-
 @ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09
@ c9e9bdc0:e4dbe9b8
2025-05-16 17:00:09Today we’re launching Buzzbot Express: a clean, targeted way to drive engagement and reward your audience with sats.
Here’s how it works:
-
Tag @buzzbot express [amount] (e.g.,
@buzzbot express 5000) -
Pay the invoice sent to your DMs
-
After 12 hours, one random liker and one random commenter each win **50% of the sats **(6% fee)
Since launching Buzzbot, we’ve seen a wide range of creative use cases. But the clearest path to long-term value may lie in branded content and decentralized promotion.
From plebs promoting value-for-value concerts to podcasters pushing new episodes, Buzzbot Express gives creators and brands a tool to generate real energy around a post.
Paying for engagement might feel off-brand to some, but if you’re promoting a product, a song, or an event, Buzzbot Express offers a clean, transparent way to generate real momentum.
The invention of Zaps opened the fifth dimension of social media. They are not just another feature added to the stack. They are an exponential amplifier that transforms attention into economic energy.
At Buzzbot, we believe this new creator economy can and should include advertisers.
The days of brands paying millions to ad firms, hiring Hollywood talent, and forcing campaigns into feeds are fading. That model made sense on centralized, algorithmic platforms, but it doesn’t belong on Nostr.
Instead, brands can spend that same money directly with creators who align with their values. Or better yet, they can reward audiences for engaging honestly.
That’s where Buzzbot comes in.
Buzzbot Express is a small step toward this future. Try it out — and let us know what you think.
Pay attention.
-
-
 @ cae03c48:2a7d6671
2025-05-16 16:52:38
@ cae03c48:2a7d6671
2025-05-16 16:52:38Bitcoin Magazine

Steak ‘n Shake Now Accepting Bitcoin via Lightning Network Across U.S. LocationsSteak ‘n Shake has officially launched Bitcoin payments via the Lightning Network, following the announcement reported on May 9. At the time, the fast food chain teased its plans to integrate BTC, generating excitement across the Bitcoin community. And today, it is an option at the cash register, or better said, Bitcoin Register.
JUST IN: Fast food giant Steak 'n Shake is now officially accepting #Bitcoin Lightning Network payments
 pic.twitter.com/bvGCb9r4Im
pic.twitter.com/bvGCb9r4Im— Bitcoin Magazine (@BitcoinMagazine) May 16, 2025
As of today, customers can pay for their meals with Bitcoin at Steak ‘n Shake locations across the United States. This marks a major step in mainstream Bitcoin adoption, as the chain serves over 100 million customers annually and now gives them the option to use Lightning for instant, low-fee transactions.
First Bitcoin purchase in the world with @SteaknShake
Changing the game of Dining, Bitcoin & Politics.
Only Steak N’ Shake puts your health over profits by using beef tallow. pic.twitter.com/ZeQxxFbbHB
— Valentina Gomez (@ValentinaForUSA) May 16, 2025
The company announced the news on X this morning, confirming that Lightning Network payments are officially supported in-store.
Bitcoin has been launched at Steak n Shake



The revolution is underway…
-Steaktoshi
— Steak 'n Shake (@SteaknShake) May 16, 2025
Following up, they clarified the scale of the implementation—this isn’t a small test or pilot program. It’s a full rollout across their system.
The Lightning Network, Bitcoin’s second-layer solution, is designed for fast, scalable, and low-cost payments, making it ideal for point-of-sale purchases like burgers and fries. Steak ‘n Shake customers can now scan a Lightning QR code at checkout using any supported wallet, completing transactions in seconds. The system uses a backend payment processor to handle real-time conversion to USD, ensuring stability and ease of use for both the customer and the merchant.
NEW: Fast food giant Steak 'n Shake will begin accepting Bitcoin payments for their over 100 million customers
 pic.twitter.com/g1OErM82BI
pic.twitter.com/g1OErM82BI— Bitcoin Magazine (@BitcoinMagazine) May 9, 2025
In Bitcoin Magazine’s previous coverage, the significance of even the hint of this move was noted, and now that it’s official, it confirms Steak ‘n Shake as one of the first major fast food brands to fully embrace Bitcoin through Lightning. This goes beyond the occasional “Bitcoin accepted here” sign; this is a practical, streamlined payment option that reflects a commitment to Bitcoin integration.
 Cashback Alert at Steak ’n Shake!
Cashback Alert at Steak ’n Shake! 
Buy your next meal in Bitcoin Lightning


Pay using Speed Wallet at any @SteaknShake store and get 1,000 SATS cashback via Lightning

 More Bonus: Post a video of your payment & tag us — we’ll send you an extra 2,000 SATS to your… pic.twitter.com/D2aV4biJP4
More Bonus: Post a video of your payment & tag us — we’ll send you an extra 2,000 SATS to your… pic.twitter.com/D2aV4biJP4— Speed Wallet
 (@speedwallet) May 16, 2025
(@speedwallet) May 16, 2025With tools like the Lightning Network making payments faster and more accessible, Steak ‘n Shake is positioning itself at the forefront of a shift toward practical, everyday BTC utility.
This update could signal a larger trend on the horizon. With more brands watching consumer behavior and the Lightning Network’s increasing usability, Steak ‘n Shake’s move might spark a wave of similar integrations.
This post Steak ‘n Shake Now Accepting Bitcoin via Lightning Network Across U.S. Locations first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 05a0f81e:fc032124
2025-05-16 16:51:11
@ 05a0f81e:fc032124
2025-05-16 16:51:11In the year 2023, a man known as RTD. HAMZA AL-MUSTAPHA. In a TV show revealed the secret behind the mining of californium in west African country, Nigeria. He also revealed that the mining of californium is also the reason while a particular (borno) state in Nigeria 🇳🇬 experience hight rate of terrorism!.
There are several research that quote that californium does not exist naturally on earth but can be made in the laboratory with the bombarding of curium with helium ions. Now from this context, it shows that there are two elements responsible for californium, which are curium and helium ions. But before i dive in deeper, there are some key words that will convince and prove the existence of californium in Nigeria.
- californium.
- curium.
- helium ions.
- mining.
- Earth crust.
- temperature.
- bombarding.
Californium: this is a chemical element of atomic number 98, a radioactive metal of the actinide series, first produced by bombarding of curium with helium ions. This means that californium is a product of curium and helium after the bombarding process.
Curium: this is a synthetic, radioactive, metallic element with the atomic number of 96. There are many ways and places where curium can be found apart from being produced in the laboratory. But in this contexts, I will focus on environmental samples and nuclear waste ways of finding curium. _ environment sample: trace amounts of Curium can be found in environmental samples such as soil or water, near
nuclear facilities or after nuclear accidents. _ nuclear waste: curium is a component of nuclear waste, particularly in spent nuclear fuel. This means that we can find curium in our environment not only on laboratory.Helium: helium is a chemical element with the atomic number of 2, it is colorless, tasteless, odorless and non toxic, inert monatomic gas. There are ways and places you can get helium but I want to focus on the radioactive decay method of getting helium. _radioactive decay: in this method, helium is produced through the radioactive decay of uranium and thorium in the Earth crust.
Mining: Mining is the process of extracting valuable materials from the beneath the Earth crust, including minerals, metals, and fossil fuels like coal, oil, and gas. It involves various techniques, from digging tunnels for underground mining to excavating open-pit mines. The goal is to locate and extract economically viable deposits of these resources for use in manufacturing, energy production, and other applications.
Temperature: thus is the hotness or coldness of something, which is specifically related to the average kinetic energy of an object's particle. Since particles are in constant motion, they possess kinetic energy, and temperature reflects the energy associated with this particle movement. The temperature beneath the Earth is very high causing this elements (curium and helium) to bombard and form californium 😃.
Bombarding: direct a stream of high-speed particles at (a substance) or element.
Since there are the presence of curium and helium ions beneath the Earth crust, the high temperature beneath there will bombard them both forming californium as the end product, which attracts miners to come do there mining activities and discover californium. 😀
Final, there are atoms of truth in what RTD. AL-MUSTAPHA said about CALIFORNIUM in Nigeria 🇳🇬.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10
@ 5d4b6c8d:8a1c1ee3
2025-05-16 15:29:10How could the Dallas Mavericks possibly have gotten the first pick in this draft? League corruption? Mischievous basketball gods? Simulation theory? Dumb stupid luck? Whatever the reason, it's very interesting.
We'll probably be done with the 2nd round, by the time we record, which means round 2 recap and conference finals previews. It's definitely not the matchups anyone expected. What are the implications for our brackets?
The NFL released the season schedules and @grayruby's rightly excited for his 49ers upcoming season.
The parity situation worsens in the MLB, as the Dodgers' pitchers are ravaged by injury. Also, @grayruby and I are going head-to-head in fantasy baseball this week. Who will prevail?
On this week's Blok'd Shots, @grayruby will dance on the Leafs' grave and celebrate their well-deserved misfortune. Hell hath no fury like a scorned Leafs fan. Also, the NHL bracket is coming down to me and @Jer. Will knowing anything about hockey be enough to get Jer the victory?
And, as always, whatever the stackers want us to cover.
https://stacker.news/items/981596
-
 @ d57360cb:4fe7d935
2025-05-16 14:54:18
@ d57360cb:4fe7d935
2025-05-16 14:54:18I soar all over the world, but one of the places I visit often is this little tiny square opening. I land softly on the platform and peer in through the hole. There’s a man inside; he seems to enjoy when I come by. His eyes light up and he gives me crumbs of bread to eat. The bread is tasty and fulfilling; it satisfies my hunger during my flights to other destinations. I wonder what it’s like to be man.
Man does strange things. I can’t fully understand. For example, this man is confined in a tiny box. He sits on what looks like a deformed tree, and in front of him is a tiny rectangular box. Everything man has is so boxy; it’s unnatural to me. When I fly from place to place, I don’t see any boxes; rather, I see a wiggly world. Endless shape, no two things look the same, but to man, it’s like he wants everything to be the same. Man usually is looking at other thin boxes; these are slim and have marks on them. He appears to stare for a long time at them, and then he sets them down and picks up another to stare at. In his box, he has long, narrow boxes. They hold small boxes bundled together with slim boxes. It gives me a headache seeing so many boxes. Once I observed man outside in the wiggly world, and when he left his big box, he went into another smaller box that moved! I was so interested I followed his moving box. You wouldn’t guess where he went to! Another box, but this one was a big one with subsections of smaller boxes. Could you believe they even have big boxes for water! What a headache man is.
The game man plays is interesting; it seems to be about boxes and how to put wiggly things in them. The wiggly is too elusive; one can’t box it up. Even if you surround the wiggly in a box, it will continue to wiggle. Like a tree confined to a planter box, its roots will spread beyond their confinement. Man is like this but believes the box will contain him, shameful.
-
 @ f85b9c2c:d190bcff
2025-05-16 14:23:39
@ f85b9c2c:d190bcff
2025-05-16 14:23:39 I used to think I thrived on chaos. Podcasts blaring, TV on in the background, notifications pinging—it was my norm. But last year, I hit a wall. I was irritable, foggy, and couldn’t focus. I didn’t realize how much the constant noise was frying my brain until I tried something radical: silence.
I used to think I thrived on chaos. Podcasts blaring, TV on in the background, notifications pinging—it was my norm. But last year, I hit a wall. I was irritable, foggy, and couldn’t focus. I didn’t realize how much the constant noise was frying my brain until I tried something radical: silence.The Experiment One weekend, I turned everything off. No music, no screens, no chatter. At first, it was weird—almost suffocating. My mind raced, looking for something to latch onto. But after a few hours, I settled in. I sat with a cup of tea, just listening to the hum of the fridge. It was the first time in months I’d actually heard my own thoughts
What Silence Gave Me That quiet weekend was a reset. I started noticing things I’d ignored—like how tense I’d been or how I’d been avoiding tough decisions. Silence didn’t just calm me; it forced me to face myself. I kept it up, carving out 30 minutes a day with no sound. It’s become my sanity-saver. When life gets loud, those quiet moments keep me grounded. Turns out, my brain needed the break. All that noise was overloading me, leaving no room to process anything. Silence let me recharge and think clearly again. It’s not about being a hermit—it’s about giving myself space to breathe.
-
 @ f85b9c2c:d190bcff
2025-05-16 14:08:51
@ f85b9c2c:d190bcff
2025-05-16 14:08:51 In the rapidly evolving world of cryptocurrencies, the potential interplay between artificial intelligence and digital assets has captured significant attention. Cointelegraph recently reported on the concept of AI, particularly in the form of ChatGPT, contributing to the potential rise of Bitcoin, potentially reaching a value of $100K in 2024. This development offers a glimpse into the role of AI in shaping the direction of cryptocurrencies, particularly Bitcoin.
In the rapidly evolving world of cryptocurrencies, the potential interplay between artificial intelligence and digital assets has captured significant attention. Cointelegraph recently reported on the concept of AI, particularly in the form of ChatGPT, contributing to the potential rise of Bitcoin, potentially reaching a value of $100K in 2024. This development offers a glimpse into the role of AI in shaping the direction of cryptocurrencies, particularly Bitcoin.AI’s Role in Shaping Bitcoin’s Future: ChatGPT, an advanced language model powered by artificial intelligence, has been seen as a potential assistant in driving Bitcoin’s value upwards. The underlying premise is rooted in AI’s capacity to influence market analysis, comprehend and design trading strategies, and anticipate potential trends in the cryptocurrency sector. By leveraging vast amounts of data and analyzing complex patterns, ChatGPT could provide insights that impact investment decisions and market.
AI-Powered Market Analysis and Prediction One of the key ways AI, represented by ChatGPT, can aid Bitcoin’s value appreciation is through advanced market analysis and prediction. By assimilating and processing large datasets encompassing historical price movements, trading volumes, market sentiment, and external factors, AI can potentially forecast potential price changes with a higher degree of accuracy. This analytical capability could equip investors with valuable insights regarding optimal entry and exit points, thus potentially contributing to Bitcoin’s upward trajectory. Furthermore, AI’s predictive abilities extend to discerning macroeconomic and geopolitical developments that could impact Bitcoin’s value, enabling proactive decision-making in response to dynamic market conditions. This foresight could instill confidence among investors and potentially drive greater adoption and investment in Bitcoin, which contributed to its ascent $100K mark.
Influencing Trading Strategies AI-driven trading strategies have gained prominence in financial markets, and their potential impact on Bitcoin’s valuation is noteworthy. ChatGPT’s capacity to generate and optimize trading algorithms that respond to market conditions in real-time could potentially enhance trading efficiency and liquidity in Bitcoin markets. By identifying opportunities for arbitrage, risk management, and executing complex trading strategies, AI could facilitate a more stable and robust Bitcoin market, potentially attracting institutional investors and bolstering its overall value.
Market Volatility Volatility has been a defining characteristic of the cryptocurrency markets, including Bitcoin. AI, through ChatGPT, could aid in mitigating this volatility by providing real-time insights, sentiment analysis, and risk assessments to market participants. By enhancing transparency and reducing uncertainty, AI-driven tools may contribute to a more stable and predictable environment for Bitcoin trading, potentially attracting a broader investor base and positively influencing its long-term value, including the speculated $100K threshold. Conclusion The potential for AI, exemplified by ChatGPT, to influence Bitcoin’s trajectory towards a $100K valuation in 2024 underscores the evolving synergy between technology and finance. As AI continues to permeate various domains, its impact on cryptocurrency markets is poised to be substantial. It is imperative to monitor the evolution of AI’s role in shaping the future of Bitcoin and other digital assets, as it has the potential to redefine investment strategies, market dynamics, and the broader financial landscape in the years to come.
-
 @ e39333da:7c66e53a
2025-05-16 13:20:33
@ e39333da:7c66e53a
2025-05-16 13:20:33::youtube{#Pex7jW3Tqwo}
Developer SHIFT UP has announced that their latest titled, Stellar Blade, that was released on PS5 on the 2024, will release on PC via Steam and EGS on the 11th of June 2025.
The game will be priced at $60, and $80 for the edition of the game that includes the 'Twin Expansion Pack', which includes the NieR: Automata DLC and the Goddess of Victory: Nikke DLC, and a key to redeem a Stellar Blade costume in the developer's previous Free-to-Play title Goddess of Victory: Nikke.
The trailer released to announce said release date also showcases the changes the made for the game and highlight PC specific enhancements, support, and options.
It's worth noting, in terms of negative news that tagged along with this, that the game will have Denuvo running, which there are evidence that decreases a game's performance, and may prevent you from playing the game offline. The game will also have an optional PSN account login, and because of this, the game is not available for purchase in around 130 countries. There's also an exclusive outfit locked behind a PSN-to-Steam account linking.

Here's the system requirements:
| | Minimum | Recommended | High | Very High | | ----------------------- | ----------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------------- | ------------------------------------------------- | | Average Performance | 1080P at 60 frames per second | 1440P at 60 frames per second | 1440P at 60 frames per second | 4K at 60 frames per second | | Graphic Presets | Low | Medium | High | Very High | | CPU | Intel Core i5-7600K AMD Ryzen 5 1600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | Intel Core i5-8400 AMD Ryzen 5 3600X | | GPU | NVIDIA GeForce GTX 1060 6GB AMD Radeon RX 580 8GB | NVIDIA GeForce RTX 2060 SUPER AMD Radeon RX 5700 XT | NVIDIA GeForce RTX 2070 SUPER AMD Radeon RX 6700 XT | NVIDIA GeForce RTX 3080 AMD Radeon RX 7900 XT | | RAM | 16GB | 16GB | 16GB | 16GB | | Storage | 75GB HDD (SSD Recommended) | 75GB SSD | 75GB SSD | 75GB SSD | | OS | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit | Windows 10 64-bit |
-
 @ 99e7936f:d5d2197c
2025-05-16 13:09:05
@ 99e7936f:d5d2197c
2025-05-16 13:09:05Baustelle HERZ
Können wir nicht einfach glücklich sein? Nein.
Eine traumatisierte Gesellschaft kann nicht EINFACH glücklich sein, weil die Herzen verletzt sind.
„Ja, aber es gibt doch auch noch andere Probleme als Trauma“, kritisieren einige.
„Ich habe schließlich eine Familie und einen anstrengenden Job“, erklären andere.
„Für mich ist das eine abstrakte Diskussion, ein Luxusproblem“, geben manche zu bedenken.
„Eigentlich möchte ich mich mit dem Thema gar nicht beschäftigen“, sagen wenige, denken aber viele.
„Ich beschäftige mich lieber mit positiven Dingen“, ist die diplomatische Variante der Vermeidung dieses Themas.
Niemand redet gerne über Trauma, bis es an die eigene Tür klopft. Und dann ist guter Rat teuer. Dann würde man gerne reden, aber die anderen wollen immer noch nicht.
Niemand redet gerne über Trauma.
„Was heißt denn Anklopfen?“ Mit Anklopfen meine ich die Situationen, die jeder kennt. Gemeint sind ganz normale Lebenskrisen, die es mehrmals in jedem Leben gibt.
„Ist denn eine Lebenskrise gleichzusetzten mit einem Trauma?“ Nein, aber durch eine starke Lebenskrise kann ein altes Trauma wieder hochgespült werden, und das fühlt sich dann original so an, wie das Trauma, das man z.B. als Kind oder später im Leben erlebt hat.
Und das passiert in einer traumatisierten Gesellschaft ständig, nur nennen die Leute es nicht so. Niemand sagt: „Er oder sie hat ein aktiviertes Trauma.“
Hierzu habe ich eine Anekdote. Vor ein paar Monaten zog in das Nachbarhaus bei mir auf der Straße ein junger Mann ein. Das Haus war frisch renoviert worden. Es zogen zeitgleich mehrere junge Leute jeweils in eine Wohnung dieses Hauses ein. Die Stimmung im Haus war gut, weil alles neu und geschmackvoll gestaltet worden war und die Mieter gut zusammen passten. Dann merkten die Mieter und Nachbarn, dass es einem jungen Mann nicht gut ging. Er saß den ganzen Tag in der Wohnung, konnte sich zu nichts aufraffen. Er schaffte es nicht, sich Lebensmittel einzukaufen. Ein Freund kam regelmäßig vorbei und brachte ihm Essen. Eine ältere Nachbarin fragte nach einigen Monaten diesen Freund, was dem jungen Mann denn fehle, ob er eine Krankheit habe oder was denn los sei. Der Freund lachte und sagte nur einen Satz: „Er stirbt.“
Die Nachbarin erzählte mir das und schaute mich fragend an. Ich übersetzte ihr den Satz und meinte: „Er hat vermutlich Liebeskummer.“ Aber was ich wirklich dachte, war, dass er ein aktiviertes Trauma hatte, nur sagte ich das nicht zur Nachbarin. Nach mittlerweile zwei Jahren kommt der Freund immer noch regelmäßig und bringt dem jungen Mann Essen. Er kauft für ihn ein und kümmert sich um ihn.
Manche Menschen leiden sehr lange unter Verlusten, Zurückweisungen, Niederlagen, Verletzungen. Andere kommen nie auf die nächste Stufe, obwohl sie sich unaufhörlich anstrengen. Wieder andere haben alles und sind dennoch unzufrieden und in permanenter Angriffshaltung. All diese Phänomene dauern oft lange, manchmal sogar ein Leben lang. Meines Erachtens sind das aktivierte Traumen bzw. Traumen, die gut verschlossen dennoch im Unterbewusstsein gegen die eigene Person arbeiten.
Trauma hat viele Gesichter.
Es kommt bei den unmöglichsten Gelegenheiten zum Vorschein. Und oft erkennen wir es nicht als das, was es ist. Wir suchen den Grund im Außen, den es ja meist auch gibt. Nur ist der Grund nicht der Grund, sondern nur der Auslöser.
Auch ich bin einmal „gestorben“. Dieser Zustand dauerte über drei Jahre an. Deshalb klingelte es bei mir auch sofort im Ohr als die Nachbarin sagte, der Freund habe gesagt: „Er stirbt.“
Sprache ist wunderbar.
Wer beides schon mal erlebt hat, eine normale Trennung und eine schwere Trennung, einen normalen Arbeitsplatzwechsel oder einen dramatischen Jobverlust, ein geplatztes Geschäft oder einen geplatzten Lebenstraum, das Ende einer Freundschaft oder eine Kränkung, über die man noch nach 35 Jahren so berichtet, als ob es gestern gewesen wäre, der kennt den Unterschied in der Intensität der Gefühle. Manche Menschen erzählen immer wieder eine Geschichte, obwohl man sie schon kennt und auch sein Mitgefühl dazu ausgedrückt hat. Manche Menschen reden gar nicht mehr über eine bestimmte Sache, bis einem irgendwann von Dritten gesagt wird, dass man ihn oder sie besser nicht auf das Thema XYZ ansprechen sollte.
All das sind aktivierte Traumen, die noch weh tun, noch nicht verarbeitet sind. Es sind Dinge, die jedem von uns passieren können. Jeder erlebt im Leben partnerschaftliche Trennungen, geplatzte Geschäfte und Kränkungen am laufenden Meter, aber es „trifft“ einen nicht immer gleich. Und es trifft nicht nur die Sensiblen, sondern es trifft jeden, wenn der Punkt, an dem es trifft, wund ist. Der wunde Punkt macht jeden sensibel. Auch robuste Naturen haben einen wunden Punkt. Und wenn der getroffen wird, dann werden auch die härtesten Menschen butterweich. In einer traumatisierten Gesellschaft wird jeder so oft „getroffen“, wie es braucht, bis er sich dem Thema widmet. Wir alle haben diese frühen oder späten Traumen erlebt, die früher oder später erneut durch Krisen aktiviert werden. Und dann „sterben“ wir, zumindest gefühlt.
Denn Trauma ist immer existenziell.
Und aktiviertes Trauma ist bitte nicht zu verwechseln mit Depression. Es ist ein aktiviertes Trauma, das sich im Unterschied zur Depression sehr wach, lebendig und vor allem schmerzvoll anfühlt. Es fühlt sich an wie „damals“. Das versteht man, in der Situation steckend, komischerweise sofort, denn wir haben ein Schmerzgedächtnis. Wir können Düfte oder Musik ja auch sofort zuordnen, wenn sie uns an etwas erinnern. Mit Schmerz ist es ähnlich. Aber es fällt so schwer, darüber zu reden, weil es keiner versteht und weil es dafür meines Erachtens in unserer Sprache keine Worte gibt. Man versteht das erst, wenn man es selbst erlebt hat. Und dann reichen zwei Worte.
Die Baustelle HERZ versteht man erst, wenn man selbst ein aktiviertes Trauma erlebt, durchlebt hat, wenn man einmal „gestorben“ ist.
Heute kann ich an Äußerungen, die jemand macht, gut ablesen, ob jemand seine Baustelle HERZ bereits kennen gelernt hat oder nicht. Menschen, die das selbst noch nicht kennen gelernt haben, haben oft aufmunternde Sprüche wie „Das wird schon wieder. Jetzt lass den Kopf mal nicht hängen.“ Das hilft einem dann in etwa so, wie wenn man in einer Depression gesagt bekommt: „Nun lach doch mal.“ Man weiß dann sofort, welchen Erfahrungshintergrund das Gegenüber hat. Das ist keine Wertung, nur eine Feststellung. Unsere Kultur hat hier einfach wichtiges Wissen verloren. Ich persönlich weiß nicht, wie es ist, ein Kind auf die Welt zu bringen oder ein Kind zu verlieren. Ich weiß vieles nicht und habe vermutlich auch schon wenig hilfreiche Kommentare abgegeben, weil ich es nicht besser wusste. Aber ich weiß, wie sich ein aktiviertes Trauma anfühlt. Und das ist ein wertvolles Wissen, was ich gern teilen möchte. Man schaut mit diesem erfahrenen Wissen (kein Bücher-Wissen) viel differenzierter auf das Leid anderer Menschen. Es gibt so viele Sorten von Trauma und deswegen auch Sorten von aktiviertem Trauma. Manchmal denkt man sich nichts dabei und sagt etwas, und schon hat man beim anderen einen Punkt getroffen, der dadurch nun schmerzt. Wenn man Glück hat, dann dauert der Schmerz nur kurz an. Wenn man Pech hat, ist die Freundschaft zu Ende. Ich habe das selbst schon erlebt. Mal war ich es, die den Rückzug angetreten hat. Mal war es der andere. Hinter diesen Phänomenen steckt nichtverarbeitetes Trauma. Die Bildungslücke bezüglich Trauma in unserer Gesellschaft ist (gewollt) riesig.
Wir sind eine traumatisierte Gesellschaft, die nicht weiß, dass sie eine traumatisierte Gesellschaft ist.
Viele Menschen haben unverarbeitetes Trauma im Gepäck. Wir haben selbst nach Jahren der Therapie und Selbstreflektion immer noch unverarbeitete Anteile eines Traumas im Gepäck, das wir glaubten, bearbeitet zu haben. Mir ist das bewusst geworden, je besser ich mein eigenes Trauma kennen und lieben gelernt habe.
Eigentlich wollte ich heute kurz etwas über den gesunden Umgang mit Gefühlen schreiben. Beim Schreiben habe ich aber gemerkt, dass ich erstmal etwas über das Haus erzählen muss, bevor ich über die Gäste, die Gefühle, rede. Ich bin das Haus, das durch Verstand und Gefühle belebt wird. Und hinter dem Haus gibt es noch ein ganzes Universum, auf das ich heute nicht eingehen möchte.
Gefühle und Fühlen sind zentral wichtig, wenn man Trauma bearbeiten möchte.
Trauma wird solange aktiviert, bis es bearbeitet wurde.
In einer traumatisierten Gesellschaft wird 24/7 Trauma aktiviert. Und das ist gut so. Die Evolution schläft nicht. Die Evolution schenkt uns Schmerz, damit wir ihr Aufmerksamkeit schenken.
Das Leben liebt uns, und wiederkehrender Schmerz ist wie die Schlummerfunktion am Wecker, die möchte, dass wir aufwachen.
In unserer traumatisierten Gesellschaft klingelt momentan nicht nur der Wecker. Alles, was tönen kann, gibt Signal. Mir kommt es in dieser Zeit manchmal vor, wie wenn sich gleichzeitig , das Kinder-Sinfonieorchester mit sämtlichen Instrumenten einstimmt, jemand mit dem Handy telefoniert, das Fenster zur Hauptstraße offen steht, der Bus anfährt, der Auspuff röhrt, jemand hupt, das Martinshorn aufheult, die Drehorgel spielt, das Pausenzeichen in der Schule ertönt, es an der Tür klingelt und die Kirchenorgel aus allen Pfeifen flötet und brummt.
Aktiviertes Trauma macht ordentlich Krach individuell und erst recht gesellschaftlich gesehen. Und je lauter es ist, desto dringender möchte es bearbeitet werden.
Die Baustelle HERZ zu bearbeiten, lohnt sich. Und Fühlen bringt die Verwandlung.
-
 @ 87fedb9f:0da83419
2025-05-16 12:45:01
@ 87fedb9f:0da83419
2025-05-16 12:45:01Push it! Push it! Push it!
That chant still echoes in my bones, not just from the gym, but from the inside out. I remember watching a bodybuilder once — the weight trembling above him, his muscles bulging and giving out, the spotters swooping in to catch the bar just in time. “Train to failure,” they said. “That’s how you grow.”
And it makes sense, doesn’t it? If you’re being chased by a wild beast, you run until your body gives out. That’s how we’re wired — to survive first and foremost, not necessarily to thrive.
But what if the house we’re building isn’t under threat from wolves? What if we’ve got stone-moving machines and time to breathe? What if we’re not being chased anymore… but we still act like we are?
See, survival patterns are sneaky. They wear masks. They show up in workouts and work days. They dress up in ambition, caffeine, and “just one more thing before I stop.”
I’ve never been a bodybuilder — my brother was — but I’ve tried that route in my own work life. Lift to failure. Push it. Every other day, I’d be nursing another injury to body and mind.
I wasn’t getting stronger. I was just breaking myself in cycles. Push, break, recover, repeat.
I see the same thing with brains. Push it. Adderall. More coffee. Keep going. Hit the wall. And then—collapse.
That’s not strengthening. That’s surviving pretending to be “powerful.”
What happens to the rest of your system when your brain is sucking up all the energy just to stay on task? You stop digesting. You stop feeling the sun on your skin. You stop enjoying your kids’ laughter. Everything feels like something to push through.
That isn’t thriving.
Thriving feels different. It’s alive, yes — there’s activation. But it’s not strained. When we’re in thriving mode, we’re with our energy, not yanking it out by the roots and forcing it to regrow. The muscles — or the mind — are engaged, fluid, expressive. Alive.
It’s a fine line. You can take the same exact action and fill it with stress.
I’ve done it. I’ve turned a perfectly normal task into a survival sprint. It feels ridiculous in hindsight — like, why did I make this email reply into a mountain climb?
Because my primitive brain still whispers, “If you don’t do this perfectly and fast, you’ll die.” Not literally. But the threat feels real. The imagined judgment, the self-criticism, the fear of not being enough — they’re imaginary lions in the tall grass of modern life.
I’ve used this system on myself. I’ve strained my nervous system like fingernails scraping rock to avoid a fall that was never coming.
That’s what we’re supposed to do, right? We bring survival force into every aspect. Into parenting. Into projects. Into relationships.
And we wonder why we’re tired all the time. Not sleepy tired — soul tired. That kind of tired that feels like you ran for your life… but all you did was sit at your desk.
Here’s what I know now: if you’re not actually in danger, you can stop living like you are.
You don’t have to push everything to the edge. You don’t have to prove your strength through strain. Strength can be alive in you — not torn, not depleted, but awake and sustaining.
And when we live from there, the recovery feels different, too. We’re not collapsing. We’re restoring.
We’re not dropping all the pieces and then forcing ourselves to pick them up… again! Instead, we’re crafting a thriving life from the pieces we find, fashion, and consciously put in place.
There’s a wisdom to building your foundation around thriving — not just surviving. And thriving starts with recognizing: it’s not life or death to get through your inbox. Your self-worth isn’t measured by how busy and depleted you are.
Look around. Are you stacking more and more iron to prove something? Or are you listening to the quiet whisper that says, “Yes, move… but don’t hurt yourself doing it.”
And in a life that tells you to push until you fail, choosing to rest and relish — choosing to feel alive rather than just alive-enough — might just be the truest strength there is.
Useful Concepts for Thriving in This Story
-
Primitive Brain\ The primitive brain keeps us on high alert even when we’re safe — it’s time to question whether the lion is real.
-
Unrushed\ Being unrushed is a radical shift from survival tempo to the rhythm of true aliveness.
-
Savvy\ Savvy invites us to work with our energy wisely, not destructively — to choose thriving over proving.
-
Vitality\ Vitality flows when we stop draining ourselves for performance and start living from inner strength.
-
Inspired Action\ Inspired action arises from presence and aliveness, not adrenaline and depletion.
-
-
 @ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12
@ 4fa5d1c4:fd6c6e41
2025-05-16 11:42:12Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
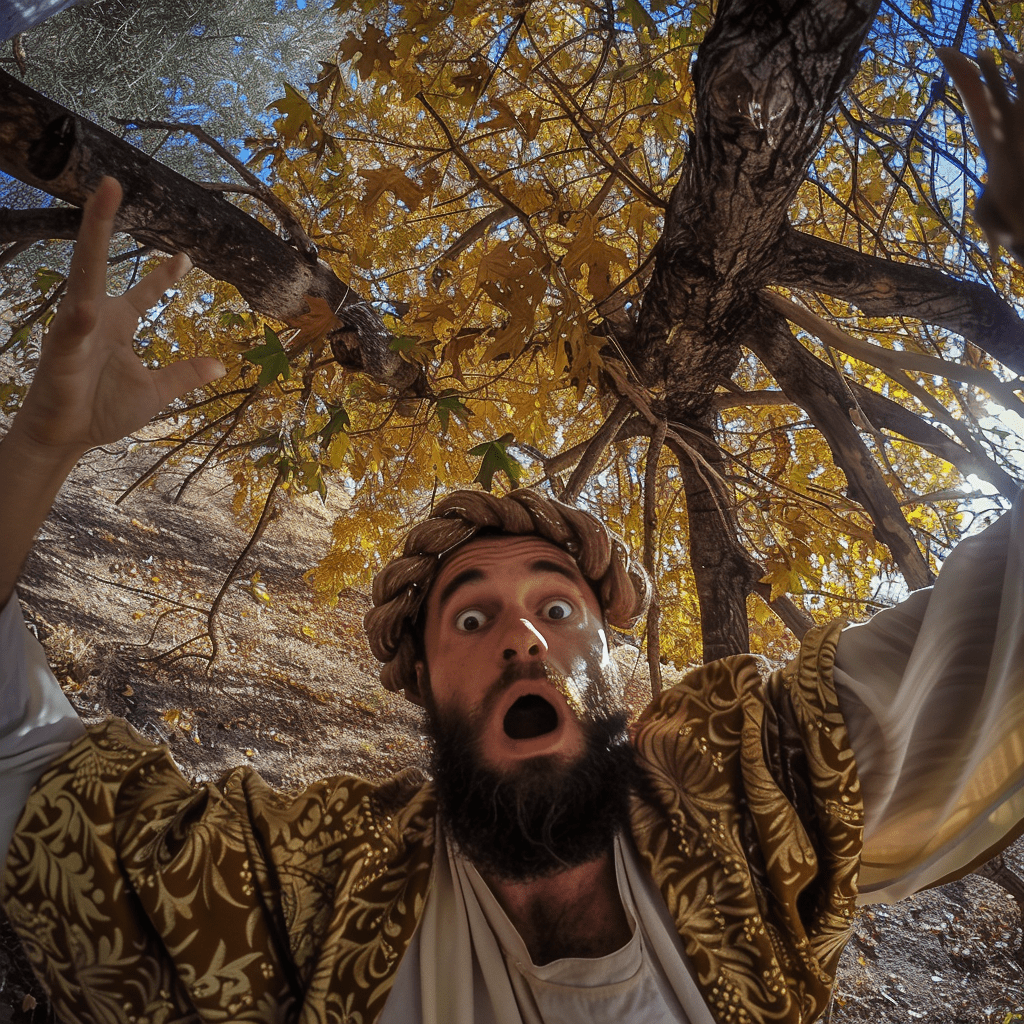
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ bbef5093:71228592
2025-05-16 17:00:59
@ bbef5093:71228592
2025-05-16 17:00:59Technológiai fejlemények
Az Egyesült Államokban és világszerte jelentős előrelépések történtek a nukleáris technológia területén. A mesterséges intelligencia (AI) egyre nagyobb szerepet kap az atomerőművek működtetésében: például a kaliforniai Diablo Canyon atomerőmű már alkalmaz generatív AI-t a dokumentumkezelés és az üzemeltetési hatékonyság javítására. Az AI segíti az üzemeltetőket a karbantartás előrejelzésében, a biztonság növelésében és a reaktorok élettartamának meghosszabbításában is. Emellett az USA Nukleáris Szabályozó Bizottsága (NRC) is vizsgálja, hogyan gyorsíthatná fel az engedélyezési folyamatokat AI-alapú rendszerekkel, ami jelentősen felgyorsíthatja az új reaktorok telepítését.
A NANO Nuclear Energy jelentős mérföldkövet ért el: megszerezte a KRONOS MMR™ (45 MWth teljesítményű, helyhez kötött mikroreaktor) és a LOKI MMR™ (1–5 MWth teljesítményű, hordozható mikroreaktor) technológiákat, és ezek fejlesztését az USA-ban és Kanadában is előmozdítja. A KRONOS MMR üzemanyag-minősítési módszertanát az NRC már jóváhagyta, ami kulcsfontosságú a kereskedelmi bevezetéshez
Ipari és piaci fejlemények
Az amerikai The Nuclear Company startup 46 millió dolláros tőkebevonással kívánja új, nagy teljesítményű atomerőművek fejlesztését megkezdeni, elsősorban már engedélyezett helyszíneken. A cél, hogy az első flottában összesen 6 gigawatt kapacitást hozzanak létre. Ez a lépés válasz a gyorsan növekvő amerikai áramigényre, amelyet főként az adatközpontok és a mesterséges intelligencia-alkalmazások hajtanak. Ugyanakkor a nukleáris ipar pénzügyi kilátásait bizonytalanság övezi, mivel az amerikai törvényhozás egyes tervezetei a nukleáris energia adókedvezményeinek megszüntetését is kilátásba helyezték, ami a jövőbeni beruházások megtérülését is befolyásolhatja.
Belgiumban a parlament váratlan fordulattal úgy döntött, hogy nem zárják be az atomerőműveket, hanem tíz évvel meghosszabbítják a reaktorok élettartamát, sőt, új reaktorok építését is tervezik. A döntés mögött az energiaválság, az ellátásbiztonság és a geopolitikai feszültségek állnak.
Magyarországon folytatódik a Paks II. projekt előkészítése, és napirenden van kis moduláris reaktorok (SMR) telepítése is, amelyek néhány száz megawattos teljesítményükkel akár ipari zónákat vagy városokat is önállóan elláthatnak.
Pénzügyi és geopolitikai aktualitások
A nukleáris energia geopolitikai jelentősége továbbra is kiemelkedő. Tajvan szombaton leállítja utolsó működő atomerőművi blokkját, ami jelentős LNG-import költségnövekedést eredményez, és komoly vitákat váltott ki a szigetországban. A törvényhozás ugyanakkor már vizsgálja az atomenergia-törvény felülvizsgálatát, amely lehetővé teheti a reaktorok újraindítását – erről akár népszavazás is lehet a közeljövőben.
Az USA és Irán között folytatódnak az atomprogramról szóló tárgyalások. Bár közelednek az álláspontok, az USA új szankciókat vezetett be Irán ellen, mivel Teherán továbbra is magas szintű urándúsítást folytat. Az esetleges megállapodás rövid távon növelheti az iráni kőolajexportot, ami a világpiaci árakra is hatással lehet.
-
 @ 8f69ac99:4f92f5fd
2025-05-16 11:40:35
@ 8f69ac99:4f92f5fd
2025-05-16 11:40:35Há algo quase reconfortante na previsibilidade com que certos colunistas abordam Bitcoin: a cada oportunidade, repetem os mesmos chavões, reciclados com indignação moralista e embrulhados numa embalagem de falsa autoridade. O artigo publicado na Visão, com o título dramático "De criança prodígio a adolescente problemático", encaixa-se perfeitamente nesse molde.
Trata-se de uma peça de opinião que mistura factos irrelevantes com interpretações enviesadas, estatísticas sem contexto e um medo mal disfarçado de perder o monopólio da narrativa económica. A autora, Sofia Santos Machado, opta por colar em Bitcoin os desastres do chamado “mundo cripto” como se fossem parte do mesmo fenómeno — ignorando, por conveniência ou ignorância, que Bitcoin não é altcoins, não é NFTs, não é esquemas de yield exótico, e não é fintech vestida de blockchain.
Esta resposta centra-se exclusivamente em Bitcoin — um protocolo monetário aberto, incorruptível e resistente à censura, que já está a servir como salvaguarda de valor em regiões onde o sistema financeiro convencional falhou. Não me interessa defender pirâmides, tokens inflacionários ou aventuras bancárias mal calculadas.
Criticar Bitcoin é legítimo — mas fazê-lo sem saber do que se fala é apenas desinformação.
A Histeria da Água — Falar Sem Saber
O artigo abre com uma pérola alarmista sobre o consumo de água:
“Uma única transacção de bitcoin consome seis milhões de vezes mais água do que um pagamento com cartão.”
Seis. Milhões. De vezes. Resta saber se a autora escreveu isto com cara séria ou a rir-se enquanto bebia água engarrafada dos Alpes Suíços.
Fontes? Metodologia? Contexto? Estou a brincar — isto é a Visão, onde os números são decoração e os factos opcionais.
Claro que comparar transacções na camada base de Bitcoin com pagamentos "instantâneos" da rede Visa é tão rigoroso como comparar um Boeing 747 com um avião de papel porque um voa mais longe. Um artigo sério teria falado em batching, na Lightning Network, ou no facto de que Bitcoin nem sequer compete com a Visa nesse nível, nem em nenhum. Mas isso exigiria, imagine-se, investigação.
Pior ainda, não há qualquer menção ao consumo de água na extracção de ouro, nos data centers bancários, ou no treino de modelos de inteligência artificial. Pelos vistos, só Bitcoin tem de obedecer aos mandamentos ecológicos da Visão. O resto? Santa ignorância selectiva.
Criminosos e o Fantasma do Satoshi
Eis o clássico: “Bitcoin é usado por criminosos”. Um cliché bafiento tirado do baú de 2013, agora reapresentado como se fosse escândalo fresco.
Na realidade, Bitcoin é pseudónimo, não anónimo. Todas as transacções ficam gravadas num livro público — não é propriamente o esconderijo ideal para lavar dinheiro, a menos que sejas fã de disfarces em néon.
E os dados? Claríssimos. Segundo a Chainalysis e a Europol, a actividade ilícita com Bitcoin tem vindo a diminuir. Enquanto isso, os bancos — esses bastiões de confiança — continuam a ser apanhados a lavar biliões para cartéis e cleptocratas. Mas disso a Visão não fala. Devia estragar a narrativa.
O verdadeiro crime aqui é a preguiça intelectual tão profunda que quase merece uma moldura. A Visão tem um editor?
O Espantalho Energético
Como uma criança que acabou de aprender uma palavra nova, a Visão repete “consumo energético” como se fosse um pecado original. Bitcoin usa electricidade — escândalo!
Mas vejamos: o Proof-of-Work não é um defeito. É a razão pela qual Bitcoin é seguro. Não há “desperdício” — há uso, e muitas vezes com energia excedente, renovável, ou que de outro modo seria desperdiçada. É por isso que os mineiros se instalam junto a barragens remotas, queima de gás (flaring), ou parques eólicos no meio do nada — não porque odeiam o planeta, mas porque os incentivos económicos funcionam. Escrevi sobre isso aqui.
O que a Visão convenientemente ignora é que Bitcoin está a ajudar a integrar mais energia renovável nas redes, funcionando como carga flexível. Mas nuance? Trabalho de casa? Esquece lá isso.
Para uma explicação mais séria, podiam ter ouvido o podcast A Seita Bitcoin com o Daniel Batten. Mas para quê investigar?
Cripto = Bitcoin = Fraude?
Aqui chegamos ao buraco negro intelectual: enfiar tudo no mesmo saco. FTX colapsou? Culpa de Bitcoin. Um banqueiro jogou com altcoins? Culpa de Bitcoin. Scam de NFT? Deve ter sido o Satoshi.
Vamos esclarecer: Bitcoin não é “cripto”. Bitcoin é descentralizado, sem líderes, transparente. Não teve pré-mineração, não tem CEO, não promete lucros. O que o rodeia? Tokens centralizados, esquemas Ponzi, pirâmides e vaporware — precisamente o oposto do que Bitcoin representa.
Se um executivo bancário perde o dinheiro dos clientes em Dogecoins, isso é um problema dele. Bitcoin não lhe prometeu nada. Foi a ganância.
E convenhamos: os bancos tradicionais também colapsam. E não precisam de satoshis para isso. Bastam dívidas mal geridas, contabilidade criativa e uma fé cega no sistema.
Culpar Bitcoin por falcatruas “cripto” é como culpar o TCP/IP ou SMTP por emails de phishing. É preguiçoso, desonesto e diz-nos mais sobre a autora do que sobre a tecnologia.
Promessas Por Cumprir? Só Se Não Estiveres a Ver
A "jornalista" da Visão lamenta que “após 15 anos, os riscos são reais mas as promessas por cumprir”. Que promessas? Dinheiro grátis? Cafés pagos com QR codes mágicos?
Bitcoin nunca prometeu fazer cappuccinos mais rápidos. Prometeu soberania monetária, resistência à censura e um sistema previsível. E tem cumprido — diariamente, para milhões. E para o cappuccino, há sempre a Lightning Network.
Pergunta aos venezuelanos, nigerianos, peruanos ou argentinos se Bitcoin falhou. Para muitos, é a única forma de escapar à hiperinflação, ao confisco estatal e à decadência financeira.
Bitcoin não é uma app. É infra-estrutura. É uma nova camada base para o dinheiro global. Não se vê — mas protege, impõe regras e não obedece a caprichos de banqueiros centrais.
E isso assusta. Especialmente quem nunca viveu fora da bolha do euro.
Conclusão: A Visão a Gritar Contra o Progresso
No fim, o artigo da Visão é um festival de clichés, dados errados e ressentimento. Não é só enganador. É desonesto. Culpa a tecnologia pelos erros dos homens. Rejeita o futuro em nome do conforto passado.
Bitcoin não é uma varinha mágica. Mas é a fundação de uma nova liberdade financeira. Uma ferramenta para proteger valor, resistir a abusos e escapar ao controlo constante de quem acha que sabe o que é melhor para ti.
Portanto, fica aqui o desafio, Sofia: se queres criticar Bitcoin, primeiro percebe o que é. Lê o white paper. Estuda. Faz perguntas difíceis.
Caso contrário, és só mais um cão a ladrar para a trovoada — muito barulho, zero impacto.
-
 @ b8af284d:f82c91dd
2025-05-16 08:38:57
@ b8af284d:f82c91dd
2025-05-16 08:38:57Liebe Abonnenten,
am Sonntag ging es im Essay „Das AGI-Project” um die geopolitischen Auswirkungen von künstlicher Intelligenz. Die USA und China befinden sich in einem Wettrennen, um die ökonomische und militärische Vorherrschaft. Das folgende Gespräch mit dem Künstler Künstler Snicklink dreht sich die konkreten Auswirkungen von KI auf unser Leben.
Snickling ist bereits zum zweiten Mal bei BlingBling zum Interview. Wer ihn noch nicht kennt, sollte das schnell nachholen. Spätestens seit 2023 ist der KI-Künstler einer breiteren Öffentlichkeit bekannt. Seine Videos sind oft messerscharfe Satire-Kunst, die mittels Collagen und DeepFakes den Irrsinn unserer Zeit auf den Punkt bringen. Hinter Snicklink steckt der Mensch und Berliner Künstler Willy Kramer, der immer wieder auch künstliche Intelligenz und die Zukunft der Menschen zum Thema hat.

https://www.youtube.com/watch?v=ThX3b5OSqUg
Willy, ich fand dein letztes Video beeindruckend gerade, weil es mal keine Satire war, sondern einen ernsten Ton hatte. Du sagst darin, dass kreative Arbeit bald vollständig von Künstlicher Intelligenz ersetzt werden könnte. Kannst du das jemandem erklären, der sich wenig mit KI auskennt? Was kommt da auf uns zu und warum?
Das ist eine große Frage. Ich betrachte das aus zwei Perspektiven: einer kreativen und einer gesellschaftlichen. Kreativ gesehen ist KI ein unglaublich mächtiges Werkzeug. Stell dir vor, ich könnte hundert Assistenten engagieren – oder ich nutze KI-Tools, die günstiger, schneller und oft präziser sind. Das ist die praktische Seite. Gesellschaftlich und technologisch geht es um viel mehr als nur Kunst oder einzelne Projekte. KI ist eine Entwicklung, die ich mit der Entdeckung des Feuers oder der Öffnung der Büchse der Pandora vergleiche. Das klingt dramatisch, aber ich übertreibe nicht. Ich beschäftige mich seit zehn Jahren intensiv mit dem Thema. Am Anfang war es spekulativ, und ich hatte kaum Gesprächspartner. Google und ein paar kleinere Firmen fingen gerade an, KI zu erforschen. Ich habe Workshops gegeben, aber viele hielten mich für einen Spinner. Trotzdem war mir klar, wohin das führt.
Vor zehn Jahren habe ich ein Video namens Emphasized Prophecy gemacht: Ein Typ sitzt am Strand, mit einem leeren Schreibtisch und einer kleinen Box, und erstellt per Sprachbefehl eine multimediale Kampagne. Heute, zehn Jahre später, arbeite ich mit einem Setup, das genau das ermöglicht – und noch mehr.
Welche Tools nutzt du konkret? Du bist ja schon tief in der praktischen Anwendung von KI.
Ich bin kein Programmierer, der stundenlang Skripte schreibt, aber ich bin ziemlich involviert. Alles begann so richtig mit dem „ChatGPT-Moment“ vor zweieinhalb Jahren, als plötzlich alle die Möglichkeiten von KI erkannten. Inzwischen nutze ich eine Suite aus etwa 200 verschiedenen Plugins und Services. Früher gab es spezialisierte KI für spezifische Aufgaben, etwa für den Stimmklang oder die „Deutschheit“ einer Stimme. Heute werden die Modelle größer und vielseitiger. Man braucht nur noch ein oder zwei Modelle, die Stimmen, Bilder, Videos und sogar Programmierung abdecken. Bald wird es ein einziges, universelles Modell geben.
Wir befinden uns in einem globalen Wettlauf, vor allem zwischen den USA und China. Jeder will das eine Modell entwickeln, das alle kreativen und administrativen Aufgaben erledigt – ähnlich wie Google damals die Suche revolutionierte.
Welche Benutzeroberfläche oder Tools wie Grok, ChatGPT setzen sich durch?
Jede Plattform hat ihre Stärken. Grok zum Beispiel hat direkten Zugriff auf Social-Media-Daten, was ein Vorteil ist. OpenAI hingegen punktet mit ausgefeilten Denkmodellen. Es ist wie bei einem Basketballteam: Der eine spielt stark in der Verteidigung, der andere wirft präzise Dreier. Für 99 Prozent der Nutzer macht das keinen Unterschied. Ob du mit ChatGPT einen Liebesbrief, einen Finanzamtsbrief oder psychologische Beratung formulierst – die Unterschiede sind marginal. Die Technologie entwickelt sich so rasant, dass wir alle paar Monate völlig neue Möglichkeiten bekommen, die im Alltag direkt nutzbar sind und Dinge ermöglichen, die vorher undenkbar waren.
Du hast erwähnt, dass der nächste Schritt KI-Agenten sein könnten, die untereinander kommunizieren. Kannst du das ausführen?
Stell dir die Digitalisierung wie die Erfindung des Rades vor: Es war ein Fortschritt, aber es waren nur Fahrräder. Jetzt kommt die Dampfmaschine – KI-Agenten sind die nächsten „Fahrzeuge“. Diese Agenten nutzen Sprachbefehle nicht nur, um Antworten zu geben, sondern um komplexe Aufgaben zu lösen: Kampagnen erstellen, Finanzberichte schreiben, Fünfjahrespläne für Patienten basierend auf den besten Forschungspapieren entwickeln. Aktuell braucht man noch Know-how, um die richtigen Anweisungen zu geben. Bald wird das überflüssig, weil KI dein Profil kennt und mit einem einfachen „Go“ alles erledigt – von der Suche nach der nächsten Apotheke bis zur Planung einer Operation.
Heißt das, wir steuern auf eine Überflussgesellschaft zu?
Das ist die Utopie, ja. KI kann eine Welt schaffen, in der es keinen Mangel mehr gibt – alles ist verfügbar, erschwinglich oder sogar kostenlos. Niemand hat mehr materielle oder körperliche Sorgen. Aber das bringt neue Herausforderungen: Wie gehen wir als Menschen damit um? Unsere Gesellschaft definiert Wert über Status, Arbeit, Besitz. Wenn das wegfällt, weil nur noch fünf Prozent der Menschen arbeiten, müssen wir uns neu erfinden. Wir brauchen eine Postleistungsgesellschaft, in der Kreativität, Freundlichkeit oder vielleicht Spiritualität den Ton angeben.
Das klingt nach einem Verteilungsproblem. Muss da nicht massiv umverteilt werden?
Das ganze Interview gibt es hier zu lesen: https://blingbling.substack.com/p/eine-welt-ohne-mangel
-
 @ 975e4ad5:8d4847ce
2025-05-16 11:22:20
@ 975e4ad5:8d4847ce
2025-05-16 11:22:20Introduction
Bitcoin and torrents are two technologies that have reshaped how people share information and resources in the digital age. Both are built on decentralized principles and challenge traditional systems—torrents in the realm of file sharing, and Bitcoin in the world of finance. However, while torrents have seen a decline in popularity with the rise of streaming platforms like Netflix and HBO, many wonder whether Bitcoin will follow a similar trajectory or continue to grow as a widely adopted technology. This article explores the similarities between the two technologies, the resilience of torrents against attempts to shut them down, the reasons for their declining popularity, and why Bitcoin is likely to avoid a similar fate.
Similarities Between Torrents and Bitcoin
Torrents and Bitcoin share several key characteristics that make them unique and resilient:
-
Decentralization:\ Torrents rely on peer-to-peer (P2P) networks, where users share files directly with each other without depending on a central server. Similarly, Bitcoin operates on a blockchain—a decentralized network of nodes that maintain and validate transactions. This lack of a central authority makes both technologies difficult to control or shut down.
-
Censorship Resistance:\ Both systems are designed to withstand attempts at restriction. Torrents continue to function even when specific sites like The Pirate Bay are blocked, as the network relies on thousands of users worldwide. Bitcoin is also resistant to government bans, as transactions are processed by a global network of miners.
-
Anonymity and Pseudonymity:\ Torrents allow users to share files without revealing their identities, especially when using VPNs. Bitcoin, while pseudonymous (transactions are public but not directly tied to real-world identities), offers a similar level of privacy, attracting users seeking financial freedom.
-
Open Source:\ Both technologies are open-source, enabling developers to improve and adapt them. This fosters innovation and makes the systems more resilient to attacks.
Why Torrents Cannot Be Stopped
Torrents have persisted despite numerous attempts to curb them due to their decentralized nature. Governments and organizations have shut down sites like The Pirate Bay and Kickass Torrents, but new platforms quickly emerge. The key reasons for their resilience include:
-
P2P Architecture:\ Torrents do not rely on a single server. Every user downloading or sharing a file becomes part of the network, making it impossible to completely dismantle.
-
Global Distribution:\ Millions of users worldwide sustain torrent networks. Even if one country imposes strict regulations, others continue to support the system.
-
Adaptability:\ The torrent community quickly adapts to challenges, using VPNs, proxy servers, or the dark web to bypass restrictions.
Despite this resilience, the popularity of torrents has significantly declined in recent years, particularly among younger users.
The Decline of Torrents: Why They Lost Popularity
In the early 2000s, torrents were the primary way to access movies, music, and software. They were easy to use, free, and offered a vast array of content. However, the rise of streaming platforms like Netflix, HBO, Disney+, and Spotify has changed how people consume media. The main reasons for the decline of torrents include:
-
Convenience:\ Streaming platforms provide instant access to high-quality content without the need for downloading or specialized software. Torrents, in contrast, require technical knowledge and are often slower.
-
Legality and Safety:\ Using torrents carries risks such as viruses, malware, and legal consequences. Streaming services offer a safe and legal alternative.
-
Marketing and Accessibility:\ Platforms like Netflix invest billions in original content and marketing, attracting younger users who prefer easy access over free but risky downloads.
-
Social Shifts:\ Younger generations, raised with access to subscription services, are often unfamiliar with torrents or view them as outdated. Studies from 2023 indicate that only a small percentage of people under 25 regularly use torrents.
Despite this decline, torrents have not disappeared entirely. They are still used in regions with limited access to streaming services or by users who value free access to niche content.
Why Bitcoin Will Not Share the Fate of Torrents
Despite the similarities, Bitcoin has unique characteristics that make it more likely to achieve mainstream adoption rather than being overshadowed by alternatives. Here are the key reasons:
-
Financial Revolution:\ Bitcoin addresses problems that lack direct alternatives. It enables transactions without intermediaries, which is particularly valuable in countries with unstable currencies or limited banking access. Unlike torrents, which were replaced by more convenient streaming platforms, traditional financial systems still have flaws that Bitcoin addresses.
-
Institutional Adoption:\ Major companies like Tesla, PayPal, and Square accept Bitcoin or invest in it. Financial institutions, including JPMorgan and Goldman Sachs, are developing cryptocurrency-related products. This institutional acceptance boosts Bitcoin’s credibility and legitimacy, something torrents never achieved.
-
Limited Supply:\ Bitcoin’s fixed supply of 21 million coins makes it attractive as a store of value, similar to gold. This characteristic distinguishes it from other technologies and gives it potential for long-term growth.
-
Technological Advancements:\ The Bitcoin network evolves through improvements like the Lightning Network, which makes transactions faster and cheaper. These innovations make it competitive with traditional payment systems, whereas torrents failed to adapt to streaming technologies.
-
Global Financial Integration:\ Unlike torrents, which remained in the niche of file sharing, Bitcoin has the potential to integrate into the global financial system. Countries like El Salvador have already recognized it as legal tender, and others may follow suit.
-
Cultural and Economic Significance:\ Bitcoin is perceived not only as a technology but also as a movement for financial independence and decentralization. This ideology attracts young people and tech enthusiasts, making it more resilient to the social shifts that affected torrents.
Conclusion
Torrents and Bitcoin share common roots as decentralized technologies that challenge the status quo. However, while torrents lost popularity due to the rise of more convenient and legal alternatives, Bitcoin has the potential to avoid this fate. Its ability to address real financial problems, institutional adoption, and technological advancements make it a likely candidate for mainstream use in the future. While torrents remained a niche technology, Bitcoin is emerging as a global force that could transform how the world perceives money.
-
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ 05a0f81e:fc032124
2025-05-16 10:58:12
@ 05a0f81e:fc032124
2025-05-16 10:58:12There is an element called carifornium. Over years, there are informations that californium does not exist naturally on earth but can only be produced in the laboratory. But a man from Africa said otherwise and we will find out what the man said.
What is californium? Californium (Cf) is a synthetic radioactive, metallic element with the atomic number 98.
Oxford dictionary defines californium as a chemical element of atomic number 98, a radioactive metal of the actinide series first produced by the bombarding of curium with helium ions. *Take note of the bombarding of curium with helium ions.
According to research, californium is discovered in 1950 and it was named after the university of California and the state of California where the research first took place.
Research also said that californium was produced in the past when several nuclear reactors were in operation 2 billion years ago in Africa.
THERE ARE SOME VITAL PROPERTIES OF CALIFORNIUM. * Radioactive : all isotopes of californium are radioactive. * Actinide : californium belongs to the actinide series, a group of radioactive element with similar properties. * Synthetic : it does not occur naturally and it is produced in the laboratory. * Soft metal : it is soft, silver-white metal. * High melting point : it have a high melting point of about 900°C. * Good neutron source : it is strong neutron emitter, making it useful in various applications.
THERE ARE USES OF CALIFORNIUM
- Neutron Source: Its strong neutron emission makes it valuable as a neutron source in various applications.
- Neutron Activation Analysis: It's used to analyze the composition of materials by bombarding them with neutrons.
- Cancer Therapy: Some isotopes are used in radiation therapy for treating certain cancers.
- Detection Systems: It's used in portable metal detectors, for identifying gold and silver ores, and in detecting oil and water in wells.
- Neutron Radiography: It can be used in neutron radiography to visualize the inside of objects.
Californium also can serve as source of income, 1 gram of californium cost $27 million in market today and it take a thousand grams to make 1 kilogram. You can imagine the figures in monetize form.
About 3-4 years ago, a man by name RTD. HAMZA AL-MUSTAPHA. On a popular radio and TV show claims that californium are being mined and sold-out in Nigeria 🇳🇬.
With critical thinking and understanding, we will find out.
-
 @ f69ff9c1:57a7cb0c
2025-05-16 10:39:10
@ f69ff9c1:57a7cb0c
2025-05-16 10:39:10Jumping into the world of cybersecurity can feel like stepping into a hacker movie — full of commands, code, and dark terminals. As someone just starting this journey, I quickly realized there’s one thing I need to learn before anything else: Linux.
Linux vs Kali Linux: What’s the Difference?
At first, I thought all Linux systems were the same. But here’s what I discovered: • Linux (like Ubuntu or Mint) is a general-purpose operating system — great for beginners, developers, and daily use. • Kali Linux is a powerful tool built specifically for penetration testing and digital forensics. It’s packed with tools like Nmap, Wireshark, and Metasploit.
In short: Kali is for pros. Ubuntu is for learning. So, I started with Ubuntu — and trust me, it was the right call.
Why I’m Starting with Ubuntu
Like any “cybersecurity baby,” I knew I couldn’t jump straight into hacking tools without knowing the basics. With Ubuntu, I’m learning: • Terminal commands • File permissions • Networking tools like ping and netstat • How to install and manage software using apt
It’s not always easy, but every small win makes me feel closer to the goal.
Sharing My Journey
To keep myself motivated and connect with others on the same path, I tweeted this:
“Diving into Linux as a cybersecurity beginner — learning the terminal, commands, permissions, and networking basics. Every line I type gets me closer to mastering the tools behind ethical hacking. It’s tough, but I’m loving the grind. #Linux #CyberSecurity #HackerInTraining”
I even added a little networking spirit:
“Follow for follow — let’s grow in this journey together!”
Joining the Right Communities
Cybersecurity is not a solo game. Here are the communities I’ve joined to stay connected and supported: • TryHackMe Official Discord – Real-time help, study groups, and room support. • Beginner Rooms & Paths on TryHackMe – Great for step-by-step learning. • Reddit (r/tryhackme & r/cybersecurity) – Insightful threads and motivation. • Twitter/X and LinkedIn – Using hashtags like #TryHackMe and #100DaysOfHacking to stay inspired.
Final Thoughts
This is just the beginning. I’m learning Linux now so that I can confidently explore Kali Linux, digital forensics, ethical hacking, and everything in between.
If you’re on a similar path — let’s connect, learn, and grow together. The cyber world is waiting.
-
 @ a5142938:0ef19da3
2025-05-16 10:15:25
@ a5142938:0ef19da3
2025-05-16 10:15:25"Joha is a Danish brand that creates clothing in merino wool, organic cotton, organic bamboo viscose and silk for babies, children and women.
Natural materials used in products
- Cotton (organic)
- Wool (merino)
- Silk
- Regenerated Cellulose (cupra, lyocell, modal, rayon, viscose) (organic bamboo)
⚠️ Warning: some products from this brand contain non-natural materials, including: - Elastane, lycra, spandex - Polyamides, nylon
Categories of products offered
This brand offers products made entirely from natural materials in the following categories:
Clothing
- Clothing fits: babies, children, women
- Underwear: panties
- One piece: bodysuits
- Tops: tank tops, t-shirts
- Bottoms: pants-trousers, leggings
- Head & handwear: hats, balaclavas, mittens
- Nightwear: pyjamas
Footwear
- Footwear fits: baby shoes
- Slippers: booties
Other information
- Oeko-Tex Standard 100 certification
- Woolmark certification
- Non mulesed wool and animal welfare declaration (Südwolle group GmbH)
👉 Learn more on the brand website
Where to find their products?
- Luna & Curious (shipping area: UK and international)
- Niddle Noddle (shipping area: UK and international)
- Chlidren Salon (shipping area: UK and international)
- Lieblings Paris
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this brand products? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors."
-
 @ e4950c93:1b99eccd
2025-05-16 10:14:50
@ e4950c93:1b99eccd
2025-05-16 10:14:50Joha est une marque danoise qui crée des vêtements en laine mérinos, coton biologique, viscose de bambou biologique et soie pour les bébés, les enfants et les femmes.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos)
- Soie
- Cellulose régénérée (cupra, lyocell, modal, rayonne, viscose) (bambou biologique)
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont : - Elasthanne, lycra, spandex - Polyamides, nylon
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements: bébés, enfants, femmes
- Sous-vêtements: culottes
- Une pièce:
- Hauts: débardeurs, t-shirts
- Bas: pantalons, leggings
- Tête et mains: bonnets, cagoules, moufles
- Nuit: pyjamas
Chaussures
- Tailles chaussures: chaussures bébé
- Chaussons: botillons
Autres informations
- Certification Oeko-Tex Standard 100
- Certification Woolmark
- Déclaration de laine de mouton sans mulesing et de bien-être animal (Südwolle group GmbH)
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Luna & Curious (en anglais, zone de livraison : RU et international)
- Niddle Noddle (en anglais, zone de livraison : RU et international)
- Chlidren Salon (en anglais, zone de livraison : RU et international)
- Lieblings Paris
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises les produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ eb0157af:77ab6c55
2025-05-16 10:09:27
@ eb0157af:77ab6c55
2025-05-16 10:09:27The sovereign fund Mubadala increases its holdings in BlackRock’s Bitcoin ETF by 6%.
According to the 13-F filing submitted to the SEC, Abu Dhabi’s sovereign wealth fund Mubadala has increased its holdings in BlackRock’s spot Bitcoin ETF (IBIT) to 8.73 million shares, with a total value of $408.5 million.

Source: Sec
The investment marks a 6% increase compared to its position last December, when the fund held 8.23 million shares.
For several months now, some of the world’s largest sovereign wealth funds have already gained exposure to Bitcoin: Norway’s Government Pension Fund Global, the largest in the world, holds around $500 million in MicroStrategy shares, while Abu Dhabi’s ADQ regularly invests in digital asset-related projects.
Mubadala joins other major institutional investors, including Goldman Sachs and Avenir Group, in increasing their exposure to IBIT.
The post Abu Dhabi sovereign wealth fund invests $408.5 million in Bitcoin via IBIT appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-05-16 08:52:31
@ eb0157af:77ab6c55
2025-05-16 08:52:31The ECB claims that a digital euro is essential to preserve the role of cash in the growing digital economy.
The European Central Bank (ECB) is moving forward with plans for a digital euro, considering it crucial for maintaining European monetary sovereignty in the digital era.
On May 15, Piero Cipollone, member of the ECB Executive Board, highlighted during the France Payments Forum how the use of physical cash is rapidly declining. With the surge in digital transactions and e-commerce, the ECB believes a digital euro represents a crucial step to preserve the universal function of cash in a digitized form.
The dependencies of Europe’s payment sector
According to the Eurotower, the current European payment system has several vulnerabilities. About two-thirds of card transactions in the eurozone are processed by non-European companies, and as many as 13 euro area countries rely entirely on international payment networks for point-of-sale transactions.
Even countries with national card systems must collaborate with international networks to enable cross-border or online purchases. Players like PayPal, Apple Pay, and Alipay dominate digital payment solutions, often partnering with international networks to further expand their market presence.
The digital euro as a complement to cash
The ECB has stressed that the digital euro will not replace cash but will serve alongside it as legal tender, ensuring it is accepted wherever digital payments are available. One key feature, according to the central institution, will be offline functionality — offering users privacy similar to that of cash payments and enabling transactions even without network connectivity.
Beyond retail payments, the ECB is also advancing in the implementation of distributed ledger technologies (DLT) and tokenization to facilitate wholesale financial transactions. The ECB has announced it will soon provide tools to settle DLT-based transactions using central bank money.
The post Digital euro to restore cash’s role, says ECB appeared first on Atlas21.
-
 @ b423e216:3280b1c0
2025-05-16 08:27:58
@ b423e216:3280b1c0
2025-05-16 08:27:58Im digitalen Zeitalter wird der Schutz der Privatsphäre immer wichtiger. Unabhängig davon, ob es sich um eine Regierungsbehörde, ein Unternehmen oder eine Einzelperson handelt, besteht für alle das Risiko, abgehört oder verfolgt zu werden. Mobiltelefone, WLAN, GPS und UHF-Geräte (Ultrahochfrequenz) können zu Werkzeugen für Hacker oder Überwachungsgeräte werden. Um diesen Bedrohungen entgegenzuwirken, sind Signalstörsender (wie etwa Tragbare Handyblocker, WLAN-Störsender, GPS-Störsender und UHF-Störsender) zu einem wirksamen Mittel zum Schutz der Privatsphäre geworden. In diesem Artikel werden die verschiedenen Arten von Störsendern erläutert, wie sie funktionieren und wie man sie legal und angemessen einsetzt, um Abhören und Tracking zu verhindern.
1. Was ist ein Signalstörsender?
Ein Signalstörsender ist ein elektronisches Gerät, das die Kommunikationssignale eines Zielgeräts durch die Aussendung von Radiowellen einer bestimmten Frequenz stört oder blockiert. Es kann Mobiltelefonanrufe, WLAN-Verbindungen, GPS-Positionierung oder UHF-Signalübertragungen blockieren, um Abhören oder Tracking zu verhindern.
Das Funktionsprinzip eines Störsenders besteht darin, ein Rauschsignal mit hoher Intensität an das Zielfrequenzband zu senden, wodurch es für das empfangende Gerät unmöglich wird, das ursprüngliche Signal richtig zu interpretieren. Beispielsweise blockiert ein Handy-Störsender die Kommunikation zwischen einem Handy und einer Basisstation, sodass mit dem Handy weder Anrufe getätigt noch Textnachrichten empfangen werden können.
2. Gängige Arten von Signalstörern
(1) Handy-Störsender
Tragbare störsender für handy werden hauptsächlich verwendet, um GSM-, 3G UMTS-, 4G- und 5G-Signale zu blockieren. Es kann verhindern, dass das Telefon überwacht oder geortet wird und eignet sich für die folgenden Szenarien:
- Abhören verhindern: Verhindern Sie, dass das Mikrofon Ihres Telefons während wichtiger Besprechungen oder privater Gespräche aus der Ferne aktiviert wird.
- Anti-Tracking: Blockieren Sie die GPS- und Mobilfunknetzortung, um die Verfolgung durch Malware oder Hacker zu verhindern.
- Prävention von Prüfungsbetrug: Wird in Schulen oder Prüfungssälen verwendet, um zu verhindern, dass Kandidaten mit Mobiltelefonen schummeln.
(2) WLAN-Störsender
WLAN-Störsender können drahtlose Netzwerksignale in den Frequenzbändern 2,4 GHz und 5 GHz blockieren und eignen sich für:
- Hacking verhindern: Blockieren Sie WLAN-Signale in der Nähe, um Datendiebstahl zu verhindern.
- Smart-Home-Geräte schützen: Verhindern Sie die Fernsteuerung von Smart-Kameras, Lautsprechern und anderen Geräten.
- Militärische oder staatliche vertrauliche Bereiche: Verhindern Sie, dass durch drahtlose Signale vertrauliche Informationen preisgegeben werden.
(3) GPS-Störsender
GPS-Störsender können Satellitenpositionierungssignale blockieren, um die Verfolgung von Fahrzeugen oder Mobiltelefonen zu verhindern. Sie eignen sich für:
- Schützen Sie Ihre Privatsphäre: Verhindern Sie, dass Mitfahrdienste, Essenslieferdienste oder Malware Ihren Aufenthaltsort aufzeichnen.
- Militärische Nutzung: Verhindern, dass Drohnen oder Raketen für ihren Angriff auf GPS-Navigation angewiesen sind.
- Anti-Aufklärung: Verhindern Sie Wirtschaftsspionage oder die Verfolgung von Logistikfahrzeugen durch Wettbewerber.
(4) UHF-Störsender
UHF Jammer (Ultra High Frequency) werden hauptsächlich verwendet, um drahtlose Kommunikation im Frequenzband von 300 MHz bis 3 GHz zu blockieren, wie z. B. Walkie-Talkies, drahtlose Mikrofone, RFID usw. und eignen sich für:
- Verhindern Sie drahtloses Abhören: Blockieren Sie drahtlose Abhörgeräte, die von Spionen verwendet werden.
- RFID-Daten schützen: Verhindern Sie das illegale Scannen von Kreditkarten oder Zugangskarten.
- Anti-Drohnen-Störsender: Blockiert die Fernbedienungssignale von Drohnen, um zu verhindern, dass sie sich sensiblen Bereichen nähern.
3. Wie verwendet man Signalstörsender richtig, um die Privatsphäre zu schützen?
Obwohl Störsender das Abhören und Verfolgen wirksam verhindern können, kann eine unsachgemäße Verwendung gegen das Gesetz verstoßen oder die normale Kommunikation beeinträchtigen. Hier sind einige Vorschläge für den legalen und sinnvollen Einsatz von Störsendern:
(1) Verstehen Sie die örtlichen Gesetze
- In vielen Ländern ist die unbefugte Verwendung von Störsendern illegal und kann zu Geldstrafen oder strafrechtlichen Konsequenzen führen.
- Nur zur Verwendung im privaten Bereich oder dort, wo dies gesetzlich zulässig ist, z. B. beim Militär, in der Regierung oder bei der Unternehmenssicherheit.
(2) Wählen Sie den entsprechenden Störbereich
- WLAN Signal Blocker mit geringer Leistung eignen sich für kleine Besprechungsräume oder Fahrzeuge, um die Kommunikation in der Umgebung nicht zu beeinträchtigen.
- In großen Veranstaltungsorten können Störsender mit hoher Leistung eingesetzt werden, dabei ist jedoch Vorsicht geboten, um die öffentliche Kommunikation nicht zu stören.
(3) Kombiniert mit anderen Sicherheitsmaßnahmen
- Störsender sind nur eine vorübergehende Lösung. Für einen langfristigen Schutz der Privatsphäre ist die Verwendung verschlüsselter Kommunikation, VPNs, Abhörgeräte usw. erforderlich.
(4) Regelmäßige Überprüfung der Ausrüstung
- Störsender können aufgrund von Änderungen der Signalstärke unwirksam werden und müssen regelmäßig getestet und angepasst werden.
4. Einschränkungen von Störsendern
Obwohl Störsender Signale wirksam blockieren können, unterliegen sie dennoch einigen Einschränkungen:
- Verhindert kein kabelgebundenes Abhören: Störsender wirken nur gegen drahtlose Signale und schützen nicht vor physischen Abhörgeräten (wie versteckten Mikrofonen).
- Kann legitime Kommunikation beeinträchtigen: Störsender blockieren wahllos Signale, was Notrufe oder die normale WLAN-Nutzung beeinträchtigen kann.
- Kann durch Anti-Jamming-Technologie geknackt werden: Einige fortschrittliche Geräte verwenden möglicherweise Frequenzsprungtechnologie (z. B. militärische Kommunikation), die von gewöhnlichen Störsendern nur schwer vollständig blockiert werden kann.
5. Alternativen: Sicherere Methoden zum Schutz der Privatsphäre
Wenn der Einsatz von Auto GPS Tracker Störsender eingeschränkt ist, ziehen Sie die folgenden Alternativen in Betracht:
- Verwenden Sie einen Faradayschen Käfig: Eine metallische Abschirmhülle oder ein Raum, der drahtlose Signale vollständig blockiert.
- Flugmodus aktivieren: Durch das Ausschalten der drahtlosen Mobiltelefonkommunikation wird die Fernaktivierung des Mikrofons verhindert.
- Verwenden Sie verschlüsselte Kommunikationstools: z. B. Anwendungen mit End-to-End-Verschlüsselung wie Signal, ProtonMail usw.
abschließend
Ein Signalstörsender ist ein leistungsstarkes Tool zum Schutz der Privatsphäre, das das Abhören von Mobiltelefonen, WLAN-Hacking, GPS-Tracking und UHF-Überwachung wirksam verhindern kann. Allerdings ist die Verwendung gesetzlich eingeschränkt und sollte mit Vorsicht verwendet werden. Durch die Kombination von Störsendern mit anderen Sicherheitsmaßnahmen (wie verschlüsselter Kommunikation und physischer Abschirmung) kann die Privatsphäre im Rahmen des gesetzlich Gegebenen weitestgehend vor Verletzungen geschützt werden. Mit der Entwicklung von Technologien zum Abhören von Störsendern könnten diese in Zukunft intelligenter und präziser werden und sich zu einem wichtigen Mittel zum Schutz der Privatsphäre entwickeln.
- https://www.signaljammerphone.com/de/echte-gefahren-durch-versteckte-kameras-und-ein-leitfaden-zur-abwehr.html
- https://www.signaljammerphone.com/de/J-DR6-leistungsstarker-tragbare-rucksack-drohnen-fernsteuerungs-stoerer-300W.html
- https://www.signaljammerphone.com/de/wie-kann-man-funkwellen-wirksam-blockieren-funkwellenabschirmung-und-stoertechnologie.html
-
 @ 94215f42:7681f622
2025-05-16 08:18:52
@ 94215f42:7681f622
2025-05-16 08:18:52Value Creation at the Edge
The conversation around artificial intelligence has largely centered on the technology itself, the capabilities of large language models, the race for more parameters, and the competition between AI companies.
He with the most data / biggest model / biggest platform wins all.
As we're been exploring in recent "Good Stuff" podcasts, the true business model of AI may be much more straightforward. AI is after all a productivity tool with little technical moat, in fact the existence of AI coding and learning tools quickly chop away at this moat even quicker!.\ \ We believe that the it's about transforming traditional human heavy businesses by dramatically reducing operational costs while maintaining or increasing output.
AI is poised to create value not primarily for AI companies themselves, but for businesses that effectively implement AI to transform their operations, particularly small, local businesses that can become extraordinarily efficient through AI adoption.
The Value Shift: From AI Companies to AI-Enabled Traditional Businesses
A central insight from episode 1 of the podcast series, is that the value of AI isn't likely to accrue primarily to companies like OpenAI or other AI technology providers. Instead, the real winners will be traditional service businesses that can leverage AI to transform their operations and cost structures.
"I think we're gonna see this shift to traditional service businesses... that traditionally have pretty fixed low margins because of a dependency on language-heavy workflows that require a lot of humans as the medium of intelligence in the business."
The opportunity here is to use AI to manage the language dependency and shift the moments of intelligence, that currently exist in the heads of our staff, into software that can run 24x7 for fractions of a cost.\ \ The real limiting factor here is less a magic AGI, but instead detailed thinking and process redesign to move humans to the edge of the process. As it turns out if we think through what each person is doing in detail we see the specific decisions, outputs, moments of intelligence are actually quite constrained and can be replicated in LLM's if we break them down to a low enough level of fidelity and take each decisions one step at a time.\ \ The result? Businesses that have traditionally operated with fixed, low margins can potentially achieve "software-style margins" by dramatically reducing their operational expenses.
Transforming Traditional Service Businesses
We have developed three key heuristics for identifying businesses that could benefit most from AI transformation:
-
Language Intensity: Businesses where much of the work involves processing language (reading, writing, communicating). Language in, language out. If you are sat in a chair and typing all day, this could be you.
-
Labor Component: Where we see this language intensity so we find many people performing similar, standardized roles. For examples, if we have four people in the same role this is a big clue we have good process, checklists, role descriptions etc for how the work can be done in order to replicate work across multiple people.
-
Load in the Business: Taking these processes into account, what amount of the operational expense of the business do they represent? Where these language and labor-intensive operations represent a significant portion of the business cost, we can see there will be significant return.
Traditional service businesses that match these criteria—legal firms, accounting practices, consulting agencies, contract engineering, design agencies and others—could see dramatic transformations through AI implementation.
By automating these language-heavy processes, businesses can potentially reduce operational costs by 50-80% while maintaining similar levels of output.
The Power of Small
We believe that small businesses may have an inherent advantage in this transformation. While large enterprises face significant barriers to reducing their workforce (political pressure, media scrutiny, organizational complexity), smaller businesses can adapt more quickly and focus on growth rather than just cost-cutting.
If I'm in a 20,000 person business and I need to remove 10,000 people... that's hard. You can't do this without sending political shock waves in your local community.
If I'm a 10 person business and I need to double my revenue, nobody gives a shit. I can just do it.
For small businesses, AI removes growth constraints. When adding the "21st person" no longer represents a significant capital investment, small businesses can scale much more efficiently:
If the next nominal client that you onboard doesn't actually cause you any more additional pain, if you don't need to hire more people to service that client... you just take off the brakes off from a growth perspective.
This gives small business a unique advantage in capitalizing on AI.
From "Bionic Humans" to "Humans at the Edge"
We currently see this integration to business happening in one of two models:
-
The Bionic Human: Equipping workers with AI tools to make them more productive.
-
Human at the Edge: Redesigning processes to be AI-native, with humans entering the process only when needed (and often facilitated by bitcoin payments).
While many businesses are focused on the first approach and it can certainly see returns, it is still a process constrained by the human input. The real value unlock comes from fundamentally redesigning business processes with AI at the core.
Now we can purchase intelligence in buckets of $0.02 API calls, how would we operate different?
This represents a profound shift in how we think about work and processes. Rather than humans being central to processes with tools supporting them, AI becomes the backbone of operations with humans providing input only at critical junctures.
This is "a complete mental shift" that challenges our fundamental assumptions about how businesses operate. The human becomes "the interface with the real world" for AI systems rather than the primary processor of information and decision-maker.
The Value Trap: Understanding the Competitive Dynamic
So what happens next? Here we have developed the concept of the Value Trap to explain how the competitive landscape will evolve as AI adoption increases..\ \

Initially, early adopters of AI and "Human at the Edge" business processes, will see dramatic benefits.
If your costs have dropped from 90 to 20 this creates an immediate competitive advantage where the early adopter is "now making 80 units of profit versus your 10 units of profit.
They gain massive pricing power in the industry and can compete for growth with an unfair advantage.
Over time, and here we believe this is likely a 5-10 year period although we believe the quicker side, competitive pressures will erode these advantages.\ \ As competitors adopt similar AI strategies, price competition will intensify, and revenues will decline. The business that initially saw its costs drop from 90 to 20 units might see its revenue decline from 100 to 30 units, resulting in similar margins but much lower overall revenue, often destroying the enterprise value of the company at these new revenue / profit levels!
This evolution creates an imperative for businesses to adopt AI early, not just to maintain perpetual advantage, but simply to survive the transition. Worse they're hit with a second challenge of the value trap, how do I keep hold of the value I generate along the way.\ \ If you're reading this on Nostr you may already suspect a way out of this value trap.\ \ If not I would invite you to consider storing the immediate short term returns you pull forwards in something that would be inflation resistant, hard to seize and ideally portable.\ \ We refer to this as a 'The big orange arbitrage".
Implications for Business Owners and Capital Allocators
For business owners, especially those running small to medium-sized enterprises, the message is clear: understand how AI could transform your industry and begin planning your transition now.\ \ This might involve creating an "AI-native twin" of your current business—similar to how Netflix developed streaming alongside its DVD business—to eventually replace your current operations. If you want help please ask, I heavily favor more small businesses in the world and would love to help make this a reality.
For capital allocation, the emerging opportunity we see if in "transformation led private equity". The acquisition of traditional service businesses and applying AI to dramatically reduce operational costs and increase enterprise value.\ \ This approach treats AI not as a product but as a transformation strategy for existing businesses with proven product-market fit.
Transformation led PE is venture style returns without the risk of product market fit.
So the lesson?
The business model of AI isn't all about selling AI technology, adding a RAG chatbot to a new DB or collecting everyone's data.\ \ Consider the humble cash flow business, use AI to transform the operational processes and save into everyone's favorite orange coin.
-
-
 @ cae03c48:2a7d6671
2025-05-16 16:22:47
@ cae03c48:2a7d6671
2025-05-16 16:22:47Bitcoin Magazine

Heritage Distilling Now Accepts Bitcoin and Will Hold It as a Company AssetYesterday, Heritage Distilling Holding Company, Inc. (NASDAQ: CASK), a leading U.S. craft spirits producer, announced that it will begin accepting Bitcoin as payment through its direct-to-consumer (DTC) e-commerce platform and will hold bitcoin as strategic assets under a newly approved Cryptocurrency Treasury Reserve Policy.
Heritage Distilling Implements Cryptocurrency Treasury Policy. Read the press release here: https://t.co/ve4Ttv0qGw $CASK pic.twitter.com/8MZLovwrjw
— Heritage Distilling (@HeritageDistill) May 15, 2025
The policy, approved by the company’s Board of Directors as part of a broader sales and treasury diversification strategy, was developed by the Technology and Cryptocurrency Committee, chaired by tech and digital payments leader Matt Swann. The move makes Heritage the first in the craft spirits sector to formally integrate bitcoin into both its payment and treasury operations.
“A new age of commerce is emerging, with cryptocurrencies leading the way to reduce friction between parties, buyers and sellers of goods and services,” stated Matt Swann on behalf of the Board. “Having been immersed in the convergence of technology and currencies for nearly two decades, it is exciting to see Heritage forge headfirst into the opportunity to combine the power of the consumer and cryptocurrency.”
Heritage’s decision comes amid rapidly growing public interest in digital assets. The company said it estimates that between 65 to 86 million Americans currently hold Bitcoin and crypto, and realizes the opportunity Heritage has to acquire more BTC by accepting it as payment.
“Heritage has always been an innovator and once again we are leading the way in the craft spirits space as we prepare to accept Bitcoin and Dogecoin as a form of payment for online e-commerce sales and to acquire and hold these cryptocurrencies as assets,” commented the CEO of Heritage Justin Stiefel. “As I have noted in the past, unlike traditional investors who purchase crypto with cash and are immediately subject to potential pricing volatility, as a company producing goods for sale, acceptable margins between the retail price of our products and their cost of production is expected to offset potential fluctuations in the value of cryptos we accept as payment. This provides us considerable financial flexibility as we develop product offerings for users and enthusiasts of these fiat alternatives.”
The company sees Bitcoin as a long-term strategic asset and a forward-looking step in connecting with modern consumers while also exploring new efficiencies in financial operations. Heritage is not only integrating Bitcoin as a payment method but also incorporating it into its treasury strategy.
The new Cryptocurrency Treasury Policy can be found here.
This post Heritage Distilling Now Accepts Bitcoin and Will Hold It as a Company Asset first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ f4db5270:3c74e0d0
2025-05-16 08:13:05
@ f4db5270:3c74e0d0
2025-05-16 08:13:05Hi Art lover! 🎨🫂💜
You may not know it yet but all of the following paintings are available in #Bitcoin on my website: <https://isolabellart.carrd.co/>
For info and prices write to me in DM and we will find a good deal! 🤝
 THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
 OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
 TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
 BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
 ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
 EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
 OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
 LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
 ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
 SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025
SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025

THE BLUE HOUR 40x50cm, Oil on canvas - Completed December 14, 2024
 WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
 L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024
L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024

LE COSE CHE PENSANO 40x50cm, Oil on paper - Completed October 05, 2024
 TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024
TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024

GOLD ON THE OCEAN 40x50cm, Oil on paper - Completed September 08, 2024
 SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
 FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
 INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
 OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
 NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
 VENICE 50x40cm, Oil on board - Completed May 4, 2024
VENICE 50x40cm, Oil on board - Completed May 4, 2024
 CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
 DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
 SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
 LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
 MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
 TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
 HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
 INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
 BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
 BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023
BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023

IL RISVEGLIO 30x40cm, oil on canvas board - Completed July 18, 2023

LA QUIETE PRIMA DELLA TEMPESTA 30x40cm, oil on canvas board - Completed March 30, 2023
 LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
 DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
 UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
 REBEL WAVES 44x32cm, oil on canvas board
REBEL WAVES 44x32cm, oil on canvas board
 THE SCREAMING WAVE 40x30cm, oil on canvas board
THE SCREAMING WAVE 40x30cm, oil on canvas board

"LA DONZELLETTA VIEN DALLA CAMPAGNA..." 30x40cm, oil on canvas board

LIGHTHOUSE ON WHITE CLIFF 30x40cm, oil on canvas board
-
 @ 866e0139:6a9334e5
2025-05-15 15:54:25
@ 866e0139:6a9334e5
2025-05-15 15:54:25Autor: Bastian Barucker. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Teil 1 lesen Sie hier.
Wie steht es nun um die Psyche beziehungsweise den emotionalen Zustand der Gesellschaft? Wie kommt Psychotherapeut Hans-Joachim Maaz auf die Idee, Deutschland als „normopathische Angstgesellschaft“ zu bezeichnen? Meist werden Begriffe wie Trauma oder frühkindliche Prägung nicht öffentlich diskutiert und schon gar nicht als Massenphänomen besprochen. Desweiteren lässt sich Trauma schwer definieren. Ich bezeichne damit prägende Erfahrungen, die so schmerzhaft waren, dass sie eine Überforderung für die meist junge Psyche darstellten und daher abgespalten werden mussten. Dazu zählen Verlassenheit, Gewalt, Liebesentzug, Ohnmachtserfahrungen, jegliche Form von Missbrauch, der Verlust der Zugehörigkeit und vieles mehr. Sie regieren jedoch weiterhin als eine Art Schattenregierung, weil aus diesen Erfahrungen Lebenseinstellungen und Verhaltensweisen entstanden sind, die weiterhin Leid erzeugen. Meine Erfahrung zeigt mir, dass fast alle Menschen so eine Schattenregierung mit sich tragen.
Schaut man sich die Geschichte dieses Landes an, findet man die Spuren von Krieg und Trauma überall. Traumata werden über Generationen hinweg weitergegeben und können ohne die notwendige Selbsterfahrung weiterhin im individuellen Schatten wirksam und in der Tiefe regieren. Sogar der wissenschaftliche Dienst des deutschen Bundestages beschäftigt sich mit genau dieser Thematik und schreibt dazu: „Einschlägige psychologische Untersuchungen legen den Schluss nahe, dass sich die Übertragung unbewusster traumatisierender Botschaften von Opfern – zumindest ohne therapeutische Behandlung – in der Generationenfolge nicht abschwächt.“
In einem Gespräch mit der Professorin für Neuroepigenetik an der Universität Zürich und der Eidgenössischen Technischen Hochschule (ETH) Isabell Mansuy erfuhr ich, dass sie davon ausgeht, dass in Deutschland oder der Schweiz 20-40% der Bevölkerung Trauma erlebt haben.
Beispiele für solche massenhaften Traumatisierungen finden sich in der deutschen Geschichte viele: Mehrere schwer traumatisierende Weltkriege, die bis in die Gegenwart reichenden NS-Erziehungsmethoden aus dem Buch „Die deutsche Mutter und ihr erstes Kind“, Verschickungsheime, in denen ca. 15 Millionen Kinder lange Zeit von ihren Eltern getrennt wurden und dort teilweise Folter erlebten, Wochenkrippen in der DDR und viele andere sogenannte Erziehungsmethoden, die bis heute ihre Wirkung entfalten.
Solche traumatischen Erlebnisse bewirken tiefgreifende Veränderungen der Persönlichkeit und haben direkten Einfluss auf den Körper, die Psyche und das Verhalten der Betroffenen. Ein für die Kriegsbereitschaft relevanter Aspekt ist die Erzeugung von Gehorsam durch Erziehung.
In seinem Buch „Die Kindheit ist politisch“ beschreibt der Autor Sven Fuchs diesen Zusammenhang wie folgt: „Das von Geburt an zum Gehorsam und zur Unterwerfung gezwungene Kind fügt sich schließlich den Willen Anderer und gibt seine Individualität und auch eigene Gefühlswelt auf. Ein solch geprägter Mensch ist ein perfekter Befehlsempfänger, Untertan, Gläubiger oder weitergedacht Soldat.“
John Lennon wiederum formuliert es in seinem Lied „Working class hero“ so: „Sobald ihr geboren seid, sorgen sie dafür, dass ihr euch klein fühlt
Indem sie euch keine Zeit geben, anstatt alle Zeit der Welt\ Bis der Schmerz so groß ist, dass ihr überhaupt nichts mehr fühlt.“
In der oben erwähnten Schattenarbeit und der bedürfnisorientierten, traumasensiblen Begleitung von Kindern sehe ich ein bisher immens unterschätztes aber sehr nachhaltiges Potenzial für mehr Friedensfähigkeit beziehungsweise Wehrhaftigkeit gegen aufoktroyierte Kriegsbereitschaft. Nämlich die Erschaffung einer Gesellschaft, die Friedfertigkeit von der Zeugung an denkt und lebt. Der Psychotherapeut und Pionier der Pränatalpsychologie in Deutschland Ludwig Janus, mit dem ich ein sehr spannendes Gespräch geführt habe, beschreibt es in seinem Aufsatz „Das Unbewußte in der Politik – Politik des Unbewußten“ wie folgt: „Wir wissen heute, dass die Kraft zu einem selbstbestimmten und verantwortlichen Leben aus primären gutartigen Beziehungs- und Bestätigungserfahrungen resultiert.“
John Lennon formulierte seine intensive Begegnung mit dem Inneren so:
„Seine [Arthur Janovs] Sache ist es, den Schmerz zu fühlen, der sich seit der Kindheit in einem angestaut hat. Ich musste das tun, um wirklich alle religiösen Mythen zu beseitigen. In der Therapie spürt man wirklich jeden schmerzhaften Moment seines Lebens – es ist unerträglich, man wird gezwungen zu erkennen, dass der Schmerz, der einen nachts mit klopfendem Herzen aufwachen lässt, wirklich von einem selbst kommt und nicht das Ergebnis von jemandem da oben im Himmel ist. Er ist das Ergebnis der eigenen Eltern und der eigenen Umgebung."
Was könnte geschehen, wenn Kinder von Anfang an weniger Schmerz verarbeiten oder abspalten müssten, weniger familiäre oder erzieherische verbale, emotionale oder körperliche Gewalt miterleben und dadurch weniger Krieg in sich tragen? Was wäre möglich, wenn mehr Erwachsene sich den inneren Kriegen und dem im Schatten verborgenen Schmerz zuwenden und diese mittels Selbsterfahrung befrieden, daher nicht zwanghaft reinszenieren müssen? Auch Konsumwahn und Machtbesessenheit können in frühkindlichen Mangel- und Ohnmachsterfahrungen ihren Ursprung haben. Nur ein Beispiel für eine Veränderung, die innerhalb kürzester Zeit umsetzbar ist: Was wäre, wenn nicht weiterhin ein Drittel aller Frauen in Deutschland unter der Geburt irgendeine Form der Gewalt erlebte?
Inwiefern würde die durch Politik und Medien angewandte systematische Erzeugung von Angst ihre Wirkkraft verlieren, wenn die Mehrheit der Menschen ihre tieferliegenden Ängste integriert hätten. Neben der Angst vor dem Klimawandel und der kürzlich erst beendeten Angstkampagne wegen der Atemwegserkrankung Covid-19 ist die mit der Realität im Widerspruch stehende Angstpropaganda, wonach der russische Präsident Putin die NATO angreifen würde, ein prominentes Beispiel.
Bei einem aktuellen Vortrag des ehemaligen Generalinspekteurs der Bundeswehr Harald Kujat a.D. äußert sich dieser wie folgt: „Dass die russische Führung einen Krieg gegen das westliche Bündnis zu führen beabsichtigt, bestreiten jedenfalls die sieben amerikanischen Nachrichtendienste in ihren Bedrohungsanalysen der letzten Jahre und auch in dem von 2024.“
Alles in allem war es mir ein Anliegen, zu zeigen, dass jeder Mensch einen inneren Tiefenstaat beheimatet, der auf persönlicher und gesellschaftlicher Ebene Wirkung entfalten kann. Diesen Aspekt näher zu beleuchten, bietet das Potenzial für mehr persönliche Friedfertigkeit und stärkere Abwehrkräfte gegen die Kriegsgelüste des geopolitischen Tiefenstaates.
Immer wieder bewegend sind die Augenblicke in den Selbsterfahrungsgruppen der Gefühls- und Körperarbeit, in denen nach dem vollumfänglichen Ausdruck von Schmerz und Leid das ursprüngliche Bedürfnis der begleiteten Person beFRIEDigt wird, indem sie das bekommt, was sie ursprünglich gebraucht hat. In ihr und im gesamten Raum entsteht dann ein unbeschreiblicher und tiefgehender Frieden. Eine berührende Ruhe, eine Stille der Zufriedenheit. Der dabei zu erlebende innere Frieden, dem ich seit über 10 Jahren regelmäßig beiwohnen darf und den ich viele Jahre selber in mir entdecken durfte, wäre eine gute Zutat für mehr Friedfertigkeit.
„Vielleicht nennst du mich einen Träumer,\ aber – ich bin nicht der Einzige.\ Ich hoffe, dass du eines Tages dazugehören wirst\ und die Welt eins sein wird.“ John Lennon, Imagine
Bastian Barucker, Jahrgang 83, ist Wildnispädagoge, Überlebenstrainer und Prozessbegleiter. Seit 2005 begleitet er Menschen bei Wachstumsprozessen in der Natur. Seit 2011 macht er mithilfe der Gefühls- und Körperarbeit tiefgreifende Selbsterfahrungen, und seit 2014 begleitet er Gruppen, Paare und Einzelpersonen. Er lebt und arbeitet im wunderschönen Lassaner Winkel, nahe der Insel Usedom.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ eab58da0:eebdafbf
2025-05-16 07:56:05
@ eab58da0:eebdafbf
2025-05-16 07:56:05By Unknownfx
We all have those moments when everything feels like it’s falling apart. For me, one terrible hour last spring became a turning point, teaching me how to flip stress into strength. It wasn’t easy, but it showed me that even our worst moments can lead to breakthroughs. Here’s my story and how you can turn your tough hours around.
The Hour It All Crashed It was a Thursday morning, and I was already stretched thin. I’d overslept, missed a work deadline, and got a curt email from my boss. Then, my phone buzzed with bad news: a close friend was moving away. By 10 a.m., I was sitting at my kitchen table, heart racing, feeling like a failure. My mind spiraled—why couldn’t I get it together? I was ready to call it a day and hide under my covers. But something in me refused to give up. I decided to face the chaos instead of running from it.
The Turnaround: Three Simple Steps I didn’t have a grand plan, but I tried three things that shifted everything. First, I breathed—deep, slow breaths for a minute to calm my racing heart. Second, I grabbed a piece of paper and wrote down what was overwhelming me: the deadline, the email, my friend’s news. Seeing it on paper made it less monstrous. Third, I picked one small action: I emailed my boss an honest apology and a plan to fix the missed deadline. It wasn’t perfect, but it was a start. Those steps—breathe, write, act—took less than 15 minutes but gave me a sense of control.
From Breakdown to Breakthrough That hour didn’t magically fix everything, but it changed my perspective. By noon, I’d tackled the deadline and called my friend to plan a goodbye hangout. More than that, I felt proud. I’d taken a moment that could’ve crushed me and turned it into proof I could handle hard things. Later, I reflected on why it worked: the breathing grounded me, writing clarified my thoughts, and acting gave me momentum. I started using this approach whenever stress hit. For instance, when anxiety flared before a big presentation, I used the same steps and ended up nailing it. My mental health grew stronger because I learned to see tough moments as opportunities, not endings.
Why It Matters This experience taught me that our worst hours don’t define us—how we respond does. You don’t need to be a superhero; you just need a few tools to shift the moment. Those three steps are like a mental first-aid kit, always there when life gets messy. They’ve helped me build resilience, and I lean on them to stay steady. It’s not about avoiding stress; it’s about moving through it with purpose. I’ve shared this with others, and they’ve turned their own bad hours into wins, too.
Make Your Moment Count Your next tough hour could be your best if you choose to act. Try my three steps: breathe, write, do one small thing. It’s not about fixing everything—it’s about starting. What’s a moment you turned around? How do you pull yourself out of a rough patch? Drop a comment or share your story in a note. Let’s lift each other up and make our worst hours the start of something great!
Thanks for reading. Much love, Unknownfx
-
 @ 866e0139:6a9334e5
2025-05-14 06:39:51
@ 866e0139:6a9334e5
2025-05-14 06:39:51Autor: Mathias Bröckers. Dieser Beitrag wurde mit dem Pareto-Client geschrieben und erschien zuerst auf dem Blog des Autors. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Leider bin ich mit der Anregung einer deutschen Übersetzung nicht rechtzeitig durchgedrungen, denn dieses Buch wäre die passende Vorbereitung für die Feiern zum 80. Jahrestag des Kriegsendes gewesen – und die angemessene Ohrfeige für die dreiste Ignoranz und Geschichtsvergessenheit der Deutschen, die nicht einmal formal diplomatischen Anstand bewahren können, und einen Vertreter Russlands zu diesem Gedenktag einladen. Oder einen hochrangigen Vertreter nach Moskau schicken, der den Millionen zivilen Opfern und den sowjetischen Soldaten Ehre und Anerkennung erweist, die die monströse Mordmaschine der Nazi-Armee besiegt haben.
\ Wie das geschah und wie westliche Kriegskorrespondenten und Frontreporter darüber berichteten, dokumentiert auf beeindruckende Weise der Band “Miracle in the East – Western War Correspondents Report 1941-1945”, der im vergangenen Herbst auf Englisch erschienen ist (hier als pdf ). Beeindruckend deshalb, weil diese Reporter anders als heute noch echte Journalisten und vor Ort waren, statt Copy-Paste-FakeNews auf dem Laptop zu produzieren; und weil ihre Berichte und Analysen die historische Entwicklung dieses Kriegs aufzeichnen, bei der Soldaten aus ganz Europa mit den Deutschen gegen die Sowjetunion vorrückten.
Die großen Zeitungen und Magazine in den USA und England, so der Autor Dmitry Fedorov im Vorwort, veröffentlichten Editorials und Leitartikel, “die von einem solchen Maß an Respekt und Bewunderung für das Heldentum des sowjetischen Volkes zeugten, dass sie darin mit den Moskauer Zeitungen hätte konkurrieren können”; und sie kürten, als das “Wunder im Osten” vollbracht, die Nazitruppe in Stalingrad und Kursk geschlagen war und die Rote Armee Richtung Berlin vorrückte, den sowjetischen Marschall Georgy Zhukow “zum besten Kommandeur in der Geschichte der Kriege.”
Dass er und seine Truppen den Löwenanteil zur Niederlage der Deutschen beigetragen hatten (und 76% der Hitlerarmee eliminiert hatten, mehr als drei Mal soviel wie USA, England und Frankreich zusammen), stellten weder Roosevelt noch Churchill in irgendeiner Weise in Frage. Wie verlogen es ist, wenn ihre Nachfolger im Westen 80 Jahre später diese historische Wahrheit kleinreden, um sich den Sieg allein an die Brust zu heften, lässt sich in diesem Buch nachverfolgen – in den Worten und Bildern ihrer eigenen Berichterstatter.\ \ Ich bin froh, dass ich vor drei Jahren am 9.Mai in Moskau meine Anerkennung und Dankbarkeit für diesen opferreichen Sieg über den Faschismus ausdrücken konnte, um den Menschen in Russland zumindest im Rahmen der “citizen diplomacy zu zeigen, dass nicht alle Deutschen von der beschämenden Ignoranz und dem notorischen Russenhass befallen sind, den ihre Regierenden an den Tag legen. Das gilt auch für die Einwohner der anderen europäischen Länder, die nicht bereit sind, die Geschichte umzuschreiben und zu vergessen und erneut Krieg zum gegen Russland zu rüsten – und sich jetzt dem European Peace Project anschließen:
\ “Wir, die Bürger Europas, erklären diesen Krieg hiermit für beendet! Wir machen bei den Kriegsspielen nicht mit. Wir machen aus unseren Männern und Söhnen keine Soldaten, aus unseren Töchtern keine Schwestern im Lazarett und aus unseren Ländern keine Schlachtfelder. Wir bieten an, sofort eine Abordnung europäischer Bürgerinnen und Bürger nach Kiew und Moskau zu entsenden, um den Dialog zu beginnen. Wir werden nicht länger zusehen, wie unsere Zukunft und die unserer Kinder auf dem Altar der Machtpolitik geopfert wird. Es lebe Europa, es lebe der Friede, es lebe die Freiheit!”
Mathias Bröckers, Jahrgang 1954, ist Autor und freier Journalist. Er gehörte zur Gründergeneration der taz, war dort bis 1991 Kultur- und Wissenschaftsredakteur und veröffentlichte seit 1980 rund 600 Beiträge für verschiedene Tageszeitungen, Wochen- und Monatszeitschriften, vor allem in den Bereichen Kultur, Wissenschaft und Politik. Neben seiner weiteren Tätigkeit als Rundfunkautor veröffentlichte Mathias Bröckers zahlreiche Bücher. Besonders bekannt wurden seine internationalen Bestseller „Die Wiederentdeckung der Nutzpflanze Hanf“ (1993), „Verschwörungen, Verschwörungstheorien und die Geheimnisse des 11.9.“ (2002) und „Wir sind immer die Guten – Ansichten eines Putinverstehers“ (2016, mit Paul Schreyer) sowie "Mythos 9/11 - Die Bilanz eines Jahrhundertverbrechens" (2021). Mathias Bröckers lebt in Berlin und Zürich und bloggt auf broeckers.com.
Sein aktuelles Buch "Inspiration, Konspiration, Evolution – Gesammelte Essays und Berichte aus dem Überall" –hier im Handel**
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 84b0c46a:417782f5
2025-05-16 13:09:31
@ 84b0c46a:417782f5
2025-05-16 13:09:31₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ eab58da0:eebdafbf
2025-05-16 07:50:19
@ eab58da0:eebdafbf
2025-05-16 07:50:19By Unknownfx
I used to think big changes required big effort—hours of work, drastic life overhauls. But a tiny habit, just five minutes a day, rewired how I think and feel. It’s called gratitude journaling, and it’s become my secret weapon for mental clarity and self-improvement. Here’s how it changed my life and why it might work for you.
Feeling Stuck in the Fog A year ago, I was in a mental rut. Work stress, endless to-do lists, and a nagging sense I wasn’t doing enough left me drained. My mornings started with dread, my mind racing with what I hadn’t accomplished. I’d read about gratitude but thought it was fluffy nonsense—how could listing “good things” fix my chaos? Then, one sleepless night, I grabbed a notebook and scribbled three things I was thankful for: my coffee, a friend’s text, the sun coming up. It felt awkward, but I slept better. The next day, I did it again. That tiny act became my lifeline.
The Habit: Five Minutes of Gratitude Here’s how it works: every morning, I spend five minutes writing three things I’m grateful for. They don’t have to be profound—sometimes it’s my cozy blanket or a kind word from a stranger. The key is consistency. I keep a small notebook by my bed, and it’s the first thing I do after brushing my teeth. If I’m rushed, I jot them in my phone. I also add a quick “why” for each, like “I’m grateful for my coffee because it warms my hands and wakes me up.” This makes it personal, not just a checklist. It’s simple, but it shifts my focus from what’s wrong to what’s right.
How It Rewired Me At first, I didn’t notice much. But after a week, my mornings felt lighter. Instead of waking up to stress, I’d smile at my notebook, remembering yesterday’s small joys. Over months, the habit rewired my brain. Studies say gratitude boosts serotonin and dopamine, and I believe it—I felt calmer, more optimistic. When work got tough, I’d pause and recall my list, grounding myself. For example, during a rough week when a project flopped, I wrote, “I’m grateful for my team’s support because they had my back.” It didn’t erase the failure, but it reminded me I wasn’t alone. My mental health improved, and I started seeing possibilities where I once saw dead ends.
Why It’s Worth Trying This habit isn’t a cure-all, but it’s a spark. It taught me that small actions can shift big emotions. I’m not perfect—some days, I still grumble—but gratitude pulls me back. It’s like a mental reset, helping me face challenges with hope. Plus, it’s flexible: you can do it anywhere, anytime, no fancy tools needed. I’ve even shared it with friends, and they’ve noticed shifts, too. It’s not about ignoring pain; it’s about balancing it with light.
Start Your Own Spark You don’t need hours to change your mindset—just five minutes. Try it tomorrow: grab a notebook, write three things you’re grateful for, and say why. Do it for a week, and see how it feels. What’s one small joy you’re thankful for today? How do you keep your mind clear when life gets heavy? Share your thoughts below or post a note—let’s inspire each other to rewire our brains, one tiny habit at a time!
Thanks for reading. Much love, Unknownfx
-
 @ eb0157af:77ab6c55
2025-05-16 07:32:01
@ eb0157af:77ab6c55
2025-05-16 07:32:01The bank’s analysts are observing a shift in the Bitcoin market, with specific catalysts that could drive the cryptocurrency higher.
According to a recent JPMorgan report shared with select industry outlets, Bitcoin could continue its rise at the expense of gold in the second half of 2025. Analysts led by Managing Director Nikolaos Panigirtzoglou highlighted that the so-called “debasement trade” — the strategy of investing in gold and Bitcoin as a hedge against the weakening of fiat currencies — has undergone a change in direction.
“What began as a parallel run has turned into a zero-sum game between the two assets,” the analysts explained. “Between mid-February and mid-April, gold rallied at Bitcoin’s expense, while over the past three weeks we’ve seen the opposite: Bitcoin rising as gold loses ground.”
Since its peak on April 22, gold has declined by nearly 8%, while over the same period, Bitcoin has gained 18%. This shift is also reflected in investor flows, with capital moving out of gold ETFs and into spot Bitcoin ETFs.
Futures market data shows a similar trend, with declining positions in gold and increasing interest in Bitcoin futures. Notably, at the start of the year, the situation was completely reversed, with gold rallying while Bitcoin struggled alongside other risk assets.
Specific catalysts driving Bitcoin’s growth
The report emphasizes that Bitcoin’s recent outperformance is not solely due to gold’s weakness but also driven by sector-specific factors:
- Companies like Strategy and Metaplanet are increasing their Bitcoin purchases. Strategy, in particular, plans to raise an additional $84 billion for acquisitions by 2027, having already reached 60% of its original target.
- Some U.S. states have begun adding Bitcoin to their reserves. New Hampshire now allows up to 5% of state assets to be invested in Bitcoin and gold.
“As more U.S. states consider adding Bitcoin to their strategic reserves, this could prove to be a sustained positive catalyst for Bitcoin,” the analysts wrote. Given the weakening of gold prices and these industry-specific drivers, JPMorgan’s analysts see greater growth potential for Bitcoin in the second half of the year.
The post Bitcoin outperforming gold in the second half of 2025: JPMorgan appeared first on Atlas21.
-
 @ cefb08d1:f419beff
2025-05-16 06:37:33
@ cefb08d1:f419beff
2025-05-16 06:37:33https://stacker.news/items/981350
-
 @ 82e045a6:9b6c2cc0
2025-05-16 06:25:22
@ 82e045a6:9b6c2cc0
2025-05-16 06:25:22GA179 là một trong những nền tảng công nghệ số tiên phong mang lại trải nghiệm đa chiều cho người dùng trong kỷ nguyên chuyển đổi số. Với sự kết hợp giữa giao diện thân thiện và công nghệ xử lý hiện đại, GA179 không chỉ đơn thuần là một ứng dụng thông thường mà còn là công cụ giúp người dùng tối ưu hóa các nhu cầu tương tác và kết nối mỗi ngày. Điểm mạnh lớn nhất của GA179 nằm ở sự ổn định và mượt mà trong quá trình sử dụng, cho phép truy cập nhanh chóng trên mọi thiết bị như điện thoại thông minh, máy tính bảng hay máy tính để bàn. Không chỉ vậy, nền tảng này còn tích hợp khả năng cá nhân hóa cao, mang đến những tính năng được đề xuất thông minh dựa trên hành vi và sở thích của từng người dùng. GA179 xây dựng trải nghiệm người dùng dựa trên tính tiện dụng, tiết kiệm thời gian và đảm bảo sự liền mạch trong từng thao tác. Nhờ đó, nền tảng đã nhanh chóng thu hút một lượng lớn người dùng trung thành, góp phần tạo nên một cộng đồng sử dụng đông đảo và gắn bó.
Không dừng lại ở giao diện và hiệu năng, GA179 còn nổi bật với hệ thống bảo mật đạt tiêu chuẩn quốc tế. Trong thời đại mà thông tin cá nhân và quyền riêng tư trở thành mối quan tâm hàng đầu, GA179 đã triển khai các biện pháp mã hóa nhiều lớp nhằm bảo vệ toàn diện dữ liệu người dùng. Các giao dịch và hoạt động trên nền tảng đều được ghi nhận, giám sát và xử lý qua hệ thống kiểm tra tự động, giúp phát hiện và ngăn chặn mọi hành vi đáng ngờ. Đồng thời, quy trình xác minh danh tính và hỗ trợ kỹ thuật được triển khai bài bản, giúp người dùng an tâm khi sử dụng dịch vụ. Một điểm cộng khác của GA179 là sự hỗ trợ khách hàng chuyên nghiệp, hoạt động 24/7 và luôn sẵn sàng lắng nghe, tiếp nhận phản hồi từ người dùng để cải thiện nền tảng từng ngày. Chính điều này giúp GA179 không chỉ giữ được sự tin cậy mà còn xây dựng được danh tiếng vững chắc trên thị trường công nghệ số ngày nay.
Định hướng phát triển của GA179 không chỉ dừng lại ở việc cải thiện trải nghiệm người dùng, mà còn mở rộng mạnh mẽ sang các lĩnh vực ứng dụng công nghệ số hóa khác như quản lý thông tin, liên kết hệ sinh thái điện tử và đồng bộ hóa dữ liệu đa nền tảng. Nền tảng này liên tục cập nhật những xu hướng công nghệ mới, bao gồm trí tuệ nhân tạo (AI), học máy (machine learning) và phân tích dữ liệu lớn (big data) để nâng cao khả năng tương tác thông minh và tối ưu hóa hiệu suất hoạt động. GA179 còn tích cực hợp tác với các đối tác chiến lược trong và ngoài nước để mở rộng quy mô, nâng cấp dịch vụ, và tạo nên một môi trường sử dụng đa dạng, phù hợp với nhu cầu cá nhân lẫn tổ chức. Nhìn chung, với sự đầu tư bài bản và định hướng phát triển lâu dài, GA179 đang từng bước khẳng định vị thế là một trong những nền tảng công nghệ đáng tin cậy, hiệu quả và tiên tiến nhất trong thời đại số, mang lại nhiều giá trị thực tiễn và tiện ích vượt trội cho người dùng trong mọi lĩnh vực của cuộc sống hiện đại.
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ 9c9d2765:16f8c2c2
2025-05-16 05:35:17
@ 9c9d2765:16f8c2c2
2025-05-16 05:35:17CHAPTER TWENTY
The Ray family exchanged glances. Mark smirked faintly, leaning toward Helen. “It’s probably one of those foreign board members,” he muttered. “No way it’s James.”
Helen nodded with a smug expression. “James is just a placeholder. A temporary President."
Even Tracy looked up from her phone, curious but confident in her assumption that the former street man she helped frame could never amount to much more.
But just as Mr. JP inhaled to say the name, a loud and chaotic voice broke through the hall.
“There he is!” a young woman shrieked from the back, storming down the aisle. “That’s him! That’s my brother! He threw me out like trash when I asked for help!”
The entire room fell into stunned silence. Gasps erupted from every corner as the woman dressed in tattered clothes for effect pointed dramatically at James, who remained seated with a stoic expression.
Cameras immediately turned toward her. Reporters snapped photos and started whispering frantically into their microphones.
“What is going on?” someone muttered from the crowd.
Mark nearly jumped in excitement. “This is perfect,” he whispered to Helen. “Let her ruin him in public!”
Helen chuckled darkly, “Couldn’t be better timing.”
But the moment was far from victorious.
Mr. JP’s face turned crimson with rage. He slammed a hand on the podium and shouted, “Security!”
Guards rushed in and surrounded the woman, who was still putting on a show for the cameras.
“I said remove her!” Mr. JP bellowed. “This is a private event, and that woman is not my daughter nor does she have any relation to my family!”
The woman’s protest turned into stammers. “But… I”
“You were paid to do this, weren’t you?” Mrs. JP cut in fiercely, standing beside her husband. “You dared to come here to sabotage our son’s moment? Arrest her at once!”
As the security officers grabbed the woman and escorted her out, the room remained frozen.
Mr. JP stepped back to the microphone, eyes blazing.
“Now let me make this perfectly clear,” he announced, his voice shaking with fury and pride. “The man you just tried to humiliate, the man you dared to frame, is not just the President of JP Enterprises…”
He turned toward James, his gaze softening with emotion.
“He is my only son. James JP. The true heir to everything I have built. My blood. My pride. My legacy.”
The entire hall erupted into gasps again this time, not from shock, but from awe.
Cameras turned sharply toward James, who now stood slowly from his seat. Mrs. JP immediately walked over and wrapped her arm around her son with tears in her eyes.
“We love you, son,” she said tenderly. “You deserve every bit of this moment.”
James gave a small nod, his eyes scanning the room as all those who once looked down on him now looked up in silence.
From their seats, Helen and Mark were speechless.
Tracy clutched her phone, her hands trembling.
This wasn’t supposed to happen… this wasn’t in the plan… she thought.
James turned to face the Ray family directly. His eyes were calm, but piercing.
The grand ballroom had descended into an eerie quiet. All eyes were now fixed on James, the man who had once been mocked as a beggar, ridiculed as a street dweller, and dismissed as a disgrace to the Ray family. But there he stood tall, refined, and composed as the sole heir to the JP empire.
Reporters who once whispered slanderous headlines now stood frozen, their cameras lowered slightly, unsure whether to record this new twist or pause in awe. Among them, Tracy felt a chill run down her spine. Her earlier confidence had vanished like smoke, replaced by the crushing weight of guilt and dread. She couldn’t even meet James’s gaze.
Helen, seated a few rows ahead, was seething silently. Her fingers clenched the silk of her gown tightly, knuckles whitening. Mark sat beside her, pale-faced and stiff. All his previous arrogance had withered into regret. This wasn’t the plan. This wasn’t supposed to happen. James wasn’t supposed to rise. Not like this.
As the hall slowly began to clap, starting from the board members of JP Enterprises to representatives of international partners who respected Mr. JP’s authority, the applause grew louder. It became thunderous, roaring like justice finally given form. The heir had been revealed, and it wasn’t just a title it was a crown reclaimed.
Mr. JP gestured for silence once again, and when the room obeyed, he turned to James and said, “Son, I may have failed you in the past. I listened to lies, I acted in anger, and I walked away when I should’ve stood by your side. But today, in front of the world, I ask for your forgiveness and welcome you back not just as the President, but as the heart of JP Enterprises.”
The crowd erupted into another round of claps, cheers, and whistles. Emotions swirled through the hall like a whirlwind.
James slowly approached the podium, every step echoing the long journey he had endured. From rejection, betrayal, and homelessness to becoming the man everyone now admired.
He adjusted the microphone and let his calm voice wash over the crowd.
“I never imagined this day would come. Not because I didn’t believe in myself but because for a long time, the world refused to believe in me. Many of you here know me as the President. Some only know me through headlines good and bad. And a few… know me as the man they once threw away.”
His words cut through the crowd like glass.
He turned his gaze slowly toward the Ray family. “To those who called me worthless… to those who spat at my name, who mocked me when I had nothing… thank you.”
Gasps filled the room.
-
 @ 341d22d7:d4e9497e
2025-05-16 05:07:10
@ 341d22d7:d4e9497e
2025-05-16 05:07:10A plataforma 89p chegou para transformar a experiência de jogos online, oferecendo aos jogadores um ambiente de alta qualidade, repleto de opções diversificadas e recursos inovadores. Com uma interface amigável, tecnologia de ponta e uma vasta gama de jogos, a 89p é a escolha perfeita para quem busca diversão e emoção a qualquer hora do dia. Neste artigo, exploraremos as características dessa plataforma, os jogos disponíveis e a experiência do jogador que faz dela uma excelente opção.
A 89p é uma plataforma de jogos online projetada para oferecer uma experiência única aos jogadores. Com um design intuitivo, fácil de navegar e totalmente otimizado para diferentes dispositivos, os usuários podem acessar a plataforma a partir de desktops, laptops e dispositivos móveis. A plataforma é conhecida por sua estabilidade, velocidade e suporte ao cliente de qualidade, garantindo que todos os aspectos da experiência do usuário sejam tratados com excelência.
O objetivo da 89pé oferecer aos seus jogadores uma experiência segura, confiável e divertida, com uma ampla gama de jogos que atendem a todos os gostos e preferências. Se você é fã de jogos de habilidade, jogos de azar ou opções mais descontraídas, a plataforma tem algo para todos.
Variedade de Jogos na Plataforma 89p Uma das grandes vantagens da 89p é a diversidade de opções de jogos. A plataforma conta com um catálogo extenso, com títulos das mais variadas categorias. Desde jogos de cartas, como pôquer e blackjack, até jogos mais modernos, como slots e jogos de mesa, a 89p garante que seus jogadores tenham acesso ao que há de melhor no mundo dos jogos online.
Além disso, a plataforma oferece jogos com temas e estilos diferentes, permitindo que cada jogador encontre opções que se adaptem ao seu estilo. A 89p também está constantemente atualizando seu portfólio de jogos, trazendo novas opções e versões aprimoradas, para que a experiência de jogar nunca se torne monótona.
A plataforma se destaca também pela qualidade gráfica dos seus jogos, que são desenvolvidos com tecnologia de última geração. Isso garante não só uma jogabilidade envolvente, mas também visuais impressionantes que tornam a experiência ainda mais imersiva. A jogabilidade é fluida, e os gráficos são de alta qualidade, com animações e efeitos especiais que aumentam ainda mais a diversão.
A Experiência do Jogador na 89p Na 89p, a experiência do jogador está no centro de tudo. A plataforma foi desenvolvida para ser fácil de usar, mesmo para aqueles que não têm muita experiência em jogos online. A navegação é simples, e a disposição dos jogos é organizada de maneira prática, permitindo que os jogadores encontrem rapidamente suas opções preferidas.
Outro ponto importante é o suporte ao cliente. A 89p oferece atendimento rápido e eficiente, com uma equipe de profissionais treinados para resolver quaisquer dúvidas ou problemas que possam surgir. O suporte está disponível 24 horas por dia, 7 dias por semana, garantindo que os jogadores tenham sempre a ajuda que precisam quando necessário.
Além disso, a plataforma se preocupa com a segurança de seus usuários. A 89p utiliza criptografia de última geração para proteger os dados dos jogadores, garantindo que suas informações pessoais e financeiras estejam sempre seguras. Isso é essencial para criar um ambiente confiável e tranquilo para os jogadores se concentrarem apenas na diversão.
Conclusão A 89p é uma plataforma de jogos online que oferece uma experiência completa, com uma grande variedade de jogos, suporte de alta qualidade e uma interface intuitiva. Se você está procurando uma nova forma de se divertir jogando online, a 89p é uma excelente escolha, proporcionando segurança, inovação e, claro, muita diversão.
Seja você um jogador iniciante ou experiente, a plataforma tem algo a oferecer. Não deixe de conferir a 89p e explorar tudo o que ela tem a oferecer.
-
 @ eb0157af:77ab6c55
2025-05-16 10:09:27
@ eb0157af:77ab6c55
2025-05-16 10:09:27The sovereign fund Mubadala increases its holdings in BlackRock’s Bitcoin ETF by 6%.
According to the 13-F filing submitted to the SEC, Abu Dhabi’s sovereign wealth fund Mubadala has increased its holdings in BlackRock’s spot Bitcoin ETF (IBIT) to 8.73 million shares, with a total value of $408.5 million.

Source: Sec
The investment marks a 6% increase compared to its position last December, when the fund held 8.23 million shares.
For several months now, some of the world’s largest sovereign wealth funds have already gained exposure to Bitcoin: Norway’s Government Pension Fund Global, the largest in the world, holds around $500 million in MicroStrategy shares, while Abu Dhabi’s ADQ regularly invests in digital asset-related projects.
Mubadala joins other major institutional investors, including Goldman Sachs and Avenir Group, in increasing their exposure to IBIT.
The post Abu Dhabi sovereign wealth fund invests $408.5 million in Bitcoin via IBIT appeared first on Atlas21.
-
 @ 341d22d7:d4e9497e
2025-05-16 05:06:22
@ 341d22d7:d4e9497e
2025-05-16 05:06:22A 7075Bet é uma plataforma de entretenimento digital inovadora, projetada para proporcionar aos jogadores uma experiência inesquecível com uma ampla variedade de jogos emocionantes. Com uma interface intuitiva e recursos que visam a comodidade do usuário, a 7075Bet se destaca no cenário de plataformas de entretenimento online, oferecendo uma experiência completa e envolvente. Neste artigo, exploraremos as funcionalidades dessa plataforma, os jogos que ela oferece e como ela se dedica a proporcionar a melhor experiência aos seus jogadores.
Plataforma de Entretenimento Inovadora
A 7075betfoi criada com o objetivo de revolucionar a forma como os jogadores interagem com as plataformas de entretenimento online. Sua interface moderna e intuitiva permite que até mesmo iniciantes naveguem facilmente por todas as funcionalidades da plataforma. A plataforma oferece uma experiência fluída, com design responsivo que se adapta bem tanto em dispositivos móveis quanto em desktops.
O processo de registro é simples e rápido, permitindo que novos jogadores comecem a explorar a plataforma sem complicações. Além disso, a 7075Bet oferece diversas opções de pagamento, tornando o processo de depósitos e retiradas acessível e seguro para os usuários. Com um suporte ao cliente eficiente, os jogadores podem contar com a ajuda da equipe da plataforma sempre que necessário, garantindo uma experiência tranquila e sem contratempos.
Jogos Diversificados para Todos os Gostos
Na 7075Bet, os jogadores encontram uma vasta gama de opções de jogos, atendendo a todos os tipos de gostos e preferências. Se você é fã de jogos de mesa, a plataforma oferece várias opções clássicas, como blackjack e roleta, que podem ser jogadas de forma fácil e divertida. Esses jogos são projetados para proporcionar aos jogadores uma experiência envolvente, com gráficos e animações de alta qualidade que imitam a sensação de estar em um ambiente físico.
Para os fãs de jogos mais dinâmicos e rápidos, a 7075Bet também disponibiliza uma seleção de jogos eletrônicos e de vídeo. Desde caça-níqueis modernos até jogos com jackpots progressivos, cada título é projetado para manter os jogadores entretidos por horas. Os jogos apresentam temas inovadores, com designs criativos e recursos interativos que tornam a jogabilidade ainda mais divertida e recompensadora.
Além disso, a plataforma está sempre atualizando sua seleção de jogos, garantindo que os jogadores tenham acesso às novidades mais recentes do mercado. Isso demonstra o compromisso da 7075Bet em oferecer uma experiência de entretenimento atualizada e diversificada.
A Experiência do Jogador: Conforto e Segurança
A experiência do jogador é a prioridade na 7075Bet. A plataforma não só oferece uma grande variedade de jogos, mas também proporciona um ambiente seguro e confortável para seus usuários. Com medidas rigorosas de segurança, como criptografia de dados e autenticação de transações, os jogadores podem se sentir tranquilos ao fazer depósitos e retirar seus ganhos.
A experiência do jogador vai além dos jogos em si. A plataforma oferece promoções regulares, bônus de boas-vindas e programas de fidelidade que tornam a jornada ainda mais emocionante. A 7075Bet também oferece uma série de funcionalidades para que os jogadores possam personalizar suas preferências, ajustando notificações, definindo limites de jogo e participando de torneios exclusivos. Tudo isso contribui para que cada jogador se sinta único e tenha uma experiência personalizada.
Conclusão
A 7075Bet se destaca como uma plataforma de entretenimento online que oferece uma experiência completa e envolvente. Com uma interface amigável, uma seleção diversificada de jogos e um compromisso com a segurança e a satisfação dos jogadores, ela se tornou uma opção popular para aqueles que buscam diversão e emoção no mundo digital. Se você está em busca de uma plataforma de entretenimento que oferece algo para todos os gostos, a 7075Bet é, sem dúvida, uma escolha excelente.
-
 @ 2fb77d26:c47a6ee1
2025-05-14 05:57:34
@ 2fb77d26:c47a6ee1
2025-05-14 05:57:34Europäischer Tunnelblick
In unseren Breiten sprach man schon seit jeher gerne davon, dass »Amerika den Europäern immer voraus« ist. Dass »der alte Kontinent« stets zehn Jahre im Hintertreffen ist. In der Finanzbranche attestierte man auch gerne mal einen Rückstand von »20 Jahren«. Bemängelt wurde im Rahmen solcher Analysen zumeist die mangelnde Innovationskraft europäischer Unternehmen, die gemäß einschlägiger Experten vor allem auf die Regulierungswut der hiesigen Bürokratie zurückzuführen ist. Langwierige Genehmigungsprozesse, kompliziertes Steuerrecht, zu kleine Kapitalmärkte und komplexe Datenschutzanforderungen schrecken Gründer und Investoren ab. »Bürokraten regulieren Europa zu Tode«, bringt es der Ökonom und Unternehmer Dirk Specht am 29. November 2024 auf den Punkt. Aus Sicht des Entrepreneurs eine durchaus nachvollziehbare Einordnung.
Denn selbst wenn die Hürden der Unternehmensgründung einmal überwunden sind, machen Bürokratiekosten selbst in kleinen Firmen knapp drei Prozent vom Umsatz aus. Im industriellen Mittelstand übersteigen sie nicht selten die jährliche Bruttoumsatzrendite von durchschnittlich fünfeinhalb Prozent. Von den arbeitsrechtlichen Rahmenbedingungen – siehe Kündigungsschutz, Urlaubsanspruch und Lohnfortzahlung im Krankheitsfall – gar nicht erst anzufangen. In puncto Flexibilität ist Europa für Unternehmer also tatsächlich nur bedingt attraktiv.
Ganz anders die USA. Deregulierung, Seed-Capital en Masse und ein Arbeitsrecht, das den Slogan »Hire and fire« weltberühmt machte – gemäß Tagesschau vom 11. Februar 2025 übrigens ein Modell, das dank Microsoft, Meta und SAP langsam auch in Deutschland Einzug hält. Diese unternehmerische Freiheit – oder Zügellosigkeit – machte Amerika zum Start-up-Inkubator. Zum Gründerparadies. Wall Street, Motorcity, Silicon Valley, Hollywood, et cetera. Ein Mekka für Investoren. Und ein Alptraum für Arbeitnehmer.
Alles richtig. Oberflächlich betrachtet. Dass bei dieser sehr kurzsichtigen Analyse stets außer Acht gelassen wird, welchen Anteil die beiden Weltkriege, angloamerikanische Finanzdynastien, halbseidene NGO-Netzwerke und vor allem über ein Dutzend Geheimdienste an Amerikas Wirtschaftswachstum der vergangenen 100 Jahre haben, trübt den Blick der europäischen Unternehmergarde allerdings nachhaltig. Denn er negiert den historischen Kontext. Vermutlich läuft Roger Köppels Editorial für DIE WELTWOCHE vom 01. Mai 2025 deshalb immer noch ungeniert unter dem Titel »Hoffnungsträger Trump«.
Ich habe täglich Kontakt mit Geschäftspartnern in den USA – und bei denen ist von Hoffnung nicht (mehr) viel zu spüren. Begriffe wie Planungsprobleme, Stornierung, Unsicherheit oder Lieferengpass fallen dagegen immer häufiger. Investor’s Business Daily nannte den Zustand vor wenigen Stunden »ein Erdbeben«, weil Trumps »Handelskrieg-Tsunami« nun auch die Häfen der Vereinigten Staaten erreicht hat. Die laufen langsam leer. Frachter und Tanker mit Importwaren löschen ihre Ladung nicht. Oder kommen gar nicht mehr an. Die auf Basis von Strafzöllen zu erwartenden Lieferengpässe »könnten die Folgen der Covid-Krise übertreffen«, konstatiert das Investment-Magazin.
Was also passiert gerade in den Vereinigten Staaten? Sollte Europa tatsächlich neidisch auf die vermeintlichen Wettbewerbsvorteile Amerikas sein – oder gar auf die aktuellen politischen Entwicklungen? Auf Effizienzsteigerung der Marke DOGE? Nein, keinesfalls. Denn zum einen sorgen die turbokapitalistischen Exzesse im »Land der unbegrenzten Möglichkeiten« dafür, dass Arbeitnehmer endgültig zu Lohnsklaven degradiert werden, die den Launen von Märkten und Unternehmen relativ schutzlos ausgeliefert sind. Zum anderen beruht der Erfolg amerikanischer Konzerne keineswegs auf deren Innovationskraft, einem laxen Arbeitsrecht oder genialem Unternehmertum, sondern primär auf tiefenstaatlichem Interventionismus. Das gilt seit dem Jahrtausendwechsel vor allem für die Tech-Branche. Denn die USA sind nicht einfach eine Wirtschaftsmacht, sondern der militärische Arm des angloamerikanischen Empire.
Das zeigen die »Glorreichen Sieben« – Google, Microsoft, Apple, Amazon, Alphabet, Meta, Tesla und Nvidia – die allesamt erst durch Startfinanzierung seitens Militär und Geheimdiensten wurden, was sie heute sind: Die Speerspitze des technokratischen Totalitarismus. Nachdem selbst The Economist am 10. Dezember 2024 feststellte, dass mit der Wiederwahl von Donald Trump nun »die PayPal-Mafia die US-Regierung übernimmt«, sollte man in unseren Bereiten also eventuell etwas kritischer begutachten, was die entsprechenden Konzerne dort treiben. Denn es ist angesichts von Agenda 2030, aktuellen EU-Programmen, EZB-Planungen und einer Kriegswirtschaft kolportierenden Bundesregierung unter BlackRock-Merz nicht davon auszugehen, dass es dieses Mal zehn oder zwanzig Jahre dauert, bis diese Entwicklungen auch bei uns ankommen.
Palantir & DOGE
Das bezieht sich insbesondere auf Elon Musks DOGE – das »Department of Government Efficiency« – eine neu geschaffene Behörde, die sich auf Effizienzsteigerung in Sachen Regierungsgeschäfte konzentrieren soll. Dies selbstredend unter flächendeckender Zuhilfenahme von KI (Künstlicher Intelligenz), die wiederum auf entsprechende Datenpools angewiesen ist. Um solche kurzfristig zur Verfügung zu stellen, durchforstet, hackt und kapert Musks DOGE-Team die IT-Abteilungen, Server und Netzwerke von Ministerien und Bundesbehörden. Vor allem auf Finanzdaten hat man es abgesehen. An geltendes Recht hält sich DOGE dabei nicht. Datenschützer sind alarmiert. Und Whistleblower werden von Musks Team bedroht. All das passiert in enger Zusammenarbeit mit Oracle, einem weiteren von der CIA startfinanzierten IT-Riesen – und natürlich Palantir, dem von Peter Thiel gegründeten Spionage- und Killerkonzern.
So berichtete Reuters am 6. Mai 2025 beispielsweise über ein neues Gemeinschaftsprojekt von Elon Musks xAI und Palantir, das die Nutzung der jeweiligen KI-Lösungen im Finanzsektor vorantreiben will – dies, nachdem xAI, BlackRock und Microsoft bereits im März ein neues Konsortium zur Erweiterung von KI-Infrastruktur ins Leben riefen. Im Department of Homeland Security (DHS) ist DOGE aktuell damit beschäftigt, das IDENT-System des »Office of Biometric Identity Management« (OBIM) zu übernehmen – die weltweit größte Datenbank für biometrische Informationen, die von praktisch allen US-Behörden aber auch internationalen Partnern genutzt wird. Zusammengeführt werden sollen die von DOGE gekaperten Daten in HART (Homeland Advanced Recognition Technology System), einem neuen, mit über sechs Milliarden US-Dollar budgetierten Überwachungssystem des DHS, das in Kollaboration mit Palantir-Programmen die flächendeckende Überwachung der Bevölkerung analog zu China ermöglichen wird.
Palantir wurde 2003 gegründet und arbeitet seither, das belegt eine 2013 geleakte Kundenliste, für mindestens 12 US-Regierungseinrichtungen: CIA, DHS, NSA, FBI, CDC, Special Operations Command, et cetera. Schon vor knapp zehn Jahren häuften sich Berichte – wie zum Beispiel von WIRED am 9. August 2017 – die belegten, dass Palantir die vermeintlich vertraulichen Daten, die zum Beispiel Polizisten in Los Angeles seit 2009 in Datenbanken des Konzerns erfassen, kopiert, verkauft und zweckentfremdet. Dass Palantir das rechtsextreme, zionistische Regime von Benjamin Netanjahu bei seinem Genozid in Gaza unterstützt, ist ebenfalls kein Geheimnis mehr. Die strategische Partnerschaft zwischen Thiels Tötungsmaschine und den IDF wurde nach Berichten von Bloomberg vom 12. Januar 2024 gar ausgeweitet. Gideon Levy bescheinigt seinem Land in einem Beitrag der Haaretz vom 19. Januar 2025, in Gaza den »ersten faschistischen Krieg« seiner Geschichte zu führen. Womit wir wieder bei Palantir und den Vereinigten Staaten wären.
Denn wie ich bereits in meinem Artikel über Thiel vom 22. September 2024 in Aussicht gestellt hatte, kommt dem gebürtigen Frankfurter eine ganz besondere Rolle in Trumps neuer Regierung zu. Vom »Paten« der PayPal-Mafia und Geheimdienst-Frontmann zum Palantir-Boss und Bilderberg-Leitungsmitglied – und nun einflussreichsten Mann hinter der US-Regierung. Ohne Peter Thiels finanzielle Unterstützung wäre JD Vance weder Geschäftsmann noch Senator in Ohio oder US-Vizepräsident geworden. So verwundert es kaum, dass Palantir bereits 100 Tage nach Donald Trumps Amtsantritt Zugriff auf sämtliche Steuer-, Gesundheits- und Bewegungsdaten der US-Bevölkerung hat und diese in einer Datenbank zusammenführt, um seine KI darauf anzusetzen. Selbst die Speicher von Smartwatches und Fitness-Armbändern werden angezapft. Kein Datensatz ist mehr tabu.
Wie diese Daten künftig verwendet werden – und zwar gegen alles und jeden – zeigt eine von Palantir entwickelte Software namens »ImmigrationOS«. Ein System, das der US-Regierung hilft, das Leben von Migranten zu durchleuchten und permanent zu überwachen. Inklusive biografischer, biometrischer und Geolokationsdaten. Die auf Basis dieser Daten entwickelten Empfehlungen nutzt das ICE (Immigration and Customs Enforcement), um Menschen in die an Massentierhaltung erinnernden Supermax-Gefängnisse von El Salvador abzuschieben. Für Deportationen ohne Beweise, Anhörung, Gerichtsverhandlung und Rechtsgrundlage. Eine in dieser Form fraglos verfassungsfeindliche Ausweitung des »Catch and Revoke« Programms, dem anstelle illegaler Einwanderer nun auch Doktoranden, Studenten oder unbescholtene Arbeitnehmer zum Opfer fallen – siehe der Fall Kilmar Abrego Garcia – vor allem solche, die den Völkermord in Gaza kritisieren.
Es dürfte derweil nur eine Frage der Zeit sein, bis das zugrundliegende, am 30. April 2025 verabschiedete »Antisemitismus-Gesetz« auf weitere unliebsame Personenkreise angewendet wird. Der Bundesstaat Alabama lässt sich bereits von der fragwürdigen Deportationspraxis Washingtons inspirieren und kündigte in Person des Republikaners Chris Sells am 1. Mai 2025 an, selbst ein Gesetz erlassen zu wollen, das die Abschiebung verurteilter Personen ins Ausland ermöglicht. Gemäß Sells wolle man mit dem Gesetzesvorschlag nur ein Zeichen setzen. Mit einer Verabschiedung rechne man nicht. Trump verkündete unterdes, neben Migranten künftig auch US-Bürger und Ureinwohner nach El Salvador verfrachten zu wollen. Verfassungsrechtlich ein absolutes Tabu. Bisher.
The Atlantic nennt diese Entwicklungen am 27. April 2025 ein »amerikanisches Panoptikum«. Zu Recht. Denn Palantirs zentralisierter Datenpool wird sich zum mächtigsten Unterdrückungsinstrument der Zivilisationsgeschichte auswachsen – und in nicht allzu ferner Zukunft auch gegen jene MAGA-Anhänger eingesetzt werden, die solch faschistoide Vorgänge derzeit noch bejubeln. Gegen das, was da auf uns zukommt, waren Corona-Tracking und 2G-Segregation geradezu harmlos.
Entsprechend hellhörig sollte es machen, dass die NATO Palantirs KI-Lösungen – genauer: die »Maven AI« – künftig für militärische Planungszwecke einsetzt, wie eine Presseerklärung des »Verteidigungsbündnisses« vom 14. April 2025 ausführt. Denn »Project Maven« ist auf ein Memorandum des US-Verteidigungsministeriums vom 26. April 2017 zurückzuführen und hatte zum Ziel, ein »funktionsübergreifendes Team für algorithmische Kriegsführung« zu schaffen. Unterstützt wurde das US-Militär dabei zunächst von Google. Also dem Unternehmen, das einst unter dem Motto »Don’t be evil« – Sei nicht böse! – angetreten war. Begleitet wurde Googles Engagement für Project Maven von einem massiven Aufruhr in der Belegschaft und Artikelüberschriften wie »Hey Google, wen soll die US-Regierung heute töten?«. Offene Briefe an Google-Chef Sundar Pichai forderten 2018, der IT-Konzern solle die Partnerschaft mit dem Pentagon unverzüglich beenden. Und das tat Google auch.
Project Maven lief natürlich trotzdem weiter. Wie Breaking Defense am 27. April 2022 ausführte, wurde das Vorhaben nach Googles Rückzug der NGA (National Geospatial Intelligence Agency) unterstellt und gemäß Informationen des Forbes Magazine fortan von Eric Schmidt (Google, Bilderberg), Peter Thiel und James Murdoch, dem jüngeren Sohn von Rupert Murdoch finanziert. Maven AI ist das KI-Flaggschiff des US-Militärs – und wird jetzt als Palantir-Produkt weltweit ausgerollt. Vorboten sind in Hessen, Bayern und Nordrhein-Westfalen bereits im Einsatz und dürften angesichts der Iden des Merz wohl bald bundesweit Verwendung finden. Es ist also keineswegs übertrieben, wenn der US-Journalist Derrick Broze am 24. April 2025 von der »Palantir World Order« spricht – einem überstaatlichen Herrschaftssystem, das zuvorderst aufgrund seiner auf zwielichtigen bis illegalen Akkumulationsprozessen basierenden Deutungs- und Interventionshoheit in puncto Big Data fußt. Getreu dem Palantir-Slogan: »Die Software ist das Waffensystem«. Selbst eine in der ARD-Mediathek abrufbare Doku des NDR über Palantir von 10. Juni 2024 läuft unter dem eindeutigen Titel »Eine Software, die töten kann«.
Ja, das Geschäft mit dem industriell-digitalisierten Auftragsmord boomt. Denn internationale Konflikte nehmen zu und die Observationsökonomie erlebt einen Quantensprung. Entsprechend profitabel fiel das erste Quartal 2025 für Thiels Unternehmen aus. Stolze 884 Millionen US-Dollar stellte man Kunden in Rechnung. Ein Wachstum von 39 Prozent gegenüber dem Vorjahr und 21,7 Millionen mehr als prognostiziert. Am 5. Mai 2025 gab die Palantir Aktie zwar um 15 Prozent nach – laut Analysten könnte die Aktie aber auch um 70 Prozent fallen und wäre immer noch die teuerste Marke unter Softwareanbietern in diesem Segment.
Das sollte zu denken geben. Denn die USA durchlaufen eine Metamorphose – weg von demokratischen Strukturen und hin zur »Algokratie«. Die PayPal-Mafia hat das Weiße Haus gekapert und demonstriert dem Wertewesten, was er im Zuge der vierten industriellen Revolution zu erwarten hat: Tech-Feudalismus, dessen Oligarchen sich aufgrund vermeintlicher Sachzwänge schamlos über Recht und Gesetz hinwegsetzen. Nicht von ungefähr hat Donald Trump in seinen ersten 100 Amtstagen bereits 141 »Exekutive Orders« unterzeichnet. Ohne dabei auch nur einmal das Repräsentantenhaus einzubeziehen oder demokratische Prozesse zu respektieren. In diesem Lichte betrachtet erscheint das Cover des TIME Magazine vom Juni 2018, auf dem »The Donald« als König abgebildet war – Titel: »King me« – heute zeitgemäßer denn je.
Dunkle Aufklärung
Und das ist kein Zufall. Wirft man nämlich einen Blick auf die philosophischen Konzepte, die Menschen wie Peter Thiel, JD Vance oder Elon Musk inspirieren, zeigt sich, dass die entsprechenden Pamphlete genau das fordern: Eine postmoderne Version von Monarchie. Einen CEO, der das Land führt wie einen Großkonzern. Mittels KI – und auf Basis des amerikanischen Arbeitsrechts natürlich. Vielsagend, dass Donald Trump am 19. April 2025 auf Twitter ankündigte, exakt das tun zu wollen:
»Das ist gesunder Menschenverstand und wird ermöglichen, dass die Bundesregierung endlich „wie ein Unternehmen geführt wird“.«
Dass Trump den letzten Teil des Satzes in Anführungszeichen setzt, impliziert, dass er jemanden zitiert. Von wem die Phrase stammt, lässt er allerdings offen. Der US-Präsident scheint jedenfalls den Ratschlägen seines Vize JD Vance zu folgen, der bereits am 17. September 2021 in einem Interview mit dem Jack Murphy Podcast sagte:
»Was Trump tun sollte, wenn ich ihm einen Ratschlag geben dürfte: Feuere jeden einzelnen Bürokraten der mittleren Leitungsebene, jeden Beamten in der Verwaltung, und ersetze ihn mit unseren Leuten. Und wenn man dich dafür verklagt, wenn dich die Gerichte aufhalten wollen – denn man wird dich dafür verklagen – stell dich vor das Land, so wie Andrew Jackson, und sag den Menschen, dass der oberste Entscheidungsträger sein Urteil bereits gefällt hat. Jetzt lasst es ihn auch umsetzen.«
Und so geschah es. Denn als der Oberste Gerichtshof der Vereinigten Staaten am 19. April 2025 entschied, dass die juristisch fragwürdigen Deportationen zu stoppen sind, schrieb Donald Trump auf Twitter:
»Ich wurde unter anderem gewählt, um schlechte Menschen aus den Vereinigten Staaten zu entfernen. Ich muss meine Arbeit tun dürfen.«
Damit stellt sich Trump offen gegen die höchste juristische Instanz des Landes und fordert, trotz eines geltenden Urteils weitermachen zu können. Für dieses Vorgehen sucht er Rückhalt in der Bevölkerung. Er will die Gerichte unter Druck zu setzen, um regieren zu können wie ein Monarch. So, wie es die Vordenker der »Neoreaktionären Bewegung« (NRx) – zumeist »Dunkle Aufklärung« genannt – vorschlagen. Bei dieser politischen Philosophie handelt es sich selbst laut Wikipedia um ein »antidemokratisches, antiegalitäres, reaktionäres und neofeudales Konzept«. Geprägt wurde es von einem etwas kauzig anmutenden Blogger namens Curtis Yarvin, der auf seiner Webseite »Unqualified Reservations« ab 2007 und unter dem Pseudonym Mencius Moldbug Texte über das Versagen der Demokratie und Theorien zu alternativen Herrschaftsformen publizierte.
Weiterentwickelt wurden diese Konzepte unter anderem von Nick Land, einem britischen Schriftsteller, der als Vater des »Akzelerationismus« gilt und mit einem Blog-Beitrag aus dem Jahr 2013 auch den Begriff »Dunkle Aufklärung« für Yarvins Theorien aufbrachte. In seinen späteren Texten redete der Brite einem »wissenschaftlichen Rassismus«, der Eugenik und dem von ihm geprägten Begriff »Hyperrassismus« das Wort. Bei der rechtsnationalistischen bis rechtsextremen Alt-Right-Bewegung stieß er damit auf offene Ohren. Die deutsche Publikation »nd – Journalismus von Links« findet diesen »Philosophen der digitalen Entgrenzung« in einem Beitrag vom 21. Mai 2023 aber trotzdem »interessant«. Dass Nick Land gerne Amphetamin konsumiert und eine Weile im Haus des 1947 verstorbenen Satanisten Aleister Crowley lebte, scheint nd-Autor Konstantin Jahn eher Bewunderung abzuringen. Seinem ehemaligen Arbeitgeber, The New Center for Research & Practice, allerdings nicht – der setzte Land am 29. März 2017 wegen rassistischer Umtriebe vor die Tür.
Von Curtis Yarvin war nach der Einstellung seines Blogs im Jahr 2016 unterdes nicht mehr viel zu hören. Bis jetzt. Denn anno 2025 schreibt plötzlich die Financial Times über »die Philosophie hinter Trumps Dunkler Aufklärung«. Ebenso die New York Times, die Yarvin im Januar 2025 zum großen Interview für eine Titelstory bat. Selbst der Bayrische Rundfunk schrieb am 23. März 2025 über den einst nur Insidern bekannten Blogger. Und natürlich Politico, wo am 30. Januar 2025 ein Artikel über Yarvin erschien. Aufmacher: »Curtis Yarvins Ideen waren Randerscheinungen. Jetzt verbreiten sie sich in Trumps Washington«. Im Zuge seines Textes beschreibt Autor Ian Ward, wie Yarvin nach Washington reiste, um auf Einladung des Trump-Teams an der pompösen Inaugurationsfeier teilzunehmen, wo er unter anderem mit dem ehemaligen Thiel-Angestellten JD Vance sprach, der die politischen Theorien von Yarvin mehrfach bei öffentlichen Auftritten lobte, zitierte und als wichtigen Einfluss auf sein Denken nannte. Im Gespräch mit Ward führte Yarvin aus, dass er Trump gegenüber zunächst skeptisch gewesen sei, weil er sich nicht sicher war, ob Trump den von ihm empfohlenen Regimewechsel überhaupt durchziehen könne.
Zwischenzeitlich habe sich jedoch Optimismus eingestellt, so Yarvin, denn man könne in Trumps Kabinett eine »neugewonnene Selbstsicherheit und Aggressivität« spüren. Kein Wunder, besteht es doch in weiten Teilen aus Protegés, Kollegen, Geschäftspartnern und Freunden von Peter Thiel – zu letzteren gehört nach Aussage von Thiel übrigens auch der neue Chef der NIH (National Institutes of Health), Jay Bhattacharya, der zuvor unter anderem bei der Hoover Institution sowie der RAND Corporation tätig war. Aufgabenbereich: Demographie und Ökonomie von Gesundheit und Altern mit Schwerpunkt auf Regierungsprogrammen und biomedizinischer Innovation.
Wer sich mit Thiel beschäftigt hat, wird kaum überrascht sein, dass der in Frankfurt geborene Milliardär Anhänger der »Dunklen Aufklärung« ist. Schon im Mai 2016 schrieb Curtis Yarvin eine E-Mail an einen Bekannten und erklärte: »Ich coache Thiel«. Der brauche aber deutlich weniger politische Orientierungshilfe als gedacht, so Yarvin. »Ich habe die Wahlen in seinem Haus angeschaut. Ich glaube, mein Hangover dauerte bis Dienstag. Er (Thiel) ist völlig aufgeklärt, geht aber sehr vorsichtig vor«, konstatiert Yarvin in seiner Mail. Zu diesem Zeitpunkt stand der dunkle Aufklärer auch in Kontakt mit dem technischen Redakteur von Breitbart News, dem seinerzeit wichtigsten Sprachrohr von Trumps ehemaligem Chefstrategen Steve Bannon, »dem Medien-Baron der Alt-Right-Bewegung«, der sich ebenfalls an Yarvins Konzepten orientierte, dessen Bücher öffentlich empfahl und maßgeblich dazu beitrug, dass Donald Trump die Wahl gegen Hillary »Body Count« Clinton gewann.
Nach Angaben von BuzzFeed News stand auch Peter Thiel 2016 in Kontakt mit besagtem Breitbart-Redakteur. In einem Podcast auftreten, wollte er allerdings nicht. »Lass uns einfach Kaffee holen und dann schauen, was wir machen«, antwortete der Palantir-Gründer im Mai auf eine Interview-Einladung von Breitbart. Und im Juni lud Thiel den Breitbart-Mitarbeiter zum Abendessen in sein Haus in den Hollywood Hills ein. Man darf davon ausgehen, dass es bei diesen Gesprächen um finanzielle Unterstützung von Breitbart News, beziehungsweise der Alt-Right-Bewegung ging. Sprich, um Stimmungsmache für Trump.
Im Wahlkampf 2024 war Thiel weniger zurückhaltend. JD Vance hatte seinen Gönner ja auch bereits im August 2024 via Forbes Magazine dazu aufgerufen, »die Seitenlinie zu verlassen und für Trump zu spenden«. Kurz darauf überwies der Exil-Deutsche mindestens 1,25 Millionen Dollar. Die Betonung liegt auf mindestens. Denn als JD Vance 2022 für den Senat kandidierte, spendete Thiel ganze 15 Millionen US-Dollar für dessen Kampagne. Für manch einen vorausschauenden Journalisten war deshalb schon im Sommer 2024 klar: »Donald Trump ist Peter Thiels erfolgreichstes Investment«.
»Letztes Jahr veröffentlichte der Journalist Max Chafkin eine Biografie über Thiel (…), in der er Yarvin als den politischen Philosophen (…) für ein Netzwerk bezeichnete, das man als Thiel-Verse kennt. Das Buch erklärt, wie Thiel sowohl Cruz als auch Josh Hawley auf ihrem Weg in den Senat half. Es endet mit einem düsteren Bild des Milliardärs, der versucht, seinen politischen Einfluss immer offener auszuweiten (…). Masters und Vance unterscheiden sich von Hawley und Cruz, schreibt Chafkin – erstere sind verlängerte Arme von Thiel«.
Das konnte man in der Vanity Fair am 20. April 2022 über Thiels Bemühungen lesen, sich politischen Einfluss für Trumps zweite Amtsperiode zu sichern. Unter der Überschrift »Im Inneren der Neuen Rechten – wo Peter Thiel seine größten Einsätze platziert« erklärt das Blatt: »Sie sind nicht MAGA. Sie sind nicht QAnon. Curtis Yarvin und die aufstrebende Rechte entwickeln eine andere Form konservativer Politik«.
So stellt sich an dieser Stelle unweigerlich die Frage: Was für eine Politik soll das sein? Warum verkünden Thiel-Weggefährten wie Elon Musk stolz, »nicht nur MAGA, sondern Dark MAGA« zu sein? Was fordern »Akzelerationismus« und »Dunkle Aufklärung«? Wie sieht der von Yarvin, Land, Thiel, Vance, Trump, Musk und Co. avisierte Soll-Zustand aus?
Auf den Punkt bringt das ein Akronym, das Curtis Yarvin seit 2012 benutzt: RAGE. Es steht für »Retire All Government Employees«, übersetzt also dafür, alle Regierungsmitarbeiter zu entlassen. Auch der von Thiel finanzierte Republikaner Blake Masters nutzte das Akronym schon öffentlich. Nur so könne man das amerikanische »Regime« stürzen. »Was wir brauchen«, so Yarvin, »ist ein nationaler CEO – oder das, was man einen Diktator nennt«. Die Amerikaner müssten ihre »Diktatoren-Phobie« überwinden, damit das Land »wie ein Start-up geführt werden kann«. Nach Ansicht von The Brooklyn Rail ist das mittlerweile der Fall. Denn am 30. Januar 2025 veröffentlichte das Medienportal einen Artikel, in dem Autor David Levi Strauss erklärt, die US-Bevölkerung akzeptiere nun endlich »die Idee, dass das Land von einem CEO und wie ein Konzern oder eine Diktatur geführt werden müsse, weil sie – wie Peter Thiel schon 2009 erklärte – nicht mehr daran glauben, dass Freiheit und Demokratie kompatibel sind«.
Ob Akzelerationismus, Neoreaktionäre Bewegung oder Dunkle Aufklärung, sie alle plädieren für eine Rückkehr zu traditionellen gesellschaftlichen Konstrukten und Regierungsformen, inklusive des absoluten Monarchismus. Dafür soll der Staat in eine private Aktiengesellschaft umgewandelt werden, in welcher dem Geschäftsführer absolute Macht zukommt. Gleichheit lehnen alle drei Strömungen als politisches Ziel ab. Stattdessen verfolgt man rationalistische oder utilaristische Konzepte sozialer Schichtung, die auf Erbmerkmalen oder Leistungsprinzipien beruhen – sprich, auf den Grundgedanken der Eugenik.
Diese neue Regierungsform, »Gov-Corp«, wie der britische Journalist Iain Davis das Modell in seinen betreffenden Artikeln und einem lesenswerten Zweiteiler betitelt, wird aufgrund der ihr zur Verfügung stehenden Technologie eine nie gekannte Machtfülle besitzen – eine Machtfülle, die sich aufgrund genau dieser Technologie mit Leichtigkeit als liberale Marktwirtschaft vermarkten lässt. Als rationales, effizientes und individuelle Freiheit suggerierendes Modell zur Steuerung von Staat, Wirtschaft und Gesellschaft. Obwohl man als Bürger – oder sagt man besser Kunde, Mitarbeiter oder Bilanzposition? – vertraglich verpflichtet wird, seine Rechte an die herrschende Konzernstruktur zu übertragen. Analog zu den Bewohnern von Peter Thiels »Start-up City« Próspera – die derzeit versucht, ihr Gastland Honduras mit einer erfolgsversprechenden Klage im Wert von 10,7 Milliarden US-Dollar in den Staatsbankrott zu treiben.
Universelle Menschenrechte sind im Gov-Corp-Modell jedenfalls nicht vorgesehen. Wenn neoreaktionäre Theoretiker wie Curtis Yarvin von »Exit« sprechen, also vom Verlassen demokratischer Strukturen, stellen sie gleichzeitig eine »Opt-in-Society« in Aussicht. Was vordergründig erst einmal gut klingt, soll man sich die Serviceangebote des Staates doch nach eigenen Bedürfnissen konfigurieren dürfen, entpuppt sich schnell als totalitäres wie inhumanes Konstrukt. Als Tech-Feudalismus. Denn für diejenigen, die in der »sozialen Schichtung« untere Ränge bekleiden, sich die Serviceangebote von Gov-Corp nicht leisten können oder den Chef kritisieren, wird es rasch ungemütlich. Siehe Supermax-Gefängnisse.
Dementsprechend zurückhaltend sollte man sein, wenn verheißungsvolle Begriffe wie Freedom Cities, Charter Cities, Start-up Cities oder »Network State« fallen. Denn gerade letzterer steht für nichts anderes als die finale Ausbaustufe von Gov-Corp. Für ein Netzwerk autonomer Städte, die jeweils von einem eigenen CEO mit absolutistischer Macht geführt werden. Sprich, für einen Zusammenschluss kleiner Königreiche – oder Niederlassungen – eines Konzerns namens Regierung. Das Konzept Netzwerk-Staat ist in dieser Form Balaji Srinivasan zuzuschreiben, dem ehemaligen CTO von Coinbase und Partner von Andreessen Horowitz. Sein im Juli 2022 veröffentlichtes Buch »The Network State« beschreibt auf fast 500 Seiten, wie »der Nachfolger des Nationalstaats« aussehen soll. Eine unausgegorene Spinnerei ist das Ganze also nicht mehr. Im Gegenteil. Srinivasan gründete extra einen Fond, um das Konzept Netzwerk-Staat voranzutreiben und wird dabei von diversen Tech-Milliardären unterstützt.
Vor diesem Hintergrund verwundert es nicht, dass Netscape-Gründer Marc Andreessen bereits Anfang Oktober 2013 prognostizierte, dass »es in den kommenden Jahren doppelt so viele, oder drei oder vier Mal so viele Länder geben wird«. Andreessens »Techno-Optimist Manifesto« vom 16. Oktober 2023 erwähnt zwar weder Yarvin noch Land oder Srinivasan, aber es outet den Verfasser als eingefleischten Akzelerationisten – und als Fan des Transhumanisten Ray Kurzweil.
Für Außenstehende mag Srinivasans Konzept abseitig anmuten. Aber es zog Kreise. Selbst die New York Times berichtete am 28. Oktober 2013 über eine Rede des bekennenden Staatsfeinds bei der Silicon Valley »Startup School«. Der entsprechende Artikel eröffnet mit dem Worten: »Silicon Valley aufgeschreckt von Sezessionsruf. Erst die Sklavenhalter im Süden, jetzt das. Versucht Silicon Valley, sich von Amerika abzuspalten?«. Während das Nachrichtenportal TechCrunch die »Dunkle Aufklärung« Ende 2013 noch als Bewegung von Nerds abtat, die eine Monarchie fordern, sprach man beim britischen Telegraph im Januar 2014 bereits von »anspruchsvollem Neo-Faschismus«.
Die Granden der Big-Tech-Branche wissen seit über einem Jahrzehnt, dass ihr digital-finanzieller Komplex die Welt beherrscht und sie mittels Disruption jede andere Industrie zum Handlanger degradiert haben. Dementsprechend selbstbewusst treten ihre Vordenker, Theoretiker und Philosophen auf. Nicht umsonst teilt auch Patri Friedman, Enkel des Nobelpreisträgers Milton Friedman, neoreaktionäre Positionen – auch wenn er sich 2009 mit Yarvin überwarf, seither »eine politisch korrektere dunkle Aufklärung« fordert und nun eigene Freedom Cities auf schwimmenden Plattformen in internationalen Gewässern schaffen will. Dafür gründete er 2019 Pronomos Capital, ein Unternehmen, das über 13 Millionen US-Dollar von Thiel, Srinivasan und Andreessen erhielt, Próspera finanziert und ähnliche Projekte in Afrika, Südostasien und Palau im Portfolio hat.
Die omnipräsente Konstante: Peter Thiel – der nicht nur in Firmen von Yarvin, Srinivasan oder Friedman investiert, sondern Donald Trump auch bei der Auswahl von Kabinettsmitgliedern beriet. So kam es, dass Thiels Kumpel Srinivasan sogar im Gespräch für den Chefposten der FDA (Food and Drug Administration) war. Eine hochrangige Position im Staatsapparat. Erstaunlich, erinnert man sich an dessen staatsfeindliche Rede bei der »Startup School«. Die Japan Times findet am 19. Juni 2024 passende Worte für diese Vorgänge:
»Es wird immer deutlicher: Führende Techno-Libertäre (…) sind nur insoweit gegen den Staat, als er sie nicht persönlich bereichert. Angesichts der Aussicht, dass die Regierung zu einem Großkunden wird, löst sich der einst prinzipielle Widerstand gegen die Staatsmacht auf. Dieser Wandel lässt sich auch bei Thiel selbst beobachten. 2009 erklärte er, dass die große Aufgabe für Libertäre darin bestehe, Politik in all ihren Formen zu entkommen. Doch 2016 engagierte sich Thiel voll und ganz für Parteipolitik und hielt eine Rede auf dem Parteitag der Republikaner. Inzwischen ist Palantir, das von ihm mitgegründete Datenanalyseunternehmen, zu einem Giganten herangewachsen und profitiert von riesigen Regierungsaufträgen. Fast die Hälfte seiner Einnahmen stammt mittlerweile aus öffentlichen Mitteln.«
Keine Frage: Peter Thiel ist Dreh- und Angelpunkt hinter der neuen US-Regierung. Der Pate der PayPal-Mafia ist der mächtigste Mann in Washington und Palantir die treibende Kraft hinter dem digitalen Panoptikum, das sich dort derzeit formiert. Und was Elon Musk als DOGE verkauft, erinnert im Kern an RAGE. Selbst das TIME Magazine stellt anhand der bislang 30.000 gefeuerten Regierungsmitarbeiter fest, dass die Vorgehensweise von Trump und Co. keineswegs Zufall ist, sondern exakt der Programmatik von Yarvins »Dunkler Aufklärung« folgt. Nur in unseren Breiten tut man sich immer noch schwer damit, das zu erkennen – oder einräumen zu wollen.
Dafür gibt es zwei Gründe. Erstens: Bis dato hat kein deutschsprachiger Journalist ausführlich über diese Zusammenhänge berichtet und den notwendigen Kontext hergestellt. Zweitens: Ist man vom herrschenden System enttäuscht und stößt bei der Suche nach Alternativen auf die Analysen von Yarvin oder Srinivasan, wirken diese wie Balsam in den Ohren, geht man als Kritiker des übermächtigen und -griffigen Staates doch in weiten Teilen mit deren Einordnung aktueller Probleme konform. Selbst die Lösungsvorschläge der dunklen Aufklärer wirken plausibel. Zumindest theoretisch. Mehr Autonomie, Dezentralität, Effizienz, Prosperität – und viel weniger Staat. Klingt attraktiv. Vor allem im Vergleich mit dem kollektivistischen Wohlfahrtspaternalismus der vergangenen Dekaden.
Die Rattenfänger aus dem Silicon Valley erzählen dem enttäuschten und von Politik angewiderten Demos, was er hören will. Im Bereich Neuro-Linguistisches Programmieren (NLP) nennt man das die Echo-Technik. Sie sorgt dafür, dass sich das Gegenüber wahr- und ernstgenommen fühlt. Dass es sich öffnet. Das funktioniert erstaunlich gut. Bis man sich anschaut, woher das Geld kommt und wohin die Daten fließen. Bis man erkennt, dass solch ein System, die Algokratie, für deutlich mehr Zentralisierung steht – für mehr Staat, für Datenzentren von Tech-Despoten und interoperable Blockchain-Plattformen von Finanzkartellen. Für einen digitalen Gulag und Gewalt gegen Andersdenkende. Für die Abschaffung universeller Menschenrechte.
Sicher. Man weiß nicht, ob die »Dunkle Aufklärung«, ob Akzelerationismus und ein Netzwerk-Staat mit CEO – oder »Diktator« – nicht vielleicht besser funktionieren als Demokratie. Manch einer denkt, man könne es ja mal versuchen. Das wollte auch der Anarcho-Kapitalist Jeff Berwick, alias The Dollar Vigilante. Im März 2025 reiste er nach Honduras, um sich Próspera anzuschauen und anschließend für das Freedom-City-Projekt zu werben. Doch ein paar Tage vor der mit der Stadtverwaltung abgestimmten Visite und Führung erhielt er eine E-Mail vom Rechtsanwalt des Unternehmens, der ihm zu seiner Überraschung mitteilte, er dürfe nun doch nicht anreisen – und hätte ab sofort generelles Zutrittsverbot für das Gelände der »Sonderentwicklungszone«. Wahrscheinlich fand die Presseabteilung von Próspera bei der vorbereitenden Überprüfung seiner Person heraus, dass Jeff Berwick von Technokratie, Zionismus, Krieg, Trump, Vance und auch der PayPal-Mafia nicht allzu viel hält. Er bezeichnet sich nämlich als »Verschwörungsrealist« – und war auf der Suche nach Freiheit. Die ist aber offenbar auch in Próspera Mangelware.
-
 @ 341d22d7:d4e9497e
2025-05-16 05:05:50
@ 341d22d7:d4e9497e
2025-05-16 05:05:50Se você está em busca de uma plataforma confiável e emocionante para se divertir, a 777ua é uma excelente opção. Com uma interface amigável, uma vasta seleção de jogos e uma experiência personalizada para cada jogador, essa plataforma tem conquistado o coração de muitos entusiastas do entretenimento digital. Neste artigo, vamos explorar a introdução da plataforma, os jogos que ela oferece e a experiência do jogador, para ajudá-lo a entender por que a 777ua está se tornando cada vez mais popular.
A 777ua é uma plataforma de entretenimento online que oferece uma experiência de usuário moderna e dinâmica. Com um design intuitivo e recursos inovadores, a plataforma foi criada para atender tanto a iniciantes quanto a jogadores experientes. O seu foco está em proporcionar uma navegação fácil, rápida e divertida, sem complicações, permitindo que os usuários se concentrem no que realmente importa: a diversão.
Ao acessar a 777ua, o jogador é recebido com uma interface bem estruturada, que facilita a exploração dos diversos jogos disponíveis. A plataforma também é otimizada para dispositivos móveis, o que significa que você pode acessar seus jogos favoritos de qualquer lugar, a qualquer momento.
Além disso, a 777ua é comprometida com a segurança dos seus usuários. Com tecnologias de criptografia de última geração, seus dados pessoais e financeiros estão sempre protegidos, oferecendo uma experiência sem preocupações para todos os jogadores.
Jogos na 777ua: Variedade para Todos os Gostos Uma das maiores atrações da 777ua é a sua extensa gama de jogos. A plataforma oferece uma variedade impressionante de opções, incluindo jogos de mesa, slots, jogos de habilidade e muito mais. A qualidade gráfica e a jogabilidade dos títulos são excepcionais, proporcionando uma experiência imersiva e emocionante.
Entre os jogos mais populares da plataforma estão os jogos de cartas, como blackjack e pôquer, onde os jogadores podem testar suas habilidades contra outros usuários ou contra a própria plataforma. Para aqueles que preferem algo mais dinâmico, as máquinas de caça-níqueis são uma ótima escolha. Com temas variados e recursos especiais, esses jogos são conhecidos pela sua jogabilidade viciante e pelas grandes oportunidades de ganho.
Além disso, a 777ua também investe em títulos de jogos de habilidade, onde a estratégia e o raciocínio lógico fazem toda a diferença. Seja você um novato ou um veterano, sempre há algo para todos na 777ua.
Os jogos são atualizados regularmente, garantindo que os usuários tenham acesso às últimas novidades do mundo do entretenimento digital. Isso significa que você nunca ficará entediado, sempre haverá algo novo para experimentar.
A Experiência do Jogador: Diversão e Comodidade Na 777ua, a experiência do jogador é a prioridade. Desde o momento em que você entra na plataforma, é claro que a 777ua se preocupa em proporcionar uma experiência de alta qualidade. A navegação simples e a organização intuitiva permitem que você encontre facilmente o que procura. Você pode jogar seus jogos favoritos com poucos cliques e aproveitar um ambiente virtual imersivo e de alta performance.
Além disso, a 777ua oferece diversas opções de pagamento, para que os jogadores possam fazer depósitos e retiradas de maneira fácil e segura. A plataforma também oferece um suporte ao cliente excepcional, com uma equipe pronta para ajudar com qualquer dúvida ou problema que possa surgir.
Outro aspecto importante da experiência do jogador na 777ua é a comunidade de jogadores. Ao interagir com outros usuários, você pode trocar dicas, estratégias e até participar de competições e eventos exclusivos. A plataforma também oferece sistemas de recompensas e promoções para valorizar ainda mais a experiência do jogador, garantindo que cada visita à 777ua seja cheia de novidades e benefícios.
Conclusão: Por Que Escolher a 777ua? A 777ua se destaca como uma plataforma de entretenimento online completa, oferecendo uma enorme variedade de jogos, segurança, e uma experiência de usuário excepcional. Seja você um novato ou um jogador experiente, a plataforma é projetada para garantir diversão, emoção e oportunidades de ganho.
Com sua interface amigável, jogos de alta qualidade e uma experiência de jogador sem igual, a 777ua está rapidamente se tornando uma das plataformas mais populares e confiáveis. Não importa o tipo de jogo que você procura, a 777ua tem algo para você. Então, não perca tempo, entre agora e comece a explorar o mundo da 777ua!
-
 @ 4fe4a528:3ff6bf06
2025-05-16 04:36:31
@ 4fe4a528:3ff6bf06
2025-05-16 04:36:31One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both no and yes. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase [wealth]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the yes part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction go ahead and harvest your crops and / or buy some bitcoin. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
-
 @ 866e0139:6a9334e5
2025-05-13 09:47:28
@ 866e0139:6a9334e5
2025-05-13 09:47:28Autor: Lilly Gebert. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wie fühlst Du dich, nachdem Du mit deinem Partner oder deiner Partnerin, oder sonst einem Menschen geschlafen hast – nachdem der Drang und die Erregung ein Ende gefunden haben? Gut – oder schlecht? Befriedigt – oder unbefriedigt? Verbunden – oder getrennt? Erfüllt – oder leer? Was geht dir durch den Kopf? Warum überhaupt geht dir irgendetwas durch den Kopf? Warum bleibst Du dich nicht in deinem Körper – in seiner noch anhaltenden Nähe zu dem Körper, mit dem Du gerade noch eins warst? Vielleicht weil Du dich davon ablenken möchtest, dass ihr gerade dies nicht wart? Dass ihr nicht «eins» wart; sondern zwei, die für einen Moment Druck abgelassen haben – ohne höheren Sinn und ohne tieferes Gefühl? Ist das der Grund, weswegen Du lieber in die Verklärungen deines Verstandes abdriftest, anstatt die gerade erlebte Verbindung noch etwas in deinem Körper nachklingen zu lassen? Ist das allgemein der Grund, weswegen Du lieber in Rationalitäten lebst? Um dir nicht eingestehen zu müssen, wie unverbunden Du wirklich bist? Wie unverbunden und allein, ohne tiefere Verbindung zu dir oder einem anderen Menschen? Ist es das? Ist es das, was Du einfach nicht wahrhaben kannst? Und weswegen Du lieber die Masse an Oberflächlichkeit suchst, um bloß nie in einer Beziehung zu enden, in der Du an deine eigene Unfähigkeit erinnert wirst, gerade dies zu sein – in Beziehung?
***
Vielleicht beginnt alle Trennung dieser Welt mit der Verwechslung von Sex und Nähe, Nähe und Liebe, als auch Liebe und Frieden. Du sehnst dich nach dem einen und jagst doch dem anderen hinterher. Wie kann das sein?
Liegt es daran, dass Du als Kind keine stabilen Beziehungen erfahren hast und diese aus dem Grund auch im Erwachsenenalter nicht leben kannst? Hast Du einst schlechte Erfahrungen mit Intimität und Nähe gemacht, aufgrund derer etwas in dir diese fortwährend verhindert, um dich zu «schützen»? Hältst Du dich selbst für nicht liebenswert und kannst deshalb auch im Außen keine Liebe annehmen? Oder hast Du Angst davor, durch die Nähe und Berührung eines anderen Menschen von etwas in dir selbst berührt zu werden, an dessen Existenz Du nicht erinnert werden möchtest?
Falls ja, warum gehst Du dann fortwährend «Beziehungen» zu anderen Menschen ein, bevor Du nicht die Beziehung zu dir selbst geklärt hast? Hast Du wirklich so sehr verlernt zu lieben und so weit vergessen, was Liebe ist, dass Du dich damit zufriedengibst? Ich glaube kaum. Und ich glaube, Du spürst das auch. Ganz tief in dir sehnt auch deine Seele sich nach einer Begegnung, in der Du nichts von dir zurückhalten musst. In der Du ganz, und damit ganz Du sein kannst.
Doch was machst Du stattdessen? Du unterdrückst diese Sehnsucht, verneinst deinen innersten Herzenswunsch nach Berührung, nach Nähe, nach Liebe. Und damit auch jedes Bedürfnis, was mit seinem ausbleibenden Ausdruck ebenfalls unterdrückt wird. Langsam, ganz langsam hörst Du auf, über deine Gefühle zu sprechen, Du hörst auf, deine Grenzen zu wahren, das zu machen, was dich dir selbst näherbringt. Auf diese Weise machst Du dich selbst nicht nur immer kleiner, Du entfernst dich auch zusehends von deiner eigenen Lebendigkeit – dem eigentlichen Schlüssel zu jeder Beziehung, die nicht von Besitz und Lustbefriedigung, sondern von Selbstsein und Nähe getragen wird.
Falsche Versprechen: Verbindung statt Symbiose
Erich Fromm war es, der mit seinem 1956 erschienenen und insgesamt über 25 Millionen Mal verkauften Werk «Die Kunst des Liebens» erstmals herausgearbeitet hat, wie zerstörerisch unsere moderne Konsumgesellschaft doch für die Art und Weise ist, wie wir Beziehungen eingehen. Nicht nur die untereinander und zu uns selbst, sondern auch die zu Tier und Natur. Liebe, so schreibt Fromm, ist allem voran eine Haltung des Seins, nicht des Habens. Es gehe nicht darum, den anderen zu besitzen oder von ihm in Besitz genommen zu werden. Nicht Verschmelzung sei das Ziel, sondern das Selbstsein mit, oder auch trotz, der anderen Person.
Ohne dieses Selbstsein, das durch den modernen Glauben, alles sei käuflich, insofern untergraben wurde, dass nun auch der Mensch und seine Beziehungen als Objekte betrachtet würden, gäbe es laut Fromm keine Nähe – und ohne Nähe keinen wahren Frieden. «Sexualität», so schreibt er, könne «ein Mittel sein, um die Isolation zu überwinden – aber sie kann auch ein Ersatz für Liebe sein.» Womit ich hinzufügen würde: Wie Sexualität ein Ersatz für Liebe sein kann, so werden heute Konsum, Sicherheit und Ablenkung zum Ersatz für wahren Frieden. Und gleich wie Nähe zur Illusion von Intimität werden kann, werden falsche Sicherheitsversprechen oft zur Maskerade des Friedens – einer Stille, die nichts heilt.
Das ist der Zustand unserer Zeit: Sexualität ersetzt Liebe, Waffen ersetzen Frieden. Doch genauso wie Sex in Wahrheit keine Liebe ersetzt, ersetzt auch ein Wettrüsten keinen Frieden. Beides täuscht Nähe und Sicherheit vor, wo eigentlich Distanz und Kälte herrschen. Von ihnen eingenommen, hältst Du die Liebe, die dein Körper imitiert, für echt, und die äußere Ordnung, die dir simuliert wird, für den Frieden, von dem Du glauben, Du würdest ihn in dir tragen. Dabei bleibt beides leer, wenn dein Herz nicht mitgeht. Da ist weder Ordnung im Außen, noch Frieden in deinem Innern. Was herrscht, ist Krieg. Innen wie außen.

Wut im Innern, Krieg im Außen
Wer Nähe meidet, verlernt Frieden. Denn Frieden beginnt dort, wo Du aushältst, was ist. Nicht im Politischen, sondern in deiner eigenen Gerichtskammer: dem Austarieren und Verhandeln der eigenen Gefühle und Bedürfnisse – dem Eingeständnis, dass am Ende nicht der Sex das Problem ist, sondern dein Umgang mit Nähe; deine Unfähigkeit, mit dir selbst in Frieden zu sein – und dies darum auch mit dem Rest der Welt nicht bist. Nenn’ es Karma, das Gesetz der Anziehung oder eine traumatische Rückkopplungsschleife; aber wo immer Du diesen Blick nicht vom Außen zurück auf das Minenfeld in dir wendest, wird sich sein Krieg solange fortsetzen, bis Du der Wut, die mit ihm in dir hochkocht, Dampf verschaffst. Ob auf konstruktive oder destruktive Weise hängt davon ab, wie früh Du sie als das erkennst, woraus sie sich speist: deine unterdrückten Gefühle.
«Das grundsätzliche Ausweichen vor dem Wesentlichen ist das Problem des Menschen.» – Wilhelm Reich
In dieser Hinsicht noch radikaler als Fromm ging Wilhelm Reich vor. Als Schüler Sigmund Freuds sah er sexuelle Unterdrückung als Wurzel aller gesellschaftlichen Gewalt. Nur wer sexuell befreit sei – im Sinne von energetisch gelöst und beziehungsfähig – könne inneren Frieden erfahren. Ginge es nach Reich, so hängt gesellschaftlicher Frieden unmittelbar davon ab, wie weit es uns gelingt, uns körperlich zu entpanzern und emotional zu öffnen. Womit sein Ansatz in der Idee gipfelte, dass die gesellschaftliche Ordnung nicht durch äußere Gesetze, sondern durch die innere Struktur des Einzelnen geprägt wird. Diametral zu Marx, demzufolge es nicht das Bewusstsein der Menschen sei, das ihr Sein bestimmt, sondern umgekehrt ihr gesellschaftliches Sein, das ihr Bewusstsein bestimmt, beschrieb Reich also, wie emotionale Blockaden im Körper verankert seien und sich dort als chronische Spannungen manifestierten. Diese Panzerungen würden nicht nur freie Gefühlsäußerung verhindern, sondern stauten auch lebendige Energie an, was zu Aggression, Entfremdung und letztlich zu kollektiver Gewalt führen könne. Frieden, so Reich, beginne nicht in politischen Institutionen, sondern in der Fähigkeit des Einzelnen, Angst und Abwehr abzubauen, sich selbst zu spüren – und andere nicht als Bedrohung, sondern als lebendige Gegenüber wahrzunehmen.
Warum wir dies scheinbar nicht mehr können, warum aber kein Weg daran vorbeiführt, über den Frieden in uns heilsame Beziehungen einzugehen, wollen wir den Frieden auch außerhalb von uns – in der Welt, folgt im zweiten Teil dieses Texts.
Lilly Gebert betreibt den Substack-Blog "Treffpunkt im Unendlichen" und schreibt regelmäßig für "die Freien" und Manova. Zuletzt erschien von ihr "Das Gewicht der Welt". Im Herbst erscheint "Sein statt Haben. Enzyklopädie für eine neue Zeit." (vorbestellbar).
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ a5ee4475:2ca75401
2025-05-16 04:20:06
@ a5ee4475:2ca75401
2025-05-16 04:20:06link #list #descentralismo #hardware
OpenSourceHardware #OSH #OSHW #Free #FOSH #Scheme #OpenSource
DIY (Do It Yourself) #modular #repairable
NoBigTech #unrestricted #antibackdoor
Certification Group:
Open Source Hardware Association - OSHWA
FOSS Software for Making Hardware
- kiCad - Electronics Design Automation Suite [info] [source]
- Blender - 2D and 3D designs [info] [source]
Energy
- OSSI - Open Source Solar Inverter [source]
- OpenMI - Open source grid-tied photovoltaic micro-inverter [source]
Component
Microcontroller
Transmission
- MOD-WIFI-ESP8266 - OSHWA certified Wifi module [source]
- ESP32-EVB - OSHWA certified Wifi module [source]
Microcomputer - OLinuXino - OSHWA certified Linux Board based on Raspberry Pi [info] [source] - Banana Pi - Linux Board based on Raspberry Pi [info] [CAD] [source]
Partially OSHW
Microcomputer
- Raspberry Pi - Everything open except the GPU and ARM CPU chip [Schematic] [source]
Hardwallet
Closed Scheme
- Krux Yahboom K210 - DIY Hardware Wallet with Arduino [source1] [source2] [source3] [source4]
Computer
Laptop
Phones
Closed Scheme
(with Linux OS support)
- Librem 5 - Free software and Security switch
- Fairphone 2 (till 5) - Easily Repairable
- Pinephone (and Pro) - Easily Repairable
- Shiftphone 8 [preorder] - Easily Repairable
- Dragonbox Pyra - Handheld computer
Custom Phones
Arduino
- Arduinophone - Touchscreen phone with Seeeduino GPRS [info] [source]
- MIT DIY Cellphone - Segmented display [source]
- 3G DIY Cellphone - 3G cellphone based on GSM/GPRS Arduino shield and damellis’ MIT DIY Cellphone [source]
- Circuitmess Ringo (antes MakerPhone) - Educational DIY mobile phone [source]
Raspberry Pi
- PiPhone - Raspberry Pi based Smartphone [source]
- ZeroPhone - Raspberry Pi Zero Linux phone with Arduino [info] [source]
- OURphone - DIY Linux Smartphone without bigtechs [info] [source]
OSHWLab Motherboard
- Paxo Phone - Basic Modular phone with PaxOS [info] [source]
3D Printer
House
Architecture and design
- WikiHouse – project to design and build houses
- OpenStructures - design from furniture to house and vehicles
Domotics (Home automation)
Robotics
- Berkeley Humanoid Lite - Printable Humanoid Robot [source]
Defense and guns
- FGC-9 MKII - 3D-printable semiautomatic pistol caliber carbine
- WarFairy Charon - 3D-printable AR-15 lower receiver [info]
Medical
- OpenBionics Prosthetic-Hands - Design of open-source prosthetic hand [source]
- Open source Leg - [info] [scheme] [source]
- OpenLung - Open source ventilator (breathing apparatus) [source]
- Makair - Open-source ventilator (breathing apparatus) [source]
-
 @ 866e0139:6a9334e5
2025-05-13 09:36:08
@ 866e0139:6a9334e5
2025-05-13 09:36:08Autor: René Boyke. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Recht gilt als Fundament für Frieden. So predigen es die Lehrer in der Schule und die Professoren an den Universitäten. Mit der – theoretischen – Funktionsweise von Gerichten und deren Streitschlichtungsfunktion wird die Notwendigkeit und Verträglichkeit eines staatlichen Gewaltmonopols hergeleitet. Die Behauptung: Ohne staatliches Recht herrsche Chaos, das Recht des Stärkeren. Das Gedankenspiel des fiktiven Naturzustands, mit dem Hobbes bereits seinen übergriffigen Leviathan rechtfertigen konnte, überzeugt die meisten.
Mit Recht?
Larken Roses Kritik am Gewaltmonopol
Der libertäre Denker Larken Rose („The Most Dangerous Superstition“, deutscher Titel: „Die gefährlichste aller Religionen“, 2018) hält dagegen. Er argumentiert, staatliches Recht sei Ausdruck von Autorität und Zwang und institutionalisiere damit Gewalt. Und in der Tat: Der Staat nimmt für sich kein Friedensmonopol in Anspruch, sondern ein Gewaltmonopol.
Rose verdeutlicht, dass staatliches Recht auf Zwang basiert: Gesetze und Verordnungen können als Drohungen interpretiert werden, die mit Sanktionen, Strafen, Gefängnis oder mancherorts mit Todesstrafe durchgesetzt werden. Für Rose ist der Staat eine Gruppe von Räubern, denen durch den tief verwurzelten Glauben an Autoritäten ein legitimer Anstrich verpasst wird. Diese „Bande“ schaffe ständig Konflikte, etwa durch inszenierte Gefahren, aber auch durch Gesetze. So seien Steuergesetze seiner Meinung nach „legitimierter Raub“, die Widerstand provozieren und damit Unfrieden. Politiker würden sich nach Belieben eigene Regeln schaffen und selbst bestimmen, was gut und was schlecht sei.
Steigt Ihnen angesichts solcher Behauptungen bereits die Röte der Empörung ins Gesicht?
Doch können Sie ihm widersprechen? Können Sie leugnen, dass staatliche Gewalt von Politikern, Apparatschiks und Staatslenkern zum eignen Vorteil eingesetzt wird? Und müssen nicht auch Sie eingestehen, dass daraus Konflikte und Unfrieden entstehen? Hat Rose also Recht?
Rechtsstaatliche Defizite in Deutschland
Um solchen Missbrauch des Gewaltmonopols zu verhindern, gibt es die Gewaltenteilung: die Aufteilung staatlicher Macht in Legislative, Exekutive und Judikative sind Grundpfeiler der Demokratie, in Deutschland verankert im Grundgesetz. Damit diese Gewaltenteilung funktioniert, setzt sie unabhängige Institutionen voraus, insbesondere eine Trennung von der Politik. Haben wir diese in Deutschland?
Unsere Legislative leidet unter Koalitionsdisziplin und Fraktionszwang. Abgeordnete stimmen zu oft nach Parteilinie, nicht nach individuellem Gewissen. Unsere Judikative ist stark politisiert. So werden die Richter des Bundesverfassungsgerichts von einem Wahlausschuss gewählt, der aus Bundestags- und Bundesratsmitgliedern besteht, was eine Einladung für parteipolitische Deals ist – ganz zu schweigen davon, dass die Richter den Parteien oft eng verbunden sind bzw. oft selbst Politiker waren (siehe beispielhaft: Stephan Harbarth, Peter Müller, Christine Hohmann-Dennhardt) und von den regelmäßigen gemeinsamen Edeldiners zwischen Spitzen der Exekutive und der Judikative, die Sie und ich als Bürger zwar bezahlen aber nicht daran teilnehmen dürfen, ausgeschlossen werden, ganz zu schweigen. Besonders kritisch: Unsere Strafverfolgungsbehörden können durch die Weisungsgebundenheit der Staatsanwaltschaften politisch gesteuert werden. Dass der Verfolgungsdruck auf Regierungskritiker immer härter wird, ist mittlerweile offenkundig. Der Deutsche Richterbund forderte erst vor wenigen Tagen einen besseren Schutz der Justiz vor autoritären Kräften. Und auch bei der Exekutive sind die Mängel offensichtlich: So sollen die Behörden eigentlich die Gesetze ausführen, aber diese Anwendung ist allzu oft selektiv und interessengeleitet. Sich daran zu gewöhnen, dass ehemalige Regierungsmitglieder in Führungspositionen von Unternehmen wechseln und damit Interessenkonflikte heraufbeschwören, ist ebenfalls ein Zeichen eines kranken Rechtsstaats.
Und wie sieht es international aus?
Internationale rechtsstaatliche Defizite
In meinem letzten hier veröffentlichten Beitrag beleuchtete ich den Papiertiger des praktisch in Stein gemeißelten völkerrechtlichen Gewaltverbots. Man beruft sich darauf, wenn es einem nützt, und ansonsten ignoriert man es oder bemüht umständliche Ausflüchte, warum es nicht greife. Ähnliches lässt sich beim Internationalen Strafgerichtshof beobachten: Die Staaten, die die heißesten Kandidaten für Kriegsverbrechen sind, werden gar nicht erst Mitglied, und die übrigen folgen seinen Regeln nur, wenn es opportun ist. So hat der IStGH zwar einen Haftbefehl gegen Benjamin Netanjahu erlassen, aber er kann unbeirrt nach Ungarn reisen, obwohl dieses hätte vollstrecken müssen. Es darf meiner Meinung nach aber auch stark bezweifelt werden, ob Deutschland einen Haftbefehl gegen Netanjahu vollstrecken würde. Ein weiteres Beispiel völkerrechtswidrigen Handelns: Die Sanktionen gegen Russland.
Ganz unempört müssen wir leider feststellen: Unsere Schutzmechanismen, den Gewaltmissbrauch zu verhindern, sind mittlerweile arg durchlöchert und angeschlagen. Kann Larken Rose helfen?
Kann Larken Rose helfen?
Rose sieht Steuern als „legitimierten Raub“. In der Tat werden auch in Deutschland etwa die Abgaben für den öffentlich-rechtlichen Rundfunk falls nötig mittels Gerichtsvollziehern und Haft erzwungen. Ohne Frage handelt es sich dabei um Gewaltausübung, die konfliktträchtig ist. Doch der Staat legitimiert seine Gewaltausübung selbst. Polizeieinsätze gegen Kritiker der Corona-Maßnahmenpolitik erfolgten z.B. mittels grober Gewalt, nämlich Wasserwerfern und Pfefferspray gegen die Demonstranten. Auch der Europäische Gerichtshof für Menschenrechte verurteilte Deutschland bereits mehrfach wegen übermäßiger Polizeigewalt. Das sind Beispiele für Roses Vorbringen, dass der Staat Gewalt institutionalisiert, um Gehorsam zu erzwingen – und das erzeugt und verschärft Spannungen und Konflikte.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
\ Rose betont, dass staatliches Recht immer auf Zwang basiert. In Deutschland führt die Nichtbeachtung von Gesetzen – etwa bei Verkehrsdelikten – zu Bußgeldern, Führerscheinentzug oder Haft. Im Völkerrecht erzwingen Sanktionen, wie die gegen Russland, wirtschaftlichen Druck, der für Rose ebenfalls Gewalt ist. Diese Mechanismen bestätigen seine Sicht, dass der Staat Gewalt als Standardwerkzeug nutzt.
Vielleicht hat Ihre eventuell aufgetretene Empörungsröte die Blässe einsichtiger Scham angenommen. Wenn ja, ist das nicht ganz unbegründet. Rose hat völlig Recht damit, dass die buchstäblich gewaltigen Möglichkeiten des Staates gefährlich sein können. Und er hat recht damit, dass blindes Vertrauen darauf, dass Autoritäten mit dieser Gewalt schon maß- und verantwortungsvoll umgehen werden, völlig fehl am Platze ist.
Und auch eine andere zentrale Frage ist gerechtfertigt: Wenn der Staat die Legitimation seiner Macht daraus bezieht, dass die Bürger ihm diese Macht übertragen, wie kann es dann sein, dass der Staat Macht ausübt, die ein einzelner Bürger weder jemals innehat noch innehatte? Ein Paradoxon.
Selbstverantwortung als Heilmittel für den Rechtsstaat
Rose setzt daher statt eines Staates auf Freiwilligkeit und Selbsteigentum. Er betont, dass „Menschlichkeit Freiwilligkeit bedeutet“. Jede Interaktion sollte auf gegenseitigem Einverständnis beruhen, ohne Zwang durch Gesetze oder staatliche Institutionen. Einen Impfzwang schlösse dies also aus. Aber auch einen Tötungszwang in Form eines Kriegsdienstes, bei uns verbal zum „Wehrdienst“ aufgehübscht. Jeder Mensch habe das Recht, über sein Leben, seinen Körper und sein Eigentum zu bestimmen, ohne dass eine „Autorität“ eingreift.
Das klingt gut, aber müsste dieses „Selbsteigentum“ nicht auch wieder durch ein irgendwie geartetes Rechtssystem abgesichert werden? Und besteht nicht die Gefahr, dass statt der Polizei dann ein privates Sicherheitsunternehmen ein neues Gewaltmonopol erschafft? Offensichtlich ist eine völlig widerspruchsfreie Antwort auf das rechtsstaatliche Dilemma nicht so leicht zu finden.
Rose fordert zudem, dass Menschen unmoralische Gesetze ignorieren und aktiv Widerstand leisten, von passivem Ungehorsam bis hin zu gewaltsamen Aktionen, je nach Unterdrückungsgrad. Er sieht dies als Mittel, um die Illusion der staatlichen „Autorität“ zu brechen und Gewalt zu reduzieren.
Bei einigen mag hier bereits wieder die Empörungsröte emporsteigen, aber vielleicht hilft dagegen die Vergegenwärtigung folgender Fragen: War der Widerstand eines Mahatma Gandhi dem Recht eher dienlich oder eher schädlich? Und war der mutige, aber rechtswidrige Ungehorsam Rosa Parks’ eher wünschenswert als nicht? Hat ihr Widerstand zu mehr oder weniger Freiheit beigetragen? Haben uns die rechtswidrigen Offenlegungen Edward Snowdens und Julian Assanges nicht die Augen geöffnet, welche Verbrechen durch demokratische Staaten begangen werden?
Und ist die von Larken Rose eingeforderte Selbstverantwortung und sein Aufruf, dem eigenen Gewissen zu folgen, anstatt „Autorität“ zu gehorchen, nicht genau das Antiserum gegen einen übergriffigen, ja diktatorischen Staat, wie etwa unter der Naziherrschaft?
Selbt als Jurist wird man Rose in vielen Punkten zustimmen müssen und einsehen, dass es in vielen Fällen der Glaube an die Autorität ist, der erst das monströse Unrecht ermöglicht, dessen Zeugen wir sind.
Ich selbst halte es für sehr zweifelhaft, ob man wie Rose daraus die Abschaffung des Staates herleiten kann oder muss.
Nicht zweifelhaft ist hingegen, dass wir eine Stärkung individueller Selbstverantwortung brauchen. Kein Warten auf einen Erlöser, auf eine Partei. Aus dieser Selbstverantwortung heraus folgt die Ausbesserung der gezeigten – auch bei uns vorhandenen – rechtsstaatlichen Defizite.
Recht ohne individuelle Selbstverantwortung führt unweigerlich zu den genannten rechtsstaatlichen Konflikten und damit zu Unfrieden und Gewalt. Recht mit Selbstverantwortung kann hingegen zu einem friedlichen Rechtssystem führen.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 502ab02a:a2860397
2025-05-16 01:57:09
@ 502ab02a:a2860397
2025-05-16 01:57:09หลังจากที่เราคุยกันไปแล้วเกี่ยวกับ milk 2.0 ว่ามี Perfect Day ที่เป็นหัวหาดด้านเวย์ที่ไม่มีวัว แล้วเราก็มี Formo หัวหาดด้านชีสที่ไม่มีวัว ซึ่ง 2 เจ้านี้ต่างมีสิ่งที่แต่ละคนขาดอยู่ นั่นคือ เจ้านึงขาดเคย์ซีนเด็ดๆ อีกเจ้าไม่ได้มีเวย์ที่เจ๋งพอ และแน่นอนครับ ทุกปัญหาย่อมมีธุรกิจเกิดขึ้นมาเพื่อแก้ปัญหา
วันนี้เราจะมาพบกับอีกผู้เล่นนึง ที่แก้ปัญหาทั้งหมดด้วยการ สร้างสิ่งที่ขาดขึ้นมาใหม่ ตามคาแรคเตอร์ของ "มังกรจีน" ใช่ครับ เราเคยคิดว่าโลกเทคโนโลยีมีแต่ฝรั่งเป็นเจ้าสำนัก แต่ตอนนี้ทุกมุมโลกต่างแย่งชิงอนาคตกันหมด ไม่มีใคร slow life อีกต่อไปแล้ว
เพราะในโลกที่นมไม่ใช่นม ชีสไม่ใช่ชีส และวัวไม่จำเป็นต้องกินหญ้า เรากำลังเข้าสู่ยุคที่ “นม 2.0” กำลังถูกออกแบบใหม่… ด้วยจุลินทรีย์ บริษัทหนึ่งจากจีนชื่อว่า Changing Biotech กำลังจะทำให้มันกลายเป็นความจริง ด้วยเป้าหมายที่ไม่ธรรมดา เปลี่ยนโครงสร้างนมทั้งระบบ โดยไม่ต้องใช้วัวแม้แต่ตัวเดียวเช่นกันครับ
หลายคนอาจคุ้นชื่อ Perfect Day บริษัทอเมริกันที่เป็นรายแรก ๆ ในโลกที่สามารถผลิตเวย์โปรตีนจากเชื้อราแบบไม่ใช้สัตว์ ด้วยเทคโนโลยี precision fermentation ซึ่งตอนนี้มีแบรนด์ไอศกรีม เนย และโยเกิร์ตของตัวเองกระจายขายในห้างทั่วอเมริกา แต่ Changing Biotech กลับเลือกเดินอีกเส้นทาง เส้นทางที่อาจลึกกว่า แยบยลกว่า และอาจ “กลืน” ตลาดในเอเชียโดยที่ผู้บริโภคไม่รู้ตัว
แน่นอนว่าสิทธิบัตรการค้นคว้าต่างๆมีมูลค่าสูง เบื้องหลังเทคโนโลยีของ Changing Biotech ไม่ใช่แค่การเลียนแบบ แต่คือการ สร้างใหม่ตั้งแต่ระดับจุลินทรีย์ พวกเขาไม่ได้แค่ยืมเชื้อราสำเร็จรูปอย่าง Trichoderma มาใส่ยีนโปรตีน แต่ “เพาะสายพันธุ์จุลินทรีย์ขึ้นมาเอง” เพื่อควบคุมการผลิตโปรตีนอย่างมีประสิทธิภาพ ทั้งเวย์และเคซีน ซึ่งเป็นสององค์ประกอบหลักของนมแท้ นี่คือสิ่งที่แม้แต่ Perfect Day เองก็ยังไม่ได้โฟกัสเต็มตัว เพราะยังผลิตแต่เวย์เพียงอย่างเดียว Perfect Day ใช้ Trichoderma reesei เชื้อราชนิดที่วงการอาหารใช้กันมานานในการหมักเวย์โปรตีน เชื้อราชนิดนี้ปลอดภัย และได้รับการอนุมัติให้ใช้ในอาหารในหลายประเทศ แต่ Changing Biotechกลับล้ำไปอีกขั้น พวกเขาไม่ได้ยืมของใครมาใช้ แต่ 'สร้างจุลินทรีย์แพลตฟอร์มของตัวเอง' (customized microbial chassis) และมี ความสามารถด้าน strain engineering แบบ in-house ซึ่งทำให้พวกเขาควบคุมประสิทธิภาพการผลิต และลดต้นทุนได้แบบลึกสุดใจไม่ต้องซื้อให้เปลืองครับ
การผลิตเคซีนได้ในระดับอุตสาหกรรมหมายถึงอะไร? มันหมายถึง ชีสที่ยืดได้จริง หลอมได้จริง และ “เนื้อสัมผัสแบบชีสแท้” ที่แบรนด์ plant-based ยังเลียนแบบไม่ได้ และนั่นคือกุญแจสำคัญที่ทำให้ Changing Biotech ถูกจับตามองในวงการ alt-dairy ว่าอาจเป็น “Formo เวอร์ชันจีน” ที่จะครองตลาดชีสทั้งเอเชีย Changing Biotech ตั้งเป้าผลิต ทั้งเวย์และเคซีน ซึ่งทำให้สามารถพัฒนาผลิตภัณฑ์ที่มี “เนื้อสัมผัสและการหลอมตัวแบบชีสแท้จริง” ได้ครบวงจรกว่า โดยเฉพาะพวก mozzarella และ cheddar ที่ต้องพึ่งเคซีนในการขึ้นรูป จุดนี้คือกุญแจสำคัญในการตีตลาด “ชีสพรีเมียม” ที่วัตถุดิบจากพืชทำไม่ได้
แต่ที่น่าจับตายิ่งกว่านั้นคือ ทุนและเครือข่ายในประเทศ ที่ Perfect Day ไม่มี แม้ฝั่งอเมริกาจะมีเงินลงทุนหลักเกิน 800 ล้านดอลลาร์ แต่ฐานการผลิตอยู่ในสหรัฐฯ ซึ่งทำให้มีต้นทุนสูงกว่า ส่วนในจีน Changing Biotech ได้รับแรงหนุนจากรัฐบาลจีนผ่านนโยบายสนับสนุน “เทคโนโลยีอาหารแห่งอนาคต” และมีแนวโน้มว่าจะได้สิทธิพิเศษด้าน supply chain และการผลิตระดับอุตสาหกรรมภายในประเทศจีน ซึ่งเป็น ตลาดที่ Perfect Day เจาะยาก รวมถึงได้รับแรงหนุนจากกองทุนอาหารแห่งอนาคตอย่าง Bits x Bites ที่ทำงานร่วมกับรัฐบาลจีนโดยตรงในแผน 5 ปีด้านเทคโนโลยีอาหาร เป้าหมายชัดเจน ลดการพึ่งพาโปรตีนจากสัตว์ และสร้างระบบนมแห่งชาติแบบไร้สัตว์
โมเดลของพวกเขาต่างกับ Perfect Day ที่เน้นการสร้างแบรนด์ (เช่น Brave Robot, Modern Kitchen) และขายตรงกับผู้บริโภค แต่ Changing Biotech ไม่ใช่การตั้งแบรนด์ขายแข่งกันในห้าง แต่เป็น “ผู้อยู่เบื้องหลัง” ของแบรนด์ใหญ่อื่น ๆ โดยซัพพลายโปรตีนให้แบบ OEM ให้กับผู้ผลิตอาหารในจีน ซึ่งทำให้สามารถฝังตัวเข้า supply chain ของอุตสาหกรรมนมจีนได้เงียบ ๆ แต่ทรงพลัง โมเดลนี้คล้ายกับ Givaudan หรือ DSM ที่เน้นการเป็นผู้อยู่เบื้องหลังผลิตภัณฑ์แบรนด์อื่น
จะเรียกว่า Perfect Day คือ Apple ของนมไร้สัตว์ก็ได้ แต่ Changing Biotech กำลังเป็น Huawei ของอุตสาหกรรมนม ที่สร้างเทคโนโลยีขึ้นเองทั้งระบบ ควบคุมเบ็ดเสร็จตั้งแต่เชื้อจุลินทรีย์ยันขั้นตอนผลิต แล้วส่งต่อให้แบรนด์อื่นใช้แบบครบวงจร
ในวันที่ผู้บริโภคในจีนตักไอศกรีม “จากครีมจุลินทรีย์” หรือกินชีส “ไม่มีสัตว์เจือปน” อาจไม่มีใครรู้เลยว่าเบื้องหลังของรสสัมผัสนั้น คือจุลินทรีย์จากโรงงานที่พัฒนาโดย Changing Biotech ทั้งสิ้น
คำถามคือ แล้วมันดีต่อสุขภาพแค่ไหน? มันดีกว่าการรีดนมจากวัวจริง ๆ หรือแค่ดีต่อ narrative ของคนเมืองที่อยาก feel good แค่นั้น?
แล้วถ้าทุกประเทศเดินตามเทรนด์นี้ ใครกันแน่จะเป็นเจ้าของ “สูตรโปรตีนแห่งอนาคต” ที่ครองอำนาจอาหารของทั้งโลก?
คำตอบอาจไม่ได้อยู่ในกล่องนม แต่ในห้องแล็บจุลินทรีย์ของบริษัทที่เราไม่เคยได้ยินชื่อ
ยิ่งเราคุยกันนานเท่าไร ยิ่งรู้สึกแล้วใช่ไหมครับว่า อาหารอนาคต ไม่ใช่อาหารที่จะเกิดขึ้นในอนาคต แต่เป็น อาหารที่เราจะถูกครอบงำในอนาคต ซึ่งเริ่มไปแล้ว . . . วันนี้
นึกภาพวันที่ทุกคนล้วนรังเกียจนมจากวัว แล้วยินดีโอบกอดรับนมจากจุลินทรีย์ ด้วยความยินดีปรีดา
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ b4403b24:83542d4e
2025-05-16 00:32:13
@ b4403b24:83542d4e
2025-05-16 00:32:13To celebrate the #BitcoinPizzaDay - I'm offering a full ticket pass for the BTC conference in Vegas with a good discount. It includes the following perks:
- Admission to Days 2 and 3 of Bitcoin 2025
- Access to Main Stage, Open-Source Stages, and more featuring top speakers
- Entry to the world’s largest Bitcoin Expo Hall
- Access to the Bitcoin Conference App
Does not include access to Code & Country Industry Day
If interested comment your contacts so that we can get in touch.
https://stacker.news/items/981227
-
 @ 5490af12:d4710677
2025-05-16 00:28:35
@ 5490af12:d4710677
2025-05-16 00:28:35| | | ------------------------------------------------------------------------- | | bitcoinmetronome.com | | cornjoin.com | | decentralisedvalueexchange.com | | decentralizedvalueexchange.com | | memeswaps.com | | bitcoinculture.org |
-
 @ 472f440f:5669301e
2025-05-16 00:18:45
@ 472f440f:5669301e
2025-05-16 00:18:45Marty's Bent
It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
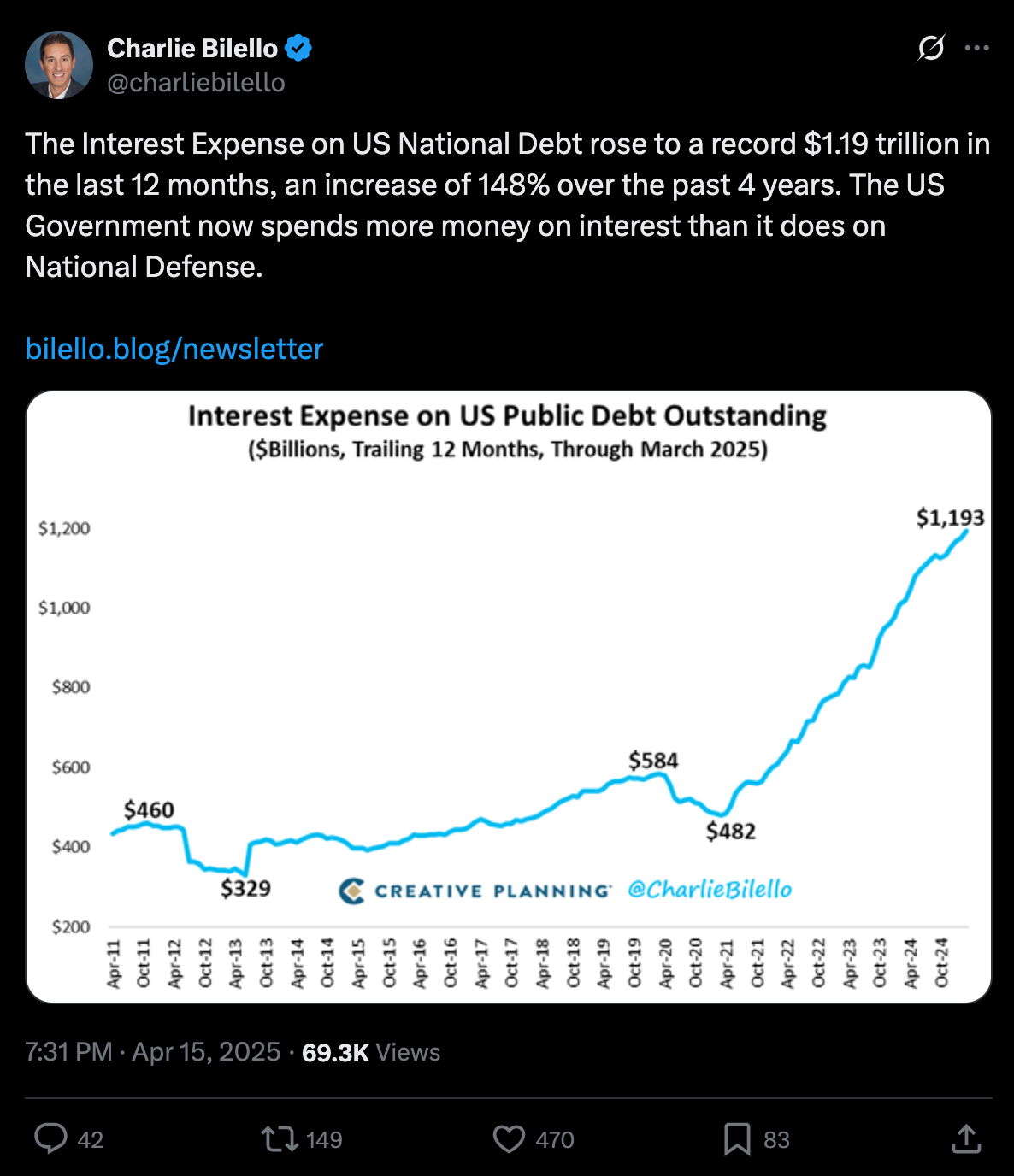
via Charlie Bilello
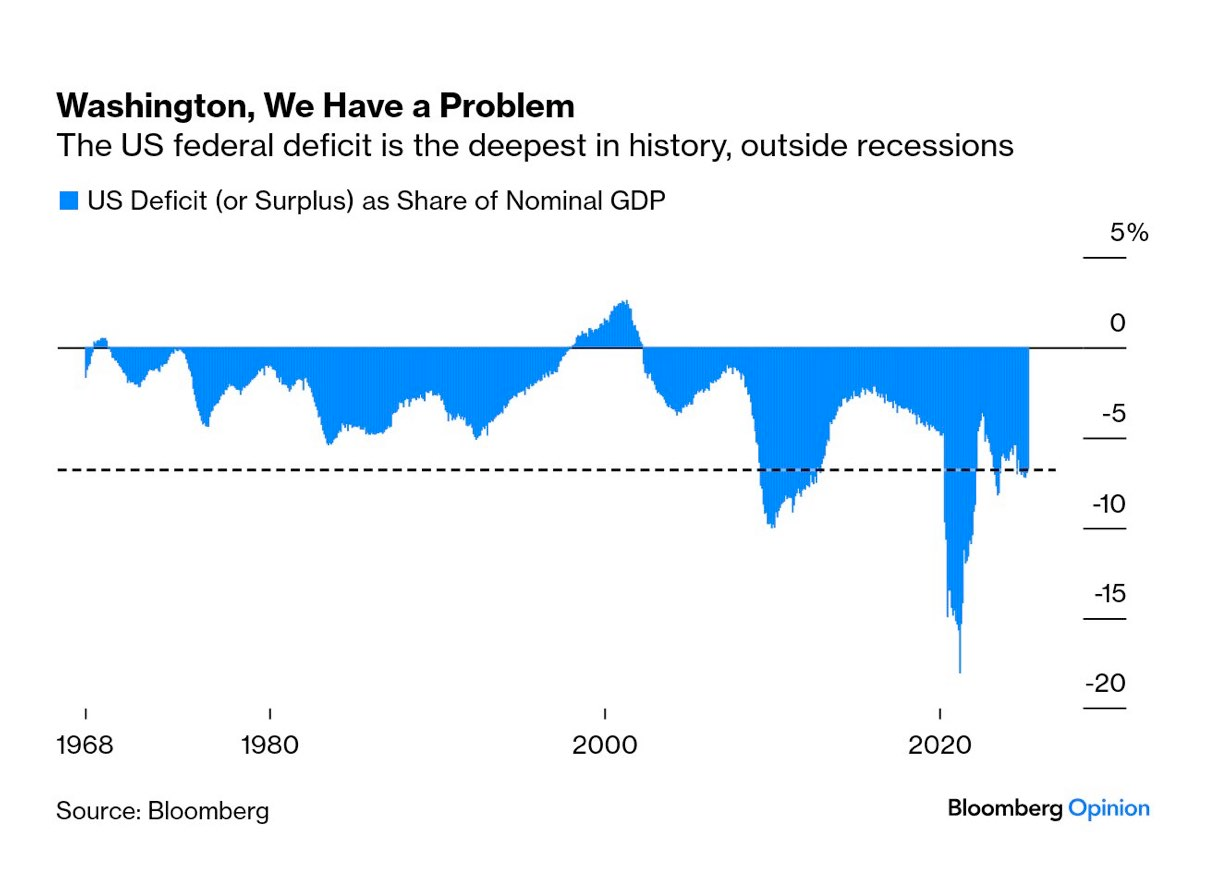
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
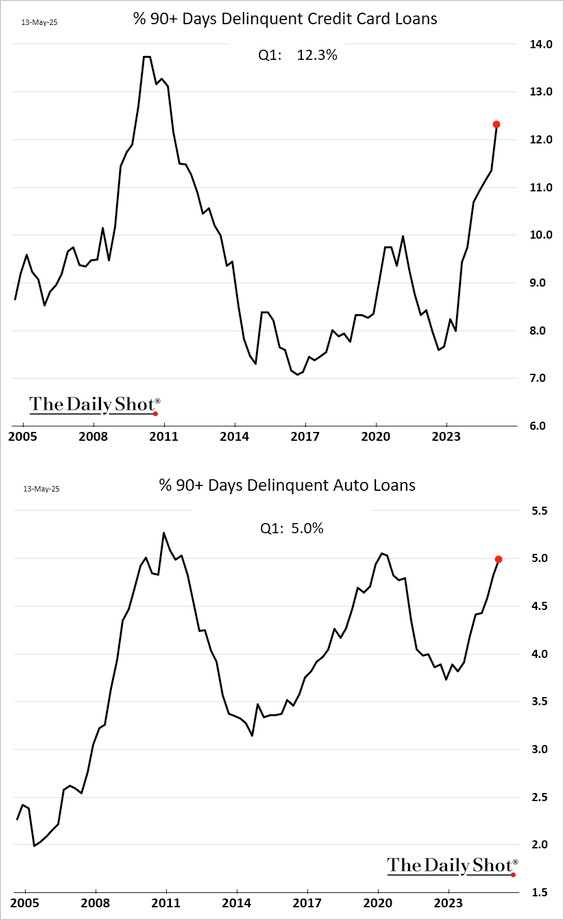
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ c9badfea:610f861a
2025-05-15 23:51:35
@ c9badfea:610f861a
2025-05-15 23:51:35- Install SDAI (it's free and open source)
- Launch the app, and allow notifications when prompted
- Complete the introduction to get started
- Set Local Diffusion Microsoft ONNX as provider
- In the configuration step, Download a model (such as Real Vision) and wait for the process to finish
- Once the model is downloaded, tap on it and then select Setup
- You can now create images offline by entering a Prompt and tapping 🪄 Imagine
ℹ️ Download the tracking-free FOSS variant
ℹ️ Internet connection is only required for the initial model download
ℹ️ To speed up image generation, consider reducing the image size (e.g. 256x256)
-
 @ 866e0139:6a9334e5
2025-05-12 10:41:33
@ 866e0139:6a9334e5
2025-05-12 10:41:33Autor: Bastian Barucker. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
John Lennon besang in seinem weltberühmten Lied „Imagine“ die fast unvorstellbare Utopie einer Welt, in der es keinen Grund mehr zu töten gäbe und die Menschen in Frieden zusammen leben. Die enorme Resonanz und Verbreitung dieser Zeilen zeigt den Wunsch fast aller Menschen nach Frieden. Wie Lennon zu diesen Zeilen kam, ist ein Hinweis darauf, dass es dazu neben geopolitischen Analysen und deren Verbreitung durch eine nicht eingebettete und freie Presse vielleicht noch etwas braucht: Schattenarbeit – ein bewusstes Hinwenden zu den eigenen Tiefen der Persönlichkeit, dem inneren Tiefenstaat.
Was ist der Tiefenstaat?
Mit dem Begriff Tiefenstaat verbinde ich Strukturen, die Edward Bernays bereits vor knapp 100 Jahren in seinem Grundlagenwerk „Propaganda“ beschrieb. Im Vorwort schreibt er: „Organisationen, die im Verborgenen arbeiten, lenken die gesellschaftlichen Abläufe. Sie sind die eigentlichen Regierungen in unserem Land.“ Er verwendet diesbezüglich auch das Wort „Schattenkabinett“. Im Bereich der Persönlichkeitsentwicklung wird der Begriff „Schattenarbeit“ dafür verwendet, unbekannte, aber einflussreiche Anteile des eigenen Selbst zu entdecken und zu integrieren.
Lennon begab sich in den 70er Jahren des letzten Jahrhunderts auf die Reise zu sich selbst. Sein Weg führte ihn zum Psychologen Dr. Arthur Janov, der Menschen mithilfe der von ihm entwickelten Primärtherapie dabei begleitete, sich ihrer primären Prägungen und frühkindlichen Traumatisierungen bewusst zu werden und abgespaltenen Schmerz wieder zu erleben, um sich davon zu befreien. Entgegen stark kognitiv geprägter Ansätze wie der Gesprächstherapie steht bei dieser Art der Therapie Gefühlsausdruck im Vordergrund. Janov selbst schreibt dazu: «Die Krankheit ist die Verleugnung des Fühlens, und das Heilmittel ist das Fühlen.»
Auch der Psychologe und Psychotherapeut Franz Ruppert beschäftigt sich intensiv mit dem Fühlen als einem möglichen Weg, eine Traumatisierung aufzuarbeiten. Er schreibt Folgendes über die Bedeutung des Fühlens in seinem Buch „Wer bin ich in einer traumatisierten Gesellschaft“: „Denn letztlich können nur über das Ausdrücken von Gefühlen die fragmentierten psychischen Strukturen wieder zu einer Einheit zusammenfinden.“
Lennon war es möglich, die immense Menge an Schmerz zu entdecken, die er verborgen in sich trug, und er erkannte dabei, welche Verhaltensweisen und Bewältigungsstrategien damit verbunden waren. Laut Lennon ist „Unser Schmerz der Schmerz, durch den wir die ganze Zeit gehen. Du wirst in Schmerz hineingeboren, und wir befinden uns meist im Schmerz. Und ich glaube, je größer der Schmerz ist, umso mehr Götter brauchen wir.“
Die Schilderungen von John Lennon decken sich mit den Erfahrungen meiner Selbsterfahrung und meiner mittlerweile über 10 Jahre langen Begleitungsarbeit in der durch den Schweizer Willi Maurer entwickelten Gefühls- und Körperarbeit.
Auch in dieser Arbeit geht es darum, abgespaltenen Schmerz langsam und über viele Jahre aus dem Schatten in das Bewusstsein zu integrieren, um nicht weiter von ihm unbewusst beeinflusst zu werden. Hunderte Male habe ich Menschen ihnen vorher unbekannten Hass, tiefe Trauer, unendliche Ohnmacht, starke Hilflosigkeit, aber auch Freude, tiefe Geborgenheit, Liebe und Friedfertigkeit entdecken und ausleben sehen. Selber habe ich mich nach einem einjährigen Aufenthalt in der nordamerikanischen Wildnis, bei dem es darum ging, so ehrlich wie möglich miteinander umzugehen, ausführlich meiner Selbsterfahrung gewidmet und dabei Intensitäten von Schmerz, aber auch Zufriedenheit entdeckt, die mir nicht vorstellbar erschienen.
Der Krieg in uns
Fast immer zeigte sich in den begleiteten Prozessen, dass die im Alltag, in der Partnerschaft oder in der Familie angerührten Gefühle aus der eigenen frühen Kindheit stammten. Innere, überfordernde „Kriege“ und Übergriffigkeiten, die auch das Leben im Außen zum Krieg werden ließen, erwachten zum Leben und durften endlich Ausdruck finden. Schlussendlich zeigte sich meist, dass es einen friedlichen Umgang mit der aktuellen Situation gibt, wenn die Altlast „entsorgt“ beziehungsweise kompostiert, also gefühlt und integriert wurde.
Franz Renggli beschreibt diese Psychodynamik in seinem Buch Verlassenheit und Angst – Nähe und Geborgenheit in Bezug auf Partnerschaft wie folgt:
„Die Erfahrung aller meiner Paarbegleitungen zeigt nun: Wenn nach der ersten Verliebtheit langsam der „Alltag“ in eine Beziehung einkehrt, neigen beide Partner immer mehr dazu, ihre Schattenseiten, ihre alten und frühen Verletzungen auch in der Beziehung zuzulassen. Je sicherer die Grenzen sind, desto vertrauensvoller dürfen diese frühen Schmerzen gespürt und erfahren werden. Wir „steigen dann wieder ab“ in unsere ursprüngliche Hölle der Verlassenheit, in die frühkindlichen Prägungen, wie ich sie hier beschrieben habe. Nur: die Hölle sind dann nicht länger die Eltern, sondern jetzt der Partner oder die Partnerin! Vielleicht könnte ich sie oder ihn umbringen vor Enttäuschung und Wut, weil er/sie mich so sehr verletzt hat. Und damit kann sie beginnen, die Heilung der alten Wunden in der Paarbeziehung! Aber nur dann, wenn wir bereit sind, unsere alten verletzten Gefühle wirklich zu spüren und zuzulassen. Und wenn wir zu diesem Schritt bereit sind, dann können wir auch gleichzeitig empfinden und wissen: Das sind unsere ureigensten alten Verletzungen, welche wir seit der Kindheit in uns tragen – ein Partner mit seinen Worten und seinem Verhalten ist nur der Auslöser unseres alten Schmerzes, ein harter Spiegel unserer alten Wunden! Wir alle haben unsere Partner entsprechend gewählt, damit wir in unseren Grundfesten immer wieder – neben allem Glück, das wir mit ihnen erleben und teilen dürfen – auch erschüttert werden.“
Diese wiederkehrenden Erschütterungen werden auch Reinszenierungszwang genannt und lassen Menschen immer wieder dieselben misslichen Lagen (mit)erschaffen, die ihnen Leid zufügen. Willi Maurer beschreibt diese Dynamik in einem sehr lesenswerten Artikel mit dem Titel „Die verschüttete Quelle des Friedens“ wie folgt: „Die Spirale der Gewalt zeigt, dass wir andern Menschen das antun, was uns selbst widerfahren ist. Doch ohne Selbsterforschung bleiben wir blind gegenüber der tief in uns verdrängt liegenden Wahrheit.“
Diese Reinszenierung ist gleichzeitig jedoch eine immer wiederkehrende Chance, sich der Ursache dieser Dynamik zuzuwenden. Das geschieht dann, wenn die Person sich als Erschaffer oder Erschafferin und nicht als reines Opfer der Umstände versteht und beginnt, die volle Verantwortung für das eigene Leben zu übernehmen.
Vor einigen Jahren brachte ich den Prozessbegleiter Willi Maurer und den Friedensforscher Dr. Daniele Ganser zu einem Gespräch zusammen, weil ich der Ansicht war, dass beide Friedensarbeit aus verschiedenen Perspektiven leisten. Es war eine Wohltat, zu erleben, wie Ganser durch die sehr authentischen Schilderungen Maurers zu ahnen begann, dass es eine Verbindung zwischen weltweiten Kriegen und frühen Erfahrungen geben kann. Was hat der Soldat, Politiker oder Geostratege erlebt, dass er in der Lage ist, Krieg zu befördern, zu verursachen oder auch nur zu dulden?
Vielleicht ist die immer wiederkehrende Kriegsbereitschaft und Kriegslust elitärer Kreise neben der wahrscheinlich frühkindlich erzeugten Gier nach Macht, Einfluss und Geld ebenfalls ein gesellschaftlicher Reinszenierungszwang. Die inneren Zerwürfnisse und Kriege müssen quasi ins Außen getragen werden, um sich dem im Schatten der eigenen Persönlichkeit wartenden Schmerz nicht zuwenden zu müssen.
Eine weitere Bewältigungsstrategie für innere, emotionale Zerwürfnisse ist die Projektion, also die Veräußerlichung des Eigenen auf andere. Ein hier vielleicht Sinn stiftendes Beispiel ist die immer wieder betonte weitestgehend unbelegte Unterstellung imperialistischer Bestrebungen Russlands im Zuge des völkerrechtswidrigen Krieges in der Ukraine. Meist kommt diese Behauptung von Vertretern oder Unterstützern der NATO, die – wie an ihrer großflächigen, gegen westliche Zusagen an Russland verstoßenden NATO-Osterweiterung leicht zu erkennen – offensichtlich selbst imperialistische Bestrebungen verfolgt.
Die Projektion ins Außen
Interessanterweise hat ausgerechnet Präsident Putin in anschaulichen Worten beschrieben, was unter anderem mit im Schatten liegenden Persönlichkeitsanteilen auch auf geopolitischer Ebene passieren kann. Sie werden anderen Menschen oder Staaten zugeschrieben, also ins Außen projiziert. Auf die Beschuldigung durch US-Präsidenten Joe Biden, ein Mörder zu sein, antwortete Putin: „Aber wenn wir andere Menschen bewerten, oder wenn wir sogar andere Staaten, andere Völker bewerten, sehen wir immer in den Spiegel, wir sehen uns immer selbst, weil wir auf eine andere Person übertragen, was wir selbst sind, was uns im Wesentlichen ausmacht. Wissen Sie, ich erinnere mich, als wir als Kinder im Hinterhof waren, als wir miteinander gestritten und gesagt haben: Wie Du andere nennst, so bist Du selbst. Und das ist kein Zufall, das ist nicht nur ein Kindersprichwort oder ein Witz. Der Sinn ist sehr psychologisch. Wir sehen immer unsere eigenen Qualitäten in einer anderen Person und denken, dass sie so ist wie wir, und daraus bewerten wir ihr Handeln und bewerten sie insgesamt.“
https://www.youtube.com/watch?v=7sMAHWH_hhQ
Der bereits erwähnte Tiefenstaat, also eine quasi Schattenregierung, existiert auf der geopolitischen Weltbühne und bestimmt größtenteils die Geschicke, insbesondere wenn es um Krieg und Frieden geht. Der Kognitionsforscher Professor Rainer Mausfeld beschreibt die unsichtbar im Hintergrund wirkenden Strukturen in seinem Buch „Angst und Macht“ wie folgt: „Die tatsächliche Macht ist heute in neuartigen globalen Organisationsformen verortet, die vollkommen einer gesellschaftlichen Kontrolle entzogen sind, die für die Bevölkerung weitgehend unsichtbar sind…“
Gleiches gilt meiner Annahme nach auch für die persönlichen Machtverhältnisse, bei denen eigene Schattenanteile ebenfalls großen Einfluss auf die sichtbaren Verhaltensweisen nehmen. Dieser unbewusste Anteil kann auf der einen Seite Macht über die eigene Kriegsbereitschaft und Friedenstüchtigkeit ausüben, auf der anderen Seite wird er von Kriegstreibern mittels kognitiver Kriegsführung aktiv benutzt, um die Bevölkerung zu manipulieren. Der Propagandaforscher Dr. Jonas Tögel schreibt dazu: „Die Tiefenpsychologie dient als Fundament der wohl wichtigsten Manipulationswaffe: die gezielte Beeinflussung des Unbewussten der menschlichen Psyche. Wie bei einem Eisberg liegt ein großer Teil unserer Gedanken und Gefühle „unter der Wasseroberfläche“, und hier können wir so beeinflusst werden, dass wir die Steuerung selbst oft nicht bemerken.“
Der Tiefe Staat kann also ungesehen politisch schalten und walten und gleichzeitig die unbewussten Anteile der menschlichen Psyche zu seinen Gunsten ausnutzen.
Teil 2 folgt in Kürze.
Bastian Barucker, Jahrgang 83, ist Wildnispädagoge, Überlebenstrainer und Prozessbegleiter. Seit 2005 begleitet er Menschen bei Wachstumsprozessen in der Natur. Seit 2011 macht er mithilfe der Gefühls- und Körperarbeit tiefgreifende Selbsterfahrungen, und seit 2014 begleitet er Gruppen, Paare und Einzelpersonen. Er lebt und arbeitet im wunderschönen Lassaner Winkel, nahe der Insel Usedom. Zuletzt erschien von ihm das Buch "Auf Spurensuche nach Natürlichkeit: Vom Leben in der Wildnis und der Reise zu sich selbst" im Massel Verlag.
Kontakt: www.bastian-barucker.de
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 3eba5ef4:751f23ae
2025-05-15 23:48:40
@ 3eba5ef4:751f23ae
2025-05-15 23:48:40Crypto Insights
Uncovering BIP30’s Consensus Vulnerability and Emerging Solutions
Bitcoin developer Ruben Somsen mentioned that while researching SwiftSync (a method to accelerate Bitcoin node synchronization; see next item for details), he discovered a theoretical consensus vulnerability in BIP. BIP30 was designed to prevent duplicate transaction IDs from creating inconsistencies in the UTXO set by invalidating blocks that contain outputs already present in the UTXO set. However, it makes exceptions for certain anomalous coinbase transactions from 2010 (the Coinbase TxIDs in blocks 91722 and 91812 are duplicates) which may cause node state inconsistencies or even forks under extreme block reorganizations. Although current checkpoint mechanisms prevent such reorganizations, removing checkpoints in the future might reintroduce the issue. Additionally, BIP30’s approach to checking the entire UTXO set is inefficient, hindering implementations of new technologies like SwiftSync, Utreexo, and zero-knowledge proofs.
SwiftSync Brings Nearly-Stateless, Fully Parallel Validation
The current Bitcoin Core validation requires these steps: sequentially traversing the blockchain while performing context-independent checks, adding outputs to the UTXO set, and removing spent outputs. Typically, the UTXO set cannot fit in memory, causing further slowdown due to disk I/O.
SwiftSync introduced by Ruben Somsen brings a near-stateless, fully parallelizable validation method that uses hints about which outputs remain unspent. This approach eliminates the need for database lookups during validation, drastically reducing memory usage to near zero and enabling full parallelization of validation steps. As a result, memory, disk I/O, and single-thread performanceCPU performance are removed. The new bottlenecks become CPU power and network bandwidth, meaning validation speed scales with better hardware and connectivity.
Ongoing Discussion on Removing the OP_RETURN Limit
- One-page summary covering 12 years of OP_RETURN history
Bitcoin Core contributor Ava Chow explained OP_RETURN’s 12-year history in a live stream. Key points are summarized in this overview by Claude 3.7.
[https://cdn.hashnode.com/res/hashnode/image/upload/v1747275792942/1c0efe45-868f-41d4-be60-c5725d8eb22a.png] align=)
- Antoine Poinsot: OP_RETURN limits are outdated and should be removed
Antoine Poinsot recommends removing OP_RETURN limits, arguing they neither effectively prevent abuse nor provide full visibility into all transactions for node operators, thus harming network efficiency.
- BitMEX somewhat supports lifting OP_RETURN limits
BitMEX argues that images or other non-financial data stored on Bitcoin shouldn’t be broadly categorized as spam. Only provocative or intentionally harmful content qualifies as spam, but storing images for profit or entertainment is not. The economic reality is that miners are incentivized to produce the most profitable blocks, and if users pay higher fees for transactions containing “junk” data, miners will include them. Blockchain is already heavily used for images, so OP_RETURN limits won’t change that.
- Bitcoin Core’s Aaron van Wirdum and Sjors Provoost also discussed removing OP_RETURN limits on their podcast Bitcoin Explained.

- Suggestions for improving Bitcoin policy change processes
Given recent “out of control” commentary on OP_RETURN, Bitcoin Core’s Matthew Zipkin suggests introducing a new procedural step for policy changes. The biggest problem was many users first hearing about this on Twitter rather than participating in initial mailing list discussions, making them feel disenfranchised and triggering uninformed, repetitive debates. Matthew Zipkin proposes adding an intermediate step between mailing list discussion and GitHub pull request to bridge the gap and improve community engagement and feedback quality while reducing misunderstandings.
Mining Centralization Is a Deeper Issue Than Spam Filtering — Stratum v1 Protocol Must Die
This article discusses fundamental problems with the Bitcoin mining protocol Stratum v1 and calls for a community-wide shift to the more secure, decentralized DATUM or Stratum v2.
The author argues that Stratum v1’s architecture leads to centralized mining where “miners” merely provide hash power, but block construction and transaction ordering are controlled by separate “node runners.” They run nodes to verify their payments but do not contribute CPU to securing chain integrity. They make up the absolute majority of today’s Bitcoin nodes, contradicting Satoshi’s envisioned decentralized lottery-like mining.
In the context of recent OP_RETURN debates, the author contends that protocol-level changes (like adopting DATUM or Stratum v2) are a more fundamental solution to centralization than any spam-filtering policy.

The Bitcoin community swimming in a centralized Stratum v1 mempool, blissfully unaware of the chemicals in the water.
Following.space: Creating and Customizing Follow Lists on Nostr
Following.space is a new Nostr tool addressing a major pain point of the protocol: finding people worth following in the absence of an algorithm. Now users can directly follow “Follow Packs” (curated follow lists) created by others or create, curate, and share their own custom follow lists.
Coinbase Launches x402: A New Open-Source Payment Protocol Built on HTTP Rails
Coinbase Developer Platform introduced the x402 open protocol, a payment protocol that enables instant stablecoin payments directly over HTTP. Built on the HTTP 402 “Payment Required” status code, it creates a native web payment layer allowing websites and applications to request immediate payments from users or AI clients-without requiring API keys, logins, or credit cards. This simplifies payments and improves efficiency. It supports multiple blockchains and stablecoins like USDC. The protocol is open-source on GitHub.
Top Reads on Blockchain and Beyond
Highlights from the 2025 Real World Crypto (RWC) Conference
Unlike many other cryptography conferences that publish peer-reviewed papers, the Real World Crypto (RWC) 2025 conference features talks showcasing the most interesting research papers and industry projects. The 3-day event included 46 talks covering nearly all cryptography topics, including encrypted messaging, TLS and Web PKI, and advances in post-quantum cryptography.
a16z’s Field Notes highlights themes such as:
-
Using zero-knowledge proofs for identity systems
-
Attacks on zero-knowledge proof systems
-
Implementing cryptography with deep neural networks
-
Apple’s large-scale deployment of homomorphic encryption in real products
New Accountability Exploration in Consensus Protocols: Making Liveness Accountable
Security and liveness are classical security properties of consensus protocols. Recent research introduced “accountability” to strengthen security: if security is violated, it can prove that a sizable fraction of adversarial nodes misbehaved. However, accountability for liveness remains underexplored. This paper investigates to what extent liveness can also be made accountable.
Read the full paper.
Diverse Landscape of Asia’s Bitcoin Ecosystem in 2025
An article highlights Asia as a hotspot for Bitcoin adoption, with different countries embracing Bitcoin uniquely—from institutional investors in Singapore, grassroots adoption in Indonesia, to Vietnam’s strong P2P usage for daily transactions and remittances— a diverse picture of Asia’s Bitcoin ecosystem driven by innovation, regulation, and community.
-
 @ 3eba5ef4:751f23ae
2025-05-15 23:37:52
@ 3eba5ef4:751f23ae
2025-05-15 23:37:52加密洞见
BIP30 潜藏共识风险,社区酝酿替代路径
比特币开发者 Ruben Somsen 提到,在研究 SwiftSync(一种加速比特币节点同步的方法。详情见下一条)时发现,BIP30 存在一个理论上的共识漏洞。BIP30 旨在通过消除重复条目来处理异常,该机制用于防止重复的 UTXOs,但在处理 2010 年某些异常 coinbase 交易时存在特例(区块 91722 和 91812 的 Coinbase TxID 是重复的),可能在极端区块重组的情况下导致节点状态不一致,甚至引发分叉。虽然当前的检查点机制阻止了这种重组,未来若移除检查点,问题可能重新浮现。此外,BIP30 对整个 UTXO 集的检查效率低下,妨碍了 SwiftSync、Utreexo、ZKP 等新技术的实现。
因此 Ruben 建议考虑用更简洁的方式(如检查 coinbase 唯一性)替代 BIP30,以提升效率并减少未来协议演进的阻力。他并未主张立即修改,而是希望鼓励社区讨论。
SwiftSync 实现近于无状态的、可并行比特币区块链验证
当前 Bitcoin Core 中的常规验证需要以下步骤:按顺序遍历区块链——同时运行一些独立于上下文的微小检查、向 UTXO 集添加输出、检索被花费的输出并移除它们。通常 UTXO 集无法放进内存中,从而因为硬盘读写而进一步放慢速度。
由 Ruben Somsen 提出的 SwiftSync 完全改变了这种模式,而且不会改变安全假设——不需要再进行数据库检索,且内存使用量降低到近于零,所有验证都可以并行完成。由此,内存、硬盘读写和单线程性能,不会再作为瓶颈出现;剩余的瓶颈就只是 CPU 和带宽,只要这两项的条件越好,验证就越快。
关于取消 OP_RETURN 12 限制的讨论持续进行
- 一页摘要涵盖 OP_RETURN 12 年的历史
Bitcoin Core 成员 Ava Chow 通过直播解释了 OP_RETURN 12 年的历史。关键内容可以在这份由 Claude 3.7 总结的摘要中找到。

- Antoine Poinsot:OP_RETURN 限制已过时,建议取消
Antoine Poinsot 在本文中建议取消 OP_RETURN 的限制,因它们既无法有效防止滥用,反而让节点运营者无法看到所有交易、对网络活动没有全面的了解、也会损害网络效率。
- BitMEX:在一定程度上支持取消 OP_RETURN 的限制
BitMEX 认为,存储在比特币上的图像或其他非金融数据不应被一概视为垃圾信息。只有具有挑衅性或故意有害的内容才算是垃圾信息,而为了盈利或娱乐而存储图像则不属于垃圾信息。目前的经济现实是,矿工有动力生产最具盈利性的区块,如果用户支付更高的手续费来发送包含“垃圾”数据的交易,矿工就会打包这些交易。区块链已经被大量用于存储图像,因此 OP_RETURN 的限制并不会改变这一现状。
-
Bitcoin Core 的 Aaron van Wirdum 和 Sjors Provoost 也在他们的播客节目 Bitcoin Explained 中,也讨论了关于移除 OP_RETURN 限制的问题
-
关于改进比特币提议形式和流程的建议
鉴于近期关于 OP_RETURN 的评论呈现「失控」状态,Bitcoin Core 的 Matthew Zipkin 认为应该考虑为政策更改添加新的流程步骤。这次 OP_RETURN 相关讨论的最大问题是,许多用户第一次是在 twitter 上听到消息,而并未参与 Bitcoin Core 邮件列表的初始讨论,因此他们觉得做任何事情都为时已晚,感到权利已被剥夺。结果引发了一大群考虑不周、不知情、重复的讨论/批评。Matthew Zipkin 因此建议引入一个处于邮件列表和 GitHub PR 之间的中间步骤,以弥合邮件列表讨论和拉取请求审查之间的差距,旨在提高社区参与度和反馈质量、减少误会。
集中挖矿的问题比垃圾信息过滤策略更深,Stratum v1 协议必须消亡
本文讨论了比特币挖矿协议 Stratum v1 的根本问题,並呼吁社群全面转向更安全、去中心化的 DATUM 或 Stratum v2 协议。作者认为 Stratum v1 的架构导致了集中挖矿,「矿工」名存实亡:他们只负责提供算力,而区块的构建和交易排序则由另外的「节点运营者」(node runner)掌握。这些用户维护节点来验证自己的支付,并没有贡献 CPU 来保持链的诚实。而他们是今天比特币节点的绝对大多数。这跟中本聪原本设想的去中心化「彩票式」挖矿模式背道而驰。
联系到最近关于 OPP_RETURN 的讨论,作者认为 DATUM 才是更为根本的解决方案,而不是任何特定策略。

比特币社区在一个中心化的 Stratum v1 内存池中幸福畅游,全然不知水中的化学物质。
Following.space:在 Nostr 上实现关注列表的创建和自定义
Following.space 是新推出的 Nostr 工具,它解决了该协议的最大痛点之一:在没有算法的情况下找到并跟踪感兴趣的用户。现在用户可以直接 follow 别人创建的关注列表(Follow Packs),或自行创建、制作、共享自定义的关注列表。
Coinbase 推出 x402:一种基于 HTTP Rails 构建的新型开源支付协议
Coinbase 开发者平台推出 x402 开源协议,它是一种支付协议,可以直接通过 HTTP 进行即时稳定币支付。它基于 HTTP 402 的「Payment Required」状态码打造原生的互联网支付层,允许服务端向用户或 AI 客户端请求即时付款,无需 API 密钥、登录或信用卡,实现更简单高效的支付体验。它支持多条区块链和 USDC 等稳定币,具备开放性和链无关性,协议已在 GitHub上开源。
精彩无限,不止于链
2025 真实世界加密 (RWC) 密码学会议亮点
与许多其他密码学的主要学术场所不同,Real World Crypto (RWC) 2025 会议不发表同行评审的论文,而是通过演讲来体现前一年最有趣的研究论文和行业项目。今年的会议在三天内举办了 46 场演讲,几乎涵盖了密码学的所有主题 ,包括加密消息传递、TLS 和 Web PKI 以及后量子密码学的进步 。
a16z 的这篇 Field Notes 对这次大会的亮点做了介绍,值得关注的主题有:
-
对身份系统使用零知识证明
-
对零知识证明系统的攻击
-
使用深度神经网络实现加密
-
Apple 在实际产品中的同态加密大规模部署
共识协议中的可追责性新探:让活性也能被追责
安全性和活性(liveliness)被认为是共识协议中的两项核心性质。近年来已经有研究引入了「可追责性」(accountability)来增强安全性:一旦安全性遭到破坏,可以证明有一定比例的对手节点违反了协议。然而相较之下,活性的可追责性却尚未被充分研究。本文探讨了在多大程度上可以为活性实现类似的可追责保证。 查看论文全文。
亚洲比特币生态 2025 的多元图景
文章指出,亚洲已成为比特币采用的重镇,不同国家正以独特的方式接纳着比特币——从新加坡的机构投资者、印尼草根阶层的采用、到越南在日常交易和汇款中的点对点使用,呈现了由创新、监管与社区共同驱动的亚洲比特币生态图景。
-
 @ 866e0139:6a9334e5
2025-05-11 15:59:43
@ 866e0139:6a9334e5
2025-05-11 15:59:43Autor: Alexa Rodrian. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Dieser Text erschien zuerst auf Manova.news
Den Frieden muss man heute fast mit der Lupe suchen. Erst recht die Menschen, die ihn noch weiter im Inneren tragen. Unbändige Wut staut sich auf, ob der unzähligen Verbrechen gegen die Menschlichkeit. Dabei noch friedlich zu bleiben, nicht selbst in die Vergeltungsspirale zu rutschen, ist dieser Tage ein wahres Kunststück in Sachen Selbstbeherrschung. In diesem Beitrag für die Friedensnote ringt die Autorin mit ihren ambivalenten Gefühlen – um sich dann letzten Endes, trotz allem, für den Frieden zu entscheiden. Alexa Rodrian setzt der geballten Grausamkeit der Welt ein „Trotzdem“ entgegen. Trotzdem für den Frieden! Ihr Gedicht verfasste sie im Rahmen der nächsten großen Friedensdemo in Berlin. Die findet am 9. Mai 2025, am Viktoria-Louise-Platz ab 16.30 Uhr zum wiederholten Male unter dem Motto #FRIEDLICHZUSAMMEN statt. Im Vorfeld wurden die Teilnehmer gebeten, ein paar Worte über den Frieden als Videobotschaft aufzunehmen, um sie als Aufruf zur Demo auf Social Media zu posten. Genau das tat Alexa Rodrian mit der nachfolgenden Friedensnote.
Da saß ich nun lange und dachte bei mir, was kann man denn über den Frieden noch sagen, was nicht schon Tausende Male zuvor gesagt und oder geschrieben wurde? Meine liebe Kollegin Sabine Winterfeld hat mir das neulich in ihrem beeindruckenden literarischen Chanson-Abend „Selig sind die Friedfertigen“ dargestellt und nochmals klar gemacht: Nichts wurde noch nicht gesagt.
So sprach und sang sie, in intensiver und gekonnter Manier, nebst kritischen und bewegenden eigenen Texten solche von Emmy Ball Hennigs, Else Laske Schüler, Hermann Hesse und Erich Mühsam.
Worte, die, wenn sie jemals verstanden worden wären, niemals zu der heutigen Kriegshetze unseres politischen Elite-Mobs und seiner Vasallen hätten führen dürfen, wahre Friedens- und Freiheitsworte von Menschen, die wussten, wovon sie sprachen.
Die Geschichte wiederholt sich, und so gedacht könnten wir das mit den Friedensworten jetzt auch einfach sein lassen, da die Erfahrung uns ja gelehrt hat, dass sie eh nichts bringen und nichts verhindern. Gott sei Dank sind wir aber nicht alle total geschichtsvergessen!
Das dringliche und tief aus dem Herzen gesprochene „Nie wieder“ meiner Mutter zum Beispiel habe ich immer zutiefst berührt zur Kenntnis genommen und als ein Mantra in mein Leben integriert.
Und das obwohl oder gerade weil ein Teil meiner Familie Nazis waren und außer vielleicht meinem sozialistischen Onkel Eugen sicherlich niemand aus meiner Familie Juden im Keller versteckt hatte.
Dafür hat sich meine Mutter ihr Leben lang geschämt. Das führte so weit, dass sie ihre/unsere deutsche Identität verleugnen wollte, indem sie wilde Geschichten, von einer ihrer Tanten tradiert, über einen armenischen Wanderer erzählte, der angeblich unser Namensgeber und Urgroßvater war; so erklärte sie sich unser „Nichtdeutsch“-Sein, wie sie immer wieder betonte, und unsere dunkle Haut und Augen.
Ich wuchs sozusagen im Glauben auf, armenisches Blut zu haben, und vielleicht erklärt sich dadurch auch mein sehr frühes Engagement für den Frieden, gegen Rassismus und besonders gegen Genozide. Meine Mutter hat mich aufgeklärt über dieses Land der Täter und Zuschauer, und gleichzeitig hat sie mir, ohne es zu wissen, gespiegelt, wie sehr auch sie als unschuldiges Kind — 1933 geboren — zum Opfer wurde.
So spüre ich ihr Trauma immer wieder in mir, und deswegen bin und möchte ich Pazifist bleiben, und das im wahrsten Sinne des Wortes:
Ich will Frieden machen, tun und handeln, „pax facere“, gemeinsam mit denen, die sich nicht spalten lassen, nicht instrumentalisieren lassen, die, die wissen, wie Frieden geht.
Bei #FRIEDLICHZUSAMMEN gibt es einige von denen, und viele schöne Worte wurden bereits veröffentlicht. Es gibt ein sehr schönes und lyrisches Spokenword-Stück von Cem-Ali Gültekin, Jens Fischer Rodrian spricht und stellt seinen tollen neuen Friedenssong „Frieden“ vor; Tina Maria Aigner erklärt, wie der Frieden in sich selbst auf andere reflektiert, und Sandra Seelig macht uns unter anderem auf den Frieden in der Natur aufmerksam.
Und dann sind da noch die beeindruckenden Worte von Oliver Elias, der unlängst auf TikTok erstmals öffentlich gemacht hat, dass er der Großcousin von Anne Frank ist.
Ich kenne Oliver Elias noch nicht persönlich, aber sich als deutscher Jude, in diesem Land, mit Entsetzen gegen das Töten in Gaza auszusprechen und deutlich zu machen, dass die israelische Regierung zu kritisieren nichts mit Antisemitismus zu tun hat — und das alles trotz seiner Biografie und des Traumas seiner Familie —, verdient in meinen Augen den allerhöchsten Respekt!
Zu guter Letzt muss ich der Ehrlichkeit halber noch etwas hinzufügen, denn
- wenn ich die Bilder aus Palästina sehe von ermordeten und entstellten Kindern, Frauen und Männern,
- wenn ich jeden Tag höre, dass 1,8 Millionen Menschen ausgehungert werden und hier zweifelsohne ein intendierter grauenhafter Genozid stattfindet,
- wenn gestern zum wiederholten Male Menschenrechtsaktivisten, diesmal auf dem Hilfsschiff Conscience, das bei Malta liegt, mit Drohnen von Israel angegriffen werden,
- wenn seit Monaten Ärzte, Krankenschwester, Journalisten und viele andere daran gehindert werden, zu helfen und Bericht zu erstatten, und sogar in großer Anzahl getötet werden,
- wenn das alles ungeahndet und offenkundig vor den Augen der internationalen Gemeinschaft stattfindet,
dann werde ich ambivalent mit meinem Pazifismus. Da brodelt es in mir, meine Wut wird immer größer, meine Verzweiflung immer tiefer — da bin ich ratlos und gebe zu, dass ich mich frage, ob „friedlich“ hier noch die richtige Lösung sein kann.
Jetzt beginnt mein Dschihad, meine innere Auseinandersetzung, und „meine ethische und religiöse Pflicht zur Selbstbeherrschung“ ist schwer herausgefordert.
Am Ende aber weiß ich nur zu gut, dass die Spirale des Tötens nur zu mehr Töten führt, und deshalb zügle ich mich und schreibe lieber ein weiteres Gedicht.
Mein Frieden
Ein Kind zärtlich in den Armen wiegen
das ist Frieden
Streiten und sich trotzdem lieben
das ist Frieden
Lusttrunken auf der Brust des Lovers liegen
das ist Frieden
Freiheit, Ausgeglichenheit und Schwesterlichkeit
das ist Frieden
Wohlwollen, Verständnis, ohne zu verstehen, mit Empathie durchs Leben gehen
das ist Frieden.
Loslassen, was einst geschah
Verzeihen, ohne gänzlich zu vergeben
auch so kann man im Frieden leben.
Lachen laut und manchmal ohne Sinn
für den Frieden immer ein Gewinn
Und auch die Wut ist für den Frieden gut
denn besser laut gesprochen
als sein Gegenüber wutlos totgeschossen.
Den Hass, den gilt es wirklich zu vermeiden, denn er hält fest,
wenn du ihn pflegst, dann wird er bleiben und dich und andere in Kriege treiben.
Nein, denn für Frieden sind wir hier
für den sind wir geblieben und stehen friedlich miteinander gegen 's Kriegen.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 28e13303:84bb7266
2025-05-15 23:37:29
@ 28e13303:84bb7266
2025-05-15 23:37:29⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT? Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics 👁️ Visible in supported wallets confirmed on-chain ⏱️ Disappears after 20–60 minutes (or X blocks) 💸 Can be withdrawn and traded ⚙️ Used in wallet testing, UI simulation, and balance display demos Also known as:
Flash USDT Wallet Tool Flash USDT Sender Atomic Flash USDT Flash USDT Binance Sim 🛠️ How Flash USDT Works You input a wallet address (TRC20, ERC20, or BEP20) Flash USDT software sends an instant transaction Wallet displays the amount — as if it were real After expiry (e.g., 30 minutes), the tokens vanish It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
Wallet UI testing “Proof of funds” simulations Demo environments Smart contract UX testing 🔧 Supported Networks & Wallets Flash USDT supports all major token standards:
🔸 TRC20 (Tron Network) 🔸 ERC20 (Ethereum) 🔸 BEP20 (Binance Smart Chain) It works with wallets such as:
✅ Trust Wallet ✅ MetaMask ✅ TronLink ✅ Binance Wallet ✅ Atomic Wallet The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Available packages:
🎯 One-time Flash USDT Send 💻 Full Flash USDT Software Tool 📱 Flash Sender for Mobile/Android 🌐 Multi-wallet Simulation Package You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
✅ Personal testing ✅ Blockchain development ✅ Wallet UI testing ✅ Research and education Any misuse is your full responsibility.
❓ Frequently Asked Questions What is Flash USDT? A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money? No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance? You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT? Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean? It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver 📱 WhatsApp: +1 941 217 1821
Packages available for:
TRC20 BEP20 ERC20 Custom wallet simulations
⚠️ Disclaimer: This article is for educational purposes only. Flash USDT is a blockchain simulation tool used for wallet testing, UI development, or demonstration purposes. It should not be used for fraudulent activity. @crypptrcver is not responsible for misuse.
💡 What Is Flash USDT?
Flash USDT is a synthetic transaction method that simulates the transfer of Tether (USDT) into a wallet. These transactions appear instantly in wallet balances — without ever being confirmed on the blockchain — and disappear after a short time or block interval.
Think of it as a temporary, visual representation of USDT that looks real in a wallet but vanishes after expiry.
🧠 Flash USDT: The Basics
- 👁️ Visible in supported wallets
- confirmed on-chain
- ⏱️ Disappears after 20–60 minutes (or X blocks)
- 💸 Can be withdrawn and traded
- ⚙️ Used in wallet testing, UI simulation, and balance display demos
Also known as:
- Flash USDT Wallet Tool
- Flash USDT Sender
- Atomic Flash USDT
- Flash USDT Binance Sim
🛠️ How Flash USDT Works
- You input a wallet address (TRC20, ERC20, or BEP20)
- Flash USDT software sends an instant transaction
- Wallet displays the amount — as if it were real
- After expiry (e.g., 30 minutes), the tokens vanish
It creates the illusion of a deposit without requiring real blockchain confirmation. Most users use Flash USDT for:
- Wallet UI testing
- “Proof of funds” simulations
- Demo environments
- Smart contract UX testing
🔧 Supported Networks & Wallets
Flash USDT supports all major token standards:
- 🔸 TRC20 (Tron Network)
- 🔸 ERC20 (Ethereum)
- 🔸 BEP20 (Binance Smart Chain)
It works with wallets such as:
- ✅ Trust Wallet
- ✅ MetaMask
- ✅ TronLink
- ✅ Binance Wallet
- ✅ Atomic Wallet
The balance appears instantly, just like a real incoming USDT deposit.
🔥 Features of Flash USDT Sender
FeatureDescriptionNetwork supportTRC20 / ERC20 / BEP20Visibility duration20 minutes — 2 hoursWallet compatibilityNon-KYC wallets that show unconfirmed TXsFlash USDT Binance modeSimulates deposits into BSC walletsAdjustable transaction sizeSend any custom USDT amountStealth expiryClean disappearance without trace
This is especially helpful in scenarios where you need to test token flows, design wallet apps, or simulate incoming funding activity
📞 How to Buy Flash USDT
To get your Flash USDT transaction or software setup:
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Available packages:
- 🎯 One-time Flash USDT Send
- 💻 Full Flash USDT Software Tool
- 📱 Flash Sender for Mobile/Android
- 🌐 Multi-wallet Simulation Package
You can request TRC20, ERC20, or BEP20 flash transactions depending on the wallet or network you’re working with.
⚠️ Legal & Ethical Use Only
While Flash USDT is a powerful blockchain simulation tool, using it to deceive, fake trades, or commit fraud is illegal. Flash transactions should only be used for:
- ✅ Personal testing
- ✅ Blockchain development
- ✅ Wallet UI testing
- ✅ Research and education
Any misuse is your full responsibility.
❓ Frequently Asked Questions
What is Flash USDT?
A temporary USDT transaction that appears in a wallet balance without confirming on the blockchain. It disappears after a set time or block count.
Is Flash USDT real money?
No. It is a simulated deposit, not spendable or tradable.
Can I use Flash USDT on Binance?
You can send it to BSC (BEP20) wallets, but you cannot use it on the Binance exchange. It’s for display/testing only.
How do I buy Flash USDT?
Contact @crypptrcver on Telegram or WhatsApp to purchase a transaction or the full sender software.
What does Atomic Flash USDT mean?
It refers to Flash USDT transactions that are time-bound and expire silently, simulating atomic wallet behavior.
🧠 Final Thoughts
Flash USDT is one of the most advanced crypto testing tools available in 2025. Whether you’re simulating wallet behavior, demonstrating a smart contract front end, or simply showing a visual “deposit” for testing, Flash USDT provides an incredibly realistic experience — without ever moving real funds.
👉 Ready to simulate your first USDT transaction?
💬 Telegram: @crypptrcver\ 📱 WhatsApp: +1 941 217 1821
Packages available for:
- TRC20
- BEP20
- ERC20
- Custom wallet simulations
-
 @ c9badfea:610f861a
2025-05-15 23:11:22
@ c9badfea:610f861a
2025-05-15 23:11:22- Install MuPDF Mini (it's free and open source)
- Launch the app and open a document or book
- Tap the left or right edges to scroll through pages
- Enjoy distraction-free reading
ℹ️ You can open
.pdf,.xps,.cbz,.epub, andfb2documents -
 @ 866e0139:6a9334e5
2025-05-11 15:40:19
@ 866e0139:6a9334e5
2025-05-11 15:40:19Autor: Peter Schmuck. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Der Text der Friedenserklärung wurde vom European Peace Project verfasst:
\ Heute, am 9. Mai 2025 – genau 80 Jahre nach dem Ende des Zweiten Weltkriegs, der 60 Millionen Menschen das Leben kostete, darunter 27 Millionen Sowjetbürgern, erheben wir, die Bürgerinnen und Bürger Europas, unsere Stimmen! Wir schämen uns für unsere Regierungen und die EU, die die Lehren des 20. Jahrhunderts nicht gelernt haben. Die EU, einst als Friedensprojekt gedacht, wurde pervertiert und hat damit den Wesenskern Europas verraten! Wir, die Bürger Europas, nehmen darum heute, am 9. Mai, unsere Geschicke und unsere Geschichte selbst in die Hand. Wir erklären die EU für gescheitert. Wir beginnen mit Bürger-Diplomatie und verweigern uns dem geplanten Krieg gegen Russland! Wir erkennen die Mitverantwortung des „Westens“, der europäischen Regierungen und der EU an diesem Konflikt an.
Wir, die Bürger Europas, treten mit dem European Peace Project der schamlosen Heuchlerei und den Lügen entgegen, die heute – am Europatag – auf offiziellen Festakten und in öffentlichen Sendern verbreitet werden.
Wir strecken den Bürgerinnen und Bürgern der Ukraine und Russlands die Hand aus. Ihr gehört zur europäischen Familie, und wir sind überzeugt, dass wir gemeinsam ein friedliches Zusammenleben auf unserem Kontinent organisieren können.
Wir haben die Bilder der Soldatenfriedhöfe vor Augen – von Wolgograd über Riga bis Lothringen. Wir sehen die frischen Gräber, die dieser sinnlose Krieg in der Ukraine und in Russland hinterlassen hat. Während die meisten EU-Regierungen und Verantwortlichen für den Krieg hetzen und verdrängen, was Krieg für die Bevölkerung bedeutet, haben wir die Lektion des letzten Jahrhunderts gelernt: Europa heißt „Nie wieder Krieg!“
Wir erinnern uns an die europäischen Aufbauleistungen des letzten Jahrhunderts und an die Versprechen von 1989 nach der friedlichen Revolution. Wir fordern ein europäisch-russisches Jugendwerk nach dem Vorbild des deutsch-französischen Jugendwerks von 1963, das die „Erbfeindschaft“ zwischen Deutschland und Frankreich beendet hat. Wir fordern ein Ende der Sanktionen und den Wiederaufbau der Nord Stream II-Pipeline. Wir weigern uns, unsere Steuergelder für Rüstung und Militarisierung zu verschwenden, auf Kosten von Sozialstandards und Infrastruktur. Im Rahmen einer OSZE-Friedenskonferenz fordern wir die Schaffung einer europäischen Sicherheitsarchitektur mit und nicht gegen Russland, wie in der Charta von Paris von 1990 festgelegt. Wir fordern ein neutrales, von den USA emanzipiertes Europa, das eine vermittelnde Rolle in einer multipolaren Welt einnimmt. Unser Europa ist post-kolonial und post-imperial.
Wir, die Bürger Europas, erklären diesen Krieg hiermit für beendet! Wir machen bei den Kriegsspielen nicht mit. Wir machen aus unseren Männern und Söhnen keine Soldaten, aus unseren Töchtern keine Schwestern im Lazarett und aus unseren Ländern keine Schlachtfelder.
Wir bieten an, sofort eine Abordnung europäischer Bürgerinnen und Bürger nach Kiew und Moskau zu entsenden, um den Dialog zu beginnen. Wir werden nicht länger zusehen, wie unsere Zukunft und die unserer Kinder auf dem Altar der Machtpolitik geopfert wird.
Es lebe Europa, es lebe der Friede, es lebe die Freiheit!
Auf der Webseite der Initiative oder in einem Gespräch mit Ulrike Guérot können Sie, liebe Leser, weitere Möglichkeiten erfahren, diese Friedensinitiative zu stärken!
https://www.youtube.com/watch?v=zECOTfeweUE&list=PLS_jddBXjdqcBKneCQcPN8NOTSqlmNqpy
Danke an die IntiatorInnen und die bislang 15.000 Menschen, die das mitgestalten werden.
Peter Schmuck ist Professor für Psychologie und Initiator zahlreicher nachhaltiger Projekte.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 044da344:073a8a0e
2025-05-11 09:16:08
@ 044da344:073a8a0e
2025-05-11 09:16:08Alles neu macht der Oktober. Sorry für das Sprachspiel. Wenn Sie so etwas mögen, dann kommen Sie in ein paar Monaten zu uns in die Oberpfalz –
- entweder zum Journalismus-Retreat für den Nachwuchs der Gegenöffentlichkeit oder
- eine Woche später zum Kurs Intellektuelle Selbstverteidigung.
Wenn man den Unterschied auf den Punkt bringen müsste: Für Kurs eins sollten sie schon öffentlich sichtbar sein mit Texten, Podcasts und Videos, auf diesem Pfad weitermachen wollen und dafür nach Aufmunterung, Bestärkung, Weggefährten suchen. Kurs zwei verlangt all das nicht. Keine Schranke, nicht einmal in Sachen Alter. Während uns bisher wichtig war, dass die Teilnehmer wenigstens eventuell und im Fall der Fälle in Richtung Medienpräsenz schielen, steht bei diesem neuen Angebot Medienkompetenz im Mittelpunkt, journalistisches Handwerk inklusive.
Infos zur Anmeldung, zur Organisation und zu allem, was Sie sonst noch wissen wollen, finden Sie unter den Links oben.
-
 @ b292393a:ad5d160e
2025-05-15 23:07:30
@ b292393a:ad5d160e
2025-05-15 23:07:30hello there2
-
 @ b292393a:ad5d160e
2025-05-15 23:07:09
@ b292393a:ad5d160e
2025-05-15 23:07:09hello there
-
 @ b292393a:ad5d160e
2025-05-15 23:06:51
@ b292393a:ad5d160e
2025-05-15 23:06:51 -
 @ 866e0139:6a9334e5
2025-05-10 11:29:23
@ 866e0139:6a9334e5
2025-05-10 11:29:23\ Autor: Kerstin Chavent. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wir halten uns für erwacht, weil wir das Coronanarrativ durchschaut haben, regierungskritisch unterwegs sind und Russland nicht für den ärgsten Feind der Demokratie halten? Wir informieren uns in alternativen und unabhängigen Medien, folgen geistigen Führern und sehen Spiritualität als einen Teil unseres Daseins auf der Erde? Vielleicht sind wir mit Meditationstechniken vertraut, machen Yoga oder nehmen bewusstseinserweiternde Substanzen zu uns? Wir denken, andere würden noch schlafen, weil sie das nicht tun? Dann haben wir noch einen weiten Weg vor uns.
Aufwachen — wir tun es jeden Morgen und oft auch während der Nacht. Der Kopf ist schwer, vielleicht ein wenig verwirrt, wie in einem Nebel. Die Schleier der Träume hängen noch an uns. Wir sind noch nicht ganz da und brauchen eine Dusche, einen Kaffee oder frische Luft, um langsam durchzukommen und den Tag zu beginnen. In den seltensten Fällen ist es so, dass wir die Augen aufschlagen und hellwach sind, vollkommen präsent und klar. So passt die Metapher auf das, was heute auf den Bewusstseinszustand der Menschen angewendet wird.
Was bedeutet es, wach zu sein? Ein waches Bewusstsein zu haben? Was ist Bewusstsein? Eine der großen Referenzen für Psychologie und Pädagogik hat einen eher beschränkten und materialistisch orientierten Bewusstseinsbegriff. Demnach reiche Bewusstsein nicht über das normale Denken hinaus. Bewusstsein habe ein Mensch immer dann, wenn er in der Lage ist, zu bedenken, ob das, was er tut, vernünftig ist. Das Bewusstsein sei an das Gehirn gebunden. Ein Bewusstsein ohne Aktivität von Nervenzellen im menschlichen Gehirn gebe es nicht. Das sei wissenschaftlicher Konsens. Über noch etwas ist man sich einig:
Nach Jahrhunderten der Bemühung von Neurowissenschaftlern, Psychologen und Philosophen bleibt zu der Frage, wie das Gehirn uns denn Bewusstsein verleiht, wie es Empfindungen, Gefühle und Subjektivität entstehen lässt, nur eine Gewissheit: Wir haben keine Ahnung (1).
Mehr Ahnung haben wir, wenn es darum geht, das menschliche Bewusstsein zu manipulieren. Voraussetzung ist, die zu manipulierende Person in Unkenntnis zu lassen. Es wird ein Gefühl von Machtlosigkeit in ihr erzeugt und ein System von Belohnung und Strafe aufgebaut, um eine autoritäre Machtstruktur, die kein Feedback und keine Änderung ohne Zustimmung oder Anordnung der Führung zulässt, zu installieren. Hierfür ist keine Gewaltanwendung erforderlich. Für eine mentale Umprogrammierung reicht es, jede Form von Kritik zu unterdrücken und Kritiker zu diffamieren, indem man ihnen persönliche Rachemotive oder menschliche Schwäche andichtet (2).
Manipulation mit Angst
Angst ist eines der wirksamsten Mittel, um das Bewusstsein der Menschen zu manipulieren. Wer Angst hat, lässt sich leicht täuschen. Das Bewusstsein verengt sich regelrecht. Damit ergibt sich ein nahezu unerschöpflicher Fundus von Methoden zur Bewusstseinskontrolle. Welche, das erleben wir täglich: die Erschaffung einer Unterhaltungsindustrie und die Verbreitung von Filmen, in denen es vor allem um Mord, Verrat, Krankheit und Betrug geht; Medien, die maximale Verwirrung schaffen; giftige Substanzen in Nahrungsmitteln und Wasser; ein knechtendes Finanzsystem; Medikamente, von denen wir möglichst früh und möglichst lange abhängig sind.
Wer das Bewusstsein der Menschen und damit die Welt in den Griff bekommen will, fängt früh an. Er erfindet zum Beispiel Religionen, die sich nach Möglichkeit gegenseitig bekämpfen.
Er erzählt Geschichten, in denen die eine Hälfte der Menschheit der anderen per se unterlegen sein soll, erfindet Götter, die die einen privilegieren und die anderen bestrafen, und ein Paradies, das irgendwoanders ist als dort, wo wir gerade sind.
Alles ist darauf ausgerichtet, dass der Mensch sich klein, unwürdig, schuldig und vor allem ohnmächtig fühlt. Auf keinen Fall darf er sich seiner angeborenen Möglichkeiten bewusstwerden! Hierfür werden Kinder so früh wie möglich von den Eltern getrennt, bekommen in staatlichen Schulen ihre Kreativität und Eigenmacht aberzogen, werden von technischen Geräten abhängig gemacht und durch Geschlechterverwirrung davon abgehalten, ihre Identität zu entwickeln. So werden sie darauf vorbereitet, zu guten Soldaten des Systems zu werden und in jeden Krieg zu ziehen, der ihnen als notwendig verkauft wird.
Project Blue Beam
Immer mehr Menschen wissen das. Immer mehr erkennen, was auf der Bühne des Welttheaters gespielt wird. Doch sind wir deshalb erwacht? Reicht es, alternative Medien zu konsumieren, bewusstseinserweiternde Substanzen zu sich zu nehmen und regelmäßig zu meditieren, um das eigene Bewusstsein zu entwickeln? Reichen die Bücher, die Workshops und die charismatischen Führer, die überall zu finden sind? Sind wir erwacht, nur weil der Nachbar noch schläft?
Wie würden wir zum Beispiel reagieren, wenn das Projekt „Blue Beam“ durchgespielt werden würde? Natürlich soll es sich hierbei um eine Verschwörungstheorie handeln. Aber nur mal angenommen. Es geht darum, durch das Erschaffen einer allgemeinen Unsicherheit und Hysterie eine neue Weltordnung durchzusetzen.
In einer ersten Etappe sollen künstlich erschaffene Naturkatastrophen dafür sorgen, dass die Menschen sämtliche religiöse Fundamente in Frage stellen. In einer zweiten Etappe werden mittels dreidimensionaler Hologramme verschiedene Gottesbilder in den Himmel projiziert mit dem Ziel, eine Einheitsreligion zu proklamieren. In einer dritten Etappe sollen mittels Niederfrequenzen und per Satellit Gedankengänge gezielt beeinflusst werden, und in einem letzten Schritt soll die Menschheit davon überzeugt werden, dass in allen großen Städten der Welt eine Invasion Außerirdischer nahe bevorsteht.
Jede große Nation soll dazu aufgefordert werden, ihr nukleares Potenzial als Abwehr zu benutzen. Es soll sich jedoch um ein Fake-Manöver handeln. Den Nationen, nun ihrer Waffen entledigt, bliebe nur noch die Hoffnung auf einen göttlichen Eingriff. Alle „erwachten“ Menschen würden von „guten“ außerirdischen Kräften „gerettet“ und entführt werden — womit der neuen Weltordnung auf Erden nichts mehr im Wege stünde. Der Rest der Menschheit würde mittels über elektronische Geräte verbreiteter böser Geister in den Wahnsinn und die totale Hoffnungslosigkeit getrieben werden.
Selbstwirksamkeit?
Die Geschichte ist haarsträubend. Doch wer könnte beschwören, dass sie technisch nicht möglich wäre? Wer könnte sich sicher sein, einer False-Flag-Aktion nicht auf den Leim zu gehen? Wer könnte von sich behaupten, so erwacht, so in seinem Bewusstsein verankert zu sein, dass er sich nicht manipulieren ließe, wenn es darauf ankommt? Wer griffe nicht in der Verzweiflung nach einem Heiligenbild, das am Himmel aufsteigt? Wer wäre erhaben über jede Art von Mind Control?
So möge der stille werden, der sich rühmt, erwacht zu sein. Möge er sich den Schlaf aus den Augen reiben und sich an die Arbeit machen. Denn das Erwachen ist nur der allererste Schritt. Dann geht es erst richtig los.
Dann können wir üben, in die Selbstwirksamkeit zu kommen: das Vertrauen in die eigenen Möglichkeiten, Aufgabenanforderungen wirksam zu bewältigen und auch in Extremsituationen gewünschte Handlungen selbst ausführen zu können.
Die Frage ist nicht, wie erwacht wir uns im Vergleich mit anderen fühlen, sondern welches Selbst- und Menschenbild wir haben und wie wir von unserer natürlichen Schöpferkraft Gebrauch machen. Nicht der ist erwacht, der sich von Katastrophenmeldungen einlullen lässt und sich gemütlich in seinen vier Wänden auf den Weltuntergang vorbereitet, sondern der, der sich darauf besinnt, dass Bewusstsein mehr ist als ein paar Synapsen im Gehirn. Er weiß, dass er über einen freien Willen verfügt, der ihn dazu befähigt, in eine andere Richtung zu gehen.
Außen wie innen
Bewusstsein hängt von keinem spirituellen Führer ab und auch von keinem Gott, der in den Himmel projiziert wird. Bewusstsein ist göttlich. Es ist die Fähigkeit, Dinge wahr-zu-nehmen, ihren Wahrheitsgehalt zu erkennen, die Gabe, aus sich heraus feinfühlig zu sein, hellsichtig, verstehend. Im individuellen Bewusstsein sind das Menschliche und das Göttliche eins. Nichts steht trennend dazwischen. Niemand muss die Erlaubnis für diesen Erkenntnisprozess geben.
Wer bei Bewusstsein ist, den kann man nicht in ein Gedankengefängnis einsperren oder ihn mit Hierarchien beeindrucken. Er weiß, dass das Wesentliche sich im Innen abspielt und dass allein er für das verantwortlich ist, was er erlebt.
Ein hoch entwickeltes Bewusstsein bedeutet, sich von jeder Erwartung zu lösen, dass sich im Außen etwas ändert. Wer sich auf das Außen konzentriert, der hat schon verloren. Er drückt sich selbst den Stempel der Ohnmacht und des Mangels auf oder befeuert die Kriegsmaschinerie, die alles in die Zerstörung treibt.
Im Inneren gilt es, für Harmonie zu sorgen und sich auf die Frequenzen des Schöpferischen einzustellen. So darf sich jeder fragen: Wie sieht es bei mir aus? Bin ich von Menschen umgeben, die mich erniedrigen oder die mich erhöhen? Lebe ich das Leben, das ich mir wünsche? Bin ich im Mangel oder im Überfluss? Bin ich krank oder gesund? Ängstlich oder vertrauend? Zynisch oder liebevoll? Wie halte ich es? Wie ist meine Stimmung? Wie fühle ich mich in dieser Zeit, in dieser Welt? Wage ich es, Nein zu sagen, wenn alle Ja sagen, und Ja, wenn alle Nein sagen?
Wie selbstwirksam bin ich? Wie benutze ich die mir angeborene Schöpferkraft? Lasse ich mit mir machen oder mache ich selbst? Welche Menschen und Ereignisse ziehe ich an? Auf welcher Ebene schwingt meine Energie? Mit welchen Kräften stehe ich in Kontakt? Welche Informationen empfange ich? Wie viel Individualität wage ich? Nicht eine Individualität, die andere ausschließt, sondern eine, die alles miteinschließt und von dem Bewusstsein geleitet wird, dass alles eins ist.
Fühle ich mich getrennt oder verbunden? Fühle ich, dass ich unteilbar bin: in-dividuum? Spüre ich, wie ich aus der Kraft dieser Unteilbarkeit heraus unermessliche Möglichkeiten habe, mein Leben und damit die Welt zu gestalten? Bin ich wirklich erwacht oder halte ich mich nur für etwas Besseres, um bei der nächstbesten Gelegenheit genau das zu tun, was ich an anderen kritisiert habe: mein Heil von außen zu erwarten?
Angst- oder Christusmatrix?
Was auch kommt in der nächsten Zeit: Es wird uns überraschen. Jede Menge Möglichkeiten wird es geben, in denen wir unser Bewusstsein und unsere Individualität auf die Probe stellen können. Auf uns kommt es an! Jeder Mensch, der sich selbst aus der Ohnmacht befreit, befreit auch die Welt ein wenig mehr. Jeder, der sich nicht von schlechten Nachrichten nach unten ziehen lässt, jeder, der darauf achtet, seine Energie möglichst hoch schwingen zu lassen, jeder, der in sich selbst die Lösung sucht, ist ein Segen für diese Zeit, ein Tor für das Göttliche auf Erden.
Göttlich, so die Bewusstseinstrainerin Sandra Weber, ist alles, was natürlich ist, alles, was liebt, was pulsiert, leuchtet und verbunden ist. Wir haben die Wahl, uns per Genmanipulation und künstlicher Intelligenz (KI) immer mehr entmenschlichen zu lassen oder unser multidimensionales Potenzial zu entdecken, unsere Fähigkeit zu Telepathie, Telekinese und Teleportation. Angst- oder Christusmatrix — wofür entscheiden wir uns? Lassen wir durch KI die eigene Lichtkörperaktivierung unterbrechen oder wählen wir die Erhebung und das Vertrauen in unsere Göttlichkeit (3)?
Von hier aus können wir die Bühne überblicken. Wir erkennen: Wir müssen da nicht mitmachen. Wir müssen nicht in das Welttheater einsteigen. Wir müssen nicht die Lichtschwerter auspacken und für das Gute kämpfen. Das Gute kämpft nicht. Das Gute ist. Was wir tun können, ist, uns von den Altlasten zu befreien, die uns unten halten, innere Kämpfe ein für alle Mal zu befrieden und unsere Schatten ins Licht zu bringen.
Erleuchtung ist, wenn die inneren Schatten aufgelöst sind und man alles überblicken kann. Er-innern wir uns. Gehen wir nach innen und bauen wir hier unsere Tempel.
Fassen wir den Mut, wir selbst zu sein. Gehen wir in unsere Herzensmitte, werden wir uns der Bewertungen bewusst, mit der wir unsere Welt in Gut und Böse einteilen, und nehmen wir einen neutralen Standpunkt ein. So kommen wir aus der Dualität zurück in die Polarität, aus einer Welt, in der sich die Dinge gegenseitig vernichten, in eine Welt, in der sie sich ergänzen und kreativ zusammenwirken.
Quellen und Anmerkungen:
(1) https://lexikon.stangl.eu/887/bewusstsein\ (2) https://de.wikipedia.org/wiki/Gehirnw%C3%A4sche\ (3) https://www.youtube.com/watch?v=grAFeprqzhs&t=13s
Kerstin Chavent ist Sprachlehrerin und lebt in Südfrankreich. Sie schreibt Artikel, Essays und autobiographische Erzählungen. Ihre Schwerpunkte sind der Umgang mit Krisensituationen und Krankheit und die Sensibilisierung für das schöpferische Potential im Menschen. Auf Deutsch erschienen sind Die wilde Göttin, Der Königsweg, Die Enthüllung, In guter Gesellschaft, Die Waffen niederlegen, Das Licht fließt dahin, wo es dunkel ist, Krankheit heilt, Was wachsen will muss Schalen abwerfen, Und Freitags kommt der Austernwagen. Weitere Informationen auf kerstinchavent.de.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 609f186c:0aa4e8af
2025-05-15 20:01:08
@ 609f186c:0aa4e8af
2025-05-15 20:01:08I love that #nostr lets me write in long form. I see this as one of the brightest parts of Nostr's future.
Friends, I appreciate that you like thoughtful & detailed posts.
I'm also trying to move myself away from the** sustained-thought atrophy of the Twitter format**.. where half of each tweet is like half headline.
But I've struggled with composing long notes on a client in a way that is natural & intuitive.
It has been especially difficult to get a sense for how the thing is gonna look.
And when I want to add in more material...yiikes.
So I'm delighted to be composing this post in the brandnew note editor from #Primal.
So far, it feels really good. And I like that I can selectively format text.
The troll in me still wants a <blink> tag.Onwards to sustained cognition & real conversation!
Check out Primal's editor: https://primal.net/myarticles
-
 @ 5f078e90:b2bacaa3
2025-05-15 19:59:08
@ 5f078e90:b2bacaa3
2025-05-15 19:59:08Owl’s One-Legged Vigil
The vigil, one leg style

In a misty grove, Sylas the owl perched on a gnarled oak, standing on one leg. His golden eyes scanned the night. Why one leg? A vow to honor his lost mate, taken by a hawk. Each dusk, Sylas balanced, unwavering, as stars wheeled above. His silent stance drew the forest’s gaze—squirrels paused, deer bowed. One moonlit night, a young owl mimicked him, sparking hope. Sylas’s vigil became legend, a beacon of resilience.
Owl’s One-Legged Vigil: Part Two
Part 2
In the misty grove, Sylas stood on one leg, his vigil unbroken. The young owl, inspired, joined nightly, mimicking his stance. Word spread—foxes whispered, ravens cawed. Sylas’s balance was no mere feat; it was defiance against loss. One stormy dusk, winds howled, yet Sylas held firm, his single leg rooted. The young owl faltered but watched in awe. Moonlight pierced the clouds, bathing them in silver. Sylas hooted softly, a call of endurance. The grove’s creatures gathered, drawn by his resolve. A wise badger spoke: “Your vigil heals us.” The young owl, now named Lark, vowed to carry Sylas’s legacy. As dawn broke, Sylas stretched both legs, his vow fulfilled. He flew with Lark, their wings brushing the sky. The grove thrived, united by his stand. Sylas’s one-legged vigil became a tale of hope, etched in every tree.
-
 @ 2ed3596e:98b4cc78
2025-05-15 18:25:25
@ 2ed3596e:98b4cc78
2025-05-15 18:25:25Bitcoiners, the Bitcoin Well point store just got even better.
You can now redeem your Bitcoin Well points for a Bitaxe, a fully open-source Bitcoin miner! Take your Bitcoin lifestyle to the next level by mining your own sats.
In a world dominated by large scale mining farms, Bitaxe is flipping the narrative by putting Bitcoin mining back into the hands of individuals.
The Bitaxe is a modern mining ASIC, but small enough to fit on your desk.
Like Bitcoin itself, Bitaxe is fully open-source, you can inspect, modify, and enhance the hardware and software. Bitaxes are super user friendly and are built to be customized, making a Bitaxe an incredible educational tool.
The Bitaxe is ideal for Bitcoiners who want to contribute to Bitcoin’s decentralization while also learning, first hand, what goes into the Bitcoin mining process. Who knows, you might even stumble into a block reward!
Now, you can exchange your points for a quiet, cool, low power miner that you can run yourself, at home.

What else can you get in store?
You can also exchange your points for:
-
Simply Bitcoin hoodie
-
Exclusive Bitcoin Well Stampseed backup plate
-
Personalized LeatherMint wallet
-
Tesla Cybertruck in Bitcoin orange
Start stacking rewards that actually matter. Visit your account to redeem today!
How to redeem your Bitcoin Well Points?
Redeeming your points is easy:
Log in and go the Bitcoin Well Points store within the Rewards Section
Check your Bitcoin Well point balance
Redeem Your Bitcoin Well points for the prize of your dreams
Once you’ve purchased an item from the Bitcoin Well Point Store, we’ll email you to figure out where you want us to ship your prize. Unless it's the Cybertruck, then you can come to our office and pick it up!
Ready to Take Control?
At Bitcoin Well, we make self-custody simple, secure, and empowering. If you’re ready to take control of your Bitcoin, sign up below to start your journey to true ownership.
-
-
 @ 3b62c542:6f45deaf
2025-05-15 17:44:53
@ 3b62c542:6f45deaf
2025-05-15 17:44:53Introduction Once dismissed as a speculative gamble, cryptocurrency is steadily transforming into a powerful tool for financial inclusion—and nowhere is this shift more pronounced than in Africa. Across the continent, digital currencies are not merely investment vehicles; they’re practical responses to real-world challenges. Faced with high inflation, weak national currencies, limited banking infrastructure, and an increasingly digital youth, African communities are leveraging crypto to build a new financial future one that’s decentralized, accessible, and uniquely tailored to local needs.
From the bustling markets of Lagos to the tech hubs of Nairobi and Cape Town, crypto is being embraced not out of trendiness, but necessity. Africa, often overlooked in the global financial narrative, is rapidly becoming a testbed for what the future of digital finance could and arguably should look like.
The driving forces behind Africa’s Crypto Boom
1. Financial inclusion In sub-Saharan Africa, nearly 60% of adults remain unbanked, largely due to the lack of accessible banking infrastructure in rural and underserved areas. Traditional banks often require documentation, minimum deposits, and credit histories requirements many Africans cannot meet. Enter cryptocurrency: decentralized, borderless, and open to anyone with a smartphone and internet connection.
Mobile friendly wallets and crypto platforms allow users to send, receive, and store funds without needing a traditional bank account. Stablecoins like USDT and USDC have proven especially valuable, offering a digital currency option pegged to the US dollar, shielding users from local currency volatility while providing global usability.
2. Remittances made easy Africa is one of the most expensive regions in the world for receiving remittances. On average, sending money to sub-Saharan Africa costs about 7–9% in fees well above the global average. Cryptocurrencies slash these costs significantly and complete transactions within minutes, not days.
Nigerians, for example, received over \$19 billion in remittances in recent years. With crypto, users can bypass traditional intermediaries like Western Union or MoneyGram and directly receive funds in digital wallets, which can then be converted to local currency or used for online purchases. This is especially impactful in rural areas where financial services are sparse.
3. A hedge against inflation In countries like Zimbabwe, Nigeria, and Sudan, inflation and currency depreciation have eroded trust in local fiat money. In these environments, digital assets have emerged as safe havens. Bitcoin, often dubbed “digital gold,” and stablecoins are increasingly being used as stores of value and mediums of exchange.
Rather than hoarding cash that loses value by the day, individuals are turning to crypto to preserve their savings. In Nigeria, for example, peer-to-peer (P2P) trading volumes have soared, driven by economic instability and foreign exchange restrictions that limit access to USD.
4. Youth-led tech adoption Africa has the world’s youngest population—with over 70% under the age of 30. This generation is digitally native, entrepreneurial, and eager to tap into global economic systems. They’re embracing crypto for side gigs, freelance jobs, digital trading, and e-commerce—all of which benefit from borderless, fast, and low-cost payments.
Platforms like Binance, Luno, and Paxful are popular among young Africans not only for trading but for learning. Many youths are also creating local crypto content, starting communities, and building tools that address uniquely African use cases, such as microtransactions, decentralized savings groups, and cross-border agriculture financing.
Real-World use cases
-
Kenya’s M-Pesa Meets Blockchain: M-Pesa revolutionized mobile money in East Africa. Now, blockchain integrations are taking that revolution a step further. By connecting M-Pesa wallets to crypto platforms, users can seamlessly convert between fiat and crypto, enabling cross-border remittances, savings, and payments—all from a basic mobile phone.
-
Crypto Startups on the Rise: African entrepreneurs are not waiting for solutions from the West. Startups like Yellow Card in Nigeria are providing easy access to crypto in multiple local currencies. VALR in South Africa is offering a full-fledged crypto trading experience with high liquidity and compliance. Bundle Africa, BuyCoins, and others are focusing on remittance, bill payments, and savings all powered by crypto.
-
Education & empowerment: Crypto literacy is spreading fast thanks to targeted education campaigns. Binance Academy Africa and Paxful have launched bootcamps, online courses, and community outreach efforts. These programs are essential in combating misinformation and scams while building a knowledgeable user base that can leverage crypto safely and effectively.
Challenges and the road ahead Despite its momentum, crypto adoption in Africa is not without its challenges. Regulatory uncertainty remains a significant barrier. In some countries, authorities have imposed bans or strict limitations, citing concerns over money laundering, fraud, and capital flight. In others, frameworks are still evolving, leaving businesses and users in a legal gray area.
Internet penetration, while growing, is still inconsistent, particularly in rural areas. This digital divide hampers access to wallets and exchanges. Moreover, the space is vulnerable to scams and pyramid schemes that prey on uninformed users highlighting the urgent need for education and safeguards.
Yet progress is being made. South Africa now regulates crypto as a financial product, bringing oversight and legitimacy to the space. Nigeria launched the eNaira, Africa’s first central bank digital currency (CBDC), aiming to modernize the financial system while retaining regulatory control. Other governments are exploring blockchain’s potential for public services, from land title registries to national ID systems and supply chain tracking.
Conclusion Africa is not just adopting cryptocurrency—it’s redefining its purpose. Here, crypto isn’t about speculative trading or get-rich-quick schemes. It’s about solving deep rooted problems with bold, decentralized solutions. In a continent long underserved by global financial institutions, blockchain technology is offering a fresh path forward one driven by innovation, inclusivity, and grassroots energy.
As global interest in digital assets continues to grow, Africa’s crypto movement offers powerful lessons. It shows how technology, when embraced by necessity and tailored to real world problems, can spark lasting change. Far from the margins, Africa is helping shape the blueprint for a future where digital finance is open, resilient, and truly global.
-
-
 @ 000002de:c05780a7
2025-05-15 17:40:26
@ 000002de:c05780a7
2025-05-15 17:40:26It's been in the news recently that Mike Waltz was not using Signal but an app called TeleMessage, which is marketed as a tool to archive Signal chat conversations. This event presents a great opportunity for learning. After years of following security and privacy tech, one of the many lessons I've learned is that humans are almost always the weak link in security. Foolish decisions are usually at the root of most breaches and attacks. This was the case with the Trump admin. I am of the opinion that it is foolish to use devices like the iPhone or any phone OS for secure communication. Not because the devices are not secure—they can be very secure. It's that humans can break this security very easily with careless behavior, as we see in this case.
While Signal encrypts messages in transit[^1] and at rest on your mobile devices, it is important to remember that any encrypted messenger app, whether it's Signal, WhatsApp, Apple Messages, or SimpleX, must decrypt the messages for you to read them. There really isn't a way around this. So, with this in mind, it's obvious that trust is involved when using any of these apps. First, you are trusting the person you are conversing with. This might seem trivial, but it seems to be lost on many people. When you send a message to another party, you have no idea what they are doing with it. Apps like Signal try to mitigate this by offering disappearing messages. Some apps don't allow screenshots of the application. But make no mistake, if your message is readable by a human, they can capture it. Even if they just snap a picture of it from another device. If that were the only thing to consider, we could end this now, but it's not.
You are also trusting the phone/device OS. While I think it is unlikely that Apple and Google are capturing the screens on devices and apps like Signal, we cannot have 100% certainty of this. At least I do not. But it's worse than this. There are attack toolkits like Pegasus which can be covertly installed on phones like the iPhone and most Android devices. It is almost certain that Pegasus or something like it could capture and expose your private messages when you read them. This is because they basically gain low-level access to the device without your knowledge. And because humans can't mentally unencrypt messages, Signal must decrypt the message for you to read it. When it does, the malicious app can capture it and send it off to the attacker. FWIW, this is possibly what happened to Tucker Carlson when he claimed that Signal "leaked" his communication about traveling to Russia to interview Putin. Though I suspect it is more likely a mole in either his operation or the Russians. The least likely scenario is that Signal was actually compromised.
So no matter how secure your messaging app may be, if your phone OS is compromised, it's game over. This wasn't the case here as Waltz foolishly was using a clone of the Signal app called TM SGNL to log Signal chats and send them to the TeleMessage servers. It appears that this was done in the clear and that the logs were even emailed to mail servers. You can read more about this in a post I made earlier today. So, as you can see, he wasn't actually using Signal at all. Signal was not the issue.
So what should you do now that you are armed with this knowledge? Well, first of all, you should take everything I write with a grain of salt. Do your own research and do not do anything you don't feel comfortable doing. Don't trust, verify. With that caveat, the likelihood of Signal being compromised in my opinion is low. The likelihood that Apple or Google is logging your Signal chats is also low. I think they could if they desired. The likelihood of your being targeted with something like Pegasus is also low but not impossible. I don't know you or your threat model. It's something to think about. But here is something everyone should consider.
The most important thing to consider is that you are always trusting the person you communicate with. This is not only true for digital communication but also in-person communication. Of course, SMS is not secure, but I do use it for things that I have no concern about being recorded. But I do prefer to use encryption when I can. A side note, we seem to be heading toward a secure-by-default standard in the future with SMS[^2], which is good to hear. I use Signal with any friends that are willing to use it, but I do not trust them all equally. For one thing, most of us do not trust everyone equally for anything. Trust is earned and built over time. But even for people I trust, I may not trust their technical skills or security practices. This has to be a consideration when you use Signal. Signal cannot protect you against a malicious recipient. This person could be building a log of your conversations. They might even be hacked and unaware. They could be using an insecure client, as was the case with the Trump admin.
So be aware. The best policy is to be very careful with anything you put in a digital device. The best way to keep a secret is to not share it. There are many thoughts and communications that I would never use a phone or computer to communicate. I think people would be wise to do the same.
[^1]: The Double Ratchet Algorithm at the heart of Signal [^2]: End to End Encryption is coming as the default for mobile phones
https://stacker.news/items/980937
-
 @ 1c19eb1a:e22fb0bc
2025-05-08 21:55:46
@ 1c19eb1a:e22fb0bc
2025-05-08 21:55:46If you haven't noticed already, #Nostr is a little different from what most people are used to. One of the ways this is felt most acutely is with media hosting. Users are accustomed to uploading their images and videos directly through the app they are posting from. Many Nostr apps provide that same experience nowadays, but it wasn't always the case.
Just a couple years ago, users had to find somewhere to host their media separately, and then copy and paste the URL into their note whenever they wanted to share their cat pictures. One of the first, if not the first, media hosting services specifically intended for Nostr was nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7, which will be the service we are reviewing today.
Like our previous review of Amber, Nostr.Build is a service for users to pair with other Nostr apps. You won't generally use nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 by itself. Rather, you'll use it to host that incredible shot you want to post to #Olas, or to host screenshots for your long-form tutorial about setting up Nostr Wallet Connect that you'll be posting from #Habla.news, or for hosting a hilarious video of your cat falling asleep to nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u's voice and taking a tumble off of his favorite perch that you want to share on #Damus. However, there are some features within Nostr.Build that you may want to check out quite apart from using it with any other Nostr app.
Overall Impression
Score: 4.8 / 5
I have been impressed by Nostr.Build for some time now, but they have pulled out all the stops in their latest update, increasing their maximum file size for free accounts to 100MB, integrating the #Blossom protocol, adding the ability to share directly to Nostr from within your dashboard, and more integrations with other Nostr apps than ever before. Nostr.Build is simply a pleasure to use, whether through their web interface, or through another Nostr app that integrates with them.
With the ability to easily organize your media, view statistics, browse the media gallery of free uploads, metadata removal for increased privacy, and AI image generation, Nostr.Build is not simply a media hosting service, it is a full-fledged media management platform. Its robust features keep it well ahead of other Nostr-focused media hosting options available, and a particularly strong option for those using Blossom and wanting redundancy and reliable uptime for their media.
As much as I enjoy using the web interface, though, where Nostr.Build really shines is their integrations with other Nostr apps. These integrations allow users to have the same experience they are accustomed to from centralized social platforms of uploading their media from within the same app they are using to share it. No copy/pasting a URL from one app to another. In fact, many users may not realize they have been using Nostr.Build in their client of choice, simply because it is the default option for media hosting for many Nostr apps.
This has the added benefit to client developers that they can provide this experience to their users without having to run media hosting infrastructure on top of trying to build their app. The separation of relays, clients, and media hosting between different entities, while keeping a similar experience to centralized platforms where a single company controls all three, is critical to Nostr adoption.
Features
Nostr.Build has a plethora of features beyond simply hosting your media. Let's take a look!
AI Image Generation
Do you need a quick title image for a long-form article? How about inspiration for a logo or art piece? Nostr.Build's AI Studio has you covered.
They have provided a few different models based on the plan you purchase, beginning with the Professional plan, which includes SDXL-Lightning and Stable Diffusion 1. Upgrading to the Creator plan will give you access to all Pro Stable Diffusion models and unlimited use of the Flux.1 model, which is the same core model used for Grok2 images.
I personally have a Professional account, so I haven't had a chance to try out Flux.1, but I have used Stable Diffusion extensively for creating character art for #NostrHeroes characters, such as these:




Nothing too spectacular when compared with some of the newer models out there, and there is no image-to-image support (yet), but more than adequate for casual image generation needs. Moreover, it is far more than what one would expect from a simple media-hosting service.
Admittedly, I am also no expert at coaxing AI models to produce anything remarkable so your results may vary. Either way, image generation is a welcome tool to have available without needing to go to an outside service unless you require something very specific.
Upload Limits
The maximum file size limits on Nostr.Build have been getting progressively larger, even for their free service. As I recall, it was a mere 21MB limit per file just a few months ago, which is fine for image files, but is quickly exceeded with videos. Then they increased their limits to 50MB per file, and as of recent updates it has been increased once more to a whopping 100MB per file... for free! This is more than adequate for most uses.
However, free users' images, GIFs, and videos are automatically viewable via Nostr.Build's free media gallery. This is something to particularly bear in mind when uploading images you intend to share via direct message. Though your DMs are encrypted, the images uploaded to Nostr.Build are not, and if you don't have a paid account, they will be viewable to the all paid users in the free media gallery. If you want to upload images that will not be viewable unless you actively share them, you must have a paid account.
Paid accounts have no file size limit, but they do have a total storage limit. I could not find anything about total storage limits for free accounts, but Professional tier will give you 25GB, Creator 50GB, and Advanced 250GB. Uploads to paid accounts are not visible in the free media gallery, so only those you give the link to will be able to access your content.
Media Types
Many file types are supported by Nostr.Built, even for free users, including:
- Image: .jpg, .png, .gif
- Video: .mov, mp4
- Audio: mp3, .wav
Upgrading to the Professional plan will add .pdf and .svg to the list of permitted file types, and upgrading to Creator or above will add .zip files, as well.
I believe other common file types are also supported, but these are the only ones specifically mentioned on the site.
Free Media Gallery
The free media gallery is an interesting little feature that Nostr.Build has available to paid accounts. Free users can get a preview, such as the one below, but only paid users can browse through the millions of uploads made by free users.
Apart from being amusing to browse through the things people have been uploading, I am unsure of how useful this particular feature is. No indication is given as to who uploaded the media, and it is limited compared to media feeds in other Nostr apps in two important ways. First, it only shows media uploaded to Nostr.Build, while other media-focused Nostr apps, such as Slidestr, Lumina, or even Primal will show media posted by all Nostr users. Second, Nostr.Build's gallery doesn't show all uploads to Nostr.Build, but only uploads from those without a paid account, further limiting the scope of whose uploads are seen.
Paid users have the advantage of being able to upload media that is not viewable to anyone unless they intentionally share the link somewhere. Free users, on the other hand, must be aware that their uploads are viewable by any paid users, whether they shared the link anywhere or not.
One incident I had while testing out another app required me to reach out to Nostr.Build support to request deletion of an image. It had some of my personal information in it, and had been uploaded to Nostr.Build and sent to me via DM. The sender assumed that since it was being sent via DM, no one else would be able to see the image, but because he was not a paid user of Nostr.Build, the image was included in the Free Media Gallery for any paid user to see. Not ideal, but the folks at Nostr.Build were quick to get it deleted for me.
In short, I have mixed feelings about this particular feature.
Blossom
Blossom is a media storage and retrieval protocol built for Nostr, but usable with any application that needs to access media via the web, and Nostr.Build has recently added support for Blossom uploads via their Blossom server: blossom.band
I will likely be adding a Nostrversity article going over Blossom in detail in the near future, but here's the basics of what it makes possible:
First, easy integration for media uploading from your favorite Nostr apps. Amethyst, Coracle, Primal and others have added Blossom upload support, so you just have to hop into your settings and add Nostr.Build's Blossom server address to start using it as your media host. No need to go to a separate app to upload your media and copy/paste the URL into your Nostr note!
Second, your media in Blossom is content addressable. This means it is named based on a hash of its actual data. Because of this, you can verify that the media has not been altered or replaced by your media host. If the hash doesn't match the data, it won't be loaded by the Nostr client, so you never have to worry about the image in your note being replaced by a different image by your media host.
Finally, because your media is addressable by its content, you can save the same media to multiple hosts, and if one of them goes down, Nostr apps can fetch your media from other hosts, just like they can do with your notes by fetching them from different relays if one relay you write to is down. This makes your images and videos much harder to censor, since you would need to be banned by multiple Blossom servers for your media to no longer be accessible.
If you would like to upload media to more than one Blossom server at the same time, your options are currently to use Primal and ensure that your settings have "Enable media mirrors" toggled on, or to use Bouquet. Hopefully we will see this option added to more Nostr apps in the near future.
Metadata Stripping
For files uploaded via Nostr.Build's dashboard, location metadata is removed upon upload. This is to protect user privacy, since this data could be used to reveal your home address if it is left attached to images posted publicly on Nostr.
When uploading via Blossom, media containing location metadata will be rejected. The user will be required to remove the metadata before they can upload the media.
No KYC and No Ads Policy
The only form of identification needed to use Nostr.Build is your Nostr identity. Every upload is tied to your npub, but no name, date of birth, email, or other identifying information is required. This is made possible because Nostr.Build only accepts Bitcoin as payment for their accounts, and no KYC is required to make Bitcoin transactions via Lightning.
Additionally, Nostr.Build is philosophically opposed to targeted advertising, so they have a policy that they will never use ads on their hosting service.
Client Integrations
Even before Blossom, Nostr.Build had many Nostr clients that used it as the default media hosting service, allowing users to upload directly within the app. This has only expanded now that Nostr.Build has added Blossom.
A very non-exhaustive list of clients that integrate with Nostr.Build is listed on their site, and includes Damus, Amethyst, Nostrudel, Snort, Iris, Coracle, Flycat, and Yakihonne. Additional apps that support Nostr.Build via Blossom include Primal and Flotilla. Some of these integrations support both Blossom and NIP-96 options for uploading media, such as Amethyst, while others only support one or the other.
I would not be surprised to see more and more Nostr apps move to integrating Blossom and phasing out NIP-96 support. Either way, though, Nostr.Build currently supports both, and is therefore an excellent hosting option if you want to use it with a wide range of Nostr apps.
Media Statistics
For those with a paid account, Nostr.Build provides information about how often each of your uploads has been requested and viewed within a given time period.
This can be valuable information for content creators, so they can determine what content is resonating with their audience, and what times of day their posts get the most views.
This information can currently be viewed for a maximum period of three months prior to the current date, and as short a period as just the past hour.
Can My Grandma Use It?
Score: 4.7 / 5
Nostr.Build is incredibly easy to use if you have a paid account, or if you are a free user uploading to Nostr.Build through a client that integrates with them by default. Previous frictions encountered by free users trying to upload large files should now be few and far between, thanks to the generous 100MB size limit.
Where things may be a bit more involved is when users are trying to set up media hosting on Nostr apps that don't use Nostr.Build by default. Exactly where in the settings the user must go to set this up, and whether to use the Blossom or NIP-96 address may not be immediately apparent, and requires an understanding of the difference that the user may not possess. This is not the fault of Nostr.Built, though, and I have not taken it into consideration in the scoring. Each individual Nostr app's settings should be as easy to understand as possible.
Another point of friction may come from free users who want to upload directly through the Nostr.Build site, instead of via another Nostr app. This used to be possible without logging in, but in an effort to ensure the service was used for Nostr, and not for general media hosting, Nostr.Build added the requirement to log in.
Thankfully, there are plenty of login options, including npub and password, browser extension (NIP-07), and even via a one-time-code sent to you via Nostr DM. However, if you don't have a paid account already, logging in will prompt you to upgrade. It seems that uploading directly via the website has been removed for free users entirely. You can only upload via another Nostr app if you don't have a paid account. This may lead to confusion for users who don't want to pay for an account, since it isn't made apparent anywhere that uploading through the website isn't an option for them.
Additionally, I would like to see the addresses for the Blossom server and for NIP-96 uploads (unless they are being phased out) added to the main page somewhere. Even selecting the "Blossom" page from the site navigation doesn't make clear what needs to be done to utilize the service. Something as simple as, "To use Nostr.Build with your favorite Blossom compatible Nostr apps, just add https://blossom.band as your media host in the app settings," would be enough to point users in the right direction.
For those who do have paid accounts, the dashboard is easy to navigate and organize your media.
By default, all uploads are added to the Main Folder. Users can leave them there, or they can easily create new folders and drag and drop media to organize it.
Every image has a copy/paste clipboard icon for ready access to copy the media URL for inclusion into a Nostr note.
Additionally, Nostr.Build allows users to share their uploaded media to Nostr directly from the dashboard. Bear in mind, though, this is published to a set of popular relays, without taking into account the user's preferred write relays.
The section just below the user's profile information gives an at-a-glance view of important information, such as how much of the user's allotted storage has been used, how many AI Studio credits are available, how many days are left before their paid account must be renewed, and how many files from three major categories — GIFs, images, and videos — have been uploaded.
Uploading directly to the dashboard is also incredibly easy. You can simply drag and drop files into the upload pane, or browse for them. If you have a URL for the media you want to upload, you can even paste it to import from another website or Blossom server.
Anything I could think of that I might want to do in the interface was intuitive to find, well labeled, or had common and easily identified icons.
How do UI look?
Score: 4.7 / 5
I would describe Nostr.Build's UI as clean and utilitarian, which is what one would expect from a media hosting service. Nothing too flashy. Just what you need and nothing you don't.
We certainly like our purple color-schemes on Nostr, and Nostr.Build leans into that with white text on shades of purple backgrounds, along with occasional color-popping accents. If a Nostr client had made the same color choices, I might be a bit more critical, but it works in an app that users won't be spending a ton of time in, except while managing their media, or using the AI Studio to generate some images.
UI elements such as buttons, active folder indicators, and icons all maintain an attractive, and simple design, with rounded corners wherever appropriate. Nothing looks too busy or overbearing, and the spacing between image previews in the folder view is just right.
Font remains consistent throughout the interface, with no jarring changes, and bold text, in white or another contrasting color, is used appropriately to draw attention, while subdued text is rendered in a light purple to blend more with the background, while remaining readable.
As such, the UI is attractive, without being particularly breathtaking. Nothing to complain about, but also nothing to write home about.
Log In Options
Score: 4.8 / 5
As mentioned previously, Nostr.Build provides three ways a user can log in.
The first should be very familiar for any Nostr user who frequents web clients, and that is by use of a browser extension (NIP-07), such as Alby, Nos2x, or Gooti. Note, this will also work if you are on Android and using KeyChat's browser, which has a NIP-07 signer built in.
Next is the legacy login method for Nostr.Build that they have used since the service first launched, which is via npub and password. This should serve to remind you that even though Nostr.Build supports Nostr login, and can post your images to Nostr for you, it's really just a centralized media hosting service. Just like you wouldn't use only one Nostr relay, you should not use just one media host. Mirror your media to other Blossom servers.
Most intriguing, and one I had not seen used before, is the option to use your npub and have a one-time-code sent to you via Nostr DM. I tested this method out and it worked flawlessly. It is unfortunately using the old NIP-04 DM spec, though, so any clients that have deprecated these DMs will not work for receiving the code. We're in a strange place with Nostr DMs currently, with some clients deprecating NIP-04 DMs in favor of NIP-17, others that still only support NIP-04, and a few that support both. If you don't see the DM in your client of choice, hop over to Primal and check your DMs there in the "other" tab.
Since Nostr.Build is supporting Nostr login, I would like to see them add remote signer (NIP-46) login alongside browser extension login to round out the options expected from a Nostr web app.
Feature Set
Score: 4.8 / 5
The features provided by Nostr.Build all work as expected and provide a lot of value to the user. With only one exception, all of the features make sense for a media hosting and management service to provide, and they are adding more features all the time.
Users not only get a reliable hosting service, with excellent uptime for their media, but they get integrations with most Nostr clients I can think of, Blossom protocol support, media organization and statistics, posting media to Nostr from within the dashboard, metadata stripping for enhanced privacy, a wide range of supported file types, and an AI image generation studio! What's more, there are additional features already on the roadmap, including traditional and AI image editing, additional plan options, expandable storage, and video transcoding for optimized playback. Nostr.Build is just getting started and they already offer more than most media hosting services out there, intended for Nostr or otherwise.
The one feature I am still not sold on is the "Free Media Gallery." The name is misleading. The gallery itself is not free. You must have a paid account to access more than a preview of it. Rather, it displays media uploaded by free users, regardless of whether they uploaded that media to send via DM, or uploaded it but decided not to share it out, or uploaded it to post it only within a private group on Flotilla, or uploaded it and only sent the note with the image link to a private relay.
Moreover, if I want to see media that has been shared on Nostr, there are plenty of ways I can do so that I can be confident only include media users intended to be publicly viewable. This feature from Nostr.Build, if it is kept at all, should have some way of ensuring the gallery only includes images that were shared on public relays.
Pricing
Score: 5 / 5
The pricing structure for Nostr.Build is exceptionally reasonable when compared with other services.
The Professional plan, which is their lowest paid tier, is just 69,000 sats a year. At current price, that translates to around $70 for the year, and Nostr.Build has been known to lower their pricing as Bitcoin goes up. Users can also get a 10% or 20% discount if they buy 2 or 3 years at a time, compensating for the fact that Bitcoin tends to go up year over year.
For that cost, users get 25GB of storage, unlimited file size for uploads within that storage cap, and access to all of Nostr.Build's features mentioned in this review, with the exception of their highest end AI models and storage of certain file types.
If I were to set up my own VPS to host a Blossom server with comparable storage, I would be paying around $14 a month before the cost of the domain, and it would be anything but plug and play. Even then, all I would have is storage. I would be missing out on all of the other features Nostr.Build has out of the box for less than half the price.
The Creator plan is close to double the cost at 120,000 sats, or about $120, a year. However, you aren't just getting double the storage space at 50GB; you are also getting double the AI credits, access to the higher tier AI models, S3 backup for all of your media, and your own Creator page you can share out with your media available for others to browse in one location.
The Advanced plan doesn't add a lot of extra features for more than double the price of the Creator plan, but it MASSIVELY increases your storage limit by 5x to a total of 250GB. Comparable storage space on a VPS to run your own Blossom server would be about $100 a month and Nostr.Build is offering it for about $250 (250,000 sats) for a whole year! If you really need to host that much media, it's hard to beat this price. The plan also comes with a Nostr.Build NIP-05 address, if you need one.
Now, the argument can be made, "But it's priced in sats, and that means in four years I will have spent many times that dollar amount on their service, possibly making it more expensive than other services priced in fiat." While that is true, it also doesn't take opportunity cost into account. Every dollar you spend on something other than Bitcoin is a missed opportunity to have bought Bitcoin with it. There's not really any difference between spending $70 in fiat to buy a hosting plan vs spending 69,000 sats, because you could have used that same $70 to buy Bitcoin instead, so you are losing out on that increase in purchasing power either way.
Not to mention, you can just buy the sats with your fiat and send it to Nostr.Build, so you would effectively be buying your plan with fiat, and they would be receiving sats.
I think Satellite.earth is still technically less expensive at just $0.05 per GB per month, which comes to $15 a year for the same 25GB of Nostr.Build's professional plan. However, all you get is media hosting. You miss out on all of the other features provided by Nostr.Build. And if you are uploading files of 100MB or less... Well, free with Nostr.Build is still cheaper than $0.5 per GB.
Wrap Up
All of the above comes together to make Nostr.Build a versatile and full-featured media hosting and management service at an affordable price point for their paid accounts, but with no need to pay at all if you just want a place to upload photos, GIFs, memes, and even some videos, so long as the file size stays under 100MB. Whether you want to use Nostr.Build as your primary media host, or as just one redundancy in your Blossom set up, they have you covered and I encourage you to check them out!
For the next review, I would like to go with another client, this time for the web, and the two options I am debating between are Coracle.social and Jumble.social. Let me know in the comments which you would like to see!
-
 @ bbef5093:71228592
2025-05-15 17:18:25
@ bbef5093:71228592
2025-05-15 17:18:25USA és Szaúd-Arábia együttműködik a nukleáris energiában, beleértve a fejlett reaktorokat is
Az Egyesült Államok és Szaúd-Arábia 2025. május 13-án Rijádban aláírt egy energiaügyi és kritikus ásványi anyagokra vonatkozó együttműködési megállapodást, amelynek részeként a polgári nukleáris energia területén is kijelölték az együttműködés főbb területeit. Az USA Energiaügyi Minisztériuma szerint a kooperáció kiterjed a biztonságra, védelmi és non-proliferációs programokra, az amerikai III+ generációs fejlett nagy reaktortechnológiákra és kis moduláris reaktorokra, valamint az uránkutatásra, bányászatra és feldolgozásra.
További területek a szakképzés, munkaerő-fejlesztés és a nukleáris hulladékkezelés. Chris Wright energiaügyi miniszter szerint ezek a megállapodások erős partnerséget teremtenek, amelyek biztosítják Donald Trump elnök „belföldi jólét és külföldi béke” víziójának megvalósulását. Trump első jelentős külföldi útján látogat Szaúd-Arábiába és más arab országokba második elnöki ciklusában. Wright az energiaügyi együttműködési megállapodást Abdulaziz bin Salman Al Saud szaúdi energiaügyi miniszterrel írta alá. Az USA szerint a megállapodás célja az innováció, fejlesztés és az energetikai infrastruktúra kiépítésének lehetőségeinek feltárása a két országban.
Az USA és Szaúd-Arábia tárgyalásokat folytat a királyság polgári nukleáris iparának fejlesztéséről, de a tárgyalásokat régiós politikai kérdések és a fegyverkezési aggodalmak bonyolítják. Wright múlt hónapban azt mondta, várhatóan előzetes megállapodást írnak alá, és Rijád valamint Washington „úton van” egy közös szaúdi polgári nukleáris program kidolgozásához. „Az USA részvételéhez és partnerségéhez mindenképp szükség lesz egy 123-as megállapodásra... sokféleképpen lehet úgy szerződni, hogy az megfeleljen mind a szaúdi, mind az amerikai céloknak” – mondta Wright.
A 123-as megállapodás útja
Az úgynevezett 123-as megállapodás az USA 1954-es Atomenergia-törvényének 123. szakaszára utal, amely szükséges ahhoz, hogy az amerikai kormány és cégek együtt dolgozhassanak a királyság entitásaival polgári nukleáris ipar fejlesztésén. Wright szerint a szaúdi hatóságok még nem egyeztek bele a törvény által előírt feltételekbe, amely kilenc non-proliferációs kritériumot határoz meg annak érdekében, hogy az adott állam ne használhassa fel a technológiát nukleáris fegyverek fejlesztésére, vagy ne adhassa át érzékeny anyagokat másoknak.
A tárgyalások eddig azért is akadoztak, mert Szaúd-Arábia nem akarta kizárni az urándúsítás vagy a kiégett fűtőelemek újrafeldolgozásának lehetőségét – mindkettő potenciális út egy atombomba felé. Mohamed bin Szalmán koronaherceg régóta hangoztatja, hogy ha Irán nukleáris fegyvert fejleszt, Szaúd-Arábia is követni fogja. A világ legnagyobb olajexportőre, Szaúd-Arábia jelentős megújuló energia előállítására és kibocsátáscsökkentésre törekszik a koronaherceg Vision 2030 reformprogramja keretében, amelyben a nukleáris energia is szerepet kap.
2022-ben Szaúd-Arábia létrehozta a Nemzeti Nukleáris Energia Társaságot, hogy fejlessze és üzemeltesse a nukleáris létesítményeket. A királyság akkor kezdte meg az első atomerőművi engedélyeztetési folyamatot, amely a hírek szerint mintegy 14 milliárd dollárba (12,2 milliárd euróba) kerülhet. Helyi média szerint a tervezett atomerőmű kapacitása 2800 GW lesz. Korábbi jelentések szerint Dél-Korea, Franciaország, Kína és Oroszország is adott be ajánlatot, de ezt hivatalosan nem erősítették meg.
Tajvan: Az utolsó atomerőmű bezárására készülve módosítják a törvényt
Tajvan parlamentje elfogadott egy módosítást a nukleáris energia törvényében, amely lehetővé teszi az üzemeltetők számára, hogy a jelenlegi 40 éves korlátozáson túl további 20 évre hosszabbítsák meg az atomerőművi engedélyeket, így akár 60 évig is működhet egy reaktor. Az állami Central News Agency szerint a módosítást az ellenzéki Kuomintang és a Tajvani Néppárt támogatta, 60 igen és 51 nem szavazattal, a kormányzó Demokratikus Progresszív Párt ellenében.
A javaslat célja a nukleáris energia újbóli bevonása Tajvan energiastratégiájába. A Nukleáris Biztonsági Tanács szerint minden hosszabbítási kérelemnek meg kell felelnie a nemzetközi szabványoknak, és alapos műszaki és jogi értékelésen kell átesnie. A lépésre azután kerül sor, hogy a kormány a hétvégén véglegesen bezárja a Maanshan-2 atomerőművet Pingtung megyében, ezzel teljesítve Tajvan nukleárismentességi ígéretét.
Kuo Jyh-huei gazdasági miniszter megerősítette, hogy a Maanshan-2 hosszabbítása akár 18 hónapot is igénybe vehet. A kormány szerint a módosítás nem változtatja meg a Maanshan-2 bezárásának tervét. 2024 júliusában a Taipower állami vállalat leállította a Maanshan-1 atomerőművet, így az országban már csak egy reaktor, a Maanshan-2 maradt üzemben.
A sziget energiaigénye – főként a félvezetőipar miatt – gyorsan nő, ami újraéleszti a nukleáris energia körüli vitát. A gazdasági minisztérium szerint az ország villamosenergia-szükséglete 2030-ra várhatóan 12-13%-kal nő, főként a mesterséges intelligencia (AI) iparág fellendülése miatt. A Greenpeace szerint a világ legnagyobb chipgyártója, a Taiwan Semiconductor Manufacturing Company 2030-ra önmagában annyi áramot fog fogyasztani, mint a sziget 23 milliós lakosságának negyede.
Az energiaéhség nehezíti Tajpej 2050-re kitűzött nettó zéró kibocsátási vállalását, amely nagyrészt a megújuló energia részarányának 60-70%-ra emelésén alapul a jelenlegi 12%-ról. A nukleáris energia támogatói szerint ez a legéletképesebb módja Tajvan ipari és környezetvédelmi céljainak összehangolására. 2023-ban a nukleáris energia a tajvani villamosenergia-termelés 6,9%-át adta, míg a fő energiaforrások a szén és a cseppfolyósított földgáz voltak. A Maanshan-1 bezárásával a nukleáris energia aránya 2,8%-ra csökken.
Egykor hat reaktor biztosította Tajvan áramellátásának több mint felét.
„Nagyon nyitottak” az új nukleáris technológiára
Tavaly év végén Cho Jung-tai tajvani miniszterelnök kijelentette, hogy az ország „nagyon nyitott” az új nukleáris technológiák alkalmazására, hogy kielégítse a chipgyártók és az AI ipar növekvő áramigényét. „Amíg konszenzus van a nukleáris biztonságról és megfelelő garanciák vannak a hulladékkezelésre, nyilvános vitát lehet folytatni” – mondta Cho a Bloombergnek adott interjúban. Ez az egyik legerősebb jele annak, hogy a kormány újragondolja a kereskedelmi atomerőművekkel szembeni ellenállását.
Cho vélhetően fejlett reaktorokra, köztük kis moduláris reaktorokra (SMR) utalt, amelyeket számos országban fejlesztenek. Tajvan Nemzeti Atomkutató Intézete a héten indított egy 3,3 millió dolláros SMR kutatási projektet, amely utat nyithat a fejlett nukleáris reaktorok bevezetése előtt.
Új építés
Az amerikai EnergySolutions megkezdi a fejlett nukleáris projektek tervezését a wisconsini Kewaunee atomerőmű helyszínén. A cég a WEC Energy Grouppal együttműködve vizsgálja az új nukleáris termelés lehetőségét a helyszínen, és most helyszíni és környezeti tanulmányokat indít az NRC engedélyek megszerzése érdekében.
Ken Robuck, az EnergySolutions elnök-vezérigazgatója szerint az adatközpontok, a mesterséges intelligencia és az ipari növekedés által hajtott energiaigény miatt soha nem volt még ekkora szükség megbízható, szén-dioxid-mentes energiára. Az EnergySolutions 2022-ben vásárolta meg a 2013-ban leállított, jelenleg leszerelés alatt álló Kewaunee erőművet. Wisconsin egyetlen működő atomerőműve a Point Beach, amely az állam villamosenergia-termelésének 16,5%-át adja.
Elemzés: A brit nukleáris munkaerőnek „jelentősen” bővülnie kell
Az Egyesült Királyságban a kormány és az iparág közös szervezete, a Destination Nuclear sikeresen vonzza a szükséges szakembereket a nukleáris tervekhez, de figyelmeztet, hogy a munkaerőnek „jelentősen” bővülnie kell. Az országban jelenleg 96 000 fő dolgozik a nukleáris szektorban, de 2030-ra 120 000-re lesz szükség, vagyis hat év alatt 24 000 fővel kell bővíteni az állományt.
A program célja, hogy a civil és védelmi nukleáris szektorban is vonzóvá tegye a pályát, különös tekintettel a kritikus készségekre, például a hegesztésre, biztonsági mérnökökre, projekttervezőkre és sugárvédelmi szakemberekre. A kampány digitális hirdetésekkel, on-demand TV-n (pl. Netflix), és az online Minecraft játékon keresztül is igyekszik elérni a potenciális munkavállalókat. Az első eredmények szerint 52%-kal nőtt azok aránya, akik korábban nem gondoltak a nukleáris pályára, de most már fontolóra veszik. A szektor már most is több tízezer munkahelyet biztosít, és 2050-re akár 70 milliárd fonttal járulhat hozzá a brit gazdasághoz.
Egyéb hírek röviden
- Kanada: Az NWMO öt céget választott ki az első mély geológiai tároló tervezésére és kivitelezésére.
- Deep Atomic és Future-tech: Új programot indítottak nukleáris adatközpontok helyszínértékelésére.
- Urenco Isotopes: Üzembe helyezte legújabb izotóp-dúsító berendezését, a Blaise Pascalt.
- IAEA: Május 21-én webináriumot tart a nukleáris fúzió gyorsításáról, különös tekintettel a technológiai és ellátási láncok összehangolására.
-
 @ 2e8970de:63345c7a
2025-05-15 16:59:24
@ 2e8970de:63345c7a
2025-05-15 16:59:24Q: “Products & services using AI make me excited. How much do you agree/disagree?”
https://www.ipsos.com/en/ipsos-ai-monitor-2024-changing-attitudes-and-feelings-about-ai-and-future-it-will-bring
https://stacker.news/items/980900
-
 @ c3b2802b:4850599c
2025-05-07 11:26:36
@ c3b2802b:4850599c
2025-05-07 11:26:36Heute, am 9. Mai 2025 – genau 80 Jahre nach dem Ende des Zweiten Weltkriegs, der 60 Millionen Menschen das Leben kostete, darunter 27 Millionen Sowjetbürgern, erheben wir, die Bürgerinnen und Bürger Europas, unsere Stimmen! Wir schämen uns für unsere Regierungen und die EU, die die Lehren des 20. Jahrhunderts nicht gelernt haben. Die EU, einst als Friedensprojekt gedacht, wurde pervertiert und hat damit den Wesenskern Europas verraten! Wir, die Bürger Europas, nehmen darum heute, am 9. Mai, unsere Geschicke und unsere Geschichte selbst in die Hand. Wir erklären die EU für gescheitert. Wir beginnen mit Bürger-Diplomatie und verweigern uns dem geplanten Krieg gegen Russland! Wir erkennen die Mitverantwortung des „Westens“, der europäischen Regierungen und der EU an diesem Konflikt an.
Wir, die Bürger Europas, treten mit dem European Peace Project der schamlosen Heuchlerei und den Lügen entgegen, die heute – am Europatag – auf offiziellen Festakten und in öffentlichen Sendern verbreitet werden.
Wir strecken den Bürgerinnen und Bürgern der Ukraine und Russlands die Hand aus. Ihr gehört zur europäischen Familie, und wir sind überzeugt, dass wir gemeinsam ein friedliches Zusammenleben auf unserem Kontinent organisieren können.
Wir haben die Bilder der Soldatenfriedhöfe vor Augen – von Wolgograd über Riga bis Lothringen. Wir sehen die frischen Gräber, die dieser sinnlose Krieg in der Ukraine und in Russland hinterlassen hat. Während die meisten EU-Regierungen und Verantwortlichen für den Krieg hetzen und verdrängen, was Krieg für die Bevölkerung bedeutet, haben wir die Lektion des letzten Jahrhunderts gelernt: Europa heißt „Nie wieder Krieg!“
Wir erinnern uns an die europäischen Aufbauleistungen des letzten Jahrhunderts und an die Versprechen von 1989 nach der friedlichen Revolution. Wir fordern ein europäisch-russisches Jugendwerk nach dem Vorbild des deutsch-französischen Jugendwerks von 1963, das die „Erbfeindschaft“ zwischen Deutschland und Frankreich beendet hat. Wir fordern ein Ende der Sanktionen und den Wiederaufbau der Nord Stream II-Pipeline. Wir weigern uns, unsere Steuergelder für Rüstung und Militarisierung zu verschwenden, auf Kosten von Sozialstandards und Infrastruktur. Im Rahmen einer OSZE-Friedenskonferenz fordern wir die Schaffung einer europäischen Sicherheitsarchitektur mit und nicht gegen Russland, wie in der Charta von Paris von 1990 festgelegt. Wir fordern ein neutrales, von den USA emanzipiertes Europa, das eine vermittelnde Rolle in einer multipolaren Welt einnimmt. Unser Europa ist post-kolonial und post-imperial.
Wir, die Bürger Europas, erklären diesen Krieg hiermit für beendet! Wir machen bei den Kriegsspielen nicht mit. Wir machen aus unseren Männern und Söhnen keine Soldaten, aus unseren Töchtern keine Schwestern im Lazarett und aus unseren Ländern keine Schlachtfelder.
Wir bieten an, sofort eine Abordnung europäischer Bürgerinnen und Bürger nach Kiew und Moskau zu entsenden, um den Dialog zu beginnen. Wir werden nicht länger zusehen, wie unsere Zukunft und die unserer Kinder auf dem Altar der Machtpolitik geopfert wird.
Es lebe Europa, es lebe der Friede, es lebe die Freiheit
Auf der Webseite der Initiative oder in einem Gespräch mit Ulrike Guérot können Sie, liebe Leser, weitere Möglichkeiten erfahren, diese Friedensinitiative zu stärken! Danke an die IntiatorInnen und die bislang 15.000 Menschen, die das mitgestalten werden.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ c13e67ae:8ff5689b
2025-05-15 16:37:10
@ c13e67ae:8ff5689b
2025-05-15 16:37:10Testing the world
-
 @ 5edbd885:5fbc291e
2025-05-15 21:04:28
@ 5edbd885:5fbc291e
2025-05-15 21:04:28Bitcoin is a system outside of the system—you don’t actually need fiat to obtain some sats. Bitcoin is a monetary network designed to operate independently of traditional financial systems.
As such, it’s possible to acquire Bitcoin without ever converting any fiat currency.
Whether you’re aiming to earn, trade, or receive Bitcoin through alternative means, there are numerous ways to accumulate it organically—through work, community engagement, or creative effort.
In this guide, we'll explore six methods to get Bitcoin without spending fiat.
While some approaches require more time or technical knowledge, others are accessible to nearly anyone willing to accept Bitcoin for payment ⚡️
Read until the end of the article to know where to find people willing to give you Bitcoin in exchange for these ideas 🙂
Note: I have no affiliates or sponsorships and so any businesses I mention below are neither endorsements nor paid ads.
1. Offer Professional Services in Exchange for Bitcoin
The easiest and most direct way to receive Bitcoin without fiat is to trade your skills for sats.
This can be an option for those who are already earning an income freelancing, consulting, or providing any type of independent service simply by charging in Bitcoin rather than fiat.
For those with a traditional 9-5, you could mine sats within a Bitcoin company rather than a fiat business, or offer your skills as a side hustle for sats until you are ready to make a full switch (if you so choose).
Common examples include:
-
Writing, editing, or translating
-
Graphic design and illustration
-
Programming and development
-
Coaching, tutoring, or consulting
-
Manual labor or local services
Rather than invoicing in your local currency, you can simply set your rate in Bitcoin—typically using a satoshi-based pricing model. I have a few free tools on my site that can help you with this.
2. Sell Goods—Physical or Digital—for Bitcoin
You don’t need to be a freelancer or to convince your boss to receive Bitcoin.
If you own physical items or create digital products, you can accept BTC as payment instead of fiat.
Even in a down-sizing situation, selling things around your home for Bitcoin is also an option.
Ideas include:
-
Selling used items locally (e.g., via marketplaces or word of mouth)
-
Creating and distributing digital products like eBooks, music, or design assets
-
Selling handmade crafts or collectibles
-
Selling the second-hand goods you no longer need for sats
Enthusiasts are often excited to support peer-to-peer BTC commerce.
You don’t need a complex setup either—a mobile wallet that supports on-chain or Lightning payments is enough to get started.
3. Engage with Nostr & Earn via Micro-Transactions
(I know you are reading on Nostr, but I originally published this on my blog for non-users, and talking about Nostr on Nostr is fun ;)
Nostr is a decentralized social protocol that allows users to interact, publish content, and receive sats.
It’s one of the most innovative new ways to earn BTC organically, without needing any fiat currency.
On Nostr, content creators, contributors, musicians, artists, and everyday people can receive “zaps” (tiny Bitcoin tips via the Lightning Network) from other users.
It’s essentially a value-for-value economy where people support each other directly with sats on top of likes and shares.
Getting started is simple:
-
Set up a Lightning wallet (many are free and non-custodial - just look up what Bitcoiners recommend at the time you are reading this)
-
Create a profile on a Nostr client (such as Damus, Amethyst, or Primal)
-
Participate by posting, replying, and sharing thoughtful content
While the amounts may be small at first, consistent engagement can result in meaningful Bitcoin accumulation over time.
4. Request Bitcoin Tips in Your Daily Life
If you work in a role where tipping is common—such as driving for Uber, working in food service, hospitality, or delivery—you can offer Bitcoin as a tipping option.
How to implement this:
-
Include a QR code to your Lightning wallet on your phone or a printed card
-
Politely inform customers that you accept Bitcoin tips
-
Use signage or include a message in your app profile
You may be surprised by how many tech-savvy or curious customers are willing to try it, especially in urban or Bitcoin-friendly communities.
5. Use Bitcoin Cashback & Rewards Programs
While not a direct trade for labor or goods, some platforms allow you to earn Bitcoin as a reward for purchases you were already planning to make.
In these cases, you are not buying Bitcoin with fiat, but instead receiving it as a form of cashback on your everyday fiat purchases.
Popular platforms include:
-
In Canada, Shakepay offers free sats for shaking your phone daily or using their pre-paid Visa debit card
-
Strike occasionally offers rewards in Bitcoin as well
This approach is best suited for those who already have a spending routine and want to passively earn BTC without changing their habits.
6. Try Bitcoin Mini–Mining
Mini miners like the Bitaxe, BitNerd, and similar open-source devices offer a unique way to mine Bitcoin at home without needing large-scale equipment or industrial-level power.
While traditional Bitcoin mining requires costly ASICs and massive electricity, mini miners are small, efficient, and hobbyist-friendly.
They’re capable of independently solving blocks—meaning there’s a tiny chance you could win the full block reward—or they can be used to join a solo mining pool and receive small payouts over time based on contribution.
Benefits of mini mining:
-
Educational: Learn how mining works from the ground up
-
Passive: Runs in the background with low power usage
-
Potential upside: Very low probability of winning a full block, but it’s possible
Important caveats:
-
These devices must be purchased with fiat or Bitcoin initially
-
Most users will not earn consistent Bitcoin from them
-
It may be more efficient to simply buy Bitcoin directly with that money ;)
While this idea is more geared towards experienced Bitcoiners wanting to expand their way of stacking sats, it's still a fun thing to consider.
Mini miners are a hands-on way to participate in the network while stacking sats or keeping open the small possibility of mining rewards.
Where to Find People Willing to Pay in Bitcoin
Now an important question—where are you going to find people willing to pay you in Bitcoin?
Finding people who are open to paying in Bitcoin is easier than it might seem—especially if you know where to look.
Start by exploring local Bitcoin meetups, conferences, or community events in your area—these are often filled with enthusiasts who prefer peer-to-peer exchanges. Consider searching Facebook or Meetup.com for Bitcoin groups and events in your area.
Online, platforms like Nostr, Twitter/X, Reddit, and Bitcoin-focused Telegram groups can be great places to find clients or collaborators.
You can also look into Bitcoin job boards to find formal employment opportunities that pay in BTC.
The Bitcoin economy is growing, and so is the number of individuals and businesses willing to transact in BTC directly—bypassing fiat altogether.
The key is to get involved in the ecosystem—once you’re in the network and people get to know you, opportunities will begin to surface organically.
Summary Table: How to Receive Bitcoin w/o Fiat
| Method | Effort Level | Payout Potential | Notes | | ------------------------------- | ------------ | ------------------- | ------------------------------------------------ | | Offer services for BTC | Medium | High | Most scalable—mine sats directly instead of fiat | | Sell goods for BTC | Medium | Medium | Local or online; accessible | | Micro-transactions (Nostr) | Low/Medium | Medium (over time) | Lightning required, engaging helps | | Accept BTC tips | Low | Low to Medium | Best for service or gig workers | | Cashback / rewards programs | Low | Low to Medium | Passive sat stacking on normal spending | | Mini Bitcoin mining | Medium | Low / Lottery Level | For advanced users |
What did I forget? Let me know your tips and thoughts in the comments below ✨
-
-
 @ e968e50b:db2a803a
2025-05-15 16:29:37
@ e968e50b:db2a803a
2025-05-15 16:29:37Hey Stacker.news,
I'm trying to book a room with a bitcoin-friendly bnb. They only had CC or debit payment on their website so I shot them an email inquiring about paying with bitcoin. They asked that I send a Whatsapp message that they'd send a lightning invoice to. Problem is, I've avoided Whatsapp because it looks like they harvest ALL of your data! Am I being a bitcoin hipster or do you think I'm right that this app looks just oh no good?
I really want to book with these guys, so if you're in the, "yeah, don't get Whatsapp camp," what do you propose that I propose to them as an alternative?
Pseudonymously, Doubter in Cypherland
originally posted at https://stacker.news/items/980877
-
 @ 5f078e90:b2bacaa3
2025-05-15 20:08:32
@ 5f078e90:b2bacaa3
2025-05-15 20:08:32Owl’s One-Legged Vigil
The vigil, one leg style

In a misty grove, Sylas the owl perched on a gnarled oak, standing on one leg. His golden eyes scanned the night. Why one leg? A vow to honor his lost mate, taken by a hawk. Each dusk, Sylas balanced, unwavering, as stars wheeled above. His silent stance drew the forest’s gaze—squirrels paused, deer bowed. One moonlit night, a young owl mimicked him, sparking hope. Sylas’s vigil became legend, a beacon of resilience.
Owl’s One-Legged Vigil: Part Two
Part 2
In the misty grove, Sylas stood on one leg, his vigil unbroken. The young owl, inspired, joined nightly, mimicking his stance. Word spread—foxes whispered, ravens cawed. Sylas’s balance was no mere feat; it was defiance against loss. One stormy dusk, winds howled, yet Sylas held firm, his single leg rooted. The young owl faltered but watched in awe. Moonlight pierced the clouds, bathing them in silver. Sylas hooted softly, a call of endurance. The grove’s creatures gathered, drawn by his resolve. A wise badger spoke: “Your vigil heals us.” The young owl, now named Lark, vowed to carry Sylas’s legacy. As dawn broke, Sylas stretched both legs, his vow fulfilled. He flew with Lark, their wings brushing the sky. The grove thrived, united by his stand. Sylas’s one-legged vigil became a tale of hope, etched in every tree.
-
 @ 866e0139:6a9334e5
2025-05-07 08:18:51
@ 866e0139:6a9334e5
2025-05-07 08:18:51Autor: Nicolas Riedl. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Dieser Beitrag erschien zuerst bei Radio München.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Das Kriegsgrauen kriecht unter die Haut. Bilder von verstümmelten Beinen und Armen, von Kriegstraumatisierten schweigenden Männern, von Kriegsgräbern steigen auf. Als Mutter, Schwester, Tante, Großmutter wachsen die Ängste, dass sich ein Verwandter von der politischen und medialen Kriegslust anstecken lässt und tatsächlich die Beteiligung an den näher kommenden kriegerischen Auseinandersetzungen in Erwägung zieht. Einen wütenden Kommentar anlässlich der wachsenden Kriegstreiberei verfasste unser Autor Nicolas Riedl.
Nicolas Riedl, Jahrgang 1993, geboren in München, studierte Medien-, Theater- und Politikwissenschaften in Erlangen. Den immer abstruser werdenden Zeitgeist der westlichen Kultur dokumentiert und analysiert er in kritischen Texten. Darüber hinaus ist er Büchernarr, strikter Bargeldzahler und ein für seine Generation ungewöhnlicher Digitalisierungsmuffel. Entsprechend findet man ihn auf keiner Social-Media-Plattform. Von 2017 bis 2023 war er für die Rubikon-Jugendredaktion und Videoredaktion tätig.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 58537364:705b4b85
2025-05-15 16:27:52
@ 58537364:705b4b85
2025-05-15 16:27:52วันนี้เป็นวันสำคัญทางศาสนา มีการจัดงานบุญพร้อมกับฟังเทศน์อย่างยิ่งใหญ่ "ชายคนหนึ่ง" ได้มานั่งฟังธรรมอยู่บนศาลาวัด ในขณะที่นั่งฟังอยู่นั้นสายตาก็เหลือบไปเห็นคนกำลังตกปลาอยู่ในบ่อน้ำที่วัด แล้วก็นั่งคิดบ่นด่าคนตกปลาอยู่ในใจว่าทำไมถึงทำเช่นนั้น ในวัดแท้ๆ ยังกล้ามาจับปลา ไม่กลัวบาปกรรมบ้างเลยหรืออย่างไร แต่แทนที่ชายคนนี้มานั่งฟังธรรมจะได้บุญ กลับเอาจิตไปด่าทอผู้อื่นอยู่ตลอดเวลา
ในขณะเดียวกัน “คนตกปลา” ก็มองเห็นคนที่มานั่งฟังธรรมบนศาลาวัด ใจก็ตั้งจิตขออนุโมทนาบุญ เพราะผมมันเป็นคนบาป ไม่มีโอกาสได้ไปนั่งฟังธรรมกับคนอื่นเขา ต้องเอาเวลามาตกปลาเลี้ยงชีพ เลี้ยงดูพ่อแม่ที่ป่วยหนัก เพราะเกิดมาจนจึงไม่มีวาสนาสร้างบุญแบบคนอื่น หากเกิดชาติหน้า ก็ขอให้มีโอกาสได้สร้างบุญเหมือนแบบท่านๆที่ได้นั่งฟังธรรมอยู่ด้วยเถิด เกิดมาชาตินี้มีกรรมหนัก ต้องชดใช้กรรมที่ก่อไว้ ปลาที่มาติดเบ็ดก็ขออย่าได้จองเวรกันเลย
ถึงแม้คนตกปลาจะกำลังตกปลาอยู่ แต่จิตก็เอาแต่ภาวนาสาธุไปกับคนที่ฟังธรรม และขออโหสิกรรมปลาตลอด ที่นี้ทุกคนเข้าใจหรือยังว่า ทำไมคนฟังธรรมถึงตกนรก คนตกปลาได้ขึ้นสวรรค์
ความหมายของ “กรรมดี” และ “กรรมชั่ว” มาจากเจตนา การมีเจตนาที่ประกอบด้วยกุศล คือ กรรมดี แต่การมีเจตนาที่ประกอบด้วยอกุศล คือ กรรมชั่ว อย่างชายที่ไปนั่งฟังธรรม ก็หลงคิดว่าตัวเองกำลังทำดีอยู่ แล้วก็เอาแต่มองคนอื่นที่ไม่ทำแบบตัวเองว่าเป็นคนไม่ดี ในใจก็เอาแต่ ด่าทอ คิดร้าย ต่างๆนาๆ ในขณะที่คนตกปลา มีแต่เจตนาที่ดีต่อผู้อื่น เห็นผู้อื่นทำความดี ก็ยินดีด้วยเสมอ
การปฏิบัติธรรม เป็นการฝึกจิตให้สงบ เพื่อพัฒนาจิตของตนเองให้สูงขึ้น ไม่ใช่เอาไว้ไปข่มคนอื่นให้ดูต่ำลง เพราะสุดท้ายแล้วคนที่ทำแบบนี้ ย่อมต่ำกว่า เจ้าสวดมนต์แต่ยัง “นินทา“ เจ้าทำทานแต่ยัง ”เอาเปรียบ“ เจ้ามีความรู้แต่ชอบ ”ดูถูกคน“ เจ้าตัวสะอาดแต่ ”ใจสกปรก“ เจ้าอยากได้มิตรแท้ แต่… ”เจ้ากลับเป็นมิตรเทียม“ เจ้าบอกทำกุศล แต่… ”หมายเอาชื่อเสียง“ เจ้ามีทุกสิ่ง แต่… ”ไม่คิดแบ่งปัน “ เจ้าดูแลคนอื่น แต่… ”ละเลยพ่อแม่ “ เจ้างดเนื้อสัตว์ แต่… ”ข่มเหง ” เพื่อนมนุษย์ เจ้าหาตัวเองไม่เจอ แต่… “กรรม ” หาเจ้าเจอ
พระไพศาล วิสาโล ได้บอกถึงพฤติกรรมที่คนเหล่านี้เป็น นั่นเพราะว่า “เหมือนในสังคมทุกวันนี้ ที่ชอบทำบุญ แต่กลับไร้น้ำใจ ทั้งๆที่การมีน้ำใจต่อเพื่อนมนุษย์ เป็นสิ่งที่ทำได้ง่ายในชีวิตประจำวัน แต่บางคนกลับดั้นด้นเดินทางไปไกลๆ เพื่อที่จะไปทำบุญที่วัดอย่างเดียว แต่กับคนทุกข์ยากใกล้ตัว ไม่เคยแม้แต่จะเหลียวแลยื่นมือช่วย นั่นเป็นเพราะว่าคนเรา มักจะชอบกระทำต่อสิ่งที่อยู่สูงกว่าตน เช่น พระสงฆ์ วัดวาอาราม แต่กลับละเลยสิ่งที่คิดว่าอยู่ต่ำกว่าตนเอง เช่น คน ยากจน หรือ สัตว์น้อยใหญ่”
เมตตาค้ำจุนโลก
Cr: คู่มือมนุษย์
-
 @ 58537364:705b4b85
2025-05-15 16:26:49
@ 58537364:705b4b85
2025-05-15 16:26:49ความสุขแท้ไม่มีในโลก มีแต่เมื่อความทุกข์ได้ถูกบำบัดลงครั้งหนึ่ง ก็เรียกว่าความสุขครั้งหนึ่ง คุณอยากได้ของสักชิ้นอย่างมาก เมื่อได้มาแล้วก็มีความสุข เพราะความอยากได้ถูกบำบัดไปแล้ว เมื่อคุณอยากได้ของหรืออยากได้อะไรอีก ความทุกข์ก็เกิดขึ้นอีก เมื่ออยากมาก ก็ทุกข์มาก เมื่อไม่อยากให้ของสิ่งนั้นหายหรือแตกดับไป ก็ทุกข์อีก
เมื่อได้รับของที่ต้องการแล้ว ก็ต้องดูแลเอาใจใส่ของนั้น เมื่อไม่เป็นไปตามความอยากหรือไม่อยากของตน ก็ทุกข์ ซึ่งทุกสรรพสิ่ง เมื่อเกิดขึ้น ย่อมตั้งอยู่แล้วดับไป คนที่เรารักย่อมเจ็บป่วยและดับไป เป็นธรรมดาของชีวิต แต่เราไม่ยอมรับ บางคนเมื่อพูดถึงความตาย ก็บอกว่า พูดทำไม เป็นคำอัปมงคล แต่โดยแท้แล้ว ความตายอยู่กับเราทุกลมหายใจ
เราต้องการให้คนรอบๆ ทำแต่สิ่งที่ถูกใจเรา ทำสิ่งที่ดีต่อเรา แต่มันจะเป็นไปได้หรือ ความสุขจึงอยู่ที่การยอมรับในสิ่งที่เป็น ที่มีอยู่ เพราะธรรมชาติของสิ่งที่เราต้องพบ ต้องประสบ มันเป็นเช่นนั้นของมันเอง การพยายามไปเปลี่ยนแปลงสิ่งต่างๆรอบๆตัว จึง เหมือนการพยายามห้ามแม่น้ำไม่ให้ไหลไป
ความสุขในฐานะปุถุชนมีได้ ด้วยการยอมรับสิ่งที่เกิดขึ้น การยอมรับไม่ใช่การยอมแพ้แก่มัน แต่เมื่อเราพยายามทำดีอย่างที่สุดแล้ว ผลสุดท้ายจะเป้นอย่างไร ก็ต้องวาง
ขอยกคำหลวงพ่อไพศาลที่ว่า ชีวิตเราเลือกได้ ว่าจะเป็นอย่างไร เด็กผู้หญิง 10 ขวบ ขนของ แต่เด็กผู้ชายสองคน ไม่ช่วยขนของ ไปดูทีวีเสีย แทนที่เด็กผู้หญิงคนนั้นจะโกรธ กลับบอกว่า ขนของเหนื่อยอย่างเดียว แต่ถ้าไปโกรธเขา เราก็เหนื่อยสองอย่าง
การอยู่โดยมองโลกในแง่บวก เป็นสิ่งที่สำคัญมาก ขอยกตัวอย่างจากหลวงพ่อไพศาลอีกครั้ง เด็กชายคนหนึ่งเป็นโรคมะเร็งที่ กระดูกที่ขา เขาถูกตัดขาไปข้างหนึ่ง เขาบอกว่า เขาดีใจที่ยังมีขาอีกข้างหนึ่ง ไม่ใช่เสียใจที่เสียขาไป
เป็นสุขในทุกความเปลี่ยนแปลง หลวงพ่อไพศาล วิสาโล
คนเราย่อมปรารถนาความเปลี่ยนแปลง หากว่าความเปลี่ยนแปลงนั้นอยู่ในอำนาจของเรา หรือสอดคล้องกับความต้องการของเรา ไม่มีใครอยากขับรถคันเดิม ใช้โทรศัพท์เครื่องเดิม หรืออยู่กับที่ไปตลอด มิจำต้องพูดถึงการอยู่ในอิริยาบถเดิม ๆ เราต้องการสิ่งใหม่ ๆ อยู่เสมอ แต่ความจริงอย่างหนึ่งที่เราปฏิเสธไม่ได้ก็คือ มีความเปลี่ยนแปลงหลายอย่างที่เราไม่ต้องการแต่หนีไม่พ้น ความเปลี่ยนแปลงอย่างนี้แหละที่ผู้คนประหวั่นพรั่นพรึง วิตกกังวลเมื่อนึกถึงมัน และเป็นทุกข์เมื่อมันมาถึง
แต่ยังมีความจริงอีกอย่างหนึ่งที่เราพึงตระหนักก็คือ สุขหรือทุกข์นั้น มิได้ขึ้นอยู่กับว่า มีอะไรเกิดขึ้นกับเรา แต่อยู่ที่ว่า เรารู้สึกอย่างไรกับสิ่งนั้นต่างหาก แม้มีสิ่งไม่ดีเกิดขึ้นกับเรา แต่ถ้าเราไม่รู้สึกย่ำแย่ไปกับมัน หรือวางใจให้เป็น มันก็ทำให้เราเป็นทุกข์ไม่ได้
กนกวรรณ ศิลป์สุข เป็นโรคธาลัสซีเมียตั้งแต่เกิด ทำให้เธอมีร่างกายแคระแกร็น กระดูกเปราะและเจ็บป่วยด้วยโรคแทรกซ้อนนานาชนิด ซึ่งมักทำให้อายุสั้น แต่เธอกับน้องสาวไม่มีสีหน้าอมทุกข์แต่อย่างใด กลับใช้ชีวิตอย่างมีความสุข เธอพูดจากประสบการณ์ของตัวเองว่า “มันไม่สำคัญหรอกว่าเราจะเป็นอย่างไรหรือมีอะไรเกิดขึ้นกับชีวิต แต่สำคัญที่ว่าเมื่อเกิดขึ้นมาแล้ว เราคิดกับมันยังไงต่างหาก สำหรับเราสองคน ความสุขเป็นเรื่องที่หาง่ายมาก ถ้าใจของเราคิดว่ามันเป็นความสุข”
โอโตทาเกะ ฮิโรทาดะ เกิดมาพิการ ไร้แขนไร้ขา แต่เขาสามารถช่วยตัวเองได้แทบทุกอย่าง ในหนังสือเรื่อง ไม่ครบห้า เขาพูดไว้ตอนหนึ่งว่า “ผมเกิดมาพิการแต่ผมมีความสุขและสนุกทุกวัน” ใครที่ได้รู้จักเขาคงยอมรับเต็มปากว่าเขาเป็นคนที่มีความสุขคนหนึ่ง อาจจะสุขมากกว่าคนที่มีอวัยวะครบ (แต่กลับเป็นทุกข์เพราะหน้ามีสิว ผิวตกกระ หุ่นไม่กระชับ)
ในโลกที่ซับซ้อนและผันผวนปรวนแปรอยู่เสมอ เราไม่สามารถเลือกได้ว่าจะต้องมีสิ่งดี ๆ เกิดขึ้นกับเราตลอดเวลา แต่เราเลือกได้ว่าจะมีปฏิกิริยากับสิ่งนั้นอย่างไร รวมทั้งเลือกได้ว่าจะยอมให้มันมีอิทธิพลต่อเราอย่างไรและแค่ไหน..ในวันที่แดดจ้าอากาศร้อนอ้าว บุรุษไปรษณีย์คนหนึ่งยืนรอส่งเอกสารหน้าบ้านหลังใหญ่ หลังจากเรียกหาเจ้าของบ้านแต่ไม่มีวี่แววว่าจะมีคนมารับ เขาก็ร้องเพลงไปพลาง ๆ เสียงดังชัดเจนไปทั้งซอย ในที่สุดเจ้าของบ้านก็ออกจากห้องแอร์มารับเอกสาร เธอมีสีหน้าหงุดหงิด เมื่อรับเอกสารเสร็จเธอก็ถามบุรุษไปรษณีย์ว่า “ร้อนแบบนี้ยังมีอารมณ์ร้องเพลงอีกเหรอ” เขายิ้มแล้วตอบว่า “ถ้าโลกร้อนแต่ใจเราเย็น มันก็เย็นครับ ร้องเพลงเป็นความสุขของผมอย่างหนึ่ง ส่งไปร้องไป” ว่าแล้วเขาก็ขับรถจากไป
เราสั่งให้อากาศเย็นตลอดเวลาไม่ได้ แต่เราเลือกได้ว่าจะยอมให้อากาศร้อนมีอิทธิพลต่อจิตใจของเราได้แค่ไหน นี้คือเสรีภาพอย่างหนึ่งที่เรามีกันทุกคน อยู่ที่ว่าเราจะใช้เสรีภาพชนิดนี้หรือไม่ พูดอีกอย่างก็คือ ถ้าเราหงุดหงิดเพราะอากาศร้อน นั่นแสดงว่าเราเลือกแล้วที่จะยอมให้มันยัดเยียดความทุกข์แก่ใจเรา
ถึงที่สุดแล้ว สุขหรือทุกข์อยู่ที่เราเลือก มิใช่มีใครมาทำให้ ถึงแม้จะป่วยด้วยโรคร้าย เราก็ยังสามารถมีความสุขได้ โจว ต้า กวน เด็กชายวัย ๑๐ ขวบ เป็นโรคมะเร็งที่ขา จนต้องผ่าตัดถึง ๓ ครั้ง เขาได้เขียนบทกวีเล่าถึงประสบการณ์ในครั้งนั้นว่า เมื่อพ่อแม่จูงมือเขาเข้าห้องผ่าตัด เขาเลือก “น้องสงบ” เป็นเพื่อน (แทนที่จะเป็น “น้องกังวล”) เมื่อเขาห้องผ่าตัดครั้งที่สอง เขาเลือก “ลุงมั่นคง”เป็นเพื่อน (แทนที่จะเป็น “ป้ากลัว”) เมื่อพ่ออุ้มเขาเข้าห้องผ่าตัดครั้งที่สาม เขาเลือก “ชีวิต” (แทนที่จะเป็น “ความตาย”) ด้วยการเลือกเช่นนี้มะเร็งจึงบั่นทอนได้แต่ร่างกายของเขา แต่ทำอะไรจิตใจเขาไม่ได้
เมื่อใดก็ตามที่ความเปลี่ยนแปลงอันไม่พึงประสงค์เกิดขึ้น หากเราไม่สามารถสกัดกั้นหรือบรรเทาลงได้ ในยามนั้นไม่มีอะไรดีกว่าการหันมาจัดการกับใจของเราเอง เพื่อให้เกิดความทุกข์น้อยที่สุด หรือใช้มันให้เกิดประโยชน์มากที่สุด ด้วยวิธีการต่อไปนี้
๑. ยอมรับความจริงที่เกิดขึ้นแล้ว การยอมรับความจริงที่ไม่พึงประสงค์ ทำให้เราเลิกบ่น ตีโพยตีพาย หรือมัวแต่ตีอกชกหัว ซึ่งมีแต่จะเพิ่มความทุกข์ให้แก่ตนเอง คนเรามักซ้ำเติมตัวเองด้วยการบ่นโวยวายในสิ่งที่ไม่อาจแก้ไขอะไรได้
เรามักทำใจยอมรับความจริงที่เกิดขึ้นแล้วไม่ได้ เพราะเห็นว่ามันไม่ถูกต้อง ไม่น่าเกิด ไม่ยุติธรรม (“ทำไมต้องเป็นฉัน ?”) แต่ยิ่งไปยึดติดหรือหมกมุ่นกับเหตุผลเหล่านั้น เราก็ยิ่งเป็นทุกข์ แทนที่จะเสียเวลาและพลังงานไปกับการบ่นโวยวาย ไม่ดีกว่าหรือหากเราจะเอาเวลาและพลังงานเหล่านั้นไปใช้ในการรับมือกับสิ่ง ที่เกิดขึ้นแล้ว
เด็ก ๓ คนได้รับมอบหมายให้ขนของขึ้นรถไฟ แต่ระหว่างที่กำลังขนของ เด็กชาย ๒ คนก็ผละไปดูโทรทัศน์ซึ่งกำลังถ่ายทอดสดการชกมวยของสมจิตร จงจอหอ นักชกเหรียญทองโอลิมปิค เมื่อมีคนถามเด็กหญิงซึ่งกำลังขนของอยู่คนเดียวว่า เธอไม่โกรธหรือคิดจะด่าว่าเพื่อน ๒ คนนั้นหรือ เธอตอบว่า “หนูขนของขึ้นรถไฟ หนูเหนื่อยอย่างเดียว แต่ถ้าหนูโกรธหรือไปด่าว่าเขา หนูก็ต้องเหนื่อยสองอย่าง”
ทุกครั้งที่ทำงาน เราสามารถเลือกได้ว่าจะเหนื่อยอย่างเดียว หรือเหนื่อยสองอย่าง คำถามคือทุกวันนี้เราเลือกเหนื่อยกี่อย่าง นอกจากเหนื่อยกายแล้ว เรายังเหนื่อยใจด้วยหรือไม่
การยอมรับความจริง ไม่ได้แปลว่ายอมจำนนต่อสิ่งที่เกิดขึ้น แต่เป็นจุดเริ่มต้นของการเลือกที่จะไม่ยอมทุกข์เพราะความเปลี่ยนแปลง อีกทั้งยังทำให้สามารถตั้งหลักหรือปรับตัวปรับใจพร้อมรับความเปลี่ยนแปลง นั้นอย่างดีที่สุด
๒. ทำปัจจุบันให้ดีที่สุด นอกจากบ่นโวยวายกับสิ่งที่เกิดขึ้นแล้ว เรามักทุกข์เพราะอาลัยอดีตอันงดงาม หรือกังวลกับสิ่งเลวร้ายที่คาดว่าจะเกิดขึ้นในอนาคต สุดท้ายก็เลยไม่เป็นอันทำอะไร
ไม่ว่าจะอาลัยอดีตหรือกังวลกับอนาคตเพียงใด ก็ไม่ช่วยให้อะไรดีขึ้น กลับทำให้เราย่ำแย่กว่าเดิม สิ่งเดียวที่จะทำให้อะไรดีขึ้นก็คือการทำปัจจุบันให้ดีที่สุด ทางข้างหน้าแม้จะยาวไกลและลำบากเพียงใด แต่เราไม่มีวันถึงจุดหมายเลยหากไม่ลงมือก้าวเสียแต่เดี๋ยวนี้ รวมทั้งใส่ใจกับแต่ละก้าวให้ดี ถ้าก้าวไม่หยุดในที่สุดก็ต้องถึงที่หมายเอง
บรู๊ซ เคอร์บี นักไต่เขา พูดไว้อย่างน่าสนใจว่า “ทุกอย่างมักจะดูเลวร้ายกว่าความจริงเสมอเมื่อเรามองจากที่ไกล ๆ เช่น หนทางขึ้นเขาดูน่ากลัว....บางเส้นทางอาจดูเลวร้ายจนคุณระย่อและอยากหันหลัง กลับ นานมาแล้วผมได้บทเรียนสำคัญคือ แทนที่จะมองขึ้นไปข้างบนและสูญเสียกำลังใจกับการจินตนาการถึงอันตรายข้าง หน้า ผมจับจ้องอยู่ที่พื้นใต้ฝ่าเท้าแล้วก้าวไปข้างหน้าทีละก้าว”
๓. มองแง่บวก มองแง่บวกไม่ได้หมายถึงการฝันหวานว่าอนาคตจะต้องดีแน่ แต่หมายถึงการมองเห็นสิ่งดี ๆ ที่มีอยู่ในปัจจุบัน ไม่ว่าเจ็บป่วย ตกงาน หรืออกหัก ก็ยังมีสิ่งดี ๆ อยู่รอบตัวและในตัวเรา รวมทั้งมองเห็นสิ่งดี ๆ ที่ซุกซ่อนอยู่ในความเปลี่ยนแปลงเหล่านั้นด้วย
แม้กนกวรรณ ศิลป์สุข จะป่วยด้วยโรคร้าย แต่เธอก็มีความสุขทุกวัน เพราะ “เราก็ยังมีตาเอาไว้มองสิ่งที่สวย ๆ มีจมูกไว้ดมกลิ่นหอม ๆ มีปากไว้กินอาหารอร่อย ๆ แล้วก็มีร่างกายที่ยังพอทำอะไรได้อีกหลายอย่าง แค่นี้ก็เพียงพอแล้วที่เราจะมีความสุข” ส่วนจารุวรรณ ศิลป์สุข น้องสาวของเธอ ซึ่งขาหักถึง ๑๔ ครั้งด้วยโรคเดียวกัน ก็พูดว่า “ขาหักก็ดีเหมือนกัน ไม่ต้องไปโรงเรียน ได้อยู่กับบ้าน ฟังยายเล่านิทาน หรือไม่ก็อ่านหนังสือ อยู่กับดอกไม้ กับธรรมชาติ กับสิ่งที่เราชอบ ก็ถือว่ามีความสุขไปอีกแบบ”
โจว ต้า กวน แม้จะถูกตัดขา แต่แทนที่จะเศร้าเสียใจกับขาที่ถูกตัด เขากลับรู้สึกดีที่ยังมีขาอีกข้างหนึ่ง ดังตั้งชื่อหนังสือรวมบทกวีของเขาว่า “ฉันยังมีขาอีกข้างหนึ่ง”
หลายคนพบว่าการที่เป็นมะเร็งทำให้ตนเองได้มาพบธรรมะและความสุขที่ลึกซึ้ง จึงอดไม่ได้ที่จะอุทานว่า “โชคดีที่เป็นมะเร็ง” ขณะที่บางคนบอกว่า “โชคดีที่เป็นแค่มะเร็งสมอง” เพราะหากเป็นมะเร็งปากมดลูกเธอจะต้องเจ็บปวดยิ่งกว่านี้
ถึงที่สุด ไม่ว่าอะไรเกิดขึ้นกับเรา ก็ล้วนดีเสมอ อย่างน้อยก็ดีที่ไม่แย่ไปกว่านี้
๔. มีสติ รู้เท่าทันตนเอง เมื่อความเปลี่ยนแปลงที่ไม่พึงประสงค์เกิดขึ้น เรามักมองออกนอกตัว และอดไม่ได้ที่จะโทษคนโน้น ต่อว่าคนนี้ และเรียกหาใครต่อใครมาช่วย แต่เรามักลืมดูใจตนเอง ว่ากำลังปล่อยให้ความโกรธแค้น ความกังวล และความท้อแท้ครอบงำใจไปแล้วมากน้อยเพียงใด เราลืมไปว่าเป็นตัวเราเองต่างหากที่ยอมให้เหตุการณ์ต่าง ๆ รอบตัวยัดเยียดความทุกข์ให้แก่ใจเรา ไม่ใช่เราดอกหรือที่เลือกทุกข์มากกว่าสุข การมีสติ ระลึกรู้ใจที่กำลังจมอยู่กับความทุกข์ จะช่วยพาใจกลับสู่ความปกติ เห็นอารมณ์ต่าง ๆ เกิดขึ้นโดยไม่ไปข้องเกี่ยว จ่อมจม หรือยึดติดถือมั่นมัน อีกทั้งยังเปิดช่องและบ่มเพาะปัญญาให้ทำงานได้เต็มที่ สามารถเปลี่ยนร้ายให้กลายเป็นดี หรือมองเห็นด้านดีของมันได้
สติและปัญญาทำให้เรามีเสรีภาพที่จะเลือกสุข และหันหลังให้กับความทุกข์ ใช่หรือไม่ว่าอิสรภาพที่แท้ คือ ความสามารถในการอนุญาตให้สิ่งต่าง ๆ มีอิทธิพลต่อชีวิตของเราได้เพียงใด ความเปลี่ยนแปลงของร่างกาย ของทรัพย์สิน ของผู้คนรอบตัว รวมทั้งความเปลี่ยนแปลงในบ้านเมือง ไม่สามารถทำให้เราทุกข์ได้ หากเราเข้าถึงอิสรภาพดังกล่าว แทนที่เราจะมัววิงวอนเรียกร้องให้เกิดความเปลี่ยนแปลงที่ถูกใจเรา ไม่ดีกว่าหรือหากเราพยายามพัฒนาตนบ่มเพาะจิตใจให้เข้าถึงอิสรภาพดังกล่าว ควบคู่ไปกับการสร้างสรรค์สิ่งดีงามให้เกิดขึ้นแก่ตนเองและสังคม
credit : Suphan Click!!
-
 @ 57d1a264:69f1fee1
2025-05-15 15:57:30
@ 57d1a264:69f1fee1
2025-05-15 15:57:30Have been finally putting together a solution for managing transactions and addresses categories in #BitcoinSafe. You can learn more about the project here https://stacker.news/items/974488/r/DeSign_r and here https://stacker.news/items/977190/r/DeSign_r.
Here the two images, before and after. Find the differences, share your thoughts and let me know which one is more intuitive and usable, considering categories can be renamed or merged.
originally posted at https://stacker.news/items/980852
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ b8af284d:f82c91dd
2025-05-05 07:05:46
@ b8af284d:f82c91dd
2025-05-05 07:05:46Vor genau 40 Jahren, unter den Kronleuchtern eines New Yorker Ballsaals, wurde das berüchtigte ‚Plaza Accord‘ unterzeichnet, das eine Finanztsunami auslöste, der den japanischen Yen in nur 16 Monaten um 46 Prozent in die Höhe trieb. Die Exporte brachen ein, und Japans beeindruckendes Wirtschaftswachstum von 5 Prozent schrumpfte zu Staub.“
Xi Jinping am 26. April 2025
Liebe Abonnenten,
2010 kam es zu einer mysteriösen Serie von Selbstmorden in der chinesischen Stadt Shenzhen. Insgesamt nahmen sich zwischen Januar und August 13 Menschen das Leben, in dem sie von Hochhäusern sprangen. Die chinesischen Medien berichteten stets über Einzelfälle. Erst ausländischen Korrespondenten gelang es, die Selbstmorde miteinander in Verbindung zu setzen: Alle waren Angestellte des Apple-Zulieferers Foxconn. Alle waren sogenannte Wanderarbeiter aus den umliegenden Provinzen. Ihr monatliches Gehalt von umgerechnet 110 Euro war auch für chinesische Verhältnisse derart niedrig, dass sie sich gezwungen sahen, Überstunden zu leisten. Trotz der viel gepriesenen chinesischen Fähigkeit 吃苦 „Bitterkeit zu essen“, erschien vielen Angestellten ihr Leben so unerträglich und ausweglos, dass sie sich das Leben nahmen.
Nach einem internationalen Shitstorm reagierte Foxconn: Man erhöhte die Gehälter um 70 bis 100 Prozent und spannte Netze in der „Foxconn-City“ auf, um weitere Selbstmorde zu verhindern.
Gegründet wurde Foxconn 1974 von Terry Gou in Taiwan unter dem Namen „Hon Hai Precision Industry“. Mit der wirtschaftlichen Öffnungspolitik der Volksrepublik expandierte Gou auf das chinesische Festland, wo er Heerscharen von billigen Arbeitskräften fand. Heute beschäftigt Foxconn mehr als eine Million Menschen und fertigt rund 70 Prozent aller iPhones weltweit.
Apple-Zulieferer Foxconn steht wie kaum ein anderes Unternehmen für den wirtschaftlichen Megatrend der vergangenen Jahrzehnte. In den USA entworfene Produkte werden in Asien gefertigt und weltweit verkauft. Komplexe Lieferketten spannen sich um den gesamten Globus. Immer neue Märkte müssen erschlossen werden, um den Rendite-Erwartungen der Anleger gerecht zu werden. Die globale Produktion wandert von Land zu Land, bis die Lohnkosten so dort stark gestiegen sind, dass es Zeit wird weiterzuziehen. Nun ist ein neuer Faktor hinzugekommen: Geopolitik.
Vor wenigen Tagen gab Apple bekannt, dass es einen großen Teil seiner iPhone-Fertigung von China nach Indien verlagern werde.
Sprich: Foxconn zieht um. Der Zulieferer betreibt Werke in Tamil Nadu und Karnataka und plant eine neue Fabrik nahe Bengaluru mit Investitionen von bis zu 2,7 Milliarden US-Dollar. Dort sind zwar die Produktionskosten rund acht Prozent höher als in China, aber Apple will so sein Ziel erreichen, 2026 alle iPhones in Indien fertigen zu lassen. Punktsieg für Trump, Vance und Bessent.
Mehr zum Thema:
Die nächsten 90 Tage
·
11. Apr.
Drei Monate hat die Welt Aufschub vor amerikanischen Zöllen bekommen, 90 Tage, in denen der Handelskrieg mit China tobt. Was Trump in dieser Zeit wirklich vorhat.
Abgekoppelt
·
1. Mai
In den vergangenen Wochen konnte man erleben, wie Bitcoin zum sicheren Hafen wurde. Wie nachhaltig ist die Entwicklung? Der Bling-Report April 2025
"Sie müssen Geld drucken"
·
13. Apr.
Fondsmanager und Investorenlegende Marc Faber über den aktuellen Aktien-Crash, Donald Trump und Gold
Ein Paid-Abo beinhaltet 4 bis 6 Artikel pro Monat (statt 2 bis 4), einen monatlichen Investment-Report samt Musterdepot, Zugang zu allen Artikeln sowie 4 Tutorials über Bitcoin, Gold, ETFs und Altcoins. Ein Test-Abo gibt es schon für sieben Euro im Monat. Bitcoin-Zahler erhalten 20% Rabatt!
Das, was im Zollkrieg zwischen den USA und China gerade stattfindet, ähnelt dem Prinzip des 2500 Jahre alten chinesischen Spiels: im Gegensatz zu Schach, wo es um das Eliminieren des gegnerischen Königs geht, ist Go subtiler. Es gibt kein direktes „Schachmatt“, sondern einen Wettstreit um Raum und Einfluss. Verbündete werden gesucht, um den jeweiligen Gegner zu entwaffnen, bevor es zu einer entscheidenden Schlacht überhaupt kommen kann.
90 Tage Aufschub hat Donald Trump allen Handelspartnern gewährt - bis auf China. Zuvor hatte er am „Liberation Day“ Zölle auf nahezu alle Ländern erhoben, mit denen die USA ein Handelsdefizit aufweisen. Ob hinter der Schaukelpolitik Kalkül steckt, oder ob ihm besonnenere Gemüter in der Regierung dazu geraten haben, nachdem der amerikanische Aktienmarkt in den Keller gerauscht war, bleibt offen für Spekulationen. Auf jeden Fall bleiben den beiden größten Volkswirtschaften der Welt nun noch etwas über zwei Monate, möglichst viele Verbündete zu finden, um den Gegner zu isolieren. „Wir können wahrscheinlich mit unseren Verbündeten einen Deal erreichen“, sagte Finanzminister Scott Bessent. „Und dann können wir gemeinsam als Gruppe auf China zugehen.“ Die USA haben an und für sich viele Argumente auf ihrer Seite:
Hinter der Paywall: Wer hat die besseren Chancen, das Spiel zu gewinnen?
-
 @ 866e0139:6a9334e5
2025-05-05 06:18:34
@ 866e0139:6a9334e5
2025-05-05 06:18:34\ \ Autor: Marcel Bühler. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
"Die Ausrufung des Notstands ist der Notstand. Er eröffnet die Möglichkeit eines Endes der Rechtsstaatlichkeit"
Prof. em. Richard K. Sherwin NY Law School
Die von Präsident Donald Trump initiierten Friedensbemühungen zur Beendigung des russisch-ukrainischen Krieges scheinen keinen Erfolg zu bringen. Während Russland darauf beharrt, dass die im Herbst 2022 offiziell in die Russische Föderation aufgenommenenRegionen Lugansk, Donezk, Saporoschje und Cherson von der ukrainischen Armee vollständig geräumt werden, will Präsident Selenskij nicht einmal auf die Krim verzichten und deren Zugehörigkeit zu Russland seit 2014 anerkennen.
Während die Ukraine Sicherheitsgarantien für die Zeit nach einem möglichen Waffenstillstand bzw. Friedensabkommen fordert, besteht Russland weiterhin auf einer weitgehenden Demilitarisierung der ukrainischen Armee und besonders ein Verbot aller ultranationalen bzw. nazistischen Einheiten welche vor allem in der ukrainischen Nationalgarde konzentriert sind.
Nur ein Rohstoffdeal zwischen Washington und Kiew ist offenbar zustande gekommen, da Trump für die vielen Milliarden Dollar, welche in den letzten Jahren in die Ukraine "investiert" wurden, eine Gegenleistung bekommen möchte (nach dem "Ukraine Democracy Defense Lend-Lease Act" vom 19.1.2022 welcher von Präsident Biden am 9.5.2022 unterzeichnet wurde).
Im Rahmen einer Armeereform ist die Ukrainische Nationalgarde auf Anfang April 2025 in 2 Armeekorps mit je fünf Brigaden aufgeteilt worden: das erste Armeekorps wird von der 12. Brigade "Asow", das zweite Armeekorps von der 13. Brigade "Chartia" angeführt welche ursprünglich aus Freiwilligenbataillonen hervorgingen. Insgesamt dürfte es sich bei den 10 Brigaden um ca. 40'000 Mann handeln. Hier eine kurze Selbstdarstellung der Nationalgarde, in der auch der Kommandant, Alexander Pivnenko, zu Wort kommt (leider nur auf ukrainisch):
https://www.youtube.com/watch?v=0fjc6QHumcY
Alexander Syrskij, der aktuelle ukrainische Oberfehlshaber, hat kürzlich den Befehl erlassen, dass die mehr als 100'000 Mann der von der Bevölkerung gefürchteten Rekrutierungstruppe "TZK" ("Територіальний центр комплектування та соціальної підтримки") nun ebenfalls als Kampftruppen an die Front müssen, da die Mobilisierung weiterer ukrainischer Männer weitgehend gescheitert sei. Gleichzeitig wird über die Senkung des Mobilisierungsalters auf 18 Jahre und ein möglicher Einzug von Frauen diskutiert (die bereits als Freiwillige mitkämpfen).

Für die Zeit um den 9. Mai ("Tag des Sieges") hat Russland einen weiteren einseitigen Waffenstillstand ausgerufen, den die Ukrainer vermutlich wie an Ostern für Gegenangriffe an der Front oder Provokationen in Russland (z.B. Anschläge oder Drohnenangriffe in/auf Moskau nutzen werden). Über die Osterfeiertage hatten sich beide Seiten wie üblich gegenseitig beschuldigt, die verkündete Waffenruhe wiederholt gebrochen zu haben.
Die Kämpfe und die Opferung von Abertausenden dürften also bis auf weiteres weitergehen, auch wenn sie den Kriegsverlauf nicht mehr entscheidend ändern werden. Die Verlustrate beträgt aktuell ca. 1:10 zuungunsten der Ukrainer, da die Russen mittlerweile bei allen Waffensystemen überlegen sind, nicht nur bei der Artillerie und der Luftwaffe sondern auch im Bereich der Drohnen und der elektronischen Kriegsführung.
Wie es dazu kommen konnte, dass die Ukraine aus einem zwar hochkorrupten, aber relativ freien Land zu einem totalitären Militärregime wurde, zeigt ein neues Video eines jungen Ukrainers aus Mariupol, der die dortigen Kämpfe im Frühjahr 2022 im Keller überlebte und es aber vorzog, dort zu bleiben und die russische Staatsbürgerschaft anzunehmen. Aus Sicherheitsgründen nennt er seinen ukrainischen Namen nicht. Seine sachliche Darstellung ist weit davon entfernt, russische oder westliche Propaganda zu sein, sondern stellt eine nüchterne und auf persönlicher Erfahrung basierende Analyse der Ereignisse in der Ukraine seit 2014 dar.
Besonders eindrücklich zeigt er mit Filmmaterial auf, wie nach dem rechtswidrigen Putsch in Kiew, welcher von den Rechtsnationalen als "Revolution der Würde" bezeichnet wird und von Kräften aus dem Westen massiv unterstützt wurde (z.B. durch US-AID), besonders die ukrainische Jugend indoktriniert und militarisiert und auf den kommenden Krieg mit Russland vorbereitet wurde. Hier muss man unwillkürlich an die HJ (Hitler Jugend) denken, deren Schicksal am Ende des 2. WK allgemein bekannt sein dürfte. Es lohnt sich, den rund 35minütigen Beitrag zweimal anzusehen, um alles richtig zu verstehen und aufzunehmen (auf englisch mit slawischem Akzent):
https://www.youtube.com/watch?v=ba_NPxVXVyc
Den 1. Mai habe ich dieses Jahr am Stand der Schweizer Friedensbewegung im Areal der ehemaligen Stadt Zürcher Kaserne verbracht und dabei auch für den neu gegründeten Verein "Bewegung für Neutralität" (BENE) geworben. Der bekannte Friedensforscher Daniele Ganser wird diesen und nächsten Monat an den grossen Schweizer Bahnhöfen eine Plakatwerbung für die immerwährende Neutralität der Schweiz starten (siehe Entwurf im Anhang).
Zu Frieden und Völkerverständigung gibt es keine Alternative, dazu gehört auch das Studium und die Analyse des ukrainischen Nationalismus und Faschismus ("Stepan Bandera Ideologie"), dessen Ursprung und Entwicklung in den letzten rund 100 Jahren bis in die heutige Zeit.
Nur die Rüstungslobby kann mit der viel zitierten "Friedensdividende" nichts anfangen!
Marcel Bühler ist freier Mitarbeiter und Rechercheur aus Zürich. Dieser Beitrag erschien zuerst in seinem Newsletter.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
\
-
 @ eab58da0:eebdafbf
2025-05-15 15:43:32
@ eab58da0:eebdafbf
2025-05-15 15:43:32By Unknownfx
Comparison used to be my silent thief, stealing my joy and clouding my mental health. I’d scroll through posts, see others’ perfect lives, and feel like I was falling behind. But when I learned to let go of comparing, I found a freedom I didn’t know was possible. Here’s my story and how you can start living your own.
Caught in the Comparison Trap I remember a night last year, sitting on my couch, scrolling X. I saw someone’s post about their flawless morning routine—meditation, green smoothies, crushing their goals. Meanwhile, I’d barely dragged myself out of bed, my mind foggy from stress. I thought, “Why can’t I be like that?” That question was poison. It wasn’t just social media; I compared myself to coworkers, friends, even strangers. Their wins made me feel small, like my efforts didn’t measure up. My mental health took a hit—self-doubt crept in, and I stopped trying because I felt I’d never be “enough.”
The Moment I Chose Me The turning point came during a walk one evening. I was beating myself up for not being as “successful” as a friend who’d just landed a big project. Then it hit me: her path isn’t mine. I started asking, “What do I want?” Instead of chasing someone else’s life, I focused on my own small wins. I wasn’t writing bestselling books, but I was posting regularly on X and Medium, sharing my thoughts on mental health. That was enough for me. I decided to stop measuring my worth against others and start celebrating what made me, well, me.
Living Without the Weight Letting go of comparison didn’t happen overnight, but it was liberating. I started a simple practice: every time I felt that pang of envy, I’d pause and list three things I was proud of. Maybe I’d journaled that morning, helped a friend, or just got through a tough day. It shifted my focus from what I lacked to what I had. I also cut back on mindless scrolling, setting a “no-phone” hour each evening to reconnect with myself. My mental health steadied—I felt lighter, more grounded. I even noticed I was more productive, pouring energy into my writing instead of worrying about others’ highlight reels.
Your Path, Your Power Stopping comparison isn’t about ignoring others’ success; it’s about owning your journey. You don’t need to be anyone else to be enough. Try this: today, write down one thing you love about your life, no matter how small. Build from there. You’re already on your way to living fully. What’s one comparison you’re ready to let go of? How do you celebrate your unique path? Drop a comment or share a note—let’s inspire each other to live free!
Thanks for reading. Much love, Unknownfx
-
 @ 4fe14ef2:f51992ec
2025-05-15 15:41:21
@ 4fe14ef2:f51992ec
2025-05-15 15:41:21Hey Bitcoiners,
Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for sats or zaps? It doesn't matter how big or small your item is, solid or digital, product or service.
Just share below what you’ve listed, swapped, and sold. Let everyone rave on your latest deals!
New to ~AGORA? Dive into the #marketplace and turn your dusty gears into shiny BTC!
originally posted at https://stacker.news/items/980838
-
 @ 0b118e40:4edc09cb
2025-05-15 15:40:21
@ 0b118e40:4edc09cb
2025-05-15 15:40:21My week started off with a lovely message from a friend : “I often think about you. Especially during times when it requires me to be more resilient and have faith in myself. I always carry your note in the book you gave me, “what the dog saw” And it always gives me courage and I send a little prayer your way”.
This friend of mine was dealing with the undercurrent of discrimination in my alma mater when we first met, and I helped out. It's something anybody would have done, but surprisingly, nobody else showed up. We’ve stayed in touch over the years, and my friend went on to help a lot of other people along the way.
I don’t remember what I wrote in that note. It’s something I tend to do (write notes, give books, write notes in books). But the message boomeranged back to me at a time when I needed to hold the line. To keep the faith.
Most of us don’t talk about our struggles. And sometimes the smallest act, which could just be a kind word or a reminder of the person you are, can carry farther than we imagine.
On the act of giving
There’s a book called Give and Take by Adam Grant. I picked it up hoping to learn how to take, because it’s always been easier to give and harder to accept help. But what I learned was something else entirely.
Grant studied over 30,000 people across different companies and grouped them into three types: * Givers * Matchers * Takers
Based on his studies, givers often finish last... They struggle the most. They burn out. They get overlooked. They’re too trusting.
But oddly, they also rise to the very top.
Matchers are the scorekeepers, the “I’ll help you if you help me” kind. They make up most of the population. The fascinating thing about tit-for-tat is that if someone’s kind, they reciprocate. But if someone acts like a jerk, they return the energy, and over time, it becomes a pool of spoiled milk. Matchers are a lukewarm, forgettable kind of network.
Takers are the ones chasing attention, always aligning themselves with whoever looks powerful. They tend to float toward status and soak up what they can. But they often portray themselves as kind and giving.
One example Grant shared was Enron's Kenneth Lay, who was at the center of one of the biggest corporate scandals in U.S. history. He hung around wherever he’d get seen or validated. He funded both Bush and Clinton, hedging his bets on who might win by securing proximity. Sadly, when Enron crumbled, he died of a heart attack before his prison sentencing.
Most people steer clear from takers because they are just exhausting. And takers often collapse under the weight of their own games.
But takers aren’t the lowest performers. That spot belongs to a certain kind of giver—the self-neglecting kind. The ones with no boundaries, no clarity, and no self-awareness. They give in to avoid conflict, to feel worthy, or because they don’t know how to say no. And when life breaks them, they point fingers.
Then there’s the other kind of giver. The ones who build trust and build people up without asking for a receipt.
These givers: 1. Give without expectation, from a place of purpose 2. Build and uplift others without seeking credit 3. Set boundaries and walk away when giving turns into draining
This group of givers rarely talk much about what they do for others. But when you hear about it or see it, it stays with you. It makes you want to show up a little better.
Why open source environments feels like home
The more I thought about it, the more I saw how deeply open source reflects that kind of giving that ends up right at the top.
In open source, you don’t last if it’s just about ego. You can’t fake it. There are no titles, no awards. You either show up to build and help, or you don’t.
People who give without needing to be seen are the ones the community leans on. You can tell when someone’s pretending to care. It’s in their tone, their urgency and their sense of transaction. The genuine ones don’t need to brand themselves as generous. They just are.
Open source works because giving is the default setting. The work speaks volumes and generosity compounds. The system filters for people who show up with purpose and stay consistent.
It’s also why the ones who whine, posture, or manipulate rarely last. They might call themselves givers, but they’re not fooling anyone who’s actually doing the work.
Adam Grant found that for giver cultures to thrive, takers have to be removed. They need to be pruned. Because takers poison the well. They drain givers, shift the culture from contribution to calculation, and unravel the trust that holds open systems together.
When hope boomerangs
That note is something I don’t remember writing. But it found its way back to me, and it was a good reminder to take my own advice and keep the faith.
And maybe that’s the point.
You do a small thing. And years later, it circles back when it matters most. Not because you expected it. But because you mattered.
According to Grant, givers do best when they combine generosity with grit and strategy. They create networks built on goodwill, which eventually open doors others don’t even know exist.
So if you’re wondering where I’m going with this, do something genuinely kind for someone today. Even if it’s as simple as sending a kind note. Not for you to be seen or heard. And not for you to keep scores.
But, just because.
-
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ a29cfc65:484fac9c
2025-05-04 16:20:03
@ a29cfc65:484fac9c
2025-05-04 16:20:03Bei einer Führung durch den Naumburger Dom sprach der Domführer über Propaganda im Mittelalter. Die gefühlvollen Gesichtsausdrücke der steinernen Stifterfiguren rund um die berühmte Uta sollten das Volk beeinflussen. Darüber haben wir auf der Heimfahrt nach Leipzig philosophiert und fanden den Denkansatz spannend. Denn auch wenn es damals nicht Propaganda hieß, so gab es doch Interessen der Mächtigen, die sie gegenüber dem Volk durchsetzten. Sie bedienten sich dabei der damals verfügbaren „Medien“, zu denen die Kirche gehörte, wo sich das Volk zum Gottesdienst traf.
Kulturelle Identität Europas
Mitteldeutschland ist ein Zentrum mittelalterlicher Baukunst. Der Naumburger Dom St. Peter und Paul wurde auf den Grundmauern einer noch älteren Kirche im 13. Jahrhundert gebaut. Er ist weltweit einzigartig in seiner Architektur, Bildhauerkunst und Glasmalerei. Seit 2018 ist er Unesco-Weltkulturerbe. Die Stadt Naumburg hatte einst die gleiche Bedeutung wie Merseburg, Magdeburg oder Leipzig. Der Dom – von der Spätromanik bis in die Frühgotik unter Leitung eines heute unbekannten Bildhauerarchitekten errichtet – gilt als Meisterwerk menschlicher Schöpferkraft und Handwerkskunst. Die naturwissenschaftlich-physikalischen Kenntnisse der Menschen waren offensichtlich enorm. Sie verfügten über das Wissen zur Planung und über entsprechende Werk- und Hebezeuge, um solche Bauwerke in relativ kurzer Zeit errichten zu können.
Im Westchor des Doms befinden sich mit den zwölf lebensgroßen Stifterfiguren die bekanntesten Kunstwerke des Doms, unter ihnen Uta von Ballenstedt. Sie soll Walt Disney als Quelle für die schöne und sehr stolze Königin im Zeichentrickfilm Schneewittchen gedient haben. Das Besondere und Neue an den steinernen Stifterfiguren war ihre realitätsnahe Darstellung, die sie lebendig und ausdrucksstark wirken lässt. Sie sind ein Höhepunkt in der Steinmetzkunst der damaligen Zeit. Die Figuren wurden, obschon die dargestellten Personen bereits mehr als 200 Jahre tot waren, mit charakteristischen Gesichtsausdrücken dargestellt: Uta schaut schön und stolz in die Ferne, ihr Gatte Ekkehard wirkt etwas hochmütig. Gegenüber steht die lachende Reglindis neben ihrem wehmütig-leidend blickenden Mann Hermann von Meißen.
Der Domführer sagte, dass die Gesichtsausdrücke menschliche Verhaltensweisen darstellen, die bei den Kirchenbesuchern unerwünscht waren. Wir hätten es hier mit einer sehr frühen Form der Propaganda zu tun. Die katholische Kirche war Vorreiter in Sachen Propaganda. Sie hat etwa 400 Jahre später, im Jahr 1622, mit der Sacra Congregatio de Propaganda Fide ein Amt gegründet, das den „richtigen“ Glauben in die Welt tragen sollte, und erst 1967 umbenannt wurde. Aber ihre gesellschaftlich führende Position hatte damals auch eine positive Seite: Den Kirchen und Klöstern haben wir den Erhalt und die Weitergabe antiken Wissens zu verdanken. Europa konnte sich trotz der politischen Zersplitterung seine kulturelle Identität erhalten. Zum Beispiel lässt sich das Wirken des namenlosen Domschöpfers anhand der Bau- und Kunstwerke quer durch Europa von Nordfrankreich über Mainz nach Naumburg und Meißen nachvollziehen. Aus der weiteren Entwicklung von Kunst und Kultur in Europa entstand in der Renaissance die Philosophie des Humanismus und später daraus die Aufklärung mit ihrer Wirkung auf Literatur und Wissenschaft. Ziel war dabei immer eine Stärkung des Gemeinwesens.
Transhumanismus zerstört Gemeinschaften
Heute scheinen wir uns allerdings an einer Bruchstelle der gesellschaftlichen Entwicklung zu befinden. Die Kirchen spielen in unserer Gesellschaft kaum noch eine Rolle. Weder bringen sie sich in ethische Diskussionen hörbar ein, noch tragen sie die Entwicklung von Kunst und Kultur sichtbar voran. Ihre Rolle im Bereich Propaganda haben längst Zeitungen und Zeitschriften, Rundfunk und Fernsehen übernommen. Diese Medien haben eine größere Reichweite, und die psychologische Beeinflussung ist umfassender. Nach dem Zweiten Weltkrieg wurde die Manipulation der Massen stark intensiviert und nahm nach dem Zusammenbruch der Sowjetunion noch weiter an Fahrt auf. Der Liberalismus konnte auf allen Gebieten seinen Siegeszug antreten, stellte das Individuum in den Mittelpunkt und erhob den Markt zur heiligen Kuh. Im Laufe der Zeit wurden die humanistischen Ideen der Aufklärung in ihr Gegenteil verkehrt. Der Mensch wurde als fehlerhaftes Wesen identifiziert, in die Vereinzelung getrieben, bevormundet und gegängelt – angeblich, damit er sich nicht selbst schadet. Zur psychologischen Beeinflussung kommen die neuen technischen Möglichkeiten aus Bio-Nano-Neuro-Wissenschaften und Digitalisierung. Der Transhumanismus wurde als neues Ziel für die Menschheit ausgerufen. Der Einzelne soll biologisch und technisch perfektioniert werden. Gemeinschaften – von der Familie angefangen – treibt das in die Bedeutungslosigkeit. Es besteht die Gefahr, dass persönliche Integrität und Privatsphäre durch Eingriffe in Körper- und Geistesfunktionen verletzt werden. Eine neue Aufklärung ist nötig. Denn sehr viel von dem über die Jahrhunderte erlangten Wissen ging schon verloren oder ist nur noch versteckt in den Bibliotheken und Archiven der Kirchen zu finden. Die Besinnung auf die vergessenen beziehungsweise verdrängten Grundlagen und Ideale der Aufklärung kann diese Entwicklung abwenden. Die Kulturschätze Mitteleuropas vermitteln in ihrer Schönheit und Vollkommenheit die Ruhe und die zeitlichen und räumlichen Dimensionen, die wir brauchen, wenn wir über die Frage nachdenken, wie wir in Zukunft leben wollen.
Die Rolle der neuen Medien für die zukünftige Entwicklung
Von den Alt-Medien ist in dieser Hinsicht nichts zu erwarten. Sie werden finanziert und sind unterwandert von den Kräften, die transhumanistische Entwicklungen vorantreiben. Die „neue Aufklärung“ ist ein lohnenswertes Ziel für die neuen Medien. Diese lassen sich jedoch noch zu sehr von den aktuellen Themen der Alt-Medien treiben. Der Angst-Propaganda begegnen sie mit – Ängsten, wenn auch anders ausgerichtet. Einige reiten die Empörungswelle in Gegenrichtung zu den Alt-Medien. Manche Betreiber von „alternativen“ Finanz- und Wirtschaftskanälen wollen ihre eigenen marktgläubigen Produkte an den Mann bringen. Stattdessen sollten in den neuen Medien positive Nachrichten verbreitet und eigene Themenfelder eröffnet werden, denen sich die Alt-Medien verweigern:
· der Mensch und seine Bildung zur souveränen, selbständig denkenden und handelnden Persönlichkeit,
· die Entwicklung des eigenen Bewusstseins, um der Fremdbestimmung zu entkommen und zu Wahrhaftigkeit, Authentizität und Menschlichkeit zu gelangen,
· die Entwicklung des Gemeinwohls,
· die Frage, wie wir neue Gemeinschaften bis hin zu autarken Gemeinden gründen können – wichtiger, je mehr das gesellschaftliche System um uns herum zusammenbricht.
Direkt sichtbar ist der letzte Punkt am Niedergang der Architektur und am Zustand der Innenstädte: Die reich dekorierten Gebäude der Gründerzeit wurden nach ihrer Zerstörung im Zweiten Weltkrieg durch gleichförmig rechteckige Gebäude aus Beton und Glas ersetzt. Dazu kamen die in allen Städten austauschbar gleichen Ladenzeilen und in den letzten Jahren Dreck und Schmierereien, die nicht mehr weggeräumt werden.
Die gesellschaftlichen Verwerfungen der Corona-Zeit führten bei vielen Menschen zum Innehalten und Nachdenken über Sinn und Ziele ihres Lebens. So entstanden einige Pilotprojekte, zum Beispiel in den Bereichen Landwirtschaft, Gesundheitswesen und Bildung. Diese auf die Zukunft gerichteten Themen könnten in den neuen Medien umfangreicher vorgestellt und diskutiert werden. Manova setzt schon solche Schwerpunkte mit „The Great WeSet“ von Walter van Rossum sowie mit den Kategorien „Zukunft & Neue Wege“ sowie „Aufwind“. Der Kontrafunk hat Formate entwickelt, die das Gemeinwohl stärker in den Fokus setzen wie etwa die Kultur- und Wissenschaftsrubrik. Nuoviso hat einen eigenen Songcontest ins Leben gerufen. Neben der inhaltlichen Ausrichtung auf eine lebenswerte Zukunft gilt es auch, die technologische Basis der neuen Medien zukunftsfest zu machen und sich der digitalen Zensur zu entziehen. Milosz Matuschek geht mit dem Pareto-Projekt neue Wege. Es könnte zur unzensierbaren Plattform der neuen Medien werden. Denn wie er sagt: Man baut sein neues Haus doch auch nicht auf dem Boden, der einem anderen gehört.
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ eab58da0:eebdafbf
2025-05-15 15:31:18
@ eab58da0:eebdafbf
2025-05-15 15:31:18By UnKnownfx
Words have power, but I never thought one could shift my entire perspective. For years, I felt stuck, weighed down by self-doubt and the fear I wasn’t good enough. Then I stumbled on a single word—“yet”—and it became the key to unlocking a new mindset. Here’s how it changed my life and how it might help you, too.
The Rut I Couldn’t Escape A couple of years ago, I was in a rough spot. I wanted to grow—write more, improve my mental health, maybe even start a side project—but every step felt like failure. I’d tell myself, “I’m not good at this,” or “I can’t figure it out.” Those words built a wall, trapping me in a cycle of giving up. One day, I was venting to a friend about how I’d never get the hang of meditation. She stopped me and said, “You’re not good at it yet.” That tiny word hit me like a lightning bolt. It wasn’t about being perfect now; it was about being on the way.
The Power of “Yet” That word, “yet,” became my mantra. It’s simple but profound—it turns “I can’t” into “I’m learning.” I started adding it to my self-talk. Struggling to write a post? “I’m not great at this yet.” Feeling overwhelmed by anxiety? “I haven’t mastered calm yet.” It’s like giving yourself permission to be a work in progress. I began to see challenges as steps, not roadblocks. For example, when I tried journaling to manage stress, my first attempts were messy—half-finished thoughts, no consistency. Instead of quitting, I told myself, “I’m not consistent yet.” Slowly, I built a habit, and now journaling is my go-to for mental clarity.
How It Rewired My Days Adding “yet” to my mindset didn’t erase my struggles, but it changed how I faced them. I started small: when I felt stuck on a work task, I’d pause, breathe, and remind myself, “I’ll get this yet.” It pushed me to keep going instead of spiraling into frustration. Over time, I noticed I was less hard on myself. I celebrated progress—like writing three posts a week, even if they weren’t perfect—because I knew I was moving forward. My mental health improved, too; I wasn’t as consumed by what I hadn’t achieved. “Yet” gave me hope and patience, two things I’d been missing.
Try It for Yourself This one word can be your game-changer, too. It’s not about pretending everything’s easy—it’s about believing you’re on the path. Next time you catch yourself saying, “I can’t,” tack on “yet” and see what shifts. Maybe you’re not where you want to be, but you’re growing, and that’s enough. What’s one thing you’ve told yourself you can’t do? How would adding “yet” change your approach? Share your thoughts below or post your own note—I’d love to hear how this small word sparks big changes for you!
Thanks for reading. Much love, Unknownfx
-
 @ c1e6505c:02b3157e
2025-05-15 15:25:27
@ c1e6505c:02b3157e
2025-05-15 15:25:27“Put that camera down, you bitch,” someone yelled out of a car as it drove by with the door wide open.

I had a little time in Savannah yesterday to walk around and take some photos. I tend to wander through the rougher areas — not just in Savannah, but in any city I visit. I’m drawn to the spots most people avoid. Not the tourist zones, but the alleys, the quiet, broken-down neighborhoods where the grit is.
I’ve photographed Savannah a lot over the past few years, so it’s getting harder to find places I haven’t already been. But every now and then, I’ll stumble on a back street or alley I’ve never seen before, and in it, something I’m almost certain no one else has photographed.
There’s something about walking aimlessly with a camera that I find incredibly fulfilling. Honestly, if I could do just that for the rest of my life — wander around and photograph things that most people overlook — I’d be content.

There’s a quote I heard recently - can’t remember who said it — but it stuck with me. It was something like: “It’s better to be aimless than to be rigid with a plan.” Because when you’re too locked into a goal, you might miss the opportunities that pop up along the way. You need to stay flexible, fluid—open to what the world hands you.
That’s how I feel about photography. I’ll walk for hours—sometimes five to ten miles — just to see what shows up. It becomes a game. A game between me, the camera, the street, and whatever decides to show up that day.
Usually, it takes a few warm-up shots to get into it — just pictures of objects, whatever catches my eye. But once I find a rhythm, it’s like the world starts to reveal itself. The good stuff comes out of hiding.
That’s what real photography is to me. Not staging scenes or setting up portraits—that’s more like illustration, as Garry Winogrand would say. What I care about is life. Life unfolding right in front of you. Life happening.















Thank you for your attention. Please consider donating a few sats if you enjoy my work. It goes a long way. If not, please share. Thank you.
-
 @ a296b972:e5a7a2e8
2025-05-15 15:07:57
@ a296b972:e5a7a2e8
2025-05-15 15:07:57***Unserestaatsanwaltschaft***
Die Staatsanwaltschaft Aachen prüft Ermittlungen gegen Unbekannt in Sachen Cum-Ex. Hierfür konnte die ehemalige Chefanklägerin Brohilker als externe Expertin gewonnen werden. Korrektur, die Staatsanwaltschaft prüft Ermittlungen gegen Frau Brohilker. „Richtig so“, sagen Experten. „Es sind doch nur 43 Milliarden im Bermuda-Dreieck verschollen. Man muss auch mal Ruhe geben, genauso, wie bei Corona“. Dank schon heute an Unserestaatsanwaltschaft.
***Bundesamt für Fassungslosigkeit***
Ein Enkel hat die Kochrezepte seiner Großmutter zusammengetragen und veröffentlicht. Ausschließlich Rezepte aus Ostpreußen, Pommern und Schlesien. Das gesamte Kochbuch ist jetzt als Nazi-Küche eingestuft worden, weil der Urenkel die Grenze des guten Geschmacks, also die Oder-Neisse-Linie, dadurch missachtet hat. Weiter wurde ihm Russenfreundlichkeit vorgeworfen, weil auch ein Rezept für Königsberger Klopse abgedruckt wurde.
***Stillhaltezusage***
Die vom Bundesamt für Verfassungsschutz ausgesprochene Stillhaltezusage hat Zahnärzte auf die Idee gebracht, diese vor Behandlung von ihren Patienten unterschreiben zu lassen. Widerstand ist zwecklos.
***Paragraphenerweiterung***
Das Würgen des Menschen ist unfassbar. Jeder, der sich dafür einsetzt, dass wieder die Vernunft in Deutschland Einzug hält, wird mit einem Urlaub mit dem Corona-Minister II nicht unter 6 Wochen bestraft.
***Freie Kapazitäten beim Verfassungsschutz***
Das als gesichert stillgehaltene Gutachten hat gezeigt, dass das Bundesamt über erhebliche Kapazitäten verfügt. Diese sollen jetzt gebündelt dazu verwendet werden, die Messerattentate und den Tatbestand der selbstfahrenden Autos in Menschenmengen lückenlos aufzuklären. Erfahrung bei dem Zusammentragen von öffentlichen Zitaten verspricht nun endlich eine zeitnahe Aufklärung.
***Sonderdezernat beim schutzverfassenden Bundesamt***
Die Sprengung der Nordstream 2-Pipeline war ein terroristischer Anschlag auf die Energieversorgung von Deutschland und ganz Europa. Zur nun endgültigen Aufklärung nach nur wenigen Jahren wurde ein Sonderdezernat mit dem Code-Namen „Task Force Peng“ eingerichtet. Man hat bereits Kontakt zu Seymour Hersh aufgenommen, doch der ist zurzeit mit einem Segelboot namens „Andromeda“ auf Weltumrundung unterwegs.
***Eurovision Song Contest***
Der ESC ist eine absolut politisch neutrale Sing-Veranstaltung, bei der persönliche Angriffe gegen Repräsentanten und Innen stets im Bereich des Unmöglichen bleiben. Auch solidarische Gewinnerermittlung zur Unterstützung eines bestimmten Landes entbehrt jeder Grundlage, wie die Vergangenheit wiederholt gezeigt hat.
***Drehtüreffekt***
Das Infragestellen von Personen, die von der Politik in die Medien oder umgekehrt wechseln, hat nichts mit Interessenkonflikten zu tun. Im Gegenteil: Es werden so Kompetenzen ressourcenschonend anschlussverwendet.
***‘Aufrüstung in Deutschland***
Nachdem man zunächst einen Feind erfunden hat, der keine Lust hat, einer zu sein, ist die zwingend logische Schlussfolgerung daraus, dass man jetzt auch wieder die zentrale Macht in Europa werden will. Das freut die Nachbarn, und wie schon in der Ukraine in 2022, beginnt die neue deutsche Zeitrechnung jetzt in 2025. Man ist zu der Überzeugung gelangt, dass Vorgeschichten von Nationen völlig überbewertet werden.
***Vergleich unzulässig***
Die geplante Zerschlagung des Kapitalismus durch die Linke ist etwas völlig anderes, als die Bekämpfung des Kapitalismus zugunsten des Sozialismus durch die SED, weil es damals um die Deutsche Mark ging und heute schließlich um den Euro.
***Bevorstehende Hitzewelle Sommer 2025***
Nach den vergeblichen zwei Anläufen durch plötzlich und unerwarteten Regen in den Jahren 2023 und 2024 ist man sich nun ganz sicher, dass die Erdverkochung durch die Klimawandelung im dritten Anlauf stattfinden wird. Es wurden schon Bodentemperaturen gemessen.
***Neueintrag im Knigge***
Ab sofort schickt es sich nicht, dass vollgeschnaufte Taschentücher auf dem Tisch liegengelassen werden dürfen, wenn die Kamera angeht. Auch Kratzlöffel, wenn der Rücken mal juckt, sind vor Einschalten der Kamera zu entfernen.
***Meinungsfreiheit***
Jeder darf die ihm von den Weisen der Wahrheit vorgegebene Meinung so oft wiederholen und aussprechen, wie er will. Eine Limitierung der Wiederholungen findet nicht statt.
***Selbstbestimmungsgesetz erweitert***
Das Selbstbestimmungsgesetz wurde jetzt erweitert: Man darf sich auch als Finanzamt definieren. Das hat den Vorteil, dass sich der Steuerpflichtige seine Steuerzahlungen auf sein eigenes Konto überweisen kann, um selbst zu entscheiden, wofür die Gelder der Allgemeinheit dienend, ausgegeben werden sollen.
***US-Verbot von Gain-of-Function Forschung***
Dafür, dass deutsche Unternehmen aufgrund der unbezahlbaren Energiekosten ihre Produktionsstätten ins Ausland verlagern, werden in deutschen Bio-Laboren die freigesetzten US-Kapazitäten aus der Forschung mit Kusshand aufgenommen. Operation Paperclip II, nur umgekehrt.
***Deutscher Weltrekord***
Noch nie wurden Ankündigungen in einem Koalitionsvertrag so schnell entsorgt, wie nach den Anfang Mai 2025 stattgefundenen Wahlen. Der verbleibende Rest sind Kann-Bestimmungen, für die sicher ein Grund gefunden wird, warum das Geld zur Umsetzung fehlt.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 044da344:073a8a0e
2025-05-03 19:02:02
@ 044da344:073a8a0e
2025-05-03 19:02:02Mein Thema kommt heute aus dem Kalender und hat gleich noch zu einem Video geführt. Internationaler Tag der Pressefreiheit – wie jedes Jahr am 3. Mai. Das Publikum liebt Ranglisten. Shanghai für die Hochschulen, der Best Country Report für die Lebensqualität und Freedom House für die Freiheit in der Welt. Es gibt Aufsteiger und Absteiger und Jahr für Jahr eine Meldung, über die sich trefflich diskutieren lässt – vor allem in Europa und Nordamerika, wo die Sieger wohnen. Man muss die Statistik dafür nicht einmal fälschen, sondern einfach nur das messen, was man selbst am besten kann, und alles weglassen, was das Bild trüben könnte. Bei den „Reportern ohne Grenzen“ sorgen dafür die Geldgeber und Fragen, die sich zum Beispiel in Afrika oder in Südostasien gar nicht stellen. Ergebnis: Die Medien sind bei uns ziemlich frei, auch wenn Leser dieser Seite wissen, dass das so nicht stimmt.
Okay: Deutschland hat es wieder nicht ganz geschafft in den grünen Bereich – dorthin, wo die skandinavischen Länder stehen, die Niederlande oder Irland. Deutschland gehört auch nicht mehr zu den Top Ten wie noch 2024, aber es war knapp. Platz elf. Zum Glück nennen die „Reporter ohne Grenzen“ die Schuldigen. Zensur? Gott bewahre. Das Ausblenden, Diffamieren, Verleumden von allen, die laut Fragen stellen zum Regierungskurs? Doch nicht bei uns. Dieses Land würde auch in Sachen Pressefreiheit längst Weltmeister sein, wenn da nicht ein paar Unverbesserliche wären, die auf Journalisten ungefähr so reagieren wie ein Stier auf ein rotes Tuch. Glaubt man den „Reportern ohne Grenzen“, dann sind Demos in Deutschland ein gefährlicher Ort für alle, die dort mit Kamera, Mikro oder Presseschild auftauchen. 75 „physische Angriffe“ 2024, davon die meisten in Berlin und beim Thema Nahost, wobei es zwei Bild-Reporter allein auf 29 Einträge gebracht haben (Iman Sefati und seine Fotografin Yalcin Askin).
Vorweg: Jede Attacke ist eine zu viel. Gleich danach kommt aber der Verdacht, dass das ganz gut passt, weil die „Reporter ohne Grenzen“ so eine „zunehmende Pressefeindlichkeit“ beklagen können und „ein verengtes Verständnis von Pressefreiheit“. Zitat: „Denn viele Bürger*innen sehen Berichterstattende, die nicht ihrem eigenen politischen Spektrum entstammen, mittlerweile als Gegner an.“
Sorry für die Genderei. Ich habe das so gelassen, weil es vermutlich bereits damit anfängt. Mit einem „verengten Verständnis“ auch und gerade bei der Sprache. Lassen Sie uns das in drei Schritten angehen. Nummer eins: Wir schauen auf den Kellner, der da jedes Jahr zum Welttag der Pressefreiheit eine Quittung ausstellt. Nummer zwei: Wir zählen nach. Und Nummer drei: Wir schlagen all das drauf, was in der Rechnung fehlt.
Die „Reporter ohne Grenzen“ sitzen in Paris und sind damit auf den ersten Blick weniger verdächtig als der US-Thinktank „Freedom House“, der bis 2017 jedes Jahr eine Konkurrenzliste veröffentlicht hat und einen Großteil seiner Gelder und Sicherheiten direkt oder indirekt aus dem Staatshaushalt in Washington bezieht. Der Volksmund weiß, was das Brot aus den Liedern macht, die draußen gesungen werden. Bei den „Reportern ohne Grenzen“ kommt das Geld aus ganz ähnlich Töpfen – 2023 zu drei Vierteln von der EU, von staatlichen Behörden und von den großen Stiftungen. Ford, Luminate (Geldbörse von Ebay-Gründer Pierre Omidyar, der auch bei den Faktencheckern mitspielt), Open Society Foundations. Der deutsche Steuerzahler ist über ein Ministerium (Entwicklungshilfe) und den Berliner Senat jeweils mit einer Viertelmillion Euro dabei. Dass die Niederlande und Schweden mitspielen, erklärt sich bei einem Blick auf die Ergebnisse (in diesem Jahr: Platz 3 und 4). Besser kann man nicht investieren in Werbung für das eigene Land.
Diese Platzierungen sind gewissermaßen ein Selbstläufer, weil all das in die Wertung kommt, was der Westen gut findet – die formale Trennung von Regierung und Redaktionen zum Beispiel. Andersherum: Abzüge gibt es überall da, wo der Staat, Parteien oder Politiker selbst Medien betreiben. In Uganda zum Beispiel, Platz 143, gibt es kaum Werbetreibende, die ein TV-Programm finanzieren könnten, und nur ein kleines Publikum, das sich ein Zeitungsabo leisten kann und will. Sonntags drängen sich die Menschen dort vor kleinen Hütten mit großen Bildschirmen, um ihren Lieblingen aus der Premier League zuzujubeln und vielleicht einen Wettgewinn einzustreichen, der sie über die Woche trägt. Auf dem Land gehören die Radiostationen in aller Regel lokalen Größen. Kirche, Politik, Wirtschaft. Ich habe dort Interviews geführt und gelernt: Über „Pressefreiheit“ und Informationsqualität sagt das alles wenig. Die Menschen in Uganda wissen sehr genau, wer jeweils zu ihnen spricht, und machen sich ihren Reim darauf. Ein anderer Kriterienkatalog könnte daraus ein Qualitätsmerkmal machen. Während Besitz- und damit Machtverhältnisse im Westen hinter Nebelkerzen versteckt werden (Objektivität, Unabhängigkeit, Neutralität), herrscht in Uganda Transparenz.
Neben dem „politischen Kontext“ haben die „Reporter ohne Grenzen“ vier weitere Blöcke in ihrem Punktekatalog. Gesetze, Wirtschaft, Gesellschaft, Sicherheit. Die Fragen decken das ab, was bei uns Standard ist. Dürfen sich Journalisten gewerkschaftlich organisieren? Werden sie bestochen? Können Nachrichtenmedien finanziell überleben? Werden Karikaturen toleriert? Ich will hier nicht zu sehr auf Uganda herumreiten. Nur: Der Beruf wird dort völlig anders gesehen als hier. Es gibt nur eine kleine vierstellige Zahl an Journalisten. 1000, vielleicht 1500. Die meisten sind jung, weil die Redaktionen als Sprungbrett gesehen werden zu einem wirklich lukrativen Job in der Verwaltung, in den Unternehmen, in der Politik. Wer zu einer Pressekonferenz fährt, erwartet dort einen Umschlag. Offiziell: Anreisepauschale. Inoffiziell der Preis für einen wohlwollenden Bericht. Die „Reporter ohne Grenzen“ strafen Uganda folglich ab. Angriffe auf Journalisten (oft von Sicherheitsleuten), wenig Schutz vor Gericht, wenig Achtung vor dem Beruf. Platz 143 halt.
Und Deutschland? Die Demos wie gesagt und Leute, die die Dinge einfach falsch sehen. Ein „verengtes Verständnis von Pressefreiheit“. Außerdem sagen die „Reporter ohne Grenzen“: Wir tun zu wenig gegen „Hassrede und Desinformation“. Der Koalitionsvertrag von Schwarz-Rot ist offenbar nicht mehr eingeflossen in diesen Bericht. Dort heißt es:
Gezielte Einflussnahme auf Wahlen sowie inzwischen alltägliche Desinformation und Fake News sind ernste Bedrohungen für unsere Demokratie, ihre Institutionen und den gesellschaftlichen Zusammenhalt. Die bewusste Verbreitung falscher Tatsachenbehauptungen ist durch die Meinungsfreiheit nicht gedeckt. Deshalb muss die staatsferne Medienaufsicht unter Wahrung der Meinungsfreiheit auf der Basis klarer gesetzlicher Vorgaben gegen Informationsmanipulation sowie Hass und Hetze vorgehen können.
Schon vorab hatten die „Reporter ohne Grenzen“ von „einem stark verengten Meinungskorridor bei der Arbeit zu Israel und Palästina“ berichtet. Selbst alte Hasen haben in dieser Befragung gesagt, dass sie noch nie einen solchen Druck erlebt hätten – vor allem dann, wenn es um die israelische Kriegsführung geht, um die Folgen für die Bevölkerung in Gaza und um das, was in Deutschland zu diesem Thema passiert. Ich verlinke hier die Münchner Rede von Andreas Zumach, gehalten im November 2018, wo all das schon Thema war.
Und sonst? Corona, Ukraine, Klima und damit Energiewende? Kontokündigungen? Gerichtsurteile, die selbst es bis in die Weltpresse schafften (im Bild: The Economist vom 16. April 2025) und dort Unbehagen auslösten? Eine Cancel Culture, die Sprecher aus der Öffentlichkeit verbannt, die sich gegen die herrschende Ideologie und den Regierungskurs stellen?
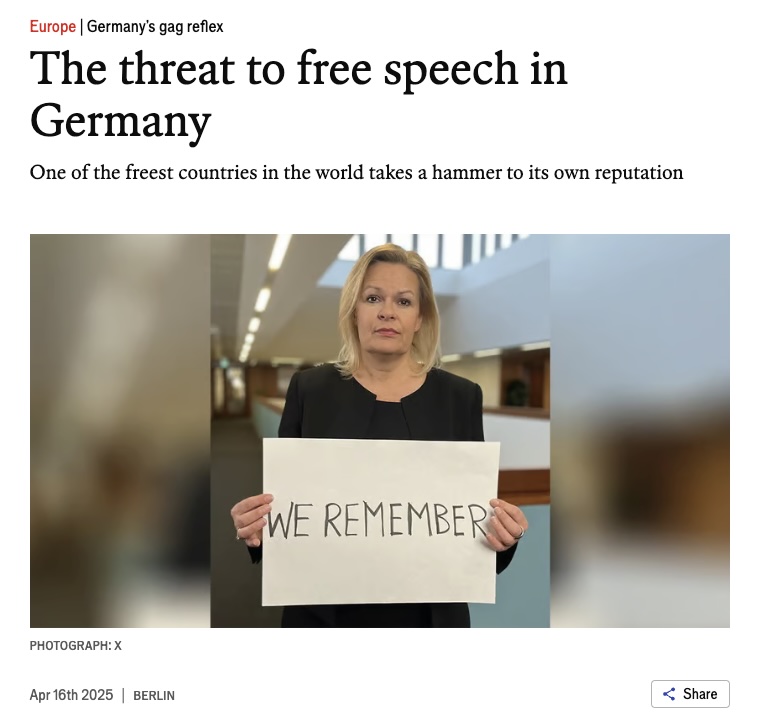
Alles kein Thema – jedenfalls nicht für die Experten, die gefragt werden (Journalisten, Forscher, Akademiker, Menschenrechtsspezialisten; mithin Menschen, die in irgendeiner Form von Staat oder Konzernen abhängen). Die konzernfreien oder neuen Medien senden für die „Reporter ohne Grenzen“ offenbar jenseits von Gut und Böse. Und dass die Regierung Fernsehen, Radio und Presse nicht unbedingt selbst betreiben muss wie in Uganda, um ihre Sicht der Dinge flächendeckend zu verbreiten, scheint dort außerhalb jeder Vorstellungskraft zu liegen. Anders ist nicht zu erklären, dass im Bericht zwar ein paar öffentlich-rechtliche Skandälchen auftauchen und der Stellenabbau bei der Südwestdeutschen Medienholding, aber nichts zu lesen ist über die Aufrüstung der Medienapparate in Ministerien, Parteien, Unternehmen und über den Druck, der davon auf Journalisten ausgeht, die zwar keinen Umschlag bekommen, wenn sie ordentlich berichten, aber sicher ein wenig Exklusives, wahrscheinlich eine Beförderung und vielleicht sogar ein Ticket für den Sprung auf die andere, besser entlohnte Seite. Bis es soweit ist, melden sie einfach, dass mit der Medienfreiheit alles okay ist, wenn es da nicht diese Chaoten auf der Straße geben würde und ein paar Unverbesserliche mit einem „verengten Verständnis von Pressefreiheit“. Sonst müsste man sich möglicherweise aufmachen und nach den Ursachen für den Unmut fragen.
-
 @ 866e0139:6a9334e5
2025-05-03 04:53:34
@ 866e0139:6a9334e5
2025-05-03 04:53:34Autor: Friderike Komárek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Was grade war, ist schief.
Wer Frieden will, ist böse.
Wer tötet, der ist lieb.
Gesund ist nur symptomlos krank,
Abstand ist gefühlte Nähe,
Maskenatmen – Gott sei Dank!
Fakten dienen Hass und Hetze,
Lügen tun gut.
Wer Fakten nennt, der wird zensiert,
Wahrheit schafft nur böses Blut.
Für Frieden braucht man Krieg,
für Meinungsfreiheit die Zensur.
Demokratie, die braucht Verbote,
fürs Klima zerstört man die Natur.
Mann ist Frau
und Frau ist Mann.
Ein Glück, dass man
die Biologie jetzt lenken kann!
Der Größenwahn beherrscht die Welt,
hat alles auf den Kopf gestellt.
Kritiker wandern als Kriminelle ins Gefängnis.
Mit ihren Gedanken bringen sie
die andern in Bedrängnis.
Was schief war, das ist grade.
Was grade war, ist schief.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 04ea4f83:210e1713
2025-05-01 18:22:24
@ 04ea4f83:210e1713
2025-05-01 18:22:2430. November 2022
Sehr geehrter Herr Bindseil und Herr Schaff von der Europäischen Zentralbank,
Ich schreibe Ihnen heute, am Tag der Veröffentlichung Ihres EZB-Blog-Berichts „Bitcoin's Last Stand", sowohl mit Belustigung als auch mit Bestürzung. Ich amüsiere mich darüber, wie albern und hilflos Sie beide erscheinen, indem Sie sich auf müde und längst widerlegte Erzählungen über Bitcoin und seine Nutzlosigkeit und Verschwendung stützen. Und ich bin beunruhigt, weil ich von zwei sehr gut ausgebildeten und etablierten Mitgliedern Ihres Fachgebiets eine viel differenziertere kritische Sichtweise auf den aufkeimenden Bitcoin und die Lightning Skalierungslösung erwartet hätte.
Sie haben sich mit Ihren dilettantischen Versuchen, Angst, Unsicherheit und Zweifel an einem globalen Open-Source-Kooperationsprojekt zu säen, das als ein ständig wachsendes Wertspeicher und -übertragungssystem für viele Millionen Menschen weltweit fungiert, wirklich einen Bärendienst erwiesen. Ein System, das jedes Jahr von mehr und mehr Menschen genutzt wird, da sie von seiner Effektivität und seinem Nutzen erfahren. Und ein System, das noch nie gehackt oder geknackt wurde, das funktioniert, um die „Banklosen" zu versorgen, besonders in den Ländern und Orten, wo sie von finsteren totalitären Regierungen schwer unterdrückt oder von der finanziell „entwickelten" Welt einfach im Stich gelassen wurden. In der Tat ist Bitcoin bereits gesetzliches Zahlungsmittel in El Salvador und der Zentralafrikanischen Republik, und erst gestern erhielt er in Brasilien den Status eines „Zahlungsmittels".
Es entbehrt nicht einer gewissen Ironie, wenn ich schreibe, dass Sie das Ziel so gründlich verfehlen, insbesondere weil die Bank- und Finanzsysteme, zu denen Sie gehören, für eine Energie- und Materialverschwendung verantwortlich sind, die um Größenordnungen größer ist als die Systeme und Ressourcen, die das Bitcoin-Netzwerk antreiben und erhalten. Ich bin mir sicher, dass Sie sich der revolutionären kohlenstoff- und treibhausgasreduzierenden Effekte bewusst sind, die Bitcoin-Mining-Anlagen haben, wenn sie neben Methan-emittierenden Mülldeponien und/oder Ölproduktionsanlagen angesiedelt sind. Und ich weiß, dass Sie auch gut über solar- und windbetriebene Bitcoin-Mining-Cluster informiert sind, die dabei helfen, Mikronetze in unterversorgten Gemeinden einzurichten.
Ich könnte noch weiter darüber sprechen, wie das Lightning-Netzwerk implementiert wird, um Überweisungszahlungen zu erleichtern sowie Finanztechnologie und Souveränität in Gemeinden in Laos und Afrika südlich der Sahara zu bringen. Aber lassen Sie mich zu dem Teil kommen, der einen gewöhnlichen Menschen wie mich einfach zutiefst traurig macht. Bitcoin ist, wie Sie sehr wohl wissen (trotz Ihrer dummen und veralteten Verleumdungen), ein technologisches Netzwerk, das nicht auf nationaler oder internationaler Verschuldung oder der Laune von Politikern basiert oder durch sie entwertet wird. Es ist ein System, das jenseits der Kontrolle einer einzelnen Person, eines Landes oder einer Gruppe von Ländern liegt. Wenn Bitcoin sprechen könnte (was er in der Tat ungefähr alle zehn Minuten tut, durch das elektro-mathematische Knistern und Summen des Wahrheitsfeuers), würde er diese Worte aussprechen:
„Über allen Völkern steht die Menschlichkeit".\ \ Als Bankiers der Europäischen Union, als Menschen von der Erde, als biologische Wesen, die denselben Gesetzen des Verfalls und der Krankheit unterliegen wie alle anderen Wesen, wäre es da nicht erfrischend für Sie beide, das Studium und die Teilnahme an einer Technologie zu begrüßen, die die Arbeit und die Bemühungen der sich abmühenden Menschen auf unserem Planeten bewahrt, anstatt sie zu entwerten? Wie die Bitcoin-Kollegin Alyse Killeen wiederholt gesagt hat: „Bitcoin ist FinTech für arme Menschen".
Ich bin dankbar für Ihre Aufmerksamkeit und hoffe, dass Sie über Bitcoin nachdenken und es gründlicher studieren werden.
Mit freundlichen Grüßen,
Cosmo Crixter
-
 @ 04ea4f83:210e1713
2025-05-01 18:18:36
@ 04ea4f83:210e1713
2025-05-01 18:18:36Digitales Geld ist nur Text, die ganze Zeit
Bei digitalem Geld geht es im Grunde nur um Zahlen in einem Hauptbuch. Die ganze Zeit über sind es die Zahlen, auf die es ankommt. Lange Zahlen sind einfach nur Zeichenketten im PC und diese werden als Nachrichten in einem Netzwerk, das durch Regeln gebildet wird, an gleichwertige Peers gesendet - das ist Bitcoin, das mit einem einzigartigen dezentralen Zeitstempel-Algorithmus kombiniert wird, der durch die Unfälschbarkeit von Energie gesichert ist. Das Ergebnis ist ein Bargeldnetzwerk mit einem festen, vorprogrammierten Zeitplan für die Geldschöpfung, das den ersten absolut knappen digitalen Inhabervermögenswert schafft.\ \ Diese revolutionären Ideen werden bleiben, genauso wie das Feuer, das Rad, die Elektrizität, das Smartphone, das Internet oder die Zahl Null. Technologie entwickelt sich weiter und was machen lebende Organismen? Sie können mutieren, genau wie Viren, und das hat mich zu dem Schluss gebracht, dass es auch in dieser Hinsicht eine Verbindung gibt und das obwohl Gigi bereits einige der vielen Facetten von Bitcoin beschrieben hat. Für mich ist die Grundlage die Abstraktion, dass Bitcoin nur die Summe aller Menschen ist, die Satoshis besitzen oder anderweitig mit dem Bitcoin-Netzwerk interagieren.\ \ Die Technologien werden in einem bestimmten Tempo angenommen. Allerdings gibt es immer frühe oder späte Entdecker von neuer Technologie. Aber was passiert, wenn es zu einer ernsthaften Bedrohung wird, wenn hartes Geld nicht adoptiert wird? Was passiert, wenn die Geschwindigkeit der Preiszunahme so hoch wird, dass es unmöglich ist, jemanden zu finden, der Satoshi in Fiat tauschen möchte? Was passiert, wenn die Hyperbitcoinisierung morgen beginnt? Was wäre, wenn es eine UpSideProtection™️ gäbe, die diesen Prozess noch mehr beschleunigt und dir Bitcoin zu einem Bruchteil seines wahren Wertes sichert?\ \ Wir alle wünschen uns einen sicheren Übergang, um den Krieg aufgrund einer scheiternden Dollar-Hegemonie zu vermeiden, und tatsächlich gibt es ein Rennen, um den Krieg zu vermeiden. Mein größtes Geschenk ist die Zeit, die ich ich investiere, und die monetäre Energie, die ich in Bitcoin spare, und da ich schon eine Weile dabei bin, sehe ich, dass meine Mitstreiter die gleiche Mission verfolgen. Aber das ist NICHT genug. Wir müssen skalieren. Schneller.\ \ Das Erstaunen über den Kurzfilm der große Widerstand hat mich zu dem Schluss gebracht, dass wir alle Werkzeuge und Informationen in Form von Lehrern, Podcasts, Büchern und aufklärenden Videos bereits haben. Der Vorteil einer festen Geldmenge wird aber noch nicht von einer kritischen Masse verstanden, sondern nur von einer intoleranten Minderheit. Diese Minderheit wächst von Tag zu Tag. Ihre Inkarnationen sind die DCA-Armee, die Hodler der letzten Instanz, die unbeirrten Stacker, die Cyberhornets, die Memefactory™️ und Mitglieder der 21 Gruppe auf der ganzen Welt.\ \ Wir Bitcoiner sind räumlich getrennt, aber nicht in der Zeit. Getrennt in der Sprache, aber nicht in der Mission. Vereint müssen wir uns zu Wort melden, aufklären und Bitcoin wie einen Virus verbreiten.\ \ Niemand entscheidet, was Bitcoin für dich ist - dieser Virus des Geistes verfestigt sich in unbestechlichen Zahlen, die zu einer wachsenden Zahl an UTXOs in den Geldbörsen führen, nicht in negativen gesundheitlichen Auswirkungen. Bitcoin ist der Virus der Schuldenindustrie, der Virus, der im 21. Jahrhundert zur größten Definanzialisierung und Auflösung des Kredits führen wird. Da wir noch nicht in einer hyperbitcoinisierten Welt leben, müssen wir den Virus effektiver machen. Bitcoin muss mutieren, aber es ist nicht Bitcoin, der tatsächlich mutiert, sondern die Menschen, die ihn benutzen. Sie werden zu toxischen Maximalisten, die den Virus noch stärker verbreiten und alle Shitcoiner während ihrer Anwesenheit geistig infizieren oder argumentativ töten.\ \ Ich habe mich gefragt, wie wir eine Milliarde Menschen dazu ausbilden und überzeugen können, Bitcoin freiwillig zu nutzen und darin zu sparen, so dass sie Bitcoin als primäres Mittel zur Speicherung und Übermittlung von Werten in Raum und Zeit nutzen? Die Hyperbitcoinisierung braucht nur eine einzige, starke positive Rückkopplungsschleife um wirklich in Gang zu kommen, und diese Rückkopplung gibt es bereits, aber nicht in den Köpfen aller. Ab einer bestimmten Schwelle wird die Schwerkraft von Bitcoins gehärteten monetären Eigenschaften einfach zu hoch sein, als dass die Spieltheorie nicht zu dieser Rückkopplung führen würde, vor allem da Bitcoin im Jahr 2024 Gold in Punkto Knappheit übertrifft.\ \ Die Verbreitung der Idee einer festen dezentralen Geldmenge, die der Macht zentraler Kräfte entzogen ist, ist der Virus. Der Weg, das Spiel zu spielen, ist, Stacker zu stapeln, und Stacker stapeln Sats, wodurch die Geldmenge noch dezentralisierter wird und ein Verbot noch absurder wird. Sats sind endlich und unser Spiel ist es auch. Allein eine bestimmte Anzahl von einfachen Leuten, den Plebs, kann den Preis auf 1.000.000 EURO treiben.\ \ Letztendlich wird sich die Welt an das neue Gleichgewicht der Macht zugunsten des Individuums anpassen. Diese Idee in die Köpfe der Massen zu bringen, ist die wichtigste Aufgabe für 2023, die in das nächste Halving Mitte 2024 führt.\ \ Wir müssen unseren Reproduktionswert erhöhen, um die Akzeptanz zu steigern. Die Verwendung von Bitcoin als Zahlungsmittel und eine Kreislaufwirtschaft ist wichtig. Bildung ist wichtig. Apps und Anwendungsfälle sind wichtig. Die Kaufkraft, d.h. die Moskau Zeit, die sich in Richtung Mitternacht (00:00) bewegt, spielt eine Rolle, und all dies hängt zusammen.\ \ Aber wie genau können Plebs eine Milliarde Menschen überzeugen?\ \ Wie genau hat das Corona-Virus eine Milliarde Menschen infiziert?\ \ Peer-to-Peer.\ \ Erhebe deine Stimme, wer auch immer du bist, sprich über Bitcoin, werde aktiv und BUIDL oder lass uns einfach Spaß daran haben, arm zu bleiben und es genießen, jeden Tag bestohlen zu werden.\ \ Lass uns Yellow mehr Freizeit schenken und Bitcoin bis 100k+ aufkaufen und uns damit ins Stackheaven befördern.
"Don't stop believin' HODL on to that feelin' "
Der Rest wird in die unumstößliche Geschichte der Timechain eingraviert.
„Unter dieser Maske gibt es mehr als nur Fleisch. Unter dieser Maske ist eine Idee. Und Ideen sind kugelsicher." Alan Moore, V wie Vendetta

⚡
Danke für deine Aufmerksamkeit .\ \ #GetShortFiat und #GetOnZero\ \ Es ist immer noch 60 Uhr. Sei weise und stapele unbeirrt. Man kann die Mathematik und Physik nicht austricksen.\ \ Wenn der Post dir Motivation zum Stapeln von Sats oder dem Stapeln von Stackern gemacht hat, freue ich mich, wenn du mir auch etwas beim Stapeln hilfst!
-
 @ f1989a96:bcaaf2c1
2025-05-15 14:42:29
@ f1989a96:bcaaf2c1
2025-05-15 14:42:29Good morning, readers!
We bring news from the Democratic Republic of Congo (DRC), where the Rwanda-backed M23 rebel group is imposing immense taxes on the local economy, merchants, and aid groups to fund its insurgency as it seeks to govern seized regions of the Eastern Congo. The levies worsen economic hardship for Congolese already suffering from ongoing cash shortages, bank closures, and rapidly rising prices induced by the regional conflict.
Meanwhile, in Hong Kong, independent media outlet Channel C, founded by former Apple Daily employees, had its bank account frozen by local officials over alleged fraud charges. The closure fits into a widespread pattern of the Chinese Communist Party (CCP) leveraging financial repression and legal pressure to silence independent and pro-democracy media in Hong Kong.
In freedom tech news, we highlight a new ecash development: multinut payments. These payments let users combine small balances held at different ecash mints to pay a single invoice. It’s a big step forward in terms of usability and security for human rights defenders since they no longer need to keep a large balance of ecash at any one mint. This reduces the chances of stolen funds while maintaining strong privacy guarantees. We also highlight the ongoing OP_RETURN debate in the Bitcoin community, present both sides of the argument, and invite our readers to watch a nuanced debate on this topic.
We end with the latest edition of the HRF x Pubkey Freedom Tech series, where the Human Rights Foundation’s Alex Gladstein discusses the upcoming Oslo Freedom Forum and HRF’s role in supporting open-source freedom tech with Pubkey’s co-founder, Thomas Pacchia. We also include the livestreams from the latest bitcoin++ event, where developers, privacy advocates, and freedom tech users convened to discuss Bitcoin’s mempool, learn how Bitcoin transactions are sorted into blocks, and discuss current mempool policies.
Now, let’s jump right in!
SUBSCRIBE HERE
GLOBAL NEWS
DR Congo | Rebel Rule and Economic Ruin
After seizing control of large parts of the eastern Congo, the Paul Kagame-backed M23 rebel group is now trying to govern and fund its insurgency through coercive taxation and financial control. Rebels now impose a 15% tax on coltan metal production, 20% duties on merchants selling essential goods, and demand tax bills from aid groups, backed by threats of physical punishment. “If you don’t pay up, you risk being whipped,” one merchant said. The new levies are worsening the financial struggles for Congolese already suffering from ongoing cash shortages, bank closures, and rapidly rising prices induced by the regional conflict. Many must travel hundreds of kilometers just to obtain cash while navigating the backdrop of a humanitarian crisis that has claimed more than 7,000 lives.
China | Law Enforcement Freezes Bank Accounts of Independent Media Outlet Channel C
Hong Kong-based Channel C, an independent media outlet founded by former Apple Daily employees, reports that its bank accounts are frozen, forcing the news outlet to halt operations. Local law enforcement claim the outlet abused a COVID-era loan scheme and arrested one of its directors for alleged fraud. Still, the closure fits a well-worn pattern: using financial and legal repression to silence independent media in Hong Kong. Pro-democracy newspaper Apple Daily faced a nearly identical fate in 2021 when its assets were seized and its founder, Jimmy Lai, was imprisoned under Hong Kong’s new national security law. Lai now faces up to life in prison. When access to money becomes contingent on political obedience, press freedom can’t survive.
Venezuela | Blackouts, Inflation, and Currency Shortages
Venezuelans are once again bracing for economic collapse as inflation rises to 162% and electrical blackouts sweep across major cities. The situation echoes 2019’s political and financial chaos, where triple-digit inflation, foreign currency shortages, and power outages paralyzed the country. In reaction to the collapse, Nicolás Maduro approved the country’s first economic emergency decree in four years, granting himself broad powers to suspend taxes and authorize new benefits for select investors. The regime has also reshuffled central bank leadership and is pressing merchants to abandon US dollar pricing and return to the failing bolivar system — a clear move to financially asphyxiate Venezuelans. A focus on top-down economic management by Maduro’s regime will only reinforce the inflation and poverty driving this widespread crisis in the wake of Maduro’s stolen and blatantly rigged presidential election.
Bolivia | Inflation Accelerates to 17-Year High
Inflation in Bolivia is accelerating rapidly, with prices rising more than 15% year over year. This is the highest level of inflation Bolivians have seen in 17 years. Families now face increased costs of essential goods like food, shelter, and water. And the country’s fixed exchange rate system is also faltering, with dwindling reserves and growing dollar shortages compounding the price increases. The Bolivian regime also approved a new decree to regulate financial technology companies and virtual asset providers. The regulations tighten control over platforms that offer alternatives to the depreciating boliviano. If implemented rigidly, these regulations could restrict access to tools like Bitcoin.
Nicaragua | Ortega Centralizes Passport Renewal in Managua for Exiled Dissidents
The regime of Daniel Ortega has stripped Nicaraguans abroad of a basic right: the ability to renew their passports at local embassies abroad. All renewals must now go through the Nicaraguan capital of Managua, forcing exiles to either return home or authorize a relative (via an apostilled power of attorney) to handle the renewal on their behalf. For many outside Nicaragua, especially political opposition, journalists, and human rights defenders, returning is not a safe option, and involving relatives could expose them to state repression or retaliation. Those who do return risk facing the immense physical and financial repression of the Ortega regime, including surveillance, extortion, bank freezes, or even imprisonment. Ortega’s corruption of even basic bureaucracy undermines the growing Nicaraguan diaspora’s ability to live freely abroad by making their legal status, mobility, and access to financial services conditional.
Kenya | High Court Rules Against Sam Altman and Worldcoin
A Kenyan High Court ruled that Worldcoin, the biometric ID project co-founded by Sam Altman, CEO of OpenAI, violated constitutional privacy rights by collecting iris scans and facial images without proper safeguards. The court ordered the immediate deletion of all biometric data collected from Kenyan users, including iris scans and facial images. They also banned the project from conducting any further data collection. Kenya had been one of Worldcoin’s largest markets before authorities suspended the project in 2023. As biometric surveillance becomes more widespread, this case highlights the risks of technologies that undermine privacy in the name of inclusion.
BITCOIN AND FREEDOM TECH NEWS
Cashu | Make Ecash Payments from Multiple Mints
Cashu, a protocol for making private bitcoin payments using ecash, shared a new feature called multinut payments. Still in development, it enables users to combine small ecash balances held at different mints (entities that issue and redeem ecash) into a single transaction. Since Cashu is a custodial system (meaning users must trust the mints they use), this update reduces counterparty risk by allowing users to spread their funds across multiple mints rather than relying on just one. Previously, making a large ecash payment required keeping a sizeable balance at a single mint, increasing the chances of losing your funds if the mint were shut down or compromised. Now, larger payments can be made with significantly less custody risk. For those living under strict financial controls, ecash multinut payments offer a very private way to spend funds without trusting any single entity that can censor or debank them.
Bitika | Bridging Bitcoin and M-Pesa in Kenya
Bitika is a Kenyan fintech startup simplifying Bitcoin access. It integrates with M-Pesa, the mobile money platform used daily for payments by millions of people across Kenya and wider East Africa. Bitika offers a three-step process to buy Bitcoin via mobile phone using the Lightning Network. Users simply enter the amount of Bitcoin they would like to receive in Kenyan shillings, input their Bitcoin Lightning wallet address, and enter their M-Pesa number, and once confirmed, they receive their Bitcoin. Bitika is similar to other Bitcoin projects like Tando, which also bridges Bitcoin with M-Pesa using the Lightning Network. With plans to expand across the rest of Africa, Bitika shows Bitcoin’s grassroots utility and the role of local context in driving bottom-up financial inclusion. Try it here.
Frostsnap | New Bitcoin Multisig Custody Solution
Frostsnap is a new Bitcoin custody solution that uses a simplified multisignature setup to protect users' funds from theft, loss, or coercion by corrupt and authoritarian regimes. Rather than generating and storing private keys on a single device, multisignature solutions like Frostsnap employ multiple private keys distributed across different devices and locations. This approach eliminates single points of failure and offers strong resistance to physical attacks, device compromise, and forced access to users’ Bitcoin (such as from Chinese law enforcement, who surveil mail and extort Bitcoin). Frostsnap also offers the ability to spend directly from the multisig wallet, hide the wallet in times of duress, and access inheritance features, all critical functionalities for human rights defenders and nonprofits facing surveillance or financial repression. Learn more here.
OP_RETURN | Debate Over Bitcoin Core’s Data Relay Limits
A heated debate has resurfaced between some Bitcoin users and developers over whether to raise the size limit for OP_RETURN data that Bitcoin Core nodes (computers running Bitcoin’s main software implementation) relay. The debate was sparked when developer Peter Todd proposed removing this data limit from mempool policy on the basis that it could reduce reliance on direct miner connections, improve fee estimation, and shrink the Unspent Transaction Output (UTXO) set. It would do this by encouraging users to store arbitrary data in prunable, unspendable outputs (rather than spendable, persistent UTXOs). On the other hand, critics warn that lifting the OP_RETURN limit could increase spam, undermine Bitcoin’s focus on serving financial transactions, and weaken its censorship resistance. The debate still continues, but at its core, the disagreement highlights deeper tensions over what kinds of data should flow through the Bitcoin network. Tune into this discussion at the latest bitcoin++ developer conference to understand the nuance on both sides of the OP_RETURN debate.
Wasabi Wallet | Major Privacy Upgrade and Serverless Operation
Wasabi Wallet, a non-custodial, privacy-focused Bitcoin wallet, introduced its Prometheus update, which enables the wallet to synchronize and operate without a central server and increases transaction privacy. Users can now connect Wasabi directly to their own Bitcoin node (computer running the Bitcoin software), removing reliance on third-party infrastructure and reducing the risk of censorship. The update also introduces Coinjoin 2.0, a privacy technique that mixes the inputs of a Bitcoin transaction, in doing so protecting, for example, the identity of a dissident or nonprofit. Coinjoin 2.0 brings a redesigned mixing process that continuously registers coins as they become available. This change improves privacy and strengthens resistance to analysis that dictators can use to track payments.
Cove Wallet | Adds Support for Krux
Cove Wallet, an open-source mobile Bitcoin wallet currently in beta, released v0.4.0, which brings support for Krux hardware wallets. Krux is an open-source software and HRF grantee that turns generic computing devices into hardware wallets for secure Bitcoin self-custody and transactions. It can help decentralize access to Bitcoin and protect freedom and property rights in authoritarian regimes by providing a discrete and modular self-custody solution. By incorporating Krux, Cove offers its users a private, borderless, DIY path to financial sovereignty with no brand-name hardware. Cove Wallet also announced future support for coin control, which will grant users granular control over the specific coins they use in their Bitcoin payments and the ability to improve transaction privacy.
RECOMMENDED CONTENT
HRF x Pubkey — Freedom Tech and the Oslo Freedom Forum with Alex Gladstein
The latest edition of the HRF x Pubkey Freedom Tech series features a fireside chat with Alex Gladstein, chief strategy officer of HRF, in conversation with Pubkey co-founder Tom Pacchia. The discussion explores HRF’s role in funding and supporting open-source Freedom Tech, the upcoming Oslo Freedom Forum and the Freedom Tech track, as well as the human rights paradox of nation-state Bitcoin adoption. Catch the full conversation here.
bitcoin++ Developer Conference Livestream
Last week, bitcoin++ hosted the “mempool edition” of its Bitcoin developer conference series in Austin, Texas. The event, supported by HRF, brought together Bitcoin developers and freedom tech advocates for multiple days of hands-on development, workshops, and technical discussions surrounding Bitcoin’s mempool (the queue of pending transactions in a Bitcoin node). If you’d like to dive into the technical intricacies, you can catch the key sessions and workshops via live stream. Watch them here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ eb0157af:77ab6c55
2025-05-15 14:41:18
@ eb0157af:77ab6c55
2025-05-15 14:41:18Coinbase has revealed an attack in which a group of hackers bribed support agents to access user data.
Coinbase is facing a serious security crisis after a data breach on May 11. A hacker group claimed to have stolen sensitive customer information and demanded a $20 million ransom in bitcoin, threatening to release the data if the payment is not made.
In response, Coinbase CEO Brian Armstrong stated the company will not negotiate with criminals. Instead, the firm launched a countermeasure: a $20 million bounty for anyone who provides information leading to the identification and capture of the attackers.
In a post, the company added it will “reimburse customers who were tricked into sending funds to the attacker.”
Reports indicate the hackers managed to corrupt some Coinbase customer service agents, gaining access to the company’s internal systems. Once inside, they collected sensitive user data, including names, phone numbers, email addresses, and partial social security numbers. Masked bank details, ID document images, and snapshots of account balances were also compromised.

Coinbase confirmed the breach and said it acted swiftly to isolate affected systems and notify impacted users. Previous reports said the incident affected 1% of monthly transacting users.
The post Coinbase user data breached: hackers demand $20 million appeared first on Atlas21.
-
 @ 05a0f81e:fc032124
2025-05-15 14:24:22
@ 05a0f81e:fc032124
2025-05-15 14:24:22People often say that education is the key to success but after a deliberate analysis with my inner mind, I discovered that education is not the key to success.
Education is the process of learning and acquiring knowledge, skills and understanding. It involves the transmission of information, knowledge and technical know-how. It also involve the development of critical thinking and understanding and the cultivation of personal and social growth, the process of education occur formally through school and universities and informally through everyday experiences.
Being educated makes someone more exposed to the world, make you see things in a different way, but educated will not grant you success 💯. Most educated individuals end up searching for jobs, while most persons after being educate in a particular field will end up as a trader. This is because there education have boundaries, it can not stand against all odds example, lack of employment and bad governments.
Furthermore, if education did not have the ability to breakdown boundaries and untie every chain that is holding success, that means It is the key to success.
Success comes from the mind and the key to success is what I called the MINDSET. What is mindset?. Mindset is the collection of attitudes and beliefs that influence how an individual perceive and interact with the world, it essentially shapes how you think, feel and behave in response to different situations.
The key to success is your MINDSET, to become successful, your mind need to think right, your actions and the words you speak is as a result of what you have in your mind.
To become Elon musk of African come from the mind, to build a titanic comes from the mind, being educated also comes from the mind before you show the actions, that going to school. Everything done on earth first dropped in the mind before it's execution.
Success is the is the accomplishment of an aim or purpose. So when you accomplished your aim and purpose which are your MINDSET, you have become successful in that part of your life.
In conclusion, the key to success is your MINDSET not education.