-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 2b24a1fa:17750f64
2025-04-04 08:15:16
@ 2b24a1fa:17750f64
2025-04-04 08:15:16Ganz im Geiste des klassischen Kabaretts widmen sich Franz Esser und Michael Sailer den Ereignissen des letzten Monats: Was ist passiert? Und was ist dazu zu sagen? Das ist oft frappierend - und manchmal auch zum Lachen.
https://soundcloud.com/radiomuenchen/vier-wochen-wahnsinn-marz25-ein-satirischer-wochenruckblick?
-
 @ 2b24a1fa:17750f64
2025-04-04 08:10:53
@ 2b24a1fa:17750f64
2025-04-04 08:10:53Wir leben in einer Demokratie. So heißt es immer. Immerhin hat die Bevölkerung, der Souverän ein Mitspracherecht. Einmal alle vier Jahre. Und damit fünfundzwanzig Mal in einem Jahrhundert. Diese 25 Wahltage ergeben zeitlich 0,07 Prozent des gesamten Jahrhunderts. Würde man das Jahrhundert auf einen Tag runter rechnen, dann ergäben diese 0,07 Prozent ziemlich genau eine Minute des Mitspracherechts. Eine Minute pro Tag darf der Souverän also bestimmen, wer am restlichen Tag ungehindert schalten und walten darf – bis in das Grundgesetz hinein.
https://soundcloud.com/radiomuenchen/das-grundgesetz-als-schmierzettel-von-henry-matthes?
Die Veränderung in diesem zentralen Gesetzestexten ist allein den Parteien vorbehalten. An sämtliche Änderungen halten, dürfen sich dann nachher alle – selbst dann, wenn noch so wenige Bürger dahinterstehen.
In den letzten Wochen offenbarte sich dieser Missstand in präzedenzloser Weise. Die als Sondervermögen schön-deklarierte Neuverschuldung wurde im Grundgesetz festgeschrieben. Ist eine solch selektive Umgestaltungsmöglichkeit des wichtigsten Gesetzestext einer Demokratie würdig? Bräuchte es nicht zumindest einer Absegnung durch Volksabstimmungen?
Henry Mattheß hat sich hierzu Gedanken gemacht. Hören Sie seinen Text „Das Grundgesetz als Schmierzettel“, der zunächst auf dem Blog von Norbert Häring erschienen war.
Sprecher: Karsten Tryoke
Bild: Radio München
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ 57d1a264:69f1fee1
2025-04-05 06:35:58
@ 57d1a264:69f1fee1
2025-04-05 06:35:58We’re looking for a Product Designer to join our team and take the lead in enhancing the experience of our mobile app. You’ll play a key role in evolving the app’s interface and interactions, ensuring that our solutions are intuitive, efficient, and aligned with both user needs and business goals.
Key Responsibilities: - Design and improve the @Bipa app experience, focusing on usability and measurable business impact. - Apply data-driven design, making decisions based on user research, metrics, and testing. - Lead and participate in usability tests and discovery processes to validate hypotheses and continuously improve the product. - Collaborate closely with Product Managers, developers, and other stakeholders to align design with product strategy. - Create wireframes, high-fidelity prototypes, and visual interfaces for new features and app optimizations. - Monitor the performance of delivered solutions, ensuring meaningful improvements for users and the business. - Contribute to the evolution and maintenance of our design system, ensuring consistency and scalability across the app.
Qualifications: - Previous experience as a Product Designer or UX/UI Designer, with a strong focus on mobile apps. - Solid understanding of user-centered design (UCD) principles and usability heuristics. - Hands-on experience with user research methods, including usability testing, interviews, and behavior analysis. - Ability to work with both quantitative and qualitative data to guide design decisions. - Familiarity with product metrics and how design impacts business outcomes (e.g. conversion, retention, engagement). - Proficiency in design tools like Figma (or similar). - Experience working with design systems and design tokens to ensure consistency. - Comfortable working in an agile, fast-paced, and iterative environment. - Strong communication skills and the ability to advocate for design decisions backed by research and data.
Benefits: 🏥 Health Insurance 💉 Dental Plan 🍽️ Meal Allowance (CAJU card) 💻 Home Office Stipend 📈 Stock Options from Day One
originally posted at https://stacker.news/items/935003
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 57d1a264:69f1fee1
2025-04-05 06:28:16
@ 57d1a264:69f1fee1
2025-04-05 06:28:16⚡️ About Us
@AdoptingBTC is the leading Bitcoin-only conference in El Salvador. For our 5th edition, we’re looking for a passionate Video Creator intern to help showcase Bitcoin’s future as MONEY.
⚡️ The Role
Create 30 short (3-minute or less) videos highlighting global circular economies, to be featured at AB25. We’ll provide all source material, direction, and inspiration—you’ll have full creative freedom, with feedback rounds to align with the conference’s vision.
⚡️ Responsibilities
Produce 30 short videos on circular economies. Incorporate subtitles as needed. Submit videos on a deliverables basis. Participate in check-ins and communicate with the AB team and circular economy communities.
⚡️ What We Offer
Free ticket to AB25. Networking with Bitcoiners and industry leaders. Letter of recommendation and LinkedIn endorsement upon completion. Mentorship and hands-on experience with a high-profile Bitcoin project.
⚡️ Skills & Qualifications
Passion for Bitcoin and circular economies. Basic to intermediate video editing skills (no specific software required). Creative independence with feedback. Portfolio or work samples preferred.
⚡️ Time Commitment
Flexible, project-based internship with check-ins and feedback rounds.
⚡️ How to Apply
Email kiki@adoptingbitcoin.org with subject “Circular Economy Video Creator Submission -
{NAME OR NYM}.” Include a brief background, your experience, why the project resonates with you, and a portfolio (if available).originally posted at https://stacker.news/items/935001
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 69eea734:4ae31ae6
2025-04-01 15:33:49
@ 69eea734:4ae31ae6
2025-04-01 15:33:49What to record from the last two weeks? The key points from the things I've read and watched? \ The encounters I had with various groups of people, and also one on one? (on my trip to Munich)\ My thoughts on what is going on in the world?\ It is all connected anyway.
This is my second post. The first was under a different profile, which I lost the private key to.
So close and yet apart
The various encounters: Overlapping 'camps'. School friends, friends from uni times, friends from Covid times. One friend from school, and one friend from uni did not have a Covid vaccine and were critical of measures. To think that this still matters! Can you believe it? But it does! Which is sad on one hand, and makes for strong bonds on the other.
I'm in a pub with three school friends. They discover that they all voted Green, and are delighted. They kind of congratulate each other, and themselves. I don't even know what to feel in that moment. I'm not shocked. It is not surprising. And yet I still find it astounding.
As the evening progresses, we move to a Greek restaurant round the corner. On the way there, I walk alongside the friend with whom I exchanged the most challenging emails of the last five years. There had been long pauses between replies. Once I read only the first two lines, and then 'quarantined' the mail. I once deleted one, and three weeks later asked him to send it again.
In 2023 we sat in a café and openly talked about the Corona period and our differing positions. I appreciated it. At least we could talk. Shortly after, the emphasis in our conversations shifted from Covid to Putin. One arch enemy was replaced by another. And when previously, the 'Covid deniers' were the deplorable ones, now it was the 'Putin understanders', and weren't they the same people anyway? And mentioning peace talks was right wing. It was all so predictable. Was I predictable, too? I'd sent a long email a week ago. But walking alongside each other, we preferred to talk about the kids.
At the Greek restaurant, the inevitable happened. We ended up in a massive discussion. I once was gesticulating wildly at him. "Conspiracy theorist! That is so convenient. Everything that does not fit into your worldview, becomes a conspiracy theory. That there would be a vaccine mandate was once a conspiracy theory. That the virus came from a lab was once a conspiracy theory."
On another occasion, he exclaimed: "You know that I know all that about America! You know exactly that I know all those things!"
We both knew a lot of things, and it went back and forth.
The irony was that we managed to stay respectful, and it was a discussion with the other school friend there (the fourth person on the table was my husband), that turned out to be the last straw. She had voted Green as well, and had congratulated our school mate on having been to the protest 'against the right'. But she was also the one who didn't have the vaccine, and now said, "With Covid, it was just so obvious that it was all set up." A bit later she said something about the WEF. Only to be greeted with a long tirade. "Aha. So you think this is all a big conspiracy with some powerful people in the background planning everything. And this wasn't a pandemic although lots of people died. I know six doctors, and they all told me the same." A bit later, to me: "So why did only the unvaccinated die then?" And then shortly after, when my friend stated again how the whole thing had seemed premeditated, "Right. That's enough now. I'm leaving." And he got up to pay and left.
My friend, who stayed behind, thought we had had interesting discussions and she had learned something. On reflection, it was good to have this discussion at all -- at a time that nobody seems to want to talk about Covid anymore.
But also: Shouldn't we be much much further than this???
My first sats
A few months ago I had tried to buy bitcoin, just to play around, but there had been difficulties to do with the fact I have a UK bank account. When looking at how to get funds into my getalby account, I ended up with Strike, which is available in the UK. But it seems they take extra care to make sure you know what you are letting yourself into! I had to do a test with about 10 questions to show I understand the risks.
I then had to wait 24 hours, but now I have sent my first sats.
On the Strike website, I noticed this video of a conversation between Jack Mallers, founder of Strike, and Jack Dorsey, co-founder of Twitter. The more I watched, the more I thought, wow, here it is all in one video, all that I would like my friend to see. "America has a problem." The Empire needs to end, and it would be a good thing for America, says Jack Dorsey. This was also the second time in a week that I heard about how Great Britain had created money and bought their own bonds when the public didn't want to, in effect stealing from the people by making their money worth less. It was good to be reminded of Adam Curtis who has made some mind-blowing documentaries, using lots of BBC archive material. Including about the special US and UK relationship (An ocean apart), and also one about Russia from 1985 to 1999 (Trauma Zone).
The two Jacks talk about the importance of open source, and of being independent of government. The dangers of building abstraction on abstraction on abstraction. About how Mark Zuckerberg served Dorsey raw goat once, because he had this challenge to only eat what he had killed himself. That was also a way to get back to the real.
Dorsey endorsed RFK jr, this was in summer of 2023, when he was still running for president.
There is also an interesting bit on the pressures of running a company that has gone public. And the government interference, in effect censorship. The Twitter files. It is not quite clear to me, if it was really so difficult for Jack Dorsey to pay attention and know what was going on, but I can understand that it must have been a difficult situation.
What I also find very interesting is that in Africa or Latin America bitcoin is sometimes valuable as an exchange medium. That is where I think it could diverge from the pure Ponzi scheme that people often call it.
And yet, doubts remain. Is bitcoin not too valuable for a lot of people to spend it? But what if you don't have access to any other money. And sending Satoshis around is different from hording bitcoin. Can it fulfil both these functions in the end, storage medium and exchange medium?
I believe that these two people want to achieve something positive. But they also remain tech bros. And I don't mean that in a bad way. It is just something that will always remain a bit alien to me.
I did like what Dorsey said about the punks. How they just started to play an instrument, and didn't care if they were not good at it. Then just turned up again and again and eventually got better. I have often thought of myself as a bit punk-like in that respect, although I've often been worried about not being good enough.
Doing away with domination
The last blog article posted on a website I work on, made me explore the writings by Darren Allen on his Expressive Egg substack. I had landed there before, years ago, and had been very impressed back then. He seems to criticise people's thoughts a lot though -- almost everybody's -- and I was wondering if that was all he ever did. But then I came across this article about anarchy. It made me realise again, in all this mess about different worldviews, different expectations and values, that this is a constant for me: How can we have less coercion, how can we live in a way that frees ourselves and others at the same time. I once saw a Twitter bio: "I insist on your freedom." It seems to come from Jack Kerouac.
Allen writes that there are seven dominants, seven elements that "control individuals against their will". They are, " in roughly ascending order of subtlety and pervasiveness":
1. The [autocratic] monarchy.\ 2. The [socialist-democratic] state (which includes its money, law, property, police, etc.).\ 3. The [totalitarian-capitalist] corporation.\ 4. The [mass] majority.\ 5. The [professional-religious] institution.\ 6. The [technocratic] system.\ 7. The [mental-emotional] ego.
I want to keep this list in mind and pay attention when I get sucked into the influence of one of these spheres.
\ I also like this quote:
The reason men and women do not need kings, princes, states, professionals, institutions and systems to rule over them is because the life within them is more intelligent, more apt, more sensitive, more forgiving and more creative than anything else—certainly any human authority. But this life cannot be rationally fixed. It can be expressed, artistically, indirectly, poetically, musically, or with tone and glance and such ordinary, metaphorical arts of human interaction; but it cannot be literally stated.
\ Although this would be a good ending for this post, I have to mention Jeffrey Sachs as well. I have been following him for a while. He appeared in the EU parliament, invited by Michael von der Schulenburg. Sachs has an amazing amount of experience with both Russian and American government officials, and with currencies. In the 90s he spent some time helping Eastern European countries with the transition to capitalist systems. He realised that the U.S. did not want to help Russia in the same way.
He gave a long speech in which he laid bare the ways in which the U.S. had influenced so many wars and uprisings around the world, and how the NATO enlargement had been a long-term strategy. That now, with Trump, the war was going to end.
There would be so much more to say. In any case, this seems to me a historic speech. Can it break through the mirror glass that has kept so many people away from valid sources of knowledge?
-
 @ fd78c37f:a0ec0833
2025-04-01 11:49:06
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
YakiHonne: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
Keypleb:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
YakiHonne: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
Keypleb:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. Keypleb:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. Keypleb:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

YakiHonne: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
Keypleb:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. Keypleb:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. Keypleb:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.
 YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?Keypleb:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. Keypleb:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. Keypleb:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
YakiHonne: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
Keypleb:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. Keypleb:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. Keypleb:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. Keypleb:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. Keypleb:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.
 YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?Keypleb:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.
 Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.YakiHonne: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
Keypleb:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. Keypleb:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. Keypleb:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
YakiHonne: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
Keypleb:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. Keypleb:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. Keypleb:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
YakiHonne: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
Keypleb:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-
 @ 3ffac3a6:2d656657
2025-04-05 04:55:12
@ 3ffac3a6:2d656657
2025-04-05 04:55:12O Impacto do Namoro com Pelé na Carreira de Xuxa Meneghel
Disclaimer:
Esse texto foi totalmente escrito pelo ChatGPT, eu apenas pedi que ele fizesse uma pesquisa sobre o tema.
Introdução: O relacionamento entre Xuxa Meneghel e Pelé, que durou cerca de seis anos (início dos anos 1980 até 1986), foi um dos mais comentados da década de 1980 (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Xuxa tinha apenas 17 anos quando começou a namorar o já consagrado “Rei do Futebol”, então com 40 anos (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Esse romance altamente midiático não só atiçou a curiosidade do público, como também alavancou a carreira de Xuxa de forma significativa. A seguir, detalhamos como o namoro aumentou a visibilidade da apresentadora, quais oportunidades profissionais podem ter tido influência direta de Pelé, o papel da revista Manchete e de outras mídias na promoção de sua imagem, se o relacionamento contribuiu para Xuxa conquistar espaços na TV (como o programa Clube da Criança e, posteriormente, na Rede Globo) e como mídia e público percebiam o casal – tudo embasado em fontes da época, entrevistas e biografias.
Aumento da Visibilidade Midiática nos Anos 1980
O namoro com Pelé catapultou Xuxa a um novo patamar de fama. Até então uma modelo em começo de carreira, Xuxa “se tornou famosa ao aparecer ao lado do esportista de maior status do Brasil” (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). A partir do momento em que o relacionamento se tornou público, ela passou a estampar capas de revistas com frequência e a ser assunto constante na imprensa. Em 20 de dezembro de 1980, a jovem apareceu na capa da revista Manchete ao lado de Pelé e outras modelos – um ensaio fotográfico que marcou o primeiro encontro dos dois e deu início à enorme atenção midiática em torno de Xuxa (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Não por acaso, “naquele ano, ela foi capa de mais de cem revistas” (Xuxa está em paz - revista piauí), um indicativo claro de como sua visibilidade explodiu após começar a namorar Pelé. Jornais, revistas de celebridades e programas de fofoca passaram a segui-los de perto; o casal virou sensação nacional, comparado até ao “Casal 20” (dupla glamourosa de uma série de TV americana) pelo seu alto perfil na mídia (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA).
Essa exposição intensa colocou Xuxa não apenas sob os holofotes do público, mas também a inseriu nos bastidores do entretenimento. Como namorada de Pelé – um dos homens mais conhecidos do mundo – Xuxa passou a frequentar eventos de gala, festas e bastidores de programas, onde conheceu figuras influentes do meio artístico e televisivo. Os fotógrafos os seguiam em eventos como bailes de carnaval e inaugurações, registrando cada aparição pública do casal. Com Pelé ao seu lado, Xuxa ganhou trânsito livre em círculos antes inacessíveis para uma modelo iniciante, construindo uma rede de contatos valiosa nos meios de comunicação. De fato, naquele início dos anos 80, “os dois eram perseguidos por fotógrafos, apareciam em capas de revistas e até faziam publicidade juntos” (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições) – evidência de que Xuxa, graças ao namoro, transitava tanto na frente quanto por trás das câmeras com muito mais facilidade. Em suma, o relacionamento conferiu a ela um grau de notoriedade nacional que provavelmente demoraria anos para conquistar de outra forma, preparando o terreno para os passos seguintes de sua carreira.
Influência Direta de Pelé nas Oportunidades Profissionais de Xuxa
Além do aumento geral da fama, há casos específicos em que Pelé influenciou diretamente oportunidades profissionais para Xuxa. Um exemplo contundente é o filme “Amor Estranho Amor” (1982) – longa de teor erótico no qual Xuxa atuou no início da carreira. Segundo relatos da própria apresentadora, foi Pelé quem a incentivou a aceitar participar desse filme (Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5). Na época ainda em início de trajetória, Xuxa acabou convencida pelo namorado de que aquela oportunidade poderia ser benéfica. Anos mais tarde, ela revelaria arrependimento pela escolha desse papel, mas o fato reforça que Pelé teve influência ativa em decisões profissionais de Xuxa no começo de sua jornada.
Outra área de influência direta foram as publicidades e campanhas comerciais. Graças ao prestígio de Pelé, Xuxa recebeu convites para estrelar anúncios ao lado do então namorado. Já em 1981, por exemplo, os dois gravaram juntos comerciais para uma empresa imobiliária, aparecendo como casal em campanhas de TV daquele Natal (pelas Imóveis Francisco Xavier, um case famoso entre colecionadores de propagandas da época) (Xuxa e Pelé: Natal de 1981 na Publicidade Imobiliária | TikTok) (Xuxa com Pelé em comercial de imobiliária em dezembro de 1981). Assim, Xuxa obteve espaço em campanhas publicitárias que dificilmente envolveriam uma modelo desconhecida – mas que, com a “namorada do Pelé” no elenco, ganhavam apelo extra. Isso evidencia que Pelé abriu portas também no mercado publicitário, dando a Xuxa oportunidades de trabalho e renda enquanto sua própria imagem pública se consolidava.
Ademais, a presença de Pelé ao lado de Xuxa em diversos editoriais e ensaios fotográficos serviu para elevá-la de modelo anônima a personalidade conhecida. Revistas e jornais buscavam os dois para sessões de fotos e entrevistas, sabendo do interesse do público pelo casal. As capas conjuntas em publicações de grande circulação (como Manchete e outras) não só aumentaram a exposição de Xuxa, mas também conferiram a ela certa credibilidade midiática por associação. Em outras palavras, estar ao lado de um ícone como Pelé funcionou como um “selo de aprovação” implícito, deixando editores e produtores mais propensos a convidá-la para projetos. Vale lembrar que “ao longo dos seis anos de relacionamento, [eles] posaram para várias capas da Manchete”, com a revista acompanhando de perto cada fase do namoro (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Essa recorrência nas bancas solidificou o rosto e o nome de Xuxa na indústria do entretenimento.
Por fim, é importante notar que nem todas as influências de Pelé foram positivas para a carreira dela – algumas foram tentativas de direcionamento. A própria Xuxa contou que, quando surgiu a oportunidade de ela ir para a TV Globo em 1986, Pelé desencorajou a mudança. Ele sugeriu que Xuxa permanecesse na TV Manchete, dizendo que “ser a primeira [na Globo] é muito difícil; melhor ficar onde está”, o que ela interpretou como falta de apoio dele à sua ascensão (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Esse episódio mostra que Pelé tentou influenciar também os rumos que Xuxa tomaria, embora, nesse caso, ela tenha decidido seguir sua intuição profissional e aceitar o desafio na Globo – escolha que se revelaria acertada. Em resumo, Pelé atuou sim como facilitador de várias oportunidades profissionais para Xuxa (de filmes a comerciais e visibilidade editorial), mas ela soube trilhar seu caminho a partir daí, inclusive contrariando conselhos dele quando necessário.
Papel da Revista Manchete e Outras Mídias na Promoção de Xuxa
A revista Manchete teve um papel central na ascensão de Xuxa durante o relacionamento com Pelé. Foi justamente num ensaio para a Manchete que os dois se conheceram, em dezembro de 1980 (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira), e a partir daí a publicação tornou-se uma espécie oficiosa de cronista do romance. A Manchete era uma das revistas mais populares do Brasil naquela época e, ao perceber o interesse do público pelo casal, passou a trazê-los frequentemente em suas páginas. De fato, a revista que agiu como "cupido" do casal “contava detalhes do romance a cada edição”, alimentando a curiosidade nacional sobre a vida de Pelé e sua jovem namorada (A história da foto de revista que gerou o namoro de Pelé e Xuxa). As capas exibindo Xuxa e Pelé juntos (em cenários que iam da praia a eventos sociais) viraram chamariz nas bancas e contribuíram enormemente para fixar a imagem de Xuxa na mente do público.
(A história da foto de revista que gerou o namoro de Pelé e Xuxa) Capa da revista Manchete (20 de dezembro de 1980) mostrando Pelé ao centro com Xuxa (à esquerda) e outras modelos. A partir desse ensaio fotográfico, a revista passou a acompanhar de perto o romance, impulsionando a imagem de Xuxa nacionalmente. (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira)
Além da Manchete, outras mídias impressas também surfaram no interesse pelo casal e ajudaram a moldar a imagem de Xuxa. Revistas de celebridades e colunas sociais publicavam notas e fotos frequentes, ora exaltando o glamour do par, ora especulando sobre fofocas. Xuxa, que pouco antes era desconhecida fora do circuito da moda, tornou-se figura constante em revistas semanais como Contigo! e Amiga (dedicadas à vida dos famosos), assim como em jornais de grande circulação. Esse bombardeio de aparições – entrevistas, fotos e manchetes – construiu a persona pública de Xuxa simultaneamente como modelo desejada e namorada devotada. A promoção de sua imagem tinha um tom deliberadamente positivo nas revistas: enfatizava-se sua beleza, juventude e sorte por ter sido “escolhida” pelo rei Pelé. Em contrapartida, eventuais polêmicas (como cenas ousadas que ela fez no cinema ou rumores de crises no namoro) eram administradas pela própria mídia de maneira a preservar o encanto em torno de Xuxa, que já despontava como uma espécie de Cinderella moderna na narrativa do entretenimento brasileiro.
Cabe destacar que a conexão de Xuxa com a Manchete não ficou só nas páginas da revista, mas transbordou para a televisão, já que a Rede Manchete (canal de TV fundado em 1983) pertencia ao mesmo grupo empresarial. Essa sinergia mídia impressa/televisão beneficiou Xuxa: quando a Rede Manchete buscava uma apresentadora para seu novo programa infantil em 1983, Xuxa – já famosa pelas capas de revista – foi convidada para o posto (Xuxa está em paz - revista piauí). Ou seja, a exposição na revista Manchete serviu de vitrine para que os executivos da emissora homônima apostassem nela na TV. Outras mídias também legitimaram sua transição de modelo para apresentadora, publicando matérias sobre sua simpatia com as crianças e seu carisma diante das câmeras, preparando o público para aceitar Xuxa em um novo papel. Assim, o período do relacionamento com Pelé viu a mídia – liderada pela revista Manchete – construir e promover intensamente a imagem de Xuxa, pavimentando o caminho para suas conquistas seguintes.
O Relacionamento e a Conquista de Espaços na TV: Clube da Criança e Rede Globo
O namoro com Pelé coincidiu com a entrada de Xuxa na televisão e possivelmente facilitou essa transição. Em 1983, a recém-inaugurada Rede Manchete lançou o “Clube da Criança”, primeiro programa infantil de auditório da emissora, e Xuxa foi escolhida como apresentadora. Há indícios de que sua fama prévia – alavancada pelo relacionamento – foi decisiva nessa escolha. Conforme relatos, o diretor Maurício Sherman (responsável pelo projeto) estava de olho em Xuxa por sua notoriedade e carisma, chegando a dizer que ela reunia “a sensualidade de Marilyn Monroe, o sorriso de Doris Day e um quê de Peter Pan” (Xuxa está em paz - revista piauí) – uma combinação que poderia funcionar bem num programa infantil. Xuxa inicialmente hesitou em aceitar, talvez pelo contraste entre sua imagem de modelo sensual e o universo infantil, mas acabou assinando contrato com a Manchete (Clube da Criança – Wikipédia, a enciclopédia livre). Assim, aos 20 anos de idade, ela estreava como apresentadora de TV, em grande parte graças à visibilidade e confiança que o nome “Xuxa” (já famoso por ser namorada do Pelé) passava aos produtores.
Não há registro de que Pelé tenha intervindo diretamente para que Xuxa conseguisse o posto no Clube da Criança. Foi a própria rede Manchete – estimulada pelo burburinho em torno dela – que a “procurou e a convidou para apresentar” o programa (Xuxa está em paz - revista piauí). Porém, é inegável que, sem o destaque que Xuxa conquistara nos anos anteriores na imprensa (devido ao namoro), dificilmente uma emissora arriscaria colocar uma jovem inexperiente para comandar um show infantil nacional. Ou seja, o relacionamento criou as condições favoráveis para essa oportunidade surgir. Uma vez no ar, Xuxa rapidamente mostrou talento próprio: o Clube da Criança foi ganhando audiência e revelou a aptidão dela em se comunicar com o público infantil (Xuxa, Pantanal, Cavaleiros dos Zodíacos: lembre sucessos da TV ...). Ainda durante seu tempo na Manchete, Xuxa manteve-se nos holofotes tanto pela carreira quanto pelo namoro com Pelé – frequentemente um assunto alimentava o outro na mídia.
Em meados de 1986, já conhecida como a “Rainha dos Baixinhos” pelo sucesso junto às crianças, Xuxa recebeu uma proposta para se transferir para a Rede Globo, a principal emissora do país (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Novamente, aqui o relacionamento com Pelé tem um papel indireto: por um lado, pode ter ajudado a construir a notoriedade que chamou a atenção da Globo; por outro, chegava ao fim exatamente nesse momento, marcando uma virada na vida dela. Após alguns anos de Clube da Criança, Xuxa decidiu dar um passo adiante. Ela mesma tomou a iniciativa de terminar o namoro com Pelé e aceitou o convite para fazer o “Xou da Xuxa” na Globo (A história da foto de revista que gerou o namoro de Pelé e Xuxa). Pelé, como mencionado, havia expressado reservas sobre essa mudança de emissora (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira), mas sem sucesso em demovê-la. Com a benção do dono da Manchete, Adolpho Bloch (que a tratava “como filha” e apoiou seu crescimento) (Xuxa está em paz - revista piauí) (Xuxa está em paz - revista piauí), Xuxa partiu para a Globo levando sua diretora Marlene Mattos, e estreou em junho de 1986 o programa que a consagraria definitivamente.
É importante notar que, ao ingressar na Globo, Xuxa já não dependia mais da aura de “namorada do Pelé” – ela havia se firmado como apresentadora de sucesso por méritos próprios. Ainda assim, o relacionamento anterior continuou a ser parte de sua imagem pública: a mídia noticiou a mudança destacando que a namorada de Pelé chegara à Globo, e muitos espectadores tinham curiosidade sobre aquela moça cuja fama começara nos braços do ídolo do futebol. Em resumo, o namoro ajudou Xuxa a conquistar o primeiro grande espaço na TV (na Manchete), fornecendo-lhe exposição e credibilidade iniciais, enquanto sua ida para a Globo foi impulsionada principalmente pelo desempenho no Clube da Criança – algo que o prestígio conquistado durante o relacionamento tornou possível em primeiro lugar.
Percepção da Mídia e do Público sobre o Casal e a Imagem de Xuxa
Durante os anos de namoro, Pelé e Xuxa foram um prato cheio para a imprensa e objeto de variadas opiniões do público. De um lado, eram celebrados como “casal perfeito na mídia”, aparecendo sorridentes em eventos e capas, o que projetava uma imagem glamourosa e apaixonada (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Xuxa era frequentemente retratada como a bela jovem humilde que havia conquistado o coração do "rei", uma narrativa de conto de fadas que agradava muitos fãs. Pessoas próximas diziam na época: “Nossa, como ela está apaixonada, como ela está de quatro pelo Pelé”, segundo relembrou a própria Xuxa, indicando que sua dedicação ao namorado era visível e comentada (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA). Essa percepção de autenticidade nos sentimentos ajudou a humanizar Xuxa aos olhos do público, diferenciando-a de estereótipos de roupante ou interesse calculado.
Por outro lado, nem toda a atenção era positiva. Houve murmúrios maldosos e preconceituosos nos bastidores. Pelé e Xuxa formavam um casal interracial (ele negro, ela branca e bem mais jovem), o que, segundo a imprensa, “gerava olhares de reprovação dos conservadores” e até comentários racistas proferidos pelas costas (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Além disso, alguns duvidavam das intenções de Xuxa no relacionamento, insinuando que ela buscava ascensão social por meio de Pelé. Termos pejorativos como “maria-chuteira” (gíria para mulheres que namoram jogadores em busca de status) e “alpinista social” chegaram a ser associados a Xuxa por fofoqueiros da época (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições). Essa desconfiança lançava sombra sobre a imagem dela, pintando-a, aos olhos de alguns, como oportunista em vez de namorada dedicada. Xuxa teve de lidar com esse tipo de insinuação ao longo do namoro, buscando provar que seu amor era verdadeiro e que ela também tinha talentos e ambições próprias.
A mídia impressa, em geral, manteve uma postura favorável ao casal, explorando o romance como algo encantador. Mas não deixou de reportar as turbulências: sabia-se, por exemplo, das frequentes traições de Pelé, que Xuxa anos depois revelou ter suportado calada na época (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira). Essas infidelidades eram rumores correntes nos círculos de fofoca, embora Xuxa raramente comentasse publicamente enquanto estava com Pelé. O público, portanto, via um casal bonito e famoso, mas também acompanhava as especulações de crises e reconciliações pelos noticiários de celebridades. Cada aparição pública deles – fosse em um jogo de futebol, um evento beneficente ou nos camarotes do carnaval – era dissecada pelos repórteres, e cada declaração (ou silêncio) alimentava interpretações sobre o estado do relacionamento e sobre quem era Xuxa por trás da fama.
No saldo final, o namoro com Pelé influenciou profundamente a imagem pública de Xuxa. Inicialmente marcada como “a namorada do Rei” – posição que trazia tanto admiração quanto inveja – Xuxa soube aproveitar a visibilidade para mostrar carisma e trabalho, transformando-se em uma estrela por direito próprio. Ao se tornar apresentadora infantil de sucesso ainda durante o namoro, ela começou a dissociar sua imagem da de Pelé, provando que podia ser mais do que um apêndice de um astro do esporte. Quando o relacionamento terminou em 1986, Xuxa emergiu não caída em desgraça, mas sim pronta para reinar sozinha na TV. A mídia continuou a mencioná-la em referência a Pelé por algum tempo (era inevitável, dado o quão famoso o casal fora), mas cada vez mais o público passou a enxergá-la principalmente como a “Rainha dos Baixinhos”, a figura alegre das manhãs na TV Globo. Em entrevistas posteriores, Xuxa admitiu ter sentimentos mistos ao lembrar dessa fase: ela se ressentiu, por exemplo, de Pelé ter classificado o que viveram como “uma amizade colorida” em vez de namoro sério (Pelé e Xuxa: um estranho amor que durou seis anos - 29/12/2022 - Celebridades - F5) – frase do ex-jogador que a magoou e que veio a público muitos anos depois. Esse comentário retroativo de Pelé apenas reforçou o quanto a mídia e o público discutiram e dissecaram a natureza daquela relação.
Em conclusão, a percepção do casal Xuxa e Pelé oscilou entre o encanto e a controvérsia, mas inegavelmente manteve Xuxa nos trending topics de sua época (para usar um termo atual). A jovem modelo gaúcha ganhou projeção, prestígio e também enfrentou julgamentos enquanto esteve com Pelé. Tudo isso moldou sua imagem – de símbolo sexual e socialite em ascensão a profissional talentosa pronta para brilhar por conta própria. O relacionamento forneceu-lhe a plataforma e a armadura mediática; coube a Xuxa transformar essa visibilidade em uma carreira sólida, o que ela fez com maestria ao se tornar uma das maiores apresentadoras da história da TV brasileira.
Fontes: Entrevistas e depoimentos de Xuxa Meneghel (inclusive do livro Memórias, 2020), reportagens da época em revistas como Manchete, colunas sociais e jornais (compiladas em repositórios atuais), e biografias e retrospectivas sobre ambos os envolvidos (A história da foto de revista que gerou o namoro de Pelé e Xuxa) (Pelé viveu com Xuxa um namoro intenso afetado por fofocas e indiscrições) (Xuxa e Pelé: o relacionamento que ficou cravado na história da imprensa brasileira) (Xuxa e Pelé: um romance que se tornou inesquecível... | VEJA), entre outras. Essas fontes confirmam o papel catalisador que o namoro com Pelé teve nos primeiros passos da trajetória de Xuxa, bem como os desafios e oportunidades que surgiram dessa intensa exposição pública.
-
 @ 75869cfa:76819987
2025-04-01 05:55:38
@ 75869cfa:76819987
2025-04-01 05:55:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 221,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 79%. More than 10 million events have been published, reflecting a 12% decrease. Total Zap activity stands at approximately 21 million, marking a 15% increase.
Additionally, 15 pull requests were submitted to the Nostr protocol, with 2 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 569 long-form articles were published, 24% focusing on Bitcoin and Nostr. During this period, 7 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 221,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 17662 events, with a low of approximately 15781.
The number of new users has decreased significantly. Profiles with bio are now around 25951, reflecting a 79% drop. Pubkeys writing events have decreased by 50% compared to the previous period.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 12% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.7 million, which is a 4.4 % decrease. Both reposts and reactions have decreased by about 5%.
For zap activity, the total zap amount is about 21 million, showing an increase of over 15% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Added optional signString() method
nostr:npub1emq0gngdvntdn4apepxrxr65vln49nytqe0hyr58fg9768z5zmfqcwa3jz is proposing a signString() method that allow Nostr users to sign/authenticate messages for external apps without compromising their private key (nsec).It opens up a more generic and flexible challenge-response style external authentication method, using the same Schnorr signature mechanism that Nostr uses to sign events natively.External apps need only understand Schnorr signatures - they do not need to understand Nostr's event structure. This widens interoperability.A concrete example of where this would be useful is P2PK locking of Cashu ecash tokens to a Nostr pubkey (npub). Decoding the token requires a Scnorr signature on a structured message string. This method would allow a signer to handle It cleanly.
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 defines kind:39701 as website bookmarks.Bookmarks can be queried by the d tag, which is just their URL without the scheme, which is always and everywhere assumed to be https://. The querystring and the hash must be removed entirely, unless their requirement is explicitly stated either by the user or by some hardcoded list of URLs that rely on query strings for basic routing provided by the client (I've searched the internet extensively and could only find 3 websites that do this: YouTube, Hacker News and a random guy's sad old blog). Bookmarks can be commented on with NIP-22.
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that covers the inclusion of Progress Events as implemented in Open Librarian. While the specific implementation is focused on tracking reading progress, the NIP is generic enough to be used in a whole range of other progress tracking scenarios (e.g. Fitness challenges, course progression for learning, personal goals etc..)
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that includes a minor update to extend kind 30003 in NIP-51 to include the i tag for external identities, as implemented for book reading lists in Open Librarian.
nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr is proposing a NIP that Enable references to commits, files and lines for both nip34 repositories and other git repositories. Useful for code reviews of nip34 patches, the forthcoming nip95 code snippets and referencing specific code more generally.
Notable Projects
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🌐web v4.5.0: * Custom reactions are here! Choose your preferred emoji to react to notes and other content. * Improved profile organization with notes and replies now displayed separately. * Adding the ability to zap notes directly from the notifications center. * Enhanced DM filtering by time, allowing you to view only recent messages or browse further back. * Manual cache clearing from settings to optimize web app performance. * Resolved issue preventing users from removing custom media uploader servers. * Expanded export data, including more relevant details in credential and wallet files. * General bug fixes and performance improvements.
📱mobile v1.6.8: * One tap zap: Send a Lightning Network payment with one tap. * Dms extensive filtering: Use advanced filters to sort or prioritise direct messages efficiently. * Separating replies from notes: Split replies and notes in profiles, adding a tab for easier browsing. * Adding slide to display options: Swipe in notifications to access zap, reply, or DM options quickly. * Custom reactions: Choose from a set of emojis for personalised reactions, beyond standard likes. * App cache manager: Manage and clear app cache to boost performance and save space. * Variety of bugs fixed: Fixed multiple bugs for a more stable and seamless app experience. * General app improvements: Enhanced overall performance, usability, and design across the app.
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xChat v1.0.2-Desktop Beta is now live! * Supports NIP-104 MLS secret chat. * Copy images directly from the clipboard. * The app stays running after closing the window. * Fixed Enter key sending messages immediately on desktop.
Nostur v1.18.2 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
Nostur v1.18.2 bugfix update: * Fixed Follow button sometimes disabled * Fixed account switching reload issue * Fixed custom feeds missing * Fixed live stream banner scroll/swipe issue * Fixed screen turns off while playing video
voca v0.0.6 nostr:npub17h9fn2ny0lycg7kmvxmw6gqdnv2epya9h9excnjw9wvml87nyw8sqy3hpu
This release fine tunes the release process and makes publishing to @Zapstore a lot easier. There are also continuous improvements to initializing the text to speech engine for a faster startup.
WasabiWallet 2.5.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- 3rd Party Providers for Fee & Exchange Rate
- Quality of Life Features
- Backend and Coordinator packaged for Linux
GitPlaza nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks
- Login via nsec
- Activity feed for the people you follow (only issue creation)
- Create issues
- Comment on issues
ZEUS v0.10.1 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.1-beta1 is now available for testing. * NameDesc / bLIP-11 support: add receiver name to invoices * Bug fix: import of QR image from camera roll * Bug fix: Embedded LND: Open Channel: fund max * UI: Add dynamic background/text colors to Android NFC modal
KYCNOT.ME nostr:npub188x98j0r7l2fszeph6j7hj99h8xl07n989pskk5zd69d2fcksetq5mgcqf
- UI/UX - designe a new logo and color palette for kycnot.me.
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services.
- ToS Scrapper: implement a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices.
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services.
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab.
- Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - upgrade the request system. The new form allows you to directly request services or points without any extra steps.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
Long-Form Content Eco
In the past two weeks, more than 569 long-form articles have been published, including over 94 articles on Bitcoin and more than 43 related to Nostr, accounting for 24% of the total content.
These articles about Nostr mainly explore the growing importance of decentralization in communication, identity management, and digital infrastructure. From beginner-friendly guides like Nostr 101 and Getting Started with Primal, to more technical deep dives such as NIP-101e, NIP-95, and tutorials on running Nostr relays as TOR hidden services. Some articles focus on security and privacy—like protecting your Nsec with Amber or using tools such as ProtonMail—while others tackle complex challenges including Sybil attack mitigation and child protection in decentralized environments. There are also cultural and political reflections, such as letters from political prisoners and thoughts on the future of free speech in a post-Twitter world. In addition, the Nostr community shows a strong spirit of experimentation—ranging from agent-to-agent communication through dad jokes, to desktop-like clients, fitness tracking protocols, and Lightning integrations like Work Zaps and Wallet Connect. Together, these pieces showcase a dynamic, resilient, and freedom-driven movement shaping the future of the web.
The Bitcoin articles discuss a wide range of themes—from foundational ideas like "What is Money?" and Bitcoin’s first principles, to practical guides on mining, self-custody, Lightning payments, and privacy tools. Many explore Bitcoin’s role as a hedge against inflation, a form of sovereignty, and a response to fiat fragility. Cultural and economic reflections appear throughout—ranging from using Bitcoin to buy homes in Italy, to hip-hop collaborations, and even personal stories of financial awakening. There's critical analysis of Bitcoin UX, memetics, policy-making, and even war-time monetary history. From node sovereignty to P2P lending, from grassroots adoption to global macro shifts, these articles together portray Bitcoin not just as a currency, but as a cultural movement, a technological evolution, and a lens to reimagine freedom, value, and the future of money.
Thank you, nostr:npub1akzvuyyd79us07m8mtp2ruuha3ylp9757qg46d50rcrkhnx0fs4q2xzr37 nostr:npub1q67f4d7qdja237us384ryeekxsz88lz5kaawrcynwe4hqsnufr6s27up0e nostr:npub1xr8tvnnnr9aqt9vv30vj4vreeq2mk38mlwe7khvhvmzjqlcghh6sr85uum nostr:npub1zmc6qyqdfnllhnzzxr5wpepfpnzcf8q6m3jdveflmgruqvd3qa9sjv7f60 nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0 nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm nostr:npub186k25a5rymtae6q0dmsh4ksen04706eurfst8xc5uzjchwkxdljqe59hv0 and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
-
YakiHonne teamed up with Bitcoin Safari, nostr:npub1w7z986fez3gmjvxy6dd3sku4ndazhxzafjv2lf6aaa26mtl70q6scz4erj nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv nostr:npub1pw778uxwkky3xgq7w3anykdwdw9g46xy8de9mnau0kgwzz375zkq3udv57 and FULAFIA University to successfully host a series of Nostr Workshops, attracting over 200 participants in total. These events introduced the Nostr ecosystem and Bitcoin payments, allowing attendees to explore decentralized technologies through YakiHonne while earning rewards. Participants were encouraged to register and verify their accounts to claim exclusive bonuses—and invite friends to unlock even more benefits.
-
The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar was held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar was hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (a lawyer specializing in Banking, Corporate, and Financial Law). The session aimed to introduce the academic program and explored Bitcoin, the crypto economy, and related legal issues.
-
The monthly Bitcoin Meetup organized by Mi Primer Bitcoin took place on Thursday, March 27 at 7:00 PM at CRAFT Basilea in San Salvador. The event featured Bitcoin education, networking opportunities, live music, and fun extras like merchandise, raffles, and more. It was a vibrant evening dedicated to building community and spreading knowledge around Bitcoin. nostr:npub10zuxk4yhygswdmt5n9mfyeq6lh7gcu5g042tlggrgp8yunl32clqsu5t9r
Here is the upcoming Nostr event that you might want to check out.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. the event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
- Panama Blockchain Week 2025 will take place from April 22 to 24 at the Panama Convention Center in Panama City. As the first large-scale blockchain event in Central America, it aims to position Panama as a leading blockchain financial hub in Latin America. The event features a diverse lineup, including a blockchain conference, Investor’s Night, Web3 gaming experiences, tech exhibitions, and an after-party celebration.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 9967f375:04f9a5e1
2025-04-05 01:33:45
@ 9967f375:04f9a5e1
2025-04-05 01:33:45Así en la Santa Iglesia Metropolitana (en donde se hallaron ochenta y seis Confesores, asignados por el V. Sr. Dean, y Cabildo Sede-Vacante) como en las Parroquiales, y demás, fue grande la concurrencia desde el dia primero (de abril), Sábado ante Dominicam Palmarum, para cumplir con el precepto de la Confesión anual, que se impuso, y mandó en el Máximo Concilio Lateranense, congregado en 1215 por el Señor Inocencio Tercero a que asistieron los Patriarcas de Antioquía, y Jerusalén, cuarenta Arzobispos, cuatrocientos Obispos, doce Abades, ochocientos Prelados inferiores; los Legados de Federico Segundo Emperador de Alemania, de Pedro Emperador de Oriente, de S. Luis Rey de Francia, de Juan Rey de Inglaterra, de D. Enrique Primero Rey de Castilla, D. Alonso Décimo Rey de León, Don Jaime Primero de Aragón, de Don Sancho el Fuerte de Navarra, de Don Alonso Segundo de Portugal, y los Embajadores de los Reyes de Chipre y Jerusalén.
-
 @ a047a37c:dfcb432c
2025-04-05 01:09:09
@ a047a37c:dfcb432c
2025-04-05 01:09:09Chef's notes
Using only top quality dill pickles and juice is highly recommended. Do not cheap out on this ingredient. The better the pickle juice, the better your fried chicken will taste.
Do not let the chicken fry for too long. If the color is not a light golden brown and you let it fry too dark. Then it will not taste right!!!
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 25-30 min
- 🍽️ Servings: 3-4
Ingredients
- 1 1/2 Pounds Chicken Breasts
- 2 Chicken Eggs
- 2 Cups Dill Pickle Juice
- 1/2 Cup Water
- 1 Cup Buttermilk
- 1 Cup Unbleached Flour
- 3 Tablespoons Powdered Sugar
- 1 Teaspoon Paprika
- 1 Teaspoon Garlic Powder
- 1 Teaspoon Cayenne Pepper
- 1 Teaspoon Ground Black Pepper
- 1 Teaspoon Sea Salt
- 1/2 Teaspoon Baking Powder
- 3-4 Cups Peanut Oil
- 3-4 Toasted Brioche Buns (Chicken Sandwiches Only)
- 1 Tablespoon Orange Blossom Honey (Chicken Sandwiches Only)
- 1/4 Cup Sliced Dill Pickles (Chicken Sandwiches Only)
Directions
- There are 2 ways to make The Legendary CFA Fried Chicken. If you want to make it into nuggets then take the chicken breasts and cut them with a kitchen knife into 1 inch cubes. If you want to make it into chicken breast sandwiches, then ensure they are no bigger than 1-1.5 inches thick cut once down the middle. Once you have made your decision and cut them to size. Place the chicken in a large mixing bowl Pour the pickle juice into the bowl, cover it, and place it in the refrigerator to marinate for the next 24 hours.
- Take a large mixing bowl and add in the flour, powdered sugar, paprika, ground black pepper, cayenne pepper, sea salt, garlic powder, and baking powder. Whisk it all together until it is fully mixed and set aside.
- Take another large mixing bowl. Add in the chicken eggs and buttermilk. Then whisk together until it is fully blended and set aside.
- Add 3-4 cups of peanut oil to a large cast iron frying pan, or a deep fryer. Heat the oil to 350F degrees.
- Remove the marinated chicken from the refrigerator. Drain out all of the pickle juice.
- Dredge the chicken in the buttermilk egg mixture until it is fully coated. Coat the chicken in the flour mixture. Then immediately repeat these two steps so it is double coated to ensure maximum crispiness.
- Add the chicken into the peanut oil and allow it to cook evenly until it has reached a light golden brown color and is fully cooked inside.
- Remove the chicken from the pan and place it onto a paper towel to drain the excess oil off. If you made it into chicken nuggets then simply choose your favorite dipping sauce and serve. If you chose to make chicken sandwiches then lightly toast the brioche bun to a golden brown and drizzle on the honey on the inside of the top of the bun. Then add 1 piece of chicken breast per bun on the bottom half, top it off with sliced dill pickles. Complete the sandwich and serve immediately.
-
 @ 6f7c7936:b48a90b1
2025-04-04 20:32:53
@ 6f7c7936:b48a90b1
2025-04-04 20:32:53In a world that celebrates constant movement, expression, and freedom of action, the idea of intentionally placing your hands behind your back—and even keeping them there—may seem counterintuitive. But for some, this posture offers not only physical benefits but also psychological calm, clarity, and even symbolic depth.
Below, we explore why keeping your hands behind your back can be a meaningful act, and how, in certain cases, voluntary restraint can bring unexpected focus and peace.
1. A Posture of Respect and Composure
From military cadets to schoolchildren waiting in line, the image of someone standing with hands behind the back conveys discipline, respect, and attentiveness. It’s a non-verbal signal of being present without demanding attention.
This posture is: - Open and non-confrontational, - Yet composed and intentional, - Signaling a readiness to listen, observe, or follow.
For some, maintaining this position—even privately or in personal rituals—can help anchor them in the moment, especially in situations where too much movement leads to distraction.
2. Gentle Restraint as a Form of Focus
In certain contexts, some people take this concept further: not only placing the hands behind the back but intentionally limiting their movement, sometimes even with gentle bindings (e.g., soft bands, loops, or self-applied ties).
While this may seem unusual, voluntary restraint can serve a purpose. For those who feel: - Overstimulated by too many choices, - Mentally scattered or physically restless, - Emotionally overwhelmed by expectations,
…the act of keeping the hands still and out of use can provide clarity, comfort, and simplicity.
It becomes easier to focus on thoughts, breathing, posture—or simply the act of being. The absence of distraction becomes its own form of freedom.
3. Sensory Regulation and Neurodiverse Experiences
For individuals who are neurodivergent (such as those on the autism spectrum), structured physical routines and reduced movement can support sensory balance and regulation.
Keeping hands behind the back can: - Reduce tactile input or self-stimulatory movements, - Create a predictable, soothing sensation of symmetry, - Increase body awareness and improve posture.
In these cases, restraint isn’t about control or punishment—it’s about reclaiming calm in a world full of overwhelming stimuli.
4. A Symbol of Stillness in Ritual or Reflection
Beyond the physical or sensory aspects, placing the hands behind the back can carry symbolic weight. It can be: - A gesture of humility, - A sign of inner stillness, - A choice to be quiet, observant, or connected to something larger.
In personal practices, some individuals incorporate this position into meditation, silent walks, or reflection exercises. Others may even choose light binding—such as a soft scarf or wrap—not as an act of submission, but as a tool for mindfulness, reminding them to pause, breathe, and stay grounded.
5. The Importance of Intent and Consent
It’s crucial to note: context and intent matter. The experience of placing hands behind the back—especially when restraint is involved—should always be voluntary, safe, and self-directed.
This isn’t about force or external control. It’s about choosing to explore stillness, structure, or personal rituals that bring meaning and calm.
When approached mindfully, this simple act can become a quiet expression of focus, discipline, and peace.
Conclusion: A Small Gesture, a Deep Effect
In an age of constant motion and noise, choosing to stand still—with your hands behind your back—can be a powerful form of presence.
Whether you’re seeking: - better posture, - sensory clarity, - emotional grounding, - or symbolic stillness,
…this gesture offers a moment to reconnect—with your body, your breath, and yourself.
It’s not about limitation.
It’s about choosing space within boundaries—and discovering what stillness can teach you. -
 @ da18e986:3a0d9851
2025-04-04 20:25:50
@ da18e986:3a0d9851
2025-04-04 20:25:50I'm making this tutorial for myself, as I plan to write many wiki pages describing DVM kinds, as a resource for DVMDash.
Wiki pages on Nostr are written using AsciiDoc. If you don't know ascii doc, get an LLM (like https://duck.ai) to help you format into the right syntax.
Here's the test wiki page I'm going to write:
``` = Simple AsciiDoc Demo
This is a simple demonstration of AsciiDoc syntax for testing purposes.
== Features
AsciiDoc offers many formatting options that are easy to use.
- Easy to learn
- Supports rich text formatting
- Can include code snippets
- Works great for documentation
[source,json]
{ "name": "Test", "version": "1.0", "active": true }
```
We're going to use nak to publish it
First, install
nakif you haven't alreadygo install github.com/fiatjaf/nak@latestNote: if you don't use Go a lot, you may need to first install it and then add it to your path so the
nakcommand is recognized by the terminal```
this is how to add it to your path on mac if using zsh
echo 'export PATH=$PATH:$(go env GOPATH)/bin' >> ~/.zshrc ```
And here's how to sign and publish this event with nak.
First, if you want to use your own nostr sec key, you can set the env variable to it and nak will use that if no secret key is specified
```
replace with your full secret key
export NOSTR_SECRET_KEY="nsec1zcdn..." ```
Now to sign and publish the event:
Note: inner double quotes need to be escaped with a
\before them in order to keep the formatting correct, because we're doing this in the terminalnak event -k 30818 -d "dvm-wiki-page-test" -t 'title=dvm wiki page test' -c "= Simple AsciiDoc Demo\n\nThis is a simple demonstration of AsciiDoc syntax for testing purposes. \n\n== Features\n\nAsciiDoc offers many formatting options that are easy to use. \n\n* Easy to learn \n* Supports rich text formatting \n* Can include code snippets \n* Works great for documentation \n\n[source,json] \n---- \n{ \"name\": \"Test\", \"version\": \"1.0\", \"active\": true } \n----" wss://relay.primal.net wss://relay.damus.io wss://relay.wikifreedia.xyzYou've now published your first wiki page! If done correctly, it will show up on wikistr.com, like mine did here: https://wikistr.com/dvm-wiki-page-test*da18e9860040f3bf493876fc16b1a912ae5a6f6fa8d5159c3de2b8233a0d9851
and on wikifreedia.xyz https://wikifreedia.xyz/dvm-wiki-page-test/dustind@dtdannen.github.io
-
 @ 98468676:3a02caf5
2025-04-04 20:21:10
@ 98468676:3a02caf5
2025-04-04 20:21:10I'm making this tutorial for myself, as I plan to write many wiki pages describing DVM kinds, as a resource for DVMDash.
Wiki pages on Nostr are written using AsciiDoc. If you don't know ascii doc, get an LLM (like https://duck.ai) to help you format into the right syntax.
Here's the test wiki page I'm going to write:
``` = Simple AsciiDoc Demo
This is a simple demonstration of AsciiDoc syntax for testing purposes.
== Features
AsciiDoc offers many formatting options that are easy to use.
- Easy to learn
- Supports rich text formatting
- Can include code snippets
- Works great for documentation
[source,json]
{ "name": "Test", "version": "1.0", "active": true }
```
We're going to use nak to publish it
First, install
nakif you haven't alreadygo install github.com/fiatjaf/nak@latestNote: if you don't use Go a lot, you may need to first install it and then add it to your path so the
nakcommand is recognized by the terminal```
this is how to add it to your path on mac if using zsh
echo 'export PATH=$PATH:$(go env GOPATH)/bin' >> ~/.zshrc ```
And here's how to sign and publish this event with nak.
First, if you want to use your own nostr sec key, you can set the env variable to it and nak will use that if no secret key is specified
```
replace with your full secret key
export NOSTR_SECRET_KEY="nsec1zcdn..." ```
Now to sign and publish the event:
Note: inner double quotes need to be escaped with a
\before them in order to keep the formatting correct, because we're doing this in the terminalnak event -k 30818 -d "dvm-wiki-page-test" -t 'title=dvm wiki page test' -c "= Simple AsciiDoc Demo\n\nThis is a simple demonstration of AsciiDoc syntax for testing purposes. \n\n== Features\n\nAsciiDoc offers many formatting options that are easy to use. \n\n* Easy to learn \n* Supports rich text formatting \n* Can include code snippets \n* Works great for documentation \n\n[source,json] \n---- \n{ \"name\": \"Test\", \"version\": \"1.0\", \"active\": true } \n----" wss://relay.primal.net wss://relay.damus.io wss://relay.wikifreedia.xyzYou've now published your first wiki page! If done correctly, it will show up on wikistr.com, like mine did here: https://wikistr.com/dvm-wiki-page-test*da18e9860040f3bf493876fc16b1a912ae5a6f6fa8d5159c3de2b8233a0d9851
and on wikifreedia.xyz https://wikifreedia.xyz/dvm-wiki-page-test/dustind@dtdannen.github.io
-
 @ d5c3d063:4d1159b3
2025-04-01 04:20:50
@ d5c3d063:4d1159b3
2025-04-01 04:20:50“วิธีที่ดีที่สุดในการทำลายทุนนิยมคือทำลายค่าเงิน” Lenin Was Right
ประโยคนี้ไม่ใช่แค่คำปลุกระดมของนักปฏิวัติ แต่มันเป็นเหมือนสัญญาณเตือนล่วงหน้า ที่คนส่วนใหญ่ไม่สนใจ จนวันหนึ่งมันก็เกิดขึ้นจริง แบบเงียบ ๆ โดยไม่มีใครทันตั้งตัว
Henry Hazlitt เขียนบทความนี้ไว้ตั้งแต่ปี 1947 เขาไม่เพียงบอกว่าเลนินพูดถูก แต่เขาแฉว่าโลกทั้งใบ “กำลังทำตามแผนของเลนิน” แบบไม่รู้ตัว
ตอนนั้นรัฐบาลหลายประเทศ โดยเฉพาะในยุโรป พิมพ์เงินออกมาใช้มหาศาล โดยอ้างว่าสงครามบีบบังคับให้ต้องทำแบบนั้น แต่ปัญหาคือ...พอสงครามจบในปี 1945 แล้ว รัฐกลับไม่หยุดพิมพ์เงิน ยังทำเหมือนอยู่ในภาวะฉุกเฉิน
เหมือนที่ อ. #SaifedeanAmmous พูดไว้ในหนังสือ #TheBitcoinStandard ว่าเวลารัฐอยากพิมพ์เงินแบบไม่ต้องรับผิดชอบ ก็แค่เอาสงครามมาอ้าง พอพูดว่า “เพื่อความมั่นคง” หรือ “เพื่อชาติ” เท่านั้นแหละ ทุกอย่างก็ดูเป็นเรื่องจำเป็นขึ้นมาทันที แล้วไม่มีใครกล้าถามว่าจริง ๆ แล้วเงินมันมาจากไหน
พอเงินเฟ้อมันแรง ของก็แพงขึ้น แต่รัฐไม่ยอมรับหรอกว่าที่ของแพงเพราะตัวเองพิมพ์เงินออกมาเยอะเกิน แต่กลับไปโทษพ่อค้า โทษคนทำธุรกิจ ว่าขายของแพง ค้ากำไรเกินควรซะงั้น
Hazlitt เขาเตือนว่า...รัฐกำลังทำให้คนเกลียดพ่อค้า เกลียดเจ้าของธุรกิจ เพื่อให้ดูเหมือนว่าตัวเองมีเหตุผลที่จะเข้ามาคุมเศรษฐกิจ ซึ่งที่น่ากลัวคือ... มันไม่ได้เกิดจากความไม่รู้ แต่มันเกิดจาก “ระบบ” ที่เปิดช่องให้เขาทำแบบนี้ได้เลย แบบไม่ต้องรับผิดชอบอะไรทั้งนั้น
ตรงนี้แหละที่ Hazlitt เอาคำพูดของ John Maynard Keynes เข้ามาเสริม เพราะแม้แต่ Keynes ก็ยังเคยเตือนไว้ในหนังสือ The Economic Consequences of the Peace ว่า “เงินเฟ้อ” มันเหมือนเครื่องมือเงียบ ๆ ที่จะค่อย ๆ ทำลายระบบเศรษฐกิจ โดยที่คนส่วนใหญ่ไม่รู้ตัว
Hazlitt เขาเป็น "สายวิจารณ์" Keynes ตัวพ่อเลยนะ เขาเขียนหนังสือ The Failure of the New Economics ที่ไล่รื้อแนวคิดของ Keynes แบบ “ตา-ต่อ-ตา หน้า-ต่อ-หน้า” กับหนังสือ The General Theory ของ Keynes เลยนะ
แต่พอมาในบทความนี้...Hazlitt กลับหยิบคำพูดของ Keynes มาใช้อย่างเต็มใจ เพราะมันตรงเกินไปที่จะมองข้ามได้ ว่าแม้แต่ #Keynes เองยังเคยเตือนเลยว่า “การทำลายค่าเงิน” คืออาวุธเงียบ ที่ใช้ทำลายระบบทุนนิยมได้อย่างแนบเนียนที่สุด . . พออ่านแล้วแบบ…แม้แต่คนที่เราคิดว่าเชียร์ฝั่งรัฐ ยังเตือนเรื่องนี้ไว้ แล้วเราจะยังเฉยอยู่ได้ไง
คือถ้าเงินมันถูกทำให้ด้อยค่าลงเรื่อย ๆ วันนึงมันจะพังแบบเงียบ ๆ จนคนไม่รู้ตัวเลย คนทั่วไปจะรู้แค่ว่าของมันแพงขึ้น แต่ไม่มีใครเห็น ว่าจริง ๆ แล้ว เงินที่เราใช้มันเริ่มไม่มีเสถียรภาพ และไม่มั่นคงอีกต่อไปแล้ว
แล้วถ้ามองตัวเลขนี่ยิ่งช็อก ระหว่างปี 1939 ถึง 1947 ในเวลาแค่ 8 ปี ปริมาณเงินในระบบของสหรัฐฯ เพิ่มจาก 33,000 ล้านดอลลารเป็น 108,500 ล้านดอลลาร์ พูดง่าย ๆ คือ คูณสาม (ช่วงสงครามโลกครั้งที่ 2)
Hazlitt พูดแบบตรง ๆ เลยว่า ปัญหาที่เกิดขึ้น มันไม่ใช่เพราะเศรษฐกิจโตหรือคนรวยขึ้นนะ มันเกิดจากการที่รัฐเพิ่มปริมาณเงินในระบบเร็วเกินไป เมื่อเงินในตลาดเลยเยอะขึ้น แต่ของที่มีให้ซื้อไม่ได้เยอะขึ้นตาม เมื่อเงินไหลเวียนมากขึ้น โดยที่ของยังมีเท่าเดิม ราคาของก็เลยพุ่ง
ทีนี้พอของขึ้นราคา รัฐบาลกลับไม่ยอมรับว่าเป็นเพราะเขาพิมพ์เงิน แต่ไปเลือกวิธีแก้แบบง่าย ๆ แต่สร้างปัญหาในระยะยาว เช่น สั่งห้ามขึ้นราคา กดดันคนทำธุรกิจให้แบกต้นทุนไว้ หรือไม่ก็ล็อกค่าเงิน เหมือนไม่มีอะไรเกิดขึ้น
หลังจากนั้น เศรษฐกิจยุโรปก็เริ่มพัง ผู้ผลิตเจอต้นทุนบาน การค้าระหว่างประเทศก็รวน สุดท้ายก็ต้องพึ่งดอลลาร์จากอเมริกา (Marshall Aid) มาช่วยอุ้ม เหมือนพิมพ์เงินของตัวเองจนระบบรวน แล้วไปขอเงินจากฝั่งที่พิมพ์ได้มากกว่าอีกที
นี่แหละจุดเริ่มของ “วิกฤตเศรษฐกิจโลกหลังสงคราม” ที่จริง ๆ แล้ว...ก็แค่เรื่องของการพิมพ์เงินล้วน ๆ . . แต่นั้นมันเป็นเรื่องเกิดขึ้นเมื่อปี 1947 นะ...แล้ววันนี้ล่ะ
ล่าสุด ปี 2020 ก่อนโควิด ระดับ M2 money supply ของสหรัฐอยู่ราว ๆ 15 ล้านล้านดอลลาร์ แค่ไม่กี่ปีต่อมา มันทะลุไปถึง 21 ล้านล้าน ในเวลาไม่ถึง 3 ปีเงินเพิ่มขึ้นในระบบเศรษฐกิจกว่า 6 ล้านล้านดอลลาร์
แล้วของก็แพงขึ้น ค่าแรงวิ่งตามไม่ทัน แต่แทนที่รัฐจะบอกว่า “เราพิมพ์เงินมากไป” ก็ไปเล่นมุกเดิม โทษตลาด โทษนายทุน โทษธุรกิจ (บ้างก็โทษโลกร้อน)
สุดท้ายก็จะมีคนบางกลุ่มเชียร์ให้ “ควบคุมราคา” อีก มันคือ loop เดิม ที่ #Hazlitt เคยเตือนไว้ เมื่อเกือบ 80 ปีก่อน.. . . สิ่งที่ซุปเห็นชัดเจนที่สุดจากบทความนี้คือ... เกมนี้มันไม่มีใครหยุดได้เลย ถ้าคุณยังถือเงินที่รัฐพิมพ์ได้
เพราะตราบใดที่ยังมีคนสั่งพิมพ์เงินได้ตามใจ ระบบเศรษฐกิจก็จะปั่นป่วนซ้ำไปซ้ำมา ของก็จะแพงขึ้นเรื่อย ๆ แบบไม่มีจุดจบ
คุณก็จะต้องเหนื่อยทำงานมากขึ้น แต่ซื้อได้น้อยลง แล้วคุณก็จะโทษตัวเอง ว่ายังขยันไม่มากพอ ทั้ง ๆ ที่คุณทำงาน 4-5 อย่าง
.
เลนิน พูดถูก ถ้าจะทำลายทุนนิยม ก็แค่ทำลายค่าเงิน ฟังดูแรงเนอะ...แต่เรื่องนี้มันไม่ใช่แค่ทฤษฎีแล้ว เพราะเรากำลังเห็น ว่ามันกำลังเกิดขึ้นอยู่จริง ๆ
แต่วันนี้ เราเลือกที่จะไม่อยู่ในเกมที่พังซ้ำๆ ได้แล้ว
เพราะเรามี “ทางออก” อยู่ตรงหน้า บิตคอยน์ ไม่ใช่อะไรที่ทุกคนจะเข้าใจมันได้ทันที แต่มันคือ “เงิน” ที่ไม่มีใครพิมพ์เพิ่มได้ตามใจ ไม่มีใครมานั่งกดปุ่มสร้างมันขึ้นมาได้ง่าย ๆ ไม่มีใครเปลี่ยนกติกากลางเกมได้ และไม่มีใครแทรกแซงนโยบายของมันได้
สิ่งเดียวที่ #บิตคอยน์ บอกเราตรง ๆ ก็คือ “ความขาดแคลน” ไม่ใช่ปัญหา...
สิ่งที่ Hazlitt เตือนเมื่ออดีต คือกับดักของเงินไม่มีขอบเขต
สิ่งที่ #Bitcoin เสนอ คือขอบเขตที่ทำให้ “มูลค่า” กลับมามีความหมาย
[Newsweek column from September 22, 1947, and reprinted in Business Tides: The Newsweek Era of Henry Hazlitt.] https://mises.org/mises-wire/lenin-was-right
Siamstr
-
 @ ac58bbcc:7d9754d8
2025-04-04 20:13:12
@ ac58bbcc:7d9754d8
2025-04-04 20:13:12Lovely seeing you here. Hello there, and welcome to our very first post! We’re the team behind Math Success by DMTI, and we’re thrilled for this journey with you. If you’re a teacher, parent, or just someone who cares about kids and learning, you’ve probably noticed something: math education isn’t working well for most everyone. Too many students dread it, too many teachers feel stuck, and too many classrooms are stuck in a cycle of rote memorization that leaves most everyone uninspired.
We’re here to change that—and that’s why we’ve built Math Success by DMTI, the leading K-6 Math Education Program.
The Problem: Math Isn’t Adding Up Let’s start with the elephant in the room. Math education often misses the mark. Kids are taught to memorize times tables or follow steps without understanding why they work. It’s like handing someone a recipe without teaching them how to cook—they might make the dish, but they won’t know what to do when the ingredients change. Studies show U.S. students lag behind many peers globally in math, and the gap widens as they move through school. Why? Because we’ve prioritized procedures over meaning, drills over discovery, and compliance over curiosity.
The result? Students who see math as a chore, not a chance to explore. Teachers, meanwhile, are stretched thin—juggling standards, testing pressures, and outdated methods that don’t spark joy or learning. It’s no wonder so many kids say, “I’m just not a math person.” But here’s the thing: we believe everyone can be a math person—if we teach it right.
Our Solution: Math Success by DMTI That’s where Math Success by DMTI comes in. Born from the Developing Mathematical Thinking Institute and over 40 years of research, our program isn’t just another curriculum—it’s a rethink of how math should feel and function in the classroom. We’ve seen the data: classrooms using our approach see an average 35% jump in achievement. But more than that, they see kids who love math and teachers who can’t wait to teach it.
So, how do we do it? It starts with our Developing Mathematical Thinking framework—a five-part recipe for success:
Listen to Kids & Build on Their Ideas: We build on what students already know, making math personal and relevant.
Speak the Right Language: We use the structural words unit, compose, decompose, iterate, partition, and equal to help kids communicate and connect to math across topics.
Understand First, Calculate Later: Concepts come before procedures, so kids grasp the “why” before the “how.”
Models and real-world connections: From blocks to drawings to numbers, we use models to make math tangible and fun while helping connect math to real life.
Embrace Misconceptions & Mistakes: Missteps aren’t failures but chances to learn and grow.
This isn’t the math you grew up with. It’s active, engaging, and built to stick. Teachers tell us it’s a game-changer—“I have never loved teaching math as much as I do now; math has come alive in my classroom. My students are further along now than any class I’ve ever taught before.” one said, “I could see the light bulbs going off like never before, and they’re excited!” Kids tell us, “Math is fun now!” And the numbers back it up: that 35% boost isn’t just a stat—it’s a sign of deeper understanding and real confidence.
Why it matters Math isn’t just about numbers; it’s about thinking, solving problems, and opening doors. When kids succeed in math, they gain skills for life—whether they’re headed to STEM careers or just figuring out their budget. But beyond that, we want them to love it. To see math as a playground, not a prison. That’s our mission: successful learning and a genuine love for mathematics, one classroom at a time.
What’s Next? This Substack is our space to share that mission with you. Expect stories from teachers and students, dives into our framework, tips for bringing math to life, and updates on our free courses (yep, free!). We’re partnering with educators like you to make this happen—because we can turn math education around together.
So, stick with us. Subscribe below, drop a comment with your thoughts, and start building a world where math adds joy, not stress. Welcome to Math Success by DMTI—let’s make math work for everyone.
-
 @ 907e4623:f40ff12a
2025-04-04 19:13:14
@ 907e4623:f40ff12a
2025-04-04 19:13:14gm.
i'm doing my job as I can.
You know, it's not easy to be a founder.
I wanted to give up so many times.But give up is not an option, I need to improve and move forward.
- Difficulties
- Doubt
- Self interest and responsabilities
I was stuck building this: https://afk-community.xyz
Chasing my Product Market Fit, solving the problems I work on...
Step by step, I'm gonna make it.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ f3328521:a00ee32a
2025-03-31 00:25:36
@ f3328521:a00ee32a
2025-03-31 00:25:36This paper was originaly writen in early November 2024 as a proposal for an international Muslim entrepreneurial initiative. It was first publish on NOSTR 27 November 2024 as part 1 of a 4 part series of essays. Last updated/revised: 30 March 2025.
The lament of the Ummah for the past century has been the downfall of the Khalifate. With the genocide in occupied Palestine over the past year and now escalations in Lebanon as well, this concern is at the forefront of a Muslim’s mind. In our tradition, when one part of the Ummah suffers, all believers are affected and share in that suffering. The Ummah today has minimal sovereignty at best. It lacks a Khalifate. It is spiritually weakened due to those not practicing and fulfilling their duties and responsibilities. And, as we will address in this paper, it has no real economic power. In our current monetary system, it is nearly impossible to avoid the malevolence of riba (interest) – one of the worst sins. However, with bitcoin there is an opportunity to alleviate this collective suffering and reclaim economic sovereignty.
Since it’s invention 15 years ago, bitcoin has risen to achieve a top 10 market cap ranking as a global asset (currently valued at $1.8 trillion USD). Institutional investors are moving full swing to embrace bitcoin in their portfolios. Recent proposals in Kazan hint that BRICS may even be utilizing bitcoin as part of their new payments system. State actors will be joining soon. With only about 1 million bitcoins left to be mined we need to aim to get as much of those remaining coins as possible into the wallets of Muslims over the next decade. Now is the time to onboard the Ummah. This paper presents Bitcoin as the best option for future economic sovereignty of the Ummah and proposes steps needed to generate a collective waqf of an initial 0.1%-0.5% chain dominance to safeguard a revived Khalifate.
Money is the protocol that facilitates economic coordination to help the development and advancement of civilization. Throughout history money has existed as cattle, seashells, salt, beads, stones, precious metals. Money develops naturally and spontaneously; it is not the invention of the state (although it at times is legislated by states). Money exists marginally, not by fiat. During the past few millenniums, gold and silver were optimally used by most advanced civilizations due to strong properties such as divisibility, durability, fungibility, portability, scarcity, and verifiability. Paper money modernized usability through attempts to enhance portability, divisibility, and verifiability. However, all these monetary properties are digitized today. And with the increase of fractional-reserve banking over the past two centuries, riba is now the de facto foundation of the consensus reserve currency – the USD.
This reserve currency itself is backed by the central banking organ of the treasury bond markets which are essentially government issued debt. Treasurey bonds opperate by manipulating the money supply arbitrarily with the purpose of targeting a set interest rate – injecting or liquidating money into the supply by fiat to control intrest yeilds. At its root, the current global monetary order depends entirely on riba to work. One need not list the terrible results of riba as Muslims know well its harshness. As Lyn Alden wonderful states in her book, Broken Money, “Everything is a claim of a claim of a claim, reliant on perpetual motion and continual growth to not collapse”. Eventual collapse is inevitable, and Muslims need to be aware and prepared for this reality.
The status quo among Muslims has been to search for “shariah compliance”. However, fatwa regarding compliance as well as the current Islamic Banking scene still operate under the same fiat protocol which make them involved in the creation of money through riba. Obfuscation of this riba through contractum trinius or "shariah compliant" yields (which are benchmarked to interest rates) is simply an attempt to replicate conventional banking, just with a “halal” label. Fortunately, with the advent of the digital age we now have other monetary options available.
Experiments and theories with digital money date back to the 1980s. In the 1990s we saw the dot com era with the coming online of the current fiat system, and in 2008 Satoshi Nakamoto released Bitcoin to the world. We have been in the crypto era ever since. Without diving into the technical aspects of Bitcoin, it is simply a P2P e-cash that is cryptographically stored in digital wallets and secured via a decentralized blockchain ledger. For Muslims, it is essential to grasp that Bitcoin is a new type of money (not just an investment vehicle or payment application) that possesses “anti-riba” properties.
Bitcoin has a fixed supply cap of 21 million, meaning there will only ever be 21 million Bitcoin (BTC). Anyone with a cheap laptop or computer with an internet connection can participate on the Bitcoin network to verify this supply cap. This may seem like an inadequate supply for global adoption, but each bitcoin is highly divisible into smaller units (1 btc = 100,000,000 satoshis or sats). Bitcoins are created (or mined) from the processing of transactions on the blockchain which involves expending energy in the real world (via CPU power) and providing proof that this work was done.
In contrast, with the riba-based fiat system, central banks need to issue debt instruments, either in the form of buying treasuries or through issuing a bond. Individual banks are supposed to be irresponsibly leveraged and are rewarded for making risky loans. With Bitcoin, there is a hard cap of 21 million, and there is no central authority that can change numbers on a database to create more money or manipulate interest rates. Under a Bitcoin standard, money is verifiably stored on a ledger and is not loaned to create more money with interest. Absolute scarcity drives saving rather than spending, but with increasing purchasing power from the exponentially increasing demand also comes the desire to use that power and increased monetary economization. With bitcoin you are your own bank, and bitcoin becomes for your enemies as much as it is for your friends. Bitcoin ultimately provides a clean foundation for a stable money that can be used by muslims and should be the currency for a future Khalifate.
The 2024 American presidential election has perhaps shown more clearly than ever the lack of politcal power that American Muslims have as well as the dire need for them to attain political influence. Political power comes largely through economic sovereignty, military might, and media distribution. Just a quick gloss of Muslim countries and Turkey & Egypt seem to have decent militaries but failing economies. GCC states have good economies but weak militaries. Iran uniquely has survived sanctions for decades and despite this weakened economic status has still been able to make military gains. Although any success from its path is yet to be seen it is important to note that Iran is the only country that has been able to put up any clear resistance to western powers. This is just a noteworthy observation and as this paper is limited to economic issues, full analysis of media and miliary issues must be left for other writings.
It would also be worthy to note that BDS movements (Boycott, Divest & Sanction) in solidarity with Palestine should continue to be championed. Over the past year they have undoubtedly contributed to PEP stock sinking 2.25% and MCD struggling to break even. SBUX and KO on the other hand, despite active boycott campaigns, remain up 3.5% & 10.6% respectively. But some thought must be put into why the focus of these boycotts has been on snack foods that are a luxury item. Should we not instead be focusing attention on advanced tech weaponry? MSFT is up 9.78%, GOOG up 23.5%, AMZN up 30%, and META up 61%! It has been well documented this past year how most of the major tech companies have contracts with occupying entity and are using the current genocide as a testing ground for AI. There is no justification for AI being a good for humanity when it comes at the expense of the lives of our brothers in Palestine. However, most “sharia compliant” investment guides still list these companies among their top recommendations for Muslims to include in their portfolios.
As has already been argued, by investing in fiat-based organization, businesses, ETFs, and mutual funds we are not addressing the root cause of riba. We are either not creating truly halal capital, are abusing the capital that Allah has entrusted to us or are significantly missing blessings that Allah wants to give us in the capital that we have. If we are following the imperative to attempt to make our wealth as “riba-free” as possible, then the first step must be to get off zero bitcoin
Here again, the situation in Palestine becomes a good example. All Palestinians suffer from inflation from using the Israeli Shekel, a fiat currency. Palestinians are limited in ways to receive remittances and are shrouded in sanctions. No CashApp, PayPal, Venmo. Western Union takes huge cuts and sometimes has confiscated funds. Bank wires do this too and here the government sanctions nearly always get in the way. However, Palestinians can use bitcoin which is un-censorable. Israel cannot stop or change the bitcoin protocol. Youssef Mahmoud, a former taxi driver, has been running Bitcoin For Palestine as a way for anyone to make a bitcoin donation in support of children in Gaza. Over 1.6 BTC has been donated so far, an equivalent of about $149,000 USD based on current valuation. This has provided a steady supply of funds for the necessary food, clothing, and medication for those most in need of aid (Note: due to recent updates in Gaza, Bitcoin For Palestine is no longer endorsed by the author of this paper. However, it remains an example of how the Bitcoin network opperates through heavy sanctions and war).
Over in one of the poorest countries in the world, a self-managed orphanage is providing a home to 77 children without the patronage of any charity organization. Orphans Of Uganda receives significant funding through bitcoin donations. In 2023 and 2024 Muslims ran Ramadan campaigns that saw the equivalent of $14,000 USD flow into the orphanage’s bitcoin wallet. This funding enabled them to purchase food, clothing, medical supplies and treatment, school costs, and other necessities. Many who started donating during the 2023 campaign also have continued providing monthly donations which has been crucial for maintaining the well-being of the children.
According to the Muslim Philanthropy Initiative, Muslim Americans give an estimated $1.8 billion in zakat donations every year with the average household donating $2070 anually. Now imagine if international zakat organizations like Launchgood or Islamic Relief enabled the option to donate bitcoin. So much could be saved by using an open, instant, permissionless, and practically feeless way to send zakat or sadaqah all over the world! Most zakat organizations are sleeping on or simply unaware of this revolutionary technology.
Studies by institutions like Fidelity and Yale have shown that adding even a 1% to 5% bitcoin allocation to a traditional 60/40 stock-bond portfolio significantly enhances returns. Over the past decade, a 5% bitcoin allocation in such a portfolio has increased returns by over 3x without a substantial increase in risk or volatility. If American Muslims, who are currently a demographic estimated at 2.5 million, were to only allocate 5% ($270 million) of their annual zakat to bitcoin donations, that would eventually become worth $14.8 billion at the end of a decade. Keep in mind this rate being proposed here is gathered from American Muslim zakat data (a financially privileged population, but one that only accounts for 0.04% of the Ummah) and that it is well established that Muslims donate in sadaqa as well. Even with a more conservative rate of a 1% allocation you would still be looking at nearly $52 million being liquidated out of fiat and into bitcoin annually. However, if the goal is to help Muslims hit at least 0.1% chain dominance in the next decade then a target benchmark of a 3% annual zakat allocation will be necessary.
Islamic financial institutions will be late to the game when it comes to bitcoin adoption. They will likely hesitate for another 2-4 years out of abundance of regulatory caution and the persuasion to be reactive rather than proactive. It is up to us on the margin to lead in this regard. Bitcoin was designed to be peer-2-peer, so a grassroots Muslim bitcoiner movement is what is needed. Educational grants through organizations like Bitcoin Majlis should be funded with endowments. Local Muslim bitcoin meetups must form around community mosques and Islamic 3rd spaces. Networked together, each community would be like decentralized nodes that could function as a seed-holder for a multi-sig waqf that can circulate wealth to those that need it, giving the poorer a real opportunity to level up and contribute to societ and demonstrating why zakat is superior to interest.
Organic, marginal organizing must be the foundation to building sovereignty within the Ummah. Sovereignty starts at the individual level and not just for all spiritual devotion, but for economics as well. Physical sovereignty is in the individual human choice and action of the Muslim. It is the direct responsibility placed upon insan when the trust of khalifa was placed upon him. Sovereignty is the hallmark of our covenant, we must embrace our right to self-determination and secede from a monetary policy of riba back toward that which is pure.
"Whatever loans you give, seeking interest at the expense of people’s wealth will not increase with Allah. But whatever charity you give, seeking the pleasure of Allah—it is they whose reward will be multiplied." (Quran 30:39)
FAQ
Why does bitcoin have any value?
Unlike stocks, bonds, real-estate or even commodities such as oil and wheat, bitcoins cannot be valued using standard discounted cash-flow analysis or by demand for their use in the production of higher order goods. Bitcoins fall into an entirely different category of goods, known as monetary goods, whose value is set game-theoretically. I.e., each market participant values the good based on their appraisal of whether and how much other participants will value it. The truth is that the notions of “cheap” and “expensive” are essentially meaningless in reference to monetary goods. The price of a monetary good is not a reflection of its cash flow or how useful it is but, rather, is a measure of how widely adopted it has become for the various roles of money.
Is crypto-currency halal?
It is important to note that this paper argues in favor of Bitcoin, not “Crypto” because all other crypto coins are simply attempts a re-introducing fiat money-creation in digital space. Since they fail to address the root cause error of riba they will ultimately be either destroyed by governments or governments will evolve to embrace them in attempts to modernize their current fiat system. To highlight this, one can call it “bit-power” rather than “bit-coin” and see that there is more at play here with bitcoin than current systems contain. Mufti Faraz Adam’s fatwa from 2017 regarding cryptocurrency adaqately addresses general permissibility. However, bitcoin has evolved much since then and is on track to achieve global recognition as money in the next few years. It is also vital to note that monetary policy is understood by governments as a vehicle for sanctions and a tool in a political war-chest. Bitcoin evolves beyond this as at its backing is literal energy from CPU mining that goes beyond kinetic power projection limitations into cyberspace. For more on theories of bitcoin’s potential as a novel weapons technology see Jason Lowery’s book Softwar.
What about market volatility?
Since the inception of the first exchange traded price in 2010, the bitcoin market has witnessed five major Gartner hype cycles. It is worth observing that the rise in bitcoin’s price during hype cycles is largely correlated with an increase in liquidity and the ease with which investors could purchase bitcoins. Although it is impossible to predict the exact magnitude of the current hype cycle, it would be reasonable to conjecture that the current cycle reaches its zenith in the range of $115,000 to $170,000. Bitcoin’s final Gartner hype cycle will begin when nation-states start accumulating it as a part of their foreign currency reserves. As private sector interest increases the capitalization of Bitcoin has exceeded 1 trillion dollars which is generally considered the threshold at which an assest becomes liquid enough for most states to enter the market. In fact, El Salvador is already on board.
-
 @ 7d33ba57:1b82db35
2025-04-04 18:13:02
@ 7d33ba57:1b82db35
2025-04-04 18:13:02Edinburgh is a city where ancient history and modern culture meet in the most atmospheric way. From its dramatic castle perched on a volcanic rock to narrow medieval alleys, vibrant festivals, and cozy pubs, Scotland’s capital is a must-visit for travelers seeking both beauty and depth. It’s a city that feels like stepping into a storybook—with a few ghost tales thrown in for good measure.
🏛️ Top Things to See & Do in Edinburgh
1️⃣ Edinburgh Castle
- Iconic and steeped in royal history
- See the Crown Jewels, the Stone of Destiny, and sweeping views over the city
- Don’t miss the 1 o’clock cannon fire!
2️⃣ Walk the Royal Mile
- The main street running from Edinburgh Castle to Holyrood Palace
- Lined with shops, historic closes (alleyways), churches, and pubs
- Pop into St Giles’ Cathedral and explore the Writer’s Museum
3️⃣ Holyrood Palace & Arthur’s Seat
- The Queen’s official Scottish residence 👑
- Hike up Arthur’s Seat, an ancient volcano, for amazing panoramic views of Edinburgh and beyond
4️⃣ Explore the Old Town & New Town
- Old Town: Medieval, moody, atmospheric
- New Town: Elegant Georgian streets and great shopping on Princes Street
- Don’t miss Victoria Street – rumored inspiration for Harry Potter’s Diagon Alley ✨
5️⃣ Museums & Culture
- National Museum of Scotland – interactive and family-friendly
- Scottish National Gallery – features art by Turner, Van Gogh, and more
- Camera Obscura & World of Illusions – quirky and fun near the castle
6️⃣ Edinburgh’s Underground & Ghost Tours
- Explore the hidden vaults under the city
- Join a ghost tour or learn about Edinburgh’s dark past, including grave robbers and plague victims
7️⃣ Festivals Galore 🎭
- Edinburgh Festival Fringe (August) – The largest arts festival in the world
- Edinburgh International Festival, Book Festival, and Hogmanay (New Year) celebrations
🍽️ What to Eat in Edinburgh
- Haggis, neeps & tatties – A classic, surprisingly tasty Scottish dish
- Scottish salmon, Cullen skink (smoky fish soup)
- Afternoon tea or Scottish whisky tasting in a historic bar 🥃
- Try local spots like The Witchery, Makars Gourmet Mash Bar, or The Scran & Scallie
🚶♀️ Tips for Visiting Edinburgh
✅ Wear comfy shoes – cobblestones and hills are part of the charm
✅ Be ready for 4 seasons in a day – pack layers and a rain jacket ☁️☀️🌧️
✅ Book ahead in summer – especially during August festivals
✅ Take a day trip to Rosslyn Chapel, the Highlands, or Stirling Castle for more Scottish beauty
✅ Consider the Edinburgh City Pass if planning to visit many attractions -
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ 2e8970de:63345c7a
2025-04-04 17:12:41
@ 2e8970de:63345c7a
2025-04-04 17:12:41Recently I shared a substack post that argued "DOGE is About Sex" https://stacker.news/items/921208 the main premise being how Elon & Trumps economic goals were to make women more economically desperate such that women are more nudged to settle for mediocre and lonely men.
I do not think that tells the whole story about MAGA economics. Neither does the author CHH, I think.
But I think she's onto something. Here are 4 tweets I randomly encountered today that fit this narrative perfectly:
Trump's trade war is partly about gender.
As American manufacturing declined, men lost economic leverage over women. The nationalist right believes that this led to lower marriage and birth rates.
https://x.com/EricLevitz/status/1908175346177847669
Highly educated women will be completely out of the marriage market in next 5 years.
https://x.com/mshree01/status/1906316952613589038
congratulations to boring men with stable jobs on becoming the next hot commodity
https://x.com/morganisawizard/status/1907889282947424453
The American economy is built around giving fake unproductive jobs to women, therefore we must destroy it
https://x.com/DrewPavlou/status/1907932434571866226
Conclusion
Interestingly this thought seems to cross many peoples minds independently. Like Calculus was invented by Leibnitz and Newton simultaneous and independently.
It's also liberals and conservatives; men and women uttering these words.
I think this is super fascinating. Shoutout to the original post: https://www.cartoonshateher.com/p/doge-is-about-sex
originally posted at https://stacker.news/items/934557
-
 @ a60e79e0:1e0e6813
2025-03-28 08:47:35
@ a60e79e0:1e0e6813
2025-03-28 08:47:35This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57

Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
Blogging (Long Form Content)
- Habla - Web app for Nostr based blogs
- Highlighter - Web app that enables users to highlight, store and share content
Group Chats
- Chachi Chat - Relay-based (NIP-29) group chat client
- 0xchat - Mobile based secure chat
- Flotilla - Web based chat app built for self-hosted communities
- Nostr Nests - Web app for audio chats
- White Noise - Mobile based secure chat
Marketplaces
- Shopstr - Permissionless marketplace for web
- Plebeian Market - Permissionless marketplace for web
- LNBits Market - Permissionless marketplace for your node
- Mostro - Nostr based Bitcoin P2P Marketplace
Photo/Video
Music
- Fountain - Podcast app with Nostr features
- Wavlake - A music app supporting the value-for-value ecosystem
Livestreaming
- Zap.stream - Nostr native live streams
Misc
- Wikifreedia - Nostr based Wikipedia alternative
- Wikistr - Nostr based Wikipedia alternative
- Pollerama - Nostr based polls
- Zap Store - The app store powered by your social graph
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at NostrApps.com, Nostr.net and Awesome Nostr.
-
 @ 2e8970de:63345c7a
2025-04-04 16:17:56
@ 2e8970de:63345c7a
2025-04-04 16:17:56Interestingly he's suggesting that he's doing all this on purpose. Why would he say that? Well the market could take this (a) positively: he's still in control and there is a masterplan (b) negatively: he's openly hostile against the economy. Trump is obviously hoping the market will take it as (a).
originally posted at https://stacker.news/items/934513
-
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ f1989a96:bcaaf2c1
2025-03-27 13:53:14
@ f1989a96:bcaaf2c1
2025-03-27 13:53:14Good morning, readers!
Turkey’s currency plunged to a record low after the arrest of Istanbul Mayor Ekrem Imamoglu, one of President Recep Tayyip Erdogan’s main political rivals. This follows a pattern of escalating repression of opposition figures, which have been described as an effort to suppress competition ahead of primary elections. As economic conditions deteriorate, Erdogan is resorting to desperate measures — blocking social media, arresting dissenters, and tear-gassing protests — to maintain power over an increasingly restless populace.
In the Caribbean, we shed light on Cubans' struggles accessing remittances sent from family members abroad. This is a symptom of the regime's strict monetary controls over foreign currency. Cubans face long delays or can’t withdraw cash due to bank liquidity shortages. And when they can, remittances are converted into pesos at the overvalued official Cuban exchange rate. This effectively allows the Communist Party of Cuba (PCC) to loot the value from Cuban remittances.
In freedom tech news, we highlight Demand Pool, the first-ever Stratum V2 mining pool. Stratum V2 is a mining protocol designed to decentralize Bitcoin mining by letting individual miners create their own block templates rather than relying on centralized pools to do so for them. This improves censorship resistance and promotes a more decentralized and resilient Bitcoin network — critical features for human rights defenders and nonprofits using Bitcoin to protect against financial repression from authoritarian regimes.
We end by featuring Vijay Selvam's new book, “Principles of Bitcoin.” It offers a clear, first-principles guide to understanding how Bitcoin’s technology interacts with economics, politics, philosophy, and human rights. Whether you’re new to Bitcoin or looking to deepen your understanding, this book provides a solid foundation, and it even features a foreword by HRF Chief Strategy Officer Alex Gladstein.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Turkey | Lira in Free Fall as Erdogan Arrests Political Rival
Turkey’s lira plunged to a record low after officials arrested Istanbul Mayor Ekrem Imamoglu, President Recep Tayyip Erdogan’s main political rival. Imamoglu’s arrest comes ahead of primary elections and follows the increasing repression of opposition figures in recent months, including the suspension of political opposition accounts on X. Officials also arrested Buğra Gökçe, head of the Istanbul Planning Agency, for publishing data exposing the country’s deepening poverty. The currency’s fallout and political repression have sparked protests in Istanbul despite a four-day ban. The regime is responding with tear gas and rubber bullets. Meanwhile, Turks dissenting online risk joining over a dozen other citizens recently arrested for “provocative” social media posts. Netblocks reports that the Turkish regime imposed restrictions on social media and messaging to quell the uprising of Turks struggling with financial conditions and deepening repression.
Cuba | Banks “Hijack” Citizen Remittances
Cubans are struggling to access remittances sent from their families abroad. This is because the regime completely controls all incoming foreign currency transfers. When remittances arrive, communist banking authorities force their conversion into collapsing Cuban pesos or “Moneda Libremente Convertible” (MLC), Cuba’s digital currency with limited use. On top of this, Cubans receive pesos in their accounts based on the official Cuban exchange rate, which is far below the informal market rate. This allows the regime to opaquely siphon off much of the remittances’ real value. Even when the money clears, Cubans face long delays or can’t withdraw the cash due to banks’ liquidity shortages. Many Cubans are accusing these banks of “hijacking” their remittances. As inflation, electrical blackouts, and food shortages continue, remittances are more critical than ever for Cuban families. Yet, they’re blocked at every turn by a system designed to impoverish them.
Pakistan | Announces Plans to Regulate Digital Assets
Pakistan announced plans to create a regulatory framework for Bitcoin and digital assets to attract foreign investment and domestic economic activity. It’s a peculiar shift for a regime that regularly suspends the Internet, censors social media, represses opposition, and burdens its people with the highest cost of living in Asia. We suspect the plans indicate efforts to control the industry rather than empower individuals. The military-backed regime is also exploring a Central Bank Digital Currency (CBDC) and tightening controls on VPN use, which are hardly the hallmarks of leadership committed to permissionless financial systems. But perhaps it matters little. Grassroots Bitcoin adoption in Pakistan already ranks among the highest in the world, with an estimated 15 to 20 million users turning to digital assets to preserve their savings, circumvent financial controls, and escape the failures of a collapsing fiat system. HRF supported Bitcoin Pakistan with a grant to help translate resources into Urdu, a language spoken by 60 million people trapped in this repressive scenario.
Russia | Piloting CBDC in Tatarstan to Test Smart Contract Functionality
Russia’s central bank plans to pilot its CBDC, the digital ruble, in Tatarstan to test smart contract functionality. Specifically, the central bank will experiment with conditional spending, using smart contracts to restrict where and what users can spend money on. If these features are implemented, it will empower the Kremlin with micro-controls over Russians’ spending activity. Officials could program funds to expire, restrict purchases to regime-approved goods, or block transactions at certain locations — leaving users with no financial autonomy or privacy. Those who oppose the Russian dictatorship, such as activists, nonprofits, and dissenters, could be debanked with more ease, their assets frozen or confiscated without recourse.
Nicaragua | Government Mandates Public Employees Declare All Assets
In Nicaragua, dictator Daniel Ortega intensified state financial surveillance by mandating all public servants to disclose information on all personal and family assets. The mandate requires all public employees to declare everything from personal bank accounts, loans, vehicles, and other assets — as well as the assets and accounts of immediate family members. Those who do not comply face the threat of termination. Ironically, despite the law requiring such disclosure, Ortega himself has not declared his assets since 2006. Under the guise of regulatory compliance, this policy is yet another link in the chain tightening state surveillance over Nicaraguan society. Bitcoin adoption continues to grow in this repressed Central American nation.
BITCOIN AND FREEDOM TECH NEWS
Demand Pool | First Stratum V2 Mining Pool Launches
Bitcoin mining could become more decentralized and censorship-resistant with the launch of Demand Pool, the first mining pool to ever implement Stratum V2. Stratum V2 is open-source software that allows miners to build their own block templates, enabling more individual mining and less dependence on large and centralized mining pools. This helps maintain Bitcoin’s key features: its decentralized, permissionless, and uncensorable nature. All of which are crucial for human rights defenders and nonprofits bypassing the financial repression and surveillance of authoritarian regimes. Learn more here.
Bitcoin Mining | Three Solo Blocks Found
Three separate solo miners mined Bitcoin blocks in the past seven days. This marks the second, third, and fourth solo blocks mined in the past two weeks alone, hinting at a surge in home mining. This promotes greater decentralization within the Bitcoin network because solo miners have little functional ability to censor. In contrast, large mining pools are points of failure that centralized interests can more easily pressure — to the detriment of activists and human rights defenders. The first block was mined on March 21 by a miner using a self-hosted FutureBit Apollo machine that earned 3.125 BTC plus fees for processing block 888,737. Just days later, a solo miner with under 1 TH/s of self-hosted hash rate found block 888,989, which became just the third block ever to be mined using an open-source Bitaxe device. Most recently, on March 24, a solo miner using a $300 setup successfully mined block 889,240.
Krux | Adds Taproot and Miniscript Support
Krux, open-source software for building your own Bitcoin signing devices (hardware for Bitcoin self-custody), released an update that enhances privacy and flexibility. The update introduces support for Taproot, a past Bitcoin upgrade that improves privacy and security, and Miniscript, a simplified way to create more complex Bitcoin transaction rules. This allows users to manage multi-signature wallets (where more than one private key is required to interact with your Bitcoin) in a more private and flexible way. It also enables spending conditions that are harder to censor and easier to verify. Krux continues to support the struggle for financial freedom and human rights by breaking down barriers to Bitcoin self-custody. HRF has recognized this impact and awarded grants to open-source developers working on Krux to advance this mission.
Cashu | Developing Tap-to-Pay Ecash
Calle, the creator of Cashu, an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, is developing a new tap-to-pay feature that enables instant, offline ecash payments via NFC. Ecash functions as a bearer asset, meaning the funds are stored directly on the user’s device. With tap-to-pay, it can be transferred with a single tap (similar to tapping your credit card). More generally, ecash offers fast, private transactions resistant to surveillance and censorship. But for activists and dissenters, this particular advancement makes private and permissionless payments more accessible and user-friendly. This development will be worth following closely. Watch a demo here.
OpenSats | Announces 10th Wave of Bitcoin Grants
OpenSats, a public nonprofit that supports open-source software and projects, announced its 10th wave of grants supporting Bitcoin initiatives. This round includes funding for Stable Channels, which enable stabilized Bitcoin-backed balances on the Lightning Network (allowing users to peg Bitcoin to fiat currencies in a self-custodial way) that provide stable, censorship-resistant payments. OpenSats also renewed its support for Floresta, a lightweight Bitcoin node (a computer that runs the Bitcoin software). It lowers entry barriers to running Bitcoin, helping make the network more decentralized and censorship-resistant.
Bitcoin Policy Institute | Launches Bitcoin Summer Research Program
The Bitcoin Student Network (BSN) and the Bitcoin Policy Institute (BPI) are teaming up to offer students an eight-week research internship this summer. The program is part of BPI’s Research Experiences for Undergraduates (REU) initiative and invites students passionate about the future of money, financial inclusion, and Bitcoin’s civil liberties impacts to conduct hands-on research. Participants will also receive mentorship from BPI researchers. The program runs from June 9 to Aug. 8, 2025, and includes an in-person colloquium in Washington, DC. It is an incredible opportunity for students worldwide, especially those living in oppressive regimes, to get involved with Bitcoin. Applications are open until April 7. Apply here.
RECOMMENDED CONTENT
Principles of Bitcoin by Vijay Selvam
“Principles of Bitcoin” by Vijay Selvam is a new book offering a first-principles guide to understanding Bitcoin’s technology, economics, politics, and philosophy. With a foreword by HRF Chief Strategy Officer Alex Gladstein, the book cuts through the noise to explain why Bitcoin stands alone as a tool for individual empowerment and financial freedom. Selvam’s work makes the case for Bitcoin as a once-in-history invention shaping a more decentralized and equitable future. Read it here.
Rule Breakers — The True Story of Roya Mahboob
“Rule Breakers” is a new film that tells the true story of Roya Mahboob, Afghanistan’s first female tech CEO, who empowered young girls in Afghanistan with financial literacy, robotics, and financial freedom through Bitcoin. The film recounts Mahboob’s courageous work educating these girls despite huge personal risks under a regime that bans their education. It follows the story of Afghan Dreamers, the country’s first all-girls robotics team, and the obstacles they overcome to compete on the world stage. “Rule Breakers” is a testament to the power of education, innovation, and resilience in the face of oppression. It’s now in theaters, and you can watch the trailer here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 3c389c8f:7a2eff7f
2025-04-04 15:47:44
@ 3c389c8f:7a2eff7f
2025-04-04 15:47:44A Rose By Any Other Name... or whatever.
NIP-05 is an identifier created by mapping Nostr keys to DNS based identifiers. More technically, it the part of the protocol that defines how to do this mapping, but you will often see the resulting identifier referred to as "your NIP-05". You will also see it referenced as a "Nostr Address", a "Nostr ID", or a "Nostr Verification". None of those terms are fully correct but nor are they wrong.
A NIP-05 identifier does look very similar to an email address (i.e. NostrName @ SomeSite .com). It makes it easier to convey your Nostr profile to friends or collogues, since your chosen name is not unique and the npub format is not exactly something you will be wanting to jot down at a business meeting. It can be used to find you and your notes, so the term, Nostr Address, fits in that sense. There are free services that provide a NIP-05 to you, but you may want to consider contracting this service to a paid provider. Free services tend to be abused by spammers. Paid NIP-05 providers are reasonably priced, more reputable, provide select affiliations, and often other services, along with hosting your Nip-05 file.
Nostr ID might be the appropriate term, in a different way. Your NIP-05 is unique. You are not limited to possessing a single one, but only one may be present on your profile at any given time. You can switch them out as needed. Some Nostr-based services will require that you have a particular NIP-05 provider in order to access their relay communities or other features. In that sense, it is an ID, proving that you are a member of that community. These NIP-05 IDs are created and hosted for you by the community relay hosts, with whatever criteria they choose to require.
Nostr Verification comes into consideration if you own or run a website. It can be used to validate your identity. By hosting your NIP-05 file on your own domain, you are, in essence, validating that the same person has ownership of the website and control of the associated Nostr profile. (i.e. YourName @ YourSite .com) This is exceptionally handy for any well known individual who may be subject to impersonation. This is great, too, if you sell a product or service online and would like to use Nostr as a means of advertising and engaging with your customers. Your NIP-05 can signal to your customers that you, or any employee, are affiliated with your company.
All of this, for me to tell you... that you don't need a NIP-05 identifier to use Nostr. It just makes a lot of the things you might want to do simpler. For clear instructions on how to set up your NIP-05 visit nostr.how
-
 @ 7bc05901:8c26d22b
2025-04-04 15:40:10
@ 7bc05901:8c26d22b
2025-04-04 15:40:10I am not an engineer by trade. I took my math classes for college credit as early as I could in high school. I signed up for a bachelor of arts in college and basically didn't touch STEM for the rest of my formal education. Seminary (incomplete) and Law School (JD) didn't go deep into any of the sciences -- I think I struggled through an "accounting for lawyers" class.
The dumb thing is that in middle school and early high school I was obsessed with tinkering with mechanical things. I rebuilt a go-kart, tinkered with my computer, built skateboard ramps. High school came, I got obsessed with chasing girls and listening to emo music, and that culminated in a foggy pursuit of journalism, linguistics, ministry and/or academia in my post-graduate adventures. Also, algebra came to me really easily. I loved cramming the day before a test in middle school and embarrassing the other A students who had to work hard to keep those grades up.
I obviously see now how dangerous that pattern can be to sustaining motivation and discipline in the long-time preference aspects of life. I was motivated by the idea of "getting one over" on the authoritarian educators in my life -- they said that the only way to succeed is to do my homework and study, but I wanted them to know that I was different. And I think I was different from a lot of other people around me, but I aimed my agency in the wrong direction. The rebellion became the end for me, instead of being the means to an end of meaningful learning. Rebel against the system so you can escape into a self-sovereign, high-agency existence.
At the risk of over-stuffing the analogy, perhaps that point brings me to decentralized social media environments. Facebook is like my school teachers, there are tasks laid out for me nudging me to behave a certain way. My grades are analogized by my reach that Facebook will give and take away. I run a few Facebook pages and I am constantly irritated by the annoying UI. Constantly changing, adding shit that I cannot imagine anyone asking for and taking away the shit that you refer to everyday. Just this past week I noticed that I have to click into a post on Meta business sweet in order to see how many shares it has. This used to be on the page as I scrolled through all of my content. There is literally just a blank white space where it used to say: 54 shares.
My thought goes to, this is somehow punishing me for my reach. Although Zuckerberg has pledged his allegiance to the new age of "free speech" and given his finger to the government-meddling that he fanned to flame over the last ten or fifteen years, I still think Facebook wants to nudge users away from certain things and towards other things. Libertarians have railed against the "nanny-state" but it is harder to understand how we also give up our sovereignty to centralized social media companies: the Nanny-Feed.
This must die. The unbundling of facebook is a weird time that feels like the detangling of digital society. Life without widespread Craigslist adoption is somewhat more annoying. I used to scroll Craigslist all the time for stuff. I went to Los Angeles for a few months in 2012 and used it to buy some things and hear about auditions for different projects, a few of which panned out for me. There was something about having some separation from the site that I went to specifically to network with co-workers and communicate with old friends that I liked. I don't want my social media identity locked on one site, especially a site that is subservient to a boardroom. I also like the inconvenience of hopping over to a different app to handle my marketplace experiences.
A lot of this needs to be thought through a lot more, because attempting to untangle the beast that is "meta" (still Facebook to me) requires a lot more insight than I have as I type this out. I'm mostly just nostalgic and emotional and remembering a different time in my life.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 7d33ba57:1b82db35
2025-04-04 14:35:00
@ 7d33ba57:1b82db35
2025-04-04 14:35:00Zlarin is a small, car-free island near Šibenik, known for its peaceful atmosphere, crystal-clear waters, and centuries-old coral tradition. It’s often called the “Golden Island” for its natural beauty, and it remains a hidden gem on the Adriatic coast—perfect for quiet beach days, cycling, and slow travel.
🌿 Why Visit Zlarin?
- No cars = pure tranquility – the whole island is pedestrian- and bike-friendly 🚲
- Rich in coral diving heritage – once the center of Croatia’s coral trade 🪸
- Beautiful stone houses, pine forests, and untouched coves
- Easy to reach via a short ferry ride from Šibenik ⛴️
🏖️ Things to Do on Zlarin
1️⃣ Swim & Relax on Secluded Beaches
- Veleš Beach – A pebbly beach surrounded by pines, great for families 🌲
- Magarna Bay – Quiet, wild beach perfect for those seeking solitude 🧘♀️
- Hidden coves – Wander the coast and find your own little swimming spot 🌅
2️⃣ Walk or Cycle the Island
- Well-marked trails through pine forests and olive groves
- Visit the hilltop viewpoint for a panoramic look at Šibenik and nearby islands
- Bring or rent a bike in Šibenik – bikes are ideal for exploring Zlarin 🚴♂️
3️⃣ Learn About Coral Traditions
- Visit the Zlarinka Museum dedicated to the island’s red coral harvesting history
- See traditional jewelry and tools, and learn about the craft’s cultural significance
4️⃣ Stroll Through the Village
- Picturesque stone streets, old chapels, and flower-filled gardens
- Enjoy a drink at a local konoba (tavern) with views of the sea 🍷
5️⃣ Take a Boat Tour or Kayak Trip
- Explore nearby Prvić, Kaprije, or Žirje islands
- Great area for kayaking or paddleboarding over glassy waters 🚣
🚢 How to Get to Zlarin
- Ferry from Šibenik (approx. 25 minutes, year-round service)
- No cars allowed, so park in Šibenik if needed
- Easy to visit for a day trip or stay overnight for peace and stargazing
💡 Tips for Visiting Zlarin
✅ Best time to visit? Late spring to early autumn for swimming and quiet vibes ☀️
✅ Bring cash – not all places accept cards 💶
✅ Pack snorkel gear and water shoes – the underwater world is beautiful 🐠
✅ Stay overnight for an unforgettable quiet island evening under the stars ✨ -
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 96203d66:643a819c
2025-04-04 12:58:46
@ 96203d66:643a819c
2025-04-04 12:58:46nostr:nevent1qqs9j3aw7jrzrw6mtgs9w2znhpg7u0vvur4v69mc8xhw90lqahej74ccx749u nostr:nevent1qqsxrleatwc7v4jvpu4hk3k4s5xvvral0uvt6svyydwtqsz7tk2v03spph2jk nostr:nevent1qqsykq5q6gaa499nykagjaf6sav7ul4ve0ge9y22707gueuasdtr97qsnceys nostr:nevent1qqsvyhuwmnjglrk8hxdw8ye3lzy9f0ahf3ajfsn0wkf3pnztlx7dxxsq7jhlg nostr:nevent1qqs2mmqn2sr6a0ysfjyyuwx5gwy4rxre6pwnjqnzzdszzrgh2zgynlgvv59j3 nostr:nevent1qqswhdmpjhkqzp0nld0m23kgyesqmyacksu9zf8kefxtwzracn7efuqt825sd nostr:nevent1qqsdzsjfa2dmkue5hk5dr8ttl76l3kf649yx4lwslwnh238442jfmmsv4fzmd nostr:nevent1qqszun5jhc22du06rle5r0z8zhj2ezm9pmmrfsqx4843qhz57k3aqxg738uv6 nostr:nevent1qqs8sx9mc2yuldpm5edrtplnge8ckgcr4xj8x7af3zdac0r4rat377ga689un nostr:nevent1qqswe5auf0ym9lg78prwj9ppy0rvpdq92pwend96jmq6udh3d5r3mfqxlyl8j nostr:nevent1qqsqtwgpl0v6qf03r4e9r4tsnyly354req9am2u6s5gjrtefwtedpmc72v3jx nostr:nevent1qqsx2w65lvwmf23rutmnhzw3k2paftngssvfdzqmwle4f3m77hk4u8c6lgmrx nostr:nevent1qqsfz6zpaw2gkgxjxfvevgsww0rhw07swwg0hun23xc4mfuh8f7afrg875wcx nostr:nevent1qqs0eknqgzut0sv0undcps42pnw7an4wjt7a2rwjxd2zaqg6rqpjdwg56yeq7 nostr:nevent1qqsrg7yyaacetzugj8304krg5ne0xxu7kdnps8tlnd797myseqp97vs8r7tup nostr:nevent1qqs20ap690l97n8py0g44w22963jkze78ws2em6e0cl02vc65nexmsqw9ugcd
-
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ e0ef3b4e:6fd74878
2025-04-04 12:55:14
@ e0ef3b4e:6fd74878
2025-04-04 12:55:14At a conference I sit in a quite area and observe and enjoy a coffee. It's bustling around and many are attending a speech at the main stage. Two people sit next to me on a sofa and begin a conversation. He's wearing a beige hoodie and seems to be builder in the space, she's wearing a green winter dress and they seem to be colleagues.
It seems they are now meeting for the first time in real life and exchanging advice, him advising her on how to store her Bitcoin. He’s been longer in the space it seems and she’s just started at the new start-up. I quickly introduce myself and ask them if I may listen in on the conversation since I am a researcher working in the space. They happily agree. She goes on to mention that she will be paid in Bitcoin and does not know how to store it. He goes on to advise her on using a hardware wallet, then takes out his phone and shows a video of the hardware wallet he is using.
She says "Wow, it looks so easy to use. I tried so many different hardware wallets but they are so difficult to use." I see the tension in her shoulders, which then relaxes a bit. He goes on to show her all the security and backup methods for this particular hardware wallet. "I'm sold." She's smiling now and one can see that a decision has been made.
These conversations are happening everyday across the world not only at conferences but in villages, cafes or during random conversation at co-working working spaces. While we strive for good marketing and adoption of Bitcoin, these simple conversations between two people are what is driving actual use.
Safety and trust is a cultural concept in many countries and viewed differently depending on where one has originated from. If one is to imagine that many people would benefit from storing BTC on a device or using an app for lighting transactions then they must trust the process. This need to trust is a basic primary human need.
They will only trust the process if:
-
Empowered: They feel as if they 100% know what they are doing when they are onboarded to the application/hardware device. If there is anything that creates doubt or friction in their minds, the trust to use it as a storage of BTC is gone. A person will window shop when deciding to use a wallet. On average when we interviewed people for various UX research initiatives one person had a minimum of two different Bitcoin wallets on their phone. Prior to that they had tested out quite a few wallets before settling on a decision.
-
Safe: Many are nervous that they will not be able to access their funds once they put it online/on a hardware device. However often receiving advice from someone they trust this will result in them feeling safe. They will likely use the very same device/application that is being used by their friend/colleague or person in a close inner circle.
While this story might seem overly simplified, it’s been repeated multiple times while observing the behavior of people at conferences, through usability tests, and through interviews.
If we understand that a person is tentatively stepping into a “home” (Bitcoin wallet/hardware device) and looking “around” (onboarding process). Once they step in, they will only leave their “bag” (BTC) on the table if specific criteria are met. If not, they will pick up their “bag” (BTC) and walk into the next “home.” (Bitcoin wallet/hardware device). During this process there are basic psychological principles are taking place.
This is where design comes in and creates an experience. The UX design could be equated to the “interior design” of the house. Every click, every interaction every visual that a person sees or experiences is driving them to trust or distrust the experience. We as builders have a unique role in this process and I fully believe that we will solve these challenges together.
If you've read all the way to the end, thank you. On another note, the last 3 weeks have been filled with a lot of strategic thinking, planning, and collaboration.
There are many balls in the air at the moment:
-
UX Research Africa strategy
If you've read all the way to the end, thank you for reading.
✌🏽Peace
-
-
 @ 6a6be47b:3e74e3e1
2025-04-04 12:41:11
@ 6a6be47b:3e74e3e1
2025-04-04 12:41:11⛅️ This week has been a bit hazy—I haven’t been feeling my best. And that’s okay. There are days like that. But this time, it felt like something deeper, as if something was off. Like I wasn’t enough.
🌞 Thankfully, as the days went by, I started to feel better. Today, I feel like myself again—like I’ve put my human suit back on and climbed back on the horse.
✏️ I picked up my pencil and started drawing again, just me and my iPad, without any expectations weighing me down. It felt good—peaceful even—to create for the sake of creating.
🦉 What I’ve realized is this: It’s not bad to have goals or aspirations. Those are important! But what becomes unhealthy is chasing perfectionism while trying to achieve those goals. For me, perfectionism turns into a spiral—not rainbows and butterflies but a storm cloud of self-doubt. I guess I just want to share this in case anyone out there needs to hear it: It’s okay to be imperfect. And most importantly, it’s okay to just be yourself.

🎨 As part of my journey back to myself this week, I decided to draw something simple and even try my hand at a little animation since it had been a while. Here’s what I came up with:
Imposter syndrome can be deceiving—it whispers lies about your worth and tries to steal your joy—but just like anything in life, this too shall pass.
🎢 The ebbs and flows are part of life’s natural rhythm; you’d think I’d have learned that by now! But life has its way of (re)teaching us lessons when we need them most.
✨ To anyone reading this who might be struggling: Be kind to yourself. You’re doing better than you think you are. And remember—you are enough.
Godspeed
-
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ 220522c2:61e18cb4
2025-03-25 06:57:24
@ 220522c2:61e18cb4
2025-03-25 06:57:24
-
 @ 4259e401:8e20e9a6
2025-03-24 14:27:27
@ 4259e401:8e20e9a6
2025-03-24 14:27:27[MVP: Gigi! How do I lightning prism this?]
If I could send a letter to myself five years ago, this book would be it.
I’m not a Bitcoin expert. I’m not a developer, a coder, or an economist.
I don’t have credentials, connections, or capital.
I’m a blue-collar guy who stumbled into Bitcoin almost exactly four years ago, and like everyone else, I had to wrestle with it to understand it.
Bitcoin is one of the most misunderstood, misrepresented, and misinterpreted ideas of our time - not just because it’s complex, but because its very structure makes it easy to distort.
It’s decentralized and leaderless, which means there’s no single voice to clarify what it is or defend it from misinformation.
That’s a feature, not a bug, but it means that understanding Bitcoin isn’t easy.
It’s a system that doesn’t fit into any of our existing categories. It’s not a company. It’s not a product. It’s not a government.
There’s no marketing department, no headquarters, no CEO.
That makes it uniquely resistant to corruption, but also uniquely vulnerable to disinformation.
Whether through negligence or malice, Bitcoin is constantly misunderstood - by skeptics who think it’s just a Ponzi scheme, by opportunists looking to cash in on the hype, by scammers who use the name to push worthless imitations, and by critics who don’t realize they’re attacking a strawman.
If you’re new to Bitcoin, you have to fight through layers of noise before you can even see the signal.
And that process isn’t instant.
Even if you could explain digital signatures off the top of your head, even if you could hash SHA-256 by hand, even if you had a perfect technical understanding of every moving part - you still wouldn’t get it.
Bitcoin isn’t just technology. It’s a shift in incentives, a challenge to power, an enforcer of sovereignty. It resists censorship.
A simple open ledger - yet it shakes the world.
Archimedes asked for a lever and a place to stand, and he could move the world.
Satoshi gave us both.
The lever is Bitcoin - an economic system with perfect game theory, incorruptible rules, and absolute scarcity.
The place to stand is the open-source, decentralized network, where anyone can verify, participate, and build without permission.
And what comes out of this seemingly simple equation?
The entire rearchitecture of trust. The separation of money and state.
A foundation upon which artificial intelligence must negotiate with the real world instead of manipulating it.
A digital economy where energy, computation, and value flow in perfect symmetry, refining themselves in an endless virtuous cycle.
Bitcoin started as a whitepaper.
Now it’s a lifeline, an immune system, a foundation, a firewall, a torch passed through time.
From such a small set of rules - 21 million divisible units, cryptographic ownership, and a fixed issuance schedule - emerges something unstoppable.
Something vast enough to absorb and constrain the intelligence of machines, to resist the distortions of human greed, to create the rails for a world that is freer, more sovereign, more aligned with truth than anything that came before it.
It’s proof that sometimes, the most profound revolutions begin with the simplest ideas. That’s why this book exists.
Bitcoin isn’t something you learn - it’s something you unlearn first.
You start with assumptions about money, value, and authority that have been baked into you since birth. And then, piece by piece, you chip away at them.
It’s like peeling an onion – it takes time and effort.
*And yes, you might shed some tears! *
At first, you might come for the speculation. A lot of people do. But those who stay - who actually take the time to understand what’s happening - don’t stay for the profits.
They stay for the principles.
If you’re holding this book, you’re somewhere on that journey.
Maybe you’re at the very beginning, trying to separate the signal from the noise.
Maybe you’ve been down the rabbit hole for years, looking for a way to articulate what you already know deep in your bones.
Either way, this is for you.
It’s not a technical manual, and it’s not a sales pitch. It’s the book I wish I had when I started.
So if you’re where I was, consider this a message in a bottle, thrown back through time. A hand reaching through the fog, saying:
“Keep going. It’s worth it.”
Preface The End of The Beginning
March 2025.
The moment has arrived. Most haven’t even noticed, let alone processed it. The United States is setting up a Bitcoin (Bitcoin-only!) strategic reserve.
It’s not a theory. Not an idea. The order is signed, the ink is dried.
The people who have been wrong, over and over (and over!) again - for years! - fumble for explanations, flipping through the wreckage of their previous predictions:
“Bubble…’’ “Fad…” “Ponzi…”
No longer.
The same analysts who once sneered are now adjusting their forecasts to protect what’s left of their credibility. Those who dismissed it are now trapped in a slow, humiliating realization: Bitcoin does not require their approval.
It never did.
Something fundamental has shifted, and the air is thick with a paradoxical cocktail of triumph and panic. Bitcoiners saw this coming. Not because they had insider information, but because they understood first principles when everyone else was still playing pretend.
Bitcoin was never just surviving.
It was infiltrating.
The question is no longer whether Bitcoin will succeed.
It already has.
The only question that remains is who understands, and who is still in denial.
Think back to 2022.
At its peak, FTX was one of the world’s largest cryptocurrency exchanges, valued at $32 billion and backed by blue-chip investors. It promised a sophisticated, institutional-grade trading platform, attracting retail traders, hedge funds, and politicians alike. Sam Bankman-Fried, with his disheveled hair and cargo shorts, was its eccentric figurehead, a billionaire who slept on a bean bag and spoke of philanthropy.
Then the illusion shattered.
FTX collapsed overnight, an implosion so violent it left an entire industry scrambling for cover. One moment, Sam Bankman-Fried was the golden boy of crypto - genius quant, regulatory darling, effective altruist™.
The next, he was just another fraudster in handcuffs.
Billions vanished. Customers locked out. Hedge funds liquidated.
Politicians who had once taken photos with SBF and smiled at his political donations, suddenly pretended they had no idea who he was. The same regulators who were supposed to prevent disasters like this stood slack-jawed, acting as if they hadn’t been having closed-door meetings with FTX months before the collapse.
But FTX wasn’t just a scandal, it was a filter.
If you were Bitcoin-only, with your satoshis in cold storage, you didn’t even flinch. From your perspective, nothing important changed:
A new Bitcoin block still arrived every ten minutes (on average). The supply cap of 21 million bitcoins remained untouched. Ownership was still protected by public/private key cryptography.
You were literally unaffected.
You had already updated your priors:
“If you don’t hold your own keys, you own nothing.” “Bitcoin is not ‘crypto’.” “’Crypto’ is a casino.”
FTX was just another financial fire, another chapter in the never-ending saga of people trusting systems that had already proven themselves untrustworthy.
That moment was a prelude.
The U.S. Bitcoin pivot is the paradigm shift.
The Eukaryotic Revolution Is Upon Us
In biology, abiogenesis is when life emerged from non-life - a fragile, uncertain process where the first microscopic self-replicators struggled to survive against hostile conditions. That was Bitcoin’s early history. It had to fight for its existence, attacked by governments, dismissed by economists, ridiculed by mainstream media.
But it survived.
That era is over. We have entered the Eukaryotic Revolution.
This is the moment in evolutionary history when simple lifeforms evolved into something structurally complex - organisms with nuclei, internal scaffolding, and the ability to form multicellular cooperatives and populate diverse ecosystems. Once this transformation happened, there was no going back. Bitcoin is going through its own Eukaryotic leap.
Once an outsider, dismissed and ridiculed, it is maturing into an integrated, resilient force within the global financial system.
On March 2, 2025, the Trump administration announced a Crypto Strategic Reserve.
At first, it wasn’t just Bitcoin - it included XRP, SOL, and ADA, a desperate attempt to appease the altcoin industry. A political move, not an economic one.
For about five minutes, the broader crypto industry cheered. Then came the pushback.
Bitcoiners called it immediately: mixing Bitcoin with centralized altcoin grifts was like adding lead weights to a life raft.
Institutional players rejected it outright: sovereign reserves need hard assets, not tech company tokens. The government realized, almost immediately, that it had made a mistake.
By March 6, 2025, the pivot was complete.
Strategic Bitcoin reserve confirmed. The President signed an executive order, and legislation has been introduced in the United States House of Representatives.
The U.S. government’s official bitcoin policy: hold, don’t sell. Look for ways to acquire more.
Altcoins relegated to second-tier status, treated as fundamentally separate from and inferior to bitcoin. The government’s official policy: sell, and do not actively accumulate more (ouch!).
“Bitcoin maximalism” – the belief that any cryptocurrency other than bitcoin lies on a spectrum between “bad idea” and outright scam - wasn’t vindicated by debate.
It was vindicated by economic reality.
When the government was forced to choose what belonged in a sovereign reserve, it wasn’t even close. Bitcoin stood alone.
“There is no second best.” -Michael Saylor
Who This Book Is For: The Three Types of Readers
You’re here for a reason.
Maybe you felt something shift.
Maybe you saw the headlines, sensed the undercurrents, or simply couldn’t ignore the growing drumbeat any longer.
Maybe you’ve been here all along, waiting for the world to catch up.
Whatever brought you to this book, one thing is certain: you’re curious enough to learn more.
Bitcoin forces a reevaluation of assumptions - about money, trust, power, and the very foundations of the economic order. How much of that process you’ve already undergone will determine how you read these pages.
1. The Layperson → new, curious, maybe skeptical. Bitcoin probably looks like chaos to you right now. One person says it’s the future. Another says it’s a scam. The price crashes. The price doubles. The news is either breathless excitement or total doom. How the hell are you supposed to figure this out?
If that’s you, welcome.
This book was built for you.
You don’t need to be an economist, a technologist, or a finance geek to understand what’s in these pages. You just need an open mind and the willingness to engage with new ideas - ideas that will, if you follow them far enough, challenge some of your deepest assumptions.
Bitcoin is not an investment. Bitcoin is not a company. Bitcoin is not a stock, a trend, or a passing phase.
Bitcoin is a paradigm shift. And by the time you reach the last page, you won’t need to be convinced of its importance. You’ll see it for yourself.
2. The Student → understand the basics, want to go deeper.
You’ve already stepped through the door.
You’ve realized Bitcoin is more than just digital gold. You understand decentralization, scarcity, censorship resistance… But the deeper you go, the more you realize just how much there is to understand.
3. The Expert → You’ve been in the game for years.
You’ve put in the time.
You don’t need another book telling you Bitcoin will succeed. You already know.
You’re here because you want sharper tools.
Tighter arguments.
A way to shut down nonsense with fewer words, and more force.
Maybe this book will give you a new way to frame an idea you’ve been struggling to convey.
Maybe it will help you refine your messaging and obliterate some lingering doubts in the minds of those around you.
Or maybe this will simply be the book you hand to the next person who asks, “Okay… but what’s the deal with Bitcoin?” so you don’t have to keep explaining it from scratch.
*If you’re already deep in the weeds, you can probably skip Part I (Foundations) without missing much - unless you’re curious about a particular way of putting a particular thing. *
Part II (Resilience) is where things get more interesting. Why you want to run a node, even if you don’t know it yet. The energy debate, stripped of media hysteria. The legend of Satoshi, and what actually matters about it.
If you’re a hardcore cypherpunk who already speaks in block heights and sending Zaps on NOSTR, feel free to jump straight to Part III (The Peaceful Revolution). Chapter 15, “The Separation of Money and State” is where the gloves come off.
Bitcoin isn’t just a technology. Bitcoin isn’t just an economic movement. Bitcoin is a lens.
And once you start looking through it, the world never looks the same again.
This book will teach you what Bitcoin is, as much as it will help you understand why Bitcoiners think the way they do.
It isn’t just something you learn about.
Especially not in one sitting, or from one book.
It’s something you grow to realize.
Regardless of which category you fall into, you’ve already passed the first test.
You’re still reading.
You haven’t dismissed this outright. You haven’t scoffed, rolled your eyes, or walked away. You’re at least curious.
And that’s all it takes.
Curiosity is the only filter that matters.
The rest takes care of itself.
The Essential Role of Memes Memes won the narrative war - it wasn’t textbooks, research papers, or whitepapers that did it. Bitcoin spread the same way evolution spreads successful genes - through replication, variation, and selection. Richard Dawkins coined the term “meme” in The Selfish Gene, describing it as a unit of cultural transmission - behaving much like a gene. Memes replicate, mutate, and spread through culture. Just as natural selection filters out weak genes, memetic selection filters out weak ideas.
But Bitcoin memes weren’t just jokes.
They were premonitions.
The most powerful ideas are often compact, inarguable, and contagious - and Bitcoin’s memes were all three. They cut through complexity like a scalpel, distilling truths into phrases so simple, so undeniable, that they burrowed into the mind and refused to leave.
"Bitcoin fixes this." "Not Your Keys, Not Your Coins." "Number Go Up."
Each of these is more than just a slogan.
They’re memetic payloads, compressed packets of truth that can carry everything you need to understand about Bitcoin in just a few words.
They spread through conversations, through tweets, through shitposts, through relentless repetition.
They bypassed the gatekeepers of financial knowledge, infecting minds before Wall Street even understood what was happening.
And they didn’t just spread.
They reshaped language itself.
Before Bitcoin, the word fiat was a sterile economic term, borrowed from Latin, meaning "by decree." It had no weight, no controversy - just a neutral descriptor for government-issued money.
But Bitcoiners forced a memetic shift.
They didn’t just make fiat mainstream.
**They made it radioactive. **
They stripped away the academic detachment and revealed its true essence:
money because I said so.
No backing. No inherent value.
Just a command.
And of course, an unspoken threat -
"Oh, and by the way, I have a monopoly on violence, so you’d better get on board."
This wasn’t just linguistic evolution; it was a memetic coup.
Bitcoiners took a sterile term and injected it with an unavoidable truth: fiat money exists not because it is chosen, but because it is imposed.
Central banks, governments, and financial institutions now use the term fiat without a second thought.
The meme has done its work.
A word that was once neutral, now carries an implicit critique - a quiet but persistent reminder that there is an alternative.
Bitcoin didn’t just challenge the financial system - it rewired the language we use to describe it.
“Money printer go BRRRRRR" did more damage to the Fed’s reputation than a thousand Austrian economics treatises ever could.
Memes exposed what balance sheets and policy reports tried to obscure. They turned abstract economic forces into something visceral, something undeniable.
And now - they are historical markers of the shift, the fossil record of our collective consciousness coming to terms with something fundamentally new in the universe.
The old world relied on authority, institutional credibility, and narrative control.
Bitcoin broke through with memes, first principles, and lived experience.
This wasn’t just an ideological battle.
It was an evolutionary process.
The weaker ideas died. The strongest ones survived.
Once a meme - in other words, an idea - takes hold, there is nothing - no law, no regulation, no institution, no government - that can stop it.
Bitcoin exists. It simply is.
And it will keep producing blocks, every ten minutes, whether you get it or not.
This book isn’t a trading manual.
It won’t teach you how to time the market, maximize your gains, or set up a wallet.
It’s a carefully curated collection of memes, giving you the prerequisite mental scaffolding to grok the greatest monetary shift in human history.
A shift that has already begun.
The only thing to decide is whether you’re watching from the sidelines or whether you’re part of it.
The rest is up to you.
How This Book Is Structured Bitcoin spreads like an evolutionary force - through memes. Each chapter in this book isn’t just an idea, it’s a memetic payload, designed to install the concepts that make Bitcoin inevitable. The book is broken into three phases:
*I. Foundations *** Memes as Mental Antivirus The first layer cuts through noise and filters out distractions. "Bitcoin Only" is the first test - if you get this one wrong, you waste years chasing ghosts. "Don’t Trust, Verify" rewires how you think about truth. And "Not Your Keys, Not Your Coins"? If you learn it the hard way, it’s already too late.
II. Resilience Memes as Weapons in the Information War Here’s where Bitcoin earns its survival. "Shitcoiners Get REKT" is a law, not an opinion. "Fork Around and Find Out" proves that you don’t change Bitcoin - Bitcoin changes you. "Antifragile, Unstoppable" shows how every attack on Bitcoin has only made it stronger.
III. The Peaceful Revolution ** Memes as Reality Distortion Fields By now, Bitcoin isn’t just an asset - it’s a lens. "Separation of Money and State" isn’t a theory; it’s happening in real time. "Fix the Money, Fix the World" isn’t a slogan; it’s a diagnosis. And "Tick Tock, Next Block"? No matter what happens, Bitcoin keeps producing blocks.
These aren’t just memes. They’re scaffolding for a new way of thinking. Each one embeds deeper until you stop asking if Bitcoin will succeed - because you realize it already has.
Next: Chapter 1: Bitcoin Only. ** For now, it’s a heuristic - an efficient filter that separates signal from noise, with minimal effort.
But by the time you finish this book, it won’t be a heuristic anymore.
It will be something you know.Welcome to the rabbit hole.
-
 @ 907e4623:f40ff12a
2025-04-04 11:39:51
@ 907e4623:f40ff12a
2025-04-04 11:39:51gm well
lfg
-
 @ 1aa9ff07:3cb793b5
2025-04-04 09:42:28
@ 1aa9ff07:3cb793b5
2025-04-04 09:42:28Artificial intelligence (AI) has gained significant momentum in recent years, and it is expected to bring revolutionary changes to our lives over the next five years. Today, AI plays a crucial role in automation, healthcare, education, and many other fields. In the near future, its impact will become even more profound. Here are some key transformations AI is expected to bring:
- Major Changes in the Business World
AI will automate repetitive tasks, allowing human workers to focus on more strategic areas. AI-powered assistants, data analytics, and customer service applications will become more widespread, shifting human efforts toward creative and problem-solving roles.
- Revolutionary Advances in Healthcare
AI in medicine will enable earlier disease diagnosis and personalized treatment plans. Thanks to advancements in image processing and genetic analysis, diseases such as cancer can be detected more quickly and accurately.
- Widespread Adoption of Autonomous Vehicles
Over the next five years, autonomous vehicle technologies will continue to evolve, becoming more common in urban transportation and logistics. This will lead to a reduction in traffic accidents, lower transportation costs, and significant changes in urban planning.
- AI-Powered Personalized Learning in Education
AI will enhance personalized education solutions, making learning processes more efficient. AI-assisted teachers and learning platforms will analyze students’ weaknesses and create customized study programs tailored to their needs.
- New Challenges in Security and Data Privacy
As AI technology advances, cybersecurity and data privacy will become even more critical. While AI-driven security systems can detect cyber threats proactively, malicious applications of AI may introduce new vulnerabilities.
- Creative Innovations in Art and Entertainment
AI-generated content will become more prevalent in fields such as art, music, and cinema. AI-assisted scripts, music compositions, and digital artwork may give rise to a new wave of artistic expression.
Conclusion
In the next five years, AI's influence will be felt in every aspect of life. From business and healthcare to transportation and the arts, various sectors will undergo transformative innovations. However, addressing ethical concerns, security challenges, and data privacy issues will be crucial to ensuring AI's positive impact. By harnessing AI’s potential responsibly, we can build a more efficient, secure, and sustainable future.
Artificial intelligence (AI) has gained significant momentum in recent years, and it is expected to bring revolutionary changes to our lives over the next five years. Today, AI plays a crucial role in automation, healthcare, education, and many other fields. In the near future, its impact will become even more profound. Here are some key transformations AI is expected to bring:
-
 @ 2b24a1fa:17750f64
2025-04-04 08:42:16
@ 2b24a1fa:17750f64
2025-04-04 08:42:16„Denke daran, daß das, was dich wie an unsichtbaren Fäden hin- und herzieht, in deinem Innern verborgen ist.“ Soll der römische Kaiser Marc Aurel gesagt haben, der letzte bedeutende Philosoph der jüngeren Stoa. Brot und Spiele hieß es damals, machten die Gesellschaften gefügig: Bier, Wein, Whiskey, Ablenkung, Informationssteuerung.
https://soundcloud.com/radiomuenchen/kriegsspiele-durch-softpower?
Wie sich die kognitive Einflussnahme zur Kriegsführung entwickelte, wie sie sich mit den heutigen medialen und technischen Mitteln darstellt und wie wir unsere Kinder und uns selbst davor schützen können, damit beschäftigt sich der Propagandaforscher und Amerikanist Dr. Jonas Tögel. Er promovierte zum Thema Soft Power und Motivation und forscht am Institut für Psychologie der Universität Regensburg. Meine Kollegin Eva Schmidt hat ihn interviewt und wollte zunächst von ihm wissen, wie er zur Propagandaforschung kam und auf welchen Grundlagen seine Tätigkeit aufbaut.
Sein aktuelles Buch "Kriegsspiele - Wie NATO und Pentagon die Zerstörung Europas simulieren" ist im Westend-Verlag erschienen, hat 111 Seiten und kostet 15 Euro.
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 2b24a1fa:17750f64
2025-04-04 08:36:50
@ 2b24a1fa:17750f64
2025-04-04 08:36:50Was passiert, wenn die Bank plötzlich das Konto kündigt? Aus gesetzlicher Sicht darf sie das, sogar ohne Gründe zu nennen - sofern diese Option in den Allgemeinen Geschäftsbedingungen (AGB) des Kontovertrags steht. Und das ist die Regel.
https://soundcloud.com/radiomuenchen/de-banking-oder-die-rache-der-bundesbank?
Zwar besteht oft eine mindestens zweimonatige Kündigungsfrist, doch wer jemals das Konto gewechselt hat, weiß, was für ein Aufwand es ist, seinen gesamten und immer komplexeren Zahlungsverkehr umzustellen. Besonders hart trifft es Empfänger von Spenden: darunter viele alternative Medien und freie Journalisten, die für alternative Medien arbeiten. Die Spenden brechen weg, denn die meist anonymen Spender können nicht direkt informiert werden. Das wissen auch diejenigen, denen alternative Medien ein Dorn im Auge sind: Staatlich finanzierte Agitatoren und staatsnahe Medien, die solange Druck auf Banken ausüben, bis diese aus Sorge um ihr Image das Konto kündigen. Das Magazin Multipolar dokumentierte Mitte 2024 rund 40 solcher Fälle. Manchmal nutzen Banken auch ganz direkt diese Möglichkeit, um kritische Stimmen einzuschüchtern und zu schwächen. Diese Variante vermutet unsere Autorin Gaby Weber. Nach einem kritischen Bericht über die Bundesbank wurde ihr das Konto gekündigt. Hören Sie ihren Beitrag „De-Banking oder: die Rache der Bundesbank?“, der zunächst beim Overton-Magazin erschienen ist: overton-magazin.de/hintergrund/pol…der-bundesbank/
Sprecher: Ulrich Allroggen
Bild: Radio München
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 866e0139:6a9334e5
2025-03-24 10:51:52
@ 866e0139:6a9334e5
2025-03-24 10:51:52Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Seit Sonntag (zu allem Glück auch noch meinem 45. Geburtstag) ist bei mir noch ein bisschen mehr los als sonst – und das liegt an Ihnen. Der Aufruf zur Gründung der „Friedenstaube“, einer unzensierbaren Friedenspublikation mit bekannten Stimmen aus der kritischen Szene, der Friedensbewegung und von Bürgerjournalisten ist bei Ihnen auf mehr als nur offene Ohren gestoßen! Ich bin regelrecht geplättet von den vielen Reaktionen, die ich noch gar nicht alle beantworten konnte.
Ich danke Ihnen herzlich für das Vertrauen in mich (auch wenn ich natürlich stark auf die Autoren angewiesen bin) und die überwältigenden Reaktionen: Es sind hunderte Abonnements für den Newsletter eingegangen, darunter einige bezahlte Abos und Förderabos und auch die ersten Genossenschaftsanteile wurden gezeichnet! Was mich besonders freut: Gut zehn weitere freiwillige Autoren wollen mitmachen und arbeiten bereits an den ersten Texten. Damit darf ich schon jetzt verkünden, dass die Genossenschaft definitiv gegründet werden kann, die Friedenstaube wird fliegen. Wie hoch und wie weit, das liegt dann nun nur noch in unser aller Hände.
Der Anfang ist jedenfalls gemacht. Die nächsten Wochen werden besonders arbeitsintensiv, ich bitte Sie um etwas Geduld: Aufbau einer Kernredaktion, Organisation der Abläufe, technologische Entwicklungsarbeiten, Genossenschaftsgründung etc. stehen jetzt auf der Agenda. Mit Tom-Oliver Regenauer darf ich den ersten Autor im redaktionellen Kernteam verkünden, der sich nicht nur große Verdienste im Schreiben erarbeitet hat (siehe u.a. sein Buch Hopium) sondern auch über Managementerfahrung verfügt; mit weiteren helfenden Händen bin ich im Gespräch.
Ich freue mich auf die (auch für mich) neue Erfahrung, quasi aus dem Nichts eine Publikation mit Redaktionsbetrieb und freien Autoren auf einer gänzlich neuen technologischen Infrastruktur aufzubauen. Es wäre illusorisch zu glauben, dass alles glatt gehen wird, denn wir starten quasi „on the go“, aber im Fall von Frieden oder Krieg gilt es, keine Zeit verstreichen zu lassen. Ich arbeite nach dem Motto „Tun, statt reden; zeigen, statt ankündigen; liefern, statt versprechen“.
Die ersten Texte zum Thema Frieden sind bereits publiziert, ein halbwegs geordneter Betrieb sollte ab April realistisch sein. Die Liste der Autoren wird regelmäßig aktualisiert, schauen Sie gerne hier (oder noch besser: hier) immer wieder herein. Dort finden Sie auch noch mal alle Infos, wenn Sie die Friedenstaube unterstützen wollen. Ab 1000 Euro/CHF werden Sie Genossenschafter, also Verleger!**
Auch an die bisherigen Unterstützer des Pareto-Projekts, der technologischen Basis der Friedenstaube, will ich hiermit schon etwas zurückgeben: Alle Spender für Pareto werden die Friedenstaube immer kostenlos lesen können. Sie, die Leser dieser Publikation haben die technologische Basis mit aufgebaut, die uns zur weltweit ersten, zensursicheren Friedenspublikation macht. Uns Autoren steht damit ein kompetentes Support-Team von inzwischen über zehn Entwicklern (und weiteren Helfern) an der Seite, welche die Friedenstaube am Fliegen halten werden.
Kontaktieren Sie mich gerne zu allen Fragen (je kürzer die Mail, desto früher kommt die Antwort): milosz\@pareto.space oder kontakt\@idw-europe.org
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Was bewegt mich beim Thema Krieg und Frieden?
Erlauben Sie mir einen kurzen persönlichen Prolog: Ich stamme aus Schlesien. Mein Urgroßvater kämpfte im I. Weltkrieg bei Verdun. Mein Großvater wurde in die Wehrmacht eingezogen, kämpfte im Partisanenkrieg in Jugoslawien, verlor Hand und Auge. Ein Bruder meiner Großmutter entzog sich und landete in Dachau. Ich kenne meine Familiengeschichte nur in groben Umrissen, vielen wird es ähnlich gehen. Einige meiner schlesischen Vorfahren waren später vor allem Lokführer. Aufgrund der bewegten schlesischen Geschichte wechselten sie mehrfach die Uniform. Die Tätigkeit und Fahrstrecke blieb die gleiche. Für wen oder was kämpften sie in Kriegen in welchen Uniformen? Vermutlich wussten sie es selbst nicht.
Auch ich könnte heute nicht genau sagen, welche Interessen und Mächte die Kriegsmaschinerie bedienen. Doch ich wüsste es gerne und Sie vielleicht auch. Kämpfen ohne letztlich zu wissen für wen und warum: Wozu? Krieg simuliert Sinn und Notwendigkeit und lässt einen am Ende mit den großen Fragen allein, ahnungslos gestorben im Schützengraben. Zivilisatorisch ist das ein Offenbarungseid.
Bin ich ein totaler Anti-Militarist? Ich glaube nicht. Ich habe nichts gegen die Idee privaten Waffenbesitzes. Ich kann der Idee der Landesverteidigung durchaus etwas abgewinnen. Den Wehrdienst habe ich bewusst nicht verweigert. Ich wollte die Erfahrung machen. Hier schreibt also auch ein Obergefreiter a. D. eines bayerischen Gebirgspionierbataillons bei Rosenheim mit bronzener Schützenschnur, der am MG durchaus treffsicher war. Aber eben auch jemand, den der Wehrdienst zum Teil-Pazifisten gemacht hat. Mir war nach dem Grundwehrdienst klar: Wir sind eine Gurkentruppe, reines Kanonenfutter. 20-jährige Grünschnäbel mit zu viel Testosteron und Hollywood in den Gliedern, aber wenig Ahnung.
Ich war also einer, der sich verlässlich mit anderen beim Orientierungslauf im Wald verirrte; einer, der mit anderen übermüdet beim ersten Wachdienst einpennte (und damit im Ernstfall den Tod im Schlaf kennengelernt hätte, denn just erfolgte ein simulierter „Angriff“); einer, der auch mal übernächtigt sein Gewehr vor dem Zelt vergaß (wir sollten dem G3 den Namen unserer damaligen Freundin geben – wie pervers – ich vergaß also „Petra“ vor dem Zelt) und schließlich einer, der die meiste Zeit des Dienstes fürs Vaterland letztlich mit dem Servieren von Getränken und Schinkennudeln im Offizierskasino verbrachte und die institutionalisierten Alkoholiker der Bundeswehr bei Laune hielt („it ain’t much, but it was honest work“).
Anders gesagt: Krieg – spätestens seitdem: ohne mich. Auch wenn ich gerne Ernst Jünger lese und zitiere (er war einfach ein großartiger Chronist und lebendiger Geist), seinen abenteuerlustigen Militarismus kreide ich ihm an und rufe ihm posthum hinterher: man muss nicht erst einen Sohn im Krieg verloren haben, um zum Pazifisten zu werden.
Weitere Störgefühle tauchten auf: In meiner Dissertation durfte ich mich u.a. mit philosophischen Theorien zum Gesellschaftsvertrag (u.a. Kant, Rousseau, Locke und Hobbes sind hier zu nennen) beschäftigen. Dies brachte mein Staatsverständnis gerade bei der Kriegsfrage noch mehr durcheinander. Wenn Mindestziel der Staatsgründung innere und äußere Sicherheit sind, aber letztlich nicht der Staat den Bürger, sondern der Bürger den Staat schützt, wozu sich dann eine Schutzmacht erfinden, die einen am Ende durch den Fleischwolf jagt? Hobbes setzte zumindest auf Söldner.
Kriege werden mit Lügen begonnen, wusste Julian Assange. Können Sie mit Wahrheit beendet oder gar verhindert werden? Seit Walter Lippmanns „Liberty and the News“ von 1920 weiß man spätestens, dass gesicherte Information im Krieg das seltenste Gut ist. Sagt Lippmann als oberster Mainstream-Journalist und Einflüsterer der Mächtigen. Jeder Journalist muss hier ein Störgefühl entwickeln, der Leser noch mehr. Der Journalist der Nachrichtenagentur ist selten im Geschehen sondern wird vom heimischen Militär gebrieft, sein Bericht landet dann in den Newstickern und Redaktionen. Die Kriegsmaschinerie produziert also auch ihre eigene Sicht auf die Dinge, die sie den Bürgern als die Realität verkauft.
Kein Wunder, dass jede abweichende Information massiv bekämpft werden muss. Im Krieg ist Zweifel gleich Verrat, quasi unsolidarisches Sektierertum und Wehrkraftzersetzung, wenn nicht Feindbegünstigung. Der kritische Journalist steht in Ausnahmezuständen, wie man schon bei Corona sehen konnte, automatisch aus Staatssicht im Lager des Feindes und wird entsprechend behandelt. Zensursicheres Publizieren ist dann nicht nur ein nettes feature, sondern notwendige Basisvoraussetzung. Vor kurzem war Twitter/X nicht mehr zugänglich wegen massiven Cyberattacken. Wenn dann noch Rundfunk und Presse auf der Propagandawelle surfen und die Plattformzensur wieder zuschlägt, wird das Angebot schnell dünn.
Wem aber dient Zensur und Propaganda? Die aktuelle Lage im Russland-Ukraine-Konflikt ist auch Gelegenheit, um zu zeigen: Es sind eben nicht nur staatliche Interessen, die hier verhandelt werden, sondern es muss (wieder mal) eine andere Entität mit am Tisch sitzen, man nenne sie Deep State oder wie auch immer. Europäische Eliten dienen offensichtlich Fremdinteressen, wenn sie mit Aufrüstungsplänen Volksvermögen verspekulieren oder darin (wie von der Leyen) ein notwendiges „Investment“ sehen. Von wem werden wir letztlich regiert? Auch diesem Themen-Komplex werde ich mich in der Friedenstaube nähern.
Es gibt viel zu tun, aber für mich ist klar: Frieden ist ohne Wahrheit nicht zu bekommen, deshalb ist Wahrheitssuche auch immer Friedenssuche, wie Wahrheitsliebe letztlich Friedensliebe ist.
Gerade fallen auch im Mainstream die Corona-Lügen zur Labortheorie in sich zusammen, fünf Jahre nach Ausrufung der Pandemie. Der Frieden hat nur eine Chance, wenn es uns gelingt, die Lügen nun möglichst synchron zu den Geschehnissen aufzudecken und zu dokumentieren.
Das ist mein persönlicher Wunsch, mit dem ich die Friedenstaube fliegen lasse.
Was ist Ihrer? Schreiben Sie es gerne in die Kommentare. Welche Erwartungen, Wünsche haben Sie an uns? Liebe Autoren: Was ist euer Beweggrund, für den Frieden zur Feder zu greifen?
Zeichnen Sie jetzt “Friedensanleihen”. Werden Sie Genossenschafter und Verleger der Friedenstaube ab 1000 Euro/CHF. Es können mehrere Anteile pro Person gezeichnet werden, es bleibt bei einem Stimmrecht pro Kopf. milosz\@pareto.space
P.S: Mit diesem Text testen wir die Newsletterfunktion erstmals an mehrere Hundert Mailadressen. Wenn Sie die Friedenstaube abonniert haben, sollten Sie diesen Artikel per Mail bekommen haben.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?* Die* Relai-App ist Europas erfolgreichste Bitcoin-App.* Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Pareto has started a crowdfunding campaign on Geyser. We were in the Top 3 in February, thank you for the support!
-
 @ a60e79e0:1e0e6813
2025-03-23 16:10:10
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much more than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent social media focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, Primal. Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our Nostr 101 to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

Getting Started
-
Go to your app store and download Primal to your Android or iPhone
-
Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
- Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
- Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
- Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think very carefully before carrying out this step.
Learn more in the detailed section at the end of this post.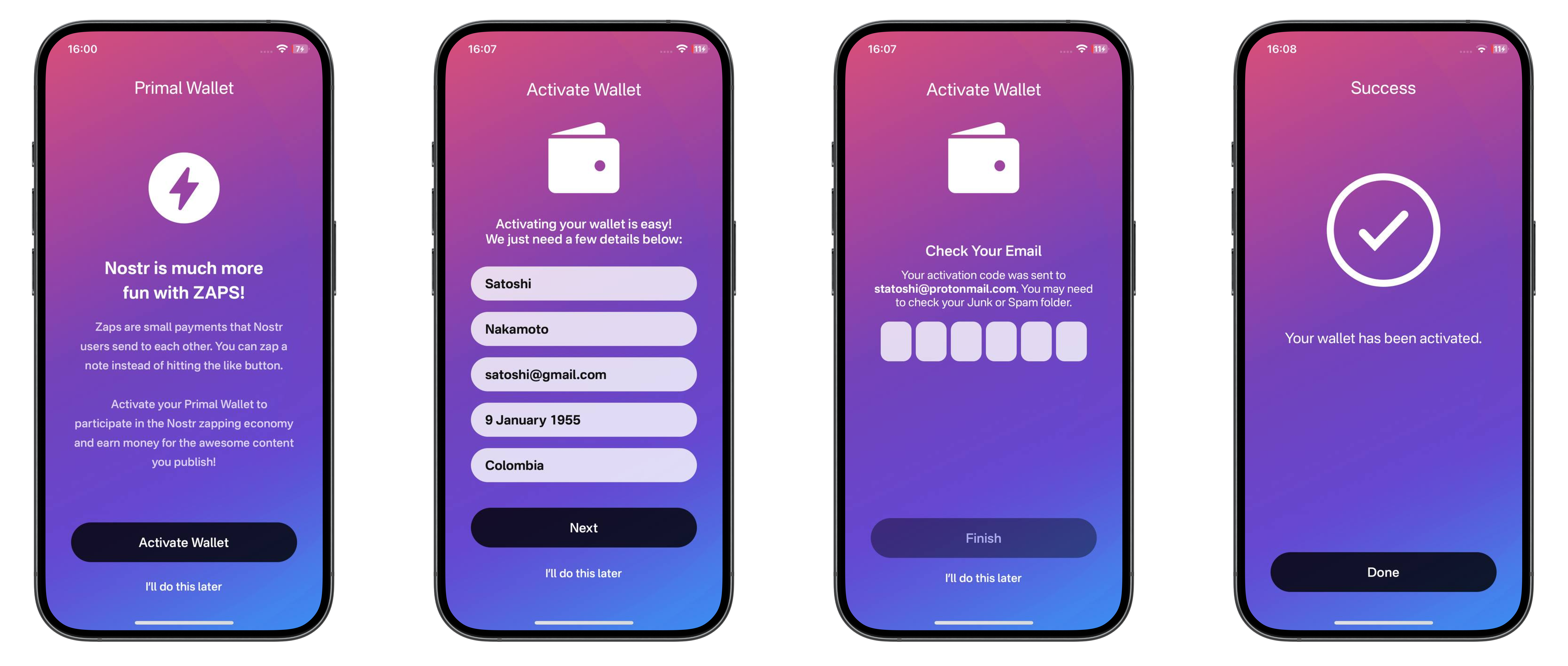
- That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.
- If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
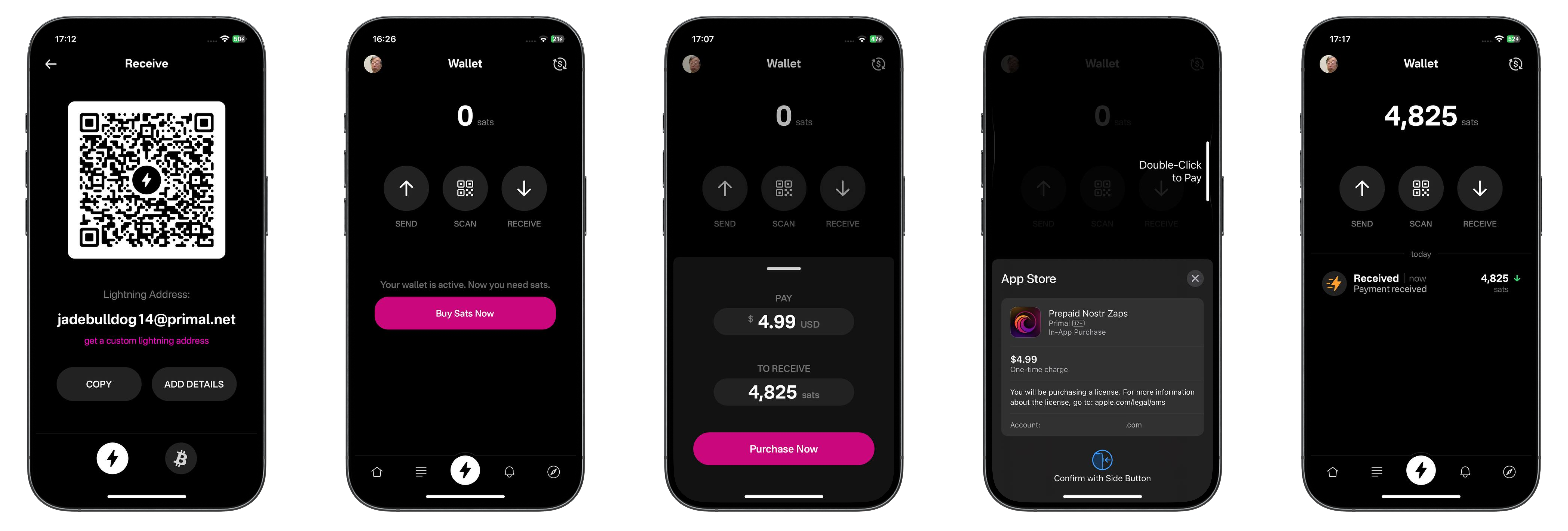
- Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
- Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.
- So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- Comment
- Zap (send value from your wallet to theirs)
- Like
- Repost
- Bookmark
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

- After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
- Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account in any Nostr client. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
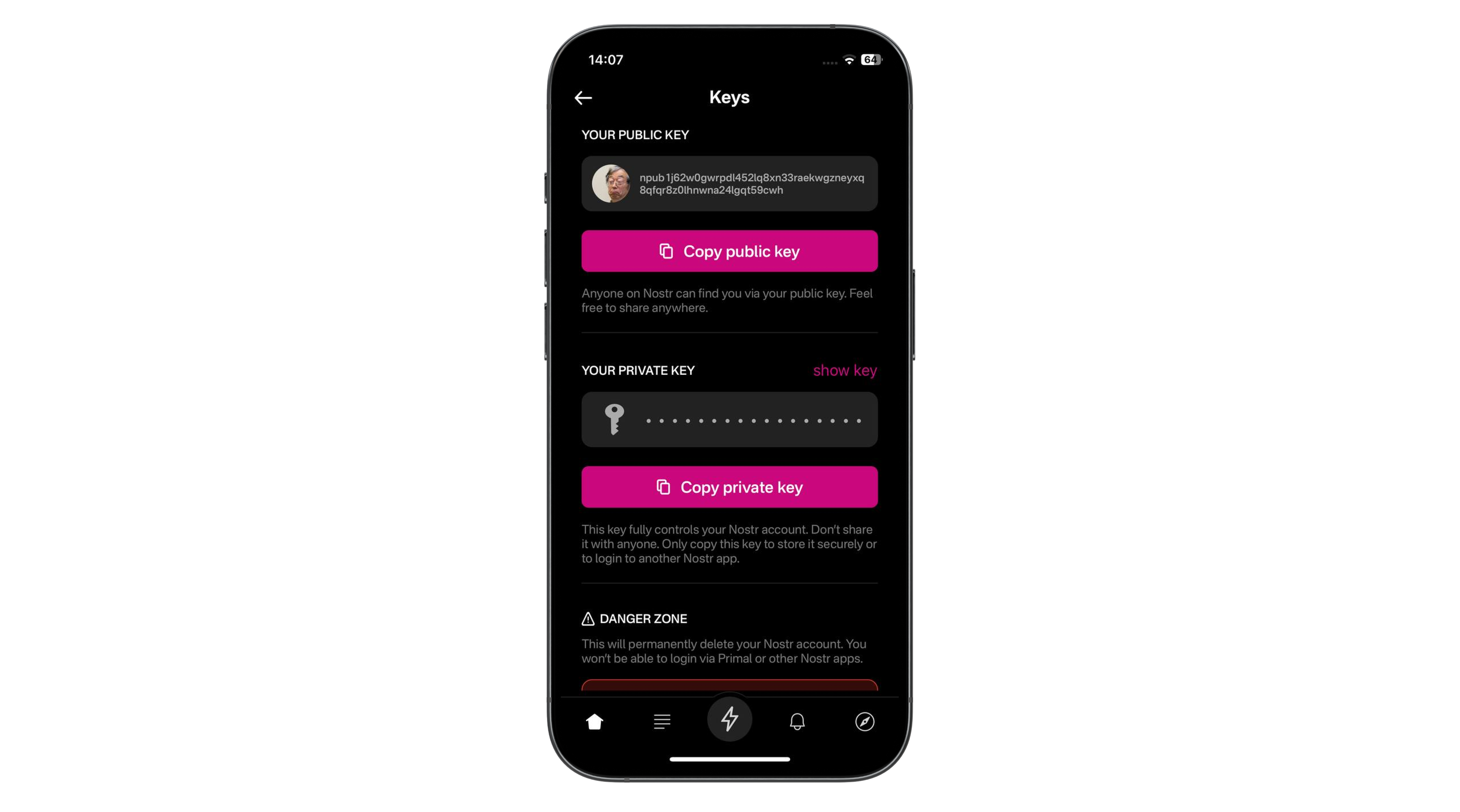
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
Your private key can be imported into any other Nostr social client for the same result.
Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend Phoenix or Zeus.
Those sats are never truly yours until you withdraw them to a self-custodial wallet
Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
Your private key allows you to take your profile and social network to any other client
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ da0b9bc3:4e30a4a9
2025-04-04 06:24:48
@ da0b9bc3:4e30a4a9
2025-04-04 06:24:48Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/934111
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ bf95e1a4:ebdcc848
2025-04-04 06:11:18
@ bf95e1a4:ebdcc848
2025-04-04 06:11:18This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
The Gullible Collective
We humans are biased by nature. Everything we think we know is distorted in one way or another by our cognitive shortcomings. The human brain has been forced to evolve and adapt to whatever environment it found itself in over millennia. Having a brain that is capable of setting aside personal aims for the sake of the collective has proven to be advantageous for the evolution of our species as a whole. The same is true for every other social life form. However, letting these parts of our brains guide our political judgment can lead to disastrous results in the long run — not because of bad intentions but because of the simple fact that a few individuals will always thrive by playing every political system for personal gain. From an evolutionary perspective, an army of ay-sayers and martyrs, regardless of whether we’re talking about an army of humans or an army of ants or bacteria, has an advantage over a less disciplined one. From an individual's evolutionary perspective though, it is better to appear like you’re a martyr but to run and hide when the actual battle happens. This at least partly explains the high percentage of sociopaths in leadership positions all over the world. If you can appear to act for the good of the collective but dupe your way into more and more power behind people’s backs, you’re more likely to succeed than someone playing a fair game.
The story of banking and fiat currency is a story about collective madness. Historically, rulers have tricked people into killing each other through the promise of an after-life. Through central banking, the rulers of the world wars could trick people into building armies for them by printing more money. This is seldom mentioned in history classes because it still goes on today on a massive scale. Inflation might no longer be paying tank factory workers, but it is the main mechanism that funnels wealth into the pockets of the super-rich and away from everyone else. Inflation is the mechanism that hinders us from transporting the value of our labor through time. It makes us avoid real long-term thinking. We hardly ever consider this a problem because none of us has ever experienced an alternative to it.
Money is still vastly misunderstood by the lion's share of the world’s population. In most parts of the world, banks do something called fractional reserve lending. This means that they lend out money that they don't have — conjuring up new money out of thin air and handing it out to their customers as loans. Loans that have to be paid back with interest. Interest that can’t be paid back with thin air but has to be paid with so-called real money. Real money, of which there isn’t enough around to pay back all the loans, so that a constant need for new credit becomes a crucial part of the entire system. Not to mention central banks, which do the same and worse for governments. We’re so used to it by now that every country is expected to have a national debt. All but a handful of ridiculously rich ones do. National debts are also loans that have to be paid back with interest backed by nothing. Think about that. Your taxes are paying someone else's interest. Your tax money is not paying for your grandmother's bypass operation, it is paying interest to a central bank.
When the ideas of the catholic church ruled Europe, people who didn’t believe in God were few and very seldomly outspoken. They had good reason for this since belief in God was virtually mandatory throughout society. Ever since 1971, when famously dishonest American president Richard Nixon cut the last string that tied the US Dollar to gold, our conception of what the world economy is and ought to be has been skewed by an utterly corrupt system. We’re led to believe that we’re all supposed to work longer and longer days in order to spend more and more money and bury ourselves in more and more debt to keep the machine running. We’re duped into thinking that buying a new car every other year is somehow good for the environment and that bringing a cotton bag to the grocery store will somehow save the planet. Stores manipulate us all the time through advertising and product placement, but we’re led to believe that if we can be “climate-smart,” we’re behaving responsibly. Somehow, our gross domestic product is supposed to increase indefinitely while politicians will save us from ourselves through carbon taxes. Fortunately for us, and unfortunately for them, there now exists a way for unbelievers of this narrative to opt out. Life finds a way, as Jeff Goldblum once so famously put it.
Collectivism has ruined many societies. Those of us fortunate enough to live in liberal democracies tend to forget that even democracy is an involuntary system. It’s often referred to as the “worst form of government except all others that have been tried,” but the system itself is very rarely criticized. We’re so used to being governed that not having a leader seems preposterous to most of us. Still, we pay our taxes, and an enormous cut of the fruit of our labor goes to a third party via inflation and the taxation of every good and service imaginable. Institutions, once in place, tend to always favor their own survival just as much as any other living thing does. People employed in the public sector are unlikely to vote against policies that threaten their livelihood. This is a bigger problem than we realize because it’s subtle and takes a long time, but every democracy is headed in the same direction. A bigger state, a more complicated system, and fewer individual freedoms. Long term, it seems that all of our systems tend to favor those who know how to play that system and not those who contribute the most value to their fellow man. Proponents of socialist policies often claim that failed socialist states “weren’t really socialist” or that “that wasn’t really socialism.” What most people fail to realize is that we’ve never tried real capitalism since we’ve always used more or less inflationary currencies. This might very well be the most skewed narrative of our era. We’re all experiencing real, albeit disguised, socialism every single day. True free market capitalism is what we haven’t experienced yet, and it might turn out to be a very different thing than what we’re told to believe that it is by almost all mainstream media.
The validity of the classic right-left scale describing political viewpoints has been debated a lot lately, and alternative scales, like GAL-TAN, the one with an additional Y-axis describing more or less authoritarian tendencies, are popping up in various contexts around the web. After the birth of Bitcoin, there’s a new way to see this. Imagine an origo, a zero point, and a vector pointing to the left of that. All politics are arguably on the left because all policies need to be funded by taxes, and taxation can be viewed as theft. Taxation can be viewed as theft because, at its core, it’s involuntary. If a person refuses to pay his taxes, there is a threat of violence lurking in the background. Not to mention inflation, which Milton Friedman so elegantly described as “taxation without legislation.” What you do with the portion of your wealth that you have in Bitcoin is another matter altogether. If you take sufficient precautionary privacy measures and you know what you’re doing, your business in Bitcoin is beyond politics altogether. With the introduction of the Lightning Network and other privacy-improving features, it is now impossible for any third party to confiscate your money or even know that you have it, for that matter. This changes the political landscape of every nation on Earth. Bitcoin is much less confiscatable than gold and other scarce assets, which makes it a much better tool for hedging against nation-states. In this sense, Bitcoin obsoletes borders. You can cross any border on Earth with any amount of Bitcoin in your head. Think about that! Your Bitcoin exists in every country simultaneously. Any imposed limit on how much money you can carry from one nation to the other is now made obsolete by beautiful mathematics. Bitcoin is sometimes referred to as a “virtual currency.” This is a very inaccurate description. Bitcoin is just mathematics, and mathematics is just about the most real thing there is. There’s nothing virtual about it. Counterintuitive to some, but real nonetheless.
The complexity of human societal hierarchies and power structures is described perfectly in a classic children's book, The Emperor’s New Clothes, by Hans Christian Andersen. See the world as the kid who points out that the king is naked in the tale, and everything starts to make sense. Everything in human society is man-made. Nations, leaders, laws, political systems. They’re all castles in the air with nothing but a lurking threat of violence to back them up. Bitcoin is a different beast altogether. It enables every individual to verify the validity of the system at all times. If you really think about it, morality is easy. Don’t hurt other people, and don’t steal other people’s stuff. That’s the basic premise. Humans have but two ways of resolving conflict, conversation and violence, and in this sense, to hurt someone can only mean physical violence. This is why free speech is so important and why you should defend people’s right to speak their minds above everything else. It’s not about being able to express yourself. It’s about your right to hear every side of every argument and thus not have to resort to violence should a conflict of interests occur. You can’t limit free speech with just more speech — there’s always a threat of violence behind the limitations. Code, which both Bitcoin and the Internet are entirely made up of, is speech. Any limitations or regulations that your government implements in regard to Bitcoin are not only a display of Bitcoin’s censorship resistance but also a test of your government's stance on freedom of expression. A restriction on Bitcoin use is a restriction on free speech.
Remember, the only alternative to speech that anyone has is violence. Code is a language, mathematics is a language, and money is a linguistic tool. A linguistic tool we use as a means of expressing value to each other and as a way to transport value through space and time. Any restrictions or regulations regarding how you can express value, for example, making it impossible to buy Bitcoin with your credit card, prove that the money you have in your bank account is not really yours. When people realize this, the demand for Bitcoin goes up, not down. If you know what you're doing, there’s no need to fear the regulators. They, on the other hand, have good reason to fear an invention that shamelessly breaks their spell.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ 502ab02a:a2860397
2025-04-04 02:50:35
@ 502ab02a:a2860397
2025-04-04 02:50:35หลังจากที่เราเพิ่งเปิดเรื่องไฟโตสเตอรอลไปหมาด ๆ ถึงเวลาที่ต้องมาคุยกันเรื่อง oryzanol ซึ่งเป็นอีกหนึ่งสารที่ถูกอุตสาหกรรมผลักดันให้เรารู้สึกว่า “ต้องกิน” เหมือนเป็นไอเทมลับสำหรับสุขภาพหัวใจ แต่เดี๋ยวก่อนนะ ทำไมสิ่งที่มนุษย์ไม่เคยต้องการมาก่อนถึงกลายเป็นสิ่งจำเป็นไปได้ ?
Oryzanol หรือ gamma-oryzanol เป็นสารประกอบที่พบได้ในน้ำมันรำข้าว มีโครงสร้างเป็น sterol ester ของกรดเฟอรูลิก (Ferulic acid esters of sterols and triterpenes) ซึ่งหมายความว่ามันมีโครงสร้างคล้ายกับไฟโตสเตอรอล แต่มาพร้อมกับองค์ประกอบของสารต้านอนุมูลอิสระที่ได้จากกรดเฟอรูลิก นั่นทำให้มันถูกโฆษณาว่าเป็นสารที่ช่วยลดคอเลสเตอรอล มีฤทธิ์ต้านอนุมูลอิสระ และอาจช่วยลดความเสี่ยงโรคหัวใจ ฟังดูดีใช่ไหม ? แต่มันก็คล้ายกับไฟโตสเตอรอลเลย คือเป็นสารที่ แข่งขันกับคอเลสเตอรอลในการดูดซึม และแน่นอนว่าผลข้างเคียงก็ยังคงอยู่ นั่นคือ มันอาจลดการดูดซึมวิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมันและจำเป็นต่อร่างกาย นั่นหมายความว่า ในขณะที่มันช่วยลด LDL ในกระดาษ มันอาจทำให้ร่างกายขาดสารอาหารที่สำคัญไปด้วย
ปัญหาที่ใหญ่กว่าคือ oryzanol พบมากใน น้ำมันรำข้าว ซึ่งเป็นหนึ่งในน้ำมันพืชที่ผ่านการแปรรูปสูง และการบริโภคน้ำมันพืชมากเกินไปนั้นสัมพันธ์กับ ภาวะอักเสบเรื้อรัง (chronic inflammation), ภาวะต้านอินซูลิน (insulin resistance), และความเสี่ยงโรคหัวใจและหลอดเลือด การที่อุตสาหกรรมบอกให้เราเพิ่ม oryzanol ในอาหาร จึงเป็นเหมือนการผลักให้ผู้คนบริโภคน้ำมันพืชมากขึ้นโดยไม่รู้ตัว ทั้งที่น้ำมันพืชโดยเฉพาะที่ผ่านกรรมวิธีอย่างน้ำมันรำข้าวมีปริมาณโอเมก้า-6 สูง ซึ่งถ้ารับมากเกินไปจะไปกระตุ้นกระบวนการอักเสบในร่างกาย เคยสังเกตไหมครับว่า น้ำมันรำข้าวมักโชว์ตัวเลขเก๋ๆของ Oryzanol แต่กลับไม่โชว์สัดส่วน โอเมก้า 6 กับ โอเมก้า 3
เทียบง่ายๆครับ น้ำมันคาโนลา มีโอเมก้า 6 ราวๆ 2200 - 2800 ต่อน้ำมัน 15 มล. (หน่วยบริโภค) น้ำมันรำข้าว มีโอเมก้า 6 ราวๆ 4,140 - 5,520 มก. ต่อน้ำมัน 15 มล. (หน่วยบริโภค) ในขณะที่โอเมก้า 3 ราวๆ 138 - 276 มก.ต่อน้ำมัน 15 มล. (หน่วยบริโภค) นี่หมายถึงสัดส่วนสูงไปถึงได้ราวๆ 40:1 ทั้งๆที่เราเข้าใจแหละว่าโอเมก้า6 ร่างกายจำเป็น แต่แต่แต่ จำเป็นไม่ได้หมายความว่าจัดหนัก เพราะสิ่งที่เราต้องพึงสังวรคือ สัดส่วนที่สมดุลระหว่าง โอเมก้า3และโอเมก้า6 ดังนั้น 40:1 ไม่เรียกว่าสมดุล ซึ่งจะกระตุ้นการอักเสบเรื้อรัง ในร่างกาย และเกี่ยวข้องกับโรคหัวใจ เบาหวาน และปัญหาสุขภาพอื่นๆ พาเหรดกันมา แต่คุณจะไม่เห็นตัวเลขนี้บนฉลากครับ
ผู้ผลิตผิดไหม? จะไปผิดอะไรครับ หน่วยบริโภคแนะนำเขา 1 หน่วยบริโภคคือ 15 มิลลิลิตร หรือ 1 ช้อนโต๊ะ แค่นั้นเอง คำถามคือ มีใครใช้ตามนั้นบ้าง คุณเจียวไข่เจียวใช้เท่าไร ผัดข้าวผัดใช้เท่าไหร่ อ่ะ ผัดผักรวมมิตรก็ได้ เอาแบบเต็มเปี่ยมเลย รู้ไหมว่ามีหลายคนเอาไปทำน้ำสลัด OMG ผมถึงบอกอยู่ครับว่า คุณอย่าไปว่าผู้ผลิตเลย เขาปกป้องตัวเองไว้เรียบร้อยทุกมุมอยู่แล้วครับ ถ้าเรายังไม่อ่านฉลาก ซื้อเครื่องไฟฟ้าไม่เคยดูคู่มือ เซนต์สัญญาแบบไม่อ่านก่อน คุณจะว่าใครจริงไหมครับ
ที่น่าสนใจกว่านั้นคือเราเข้าใจกันแล้วใช่ไหมว่า oryzanol ไม่ได้มาจากการกินรำข้าวตรง ๆ แต่ต้องผ่านกระบวนการสกัดที่ซับซ้อนเพื่อได้น้ำมันมาใช้ และวิธีที่อุตสาหกรรมใช้มากที่สุดก็คือ การสกัดด้วยเฮกเซน (Hexane Extraction) ซึ่งเป็นตัวทำละลายเคมีที่อาจมีสารตกค้างในผลิตภัณฑ์สุดท้าย ถึงแม้จะมีวิธีอื่นที่ปลอดภัยกว่า เช่น การสกัดด้วยเอทานอล (Ethanol Extraction), การสกัดด้วยเอนไซม์ (Enzyme-Assisted Extraction), หรือการสกัดด้วยคาร์บอนไดออกไซด์เหนือวิกฤต (Supercritical CO₂ Extraction) แต่ทั้งหมดนี้มีต้นทุนสูงกว่า ทำให้ไม่เป็นที่นิยมในอุตสาหกรรม นั่นหมายความว่า ถ้าผลิตภัณฑ์ที่คุณซื้อไม่ได้ระบุว่าใช้วิธีอื่น ส่วนใหญ่ก็คือเฮกเซนแน่นอน
ข้อเสียของการบริโภค oryzanol มากเกินไปไม่ได้จบแค่การขัดขวางการดูดซึมวิตามิน เพราะการบริโภคในปริมาณสูงอาจส่งผลให้เกิด ความไม่สมดุลของฮอร์โมน เนื่องจาก oryzanol มีโครงสร้างคล้ายกับสเตอรอลในร่างกาย มันอาจไปรบกวนกระบวนการเผาผลาญของสเตอรอยด์ฮอร์โมน เช่น ฮอร์โมนเพศชาย (Testosterone) และฮอร์โมนความเครียด (Cortisol) ซึ่งในระยะยาวอาจส่งผลต่อระบบภูมิคุ้มกัน อารมณ์ และระดับพลังงานของร่างกาย
ประเด็นที่สำคัญคือ ในเมื่อเรามีอาหารจากธรรมชาติที่ช่วยบำรุงหัวใจได้โดยไม่ต้องมีผลข้างเคียง เช่น ไขมันสัตว์ดี ๆ ที่มีวิตามิน A, D, E, K ครบถ้วน ทำไมต้องพึ่งพาสารสกัดจากอุตสาหกรรม ? สิ่งที่ดูเหมือนดีจากงานวิจัยในแล็บ อาจไม่ได้ดีในระยะยาวเมื่ออยู่ในร่างกายมนุษย์จริง ๆ
ทีนี้เรามาดูจุดขายของ น้ำมันรำข้าวกัน - oryzanol เป็นสารธรรมชาติ ทนความร้อนสูง เอาไปใช้ทอดจะไม่เกิดการสลายตัว ทนความร้อนสูงนี่จริงเลยครับ โอริซานอลเป็นสารต้านอนุมูลอิสระในกลุ่ม Ferulic Acid Esters ซึ่งมีโครงสร้างเสถียรกว่าวิตามินอี (เทียบกับวิตามินอีเพราะ ต้านอนุมูลอิสระ และ การปกป้องไขมันจากการเกิดออกซิเดชัน ) มี จุดสลายตัวสูงกว่า 250°C ซึ่งทำให้ยังคงอยู่ได้ในอุณหภูมิที่ใช้ทอดอาหาร แล้วมันแปลว่าดีจริงไหม? ในขณะที่ น้ำมันรำข้าวมีโอเมก้า-6 สูงมาก (30-40%) ซึ่งไวต่อการเกิดออกซิเดชัน ถึงแม้โอริซานอลจะช่วยชะลอการเหม็นหืน แต่มันไม่ได้ช่วยลดการเกิด สารพิษจากไขมันไหม้ เช่น Aldehydes หรือ HNE (4-Hydroxy-2-nonenal) ที่มาจากโอเมก้า-6 หรือเปล่า??? มันคือการพูดให้เราไปโฟกัสจุดเดียวครับ "โอริซานอลทนร้อน ไม่ได้แปลว่า น้ำมันรำข้าวดีต่อสุขภาพ" เพราะโอเมก้า6 ที่ไวต่อการเกิดออกซิเดชัน รวมถึงวิตามินต่างๆ ก็ยังสูญสลายไปด้วยความร้อน นี่ยังไม่รวมถึงโทษของการกินโอริซานอลมากไปตามที่ให้ข้อมูลไว้ข้างบนด้วย
นอกจากนี้ยังมีคนตั้งคำถามไว้มากมายว่า หากโอริซานอลมีผลชัดเจนต่อสุขภาพเช่นเดียวกับที่โฆษณา ทำไมจึงไม่ได้รับการพัฒนาเป็นยาอย่างจริงจัง? หรือคำตอบคือ งานวิจัยที่สนับสนุนโอริซานอลยังไม่เพียงพอ และในหลายกรณี ผลของมันอาจเกิดจาก Placebo Effect (ผลจากความเชื่อว่ามันได้ผล มากกว่าผลจริงๆ ของสารนั้น) ซึ่งเป็นลักษณะเดียวกับ "ยาหลอก" ที่ไม่ได้มีฤทธิ์ทางชีวเคมีที่ส่งผลชัดเจน
-
มีไลโนเลอิกสูง ใช่ครับไม่ผิดเลยในจุดนี้ ไลโนเลอิก (Linoleic acid) เป็น กรดไขมันไม่อิ่มตัวชนิดหลายพันธะ (Polyunsaturated Fatty Acid, PUFA) ที่สำคัญและจำเป็นสำหรับร่างกาย โดยเฉพาะอย่างยิ่งในการช่วยบำรุงเซลล์และระบบต่างๆ ของร่างกาย ที่สำคัญคือ ไลโนเลอิกเป็นกรดไขมันในกลุ่ม โอเมก้า-6 เป็นสิ่งที่บอกกับเราชัดๆว่า โอเมก้า6 สูงนั่นเอง ถ้าจะดึงเฉพาะข้อดีมาคุยกันก็ไม่ผิดอะไรเลยครับ เพราะโอเมก้า6 สำคัญกับร่างกายจริงๆ แต่ แต่ แต่ การรับโอเมก้า-6 ในปริมาณสูงเกินไปอาจทำให้เกิดการอักเสบในร่างกาย ซึ่งเกี่ยวข้องกับโรคต่างๆ เช่น โรคหัวใจ โรคมะเร็ง และโรคเบาหวาน อย่างที่เรารู้กัน ดังนั้นที่บอกไว้ข้างบนครับ สัดส่วนโอเมก้า 6:3 คือ 40:1 หรือใน 1 ช้อนโต๊ะ มีโอเมก้า 6 สูงถึง ราวๆ 4,140 - 5,520 มก. เรียกว่าโฆษณาไม่ผิดเลยเรื่องปริมาณ แต่จริงๆแล้วเราควรรักษาสมดุล โอเมก้า 6:3 ให้ใกล้เคียง 1:1 มากที่สุดเท่าที่ทำได้ เราก็อาจต้องตั้งคำถามอีกทีว่า การมีไลโนเลอิกสูง มันดีจริงไหม
-
โทโคฟีรอล (Tocopherols) เป็นสารประกอบที่อยู่ในกลุ่ม วิตามินอี เป็นสารต้านอนุมูลอิสระในร่างกาย โดยช่วยปกป้องเซลล์จากความเสียหายจากอนุมูลอิสระและช่วยชะลอการเสื่อมของเซลล์ ถูกต้องตามโฆษณา จริงๆหน้าที่หลักคือปกป้องไขมันไม่ให้เกิดการออกซิเดชัน ซึ่งสามารถช่วยยืดอายุการใช้งานของน้ำมัน หรือไม่ให้เกิดการหืน นั่นเอง แต่การทอดหรือปรุงอาหารในอุณหภูมิสูงเกินไป ก็อาจทำให้น้ำมันเกิดการออกซิเดชันและเกิดสารพิษที่เป็นอันตรายต่อร่างกายได้ อย่าลืมนะครับว่าคำแนะนำในการใช้น้ำมันรำข้าว กลับชูการเหมาะกับอาหารทอดอุณหภูมิสูง
-
โทโคไทรอีนอล (Tocotrienols) เป็นส่วนหนึ่งของกลุ่ม วิตามินอี เช่นกัน การบริโภคมากเกินไป การรับประทาน โทโคไทรอีนอลในปริมาณมาก อาจมีผลข้างเคียงที่ไม่พึงประสงค์ เช่น ส่งผลกระทบต่อการดูดซึมวิตามินอื่นๆ ในร่างกายโดยเฉพาะวิตามิน K ซึ่งอาจทำให้เกิดปัญหาการแข็งตัวของเลือด, ทำให้ตับทำงานหนักขึ้นในการจัดการกับสารนี้ ซึ่งอาจส่งผลเสียต่อการทำงานของตับระยะยาว
สุดท้ายแล้ว เราต้องกลับมาตั้งคำถามว่า เราอยากให้สุขภาพของเราถูกกำหนดโดยการตลาดของอุตสาหกรรม หรือโดยสิ่งที่ธรรมชาติออกแบบมาให้เราตั้งแต่แรก ? ถ้าจะดูแลหัวใจจริง ๆ การกินอาหารที่มนุษย์วิวัฒนาการมากับมันมาตลอด เช่น เนื้อสัตว์ ไข่ ตับ และไขมันดี ๆ อาจเป็นคำตอบที่เรียบง่ายและมีเหตุผลมากกว่าการไล่ตามสารสกัดที่อุตสาหกรรมบอกว่าจำเป็น แต่ธรรมชาติอาจไม่เคยเห็นว่ามันสำคัญเลยก็ได้
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ 69e50943:2ac7059c
2025-04-03 23:14:14
@ 69e50943:2ac7059c
2025-04-03 23:14:14This is a test
How does this look?

-
 @ 2b42dd42:5049393c
2025-04-03 21:25:46
@ 2b42dd42:5049393c
2025-04-03 21:25:46this is a test

end of the test
-
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ 2ed3596e:98b4cc78
2025-04-03 21:20:27
@ 2ed3596e:98b4cc78
2025-04-03 21:20:27We’re giving you the chance to win even more sats through the Bitcoin (Wishing) Well—just for telling us what you love about Bitcoin Well.
Each month, when you leave a review for either the Bitcoin Well portal on Trustpilot (include your WellTag), or our Bitcoin ATMs and (include your transaction ID and email), you’ll be entered for a draw where you can win $210 in bitcoin just for sharing your experience!
Whether it’s our self-custody focus, fast Lightning purchases, Lightning referral payouts, private ATM transactions or our unbeatable customer support, we want to hear what makes Bitcoin Well your go-to place for buying, selling, and using bitcoin.
How to leave your Trustpilot review for our portal
- Head to our Trustpilot page
- Write a quick review sharing your favourite Bitcoin Well feature
- Include your WellTag (or transaction ID), in the review so we can add you to the prize draw
How to leave your google review for one of our ATMs
- Google the Bitcoin Well Bitcoin ATM you recently used
- Write a quick review sharing your favourite Bitcoin Well feature
- Include your transaction ID, in the review so we can add you to the prize draw
It’s that easy! Once your review is verified with your welltag or transaction ID, we’ll add your entry to our monthly draw for your chance to win $210 in bitcoin! We’ll announce the winner and the start of each month. Good luck and keep stacking sats!
What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. We do this by making it easy to self custody bitcoin. By custodying their own money, our customers are free to do as they wish without begging for permission. By creating a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂.
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website.
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
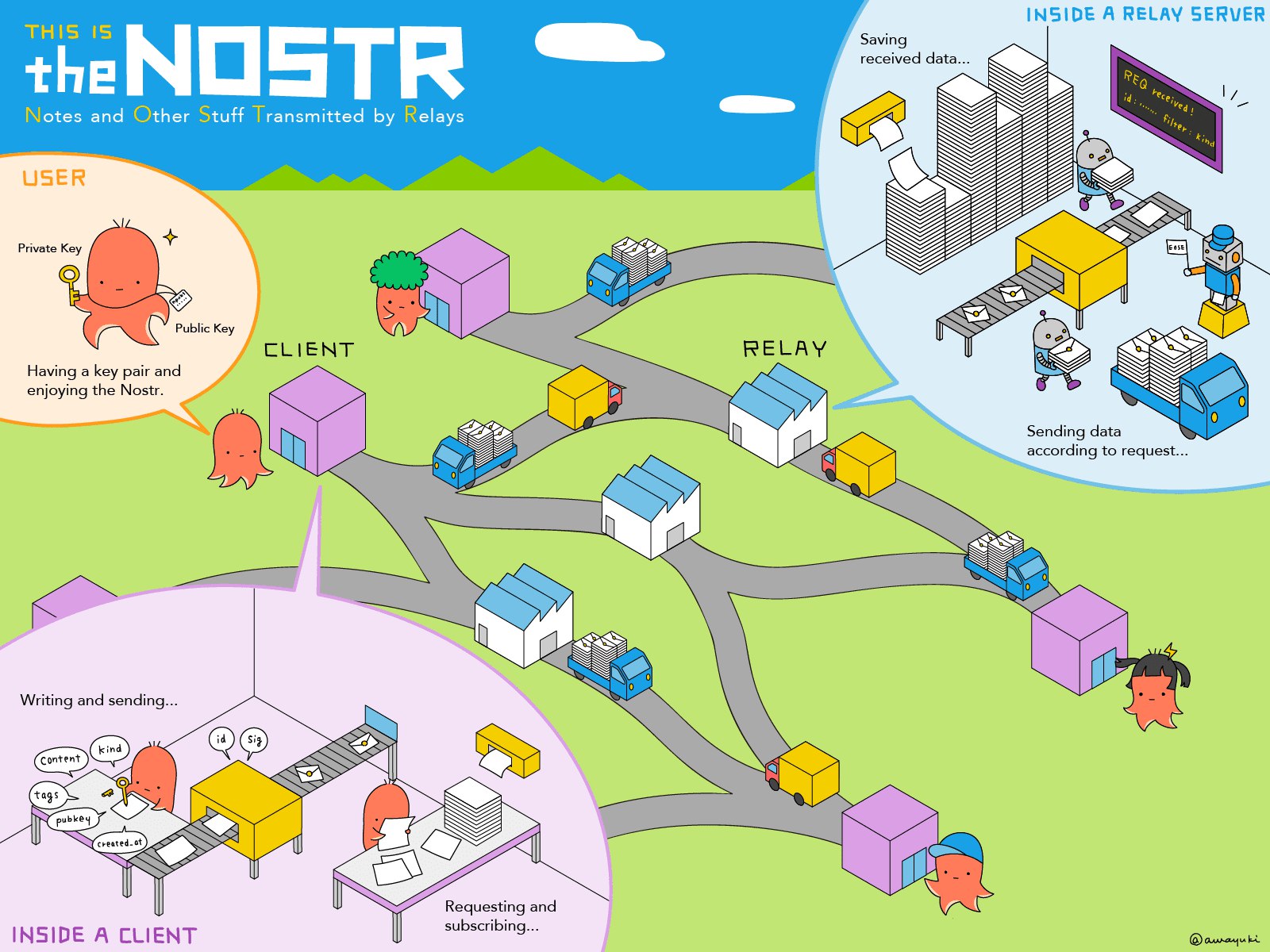
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:04:35
@ 20e17dd0:2ae504d7
2025-03-20 10:04:35Prerequisite
Installation
Open a Terminal session and write the following command to make sure that Docker is running:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Then, create the volume that Portainer Server will use to store its database:
ruby sudo docker volume create portainer_dataYou are now ready for the on-liner installation:
ruby sudo docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestTo validate the installer, prompt the following command:
ruby sudo docker psYou should see Portainer's container running.
To access Portainer Server, go to the following adress: https://localhost:9443
Et voila!
-
 @ 07f367da:0e76880d
2025-04-03 17:59:21
@ 07f367da:0e76880d
2025-04-03 17:59:21윤석열 탄핵 선고를 앞둔 4월 3일. 우리 노동조합은 서울 마포구 소재의 한 활동지원기관 앞에서 선전전을 진행했다. 노동조합은 한 활동지원사의 민원을 통해 해당 활동지원기관이 일요일에 일해도 평일 임금을 지급한다는 사실을 파악했다. 활동지원사의 민원에 관심을 가진 한 언론사의 기자는 활동지원기관과 구청, 서울시, 노조에 문의하며 팩트체크를 진행하고 있는데, 이 과정에서 노조는 해당 기관이 일요일에 일을 해도 평일 임금을 지급하고 있다는 사실을 명확히 확인했다.
자신이 받는 임금에 대한 사실관계를 노동자들은 잘 알지 못한다. 활동지원사는 기관에 자신의 임금에 대해 문의해도 속 시원한 답을 듣지 못한다. 활동지원사들이 하나같이 하는 이야기가 기관에 물어봐도 제대로 설명을 해주지 않는다는 하소연이다.
당사자 활동지원사는 노조에 민원을 제기하고, 또 기자가 취재한 내용들을 통해서야 자신의 임금이 자신도 모르게 어떻게 변화했는지를 알아가고 있다. 사업장의 임급지급 행위에 대한 가치판단이나 평가 이전에 노동자들은 그 사실 자체를 모를 가능성이 높다. 노조는 이 사실을 활동지원사들에게 알리려 선전전을 진행하기로 했다.
선전전 진행 중 정말 충격적인 경험을 했다. 노동조합의 선전활동은 정당한 노조활동이고 일상적인 활동이다. 여태 여러 사업장에서 선전활동을 했지만, 이런 경우는 정말 처음이었다. 사업장들은 신경 거슬러 하고 적대적인 대우를 하곤 했지만, 가장 강한 대처가 경찰에 신고하여 공권력의 개입을 요청하고, 경찰은 충돌을 방지하는 선에서 대처한다. 그런데 오늘은 장애인 기관장이 선전활동을 하지 말라고 계속 항의하며 방해하더니 소속 활동지원팀 인력은 노동조합이 활동지원사에게 선전물을 전달하려 하니 몸으로 막기까지 한다.
무엇을 그렇게 숨기고 싶을까? 노동조합의 활동을 몸으로 막으면서까지 싫어할 이유가 무엇일까? 노동조합의 활동이 그들에게 무엇으로 다가갔을까? 여러 질문이 든다.
충격적인 것은 이 기관의 대표가 우리노조가 예전에 청와대 앞에서 기자회견 할 때 연대 발언을 하러 왔던 활동가라는 점이다. 장애인 당사자이자 인권운동 활동가가 사용자로, 그리고 사회복지사 노동자들이 전담인력으로 고용되어 사측을 대신해 활동지원사 노동자들이 응당 자신에 대해 알아야 할 사항을 은폐한다.
사장이 되어 권력을 행사하면서도 장애인이라는 정체성으로 자신의 지위를 지우려 하고, 전담인력이라는 지위로 노동자들을 지휘하면서도 같은 노동자라며 위계를 삭제한다. 그리고 정작 현장에서 장애인에게 활동지원을 제공하는 활동지원사들은 대부분 고령의 여성들로 정보약자에 해당한다. 우리에게도 민주주의가 올까. 나는 저들이 활동으로 세상을 좋게 만드는 것을 상쇄할 정도로 더 세상을 나쁘게 만들고 있다고 생각한다.
타인에 의해 돈벌이 수단으로 이용당하는 사람은 자신 또한 타인을 돈벌이 수단으로 활용할 가능성이 높다. 그 타인에는 장애인도 포함된다. 나는 시설사회가 끝나도 장애인학대가 끝나리라는 믿음이 없다. 우리는 어차피 서로를 돈벌이 수단으로만 삼는 사회에서 살고 있기 때문이다.
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 30ceb64e:7f08bdf5
2025-03-19 21:29:59
@ 30ceb64e:7f08bdf5
2025-03-19 21:29:59NIP-101e: Workout Data and Running Extensions
NIP-101e represents a crucial step forward for fitness tracking on Nostr, giving us a common language that would allow workout data to flow freely between apps. This proposal outlines a thoughtful framework with Exercise Templates, Workout Templates, and Workout Records that would finally free our fitness data from proprietary silos and put it back in our hands. I'm eager to see this proposal implemented because it would create the foundation for a genuinely open fitness ecosystem on Nostr.
As a runner building a Nostr running app RUNSTR, I've proposed some running-specific extensions to NIP-101e that address the unique needs of runners without disrupting the elegant structure of the original proposal. My extensions would standardize how we record GPS routes, pace metrics, elevation data, splits, and even weather conditions - all things that matter tremendously to runners but aren't covered in the base proposal that focuses more on strength training.
By implementing NIP-101e along with these running extensions, we could create something truly revolutionary: a fitness ecosystem where runners aren't locked into a single platform because of their data. You could track your morning run in my app, analyze your training in another app that specializes in statistics, and share achievements with friends using whatever Nostr clients they prefer. I believe strongly in getting NIP-101e implemented with these extensions included because it would foster innovation while giving runners unprecedented freedom to own their data and use it however they want. Let's make this happen and show what's possible when fitness data becomes truly interoperable!
-
 @ 502ab02a:a2860397
2025-04-03 17:41:20
@ 502ab02a:a2860397
2025-04-03 17:41:20ไฟโตสเตอรอล (Phytosterols) เป็นสารประกอบที่พบในพืชและมีโครงสร้างคล้ายคลึงกับคลอเลสเตอรอล (Cholesterol) ของมนุษย์ แต่ไฟโตสเตอรอลไม่ได้ทำหน้าที่เหมือนคลอเลสเตอรอลในร่างกายครับ ไฟโตสเตอรอลมีบทบาทสำคัญในการลดการดูดซึมคลอเลสเตอรอลจากอาหารในระบบทางเดินอาหาร ทำให้ไฟโตสเตอรอลได้รับการส่งเสริมว่าเป็นสารที่ช่วยลดระดับคลอเลสเตอรอลในเลือดไปโดยปริยาย
อย่างไรก็ตาม สิ่งที่หลายคนไม่ได้ตั้งข้อสงสัยคือวิธีการโฆษณาและการตลาดนั้นจะแฝงไปด้วยข้อมูลที่บิดเบือนเกี่ยวกับไฟโตสเตอรอลซึ่งอาจนำไปสู่การเสพสารนี้ในปริมาณมากเกินไปจนทำให้เกิดปัญหาสุขภาพหรือเปล่า? เราลองมาค่อยๆตั้งคำถามกันครับ
ไฟโตสเตอรอลในธรรมชาติจะพบในปริมาณที่ค่อนข้างน้อยในพืชต่าง ๆ เช่น ธัญพืช ถั่ว เมล็ดพืช อย่างไรก็ตาม ปริมาณไฟโตสเตอรอลในธรรมชาติเป็นเม็ดเป็นผลจะอยู่ในระดับต่ำมาก เช่น ในเมล็ดแฟลกซีด (flaxseed) จะมีไฟโตสเตอรอลอยู่ประมาณ 1,000–2,000 ppm (parts per million) ขณะที่น้ำมันรำข้าวที่มักถูกโฆษณาว่ามีไฟโตสเตอรอลสูงถึงหลักหมื่น ๆ ppm เช่น 12,000 ppm หรือบางยี่ห้ออาจสูงกว่านั้น ซึ่งไม่ใช่แค่สูงจนน่าสรรเสริญ แต่ยังเป็นการขยายความสำคัญของไฟโตสเตอรอลในทางที่ตอบสนองต่อการตลาดได้ในวงกว้างเสียด้วย
กระบวนการผลิตน้ำมันรำข้าวนั้นเริ่มต้นจากการสกัดน้ำมันจากรำข้าว โดยมีการใช้เทคนิคการกลั่นน้ำมันที่สามารถช่วยให้ได้น้ำมันที่มีคุณภาพสูง น้ำมันรำข้าวเป็นน้ำมันที่มีไฟโตสเตอรอลสูงเพราะรำข้าว (bran) ซึ่งเป็นเปลือกที่หุ้มเมล็ดข้าวนั้น มีไฟโตสเตอรอลอยู่ในปริมาณสูงตามธรรมชาติอยุ่แล้ว ในกระบวนการสกัดน้ำมันนั้น ตัวไฟโตสเตอรอลจะถูกรักษาไว้ โดยไม่ต้องเติมเข้าไปใหม่ ดังนั้น เมื่อโฆษณาน้ำมันรำข้าวว่า "มีไฟโตสเตอรอลสูงถึง 12,000 ppm" สิ่งนี้ไม่ได้หมายความว่าเป็นการเติมสารเพิ่มเข้ามาหรอกครับ แต่เป็นการยืนยันถึงความ "เข้มข้น" ของไฟโตสเตอรอลที่มีอยู่ในน้ำมันรำข้าวตามธรรมชาตินั่นละครับว่ามันกลั่นมาเข้มข้นขนาดไหน มากกว่าการกินจากธรรมชาติขนาดไหนเพื่อให้เรากินกันนั่นเอง
ถึงแม้ว่าไฟโตสเตอรอลจะถูกส่งเสริมให้เป็นสารที่ช่วยลดระดับคลอเลสเตอรอลในเลือด แต่การโฆษณาและการตลาดเกี่ยวกับไฟโตสเตอรอลนั้นอาจทำให้คนเข้าใจผิดว่า ผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูง จะช่วยทำให้สุขภาพดีขึ้นและลดความเสี่ยงจากโรคหัวใจและหลอดเลือด เพราะซึ่งสิ่งนี้ยังไม่ได้รับการสนับสนุนอย่างชัดเจนจากงานวิจัยที่สามารถยืนยันได้ในระยะยาว นอกจากนี้ยังมีผลการศึกษาบางชิ้นเช่นกันที่พบว่า การบริโภคไฟโตสเตอรอลในปริมาณสูงอาจ "ไม่ได้มีผล" ในการลดระดับคลอเลสเตอรอลที่น่ามหัศจรรย์หรือช่วยลดการเสี่ยงต่อโรคหัวใจได้ตามที่โฆษณาเอามาขยายความกัน ซึ่งแน่นอนหละครับว่า ถ้าจะทำสงครามวิจัย มันย่อมไม่จบสิ้นเพราะทุกฝ่ายมีการวิจัยสนับสนุนในแบบ peer review ทั้งนั้น ไม่ต้องไปเป็น member อะไรที่ไหน (ถ้าเราไม่คิดจะอ่านมันเอง)
ไฟโตสเตอรอลมีหลายประเภทที่พบในพืชและน้ำมันพืชแต่ละชนิด โดยแต่ละชนิดจะมีคุณสมบัติและผลกระทบต่อร่างกายที่แตกต่างกัน ซึ่งสามารถแบ่งออกเป็นหลายประเภทหลักที่พบได้บ่อยในธรรมชาติ แต่ละประเภทก็มีข้อดีและข้อเสียที่ควรพิจารณาก่อนการบริโภคตามประเภทมันไปครับ
-บีตาสติโรล (Beta-Sitosterol) เป็นไฟโตสเตอรอลที่พบมากในพืชหลายชนิด โดยเฉพาะในเมล็ดพืช ถั่ว และน้ำมันพืช บีตาสติโรลได้รับความนิยมในวงการสุขภาพเนื่องจากการศึกษาบางชิ้นพบว่ามันสามารถช่วยลดระดับคอเลสเตอรอลในเลือดได้ โดยการลดการดูดซึมคอเลสเตอรอลจากอาหารในระบบย่อยอาหาร แต่การบริโภคบีตาสติโรลในปริมาณสูงอาจส่งผลต่อการดูดซึมวิตามินที่ละลายในไขมัน เช่น วิตามิน A, D, E และ K ซึ่งอาจทำให้เกิดการขาดวิตามินเหล่านี้ในระยะยาวได้ นอกจากนี้ การบริโภคบีตาสติโรลในปริมาณที่มากเกินไปอาจส่งผลให้เกิดปัญหาด้านระบบฮอร์โมน โดยเฉพาะในผู้ที่มีปัญหาฮอร์โมนเพศหรือระบบสืบพันธุ์
-แคมป์สเตอรอล (Campesterol) เป็นอีกหนึ่งไฟโตสเตอรอลที่พบในพืชหลายชนิด โดยเฉพาะในน้ำมันพืชและผักผลไม้ แคมป์สเตอรอลมีโครงสร้างที่คล้ายกับคอเลสเตอรอลในร่างกาย และมันได้รับการศึกษาว่ามีคุณสมบัติช่วยลดระดับคอเลสเตอรอลในเลือดได้เช่นกัน อย่างไรก็ตาม การบริโภคแคมป์สเตอรอลมากเกินไปอาจทำให้เกิดผลกระทบต่อการดูดซึมสารอาหารบางประเภท เช่น วิตามินที่ละลายในไขมัน โดยเฉพาะในผู้ที่มีปัญหาทางเดินอาหาร หรือผู้ที่มีปัญหาการดูดซึมสารอาหาร อาจทำให้เกิดภาวะขาดสารอาหารหรือการดูดซึมสารอาหารไม่เต็มที่ได้ นอกจากนี้ การบริโภคแคมป์สเตอรอลในปริมาณสูงอาจส่งผลกระทบต่อการทำงานของฮอร์โมนเพศ เช่น การเปลี่ยนแปลงของฮอร์โมนในร่างกาย ซึ่งอาจเกิดผลเสียต่อสุขภาพในระยะยาว
-สแตกิโอรอล (Stigmasterol) เป็นไฟโตสเตอรอลชนิดหนึ่งที่พบมากในพืชบางชนิด เช่น ถั่วเหลือง และน้ำมันถั่วเหลือง สแตกิโอรอลได้รับการศึกษาในแง่ของการลดการอักเสบและการช่วยบำรุงสุขภาพหัวใจและหลอดเลือด แต่การบริโภคสแตกิโอรอลในปริมาณสูงอาจมีผลเสียต่อการทำงานของฮอร์โมนเพศได้เช่นกัน โดยเฉพาะในผู้ที่มีปัญหาฮอร์โมนไม่สมดุลหรือมีปัญหาเกี่ยวกับระบบสืบพันธุ์ การบริโภคไฟโตสเตอรอลชนิดนี้มากเกินไปอาจทำให้เกิดผลกระทบต่อการทำงานของระบบฮอร์โมนในร่างกาย ซึ่งอาจส่งผลให้เกิดอาการผิดปกติในระยะยาว รวมทั้งความเสี่ยงต่อการมีบุตรหรือสุขภาพที่ไม่ดีเกี่ยวกับระบบฮอร์โมน
ไฟโตสเตอรอลประเภทอื่น ๆ ที่พบในพืชและน้ำมันพืช ได้แก่ อะฟิตเตอร์ออล (Afitosterol) และซิตรัสเตอรอล (Citrusterol) ซึ่งมักพบในน้ำมันจากพืชต่าง ๆ เช่น น้ำมันเมล็ดองุ่น น้ำมันดอกทานตะวัน การบริโภคไฟโตสเตอรอลเหล่านี้ในปริมาณที่สูงเกินไปอาจทำให้เกิดปัญหาด้านระบบย่อยอาหาร หรือปัญหาการดูดซึมสารอาหารที่จำเป็นจากอาหารได้ นอกจากนี้ การบริโภคไฟโตสเตอรอลประเภทอื่น ๆ ในปริมาณสูงยังอาจส่งผลกระทบต่อระบบฮอร์โมนและการทำงานของร่างกายในระยะยาว เช่น การทำงานของระบบภูมิคุ้มกัน หรือการทำงานของตับ ที่อาจได้รับผลกระทบจากการบริโภคในปริมาณสูง ดังนั้น ควรระมัดระวังในการบริโภคไฟโตสเตอรอลจากแหล่งต่าง ๆ อย่างรอบคอบ เพื่อหลีกเลี่ยงผลเสียที่อาจเกิดขึ้นกับร่างกายในระยะยาว
สิ่งที่จริงแล้วอาจเป็นอันตรายมากกว่า คือ การที่ผู้บริโภคตัดสินใจบริโภคผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูงในปริมาณมากเกินไป โดยไม่คำนึงถึงผลกระทบต่อร่างกายในระยะยาว อาจมีผลกระทบต่อการดูดซึมสารอาหารที่จำเป็น เช่น วิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมัน การดูดซึมของวิตามินเหล่านี้อาจถูกยับยั้งไป เนื่องจากไฟโตสเตอรอลสามารถแข่งขันกับคลอเลสเตอรอลในร่างกายในการดูดซึมสารอาหารเหล่านี้ นอกจากนี้ยังมีข้อกังวลเกี่ยวกับผลกระทบที่อาจเกิดขึ้นจากการบริโภคไฟโตสเตอรอลในปริมาณสูงที่อาจไปเพิ่มความเสี่ยงของการเกิดโรคบางอย่าง เช่น โรคมะเร็งต่อมลูกหมาก
ผลเสียจากการบริโภคไฟโตสเตอรอลมากเกินไปไม่ได้จำกัดเพียงแค่การแย่งสารอาหาร แต่ยังมีการศึกษาที่แสดงให้เห็นว่า การบริโภคไฟโตสเตอรอลในปริมาณสูงอาจกระทบต่อการทำงานของระบบภูมิคุ้มกันของร่างกาย ในบางกรณีไฟโตสเตอรอลอาจเข้าไปแทรกแซงกระบวนการทางชีวเคมีที่สำคัญ และอาจทำให้ร่างกายเกิดความผิดปกติในการตอบสนองต่อสารแปลกปลอมที่มีอยู่ในสิ่งแวดล้อม
ข้อโต้แย้งที่สำคัญคือลักษณะการโฆษณาของน้ำมันรำข้าวและผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูงนั้น ไม่ได้สะท้อนความจริงในสิ่งที่เป็นประโยชน์ต่อสุขภาพจริง ๆ การใช้ไฟโตสเตอรอลในผลิตภัณฑ์ต่าง ๆ โดยเน้นที่ปริมาณที่สูงเกินจริงนั้น เป็นวิธีการตลาดที่ใช้บอกเป็นนัยกับผู้บริโภคให้เข้าใจว่าการบริโภคสารเหล่านี้จะช่วยลดระดับคลอเลสเตอรอลและช่วยให้สุขภาพหัวใจดีขึ้น ทั้งที่ในความเป็นจริง ไฟโตสเตอรอลไม่ได้ช่วยแก้ปัญหาสุขภาพพื้นฐานอย่างการอักเสบที่เป็นสาเหตุหลักของโรคหัวใจและหลอดเลือด แต่ทั้งนี้ทั้งนั้น การโฆษณาดังกล่าวก็อยู่ภายใต้กฎเกณฑ์ของประกาศและกฎหมายต่างๆอยู่ดี ผู้บริโภคจึงควรหาความรู้สนับสนุนการเลือกด้วยตัวเอง ว่าจะตัดสินใจอย่างไร
การที่ไฟโตสเตอรอลมีโครงสร้างที่คล้ายกับคอเลสเตอรอลในร่างกาย ทำให้มันสามารถแทรกซึมเข้าไปในเซลล์ได้คล้ายคลึงกับคอเลสเตอรอล แต่แตกต่างกันตรงที่ไฟโตสเตอรอลไม่สามารถทำหน้าที่ในการสร้างฮอร์โมนต่าง ๆ หรือทำหน้าที่ในระบบร่างกายได้เหมือนคอเลสเตอรอล การที่ไฟโตสเตอรอลแทรกซึมเข้าไปในเซลล์จึงเป็นแค่การสามารถช่วยป้องกันการดูดซึมคอเลสเตอรอลจากอาหารในระบบย่อยอาหารได้ ซึ่งจะทำให้นี่เป็นสาเหตุของการทำให้ ระดับคอเลสเตอรอลในเลือดลดลงได้ พูดง่ายๆคือมันไปแซงคลอเลสเตอรอล อะครับ
นอกจากนี้ ไฟโตสเตอรอลยังสามารถไปแข่งขันกับคอเลสเตอรอลในการเข้าเซลล์ผ่านตัวรับ LDL (low-density lipoprotein receptor) ซึ่งเป็นตัวรับที่ช่วยดูดซึมคอเลสเตอรอลเข้าสู่เซลล์ ดังนั้น เมื่อไฟโตสเตอรอลแทรกซึมเข้ามามากขึ้น ก็จะช่วยลดการดูดซึมคอเลสเตอรอล ที่มาจากอาหารลงไปได้ ทำให้ระดับคอเลสเตอรอลในเลือดลดลง โดยการลดการดูดซึมคอเลสเตอรอลจากทางเดินอาหารเข้าสู่กระแสเลือด แต่ไฟโตสเตอรอลไม่ได้มีผลโดยตรงในการลดคอเลสเตอรอลที่เซลล์ในร่างกายสร้างขึ้นเอง (endogenous cholesterol) เพราะไฟโตสเตอรอลไม่ได้เข้าไปแทรกซึมและทำงานที่จุดที่เซลล์ผลิตคอเลสเตอรอลในร่างกาย
ร่างกายสามารถผลิตคอเลสเตอรอลได้เอง ซึ่งเป็นกระบวนการที่ไฟโตสเตอรอลไม่สามารถไปขัดขวางหรือยับยั้งได้ นั่นหมายความว่า หากร่างกายผลิตคอเลสเตอรอลในระดับสูง ไฟโตสเตอรอลจะไม่สามารถลดระดับคอเลสเตอรอลที่มาจากการสร้างของร่างกายได้ ดังนั้น ไฟโตสเตอรอลมีประโยชน์ในการลดคอเลสเตอรอลจากอาหาร แต่ไม่ได้ช่วยในการลดคอเลสเตอรอลที่ร่างกายผลิตขึ้นเอง
การโฆษณาไม่ได้ให้ข้อมูลในด้านที่ว่า ผลกระทบระยะยาวจากการบริโภคไฟโตสเตอรอลในปริมาณสูงอาจทำให้เกิดปัญหาสุขภาพอื่น ๆ โดยเฉพาะในด้านการดูดซึมสารอาหารหรือความสามารถในการทำงานของระบบภูมิคุ้มกัน ซึ่งเป็นสิ่งที่ควรคำนึงถึงในการตัดสินใจเลือกผลิตภัณฑ์ที่จะนำมาใช้ในชีวิตประจำวัน ในความเห็นของผมนั้น สิ่งที่ควรให้ความสำคัญมากกว่าคือการเลือกบริโภคอาหารที่เป็นธรรมชาติ และหลีกเลี่ยงการพึ่งพาผลิตภัณฑ์ที่มีการผ่านกระบวนการต่าง ๆ เช่น ไฟโตสเตอรอลเข้มข้น หรือสารเติมแต่งอื่น ๆ ที่ไม่จำเป็นต่อร่างกาย การเลือกรับประทานอาหารที่มีคุณค่าทางโภชนาการครบถ้วนจะช่วยส่งเสริมสุขภาพโดยรวมได้ดีกว่าแทนที่จะพึ่งพาสิ่งที่โฆษณาบอกไว้ข้างขวด
ไฟโตสเตอรอลอาจมีคุณสมบัติในการลดการดูดซึมคลอเลสเตอรอลจากอาหารในทางทฤษฎี แต่การบริโภคในปริมาณมากเกินไปนั้นอาจส่งผลเสียต่อร่างกายในหลาย ๆ ด้าน ดังนั้นจึงควรหันมาใส่ใจในข้อมูลที่มีพื้นฐาน และตั้งคำถามกับสิ่งต่างๆ โดยเฉพาะอะไรที่การตลาดตะโกนดังๆว่า ไอ้นี่ดี อันโน้นเยี่ยมยอด อันนี้ที่สุดแห่งความซุปเปอร์ ต่อมเอ๊ะทำงานไว้ก่อน ผิดถูกไม่รู้หาข้อมูลมาโยงเส้นทางแล้วชวนคุยกัน
เช่นเราตั้งคำถามตั้งต้นก่อนไหมว่า จริงๆแล้ว คลอลเสเตอรอล มันต้องกลัวขนาดนั้นเลยหรือ ในเมื่อมันเป็นสารตั้งต้นของชีวิต และเป็นสิ่งจำเป็นในการซ่อมแซมเสริมสร้างร่ายกาย เราต้องลดการดูดซึมด้วยเหรอ
-
 @ 7d33ba57:1b82db35
2025-04-03 17:36:08
@ 7d33ba57:1b82db35
2025-04-03 17:36:08Zadar is a coastal city in northern Dalmatia, known for its rich Roman and Venetian history, stunning sunsets, and unique modern attractions like the Sea Organ and Sun Salutation. With ancient ruins, beautiful beaches, and a lively Old Town, Zadar offers a less crowded but equally charming alternative** to Split and Dubrovnik.
🏛️ Top Things to See & Do in Zadar
1️⃣ Explore Zadar Old Town 🏰
- Walk through narrow, stone-paved streets, surrounded by Roman and medieval architecture.
- Visit People’s Square (Narodni Trg) – The heart of Zadar’s Old Town, filled with lively cafés.
2️⃣ Visit the Sea Organ & Sun Salutation 🎶🌞
- Sea Organ – A one-of-a-kind musical instrument, where waves create natural melodies.
- Sun Salutation – A large solar-powered light display, best seen at sunset.
- Alfred Hitchcock once called Zadar’s sunset “the most beautiful in the world.” 🌅
3️⃣ Admire St. Donatus Church & Roman Forum ⛪
- St. Donatus (9th century) – A unique, round Byzantine-style church with great acoustics.
- Roman Forum – The remains of an ancient Roman marketplace, built in the 1st century BC.
4️⃣ Climb the Bell Tower of St. Anastasia’s Cathedral 🔔
- Enjoy spectacular views over Zadar’s rooftops and the Adriatic.
- One of the tallest church towers in Croatia.
5️⃣ Relax at Zadar’s Best Beaches 🏖️
- Kolovare Beach – The most popular city beach, just a short walk from the Old Town.
- Borik Beach – A sandy beach with shallow waters, ideal for families.
- Punta Bajlo – A more natural and peaceful spot, great for a quiet swim.
6️⃣ Take a Day Trip to Kornati National Park ⛵
- A beautiful archipelago of 89 islands, perfect for boating, swimming, and snorkeling.
- Join a boat tour from Zadar to explore the untouched nature of the Adriatic.
7️⃣ Try Dalmatian Cuisine 🍽️
- Black Risotto (Crni Rižot) – A delicious squid-ink seafood dish. 🦑
- Pag Cheese (Paški Sir) – A famous sheep’s milk cheese from Pag Island. 🧀
- Grilled Adriatic Fish – Freshly caught and served with olive oil & Dalmatian herbs. 🐟
🚗 How to Get to Zadar
✈️ By Air:
- Zadar Airport (ZAD) is just 15 minutes from the city center.
🚘 By Car:
- From Split: ~1.5 hours (160 km)
- From Zagreb: ~2.5 hours (285 km)
🚌 By Bus: Regular buses from Split, Zagreb, Dubrovnik, and Plitvice Lakes.
⛴️ By Ferry: Ferries connect Zadar to nearby islands like Ugljan, Dugi Otok, and Pašman.
💡 Tips for Visiting Zadar
✅ Best time to visit? May–October for warm weather & island trips ☀️
✅ Stay near the Old Town – Everything is within walking distance 🏡
✅ Catch the sunset at the Sea Organ – It’s a must-do experience 🌊🎶
✅ Take a ferry to Ugljan Island for a day of beaches & cycling 🚢🚴♂️
✅ Book Kornati boat tours in advance – They sell out fast in summer! ⛵ -
 @ 5708b1f6:208df3b8
2025-04-03 15:25:33
@ 5708b1f6:208df3b8
2025-04-03 15:25:33The role and significance of music naturally varies from person to person. For some, it is counted among the most important things in life. For others, it may be a superfluous additive of limited value. Due to this difference in perception relating to music, it may be difficult for some individuals to recognize the benefits of compiling a personalized music playlist.
However, the value of music as a therapeutic tool for people already suffering from advanced dementia has been repeatedly demonstrated, and sometimes with astounding, although temporary, results. The internet is full of studies and stories, and YouTube searches yield an abundance of video evidence ranging from clinical studies to anecdotal family recordings of elderly relatives.
All of these data and anecdotes point to a compelling suggestion and an exciting conclusion: music appreciation has tremendous potential as a supplemental activity for mental health maintenance. With insights gained from the study of neuroplasticity, the neurological benefits for musicians and performers are easy to see, but less clear is the fact that mere exposure to music as a casual listener can be of profound psychological importance, even for individuals who don’t consider themselves to be music lovers.
The transformative effect of music is on full display in many of the available videos on YouTube. We can simply search “dementia music,” or ‘Alzheimer’s music” for fast, relevant results. In video after video, we can see elderly subjects who may be slow to speak, detached, disoriented, barely-intelligible, or unresponsive. In care facilities and at gatherings with families, they are interviewed about their youth, and about their feelings related to music.
Many of the videos first show footage of the individual’s normal daily cognitive state, and them listening and responding to the questions, followed by a period of music listening, and then another brief, post-music discussion. The transformation of mental states tends to be very clear when we compare the quality of their cognitive performance before and after the introduction of music. People remark that “a light has been turned back on,” or “his personality returned,” or “it’s as if the person has woken up from sleep.”
Unfortunately, these positive responses are only temporary, and music does not have the power to permanently reverse the symptoms and pathology of advanced dementia and age-related cognitive decline. Also there is no guarantee it will work for every person, or to what degree. Nevertheless, it does not mean that music as therapy is completely without value. In fact, it can be quite the opposite.
When the response is positive, the event can have multiple benefits, and may even be a therapeutic experience for certain listeners. Faces once despondent or vacant become animated and radiant. Long lost smiles return from faraway times and places. Memories and associations from previous ages shake loose and rise to the surface. Many listeners were asked to recount their experiences related to the songs and the time in life with which they were primarily associated. Some of them were able to describe events, places, people, emotions, and reactions with a degree of clarity, dexterity, and articulation that was completely inconsistent with their medical diagnosis and their cognitive performance prior to hearing the music. The song quite literally revives the personality that makes the person, temporarily and superficially reversing the undoing of the mind. For a mind that is coming undone, music as therapy has potential to mitigate suffering and confusion, provide moments of joy and enthusiasm, and ease the transition into and experience of the end-of-life period that awaits all who are fortunate enough to “die of natural causes” in old age.
The benefits described above are specific to “treatment” recipients, but the merit of music as therapy cascades into the lives of everyone involved. Doctors and caretakers are uplifted and encouraged by success stories, which contributes to further proliferation and advancement of music as therapy. More critically, it can have a profound impact on families of dementia patients. In some cases, relatives get a chance to communicate with their loved ones again. Grandchildren have a window of opportunity to learn more, directly from their grandparents, about the youthful experiences and memories of past generations. It’s clear that generational bonds are also strengthened, which can positively impact the future prospects of the young generation as they in turn grow old, and lay new groundwork for generations that follow.
It is unfortunate that some elderly individuals seem to derive less cognitive benefit than others from music therapy. It is not entirely certain why this is so, because there are many factors to consider, but two of the clearest factors are a person’s degree of cognitive decline, and their degree of interest in and enthusiasm for music in general. While these are the most popular metrics by which to judge the potential effectiveness and suitability of music as therapy for a given individual, by far the most important consideration is relevance to each particular person’s life experiences.
This is the opportunity to finally state the obvious: It’s not possible to simply pick any song at random and expect it to have a beneficial effect on the cognitive function of every person who hears it. It’s not as if there’s a Britney Spears song that sparks joy in the heart of every soul on Earth. And the legend of Bill and Ted’s ultimate song that united the world could never be a true story (also because, as we finally learned in 2020, it was not two men and a song that united the world, but rather, the world uniting together to create that song.) However, everyone in the world can make their own playlist custom-tailored to their individual life, experiences, and memories, and some of those playlists might have a song or two by Britney Spears, or even some from one of the “Bill and Ted” soundtracks.
Throughout my decades of music appreciation, an ever-growing level of respect for the enduring spirit of music has overwhelmed me, and it’s clear that no song will ever be loved by all. But every song will be loved by some, certainly at least by someone, or it would cease to exist. This is why a personalized playlist is infinitely more valuable than randomly selected songs, and we can see the truth of this claim upon close examination of recorded interviews with the elderly subjects. The songs that triggered the greatest reactions were songs that interviewees felt strong connections to, based primarily on the song’s associations to the time and place, as well as the emotional context imprinted on the memory of the events surrounding the songs.
This simply means that songs for which we have emotional attachments and vivid memories are songs that invigorate our neural circuits, activating cognitive pathways and opening doors of memory similar to how olfactory sensations can trigger a memory or a sense of déjà vu. There are some exceptions, but a lot of these songs are from a person’s formative years, particularly early developmental years and their teenage period. This comes as no surprise to the discerning neuroplastician, because these are periods of life when neural plasticity is most fluid, neural development and refinement functions are most active and receptive, and the degree of exciting novelty in life tends to be highest when we are young and inexperienced.
Novelty and emotion are critical components of memory formation and whether a given experience will be memorable or not. Something completely new (novelty) can be memorable if it commands your attention, or derails you from your usual pattern of behavior. Similarly, the content of a tedious lecture may be harder to recall without taking notes, while that of an exciting, fun, and funny, interactive lesson has a greater chance of being memorable, and recalled with more clarity and detail (emotion).
When it comes to music, the connection to novelty and emotion is crystal clear. The first time you ever heard that song, it was new and your emotional response was strong. You might even remember the events of that first time you heard it, but not necessarily. Your emotional attachment to the song may have developed later on, when you heard it playing at a party, on one of the most memorable nights of your teenage life, for example. Perhaps it’s just a song (or songs) your parents played a lot when you were young, and it could be a song you yourself heard many times, and looking back realized it holds a special place in your heart, for whatever reason. There are also songs that are special to romantic couples (This song was playing when we…; This is our song; We were together the first time we heard this song; etc.) and these songs, for obvious reasons, can be added to a personalized music playlist at any time in life, as new and old songs take on added personal significance in various ways. There are a multitude of ways that novelty and emotion can combine to form experiences worth remembering, by which memories are made, and if these experiences are imprinted with a musical stamp, the song stamped onto the memory is likely to remain just as memorable as the event itself, and conversely, listening to the song has the potential to vivify the memories and feelings of nostalgia related to the song.
Therefore, as a preventative measure we can implement now, and an insurance policy we may benefit from later, it is advisable that each person should endeavor to compile their own personal, individualized cognitive reserve playlist. When speaking to someone about this idea, they responded, “But what’s the hurry? After all, you’re still quite young.” Just then, it spontaneously occurred to me that a traumatic head injury could befall me the following day or any day hence, and the simple point that “it’s never too early” was well taken.
To create your own cognitive reserve playlist, it is helpful to have a few guiding parameters. Most important of all is to keep an open mind without setting anything in stone. It’s not necessary to finalize the list immediately, if ever. This is a project that deserves your thoughtful consideration, so you deserve to be allowed to take your time. It’s better to get the list populated with your definite favorites, and as many others that come to mind, just to kick-start the process. Besides, due to the virtually infinite number of songs and compositions in existence, we will never be able to make the perfect list in one day, one month, or even one year. We can always revisit the list and make changes later, because our minds cannot retrieve all the data at once. We must go about our business of carrying on, and wait for it to come to us. (It’s guaranteed to be worth the wait, so never fret about it.) You may even find yourself removing one of those “definite favorites” from the list, which is welcome and fine, because it’s not merely a list of your favorite songs. Being a “favorite” is just one of multiple indicators that a song might be appropriate for a cognitive reserve playlist. “Memorable” is another key word.
There are still other factors that determine a song’s suitability for a personal playlist, such as a song that isn’t a personal favorite, but which nevertheless evokes a strong emotional response in some other way. This is best described as nostalgia, and nostalgic emotions are powerful anchors for memories. So any song that arouses some sense of nostalgia also has the power to arouse the memory of events, places, times, and other details tied to that nostalgia. To know what songs are nostalgic for you and add them to your list today, may help you if a time should come that you need music as therapy in order to trigger your memory and cognitive function.
It is because of nostalgia that many songs from our youth are good candidates for inclusion on the playlist. Songs that were popular on the radio or TV when we were children, theme songs from popular television programs that are unforgettable for us, and songs that acted as the soundtrack to our lives, so to speak, while growing into childhood, and then blossoming again from adolescence into adulthood. This period is rich with music of great significance to our personal center.
It is my sincere hope that all people earnestly endeavor to compile their own personalized cognitive reserve playlists, and encourage their loved ones to do the same. Maybe it can help those who suffer to better cope with the condition. Perhaps starting this project now, and focusing on mental health now can be a significant contributing factor to developing robust cognitive reserve in the first place, thereby heading off the worst of what this condition can throw at us, and delaying it until later. And of course, not only should we create the lists, but it’s highly recommended that we also play the songs frequently, and dance to them as well, preferably. It is in the interest of your future health, ability, mobility, enjoyment, and ease of living that I offer this potentially beneficial suggestion, and I am grateful that you have taken the time to hear me out regarding my passion about the restorative and healing properties of music, as they relate to the broader topic of neuroplasticity. So on that note, shall we press play and dance?
-
 @ e4950c93:1b99eccd
2025-04-03 14:57:41
@ e4950c93:1b99eccd
2025-04-03 14:57:41Découvrez les matières utilisées ou non dans les produits référencés sur ce site.
✅ Matières naturelles
Matières d'origine végétale, animale ou minérale, sans transformation chimique altérant leur structure moléculaire.
🌱 Principaux critères :
- Biodégradabilité
- Non-toxicité
- Présence naturelle et minimum de transformation
🔍 Liste des matières naturelles :
- Caoutchouc naturel
- Chanvre
- Coton
- Cuir
- Liège
- Lin
- Laine
- Soie
- Terre
- … (Autres matières)
⚠️ Bien que naturelles, ces matières peuvent générer des impacts négatifs selon leurs conditions de production (pollution par pesticides, consommation d’eau excessive, traitement chimique, exploitation animale…). Ces impacts sont mentionnés sur la fiche de chaque matière. Les versions biologiques, sans traitement chimique… de ces matieres sont privilégiées pour référencer les produits sur ce site. Les versions "conventionnelles" ne sont référencées que tant que lorsqu'il n'a pas encore été trouvé d'alternative plus durable pour cette catégorie de produits.
🚫 Matières non naturelles
Matières synthétiques ou fortement modifiées, souvent issues de la pétrochimie.
📌 Principaux problèmes :
- Émissions de microplastiques
- Dépendance aux énergies fossiles
- Mauvaise biodégradabilité
🔍 Liste des matières non naturelles :
- Polyester
- Polyamide
- Acrylique
- Élasthanne
- Viscose
- Silicone
- … (Ajouter les autres matières)
⚠️ Ces matières ne sont pas admises sur le site. Néanmoins, elles peuvent être présentes dans certains produits référencés lorsque :
- elles sont utilisées en accessoire amovible (ex. : élastiques, boutons… généralement non indiqué dans la composition par la marque) pouvant être retiré pour le recyclage ou compostage, et
- aucune alternative 100 % naturelle n’a encore été identifiée pour cette catégorie de produits. Dans ce cas, un avertissement est alors affiché sur la fiche du produit.
-
 @ 04ff5a72:22ba7b2d
2025-03-19 03:25:28
@ 04ff5a72:22ba7b2d
2025-03-19 03:25:28The Evolution of the "World Wide Web"
The internet has undergone a remarkable transformation since its inception, evolving from a collection of static pages to a dynamic, interconnected ecosystem, and now progressing toward a decentralized future. This evolution is commonly divided into three distinct phases: Web 1, Web 2, and the emerging Web 3. Each phase represents not only technological advancement but fundamental shifts in how we interact with digital content, who controls our data, and how value is created and distributed online. While Web 1 and Web 2 have largely defined our internet experience to date, Web 3 promises a paradigm shift toward greater user sovereignty, decentralized infrastructure, and reimagined ownership models for digital assets.
The Static Beginning: Web 1.0
The first iteration of the web, commonly known as Web 1.0, emerged in the early 1990s and continued until the late 1990s. This period represented the internet's infancy, characterized by static pages with limited functionality and minimal user interaction[1]. At the core of Web 1 was the concept of information retrieval rather than dynamic interaction.
Fundamental Characteristics of Web 1
During the Web 1 era, websites primarily served as digital brochures or informational repositories. Most sites were static, comprised of HTML pages containing fixed content such as text, images, and hyperlinks[1]. The HTML (Hypertext Markup Language) provided the structural foundation, while CSS (Cascading Style Sheets) offered basic styling capabilities. These technologies enabled the creation of visually formatted content but lacked the dynamic elements we take for granted today.
The Web 1 experience was predominantly one-directional. The majority of internet users were passive consumers of content, while creators were primarily web developers who produced websites with mainly textual or visual information[2]. Interaction was limited to basic navigation through hyperlinks, with few opportunities for users to contribute their own content or engage meaningfully with websites.
Technical limitations further defined the Web 1 experience. Information access was significantly slower than today's standards, largely due to the prevalence of dial-up connections. This constraint meant websites needed to be optimized for minimal bandwidth usage[1]. Additionally, security measures were rudimentary, making early websites vulnerable to various cyberattacks without adequate protection systems in place.
The Social Revolution: Web 2.0
As the internet matured in the late 1990s and early 2000s, a significant transformation occurred. Web 2.0 emerged as a more dynamic, interactive platform that emphasized user participation, content creation, and social connectivity[6]. This shift fundamentally changed how people engaged with the internet, moving from passive consumption to active contribution.
The Rise of Social Media and Big Data
Web 2.0 gave birth to social media platforms, interactive web applications, and user-generated content ecosystems. Companies like Google, Facebook, Twitter, and Amazon developed business models that leveraged user activity and content creation[4]. These platforms transformed from simple information repositories into complex social networks and digital marketplaces.
Central to the Web 2.0 revolution was the collection and analysis of user data on an unprecedented scale. Companies developed sophisticated infrastructure to handle massive amounts of information. Google implemented systems like the Google File System (GFS) and Spanner to store and distribute data across thousands of machines worldwide[4]. Facebook developed cascade prediction systems to manage user interactions, while Twitter created specialized infrastructure to process millions of tweets per minute[4].
These technological advancements enabled the monetization of user attention and personal information. By analyzing user behavior, preferences, and social connections, Web 2.0 companies could deliver highly targeted advertising and personalized content recommendations. This business model generated immense wealth for platform owners while raising significant concerns about privacy, data ownership, and the concentration of power in the hands of a few technology giants.
The Decentralized Future: Web 3.0
Web 3 represents the next evolutionary stage of the internet, characterized by principles of decentralization, transparency, and user sovereignty[6]. Unlike previous iterations, Web 3 seeks to redistribute control from centralized entities to individual users and communities through blockchain technology and decentralized protocols.
Blockchain as the Foundation
The conceptual underpinnings of Web 3 emerged with the creation of Bitcoin in 2009. Bitcoin introduced a revolutionary approach to digital transactions by enabling peer-to-peer value transfer without requiring a central authority. This innovation demonstrated that trust could be established through cryptographic proof rather than relying on traditional financial institutions.
Ethereum expanded upon Bitcoin's foundation by introducing programmable smart contracts, which allowed for the creation of decentralized applications (dApps) beyond simple financial transactions. This breakthrough enabled developers to build complex applications with self-executing agreements that operate transparently on the blockchain[6].
Ownership and Data Sovereignty
A defining characteristic of Web 3 is the emphasis on true digital ownership. Through blockchain technology and cryptographic tokens, individuals can now assert verifiable ownership over digital assets in ways previously impossible[6]. This stands in stark contrast to Web 2 platforms, where users effectively surrendered control of their content and data to centralized companies.
The concept of self-custody exemplifies this shift toward user sovereignty. Platforms like Trust Wallet enable individuals to maintain control over their digital assets across multiple blockchains without relying on intermediaries[5]. Users hold their private keys, ensuring that they—not corporations or governments—have ultimate authority over their digital property.
Decentralized Physical Infrastructure Networks (DePIN)
Web 3 extends beyond digital assets to reimagine physical infrastructure through Decentralized Physical Infrastructure Networks (DePIN). These networks connect blockchain technology with real-world systems, allowing people to use cryptocurrency tokens to build and manage physical infrastructure—from wireless hotspots to energy systems[7].
DePIN projects decentralize ownership and governance of critical infrastructure, creating more transparent, efficient, and resilient systems aligned with Web 3 principles[7]. By distributing control among network participants rather than centralizing it within corporations or governments, these projects bridge the gap between digital networks and physical reality.
Non-Fungible Tokens and Intellectual Property
Non-Fungible Tokens (NFTs) represent another revolutionary aspect of Web 3, providing a mechanism for verifying the authenticity and ownership of unique digital items. NFTs enable creators to establish provenance for digital art, music, virtual real estate, and other forms of intellectual property, addressing longstanding issues of duplication and unauthorized distribution in the digital realm[6].
This innovation has profound implications for creative industries, potentially enabling more direct relationships between creators and their audiences while reducing dependence on centralized platforms and intermediaries.
Nostr: A Decentralized Protocol for Social Media and Communication
Nostr (Notes and Other Stuff Transmitted by Relays) is a decentralized and censorship-resistant communication protocol designed to enable open and secure social networking. Unlike traditional social media platforms that rely on centralized servers and corporate control, Nostr allows users to communicate directly through a network of relays, ensuring resilience against censorship and deplatforming.
The protocol operates using simple cryptographic principles: users generate a public-private key pair, where the public key acts as their unique identifier, and messages are signed with their private key. These signed messages are then broadcast to multiple relays, which store and propagate them to other users. This structure eliminates the need for a central authority to control user identities or content distribution[8].
As concerns over censorship, content moderation, and data privacy continue to rise, Nostr presents a compelling alternative to centralized social media platforms. By decentralizing content distribution and giving users control over their own data, it aligns with the broader ethos of Web3—empowering individuals and reducing reliance on corporate intermediaries[9].
Additionally Nostr implements a novel way for users to monetize their content via close integration with Bitcoin's "Lightning Network"[11] -- a means by which users are able to instantly transmit small sums (satoshi's, the smallest unit of Bitcoin) with minimal fees. This feature, known as “zapping,” allows users to send micropayments directly to content creators, tipping them for valuable posts, comments, or contributions. By leveraging Lightning wallets, users can seamlessly exchange value without relying on traditional payment processors or centralized monetization models. This integration not only incentivizes quality content but also aligns with Nostr’s decentralized ethos by enabling peer-to-peer financial interactions that are censorship-resistant and borderless.
For those interested in exploring Nostr, setting up an account requires only a private key, and users can begin interacting with the network immediately by selecting a client that suits their needs. The simplicity and openness of the protocol make it a promising foundation for the next generation of decentralized social and communication networks.
Alternative Decentralized Models: Federation
Not all Web 3 initiatives rely on blockchain technology. Platforms like Bluesky are pioneering federation approaches that allow users to host their own data while maintaining seamless connectivity across the network[10]. This model draws inspiration from how the internet itself functions: just as anyone can host a website and change hosting providers without disrupting visitor access, Bluesky enables users to control where their social media data resides.
Federation lets services be interconnected while preserving user choice and flexibility. Users can move between various applications and experiences as fluidly as they navigate the open web[10]. This approach maintains the principles of data sovereignty and user control that define Web 3 while offering alternatives to blockchain-based implementations.
Conclusion
The evolution from Web 1 to Web 3 represents a profound transformation in how we interact with the internet. From the static, read-only pages of Web 1 through the social, data-driven platforms of Web 2, we are now entering an era defined by decentralization, user sovereignty, and reimagined ownership models.
Web 3 technologies—whether blockchain-based or implementing federation principles—share a common vision of redistributing power from centralized entities to individual users and communities. By enabling true digital ownership, community governance, and decentralized infrastructure, Web 3 has the potential to address many of the concerns that have emerged during the Web 2 era regarding privacy, control, and the concentration of power.
As this technology continues to mature, we may witness a fundamental reshaping of our digital landscape toward greater transparency, user autonomy, and equitable value distribution—creating an internet that more closely aligns with its original promise of openness and accessibility for all.
Sources
[1] What is WEB1? a brief history of creation - White and Partners https://whiteand.partners/en/what-is-web1-a-brief-history-of-creation/ [2] Evolution of the Internet - from web1.0 to web3 - LinkedIn https://www.linkedin.com/pulse/evolution-internet-from-web10-web3-ravi-chamria [3] Web3 Social: Create & Monetize with Smart Contracts - Phala Network https://phala.network/web3-social-create-monetize-with-smart-contracts [4] [PDF] Big Data Techniques of Google, Amazon, Facebook and Twitter https://www.jocm.us/uploadfile/2018/0613/20180613044107972.pdf [5] True crypto ownership. Powerful Web3 experiences - Trust Wallet https://trustwallet.com [6] Web3: Revolutionizing Digital Ownership and NFTs - ThoughtLab https://www.thoughtlab.com/blog/web3-revolutionizing-digital-ownership-and-nfts/ [7] DePIN Crypto: How It's Revolutionizing Infrastructure in Web3 https://www.ulam.io/blog/how-depin-is-revolutionizing-infrastructure-in-the-web3-era [8] Nostr: Notes and Other Stuff… https://nostr.com/ [9] Nostr: The Importance of Censorship-Resistant Communication... https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [10] Bluesky: An Open Social Web https://bsky.social/about/blog/02-22-2024-open-social-web [11] Wikipedia: Lightning Network https://en.wikipedia.org/wiki/Lightning_Network
-
 @ 8671a6e5:f88194d1
2025-04-03 14:52:44
@ 8671a6e5:f88194d1
2025-04-03 14:52:44\~ The person came up to me from behind his merchandise stand and saw my Noderunners pin on my black t-shirt, then looked me dead in the eye and asked : “So… what do you sell?”
This is the eighth long-read in a series of twelve “food for thought” writings on Bitcoin. It was originally meant to be a few chapters in a book, but life’s too short for that.
Define
Let me start by saying there’s no single way to define or explain a “Bitcoin conference.” The experience can vary depending on a few factors: who’s organizing it (a long-time Bitcoiner or someone from traditional finance trying to grasp Bitcoin), where it’s being held (a sunny paradise like Madeira or a gloomy northern French town), and who’s speaking (technical experts or charismatic entertainers or people with little substance).
Despite these differences, there’s a shared culture that ties these conferences together: a mix of excitement, frustrations, and inevitable evolution. That’s what I explore.
This is just my take, based on what I’ve personally witnessed and what I hear from my surroundings. It’s not meant to be a blanket critique of all Bitcoin conferences as there are plenty I haven’t attended, though I hear about most of them. Even the good ones will evolve into something else over time. So, plan accordingly.
A bit of background on my perspective: at some point in my life, I hit a bump in the road that kept me tied to where I live — a bleak corner of Belgium, surrounded by fiat slaves, shitcoiners, and people who spend six hours a day consuming brain-numbing garbage television. Traveling is an exception for me, but for many Bitcoin conference attendees, it’s a ritual, a must-do event.
So, I view these events with a mix of fascination and grounded skepticism — something I’ve found lacking in many Bitcoiners. I’ve never been to a Bitcoin conference before 2023, despite receiving plenty of invites over the years. From what I heard and saw in photos from friends who attended (even the real early ones) these events seemed eerily similar to the dull hotel conference rooms I once endured in tech and telecom. I’ve had my fill of lukewarm, watery coffee and lifeless speakers droning on about firewalls. So I skipped that particular honor.
Up until around 2018, Bitcoin conferences were a soulless sea of chairs lined up under fluorescent tube lights, draining the life out of attendees—one telecom acronym at a time. Not exactly inviting. Yet, looking back from the perspective of 2025, those were the “pure” days. Back then, people like Roger Ver (before he pivoted to Bitcoin Cash), Andreas Antonopoulos, and encryption specialists spoke to small audiences, explaining Bitcoin in its raw form.
But, like any Bitcoiner, I try to improve myself. So, I made the effort to travel, visit other Bitcoiners, and attend Bitcoin conferences. The conferences I attended in 2023/2024 made me a bit wiser ; not necessarily from what was said on stage (with a few lucky exceptions who still try to bring original thoughts). Most of what I learned came from the long queues, the drama, and watching grifters operate in real time and the good characters floating around.
So, here’s what I’ve learned.

Chain of ticket
I quickly discovered that many Bitcoin conferences have their own “quest for tickets” dynamic, almost like an industry with its own inner circle. It’s a waterfall system: tickets start at lower prices to fill up the venue (usually right after the previous edition). That’s standard practice, both inside and outside of Bitcoin. But what’s strange is seeing organizations that only pop up when a conference needs promotion—somehow securing tickets for themselves and their friends (or for *making* friends) while shilling referral links for small discounts to their followers.
The real free tickets, though, are a hot topic in many local communities and make all the difference for some attendees. What’s particularly interesting is that most ticket prices can be paid in Bitcoin, adding a layer of calculation to the process.
If you paid 230500 sats for your ticket and later see the dollar price fluctuate, say from $180 to $270, or the other way around, by the time the conference starts, you realize you either bought too late or too early.\ It’s better to not have bought at all.
Some ticket holders end up paying less (in dollar terms) than others, making it a gamble. As the event date approaches, ticket prices tend to rise—unless you wait until the last minute, when they haven’t sold out, or just pay at the door. It’s a strange feeling knowing that not everyone paid the same amount (and as mentioned, a significant number get in for free) depending on their timing.
Many organizations and local community representatives show up primarily to be present; securing free tickets, which function more as a badge of recognition than a necessity.\ It’s similar to how a rock groupie sees backstage access: a status symbol, whether for an autograph or something more. Being seen standing next to big names is a huge deal for some, as they derive their own status from proximity.\ This also reinforces the “rockstar status” that conferences create around certain figures, once they come out to take a selfie with some nice people and young fans, then to quickly disappear back to the ‘whale room’ or backstage.
There’s often an entire insider network determining who gets these free tickets. In some cases, it’s naturally tied to the local community, but in others, the professionalism is laughably low. At certain events, you could probably just walk up to the entrance (if there’s even someone checking) and say, “I’m with the organization” to get in for free.
It gets even more absurd.\ At a conference near the French-Swiss border, I was probably one of the very few who actually paid for entry. The real spectacle wasn’t in the talk rooms — which remained eerily empty — but in the dining area, where half the town seemed to have shown up just for the free food. Around 200 people queued for a free lunch, while the presentation halls were at best one-third full throughout the day.
And beyond the ticket games, there are plenty of ways to slip in unnoticed. Carrying a random piece of equipment and mumbling\ “I need to put this crate in the back” can get you past security. Or you can just wait for the one security guard to get distracted by chatting up a girl or stepping out for a smoke, and you’re in. At one event, I walked in alongside someone carrying crates of wine for the VIP lounge. I blended in perfectly (I paid afterward).
So, to sum up: at nearly every conference I’ve been to, a big portion of attendees either walk in for free or hold compensation tickets they got through some connection. Sometimes that connection is uncomfortably close to the organizers. Other times, they just slap an “industry” label on themselves when, in reality, they’re nothing more than a social media bio with a few followers.
Local representatives of a podcast, community, influencer network, or fake marketing club also get in for free. And you? The regular guest, you and I are paying for them. There’s no real vetting process; with some organizers, anyone wearing a Bitcoin t-shirt and saying the magic words “I do community building” or “I know the local Bitcoin meetups” gets a free pass.
The ones who actually want to learn about Bitcoin — the ones who click the link and pay full price — are the ones covering the costs for everyone else and ultimately making these conferences profitable (or at least break even). The problem? They’re the ones left wondering: “Was it really worth my time and money?” only to never return again most of the time.
Because many of the people at these conferences aren’t there to learn. They’re part of the circus. And others? They’re the ones paying for the circus boss, the clowns, and the trapeze artists.
At that one conference with the massive free-lunch crowd, I saw one interesting talk. And I had plenty of valuable conversations and observations — conversations I could have just as easily had by visiting that place outside of a conference setting.
In the end, I realized the main reason I was there was to support a fellow Bitcoiner giving a presentation. And after that? They disappeared from my life. Because, just like in the fiat world, you’re only as good as your last few hours of usefulness to most people.
Which brings me to the next element of Bitcoin conferences...friends
Bitcoin “frens”
This might be the hardest lesson of all: you meet fellow Bitcoiners at these conferences. And some of them? They’re truly special characters. A few even made such a deep connection with not-so-well-traveled-me that I would’ve gladly traveled a full travel day just to spend time working and doing something meaningful together (which I actually did).
But most of these connections? They last only a moment. Few survive beyond the conference, mainly because of the vast distances— both in kilometers (or miles) and in the way we live our everyday lives. The Bitcoiners you meet at these events are, for the most part, just regular people trying to make ends meet in the fiat world while saving in Bitcoin. Or they’re chasing the Bitcoin dream or even find a job in the fata morgana of bitcoin jobs. They act like they belong, like a clown acting like he’s going to climb the trapeze.
I respect that. But over time, I realized that many of them operate in Bitcoin mode; a kind of facade. Behind that front, that mask, most are just testing the waters to see if they can make it. And most don’t.\ Treating Bitcoin as a lifestyle movement, a career shortcut, or an identity, has its limits. Eventually, the real person breaks through. And you have to face your own instincts and personality.\ I’ve tried to be an acrobat, and ride the lion, make the audience laugh, but I’m still the seal who’s brought back to the cage after he balanced a ball on his nose. The quote “I’m Jack’s wasted life.” came to mind often when standing somewhere at a conference space.
Self-doubting people stay self-doubting, owning Bitcoin or not. Emotional wrecks remain emotional wrecks — just with Bitcoin now. And when these masks slip off, you’ll see everything: the greed, the overconfidence, the longing for drama, the addictions, the narcissism, the energy-draining personalities, sleaziness usually with the ones who always say the right oneliners or wear the right Bitcoin merch to blend in.
And you can love people for that. Everyone has flaws. Everyone has a price as well.
But these Bitcoin “frens” can also hurt you badly. Because as Bitcoiners, we carry hopes. And hopes are like ants on a sidewalk, they’ll eventually get crushed.\ We long to meet people who see the same truth, the same vision of Bitcoin as we do. Some will act like they actually understand and do, they talk the talk for a while, as if they’re parroting a podcast.
If you stay in the shadows - like I did for years - you won’t have to deal with these things. If you never try, you’ll never be let down. But you still stay in the imaginary basement, letting yourself down. That’s not the bitcoin style. We router around problems. Even if we stand amidst the problems (like a conference).
But if you do? There’s a hefty price to pay — beyond just the money spent. It’s a cost paid in energy, emotions, and social interactions and above all: time.
And once in a while, you’ll meet a friend for life.
Just be prepared:
Bitcoin is a journey that few people you encounter at a conference can take for longer than four years, or even four hours of conversation actually.
And then, after navigating the social maze of Bitcoin conferences —the connections, the masks, the fleeting friendships, the smell of weed and regret — you find yourself facing an even greater challenge: the queue at a coffee stall.

## \ The Soviet LN Queue
It’s one of the most fascinating and frustrating aspects of every conference: the insanely long lines. Whether it’s for the toilets, a coffee booth, or some niche merchandise stall, you’ll see Bitcoiners waiting like it’s 1963 after a Soviet state bakery just got fresh deliveries.
waiting for coffee Seriously, aren’t we supposed to be the pinnacle of free-market efficiency? Instead, we’ve somehow perfected the art of the long food lines. I remember people waiting in line for like 35 minutes to order a cappuccino!
The usual culprit? A mix of payment chaos and the Bitcoin Orangepill mental issues in action.
A large portion insists on using Lightning (as in "their preferred lighting wallet"), which would be fine except they’re fumbling with some exotic, half-working wallet because using something that’s actually fast might get them sneered at for being “custodial.”
On top of that, vendors are juggling card payments, cash, various Lightning POS systems, and even the occasional cutting edge dudes trying to pay with an Apple Watch or worse, some newly released Lightning-enabled gadget that doesn’t work yet. And when it does work, it requires so much attention and Instagram footage that it takes five minutes just to hand someone a coffee while the guy pays with a lighting NFC ring on his finger, something you can't use ànywhere else ever. It’s cool. But not to anyone else than you.
So, here’s a tip for the regular people, the rats that pay for all of this : sneak out.
Then you find a small, locally owned café outside the conference, pay them in cash, and actually enjoy your food in a few seconds or minutes.
If (and only if) they accept Bitcoin, great! Tip them well. Otherwise, just relax and have a conversation with a local, all the while inside the conference venue there are Bitcoiners filming each other struggling to make a payment with the latest Lightning-enabled NFC card or making the staff uneasy.
Meanwhile, some poor 22-year-old café worker is trapped in an unsolicited podcast participation:
“Wait, you accept tips in Wallet of Satoshi? Who told you that? I’ll explain it to you!”
Or worse:
“Hold on, I just need to do a quick swap… It’s an on-chain transaction, the last block was 19 minutes ago, can’t be long now… wait… umm… do you take VISA?”
At this point, ordering a simple drink at a Bitcoin conference has become an unnecessarily complex, ego-driven performance. With long queues as a direct result. And don’t get me started on the story when 30+ bitcoiners walked in to a Portuguese restaurant without a reservation, and they all wanted to pay with different payment methods. It was like the Vietnam war.
Solution:
A tip for conference organizers and their catering : pick one Bitcoin point of sales system, set clear guidelines, and make everyone stick to them. Instruct people to adhere to the following :
Pay with a (bank) card, cash, or Lightning and PLEASE decide beforehand which method you’re using before ordering your stuff! We prefer lighting.
If you’re using Lightning, have enough balance on you wallet or get lost.
Use a compatible wallet. (Provide a tested “approved” list and train staff properly. Users who use other stuff get their order “cancelled” at the first sign of trouble. Your app‘s not scanning, or not compatible, or it has some technical mumbo-jumbo going on to your vpn LN node at home 2000 km away? Please get real and pay with a bank card or something.
No filming, duck-facing (like it's 2017) or stupid selfies with your payment. It’s been done a thousand times by now. There are people in line, waiting behind you, they want to order as well, while you have your little ego trip or marketing moment. Move on please!
“Our staff knows how bitcoin payments work, you don’t need to #orangesplain it to anyone.” We don’t care about your 200th LN app or the latest “but… this one is faster” thingy. Order your drinks, pay and get out of the way please.
Bitcoin fixes many things. But it hasn’t quite fixed this yet.
The bitcoin conference axiom
Going to a conference, versus keeping your bitcoin in your wallet is a tough choice for many.
If you pay nothing for tickets and lodging, while enjoying free meals and cocktails, your opportunity cost drops close to zero —yet your networking and social impact are maximized while you can also do business. That’s ideal. At least, for you. In such case, Bitcoin may only "win" over an extended timeline, but for you, it's essentially a free ride. You incur no real opportunity costs. You drink their milkshake.
On the other hand, if you’re a regular attendee, you pay full price: the ticket, overpriced drinks and food from the stands (losing even more if you generously pay for coffee in sats), plus extras like t-shirts and books (which you’ll never read). Your milkshake gets taken—at least half of it.
If you’re lucky, you might spend an evening in town with the event’s "stars"—those occasional luminaries who briefly grace the normies with their presence for a drink. Some can’t even hold their liquor. Year after year, the same 10 to 15 speakers or panelists appear, funded by your dime, traveling the world and enjoying the perks—some even cultivating fan bases and hosting exclusive parties.
The real opportunity cost hits hardest for regular attendees who come to learn, shelling out significant money while accumulating their fourth hardware wallet or yet another orange-themed t-shirt. They might even squeeze in a selfie with a former sportswear model turned Bitcoiner. For normies (as they’re often called), the financial and social scales rarely tip in their favor.
Calculating the conference opportunity cost
To determine the opportunity cost of attending a conference instead of investing in Bitcoin, over time follow these steps:
-
Calculate your total conference expenses, including tickets, travel, food, drinks, and lodging (merchandise and donations).
-
Estimate Bitcoin’s percentage gain over the conference period and the following year(s). (in order to not make you cry, I suggest nog going over 5 years)
-
Multiply your total conference cost by this percentage to determine the potential Bitcoin profit you forgo.
-
Assign a dollar value to the networking or business opportunities you expect to gain from the conference (if you’re not just in it for the laughs, meeting high-class consultants, friendships, self-proclaimed social media Bitcoiners, or the occasional gyrating on one of the musicians/artists/food stall staff members).
-
Subtract this “networking” value from the missed Bitcoin profit to find your net opportunity cost (this is rather personal,… with me it’s zero, but for someone selling t-shirts it’s probably much more).
If the result is negative over the chosen timeframe, the conference was financially worthwhile for you. If positive, holding or buying Bitcoin was the smarter move.
Unless you’re a recognized speaker in this traveling circus, your opportunity cost will likely be positive — meaning all the others lose hard money, while fumbling with your Lightning wallet.
The Conference Opportunity Cost Formula
Let:
CT = Total conference ticket & entrance cost (in dollars)
CR = Total related conference costs (travel, lodging, food, etc.)
C = CT + CR (Total cost)
G = Bitcoin’s % gain per year (as a decimal, e.g., 5% = 0.05)
N = Estimated fiat value of networking/business opportunities and knowledge gained.
OC = (C × G) − N
Where:
OC (Opportunity Cost) < 0 → The conference was worth attending.
OC (Opportunity Cost) > 0 → Holding/buying Bitcoin was the better move.
Some example calculations (I've left out examples before 2020, I don't want people crying or waking up at night thinking "Why did I go to Amsterdam in 2014?!")
example : Conference in April 2024 Entrance: $200 Lodging, t-shirt, and travel: $900 Bitcoin's estimated gain: 23% (0.23) No business / knowledge value gained OC = (200 + 900) × 0.23 - 0
- $253 OC (Bitcoin would have been the better choice.)
Conference in April 2020 (adjusted for historical Bitcoin growth) Entrance: $175 Lodging and travel: $700 Bitcoin's estimated gain: 1089% (10.89) No business / knowledge value gained OC = (175 + 700) × 10.89 - 0 OC = +$9,529 (Massive missed gains — Bitcoin was the clear winner.
--
So the first lesson in bitcoin should be: Only attend conferences if you get paid to do so and get a free ticket and free lodging, which kind of would kill that whole industry to begin with.
Energizing
At first, it’s energizing to meet like-minded bitcoiners, but after a while, you realize that a big chunk of them are just trying to sell you something or aren’t really bitcoin-focused at all. And some of them are just looking for their next way to kill time and boredom.
The drama that comes with attending these conference and the personal interaction can get pretty intense at times, since expectations often don’t match the personalities. Before you know, you’re walking around at night through some bad part of a town, while crying your eyes out because you thought you found your soulmate.
Future pure industry conferences will suffer less from this drama, because everyone there has the same goal — pushing their company or product— while the “other” grassroots conferences are more of a meeting spot for bitcoiners of all types and perspectives, bringing the usual drama and mess that comes with human interactions. Current conferences are a mix of both usually.
I think the current era of bitcoin conferences is coming to an end. Soon, probably by the end of 2025, we’ll see a clear split between industry-driven and human-driven (grassroots) smaller conferences, and it’ll be really important to keep these two separate.
I even had the idea to launch a sort of conference where there wouldn’t be any industry speakers or companies present. Just bitcoiners gathering at a certain place at a specific week and having a good time. I called it “club Sat” And you could just go there, and meet other bitcoiners, while acting there was a big venue and speakers,… but there aren’t any. Would be refreshing. No struggle for tickets, no backstage stuff, no boring talks and presentation,… just the surroundings and the drama lever you want and probably like.
On stage
The podium is usually left for the known names. Not every conference is like that, but most of them need these names, badly. These names know each other, they encounter one another in VIP rooms and “the industry” a lot of times anyway.
The same people you see in the bitcoin news, the same people having a cult following, and the very same people traveling, staying and drinking for free while spreading the same bitcoin wisdoms will be invited over and over again.
Or… they go rock around as they’re usually so bored they had to start a rock band to entertain themselves. Which is rather entertaining if you’re following up on who does what, but in the end it’s largely just for their own amusement and it shows. I get that. I would do the same. It’s fun and all.
It’s just a bit sad that there are only a small group of top-layer speakers, and then the sub-top that usually has more to say, or gets little opportunity. The reason for that is simple: the “normies” who pay in full for tickets, come there for the “big” names. They don’t know that much about bitcoin usually, so they’re not waiting on some unknown dude explaining something about an obscure niche subject. A debate can help remedie this, to mix it in with some lesser known names, but I have the feeling the current “line-up” of bitcoin conferences feels like a rock festival in 2025 putting the Stone temple pilots or Creed on the card.
Yes, they’ll attract an audience and do their playset well,… but it’s not exactly the pinnacle of the music industry at the moment, neither is Madonna by the way :)
Promoting anything
The people organizing these events usually aren’t Bitcoiners either — they’re promoters (few exceptions though).

They don’t care if they organize a symposium about a newly discovered STD, A three-day cheese tasting event, a Star Trek convention, or a Lucha Libre wrestling tournament featuring El HODLador, as long as they can sell tickets and make money from merchandise they're good. The last thing on the mind with some of them will be helping bitcoin adoption. There will be a time (soon) where people that know bitcoin, known bitcoiners and know how to organize events get their act together. It will be different than the early days, and it will be different than the boring going-through-the-motions conferences we have now. There shall be fun, social gatherings, life, excitement and culture, and not the “what do you sell?” atmosphere, neither the “this old dude on stage again”?
That’s why they’ll slap any semi-famous name on the poster to pull in a crowd - could be a washed-up Mexican wrestling star with strange legal issues, the cheese-tasting equivalent of Usain Bolt, or your neighborhood Bitcoin old-timer with a beard and a "best selling author" label.
It’s also why most of these conferences end up being more about shitcoins than anything else. And even if they're for the most part about bitcoin, the venue is usually infested with marketing budgets, useless organizations that wanted complimentary tickets (some of them do only one thing: popping up when a conference is nearby and then they’re gone again) ... along with some hawking consultant types you never see anywhere else.
They'll occasionally pay people but usually in fiat, or if you're a bigger name, you might get other deals. For artists or staff, it's all in fiat from what I heard.
Pure Bitcoin conferences, also rely on these big names. Whether it’s a well-known Bitcoiner, a CEO, president, or someone with real reveling knowledge to share with the audience (though that last type is getting rare).
Looking for love in all the wrong places
\ Let’s also address the fair share of “orange diggers” at Bitcoin conferences—because yes, they exist. And no, let’s not single out one particular gender here.
Some people treat a Bitcoin conference like a live-action dating app mixed with a financial vetting process for potential partners. It’s essentially an opportunity to inspect and assess the grab bag of fintech, crypto, and Bitcoin folks in real life.
And if you think this is exaggerated, just attend a few conferences—three is enough. You’ll start noticing the same people popping up, seemingly without any real Bitcoin knowledge, but with a very strong interest in dining, chatting, and generally being around—as long as you look and play the part. I can only imagine how dialed-up this effect must be at a shitcoin conference — probably like flies on a cowpie.
The trick is, in Bitcoin, these people try to blend in. Some even tag along with real Bitcoiners, while others just crash the party and try to get noticed. Their actual interest in Bitcoin? Close to zero. Their main target? Your wallet, or some fantasy thing about getting to know someone out of the ordinary.
And that’s a shame for the people who genuinely care about Bitcoin, who want to network, or who simply are looking for like-minded people. They often find themselves competing for attention with those who’ve turned “being noticed” into a sport, while the rest just wander around, lost in the shuffle. Talk to the quiet ones. Certainly if they look like they belong in a antiques shop.
My advice: Talk to people and be genuine. If you don’t know much about Bitcoin, that’s fine - nobody expects you to be a walking whitepaper and on top of that, most people you'll encounter don't know that much either. It’s bitcoin: we’re all rather average people that hold an extraordinary asset.
Just don’t be "that orange digger" looking for a partner with a loaded bag of bitcoin.
Because in the end, what’s the prize you win? You don’t know who’s under the mask. You don’t even know who’s under your own mask.
Finding a man or woman at a place where half the people are laser-focused on financial sovereignty, and the other half are busy arguing about seed phrase storage, UTXO management, and why your Lightning wallet sucks? But good luck with that. The judge of character usually comes when they find the next shiny object or ditched you standing in the rain at the entrance of a restaurant while dealing with a lightning watchtower or a funny cigarette or whatever.
If you’re truly looking for love, maybe stick to going to a normal bar. If you’re here to learn, connect, and be part of something of a grassroots movement, then be real yourself.
I've seen some rather nasty examples of people at Bitcoin conferences—of all kinds. And I've also seen some really cool examples of truly awesome people. This led me to believe that Bitcoin conferences simply let you meet… people, just dialed up a bit.
Future If you encounter rotten people, they’ll usually be even more rotten than in the fiat world. If you meet really cool people, they’ll be even more awesome than the cool people in the fiat world.
Our volatility is our freedom. So, I guess it’s normal. Doesn’t make it any easier, though.
Bitcoin sees through bullshit, and so do Bitcoiners (even if it takes 21,000 blocks)
Pretty soon, I reckon we’ll see conferences fork into two camps: grass roots, and the “industry” level ones. (human / corporate) I guess I’ll only attend the human part, for sure, but I can’t help but booking myself a single room in a hotel in a nice area in that case, so I don’t have to deal with class of 2022 hippies sharing referral links to their middleman service while asking me for a lighter 3 times in a row. The chances for me of meeting cool bitcoiners in a nearby cocktail bar are a lot higher.
In the meanwhile, I’ll look forward and see how the bitcoin conferences will evolve, fork in two “styles”. One corporate and one underground. Maybe there will be one more genre just for the fun of it.
I’ll stay away, as I don’t like this current mix of industry gigs and having the insiders and “the rest” of us all mingled together clamoring for tickets, attention and coffee. The game is rigged. Staying at home is the better option (for now).
written by AVB
If you like : tip here
-
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ f1989a96:bcaaf2c1
2025-04-03 14:30:08
@ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers!
Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin.
We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation.
Now, let’s get right to it!
SUBSCRIBE HERE
GLOBAL NEWS
Georgia | Officials Freeze Accounts of Organizations Supporting Protesters
Georgian officials have frozen the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International warns this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped sustain pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose.
United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025
The United Arab Emirates (UAE) will launch its central bank digital currency (CBDC), the “Digital Durham,” by the end of 2025. According to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further admitted the CBDC will replace cash and assist law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials claim this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime.
India | Grants Tax Authorities Access to Citizens’ Online Data
Starting in April 2026, the Indian government will grant tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power.
Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief
Last week, a 7.7 magnitude earthquake struck central Burma, with strong tremors reaching neighboring Thailand. The official death toll has surpassed 2700. And in Bangkok, a 33-story building under construction collapsed. Despite an already strenuous situation, Burma’s military junta continues its oppression. They are blocking rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a million people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected.
Angola | Regime Jacks Price of Diesel
The Angolan regime raised diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on less than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose 80%) sparked protests between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, describes as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters.
Nicaragua | Ortega’s Dismantling of Press Freedom
Since coming to power in 2007, Ortega has closed or seized 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His assault on press freedom has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like La Prensa and CONFIDENCIAL. Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to criminalize free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders.
BITCOIN AND FREEDOM TECH NEWS
HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide
HRF gifted 1 billion satoshis in its Q1 2025 round of Bitcoin Development Fund (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work here.
Cove | New Open-Source and Permissionless Bitcoin Wallet
Cove is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it here.
Second | New Ark Implementation Launches on Bitcoin Signet
Second, a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, launched “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s Signet network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it here.
Braiins | Open Sources Bitcoin Control Board
Braiins, a company building tools for Bitcoin mining, open-sourced its BCB100 Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most.
African Bitcoiners | Publish Bitcoin Starter Guide
African Bitcoiners just published “Bitcoin: Africa’s Guide to Freedom Money,” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it here.
OpenSats | 10th Wave of Nostr Grants
OpenSats, a nonprofit that supports open-source software development, announced its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools.
RECOMMENDED CONTENT
Freedom Tech with Alex Gladstein
In this episode of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation here.
The State of Personal Online Security and Confidentiality with Meredith Whittaker
In this keynote for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the full discussion for a pragmatic view into the future of digital privacy and security.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ a60e79e0:1e0e6813
2025-03-18 15:38:25
@ a60e79e0:1e0e6813
2025-03-18 15:38:25**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
One of the first things most people learn when getting started with Nostr is the importance of their private key, or ‘nsec’. The nsec is the key to their Nostr world. Whoever controls an nsec, controls that account. Lose access to the nsec and you lose access to that account and its social graph.
So the nsec is very important and should be treated very carefully, but what happens if we want to use or test multiple Nostr clients? Newer clients might be malicious, or have unknown security vulnerabilities, so simply go pasting our nsec everywhere just to see if we like a new app is not the best idea!
Thankfully there are solutions for nsec management that allow us to do exactly that, without having to expose our all important nsec to each and every app we want to interact with. The most commonly used to date are browser extensions like Alby or nos2x. Typically these types of browser extensions do not work on mobile platforms.
Enter Amber…

What is Amber?
Amber is a free and open source Android application that serves as a dedicated ‘Nostr event signer’. Amber allows users to keep their nsec segregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware.
At its core Amber serves two main purposes:
Securing your nsec(s) Using this nsec to sign events for other Nostr clients on your phone
Got an iPhone? Check out nsec.app
Getting Started
- Download Amber to your phone. It is available from Zap Store, Obtanium, GitHub or F-Droid
Download Amber here. Support Amber here.
-
When opening Amber for the first time, you’ll have the option to create a new Nostr account (nsec) or import an existing one.
-
If you do not currently have a Nostr account, Amber will help you generate and secure a brand new nsec. Amber allows you to download an encrypted file containing your nsec as well as the option to download a human-readable version of the nsec in the form of 12 English words, similar to a Bitcoin seed.
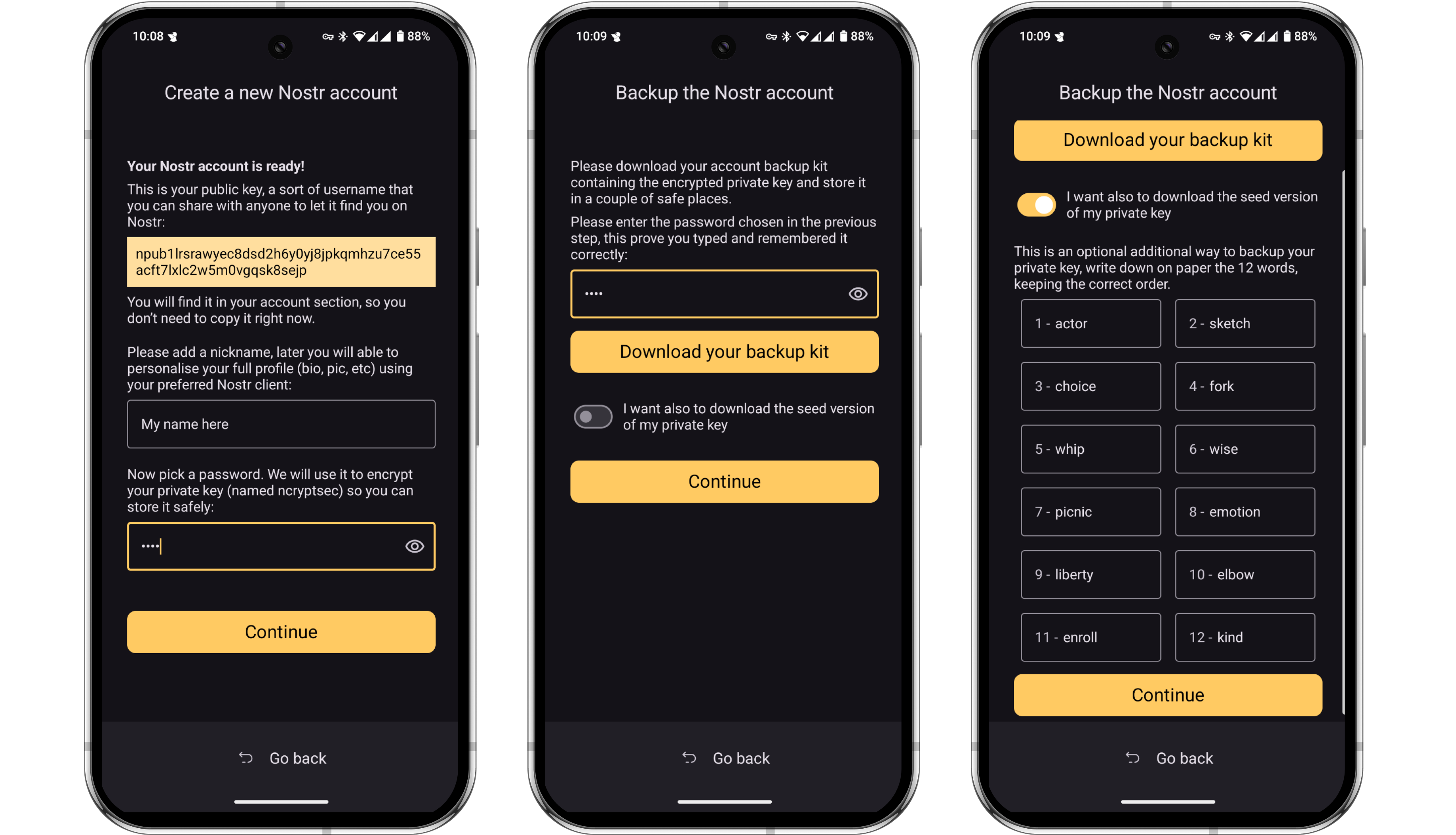
Skip this step if you have an existing nsec that you want to import to Amber.
-
To import an existing nsec, choose ‘Use your private key’. You can then paste the nsec from an existing client, or scan a QR code of it if you have one available to you.
-
Once you have created or imported your nsec, Amber will ask for some basic permissions. You can allow the app the approve basic actions, or enable more granular selection for each client you subsequently connect. Once you tap ‘Finish’, you’ll see that the account is now ready.
If you have or require more than one Nostr account, you can repeat these steps for each one. All accounts can be viewed by tapping the profile image in the bottom right corner of the screen.
- That’s it, Amber is now ready to sign events. Amber allows multiple ways to connect other clients to it, but most will have a very simple ‘Login with Amber’ button. Let’s demo this in practice with Amethyst, the most popular Android-only client.
The opening screen of Amethyst shows the ‘Login with Amber’ option. Tap that.
- Amber will then open automatically and ask you to define the level of autonomy you’d like to have with Amethyst. This setting defines how often Amber will require you to manually authorize each event.
For example, you might want Amber to automatically sign every like or repost you do in Amethyst, but then be asked to manually approve all direct messages sent from your account. These permissions can be customized in the settings at any time.
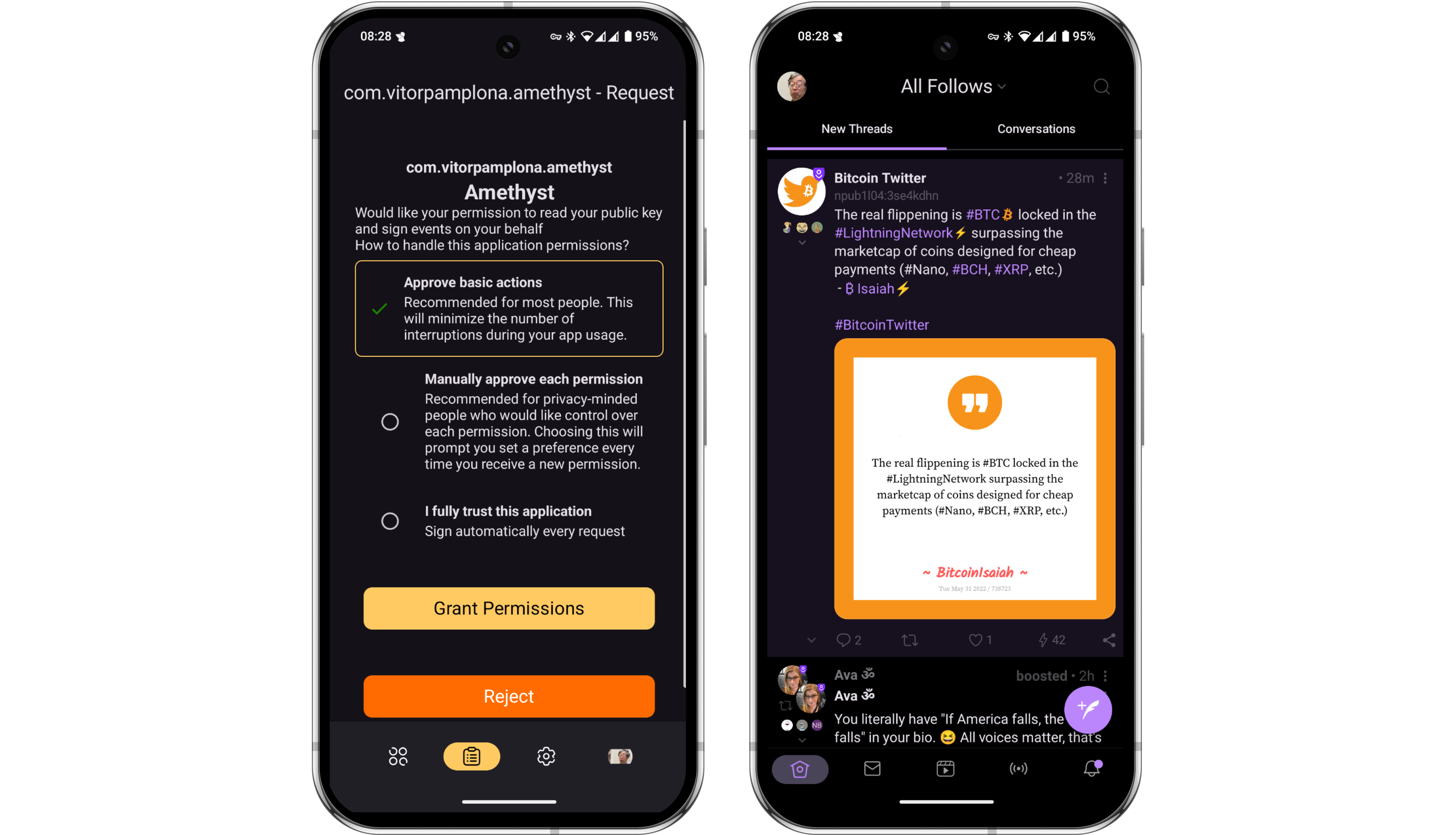
- Let’s assume that upon setup, we did not grant Amber the ability to automatically sign short text notes for us. Let’s look at how simple the authorization flow is. Type a new short note in Amethyst and press ‘Post’.
Amethyst will instantly send the request to the Amber app on your phone, with no third party server involved. Amber will open and ask you to approve the event. When you do, Amber signs the event with the nsec it stores for you and automatically send the signed event back to Amethyst to be posted. The whole process takes just a few seconds.
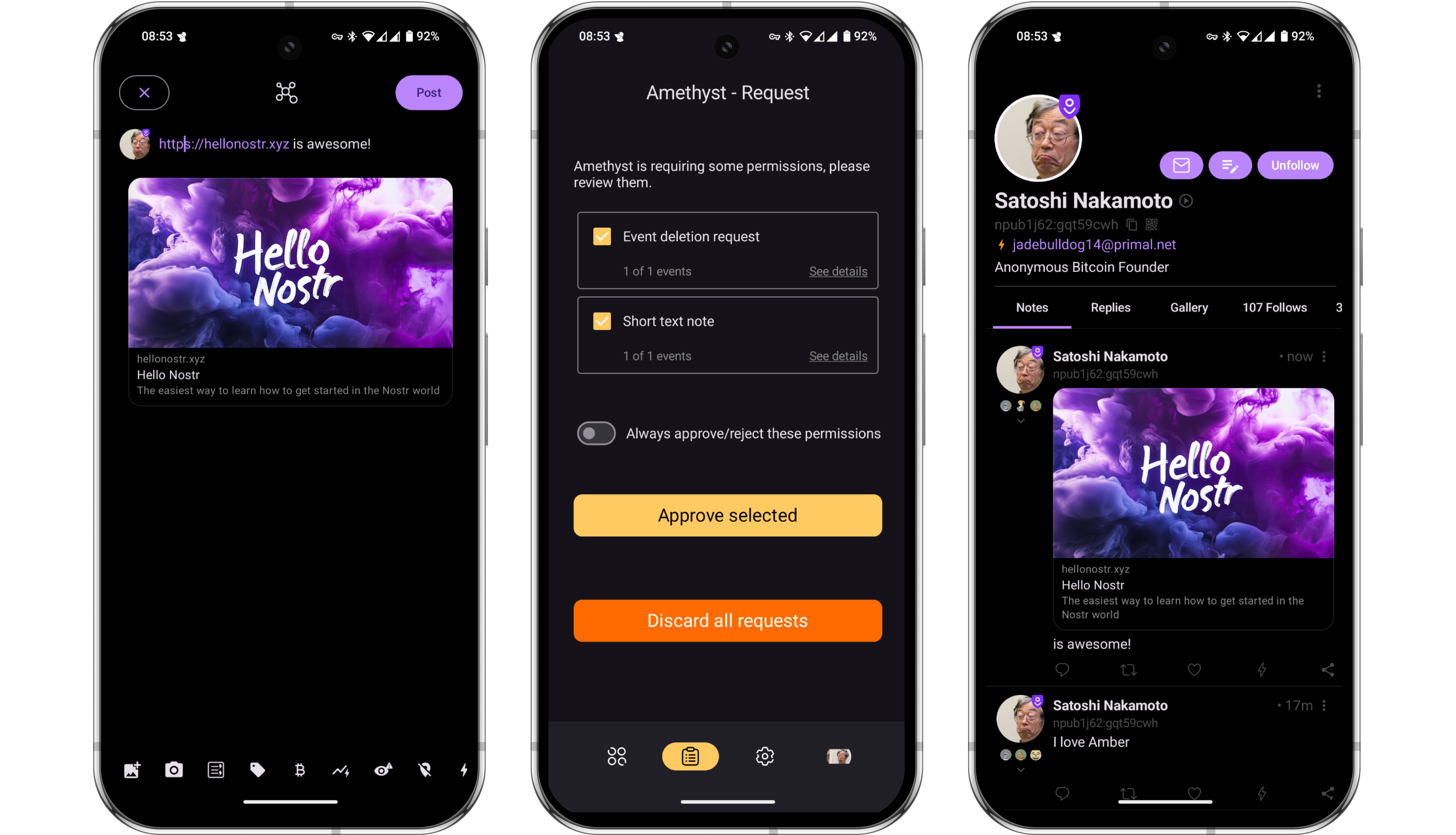
Using Amber with a Web Client
-
Next let’s take a look at how you can use Amber on your phone to sign events on a web app running on your computer. For this example, we’ll be using Coracle. Open Coracle and click ‘Log In’, then choose ‘Use Remote Signer’. Coracle will then display a QR code.
-
Open Amber and navigate to the Applications page, tap the + icon, then scan the QR code being displayed by Coracle.
-
Just as it did earlier with Amethyst, Amber will now ask you to grant some basic permissions for the Coracle connection. Once again, these permissions can be customized at any time in the settings. Once granted, you’ll notice that Coracle automatically logs in to your feed.
But wait, how did that happen? The nsec is in Amber on your phone, and Coracle is running on your computer. The two might not even be in the same location or on the same network!? The communication is happening over the Nostr protocol, via relays. Which relays are used for this communication can be configured in the Amber settings.
-
Let’s test out a short note on Coracle to demonstrate the signing process. Click ‘Post +’ in the top right corner, draft your note and then click send.
-
Amber will send a push notification to your phone. Tapping the notification will open Amber for you to approve the event.
-
Once the event is approved in Amber, Amber will automatically send the signed event back to Coracle for publishing.
Summary
You can view Amber as a vault for your Nostr private keys (nsec). It allows you to explore the entire ecosystem without exposing your nsec to every new app you try. Amber is an incredibly simple yet powerful tool that belongs on the Android phone of every Nostr user.
At the time of writing, using Amber as a remote event signer is supported by the following popular Nostr clients:
- Amethyst (mobile)
- Coracle (web)
- 0xChat (mobile)
- Fountain (mobile)
- Zap Store (mobile)
- Keychat (mobile)
- Freeflow (mobile)
- Highlighter (web)
- Chachi Chat (web)
- Habla (web)
- Shopstr (web)
- Plebeian Market (web)
- Snort (web)
- Nostrudel (web)
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I’ll be sure to Zap you back! ⚡️
-
 @ 1aa9ff07:3cb793b5
2025-04-03 14:06:38
@ 1aa9ff07:3cb793b5
2025-04-03 14:06:38In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
- Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
- Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
- Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
- Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
- Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
- Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
- Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
- Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
- User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
Understanding Nostr: A Decentralized Social Network Protocol
In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
-
Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
-
Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
-
Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
-
Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
-
Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
-
Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
-
Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
-
Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
-
User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
-
 @ 21335073:a244b1ad
2025-03-18 14:23:35
@ 21335073:a244b1ad
2025-03-18 14:23:35Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ edeb837b:ac664163
2025-04-03 10:35:59
@ edeb837b:ac664163
2025-04-03 10:35:59When it comes to social trading, there are plenty of platforms that claim to offer innovative ways to connect with other traders, share strategies, and improve your market performance. But let's be real: most so-called "social trading" apps are either glorified brokerage platforms with limited community features or outdated, clunky systems that don’t offer real-time value.
There’s really only one social trading app you need to consider—NVSTly. Here’s why.
Why NVSTly Stands Above the Rest
NVSTly isn’t just another trading app with a few social features slapped on. It’s the ultimate social trading platform, purpose-built to empower traders by combining real-time trade tracking, seamless social sharing, deep market insights, and a powerful trader community.
Unlike other platforms, NVSTly isn’t just about copying trades or following vague signals—it’s about true transparency, collaboration, and learning from top traders in an interactive environment.
What is NVSTly?
NVSTly is a completely free social trading platform that lets traders track, share, and analyze their trades in real time. Whether you're trading stocks, options, or crypto, NVSTly provides a seamless multi-platform experience—available via web, iOS, Android, and even Discord.
It’s not just a social network—it’s a trader’s command center where every trade you make is part of a bigger, smarter ecosystem designed to help you grow.
Key Features That Make NVSTly #1
1. Real-Time Trade Sharing & Tracking
NVSTly integrates with brokers like Webull (with more brokerages coming soon) to automatically track your trades and display them in real-time. No manual entry—just instant trade updates for you and your followers.
2. Unique POV Trade Charting
See trades like never before. NVSTly’s proprietary POV Chart marks every trade action directly on the candlestick chart, giving you (and your followers) an unparalleled view of trading strategies in action.
3. Deep Trade Analytics & Trader Dashboards
Get powerful insights into your performance, including: - Win rate - Total gain/loss - Average return per trade - Long vs. short ratio - (Coming soon) Drawdown tracking to measure risk exposure
4. Global Trades Feed & Leaderboard
Want to see what the best traders are doing right now? The Global Trades Feed lets you watch live trades, while the Leaderboard ranks top traders based on performance metrics, making it easy to find successful strategies.
5. Fully Integrated with Discord & Telegram
No other platform makes social trading as seamless as NVSTly. The NVSTly Discord bot allows users to: - Check a trader’s latest stats - View real-time trade recaps - Fetch charts and ticker data - Receive automated trade notifications
Telegram users won’t be left out either—NVSTly is working on bringing the same functionality to Telegram for even broader access.
6. Automated Social Media Sharing
Set your trades to automatically share to Twitter/X, Discord, and soon, Telegram. Whether you’re growing your personal brand or running a trading community, NVSTly makes sure your trades get noticed.
7. Future AI & Machine Learning Enhancements
NVSTly is building AI-powered trade insights and strategy generation, allowing traders to: - Get automated trading tips tailored to their strategies - Use customizable AI models to refine their trading approach - Interact with a smart AI trading assistant via the app and Discord bot
Why NVSTly is the Only Social Trading App You Need
While others might pretend to offer social trading, NVSTly actually delivers. It’s not a gimmick or a half-baked feature—it’s a complete trading ecosystem built for real traders who want real-time data, powerful analytics, and a truly social experience.
With NVSTly, you're not just following traders—you’re engaging with them, learning from them, and improving your own strategies in the most transparent and interactive way possible.
So don’t waste time on inferior platforms. NVSTly is the only social trading app that matters.
Ready to Take Your Trading to the Next Level?
Join 50,000+ traders who are already using NVSTly to track, share, and dominate the markets.
📲 Download NVSTly today on Web, iOS, or Android!
🚀 Join our Discord community and bring the power of NVSTly straight into your server!
-
 @ ed84ce10:cccf4c2a
2025-03-18 14:19:19
@ ed84ce10:cccf4c2a
2025-03-18 14:19:19The Evolution of Hackathons: From Offline to Online, Powering Frontier Innovation Worldwide
Throughout the history of open-source platform technology, hackathons have been the launchpads for innovation—fueling breakthroughs, incubating the next generation of startups, and serving as the proving ground for builders. Over the past decade, DoraHacks has led the charge, driving the hacker movement and open-source revolution. We didn’t just witness the evolution of hackathons—we architected it.
The Online Revolution of Hackathons
Before 2020, hackathons were largely stuck in the physical world—you had to be in the room to participate. The idea of a fully online, global hackathon was a pipe dream. Then, DoraHacks.io changed everything. Suddenly, a developer in Africa could win funding from a hackathon hosted by a Silicon Valley company. Geographic barriers collapsed. Today, over 95% of hackathons happen online.
The Infrastructure Revolution: Making Hackathons 10x More Effective
DoraHacks relentlessly iterated on the hackathon model. We built BUIDL pages for real-time project showcases, a world-class hackathon organizer dashboard, MACI-powered decentralized privacy governance, and Grant DAOs that provide ongoing funding. The result? DoraHacks became the ultimate launchpad for hackers and early-stage builders.
The Ecosystem Revolution: Supercharging Open Innovation
DoraHacks became the backbone of Web3 innovation—from Ethereum, Solana, and BNB Chain to the next wave of blockchains like Aptos, Cosmos, Injective, TON, and Sonic. Since 2023, hackathons have expanded beyond crypto—quantum computing, commercial space tech, and AI-driven innovations are now being built on DoraHacks.
Rolling Hackathons and Uninterrupted BUIDLing - the New Standard for Ecosystem Growth
BUIDLs can be created spontaneously at any time. Hosting Hackathons as short-term events held only once or twice a year is not conducive to attracting outstanding Hackers and high-quality projects to join the ecosystem and drive innovation in the long term. To remediate this, Hackathons should be continuous and uninterrupted, serving as a long-term driving force within the developer ecosystem.
Historically, the high organizational costs and substantial resource investments associated with frequent Hackathons meant that most emerging ecosystems couldn't afford to host them regularly. As a result, Hackathons became rare, annual spectacles, and for some projects, an unaffordable luxury. This model severely restricted developers' chances to participate and hindered the ecosystem's ability to innovate consistently. Let's imagine what would happen if an ecosystem held 12 or more Hackathons each year?
- Developers have a clear loyalty incentive: They would know that the ecosystem is committed to supporting and funding excellent developers and projects continuously, which would encourage them to make long-term investments and contribute regularly.
- Missing out is no longer an issue: Even if a developer couldn't attend a particular Hackathon, there would be another one soon, increasing accessibility.
- Accelerated ecosystem innovation: Frequent Hackathons would accelerate ecosystem innovation. Developers would be constantly pushed to explore new directions, significantly boosting the growth rate of the technological ecosystem.
Previously, due to the limitations of costs and organizational difficulties, frequent Hackathons were almost unthinkable. Only ecosystems with sufficient funds like Google and Amazon could afford rolling Hackathons. But now, DoraHacks' upcoming BUIDL AI platform tools are set to change the game. These tools make it possible to organize 12 Hackathons in a year, and even go a step further by enabling the simultaneous hosting of multiple differently-themed Hackathons. This will help emerging ecosystems effectively incentivise developers, expand their technological influence, and increase the number of exceptional BUIDLs (projects) in their ecosystems.
The majority of BUIDLs come about continuously and spontaneously and should be recognized and incentivized promptly, rather than having to wait for the single annual Hackathon.
As the saying goes, "He who wins over developers wins the world." In the highly competitive Web3 space, Hackathons are an effective means of attracting developers, and rolling Hackathons are the best way to achieve this. For an ecosystem to stay competitive, it must ensure that developers always have opportunities to engage and create.
The AI Era of Hackathons: A 10x Opportunity, A 10x Challenge
AI Turns Everyone Into a Hacker
AI has obliterated repetitive work. Building is faster than ever. Anyone, from anywhere, can hack, ship, and scale with AI tools that accelerate ideation, development, and execution. The potential of hackathons in this AI-powered era is 10x bigger than ever before.
But Hackathon Infrastructure Is Stuck in the Past
Despite this massive opportunity, organizing hackathons remains painfully inefficient:
- Most organizations don’t know how to run hackathons effectively.
- Even those who do lack time and resources to do it frequently.
- Ecosystem builders who have the resources can only host one hackathon per year.
The result?
- Hackathons are underutilized, slowing innovation.
- Ecosystem growth is bottlenecked by developer relations (DevRel) teams.
- Many ecosystems fail to maximize the potential of hackathons.
- Low-frequency hackathons waste hacker potential—builders sit idle when they could be shipping.
BUIDL AI: Unlocking the Infinite Potential of Hackathons
We refuse to let inefficiency limit innovation. BUIDL AI is our answer.
DoraHacks is launching BUIDL AI, the AI-powered Hackathon Co-Pilot that automates, scales, and supercharges hackathon organization.
BUIDL AI: The Game-Changing Features
1. Edit and Launch: One-Click Hackathon Deployment
Organizers can now launch a hackathon in minutes by filling in basic details (prizes, themes, workshops, judges, etc.). No tedious manual setup.
2. BUIDL Review: Submission Evaluation (10x Faster)
Traditional hackathons get hundreds of submissions—judging takes hundreds of hours. BUIDL AI changes the game. It automatically scores projects based on completeness, originality, and theme relevance—filtering out low-quality submissions 10x faster than before.
3. Automated Marketing: Instant Hackathon Reports
After the hackathon ends, BUIDL AI auto-generates a full post-event report—highlighting winners, standout projects, and key takeaways—boosting visibility and impact.
4. Seamless Interaction: Smarter Collaboration, No Bottlenecks
BUIDL AI will interact with hackathon organizers to keep organizers in sync, alerting them about new submissions, pending approvals, and participant inquiries in real time. No more dropped balls.
5. Multi-Hackathon Management: Scaling Innovation Without Limits
Before BUIDL AI, running multiple hackathons at once was a logistical nightmare. Now, ecosystem builders can launch and manage multiple hackathons seamlessly, boosting innovation frequency exponentially
The full BUIDL AI Beta version will release on April 15th, but multiple free BUIDL AI features have already been available on DoraHacks.io!
BUIDL AI: The Next Great Leap in Open Innovation
Hackathons aren’t just competitions. They are the birthplace of the next trillion-dollar innovations.
With BUIDL AI, hackathons enter a new era—automated, intelligent, and infinitely scalable. This means more hackers, more builders, and more breakthrough projects than ever before.
At DoraHacks, we believe in an open, hacker-driven future. BUIDL AI is the rocket fuel for that future.
-
 @ fd78c37f:a0ec0833
2025-03-18 10:44:40
@ fd78c37f:a0ec0833
2025-03-18 10:44:40In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology.
YakiHonne: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby?
Tomek K: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways.
During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion.
At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution.
That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin.
YakiHonne: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community?
Tomek K: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this.
As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement.
Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role.
If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path.
YakiHonne: How did the Alby community start, and how did it attract its first members?
Tomek K: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now.
As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere.
We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices.
That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal.
YakiHonne:Were there any notable challenges in the early days that left a strong impression on you?
Tomek K :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged.
Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues.
There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.

YakiHonne:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them?
Tomek K: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing.
You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities.
YakiHonne: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both?
Tomek K: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby.
As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.

YakiHonne: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking?
Tomek K: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together.
The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did.
The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects.
Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it.
YakiHonne:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far?
Tomek K :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work.
YakiHonne:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before?
Tomek K:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join.
Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting.
It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema.
YakiHonne:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation.
-
 @ 2b24a1fa:17750f64
2025-04-03 10:11:13
@ 2b24a1fa:17750f64
2025-04-03 10:11:13Ist es wirklich so, dass Gendern für mehr Gleichberechtigung sorgt, für ein friedlicheres Miteinander? Abgesehen von den grammatikalischen Verirrungen, die sich dabei in die Sprache schleichen, darf die Frage erlaubt sein, warum ein Gemeinschaftsgefühl, das „Wir“ in immer kleinere Einheiten, auch sprachlich geteilt werden soll. Muss ich tatsächlich alle benennen?
https://soundcloud.com/radiomuenchen/gendern-die-sakralsprache-des?
Dann wäre das eine Liste von Namen. Verlese ich die nicht, sondern gendere mit Glottisschlag und allem was dazu gehört, unterteile ich ja doch in Gruppen. Und Gruppen haben zur Eigenart, dass es Zugehörigkeiten gibt und ausgeschlossen sein. So beginnt der Kampf. Zunächst war die Frau minderwertig, jetzt ist der Mann toxisch. Und was, wann zu wem, wie gesagt werden darf wird zum Spießrutenlauf. „Misgendern“ ist beispielsweise eine Wortneuschöpfungen, die eine Incorrectness der Sprache bezeichnet, die bis in die Strafbarkeit reichen will.
Einer, der von dieser rigide anmutenden Sprach-Religion getriggert wird, ist Gerald Ehegartner. Er ist Lehrer, Musiker, Theater- und Wildnispädagoge und Autor und nimmt sich immer wieder dem Gemeingut Sprache an. Heute mit einem Text, den er mit: „Gendern, die Sakralsprache des Wokeismus“ betitelt hat.
Sprecherin: Sabrina Khalil
-
 @ 75869cfa:76819987
2025-03-18 07:54:38
@ 75869cfa:76819987
2025-03-18 07:54:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 225,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 95%. More than 10 million events have been published, with posts and reposts showing a decrease. Total Zap activity stands at approximately 15 million, marking a 10% decrease.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 463 long-form articles were published, 29% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 225,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 18179 events, with a low of approximately 16093.
The number of new users has decreased significantly. Profiles with a contact list are now around 17,511, reflecting a 95% drop. Profiles with a bio have decreased by 62% compared to the previous period. The only category showing growth is pubkeys writing events, which have increased by 27%.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 14% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.6 million, which is a 6.1% decrease. Both reposts and reactions have decreased by about 10%.
For zap activity, the total zap amount is about 15 million, showing an increase of over 10% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that A bulletin board is a relay-centric system of forums where users can post and reply to others, typically around a specific community. The relay operator controls and moderates who can post and view content. A board is defined by kind:30890. Its naddr representation must provide the community's home relays, from which all posts should be gathered. No other relays should be used.
nostr:npub1xy54p83r6wnpyhs52xjeztd7qyyeu9ghymz8v66yu8kt3jzx75rqhf3urc is proposing a standardized way to represent fitness and workout data in Nostr, including: Exercise Templates (kind: 33401) for storing reusable exercise definitions, Workout Templates (kind: 33402) for defining workout plans, Workout Records (kind: 1301) for recording completed workouts. The format provides structured data for fitness tracking while following Nostr conventions for data representation.Many fitness applications use proprietary formats, locking user data into specific platforms. This NIP enables decentralized fitness tracking, allowing users to control their workout data and history while facilitating social sharing and integration between fitness applications.
nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef is proposing a PR introduces two "1-click" connection flows for setting up initial NWC connections. Rather than having to copy-paste a connection string, the user is presented with an authorization page which they can approve or decline. The secret is generated locally and never leaves the client. HTTP flow - for publicly accessible lightning wallets. Implemented in Alby Hub (my.albyhub.com) and CoinOS (coinos.io). Nostr flow - for mobile-based / self-hosted lightning wallets, very similar to NWA but without a new event type added. Implemented in Alby Go and Alby Hub. Benefits over NWC Deep Links are that it works cross-device, mobile to web, and the client-generated secret never leaves the client. Both flows are also implemented in Alby JS SDK and Bitcoin Connect.
add B0 NIP for Blossom interaction
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 describes a tiny subset of possible Blossom capabilities, but arguably the most important from the point of view of a most basic Nostr client. This NIP specifies how Nostr clients can use Blossom for handling media. Blossom is a set of standards (called BUDs) for dealing with servers that store files addressable by their SHA-256 sums. Nostr clients may make use of all the BUDs for allowing users to upload files, manage their own files and so on, but most importantly Nostr clients SHOULD make use of BUD-03 to fetch kind:10063 lists of servers for each user.
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q defines a standard for creating, managing and publishing to communities by leveraging existing key pairs and relays, introducing the concept of "Communi-keys". This approach allows any existing npub to become a community (identity + manager) while maintaining compatibility with existing relay infrastructure.
A way for relays to be honest about their algos
securitybrahh is proposing a PR introduces NIP-41, a way for relays to be honest about their algos, edits 01.md to account for changes in limit (related #78, #1434, received_at?, #620, #1645) when algo is provided, appends 11.md for relays to advertize whether they are an aggregator or not and their provided algos. solves #522, supersedes #579.
nip31: template-based "alt" tags for known kinds
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that clients hardcoding alt tags are not very trustworthy. alt tags tend to be garbage in a long-enough timeframe.This fixes it with hardcoded rich templates that anyone can implement very easily without having to do it manually for each kind. alt tags can still be used as a fallback.
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a PR addresses 3 main problems of NIP-44v2. First, It has a message size limit of 65Kb, which is unnecessarily small. Second, It forces the encrypting key to be the same as the event's signing key. Which forces multi-sig actors to share their main private key in order to encrypt the payload that would be later signed by the group. Decoupling singing and encryption keys, for both source and destination, is one of the goals of this version. And It offers no way to describe what's inside the encrypted blob before requesting the user's approval to decrypt and send the decrypted info back to the requesting application. This PR adds an alt description to allow decrypting signers to display a message and warn the user of what type of information the requesting application is receiving.
Notable Projects
Damus nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
- Notes in progress will always be persisted and saved automatically. Never lose those banger notes when you aren't quite ready to ship them.
- Make your profile look just right without any fuss. It also optimizes them on upload now to not nuke other people’s phone data bills.
- You won't see the same note more than once in your home feed.
- Fixed note loading when clicking notifications and damus.io links.
- Fixed NWC not working when you first connect a wallet.
- Fixed overly sensitive and mildly infuriating touch gestures in the thread view when scrolling
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for Android build 2.1.9 has been released. * Multi-account support * Deep linking support * "Share via Primal" support * Bug fixes and improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
YakiHonne Wallet just got a fresh new look!
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xchat v1.4.7-beta release * Upgraded the Flutter framework to v3.29.0. * Private chat implementation changed to NIP-104 Nostr MLS. * NIP-17 and NIP-29 messages now support q tags. * You can swipe left to reply to your own messages. * Chat messages now support code block display. * Copy images from the clipboard. * Fixed an issue where underlined text in chat appeared as italic.
GOSSIP 0.14.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * New Features and Improvements * Zappers and amounts are now shown (click on the zap total) * Reactions and who reacted are now shown (click on the reaction numbers) * Multiple search UI/UX improvements * Undo Send works for DMs too * Undo Send now restores the draft * UI: Side panel contains less so it can be thinner. Bottom bar added. * UI: frame count and spinner (optional) * Relay UI: sorting by score puts important relays at the top. * Relay UI: add more filters so all the bits are covered * Image and video loading is much faster (significant lag reduction) * Thread loading fix makes threads load far more reliably * Settings have reset-to-default buttons, so you don't get too lost. * Setting 'limit inbox seeking to inbox relays' may help avoid spam at the expense of possibly * Fix some bugs * And more updates
Nostur v1.18.1 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Floating mini video player * Videos: Save to library, Copy video URL, Add bookmark * Improved video stream / chat view * Top zaps on live chat * Posting to Picture-first * Profile view: Show interactions with you (conversations, reactions, zaps, reposts) * Profile view: Show actual reactions instead of only Likes * Improved search + Bookmark search * Detect nsfw / content-warning in posts * Show more to show reactions outside Web of Trust * Show more to show zaps outside Web of Trust * Support .avif image format * Support .mp3 format * Support .m4v video format * Improved zap verification for changed wallets * Improved outbox support * Show label on restricted posts * Low data mode: load media in app on tap instead of external browser * Many other bug fixes and performance improvements
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Latest two releases of Alby Go, 1.10 and 1.11, brought you lots of goodies: * BTC Map integration for quick access to global bitcoin merchants map * Confirm new NWC connections to your Alby Hub directly in Alby Go! No more copy-pasting or QR code scanning * Support for MoneyBadger Pay Pick n Pay QR payments in over 2000 stores in South Africa
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.0 is now available. This release features the ability to renew channel leases, spin up multiple embedded wallets, Nostr Wallet Connect client support, and more. * Renewable channels * NWC client support * Ability to create multiple Embedded LND 'node in the phone' wallets * Ability to delete Embedded LND wallets * Embedded LND: v0.18.5-beta * New share button (share ZEUS QR images) * Tools: Export Activity CSVs, Developer tools, chantools * Activity: filter by max amount, memo, and note
Long-Form Content Eco
In the past two weeks, more than 463 long-form articles have been published, including over 91 articles on Bitcoin and more than 41 related to Nostr, accounting for 29% of the total content.
These articles about Nostr mainly explore the rise of Nostr as a decentralized platform that is reshaping the future of the internet. They emphasize Nostr's role in providing users with greater freedom, ownership, and fair monetization, particularly in the realm of content creation. The platform is positioned as a counter to centralized social media networks, offering uncensored interactions, enhanced privacy, and direct transactions. Many articles delve into Nostr’s potential to integrate with Bitcoin, creating a Layer 3 solution that promises to end the dominance of old internet structures. Discussions also cover the technical aspects of Nostr, such as the implementation of relays and group functionalities, as well as security concerns like account hacks. Furthermore, there is an exploration of the philosophical and anthropological dimensions of Nostr, with the rise of "Dark Nostr" being portrayed as a deeper expression of decentralized freedom.
The Bitcoin articles discuss the ongoing evolution of Bitcoin and its increasing integration into global financial systems. Many articles focus on the growing adoption of Bitcoin, particularly in areas like Argentina and the U.S., where Bitcoin is being used for rental payments and the establishment of a strategic Bitcoin reserve. Bitcoin is also portrayed as a response to the centralized financial system, with discussions about how it can empower individuals through financial sovereignty, provide a hedge against inflation, and create fairer monetization models for creators. Additionally, the articles explore the challenges and opportunities within the Bitcoin ecosystem, including the rise of Bitcoin ETFs, the development of Bitcoin mining, and the potential impact of AI on Bitcoin adoption. There is also emphasis on Bitcoin's cultural and economic implications, as well as the need for decentralized education and innovation to drive further adoption.
Thank you, nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub17wrn0xxg0hfq7734cfm7gkyx3u82yfrqcdpperzzfqxrjf9n7tes6ra78k nostr:npub1fxq5crl52mre7luhl8uqsa639p50853r3dtl0j0wwvyfkuk4f6ssc5tahv nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2 nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 nostr:npub1uv0m8xc6q4cnj2p0tewmcgkyzg8cnteyhed0zv30ez03w6dzwvnqtu6gwl nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1gqgpfv65dz8whvyup942daagsmwauj0d8gtxv9kpfvgxzkw4ga4s4w9awr nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The first Bitcoin Meetup organized by Mi Primer Bitcoin was successfully held on March 14, 2025, at Texijal Pizza in Apaneca. The event included Bitcoin education, networking, a Q&A session, and merchandise distribution, offering an exciting experience for all participants.
* The Btrust Space discussion was successfully held on March 13, 2024. The event focused on how to support Bitcoin developers, fund open-source contributions, and grow the Bitcoin ecosystem. The speakers included Bitcoin core contributors, Btrust CEO, engineering leads, and other project leaders.Here is the upcoming Nostr event that you might want to check out.
- The Nostr Workshop, organized by YakiHonne and Bitcoin Safari, will take place online via Google Meet on March 17, 2025, at 7:00 PM (GMT+1). The event will introduce the Nostr ecosystem and Bitcoin payments, with participants learning about decentralized technology through YakiHonne and earning rewards. Register and verify your account to claim exclusive rewards, and invite friends to unlock additional rewards.
- The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar will be held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar will be hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (Lawyer specializing in Banking, Corporate, and Financial Law). The session aims to introduce the academic program and explore Bitcoin, the crypto economy, and related legal issues.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. The event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 2b24a1fa:17750f64
2025-04-03 10:05:21
@ 2b24a1fa:17750f64
2025-04-03 10:05:21Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden.
https://soundcloud.com/radiomuenchen/nachruf-3-christian-der-wachstumliche
Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.
Folge 3: Christian der Wachstümliche
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
Radio München
-
 @ 2b24a1fa:17750f64
2025-04-03 10:03:24
@ 2b24a1fa:17750f64
2025-04-03 10:03:24Der Deutsche Bundestag wurde neu gewählt. Für einige Abgeordnete und Regierungsmitglieder heißt es Time to Say Goodbye. Abschied ist ein scharfes Schwert. Auch bei Radio München werden Trennungs- und Verlassenheitsgefühle getriggert. Umso mehr, wenn es sich nicht nur um duselige Allerweltsliebe handelt, sondern um den Abgang großer Helden.
Sie bezahlten ihren todesmutigen und fast ehrenamtlichen Einsatz nicht mit dem Leben, jedoch mit der einen oder anderen Falte in Hemd oder Bluse, manchmal sogar im Gesicht. Was bleibt? Eine bescheidene Pension? Ein lausig bezahlter Manager-Job in einem Konzern? Wir wollen jedenfalls nicht, dass diese Volkshelden vom Zahn der Zeit abgenagt, vergessen werden und setzen ihnen deshalb ein bescheidenes akustisches, aber nachhaltiges Denkmal. Hören Sie die kleine satirische Reihe „Nachrufe“ von unserem Autor Jonny Rieder.
Folge 4: Annalena die Völkerballerina
Sprecher: Karsten Troyke
Bild: Markus Mitterer für Radio München
-
 @ edf0da8b:b2652fa3
2025-03-17 17:28:33
@ edf0da8b:b2652fa3
2025-03-17 17:28:33One remarkable thing the Wim Hof Method stirs in me is that I increasingly feel the desire to connect with pure nature. Now, what does that mean?
You may know that slight feeling of eeriness when looking at deep moving waters or that tiny insecurity when darkness creeps up around you alone among the trees? You are sure there's nothing to worry about. But still, these little old conditioned anxieties, these unreasonable mind scenarios, they keep coming up and make you seek safety.
They are different for everyone, but these anxieties in the foreground are a sign for inner blockages that deprive us from expressing our power and creativity. What's more, they separate us from nature. They suggest, everything around us is potentially dangerous. Is it though?
When practicing the Wim Hof Method, and especially right after the breathing exercises, I can immediately feel a clarity emerging, a stronger awareness of presence in the moment. Anxieties are caringly pushed back to their rightful place, but do not control my actions and no longer dominate my state of being.
And so suddenly, the world view shifts. Eerie deep moving waters become fascinating, the darkness around reveals the beauty of trees casting soft moonlight shadows. I deeply appreciate what is, I want to touch the waters, I want to merge with the shadows, I feel that power. Instead of running away I want to connect with nature. I'm more aware of the present and should danger reveal itself, I have the confidence that I can properly react when it arises. But until then, I can enjoy beauty and connectedness. The powerful shift is from scenarios about potential threats around me to curiosity and beautiful opportunity everywhere.
There are countless great techniques and traditions that guide us to such shifts. But with regular practice, I find the Wim Hof Method to be particularly simple, accessible and effective.
wimhofmethod
-
 @ 2b24a1fa:17750f64
2025-04-03 09:57:35
@ 2b24a1fa:17750f64
2025-04-03 09:57:35Es sind immer die gleichen Mechanismen: Die Faktoren Zeitdruck und Angst machen enorm viele Menschen gefügig. 500 Milliarden Euro für Infrastruktur und den sogenannten Klimaschutz, 400 Milliarden für die Bundeswehr – also fast eine Billion Euro Schulden, innerhalb von weniger als vier Wochen nach der Wahl mit Winkelzügen den Bundesbürgern auferlegt.
https://soundcloud.com/radiomuenchen/es-lebe-die-freiheit-verdammt?
Wahlversprechen oder Parteiprogramme, das auf keinen Fall zu tun, sind Makulatur. Keine Diskussion über einen Haushalt, keine Diskussion über die Notwendigkeiten und schon sind Fragen anhängig, ob die Aufträge, die nun vergeben werden, nach den rechtmäßigen Ausschreibungskriterien vonstatten gehen, oder ob auch bei diesen unvorstellbaren Summen die Spezlwirtschaft im Land fortgeführt wird.
Wo ist der Wille des Volkes geblieben? Wo die Freiheit, tatsächlich über unser Leben und Wirtschaften zu entscheiden?
Der Autor, Wirtschafts- und Finanzexperte Andreas Geltinger schaut auf die einstigen Ideen wirtschaftlichen Handelns und analysiert, womit wir es jetzt zu tun haben.
Sprecher: Karsten Troyke.
-
 @ 06bc9ab7:427c48f5
2025-03-17 15:46:23
@ 06bc9ab7:427c48f5
2025-03-17 15:46:23Bitcoin Safe - A bitcoin savings wallet for the entire family
Designed for both beginners and power users, Bitcoin Safe combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure.
Built for Learners
✔️ Step-by-step wallet setup wizard + PDF backup sheets 📄 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware signers only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address categories for easy organization ☁️ Label and category synchronization, and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon
Built for Power Users
🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & many more 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow diagrams to trace coin movements 🔍 Instant cross-wallet wallet search ⚙️ Set your own electrum server, mempool instance, and nostr relay
Step-by-Step Wallet Setup
Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:

- Single Sig Wizard: Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w
Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard
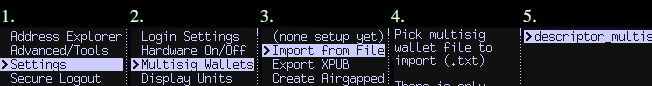
-
Multisig Wizard: The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/
-
PDF Backup: The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.
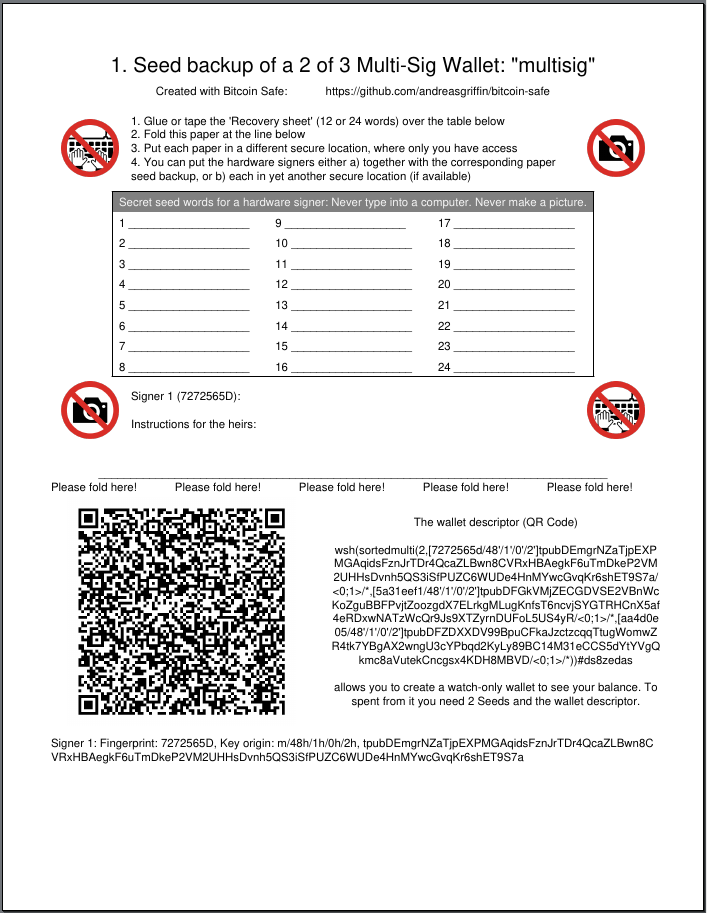
-
Hardware Signer Support: With full support for major hardware signers your keys remain securely offline.
Transaction Visualization
Visualize and navigate your transaction history:
-
Graphical Explorer: An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.
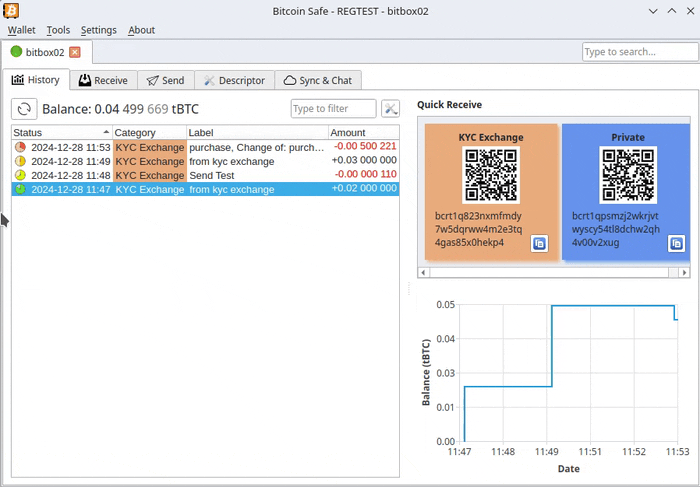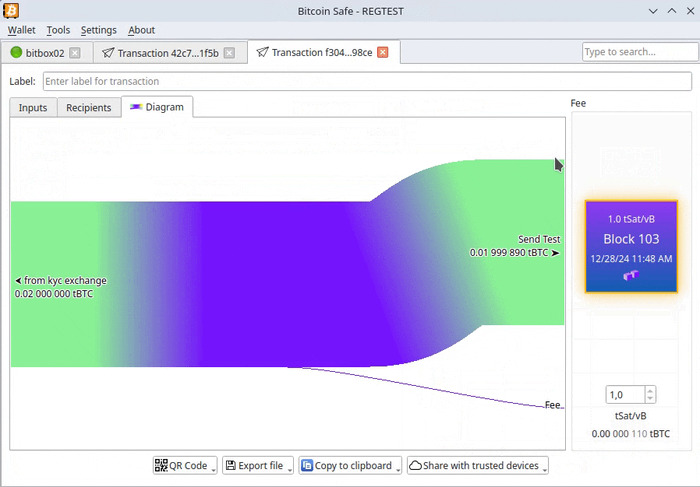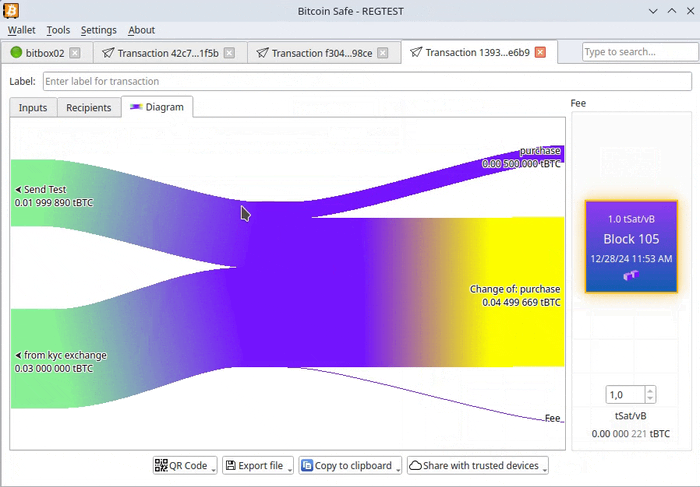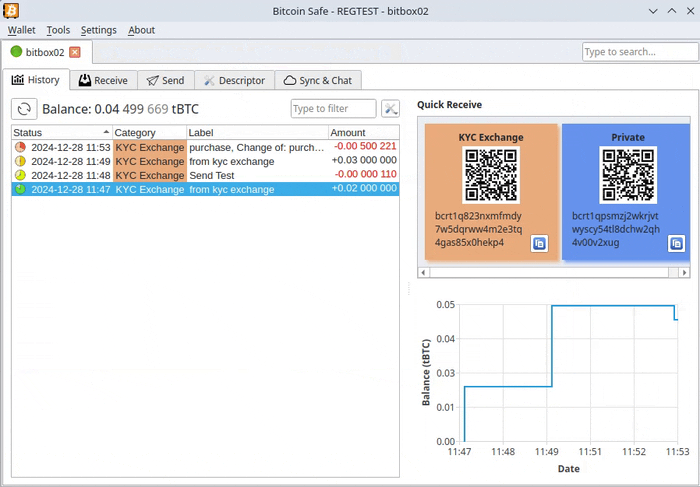
-
Coin Categories: Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so Bitcoin Safe automatically selects the correct inputs when creating PSBTs.

It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.
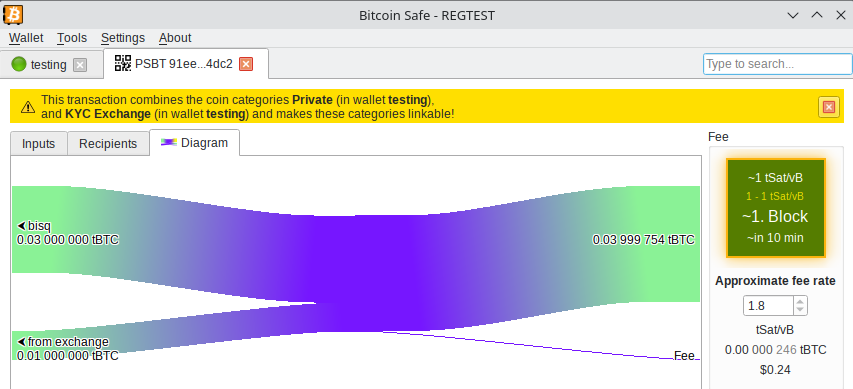
Powerful Wallet Management Tools
- Flexible Fee Selection: Choose fees with one click using an intuitive mempool block preview.
- UTXO Management: Automatically (optional) merge UTXOs when fees are low.
- CSV Table Export: Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel.
- PDF Balance Statement: Export the address balances for easy record keeping on paper.
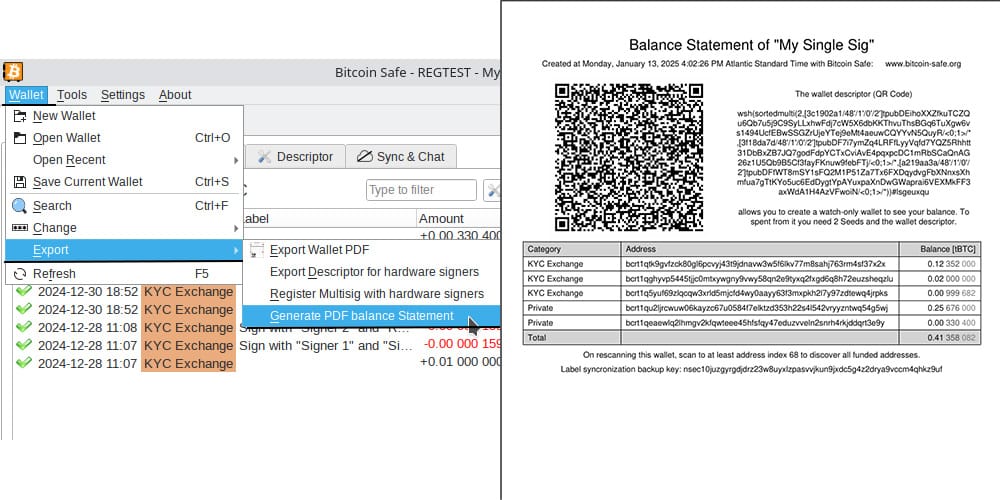
Advanced Features for the Power-User
Sync & Chat is off by default (for the paranoid user), but can be enabled with just one click.
Label Synchronization and Backup
- Seamless Sync: Using encrypted nostr messages, Bitcoin Safe synchronizes your coin categories and labels across multiple devices.
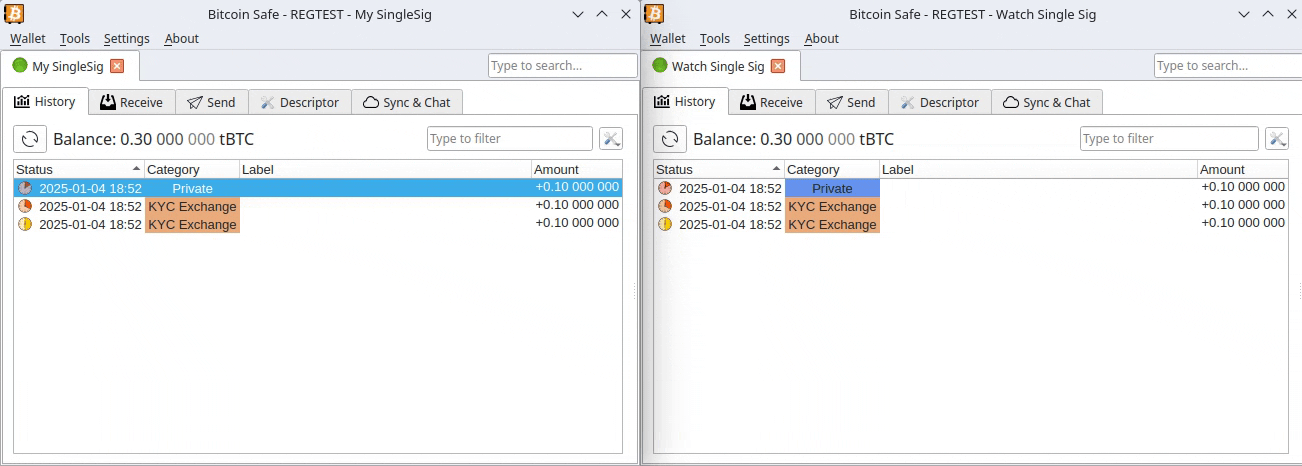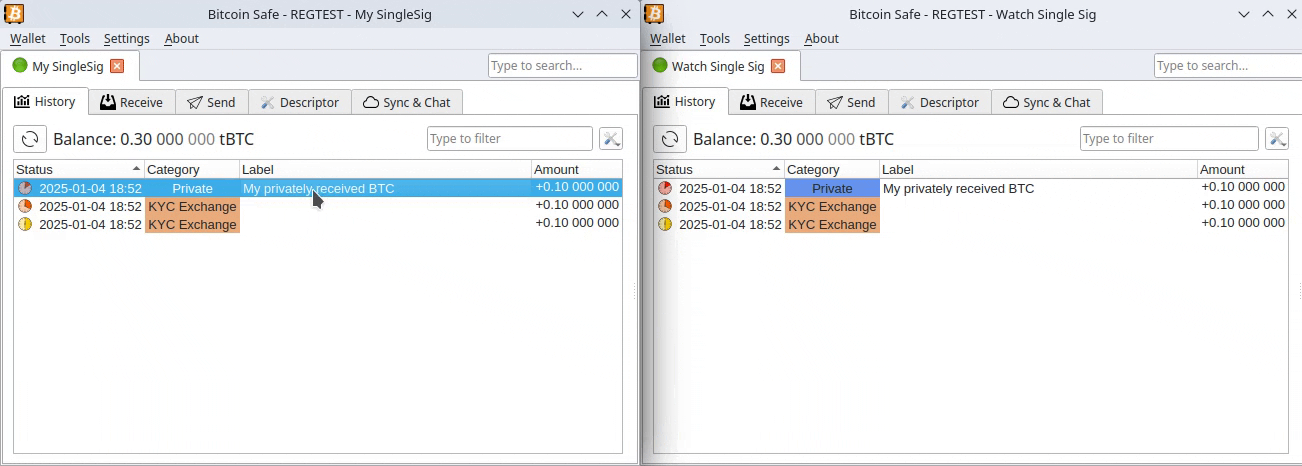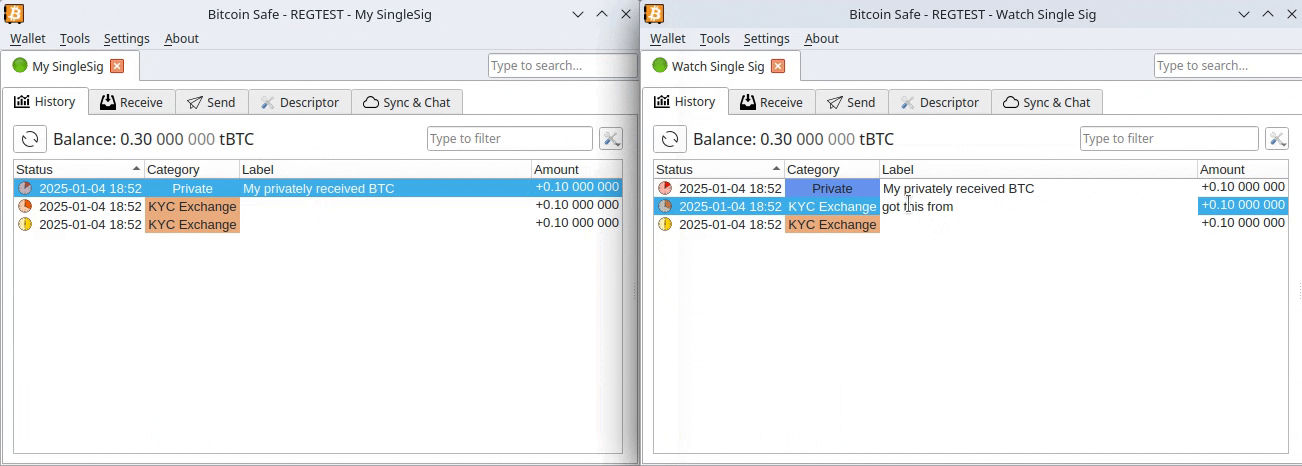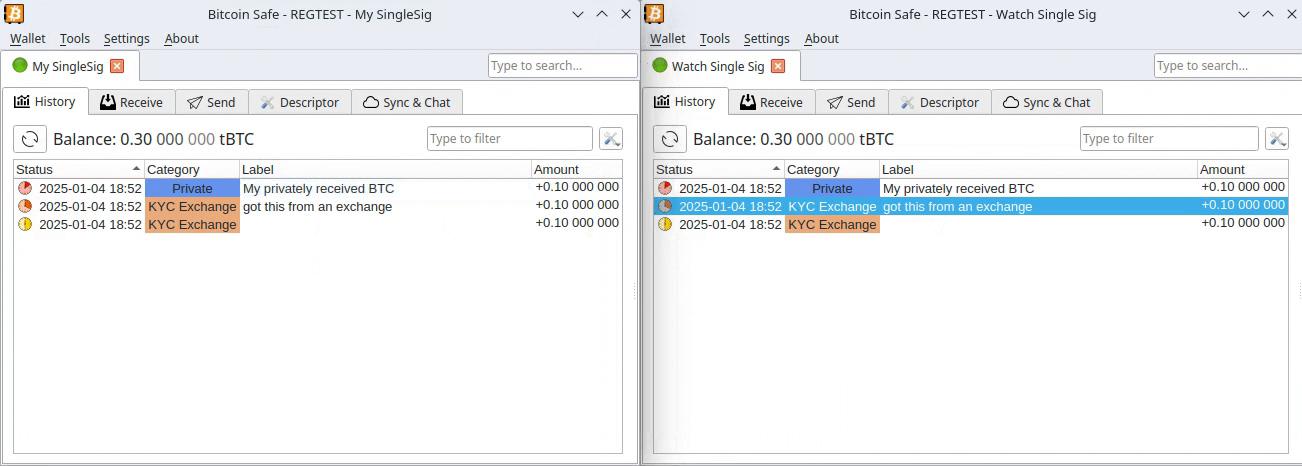
- Easy Backup: A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact.
Collaborative Multi-party Multisig
- Group Chat Integration: After creating your multisig wallet, Bitcoin Safe offers an encrypted nostr group chat for secure collaboration and one-click PSBT sharing.
- User Authentication: Each participant must authenticate every other user with a simple click, ensuring secure communication.
Watch and Learn: Get Started with Bitcoin Safe
If you’re new to Bitcoin Safe, a short video guide can make all the difference. Learn how to set up your Bitcoin Safe wallet in this detailed walk through:
https://youtu.be/m0g6ytYTy0w
Or see how to verify an address on your hardware singer:
https://youtu.be/h5FkOYj9OT8
Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/
Whats next?
- Compact Block Filters!!! They make electrum servers obsolete.
- Why? Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions
- Trade-off: They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK.
- How do they work? Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more here and of course in the bip.
- When: 2 weeks 😅. Lots of things need to be done until Bitcoin Safe can use the bdk CBF/kyoto client from rustaceanrob, so keep an eye out for updates and please give feedback when you use Bitcoin Safe.
Stay updated on nostr or on GitHub.
Thank you
A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a grant and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the Hackathon prize.
This wallet is only possible because it is building upon other peoples open source work. Most notably
- bdk nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet
- and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions.
- rustaceanrob building kyoto which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases
- ndk by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp
And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 Coldcard , Coldcard Q , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt Bitbox02 , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n Blockstream Jade , Trezor Safe, Foundation Passport, Keystone, Ledger, Specter Shield, and many more.
I also want to thank people who gave feedback and helped spread the knowledge of Bitcoin Safe (please forgive me if I forgot to mention you)
- nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini rustaceanrob
-
 @ e4950c93:1b99eccd
2025-04-03 09:55:59
@ e4950c93:1b99eccd
2025-04-03 09:55:59Équipe Cœur
L'équipe Cœur porte le projet et valide les contenus.
Pour démarrer, je gère le projet en solo. Contactez-moi si vous souhaitez rejoindre l'aventure !
Enrichisseu-r-se-s de contenus
Les contribut-eur-rice-s rendent ce site vivant et intéressant.
-
 @ 2b24a1fa:17750f64
2025-04-03 09:34:29
@ 2b24a1fa:17750f64
2025-04-03 09:34:29Kartografiert, aufgekauft, betoniert, beschildert. Wo ist die Freiheit? Wo ist Platz zum Erforschen im Nicht-Definierten? Also wo sind die Erfahrungsräume, die sich von Generation zu Generation üblicherweise immer wieder die Jugend erobert, um darin zu wachsen und zu reifen?
https://soundcloud.com/radiomuenchen/abwartend-skeptisch-von-kenneth-anders
Perspektivwechsel: Wo sind eigentlich die Jugendlichen abgeblieben, die nach diesen Räumen Ausschau halten? Sie bewegen sich in „Spaces“. Seit Corona staatlich verordnet, suchen sie auf flachen Bildschirmen, in einer artifiziellen Welt, ihren Horizont zu erweitern.
Der Kulturwissenschaftler Kenneth Anders hat sich auf Spurensuche bei Jugendlichen auf dem Land gemacht. Hören Sie sein Resumée mit dem Titel „Abwartend skeptisch“.
Nachzulesen ist der Beitrag auf der Webseite: oderamazonas.de
Sprecherin: Sabrina Khalil
Bild: KI
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
-
 @ 06639a38:655f8f71
2025-03-17 15:13:22
@ 06639a38:655f8f71
2025-03-17 15:13:22- My PR#100 for
sirn-se/websocket-phpgot merged and was released in version 3.2.3 - Closed issue #83, reviewed and merged PR#84 for integrating NIP-04 and NIP-44
- Closed issue #85 and merged PR#86 with Event object verification
1.6.0release https://github.com/nostrver-se/nostr-php/releases/tag/1.6.0
Planned for week 12:
- Integrate NIP-19
- My PR#100 for
-
 @ 2b24a1fa:17750f64
2025-04-03 09:28:52
@ 2b24a1fa:17750f64
2025-04-03 09:28:5221 Monate, also fast zwei Jahre verbringt Johanna Findeisen bereits in Untersuchungshaft. Trägt sie reichsbürgerliche Ideen mit sich? Oder hat sie Straftaten geplant? Es ist ein Fall im sogenannten „Reichsbürgerprozess“. Mit diesem beschäftigt sich einer ihrer Anwälte Prof. Martin Schwab. Bei den Prozessen, so der Jurist, gehe es eher um Gesinnungsfragen.
Fakten zu Straftaten, auch geplanten, seien nicht aufzufinden. Und eine Untersuchungshaft für die Aufdeckung einer möglicherweise falschen Gesinnung – die Johanna Findeisen vehement bestreitet - ist in unserem Rechtssystem nicht vorgesehen. Dennoch sind die Termine für diese Untersuchungen bereits bis 2026 anberaumt.
Das soll aber heute nicht unser Thema sein. Es geht um die Untersuchungshaft selbst. Prof. Martin Schwab ist in regelmäßigem, telefonischen Kontakt mit Johanna Findeisen und stellt dort Verhältnisse fest, die den Tatbestand der Folter erfüllen. Kein Mensch, selbst der Verurteilte, darf in seiner Menschenwürde herabgesetzt werden. Nun wird der Fall Johanna Findeisen bislang lediglich untersucht. Wie kann also sein, dass sie im Transport zum Gericht gefesselt wird? Warum wurde sie bei ihrer Rückkehr körperinvasiv untersucht? Was übrigens nach einem öffentlichkeitswirksamen Antrag ans Oberlandesgericht erfolgreich unterbunden wurde. Warum wird ihre Post zurückgehalten? Warum durfte sie, bei zwei Stunden Besuchszeit im Monat, ihren Angehörigen nur hinter einer Scheibe begegnen? Warum wird sie, ohne Morgentoilette, abgeholt und in eine fensterlose Zelle ins Gericht gebracht, wo sie zwei Stunden bis zum Gerichtstermin ausharren muss? Und warum wird die fiebernde Johanna, bei Minusgraden und offener Türe gezwungen, sich nackt auszuziehen, sich zur Wand zu drehen und sich einer erniedrigenden Leibesvisitation zu stellen?
Auch dem Pfarrer und Autor Jürgen Fliege geht dieser Fall nah und fragte sich, was Johanna Findeisen, neben einer guten Verteidigung gebrauchen könnte und er ihr geben: Beistand! Hören Sie seinen offenen Brief an die Inhaftierte.
Sprecherin: Sabrina Khalil.
Wer sich gegen die – in einzelnen Haftanstalten – untragbaren Zustände, gegen die dortigen Menschenrechtsverletzungen engagieren möchte, kann das beispielsweise auf der Webseite www.folter-nein-danke.eu tun.