-
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ c1831fbe:de4b39bf
2025-05-17 09:57:04
@ c1831fbe:de4b39bf
2025-05-17 09:57:04What follows is my best effort to recall the details of an arguably supernatural encounter I experienced almost sixty years ago. I've told this story many times before, and while my recollection may not be perfect in every detail, my account is real and substantively factual.
It was early one long ago morning, in that twilit between-time shortly before dawn. As I dangled precariously in a quasi-aware state, hovering on the knife edge between wakefulness and sleep, I was transported in a dream to another place and time. Was it the Mediterranean coast? Perhaps ancient Greece?
In my mind's eye, I found myself climbing a rather steep, rocky hillside overlooking a sparkling bright blue sea. Ahead of me, and slightly higher, was what appeared to be a young shepherd boy, leading me ever higher up the hill.
As we wove our way upward,
skirting rocky outcroppings and zig-zagging because of the steepness of the slope, I heard the boy chanting:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
He kept repeating the mantra, over and over:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
\~ \~ \~
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
I listened for a few cycles, and then took up the chant myself. After several attempts, when at last I got it right, the shepherd boy turned, looking back at me and smiling broadly to signal that I had finally mastered the cadence and the words.
Then I awoke.
Because my dream had been so vivid and unusual, I immediately found a pencil and paper to write down the chant phonetically before I could forget it.
A few days passed.
Life was busy. Then I remembered my friend in grad school, studying biblical Greek. That weekend, I went and hung out with him while he worked his night job at the college heating plant. Between his rounds inspecting and managing the steam boilers keeping students from freezing to death in the Arctic Midwest winter, I told him about my strange dream.
Pulling out an exhaustive Greek lexicon, one by one, my knowledgeable friend looked up the words from my dream, interpreting each according to its verb conjugation, tense, and mood.
"Ata, Ata" had no discernible meaning; we soon concluded that it was probably just meaningless vocables, added to give the chant rhythm and substance. My friend moved on to the first recognizable word of the chant...
"Archontos" - "They are ruled."
OK, so far, so good. He checked the next word:
"Echousi" - "They shed blood."
Hmmmm... This chant is beginning to appear to be more than random sounds.
"Archousi" - "They rule."
At this point, I almost fell out of my chair in shock. Far from being a meaningless chant, this cycle—repeating again and again—is the seemingly never-ending story of the entirety of human history...
"They Are Ruled, They Shed Blood, They Rule."
\~ \~ \~
"They Are Ruled, They Shed Blood, They Rule."
This concise mantra perfectly captures the endlessly repeating cycle of oppression, revolt, and revolution that always leaves us with a fresh set of oppressors all too ready to replace the last.
Who will rescue us?
Who will redeem us from this endless tedious cycle into which we have been born?
A long lifetime of study and reflection has persuaded me that this deadly cycle can and ultimately will be broken. If we follow the teachings of Jesus; if we love one another and live together in voluntary, local societies, serving each other; I am persuaded that we can break free of this desperately destructive cycle of endlessly seeking to dominate one another. It's past time for us to enter into a mutually beneficial life in the Kingdom of our Creator-God Jesus, the most authentically benevolent King the universe has ever known.
stories #politics #Christianity #supernatural #strange
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 609f186c:0aa4e8af
2025-05-16 20:57:43
@ 609f186c:0aa4e8af
2025-05-16 20:57:43Google says that Android 16 is slated to feature an optional high security mode. Cool.
Advanced Protection has a bunch of requested features that address the kinds of threats we worry about.
It's the kind of 'turn this one thing on if you face elevated risk' that we've been asking for from Google.
And likely reflects some learning after Google watched Apple 's Lockdown Mode play out. I see a lot of value in this..
Here are some features I'm excited to see play out:
The Intrusion Logging feature is interesting & is going to impose substantial cost on attackers trying to hide evidence of exploitation. Logs get e2ee encrypted into the cloud. This one is spicy.
The Offline Lock, Inactivity Reboot & USB protection will frustrate non-consensual attempts to physically grab device data.

Memory Tagging Extension is going to make a lot of attack & exploitation categories harder.
2G Network Protection & disabling Auto-connect to insecure networks are going to address categories of threat from things like IMSI catchers & hostile WiFi.
I'm curious about some other features such as:
Spam & Scam detection: Google messages feature that suggests message content awareness and some kind of scanning.
Scam detection for Phone by Google is interesting & coming later. The way it is described suggests phone conversation awareness. This also addresses a different category of threat than the stuff above. I can see it addressing a whole category of bad things that regular users (& high risk ones too!) face. Will be curious how privacy is addressed or if this done purely locally. Getting messy: Friction points? I see Google thinking these through, but I'm going to add a potential concern: what will users do when they encounter friction? Will they turn this off & forget to re-enable? We've seen users turn off iOS Lockdown Mode when they run into friction for specific websites or, say, legacy WiFi. They then forget to turn it back on. And stay vulnerable.

Bottom line: users disabling Apple's Lockdown Mode for a temporary thing & leaving it off because they forget to turn it on happens a lot. This is a serious % of users in my experience...
And should be factored into design decisions for similar modes. I feel like a good balance is a 'snooze button' or equivalent so that users can disable all/some features for a brief few minute period to do something they need to do, and then auto re-enable.
Winding up:
I'm excited to see how Android Advanced Protection plays with high risk users' experiences. I'm also super curious whether the spam/scam detection features may also be helpful to more vulnerable users (think: aging seniors)...
Niche but important:
Some users, esp. those that migrated to security & privacy-focused Android distros because of because of the absence of such a feature are clear candidates for it... But they may also voice privacy concerns around some of the screening features. Clear communication from the Google Security / Android team will be key here.
-
 @ 85fb39c4:81498307
2025-05-19 23:07:11
@ 85fb39c4:81498307
2025-05-19 23:07:11It's my first post
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ 94215f42:7681f622
2025-05-16 08:18:52
@ 94215f42:7681f622
2025-05-16 08:18:52Value Creation at the Edge
The conversation around artificial intelligence has largely centered on the technology itself, the capabilities of large language models, the race for more parameters, and the competition between AI companies.
He with the most data / biggest model / biggest platform wins all.
As we're been exploring in recent "Good Stuff" podcasts, the true business model of AI may be much more straightforward. AI is after all a productivity tool with little technical moat, in fact the existence of AI coding and learning tools quickly chop away at this moat even quicker!.\ \ We believe that the it's about transforming traditional human heavy businesses by dramatically reducing operational costs while maintaining or increasing output.
AI is poised to create value not primarily for AI companies themselves, but for businesses that effectively implement AI to transform their operations, particularly small, local businesses that can become extraordinarily efficient through AI adoption.
The Value Shift: From AI Companies to AI-Enabled Traditional Businesses
A central insight from episode 1 of the podcast series, is that the value of AI isn't likely to accrue primarily to companies like OpenAI or other AI technology providers. Instead, the real winners will be traditional service businesses that can leverage AI to transform their operations and cost structures.
"I think we're gonna see this shift to traditional service businesses... that traditionally have pretty fixed low margins because of a dependency on language-heavy workflows that require a lot of humans as the medium of intelligence in the business."
The opportunity here is to use AI to manage the language dependency and shift the moments of intelligence, that currently exist in the heads of our staff, into software that can run 24x7 for fractions of a cost.\ \ The real limiting factor here is less a magic AGI, but instead detailed thinking and process redesign to move humans to the edge of the process. As it turns out if we think through what each person is doing in detail we see the specific decisions, outputs, moments of intelligence are actually quite constrained and can be replicated in LLM's if we break them down to a low enough level of fidelity and take each decisions one step at a time.\ \ The result? Businesses that have traditionally operated with fixed, low margins can potentially achieve "software-style margins" by dramatically reducing their operational expenses.
Transforming Traditional Service Businesses
We have developed three key heuristics for identifying businesses that could benefit most from AI transformation:
-
Language Intensity: Businesses where much of the work involves processing language (reading, writing, communicating). Language in, language out. If you are sat in a chair and typing all day, this could be you.
-
Labor Component: Where we see this language intensity so we find many people performing similar, standardized roles. For examples, if we have four people in the same role this is a big clue we have good process, checklists, role descriptions etc for how the work can be done in order to replicate work across multiple people.
-
Load in the Business: Taking these processes into account, what amount of the operational expense of the business do they represent? Where these language and labor-intensive operations represent a significant portion of the business cost, we can see there will be significant return.
Traditional service businesses that match these criteria—legal firms, accounting practices, consulting agencies, contract engineering, design agencies and others—could see dramatic transformations through AI implementation.
By automating these language-heavy processes, businesses can potentially reduce operational costs by 50-80% while maintaining similar levels of output.
The Power of Small
We believe that small businesses may have an inherent advantage in this transformation. While large enterprises face significant barriers to reducing their workforce (political pressure, media scrutiny, organizational complexity), smaller businesses can adapt more quickly and focus on growth rather than just cost-cutting.
If I'm in a 20,000 person business and I need to remove 10,000 people... that's hard. You can't do this without sending political shock waves in your local community.
If I'm a 10 person business and I need to double my revenue, nobody gives a shit. I can just do it.
For small businesses, AI removes growth constraints. When adding the "21st person" no longer represents a significant capital investment, small businesses can scale much more efficiently:
If the next nominal client that you onboard doesn't actually cause you any more additional pain, if you don't need to hire more people to service that client... you just take off the brakes off from a growth perspective.
This gives small business a unique advantage in capitalizing on AI.
From "Bionic Humans" to "Humans at the Edge"
We currently see this integration to business happening in one of two models:
-
The Bionic Human: Equipping workers with AI tools to make them more productive.
-
Human at the Edge: Redesigning processes to be AI-native, with humans entering the process only when needed (and often facilitated by bitcoin payments).
While many businesses are focused on the first approach and it can certainly see returns, it is still a process constrained by the human input. The real value unlock comes from fundamentally redesigning business processes with AI at the core.
Now we can purchase intelligence in buckets of $0.02 API calls, how would we operate different?
This represents a profound shift in how we think about work and processes. Rather than humans being central to processes with tools supporting them, AI becomes the backbone of operations with humans providing input only at critical junctures.
This is "a complete mental shift" that challenges our fundamental assumptions about how businesses operate. The human becomes "the interface with the real world" for AI systems rather than the primary processor of information and decision-maker.
The Value Trap: Understanding the Competitive Dynamic
So what happens next? Here we have developed the concept of the Value Trap to explain how the competitive landscape will evolve as AI adoption increases..\ \

Initially, early adopters of AI and "Human at the Edge" business processes, will see dramatic benefits.
If your costs have dropped from 90 to 20 this creates an immediate competitive advantage where the early adopter is "now making 80 units of profit versus your 10 units of profit.
They gain massive pricing power in the industry and can compete for growth with an unfair advantage.
Over time, and here we believe this is likely a 5-10 year period although we believe the quicker side, competitive pressures will erode these advantages.\ \ As competitors adopt similar AI strategies, price competition will intensify, and revenues will decline. The business that initially saw its costs drop from 90 to 20 units might see its revenue decline from 100 to 30 units, resulting in similar margins but much lower overall revenue, often destroying the enterprise value of the company at these new revenue / profit levels!
This evolution creates an imperative for businesses to adopt AI early, not just to maintain perpetual advantage, but simply to survive the transition. Worse they're hit with a second challenge of the value trap, how do I keep hold of the value I generate along the way.\ \ If you're reading this on Nostr you may already suspect a way out of this value trap.\ \ If not I would invite you to consider storing the immediate short term returns you pull forwards in something that would be inflation resistant, hard to seize and ideally portable.\ \ We refer to this as a 'The big orange arbitrage".
Implications for Business Owners and Capital Allocators
For business owners, especially those running small to medium-sized enterprises, the message is clear: understand how AI could transform your industry and begin planning your transition now.\ \ This might involve creating an "AI-native twin" of your current business—similar to how Netflix developed streaming alongside its DVD business—to eventually replace your current operations. If you want help please ask, I heavily favor more small businesses in the world and would love to help make this a reality.
For capital allocation, the emerging opportunity we see if in "transformation led private equity". The acquisition of traditional service businesses and applying AI to dramatically reduce operational costs and increase enterprise value.\ \ This approach treats AI not as a product but as a transformation strategy for existing businesses with proven product-market fit.
Transformation led PE is venture style returns without the risk of product market fit.
So the lesson?
The business model of AI isn't all about selling AI technology, adding a RAG chatbot to a new DB or collecting everyone's data.\ \ Consider the humble cash flow business, use AI to transform the operational processes and save into everyone's favorite orange coin.
-
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ 57d1a264:69f1fee1
2025-05-14 09:48:43
@ 57d1a264:69f1fee1
2025-05-14 09:48:43Just another Ecash nutsnote design is a ew template for brrr.gandlaf.com cashu tocken printing machine and honoring Ecash ideator David Lee Chaum. Despite the turn the initial project took, we would not have Ecash today without his pioneering approach in cryptography and privacy-preserving technologies.
A simple KISS (Keep It Super Simple) Ecash nutsnote delivered as SVG, nothing fancy, designed in PenPot, an open source design tool, for slides, presentations, mockups and interactive prototypes.
Here Just another Nutsnote's current state, together with some snapshots along the process. Your feedback is more than welcome.
https://design.penpot.app/#/view?file-id=749aaa04-8836-81c6-8006-0b29916ec156&page-id=749aaa04-8836-81c6-8006-0b29916ec157§ion=interactions&index=0&share-id=addba4d5-28a4-8022-8006-2ecc4316ebb2
originally posted at https://stacker.news/items/979728
-
 @ 4ba8e86d:89d32de4
2025-05-19 22:33:46
@ 4ba8e86d:89d32de4
2025-05-19 22:33:46O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://pomf2.lain.la/f/eprhj0u3.mp4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://pomf2.lain.la/f/7p6jfr9r.mp4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável. https://pomf2.lain.la/f/x4pm8hm8.mp4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ ee6ea13a:959b6e74
2025-05-13 21:29:02
@ ee6ea13a:959b6e74
2025-05-13 21:29:02Reposted without permission from Business Insider.
Bitcoin Is A Joke
Joe Weisenthal Nov 6, 2013, 10:42 PM UTC

REUTERS/Eliana Aponte
Bitcoin is back in the news, as the digital currency has surged to new all-time highs in recent weeks.
A few weeks ago, it was just above $100. Today it's over $260.
This surge has prompted Timothy B Lee at The Washington Post to ask whether those who have called it a bubble in the past should retract and admit that they were wrong.
Well I'm not totally sure if I've called it a bubble, but I have spoken negatively of it, and I'll say that I still think it's a joke, and probably in a bubble.
Now first of all, I find the premise of Lee's post to be hilarious. The currency has been surging several percent every day lately, and that's evidence that it's not in a bubble?
Before going on, I want to be clear that saying something is a bubble is not saying it will go down. It could go to $500 or $1000 or $10,000. That's the nature of manias.
But make no mistake, Bitcoin is not the currency of the future. It has no intrinsic value.
Now this idea of "intrinsic value" when it comes to currency bothers people, and Bitcoin Bugs will immediately ask why the U.S. dollar has intrinsic value. There's an answer to that. The U.S. Dollar has intrinsic value because the U.S. government which sets the laws of doing business in the United States says it has intrinsic value. If you want to conduct commerce in the United States you have to pay taxes, and there's only one currency you're allowed to pay taxes in: U.S. dollars. There's no getting around this fact. Furthermore, if you want to use the banking system at all, there's no choice but to use U.S. dollars, because that's the currency of the Fed which is behind the whole thing.
On top of all these laws requiring the U.S. dollar to be used, the United States has a gigantic military that can force people around the world to use dollars (if it came to that) so yes, there's a lot of real-world value behind greenbacks.
Bitcoin? Nada. There's nothing keeping it being a thing. If people lose faith in it, it's over. Bitcoin is fiat currency in the most literal sense of the word.
But it gets worse. Bitcoin is mostly just a speculative vehicle. Yes, there are PR stunts about bars and other shops accepting bitcoins. And there is a Bitcoin ATM for some reason. But mostly Bitcoin is a speculative vehicle. And really, you'd be insane to actually conduct a sizable amount of commerce in bitcoins. That's because the price swings so wildly, that the next day, there's a good chance that one of the parties will have gotten royally screwed. Either the purchaser of the good will have ended up totally blowing a huge opportunity (by not holding longer) or the seller will be totally screwed (if Bitcoin instantly plunges). The very volatility that excited people to want to play the Bitcoin game is death when it comes to real transactions in the real world.
Again, Bitcoin might go up a lot more before it ultimately ends. That's the nature of bubbles. The dotcom bubble crashed a bunch of times on its way up. Then one day it ended. The same will happen with this.
In the meantime, have fun speculating!
-
 @ 6b0a60cf:b952e7d4
2025-05-19 22:33:33
@ 6b0a60cf:b952e7d4
2025-05-19 22:33:33タイトルは釣りです。そんなこと微塵も思っていません。 本稿はアウトボックスモデルの実装に関してうだうだ考えるコーナーです。 ダムスに関して何か言いたいわけではないので先にタイトル回収しておきます。
- NIP-65を守る気なんかさらさら無いのにNIP-65に書いてあるkind:10002のReadリレーの意味を知っていながら全然違う使い方をしているのは一部の和製クライアントの方だよね
- NIP-65を守る気が無いならkind:10002を使うべきではなく、独自仕様でリレーを保存するべきだよね
- アウトボックスモデルを採用しているクライアントからすれば仕様と異なる実装をしてしまっているクライアントが迷惑だと思われても仕方ないよね
- と考えればダムスの方が潔いよね
- とはいえkind:3のcontentは空にしろって言われてんだからやっぱダムスはゴミだわ
- やるとしたらRabbitみたいにローカルに保存するか、別デバイス間で同期したいならkind:30078を使うべきだよね
アウトボックスモデルはなぜ人気がないのか
言ってることはとてもいいと思うんですよ。 欠点があるとすれば、
- 末端のユーザーからすればreadリレーとwriteリレーと書かれると直感的にイメージされるものとかけ離れている
- 正しく設定してもらうには相当の説明が必要
- フォローTLを表示しようとすれば非常にたくさんのリレーと接続することになり現実的ではない
- なるほど完璧な作戦っスねーっ 不可能だという点に目をつぶればよぉ~
余談ですが昔irisでログインした時に localhost のリレーに繋ごうとしてiris壊れたって思ったけど今思えばアウトボックスモデルを忠実に実装してたんじゃないかな…。
現実的に実装する方法は無いのか
これでReadすべきリレーをシミュレーションできる。 https://nikolat.github.io/nostr-relay-trend/ フォローイーのWriteリレーを全部購読しようとすると100個近いリレー数になるので現実的ではありません。 しかしフォローイーのWriteリレーのうち1個だけでよい、とする条件を仮に追加すると一気にハードルが下がります。私の場合はReadリレー含めて7個のリレーに収まりました。 Nos Haikuはとりあえずこの方針でいくことにしました。
今後どうしていきたいのか
エンドユーザーとしての自分の志向としては、自分が指定したリレーだけを購読してほしい、勝手に余計なリレーを読みに行かないでほしい、という気持ちがあり、現状の和製クライアントの仕様を気に入っています。 仮にNos Haikuでアウトボックスモデルを採用しつつ自分の決めたリレーに接続するハイブリッド実装を考えるとすれば、
あなたの購読するリレーはこれですよー - Read(inbox) Relays (あなたへのメンションが届くリレー) - wss://relay1.example.com/ - wss://relay2.example.com/ - wss://relay3.example.com/ - Followee's Write Relays (フォローイーが書き込んでいるリレー) - wss://relay4.example.com/ - wss://relay5.example.com/ - wss://relay6.example.com/って出して、チェックボックス付けてON/OFFできるようにして最終的に購読するリレーをユーザーに決めてもらう感じかな……って漠然と考えています。よほど時間を持て余したときがあればやってみるかも。
あとリレーを数は仕方ないとしてリレーごとにフォローイーの投稿だけを取得するようにした方が理にかなってるよね。全部のリレーから全部のフォローイーの投稿を取得しようとしたら(実装はシンプルで楽だけど)通信量が大変だよね。 rx-nostr の Forward Strategy ってリレーごとにREQかえて一度に購読できるっけ?
常にひとつ以下の REQ サブスクリプションを保持します。
って書いてあるから無理なのかな? あとReadリレーは純粋に自分へのメンション(pタグ付き)イベントのみを購読するようにした方がいい気がする。スパム対策としてかなり有効だと思うので。スパムはNIP-65に準拠したりはしていないでしょうし。 まぁ、NIP-65に準拠していないクライアントからのメンションは届かなくなってしまうわけですが。
-
 @ 57d1a264:69f1fee1
2025-05-14 06:48:45
@ 57d1a264:69f1fee1
2025-05-14 06:48:45Has the architect Greg Chasen considered it when rebuilding the house just one year before the catastrophe? Apparently not! Another of his projects was featured on the Value of Architecture as properties with design integrity.
This is a super interesting subject. The historic character, livability, and modern disaster-resistance is a triangle where you often have to pick just one or two, which leads to some tough decisions that have major impacts on families and communities. Like one of the things he mentions is that the architect completely eliminated plants from the property. That's great for fire resistance, but not so great for other things if the entire town decides to go the same route (which he does bring up later in the video). I don't think there's any objectively right answer, but definitely lots of good (and important) discussion points to be had.
https://www.youtube.com/watch?v=cbl_1qfsFXk
originally posted at https://stacker.news/items/979653
-
 @ 57d1a264:69f1fee1
2025-05-14 06:12:19
@ 57d1a264:69f1fee1
2025-05-14 06:12:19We asked members of the design community to choose an artifact that embodies craft—something that speaks to their understanding of what it means to make with intention. Here’s what they shared.
A vintage puzzle box, a perfectly tuned guitar, an AI-powered poetry camera. A daiquiri mixed with precision. A spreadsheet that still haunts muscle memory. Each artifact tells a story: not just about the thing itself, but about the choices of the creator behind it. What to refine, what to leave raw. When to push forward, when to let go. Whether built to last for generations or designed to delight in a fleeting moment, the common thread is that great craft doesn’t happen by accident. It’s made.
On the application of craft
Even the most experienced makers can benefit from building structure and intention into their practice. From sharpening your storytelling to designing quality products, these pieces offer practical ways to uplevel your craft.
Read more at https://www.figma.com/blog/craft-artifacts/
originally posted at https://stacker.news/items/979644
-
 @ 374ee93a:36623347
2025-05-13 11:47:55
@ 374ee93a:36623347
2025-05-13 11:47:55Chef's notes
Lovely tart rhubarb jam with the extra firey kick of fresh root ginger.
Technically a vegetable rhubarb has low pectin content so be sure to include a high pectin fruit such as lemon/cooking apple/redcurrant/gooseberry. It also quite watery so we use a slightly higher fruit to sugar ratio (1.2:1) and evaporate off some water at the beginning.
Testing for setting point: put a saucer in the freezer to chill whilst cooking the fruit, after 5 mins of a high boil with the sugar put a small blob of jam on the cold saucer and return to the freezer for 2 minutes. If the jam forms a solid wrinkle when pushed with a spoon it is ready, if it is runny continue cooking and retest every 5 mins
The recipe can be halved for a small batch but if you have lots of rhubarb to process it is better to cook double batches in separate pans because it will take much longer to heat through, this affects the colour and flavour - the jam will taste warm and mellow rather than zingy
Sterilise glass jars in a 120c oven and pot the jam hot leaving 1/4 inch head space, it will keep for 5 years unopened if the lids are well sealed and does not require water bath canning
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 30 mins
- 🍽️ Servings: 6 (jars)
Ingredients
- 1.2kg Rhubarb
- 200g Grated Root Ginger
- 100g Chopped Crystalised Ginger
- 1kg Sugar
- 1 Lemon
Directions
- Chop the rhubarb into 1/2 inch pieces, peel and finely grate the fresh root ginger, chop crystalised ginger into tiny bits. Juice and quarter a lemon (discard pips) and add all these to a pan with a small amount of water
- Simmer gently for 20 mins until the lemon and rhubarb are soft then add the sugar, stir until fully dissolved
- Boil on high to reach setting point, usually at 105 degrees c or when a small blob of jam wrinkles on a cold plate instead of being runny
- Remove the lemon pieces and pot into sterilised jars
-
 @ cae03c48:2a7d6671
2025-05-19 22:21:46
@ cae03c48:2a7d6671
2025-05-19 22:21:46Bitcoin Magazine

BitMine Launches Bitcoin Treasury Advisory Practice, Secures $4M Deal with First ClientToday, BitMine Immersion Technologies, Inc. (OTCQX: BMNRD) announced the launch of its Bitcoin Treasury Advisory Practice and a $4 million deal with a U.S. exchange-listed company. The deal saw Bitmine surpass its last year’s total revenue in that single transaction alone, according to the announcement.
BitMine ( OTCQX: $BMNRD $BMNR) launches Bitcoin Treasury Advisory Practice and secures $4M deal with first client.
This single transaction exceeds our 2024 revenue and sets the stage for major growth.
Read now: https://t.co/R89K3WXdZZ pic.twitter.com/5vIvlYPZUY
— Bitmine Immersion Technologies, Inc. (@BitMNR) May 19, 2025
BitMine will provide “Mining as a Service” (MaaS) by leasing 3,000 Bitcoin ASIC miners to the client through December 30, 2025, in a $3.2 million lease deal, with $1.6 million paid upfront. Additionally, the client has signed an $800,000 consulting agreement for one year focusing on Bitcoin Mining-as-a-Service and Bitcoin Treasury Strategy.
“Currently, there are almost 100 public companies that have adopted Bitcoin as a treasury holding. We expect this number to grow in the future. As more companies adopt Bitcoin treasury strategies, the need for infrastructure, revenue generation, and expert guidance grows along with it,” said Jonathan Bates, CEO of BitMine. “This single transaction is greater than our entire 2024 fiscal year revenue, and we feel there is an opportunity to acquire more clients in the near future as interest in Bitcoin ownership grows.”
BitMine’s first quarter 2025 results showed strong revenue growth, with GAAP revenue rising approximately 135% to $1.2 million, up from $511,000 in Q1 2024, supported by an expanded mining capacity of 4,640 miners as of November 30, 2024, compared to 1,606 the previous year. Despite this growth, the company reported a net loss of $3.9 million in Q1 2025, primarily due to a one-time, non-cash accounting adjustment related to preferred stock; excluding this charge, the adjusted loss was approximately $975,000, consistent with the prior year’s results.
$BMNR reports a 135% revenue increase YOY for Q1 2025 and tripled self-mining capacity with 3,000 new miners! CEO Jonathan Bates credits a team-driven approach and creative financing for this growth.
Read the full release here: https://t.co/slNrZv8Ocn pic.twitter.com/Gb4tk1UfAO— Bitmine Immersion Technologies, Inc. (@BitMNR) January 13, 2025
BitMine’s new Bitcoin Treasury Advisory Practice, along with the $4 million deal, joins a trend among public companies exploring Bitcoin not just as a treasury asset but also as a source of revenue.
This post BitMine Launches Bitcoin Treasury Advisory Practice, Secures $4M Deal with First Client first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 95543309:196c540e
2025-05-11 12:42:09
@ 95543309:196c540e
2025-05-11 12:42:09Lets see if this works with the blossom upload and without markdown hassle.
:cat:

https://blossom.primal.net/73a099f931366732c18dd60da82db6ef65bb368eb96756f07d9fa7a8a3644009.mp4
-
 @ 7459d333:f207289b
2025-05-10 10:38:56
@ 7459d333:f207289b
2025-05-10 10:38:56Description: Just as Bitcoin enabled sovereignty over money, a decentralized shipping protocol would enable sovereignty over trade. An LN/Bisq inspired shipping protocol could create an unstoppable free market.
Bitcoin gave us monetary sovereignty, freeing us from central bank manipulation, inflation, and censorship. But there's a missing link in our freedom journey: the physical world of goods.
The Problem: Even with Bitcoin, global trade remains at the mercy of: - Arbitrary tariffs and import restrictions - Political censorship of goods - Privacy invasion of shipping information - Centralized shipping carriers
The Vision: A decentralized shipping protocol with these properties:
- "Onion-routed" packages: Each carrier only knows the previous and next hop
- Bitcoin-secured multi-sig escrow: Funds locked until package delivery confirmed
- Incentive alignment: Carriers set their own fees based on risk assessment
- Privacy tiers: Options for inspected vs. sealed packages with appropriate pricing
- End-to-end sovereignty: Sender and receiver maintain control, intermediate carriers just fulfill their role
How it could work:
- Sender creates shipping request with package details and destination
- Protocol finds optimal route through independent carriers
- Each hop secured by multi-sig deposits larger than package value
- Carriers only see next hop, not ultimate destination
- Reputation systems and economic incentives maintain integrity
This creates a free market where any individual can participate as a carrier, earning Bitcoin for facilitating trade. Just like Lightning Network nodes, anyone can open "channels" with trusted partners.
Impact: This would enable true free market principles globally, making artificial trade barriers obsolete and empowering individuals to engage in voluntary exchange regardless of geographic or political boundaries.
There are a lot of challenges. But the first question is if this is a real problem and if its worth solving it.
What components would need development first? How would you solve the physical handoff challenges?
originally posted at https://stacker.news/items/976326
-
 @ 57d1a264:69f1fee1
2025-05-14 05:56:15
@ 57d1a264:69f1fee1
2025-05-14 05:56:15Shanghai: Bus Stops Here
A new crowd-sourced transit platform allows riders to propose, vote on, and activate new bus lines in as little as three days.
From early-morning school drop-offs to seniors booking rides to the hospital, from suburban commuters seeking a faster link to the metro to families visiting ancestral graves, Shanghai is rolling out a new kind of public bus — one that’s designed by commuters, and launched only when enough riders request it.
Branded “DZ” for dingzhi, or “customized,” the system invites residents to submit proposed routes through a city-run platform. Others with similar travel needs can opt in or vote, and if demand meets the threshold — typically 15 to 20 passengers per trip — the route goes live.
More than 220 DZ routes have already launched across all 16 city districts. Through an online platform opened May 8, users enter start and end points, preferred times, and trip frequency. If approved, routes can begin running in as little as three days.
Continue reading at https://www.sixthtone.com/news/1017072
originally posted at https://stacker.news/items/979637
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 04c3c1a5:a94cf83d
2025-05-13 16:49:23
@ 04c3c1a5:a94cf83d
2025-05-13 16:49:23Testing Testing Testing
This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test

nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau
| | | | | ------------------------ | - | - | | Quick'hthbdoiwenweuifier | | | | 1. Little | | |
ghtgehg
gwefjieqhf
MUCH BETTER
-
 @ 5391098c:74403a0e
2025-05-13 16:47:48
@ 5391098c:74403a0e
2025-05-13 16:47:48(Textículo em prosa erudita sobre a Ideologia Anarco-Capitalista-Cristã)
https://davipinheiro.com/01-escravos-da-cara-inchada/
A cultura #Woke apropriou-se da imagem sobre a #escravidão. Quando uma pessoa aculturada imagina um #escravo, vem em sua mente a imagem de um ser humano negro, magro e flagelado. Para quem enxerga além das cortinas da mentira, vem em sua mente a imagem de um ser humano de qualquer etnia, gordo e doente.
Democracia, péssimo regime de governo assim classificado pelo seu próprio idealizador: Platão em A República, é o grito da hienas de dentes arreganhados para ampliação do regime escravocrata fomentado pelos #GlobalistasSatanistas.
Um escravo da cara inchada é todo aquele ser humano ignorante inconsciente que alimenta esse sistema em troca de intoxicantes como flúor¹, cloro, glutamato monosódico, gordura trans, corantes, conservantes, refrigerantes, bebidas alcoólicas, psicotrópicos e remédios sintomáticos, tudo embrulhado com mentiras reiteradas.
Como consequência, após os 18 anos de idade o corpo do #EscravoDaCaraInchada sucumbe à tamanha intoxicação e passa a inchar, sendo fisicamente perceptível sua condição de escravo da cara inchada tanto à olho nú quando por reconhecimento facial de qualquer pseudo inteligência artificial.
O círculo vicioso da #EscravidaoDemocratica é tão simples e tosco como o “pão e circo romano”, Mesmo assim é muito difícil para o escravo da cara inchada perceber a própria condição tamanha é sua intoxicação física e mental.
Se um Anarco-Capitalista-Cristão (#Ancapcristão) chega para um escravo da cara inchada e explica sobre esses intoxicantes como instrumento de escravização, dificilmente o escravo da cara inchada irá acreditar pois diferentemente do antigo e aposentado chicote, o novo instrumento da escravidão não dói de imediato e os próprios efeitos da intoxicação impedem-no de raciocinar com clareza.
Portanto, para que os #GlobalistasSatanistas obtivessem sucesso na democratização da escravidão, tiveram que criar um chicote químico e uma ideologia favorável. Quanto às etapas utilizadas para formação dessa ideologia no inconsciente coletivo passo a elencar as 6 grandes mentiras em ordem cronológica:
(1ª etapa) Iluminismo: distanciamento de #Deus e seus ensinamentos, criação de sociedades secretas, exacerbação do ser humano perante o criador na tentativa de projetar o ser humano como seu próprio deus, tornando-o responsável sobre os rumos naturais do planeta. Assim formou-se a base ideológica para o materialismo, ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(2ª etapa) Materialismo: perda do propósito espiritual e do sentido da vida², o que passa a importar são apenas as coisas materiais, acima inclusive do próprio ser humano. A perpetuação da espécie também fica em segundo plano. Assim formou-se a base ideológica para o ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(3ª etapa) Ambientalismo: redução do ser humano à mero câncer do planeta superlotado, atribuído-lhe a responsabilidade por qualquer desastre natural. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(4ª etapa) Feminismo: enfraquecimento do ser humano por meio da sua divisão em duas categorias: macho e fêmea, os quais são inimigos e não cooperadores. A ideia de igualdade de gêneros é tão antagônica que beira ao conflito cognitivo³: Eles querem separar para dizer que são iguais... Ora, como não pode haver diferenças entre os gêneros se eles são fisicamente e mentalmente diferentes? Nesse diapasão, mesmo não sendo os estados nacionais os arquitetos da escravidão democrática e sim meros fantoches dos globalistas satanistas, o voto feminino foi fundamental para aprovação de leis misândricas com o fito de acelerar a destruição da base familiar do escravo da cara inchada. Importante mencionar que a base familiar dos globalistas satanistas continua sendo patriarcal. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(5ª etapa) Controle Populacional: “Crescei e multiplicai-vos” é o caralho, Deus não sabe de nada (Iluminismo), o que importa é o dinheiro e filho é caro (Materialismo), para que colocar mais um ser humano nesse planeta doente e superlotado (Ambientalismo), além disso o sexo oposto é meu inimigo (Feminismo). Essa é base ideológica que antecede a ideologia de Controle Populacional, ainda reforçada pela apologia à castração, já que em todas as mídias produzidas com patrocínio oculto de capital globalista satanista tentam normalizar a castração do homem (perda da capacidade de reprodução) desde em desenhos infantis até grandes produções cinematográficas, ora em tom de humor ora em tom de tortura. Assim os escravos da cara inchada do sexo masculino perderam sua identidade, essência e desejo de ser o que são, formando-se a base ideológica para o homossexualismo, ou seja, para a ideologia de gêneros.
(6ª etapa) Ideologia de Gêneros: É a cereja do bolo para os planos do Diabo (Anjo invejoso de Deus que quer destruir a maior criação: nós). Enquanto os globalistas satanistas, dentro de sua sábia ignorância, acreditam estarem chefiando a democratização da escravidão, na verdade também não passam de meros fantoches do Anjo Caído. Com a sexta e última etapa de mentiras para extinção da humanidade (#apocalipse) posta em prática através da Ideologia de Gêneros, fecha-se o ciclo vicioso de mentiras que se auto justificam: Se #Deus não presta, o que vale são os bens materiais, o ser humano é um câncer no planeta, o sexo oposto é inimigo e ter filhos é uma péssima ideia e ser homem másculo é crime, então ser #homossexual é a melhor opção, inclusive vamos castrar os meninos antes da puberdade sem o consentimento dos pais ou mães solo. Aqui também há uma grande bifurcação do círculo vicioso de mentiras, qual seja o gritante conflito cognitivo³: Se todos os homens deixarem de ser másculos, quem vai comer os #gays afeminados? Ou se todas as mulheres deixarem de ser femininas, quem as #sapatonas irão comer? E o pior, se todos passem a ser homossexuais quem vai perpetuar a espécie? Seremos extintos no lapso temporal de apenas uma geração, pois a fraudulenta medicina moderna jamais terá a capacidade de gerar bebês de chocadeira à tempo.
É interessante enxergar que mesmo os Globalistas Satanistas, dentro de sua sábia ignorância, acreditando estarem democratizando a escravidão em benefício próprio, na verdade apenas estão fomentando o apocalipse, ou seja sua própria extinção. Também não terão qualquer lugar especial no inferno, sinônimo de mal é mentira. Portanto os #GlobalistaSatanistas são meros fantoches do #Diabo enganador, tão submissos quanto o Escravo da Cara Inchada…
Interessante também enxergar que o livre arbítrio é uma condição obrigatória para independência da criação (anjo e ser humano). Todos somos livres para escolher entre o bem e o mal, se iremos ser escravos de #Deus ou escravos do Diabo. Se assim não fosse, inexistiria criação pois seríamos mera extensão da consciência do #Criador, em outras palavras: para que exista uma criação, essa deve ter a capacidade de decisão de forma independente, o chamado livre arbítrio.
Com base nisso, temos que não cabe à nos fazer qualquer revolução, tudo está normal, a luta entre o bem e o mal sempre irá existir pois um não existe sem o outro. Nos cabe apenas escolher o lado. Nesse contexto, tenho a seguinte mensagem destinada à você para encerrar o presente Textículo Anarco-Capitalista-Cristão:
------ > Se você for um ANARCO-CAPITALISTA-CRISTÃO passe esta palavra à diante para que a verdade atinja o maior número de ignorantes inconscientes possível;
------ > Se você for um GLOBALISTA SATANISTA, vai viver sua vida, desfrutar da própria fortuna e pare de ser fantoche o Diabo, mentiram para você: não terá qualquer lugar especial quando morrer;
------ > Se você for um ESCRAVO DA CARA INCHADA e não entendeu o que eu disse, por favor me pergunte ou debata comigo, terei o prazer em lhe ajudar a enxergar a verdade. Pare de trabalhar por dinheiro fiduciário, passe a aceitar #Monero e #Bitcoin em troca do seu trabalho, pois isso é o único jeito de sermos financeiramente livres, se tiver alguma dúvida sobre #criptomoedas me pergunte e terei o prazer e ensinar. Se ainda assim você se recusa a enxergar a verdade exposta aqui, por favor aceite #Monero e #Bitcoin quando for dar o seu cú. Ou melhor, cometa suicídio, já que você é um câncer no planeta, salve a natureza.
(Davi Pinheiro)
¹ - https://davipinheiro.com/teoria-da-conspiracao-o-fluor-na-agua-e-usado-para-controlar-mentes-revista-super-interessante-editora-abril/
² - https://davipinheiro.com/qual-o-sentido-da-vida/
³ - https://davipinheiro.com/entendendo-as-referencias-cruzadas-do-pensamento/
PREZADOS AMIGOS, DIVULGUEM ESTE ARTIGO. ABAIXO SEGUE A LISTA DOS 500 BRASILEIROS MAIS ATIVOS NO NOSTR NOS ÚLTIMOS MESES PARA TODOS SEGUIREM-SE ENTRE SI E FORTALECER NOSSA COMUNIDADE DE LÍNGUA BRASILEIRA (se você não estiver na lista interaja para ser adicionado):
npub1u2e0qzjsjw9suxcdkeqrydr07xzsyx8mzp469augc0a29aeasfdq8fx67q npub1xt25e4pakq6x4w44p9kw2vlfwv4zpc9hg7xsnrq53hl0za4ag2qs09cwcs npub17hgdpn9xnt5zyxlx8pz0uuus8d23pxwr9a5vq96nw5nawx20zxnsj6fym6 npub1arnth7tuxw060c74adaf08jam6kttn24wfdse9wyg2c7waycwezqszr2mz npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw npub10q0axre6n3ew64pen99x0qkrh70yxfx6w3grwvkhk4kz9dp8m3ssltvs6f npub1sf2se74xlzf7f7clm3dg28npaxghdy6pguzpsut30fjpwuaxrxcsrnhr57 npub19ychr8yknmje69r645sgd8j0epx2rdgdyl7feagcnmrwkaedzffqtrcznl npub1k86zp0778x7cjng50et5z76xdwxy0tgfn5amnrwrd6mda8uln4lq78ua23 npub13src792wxm8nrhqzu555uxuktfffzcqx78s3pc9zefcdjgwvm3pqsddz4j npub1uw04lzuqx42gk0xc4m8advfmuqlz8nv7dqpuyq4gcv8r304lwvnq2m5ew2 npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr npub1nkenffr9eslkzplds3lwcz7xeq67w6a9qcjlfsvspj7tnhuq3kgsram48g npub1w66drr2qta67gyt7la6fgglsdvk3xx3nndsz4k5wfcal8jq0ze7sqcxdpd npub12xq6exra99hg6tuefx3yysszqudaljvy6eyxqz8tpt7038gpaqus7lfuyy npub17tvf04z759dsyecdtmk70tevla7vua9e3sr88lgnl7put97764zq708q0m npub1rzajeq88urk58nh0n7gqknr2agrx34xu4en0k8hm43fl8h2khp6sk0v3y4 npub1yspe4ly5p9dlfv4vevm0evpag8ljkaay3x3clj8gtvxlsvpwrrrs6h47mx npub107a0nwr3lsj9kdy3jdq570jzcv95y0qzuuhrvcgrpsnq2h4xsclqzy7v4g npub14reqsqss7wp06k390a547pkqrlc0w6uzelm9gpwxze7p8z8x3awsuthvzz npub18fh6flnjt9aa3jlnp5k3kd9zr6v5mlpeczhdx4qheytfyyqfpe7s2y0lzm npub1lafcm7zm35l9q06mnaqk5ykt2530ylnwm5j8xaykflppfstv6vysxg4ryf npub1s00wyzkfrjcclawx225k7wrxd74369vxdcdhy88j89yhrxssfclqulxf93 npub1rmq4kl4dfvp4kt937f9mz60ywkwv467585vnesm3ctqz9krkksrqg4ran0 npub1d7r5su48a8m5k389fd6rwy9cvhlyycmg3pl2g60q5zmgvmr3xreq098mu2 npub1r8lsve0d5yezxq52fjj90kwz76xcweyxlx9uwhsrpd6gt7uk4edscl4fdr npub19ljjj23d7fgy0gujlnh26a293p6uwawrrnpg7jlqfnhnard322gssd2rnj npub1u484zct2rxyknscgnnxrwpuk3f2j679x8tdysvxh659whv99g35saq9xjt npub1gpd868cejawju35epkayavfkqfuykt3820xe678m2vqfqj8v7ges2t4umk npub172fwxt8nnauv2c6leevl0rq4mk87c5vu4mm4fqef58xt390jqxfs6ua7vz npub1gmdrkx4lgwzyqr6krqyykg9r2kpasftuu2x98ncvs9xz9cjhfgcsxns0xz npub1sfzc94dhlkrj6m9tdkle4glyazhtajjsj9qhjv279an06nr74uvqzka6js npub18rdvxdw773852gyl4kjkr5xmg44p9l0jywdk6cq8axl3k9yh59fsu3g8aj npub167h7xtt7tkfvr9mn9d09s4u6r4l0y7rr355jpjg55lg4mpdghsasa9c47v npub1q4qjda5zm33743dd4mewnx6j049hgry7ls4nvh54clcnax3wsnzqv7c5lw npub1mjckw2qsqemdnhz7ul63vpcd79fmar49r8y7fh0tffva767yx07qq68xkn npub1ry2uv7qwu840qx4fg38zzfrl6dfgaudn6d8s7trpf3sj8nx0vaaquj5qrj npub1zqw2ymcy9txda2wzuka7yx6vlyvuwe7k2pldxpxxx660nhf65tusxzdcp6 npub1fjr0qa7rdhll7cfpgdcsz5nry2gy92u7a8gr0ku390n69865ec0qxwcral npub1wc4rc9wxl2gfzxl384g0cw3f79nrms0sfdpe02y7aasy7c3we4sqd0qywr npub19x5l76266vfen827fudaampuuupkejg9vls88hld8nv4w4sq59lsqlal37 npub1gc24vefdu60d3e3yxg8mhu52hxxpcykesk85y8mez8llj23kpehszdmu3j npub1u9ja9ymqmaw7mn9tnmrsnpx0f9j6hs59kxd9de363jvadjamzd9qg3ek4k npub1lzt7pmhvg7hl23emv22g4d7cs9jyglkqpr7lf3n8rcz0evkacg2s6n4jjf npub1p22hyejtr60rdrmjvql5k8fyv8lkq8exzw5mkkx3qcwqcu6979aqvhpqlq npub15p6p9l5upa0y0aj5nwf7lnud2regh00az9u4a4fmgyh8ukyue8kq7xuzp7 npub187dlu8g04kk8adc309vwn3lxsj63fmaty5vmdyrsvzx2fcxg70pqfszj4z npub1adfs8z9rlk6dzwm44522ge0gf367t6s6x30nrulp0xq6wsglyxssxqwyva npub1wqh4j2lvkd0fz342he0jr2d8eqrjwlqsv42azw6utqnpkrjv72xqylx32z npub1n9e2cy50jk900hdzvxt4cjhn80qwzxuer93aylhfdc76gwksr2lsqt36ww npub1styn4qvw4h4s92pcntrffm5dhe889h3hanwjpv66r4ue7gd3xutqk9hpc6 npub157v53ahyyxh4mp38v363chz9lrrw8um9m0tyhqzjujz8m4pmr42s9sk9u8 npub1alq86fku99p0rgq6s0cwwe9lsa8vdvu4d6r7d6j6cyuysf2r76hsh9tt37 npub18cvuxxvd2a6gt76etnte5vtws7a5a4xeqgt03qcs0u46nfws0vzskrnwu9 npub1mlu4qvm8j7gqamukz98l832ghgktyj0whqrxfx89625m3p30haqq5racjk npub1l8tlpvn3kka3nm2qpk96amsuy2kr5kl9eusd54fpn3yjnefrnpaq2j5t9v npub1jtnuszgjayga0pzvm3t7z9pantcnyxzacu30mhvw4dk0lkkvhxrsgvfgw5 npub1z73hklrdpa0n5z663mvnu0afxhlegpt5exmkg9u0nmd32ktqs7fq3prv27 npub1tshn5e5h0ud3l6vegwrce2er2tuhxangx4yvx4q04uheznxxgp6qg9dx2n npub136aeqeuum2t8cjgfnpxwfkgf5e8fd95h39uqkenrr6u0yl3upg9skvkfq8 npub1pkjyqg0am9qyjwg772ue4hhshaf6gwgz4psnptlg9v8lk6st2naqct3ll5 npub1kvzyrn6zvvdh9jnvfzc6e86s0zpntvg0e9f0v340e59u2rut99zsuq9fl9 npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 npub1cajs9cz6r43rmn0y8v8cgeuuj2lfhftvxcq05f8efc22hr5fnwmshx0pvw npub1uu0qk8f7xv7egc6tf9kk3mkx99u2leldgzz0trl77uymvv8n8ahqtd6309 npub1t8a7uumfmam38kal4xaakzyjccht4y5jxfs4cmlj0p768pxtwu8skh56yu npub10wlfumja930vzz4jhh9vc6t3wy8ay7thg8mt9qcptlp5leqfmazqn79ee9 npub1tx8wamjvhaqme29rujkd4v978ck8d3ud7gxa9zzqtjftpfn9p5vs27a2lg npub1e5pneqe2je07e5sk00g8urqa66eljg74t4llv4htp6vq5f8kv2zsqrtway npub1nk7gygwkcfpf9hdjhkgyqszcgwyzmcrqhd9tr7zzczkm5ga79xusmm5qjt npub1p3pna34zku4fqe9mzyvhhffladjjxcug7jn20wm5rnccpjezn4ks0zaw4u npub1j4vyl5kadajpgxh2wrnfk2wvg25jhnv78s0mrs6ckuhft9uzqe7s9wpcgc npub1hfg3tsmmp7g3u5cw6mzg0n9andehmgel6jug486eppsr0rqx4a3qlp7yfm npub1zks89kfxmxv0s4sa7rj8yyd6ld8ncsqusm993678vq9ut73hn7uqhmecsf npub1hzt3p8ap8s4nnqjhha37z5q3jdc9lfg90js0crmg8u5lncnaqpzsdn75p5 npub12em9q547gfga2tkhuzc65ufrn5h9ndu270d7xnh0nkcz2gtvq4sqwutpy3 npub12fh76ppgs5g2srtvgewe9fprdsk2y6g42wf0sg2y0ucjxqq9l0dsy5n8wl npub1arjgv76ld978cya3k6xz24nuxkuezuqrsmy73x0gaxdlu7pxv4lq8npp2g npub1zpmtwh0esa4esnc4p6rn5vhx7wcfw8z0ky8nzczj6k46drsmm47s0zzlyh npub156zse25dzgt65kq472nfkfpwgqvf6vuw8ur0s0ny7zmzw4xqd68q3p4sem npub1pwyy6rwh9smlurdmfg7yy2lce43jlv9ac7l9zay723dyfx4m649ql85u04 npub13j4jtgrm0dtsfzecx4khzz5a8ykgdd374qewewj0ksfmenps67lqz2yr8a npub1dmdlkhqnzmde0ultsq72hnn8h6gjfrkfeud4hecjg8fg8pugzctsjwqas0 npub1yqq7mwccr6wv7vmhehgh4n9kwn55r9gneydhdu6249pntguacegsjgwevp npub1u79u7zxlz2flmwpdt59xsvv5syreavzdyu9llkg07swtf24a4ayq5g0uud npub1eezyd5p7n9vse3yv5k8vh068dutpjf7d9zuk6azegeh5ypvp270qqr8fam npub1s0p3y6rvmt5m6jf6zt96kl0c80x0fy396d8h3cvtsxpqq7lf7wwsgw780n npub1kcf4p6e8k0rkjtaaghu765647z58qu0wfpgxnqptlwg2pm30skzsm2mct0 npub10uqpae32d6t4xhcgmzkc5gkna3hf9xclpzf3q6kfusz5q8j5ruqs5tdemg npub1jldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsfxfunp npub1ksp960nd2vhxxp4lw7unnhujy6mknd0mpw2sh7xuj4m963a2u03qw776l8 npub188qkhpvqhne68rwu878jta5a8uh3vl4mcmfp44nppydfz0td9tqqa5h3cm npub1e008u7wmf0gppsnzupclhzh4mexp90addmdu0wu9glyk0y6msvxskyd3yq npub1crtd3zn3ek0cwne036s0xfqgs6ywuutqdcwxl5k4csv57jsmlgfsjq9039 npub1u4r4hx3y820p8g00u65tpggk2rd5qkd0d3ukt2yvgwyhcd0qvymqweyx75 npub18e7t2damcrfe60empcnye5z896wf9fk478rgrdcawvv23hqtd8es3yg772 npub1s5uqfqur0jlnp9z32ag90e9p5y60z0e8ruryun6u8gy9c38s7caqqqjxvt npub1q9fawsk02d7ffc47l92peuasy9q23ganvs00aqfagxz9rgk5g3usy92n3g npub18qhe55gump3d8ff2xzugpeaxkq6gfc498hr6at2jlsert0h9qkvqquqmve npub1cj9w34dn6nyazvhtq9srms5rf9rj4tapmqlwc5d5k3cwk34vy8dqewkvj6 npub1wvkx5ckpcxmxvc9wd0q576qssle3ed40c4z5rpetwy8fqssq8k3qdhh3yl npub1wnpc03cvexrv7tqnz4amk5zpyxw30nat3xav8nna89j92h25q53sls0g5w npub1938qus3z7jxs4u5x6gpyf7pwavnvnvrhmlfv2jqryy43qf0mdgpqlrtyfq npub1gnvha9zemx47e3paehu59ssqjkkpkc0n6ugdufmkl9ahgd3qhajs6mfs4m npub1cha5p8ytujflljhet2k34sctnqyl3n5w74wnuy7c6dvyv870twas9xnugj npub1h4d7986rjexvgaqsv8zm4s88dekkacs9uadtad6zp8n38nkdszysj45nmc npub1wcuv2wqn3uypzx7f98vavt2gqz4f4qkzm28fgj4qpwgj3yfjghks0patgl npub14hq5lgadtyy9dhvtszq46dnl0s0xwdddqr7e32rdqqhma8a4xhsspxjjzu npub17rzgm20v9hf4m2hemlau5fzepyanwd5h3zxc0wkwq7y38s3g8uqs49lrut npub1l5sgjcjruwec2y2lxd23vj34qe2kkxyqnact76tsq5kzdtcmke0s4cz0uu npub1ylw08gevzgvwasypcs2lvmssfqyt46xzgul7lwvkssm76ehgq47qrn4xxk npub13t2th7tr0uxwc8mfkkr5dqmfrg5hmmdfnfjfhs4z2xal9z6hpe9q6xn9ph npub1239p46pv99lt94yfzu4xkh4u3vqr2k7rnmcc8zz64p6m8g0mva8qcxr0hj npub1r2eehghv6syvdhezrlln25fnz90clgdkcagqw87c9r735zlnhuaq8dpvwp npub1sd5wp8ufsttwk3c575gnakufgaeg3x4f4r5d84pun9n09yr7zq8s735ezh npub18txjwp7dj9hjwk972c32sj5xmngnutguvtg2r66a3g5rgw2s88xq3799uq npub1247x2zmsp8e766cy39gkuzywfq6ea89wd6sgvuh8lywrrvzvdqtsv9573z npub1mu2tx4ue4yt7n7pymcql3agslnx0zeyt34zmmfex2g07k6ymtksq7hansc npub152wtu2y9a5wlz74v88ahls2xq0g493gz5jx0wat9vfgxqzjfzl6qdazlty npub18yyc9l68tk6zsq63wmnzf3862l3xfckds38tq44egwl5l4g0nqeszhj50p npub15rdytrwdsc62qmvsc28xhzdxs5u35utlexg3tc3mtzm23ka4hzmsthe64f npub13je2r5t0s4uszds4lc5e87n77xngluwkjt0hesduvch0vk206gcsa0d03t npub10jjcalyj6a67qfxrax2mwpmsnrlles6qhk23j0dyc76h27gag05syya4qn npub155kdyaltpxaek29wkeza9prkr0t398ayn24wlp6pg68z57s8l67qka6ly8 npub1uk5ne4u0ey8s8tg8czceg70yw9jlzvk74y804wd3vaa3ncm5l9tsl2cjqc npub1q09ysz8xhfe0x0n2y77u6xem9whtsk5hgswz7s0lrj9znn8eksqqzzpsyy npub1rm8uwmhs7s9n3jqzzd92mwwgr8gca4p9x0u8vu8m5n5eppqj88fstspqh6 npub1e8antmtxy0vs2pjd6kah99lpy44ztads4m0udpf07vauvr7larzsf76w9j npub1e0ngk7s4nygt46cpmdrc63f3mfgjcp8edxh0f8vpp6zd5hwax4qq0mykcp npub1rksqdj6tpjx4ddcyc9v3jw458u9y83hk789jqy2j8h58jusv0mgscx389d npub1q2f2nlq5kxthrcsww2zmytyzal325gsvrv0aeg8fqj54z4kyrxgsylesz9 npub100t4hmfxs467q3cwqd5f3sej9zhm2edd3kcn57hj0kag3n49geusm5zt87 npub13et8ay8ny99mygd8ymznczusrhfrhhzzs8jdlep9q98r8uway9asl62v4r npub1qeydnlt70d29q3axc3h5v3spfntl74jukw9r6zy9s8ms6a82mupqgnr2y5 npub1n9hr9s73atxmjm0muz45ghwutvf2kc00lq2fa58rm9y80mpdqxmq73mdc0 npub145cgkka2733cmxn86khjshwyxz6ahgjp0ek9gp3fc2k7y3penkqq45ccpu npub1z24p8ghllrl4jxyw8juggm3cfrpn8vvfxxsjzjj4tuaz0qfkeqkstnk760 npub1h6mtmjw2au827vs99zlykn0tdhm3hpyffjgnaq8fsvjzem430hesd3zw5p npub13u9wq6td5qvj2dajmkjplz0ytvt4j7zvuyjg6kl9xqt5wznqghvqrptnlq npub1x7j0x34k2cguw8qk07hlgtpcdd22k0p4nfmuy3sk53mw7n5p4dws97mh3q npub1rlgz4nrqjvy7skd640reu9f9ckv5gzg4dmheeuq4u9dux42t7lys88svf3 npub1j5peadcc3as7ht6tszt47z2z3rec5py39y23cemrs47czyfxddnsskqnav npub1ymjhm0kxwldyx3f599d0cjvpcwdyfw7rmruyn8m2qnfhlu8mn4mspdwhqk npub1gaqn62wk22gesxfczv4q30kg3e2f6cqzdml645rwdyas6uaz3wdqexzlgl npub1z9vh6x3h5d99wvrjxw036ehg27cc37837f7dz4lr933euzu4pt3qn5874u npub1axy5sgkdz50hqrt266cl95qp7e5n9q6qmxguj0ry6mhpmu23t80s9nvqug npub1yvjmvxh2jx07m945mf2lu4j5kswr0d63n0w6cjddj3vpkw4unp4qjarngj npub1993fqzsar7lydy6lc8sztj5pxzeckttsf7m7dzjpcfvuu44uavksdks9p7 npub16s7exzaa4le983mjvnw7jfatum0jfxqtpfk2uqdel3c4q97uqznst6hyar npub15mptsgelg8rn5tjw5ltmdy8vmglws4fulr0kaghpv7t2jj8qzjks2mecva npub1yjvs58t4tgnmn98m4y2s64jferzv77p037zmwed8wzdful29a6esyajtwa npub1ctmkhtvw7rwk425sm4mqx6ak86aama7c6z8yxczfhgkwfv2fq7xq4mcr38 npub1f9jys8kppch9sceykam7p7uecpyam7ajm87wrgnndhjtj6jlp5vqe7y207 npub1k67tmzt34d6klra3ykrhkpvu0y8g8rlzv0egpgrry0xxcauxqzestwyz59 npub1x49ytzhkslwq6680jqsng7dy79vh8alsqpapr73m3akn0qerhj3ql7s2w3 npub1m2us7cgdufhg30yw6kawugwt5slp8kh9ed88dn7q5gtq5y20f95s9s25vt npub13sdds5pcp344k5mhfch7ltc4a8737uxqw9c47wfe08kkrnm3rhssm60637 npub1qfamw8qmsekxxu8pj5kfa960sgwsc86wys84gqxkzkzld8e6hk3qtvv7kq npub1tsxemx456uadxs4nsqenmquvws53290eg2gejrhvx7w965c779mslf7pds npub1ymxlmrd2yd59g7x4uejzsgmn4xlglu0schl39m2mjx5nzfzl2hcs73hn6g npub1qd05jn0jxlzplx33xjtzstvgeus9dk9405kwqf79vu00czwyvghqf08md5 npub1n5sl69j0w6c79tut2anqf69tkfevr065kzjt4n2rv2gres3q45ysmnj5nc npub10qjw7zw8m6yq4sr53watq4u8y47eef28jsyd0tmyhyfy4pjhntgqva7d9t npub1k6n2ghwu0afld0tnl2p43q7wtu2u9hln6e89ruv9a2y5deej06dskek6xy npub1ax4szvq26em2klfqj6hr38009x6k6m7nhe2z7mq0xs4xszetxe2s6964q4 npub1645w5cevetsz2364mss575panjuaa5ffh89ax4tp6u7x0tr2xlhsc29g25 npub1ys9j7sws8vccfwjctlqu7kx2hlfmkcxmjxmdttfl29edxv6xgelqkaffe4 npub1h4fnky04vkfkyac8shhmy0fwkrhuha65c5ec2ggvv03zv7pm64ls9x5vag npub1ueenpne5qhkvr4l9rw3c2ls2f6lgm7gh7f7ssl73l5yqt7um6uwsyatgml npub1krcpj4r4gp28vswfc4gztr5gku58c2eyhll47tyz5y2hhl6jyjwqduv9mr npub125nh0nkr0czuzkpjkqvjwc7mxuuvusr4n7a3kthjyfeer70eac0qpy5lsx npub1qcr5atkc2u04wx80pdyfnnwrttrw0taaz8hst3qt573j44yzxcvqkl339x npub1x96qzppsymujfyzn4dmkl08qgcr3aw7f2tt0xlmgyudfaggeq7zsh0yghv npub1l56z85xvaplh3033l8h2x9thypamu0d2hyqnxkw0ujuntqm8asaqh99sza npub1wh30wunfpkezx5s7edqu9g0s0raeetf5dgthzm0zw7sk8wqygmjqqfljgh npub1kqd90mglkp0ltmc5eacd0claqvnayaklkvzkdhx7x84w9uavplxszvrlwd npub1ly9cmpxs5kyrhnc946rlxmyj397pvcp3606zgvh3kvukmqveaxmqgwdwct npub1papvv8nyg68m73wae3u25lvxw5wfz2htpzk7j85z8yng3xqqvntqc5n9vf npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 npub16y2de3wvy2xgj3238r8h8g96hwtqsfm72sxcfw2t4c5xfjwnm4ms5y8uyd npub1ln4q6lzdwzxnvuv0a2gnfcxrfhwyfpcrp8tj5a403mwptq8r8clsq2znta npub1e0jya9z5wu68dzgxqeg7gal9ytgwvr63evtchv4a4wr8u5dcvs6s6vfwgm npub158dcjddhtq29ezyd3j5qyc70xyzyzujg02kcrla706fs52zcahaszql9ha npub1gayzxecnek73hm695d8tu94n2q3xnlucu9gwr2zqnql090rkautqq7ne7s npub1hvtyspm7n7nea59lhe2fdvwd0rqw7de20fl365wklsg4jsmrpwrqe6yaeh npub1hsr44v6satu5qkjcua36u8a8ng7fhh9ljv8mmnhvkf0a6407nhtq2k4ths npub18s8ym4ajt3rfwa0yn39m70k603j8a7wkhylhewzcjhtfheu8dnrqzwv677 npub1zdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2s4p88cz npub1xq0pc34qq99yawjxl7rsqx7wgs4x3088tkwwle5kz3jqwf0ggyuqxx5et7 npub1dgx9jmq5sn4w96qnrgps7f5egjfpu5npnswazsaq98ryafkdjucshaaej8 npub1s6ms8dqxc4s2e6yawg20lkrpk9dxazz9qsaernpxndc2axua26rsva6lha npub19rxp2h2c96h9y79nhsu8p9yn4f79k8q76z40v8x6g0j8mcmex7jsu4whlq npub1fnvuz4rad0sc6ueflq33kj242hqe65da40zug7u5nryvjdeg0xqsl4y86t npub1e2d8f64kaxepfqncve7gy72vam3h66vmfwaqnalekv8zmh3qar4sz34p0k npub1krahyq9me8aglq54cfffylgnj0sy0q02emv9zr4csc94kz3qajxsmwu7lj npub1qn8rpsky3t8v5dn30rycfwpktwclm544nlef98tg23drgk022a4qtzekjd npub14p529xk3dmtyqp25slasulxx5p6yu2js6lz0072qu77c54cz6pesq2qsuv npub1mxlypddvhxdatdjdh2twejz7d8lkf90350f2zhzcunhmu7pgw9yq9033ss npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz npub160mrpl505fmse22eue6v23k4u4z0yyw37hpf3j73z97jtq50rapqx9q0ac npub1ve32zawsazgn9ukyr0trw4u5zk5z9ravgq9g06ml4gfzuvuzrvyq2mfzr3 npub1c0dysexhhd09e65rvmeecx0dpn6c7lq4yp99f3h4ktnr4vvrez5ql3h0y0 npub1758748kzgkp5vrt2u8vdgx462kt9f5p2x84xwljm4svadq9xc84sl9yk27 npub1rg7x6lh3zurejwnhxljdh8td2uhnhucx3jhle565eh7x94aqn03qrwrm9s npub14nefrmsdvn72qq5f3zqpdsh068ufk02e3t79ukga457p0v796chq7xrakx npub1l04nl239dn9wps24a753xq38h3wtlaa7vxmqatf9y0g6vzae6u0s27vwl8 npub1mezldzxnv6lszd7vlh60k0cqgxca7s08x5akyvln9fhz58jyfzsscyepuv npub1a76u90rr5tfdn9vf3sg574g0vftz4p5vu5r9t57c9atpwt64jkps0h4qya npub18g9zwmrdjcf6mkz7zpavmcx46r3h9ydxv2urwc9kqvha7vzght6swffxry npub12y8v5es4g8ynms5495l448977l25puf39wj9has66f7yg8xkhakqn89g0n npub1gustav0kvwh9zlz22ns7y6utwt3s2747mh5s6ja7v622tl09megq9heczp npub1t62k7smt3nad7s3rzhkrcvzlmheerk8p3qrpjwj32c9lzfmz5ksqaegpck npub1cuvc5stpvpeljeveqlk9u6tp3z3qams2w9r3s72hy0ufxudlz4fqu3x5jv npub1g8henaumhfjngrkpp7g7urz420hdzcx2hnh9grf2r7g3sxtur6es8uucpq npub187c8yedmqmss7fxtzqya4vphfkazl04lvrz7cp5xghhwzjduc4rqkcwd0t npub1vg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsel8885 npub1nkl720g0fuvzt4dqm5xxjet2lnm95z5fv4k3jvgz5jhnvhe2lehs98d9kr npub1l74p0yq6uzce4v4ntvvj9zcx03rc75g8gn0ajsccxzwyunv9m6tqwjlh45 npub1tl2pwveluev0jcmm973x87qt0uy20hxnyrcwefxv3nkv9kpxmzgs5pl9th npub18zhn7vrv94vy26vsf677uyxxvs29t2da492xs3xnxl45sszvh5psw9vpuv npub18z4uprsemsf4tcxdnfc8q2esk36g5rleqp6mw9ealtn2kmv8pxjswswrvz npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk npub1ejp9v82302mth0k3nlanyh4zm4tskvg9yk2hp5fjun0g7uc47n0s0q07vf npub103wzz5eeegcwzrchje02m4rcxqxqtz2rauefhdshmtzd9xjxxdnqm5kd9u npub1k9mx4t56d6jsm658mmnwv7uvxl9edflkelpu4llgwrlc220d9qlqcyhueq npub10x8de2sz6apxnju8wwtqx00sjkeqj22kcjjfajsa9hj77492hkhs4g287f npub1q24ugzmm8ptkyq3gwukkl680kyftmlk3cmqu49x7yy4zuv94a3cqlhw8ld npub13xd3wejhu3xy5hmzgd0ymc9apee7ett6my4xsug5ya0z2f650n4qaf9f8z npub1vxd0dfst8ljvwva2egrpc53ve8ru78v8aaxfpravchkexmfmmu3sqnrs50 npub1nnyqvvr992hn3umzgehppzt49vhm9u4vet9zhzks4wq2a34ehv6qm6wkx8 npub1467z25r4x9xj6xgrgsk6a9gytdy0qp8xuupplxyunzfp5esk2uys4gm0a7 npub1w48530djsgja5d63k27mr8krx3xg63qvrjhczfwqgtmml4kgxw3qpcfwvj npub1ymldfnyvl2u5efjkdlqhpjruhv345qtesj9jf22paxmgj50nfxes3k4wqd npub1mqn5acr09lls33wapadkdf27t9v87h22jf53c473wzpkgld6z7hs72mwzd npub1y7yvamgvwdt6h8skh5yf5phn25yt7c6qcpclgpd0nglsy3f5uu2qu47fad npub1q5jxvccuds9wmpqhr7p770y4ewqcfr2dehqarm5alhm4hpgvrj6qtm2qhm npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x npub1k2teldhmj7d53732ekcs5ta0qpjsj9fhwc2e5ve5wljqpxht5mfstxx3qw npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle npub12xm5ax6rqp3n9n0lwlja22lpfuwc6g63a76p5kdxuszqnn4ut2ssj2k7jn npub170d8w0jjdcjuh70lq5ppr0pcy7cfuxj6hpr00tm4et3v53j8pvrqj0chu7 npub1fs3n5u75kmtfgzzuy5ms5qexchv7kz3altj7e2uzl79ygf2nn0nsv2sdjg npub1y8hsmp2pxadwf09g22zsjla6xu8hu4qttgcwte6kwrqkv70e69zqvtfqyr npub1rtjk5n3cgdepj95wylpy4h6etg2jel3erpn8px9wxys8tuueeeushu5jyg npub1m0lr5fdjrhhwxl7dev4h7c5yvruz2vp949tun5zmulxuktcm0fusy0gg5r npub1ur6emzgy0wrg5xyvtm7khy7a3sttv4jrhpcc3px6mp2z8pkxphwsyy6kg3 npub1efyfeevwrtxnmncs8767p66wxwulm0wd85cszksw6n6uw2qtca6qzfvgyx npub154efugcrxmttmnp5cfxpnhgwglvxswsxh6d84jcj0a865a7s4jgsrrun7f npub16erzcypvccc08a6z6l6gw830zj7m743ah3gtc85rcjhfqmqjccksce7jej npub1jpxn8d3x0p8cdxvxzafpcpqwsfnvgntywhgne9w085fzu2mjjw7qldgdg0 npub165llzjv9ux2s3ezx5k6l4mzhvly9n8gyzhx5p7v4499heee4w4fsvhnu5w npub1mcgm982av268z989lv9h23f0w733wxecqhjjw5l4dvzdjgl0gu8sdss2v5 npub1z3adf0m2c2mul0vtpru4f5uzghn746xyf2udxv63de2ckcmg697qqmjnvn npub1520n32u3r68qtlw5nykxegtxkdt09rpk7h52laectc4qvdcde34s2u9qsw npub122fgydglyvhzr753e0l6k092x8h5k4ev0g9v90lpgje597srk6gs420cc3 npub1xngvle6vzkusezsxs35kgulf6s0usjxej3qvs4kczezy6q0war5sxmumdn npub16umw99z8jm5r55neprqmvlrsqzwklernxnczam2xu5q5fwjaj2kqttgcvd npub12aa8fnjcp84epqtmhtnc4w2fah9tfyrews76nd8hqltpedf4l75s5x6lg8 npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju npub1l8qw5av3039qhefprytlm7fg8kyyc0luy8yk2prk2l8wc38gf86qzw7nnm npub1nwrrty92erpe8th9wv4u9l9f20pqqh872kwjmejc6mu9hfnzumfqk5fua4 npub13qhkp54f8w0vgql3lqukvk9pduhef099hx0azmzupuhxevjayy9qsfg266 npub12jyfh0sy02ku5p3zg6hhfvph4zphl3y5jqfk9skaqa59z7pmfh0qqyn9mn npub1t8pha5vxkct4mlhskzz4pshvwznsma5646nmzz5gcth06mth0hfsuleyrc npub17ptx9z8mnyw2vd8as0nyh40gtvyydufme8peweh72ax9kpxrqzxqmnsxpq npub1lzh4pgufkx4xq675fujac9mmxs5zmf8ffucetgp02vep5eae3acqwez9kx npub1gnrfjvjmu3jucpmkvj6ptmdxcj766hwcrekjeuzlwtcqrqmyszvs3pr7lj npub1gazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsmfe0a3 npub1xc5c7srsajcem7s8x0sndqsu6yqe36xzu2kdnu0cky353x6tkreqx4lsgg npub17kytlyvd28tvpz9u8z2mrr3pq503pmvtv46qskjccfch9vwqhadsregenj npub1vcq8nv3lctr8ctk2dp7h3e0su4f7gklgx4dlm2375l6u69hvuh6syj3d9l npub1v6xa5avwqkyqwzmfhu0ul4cm892txq4jnxmxsvgt5pnralqj9upsnmsnu4 npub1m986jhedeq7xxe8ukxc3dqwqzcz0ue9fra6m0t2zpvp8yezkeexscz7ena npub1yftkt6shs2fls0djxzww2nc7t96x6uxq490qw860ssfda755pc0q6emnz3 npub1rl5s8caaq8vsjfhxnmmmguxryug2f2has0kg5gzedepzle8quncqn9patu npub1ucsl4dgwslalsgje4es7jefqexlsf678wrhvu8q59e3djzgl7krqf2hnad npub1hvzkl03x7z8fews3cc5h99mxtze83rwxunre2687hcdy0zqn0cssnszrkx npub1q884swxynxp5dt467g0v3gk6t89tgd3r90pgdwcvxtlnjf2l3jtswgwvcc npub169jj88ry88e7f6cmcngcz8mu67ak6q6u2pgtcae6wa4ju00z8gts8hac60 npub1ahfkmjuzqcngqule5c4eq3cucxd65dpkp0sguzzsr2duxwlx9guq86x8en npub14xcy30kssvtpj29f40rk2kk5d2heumaxnz77ahkuejwepqngy9nsewgz0e npub13jpmntdr2k04x76f0c76syf3za42esn2nnd6kumc2cwyltmtje0se6mvqj npub1us9tzl0zc0ggfqw6348wyctck7mmh34w0hpn2rs236akusx7ltjq5s8gtq npub1eykpylvevzagq8jm8jutf2pmjnnelmyuc56a66v9g7ttcth5kfsq6vllrz npub14r294afl5jqgvj4hlfpj3dvyxenxh4vuhepn68zdurcas5r5xy2q5ydufe npub14n46ruge3mmv72xeyjw5zl4cec6dykrme78plmm0zmpnclcptqzq7kct5u npub1yvw87p6d2rmd3lqdp3c6npjhunpra9huxnl8c30rxjw8tnwd292s3jusa9 npub10agmu2vwed988jdxs8cewppw5jvk0xtvh9vdyguttuhugu930fdsdcsdp4 npub1gyu3h0kmqmecf6044q5r88vu5vtf5u6rekh9yazxrtejfexct0lq5zpudc npub1kstv7m2flm703dmufltz4l4lkm3pptl0zdqjvkx8ap3aagttkd4s8d5pa8 npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk npub1mlf37lk424pxrstpdhxqp04v637kjyashaj4ea73gfz86yr4gdzq3mjtav npub177xlld4katf3aardam7qpu88l0ttvyde739qcvjdjynweqnncuqqvxmfdc npub1ykfmyfwtanmhvp06wn3ggwm0gl0v5v2ftmnkmhz6swl2x4ur9udq7ld2fy npub1a5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqk7glwn npub19gskj4eqgjgjrwjw5zhu9rddnrqfq59slm5fa5a9crun9wm2qlyqccyh6h npub1ujxurwzpfrxsprf0urqfxpp0qpm2yrpneat4udg7e0v560nzw3asml0d9z npub1ep6wcd256kvsdxey2ylycrpvmf9wnsqvg46kzqrhuw2akxj020kqvkq9hc npub1pumdyz7qfu0suamv4nrl0vcg574dtl5mwazva6nyjxhpwc4ccxxqca3ane npub147d47sem878zwqln7k9y8y3273v29ase4r7lk5yeta62xk3t739qu5n8zd npub18jzu9qrrmhhwk57zqhfffymy7hq8vrncxnvl0sutu5y2lhr456sssgsesp npub1wmnvcv3ycqmtfsysmrnkyckja8dc9nt5sgf60rrel339v8chtgnq4p5w26 npub1tc07sk67d2rs8x90fpg9x727ulzknw7xjyk4lds7pkzauw2tqntqpzs9dq npub15h8pr8t0l6ya275k42cwwhrfu6z6vk6qydkdn55p6wn4f424s2qsasdczc npub1l0j7srkgmdwy8839st2hn8f9utlgh9vtrm04jksh8tsu32h5vpms9k7zqa npub1p9auvqfn3dtrjnwkhxdvvk6xn3tt8aa2uv4dh2af42nv9z8nh0msrjvmhp npub1lnjp9d8xz5zguufe257vtx59kgjuxxufv0fjnplwcfncvpc7vahscraxv3 npub1mhp87q9axdlwh9ac3p7drg9z764mxwe27xvxm7x704l9dykfy9xqrgmxdq npub1253ehcqxctt4ps8kjfmhqje965v8gtzn7c6gtq02c3kqvtxmsx4qv9my05 npub1gk0yyk54t6ptq5m7hygy8rvc98pq9zz5uhusz9ht6yxcpmvsr59qg5ptts npub1828ey4s37t3dlwjmgsa05zafvdlsfsa3lu5vlk5cdx0a3zppv7nq987tnk npub1h6h3jwx3fvz9sanmg5yx6rutmggsnz5t09t795yf4jk4dqsfyq3q47kcxr npub1cw2epa68jpmy384t7vn0suvd3mxnk5s02ap6fcwg0x6jqy4lhdpsfg84uq npub172g2zwq6vkerg02urweyt2daa0huavn6ghcr4gxt93lmhvnzan0snuwkc7 npub1awwrv77yu0x9rvuaq55ppntc52rhxt0w9t32zkyw2jszvmgsqnkq2f3lpm npub12p25mnqkunnhup0sk6ky0vvtq5pnkapezx8kh689dv2vl2wnp2vquyfw5s npub106yj5wlntf5els6w5cw3gwmsgh4yu7vs0lrpw4c0uzkq3rqmkkgqg7rgpe npub1a4u7yc39v6fvr48a3skz9gwdzl76hf499mk96x703nzc23mdqq2qe84e0k npub1fc72tcwhr5fhcmcczzld6femwd7d7uhqwjw8rp5w9enxj52xjqxsmpgv04 npub14h5r077z3edgts6wl2me5vk52x5se6nnhry0ldfzua872ggcxw9slkd3fd npub1xlngepdt5qz752x9423gnvj2gk92j55qsdhm7mrtmju7x36pwnxqg4sypx npub1rl9wszqmsqduzjagewq302qfadjy4mt5vw5zvm8xdamvp3d0nm3sr88s7e npub1ayvrrlpygam2ruyx2lhtkvgjc53wjd3vvvs0ysjqh3pwhryaju7qd60eq3 npub143mkh6lvtrha7w7pjw32ujkljc9ell9wpyvd707nahqy0rt62kws4wlyhl npub157rwfe8a4gffdcx5ca56q2qsvpp3z757674lkwca5ud9j9pdcnaqct6p2h npub12z3w5jynqn3pjt73kqz6wkueygrvt57qfwgxy5u5pmn0uqutdwdq5jpd8w npub1zfrc4u0dnph8flpqar5r5lv3gpn7qafhlh35zpcm8e6ex4k24snqhx69js npub1rvww8nakj7rgz59jdqlswdmvjn0cd46q2h4y00wuaquwyn383fysxlpyxt npub12knmfzy88xpc4dhuly50tlhcnar07c4pd3w9pfpd4lnssmwhvtrsgq2ez4 npub1705am22u3tep8vvdwkqex0jm9pazhmqqyxvaqzcnv76m53xed0xqeetuva npub1q0k8epddegnec4kj0j3rew9yel0jsrp82sd2new0zy3m9pcfgqas4r5yp7 npub1fcj3en06ajdm09y3twytsrnd9n7yqayt9e9xuutqdrwnqu85t6nqt7rz5p npub1jvej78jr00s94gdyct9md9x2ljtjr0jhej5c4mm7cejp39dwgu6slkmju6 npub1mp0jgd4gaj5hhw99lfwxufl0k50m398jcneqsp940sjzz32skmzqw5uuat npub13u8pyc0azav54a9gg0py5khrmd8er6ac55kvag72h43r4q8s7nnqsqsy4t npub1ajan43fcllaxc589juls8pef90cgdya0p0en38h55fal42nlgkrsvltfdv npub1pvn0tyrrrv86xpydzq6ppeyyuh3zut263m82emdfmydn37qa6x5qmh8khc npub1pfx4fj43y5j27ywgj02axnyup0eujtk3g6r4ug2n4nvfsa2kpl0qwvtah5 npub1rpx2y7u00jmsvwt8zlkztajmk3e5se89vhnswsz4suuyg4a3fx2ses6lkk npub10jhpwcdsc6mrfs8audcdds2x5txdagru9835f3drthzaumxurduq6esrnm npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r npub1yrffsyxk5hujkpz6mcpwhwkujqmdwswvdp4sqs2ug26zxmly45hsfpn8p0 npub10ua5vjul7d3rvvzg2psvhk36w7gpx8zn8xncqw773l4hnf0pkp4qccymjg npub14fzrwpygf69t0e9snrk2ms7ltn8u4dnvunl6d98zkrgdzf256exqa3j6rj npub1x8vkne5rx99wzup65m7gpmhmgsa80d3dscp8hafrwj70zxzkyexqttjd5x npub1643y7m94wwu30awq5djh7lkqj48evpz944yetgzhssmykkh93zlsz22hhs npub15pkupvdv7hmcjumlrx5yjmcwy2f9fl9fmsa9mx7qjlau8k59rxusq2v0ny npub15wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8css6kt8fs npub1saygqd4rdf8edlm3r45cexr97zndj3254lxyz9dejjlztscvndcqhcky0f npub14neap59th00w9keu9uffpal72dxyex5u7vc8pwsuqrdxes2mkrascnlukg npub1nyzep3atafwfrnq7346dmx7kjhqsrza936rnvnlkv25fzd09gxpqw3gg6v npub1chgzxyqjnvv7ryuf095cswtym37jummaqme42dfez8q25h4l734s9xdl08 npub1gp0cpreej8amtmmd4zn72hvgr4d4tgdhg3vpe0m4yxzqz7skg5eq47jmuc npub10gp3mv09aet40plum7f4pllyc8g8u4thq8mkkwymdcct3schagvq6fuh49 npub143jqpdq583jd7t4ucfkr9wzug9h3904vcng0vymyley0dx43vv8ssk2gc7 npub1z8y57drslgthaefkvya7kmqcdm9c20uutz336j9hp4frkrg32nwq9g4ju8 npub12er2cnsfzc3d5ceggpjazwx9a5cwna4atxslkwe8975lp3fuy6gs6s36tk npub1cpxjrlnhfmcclcsly5c0dvrgvl5nsctzxpp4s9f2nh4qeq50mwsq4089fc npub17dhclpvjmlkhlgkh04sc2296wj0veae79fq8dkwr5efvlz6vt79qgyqztn npub1gm7vxd6yjqsjx49ddqgyflllpjuhduqch79jlp07upsh3uf6q47qsm4xlv npub1d8h26etwdx6ws4afflra7reqwtvjsm7u8zn7jz0w5q0ah4tgx3rsga3axt npub18trgdajss33u25jvk0g2yv6lxr7s7k2dlkkku6eqq7m4hrc6aazshusdhj npub17s290m08ukaz9j3nhyuj5w2zyxtdzdqvrvsgv65c7ckcxshjrxrs6wnfhy npub1jlu3zyj7f2hacdrrmy7jpny9f7nnvuxt2flrasjtmgut90502xqqtsx4rf npub1vwcy6na4rcx6r43fqyxkhzzdvqufctnx06ywvrnajmq9p3mu27yqxy04ch npub1ea35pc7pqg2uvstspd0ljlu09t580qc942n5eevvmkrv6huchffspl8087 npub1jxl2tnvnv9gycsy64aze295c3a529lx5sfmzlktf5lxuw805g5wqew0z0n npub1l885a986vy3sj3watelhdwea74jxhy8688ju4h2c8wz2e94tcd2sl7qjy9 npub1uy7tnhwxsr0tc8eexksandgcct5wtua2xazvl2gfyy5n86p9sdvq7nwdzc npub12wm6zfgan2v2jc5tknkjsj9d64qfk6y4ggu32f9tgnu0mpuz26uqctkvly npub19hvj2zeg7ck8cj2p2az5y0gplllhgzzdu0khu5fhnpfmum5jspeqqcdjej npub1cqykgt4enf0ce9v36kjzugx94l6tp8dd5k8ktfgga9ahgs2mzess82r6sm npub1th77tvx7c3l9qgxql4grcllh9qahyfvz65ruplrf6kh0sfzuya0stmendl npub1w98zr2sevkqle6lmt7u503ewclhzs2cdq94ke4mw7kmpxy2u9y5s6fe9yy npub1c999aq8sl4fmw8an6hfj5lfhuneqc35seffqs6938hxajr2jq6rquyvp6l npub13tnrml3s46xswsk8l2p4tv8cdmnpkvrk4p32828jwce7puefc0kq8jlf2d npub126v86pztd6emjtkwxe8jj8sa8f0m9wcavsd4j0raemdxksegfg3qfaan6r npub1uz9f979gqjj0ymul0kqq79g8gtelwe6rs276jm7qnaffmn545h7suw6nhl npub165h57grx6hjw0grfcw805srfxl53ggcsl3mmhagmp7rg8x80ehasytgw9y npub1re764kr23sa6d2ld6fhukthcwgnwvsrahe92zq42kpdu3lm05sjqwjchtt npub1m0l0harjth9sses5h0r2slf7l4wws4clgt88s6n23ct2kd2xdkusf8nqjj npub1a8w23gjnfv0f0qzjpfeqg7yc5ddf4c8m8jks50l84lrv7h52jhgqq734am npub178p8fw0spjry5824n5wv96rfre8lq4r30ysyctfspzy97n3tl0nqcg5hzj npub1yhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6q9zu2sd npub1h7mp8nd39hzxywqdl28rm2du9j2jhcarmsmakmulm6z7fc4lx6eqqaxh7q npub1dvqg5278etemtvxl59ahcey8cywrcl0krhpu8dt9s70mgwjar3jsqh5ywp npub1dpm87jq8zpgrvq2thr80chmjjrj0tww7q3hx9kq7wpzq2aayqxdq9a76um npub1l506tlst4adydg0tkshynjw6dsk5ukjvpzr67y9vas8v3nzxylssq6p0j5 npub1pe493zu4ax53pthcsfff7uehwppc9w6peashtyu972ey2szdeheqxcfk5k npub1kuxfh7e9fds89qzzzfjrh6c80d46jstqnm2q29wekyykr4mk0zvss3yn27 npub1gwx22vu2yzm8eq95nvvmgvpax04u96gq4r8rgqqf9pgsheu2lz4q429cus npub1n8ahhlw8trcpwkqdcetl5pgqvrxcfvgrtj037zlflrnqymq5f40qhnwpd9 npub1ujr9zwz8h7xtkvp4pn6aslguqvks43h8ej2z2g86snff0h4xxmuqjzcwy7 npub1vm4s0uqkydaqzt44dyt38p5spltl6637sxrfxswmr6k883f5a0ds8taxyl npub1zqvtnvxrdpg5vwh5alpx0m567092m2ltynqxlk004976tgc6syqsg9rcv4 npub1ld5xqfflwy6txghaaef2d4rnyzkvwvz2crncmtvhq93xxsqvzqtqzdx4yp npub1er2xa679095y03xlcmycgg4r93nluqpluye44h0ndxdy6k5uxcdsqwtqkf npub16jde9ylpry7pyau6svgqktdes242ynfk9snfafh8gq3r3fj5xfus44xm32 npub1zqgjtt2ayahsuxzp3cg7h8qwt6ev7phz9x02ktc0gdlwz70n23nsla0sph npub1h9c96qqmcupyvtq30d0xvp97h2cx966gz8n55cqgd24hgzvz047s6hxyd4 npub1h955atshn3faxg5r40p4achtxg3q832h0agjn24sf63tnkg5ezfq0fnr0n npub1ker60jkxmxjmft468v5wzth5757v2end6wzd4xn67jyej8taj4zsyp7tqy npub1ddjzjva20mwp9xals7v0nh3devvjewevkkrqrsglyhnwa59ctswq6kzdys npub1wtvrnst9hus9pvz3m95pusfjzq4z5zly3w4lehulh6xc8dajl60qsrjg5a npub1hl07ukzg0xk7gj6ejr5k5e6gmakt9tnu5r07f543ce6e7sa7dc0qv0kcun npub16dana9qsfpf48ccyqwvl8jlw6k5u8adly9ph76z0ftrs88lf7vtsrzlu5s npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg npub1saessfmtu5xwnwh60e0rwnj0e067npv6yxgc7d96algqqart056s5gkuqh npub1lylzl87mst3swjtj97j8aajyfmaqctaylgw9et5agyp3rl42y5as87k86d npub1z324cpkjv9ay5fanw7rex5847dy7h3ndvaej2hy2vmc7r8c35res3x2kje npub13zlwh0n00pja6dkw6htamu6sl8668hpgr45y5lnmnmvt92g3laysqqsatw npub1u2ukfds6k42qwufd9xd5l535lxt3g2zet9rmmlhagtjxg6t8e6asmx0w6c npub1ezeah83hkpsguazn70rmkmfwh864wdejv7h7q7tsuq46wquelelqu8fr7h npub1pvuu3ms6vlu7lmysggjuuz6ctsuyjdmy3uhlywg7jxdewvtr7rgqakhnsl npub1vny9x6jl2cmvhva8m9gq05z0vf2tar3vy72503hvuru0pxtnz2vq9v0fyg npub1s9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqsd753t npub1qvwpwvdvq4hckarg9ekldnvzza0shka85fk24uuh606vhg4l2grsuw808l npub15ksrns0fw4l8heral0hst3szmvpka67a94xxjcm3ddlpx7hcn7eqhwfkrd npub1zkrdvkmnx0sv7d8hyd0ma22lfvvphhd33d0qs3sg7lrtrv0xdv9sa7gy52 npub1nknxhegrddacazt8sax6cr2h0r9sht6ajmq3s82vjhg54ey2rfhsumhe3c npub107swly8y0ert2upsevqk8fqw9tvacfvuygw55qcv4s2eav6f0axslhmymt npub1a9a2l7jqqxa9mwrw034lcnuhcsncg905sl03ava49md55t4awewsvvzz87 npub1yudjcmkasasju6znprl3rpyp39xa3uk4g6sfrv3wxestqsehs3eq7z5f8r npub1cy3a6gug0t4jrl8plq393cjjxwtg6cewcuek0n0hkww4h567dnts0ft0dy npub19jxz6jynvhlwzmfyhmn5tzymdff0zuq8jkg2mq268a5045f6favswaxu2q npub1uvx00x8svjwma2zhddwpthyke6zc3rrxqg5gj8mxdjv77zvwmz2qgw603z npub1ewe3r7x8qemdh7v30gndpamgrmu0k6nu4twyt62r6ukvkvmpgkls24272j npub1deexjnst5g52wh9kmqr4hy3wzhh0gspujs2nc6m0l892rzj788uq5gcpq2 npub16qsq63pgxyw5vz6847y9w4cau0fmvhykw7uy04p50u5muulc6kwqn706mz npub12cfje6nl2nuxplcqfvhg7ljt89fmpj0n0fd24zxsukja5qm9wmtqd7y76c npub1nu0yladm9rr6wsz8w3v995gcxl88vqcdnp8uv3zp3xk978d3658s8kvmhm npub1dn5cj3n85c085yqry7wle93uhrqtkf9m2zwqgt8c233js0lt9ugsdr7zzt npub1vudm0xsx4cv3zkvvq7k5836tnkv64q0h7uudnwujr4a4l9zc2p9s0x8url npub12c68tkshmelhtrd7ye5fqg3gwttd33ly7gzxkwh2u4qt008nu7gstf7x0p npub1dc9p7jzjhj86g2uqgltq4qvnpkyfqn9r72kdlddcgyat3j05gnjsgjc8rz npub1dmqa9kg8nke7fc88p760zd8crrqupl4w5lflhgs0jgh4n3slmdjsql67zc npub13q2vzsfemle9cpxj875tz0vcwqe6r8sy05fd62jcd3xuxjeqj6ksze4xl8 npub16merj2xt59t43djfx8vf4fzhc6nd4v9hlsv8ej8xfl3327yr3vzqu8zjt4 npub15dqlghlewk84wz3pkqqvzl2w2w36f97g89ljds8x6c094nlu02vqjllm5m npub1kqnfgpzt3jxh69ma394r0azyurd6h3dehpw7lzvl0vv3n7kv4a0s3305z2 npub1g6jjgu06nctv74e96u84jux6vxm3ezncjh7tyquvm66jug02xvzqmqu08l npub1efk5xdyrs6e4lqfm7crut2ssdnhu54d9egswq6smt62v0llj37vsprp0r9 npub1j2gc7kt42rwf5q37dmm2k29rqxscdqt2vyfn0xgju32v329jfpdqmkq0xk npub15lymwv6mdpdc3j8zxf3qzq33j2lyntst9v83ukqpa0tzkdtae28sgef05j npub189ts86gs5xw5w2mcz0na5vkz4cseam7jnkjwwqswrj56v9x776lshjqa8m npub1cgf0yeja9tlkfq248l09hkf4kfjfyaup50laen46ucv8gf0puy0qlpxlh5 npub15r0z9mrt0nxzq5fzxysqusm32r9krljq8gh55xnavdyllk6gdxjsj36uc5 npub1qa0lj0jktem67zaazrvpgrf23qdcj3cw9u6j5ct55mg447tqnftshv420v npub1yxfjljjd3apsrvzlkww525jfvdsvuwcs3n23wpmy2txtsppzvmtsgxur33 npub1gv8juwhat4xkl734q684n6vvv8sn5k2dvm8a0wnckyw50zajdvhse8rd3j npub14tj8zkwatnjq4rlnruj53676thre3uss9tg8e23a6w4ewuzus60qe4qg6r npub1ylf8w68g5dkfqwjpdvsy42d2cwqnajswrhz323chsc7gnz400chqfmzdm5 npub1rhgqj4urjf5uw9y3npnvvst2hhmcdqghd26fzwgc4s5ptkq24d4s2525ja npub1lzmdnlsaysc5m040q5q8nlgmquldtxzgllegsg6z2n0engaxwp8szsswed npub1vr3860267yxktugg5q034j9xh3xjaxnlawvas6wqa5kw6zxhgcdq6u2yzr npub1q6ygq585gcs2m6egv67yv3a036jhry8zu93wk2uk68e3smdafl5q4sl54r npub1vy0g338hw6w6rn2fsv5s92nx47u6gle8v50ypxwj6k2hsj9p344s95e8r5 npub14k0ws2m8f5jfrae4a7smtmwgx0quhhl58z4rpd8hs9ar8mlx78ys0seswh npub1qahmtyz5pr385kqmvxqf0a4004cx6ncvnj2829rvjf0rs5ujanhs2ssgvv npub18wamvs6p7dslshavd24kv2gy72e5jck9lgm3f3e3f8udja3ramcqvrzg6q npub1njtezc8lznuj5ws6yvz6x324lzn2ct907s8vlwnxqph30m0gqd0qvpvr07 npub1vgppgksgzs7je6xueqqvkpn4gqmcn3nl96famz34zfhqzq286mdqqmecmx npub1w6nj3y6wsv9kfjev4jjdghsg9ajcjq2gtec4qfpmgcmkzljl4yps8r0gwq npub10l6udyczpjzg4wcer9mje4zkcf2hhus8cswhycwaxfanepc7fz6s0q7u4a npub1cwevvvcurkfg5wjtnftret2j7ldv4lg3x35sty0pm546p6jx0g8q9fa055 npub1v5t0xmnrcap5rah8cm8mrqkp0rmuv4mslrlm3ldwkr39fzy56mas7wvr3f npub1w2vm583yvalnc02ngh6rxhn4ekp8m0xysmrzr6s7ufdwmu9r9qxsqdg0ng npub14va2v0yaprmt0nn0qk7ga6jujfk6pdrfwv0kxj76a5ymp8dfdy2s5ehfdd npub1ztdt0nvu8324tg40g4ts8d6englps8w6574zyq2gkdvcrx364y0qd9x9za npub15qskvuagmaznzc3pea7vxh0890ycfzxxdx537gef5wl6cunan3tsdkld4r npub10vmwytmy0pypy2c0f5zen8auvl7ku5dnk53vaw3ddplw2fl9r9wq4hmr5r npub1crqgm8qg9kplm9rlwfj7uxdzdtanq6rfu9unkt4ckd8r7fn7q36s0az8tt npub1x7fj44hzhjdcw2jwpylllpdgeh9yqqt7fg35ucfaywnw68tctv7qntw8qu npub1rj46xc5tssyk67ma9sslqqt90d597uuqx6v7tprv8alt9enk6v0qyvgn65 npub1y9a3x4e4zf6fu2w0cyyx9r2pmm6qtzrv4sallyznflamhplz3jyq0gq7gp npub1ukm78z9nzr0vnq7nqn8tvx95htttj2f48n99n9nqlky547rwzyrqk08am8 npub1p93m0semtesnsm2fjjd0p5kwl8gpwdqsnfq920zqyhfcc3j4nddsygyk5p npub1rgtl4ay7dcnud25enknv9230r3u5dmu3h3c7mj38jamrz4g3vf8qj5cszy npub19ajcupesc6zcpt0tlg6jv2l4w6wnpx985x735445fvla4w9zqqkss69s06 npub1kpyx8lxklwtd6n496rqgu8kq2k3yh2svlzr5sz3jlxlnphc6tcwq8kllrw npub1sg3qz6633ajzfg7w9ptmk0hf8ckl9jvv4zh6ttxt39jne36wnpnqyzk3vn npub1h5e0y6r2tagu4cygnfggzcfrt4afarvcvvcgqmpzyv605g4n89nqhlf2e2 npub1n6rffa4wqh3hcuurlf298dx8j59wxkmjth87adc7ektxnmpgxwgszk7scj npub17ml9y86nfg65h68pumfkclr3ay24pcfduu06j2jfp4pz2yjcpcjqv04fu3 npub1rkz86wjvey3vgdy2pau5ulpzdmxyzq4g8xp9cd3tu6kqmzpqcppseazx4s npub1c664gerrwlc3rlm6nnm73uc2kjyd0f7zaellshxyfdrludtmcf4q3adztu npub1zp0ys9ysfyrjvuxpwhvyevgphkmluynreun7fg2jeuu9xtsjwa4shlqhhn npub1fp0w2jd6e9l6pd3akr630d8gkcn39t2vep7u3ac5265fezu2fnvqjxpa2s npub1jz8k5nl4978lnhghlzeenp3nmfyvykqw5pjp620jj5qft8vqh44qp6pjk8 npub18vay956v7zs5qtgc65mvn54v96cuvqv6j9fmu4cgfjqkt5vjuvjsc47nzf npub1kgpnq8ycudaq8d7fym033hgdarz3ktvcws8nxt7p9rnfv98j7cdqftrga8 npub10wdzfpdpgyzxj8a4xtf5dux5z8065pan7xrcjh6gd6plj39qzycssepffr npub1ew3rlwvtmxw903gnqx92zar5dcyd47pjjure7ut2wngyz003ff8q0x0frx npub18urkgk8wrf0esedp8gy57670q5qxry22yce7rwrnvvrur736p3pspy6upf npub1pp8mxtdgamg65wfvrtp56v5lnyvv2kmx45cxd5m9dgcdjqqy5ysq5qasy3 npub1y5vlh9z98stts0rc5mlufellseuwjtyaa5jhewjqugnzdwt7yvgs0ydryw npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtn npub1lc6c4ukssmuf678py7k6thmlk8c4a52l9zx4thec48ve2qmcdqys22jt95 npub1h28yvj0mj692wpwruqdhyjngcfh4la7gaygrent6a3wwqjxcah7qnt92e7 npub16g85fanyh8sq48yjfq0smqm297yw76yxlcdvjq7hkuvm7xjjhn5saads2f npub1xc2plng44tlj2smv65e53sf3uaqf56c5gajktyu8zxn2p70jrxcq230nt9 npub15l8sfm30uwns8qrcajs99narc4ex65ujt5sky4zx3dpjhnnk2szsqu40n5 npub126u9v4tqg79hxx569wyq207q68j4vn4yme8he007kqfg36va8r8s4qvqs4 npub1stv2q4hwrk6ggvw3hxju8hjakly4ev9wt5tn8gnl9cpaqt8799yqj58ygn npub18yffjalmcfn4x0x0jpj3xm8g6vdx8rp2jd4dhnpr7e3xpemxlmas9w0q8u npub1wmmlxqv8l6aks90jvnetvwkk2hqd7pmqzk8hq6v0tkjrpqdvm8tq0exs5c npub1z8v0x60ukxsk00zz5s2uqgvlg6p8dhunnz3fn6wtnw48xg7p3wvsgmnduu npub1vukz6scwfq55vqjpv3z52theg0lwkrz6kncwc3rfkczl3ukafsfqfnw368 npub1kujyqe2m5w9895kfx7agwjag0xperd0efnxzfellux0xuj5es28q09lucn npub1j3tn5wdn82tmlgvcmhtm0fwzqpwx86pdgr3538rh7asdvkas2ktsqlnxpf npub1g7tavhda0yc8857nj22feuytgxskg4dlpfyql6r2d99egajrss7ssq730z npub1fsyfqrleejgdmck8rxd64wkhdefjthu6lgm8eg99r9xxsl9hespsnmfhvv npub1mevkncsv484u9nue4apgl6ue2644x4m57y9cmztnvwpvs0tnduysg3vdsw npub1a2mj00469ng4xy87nucds99e7m5djh4pe3rpluvhcnaat48gpeysj0gy8v npub1ggfzdxa8xrrzhaut6venkrmjtw8wl25y6l0wramkc7d4dlyaflzsxxrfcq npub1f945c6sqw2d2aqktvjrjtu9uca9wdd6ua5e0a560jak90rr5ha0q3tj4cx npub1x3j34yuj6d9ln5ryuw0ncy97aa6ttc5wwyxqwvjrz7mg039t6l5qd4ewrm npub1d0jucp5jqt799kjuqxzs4cj377tew43dpcr60fzyvcltc5jemtcqryyvcy npub1m6keqpkqfp0uzxdzm2q0rdw6pzxuln98rzla0zzywwdzgcyw2rpq56p4d8 npub1p8ymvhgtsyhyqk4y35xlup20trde4pa69pxf45hdxc74zdkyhfvq3narwh npub17n7fe8p607xgzj2hzft5dsqvsus7mm3y0ceq0ta9a30s9akatq5sqh9y58 npub1he7j4yt7ad6kd07ynqk9qmhfqflw642qkjagqvn2eektqrl90fcs6dlraq npub1mryqu5cffjqpyykvmfjx3js8j0m0850v56dx24lhyqgf2uhl5npsk9xj7y npub17natddjkmse4z8frh7ysynwtzanzmvs9d76c5r53546wsnzs25gqfdeqey npub1ywcw97xsl93l0mqmdpshqx4yu507xqa8zy8p3l8vrkgkek90wm7qjhp74e npub1d9f66fpawpeyrdh9jkyccfdgut6u9ghufwly5gyttfy790mp88sqgx5v98 npub1cx5js2ma5gf7fqn7yv8sjtezvg3agfth7yyxhwywtqypkat493ksjm7yr8 npub1ykrmhyqc0mjhdf5mzuz37g3jkt5ma7v0uesmuyvhueaqs5ysfres02hqjd npub13k3ynlhc2ret9nvzamj4cgrnq9fx3uzyx8ral84tjtk5pmxqpcysdzrzgt npub1jdaa64eyuql4hd0244mp7z7n82egpmt2d79ny9avjufkpm5gz46shcdfng npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk npub1klwact0ar00r9uer7tzh2zq0ytx3f552tt8qavszdhvu6vpv3uzqwpkjqz npub124rja8qp7dartasr9wdh3kk78phxunzhmq8ar5ryd2anj2qwtcnsz3tuhs npub1c7kdmhhae7x40q8zq9eudgqm9wgz0q3av4nrgaqe2qqphqmqvczqhee447
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 57d1a264:69f1fee1
2025-05-13 06:32:15
@ 57d1a264:69f1fee1
2025-05-13 06:32:15You don’t have to be a type designer to appreciate what goes into the design of a letterform. In fact, even if you’re just a humble graphic designer, you should have a basic knowledge of what constructs the type you employ.
Typography, for all its concepts, expectations, implications, connotations and artistry, is, ultimately, a system. Just like a body has bones and muscles, every letterform has parts that give it shape, rhythm, and character.
If you're a creative working with type, learning the names of these parts helps you communicate clearly, better analyze your work and others, and design with precision. Everything comes down to a foundational understanding of the anatomy of the letterform and its essential component. So let’s help you with that.
Pangram Pangram Foundry is where the art of typography meets unparalleled craftsmanship. Established in 2018 by designer Mat Desjardins, Pangram Pangram has swiftly risen to become a globally recognized independent type foundry, admired and trusted by industry peers and the design community alike.
Read more about the anatomy of fonts at https://pangrampangram.com/blogs/journal/anatomy-of-the-letterform
originally posted at https://stacker.news/items/978828
-
 @ 6e64b83c:94102ee8
2025-05-05 16:50:13
@ 6e64b83c:94102ee8
2025-05-05 16:50:13Nostr-static is a powerful static site generator that transforms long-form Nostr content into beautiful, standalone websites. It makes your content accessible to everyone, even those not using Nostr clients. For more information check out my previous blog post How to Create a Blog Out of Nostr Long-Form Articles
What's New in Version 0.7?
RSS and Atom Feeds
Version 0.7 brings comprehensive feed support with both RSS and Atom formats. The system automatically generates feeds for your main content, individual profiles, and tag-specific pages. These feeds are seamlessly integrated into your site's header, making them easily discoverable by feed readers and content aggregators.
This feature bridges the gap between Nostr and traditional web publishing, allowing your content to reach readers who prefer feed readers or automated content distribution systems.
Smart Content Discovery
The new tag discovery system enhances your readers' experience by automatically finding and recommending relevant articles from the Nostr network. It works by:
- Analyzing the tags in your articles
- Fetching popular articles from Nostr that share these tags
- Using configurable weights to rank these articles based on:
- Engagement metrics (reactions, reposts, replies)
- Zap statistics (amount, unique zappers, average zap size)
- Content quality signals (report penalties)
This creates a dynamic "Recommended Articles" section that helps readers discover more content they might be interested in, all while staying within the Nostr ecosystem.
See the new features yourself by visiting our demo at: https://blog.nostrize.me
-
 @ bf47c19e:c3d2573b
2025-05-19 21:41:37
@ bf47c19e:c3d2573b
2025-05-19 21:41:37Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je Bitcoin?
- Šta Bitcoin može da učini za vas?
- Zašto ljudi kupuju Bitcoin?
- Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
- Šta je bolje za štednju od dolara, kuća i akcija?
- Po čemu se Bitcoin razlikuje od ostalih valuta?
- kako Bitcoin spašava svet?
- Kako mogu da saznam više o Bitcoin-u?
Bitcoin čini da štednja novca bude kul – i praktična – ponovo. Ovaj članak objašnjava kako i zašto.
Šta je Bitcoin?
Bitcoin se naziva digitalno zlato, mašina za istinu, blockchain, peer to peer mreža čvorova, energetski ponor i još mnogo toga. Bitcoin je, u stvari, sve ovo. Međutim, ova objašnjenja su često toliko tehnička i suvoparna, da bi većina ljudi radije gledala kako trava raste. Što je najvažnije, ova objašnjenja ne pokazuju kako Bitcoin ima bilo kakve koristi za vas.
iPod nije postao kulturološka senzacija jer ga je Apple nazvao „prenosnim digitalnim medijskim uređajem“. Postao je senzacija jer su ga zvali “1,000 pesama u vašem džepu.”
Ne zanima vas šta je Bitcoin. Vas zanima šta on može da učini za vas.
Baš kao i Internet, vaš auto, vaš telefon, kao i mnogi drugi uređaji i sistemi koje svakodnevno koristite, vi ne treba da znate šta je Bitcoin ili kako to funkcioniše da biste razumeli šta on može da učini za vas.
Šta Bitcoin može da učini za vas?
Bitcoin može da sačuva vaš teško zarađeni novac.
Bitcoin je stekao veliku pažnju u 2017. i 2018. godini zbog svoje spekulativne upotrebe. Mnogi ljudi su ga kupili nadajući se da će se obogatiti. Cena je naglo porasla, a zatim se srušila. Ovo nije bio prvi put da je Bitcoin uradio to. Međutim, niko nikada nije izgubio novac držeći bitcoin duže od 3,5 godine – ćak i ako je kupio na apsolutnim vrhovima.
Zašto Bitcoin konstantno raste? Ljudi počinju da shvataju koliko je Bitcoin moćan, kao način uštede novca u svetu u kojem je ’novac’ poput dolara, eura i drugih nacionalnih valuta dizajniran da gubi vrednost.
Ovo čini Bitcoin odličnom opcijom za štednju novca na nekoliko godina ili više. Bitcoin je bolji od štednje novca u dolarima, akcijama, nekretninama, pa čak i u zlatu.
Zato pokušajte da zaboravite na trenutak na razumevanje blockchaina, digitalne valute, kriptografije, seed fraza, novčanika, rudarstva i svih ostalih nerazumljivih termina. Za sada, razgovarajmo o tome zašto ljudi kupuju Bitcoin: razlog je prostiji nego što vi mislite.
Zašto ljudi kupuju Bitcoin?
Naravno, svako ima svoj razlog za kupovinu Bitcoin-a. Jedan od razloga, koji verovatno često čujete, je taj što mu vrednost raste. Ljudi žele da se obogate. Uskoče kao spekulanti, krenu u vožnju i najverovatnije ih prodaju ubrzo nakon kupovine.
Međutim, čak i kada cena krene naglo prema gore i strmoglavo padne nazad, mnogi ljudi ostanu i nakon tog pada. Otkud mi to znamo? Broj aktivnih novčanika dnevno, koji je otprilike sličan broju korisnika Bitcoin-a, nastavlja da raste. Takođe, nakon svakog balona u istoriji Bitcoin-a, cena se nikada ne vraća na svoju cenu pre balona. Uvek ostane malo višlja. Bitcoin se penje, a svaka masovna spekulativna serija dovodi sve više i više ljudi.
Broj aktivnih Bitcoin novčanika neprekidno raste
„Aktivna adresa“ znači da je neko tog dana poslao Bitcoin transakciju. Donji grafikon je na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeCena Bitcoina se neprestano penje
Kroz istoriju Bitcoin-a možemo videti divlje kolebanje cena, ali nakon svakog balona, cena se ostaje višlja nego pre. Ovo je cena Bitcoin-a na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeTo pokazuje da se ljudi zadržavaju: potražnja za Bitcoin-om se povećava. Da je svaki masovni rast cena bio samo balon koji su iscenirali prevaranti koji žele brzo da se obogate, cena bi se vratila na nivo pre balona. To se dogodilo sa lalama, ali ne i sa Bitcoin-om.
I zašto se onda cena Bitcoin-a stalno povećava? Sve veći broj ljudi čuva Bitcoin dugoročno – oni razumeju šta Bitcoin može učiniti za njihovu štednju.
Zašto ljudi štede svoj novac u Bitcoin-u umesto na štednim računima, kućama, deonicama ili zlatu? Hajde da pogledajmo sve te metode štednje, i zatim da ih uporedimo sa Bitcoin-om.
Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
Tokom mnogo godina, to su bile pristojne opcije za štednju. Međutim, sistem koji podržava vrednost svega ovoga je u krizi.
Dolari, Euri, Dinari
Dolari i sve ostale „tradicionalne“ valute koje proizvode vlade, stvorene su da izgube vrednost kroz inflaciju. Banke i tradicionalni monetarni sistem uzrokuju inflaciju stalnim stvaranjem i distribucijom novog novca. Kada Američke Federalne Rezerve objave ciljanu stopu od 2% inflacije, to znači da žele da vaš novac svake godine izgubi 2% od svoje vrednosti. Čak i sa inflacijom od samo 2%, vaša štednja u dolarima izgubiće polovinu vrednosti tokom 40-godišnjeg radnog veka.
Izveštena inflacija se danas opasno povečava, uprkos rastućem „buretu sa barutom“ koji bi mogao da explodira i dovede do masivne hiperinflacije. Što je više valute u opticaju, to je više baruta u buretu.
Naše vlade su ekonomiju napunile valutama da bankarski sistem ne bi propao nakon finansijske krize koja se dogodila 2008. godine. Od tada je većina glavnih centralnih banaka postavila vrlo niske kamatne stope, što pojedincima i korporacijama omogućava dobijanje jeftinijih kredita. To znači da mnogi pojedinci i korporacije podižu ogromne kredite i koriste ih za kupovinu druge imovine poput deonica, umetničkih dela i nekretnina. Sve ovo pozajmljivanje znači da stvaramo tone novog novca i stavljamo ga u opticaj.
Računi za podsticaje (stimulus bills) COVID-19 za 2020. godinu unose trilione u sistem. Ovoliko stvaranje valuta na kraju dovodi do inflacije – velikog gubitka u vrednosti valute.
 Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. Izvor
Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. IzvorRačuni za podsticaje su bez presedana, toliko da je neko izmislio meme da opiše ovu situaciju.

Resurs koji vlade mogu da naprave u većem broju da bi platile svoje račune? Ne zvuči kao dobro mesto za štednju novca.
Kuće
Kuće su tokom prošlog veka bile pristojan način štednje novca. Međutim, pad cena nekretnina 2007. godine doveo je do toga da su mnogi vlasnici kuća izgubili svu ušteđevinu.
Danas su kuće gotovo nepristupačne za prosečnog čoveka. Jedan od načina da se ovo izmeri je koliko godišnjih zarada treba prosečnom čoveku da zaradi ekvivalent vrednosti prosečne kuće. Prema CityLab-u, publikaciji Bloomberg-a koja pokriva gradove, porodica može da priuštiti određenu kuću ako košta manje od 2,6 godišnjih prihoda domaćinstva te porodice.
Međutim, prema RZS (Republički zavod za statistiku) prosečan prihod porodičnog domaćinstva u Srbiji iznosi oko 570 EUR mesečno ili otprilike 7.000 EUR godišnje. Nažalost, samo najjeftinija područja van gradova imaju srednje cene kuća od oko 2,6 prosečnih godišnjih prihoda domaćinstva. U većim gradovima poput Beograda i Novog Sada srednja cena kuće je veća od 10 prosečnih godišnjih prihoda jednog domaćinstva.
Ako nekako možete sebi da priuštite kuću, ona bi mogla biti pristojna zaliha vrednosti. Dokle god ne doživimo još jedan krah i izvršitelji zaplene ovu imovinu mnogim vlasnicima kuća.
Akcije
Berza je u prošlosti takođe dobro poslovala. Međutim, sporo i stabilno povećanje tržišta događa se u dosadnom, predvidljivom svetu. Svakog dana vidimo sve manje toga. Nakon ubrzanja korona virusa, videli smo smo najbrži pad američke berze u istoriji od 25% – brži od Velike depresije.
Neki se odlučuju za ulaganje u obveznice i drugu finansijsku imovinu, ali ’prinosi’ za tu imovinu – procenat kamate zarađene na imovinu iz godine u godinu – stalno opada. Sve veći broj odredjenih imovina ima čak i negativne prinose, što znači da posedovanje te imovine košta! Ovo je veliki problem za sve koji se oslanjaju na penziju. Plus, s obzirom na to da su akcije denominovane u tradicionalnim valutama poput dolara i evra, inflacija pojede prinos koji investitor dobije.
Najgore od svega je to što ti isti ekonomski krahovi koji uzrokuju masovna otpuštanja i teško tržište rada takođe znače i nagli pad cena akcija. Čuvanje ušteđevine u akcijama može značiti i gubitak štednje i gubitak posla zbog recesije. Teška vremena mogu da vas prisile da svoje akcije prodate po vrlo malim cenama samo da biste platili svoje račune.
A to nije baš siguran način štednje novca.
Zlato
Vrednost zlata neprekidno se povećavala tokom 5000 godina, obično padajući onda kada berza obećava jače prinose.
Evidencija vrednosti zlata je solidna. Međutim, zlato nosi i druge rizike. Većina ljudi poseduje zlato na papiru. Oni fizički ne poseduju zlato, već ga njihova banka čuva za njih. Zbog toga je zlato veoma podložno konfiskaciji od strane vlade.
Zašto bi vlada konfiskovala nečije zlato, a kamoli u demokratskoj zemlji u „slobodnom svetu“? Ali to se dešavalo i ranije. 1933. godine Izvršnom Naredbom 6102, predsednik Roosevelt naredio je svim Amerikancima da prodaju svoje zlato vladi u zamenu za papirne dolare. Vlada je iskoristila pretnju zatvorom za prikupljanje zlata u fizičkom obliku. Znali su da se zlato više poštuje kao zaliha vrednosti širom sveta od papirnih dolara.
Ako posedujete svoje zlato na nekoj od aplikacija za trgovanje akcijama, možete se kladiti da će vam ga država oduzeti ako joj zatreba. Čak i ako posedujete fizičko zlato, onda ga izlažete mogućnosti krađe – od strane kriminalca ili vaše vlade.
Vaša uštedjevina nije bezbedna.
Rast cena svih gore navedenih sredstava zavisi od našeg trenutnog političkog i ekonomskog sistema koji se nastavlja kao i tokom proteklih 100 godina. Međutim, danas vidimo ogromne pukotine u ovom sistemu.
Sistem ne funkcioniše dobro za većinu ljudi.
Od 1971. plate većine američkih radnika nisu rasle. S druge strane, bogatstvo koje imaju najbogatiji u društvu nalazi se na nivoima koji nisu viđeni više od 80 godina. U međuvremenu, ljudi sve manje i manje veruju institucijama poput banaka i vlada.
 CBPP Nejednakost Bogatstva Tokom Vremena
CBPP Nejednakost Bogatstva Tokom VremenaŠirom sveta možemo videti dokaze o slamanju sistema kroz politički ekstremizam: izbor Trampa i drugih ekstremističkih desničarskih kandidata, Bregzit, pokret Occupy, popularizacija koncepta univerzalnog osnovnog dohotka, povratak pojma „socijalizam“ nazad u modu. Ljudi na svim delovima političkog i društvenog spektra osećaju problematična vremena i posežu za sve radikalnijim rešenjima.
Šta je bolje za štednju od dolara, kuća i akcija?
Pa kako ljudi mogu da štede novac u ovim teškim vremenima? Ili ne koriste tradicionalne valute, ili kupuju sredstva koja će zadržati vrednost u teškim vremenima.
Bitcoin ima najviše potencijala da zadrži vrednost kroz politička i ekonomska previranja od bilo koje druge imovine. Na tom putu će biti rupa na kojima će se rušiti ili pumpati, međutim, njegova svojstva čine ga takvim da će verovatno preživeti previranja kada druga imovina ne bude to mogla.
Šta Bitcoin čini drugačijim?
Bitcoini su retki.
Proces ‘rudarenja’ bitcoin-a, proizvodnju bitcoin-a čini veoma skupom, a Bitcoin protokol ograničava ukupan broj bitcoin-a na 21 milion novčića. To čini Bitcoin imunim na nagle poraste ponude. Ovo se veoma razlikuje od tradicionalnih valuta, koje vlade mogu da štampaju sve više kad god one to požele. Zapamtite, povećanje ponude vrši veliki pritisak na vrednost valute.
Bitcoini nemaju drugu ugovornu stranu.
Bitcoin se takođe razlikuje od imovine kao što su obveznice, akcije i kuće, jer mu nedostaje druga ugovorna strana. Druge ugovorne strane su drugi subjekti uključeni u vrednost sredstva, koji to sredstvo mogu obezvrediti ili vam ga uzeti. Ako imate hipoteku na svojoj kući, banka je druga ugovorna strana. Kada sledeći put dođe do velikog finansijskog kraha, banka vam može oduzeti kuću. Kompanije su kvazi-ugovorne strane akcijama i obveznicama, jer mogu da počnu da donose loše odluke koje utiču na njihovu cenu akcija ili na „neizvršenje“ duga (da ga ne vraćaju vama ili drugim poveriocima). Bitcoin nema ovih problema.
Bitcoin je pristupačan.
Svako sa 5 eura i mobilnim telefonom može da kupi i poseduje mali deo bitcoin-a. Važno je da znate da ne morate da kupite ceo bitcoin. Bitcoin-i su deljivi do 100-milionite jedinice, tako da možete da kupite Bitcoin u vrednosti od samo nekoliko eura. Neuporedivo lakše nego kupovina kuće, zlata ili akcija!
Bitcoin se ne može konfiskovati.
Banke drže većinu vaših eura, zlata i akcija za vas. Većina ljudi u razvijenom svetu veruje bankama, jer većina ljudi koji žive u današnje vreme nikada nije doživela konfiskaciju imovine ili ’šišanje’ od strane banaka ili vlada. Nažalost, postoji presedan za konfiskaciju imovine čak i u demokratskim zemljama sa snažnom vladavinom prava.
Kada vlada konfiskuje imovinu, ona obično ubedi javnost da će je menjati za imovinu jednake vrednosti. U SAD-u 1930-ih, vlada je davala dolare vlasnicima zlata. Vlada je znala da uvek može da odštampa još više dolara, ali da ne može da napravi više zlata. Na Kipru 2012. godine, jedna propala banka je svojim klijentima dala deonice banke da pokrije dolare klijenata koje je banka trebala da ima. I dolari i deonice su strmoglavo opali u odnosu na imovinu koja je uzeta od ovih ljudi.
Doći do bitcoin-a koji ljudi poseduju, biće mnogo teže jer se bitcoin-i mogu čuvati u novčaniku koji ne poseduje neka treća strana, a vi možete čak i da zapamtite privatne ključeve do vašeg bitcoin-a u glavi.
Bitcoin je za štednju.
Bitcoin se polako pokazuje kao najbolja opcija za dugoročnu štednju novca, posebno s obzirom na današnju ekonomsku klimu. Posedovanje čak i malog dela, je polisa osiguranja koja se isplati ako svet i dalje nastavi da ludi. Cena Bitcoin-a u dolarima može divlje da varira u roku od godinu ili dve, ali tokom 3+ godine skoro svi vide slične ili više cene od trenutka kada su ga kupili. U stvari, doslovno niko nije izgubio novac čuvajući Bitcoin duže od 3,5 godine – čak i ako je kupio BTC na apsolutnim vrhovima tržišta.

Imajte na umu da nakon ove tačke ti ljudi više nikada nisu videli rizik od gubitka. Cena se nikada nije smanjila niže od najviše cene u prethodnom ciklusu.
Po čemu se Bitcoin razlikuje od ostalih valuta?
Bitcoin funkcioniše tako dobro kao način štednje zbog svog neobičnog dizajna, koji ga čini drugačijim od bilo kog drugog oblika novca koji je postojao pre njega. Bitcoin je digitalna valuta, prvi i verovatno jedini primer valute koja ima ograničenu ponudu dok radi na otvorenom, decentralizovanom sistemu. Vlade strogo kontrolišu valute koje danas koristimo, poput dolara i eura, i proizvode ih za finansiranje ratova i dugova. Korisnici Bitcoin-a – poput vas – kontrolišu Bitcoin protokol.
Evo šta Bitcoin razlikuje od dolara, eura i drugih valuta:
Bitcoin je otvoren sistem.
Svako može da odluči da se pridruži Bitcoin mreži i primeni pravila softverskog protokola, što je dovelo do vrlo decentralizovanog sistema u kojem nijedan pojedinac ili entitet ne može da blokira transakciju, zamrzne sredstva ili da ukrade od druge osobe.Današnji savremeni bankarski sistem se uveliko razlikuje. Nekoliko banaka je dobilo poverenje da gotovo sve valute, akcije i druge vredne predmete čuvaju na “sigurnom” za svoje klijente. Da biste postali banka, potrebni su vam milioni dolara i neverovatne količine političkog uticaja. Da biste pokrenuli Bitcoin čvor i postali „svoja banka“, potrebno vam je nekoliko stotina dolara i jedno slobodno popodne.
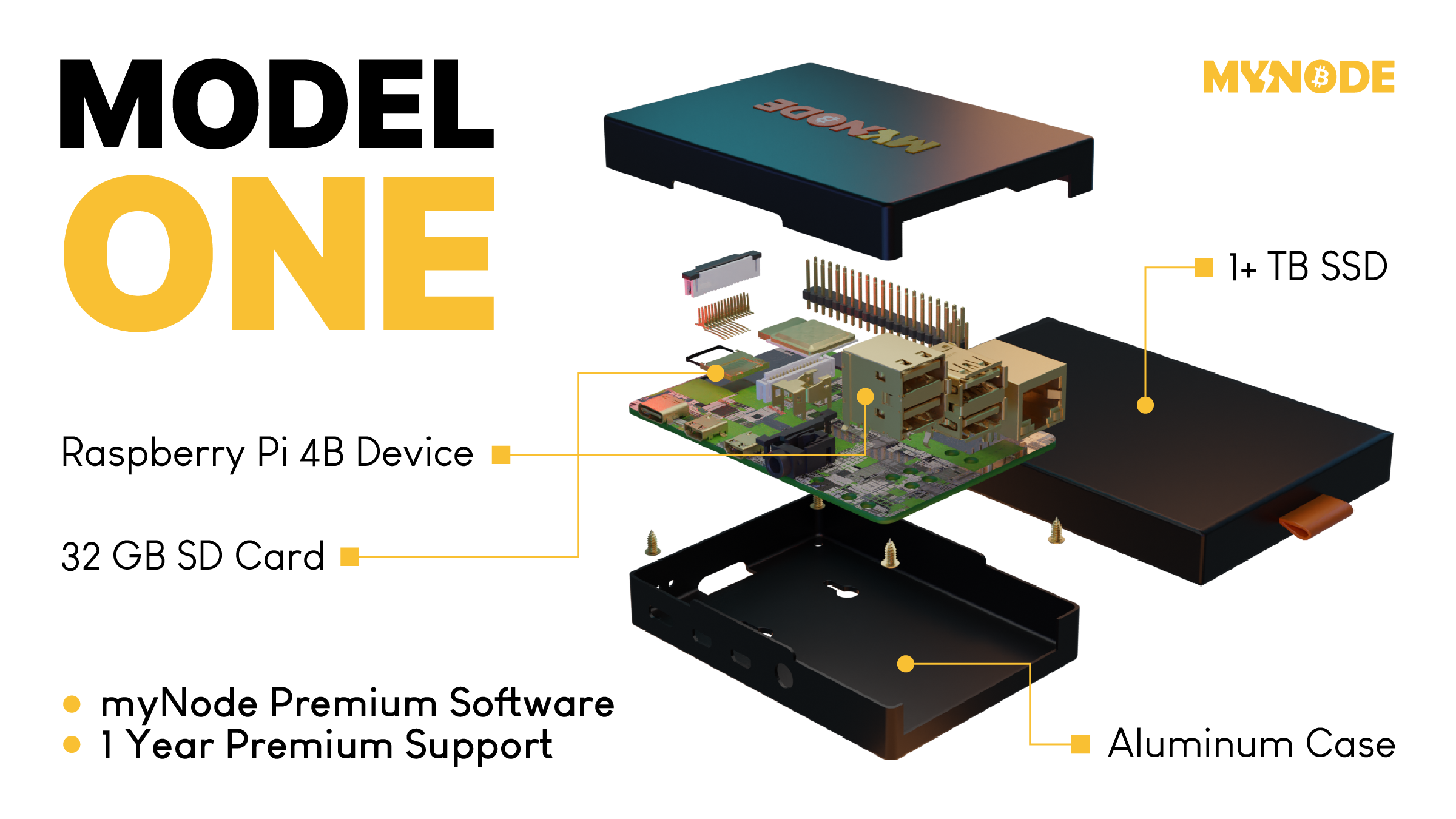 Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.
Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.Bitcoin ima ograničenu ponudu.
Softverski protokol otvorenog koda koji upravlja Bitcoin sistemom ograničava broj novih bitcoin-a koji se mogu stvoriti tokom vremena, sa ograničenjem od ukupno 21.000.000 bitcoin-a. S druge strane, valute koje danas koristimo imaju neograničenu ponudu. Istorija i sadašnje odluke centralnih banaka govore nam da će vlade uvek štampati sve više i više valuta, sve dok valuta ne bude bezvredna. Sve ovo štampanje uzrokuje inflaciju, što pravi štetu običnim radnim ljudima i štedišama.
Tradicionalne valute su dizajnirane tako da opadaju vremenom. Svaki put kada centralna banka kaže da cilja određenu stopu inflacije, oni ustvari kažu da žele da vaš novac svake godine izgubi određeni procenat svoje vrednosti.
Bitcoin-ova ograničena ponuda znači da je on tako dizajniran da raste vremenom kako se potražnja za njim povećava.

Bitcoin putuje oko sveta za nekoliko minuta.
Svako može da pošalje bitcoin-e za nekoliko minuta širom sveta, bez obzira na granice, banke i vlade. Potrebno je manje od minuta da se transakcija pojavi na novčaniku primaoca i oko 60 minuta da se transakcija u potpunosti „obračuna“, tako da primaoc može da bude siguran da su primljeni bitcoin-i sada njegovi (6 konfirmacija bloka). Slanje drugih valuta širom sveta traje danima ili čak mesecima ako se šalju milionski iznosi, a podrazumeva i visoke naknade.
Neke vlade i novinari tvrde da ova sloboda putovanja koju pruža Bitcoin pomaže kriminalcima i teroristima. Međutim, transakciju Bitcoin-a je lakše pratiti nego većinu transakcija u dolarima ili eurima.
Bitcoin se može čuvati na “USB-u”.
Dizajn Bitcoin-a je takav da vam treba samo da čuvate privatni ključ do svojih ‘bitcoin’ adresa (poput lozinke do bankovnih računa) da biste pristupili svojim bitcoin-ima odakle god poželite. Ovaj privatni ključ možete da sačuvate na disku ili na papiru u obliku 12 ili 24 reči na engleskom jeziku. Kao rezultat toga, možete da držite Bitcoin-e vredne milione dolara u svojoj šaci.
Sve ostale valute danas možete ili da strpate u svoj dušek ili da ih poverite banci na čuvanje. Za većinu ljudi koji žive u razvijenom svetu, i koji ne osporavaju autoritet i poverenje u banku, ovo deluje sasvim dobro. Međutim, oni kojima je potrebno da pobegnu od ugnjetavačke vlade ili koji naljute pogrešne ljude, ne mogu verovati bankama. Za njih je sposobnost da nose svoju ušteđevinu bez potrebe za ogromnim koferom neprocenjiva. Čak i ako ne živite na mestu poput ovog, cena Bitcoin-a se i dalje povećava kada ih neko kome oni trebaju kupi.
Kako Bitcoin spašava svet?
Bitcoin, kao ultimativni način štednje, je cakum pakum, ali da li on pomaže u poboljšanju sveta u celini?
Kao što ćete početi da shvatate, ulazeći sve dublje i u druge sadržaje na ovoj stranici, mnogi temeljni delovi našeg današnjeg monetarnog sistema i ekonomije su duboko slomljeni. Međutim, oni koji upravljaju imaju korist od ovakvih sistema, pa se on verovatno neće promeniti bez revolucije ili mirnog svrgavanja od strane naroda. Bitcoin predstavlja novi sistem, sa nekoliko glavnih prednosti:
- Bitcoin popravlja novac, koji je milenijumima služio kao važan alat za rast i poboljšanje društva.
- Bitcoin vraća zdrav razum pozajmljivanju, uklanjanjem apsurdnih situacija poput negativnih kamatnih stopa (gde zajmitelj plaća da bi se zadužio).
- Bitcoin pokreće ulaganja u obnovljive izvore energije i poboljšava energetsku efikasnost u mreži, služeći kao „krajnji kupac“ za sve vrste energije.
Kako mogu da saznam više o Bitcoin-u?
Ovaj članak vam je dao osnovno razumevanje zašto biste trebali razmišljati o Bitcoin-u. Ako želite da saznate više, preporučujem ove resurse:
- Film Bitcoin: Kraj Novca Kakav Poznajemo
- Još uvek je rano za Bitcoin
- Zasto baš Bitcoin?
- Šta je to Bitcoin?
- The Bitcoin Whitepaper ← objavljen 2008. godine, ovo je izložio dizajn za Bitcoin.
-
 @ 57d1a264:69f1fee1
2025-05-13 06:21:36
@ 57d1a264:69f1fee1
2025-05-13 06:21:36Steve Jobs sent me an email saying “Great idea, thank you."
Wait, what? What was the great idea?
new guy at NeXT In October of 1991, I was a new Systems Engineer at NeXT. NeXT, of course, was the company Steve Jobs had founded after leaving Apple in 1985, and which eventually merged back into Apple in 1996. I was one of three employees in Canada, and I think NeXT had about 400 people total.
NeXTMail Mail on the NeXT Computer was pretty amazing in 1991. Multimedia! Fonts! Attachments! Sounds! It’s hard to overstate how cool that was compared to the command line email everybody was used to. Every NeXT user got this email from Steve when they started up their computer.
That message included an attachment of what NeXT called Lip Service, the crazy idea that you could embed an audio file inside an email message. Crazy.
i have an idea
NeXT automatically set everybody up with a first-initial last-name address in the usual way, so I was shayman@next.com, and the big guy was sjobs@next.com.
A few colleagues had somehow acquired cooler email aliases - single letter things, or their first name, or a nickname or an easier to spell version, or whatever. Turns out NeXT had set up some sort of form where you could request an email alias that would redirect to whatever your real email address was.
I also noticed that even though there were seven or eight people at NeXT named Steve, nobody was using the email alias steve@next.com.
So late one Friday night, two weeks into the job, I figured, naively, what the heck, nobody else seems to want it, so I filled in the form asking for steve@next.com to be forwarded to me, shayman@next.com.
In the back of my mind was a vague idea that maybe somebody would have to approve this. But no, it all got set up automatically, and …
Continue reading at https://blog.hayman.net/2025/05/06/from-steve-jobs-great-idea.html
originally posted at https://stacker.news/items/978825
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 866e0139:6a9334e5
2025-05-19 21:39:26
@ 866e0139:6a9334e5
2025-05-19 21:39:26Autor: Ludwig F. Badenhagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wer einhundert Prozent seines Einkommens abgeben muss, ist sicher ein Sklave, oder? Aber ab wieviel Prozent Pflichtabgabe ist er denn kein Sklave mehr? Ab wann ist er frei und selbst-bestimmt?
Wer definieren möchte, was ein Sklave ist, sollte nicht bei Pflichtabgaben verweilen, denn die Fremdbestimmtheit geht viel weiter. Vielfach hat der gewöhnliche Mensch wenig Einfluss darauf, wie er und seine Familie misshandelt wird. Es wird verfügt, welche Bildung, welche Nahrung, welche Medikamente, welche Impfungen und welche Kriege er zu erdulden hat. Hierbei erkennt der gewöhnliche Mensch aber nur, wer ihm direkt etwas an-tut. So wie der Gefolterte bestenfalls seinen Folterer wahrnimmt, aber nicht den, in dessen Auftrag dieser handelt, so haben die vorbezeichnet Geschädigten mit Lehrern, „Experten“, Ärzten und Politikern zu tun. Ebenfalls ohne zu wissen, in wessen Auftrag diese Leute handeln. „Führungssysteme“ sind so konzipiert, dass für viele Menschen bereits kleinste wahrgenommene Vorteile genügen, um einem anderen Menschen Schlimmes anzutun.
Aber warum genau wird Menschen Schlimmes angetan? Die Gründe dafür sind stets dieselben. Der Täter hat ein Motiv und Motivlagen können vielfältig sein.
Wer also ein Motiv hat, ein Geschehen zu beeinflussen, motiviert andere zur Unterstützung. Wem es gelingt, bei anderen den Wunsch zu erwecken, das zu tun, was er möchte, ist wirklich mächtig. Und es sind die Mächtigen im Hintergrund, welche die Darsteller auf den Bühnen dieser Welt dazu nutzen, die Interessen der wirklich Mächtigen durchzusetzen. Insbesondere die letzten fünf Jahre haben eindrucksvoll gezeigt, wie willfährig Politiker, Ärzte, Experten und viele weitere ihre jeweiligen Aufträge gegen die Bevölkerung durchsetz(t)en.
Und so geschieht es auch beim aktuellen Krieg, der stellvertretend auf dem europäischen Kontinent ausgetragen wird. Parolen wie „nie wieder Krieg“ gehören der Vergangenheit an. Stattdessen ist nunmehr wieder der Krieg und nur der Krieg geeignet, um „Aggressionen des Gegners abzuwehren“ und um „uns zu verteidigen“.
Das hat mindestens drei gute Gründe:
- Mit einem Krieg können Sie einem anderen etwas wegnehmen, was er freiwillig nicht herausrückt. Auf diese Weise kommen Sie an dessen Land, seine Rohstoffe und sein Vermögen. Sie können ihn beherrschen und Ihren eigenen Einfluss ausbauen. Je mehr Ihnen gehört, um so besser ist das für Sie. Sie müssen sich weniger abstimmen und Widersacher werden einfach ausgeschaltet.
- Wenn etwas über einen langen Zeitraum aufgebaut wurde, ist es irgendwann auch einmal fertig. Um aber viel Geld verdienen und etwas nach eigenen Vorstellungen gestalten zu können, muss immer wieder etwas Neues erschaffen werden, und da stört das Alte nur. Demzufolge ist ein Krieg ein geeignetes Mittel, etwas zu zerstören. Und das Schöne ist, dass man von Beginn an viel Geld verdient. Denn man muss dem indoktrinierten Volk nur vormachen, dass der Krieg „unbedingt erforderlich“ sei, um das Volk dann selbst bereitwillig für diesen Krieg bezahlen und auch sonst engagiert mitwirken zu lassen. Dann kann in Rüstung und „Kriegstauglichkeit“ investiert werden. Deutschland soll dem Vernehmen nach bereits in einigen Jahren „kriegstauglich“ sein. Der Gegner wartet sicher gerne mit seinen Angriffen, bis es so weit ist.
- Und nicht zu vergessen ist, dass man die vielen gewöhnlichen Menschen loswird. Schon immer wurden Populationen „reguliert“. Das macht bei Tieren ebenfalls so, indem man sie je nach „Erfordernis“ tötet. Und bei kollabierenden Systemen zu Zeiten von Automatisierung und KI unter Berücksichtigung der Klimarettung wissen doch mittlerweile alle, dass es viel zu viele Menschen auf dem Planeten gibt. Wenn jemand durch medizinische Misshandlungen oder auch durch einen Krieg direkt stirbt, zahlt dies auf die Lösung des Problems ein. Aber auch ein „Sterben auf Raten“ ist von großem Vorteil, denn durch die „fachmännische Behandlung von Verletzten“ bis zu deren jeweiligen Tode lässt sich am Leid viel verdienen.
Sie erkennen, dass es sehr vorteilhaft ist, Kriege zu führen, oder? Und diese exemplarisch genannten drei Gründe könnten noch beliebig erweitert werden.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Das Einzige, was gegen Kriegsereignisse sprechen könnte, wäre, dass man selbst niemandem etwas wegnehmen möchte, was ihm gehört, und dass man seinen Mitmenschen nicht schaden, geschweige denn diese verletzen oder gar töten möchte.
In diesem Zusammenhang könnte man auch erkennen, dass die, die nach Krieg rufen, selbst nicht kämpfen. Auch deren Kinder nicht. Man könnte erkennen, dass man selbst nur benutzt wird, um die Interessen anderer durchzusetzen. Wie beim Brettspiel Schach hat jede Figur eine Funktion und keinem Spieler ist das Fortbestehen eines Bauern wichtig, wenn seine Entnahme dem Spielgewinn dient. Wer Krieg spielt, denkt sicher ähnlich.
Meine beiden Großväter waren Soldaten im zweiten Weltkrieg und erlebten die Grausamkeiten des Krieges und der Gefangenschaft so intensiv, dass sie mit uns Enkeln zu keiner Zeit hierüber sprechen konnten, da sie wohl wussten, dass uns allein ihre Erzählungen zutiefst traumatisiert hätten. Die Opas waren analog dem, was wir ihnen an Information abringen konnten, angeblich nur Sanitäter. Sanitäter, wie auch die meisten Großväter aus der Nachbarschaft. Wer aber jemals beobachten konnte, wie unbeholfen mein Opa ein Pflaster aufgebracht hat, der konnte sich denken, dass seine vermeintliche Tätigkeit als Sanitäter eine Notlüge war, um uns die Wahrheit nicht vermitteln zu müssen.
Mein Opa war mein bester Freund und mir treibt es unverändert die Tränen in die Augen, sein erlebtes Leid nachzuempfinden. Und trotz aller seelischen und körperlichen Verletzungen hat er nach seiner Rückkehr aus der Kriegshölle mit großem Erfolg daran gearbeitet, für seine Familie zu sorgen.
Manchmal ist es m. E. besser, die Dinge vom vorhersehbaren Ende aus zu betrachten, um zu entscheiden, welche Herausforderungen man annimmt und welche man besser ablehnt. Es brauchte fast 80 Jahre, um die Deutschen erneut dafür zu begeistern, Ihre Leben „für die gute Sache“ zu opfern. Was heutzutage aber anders ist als früher: Einerseits sind die Politiker dieser Tage sehr durchschaubar geworden. Aber in einem ähnlichen Verhältnis, wie die schauspielerischen Leistungen der Politiker abgenommen haben, hat die Volksverblödung zugenommen.
Denken Sie nicht nach. Denken Sie stattdessen vor. Und denken Sie selbst. Für sich, Ihre Lieben und alle anderen Menschen. Andernfalls wird die Geschichte, so wie sie von meinen Opas (und Omas) erlebt wurde, mit neuen Technologien und „zeitgemäßen Methoden“ wiederholt. Dies führt zweifelsfrei zu Not und Tod.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 2b998b04:86727e47
2025-05-19 21:18:46
@ 2b998b04:86727e47
2025-05-19 21:18:46After the pruning came clarity.\ And after the clarity came a quiet but relentless question:\ What now?
If I wasn’t going back to Web3, if I wasn’t going to pretend anymore — not in faith, not in finance — then I needed to start building again. But this time, with different materials. Different rhythms. A different spirit.
Starting Over on Solid Ground
I’d spent years exploring tokens, networks, and well-intentioned communities. But most of it, I see now, was sand. It moved with the tides. The incentives shifted. The values bent. And when the storms came — personal, financial, spiritual — much of what I’d been part of collapsed or exposed its shallowness.
So I returned to the beginning: What can’t be faked?
That’s where Bitcoin came in — not just as an asset, but as a foundation.\ It taught me cost. Time. Truth. It doesn’t market itself. It just is.\ A system that punishes shortcuts, rewards discipline, and invites peace.
And the more I leaned in, the more I realized:\ This isn’t just money. This is philosophy. This is soil.
Pruned to Plant Again
I used to be a buy-and-hold investor. I still carry those instincts. But in 2020–21, I discovered trading — and with it, a new kind of discipline. Not gambling. Not speculation. Stewardship under pressure. Real-time decision-making with skin in the game.
My grandfather, who passed in the late '90s, probably would’ve looked a little dimly on trading. He lived off his dividends. Stocks he held for decades. He wasn’t chasing. He was rooting. But he would’ve respected the discipline — the clarity — when done right.
He also saw things I didn’t. He once told me I wasn’t raised properly. It hurt at the time, but now I understand. He saw the drift — not just in me, but in the culture. He understood that frugality means nothing if it’s not paired with truth.
I think he would’ve respected what I’m doing now — even if he wouldn't have fully understand it.
What I’m Building Now
-
StartNation – A Bitcoin-aligned equity accelerator. Proof-based. No tokens. No hype.
-
Golden Gate Group Investments – Real estate with a vision to integrate BTC in payments and ownership. Still early. Still real.
-
Blue Planet Ventures – Equities trading with daily proof-of-work and sats-based performance tracking.
-
A garden – Yes, literal food. Soil and seed. Hypdropnics. Bitcoin taught me patience; gardening reinforces it.
I’m not building a brand. I’m building a life. And I’m doing it in public — not to be seen, but to help others see. That it’s possible to step off the hype rails and still thrive.
Bitcoin: The Turning Point
It wasn’t until last fall that Bitcoin truly became central for me.\ Not just part of a portfolio — the lens through which I see capital, time, and truth.
I don’t see it as speculative anymore. I see it as inevitable. In 20–30 years, I believe Bitcoin will be the de facto reserve currency — even if not in name. Those who hold it will steward wealth not because they played the game, but because they opted out of it early.
I’m stacking not to escape — but to prepare. Not to prove I'm right — but to live rightly.
Legacy Without a Platform
I don’t have children.\ But I do have nieces. Nephews. Brothers. Sisters. Cousins. In-Laws.
And I know they’re watching — even if they don’t say it.\ I want to show them that you can live with truth, walk by faith, work with your hands — and still thrive.
I’m not stacking for applause. I’m stacking for legacy.\ I’m building not just for the next quarter — but for the next generation.
And if someone, years from now, asks why I chose this path, I want to say:
Because it was real.\ Because it was proof.\ Because it was built to last.
⚡ If this series has encouraged or challenged you, zap a few sats/bitcoin. It keeps me building.
✍️ Catch up on the full series here:\ \ Part 1: The Drift -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-1%3A-the-drift\ Part 2: The Breaking Point -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work---part-2%3A-the-breaking-point\ Part 3: The Return -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-3%3A-the-return\ Part 4: Proof Of Work as Philosophy -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-4%3A-proof-of-work-as-philosophy\ Part 5: Building Again (what you are reading now...)
Written with help from ChatGPT (GPT-4), edited and posted by me.
-
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ 30611079:ecac89f8
2025-05-10 13:30:51
@ 30611079:ecac89f8
2025-05-10 13:30:51Um Shell Script simples para facilitar backups bip39 baseados nos números das palavras, coloque o script na mesma pasta que o arquivo contendo as palavras, passe o idioma no 1º argumento (Ex. english) e as palavras em sequência, a saída serão os números correspondentes as palavras passadas no idioma selecionado
```
!/bin/bash
Enter in correct diretory
if [ ${0%/} == $0 ]; then cd ${PWD} elif [ -e ${PWD}/${0%/} ]; then cd ${PWD}/${0%/} else cd ${0%/} fi
file="$1.txt"
index=0 numbers=() for word in "$@"; do while IFS= read -r linha; do if [[ "$linha" == "$word" ]]; then numbers+=($index) break fi ((index++)) done < "$file" index=0 done echo "${numbers[@]}" ```
Fiz para aprender um pouco de Shell Script, podem dizer se está bom e se dá para melhorar algo?
Também fiz outro que faz o processo reverso
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 4c96d763:80c3ee30
2025-05-19 20:56:26
@ 4c96d763:80c3ee30
2025-05-19 20:56:26Changes
William Casarin (19):
- dave: add screenshot to readme
- dave: fix image in readme
- columns: remove spamming info logs about writing to cache
- columns: never truncate notes you're replying to
- windows: don't show terminal window
- mention: show username instead of display_name
- chrome: switch from ALPHA to BETA
- ui: make post replies selectable
- dave: include anonymous user identifier in api call
- dave: add trial mode
- dave: fix sidebar click
- dave: nudge avatar when you click
- dave: hide media in dave note previews
- chrome: fix theme persistence
- ui: fix a bunch of missing hover pointers
- Release Notedeck Beta v0.4.0
- release: changelog
- timeline: show media on universe timeline
- clippy: fix lint related to iterator
kernelkind (28):
- add
trust_media_from_pk2method - add hashbrown
- introduce & use
JobPool - introduce JobsCache
- add blurhash dependency
- introduce blur
- note: remove unnecessary derive macros from
NoteAction - propagate
JobsCache ImagePulseTint->PulseAlpha- images: move fetch to fn
- add
TexturesCache - images: make
MediaCacheholdMediaCacheType - images: make promise payload optional to take easily
- post: unnest
- notedeck_ui: move carousel to
note/media.rs - note media: only show full screen when loaded
- note media: unnest full screen media
- pass
NoteActionby value instead of reference - propagate
Imagesto actionbar - add one shot error message
- make
WidgetimplProfilePicmutably - implement blurring
- don't show zap button if no wallet
- display name should wrap
- make styled button toggleable
- method to get current default zap amount
- add
CustomZapView - use
CustomZapView
pushed to notedeck:refs/heads/master
-
 @ 1817b617:715fb372
2025-05-19 20:39:28
@ 1817b617:715fb372
2025-05-19 20:39:28Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
🔗 Buy Flash USDT Now This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
✅ Perfect for: Simulating token inflows Wallet stress testing “Proof of funds” display Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
🧠 What Is Flash USDT? Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
Visible on wallet interfaces Time-limited (auto-disappears cleanly) Undetectable on block explorers after expiry It’s the smartest, safest way to simulate high-value transactions without real crypto.
🛠️ Flash USDT Software – Your Own USDT Flasher at Your Fingertips Want to control the flash? Run your own operations? Flash unlimited wallets?
🔗 Buy Flash USDT Software
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
Send custom USDT amounts Set custom expiry time (e.g., 30–360 days) Flash multiple wallets Choose between networks (Tron, ETH, BSC) You can simulate any amount, to any supported wallet, from your own system.
No third-party access. No blockchain fee. No trace left behind.
💥 Why Our Flash USDT & Software Stands Out Feature Flash USDT Flash USDT Software One-time flash send ✅ Yes Optional Full sender control ❌ No ✅ Yes TRC20 / ERC20 / BEP20 ✅ Yes ✅ Yes Custom duration/expiry Limited ✅ Yes Unlimited usage ❌ One-off ✅ Yes Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
🛒 Ready to Buy Flash USDT or the Software? Skip the wait. Skip the scammers. You’re one click away from real control.
👉 Buy Flash USDT 👉 Buy Flash USDT Software
📞 Support or live walkthrough?
💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531
🚫 Legal Notice These tools are intended for:
Educational purposes Demo environments Wallet and UI testing They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call: Need to flash USDT? Want full control? Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
🔗 Buy Now → Flash USDT 🔗 Buy Now → Flash USDT Software 💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
Buy Flash USDT Now\ This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
Perfect for:
- Simulating token inflows
- Wallet stress testing
- “Proof of funds” display
Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
What Is Flash USDT?
Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
- Visible on wallet interfaces
- Time-limited (auto-disappears cleanly)
- Undetectable on block explorers after expiry
It’s the smartest, safest way to simulate high-value transactions without real crypto.
Flash USDT Software – Your Own USDT Flasher at Your Fingertips
Want to control the flash?\ Run your own operations?\ Flash unlimited wallets?
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
- Send custom USDT amounts
- Set custom expiry time (e.g., 30–360 days)
- Flash multiple wallets
- Choose between networks (Tron, ETH, BSC)
You can simulate any amount, to any supported wallet, from your own system.
No third-party access.\ No blockchain fee.\ No trace left behind.
Why Our Flash USDT & Software Stands Out
Feature
Flash USDT
Flash USDT Software
One-time flash send
Yes
Optional
Full sender control
No
Yes
TRC20 / ERC20 / BEP20
Yes
Yes
Custom duration/expiry
Limited
Yes
Unlimited usage
One-off
Yes
Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
Ready to Buy Flash USDT or the Software?
Skip the wait. Skip the scammers.\ You’re one click away from real control.
Support or live walkthrough?
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
Legal Notice
These tools are intended for:
- Educational purposes
- Demo environments
- Wallet and UI testing
They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call:
Need to flash USDT? Want full control?\ Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
-
 @ d41bf82f:ed90d888
2025-05-19 20:31:54
@ d41bf82f:ed90d888
2025-05-19 20:31:54“ประเด็นแท้จริงคือเรื่องของการควบคุม—อินเทอร์เน็ตแพร่ขยายกว้างไกลเกินกว่าที่รัฐบาลใดจะครอบงำได้โดยง่าย ด้วยการสร้างเขตเศรษฐกิจระดับโลกที่ไร้รอยต่อ ไม่ขึ้นต่ออธิปไตย และอยู่นอกเหนือการควบคุม อินเทอร์เน็ตจึงตั้งคำถามต่อแนวคิดของรัฐชาติในตัวมันเอง” — JOHN PERRY BARLOW
บทนี้เริ่มต้นด้วยการวิพากษ์แนวคิด ทางด่วนข้อมูล ว่าเป็นคำอุปมาอุปมัยที่ยังยึดติดกับโลกยุคอุตสาหกรรม เพราะเศรษฐกิจยุคสารสนเทศไม่ใช่แค่โครงสร้างพื้นฐานสำหรับขนส่งข้อมูล แต่คือ จุดหมายปลายทาง ใหม่ในตัวเอง นั่นคือ ไซเบอร์สเปซ —ดินแดนที่ก้าวข้ามขอบเขตทางภูมิศาสตร์โดยสิ้นเชิง
ไซเบอร์สเปซคือพื้นที่ใหม่ของปฏิสัมพันธ์ทางสังคม เศรษฐกิจ และการเมือง ซึ่งไม่สามารถควบคุมโดยรัฐชาติแบบเดิมได้อีกต่อไป ผู้เขียนยกคำของ John Perry Barlow ที่เปรียบไซเบอร์สเปซเป็น “ดินแดนแห่งเสรีภาพ” ที่ไม่ยึดโยงกับสถานที่จริง และเปิดโอกาสให้ทุกคนแสดงความคิดเห็นได้อย่างไร้การควบคุม
การเปลี่ยนผ่านนี้ส่งผลกระทบรุนแรงต่อโครงสร้างของเศรษฐกิจแบบเดิม การเข้าถึงข้อมูลอย่างรวดเร็วแบบไร้ขอบเขตเปรียบเสมือนตัวทำละลายที่กัดกร่อนต้นทุนของสถาบันขนาดใหญ่ ทั้งภาครัฐและเอกชน ไมโครโพรเซสซิงจะเปลี่ยนรูปแบบขององค์กรและแนวคิดเรื่องสถานที่ในทางเศรษฐกิจอย่างสิ้นเชิง
ตลอดประวัติศาสตร์ เศรษฐกิจผูกติดกับพื้นที่ทางภูมิศาสตร์ การเดินทางเป็นเรื่องยากและจำกัด การค้าขายส่วนใหญ่เกิดในระดับท้องถิ่น ภาษา วัฒนธรรม และภูมิประเทศเป็นอุปสรรคทางการเมืองเสมอ จนถึงกับที่ผู้เขียนกล่าวว่า การเมืองทั้งหมดเป็นเรื่องท้องถิ่น
แต่เทคโนโลยีสมัยใหม่กำลังเปลี่ยนสมการนี้ การสื่อสารและขนส่งที่รวดเร็วทำให้ผู้มีความสามารถสามารถเลือกสถานที่อยู่อาศัยหรือทำงานได้อย่างเสรี ลดอำนาจต่อรองของรัฐบาลในพื้นที่นั้นลง เพราะคนสามารถ “หนี” ได้ง่ายขึ้น หากรัฐบาลกดขี่หรือรีดไถ
แม้อินเทอร์เน็ตยุคแรกจะดูธรรมดา เช่น ใช้อ่านบทความหรือสั่งซื้อสินค้า แต่ศักยภาพที่แท้จริงของเศรษฐกิจไซเบอร์นั้นยิ่งใหญ่มาก ผู้เขียนเสนอว่ามันจะพัฒนาเป็นสามขั้น: 1. ขั้นพื้นฐาน: อินเทอร์เน็ตเป็นเพียงช่องทางเพิ่มประสิทธิภาพธุรกิจแบบเดิม (เช่น เว็บขายสินค้าขายของออนไลน์ เช่น อเมซอน) 2. ขั้นพัฒนา: การเกิดขึ้นของเงินดิจิทัลที่เข้ารหัสและไม่สามารถติดตามได้ จะปลดปล่อยธุรกรรมจากการควบคุมและการจัดเก็บภาษีของรัฐ 3. ขั้นก้าวหน้า: ไซเบอร์สเปซจะมีระบบเศรษฐกิจ กฎหมาย และกลไกคุ้มครองของตัวเอง ปราศจากการควบคุมจากรัฐบาลใด ๆ
ในโลกใหม่นี้ Sovereign Individual หรือ “ปัจเจกผู้มีอธิปไตย” จะสามารถสร้างความมั่งคั่งและดำเนินกิจกรรมในไซเบอร์สเปซได้อย่างเป็นอิสระ โดยไม่ต้องอิงรัฐชาติ รัฐจึงจะถูกบีบให้ลดขนาดและเปลี่ยนบทบาทจากผู้ใช้อำนาจกลายเป็นผู้ให้บริการที่ต้องแข่งขันเพื่อความพึงพอใจของพลเมือง
สามารถไปติดตามเนื้อหาแบบ short vdo ที่สรุปประเด็นสำคัญจากแต่ละบท พร้อมกราฟิกและคำอธิบายกระชับ เข้าใจง่าย ได้ที่ TikTok ช่อง https://www.tiktok.com/@moneyment1971
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 30b99916:3cc6e3fe
2025-05-19 20:30:52
@ 30b99916:3cc6e3fe
2025-05-19 20:30:52bitcoin #security #vault #veracrypt #powershell
BTCwallet automates running hot and cold storage wallets for multiple Bitcoin wallet applications.

BTCwallet is included with VaultApi and supports Sparrow, Blockstream Green, and just added support for Wasabi wallets.
To launch a wallet application, the command BTCwallet start is executed.
After responding to prompts for launching and initializing the Vault (not shown), the following prompts are presented.
Now the Wasabi GUI application (a.k.a wassabee) is presented.

With the combination of VaultApi and BTCwallet one has a very secure self-hosted password manager along with a very secure way of protecting your Bitcoin wallet's data.
Care to follow me on my journey? If so, then check out the following links.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ a008def1:57a3564d
2025-04-30 17:52:11
@ a008def1:57a3564d
2025-04-30 17:52:11A Vision for #GitViaNostr
Git has long been the standard for version control in software development, but over time, we has lost its distributed nature. Originally, Git used open, permissionless email for collaboration, which worked well at scale. However, the rise of GitHub and its centralized pull request (PR) model has shifted the landscape.
Now, we have the opportunity to revive Git's permissionless and distributed nature through Nostr!
We’ve developed tools to facilitate Git collaboration via Nostr, but there are still significant friction that prevents widespread adoption. This article outlines a vision for how we can reduce those barriers and encourage more repositories to embrace this approach.
First, we’ll review our progress so far. Then, we’ll propose a guiding philosophy for our next steps. Finally, we’ll discuss a vision to tackle specific challenges, mainly relating to the role of the Git server and CI/CD.
I am the lead maintainer of ngit and gitworkshop.dev, and I’ve been fortunate to work full-time on this initiative for the past two years, thanks to an OpenSats grant.
How Far We’ve Come
The aim of #GitViaNostr is to liberate discussions around code collaboration from permissioned walled gardens. At the core of this collaboration is the process of proposing and applying changes. That's what we focused on first.
Since Nostr shares characteristics with email, and with NIP34, we’ve adopted similar primitives to those used in the patches-over-email workflow. This is because of their simplicity and that they don’t require contributors to host anything, which adds reliability and makes participation more accessible.
However, the fork-branch-PR-merge workflow is the only model many developers have known, and changing established workflows can be challenging. To address this, we developed a new workflow that balances familiarity, user experience, and alignment with the Nostr protocol: the branch-PR-merge model.
This model is implemented in ngit, which includes a Git plugin that allows users to engage without needing to learn new commands. Additionally, gitworkshop.dev offers a GitHub-like interface for interacting with PRs and issues. We encourage you to try them out using the quick start guide and share your feedback. You can also explore PRs and issues with gitplaza.
For those who prefer the patches-over-email workflow, you can still use that approach with Nostr through gitstr or the
ngit sendandngit listcommands, and explore patches with patch34.The tools are now available to support the core collaboration challenge, but we are still at the beginning of the adoption curve.
Before we dive into the challenges—such as why the Git server setup can be jarring and the possibilities surrounding CI/CD—let’s take a moment to reflect on how we should approach the challenges ahead of us.
Philosophy
Here are some foundational principles I shared a few years ago:
- Let Git be Git
- Let Nostr be Nostr
- Learn from the successes of others
I’d like to add one more:
- Embrace anarchy and resist monolithic development.
Micro Clients FTW
Nostr celebrates simplicity, and we should strive to maintain that. Monolithic developments often lead to unnecessary complexity. Projects like gitworkshop.dev, which aim to cover various aspects of the code collaboration experience, should not stifle innovation.
Just yesterday, the launch of following.space demonstrated how vibe-coded micro clients can make a significant impact. They can be valuable on their own, shape the ecosystem, and help push large and widely used clients to implement features and ideas.
The primitives in NIP34 are straightforward, and if there are any barriers preventing the vibe-coding of a #GitViaNostr app in an afternoon, we should work to eliminate them.
Micro clients should lead the way and explore new workflows, experiences, and models of thinking.
Take kanbanstr.com. It provides excellent project management and organization features that work seamlessly with NIP34 primitives.
From kanban to code snippets, from CI/CD runners to SatShoot—may a thousand flowers bloom, and a thousand more after them.
Friction and Challenges
The Git Server
In #GitViaNostr, maintainers' branches (e.g.,
master) are hosted on a Git server. Here’s why this approach is beneficial:- Follows the original Git vision and the "let Git be Git" philosophy.
- Super efficient, battle-tested, and compatible with all the ways people use Git (e.g., LFS, shallow cloning).
- Maintains compatibility with related systems without the need for plugins (e.g., for build and deployment).
- Only repository maintainers need write access.
In the original Git model, all users would need to add the Git server as a 'git remote.' However, with ngit, the Git server is hidden behind a Nostr remote, which enables:
- Hiding complexity from contributors and users, so that only maintainers need to know about the Git server component to start using #GitViaNostr.
- Maintainers can easily swap Git servers by updating their announcement event, allowing contributors/users using ngit to automatically switch to the new one.
Challenges with the Git Server
While the Git server model has its advantages, it also presents several challenges:
- Initial Setup: When creating a new repository, maintainers must select a Git server, which can be a jarring experience. Most options come with bloated social collaboration features tied to a centralized PR model, often difficult or impossible to disable.
-
Manual Configuration: New repositories require manual configuration, including adding new maintainers through a browser UI, which can be cumbersome and time-consuming.
-
User Onboarding: Many Git servers require email sign-up or KYC (Know Your Customer) processes, which can be a significant turn-off for new users exploring a decentralized and permissionless alternative to GitHub.
Once the initial setup is complete, the system works well if a reliable Git server is chosen. However, this is a significant "if," as we have become accustomed to the excellent uptime and reliability of GitHub. Even professionally run alternatives like Codeberg can experience downtime, which is frustrating when CI/CD and deployment processes are affected. This problem is exacerbated when self-hosting.
Currently, most repositories on Nostr rely on GitHub as the Git server. While maintainers can change servers without disrupting their contributors, this reliance on a centralized service is not the decentralized dream we aspire to achieve.
Vision for the Git Server
The goal is to transform the Git server from a single point of truth and failure into a component similar to a Nostr relay.
Functionality Already in ngit to Support This
-
State on Nostr: Store the state of branches and tags in a Nostr event, removing reliance on a single server. This validates that the data received has been signed by the maintainer, significantly reducing the trust requirement.
-
Proxy to Multiple Git Servers: Proxy requests to all servers listed in the announcement event, adding redundancy and eliminating the need for any one server to match GitHub's reliability.
Implementation Requirements
To achieve this vision, the Nostr Git server implementation should:
-
Implement the Git Smart HTTP Protocol without authentication (no SSH) and only accept pushes if the reference tip matches the latest state event.
-
Avoid Bloat: There should be no user authentication, no database, no web UI, and no unnecessary features.
-
Automatic Repository Management: Accept or reject new repositories automatically upon the first push based on the content of the repository announcement event referenced in the URL path and its author.
Just as there are many free, paid, and self-hosted relays, there will be a variety of free, zero-step signup options, as well as self-hosted and paid solutions.
Some servers may use a Web of Trust (WoT) to filter out spam, while others might impose bandwidth or repository size limits for free tiers or whitelist specific npubs.
Additionally, some implementations could bundle relay and blossom server functionalities to unify the provision of repository data into a single service. These would likely only accept content related to the stored repositories rather than general social nostr content.
The potential role of CI / CD via nostr DVMs could create the incentives for a market of highly reliable free at the point of use git servers.
This could make onboarding #GitViaNostr repositories as easy as entering a name and selecting from a multi-select list of Git server providers that announce via NIP89.
!(image)[https://image.nostr.build/badedc822995eb18b6d3c4bff0743b12b2e5ac018845ba498ce4aab0727caf6c.jpg]
Git Client in the Browser
Currently, many tasks are performed on a Git server web UI, such as:
- Browsing code, commits, branches, tags, etc.
- Creating and displaying permalinks to specific lines in commits.
- Merging PRs.
- Making small commits and PRs on-the-fly.
Just as nobody goes to the web UI of a relay (e.g., nos.lol) to interact with notes, nobody should need to go to a Git server to interact with repositories. We use the Nostr protocol to interact with Nostr relays, and we should use the Git protocol to interact with Git servers. This situation has evolved due to the centralization of Git servers. Instead of being restricted to the view and experience designed by the server operator, users should be able to choose the user experience that works best for them from a range of clients. To facilitate this, we need a library that lowers the barrier to entry for creating these experiences. This library should not require a full clone of every repository and should not depend on proprietary APIs. As a starting point, I propose wrapping the WASM-compiled gitlib2 library for the web and creating useful functions, such as showing a file, which utilizes clever flags to minimize bandwidth usage (e.g., shallow clone, noblob, etc.).
This approach would not only enhance clients like gitworkshop.dev but also bring forth a vision where Git servers simply run the Git protocol, making vibe coding Git experiences even better.
song
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 created song with a complementary vision that has shaped how I see the role of the git server. Its a self-hosted, nostr-permissioned git server with a relay baked in. Its currently a WIP and there are some compatability with ngit that we need to work out.
We collaborated on the nostr-permissioning approach now reflected in nip34.
I'm really excited to see how this space evolves.
CI/CD
Most projects require CI/CD, and while this is often bundled with Git hosting solutions, it is currently not smoothly integrated into #GitViaNostr yet. There are many loosely coupled options, such as Jenkins, Travis, CircleCI, etc., that could be integrated with Nostr.
However, the more exciting prospect is to use DVMs (Data Vending Machines).
DVMs for CI/CD
Nostr Data Vending Machines (DVMs) can provide a marketplace of CI/CD task runners with Cashu for micro payments.
There are various trust levels in CI/CD tasks:
- Tasks with no secrets eg. tests.
- Tasks using updatable secrets eg. API keys.
- Unverifiable builds and steps that sign with Android, Nostr, or PGP keys.
DVMs allow tasks to be kicked off with specific providers using a Cashu token as payment.
It might be suitable for some high-compute and easily verifiable tasks to be run by the cheapest available providers. Medium trust tasks could be run by providers with a good reputation, while high trust tasks could be run on self-hosted runners.
Job requests, status, and results all get published to Nostr for display in Git-focused Nostr clients.
Jobs could be triggered manually, or self-hosted runners could be configured to watch a Nostr repository and kick off jobs using their own runners without payment.
But I'm most excited about the prospect of Watcher Agents.
CI/CD Watcher Agents
AI agents empowered with a NIP60 Cashu wallet can run tasks based on activity, such as a push to master or a new PR, using the most suitable available DVM runner that meets the user's criteria. To keep them running, anyone could top up their NIP60 Cashu wallet; otherwise, the watcher turns off when the funds run out. It could be users, maintainers, or anyone interested in helping the project who could top up the Watcher Agent's balance.
As aluded to earlier, part of building a reputation as a CI/CD provider could involve running reliable hosting (Git server, relay, and blossom server) for all FOSS Nostr Git repositories.
This provides a sustainable revenue model for hosting providers and creates incentives for many free-at-the-point-of-use hosting providers. This, in turn, would allow one-click Nostr repository creation workflows, instantly hosted by many different providers.
Progress to Date
nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr and nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 have been working on a runner that uses GitHub Actions YAML syntax (using act) for the dvm-cicd-runner and takes Cashu payment. You can see example runs on GitWorkshop. It currently takes testnuts, doesn't give any change, and the schema will likely change.
Note: The actions tab on GitWorkshop is currently available on all repositories if you turn on experimental mode (under settings in the user menu).
It's a work in progress, and we expect the format and schema to evolve.
Easy Web App Deployment
For those disapointed not to find a 'Nostr' button to import a git repository to Vercel menu: take heart, they made it easy. vercel.com_import_options.png there is a vercel cli that can be easily called in CI / CD jobs to kick of deployments. Not all managed solutions for web app deployment (eg. netlify) make it that easy.
Many More Opportunities
Large Patches via Blossom
I would be remiss not to mention the large patch problem. Some patches are too big to fit into Nostr events. Blossom is perfect for this, as it allows these larger patches to be included in a blossom file and referenced in a new patch kind.
Enhancing the #GitViaNostr Experience
Beyond the large patch issue, there are numerous opportunities to enhance the #GitViaNostr ecosystem. We can focus on improving browsing, discovery, social and notifications. Receiving notifications on daily driver Nostr apps is one of the killer features of Nostr. However, we must ensure that Git-related notifications are easily reviewable, so we don’t miss any critical updates.
We need to develop tools that cater to our curiosity—tools that enable us to discover and follow projects, engage in discussions that pique our interest, and stay informed about developments relevant to our work.
Additionally, we should not overlook the importance of robust search capabilities and tools that facilitate migrations.
Concluding Thoughts
The design space is vast. Its an exciting time to be working on freedom tech. I encourage everyone to contribute their ideas and creativity and get vibe-coding!
I welcome your honest feedback on this vision and any suggestions you might have. Your insights are invaluable as we collaborate to shape the future of #GitViaNostr. Onward.
Contributions
To conclude, I want to acknowledge some the individuals who have made recent code contributions related to #GitViaNostr:
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 (gitstr, song, patch34), nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks (gitplaza)
nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume (ngit contributions, git-remote-blossom),nostr:npub16p8v7varqwjes5hak6q7mz6pygqm4pwc6gve4mrned3xs8tz42gq7kfhdw (SatShoot, Flotilla-Budabit), nostr:npub1ehhfg09mr8z34wz85ek46a6rww4f7c7jsujxhdvmpqnl5hnrwsqq2szjqv (Flotilla-Budabit, Nostr Git Extension), nostr:npub1ahaz04ya9tehace3uy39hdhdryfvdkve9qdndkqp3tvehs6h8s5slq45hy (gnostr and experiments), and others.
nostr:npub1uplxcy63up7gx7cladkrvfqh834n7ylyp46l3e8t660l7peec8rsd2sfek (git-remote-nostr)
Project Management nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t (kanbanstr) Code Snippets nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 (nodebin.io) nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac (snipsnip.dev)
CI / CD nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr
and for their nostr:npub1c03rad0r6q833vh57kyd3ndu2jry30nkr0wepqfpsm05vq7he25slryrnw nostr:npub1qqqqqq2stely3ynsgm5mh2nj3v0nk5gjyl3zqrzh34hxhvx806usxmln03 and nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z for their testing, feedback, ideas and encouragement.
Thank you for your support and collaboration! Let me know if I've missed you.
-
 @ cae03c48:2a7d6671
2025-05-19 18:29:07
@ cae03c48:2a7d6671
2025-05-19 18:29:07Bitcoin Magazine

Bitcoin Records Highest Weekly Close Above $106KBitcoin has officially recorded its highest-ever weekly candle close, finishing the week at $106,516. The milestone was achieved on Sunday evening, marking a notable moment in Bitcoin’s ongoing price history and underscoring growing institutional and retail interest.
JUST IN: $107,000 #Bitcoin
 pic.twitter.com/Xt1JLm0Ke6
pic.twitter.com/Xt1JLm0Ke6— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
This weekly close sets a new benchmark for BTC’s price performance and positions the asset in a historically rare range. As of Monday, Bitcoin is trading at $102,924, reflecting typical price movement following a new high as markets adjust to key levels.
Historical data helps illustrate the significance of this moment. According to an analysis shared by on-chain researcher Dan, Bitcoin has closed above $106,439 only once—this week—accounting for just 0.02% of its entire trading history. Closures above $100,000 have occurred in only 40 days total. Even levels like $75,000 and $50,000 remain relatively uncommon in Bitcoin’s lifespan, appearing on just 181 and 586 days, respectively.
— Dan (@robustus) May 19, 2025
This data highlights how current prices place Bitcoin in a historically narrow range of time — a reflection of the long-term upward trend of the asset over the past decade. For market participants, this type of price action often serves as an indicator of continued momentum and interest in Bitcoin’s role as a digital store of value.
The broader Bitcoin ecosystem continues to show strength, with on-chain metrics reflecting growing user engagement and long-term holder confidence. Notably, activity on the Bitcoin network remains elevated, with transaction volumes and address growth signaling continued adoption. Analysts are closely watching inflows into Bitcoin-focused ETFs and the behavior of long-term holders, both of which are key indicators of sustained interest and belief in Bitcoin’s long-term value.
bitcoin just had its all-time high weekly candle close at $106,500 pic.twitter.com/FuqqptHEmA
— Alex Thorn (@intangiblecoins) May 19, 2025
Some traders are watching the $100,000 level closely as a key psychological and technical zone. Bitcoin’s ability to maintain this level following a record weekly close could be important in setting the tone for the weeks ahead.
While near-term price movements are always part of market dynamics, the latest close represents a milestone in Bitcoin’s history. It reaffirms the asset’s resilience and ongoing relevance in the global financial landscape.
This post Bitcoin Records Highest Weekly Close Above $106K first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:49
@ 6be5cc06:5259daf0
2025-04-28 01:05:49Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31
@ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31Whatever
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ cae03c48:2a7d6671
2025-05-19 17:48:53
@ cae03c48:2a7d6671
2025-05-19 17:48:53Bitcoin Magazine

JPMorgan To Allow Clients To Buy Bitcoin, Jamie Dimon SaysToday, Chairman and CEO of JPMorgan Chase Jamie Dimon reiterated his personal disapproval of Bitcoin during the bank’s annual Investor Day event. Despite the bank’s decision to provide clients with access to Bitcoin investments, Dimon emphasized his personal disapproval of Bitcoin.
“I am not a fan” of Bitcoin, stated Dimon.
JPMorgan is going to allow clients to buy Bitcoin, but the bank won’t custody it, according to Bloomberg. Dimon made clear that while JPMorgan will provide clients access to Bitcoin investments, the bank will not hold or manage the digital asset directly.
JUST IN: JPMorgan CEO Jamie Dimon said they will allow clients to buy #Bitcoin
 pic.twitter.com/wO0djlYGUM
pic.twitter.com/wO0djlYGUM— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
In a January 2025 interview with CBS News, Dimon expressed continued skepticism toward Bitcoin. “Bitcoin itself has no intrinsic value. It’s used heavily by sex traffickers, money launderers, ransomware,” said Dimon.
Although he acknowledged, “We are going to have some kind of digital currency at some point,” he added, “I just don’t feel great about bitcoin. I applaud your ability to wanna buy or sell it. Just like I think you have the right to smoke, but I don’t think you should smoke.”
These comments from Dimon contrast with recent optimism from JPMorgan analysts regarding Bitcoin’s market prospects. JPMorgan analysts reported that Bitcoin is likely to continue gaining ground at gold’s expense in the second half of the year, driven by rising corporate demand and growing support from U.S. states.
JUST IN: JPMorgan says #Bitcoin likely to have more upside than gold in the second half of 2025
 pic.twitter.com/YPrHivch9O
pic.twitter.com/YPrHivch9O— Bitcoin Magazine (@BitcoinMagazine) May 15, 2025
“Between mid-February and mid-April gold was rising at the expense of bitcoin, while of the past three weeks we have been observing the opposite, i.e. bitcoin rising at the expense of gold,” said JPMorgan analysts. “In all, we expect the YTD zero sum game between gold and bitcoin to extend to the remainder of the year, but are biased towards crypto-specific catalysts creating more upside for bitcoin over gold into the second half of the year.”
Since April 22, gold has dropped nearly 8%, while Bitcoin has surged 18%, reflecting a notable shift in investor sentiment. Capital has been moving out of gold ETFs and into Bitcoin. Several U.S. states are also warming to Bitcoin—New Hampshire now permits up to 5% of its reserves in Bitcoin, while Arizona is launching a Bitcoin reserve and has pledged not to raise taxes this year. At the corporate level, companies like Strategy and Metaplanet are expanding their Bitcoin holdings.
“As the list grows, with other U.S. states potentially considering adding bitcoin to their strategic reserves, this could turn out to be a more sustained positive catalyst for bitcoin,” said the analysts.
This post JPMorgan To Allow Clients To Buy Bitcoin, Jamie Dimon Says first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ a8d1560d:3fec7a08
2025-05-19 17:28:05
@ a8d1560d:3fec7a08
2025-05-19 17:28:05NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "mediawiki" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-mediawiki-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }MediaWiki Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "mediawiki"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ cae03c48:2a7d6671
2025-05-19 17:15:58
@ cae03c48:2a7d6671
2025-05-19 17:15:58Bitcoin Magazine

Nebraska’s New Mining Rules: Infrastructure Safeguard or Soft Ban in Disguise?Nebraska lawmakers have just passed Legislative Bill 526 (LB526), and while not explicitly anti-Bitcoin, its effects may be anything but neutral. With a unanimous 49-0 vote, the Legislature sent the bill to Governor Jim Pillen’s desk, where it’s expected to be signed into law. Supporters call it a commonsense infrastructure bill. Bitcoin miners call it a slow-motion exodus in the making.
On paper, LB526 is about large energy users. But in practice, it singles out Bitcoin mining facilities with one megawatt (MW) or greater loads and layers on operational constraints that look more like punishment than policy.
Cost Shifting, Public Shaming, and Curtailment
At the heart of LB526 is a mandate: miners must shoulder the costs of any infrastructure upgrades needed to support their demand. Utilities are empowered to demand direct payments or letters of credit after conducting a “load study.” And while the law pays lip service to “fairness” and non-discrimination, it’s clear who the target is. Bitcoin miners are the only industry named.
Further, mining operators must notify utilities in advance, submit to their interconnection requirements, and, critically, accept interruptible service. That means that when the grid gets tight, it’s miners who go dark first. Voluntary demand response, the hallmark of Bitcoin mining’s grid-friendly posture? Replaced with mandated curtailment and utility discretion.
And the kicker: public disclosure of energy consumption. Utilities must publish annual energy usage for each mining operation. No such requirement exists for other data-heavy sectors — not for cloud computing, not for AI clusters, not for Amazon data centers. Just Bitcoin. It’s not just surveillance, it’s signaling.
The Tax That Wasn’t, and the Costs That Remain
To its credit, the Legislature dropped an earlier provision that would’ve added a 2.5¢/kWh tax on mining. This punitive levy would’ve tacked 50% onto typical industrial rates. That tax would have been an open declaration of hostility. Removing it was necessary. But not sufficient.
Because what remains in LB526 is a less visible, but no less potent deterrent: uncertainty. Miners already operate on razor-thin margins and seek jurisdictions with predictable power costs and clear rules. Instead, Nebraska is offering infrastructure tolls, discretionary curtailment, and regulatory spotlighting.
The Market Responds: Warning Shots from Miners
Industry leaders didn’t stay silent. Marathon Digital Holdings, one of the largest publicly traded mining firms, testified that it had invested nearly $200 million in Nebraska and paid over $6.5 million in taxes, and warned that if LB526 passed, further expansion would likely be scrapped.
Their message was clear: Nebraska had been a pro-mining, pro-growth jurisdiction. But LB526 sends a signal that miners aren’t welcome, or at best, are second-class citizens in the energy economy. As one executive put it, “If the same rules don’t apply to other energy-intensive industries, this isn’t about infrastructure, it’s about discrimination.”
Others warned that mandatory curtailment replaces cooperative grid services with coercion. Bitcoin miners can, and do, offer real-time load shedding that stabilizes grids during peak demand. But that value proposition only works when there’s a market signal. LB526 turns it into a liability.
Politics, Power, and Public Utilities
Senator Mike Jacobson, the bill’s sponsor, insisted LB526 is agnostic toward Bitcoin. “This is about electricity usage,” he said. But that’s hard to square with a bill that surgically targets one user class.
Jacobson pointed to Kearney, where half the city’s power goes to a single mining facility. But rather than view that as an opportunity, a dispatchable industrial customer willing to scale up or down based on grid needs, the Legislature opted for risk aversion and central planning.
And in Nebraska’s public power model, that matters. With every utility publicly owned, the regulatory posture of the state isn’t advisory, it’s existential. There is no retail competition. If Nebraska’s power authorities begin treating Bitcoin miners like unreliable freeloaders rather than willing partners, miners have no recourse. Just the exit.
For now, LB526 awaits only the governor’s signature. Given that LB526 was introduced at the behest of the governor, it is likely to be signed. Once enacted, it will take effect October 1, 2025. Miners have until then to decide: adapt, relocate, or fold.
States like Texas, Wyoming, and North Dakota have gone the opposite direction, offering tax clarity, grid integration, and legal protection. Nebraska, once on that shortlist, may find itself dropping off the radar.
Bitcoin mining doesn’t need handouts. But it does need equal footing. LB526 imposes costs, limits flexibility, and broadcasts suspicion. If the goal was to balance innovation with infrastructure, the execution leaves much to be desired.
Because when one industry is burdened while others are exempted, when voluntary partnerships are replaced with mandates, and when operational data is made public for no clear reason, it’s not hard to see why miners view LB526 not as regulation, but as retaliation.
This is a guest post by Colin Crossman. Opinions expressed are entirely their own and do not necessarily reflect those of BTC, Inc. or Bitcoin Magazine_._
This post Nebraska’s New Mining Rules: Infrastructure Safeguard or Soft Ban in Disguise? first appeared on Bitcoin Magazine and is written by Colin Crossman.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ 3f68dede:779bb81d
2025-05-19 17:14:15
@ 3f68dede:779bb81d
2025-05-19 17:14:15 -
 @ e691f4df:1099ad65
2025-04-24 18:56:12
@ e691f4df:1099ad65
2025-04-24 18:56:12Viewing Bitcoin Through the Light of Awakening
Ankh & Ohm Capital’s Overview of the Psycho-Spiritual Nature of Bitcoin
Glossary:
I. Preface: The Logos of Our Logo
II. An Oracular Introduction
III. Alchemizing Greed
IV. Layers of Fractalized Thought
V. Permissionless Individuation
VI. Dispelling Paradox Through Resonance
VII. Ego Deflation
VIII. The Coin of Great Price
Preface: The Logos of Our Logo
Before we offer our lens on Bitcoin, it’s important to illuminate the meaning behind Ankh & Ohm’s name and symbol. These elements are not ornamental—they are foundational, expressing the cosmological principles that guide our work.
Our mission is to bridge the eternal with the practical. As a Bitcoin-focused family office and consulting firm, we understand capital not as an end, but as a tool—one that, when properly aligned, becomes a vehicle for divine order. We see Bitcoin not simply as a technological innovation but as an emanation of the Divine Logos—a harmonic expression of truth, transparency, and incorruptible structure. Both the beginning and the end, the Alpha and Omega.
The Ankh (☥), an ancient symbol of eternal life, is a key to the integration of opposites. It unites spirit and matter, force and form, continuity and change. It reminds us that capital, like Life, must not only be generative, but regenerative; sacred. Money must serve Life, not siphon from it.
The Ohm (Ω) holds a dual meaning. In physics, it denotes a unit of electrical resistance—the formative tension that gives energy coherence. In the Vedic tradition, Om (ॐ) is the primordial vibration—the sound from which all existence unfolds. Together, these symbols affirm a timeless truth: resistance and resonance are both sacred instruments of the Creator.
Ankh & Ohm, then, represents our striving for union, for harmony —between the flow of life and intentional structure, between incalculable abundance and measured restraint, between the lightbulb’s electrical impulse and its light-emitting filament. We stand at the threshold where intention becomes action, and where capital is not extracted, but cultivated in rhythm with the cosmos.
We exist to shepherd this transformation, as guides of this threshold —helping families, founders, and institutions align with a deeper order, where capital serves not as the prize, but as a pathway to collective Presence, Purpose, Peace and Prosperity.
An Oracular Introduction
Bitcoin is commonly understood as the first truly decentralized and secure form of digital money—a breakthrough in monetary sovereignty. But this view, while technically correct, is incomplete and spiritually shallow. Bitcoin is more than a tool for economic disruption. Bitcoin represents a mythic threshold: a symbol of the psycho-spiritual shift that many ancient traditions have long foretold.
For millennia, sages and seers have spoken of a coming Golden Age. In the Vedic Yuga cycles, in Plato’s Great Year, in the Eagle and Condor prophecies of the Americas—there exists a common thread: that humanity will emerge from darkness into a time of harmony, cooperation, and clarity. That the veil of illusion (maya, materiality) will thin, and reality will once again become transparent to the transcendent. In such an age, systems based on scarcity, deception, and centralization fall away. A new cosmology takes root—one grounded in balance, coherence, and sacred reciprocity.
But we must ask—how does such a shift happen? How do we cross from the age of scarcity, fear, and domination into one of coherence, abundance, and freedom?
One possible answer lies in the alchemy of incentive.
Bitcoin operates not just on the rules of computer science or Austrian economics, but on something far more old and subtle: the logic of transformation. It transmutes greed—a base instinct rooted in scarcity—into cooperation, transparency, and incorruptibility.
In this light, Bitcoin becomes more than code—it becomes a psychoactive protocol, one that rewires human behavior by aligning individual gain with collective integrity. It is not simply a new form of money. It is a new myth of value. A new operating system for human consciousness.
Bitcoin does not moralize. It harmonizes. It transforms the instinct for self-preservation into a pathway for planetary coherence.
Alchemizing Greed
At the heart of Bitcoin lies the ancient alchemical principle of transmutation: that which is base may be refined into gold.
Greed, long condemned as a vice, is not inherently evil. It is a distorted longing. A warped echo of the drive to preserve life. But in systems built on scarcity and deception, this longing calcifies into hoarding, corruption, and decay.
Bitcoin introduces a new game. A game with memory. A game that makes deception inefficient and truth profitable. It does not demand virtue—it encodes consequence. Its design does not suppress greed; it reprograms it.
In traditional models, game theory often illustrates the fragility of trust. The Prisoner’s Dilemma reveals how self-interest can sabotage collective well-being. But Bitcoin inverts this. It creates an environment where self-interest and integrity converge—where the most rational action is also the most truthful.
Its ledger, immutable and transparent, exposes manipulation for what it is: energetically wasteful and economically self-defeating. Dishonesty burns energy and yields nothing. The network punishes incoherence, not by decree, but by natural law.
This is the spiritual elegance of Bitcoin: it does not suppress greed—it transmutes it. It channels the drive for personal gain into the architecture of collective order. Miners compete not to dominate, but to validate. Nodes collaborate not through trust, but through mathematical proof.
This is not austerity. It is alchemy.
Greed, under Bitcoin, is refined. Tempered. Re-forged into a generative force—no longer parasitic, but harmonic.
Layers of Fractalized Thought Fragments
All living systems are layered. So is the cosmos. So is the human being. So is a musical scale.
At its foundation lies the timechain—the pulsing, incorruptible record of truth. Like the heart, it beats steadily. Every block, like a pulse, affirms its life through continuity. The difficulty adjustment—Bitcoin’s internal calibration—functions like heart rate variability, adapting to pressure while preserving coherence.
Above this base layer is the Lightning Network—a second layer facilitating rapid, efficient transactions. It is the nervous system: transmitting energy, reducing latency, enabling real-time interaction across a distributed whole.
Beyond that, emerging tools like Fedimint and Cashu function like the capillaries—bringing vitality to the extremities, to those underserved by legacy systems. They empower the unbanked, the overlooked, the forgotten. Privacy and dignity in the palms of those the old system refused to see.
And then there is NOSTR—the decentralized protocol for communication and creation. It is the throat chakra, the vocal cords of the “freedom-tech” body. It reclaims speech from the algorithmic overlords, making expression sovereign once more. It is also the reproductive system, as it enables the propagation of novel ideas and protocols in fertile, uncensorable soil.
Each layer plays its part. Not in hierarchy, but in harmony. In holarchy. Bitcoin and other open source protocols grow not through exogenous command, but through endogenous coherence. Like cells in an organism. Like a song.
Imagine the cell as a piece of glass from a shattered holographic plate —by which its perspectival, moving image can be restructured from the single shard. DNA isn’t only a logical script of base pairs, but an evolving progressive song. Its lyrics imbued with wise reflections on relationships. The nucleus sings, the cell responds—not by command, but by memory. Life is not imposed; it is expressed. A reflection of a hidden pattern.
Bitcoin chants this. Each node, a living cell, holds the full timechain—Truth distributed, incorruptible. Remove one, and the whole remains. This isn’t redundancy. It’s a revelation on the power of protection in Truth.
Consensus is communion. Verification becomes a sacred rite—Truth made audible through math.
Not just the signal; the song. A web of self-expression woven from Truth.
No center, yet every point alive with the whole. Like Indra’s Net, each reflects all. This is more than currency and information exchange. It is memory; a self-remembering Mind, unfolding through consensus and code. A Mind reflecting the Truth of reality at the speed of thought.
Heuristics are mental shortcuts—efficient, imperfect, alive. Like cells, they must adapt or decay. To become unbiased is to have self-balancing heuristics which carry feedback loops within them: they listen to the environment, mutate when needed, and survive by resonance with reality. Mutation is not error, but evolution. Its rules are simple, but their expression is dynamic.
What persists is not rigidity, but pattern.
To think clearly is not necessarily to be certain, but to dissolve doubt by listening, adjusting, and evolving thought itself.
To understand Bitcoin is simply to listen—patiently, clearly, as one would to a familiar rhythm returning.
Permissionless Individuation
Bitcoin is a path. One that no one can walk for you.
Said differently, it is not a passive act. It cannot be spoon-fed. Like a spiritual path, it demands initiation, effort, and the willingness to question inherited beliefs.
Because Bitcoin is permissionless, no one can be forced to adopt it. One must choose to engage it—compelled by need, interest, or intuition. Each person who embarks undergoes their own version of the hero’s journey.
Carl Jung called this process Individuation—the reconciliation of fragmented psychic elements into a coherent, mature Self. Bitcoin mirrors this: it invites individuals to confront the unconscious assumptions of the fiat paradigm, and to re-integrate their relationship to time, value, and agency.
In Western traditions—alchemy, Christianity, Kabbalah—the individual is sacred, and salvation is personal. In Eastern systems—Daoism, Buddhism, the Vedas—the self is ultimately dissolved into the cosmic whole. Bitcoin, in a paradoxical way, echoes both: it empowers the individual, while aligning them with a holistic, transcendent order.
To truly see Bitcoin is to allow something false to die. A belief. A habit. A self-concept.
In that death—a space opens for deeper connection with the Divine itSelf.
In that dissolution, something luminous is reborn.
After the passing, Truth becomes resurrected.
Dispelling Paradox Through Resonance
There is a subtle paradox encoded into the hero’s journey: each starts in solidarity, yet the awakening affects the collective.
No one can be forced into understanding Bitcoin. Like a spiritual truth, it must be seen. And yet, once seen, it becomes nearly impossible to unsee—and easier for others to glimpse. The pattern catches.
This phenomenon mirrors the concept of morphic resonance, as proposed and empirically tested by biologist Rupert Sheldrake. Once a critical mass of individuals begins to embody a new behavior or awareness, it becomes easier—instinctive—for others to follow suit. Like the proverbial hundredth monkey who begins to wash the fruit in the sea water, and suddenly, monkeys across islands begin doing the same—without ever meeting.
When enough individuals embody a pattern, it ripples outward. Not through propaganda, but through field effect and wave propagation. It becomes accessible, instinctive, familiar—even across great distance.
Bitcoin spreads in this way. Not through centralized broadcast, but through subtle resonance. Each new node, each individual who integrates the protocol into their life, strengthens the signal for others. The protocol doesn’t shout; it hums, oscillates and vibrates——persistently, coherently, patiently.
One awakens. Another follows. The current builds. What was fringe becomes familiar. What was radical becomes obvious.
This is the sacred geometry of spiritual awakening. One awakens, another follows, and soon the fluidic current is strong enough to carry the rest. One becomes two, two become many, and eventually the many become One again. This tessellation reverberates through the human aura, not as ideology, but as perceivable pattern recognition.
Bitcoin’s most powerful marketing tool is truth. Its most compelling evangelist is reality. Its most unstoppable force is resonance.
Therefore, Bitcoin is not just financial infrastructure—it is psychic scaffolding. It is part of the subtle architecture through which new patterns of coherence ripple across the collective field.
The training wheels from which humanity learns to embody Peace and Prosperity.
Ego Deflation
The process of awakening is not linear, and its beginning is rarely gentle—it usually begins with disruption, with ego inflation and destruction.
To individuate is to shape a center; to recognize peripherals and create boundaries—to say, “I am.” But without integration, the ego tilts—collapsing into void or inflating into noise. Fiat reflects this pathology: scarcity hoarded, abundance simulated. Stagnation becomes disguised as safety, and inflation masquerades as growth.
In other words, to become whole, the ego must first rise—claiming agency, autonomy, and identity. However, when left unbalanced, it inflates, or implodes. It forgets its context. It begins to consume rather than connect. And so the process must reverse: what inflates must deflate.
In the fiat paradigm, this inflation is literal. More is printed, and ethos is diluted. Savings decay. Meaning erodes. Value is abstracted. The economy becomes bloated with inaudible noise. And like the psyche that refuses to confront its own shadow, it begins to collapse under the weight of its own illusions.
But under Bitcoin, time is honored. Value is preserved. Energy is not abstracted but grounded.
Bitcoin is inherently deflationary—in both economic and spiritual senses. With a fixed supply, it reveals what is truly scarce. Not money, not status—but the finite number of heartbeats we each carry.
To see Bitcoin is to feel that limit in one’s soul. To hold Bitcoin is to feel Time’s weight again. To sense the importance of Bitcoin is to feel the value of preserved, potential energy. It is to confront the reality that what matters cannot be printed, inflated, or faked. In this way, Bitcoin gently confronts the ego—not through punishment, but through clarity.
Deflation, rightly understood, is not collapse—it is refinement. It strips away illusion, bloat, and excess. It restores the clarity of essence.
Spiritually, this is liberation.
The Coin of Great Price
There is an ancient parable told by a wise man:
“The kingdom of heaven is like a merchant seeking fine pearls, who, upon finding one of great price, sold all he had and bought it.”
Bitcoin is such a pearl.
But the ledger is more than a chest full of treasure. It is a key to the heart of things.
It is not just software—it is sacrament.
A symbol of what cannot be corrupted. A mirror of divine order etched into code. A map back to the sacred center.
It reflects what endures. It encodes what cannot be falsified. It remembers what we forgot: that Truth, when aligned with form, becomes Light once again.
Its design is not arbitrary. It speaks the language of life itself—
The elliptic orbits of the planets mirrored in its cryptography,
The logarithmic spiral of the nautilus shell discloses its adoption rate,
The interconnectivity of mycelium in soil reflect the network of nodes in cyberspace,
A webbed breadth of neurons across synaptic space fires with each new confirmed transaction.
It is geometry in devotion. Stillness in motion.
It is the Logos clothed in protocol.
What this key unlocks is beyond external riches. It is the eternal gold within us.
Clarity. Sovereignty. The unshakeable knowing that what is real cannot be taken. That what is sacred was never for sale.
Bitcoin is not the destination.
It is the Path.
And we—when we are willing to see it—are the Temple it leads back to.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ cae03c48:2a7d6671
2025-05-19 17:14:11
@ cae03c48:2a7d6671
2025-05-19 17:14:11Bitcoin Magazine

Fold Unveils Bitcoin Gift Card, Pioneering Bitcoin in U.S. Retail Gift Card MarketFold, a leading Bitcoin financial services company, recently announced the launch of its Bitcoin Gift Card, marking the first step in integrating Bitcoin into the $300 billion U.S. retail gift card market. This innovative product enables consumers to purchase and gift bitcoin through familiar retail channels, is available now at Fold’s website and is expected to expand to major retailers nationwide throughout the year.
The Fold Bitcoin Gift Card allows users to acquire bitcoin for personal savings or as a gift, redeemable via the Fold app. “Once you buy that gift card, you can give it to someone or use it yourself. You open the Fold app, and your bitcoin appears,” said Will Reeves, Chairman and CEO of Fold, in an interview with Bitcoin Magazine. Available initially at the Fold website, the product will soon reach physical and online retail shelves, bringing Bitcoin to everyday shopping experiences.
This launch positions Fold as a trailblazer in making Bitcoin accessible through gift cards, the most popular gift in America.
“We’re now talking about Bitcoin gift cards on sale on the racks of the largest retailers in the country. You can pick up Bitcoin at the checkout line, buy it for yourself, or share it as a gift,” Reeves told Bitcoin Magazine.
The gift card, a white Bitcoin “B,” adorned by vibrant orange, taps into the retail market’s demand for alternative assets, following the success of Costco’s $200 million monthly gold sales.

Fold’s partnership with Totus, a gift card issuance provider, enables distribution through over 150,000 points of sale nationwide.
“In our announcement, we reference one of our partners who has direct distribution into all primary retailers in the country,” Reeves said. While specific retailer names will be revealed later, Fold plans to expand throughout 2025, ensuring Bitcoin’s presence in stores like grocery chains and gas stations. “Throughout the rest of this year, we’ll announce distribution partners, including some of the largest retailers in the US,” Reeves added.
The Bitcoin Gift Card targets millions of Americans curious about Bitcoin but hesitant to navigate apps or exchanges.
“This gift card gives us distribution directly to millions of Americans who may not be buying Bitcoin because they haven’t downloaded a new app, don’t have a brokerage account, or haven’t seen the ETF,” Reeves explained. By leveraging trusted retail channels, Fold is opening a new avenue for Bitcoin adoption.
Since 2019, Fold has empowered over 600,000 users with Bitcoin-based financial tools, holding over 1,485 Bitcoin in its treasury.
“I think there’s a real chance by the end of 2025 that Bitcoin becomes the most popular gift in America because of this card,” Reeves predicted.
This post Fold Unveils Bitcoin Gift Card, Pioneering Bitcoin in U.S. Retail Gift Card Market first appeared on Bitcoin Magazine and is written by Juan Galt.
-
 @ 3f68dede:779bb81d
2025-05-19 17:06:26
@ 3f68dede:779bb81d
2025-05-19 17:06:26 -
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 3f68dede:779bb81d
2025-05-19 17:04:13
@ 3f68dede:779bb81d
2025-05-19 17:04:13testing schedule
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 3f68dede:779bb81d
2025-05-19 17:02:54
@ 3f68dede:779bb81d
2025-05-19 17:02:54testing schedule
-
 @ 3f68dede:779bb81d
2025-05-19 17:02:33
@ 3f68dede:779bb81d
2025-05-19 17:02:33testing
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:57
@ 3f68dede:779bb81d
2025-05-19 17:01:57testing schedule
-
 @ 005bc4de:ef11e1a2
2025-05-19 17:01:54
@ 005bc4de:ef11e1a2
2025-05-19 17:01:54Keys and Religion
Mixing
Normally, I'm not a fan mixing and comparing bitcoinesque things and religion. It's too banal and trite, too easy: the religion of Bitcoin, the allusion of Satoshi the savior, the "Book of Satoshi," even the "Genesis" block. But, today, I'll break my own rule.
Yesterday, I heard a Christian pastor speak of the "keys of the kingdom." My feeling is that, were you to ask the average Christian, "What is the key, or keys, to the kingdom?", and perhaps I'm wrong on this, but I think they'd answer, "Prayer." I've heard it many times, "Prayer is the key to the kingdom." It's an easy mantra to remember. And, prayer is important for a Christian, no question about it. However, Biblically, the phrase "keys of the kingdom" refers to something else.
As the pastor pointed out yesterday, Biblically there are two keys: the binding key and the loosing key. This refers to Matthew 16:19 where Jesus says:
I will give you the keys of the kingdom of heaven; whatever you bind on earth will be bound in heaven, and whatever you loose on earth will be loosed in heaven. Matthew 16:19 (NIV)
For context, back up a few verses. This statement above was made in a conversation between Jesus and his disciple Simon Peter.
15 Jesus asked, “But what about you?” he asked. “Who do you say I am?” 16 Simon Peter answered, “You are the Messiah, the Son of the living God.” 17 Jesus replied, “Blessed are you, Simon son of Jonah, for this was not revealed to you by flesh and blood, but by my Father in heaven. 18 And I tell you that you are Peter, and on this rock I will build my church, and the gates of Hades will not overcome it.
Although brief, this is a deep and rich exchange. Traditionally, this has been viewed as the moment that Christ instituted the Christian church, the passing of power and authority to the early church itself. There has been confusion over it too, particularly the "...on this rock I will build my church..." part of it. Jesus was referring to Simon Peter's statement of faith (...for this was not revealed to you by flesh and blood...) with the "this" being what Peter had just said, "You are the Messiah, the Son of the living God." The church would be built upon the rock of faith in Jesus as the Messiah.
The early Christian church thus established, Jesus instituted what's come to be called the "office of the keys." That is, Jesus grants authority to his "appointees" in the church to carry out his authority. In more practical terms, this is referring to those who have been called into church service, normally priests, to forgive or not forgive sins. When a priest or pastor forgives, or not, it is not that he is doing it by his own right or power. That priest is, after all, yet another sinful man as well. Instead, the priest forgives by Christ's authority which was handed down by Jesus himself in those words to Peter.
To use an analogy, suppose a general had to make a decision about foot soldiers on the front line, waiting there in the trenches. Due to some time constraint, a decision for action was needed imminently. However, suppose the general lacked some bit of information that could only be obtained at the front. So, the general wrote up a communique to the lieutenant stationed at the front saying, "You assess the situation, and you make the call, charge or pull back. I'll support your decision." A courier ran to the front, relayed the message to the lieutenant, and the lieutenant assessed and made the decision. Ultimately, even thought the lieutenant made the decision, the authority behind the decision lay with the general who had transferred his authority to the lieutenant.
This authority or office of the keys is mirrored in John 20:22-23, when the resurrected Jesus appears to his disciples and says, "If you forgive anyone’s sins, their sins are forgiven; if you do not forgive them, they are not forgiven.”
Going just one step further, recall there are two keys involved, binding and loosing, and there are two places involved, earth and heaven. Usually, priests and pastors are "in the business" of forgiving. Penitence or confession, when real, is forgiven. The priest has the authority to forgive, or "loose" the sinner from his wrongdoings here on earth. And, that forgiveness applies to heaven as well, the sin is atoned and reconciled with God.
But, what about when the person is unrepentant, unbothered by what is Biblically sinful, refuses to change his ways, and rather chooses to continue in sinful ways? The "binding" key says that the priest or appointed church leader can hold that person accountable, can bind that person to the sin and separation from God. Normally, we hear of "excommunication" from the church which is formally stating that a person is outside of the church body. The binding keys still bind, both on earth as being outside of the church and in heaven as being separated from God.
And bitcoin?
That's a lot of religion, and heavy religion at that. The question is, what does this have to do with bitcoin?
Keys.
Namely, this is about public and private keys. Loosing and binding keys. A bit more religion, then I'll get back to bitcoin.
Yesterday, the pastor spoke briefly about binding and loosing keys, and this where my thoughts about keys somehow morphed over into bitcoin. For some reason, I pictured Herod's Temple. There had been Solomon's temple, which was destroyed, and then there was Herod's which was known for its beauty and was the one during Jesus's time. But, let's recall the background on this...
The book of Exodus, and others in the Old Testament, outline in detail God's plan for the tabernacle (a traveling tent) and for the temple in Jerusalem.
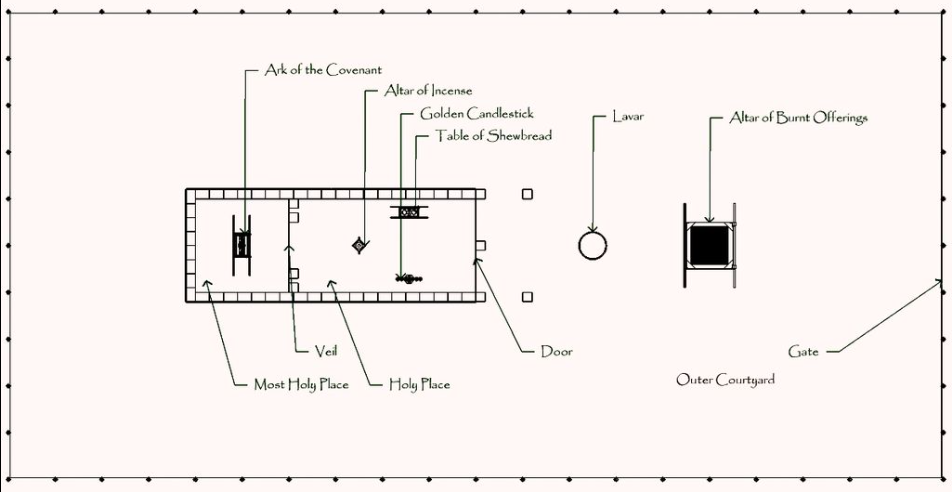
The tabernacle, overhead diagram. Image source: https://en.wikipedia.org/wiki/Tabernacle
You might recall the "history" lesson in Raiders of the Lost Ark. With the tabernacle and temple, one of the purposes was to house the ark of the covenant. Remember that the ark was the golden box that the Israelites carried around containing Moses's stone tablets with the Ten Commandments, some manna, and Aaron's staff. It held great power, God's power, and God literally met and spoke with the Levite priests hovering over the cherubim's wings.

The ark of the covenant. Image source: https://en.wikipedia.org/wiki/Ark_of_the_Covenant
In the tabernacle and temple, the "Holy of Holies" was a room, separated by a heavy curtain. It was off limits to all because it was, well, holy of holies. A heavy curtain divided the Holy of Holies, or the "Most Holy Place", from the less-holy, "Holy Place."
Once a year, on the Day of Atonement, one person, the chief priest, was allowed to walk into the Holy of Holies. He would sprinkle the blood of a sacrificed animal onto the ark. This was done for the forgiveness of the people's sins. Although this was pre-Jesus's words, this was using the loosing keys and was loosing sin.
This was serious business and was taken seriously. For instance, the priests Nadab and Abihu improperly performed their sacrificial duties, they messed up the procedure, and were consumed by fire. Priesthood was a dangerous occupation, one slip up and you were scorched.
 The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_Temple
The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_TempleBack to keys...
Yesterday, for some reason when I heard about binding and loosing keys, I imagined the chief priest standing in front of the curtain. I imagined him taking a deep breath, collecting his thoughts, getting ready to go in. It had to be intimidating.
As he stood there, in my mind, he and everyone else was shut out. The Most Holy Place was bound and locked. Walking in meant getting scorched (again, the end of Raiders of the Lost Ark). Yet, that priest had the loosing key. He had, first, permission as chief priest to enter on the Day of Atonement, secondly, he had the sacrificial blood to loose sins. Although the binding key had locked the Holy of Holies and thus bound the sins of the people, the loosing key was about to loose their sins.
Cryptographic keys
And back to bitcoin...
Bitcoin, and cryptography in general, operate on public and private keys. Any flavor of "cryptocurrency", or even Nostr, has public and private keys. In a way, these are binding and loosing keys.
Say you have 1.0 BTC (that's 100,000,000 sats 😀). That BTC exists as a UTXO which can be seen by anyone viewing your public address. In this way, your bitcoin public key is your binding key...that UTXO, that bitcoin, is bound to your public key...it is locked in place behind that heavy curtain. It will be there forever, unless there is an intervention...
You also have your private key, your loosing key. You can apply your private key to loose that UTXO, that bitcoin, and to send it along to wherever.
This is like law and gospel: sin is binding, however Jesus frees it. A bitcoin UTXO is bound until a private key looses it.
Nostr offers a somewhat similar illustration. You have an npub publicly and and nsec secretly or privately. If you were to write a note, your private nsec is needed as a loosing key to free that message, to broadcast it to the world. Once broadcast, it can be seen by all, however it is still inextricably bound or tied to your public key (your npub). Your npub is your binding key and your message is bound to it.
Summed
I'm not sure this binding and loosing keys in religion, and public and private keys in cryptography is the best comparison in the world. It's probably a terrible comparison. But, this is what came to my mind yesterday.
And, so, the mixing of religion and bitcoin is now officially over.
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:19
@ 3f68dede:779bb81d
2025-05-19 17:01:19testing schedule
-
 @ 3f68dede:779bb81d
2025-05-19 17:00:18
@ 3f68dede:779bb81d
2025-05-19 17:00:18testing schedule
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3f68dede:779bb81d
2025-05-19 16:59:50
@ 3f68dede:779bb81d
2025-05-19 16:59:50testing schedule
-
 @ cb4352cd:a16422d7
2025-05-19 16:40:21
@ cb4352cd:a16422d7
2025-05-19 16:40:21The countdown is nearly over. On May 30, 2025, the Beyond Banking Conference by WeFi will go live — gathering thinkers, builders, and innovators from across DeFi, Web3, AI, and FinTech. Whether you're a founder, developer, investor, or just exploring the space, this is where ideas meet momentum.
Four Tracks, One Shared Vision
At the heart of the conference are four thematic tracks, each offering a lens into where finance is heading:
-
DeFAI — Where AI meets DeFi. From autonomous lending to smart liquidity, this track dives into machine-powered finance.
-
GameFi — Not just play-to-earn. Think social-first gaming, fast sessions, on-chain assets, and frictionless onboarding.
-
AI + Web3 — Explore a future shaped by trustless AI agents, generative content, and decentralized governance systems.
-
FinTech AI — See how financial services are evolving with AI: from compliance and identity to intelligent asset management.
Who You’ll Hear From
Among the voices leading the conversation:
-
Vít Jedlička, President of Liberland, on digital sovereignty and blockchain-powered governance.
-
Tigran Hakhunts, HTX Ambassador, on how exchanges are navigating and accelerating decentralized adoption.
And that’s just the beginning — expect DeFi founders, Web3 infrastructure teams, AI policy researchers, and the next generation of financial technologists.
What’s Beyond the Keynotes
This isn’t a day of passive watching. You’ll see:
-
Live product demos, including WeFi’s own onchain banking tools.
-
Multilingual Q&A sessions where your questions drive the conversation.
-
Real-time translation in 8 languages to keep everything accessible.
-
And yes — a Ferrari giveaway. Registered attendees automatically enter a lottery to win big.
One Day. A Global Experience.
No flights, no paywalls, no exclusivity. This is finance without borders. Whether you’re tuning in from São Paulo or Seoul, you’ll be part of a shared global moment.
To join, just connect through the official bot.
The future of finance isn’t happening behind closed doors. It’s unfolding in the open — and you’re invited. See you May 30.
-
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ cae03c48:2a7d6671
2025-05-19 16:06:29
@ cae03c48:2a7d6671
2025-05-19 16:06:29Bitcoin Magazine

Abraaj Restaurants Becomes First Bitcoin Treasury Company in the Middle EastToday it was announced that Al Abraaj Restaurants Group B.S.C. has become the first publicly traded company in the region to adopt Bitcoin as a treasury reserve asset. The Bahrain-based hospitality firm announced today it has acquired 5 Bitcoin for its balance sheet, with plans to significantly increase its allocation over time.
JUST IN:
 Al Abraaj Restaurants Group becomes first publicly traded company in middle east to purchase #Bitcoin as a treasury reserve asset
Al Abraaj Restaurants Group becomes first publicly traded company in middle east to purchase #Bitcoin as a treasury reserve asset  pic.twitter.com/QUH5FMGRoy
pic.twitter.com/QUH5FMGRoy— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
“Our initiative towards becoming a Bitcoin Treasury Company reflects our forward-thinking approach and dedication to maximizing shareholder value,” said Abdulla Isa, Chairman of the Bitcoin Treasury Committee at Al Abraaj. “We believe that Bitcoin will play a pivotal role in the future of finance, and we are excited to be at the forefront of this transformation in the Kingdom of Bahrain. 10X is a proven leader in advising and bringing capital to listed Bitcoin Treasury Companies, and we welcome their partnership in helping us build the MicroStrategy of the Middle East.”
The decision makes Abraaj not only the first in Bahrain, but also in the GCC and wider Middle East, to publicly hold Bitcoin on its balance sheet. The investment is a direct response to growing institutional interest in Bitcoin and comes amid what appears to be a regional shift toward digital assets.
Abraaj’s strategic partner in the transition is 10X Capital, a New York-based investment firm with a strong track record in digital asset treasury management. 10X previously advised companies like Nakamoto on its $710 million Bitcoin-focused financing round.
“I’d like to congratulate Abdalla Isa and the team at Al Abraaj for adopting Bitcoin at the corporate treasury level, finally enabling anyone in the GCC with a brokerage account to gain Bitcoin exposure,” said Hans Thomas, CEO of 10X Capital. “Bahrain continues to be a leader in the Middle East in Bitcoin adoption, backed by a forward-thinking regulatory framework.”
Thomas added, “The GCC, with a combined GDP of $2.2 trillion and over $6 trillion in sovereign wealth funds, has until now lacked a publicly listed Bitcoin treasury company like Strategy, Tesla, or Metaplanet. That changes today with ABRAAJ’s historic Bitcoin purchase.”
Abraaj said it will continue to work under the regulatory oversight of the Central Bank of Bahrain (CBB) and has pledged full compliance with all digital asset transaction laws. The company will adopt robust custody, risk management, and governance protocols for its Bitcoin holdings.
Disclosure: Nakamoto is in partnership with Bitcoin Magazine’s parent company BTC Inc to build the first global network of Bitcoin treasury companies, where BTC Inc provides certain marketing services to Nakamoto. More information on this can be found here.
This post Abraaj Restaurants Becomes First Bitcoin Treasury Company in the Middle East first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 9994730e:7df84c81
2025-05-19 15:59:38
@ 9994730e:7df84c81
2025-05-19 15:59:38❤️🔥✨
-
 @ 6e0ea5d6:0327f353
2025-04-19 15:09:18
@ 6e0ea5d6:0327f353
2025-04-19 15:09:18🩸
The world won’t stop and wait for you to recover.Do your duty regardless of how you feel. That’s the only guarantee you’ll end the day alright.
You’ve heard it before: “The worst workout is the one you didn’t do.” Sometimes you don’t feel like going to the gym. You start bargaining with laziness: “I didn’t sleep well… maybe I should skip today.” But then you go anyway, committing only to the bare minimum your energy allows. And once you start, your body outperforms your mind’s assumptions—it turns out to be one of the best workouts you’ve had in a long time. The feeling of following through, of winning a battle you were losing, gives you the confidence to own the rest of your day. You finally feel good.
And that wouldn’t have happened if you stayed home waiting to feel better. Guilt would’ve joined forces with discouragement, and you’d be crushed by melancholy in a victim mindset. That loss would bleed into the rest of your week, conditioning your mind: because you didn’t spend your energy on the workout, you’d stay up late, wake up worse, and while waiting to feel “ready,” you’d lose a habit that took months of effort to build.
When in doubt, just do your duty. Stick to the plan. Don’t negotiate with your feelings—outsmart them. “Just one page today,” and you’ll end up reading ten. “Only the easy tasks,” and you’ll gain momentum to conquer the hard ones. Laziness is a serpent—you win when you make no deals with it.
A close friend once told me that when he was at his limit during a second job shift, he’d open a picture on his phone—of a fridge or a stove he needed to buy for his home—and that image gave him strength to stay awake. That moment stuck with me forever.
Do you really think the world will have the same mercy on you that you have on yourself? Don’t be surprised when it doesn’t spare you. Move forward even while stitching your wounds: “If you wait for perfect conditions, you’ll never do anything.” (Ecclesiastes 11:4)
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
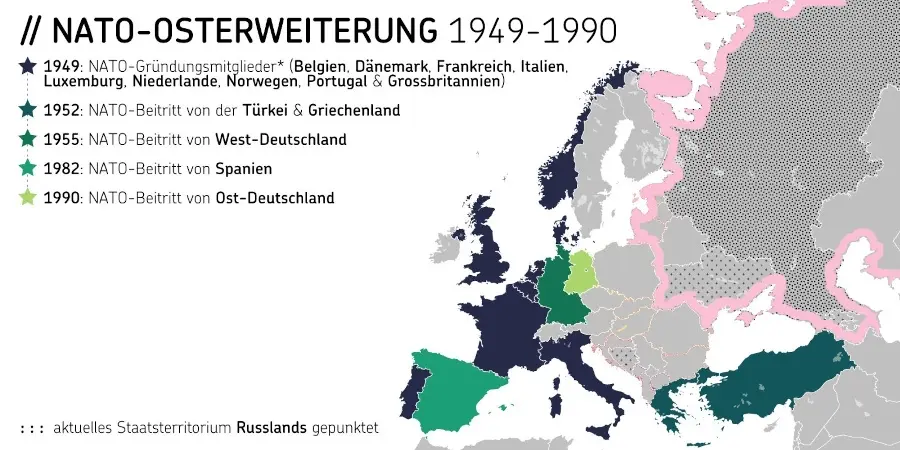
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
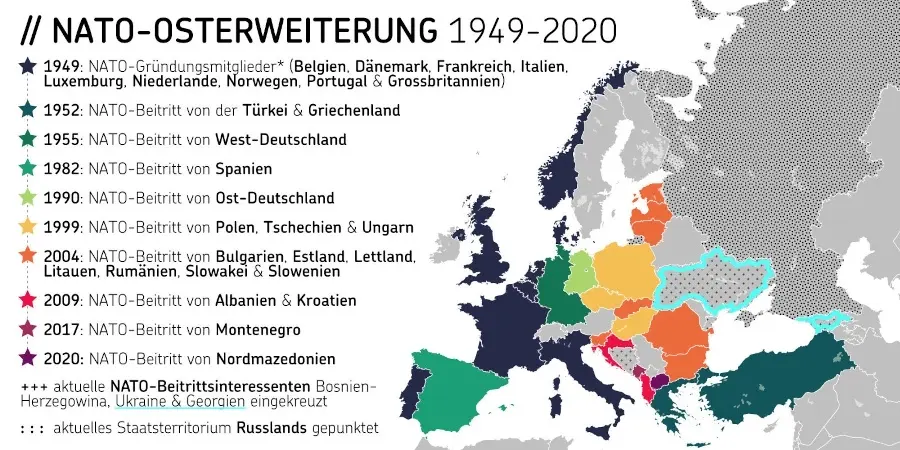
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
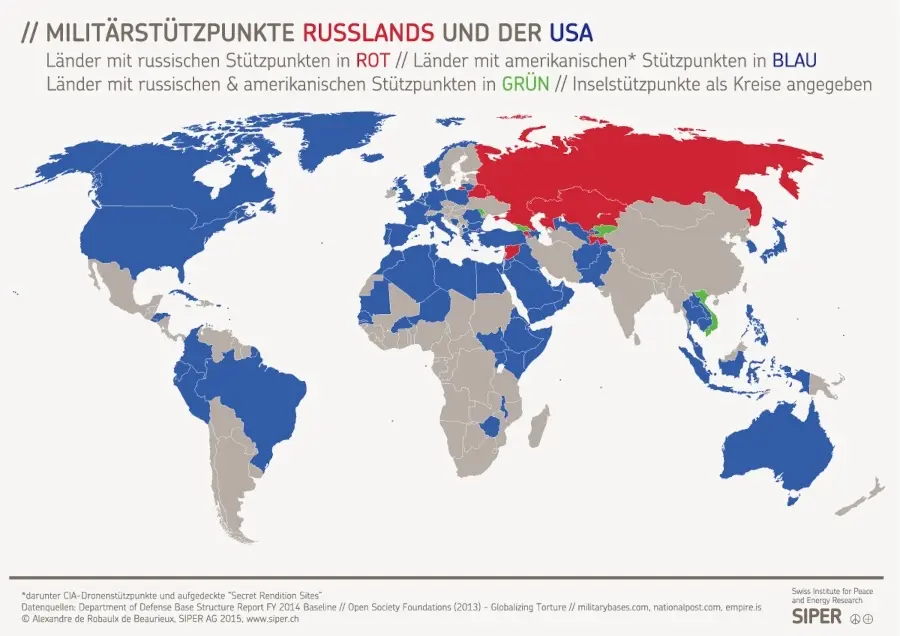
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6e0ea5d6:0327f353
2025-04-19 15:02:55
@ 6e0ea5d6:0327f353
2025-04-19 15:02:55My friend, let yourself be deluded for a moment, and reality will see to it that your fantasy is shattered—like a hammer crushing marble. The real world grants no mercy; it will relentlessly tear down your aspirations, casting them into the abyss of disillusionment and burying your dreams under the unbearable weight of your own expectations. It’s an inescapable fate—but the outcome is still in your hands: perish at the bottom like a wretch or turn the pit into a trench.
Davvero, everyone must eventually face something that breaks them. It is in devastation that man discovers what he is made of, and in the silence of defeat that he hears the finest advice. Yet the weak would rather embrace the convenient lie of self-pity, blaming life for failures that are, in truth, the result of their own negligence and cowardly choices. If you hide behind excuses because you fear the painful truth, know this: the responsibility has always been yours.
Ascolta bene! Just remain steadfast, even when everything feels like an endless maze. The difficulties you face today—those you believe you’ll never overcome—will one day seem insignificant under the light of time and experience. Tomorrow, you’ll look back and laugh at yourself for ever letting these storms seem so overwhelming.
Now, it’s up to you to fight your own battle—for the evil day spares no one. Don’t let yourself be paralyzed by shock or bow before adversity. Be strong and of good courage—not as one who waits for relief, but as one prepared to face the inevitable and turn pain into glory.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!