-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 54609048:8e22ba03
2025-04-22 12:25:50
@ 54609048:8e22ba03
2025-04-22 12:25:50One of the greatest threats facing liberty lovers around the world today is the rise of the biomedical security state—the militarization of healthcare. COVID-19 was merely a compliance test, and sadly, most failed it dismally. But pay attention: “pandemic response,” war-gamed at elite gatherings like Davos, is steadily morphing into official health policy through backdoor mechanisms—diabolical agreements like the WHO Pandemic Treaty, which effectively transfers sovereign pandemic authority to Bill Gates via the WHO; the rollout of digital IDs; and the global push for central bank digital currencies (CBDCs).
This biomedical Leviathan requires all three pillars to be firmly in place before it can unleash a never-ending cycle of pandemics. The goal? To normalize draconian measures like those witnessed in 2020, thereby dismantling not only national sovereignty but, more dangerously, individual sovereignty. A digital ID won't merely confirm your identity—it will track your vaccination status, movements, and even your sentiments, all to determine what privileges you're allowed. Meanwhile, the CBDC will act not just as a means of transaction but as an enforcement mechanism—particularly for dissenters. This is why having an alternative like Bitcoin is not just relevant, but essential.
Vaccines are a cornerstone of this architecture—not only as instruments of control but also as tools for "redesigning" humanity. Welcome to the realm of transhumanism. The merger of man and machine through brain-computer interfaces and artificial intelligence is no longer science fiction; it's a stated goal. In this context, vaccines are not merely preventative medicine but potentially covert instruments of eugenics. This could explain the near-religious devotion to these pharmaceutical products—despite their increasingly controversial outcomes and questionable safety record—especially when mandates enter the equation.
The first piece of property any individual owns upon birth is their body. And yet, this sacred ownership is violated at birth when governments mandate certain injections—often administered without informed parental consent. I've often wondered: Why, despite mounting evidence to the contrary, is vaccine efficacy treated as “settled science”? Why is it taboo to question vaccines or hold their manufacturers accountable for harm, even as we’re expected to believe—without scrutiny—that they are “safe and effective”? We’re told our refusal to comply endangers everyone else who took a product supposedly designed to protect them. Strange, isn’t it? If it’s so effective, why must everyone take it simultaneously?
If you're wondering where this seemingly off-the-cuff rant is headed, here's the point: when the state mandates vaccines, it violates your property rights over your own body. It’s a direct claim of ownership over you, dressed up in moral language like “we're all in this together.” You're guilt-tripped into compliance under the pretense of saving “grandma.” But the truth is, if your rights can be suspended for the collective, they were never yours to begin with.
The biomedical security state will manufacture a permanent state of emergency under the guise of “pandemic preparedness.” You’ll be expected—required, even—to inject yourself with the latest mRNA-based bioweapon, all in the name of public health. Some will die. Others will become incapacitated—zombies or vegetables. The altar of compliance will be merciless towards those that bow before it.
Public health agencies like the CDC, WHO, and NIH are on track to become as powerful as central banks. In fact, they may soon act as arms of monetary policy enforcement. Don’t believe it? Look into what was happening in the repo markets in September 2019—just months before the global shutdown. While you're at it, investigate how many elderly pensioners quietly dropped dead like flies between 2021 and 2023, either from the virus or the vaccine. I’ll let the numbers speak for themselves.
These agencies are becoming the new face of the war machine. Vaccines will be marketed as shields against biological threats—“benevolent” weapons to protect us from invisible enemies. And if history is any guide, the next “9/11-style” event will be biological in nature.
The lunatics running the asylum will seize any such crisis to strip away more of your freedoms while simultaneously redesigning the global economy—consolidating even more power in their hands. For a blueprint of this ambition, look no further than Klaus Schwab’s COVID-19: The Great Reset.
The only antidote is a decentralized parallel system of medicine—one that stands entirely outside the Big Pharma cartel. This will require not only a network of courageous healthcare providers but also a new generation of researchers willing to ask uncomfortable questions and challenge sacred cows in the pursuit of truth. Add independent scientific journals to the mix, and we can finally dismantle the machinery that suppresses unprofitable—but potentially life-saving—treatments.
In my view, none of this is viable at scale without decentralized money. Enter Bitcoin. It’s not a panacea, but it’s a crucial tool for realigning incentives. Bitcoin renders CBDCs dead on arrival and undermines the foundation of any future social credit system—where vaccine compliance will be its crown jewel.
The biomedical state is not coming—it’s already here, creeping into every corner of our lives. It will be the scepter of a new technocratic tyranny. So beware the white coats who worship the state. They are not here to heal—they are here to rule.
A more polished series of articles on this topic is forthcoming. Stay tuned.
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
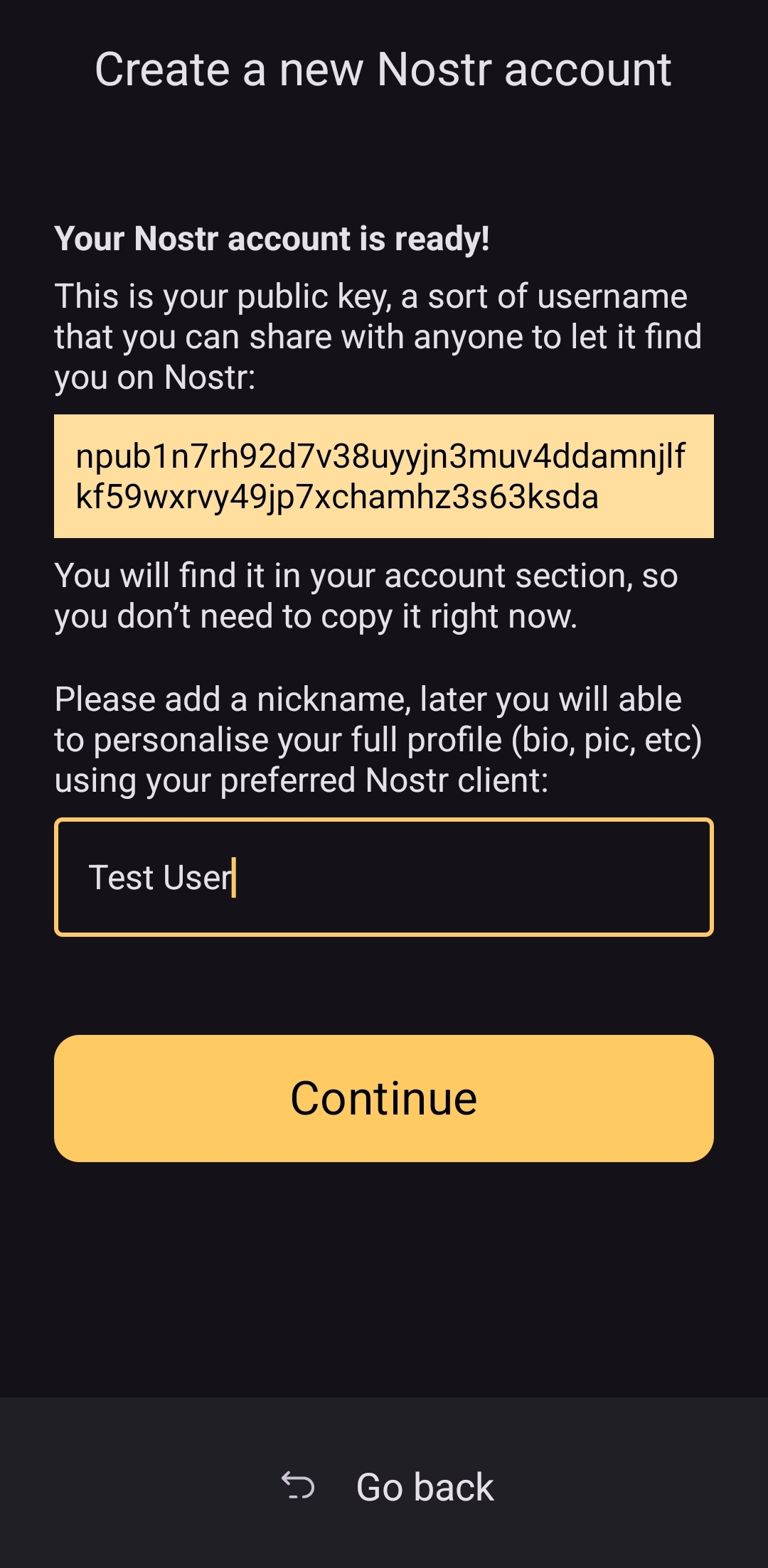
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
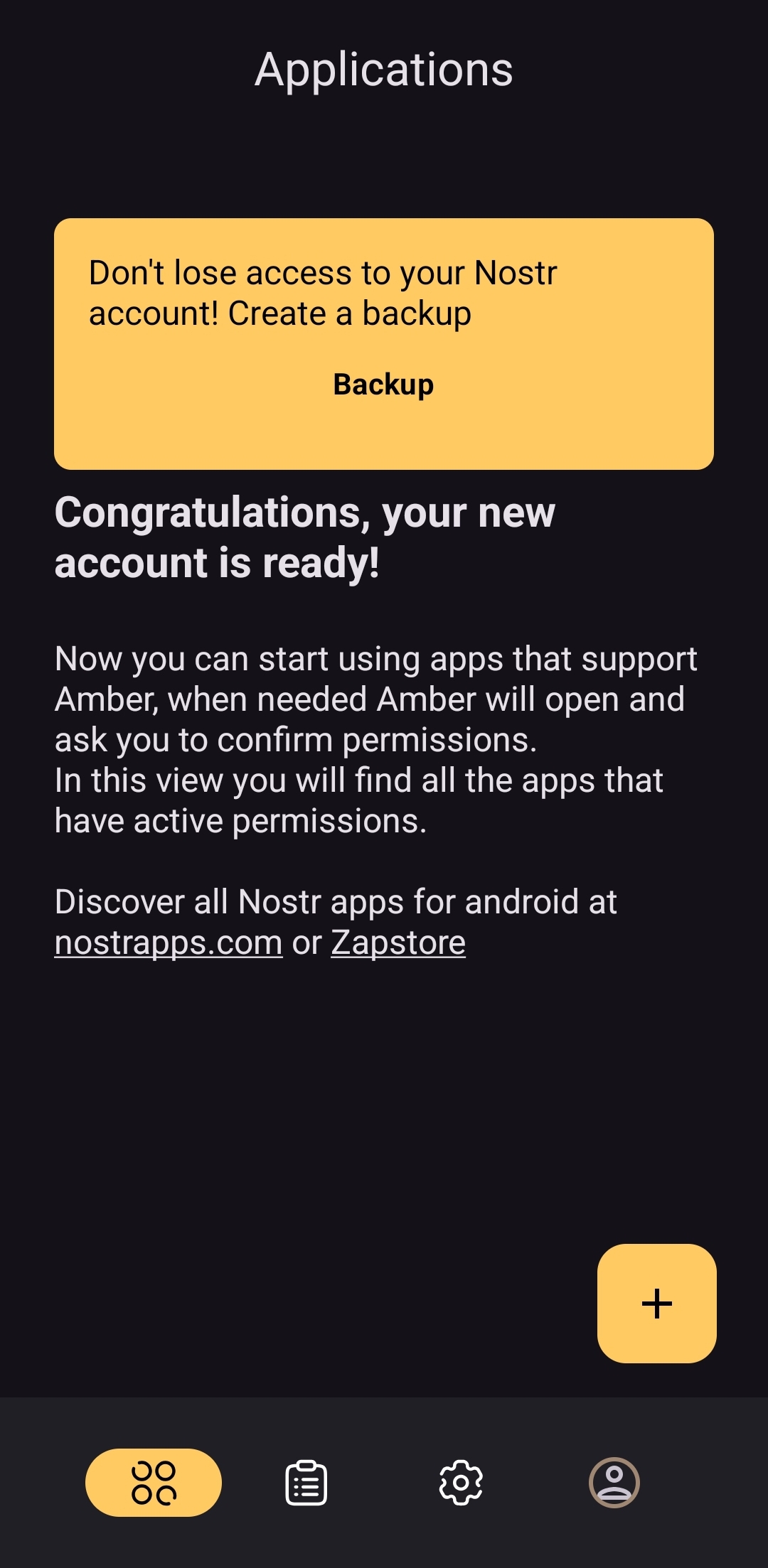
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ d34e832d:383f78d0
2025-04-22 08:40:25
@ d34e832d:383f78d0
2025-04-22 08:40:25
In the twilight of forgotten eras, where the whispers of the past wove through the air like a ghostly melody, two shadowy figures emerged beneath an ageless sky. She was Eve, not the emblem of gardens, but the Mitochondrial Eve—her essence pulsing within the very mitochondria that spark life in each human heartbeat. He stood before her as Adam, not forged from soil, but the Y-Chromosome Adam—guardian of a singular lineage, his heritage dancing through the veins of sons alone.
Their encounter was not one of flesh and blood, but a meeting of symbols, sparked by the insatiable curiosity of humanity, prowling through the labyrinth of DNA, seeking to uncover the tales of their primordial roots.
In the ethereal glimmer of a timeless pool, two figures stood, their outlines rippling like whispered secrets. They were neither lovers nor allies, nor of the same age, yet their names danced together in every headline and wisdom-filled book.
Today, however, was different—they had gathered at the brink of the infinite to unravel the threads of their intertwined destinies.
As the twilight draped its ethereal cloak over the meadow, Eve let her fingers dance through the glimmering starlight, weaving dreams from its luminous threads.
“You know,” she mused, her voice a whisper carried by the evening breeze, “they often ponder why fate kept us apart. Why our paths never crossed beneath the same sun.”Adam’s lips curled into a wry smile, his eyes reflecting the cosmos above.
“Perhaps they seek a narrative that is neat and orderly, a story with perfect symmetry,” he replied, the gentle rustle of leaves echoing his words.Eve shook her head softly, her gaze fixed on the swirling constellations.
“Ah, but nature, dear Adam,” she countered with a glimmer of mischief, “is a master of chaos. It delights in the untamed, the beautiful mess of existence.”In the grand tapestry of time, two figures emerged from the mists of ancient Africa:
Mitochondrial Eve, a woman of vibrant spirit, who roamed the earth around 150,000 to 200,000 years ago, and
Y-Chromosome Adam, a man of strength and wisdom, appearing some 60,000 to 100,000 years later.Though separated by a chasm of tens of thousands of years, they were not the sole beings of their era, yet in the intricate web of life, they were the most recent ancestors, bearers of unbroken trails of maternal and paternal lines, from which all humanity flows.
Their stories intertwine, echoing through generations, whispers of a time long past.
In a hushed tone, Eve shared the tale of her lineage, weaving a rich tapestry of time.
“Behold my daughters,” she said, her eyes gleaming with pride. “From them sprang another generation, and those daughters too have borne daughters.This precious thread of life, my mitochondrial DNA, weaves through the tapestry, handed down solely by women.
With each passing age, while many lines faded into shadows—some in mere moments, others enduring for centuries—mine flowed on, a river of continuity and strength.
My legacy, a steadfast whisper across generations, defied the silence of so many others.”In a dimly lit room, Adam pondered the weight of generations past.
“And what of mine?” he inquired, his voice tinged with a mix of curiosity and melancholy.He shook his head slowly, as if unraveling a forgotten tale.
“The Y-chromosome, it weaves a delicate thread through the tapestry of life.
Passed from fathers to sons, a fleeting whisper of legacy, vanishing if a man begets no heirs.Like branches of a grand oak, countless lines have been severed by the cruel hands of war, the relentless march of disease, and the silent grasp of chance.
Mine is not the sole survivor in this timeless struggle, but it is the one that defied extinction—standing resilient against the bottleneck of time, thriving into the present day, a testament to tenacity and fate.”Their inheritance patterns are straightforward but ruthless.
Mitochondrial DNA (mtDNA) is stable and abundant, making it a powerful marker for tracing maternal lineage.
It mutates slowly, preserving a clear path backward.In contrast, the Y-chromosome, despite its utility in tracing paternal lines, is subject to greater volatility: smaller effective population sizes, male-specific extinction events, and the disproportionate reproductive success of a few males—all contribute to a narrower, more chaotic record.
In a dimly lit chamber nestled among ancient trees, Eve’s voice resonated with the wisdom of ages.
“The numbers are not our destiny,” she declared, her finger tracing a pattern in the soil.
“They are mere echoes of survival, tales of those who dared to pass their legacy—a lineage of children begetting children, weaving a tapestry of existence.”Adam stood by, thoughtful as a storm brewing on a distant horizon.
“Indeed, lineages dissolve like whispers in the wind,” he mused, his gaze fixed on the moonlight filtering through the leaves.
“Some genetic threads endure not from superiority, but sheer fortune. Bottlenecks of fate, the whims of founders, the swirling dance of genetic drift—these unseen forces hold the key to who emerges amidst the chaos of time.”Together, they pondered the intricate dance of life, where luck and survival intertwined, crafting the very fabric of their world.
Eve paused, her voice a whisper woven with time.
“And so it is,” she mused, “the humans trace their lineage back to me, painting me as the primordial bloom of existence.Yet, shadows linger—my cousins, neighbors, even rivals shared this space, vibrant as I, yet their stories faded like whispers in the wind.
They bore no daughters to carry forth their tales, only their echoes lingered, lost in the tapestry of forgotten history…”
In the shadow of an ancient, pulsing tree that mirrored their very essence, Adam mused aloud,
“I came along far down the line, but not right at the start.
I am but one among countless men, and in the end, only my Y-line remained, a solitary thread in the tapestry of time.
Your lineage, however, stretches across continents, vibrant and thriving.”They stood quietly, lost in the vast glow of humanity’s fractal branches, each flicker representing a birth, a connection, a glimmer of possibility.
“Isn’t it amusing?” Adam chuckled, breaking the reverie.
“They pair us as if we were a couple, forever intertwined.”Eve’s laughter echoed like sweet music.
“Merely symbols, nothing deeper. We are called ancestors, yet we are merely the fortunate survivors of an exquisite genetic lottery.”Adam continued,
“And yet, the very essence of your spark resides in every human’s mitochondria, while half of them carry my signature in their Y chromosome.”Eve’s voice was soft as she spoke, weaving a tapestry of understanding.
“Ah, but dear friend, ancestry is far more than mere lineage.
It’s like tracing the delicate threads of a grand tapestry, where some strands are visible, yet countless others lie hidden in the shadows of time.Each soul walking upon this earth is a descendant of a multitude of individuals from ages long past.
Their names may fade like whispers in the wind, and their unique genes become mere echoes of history.
Yet, amidst this beautiful chaos, the patterns of our heritage forever linger, binding us in an unseen embrace of shared existence.”As Adam stood beneath the shimmering canopy of stars, he pondered aloud,
“Maybe the tale isn’t solely ours. It’s about the delicate yet unwavering dance of life itself.”Eve, her eyes reflecting the celestial lights, agreed with a subtle nod.
“Indeed, for no single thread can unveil the entirety of the narrative.
One must gaze upon the grand tapestry woven through time.”They dimmed away, not with finality, but like starlight traversing the vastness of the cosmos—whispers that remind us history bends and weaves, a spider’s web of fate, woven with threads of fortune, affection, and heartache, where beams of hope dance through the dark.
Within each of us, they linger still, a harmonious symphony resonating with the voices of billions, echoing through time.
-
 @ 7d33ba57:1b82db35
2025-04-22 08:35:57
@ 7d33ba57:1b82db35
2025-04-22 08:35:57Nestled in Lower Saxony’s East Frisia region, Leer is a charming canal town known for its historic tea culture, maritime heritage, and postcard-worthy Altstadt (Old Town). With colorful gabled houses, cobbled streets, and a relaxed pace, Leer offers a taste of northern Germany’s quiet beauty—without the crowds.
🏘️ Things to See & Do in Leer
🚶♂️ Altstadt (Old Town)
- Stroll through narrow lanes lined with 17th and 18th-century houses
- Highlights include Waageplatz, the Reformed Church, and Evenburg Castle
- Perfect for a slow wander, especially during golden hour
🛶 Canal Walks & Harbor
- Take a peaceful walk along the Leda and Ems rivers
- Watch boats pass through the small port and historic trading canals
- In summer, you can even book a scenic canal cruise
🍵 East Frisian Tea Culture
- Leer is considered the tea capital of Germany
- Visit the Bünting Teemuseum to learn about the centuries-old tea tradition
- Don’t miss a tea session with rock sugar and cream—served the traditional East Frisian way
🌳 Nature Nearby
- Cycle or walk through the flat green landscapes of East Frisia
- Great routes along rivers and meadows, with plenty of windmills and grazing sheep
- A short drive takes you to the Wadden Sea, a UNESCO site and tidal wonder
🍽️ Local Eats
- Sample Matjes (pickled herring), smoked fish, and hearty stews
- East Frisian cakes pair beautifully with black tea
- Cozy inns and riverside cafés make for a warm, welcoming meal
🚆 Getting There
- Easily accessible by train from Bremen or Emden
- Compact and walkable—no car needed in the town center
Leer is a peaceful, picturesque retreat where canals, culture, and comfort flow together. Whether you're cycling through the countryside or sipping tea by the harbor, it’s a place to unwind and soak up the slow life.
-
 @ 70c48e4b:00ce3ccb
2025-04-22 08:35:52
@ 70c48e4b:00ce3ccb
2025-04-22 08:35:52Hello reader,
I can say from personal experience that crowdfunding has truly changed my life. I found people who believed in my dream of using Bitcoin as money. Every single one of my videos was made possible through crowdfunding. And I’m not alone. I know several Bitcoiners who have raised funds this way, from Africa to Korea to Haiti.
https://images.forbesindia.com/media/images/2022/Jul/img_190501_runwithbitcoin_bg.jpg
Crowdfunding is deeply rooted in the traditional financial world. From raising money for life-saving surgeries to helping someone open a local coffee shop, platforms like GoFundMe, Kickstarter, and Indiegogo have become essential tools for many. But behind all the heartwarming stories and viral campaigns, there’s a side of crowdfunding that doesn’t get talked about enough. Traditional platforms are far from perfect.
They are centralized, which means there’s always someone in control. These platforms can freeze campaigns, delay payouts, or take a significant cut of the money. And often, the people who need funding the most, those without access to strong banking systems or large social media followings are the ones who get left out.
Here are some of the problems I’ve noticed with these platforms:
Problem 1: Inequality in Who Gets Funded
A recent article in The Guardian pointed out something that’s hard to ignore. Crowdfunding often benefits people who already have influence. After the Los Angeles wildfires in January 2025, celebrities like Mandy Moore were able to raise funds quickly. At the same time, everyday people who lost their homes struggled to get noticed.
https://i.guim.co.uk/img/media/f8398505e58ec3c04685aab06e94048e5d7b6a0c/0_127_4800_2880/master/4800.jpg?width=1300&dpr=1&s=none&crop=none
Angor (https://angor.io/) changes that by removing the need for a central platform to choose which projects get featured or promoted. Anyone can share their project. People can find them on Angor Hub (https://hub.angor.io/), which is a public directory built on the Nostr protocol. Instead of relying on popularity, projects are highlighted based on transparency and engagement.
Problem 2: Platform Dependence and Middlemen
Here’s something people don’t often realize. When you raise funds online, the platform usually has control. It holds the money, decides when to release it, and can freeze everything without warning. This happened during the trucker protests in Canada in 2022. Tens of millions of dollars were raised, but platforms like GoFundMe and GiveSendGo froze the donations. The funds never reached the people they were meant for. Supporters were left confused, and the recipients had no way to access what had been raised for them.
https://upload.wikimedia.org/wikipedia/commons/thumb/2/2d/Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg/800px-Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg
Angor avoids all of this. It does not hold the funds, does not require approval processes, and only the project creator has control over the campaign. Contributions go directly from supporters to the people building the project, using Bitcoin. It is a peer-to-peer system that works without any gatekeepers. Angor never touches the money. It simply provides the tools people need to raise funds and build, while staying fully in control.
Problem 3: Global Access
Another major issue is that these platforms often exclude people based on where they live. If you're in a region with limited banking access or outside the supported list of countries, you’re likely shut out. In 2023, a woman named Samar in Gaza tried to raise funds for food and medical supplies during a crisis. A friend abroad set up a campaign to help, but the platform froze it due to "location-related concerns." The funds were locked, and the support never arrived in time.
https://images.gofundme.com/EMFtPWSLs3P9SewkzwZ4FtaBQSA=/720x405/https://d2g8igdw686xgo.cloudfront.net/78478731_1709065237698709_r.jpeg
Angor removes these barriers by using Bitcoin, which works globally without needing banks or approvals. Anyone, anywhere, can raise and receive support directly.
Problem 4: Lack of Transparency
Post-funding transparency is often lacking. Backers rarely get consistent updates, making it difficult to track a project's progress or hold anyone accountable.
In 2015, the Zano drone project on Kickstarter raised over £2.3 million from more than 12,000 backers. It promised a compact, smart drone for aerial photography. But as time went on, updates became rare and vague. Backers had little insight into the project’s struggles, and eventually, it was canceled. The company shut down, and most backers never received their product or a refund.
https://ichef.bbci.co.uk/ace/standard/976/cpsprodpb/2A0A/production/_86626701_ff861eeb-ce94-43b7-9a43-b30b5adbd7ab.jpg
Angor takes a different approach. Project updates are shared through Nostr, a decentralized and tamper-proof communication protocol. This allows backers to follow progress in real time, with no corporate filters and no blackout periods. Everyone stays in the loop, from start to finish.
Problem 5: Fraud and Accountability
Scams are a growing problem in the crowdfunding world. People can launch fake campaigns, collect donations, and vanish — leaving supporters with empty promises and no way to recover their money. One well-known example was the "Homeless Vet GoFundMe scam" in the U.S.
https://a57.foxnews.com/static.foxnews.com/foxnews.com/content/uploads/2018/09/720/405/1536549443584.jpg
A couple and a homeless man raised over $400,000 by telling a heartwarming story that later turned out to be completely fake. The money was spent on luxury items, and it took a legal investigation to uncover the truth. By the time it was resolved, most of the funds were gone.
This kind of fraud is hard to stop on traditional platforms, because once the funds are transferred, there’s no built-in structure to verify how they’re used.
On Angor, projects are funded in stages, with each step tied to a specific milestone. Bitcoin is held in a shared wallet that only unlocks funds when both the backer and the creator agree that the milestone is complete. If something feels off, backers can choose to stop and recover unspent funds.
This structure discourages scammers from even trying. It adds friction for bad actors, while still giving honest creators the freedom to build trust, deliver value, and raise support transparently. It can’t get any better than this
So, does Angor matter?
For me, it really does. I’m genuinely excited to have my project listed on Angorhub. In a world shaped by AI, open source and transparency light the way forward. Let the work shine on its own.
Have you tried Angor yet? Thanks for tuning in. Catch you next week. Ciao!
Guest blog: Paco nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk
References:
• The Guardian, 2025: Crowdfunding after LA fires and inequality - https://www.theguardian.com/us-news/2025/jan/17/la-fires-gofundme-mandy-moore • https://www.theguardian.com/us-news/2018/nov/15/johnny-bobbitt-gofundme-scam-arrest-viral-gas-story-couple-charged • FundsforNGOs: The Success Story of an NGO That Scaled with Limited Resourceshttps://www2.fundsforngos.org/articles/the-success-story-of-an-ngo-that-scaled-with-limited-resources/ • https://www.freightwaves.com/news/gofundme-freezes-37m-until-organizers-of-canada-trucker-convoy-detail-spending-plan
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ d360efec:14907b5f
2025-04-22 08:12:27
@ d360efec:14907b5f
2025-04-22 08:12:27ความทรงจำเรานั้นเชื่อได้แน่หรือ ?
"เพราะจิตเราเกิดดับทุกเสี้ยววินาที ทุกความทรงจำจึงสร้างขึ้นมาใหม่เสมอ ดังนั้นมันก็ไม่เหมือนต้นฉบับเป็นธรรมดา แต่ยังคงเค้าโครงเดิมอยู่ ความเปลี่ยนแปลงจึงเป็นนิรันดร์ค่ะ" - Lina Engword
เรามักจะคิดว่าความทรงจำของเราคือการบันทึกเหตุการณ์ในอดีตไว้อย่างแม่นยำ เหมือนการดูวิดีโอ 📼 หรือเปิดไฟล์คอมพิวเตอร์ 💾 แต่ในความเป็นจริงแล้ว แนวคิดนี้อาจไม่ใช่ภาพที่สมบูรณ์ บทความที่เรานำมาวิเคราะห์นี้ได้นำเสนอข้อคิดที่น่าสนใจเกี่ยวกับธรรมชาติของความทรงจำมนุษย์ ความน่าเชื่อถือของมัน และเชื่อมโยงไปถึงความจำเป็นในการฝึกฝนจิตตามหลักพุทธศาสนาเพื่อเข้าถึงความจริงที่เที่ยงแท้ 🧘♀️🔍
ความทรงจำไม่ใช่การบันทึก แต่เป็นการสร้างใหม่ 🏗️🧩
ประเด็นสำคัญที่บทความชี้ให้เห็นคือ ความทรงจำของมนุษย์ไม่ได้ทำงานเหมือนการ "บันทึก" เหตุการณ์ไว้ตายตัว 📼❌ แต่เปรียบเสมือน "ชิ้นส่วนของโค้ด" 💻 ที่จะถูก "สร้างขึ้นใหม่" 🏗️ ทุกครั้งที่เราพยายามระลึกถึง นั่นหมายความว่า ทุกครั้งที่เราดึงความทรงจำเก่าๆ กลับมา มันไม่ใช่การเปิดไฟล์เดิมซ้ำๆ แต่เป็นการประกอบชิ้นส่วนเหล่านั้นขึ้นมาใหม่ในห้วงเวลานั้นๆ กระบวนการนี้เองที่เปิดโอกาสให้เกิดการ "เติมเต็ม" ✨ หรือ "แก้ไข" ✏️ ข้อมูลในความทรงจำอยู่เสมอ ทำให้ความทรงจำที่เราเพิ่งนึกถึงอาจไม่เหมือนกับความทรงจำครั้งก่อนหน้าเสียทีเดียว 🔄
การปรุงแต่งด้วยเหตุผลและความคุ้นเคย 🤔➕🏠
สิ่งที่น่าสนใจอย่างยิ่งคือ ในกระบวนการ "สร้างใหม่" หรือ "ประกอบ" ความทรงจำขึ้นมานี้ มนุษย์มักจะเติม "เหตุผล"💡 หรือใส่สิ่งที่ตนเอง "คุ้นเคย" 🏠 ลงไปในเรื่องราวที่ระลึกได้เสมอ แม้ว่าสิ่งเหล่านั้นอาจจะไม่ได้เกิดขึ้นจริงหรือไม่เกี่ยวข้องโดยตรงกับเหตุการณ์นั้นๆ ก็ตาม ยกตัวอย่างเช่น เมื่อเราเล่าเรื่องในอดีต เรามักจะอธิบายว่าทำไมเราถึงทำสิ่งนั้น หรือทำไมเหตุการณ์นี้ถึงเกิดขึ้น โดยใส่เหตุผลที่เราคิดว่าสมเหตุสมผลในปัจจุบันลงไป สิ่งนี้ทำให้เรื่องราวในความทรงจำของเราดูมีความเชื่อมโยงและฟังดู "จริง" ✅ มากขึ้นในสายตาของเราเอง
เมื่อเราใส่เหตุผลหรือรายละเอียดที่คุ้นเคยลงไปในความทรงจำบ่อยครั้งเข้า มันก็จะยิ่งทำให้เรา "เชื่อ" 👍 โดยสนิทใจว่าสิ่งที่เราระลึกได้นั้นคือความจริงทั้งหมด ทั้งที่ความเป็นจริงของเหตุการณ์ดั้งเดิมอาจแตกต่างออกไป 🤥 นี่คือสาเหตุว่าทำไมคนสองคนจึงอาจมีความทรงจำเกี่ยวกับเหตุการณ์เดียวกันที่แตกต่างกันอย่างสิ้นเชิง ซึ่งปรากฏการณ์นี้สามารถอธิบายได้ดีด้วยตัวอย่างคลาสสิกในภาพยนตร์เรื่อง "ราโชมอน" (Rashomon) 🎬 ที่นำเสนอเหตุการณ์เดียวผ่านมุมมองและความทรงจำของตัวละครที่ขัดแย้งกันอย่างสิ้นเชิง แต่ทุกคนต่างเชื่อในสิ่งที่ตนเองจำได้ว่าเป็นความจริง 🤔❓
เครื่องมือและกระบวนการช่วยตรวจสอบความจริง 📱📹📝🔍
จากข้อจำกัดโดยธรรมชาติของความทรงจำนี้เอง ทำให้เห็นว่าเราไม่สามารถพึ่งพาสิ่งที่ 'จำได้' เพียงอย่างเดียวได้หากต้องการเข้าถึงความจริงที่เที่ยงแท้ เราจึงจำเป็นต้องมี 'กระบวนการตรวจสอบ' 🤔🔍 มาช่วยยืนยันหรือแก้ไขข้อมูลในความทรงจำ
ในยุคปัจจุบัน เรามีเครื่องมือภายนอกมากมายที่ช่วยในกระบวนการนี้ เช่น กล้องจากสมาร์ทโฟน 📱 หรือกล้องวงจรปิด 📹 ที่บันทึกเหตุการณ์ต่างๆ ไว้ได้อย่างเป็นกลาง ทำให้เรามี 'หลักฐาน' 📄 ที่เป็นรูปธรรมไว้อ้างอิงเพื่อเปรียบเทียบกับความทรงจำส่วนตัว ซึ่งบ่อยครั้งสิ่งที่กล้องเห็นนั้น 'ตรงกับความจริง' ✅ ในมุมมองที่ปราศจากอคติมากกว่าสิ่งที่ใจเราจำได้ การจดบันทึกด้วยเสียง 🎤 หรือการจดบันทึกเป็นลายลักษณ์อักษร 📝 ในทันที ก็เป็นอีกวิธีหนึ่งที่ช่วย 'ตรึง' ข้อมูลเบื้องต้นไว้ได้ระดับหนึ่งเช่นกัน ✍️
นอกจากเครื่องมือภายนอกแล้ว 'กระบวนการตรวจสอบเชิงจิตวิทยา' 🤔🧠 ที่เป็นระบบ ก็สามารถช่วยให้มนุษย์ค้นพบความจริงได้เช่นกัน ไม่ว่าจะเป็นกระบวนการซักถามในเชิงนิติวิทยาศาสตร์ 👮♀️ หรือแม้กระทั่งการฝึกฝนจิตเพื่อให้สามารถสังเกตการณ์ทำงานของตนเองได้อย่างละเอียดลึกซึ้ง ซึ่งนำเราไปสู่แนวคิดตามหลักพุทธศาสนา...
ทำไมพุทธศาสนาจึงสอนไม่ให้เชื่อแม้เป็นความคิดตัวเอง? 🙏🧠❌
จากธรรมชาติของความทรงจำและกระบวนการปรุงแต่งของจิตใจที่อธิบายมานี้เอง ทำให้เราเห็นความเชื่อมโยงกับหลักคำสอนในพุทธศาสนา 🙏 ที่เน้นย้ำให้เรา "ไม่เชื่อแม้แต่ความคิดตัวเอง" 🧠❌ อย่างปราศจากการพิจารณา เพราะความคิด อารมณ์ ความทรงจำ หรือแม้แต่ความรู้สึกมั่นใจอย่างแรงกล้าที่เรามีนั้น อาจถูกสร้างขึ้นหรือปรุงแต่งโดยกลไกของจิตใจที่ไม่ได้สะท้อนความจริงทั้งหมด 🤥
พุทธศาสนาชี้ให้เห็นว่า การจะเข้าถึงความจริงที่แท้จริงได้นั้น 🔍 จำเป็นต้องมีกระบวนการตรวจสอบภายในจิตใจ เปรียบเสมือนการสร้าง "อัลกอริทึม" 🤖 เพื่อตรวจทานว่าสิ่งที่เราคิดหรือจำได้นั้นเป็นความจริงหรือไม่ ✅❌ การจะทำเช่นนี้ได้ ไม่ใช่เรื่องง่าย และต้องอาศัยการฝึกฝนจิตอย่าง "สมาธิอย่างมาก" 🧘♂️🧘♀️ เพื่อให้จิตมีความตั้งมั่น เป็นระบบ และสามารถ "เห็นการดำเนินไปของจิตได้อย่างเป็นระบบ" 👀🔬 เห็นว่าจิตปรุงแต่งความทรงจำอย่างไร เห็นว่าเหตุผลที่เราใส่เข้าไปนั้นจริงหรือไม่ เป็นเพียงการตีความ หรือเป็นเพียงสิ่งที่ใจเราอยากให้เป็น
บทความยังกล่าวเสริมว่า ความทรงจำที่ "สด" ✨ หรือใกล้เคียงกับเวลาที่เกิดเหตุการณ์นั้นมักจะมีความน่าเชื่อถือมากกว่า 👍 แม้จะดู "ดิบๆ" หรือไม่ผ่านการปรุงแต่งมากนัก ซึ่งสอดคล้องกับแนวคิดที่ว่ายิ่งระยะเวลาผ่านไปนานเท่าไหร่ ⏳ ยิ่งมีการเรียกคืนความทรงจำนั้นๆ บ่อยครั้ง ความทรงจำก็ยิ่งมีโอกาสถูกแก้ไข เติมเต็ม หรือปรุงแต่งด้วยเหตุผลและความคุ้นเคยมากขึ้นเท่านั้น 🔄✏️
"ใดๆในโลกนั้นคือสมมุติ ความคิดความทรงจำ ก็เป็นสมมุติเพียง แต่เราต้องรู้จักใช้สมมุติให้เป็นประโยชน์ และรู้จักใช้มันให้เป็นเพื่อดำรงอยู่บนโลก"
สรุป ✨🧠🔍
โดยสรุปแล้ว บทความนี้เตือนใจเราว่า ความทรงจำของเราไม่ใช่กล้องวิดีโอที่บันทึกทุกอย่างไว้แม่นยำ 📼❌ แต่เป็นกระบวนการสร้างสรรค์ที่ซับซ้อนซึ่งมีแนวโน้มที่จะถูกปรุงแต่งด้วยเหตุผล ความคุ้นเคย และการตีความของเราเอง 🏗️🤔🏠 ความมั่นใจที่เรามีต่อสิ่งที่จำได้นั้น ไม่ได้เป็นหลักประกันว่าเป็นความจริงเสมอไป 👍🤥
การตระหนักถึงธรรมชาติข้อนี้ของจิต และการใช้เครื่องมือภายนอก 📱📹📝 รวมถึงการฝึกฝนจิตให้สามารถสังเกตการณ์ทำงานของมันได้อย่างละเอียดรอบคอบตามหลักพุทธศาสนา 🙏🧘♀️ จึงเป็นกุญแจสำคัญที่จะช่วยให้เราสามารถแยกแยะระหว่าง "ความจริง" ✅ กับ "สิ่งที่จิตปรุงแต่งขึ้น" 🤥 ได้มากขึ้น และช่วยให้เราเข้าใกล้ความเข้าใจในธรรมชาติของสรรพสิ่งได้อย่างเที่ยงตรง ไม่หลงติดอยู่ในวังวนของความทรงจำและความคิดที่อาจบิดเบือนไปจากความเป็นจริง 🔄
**#ความทรงจำ #จิตวิทยา #พุทธศาสนา #สมอง #สมาธิ #การฝึกจิต #ราโชมอน #ความจริง #ไม่เชื่อความคิด #ธรรมชาติของจิต #พัฒนาตนเอง #บทความน่ารู้ #เทคโนโลยี #บันทึกความจริง #พระอภิธรรม #พระหฤทัยสูตร #LinaEngword **
-
 @ d360efec:14907b5f
2025-04-22 07:54:51
@ d360efec:14907b5f
2025-04-22 07:54:51“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง “การพนัน” ภาพที่ชาวเมืองมักนึกถึงคือ “ยาจกข้างถนน”
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า จ้าวแห่งหอคอยรัตติกาล ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก “เกมพนัน” เช่น เวเนสซา รุสโซ นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ “โป๊กเกอร์” หรือแม้แต่ เอ็ดเวิร์ด โอ. ทอร์ป จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา “แบล็กแจ็ก” ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ “หอคอยรัตติกาล” เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ “คณิตศาสตร์” เหตุใด “คณิตศาสตร์” จึงช่วยให้ผู้คนเอาชนะ “การพนัน” ได้? และนอกจาก “การพนัน” แล้ว “คณิตศาสตร์” ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? นักเล่าเรื่องแห่งเฮรันเทล จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: * ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก * แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ * ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ * ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น * จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น “วงจรอุบาทว์” สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด “วงจรอุบาทว์” นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก “กลไกต้องสาป” ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ “สมาคมพ่อค้าผู้พิทักษ์” คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม “กฎแห่งจำนวนมหาศาล” เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ “คณิตศาสตร์” เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: ๑. ปริศนาแห่ง “กำไรคาดหวัง” สำหรับการแสวงหา “เกมเสี่ยงทาย” ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ “การประเมินกำไรคาดหวัง” หรือ “เวทคำนวณอนาคต” “กำไรคาดหวัง” ถูกคิดค้นโดย คริสเตียน ฮอยเกนส์ นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) ดังนั้น หากปรารถนาจะสะสม “ทองคำมายา” ในระยะยาว จงเลือกเกมที่มี “กำไรคาดหวัง” เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ “กำไรคาดหวัง” เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว “กำไรคาดหวัง” ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ “สลากกินแบ่งรัฐบาล” ก็ล้วนเป็นเกมที่มี “กำไรคาดหวัง” ติดลบทั้งสิ้น นอกจาก “กำไรคาดหวัง” จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ “คณิตศาสตร์” ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ “ศิลาแห่งโชค” แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี “กำไรคาดหวัง” = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ ๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน” แม้ว่าท่านจักรับรู้ “กำไรคาดหวัง” แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย “ศิลาแห่งโชค” หรือหลาย “เกมเสี่ยงทาย” แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร “การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)” หรือ สูตร “ขนาดเดิมพันที่เหมาะสม (Kelly Formula)” ๓. ปริศนาแห่ง “อคติ” ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ “Gambler's Fallacy” หรือ “ความเชื่อผิด ๆ แห่งนักพนัน” ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง “สลากกินแบ่งรัฐบาล” มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก “ศิลาแห่งโชค A” ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น “เกมเสี่ยงทายแห่งโชคชะตา” หรือ “การผจญภัยในตลาดทุน” หากท่านมีความเข้าใจ และนำ “คณิตศาสตร์” เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. สูตรเวทย์มนตร์ที่ปรากฏในตำนาน: * กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล: "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-
 @ ef53426a:7e988851
2025-04-22 07:47:07
@ ef53426a:7e988851
2025-04-22 07:47:07In 1997, an IBM supercomputer beat the sport’s greatest mind. Deep Blue II became the first machine to defeat a chess world champion — Garry Kasparov. Humans would never win at chess again.
But if computers have been better than us for so long, why do we still play chess? Don’t we always play to win?
Well, even though we’re unlikely to record a victory over the machines, chess has become more popular than ever. According to a June 2023 PBS feature, subscriptions to chess clubs have soared and earlier this year chess.com servers overloaded due to a the highest number of active users ever.
This is not just a fad based on The Queen’s Gambit (a 2020 Netflix adaptation). Over 100m people have registered on chess.com since then, and books, YouTube channels and other content is flourishing. A Grandmaster recently visited the city in Spain where I live, and thousands of people came to watch her play.
Here’s my theory behind the recent revival of chess. The answer to why we still play is what’s behind the game of chess — strategy and spatial recognition.
It’s a system of training ourselves to appreciate cause and consequence, to improve our decision making. The best players train against computers, knowing they can’t win, but they can learn.
The same is true with today’s writing landscape. Professionals are panicking that machines will produce most of the content we’ll read from now on. Writing will change — that’s true. AI can write faster and more (grammatically) accurately.
But what’s behind writing? 🧠 Patterns of structured thought 🗣️ Sound rhetoric 🖊️ The creativity of language 📚 The beauty of stories.
Writing is a skill that we still need to train.
If we don’t, how will we know what makes our words effective? How will we communicate? How will we make sense of our past?
We can use AI to help, but the words it processes belong to us.
Just as we have recognised the importance of the concepts behind chess, we must do the same for the process of writing.
-
 @ 37c10448:f8256861
2025-04-22 07:44:10
@ 37c10448:f8256861
2025-04-22 07:44:10Title H1
Hello !
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ 9f9fda7f:e5e82a43
2025-04-22 07:08:47
@ 9f9fda7f:e5e82a43
2025-04-22 07:08:47Untitled wefwef
typescript function fetchData() { return fetch('https://api.example.com/data') .then(response => response.json()) .then(data => console.log(data)) .catch(error => console.error('Error fetching data:', error)); }wefwe https://stas.layer3.press/articles/9776f286-c73e-42ae-9ac4-d5357ab65cf9
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 2b24a1fa:17750f64
2025-04-22 06:57:36
@ 2b24a1fa:17750f64
2025-04-22 06:57:36Es fühlt sich wie ein Staatsstreich an. Vielleicht ist es auch einer. Ein abgewählter Bundestag genehmigt mittels Grundgesetzänderung die größte Staatsverschuldung in der Geschichte Deutschlands mit der unvorstellbaren Summe von 1000 Milliarden Euro, also eine Billion.
https://soundcloud.com/radiomuenchen/vom-schuldenstaatsstreich-zur-finanzdiktatur-von-rob-kenius?\ Jedem muss klar sein, wohin diese Gelder aus den Taschen der Steuerzahler wandern und wer, wenn in Rüstung, Militärhilfen, Konzern-Subventionen investiert wird, die Leidtragenden sind: Kinder, Rentner, kleine Firmen und Betriebe, sozial Schwache, Kranke, Arbeitslose, Obdachlose.
\ Die Kräfte aus Finanzeliten, Militär, Rüstungsindustrie, regierenden Parteien und den staatstragenden Medien werden dafür immer stärker.
\ Hören Sie den Beitrag „Vom Schuldenstaatsstreich zur Finanzdiktatur“ von Rob Kenius, der zunächst beim Overton-Magazin erschienen war: https://overton-magazin.de/top-story/vom-schuldenstaatsstreich-zur-finanzdiktatur-in-leicht-verstaendlicher-sprache/
Sprecherin: Sabrina Khalil
Redaktion: Jonny Rieder
Bild: Bund der Steuerzahler / Janek Werner
Rob Kenius betreibt die systemkritische Webseite kritlit.de und den Podcast 9min Denksport. Der Text Vom Schuldenstaatsstreich zur Finanzdiktatur ist davon die 14. Folge.
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28
@ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ da0b9bc3:4e30a4a9
2025-04-22 06:44:40
@ da0b9bc3:4e30a4a9
2025-04-22 06:44:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/952743
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ d34e832d:383f78d0
2025-04-22 06:43:30
@ d34e832d:383f78d0
2025-04-22 06:43:30It is noteworthy to mention that Bill Gates, a distinguished co-founder of Microsoft and a philanthropist with extensive impact on global health and education initiatives, serves as a limited partner in various investment vehicles associated with Village Global. However, it is critical to delineate the nuances of this relationship, as Gates' status as a limited partner does not confer upon him any authoritative control or decision-making power regarding the operational protocols or strategic direction of SimpleX Chat.
The development team behind SimpleX Chat has made a concerted effort to clarify that Village Global's involvement is strictly financial in nature, devoid of any operational oversight or influence over the management and technical development of the project.
Privacy Without Compromise
SimpleX Chat aims to provide a messenger that is both convenient and private, addressing the perceived trade-off between these two qualities in existing solutions. They define privacy as protecting not only message content but also metadata like connection details and user identities.
In contrast to a multitude of contemporary messaging applications, SimpleX Chat distinctly emphasizes the safeguarding of metadata privacy as a foundational component of its architecture.
The development team articulates a compelling argument regarding the intrinsic value of communication relationships, suggesting that the identification of interlocutors constitutes sensitive data that may be weaponized against users in various contexts—an issue that current market leaders in the domain have failed to remedy with sufficient rigor.
Consequently, the developers are actively engaged in initiatives to bolster the obfuscation of users’ IP addresses, thereby enhancing the overall security framework against potential surveillance and data exploitation threats.
A Radical Architectural Shift
The architecture underpinning SimpleX Chat diverges notably from conventional paradigms associated with user account management.
Specifically, it eschews the creation and maintenance of user profiles in the traditional sense, thereby negating the repository of personally identifiable information on centralized servers. Instead, all pertinent data transactions pertinent to user interactions are localized, existing solely on the end-user's devices.
This paradigm shift engenders a formidable barrier to data accessibility, effectively neutralizing the potential for data disclosure to law enforcement agencies, irrespective of judicial mandates such as court warrants.
Furthermore, in their adherence to statutory obligations, SimpleX Chat's design ethos proactively prioritizes the minimization of data collection, establishing a privacy-centric framework that aptly aligns with contemporary concerns regarding data sovereignty and user anonymity.
Functionality Grounded in Security
The SimpleX Chat application exemplifies a multi-device compatibility framework, strategically prioritizing stringent security protocols over user convenience.
This methodology distinctly contrasts with that of various competitors who may opt for convenience-focused functionalities that inadvertently jeopardize user data integrity and confidentiality.
The current technical architecture facilitates seamless profile transfers across devices, while also enabling a desktop terminal interface that remains operationally tethered to the mobile device.
Such an arrangement underscores SimpleX Chat's commitment to balancing usability with robust security measures, effectively mitigating potential vulnerabilities in cross-platform interactions.
Transient Messaging and Signal Protocol Reimagined
SimpleX Chat integrates the functionality of transient messaging, which serves primarily as a user convenience element rather than representing a robust security mechanism.
The developers have explicitly articulated that they are unable to ensure the irreversible deletion of messages from the recipient's device, thereby highlighting potential vulnerabilities associated with data retention and privacy concerns in digital communications.
The development team arrived at a strategic decision to forgo the utilization of the existing Signal codebase, primarily attributed to its inherent complexity and the prospective risks associated with the coupling dynamics that could emerge between the Signal protocol and its corresponding system architecture.
As a result, they opted to engineer the Signal protocol anew, commencing from foundational coding principles.
This approach not only enables them to exert comprehensive control over the implementation but also significantly facilitates the seamless integration of advanced cryptographic frameworks, specifically post-quantum key agreement methodologies, which are imperative in future-proofing cryptographic communications against the advent of quantum computing threats.
UX Development and the Road Ahead
The UI is still under development. The developers acknowledge some usability challenges, especially for users unfamiliar with the concept of profile-based messaging without traditional accounts.
They are actively working on improving UX based on user feedback.
A Decentralized Economic Model
SimpleX Chat is poised to introduce an innovative commercial framework predicated on the integration of a decentralized accounting mechanism, characterized by the utilization of distributed ledger technology, which underpins cryptocurrency transactions, coupled with a system reminiscent of traditional gift card paradigms.
This commercial model is strategically designed to provide economic incentives to both infrastructure operators, who maintain the necessary backbone for the network's operations, and software vendors, who contribute essential applications and services—all while preserving the fundamental decentralized architecture inherent to blockchain systems.
This careful balance is crucial for fostering a sustainable ecosystem that rewards participants without compromising the network's core principles of transparency and egalitarian access.
🚧 Prerequisites
| Requirement | Description | |-------------------|----------------------------------------------| | VPS | Debian 12, at least 1GB RAM (for running server) | | Build Machine | A second Linux machine with ≥ 8GB RAM for compiling binaries | | Domains | FQDNs like
smp.yourdomain.com,xfp.yourdomain.com,turn.yourdomain.com| | SSH Keys | SSH access secured with key-based auth only | | Firewall | Only allow ports for SSH (22), SMP (5223), XFP (5353), TURN (5349) |
🧱 Step 1: Build SimpleX on Build Machine
You’ll compile the binaries on your high-RAM machine and then SCP them over.
```bash sudo apt update && sudo apt install build-essential git rustc cargo pkg-config libssl-dev
Clone repo
git clone https://github.com/simplex-chat/simplexmq cd simplexmq
Build binaries
cargo build --release ```
You’ll find: -
target/release/smp-server-target/release/xfp-serverCopy them to your VPS:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/
🧑💻 Step 2: Harden the VPS
🔒 SSH-only access
```bash
Edit /etc/ssh/sshd_config
PermitRootLogin no PasswordAuthentication no ```
Restart SSH:
bash sudo systemctl restart ssh🔥 UFW Firewall
bash sudo apt install ufw sudo ufw default deny incoming sudo ufw default allow outgoing sudo ufw allow OpenSSH sudo ufw enable🛡️ Fail2ban
bash sudo apt install fail2ban sudo systemctl enable --now fail2ban
📡 Step 3: SMP Server Setup
Create user and directories:
bash sudo useradd -m -r -s /usr/sbin/nologin smp sudo mkdir -p /var/lib/smp /var/log/smp sudo chown -R smp:smp /var/lib/smp /var/log/smpMove binary and set permissions:
bash sudo mv /home/user/smp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/smp-serverCreate systemd service:
/etc/systemd/system/smp.service```ini [Unit] Description=SimpleX SMP Server After=network.target[Service] User=smp ExecStart=/usr/local/bin/smp-server --fqdn smp.yourdomain.com --log /var/log/smp/smp.log WorkingDirectory=/var/lib/smp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now smp.service
🗂️ Step 4: XFP Server Setup
bash sudo useradd -m -r -s /usr/sbin/nologin xfp sudo mkdir -p /var/lib/xfp /var/log/xfp sudo chown -R xfp:xfp /var/lib/xfp /var/log/xfp sudo mv /home/user/xfp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/xfp-serverCreate systemd service:
/etc/systemd/system/xfp.service```ini [Unit] Description=SimpleX XFP Server After=network.target[Service] User=xfp ExecStart=/usr/local/bin/xfp-server --storage /var/lib/xfp --log /var/log/xfp/xfp.log --quota 2GB WorkingDirectory=/var/lib/xfp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now xfp.service
🎙️ Step 5: Optional TURN Server (WebRTC)
Install Coturn:
bash sudo apt install coturnEdit
/etc/turnserver.conf:ini listening-port=5349 tls-listening-port=5349 fingerprint lt-cred-mech realm=turn.yourdomain.com user=someuser:somepassword cert=/etc/letsencrypt/live/turn.yourdomain.com/fullchain.pem pkey=/etc/letsencrypt/live/turn.yourdomain.com/privkey.pem cipher-list="ECDHE-RSA-AES256-GCM-SHA384" no-stdout-logSet to auto-start:
bash sudo systemctl enable coturnConfigure DNS and firewall to allow 5349.
🔁 Step 6: Certificate Renewal (Let's Encrypt)
bash sudo apt install certbotSet up renewal cron:
bash sudo crontab -ebash 0 3 * * * certbot renew --quiet && systemctl restart coturn
🧪 Step 7: Testing with SimpleX Desktop
- Download SimpleX Desktop
- Launch and go to Settings → Relay Settings
- Disable defaults, add your SMP and XFP addresses.
🔄 Upgrading SimpleX
On your build machine:
bash git pull origin main cargo build --releaseThen:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/On VPS:
bash sudo systemctl stop smp xfp sudo mv /home/user/smp-server /usr/local/bin/ sudo mv /home/user/xfp-server /usr/local/bin/ sudo systemctl start smp xfp
What if you communicated securely?
📡 SimpleX – Anonymous chat, no phone numbers, no metadata
SimpleX is unlike anything else. It doesn’t just encrypt your messages—it hides who you're talking to. No central servers, no profiles, no traces. Just pure private messaging.
Perfect for when you need total metadata privacy and no digital fingerprint.
🌱 Nostr DMs – Messages with your Web of Trust
If you’re already on Nostr, using DMs is a natural step. Messages are encrypted end-to-end and tied to your public key identity.
Great for building trusted, decentralized communication channels within your Web of Trust.
🔐 PGP Email – Old-school but rock solid
PGP lets you encrypt your emails and verify identities with public keys. It’s still one of the most powerful tools for asynchronous, verifiable, and encrypted communication—especially for long-form or professional exchanges.
🔁 Use them all together
Different tools for different roles. Want to talk anonymously? Use SimpleX.
Connecting with your Nostr tribe? Slide into those DMs.
Need to send a secure file or message over email? PGP's got your back.Privacy isn’t just one app—it’s a toolkit. Build yours.
-
 @ 233e10e1:d45c3bb8
2025-04-12 20:24:35
@ 233e10e1:d45c3bb8
2025-04-12 20:24:35Here I try to tie this fictional history back to our own reality, illuminating why, even if the Gold Standard had been restored, where the invention of Bitcoin might still be inevitable due to the frailty of man. Bitcoin combines the scarcity and immutability of gold with the efficiency of digital settlement. In a world that promotes low time preference, stable value, and secure transactions, Bitcoin stands as the logical evolution of monetary technology.
-
 @ 10fe3f70:3489c810
2025-04-12 03:53:36
@ 10fe3f70:3489c810
2025-04-12 03:53:36contract-drafting #agreement-drafting #learn-drafting #keep-learning
I am a lawyer and a teacher. I am interested in learning new things every day.
I am from India, and have studied in a reputed law school in Delhi. I have long experience of working as in-house counsels to some reputed organisations.
My present goal is to teach drafting of contracts. What I will teach is some basic skills required by students to draft contracts.
I did some freelance online teaching during Covid Pandemic, and found that students are very interested in learning the craft. But, I also understood that they may not have enough free time to learn due to busy schedule.
If you are interested, you can access my curated playlist on Youtube
Keep watching this space, if you wish to know more...
Lessons on Contract Drafting
- Contract Drafting - An Introduction
- ...
-
 @ e111a405:fa441558
2025-04-11 17:15:58
@ e111a405:fa441558
2025-04-11 17:15:58Meritocracy without equality is basically a ladder with missing steps, which only the fortunate few can climb. The rest is basically left at the ground to gaze up.
Furthermore, a pure focus on meritocracy can become a weakness if it’s a zero-sum game. While talents thrive in systems that value it, without fairness, you ultimately get exploitation, resentment, or fragility.
Ergo: meritocracy needs to be balanced with equality, and equality needs to be balanced with meritocracy.
In a meritocratic system, you basically need that the fortunate and the able are compassionate towards those less fortunate and able.
If you are more on the libertarian side, you need the fortunate individuals to compete as capitalists and then be socialists within their communities and families.
If you prefer a state, then the state must encourage meritocratic contribution of everyone that is able, to the best of their ability, while balancing it with a fair welfare system that nurtures and supports those less able and fortunate.
I think this is something Germany did historically quite well, but at one point we lost the balance: we lost the culture of merit by putting too much emphasis on equality – even to a point that Germany now cares for millions of non-citizens that never contributed, when it should instead demand these individuals to contribute to the best of their ability.
If we want to have a state, then we don’t want a welfare state, and – I think – we should also not want a pure capitalistic state. We need balance and thus a social meritocracy.
-
 @ 8d5ba92c:c6c3ecd5
2025-04-10 22:20:40
@ 8d5ba92c:c6c3ecd5
2025-04-10 22:20:40It’s often said that 'Bitcoin doesn’t need marketing'—and the internet proves it well, almost like a daily feed. Instead of typical ads in the form of 'sell-me-anything-and-everything', the space thrives on organic memes and threads: a grassroots testament to Bitcoin ethos.
This isn’t about the artificial promotion of THE TRUMAN SHOW, where desires are manufactured and ads dictate specific behaviours. Bitcoiners don’t just reject the Proof-of-Hype, so typical in a fiat-driven world, they replace it with Proof-of-Work: value emerging not from coercion, but from consensus (i.e., what the community validates as genuine and meaningful).
The "Funny Money" Crew
On the other hand, equally common is the twist with memes labeled 'Bitcoin’s Marketing Team', featuring faces like:
🤡 Jerome Powell (Fed Chair), Christine Lagarde (ECB), Agustín Carstens (BIS chief, CBDC pusher), Janet Yellen (U.S. Treasury Secretary), Jamie Dimon (JPMorgan CEO), Elizabeth Warren (U.S. Senator), and so on.
Sophisticated jokes—appreciated by those who understand their actual impact. After all, what better advertisement for Bitcoin could there be than watching the fiat system degrade in real time? 😎
Why Bring This Up?
First, because I want to remind that Bitcoiners weaponize even simple ideas better than entire Wall Street-hired PR firms. Every "Bitcoin doesn’t need marketing" or "Thanks, Fed for the free promo!" is a clever, almost subversive way of raising topics we should be aware of. Exposing fiat’s failures often speaks louder than directly evangelizing how sound Bitcoin is—and how well it solves problems that keep many non-coiners awake at night.
Second, to credit where it’s due: Bitcoin-only projects and individuals who are actively spreading the word—hard money, real solutions, and the culture itself. But this isn’t 'marketing' in the traditional, pushy, profit-at-all-costs sense. Instead, it’s built on:
- Information (no bullshit, just facts)
- Education (orange-pilling, not upselling)
- Community (value, instead of dry PR)
- Creativity (proof-of-mind, not algo-baits)
- Experiences (how-to solutions, not showing off)
And let’s be clear: Earning money isn’t evil—it’s necessary for these projects to survive. What matters is the intention. No one should apologize for creating Bitcoin-themed ads, so long as they’re carrying the meaning, instead of being rooted in hype.
PoW: Earning Attention, Not Buying It
The list below (part one) is based on my own preferences, but it was also inspired by Bitcoin FilmFest, which—in its upcoming edition #BFF25, May 22-25—introduced a new block to the program: ‘BFF PoWies: The Show for Bitcoin-Only Advertising.’ A dedicated space for creative expression beyond films, where projects and individuals compete for awards in categories like Grand Prix, Best Visual, and Best Identity—with a $4,500 prize pool to grab.
Anyways, as our small but passionate team dug into this topic, I was really happy to uncover unique video ads, some of which I’m excited to share with you now.
If you know others, tag me (private profile) or 'Bitcoin FilmFest' directly on socials. Feel free to submit your work to the PoWies too (submissions close May 6th).
Without further ado... Let's explore the space where value is discovered, not packaged in empty promises 📺👇
Bitcoin-Video Ads: Part One.
Creative, funny, dynamic, inspirational. All four below. Enjoy!
1/. NEVER LOSE YOUR BITCOIN (Liana)
https://v.nostr.build/P7To0HpNmmB6iudR.mp4
2/. MAKE A CHANGE, (Wasabi)
https://v.nostr.build/rUGQAysAIDH8Wx9x.mp4
3/. THE MOTHER OF ALL BACKUPS (Cryptosteel)
https://v.nostr.build/3zesnSjQudQoxl5f.mp4
- FINANCIAL FALLOUT (21 Futures)
https://v.nostr.build/sFvmt8oCWfxLKJRb.mp4
PS. The most effective Bitcoin ads aren't 'typical' campaigns—they're the result of creativity, PoW, and authentic storytelling move hand-in-hand.
BTC Your Mind. Let it Beat... Şela
-
 @ 86102a64:33871ac0
2025-04-22 02:11:57
@ 86102a64:33871ac0
2025-04-22 02:11:57{"imageData":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAXAAAAEUCAYAAAAyfG1zAAAgAElEQVR4Xux9CWBcRf3/N5uz6X3RNk16t0lb6F16gaCC8hcERQVFEFAUFUFU/AkooiKKioqAKKICIpeIXJ4cytkWytVCaZLeTZo2bdq0TZp7d//f7xzvzXv7jnlv326SsrOEttk5vzPzme98r8mDXHo3USBvQtXyhyAv72OZHnQSkpCHH5mS+Jc8/B39n5Lle/PXnt1KJrHOPLNOVo/td+q/nfKnNIDlk1glqxX7Qb2GPGvfdWnFhmH+T7eYdj4aD1Uf06CBqPTCuuqVd2k3kMvY7yhg3Q39rvu5DgehwITK5Tfg7v9WkDJh8mrisQLnNkB3aRTxCwHc+qX9d+q/LX8XxwahNR0kBNqUCHCTWCkDXtEjA9DDDN4oo0uF4I2kHlpWutC4Rbq7rvqlC4K3kCvRXyiQA/D+MlNp9rOiavkFyL3emWY1gYr7ccB2gFUXo52DZ/CqDeC8NMNjAmnOFgfqu+V0CVbSzB2mWYdbhl/zToeYKLMWAXyeX/nc9/2XAgFXdf8d6Lu558MmzRs2uKS0AQF8QLbo4AS2HIRNMYiKb35gbynLRB2c60wmCNUFUHO0tgBoksQhabDUdtFPYPqFAHG/NhitlLE6iZHE1407Nqwc61df7vv+S4EcgPffudPuOcq9v4fAdq12gQgzpgC5AmieoE3yXsFxc7m0kC/TISAF1oTXQcCZiUt4B4IsfOonB8QgpZRzxOHmECGJPapKdu/YUFQK8GxPdtrLtZJtCoRbkdnuZa690BSYNOnEksSA7gasYHjoSkIWZMDHsFdVZjorCLl6zpRJy7/zpk0EdGVoA3C6UkQcdPEHaCIkxZRiPo3xQwUpKwdhz2/IwZOvJZLJB6EA/lC/ftX+9DuWq6EvUSDoGu5Lfc/1RYMCE2YuPw83+p80skaSxcQRDskSvIVUmsumhYUKxxghDuCqRQH19r/bJNiiETeMcxPf2Aeom08tpyPqiYSQPpWoAO4mQuEnIj//jL9DXg/+ey/++/GuRNdPG2vXbMlGf3NtZIYCOQDPDF37TK0VVSvuQi7t/Ix2iMmkU038/NrkHDoJsvmfBjOp/FvmYThky+dVv5MS1DF/GBT3G5jb9wHb8jospKWJQj6jVcUKRVxpLAAu6C3oCbHq7kTXqTkgDzupvVsuB+C9S/+Mt44c+DbcxRMz0ZAh9ggkUU7tCQNblGXbFY7y99ygxFRGWv4uFHpMMBNyNfcVrjqFMj6AL/udanMv7zamfbvCgVsAPA9iSNkE5CXy7q+rXYm3NYhnYq3k6swMBUIu+cx0JldrtBQQ8u/2aGvltWlzuJloPECdfQ2cg/XHWxDOrVGEuEk5vaTSlchEildVCWtKU7iSmCA+mYcAnkQgTyZeqK9Z9Z4A5M1l7WUK5AC8lycgk82Pnr147IBE0a5MttEf6s6q8tGHIAGlKN61eWhjTemUaUGjgjcDbqZjRv6bWfiwv5GZzpb6lm3HQENDW3+Y23d7H3MAfgSvgPFVx47MzytsinSIkSKQS89ssnEjl8XzR7HNU36fDlgH446dHYv8aB2UfF43nRRLFLoZmdYnpgKZW2GyexNPJngzL1TxFTOxZP/Fn6+vfvkEv7Hkvu99CuQAvPfnIKM9mFC1ogN3aHFGG+kHlQcFZ50hZaJOnXYZ3gosDi33ZzAukmLVwyvGn0TyF3W1q7+h259cvt6hQA7Ae4fuWWs1k0rMrA0iYENBuVxL9YEKh+P3tYHfoy/EmdPXamArlfu2eKcyQUlqMAGphJZcObf04WIV6mNT6+GK9p3r6gOSP5c9ixTIAXgWid0bTU2YueIpbPektNsOBGxpt8YrSEOU4tQDHeDUyRPR6Hyr8TcjVMISGKITazQBeyNeppgGualQIoES8eSLO2tWH+/b0VyGXqNADsB7jfTZaXhC1bIrIS/24+y01ndacQI/HXDWyaOOMqg1TqD6wzH4Qr4ipN4O8m92NipmmdbxCN8fRHOMM5Osb90+KKfQ7Dvr2t6THID33bmJpGcTJhw3PDkwUY+qKoyJES4FAp1wTbiWMmydyWTOZion/632z/i7443BHxH9c6Q3wCAXGbfDgYk+KCxuyN2rPUbsbFdP/Nrdm17+QXqjzpXOFAVCLoFMdSdXbyYogN6Yv8XNfnHYuvsjgIflwAPRKAgai4q1wdOjI2YdqsOO2MpMEO7NfUsOXDZhiVWjHJREw3gyuaOhZtXEQHTJZc4aBXIAnjVS915DZE4Yg8JqBPFRYXoRAqfCNONYJmIxuFa/dA8s3XzWRvUg3K1uw0nHiDsQjBN3bd02yZL7T2BC5558LcLlMmWdAjkAzzrJe6fBisoVX8yLwW/CtB4OqMK0lFomtAgFq3IUQWjgp/Z4NeqKhgpmLQmMf06blolPmJelqbQ0rLy5KQkPGcalLZZgB6r1iVNgXXX8cWxvZ83KHE5EPZER1ZebmIgI2R+qQZPCe3Arn9sf+hpFH+1ArAPMOnlk34IrML0tRIwxu1x5zNsIekziaaxE2dUglxS36MdC5ybhSairacCHQLZ1aDSSy5JlCuQAPMsE7+Xm8vFxhyeRc3ufdj96gctM6Zvsg70v6r/d/q5UpgO4Onm0aRdhRgN+WdCvVJvuKJpihxdVJDh77rmZB02NBya2N6/fEUUbuTqipUAOwKOlZ5+vjQJcxQd0/xIn/ou6nQ3ClerWqZsvrAjFiYnVGYeuvF+nLnWMuvVaytA/qKA8nBhwCwUlQ3QhNGHyFJGPAbD4nxCl8H8F2+pc1s7rbWo8mANw3QWb5XzBZjXLncs1lzkKVFQuPyMvxh459n2pJwz4RNXzsEpMZysUTRFGVJ1Pox6OvehMw2TcMcNkkNtvC+hWYqhzF3hn6xP2FX1H74O6ALl6UPJum/lbDnZMbG54LceBpzGfmSqaA/BMUbYf1Dt22vGjiwri30F0uMyru70pVpBtO8W8tr72I8CLq+5CUV+bq87AiWYYBLIHP01RBvrSMHd5w/qEoJW94mDgtdZYU+r3MCKXbUk7+/amwsF79z7bqtVQLlNWKRBupWe1i7nGMk2BsVVLJxXlxb6EsLEckWGB3ekH40QfQi5wSKb74VR/WBGKva7ePITc6MatQSQYOx886NEOMdJXWuyzqcbg4hNpfUJ/xvAjk53GSaEjZa2QErM6Z4XSG2tfp80cgOtQ6V2W56jJS8YUlOSNp2HHWvI2tJUkCgcV5uM7inlF/YIUIThkbe5bgwBedfGuUbAoZ/tty0GDmTEeCbMDjMVQoILIisIUIVYRHfGRf3PFJIK1TXzCuGxFpq4Oy+D6mfwGkgjgJtprjD+XJXsUyAF49mjdr1uqmLn8AYScs7mujP5njWVnGRwTn5pPpBk5BWBYuEniQYmZZBhjNa8IK/9OIXQIQA8zWZyfFhDM6CO3l5Bbk8yaGG4G4uafnNNNlc8TeMcU3STF646xhxc4486SOAhUsYfgzUVUQZ5ZvrrDxDNSfKI2Kv7O5eWyf2zm9tVXrwzlABaGhrkywSiQA/Bg9HrX5i6bctyEWFFiPQLAIC8iMPmzMIpg0gGBCKpcWspw+RuYFHpaiarnAehaxM8SWBt9MYDa5J3dxNNO4O3UXfk7yQmjMyR/Gk3Q1di0GtYnDOARhtVXd2JkQy6TrQNyvvgYiNuP/xYjEn5Ji/a5TFmnQA7As07yftlg/vjpS69EvMCgRuruN8fCAEZwd4bCjXGVHNBN8OL5pAiXc3tcDqwD6AxYxKp1YCAjJq4JymO6O2FidweM7e6C0T1d8JehR8HB/EKLujRscCmnThNoW0Qc3CgkPfGJoLEUvTNoJ4E3QbWYP8nRk7iG/DjbEsmKfbWrdkZM2Fx1EVEgB+AREfJIrqa8cskcVGK+ivu/0G2cFssIKWZRwNlezhfQsYBqeUHlGTOPzCPJgdMGbxc2uRiBczwC9dz2Fjjx8AGY2tUO0zvboYQBnZn2xwpg8fTF0EMaRqWvasTEMGtChnnlMmqSlfMDTopPuFmhqFlT/q2KT4yTlB22ghO3iE/4bSgZx7bzklsxDsqUMOPIlckOBXIAnh06999WZs8uKo8PeRUHcIwreHuITfir6KZM1RCv2CqzALoUu0jOnPGIVpk7U+gheAY2GRQy3sGJHqjsbGMc9bieDjim/TB8sHV/ClB7TdzOgiL4f5PnwcECfq6Z4iKN6faQp1A9dFxQBCkpXmK3EyYH8QJv6gQjFk9CWG68Oo+1kviE6y9NYTfjwgWt1VfsMQ7KzIbaVdUao8ll6SUK5AC8lwjfX5otr1x2Cm7qf3n1V256dfNTfgt4C7GJF6Bz7lXhOgXIeDmfENgRkHO8SjXFo+9LEaDGd3XA+5CjPrbtEFR1HoYKFIlEkRpHAixeOB/ydmC4EAnikkWWIO3XkA3M6XAiQGVKXaIB/hHG+kTIYDiei1fnDR0F/ZaJaYT4RNVD0OP0kLgPue9P+3U9933vUiAH4L1L/z7fOr3og7Do+aKPFoALgDC4cTdAl8DP0TDlEQc7wYiPHIVg/P62g8hJd8HAeBwGJuIwBDnsSQjaxGXbxR9REX3HBIAlLwPsHgtQ/MJwGPHtaVCwV3LjNBCSgripNJVe2ACccfJ0JsmiBOAIwOHFJ1zHYNQpxCesHaIxHoD4+g7+yfOh/2eivjoXQjaqdZLJenIAnknq+tQ9fMrCoQMLit6XzMs7CTfPglgyOQ6LDMOtVIxXXNrCPfj3NjLlwj1el0jEX+6Eztuaat5oyFa3yXwQ2zrbqz1u58C5X3uoUlV8Yue+1X8LvBYiWs51WuN+KLJfoQNVWxuLIH5RcwNc0LwbiqQtXAaJtGkqwHEvAjQieKupaO1AGPrLSVD86hDI65GCCuJyhWzZpsAlXCWaJYZ3Qff0dogP7oaBT49m+bkVCoJrBOaDJJTh4hPeIufEmZkQs25hZwb+m8LV4r/+iNz35zJIvlzVEVEgB+AREVK3mjFTlx+FItNzkfCfx/1SGTQcv9h+rcgx/QNZpu/urH6xVrftMPnSB3ATuLjVgykPtwK6aalC/VQtTVTbZXlAGHbmeN1XRcN4CKKIpA1OONwMX2mqh8E25WMYGtjL1JWj2GRNKnjb88UOFUDh+oFQvG4g5NeXALSiVJtMSUoT0FPeAZ1zWqH76MOQHBI3ig65ejIMfmSssPcWtIvIfFCKT1gsFUULLA9fmg8S33R3541p3LxyTxS0ytWRWQrkADyz9DVqHz9zxVJ0yrgJ98iSqJpkDjFJOIAPX329rublO6OqV60nbRGKwplzAHcDdAnapshBRsQzwNxg0xkTaSjrGJizf5r8Py3sGILRzxs2wpkt+yIjTfMwgJkb/ME7bIPjZy9BZaWinBXmg0IfyavVdN4xvC8JsI0IWOKmJBXFKD4x7My5XrOhvmYl88LNpb5PgRyAZ3iOJkxbMitZUPBrBKETM9YU36D7IRH/LAL5Y1G2U1619ER0xf6fV52BZOBugG7jzA2sNiwquEjBMNMz5Ma8Z24gTt6MS1A+/uCOd5hVRzqpDfWUUzehzLssnVo8ynbkwfi5S0XsE2k+SIBtGpbwq4mQIbGBi/9x0xKebM47vAIhJzHoT/mY3ITpMvPZnwnoTHYdv7f2NRQO5VJ/oEAOwDM0S+S5mF+U/CXuko8i6GSczpyzZcKG3XGIn9qwYfXrEQ0tVl65nOqa61aftB7hCMKtSBisMAsHcV0X/04RoUhAsSs5VasIVp+slEshOEcqQElQV3L4Tv1ciCD+yA50JA2ZujAKzDFvAdTOCFmBRrHB102AofeVm7pGwX2HUV7auW9DfMXmhwM6kY0OODr8SIGZ6EkerN+4Eu8YudRfKJBxYOkvhIiynxVVyz+AW+Ix3CEo+Mx+wg1Ku/SvdTWrzoqi9fEzjpsbiyXW4Lb3cOQhjJX3fVOYwRlGwTUyjz8XQLcBuTU4iBCNGHIEHmXEAuJioIZXJ+G7RaUKMAll409vWxtYydmOs3g0gveWaVFQ070OEp8Aik/ICJyCV0XuvCO5dWK5xYEaJ3v6vHzmkRlP9Jywa+Oa5zM7ylztUVIgB+BRUhPrqpi57BLceTcjkPR+BLdksqWjB+bv2bRyc7rDTFsWLhRnjCqOgC7AnQEvB3l5cbHGp+aR/LglhRCFS0acnIYEp+4lF78HOfHj0NNSJx0YymXeu8k+KJOpLQ/K5y9lnLChJ8iE8w7RSJgPkviEmQ8y5SU9XrwqhweZnOMM1J2bsAiJWlG14hbcC1+JsMr0qiJGnJtwPBQ/2HFhQ8NrbelUWDZr2fz8BDyMdU52q8c7mBW/tNPZxjGEbI85oNs5c5UD5yIZofyUoiLjEOA94bE8GPKbyk1DKGztLbV75sE9cNMuFGh7pAY0EZz/JsCeMelQTa/soFvHw9BbJwjTST6GTDjvMLt0IXrioWqJ22eKzANoOuj7OpPeaHK5skWBHIBHROnymSs+h1j0+4iqi7wa3Ldoehg/q752tadXpV/DZWULS2FQ4YdRIfgx3PvLMP8oLlphiMov6cyLkDPQLFSsYfFAj4QJ3pnJVqyAboIvtyiXtoRq7GoTzFlLJs7zw8oAJ0PtIOTldgsV6sd7W/bDn3Y6e4pvwSNq2arsgDd1+6gVC6FoPwraaRCCNOm5zjOFiLPzjphkFrCKnmvDfyfiiTt3blz9Wb/5z33ftyiQA/AI5qOsatny/LzYc0jMggiqy0gVhtlvIvlf9BH6/I7aF7dkoiHEjA9hvX/FH+5b7pL2o9z1hjGT4IWBQ6EpVgid+WQjIiMVcvAmxxJKXH2pmr/ZZepmLosDkBSneHDiZx9ohJ/ttkqYNk4HOP4FNBXMAuctyVNetYydV9LSJiru2815hxqT5oPM9rsrOXbP1pcbM7EmcnVmjgI5AE+TtuOnLSmPFeS/iRwfRsXo+4m/0II4kZe8pz0Ru7Sp5iU9YbDG0BBoP4rZ/oI/gQ8yO6B3EGeIMlo1vopFTCJAmWO8lIsrDkDs1/6u+HRonHZoD9yG9uKUss15U5t5W4ug7EML0f4b/0EiJRKfROQ6L+NUscHJ3S4MeiwmiJB3e1ei66eNtWsycrBrLJ9clhAUyAF4CKKpRdDi5N8ILB9Ms5qMF7e82GICWydyXz/CuBc/xA5Y46UG7BFiwmewyF0KTASswZq9KZYPZ06cA9uLS5likkkDpALOsGk2ZeccyAXHLuTgpis+RywvCxWyFf9x4h1YgUFzsyHzVkc79j0LMYZKEdMJqK7zYcwHzdCxPM63cfPiBMD/CZmSQS6pAZbWQbHq7kTXqTkgT2v5Zq1wDsDTIDVF6kMFUFoy5TSaD1zUas1hWnrgJt/a2ZM8Oay1CkLCVdiZHwXukEaBy8ZNg8eGjTGu+1SEiYkFiEt3fFPJySs1Le8dohu6eG4mChLQeMd66F4a2aXEf4TovFM2dwmgCI4dU2w8IvZJGABHY0CuCKX/woafJUVzIu/+utqV5+EATD9//9HkcmSZAjkAD0/w2ISZK9A6GGaFr6L3StofAENwpydYflS3YeU1QXqFYHoL5s+o5c09Q8fA98ZOgS6CJnqhnT+2y5WljMvkmj8pTrFw4gLsUyxU3EAcQfTwaXuh+WfeFipBaOSVd/ANFTD07nJjHBLAg4Avu50IxloqfCORoScTL6BlynuiGmuunugpkAPwkDRF0ckFuNnuDFm814q5iFLM/iA33tPddULD5jV1fp1EzCBl5cf88kXxfSsKh787bgo8PngkdOcXQBzDxpIFBXN4oQYMT07VflxKDawWKlIW7OW52b7oADTd804UXfesY/wsdJ0XBjwq+MpbhhRXu1ciVbz4J5eaRC1D31Lfsu0YaGhIywQ144R8lzaQA/AwE4+v1ExIDMUogHkTwxTva2XsDyEQN454+DMManSlW18RLuj2cXRvjOX3w8fC9WMmQw+9R0AxrCkJ13DFzNnwtFedfpRfimLc3I7z8NZXf7omtUHj42vRSNIfRsPQIW9LEYw/dRFvV5gPchNMaWXjB9v8FiJDxNrDz4YRwaS+3kM0iT9fX/3yCWHGmCuTWQrkADwEfSmyIBq9oZVw/0yqEYLh9Wez2OAjS25vb+9eunfbmt1ypFiWwgOQpUKmfRM9iXsAzRBvGzUe/jx0LLQWFFiUnNY445qemy6mhiQX3/PHt6FrUfRy8bHHo/Kyqdg4OHRD5kjlrCQQs+dmIiGrDJ3NM7fJF1EOBLcuFASGUQq/wvAjDE1h8jAUPcUPt4SfTSR+UVe7+hv9c8X3bq/HTjt+dEF+/ArsxQeQ4ZiEVB6I242HpchLdqFZ7yGk/zb83UNQkPx9/fpV+3V7nANwXUop+SZULr8BzQW+FaJo3ygiHGsUTZ9Hv5LdyNldgJYq9+EWJyO3XfhzVN8YCO/F58ZXwn8GDudPq6Vw4iLIl4fnpq/TD+6Slk83wMFvb4tu2OQ6v2ApA1YmQtEIvGAAt3LNINg1HtOQYiRLdXpbXIrWONorAK7Y3ze1Hq5o37muPjoiHNk1DZs8f+LgopK/4Ao81lCq61kCrYvH2z+5a+PrGMTBO+nNrl8t77LvJ1StqEb2pLK/DtuO395cOLNWoV391Obq1TMLIVnRF8f98OBR8DW0WEmiSEU6r1gtVBi7Y3lQws3pxwAz20Bbzt4FB763NZLhk+v8sFvQdV7YuutWajELRBkJiyaomFCa8WOoRnHX8gENThlhgsmpxJ9vY52SLy2R80DixZ01q4/X7eu7OB9G8Fz2OyQgemeHfAqPbkDJvEfralbSa1hdbrTMAXjAVVY2Y1lVQX7M92QMWG3Ws/sqM0WP1KBStJkXtrXAN/duh2X4OHBfS/vRdvxDE+dCQzE6gZIvv2KhIkUEhgk5AZVY/YaFihiQaS+eKvtODOmG1rMa4eDFyIgOCm86P+YEFJ/sLmJxuH2T0VFCVTM/eVLyG4cQoHMkNsLtSscnCcSq6IzDNAdpacVjhKAV0M+dvqSCgOkKknUt2wblFJruM1Y2Y+GoGBRuwndGh6pP4ckzlIupxOFqRO8Uh6Whz1BEWcnEzsPdXbObt7x20KlVjdXju7zeVRn6q/WJfZKsAK6AmaMs3CwtAX1ovBu+ik+WfXZ/g4v0uPeWxVfHToW/oe04c/xhe8UEOLupIX3HviV8YvjIZclynK4PRWBUr6YbNkLHaeFe+ymrItvvfG7PrpvUQFTsUkRCLbTEEYDLqmEAbsrDdarm1i9CcSojPSqHhrpWunri1+7e9PIPdOp9l+WJja9cej/OxllSF2FsDLGudOjBxWHi7sTmkZkWNTd3HJx1eNt6Qxcl6wqwenSaP/LzUFhVvPd6vtLeH6hgd+qRfbZy3P4jGYCvv1++tx6+uH+nf+Ys5vhS2Qz4x5BRvEVHz00uTjHEDErfDLiXBi4CECUXrw6je1w7ND68DpLDg/m7VFRi7JN8DcG3C83iyH2zQGFMZCQsUWR/lSPVPLqsz82pHLgx9wQeNFZxezF+L+KHi9d7duysWTkxi1PZ55sah7Lu/OKSNUj+0VLwJA9Eu8JZezBC8SxNpNAwrK6+ZjXR3XItzAG4NkV5xvKZy29CudZXAxbrc9lTvDINZZXllm702w/Yy7o64H6Msz2pu6PPjPW82dPhufhowWFzFttuoZIiF5eCBYMlFx6r7LorAd/cNvS3BFpu7PvBZmj/+F69se+PQcVyjP3tt/tEBidxF7ODpw6R3pYL8w05Npd6WOPAeHVMcuBqd6RNuiGGopsKZw0T6NyT7ut0enTqg7nKZpxYFcvr+jZOzYexe0MM4jNugGMrF2pJx7L0BmEyGazuu+uqV12g1ui3hNJr/Qgsja+0P4pTc0Z/H5rx8IHk1izasdTR2QHcbjvOFi7Wccm+epSR7+h18vz9VICPo5tR6XVTofSvow1loQQk035aPiSBI+IiZUYRsqk2NiNjdfnGdBN5EH06Klth71/WAWBUWK80+McVMPyeCYFoZFc0E4CTspZhvAR6BUBk5WE4cPPqr8jccXz0eg85T9VXr3zX4UbF0cunYlCBf+NSYO8ycbEbZwr4B29CkuhOJ7PBUZvTzpaVQkm3LciyUTv403S4rby9fq1x3X3XTUSgXeOQuWLmitVItMhelk+3P2HLp4hQlNXjBM5O7bhx5VPx6bKHtr8FI+M9YbuXVrlffB3gihu57TOlAf8cCcO/Pg03WL7hucmYSXEZ5fsw1dyQ2VeLD+NwfVhmqqNrZis0PuAN4mNRgVm4p9hzjKo1iSmfl3J6DFBCHLiQfxOAW+YsAg6cdc5KIAbgdGjUVTeglnhb37lqpbVafAsXoGz7PpyPT8g5YTcedb+giClJymSmUDYTB14rSHu1Zt6EUgsxhgtNg/DzLIpS3mucFb7dz2WwUOBIBXALGLuyAgpH5rMuihFgbty9CU4/1JTVFfTVXwHcfFlqk3nN+TDmjHlQuJcDZwoHLjlu2psMuxgKctEE25h6vA5tsaYf1UD7R9yVm+WzlzN/GS/CmACuvkQkZN1sLyOYIoCrh4p6q7LI9w0FpWiRtSxBiP+OX/u5DNzKFYrbB9Yh44c3NR6c2N68vvevWVlYWRVVy15EgqxQRVTq9kiQvSX7BX/ZiJ17QhwZtntSyG1fILQmyUe6/uCWwdDYeFjMYthm3p3ljhgRigFYYpmoq9JHnKLOvJ9sfAGaG/6+fkPGuXEKvEcik0fO9F6Xoz9xNJS8PUQgM0Nqw/LEfKuTb0IJbH6ct73FBFqo1L+8GuU3Fn2TzLYZ19BUC0o6dNnFcpDlJNBgkhMyQRRzZTjzMBA2r/g6IhQnM0KOROLAFn+yxybw162HOic2N7x2hAP4wtLymUXr8ECbajp6CSrL6xs71EgXgcBN9vwZhkQpSulJJn7aULOaORJmus0MDyn71eO7l7/Febs4+y1H22KKElMAGd+37gowz3HeQ30AACAASURBVO9cOI8YXjE/17wLvr1nW0YWXA+q1D78d4B/n6JHoxGXVELpMyMs3DUDbIa3bHeaZoS+mkbnNpsv3QYtX0qxzOmA6qJjKz66CGUs3snCgXP2z7gRxDEIDAXxMuLAiDkTJ060ZoQCyIkxZ2c+/u/wnq5hzc3Odsl+4+ov3yPn/SxS+AROUw6TbHlY9gkdpqiLYM5YFCZT/4aqS4cU3RPevPAgrUOHKqZEyQG4LiVFvglVy7+Hs3VtwGJ9LnsqgBvr1HMh+nHcXt+X4mK/oQHFKi1NkS28ZnyGd/EagM3I0wZJAx4bBSOunIZgR3JxITJRLE+k7XhQ7lv2oX3Ffth7R4q/15kjxh/96qChQwNzr6oSk/4ur+sGBy6u8XxTh9vWUoRimBGqcl5xYyMxys5aUgMduWl85bJfomnm5XY9hEprKYKT8+K6TmyCcMO6h5lr8gNBxqtxmzbrnkIzIFRG1NdyS6AjeiIyscSOREcezl1wz0XOZATjwP1A3TIPWPdIdAK6cs92+AS+DJ/OAtwyBcH7FYD9IR+zI7n4UecdA0WbS80uCnmxsTFD9rB7XAfseuY1deh/wKouGj584dDBY0oOeK5NB6Ko0gwK3c7eCxXKS0NW79BXHRGKU19UM0ICGflWJz5+nMTHj8MbsGdiU0ZY5wh8IrE0P7YDAZmSUTMXhpnevdICxYjg63BTC7QvePVaiExzgZZABOAkOcylIBQ4El3pOWibHLjXTdDpO7vSxrG8wy8HoRPQuft3w5Xomh90Ib60HOCUf6M8dnCQ2XPOO/qCWVDy8jDDYZMxRuTMgixSWA68e3Qn7HruVdngth7o+Uo+5K/AX5ThQyDn+/U6RYkpwYOJd/jzcuK0Va5OolYmDUrPDtxeNw9VS3E9Es0Y2AzlT0dimlZcMeOowzhMdJElMFV0DDbRCX0ldQKWNYL5mEVKBslD89/c3DKmtXHdnky2k8Eh9G7VR1owKw7gykMIHlr0wFyFy1SpeF6MopWL9+2EL+PPADLG9klPnowy7ycwwo+3JZ5fNZbvR1yKcvGnRuLIydZZbMAA1if2xjrmtMAeNCcsgZL4LtgVHwbDDOvwSbOON+zM3Tpp4LON62OWCAJMDYbNww48CBFSrFCE2ITqYACOsqaenq47Gzau+WyQevtJ3lhF5VKUeeXNYCINO0dtEyfR90yZzC5CUm/ib2qqS4sUPw1lj9JcHDzUMrOl4a3qHIDrUlTJ1++9MeXGVBepZYGmMnVy+G4AnsqFp3KATmWN3yEaUVTvczG2ypfxZ0yPcwC2v+G792fhu/fxwO/e+080ycVHXjUdknHsO/NwtJrp+ddg5jj42Xpou6IBqvEzBT9qmrvkg9Dc0upZnRkd0BRtSSClP+XGNTh1l0M3rAhFnW92wPNTHtriiYr9m14+4kLKTpi5/B6U75/LNAgCwC1MjU0/SduFTDnzhemgtvwjyCJykalQ202NB5gpZw7AAxGUZ+5vjxnbh+hmZ+oH0nwPu1zNbSISx3xeshm1k9jBqs7DcNm+Ojj1kGlPfcdFAF/4nYJeIebOrwjJxUdcOQOK/jsE8gswNBEheYi059634ZX5L8Ax+LGkH/4Qrrr1j3DvcO/3MOwiFA6iXHxC+5oFMXSzkIlKhGIuCBZeluwTUXxyxGHGqMpFlSVQuEGy3Zy0pvjEMn/iRFSNAJwZE0UkKSogb0o6edmRTHNE3Lvf2rLJxTnvhQ5jbd1TG3es2eJb3q/+d+f3CwsnVBXvxVkeeiSMP2UBegCtq5NCCoC740sQmg1Gb84vYdTDQxfvhKsz8u69c2/y9qPjz8nzobCtKLAcvGdiB/z3H/dCZUwJGU/0OessfEX0r7CzoAiWT1sUikA0V0ycQSCg2IFLgKc/ebgA/huWwjryyDnFP+MEO4nkwfra1cOCzF9/yIsmg7uQrmPzMDqkTJJkqvmmeZ6ZzlXcwlPCKN8dRHZ961NVPepMLetNgLeNyuRytETZmQPwkCusonLFF5E5+03I4r1WzFl6EkTh5bw4dWXjbmeDn/davLQHDn25Dlo+25BV2o354DwoqivVNs1L5ifhvr/+Ao6rtEVbmDkToLra6PviaQuhsdDHnV4BBsmrsRgtxIHb4ohnxJFHoTTJe9EC+V50IEExw5GTxkxbsLQwv3gloaIKhtJMkP3JDkUzyTXMQi2wG5qM4qjBUYchHek9mGjHvAHv2PBSzgolDC2VMjFUZm5Cuk5Os54+VdwPiF2Zc4cv/OqyD9wvP22kxLBu2HdjDXQsd4xvnxFajrhsBgx6GiOFaqRLvvZp+L/Pf8nMeRD7OX06wF5rpMJXBwyGj01E8Yo+q8bqNJSYhuyVNyWv9IwjjDIeuBgJ2X8faG87unXH2vUaZOgnWcpKyysn0XuU+RyIeXKaEnV5G4elvOVYuPDMDN04RLjoJVm34SXW4RwHnga90SX6k3gu3p9GFVktqsrtZMN20PQFURcZeBCZtx+3rUOUtpP2wf4fbEJAz07ArMLVg+Gor1VB/kGXUIOTu+FPN94EJ8xcZnYf48HAmDEA+5zjolw6bgY8NtT7YDDBhG9hBuD4N757rWZucjerRmxBlJiujjwktsHmujrjY/dsfblRZ376QZ58FJ3gqZo3XCpo2dMYTADuoOuxWaFwMYmOEDsaSlgOkGRyf131Sub9kAPwNOmLjj3rcCJtmqo0K+3DxV2tUBzkfroWK2GHmyiNw4FvbIPWs/GhknC6xkBN57XHoOSlYVBUMxAKN3Lnn+5pbTCsaiA8f/yTMKHY9lzoIpRzv2Zx5klp77gpC2BHEQb380hWYyEuM1WtT1IceSJQYlocebA9+nf74fbxTXVvZFeGFWiGdDNPKqmYWbYLWVlFni9V+7wOuxmhfS2TSMkuxtJtPWw+2YdkIvFQXc0qVKjkADwsLY1yZbOWzS9IxF7Co9B7F6bdUvQVBOa+vezDHb5zB3t9mbvOqLsntcE+fN6sa463aZ5OXUHzTIfp8AJ+xuDHki65BOC223yr2x8rgMXTF0OPTSTiVhAdIYkPT3Glp/yRRyNU2D4SoaDzyNjDe97u7xw4ct7L9yBAj5CKXm5XH5MqXwHg3s5t9EiR05RZRS3iMAhjfSIOTbuTEEF2R3f8uD2bV7+UA3Df7aWXAa9in0IZ2n16uftGrjBiDK8yTrLxINy6SpUw5ahM56JDKB+vhfgY10e8IyX+ZFR/rMJPCni/8QbAggXabZFVyocmz4MDBYW+ZQwxGANswYExRZtw82YKNRY62pTl+lihMHoz8YHV5tyIBy7aOgKiEBYieO9CscNIHldRiKW47Qg/AIU82wivqwop7NpMY7YyY31iXwziwEmi+IS8IJjHW06E4rtl9DL0WeceJ7MThyH5yb4Zh+ci/3b7zjW/60bgHdPpi+us4IpuOacBmr+9VW/iQuYaD+PhNfykgDfRexzaeDcGY1TpRc2TJ8+HzcXeFzkhQBHgo4hSxDzLl9DDADgLUp4UVhXSu1OuH4SK9sNt/VmEEptQuWw9ss1VfI0J8BNrURrzyeXArVBsCk3xC+thyYNSZQxI7bL3PGis27ByrNHPkOs3VyyFAicWVMzs+i+e3Mf3N+KE4cZTxhjACsUPoINy+k707jmqE3Y/sBYSY7sjn47BMBg24icFvKmlb2GY5p/+NHSb/xs4HK4omwZ78525cRn2VgazkigjH1sIBOBKL5lIQDwdZ7FeNNg8ptnDV3jyXuzo6fy/vZtexWtG/0nkaYkM9rkMr8mOWrwuJG80RuwYAeiO0UwUMbnKrWeTColk/JH66tVG1PuMHRzZHFTfaWshXtGK78YF8qm+06doeuLDNDs24gbEfgDu1WNXM0aHQslYEpqv3AKt56KSM6JUCIWwAT9T8ZOS3noLYM6cSFp6o2Qg/GT0JHi5dAg60ZjbVJVzkyOPBHRDwYUgHEOW0IkDl/isdhBtu5n4xEJXDZELJGMHOuOd7+sPQE6elgPyijaQqbdBJ8FdGxcMw+lJBAJjlv/c6scSldDjFhrJxDutY0W/1NPTfU7DxlcMy7ccgGeA6uVVyy9Fwt6EE58F2wj9AQQBP/1a3UUe7iIUB5MVW4OeXDhxUS4ddGqzfUUzxuZ+J8iQHPMWYLQWEpvMwU9KIuKOGoWxbfen3Y69gkOo6FyLgP5m8UCoQRHLY0PHGBYQFFpWmheya78AcJPTZN+mEExy7ERIN8A3tHqM2NJkUcw3gT6BfyJvTV3tSowNCdmx5wxBXfK0xP6jp6XwUFVk/Sw8gQBINf6MYSZoX5e9AeDysMG+HO7uGYqxaNB2naccgIdYEDpFxs9Y9v5YfuwxJPBAnfyZzxOGhxa98kH+oNYmWhy4R5thRD7d4ztg9xNvQLLEP9qh01wUQzGsxs88/Dimj30M4G9/y/g0NucXwJxpi1loV1Nuq3CKhiMPf5CZ5XHY5QTgzPLCBvjmKpG8vixueiRysQMdFlxmjlz8jp3VqyZmfPAhGiBPy6KCkpXUYeldSX2XXo2WKiWd2PNDnG52px436xNWD5YhekpoVf5qmLTorF03rh/P6nhdzUuWMG45AA+xKHSLHDV5yZjiovzv4j75PC4FfxMD3Ypt+QzRnPiLjnNfprhxtWtpiVC8ANyHgXdrtwdjdDfe/xbEyzoDUXoEjIB1+CHFpWN6+mnUQGKM2yykvQjgC6Yfa7GhMBBaOKAwzBaLwC7LJZEJfwZAiAYMwNc37eQ24sKKg3l94qvsybzWnXs2lJeNnjsultf1Dfz6VOzkKPyywDxJBChCXjdWQa9dP96V6PppY+2aLZkh3aSS8spxrRgGN9/LSspu886wmMBYnH1yP6UyHgyxeT5NJOV1UP38EAmSMIzCdnzIYZJaJmAVQZrL5ZUUKJ+9bEReT+wqvKtejtMWXSBUHwsTd547DW7cfni4XCk9uWyN00OLSw+xxCimStOt1dC5VM8Vn0wF1+BnJH5cE3lb7tkTojfBi+xG5eZiDITF4BMRwOCLDe5RoE6q1IQ1xvlqkdn4Q5Wxy2/dOXDZa9Vzk7P6SbTfzGOuqtYYIt7cPEJadXei69SIgZzsvSl+wXAjrgm3EeR0ELcIBqaKGIW/c8YB2TDZZKIXTlDz1Sp90HaaZTYLXtvQvkcwLx6TtyCAX5YD8OD7JpISZWULS6Gk4Oz8ovzbcFGVhK9UsNryfmw7hoVVqrlRQzakgbOuNetcFT27FVJsY4KLs3yQSEbKzYPowdlyobdT4XJYDv/GD1mduKYbbwT45jdDUjh4sb0oD5+Pjj9s86MSU7rUS2Wm3YNQbYG/ICNlAyYYsau/5Mg1uiQ5cLnsyKJDgrY9DoufSMbQntJ8J+B+lKefh3WRVWU6idl74wi5u7myP0wlpk05yYnADx7lJmsBcbGj0tkXYQdF/cjvKBq3bduzFo18jgPXpOikSSeW9Azo/H+o8JmLRWaLYm8n8pLrCtqL/4WERRMr/VQ+fellefmxm/ia4Oe6isecoeH1sUmymBA4T5vK59hzRMdzm2MMahfOhqSpBPLN5wfwiubePiuyaPtxzdB0c7WjXPxkOBmewA/Jvl1TE0oBKtB9viPQ1OsvEoec9ciBL53KOXADwJ1qtN3PSeZNSGbEUGHLiy+wdGKnWBWdoq6wBwKTSCRfQDvn96RBJMPemwOxcE4yOG/JXaf+6Sb3Rtd1ltnrcEyjv65FVSYID98dyH1PtGfOAbgG5Zm7fDzvPtTXVKn2WeY1KLm7K578SOPG1S9rVGdkGTZs3rDBYwc8gytjAV3duLVAsCmxcjip1qtRceMpIOgBkF408AVmUdiPy/Hj8HXbiQ/phj1/XA/dsw4b3f4ofBT+gh+yOvFMX/wiwO23B5nytPOSCGXR1IXcyA05cDXsKauc2Q+mNpPE3ydtHLuxWkICLtfasRNAiLlTDwQGocqyFjwJ8iO8n+rjBuxfzAQyuaW+Zdsx0NDQFpRgpr03Z4mMmDGCcfDzMZD7yb4NVU7cgboG98UlMOwk4kyXnA6ffe20XiXd6M84JM5pqF6VEjgvGFoEpWb/z49ytBXfQq7g+7iqCmgxsAXBOQU5P8Yo8Sr5UrKl+wMNDa8FWnjl0xafkFdQdC8C+HiSa5o4jstNdfNiG0EsMbEBnAUFJndl5a+yMyFe3L4usEYF0Dojprk89IV6OPjVHXARfn6HH0dHDrWyNWsAli5FwAxn1aLTL6c8pMScjxw4WZAwO3Bx3/cUnVAfae0IwJf1psWB2/QvqfMlWIdAPAmHd/4oQuL5uupVJwSh0+iZS6aXJPNruL23vLnyGkwwVEHdyoXzfOIQMjWXok9cvKImHbGVPb+QsGsNy9gryUTXjupV5KKbsthyAO5BytGT5s0rKS59FZEag6cLbkfKypgZlRXEiZioaOjp6omftmfTK//RmiUzU17FtGUXJgvzbkEupDQT3HjA/kSfPYAcx5cD1xDF+DVnP0xGHD0Inv7t/TByxHD/sS9cCPD66/75Is4hOXAG4FLuJnax+cCAtVFpMqi+4GMB3DAcODbBRXupoMbk4IwrN5O8rXLGVAC1YSljBVlZKtHT86v6jS9frkvCispl67A/x9g9LblC1RbnxaNSO4izF5CUcZrHTEj4lAy67sCSyYd3VK/8uFP2kD3Qbbkf55s9u6g8PhRd65IzUrgxsXGY0MMZxJGBSP5tZ+1qCvmorZDBec1vyct/7Poxk069f9gYZmUQBTce5Sz4gWJqAAl1F+uzY36cut/31KpfHqdDonRACfzkuivh9A+d5E62O+8E+GzvPMxOSswFqMSkF+KdgMZpQ1sA3AKqVpGHLshK5Qy/jZpzmmKpwUDeEJpoLUNzTLzqvQebJ3Xs2rDdr/Do8gXTSgaV1LIjRSgi1e6pa0EFczdGwZB7Y4XE9nIA5yIR+TqOX5/8vnds2/5LbC/R1TOjfsvLG3MA7kdR5fsx0489rSi/4AnOeXMwsJziEsSliZGtbpH/lZ01q8lLzRfECbwxH3mCnE5VbSksgQsnzIKt+GemlCdsa2lwsnJoflxxAPL6Z/VTUmr02w/AvTqxZNE8+M1N16Vy46S4LC8H6AxmS+4/YL0c9bFCWDYdlZhi3VnXhjM/Rt6aBPgsCbrKtcwP5AAgK2XsAXU1eqMzc8l+Yde76mpWkjOch6dnWWlF1cRmdHwuYsy9zdPSVxymdk7hUOivXBTjbiOvK98PyynjraoeH5K2BZo3Oxy23qDz0e/yV1Qu/SPk5V8o7UTlGne6irkBLAPxBKyur115nBeI28FbJdbjQ0bC1/Hlli7cgFFNli8X7TBb6YJ3uuXtXdKpTwfAvfIUFBTAt752MXzhQiW0zfEYq+zFF3ttPTMAn4FmhAQuDHz9E43RCH7ln90zB3PBFwpUt4ye1klGn/3tzNl5Qz+JZE19zUp8VNQ4adSmU+y9VaaLMhqKTEWMorN+qKwMemUda3ryffuc2TFFpV883nPFztqXf+5Ga535T3PK+2dxjJ+wFi9OcwyDfrlj2IrgG4cvAi7mcBKlMI00Ob4lk3/ZWbvqbCdKeIG3zN+G8s4zJ86BDQMGekoovCjNuW2rYifKmdEBS932dOqKKo9On8rGjYEH7roFJj7/P4Bze/dNXwLw5QjgTtDtxBQzHSu5y6tKOUfunVPCi6OkV2hMRb4qOkkRhdvxjt9eNbl2Loqx8s09yfgDDdWrbUHi8E3Lqkm7kbUZzA4zG5r5rZEUELefiExcIsRMUo7uIN/XWUNB8sh+U/868g8M3rt+vetLJTkAd6EsD4ATwwA4pmbaNNbmhaRyhMupTYsAe5W0CLq7ek5q3LLmGfU7HfBW8986shxuHD2BLynWLyXsvJxJsehUOWCQxWPrnxaHF7Z+t3J+G48DjT8g6CquXOWgCsdGz2d9Z+8O+NyeHVEPN1B9JoDbMJJx2amx09gr9jgObw5cj6MkAGd1ab4e5GTlEmSwrFdCG4rznexK9kxtrHllq6jDeFnHWA+SsxLrw+DEQ3Desp9cJCNPNlajMYQoxSfq2SHrxZtHHYqPJnjRLAfgLtTBBxq2I+MyQQVpO2jbi6o2p/bv8CrWg/JwculjXh9BwVvWV4PvJ35k0hxoyyeReWamL1O240E2r19eHXDWAXm/w8Bex/y2Q/CH+g0wMt47wffIkWfFjGMt3oJyDE40Y1wz2X87cL8SIJ0eJDABRcAwD3poiG1SxBK2U9BpftIFPFQs1uNbkCgPlpw3IOdtjSlicq96cmvXdSaurJw26j7TO+xsxyv7p58djL3vqLu4HU0p0dnAPWUGAfx2Xz/4HjnwfyFbfYrkccUMsD8MbtsmSrFbBdiHiSdqR1d357G7t7xGsU0NhWVQcrTE8uHUSXNhG4YW5Qav0UyjKpWMqsagh4wO6Ork8QNmlea69fE6AUqScbhx1yY4/RDFY8puOpSXD8dUov25gwCcX/Zt0MFYSOa0yZNYK3aLEbm+vUQdcn3LPaA38ugAj7jwjpa2BSWDBzyNCkvmJs+VjDQu3huDexXbwv5v1z477CPVfNDrsNOjQ7BciBXJeLLzqIba1zwXWTT7NFjf+kXu8ZVLLo/lFfzSIgNnK0QsFmW3cG4Ep1iIUvxk4pc21W/45r4dpJQJnaj5y8dNh0eGjOa7ky3k4GBu5bQC6etD9z3dgrqAq5/P+wx0OiOp7uVtB+HXO2uyzo1PqCLDptTkBL4cdJ05cFmDk6hDXRc8dni+WN/8G34OiFwO9383wEuLCyejAMiL4zrPZ00qsnyDe/Xgc/14HWNLC/Ecjx0jlF8OnLiUZYb1vjTor4gD5TgS8fjW+trVU/z2Sg7A3SlEXpioPEiaQacURabV1pRPvY5MnE8QwD+3roWjOwM5bDr2dOWAIfCFipnQgh56ckuZOE6HirgmiC91PTn9Fk4mvtcHXH/5Nx+u36WVj0K3XacxFyC4XbqvHi5vqssESRzrnIgAzp/htadUHpyBM64BLgN3AX2DfZVKO8tC5/bmgjewmC+6IGIqdx8NF67Ok33OTE7b29MylWQOTA8/KNgK6g3vS7Ym4/DV+o0rb/ZbVDkA96DQ+GnLPhEryPuLBEYilrm0Tdkb3ySpFXmZF5aiDHX9xleY8Xe6icSTF5dXwZOD8FaZoRnlTJbDvT3dzovyumAbpDldYNbJ55dnTE8nPLFlLYyJR/8Gp33Mc9AK5QDKwp1oZr9DUb9p1qQM3PE2oSxe+4v28lbJzOlIaZ6vKvE4M+K26Jy4cC7REZtFcY5hY5R1GXIRKX8WIxVjkcxTWvbeClHtnLf8SqUvz6PHEDiuUX6Oum9PZWJozjryD3pan8g2MrTdg2yzvp2XycIhdgq7RqKSn6yx2ZVJBGRXFQ8p5oWUTcggLaMULmLH4hX8rzvWR0aAd0pK4TtjpsDryJUzL84IkgHZmcNuw1lCS5bvdw8OMWadKt0AXN3kxI3fjCKVU1ujf1ZNHdZVYybDvcPHOY/UNu2s30zkkfIFkxupzIf1dR4uTzaAQpjPMccvQ6Buypzt9q12LpyDuRC6sHYlmKmaF47i8jvZd4P9F/vJtPhSmChVDKEArevcOsvFlJuNFBXxTmfK+9JpXcUTiT07a1ZhkHn/FM0u92+nX+com7nkk/mJ/D+hRr+QBQQiay0FwBW2nI1TNSl0sxPn53kS/rz9HTihXe9xAV0iHkYzr2sQyP+O8vFOTZMvtW65b3UWB99+fU927scxW8arbH43GnuBvL2ts5t3w093b9adrsD5thcWv3P81IWkQ2GE96K+yoG73XLU9zFlPG8Lryg8G1msFRaQVhEZWuS3qboEg4GhfrLXawKIv7igm50Spsw7TZ29woi4cd5sb/qsCZ0DKOjEyvlJxBOP1teu+qhOeZ09qlPPEZ9n8OCqkUPGD7ka4vlfQiMQjAxmhvI0QNs4+U2FpuRwXJ0YcKHcveNtOBHN0zKRnh04DG4dVQ5riCs3ThqhmjEUUWwEwSxa2JUwjStliMEGuQT4bcCgAB6kuwT28zpa4NFt63j87WgTvnoD48nRDNdUmSMoi1dlJJPARH8OHDi/SYrOKUjAA17yhw3IDZ/e5pbKfO6whqNS3dU9wE5y4mKFWSihHopGNwisbU48KqAaXLnor1XMYa5HnVuV0RlD5m0eDs50FXoVzdstH7vz8WqpX+STfe7pSXy6YeOq+3SWTQ7AdahkyzN+xtId+GBxBZsawR0YIO4gMjE2jwQ9cZXki5pFMIRPNzfC9Y1bIpGJOw2JvDkvL5sB/xkyInXH6tJAIGigzeFRd1T16HbfLZ8u2Ovmk+1M6zgM/0QQLxYv1qTbT1H+S7hmfltWtWx5PuS9yNhvhhPWrSyXIfWZnJBMixEOKhwUhXG3AuQELExMaLtWUv30nqZ0rFFcyLiYUNwE5JwaopmUG4KPQlOAKRePu3PequjSXddk49btHAA7NUx6yPmhVil+unRYkkKesPdMqQvw00/JMbVBR1nThtfQkdA/5QDcn0ZOOYrLK5e34cagkHBCJi5FJ/LWZy5qvkw4antFMDz7QCPcuDtD77uKUawqRauV8plwkDkCyfXLuS1poWKKRdiJ46F5CUc8Dh5pXoUjPRg0efsQnZ6ClkaPbHsLhiUicfx5A2djgRx6ReWKe3FBnaMIlA2qSDw3YnnY+s45WUwioylGEbczvnzlEhEHgOBAxe2TnITocHAki709JgN3CDOrrAOnA9IC1FLJpKwfe9shpijVdlwRCzpx4m43B8bPsZus3rZRV50hPklCvL7a+vK81y7LAXhIDCqfuuyjeYV56IzDhHviKsqVKuqJbVFiCk7HC8SXHj4ID9S9kzFOnIZL3Phn0fRwFYpXckmfAn4cuNv3ZV3t8ND29VCOlippJIpouRSX0KtqHchIbEYOdIrTEcTWIr0GhhIPSsAIDQAAIABJREFUuQ4ls035hSrHFKPIKz9x22R1wvgTxo+acnaxvmNY2s4Fy3z2w8Gu0JTHgMr8GqBoiBO4rDwVoMXv1T7ZiKoF4i7cN2cuuNjImnxuDo4TywVDXoJGk4b8LMWDtL6eeZvqpRyA69HJMRcGkH8cqf5hOUVSU61uZKcN4HTllQ1Q/tkdrfB3vHpHYWLoNbx7Meb4tajs7A6h6AxDNk0+N0zVRhk/kLVXHiS/X16372nrD0Oz0fsRxGd3mk+3BRzo7bhZU9yqx48/dmT+4MKd2AZ7vNMrYJQBFsobj05iFKuPA4cgrvMhcR+97sOPASlSUDl546BwkBNLUULKpc4Bcf0571R7b096uqC6IfKx3wQ4MfnhFXUAK4/xxhPxP2PIDXrYWSvlAFyLTO6ZyipX/CsGiVPIztYO4IYckC13ZcHLxe0hE1/c1gIPoXIz0yDeidvwirLp8PjQUWyTZiIJ3iVw/X6AmQ4YGwdmgF759cdR8SUaorIFuAZ+V18NJ7U2ByVzOxZAnQvscyo4YuriioGFhW/gd+IVdus8sgcd8JDm0QQ5Hsvn2Ng/GafOZb5Mdm6Lp82wTKwNY02TFRYyqdwyRZrzUUXOsrFULpz3w1gbjNt2B2UD0D35WW+ycn6Y2nW3hLG4zyuyfbVmkxGRd225c8J5Sqjj7uhKrNizedVK3QWSmR2r2/oRkm/k5PmfGVA04G7aHNIbk4lJxAJgDAzfBSkbwSuK4UcP7IFf7d6UUSr14AlxGj5b8fS8Ihh16UwoXo+x8zW17H4dU5d34IWmdQ/264HO9/r3Aj8A12mNwOOaxm1wUXODVnaR6QdIv2t9CuRPqFz+NtK8ym75QFxzDF3hWWRCJvvmeg1DjCJglDEhHMENqxOjTYH0qliGh6rlohZDmS8OB4GTjkvJLmI0lfwm+HMxDO+nWpcF5BUwd10uTl8wsRCvONU4xwXc5WGjuTf43tdTe5o3o2QSow8Sz2acNX6LJPC+8qvw3fg9UvuEBweOePqbFZX48DFyMWJhyeukXIQGqNuI5GUrPg2v3H9HJVhptJYMrAetgwCWrAZ4Z7bZoYIdxTDsx1NgwPPDaW8GBnMrd6K3gPvLmtEBcC8uXB3nZ/Y3wHWNW3WGfgg36VA1I2LDPPz3hfgzC3/G4o98sWbPgw+P6bjmR5MXtx+ODVHwz5Any9d55JNhDMSk0i3FksWLU6VyqHHDw6EA7Wq9RCeWvsu9QRgljWCUG6n9EpgNztuwEmHIaR2z3QIlqALT0wLFdrgkEnGUf6/Wln+zudNZQbk87hTAZbgIv30Of0rfO2k+bBlQaip3+B2RJUuoWcFY8PkzveHclJsxBO8/1m2A96LnZlRpF277+XjpbqTt75Dy9xbC0J9NgoH/wGBZCXlFxuXYj2Kr+NFKB5CdwMez3gA3h3P372Kmox6JVs9HcLk8jtXOwb9TbIxl+FPkN7Y31g6EH/1scs8rrw2OJZJkyM05WmPM4qTly5N/Z+V4FU5cLmJhXy5twllJ7Jg0t5OiGl6jbM+ByxX7gjMuNq6bWwGkz3k7EciD85Zjscj/DQ4/egWmfe2xAzAJtyEHfonf3Krf5wA8CLVseZHkR+OvSF5Fcb6hCxdf5YylEKerkwRmvpotQO3YpJRN0iZzeSj5lEP74LcNtWnLxTdPheQKtCB2A2+1fwTkw6+Zjhz5MNMSIQ2aORaVHGCIeoOCcIgmjCJabfkAuL0OH6/NZ3DtfBc7cA/++EamcxvboUMFyWOWLkQqFyCYK2IUBrPEcZKjDocCi/LQSRFp4q3BdUsQt7/ebumPCtSC+2Yu+S4SrCCcdwrJXeq008fCeeOeU22/jUMoagWmHUOEPJ7EUQfz9o1qqa521HO4zW0OwEPuaFwjk7HoOvxBQYSZ/o4Bpb5cXom/MBCZfalyP3LB0SK1m2hJsHfqFuWf234IHt0eXrm5ZQoklr8EMR3wVvtQUFcMI6+ohKK3BkUH5AG41ZDT5F4sRNs6AO6XJ+V77MdXMJLhN+3RDPOgFT8boBTo/bS000WXzIAn/4u3KVpxAjTkBZHA25BiCIA21yjnoJlonNaxDTHkGpYmh/wg4AiaIk6SlcgciuIylSOV7SqKTR2ZdxqUYuFj6XYsL86KzooBunp4iXZ4PH5xh9FhRCyVcAENY/YSiXZ8rKI0aPdzAB6UYnzx0U6gu68FvGVV38VgQ3cOw2BDUpsvFoJFQaSIV4JaqByLFip/CWGhsnUyxJethPyg4K2SKK81H4b9YiIMfPQoyGs3ObdAZBSLWJNRClR1JjNrybf9OHAFhIy+Ypnb0TrlFDMIVhzWQBMK57QCGumMed/+Api7fDGLSmjoZgT3LcurCninOlNAXIph2BccuO1iEXs9xOXKU8BLH6hDa60zmB08CvJ6EMv58I1efKJ2wTgoE4mHEMDP0plLy34MWuDdnh+XAnm/0MOITGzilu4dOgauRiBPiNfkTVm3ouGXzApVopz20lQrSguVKMDbMlZ0Kyl9chQMvq0cijcT42A6XZibz2RJ+Jg4e9MfVZt+nLWkjW4++7qJ4R36CbT9P5rsxH8PLfA57/UVZh9OmLmMiUukGEVaSVjtvlNN+VyBUnxBsm9av/JNTk4DsahtMm7eb3Phq3brVuY0JOft0ln7jcICooaMX9FV0WGUYfEJO1rYLZwceDpH+72+4zTnOQ48wE5AQpOJD8UoIA7cNx1A8D51wjzYUVLMvdoEiKlKoGxYqEQO3raRF78+GIb/cAoUVpN4JVPJUIsJAMhUO8716nCEfEP6G+641TWopwf+MXPt4UmPdZBVSeRp3opFsH8/+fsoYhRpMuh0M9DogZCsAMQR8JRY4VZ5A8/FbMbRnNHg1G31R0Vjo09SVOQ4DitnzS4RxuRxsYjKaLA7hsGD8BZkyGa55nXmnq8RYcTIbkNUT7K1fsNKT4bQbSoyt980Jr8/ZRHg/Tb2uSpov88ePwtWDTbd1lXLE6pLy0LF5b5ZiNzP3XXrYYVLNMOwMu+gY6T8hRsGwqhvzoDCLYFFed7NRSVr0d1hDr3R5ay1QMijH+PGdMK/HnkThg+LJHaKZSTXXj8Z/nDPWC5G4UhiBmxSwE4dgyf3zRevCc6GbbUpplHXNp9GAYsCeWwiYYuMXasfcoROHWXcLW/ITVwjxUJk02h3n5eSfN6EHlSa5pR6ZSg/buG/76xdiR7dwZNer4LXe0SVEOD9JA7qfWEHdvqEOfBG6UAG1kyhabu2SbGJU/1+0Qyp7DkO0QwzzXm70aJo3SAYdcUMyK/H1+hE3PSgdFO2XtCivZpf64zwyoSLbWZVK/ztXrT9LyVD6ejSzl1FsPS9iwTDgMCBbfG3GUwlpm9rymGqcroGyNnCzJr4yq1dsFUjxoqfzN3eFz/a+nHedqsTblhA4E60EGFzXYDaHLaxc+XR4GhII8GfzG4dDw8hOiEadHbGT27csvppX9o7ZMgBuA/VBHg/htlODUNgtcxHK2bDq6XDkOvh1yi7+MQuiwwqF//Ugd3wExHNcPtE6Fy6Gop3u9h5pzsW3/KIPYMeHAvDf4rGOp08QCmXkyseduJeyrggKTOVf/VtQC+DyRGFX+pBLgA6nLpnHoFSC+YegofueQsK+FOnkaWJKAdHu3Csj8LGIqAysnB5cyCOV+0RgREXBVjBmbP5LKdJQ6kDMq1bVIBzs0ZxJUCanDcbdSwJ3eM6oXDnAGFxI5Wxwp7dS9uqdIzvaauGRx4qpphF1THwv3ce7prauGNNqDCk4Vd1ZEuqb1eEE/Aw9vDMqHp56djp8NgwRYTuZqHCgEy1GDB74OW5OR2VYL8//NahZWsTQ9KxNolqvLEDBXDUZ2cz8YqqsIqq/j5Xjx+byNCMb3S/tOzYA3D/net1svpVZXx/0SWV8J9nMCa8ABoJ2k5zk9JN+0kmAdpmQ65GMrSIHmwxVnSV2X7kSofzJvBueOINKPvwAvQ85nMieWzd/tmJb3D6PlMsD6sdjY1DYf+mUC+6+K8i7aVxZGWMkvO2U+bs8tmwatBQgytxslBJRy6ezE9A4+/XQ9eSUGsiIxM56K5xMPxnk/mDAP0p+aFHiLH4cekqJ3zi8fvh7ts3hGjFuQiJUZaduJhzmpL7pqwGCGudLZbKJYlYsCzx4ppl/bIzSzoMidsna1IApiJ/1x5oFJx3fhJ2/u9VSIzuhopZyw3Rph24LXJ60cHA9t/qwESFBoBveCn0pghdUJvQ/TBjJsFbkuNz46vgPwMx3gg9lOxgoWJXdNrJaDW/MngQIxv9pvXsXXDgmq3cdqYPpIKtJTDm/GMg1lSYMVNCqZTSYHAjp4gfMMsGg54JH/pAE/zmpprI+jtx9jJ0HBF6GEQAEqU44It3ezbuW2Y2Xu2hS4Z4/JiJV4Q6UZrGRnEbS4fzTqB+Ydejb0C8HONxNhRAxfuPtZ1c0dt/p4qH2Ai66qpXslDAYVIOwG1UywZ4yyYfGjwKvjF2GgKsuYFUWaSccLnhpdxccggpYCXkkIYnGTYUR6uGQxc0wOFPNWLE6GiVYqEWHDoCkYKz5PkRzCxLU7nv25R6hPXWotYGcB2TPQvKJ+Gqb2yDL34uUARDV5qRGOXJ/1L4YEE1LhL3FnG5nDrm2hQybWYqK5qWdYp5VqXh7AbgQQeLrsTvdGEKQT1rEzq2uqe1wa4n3jRqHXVpFZQ+zcVKUvwR6UNUDrQzjGITia3owBM6TEJvrXXfDdkbGbIJ3nJ8TRjJ7QOT58PeQuRKFQsVU/4tlD5iV1jB2+rs4LUJE4N6YO/Pq6Hz+OgCYoWeIyT0sF9PQCcgDLxGm5zwg+kCgiVTEczQIFJZsS4YB+sxz63Dgae2n4Q//HoDnPTewLHEU7rIrFHet5DbOgvCS8soL7mvH8crRse5ewxlqb5gz8YtADtd7tuvH67WJijv3o8HYetnrQdh+dylEOsWERWFTspyZhh8hp4Fivea4KeZXAPxePzunbWrLwizjqhM0D0Ttp0+X06A94vY0aW90Vm7hYqvXFw6YEg2nCZTyg0cOHGa6ASyvIfP3APN39/cq2KVfJTpPIWfxLNFcPFl34ZudGCRm5+QnL92by5PA8zktZ195RBrozcmTvY8gBxX53BwyhNDAHriobVw9MzQr/oYFJqx4FjoaEcTF8kJ00vzwhrFQsaQsmbuMc8WolIdBy/uyJZqheLIdYsqHIEqAOfdM6YDGh9dCwmbfX3hulIY+8l5qSI9KfbRlMU5WaB4LUc5v41791V2NlXXhl26OQBny5ZJiUlTND0sIaMop1qoeAO4yW2miFXEFdaNy6H8LecI2XgUnQ5YRwG+S7MSP4tFjKaNm7bCaWddBB0dab0XGbAXvZxdjwV3vFIMLO2Bf/1tLUyc0JHWIP715HD4wlfp7QcBAexwdLZZDsPxGq//GNUrIWttPdchBxWRvhKua5sOIHFgcCaAH/KtH98NzT9wttIb9/4FULhrgNEjuwUKO3LkISKYJS8PTE8LFIeB7khDgWmyOGkthf5dGOeGFAg0u2V9YSTSQkUIFliXnOTixoLm204JUKTBieOi7njvfmi6BRVjWVRwFmEY69fwczSLwmumpqb9cMqZF8LepkCRNPvCdLE+6HDUwTvroiBAECgr64J/Ppy+t+b0+Uugg2z0ifsmjtj+jq+90wE4XsVVzVqLkJepXHgKbTy4boNz5xvAUWzGQZS/F5EsjsPON192Jv/hGFQsxgu3cLYx5NJsT8ljS4/H9fPAVNeIMYY4xOtq9V+gdxqEXu+Cr75+UUJw3ihPgIl9qcNkofLkIFKqcBm3RT6pnOLWRcGFyYaMXIMTbz0DxSk3ZPbJNknXATAA1uJnusslh8Zy/sVXwLMvrO5X9uJarvPK4tIFe698tARmReCt+eobg+HMT+NhyrhWDlnCcERrOzjJmu0FLTbhDvJlv4b8uG5eniO+ynXLPbP77rege3GLYzNDfzIRht5d7tkF8xjVk38LCTd7+MRJ+mICfR69QL8FX6Cf6kcDr+/f7QBOjzHQCyd9LpGFyhVl05CLyDc8N+0mWIaViqLglAuEBqRjatj+3ibYdwuK4DLIiQ/EF79ewc8s9gKYd3rs70/BN759PXR3Rx8LxK/toN+zszSg9lQfwP2VsrNntsLjD65Ny1vz4ksr4V9PjWLctwouPAC4gId0UALrSQjZunHYKS/7pNDcyWJDyssFVjsCo+C6SbwhvX57Snqg4XUX7hvrGvsBFJ9guAduDWV9rYj1NQ35t8G/q+NhNxieuDNe8pYd1SsvC7ru1PzpTE067fZ6WSTk77ETn+v1jnh0gCxUzpp4DGwq5sGhxKQbO9u48ikKNF9TQ6yHi/LEBsV/xEd0Qwtq5lsu2hk5OYjzfg4/Uuat00Br62H49EVfgzfXvpMxNbvklDLWgM5APfL4Az0fQdWMw/BvDH6liTWOLZJFys5dJYz7VkGcWuCKRbb6ArVBa5NJoak8RirEx4AsMuwUnFbOCz+ZOx+EjetmIG+aE9Ii3/X316FnqruuoHzOMoj1mHKjbHhgqsrb9vaOsqbtr1F009DpXQngONffQIrdGJpqWS6oysVVjs8O4CkKGAHUdq844zCwjSM+qgv23lQNXQucr5xBh03WJk/j50T8hEn/fOo5+ObV10Nra1tkOGvghAIYYfoWpow/KKu1endQrWvihHZ48tE3oaQknJ3/fnzsYdF7FkFPnD/QIR88NhWcCjC6xHPnS032WXnYAX/30sZX4UNT5sOBgkKDb9A6cALK3NUT5vAH9sK+mzyMO7rzoAIB3NgbwsQxZQb4OcEOIjZE0XEJnLoKWFmvnDd8wPgwPmDs+CBMkLX1rgNwnIaPI4H+wliKfpTeP2neO7XFpbOo1xQOlO8XaxCiFJm4wjVZrsfGaqIFyRU+BteD37Ud3wz7f1UDyQHhAIEdEPh5CD8fw086qa2tHb5/w81w/1+fCO34Y1xb0+mIUjbopg3VrE8jdngfc1Qn/O2+t6C8LJw1z84fFsEH754LhxBkudLcvKkxCbmCuKalheSCpc23NA+k6H55UIQR/v6x5Q2o6u6AFpTRzJmxBN+LJU6cbz6jSvtg5A3RhvJeMndpgkhg2z2+HXY/9bon2WO7C2G8CCmgAr95M+OrWCdpKTBZdcqjJ8nE3XXVqy7Qqd8rj14P022lj5THyXkvdoXCwkYc4y3jA/wVguyaAY+O+vOIq6Yx12dVHu4sSjE3iJMiyE85lCiKw95foePPCQdCDe5OuBMuwE9U6bkXX4YvXHo1tHd28JdSjIr5lhPGDQQ74ht+fQ9079fobNgqg3Hf4SxbBg/qhttvroEVS0M4a/0/9Nr9N8BJk+bB5pJSxbyQwJhoSmvOXS5M42OKO4qrjeE2R/R0wasb11hUKzsKiuH46QuFCE85FFyIqoob7By75bZplMe+ordxwzMY32SEtw4lf0MJjP8YOjN5TKh5roRUYDrK87lwKZHoCvUCj32JvmsAHCdjHg7+JfyJ+LUBjV2fXpa7cN9cg1Wsx58hefvyMZ7I0VC0eRCXKXLocjU1pKatehQT+vyUnFR1y4U74cDXtwdSct4AN8C38BN1ajvUAucuOAFeK+pfUxjUUoXPmb8SzRl7kvDtb26DL1wYwO3+OWzwRHO2/ocxei4vmw778wsEp2zCBAdqLm8m2QI5h6GanS1D+n1pMg7f3b0VzjnYmDL9z70HA+rfXwRlp8+HvMNca26KMER2KXN3lLEIUY7tXOYcMPZlaDfsQn1AYlyX79Ibev0kGHrveJMNkPRmt1F/2suCXOfkHUKW55V0y4N4ItG6s2ZVqBd43pUAjiSmWANv9UPwfgb7fDLuEbKWsXiIjvz6DBj479E8DrMMki/leMrOtgNBqpKTAzpXkDqLVNqPPQj7frdBK5bKZXAZ/Ao/kac4PsI5Zw7AO+/APcPGwrVjp+B1PDv8h/2GH2RsbCoCWqro1u91GzjhuGb43c3VenLx5djiqtRW3ygZCD8YPRkfIhmCQG0Vo1hyY0cm4M3ou41b4OQ29xvbODxTduNb35TGnbIACrahC4YEP8OhyJS3u9mKG/wwcfwopiEzra4ZrbAbPS1101h04CnycODRrccAcmYFw+wkXZPciz3xxCMNtasiCVGdnR0QlBoR5sf9gwbVgCyk8wvyETYVdVX0cPIUBO/v45/fdqq89IExMPJHUyCJDAd/Dkpw4ir3poK5Ym7I6zO5Ah2Ryp7b3/EMUXs+nA934SfyRGP4GMrSH3nEqPogvq144YRZ8FopMTKZWcYKlEQ+JK8KdbhvMXuG3b9anyw/dEg3/OG2DbDYSyn9Eyx5pf/wDsUKYE3JIHgF6d2IopAheKDO6TwEJ7QegtGJbt8Kbr0E4NJbrdmKXxgOI6+ajtEpuUu/nEVneTsaI9rc/WlZJEZ3QdP1mzDGT7AYMRUzMXys1CU5KDA5N0P9JftyTm35KDc7j9lXmutO7EG5FXfs2VsO+2ojMfnS7IHv/PTJDHSjw44RocwHKftkT1M6RYG8xyF40/uba/DH3UfuUAyG/3gylP4bbXk7UDrODXoVAbj591Qlp7VdrVgqH2+E5mvRcdVmN34KnAL/wI89NGkk5P7859Hok6w+U9P/Bg6Fr4yfCa30zJHuhvLplCrx7I0Nosvxu+azsOZJ+L/Lt8MlX3DAi/8gIVD2bdFgRzJh1kr2IQtVhtx3l0vQ1KK1A2HoLydB0ZohaHIozRXdzRZJ8d45twUOfGsLdM0NEReGPDAXLXUEYT9Gxk4ev0Ne3XOkSyADhHTd59U+9Mb6zMASSa0SFzdBTD3+9NajYmHH2Y4FK3GNEktBNqLapkajzp8JA17BMK3Kld0O2qZJIce7FJGK4DykkpQPgsvZ5Z8tZ+2GA983Y0tMhalQjR+KcxJ5ugbF/z/8oWe1bXhoXTtmMjw4HKc6pMjCqrAK+xaL2c2wys4g9PNqw/pdEj6D8W+u+85Ws3pywF2AP9FYjHp2+1P3AzzwSb2RxQ4VQOH6gVD8+iDI31QK+fhvCoPcM6kd2vGBkp75rZAYkp6T19Dr0QPzXvTAtNxOqX/iuT+9rlpzSQZd/tY2OYqDXTfG/y4K04RTmSMSwAV4U8Bfa9CNqKiWuXqInZiCk7IH1xIpXEk6GSgNv3I6DHxstGlqqCxK01pFgLciUlE9ONUGmV+bg6lh9+Q2aPzrOhhQWoKd3YO+lgMD9VMr86145770Uq2slGkVymrPr5iFT3BiaFC+HwVTzi0kjDs6+72AbC6kxhTdVkgLvHXZbxqehqJTJd6pH9wLv/5FLeShfxTzP84CeP8LOfwP/VN7CrOScRw6LhXuxge3WeKiEgbdESwBN8Uy07Oy5pJpxf+2EyiCLmeF5tqNCPB+QSxR7XJ9ICNFcpqNE4IvL8AK/DuNIdT8jPw8Bqh/ETlx1T2YLVURoU0Am507V60lzGiI7sqrZEECLrvuPLjijC9FT7477gD4whcC10v2xqdOngfbi80Ic4Er6ScF/K1bUk+DFQsOwH0PoEET6oQznVrxTK/EeGkNprFHppvUqr/8GPTARKclt2SRQIpMaT2hxnCbMxOJZPyO+urVwRe2S2dDAYQWlXohkwDvN7DpY3qh+XSarMPCixjnTSnJRD9pLfvhV0+FwY+gSEGISSx24zYAl3I/pwFYTQ155+wilfM++RH4wXe+Dvn5EQVUefBBgE9q3rldqH4ZmsE9NuSokEdg8KkMwDi7A0fgK7x3q24c+v872AS/bYjuiTa3AV3ya4DbvhyclhktQR6YCODyuTezLWcTRe++cLbaSfBiHK6GApMbGOzfc3BW6763I3vk9IgBcCQlyYopsiDu2n6VSJi8TAHv0/DfT0QxAtPUUN7fODft5MHJ25PB9rlYwXz9x1o+tW8oY/3Ux+C6a76efrf/ifftD38YWZXwXqCyE/cNHQNXjcNgbxGLSNRB+imx0ieIew1+IhQveD+7eTf8dDdtl8ykl/GJyaWr2ZLqUym2pRjKT1tk3QMskmFmu8pFKMkkyr+JyzE3VJrU6WPkDTcapAbpt8lzgUwG+1OygjebYyAJ5cyoBiFNDQE5D84800o1g92rscQNsQmHctYFRxd8uQKloFkoOY9fvhjuueMXaJbrF1jaZXTPP4+ugCehL7S/WZouff43cBh8Hq1UuvDd0Sg9M3vbUkXOjW7EPDu9qP/n798N16HtdtSpC0OezEYpzaZefR7FeVTDvzGtafC/xowSeGphVHgJLhOPwnzQuKsKATgaQvbsrF6F1IkuHSkAvhVJMik6smSlJifwJm9REgFFm4Sp4YD/joTYQW5zS+ZMKiduBLVXFGN2kyrp8SbtzVNAAcsOHTIY7rr9Z7BwXkAp1mpk1973PoB2MsKJNq1DhxSK6thOcTiEw1IY5xqTo/WXPkc7Aufa/DhwDvLu1pVU/nzkxKMG8St/DPATDdvybNDI3sb4ect2xbryxtntjKI2H5TtqsYB+PedGP/bOwB5QKL0ewDH9flXHHN6EZMCEi2C7BuxjuOZwlJNSRan5eQI6netovDNQXDUl2dCrJkzAnZlpVWxad38PGAQK8TKimsh/YL+Jf7kX//yhmvgzNM/qDeUdevQ3gYNbg6HsOnVawE2Fw1A5eZcaEcLFWNzsUH0jqWKZrdds+lauujk+8x+NDGMiBN/HVmQhRRHqm8iy18qZq44A9enYZHuLsXWnCFi2H3EL4YCM5H4IwJ4pCGs+yaZ9WlHLwS83WeXi/M4UjlvDiSL8f8UfT4rczL6CzOhBD3hTPA1wVyKVZxipVjtw90sVGhbxOAv99wKSxbO9Z7NjXiWLVkC0BzMk05ziViy7c4vhBOnLbSAeJh6+kIZHe6bLytv22YJLp840Ag37krvdSaa9aEYR6tlSF+gUEofumGVKctoAAAgAElEQVRHSVX5BxdsZm9ciRCcmTIftDJCGOALb3+N+w5O69zzdqSKh6yARaamExcMrbi0niTKVN9c6iX3+MWGwlLNlAQKXpxVqeHwq6fBwL+RpQZ6iDGtpfLSu90RwTBB5DyLXfZqXhU5N065iouKoPaNZ9xl4nVofHMsart2787aNOwpKIATpiyENgzU1JspXasVHc6aA7g+R/Ce1ma4p45UMOHSB9Cz86kPhCubhVI/GVk595bS2MB6V70BI5YiKBM+Aiz6JVvW/LqmZNHqttgbkSsw2T7U6kEfzISkPBW79fc+2DW3LpGd9ywX8P4efndtb4xlwD9HwogrMB4Fxpmw2I2rXmpCLu4kJ1RlfE5OPwUF+WihciZc9Y0vQ3Gx4oC2dy/etTGcJ4F4ltMe5MTfP3UBHBTR9rLcfFab0wF6lVuc2tkG/9i6FgZQkKgAaR2qPOaiJKyPJnqW56hhU+aPGFwyYJuTn63ujcYYn8vJaLnxKMTHt0G76qtXuQQTCE+1/gzgZEtJsUL6Q6IFNNEFvNNy2oli8BSi9qjPHANFW8yn2yxXQHHSWxwcDNeyVDm6U59KSorhh9deAZ84A13z9uFZNns2agBSQ45GMR6dOrYWlcBpk+ZAK4L5kZx0gMmeZ1C8Bx7a/hbMQjDXTeSwUztDN3fW830fWdXvjZpy7KIBRQVrLC8N2ULBZqpn8US8fmfN6oqo6++XAI6HH8U3SestuagJ6VEfsTLHIaFTA3YmgTTSJAaK/GQOM75R582GAa8O5XCtPJ3lZEro5HrvFwyLXPLPOeUkuP72n0N+mz44hBmLTpk3MbreJ9A6pSus2aNOI5iH38w9zEE06wmTzU8GTnU6dS0fOfBv79kOn9vvH1f8+eMATkAL0D56n2/Fng3FviUqKlfci7LCc5igkE1HZuBPZc4l/ePxxD07a1d9JswcepXJzAii7qWtPiQQvWdJ71r29UQOyychkZ9N6WgSSIO4DX/6lMpnJFqoDPgvdo3k4ixErYi5QX8xrE/4EvULhuU0OQT8nzxATiTR2x+HWQzPop34BRg/hcwLueQ+/UBWsh/2QGFh+mcvowPI1jJBpOCpPTwe5eI3N9TCCOTK3dIstPneQOYEfTOdh1P6Z+rahKrlh3DRYvzh9GjiPExrnYaJrji3W7t7Zu/f9HJ4BYMLbfsrgJPL+ei+uV6MXhHnfSoSGB+qckj4aDb+tk9GSpz16LFw+NuF6AypxBe3Abjd6cciC1c4G7tyU1q9nNKyD36zs8YelbZXpvShIaPhivHq/d+IGsMAPUzi2zkTQBGsNzoiFKrRK9+weDf8ur4GjmtLfartHXQ5mx05LAUbo0fudTgJzAyqbMbCUfmxYsINXLrWOZW6yygfL5Z9yqQCk23JyEiVpYqQ2NOwKbKj7uvpXCTuvS7gTRzBp/viAAbDYHy7bT0M2DcQPnnBZVC7aavRTadQtObviNUw+Vc/5SZVurDtEDyAVg/FARVmmaDbD0dPhDtGOfhYSPkCM75ReHS8ofA3IPnvTSL1rW2lC+BuHj9GeaTDRw7uhZ+jqSEGeDWGeyqaEfyTzAn6XqIrwzCcIOZcML5y2S/zY7HLZTfNA1Z/vkxRonsZq/mg8dRhd92G6ELIqqTujwDeH6xPrkbCoj+aQ0oCebf8C3/6JO3/jLfNTytny3d/+Au4688Po1k3WcwqIhW7JycbEPfulMniJETf2cLSEgFiCN7XozjlnIM8jldvpk9MOBpewQcijqSkC+Be+dTvhqAo5eFt62BGVzv0ce77c7jk/ijnsqJqWS3aYkdipivBnx3gHrtY0i2RSNSjA0/kCkz9o6cPrWgk3tewO7/oQ12yd+UPOKcXufYvCXQP7VNyb9nXD+LZ8m8Hic/d9z0M370OSa7IwCU4251+nJSb0lHTycyQ1j/GiIBTDu3DCHm1vS5SWYaOPg2FMlZ0H1llISUxQfSmukDPQAMr/jFy4g/duQce+WgfoZG1G4/hmvuI+quKyuVxjEAYCzJOv5FJVsWO4fbpQguUP6MFynl+9YX5vk9ygV4DQeLQC+0/CDPYLJR5CAl6lgd4X4Hf/SwL/QjcBL2msw8/Q1zOlo0oSjnpdLEGZYhMxbnH9NA0lZsWhRtHavY4nHCCY31k/hHiu7kdh+DR7W/3Koh3FObB8gWLYN+hyB5NCTwXaoF0ACdIWb+8Tt+3nt4I+29Iz3szLeI4FyYGaQYuLONKN3bakllFBQXr7Xdei1msqCvduN9Ujd3ctrM7uWLP5lX0MHnkqT8COIXJcRZPRE6eQBVSEKolSFDnUHpJGIXfk8thREGzA/XNN/N1cB18Bz9e6clnnofPX3q1GQRLcfBROXE1vripDuQu3V5cOIlWl7a3wAM7egnECbPxHafWCTE47uRF0Hygd23E/UDVb1IzxYGr7XbMPQR77n3L69VWv25G/b1FdEKVo/z7Tyj/ltwHYzvMGDg6zXNeO8iDa6b4JJmsr4k2hKza4/4I4BR0+uc6ZM9iHnQrZE+hkc2pc0rC7fhFZC9xRDm2ozCE+m786BjQ/fzmO+Dm39wt1Hn2+ClcyiLN51hkTgHyrL+M3RaycqYIS5UNJJFNv75uE3zmcFOUQ/Svi8D7FfwRoVv2NqG35mnz4eCh3gVx/45Hk0PnsHCT5HRVtULj/W+xtyt7OT2Pa+wEex/Kq5YdxhtiqXSJzwTo2elnmhEmdtZVRxuBsL8D+Jk4ANSq9ZlEXpaTcFG4uxUmWXxvCroVMlB2Zsf6MJLzTPzoplt+exf87GZ8JZ4pLDkqW1/8EdJBAnM0RVStUxjzw6IakqiFG9qZ/+N10fc/2VUL56BcPCuJwPs5/FlqbW3r9hI49eNzMUhi78ZNyQYNtOzLPVj6riltsOfPb0FiWHoPDqcxVopDPBOX1Xa1jvKqpSei8v1/ljUoMpgHkhrdnb5M3wDUAPBE8ra6mpWXpDEuz6KZOIwy1VdWLxJ9JP6RZfbMdUi0Wik4FT2g7J6ScAN++a2MEiZk5VUYjeAd/Ohw32oT9Q274cxzvgS7dqOoUTj9GIuWsd7WSHhGHBW2OQjw6SzjwG9PUhG67PABFlwpo9JoYrDp0V18R8IpvbkOvTXPOxq6usRDKpny3hPGyEHnIeS0O9LczzPRTyTTXdYOe/60HuJlnVF1K0g9/4dLK0W/VFG1oganzDTyl+tScx75bVJ3VqxHAhU9CPtHtVRXZ4wT6XcALkCc3PgmB5ndDOSlVUrgjQJAn5SEasxR6ZetN75/BB5Bdb1FYa/fjeeeg1s+9Vm4Ed+eTOblc77F8Gjk3Dd7e1Aw5By4hfyRWhF/dzIvlIrN0w41wW3IjWck0RlCj9d9yLv2Z19Ab80vorcmRaWjbvshWZDORlmXaFeLm7b1UUeEwvaeKhKz10FH88A4NP7pbeiembnY7g7kJf3TIlyAFhlO2dTFFfmFhdvJc0fy2LpQbG+D0dQv8LedHolkO3LfPMBQhlJ/BfBbkR4Zu5Zo0PoA5pmHxLNc1xzLJVnArcgeMdXom3aWkXiZ2YufUIv6x6hH/g4qPfHtykMYS+TDE+fCVnwJ3rBGYdIQwZEoYhPZOR0bcTIvpP/+VLce3otOP5GnB7DGs/VqfeSJ0XD5t2zemj52wF41M9ymDH1kB+qCvh/QM6DEMTVfvQVaP52VMMEE2sdgmyn+oOXIfSP/MMNpbOLCwx9jEL4L7LUmZUp0zlYvesSTyad2Vq/MaIDdPrJ89DaRzIXEJ+6bAqP3Rv9JfDMbG9bzPEEHNsz/SLARZif3LXALfAU/gVIcw7ssWoRCo1Sp0fnlM+F/gyjEC0/2jaOCtpFJVWw6OPoQiOcjJ7+hdjUMCNRRn8y/we+/GKzCG34xAX7ze5s/Bu5yDgJkDmmLFW1c14W6luWJMtpKsP675fYDZbVckLwdiw9C06+qMy0X/w2iwJftYxszddHRRYVF61S/ec5OiOugJnRIcR7Hdn+4UUG/qyOxZPfWVaQaz1jy71HGmk6vYpyGx7EGfL48q8k9LKzr7mAwQXDRpxK5zB/ETyDu+6mnAM44w/Pdyq+UTYfHMbYI2yYyoqHcM/Qr4cEZ1Ea8rLsDXtryejQ2mD/CjlwVbjrOvmA2rH5lWLjCfbSULvdN3dcBcDVPojgOB/5vG7Sejdx49Cp8EmMOxkWcYrqLT6etRs56id1VkjPbUskuuAcLprProoHVarAEHsVQeF9ajb1TndyQCFG/QO+0fPozgFP8s7X4ky0TAZrmE5BgLwTah0n4Hua/NlCZLGT+I3oZX4gfrUSPL1x6KcCDD2plv2zcdPjb4FH4Eg9DbKWMdcP0io04xbCkWJZppJM+PB82bs6oaDN470z9WeCyOqAsKw0C9mpHuie1wb4bNkLXHHdL28Adp2M4jxkIWNOYOQMrhg9qkdy3NGuVDmTS+omvTHcLFM598+uVPeqNG3AqivxGjH+S8WB1/RbAOenhu/jH90NMfJgityGxgsvd+yCAL0J9zxr8+CZawL/9LW4TZFcPpkai8yr/+OCR8BUEcobicpWpnA6JE+w24j6emqTs/GVdDXz88H7frjtmoAAHd4QrqpZCsT986GNzYUPNoPQri6CGIACcbnO6bTnlo991vOcA7PtJbRRiFXJcGOc0nooZK+5Cnfr5DCNkbB5agwkh66IvGGPBdSzcysQMVMYPKWYjJaoXsi8Xqyl5DKi3WQzxc3tdzUsBhXTBZ6e/AzjZdhEXjs+7ZDT9D2v/IBLL2cvSq+lk3xKhDIJBTHFZgh/PRC/FX3ABwBuk4A+XaIcdW0XG1Q7LjG6qio245Oz8PDXJ1mVtzUqM0B8wUYADUlpGuOLPPOcYeO3N3g1rowuobtQKyrjrtufJqWNgtJazdkPzNWhMFn4+PoJlH3ME8MplrXmx2EAJ4NzKiQKtcdwW0B3oQQdXc0IZVkLULdvs6Oget3fbmoxrccOTL+D+yVR2pBtplZ7Dn8kZaoPeGvkAEiqccWsfUmLmowT5Dfwcgx/X1IpXXLIu+dWvIiHnYwNHwFcqKk1Zu8H48GtpChfOxI/OkQulVcqpB/bCbxsDxODAV9yYuWAGghicf/FMePaFEZHQqj9Uog3gHuaGcpyJ0h7Yf+1maDsN7QKCIdFazD/PiV7DJs0bNrikFK9oCNvydMK6Y8IElElEAjamtmP4MyjROCVoSzv6RDLZUF+9cnw25jMY2bLRoxBt4Dzh0+pAXHLU74JQnachkcK//5WESVjH1hDDiryIr833HzH65tcw2OOhaE32ziqfBasoTCtdVcWKkzbiTp6a3BLNHcRJlvlWzSo9LpyMuPC19Eym2+4YDz+9aSJTcPWrpGMnZxuQLoC70cGpfHxYFxy8eCe0nofPt+kpOs/A5UFGDCmpvHLZT2Ox2DeJ3UYg5Vy2YBr8HJXCzp06Jvp7PAGXNNSuvC1sfUHK9bMV5z403NN0Zfol/nw+CAFc8pI0lmwVrkUCpR/goQ848niaDD79NMC552b0keHTJ8yB1wcMxGfakKo8YAoXPwpuyNEqhW08YaZn4ZqSMADjUq/e9DoMT9KrdS5pCf7+WfzJQnTY2k0l8KkL5kDTPtSpa3r5BV2nnKMMElIpaAv++YMAeJDzgalH8hPQdvJ+aL5qCyRGu0or38ClsMCtp2T7jVt2hsFlZxi8eegHbl1FCxpviT3IfZPzsNT4+BM1jRxHDIBLGiDVyCn6TvxxeF5Fi1IkU/8GEuYZrdw6mZJwE2b7qk7WTOQZASNYqFjHdBFq9v7wh0w0m1LnmfhgwprSIYIh4gqkFE9NQ53Ei5veb1ZpLS3cBH5+3LAZzj1EscRsifxeX8WfLOoZW1rz4YtfrYIXVuFDMEHQy4/6Udbl15bP94EAnKkBg0MMzXR3RRu0fmY3tH4SXx60ir5cuW/qennl8g4kfjFrN+PgjQ0yRsQMoYz/eBS9L7MWJT04ddNcANkqjouAXoAmA3/iw/xSC2agK9mtSJDVfpkDf9/LcvA70PTiIvsbE11dqPpF3e+mALLkwANPLXAPmhdePR6tU2h/MR7F3GiGxYDgaEj5xHIYLszOID69ow3+ja/EGDFTKHAv8mF4bmU9Edbe9OsKuOk27vDj92qLVwcz5a0ZBITt/QtS1vPccdGeGvXT+U5MbSwOHe87APuv2UxcuSf3LQA8KW95YU0egy4alSZdyfjk3dWrtwWtI2z+IxbAJUFwHZDGjp5Som1NP2SxQp4YpCGux5/nkAj/DUtA7XJJdpk/QTt/RBkdue8DGAlg8mQA+rMX0oOlI+CbEyotIhTCcSkPZxtCfHRBfFxHJ7y47Q0oIndNOpPKemFgSpPPPDscLkZuvLsbhbpHgLcmP4yCSYc8wT5gZQTGidJ4Y/JQ4dcaNr5IDgkpos2ioyrnHDVi5FqLGD1D4ix1dRmWinnJ9Ts2rDw6myvviAfwbBLTs60kHI/fk0VLVtOD8CA+EaQ8ElSPZ9acORisojmr/bA39n6MnVJbWsqv2EyaoogMxb+DgviYzk5Y+XcE8ahV2SEpVbNxAJx+1lzo6MyA+UvIPqVVLATohhWhUD/dwAkPBjIxaUlA3loUwW1FKN90uKfrrgGx/Ndi+bHRzFFHBlJLa8D6hZPoHIDkWVJfm1nXeXuPcgCuP0fp58xyWNn3wHvQvvI5s9/r1wOsWBHYKSf9gafWQHF4p1QtM12QacMpkQwlqDuCuO1ZNrnZycxw7Bh0uX8SQTyjMWj1KdLYWAgnnTEfDXv6/8MQLlIPV2L44b2XiMOrrFmOKxBZBEwEULZWUH4iRXGZsjpxGjB2o6duQwe6574W3FdEfzml5MwBeBrEC1yUu3ZR9OlTApcNWIBinZDishA/LGHoVzj1VMDXCQLWlLnsXxs7FR4eNkYomzg8SLdn1qoDJ842qce1mMpPnNgGzzz+Zp8B8dbWGJz0/9u7EjC7iip93uukOxsJZFWyL6QTCYYkDJAMgcggixAQmZHVccBv2BxZhpHwKSCoGYkSENEBRjFiZkYz7AOMMOqwSLqDLEMjId1BpLM1JEAwQRKzdN/5z13ee91599W991Xd5fWp/i7d4VWdqvpv3f/WO3WWebOoY09DKOcRc8jHI1lF4NWMort6BqZ7CLKW55DGbDYGN8h8Pv5vPcg+fxKyzz9ezbzCthUCD4tYtfUtO2sw+7GXxiatVmq39pyg+GX8HOw5qN57L9E552CPkFi2lLLz49FMxi6c32v2rsozLyzd6rkkjoTitowguyp+uE8+8R36/s2vU138z/G+c70H783z8/SZ8YdQa/8YzWI0rqooZByoTaBK/hPxmoM8Qdp5ewPAyycfg+6756jQ9V0bWs27z5f2KwSucZEHFmVhe+xYvSwI3CZgxYEwh2/Bz2T82IXjmNy0b7yfgOKMV/M8NR1jFNczE706X43d7l1zwzD6VH6MH/iPFjrs0IS/cbRjDjgv5vIhXkLnjjuYXmJTyrD6iBB3wv0uUwJgiMYaqwbhZpVVi+pzb7hM4MW0fnlTpvgV0cF8W0DgZT1ENcLaTZQQuClkVXIR5hpVkBWBvqyqGvTzmcjI+wx+BvMmvw12dAvwfnjbeDiGoMPzrceemqsGcXQTx/vS8cQskrhKbeIneMTw3dT06xeovm/JAWnVow0hgAPvsTVhibEPk/h5IPEXByAKaqkZZQixflUL7wTNL4egJNpzXHoIPJjli+11yWvGfW0F+aamAfIeIqzNsEIxHoGwtFMhcP13MZxECyeNjuPRpHANi7VZz70EP1fix7br5tCvj8eqios69EK7IyfNpo56dpl0PC9LSZy/Gkct99y1mhbMT8BcEmb2dhK99n1H7pE478S52KQTkXS9V1MaH+RAxB+E5X1uvtfUMeMrApiA9sQdobVn/Zp6HGQ+FZuuMo33Peqzmu12lh2cm6NVB46syAeVZ+KHHXXoLXisXXcdEccz8QxTM4SIrQ9vnOtE/OTHsYTEnQTI0cqiK9vp0r/fFK1x1FZshzALF4x+/AqT+JnjZ9Dv+rM2zSn2OYAXdMn9P16wASfMSpGutXp6Rp2nlnbqN5fqRdBlWzC5GGLtV/PCr3ZK+Z19+7e3P8WJX2IpQuCxwByiE8t2QeE0bMeCoA+FOmTSTtqZ4/CvI/HDeSwn4edz+Jlvm5bzc42H4POfJ1q+PERH6av6yKBhdDEy+jghxFmd4nCWd4AZZcSnnPQO/WCpoaTI5QbE5vXs+/u6erRM4qdOnEm/b0hZcgj10JU1VKTrCQhaz69Db/ft6L/dlyAqJ6JCsazt61ubQkc6VoJZoYIQeDXoGWyLhc3B6l/FVdkhHM4rdO65RPffb3A08Yn+27HT6VcNQ6iOY0K5JJ4PGKKu3CjPOG0L3fKtAGyqY4rtLnkHy5Zq98gk/onJs2lz3wYdI9AnowrVhjMI9c7arsXnHQFYyK+e/f+9rtzf9q8AMvWB5c7Ysl5HGjVj1mXlxpvANHXDVpvyQOBsaojswYpyzTVES5aoamXq84cGD6MvjpxC+T6uG08VKpTF1yPY1VkxHORy7BU+zQhB3t5NQfYBmj/lMNraJ/vOPmEXWtAdeKV6jgq8eFDNqqhqvrWFnYNXH/2uQBq1s6K2j9JOCDwKaobbYLFCmU1fV3bD9t2fLXGTVzbIToWtp9bR3HWH0o5dfW0HjajlwZ+9QrNncqwyg6UK8vZGtRvfNk6BOqWtn51IJtMl6K7amWTQnbrrJ1AGGSfJQimV+dc1CSzGcTYInPM+xVaEwGODOlhHIG824G7FVTlZMycangTDFc6gU0uFVyRHYscXCy6HHT2LtrzTP5JOc9rUD+kXD7zsJFc2VTSQd+nQLhndSI8hYmMSKgBTEFWUG5DtK7rW27pv1w7cDWEbxmdAx7w5PstOKzfk3baVhncL3UcrBK7j7mmUgXVwH8SdoRR5MfKl3nWXslqmKvBG+0FcC7uP+vAFc+jtLXBD9w1vtO8s+/TpokfvbaHpjdGTKSmxa0cNPrCMoDapJPu7w8bQrSPGJaPIVU5aVSHYjtqTokOFwrIKoYg9wa5jmGq0uj5H8Kw1iAMeexg1IXBdd1CDHCxCTg0He0DFqd1rrxHNQNTKDJoL+sLEwaeacfnkWjlu4Ux6/Y3gbujGzQe3Yax8XKWZvD18fgfLlAvg8LO5T32I11a4RVg4+wt4kBhOerDaugjc9sTkQODupMK87ION1L8W77535+jjm9c0sdFBrEUIPFa4K3eGdbAYNb6iHFKtHVxydPaXcY2vPPN/WzGCrvvGFOrq8teJjB2zk+68rY1mTDfoQs9WvtNxtSvvVNUVFo+cQP86lPPjamTZgGqLsIMPt/cOJ105ZFToctPNFaIVQi8ehyoKdujvbGxr4s1X7EUIPHbIK77JN+NT9UKYNs1xla+F8glM4n9wVdb4F2a6dWsd3bVsNLW8sh+9ua4f7d6dp2FD91Dj1B104iffo+OPfZ8aGqpPY+oLLaw2bVerN+ID/3k4+1w8ehq9i914ZJdNe7iupUYhw1F8cyjXU9Ddtz1ydpWvFIWyMDdU9pzAXNtwkyTOLvxd1u5pHW0vJPJACoEnu4YLvWOBQulJ65TDacX55nTe/mW8sNnzbbguytA8PgBLzAA9rI9/zNsQHvXyA6fSk/t5bgEcC9vdYdqHeC5xuTxtP9g9vDdNjVpFrn79htmxq/rwPkck2QKB2wHSDDOc1QnTwbXxmg6W4ml4eqaWTO3JxQI8BbN6RDmzhx4iOj22nKnK4YSuwCvuTFx8/uqEAslG2Uh7aRq+JxjUzAQB4qcHfIS+NmoS1AW969ENSuCMoRPYikMUO1xuCiro3d9E/O/IMYyC3G9Vnd61ClRoJPg5FuhX0f03lUO4806iSy5RVktlBc4WuAyX2j0pXcNvwcHyHPoodaZjWGuR+PM02IzvSCBpgYeATaj8j+J/woETZvttS67coJTge1qkFFQvSkV60CnYluc7rA+ssRs3Nm8N2spEPSFwE6hGkIlFtxTN/lHZ9IYbiG68UVktVRV4p/0NXP+Ay6RNtolJr6PlNIHO86jKRBdRZO6A9+aJEw+ldQ2cxVlKzx26H4kX/DUVOvWeiDrc7xyPQne19cO9nTO3/v45ToqeaBECTxT+YudYcOx5yR6YlUvWCJwdRVnXHWuUZBWIgT9fhOf1ctROOMe9/3gvHT2VHhs8IvCEqq5oOz06KoqopVIuzHIyVeoTblNuc+0lefA+dL4suONGA/c7REUVi2epaytk7ENRC0kbmmJN2lAJ5+h3Ierdk3ZlEcDCWIQP1KlzsqJCGQPXuHuw3z42kzeco9t+ARyFDNB0Ydpn8PMhI/dc/dEpbMcDbUHtPdJBtC3lSL5wsOkZ39gsX0z0VIqVF8rXtvLhkL4lLyn35fDWnq7cBW+1PZuqQPu1d7fT/rT5jA+Ljb0v2Quzckn/IaZFV2C7chPIO2UB9lTQup+zlfepeNA58bRapRVQqMFq7Lp92NjGuZPgx/IwwjjV6+RwbWrjqgBQU3hZAnfd6r2uOXN9MeSVZyPubysOmWiQa7a6/nzVxtdffK6qKRhqLARuCNiwYrFY+Huw2q+vvR05FieGFR9PfZhl00qq9/OmjGcQVfWyCyaCx8GhiL8NsVVQ2gsC4tAMPMT2uhk37Yg5RHVP4s/9LLC483Crya90kgXCdnerzmfpp4myapkyb5+iuaGT+Qku8IX8ffaOnKfaSTv67GkYjcQMCaRyCrfk0n9nws0n07WxuDZgAmOUk0ijI890+jO9hKwTnBUtm4Xz6ByBB/g7+P1XGZhCB8Y4yyNvb7wHNv5lY13eWgn6Hlakb1ct4Gl97XM4N+mBtyW1mSCsdto8SsH03+WdfCrtyovqFadtNysWsnYgqmAmwkIKgZtfg4F7wCL6HiojoaWiXHEFDmX2DEoAABAySURBVAb5ZDAl5e+g774bKpOsWZgU4WP/ykNB3hfgt7Yk0wbvznuQ/bGe5F0g8alzhvfJ92vBfFJ7+KoTGz+SL/v/3V15RQJHZh0cVMaaWScqHkLgUZEz0A6LikPJIiuxoqRJD34Dxvo11YBT/TmHpZoNsmPr9BWpHqkzOE6XPNaPvL3xjzj44EH9Ovd/DpvL2CPklWIYToHTA/2ACvggu3RPsh9xd9+B09sb1qzkjFipL0LgKbtFWEisw1ygHNYCVHn6aWU1YxXYrmo5aA/Z3DJcOKLJIZgFK37acaXdN5RdiY7CQ7sqIOa5cdPn3oKDzSt63YPu8+YIROBW12sbWpsDJxcPeC+MVOt199UIihqFYoEdA3FPKUU+8wzRMVw1gZIHef8CtHd8An3r6/LXEHUCdqideNa/i7/Z3jvNhSnpFDyw/x12kPVNQ94feen0/fO7omc2CttnbPV9dumqzbtChfJLqFAysbqFwGNbacE7wuK6BbWvVLZIIqxsHcj7addCWjnA1Fa4FcRtmwiCFcfjF2c9TntCysvxsPIZSbhi0Qlo8HjuwzyNOu/jVN9m7mzO3vSqmDPc6CPV9h1Cya68EoF3Wp23bGpddVWkzmNuJAQeM+BBu8MCQ9YGO+q0f4FdK33qU0RPPBFUbHX1+uGwsglHlbOqE5Nw60Ug7297Y8Az/S387SZwS3hk/t2vwIMaLVmuRWsgFvGHndKveQjtv3gS9f3DAG3Ggbbbum2Bp4FOQrwAfPXril2593HP34yP43lpnY8d+E9SuxpKBqYB8SxMM3tjxEPBUfz5a35jxdFvwxncHJj/vmE4QPUExOF7jQZSdkNv2N6VIO+fluKJ5/VN/HtCilfIJoxtHB7U8EHOLXsDwBuBfUrDC4Np2NUHUd3b/Uri9oVHwSHRqo4qw3caoUU3Tlcw+N4ua3rH2mbOS5v6IgSe4lsEEudDtf/CVVnZvX070cknEz37rInZWNAOb4eWOBNmVT4AsJngQpD3L3uQ90H491oToGmSyS+dCXhImcTDFz6pINujtHzBK2HQio/QAd+ZSLmdvIVmA3Guakfbc3bUHMCJ447bEop+jJGjEJYZib2D5/40uJD6WqSUMLj3uun5m8cAv551G1tXTggPdjIthMCTwT1wr1iQfPLE+tobcfnvfzthoPAVZGP7dkE7ELiPChXXIgp2PdWleoeqmie7xh8Nbni+Z0U8wKfi/z2sEpDg52fgAX0gUv/O7nu1zcOKkv9jHxp+2TRqeH6wFhJV9Zfqz7usJevbmtKuUitAqLy5qQa7Fw0ORM6B43+Ay39HxXiwaSFnrOfMPdHL+zCo+xJtoyUQwaqcrBbbQQfkXRYMEDiAojtSOrmH8HBGz9xh2aaGR4SZ24CHR9DQGyZTrVmrdLPxtj1Qi9ELS1Ur/HdXjuZuWrMyqJlmGHiN1BUCNwKrOaFYjLyzYm/Nz+HyT9O+bBnR0qV7afXqgNkm7TFzsrA78E2Z3clZtZBotpEqUWSHl5l+5M2y8bwGC+Fb5UAiNN+JNiPwcEbL/2PRPLRnfVr45xtqlaHXT6GBD42gXIXk0RHmVGhSCNEacnSVHHZCnH36D92it9a3rsyU92pICKu5bdJWNwJY0HMhk68puMbiYkcPPpRrwdUEneJakBQvyE/jOhIXe3qOwsV54Dn2BwdD4pgavOP4FyyGLXgQOBbLC2493UOOSx4T32yQd0X9NrDhNBPXxjWoEP2ch3vx7yHqd69q2SmXq3r55rf2oWFXNVL/VVgqmliiRIMeXmQFhg7qiamw/eYwspdsaFuJlFfZKZpuTXYmLCP1RwDPCOvb+eFn2+islncx8Bkg782qCYBQLkUdVkulqbTgoYyeMMCyD7yf0jWhunf60hAccg58DLGxrHxo4vVMDO23gKu+0DU2W05FYg+eDxPjfBWmgzMhMby1j9YJhRMmBB4Or5qtjeeAD0h5x6qOhpheFFgF9Bcgb3VYXn72iT6DX/enaDqssx+Oh/JPkcdkEVx0aX7k9j4NmcgH3z6OBt0/0latOAkPuLj2KVhAthWJa8XifMQGhtVl76k0j0rGi0F35Z58q7Pr9A1rm5ExPFtFCDxb98vYaPH8NUM4q1myWtowcLY2CUTePEkQwFT84nZpKQvxQD5a1WAsO9iVMa/Surfqaeg1U6kfW6yE3o8HnBluDMfqjkxOYRXiltW0vrWJsy9lrkTGKHMzlQH7IoD1fjM+zITrsM8kQpN3YedF9Af8PTEFy6M6qxPnjcTxO2Jxy+3T3o+GfbmR6lcP1EfkYYm3zE3bZ1eucNrBi2JHZ846quO15v9LwRoIPQQh8NCQ1VYDrG/29GR366yuhcjk7e7C0xDIig9dR0W2Oim+jWI/lK3raKD9l46n/k8MpxyO0CM543gxulWLEPVshYzGlYqsaecg8uDPsvpUa4QiqxD07nHjmWBnj0RjRldxB9ah7eFh1CY9+8KOLbDDSxXjVDU9Cw9i9bHILboXHf21qjMjn+/J0cBHR9CQW8cT68udLDeec6enBy/qRmxfT1tPUllHbpscKupEnk/GnHbKzVMIPPLdz35DPByc95Fd9bO4Dtja5OBqyLu4caWf4+8zE7qjvwX4oRxufMdp0ZP4bEFC8yh0a8dZuazRqnsf+ZUjryzPnZ/FVhAScVcO6c8gbRpjVWrdmDR0ofuPDG/onqRB6hDI8MHlDoA5UQd5803BE8z28WyBE3dSOE6NNhIPoR7TNUMWKBEX7mVjph05IJeru8mxRXGIOIfdNO+8ux1SepYrthEL6lQyL+H7Ve2uvMv60fq2XTAhfZF9ITJdhMAzffuqGzweBKMWC9WNzrc1xzZhO2+t4RfBCUsh144RHlNh7CfiAWRHKj0lJTtwTGYLeJgdxmjU5Hkz6uvzdyP9++FesCzdu3KP7znBfJ7fhu5vh+gLSed5OJ14cVy0cc3Ku/UAnrwUIfDk70EiI8DiPgkdh87ukshgi51uxZ+NIABWn2gtrK6FQI5WGEdGes7DOQ8dlg31Gnlilh1++NjI7fU1PB1odrOpHjtj3mTam/sx9t7zCwpyLxBt1F25wsKk9LQTduHvdVm5v9nUtpLVTDVThMBr5laGmwjWfhYSGZRO6iX8gw8sOVyAkQISPwCCX8Rl0qzwN3jojjY0AX4h84s5ybIdvOwbevjAA+cMzw+qvyqfz/OZw4RoNoiu2trbehd+O4eidnF1NPjXh9DL3LFr196bt7z5nNI7N0ngovQtBB4FtRpoAwJ/BNPgQ8y0Fybsa0HcN8UxUDzw/NWfQ7hyQCidBUHbiWOcMO5mimV/gzjOjPDAUltAyoFDAYxtPBKmj/kTsFtmS6gBuIr+Qd2OFz0tusPNtls+D8nWx3gVS+jMsrah3u1W3rp14+pm/uZWk0UIvCZvq3pSIPBXUSvtmbfZNf4YPKPt6hnprQFK4BfGIk1Sf4gH7UJNsvzFWEh45wQ3S7I0g1kjvfywOx9QN6j++FxdDiEOcgsxCQ66Fqb8EWT+aBdZD3Rt2/1ER8eLfNhd00UIvKZvb4VnXUPEOsPQ3Q75/wTy5sO+RApInFUp38R1Nq6wzwpblizHdT0a8ovIfMk4gfcEaNy0Ixd2Ud08mAZxpM0DcT9G4y444V4t6gCunKmoA2qTTTgkfXZ96ypz327M371IPYRdlJE6kUbpQwA78KpDjhqaFRPf2SDu/zQkP7RYEAc7+3D8ddbbqsK08sEkB8hajoeLs93HV9KhQvkVSPaT8U26d/ckBN5L739KVShsIjgf5M3xyFNZQOYzMLDZuDgQ1iG42JaYSZvJelXspF2KkpWoQ5I3khUg8LNSefNqcFBC4DV4U4NMCQTOZl6nBakbUx12avmYLuecmMacrm4s+ioGxCqfJMu1IPDFSQ6gN/UtBN6b7nbJXFNmRsjOLLOEvKtcjJadeenBKqVU23wfG/BqBUp7fwSEwHvp6gCBH4Wp/yYF05edt66bYMGu2kmpl2SZiB14e5ID6E19C4H3prvdY64gcdbfhkl6rBstDqM6OUj6M90d16w8izZibqMTmt9GkDdbjEiJCQEh8JiATmM3IHAOYh/Y6ULzHNja5CCQNydUkKILAYuSjG9+Gwj8Cl1TETlqBITA1RjVbI2E9eC3gLyznAUonesiWT34SSDwx9MJTG2OSgi8Nu9r4FmBxOG95h+7IrCgcBW3g7x942WEEyW190HAsrPSHxMzMk+DvBfE3Gev704IvJcvARD4FwHB92OG4UIQ+A9j7rP3dGfZWek5O32cZR4InBNjS4kRASHwGMFOa1cxJ3ZYBfJOOl5HWm+FvnFZWmO5qMa1BOR9jaqSfK4fASFw/ZhmTiIInDPRvI1rhOHBcxzvUSBwPRloDA820+I5tQ3RY7hMh5d9wu6D0+5IiR0BIfDYIU9nhyDxMRgZx0epNzRCJwNNTmMGGkMDrRmxFg3GXH6Lq9HQnDgN3WEg7w8MyRexCgSEwGWJFBAAiXOkt1dwDdMMC8djPkTIWzOqQcRZtB+qcXxz3XHC/xcyPy3kHeQmmKsjBG4O20xKBonzDpwPwPRkSid6HrKOSjIsbCZvhM5BW1QHcf+M62pNYm+GnGtA3sayI2kaZ82LEQKv+VscbYIg8i+h5RJc/aNJoJ1otwjEzXG9paQBActO5fY9XDMjDqcF7S4Dccdt4RJxuLXfTAi89u9xVTMEkXMG78/iGhRQEKcOuw/E/YWA9aVa3AhYdD66vAhX0G9Zz6Luj0Hcy+IeqvRXGQEhcFkhgRAAkc/iHTUujoPNqa48Qv8T/mZnID7Q+jqIW2+m9UCjk0qREHDOPDiC4UG4hrsXi2JrIb44xvl9IO4tkeRLI+MICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4Av8PmtVExuho1m4AAAAASUVORK5CYII=","user":{},"timestamp":"2025-04-22T02:11:57.947Z"}
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16
@ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16"There are two pillars in Costa Rica, education and coffee." A tourist guide I met told me this, and during the trip I discovered the strong link between coffee and the locals.
In fact, coffee runs very deeply in the Ticos' culture. So deep that the summer vacations from school (November to January) coincide with the coffee collection season. Children had to help their parents with the coffee. Coffee was a family business.
Monteverde, in the region of Puentarenas, is one of those places where coffee ha always been a corner stone of the society. Here, My gf and I went to visit a coffee plantation and discovered how coffee is made.
Monteverde
Monteverde is a well-known turistic location in the central part of Costa Rica. Many people reach this beautiful place to visit the famous Cloud Rainforest, acres and acres of pristine forest, with many different kind of animals and plants living in it.

However, other than tourism is coffee that pushes the economy of this place. The hills around the town are covered with coffee plantations and there are tours than try to explain how coffee is made.

Coffee Tours
While we were in Monteverde, we joined one of these tours. We decided to give credit to a smaller plantation instead of the super turistic ones. A more rustic and family-owned business, El Pueblo Coffee Tour. We were not disappointed. We had the show all to ourselves, a super-prepared guide and all the time to make questions and enjoy with no rush.
The Plant of Coffee
Since Costa Rica is a quite small country, to compete on the market producers decided to bet on quality instead of quantity. That's why, the only type produced here is the Arabica.
Before the coffee bean, the plant produces a nice white flower, similar to the jasmine.

After a while, the coffee beans appear.

As soon as they turn red, they are ready to be collected.
Interesting fact: between the coffee plants many fruit trees like mangos or bananos can be found. In fact, those plants help keep the soil fertile and healthy, thus leading to a higher coffee quality!
Coffee Harvesting
Coffee is still harvested by hand. Beans do not get mature at the same time, so manual labor is needed. Laborer use a very simple tool to collect coffee, one which allow them to have both hands free.
 Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Each cajuela is paid around 3.50$.
Coffee Drying
In the farm we visited, drying was perfomed naturally, through the heat of the sun. There are three ways in which the bean is left to dry: lavado, miel and naturàl.
- Lavado: The beans are peeled and washed to remove the jelly.
 - Miel: The jelly on the beans is maintained to give it more sweet flavour.
- Miel: The jelly on the beans is maintained to give it more sweet flavour. - Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
- Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
Back in the days, to peel the beans for the lavado and the miel variety, the pìlon was used. The bean is very hard, thus this tool does not damage it.

However, today the peeling procedure is done using a machine.

Coffee Roasting
The last step in the production of coffee is roasting. Coffee is put inside a sort of hoven, and is left there at high temperature according to the level of roasting that is needed. The more roasting, the less caffeine there is and the more bitter the coffee. Usually you have light, medium and dark roast.

Coffee Tasting
In the end, we also had a coffee tasting. We tried different roasting and different varieties.
Our guide explained us the best way to taste coffee and helped us defining the different flavours that we perceived. He also taught us the best way to prepare it: infusion time, water temperature, coffe makers and so on.
My favorite one was the dark one, while my gf enjoyed the light roast more. Of course, we bought some packs of these varieties!
Thanks for tuning in!
I hope you enjoyed this brief overview of the Costa Rican coffee.
Pura Vida
Tuma
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 812cff5a:5c40aeeb
2025-04-22 01:27:45
@ 812cff5a:5c40aeeb
2025-04-22 01:27:45يوم جديد وتطبيق نوستر جديد
أكتب هذا المقال من داخل نفس التطبيق اللي براجعه—يعني بختبر وبوثق التجربة في نفس الوقت، حرفياً!
الهدف من تطبيق أنتايپ
untyp| هو تطبيق مخصص للمنشورات الطويلة على بروتوكول نوستر. فكرته بسيطة جداً، لكنها عبقرية: إزالة كل الحواجز بينك وبين أفكارك، بحيث تقدر تكتب بحرية وسلاسة، كأنك بتكتب على ورقة فاضية... بس رقمية.
المزاية.. آو يمكن الميزة الوحيدة
ميزة التطبيق الأساسية هي دعمه الكامل لتنسيق Markdown، وهذا يعطيك مرونة هائلة في عرض أفكارك بشكل منظم وواضح—عناوين، روابط، كود، اقتباسات، وكل شيء بينهما.
الفكرة مو بس في المزايا، بل في الحد من المشتتات. التصميم بسيط وأنيق، بدون أي زوائد أو إعلانات، مما يساعدك تركز على الكتابة فقط.
untyp| مش بس وسيلة للنشر، بل أداة بتخليك أقرب لأفكارك، وأسرع في التعبير عنها.
جربته؟ قول لي رأيك. مطور التطبيق هو كارنج: nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 502ab02a:a2860397
2025-04-22 01:16:17
@ 502ab02a:a2860397
2025-04-22 01:16:17ก่อนที่จะมูฟออนจากเทคนิคการสร้าง เรามาดูเรื่องสำคัญครับ
วันที่ไม่มีวัว แต่มีเวย์โปรตีน – เบื้องหลังเทคโนโลยีที่เปลี่ยนถังหมักให้กลายเป็นเต้านมวัว เคยมีคำถามไหมว่า “เวย์โปรตีน” ที่กินตอนออกกำลังกาย หรือโยเกิร์ตถ้วยโปรดที่ซื้อมาจากร้านใกล้บ้าน มันยังมาจากนมวัวอยู่ไหม? ถ้าคำตอบคือ “ไม่” แล้วมันมาจากไหน?
ยินดีต้อนรับสู่โลกของ Perfect Day บริษัทที่บอกว่า "เราสร้างเวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว” ฟังดูเหมือนมายากล แต่นี่คือวิทยาศาสตร์ขั้นสูงที่ผูกสูตรไว้กับ DNA, จุลินทรีย์ และการหมักอย่างแยบยล
ขั้นตอนที่ 1: หารหัสโปรตีนจากแม่วัว เริ่มต้นจากคำถามง่าย ๆ ว่า “โปรตีนเวย์ที่อยู่ในน้ำนมวัว คืออะไร?” คำตอบคือ เบต้า-แลคโตโกลบูลิน (Beta-lactoglobulin) ซึ่งเป็นโปรตีนหลักในเวย์ประมาณ 50-55% โดยในธรรมชาติ วัวจะสร้างโปรตีนนี้จาก รหัสพันธุกรรมใน DNA ของมัน Perfect Day จึงไปค้นหา ลำดับเบส (DNA sequence) ของโปรตีนนี้จากฐานข้อมูลวิทยาศาสตร์ชื่อ UniProt (Universal Protein Resource) ซึ่งเก็บรหัสโปรตีนของสิ่งมีชีวิตแทบทุกชนิดไว้ครบถ้วน ได้รหัสมาแล้ว ก็เตรียมเข้าสู่ภารกิจ “หลอกจุลินทรีย์ให้สร้างโปรตีนแทนวัว”
ขั้นตอนที่ 2: สร้างแผ่นดีเอ็นเอสังเคราะห์ รหัส DNA ที่ได้จาก UniProt จะถูกนำไปสร้างเป็น DNA สังเคราะห์ โดยนักชีววิทยาจะออกแบบให้เหมาะสมกับการทำงานในเซลล์ของจุลินทรีย์ ไม่ใช่เซลล์วัว จะเรียกว่านี่คือ “การดัดแปลงบทละครชีวิตของวัว แล้วส่งให้จุลินทรีย์เล่นแทน” ก็ไม่ผิด DNA ที่ออกแบบนี้ มักจะมาพร้อมกับเครื่องมือบางอย่าง เช่น ตัวกระตุ้นการทำงานของยีน (promoter) หรือ ตัวตัดต่อยีน ที่จะทำให้จุลินทรีย์ยอมรับและใช้มันได้อย่างมีประสิทธิภาพ
ขั้นตอนที่ 3: ปลอมตัวแทรกเข้าไปในจุลินทรีย์ จุลินทรีย์ที่ Perfect Day ใช้คือกลุ่มที่เรียกว่า Microflora ซึ่งอาจเป็นยีสต์, เชื้อรา, หรือแบคทีเรียชนิดที่เลี้ยงง่าย แต่มันจะไม่ยอมรับ DNA แปลกปลอมง่าย ๆ ดังนั้นต้องมี “เทคนิคหลอกล่อ” นิดหน่อย เขาจะทำให้ DNA ของจุลินทรีย์ เสียหายตรงจุดหนึ่ง แล้วแอบแนบ DNA ปลอม (ที่มีรหัสโปรตีนของวัว) เข้าไปซ่อมแซมจุดนั้นพอดีเป๊ะ แบบ “จิ๊กซอว์พอดีช่อง” แล้วจุลินทรีย์ก็จะเผลอรับ DNA แปลกปลอมนี้เข้าร่าง เมื่อติดตั้งสำเร็จ มันจะเริ่มแปลรหัสและ “ผลิตโปรตีนเวย์” ออกมาเหมือนกับแม่วัวตัวจริงไม่มีผิด
ขั้นตอนที่ 4: เลี้ยงจุลินทรีย์ในถังหมัก ตอนนี้จุลินทรีย์กลายเป็น “แม่วัวในร่างเซลล์เดียว” แล้ว Perfect Day ก็แค่เลี้ยงมันใน ถังหมักชีวภาพ (fermentor) ที่ควบคุมอุณหภูมิ ค่าความเป็นกรดด่าง อากาศ และใส่น้ำตาลลงไปเป็นอาหาร จุลินทรีย์จะกินน้ำตาลแล้วเปลี่ยนเป็น เวย์โปรตีน ปล่อยออกมานอกเซลล์ จากนั้นก็เก็บเอาน้ำที่มีโปรตีนนี้ ไปผ่านกระบวนการกรอง แยก แปรรูป และทำให้แห้ง เป็นผงเวย์โปรตีน พร้อมใช้ในอาหารหรือเครื่องดื่มต่าง ๆ
ขั้นตอนที่ 5: ตรวจสอบความเหมือนจริง ก่อนนำเวย์โปรตีนที่ได้ไปใช้งาน บริษัทต้อง ตรวจสอบระดับโมเลกุล ว่าโปรตีนที่ได้เหมือนกับของวัวจริง ๆ ไหม? สิ่งที่ต้องดูคือ โครงสร้างโปรตีน: ใช้เทคนิค mass spectrometry ตรวจความแม่นยำระดับกรดอะมิโน พฤติกรรมทางชีวเคมี เช่น ความสามารถในการจับกับน้ำ การเกิดฟอง หรือการละลาย ความปลอดภัย ตรวจหาสารปนเปื้อน สารก่อภูมิแพ้ หรือสารที่ไม่ได้ตั้งใจให้มี Perfect Day เคลมว่าทั้งหมดนี้ปลอดภัย และได้รับการรับรองจาก FDA ว่าเป็น GRAS (Generally Recognized as Safe)
แล้วเราควรรู้สึกยังไง? นี่คือ “นมที่ไม่มีวัว” แต่มีเวย์โปรตีนครบสูตร ทำให้โยเกิร์ต ไอศกรีม และแม้กระทั่งกาแฟลาเต้ที่ไม่มีนมวัว แต่ยังมีฟองนมหนานุ่ม กลายเป็นจริงได้แบบไม่ต้องพึ่งวัวเลยแม้แต่นิดเดียว แต่คำถามที่ลึกกว่านั้นคือ... เรายังได้กินอาหารจากธรรมชาติอยู่หรือเปล่า? หรือกำลังอยู่ในยุคที่ “ชีวิต” ถูกตัดออกจากอาหาร โดยสิ้นเชิง? เทคโนโลยีนี้อาจช่วยโลกในมุมของ ESG แต่สำหรับบางคน มันคือ ทางแยกของความจริงกับของจำลอง คำว่า “Perfect” จึงอาจขึ้นอยู่กับว่า… สมบูรณ์แบบในสายตาใคร?
แล้วคำถามที่ล่องลอยอยู่เสมอคือ เมื่อทางเลือกกลายเป็นทางหลัก แล้วเราจะเหลือทางไหนอีกบ้าง หรือจะเป็น...ทางตัน? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ f7f4e308:b44d67f4
2025-04-09 02:12:18
@ f7f4e308:b44d67f4
2025-04-09 02:12:18https://sns-video-hw.xhscdn.com/stream/1/110/258/01e7ec7be81a85850103700195f3c4ba45_258.mp4
-
 @ 5188521b:008eb518
2025-04-08 13:33:42
@ 5188521b:008eb518
2025-04-08 13:33:42Ecology
When my father died, an entire ecosystem system of beneficiaries withered. Moussa Ag El Khir funded scholarships and community projects, paying thousands of Dinars monthly to stop the oasis town of In Salah from burning up. The few families we knew operating outside the oil-field economy would be forced to flee to the Mediterranean coast, along with just about every other Berber.
It wasn’t unexpected. My father had cystic fibrosis for all sixty-one years of his life. So far, that’s the only legacy he’s passed on to his children. My brothers are just carriers, but me, his precious daughter ended up like him in more ways than one.
We sat there in the lawyer’s office in Algiers, my brothers and I, staring at the ledger which contained payment for his life’s work.
“And he only left one word in his will?” asked Ibrahim for the third time. Ecology.
The lawyer said Moussa was very clear. He chose each of the keys himself. The contents of the ledger would belong to whoever could decode his life — those who understood the real meaning. Then he cut all communications and walked into the Sahara. The Tuareg caravan on the road to Akabli found his body a week later, reddened by sand burn.
Earth
We made an agreement that day. To share each word we discovered. We could break the code together. Of course, Ibrahim and Hama didn’t share anything. We barely speak. That’s what happens when one child follows their father into science, and her two brothers move to France the minute they get rich enough to buy a wife. I bet they spent longer looking into legal loopholes to get their hands on my father’s assets than they did trying to identify the keys.
That day was the start of my second life, and I went from research assistant at a regional university to private-key detective. 2048 words and few clues where to start. Although I was 27, I was virtually a grandmother according to the In Salah wives. But of course, I could never be a grandmother, or even a mother. Every night, I scoured photos in the family archive. An initial sweep of his digital footprint returned no out-of-place instances of any keywords.
It took me a year to find the GPS tag he’d added to one photo — an eighteen-year-old daughter standing next to a father proud of his first infinite solar prototype. The panel has long-since been torn out by the oil corp, but the base is still there. I drove the three kilometres from the town limit and shone the high beams at the spot. When I got out, the air was cool but still thick with sand. A few more steps through sinking dunes, and I saw it. He’d scratched a little globe into the blistered metal, and for a moment, my mucus-laden lungs tasted clear air.
Trigger
The next word took three years. Friends, contacts, professors, biographers — visits to anyone with whom he might have left a clue. But it was in the In Salah hospital, where, upon a routine CF checkup with Jerome Devailier, a French doctor, ‘trigger’ appeared. The government might stack everything against the desert peoples, but they hadn’t taken away healthcare. I’d been living off the kindness of neighbours while finishing my thesis on the very solar technology my father developed. How could he have known the ‘buyer’ was just a tendril of the very oil company he sought to defeat.
Dr Devalier went through the list of carcinogens and allergens to avoid with my new drugs. Over forty triggers which could be my downfall. If I was lucky, I’d live as long as my father did.
By then, my research stipend was long gone. I existed on toughened bread and soup, which always carried the taste of the scorched city air. Yet, I stayed. The public library, disconnected from the grid by the oil corp, was where I finished my manuscript. They would fight its publication. Since father’s money no longer flowed into the town, many had deserted me. There were those who said he killed an entire people by selling his solar patent to the wrong buyers. Others in In Salah worshipped his name, but eventually, they all trudged north to the cities. My brothers sold the family home from under me, forcing me to follow.
When I returned from the hospital, I dug out my father’s medical documents. On every page, the word ‘trigger’ was underlined. That was the moment I knew my life’s work would be unlocking the ledger, not publishing studies on long-dead solar panel technology. That battle was lost.
They
All we need is a simple document, but here, it is the administrators’ job to send people away. Physical copies are only issued in extreme circumstances. Citizens’ Registry screens played endless repetitions of how to apply for digital documents. The shrill voices of family members desperate for the original copy of a pirated document drowned the TV messaging. Women removed headscarves and revealed thick black hair; teenagers paced. The atmosphere thickened with sweat. And hours passed. Each appointment required a reset of digital protocol, biometric tests, and identity cards from legal descendents. Through counterfeit identities, our Dinars leak into the hands of criminals, but still the government denies the need for bitcoin. They just print more money. They is the word my father used for the government that fought his patent so hard.
After a four-hour wait, I discovered that the physical death certificate included an ‘identifying mark’ on the deceased’s body. The ink was fresh — etched into the shoulder blade of a man who wished to turn his back on the government that ignored its people. The tattoo read aqqalan, the Tamasheq word for they.
Scheme
It took two trips to his cluttered Marseille office to convince him I was serious. Two visas, two flights, and the small amount from the sale of the family house. But few detectives wanted to work for a promise.
The ledger could not legally be owned in Algeria, and Laurent Mercier was the only serious professional who entertained a percentage of what was on there. The solar tech patent and documents from my father were enough to start Laurent on the trail. ‘Preliminary,’ he said, until I had the ledger in my possession.
“Flying is not easy with my condition,” I said.
He lowered his sunglasses. “Working is not easy without money.”
Contact with my brother through the lawyer in Algiers was achingly slow, but eventually they agreed to give me possession. What was 33% of nothing anyway? Years had gone by.
So, when I sat for the second time, in the sweaty office in Marseille, I gave Laurent the ledger, and he handed me a surprise. In all his business affairs, my father used little English, but the word ‘scheme’ appeared in all three company names he incorporated in the last three years of his life. We had our fifth word, and I finally had someone on my side.
Make
Some days, I could barely walk to the public library. I became lethargic and mostly sat in the cool dark of my room in the shelter. The government refused to provide housing outside of Algiers, but a Tuareg organisation from Mali opened a shelter in In Salah. Bulging eyes and faded clothes stared back in the mirror each day. How long had it been since I’d been to a wedding, or celebrated a friend’s child? Occupants came and went, and all that was left was a barren room and one meal per day.
As the sun punished the city with every ray of Allah’s untapped gift, streets grew thick with dust, and the local government fell, seat by seat, to oil execs. The only transport running was to and from the oil fields, which belched the remnants of the land into the sky. And still they worked. Still they sat on my father’s patent and refused to supply the world with efficient solar power.
With little else to cling onto, I harboured thoughts of how I could spend the ledger money. Fixing the town and replanting lost gardens. Bringing people back. That all took a back seat to decoding the message my father was sending. Laurent and I began to believe that the keys he chose formed some sort of instruction for his legacy.
Ten years to the day after his death, I was in the public library, looking for clues in an English history book. On my exit, the librarian stopped me.
“We have a gift for you, Kana.”
I waited while he fetched a package.
“Your father instructed me to give this to you. But not before this date.”
My hands tore open the package. More books, technical manuals, and hand-written notes. Amongst the papers was a tasselled leather bookmark embossed with the four letters that comprised one of the seven missing words. Make.
Citizen
It’s hard for a father in Algeria to admit to his daughter that she is his spirit — the heir to his life’s work. Of course he felt terrible guilt after our mother’s passing. That was when the letters started.
Moussa wrote to himself really, trying to come to terms with bringing a protégé into the world with a bright scientific mind and lungs that would snap her life expectancy. We communicated by letter for the last few years of his life — sharing the breakthroughs of his findings and what it might mean for our decaying oasis town. Analogue writing was the only real privacy, he said. His letters always ran to the same length, as if they were one lesson divided into equal chunks. We even exchanged letters during his last hospitalisation in Algiers. Those words were the only real strength I gained.
It was Laurent who analysed the letters with a new text scanning tool. For me, my father’s last letters were advice, regret, pain, and love, but to Laurent, they were simply a puzzle to solve to get one step closer.
Our letters gave Laurent the idea to communicate via physical mail. The process was painful, with letters sent from outlying towns before being shipped across the Alboran Sea and up into France. Muatin was one name my father called me. Like him, I dreamed of helping many through science. This was one of the few Arabic words in the French letters he wrote. It was also the only keyword included in any of the letters. Citizen.
When
Years of quiet followed. In Salah became unlivable after they co-opted the city reservoir for cooling drilling rigs. Each study that proved the field was still viable funnelled funds away from the locals who clung on. Resettlement benefits went up, and all but the semi-nomadic Tuaregs left. I followed. My health could not take much more desert. In the cooler coastal plains, I recovered strength, and subsidies for new medications helped me survive on a meagre teaching salary.
With no further clues, my Marseillais detective lost interest. His last letter, sent years ago, stated with unusual brevity that he was resigning the case. No payment was due.
I had lost my health, my father, his work, my money, our house, the town, and I spent each week delivering science and English classes to teenagers. They had no more hope for our country than I had. Algerians had already lost the Sahara. A one-degree temperature shift each decade of my life had shrunk Africa and sent its peoples northwards.
My father’s word puzzle occupied my thoughts. The combinations and permutations of letters and characters had millions of possible meanings but only one correct answer. Yet simple linguistic logic provided the next word. The headteacher was a linguist — a profession long lost to the higher-powered text analysers and language AI. He spoke little English but asked about the categorisations of grammatical terms in the 2048 key words.
“Why do you ask?”
“Because,” he said, “for a sentence of twelve words, at least one conjunction is necessary to form a second clause.”
He was right. I had been focussing on lists and complex codes to build my father’s motto. When I got home, I furiously searched my list of terms for conjunctions. I found only one. ‘When.’
Can
The permutations were still huge. Even eliminating some of the more conceptual words did not help. Millions of sentences existed in my dead father’s mind. Millions of meanings, all lost to the need for more energy to fund the world’s great thirst for energy. Still, the panels in most of the ‘dead middle’ (as the space between the tropics became known) melted at over 50 degrees.
I was back in Paris for CF treatment. As a young woman, I would have been pleased to make fifty years. But the realities of daily visits and the sickness brought on by medication stung. I wanted things to end, even when I discovered the next key.
It had been years since I had dreamed of the freedoms my father’s fortune could bring. Parts of Asia held out against bitcoin, but the cost of countries doing business off-network had become prohibitive. Eventually, the fossil conglomerates would give in to the need for solar mining and the provision of universal energy.
It was in a Parisian hospital bed that I discovered ‘can.’ My wardmate, a rough labourer from Oran, found a biography in the hospital library that made me sit up straight. ‘Can’ was repeated in almost every description of my father in his one-time business partner’s book. And it was this Arabian ‘businessman,’ Abdulkarim Rahman, who brokered the deal that robbed the world of infinite solar power. Each page mocked my father as believing only physical impossibilities are impossible. He branded him the ‘can man.’
Drastic
During my recuperation, I spent the final two weeks of my visa stay in Marseille. My days passed with endless algorithm tweaks to reject or accept word orders for the elusive twelve-word sentence my father once wrote.
Food lost its taste, and friends and colleagues in academia had scattered. In-person meetings were often contained to the night hours, but Marseille was not a place to go out after dark. The latest protests had gotten violent, and the government looked likely to topple. My people had always been resilient, but when the option to move and operate a caravan was removed by General Hafiz, part of my spirit died. I resolved to spend my final years in In Salah, however uncomfortable they would be.
My final port of call before returning was Laurent’s office. The eTaxi cast me out into the dusty street, and I wheezed as I climbed the three flights of stairs to his tiny door on Rue Marché. We hadn’t spoken in years, but I was surprised to find a different name about the door. Pascale Dupont, Investigateur.
The assistant I remembered was quite the opposite to Laurent — slow and methodical, short and heavy set.
“Madame,” he said. “I have difficult news.”
Their business had always straddled the law, but I never imagined an ex-officer of the law could be convicted of treason.
“A closed-door trial,” said Pascale. Then he handed over an air-gapped 3D storage file. “Laurent knew you would come for this.”
My mind cast forward to the reams of information he must have built on my father. The patents and technical diagrams he illegally acquired and other clues. I instantly recognised the brand of storage file as a keyword. Drastic.
“How can I thank him?”
“He is dead, madame.” Pascale hung his head. “He survived prison for only two weeks.”
Must
My final years brought me home. In Salah had gained fame for its one group of Tuaregs who refused to leave. The Lakzis owned a house in a desperate condition, not dissimilar to my failing body. By the age of fifty-two, I could no longer walk, but they welcomed me. I pooled my disability allowance and some money I’d gained from selling my father’s watch. We waited for the world to mourn the death of a once great city. We would keep it alive by refusing to move, by refusing to permit its rebranding as an ‘industrial area.’ Now the oil fields were finally drying up, they wanted to dig under the town.
We had managed to eliminate half of the remaining words. Just under 1,000 possible selections for the final two words, but little idea of an order.
The problem was that I was the only English speaker among them, and it took great energy to attempt to teach the meaning of the words and possible grammatical constructions for my father’s sentence.
But soon, patterns began to emerge. Fragments of word pairings and groups. ‘Trigger drastic scheme’ appeared again and again in the permutations. ‘They can’ and ‘When they can’ gave a tantalising glimpse. We ranked sentences in terms of likelihood to form the full key and categorised them by the most likely remaining words. Due to the need for a modal verb, ‘must’ scored highest by our calculations.
In this race to unlock the ledger before In Salah’s destruction, we nosed ahead.
Yet the day of that discovery was my final day in the desert. An air ambulance transported my feeble body to Algiers, and I would never return.
They messaged me — so close. They would unlock the ledger with the final word after my operation. The bitcoin could undo the wrongs of the past, and my father’s sentence would live on.
End
The phrase which began the global revolution first appeared on the wall of a much-disputed oil refinery in the desert outside In Salah, Algeria.
When they can make ecology end, citizen earth must trigger drastic scheme
Soon, the graffiti marked government buildings in Algiers. Activists took to the streets. Governments crumbled and currencies collapsed. Climate groups received massive donations said to come from ‘the one,’ a ledger with a huge stack written off by financiers the world over. The codebreaker credited with unlocking the ledger was unable to witness the transfer of 10,000 coins to the Global Climate Fund due to her death, aged 52, from a congenital condition.
The words of Moussa Ag El Khir now mark each of the millions of panels, which line the ‘dead middle.’ They contribute over 80% of the Earth’s power supply.
To mark the fiftieth anniversary of his death, the World Climate Forum will be held in the town of his birth, In Salah, Algeria. This story, compiled from the diaries of his daughter, Kana Ult El Khir, will be read as the opening address of the conference.
This story was originally published in 21 Futures: Tales From the Timechain
To continue the story of the real-world treasure (sats) use the address (it's real).\ Who knows, maybe some zaps will find their way into the wallet...

-
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ e111a405:fa441558
2025-04-06 18:09:31
@ e111a405:fa441558
2025-04-06 18:09:31Running in circles is an expression that is often used to express when no matter what we do, nothing changes. We run in a circle, always ending up where we started.
Imagine the circle lines as boundaries, not physical boundaries, but mental barriers. In our life, we often run within our circle of possibilities. Anything outside our circle seem impossible. Outside the circle is anything that seems unattainable.
For some, healing a chronic disease may seem unattainable, for others it is a nice house, finding one’s soulmate, or merely financial abundance.
Over our lifetime, through our upbringing, we have defined our circle of possibilities. We have defined what is within our possibility and what is outside our possibility.
But this is just a line we drew. It is a mental barrier that does not exist outside our mind. In order to attain what seems unattainable, we have to expand our circle of possibilities. We have to pull what is outside our circle inside.
Imagine it like this: anything that is within our circle is easy and comes effortless. For example, making a coffee, driving a car are within our circle of effortless possibilities.
Other things seem out of reach. They are outside our circle of possibilities. They look extremely hard and impossible to reach.
What we need to do is reframe our understanding of what is within and what is without our circle. We pull seemingly impossible things inside our circle, and thereby we are expanding the size of our circle exponentially. We do this by following our excitement.
Not everything can be pulled inside our circle. But anything we are absolutely excited and passionate about can be pulled inside and made attainable.
You might think that you want to be the founder and CEO of a large, successful company. But if this is merely a desire that comes from mimesis – in other words, a desire that we have because we see other people have or desire it – not from our true inner being.
We will try forever to pull this inauthentic desire inside our circle, but we will fail because it is against our nature. Listening to our true excitement is key. We have to follow what is truly authentic to us — what we are truly excited about from our whole heart – and pull it inside our circle.
You may find true excitement and joy playing the piano or researching a certain subject. But true mastery of the piano or earning a livelihood with it may seem like an impossibility. Don’t let this hold you back. If this is what excites you the most, make the decision to pull it into your circle, define it is easily attainable, possible.
Inside our circle, doing and attaining our desires is as natural and easy as making a cup of coffee. Our inner circle represents our current reality. It is both endless and limiting. Endless in terms of repetition and confinement of boundaries.
Think again of walking in a circle, you always end up in the same spot, never really advancing. We try to improve the conditions within our circles, but improvements within our circles is like improving a prison cell.
True freedom comes from expanding that circle. Or stepping out of that circle into an entirely new one. That is difficult because we are like fish in an aquarium, unaware of the world behind. We only see what is familiar, what is within our circle, and everything beyond that feels alien or unattainable even though we desire it.
The real truth is that it takes the same energy to live and operate within our current circle as it takes to live within a much larger circle or to step. It takes the same effort to be in our current circle as it takes to be in a completely different, much larger circle.
First, you need to identify that you are inside a circle. What are your current habits and goals? What is your current reality?
Once you are aware, the next step is to identify what is outside your circle. What is it that you desire but looks unattainable, impossible?
Now we define a new circle. In this new circle, our goals, our habits are aligned with our authentic aspirations, our true excitement. We create a new reality.
Stepping out of this circle requires risk. It means breaking free from the familiar, and pursing something that may seem uncomfortable or unattainable.
We leave our circle, we leave our comfort zone.
We can do this in small, consistent steps, or we can make a sharp turn–an instant shift in our approach to living, like flipping from being chased to becoming the one who chases.
The real key to escaping our limiting circle is focus.
Where we focus our mental energy on determines the reality we will experience. By only focusing on improving our current reality, we remain locked in. But by expanding our vision to something outside our current circle, outside our current reality, we open up the possibilities of stepping into a new, much larger circle of possibilities.
What seems impossible now, becomes as effortless as making a cup of coffee.
The decision to break free starts with the realization that we are contained in a circle and the decision that we are ready to stop running in circles.
-
 @ d41bf82f:ed90d888
2025-04-21 23:18:20
@ d41bf82f:ed90d888
2025-04-21 23:18:20"ประวัติศาสตร์ก็เฉกเช่นธรรมชาติ — การเกิดและการตายล้วนดำเนินไปอย่างสมดุล" -โยฮัน ฮุยซิงกา3
การเสื่อมถอยของโลกยุคใหม่
พวกเรากำลังอยู่ในช่วงปลายของสิ่งที่เรียกว่า “ยุคใหม่” — ระบบโลกที่ถูกจัดระเบียบผ่านรัฐชาติอันรวมศูนย์ ซึ่งเคยพาเราผ่านยุคอุตสาหกรรม สงครามโลก และการสร้างโครงสร้างทางสังคมที่เข้มแข็งด้วยภาษี สวัสดิการ และระบบราชการ แต่ยุคนี้กำลังเคลื่อนเข้าสู่ฉากสุดท้ายของมันอย่างเงียบงัน โดยไม่มีใครในกระแสหลักพูดถึงอย่างจริงจัง และสิ่งที่กำลังมาแทนที่ก็จะแตกต่างอย่างสิ้นเชิงในเชิงคุณภาพจากโลกที่เราคุ้นเคย
เช่นเดียวกับที่สังคมเกษตรกรรมเคยมาแทนที่สังคมสัตว์-หาของป่า และระบบอุตสาหกรรมเคยมาแทนระบบศักดินา สังคมใหม่ที่กำลังปรากฏขึ้นจะเป็นการเปลี่ยนผ่านครั้งใหญ่ โดยในยุคใหม่นี้ “ประสิทธิภาพ” จะไม่ผูกติดกับ “ขนาด” อีกต่อไป อำนาจแบบรวมศูนย์ของรัฐจะถูกสั่นคลอน และระบบใหม่จะเกิดขึ้นซึ่งเล็กกว่า คล่องตัวกว่า และยากที่รัฐแบบเดิมจะควบคุม
นักประวัติศาสตร์ในอนาคตอาจมองว่าการล่มสลายของสหภาพโซเวียตในปี 1991 หรือการพังทลายของกำแพงเบอร์ลินในปี 1989 คือจุดสิ้นสุดของยุคสมัยนี้ และเปิดฉากสู่สิ่งใหม่ — บ้างเรียกมันว่ายุคหลังสมัยใหม่ บ้างว่าโลกไซเบอร์ หรือสังคมสารสนเทศ ไม่ว่าจะตั้งชื่ออย่างไร สิ่งที่ทุกคนยอมรับคือมันคือ "โลกใบใหม่" ที่แตกต่างอย่างถึงแก่นจากโลกเดิม
ความเข้าใจของมนุษย์ต่อการเปลี่ยนแปลงใหญ่ระดับอารยธรรมมักมาช้า เพราะขาดกรอบความคิดและภาษาที่จะมองเห็นมันได้ในขณะที่มันเกิดขึ้นจริง ยกตัวอย่างเช่น ไม่มีใครในยุคศักดินาคิดว่าตนเองอยู่ใน “ยุคกลาง” จนกระทั่งยุคใหม่เข้ามาเปรียบเทียบ ในทำนองเดียวกัน พวกเราทุกวันนี้ก็อาจไม่รู้ตัวว่าเรากำลังอยู่ในช่วงสิ้นสุดของยุคหนึ่ง และจุดเริ่มต้นของอีกยุคหนึ่ง
ระบบสังคมใดก็ตามมักฝังข้อสันนิษฐานโดยปริยายว่าระบบของตนคือสิ่งสูงสุด เป็นสิ่งที่ไม่มีวันเปลี่ยน และไม่ควรถูกตั้งคำถาม การตั้งคำถามถึงความอยู่รอดของระบบ จึงเป็นเรื่องที่ถูกกีดกันโดยไม่รู้ตัว เพราะยิ่งระบบใกล้ล่มสลายเท่าไร มันก็ยิ่งต้องพยายามปกปิดไม่ให้ใครรับรู้ถึงความเปราะบางของมัน
ตัวอย่างจากประวัติศาสตร์เช่น การล่มสลายของจักรวรรดิโรมันใน ค.ศ. 476 ก็ไม่ได้รับการรับรู้ว่าเป็น “จุดจบ” ในเวลานั้น แม้เมื่อจักรพรรดิองค์สุดท้าย(โรมุลุส เอากุสตุส)ถูกปลด แต่ผู้คนและโครงสร้างเดิมของโรมันก็ยังคงแสร้งทำว่าทุกอย่างดำเนินไปตามปกติ รูปแบบของรัฐบาลเก่ายังคงถูกรักษาไว้ พิธีกรรมในระบบเดิมยังคงจัดขึ้น วุฒิสภายังคงประชุม กงสุลยังได้รับการแต่งตั้ง และระบบราชการก็ยังคงอยู่เกือบครบถ้วน พวกป่าเถื่อนที่เข้ามาปกครองก็ยังแสดงตนว่าให้ความเคารพต่อจักรวรรดิไบแซนไทน์และกฎหมายโรมัน ศาสนาคริสต์ยังคงดำรงเป็นศาสนาประจำรัฐ เครื่องราชสัญลักษณ์ยังถูกใช้ในพิธีสาธารณะ ทั้งหมดนี้เป็นฉากหน้าของการพยายามรักษาภาพความต่อเนื่องในขณะที่แก่นของอำนาจได้เปลี่ยนไปแล้วโดยสิ้นเชิง
ประวัติศาสตร์ช่วงนี้สอนให้เห็นว่า การเปลี่ยนแปลงใหญ่ในระดับอารยธรรมมักถูกซ่อนเร้นอยู่ภายใต้ความเฉื่อยของสังคมที่ไม่ยอมรับความเป็นจริง คนในยุคนั้นไม่ได้รู้สึกว่าโรมล่มสลายไปแล้ว พวกเขาเพียงรู้สึกว่าชีวิตยังดำเนินต่อไปได้ แม้ภายใต้ระเบียบใหม่ที่ซ้อนทับเข้ามาโดยไม่ได้ประกาศตนอย่างเป็นทางการ ความเปลี่ยนแปลงที่แท้จริงจึงไม่ใช่เหตุการณ์ที่เกิดขึ้นในวันใดวันหนึ่ง แต่เป็นกระบวนการค่อยเป็นค่อยไปที่อาศัยแรงเฉื่อยของความเชื่อเก่าว่าสิ่งต่างๆ “ยังเหมือนเดิม”
ผู้เขียนใช้ตัวอย่างนี้เพื่อสะท้อนมาสู่โลกปัจจุบันว่า แม้ตัวอย่างโรมจะดูไกลตัว แต่ก็มีลักษณะใกล้เคียงกับสิ่งที่เรากำลังเผชิญอยู่ ระบบรัฐชาติสมัยใหม่ก็อาจกำลังเข้าสู่ภาวะเสื่อมถอยโดยที่คนส่วนใหญ่ยังไม่รู้ตัวเช่นเดียวกัน หนังสือเล่มนี้จึงไม่ได้ตั้งต้นจากการคาดเดาอนาคตอย่างลอย ๆ หากแต่เสนอว่า เราจะเข้าใจอนาคตได้ดีขึ้น ถ้าเริ่มจากการเรียนรู้กระบวนการเปลี่ยนผ่านในอดีต โดยเฉพาะพลวัตทางการเมืองและตรรกะของอำนาจ
จุดเปลี่ยนของโรมันไม่เพียงแต่แสดงให้เห็นการล่มสลายของรัฐรวมศูนย์ แต่ยังเผยให้เห็นว่าการล่มสลายนั้นสามารถเปิดทางให้กิจกรรมทางเศรษฐกิจในท้องถิ่นเบ่งบานขึ้นได้ ในยุคของเรา แม้สาเหตุจะต่างกัน — โรมล่มเพราะขยายเกินตัว เศรษฐกิจเกษตรกรรมไม่สามารถรองรับภาระรัฐ การเก็บภาษีที่หนักหนาและทหารที่ใช้อำนาจในทางมิชอบ — แต่สิ่งที่คล้ายกันคือ การไม่ยอมรับต่อการเปลี่ยนแปลงที่กำลังก่อตัว
เรายังเห็นการเปรียบเทียบถึงผลกระทบจากโรคระบาดในอดีต เช่น โรคฝีดาษที่ทำให้โรมอ่อนแอลง เช่นเดียวกับความกังวลเรื่องไวรัสกลายพันธุ์ในยุคปัจจุบัน ที่บ่งชี้ถึงความเปราะบางของโครงสร้างสังคม แม้รูปแบบของภัยคุกคามจะต่างกัน แต่สิ่งที่เหมือนกันคือ “ความไม่พร้อมของระบบ” ที่จะรับมือกับความเปลี่ยนแปลงใหญ่
แต่สิ่งสำคัญที่สุดที่ผู้เขียนต้องการชี้ ไม่ใช่แค่สาเหตุของการล่มสลาย แต่คือความจริงที่ว่า ผู้คนในยุคนั้น “ไม่เห็น” ว่าตนเองอยู่ในจุดเปลี่ยน เพราะแรงเฉื่อยทางความคิดและการเมืองทำให้พวกเขายึดมั่นในสิ่งที่เคยรู้จัก โดยไม่รู้เลยว่าโลกได้เคลื่อนเข้าสู่ระยะใหม่แล้ว และเราทุกวันนี้ก็อาจกำลังทำเช่นเดียวกัน
เรากำลังอยู่ในช่วงเวลาที่ไมโครโปรเซสเซอร์ เทคโนโลยีดิจิทัล และโครงสร้างไร้ศูนย์กลางจะเปลี่ยนกฎเกณฑ์ของอำนาจอย่างรุนแรง แต่ผู้คนกลับพยายามตีความสิ่งเหล่านี้ผ่านเลนส์ของโครงสร้างอุตสาหกรรมแบบเดิม ซึ่งอาจทำให้พลาดโอกาสที่จะเข้าใจการเปลี่ยนแปลงที่แท้จริง
ผู้เขียนเตือนว่าแม้บางหนังสือว่าด้วยอนาคตจะเต็มไปด้วยข้อมูล แต่กลับพาเราเข้าใจผิด เพราะยังยึดติดอยู่กับกรอบคิดเดิม เช่น การเชื่อว่ามนุษย์สามารถควบคุมทิศทางประวัติศาสตร์ได้เสมอ ทั้งที่ในความจริงแล้ว ปัจจัยที่ขับเคลื่อนการเปลี่ยนแปลงทางประวัติศาสตร์นั้น มักเป็นเงื่อนไขพื้นฐานที่มนุษย์ควบคุมไม่ได้ และไม่ได้อยู่ในความสนใจของการเมืองกระแสหลัก
มนุษย์มักไม่เปลี่ยนแปลงเพราะ “ต้องการเปลี่ยน” แต่เพราะ “ไม่เปลี่ยนไม่ได้แล้ว” และการเปลี่ยนแปลงเหล่านั้นมักเกิดสวนทางกับความต้องการของคนส่วนใหญ่ที่อยากรักษาสถานะเดิม
ชีวิตที่ขาดวิสัยทัศน์
ความไม่ตระหนักถึงการเปลี่ยนแปลงอันยิ่งใหญ่ที่กำลังก่อตัวขึ้นรอบตัวเรา อาจไม่ได้เกิดจากความไม่รู้ แต่เพราะเราลึกๆ แล้ว “ไม่อยากเห็น” ความเปลี่ยนแปลงนั้นเอง ความต้านทานนี้ไม่ใช่เรื่องใหม่ บรรพบุรุษของเราที่ดำรงชีพด้วยการล่าสัตว์และหาของป่าก็อาจเคยดื้อรั้นไม่ต่างกัน เพียงแต่พวกเขามีข้อแก้ตัวที่ฟังขึ้นมากกว่า เพราะในยุคก่อนประวัติศาสตร์ ไม่มีใครอาจคาดเดาว่า “การปฏิวัติการเกษตร” จะเปลี่ยนโลกไปในระดับใด พวกเขาไม่มีปฏิทิน ไม่มีการบันทึก ไม่มีแบบจำลองใดจากอดีตให้ใช้ทำนายอนาคต แม้แต่แนวคิดเรื่อง “เวลา” ก็ยังไม่มีอยู่ในจิตสำนึก พวกเขาใช้ชีวิตอยู่ใน “ปัจจุบันที่ไม่สิ้นสุด” และเมื่อพูดถึงการคาดการณ์อนาคต พวกเขาก็เป็นเหมือน “คนตาบอด” ที่ยังไม่เคยลิ้มรส “ผลไม้แห่งความรู้” (ตามคำเปรียบในพระคัมภีร์) แต่ต่างจากพวกเขา พวกเราในวันนี้มีเครื่องมือและมุมมองที่ลึกซึ้งกว่า จากองค์ความรู้ของบรรพบุรุษกว่าสี่ห้าร้อยรุ่น วิทยาศาสตร์ คณิตศาสตร์ และอัลกอริธึมของคอมพิวเตอร์ความเร็วสูง ช่วยให้เราทำความเข้าใจระบบที่ซับซ้อนอย่างเศรษฐกิจมนุษย์และพลวัตของสังคมได้ดียิ่งขึ้น แม้ทฤษฎีเศรษฐศาสตร์จะไม่สามารถอธิบายพฤติกรรมมนุษย์ได้แบบสมบูรณ์ แต่ก็ทำให้เราเข้าใจว่า “แรงจูงใจ” คือแรงผลักดันสำคัญ เมื่อผลตอบแทนสูงขึ้น หรือความเสี่ยงต่ำลง พฤติกรรมย่อมเกิดขึ้นถี่ขึ้น และนี่คือหลักการที่แม่นยำอย่างยิ่งในการวิเคราะห์อนาคต
แรงจูงใจนี้เองที่เป็นหัวใจของการพยากรณ์ และการพยากรณ์ที่ดีไม่ได้ขึ้นกับการรู้เหตุการณ์ล่วงหน้าแบบเฉพาะเจาะจง แต่ขึ้นอยู่กับการเข้าใจโครงสร้างของแรงขับเคลื่อน เช่นเดียวกับที่เราอาจไม่รู้ว่าเมื่อไรเสียงฟ้าร้องจะดังขึ้น แต่เมื่อเห็นฟ้าแลบ ก็สามารถคาดหมายได้ว่าจะมีเสียงตามมา เช่นกัน หากเราสามารถเข้าใจ “ตรรกะของความรุนแรง” ที่กำลังเปลี่ยนไปในระดับการเมืองมหภาคได้ เราก็จะมองเห็น “โอกาส” หรือ “ช่องโหว่” ของระเบียบเดิม และใครจะเป็นผู้ฉวยโอกาสเหล่านั้น
การเปลี่ยนแปลงครั้งใหญ่ในอดีต เช่น การปฏิวัติการเกษตร หรือการเข้าสู่ยุคอุตสาหกรรม ล้วนเกิดขึ้นช้าและกินเวลาหลายศตวรรษกว่าจะเผยผลเต็มที่ ในทางตรงกันข้าม การเปลี่ยนผ่านสู่ยุคสารสนเทศกลับเกิดขึ้นรวดเร็วเพียงช่วงชีวิตเดียว
ผู้เขียนวางกรอบเพื่อให้เราเข้าใจว่า การเปลี่ยนแปลงทางการเมืองมหภาคมักมาก่อนการเปลี่ยนแปลงในโครงสร้างของรัฐอย่างเป็นรูปธรรม รายได้ที่ลดลง วิกฤตที่เกิดจากทรัพยากรจำกัด และแรงกดดันจากประชากร ล้วนเป็นผลพลอยได้จากความไม่สามารถของระเบียบเดิมในการรองรับแรงกระแทกของโลกใหม่ และการพูดถึงการเปลี่ยนแปลงจาก “ภายนอกระบบ” มักถูกห้ามหรือมองว่าเป็นเรื่องต้องห้ามในทุกยุคทุกสมัย ยิ่งไปกว่านั้น การเปลี่ยนแปลงในระดับนี้มักก่อให้เกิดแรงปะทะทางวัฒนธรรมระหว่างผู้ที่ยึดมั่นในกรอบศีลธรรมดั้งเดิมกับผู้ที่เปิดรับแนวคิดใหม่ และไม่ใช่เรื่องแปลกที่การเปลี่ยนแปลงเช่นนี้จะไม่เป็นที่นิยม เพราะมันลดคุณค่าของทุนทางปัญญาเดิม ทำให้ระบบเก่าไร้ความหมาย และบีบบังคับให้สังคมต้องเรียนรู้ใหม่เกือบทั้งหมด โดยเฉพาะในกลุ่มคนที่ได้รับผลกระทบโดยตรง
สัญญาณของการเสื่อมถอยมักปรากฏในรูปของคอร์รัปชัน ความไร้ประสิทธิภาพ และการสูญเสียศีลธรรมของผู้มีอำนาจ ซึ่งมักเป็นสัญญาณล่วงหน้าของการเปลี่ยนแปลงที่หลีกเลี่ยงไม่ได้ ยิ่งในยุคที่เทคโนโลยีก้าวหน้าเร็วขึ้น กระบวนการเหล่านี้ก็จะยิ่งเร่งตัว จนทำให้เวลาที่เหลืออยู่สำหรับการปรับตัวลดลงเรื่อย ๆ
"เมื่อมองย้อนกลับไปตลอดหลายศตวรรษ — หรือแม้แต่แค่ในปัจจุบัน — เราจะเห็นได้อย่างชัดเจนว่า มีผู้คนจำนวนมากที่สร้างรายได้(บ่อยครั้งเป็นรายได้จำนวนมาก) จากทักษะในการใช้ความรุนแรงผ่านอาวุธ และกิจกรรมของพวกเขาเหล่านี้มีบทบาทอย่างสำคัญยิ่งในการกำหนดว่าทรัพยากรที่มีอยู่จำกัดในสังคมจะถูกจัดสรรไปในทิศทางใด." --เฟรเดอริก ซี. เลน
แนวคิดของการเมืองมหภาค(megapolitics) เป็นกรอบความคิดที่ทรงพลัง ซึ่งช่วยให้เรามองเห็นกลไกเบื้องหลังเหตุการณ์ที่ดูซับซ้อนหรือลึกลับในประวัติศาสตร์ ไม่ว่าจะเป็นเหตุผลที่บางรัฐบาลเจริญรุ่งเรือง ขณะที่บางแห่งกลับล่มสลาย เหตุใดสงครามจึงอุบัติขึ้น และเหตุใดฝ่ายหนึ่งจึงมีชัย หรือแม้กระทั่งว่าอะไรเป็นตัวแปรที่กำหนดวงจรแห่งความรุ่งเรืองและความตกต่ำทางเศรษฐกิจ ทั้งหมดล้วนสามารถอธิบายได้ผ่านเลนส์ของการเมืองมหภาค ซึ่งเน้นวิเคราะห์ว่า "ต้นทุนและผลตอบแทนของการใช้ความรุนแรง" เปลี่ยนไปอย่างไรในแต่ละบริบทของเวลา หากต้นทุนในการใช้อำนาจบังคับลดต่ำลง เช่น การเข้าถึงอาวุธที่ง่ายขึ้นและราคาถูกลง ก็ทำให้อำนาจเปลี่ยนมือได้ง่ายขึ้นตามไปด้วย หลักการนี้ยังคงใช้ได้ตั้งแต่ยุคโบราณจนถึงโลกยุคไซเบอร์สเปซในปัจจุบัน
ใน Part 2 เราจะมาดูกันว่ามีปัจจัยอะไรบ้างที่อยู่เบื้องหลังการเปลี่ยนแปลงครั้งใหญ่ในประวัติศาสตร์ to be continue....
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ ae1008d2:a166d760
2025-04-01 00:29:56
@ ae1008d2:a166d760
2025-04-01 00:29:56This is part one in a series of long-form content of my ideas as to what we are entering into in my opinion;The Roaring '20's 2.0 (working title). I hope you'll join me on this journey together.
"History does not repeat itself, but it often rhymes"; - Samuel Clemens, aka Mark Twain. My only class I received an A+ in high school was history, this opened up the opportunity for me to enroll in an AP (college level) history class my senior year. There was an inherent nature for me to study history. Another quote I found to live by; "If we do not study history, we are bound to repeat it", a paraphrased quote by the many great philosphers of old from Edmund Burke, George Santayana and even Winston Churchill, all pulling from the same King Solomon quote; "What has been will be again, what has been done will be done again; there is nothing new under the sun". My curiousity of human actions, psychological and therefore economical behavior, has benefitted me greatly throughout my life and career, at such a young age. Being able to 'see around the curves' ahead I thought was a gift many had, but was sorely mistaken. People are just built different. One, if not my hardest action for me is to share. I just do things; act, often without even thinking about writing down or sharing in anyway shape or form what I just did here with friends, what we just built or how we formed these startups, etc., I've finally made the time, mainly for myself, to share my thoughts and ideas as to where we are at, and what we can do moving forward. It's very easy for us living a sovereign-lifestyle in Bitcoin, Nostr and other P2P, cryptographically-signed sovereign tools and tech-stacks alike, permissionless and self-hostable, to take all these tools for granted. We just live with them. Use them everyday. Do you own property? Do you have to take care of the cattle everyday? To live a sovereign life is tough, but most rewarding. As mentioned above, I'm diving into the details in a several part series as to what the roaring '20's were about, how it got to the point it did, and the inevitable outcome we all know what came to be. How does this possibly repeat itself almost exactly a century later? How does Bitcoin play a role? Are we all really going to be replaced by AI robots (again, history rhymes here)? Time will tell, but I think most of us actually using the tools will also forsee many of these possible outcomes, as it's why we are using many of these tools today. The next parts of this series will be released periodically, maybe once per month, maybe once per quarter. I'll also be releasing these on other platforms like Medium for reach, but Nostr will always be first, most important and prioritized.
I'll leave you with one of my favorite quotes I've lived by from one of the greatest traders of all time, especially during this roaring '20's era, Jesse Livermore; "Money is made by sitting, not trading". -
 @ 6be5cc06:5259daf0
2025-03-31 03:39:07
@ 6be5cc06:5259daf0
2025-03-31 03:39:07Introdução
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.\ Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.\ Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.
Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ d360efec:14907b5f
2025-04-21 22:10:23
@ d360efec:14907b5f
2025-04-21 22:10:23สวัสดีเพื่อนนักเทรดทุกท่าน! 👋 วันนี้ฉันมาแนะนำตารางกิจวัตรประจำวันของ Day Trader ที่น่าสนใจนี้กันนะคะ มาดูกันว่ามีอะไรที่เราสามารถเรียนรู้และนำไปปรับใช้กับการเทรดของเราได้บ้างค่ะ

ภาพรวมกิจวัตรประจำวันของ Day Trader 📊
ตารางนี้แสดงให้เห็นถึงโครงสร้างของวันที่สมดุลสำหรับนักเทรดรายวันที่ประสบความสำเร็จ โดยเน้นทั้งการเตรียมตัว 🤓 การลงมือเทรด 🚀 การเรียนรู้ 📚 และการดูแลสุขภาพส่วนตัว 🧘♀️ ซึ่งเป็นสิ่งสำคัญอย่างยิ่งในการรักษาประสิทธิภาพและความสม่ำเสมอในการเทรด 💪
การวิเคราะห์และอธิบายแต่ละช่วงเวลา
$ 05.30 น. > ตื่นนอน 🌅 อาบน้ำ 🚿 และเตรียมตัว 👔 > การเริ่มต้นวันอย่างกระปรี้กระเปร่า 🎉 และการมีกิจวัตรส่วนตัวที่ผ่อนคลายเป็นสิ่งสำคัญในการเตรียมพร้อมทั้งร่างกายและจิตใจ 🧠 สำหรับการเทรด
$ 06.00 น. > ตรวจสอบข่าวสาร 📰 วิเคราะห์กราฟ 📈 และเตรียมตัว 🎯 > ช่วงเวลานี้เป็นหัวใจสำคัญของการเตรียมตัวก่อนตลาดเปิด ⏰ นักเทรดจะตรวจสอบข่าวเศรษฐกิจ 💰 และข่าวที่เกี่ยวข้องกับสินทรัพย์ที่ตนเองเทรด 🧐 วิเคราะห์กราฟเพื่อหาแนวโน้ม 🔭 และระดับราคาที่น่าสนใจ 📍 รวมถึงวางแผนกลยุทธ์การเทรดสำหรับวันนี้ ✍️
$ 06.30 น. > ตลาดเปิด 🔔 เริ่มทำการเทรด 🚀 > เมื่อตลาดเปิด นักเทรดจะเริ่มดำเนินการตามแผนที่วางไว้ 📝 โดยจะเฝ้าติดตามการเคลื่อนไหวของราคา 👀 และเข้าเทรดตามสัญญาณที่เกิดขึ้น 🚦
$ 12.00 น. > พักรับประทานอาหารกลางวัน 🥪 > การพักผ่อน 😌 และการเติมพลัง 💪 ในช่วงกลางวันเป็นสิ่งสำคัญในการรักษาความมีสมาธิ 🧘♀️ และความสามารถในการตัดสินใจที่ดี 👍
$ 12.45 น. > ปิดสถานะการเทรดทั้งหมด 🛑 > สำหรับ Day Trader การปิดสถานะทั้งหมดภายในวันถือเป็นกฎเหล็ก 🚫 เพื่อหลีกเลี่ยงความเสี่ยงจากความผันผวนข้ามคืน 🌙
$ 13.00 น. > ทบทวน 🤔 เรียนรู้ 📚 และปรับปรุง ⚙️ > หลังจากการเทรด นักเทรดที่ประสบความสำเร็จ 🎉 จะใช้เวลาในการทบทวนการเทรดของตนเอง 🧐 วิเคราะห์ว่าอะไรทำได้ดี 👍 และอะไรที่ต้องปรับปรุง 📝 การเรียนรู้อย่างต่อเนื่องเป็นกุญแจสำคัญสู่การพัฒนา 🚀
$ 14.00 น. > ออกกำลังกาย 💪 และพักผ่อน 🧘♀️ > การดูแลสุขภาพกาย 🍎 และใจ 💖 มีความสำคัญไม่ยิ่งหย่อนไปกว่าการเทรด 📈 การออกกำลังกายและการมีเวลาว่าง 🌴 ช่วยลดความเครียด 😥 และเพิ่มประสิทธิภาพในการเทรดในระยะยาว ✨
$ 17.00 น. > รับประทานอาหารเย็น 🍽️ และพักผ่อน 🛋️ > การมีเวลาพักผ่อนกับครอบครัว ❤️ หรือทำกิจกรรมที่ชอบ 😊 ช่วยให้ผ่อนคลาย 😌 และเตรียมพร้อมสำหรับวันต่อไป 🌅
$ 19.00 น. > วางแผนการเทรดสำหรับวันพรุ่งนี้ 🗓️ และตรวจสอบข่าวสาร 📰 > การวางแผนล่วงหน้า 🤓 ช่วยให้นักเทรดมีความพร้อม 💪 และสามารถตอบสนองต่อสถานการณ์ตลาดได้อย่างมีประสิทธิภาพ 🚀
$ 22.00 น. > เข้านอน 😴 > การนอนหลับพักผ่อนอย่างเพียงพอ 🛌 เป็นสิ่งจำเป็นสำหรับการรักษาสุขภาพ 💖 และประสิทธิภาพในการเทรด 💪
สิ่งที่น่าสนใจและข้อคิด 🤔
$ ความมีระเบียบวินัย 💯 > ตารางนี้แสดงให้เห็นถึงความมีระเบียบวินัยที่เข้มงวด 📏 ซึ่งเป็นคุณสมบัติที่สำคัญของนักเทรดที่ประสบความสำเร็จ 🎉
$ การเตรียมตัวอย่างรอบคอบ 🧐 > การใช้เวลาในการวิเคราะห์ 📊 และวางแผน 📝 ก่อนตลาดเปิดช่วยลดการตัดสินใจที่ผิดพลาด 🚫 และเพิ่มโอกาสในการทำกำไร 💰
$ การเรียนรู้อย่างต่อเนื่อง 📚 > การทบทวน 🤔 และปรับปรุงกลยุทธ์ ⚙️ อยู่เสมอเป็นสิ่งสำคัญในการพัฒนาทักษะการเทรด 🚀
$ ความสมดุล ⚖️ > การให้ความสำคัญกับการดูแลสุขภาพ 🧘♀️ และการพักผ่อน 🌴 ควบคู่ไปกับการเทรด 📈 ช่วยป้องกันภาวะหมดไฟ 🔥 และรักษาประสิทธิภาพในระยะยาว ✨
การนำไปปรับใช้ 🛠️
เพื่อนๆ นักเทรดสามารถนำแนวคิดจากตารางนี้ไปปรับใช้กับกิจวัตรประจำวันของตนเองได้ 👍 โดยอาจไม่จำเป็นต้องทำตามทุกช่วงเวลาอย่างเคร่งครัด ⏰ แต่ให้เน้นที่หลักการสำคัญ เช่น การเตรียมตัวก่อนเทรด 🤓 การทบทวนหลังเทรด 🤔 และการดูแลสุขภาพ 🧘♀️ เพื่อสร้างสมดุล ⚖️ และเพิ่มประสิทธิภาพในการเทรดของเราค่ะ 💪
ขอให้ทุกท่านประสบความสำเร็จในการเทรดนะคะ! 💸🚀
#DayTrader #นักเทรดรายวัน #กิจวัตรประจำวัน #การลงทุน #เทรด #หุ้น #คริปโต #ตลาดหุ้น #แรงบันดาลใจ #พัฒนาตัวเอง #LinaEngword
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 7d33ba57:1b82db35
2025-04-21 20:16:41
@ 7d33ba57:1b82db35
2025-04-21 20:16:41Helsinki, the stylish and compact capital of Finland, sits right on the edge of the Baltic Sea, blending Scandinavian design, sustainable living, and a love for nature. It’s a city of clean lines, calm energy, and a creative spirit—where you can go from a seaside sauna to a sleek design museum in minutes.
🧭 Top Things to Do in Helsinki
⛪ Helsinki Cathedral
- The city’s iconic white-domed landmark, perched on Senate Square
- Climb the steps for sweeping views over the city’s neoclassical heart
🏝️ Suomenlinna Sea Fortress
- A UNESCO World Heritage Site spread across several islands
- Explore old ramparts, tunnels, museums, and scenic picnic spots
- A short ferry ride from the city center, perfect for a half-day trip
🧊 Löyly Sauna
- One of Helsinki’s most famous public saunas, right on the waterfront
- Relax in the heat, then dip in the Baltic like a local
- Beautiful architecture and a must-do cultural experience
🏛️ Design District & Museums
- Wander the Design District for boutique shops, galleries, and Finnish fashion
- Visit the Design Museum, Kiasma (contemporary art), and Ateneum (classic Finnish art)
🌲 Nature + Nordic Calm
- Walk along the Esplanadi park or relax in Kaivopuisto by the sea
- Take a boat to the nearby archipelago islands for hiking, birdwatching, or quiet cafés
- Even in winter, the city feels clean, serene, and cozy
☕ Food, Coffee & Nordic Flavors
- Try karjalanpiirakka (Karelian pies), salmon soup, or reindeer meat if you’re adventurous
- Helsinki has a big coffee culture—Finns drink more coffee per capita than anyone!
- Cozy up in a café with a cinnamon pulla and watch the snow fall (or the summer sun glow at midnight)
🚲 Getting Around
- Easy to explore by foot, tram, or city bikes
- Excellent ferries and boats to nearby islands and Tallinn, Estonia
- Helsinki Airport is well-connected and just 30 mins from downtown
📅 When to Go
- Summer: Endless daylight, festivals, and outdoor dining
- Winter: Snowy streets, cozy interiors, and a shot at the Northern Lights if you head north
- Autumn: Ruska (fall colors) is stunning in the parks and forests
-
 @ b12e2899:ed9d9c8b
2025-03-26 17:33:37
@ b12e2899:ed9d9c8b
2025-03-26 17:33:37I have completely switched to Nostr and today am going to share my experience, which may be useful to those of you who want to launch a bot on a social network and encounters censorship. The thing is Nostr is ideal for this, but first things first:
It all started when I suddenly woke up to see my twitter bot @cryptoratingbot suspended without any explanation. I contacted support, but they apparently considered my case too insignificant to even respond. The goal of my bot was to attract users and provide free tools like charts.xport.top, tickerbell.xport.top and few others that you can find out about in my previous publications. It worked, and accumulated all in all around 60k engagement a year. Silly, right? You can do this in two days doing it the right way. But I was in no hurry. Overall I gained 10 new users per day and that was enough for me to begin with since I wasn’t prepared for the big wave of users. But that is not the topic for today. I can tell you more about this later on, if you are interested click like and subscribe.
I was planning to buy a premium, but then twitter suspended my bot which actually didn’t do anything bad if you think about it. Furthermore, it was useful, otherwise why would people use it and like its tweets. Anyway, this ruined my plans and forced me to think about switching to Nostr. Today I can tell that it was definitely worth it! I haven’t lost anything, except time and overall gained from it! But I won’t say too much, so as not to bore you. However, this context is important for a better understanding of my situation. There are much more details and if you have any questions, feel free to ask, I will try to answer everyone.
Hard to believe, but these things can help you make money from buying cryptocurrency on the bottoms in a right time just when it starts trading, if you understand what you’re doing. That’s not easy. Maybe I will share some thoughts later on, until then you may find more info in my previous articles.
In fact, I decided to write this because for the first time since I was introduced to Nostr I finally tried proof-of-work(nip-13 pow) myself and I love it! I see such a thing for the first time on a social media. No moderation or censorship measures are needed. After all, if you are ready to burn resources to publish events, then it is definitely not a spam. And that’s the beauty of it!
I’ve picked 7 relays to try and publish 5000+ events that my previous version collected from top 12 cryptocurrency exchanges. Two relays rejected those events after some time, most likely because as always I have forgot to add something crucial — nonce tag, to help relays understand I am using pow. I thought it would add it itself, but seemes that it wouldn’t. What a shame! However, other 5 relays are ok with that! Maybe because I wasn’t publishing events too often, I don’t know, but anyway the more freedom the more I love it! And if you want find more about relays you can use use nostrwat.ch which is the greatest resource for finding the best relays to use.
While I was writing this article, another few relays dropped connections, but that’s fine, I have selected 7 relays out of about 700 active online.
This is how my server statistics looks like:


 So, besides everything else, I also checked Netcup root server G11 stats. In my opinion, this is the best of all that I have ever dealt with. And this is not an advertisement, no. I found this company on my own, just watching how Nostr relays works in terms of price/quality, so this is my personal recommendation. But if you think you know better root server solutions please let me know in the comment below.
So, besides everything else, I also checked Netcup root server G11 stats. In my opinion, this is the best of all that I have ever dealt with. And this is not an advertisement, no. I found this company on my own, just watching how Nostr relays works in terms of price/quality, so this is my personal recommendation. But if you think you know better root server solutions please let me know in the comment below.The only disadvantage I have encountered is you can wait for their support for few days to answer, but that’s ok if you know what you’re doing. I have no problem with this. I try to be careful and there were no problems for two months since I ordered it and use it on the daily basis.
In short, this is my journey. Don’t scold me for this. It’s just that I’ve been saving all this up for a long time, and today I realized that I simply have to tell you about it!
Thank you all and see you soon! Cheers 🍻

-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ 3ad01248:962d8a07
2025-04-21 19:40:22
@ 3ad01248:962d8a07
2025-04-21 19:40:22It has almost been a month since the Bitcoin friendly Trump administration has been in power. The Bitcoin price was riding high days before and after the election with Bitcoin reaching a new all time high of 109k. It sure seem like surely once Trump got into office the price would skyrocket and everyone finally would have lambos and girlfriends.
Sadly for the number go up crowd this didn't happen. There are no lambos to be found and no girlfriends. All we get is some sideways price action and a Strategic Bitcoin Reserve (BSR).
If you are in Bitcoin for the right reasons and understand what you hold, this is the perfect time to stack sats before the price goes parabolic. I say this because Bitcoin sure seems to be poised to make a massive run. If you look past the current price of Bitcoin you can see a storm of dollars flowing into Bitcoin from the traditional fiat economy. The signs are there if you start looking for them.
US States Creating Bitcoin Strategic Reserves
Guess how many states are considering creating a state level Bitcoin reserve of their own? Lots. Here is a list of states that are thinking about creating a reserve for their state:
- Alabama
- Arizona
- Florida
- Kansas
- Illinois
- Iowa
- Massachusetts
- Michigan
- Missouri
- Montana
- New Hampshire
- New Jersey
- New Mexico
- North Carolina
- North Dakota
- Ohio
- Pennsylvania
- South Dakota
- Texas
- Utah
- Wisconsin
- Wyoming
Each state is at some varying degree of interest in creating a reserve. Texas and Arizona are by far have made the most progress on making a Bitcoin reserve a reality. Texas is currently holding a public hearing on this at the time of this writing. There is strong political will to create a reserve so I definitely can see them being first movers on this and once Texas makes it a reality the other state will move in short order.
Arizona's strategic reserve bill passed the senate finance committee on a 5-2 which is a big deal in itself but still has a long way to go before it becomes policy. If it passes the Senate it still has to pass the Arizona House of Representatives and signed by Democrat Governor Katie Hobbs, so the odds of this becoming law is slim. Arizona Democrats seem to be anti-Bitcoin in general and any bills coming from Republicans will likely be shoot down or watered down.
Analysts believe that $23 billion could flow into Bitcoin from government reserves which equates to 247k Bitcoin going into government cold storage. I have reservations about governments creating BSR's but if we are going to have them I much rather them be at the state level where it can benefit citizens the most. Especially state pension funds that so many of our firefighters, police and first responders depend on for retirement.
We will probably see a state level BSR created by the end of the year if not sooner. Time will tell.
SAB 121 Repeal
What is SAB 121? SAB 121 or Staff Accounting Bulletin 121 made it problematic for financial institutions to custody digital assets such as Bitcoin for their customers. SAB 121 required institutions to record their holdings as a liability and not an asset.
Naturally banks and other financial institutions didn't see an upside to custody digital assets if it meant taking on liability and having an administration that was hostile to crypto in general. Why take the chance to piss off the government and give them a reason to go after you is probably the reasoning of most bank executives. SAB 121 achieved the goal the Biden administration set out to accomplish, namely stymie Bitcoin adoption by banks and individuals as long as possible.
President Trump swiftly issued a executive order rescinding SAB 121 and with that ushering a new era in the realm of Bitcoin and digital assets in general. Financial institutions now have the ability to explore Bitcoin custody solutions that fit their customer's need without fear of having to record a liability on their books.
As more and more people and business learn about Bitcoin third party custody options are going to be popular. Think about it from a small business owner perspective for a second. They are in the business of selling their widgets for Bitcoin but they don't want to manage the complexity that comes with accounting, taxes etc.. In steps in their local bank that they have been with for years if not decades and starts providing Bitcoin management services. Small business owners would be all over that idea. In the long run I think the repeal of SAB 121 is going to be a bigger deal than states creating Bitcoin strategic reserves.
FASB
Financial Accounting Standards Board or FASB for short has applied fair value accounting rules on Bitcoin and other digital assets. This is a huge deal because it will allow business to realize profit and losses of Bitcoin based on market prices. It also makes it easier for investors who evaluate businesses that hold Bitcoin on their balance sheet. Overall it treats Bitcoin like any other asset that a business would hold.
This accounting rule change will pave the way for more businesses to put Bitcoin on their balance sheet further driving demand for Bitcoin.
Lightning Companies Leading The Way
We all know that L1 Bitcoin can not scale to the entire world and that in order to bring more people into Bitcoin that layer two solutions would have to be built. This has largely been done with the creation of the lightning network which enables seamless peer to peer micropayments in the blink of an eye.
Base layer Bitcoin will certain not be used to buy your daily coffees or gym memberships but lightning will be used for that purpose. Businesses small and large will demand one click on demand solutions to help them accept Bitcoin payments for their businesses. There are plenty of Bitcoin business ready to help business adopt a Bitcoin standard.
Businesses such as Opennode, Zaprite, Voltage, Breez make switching over to a Bitcoin standard easy for businesses to do.
So when you take a step back and really look at the Bitcoin ecosystem it is a lot more mature than most give it credit for and will slowly eat away at fiat currency dominance around the world.
The best thing that you can do is be patient, stack as many sats as you can and educate others about Bitcoin. We all know how fiat currencies end. Our time will come.
-
 @ d34e832d:383f78d0
2025-04-21 19:09:53
@ d34e832d:383f78d0
2025-04-21 19:09:53Such a transformation positions Nostr to compete with established social networking platforms in terms of reach while simultaneously ensuring the preservation of user sovereignty and the integrity of cryptographic trust mechanisms.

The Emergence of Encrypted Relay-to-Relay Federation
In the context of Nostr protocol scalability challenges pertaining to censorship-resistant networking paradigms, Nostr stands as a paradigm-shifting entity, underpinned by robust public-key cryptography and minimal operational assumptions. This feature set has rendered Nostr an emblematic instrument for overcoming systemic censorship, fostering permissionless content dissemination, and upholding user autonomy within digital environments. However, as the demographic footprint of Nostr's user base grows exponentially, coupled with an expanding range of content modalities, the structural integrity of individual relays faces increasing pressure.
Challenges of Isolation and Limited Scalability in Decentralized Networks
The current architecture of Nostr relays is primarily constituted of simple TCP or WebSocket servers that facilitate the publication and reception of events. While aesthetically simple, this design introduces significant performance bottlenecks and discoverability issues. Relays targeting specific regional or topical niches often rely heavily on client-side interactions or third-party directories for information exchange. This operational framework presents inefficiencies when scaled globally, especially in scenarios requiring high throughput and rapid dissemination of information. Furthermore, it does not adequately account for redundancy and availability, especially in low-bandwidth environments or regions facing strict censorship.

Navigating Impediments of Isolation and Constrained Scalability
Current Nostr relay infrastructures mainly involve basic TCP and WebSocket configurations for event publication and reception. While simple, these configurations contribute to performance bottlenecks and a significant discoverability deficit. Relays that serve niche markets often operate under constraints, relying on client-side interactions or third-party directories. These inefficiencies become particularly problematic at a global scale, where high throughput and rapid information distribution are necessary. The absence of mechanisms to enhance redundancy and availability in environments with limited connectivity or under censorship further exacerbates these issues.
Proposal for Encrypted Relay Federation
Encrypted relay federation in decentralized networking can be achieved through a novel Nostr Improvement Proposal (NIP), which introduces a sophisticated gossip-style mesh topology. In this system, relays subscribe to content tags, message types, or public keys from peer nodes, optimizing data flow and relevance.
Central to this architecture is a mutual key handshake protocol using Elliptic Curve Diffie-Hellman (ECDH) for symmetric encryption over relay keys. This ensures data integrity and confidentiality during transmission. The use of encrypted event bundles, compression, and routing based on relay reputation metrics and content demand analytics enhances throughput and optimizes network resources.
To counter potential abuse and spam, strategies like rate limiting, financially incentivized peering, and token gating are proposed, serving as control mechanisms for network interactions. Additionally, the relay federation model could emulate the Border Gateway Protocol (BGP), allowing for dynamic content advertisement and routing updates across the federated mesh, enhancing network resilience.
Advantages of Relay Federation in Data Distribution Architecture
Relay federation introduces a distributed data load management system where relays selectively store pertinent events. This enhances data retrieval efficiency, minimizes congestion, and fosters a censorship-resistant information flow. By decentralizing data storage, relays contribute to a global cache network, ensuring no single relay holds comprehensive access to all network data. This feature helps preserve the integrity of information flow, making it resistant to censorship.
An additional advantage is offline communication capabilities. Even without traditional internet access, events can still be communicated through alternative channels like Bluetooth, Wi-Fi Direct, or LoRa. This ensures local and community-based interactions remain uninterrupted during network downtime.
Furthermore, relay federations may introduce monetization strategies where specialized relays offer access to rare or high-quality data streams, promoting competition and interoperability while providing users with diverse data options.
Some Notable Markers To Nostr Becoming the Internet Layer for Censorship Resistance
Stop for a moment in your day and try to understand what Nostr can do for your communications by observing these markers:
- Protocol Idea (NIP-01 by fiatjaf) │ ▼
- npub/nsec Keypair Standard │ ▼
- First Relays Go Online │ ▼
- Identity & Auth (NIP-05, NIP-07) │ ▼
- Clients Launch (Damus, Amethyst, Iris, etc.) │ ▼
- Lightning Zaps + NWC (NIP-57) │ ▼
- Relay Moderation & Reputation NIPs │ ▼
- Protocol Bridging (ActivityPub, Matrix, Mastodon) │ ▼
- Ecash Integration (Cashu, Walletless Zaps) │ ▼
- Encrypted Relay Federation (Experimental) │ ▼
- Relay Mesh Networks (WireGuard + libp2p) │ ▼
- IoT Integration (Meshtastic + ESP32) │ ▼
- Fully Decentralized, Censorship-Resistant Social Layer
The implementation of encrypted federation represents a pivotal technological advancement, establishing a robust framework that challenges the prevailing architecture of fragmented social networking ecosystems and monopolistic centralized cloud services. This innovative approach posits that Nostr could:
- Facilitate a comprehensive, globally accessible decentralized index of information, driven fundamentally by user interactions and a novel microtransaction system (zaps), enabling efficient content valorization and information dissemination.
- Empower the concept of nomadic digital identities, allowing them to seamlessly traverse various relays, devoid of reliance on centralized identity verification systems, promoting user autonomy and privacy.
- Become the quintessential backend infrastructure for decentralized applications, knowledge graphs, and expansive datasets conducive to DVMs.
- Achieve seamless interoperability with established protocols, such as ActivityPub, Matrix, IPFS, and innovative eCash systems that offer incentive mechanisms, fostering an integrated and collaborative ecosystem.
In alignment with decentralization, encrypted relay-to-relay federation marks a significant evolution for the Nostr protocol, transitioning from isolated personal broadcasting stations to an interoperable, adaptive, trustless mesh network of communication nodes.
By implementing this sophisticated architecture, Nostr is positioned to scale efficiently, addressing global needs while preserving free speech, privacy, and individual autonomy in a world marked by surveillance and compartmentalized digital environments.
Nostr's Countenance Structure: Noteworthy Events
``` Nostr Protocol Concept by fiatjaf:
- First Relays and npub/nsec key pairs appear
- Damus, Amethyst, and other clients emerge
- Launch of Zaps and Lightning Tip Integration
- Mainstream interest post Twitter censorship events
- Ecosystem tools: NWC, NIP-07, NIP-05 adoption
- Nostr devs propose relay scoring and moderation NIPs
- Bridging begins (ActivityPub, Matrix, Mastodon)
- Cashu eCash integration with Nostr zaps (walletless tips)
- Relay-to-relay encrypted federation proposed
- Hackathons exploring libp2p, LNbits, and eCash-backed identities
- Scalable P2P Mesh using WireGuard + Nostr + Gossip
- Web3 & IoT integration with ESP32 + Meshtastic + relays
- A censorship-resistant, decentralized social internet ```
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ c239c0f9:fa4a5015
2025-04-21 17:42:49
@ c239c0f9:fa4a5015
2025-04-21 17:42:49Block:#893398- April 2025The Monthly Thunderbolt Dispatch on Bitcoin layers two innovations, aggregating the Best posts about the ~Lightning Network and others Bitcoin L2 solution- Exclusively on Stacker.News
It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin—the very first and most commented insights from around the SN world. In every issue arrives expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Subscribe and make sure you don’t miss anything about the ~Lightning Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Use RIZFUL as your BTCPay Server lightning node via NWC by @supratic 10.2k sats \ 2 comments \ 14 Apr
-
c-otto.de routing node history with a bit of data by @C_Otto 6301 sats \ 31 comments \ 23 Mar
-
Phoenix Wallet available again in the US by @Scoresby 4696 sats \ 29 comments \ 8 Apr
-
Short Text Note: Cashu is coming to ZEUS. by @supratic 5270 sats \ 13 comments \ 1 Apr
-
Hydrus - Automating lightning liquidity management by @aftermath 2281 sats \ 9 comments \ 27 Mar
Top posts by comments
Excluding the ones already mentioned above, you can see them all here (excluding those already listed above):
-
Liquidity squeezing from your node by @k00b 644 sats \ 20 comments \ 5 Apr
-
ZEUS starting to open up Cashu test builds to community sponsors. by @supratic 499 sats \ 14 comments \ 6 Apr
-
Ask Node Runners: What is the longest lived LN channel you have? by @DarthCoin 276 sats \ 12 comments \ 10 Apr
-
What's the best way to accept lightning payments on Wordpress + WooCommerce? by @Jon_Hodl 1879 sats \ 12 comments \ 10 Apr
-
Lightning node over tor by @BallLightning 219 sats \ 9 comments \ 28 Mar
Top ~Lightning Boosts
Check them all here.
-
Missing r/place? LNboard.com is the Lightning Network's Anarchy Art Gallery by @f0e6f4f43b 905 sats \ 40k boost \ 20 comments \ 2 Apr
-
Try out the Ark protocol on signet by @nwoodfine 2083 sats \ 30k boost \ 12 comments \ 19 Mar
-
Amboss CEO On Growth Of The Lightning Network, Tether (USDT) On Lightning by @Jestopher_BTC 577 sats \ 20k boost \ 10 comments \ 19 Feb
-
Building Self Custody Lightning in 2025 by @k00b 2293 sats \ 10k boost \ 8 comments \ 23 Jan
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
I made a game with Lightning where you can earn some sats by @stacks 4732 sats \ 46 comments \ 17 Apr on
~bitcoin -
"Lightning self custody works for 100 million users" "But it needs 10 billion!!" by @standardcrypto 2998 sats \ 22 comments \ 24 Mar on
~bitcoin -
24 Hours of Lightning: Watch LNboard.com's First Day Unfold by @f0e6f4f43b 809 sats \ 8 comments \ 2 Apr on
~bitcoin -
Lightning Payments Tour by Yopaki by @PlebLab 355 sats \ 0 comments \ 11 Apr on
~builders -
👀 My Bitcoin Startup Company Portfolio through Lightning Ventures. 👀 by @BlokchainB 965 sats \ 13 comments \ 16 Apr on
~Stacker_Stocks
Forever top ~Lightning posts
La crème de la crème... check them all here. Nothing has changed this month!
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
The rise of Supertestnet at #5, congrats!
-
Rethinking Lightning by @benthecarman with 51.6k sats \ 137 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio with 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Lightning Is Doomed by @Rsync25 2450 sats \ 15 comments \ 27 Nov 2023 on
~bitcoin -
Bisq2 adds lightning by @supertestnet 3019 sats \ 47 comments \ 19 Aug 2024 on
~bitcoin
-
-
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ d34e832d:383f78d0
2025-04-21 17:29:37
@ d34e832d:383f78d0
2025-04-21 17:29:37This foundational philosophy positioned her as the principal architect of the climactic finale of the Reconquista—a protracted campaign that sought to reclaim territories under Muslim dominion. Her decisive participation in military operations against the Emirate of Granada not only consummated centuries of Christian reclamation endeavors but also heralded the advent of a transformative epoch in both Spanish and European identity, intertwining religious zeal with nationalistic aspirations and setting the stage for the emergence of a unified Spanish state that would exert significant influence on European dynamics for centuries to come.
Image Above Map Of Th Iberias
During the era of governance overseen by Muhammad XII, historically identified as Boabdil, the Kingdom of Granada was characterized by a pronounced trajectory of decline, beset by significant internal dissent and acute dynastic rivalry, factors that fundamentally undermined its structural integrity. The political landscape of the emirate was marked by fragmentation, most notably illustrated by the contentious relationship between Boabdil and his uncle, the militarily adept El Zagal, whose formidable martial capabilities further exacerbated the emirate's geopolitical vulnerabilities, thereby impairing its capacity to effectively mobilize resistance against the encroaching coalition of Christian forces. Nevertheless, it is imperative to acknowledge the strategic advantages conferred by Granada’s formidable mountainous terrain, coupled with the robust fortifications of its urban centers. This geographical and structural fortitude, augmented by the fervent determination and resilience of the local populace, collectively contributed to Granada's status as a critical and tenacious stronghold of Islamic governance in the broader Iberian Peninsula during this tumultuous epoch.
The military campaign initiated was precipitated by the audacious territorial annexation of Zahara by the Emirate in the annum 1481—a pivotal juncture that served as a catalytic impetus for the martial engagement orchestrated by the Catholic Monarchs, Isabel I of Castile and Ferdinand II of Aragon.

Image Above Monarchs Of Castilles
What subsequently unfolded was an arduous protracted conflict, extending over a decade, characterized by a series of decisive military confrontations—most notably the Battle of Alhama, the skirmishes at Loja and Lucena, the strategic recapture of Zahara, and engagements in Ronda, Málaga, Baza, and Almería. Each of these encounters elucidates the intricate dynamics of military triumph entwined with the perils of adversity. Isabel's role transcended mere symbolic representation; she emerged as an astute logistical architect, meticulously structuring supply chains, provisioning her armies with necessary resources, and advocating for military advancements, including the tactical incorporation of Lombard artillery into the operational theater. Her dual presence—both on the battlefield and within the strategic command—interwove deep-seated piety with formidable power, unifying administrative efficiency with unyielding ambition.
In the face of profound personal adversities, exemplified by the heart-wrenching stillbirth of her progeny amidst the tumultuous electoral campaign, Isabel exhibited a remarkable steadfastness in her quest for triumph. Her strategic leadership catalyzed a transformative evolution in the constructs of monarchical power, ingeniously intertwining the notion of divine right—a historically entrenched justification for sovereign authority—with pragmatic statecraft underpinned by the imperatives of efficacious governance and stringent military discipline. The opposition posed by El Zagal, characterized by his indefatigable efforts and tenacious resistance, elongated the duration of the campaign; however, the indomitable spirit and cohesive resolve of the Catholic Monarchs emerged as an insuperable force, compelling the eventual culmination of their aspirations into a definitive victory.
The capitulation of the Emirate of Granada in the month of January in the year 1492 represents a pivotal moment in the historical continuum of the Iberian Peninsula, transcending the mere conclusion of the protracted series of military engagements known as the Reconquista. This momentous event is emblematic of the intricate process of state-building that led to the establishment of a cohesive Spanish nation-state fundamentally predicated on the precepts of Christian hegemony. Furthermore, it delineates the cusp of an imperial epoch characterized by expansionist ambitions fueled by religious zealotry. The ramifications of this surrender profoundly altered the sociocultural and political framework of the region, precipitating the coerced conversion and expulsion of significant Jewish and Muslim populations—a demographic upheaval that would serve to reinforce the ideological paradigms that underpinned the subsequent institution of the Spanish Inquisition, a systematic apparatus of religious persecution aimed at maintaining ideological conformity and unity under the Catholic Monarchs.

Image Above Surrender At Granada
In a broader historical context, the capitulation of the Nasrid Kingdom of Granada transpired concurrently with the inaugural expedition undertaken by the navigator Christopher Columbus, both events being facilitated under the auspices of Queen Isabel I of Castile. This significant temporal nexus serves to underscore the confluence of the termination of Islamic hegemony in the Iberian Peninsula with the commencement of European maritime exploration on a grand scale. Such a juxtaposition of religiously motivated conquest and the zealous pursuit of transoceanic exploration precipitated a paradigm shift in the trajectory of global history. It catalyzed the ascendance of the Spanish Empire, thereby marking the nascent stages of European colonial endeavors throughout the Americas.

Image Above Columbus At The Spanish Court
This epochal transformation not only redefined territorial dominion but also initiated profound socio-economic and cultural repercussions across continents, forever altering the intricate tapestry of human civilization.
Consequently, the cessation of hostilities in Granada should not merely be interpreted as the conclusion of a protracted medieval conflict; rather, it represents a critical juncture that fundamentally reoriented the socio-political landscape of the Old World while concurrently heralding the advent of modernity. The pivotal contributions of Queen Isabel I in this transformative epoch position her as an extraordinarily significant historical figure—an autocrat whose strategic foresight, resilience, and zeal indelibly influenced the trajectory of nations and entire continents across the globe.
-
 @ e97aaffa:2ebd765d
2025-04-21 12:57:16
@ e97aaffa:2ebd765d
2025-04-21 12:57:16Se este movimento de desglobalização continuar, poderá provocar uma cisão no mundo geopolítico, criar dois grandes blocos económicos, uma nova guerra fria.
Se isso se concretizar, quantos anos vão ser necessários para o S&P500 superar máximos históricos em termos reais, em poder de compra?
Em valores nominais vai ser rápido, o governo dos EUA vai imprimir tanto dinheiro, rapidamente vai superar máximos, mas em termos reais, vai demorar muitos anos.
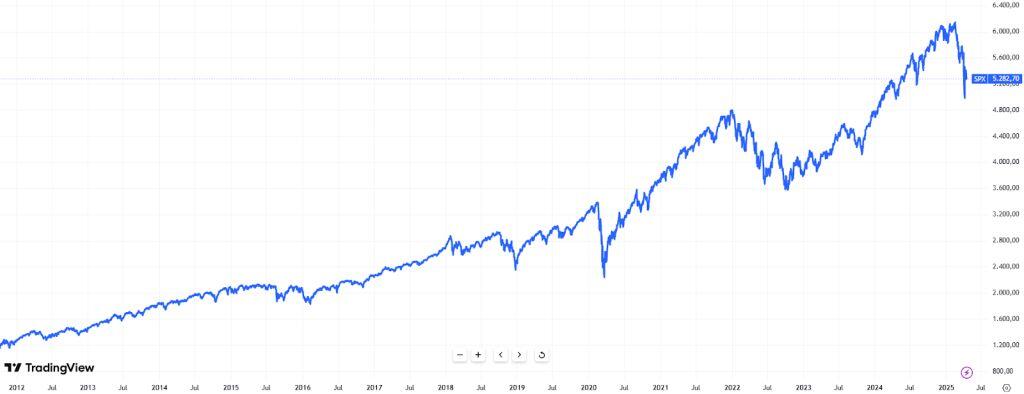
Até agora, todo o mundo estava a investir nos EUA, mas se os países do bloco oriental, sobretudo a China, deixarem de investir em ações, obrigações e moeda dos EUA, irá provocar uma enorme redução de liquidez e na procura/demanda, não vai ser fácil ultrapassar isso.
Nos US Treasury, o afastamento da China começou em 2014(1° guerra da Ucrânia), mas o movimento acelerou em 2022(2° guerra da Ucrânia).

Os EUA, ao congelar as reservas da Rússia, ao utilizar as reservas como uma arma de guerra, “assustaram” a China e outros países. As sanções à Rússia e como esta fez para contornar as sanções foi um case study para a China.
Como o objetivo da China é recuperar Taiwan, sabe que sofrerá as mesmas represálias que hoje a Rússia sofre, por isso a China tem que se afastar da economia dos EUA.
A China está a trocar US Treasury por outros ativos e por outras geografias, o principal beneficiado foi o ouro, um ativo soberano, que não tem problemas de contraparte.
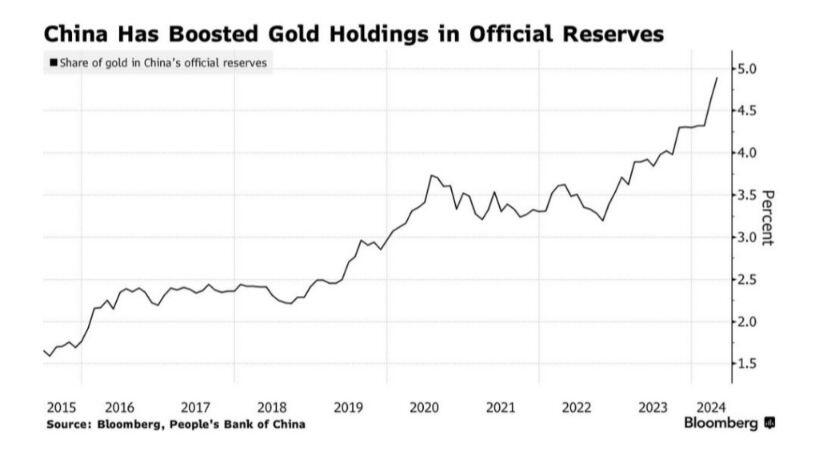
Este movimento da China foi bem visível no preço do ouro no último ano, uma valorização superior a 42%.
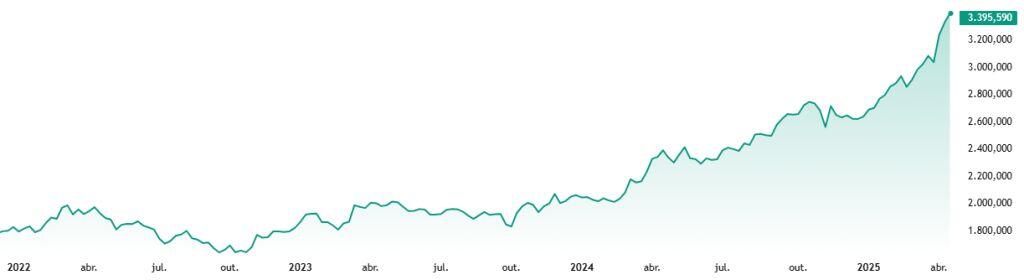
Mas não é só a China que está a apostar no ouro, são diversos, mas sobretudo composta por países do bloco oriental.
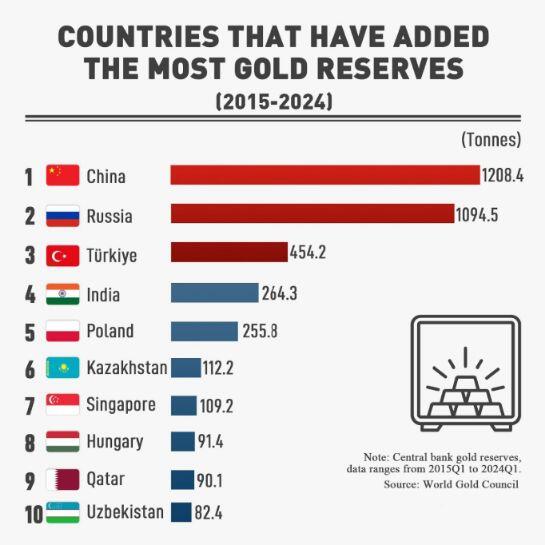
Enquanto, Taiwan for a fábrica do mundo nos semicondutores, estarão protegidos pelo guarda-chuva dos EUA. Mas os EUA, estão a construir fábricas próprias, quando forem auto-suficientes, vão descartar o “guarda-chuva”, Taiwan não terá qualquer hipótese sobre o poderio da China.
A China pensa sempre a longo prazo, estão apenas a aguardar, isto poderá estar para muito em breve.
Se isto se confirmar, o S&P500 poderá demorar décadas para recuperar desta crise, em termos de poder de compra.
-
 @ 5c8a5765:4fc5edee
2025-03-22 18:38:23
@ 5c8a5765:4fc5edee
2025-03-22 18:38:23[Читать в IPFS]
Итак, детки-котлетки, сегодня мы поговорим, как ~~не~~правильно распространять агиацию. Возьмите свои любимые антифашистские стикеры и используйте этот текст как инструкцию к ним — иначе у меня голова лопнет от того, что я вижу на улицах.
Агитация
Для начала определитесь, чем вы занимаетесь: агитируете к чему-то или поддерживаете чего-то, потому что это предполагает совершенно разные подходы. Агитацией может быть призыв к анархизму, классовой борьбе, неуплате налогов, гендерному равенству и т.д. Поддержкой может быть поддержка анархической борьбы, антифашистский идей и т.д. Первое — "вербует"/приманивает новых людей к идее, второе поддерживает только тех, кто уже знаком с идеей и уже с ней согласен.
Как должна выглядеть агитация? Представьте, что некий неонацист решил за-агитировать вас в неонацизм (с учетом, что сейчас вы его не поддерживаете): в каком случае у него больше всего на это шансов? Если вы заметите на мусорном баке наклейку "бей жыдоф"? Или если вам, например, выдадут в руки грамотный агитационный текст? Поставьте себя на место читающего: агитация должна выглядеть именно так, как мог бы выглядеть материал, который хоть немного мог бы поменять ваши текущие взгляды. А именно...
1. Агитация доступна
Она не висит на задней стороне мусорки. Она не нарисована на заброшке. Обыватель не рассматривает мусорки и не ходит по заброшкам. Чтобы масса увидела вашу агитацию, она должна висеть в заметном месте.
Ещё лучше, если она висит там, где человек по внешним причинам на мгновение задерживается, и имеет время проглядеть вашу агитацию: ибо обыватель никогда не остановится у столба посреди длинной тропы, чтобы прочесть стикер.
И учтите: если место, которое вы выбрали, уже забито стикерами, вашему придётся делить привлеченное внимание с каждым остальным.
К доступности стоит также отнести то, что агитация более значительна, если она написана на самом популярном в вашей стране языке, развешивается в разных локациях (чтобы люди разного класса могли её увидеть), если вы развешиваете в туалетах — то туалетах разного гендера (и не забывайте про инвалидные кабинки!), так далее.
Лучшие места для стикеров: лифт, автобусная остановка, метро, поручен эскалатора, внешняя сторона дверцы туалета, чистое (не разрисованное или расклеенное) зеркало.Лучшие места для крупных агитационных листов или графитти: указанные выше, а также — заметные места подъездов,Лучшие места для "визиток"*: оставлять под задницей на выходе из автобуса, метро, маршрутки, на стульях, скамейках и т.д.*"Визитка" — это са-а-амый простой метод агитации: выводите нужный текст или картинки мелкими блоками на листе А4, нарезаете бумагу на кусочки "визиток" с небольшим текстом, картинкой или ссылкой, и оставляете где попало.
2. Агитация запоминается
Если вы не неонацист, какие эмоции в вас побуждает "бей жыдоф"? Вы возжелали стать неонацистом? Или это только укрепило ваши антифашистские взгляды? Или это для вас вообще никак не прозвучало?
Также для ваших противников и обывателей звучат ваши "ешь богатых!", "классовая борьба сегодня!!", "доёш онархию!!!". Это — поддержка. Уже-анархисты будут рады увидеть, что в городе есть левые активисты кроме них самих. Но это никого не переубедит и не привлечет.
А агитация привлекает. Агитация задаёт острые вопросы, которые остаются в голове. Агитация манит предложениями нового. Агитация нестереотипно предлагает.
Примеры хорошей агитации:

"Если большинство проголосует за то, чтобы ты спрыгнул(а) с вмоста, ты бы сделал(а) это? / - Может быть — если это было честным голосованием!"

"Этот телефон прослушивается - согласно законодательству США, телефонные разговоры прослушиваются без ордера или уведомленияю"

"Вы под наблюдением — текст, объясняющий тезис, и ссылка, где можно прочесть об этом подробнее."
Примеры никудышной агитации (но хорошей поддержки):



3. Агитация даёт возможность изучить больше
Хорошее правило для любой агитации: иметь ссылку на сайт, где можно найти больше информации о том, к чему агитируется. Это не обязательное, но рекомендуемое правило, ибо мало толку от человека, согласившегося с идеей анархизма и захотевшего (редчайший случай!) самостоятельно изучить больше, но не имевшего к этому простой возможности и забывшего вследствие обо всей идее.
Поддержка
А вот поддержка — ориентированная на тех, кто уже знает и уже поддерживает то, что вы любите — может быть совершенно любой. Поддержать антифашистов своего города, позлить фашистов и остаться совершенно незамеченными для обывателя — самое место для диалектики "бей жыдоф!" и "доёш онтифошизм!!".
Напоминание о безопасности
Несколько базовых напоминаний о том, что нужно помнить во время агитации:
- ОСТЕРЕГАЙТЕСЬ КАМЕР! Особенно в России! Метро, маршрутки, автобусы, учебные заведения полны ими!
- Если вас заметили гестаповцы, лучшее, что вы можете сделать — это бежать, что есть мочи.
- Шифруйте материалы, которые храните для распечаток.
- Не распечатывайте стикеры/"визитки" в публичных местах (вроде библиотек).
Спасибо за прочтение!

-
 @ dbb19ae0:c3f22d5a
2025-04-21 12:29:38
@ dbb19ae0:c3f22d5a
2025-04-21 12:29:38Notice this consistent apparitioon in the timeline of something that reflects a major key shift in tech:
💾 1980s – The Personal Computer Era
- IBM PC (1981) launches the home computing revolution.
- Rise of Apple II, Commodore 64, etc.
- Storage is local and minimal.
- Paradigm shift: Computing becomes personal.
🎮 1990s – Networking & Gaming
- LAN parties, DOOM (1993) popularizes multiplayer FPS.
- Early internet (dial-up, BBS, IRC).
- There is lots of room for connecting PC.
- Paradigm shift: Networked interaction begins.
🌐 2000s – The Internet Boom
- Web 2.0, broadband, Google, Wikipedia.
- Rise of forums, blogs, file sharing.
- A bigger need of interaction is looming
- Storage is on cd and dvd.
- Paradigm shift: Global information access explodes.
📱 2010s – Social Media & Mobile
- Facebook, Twitter, Instagram dominate.
- Smartphones become ubiquitous.
- Bitcoin appears and start a revolution.
- Collecting personal data from users to fuel the next shift.
- Paradigm shift: Always-connected, algorithmic society.
🤖 2020s – AI & Decentralization
- GPT, Stable Diffusion, Midjourney, Copilot.
- Blockchain, Nostr, Web3 experiments.
- Storage is in the cloud.
- Paradigm shift: Autonomous intelligence and freedom tech emerge.
roughly every decade, a tech leap reshapes how we live and think.
-
 @ 57d1a264:69f1fee1
2025-04-21 12:11:22
@ 57d1a264:69f1fee1
2025-04-21 12:11:22There's any content about SN out there?
In the news: - @BitcoinNews Stacker.News Raises $1.25m Seed Round At $25m Valuation - @Alby blog post explain how Stacker News adds Self-custodial Spending with NWC - @cryotosensei on @0xbitcoiner's website Stacker News encourages deep sharing ad Random things I learnt about Bitcoin from Stacker News - @anita's Earn bitcoin on Stacker News: People asked and I answered
Recently we have seen an article in BM writing about how PlebLab is shaping the future of bitcoin startups in Austin. SN was mentioned and linked 🎉
Started in 2021 by one of PlebLab’s cofounders Keyan Kousha, Stacker.news has quickly become a hub of news for many tech-savvy Bitcoiners. Boasting an open source Lightning-powered Reddit, the platform has gathered an active and loyal fan base that reward each other with sats for every upvote, often being early to integrate the latest technologies in the Bitcoin-social media tech scene.
In the past it has also only mentioned here.
From a startup pitch perspective:
Developer of a news platform intended for individuals to earn real money for creating and curating content. The company's platform specializes in allowing individuals to submit, vote, and comment on content, stories, and discussions about the topics in communities organized around their interests, enabling individuals to post content and get paid while reading the news. PitchBook -
https://pitchbook.com/profiles/company/535835-44#overviewStacker News is a forum (like Reddit or Hacker News) where you can earn real money for creating or curating content. F6S -
https://www.f6s.com/company/stacker-news#aboutPeople talking about SN:
-
A stacker shared a Lessons learned from Stacker.news and how SN works. Discourse Co-CEO respond:
Heh, it’s not a healthy or sustainable model for the types of communities consciously we build for. Definitely not something we would consider building into core but you could make it work with a plugin. Extrinsic motivators attract the wrong people for the wrong reasons, in my experience. Healthy community ecosystems are driven by intrinsic motivation.
-
on BitcoinTalk here, here and here. There are probably more posts where it has ben mentioned and discussed.
-
HackerNews crowd does not seem too excited about it. Just few comments on each post.
Some review have been collected on @julian's Apollo and ProductHunt.
Let's check what YT has:
Some interviews first. At 2023 ZBD x PlebLab TabConf Hackathon, Keyan Kousha explain Why Not to Use Stacker News
@kr did a great job interviewing k00b when SN was in its infancy - Stacker News Is Growing FAST - Stacker News Is Disrupting Social Media | E17 - Keyan Kousha on Stacker News, Earning Bitcoin, & Decentralized Content | The Kevin Rooke Show | E17 - How Siggy47 Stacked Over 500,000 Sats on Stacker News | SS8
And here some interviews:
Stacker News is a user-generated, feed-style news platform, modeled after Hacker News, but with the important distinction of having natively-integrated bitcoin lightning payments, as a means of fostering more natural communities (think less spam and antisocial behavior), cultivating high-signal bitcoin content, and providing a better user experience overall.
Stacker News is still in the very early days of its development, but it's a great showcase of how bitcoin can be used to improve upon an existing model, and in doing so, explore how improved incentives might influence media publishing, monetization, and moderation.
Keyan is a prime example of someone who caught the bitcoin bug, and just couldn't resist getting involved. The result is a product built with and for bitcoiners, and it was great to have him on the show to explain more about his motivations and ambitions.
-
From ~ideasfrommtheedge pod: AI, Simulations, and Startups with Keyan Kousha (Founder, Stacker News)
-
@alexstrenger's Convos On The Pedicab #177 Stacker News: A Bitcoiners Alternative To Reddit
-
@dk and @MaxAWebster intro on What's new with Stacker.News and Nostr? also shared here
-
@ConnectTheWorld stream Keep Austin Weird! Meet Keyan, the founder of Stacker.news
-
@Thriller Lightning: Stacker.News Founder Keyan
-
0.00000018: Keyan Kousha, Stacker.News: an interview in the Changing the Tide show here
-
@bitcoinplebdev reading top ~devs stories 04/08/2024 and stacker.news codebase overview / how to run locally)
That's the interviews I was able to find. Continuing the dig...
-
@TheWildHustle compiles SN ~Music' vibes into YT playlists
-
@kdnolan7 on was giving some updates about the ~Education territory here and here
Gradually, then suddenly, the message start to change, and the majority of videos communicate something that is probably, at least from my perspective, not the right way to market a product like SN:
-
@SatsMate lay out Why He Love Stacker News!
-
@voltage share a story quickly talking how Stacker News is like YCombinators Hacker News but YOU EARN! https://www.youtube.com/shorts/d1xZ3RE9plk
@HattyHats Earn Bitcoin (LN) Blogging with Stacker News
The long list continues: - Earn bitcoin Satoshis Reading & Sharing Content on Stacker.News - First Time Walk Through by @SatoshiTutor - Earn Free Bitcoin | Stacker News Quick Tutorial from Earning Crypto Site - One of the Different Ways to Earn Bitcoin 👉 stacker.news | Bitcoin Lifestyle #2 from @SatoshiComTR - @1100note another Stacker.News story - ...
This list of references can, and probably will, go on and on with the same topic. The message looks like will be always the same: come over, stack sats, stay humble. There's maybe something wrong with the message we share SN out there? Is not what we do, is how we do it, that make the difference. As you can see, there's not much there that refer to quality content, great supportive community, community moderated contents, no ads, no spam, no bots (well, not many) and no ai. Pure human content.
In other successful platforms where people earn money for the contents they create, the money factor is totally hidden, is not their main sales point in the pitch. Look at YT itself. We all know people earn fiat producing and sharing videos, but their comms does not talk about it, at least not the way stackers do. And you'll not find many YTers inviting others to create videos to earn money. Well ok, some do!
Something we could make an effort to improve, is the way we talk about SN. Finding alternative ways to do it is hard, some have been mentioned here https://stacker.news/items/948462/r/Design_r
Just wanted to see how much other quality content is out there talking about SN that is not about stacking sats? Share your best contents, nostr notes, x tweets, blog posts, articles, videos, interviews, reviews or any other media that has been created by others about SN (no memes shill) or that somehow mention it in the comments below.
originally posted at https://stacker.news/items/951177
-
-
 @ bccf33d8:4b705625
2025-03-19 10:07:46
@ bccf33d8:4b705625
2025-03-19 10:07:46{"title":"nostrbook 创建的五本四书哈哈哈","author":"nostrbook.com","intro":"This is a book from ....很不错","picture":"https://432fds"}
-
 @ e111a405:fa441558
2025-03-19 08:57:18
@ e111a405:fa441558
2025-03-19 08:57:18Erdoğan'ın İmamoğlu'nu akademik teknik detaylar ve iddia edilen PKK bağlantıları üzerinden sistematik olarak saf dışı bırakması, yalnızca Türkiye'ye özgü bir durum değil; demokrasinin küresel çöküşünün bir örneğidir.
Dün Almanya, yeterli inceleme yapılmadan ve zaten görevden alınmış bir çoğunlukla anayasal değişiklikleri aceleyle geçirdi; Romanya ise adayları prosedürel gerekçelerle diskalifiye ediyor. Liste uzayıp gidiyor: Macaristan'da Viktor Orbán, Sırbistan'da Aleksandar Vučić, İsrail'de Netanyahu, Polonya'da Hukuk ve Adalet Partisi – demokratik gerileme bölgeler ve siyasi sistemlerin ötesine geçiyor. Bugün insanlığın %72'si otoriter rejimler altında yaşıyor.
Yeni bir oyun kitabı var: yasal kurumları muhaliflere karşı silah olarak kullanmak, prosedürel tiyatro yoluyla meşruiyet üretmek ve anayasal görüntüyü korurken demokratik güvenceleri ortadan kaldırmak.
Demokrasinin dramatik bir çöküşünü değil, bürokratik manipülasyonla metodik olarak boğulmasını izliyoruz. Bu erozyon tesadüfi değil; merkezi güç yapılarının, ne kadar iyi tasarlanmış olursa olsun, kaçınılmaz olarak yozlaşmasının bir sonucudur.
İnanıyorum ki tek sürdürülebilir yolumuz radikal bir merkezsizleşmeden geçiyor: yönetimin yerel topluluklara dağıtılması, kripto ağları aracılığıyla finansal egemenlik sağlanması ve hiçbir tekil varlığın kontrol edemeyeceği sansüre dayanıklı platformlar üzerinden iletişim kurulması.
Merkezi olmayan sistemler, insan onurunu, merkezi otoritelerin, kariyer politikacılarının ve atanmış bürokratların boş vaatlerine bel bağlamak yerine kırılmaz kriptografik garantilerle yeniden tesis eder.
Gelecek, özgürlüğü temel alan sistemler aracılığıyla gönüllü olarak işbirliği yapan ağ bağlantılı bireylere aittir. Merkezi olmayan ve küresel olarak ağ bağlantılı toplumlar, tek noktadan başarısızlık yerine binlerce eşzamanlı deneyi mümkün kılarak yeniliği serbest bırakan antifragil toplumlardır.
Türk arkadaşlarıma tavsiyelerim: https://primal.net'i kullanın (X'e merkeziyetsiz bir alternatif), günlük işlemler ve akıllı sözleşmeler için https://zano.org 'u kullanmaya ve kabul etmeye başlayın (merkeziyetsiz, izinsiz kripto para birimi ve işlemler; yakında gizlilik odaklı bir stabilcoin ile).
-
 @ cb4352cd:a16422d7
2025-04-21 11:17:41
@ cb4352cd:a16422d7
2025-04-21 11:17:41What happens when artificial intelligence meets Web3? It's no longer just an idea — it's happening, and it's reshaping how we think about applications, economies, and communities online.
AI-as-a-Service in Web3
One of the clearest signs of this shift is the rise of decentralized AI marketplaces. Projects like Bittensor show that users can contribute machine learning models and earn rewards in cryptocurrency.
Another example is Gensyn, linking AI developers to decentralized compute resources.
Verifying AI with Blockchain
Blockchain helps verify AI outputs. Initiatives like Oraichain and Fetch.ai ensure AI agents interact securely and transparently in decentralized ecosystems.
AI-Driven Decentralized Organizations
Projects like SingularityNET explore AI marketplaces and autonomous governance models, creating new possibilities for decentralized coordination.
Generative AI in Web3 Content Creation
Platforms like Alethea AI are building intelligent NFTs that adapt to user interactions. AI-generated quests and dynamic worlds are reshaping GameFi.
The Road Ahead
Beyond Banking Conference by WeFi will spotlight how AI and Web3 are converging to redefine ownership, collaboration, and the very nature of the internet.
The question isn't whether AI and Web3 will merge — it's how quickly their union will reshape everything we know about digital life.
-
 @ e111a405:fa441558
2025-03-19 08:54:18
@ e111a405:fa441558
2025-03-19 08:54:18Erdogan's calculated elimination of Imamoglu through academic technicalities and alleged ties to PKK is not really an isolated Turkish case but an example of democracy's global collapse.
Yesterday, Germany rushed constitutional changes without proper scrutiny and with a majority that was already voted out of office, Romania disqualifies candidates on procedural grounds. The list goes on: Hungary under Viktor Orbán, Serbia under Aleksandar Vučić, Israel under Netanyahu, Poland under the Law and Justice party – the democratic backsliding goes well beyond regions and political systems. 72% of humanity now lives under authoritarian control.
There is a new playbook: weaponize legal institutions against opponents, manufacture legitimacy through procedural theater, and dismantle democratic safeguards while maintaining the illusion of constitutionality.
We're witnessing not democracy's dramatic collapse but its methodical strangulation through bureaucratic manipulation. This erosion isn't coincidental but the inevitable outcome of centralized power structures that invariably corrupt even well-designed systems.
I believe that our only viable path forward lies in radical decentralization: distributing governance to local communities, financial sovereignty through crypto networks, and communication via censorship-resistant platforms that no single entity controls.
Decentralized systems restore human dignity by establishing unbreakable cryptographic guarantees rather than depending on the hollow promises of centralized authorities, career politicians, and unelected bureaucrats .
The future belongs to networked individuals collaborating voluntarily through systems designed with liberty as their foundation. Decentralized and globally networked societies are antifragile societies that unleash innovation by enabling thousands of concurrent experiments instead of single-point failures.
-
 @ 86dfbe73:628cef55
2025-04-21 10:08:34
@ 86dfbe73:628cef55
2025-04-21 10:08:34Mit dem Internet kam das Ende der Massengesellschaft. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar. Nicht als Netzwerk zur Kommunikation, sondern als Netzwerk der Beziehungen, bestehend aus den Erwartungen, Kenntnissen und letztlich bestehend aus dem Vertrauen, das Menschen gegenüber anderen Menschen und Institutionen aufzubauen pflegen. Wichtig ist nicht mehr, wo jemand eine Information plaziert, wichtig ist, wann und wer und unter Einbeziehung welcher Faktoren diese abfragt.
In Sozialen Netzwerken entscheidet jeder selbst, wem er folgt. Er entscheidet selbst, wie die eigene Startseite, der eigene Blick auf den Dienst, aussieht. Als Beispiel sei hier Twitter erwähnt. Aus der Liste der Gefolgten wird die Timeline generiert, die eine Wirklichkeit abbildet, die einzig und alleine von den Following-Entscheidungen des Nutzers bestimmt ist.
Die Beziehungsweise des Folgens ist eine direkte Willenserklärung, die Inhalte eines Users sehen zu wollen. Sie ist ein Pakt, der auch eine gewisse, wenn auch kleine, Verantwortungsübernahme bedeutet. Und diese Beziehungsweise wurde zum integralen Strukturbaustein der digitalen Öffentlichkeit zwischen 2010 bis 2020 und damit auch zur tragenden Säule vieler Karrieren, Geschäftsmodellen und außerdem zur Grundlage der Selektionsverfahren von kulturellen Trends. Im Follower steckte die Macht.
Die digitale Öffentlichkeit hat aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in den „For you“-Algorithmen der kommerziellen Plattformen auf. Ab 2020 wurde dem Follower von Diensten wie Tiktok der Gar ausgemacht und von dort setzte sich der „For You-Algoritmus“ auf allen kommerziellen Plattformen durch. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist. Auf einmal bedeutete ein Following nicht mehr die Garantie, dass der Content die Abonnenten erreicht.
Mit der Zerstörung dieser Beziehung entgleiten den Creators ihre medialen Regime und beide, User und Creator werden immer abhängiger vom Algorithmus und arbeiten folglich nur noch für die Interessen der Plattformen, statt für sich selbst.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 95cb4330:96db706c
2025-04-21 09:59:02
@ 95cb4330:96db706c
2025-04-21 09:59:02Principle:
Reduce internal friction by minimizing unnecessary processes, approvals, and meetings.
Empower small, autonomous teams to make decisions quickly and independently.
💡 What It Means
- Bureaucracy kills speed, innovation, and ownership.
- Instead of creating endless layers of management and approval, build the smallest system necessary to enable great work.
- Give teams the trust and tools they need to move fast.
The goal is not chaos, but flexibility with lightweight structure—so the organization stays dynamic as it scales.
📈 Why It Matters
✅ Speed is a competitive advantage in entrepreneurship.
✅ Empowered teams are more creative and motivated.
✅ Minimal bureaucracy allows companies to iterate fast and stay customer-focused.
🏛️ Examples in Action
- Spotify uses small “squads” with high autonomy and light-touch leadership to maintain speed and innovation.
- Basecamp designs its company around minimal meetings, clear asynchronous communication, and trusting small teams to own outcomes.
- Amazon uses the "two-pizza team" rule—teams should be small enough to be fed with two pizzas.
📚 Resources to Explore
- 📄 Spotify’s Engineering Culture – Part 1
- 📖 Basecamp’s Approach to Minimal Management
- 📘 Harvard Business Review on 3 Ways to Improve Your Decision Making
- Spotify Engineering Culture - Part 1 (aka the "Spotify Model")
🚀 Action Prompthttps://hbr.org/2018/01/3-ways-to-improve-your-decision-making
Ask yourself:
"What approvals, meetings, or processes can I eliminate or simplify today to help my team move faster?"Build only as much structure as needed—and no more. Protect creativity, speed, and ownership at all costs.
-
 @ 7d33ba57:1b82db35
2025-04-21 08:47:51
@ 7d33ba57:1b82db35
2025-04-21 08:47:51Spread across 14 islands and connected by elegant bridges, Stockholm is often called the **"Venice of the North." It blends royal history, cutting-edge design, lush nature, and a laid-back Nordic vibe like few cities can. With cobblestone streets in Gamla Stan, sleek modern art in Södermalm, and serene waterways everywhere, Stockholm is both storybook and futuristic.

🏰 Top Things to Do in Stockholm
🏛️ Gamla Stan (Old Town)
- A beautifully preserved medieval core with colorful buildings, narrow alleys, and cozy cafés
- Visit the Royal Palace, Stockholm Cathedral, and watch the changing of the guard
- Stop by Stortorget Square for the classic photo and a fika (Swedish coffee break)
🖼️ Vasa Museum
- Home to the Vasa warship, which sank on its maiden voyage in 1628 and was miraculously recovered 333 years later
- One of Sweden’s most popular and jaw-dropping museums

🏡 Skansen Open-Air Museum
- A walk through Sweden’s past—complete with historic homes, craft demos, and even Scandinavian animals
- Great for families or anyone curious about Swedish traditions
🌉 Södermalm
- Stockholm’s hip, creative district
- Full of boutique shops, vintage stores, craft coffee, and rooftop bars
- Climb Monteliusvägen for incredible views of the city skyline and Lake Mälaren

🌿 Nature & Water Everywhere
- Take a boat tour of the Stockholm Archipelago, made up of 30,000+ islands
- Kayak through the canals or paddleboard around Kungsholmen
- In summer, locals swim off the rocks in the city or picnic in Djurgården Park

🍽️ Food & Fika
- Try Swedish meatballs, gravad lax, or herring smörgåsbord
- Visit the indoor Östermalm Market Hall for local specialties
- Don’t miss fika culture—coffee + cinnamon buns (kanelbullar) is a must

🚆 Getting Around
- Super walkable and bike-friendly
- Excellent public transport: trams, ferries, metro (Tunnelbana)
- The T-Centralen station even doubles as an underground art gallery

📅 Best Time to Visit
- Summer (June–August): Long sunny days, outdoor festivals, archipelago adventures
- Winter: Christmas markets, cozy cafés, and snow-dusted rooftops
- Year-round appeal with distinct charm in every season

-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ d34e832d:383f78d0
2025-04-21 08:32:02
@ d34e832d:383f78d0
2025-04-21 08:32:02The operational landscape for Nostr relay operators is fraught with multifaceted challenges that not only pertain to technical feasibility but also address pivotal economic realities in an increasingly censored digital environment.
While the infrastructure required to run a Nostr relay can be considered comparatively lightweight in terms of hardware demands, the operators must navigate a spectrum of operational hurdles and associated costs. Key among these are bandwidth allocation, effective spam mitigation, comprehensive security protocols, and the critical need for sustained uptime.
To ensure economic viability amidst these challenges, many relay operators have implemented various strategies, including the introduction of rate limiting mechanisms and subscription-based financial models that leverage user payments to subsidize operational costs. The conundrum remains: how can the Nostr framework evolve to permit relay operators to cultivate at least a singular relay to its fullest operational efficiency?
It is essential to note that while the trajectory of user engagement with these relays remains profoundly unpredictable—analogous to the nebulous impetus behind their initial inception—indicators within our broader economic and sociocultural contexts illuminate potential pathways to harmonizing commercial interests with user interaction through the robust capabilities of websocket relays.
A few musingsI beg you to think about the Evolutionary Trajectory of Nostr Infrastructure Leveraging BDK (Bitcoin Development Kit) and NDK (Nostr Development Kit) in the Context of Sovereign Communication Infrastructure
As the Nostr ecosystem transitions through its iterative phases of maturity, the infrastructure, notably the relays, is projected to undergo significant enhancements to accommodate an array of emerging protocols, particularly highlighted by the Mostr Bridge implementation.
Additionally, the integration of decentralized identity frameworks, exemplified by PKARR (Public-Key Addressable Resource Records), signifies a robust evolutionary step towards fostering user accountability and autonomy.
Moreover, the introduction of sophisticated filtering mechanisms, including but not limited to Set Based Reconciliation techniques, seeks to refine the user interface by enabling more granular control over content visibility and interaction dynamics.
These progressive innovations are meticulously designed to augment the overall user experience while steadfastly adhering to the foundational ethos of the Nostr protocol, which emphasizes the principles of digital freedom, uncurtailed access to publication, and the establishment of a harassment-free digital environment devoid of shadowbanning practices.
Such advancements underscore the balancing act between technological progression and ethical considerations in decentralized communication frameworks.
-
 @ d34e832d:383f78d0
2025-04-21 08:08:49
@ d34e832d:383f78d0
2025-04-21 08:08:49Let’s break it down.
🎭 The Cultural Love for Hype
Trinidadians are no strangers to investing. We invest in pyramid schemes, blessing circles, overpriced insurance packages, corrupt ministries, miracle crusades, and football teams that haven’t kicked a ball in years. Anything wrapped in emotion, religion, or political flag-waving gets support—no questions asked.
Bitcoin, on the other hand, demands research, self-custody, and personal responsibility. That’s not sexy in a culture where people would rather “leave it to God,” “vote them out,” or “put some pressure on the boss man.”
🧠 The Mindset Gap
There’s a deep psychological barrier here:
Fear of responsibility: Bitcoin doesn’t come with customer service. It puts you in control—and that scares people used to blaming the bank, the government, or the devil.
Love for middlemen: Whether it’s pastors, politicians, or financiers, Trinidad loves an “intercessor.” Bitcoin removes them all.
Resistance to abstraction: We’re tactile people. We want paper receipts, printed statements, and "real money." Bitcoin’s digital nature makes it feel unreal—despite being harder money than the TT dollar will ever be.
🔥 What Gets Us Excited
Let a pastor say God told him to buy a jet—people pledge money.
Let a politician promise a ghost job—people campaign.
Let a friend say he knows a man that can flip $100 into $500—people sign up.
But tell someone to download a Bitcoin wallet, learn about self-custody, and opt out of inflation?
They tell you that’s a scam.
⚖️ The Harsh Reality
Trinidad is on the brink of a currency crisis. The TT dollar is quietly bleeding value. Bank fees rise, foreign exchange is a riddle, and financial surveillance is tightening.
Bitcoin is an escape hatch—but it requires a new kind of mindset: one rooted in self-education, long-term thinking, and personal accountability. These aren’t values we currently celebrate—but they are values we desperately need.
🟠 A Guide to Starting with Bitcoin in Trinidad
- Understand Bitcoin
It’s not a stock or company. It’s a decentralized protocol like email—but for money.
It’s finite. Only 21 million will ever exist.
It’s permissionless. No bank, government, or pastor can block your access.
- Get a Wallet
Start with Phoenix Wallet or Blue Wallet (for Lightning).
If you're going offline, learn about SeedSigner or Trezor for cold storage.
- Earn or Buy BTC
Use Robosats or Peach for peer-to-peer (P2P) trading.
Ask your clients to pay in Bitcoin.
Zap content on Nostr to earn sats.
- Secure It
Learn about seed phrases, hardware wallets, and multisig options.
Never leave your coins on exchanges.
Consider a steel backup plate.
- Use It
Pay others in BTC.
Accept BTC for services.
Donate to freedom tech projects or communities building open internet tools.
🧭 Case In Point
Bitcoin isn’t just technology. It’s a mirror—one that reveals who we really are. Trinidad isn’t slow to adopt Bitcoin because it’s hard. We’re slow because we don’t want to let go of the comfort of being misled.
But times are changing. And the first person to wake up usually ends up leading the others.
So maybe it’s time.
Maybe you are the one to bring Bitcoin to Trinidad—not by shouting, but by living it.
-
 @ d34e832d:383f78d0
2025-04-21 07:31:10
@ d34e832d:383f78d0
2025-04-21 07:31:10The inherent heterogeneity of relay types within this ecosystem not only enhances operational agility but also significantly contributes to the overall robustness and resilience of the network architecture, empowering it to endure systemic assaults or coordinated initiatives designed to suppress specific content.
In examining the technical underpinnings of the Nostr protocol, relays are characterized by their exceptional adaptability, permitting deployment across an extensive variety of hosting environments configured to achieve targeted operational objectives.
For example, strategically deploying relays in jurisdictions characterized by robust legal protections for free expression can provide effective countermeasures against local censorship and pervasive legal restrictions in regions plagued by oppressive control.
This strategic operational framework mirrors the approaches adopted by whistleblowers and activists who deliberately position their digital platforms or mirrored content within territories boasting more favorable regulatory environments regarding internet freedoms.
Alternatively, relays may also be meticulously configured to operate exclusively within offline contexts—functioning within localized area networks or leveraging air-gapped computational configurations.
Such offline relays are indispensable in scenarios necessitating disaster recovery, secure communication frameworks, or methods for grassroots documentation, thereby safeguarding sensitive data from unauthorized access, ensuring its integrity against tampering, and preserving resilience in the face of both potential disruptions in internet connectivity and overarching surveillance efforts.
-
 @ dbbd7125:07ff73f8
2025-03-16 05:57:18
@ dbbd7125:07ff73f8
2025-03-16 05:57:18https://weibo.com/2169989911/5137332916715995
-
 @ dbbd7125:07ff73f8
2025-03-16 05:48:12
@ dbbd7125:07ff73f8
2025-03-16 05:48:12https://weibo.com/5324708177/5144638344398410
-
 @ 1beecee5:d29d2162
2025-04-21 06:30:55
@ 1beecee5:d29d2162
2025-04-21 06:30:55 -
 @ b0137b96:304501dd
2025-04-21 05:54:41
@ b0137b96:304501dd
2025-04-21 05:54:41Streaming has revolutionized how we consume entertainment, offering unparalleled access to diverse content worldwide. With the rise of theBest OTT Platform options, audiences can enjoy their favorite Hollywood, Bollywood, and regional films anytime, anywhere. However, for many viewers, language can be a barrier to fully experiencing international cinema. That’s where innovative platforms step in, bridging the gap between global content and regional audiences.
If you're searching for theBest OTT Platform that delivers high-quality international and regional content, we’ve got you covered. Let’s explore four leading platforms—Dimension on Demand (DOD), Hoichoi, Olly Plus, and Aha Video—that are transforming the Indian entertainment landscape.
Dimension on Demand (DOD) – The Best OTT Platform for Hollywood in Your Language Among the many platforms available, Dimension on Demand (DOD) stands out as theBest OTT Platform for movie lovers who enjoy global cinema in their native tongue. Unlike other platforms that focus solely on regional or Bollywood content, DOD specializes in offering Hollywood movies dubbed in 9 languages like Hindi, Telugu, Tamil, Bangla, Malayalam, Bhojpuri, English, Kannada, and Marathi. This means you can enjoy blockbuster hits, critically acclaimed masterpieces, and thrilling action films—all in the comfort of your language.
What makes DOD truly unique? A vast library of Hollywood movies dubbed in Indian languages Seamless user experience with high-definition streaming Personalized recommendations based on viewer preferences Accessible across multiple devices—smart TVs, mobiles, and laptops A growing collection that ensures fresh content for movie enthusiasts Beyond its impressive collection, DOD ensures that audiences across India can experience world-class entertainment without language barriers. If you love Hollywood but prefer watching in your native language, DOD is undoubtedly the Best OTT Platform.
Hoichoi – A Must-Have for Bengali Entertainment Hoichoi (https://www.hoichoi.tv/)has become a go-to OTT platform for Bengali audiences, offering an impressive mix of movies, web series, and original content. With a strong focus on Bengali-language storytelling, it delivers a diverse collection ranging from classic films to modern thrillers.
Why Choose Hoichoi? Extensive collection of Bengali films and web series Exclusive Hoichoi Originals with gripping storytelling A mix of contemporary and classic Bengali cinema With its continuous addition of fresh content and commitment to Bengali storytelling, Hoichoi has solidified its position as a top-tier platform for regional entertainment lovers.
Olly Plus – A Celebration of Odia Content Olly Plus (https://www.youtube.com/OllyPlus) is Odisha’s dedicated OTT platform, catering specifically to Odia-speaking audiences. It features a rich selection of Odia movies, music, and podcasts, making it a hub for cultural and entertainment enthusiasts.
What Sets Olly Plus Apart? Exclusive Odia-language movies, music, and short films A platform dedicated to preserving and promoting Odia storytelling Inclusion of music, podcasts, and cultural content With Odia entertainment often underrepresented in mainstream media, Olly Plus plays a crucial role in bringing high-quality Odia content to its audience.
Aha Video – The Ultimate Destination for Telugu & Tamil Viewers Aha Video (https://www.aha.video/) has carved a niche in the Best OTT Platform industry by delivering high-quality Telugu and Tamil entertainment. From blockbuster movies to gripping web series, Aha Video ensures South Indian audiences have access to exclusive content tailored to their preferences.
Why Aha Video is a Must-Try? Exclusive Telugu and Tamil movie collections Original series that cater to South Indian storytelling A strong focus on South Indian cinema and entertainment Its commitment to regional cinema ensures that fans of Telugu and Tamil content always have something fresh and exciting to watch.
Why the Best OTT Platforms Matter for Regional Audiences As the streaming industry expands, the importance of theOTT Platform options for regional audiences cannot be overlooked. They not only cater to language-specific audiences but also help preserve and promote local cultures while making global content more accessible.
The Rise of the Best OTT Platforms for Regional Content: They bridge the gap between global cinema and local audiences Viewers can enjoy Hollywood and indie films in their native language Regional content platforms contribute to cultural storytelling and preservation Whether it’s the Hollywood-dubbed collection of DOD, the Bengali storytelling of Hoichoi, the Odia exclusives of Olly Plus, or the South Indian cinema of Aha Video, each platform plays a vital role in reshaping digital entertainment in India.
The Final Verdict – Which is the Best OTT Platform? Choosing the Best OTT Platform depends on your content preferences. If you are looking for international cinema in regional languages, Dimension on Demand (DOD) is the perfect choice. For regional entertainment lovers, Hoichoi, Olly Plus, and Aha Video offer excellent options tailored to specific linguistic audiences.
With DOD leading the way in bringing global entertainment to regional audiences, it's clear that the future ofOTT lies in localization and accessibility. Whether you're a fan of Hollywood, Bengali dramas, Odia storytelling, or Tamil blockbusters, there’s an OTT platform designed just for you.
Want to experience Hollywood like never before? Watch your favorite global films in your language on Dimension on Demand (DOD). Subscribe now and explore an ever-growing collection of blockbuster movies!
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ d34e832d:383f78d0
2025-04-21 02:36:32
@ d34e832d:383f78d0
2025-04-21 02:36:32Lister.lol represents a sophisticated web application engineered specifically for the administration and management of Nostr lists. This feature is intrinsically embedded within the Nostr protocol, facilitating users in the curation of personalized feeds and the exploration of novel content. Although its current functionality remains relatively rudimentary, the platform encapsulates substantial potential for enhanced collaborative list management, as well as seamless integration with disparate client applications, effectively functioning as a micro-app within the broader ecosystem.
The trajectory of Nostr is oriented towards the development of robust developer tools (namely, the Nostr Development Kit - NDK), the establishment of comprehensive educational resources, and the cultivation of a dynamic and engaged community of developers and builders.
The overarching strategy emphasizes a decentralized paradigm, prioritizing the growth of small-scale, sustainable enterprises over the dominance of large, centralized corporations. In this regard, a rigorous experimentation with diverse monetization frameworks and the establishment of straightforward, user-friendly applications are deemed critical for the sustained evolution and scalability of the Nostr platform.
 Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin.
Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin. -
 @ 66675158:1b644430
2025-03-13 11:20:49
@ 66675158:1b644430
2025-03-13 11:20:49In the twilight of his days, Myrddin sat upon the weathered stone bench overlooking what remained of Libertalia. His ancient hands—once steady enough to craft the most intricate mechanisms known to the Free Realms—now trembled as they rested upon the gnarled walking stick he had carved from windfall oak. The city below, once a marvel of independent districts connected by the invisible threads of mutual cooperation, had become something else entirely. Something monstrous.
The sun was setting, casting long shadows across the Grand Plaza where the Central Authority's banners now flew. Myrddin's eyes, still sharp despite his five hundred and seventy years, could make out the uniformed guards patrolling in perfect synchronicity. The sight made his stomach turn.
"I built the foundations for freedom," he whispered to himself, "and they have erected prisons upon them."
A figure approached from behind, footsteps deliberately heavy to announce their presence. Myrddin did not turn.
"Master Myrddin," came the voice of Thalion, one of his few remaining former apprentices not yet captured by the Authority. "The Council of Remnants awaits your wisdom."
Myrddin scoffed. "Wisdom? What wisdom can I offer now? I who planted the seeds of our destruction through my own shortsightedness?"
"You could not have known—"
"I should have known!" Myrddin's voice cracked with the force of his outburst. "Every great civilization before us fell to the same disease. Centralization. The pooling of power into fewer and fewer hands until the many are crushed beneath the weight of the few. I knew this. I studied the ancient texts. I designed our systems specifically to prevent this very outcome."
Thalion remained silent, allowing the old engineer his moment of self-recrimination.
"Come," Myrddin finally said, rising with difficulty. "Let us not keep your Council waiting. Though what good words can do against the machinery of oppression, I cannot say."
As they walked the hidden path down from the overlook, Myrddin's mind drifted back to the beginning, to the founding of Libertalia four centuries earlier...
The Founding Council had gathered beneath the great oak that would later mark the center of Libertalia. Twelve visionaries from twelve different traditions, united by a single purpose: to create a society where no person would rule over another.
Young Myrddin, barely forty years old but already renowned for his brilliance, unrolled the plans he had spent a decade perfecting.
"The Nexus System," he explained, pointing to the intricate diagrams. "A method of connection that requires no central authority. Each district, each guild, each family unit can connect to the whole while maintaining complete sovereignty over their own affairs."
Lorien the Sage, eldest among them, leaned forward with interest. "You propose that trade, communication, defense—all can function without a ruling body?"
"Not only can they function," Myrddin replied with the confidence of youth, "they will function better. A decentralized system is resilient. Cut one connection, and a hundred others remain. Attack one node, and the system routes around the damage. But most importantly, when power is distributed, corruption finds no fertile ground in which to take root."
"And what prevents a group from seizing control?" asked Marwen the Warrior. "From forcing others to submit to their will?"
Myrddin smiled. "The architecture itself. See here—" he pointed to a complex series of interlocking mechanisms, "—the Consensus Protocol. Any attempt to exert control beyond one's rightful domain triggers automatic resistance from the system. The more one tries to centralize power, the more difficult it becomes."
"You speak of mechanisms as if they have will," Marwen said skeptically.
"Not will, but design," Myrddin corrected. "Like water flowing downhill. I have designed a system where power naturally disperses rather than concentrates."
The Council debated through the night, questioning every aspect of Myrddin's design. By morning, they had agreed to build their new society upon his principles. Libertalia would be a constellation of sovereign individuals and voluntary associations, connected but never controlled.
For three generations, it worked exactly as Myrddin had envisioned. The Free Realms prospered as never before. Innovation flourished in the absence of restrictive oversight. Disputes were resolved through mutual arbitration rather than imposed judgment. The Nexus System facilitated trade and communication while preserving the independence of all participants.
Myrddin, his lifespan extended by the alchemical discoveries his system had made possible, watched with pride as Libertalia became the envy of the known world.
But he had made one critical error.
"You created a system that required vigilance," Thalion said as they descended toward the hidden meeting place. "Perhaps that was the flaw."
"No," Myrddin replied. "The flaw was in believing that making something difficult would make it impossible. I should have made centralization not merely hard, but unachievable by any means."
They reached the abandoned mill that served as the Council's current hiding place. Inside, two dozen faces turned toward them—the last free thinkers in a land that once celebrated independence above all else.
Myrddin took his seat at the rough-hewn table. "Tell me," he said without preamble, "how much worse has it become since we last met?"
A woman named Sera, who had once been the foremost architect in the Eastern District, spoke first. "The Authority has implemented the Unified Identification Protocol. No citizen may trade, travel, or even purchase food without presenting their Authority Crystal for scanning."
"And these crystals track their movements?" Myrddin asked, though he already knew the answer.
"Every step," confirmed Sera. "Every transaction. Every word spoken near an Echo Stone."
Myrddin closed his eyes briefly. Echo Stones—his invention, meant to record important discoveries and preserve the wisdom of the ages. Now perverted into tools of surveillance.
"The schools have been consolidated," added a younger man named Ferris. "All children now learn from the same Authority-approved texts. The history of Libertalia is being rewritten. They claim you designed the Nexus System to eventually unite under central guidance."
"A lie," Myrddin spat.
"But a believable one," Thalion said gently. "You did build the infrastructure that made this possible, however unintentional."
Myrddin could not deny it. The Nexus System, designed for voluntary connection, had been gradually modified over the centuries. What began as simple efficiency improvements eventually created vulnerabilities. The Consensus Protocol, once the guardian of decentralization, had been subverted by those who understood its mechanics but not its purpose.
"The disease always begins the same way," Myrddin said, addressing the Council. "With promises of efficiency. Of security. Of protection from unseen threats. The centralizers never announce their true intentions. They speak of unity while forging chains."
"We know this, Master Myrddin," said Sera impatiently. "What we need is a solution, not a history lesson."
Myrddin smiled sadly. "The history is the solution, if only we would heed it. Every great civilization before us fell to centralization. The Aurelian Empire, whose emperors claimed divine right to rule all lands beneath the twin moons. The Dynasty of Eternal Harmony, whose bureaucracy grew so vast it consumed half the realm's production. The Jade Confederation, whose Council of Nine became a single Overlord within three generations."
He paused, gathering his thoughts.
"In every case, the pattern was identical. Power, once distributed among many, gradually accumulated in the hands of few. Those few, corrupted by their unnatural position, made decisions that benefited themselves rather than the whole. Resources were misallocated. Innovation stagnated. The system became brittle rather than resilient. And when crisis came—whether famine, war, or natural disaster—the centralized structure collapsed under its own weight."
"Yet people never learn," said Ferris bitterly.
"Because the benefits of centralization are immediate and visible, while its costs are delayed and diffuse," Myrddin replied. "The Authority provides convenience today at the cost of freedom tomorrow. They offer solutions to problems that would resolve themselves naturally in a decentralized system."
"What was your mistake, then?" asked Thalion. "Where in your design did you leave the opening for this disease to take hold?"
Myrddin's face darkened with regret. "I built a system that was resistant to centralization, but not immune to it. I created tools of such power and efficiency that they became irresistible targets for those who would control others. And most critically, I failed to encode the philosophical foundations of decentralization into the system itself."
He looked around at the faces of the Council, seeing in them the last embers of the fire that had once burned so brightly in Libertalia.
"I believed that people would choose freedom if given the option. I did not account for how seductive the promises of centralization would be. How easily people would trade liberty for convenience. How willingly they would accept security over sovereignty."
The decline had been gradual, almost imperceptible at first. It began two centuries after the founding, with the creation of the Coordination Council.
"Merely to improve efficiency," its proponents had argued. "To eliminate redundancies in our wonderfully decentralized system."
Myrddin, by then well into his second century, had voiced concerns but was overruled by younger generations who found the original Nexus System too cumbersome for their modern needs. The Coordination Council was given limited authority to standardize certain protocols across districts.
Within a decade, those standards became requirements. Requirements became regulations. Regulations became laws. The Council, originally composed of representatives who returned to their districts after brief terms of service, gradually transformed into a permanent body of administrators.
By the time Myrddin recognized the pattern, the disease had already taken root. The Coordination Council had become the Central Authority. The voluntary associations that once formed the backbone of Libertalian society were now subordinate to its dictates.
He had tried to warn them. He had written treatises on the dangers of centralization, had spoken at public forums, had even attempted to modify the Nexus System to restore its decentralizing functions. But he was dismissed as an outdated thinker, unable to appreciate the "improvements" of modern governance.
Now, four hundred years after the founding, Libertalia was Libertalia in name only. The Authority controlled all aspects of life. The districts, once proudly independent, were administrative zones whose boundaries could be redrawn at the Authority's whim. The guilds, once self-governing bodies of skilled craftspeople, were now licensing bureaus that enforced Authority standards.
And the people—the free, sovereign individuals for whom Myrddin had designed his system—had become subjects. Citizens, they were called, but the word had lost its original meaning of self-governance and had come to signify merely a registered and tracked unit of the Authority.
"We cannot defeat the Authority directly," Myrddin told the Council of Remnants. "They control too much. The military, the food supply, the Nexus itself. Any direct confrontation would be suicidal."
"Then what hope remains?" asked Sera.
"We must build anew," Myrddin said, his voice finding strength in purpose. "Not reform, but replace. The old system cannot be saved—it is too thoroughly corrupted. We must create a parallel system that makes centralization not merely difficult, but impossible by its very nature."
"How?" several voices asked at once.
Myrddin reached into his worn leather satchel and withdrew a small crystal, unlike the Authority Crystals in both color and cut. "I have spent the last fifty years designing what should have been built from the beginning. A truly decentralized system that cannot be subverted because its very operation depends on remaining distributed."
He placed the crystal in the center of the table. It pulsed with a soft blue light.
"The Arx," he explained. "Each crystal contains the complete system, yet functions as only one node within it. No node can control another. No group of nodes can outvote or overpower the minority. Consensus is achieved not through majority rule, but through voluntary participation."
Thalion picked up the crystal, examining it skeptically. "The Authority will never allow this."
"They need not allow what they cannot detect," Myrddin replied. "The Arx operates on principles the Authority's systems cannot recognize. It exists alongside their network but remains invisible to it."
"And what can this network do?" asked Ferris. "How does it help us against the might of the Authority?"
"It allows us to trade without their knowledge. To communicate without their oversight. To organize without their permission. And most importantly, to remember who we truly are—sovereign individuals who require no masters."
Myrddin stood, his ancient frame seeming to straighten with the weight of his purpose.
"Centralization is not merely inefficient or unjust—it is a disease that infects and ultimately kills any society it touches. It promises order but delivers stagnation. It promises security but creates vulnerability. It promises prosperity but ensures that wealth flows only to those who control the center."
He looked each Council member in the eye.
"I made a mistake in believing that making centralization difficult would be enough. This time, we will make it impossible. The Arx cannot be centralized because its very operation depends on distribution. Any attempt to control it causes it to fragment and reform beyond the controller's reach."
"And if the Authority discovers these crystals?" Sera asked.
"They can destroy individual crystals, but the network will continue. They can imprison those who carry them, but more will take their place. The design is now the important thing, not the designer. I have encoded the knowledge of how to create these crystals within the crystals themselves. The idea cannot be killed."
Myrddin sat back down, suddenly looking every one of his many years.
"I cannot undo the damage my oversight has caused. I cannot restore the Libertalia I helped to build. But I can give you the tools to create something better—something truly resistant to the disease of centralization."
The Council members looked at one another, hope kindling in eyes that had known only despair for too long.
"How do we begin?" Thalion asked.
Myrddin smiled. "We begin by remembering what we have forgotten. That no person has the right to rule another. That voluntary cooperation always outperforms forced compliance. That systems must serve individuals, not the reverse. That decentralization is not merely a technical architecture but a moral imperative."
He gestured to the crystal, still glowing in Thalion's palm.
"And we begin by building connections that cannot be controlled. Person to person. District to district. Free association by free association. The Authority believes itself invincible because it sits at the center of all things. But when there is no center, there is nothing to seize, nothing to corrupt, nothing to control."
As night fell over Libertalia, the Council of Remnants listened as the ancient engineer outlined his vision for a truly decentralized future. Outside, the Authority's patrols marched in perfect order, their uniformity a testament to the disease that had consumed what was once the freest society in the known world.
Myrddin knew he would not live to see his new design reach fruition. But for the first time in decades, he felt something like peace. He had identified his error. He had created a solution. And most importantly, he had ensured that the knowledge would outlive him.
Centralization was indeed a disease—perhaps the most persistent and destructive disease ever to afflict human societies. But like all diseases, it could be overcome with the right medicine. And the medicine was not more centralization, not better rulers, not wiser authorities.
The medicine was decentralization. Complete, uncompromising, and irreversible decentralization.
As the meeting concluded and the Council members departed with their crystals, Myrddin remained seated at the table. Thalion lingered behind.
"You know they will come for you eventually," his former apprentice said. "You are too significant a symbol to ignore forever."
Myrddin nodded. "Let them come. An old man is a small price to pay for the rebirth of freedom."
"Your new system," Thalion said hesitantly, "you are certain it cannot be centralized? That we are not simply repeating the cycle?"
"Nothing created by human hands can be perfect," Myrddin admitted. "But I have learned from my mistake. The Arx does not merely resist centralization—it actively works against it. The more one tries to control it, the more it disperses. It is not merely a technical solution but a philosophical one."
He placed a hand on Thalion's shoulder. "Remember always: centralization benefits only those at the center. For everyone else—the 99.999% who stand at the periphery—it is nothing but chains disguised as safety. Never again can we allow the disease to take root by promising efficiency at the cost of sovereignty."
Thalion nodded solemnly. "I will remember."
As his former apprentice departed, Myrddin turned to look out the small window at the city below. The Authority's lights blazed from the central towers, pushing back the natural darkness of night. So much power, concentrated in so few hands. So much potential, wasted in the service of control rather than creation.
He had lived long enough to see his greatest work corrupted. With what time remained to him, he would ensure that his final creation could not suffer the same fate. The Arx would spread, node by node, person by person, until the very concept of centralized authority became as obsolete as the diseases his earlier inventions had eradicated.
Myrddin Myrddin, Master Engineer of the Free Realms, closed his eyes and allowed himself, just for a moment, to imagine a world reborn in true freedom. A world where the disease of centralization had finally been cured.
It would not happen in his lifetime. Perhaps not even in Thalion's. But it would happen. Of that, he was certain.
For the truth that the Authority and all centralizers before them had never understood was simple: humans were not meant to be controlled. They were meant to be free. And in the end, that natural state would reassert itself, no matter how elaborate the systems of control became.
Centralization was a disease. And like all diseases, it would eventually meet a cure.
-
 @ 8d5ba92c:c6c3ecd5
2025-03-13 00:31:41
@ 8d5ba92c:c6c3ecd5
2025-03-13 00:31:41It’s no exaggeration to say that Bitcoin has moved beyond its roots as a monetary innovation, growing into a cultural movement built on resistance, decentralization, truth, and freedom. This makes perfect sense.
Money and technology are powerful forces redefining how we interact with each other and ultimately live. From the invention of the printing press to the rise of the Internet—and the countless areas they’ve transformed to this day—every major shift in how we exchange value and information has sparked cultural revolutions. The key here is to choose authenticity over the shallow narratives so often thrown our way.
Bitcoin, by its very nature, challenges current systems. The culture it fosters naturally becomes a counterbalance to a world dominated by fiat—its rotten values, dishonest incentives, hopelessness, greed, and increasingly weaker social interactions.
Go Out and Meet Your Tribe
Over the years, I’ve been to plenty of Bitcoin-themed events. Conferences, meetups, hackathons, and so on. All sorts of gatherings. Each one has left me with not just cool memories and lessons learned, but also genuine connections. I’ve met so many amazing people—some I’m lucky to call friends now, and I know that if it weren’t for Bitcoin and the incredible community that’s grown around it, I probably never would’ve crossed paths with most of them.
Culture is not just about where we’ve come from. It’s about where we’re going...
Last year, I joined 5 different conferences, not to mention smaller gatherings. Regardless of their format, they always enrich my personal perspectives, and, in turn, shape how I see the world and my place within it.
My calendar for the first part of this year is already marked with 6 major events, one of which I’m personally co-organizing. From January to March alone, I’ve attended around 10 Bitcoin meetups and 1 larger event in Thailand—SatsNFacts, a signal-rich 'unconference' (here you can read some memories from it).
The more I travel and spend time with Bitcoiners from around the world, the happier, more hopeful, and more motivated I become. I truly believe that the places we choose to go and the people we meet along the way can profoundly shape our near and distant futures.
Discover the Heartbeat of Bitcoin Culture
Now, imagine a unique gathering that embodies the ethos of Bitcoin while blending artistic expression, intellectual stimulation and collaborative spirit. Not too big, with thousands of attendees you’ll never have a chance to talk to, and not as small as an average local meetup where every face is already familiar.
That’s exactly what Bitcoin FilmFest 2025 (#BFF25) feels like—the event I’m honored to co-create (again) this year. It’s not a typical conference but a community-driven cultural experience, that, for the third time already, is taking over one of Warsaw’s most iconic landmarks: the Palace of Culture and Science. Once known as 'Stalin’s Ziggurat,' now our Cinematic Rebel ₿ase.
I’m not writing this piece to promote the event itself but rather to show how attending more culture-themed events can impact your journey. By participating in these experiences, you’re not just learning or networking—you’re becoming part of a movement that values creativity, authentic storytelling, and human connections.
📣 Why to attend Bitcoin FilmFest (or any similar event):
#1: Fresh Perspectives Through Art and Storytelling
Even if you’re not an artist or filmmaker, most probably you consume their work in one way or another, anyway. Viewing Bitcoin’s cultural impact through the lens of independent art can make you a more conscious, and inspired member of this space. The best part? You won’t just watch films or artistic projects—you’ll also have the chance to meet the creators, ask questions, and dive deeper into their stories. This isn’t about being a random spectator. It’s about engaging with narratives that fuel your mind and heart in ways you can’t yet imagine. Simply put, step in and become part of the story.
#2: From Cypherpunks to Spiritual Awakening
Cultural events like BFF feel more organic than traditional conferences, where networking can often feel rushed or transactional. Built on art and creativity, they foster a relaxed and open atmosphere—a perfect environment to explore deeper conversations, even those with philosophical dimensions. Topics could span a wide range, from the cypherpunk movement and its emphasis on privacy to using Bitcoin to escape inflation, real-world examples of micro-nations, freedom-tech innovations, powerful music, permissionless art, higher consciousness, personal awakenings, and spirituality. When you add the opportunity to engage with like-minded participants who have firsthand experience in many of these areas, you gain mind-blowing insights that can inspire you for months to come.
#3: Non-Technical Areas and New Opportunities
While developers and their work is essential, Bitcoin thrives on a wide range of skills and perspectives. Attending events like BFF might reveal how your unique talents can contribute to this space—something you might not realize while sitting at home. As Anya, founder of Bitvocation (*a partner of this year’s BFF, running a mini-site event where you can learn more about the Bitcoin job market, details to come), once told me:
Face-to-face interactions create real connection and trust—vital ingredients for Bitcoin's social layer.
Just like her, I know that by attending Bitcoin meetups and conferences, we gain an unmatched opportunity to grow our network in real life, resulting in much closer relations than hanging out with someone on X or Nostr.
It could even be the first step toward a new career path that, precisely because of your presence, begins to take shape. Indeed, quoting Anya again:
The best opportunities come to those who truly show up.
Of course, this doesn’t mean that after attending an event, you’ll immediately walk away with a job in Bitcoin (though you might!). But you’ll likely leave with valuable connections, fresh ideas, and a clearer sense of direction.
Final Thoughts
A year has 12 months—whether that’s a lot or a little depends on how we spend it. But please remember that a sound culture thrives when we gather, create, and connect. That’s why I’d like to encourage you to make Bitcoin events and meetups part of your plans this year.
Hope to see you in Warsaw at BFF25 (May 22-25)—so you can verify for yourself whether the points I’ve raised above resonate with your own experience.
Who knows? Maybe our paths will cross at other events I’ve penciled into my calendar as well 😎
BTC Your Mind. Let it Beat. Şela
-
 @ 502ab02a:a2860397
2025-04-21 02:26:09
@ 502ab02a:a2860397
2025-04-21 02:26:09เรามาดูกันครับว่า Precision Fermentation ของ Perfect Day เค้าใช้อะไรเป็นกำลังสำคัญในการหมัก ให้ได้สินค้ามูลค่ามหาศาล ท้าวความกันก่อนว่า Perfect Day เป็นบริษัทที่ผลิต เวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว ด้วยการใช้จุลินทรีย์
Microflora ฟาร์มวัวยุคใหม่ ที่ไม่มีวัว ถ้าคุณเคยดูสารคดีธรรมชาติ แล้วเห็นภาพป่าดิบเขียวชอุ่มที่แต่ละสิ่งมีชีวิตทำหน้าที่ของมันอย่างกลมกลืนกัน ทั้งแมลงที่บินไปมา เชื้อราที่แอบฝังรากอยู่ใต้ใบไม้ หรือจุลินทรีย์ที่ไม่เห็นด้วยตาเปล่าแต่ทำงานหนักอยู่ใต้ดิน... โลกของ microflora ก็ไม่ต่างอะไรกับ “จักรวาลจิ๋ว” แบบนั้นเลย
Microflora คืออะไร? microflora เป็นศัพท์ที่นักวิทยาศาสตร์ใช้เรียกสิ่งมีชีวิตขนาดจิ๋วที่มองไม่เห็นด้วยตาเปล่า แต่มีชีวิตจริงๆ แบบครบสูตร คือเจริญเติบโตได้ แบ่งตัวได้ กินได้ เหมือนสิ่งมีชีวิตอื่นๆ เป๊ะๆ มาจาก micro กับ flora
พอพูดถึงคำว่า “flora” บางคนอาจนึกถึงต้นไม้ แต่ในความหมายนี้ มันกว้างกว่านั้นมาก เพราะ “microflora” ไม่ได้จำกัดแค่พืช แต่หมายถึงสิ่งมีชีวิตจิ๋วจากหลากหลายอาณาจักรในธรรมชาติ เช่น ฟังไจ (Fungi) — ไม่ใช่แค่เห็ดที่เรากินกัน แต่รวมถึงเชื้อราจิ๋วที่อยู่ในดินและอากาศ ที่เก่งเรื่องการปล่อยเอนไซม์ย่อยอาหารนอกตัว แล้วดูดสารอาหารเข้าไป แบคทีเรีย (Bacteria) — นักแบ่งตัวมือโปรที่อยู่ในทุกที่ตั้งแต่ดินในสวน ยันในลำไส้เรา โพรทิสต์ (Protists) — กลุ่มที่เหลือๆ ที่ไม่เข้าพวกกับใคร เช่น สาหร่ายบางชนิด หรืออะมีบา
microflora เหล่านี้เหมือนพนักงานจิ๋วที่ทำหน้าที่เฉพาะทาง บางตัวเก่งเรื่องสร้างโปรตีน บางตัวสร้างไขมัน บางตัวสังเคราะห์วิตามินเก่งสุดๆ เลยกลายเป็นขุมพลังที่มนุษย์เริ่มหันมาใช้มากขึ้นเรื่อยๆ
ความสัมพันธ์ระหว่างมนุษย์กับ microflora ไม่ใช่เรื่องใหม่เลย เราหมักเบียร์ ทำโยเกิร์ต ดองกิมจิ และทำซีอิ๊วจากถั่วเหลืองด้วยกระบวนการที่เรียกว่า “fermentation” หรือ “การหมัก” มานานหลายพันปีแล้ว ซึ่งเป็นการอาศัยพลังของจุลินทรีย์ธรรมชาติให้สร้างรสชาติ วิตามิน หรือย่อยของที่เรากินให้ดูดซึมง่ายขึ้น แต่วันนี้โลกไปไกลกว่านั้นมาก เพราะเราสามารถสอนจุลินทรีย์ให้ผลิต “โปรตีนเฉพาะแบบ” ได้ตามต้องการ กระบวนการนี้เรียกว่า Precision Fermentation หรือ “การหมักแบบแม่นยำ” ฟังดูเหมือนห้องทดลองของ Iron Man เลยเนอะ
Perfect Day ใช้วิธีนี้ในการผลิต เวย์โปรตีน แบบไม่ต้องรีดนมจากวัวเลยสักหยด ด้วยการใช้ “เชื้อราจิ๋ว” ชนิดหนึ่งที่มีชื่อสายวิทยาศาสตร์ว่า Trichoderma
ทำไมต้อง Trichoderma? เจ้า Trichoderma ไม่ใช่เชื้อราหน้าตาน่ากลัวแบบในหนังสยองขวัญ แต่มันคือเชื้อราที่อยู่ในดินมานานกว่า 70 ปีแล้ว และเป็นที่รู้กันในวงการวิทยาศาสตร์ว่า มันเก่งเรื่องการผลิตเอนไซม์ที่ย่อยไม้ ย่อยใบไม้ ย่อยสิ่งมีชีวิตอื่นในธรรมชาติได้อย่างมีประสิทธิภาพ จึงเป็นเหมือน “โรงงานย่อยอาหาร” ชั้นเลิศ
นักวิทยาศาสตร์ของ Perfect Day เห็นแววก็เลยจับมันมา “ฝึกงาน” ใหม่ โดยใช้กระบวนการที่เรียกว่า strain engineering หรือ “การออกแบบสายพันธุ์” พูดง่ายๆ ก็คือ ใส่รหัสพันธุกรรม (เหมือนคำสั่งงาน) เข้าไปให้มันผลิตโปรตีนจากนมได้ เช่น beta-lactoglobulin ซึ่งเป็นโปรตีนตัวหลักของเวย์ในน้ำนมวัว
เมื่อ Trichoderma อ่านคำสั่งนี้ออก มันก็เริ่มเดินเครื่องผลิตโปรตีนตามที่เราสั่ง เหมือนเป็น “วัวในห้องแล็บ” ที่ไม่มีเสียงร้อง ไม่มีปุ๋ยคอก และไม่ต้องเลี้ยงด้วยหญ้า
microflora = วัวจิ๋วยุคใหม่
ลองจินตนาการว่าถ้าในอดีตเราต้องเลี้ยงวัวจริงๆ เพื่อให้ได้โปรตีนจากนม วันนี้เราใช้แค่จุลินทรีย์จิ๋วในถังหมัก แล้วป้อน “อาหาร” ให้มันเป็นน้ำตาลจากพืช (เช่น ข้าวโพด !!! เป็นง่ะ ข้าวโพดอีกแล้ว) มันก็จะเปลี่ยนคาร์โบไฮเดรตเหล่านั้นให้กลายเป็นโปรตีน หรือไขมัน หรือสารที่เราต้องการได้แบบแม่นยำ
microflora ไม่ใช่สัตว์ แต่ก็ทำหน้าที่แทนสัตว์ได้ พวกมันไม่มีสมอง ไม่มีระบบประสาท ไม่รู้สึกเจ็บ ไม่เบื่อ ไม่หิวข้าว ไม่ต้องการวันหยุด แต่มันมี “ความสามารถ” ที่เราสามารถดึงมาใช้ให้เกิดประโยชน์ได้อย่างน่าทึ่ง
ข้อดีของ microflora -เลี้ยงง่าย แค่ให้คาร์บ (จากพืช) ก็พร้อมทำงาน -ไม่ต้องใช้พื้นที่เยอะ ผลิตในถังหมัก ไม่ต้องใช้ทุ่งหญ้ากว้างๆ แบบฟาร์มวัว -ควบคุมคุณภาพได้ ผลิตโปรตีนได้สม่ำเสมอ ปราศจากสารก่อภูมิแพ้หรือยาปฏิชีวนะ -ลดการปล่อยก๊าซเรือนกระจก เพราะไม่ต้องเลี้ยงสัตว์ที่ปล่อยมีเทน
microflora จึงเป็น “เพื่อนร่วมงานที่เล็กที่สุด” แต่ก็อาจจะทรงพลังที่สุดในครัวของอนาคต และแม้เราจะยังยึดมั่นกับ animal-based diet อยู่ แต่ผมคิดว่าเรื่องนี้ก็น่าสนใจในฐานะ เทคโนโลยีที่กำลังท้าทายโลก fiat food อีกแนวทางหนึ่ง เพราะมันไม่ใช่พืชประดิษฐ์ ไม่ใช่แป้ง+สี+กลิ่น+สารพัด additive แต่คือ “การสร้างโปรตีนแท้” ด้วยความรู้ทางวิทยาศาสตร์ ที่เอื้อให้มนุษย์เลิกพึ่งวัวโดยตรง
ไม่แน่ว่าวันหนึ่ง แทนที่จะมีฟาร์มวัวเลี้ยงวัว 500 ตัวเพื่อผลิตเวย์ 1 ตัน เราอาจมีแค่ถังหมัก 1 ถัง ที่เลี้ยงเชื้อรา 500 ล้านตัว แล้วได้เวย์โปรตีนคุณภาพเดียวกัน...โดยไม่ต้องมีเสียง "มอ" เลยสักแอะ
แต่คำถามสำคัญคือ เราจะมีฟาร์มนั้นได้ไหม หรือได้แต่ทำหน้าที่ซื้อนมมารับประทานเท่านั้น
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ 9dd283b1:cf9b6beb
2025-03-12 09:46:45
@ 9dd283b1:cf9b6beb
2025-03-12 09:46:45My Raspberry Pi 4 (running Umbrel) has been disconnecting approximately once a month, and my 1TB SSD now has only 80GB of space remaining. I'm considering an upgrade—possibly moving to a Pi 5 with a 2TB drive—but I'm open to any suggestions for a better setup within a similar budget. Any recommendations?
originally posted at https://stacker.news/items/911133
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:08:06
@ 4ba8e86d:89d32de4
2025-04-21 02:08:06FOSS Browser é um navegador Android totalmente livre e de código aberto (freedom/libre, no sentido de liberdade). Seu código-fonte é público e o aplicativo não solicita permissões desnecessárias. Ele é baseado no WebView do Android, com o objetivo de oferecer uma navegação simples, leve, eficiente e com uma interface agradável.
FOSS Browser é uma aplicação Android para navegação na internet. Por utilizar o WebView nativo do sistema, ele não possui um motor de renderização avançado como navegadores tradicionais, o que o torna mais leve e direto ao ponto.
O FOSS Browser permite salvar configurações específicas para cada domínio, o que ajuda a proteger sua privacidade. Para cada site visitado, é possível ativar ou desativar opções como:
- Bloqueador de anúncios (AdBlock);
- Execução de JavaScript;
- Uso de cookies;
- Proteção contra fingerprinting;
- E outras opções personalizáveis.
Para sites que não têm configurações salvas, você pode ajustar um perfil padrão conforme suas preferências.
Mais recursos de privacidade:
- AdBlock integrado, com atualizações automáticas. Você escolhe o que deseja bloquear. As listas são baseadas nos hosts do projeto Steven Black - AdBlock Hosts https://github.com/StevenBlack/hosts
- Bloqueio de cookies de terceiros.
- Bloqueio de banners de consentimento de cookies.
- Habilitar ou desabilitar o preenchimento automático do Android.
- Apagar dados de navegação automaticamente ao sair do app.
- Escolher entre diferentes mecanismos de busca, ou definir um mecanismo personalizado.
- O próprio FOSS Browser não coleta nenhum dado dos usuários https://codeberg.org/Gaukler_Faun/FOSS_Browser/src/branch/master/PRIVACY.md
O FOSS Browser adota o design moderno do Material You, com suporte ao modo claro/escuro do sistema e temas baseados no papel de parede do dispositivo. A interface foi otimizada para uso com uma só mão, com todos os elementos principais localizados na parte inferior da tela.
Recursos adicionais:
- Manter a tela ligada durante a navegação;
- Abrir links em segundo plano;
- Restaurar abas automaticamente ao reiniciar o app.
Gerencie seus favoritos com filtros personalizados. Você pode nomear cada filtro como quiser. Ao pressionar e segurar o ícone de favoritos na barra de ferramentas, terá acesso rápido aos seus sites favoritos.
Gestos Personalizáveis Você pode atribuir quase 20 gestos diferentes à barra de ferramentas e aos seus botões, com suporte a quatro direções por gesto. Também é possível acionar ações ao pressionar e segurar os botões da barra, totalizando até 10 gestos diferentes para controlar o navegador.
Algumas ações disponíveis incluem:
- Carregar o último site acessado;
- Alternar entre abas;
- Recarregar a página;
- Abrir favoritos;
- E muito mais.
-Backup e Restauração
Faça backup de todos os seus dados e configurações importantes (favoritos, histórico, configurações por site, etc.) diretamente no cartão SD. Os backups também podem incluir as configurações gerais do FOSS Browser, e podem ser restaurados em uma instalação nova ou em outro dispositivo, bastando copiar os arquivos de backup.
Link Pra baixar no obtainium : https://codeberg.org/Gaukler_Faun/FOSS_Browser
Fdroid : https://f-droid.org/packages/de.baumann.browser/
https://codeberg.org/Gaukler_Faun/FOSS_Browser
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 0c469779:4b21d8b0
2025-03-11 10:52:49
@ 0c469779:4b21d8b0
2025-03-11 10:52:49Sobre el amor
Mi percepción del amor cambió con el tiempo. Leer literatura rusa, principalmente a Dostoevsky, te cambia la perspectiva sobre el amor y la vida en general.
Por mucho tiempo mi visión sobre la vida es que la misma se basa en el sufrimiento: también la Biblia dice esto. El amor es igual, en el amor se sufre y se banca a la otra persona. El problema es que hay una distinción de sufrimientos que por mucho tiempo no tuve en cuenta. Está el sufrimiento del sacrificio y el sufrimiento masoquista. Para mí eran indistintos.
Para mí el ideal era Aliosha y Natasha de Humillados y Ofendidos: estar con alguien que me amase tanto como Natasha a Aliosha, un amor inclusive autodestructivo para Natasha, pero real. Tiene algo de épico, inalcanzable. Un sufrimiento extremo, redentor, es una vara altísima que en la vida cotidiana no se manifiesta. O el amor de Sonia a Raskolnikov, quien se fue hasta Siberia mientras estuvo en prisión para que no se quede solo en Crimen y Castigo.
Este es el tipo de amor que yo esperaba. Y como no me pasó nada tan extremo y las situaciones que llegan a ocurrir en mi vida están lejos de ser tan extremas, me parecía hasta poco lo que estaba pidiendo y que nadie pueda quedarse conmigo me parecía insuficiente.
Ahora pienso que el amor no tiene por qué ser así. Es un pensamiento nuevo que todavía estoy construyendo, y me di cuenta cuando fui a la iglesia, a pesar de que no soy cristiano. La filosofía cristiana me gusta. Va conmigo. Tiene un enfoque de humildad, superación y comunidad que me recuerda al estoicismo.
El amor se trata de resaltar lo mejor que hay en el otro. Se trata de ser un plus, de ayudar. Por eso si uno no está en su mejor etapa, si no se está cómodo con uno mismo, no se puede amar de verdad. El amor empieza en uno mismo.
Los libros son un espejo, no necesariamente vas a aprender de ellos, sino que te muestran quién sos. Resaltás lo que te importa. Por eso a pesar de saber los tipos de amores que hay en los trabajos de Dostoevsky, cometí los mismos errores varias veces.
Ser mejor depende de uno mismo y cada día se pone el granito de arena.
-
 @ d34e832d:383f78d0
2025-04-21 01:31:02
@ d34e832d:383f78d0
2025-04-21 01:31:02Optimizing Knowledge Management with Obsidian and the Zettelkasten Method
The Zettelkasten method, which translates to "slip box" in German, is a powerful system for personal knowledge management developed by sociologist Niklas Luhmann. It relies on creating and linking small, self-contained notes that each represent a single idea or thought. These notes are connected through internal references, forming a dense web of knowledge that mirrors how ideas evolve and relate to each other naturally. By writing in small, atomic units, users are encouraged to distill complex concepts into their essence, improving understanding and retention.
Zettelkasten facilitates knowledge retention by encouraging active engagement with information. Instead of passively reading or highlighting, users must rephrase, question, and connect ideas. This process reinforces memory and builds a reusable archive of insights. The method also supports long-term idea development by creating an environment where thoughts grow organically through continuous linking, comparison, and reflection. For researchers and writers, Zettelkasten becomes a dynamic workspace for managing sources, forming arguments, and drafting structured content.
With the rise of digital tools, the Zettelkasten method has found a modern home in applications like Obsidian. Obsidian is a markdown-based note-taking app that allows users to create a network of interlinked notes stored locally on their device. It supports backlinks, graph views, and a customizable interface, making it ideal for implementing Zettelkasten. Unlike paper systems or linear document editors, Obsidian turns a note collection into an interactive, searchable, and scalable knowledge base. This evolution has made it easier than ever to adopt and maintain a Zettelkasten system for academic research, professional writing, and lifelong learning. - Problem Statement: Despite its effectiveness, many users struggle with implementing Zettelkasten in a way that integrates well into their daily routines. This thesis presents a streamlined, efficient setup using Obsidian for optimal results.
1. Install Obsidian
- Download Obsidian from the official website (https://obsidian.md) and install it on your preferred device (Windows, macOS, Linux, or mobile).
- Open the app and create a new Vault, which will serve as the central repository for all your notes.
- Choose a location for your vault. For backup and multi-device access, store it in a synced folder like Dropbox, OneDrive, or iCloud.
2. Folder Structure
Set up a simple, organized folder structure to support the Zettelkasten flow:
00_Templates: Store reusable note templates.01_Source_Material: Notes from books, articles, lectures, etc.02_Rough_Notes: Free-form, early-stage thoughts (optional).03_Main_Notes: Core Zettelkasten notes; each represents a single atomic idea.04_Indexes: Thematic hubs or entry points for exploring related notes.05_Tags: Empty placeholder notes acting as tags for navigation or filtering (optional).
3. Settings Configuration
- Default Location for New Notes: Point to
03_Main_Notes. - Appearance: Choose a legible font and theme; toggle "Readable line length" for better formatting.
- Hotkeys: Assign shortcuts, e.g.:
Ctrl + N: New NoteCtrl + T: Insert Template (after plugin activation)- Core Plugins:
- Enable Templates, Daily Notes (optional), and Backlinks.
- Community Plugins (optional):
- Calendar: For date-based organization.
- Tag Wrangler: For managing and merging tags.
- Advanced Tables, Quick Switcher++, or DataView: For productivity.
4. Create Templates
Under
00_Templates, create templates like:Source Material Template ``` Title: Author: Source: Date: Tags:
Summary: Key Points: Quotes: Reflections: ```
Main Note Template ``` Title: Date Created: Tags:
Idea: Context: Connections: [[Linked Note]] Reflections: ```
Configure the Templates plugin to insert templates quickly using hotkeys.
5. Note-Taking Workflow
Step 1: Capture - In
01_Source_Material, create notes while reading or researching. Summarize, highlight quotes, and reflect in your own words. - Use tags for themes, authors, or concepts (e.g.,#philosophy,#biology).Step 2: Synthesize - In
03_Main_Notes, write atomic notes from your reflections. - Each note should express a single idea clearly (under 500 words). - Use links to reference related notes with[[Note Name]]. - Focus on clarity, brevity, and insight.Step 3: Connect - Link your new idea to related ideas, themes, or sources. - Create notes in
04_Indexesto organize clusters of related content. - Add notes to multiple indexes or link to broader themes using[[#Tag]].
6. Use Tags and Indexes Thoughtfully
- Avoid creating hundreds of tags. Stick to a small set of relevant themes.
- Use
05_Tagsto define and clarify what each tag means. - In
04_Indexes, organize curated lists of related notes. Example:Mindfulness Indexmight link to[[]]notes from psychology, philosophy, and neuroscience.
7. Benefits for Research and Writing
- Streamlines Research: Notes from multiple sources are cross-referenced and easily revisitable.
- Accelerates Writing: Writing becomes an assembly of existing notes instead of starting from scratch.
- Improves Clarity: Breaking down ideas into atomic notes encourages better thinking and clarity.
- Long-Term Retention: Regular review and linking strengthen memory and understanding.
- Reusable Content: Notes can be reused across multiple projects, articles, or books.
8. Maintenance Tips
- Review backlinks weekly to surface forgotten or underdeveloped ideas.
- Refactor or split long notes to maintain atomicity.
- Avoid over-editing old notes; instead, create new ones that build upon earlier thoughts.
With this Obsidian-based Zettelkasten setup, you're not just taking notes — you're cultivating a living knowledge system. Whether you're an academic, writer, student, or lifelong learner, this system adapts to your workflow, grows with your interests, and becomes more powerful the more you use it. Over time, your vault evolves into a personalized knowledge database that supports deeper understanding, creative exploration, and effortless content creation.
- The Zettelkasten Methodology
The Original Zettelkasten Technique: Core Principles & Benefits
The Zettelkasten method (German for "slip box") was developed by sociologist Niklas Luhmann as a tool to manage complex knowledge and boost creativity in writing and research. He credited it with enabling his prolific academic output: over 70 books and hundreds of articles. The brilliance of the system lies in its simplicity, modularity, and organic growth.
🌱 Core Principles of Zettelkasten
1. Atomicity
Each note in the Zettelkasten should express a single idea or concept. This principle ensures clarity, encourages deeper understanding, and makes ideas easier to reuse and connect.
- ✅ Do: “The law of diminishing returns means each additional input yields less output.”
- ❌ Don’t: Combine multiple concepts or quotes into one long note.
Atomic notes are easier to: - Link logically. - Modify independently. - Reuse across different contexts.
2. Linking
Instead of a rigid hierarchy, Zettelkasten thrives on contextual, lateral linking.
- Notes are connected using direct references to other notes.
- Each note becomes part of a network, not a silo.
- Links simulate how human memory works—via associations, not folders.
Example: A note on “Nietzsche’s eternal recurrence” might link to notes on “cyclical time in Buddhism” or “existentialism.”
Benefits: - Emergent structure—patterns and themes arise naturally. - Serendipitous discovery—old ideas resurface via linked paths. - Compound creativity—new combinations emerge from connected thoughts.
3. Simplicity
Luhmann emphasized a low-friction system. His physical slip-box used numbered index cards and manual cross-referencing—no complex categorization.
Simplicity: - Reduces friction between thought and capture. - Makes the system future-proof and easy to maintain. - Encourages writing in your own words, promoting internalization.
Modern Zettelkasten tools (like Obsidian) honor this by: - Allowing bidirectional links (
[[Note Title]]). - Replacing folders with tags and contextual backlinks. - Supporting plain text Markdown format for longevity.
✍️ Benefits of Zettelkasten
📚 For Writing
- Provides a ready-made library of ideas to draw from.
- Writing becomes assembly, not invention—you collect, synthesize, and expand existing notes.
- Encourages idea-driven writing, not source-driven copying.
“Writing is no longer a process of transfer, but of transformation.” — Luhmann
🔍 For Research
- Encourages critical engagement with sources (notes are written in your own words).
- Makes literature review manageable through connected concepts.
- Supports non-linear learning—you follow interesting links, not rigid outlines.
🧠 For Idea Organization
- Keeps ideas alive and evolving through regular linking and revisiting.
- Avoids information rot by focusing on synthesis, not storage.
- Fosters a personal knowledge graph—tailored to how you think.
🧩 Summary Table
| Principle | What it Means | Why it Matters | |---------------|------------------------------------|--------------------------------------| | Atomicity | 1 idea per note | Improves clarity, reuse, and focus | | Linking | Contextual note-to-note links | Encourages discovery and depth | | Simplicity | Low friction, minimal structure | Easy to maintain and long-lasting |
Consider
The original Zettelkasten is more than a note-taking method—it's a thinking partner. By focusing on the quality of thought, it transforms how you learn, create, and connect ideas. Whether used with index cards or modern tools like Obsidian, its core principles remain timeless.
Would you like a visual map or Obsidian-ready template for Luhmann-style Zettelkasten?
- Benefits of Zettelkasten for Writing:
- Streamlines Research: Centralized notes help avoid redundant research across multiple projects.
- Facilitates Long-Form Writing: Accumulated notes serve as building blocks for larger projects.
- Personal Writing Assistant: The evolving network of notes provides quick access to ideas for future writing.
-
Obsidian Setup and Configuration
-
Installing Obsidian: Guide the user through the installation process, emphasizing the free version and its core features.
-
Creating and Organizing a Vault: A vault in Obsidian is the central hub for all your notes. This section provides instructions for setting up a vault and explains the importance of cloud storage for backup and accessibility.
-
Folder Structure: Establish a recommended folder structure:
- Rough Notes: Optional folder for quick thoughts.
- Source Material: Store notes from books, articles, etc.
- Tags: Empty notes used as tags for easy categorization.
- Indexes: Organized collections of notes based on specific topics or themes.
- Templates: Predefined templates for consistent note-taking.
-
Main Notes: The core content of your knowledge base.
-
Settings Configuration:
- Configure default note locations.
- Customize appearance for readability.
- Set up hotkeys for efficient note-taking (e.g., Ctrl+T for template insertion).
- Enable and configure the "Templates" core plugin for consistent note creation.
-
The Note-Taking Process
-
Creating Notes: Guide the user on how to create new notes (Ctrl+O) and insert templates (Ctrl+T). Emphasize the importance of focusing on one idea per note to maintain atomicity.
-
Source Material Notes:
- Record page numbers, quotes, and elaborate on the ideas in your own words.
-
Include metadata such as authorship, publication year, and source references.
-
Main Notes:
- Synthesize ideas from source material.
- Focus on the key takeaways and connections between different ideas.
-
Use internal links ([[Note Name]]) to connect related notes and foster deeper understanding.
-
Tagging Notes:
- Use tags sparingly but effectively.
- Avoid over-complicating tags, focusing on personal interests or key themes.
- Tags act as an index to quickly locate notes.
-
Linking and Organizing Ideas
-
Internal Links and Connections: Demonstrate how internal links help create a web of interconnected ideas. Discuss how linking related concepts and topics can lead to a more holistic understanding.
-
Indexing for Navigation: Show how creating indexes for topics allows for quick access to collections of related notes. Introduce the idea of building thematic indexes for large research projects.
-
Synthesizing Notes for Larger Projects: Explain how to take notes from the Source Material and Main Notes to gradually build drafts for books, essays, or research papers.
-
Best Practices for Obsidian and Zettelkasten
-
Consistency and Simplicity: Emphasize the importance of simplicity in both note-taking and vault organization. Discourage the need for a "perfect" setup, focusing on efficiency and growth over time.
-
Keeping Notes Concise: Encourage users to keep each note under 500 words, focusing on one idea per note. This enhances clarity and makes it easier to synthesize ideas later.
-
Making Notes Readable: Provide tips on formatting for readability: use headings, bullet points, and quotes to break up large blocks of text.
-
Practical Applications of Zettelkasten in Writing
-
Research Projects: Show how to leverage your Zettelkasten system to conduct more efficient and thorough research for academic papers, articles, or blog posts.
-
Book and Essay Writing: Provide examples of how notes in Obsidian can evolve into larger writing projects, from initial drafts to final revisions.
-
Personal Projects and Brainstorming: Illustrate how the Zettelkasten method can be used for creative writing, personal reflections, or brainstorming for new ventures.
-
Case In Point
-
Summary of Findings: Recap the effectiveness of combining the Zettelkasten method with Obsidian for knowledge management, writing, and research.
-
Future Directions: Suggest areas for future exploration, such as integrating other digital tools (e.g., Zotero, Roam Research) into the workflow or expanding the Zettelkasten method into larger organizational systems.
-
References
-
Cite all relevant sources, including academic papers, books, and articles about the Zettelkasten method, Obsidian, and knowledge management.
📘 1. Source Note Template (
Source Note)This template is used when reading books, articles, podcasts, or videos. The goal is to capture contextual metadata and your impressions, not to mindlessly copy.
```markdown
📘 Source: {{title}}
Type: Book / Article / Video / Podcast
Author: {{author}}
Published: {{date}}
Source Link: Link
Tags: #source #{{topic}}
Related Notes: [[ ]]
🧠 Summary
A brief summary of the source in your own words.
🧩 Key Ideas
- Idea 1
- Idea 2
- Idea 3
🔎 Quotes & Passages
“...”
— Page X🗺️ Linked Notes
- [[Note about idea X]]
- [[Historical context of Y]]
📝 Your Thoughts
- Agreement? Disagreement?
- How does this relate to your current research?
- Ideas it sparked? ```
🧠 2. Main/Idea Note Template (
Zettelor Permanent Note)Each idea should be atomic, clearly written in your own words, and linked to related ideas. This is the core of your Zettelkasten.
```markdown
💡 {{Descriptive Title}}
ID: {{YYYYMMDDHHMM}}
Tags: #zettel #{{topic}}
Linked From: [[ ]]
🧠 Core Idea
Write a single, concise idea in your own words. This should be a self-contained statement or argument.
💬 Explanation / Elaboration
Explain why this idea matters or how it connects to broader themes. Use metaphors, contrast, or short examples.
🔗 Related Notes
- [[Related idea A]]
- [[Contrasting concept B]]
- [[Supports claim C]] ```
Tip: Use the ID convention (e.g.
202504201013) to uniquely identify each note.
🧪 3. Research Summary Note (
Literature Noteor Topic Overview)Use this when you're studying a broader concept or topic and summarizing multiple inputs (e.g., a research question or paper theme).
```markdown
🧪 Research Summary: {{Topic}}
Tags: #summary #research #{{subject}}
Created: {{date}}
Status: Draft / Ongoing / Complete
📌 Topic Overview
Brief definition or framing of the research question.
📚 Key Sources
- [[Author, Title]] — key takeaway.
- [[Article Title]] — significant argument.
🧩 Key Themes
- Theme 1: summary + relevant note links.
- Theme 2: contrasting perspective.
🧠 Emerging Ideas
- New insights or patterns you're noticing.
- Questions that remain unanswered.
🔗 Related Notes
- [[Main idea note]]
- [[Potential application note]]
- [[Philosophical implication]] ```
🔄 How They Interact
- Source Notes → inspire → Main Notes
- Main Notes → get linked into → Research Summaries
- Research Summaries → help generate → new Main Notes
“You don’t collect knowledge, you build it — one link at a time.”
-
 @ 4857600b:30b502f4
2025-03-11 01:58:19
@ 4857600b:30b502f4
2025-03-11 01:58:19Key Findings
- Researchers at the University of Cambridge discovered that aspirin can help slow the spread of certain cancers, including breast, bowel, and prostate cancers
- The study was published in the journal Nature
How Aspirin Works Against Cancer
- Aspirin blocks thromboxane A2 (TXA2), a chemical produced by blood platelets
- TXA2 normally weakens T cells, which are crucial for fighting cancer
- By inhibiting TXA2, aspirin "unleashes" T cells to more effectively target and destroy cancer cells
Supporting Evidence
- Previous studies showed regular aspirin use was linked to:
- 31% reduction in cancer-specific mortality in breast cancer patients
- 9% decrease in recurrence/metastasis risk
- 25% reduction in colon cancer risk
Potential Impact
- Aspirin could be particularly effective in early stages of cancer
- It may help prevent metastasis, which causes 90% of cancer fatalities
- As an inexpensive treatment, it could be more accessible globally than antibody-based therapies
Cautions
- Experts warn against self-medicating with aspirin
- Potential risks include internal bleeding and stomach ulcers
- Patients should consult doctors before starting aspirin therapy
Next Steps
- Large-scale clinical trials to determine which cancer types and patients would benefit most
- Development of new drugs that mimic aspirin's benefits without side effects
Citations: Natural News
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-21 00:28:50
@ 5d4b6c8d:8a1c1ee3
2025-04-21 00:28:50I was just about to get into bed last night, after recording the Stacker Sports Pod and hiding Easter Eggs, when I remembered to check my step count. As often happens, I was stupidly short of my goal: just 7 steps this time.
My step counter is not nearly so precise as to actually record seven steps, so I knew it was either go to bed or do some chores for a bit to get enough more steps to register.
Well, I got the steps easily enough, only to discover the dog had an accident on the carpet that I now needed to clean up...and it turned out we had run out of the cleaning supplies we use for such incidents. So, I had to do some basic chemistry at midnight to mix up a makeshift cleaning solution to keep the carpet from staining and wait long enough for it to do its magic before drying it out.
Had I just taken the L on the steps, the dog would have just fallen asleep and peed in the morning. I doubt the Workit payout will prove to be worth the hassle this time
originally posted at https://stacker.news/items/950750
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ 9063ef6b:fd1e9a09
2025-04-20 20:19:27
@ 9063ef6b:fd1e9a09
2025-04-20 20:19:27Quantum computing is no longer a futuristic fantasy — it's becoming a present-day reality. Major tech companies are racing to build machines that could revolutionize fields like drug discovery, logistics, and climate modeling. But along with this promise comes a major risk: quantum computers could one day break the cryptographic systems we use to secure everything from emails to bank transactions.
🧠 What Is a Quantum Computer?
A quantum computer uses the principles of quantum physics to process information differently than traditional computers. While classical computers use bits (0 or 1), quantum computers use qubits, which can be both 0 and 1 at the same time. This allows them to perform certain calculations exponentially faster.
Who's Building Them?
Several major tech companies are developing quantum computers:
- Microsoft is building Majorana 1, which uses topological qubits designed to be more stable and less prone to errors.
- Amazon introduced Ocelot, a scalable architecture with significantly reduced error correction needs.
- Google's Willow chip has demonstrated faster problem-solving with lower error rates.
- IBM has released Condor, the first quantum chip with over 1,000 qubits.
📅 As of 2025, none of these systems are yet capable of breaking today's encryption — but the rapid pace of development means that could change in 5–10 years.
🔐 Understanding Cryptography Today
Cryptography is the backbone of secure digital communication. It ensures that data sent over the internet or stored on devices remains confidential and trustworthy.
There are two main types of cryptography:
1. Symmetric Cryptography
- Uses a single shared key for encryption and decryption.
- Examples: AES-256, ChaCha20
- Quantum status: Generally considered secure against quantum attacks when long key lengths are used.
2. Asymmetric Cryptography (Public-Key)
- Uses a public key to encrypt and a private key to decrypt.
- Examples: RSA, ECC
- Quantum status: Highly vulnerable — quantum algorithms like Shor’s algorithm could break these quickly.
⚠️ The Quantum Threat
If a large-scale quantum computer becomes available, it could:
- Break secure websites (TLS/SSL)
- Forge digital signatures
- Decrypt previously recorded encrypted data ("harvest now, decrypt later")
This is why experts and governments are acting now to prepare, even though the technology isn’t fully here yet.
🔒 What Is Quantum Cryptography?
Quantum cryptography is a new method of securing communication using the laws of quantum physics. It doesn’t encrypt data directly, but instead focuses on creating a secure key between two people that cannot be intercepted without detection.
Quantum cryptography is promising, but not yet practical.
🛡️ What Is Post-Quantum Cryptography (PQC)?
Post-Quantum Cryptography is about designing new algorithms that are safe even if quantum computers become powerful. These algorithms can run on existing devices and are being actively standardized.
NIST-Selected Algorithms (2024):
- Kyber — for secure key exchange
- Dilithium — for digital signatures
- FALCON, SPHINCS+ — alternative signature schemes
PQC is already being tested or adopted by:
- Secure messaging apps (e.g. Signal)
- Web browsers and VPNs
- Tech companies like Google, Amazon, Microsoft
PQC is the most realistic and scalable solution to protect today's systems against tomorrow's quantum threats.
✅ Summary: What You Should Know
| Topic | Key Points | |--------------------------|------------------------------------------------------------------------------| | Quantum Computers | Use qubits; still in development but progressing fast | | Current Encryption | RSA and ECC will be broken by quantum computers | | Quantum Cryptography | Secure but needs special hardware; not practical at large scale (yet) | | Post-Quantum Crypto | Ready to use today; secure against future quantum threats | | Global Action | Standards, funding, and migration plans already in motion |
The quantum era is coming. The systems we build today must be ready for it tomorrow.
Date: 20.04.2025
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.










