-
 @ 681ec9c0:fe78b4e7
2024-07-22 12:09:04
@ 681ec9c0:fe78b4e7
2024-07-22 12:09:04A refugee from Twitter said they lost 10,000 followers
My first thought was, did they die?
If they didn't follow you here then they weren't your followers
But on that platform did you manage to talk with anyone
Did you get an impression of them as a living feeling human being
Did you connect with them
And if you did will they find you here or will they be a fleeting moment
Life is like that sometimes
Pay no heed to the slot machine numbers
Cherish the fleeting moments
-
 @ 681ec9c0:fe78b4e7
2024-07-20 17:09:50
@ 681ec9c0:fe78b4e7
2024-07-20 17:09:50I was puzzled when Mike Masnick claimed that Bluesky is everything Jack wished for in a decentralized social network, being as it is highly centralized
I think the discrepancy comes down to different views of the role of decentralization encapsulated in this term, enshittification
"Even if most of the users of a decentralized system don’t know or care about the fact that it’s decentralized, the fact that the underlying protocol is that way and is set up such that others can build and provide services (algorithms, moderation services, interfaces, etc.) means that Bluesky itself has strong, built-in incentives to not enshittify the service.
In some ways, Bluesky is building in the natural antidote to the activist investors that so vexed Jack at Twitter. Bluesky can simply point out that going down the enshittification path of greater and greater user extraction/worsening service just opens up someone else to step in and provide a better competing service on the same protocol. Having it be on the same protocol removes the switching costs that centralized enshittified services rely on to keep users from leaving, allowing them to enshittify. The underlying protocol that Bluesky is built on is a kind of commitment device. The company (and, in large part, its CEO Jay) is going to face tremendous pressures to make Bluesky worse.
But by committing to an open protocol they’re building, it creates a world that makes it much harder to force the company down that path. That doesn’t mean there won’t still be difficult to impossible choices to make. Because there will be. But the protocol is still there."
https://www.techdirt.com/2024/05/13/bluesky-is-building-the-decentralized-social-media-jack-dorsey-wants-even-if-he-doesnt-realize-it/
And echoed by Bluesky CEO Jay Graber
"There will always be free options, and we can't enshittify the network with ads. This is where federation comes in. The fact that anyone can self-host and anyone can build on the software means that we'll never be able to degrade the user experience in a way where people want to leave."
https://web.archive.org/web/20240209161307/https://www.wired.com/story/bluesky-ceo-jay-graber-wont-enshittify-ads/
It all comes down to this
"the protocol is still there"
In this view of decentralization, being there is sufficient
Decentralization is this thing that can happen if needed
It's a safety valve operated by market forces
And where I think Jack and most of nostr would disagree is that market forces do not cater to the rights of individuals
Because one person being deplatformed is not a market demand
Especially for ATProto where decentralization is relatively expensive
To service deplatformed users would require building four servers, each one capable of ingesting the entire network: a Relay, a Labeller, an AppView and a Feed Generator
Decentralization by default is necessary for censorship resistance
Jack talked about censorship in the interview that formed the basis for Mike's article
"I know it's early, and Nostr is weird and hard to use, but if you truly believe in censorship resistance and free speech, you have to use the technologies that actually enable that, and defend your rights."
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Mike's concerns over enshittification are highly valid
I would like to see Mike address Jack's concern for censorship resistance
I think that would help understanding
-
 @ 681ec9c0:fe78b4e7
2024-07-05 06:32:39
@ 681ec9c0:fe78b4e7
2024-07-05 06:32:39"I work for a Government I despise for ends I think criminal"
John Maynard Keynes
Politicians are assholes
That hasn't changed in 5,000 years
It's objectively true that Julian Assange was persecuted by multiple democratic governments
https://thedissenter.org/inside-the-assange-plea-deal-why-the-us-government-abruptly-ended-the-case/
The difference between democracy and not democracy is tens of thousands of Julian Assanges (Iran) and hundreds of thousands of Julian Assanges (Syria, North Korea)
The difference is a full stop
nostr:nevent1qqs857j7ge4daqk4frsy5md3l0e7qnxlx3fu2zld2gxacs999fp5tkspz9mhxue69uhkummnw3ezuamfdejj7q3qcpazafytvafazxkjn43zjfwtfzatfz508r54f6z6a3rf2ws8223qxpqqqqqqzxsdxpy
Someone challenged a human rights activist and former Venezuelan political prisoner to support freedom over shilling for democracy
Placing democracy and freedom in opposition can make perfect sense to someone who is living in a liberal democracy
It does not make any sense for someone who is living in Iran, Venezuela or North Korea
At this moment in time there are several hundred thousand people being forced to work in online scam centres generating tens of $ billions of revenue for organized crime
To gain freedom they must risk their lives to escape or their families pay a ransom
They are tortured if they don't meet targets
These centres are mainly located in Cambodia and Myanmar
They are in Cambodia because Cambodia is a one-party state
The Cambodian police, judiciary and government have been bought
And they are in Myanmar where regional military fiefdoms are financed by organized crime
https://bangkok.ohchr.org/wp-content/uploads/2023/08/ONLINE-SCAM-OPERATIONS-2582023.pdf
https://www.nytimes.com/interactive/2023/12/17/world/asia/myanmar-cyber-scam.html
Spreading liberal democracy reduces human trafficking
Spreading liberal democracy increases freedom of speech

In as far as human rights activists work with objective facts and the most oppressed peoples in the world, they will work to spread democracy
Expecting anything else is unrealistic
Presenting it as a choice will only go one way
But it needn't be a choice as we're all on the same side
It's in the interest of governments to split people into sides and get them to fight on Twitter
The self-sovereign tech movement is interesting as it cuts across all political contexts
It helps people in the most oppressed parts of the world as well as the freest
It's an escape hatch and a home for some of the nicest people on the planet
It has the shape of the future
But it didn't free Julian Assange
And it doesn't solve the problem of the thousands of Julian Assanges in Iran
It didn't transition Taiwan from the white terror to an open society
nostr:nevent1qqsqfc8qgsqd7gxcmw5zw3udg56utkcj0qnp9jxemj6eht9p4e2z8vgpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygqn3qlypmqmr9q2v406wa4dt5ehv44xsanedpvc8zq53wthu4j4pupsgqqqqqqsffxa78

Although it may help in all those things
Human progress toward freedom is slow and faltering
It is also inexorable
That is our history
The tide will wash away the "Supreme Leaders" and the slavers and their mad dreams
And ultimately all governments
"Many forms of Government have been tried, and will be tried in this world of sin and woe. No one pretends that democracy is perfect or all-wise. Indeed it has been said that democracy is the worst form of Government except for all those other forms that have been tried from time to time..."
Winston Churchill
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ c230edd3:8ad4a712
2025-04-09 00:33:31
@ c230edd3:8ad4a712
2025-04-09 00:33:31Chef's notes
I found this recipe a couple years ago and have been addicted to it since. Its incredibly easy, and cheap to prep. Freeze the sausage in flat, single serving portions. That way it can be cooked from frozen for a fast, flavorful, and healthy lunch or dinner. I took inspiration from the video that contained this recipe, and almost always pan fry the frozen sausage with some baby broccoli. The steam cooks the broccoli and the fats from the sausage help it to sear, while infusing the vibrant flavors. Serve with some rice, if desired. I often use serrano peppers, due to limited produce availability. They work well for a little heat and nice flavor that is not overpowering.
Details
- ⏲️ Prep time: 25 min
- 🍳 Cook time: 15 min (only needed if cooking at time of prep)
- 🍽️ Servings: 10
Ingredients
- 4 lbs ground pork
- 12-15 cloves garlic, minced
- 6 Thai or Serrano peppers, rough chopped
- 1/4 c. lime juice
- 4 Tbsp fish sauce
- 1 Tbsp brown sugar
- 1/2 c. chopped cilantro
Directions
- Mix all ingredients in a large bowl.
- Portion and freeze, as desired.
- Sautè frozen portions in hot frying pan, with broccoli or other fresh veggies.
- Serve with rice or alone.
-
 @ 00000001:b0c77eb9
2025-02-14 21:24:24
@ 00000001:b0c77eb9
2025-02-14 21:24:24مواقع التواصل الإجتماعي العامة هي التي تتحكم بك، تتحكم بك بفرض أجندتها وتجبرك على اتباعها وتحظر وتحذف كل ما يخالفها، وحرية التعبير تنحصر في أجندتها تلك!
وخوارزمياتها الخبيثة التي لا حاجة لها، تعرض لك مايريدون منك أن تراه وتحجب ما لا يريدونك أن تراه.
في نوستر انت المتحكم، انت الذي تحدد من تتابع و انت الذي تحدد المرحلات التي تنشر منشوراتك بها.
نوستر لامركزي، بمعنى عدم وجود سلطة تتحكم ببياناتك، بياناتك موجودة في المرحلات، ولا احد يستطيع حذفها او تعديلها او حظر ظهورها.
و هذا لا ينطبق فقط على مواقع التواصل الإجتماعي العامة، بل ينطبق أيضاً على الـfediverse، في الـfediverse انت لست حر، انت تتبع الخادم الذي تستخدمه ويستطيع هذا الخادم حظر ما لا يريد ظهوره لك، لأنك لا تتواصل مع بقية الخوادم بنفسك، بل خادمك من يقوم بذلك بالنيابة عنك.
وحتى إذا كنت تمتلك خادم في شبكة الـfediverse، إذا خالفت اجندة بقية الخوادم ونظرتهم عن حرية الرأي و التعبير سوف يندرج خادمك في القائمة السوداء fediblock ولن يتمكن خادمك من التواصل مع بقية خوادم الشبكة، ستكون محصوراً بالخوادم الأخرى المحظورة كخادمك، بالتالي انت في الشبكة الأخرى من الـfediverse!
نعم، يوجد شبكتان في الكون الفدرالي fediverse شبكة الصالحين التابعين للأجندة الغربية وشبكة الطالحين الذين لا يتبعون لها، إذا تم إدراج خادمك في قائمة fediblock سوف تذهب للشبكة الأخرى!
-
 @ 6b0a60cf:b952e7d4
2025-04-01 11:53:31
@ 6b0a60cf:b952e7d4
2025-04-01 11:53:31nostr:nevent1qqspynu0th85xlczqgnafy2na46mg276u0c5dmpd9utcz36npmqdmpsunn5rl nostr:nevent1qqs06cvm4qq9ymt2j58u0p7c46j2atxevjkp5vpezvlzesxcp7v03fqm0tp5k nostr:nevent1qqs8vjpu7wd5h7p0elysezzml7wzhaxgjwnp5h7yst0uudyy8pjt3pckcapzl nostr:nevent1qqswmpc5vghej8uz5mk8nta2szx3ejdsvdrvxtspmc3mld683j53mfsf0ujes nostr:nevent1qqs9cwaua4gvrxms3qz8rntj7jmuyvv953sm9lcwk5j4p8jfc4qxpgc7sfhw2 nostr:nevent1qqsx4f2m3njh0cpgqe376xpqde65ujq0aq50nj45ttfqls3yzluqujgpuum60 nostr:nevent1qqsrx7q02xfyak54zcmh233trqtpw725ywasfyg9dz08prxdvcnnuhqdnymnw nostr:nevent1qqsdllaud8mjpfhfzgu9nxjgvys5g08eu344909nyekrrn92pzhpxac56vtuj nostr:nevent1qqsxhx3skvs8xeddpwvhct3yhp02vgmdu90my67ttlj70muhcu3malqjadl5f nostr:nevent1qqs2k5q965ppnvxs7tna9wwx3njtp9r40ur4ahud8ykug85vth03haqe6m4py nostr:nevent1qqspzh3q002ssre56emu2kkhel82sd9j2sacd75fm998km8p6cxn8gg7agpxy nostr:nevent1qqsy8v9vj7u3jfnmhl6867n847d2gs7gpvdn5zdnm98nes9zlgu3rnqjkwmt9 nostr:nevent1qqsq559y4mj940540zhzxa9teknz74l9d6tqptste7l4lqu5yfvu2tg74dky7 nostr:nevent1qqs8gq3t2wk6qluhcjqy5cp8v3y20wmtw3uyfujmga7njpq3fe76pcgtgp34k nostr:nevent1qqsztaj9ut2lxru8la8lcs95lgyrpypwhgx92jc74r5nj7ss8tf9fvsr70m5v nostr:nevent1qqsghxwhmfywe40sdrq2cw750ug5f62nfh2u3jwe476zj6s0xmgcgpchj5qwx nostr:nevent1qqsdaw986p4qwujz99a0eg0yqtpjqhl6rcamxa0hn0yyg8pcwch6cysmans7p nostr:nevent1qqsyh8g0et5catuar388v56eahc4qmf7l6t79cs6scuuqa72vxj5lxq7de8wr nostr:nevent1qqszvxdc8vf2tjlayf7qf839p2j245nt7447ytqnju65s4ypz402gecrcsp8q nostr:nevent1qqspyx8mxme44n9vjspewch8s2tmtezt3z87kpytzetn68m39f0yhfsskl808 nostr:nevent1qqsdu6r2sf6npr3xn5gwkdc6st62zvy6r6r8u7sh078rjd7cjvy5jdcy8crru nostr:nevent1qqsrc0j0xa769ymehgxjem3lchwccndwj3ms922ltu7r7sy567lyzncddqjsv nostr:nevent1qqs0gcr269zzgcmrq6fjyzgqh7lqerhqqaknfrd5k563xnr9vanmtgcfzza5l nostr:nevent1qqsru4vxn5sw02zq4v44xtcpkt0qxqp9yc6gyy5pyavvvwa96dxyzscp3apme nostr:nevent1qqsp0ajlpxnvu64recf69efhxzv6sgu7yk235u59nj2v529dq92x2wgvcna9c nostr:nevent1qqsdmcrqmdkzf9tptgh5mytuan9q3ur7l50a5kjfrskfr54gxqq5k0szyhfsj nostr:nevent1qqsfk0duvuamrutcpansw3hqarnmhcr4vp0zt9r8pta9zlycma2jscs5wz0fm nostr:nevent1qqs82xxv600mtzxhhped2vn9yw7aer487ws8yy5hk5ppyuzxjw92hzs06hxp6 nostr:nevent1qqsfs96nd96mvulw9yp0dyygdtsegxkmnvytkq5xgmepkrh0504x0ns0rnm60 nostr:nevent1qqspa5f2fc5w4f9ghq2eryjnc44hs3grmaq6eyrx4s7ggkpjdmx2gjckswv0a nostr:nevent1qqs96s99kv7h207twu8s9mhmms7e5ck2s9qhndnp0m2w3uqpsh724ysnd6esu nostr:nevent1qqs8z5jzrlmeenpst0xtrm336tt0racrx63cnchskgs2d9cgmrtugdgmluxwa nostr:nevent1qqs9aqladqaf2jvanehny0mhd6mq9cdrgwr838z68p8h9clmcgf0zygqfvdd9 nostr:nevent1qqsd2m5tlpztgfqhzhc09upzzc876j6s60299m9lha2sxvnyjrvfasctaurj9 nostr:nevent1qqsg2yq7mw55vqnjmrfetc453v3z6vzzynmevt2ljgg4yppn5m2ry3ce2jlfe nostr:nevent1qqsr3vckac3re8ayyhv3m3g5s8a4rat5720un7qle8am2lfn7ew3magu6vk8f nostr:nevent1qqsg73fke3mszmuz0nh7r34sl3jlgdx70npfjc5almxrpycykhvnersq3rfaq nostr:nevent1qqsr73gdk6n0dgvg7nv6c390qf0c2j80t7qf99nftmze3dlr7k3nhpsfhl2ql nostr:nevent1qqs2mfw8a5vz3tjrnuerw6vxge0t6kd6snyeaj5jpfye7jvkqyqsv8cdw09np nostr:nevent1qqsr3qpal7xkhkttp4jrmjehm86ulh8hzarusgnyhhuf4ttdkqq0vhg7279w0 nostr:nevent1qqs0m4l3rza008tax28s3mh0tpexeqpzk8y2hlx2h8dgaqcft4rvm5c8xz2sq nostr:nevent1qqszt96jl70h9ku86s8mldsa8vk7m2vtwgfc2sksxcqfmkl2dksjntsjhz5zx nostr:nevent1qqsqdhulqcal3edfn2tu5lsj2tcgyq73zft3z6sa0xaqt4rd7m2gq4qpgs30l nostr:nevent1qqsygu35a9rrlh8ld5nuucjj9nw4up0d8mx6dmq98hqpj7j2kc6w7ts44y0wh nostr:nevent1qqsfnzz55mveegemu9nmqvfvm4wyarpevh29m778946lphw4wya23ms7z8ll2 nostr:nevent1qqs02ft4599adqeu9v3ny04k5x3mdued0rnj2hgg5lsg82xmqnpgxvsr48clp nostr:nevent1qqstkr7gr3flahhe9e6gl70sudqm5qz23rq2f2q9as3ys9s6l9c06lsgrduvd nostr:nevent1qqsqzmjj8rn6pl8wrn5km7an00cfhy5wzqzz9nlne5hzhktwlnsp0ag0qd665 nostr:nevent1qqsfc2x5vx23yyztnvr3n59dv9kyw64jc88pxxfgawt4c8m32qq5ekqqe4neh nostr:nevent1qqs0f7fkwlky42jxsdgr33xttz3rkg7gk200qkmv2rulrlauqwee7ts7mzn5q nostr:nevent1qqsg3c8qyp4n86qdtkyzcnk6kr7gnmad3sd2vhel52m3r64ala9rqugrcnnv6 nostr:nevent1qqsw9dn2cuhe4xu76z2xyugh8gaah92rdyazyg0s2mvkll0qrll02gs4uvvvk nostr:nevent1qqsv0pymkvfqz53jyqwqjj5wypp375ljlstav67zzpdlq536xpm8d6snawjc0 nostr:nevent1qqs20fpumlhmzs49mlsvd2f0s7kfgjq68auzkfvf6s3yr7a0njy782qv778m2 nostr:nevent1qqswqq7pl8g5redm0t82k4ys50w65z03m5xl6ayr374c2vknqfwjcrgguyt5s nostr:nevent1qqsp0fn3adqdq3jvcna0vwkwjnaq32lx6ac7qzpquvdt8zpugx5gvhshhkgez nostr:nevent1qqsvtd6surkas9nrvnlndk3r53aqq82dedmm8ayf2zhrv9w9lf90g8gslhagd nostr:nevent1qqsqw56qfhvkv56ss5r066yrf2hnwchcn4ldav576ldhvk3jk543clcsayyfz nostr:nevent1qqsxq9faxju2wp9zl5gw7usu00rkm7n0x9ylnlujsjjn323wppqpausm4etyu nostr:nevent1qqsrl7gdwgd5mqf3s3ygn2e5j34qnjxeldr99qwn7lge3ncfdwhf4usl70dm2 nostr:nevent1qqsd2a32drg7teet8fnkauxede52lyrau8ey24dzzqflu7pad2fhsvsdgtyr4 nostr:nevent1qqsv5uqj4zxhdtdapzk44tfuxyft55tlp900r4l7rf9vtma8d6cgjms2hjwde nostr:nevent1qqszcepleg57p2k03e06et848frekk79x3f523nmx8t3guxmuyfgsyqeat4pt nostr:nevent1qqsvklay6j4ukvc0w9n74u5hzselsrmclm9jfmezrztqf3xf74522ac0rlcen nostr:nevent1qqs909ldkkvchacs32hpj4zphwxdyxtnvv2nz0wdk7d26ec25j7xyfcsx997r nostr:nevent1qqs0nyvnc4j8xen06z9t784htam8e9jsucpm7g0xq2cdtenxrcx4qdgmgtj8q nostr:nevent1qqsfq3gqv98x97s0wu2cyenz5ng0v52fsv8erzyuj8q7ls9kwaaafggwt30r0 nostr:nevent1qqs2pu4lcqakjgkx524jvd967vk2fkuw6urtp7tw38q3accra6hf0xqd99kc3 nostr:nevent1qqsvgwlfeju2qsnllqgexscdrta9lnqamxlq2kvansadmhyy0g0eqhg02dpeg nostr:nevent1qqsvveq4k9cz0t3xh55cudydkweh58aekjrmqh6zut7ekqsnuv3hfyqdrru6x nostr:nevent1qqsfn29l63mfggnvq2j3ns9u09su2zrsahrxmczh4mk6q8mq45lxkps5alh6e nostr:nevent1qqszg3s0jdwj4qug6plqe865ul8zh6j60gue9c5f897dclmvu5xc2zqv77xmu nostr:nevent1qqswla2n4l5cu2z3czyt8vyawylv2hxj2avjg0lx6lnl7cw9p3kn5ac9nf5u8 nostr:nevent1qqsf8qufcluup4tl8rcngu5z8tarzxl7the3wfe0xnfdyjht9rzvpaqyzcn57 nostr:nevent1qqs8turf9zhsjc7uunw8wgqtd7dc5wtlrgxf2wrvsnw2cgz534wd6sghzcgw4 nostr:nevent1qqsqwngx9nxgf7slse6yeh9uvnpmwz3exa95qyh6x3ez00z72y2jvwsrfqdhk nostr:nevent1qqsv8z7leemtzl5cfexxynl7243uqd4nr7kacdaumyx8rq46kune2psgz47rc nostr:nevent1qqsp0ttn3kcnds34zjew7w7e8hwnaa8hwx29t3tej2guawf8pdt9csgz4m9nv nostr:nevent1qqszy0yufenkexssavnv0p5k98e3vu77f4r4tze5v6p94gmgcrgpx4qd27h77 nostr:nevent1qqs2xj626q46rpzwnas5259t5ywpwzltnvj3pwvrjcqseddtyu500qg5rn883 nostr:nevent1qqsw02jdkpg2vzs5k5c3ymvndsrkje6uwkxf0dqmz0yvycfwt6lvq6qjqgfgz nostr:nevent1qqs2d237yzkmuxl82fc2u7wdpzxyvjw2gje6vgadtw4dzmnp483jgrcval8vd nostr:nevent1qqsrwqj390vqwp7e6nwu3k8m6h4luks86gq3sql99k5tnvy4w52kamqp73nl8 nostr:nevent1qqstdtqpxl78ecn9x8dzylvzul0cfsxh64gfunzts72l3sqmvzt0ylqwp9c8n nostr:nevent1qqswcvajl70frlhwtuch6cwlsehl0u7f2hfw27vhxvzwhzatm2ugjss4zle92 nostr:nevent1qqszfrq6zdsclykmeke3a7znqgp7y975mslf5w0fk0hfujajj9jh4hssc4s7f nostr:nevent1qqsp253cwmp33yedu7asa6k2f09w08j34zcky52ks6jh97msqsrh9nqylwer9 nostr:nevent1qqsd3u0gms7u8gqkvhpfqlvk2jrttjzs5zuvc8qdl3g5pse4dt8ugcsqcez79 nostr:nevent1qqsxq8t0u67schrxvv0dtuf2j6nlvqytkez42f0jmhpjtnkap5ssvsgm7pdcc nostr:nevent1qqsvp878n0zlqkge6famsdwcqp8k92flz2wf97c0emxlsrf7f6gqt8gyzkgp8 nostr:nevent1qqsx3xnxupzzfvws2etneycjyvcx0n7mcqru09gyym5x20s3n9ewcrgcsetd6 nostr:nevent1qqsf666tlstrgssclusaam50nfk0xjs7m849f70fuv5hw9h7tsmqpegaduhy9 nostr:nevent1qqs23eqhwhvah5yjn54m7n5klw4e5efg8s6994pamz5ejcgnsq4d2wss89y7y nostr:nevent1qqs2q84pdl6qvf8h7yu9g6hfvfzj49z28ea5m6k4lpmwvl86tnuedxqkxxajr nostr:nevent1qqsyf0quzl6ttedn7qftse9386uh0pvp8795egxumyvs8sjckm8xgxs2srhmy nostr:nevent1qqsf7n8rqr2wsjpcuczlcee85227rylnv0kanj4mca0hllptyerd8csnyspns nostr:nevent1qqsycgshmjcqsr76tlhuppp23a49zy4e995lj5wnqm8jkz5vmv9l55cjpughr nostr:nevent1qqsp4vwephtxxlv2pjgupymfl6k288qh6gdzsy8qesmu0natsh095tsnfrpnk nostr:nevent1qqs297q9e00dpmj78rdx2qrjg3hva5ye9p7nke8avagn844jxucudwg2mtxgq nostr:nevent1qqs9c08g0fxv3vy7v5c9gsme0jx6fujkv88k3rtnmxjcd89ejpy72hcadrjas nostr:nevent1qqsvmwsetretl7dm42c3g690llwylyn37cunkauepzj3le3qhaytrjsh2ga9h nostr:nevent1qqsgyqu6zjppqek23fgpzlmg7hqfl4knryjvuflx54ypx70m58gt6rs5s9dms nostr:nevent1qqspxcsk7g56qhapmzek243az6zhv9v5hwupnyg4nn352kvc2z0fw7qklkcv7 nostr:nevent1qqsxwe7u49q4yc4ney5kt6gkfep0v9jlx68r5u0uf9upl7u9mcfxpkcqpu7z8 nostr:nevent1qqsrmyeh30f4kfdleq23w9vgcx9jcqgkv3stg9au5m593tlywlca0lgylty6g nostr:nevent1qqsg2v2e7tthtd8m39ctt7yyqw0lqkx23s7e2fqt4s2ymlnn33n5axg7fy4da nostr:nevent1qqsvtgfln33c2nllxt2797xfqttcuy6qtlh8we8q9lv9gn7r5jy4ahsfqpyg7 nostr:nevent1qqsz2al0emnaf5cjtrtdfv9c9t5ey8475yx5kp5442cg0afmlys6dgg29jq4x nostr:nevent1qqsg8lvelaeq9uyv7hzrxgpelckuz5hpf5g3ajyghj8nsk2ycckv63sllv797 nostr:nevent1qqsxhp4g53ltg7qjz2puzvsdwxk54xev46n8jmc2tlg2pdp529ckgfg2329m7 nostr:nevent1qqs82j5zgk3plkk8fugmflertrl8uc6x36elfeet643npvyuxr39tvcrr2u63 nostr:nevent1qqsd4vye657t504chaqf2d5gwgd5946t9tfg6aq0fnkjljnnmkfmadg3ss3uw nostr:nevent1qqsxhr5lanyrce0c6amgvxzd77a26fpap505hl74jztuc5svst8dtrcvtcl4f nostr:nevent1qqsrdap3r0ptlwxgd0dav04y53w04x0jzh22d4sxksuzfpetf6j8zwgtmay55 nostr:nevent1qqsvyqj4lr5g5swahxxjrpmga3569qlmd96xk6f4xwm84gmwu7aqw4c69zqtx nostr:nevent1qqsf9dntcjdmmzsu0s2t7pnlx6ver9usvaz53hvgtjggfgn8da6eydc7l5gc2 nostr:nevent1qqs9njwwgechxesqycm29asghutvq0e2fec2v4jc0gvpsk2dsnujq8c9vnuuq nostr:nevent1qqs9ahfkkycdlkemndn0dc7am5djnp8pwjnu72sng2tg0pk5kq7jv2skfv95c nostr:nevent1qqsflgngaeu8w2xz2lkzly5rvr3rudcvq4yyrn2w724dlr32p2mulpqasv6vj nostr:nevent1qqswg7qfwtdj38kr9xfp7f6gfvaxm5kpuwp22ueqny5pp6da7snl92svggqww nostr:nevent1qqs256vewt769a0q8teqh3n5eggjvw0jddl4xzejx4rykhcrrx2k4zcr70g2w nostr:nevent1qqstf7w5lej9qqm63x2r9c5ztc7s9tre65f3e27p5mhqjzy3555856g0lptxq nostr:nevent1qqsfzchhw84ldh2egvqethzychr8jvaaurdacvav3qhgelwzldy7adslwelmw nostr:nevent1qqsqy4uzgsedu94j6jyjpavrmn35khc7nsdmhxnwqehy9umdkgac79skwad40 nostr:nevent1qqsrzxkswpug72gc6eqf4qklemc29quyscds2ftwuqmf0lwvz78fckqxq9r9d nostr:nevent1qqsfzvl36d5k89q0frn9gfepwjrd65cgarh3gtj6gmqffjh9v7ncpesfxuyug nostr:nevent1qqs9vcndnjwtjcg2p5yj2jcktscn8lyf766kqtjef2a3fmyhsga0mgg6d5vp7 nostr:nevent1qqsdf65dzcvx2pkwh297amygfcdypu80g3hc2w0hzl6l8ed8ptcd83ccux9kt nostr:nevent1qqsr69tp6y6dj6agued5vqvv8wrhwngtl9nk6yln2amzg4j0fnxfsksj59765 nostr:nevent1qqs0jjfn0tnjgvech67ks5n3x9zrpredskg67twea7m2x8hvuq3zvvsjdgjcx nostr:nevent1qqs8s9wuwnqmkdjwmrxmqrjyktq3egkxlaqzx7t6q9e53yalga55xuq5ez8ug nostr:nevent1qqste2hugs0txe9xqzle5y60t2m5sakxfcq4flw9e6gtxvdlpuy2qqq3ksyc5 nostr:nevent1qqsxrns3rez8vhnym5qvqkg434w26r2paw8jm9640lzmhzs7jc00r2sk5nqq7 nostr:nevent1qqs05du8xmstnuajfj6cqetxv06xk8xgj23eepfpyjk8hdz3v5hx3hqg7tcwf nostr:nevent1qqswq92249238q2gp6cjcuup5w0e60htyqrp22cepc6uelysmewp46s3n3c76 nostr:nevent1qqspwxsck6zz60gc8tr48l4qqdnlnva0s9gay2hmdckutrz5sk8mnpcueftjt nostr:nevent1qqsywqjwwnuycnzkar8cnua5lerl80kr9wvwdr4yy07k2r7enlup08s0w3tg6 nostr:nevent1qqs87m5zz4x2cctfvxrvxx9546fe9rl5j82dxcrz4s89qzk47huyalgrd3rk7 nostr:nevent1qqst7lun76xhcmaw84s7cwqu9wu5dfterxxhjptlw54gxhnz5duxcaceaky47 nostr:nevent1qqsyexk849hlfxhnqlt4t6y23jshgeevrvtu53dh95w6xfeuuxrvz7c2aj87m nostr:nevent1qqsglmpnfw3jgl9ekwanzlgzhndce6pmncvunkswpc3y2n40vu33m0cwds2v5 nostr:nevent1qqsdaw8rm6yww2ks8300m2xw22c8xdemnkspdvwrjh2jn6hnuvuh9zc6quvml nostr:nevent1qqs0p6d8ny8kunevc8capqu9ntjmd9ze24ql2sjam0j0h8ju0xjydygkm9ffq nostr:nevent1qqswu057ppwc2lars6nu8sc8j4rupnahsrn79a8zktsqawq6p5fh46s5t4yqn nostr:nevent1qqs270vsqqtjwjyswfmqyldjnmnvrrp5g5q7wh3k5qj8cuhljwn0j5c8md0u6 nostr:nevent1qqs2ypcx6p5cqe8dqqmrm36qvgucflgvss885r8czcal6zv0axqdr7sn0x2df nostr:nevent1qqsqvf477f73gm2qfkuly89sy4sadju6wh4t6dcqgh4zwr8ds9g9txg9gppkp nostr:nevent1qqswnmvwph8x9xnqr4n6ytxnfz8nl89a7hfrk2453ldxudtql3j4yns2fj3hs nostr:nevent1qqs2ecqgkcgmlvzj90c8trmw3nld0trtuujnv28f5ezt3huhvvtegmcagpf0y nostr:nevent1qqs9s9zkznyxu6qk7svajntw0v02ldr8462dgt7n5f9slq7aleycsusl96zph nostr:nevent1qqsp7nux9qjzsx4ypcrjexrz25clr9586ar5n5ahc70r7yhakzvaeasd63ulx nostr:nevent1qqsp5gp2xg8lx4kneqrhv990x0velm85s5u2jmggkwwzt8yrxygdc8qgfsp3z nostr:nevent1qqsxdt30myarjhkprzt8xx4kfy7fhyjxshaza0z52nq0pkgwkqguhugt0jswa nostr:nevent1qqs2qq3wpva3lt07xrde3y2vehqy0cwyzye52cvhjnlyw5x3rghsgrq93jycs nostr:nevent1qqsw0959762aa5pxz9hhaa6saszqrnqjrr5umtl5kkj00prqka4fc5qnpfek9 nostr:nevent1qqsx5htpawdvx500074r0skyxhrezkfs7rctuu4afp4puykuvth9kksr9dc64 nostr:nevent1qqsf7kexs3s0g0f4dzv9c8qdns6jh6e26qvecu59d579ud0fta8a7ag7pss04 nostr:nevent1qqszkphl8n8vtgfnrpkudwe8nsm47pm95ajy9a7cdaz3k7shadjynaccpqzv6 nostr:nevent1qqsgrperqd4nrjegephrrdcj0qwkk22glfeq3msumte2evup3f5f29cv9e5vq nostr:nevent1qqsqueyp46tjgh4s6fc7af8r6nnpdetrutmemalfkk0ruqp93zt4ltc3hdj29 nostr:nevent1qqsd34zcm5gm0aws879q9t7sdm7r7rvd75sj4uzxxslwa25ffay3pnc4x9wmg nostr:nevent1qqsz233vcgpjrtkn03kh2wv93jwt0m042jpqp06uank9vfummhdrqxgvq0hnj nostr:nevent1qqsxdtchwzjvxvml4h27ta75542vgc6zpdtzeuma4hrz55v9trswdns9dpxna nostr:nevent1qqs922qlylqjrmr3uaj0f29s82smytg67cxcl208memnktx4h7fhhxqd2wzwc nostr:nevent1qqsrpzxupddee90chcj8psnlhhd8s2r68tvz5u09u7u46wj5a0hyyvs98d2z7 nostr:nevent1qqsfkl9ukp2gss96ut95rwyg3gfcdft4qnkzjc6mg2x4dnpxsezwx3g7dl4fg nostr:nevent1qqs03mv7zygd5stzm6mlh3v57mszuhvnumwfpa94m2axlwqhrtyjfacm9hfaj nostr:nevent1qqsg0k2f4l79804jydkq3ryekkjk95rcysswg02ktrg3cftwq5jnvdc6pcn0x nostr:nevent1qqsw8fnh3x09dj7m4w0engzftejh5pq0dgjzcr23erpg38kyvgz6taq9hg083 nostr:nevent1qqsycaw0y5z5te9r8m3sx8cngczuc0dtzcltf6khwgwhls4y3vxv7wcehkkgx nostr:nevent1qqswpdv0jy9ag757st0c29efprl6jttz3jvrgaxg382txm4r38shhcgfnzhvu nostr:nevent1qqswzt4yac0p8536j4venvexgt03shq94xnsp7lmxuy0vq9wl9dj69qqtr6tg nostr:nevent1qqsw5p0cm9wxvwjlv3z2kewze2t4lw073h7x5lql0g3az7h7jnd0pagxxsmwp nostr:nevent1qqsz92z4pa6zdhhchrygypy39x3j8u4mv98dflxmsw39dyuerfgy2xsp7rg2g nostr:nevent1qqsqur6s28xh68lzft7k6suklrv5knjp4hysunyr7g79caucc8vt7yq6kl0zd nostr:nevent1qqsf02sunq6yqjcpjlm8a4ku8txkyte68gmtvmhyez0lx424cxk65zsv6gk3q nostr:nevent1qqspexe5ew6dt7g3ps9tk2cd345y3jd0asfuyj8pgxv4m5ywqw990lqyhzv9m nostr:nevent1qqsyedkwvv6u4ludqgz623ftuj4mncn5c3tzf533q6xgc4k5xgn435s62yr3l nostr:nevent1qqs0qr3al6we2zeqr4lrkz6nk9cp7cvf9ymt06khw7d4377k7ar5n2gxtem3f nostr:nevent1qqsg5x0qrjk38xpmxh83n2wspg32gwwr4hxqjsc6xz60wess9efy4eg6cpn6v nostr:nevent1qqs9swl3twdd9zjr55gsq43gctczv4cjn0an58gn83wf3ujquu0l7lcff4ma9 nostr:nevent1qqsv9sc8m3e36a253p4jg5am9ay92ncjnx9nttsh5ss37ndr4znu97g0lg0hz nostr:nevent1qqs90fava6xzrjhdpkwld3utw3xl6ghddfmlu9ceql8p82mkv6luvwswptxe2 nostr:nevent1qqsrx0h5jz7vjv7ul0w30rjqzg0eey8r0ff0k9cf8jfcjjr5a57kg8s8tz2qy nostr:nevent1qqsfwln27aduh4yw80cqwml5f7vh5z6v7q80gxmrv3a97x8zfw0a7us40qsmx nostr:nevent1qqsyyl03g27p9ekau4v483800dwc02sfeay8txxn67mr3h3zt476sdqv7dc0g nostr:nevent1qqsgup96lkscndr7jdze308kt495s65uura9vjl8yucfcd0depzpe8cdvlxjr nostr:nevent1qqs0c0zwxpfv4krj0vfku448tl3jpudw56nw4wr4whlje7cexauhd0g6zqjxn nostr:nevent1qqs0dvc82lc2mmzvkmqtcua7kt0vwz4am48kj9sq0rk8xpsxjxw5pgg4qe329 nostr:nevent1qqsxzttj97g67mag82fww0aglmvt5qwvk59e7euswn3nmjtpx5j6thg6c3nz7 nostr:nevent1qqs0gxfve8yz6m93jaseldl8xzhsmpt7k3gkqlv8xlje4q6aqjnna0gezcl83 nostr:nevent1qqspj6puxtaj06z2shd9nr82t2rwwmh6mszapee4gjyj7vra6pwfj4q22x99e nostr:nevent1qqspcrj2zg0jyy7ardz4kt4d5n95wz84jl65hmrdxum7nneeglwtnzcxxzdt7 nostr:nevent1qqsd4ddx493uj3wuxscwfjl9le3f7t2f78yh385666knu26vr9luz4gwa0w24 nostr:nevent1qqsx4w8ztgk5m3wz59mm0sqr7nyzx9hzu005vae6kqaepnpxqw0svwqaq9le0 nostr:nevent1qqsztgtzz4nqf8znh8u3q5fwtnx84mzrjur8gq6dmg3mj2kn3ugx2xca4g2nv nostr:nevent1qqsv6m42nk6uerh02wnflytfvj4nuj0sp43s9lzuvd5thprz9k7jjgqgywnf9 nostr:nevent1qqsvennjay5vvk40t99jwnuefa4lw6zuhya4mg74fsd0klrwyfwjjus0atnfx nostr:nevent1qqs8awph7hzu76df5w8k4xx6j5wmc8tnddxa4sfwnuruea78wr4tg8c47rsa3 nostr:nevent1qqst2222z58smd36lltudxlme8fpyupg8t2c34z803n668t5pmt0ypgsv3ryg nostr:nevent1qqsvjphy6fz8ae244jzdha9xxmz2jcy0pz6zfcse626t9ms5xlcyeecmpdyt6 nostr:nevent1qqs93ghgzxt4ywr404yn4jm5lx8m7l964mmgqtl55khza7jfwsk3klcyup39u nostr:nevent1qqsq0lhuuwewq2kgtjk44z8wnuhv9x0lrvym08dk5p70zk3l9gupp3sv3dlrp nostr:nevent1qqsyq8u0tnangar2w7ft0cfzwglxmwk7kkczpj8k7wqjnasz3sq2sgqssvy50 nostr:nevent1qqsyh3f6lhft7mxmf57v68ypfa4j5fdkuvf43c9q0g5w83jtzwsg86gwhjqtp nostr:nevent1qqsysgrlqjk2wayzw0dymw0r0wv30lk0c5qeagc8h7lmulyffj75clg4t4anr nostr:nevent1qqswcpe2hfr6zk46p0jv65kl3wtp63smv6uxe6j4evsav9dlcpe7xmcx9kqrq nostr:nevent1qqsxv5tuzmfjm3dcz05xng5e9gl6e7vqx84h37p83d6qstzx3hwqwlqtw59hv nostr:nevent1qqs86k2c9akxtzvw7upchwu4pnesj4ds3d3fsg8m76mjdpvj38zwcac6vud53 nostr:nevent1qqszltfvvs22flkqd2v9jzuu222nq9jud78z5sjk8z6y7jmqnd3f3fgme3yek nostr:nevent1qqsrglucq53e84kgkaa2hsq6a5xahraethlykzx6znymtg4gvxenkssx4un3a nostr:nevent1qqsvaq0lwefwnrfkvmrul84fneecua2g7eg8henlkuht0r8u0sp79cqqwt7s8 nostr:nevent1qqsfrah0av2l3dc7valuqklryz2a687t7cenharuq7r6xelm0e0yv4s494vpz nostr:nevent1qqsrt7uykaetqwl2q90x6kd5xhgh6apn8kz7gvy6hgsa42xe6qmqgxcmyll46 nostr:nevent1qqsgl80erg8t5cqdz3wnxzd2g6ekhdtm7rt3nxszzvzxft7v7x8lqgc084p04 nostr:nevent1qqs8gsthklfdzy6fku378tf6807qk86kjcgrgaavrjtdffh2e57la8cwltl53 nostr:nevent1qqswjgler7slw0lncaxhtne5kz3np3tu5umdef2aqavy5atq0tvgm9gns8h40 nostr:nevent1qqsr2ka8n6zv0z4mk6ty9nztqd9qz8rkgt6cjck4ce6mtpm8sxupmsqj7s257 nostr:nevent1qqsrudy60t40q9vup3p0kxrrnlllwnwnyh8kt4x623d3f74jctpnrvsmd8zam nostr:nevent1qqsqskyce40lmwc9v94tkxy5phnzf4p55q090g02wt0x40czw8mkk4svtu7a2 nostr:nevent1qqs24dsj4x02x80lvgtj3khkcqpqv6qyypfse2676et46phrztxs75shwde3x nostr:nevent1qqs2cyspyllevj6ahmzep5jhlnnfc8448uh3jn5m2qfmn8y3dma2qggcrtvve nostr:nevent1qqs0k044ntscwad95k8347wuflpchrl0aszzltfyp2nxpv3g6kr2cass8k459 nostr:nevent1qqsqq9cce7umtkm9e3588n7nl4y3dktlskssapph5z6004hqg9setaq4zcqr3 nostr:nevent1qqsdsxzfqhwxg42a652t4234z7p703lwrulfnz9drsus8erjvnag74c3606pt nostr:nevent1qqs0wjxh4ze8xfk7sec3zu4cepwtwexqty80qpvp5nxxgvutk9lqydch9jzp4 nostr:nevent1qqsgavz69cxs6mx2y42j4qnqn7q5xdwvmnaae2tj2px8zdep0j8rs6g87hl3t nostr:nevent1qqsru6z84jtjmycunulyzf5ns3rq0dweseseyq5rxmuzvcs7ylenu9sykk9re nostr:nevent1qqs2kxhn4sl0p8wyxzcv4gpqqwztky37p2j22qhpjqgn0cy407yn03qmsctfx nostr:nevent1qqsf7ug82cd5c02jkm7uahc4p7kc8j32q2dgvuun46ywmlfmrwu6xns3r0egn nostr:nevent1qqszckunp53566u6grgw75gy2c9ce6902zd3jp9cfg20paq66lxxdjs9l259l nostr:nevent1qqs07qw0kashdjyxgj6w92p44hnd3l9jeamxhc63fkdz9cr8na85pwgqlset5 nostr:nevent1qqsga4g5haatk09u4vkm6nfmw6ngctg6p5jzam5kax27lcnc74vcsdc5fwjjf nostr:nevent1qqs8uu57ukvxfvve900uvynudvazpu8xuw7zvexkctm62rdgtpu600qcdwg0y nostr:nevent1qqsgdc297tvnh06kqrg3e68ftyu6prwjqtvxj782f549jugart2jc5gqcqjyp nostr:nevent1qqsqkus0qg7nnl5jkjzhugjpd6vfn70m0r7xtpyz3mhq9k49unuwg6shprvut nostr:nevent1qqsgxaedjvy4s3rlfg8235c7yh0uxc0e7n967p9j6uuz90tzvafzy6qrmcrwe nostr:nevent1qqsv2j2dchuyajecmrqxv9pra3cju03fwkes5qy3xrjtf55twjmx64cjvx347 nostr:nevent1qqsqmnnasdsf5zmqlq3alycl5r2uestvx5mshvnl56fdjk0qx4t2hkgnzn7ww nostr:nevent1qqsvdm79znu685uehrmmegcmq836jj3qeqtym8cv356wx8y5tscjg9c0dvw4y nostr:nevent1qqsy8wx4ujy7z3e6svmz72zaapu7xqx7y4xsuthuk6ynwkzfl9u92nsl42f8c nostr:nevent1qqswccl50t2p57wdfam07p2lvdqzxeg6dzm72vrjsf0xjl88uk03m4gzx25jj nostr:nevent1qqstv4gslzxfte85yckx07fdn5phluvcnj7a7pf28j7hgthkngs7fgqhl5fay nostr:nevent1qqspeada7h3749ex026n4gp60pkv7rtt5nzn4p76dyz9vfzyhxp5puqw6uech nostr:nevent1qqs88tlgk2gd2dsf3mre36e5nurg8afmynkafwlj59p5295wq2dycccjtp7l7 nostr:nevent1qqstu5z907epgq3rechx0ezqyge3uj7nm2j2ty93hj9rwuxxzrljffc4zr0qc nostr:nevent1qqs2r67wggz466rv4kh3vrhyl8e4t26a5s4tq7wgfrglghnhcw47n6q9mhltw nostr:nevent1qqszerzkulum87k7ykzzg0t7wa2lww8ttt7xlu6m385hl5p07lsk9ych3s90p nostr:nevent1qqs804wfmxcdt6gev9qmyasz7mxq6m8k287ulsfz39umqcgpqqf2jnca7xk42 nostr:nevent1qqsgusg06zl58x44778cskde5n8uudgwwajfdq28nvq38kt8nwsyu8qyw6hhx nostr:nevent1qqsy8ecclr3p6s9r7d0ge060fsc6qveuj8509nkndq9stzp4aslejuqw9j892 nostr:nevent1qqsyxns5ze0qm54f3nhpc0dygqnq60e2nmmgpvlhkg99zt2fp7umedc7latuk nostr:nevent1qqs27g6c4vaqxkc2gvnvuged60095fwdsk4e4ze77ylazg9lgz0mlng67q65m nostr:nevent1qqswcy0v5pn5v9wx6uzln6nr4nl4w5d0c688gx5z3qhepswmhu4zgdcrvux38 nostr:nevent1qqst3l22tc9thmnks3nxa9lqdtejktk44ved3xkyqy34dzuzcz92npcdvgtlr nostr:nevent1qqs0jnryazxjjl8g3hxw2xh4fastfy9cu47lpm2qgh2fc6tf4d78sqcphuvzg nostr:nevent1qqsva8k2qn9pjm4wpg879k37f9hxtrpa6twa4ck9uf33e4udzq308rsavs72j nostr:nevent1qqsggahcy8q0zgyvjdpxpljykjahjsx4tkg7z8qr6m28y0hjvfkredsyu0tfj nostr:nevent1qqspayr6m5dcevp96sgew5zn7dye0gm2lrvwmlhr0nlv8kcayarlp9qlntm3p nostr:nevent1qqsdssqj635ee355wdugls0lr7hgfwjjxdzr3appz2pc0wrsp228wrghtxuzg nostr:nevent1qqs0end22ejwqry63pt4yq99ez2jsxj2d35kpy3dfnkmsdx8pk53pjcw2qdwy nostr:nevent1qqsw5t6gr0svp9wefrve6przj6hqlkp7ma787ac8tauxwtc53ws2a8sru5vm9 nostr:nevent1qqsr53vq37g7mm6chgsafpgn9hscgaku6m00mu96d05lryqx285k0yq7ujhye nostr:nevent1qqs8w3ds968pe2jeazwt3ra5y6r3dlgxqgt0an7fd0zy7wm2lkgc2ucahcjqq nostr:nevent1qqs26szux5exxukg7ht579uytrcs72j2j9h2xf4dwvz044jpntsynagqv9sdz nostr:nevent1qqsrej9r6kazt3eda4hhu70tkax4j5ft9l3ve4apnh5u8p9ltj6allgmn68a7 nostr:nevent1qqsq64h92pdffc50xvmlwdfyms802x029qf5pe8fwlu9n4v4rg93t8gfa7kee nostr:nevent1qqs8hhmaww599xz682l2hx0uvn4sfluc6aa7lydk4nugxejqjeaqeugyg0glt nostr:nevent1qqs832edsy9yxhq765zfummutc0r54zc4xj7n9lcuwcf60c66q494zc7tlqgx nostr:nevent1qqs8etkcd8f2aw2s7efjdsj8w5ch8r8ej9capyx976w343ps9sm7s4g0l37gr nostr:nevent1qqsfwaetdhzn3z6fqs50usmktug5v4stcet3lus70p5hffjq8kcpuhqpu5ef4 nostr:nevent1qqswnvtzachtgqc9gwqvcu4s0mtmwxnl78v544p22u6cuud95s2jgmgaz5glx nostr:nevent1qqspmckx784xjj7mkn70tu6rfnyq0kmpcg4p8jr6dmlh98um8dcqnvgj8n426 nostr:nevent1qqsdxeatzq42tstmculgf62rhj84mpgfzsa54gjsh4hrl6e64jv3wfcvr8fec nostr:nevent1qqspcksa07zqnc0xf9h57mpvna4ke5fd5g8lw0v6wycf980lhh9fzes3k5t94 nostr:nevent1qqsy8kvy6s5spzhyfjvj6lzesj0ynnp5d30pqzuwe93d2t3xmrl77dcjz5sfg nostr:nevent1qqsyh342up3pkjfkvzr0yjaxtu4qg5syquz93xyd6fgatdwqxy8e7mgklaf0f nostr:nevent1qqsyp94g3puhpz0k9vaft8tvpqew024n3asxpklgnax6fdsu2mu4kcqkq7fqz nostr:nevent1qqsznp4zqx06tjmplxdr0q548f3kcn7pj4hvf4g4rgm74yk62c59lnswzsdn4 nostr:nevent1qqs29ffntcwt0t5zv7ecrzjgpd6v2r0nqwg9ymm5luhehgrzhlr4f4shqhwee nostr:nevent1qqsfrn6h3hjk4zrs6pamcdzapap0gvemrm2akxlur005chgh4vaps9sx4y5sl nostr:nevent1qqsql32xdfshaa73ex68fz8e4r6e0lhpcgsgdhczwfsq6e7lqqt703cuhue8l nostr:nevent1qqs952dv2ycq0a2tdvyj7st7sd87pxzh7hceth96hhhwjq7gs95m5ccdf764h nostr:nevent1qqs29kzdduhtv7v2gr40nhzkykls6pwmn9maspl2qs83gqkk23ql42cmxwq3n nostr:nevent1qqspwpz06fysr7xqyjfxg296e5d7hcycp3wkmladpe39tkwtmyyaprgycny5j nostr:nevent1qqswsj30jgpyt623gqpy5gk434xeff94cwqrpzpm2tdznhqlvs6dghcuxdx4l nostr:nevent1qqsvty7umlq35gydcj4n2tmzv334yuf5dnw9p662q22rzfq5yhwpk4gz7fnyp nostr:nevent1qqsppkpezwkyfezakg9se8uzvx8j6z33e7k3f4xrpad378m5jua5z4cms7k8m nostr:nevent1qqsykvscexq75xect594xvyp0yzlstagqa62kmpwr94wl7q0exg8h9cwfxcmz nostr:nevent1qqstfqwlc8rmrqrhdt7zdd082eehssdt4r66h3j3ns42cxvnzjegfrc7qr8wd nostr:nevent1qqs0prhhhyvtz3fwwsu93ndvc6ye32zp885eyg6rkxldc37f0jck2eqe3kqr2 nostr:nevent1qqsvr4nsccw9dehyettdc0tr4t3yycvldjxka6cte8uth5r6xz8vhxcat20d4 nostr:nevent1qqsfkxvh4h3ga60l3w3x5ngu777up09sxrqdjgkrnv3yzdhdn2ljsnsylcsge nostr:nevent1qqsfc83pkdtd4jph9r4hjyc4xqczdcem3ytkvp732zalqkl8jhxaq6c26cp54 nostr:nevent1qqszd2hpl8h2uljcgqe0r4zqrk9v0us4nwu5x03v02cx52hkgrlykjqehsv2d nostr:nevent1qqsdz3m0pc789hk8vv7ldhwnz2ydj93qatn5t6g995y9nqkylcfh8hsex7w94 nostr:nevent1qqsvpr85pg2gammm3fqzhw8lme342mplaau3zeeku0up372eps75cfssvpzkt nostr:nevent1qqsq8j9f0vg5an20rdxfpgylaslpf6nt33srglu9f2pthesfqhjgy4s8w3qmn nostr:nevent1qqsyxu3dg4fprxjc4rneslkgucnwx5h4sc7zvd0w0yydkv2hzymletcksa04g nostr:nevent1qqs08n09gvne3d46y8dhxhv68duzvlkwmg9mnv7467cz4x5utgu3rmc0dcuny nostr:nevent1qqs8tcakcm8dqnzef535ylh8j7m5n98s5qu2zydj9w8d2kfa5mgsv2ccpxcqw nostr:nevent1qqs2sm3kfej6t258k6su7krggu362slve3m9gayjyskgvwt0m49ahdsgdmjnm nostr:nevent1qqs8dvmywjutfgx5cw3r9h355dmfufsxwse495svdx79kq820g2u9fgap3umm nostr:nevent1qqsdqram3x44q994z4e93ufqqav5dwa2la28j4fmwqr5swympy5k8esk2py04 nostr:nevent1qqst0vhcp4sy6h7h6c3cfe957z9pj48ujvhw7yhmgjjmqe0d4u5x3hq45hqan nostr:nevent1qqs28z599avfsddedq8dwulzhyhqggs9wukc6jqdp60fp0kcruck7gg048zc5 nostr:nevent1qqsptwc7rfkt7lhkvwz0h2hrrwxj9v0kak9dqg0lph3pfsxq4mna8ac38gqdm nostr:nevent1qqs04rh8vcey9p78kjugs9xvlmyl5m6043n6turhg0d6xrnn745y5fcqkes8f nostr:nevent1qqs0j9h04kfesvcqeax0ynawe7g7j62jhdanmzp0eal57ayqhgn67qqvs8d6h nostr:nevent1qqsrg4gvrwhvj3np8hqyyl6nsz4twjnxdy3wtd99try3t5pkz07e3pc3sn26m nostr:nevent1qqsga3tc0kc02g726fwrwrjm2e5x7tl3vzmv80sd2as9ywht58gcztcgfcrad nostr:nevent1qqsr5srauwprlzlfl0gxnfkaya0rlqwusqnrnkjzmta03kqxx2xc25s5ctflc nostr:nevent1qqs0fjpmu9w0dgc4a808vvals2j23ny6lrp0u0dz89w5mn9749xsalqva29uj nostr:nevent1qqstrrhjlp5h0qetmyll3dzg95yj4rr0m7rzfvp4f0yla2f3g5uj7hcdkkep0 nostr:nevent1qqs9p5z3djta5r223lpdvjgrcc9y9vcm4lsvj69zqfuhrgw3zqeapccfk9dcw nostr:nevent1qqsfrz8sp6sk0u75zwfskwxqgk2t495ymf5fqtalwdptagrx85d0yhsnejvgv nostr:nevent1qqs9a6ujeew8mzmuh8tewk89cv53fahgwyl552hq2qd5zjp5dccc3uq34j4s4 nostr:nevent1qqs8rhur5klw8pfu32nrqh0cp8n6fwgppvpjzpf9q437csc48x5gmmsngq8hr nostr:nevent1qqspr3sgff05240mlyg9y0j7x45qck8x7edzfeqrdafc9l3jwl490wsm4ll68 nostr:nevent1qqs2vzfrp2082gm88uc34zh7pe5zqypgsxkhed4f2aluep2265955vsatghhe nostr:nevent1qqsfjfaz8932tlxz9gqppvmvk9jpqclp6ejg6cdk488xexp5l8jn44gslrmke nostr:nevent1qqs06kyqpy4y6p24p8rpjc728hzn5cu5yvg57nl393t3hzhs4zrhmdgx7s02z nostr:nevent1qqsw5ez3ew4jmeuvz5tg2whsggqfn4097du4jspawxpun375njduxxq4s79hy nostr:nevent1qqsxrrmedupcnyjkv9azw656c0h70x7allk6kv3wqcqq2enar97xc0qmfsdgd nostr:nevent1qqsf88gx3w544ukdxz6wsr70vnhx42ruf7mn6p93e57jqpff4ty3adcgsu5sq nostr:nevent1qqsg7tef7jx07yp4udwnr3mhk4zc9ckdymqsre2xcjcu8y3ejszk0yqes906u nostr:nevent1qqswmqh45286p5uw83kcy38e0qz65xycn06xlwwg48g99kn6mkmmh4sn4nudp nostr:nevent1qqsdgdmdrnk6mf4rcfnqanjtptkazlkry3dnv5wt49znt4xn2ycyvvq2hp8ke nostr:nevent1qqswyueph6kfgwacrdhttat5pnk732m7qcsqt59sptu3cux9hzjw3scte3kfv nostr:nevent1qqs9gw4n83hgclvurawkhpqwtfdqm257kgkzve9gf6gx6n8p0k46acclzglst nostr:nevent1qqsvf9heuqcsxw05uhmnu67884h73mhq27rcv46lhdjhvly9e5eq4lgsalqhu nostr:nevent1qqs0s3mu4k6wey5zjj7rrff26q7nxpt8r2d3qex5mww00dpfqdltpvq56r5nj nostr:nevent1qqsty4e39zsmsax4m5m06wmw3fe05tlkqujk05k9d0sdz053zguagtstnfgu0 nostr:nevent1qqs9rz3at95dava3wnp05wdp7f6s7kl0rzfzpmm04ahk7a38akspzdqw7slkq nostr:nevent1qqs0vwqx7edy8z7m6sr4tjqjscgqf2fmqynkqequq6cp2cw98te5ags908vau nostr:nevent1qqspf7ms32mqyzt46jss7e2eurk66p2j0kdjt4mxx840e4fnfmd0fpgpnanv3 nostr:nevent1qqsfjtqrw4wmzc926gzkmval7s99p0m36vkkag206y25r0yevaw5dqcvk53zu nostr:nevent1qqsdhhmptxgvjxv30r3zkg48kjangs9u9yyfncjs7j26y3xq04r0e6sgktj68 nostr:nevent1qqszzmmc2krvwn6auf9nvhr9uwau66kymjajwzlfukq7evfyee4ukecs0kgyy nostr:nevent1qqst6w7u8lhjzat6vdl5ys7m4dpr2dp07kqrw6qzflehkd2chhu3u6qlwvdha nostr:nevent1qqsgl48cu28690ns7endh3es2ydjv5wjeexv5gqhjmhmgj2alp352tgdzzss3 nostr:nevent1qqs2dzyjlj99mhxznnuvhlqrn9rma6ydatj63umwaxw7yzvlltafyqcv3f9mz nostr:nevent1qqsgu088v434nqvnnqrsltnuvhh68698gm5acgmne3k67lh48au8vtc6ys0jz nostr:nevent1qqsvvp5wg5mrnc4226c9ukl7kydyd4v0zgte24nff9l7qad4wx7xpqgc2x3h2 nostr:nevent1qqsfwqwgttstups774qu448437tn6wx9ffw7l5w5fu5ljs5s7efh0zq7csjfn nostr:nevent1qqs0n9gqdjrant7lx2vd77023kh9csr256apwv2f7lsucewuz0kzwzgtmxda2 nostr:nevent1qqsreqlk6ncm7j0zsy7ym2kthv0mc93vgjl5l5jkn3s083ztswsujfszcyhyw nostr:nevent1qqsznlsfkf7ptq4rnegqsd0uvz38mmtk2eeshkmw4y7z2klupzrmgqc2rhluu nostr:nevent1qqstfheaq9cfq96w8kyvwc4herjnt5ehru3zen2yjfh4muc8zx9kmtgehnpyc nostr:nevent1qqs8ac3g79el94kgudcce80h6j6u3nnwagh2rgh87fu0ffky09tx6ugsyxd7g nostr:nevent1qqs0vvczfx44sk9vx7f7fd0l5d8nu9jp9mgv8n0n4rx03ytsx9rh64cml8am0 nostr:nevent1qqsyrk88pql3s2ue85cuwr56pude6f7ay67ylymmtezxdl855tu0pfc2sdwre nostr:nevent1qqs06nhur8vlwf2evmjt2fujamcka38v5krpzfs0yh0n7lk25vtj03ct8nxy4 nostr:nevent1qqsdetdugy6me4l44svtrsy4nc6lsvy8fha9824lca5v9ejdfdasclqd9jf2t nostr:nevent1qqs22th6z0g63dswxjxfwnk92tmpzafec4p9j93cw99tvelervzj2ys3lrsgf nostr:nevent1qqswyktlpagzpjfmv7ldtgkpdzt93zt76s04sa96ngkl976wjpm3dagat2pny nostr:nevent1qqs9pv0457acvajt7ln7tlq39nhlt7tcn4u2l8pvmtjm0f3n3ueuvggxtjsq4 nostr:nevent1qqsztv6rh9s3mx3h237nywtz3z86w6ydsynyp9nzyu43qhuejx5kj5cmc4sv4 nostr:nevent1qqsdu6aqu9y06pw9uk5zah408f5whnuunc3eafmemh5pfeyh20gwc9gr2m00g nostr:nevent1qqsdctkdrz4d0vnendwrekj9uhfw4lkxfjny2gnyrmjvgn0huj3u2xc3aavvw nostr:nevent1qqsp477v4mk2d4qvpj4xt6ua43rj53eqs48qk6jh7lm4c300fq6nm2qxmqz68 nostr:nevent1qqsfgl3x0mv25ytjtr0p5vq2acm4hhnmuxynwxe9a0whvvylsff9ajg0r6du2 nostr:nevent1qqsyvy3qd2hg5tmatgzgzrw9nuqk7tnqtuzzvxhfj7cf9mn06nsq3psxv56se nostr:nevent1qqsgx7lwjaj65ey59m42lvquam85l0vxvx9fcky43nhff3fxy8t7a4su60nr7 nostr:nevent1qqsv6g20rdeq229sfanduu2c497gp9gttejyd9hcpalm4u2f6af3gjc8ynpjf nostr:nevent1qqsqqrmzka388vxuq3ly3urust3svxr7lewxjnhul6v2f9na0xwr3ncxu638f nostr:nevent1qqsxdx9heupdzvhepkq52j0655p94j5w5z72hsy9dcst8h9dgcnq82qwssgfj nostr:nevent1qqsrdvpmljkwdxf4m8jj3ju63w7f42cy869ukwhmgxk5u47vr9q4vsgg54903 nostr:nevent1qqswyy7rwkrfv0q98tdhv43sln0m6gt2yy585m5km70ylxds76g9shst6r9e8 nostr:nevent1qqsw2e5a6hn8hca8xe0aywrgrgd89800xy8680f7cmwc9vtnag47jwqxplvu0 nostr:nevent1qqsywxjm4ay8lcxqvrxqvfgfcfsck29w67uf6fpwas0u2vvm5e772dq6unz4j nostr:nevent1qqsxa9w7lyydy3kxwnnm0a8w2vzjt2px7xklegw2apyvr68wgeepq6qjvmm32 nostr:nevent1qqszt2x6zft0f39yxu2er5qhh7z09xh67kcas9cunwshx7pz3w2xlzg8w6yyx nostr:nevent1qqsvj9q04sw0hlwvfc9ul7yufjd8uy9v0zlhlplr36u9r9t37ffl3ggtx7ard nostr:nevent1qqsgwj2umphzxm82njqzqhm3ujhyept9wd5pvxyzl0u8yctvh4feugcl83uh6 nostr:nevent1qqs93wup3yx2l85rs427uzucujaym9xpkrq6frnhyl8cd9rl8atp6hsak3a3t nostr:nevent1qqs22gxegsg8jwqzptdu9v0m0z9a33tnr42asuujp880qegvakdfasqzzz8tn nostr:nevent1qqsvx3na0fj2k5z9n9jjmcfnxjscq4j58mhpk9yd5ga29z7tq5rayug2pd030 nostr:nevent1qqsgalz2tjnszu03qja9tqmh3fnfhmpmdav9khcwh9506wq9dx50s0gqxe550 nostr:nevent1qqstd0rl52dcjacw8v072e40kc54nyygv436fkja6k2npka0h4x8qhgg87n9y nostr:nevent1qqsyj0hhcgdj3s97zvdnlpwktru2e0f6g002674spyyektxqxky5mpsqym78u nostr:nevent1qqs8tyugskp6gyl89qeynpjp485vsfpltyqx0v5d6cvuacv773q9eqquleude nostr:nevent1qqst2u3y6w830ef6a3sp66gxceryenl3k36ch36mvl9e2d6jwfmgkwqkv4v3e nostr:nevent1qqsy8qhhxhh36xq4kaksyhxm2vy7vuyujrjdxu9m80mw889wx0va3eghz6xc6 nostr:nevent1qqsz7spxfkrzawcwge0hqt9l2q6kc5fc3s5h7pcwj8kqmdtgwsft56q32ezp9 nostr:nevent1qqsrtj4xvtx6tdjv4zmm6axugf29t8xrzp2nmdyh09rzfmaukzp79nckyr3p6 nostr:nevent1qqsrthfeuwsw8ty32lgk6jxqnt2mcr2g7sajze29tyztzys0lxavhkgn609w9 nostr:nevent1qqs8afxujdxjw2jcdjtfsmux72xufzwhhvtc6f44e4yawlcygu9mhvckpdr2f nostr:nevent1qqsfuz3xezyq9e3y99wz6u4z68e09ult0urcyk80rrd4w38jxrcp08gh2hp8f nostr:nevent1qqsrc9nth6vef28sylzxsp7a7ydzqq3slsuas2ydcm4chz76erzpy3qu52mes nostr:nevent1qqsvqr903utwyynxkqyt3nf4jd3gtk355t0rfj6vec6yfp5huqvu39g5tt923 nostr:nevent1qqsgs0alua2ftak3yjp2dkvaxtxk59q8jr6fl3z02z9dt5ecalgjsmqyvpnz8 nostr:nevent1qqsx7sg2tshm7fgku6y86krp2sfvk7evua8mzy86agqfrwphtf5zk9q0rszzc nostr:nevent1qqs95ztf6g0w0k88d8ts5zcc72sw2f0lc0anhcp0f590sxrya70vlas3p0fzr nostr:nevent1qqsq4fsrzz7r60qk7lhmpq9j3e38edee4uuuhqnlpgw90dmqyz3jkscwh3emm nostr:nevent1qqsgnsekfcu53ser5pdnrfpwghsjl57r69xdgjnrn0qxflrvwhv0yxcnw8yyu nostr:nevent1qqswwf3wnj082vrpdjzjd8th0lkes6rdvtzgx0wfftn9398hajvypqc7fvpxs nostr:nevent1qqsyjdhjarz0dmpzpqd0ywhmnyenhmmy28lwj8nkca9av3fxme3s4xsc459u8 nostr:nevent1qqsyqkuylp78memrx58atm4pjggfjpnqmv2z6u0unngpgm89xrp7wtg0qtdus nostr:nevent1qqsv9sdnzjpk98ezcldylxmp7cr5207uxq3em0qdq4mxlc9rw3uflzgsra6wt nostr:nevent1qqsqalxng8fyvyzm5x9rvmu8f6g2mc4fvl42s8qks3v23admjjva9rst7th07 nostr:nevent1qqs245rsx9q22ycamy0dcm6p8gmawzlwj8eq9lp6v0kw96ssdzs2zxswfywrz nostr:nevent1qqsxjvyqjmy9h42kz5pud7uhl87kj3ceagdv4pseyjgrst9aj4r45nqxpwv47 nostr:nevent1qqsr97gg0jm0f87dqvt5dq97jx32uj004lkvapvkqy59wspuytup8zq6skp4k nostr:nevent1qqsy7xuzq5dewwfwrvwannr6vvdxhkxg7njjhqd435nq2k4vcm2ecns4d0agk nostr:nevent1qqs9e5ztm2fhqzm0283u2mzkvgnuv94cvx2h8p0946ch75g03lwr7xsg8mqt7 nostr:nevent1qqs0fvyf9w00k7cfdr7r8hptptx5t7q9gchw40twx24l4e7jcuv605gq34ugz nostr:nevent1qqs9zswmvckn4tke053m9tvhurpf7pwuc3kq82evun9vmvczdz9r5ec95k43c nostr:nevent1qqsrxpxjylc2fjtvwjvt7grk5ae5mwtsp9frkemm2lygfhqurfnfqwcm9k48f nostr:nevent1qqsw6p2j9g9yq0lh3d794nt20flzms2nyvq2752ypfwj2rnlx5sw4tghd5rvx nostr:nevent1qqswrv27dzmtavpcz6d9aphrg8anarhv7jvzfw3twfu43j03qahuc7g3j7pu7 nostr:nevent1qqsvqjgqkw0nfj0yph2ahgfhutw28u5ntyv6s8sz7lxn4jyg6mtw99ga78gwz nostr:nevent1qqsgp93wmz9uyzmzwunh8zvaz8wndg36x04kryw565fwgs6glprlfjqxu537m nostr:nevent1qqszrqjw83xkxdwkp9k45e5fnulp7gjf9ct5zqwxuy8e0mdx2r9fsrcdyay6n nostr:nevent1qqsdyvrhkvdwz6m73sckckr4esauq09u9dhphskxa22kl408gkpmdmg4f85pz nostr:nevent1qqs9g7dhjwlnludgsnkutdf2mnuc4tvagn4jcg7z4uufr3h2w9jd5zsv777kv nostr:nevent1qqsgdwljd9dynp9zd6c2c5l6fyy0j8sh5c44tv55rn5l24lfcq0pz3q2r0hmw nostr:nevent1qqs2atfxw3lzqtawhksqdvzqx7qw3xgp30knlks6lp0rtzhhdczafdqugctck nostr:nevent1qqstr87at5uetk975gwa26evejf9uuhdja84uc602dq7u3ktgfculkc8z948c nostr:nevent1qqsw6kt9s9hqc0p6cd97gxgfdgntdc4kwsf06t8r5q8k7syllr5nffc3e2ved nostr:nevent1qqs2vvsyxxsf73g68nnfkpskyjrhd655852w9w39m4t9yfxk70t2amsqtvlc8 nostr:nevent1qqs9qha3elys5qneel0rlt0s5ch6y6hytt8umpp25knpfu5lm3kvs8snxet5m nostr:nevent1qqs2gkprq3kd4dqf7lzqhg9mgqa9dnagjgaresvgcv63syf0zma0jagdcykl0 nostr:nevent1qqsdn093lcfapk0ke2zqe0982yx66auxvnjklq0ytsxmv7txsn5l06q76jefa nostr:nevent1qqsx2yxa4y7u4trxgtkyvp4jfssdm3lfrtkk7cpkewnpuflq522mkccttn0m9 nostr:nevent1qqsfpphq39tphc0znfdvzty88fdejm4wjr5l0n7ksld3vff0kuhak2cas8yhv nostr:nevent1qqsfvzmk7cfanupzthrjh0t600z6szxj0mz40hrrm4rd7kwqqcehrec27k2qw nostr:nevent1qqsqamgz56h7lqg96p3a42mhr9f7rxjprpsaawz9n2uhgh8n7kaukvglw2xvy nostr:nevent1qqsqt3wp8htyhre4d9n22ldml7k9vs655h55n8758yeenwnc2c8yxmc4fn77d nostr:nevent1qqsrurt0gcz8jzlkyqahz288ex3mqwu8tyh0rcpwlrmu5jckhj3wg5sd6m3a8 nostr:nevent1qqsrsz2uyqvakvwpkne2aqhl3d9yjjyzz2wemsj6vv63rcvcylra6cge70xu7 nostr:nevent1qqs93dzpp2acdw7aq9nwtjg4ap6ytjrc6z99mz0x4l6gq2arpd4r8nq3vzw6u nostr:nevent1qqsvam60cggvxtgxdelm4ja6n8wkqjlsdvwau4yqpr67q85jrc8fmcs6tud72 nostr:nevent1qqsztc59n4p23tw3zwewzn88nz99pwal0fh37aw3gg3ymzlg8np5ghguh0r69 nostr:nevent1qqs9p8k384u2qmugnzusxnna2ge3wldg4rvs895zu5pq6l9df24h0ygrytc6v nostr:nevent1qqsvh2lfpxvp7x7cs9d8ttr9ra9m6xl5405lal7x6f2uf5xymlz6j9gqp4ut3 nostr:nevent1qqspndcrk2lxd86tvdy3yd5gqmytvr543pa2cpsgmjylprk33zcsk3crx34t7 nostr:nevent1qqspr3nmus3ch4zy8js73gvqxyz5p5ed8ch6rxl4ymqs2x9fql4ys8gn9x9qw nostr:nevent1qqspslhp7kzfgu0t8rgf0nhm0s4rgnj9rx329vuze8f62r0qmtpx8xcm0tprj nostr:nevent1qqsg3hk5mdre8ny2fpp5xwct7cary359ld8cx97f5h388epg9flwgeqfuzwzy nostr:nevent1qqs9d7dqsqfp2cv3mstn7fnwdsemtct44wan43uy4kkfchd49l65lxg5h2cjz nostr:nevent1qqszn7ycnfn9suns5xxam2207v70ast0w07yq9shwzv6e9cuvz2w0vq22kafd nostr:nevent1qqsdyfrj2n0mxtkgmdy562qdahj8vzrt8drjphvw4cfgp45qvwq06lgu8tzea nostr:nevent1qqs0tja3rdn95q3plklyvz2swkyj8wmfnf5sese5882mh40yj85mdkgcx9sdt nostr:nevent1qqsdfj4zf20wpg8ldkdt2pdnr0tjmjfgc0mz8e2t7l4kf7syrelxhnqnplcq8 nostr:nevent1qqsp9wva4ujkvzyl7ve05h95quq6shnvsgexkw6n588n8wym6tutujcrmdcp8 nostr:nevent1qqs2f6t7et6tag8qms6vkzwpw9tn3fvxqp86hh7dxrr4pxfeeunge6cgaykdg nostr:nevent1qqs0lnhgz0khlsjjq6404p2hug3pwvcqt6x2x6l7yfmfqwzxf364y2gawq8xh nostr:nevent1qqspj2ar7xc4zs3catcks73ppvs77sj59zfdd6vu0h99ukqdt7wf0cgpdcq7s nostr:nevent1qqsyytgaxazjm8gnj64g5l4hushyu9040r336xs4sl0s79jet77esyspcmfel nostr:nevent1qqsw0jdhk5sytywvpn4gzfy6ahrjsmarellyjwy6vm4t82l83x9h4zca63vzu nostr:nevent1qqsgs9q52e920wx0gsy29egqch5x6aey9mtt3jl8kv340uw7lmcgceg43ecjv nostr:nevent1qqsdj0awygazadajkysga3anet6s38vrxrvj55kvhyguvyagqxk2z3sjla65v nostr:nevent1qqsypmjgxeqt9rah3sfxraudpdfhfj0k0sut39n07e4xwtpw5fmju8qfdh234 nostr:nevent1qqspaqxwrg9trpcg4sp2gtjjw6jw6u2rj9yu8al2hscdfdv8ra60f2s5z56vf nostr:nevent1qqsdp3kg2f7ena80zkpw68uc8x4fatccul56jf5j87nhzaqk8mwgsccczcc57 nostr:nevent1qqs9p8wdx53y57ysg39jjgzt5gu67ntqq0u8zv7gsgp3v3xsxw6ta4ssvh6vp nostr:nevent1qqsppejxz438ummams5427fzzfg4lnuswfww6ha2yapf4kkl73mhm6sjtlans nostr:nevent1qqsfewzswnqzwkp76qp7rga0007v2er0s797eqcd2z8cee57u74xv0cn290jt nostr:nevent1qqsq9vjah3gtma3gz99y4m7ey6df8p34n8u572cmaqzwq95xl9xm72gwfrqg8 nostr:nevent1qqsw2qm4664k4f6633j57t7vrwxn9rht6x0sf2suaejjgttrgxm52ccvv9lrj nostr:nevent1qqsplx6sls8ga3eez376m6umwszjj6lmuardvzs72pyekgzyanf0c5s5d5q2r nostr:nevent1qqs8cast93yvaxl0zj20aakl6h4hz6wx8vr7sv4cy4sz20frpdj9ezslrvq4s nostr:nevent1qqswku45leeulqe574ustynud357jwneu3t02qatw0atr3zyclxzaqscxj0sj nostr:nevent1qqsfmsqlukjx47aumecfhq979c53mmyv99ftfgj2luz9h8fe54m9x7sg0jcy9 nostr:nevent1qqsyquj9cquhsmzescerqjyur4cct2eatd6yrp7cxlfjzr0502s7fccyggrwq nostr:nevent1qqsxxurfn8xd83nz52jw2z37cvc3pdnsxvtp6fn9wkzysezh600wl0qs3mdws nostr:nevent1qqsdalre0nscl5mcg8z5tj2rwc08qpjphzvdy56fqvshtuuuvaqgjtskgr03s nostr:nevent1qqszln2q627ef64djy5pn05jzuh8alnuurl4z67fagtehucfg24pkscrgnnth nostr:nevent1qqs0ztxssvt4kt7kuwyts6z4pm7k46undqpccfvn6r54snuzax66z8qw8fyvk nostr:nevent1qqsw8h3n6xc6f5tpqtcqud68tdczruae32hqwdenes34k5dup6kqxqgnwawsu nostr:nevent1qqswjh2qdz0dgmj3va747seu5eu9lnr49zt9kws4lx8lczw74x5gj0c70r6lg nostr:nevent1qqswvkdqtkxy627hvxue8jsam0m93scj7p6jjgqh0mn2r6m9u4pfq9g6q882j nostr:nevent1qqsd4uhh42gq9sj4vtwcr6cnkpwd9k3mzm0g8myakg9ynglfkxyvlqca64zcs nostr:nevent1qqs8wnayqec04sqvl6rt9kyylty09jng6g4ktv8h594x95vn352a43suhqvtu nostr:nevent1qqsfsguft8a77ttqff88emq8dfrvqs8v8lc8ka5d2pjt57wesq6tk8cz4a84y nostr:nevent1qqsf99szvuzldnvgg49dnvlttttd89xpkc9rhfn4wghsfwalrsplesqvw5tpd nostr:nevent1qqsv4vptazj68zgxvf8z5zy3ptz8vwfgkq99a65l2s7hslc5y8vafequjwp3t nostr:nevent1qqsqa5zjxcdu3t7qxlqnrgcgyvftwr8adns8eq6anevwalawpshjs2g48e9gl nostr:nevent1qqsx92uj3cg62w3fsnys7vepwvf9x347hdm3cgww4nvqetdc8h6y5aszzrs7z nostr:nevent1qqs97wu7kt8g3u9sp06rduksjh22uz28etjv7d9fqccfzh2rcajc5ssx6660y nostr:nevent1qqszrjy9qltpxrmqelm39s8f68p3mzq3mz6hy535kt576ryd4xj45rc6m42vz nostr:nevent1qqsz3tzzg2cp2qqu0wpcvg3lgdz7t5jalrl3z9vnhh4qxacx3mt370gma2eur nostr:nevent1qqs8ys6zj6ta8c9m4f47g04tyc4s0uk3rzlj8nzyvn88rqjsak8d3acd9m46w nostr:nevent1qqszc99x43vh4y6g6ufa6s4ffrppjgjmun27je898u90fdml6p2hz8g3dtnhp nostr:nevent1qqs8k903clgruktvagvadtf5huyx4leedd0w9shcrgwyg90y0g7tzmck89mzp nostr:nevent1qqsydxc8mzmsf0qyx8paweap69qaw8fgssz56xmg5q6grxqee2uz75gszqegy nostr:nevent1qqsdscwrfvt0fr0847qd2edna8lduuh7fk2g8jhktvr0r3gmrs7l4kgw08n9r nostr:nevent1qqsrf7tduyxx0h3ywed0pfjtnf7wxjde6xqzeu9qczwar50ptql64uc2cytg3 nostr:nevent1qqstnwlulgt689cwygappskjlexnt3ejzlh380w6gsx93e4mg2smt8gdrz8l9 nostr:nevent1qqsdmke8e87qvy54lz0u3twz36wsz02t8cp0qp5v5hepwd2nf4lfg3seyp84n nostr:nevent1qqszrr2k94yve0v5lxnm82x55vkwu3g36eqf8nya5cgxz9utwc7tlvccuu63k nostr:nevent1qqswgyad2qu6ltmnfasetun80hctvkx5npnwqamse33auvpm2tev5usvx5xd2 nostr:nevent1qqs9cxp7w8tjzed2aaxfscglmac4ddcqzmt667pv2qxck6zmfs7gmkcdxpzps nostr:nevent1qqsgdknwqqa6gkr0x403s6eh3xxjxqd0gy8hxp9mkxkuffaxqmffk9gya2fhh nostr:nevent1qqs0rq7r8s56jhnrysnkg4k99f0q96uphl7vjvjexaazufpzmjl2ldc8ppz5l nostr:nevent1qqsx24ratma6qgt65vj30k5vtcf8ls5l9swrxhe82t3f7xev92n2ckgxepk7g nostr:nevent1qqs06jpjgw56t0xuuu82td6sd8yjnpu9d78z4vvxc6q9gxq5axh0n6spryvch nostr:nevent1qqspa75xvvkw6zpavvrgp3mk30y6shjsg43v0yekk2nqf582xek3mvqr4vjw4 nostr:nevent1qqsvlz88ahc6uq7yqfuuus2vgk035ywa582amt3umaxq0a4hw7sdvzchnavfj nostr:nevent1qqs908tjsfvv9hwn64v800da3p2lkgwcwv695eksc6hhkavgqk6wleg3ue08p nostr:nevent1qqs97hyy2zm3lsah7r3d6u536xf5wn2w8afyqlz7zgqwmaqsn0flsnczp2q4f nostr:nevent1qqsg2hatn34sm5qpsxsykdk35nwrp68n5ggjlgac2qrhjxrzp6vgvlc8v8nuj nostr:nevent1qqsyu8evwrh0kagzjcpcfy8nhdvt5gdnf5q0pex7vukagnm3llzljycp4d3h0 nostr:nevent1qqsvj2hnvgme0zzf8p6u0ehlk27z5yn4zwlravn9ft3smgks77gnxnst533zf nostr:nevent1qqszhfx4aq8qllq3xd2cnyqyenwzu0gysqr9fdrwsx73zp5rv9uflegmeqz70 nostr:nevent1qqsqmga4dkcqkw8tzugg23p7qck622wlgxhhtfshppuzpt8a8xpneac9avf4s nostr:nevent1qqsp3tf4vamjezdpcc4d9jxjrqj6mpunehw4n0p0m6cwdzxy2rgllyqeves5g nostr:nevent1qqs8vnfc2uuvsce0c88kyz5qpn954zv5wqdksprq20c84x0m8axndlg3wc3v2 nostr:nevent1qqsgvctjju645q2yuleqmmt7ku4pwjrf0pjgher4um87k6t33h4yycg5ewtzj nostr:nevent1qqs0ud2vpw9mp59dq5pm9hyxhu6vye9z68k9syrhfjsdqed89zhureqycl52m nostr:nevent1qqszkwqymc8xhvn0afnw9j4ax3dts6e7rv5v9n5zhqmxuxgqmv09kns8rjn00 nostr:nevent1qqs8e6kcap8ae2es6t34053pfvpkeucpt34ve6hhrfgnvh7j2fa4u7qnxaaw0 nostr:nevent1qqsvjd08zysyj93ypsze3jraww4hjdqgr25kzee86c2mutz08rzjgac4k4ef0 nostr:nevent1qqsqqgqnayjy80wfa3qkws83a0ef2rxfnpdet5f33ph0csz3gcqap8gjjnyf8 nostr:nevent1qqsp5m8ar6rsuaah2s8mz8knsq7fm3vlqk60pkvs9xvgugxt99c46wq8va8vg nostr:nevent1qqszptmufg2y38v2cy6v57ptnf27mg7kvh5hmp8uhk9cjwl9m8zrnqc6vf5dx nostr:nevent1qqsg9jl952dq4qvzyfklverpt5aqkp6lmw04kzz6z3zz3n9qg5unt7qjchphg nostr:nevent1qqs9e8jgsv4kyulgz0r7x5z3mxuw2l5ya8las4tkf5z8sy97elvud8qq9s88n nostr:nevent1qqsw0w3f0jvx6pa203kqm8lmhaf2qq69tvnt0f7pedp8ksmtazmjunqzvz5d5 nostr:nevent1qqs25shxc9l6mcudx8su646etmfmx7ywv87dcewjxu87qax49lnkylglpk47n nostr:nevent1qqsfj00j5sk7fuxuxxt8wpf9d60vysfqk0mz53478tfvccx4s4ys7rc2l0uzj nostr:nevent1qqsfwdnw4qfc7j3hnhcrxdu7ecxvgpjmveftu9g29fxg4ra7k9vvehgd744hs nostr:nevent1qqsfqm6phetgyjr7f5zt67gq6k8dv2lgh7j4leax75wk0ry4wfral4sp9pv56 nostr:nevent1qqsrtl8wtsxcrmncwkjrshm3d7ys633zswz5y7r530ywlfpsjk8qtpsprkh4r nostr:nevent1qqs2mqqlpq3s5scaz9dsvn4vnqwzyyp8wtxe43k2pmlfvn9qk9ck8ksts3ll3 nostr:nevent1qqsyl7rhny5et457dm6l23z6hercuvv5hch7pm5xs4v2ekn44c27zaqjpx0r2 nostr:nevent1qqsp3yaj6hzzfd840kmvsct9nw7y94c7pdfw2cnkdgqwaswx2xr0wcqeusc5d nostr:nevent1qqs2ze6chukganrfwmnspce3nuu02zmh0r4nn3z5ed62xx8qtvdjfzsyzp75l nostr:nevent1qqs0kq8eevn32v0karl0naywzeqck2m9sqsync2p0z4phc2tdx2mf2cqer0ws nostr:nevent1qqs9h77g2c3t72q4l9n7e76me8488qkdxyjw2l95nztx36kzxd73tjq973dat nostr:nevent1qqszq5lza048954nq30pwfmqaapentajp7zjqmjtw8zvh0zunt662vsvuqzz5 nostr:nevent1qqsxwhlaqhtkhpsn209e0a7lla3upc0gyse4pyg9np44lc7vg0nuzhcjtljuf nostr:nevent1qqsg2a04k9r6mggptyxjjt9d5whjull77d3aw8xfel8e29eeje8ugzqd8frp4 nostr:nevent1qqs8sk0p79mn9cgcjgxhycyrtq0fxzxepvlnd706mfyrhyyj7jqyk5qhuqfpw nostr:nevent1qqsx9t68ffff4cnz2z36n52eezk6ayqefud340j5thdft7fjt2upd3q0vyzc7 nostr:nevent1qqsw6cn4w95ku93u9atcrduz6st8vuwf9zf4qjge3w6xkpa8lp6rzesufawc4 nostr:nevent1qqsv9yjmw4gq3xgxy4fq02rqk8gsqxk7wyh4uvhppezxrcp7utacdyq233x8j nostr:nevent1qqsrlgvn2uu0zueultxv7stkaalw7vdu2z2ukvttfdw5sj2y865g50gws5cds nostr:nevent1qqsgarz5ppp3mn4m77t2xzzjqq0tps5sjxuve3k2w0ylf55vd4a4uqsxvd9xj nostr:nevent1qqs95z85mhl75j27g5aqw8s3ntm5kasmlglsg3w3u2h6lncyrg0rvkqc5zgjf nostr:nevent1qqspdzkrtk8h8h67egltafs7s32j9vvzxcpycm8dd689e572atr8xfg30a8ce nostr:nevent1qqsq2kd7c2flkrwqz4344gpwx4al4ekrr9wxe3kt7rjz7amcutnzcpsej2atv nostr:nevent1qqsfhz5rx22f5m3x60dpe08fjjpu7mrkeqpq0z2jjn54yh3uzdw257gpws5nq nostr:nevent1qqszc7l3tp70y0ml3zvppuyj2kvs07knxq6d8je3saemv2pgthc2hgczy6pw9 nostr:nevent1qqsta6ec23jz9jpxg8cfy0ae84xcqrcka6u7vsknjfwsq7ec9cx2k2gyfmgup nostr:nevent1qqsyad6h6dpykmhehuaseh2cu53reqf4q5ff7g0k494jvqwjua2dmesxdjwtq nostr:nevent1qqs0g5nm4jajj9rfzd42cueqhakyevs0zg3zsmnv2y6va6dqfnzx79cds0u6e nostr:nevent1qqs8kzvkgq7judfywvt6vaekwn9azslavl75xe40t8wnzhtar24p3kcndx7ld nostr:nevent1qqs24ynaypvt745e0nmdux5cjt57fxs9wtda3p7nnn5jslmxv9g9q4g2zt603 nostr:nevent1qqsp2nujt5m6ypp5cn4yauz58stjn4m3jguecklw7hgyjdg73zc4ddsdz32p3 nostr:nevent1qqsx9sqkyv5afv03mdc2w0ay3t0u872nme3c6ryvs48r5hd7gjg6raq9qa7sq nostr:nevent1qqsv0jsyde7lndup8czlzft8dw9mg06w3evmhtz4ezj2zteepzxacwgdsv7jw nostr:nevent1qqsdu644w6mrn3u468vzuhprckkc8xjqznev2h602ft74c76vx2350cgrqv3a nostr:nevent1qqsg6v7z35vjrfrqkly6fewjjk0yxd5rwdepp28t9ghnt3s9kpdynhce8w5t9 nostr:nevent1qqs9l446svwqwr5h54ygrceqvf20guta566ezwkneu2hx49ha5vdalcjevmxl nostr:nevent1qqsfurxh37ap65w8c87ju4pr4jr9245drjf3ua4l7hc29429cse7e5cw46m4c nostr:nevent1qqs2q76mjpqq8p9kz86869gs65ccrjye2uml887tdau9znqg43k7phg0mzlx2 nostr:nevent1qqsdq24a356ep48la4yt74tcyt5as37ux0ejxfzpthzd5y85ws0n4xqars3lu
-
 @ 82b30d30:40c6c003
2025-03-17 15:26:29
@ 82b30d30:40c6c003
2025-03-17 15:26:29[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
[32]
[33]
-
 @ 06639a38:655f8f71
2025-03-17 14:59:40
@ 06639a38:655f8f71
2025-03-17 14:59:40https://ccns.nostrver.se is a (Drupal powered) website that I started to build in January 2024 (source on Github and Gitlab). It's a fork of an earlier (abandoned) project https://cchs.social/.
Currently CCNS is a link aggregration website and for now it's only my who is using it to save and share Nostr related links. When you post a new link, you have the option to cross-post it as a Nostr note (example here).Kind 39700
Last month Jurjen and Abir have started to work on a social bookmark client built with Nostr (inspired by Del.icio.us from the past). Earlier this month they changed to event kind 39700 for broadcasting the Nostr event with the bookmark / link data accross the network. They did this because Sep already created a social bookmark like client called Pinja when fiatjaf raised this idea.
With these developments to me it was very obvious to integrate the feature that new created CCNS links are now also published as kind 39700 events to the Nostr network. This means that links are now also distributed on multiple relays as kind 39700 events and are accessible in multiple clients (Yumyume and Pinja).
Here you can see the same data, from left to right:

Structure
The current data structure for the 39700 kind looks as follow:
- "id": "event_id"
- "pubkey": "pubkey author"
- "created_at": unix_timestamp
- "kind": 39700
- "tags":
- "description", "description text here"
- "d", "unique-slug-value"
- "t", "hashtag"
- "content": "https://book_mark_url"
- "sig": "signature"
As there is no NIP (yet) for this event kind, I see some possible improvements:
- Use the bookmark URL as
dtag so it can be used as a unique identifier for every client - Use the content field for the description
- Use the
atag for an addressable event following NIP-01:["a", "39700:pubkey_of_author:", recommended_relay_url_optional]
On short-term I don't have any plans to developer CCNS further, as most of my attention goes to the development of the Nostr-PHP library and Drupal related contribs using that library. That said, CCNS is a Drupal project but all the Nostr stuff is done client-side (Javascript) with NDK and Nostr-PHP is not used (maybe this will change in the future).
-
 @ 84b0c46a:417782f5
2025-03-13 06:44:10
@ 84b0c46a:417782f5
2025-03-13 06:44:10 -
 @ 2cb8ae56:84d30cba
2025-03-06 07:40:38
@ 2cb8ae56:84d30cba
2025-03-06 07:40:38どうも、Nostrまとめ(2024)ぶりですね。
記事として出すのはかなりお久しぶりかも、お名前変わりまして「フェゼレント」でございます。 意味としては以下の通りです
1.Fezer(フェザー)という英単語 2.ent(エント)という造語 2-1. netを崩した形、よくこれに打ち間違えます。 2-2. Entertainment(エンターテイメント)の略語、なんか娯楽とか話題を生み出せる人になりたいですね。
1と2をガッタイ!!!(トムブラウン風)しまして、フェゼレントです。
なんとググってみますと、Fezerent及びフェゼレントの検索結果が0。 これは...一種のチャンスでは!?と思って、使っています。
さて、そこで出てくるのが「薄味のキャルピス」と「IVstrook」の今後ですよね。 後者に至っては3年分の料金を払ってドメインまで取っているわけですし、前者はかなりネットとかラジオでも浸透しています。
というわけで、こんな風に置き換えます。
Nostr、YT、Discordはフェゼレント及びFezerentを使用します。 それ以外(ラジオを含む)では薄味のキャルピス、IVstrookを使用します。 そして、NHKなどAM波を使用して放送を行っているラジオ局用で使用していた「テックジャンカー」ですが、使用を停止します。 あんま浸透しなかったわけですからね
そんな感じでやっていきます 最後に、記事最後に使用する署名のような奴ですが、そちらは変更なく「IVstrook」単体で行います。
また、ニコニコ動画及び各種ポッドキャストサービスにて配信しておりました「Small Room Space」ですが、今後はzap.streamというNostrのシステムを使用したサービスを用い、番組名の変更は行わないものとします。 zap.streamでの配信開始は「4月7日」 ちょうど#1が公開されてから1年が経過した日です
重ねて、当名義を使用したニコニコ動画への投稿は「3月8日」をもって終了とし、zap.streamへ移行します。
以上、今年に入ってからまともにニコニコ動画で投稿できていませんでしたが、そのような運びとさせていただきます。
2025/03/06 IVstrook
-
 @ ec42c765:328c0600
2025-02-05 23:45:09
@ ec42c765:328c0600
2025-02-05 23:45:09test
test
-
 @ ec42c765:328c0600
2025-02-05 23:43:35
@ ec42c765:328c0600
2025-02-05 23:43:35test
-
 @ ec42c765:328c0600
2025-02-05 23:38:12
@ ec42c765:328c0600
2025-02-05 23:38:12カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ ec42c765:328c0600
2025-02-05 23:16:35
@ ec42c765:328c0600
2025-02-05 23:16:35てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
test
てs
-
 @ ec42c765:328c0600
2025-02-05 22:05:55
@ ec42c765:328c0600
2025-02-05 22:05:55カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ ec42c765:328c0600
2025-02-05 20:30:46
@ ec42c765:328c0600
2025-02-05 20:30:46カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 21ac2956:09d1e2df
2025-01-22 15:27:00
@ 21ac2956:09d1e2df
2025-01-22 15:27:00kakoi の仕様についてのメモ
キーボード操作
- 左手での操作に最適化
| キー | 動作 | |:-|:-| | ESC | 設定画面 | | F1 / F12 | ポストバーの表示と非表示 | | F2 | 時間の表示と非表示 | | F3 | ユーザーアイコンの表示と非表示 | | F4 | 名前の表示と非表示 | | F5 | Geminiによるタイムラインまとめ画面を表示 | | F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) | | F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) | | F11 | メイン画面の表示と非表示 (ポストバー表示) | | Shift + W | イベント最上行へ移動 | | W / ↑| イベント選択上移動 | | S / ↓ | イベント選択下移動 | | Shift + S | イベント最下行へ移動 | | A / ← | Webビューを開く (イベントを右クリックでも動作) | | F / → | リアクションを送信 (イベントをダブルクリックでも動作) | | 1 ~ 0 | リアクションを選択 | | R | 返信 | | B | リポスト | | Q | 引用 | | C | Webビューを閉じる | | Ctrl + Shift + A | メイン画面をアクティブにする |
タイムライン
- kind:1, 6, 7, 16を取得して表示する
- フォロイーの名前の前には * が付く
フォローリスト(kind:3)
-
参照のみで更新はしない
-
F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存)
プロフィール(kind:0)
- F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存)
返信(NIP-10 kind:1)
- kakoi のタイムラインに流れるすべてのイベント種に返信可能とする
- スレッドを考慮せず、単一イベントへの単発返信とする
- e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定
json ["e", "返信先 event-id", ""]- p タグは 返信先 pubkey ひとつだけを指定
リポスト(NIP-18 kind:6 , 16)
- kakoi のタイムラインに流れるすべてのイベント種をリポスト可能
- kind:1はkind:6。その他はkind:16でリポストする
- e タグは relay-url に空文字を設定
json ["e", "リポスト元 event-id", ""]引用(NIP-18 kind:1)
- q タグは relay-url に空文字を設定
json ["q", "引用元 event-id", ""] -
 @ 84b0c46a:417782f5
2025-01-11 01:48:46
@ 84b0c46a:417782f5
2025-01-11 01:48:46nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0df2mwnp2q6hm6zjrthkmx3fudwsuwrmgnwrdavpzgjy8nnuqm5cqpd06k
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs2muhvnev5367ywuzkhell9my86jlnzhsnuszwl46tnc3fpsx9mtgjkqnu7
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsznnkrl8qdwzgp7ry2hc7a77kwhg440gv9xtmvyfawggrpz3rhwvcx4rckf
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsyjf80k3djt96qncgvwl2yem09fdqcc0y9l8t657yc9qg2yhmg7kcnua8vn
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0s3lp0w0yclk64j0tpc5fvrulv78g2lfjz3gcgacw9mt6czek26qtqxuck
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqqs89tst72clc60wse3zq4qfs0976y7areffnhx26atvu6pv58hg6dsxvcc79
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr3mhxue69uhhxun5wfjkccte9e3j6um5v4kxcctj9ehx2aqqyp5k40r3ug02yz5y0tn67tm2lwevuwac54qyw3yyct8n8uzr7pjz2q92pyt
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyp9pennjwq2qk4dxpr440wxqm5cfwah4qccd8la62hantxdelkk82ty9mr8
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqsz9w30kxzjshwd8sq7jg2hsy2hwqg3zu7gyvxnsyrgfw0ur4rkhsg9v0re4
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqs8wkx2r8txt9q69c3zvpqs2em2s40nc8tajmcc5l8ngxn8v2ng3sc43xvzu
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyzdkacpjqvv2y79zgvufx9jh39rd7xa8v056rgn4xelmnmrq9u2tuguswek
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qy2hwumn8ghj7mn0wd68ytnyv96xztngv96hxqpqmdtjrs38fv8r20deplrlt8fma54gu43keuzquzks7673a27ud58slunr8y
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhkummnw3ezucm0d4cxjmr994jhyun0wghxuet5qqsxzpx2r5hd36pruzn2e58wh947y2t0t205fp5xtstqp5wq0qgcjuq07rqlk
-
 @ 78b3c1ed:5033eea9
2025-01-10 12:31:01
@ 78b3c1ed:5033eea9
2025-01-10 12:31:01※ライトニングノード保有者向け
Alby Hubをインストールした時なんもわからずポチポチしているとMegatlith LSPノードからインバウンドを購入してチャネルを開くことになります。2万sats(2024/12/4 午後7時時点で三千円ほど)かかります。
そこで誰もが思うに違いない 「高いなぁ。だれかタダで無料で私のHubにチャネル開いてくれないかなぁ...」
その願望をかなえる献身的なノードランナー(笑)がAlby Hubへチャネルを開いてあげるための手順書みたいなものがこの記事です。 ~~ppmをうんと高くしてぼったくってやりましょう!~~
※AlbyHubにオンチェーン資金が無くてもLNDから開く方法を発見しました。末尾に追記しました。
《これはアンカーアウトプットを利用するタイプのチャネル》 条件 ・チャネルを開く側 Clearnet IPアドレスで着信可能であること。Torノードは不可。ノードURIを公開していなくても良い。AlbyHubでピア登録できるClearnet IPアドレスと着信ポートがあればOK。
・開いてもらうAlby Hub側 オンチェーン資金25,000sats以上をデポジットしておく。ないと開けません。
手順
-
[Alby Hub側] オンチェーン資金をデポジット Hubログイン後の左メニューからNodeを選択。Saving BalanceのDepositを選択。するとbc1qではじまるオンチェーンアドレスが表示される。ここへ送金してオンチェーンをデポジットしておく。
-
[Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。 右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。
-
[開く側ノード] AlbyHubを確認、チャネルを開く ThunderhubやRide-The-Lightningなどを使い、Alby Hubのノードが表示されていることを確認。Hubにエイリアスは無いのでノードIDで表示される。 このノードに対してチャネルを開く。Private channelが望ましいと思われる。 6conf後に開設完了。
終わり!
メモ
- Alby Hubではbase feeは設定可能だがrateが設定できない。そもそもAlby Hubはルーティング向けノードとして設計されてない。セルフカストディアルウォレットです。
- public channelだとchannel_update, channel_announcementがゴシップされるまでHubへ送金できない(no route)。上記の通りウォレットとしてのノードならprivate channelだけにしてルートヒント付きインボイスが発行できるようにしとくのが望ましい。
- LDKにおいて相手からチャネルを開いてもらう場合にオンチェーン資金が必要。相手がチャネルリザーブ無しのチャネルでもOKなら不要。現にメガリスLSPからチャネルを開いてもらう時オンチェーン資金が0satsでも開けているのがその実例。
- オンチェーン資金が必要なのはチャネルタイプがanchorの場合。オンチェーン資金でアンカーアウトプットをCPFPするためみたい。anchorが登場する前のstatic-remotekeyのタイプならオンチェーン資金は不要。
<ここからが追加>
《これはアンカーアウトプットを利用しないタイプのチャネル》 LNDからチャネルを開くときにstatic remote keyを利用するタイプを指定します。
条件 ・チャネルを開く側 ※上記と同様。
・開いてもらうAlby Hub側 無し。 手順 1. [Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。 2. [開く側ノード] AlbyHubを確認、チャネルを開く SSHログイン、UmbrelならLightningのターミナルで以下のコマンドを実行します。
<ノードID>は開きたいAlbyHubのノードIDで置き換えてください。 <チャネルサイズ>は開きたいチャネルの金額、例えば20万satsなら200000としましょう。 <手数料率>はチャネル開設のトランザクションに掛ける手数料率です。mempool. spaceなどで手数料水準を確認して指定しましょう。 --channel_type tweaklessがキモです。デフォルトだとanchorになります。RTLやTHで開くとこのanchorになります。なのでlncli openchannelでやります。
lncli openchannel --node_key <ノードID> \ --local_amt <チャネルサイズ> \ --sat_per_vbyte <手数料率> \ --private --channel_type tweakless終わり!
-
-
 @ dffd3ffc:5ade7be1
2025-01-04 12:58:17
@ dffd3ffc:5ade7be1
2025-01-04 12:58:17Nostr 利用開始から 1 年を迎えて
はじめに
みなさんこんにちは。おっぱぴぃです。
ハッカーのおもちゃとしての Nostr のススメ と Nostr の面白さをエンジニア目線で解説してみるをみて Nostr にはじめて投稿をしたのが 2024/01/04 09:04:18 でした。
nostr:nevent1qqsd5v80f9zazxd4kq2r2dls5znd40ht6c7cj4slt6wtlv483vkmxdcjvq66c
Nostr で私が 1 年間をどう過ごしてきたか、振り返ってみようと思います。
初投稿日

今見たら 10 リポスト、20 そこそこのリアクションをいただいてたんですね。初投稿というだけでこんなおバズリあそばすことあるんだって思いました。~~みんな年始で暇やったんかな~~
これだけリアクションがあって、フォローもしていただいたおかげで Nostr の印象がよくなったこと、日本人話者にすぐたどり着けてことが Nostr を続けられている要因になっていると思います。あとはエアリプ文化が懐かしい&近すぎず遠すぎずで居心地がよくて沼ったところがあると思います。
その日はNostr の Scrapbox(現 Cosense)をその日中にざっと読み漁って、記事の誤字修正したり、WoS を設定してみたり、Lightning Address を設定したりしていたようです。
nostr:nevent1qqsxml4ak7g3u8gjcyuhy89sd8vlk3fu6we9ecgey69jltd42dr0etcvt0l3w
~~おまえ、このころから大欲情を…~~
のす会でのオン会(?)
Nostr 日本人ユーザーの集まる Discord サーバとして、「のす会」というものがあります。 過去ログを漁ってるとどうやら 2024/01/15 ごろにボイチャに入りはじめ、
nostr:nevent1qqszm0kv7aulxnmxr2fdxg5cvme7nyv3j6rgfa30cat8cs3npnsep9caz0xyc
その翌日にはのす会にて Geo guesser で遊んだりしていたようです。こじらさんが尋常じゃない強さでどういう事なの…となった覚えがあります。
nostr:nevent1qqs9knrf4ww8g0fsu4l74gxeeh3s9pwpnf47xn8pf5u8pplkz4yatjg03ufd5
こうした経験を経て、徐々に Nostr ユーザーの方と直接会話することのハードルが下がってきた所でした。
初のオフ会参加
2 月頭、TL で話題になっていた火鍋を食べた経験がないなぁ…ということで、2024/02/10、ゴリラ.vim#30~四谷ラボコラボ~の参加と併せて、海底撈火鍋でオフ会を開催したのが Nostr における初めてのオフ会参加&幹事でした。
この日は中国の春節初日だったのもあって異様に店舗が混んでおり、18:00 に予約したのに一行に案内されず、
nostr:nevent1qqspcttj4gv2ey7vkt0wp2nehqfwxjnp55vm4agnwu9kullep88ysccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg87v060ssxrpew6a0vrhkcy36hqppvrwjmlqnrgqrrvf8fghgg0pypsgqqqqqqs07ajzp
顔面が痙攣したり、
nostr:nevent1qqs9d5vycslspatsnx6u5qqqwpfmdt33w2v7xkytljzsfwv56acs79czyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zp6f7wn
詫び菓子を貰ったり、
nostr:nevent1qqs8a0u47alv9vexd5r5s5vygs77ecadm6dl9vlky32hjywdx8f3gtczyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zgjxmhl
病院待合室みたいな場所で検尿コップで水飲んだりと
nostr:nevent1qqsq44zs04g5zng35ks6jrvrv6uel2f9ls26d7nsc6svuggrlfnvtcgzyp4kuxwwg7530jlp8fn7adq982dnq8ncajv3gyl824y4xzyw6cknkvj37gy
トラウマになりそうなオフ会でした。当時の様子はnosli でまとめています。
今振り返ってもくちゃくちゃの体験してるなと思いますが、 ~~クレーターを作りそうな青ウサギがいたものの~~
nostr:nevent1qqsrs8y3phadhcukwjlkjkgdcs43ndkc8a42m88zayfj6p2lex6a6tgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygrtdcvuu3afzl97zwn8a66q2w5mxq083myezsf7w42f2vyga43d8vpsgqqqqqqsyfx7da
誰も怒らないし宴会自体は楽しかったので、Nostr のオフ会の原体験としては良かったな、と感じています。ひどい思い出ほど振り返ったら美化されるやつかもしれない。
各種イベント参加
Nostr には四谷ラボ参加者の方が沢山いらっしゃったこと、お声かけいただいた縁などもあり、いろいろなイベントにスタッフとして参加する経験ができました。例えば…
- Bluesky Meetup in Tokyo Vol.2
- 技術書典 16 ⇒ 関わらせていただいたのぶこ本
- Nostrasia2024
など。
微力ながら、自らの役割に合わせてイベントに貢献させていただけて、とても楽しめました。 自分に自信がなく、私生活では責任が発生する立場を回避しがちであったこともあって、自分としてはこれらのイベント参加はとても貴重な経験になりました。 関係されている方々が思い思いの仕事のやりようでイベントに取り組んでいる様が刺激になったなと思います。
オフ会履歴
私を Nostr でフォローいただいている方であれば、「こいつ、やたらオフ会行ってないか…?」と思われるでしょう。ということで、自分でも一度整理をしてみました。

うわっ...私のオフ会参加、多すぎ…? ~~1 年間は52週しかないねんぞ~~
このように、火鍋のオフ会を皮切りに、相当な数のオフ会に参加させていただきました。オフ会というかもう普通に Nostr で知り合っただけの友人との集まりみたいな感覚になっているかも。
ちなみに、人単位でお会いした回数もまとめています。
 ※:Nostrasia などのイベントでお会いした回数は除いています。
※:Nostrasia などのイベントでお会いした回数は除いています。こうみるとしおと神(かすてらふぃさん)と会った回数めちゃくちゃ多いですね。28,26回だとほぼ2週に1回ペースですが、過去どんなに親しい友人でもこんな頻度で会ってたことないかも。
思い出深かった出来事
nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygxll5llcw4tv2f34r9s3u9z5jyd5ars85ydrhhe8p52uv844hnmuypsgqqqqqqskevt6r
nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cppemhxue69uhkummn9ekx7mp0qgsdllfllsa2kc5nr2xtprc29fygmf68q0gg6800jwrg4cc0tt08hcgrqsqqqqqpaua8e8
この誤字投稿を経て、私の(たまにほかの人も)誤字は大欲情と呼ばれるようになりました。~~毎回思うけど新しく入ってきた人は何だこれってなるよなこれ~~
その後も酔ってる時を中心に結構誤字をやらかすので、那月さんによるまとめが作られています。
名前としては不名誉かもしれませんが、面白いのでOKです。
おわりに
振り返ってみれば Nostr 日本人ユーザーコミュニティの心地良さに浸った 1 年だったと思います。 Nostr の仕組み自体も好きですが、私はコミュニティの方に目が行っている気がします。
Nostr 歴 1 歳になったので、今後は私が Nostr を使う人々に心地良いと思ってもらえるような人になれるとよいなと思います。
これからもよろしくお願いします。
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 59cb0748:9602464b
2025-01-01 06:15:09
@ 59cb0748:9602464b
2025-01-01 06:15:09Nostrでお世話になっている方も、お世話になってない方も、こんにちは!
タコ頭大吉です!
NIP-23を使った初めての投稿です。
今回は、私がここ数ヶ月中にデザインをした三種類のビタキセケースの紹介記事になります!!
ビタキセを買ったもののあまり自分の好みに合う外観や仕様のケースがなく、いくつかプロトタイプを作りそれなりに時間をかけて考えたケース達です。
これら3シリーズに関しては、FDMタイプの3Dプリンタの精度、耐久性、出力後の作業性を考慮して一つのパーツで完結することに拘って設計をしました。
一定以上の充填率でプリントをすればそれなりに丈夫なはずです。
また、基本的に放熱性と保護性を両立できるように設計をしたつもります。
それぞれのモデルについて簡単に紹介をさせていただきますので、よろしければ各リポジトリに付属のREADMEを読んでいただいて自作、フィードバックをいただけましたら幸いです。
それでは、簡単に各モデルの紹介をさせていたきます。
AirLiftFrame
 最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
最初に作ったモデルです!
少し大きいのが難点ですが、分厚めのフレームをベースとし基盤周辺をあえて囲わない設計により、保護性と放熱を阻害しない事の両立を狙っています。
TwinAirLiftFrame
 ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
ビタキセを買い増ししたことにより、複数台をカッコよく運用したいという需要が自分の中に出てきたので、AirLiftFrameを2つくっつけたら良いのではと言うごくごく単純な発想でつくり始めたケースです。
しかし、ただ横並びにしただけでは廃熱が干渉するだけではなく、DCジャックやUSBポートへのアクセスが阻害されるという問題にすぐに気がつきました。
そこで、WebUI上でディスプレイの表示を上下反転出来ることに注目し、2台を上下逆向きに取り付ける事でそれらの問題を解決しました!
VoronoiShell
 AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
AirLiftFrameシリーズのサイズを小型化する事から始めたプロジョクトです。
縦横の寸法の削減だけではなく、厚みを薄くつくリたいという希望がありました。
所が単純に薄くすると、持った時に発熱する背面パーツに手が触れてしまったり、落下などでぶつかった際に背面パーツが破損する懸念がありました。
そこで、(当初は付けたくはなかった)背面保護用のグリルをデザインする必要が出てきました。
初めは多角形でしたがあまりにもダサく、調べている内にVoronoi柄という有機的なパターンに行き付き即採用しました。
結果、ビタキセを取り付けると柄が見えなくなるのが勿体無いぐらい個性的でスタイリッシュなデザインに仕上がりました。
いずれカスタム方法やインサートナットや増設ファンの選定方法等を紹介したいのですが、今回はNIP-23になれるという意図もあるので紹介に留めます! また、他の関連OSハードウェアプロジェクトのケースもデザインできたらと思っております!
今後ともタコ頭をよろしくお願いいたします。
-
 @ 84b0c46a:417782f5
2024-12-26 10:28:26
@ 84b0c46a:417782f5
2024-12-26 10:28:26- lumilumi The Nostr Web Client.
Lightweight modes are available, such as not displaying icon images, not loading images automatically, etc.
Follow List ( kind3 ) organization tool.
- NAKE NIP-19, NIP-49 Encode/Decode Tool
- chrome extension
- firefox add-on
- nostviewstr
Addressable or Replaceable Event Editor ( いろんなリストエディター )
Addressable or Replaceable Event Recovery tool ( いろいろリカバリーツール )
Bookmark event ( kind:10003,30001,30003 ) recovery tool ( ぶくま復活させたいやつ )
プロフィールを編集するやつ - nostr-bookmark-viewer
Bookmark event ( kind:10003,30001,30003 ) Editor ( ぶっくまーくをみるやつ )
Broadcast an event from relay to relay ( イベントをブロードキャストするやつ )
-
 @ ec42c765:328c0600
2024-12-22 19:16:31
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
手順
- 登録する画像を用意する
- 画像をweb上にアップロードする
- 絵文字セットに登録する
1. 登録する画像を用意する
以下のような方法で用意してください。
- 画像編集ソフト等を使って自分で作成する
- 絵文字作成サイトを使う(絵文字ジェネレーター、MEGAMOJI など)
- フリー画像を使う(いらすとや など)
データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト toimg) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
その他
- 背景透過画像
- ダークモード、ライトモード両方で見やすい色
がおすすめです。
2. 画像をweb上にアップロードする
よく分からなければ emojito からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → emojito など
- 削除できるが差し替えはできない → Gyazo、nostrcheck.meなど
- 削除も差し替えもできる → GitHub 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。3. 絵文字セットに登録する
emojito から登録します。
右上のアイコン → + New emoji set から新規の絵文字セットを作成できます。


① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
④ 追加
Add を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の Save を押すと作成完了です。

画面が切り替わるので、右側の Options から Bookmark を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには Options から Edit を選択します。
以上です。
仕様
-
 @ 2cb8ae56:84d30cba
2024-12-21 11:27:14
@ 2cb8ae56:84d30cba
2024-12-21 11:27:14ども、薄味のキャルピスでございます。
当記事は、「Nostr Advent Calendar 2024」7日目の記事です。
この記事を読んでいる人でいないとは思いますが、Nostrとはなんぞやとお思いの方は以下をご覧ください。https://hello.nostrapp.me/
僕は「Nostrで過ごした2024年」というタイトルの通り、一年間を振り返ってみようと思います。
自己紹介
まず知らん人のために軽く自己紹介をします
「薄味のキャルピス」という名前で、色んな所にいるどこかの高校生です。 左利き、箸とベースとお盆は右手。
普段は学業の傍ら、画像を弄ったり作ったりしている上に、イヤホンを集めたりラジオにメッセージを送っています。
コーディングは出来ないテクノロジーまみれのガラクタ人間(→テックジャンカー)です
参加経緯とスタンス
なぜ参加したのかを思い出しながら書いていきます まず、どんな媒体でNostr(ノスター・ノストラ)の存在を知ったのかと言うと、ネットニュースです。
https://gigazine.net/news/20230425-nostr-intro/
こちらの記事で「そんなのあるんだ」と知り、4月1日ついにjoin!!!!
現時点での参加スタンスは「気楽に、素直に」という感じで参加しています
やりたいときにやりたいことをやるって言うリアルでは到底難しいことを、Nostrのなかでやっている気もします。
後述するNostrasia 2024の開催日「9月23日」を持って、Mastodon(マストドン)から乗り換え、上記のスタンスのもと、メインで精力的に活動しています。
Nostr活動年表
2024/04/01 Nostr Join!!!
2024/06/08 人生初オフ会「たくろうさんオフ」参加、LNアドレス追加。
2024/09/23 人生初小規模イベント「Nostrasia 2024」運営メンバーとして参加
2024/10/12 2度目のオフ会「デザイン談義」主催・参加
簡易的に各種紹介!
人生初オフ会「たくろうさんオフ」 渋三魚金でご飯→猿田彦珈琲でリラックス、Linux使ってると話を切り出す(唐突)→スクランブル交差点で解散。 ウォークマンの再生画面を送付した投稿を行う
人生初イベント「Nostrasia 2024」
あ、記事出したので見てください。初版
第二版
2度目のオフ会「デザイン談義」
秋葉原の「創作空間caféアトリエ あきば店」で行われたオフ会。 ちょくちょく内容を上げているので、見ていってください。 https://nostter.app/npub19ju2u4sduewta4hxl22kke7se8yxm2puytzw47lr6y999pxnpjaqtjjfxj/2024/10/12 終了後、e☆イヤホン 秋葉原店にて、BTR13の在庫状況を確認し、在庫がないため予約しました。 (10月24日到着) 雑多すぎますが、一応こんな感じで大丈夫かな?まとめ
僕がNostrに出会い、Nostrにのめり込むまでの話はいかがだったでしょうか。 Nostrに入る前、オフ会に参加するまでは「ネットにロクな人なんていない!」と思っていましたが、Nostrは違いましたね。 いい意味で期待はずれ、本当にいい人たちばかりで、とにかく自然体で接することができるSNSであると感じました。 そんな世界にぜひとも一回足を踏み入れてみてはいかがでしょうか? それではまた、来年のアドベントカレンダー、及び開催されましたら「Nostrasia 2025」でお会いしましょう。 -
 @ ec42c765:328c0600
2024-12-15 11:13:44
@ ec42c765:328c0600
2024-12-15 11:13:44てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
-
 @ ec42c765:328c0600
2024-12-13 08:16:32
@ ec42c765:328c0600
2024-12-13 08:16:32Nostr Advent Calendar 2024 の 12日目の記事です。
昨日の 12/11 は きりの さんの 2024年のNostrリレー運営を振り返る でした。
nostr-zap-view 作った
リポジトリ: https://github.com/Lokuyow/nostr-zap-view/
動作確認ページ: https://lokuyow.github.io/nostr-zap-view/それ何?
特定の誰かや何かに宛てたZap(投げ銭)を一覧できるやつ
を
自分のWebサイトに設置できるやつ
自分のサイトに設置した例 * SNSリンク集ページ(最下部): https://lokuyow.github.io/
おいくらサッツ(Zap一覧ボタン): https://osats.money/
今日からビットコ(最下部): https://lokuyow.github.io/btc-dca-simulator/なんで作ったの?
私の去年のアドベントカレンダー
【Nostr】Webサイトにビットコインの投げ銭ボタンを設置しよう【Zap】
https://spotlight.soy/detail?article_id=ucd7cbrql/
が前提になってるけど長いので要約すると * ZapするやつはあるけどZap見るやつがないので欲しい * ZapをNostr(の典型的なkind:1クライアント)内だけに留めるのはもったいない * Webサイトの広告うざいからZap(的な何か)で置き換わって欲しいお前だれ?
非エンジニア、非プログラマー
AIにコード出させてるだけ人作った感想
できた
作った感想2
完成してから気付いた本当に作りたかったもの
こういうところにそのままZapを表示できる感じにしたい
 (ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
(ここまでちゃんとした商業ブログでなく)個人のブログやHPの端っこに「Sponsored by」欄があって名前が表示される感じ
もうZapっていう文字もビットコインっていう文字もNostrも出さなくていいし説明もしなくていいのでは感がある
イメージはWebサイトを対象にしたニコニ広告 + スーパーチャット + 祭りとか神社の奉納者一覧
で思ったのは
個人からの投げ銭なら推し活的なものにしかならないけど
企業がNostrにアカウントを作ってサイトに投げ銭をしたら企業の広告になるんでは!?
~~企業がNostrにアカウントを!?デリヘルしか見たことない!~~今後
思いつき、予定は未定
* ボタン→ダイアログ形式でなくバナー、Embed形式にしてページアクセスですぐ見れるようにする * 多分リレーに負荷がかかるのでなんかする * Zapの文字は出さず「Sponsored by」等にする * 単純な最新順でなくする * 少額Zapをトリミング * 一定期間(一か月など)ごとで金額順にソート * 多分リレーに負荷がかかるのでなんかする * 今は投稿宛てのZapをWebサイト宛てのZapと勝手に言い張ってるだけなのでちゃんとWebサイト宛てのZapにする * NIPの提案が必要 * ウォレットの準拠も必要 * リレー(wss://~)宛てのZapもできてほしい将来
インターネットのすべてに投げ銭をさせろ
おわり
明日は mono さんの Open Sats 申請編 です!!
-
 @ f0c7506b:9ead75b8
2024-12-08 10:03:35
@ f0c7506b:9ead75b8
2024-12-08 10:03:35
-
Bazı şeyleri yapmak, söylemekten daha kolaydır.
-
Bütün güzel şeyleri bize toprak verir. Bütün güzel şeyler toprağa geri döner.
-
Eğer mevsimlere bakarsanız her mevsim meyve getirir. Yazın meyve vardır, sonbaharda da. Kış farklı meyveler getirir, ilkbahar da. Hiçbir anne çocukları için bu kadar çok çeşit meyveyle buzdolabını dolduramaz.
-
Kendimi bu hayattan kurtarmaya karar verdim. Ne için mi? Bu anlamanıza yardım etmeyecektir ve bunun hakkında sizinle konuşamam; anlayamazsınız. Anlamayacağınız için değil; çünkü benim hissettiklerimi hissedemezsiniz. Duygularımı anlayıp paylaşabilirsiniz, bana merhamet gösterebilirsiniz; ama acımı hissedebilir misiniz? Hayır. Acı çekersiniz ve ben de çekerim. Sizi anlarım. Acımı anlayabilirsiniz; ama onu hissedemezsiniz.
-
İnsanın devam edemeyeceği bir an gelir.
-
Birisine yardım etmek istediğiniz zaman bunu uygun biçimde yapmalısınız, bütün kalbinizle. Bu daha iyidir. Daha adil ve daha makul.
-
İntiharın en büyük günahlardan birisi olduğunu biliyorum. Fakat mutsuz olmak da büyük bir günah. Mutsuzken başka insanları incitirsiniz. Bu da bir günah değil mi? Başkalarını incittiğinizde bu bir günah değil midir? Aileni incitiyorsun, arkadaşlarını, kendini incitiyorsun. Bu bir günah değil mi? Size yakın olan insanları incitiyorsanız bu da büyük bir günahtır.
-
Yardım, mutlaka karşılığı ödenmesi gereken bir şey değildir.
-
Size başımdan geçen bir olayı anlatacağım: henüz yeni evlenmiştim. Belaların her türlüsü bizi buldu. Öylesine bıkkındım ki her şeye son vermeye karar verdim. Bir sabah şafak sökmeden önce arabama bir ip koydum. Kendimi öldürmeyi kafama koydum. Yola koyuldum. Dut ağaçlarıyla dolu bir bahçeye vardım. Orada durdum. Hava henüz karanlıktı. İpi bir ağacın dalı üzerine attım; ama tutturamadım. Bir iki kere denedim ama kâr etmedi. Ardından ağaca tırmandım ve ipi sımsıkı düğümledim. Sonra elimin altında yumuşak bir şey hissettim: Dutlar. Lezzetli, tatlı dutlar. Birini yedim. taze ve suluydu. Ardından bir ikincisini ve üçüncüsünü. Birdenbire güneşin dağların zirvesinden doğduğunun farkına vardım. O ne güneşti, ne manzaraydı, ne yeşillikti ama! Birdenbire okula giden çocukların seslerini duydum. Bana bakmak için durdular. "Ağacı sallar mısın?" diye bana sordular. Dutlar düştü ve yediler. Kendimi mutlu hissettim. Ardından alıp eve götürmek için biraz dut topladım. Bizim hanım hâlâ uyuyordu. Uyandığı zaman dutları güzelce yedi. Ve hoşuna gitti. Kendimi öldürmek için ayrılmıştım ve dutlarla geri döndüm. Bir dut hayatımı kurtarmıştı.
-
Bir türk, doktoru görmeye gider. Ve ona der ki: "Doktor bey, vücuduma parmağımla dokunduğumda acıyor, başıma dokunsam acıyor, bacaklarıma dokunsam acıyor, karnıma, elime dokunsam acıyor." doktor onu muayene eder ve sonra ona der ki: "vücudun sağlam; ama parmağın kırık!"
-
Hayat dümdüz ilerleyen bir tren gibidir; rayların sonuna geldiğinde son durağa ulaşır. Ve ölüm son durakta bekler. Elbette, ölüm bir çözümdür; fakat ilk olarak değil. Genç yaşta hiç değil.
-
Dünya göründüğü gibi değildir. Bakış açınızı değiştirmelisiniz ki dünya değişsin. İyimser olun. Her şeye olumlu tarafından bakın.
-
-
 @ 4c5d5379:3a4383ee
2024-12-01 03:21:49
@ 4c5d5379:3a4383ee
2024-12-01 03:21:49first header
I'm testing YakiHonne article.

にほんごだよ
header
header
header
header
header
header
ヘッダ
ヘッダ
ヘッダ
ヘッダ
ヘッダ
ヘッダ
-
 @ 6b0a60cf:b952e7d4
2024-11-17 07:02:11
@ 6b0a60cf:b952e7d4
2024-11-17 07:02:11ビットコインのウォレットは取引形態によって2種類に分かれます。
- オンチェーン(L1)
- 取引がブロックチェーンに刻まれるタイプ。時間がかかるし手数料が高い。
- ライトニングネットワーク(L2)
- ブロックチェーンに刻む前の少額決済を目的としたレイヤー。高速で手数料が安い。
NostrでZapを利用する場合はライトニングネットワーク(以下、LNと呼びます)のウォレットが使われますが、さらにその中でもZap対応/非対応で分かれることになります。
また、秘密鍵を誰が管理するかによっても2種類の呼び方に分かれます。
- カストディアル
- 秘密鍵をサービスの運営に預けるタイプ。
- ノンカストディアル/セルフカストディアル
- 秘密鍵(シードフレーズ)を自分で持っておくタイプ。
Nostrで人気があるWallet of Satoshi(以下、WoSと呼びます)はLNのカストディアルウォレットです。 今回はLNのセルフカストディアルウォレットであるPhoenixを使ってみて、その仕組みや注意点など、学んだことを記録したいと思います。
Phoenixでウォレットを作る場合、初回でシードフレーズ(12個の単語)が作られますので、大切に控えておきましょう。
WoSからPhoenixに送金してみる
メイン画面左下にあるReciaveからQRCode表示画面へ遷移します。そこでcopyボタンを押して
Lightning invoice(text)をコピーしましょう。
次に、WoSの画面からSendを選択し、クリップボードからの貼り付けを選択します。

 金額を指定して送金します。
金額を指定して送金します。
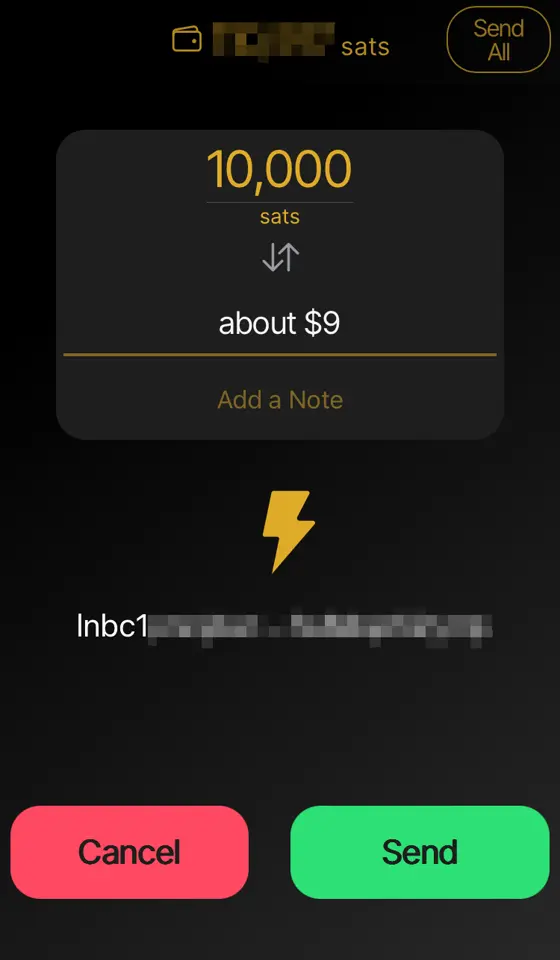
送金した額が満額届いてないんだけど?
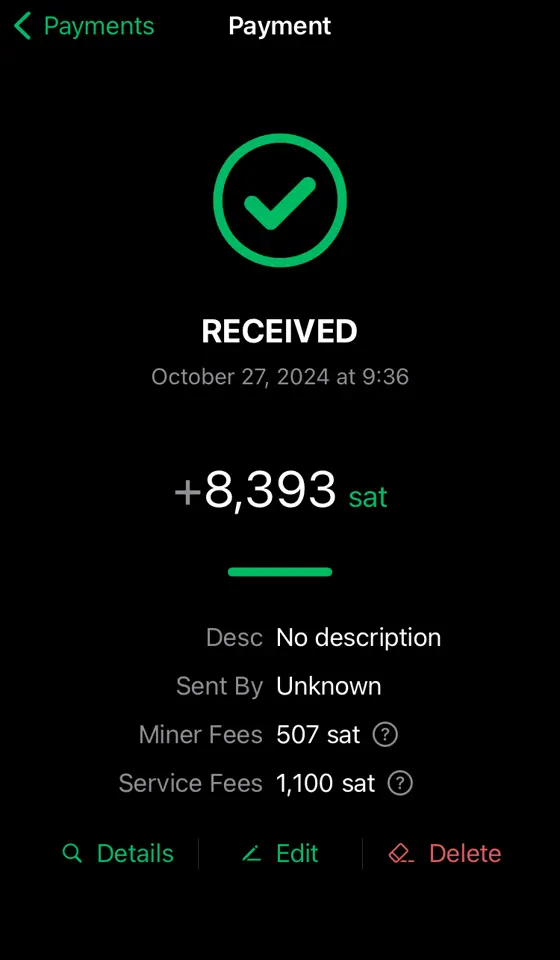
下の方に
Service Feesとありますが、これはPhoenix運営(ACINQ)へのお布施ですね。結構高く見えますが初回だけです。 またMiner Feesという項目は、mempoolのfeeに連動して変わるようですが、これはチャネルを太くする(送受信できる金額の上限を上げる)ために使われる手数料になります。財布が重たくなると手数料が取られる?
有り体に言えばそういうことになります。以下のように10,000satsをもらう度にチャネル拡張のための手数料が引かれています。
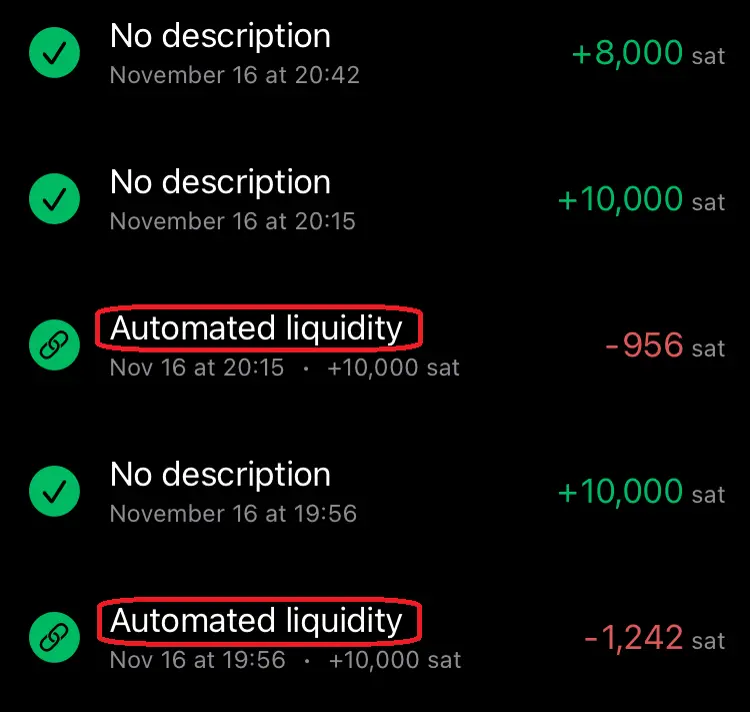
上記の8,000satsを受け取っている時には手数料が発生していませんね。これはチャネル拡張が必要ないギリギリの金額を狙って送金したためです。送金前は8,859satsの余裕がありました。送金後は1,719satsに減っています。(余裕分がぴったり8,000sats減るわけではないようです。このへんの仕組みはよくわかりません。) (画面は左上⚙️マークの設定からPayment channelsから。)
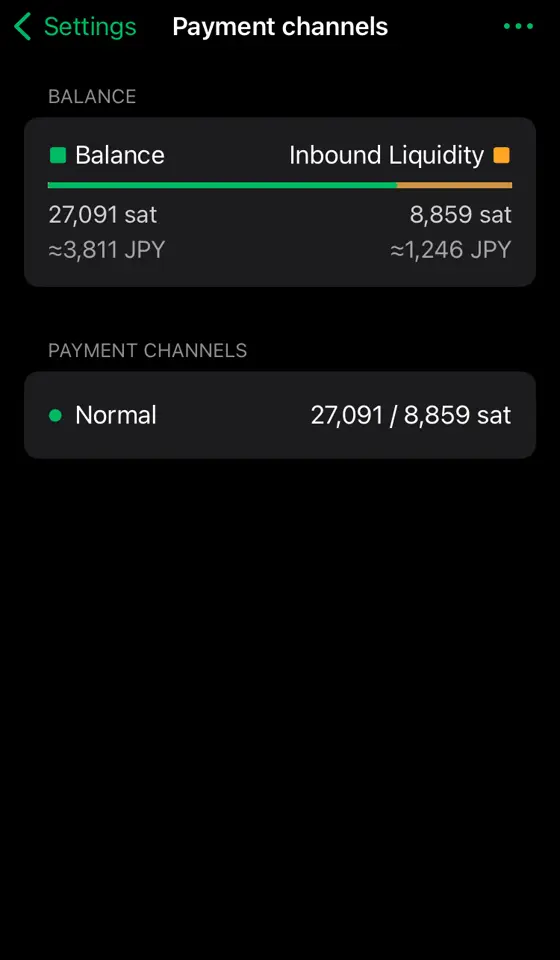
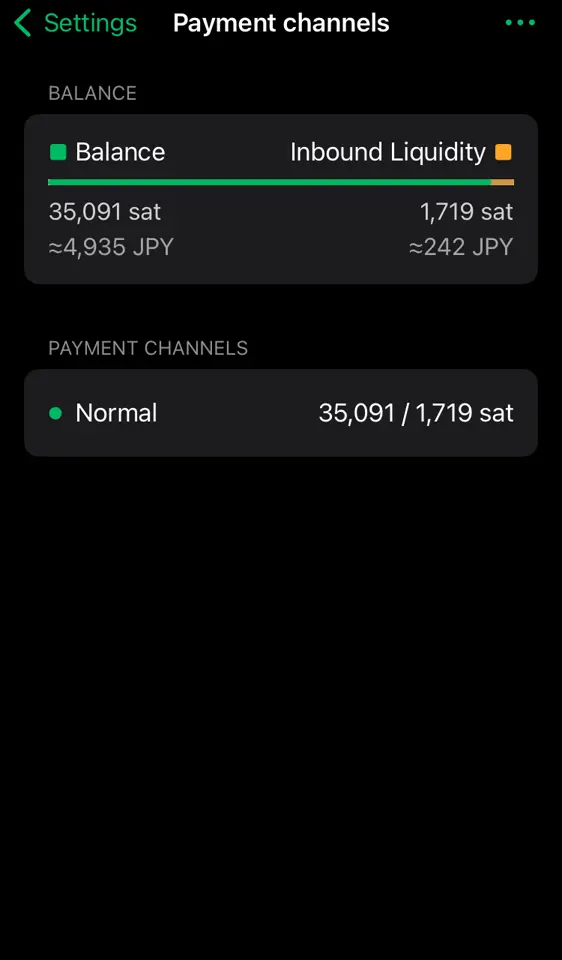
財布が軽くなると余裕が増える?
逆にPhoenixからWoSに5,000satsほど送金してみます。(手数料として24satsほど余計に抜かれました)
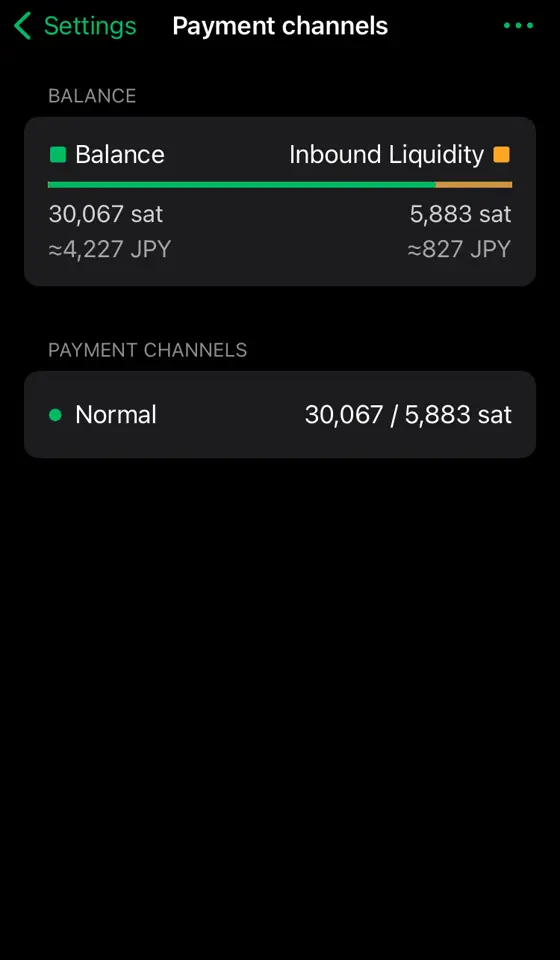
余裕(Inbound Liquidity)が5,883satsまで復活しています。受け取るばかりでなく、バランスよく送ることで財布を重たくしなければチャネル拡張せずに使い続けることができそうです。(太くしたチャネルは永遠に残るわけではなく、1年までらしいです)
自動でチャネル拡張にsatsを使われたくない!
自動チャネル拡張を設定で無効化できます。左上⚙️マークの設定から
Channel managementから。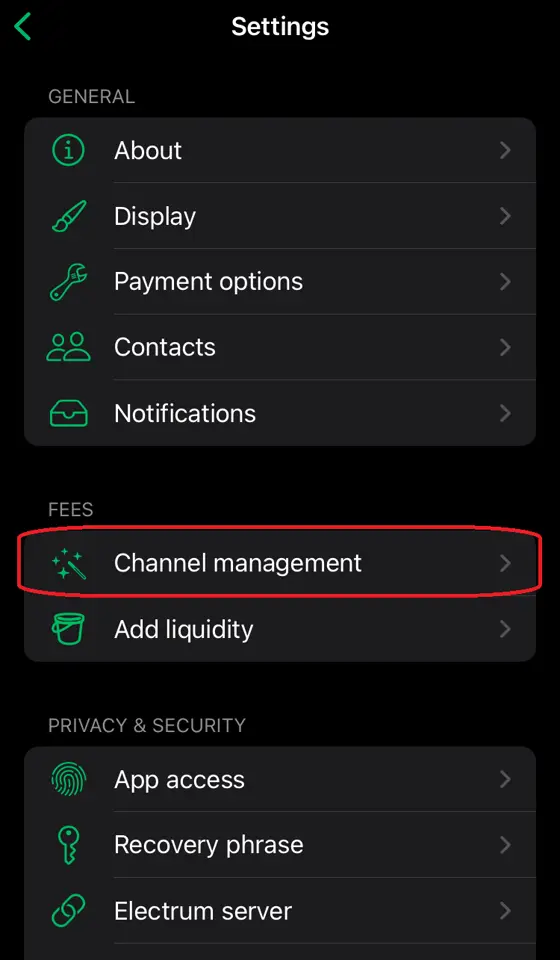
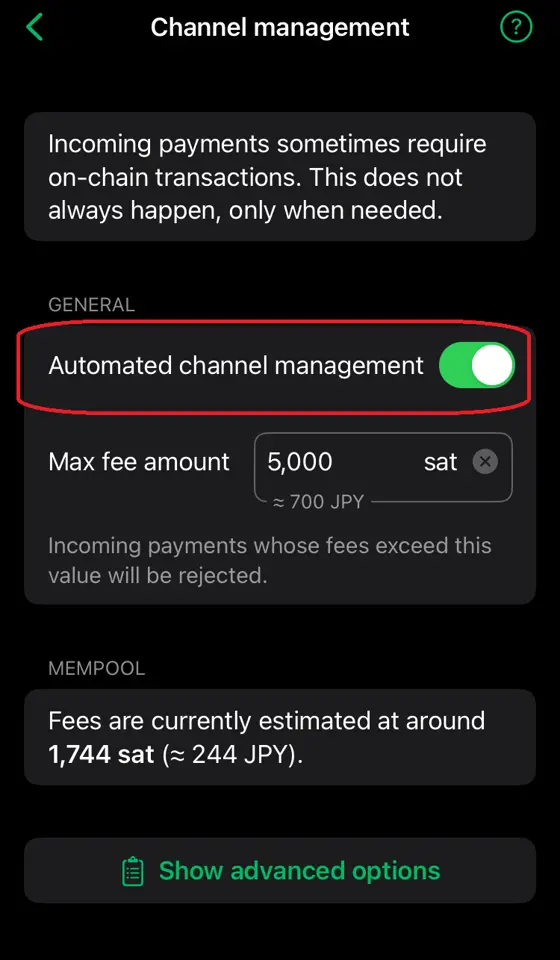
これでチャネル拡張が必要なほどの金額を送金しようとするとエラーになり失敗します。
まとめ
セルフカストディアルウォレットならではの概念があり、謎の手数料が発生したりして怖いイメージがありましたが、どういう理由で手数料が発生するのかを知り、設定でのコントロールの仕方を習得することである程度怖いイメージを払拭することができました。 しかしカストディアルウォレット(特にWoS)の使いやすさを再認識することにもなりました。ただ自分で管理することの重要性も理解していますので、徐々に知識を深めていこうと思います。
参考/謝辞
- Phoenix wallet(フェニックスウォレット)の使い方!ビットコインのセルフカストディができるアプリを解説 - 知っとこ!ビットコイン図鑑
- nostr:npub10zeurmg22wc89l8m3npw9cyu45cun0lvs6w3ep69cdpa25pna65s0994qz 様
-
 @ 6bcc27d2:b67d296e
2024-10-21 03:54:32
@ 6bcc27d2:b67d296e
2024-10-21 03:54:32yugoです。 この記事は「Nostrasia2024 逆アドベントカレンダー」10/19の分です。Nostrasiaの当日はリアルタイムで配信を視聴していました。Nostrを使ってアプリケーションの再発明をすべきという発表を聴き、自分だったらどんなものを作ってみたいかを考えて少し調べたり試みたりしたのでその記録を書きます。また、超簡単なものですがおそらく世界初となるvisionOS対応のNostrクライアントをつくってみたので最後の方に紹介します。
アプリケーションを再発明する話があったのは、「What is Nostr Other Stuff?」と題したkaijiさんの発表でした。
Nostrプロトコルを使って既存のアプリケーションを再発明することで、ユーザ体験を損なわずにゆるやかな分散を促すことができ、プロトコルとしてのNostrも成長していくというような内容でした。
自分はまだNostrで何かをつくった経験はなかったので、実装に必要な仕様の知識がほとんどない状態からどのようなアプリケーションをつくってみたいかを考えました。
最初に思いついたのは、Scrapboxのようなネットワーク型のナレッジベースです。自分は最近visionOS勉強会をやっており、勉強会でナレッジを共有する手段としてScrapboxの導入を検討していました。
Nostrコミュニティにも有志によるScrapboxがありますが、Nostrクライアントがあればそれを使うだろうから同じくらいの実用性を備えたクライアントはまだ存在しないのではないかという見立てでした。
長文投稿やpublic chatなどの機能を組み合わせることで実現できるだろうか。そう思っていた矢先、NIP-54のWikiという規格があることを知りました。
https://github.com/nostr-protocol/nips/blob/master/54.md
まだちゃんとは読めていないですが、Scrapboxもwikiソフトウェアだし参考になりそうと思っています。正式な仕様に組み込まれていないようで、採用しているクライアントはfiatjafによるリファレンス実装(?)のwikistrくらいしか見つかりませんでした。
Scrapboxのようなナレッジベースを志向するNostrクライアントがあれば、後述するvisionOS対応クライアントの存在もありアカウントを使いまわせて嬉しいので試してみたいです。もし他にも似たようなサービスをどなたか知っていたら教えてください。
また現在は、勉強会やワークショップ、ハッカソンなどのコラボレーションワークを支援するためのツールを自分たちでも開発しています。Apple Vision Proに搭載されているvisionOSというプラットフォームで動作します。
https://image.nostr.build/14f0c1b8fbe5ce7754825c01b09280a4c22f87bbf3c2fa6d60dd724f98919c34.png
この画面で自分が入りたいスペースを選んで共有体験を開始します。
スライドなどのコンテンツや自らのアバターを同期させることで、遠隔地にいてもまるでオフラインかのように同じ空間を共有することが可能になります。
https://image.nostr.build/cfb75d3db2a9b9cd39f502d6426d5ef4f264b3d5d693b6fc9762735d2922b85c.jpg
ということなので、急遽visionOS対応のクライアントを作ってみました。検索しても1つも事例が出てこなかったので多分まだ世界で実装しているアプリはないのではないでしょうか。
とはいえ、クライアントを名乗っているもののまだ大した機能はなく、リレーからデータを取得するだけの読み取り専用です。
https://image.nostr.build/96e088cc6a082528682989ccc12b4312f9cb6277656e491578e32a0851ce50fe.png
画像では自分のプロフィールデータをリレーから取得しています。
まだどのライブラリもvisionOSに対応していなかったりで手こずったものの仕様の勉強になりました。
ただvisionOSアプリはiOSアプリ同様NIP-7が使えないので秘密鍵を自分で保管しなくてはならず、今後どう対処すべきかわかりかねています。これから時間ある時に少しずつ調べていこうと思っていますが、ネイティブアプリの秘密鍵周りはあまりリソースが多くないようにも感じました。もしどなたかその辺の実装に詳しい方いたら教えていただけると嬉しいです。
準備ができたらそのうちコードも公開したいと思っています。
これから少しずつ色んな機能を実装しながらNostrで遊んでいきたいです!
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ f240c9c2:6c0c0a86
2024-08-22 06:50:33
@ f240c9c2:6c0c0a86
2024-08-22 06:50:33⚠️一部のクライアントでは表示が崩れている場合があります。HablaやYakihonneから見てください
NIP-51のkind:30007に関するPull Requestが承認され、2024/08/20時点で本家NIPsにもマージされました。今後「リポスト」や「リアクション」などの特定のkind^1をミュートするためのセット^2が対応するクライアントで使えるようになります。
kind mute set(kind:30007)にて、
"d"タグには対応するイベントの種類の番号(リポストなら"6"、リアクションなら"7")を入れ、"p"タグにはユーザの公開鍵(pubkey)を入れるそうです。nostrクライアントのnostterは、これに対応したことで、Twitter(現:X)の「リポストをオフのする」機能のように"特定ユーザーのリポストをクライアント上で非表示にする"といったことができるようになりました。リアクションも同様に非表示にできます。 nostterでは、2024/07/29以降、ユーザーのプロフィール画面からこれらの設定を行えるようになっています。
2024/06/22 20時の時点では、nostter上ではこれを設定する画面が用意されていなかったので、別アプリを用いたり、イベントを自分で投げるなどして別途設定する必要がありました。 以下は、別アプリを用いて設定した際の手順です。
手順
kind:30007はのすとびうあというWebアプリで設定しました。 以下のようにのすとびうあのホーム画面「リストの種類」で30007を入力するか、

https://nostviewstr.vercel.app/<npub文字列>/30007にアクセスして設定画面にいけました^3。左下の方にある≡を押して

ポップアップの「編集」を押して

ここではリポストのミュートのため、IDの欄に対応するイベントの種類の番号である「6」を入れて

右下にある青いボタン押して

Userの欄にリポストをミュートするユーザーの公開鍵のnpub文字列を入れ、public(ミュート状況が公開される)あるいはprivate(非公開)のボタンを押したら

そのユーザーが追加されて設定完了!

この設定を行うことで、入力した公開鍵(ユーザー)のリポストをnostter上でもミュートできました🙌
リポストやリアクションがどのように表示されるかをユーザーがコントロールできると便利なので、今後いろんなクライアントで対応されればいいな〜と思います!
-
 @ 4c96d763:80c3ee30
2024-08-19 16:26:43
@ 4c96d763:80c3ee30
2024-08-19 16:26:43Changes
Rusty Russell (3):
- Makefile: fix missing dependencies on bolt11 headers.
- bolt11: update to latest version from CLN
- bolt11: remove unneeded fields.
William Casarin (1):
- ndb_filter_from_json
pushed to nostrdb:refs/heads/master
-
 @ 27676f17:0726572a
2024-06-21 23:13:04
@ 27676f17:0726572a
2024-06-21 23:13:04foobar
-
 @ 3f770d65:7a745b24
2024-06-17 18:56:54
@ 3f770d65:7a745b24
2024-06-17 18:56:54Several months ago, nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s and I set out to do tackle a task that had never been done before throughout Nostr's short history. We decided adopt the "go big, or go home" mentality and give our best effort to Purple Pill all of the nostr:npub167n5w6cj2wseqtmk26zllc7n28uv9c4vw28k2kht206vnghe5a7stgzu3r conference.
We couldn't accomplish this monumental task without the help of the Nostr community. From every day Nostriches and plebs, to legendary developers putting their blood, sweat, and tears into building this new protocol, to several companies within the Nostr ecosystem, everyone was going to need to do their part to turn this dream into a reality.
The mission
For the original vision of Nostr at BTC Prague, we planned on supporting the smallest available booth and a small panel on the secondary stage. The plan was for any Nostr developer to contribute what they could and then use the Nostr booth as a central hub to onboard users to their applications, provide support to their users, and meet the community. I embarked on my first crowdfunding journey and was able to initially raise over 10M sats thanks to the greater Nostr community donating towards our efforts.
Shortly afterwards, I was approached by nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m from Satlantis. He had planned on doing a mainstage presentation at BTC Prague on his new Nostr powered application. He asked me if I wanted to combine our efforts to upgrade the Nostr booth to the largest booth possible to give Nostr an even larger presence. I reached out to Avi and several other trusted Nostriches to see their opinions on this potential upgrade and everyone seemed to agree that we should continue with the "go big, or go home" mentality and try our best to Purple Pill all of Prague.
Now with a larger goal at hand, we were able to garner even more support from the Nostr community in addition by adding Highlighter from nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft and Primal from nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr as larger contributors.
The final tallies for funds raised were 16M+ sats from the greater Nostr community and 38M+ sats raised from Satlantis, Primal, and Highlighter. (We did have to raise a little more than originally anticipated because the Bitcoin 58K Gang made the fiat value of Bitcoin dip down for a bit right when we were trying to finalize payment.)
Putting it all together
This support enabled us to secure one of the four large booths at BTC Prague and a main stage panel. Given that these three companies made significant contributions, enabling our acquisition of the largest booth, we decided that it was logical to feature these companies more prominently. However, it was crucial to strike a delicate balance here. While emphasizing that this booth represented the Nostr community and was a true community effort, we also wanted to acknowledge and showcase those who made it possible. These companies could have opted for smaller individual booths, but their collaboration in a unified space demonstrates Nostr's principles of openness and interoperability—demonstrating that everyone and everything can work together seamlessly.
Therefore, we included as many logos across the Nostr ecosystem as possible throughout our iconography.

And, we also had a dedicated area of the booth highlighting our larger contributors.

The results exceeded all expectations. For three days during the BTC Prague conference, the Nostr booth was continuously bustling with activity. Attendees ranged from individuals who had never heard of Nostr before to those who were curious, active users within the ecosystem, and developers creating the applications we use daily. It was a remarkable community effort, with unexpected volunteers stepping up to onboard new users and provide support. Recognizing our busy schedules and flocks of new Nostriches hatching, they chose to assist in our efforts, offering help, and answering questions. It was a truly inspiring experience. Despite the busyness, the enthusiasm and support of so many people made each day enjoyable and dynamic, ensuring there was never a dull moment and we were always surrounded by friends.
Booth takeaways
As this was our very first attempt at doing something like this, I'd like to do a personal post mortem and highlight many of our successes and even some areas where I feel we can improve upon in the future.
Several Nostriches went above and beyond, helping onboard people and answer questions for three days straight. nostr:npub17plqkxhsv66g8quxxc9p5t9mxazzn20m426exqnl8lxnh5a4cdns7jezx0 nostr:npub1spdnfacgsd7lk0nlqkq443tkq4jx9z6c6ksvaquuewmw7d3qltpslcq6j7 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1k6tqlj78cpznd0yc74wy3k0elmj4nql87a3uzfz98tmj3tuzxywsf0dhk6 nostr:npub1md39ua3h2s7204a7v5p9sdxmxx9qc7m4kr3r6naeuwfznad6d7nsxpctp9 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1zga04e73s7ard4kaektaha9vckdwll3y8auztyhl3uj764ua7vrqc7ppvc were the lifeblood of the booth, always answering questions themselves or referring them to others if they were unable to help, didn't know the answer or were busy at the time. You all put in the work and deserve much credit and thanks. Even nostr:npub1995y964wmxl94crx3ksfley24szjr390skdd237ex9z7ttp5c9lqld8vtf was helping with onboarding!

Additionally, beyond general use case questions, we also had many developers stop by and answer many more technical questions for those wanting to learn a bit more too. nostr:npub1zach44xjpc4yyhx6pgse2cj2pf98838kja03dv2e8ly8lfr094vqvm5dy5 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub1arkn0xxxll4llgy9qxkrncn3vc4l69s0dz8ef3zadykcwe7ax3dqrrh43w nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft were often seen answering more technical questions on various developmental topics.


Identifying areas for improvement is challenging, as the entire team of Nostriches performed exceptionally well, exceeding expectations. The event was a whirlwind of activity, with constant engagement and zero downtime. Volunteers seamlessly rotated at the front counter answering questions and distributing items to attendees. (Thanks nostr:npub1cgcwm56v5hyrrzl5ty4vq4kdud63n5u4czgycdl2r3jshzk55ufqe52ndy . Your nostr.how and nostrapps.com business cards were a HUGE help here!)
Full disclosure, I personally didn't leave the booth for three days all that much for two reasons. 1) Because I love to #GrowNostr and talk to people and 2) Because I was worried that the booth would turn into a corporate Primal or Satlantis show. However, this wasn't the case. While these teams did have a large presence with many team members all wearing t-shirts, none of my fears became a reality. If people asked questions about Nostr in general, that was discussed. If people asked questions about Primal or Satlantis, that was discussed. I personally recommended numerous social apps, Damus, Amethyst, Primal, Nostur, Nos.social - all of them. The booth was a true decentralized effort and I absolutely did not need to worry as much as I did, but I felt like I had an obligation to fulfill and I wanted to be there to see it through.
If I had to choose an area that needed improvement, I'd say that the three Satlantis women that nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m brought with him were supposed to shadow some of us to learn more about Nostr, so that they could then use this information to do the initial intake booth questions before making the referral to those with more information, but this just didn't happen. We were all so busy. Sorry! It was just too hard to coordinate. Maybe in the future we can prepare a bit more in this area. Although, nostr:npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa did a fantastic job, jumping right in there head first!
Secondly, we could have improved our television capabilities. We rotated from showing the live dashboard from the booth's Zap.stream livestream, to showing Primal.net/explore Nostr statistics, to showing nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz 's Nostr Documentary on loop, to playing the Satlantis promotional video. The majority of the time our TV was playing the same Nostr Documentary. It's great! I love that video, but we may be able to work out a better schedule and rotation mechanism in the future to showcase more content equally. Plus, I don't want to always be on the TV. I don't want people getting the wrong idea.
Nostr takeaways
After speaking with hundreds of people at BTC Prague, I feel that I've discovered the best way to describe Nostr.
Nostr has a portable digital social identity, allowing you to be in control of your digital social identity for the very first time, allowing you to take your entire social graph with you, every time you use a different application from Nostr's ecosystem.
Nostr is the social glue that binds all of your apps together.
In general, at BTC Prague, while explaining Nostr to people, the digital social identity route was what clicked with the most people. From there, it's not a long stretch to understand building a reputation and web of trust either.
Many people do not use the "Other Stuff" and explaining to them how to use these applications is hard. People want a native application.
Damus, Primal, and Amethyst seem to be the number one apps that people are using, with maybe Primal being the number one altogether? This is probably due to Primal being available on Android, iOS, and the web. Also, many people don't know that Damus still supports Zaps via the Nostr script workaround. I had to show many how to enable Zaps.
Everyone wants Nostr at their conference
There is significant interest in featuring Nostr at various conferences. Although not everyone has reached out, numerous individuals at BTC Prague expressed enthusiasm about incorporating a Nostr booth, along with several Nostr talks and sessions, into their upcoming events. They recognize the critical role Nostr and free speech play globally and acknowledge Nostr's popularity within the Bitcoin community. However, they also understand that more work is needed, and we must continue our efforts to onboard and engage new users.

I have two primary observations on this matter:
-
The community effort demonstrated here serves as a blueprint for success. We have proven that this approach to growing Nostr is effective, desired, and necessary. The engagement at our booth and attendance at our panels prove this with ease.
-
This fundraising initiative is likely a one-time effort. I cannot, in good conscience, continue to ask the community to bootstrap these endeavors. If we are to sustain these booths and promote Nostr at similar conferences, the conference organizers themselves must provide substantial support or discounts to foster broader Nostr adoption. While I understand that conferences entail significant operational costs, it is not feasible for Nostr developers and the broader Nostr community to finance these efforts continuously. Additionally, I would not feel comfortable requesting financial contributions from you all again for this purpose.
Looking forward
Will we do _this _again? I don't know. While our initial endeavor was a complete success, it would be unfortunate to cease our efforts just as we are gaining momentum.
Avi and I have a lot to discuss between ourselves and a lot to discuss with all of you.
Thank you all from the bottom of my heart. Thank you nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr for making all of this possible. Thank you to every single Nostrich that donated your hard earned sats to make this possible. Thank you to all of the developers that built all of this to make all of this possible. Thank you to everyone else <3
Keep building.
-
-
 @ 3bf0c63f:aefa459d
2024-06-07 15:27:10
@ 3bf0c63f:aefa459d
2024-06-07 15:27:10Report of how the money Jack donated to the cause in December 2022 is being spent.
Bounties given
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 3c984938:2ec11289
2024-06-07 11:14:17
@ 3c984938:2ec11289
2024-06-07 11:14:17The Chamorros: People of my island
They islanders for centuries took care of the island. They fished, farmed, hunted, voyaged, made tools, art, had stories, had marriages within clans. Then, the Spanish came. When they first came, the Chamorros boarded their boat to greet the weird people(I'm sure they thought they were weird too). It started peaceful until the Spaniards coffer's slowly dried up. This led to the occupation of the island and grew oppressive. Eventually, The Spanish lost the war to the Americans. Guam was then sold to the American gov't as spoils of war, trading one oppressive regime for another.
The TakeOver Process-1
The TakeOver Process-2
The TakeOver Process-3
Get a job, you lazy islanders. We need to tax you, come work for us. This was the price to become American to the indigenous islanders.
Then the war came.
close up
Guam was hit first before Pearl Harbor(The international Date line puts Guam timezone first ahead) but after this, The Japanese invaded and then occupied the island. Note at the bottom, The American Naval governor surrendered. This led to the islanders thus to become slaves to the Japanese Empire.
Recall "Day of Infamy" by FDR
Life under Japanese Rule Note Northern Marianas islands are the smaller islands above Guam. See the next image below.
Map of the island geography. Guam is referred as NYC in the Marianas. The rest are really, really small.

Nearly 16k of indigenous islander died, by the end of the war less than 6kish Chamorro survived.
The Federal Government then claimed parts of the land and since then and haven't returned it. They've returned some of it. This was a long time ago, I think it's time to let it go. Some islanders demand war repatriations. It makes zero sense to demand money from future Americans to pay for those war repatriations. The enemy is not the people, it's those that wield the pen to create unreasonable bills and the ones that enforce it.
Final Words. The islanders lived peaceful. There was no room to be a bad person of the colony because that person was risked getting shunned. Often, they sent the bad natives (thus becoming 2nd class citizens) inland, barring them from getting access to the ocean. But the land is rich and fertile. Instead of saltwater fish, they had fresh water 🐟fish, 🐍eel, 🦐shrimp and 🦞crawfish and plenty of fruit to eat and farm.
They didn't ask to become Spanish or American. It was this way or the highway. When countries want to expand they need more territories, land, money and human capital(your life energy). History doesn't repeat, it just rhymes.
🦋The best way to combat this is go back to a similar economy that is less corruptible. I believe Bitcoin can do this. History gives clues. Don't trust, verify.
Thank you for joining me on this walk (lol, reading) through the museum, please comment if you enjoyed this.
-
 @ 4c96d763:80c3ee30
2024-05-31 07:05:51
@ 4c96d763:80c3ee30
2024-05-31 07:05:51Here's a quick script for generating git shortlog longform notes on git push. It currently powers the Damus Code nostr account:
Let's say you are hosting a bare git repository on a server at
git/project. You can add apost-receivehook that generates a longform note when you push to the server:In
server:git/project/hooks/post-receive:```bash
!/usr/bin/env bash
commit_body="" last="" project="my-project" # update this with your project name sec="abcdef..." # update this with your secret key branch="master"
while read oldrev newrev refname; do branch=$refname last=$newrev relays="wss://relay.damus.io wss://nos.lol" commit_body=$(git shortlog $oldrev..$newrev | awk -f /home/user/markdown-shortlog.awk) done
if [[ $branch == "refs/heads/master" ]]; then
nostril --content "# Changes
$commit_body" \ --envelope \ --kind 30023 \ --tag title "$project" \ --tag summary "Latest codebase changes to $project" \ --tag t gitlog \ --sec $sec \ | nostcat --connect-timeout 1000 $relays fi ```
you'll need nostril, nostcat, and
markdown-shortlog.awk:```awk /^[^ ]/ { if (author) { print "" } author = $0 print "## " author }
/^ / { print "-" substr($0, 6) } ```
Now when you push, it will generate a longform note that looks something like this:
Example
William Casarin (10):
- fix warnings
- readme: add usage
- textmode: fix coloring of abbreviated names
- profiling: update puffin version
- refactor: move note into its own widget
- refactor: rename widgets to ui
- ui: simplify note widget
- get all missing ids from all timelines
- initial inline note previews
- fix until filters
kernelkind (6):
- Add custom visual themes
- Add modular custom text styles
- Apply app style to AccountLoginView
- Add MobileAccountLoginView
- Refactor 'ui tests' conception to previews
- Use custom style in app
-
 @ 4c96d763:80c3ee30
2025-04-23 19:43:04
@ 4c96d763:80c3ee30
2025-04-23 19:43:04Changes
William Casarin (28):
- dave: constrain power for now
- ci: bump ubuntu runner
- dave: initial note rendering
- note: fix from_hex crash on bad note ids
- dave: improve multi-note display
- dave: cleanly separate ui from logic
- dave: add a few docs
- dave: add readme
- dave: improve docs with ai
- docs: add some ui-related guides
- docs: remove test hallucination
- docs: add tokenator docs
- docs: add notedeck docs
- docs: add notedeck_columns readme
- docs: add notedeck_chrome docs
- docs: improve top-level docs
- dave: add new chat button
- dave: ensure system prompt is included when reset
- enostr: rename to_bech to npub
- name: display_name before name in NostrName
- ui: add note truncation
- ui: add ProfilePic::from_profile_or_default
- dave: add query rendering, fix author queries
- dave: return tool errors back to the ai
- dave: give present notes a proper tool response
- dave: more flexible env config
- dave: bubble note actions to chrome
- chrome: use actual columns noteaction executor
kernelkind (13):
- remove unnecessary
#[allow(dead_code)] - extend
ZapAction - UserAccount use builder pattern
Wallettoken parser shouldn't parse all- move
WalletStateto UI - add default zap
- introduce
ZapWallet - use
ZapWallet - propagate
DefaultZapStateto wallet ui - wallet: helper method to get current wallet
- accounts: check if selected account has wallet
- ui: show default zap amount in wallet view
- use default zap amount for zap
pushed to notedeck:refs/heads/master
-
 @ e516ecb8:1be0b167
2025-04-23 15:25:16
@ e516ecb8:1be0b167
2025-04-23 15:25:16¡Muy bien, amigo! Vamos a sumergirnos en las profundidades arquetípicas de la psique humana para desentrañar esta noción, esta chispa de sabiduría que intentamos articular, porque, verás, no es una mera declaración trivial, no, no, es una verdad ontológica que reverbera a través de los eones, en los cimientos mismos del Ser.
Permíteme, si me lo permites, desplegar esta idea como si fuera un tapiz mitológico, tejido con los hilos del caos y el orden, porque eso es lo que hacemos cuando nos enfrentamos a la condición humana, ¿no es así? Nos esforzamos por dar sentido al cosmos, por encontrar un faro en la tormenta.
Ahora, consideremos esta proposición: la felicidad, esa efímera mariposa que revolotea en los márgenes de nuestra conciencia, no es, como podrías suponer ingenuamente, el summum bonum, el pináculo de la existencia. No, señor, no lo es. La felicidad es un estado fugaz, una sombra danzante en la caverna platónica, un destello momentáneo que se desvanece en cuanto intentas apresarlo. Es como tratar de agarrar el agua con las manos: cuanto más aprietas, más se escurre. Y aquí está el quid de la cuestión, la médula de la narrativa: perseguir la felicidad como si fuera el telos, el fin último de tu peregrinaje existencial, es una empresa quijotesca, una búsqueda condenada a la futilidad, porque la felicidad no es un destino; es un subproducto, un acompañante caprichoso que aparece y desaparece según los caprichos del destino. Pero entonces, ¿cuál es el antídoto? ¿Cuál es la brújula que orienta al alma en esta travesía a través del desierto de la modernidad? Aquí, amigo mío, es donde debemos invocar el espectro del propósito, esa fuerza titánica, ese Logos encarnado que nos llama a trascender la mera gratificación hedónica y a alinearnos con algo más grande, algo más profundo, algo que resuene con las estructuras arquetípicas que han guiado a la humanidad desde las fogatas de la prehistoria hasta los rascacielos de la posmodernidad. El propósito, verás, no es una abstracción frívola; es el eje alrededor del cual gira la rueda de la vida. Es la carga que eliges llevar voluntariamente, como el héroe mitológico que levanta el mundo sobre sus hombros, no porque sea fácil, sino porque es necesario.
Y no me malinterpretes, porque esto no es un juego de niños. Asumir un propósito es enfrentarte al dragón del caos, es mirar fijamente al abismo y decir: “No me doblegarás”. Es la disposición a soportar el sufrimiento —porque, créeme, el sufrimiento vendrá, tan seguro como el sol sale por el este— y transformarlo en algo redentor, algo que eleve tu existencia más allá de los confines de lo mundano. Porque, ¿qué es la vida sino una serie de tragedias potenciales, una danza perpetua al borde del precipicio? Y sin embargo, en esa danza, en esa lucha, encontramos significado. No es la ausencia de dolor lo que define una vida bien vivida, sino la valentía de avanzar a pesar de él, de construir orden a partir del caos, de erigir un templo de significado en medio de la entropía.
Así que, cuando decimos que la felicidad es pasajera y nuestro objetivo es perseguir un propósito, no estamos simplemente lanzando una frase al éter; estamos articulando una verdad que ha sido destilada a través de milenios de lucha humana, desde los mitos de Gilgamesh hasta las reflexiones de los estoicos, desde las catedrales góticas hasta las bibliotecas de la Ilustración. Es una invitación a reorientar tu brújula interna, a dejar de perseguir el espejismo de la felicidad y, en cambio, abrazar la carga gloriosa del propósito, porque en esa carga, en esa responsabilidad autoimpuesta, encuentras no solo significado, sino la posibilidad de trascendencia. Y eso, amigo mío, es la aventura más noble que un ser humano puede emprender.
-
 @ 3ffac3a6:2d656657
2025-04-23 01:57:57
@ 3ffac3a6:2d656657
2025-04-23 01:57:57🔧 Infrastructure Overview
- Hardware: Raspberry Pi 5 with PCIe NVMe HAT and 2TB NVMe SSD
- Filesystem: ZFS with separate datasets for each service
- Networking: Docker bridge networks for service segmentation
- Privacy: Tor and I2P routing for anonymous communication
- Public Access: Cloudflare Tunnel to securely expose LNbits
📊 Architecture Diagram
🛠️ Setup Steps
1. Prepare the System
- Install Raspberry Pi OS (64-bit)
- Set up ZFS on the NVMe disk
- Create a ZFS dataset for each service (e.g.,
bitcoin,lnd,rtl,lnbits,tor-data) - Install Docker and Docker Compose
2. Create Shared Docker Network and Privacy Layers
Create a shared Docker bridge network:
bash docker network create \ --driver=bridge \ --subnet=192.168.100.0/24 \ bitcoin-netNote: Connect
bitcoind,lnd,rtl, internallnbits,tor, andi2pto thisbitcoin-netnetwork.Tor
- Run Tor in a container
- Configure it to expose LND's gRPC and REST ports via hidden services:
HiddenServicePort 10009 192.168.100.31:10009 HiddenServicePort 8080 192.168.100.31:8080 - Set correct permissions:
bash sudo chown -R 102:102 /zfs/datasets/tor-data
I2P
- Run I2P in a container with SAM and SOCKS proxies
- Update
bitcoin.conf:i2psam=192.168.100.20:7656 i2pacceptincoming=1
3. Set Up Bitcoin Core
- Create a
bitcoin.confwith Tor/I2P/proxy settings and ZMQ enabled - Sync the blockchain in a container using its ZFS dataset
4. Set Up LND
- Configure
lnd.confto connect tobitcoindand use Tor: ```ini [Bitcoind] bitcoind.rpchost=bitcoin:8332 bitcoind.rpcuser=bitcoin bitcoind.rpcpass=very-hard-password bitcoind.zmqpubrawblock=tcp://bitcoin:28332 bitcoind.zmqpubrawtx=tcp://bitcoin:28333
[Application Options] externalip=xxxxxxxx.onion
`` - Don’t expose gRPC or REST ports publicly - Mount the ZFS dataset at/root/.lnd` - Optionally enable Watchtower5. Set Up RTL
- Mount
RTL-Config.jsonand data volumes - Expose RTL's web interface locally:
```yaml
ports:
- "3000:3000" ```
6. Set Up Internal LNbits
- Connect the LNbits container to
bitcoin-net - Mount the data directory and LND cert/macaroons (read-only)
- Expose the LNbits UI on the local network:
```yaml
ports:
- "5000:5000" ```
- In the web UI, configure the funding source to point to the LND REST
.onionaddress and paste the hex macaroon - Create and fund a wallet, and copy its Admin Key for external use
7. Set Up External LNbits + Cloudflare Tunnel
- Run another LNbits container on a separate Docker network
- Access the internal LNbits via the host IP and port 5000
- Use the Admin Key from the internal wallet to configure funding
- In the Cloudflare Zero Trust dashboard:
- Create a tunnel
- Select Docker, copy the
--tokencommand - Add to Docker Compose:
yaml command: tunnel --no-autoupdate run --token eyJ...your_token...
💾 Backup Strategy
- Bitcoin Core: hourly ZFS snapshots, retained for 6 hours
- Other Services: hourly snapshots with remote
.tar.gzbackups - Retention: 7d hourly, 30d daily, 12mo weekly, monthly forever
- Back up ZFS snapshots to avoid inconsistencies
🔐 Security Isolation Benefits
This architecture isolates services by scope and function:
- Internal traffic stays on
bitcoin-net - Sensitive APIs (gRPC, REST) are reachable only via Tor
- Public access is controlled by Cloudflare Tunnel
Extra Security: Host the public LNbits on a separate machine (e.g., hardened VPS) with strict firewall rules:
- Allow only Cloudflare egress
- Allow ingress from your local IP
- Allow outbound access to internal LNbits (port 5000)
Use WireGuard VPN to secure the connection between external and internal LNbits:
- Ensures encrypted communication
- Restricts access to authenticated VPN peers
- Keeps the internal interface isolated from the public internet
✅ Final Notes
- Internal services communicate over
bitcoin-net - LND interfaces are accessed via Tor only
- LNbits and RTL UIs are locally accessible
- Cloudflare Tunnel secures external access to LNbits
Monitor system health using
monit,watchtower, or Prometheus.Create all configuration files manually (
bitcoin.conf,lnd.conf,RTL-Config.json), and keep credentials secure. Test every component locally before exposing it externally.⚡
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ f77dfdcf:17e93422
2024-05-29 04:06:39
@ f77dfdcf:17e93422
2024-05-29 04:06:39Proof of Work เป็น concept ที่คนที่เคยศึกษาการทำงานของ bitcoin อาจจะเคยได้ยินผ่านหูมาบ้าง แต่จริง ๆ แล้ว สิ่งนี้สามารถนำมาประยุกต์ใช้กับชีวิตประจำวันของเราได้อย่างเป็นธรรมชาติมาก
Proof of Work สำหรับ bitcoin เอาแบบสั้น ๆ คือ การที่เราเจอ ตัวเลขที่ถูกต้อง (Proof) ซึ่งได้จากการขุด ที่จะเกิดขึ้นได้โดยการใช้พลังงานและเวลาของเครื่องขุดในการคำนวณตัวเลข (Work)
ยิ่งมี Proof of Work ใน chain เยอะขึ้น ก็ทำให้ transaction มี confirmation มากขึ้น
ถ้าจะให้เขียนให้ครบจบตรงนี้ คนอ่านน่าจะตาลอย แนะนำให้ลองอ่านต่อใน Inventing Bitcoin ดูครับ
พอเราซูมออกมาเป็นภาพกว้าง ๆ Proof of Work จะหมายถึง “หลักฐาน” ที่เกิดขึ้น จากการทำ “งาน”
งาน (Work)ในที่นี้ คือ การลงทุนทาง “เวลา” ไปกับการทำส่ิง ๆ หนึ่ง ซึ่งจะได้ผลตอบแทนเป็น Proof of Work ในรูปแบบใดรูปแบบหนึ่ง
Proof ที่พูดถึง ไม่จำเป็นต้องเป็นชิ้นงานที่มองเห็นหรือจับต้องได้ มันอาจจะหมายถึงทักษะ ความรู้ หรือ ประสบการณ์ ก็ได้
ตัวอย่างในชีวิตประจำวันชัด ๆ เลยก็อย่างเช่น
- การที่บางคนที่มีหุ่นดี สุขภาพแข็งแรง มีกล้ามเนื้อกำยำ ก็เป็น Proof of Work ของการออกกำลังกาย กินอาหารที่ดี และความมีวินัย
- การที่เราเรียนรู้เรื่องใหม่ ๆ แล้วเรารู้สึกว่ายังไม่แน่ใจกับสิ่งที่รู้ เราเลยศึกษาเพิ่ม สิ่งนี้ก็เป็นการเพิ่ม Proof of Work ตัวเรา ซึ่งคือ knowledge ของสิ่งนั้น ทำให้เรามั่นใจในองค์ความรู้นั้น ๆ มากขึ้น และสามารถนำไปส่งมอบ valueให้กับคนอื่น ๆ ได้
- หรือจะเป็นการฝึกทักษะการทำงาน ถ้าเรารู้ว่ายังไม่เก่ง Work ที่เราจะทำเพิ่ม ก็คือการหมั่นฝึกฝน และ Proof of Work ที่ได้ คือ ทักษะที่ดีขึ้นของเรา พอมองแบบนี้ เราจะชั่งน้ำหนักได้ง่ายขึ้น ว่าเราอยากจะลงทุนเวลาของเราไปกับ Proof of Work แบบไหน เพราะทุกคนย่อมอยากได้ผลตอบแทนที่คุ้มค่าจากการลงทุน
แต่มันมีข้อสังเกตอยู่อย่างหนึ่ง คือ เราต้องมองให้ออก ว่าอะไรเป็น Proof of Work จริง ๆ ของแต่ละสิ่ง
อย่างบางที เราบอกว่า เราเข้าใจเรื่องนี้นะ เพราะเราเคยเรียนคลาสนี้มา และเราอาจจะคิดว่าเอารูปถ่ายหรือประกาศนีย์บัตรมันเป็น Proof of Work ได้ แต่จริง ๆ แล้วไม่น่าใช่ มันคือ Proof of อะไรไม่รู้
อ่ะ ๆ มันอาจจะเป็น Proof ว่าเราเคยไปเรียนมาจริง อันนี้ยอมรับได้ แต่ไม่ใช่ว่ามันจะเป็น Proof ว่าเราเข้าใจเรื่องนั้นได้โดยตรง
เพราะ Proof ของ Work ที่เรากำลังพูดถึง มันคือ knowledge ที่อยู่ในหัวเรา ถ้าเราอยากโชว์ว่ามี Proof of Work จริง ๆ เราต้องเอาสิ่งที่ได้เรียนรู้ มาแชร์ให้คนอื่นฟังได้
และสังเกตดี ๆ จะเห็นว่า Proof of Work ที่ได้พวกนี้ มันเป็นสิ่งที่จะติดไปกับตัวเราทั้งหมดเลย มันจึงเกิดเป็น quote ที่ว่า
“You are your Proof of Work”
ซึ่งสื่อว่า สิ่งที่เราเป็น ล้วนเป็น Proof of Work มาจากสิ่งที่เราทำทั้งสิ้น และยิ่งเรามี Proof of Work เยอะขึ้น เราก็จะยิ่งเติบโตขึ้นเรื่อย ๆ
บางทีเราสามารถมองได้ด้วยตาเปล่าด้วยซ้ำ ว่าใครมี Proof of Work ที่มากหรือน้อย เพราะมันจะมันสะท้อนออกมาในรูปแบบของความมั่นใจ
พอรู้จักสิ่งที่เรียกว่า Proof of Work แล้ว สุดท้าย เราต้องกลับมาถามตัวเอง ว่าสิ่งที่เราทำอยู่ มันกำลังให้อะไรกับเรา กำลังสอนอะไรกับเรา หรือมันจะมอบ Proof of Work ที่เราต้องการ สำหรับเป้าหมายของเราในอนาคตหรือเปล่า
พิจารณามันให้ดี และอย่าลืม
หมั่นสร้าง Proof of Work ให้กับตัวเอง
Reference
https://youtu.be/E0LYMhjHnBU?si=AY6ySrTy5t-OgYFT
-
 @ 7bdef7be:784a5805
2024-05-28 13:47:50
@ 7bdef7be:784a5805
2024-05-28 13:47:50I wrote Oracolo (see the announcement below) because I was brainstorming about Nostr "long format" and thinking about how to promote it. There seems to be little love for this format, why?
Long posts should have interesting value because the author usually put effort into them, and are produced for a long-term fruition. In the end, blogging was one of the most productive strands on the web, and still holds considerable importance.But in standard (kind-1) social clients they are rather hidden. I think many people don't even know they exist, they probably intuit something just because they see a particular formatting. This is quite evident if you compare the responses/zaps/reactions of the short notes with the long ones, the latter have far fewer interactions, a fact that I read as less exposure to readers.
Interlude: don't know what this "long format" stuff is?
Check https://habla.news or https://highlighter.comI think the situation can be largely improved with some adjustments in kind-1 clients:
- Add a tab/section to the user's profile, next to the usual posts/responses, that lists only the long format notes;
- Highlight/pinning recent long notes in the user's profile to give them visibility; the user picture could also have a special mark that alerts about fresh content available;
- In the feed show the preview of long notes with a special design, and allow the user to read them in a separate/immersive view (or just link to njump.me);
- In an appropriate context (es. at the footer of a long note) invite the user to discover long format and post his own content;
- Offer a filtered feed that display only long format notes;
Finally, we should probably also evaluate and agree on a new labeling in clients, because “long notes” is self-explanatory but also a bit confusing next to "plain notes”. Perhaps “articles” might be a better term.
If clients bring more interaction on articles, content creators are naturally incentivized to invest their time in this area, thus increasing the production of in-depth content that may be of interest even to those who are not as involved in social media dynamics.
Memo for kind-1 clients: interoperability is our superpower and currently your are the main entrance to Nostr, so don't be fearful or lazy, please embrace it.
nostr:nevent1qqsrrcl7sfaxd505lyezj7u54tpdg93x0swpcpe0xj5adax5l6xz3yspzamhxue69uhky6t5vdhkjmn9wgh8xmmrd9skctcpr3mhxue69uhkxmm4de68y6t9wvhxv6tpw34xze3wvdhk6tcppemhxue69uhkummn9ekx7mp0aagyzp
nostrdesign
-
 @ 6ad08392:ea301584
2024-05-27 18:31:39
@ 6ad08392:ea301584
2024-05-27 18:31:39Release announcement & short overview
Two years, six drafts, and 125,000 words later, and The Bushido of Bitcoin is almost complete.
Before the book’s release in Q3 of this year I will be doing a few things:
- Making it available for pre-order on Geyser. For the general paperback, digital and audio copies, it will save you roughly 50%. I will also include some limited edition options, like a short run of 21 leather-bound versions of the book. More on that in the coming weeks.
- Drip-feeding snippets from the book, in the form of quotes, lessons, etymology progressions and insights, across all my socials. On Substack I’ll do longer form posts, on Twitter & Nostr, I’ll keep them more succinct, and finally, I’m reviving my Instagram to wrap the insights in beautiful, shareable, bite-size visuals.
- Jumping on a bunch of podcasts, both Bitcoin and not Bitcoin-related to dig into the content of the book. I’ve recorded with Breedlove already. Many more to come - and who knows, I may even revive my old Wake Up Podcast and do a few short episodes there too.
I want to treat this book as both an ongoing work and a piece of art. So alongside the book, I’m also going to produce some pieces of visual and physical art. The video trailer, alone, I promise will blow your mind., as will the warrior-samurai artwork I’m going to have commissioned in collaboration with some soon-to-be-announced artists. I’ll probably even do a tradings cards pack with Bitcoin Trading cards next year, and some other collaborations along the way.
In any case, it’s been an incredible journey writing this book and I’m honoured to have had people like John Carter help me edit it, and Ross Stevens agreeing to do the foreword. I can’t wait to have the final version completed and in your hands.
For those who might be wondering what I am talking about…
**What is The Bushido of Bitcoin? **
This is a book I’ve been writing for almost two years now. Its genesis was a conversation I had with Erik Cason on my old Wake Up Podcast - also called “The Bushido of Bitcoin.” It was Episode 65: you can check out here. The inspiration for that episode came from a shared love of the book by James Clavell, called: Shogun (now a HBO series - which it seems they didn’t make woke..thank God), and of course we related the idea of Bushido (Way of the warrior: Code of Virtue) back to Bitcoin.
I felt that this was a seed of an idea, well worth watering. So after that, I decided to go on a history binge and start collecting ideas. What ensued was a real journey. I must’ve listened to a thousand hours of history books and Dan Carlin podcasts in the first six months and the concept began to form. But before I tell you what the concept is - let me tell you what it’s not.
This is NOT another book about the history of money, nor does it make an Austrian case for sound money, or an economic case for Bitcoin as sound money. Neither is it concerned with how Bitcoin works, or any of the technicals. We have enough of those books, and I don’t think I will add anything new to that corpus of knowledge. What this book IS about, is something so much deeper and more profound: The behaviour, virtue, culture and civilisation of greatness.
The book seeks to answer the question: “What happens when Bitcoin wins?” What happens to those who rise to the top, and become the socio-economic elite of the world?
- Will we become a new parasitic class?
- Will we become self-indulgent degenerates? Or..
- Will become men and women of virtue?
The latter is not a given, and it’s certainly not enough to just say “Bitcoin Fixes This.” To become men and women of stature and character requires actively developing the virtues which give rise to a culture of excellence. This is the only way to reclaim and rebuild civilisation - complaining and wishing about the past won’t cut it.
Over the coming weeks, I will introduce you to the Ten Virtues that make up The Bushido of Bitcoin. The book of course is more complete, but I will hold nothing back. We’ll follow the historical and etymological genesis of these virtues with an in-depth analysis on how they were embodied by the greatest leaders and warriors throughout history. We’ll also draw lessons from this analysis that will help us navigate the road ahead.

What lies before us may be a “clown world” but hope is far from lost. We’ve been here before. Many times, and against greater odds. This is our generation’s opportunity for a re-conquista.
The Bushido of Bitcoin is written to remind you there is something greater inside of you, and the only way through hell, is forward. I hope you find value in the up-coming content, and that should you pick up a copy of the book, it greatly inspires you.
Thankyou Aleksandar Svetski
Per-order the book here: https://geyser.fund/project/bushidoofbitcoin Get a free introductory chapter here: BushidoOfBitcoin.com Follow my work here: Linktree.com/Svetski
-
 @ 362ebffa:492e2719
2024-05-27 12:51:14
@ 362ebffa:492e2719
2024-05-27 12:51:14Consciousness is the subjective experience arising from the brain (as the viewer, the beholder) While reality encompasses both the objective external world and our subjective perception of it.
The two are deeply interconnected, with consciousness shaping our experience of reality and reality influencing the state and content of our consciousness.
Therefor we do live in various bubbles of reality, my reality (my perception of reality) is my own.
What do you think?
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ dbb19ae0:c3f22d5a
2025-04-21 12:29:38
@ dbb19ae0:c3f22d5a
2025-04-21 12:29:38Notice this consistent apparitioon in the timeline of something that reflects a major key shift in tech:
💾 1980s – The Personal Computer Era
- IBM PC (1981) launches the home computing revolution.
- Rise of Apple II, Commodore 64, etc.
- Storage is local and minimal.
- Paradigm shift: Computing becomes personal.
🎮 1990s – Networking & Gaming
- LAN parties, DOOM (1993) popularizes multiplayer FPS.
- Early internet (dial-up, BBS, IRC).
- There is lots of room for connecting PC.
- Paradigm shift: Networked interaction begins.
🌐 2000s – The Internet Boom
- Web 2.0, broadband, Google, Wikipedia.
- Rise of forums, blogs, file sharing.
- A bigger need of interaction is looming
- Storage is on cd and dvd.
- Paradigm shift: Global information access explodes.
📱 2010s – Social Media & Mobile
- Facebook, Twitter, Instagram dominate.
- Smartphones become ubiquitous.
- Bitcoin appears and start a revolution.
- Collecting personal data from users to fuel the next shift.
- Paradigm shift: Always-connected, algorithmic society.
🤖 2020s – AI & Decentralization
- GPT, Stable Diffusion, Midjourney, Copilot.
- Blockchain, Nostr, Web3 experiments.
- Storage is in the cloud.
- Paradigm shift: Autonomous intelligence and freedom tech emerge.
roughly every decade, a tech leap reshapes how we live and think.
-
 @ 86dfbe73:628cef55
2025-04-21 10:08:34
@ 86dfbe73:628cef55
2025-04-21 10:08:34Mit dem Internet kam das Ende der Massengesellschaft. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar. Nicht als Netzwerk zur Kommunikation, sondern als Netzwerk der Beziehungen, bestehend aus den Erwartungen, Kenntnissen und letztlich bestehend aus dem Vertrauen, das Menschen gegenüber anderen Menschen und Institutionen aufzubauen pflegen. Wichtig ist nicht mehr, wo jemand eine Information plaziert, wichtig ist, wann und wer und unter Einbeziehung welcher Faktoren diese abfragt.
In Sozialen Netzwerken entscheidet jeder selbst, wem er folgt. Er entscheidet selbst, wie die eigene Startseite, der eigene Blick auf den Dienst, aussieht. Als Beispiel sei hier Twitter erwähnt. Aus der Liste der Gefolgten wird die Timeline generiert, die eine Wirklichkeit abbildet, die einzig und alleine von den Following-Entscheidungen des Nutzers bestimmt ist.
Die Beziehungsweise des Folgens ist eine direkte Willenserklärung, die Inhalte eines Users sehen zu wollen. Sie ist ein Pakt, der auch eine gewisse, wenn auch kleine, Verantwortungsübernahme bedeutet. Und diese Beziehungsweise wurde zum integralen Strukturbaustein der digitalen Öffentlichkeit zwischen 2010 bis 2020 und damit auch zur tragenden Säule vieler Karrieren, Geschäftsmodellen und außerdem zur Grundlage der Selektionsverfahren von kulturellen Trends. Im Follower steckte die Macht.
Die digitale Öffentlichkeit hat aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in den „For you“-Algorithmen der kommerziellen Plattformen auf. Ab 2020 wurde dem Follower von Diensten wie Tiktok der Gar ausgemacht und von dort setzte sich der „For You-Algoritmus“ auf allen kommerziellen Plattformen durch. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist. Auf einmal bedeutete ein Following nicht mehr die Garantie, dass der Content die Abonnenten erreicht.
Mit der Zerstörung dieser Beziehung entgleiten den Creators ihre medialen Regime und beide, User und Creator werden immer abhängiger vom Algorithmus und arbeiten folglich nur noch für die Interessen der Plattformen, statt für sich selbst.
-
 @ 005bc4de:ef11e1a2
2025-04-19 12:23:14
@ 005bc4de:ef11e1a2
2025-04-19 12:23:14A new game is starting today, 4/19/2025, called "Moon"
https://moon.hive.pizza
I'm not a gamer and don't know much about this one, or any games for that matter, but some folks may be interested in getting in at the start.
Go-time is noon EST today, I believe.
I do get a kick out of the line "Free dopamine and tears."
😀

-
 @ 2ecde0a6:10022dcb
2024-05-25 20:28:41
@ 2ecde0a6:10022dcb
2024-05-25 20:28:41Opinion about KeepKey (hardware)
KeepKey is a hardware wallet with a high level of security and supports more than 40 different crypto assets.
The device provides a PIN code and recovery seeds. It has a feature where it switches your PIN code numbers from time to time, making it impossible for malware to copy our code. Also, the device has a system for trade where you have to press and hold to confirm the transaction to avoid external hacks.
KeepKey has only one button to manage it. This button is used for turning the device on and off. All the other processes can be managed through the mobile app. That includes entering your PIN code and setting up the recovery seed, which makes it very simple to use, unlike other complex wallets. The device has a wide screen that allows you to see the entire cryptocurrency address without the need to scroll back and forth. But it's easy to break or scratch if you don't have a protecting casing.
Its price is around $80.
But you have to remember that the device is a little big and heavy, compared to other hard wallets, so it's difficult to carry around with it.
WalletScrutiny #nostrOpinion
-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0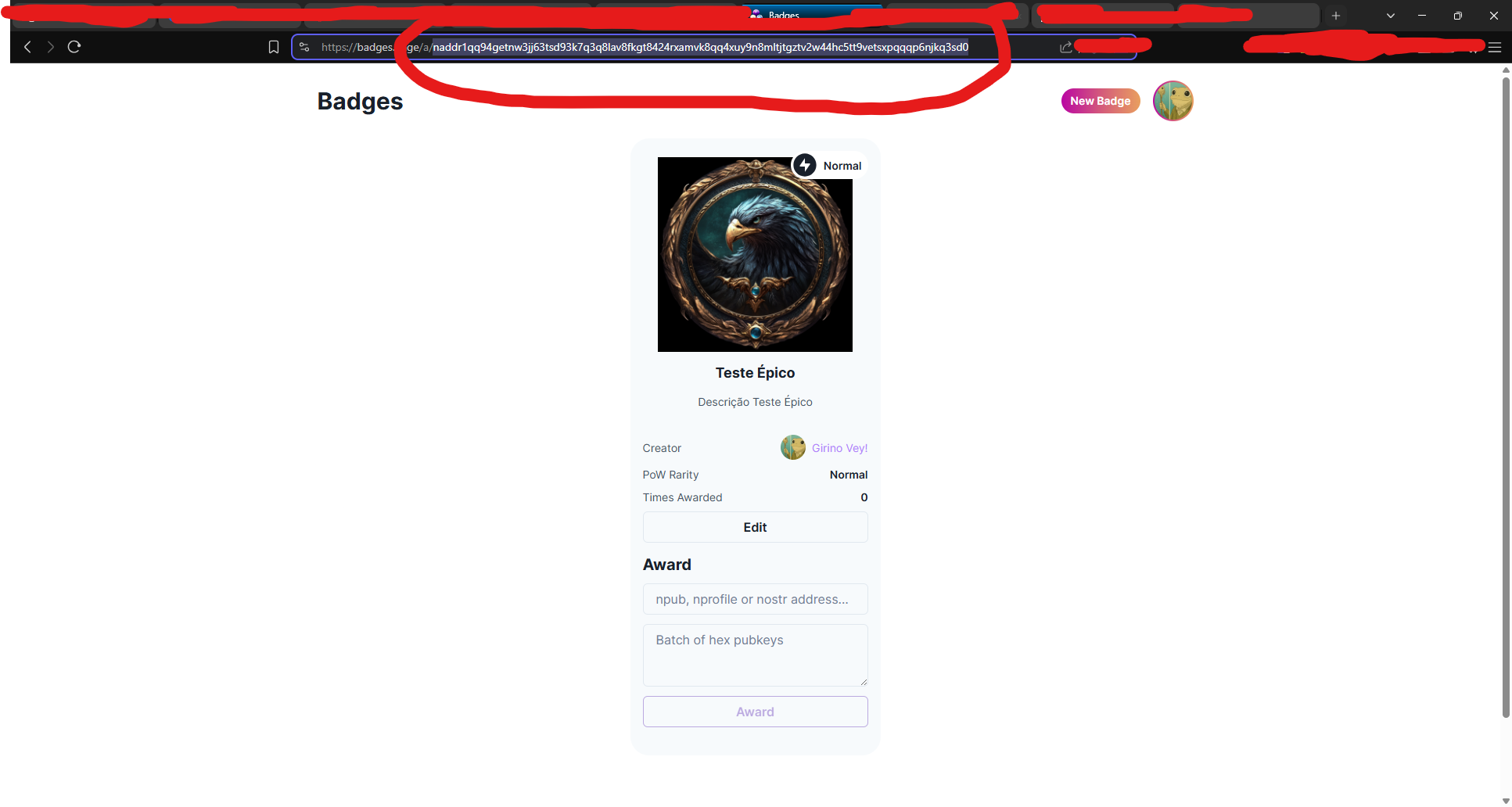
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 126a29e8:d1341981
2024-05-22 06:47:20
@ 126a29e8:d1341981
2024-05-22 06:47:20Esta es la traducción de una carta de Ross Ulbricht que se publicó en su blog en Septiembre de 2019. Podéis leer el artículo original aquí: https://rossulbricht.medium.com/bitcoin-equals-freedom-6c33986b4852
Algo especial sucedió en el primer año después de que Satoshi nos regalara Bitcoin. Algo que nadie esperaba y que muchos pensaban que era imposible. Intenta imaginar Bitcoin en aquel entonces, antes de que pudieras comprar cosas con él, antes de que hubiera un tipo de cambio, antes de que nadie supiera realmente qué pasaría con él, si es que pasaba algo. Bitcoin no empezó como dinero. Se convirtió en dinero, pero lo hizo de forma distinta a cualquier dinero anterior. A pesar de todas las cosas que Bitcoin ha hecho posibles, a pesar de todas las formas en que está cambiando nuestro mundo, no apreciamos plenamente o ni siquiera entendemos lo que sucedió en aquellos primeros días, cuando era sólo un juguete para geeks.
Cualquier otro dinero anterior al Bitcoin -en la larga historia de la civilización humana- se valoraba por razones distintas a su uso como dinero. El ganado en África, los sellos de correos en las prisiones, las conchas marinas y los metales preciosos se han utilizado como dinero y encajan en este patrón. La única excepción es el dinero fiduciario -algo declarado como dinero por una autoridad-, pero incluso las monedas fiduciarias nacionales estuvieron en su día respaldadas por algo con valor previo, como el oro.
Bitcoin cambió todo eso. Bitcoin no tenía ningún valor previo y nadie estaba obligado a utilizarlo, pero de alguna manera se convirtió en un medio de intercambio. Las personas que no entienden y se preocupan poco por Bitcoin pueden, sin embargo, aceptarlo como pago porque saben que puede ser utilizado para pagar por otra cosa o ser intercambiado por dinero convencional.
La gente suele mencionar las pizzas que se compraron por diez mil bitcoins y, en retrospectiva, se burlan del tipo que se comió lo que se convertiría en un almuerzo multimillonario. A mí me interesa más la persona que renunció a dos pizzas en perfecto estado por meros bitcoins. ¿Qué vio en esos bits y bytes, en esa firma digital de algo que la gente llamaba cadena de bloques? Lo que motivó al vendedor de pizzas pudo haber llamado también la atención de los primeros mineros, que no podían vender pero acumulaban alegremente. Quizá inspiró a los que simplemente regalaban bitcoins por miles. Fuera lo que fuese, era algo nuevo.
La teoría económica clásica dice que un intercambio no se produce a menos que ambas partes valoren más lo que reciben que lo que entregan. Entonces, ¿de dónde viene el valor? Bitcoin nunca debería haber despegado, pero lo hizo. Incluso un producto nuevo tiene algún tipo de valor, y los primeros en adoptarlo corren el riesgo de no obtener el valor de su dinero, pero aún así esperan ganar con el intercambio.
En cambio, los primeros usuarios de Bitcoin no tenían ni idea de lo que sabemos ahora. Todo lo que tenían era un sueño, una convicción y el entusiasmo suficiente para convertir un artilugio digital en un fenómeno multimillonario del que sólo estamos empezando a ver los efectos.
Te diré lo que creo que pasó, aunque lo cierto es que nadie lo sabe. Es casi magia que Bitcoin pudiera surgir de la nada y, sin valor previo ni decreto de autoridad, convertirse en dinero. Pero Bitcoin no se originó en el vacío. Fue la solución a un problema con el que los criptógrafos llevaban lidiando muchos años: Cómo crear dinero digital sin autoridad central que no pudiera falsificarse y en el que se pudiera confiar.
Este problema persistió durante tanto tiempo que algunos dejaron la solución a otros y soñaron en cambio con cómo sería nuestro futuro si el dinero digital descentralizado llegara a existir de alguna manera. Soñaban con un futuro en el que el poder económico del mundo estuviera al alcance de todos, en el que el valor pudiera transferirse a cualquier lugar con sólo pulsar una tecla. Soñaban con que la prosperidad y libertad dependieran únicamente de las matemáticas de una encriptación robusta.
Bitcoin nacía pues en terreno fértil y era reconocido por quienes lo habían estado esperando. Fue un momento histórico para ellos, mucho más importante que las pizzas o las facturas de la electricidad generadas por la minería. La promesa de libertad y el encanto del destino dieron energía a la comunidad inicial. Bitcoin se adoptó consciente y espontáneamente como dinero mientras nadie lo veía, y nuestro mundo nunca volverá a ser el mismo.
https://freeross.org
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ e516ecb8:1be0b167
2025-04-11 15:07:04
@ e516ecb8:1be0b167
2025-04-11 15:07:04¿Qué es realmente la inflación? Si alguna vez has escuchado que la inflación es “la subida constante de precios”, no estás solo. Hace poco, un economista soltó esa definición en una entrevista, y otro, desde la Fundación para el Progreso (FPP), una institución que suele citar a pensadores como Mises o Hayek, repitió lo mismo. Suena lógico, ¿no? Pero están equivocados. Y ese error, aunque parezca pequeño, puede tener consecuencias catastróficas. Para entender por qué, no hace falta ir muy lejos: miremos a Argentina.
La subida de precios no es la inflación. Es solo el síntoma. La inflación, en esencia, es la pérdida del valor adquisitivo de la moneda. Confundir la causa con el efecto es como tratar una fiebre con un paño frío sin atacar la infección. Y cuando las políticas públicas se basan en esa confusión, el desastre está garantizado.
Argentina: una lección que duele Argentina es el caso de estudio perfecto. Antes de que Javier Milei llegara al poder en diciembre de 2023, la inflación en el país vecino estaba desbocada, alcanzando picos de 211% anual según datos del INDEC. El peronismo, convencido de que el problema eran los precios, implementó medidas como los “Precios Justos”, fijando topes artificiales. ¿Resultado? Escasez total. En un país famoso por su carne, los supermercados se quedaron sin ella. Los productores, enfrentados a costos que subían sin control, preferían exportar antes que vender localmente a precios que no les daban ni para cubrir gastos. Y ahí no terminó la cosa. En lugar de atacar la raíz del problema, el gobierno peronista complicó todo aún más: restringió exportaciones y creó un sistema surrealista de múltiples tipos de dólar (¡hasta uno distinto para Netflix!). Todo porque seguían peleando con el efecto, no con la causa.
¿Por qué los argentinos corrían a ahorrar en dólares y no en pesos? Porque el peso se devaluaba a una velocidad alarmante. Si la inflación fuera solo una cuestión de precios, habría afectado a todas las monedas por igual. Pero no. Como dice Milei una y otra vez, la inflación es un fenómeno monetario: demasiados billetes circulando sin respaldo o una moneda que la gente considera “de segunda” frente a otras.
¿Por qué seguimos repitiendo el error? Entonces, si la inflación es tan claramente un problema del valor de la moneda, ¿por qué seguimos escuchando que es una subida de precios? La respuesta es sencilla: culpar a otros es más fácil. Cuando se vende esa idea, los políticos pueden apuntar con el dedo a empresarios, comerciantes o “especuladores” y lavarse las manos. Es más cómodo que admitir una emisión monetaria irresponsable, un gasto público descontrolado o una pésima gestión económica. Y no faltan economistas, a veces financiados por grupos estatistas o formados en sistemas educativos que promueven esas ideas, que les hacen el coro.
Chile: por un pelo nos salvamos Este malentendido estuvo a punto de colarse en Chile. En el segundo intento de reforma constitucional, impulsado por Chile Vamos en 2023, se propuso que el Banco Central velara por la “estabilidad de precios”, no por la estabilidad del valor de la moneda. Parece un detalle técnico, ¿verdad? Pero no lo es. Ese cambio abría la puerta a políticas que podrían habernos llevado por el mismo camino que Argentina. Por suerte, aunque muchos expertos lo pasaron por alto, la ciudadanía no: la propuesta fue rechazada en las urnas con un contundente “En Contra”.
Nos salvamos, pero no porque nuestros políticos tuvieran las ideas claras. Nos salvamos porque los chilenos dijimos “basta”. Y menos mal, porque en 2024 la inflación en Chile se mantuvo controlada, rondando el 3,5% anual según el Banco Central, lejos del caos argentino. Pero no podemos confiarnos, porque esa inflación sigue siendo alta para nuestros estándares pre-pandémicos o pre-estallido social. El retiro desde las AFP convirtió activos en consumo, en otras palabras aumentó el circulante y todavía batallamos con esa inflación.
No es un “detallito” Cada vez que alguien diga que la inflación es una subida de precios o que la solución está en controlarlos, por favor, corrígelo. No es un error menor. Argentina lleva más de un año intentando salir del pozo que cavó este malentendido. Milei ha dado pasos importantes: transparentó la inflación real, ajustó el tipo de cambio para acercarse al valor de mercado y, aunque la inflación sigue alta (cerca del 50% anual a fines de 2024, según estimaciones), empieza a estabilizarse. Pero el camino es largo, y los costos de este “detallito” los pagan todos los argentinos.
¿Y ahora qué hacemos? La próxima vez que escuches a un político o un experto hablar de inflación como si fuera solo un problema de precios, no te quedes callado. Pregúntales: ¿y el valor de la moneda qué? Comparte esta historia, porque entender la inflación es el primer paso para no repetir los errores del pasado. En Chile esquivamos la bala, pero no podemos bajar la guardia. Los errores pequeños, cuando se trata de economía, terminan costándonos caro.
¿Qué opinas? ¿Crees que Chile aprendió la lección o estamos a un paso de tropezar otra vez? ¡Déja tu comentario y comparte este post si te hizo clic!
-
 @ e17e9a18:66d67a6b
2025-04-11 14:00:27
@ e17e9a18:66d67a6b
2025-04-11 14:00:27We wrote this album to explain the inspiration behind Mutiny Brewing, and as a way to share the story of Bitcoin and freedom technologies like nostr. Through these songs, we’ve tried to capture every truth that we believe is essential to understand about money, freedom, trust, and human connection in the internet age. It’s our way of making these ideas real and relatable, and we hope it helps others see the power of taking control of their future through the systems we use.
01. "Tomorrow's Prices on Yesterday's Wage" explores the harsh reality of inflation. As central banks inflate the money supply, prices rise faster than wages, leaving us constantly falling behind. People, expecting prices to keep climbing, borrow more to buy sooner, pushing prices even higher in a vicious cycle. You're always a step behind, forced to pay tomorrow's inflated prices with yesterday's stagnant wages.
https://wavlake.com/track/76a6cd02-e876-4a37-b093-1fe919e9eabe
02. "Everybody Works For The Bank" exposes the hidden truth behind our fiat money system. When banks issue loans, they create new money from debt—but you must pay back both the principal and interest. That interest requires even more money, relying on others to borrow, creating an endless cycle of debt. If borrowing slows, the system falters and governments step in, printing more money to keep banks afloat. Ultimately, we’re all working to service debt, chained to the banks.
“Paying back what they create, working till I break” https://wavlake.com/track/4d94cb4b-ff3b-4423-be6a-03e0be8177d6
03. "Let My People Go" references Moses' demand for freedom but directly draws from Proverbs 6:1–5, exposing the danger of debt based money. Every dollar you hold is actually someone else's debt, making you personally liable—held in the hand of your debtor and at risk of their losses, which you ultimately pay for through inflation or higher taxes. As the song says, "The more you try to save it up, the deeper in you get." The wisdom of Proverbs urges immediate action, pleading urgently to escape this trap and free yourself, like a gazelle from a hunter.
https://wavlake.com/track/76214ff1-f8fd-45b0-a677-d9c285b1e7d6
04. "Mutiny Brewing" embodies Friedrich Hayek's insight: "I don't believe we shall ever have good money again before we take it out of the hands of government... we can't take it violently... all we can do is by some sly roundabout way introduce something they can't stop."
Inspired also by the Cypherpunk manifesto's rallying cry, "We will write the code", the song celebrates Bitcoin as exactly that unstoppable solution.
"Not here to break ya, just here to create our own little world where we determine our fate." https://wavlake.com/track/ba767fc8-6afc-4b0d-be64-259b340432f3
05. "Invisible Wealth" is inspired by The Sovereign Individual, a groundbreaking 1990s book that predicted the rise of digital money and explores how the return on violence shaped civilizations. The song references humanity's vulnerability since agriculture began—where stored wealth attracted violence, forcing reliance on larger governments for protection.
Today, digital privacy enabled by cryptography fundamentally changes this dynamic. When wealth is stored privately, secured by cryptographic keys, violence becomes ineffective. As the song emphasizes, "You can't bomb what you can't see." Cryptography dismantles traditional power structures, providing individuals true financial security, privacy, and freedom from exploitation.
“Violence is useless against cryptography” https://wavlake.com/track/648da3cc-d58c-4049-abe0-d22f9e61fef0
06. "Run A Node" is a rallying cry for Bitcoin's decentralisation. At its heart, it's about personal verification and choice: every node is a vote, every check’s a voice. By running the code yourself, you enforce the rules you choose to follow. This is true digital democracy. When everyone participates, there's no room for collusion, and authority comes directly from transparent code rather than blind trust.
"I verify, therefore I do." https://wavlake.com/track/ee11362b-2e84-4631-b05e-df6d8e6797f8
07. "Leverage is a Liar" warns against gambling with your wealth, but beneath the surface, it's a sharp critique of fractional reserve banking. Fractional reserves inflate asset prices, creating the illusion of wealth built on leverage. This system isn't sustainable and inevitably leads to collapse. Real wealth requires sound money, money that can't be inflated. Trying to gain more through leverage only feeds the lie.
"Watch it burn higher and higher—leverage is a liar." https://wavlake.com/track/67f9c39c-c5e1-4e15-b171-f1f5442f29a5
08. "Don't Get Rekt" serves as a stark warning about trusting custodians with your Bitcoin. Highlighting infamous collapses like Mt.Gox, Celsius, and FTX. These modern failures echo the 1933 Executive Order 6102, where the US government forcibly seized citizens' gold, banned its use, and then promptly devalued the currency exchanged for it. History shows clearly: trusting others with your wealth means risking losing it all.
"Your keys, your life, don't forget." https://wavlake.com/track/fbd9b46d-56fc-4496-bc4b-71dec2043705
09. "One Language" critiques the thousands of cryptocurrencies claiming to be revolutionary. Like languages, while anyone can invent one, getting people to actually use it is another story. Most of these cryptos are just affinity scams, centralized towers built on shaky foundations. Drawing from The Bitcoin Standard, the song argues money naturally gravitates toward a single unit, a universal language understood by all. When the dust settles, only genuine, decentralized currency remains.
"One voice speaking loud and clear, the rest will disappear." https://wavlake.com/track/22fb4705-9a01-4f65-9b68-7e8a77406a16
10. "Key To Life" is an anthem dedicated to nostr, the permissionless, unstoppable internet identity protocol. Unlike mainstream social media’s walled gardens, nostr places your identity securely in a cryptographic key, allowing you total control. Every message or action you sign proves authenticity, verifiable by anyone. This ensures censorship resistant communication, crucial for decentralised coordination around Bitcoin, keeping it free from centralised control.
"I got the key that sets me free—my truth is mine, authentically." https://wavlake.com/track/0d702284-88d2-4d3a-9059-960cc9286d3f
11. "Web Of Trust" celebrates genuine human connections built through protocols like nostr, free from corporate algorithms and their manipulative agendas. Instead of top down control, it champions grassroots sharing of information among trusted peers, ensuring truth and authenticity rise naturally. It's about reclaiming our digital lives, building real communities where trust isn't manufactured by machines, but created by people.
"My filter, my future, my choice to make, real connections no one can fake." https://wavlake.com/track/b383d4e2-feba-4d63-b9f6-10382683b54b
12. "Proof Of Work" is an anthem for fair value creation. In Bitcoin, new money is earned through real work, computing power and electricity spent to secure the network. No shortcuts, no favourites. It's a system grounded in natural law: you reap what you sow. Unlike fiat money, which rewards those closest to power and the printing press, Proof of Work ensures rewards flow to those who put in the effort. Paper castles built on easy money will crumble, but real work builds lasting worth.
"Real work makes real worth, that's the law of this earth." https://wavlake.com/track/01bb7327-0e77-490b-9985-b5ff4d4fdcfc
13. "Stay Humble" is a reminder that true wealth isn’t measured in coins or possessions. It’s grounded in the truth that a man’s life does not consist in the abundance of his possessions. Real wealth is the freedom to use your life and time for what is good and meaningful. When you let go of the obsession with numbers, you make room for gratitude, purpose, and peace. It's not about counting coins, it's about counting your blessings.
"Real wealth ain't what you own, it's gratitude that sets the tone." https://wavlake.com/track/3fdb2e9b-2f52-4def-a8c5-c6b3ee1cd194
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ e516ecb8:1be0b167
2025-04-06 18:25:12
@ e516ecb8:1be0b167
2025-04-06 18:25:12Bitcoin ha recorrido un camino fascinante: de ser un experimento cypherpunk nacido en las sombras de la crisis de 2008 a convertirse en un activo que algunos estados, como El Salvador, consideran parte de sus reservas estratégicas, una especie de "oro digital". Hace apenas 15 años, era un código curioso que valía centavos; hoy, hay países apostando su futuro económico a él. Sin embargo, no hace falta haber leído Hijacking Bitcoin para sospechar que hay nubes en el horizonte. Y no, no hablo solo de la volatilidad, ese eterno fantasma que siempre se menciona. Sí, Bitcoin sube y baja como montaña rusa —en 2021 tocó los 69 mil dólares y luego cayó a 16 mil en 2022—, pero si hacemos un zoom out —como dicen los gringos—, la tendencia a largo plazo es al alza, mientras que las monedas fiduciarias, en palabras de Huerta de Soto, no son más que "papelitos coloreados" que tienden a valer cero. Pero dejemos la poesía de lado y miremos con lupa: ¿qué problemas podrían acechar el futuro de Bitcoin? Aquí van algunos puntos que me dan vueltas en la cabeza.
1. Bloques vacíos y el dilema del HODL
En marzo de 2025, se reportó que casi el 20% de los bloques de la blockchain estaban vacíos o con pocas transacciones. Esto encaja con una teoría: Bitcoin dejó de ser la moneda peer-to-peer que soñó Satoshi Nakamoto para transformarse en un depósito de valor. Hoy, la filosofía dominante es "HODL" (sujetar y no soltar), y figuras como Michael Saylor no esconden que les conviene que la gente pierda sus llaves privadas: menos bitcoins en circulación, mayor escasez, precio más alto. Imagina a Saylor frotándose las manos cada vez que alguien olvida su contraseña. Pero si todos acumulan y nadie gasta, ¿qué pasará con los mineros cuando las transacciones escaseen? Sin ellas, sus ingresos dependen de las recompensas por bloque, que algún día desaparecerán. Claro, ahora existen billeteras con opciones de herencia, pero si la idea es holdear hasta la tumba, ¿para qué acumular?
2. La red Lightning y el fantasma de los terceros
Para revivir la red, hacen falta más transacciones. Pero cuidado: el tamaño de los bloques es limitado a 1 MB (o un poco más con SegWit). Si el volumen crece demasiado —como en 2017, cuando las tarifas llegaron a 50 dólares por transacción—, la red se congestiona y adiós practicidad. ¿Aumentar el tamaño de los bloques? Ni lo menciones, eso sería darle la razón a los de Bitcoin Cash, un pecado mortal para cualquier bitcoinero Core. La solución, entonces, son las segundas capas como la red Lightning, que promete transacciones rápidas y baratas. El problema es que sigue pareciendo un eterno beta: hay fallos técnicos que no termino de entender (y sospecho que no soy el único). Pero lo que sí entiendo es que, al usarla, mucha gente termina dependiendo de terceros. Y si "no son tus llaves, no es tu dinero", esto choca de frente con la filosofía original de Bitcoin.
3. Computación cuántica: ¿el fin de la inviolabilidad?
Pasemos a un terreno más técnico. La computación cuántica podría, en teoría, descifrar las direcciones antiguas de Bitcoin, esas basadas en algoritmos vulnerables como ECDSA. Algunos proponen "quemar" esos bitcoins para proteger la red, pero imagina el golpe a la confianza: ¿qué tan "seguro" es un activo si de pronto desaparecen millones de unidades? Este riesgo no es exclusivo de Bitcoin —afecta a casi todas las criptos—, pero solo un puñado, como QRL o IOTA en sus inicios, usa algoritmos post-cuánticos, y ninguna es mainstream. Un tema que da para pensar.
4. Filosofía traicionada: del antisistema al lobby estatal
Bitcoin nació como un grito contra los bancos, los gobiernos y el sistema monetario tras la crisis de 2008. Entonces, ¿por qué vemos a sus principales voceros viajando por el mundo, haciendo lobby para que estados y gigantes como BlackRock lo adopten como reserva de valor? Podría ser solo una contradicción filosófica menor, pero hay más: si Bitcoin es tan libre y transfronterizo, ¿por qué los aranceles de Trump lograron tumbar su precio un 5% en diciembre pasado? Algo no cuadra en el discurso de la independencia absoluta.
5. El fin de la minería y la dependencia estatal
A largo plazo, cuando se mine el último bitcoin en 2140 (sí, falta mucho), los mineros dependerán exclusivamente de las tarifas por transacción. Pero si el modelo es "sujetar y no soltar", ¿quién pagará esas tarifas? Ya hemos visto momentos en que minar sale más caro que las ganancias —en 2018, muchos apagaron sus máquinas—, y aunque hasta ahora han sido excepciones, el futuro pinta complicado. Si los costos energéticos no bajan, ¿quién mantendrá la red? ¿Empresas dispuestas a perder dinero por un "bien mayor"? Suena a utopía, salvo que hablemos de empresas estatales. Y aquí volvemos al punto inicial: ¿Bitcoin dependiendo de los estados? ¿Pagando impuestos en dinero fiduciario para subsidiar mineros? ¿No era esto lo que queríamos evitar? El oro, una vez extraído, no necesita mineros para seguir existiendo; Bitcoin, por el contrario, sí.
6. El caso argentino: libertarismo con asterisco
Para rematar, esta semana salió la noticia de que el gobierno argentino —sí, el de Milei, abanderado del libertarismo— planea exigir que los residentes declaren sus billeteras de criptoactivos. No niego las reformas positivas de su gestión, como la desregulación económica, pero esto huele a Gran Hermano. ¿Qué tan libertario es un sistema que te vigila mientras predica libertad? Otra contradicción que suma ruido.
Después de ganarme el odio de los maximalistas de Bitcoin (esperaré comentarios tipo: "¡este tipo no entiende nada!"), y quizás de algún fan de Milei, quiero aclarar: no estoy en contra de Bitcoin. Lo que me molesta son las inconsistencias. Odio igual a los políticos que dicen una cosa y hacen otra que a los predicadores de un "antisistema" que termina dependiendo del sistema para sobrevivir. Me hace tanto ruido como esos malacatosos que rayan paredes con la "A" de anarquía mientras piden más Estado.
Dicho esto, no todo está perdido. Si Bitcoin quiere ser ese oro digital y cumplir su promesa libertaria, tal vez necesite ajustes: algoritmos más robustos contra la computación cuántica y algún método para pasar los bitcoins de direcciones antiguas a nuevas de forma transparente (ni idea si es técnicamente posible), una red Lightning que realmente funcione sin intermediarios, o una comunidad que priorice la utilidad sobre el HODL ciego. En resumen, apoyo a Bitcoin siempre que sus defensores sean coherentes. Si es libertad, que no se arrodille ante nadie. ¿Es mucho pedir?
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ e516ecb8:1be0b167
2025-04-05 23:09:31
@ e516ecb8:1be0b167
2025-04-05 23:09:31En el vasto universo de "Dune", Frank Herbert nos presenta un mundo donde el poder, la religión y la economía se entrelazan de manera fascinante. A primera vista, uno podría pensar que esta saga épica no tiene mucho que ofrecer a los libertarios. Sin embargo, al examinarla a través de la lente de la Escuela Austriaca y el anarcocapitalismo, emergen lecciones valiosas sobre la naturaleza del poder, la importancia del libre mercado y los peligros del intervencionismo estatal.
El Estado y el control de los recursos
En "Dune", el Estado, representado por el Imperio Corrino, ejerce un control férreo sobre el recurso más valioso del universo: la especia melange. Este monopolio estatal sofoca la innovación y el libre intercambio, creando una economía distorsionada y propensa a la corrupción. La lucha por el control de Arrakis, el único planeta donde se produce la especia, es un claro ejemplo de cómo el intervencionismo estatal genera conflictos y guerras.
El mesianismo y el peligro del liderazgo carismático
La figura de Paul Atreides, el mesías Muad'Dib, nos advierte sobre los peligros del liderazgo carismático y el culto a la personalidad. Su ascenso al poder, impulsado por la manipulación religiosa y el miedo, desemboca en una guerra santa que se extiende por el universo, cobrando millones de vidas. Esta tragedia nos recuerda que el poder, incluso cuando se ejerce con las mejores intenciones, tiende a corromper y a generar consecuencias imprevistas.
El libre mercado y la innovación
A pesar del control estatal, en "Dune" también encontramos ejemplos de libre mercado e innovación. Los fremen, habitantes del desierto de Arrakis, han desarrollado una cultura basada en la autosuficiencia y el ingenio, adaptándose a un entorno hostil y creando tecnologías únicas. Su capacidad para sobrevivir y prosperar en un mundo sin Estado es un testimonio del poder del libre mercado y la iniciativa individual.
Lecciones para el anarcocapitalismo
"Dune" nos ofrece valiosas lecciones para el anarcocapitalismo. Nos recuerda que el Estado, incluso en sus formas más benignas, tiende a sofocar la libertad y la prosperidad. Nos advierte sobre los peligros del liderazgo carismático y la importancia de la descentralización del poder. Y nos muestra que el libre mercado y la innovación son esenciales para la supervivencia y el progreso de la humanidad.
En un mundo donde el Estado y el poder centralizado siguen siendo la norma, "Dune" nos invita a imaginar un futuro donde la libertad y la cooperación voluntaria sean los pilares de la sociedad. Un futuro donde, como los fremen en el desierto, podamos construir un mundo mejor sin necesidad de amos ni señores.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 3ffac3a6:2d656657
2025-04-05 04:55:12
@ 3ffac3a6:2d656657
2025-04-05 04:55:12O Impacto do Namoro com Pelé na Carreira de Xuxa Meneghel
Disclaimer:
Esse texto foi totalmente escrito pelo ChatGPT, eu apenas pedi que ele fizesse uma pesquisa sobre o tema.
Introdução: O relacionamento entre Xuxa Meneghel e Pelé, que durou cerca de seis anos (início dos anos 1980 até 1986), foi um dos mais comentados da década de 1980 (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Xuxa tinha apenas 17 anos quando começou a namorar o já consagrado “Rei do Futebol”, então com 40 anos (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Esse romance altamente midiático não só atiçou a curiosidade do público, como também alavancou a carreira de Xuxa de forma significativa. A seguir, detalhamos como o namoro aumentou a visibilidade da apresentadora, quais oportunidades profissionais podem ter tido influência direta de Pelé, o papel da revista Manchete e de outras mídias na promoção de sua imagem, se o relacionamento contribuiu para Xuxa conquistar espaços na TV (como o programa Clube da Criança e, posteriormente, na Rede Globo) e como mídia e público percebiam o casal – tudo embasado em fontes da época, entrevistas e biografias.
Aumento da Visibilidade Midiática nos Anos 1980
O namoro com Pelé catapultou Xuxa a um novo patamar de fama. Até então uma modelo em começo de carreira, Xuxa “se tornou famosa ao aparecer ao lado do esportista de maior status do Brasil” (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). A partir do momento em que o relacionamento se tornou público, ela passou a estampar capas de revistas com frequência e a ser assunto constante na imprensa. Em 20 de dezembro de 1980, a jovem apareceu na capa da revista Manchete ao lado de Pelé e outras modelos – um ensaio fotográfico que marcou o primeiro encontro dos dois e deu início à enorme atenção midiática em torno de Xuxa (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Não por acaso, “naquele ano, ela foi capa de mais de cem revistas” (Xuxa está em paz - revista piauí), um indicativo claro de como sua visibilidade explodiu após começar a namorar Pelé. Jornais, revistas de celebridades e programas de fofoca passaram a segui-los de perto; o casal virou sensação nacional, comparado até ao “Casal 20” (dupla glamourosa de uma série de TV americana) pelo seu alto perfil na mídia (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA).
Essa exposição intensa colocou Xuxa não apenas sob os holofotes do público, mas também a inseriu nos bastidores do entretenimento. Como namorada de Pelé – um dos homens mais conhecidos do mundo – Xuxa passou a frequentar eventos de gala, festas e bastidores de programas, onde conheceu figuras influentes do meio artístico e televisivo. Os fotógrafos os seguiam em eventos como bailes de carnaval e inaugurações, registrando cada aparição pública do casal. Com Pelé ao seu lado, Xuxa ganhou trânsito livre em círculos antes inacessíveis para uma modelo iniciante, construindo uma rede de contatos valiosa nos meios de comunicação. De fato, naquele início dos anos 80, “os dois eram perseguidos por fotógrafos, apareciam em capas de revistas e até faziam publicidade juntos” (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições) – evidência de que Xuxa, graças ao namoro, transitava tanto na frente quanto por trás das câmeras com muito mais facilidade. Em suma, o relacionamento conferiu a ela um grau de notoriedade nacional que provavelmente demoraria anos para conquistar de outra forma, preparando o terreno para os passos seguintes de sua carreira.
Influência Direta de Pelé nas Oportunidades Profissionais de Xuxa
Além do aumento geral da fama, há casos específicos em que Pelé influenciou diretamente oportunidades profissionais para Xuxa. Um exemplo contundente é o filme “Amor Estranho Amor” (1982) – longa de teor erótico no qual Xuxa atuou no início da carreira. Segundo relatos da própria apresentadora, foi Pelé quem a incentivou a aceitar participar desse filme (Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5). Na época ainda em início de trajetória, Xuxa acabou convencida pelo namorado de que aquela oportunidade poderia ser benéfica. Anos mais tarde, ela revelaria arrependimento pela escolha desse papel, mas o fato reforça que Pelé teve influência ativa em decisões profissionais de Xuxa no começo de sua jornada.
Outra área de influência direta foram as publicidades e campanhas comerciais. Graças ao prestígio de Pelé, Xuxa recebeu convites para estrelar anúncios ao lado do então namorado. Já em 1981, por exemplo, os dois gravaram juntos comerciais para uma empresa imobiliária, aparecendo como casal em campanhas de TV daquele Natal (pelas Imóveis Francisco Xavier, um case famoso entre colecionadores de propagandas da época) (Xuxa e Pelé: Natal de 1981 na Publicidade Imobiliária | TikTok) (Xuxa com Pelé em comercial de imobiliária em dezembro de 1981). Assim, Xuxa obteve espaço em campanhas publicitárias que dificilmente envolveriam uma modelo desconhecida – mas que, com a “namorada do Pelé” no elenco, ganhavam apelo extra. Isso evidencia que Pelé abriu portas também no mercado publicitário, dando a Xuxa oportunidades de trabalho e renda enquanto sua própria imagem pública se consolidava.
Ademais, a presença de Pelé ao lado de Xuxa em diversos editoriais e ensaios fotográficos serviu para elevá-la de modelo anônima a personalidade conhecida. Revistas e jornais buscavam os dois para sessões de fotos e entrevistas, sabendo do interesse do público pelo casal. As capas conjuntas em publicações de grande circulação (como Manchete e outras) não só aumentaram a exposição de Xuxa, mas também conferiram a ela certa credibilidade midiática por associação. Em outras palavras, estar ao lado de um ícone como Pelé funcionou como um “selo de aprovação” implícito, deixando editores e produtores mais propensos a convidá-la para projetos. Vale lembrar que “ao longo dos seis anos de relacionamento, [eles] posaram para várias capas da Manchete”, com a revista acompanhando de perto cada fase do namoro (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Essa recorrência nas bancas solidificou o rosto e o nome de Xuxa na indústria do entretenimento.
Por fim, é importante notar que nem todas as influências de Pelé foram positivas para a carreira dela – algumas foram tentativas de direcionamento. A própria Xuxa contou que, quando surgiu a oportunidade de ela ir para a TV Globo em 1986, Pelé desencorajou a mudança. Ele sugeriu que Xuxa permanecesse na TV Manchete, dizendo que “ser a primeira [na Globo] é muito difícil; melhor ficar onde está”, o que ela interpretou como falta de apoio dele à sua ascensão (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Esse episódio mostra que Pelé tentou influenciar também os rumos que Xuxa tomaria, embora, nesse caso, ela tenha decidido seguir sua intuição profissional e aceitar o desafio na Globo – escolha que se revelaria acertada. Em resumo, Pelé atuou sim como facilitador de várias oportunidades profissionais para Xuxa (de filmes a comerciais e visibilidade editorial), mas ela soube trilhar seu caminho a partir daí, inclusive contrariando conselhos dele quando necessário.
Papel da Revista Manchete e Outras Mídias na Promoção de Xuxa
A revista Manchete teve um papel central na ascensão de Xuxa durante o relacionamento com Pelé. Foi justamente num ensaio para a Manchete que os dois se conheceram, em dezembro de 1980 (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira), e a partir daí a publicação tornou-se uma espécie oficiosa de cronista do romance. A Manchete era uma das revistas mais populares do Brasil naquela época e, ao perceber o interesse do público pelo casal, passou a trazê-los frequentemente em suas páginas. De fato, a revista que agiu como "cupido" do casal “contava detalhes do romance a cada edição”, alimentando a curiosidade nacional sobre a vida de Pelé e sua jovem namorada (A história da foto de revista que gerou o namoro de Pelé e Xuxa). As capas exibindo Xuxa e Pelé juntos (em cenários que iam da praia a eventos sociais) viraram chamariz nas bancas e contribuíram enormemente para fixar a imagem de Xuxa na mente do público.
(A história da foto de revista que gerou o namoro de Pelé e Xuxa) Capa da revista Manchete (20 de dezembro de 1980) mostrando Pelé ao centro com Xuxa (à esquerda) e outras modelos. A partir desse ensaio fotográfico, a revista passou a acompanhar de perto o romance, impulsionando a imagem de Xuxa nacionalmente. (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira)
Além da Manchete, outras mídias impressas também surfaram no interesse pelo casal e ajudaram a moldar a imagem de Xuxa. Revistas de celebridades e colunas sociais publicavam notas e fotos frequentes, ora exaltando o glamour do par, ora especulando sobre fofocas. Xuxa, que pouco antes era desconhecida fora do circuito da moda, tornou-se figura constante em revistas semanais como Contigo! e Amiga (dedicadas à vida dos famosos), assim como em jornais de grande circulação. Esse bombardeio de aparições – entrevistas, fotos e manchetes – construiu a persona pública de Xuxa simultaneamente como modelo desejada e namorada devotada. A promoção de sua imagem tinha um tom deliberadamente positivo nas revistas: enfatizava-se sua beleza, juventude e sorte por ter sido “escolhida” pelo rei Pelé. Em contrapartida, eventuais polêmicas (como cenas ousadas que ela fez no cinema ou rumores de crises no namoro) eram administradas pela própria mídia de maneira a preservar o encanto em torno de Xuxa, que já despontava como uma espécie de Cinderella moderna na narrativa do entretenimento brasileiro.
Cabe destacar que a conexão de Xuxa com a Manchete não ficou só nas páginas da revista, mas transbordou para a televisão, já que a Rede Manchete (canal de TV fundado em 1983) pertencia ao mesmo grupo empresarial. Essa sinergia mídia impressa/televisão beneficiou Xuxa: quando a Rede Manchete buscava uma apresentadora para seu novo programa infantil em 1983, Xuxa – já famosa pelas capas de revista – foi convidada para o posto (Xuxa está em paz - revista piauí). Ou seja, a exposição na revista Manchete serviu de vitrine para que os executivos da emissora homônima apostassem nela na TV. Outras mídias também legitimaram sua transição de modelo para apresentadora, publicando matérias sobre sua simpatia com as crianças e seu carisma diante das câmeras, preparando o público para aceitar Xuxa em um novo papel. Assim, o período do relacionamento com Pelé viu a mídia – liderada pela revista Manchete – construir e promover intensamente a imagem de Xuxa, pavimentando o caminho para suas conquistas seguintes.
O Relacionamento e a Conquista de Espaços na TV: Clube da Criança e Rede Globo
O namoro com Pelé coincidiu com a entrada de Xuxa na televisão e possivelmente facilitou essa transição. Em 1983, a recém-inaugurada Rede Manchete lançou o “Clube da Criança”, primeiro programa infantil de auditório da emissora, e Xuxa foi escolhida como apresentadora. Há indícios de que sua fama prévia – alavancada pelo relacionamento – foi decisiva nessa escolha. Conforme relatos, o diretor Maurício Sherman (responsável pelo projeto) estava de olho em Xuxa por sua notoriedade e carisma, chegando a dizer que ela reunia “a sensualidade de Marilyn Monroe, o sorriso de Doris Day e um quê de Peter Pan” (Xuxa está em paz - revista piauí) – uma combinação que poderia funcionar bem num programa infantil. Xuxa inicialmente hesitou em aceitar, talvez pelo contraste entre sua imagem de modelo sensual e o universo infantil, mas acabou assinando contrato com a Manchete (Clube da Criança – Wikipédia, a enciclopédia livre). Assim, aos 20 anos de idade, ela estreava como apresentadora de TV, em grande parte graças à visibilidade e confiança que o nome “Xuxa” (já famoso por ser namorada do Pelé) passava aos produtores.
Não há registro de que Pelé tenha intervindo diretamente para que Xuxa conseguisse o posto no Clube da Criança. Foi a própria rede Manchete – estimulada pelo burburinho em torno dela – que a “procurou e a convidou para apresentar” o programa (Xuxa está em paz - revista piauí). Porém, é inegável que, sem o destaque que Xuxa conquistara nos anos anteriores na imprensa (devido ao namoro), dificilmente uma emissora arriscaria colocar uma jovem inexperiente para comandar um show infantil nacional. Ou seja, o relacionamento criou as condições favoráveis para essa oportunidade surgir. Uma vez no ar, Xuxa rapidamente mostrou talento próprio: o Clube da Criança foi ganhando audiência e revelou a aptidão dela em se comunicar com o público infantil (Xuxa, Pantanal, Cavaleiros dos Zodíacos: lembre sucessos da TV ...). Ainda durante seu tempo na Manchete, Xuxa manteve-se nos holofotes tanto pela carreira quanto pelo namoro com Pelé – frequentemente um assunto alimentava o outro na mídia.
Em meados de 1986, já conhecida como a “Rainha dos Baixinhos” pelo sucesso junto às crianças, Xuxa recebeu uma proposta para se transferir para a Rede Globo, a principal emissora do país (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Novamente, aqui o relacionamento com Pelé tem um papel indireto: por um lado, pode ter ajudado a construir a notoriedade que chamou a atenção da Globo; por outro, chegava ao fim exatamente nesse momento, marcando uma virada na vida dela. Após alguns anos de Clube da Criança, Xuxa decidiu dar um passo adiante. Ela mesma tomou a iniciativa de terminar o namoro com Pelé e aceitou o convite para fazer o “Xou da Xuxa” na Globo (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Pelé, como mencionado, havia expressado reservas sobre essa mudança de emissora (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira), mas sem sucesso em demovê-la. Com a benção do dono da Manchete, Adolpho Bloch (que a tratava “como filha” e apoiou seu crescimento) (Xuxa está em paz - revista piauí) (Xuxa está em paz - revista piauí), Xuxa partiu para a Globo levando sua diretora Marlene Mattos, e estreou em junho de 1986 o programa que a consagraria definitivamente.
É importante notar que, ao ingressar na Globo, Xuxa já não dependia mais da aura de “namorada do Pelé” – ela havia se firmado como apresentadora de sucesso por méritos próprios. Ainda assim, o relacionamento anterior continuou a ser parte de sua imagem pública: a mídia noticiou a mudança destacando que a namorada de Pelé chegara à Globo, e muitos espectadores tinham curiosidade sobre aquela moça cuja fama começara nos braços do ídolo do futebol. Em resumo, o namoro ajudou Xuxa a conquistar o primeiro grande espaço na TV (na Manchete), fornecendo-lhe exposição e credibilidade iniciais, enquanto sua ida para a Globo foi impulsionada principalmente pelo desempenho no Clube da Criança – algo que o prestígio conquistado durante o relacionamento tornou possível em primeiro lugar.
Percepção da Mídia e do Público sobre o Casal e a Imagem de Xuxa
Durante os anos de namoro, Pelé e Xuxa foram um prato cheio para a imprensa e objeto de variadas opiniões do público. De um lado, eram celebrados como “casal perfeito na mídia”, aparecendo sorridentes em eventos e capas, o que projetava uma imagem glamourosa e apaixonada (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Xuxa era frequentemente retratada como a bela jovem humilde que havia conquistado o coração do "rei", uma narrativa de conto de fadas que agradava muitos fãs. Pessoas próximas diziam na época: “Nossa, como ela está apaixonada, como ela está de quatro pelo Pelé”, segundo relembrou a própria Xuxa, indicando que sua dedicação ao namorado era visível e comentada (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Essa percepção de autenticidade nos sentimentos ajudou a humanizar Xuxa aos olhos do público, diferenciando-a de estereótipos de roupante ou interesse calculado.
Por outro lado, nem toda a atenção era positiva. Houve murmúrios maldosos e preconceituosos nos bastidores. Pelé e Xuxa formavam um casal interracial (ele negro, ela branca e bem mais jovem), o que, segundo a imprensa, “gerava olhares de reprovação dos conservadores” e até comentários racistas proferidos pelas costas (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Além disso, alguns duvidavam das intenções de Xuxa no relacionamento, insinuando que ela buscava ascensão social por meio de Pelé. Termos pejorativos como “maria-chuteira” (gíria para mulheres que namoram jogadores em busca de status) e “alpinista social” chegaram a ser associados a Xuxa por fofoqueiros da época (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Essa desconfiança lançava sombra sobre a imagem dela, pintando-a, aos olhos de alguns, como oportunista em vez de namorada dedicada. Xuxa teve de lidar com esse tipo de insinuação ao longo do namoro, buscando provar que seu amor era verdadeiro e que ela também tinha talentos e ambições próprias.
A mídia impressa, em geral, manteve uma postura favorável ao casal, explorando o romance como algo encantador. Mas não deixou de reportar as turbulências: sabia-se, por exemplo, das frequentes traições de Pelé, que Xuxa anos depois revelou ter suportado calada na época (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Essas infidelidades eram rumores correntes nos círculos de fofoca, embora Xuxa raramente comentasse publicamente enquanto estava com Pelé. O público, portanto, via um casal bonito e famoso, mas também acompanhava as especulações de crises e reconciliações pelos noticiários de celebridades. Cada aparição pública deles – fosse em um jogo de futebol, um evento beneficente ou nos camarotes do carnaval – era dissecada pelos repórteres, e cada declaração (ou silêncio) alimentava interpretações sobre o estado do relacionamento e sobre quem era Xuxa por trás da fama.
No saldo final, o namoro com Pelé influenciou profundamente a imagem pública de Xuxa. Inicialmente marcada como “a namorada do Rei” – posição que trazia tanto admiração quanto inveja – Xuxa soube aproveitar a visibilidade para mostrar carisma e trabalho, transformando-se em uma estrela por direito próprio. Ao se tornar apresentadora infantil de sucesso ainda durante o namoro, ela começou a dissociar sua imagem da de Pelé, provando que podia ser mais do que um apêndice de um astro do esporte. Quando o relacionamento terminou em 1986, Xuxa emergiu não caída em desgraça, mas sim pronta para reinar sozinha na TV. A mídia continuou a mencioná-la em referência a Pelé por algum tempo (era inevitável, dado o quão famoso o casal fora), mas cada vez mais o público passou a enxergá-la principalmente como a “Rainha dos Baixinhos”, a figura alegre das manhãs na TV Globo. Em entrevistas posteriores, Xuxa admitiu ter sentimentos mistos ao lembrar dessa fase: ela se ressentiu, por exemplo, de Pelé ter classificado o que viveram como “uma amizade colorida” em vez de namoro sério (Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5) – frase do ex-jogador que a magoou e que veio a público muitos anos depois. Esse comentário retroativo de Pelé apenas reforçou o quanto a mídia e o público discutiram e dissecaram a natureza daquela relação.
Em conclusão, a percepção do casal Xuxa e Pelé oscilou entre o encanto e a controvérsia, mas inegavelmente manteve Xuxa nos trending topics de sua época (para usar um termo atual). A jovem modelo gaúcha ganhou projeção, prestígio e também enfrentou julgamentos enquanto esteve com Pelé. Tudo isso moldou sua imagem – de símbolo sexual e socialite em ascensão a profissional talentosa pronta para brilhar por conta própria. O relacionamento forneceu-lhe a plataforma e a armadura mediática; coube a Xuxa transformar essa visibilidade em uma carreira sólida, o que ela fez com maestria ao se tornar uma das maiores apresentadoras da história da TV brasileira.
Fontes: Entrevistas e depoimentos de Xuxa Meneghel (inclusive do livro Memórias, 2020), reportagens da época em revistas como Manchete, colunas sociais e jornais (compiladas em repositórios atuais), e biografias e retrospectivas sobre ambos os envolvidos (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA), entre outras. Essas fontes confirmam o papel catalisador que o namoro com Pelé teve nos primeiros passos da trajetória de Xuxa, bem como os desafios e oportunidades que surgiram dessa intensa exposição pública.
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ 6be5cc06:5259daf0
2025-03-31 03:39:07
@ 6be5cc06:5259daf0
2025-03-31 03:39:07Introdução
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.\ Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.\ Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.
Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ 3c827db6:66418fc3
2024-05-20 12:25:27
@ 3c827db6:66418fc3
2024-05-20 12:25:27With the previous articles, we found the disconnect between paid-for work and paid-for time. We also understood that if you want to get paid you have to provide work that is valuable for others. So when the person consumes the benefit of your work, the exchange happens value for value - work for sats. But what happens if the benefit that the consumer experiences is not a momentary but a continuous process? There are a few examples of this. I will start with the one that is not that captivating but still valuable.
Streaming services, like other industries, grapple with the limitations of the fiat payment system. The burden of fees and the absence of suitable technology for streaming payments have compelled them to adopt similar mitigations as other industries. This translates to charging users on a monthly basis.
With the Lightning Network, we have the technology to stream sats for content. No longer confined to monthly subscriptions, you pay for what you consume in real time. Whether you watch sporadically or binge extensively, streaming payments allow for a more personalized and efficient payment model. This way the creator of the content and the user have a direct connection for each minute the content is broadcasted. With streaming payments now you can say goodbye to subscription payments.
Unveiling A New Era Of Fair Compensation And Accountability In Movie Production
Imagine you've created a movie or documentary. Traditionally, you'd charge people for a ticket, essentially asking them to pay upfront for future value, creating a slight disconnect. Now, with streaming payments using sats, consumers can pay as they watch. If your movie sucks, they might only pay for the first 30 minutes. However, you still receive value, and viewers won't feel overcharged for something they didn't enjoy. If your movie is great they not only stream sats the whole time but at the end, they leave a tip.
On the receiving side of the movie most people involved in it received a salary for doing their job. As we already know this is not aligning the whole structure in the same direction. Some people do not care at all how good the movie is if they have already been paid and do not receive a bonus further. Some people might care about reputation in the market but very few just want to do the best job. Again, we went through this, and as you are guessing you just do a split payment in the backend where all the people in the credits actually receive sats or even milisatoshis based on their contribution. This was something I did not expect that Bitcoin would disrupt. This way the reputation is directly linked to the payment and a lot more people will fight to have the best movie. You can be someone who contributed to a project and wants to stay anonymous for whatever reason but still receive money - Lightning instant settlement is the way to do it.
These concepts should not be new if you read through the last 3 articles. In addition, people in the Bitcoin space are familiar with the Value for Value (V4V) podcasting and that is very close to what I am describing above. While the technology for podcasting is already in place, it's surprising how few podcasts leverage this technology to implement split payments effectively. They give that responsibility to some hosting service that decides to take a 5% split for themselves and the other 95% goes to the wallet of the show. Why not do the split the proper way? The hosting service provides value so they should get a percentage but if you are 3 people involved in the production of the podcast you should have that 95% split so it goes to those individuals. There's no excuse, especially for Bitcoin podcasts, not to make this effort and implement split payments appropriately.
The Dynamic Future Of Pay-as-you-go In Content Consumption
In this example, the pay-as-you-go model holds true for continuous experiences, like streaming. Now, let's revisit the movie example. If you're a theater, you are essentially the hosting provider for the movie. The quality of the theater experience can vary; one theater might have uncomfortable chairs, while another boasts luxurious massage chairs. The theater with subpar seating might receive a 3% share of the movie's streaming sats revenue, while the one with comfortable massage chairs might earn 5% for each sat stream paying for the movie. Furthermore, if a viewer activates the massage function of the chair, additional sats are streamed for each second that the function is on. I do not know the exact payment dynamics between theaters and movie studios but I bet there are prepayments and funds held at multiple points in the fiat payment process. With the adoption of the Lightning Network, theaters no longer have to prepay for movies to be projected on their screens. They can now observe which movies are most popular in real time and adjust their projections accordingly to optimize revenues. This benefits the consumer and optimizes profits for themselves and the creators of the movie.
Now you see the content gets its value stream for the continuous experience and everyone in the film industry will fight to give the best experience for the most amount of time. The better the experience the more sats flow their way. Due to the highly subjective nature of content, where one person might deem a movie subpar, another might label it as their favorite. This subjectivity is why I believe most content streaming will not have a predetermined price. Even movies may adopt the V4V model, similar to what Adam Curry is pioneering in podcasting. For instance, you watch a movie, and during the credits, a prominent QR code appears, allowing you to decide how much you want to send to the creators of the movie. You will listen to a song or a podcast the same way. Whether you predefine a streaming rate per minute or request payment at the end, both options are technically possible. However, the market will ultimately determine which option prevails as the better one.
Also, why not have a bidding competition for any event that has assigned seats? The person who bids the most for a ticket gets to be in the first row of the concert or a sports stadium. This way the subjectivity is left for all the viewers to decide how valuable it really is. This way it ensures a full stadium also because if there is no value in attending the event people are not going to bid for the seats or just pay 1 sat for it.
Revolutionizing Taxi Transactions For Drivers And Passengers Alike
The continuous experience or service for streaming could be anything in the physical realm. I will take a look at how instant settlement could look like in transportation services. One such transportation service is the taxi service. Even though Uber decentralized the taxi companies which is great they did nothing about decentralizing the payment process. Lightning Network fixes that and more.
With a streaming payment option for each meter of movement, taxi drivers no longer need to wait until the end destination to receive their payment. In a world of instant settlement, payment occurs as you go, eliminating the risk for the taxi driver regarding whether the passenger will pay at the end of the journey. While this might not be a groundbreaking improvement, there are several additional benefits to consider.
Why do most taxis operate with cash? Taxi drivers in most places need a POS device for the customers to be able to pay for a better user experience (UX). It may be a better UX but on the other hand, it creates problems for the drivers either way:
- They have to acquire clunky devices.
- They must pay payment processing fees, negatively impacting their margins.
- Operating solely with cash exposes them to the honeypot problem, carrying a substantial amount of money, and making them vulnerable to theft.
With an app tailored for the taxi experience and integrated with the Lightning Network, these issues become irrelevant. There is no need for additional equipment, no payment processing fees for receiving money, and no exposure to visible cash, reducing the risk of being a target for theft. Now you can have a better UX with better security and better margins - an additional benefit is that it will be paid with Bitcoin. Not only that but just like the example with the movie theater chairs drivers will be incentivized to make the travel experience even better. They can offer - to watch a movie, video games like PlayStation, or massage chair. If you choose to use those extra experiences on top of the travel experience you have to increase the sats streaming their way.
An additional benefit for the travel experience of customers arises when multiple passengers in a taxi have different destinations. Traditionally, the taxi meter ticks for the entire journey, and when the first person is dropped off, determining a fair amount for their portion becomes complex. However, with the Lightning Network, it's conceivable to streamline this process. Imagine a scenario where three passengers enter a taxi, each with distinct destinations. Each person scans a QR code upon entering, linking their streaming sats to the taxi app. The app manages split-receiving, dynamically adjusting the distribution of streaming payments based on how many people are in the taxi. As passengers are dropped off one by one, the app seamlessly adjusts the split-receiving, providing a fair and efficient payment solution for each individual's share of the journey.
Optimizing City Transportation With Streaming Sats
The proposed model of split-receiving through QR codes and streaming sats can extend beyond taxi services to other modes of transportation, such as buses. The idea is to calculate the average cost per mile (or meter/foot) for providing the transportation service, including factors like fuel, maintenance, and driver salary, and add a margin for profit. Passengers entering the vehicle scan a QR code, and the app dynamically adjusts the streaming payments based on the number of people on board.
For buses, this model allows for real-time adjustment of streaming payments as passengers enter and exit. If there are 30 people on the bus the split is between them. At the next stop, 10 people are dropped off and 5 people get on board - now the sats stream is divided by 25 people. As the number of people on the bus changes at each stop, the streaming sats are proportionally divided among the passengers. This approach can lead to more efficient and flexible city transportation. Late-night buses will be more expensive for the passengers because of the fewer riders, while buses during peak hours may offer a more cost-effective traveling experience as payments are shared among more passengers.
This system encourages transportation optimization around events, such as concerts or sports games, where private buses or minivans wait to fill up before departing. Routes can be dynamically adjusted because you will have a system tracking how many people are in the vehicles at what time and at what location on the map. Importantly, this data remains anonymous, as no KYC information is required for the Lightning Network payments.
The Streamlined Pay-from-a-distance
Now with this streaming money feature, it can be applied differently. Let’s go back to the taxi service for a moment. The pay-from-a-distance feature that is available in the Lightning Network can significantly enhance the experience of ordering a taxi. Instead of the traditional model where drivers wait patiently and charge fixed fees when passengers enter the car, this model introduces streaming sats from the moment the passenger accepts the ride. Here's how it works:
- The passenger places an order in the app, specifying the destination. Nothing new here.
- Drivers see the order and can apply for it, similar to platforms like Uber.
- Streaming sats start the moment the passenger accepts the driver, and streaming payments commence. This fee will be less than the actual transportation but the user is still paying for the service of the car coming to him and not the other way around.
- The taxi arrives at the passenger's door, and the streaming payments continue. There is a fee for waiting at the door per minute.
By shifting the waiting cost to the passenger, there's a strong incentive for both parties to be prompt, and the system becomes more efficient. Additionally, the passenger's responsibility to follow the car reduces operational costs related to alerting passengers via message or a call. Any inefficient time management becomes a cost for the passenger. This model aligns incentives for both drivers and passengers, creating a more seamless cost and time-effective taxi experience.
The concept of paying from a distance can be creatively applied to various scenarios, providing convenience and peace of mind. For instance, when it comes to sending your child somewhere with a taxi, traditional concerns about trusting them with money or the driver's reliability may arise. However, with the ability to stream sats for the ride, you gain real-time visibility on your device, tracking your child's journey and ensuring they reach the intended destination safely. This pay-from-a-distance feature extends beyond transportation and can be applied to other continuous services. For example, daycare services charge per minute, allowing you to stream payments in real-time, ensuring accurate and fair compensation for the duration your child spends there. Additionally, you can send a present to a friend, such as a massage session, and pay for it in a streaming fashion, covering the cost continuously based on the duration of the service. The flexibility of streaming payments not only offers real-time tracking and control but also opens up new possibilities for various services where charging per minute or duration is relevant. Those services can be paid on the spot or from a distance. image2
I know that now it looks like we are going backwards from the original point of never paying money for time. The key distinction here is that you may be paying for time past for the service but in that time you get a continuous stream of value (work done) so you are streaming value back to pay for it. In some cases the time spent is actually an accurate measure of the work done.
It's true that developing apps with such functionalities is technically feasible, and there might be entrepreneurs and developers willing to explore these possibilities. However, a significant challenge arises when considering custodial control over users' funds. Small startups might find it financially burdensome and complex to operate as custodians, potentially steering away from such responsibilities. This will take not only high responsibility but also a very big financial wall and expertise to obtain the licenses that comply with the ever-changing regulations. On the other hand, large tech companies with substantial resources could afford to take on the role of custodians, presenting both a business opportunity for them and a risk for the users. The move by some tech giants, like X(formerly Twitter), to obtain such licenses can be seen as a strategic measure for self-preservation over their own finances. This is also an opportunity to consolidate control over not only user data but user finances within their platforms.
The Breez SDK offers a powerful solution, empowering developers to create diverse applications without having to worry about payment intricacies. Its non-custodial nature is a key advantage, eliminating the need for licenses. The infrastructure of it is made in such a way that it is peer-to-peer so no one is holding money for someone else. The app developers focus on the experience within the app and just plug in the code. This combination of features gives startups a competitive edge and reverses the advantage held by large tech companies. While they go through the complex process of getting a license the startup can integrate the global payment network (the Lightning Network) in one day. Even if certain tech giants choose to lock users' funds within their applications, alternative options will continue to be developed, and users will have the freedom to opt-out. Just like people are choosing Bitcoin over fiat.
Now who is ready to give all of us those experiences in their app?
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ b804f68e:2fb0fa1f
2024-05-20 06:07:22
@ b804f68e:2fb0fa1f
2024-05-20 06:07:22Consistently writing on SN and Obsidian has underscored for me the critical role of application in the learning process. Writing allows me to visually process, reflect, analyze, and organize the myriad ideas generated within my brain. Through this ongoing practice, I can physically sense my improvement in articulating thoughts to others and myself, both in writing and speech. However, both forms of expression still require significant practice, especially the latter.
Before I began writing regularly, I didn't fully appreciate the importance of purposeful learning. Previously, I viewed reading a book, watching an educational video, or listening to a podcast as the primary components of learning. But these activities are merely the initial stimuli that prepare our brains for deeper engagement, much like a warm-up before a workout. True learning extends beyond passive consumption; it involves actively practicing and applying what we've learned, reflecting on our experiences, and continually revisiting the material to fill in gaps and deepen our understanding. Sharing and discussing our insights with others further enriches this process, as it exposes us to diverse perspectives and feedback we might not have considered on our own. For me, writing acts as the bridge that connects acquired knowledge to practical application.
After writing on SN consistently for over a month, I've come to realize what it truly means to learn and acquire knowledge. Writing daily has exposed gaps in my understanding, often revealing that I lack the depth of knowledge I assumed I had. When I reach the limits of what I know, I'm compelled to research further, which reinforces and expands my comprehension.
Even if you never write publicly, I believe everyone can benefit from the act of writing. The more I write, the more intentional my learning process becomes, and the more organized and structured my thoughts are.
-
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b5d34eed:a7475cbf
2025-03-21 10:12:21
@ b5d34eed:a7475cbf
2025-03-21 10:12:21Introduction
In an era of increasing surveillance, data breaches, and corporate control over digital communication, privacy-focused tools have become essential. ProtonMail, a secure and encrypted email service, stands as a stronghold for those seeking privacy in their online correspondence.
At the same time, Nostr, a decentralized social networking protocol, is revolutionizing how people connect without relying on centralized platforms. Together, ProtonMail and Nostr create a powerful combination for individuals who prioritize security, anonymity, and freedom in their online interactions.
This article explores the ProtonMail application suite, its relevance to privacy, and how it aligns with Nostr’s decentralized approach to communication.
What is ProtonMail?
ProtonMail is an encrypted email service founded in 2013 by scientists at CERN, the European Organization for Nuclear Research. Unlike mainstream email providers such as Gmail or Outlook, ProtonMail does not collect personal data, does not track users, and ensures end-to-end encryption for emails.
Key Features of ProtonMail
End-to-End Encryption: Ensures that only the sender and recipient can read messages.
No Personal Information Required: Users can sign up without providing identifying details.
Open-Source Cryptography: Transparency in security protocols, allowing community audits.
Swiss-Based Privacy Laws: ProtonMail operates under Switzerland’s strict data protection regulations, shielding it from intrusive government surveillance.
Self-Destructing Emails: Allows users to send messages that automatically expire after a set time.
ProtonMail’s security-first approach makes it an ideal choice for activists, journalists, and privacy-conscious individuals who want to communicate without fear of surveillance or data mining.
ProtonMail Application Suite: A Holistic Privacy Ecosystem
Beyond encrypted email, Proton has expanded into a full suite of privacy-focused tools:
ProtonMail – Secure, encrypted email with zero access to user data.
ProtonVPN – A no-logs VPN that protects internet traffic from ISPs and surveillance.
ProtonCalendar – An encrypted calendar that ensures event data remains private.
ProtonDrive – Secure cloud storage for files with end-to-end encryption.
ProtonPass – A password manager that encrypts credentials and autofills login details safely.
This ecosystem provides a seamless experience for those looking to secure not just their emails but also their browsing, file storage, scheduling, and password management.
Why ProtonMail is a Must for Privacy-Conscious Users
-
End-to-End Encryption: Unlike Gmail and Outlook, ProtonMail ensures that even ProtonMail itself cannot access your emails.
-
No IP Tracking: Protects against metadata collection, preserving user anonymity.
-
Zero Access Architecture: Even Proton employees cannot read your emails.
-
Decentralization-Friendly: Complements Nostr’s ethos of distributed, private communication.
ProtonMail’s strict security measures align well with the values of decentralization and censorship resistance, making it a natural ally to protocols like Nostr.
ProtonMail and Nostr: A Privacy Power Duo
Nostr is an open-source, censorship-resistant social networking protocol that allows users to communicate without relying on a centralized platform. Unlike Twitter, Facebook, or even Mastodon, Nostr operates through decentralized relays, making it nearly impossible to shut down or control.
ProtonMail and Nostr share a fundamental philosophy: empowering users with control over their own data. Here’s how they complement each other:
- Secure and Private Communication
Nostr messages are cryptographically signed and relayed across decentralized nodes. ProtonMail, with its encryption-first approach, ensures that even off-platform communication remains private.
- No Central Authority
ProtonMail is protected under Swiss privacy laws and is not beholden to big tech surveillance. Nostr operates without central servers, preventing a single entity from controlling conversations.
- Protecting Metadata
While Nostr encrypts direct messages, email remains a critical form of communication for many users. ProtonMail’s metadata protection ensures that senders, recipients, and message content remain shielded.
- Enhanced Security for Activists and Journalists
Nostr is popular among privacy advocates, activists, and whistleblowers due to its resilience against censorship. ProtonMail adds an extra layer of protection for sensitive information shared over email.
By using ProtonMail and Nostr together, users can create a robust digital identity that is censorship-resistant, private, and secure.
How to Get Started with ProtonMail
If you’re ready to enhance your privacy, setting up ProtonMail is simple:
-
Sign Up: Visit ProtonMail.com and create a free or premium account.
-
Set Up Your Inbox: Customize security settings and enable two-factor authentication.
-
Explore Proton’s Suite: Utilize ProtonVPN, ProtonDrive, and ProtonPass for full privacy coverage.
-
Integrate with Nostr: Use ProtonMail for private communication outside of Nostr’s relay-based messaging system.
ProtonMail offers free plans, but for advanced security features, encrypted storage, and custom domains, premium plans are available.
Conclusion: A Privacy-First Digital Future
In a world where data privacy is constantly under threat, services like ProtonMail and Nostr pave the way for a more secure and independent digital future. Whether you are a journalist, activist, or simply someone who values personal privacy, these tools provide the protection you need.
By combining ProtonMail’s encrypted email with Nostr’s decentralized networking, users can take control of their communications, free from surveillance and corporate interference.
Now is the time to reclaim your digital privacy—sign up for ProtonMail and explore Nostr to experience a censorship-resistant, secure way of communicating.
Further Resources
ProtonMail Official Website
ProtonVPN for Secure Browsing
Nostr Documentation and GitHub
Privacy Guides for Online Security
Are you using ProtonMail and Nostr together? Share your thoughts on how these tools empower you in the comments below!
-
-
 @ 75da9402:77a65b5c
2024-05-19 00:07:36
@ 75da9402:77a65b5c
2024-05-19 00:07:36Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ ec965405:63996966
2024-05-18 18:02:00
@ ec965405:63996966
2024-05-18 18:02:00Re #introductions
For the next couple of months, the team at nos.social, led by @Rabble@nos.social, is supporting me in building engaging social media for my community with their new Nostr client. I'm an activist who is dedicating this season of my life to learning how computers and the Internet work. After stumbling across Nostr last year in search of better social media experiences, I entered a blogging contest with https://nostr.build and won a creator account. My interest and enthusiasm for this protocol has only grown.
RE #introducciones
Durante los próximos meses, el equipo de nos.social, liderado por Rabble@nos.social, me ayudará a crear una experiencia atractiva para mi comunidad con su nuevo cliente de Nostr. Soy un activisa dedicado a aprender cómo funcionan las computadoras y el Internet. Despues de encontrar a Nostr el año pasado en la busqueda de mejores experiencias en las redes sociales, participé en un concurso de blogs con [[nostr.build]] y gané una cuenta de creador. Mi interés y entusiasmo por este protocolo no ha hecho más que aumentar.
Liberation Tech
The world is having a moment right now. Social media is evolving into a tool for collective liberation. It couldn't have come at a better time. We have an opportunity to reconstruct a digital public commons. Tools like Nostr are blueprints for building resilient social media and represent a rejection of the factory of manufactured consent that defines our current political realities. A liberated fifth estate built on open protocols could channel people power into material improvements within our lifetimes. We are not going back to the way things used to be.
Tecnología de Liberación
Actualmente estamos viviendo un momento critical. Las redes sociales se estan evolucionando hacia una herramienta para nuestra liberación colectiva. No podría haber llegado en mejor momento. Tenemos una oportunidad de reconstruir la plaza digital del pueblo. Herramientas como Nostr son modelos para construir redes sociales resistentes y representan un rechazo a la fábrica de consentimiento manufacturado que define nuestras realidades políticas actuales. Un quinto estado liberado, basado en protocolos abiertas podría canalizar el poder del pueblo hacia un cambio material en el transcurso de nuestras vidas.
Explore my Asteroid
I host my main web page from an asteroid with Uberspace, a small team of supportive technologists who provide an affordable Linux server that runs on renewable energy. On it I run a personal relay for on-boarding my community to Nostr as well as learning to code. Find resources and more about what I'm working on at https://miguelalmodo.com.
Explora mi asteroide.
Mi pagina web principal se encuentra en un asteroide con Uberspace, un equipo chiquito de tecnólogos solidarios que ofrecen un servidor Linux barata que funciona con energía renovable. En él, gestiono un relevo personal para incorporar a mi comunidad a Nostr, además de aprender a programar. Encuentra rescursos y mas sobre lo que estoy creando en https://miguelalmodo.com
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ 76c71aae:3e29cafa
2024-05-16 04:48:42
@ 76c71aae:3e29cafa
2024-05-16 04:48:42The Curious Case of DSNP: Years of Effort, Minimal Output
It's been a while since I looked at DSNP. There’s news that its backer, Frank McCourt, is trying to put together a team to buy TikTok. That’s insane. The DSNP and Project Liberty team are well-meaning, but they’re even less equipped to run a social network or protocol than Elon Musk at his lowest point when he was firing engineers based on how many lines of code they’d written.
To check what’s happened with DSNP since I last looked a year ago, I just read the entire spec, and there's not actually that much to it. The amount of time and money spent on developing so little is quite stunning. While the spec is fine, it is minimal.
Key Features and Odd Choices
DSNP allows users to have a key pair, write content into a datastore, follow people, and sign messages. However, the protocol seems to mix up layers, specifying the wire protocol, signing system, and at-rest specification format that clients and user data servers might use (pds in atproto, instance in fedi, relay in nostr). They use the ActivityStreams 2.0 schema, which is a good choice. Many new protocols have created their own schemas, but I appreciate DSNP's use of the standard. I wish more protocols had not tried to reinvent the wheel in this respect.
Encrypted Direct Messages and Metadata Privacy
There’s mention in the whitepaper about encrypted direct messages, suggesting it’s possible to hide metadata using techniques from Ethereum’s Whisper. Although the specs or code about DMs don't elaborate much on this, it’s good to see an attempt to hide metadata. However, there’s nothing about double ratchet encryption, forward secrecy, or any advanced encryption techniques. So, overall, it feels quite basic.
Data Storage and Interesting Choices
For storing user data and posts, they're using Apache Parquet, a file format from Hadoop. This is probably the only neat or interesting aspect. I've been searching for a supported data format like Parquet for a while because I think it can facilitate privacy-preserving contact discovery, so it’s cool to see its inclusion here.
Minimal Data Types and Following Options
DSNP supports very minimal data types: post, follow, reaction, profile, and, oddly, location. You can follow publicly or privately, the latter being a neat feature that Scuttlebutt had but most of the current generation of emerging social protocols don't.
Lack of Comprehensive Features
There does not appear to be any client app or server code, which might not be needed. There is an SDK for some core functions, but that’s it. Their documentation lacks information on user discovery, algorithms, or anything beyond the basics.
The Verdict: A First Draft After Years of Work
It feels like someone spent millions and ended up with a naive first draft, despite working on this for years. It’s similar to the early sketches of Farcaster and Lens, but those protocols have grown significantly over the past couple of years, with real users, lots of functionality, and apps.
DSNP remains as vaporware today as it was four years ago. These clowns have wasted tens of millions of dollars on nothing. Some academics have happily taken the money to fund their research labs. Consultants have written and thrown away countless prototypes nobody’s ever used.
There are lots of serious projects to build decentralized social media protocols. All these folks had to do was either work with others or even copy them. This stuff is all open source. Yet DSNP keeps sending folks to conferences without talking to anybody or attending any talks.
It’s a shame because they’ve got their hearts in the right place. The Unfinished conferences are really well put together with lots of great speakers. They hired the supremely talented and savvy Karl Fogel and James Vasile to help them make their code and process open, but you can’t fix DSNP.
Fundamentally, software and specs are a social enterprise, even more so if you’re working on social protocols. But these folks… they’ve never figured out how to play well with others. The money and good intentions couldn’t overcome their fundamental failure to have the humility to learn and play well with others.
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 20986fb8:cdac21b3
2024-05-14 04:27:58
@ 20986fb8:cdac21b3
2024-05-14 04:27:58Relay is the soul of the decentralized Nostr network. In previous articles, we discussed who would bear the ongoing operational costs of Relay. To ensure a thriving storage network, Relay needs to be incentivized. In order to achieve better decentralization of media, YakiHonne has launched the Relay's early incentive plan to support the development of 50 Relays for a period of 6 months.

The details of the grant program are as follows:
- Grant amount: A total of $50,000, with each grant ideally being $1000.
- Application period: From May 15, 2024, to December 31, 2024.
- Applicants: Existing Relay node hosts or new hosters, with a funding ratio of 20 existing Relay nodes and 30 new Relay nodes.
Relay operational requirements:
-
The minimum requirements for Relay deployment are according to [1]:
-
1.1. High performance Intel
- 1.2. 1 vCPU
- 1.3. 2048 MB Ram
- 1.4. 50 GB NVMe SSD
-
1.5. OS Ubuntu 22.04 LTS
-
There are no restrictions on storage service providers, and you can choose any stable provider.
-
There are no restrictions on the location of Relays, but it is recommended to have geographical diversity to maintain a balanced distribution of Relays.
- Relays need to operate continuously for the next 6 months with downtime not exceeding 30 minutes.
- You can choose from the already existed relays implementations: nostr-rs-relay based on Rust, nostr-ts-relay akk nostream using Typescript, or strfry using C++.
- Relay models can be of any type: thematic Relays relying on keyword filtering for specific topics, invitation-only Relays that restrict publishing permissions through public keys, or paid and free public Relays corresponding to paid publishing and fully open modes, respectively. However, to maintain a balanced incentive, the proportion of paid and invitation-only Relays will not exceed 20%.
- Monthly reports on Relay stability and availability need to be shared to maintain good operational status.
Application process:
You need to submit a proposal including whether you are already hosting a Relay, the name of the existing Relay, specifications of the Relay hosting service, possible service provider choices, Relay development environment, Relay model, and more details to help you secure funding.
Submission: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Grant Evaluation and Disbursement:
Within one week of receiving the application, we will provide feedback on the grant decision. The grant amount will be disbursed in two installments, with 50% being provided initially and the remaining 50% being disbursed after 3 months.
Rewards:
In the early incentive program, nodes that contribute consistently to improving Relay performance, expanding functionality, and ensuring stability will receive special rewards and have the opportunity to earn more income.
The goal of this incentive program is to further decentralize Nostr, enhance its performance, and promote the development of Relay functionality. Through the early incentive program, we aim to explore sustainable incentive models for Relays and lay the foundation for their sustainable development.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 1bc70a01:24f6a411
2024-05-13 09:49:18
@ 1bc70a01:24f6a411
2024-05-13 09:49:18Thought 1: Content Creation, Discovery & Remixing
Recently I’ve been thinking about ways we could highlight nostr’s unique properties while at the same time attracting creators to the platform.
There’s been a lot of discussion about what might spark nostr’s next wave of growth. I pointed out that people come for either other people, or for content. But, I also failed to realize that people also seek ways to express themselves via new tools that enable easy or unique ways of expressing yourself.
One thing we can say with certainty is that people are not coming to nostr for other people. While generally following influencers is a proven growth strategy - after all, many of us followed Jack, we still have a catch 22 problem of lacking audience and incentives for those creators to come here. Even if we managed to convince some large influencers to try the platform, it is not likely that they would stay. They’d need to be really passionate about nostr’s principles and vision to buckle in for the long term.
Problem: creators and influencers won’t come to nostr unless they can grow their audience, and nostr lacks the audience. We’ve seen this play out with Matt Taibi. He joined nostr but was reluctant to stay because there’s little incentive to share with a small audience when Twitter/X can bring in many more eyeballs.
Possible Solution: Instead of brining creators to the platform, enable some of the current passionate user base to become decent creators themselves. We don’t need influencers with giant audiences, we just need good content that keeps people around. If we apply the 80/20 rule (Pareto’s principle), it turns out we don’t need that many creators to have a great flow of content. Enabling just a handful of people to create great content might just do the trick.
How to get there: focus on creating tools that enable expression of creativity. One such tool is Pinstr, but its value is largely untapped. On its own, pinstr is nothing interesting, it’s practically a clone of Pinterest. But, given the interoperable nature of nostr, it would be interesting to see pinned boards / content surfaced within kind 1 clients. People could then explore the board or that user’s other boards further by making their way to Pinstr.
How do we encourage more people to curate interesting pins? How about a pin extension that makes it easy to do so?
How do we enable people remixing other pins? Allow them to re-pin the content to their own boards. These are all mechanics that made Pinterest interesting, but lack in pinstr (as far as I’m aware).
Other ways that we might encourage content creation:
- Multi-account support. Can we make it SUPER easy to switch between identities when posting some curated content? Yes we can. (Select a different identity when posting)
- Surfacing “Other stuff” with a call to action to do that thing. For example, if someone shares a list, a kind 1 client should be able to render that list in a way that’s easy to browse, share and encourages to create your own list. If someone shares a music playlist (hopefully via native nostr kind), a person should be able to see the playlist and be encouraged to create their own. Watch stream? > prompt to start your own
- Gif / meme discovery with a call to action to create your own. (Plebhy, Memester)
- Styling tools (more complex) to style media, add soundtracks etc (perhaps via integration with Wavlake or other nost-native music events).
-
Content scheduling - help existing users become power users. Instead of posting everything at once, allow users to schedule it out for even distribution. Tools like Shipyard enable this already, but having this ability in-client might make it more accessible and useful.
-
Content pinning extensions - bring the outside world to Nostr. How can people 1-click pin content to nostr without having to switch tabs constantly?
-
App discovery - I think this is already in the works, but being able to surface other apps within kind 1 clients would be super interesting.
- Enable surfacing of highlighted content and paid content - with highlights, nudge people to read more of the content if it comes from within one of the nostr clients. With paid content, indicate that it is premium content and encourage creation of premium content “Become a creator” or “Join creator studio”.
- Encourage people to write long-form opinion content. When reading a long form article, perhaps have a call to action to start your own nostr publication. “Publish on Nostr and earn”
- Surface and encourage audio creation - we don’t have a nostr podcast client yet, but if there was one, kind 1 clients could surface that content automatically and encourage people to start their own podcasts, audio diaries, audio chats (nostr nests) or audio stories. Kind 1 clients could surface audio clips with waveforms and subtitles built in, or create a framework by which other developers could create this type of interaction with your kind 1 client. Can users create their own clip playlists from audio content fetched from the nostr podcast app? Why not?
The common objection to all of this might be that “you can already do all of this just by copying links”. Yes, and no. Copying links does share content - albeit in a boring preview way. It does not enable interactivity, nor prompt people to create that type of content. I think this is where nostr could shine.
Thought 2: Interoperability
One of the greatest strengths of nostr is the ability to display events across clients. I think of kind 1 clients as the glue that holds together the “other stuff”. The other stuff apps can be used to create the stuff, and kind 1 can enable discovery of said stuff, while encouraging to visit those tools to create their own.
Traditional social media platforms are encourage to put up walls and discourage leaking of users to other places. The more time a user spends on a website or app, the better for that company. But, with nostr, there’s a virtuous positive loop that does not punish leaking of attention, but instead, rewards it. The more content people create, the more interesting your kind 1 discovery client becomes.
How to get there: It’s going to take a lot of work to integrate the other stuff, but it’s already under way. As a client developer, partner up with other stuff clients to figure out how to best support them. Open up nostrapps.com to see what exists, and how your client can accommodate the surfacing of that stuff with minimal effort (since our resources are so scarce). Tap into product designers to help conceptualize and visualize interactions and growth loops. #nostrdesign is ready to help with this.


Type of content kind 1 clients could surface and create loops for:
- Playlists
- Pin boards (pinstr)
- Audio chats (nost nests, corny chat)
- Highlights (highlighter)
- Payments
- Fundraisers (Heya, Geyser)
- Communities
- Events (Flockstr)
- Streams (zapstream)
- Long form content
- Job posts / boards
- Recipes (zap cooking)
- Lists
- Torrents (Stan)
- News feeds
- Calling functionality
- DMVs
- Podcast clips, playlists
- Audio clips
- Marketplace items (Shopstr, Creatstr, Plebeian Market)
- Paid content (highlighter)
Recap
- Build tools to aid content creation
- Surface “other stuff” in kind 1 clients
- Prompt people to create their own stuff
I’m probably missing a ton, or not thinking of unique experiences that are just under the nose. What am I missing? What other cool interactions could be enabled by nostr’s interoperabilit
-
 @ 7dc16771:70ed704f
2024-05-11 06:01:39
@ 7dc16771:70ed704f
2024-05-11 06:01:39『マーダーボット・ダイアリー』マーサ・ウェルズ著・中原尚哉訳・東京創元社
「マーダーボット」と呼ばれる主人公“弊機”は保険会社に所属する人型警備ユニット。顧客に貸し出される警備システムの「構成機体」でありながら、自分で統制モジュールをハッキングして、“自由”な存在になっている。でも彼がその“自由”を使って行うのは大好きな連続ドラマ『サンクチュアリムーン』を繰り返し繰り返し見ること。――とにかく“弊機”が可愛い! 一人称を“弊機”と訳した訳者さんがすごい! 人間の作ったドラマにどハマりしながら「人間とは付き合いたくない」と思ってる自意識過剰な引きこもりオタbotによる一人称日記形式のSF小説。安倍吉俊さんの表紙イラストも可愛いので是非!
アーケードゲーム・タイポグラフィ ビットマップ書体の世界 (大曲都市・著/グラフィック社)
パックマンのフォントを覚えているでしょうか?
本書は、70〜90年代のアーケードゲーム黄金期に生まれた様々なゲームのために作られた、個性豊かなフォントを取り上げています。 そこはわずか8✕8ピクセルの小さな文字の世界。その中で工夫を凝らされた数百にも及ぶフォントにはひとつとして同じものはなく、視認性と世界観の演出を追求した試行錯誤と進化の歴史を感じることでしょう。
いわゆる8bit風、ピクセルアートがひとつのジャンルとして市民権を得て久しいですが、キャラクターや背景だけではなく、フォントにもこんな奥深い世界があることを感じてほしいと思います。
ネガティブ・ケイパビリティ 答えの出ない事態に耐える力 (帚木蓬生/朝日選書/朝日新聞出版)
本書は、医師たちが「ネガティブ・ケイパビリティ=答えの無い状況を耐える力」を発見するまでの道程からはじまります。以降、それが「医療」、「創作」、「教育」、および平和の源泉たる「寛容」の点から、実践的にも極めて重要である理由を述べています。
本書は読み物として面白いだけでなく、文献の列挙など参考書としても役に立つ様に書かれています。物語作家であり、現役医師でもある帚木氏ならではです。多くの人に一読をお薦めできます。
面白く読め、困難に直面した際に誰もが持つ根源的な力について、理解を助けてくれます。豊富な解説は、現代的な問題を俯瞰する際に、辞書的に参照することもできる一冊です。
王様のプロポーズ 極彩の魔女 (橘公司/富士見ファンタジア文庫)
この物語の始まりは不意に誘 (いざな) われた異世界、目の前で殺されたのは世界最強の魔女。 彼女に託された最後の魔法を受け取り、その犯人に迫っていく。 一見するとシリアスに感じられるストーリーに色を付けるのは主人公の一途さ。一目惚れから始まった彼女への恋愛感情はどこまでも愚直であり、故に周りから奇異の目で見られ滑稽なやり取りが発生することもある。しかし一途であるために犯人が露見した場面で主人公の決意がより重いものとなり、それまでの伏線の美しさが強く感じられる。
「人生が整うマウント大全」著:マウンティングポリス 技術評論社
登頂者(マウンティングピープル)たちの能力バトル開幕ッッ!お前の“普通”で相手を殴れーーーー!
強者は何気無い発言の全てが他者を傷つけていることに向き合え。弱者はマウントの型を取り入れて精神武装を身につけろ。
書籍の半分を占める圧倒的なマウンティング実例で、今日から実践可能な知識をインプット可能。マウンティングする“剛”の技だけではなく、マウンティングを受ける“柔”の技も身につく、全方位に特化した業界トップのハウツー本。
5年間Twitterでマウント警察をし続け、“体系的な学問”としてのマウントフルネスをぶち上げた筆者に涙が止まらない、感動の一冊。
-
 @ 6ad08392:ea301584
2025-03-14 19:03:20
@ 6ad08392:ea301584
2025-03-14 19:03:20In 2024, I was high as a kite on Nostr hopium and optimism. Early that year, my co-founder and I figured that we could use Nostr as a way to validate ambassadors on “Destination Bitcoin” - the germ of a travel app idea we had at the time that would turn into Satlantis. After some more digging and thinking, we realised that Nostr’s open social graph would be of major benefit, and in exploring that design space, the fuller idea of Satlantis formed: a new kind of social network for travel.
 ###### ^^2 slides from the original idea here
###### ^^2 slides from the original idea hereI still remember the call I had with @pablof7z in January. I was in Dubai pitching the AI idea I was working on at the time, but all I could think and talk about was Satlantis and Nostr.
That conversation made me bullish AF. I came back from the trip convinced we’d struck gold. I pivoted the old company, re-organised the team and booked us for the Sovereign Engineering cohort in Madeira. We put together a whole product roadmap, go to market strategy and cap raise around the use of Nostr. We were going to be the ‘next big Nostr app’.
A couple of events followed in which I announced this all to the world: Bitcoin Atlantis in March and BTC Prague in June being the two main ones. The feedback was incredible. So we doubled down. After being the major financial backer for the Nostr Booth in Prague, I decided to help organise the Nostr Booth initiative and back it financially for a series of Latin American conferences in November. I was convinced this was the biggest thing since bitcoin, so much so that I spent over $50,000 in 2024 on Nostr marketing initiatives. I was certainly high on something.
Sobering up
It’s March 2025 and I’ve sobered up. I now look at Nostr through a different lens. A more pragmatic one. I see Nostr as a tool, as an entrepreneur - who’s more interested in solving a problem, than fixating on the tool(s) being used - should.
A couple things changed for me. One was the sub-standard product we released in November. I was so focused on being a Nostr evangelist that I put our product second. Coupled with the extra technical debt we took on at Satlantis by making everything Nostr native, our product was crap. We traded usability & product stability for Nostr purism & evangelism.
We built a whole suite of features using native event kinds (location kinds, calendar kinds, etc) that we thought other Nostr apps would also use and therefore be interoperable. Turns out no serious players were doing any of that, so we spent a bunch of time over-engineering for no benefit 😂
The other wake up call for me was the Twitter ban in Brazil. Being one of the largest markets for Twitter, I really thought it would have a material impact on global Nostr adoption. When basically nothing happened, I began to question things.
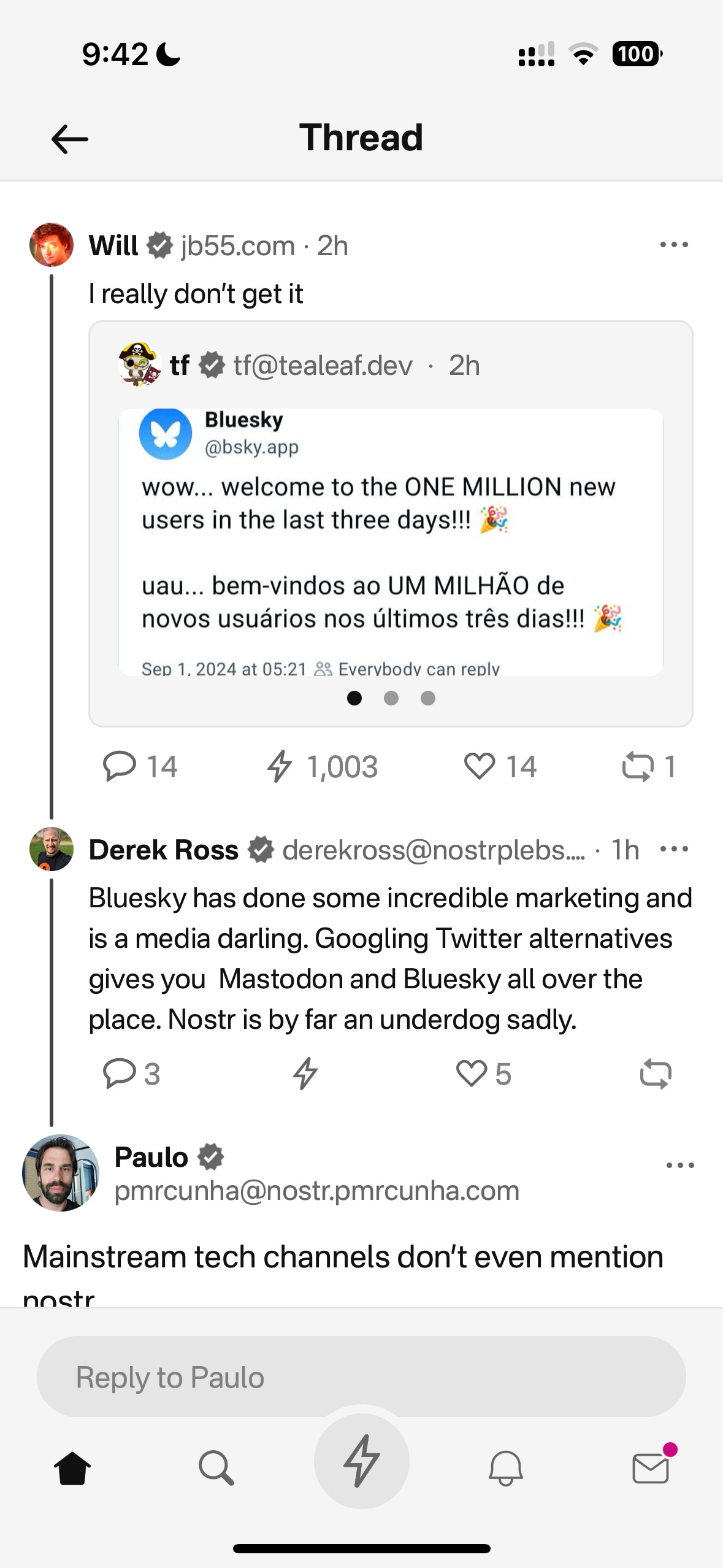
Combined, these experiences helped sober me up and I come down from my high. I was reading “the cold start problem” by Andrew Chen (ex-Uber) at the time and doing a deep dive on network effects. I came to the following realisation:
Nostr’s network effect is going to take WAY longer than we all anticipated initially. This is going to be a long grind. And unlike bitcoin, winning is not inevitable. Bitcoin solves a much more important problem, and it’s the ONLY option. Nostr solves an important problem yes, but it’s far from the only approach. It’s just the implementation arguably in the lead right now.
This sobering up led us to take a different approach with Nostr. We now view it as another tool in the tech-stack, no different to the use of React Native on mobile or AWS for infrastructure. Nostr is something to use if it makes the product better, or avoid if it makes the product and user experience worse. I will share more on this below, including our simple decision making framework. I’ll also present a few more potentially unpopular opinions about Nostr. Four in total actually:
- Nostr is a tool, not a revolution
- Nostr doesn’t solve the multiple social accounts problem
- Nostr is not for censorship resistance
- Grants come with a price
Let’s begin…
Nostr is a tool, not a revolution
Nostr is full of Bitcoiners, and as much as we like to think we’re immune from shiny object syndrome, we are, somewhere deep down afflicted by it like other humans. That’s normal & fine. But…while Bitcoiners have successfully suppressed this desire when it comes to shitcoins, it lies dormant, yearning for the least shitcoin-like thing to emerge which we can throw our guiltless support behind.
That thing arrived and it’s called Nostr.
As a result, we’ve come to project the same kind of purity and maximalism onto it as we do with Bitcoin, because it shares some attributes and it’s clearly not a grift.
The trouble is, in doing so, we’ve put it in the same class as Bitcoin - which is an error.
Nostr is important and in its own small way, revolutionary, but it pales in comparison to Bitcoin’s importance. Think of it this way: If Bitcoin fails, civilisation is fucked. If Nostr fails, we’ll engineer another rich-identity protocol. There is no need for the kind of immaculate conception and path dependence that was necessary for Bitcoin whose genesis and success has been a once in a civilisation event. Equivocating Nostr and Bitcoin to the degree that it has been, is a significant category error. Nostr may ‘win’ or it may just be an experiment on the path to something better. And that’s ok !
I don’t say this to piss anyone off, to piss on Nostr or to piss on myself. I say it because I’d prefer Nostr not remain a place where a few thousand people speak to each other about how cool Nostr is. That’s cute in the short term, but in the grand scheme of things, it’s a waste of a great tool that can make a significant corner of the Internet great again.
By removing the emotional charge and hopium from our relationship to Nostr, we can take a more sober, objective view of it (and hopefully use it more effectively).
Instead of making everything about Nostr (the tool), we can go back to doing what great product people and businesses do: make everything about the customer.
Nobody’s going around marketing their app as a “react native product” - and while I understand that’s a false equivalent in the sense that Nostr is a protocol, while react is a framework - the reality is that it DOES NOT MATTER.
For 99.9999% of the world, what matters is the hole, not the drill. Maybe 1000 people on Earth REALLY care that something is built on Nostr, but for everyone else, what matters is what the app or product does and the problem it solves. Realigning our focus in this way, and looking at not only Nostr, but also Bitcoin as a tool in the toolkit, has transformed the way we’re building.
This inspired an essay I wrote a couple weeks ago called “As Nostr as Possible”. It covers our updated approach to using and building WITH Nostr (not just ‘on’ it). You can find that here:
https://futuresocial.substack.com/p/as-nostr-as-possible-anap
If you’re too busy to read it, don’t fret. The entire theory can be summarised by the diagram below. This is how we now decide what to make Nostr-native, and what to just build on our own. And - as stated in the ANAP essay - that doesn’t mean we’ll never make certain features Nostr-native. If the argument is that Nostr is not going anywhere, then we can always come back to that feature and Nostr-fy it later when resources and protocol stability permit.
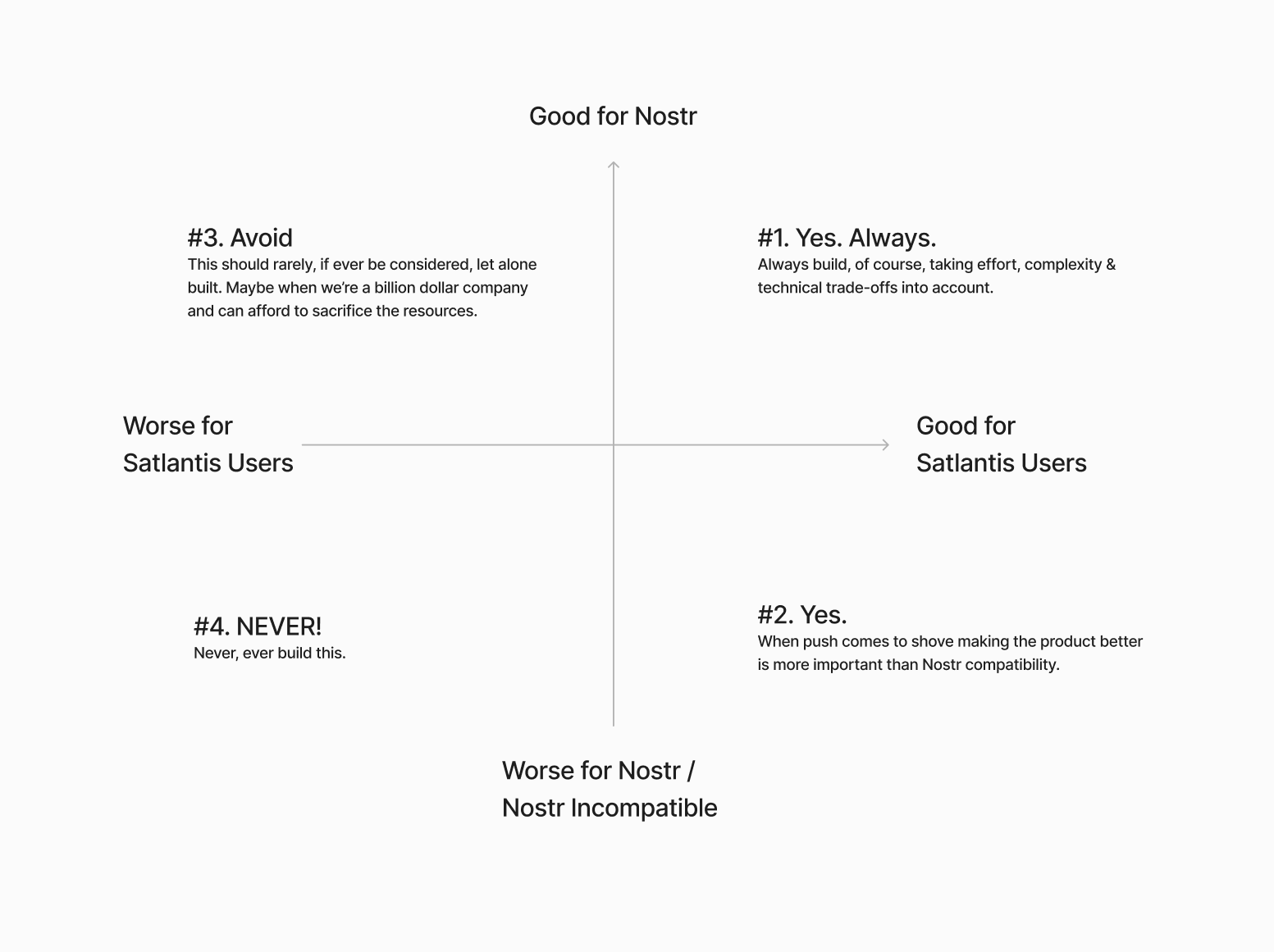
Next…
The Nostr all in one approach is not all “positive”
Having one account accessible via many different apps might not be as positive as we initially thought.

If you have one unified presence online, across all of your socials, and you’re posting the same thing everywhere, then yes - being able to post content in one place and it being broadcast everywhere, is great. There’s a reason why people literally PAY for products like Hypefury, Buffer and Hootsuite (aside from scheduling).
BUT…..This is not always the case.
I’ve spoken to hundreds of creators and many have flagged this as a bug not a feature because they tend to have a different audience on different platforms and speak to them differently depending on the platform. We all know this. How you present yourself on LinkedIn is very different to how you do it on Instagram or X.
The story of Weishu (Tencent’s version of TikTok) comes to mind here. Tencent’s WeChat login worked against them because people didn’t want their social graph following them around. Users actually wanted freedom from their existing family & friends, so they chose Douyin (Chinese TikTok) instead.
Perhaps this is more relevant to something like WeChat because the social graph following you around is more personal, but we saw something similar with Instagram and Facebook. Despite over a decade of ownership, Facebook still keeps the social graphs separated.
All this to say that while having a different strategy & approach on different social apps is annoying, it allows users to tap into different markets because each silo has its own ‘flavour’. The people who just post the same thing everywhere are low-quality content creators anyway. The ones who actually care, are using each platform differently.
The ironic part here is that this is arguably more ‘decentralised’ than the protocol approach because these siloes form a ‘marketplace of communities’ which are all somewhat different.
We need to find a smart way of doing this with Nostr. Some way of catering to the appropriate audience where it matters most. Perhaps this will be handled by clients, or by relays. One solution I’ve heard from people in the Nostr space is to just ‘spin up another nPub’ for your different audience. While I have no problem with people doing that - I have multiple nPubs myself - it’s clearly NOT a solution to the underlying problem here.
We’re experimenting with something. Whether it’s a good idea or not remains to be seen. Satlantis users will be able to curate their profiles and remove (hide / delete) content on our app. We’ll implement this in two stages:
Stage 1: Simple\ In the first iteration, we will not broadcast a delete request to relays. This means users can get a nicely curated profile page on Satlantis, but keep a record of their full profile elsewhere on other clients / relays.
Stage 2: More complex\ Later on, we’ll try to give people an option to “delete on Satlantis only” or “delete everywhere”. The difference here is more control for the user. Whether we get this far remains to be seen. We’ll need to experiment with the UX and see whether this is something people really want.
I’m sure neither of these solutions are ‘ideal’ - but they’re what we’re going to try until we have more time & resources to think this through more.
Next…
Nostr is not for Censorship Resistance
I’m sorry to say, but this ship has sailed. At least for now. Maybe it’s a problem again in the future, but who knows when, and if it will ever be a big enough factor anyway.
The truth is, while WE all know that Nostr is superior because it’s a protocol, people do NOT care enough. They are more interested in what’s written ON the box, not what’s necessarily inside the box. 99% of people don’t know wtf a protocol is in the first place - let alone why it matters for censorship resistance to happen at that level, or more importantly, why they should trust Nostr to deliver on that promise.
Furthermore, the few people who did care about “free speech” are now placated enough with Rumble for Video, X for short form and Substack for long form. With Meta now paying lip-service to the movement, it’s game over for this narrative - at least for the foreseeable future.
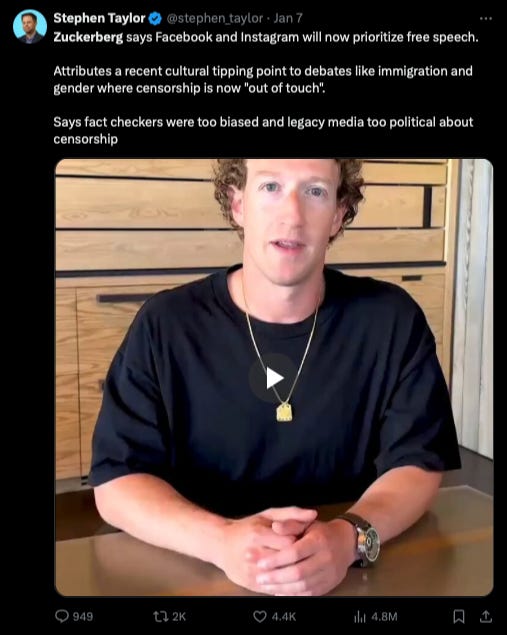 The "space in people’s minds for censorship resistance has been filled. Both the ‘censorship resistance’ and ‘free speech’ ships have sailed (even though they were fake), and the people who cared enough all boarded.
The "space in people’s minds for censorship resistance has been filled. Both the ‘censorship resistance’ and ‘free speech’ ships have sailed (even though they were fake), and the people who cared enough all boarded.For the normies who never cared, they still don’t care - or they found their way to the anti-platforms, like Threads, BlueSky or Pornhub.
The small minority of us still here on Nostr…are well…still here. Which is great, but if the goal is to grow the network effect here and bring in more people, then we need to find a new angle. Something more compelling than “your account won’t be deleted.”
I’m not 100% sure what that is. My instinct is that a “network of interoperable applications”, that don’t necessarily or explicitly brand themselves as Nostr, but have it under the hood is the right direction. I think the open social graph and using it in novel ways is compelling. Trouble is, this needs more really well-built and novel apps for non-sovereignty minded people (especially content creators) and people who don’t necessarily care about the reasons Nostr was first built. Also requires us to move beyond just building clones of what already exists.
We’ve been trying to do this Satlantis thing for almost a year now and it’s coming along - albeit WAY slower than I would’ve liked. We’re experimenting our way into a whole new category of product. Something different to what exists today. We’ve made a whole bunch of mistakes and at times I feel like a LARP considering the state of non-delivery.
BUT…what’s on the horizon is very special, and I think that all of the pain, effort and heartache along the way will be 100% worth it. We are going to deliver a killer product that people love, that solves a whole host of travel-related problems and has Nostr under the hood (where nobody, except those who care, will know).
Grants come with a price
This one is less of an opinion and more of an observation. Not sure it really belongs in this essay, but I’ll make a small mention just as food for thought,
Grants are a double-edged sword.
I’m super grateful that OpenSats, et al, are supporting the protocol, and I don’t envy the job they have in trying to decipher what to support and what not to depending on what’s of benefit to the network versus what’s an end user product.
That being said, is the Nostr ecosystem too grant-dependent? This is not a criticism, but a question. Perhaps this is the right thing to do because of how young Nostr is. But I just can’t help but feel like there’s something a-miss.
Grants put the focus on Nostr, instead of the product or customer. Which is fine, if the work the grant covers is for Nostr protocol development or tooling. But when grants subsidise the development of end user products, it ties the builder / grant recipient to Nostr in a way that can misalign them to the customer’s needs. It’s a bit like getting a government grant to build something. Who’s the real customer??
Grants can therefore create an almost communist-like detachment from the market and false economic incentive. To reference the Nostr decision framework I showed you earlier, when you’ve been given a grant, you are focusing more on the X axis, not the Y. This is a trade-off, and all trade-offs have consequences.
Could grants be the reason Nostr is so full of hobbyists and experimental products, instead of serious products? Or is that just a function of how ambitious and early Nostr is?
I don’t know.
Nostr certainly needs better toolkits, SDKs, and infrastructure upon which app and product developers can build. I just hope the grant money finds its way there, and that it yields these tools. Otherwise app developers like us, won’t stick around and build on Nostr. We’ll swap it out with a better tool.
To be clear, this is not me pissing on Nostr or the Grantors. Jack, OpenSats and everyone who’s supported Nostr are incredible. I’m just asking the question.
Final thing I’ll leave this section with is a thought experiment: Would Nostr survive if OpenSats disappeared tomorrow?
Something to think about….
Coda
If you read this far, thank you. There’s a bunch here to digest, and like I said earlier - this not about shitting on Nostr. It is just an enquiry mixed with a little classic Svetski-Sacred-Cow-Slaying.
I want to see Nostr succeed. Not only because I think it’s good for the world, but also because I think it is the best option. Which is why we’ve invested so much in it (something I’ll cover in an upcoming article: “Why we chose to build on Nostr”). I’m firmly of the belief that this is the right toolkit for an internet-native identity and open social graph. What I’m not so sure about is the echo chamber it’s become and the cult-like relationship people have with it.
I look forward to being witch-hunted and burnt at the stake by the Nostr purists for my heresy and blaspheming. I also look forward to some productive discussions as a result of reading this.
Thankyou for your attention.
Until next time.
-
 @ 6b9da920:7841cc6e
2024-05-10 23:07:42
@ 6b9da920:7841cc6e
2024-05-10 23:07:42Here is a simple chart for developers to understand when to "Nostr Native" and when to "Nostr Integrated"
Definition:
Nostr Native: Uses relays as the only network layer and storage layer and business logic is 99%+ client side.
Nostr Integrated: Has in-house solutions and only connects partially to Nostr.
Both categories could be open sourced or close sourced.
| Features | Benefit From Network Effect | Don't benefit from Network Effect | | --- | --- | --- | | Contribute To Network Effect | All in Nostr Native | Recommend Writing to Nostr | | Harm Network Effect| Don't Write to Nostr and could read from Nostr | Should be in-house solution and not write to Nostr |
Category 1
If we think we should be all-in Nostr Native no matter what (like 99%+), we are limiting ourselves to only features that both benefit from Nostr and contribute to Nostr. This is a totally valid proposition as long as developers are consciously aware that they are indeed making a product within this category.
Pretty much all public facing social features fall into this category.
But, there are many products that need features that fall into other 3 categories.
Category 2
For features that benefit from Nostr but harms it, you are basically stealing data from Nostr without contributing back. My advice to is not write to Nostr at all and only read from Nostr if you have to do it, but you should minimize this product design in general.
Pretty much any massivly bot/batch job/pipeline generated data fall into this category. Machine generated data do not necessarily mean spam data. In the data engineering & machine learning world, it's very common to generate intermediate data in data pipelines for downstream analytics. This kind of data is huge and can also be purely textual. Don't write to Nostr relays.
Category 3
Is it even possible to have features that don't benefit from the network effect of Nostr and can contribute to it?
I can't think of any. But if it exists, consider writing to Nostr even if you don't use relays as the primary storage.
Category 4
These are features that don't benefit from Nostr and also harm Nostr if writing to it.
Slack style internal organization communication falls into this category. In fact, we want to actively prevent these features from having network effects because having these data in an open network might reduce their security.
Writing them to Nostr also harms the network because these data, encrypted or not, only have semantic meaning within the organization. Posting them to Nostr reduces the overall signal(value) density of the network.
Outtro
It is very common and almost inevitable for a single product to have both lots of category 1 and lots of category 4 and some % of category 2 & 3.
Using this chart, you will know how to make wise engineering decisions that help your product design instead of harming it and help the network at the same time.
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ dbb19ae0:c3f22d5a
2025-03-11 19:09:19
@ dbb19ae0:c3f22d5a
2025-03-11 19:09:19I had this idea nostr:nevent1qvzqqqqqqypzpka3ntswp659x2yu2nru4qg8s2mpxpkgfr9d3kzpv969jlplyt26qqsdcsjaf57l9dssenlw6rt7vz2kd3kq9hqy5h6f3jx20u2j4vkmetgtg9q24
And today I wrote the python program using #nostr_sdk Using nostr_sdk 0.39 replace nsec_key with your secret key be careful, I just made like 2 or 3 test run. ``` python
!/usr/bin/env python3
import asyncio import argparse import json from nostr_sdk import Metadata, Client, NostrSigner, Keys, init_logger, LogLevel
async def write_metadata(secret_key, profile_data): try: init_logger(LogLevel.INFO) keys = Keys.parse(secret_key) signer = NostrSigner.keys(keys) client = Client(signer) public_key = keys.public_key() print(f"Public key (npub): {public_key.to_bech32()}")
# Add relays await client.add_relay("wss://relay.damus.io") await client.connect() # Parse profile content profile_content = json.loads(profile_data['content']) # Update metadata new_metadata = Metadata()\ .set_name(profile_content.get('name', '')) \ .set_picture(profile_content.get('picture', '')) \ .set_banner(profile_content.get('banner', '')) \ .set_about(profile_content.get('about', '')) await client.set_metadata(new_metadata) print("Metadata updated successfully.") except Exception as e: print(f"An error occurred in update_metadata: {e}") raiseif name == 'main': parser = argparse.ArgumentParser(description='Forcing user metadata using Nostr SDK.') parser.add_argument('json_file', type=str, help='Path to the JSON file containing profile data.') args = parser.parse_args()
with open(args.json_file, 'r') as file: profile_data_list = json.load(file) # Assuming the first profile in the JSON file is the one to be updated profile_data = profile_data_list[0] # Replace with actual secret key secret_key = "nsec_key" asyncio.run(write_metadata(secret_key, profile_data))```
-
 @ 0c469779:4b21d8b0
2025-03-11 10:52:49
@ 0c469779:4b21d8b0
2025-03-11 10:52:49Sobre el amor
Mi percepción del amor cambió con el tiempo. Leer literatura rusa, principalmente a Dostoevsky, te cambia la perspectiva sobre el amor y la vida en general.
Por mucho tiempo mi visión sobre la vida es que la misma se basa en el sufrimiento: también la Biblia dice esto. El amor es igual, en el amor se sufre y se banca a la otra persona. El problema es que hay una distinción de sufrimientos que por mucho tiempo no tuve en cuenta. Está el sufrimiento del sacrificio y el sufrimiento masoquista. Para mí eran indistintos.
Para mí el ideal era Aliosha y Natasha de Humillados y Ofendidos: estar con alguien que me amase tanto como Natasha a Aliosha, un amor inclusive autodestructivo para Natasha, pero real. Tiene algo de épico, inalcanzable. Un sufrimiento extremo, redentor, es una vara altísima que en la vida cotidiana no se manifiesta. O el amor de Sonia a Raskolnikov, quien se fue hasta Siberia mientras estuvo en prisión para que no se quede solo en Crimen y Castigo.
Este es el tipo de amor que yo esperaba. Y como no me pasó nada tan extremo y las situaciones que llegan a ocurrir en mi vida están lejos de ser tan extremas, me parecía hasta poco lo que estaba pidiendo y que nadie pueda quedarse conmigo me parecía insuficiente.
Ahora pienso que el amor no tiene por qué ser así. Es un pensamiento nuevo que todavía estoy construyendo, y me di cuenta cuando fui a la iglesia, a pesar de que no soy cristiano. La filosofía cristiana me gusta. Va conmigo. Tiene un enfoque de humildad, superación y comunidad que me recuerda al estoicismo.
El amor se trata de resaltar lo mejor que hay en el otro. Se trata de ser un plus, de ayudar. Por eso si uno no está en su mejor etapa, si no se está cómodo con uno mismo, no se puede amar de verdad. El amor empieza en uno mismo.
Los libros son un espejo, no necesariamente vas a aprender de ellos, sino que te muestran quién sos. Resaltás lo que te importa. Por eso a pesar de saber los tipos de amores que hay en los trabajos de Dostoevsky, cometí los mismos errores varias veces.
Ser mejor depende de uno mismo y cada día se pone el granito de arena.
-
 @ 4857600b:30b502f4
2025-03-11 01:58:19
@ 4857600b:30b502f4
2025-03-11 01:58:19Key Findings
- Researchers at the University of Cambridge discovered that aspirin can help slow the spread of certain cancers, including breast, bowel, and prostate cancers
- The study was published in the journal Nature
How Aspirin Works Against Cancer
- Aspirin blocks thromboxane A2 (TXA2), a chemical produced by blood platelets
- TXA2 normally weakens T cells, which are crucial for fighting cancer
- By inhibiting TXA2, aspirin "unleashes" T cells to more effectively target and destroy cancer cells
Supporting Evidence
- Previous studies showed regular aspirin use was linked to:
- 31% reduction in cancer-specific mortality in breast cancer patients
- 9% decrease in recurrence/metastasis risk
- 25% reduction in colon cancer risk
Potential Impact
- Aspirin could be particularly effective in early stages of cancer
- It may help prevent metastasis, which causes 90% of cancer fatalities
- As an inexpensive treatment, it could be more accessible globally than antibody-based therapies
Cautions
- Experts warn against self-medicating with aspirin
- Potential risks include internal bleeding and stomach ulcers
- Patients should consult doctors before starting aspirin therapy
Next Steps
- Large-scale clinical trials to determine which cancer types and patients would benefit most
- Development of new drugs that mimic aspirin's benefits without side effects
Citations: Natural News
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ f3873798:24b3f2f3
2025-03-10 00:32:44
@ f3873798:24b3f2f3
2025-03-10 00:32:44Recentemente, assisti a um vídeo que me fez refletir profundamente sobre o impacto da linguagem na hora de vender. No vídeo, uma jovem relatava sua experiência ao presenciar um vendedor de amendoim em uma agência dos Correios. O local estava cheio, as pessoas aguardavam impacientes na fila e, em meio a esse cenário, um homem humilde tentava vender seu produto. Mas sua abordagem não era estratégica; ao invés de destacar os benefícios do amendoim, ele suplicava para que alguém o ajudasse comprando. O resultado? Ninguém se interessou.

A jovem observou que o problema não era o produto, mas a forma como ele estava sendo oferecido. Afinal, muitas das pessoas ali estavam há horas esperando e perto do horário do almoço – o amendoim poderia ser um ótimo tira-gosto. No entanto, como a comunicação do vendedor vinha carregada de desespero, ele afastava os clientes ao invés de atraí-los. Esse vídeo me tocou profundamente.
No dia seguinte, ao sair para comemorar meu aniversário, vi um menino vendendo balas na rua, sob o sol forte. Assim como no caso do amendoim, percebi que as pessoas ao redor não se interessavam por seu produto. Ao se aproximar do carro, resolvi comprar dois pacotes. Mais do que ajudar, queria que aquele pequeno gesto servisse como incentivo para que ele continuasse acreditando no seu negócio.
Essa experiência me fez refletir ainda mais sobre o poder da comunicação em vendas. Muitas vezes, não é o produto que está errado, mas sim a forma como o vendedor o apresenta. Quando transmitimos confiança e mostramos o valor do que vendemos, despertamos o interesse genuíno dos clientes.
Como a Linguagem Impacta as Vendas?

1. O Poder da Abordagem Positiva
Em vez de pedir por ajuda, é importante destacar os benefícios do produto. No caso do amendoim, o vendedor poderia ter dito algo como: "Que tal um petisco delicioso enquanto espera? Um amendoim fresquinho para matar a fome até o almoço!"
2. A Emoção na Medida Certa
Expressar emoção é essencial, mas sem parecer desesperado. Os clientes devem sentir que estão adquirindo algo de valor, não apenas ajudando o vendedor.
3. Conheça Seu Público
Entender o contexto é fundamental. Se as pessoas estavam com fome e impacientes, uma abordagem mais objetiva e focada no benefício do produto poderia gerar mais vendas.
4. Autoconfiança e Postura
Falar com firmeza e segurança transmite credibilidade. O vendedor precisa acreditar no próprio produto antes de convencer o cliente a comprá-lo.
Conclusão
Vender é mais do que apenas oferecer um produto – é uma arte que envolve comunicação, percepção e estratégia. Pequenos ajustes na abordagem podem transformar completamente os resultados. Se o vendedor de amendoim tivesse apresentado seu produto de outra maneira, talvez tivesse vendido tudo rapidamente. Da mesma forma, se cada um de nós aprender a se comunicar melhor em nossas próprias áreas, poderemos alcançar muito mais sucesso.
E você? Já passou por uma experiência parecida?