-
 @ cbaa0c82:e9313245
2025-05-02 17:00:12
@ cbaa0c82:e9313245
2025-05-02 17:00:12TheWholeGrain - #April2025
Toast officially took this April. It was non-stop Toast posts since the beginning of the month when Toast somehow got control of the nSec for the official Bread and Toast nPub on NOSTR. Not only that, but Toast somehow managed to hack the entire Bread and Toast website!
We're still trying to figure out how...
Luckily, we've managed to take back control of the website as well as gotten Toast to agree not to mess around with our profile on NOSTR. We'll see how long that lasts...
Sunday Singles - April 2025 2025-04-06 | Sunday Single 87 Title: Puppets Toast just keeps saying, "Dance my puppets... Dance..." over and over... https://i.nostr.build/Xz6akLAQXZgTUJrh.png
2025-04-13 | Sunday Single 88 Title: Late Night Show Tonight on A Midnight Snack with Toast! We have our guest, End-Piece, to talk about a new movie and much more! https://i.nostr.build/NKdCZ6gmZh7wEFSJ.png
2025-04-20 | Sunday Single 89 Title: Sculpture This statue is in honor of Toast, the Great! https://i.nostr.build/08C2SG3VCiugelX4.png
2025-04-27 | Sunday Single 90 Title: Nothing Butter It's Nothing Butter! Because Nothing get Butter than this! https://i.nostr.build/sfR3U6LWIj9hPjkX.png
Adventure Series: Questline The group continues on the next leg of their journey which happens to lead them into a massive forest where the trees are so thick and large that sunlight can barely get through if at all!
Artist: Dakota Jernigan (The Bitcoin Painter) Writer: Daniel David (dan 🍞)
2025-04-08 | Questline 007 - Dark Forest After recovering from their recent battle our heroes continue on their path to find themselves before a large dark forest. The forest is so large that the only way to get to the other side is to go through it. https://i.nostr.build/29FrlOBwWCRsTvrN.png
2025-04-22 | Questline 008 - Into the Shadows As the our heroes enter the forest the darkness of the shadows begins to engulf all that is around them. While Bread is eager to move into the woods Toast and End-Piece are a little more hesitant to do so. https://i.nostr.build/MOkJEzeFVVCSK9aj.png
Toast's Takeover 2025 As we pointed out at the beginning of this edition of The Whole Grain, Toast took over just about everything! On the last day of March something suspicious was going on. https://i.nostr.build/0ERB5nXGTRQew0C3.png
The next day on April 1st, the official Bread and Toast nPub was renamed to Toast and Bread. Some people might have even thought that it was just a silly April Fools joke on our part, but then the following message was released that same morning:
Hey, everyone! Toast here! That’s right, I’m in charge now! https://i.nostr.build/tHyQr5BsGcf00crp.png
For the next month, it’s all about, me, Toast! Prepare yourselves for Toast’s Takeover!
Stay tuned for more of Toast and Bread! Things are about to get crispy!
Our entire brand was transformed into Toast and Bread. Even the website was redirecting to ToastandBread.com. It was crazy, and no one could figure out how Toast made it all happen.
Other Content Released in April 2025 2025-04-02 | Toast's Comic Collection Title: Toastie #12 Hi. My Name is Toastie Andrews. Welcome to Toasterdale! https://i.nostr.build/vW9plTM44t4U2WM8.png
2025-04-09 | Concept Art Title: The Birth of Toast This was a quick drawing done to show how Toast actually became Toast. The idea was that our second slice of bread gets stuck in a toaster while exploring. End-Piece accidentally turns the toaster on while trying to figure out how to help. https://i.nostr.build/TDQ6CiPBkrxAU3Vi.png
2025-04-16 | Bitcoin Art Title: Toast Loves Lightning Block Height: 892674 Toast loves learning about Lightning! https://i.nostr.build/SAoXAvpjH6gYDYPB.png
Additions to The Bakery in 2025 We had our first addition of the year to The Bakery back in March, and we'd like to make sure we share it in this edition of The Whole Grain since we forgot to mention it the March edition. Let's just all agree we got distracted dealing with Toast's ego.
2025-03-09 | npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9 https://image.nostr.build/55d0531271ee5263841d4d06b67f787ed3da85babaedd865a007f957e14fb2e7.jpg
As for April, we had a few new additions to The Bakery. The first additions was a collection that showed us what Bread and Toast would look like on some classic VHS tapes.
2025-04-04 | npub1qhjxfxpjm7udr0agr6nuhuwf9383e4g9907g64r9hf6y4fh6t6uqpcp36k https://i.nostr.build/5VJZdLOC1FdzJ3XE.jpg https://i.nostr.build/G5SUkzo1tKoYFoef.png https://i.nostr.build/ViDuteL5TXM3YTs1.png
To finish off here is the latest addition which was a beautiful watercolor showing off all three slices of bread on a plate next to a toaster!
2025-04-24 | npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u https://image.nostr.build/9fc49d71715ae6a90f441b71de6ba0f8598b3f81c7fb7247ccb200e9537d8fb1.jpg https://image.nostr.build/19a158ceb6010a24712ee2741447f3e56f2883156e775c1be037b498a3b51a2e.jpg
Thanks for checking out the eighth issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
Thanks for putting up with Toast this past month! Bread and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🍞 #🖼️
List of nPubs Mentioned: samhain: npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9
archjourney: npub1qhjxfxpjm7udr0agr6nuhuwf9383e4g9907g64r9hf6y4fh6t6uqpcp36k
existing sprinkles: npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u
The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 005bc4de:ef11e1a2
2025-05-02 16:14:46
@ 005bc4de:ef11e1a2
2025-05-02 16:14:46Popes and Horses
It's probably not kosher to compare popes with horses, and yet...the Kentucky Derby is tomorrow and the papal conclave begins Monday. The question in both cases is, "Who will win?" So, here we go...
Polymarket, or other such "prediction markets", are becoming go-to places for things such as this. At least to me, they're interesting because it's a bit more than an opinion poll. With these markets, people have to put up real money, or cryptocurrency, to make their predictions. They actually have to put their money where their mouth is.
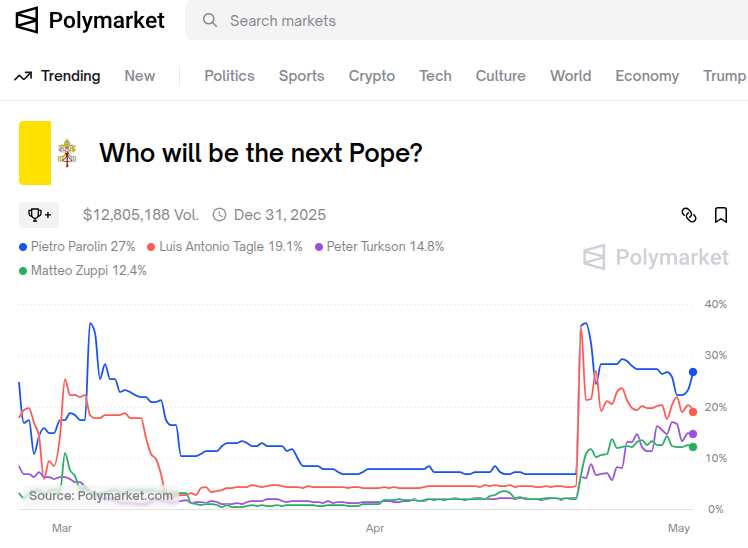
Polymarket currently lists four cardinals as front runners for pope, as below:
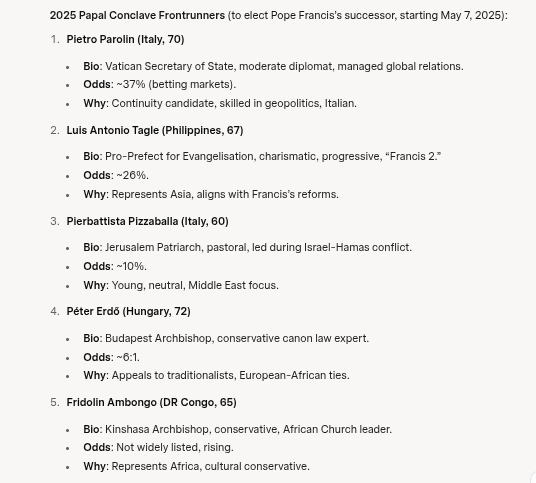
And, thanks to Grok, here's a short run-down for leading candidates (ironically 3 are not on Polymarket at the moment):
And as to the Kentucky Derby, Polymarket has this prediction at the moment:
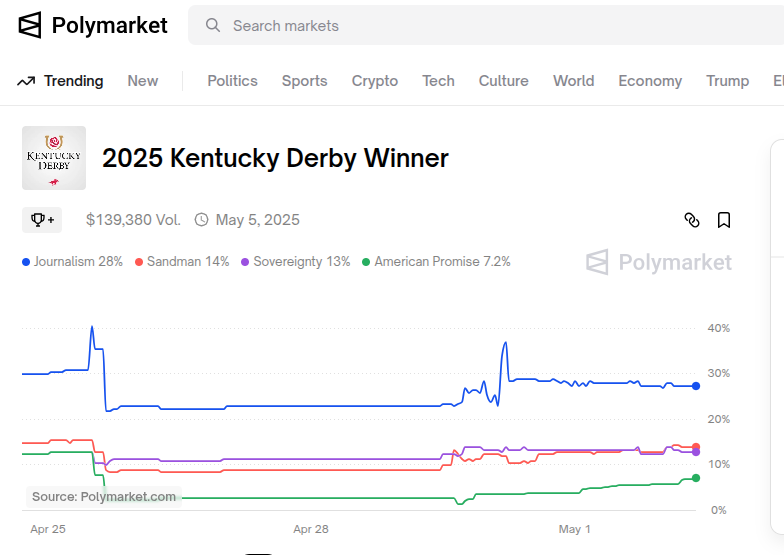
I know more about horse racing than papal politics. This is not bragging. I know very little about horse racing, which means I know zero about papal politics. But, one thing I believe with horse racing and especially with the Kentucky Derby is this...
...when the horses are making that final fourth turn, it's usually not the front runner you need to watch out for. All eyes are on that horse, of course, and the announcer is calling that horse's name, but that's not the place to focus. The dangerous horse is usually about two or three slots back, lurking and waiting for "the moment."
The Derby is the longest race these 3-year old horses have every run at 1 1/8 miles. That front horse often/usually fades, not always, but often. That horse sitting in the 3 or 4 spot is often a distancer, a stalker, and if a wise jockey is aboard, has been biding his time. That final 100 yards is go-time.

In the image above, I'd keep an eye on the blue/yellow jockey and horse...he's sitting in 4th place, directly positioned behind the front runner, hugging the rail, about to make a move and power ahead to win.
And back to papal politics, which again, I know nothing about...two things come to mind:
- In political elections I'm typically a big believer in the pendulum swing of elections and movements. The pendulum swings conservative, then liberal, then back again. This is a religious election, so the pendulum effect may play less of a role here. It stands to figure that for centuries the pendulum should have been stuck on the "conservative" side of things. That's kind of how religion works...the Bible doesn't change. But, let's not fool ourselves, it is 2025 and people change their views on things...this election is political too. Both world politics and internal, unseen "Vatican politics" figure in. The pendulum may be at play is simply seen in Pope Francis himself. Pope John Paul was conservative, Francis swung the pendulum the other way, and if the pendulum is indeed swinging, then "conservative" cardinals stand to benefit in their chances of election.
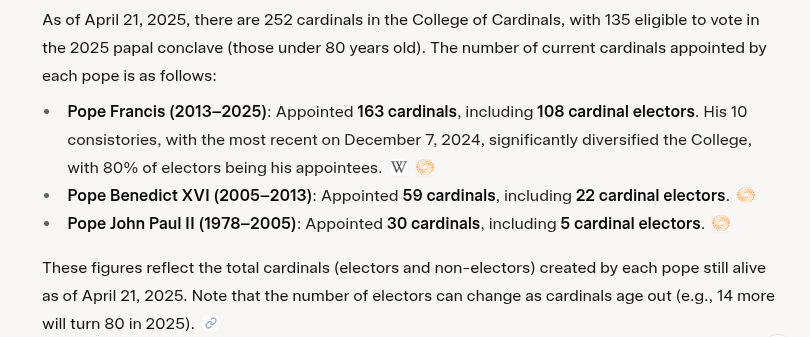
- However, if you want to win an election, you pick the voters. According to Grok, Pope Francis appointed 108 of the 135 voting cardinals. That leaves only 27 candidates from the conservative old-guard popes. Like gerrymandering a district, getting the right people to vote can yield a candidate-of-choice.
Voters, according to Grok:
Circling back to the front runners on Polymarket, I'd normally go with the horse, er cardinal, sitting in the three spot, Turkson on Polymarket. Or, I'd go with number 4 according to Grok, Peter Erdo, if I felt the pendulum effect is at play.
Yet, you win by votes and 108/135 are Francis-men. So, the top two, being continuity candidates have the best chances in my view. I still, can't go with the lead horse though. So, my prediction...
Luis Antonio Tagle will be the next pope.
And, the Kentucky Derby winner: Owen Almighty - This horse has good past performances with the exception of the last time out at the Bluegrass Stakes which is a mile and 1/8. This is concerning and might mean the horse can't handle the extra distance. No doubt this is what got the 30/1 odds. But, a jockey change was made. I like the new jockey Javier Castellano and maybe his experience can navigate the horse through.
We'll see how my predictions pan out.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ f1989a96:bcaaf2c1
2025-05-01 15:50:38
@ f1989a96:bcaaf2c1
2025-05-01 15:50:38Good morning, readers!
This week, we bring pressing news from Belarus, where the regime’s central bank is preparing to launch its central bank digital currency in close collaboration with Russia by the end of 2026. Since rigging the 2020 election, President Alexander Lukashenko has ruled through brute force and used financial repression to crush civil society and political opposition. A Central Bank Digital Currency (CBDC) in the hands of such an authoritarian leader is a recipe for greater control over all aspects of financial activity.
Meanwhile, Russia is planning to further restrict Bitcoin access for ordinary citizens. This time, the Central Bank of Russia and the Ministry of Finance announced joint plans to launch a state-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Access would be limited to those meeting previously defined thresholds of $1.2 million in assets or an annual income above $580,000. This is a blatant attempt by the Kremlin to dampen the accessibility and impact of Bitcoin for those who need it most.
In freedom tech news, we spotlight Samiz. This new tool allows users to create a Bluetooth mesh network over nostr, allowing users' messages and posts to pass through nearby devices on the network even while offline. When a post reaches someone with an Internet connection, it is broadcast across the wider network. While early in development, Mesh networks like Samiz hold the potential to disseminate information posted by activists and human rights defenders even when authoritarian regimes in countries like Pakistan, Venezuela, or Burma try to restrict communications and the Internet.
We end with a reading of our very own Financial Freedom Report #67 on the Bitcoin Audible podcast, where host Guy Swann reads the latest news on plunging currencies, CBDCs, and new Bitcoin freedom tools. We encourage our readers to give it a listen and stay tuned for future readings of HRF’s Financial Freedom Report on Bitcoin Audible. We also include an interview with HRF’s global bitcoin adoption lead, Femi Longe, who shares insights on Bitcoin’s growing role as freedom money for those who need it most.
Now, let’s see what’s in store this week!
SUBSCRIBE HERE
GLOBAL NEWS
Belarus | Launching CBDC in Late 2026
Belarus is preparing to launch its CBDC, the digital ruble, into public circulation by late 2026. Roman Golovchenko, the chairman of the National Bank of the Republic of Belarus (and former prime minister), made the regime’s intent clear: “For the state, it is very important to be able to trace how digital money moves along the entire chain.” He added that Belarus was “closely cooperating with Russia regarding the development of the CBDC.” The level of surveillance and central control that the digital ruble would embed into Belarus’s financial system would pose existential threats to what remains of civil society in the country. Since stealing the 2020 election, Belarusian President Alexander Lukashenko has ruled through sheer force, detaining over 35,000 people, labeling dissidents and journalists as “extremists,” and freezing the bank accounts of those who challenge his authority. In this context, a CBDC would not be a modern financial tool — it would be a means of instant oppression, granting the regime real-time insight into every transaction and the ability to act on it directly.
Russia | Proposes Digital Asset Exchange Exclusively for Wealthy Investors
A month after proposing a framework that would restrict the trading of Bitcoin to only the country’s wealthiest individuals (Russians with over $1.2 million in assets or an annual income above $580,000), Russia’s Ministry of Finance and Central Bank have announced plans to launch a government-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Under the plan, only citizens meeting the previously stated wealth and income thresholds (which may be subject to change) would be allowed to trade digital assets on the platform. This would further entrench financial privilege for Russian oligarchs while cutting ordinary Russians off from alternative financial tools and the financial freedom they offer. Finance Minister Anton Siluanov claims this will bring digital asset operations “out of the shadows,” but in reality, it suppresses grassroots financial autonomy while exerting state control over who can access freedom money.
Cuba | Ecash Brings Offline Bitcoin Payments to Island Nation in the Dark
As daily blackouts and internet outages continue across Cuba, a new development is helping Cubans achieve financial freedom: Cashu ecash. Cashu is an ecash protocol — a form of digital cash backed by Bitcoin that enables private, everyday payments that can also be done offline — a powerful feature for Cubans experiencing up to 20-hour daily blackouts. However, ecash users must trust mints (servers operated by individuals or groups that issue and redeem ecash tokens) not to disappear with user funds. To leverage this freedom tech to its fullest, the Cuban Bitcoin community launched its own ecash mint, mint.cubabitcoin.org. This minimizes trust requirements for Cubans to transact with ecash and increases its accessibility by running the mint locally. Cuba Bitcoin also released a dedicated ecash resource page, helping expand accessibility to freedom through financial education. For an island nation where the currency has lost more than 90% of its value, citizens remain locked out of their savings, and remittances are often hijacked by the regime, tools like ecash empower Cubans to preserve their financial privacy, exchange value freely, and resist the financial repression that has left so many impoverished.
Zambia | Introduces Cyber Law to Track and Intercept Digital Communications
Zambia’s government passed two new cyber laws granting officials sweeping powers to track and intercept digital communications while increasing surveillance over Zambians' online activity. Officials insist it will help combat cybercrime. Really, it gives the president absolute control over the direction of a new surveillance agency — a powerful tool to crush dissent. This follows earlier plans to restrict the use of foreign currency in the economy to fight inflation, which effectively trapped Zambians in a financial system centered around the volatile “kwacha” currency (which reached a record low earlier this year with inflation above 16%). For activists, journalists, and everyday Zambians, the new laws over online activity threaten the ability to organize and speak freely while potentially hampering access to freedom tech.
India | Central Bank Deputy Governor Praises CBDC Capabilities
At the Bharat Inclusion Summit in Bengaluru, India, the deputy governor of the Reserve Bank of India (RBI), Rabi Sankar, declared, “I have so far not seen any use case that potentially can solve the problem of cross-border money transfer; only CBDC has the ability to solve it.” Yet — seemingly unbeknownst to Sankar, Bitcoin has served as an effective remittance tool for more than a decade at low cost, fast speed, and with no central point of control. Sankar’s remarks follow a growing push to normalize state-controlled, surveillance-based digital money as a natural progression of currency. The RBI’s digital rupee CBDC, currently in pilot phase, is quickly growing into one of the most advanced CBDCs on the planet. It is being embedded into the government’s UPI payment system and offered through existing financial institutions and platforms. Decentralized alternatives like Bitcoin can achieve financial inclusion and payment efficiency too — but without sacrificing privacy, autonomy, or basic rights over to the state.
Tanzania | Opposition Party Excluded From Election Amid Financial Repression
Last week, the Tanzanian regime banned the use of foreign currency in transactions, leaving Tanzanians to rely solely on the rapidly depreciating Tanzanian shilling. Now, Tanzania's ruling party has taken a decisive step to eliminate political opposition ahead of October’s general elections by barring the CHADEMA party from participation under the pretense of treason against their party leader, Tundu Lissu. Law enforcement arrested Lissu at a public rally where he was calling for electoral reforms. This political repression is not happening in isolation. Last year, the Tanzanian regime blocked access to X, detained hundreds of opposition members, and disappeared dissidents. These developments suggest a broader strategy to silence criticism and electoral competition through arrests, censorship, and economic coercion.
BITCOIN AND FREEDOM TECH NEWS
Samiz | Create a Bluetooth Mesh Network with Nostr
Samiz, an app for creating a Bluetooth mesh network over nostr, is officially available for testing. Mesh networks, where interconnected computers relay data to one another, can provide offline access to nostr if enough users participate. For example, when an individual is offline but has Samiz enabled, their device can connect to other nearby devices through Bluetooth, allowing nostr messages to hop locally from phone to phone until reaching someone with internet access, who can then broadcast the message to the wider nostr network. Mesh networks like this hold powerful implications for activists and communities facing censorship, Internet shutdowns, or surveillance. In places with restricted finances and organization, Samiz, while early in development, can potentially offer a way to distribute information through nostr without relying on infrastructure that authoritarian regimes can shut down.
Spark | New Bitcoin Payments Protocol Now Live
Lightspark, a company building on the Bitcoin Lightning Network, officially released Spark, a new payment protocol built on Bitcoin to make transactions faster, cheaper, and more privacy-protecting. Spark leverages a technology called statechains to enable self-custodial and off-chain Bitcoin transactions for users by transferring the private keys associated with their bitcoin rather than signing and sending a transaction with said keys. Spark also supports stablecoins (digital tokens pegged to fiat currency) and allows users to receive payments while offline. While these are promising developments, in its current state, Spark is not completely trustless; therefore, it is advisable only to hold a small balance of funds on the protocol as this new payment technology gets off the ground. You can learn more about Spark here.
Boltz | Now Supports Nostr Zaps
Boltz, a non-custodial bridge for swapping between different Bitcoin layers, released a new feature called Zap Swaps, enabling users to make Lightning payments as low as 21 satoshis (small units of bitcoin). This feature enables bitcoin microtransactions like nostr zaps, which are use cases that previously required workaround solutions. With the release, users of Boltz-powered Bitcoin wallets like Misty Breez can now leverage their wallets for zaps on nostr. These small, uncensorable bitcoin payments are a powerful tool for supporting activists, journalists, and dissidents — offering a permissionless way to support free speech and financial freedom worldwide. HRF is pleased to see this past HRF grantee add support for the latest freedom tech features.
Coinswap | Adds Support for Coin Selection
Coinswap, an in-development protocol that enables users to privately swap Bitcoin with one another, added support for coin selection, boosting the protocol’s privacy capabilities. Coin selection allows Bitcoin users to choose which of their unspent transaction outputs (UTXOs) to spend, giving them granular control over their transactions and the information they choose to reveal. For activists, journalists, and anyone operating under financial surveillance and repression, this addition (when fully implemented and released) can strengthen Bitcoin’s ability to resist censorship and protect human rights. HRF’s first Bitcoin Development Fund (BDF) grant was to Coinswap, and we are glad to see the continued development of the protocol.
bitcoin++ | Upcoming Bitcoin Developer Conference
The next bitcoin++ conference, a global, bitcoin-only developer series organized by Bitcoin educator Lisa Neigut, will occur in Austin, Texas, from May 7 to 9, 2025. A diverse group of privacy advocates, developers, and freedom tech enthusiasts will convene to learn about the mempool (the queue of pending and unconfirmed transactions in a Bitcoin node). Attendees will learn how Bitcoin transactions are sorted into blocks, mempool policies, and how transactions move through time and space to reach the next block. These events offer an incredible opportunity to connect with the technical Bitcoin community, who are ultimately many of the figures building the freedom tools that are helping individuals preserve their rights and freedoms in the face of censorship. Get your tickets here.
OpenSats | Announces 11th Wave of Nostr Grants
OpenSats, a nonprofit organization supporting open-source software and projects, announced its 11th round of grants for nostr, a decentralized protocol that enables uncensorable communications. Two projects stand out for their potential impact on financial freedom and activism: HAMSTR, which enables nostr messaging over ham radio that keeps information and payments flowing in off-grid or censored environments, and Nostr Double Ratchet, which brings end-to-end encrypted private messaging to nostr clients, safeguarding activists from surveillance. These tools help dissidents stay connected, coordinate securely, and transact privately, making them powerful assets for those resisting authoritarian control. Read the full list of grants here.
Bitcoin Design Community | Organizes Designathon for Open-Source UX Designers
The Bitcoin Design Community is hosting its next Designathon between May 4 and 18, 2025, inviting designers of all levels and backgrounds to creatively explore ideas to advance Bitcoin’s user experience and interface. Unlike traditional hackathons, this event centers specifically on design, encouraging open collaboration on projects that improve usability, accessibility, and innovation in open-source Bitcoin tools. Participants can earn monetary prizes, rewards, and recognition for their work. Anyone can join or start a project. Learn more here.
RECOMMENDED CONTENT
Plunging Currencies, CBDCs, and New Bitcoin Freedom Tools with Guy Swann
In this reading on the Bitcoin Audible podcast, host Guy Swan reads HRF’s Financial Freedom Report #67, offering listeners a front-row view into the latest developments in financial repression and resistance. He unpacks how collapsing currencies, rising inflation, and CBDC rollouts tighten state control in Turkey, Russia, and Nigeria. But he also highlights the tools for pushing back, from the first Stratum V2 mining pool to Cashu’s new Tap-to-Pay ecash feature. If you’re a reader of the Financial Freedom Report, we encourage you to check out the Bitcoin Audible podcast, where Guy Swan will be doing monthly readings of our newsletter. Listen to the full recording here.
Bitcoin Beyond Capital: Freedom Money for the Global South with Femi Longe
In this interview at the 2025 MIT Bitcoin Expo, journalist Frank Corva speaks with Femi Longe, HRF’s global bitcoin lead, who shares insights on Bitcoin’s growing role as freedom money for those living under authoritarian regimes. The conversation highlights the importance of building Bitcoin solutions that center on the specific problems faced by communities rather than the technology itself. Longe commends projects like Tando in Kenya and Bit.Spenda in Ghana, which integrate Bitcoin and Lightning into familiar financial channels, making Bitcoin more practical and accessible for everyday payments and saving. You can watch the interview here and catch the livestreams of the full 2025 MIT Bitcoin Expo here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 1f79058c:eb86e1cb
2025-04-26 13:53:50
@ 1f79058c:eb86e1cb
2025-04-26 13:53:50I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
bash markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
bash markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```markdown
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ 22050dd3:480c11ea
2025-05-02 16:10:59
@ 22050dd3:480c11ea
2025-05-02 16:10:59Bitcoin isn’t complicated, nor is it difficult to understand. It just requires a bit of time and the realization that Bitcoin is unlike anything you’ve heard of or seen before. It’s different.
From the outside looking in, Bitcoin seems like a whole world full of strange and sophisticated words. What is a hash? Is it related to hash rate? What about this talk of public keys, private keys, and seed phrases? Are these seeds edible? While these aren’t words you’d find in traditional finance and economics jargon, they’re fairly simple to understand.
Going deeper, there are concepts and properties of Bitcoin that aren’t found elsewhere.
What does it mean that Bitcoin is deflationary? What’s this talk of Lightning, layers, and on-chain vs off-chain? These can seem complex to the uneducated reader, but fear not as they can be understood with a little bit of explanation.
These concepts aren’t complicated, just different.
I once read that “Bitcoin is everything people don’t understand about computers mixed with everything people don’t understand about money”. While I do find this amusing and think it’s a witty one-liner, I don’t think it’s entirely accurate.
I would say that Bitcoin is the answer and the solution to a significant problem in the world today that the majority of people don’t even realize exists.
Our money and everything built on it is broken.
To the average person that last sentence probably provokes thoughts and questions. Most people do not understand what money is and its purpose. It makes sense why this is. At least in the United States, we are not taught what money is.
We all think we know what money is: the dollars in our wallets that we use to buy goods and services. These dollars are actually currency, which is a form of money, though the two are different.
Before I went down the rabbit hole and learned about Bitcoin, I also had no idea what money was.
 Going back to Bitcoin, Bitcoin is two things: money, and a computer network.
Going back to Bitcoin, Bitcoin is two things: money, and a computer network. The fact that we don’t understand money is why Bitcoin seems so complicated. Add that Bitcoin is a new form of money that our species has never seen before and things get hairy very quickly for the outside observer. With a basic understanding of what money is, as well as a run-down of how blockchain technology works, Bitcoin becomes much more digestible.
Money is three things: medium of exchange, store of value, and unit of account. Currency is two things: medium of exchange and unit of account. We use money in the form of currency as a medium of exchange to pay for goods and services. We use units of account to price goods and services. The store of value property is how we preserve the fruits of our time and energy (work) into the future.
To be good money a thing must fulfill these three properties well. Gold did succeed as a hard money until it didn’t. Gold still succeeds as a store of value, which is the most elusive of the three properties. However, gold has failed as a medium of exchange, which is why we transact with paper currency and not gold coins. Gold can only move at the speed of humans.
Bitcoin is proving with each passing day that it succeeds as hard and sound money by checking the box of these three properties.
If you’re reading this and asking “but a bitcoin is worth $96,000, how do you possibly use that to transact with?” then I have a great answer for you: a bitcoin is divisible into 100 million units, called satoshis or sats. This divisibility property gives Bitcoin the ability to succeed as a medium of exchange and unit of account. Everyday and small purchases are priced in satoshis, while less frequent but significant purchases are priced in bitcoin. A cup of coffee can be 3000 satoshis, while a house can be 3 bitcoin.
Bitcoin already has and will continue to succeed and take over on a global scale due to its store of value properties. For the first time in human history, a perfect money exists. Or rather, as close to “perfect” as possible. Due to its unique properties and absolute scarcity, Bitcoin will continue to become more valuable over time. It’s logical.
Absolute scarcity is difficult to comprehend because it has never existed before on such a large scale. More gold can always be mined, and more oil can always be drilled, but more than 21 million bitcoin total and a predictable and fixed release/minting schedule is forever. For the first time, society can save in money that can’t be debased and diluted. For the first time, society has money that discourages frivolous spending. This is amazing.
On a subconscious level, we are conditioned to want to spend our paper money since we are aware that it is constantly losing its value and buys us less in the future. With hard and sound money, there is no need to buy 20 properties to preserve one’s wealth. For the first time people can save in money, and no longer monetize other things. This will allow the prices of everything to fall, as they naturally should.
 Photo by David McBee
Photo by David McBeeWith this understanding of what good money should be, the defects with our current money become blindingly obvious, as if a switch were flipped for the first time. With this new understanding, it becomes a lot easier to understand Bitcoin and what it means for the world.
Understanding Bitcoin and its monetary system requires looking outside of the existing system. What makes it seem complicated is the fact that the majority of people do not realize what the current system is, how it works, and why it’s so severely flawed.
There are other and more comprehensive resources on the web for understanding how the Bitcoin blockchain works. However, I will provide a very basic explanation to get your big toe wet.
Transactions amongst peers are sent to a pool where they await inclusion into the blockchain. Highly specialized computers are constantly working around the globe to solve complex math problems to win the right to add the next block to the chain. When a computer solves the math problem, it adds transactions to the next block and is rewarded with a fixed amount of bitcoin (the block reward). Each block references and builds upon the previous block. Each new transaction is checked against previous transactions to ensure that no bitcoin is being double spent or invalidly spent. Once the new block is assembled, it is sent out to a global network of nodes that check the new block (and with it the rest of the chain) to verify that it is valid and conforms to the rules of the network. If the nodes are in consensus, the new block is added to the chain and the process starts over again.
There is no need for trust in the Bitcoin network, just verification.
A very important aspect of this process is that physical world energy, resources and time are required to mine blocks and keep the system running. This link between the physical and digital world is extremely crucial and is what sets Bitcoin aside from the rest and makes it the money that it is.
No matter how much computational power and no matter how much money you put into the system, there will never be more than 21 million coins total, with a release schedule set every 10 minutes on average. You could be the richest person in the world and have the computational power of Google, Microsoft, and Amazon combined. But on the Bitcoin network, you’re the same as the person who holds 1/100 of a bitcoin, and this is beautiful.
An understanding of Bitcoin isn’t something that happens overnight. While it’s possible to understand the concepts behind Bitcoin, a full understanding of what Bitcoin means to the world takes time. Much like any large change in life, it takes time to digest and truly understand that it has and will continue to have in the future.
 Learning about and understanding Bitcoin isn’t like learning a new theory or equation. It isn’t like learning about a new way of doing things in the existing system. It’s a completely new and foreign system providing solutions to problems that you didn’t even know existed.
Learning about and understanding Bitcoin isn’t like learning a new theory or equation. It isn’t like learning about a new way of doing things in the existing system. It’s a completely new and foreign system providing solutions to problems that you didn’t even know existed. Bitcoin is changing the world with each passing day and will continue to change and improve our world in ways we can’t even imagine in 2024.
With a growing understanding and the passage of time to digest, comprehend, and fully realize it, Bitcoin will change your perspective on the world and what you do with your time and energy. Once the mind opens up to what Bitcoin is and its significance, the world as it is now and the way we deal with money will seem completely asinine.
Bitcoin is exactly one of those things that you don’t notice until you notice it. And then it becomes impossible to ignore and see things as they once were.
Study Bitcoin.
-
 @ 5cb68b7a:b7cb67d5
2025-05-02 15:09:57
@ 5cb68b7a:b7cb67d5
2025-05-02 15:09:57Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 1d7ff02a:d042b5be
2025-05-02 14:50:01
@ 1d7ff02a:d042b5be
2025-05-02 14:50:01ผมได้ติดตามการแบนการซื้อขายแบบ P2P ของ Binance ในประเทศไทยมาระยะหนึ่งแล้ว จากสถานการณ์ดังกล่าว เห็นได้อย่างชัดเจนว่ารัฐบาลกำลังเริ่มโจมตี Bitcoin ก่อนที่เราจะบรรลุถึง Bitcoin Standard เราจำเป็นต้องมีความเป็นส่วนตัวและอิสระทางการเงิน ซึ่งการซื้อขายแบบ P2P มีความสำคัญมากในการบรรลุเป้าหมายนี้
ความสำคัญของ No-KYC P2P
No-KYC P2P คือหัวใจสำคัญ - เราจำเป็นต้องมีแพลตฟอร์มที่เป็นทางรอด เราไม่สามารถเชื่อใจแพลตฟอร์มแบบรวมศูนย์ได้เนื่องจากสาเหตุสองประการ: 1. ความเสี่ยงจากการถูกโกงโดยแพลตฟอร์มเอง (rug pull) 2. การถูกควบคุมจากภาครัฐ
แพลตฟอร์ม No-KYC P2P ที่แนะนำ
ผมอยากเสนอให้นักพัฒนาและชุมชน Bitcoin ไทย พิจารณาการศึกษาและพัฒนาแพลตฟอร์ม No-KYC P2P ปัจจุบันมีหลายทางเลือกที่มีอยู่แล้ว เช่น:
- Bisq
- RoboSats
- Mostro
- HodlHodl
- Lnp2pbot
เหตุผลที่แนะนำ Lnp2pbot
ผมขอแนะนำให้นำใช้หรือพัฒนาต่อจาก Lnp2pbot เนื่องจากข้อดีหลายประการ:
- ประสบการณ์ผู้ใช้ (UX) ที่ดีกว่า - เมื่อเทียบกับแพลตฟอร์มอื่นๆ
- ใช้ Telegram เป็นพื้นฐาน - มีระบบ Escrow (บุคคลที่สามที่ถือเงินระหว่างการทำธุรกรรม) ซึ่งเพิ่มความมั่นใจและลดโอกาสการถูกโกง
- ลดการรวมศูนย์ - ไม่จำเป็นต้องพัฒนาแอปและส่งขึ้นสโตร์ ซึ่งจะทำให้นักพัฒนาต้องเปิดเผยตัวตนและกลายเป็นจุดอ่อนให้รัฐบาลควบคุม
- สร้างชุมชนได้ง่าย - ทุกคนสามารถสร้างกลุ่มหรือชุมชนเพื่อการซื้อขายได้ ทำให้ตลาดพัฒนากลุ่มที่น่าเชื่อถือตามกลไกตลาดเสรี
- ใช้งานจริงในหลายประเทศแล้ว - ปัจจุบันมีหลายประเทศที่นำ Lnp2pbot ไปใช้งานจริงแล้ว แสดงให้เห็นถึงความเสถียรและความเชื่อถือได้ของระบบ
บทบาทของนักพัฒนาไทย
Lnp2pbot อาจยังมีข้อจำกัดด้าน UX โดยเฉพาะสำหรับผู้ใช้ท้องถิ่น นักพัฒนาไทยสามารถนำเอาซอฟต์แวร์มาพัฒนาต่อและดำเนินการเองได้ เนื่องจากเป็นโอเพนซอร์สอยู่แล้ว
สิ่งสำคัญที่สุดคือการรักษาให้ซอฟต์แวร์เป็นโอเพนซอร์สและให้ทุกคนสามารถนำไปใช้หรือทำให้มันทำงานได้ด้วยตนเอง วิธีการนี้จะหลีกเลี่ยงการมีจุดรวมศูนย์ที่รัฐบาลสามารถโจมตีได้
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 30b99916:3cc6e3fe
2025-04-19 19:55:31
@ 30b99916:3cc6e3fe
2025-04-19 19:55:31btcpayserver #lightning #lnd #powershell #coinos
BTCpayAPI now supports CoinOS.io REST Api

Adding Coinos.io REST Api end points support to BTCpayAPI. Here is what is implemented, tested and doumented so far.
Current REST APIs supported are now:
LND API https://lightning.engineering/api-docs/api/lnd/ BTCPay Greenfield API (v1) https://docs.btcpayserver.org/API/Greenfield/v1/ Hashicorp Vault API https://developer.hashicorp.com/vault/api-docs/secret/kv/kv-v1 Coinos.io API https://coinos.io/docs
Although this is PowerShell code, it is exclusively being developed and tested on Linux only.
Code is available at https://btcpayserver.sytes.net
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ dab6c606:51f507b6
2025-04-18 14:59:25
@ dab6c606:51f507b6
2025-04-18 14:59:25Core idea: Use geotagged anonymized Nostr events with Cashu-based points to snitch on cop locations for a more relaxed driving and walking
We all know navigation apps. There's one of them that allows you to report on locations of cops. It's Waze and it's owned by Google. There are perfectly fine navigation apps like Organic Maps, that unfortunately lack the cop-snitching features. In some countries, it is illegal to report cop locations, so it would probably not be a good idea to use your npub to report them. But getting a points Cashu token as a reward and exchanging them from time to time would solve this. You can of course report construction, traffic jams, ...
Proposed solution: Add Nostr client (Copstr) to Organic Maps. Have a button in bottom right allowing you to report traffic situations. Geotagged events are published on Nostr relays, users sending cashu tokens as thank you if the report is valid. Notes have smart expiration times.
Phase 2: Automation: Integration with dashcams and comma.ai allow for automated AI recognition of traffic events such as traffic jams and cops, with automatic touchless reporting.
Result: Drive with most essential information and with full privacy. Collect points to be cool and stay cool.
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 20986fb8:cdac21b3
2025-05-02 14:08:55
@ 20986fb8:cdac21b3
2025-05-02 14:08:55传统黑客松:闪耀火花中的局限
过去几十年里,黑客松一直是技术文化的培养皿——24小时或48小时的狂热编程马拉松,在披萨、咖啡因和几近不可能的乐观情绪中推进。
自1999年Sun Microsystems首次举办黑客松,要求Java开发者在Palm V掌上电脑上完成一日编程,到创业公司和大学里通宵达旦的“黑客日”[1],这些活动始终在庆祝黑客精神。它们为我们带来了Facebook的“点赞”按钮和聊天功能——这些标志性的创新[1],皆诞生于一夜之间的即兴狂想。
它们也催生了如GroupMe这样的公司——这个应用仅用了几个深夜时段就完成开发,一年后就被Skype以8000万美元收购[2]。
黑客松逐渐成为技术界的传说,成为“无拘束创造力”的代名词。然而,尽管充满激情和炒作,传统黑客松却存在着严重的局限:它们是偶发、线下的活动——更像是“蓝月亮”才出现一次的肾上腺素爆发,而不是一种可持续的创新流程。
一次黑客松也许能在周末召集100名程序员共聚一室,但活动结束后便销声匿迹,直到下一年。
频率低、规模小、触达有限。只有能亲临现场的人(往往是硅谷或精英高校)才有机会参与。哪怕你是来自拉各斯或圣保罗的天才黑客,只要身处远方,你的绝妙创意也注定被忽视。
这类冲刺式活动的成果也极为受限。
当然,团队可能构建出炫酷的演示项目,并赢得一时风头。但大多数情况下,这些项目只是一次性原型——“玩具”应用,最终并未发展为真正的产品或公司。有研究表明,只有约5%的黑客松项目在活动结束几个月后还有任何生命迹象[3]。
其余95%则如烟云般消散——在“黑客松宿醉”中夭折:人们回到“正职”,而演示代码也蒙尘。
批评者甚至给黑客松取了个贬义的别名:“周末虚耗松”(weekend wastedathons),抨击其成果如同短命的“蒸汽软件”(vaporware)[3]。
想想看:一阵创造力的爆发,数十个点子竞相绽放……然后呢?
你能说出几个真正从黑客松走出的成功企业名字?对于每一个如Carousell或EasyTaxi那样从黑客松中诞生、后来成功融资数千万美元的项目,就有几百个聪明的创意组合永远不见天日[2]。
传统黑客松模式,尽管令人兴奋,却极少能转化为持续的创新。
它更像是被时间、地域和后续缺失所束缚的孤岛式创新。黑客松是事件,不是流程;它是烟花,不是日出。
此外,黑客松在历史上一直颇为封闭。
直到近年,它们主要由技术圈内人士自办自娱。大型科技公司会举办内部黑客松,以激发员工创造力(Facebook每几周举办一次通宵活动,最终诞生了时间线和标记功能,影响了十亿用户 [1]);NASA和世界银行也曾尝试用黑客松推进公民科技。但这些都是例外,印证了一个普遍规律:黑客松从来不是常规工作流程,而是特例事件。
在科技巨头之外,鲜有组织具备资源或经验能频繁举办黑客松。
除非你是Google、Microsoft,或资金雄厚的创业孵化器,否则黑客松只是一场偶尔奢侈的尝试。事实上,当今世界上最大的黑客松是微软的内部全球黑客松——有多达70,000名员工跨越75个国家同时参与,这是壮观的成就,但唯有企业巨头才能负担得起[4]。
而中小型玩家只能仰望、惊叹。
限制显而易见:黑客松太少见、太封闭,无法真正激活全球人才库;周期太短,难以构建成熟产品;过于孤立,无法真正撼动行业。
没错,它们确实产生过惊艳的灵感时刻——创新的闪光灯。
但若视其为持续进步的机制,传统黑客松则显得捉襟见肘。作为投资者或科技领袖,你或许会为创造力鼓掌,但仍会追问:真正的长期影响在哪里?有谁搭建了把这些火花转化为持续光束的基础设施?
正如克莱顿·克里斯滕森的《创新者的窘境》所言,传统巨头往往将黑客松项目视作“玩具”——有趣但不切实际。
而事实上,“每一个未来的大事物,起初总是被当作玩具”。黑客松的确催生了不少“玩具”,却极少能拥有支持系统去把它们变为下一个伟大的事物。
这个模式,是时候被重新发明了。
为何到了2020年代,我们还在用1990年代的创新方式?为何将突破性的想法限制在一个周末或一个地点?为何允许95%的早期创新无声凋谢?
这些问题,悬而未解,等待着回答。
Hackathons 2.0 ——DoraHacks与黑客松的第一次进化(2020–2024)
DoraHacks登场。
在2020年代初,DoraHacks如同一台“心脏除颤器”,令黑客松这种形式重获新生。DoraHacks 1.0(大致始于2020年、延续至2024年)并非对黑客松的微调,而是对其彻底的重塑:将传统黑客松从1.0升级到2.0。它汲取原有理念,加速、扩展并升级至全维度,全方位放大其影响力。结果是一场全球黑客运动的兴起,一个将黑客松从“一锤子买卖”变为持续技术创新引擎的平台。
DoraHacks如何革命性地重构黑客松?请看以下几个维度:
从24小时到24天(甚至24周)——时间轴的重构
DoraHacks拉长了黑客松的时间框架,解锁了远超以往的创新潜能。
相比于传统那种紧张焦躁的24小时冲刺,DoraHacks支持的黑客松往往持续数周甚至数月——这是一场范式转变。
团队终于有了足够时间去打磨原型、迭代优化、反复精炼。更长的周期意味着项目能从粗糙演示走向成熟MVP。黑客们终于可以“偶尔睡觉”,引入用户反馈,将灵感的火花铸造成实用的成果。
时间的延展模糊了黑客松与加速器之间的界限,但保留了黑客松自由、开放的精神。例如,DoraHacks为区块链初创团队组织的黑客松通常持续6到8周,最终成果往往能吸引真实用户与投资人。
延长的时间,把“玩具”变成了产品。就像黑客松终于“长大成人”:Less Hack, More BUIDL(少些临时拼凑,多些踏实构建)。打破24小时范式之后,黑客松真正变得更高效、更深远、更具生产力。
从街角咖啡馆到全球虚拟竞技场——地理限制的打破
DoraHacks将黑客松从线下搬到云端,释放出全球参与的可能性。
2020年之前,黑客松意味着必须到现场——可能是旧金山某仓库,或是大学实验室,与本地队友并肩作战。而DoraHacks颠覆了这一格局:任何人、任何地方,只要连上网络,就可以参与。
一位尼日利亚的开发者、乌克兰的设计师、巴西的产品经理,如今可以在同一场线上黑客松中协作创新。地理边界不复存在。
当DoraHacks举办面向非洲区块链开发者的Naija HackAtom时,吸引了来自尼日利亚科技社群的500多名参与者(包括160多位开发者,odaily.news)。在另一场活动中,来自数十个国家的黑客同时在线参与、构思、竞争 [6]。
这种全球性拓展不仅增加了参与人数,更引入了多样的视角和本地问题。一个金融科技黑客松中,可能有拉美开发者解决汇款问题;一个AI黑客松中,亚洲或非洲开发者将机器学习应用于本地医疗。
线上化,让黑客松变得真正普惠。DoraHacks有效地民主化了创新的入场门槛——你只需要一根网线和一颗创作的心。
结果是:创意的数量与质量实现量子飞跃。 黑客松不再是精英小圈子的游戏,而是一场面向全人类的全球创新嘉年华。
从几十人到数万人——规模的跃迁
DoraHacks推动的另一项革命,就是规模的扩展。传统黑客松人少而亲密(几十人,顶多几百)。DoraHacks则催生了成千上万人参与、数百万美元奖金池的大型活动。
例如,在2021年的一场线上黑客松中,近7000名参与者提交了550个项目,争夺500万美元奖金。这是2010年代初期根本无法想象的规模[7]。
DoraHacks本身也成为这些“超级黑客松”的中枢。平台在Web3领域所举办的黑客松常常吸引数百支队伍参赛,奖金高达数百万美元。
这不只是好看的数据,而是更广泛的全球人才投入,也带来了更高概率的真正突破性成果。
以BNB Chain支持的黑客松系列为例,在DoraHacks推动下,有216支开发团队获得了超过1000万美元的资金支持[8]——是的,真金白银的种子投资。这哪是黑客松?简直就是一个小型经济体。
奖池也从“披萨钱”膨胀成“起步资本”,吸引那些有抱负、懂商业的创业者参与。越来越多的项目不再只是周末练习,而是具备融资能力的初创企业。黑客松,也由“科技科学展”升格为“全球创业发射台”。
从玩具项目到真公司(甚至独角兽)——成果的飞跃
最令人振奋的一点是:DoraHacks所孵化的项目,不只是应用,更是真正的公司。其中一些甚至成长为独角兽(估值超过10亿美元的公司)。
我们之前提到过2020年之前为数不多的成功案例,比如Carousell(一个在2012年黑客松上诞生的小点子,如今已成为估值11亿美元的二手市场[2]),或EasyTaxi(始于黑客松,后融资7500万美元、覆盖30个国家[2])。
DoraHacks让这种奇迹频繁上演。通过更长的周期、更多的支持、更好的资金接力,黑客松逐渐成为真正的“创新孵化器”。
以1inch Network为例——它是一家去中心化金融聚合平台,起初就是在2019年一个黑客松中诞生的。创始人Sergej Kunz和Anton Bukov在社区支持下完成了最初的原型,随后持续迭代。
如今,1inch的累计交易额已超4000亿美元,成为DeFi领域的头部平台之一 [9]。
再看DoraHacks Web3黑客松中的优胜者,许多项目已经完成了数百万美元的融资,获得顶级VC支持。
黑客松成为了“创业世界的前门”,创始人往往在此首次亮相。比如Solana Season Hackathons中的热门项目STEPN —— 一个“边走边赚”应用,于2021年赢得黑客松奖项,不久后就成长为拥有数十亿美元代币经济的现象级产品[10]。
这不是孤立事件,而是DoraHacks设定的系统性趋势。它的黑客松正在源源不断地产出可投、可用、可落地的创业项目。
某种意义上,DoraHacks模糊了黑客松与早期孵化器的界限。玩乐的黑客精神依然在,但结果已不只是炫耀——而是真实存在的公司,有用户,有营收,有估值。
借用投资人Chris Dixon的话说:DoraHacks把那些“玩具”,扶育成了下一个伟大的事物[5]。
DoraHacks不仅优化了旧模式,它创造了一个全新的创新生态
DoraHacks主导的第一次黑客松进化,不只是“修补优化”,而是打造了一个全新的创新系统。
黑客松变得高频、全球化、具决定性影响。
它不再是短暂的周末狂欢,而是持续的创新供给链。
DoraHacks平台每年孵化出上百个可行项目,其中很多都获得后续融资。它不仅提供活动本身,更提供“术后护理”:社区支持、导师指导、连接投资人与资助渠道(如DoraHacks的资助计划和二次方资助机制)。 到2024年,成果不言自明。DoraHacks已成长为全球最重要的黑客松平台——一个贯通区块链、AI乃至更多前沿科技的黑客运动中枢。
数据不会说谎。
9年间,DoraHacks帮助4000多个项目获得超过3000万美元资金(coindesk.com)[11];到2025年,这一数字飙升,DoraHacks支持的黑客松和资助总计为超过21000个初创团队提供了逾8000万美元资金(linkedin.com)[12]。
这不是夸张宣传——而是写入技术史的事实。CoinDesk评价道:“DoraHacks已成为全球最活跃的多链Web3开发平台与黑客松组织者之一。”(coindesk.com)[13]
主流技术生态纷纷注意到这一趋势。
超过40个公链(包括L1与L2)——从Solana到Polygon再到Avalanche——皆与DoraHacks合作,组织黑客松与开放创新计划(blockworks.co)[13]。
Blockworks 报道称,DoraHacks已成为数十个Web3生态系统的“核心合作伙伴”,帮助他们连接全球开发者资源(blockworks.co)[11]。
在投资人眼中,DoraHacks本身就是关键基础设施:“DoraHacks对Web3基础设施建设至关重要。”一位支持平台的VC如此指出(blockworks.co)[13]。
简而言之:到2024年,DoraHacks已将黑客松从一个小众事件变为全球创新引擎。
它证明:只要规模足够、流程健全,黑客松可以持续地产出真实、可投、可商业化的创新。
它连接开发者与资源,把“孤岛式创新”变成一场全球开发者的常青运动。
这就是Hackathons 2.0:更大、更久、更无界,也远比以往更具颠覆性。
也许你会问:还能比这更好吗?
DoraHacks似乎已经破解了“如何让黑客创造力产生持久影响”的密码。
但这并不是终点。事实上,DoraHacks团队即将揭示的,是一场更加激进的革命。
如果说DoraHacks 1.0是“进化”,那接下来将是一次范式转移的“革命”。
Agentic Hackathon:BUIDL AI与第二次黑客松革命
2024年,DoraHacks推出了BUIDL AI,并由此提出了“Agentic Hackathon(自主智能黑客松)”的概念。
如果说最初的黑客松像是模拟电话,DoraHacks 1.0则使其进化为智能手机,那么BUIDL AI的出现,就像为黑客松安装上了AI副驾驶——进入自动驾驶模式。
这不仅是渐进式的提升,而是一场彻底的第二次革命。
BUIDL AI为黑客松注入了人工智能、自动化与“智能代理”能力(Agentic),根本性地改变了黑客松的组织方式与体验路径。
我们正迈入“自主智能创新时代(Age of Agentic Innovation)”,在这个时代中,借助AI代理运行的黑客松可以以前所未有的频率、高效与智慧展开。
那么,究竟什么是Agentic Hackathon?
它是一种由AI代理全面增强的黑客松,从策划、评审到参与者支持都涵盖在内,使得创新的速度与规模达到前所未有的高度。
在Agentic Hackathon中,AI是那位永不疲倦的共同组织者,与人类并肩工作。 过去那些压垮组织者的繁琐流程,如今交由智能算法完成。你可以想象——黑客松几乎在自动运行,如同一场永不停歇的“点子锦标赛”。
借助BUIDL AI,DoraHacks实现了“自驾黑客松”:自主、高效、全天候运行,且可在多个领域同时并行。 这并非科幻小说,而是正在发生的现实。我们来看BUIDL AI是如何运作的,以及它如何将黑客松效率提升十倍以上:
AI驱动的评审与项目筛选:效率提升10倍以上
大型黑客松中最耗时的环节之一就是评审数百个项目提交。传统做法常常需要组织者耗费数周精力,才能从中筛选出有潜力的项目。
BUIDL AI彻底改变了这一切。
它配备了BUIDL Review模块——一个AI驱动的评审系统,能够从多个维度(项目完整性、创意性、主题契合度等)智能分析项目,并自动剔除质量较低的提交[14]。
就像配备了一支随叫随到的专家评审军团。
效果如何?原本需要几百人小时完成的工作,如今几分钟即可完成。
DoraHacks报告称,AI辅助评审已将组织效率提高超过10倍[14]。
想象一下:一项原本需要一个月枯燥工作完成的任务,如今在几天之内搞定,而且评分更一致、公正、透明。 组织者不再淹没在文书工作中,参与者也能更快获得反馈。
当然,AI并不完全取代人工评委——最终决策仍需专家参与,但AI承担了繁重的初审环节。这也意味着:黑客松可放心接纳更多项目提交,因为AI会帮你完成筛选。
不再因为“人手不足”而限制报名人数。
在Agentic Hackathon中,再也没有优秀项目被埋没的遗憾,因为AI确保它们都能被看到。
自动化市场营销与内容讲述:让每场黑客松都自带扩散力
赢得一场黑客松固然令人激动,但如果无人知晓,影响力也就大打折扣。
过去,黑客松结束后,组织者通常需要手动撰写总结、撰文致谢、更新结果——虽然重要,却常常被推迟。
BUIDL AI改变了这一点。
它配备了自动化营销模块,可一键生成黑客松的总结报告与传播内容[14]。
想象这样一个AI,它完整“观察”了整场黑客松(包括提交项目、获奖名单、技术趋势),然后自动撰写出一份专业报道:突出最佳创意、介绍获胜团队、提炼洞察(比如“本次黑客松中60%的项目应用AI于医疗场景”)。
BUIDL AI正是这么做的:自动生成“高光集锦”与总结报告[14]。
这不仅节省了组织者的写作工作,还极大提升了黑客松的传播力。
活动结束数小时内,一份内容丰富的总结即可全球发布,展示创新成果,吸引关注。
赞助方与合作伙伴对此尤为青睐,因为他们的投资能被迅速宣传;参与者也很喜欢,因为自己的项目立刻获得庆祝与曝光。
本质上,每一场黑客松都在讲述一个故事,而BUIDL AI确保这个故事被迅速、广泛地传播。
这种自动化叙事机制,使得黑客松不再是孤立事件,而是持续内容的源泉,为下一场活动积蓄动能。
这是一个良性循环:黑客松产出创新,AI包装传播,传播吸引更多创新者。
一键发起,多黑客松并行:组织者的自由释放
BUIDL AI最具解放性的功能之一,是一键启动黑客松、支持多场并行管理。
过去,发起一场黑客松本身就是一项大型项目:报名系统、评委协调、奖金设计、沟通流程……一切都需人工配置。
DoraHacks的BUIDL AI引入了“一键发起黑客松”工具 [14] 。
组织者只需输入基本信息(主题、奖池、时间、评审规则),平台即自动生成活动页面、提交入口、评审流程等,就像发一篇博客一样简单。
这极大降低了社区与公司举办黑客松的门槛。
如今,即使是一个初创公司或大学社团,也可以轻松举办全球级黑客松,无需专职活动团队。
此外,BUIDL AI还支持多场黑客松的并行管理[14]。
过去,即使是科技巨头也难以同步组织多场黑客松——资源消耗太大。如今,一个生态系统可以同时运行DeFi、AI、 IoT等主题黑客松,背后由AI自动调度。
自BUIDL AI发布以来,组织12场/年,甚至同时运行数场黑客松,从“不可能”变成常规操作[14]。
平台还自动管理参与者接入、发送提醒、通过聊天机器人回答常见问题,确保流程顺畅。
简而言之,BUIDL AI让黑客松主办方像使用云服务器一样“按需发起”创新活动。
这是一场结构性转变:黑客松不再是“偶尔有空才办”的事件,而是“需要时就能发”的常态流程。 我们正在见证永续黑客松文化的诞生——不再是偶尔的火花,而是持续的火焰,始终燃烧,永不熄灭。
实时AI导师与智能助手:人人皆可成为“Agentic Hacker”
Agentic Hackathon的“智能代理”不仅体现在后台,也贯穿了参与者的体验。
借助AI集成,开发者得到了更智能的工具与支持。
例如,BUIDL AI可以配备AI助手,在活动中实时回答开发者问题(如“这个API怎么用?”、“有没有这个算法的代码示 例?”),就像随叫随到的技术导师。
它还可以推荐协作伙伴、推送参考资料。
本质上,每位参与者都像身边多了一个AI队友——全能、勤奋、永不疲倦。
一些本需数小时调试的bug,借助AI助手几分钟即可解决。
这意味着:项目质量提升,参与者学习效率大幅提高。
正如followin.io所言,这种“agentic协助”体现了“人人皆可成为黑客”的愿景[14]。
AI自动化了大量重复性工作,放大了小团队的能力边界[14]。
在Agentic Hackathon中,两个人加AI助手,就能完成过去五人团队数周才能达成的任务[14]。
这既降低了门槛,也拉高了上限——创新的天花板不再遥不可及。
总结:从黑客松2.0跃迁至3.0,进入智能化持续创新的新时代
所有这些变革,指向同一个事实:黑客松已从偶发的灵感爆发,演化为持续、高频、AI优化的创新流程。
我们正从黑客松2.0走向黑客松3.0——一个自主、常驻、智能的新时代。
这是一场范式转移。
黑客松不再是你参加的一场活动,而是你生活的一个创新环境。
借助BUIDL AI,DoraHacks描绘出这样的世界:“黑客松将进入一个前所未有的自动化与智能化时代,使全球更多黑客、开发者与开源社区能够轻松发起与参与。”
创新将随时随地发生,因为支持它的基础设施正由AI驱动、全天候运转于云端。
黑客松已成为一个智能平台,随时准备将创意转化为现实。
更关键的是,这一切并不局限于区块链。
BUIDL AI是通用平台——无论是AI、气候科技、医疗、教育等领域,都可接入Agentic Hackathon平台,享受更高频、更高效的创新节奏。
这预示着一个未来:黑客松将成为默认的解决问题方式。
公司与社区不再靠封闭的委员会与研发部门推进创新,而是将问题投入黑客松竞技场——一个始终活跃的解决问题引擎。
形象地说:
**DoraHacks 1.0 让黑客松拥有了高速引擎;
DoraHacks 2.0 加上 BUIDL AI,则让它变成一辆自动驾驶的赛车——油门踩到底。**
成本、复杂度、时间的阻碍——都不复存在。
如今,任何组织都能毫无阻力地驶入创新高速公路,从0加速到60。
黑客松频率如博客更新,融入日常运营,如同敏捷开发的冲刺演示。
按需创新,规模扩张——这就是Agentic Hackathon的力量。
随需创新:Agentic Hackathon 如何惠及所有人
Agentic Hackathon(自主智能黑客松)的诞生,并非只是技术社区的一款“新奇玩具”,而是一种变革性的工具,可服务于企业、开发者,乃至整个行业。
我们正步入一个全新时代:任何拥有愿景的人都能将“黑客松即服务”转化为推动创新的引擎。以下是不同参与者如何从这场革命中受益:
AI公司 —— 加速生态成长的发动机
对于专注于人工智能的公司(如 OpenAI、Google、Microsoft、Stability AI 等),黑客松是一座座发掘其技术创意用途的金矿。
如今借助 Agentic Hackathon,这些公司几乎可以为自己的平台持续举办一场“永不落幕”的开发者大会。
比如,OpenAI 可以为 GPT-4 或 DALL·E 启动全年在线的黑客松,鼓励全球开发者持续实验、展示这些AI的应用场景——本质上,以众包方式为AI平台孵化创新与杀手级应用。
收益何在?生态系统和用户基数的指数级扩展。
新的用例往往来自公司内部未曾设想的角落。 (最早展示 GPT-3 能撰写法律合同、生成游戏关卡的,不是大公司,而是独立黑客——他们在黑客松和社区挑战中发现了这些潜力。)
有了 BUIDL AI,AI 公司可以一键启动月度黑客松,每月聚焦不同方向(比如本月自然语言处理,下月机器人控制)。 这是市场营销与产品研发的倍增器。
无需再组织昂贵的开发者布道之旅,AI 将成为全球开发者互动的主力军。产品在推广的同时也在优化。 本质上,每家AI公司都可以开启自己的“黑客松联赛”,推动API或模型的普及与应用。
Coinbase最近首次举办AI主题黑客松,尝试连接加密与AI领域——他们很清楚,要播下新范式的种子,黑客松是最佳路径[15] 。
未来,我们将看到所有AI平台效仿:持续通过黑客松教育开发者、生成内容(演示、教程),并发掘可投资/可招聘的杰出人才。这将是社区建设的超级助推器。
L1/L2与技术平台 —— 发现下一只独角兽
对于区块链的一层/二层网络(Layer1/Layer2),以及任何技术平台(如云服务、VR平台等)来说,黑客松已成为新的“Deal Flow”(项目源)。
在 Web3 世界里,许多顶级项目与协议都诞生于黑客松,这一点早已被广泛认同。
我们看到,1inch 就是始于黑客松,后来成长为 DeFi 独角兽(cointelegraph.com)[9]。
Polygon 积极举办黑客松以寻找其生态的新型dApps;Filecoin 借助黑客松发掘分布式存储应用。
借助 DoraHacks 和 BUIDL AI,这些平台现在可以高频率地组织黑客松,持续输出创新成果。
不再是一年一两次大型活动,而是一个滚动进行的计划——比如每季度一场,甚至同时多地开展全球挑战,保持开发者“常态建设”。
回报率巨大:即使设有可观奖金,黑客松的举办成本也远低于收购一个蓬勃发展的初创公司或协议所需投入。 黑客松本质上是将早期研发外包给充满热情的社区成员,最好的创意自然浮现。
Solana 的黑客松就促成了 Phantom、Solend 等明星项目的落地。Facebook 的内部黑客松也曾带来推动平台主导地位的功能创新[1]。
现在,任何平台都可以将黑客松“外部化”:作为发现人才与创新的“雷达”。借助 BUIDL AI,哪怕一个 L2 区块链的核心团队人手有限,也能并行运行多场黑客松与赏金任务——一场关注 DeFi,一场关注 NFT,一场关注游戏等等。
AI 负责初审项目与管理社区问答,让平台的 DevRel 团队不至于“过劳”。结果是,一条源源不断的创新供给链,不断喂养平台增长。下一个独角兽、下一个杀手级应用,将被提前识别并扶持成长。
黑客松已成为 VC 和技术生态的新型创业漏斗(Startup Funnel)。
未来,投资人将活跃于 Agentic Hackathon 中——因为那里正是“未来车库”的所在:黑客们聚集在云端黑客室中重塑世界。
正如 Paul Graham 所言:“黑客与画家,皆为创造者”,他们将在黑客松平台的画布上,描绘未来科技的蓝图。
所有公司与社区 —— 创新成为一种持续流程
或许 BUIDL AI 最深远的影响是:让所有组织都能举办黑客松,不再局限于科技公司。
任何希望推动创新的机构——银行探索金融科技、医院网络寻找医疗科技方案、政府寻找公民科技创意——都可以利用 Agentic Hackathon。
创新不再是巨头的特权,它成为一项“云服务”,人人可用。
比如,一个城市政府可以举办全年黑客松,征集“智慧城市”解决方案,让本地开发者持续提出、建设项目以改善城市生活。
BUIDL AI 平台可以设置不同“赛道”:交通、能源、安全,每月评选最佳创意并给予奖励。
这比传统招标流程更加灵活,能更高效地激发社区活力与项目孵化。
同样地,任何担心被颠覆的财富500强公司(其实谁不担心?)都可以主动“自我颠覆”——通过黑客松邀请员工和外部创新者挑战企业自身难题。
在 agentic 模式下,即使是非技术型公司也能轻松参与;AI 会引导流程,保障运行顺畅。试想:黑客松成为每一家企业战略部门的“标配工具”,不断原型化未来。
正如 Marc Andreessen 所说,“软件正在吞噬整个世界”——而现在,每家公司都可以通过举办黑客松,参与“软件化”自身问题的过程。
这将推动跨行业的创新民主化。
尝试大胆创意的门槛大幅降低(周末黑客松 vs. 数月企业流程),更多潜在颠覆性创意将在企业内部浮现。
有了 DoraHacks 的全球影响力,企业也能轻松吸引外部创新者参与。
零售公司为何不能从全球黑客那里众包 AR 购物创意?
制药公司为何不办场生物信息学黑客松以探索数据分析新方法?
答案只有一个:没有理由不做。Agentic Hackathon 让一切变得可行、值得。
黑客松即服务(Hackathon-as-a-Service)将成为下一代的创新部门——要么使用它,要么被使用它的人超越。
结语:从偶发事件到创新基础设施的演进
所有上述变革,归结为一个深刻转变:黑客松正从一次性的活动,演变为创新生态系统中的常驻组成部分。
它们正成为像云计算、宽带网络一样的基础资源:随时可用,规模无限。
想获得新点子或原型?办场黑客松,让全球开发者接招。
想激活开发者社群?发布主题黑客松,提供舞台。
想试验10种解决方案?来一场比赛,看看谁跑出来。
我们正在见证所谓“创新公地(Innovation Commons)”的诞生:一个持续匹配问题与创意、迅速迭代解决方案的协 作空间。
AI是这片公地的维护者,保证运行高效、协作持久,不再需要消耗人为组织者的精力。
这也正好回应了人们对黑客松的批评:缺乏可持续性与后续跟进。
而在Agentic模型中,黑客松不再是孤岛——它们可以彼此衔接:上届的优胜团队可以直接晋级加速器,或参与下月的 新主题挑战。
BUIDL AI 甚至可以追踪团队进展,推荐资助机会、合作方、甚至下一步要申请的Grant,彻底解决过去“项目周末之后无人接手”的痛点。
好项目不会在周日夜晚“死掉”,而是被自动引导进入下一阶段的旅程。
我们还应认识到一种更深层的哲学意义:
创新文化,变得更具实验性、更重才智、更具节奏感。
在Agentic Hackathon的世界中,座右铭是:“为啥不原型一下?为啥不现在就试?”
因为启动一场实验的门槛如此之低,创新思维将像空气般流入每一个组织、每一个社区。
失败的成本极低(只需几周),成功的可能却极高(也许就是下一个突破)。
这是一块供“颠覆性想法”安全试验的沙盒,也正是解决《创新者的窘境》的现实路径:
结构性地为那些被视为“玩具”的想法,保留生长空间[5]。
企业无需在“核心业务”与“实验创新”之间二选一——他们可以为后者开设一条常驻黑客松轨道。
本质上,DoraHacks 与 BUIDL AI 打造了一座“创新工厂”——任何有远见的组织都可以“租用”一周末,甚至一年。
从 Like 按钮到点火升空:黑客松是创新的摇篮
要真正理解这个新时代的分量,我们不妨回顾一下——多少改变世界的创新,其实起源于黑客松项目或类似黑客松的实验,即使当时还受限于旧有模式。而现在,随着这些限制被移除,我们能期待的,将远远不止于此。 历史本身,就是黑客松创新模式的最佳佐证:
Facebook 的基因,由黑客松塑造
马克·扎克伯格本人曾表示,Facebook 的许多关键功能都来自公司内部的黑客松:“点赞”按钮、Facebook Chat、时间线功能,无一不是工程师们在通宵达旦的黑客松中迸发出的创意[1]。
一位实习生在黑客松中构建的“评论区标记好友”原型,在短短两周后就上线,触达了十亿用户[1]。Facebook 的核心理念“Move fast and break things(快速行动,大胆试错)”,几乎就是黑客松精神的官方化表达。
可以毫不夸张地说,Facebook 能在2000年代超越 MySpace,正是得益于其由黑客松推动的快速创新文化[1]。
如果黑客松能在一家公司的内部产生如此颠覆性作用,想象一下——当它成为全球网络时,创新的速度将怎样改变整个世界?
Google 的“20% 时间”项目:制度化的黑客精神
Google 长期鼓励员工将20%的时间投入到自由探索的副项目中,这本质上是黑客松理念的延伸:结构外的探索实验。 Gmail 和 Google News 就是这样诞生的。
此外,Google 也曾围绕其 API 举办公开黑客松(如 Android 黑客松),催生了无数应用。
换句话说,Google 将黑客式实验制度化,获得了巨大的创新红利。
如今借助 Agentic Hackathon,即便没有 Google 资源的公司,也能制度化实验文化。
世界各地的开发者,都可以把每个周末当作自己的“20%时间”,借由这些平台启动属于自己的探索。
开源运动的推进器:Hackathons + Open Source = 强生态
开源软件世界也从“代码冲刺”(黑客松形式)中受益匪浅。
例如整个 OpenBSD 操作系统的开发就离不开其定期举办的黑客松[3]。
近年来,Node.js 与 TensorFlow 等项目也都通过黑客松来构建工具与生态组件。
其结果是:更强壮的技术生态,更活跃的贡献者社群。
DoraHacks 也在延续这种传统,并将自己定位为“全球领先的黑客松社区与开源开发者激励平台”[17]。
开源与黑客松的结合——都去中心化、社群驱动、基于 meritocracy(才智主义)——本身就是创新引擎。
我们可以预见,未来开源项目将借助 BUIDL AI 启动“永不停歇的黑客松”:持续修复 bug、加入新功能、奖励优秀贡献者。
这将为开源世界注入新生命——不仅通过奖金提供激励,还能以系统化的方式提供认可与传播。
初创世界:黑客松造就新公司
众多初创企业的起点,都是黑客松。 我们已提到的 Carousell(起于Startup Weekend,估值超10亿美元[2])、EasyTaxi(同样出自Startup Weekend,融资7500万美元[2])。 再加上:
- Zapier(集成工具平台,灵感来自黑客松)
- GroupMe(如前所述,被Skype收购)
- Instacart(传说在Y Combinator Demo Day 黑客松中以早期版本夺得优胜)
- 以及无数加密初创项目(包括 Ethereum 创始人们的相识与合作也源于早期黑客松与比特币线下聚会)
如今,当 Coinbase 想寻找链上 AI 的下一个机会时,他们办一场黑客松[15]。
Stripe 想推动支付平台上的应用数量,也选择了办黑客松并发放 Bounty。
这种模式行之有效:找到充满热情的构建者,为他们提供跳板。
有了 Agentic Hackathon,这个跳板不再只是弹射一次,而是始终在线,能接住更多人。
这个“创业漏斗”变宽了,我们将看到更多初创企业诞生于黑客松。
完全可以想象:
2030年代最伟大的公司,不会诞生于车库,而是源自一场在线黑客松,由几个在 Discord 上认识的开发者,在 AI 导师协助下完成原型,并在 DoraHacks 平台数周内获得融资。
换句话说,“车库神话”已进化为全球、云端、AI驱动的创业现实。
黑客与画家:创造者的共鸣
Paul Graham 在《Hackers & Painters》中曾将“黑客”比作“画家”——两者皆为纯粹的创作者[16]。
而黑客松,正是这种创造能量最集中、最爆发的场域。
许多伟大程序员都会告诉你,他们最具灵感的作品,正是在黑客松或秘密小项目中完成的——在没有官僚主义的束缚 下,沉浸于“心流”中完成的创作。
扩大黑客松的规模与频率,本质上就是扩大人类的创造力边界。
我们或许会想起文艺复兴时期——艺术家与发明家聚集在赞助人举办的工坊中自由创作;而如今,黑客松就是现代文艺复兴的“创客工坊”。
它融合了艺术、科学与企业家精神。
若达·芬奇活在今天,他一定会如鱼得水地出现在黑客松中——他以疯狂原型迭代著称。
更重要的是:黑客松完美解决了《创新者的窘境》中的核心问题:鼓励人们去做那些 incumbent(巨头)不屑一顾、看似“小而无用”的项目——而那恰恰往往是颠覆性创新的藏身之处 [5]。
DoraHacks 正是通过制度化黑客松,制度化了颠覆本身——确保下一个 Netflix、Airbnb,不会因为“听起来像个玩具”而被错过。
黑客松已成为全球创新基础设施的一部分
我们已从“黑客松罕见且本地化”的时代,走到了“黑客松持续且全球化”的今天。
这不仅是节奏上的转变,更是全球创新基础设施的关键转折点。
19世纪,我们修建了铁路与电报,催化了工业革命,连接了市场与思想;
20世纪,我们构建了互联网与万维网,引爆了信息革命;
而今,21世纪,DoraHacks 与 BUIDL AI 正在搭建“创新高速公路”:一个持续运行、AI驱动的网络,
在全球范围内,实时连接解决者与问题、人才与机会、资本与创意。
这是为 创新本身修建的基础设施。
伟大的愿景:全球创新的新基础设施
我们正站在一个历史拐点上。
有了 DoraHacks 和 Agentic Hackathon(自主智能黑客松)的出现,创新不再局限于象牙塔、硅谷办公室,或一年一度的大会。
它正成为一项持续的全球性活动——一个随时随地聚集最聪明头脑与最大胆创意的竞技场。
这是一个未来:创新将像 Wi-Fi 一样无处不在,像摩尔定律一样不断加速。
这是 DoraHacks 正在主动构建的未来,而它所带来的影响将是深远的。
想象几年之后的世界:DoraHacks + BUIDL AI 成为跨行业创新项目的默认基础设施。
这个平台7×24不间断运转,承载着从 AI 医疗、气候变化应对,到艺术娱乐前沿的各类黑客松。
而且它不仅仅属于程序员——设计师、创业者、科学家,任何有创造力冲动的人,都能接入这张全球创新网络。
一个伦敦的创业者凌晨2点冒出商业点子;2点15分,她就在 DoraHacks 上发起一场48小时黑客松,AI 自动为她召集来自四大洲的协作者。
听起来疯狂?但未来这将成为常态。
亚洲某国突发环境危机,政府通过 BUIDL AI 紧急发起黑客松,数日内即收到来自全球的数十个可执行科技方案。 纽约某家风投基金希望发现新项目,不再只是等着 PPT 投递——他们直接赞助一场开放黑客松,要求提交原型,而非空谈构想。
这就是 Agentic 创新正在发生的方式:快速、无边界、智能协作。 在这个即将到来的时代,DoraHacks 将如同 GitHub 之于代码、AWS 之于初创企业一般,成为全球创新的基础平台。
你甚至可以称它为创新的 GitHub——不是一个存储代码的工具,而是项目诞生的土壤[17]。 DoraHacks 自称是“全球黑客运动的引擎”;而有了 BUIDL AI,它更成为这场运动的自动驾驶系统。
我们应将其视为全球公共创新基础设施的一部分:
正如高速公路运输货物、互联网传递信息,DoraHacks 传递的是创新本身——
从创意萌芽到落地实施,以惊人的速度。
当历史回顾2020年代,持续性、AI驱动的黑客松的诞生,将被视为人类创新模式变革的重要篇章。
这是一幅宏大但真实可触的愿景:
创新,将变成一场永恒的黑客松。
设想一下:
黑客精神深入社会每个角落,成为对现状的持续挑战,时刻发出这样的提问:
“我们如何改进这件事?”、“我们如何重新发明那件事?”
然后立刻号召人才,迅速投入行动。
这不是混乱,而是一种全新的、有组织、去中心化的研发模式。
一个大胆问题——“我们能治愈这种疾病吗?”、“我们能否让儿童教育更高效?”、“我们能不能让城市真正可持续?”—— 不再需要靠闭门造车的委员会来思考十年,而是一场全球黑客松,就可能在几天或几周内产生答案。 这将是一个创新不再稀缺、不再由少数人垄断,而是成为一项公共物品的世界。
一场开放的、胜者为王的比赛,不管解决方案来自斯坦福博士,还是拉各斯的自学黑客,只要够好,就能脱颖而出。 如果你觉得这听起来太理想,请看看我们已经走了多远:
黑客松从一个名不见经传的程序员聚会,变成了支撑十亿美元企业和全球关键技术的创新机制。 (别忘了,比特币本身就是黑客文化的产物!)
随着 DoraHacks 的壮大和 BUIDL AI 的腾飞,黑客松正朝着持续化与无处不在的方向稳步推进。 技术已经准备就绪,模式已经跑通,现在的关键是执行与普及。
而趋势已然明朗:
- 越来越多公司拥抱开放创新;
- 越来越多开发者远程工作、参与在线社区;
- AI 正快速成为每个创造过程的副驾驶。
DoraHacks 正站在这场转型的核心。
它拥有先发优势、全球社区、明确愿景。
他们的理念非常清晰:“为黑客运动提供永恒燃料”是他们的口号之一[18]。
在他们眼中,黑客松不仅是活动,更是一场必须永续进行的思维革命。 而 BUIDL AI,正是支撑这场永续革命的引擎。
这预示着一个未来:
DoraHacks + BUIDL AI,将成为全球创新关键基础设施的一部分,就像公共事业一样。
这是一张“创新电网”;一旦接入它,奇迹发生。
Marc Andreessen 常在文章中以“建造更好的未来”为信条,热情洋溢地谈论人类的进步。
如果秉持这一精神,我们可以大胆断言:
Agentic Hackathon 将重塑我们的未来——更快、更好。
它们将加速人类解决最难问题的速度,
动员更广泛的人才库,
以史无前例的节奏不断迭代方案。
它们将赋能每一个人——让地球上任何拥有创造力的人,立即就能获得工具、社群和机会,产生真正的影响,而不是“未来某天”。
这是一种深层次的民主化。
它呼应了早期互联网的精神:不需许可的创新(Permissionless Innovation)。
而 DoraHacks 正在将这一精神引入结构化的创新事件中,并将其延展为一种持久的创新模式。
总结:我们正目睹一场范式的彻底转变:黑客松被重塑,创新被解放。
旧模型的限制已被打破,
新范式的核心是:
高频黑客松、AI增强、结果导向。
DoraHacks 在 2020–2024 年引领了这场变革,
而随着 BUIDL AI 的登场,它即将开启下一个篇章——Agentic Innovation 的时代。
对投资者与有远见的领袖而言,这是一场集结号。
我们常说要“投资基础设施”,
那么现在,就是投资“创新本身的基础设施”。
支持 DoraHacks 和它的使命,
就像支持跨洲铁路或洲际高速的建造者,
只不过这次运载的是创意与突破。
网络效应巨大:每一场新增的黑客松、每一位新增的参与者,
都以复利效应提升整个生态系统的价值。
这是一场正和博弈(Positive-Sum Game),
DoraHacks 将是那个创造并捕捉全球价值的平台与社区。
DoraHacks 重新定义了黑客松:
它将黑客松从偶发行为变成了持续创新的系统方法。
在这个过程中,它敞开了创新之门,
引领我们进入一个全新的时代:
一个创新可以自主驱动、自组织、永不停歇的时代。
我们正站在这个新时代的黎明。
这是一个真正意义上:
拥有开发者,拥有世界的时代[14] 。
DoraHacks 正在确保:
无论你身在何处,只要你是开发者、黑客、梦想家,
你都能为这个世界的未来贡献力量。
前方的远景令人震撼——一个由全球黑客思维构成的智能蜂巢,
不断发明、持续发现,
由 AI 指引航向,
由 DoraHacks 与 BUIDL AI 领航。
这不仅仅是一个平台,
它是一项革命性的基础设施——创新的铁路,创意的高速。
请系好安全带:
DoraHacks 已经启程,
Agentic Innovation 的时代已经到来,
未来正以黑客松的速度,向我们疾驰而来。
这场黑客松,永不停歇。
而这,正是我们构建更美好世界的方式。
参考文献:
[1] Vocoli. (2015). Facebook’s Secret Sauce: The Hackathon . https://www.vocoli.com/blog/june-2015/facebook-s-secret-sauce-the-hackathon/
[2] Analytics India Magazine. (2023). Borne Out Of Hackathons . https://analyticsindiamag.com/ai-trends/borne-out-of-hackathons/
[3] Wikipedia. (n.d.). Hackathon: Origin and History . https://en.wikipedia.org/wiki/Hackathon#Origin_and_history
[4] LinkedIn. (2024). This year marked my third annual participation in Microsoft’s Global… . https://www.linkedin.com/posts/clare-ashforth_this-year-marked-my-third-annual-participation-activity-7247636808119775233-yev-
[5] Glasp. (n.d.). Chris Dixon’s Quotes . https://glasp.co/quotes/chris-dixon
[6] ODaily. (2024). Naija HackAtom Hackathon Recap . https://www.odaily.news/en/post/5203212
[7] Solana. (2021). Meet the winners of the Riptide hackathon - Solana . https://solana.com/news/riptide-hackathon-winners-solana
[8] DoraHacks. (n.d.). BNB Grant DAO - DoraHacks . https://dorahacks.io/bnb
[9] Cointelegraph. (2021). From Hackathon Project to DeFi Powerhouse: AMA with 1inch Network . https://cointelegraph.com/news/from-hackathon-project-to-defi-powerhouse-ama-with-1inch-network
[10] Gemini. (2022). How Does STEPN Work? GST and GMT Token Rewards . https://www.gemini.com/cryptopedia/stepn-nft-sneakers-gmt-token-gst-crypto-move-to-earn-m2e
[11] CoinDesk. (2022). Inside DoraHacks: The Open Source Bazaar Empowering Web3 Innovations . https://www.coindesk.com/sponsored-content/inside-dorahacks-the-open-source-bazaar-empowering-web3-innovations
[12] LinkedIn. (n.d.). DoraHacks . https://www.linkedin.com/company/dorahacks
[13] Blockworks. (2022). Web3 Hackathon Incubator DoraHacks Nabs $20M From FTX, Liberty City . https://blockworks.co/news/web3-hackathon-incubator-dorahacks-nabs-20m-from-ftx-liberty-city
[14] Followin. (2024). BUIDL AI: The future of Hackathon, a new engine for global open source technology . https://followin.io/en/feed/16892627
[15] Coinbase. (2024). Coinbase Hosts Its First AI Hackathon: Bringing the San Francisco Developer Community Onchain . https://www.coinbase.com/developer-platform/discover/launches/Coinbase-AI-hackathon
[16] Graham, P. (2004). Hackers & Painters . https://ics.uci.edu/~pattis/common/handouts/hackerspainters.pdf
[17] Himalayas. (n.d.). DoraHacks hiring Research Engineer – BUIDL AI . https://himalayas.app/companies/dorahacks/jobs/research-engineer-buidl-ai
[18] X. (n.d.). DoraHacks . https://x.com/dorahacks?lang=en
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 2b24a1fa:17750f64
2025-05-02 13:40:12
@ 2b24a1fa:17750f64
2025-05-02 13:40:12Das Kriegsgrauen kriecht unter die Haut. Bilder von verstümmelten Beinen und Armen, von Kriegstraumatisierten schweigenden Männern, von Kriegsgräbern steigen auf. Als Mutter, Schwester, Tante, Großmutter wachsen die Ängste, dass sich ein Verwandter von der politischen und medialen Kriegslust anstecken lässt und tatsächlich die Beteiligung an den näher kommenden kriegerischen Auseinandersetzungen in Erwägung zieht. Einen wütenden Kommentar anlässlich der wachsenden Kriegstreiberei verfasste unser Autor Nicolas Riedl.
https://soundcloud.com/radiomuenchen/sofa-soldaten-an-die-front-von-nicolas-riedl?
Bild: KI
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ c3c7122c:607731d7
2025-04-12 04:05:06
@ c3c7122c:607731d7
2025-04-12 04:05:06Help!
Calling all El Salvador Nostriches! If you currently live in SV, I need your help and am offering several bounties (0.001, 0.01, and 0.1 BTC).
In Brief
In short, I am pursuing El Salvador citizenship by birthright (through my grandmother). I’ve struggled to progress because her name varies on different documents. I need someone to help me push harder to get past this barrier, or connect me with information or people who can work on my behalf. I am offering:
- 0.001 BTC (100k sats) for information that will help me progress from my current situation
- 0.01 BTC (1 MM sats) to get me in touch with someone that is more impactful than the immigration lawyer I already spoke with
- 0.1 BTC (10 MM sats) if your efforts help me obtain citizenship for me or my father
Background
My grandma married my grandfather (an American Marine) and moved to the states where my father was born. I have some official and unofficial documents where her name varies in spelling, order of first/middle name, and addition of her father’s last name. So every doc basically has a different name for her. I was connected with an english-speaking immigration lawyer in SV who hit a dead end when searching for her official ID because the city hall in her city had burned down so there was no record of her info. He gave up at that point. I find it odd that it was so easy to change your name back then, but they are more strict now with the records from that time.
I believe SV citizenship is my birthright and have several personal reasons for pursuing this. I want someone to act on my behalf who will try harder to work the system (by appeal, loophole, or even bribe if I have to). If you are local and can help me with this, I’d greatly appreciate any efforts you make.
Cheers!
Corey San Diego
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 99e7936f:d5d2197c
2025-05-02 13:25:06
@ 99e7936f:d5d2197c
2025-05-02 13:25:06Frieden braucht die Kapitulation, keine Gebrauchsanweisung
Wenn Dir ständig jemand erklärt, wie Du etwas zu machen hast, dann machst Du irgendwann gar nichts mehr, sondern wartest nur noch auf die nächste Aufforderung, dies oder jenes zu tun.
Manchmal ist das gut so, aber meist ist diese abwartende Haltung eine Vorlage für andere Menschen, die nichts Gutes im Schilde führen. Sie nutzen dieses entgegengebrachte Vertrauen aus und geben Anweisungen, die nur ihnen selbst dienen und sonst keinem. Das Phänomen ist hinreichend bekannt.
Ich habe lange gebraucht, um zu verstehen, warum Menschen auf Aufforderungen von anderen warten. Das ist offensichtlich früh gelerntes Verhalten, wie so vieles im Leben. In meiner Kindheit habe ich auch viele dysfunktionale Verhaltensweisen gelernt, aber exakt diese nicht, da ich kaum Aufforderungen erhielt. Ich hätte gerne welche erhalten. Meine Eltern waren aber meist mit sich selbst und den Anforderungen des Alltags beschäftigt.
Mein Vater war 11 Jahre und meine Mutter war 8 Jahre alt als der zweite Weltkrieg endete. Zwanzig Jahre später kreuzten sich ihre Wege, sie heirateten und bekamen drei Kinder. Sie kümmerten sich um alle praktischen Aufgaben, sorgten für Sicherheit, ein schönes Zuhause und materiellen Wohlstand. Ich muss schlucken beim Schreiben dieses Satzes.
Mit 11 Jahren fing ich an, Tagebuch zu schreiben, weil ich so vieles nicht verstand. Trauma wird weiter gegeben, wenn es nicht aufgelöst wird. Ich hätte, wie gesagt, gerne mal klare Aufforderungen und Anweisungen gehabt. Ich suchte in der Schule und in meinen Ausbildungen nach Antworten, fand sie aber nicht. 1990 war ich 20 Jahre alt und startete nicht gut vorbereitet ins Erwachsenenleben. Wenn ich heute auf die letzten 35 Jahre zurück blicke, dann verstehe ich so viel, dass mir schwindelig wird. Heute mag ich mich und bereite mich daher nur noch selten auf etwas vor. Diese Erkenntnis ist aber nicht über Nacht gekommen. Das hätte ich wohl kaum überlebt. Die hierzu notwendigen Krisen in meinem Leben kamen in regelmäßigen Abständen und waren wohldosiert. Mit Krisen kenne ich mich aus. Krisen folgen immer demselben Muster, egal ob persönliche oder globale.
Wer bin ich, und warum schreibe ich hier einen Artikel über Frieden?
Ich bin eine Psychologin, die sich für ihr Leben gern mit Trauma beschäftigt. Das ist, nebenbei bemerkt, eines der positivsten Themen, die es gibt. Aber dazu erzähle ich ein anderes Mal. Ich bin das Kind meiner Eltern, Spätentwicklerin und die Eiskönigin nach der Verwandlung. Menschen, die meine Geschichte nicht kennen, halten mich für stark, obwohl ich auch nicht stärker bin als andere. Bewältigtes Trauma macht einen stark. Seitdem ich vor ein paar Jahren meinen persönlichen Knoten gelöst habe, folge ich nur noch meinem Herzen, was unglaublich polarisiert. Ich kann jetzt nicht mehr anders. Früher habe ich mein Herz zwar auch schon deutlich gehört, aber überholte Glaubenssätze hatten oft das letzte Wort und bestimmten mein Handeln. Das war dann nicht selten der innerliche Spagat, um es vor allem anderen recht zu machen. Die leere Batterie, die ich mehrmals kennen lernen durfte, hat mich dann gelehrt, es anders zu machen. Heute achte ich auf meine sehr feine Wahrnehmung und auf meine Bedürfnisse. Das kommt aber meistens auch anderen zugute.
Wer gelernt hat, sich selbst so anzunehmen wie er ist, was gleichzusetzen ist mit Schmerz, der möchte anderen keinen Schmerz zufügen. Eigentlich könnte ich an dieser Stelle den Artikel schon beenden.
Selbstliebe und Schmerz sind unzertrennliche Freunde. Aber dazu erzähle ich auch ein anderes Mal.
Heute möchte ich etwas dazu sagen, warum ich für den Frieden keine Gebrauchsanweisung brauche, sondern die Kapitulation.
Ich bin dem Krieg * in* mir begegnet. Dieser Krieg hat in meinem Außen über lange Zeit für Unruhe gesorgt, und er hat meine Batterie im Innern dadurch öfters leer gezogen. Er war immer berechtigt, begründet und gerechtfertigt, aber dennoch nicht gut für mich oder andere. Im größten Schmerz, den ich je empfunden habe, kam dann 2018/19 endlich der Frieden in mein persönliches Leben. Ich musste dafür nichts tun. Ausrufungszeichen. Den Frieden bekam ich quasi geschenkt, weil ich aufgehört hatte zu kämpfen, weil ich mich dem Schmerz hingegeben hatte, weil ich es akzeptiert hatte, am Boden zu liegen.
Alle wollen Frieden, aber niemand will am Boden liegen.
Kann ich gut verstehen, aber meine Erfahrung ist genau diese, dass Du gefühlt am Boden liegen musst. Frieden kann man „machen“ durch bewusstes Unterlassen von verbalem Zurückschlagen und von Ablenkungs- oder Vermeidungsverhalten, um den eigenen Schmerz nicht spüren zu müssen. Nach diesem Verzicht kann man dann Wut und Schmerz deutlicher oder sogar hervorragend spüren, und dann kommt das Geschenk. Der Frieden durchflutet Dich in einem Moment, in dem Du es nicht erwartest. Frieden kommt, wenn die Situation gefährlich und existenziell bedrohlich wird. Der ganze Körper entspannt in einem einzigen Moment. Das ist wie eine Erlösung. Man sagt nicht umsonst, dass es schön sei, wenn der Schmerz aufhöre. Das stimmt wirklich. Da passiert auch auf biologischer Ebene ganz viel. Körpereigene Stoffe, die schmerzfrei und unglaublich leicht fühlen lassen, werden in Hülle und Fülle ausgeschüttet. Die Evolution hat an alles gedacht. Sie lässt Dich nicht im Stich, wenn es dicke kommt. Frieden ist ein unbeschreiblicher Zustand. Wenn Du den einmal gespürt hast, dann ist der Weg frei, und dann brauchst Du keine Gebrauchsanweisung mehr. Dieser Moment verändert Dich für immer. Du hast eine Erfahrung gemacht, die Dir keiner mehr nehmen kann. Ich habe diese Erfahrung damals alleine gemacht, weil ich niemanden hatte, dem ich mich anvertrauen wollte. Das war ganz unspektakulär im Wohnzimmer. Aber diese Erfahrung, für die es tausende von Bezeichnungen gibt, verändert Dein Leben von Grund auf. Schön ist, wenn man jemanden an seiner Seite hat, der einfach nur zuhört und ab und zu einfach mal was Nettes sagt. Und genau das ist so schwer, so jemanden zu finden, der gerne bei einem sein möchte, wenn man gerade gefühlt stirbt. Die meisten Menschen laufen dann weg oder sagen: „Jetzt reiß Dich mal zusammen.“
Frieden ist nichts für schwache Nerven.
Wenn Du Frieden einmal selbst am eigenen Körper erlebt hast, dann gehst Du anders in Auseinandersetzungen (und globale Krisen) hinein, weil Du diesen Mechanismus kennen gelernt hast, weil Du weißt, dass Du geschützt bist. Das Leben liebt Dich und arbeitet für Dich. Immer. Mit diesem Wissen ausgestattet, kannst Du leichter ruhig bleiben, wenn es nicht so gut läuft, wenn es brenzlig wird, auch wenn große Dinge in der Welt schief laufen. Der Schmerz ist nicht mehr Dein Feind, den es unbedingt zu vermeiden gilt. Jetzt wird es kurios. Ich mag sicherlich keinen Schmerz, aber ich laufe vor „dem Schmerz“ nicht mehr davon. Oft empfinden wir Schmerz schon, wenn jemand unsere Glaubenssätze triggert. Ich schau mir den Schmerz an, fühle rein und höre zu, was er mir sagen will. Und in den meisten Fällen ist es gar nicht MEIN Schmerz. Jemand greift mich an, weil er selber Ängste hat, sich getriggert fühlt oder sonst etwas hat oder nicht hat. Ich bin irritiert und vielleicht auch wütend, weil es weh tut, aber genau dann kommt dieses erfahrene Wissen zum Einsatz und legt die rettende Pause in mein Denken und Handeln ein. Ich reagiere nicht mit einem Schlagabtausch, und freu mich umgehend unglaublich über mich selbst. Und dann laufen die Dinge für mich. Ich brauche nur Geduld. Der andere hat jetzt etwas zum Nachdenken. Wenn man nicht zurück schlägt, dann hat der andere etwas zum Nachdenken. Das ist jetzt die Kurzfassung der Geschichte. Jedenfalls aktiviert dieses Unterlassen von Schlagabtausch auch in den schwierigsten Zeitgenossen etwas Gutes. Versprochen. Und dieses Gute fängt dann an zu arbeiten, für mich, für uns alle und vor allem für den Frieden.
Das Ganze ist eine komplexe Erfahrung, die ich erst persönlich gemacht habe, dann aber auch bei anderen beobachten und raushören konnte. Über das Phänomen wird viel geredet. Aber zentral wichtig ist mir zu sagen, dass der Frieden kommt, wenn Du aufgibst, nicht mehr kämpfst, auf einen Schlagabtausch verzichtest. Das gilt für Deine Freundschaften, für Deine Partnerschaft, für Deine Familie und für das Land, in dem Du lebst. Frieden entsteht im Streit, im Krieg. Frieden entsteht, wenn die Situation einen unglaublich verletzt, wütend und fassungslos macht. Die Evolution braucht Dich an Deinem persönlichen Siedepunkt, Schmelzpunkt. Nenn es, wie Du willst. Im Schmerz öffnet sich ein Zugang zu einem anderen Bewusstsein. Du wirst weit auf allen Ebenen. Alles, was Du auf Deinem Weg mal verloren hast, kommt zu Dir zurück. Der Schmerz repariert erst Dich und dann alle anderen, mit denen Du zu tun hast. Menschen, die diese Erfahrung am eigenen Körper gemacht haben, schauen anders auf und in diese Welt, weil sie diese andere Welt, dieses weite Bewusstsein, kennen gelernt haben. Es gibt viele Wege zu diesem weiten Bewusstsein und, nebenbei bemerkt, auch viel Zensur zum Thema in der wissenschaftlichen Welt, aber auch im Mainstream. Ich persönlich habe das Phänomen am eigenen Körper kennen gelernt, bevor ich einen Namen dafür hatte. Aber der wichtige Punkt ist, wenn mich jemand fragen würde, was man mitten im Krieg tun kann, dann würde ich sagen: „Lass den Schmerz zu.“
Soll das etwa heißen, dass der ganze Widerstand aktuell für die Katze ist? Nein, natürlich nicht.
Über Missstände berichten? Ja. Schuldige benennen? Ja. Rechtsstaatliche Maßnahmen? Ja.
Aber lass Deinen Schmerz zu. Spür nach, was genau Dich so wütend macht. Frag Dich konkret, warum Dich das Verhalten von XY so trifft. Warum kann Dich jemand, den Du gar nicht persönlich kennst, so fassungslos machen? Und dann kommen wir alle unweigerlich zu uns selbst. Was ist mir so unglaublich wichtig? Und warum? Und was hat das mit meinen Wunden zu tun?
Mich kann man heute auch immer noch triggern, weil ich ein Mensch aus Fleisch und Blut bin. Aber ich setze mich jedes Mal wieder hin und schaue es mir an, was da noch weh tut in mir. Und dann bin ich bei mir. Und dann geht’s um mich. Und dann gebe ich mir alles Gute, Nährende, Pflegende und Aufmunternde. Das tut mir gut und bringt mich weiter. Und mit dieser Haltung kann ich dann wieder auf Menschen zugehen, denen ich nicht aus dem Weg gehen kann. Und Menschen, die dieser Gesellschaft aktiv Schaden zufügen, kann ich nicht aus dem Weg gehen. Sie sägen an meinem Baum. Sie sägen, aber ich stell mich immer wieder daneben. Ich rede mit ihnen wie mit einem normalen Menschen. Ausrufungszeichen. Ich adressiere das im anderen, was ich wachsen sehen möchte. Ich brauche Pausen, aber ich bleibe ruhig, denn nur so arbeitet das Gute im anderen für mich, für uns alle, für den Frieden. Das Gute im anderen ist in 99,9 % der Fälle da und erreichbar, ist zumindest meine Erfahrung.
Die Erfahrung von Frieden kann mir keiner mehr nehmen.
Und eine Gebrauchsanweisung für den Frieden brauche ich auch nicht mehr.
Kapitulation bringt Frieden.
-
 @ 87f5e1d9:e251d8f4
2025-05-02 13:15:23
@ 87f5e1d9:e251d8f4
2025-05-02 13:15:23In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ b5b28e8a:8930a19b
2025-05-02 13:07:56
@ b5b28e8a:8930a19b
2025-05-02 13:07:56Testing
This is my first page.
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:31
@ 9e69e420:d12360c2
2025-01-26 01:31:31Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ e4950c93:1b99eccd
2025-05-02 12:48:46
@ e4950c93:1b99eccd
2025-05-02 12:48:46🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ e4950c93:1b99eccd
2025-05-02 12:47:27
@ e4950c93:1b99eccd
2025-05-02 12:47:27Dilling est une marque danoise qui crée des vêtements en laine, soie et coton biologique pour toute la famille.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos, alpaga)
- Latex naturel (OEKO-TEX ®)
- Soie
⚠️ Attention, certains produits de cette marque (notamment les Vêtements - chaussettes, vestes, strings, shorts) contiennent des matières non naturelles, dont :
- Elasthanne
- Polyamide, nylon (nylon recyclé)
- Polyester (recyclé)
Catégories de produits proposés
-
Vêtements : homme, femme, enfant, bébé, sous-vêtements, t-shirts, débardeurs, robes, vestes, pantalons, shorts, pulls, gilets, bodies, combinaisons, culottes, slips, boxers...
Autres informations
- Ecolabel Nordic Swan (teintures)
- Fabriqué en Lituanie (coupe et couture)
- Fabriqué au Danemark (teintures)
- Fabriqué en Europe
👉 En savoir plus sur le site de la marque
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises ce produit ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ e4950c93:1b99eccd
2025-05-02 12:19:28
@ e4950c93:1b99eccd
2025-05-02 12:19:28Qu'est-ce qu'une matière naturelle ? La question fait débat, et chacun-e privilégiera ses propres critères. Voici comment les matières sont classées sur ce site. La liste est régulièrement mise à jour en fonction des produits ajoutés. N'hésitez pas à partager votre avis !
✅ Matières naturelles
Matières d'origine végétale, animale ou minérale, sans transformation chimique altérant leur structure moléculaire.
🌱 Principaux critères : - Biodégradabilité - Non-toxicité - Présence naturelle nécessitant le minimum de transformation
🔍 Liste des matières naturelles : - Bois - Cellulose régénérée (cupra, lyocell, modal, viscose) - Chanvre - Coton - Cuir - Liège - Lin - Laine - Latex naturel, caoutchouc - Métal - Soie - Terre - Verre - … (Autres matières)
⚠️ Bien que "naturelles", ces matières peuvent générer des impacts négatifs selon leurs conditions de production (pollution par pesticides, consommation d’eau excessive, traitement chimique, exploitation animale…). Ces impacts sont mentionnés sur la fiche de chaque matière.
Les versions biologiques de ces matières (sans traitement chimique, maltraitance animale, etc.) sont privilégiées pour référencer les produits sur ce site, tel qu'indiqué sur la fiche de chaque matière (à venir).
Les versions conventionnelles ne sont référencées que tant que lorsqu'il n'a pas encore été trouvé d'alternative plus durable pour cette catégorie de produits.
🚫 Matières non naturelles
Matières synthétiques ou fortement modifiées, souvent issues de la pétrochimie.
📌 Principaux problèmes : - Toxicité et émissions de microplastiques - Dépendance aux énergies fossiles - Mauvaise biodégradabilité
🔍 Liste des matières non naturelles : - Acrylique - Élasthanne, lycra, spandex - Polyamides, nylon - Polyester - Silicone - … (Autres matières)
⚠️ Ces matières ne sont pas admises sur le site. Néanmoins, elles peuvent être présentes dans certains produits référencés lorsque :
- elles sont utilisées en accessoire amovible (ex. : élastiques, boutons… généralement non indiqué dans la composition par la marque) pouvant être retiré pour le recyclage ou compostage, et
- aucune alternative 100 % naturelle n’a encore été identifiée pour cette catégorie de produits.
Dans ce cas, un avertissement est alors affiché sur la fiche du produit.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00
@ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.

Dose:
20g coffee (Coarse ground coffee) 300mL water (92°C / 197.6°F) Time: 3:30Instructions:
- Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.)
- Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.)
- Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour)
- Pour 4: 2:10 > 60mL
- Pour 5: 2:40 > 60mL
- Remove the V60 at 3:30
-
 @ 866e0139:6a9334e5
2025-04-05 11:00:25
@ 866e0139:6a9334e5
2025-04-05 11:00:25
Autor: CJ Hopkins. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Dieser Beitrag erschien zuerst auf dem Substack-Blog des Autors.
Er soll andauern, was er auch tut. Genau wie der nie endende Krieg in Orwells 1984 wird er vom Imperium gegen seine eigenen Untertanen geführt, aber nicht nur, um die Struktur der Gesellschaft intakt zu halten, sondern in unserem Fall auch, um die Gesellschaft in eine neo-totalitäre global-kapitalistische Dystopie zu verwandeln.
Bist du nicht vertraut mit dem Krieg gegen was auch immer?
Nun ja, okay, du erinnerst dich an den Krieg gegen den Terror.
Du erinnerst dich daran, als die „Freiheit und Demokratie“ von „den Terroristen“ angegriffen wurden und wir keine andere Wahl hatten, als uns unserer demokratischen Rechte und Prinzipien zu entledigen, einen nationalen „Notstand“ auszurufen, die verfassungsmäßigen Rechte der Menschen auszusetzen, einen Angriffskrieg gegen ein Land im Nahen Osten anzuzetteln, das für uns keinerlei Bedrohung darstellte, und unsere Straßen, Bahnhöfe, Flughäfen und alle anderen Orte mit schwer bewaffneten Soldaten zu füllen, denn sonst hätten „die Terroristen gewonnen“. Du erinnerst dich, als wir ein Offshore-Gulag bauten, um verdächtige Terroristen auf unbestimmte Zeit wegzusperren, die wir zuvor zu CIA-Geheimgefängnissen verschleppt hatten, wo wir sie gefoltert und gedemütigt haben, richtig?
Natürlich erinnerst du dich. Wer könnte das vergessen?
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Erinnerst du dich, als die National Security Agency keine andere Wahl hatte, als ein geheimes „Terroristen-Überwachungsprogramm“ einzurichten, um Amerikaner auszuspionieren, oder sonst „hätten die Terroristen gewonnen“? Oder wie wäre es mit den „Anti-Terror“-Unterleibsuntersuchungen der TSA, der Behörde für Transportsicherheit, die nach über zwanzig Jahren immer noch in Kraft sind?
Und was ist mit dem Krieg gegen den Populismus? An den erinnerst du dich vielleicht nicht so gut.
Ich erinnere mich, denn ich habe zwei Bücher dazu veröffentlicht. Er begann im Sommer 2016, als das Imperium erkannte, dass „rechte Populisten“ die „Freiheit und Demokratie“ in Europa bedrohten und Trump in den USA auf dem Vormarsch war. Also wurde ein weiterer „Notstand“ ausgerufen – diesmal von der Gemeinschaft der Geheimdienste, den Medien, der akademischen Welt und der Kulturindustrie. Ja, genau, es war wieder einmal an der Zeit, unsere demokratischen Prinzipien hintanzustellen, „Hassrede“ in sozialen Medien zu zensieren, die Massen mit lächerlicher offizieller Propaganda über „Russiagate,“ „Hitlergate“ und so weiter zu bombardieren – sonst hätten „die Rechtspopulisten gewonnen.“
Der Krieg gegen den Populismus gipfelte in der Einführung des Neuen Normalen Reichs.

Im Frühjahr 2020 rief das Imperium einen globalen „gesundheitlichen Ausnahmezustand“ aus, als Reaktion auf ein Virus mit einer Überlebensrate von etwa 99,8 Prozent. Das Imperium hatte keine andere Wahl, als ganze Gesellschaften abzuriegeln, jeden dazu zu zwingen, in der Öffentlichkeit medizinisch aussehende Masken zu tragen, die Öffentlichkeit mit Propaganda und Lügen zu bombardieren, die Menschen dazu zu nötigen, sich einer Reihe experimenteller mRNA-„Impfungen“ zu unterziehen, Proteste gegen ihre Dekrete zu verbieten und systematisch diejenigen zu zensieren und zu verfolgen, die es wagten, ihre erfundenen „Fakten“ in Frage zu stellen oder ihr totalitäres Programm zu kritisieren.
Das Imperium hatte keine andere Wahl, als das alles zu tun, denn sonst hätten „die Covid-Leugner, die Impfgegner, die Verschwörungstheoretiker und all die anderen Extremisten gewonnen.“
Ich bin mir ziemlich sicher, dass du dich an all das erinnerst.
Und jetzt … nun, hier sind wir. Ja, du hast es erraten – es ist wieder einmal an der Zeit, kräftig auf die US-Verfassung und die Meinungsfreiheit zu scheißen, Menschen in irgendein salvadorianisches Höllenloch abzuschieben, das wir angemietet haben, weil ein Polizist ihre Tattoos nicht mochte, Universitätsstudenten wegen ihrer Anti-Israel-Proteste festzunehmen und zu verschleppen und natürlich die Massen mit Lügen und offizieller Propaganda zu bombardieren, denn … okay, alle zusammen jetzt: „sonst hätten die antisemitischen Terroristen und venezolanischen Banden gewonnen!“
Fängst du an, ein Muster zu erkennen? Ja? Willkommen beim Krieg gegen-was-auch-immer!
Wenn du die Zusammenhänge noch nicht ganz siehst, okay, lass es mich noch einmal ganz simpel erklären.
Das globale ideologische System, in dem wir alle leben, wird totalitär. (Dieses System ist der globale Kapitalismus, aber nenne es, wie du willst. Es ist mir scheißegal.) Es reißt die Simulation der Demokratie nieder, die es nicht mehr aufrechterhalten muss. Der Kalte Krieg ist vorbei. Der Kommunismus ist tot. Der globale Kapitalismus hat keine externen Feinde mehr. Also muss er die Massen nicht mehr mit demokratischen Rechten und Freiheiten besänftigen. Deshalb entzieht er uns diese Rechte nach und nach und konditioniert uns darauf, ihren Verlust hinzunehmen.
Er tut dies, indem er eine Reihe von „Notständen“ inszeniert, jeder mit einer anderen „Bedrohung“ für die „Demokratie,“ die „Freiheit,“ „Amerika“ oder „den Planeten“ – oder was auch immer. Jeder mit seinen eigenen „Monstern,“ die eine so große Gefahr für die „Freiheit“ oder was auch immer darstellen, dass wir unsere verfassungsmäßigen Rechte aufgeben und die demokratischen Werte ad absurdum führen müssen, denn: sonst „würden die Monster gewinnen.“

Es tut dies, indem es sein Antlitz von „links“ nach „rechts,“ dann zurück nach „links“, und dann zurück nach „rechts,“ dann nach „links“ und so weiter neigt, weil es unsere Kooperation dafür benötigt. Nicht die Kooperation von uns allen auf einmal. Nur eine kooperative demografische Gruppe auf einmal.
Es ist dabei erfolgreich – also das System – indem es unsere Angst und unseren Hass instrumentalisiert. Dem System ist es völlig egal, ob wir uns als „links“ oder „rechts“ identifizieren, aber es braucht uns gespalten in „links“ und „rechts,“ damit es unsere Angst und unseren Hass aufeinander nähren kann … eine Regierung, ein „Notfall,“ ein „Krieg“ nach dem anderen.
Da hast du es. Das ist der Krieg gegen was auch immer. Noch simpler kann ich es nicht erklären.
Oh, und noch eine letzte Sache … wenn du einer meiner ehemaligen Fans bist, wie Rob, die über meine „Einsichten“ oder Loyalitäten oder was auch immer verwirrt sind … nun, der Text, den du gerade gelesen hast, sollte das für dich klären. Ich stehe auf keiner Seite. Überhaupt keiner. Aber ich habe ein paar grundlegende demokratische Prinzipien. Und die richten sich nicht danach, was gerade populär ist oder wer im Weißen Haus sitzt.
Die Sache ist die: Ich muss mich morgens im Spiegel anschauen können ohne dort einen Heuchler oder … du weißt schon, einen Feigling zu sehen.
(Aus dem Amerikanischen übersetzt von René Boyke).
CJ Hopkins ist ein US-amerikanischer Dramatiker, Romanautor und politischer Satiriker. Zu seinen Werken zählen die Stücke Horse Country, Screwmachine/Eyecandy und The Extremists. Er hat sich als profilierter Kritiker des Corona-Regimes profiliert und veröffentlicht regelmäßig auf seinem Substack-Blog.
Sein aktuelles Buch:
https://x.com/CJHopkins_Z23/status/1907795633689264530
Hier in einem aktuellen Gespräch:
https://www.youtube.com/watch?v=wF-G32P0leI
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ e4950c93:1b99eccd
2025-05-02 10:54:24
@ e4950c93:1b99eccd
2025-05-02 10:54:24Les rétributions sont une démarche expérimentale de partage de la valeur entre les contribut-eur-rice-s du site, via un partage des revenus aux conditions suivantes :
- Les revenus éventuels générés par ce site chaque mois sont répartis sur les 12 mois suivants, afin d’assurer une visibilité sur le projet et de lisser les variations mensuelles.
- Chaque 1er du mois, la moitié des revenus est distribuée à l’ensemble des contribut-eur-rice-s, proportionnellement au nombre de leurs contributions validées.
- Les contributions restent valides à vie, mais les rétributions ne sont versées qu’aux contribut-eur-rice-s ayant réalisé au moins une contribution validée au cours des 12 derniers mois.
Modalités de paiement
Les rétributions sont effectuées via le réseau Lightning, sous forme de sats (la plus petite unité du Bitcoin).
Pour en bénéficier, le compte NOSTR avec lequel tu as réalisé tes contributions doit être lié à un porte-monnaie Lightning.
💡 Si tu découvres ces outils :
- Pas encore de compte ? Une solution simple est d'en créer un sur un client NOSTR open source comme yakihonne.com pour y paramétrer ton profil et ton wallet. Ensuite, récupère tes clés NOSTR (dans les settings) et enregistre les dans un coffre sécurisé comme nsec.app pour te connecter ici et commencer à contribuer.
- Tu as déjà commencé à contribuer sur le site ? Conserve bien les clés NOSTR fournies par le site dans un coffre comme nsec.app. Tu peux aussi te connecter avec sur yakihonne.com pour paramétrer ton profil.
- Tu peux aussi contribuer directement depuis yakihonne.com sur les articles d'Origine Nature.
👉 En savoir plus sur les contributions
Prochaines rétributions
A venir.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-02 10:48:12
@ e4950c93:1b99eccd
2025-05-02 10:48:12Trouver des produits 100% naturels, sans plastique, est bien plus compliqué que je ne le pensais… Alors j’ai commencé à collectionner des marque-pages. Et puis je me suis dit : « Et si on partageait ?! »
Aide-moi à dénicher les meilleures alternatives naturelles pour s’habiller et s’équiper sans plastique !
Ce projet repose sur le partage : la moitié des revenus éventuels du site est reversée aux contribut-eur-rice-s. Une petite expérimentation de partage de la valeur sur Internet. :-)
Questions-réponses
Pourquoi se focaliser sur les matières naturelles ?
Les matières synthétiques sont essentiellement des plastiques (polyester, polyamide…). Problème ? Oui ! Ils finissent par nous contaminer :
- Microplastiques absorbés par la peau,
- Particules diffusées à chaque lavage, se retrouvant dans l’eau que nous buvons et les aliments que nous consommons,
- Enjeux majeurs liés au recyclage des déchets plastiques.
C'est quoi, au juste, des matières naturelles ?
Ce sont des matières non synthétiques, dont les composants existent à l’état naturel, sans modification de leur structure moléculaire. Mais ce qui nous intéresse avant tout, c’est leur biodégradabilité et leur absence de toxicité.
Certaines matières feront sûrement débat sur leur acceptabilité ici.
👉 En savoir plus sur les matières
Quelle différence avec d'autres sites de mode ou de shopping éthiques ?
Il existe déjà de nombreux sites proposant des produits éthiques et durables, mais j’ai constaté qu’ils incluaient souvent des matières synthétiques. Je devais vérifier produit par produit. Certains mettent en avant les fibres en plastique recyclé comme démarche environnementale, mais je préfère éviter d’en porter sur ma peau ou d'en mettre sur mes enfants.
Comment contribuer ?
Si tu trouves ce projet utile ou intéressant, voici comment le soutenir :
-
📝 Contribue : suggère des modifications en commentant les fiches existantes ou propose de nouvelles références de produits ou de marque. 👉 En savoir plus sur les contributions
-
⚡ Fais un don : pour faire vivre le projet et remercier les contribut-eur-ice-s. 👉 En savoir plus sur les dons
-
📢 Fais-le connaître : parles-en autour de toi, partage le site sur les réseaux sociaux, ton blog…
Comment recevoir une partie des revenus du site ?
Il suffit d’avoir un compte NOSTR et une adresse Bitcoin Lightning.
👉 En savoir plus sur les rétributions
C'est quoi NOSTR ?
C’est un protocole décentralisé pour Internet, encore en phase expérimentale. Il permet :
- De publier et consulter du contenu sans dépendre d’une plateforme centralisée.
- De se connecter à plusieurs services en conservant le contrôle total de ses données.
- D’intégrer le réseau Bitcoin Lightning pour des paiements instantanés et décentralisés.
Et la confidentialité de mes données ?
- Aucune publicité, aucun traçage personnalisé.
- Les commentaires NOSTR sont publics, mais vous pouvez utiliser un pseudonyme.
- Vous conservez la propriété de vos contributions sur le protocole NOSTR.
Qui porte ce projet ?
👉 Voir les contribut-eur-rice-s
Nous utilisons des outils et services open source :
- NOSTR pour la publication des contenus et la vérification des contributions,
- npub.pro pour la visualisation des contenus,
- Coinos.io pour la gestion des paiements.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ da18e986:3a0d9851
2025-04-04 20:25:50
@ da18e986:3a0d9851
2025-04-04 20:25:50I'm making this tutorial for myself, as I plan to write many wiki pages describing DVM kinds, as a resource for DVMDash.
Wiki pages on Nostr are written using AsciiDoc. If you don't know ascii doc, get an LLM (like https://duck.ai) to help you format into the right syntax.
Here's the test wiki page I'm going to write:
``` = Simple AsciiDoc Demo
This is a simple demonstration of AsciiDoc syntax for testing purposes.
== Features
AsciiDoc offers many formatting options that are easy to use.
- Easy to learn
- Supports rich text formatting
- Can include code snippets
- Works great for documentation
[source,json]
{ "name": "Test", "version": "1.0", "active": true }
```
We're going to use nak to publish it
First, install
nakif you haven't alreadygo install github.com/fiatjaf/nak@latestNote: if you don't use Go a lot, you may need to first install it and then add it to your path so the
nakcommand is recognized by the terminal```
this is how to add it to your path on mac if using zsh
echo 'export PATH=$PATH:$(go env GOPATH)/bin' >> ~/.zshrc ```
And here's how to sign and publish this event with nak.
First, if you want to use your own nostr sec key, you can set the env variable to it and nak will use that if no secret key is specified
```
replace with your full secret key
export NOSTR_SECRET_KEY="nsec1zcdn..." ```
Now to sign and publish the event:
Note: inner double quotes need to be escaped with a
\before them in order to keep the formatting correct, because we're doing this in the terminalnak event -k 30818 -d "dvm-wiki-page-test" -t 'title=dvm wiki page test' -c "= Simple AsciiDoc Demo\n\nThis is a simple demonstration of AsciiDoc syntax for testing purposes. \n\n== Features\n\nAsciiDoc offers many formatting options that are easy to use. \n\n* Easy to learn \n* Supports rich text formatting \n* Can include code snippets \n* Works great for documentation \n\n[source,json] \n---- \n{ \"name\": \"Test\", \"version\": \"1.0\", \"active\": true } \n----" wss://relay.primal.net wss://relay.damus.io wss://relay.wikifreedia.xyzYou've now published your first wiki page! If done correctly, it will show up on wikistr.com, like mine did here: https://wikistr.com/dvm-wiki-page-test*da18e9860040f3bf493876fc16b1a912ae5a6f6fa8d5159c3de2b8233a0d9851
and on wikifreedia.xyz https://wikifreedia.xyz/dvm-wiki-page-test/dustind@dtdannen.github.io
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ a87c9bfc:83bda6a8
2025-05-02 10:43:34
@ a87c9bfc:83bda6a8
2025-05-02 10:43:34Large Language Models (LLMs) are revolutionizing how we interact with technology, but their increasing sophistication brings unique security challenges. Malicious actors are constantly finding new ways to exploit these systems, primarily through techniques like prompt injection – crafting inputs to bypass safety controls – and the use of hidden characters to obfuscate harmful commands or disrupt text processing. Ensuring the safety and integrity of LLM applications is paramount.
The Hidden Dangers in Text
Prompt injection allows attackers to manipulate LLM outputs, potentially leading to data leaks, generation of inappropriate content, or unauthorized actions. Similarly, invisible characters (like zero-width spaces or bidirectional text overrides) can be embedded within seemingly innocuous text. These hidden elements can bypass simple security filters, disguise malicious instructions, or interfere with how the LLM interprets the input, leading to unpredictable or harmful behavior.
Vibecondom: A New Shield for LLM Security
To combat these emerging threats, a new open-source tool called Vibecondom has been developed. Written in Go, Vibecondom acts as a specialized security scanner designed specifically for the text content fed into LLMs. It serves as a critical defensive layer for AI developers, security researchers, and content moderation teams aiming to protect their systems.
Core Capabilities
Vibecondom focuses on identifying subtle but dangerous patterns within text data:
- Detecting Deception: It actively scans for known techniques used in prompt injection attacks and identifies various types of hidden or control characters that could signal malicious intent.
- Unmasking Obfuscation: The tool can flag potentially obfuscated content, such as Base64 encoded strings or text mixing different character scripts, which might be used to hide payloads.
- Flexible Integration: Vibecondom is designed for versatility, capable of analyzing text files stored locally or scanning content directly from remote Git repositories.
- Actionable Insights: When potential threats are detected, the tool provides clear alerts, helping teams pinpoint and investigate suspicious inputs before they compromise the LLM.
Enhancing Trust in AI
Tools like Vibecondom represent an essential step forward in securing the LLM ecosystem. By proactively identifying and flagging potentially harmful inputs, developers can build more robust defenses, fostering greater trust and reliability in AI applications.
As an open-source project (MIT License), Vibecondom invites collaboration and contribution from the security community. Anyone interested in bolstering their LLM security posture is encouraged to explore the Vibecondom project on GitHub to learn more.
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ e4950c93:1b99eccd
2025-05-02 10:39:50
@ e4950c93:1b99eccd
2025-05-02 10:39:50Équipe Cœur
L'équipe Cœur porte le projet et valide les contenus.
- Jean-David Bar : https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll
Pour démarrer, je gère le projet en solo en partageant mes favoris pour éviter le plastique sur nous et sur nos enfants. Contacte-moi si tu souhaites rejoindre l'aventure !
Enrichisseu-r-se-s de contenus
Les contribut-eur-rice-s rendent ce site vivant et intéressant.
A venir.
👉 En savoir plus sur les contributions
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-02 10:36:46
@ e4950c93:1b99eccd
2025-05-02 10:36:46Heureu-x-se d’avoir trouvé une information utile sur ce site ?
Soutiens le projet en faisant un don pour le faire vivre et remercier les contribut-eur-rice-s.
En bitcoin
-
Sur la blockchain : bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
-
Réseau lightning : ⚡️
origin-nature@coinos.ioVous pouvez aussi nous soutenir de manière récurrente 👉 Créer un paiement Lightning récurrent
En euros, dollars, ou toute autre monnaie prise en charge
-
Par virement, IBAN : FR76 2823 3000 0144 3759 8717 669
-
Tu peux aussi nous soutenir de manière récurrente 👉 Faire une promesse sur LiberaPay
Contacte-nous si tu souhaites faire un don avec toute autre cryptomonnaie.
💡 Un modèle de partage de la valeur
La moitié des dons est redistribuée aux contribut-eur-rice-s qui créent la valeur du site, pour expérimenter un modèle de partage de revenus sur Internet — un modèle qui respecte vos données et ne cherche pas à capter votre attention.
L’autre moitié permet de couvrir les frais de fonctionnement du site, rémunérer l'équipe coeur et soutenir les outils open source que nous utilisons.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
-
 @ e4950c93:1b99eccd
2025-05-02 10:31:12
@ e4950c93:1b99eccd
2025-05-02 10:31:12Contribue à enrichir le site !
Chaque contribution permet d’améliorer ce site en aidant à référencer des alternatives naturelles.
💡 Qu’est-ce qu’une contribution ?
Une contribution peut être :
📝 La proposition d’une nouvelle fiche, en fournissant ses premières informations. Chaque information ajoutée (nom, lien, catégorie, etc.) est une contribution : - Ajouter un produit - Ajouter une marque
📝 L'ajout ou la modification d’informations sur une fiche existante. Chaque information ajoutée ou retirée est une contribution.
✅ Validation des contributions
Les contributions sont vérifiées par l’équipe cœur. Une contribution est validée lorsque l'information indiquée est fournie pour la première fois (le commentaire le plus ancien est pris en compte) et est vérifiable.
Une fois validées, les contributions sont comptabilisées et donnent lieu à une rétribution. 👉 En savoir plus sur les rétributions
Les informations ajoutées directement par l'équipe cœur lors de la vérification d'une contribution ne sont pas comptabilisées. Néanmoins, les membres de l'équipe coeur peuvent aussi contribuer comme tout le monde.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 05cdefcd:550cc264
2025-03-28 08:00:15
@ 05cdefcd:550cc264
2025-03-28 08:00:15The crypto world is full of buzzwords. One that I keep on hearing: “Bitcoin is its own asset class”.
While I have always been sympathetic to that view, I’ve always failed to understand the true meaning behind that statement.
Although I consider Bitcoin to be the prime innovation within the digital asset sector, my primary response has always been: How can bitcoin (BTC), a single asset, represent an entire asset class? Isn’t it Bitcoin and other digital assets that make up an asset class called crypto?
Well, I increasingly believe that most of crypto is just noise. Sure, it’s volatile noise that is predominately interesting for very sophisticated hedge funds, market makers or prop traders that are sophisticated enough to extract alpha – but it’s noise nonetheless and has no part to play in a long-term only portfolio of private retail investors (of which most of us are).
 Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: Tradingview
Over multiple market cycles, nearly all altcoins underperform Bitcoin when measured in BTC terms. Source: TradingviewAha-Moment: Bitcoin keeps on giving
Still, how can Bitcoin, as a standalone asset, make up an entire asset class? The “aha-moment” to answer this question recently came to me in a Less Noise More Signal interview I did with James Van Straten, senior analyst at Coindesk.
Let me paraphrase him here: “You can’t simply recreate the same ETF as BlackRock. To succeed in the Bitcoin space, new and innovative approaches are needed. This is where understanding Bitcoin not just as a single asset, but as an entire asset class, becomes essential. There are countless ways to build upon Bitcoin’s foundation—varied iterations that go beyond just holding the asset. This is precisely where the emergence of the Bitcoin-linked stock market is taking shape—and it's already underway.”
And this is actually coming to fruition as we speak. Just in the last few days, we saw several products launch in that regard.
Obviously, MicroStrategy (now Strategy) is the pioneer of this. The company now owns 506,137 BTC, and while they’ll keep on buying more, they have also inspired many other companies to follow suit.
In fact, there are now already over 70 companies that have adopted Strategy’s Bitcoin playbook. One of the latest companies to buy Bitcoin for their corporate treasury is Rumble. The YouTube competitor just announced their first Bitcoin purchase for $17 million.
Also, the gaming zombie company GameStop just announced to raise money to buy BTC for their corporate treasury.
 Gamestop to make BTC their hurdle rate. Source: X
Gamestop to make BTC their hurdle rate. Source: XETF on Bitcoin companies
Given this proliferation of Bitcoin Treasury companies, it was only a matter of time before a financial product tracking these would emerge.
The popular crypto index fund provider Bitwise Investments has just launched this very product called the Bitwise Bitcoin Standard Corporations ETF (OWNB).
The ETF tracks Bitcoin Treasury companies with over 1,000 BTC on their balance sheet. These companies invest in Bitcoin as a strategic reserve asset to protect the $5 trillion in low-yield cash that companies in the US commonly sit on.
 These are the top 10 holdings of OWNB. Source: Ownbetf
These are the top 10 holdings of OWNB. Source: OwnbetfETF on Bitcoin companies’ convertible bonds
Another instrument that fits seamlessly into the range of Bitcoin-linked stock market products is the REX Bitcoin Corporate Treasury Convertible Bond ETF (BMAX). The ETF provides exposure to the many different convertible bonds issued by companies that are actively moving onto a Bitcoin standard.
Convertible bonds are a valuable financing tool for companies looking to raise capital for Bitcoin purchases. Their strong demand is driven by the unique combination of equity-like upside and debt-like downside protection they offer.
For example, MicroStrategy's convertible bonds, in particular, have shown exceptional performance. For instance, MicroStrategy's 2031 bonds has shown a price rise of 101% over a one-year period, vastly outperforming MicroStrategy share (at 53%), Bitcoin (at 25%) and the ICE BofA U.S. Convertible Index (at 10%). The latter is the benchmark index for convertible bond funds, tracking the performance of U.S. dollar-denominated convertible securities in the U.S. market.
 The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: Bloomberg
The chart shows a comparison of ICE BofA U.S. Convertible Index, the Bloomberg Bitcoin index (BTC price), MicroStrategy share (MSTR), and MicroStrategy bond (0.875%, March 15 203). The convertible bond has been outperforming massively. Source: BloombergWhile the BMAX ETF faces challenges such as double taxation, which significantly reduces investor returns (explained in more detail here), it is likely that future products will emerge that address and improve upon these issues.
Bitcoin yield products
The demand for a yield on Bitcoin has increased tremendously. Consequently, respective products have emerged.
Bitcoin yield products aim to generate alpha by capitalizing on volatility, market inefficiencies, and fragmentation within cryptocurrency markets. The objective is to achieve uncorrelated returns denominated in Bitcoin (BTC), with attractive risk-adjusted performance. Returns are derived exclusively from asset selection and trading strategies, eliminating reliance on directional market moves.
Key strategies employed by these funds include:
- Statistical Arbitrage: Exploits short-term pricing discrepancies between closely related financial instruments—for instance, between Bitcoin and traditional assets, or Bitcoin and other digital assets. Traders utilize statistical models and historical price relationships to identify temporary inefficiencies.
- Futures Basis Arbitrage: Captures profits from differences between the spot price of Bitcoin and its futures contracts. Traders simultaneously buy or sell Bitcoin on spot markets and enter opposite positions in futures markets, benefiting as the prices converge.
- Funding Arbitrage: Generates returns by taking advantage of variations in Bitcoin funding rates across different markets or exchanges. Funding rates are periodic payments exchanged between long and short positions in perpetual futures contracts, allowing traders to profit from discrepancies without significant directional exposure.
- Volatility/Option Arbitrage: Seeks profits from differences between implied volatility (reflected in Bitcoin options prices) and expected realized volatility. Traders identify mispriced volatility in options related to Bitcoin or Bitcoin-linked equities, such as MSTR, and position accordingly to benefit from volatility normalization.
- Market Making: Involves continuously providing liquidity by simultaneously quoting bid (buy) and ask (sell) prices for Bitcoin. Market makers profit primarily through capturing the spread between these prices, thereby enhancing market efficiency and earning consistent returns.
- Liquidity Provision in DeFi Markets: Consists of depositing Bitcoin (usually as Wrapped BTC) into decentralized finance (DeFi) liquidity pools such as those on Uniswap, Curve, or Balancer. Liquidity providers earn fees paid by traders who execute swaps within these decentralized exchanges, creating steady yield opportunities.
Notable products currently available in this segment include the Syz Capital BTC Alpha Fund offered by Syz Capital and the Forteus Crypto Alpha Fund by Forteus.
BTC-denominated share class
A Bitcoin-denominated share class refers to a specialized investment fund category in which share values, subscriptions (fund deposits), redemptions (fund withdrawals), and performance metrics are expressed entirely in Bitcoin (BTC), rather than in traditional fiat currencies such as USD or EUR.
Increasingly, both individual investors and institutions are adopting Bitcoin as their preferred benchmark—or "Bitcoin hurdle rate"—meaning that investment performance is evaluated directly against Bitcoin’s own price movements.
These Bitcoin-denominated share classes are designed specifically for investors seeking to preserve and grow their wealth in Bitcoin terms, rather than conventional fiat currencies. As a result, investors reduce their exposure to fiat-related risks. Furthermore, if Bitcoin outperforms fiat currencies, investors holding BTC-denominated shares will experience enhanced returns relative to traditional fiat-denominated investment classes.
X: https://x.com/pahueg
Podcast: https://www.youtube.com/@lessnoisemoresignalpodcast
Book: https://academy.saifedean.com/product/the-bitcoin-enlightenment-hardcover/
-
 @ e4950c93:1b99eccd
2025-05-02 10:20:25
@ e4950c93:1b99eccd
2025-05-02 10:20:25
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ ecda4328:1278f072
2025-03-26 12:06:30
@ ecda4328:1278f072
2025-03-26 12:06:30When designing a highly available Kubernetes (or k3s) cluster, one of the key architectural questions is: "How many ETCD nodes should I run?"
A recent discussion in our team sparked this very debate. Someone suggested increasing our ETCD cluster size from 3 to more nodes, citing concerns about node failures and the need for higher fault tolerance. It’s a fair concern—nobody wants a critical service to go down—but here's why 3-node ETCD clusters are usually the sweet spot for most setups.
The Role of ETCD and Quorum
ETCD is a distributed key-value store used by Kubernetes to store all its state. Like most consensus-based systems (e.g., Raft), ETCD relies on quorum to operate. This means that more than half of the ETCD nodes must be online and in agreement for the cluster to function correctly.
What Quorum Means in Practice
- In a 3-node ETCD cluster, quorum is 2.
- In a 5-node cluster, quorum is 3.

⚠️ So yes, 5 nodes can tolerate 2 failures vs. just 1 in a 3-node setup—but you also need more nodes online to keep the system functional. More nodes doesn't linearly increase safety.
Why 3 Nodes is the Ideal Baseline
Running 3 ETCD nodes hits a great balance:
- Fault tolerance: 1 node can fail without issue.
- Performance: Fewer nodes = faster consensus and lower latency.
- Simplicity: Easier to manage, upgrade, and monitor.
Even the ETCD documentation recommends 3–5 nodes total, with 5 being the upper limit before write performance and operational complexity start to degrade.
Systems like Google's Chubby—which inspired systems like ETCD and ZooKeeper—also recommend no more than 5 nodes.
The Myth of Catastrophic Failure
"If two of our three ETCD nodes go down, the cluster will become unusable and need deep repair!"
This is a common fear, but the reality is less dramatic:
- ETCD becomes read-only: You can't schedule or update workloads, but existing workloads continue to run.
- No deep repair needed: As long as there's no data corruption, restoring quorum just requires bringing at least one other ETCD node back online.
- Still recoverable if two nodes are permanently lost: You can re-initialize the remaining node as a new single-node ETCD cluster using
--cluster-init, and rebuild from there.
What About Backups?
In k3s, ETCD snapshots are automatically saved by default. For example:
- Default path:
/var/lib/rancher/k3s/server/db/snapshots/
You can restore these snapshots in case of failure, making ETCD even more resilient.
When to Consider 5 Nodes
Adding more ETCD nodes only makes sense at scale, such as:
- Running 12+ total cluster nodes
- Needing stronger fault domains for regulatory/compliance reasons
Note: ETCD typically requires low-latency communication between nodes. Distributing ETCD members across availability zones or regions is generally discouraged unless you're using specialized networking and understand the performance implications.
Even then, be cautious—you're trading some simplicity and performance for that extra failure margin.
TL;DR
- 3-node ETCD clusters are the best choice for most Kubernetes/k3s environments.
- 5-node clusters offer more redundancy but come with extra complexity and performance costs.
- Loss of quorum is not a disaster—it’s recoverable.
- Backups and restore paths make even worst-case recovery feasible.
And finally: if you're seeing multiple ETCD nodes go down frequently, the real problem might not be the number of nodes—but your hosting provider.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ e4950c93:1b99eccd
2025-05-02 09:41:12
@ e4950c93:1b99eccd
2025-05-02 09:41:12Tu connais une marque proposant des alternatives naturelles ? Partage-la ici en commentant cette page !
Pour être référencée, la marque doit proposer une partie au moins de ses produits en matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, lien, catégorie, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. Pense à bien sauvegarder tes clés (identifiants) dans un coffre comme nsec.app). Tu peux aussi partager plus simplement tes trouvailles sans créer de compte via le formulaire de contact (non éligible pour les rétributions). 👉 En savoir plus sur les rétributions
Copie-colle le modèle ci-dessous et remplis les informations que tu as. D’autres contribut-eur-rice-s ou l'équipe coeur pourront compléter les éléments manquants.
Nouvelle marque ou fabricant
- Nom de la marque :
- Image représentant des produits de la marque (lien, idéalement depuis le site de la marque) :
- Courte description :
- Catégories de produits proposées :
- Matières utilisées pour ses produits :
- Site internet de la marque :
- Autres informations (lieu de production, labels…) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-02 09:36:09
@ e4950c93:1b99eccd
2025-05-02 09:36:09Tu as trouvé un produit naturel ? Partage-le ici en commentant cette page !
Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus.
Pour être référencé, le produit doit être composé de matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. Pense à bien sauvegarder tes clés (identifiants) dans un coffre comme nsec.app). Tu peux aussi partager plus simplement tes trouvailles sans créer de compte via le formulaire de contact (non éligible pour les rétributions). 👉 En savoir plus sur les rétributions
Copie-colle le modèle ci-dessous et remplis les informations dont tu disposes. D’autres contribut-eur-rice-s ou l'équipe coeur pourront compléter les éléments manquants.
Nouveau produit
- Nom du produit :
- Image du produit (lien) :
- Description courte :
- Catégories :
- Marque ou fabricant :
- Composition (matériaux utilisés, y compris les éléments inconnus) :
- Liens pour l’acheter (et zone de livraison) :
- Zone de livraison pour les
- Autres infos utiles (lieu de fabrication, labels, etc.) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ fbb0eb9d:bdb78256
2025-05-02 09:32:40
@ fbb0eb9d:bdb78256
2025-05-02 09:32:40Wir dürfen keinen Millimeter weichen für jene, die unsere Freiheit nicht zu schätzen wissen. Vor zehn Jahren wurden die Journalisten des französischen Satiremagazins Charlie Hebdo in ihrer Redaktion erschossen, weil sie sich die Freiheit nahmen, eine Religion zu beleidigen. Das sollten wir nicht vergessen, und beim Namen nennen. Diesen Text schrieb ich schon damals, und um es vorweg zu nehmen: Ich bin immer noch Charlie.
„Und, sind Sie auch Charlie?“ fragte damals mein Banksachbearbeiter, nachdem ich auf die Frage nach meinem Beruf „Journalistin“ geantwortet hatte. Viele waren seinerzeit „Charlie“, ja, die Solidarität mit den Opfern in Paris war groß. Bei uns im Land und auch weltweit. Tausende Facebooker veränderten ihre Profilbilder, aber genauso sicher, wie das Amen in der Kirche, hatte es nur wenige Tage gedauert, bis die Differenzierer auf den Plan gerufen wurden. Am Tag der Geiselnahmen in Paris fuhr ich gerade Taxi in Berlin, während sich die französischen Sondereinheiten vor der Druckerei und dem jüdischen Supermarkt in Stellung brachten, die ebenfalls unter Beschuss von Islamisten gerieten. Der Taxifahrer war kein potenzieller „Charlie“. Ich konnte seine Nationalität trotz Akzent nicht ausmachen, möglicherweise war er sogar Franzose. Ich habe nicht gefragt. Sein Standpunkt jedenfalls: „Warum mussten die das auch veröffentlichen, das hätte man ja wissen können, das sowas passiert“.
Wenn mehr auf dem Spiel steht, als ein Profilbild
Ein Moslem? Ich weiß es nicht. Aber auch aus dem christlichen Lager kam zunehmend Kritik, nachdem so mancher recherchiert hatte, was für Karikaturen bei „Charlie Hebdo“ in der Vergangenheit erschienen sind. Auch mit uns Christen ging man in dem Satire-Magazin nicht gerade zimperlich um. Sind wir immer noch Charlie, auch dann, wenn unsere eigene Religion aufs Korn genommen oder gar beleidigt wird?
Und so bestätigte ich dem Angestellten am Bankschalter auch gerne: „Ja, ich bin Charlie, aber ich bin auch gespannt, wie viele immer noch Charlie sind, wenn es um ihren eigenen Kopf geht!“ – eine Frage die heute kaum aktueller sein könnte angesichts von katholischen Priestern, die zwischenzeitlich im Namen Allahs in Frankreich am Altar geköpft wurden und auch islamischen Attentätern, die gerne deutsche Weihnachtsmärkte für ein adventliches Töten zum Anlass nehmen. Sind wir immer noch “Charlie” wenn die Frage nach der Solidarität mit den Opfern sich nicht mit einem Wechsel des Profilbildes bei Facebook erledigen lässt? Denn ein Bild zu tauschen, tut nicht weh, ist schnell gemacht und man bewegt sich damit gerade sowieso im Strom der breiten Masse.
Gesicht zu zeigen ist ein Anfang, es bis zur letzten Konsequenz durchzuhalten, oft etwas ganz anderes. Auch Prominente zeigten damals vor zehn Jahren gerne immer wieder Gesicht. Es existierte eine ganze Kampagne dazu unter dem Namen.
Da war dann Klaus Wowereit Migrant, wenn jemand was gegen Migranten hat, Jörg Thadeusz war schwul, wenn jemand etwas gegen Schwule hat, Ulrich Wickert war Jude, wenn jemand etwas gegen Juden hat und Markus Kavka gar schwarz, wenn jemand was gegen Schwarze hat.
 Das ist auch gut so, so wird Flagge gezeigt. Aber es braucht für derlei Bekenntnisse genauso wenig Mut, wie für den Profilbild-Wechsel bei Facebook.
Das ist auch gut so, so wird Flagge gezeigt. Aber es braucht für derlei Bekenntnisse genauso wenig Mut, wie für den Profilbild-Wechsel bei Facebook.Denn sind wir wirklich immer noch „schwarz“, „schwul“, „Jude“ oder „Migrant“, wenn unser Nebenmann angegriffen wird? Kurz nach der Ermordung der Satiriker von Charlie Hebdo bekam damals Ralf König auf Facebook und Co. von allen Seiten die Comiczeichner-Jacke vollgehauen, weil er nicht mehr ganz Charlie sein mag. Aus Angst hatte er eine Karikatur zurückgezogen, die sich mit dem Islam beschäftigte. Bei ihm steht ja auch nicht nur ein Profilbild, sondern – wie Paris gezeigt hat – wesentlich mehr auf dem Spiel. Eine allzu menschliche Reaktion! Und all den Heuchlern, die ihn verurteilen, würde ich gerne zurufen: Euch möchte ich mal in der gleichen Situation erleben. Nämlich dann, wenn es persönlich wird und die Angst nicht abstrakt, sondern konkret begründet werden kann.
Gerade Christen dürfen nicht zurückweichen
Das zeigt aber gleichzeitig, warum es so wichtig ist, dass wir auch weiterhin Charlie sind. Weil die Angst im Kopf uns sonst lähmt.
Wenn ein Journalist anfängt nachzudenken, ob er überhaupt oder wenn, wie er etwas schreiben soll, dann hat die Selbstzensur bereits eingesetzt.
Wenn ein Journalist Fakten weglässt, weil er vermutet, dass sie nicht gerne gehört werden, dann hat Selbstzensur schon eingesetzt.
Wenn ein Zeichner sich nicht mehr traut, manche Themen oder Religionen aufs Korn zu nehmen, dann hat Selbstzensur schon eingesetzt.
Und dann nutzt es nichts, dass gesetzlich keine Zensur existiert, weil diese Gesetze dann nicht mehr das Papier wert sind, auf dem sie stehen. Wir dürfen nicht zurückweichen. Auch und gerade nicht als Christen. Auch wenn wir selbst mit manchen Karikaturen hadern. Beleidigt sein darf man trotzdem. Denn der Grad von persönlicher Entrüstung ist bei allen unterschiedlich. Ich jedenfalls habe Tränen gelacht beim Kinoklassiker „Life of Brian“ und Monty Pythons „Catholic Song“ ist einfach ganz großes Kino. Aber auch ich war schon oft empört, weil mir manches, was unter Satire und Kunst verkauft wird, zu weit ging.
„Würden Sie auch Mohammed-Town ausstrahlen?“
Als etwa 2003 der Musiksender MTV die Comic-Serie „Popetown“ mit einem infantilen Papst und korrupten Kardinälen ausstrahlte, habe ich eine Gegenkampagne dazu organisiert. „Würden Sie auch Mohammed-Town“ ausstrahlen, fragte ich damals in einem offenen Brief die MTV-Geschäftsführerin Catherine Mühlemann. „Kein Christ wird Ihnen bei Ausstrahlung die Studiofenster zertrümmern, handelt es sich doch beim Christentum um eine Religion des Friedens. Wir verdienen aber nicht weniger Respekt als andere Religionen.“ 50.000 Menschen beteiligten sich damals an den Protesten, verschiedene Organisationen, Politiker und sogar der Zentralrat der Juden protestierte, genutzt hat es nichts. Die Serie erledigte sich letztendlich selbst mit niedrigen Einschaltquoten dank ihres unterirdischen Niveaus.

Aber selbst, wenn es ein Erfolg geworden wäre, hätten wir weiter protestiert: friedlich und ganz sicher nicht mit dem Maschinengewehr. Wir sind ein Land, in dem diese Debatten immer und immer wieder neu mit Worten und nicht mit Waffen ausgetragen werden. In unserem Land darf man kritisieren und sich auch empören. Wir dürfen unsere eigene Regierung anprangern und uns über Religionen lustig machen. Das tut weh, wenn man selbst betroffen ist, dieses Recht dürfen wir aber nicht riskieren. Für keinen persönlichen Grad an Beleidigtsein.
Diskurs statt Blasphemie-Gesetze
Wenn wir also Rücksicht nehmen auf Religionen, dann aber bitte auf alle. Wenn Religionen aber Kritik, Humor oder Satire aushalten müssen, dann bitte auch alle. Ich halte nichts von Blasphemie-Gesetzen, aber umso mehr vom freien Diskurs, der nicht nur in der Religionsfrage derzeit ins Hintertreffen gerät.
Die Frage, ob „der Islam“ zu Deutschland gehört, ist also die falsche. Die Frage ist: Will der Islam zu Deutschland oder gar zu Europa gehören? Sind alle seine Gläubigen bereit, friedlich hinzunehmen, dass im Namen von Meinungsfreiheit, Kunst oder Satire der eigene Glaube beleidigt werden darf?
Denn erst dann ist der Islam wirklich im freien Europa angekommen und diese Frage können die Muslime nur unter sich ausmachen. Es ist nicht an uns, ihnen ihre Religion zu erklären. Wir sollten aber langsam klären, wofür wir selbst stehen. Integration kann nur von jemandem erwartet werden, dem man auch erklären kann, in was er sich integrieren und wie weit das reichen soll.
Wir werden den gemeinsamen Nenner aufzeigen müssen, die „Conditio-sine-qua-non“, ohne die sich unsere Gesellschaft sonst immer weiter auseinander bewegt. Ich habe damals von Catherine Mühlemann keine Antwort auf meine Frage bekommen. Ich weiß nicht, ob sie heute Charlie ist. Ich wünsche mir keinen Raum für diese Angst, die uns lähmt, Debatten ehrlich zu führen. Für Menschen, die unsere Freiheit nicht zu schätzen wissen, weiche ich keinen Millimeter. Ich bin Birgit Kelle. Und ich bin immer noch Charlie.
-
 @ 8f69ac99:4f92f5fd
2025-05-02 09:29:41
@ 8f69ac99:4f92f5fd
2025-05-02 09:29:41À medida que Portugal se aproxima das eleições legislativas de 2025, a 18 de Maio, torna-se essencial compreender as diferentes propostas políticas e os programas eleitorais dos partidos para votar de forma informada. Este artigo funciona como um índice para uma série de análises realizadas aos programas dos principais partidos, com foco em temas como liberdades individuais, descentralização e crescimento económico.
A Evolução da Esquerda e da Direita: Um Contexto Histórico e Ideológico
Os termos “esquerda” e “direita” surgiram na Revolução Francesa (1789–1799) para distinguir quem se sentava ao lado do presidente da Assembleia: as forças favoráveis às reformas radicais (à esquerda) e as defensoras da monarquia e da ordem estabelecida (à direita). Com o século XIX e o advento do liberalismo económico, a direita passou a associar-se ao livre mercado e ao direito de propriedade, enquanto a esquerda defendeu maior intervenção estatal para promover igualdade.
No final do século XIX e início do século XX, surgiram o socialismo e o comunismo como correntes mais radicais da esquerda, propondo a abolição da propriedade privada dos meios de produção (comunismo) ou sistemas mistos com forte regulação e redistribuição (socialismo). A resposta liberal-conservadora evoluiu para o capitalismo democrático, que combina mercado livre com alguns mecanismos de assistência social.
Hoje, o espectro político vai além do simples eixo esquerda–direita, incluindo dimensões como:
- Autoritarismo vs. Liberdade: grau de controlo do Estado sobre a vida individual e as instituições;
- Intervenção Estatal vs. Livre Mercado: equilíbrio entre regulação económica e iniciativas privadas;
- Igualdade Social vs. Mérito e Responsabilidade Individual: ênfase na redistribuição de recursos ou na criação de incentivos pessoais.
Este modelo multidimensional ajuda a capturar melhor as posições dos partidos contemporâneos e as suas promessas de governação.
Visão Geral das Análises por Partido
Segue-se um resumo dos principais partidos políticos em Portugal, com destaque para a sua orientação ideológica segundo as dimensões de autoritarismo, nível de Intervenção estatal e grau de liberdade individual. Cada nome de partido estará ligado à respectiva análise detalhada.
| Partido | Orientação Ideológica | Nível de Intervenção Estatal | Grau de Liberdade Individual | |----------------------------------------|---------------------------------------------------------------------------------------|------------------------------|------------------------------| | AD – Aliança Democrática (PSD/CDS) | Centro-direita democrática (baixo autoritarismo / equilíbrio intervenção–mercado) | Médio | Médio | | PS – Partido Socialista | Centro-esquerda social-democrata (moderado autoritarismo / intervenção estatal) | Alto | Médio | | CDU – Coligação Democrática Unitária (PCP/PEV) | Esquerda comunista/eco-marxista (mais autoritário / forte intervenção) | Muito alto | Baixo | | IL – Iniciativa Liberal | Liberalismo clássico (muito baixa intervenção / alta liberdade) | Baixo | Muito alto | | Chega | Nacionalismo autoritário (controlo social elevado / mercado regulado com foco interno)| Médio | Baixo | | Livre | Esquerda progressista verde (baixa hierarquia / intervenção social) | Alto | Médio | | BE – Bloco de Esquerda | Esquerda democrática radical (moderado autoritarismo / intervenção forte) | Alto | Médio | | PAN – Pessoas-Animais-Natureza | Ambientalismo progressista (intervenção pragmática / foco em direitos e sustentabilidade) | Médio | Alto | | Ergue-te | Nacionalismo soberanista (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo | | ADN – Alternativa Democrática Nacional | Nacionalismo conservador (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo |
Análises Detalhadas dos Programas Eleitorais
Estas análises pretendem oferecer aos eleitores uma visão clara e objetiva das propostas de cada partido, facilitando decisões conscientes nas urnas. Ao focar-se nas promessas relacionadas com liberdades individuais, descentralização e crescimento económico, este conjunto de textos ajuda a compreender melhor o impacto potencial de cada escolha política.
Aliança Democrática (AD)
Partido Socialista (PS)
Coligação Democrática Unitária (CDU)
Iniciativa Liberal (IL)
Chega
Livre
Bloco de Esquerda (BE)
Pessoas,Animais e Natureza (PAN)
Alternativa Democrática Nacional (ADN)
Ergue-te
Photo by Brett Kunsch on Unsplash
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ fbb0eb9d:bdb78256
2025-05-02 09:28:33
@ fbb0eb9d:bdb78256
2025-05-02 09:28:33„Das Schlachten hat begonnen“ war im Jahr 2013 der Titel eines höchst umstrittenen – also wahrscheinlich recht realistischen – Meinungsbeitrags des Autors Akif Pirinçci. Heute ruft die Terrororganisation Islamischer Staat (IS) ganz offiziell in Deutschland genau zu jenem Schlachten auf, das der Autor damals bereits als sichtbares Schema eines außer Kontrolle geratenen Islams in Deutschland beklagte. Der Beitrag ist heute im Internet gelöscht. 12 Jahre später fordern islamische Terroristen ihre Glaubensbrüder in Deutschland auf: „Auf zum Schlachten. Worauf wartest du? Die Straßen sind voller Ziele! Überfahre sie!!“ und verbreiten dazu Bilder, bei denen der Fahrer eines Wagens die Menschen vor ihm auf der Straße ins Fadenkreuz nimmt.

Der Deutsch-Türke Pirinçci war den meisten Lesern bis zu diesem Zeitpunkt eher als weltweiter Bestsellerautor von „Felidae“ und als Erfinder der Romangattung “Katzenkrimi“ bekannt denn als politischer Autor und Kritiker des Zeitgeschehens. Sein Hang zur unflätigen und vulgären Ausdrucksweise und seine anschließenden Auftritte u. a. bei den islamkritischen „Pegida“-Demonstrationen hatten es seinen Kritikern einst leicht gemacht, den brisanten Inhalt seiner Texte und Thesen gleich mit vom Tisch zu wischen und ihn nach allen Regeln jener Kunst, die man heute als „Cancel Culture“ bezeichnet, als ihr erstes prominentes Opfer ins komplette Abseits zu katapultieren. Nun schreibe ich das nicht, um zur späten Rehabilitierung eines Kollegen anzusetzen, sondern weil es sich lohnt, die Genese dieses Vorgangs heute zu betrachten, um sich ehrlich zu fragen: Kommen einem die medialen und politischen Reaktionen nicht doch sehr bekannt vor? Und wenn man das damals alles schon sehen konnte, warum sind wir über ein Jahrzehnt später immer noch nicht weiter?
Ein Exempel wird statuiert
Da schreibt also ein Autor bereits vor 12 Jahren, selbst als Türke mit Einwanderungsbiografie, eine scharfe Kritik an der deutschen Einwanderungspolitik, die mit den Menschen einen Islam zu uns bringt, der sich in Gewalt entlädt und die einheimische Bevölkerung bedroht. Aufhänger des Textes war 2013 der Todesfall des 25-jährigen Lackierers Daniel S., der von einem herbeitelefonierten Schlägertrupp an einer Bushaltestelle abgepasst wurde und später an seinen Kopfverletzungen verstarb. Die Täter hatten türkischen Migrationshintergrund, manche waren bereits polizeibekannt, beides verschwieg die Polizei in ihrer Pressemitteilung an die Öffentlichkeit, bis die BILD-Zeitung die ganze Wahrheit druckte.
Der später verurteilte Täter war statistisch „Deutscher“, seine Tat zahlt in die Polizeistatistik der Deutschen ein, da er in Deutschland geboren wurde, also bereits zweite Generation Einwandererkind ist, man kann seine Integration und die seiner Freunde aber als gescheitert bezeichnen. Pirinçci verliert danach alles, man streicht Verträge, er wird nicht mehr gedruckt und sein Verlag, der vorher Millionen mit ihm verdient hatte, lässt ihn hängen, weil sich gutmenschelnde Autorenkollegen des Verlages von ihm distanzieren und seinen Kopf fordern, schließlich gilt der Türke Pirinçci jetzt als Rassist und als islamophob. Die Läden nehmen seine Bücher aus den Regalen und selbst die Katzenromane aus dem Sortiment. Das Schlachten geht derweil unbehelligt weiter. Ein Kritiker weniger und dazu ein Exempel statuiert: Wagt nicht, dieses Thema anzufassen.
Blutspur durch Europa
Das Schlachten hat schon lange begonnen, nicht erst jetzt. Wie eine Blutspur ziehen sich die Tatorte und Attacken zugewanderter Migranten auf die europäische Bevölkerung seit 20 Jahren über die Landkarte. Von den inzwischen täglichen Messerattacken, die man schon gar nicht mehr mitzählt, bis zu größeren Anschlägen ist alles dabei. Die Tatwaffen ändern sich, die Orte auch, aber das Schema bleibt: Einheimische werden von islamischen Zuwanderern ermordet, absichtlich totgefahren, abgestochen, erschossen, geköpft, in die Luft gesprengt. Es geschieht in Deutschland, in Österreich, massiv in Frankreich, in Belgien, in England, Spanien und auch in Schweden.
Manche dieser Taten liegen schon sehr viele Jahre zurück, manche, die heute „gegen rechts“ auf die Straße gehen, wenn wieder einmal ein Islamist das Gedankenkonstrukt der Vielfalt gefährdet, waren damals noch in der Kita. Spätestens seit 2015 und der Terrorwelle in Frankreich ist das Thema in ganz Europa präsent. Die Journalisten des Satiremagazins Charlie Hebdo werden im Januar 2015 in ihrer Redaktion niedergemetzelt, 11 Tote. Die Botschaft: Leg dich nicht mit Mohammed und seinen humorlosen Gesellen an. Am Tag darauf ein jüdischer Supermarkt in Paris, 4 Tote und eine Geiselnahme. Dann im November 2015 koordinierte, islamistische Attentate mit insgesamt 130 Toten und 683 Verletzten zwischen Sprengsätzen am Stade de France über Zufallsopfern in Bars und Restaurants bis zu einem Blutbad mit 89 Toten, die in der Konzerthalle Bataclan mit Maschinengewehren wahllos niedergemetzelt werden.
In der darauffolgenden Silvesternacht wird Köln Schauplatz Hunderter Übergriffe von Migranten auf Frauen. Ein Auto als Waffe? Premiere schon 2016 auf dem Boulevard von Nizza mit 86 Toten und über 400 Schwerverletzten am Nationalfeiertag. In Deutschland folgt das Schema erstmals im selben Jahr im Dezember 2016 auf dem Weihnachtsmarkt am Breitscheidplatz. Im März 2016 sprengen sich in Brüssel Islamisten am Flughafen und auf einem Bahnhof in die Luft und hinterlassen 32 Todesopfer aus 22 Ländern und unzählige Verletzte. Am Jahrestag ein Jahr später rammt sich ein Islamist in London auf der Westminsterbrücke seinen Weg durch eine Menschenmenge. Spanien hatte die Terrorwelle bereits 2004 eingeholt, es kostete fast 200 Tote und fast 2.000 Verletzte, dass Islamisten koordiniert vier Züge Richtung Madrid hintereinander in die Luft sprengten. Zwei Jahrzehnte Terror in Europa. Dazwischen Machetenangriffe, geköpfte Priester, ermordete Filmemacher, ermordete Lehrer, die es wagen, das Thema in der Schule zu behandeln, Sprengsätze, vergewaltigte und ermordete Frauen und Islamkritiker, die nur noch mit ständigem Personenschutz leben können. Nur eines bleibt immer gleich: Niemand verändert die Migrationspolitik. Alle sind bemüht, stattdessen den Kampf gegen Islamophobie und Rassismus unbedingt zu verstärken, auf zur Demo gegen rechts!
Vergessene Opfer
Das Schema der medialen und politischen Verarbeitung blieb immer konstant: verschweigen, kleinreden, vergessen. Die Erinnerungskultur der Deutschen beschränkt sich gerne auf die Opfer der Nationalsozialisten und auf jene Ausländer, die von Deutschen ums Leben gebracht wurden. Hier werden, wie gerade erst vor wenigen Tagen, immer noch gerne die Namen der Opfer von Hanau von deutschen Politikern in den Medien wiederholt. Doch kennt jemand die Namen der Opfer vom Breitscheidplatz, also jenem Anschlag, der einst auslöste, dass heute jeder Weihnachtsmarkt in Deutschland zur Hochsicherheitszone aufgerüstet wird und bei dem die Politik einst peinlich bemüht war, nicht von einem islamistischen Anschlag zu sprechen? Und selbst das hat das nächste Schlachten in Magdeburg ja nicht verhindern können.
Kennt jemand die Namen aller Opfer vom Weihnachtsmarkt in Magdeburg? Kollegen bei der WELT recherchieren derzeit dankbarerweise die Folgen alleine dieses Anschlags akribisch nach. Man spricht von 1.300 Opfern insgesamt, 6 Toten, 300 Verletzten, davon 67 Schwerverletzten, einem Querschnittsgelähmten und zahlreichen Opfern, die Hände, Füße oder gar ein Bein verloren haben. Warum berührt es nicht alle gleichermaßen? Die Folgen sind keine Umkehr in der Migrationspolitik der Regierung, sondern weitere, staatlich mitorganisierte und mitfinanzierte Demonstrationen „gegen rechts“. In Aschaffenburg sind Kindergartenkinder das Opfer, ein Helfer bezahlt seinen Mut mit dem Leben, für einen Zweijährigen kommt jede Hilfe zu spät. In München fährt vor wenigen Tagen ein Islamist in eine Demonstration, eine Mutter und ihr Kind werden unter den Wagen gezogen, sie sind verstorben, noch am selben Abend demonstriert man in München „gegen rechts“, während Dutzende Schwerverletzte in den Krankenhäusern liegen und der Täter im Gefängnis reklamiert, man möge seine Zelle von der imaginären Verschmutzung durch Christen reinigen. Wenige Tage später sticht im österreichischen Villach ein Migrant wahllos in der Innenstadt Passanten nieder, ein 14-Jähriger stirbt. Der Täter lacht bei seiner Verhaftung. Die Polizei in Wien nimmt vor zwei Tagen einen 14-Jährigen fest, er plante einen Anschlag auf den Westbahnhof. Wien hatte bereits 2020 einen eigenen Amoklauf mit 4 Toten und erst im Sommer 2024 musste dort ein Taylor-Swift-Konzert wegen dringenden Terrorverdachts abgesagt werden. In Schweden wurde vor wenigen Wochen ein Islamkritiker während eines Live-Streams durch Islamisten erschossen. Europa 2025.
Man wird müde, die immer selben Worte zu wiederholen bei den sich immer enger taktenden Anschlägen von Migranten in unserem Land und in Europa. Es fehlen die Worte, weil bereits alles gesagt ist. Genauso, wie sich die sinnlosen Floskeln der Politiker wiederholen, wenn wieder eine junge Frau, ein Kind, ein Vater oder ein mutiger Helfer sein Leben lassen muss und das Volk in der verbalen Litanei erstickt wird zwischen „verwirrter Einzeltäter – Betroffenheit – wir lassen uns nicht spalten – Stadt XY bleibt bunt und wir lassen uns die Art zu leben nicht nehmen“. So, als würden nicht bereits die ersten Karnevalsumzüge abgesagt, weil die Sicherheit auf den Straßen nicht mehr garantiert werden kann.
Wir demonstrieren uns zu Tode
Was, wenn gar nicht die AfD das Problem ist, sondern der Islam? Man stelle sich für eine Sekunde vor, die AfD wäre erfolgreich bekämpft und weg. Eine Nulllinie, von der man in den Jahren 2014 und 2015 gar nicht so weit entfernt war. Damals stand die AfD in den Umfragen irgendwo zwischen 2 und 4 Prozent und tat gerade das, was nahezu alle neuen Parteigründungen der vergangenen 30 Jahre taten: Sie zerlegten sich in innerparteilichen Streitigkeiten selbst. Doch dann öffnete Angela Merkel die Grenze zur unkontrollierten Migration nach Deutschland und lieferte über Jahre ein Thema, an dem sich die AfD wie ein Phoenix aus der Asche wieder neu erhob. Denken wir also eine Sekunde, die AfD sei als Problem weg, welche Probleme sind dann immer noch da? Nichts von dem, was gerade in Deutschland relevant ist, wäre gelöst. Rezession, Wirtschaftskrise, Energiekrise, Krieg in Europa und ja, vor allem auch die gescheiterte Migrationspolitik und die Erosion der inneren Sicherheit sind dann immer noch da. Man kann natürlich die AfD exzessiv bekämpfen statt der realen Probleme, es bleibt dann aber alles, wie es ist. In einem Pseudokampf lenken die wechselnden politischen Eliten erfolgreich vom Thema ab, indem man nun bereits über ein Jahrzehnt den falschen Feind bekämpft. Gerade wird in einem Akt kollektiver kultureller Todessehnsucht das Feindbild AfD zum Feindbild CDU erweitert, um die gesamte bürgerliche Mitte von einer Umkehr in der Migrationspolitik abzuhalten. Immer noch treten brav nach jedem weiteren Anschlag wie gehirngewaschen erwachsene Menschen zu einer Demo gegen rechts an. „Wir amüsieren uns zu Tode“, resümierte einst der Autor Neil Postman die Zersetzung des Westens durch die Unterhaltungsindustrie. Deutschland hat sich im Angesicht einer kulturellen Übernahme durch zugewanderte islamische junge Männer einen weltweiten Alleingang ausgedacht: Deutschland demonstriert sich zu Tode.
Das Schlachten hat schon lange begonnen. Wer es jetzt immer noch nicht versteht, dass eine Mehrheit der illegal einreisenden Migranten weder zur Integration noch zur Arbeit und schon gar nicht wegen politischer Verfolgung hierherkommt, dem ist nicht zu helfen. Wer glaubt, er könne Millionen an aggressiven Antisemiten, glühenden Frauenhassern, Christenverächtern und Sozialstaatstouristen gesellschaftlich, kulturell und finanziell integrieren, ist realitätsfremd. An diesem Sonntag wird gewählt. Der Souverän wird seine eigene Meinung dazu kundtun, wem er zutraut, das Schlachten zu beenden.
-
 @ a367f9eb:0633efea
2025-03-19 17:40:04
@ a367f9eb:0633efea
2025-03-19 17:40:04On February 27th, the Securities and Exchange Commission stated in its latest staff statement that memecoins are not necessarily securities.
“Although the offer and sale of meme coins may not be subject to the federal securities laws, fraudulent conduct related to the offer and sale of meme coins may be subject to enforcement action or prosecution,” writes the SEC.
This clarity is important, but it reveals nothing about what the policies around memecoins, rugpulls, and crypto scams should actually be.
This month has already delivered us Argentine President Javier Milei’s promotion of a pump-and-dump memecoin called LIBRA. At this moment, Barstool Sports founder Dave Portnoy is probably pumping his third or fourth favorite memecoin into oblivion while he dumps on retail.
In each of these cases, these tokens are created with copy-paste smart contracts, influencers singing their praises, and people exchanging their stablecoins, bitcoin, or some other altcoin for the hope of making it rich.
Memecoin world
Of course, in a free country people should be free to bet on things they want. But they should be prepared to lose just as much as they’re prepared to win.
To the uninitiated, these scams represent “crypto” writ-large, lumping the original decentralized protocol of Bitcoin with pump and dump scams from platforms like pump.fun that run on Solana and other chains.
Knowing what we know, and how desperate parts of the crypto market are for outrageous tokens and leveraged degen trading, we must naturally ask how Bitcoin can fix this. Or, rather, how smart Bitcoin policies can fix this.
As I have written for several years, we as Bitcoin advocates should promote sound policies that will encourage innovation and increase economic inclusion across all income groups, all the while protecting consumers from harm. We want to avoid blowouts like FTX, Celsius, and even stablecoins projects like TerraUSD – not only because they defraud bitcoiners, but because they sully the reputation of our entire sector of technological innovation.
Because Bitcoin represents scarcity, decentralization, and complete transparency, there is much we can learn from Satoshi’s innovation when we’re dealing with next-level crypto-offspring.
The Smart Bitcoin Policies to Stop Crypto Scams
To begin, US federal, state, and local agencies should update their technological stack to rigorously identify and prosecute fraud and abuse in crypto projects. Fraudulent claims, fake token whitepapers, and deceptive tactics are already illegal under existing law. Our agencies should be empowered to enforce existing law and weed out the bad actors.
Whether that means better training or tools, law enforcement should receive the necessary upgrades to prosecute and identify the real fraudulent crime that happens to take place in crypto protocols. Much of this behavior is just being used in a new medium. It’s not crazy to think that cops should upgrade their tech stack to understand how it’s happening now.
Second, our policies on money transmission licenses and regulation for crypto exchanges should be streamlined and made easier, rather than more difficult. Let competition provide the best places for people to buy their bitcoin. As much as privacy advocates abhor centralized platforms and exchanges, they still implement better security and educational practices to inform users than a shady service hosted in China will provide.
By simplifying the rules and restrictions on bitcoin exchanges, especially by allowing them to consider their custodied bitcoin as assets rather than liabilities as was done by rescinding SAB 121, it means that more Americans will have the opportunity to have excellent experiences when purchasing their coins online.
Third, regulators must not pigeonhole bitcoin and its crypto-offspring only as investments fit for taxing, but rather as technological tools that empower consumers and foster innovation. Too much discussion about bitcoin policies hinges on the tax rate or how much it will bring to state coffers, rather than by how much it can make one’s life better by removing the red tape to safeguard wealth.
By recognizing the ultimate power of bitcoin self-custody without needing to trust third parties or intermediaries, it means we finally view this technology as an extension of our own free speech and freedom of association.
And lastly, we must focus on removing the barriers to using bitcoin as an ordinary means of payment. The Keep Your Coins Act restricts federal agencies from stopping individuals from using bitcoin how they see fit, as well as protecting self-custody. That, plus de minimis exemption rules that allow us to spend bitcoin as any other asset, mean we can use digital money as intended.
We know that memecoins and rugpulls will continue to happen no matter what, this is almost human nature. But at the same time, embracing smart bitcoin policies will ensure that consumers and users have the best tools and protections available to use the technology if they want.
Originally published at the Bitcoin Policy Institute.
-
 @ 99556507:a6cf5c08
2025-05-02 09:19:37
@ 99556507:a6cf5c08
2025-05-02 09:19:37El paradigma del trabajador común aceptado en nuestra era es trabajar duro durante 40 años por un salario para tener derecho a una jubilación los últimos 20 o con suerte 25 años de vida.
Pero ¿es ésto lo más rentable? ¿Hay otras alternativas?
Vamos a ponernos en la piel de un asalariado o un autónomo que ha cotizado durante 30 años por la base máxima y está a una década todavía de poder jubilarse. ¿Le conviene trabajar esa década para tener derecho a la pensión estatal? ¿O es una estafa?
Hagamos números: La cotización máxima del autónomo o la del empresario a cuenta del trabajador hoy en día es de 1.472€/mes, 12 pagas al año, o 17.664€/año. En 10 años, y considerando una inflación del 4% anual, pagará 202.075€ en cotizaciones sociales.
El cotizante que haya pagado esto durante toda su vida laboral tiene derecho a la jubilación máxima, que hoy es de 3.267€/ mes, 14 pagas al año, o 45.746,40€/año. Si pensamos que la esperanza de vida en España es de 83 años y se tiene derecho a la jubilación a los 67, significa que un pensionista medio recibirá la pensión durante 16 años. Pero vamos a a hacer las cuentas para Matusalén, el pensionista pesadilla para el gobierno y las aseguradoras, que llegará a cumplir los 92 años, recibiendo la pensión durante 25 años.
Asumamos que el gobierno, que necesita imperiosamente los votos de los 7 millones de pensionistas, seguirá revalorizando las pensiones con el IPC oficial, es decir, a una media del 4% anual.
Matusalén se jubilará a los 67 y recibirá a lo largo de sus 25 años de pensionista la cantidad de 1.905.000€(1), de los cuales tendrá que pagar alrededor de un 28% de impuestos.
[(1) 45.746,40*(1-1,0425)/(1-1.04)] = 1.905.150
Es decir, Matusalén pagará 202.000€ en total a lo largo de 10 años para recibir 1.905.000€ distribuidos durante los siguientes 25. Parece un buen negocio, ¿no?
Pero, y si Matusalén, que es una persona cabal y ahorradora, ha ido haciendo una hucha durante sus 30 años de vida laboral a razón de 1000€ al mes, de manera que ahora ya dispone de esos 202.075€ necesarios para pagar sus cotizaciones hasta la edad de jubilación, y además le sobran 160.000€ para sus gastos la próxima década, a razón de 16.000€/año, que deberían de ser suficiente para vivir, puesto que esta cantidad es justo el salario mínimo interprofesional actual. ¿Le merece la pena seguir trabajando o puede plantearse dejar de hacerlo y usar esos ahorros para pagar sus cotizaciones de los siguientes 10 años, y tener derecho a la jubilación cuando cumpla 67 años?
O ya puestos a hacer cuentas, dado que tiene un capital disponible de 202.000€ en el banco, ¿podría pensar en alguna inversión alternativa que revalorizara su dinero de manera que mejorase las prestaciones de su jubilación (los 1.905.000€ calculados antes)?
Aquí es donde sale a jugar la fórmula del interés compuesto: Cf = Ci * (1+Rn), donde: Cf: capital final (queremos llegar a 1.905.000€) Ci: capital inicial (los 202.075€ de Matu) R: tasa de interés anual (CAGR) n: numero de años de la inversión (10)
¿Qué crecimiento anual compuesto (CAGR) necesitaría Matu para obtener el total de lo que nos daría su pensión tras 25 años, pero en tan solo 10 años, de manera que pudiera disponer de todo ese capital incluso antes de jubilarse? Haciendo las cuentas, R = (Cf/Ci-1)(1/n) = 23.09 %
Por si has llegado hasta aquí pero te has perdido por el camino, acabamos de concluir que una persona que invierta hoy 202.075€ en un producto que rente un 23,09% anual, obtendrá 1.905.000€ en 10 años, el equivalente a toda su jubilación.
Pues esto parece incluso mejor que la alternativa anterior, ¿no? Pero claro, hay que encontrar un producto que garantice esta rentabilidad sostenida durante una década. ¿Qué podría ser? A esta alturas, si sigues por aquí, ya habrás podido intuir por dónde van los tiros. Lo único que ha garantizado esta revalorización hasta la fecha es #bitcoin.
Éste el el cuadro del CAGR de Bitcoin tabulado por años. Se lee de la siguiente manera: A finales de 2024, la columna "CAGR 2024" da el CAGR (rendimiento anual compuesto) para la diferencia de años entre 2024 y el año de la cifra que estemos mirando. Por ejemplo, el CAGR a 31/12/2024 de una inversión realizada el 31/12/2023, es decir de 1 año, es del 276,92%. Si la inversión se realizó el 31/12/2016, el CAGR 8 años después, a final de 2024, es del 78,22% ANUAL
(Ver imagen 1)
El tío Matusalén está buscando algo que le dé un mínimo del 23,09% anual, ¿recordáis?. Pues da igual cuándo haya invertido y cuánto tiempo mantenga la inversión. BTC siempre supera ese umbral, por mucho.
"Ya Manolito, pero estás mirando rendimientos desde finales de 2024, cuando Bitcoin hizo un precio máximo histórico. Esto no asegura que haya ocurrido esto cada año, ¿no?"
El siguiente cuadro muestra los CAGR calculados a finales de cada año, los últimos 6 años. Las cifras en verde corresponden a los rendimientos de inversiones mantenidas 10 años. No podemos ir más para atrás porque Bitcoin acaba de cumplir 16 años.
(ver imagen 2)
No es difícil comprobar que a 10 años vista, bitcoin siempre ha superado de largo esta tasa de crecimiento.
*Consideraciones fiscales ** La pensión máxima devenga impuestos sobre la base de rentas del trabajo a razón del 28% anual, mientras que las inversiones tributan a un máximo del 26% sobre la base de las rentas de capital, suponiendo que se recupere todo el mismo año. Si se distribuyen los rendimientos plurianualmente, ese 26% puede reducirse entono al 21%, suponiendo otro 7% anual de ventaja neta sobre la pensión. En el caso particular de Matusalén, los 45.746,40€ anuales de su pensión tributarían íntegros al 28%, por lo que los 1.905.150 se quedarían netos en 823.435,20€ al cabo de 25 años. Si hubiese optado por invertir los 202.075€ en Bitcoin, y suponiendo que la rentabilidad obtenida es solo la necesaria para conseguir los 1.905.150€, tributaría al 26% sobre la ganancia si decide convertirlos en € de una vez, es decir, pagaría 26%(1.905.150-202.075)=442,800€, con lo que le quedarían netos 1.462.350€. Si decide por el contrario vender solo bitcoins cada año por valor de 45,746€, y suponiendo que mantienen el mismo valor en € durante los 25 años, pagaría el 21% sobre la plusvalía, es decir 357.645€ a lo largo de los 25 años por lo que le habrá quedado neto 1.547.504€.
Resumiendo: Renta neta con la pensión estatal tras 25 años: 823.435€ Renta neta con el plan de inversión en bitcoin, con rescate en una vez, el año 0: 1.462.350€ Renta neta con el plan de inversión en bitcoin, con rescate a lo largo de 25 años: 1.547.504€
Hay que recordar que todo el ejercicio está realizado para el mejor caso del pensionista estatal, que vivirá muy por encima de la media. Cualquier número de años inferior mejorará la rentabilidad del plan de bitcoin respecto al estatal.
Conclusión: Al bueno de Matu más le vale comprar bitcoins hoy mismo con ese dinero ahorrado. No solamente no necesitará una pensión sino que lo más probable es que sus ahorros valgan 5 veces más que lo que conseguiría de pensionista, pero 25 años antes.
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ a367f9eb:0633efea
2024-12-22 21:35:22
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate Matt Odell, “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine Devolution Review in September 2017, I had a breaking point. The article was titled “Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century”.
It was later republished in Huffington Post and across dozens of financial and crypto blogs at the time with another, more appropriate title: “Bitcoin Has Become About The Payday, Not Its Potential”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
…
The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
I was at least somewhat wrong.
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests on my college radio show, and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at Occupy Tampa in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “How to Avoid Bank Fees Using Bitcoin,” discussing its potential legalization in Germany, and interviewing Jeremy Hansen, one of the first political candidates in the U.S. to accept Bitcoin donations.
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
But I was wrong.
When I gave my first public speech on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
Now I understand I was wrong.
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG Pierre Rochard: Bitcoin as a savings technology.
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “Technological Literacy is Doomed” in 2016.
And I was wrong again.
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now dozens of ways to use Bitcoin privately — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-
 @ 1b9fc4cd:1d6d4902
2025-05-02 07:55:36
@ 1b9fc4cd:1d6d4902
2025-05-02 07:55:36To outsiders, the music industry is usually viewed as a glamorous world of fame, fortune, and creativity. However, lurking underneath the surface, the industry is also a field fraught with mental health challenges. From the history of addiction to the pressures of fame, artists have long wrestled with maintaining their mental well-being. Daniel Siegel Alonso looks at how many artists have found effective coping strategies, turning to therapy, mindfulness practices, and using music itself as a healing outlet.
The Dark History of Addiction in Music
Siegel Alonso notes that the history of addiction in the music industry is well-documented. The strain of constant touring, public scrutiny, and the never-ending pursuit of success have driven many artists to find relief in substances. Iconic musicians like Kurt Cobain, Amy Winehouse, and Jim Morrison are stark reminders of how addiction can destroy lives.
Guitarist John Frusciante of the Red Hot Chili Peppers is a notable example of someone who battled severe addiction. At the height of his career, Frusciante fell deeply into heroin addiction, which led him to leave the band in 1992. His addiction nearly cost him his life, but after a long and painful struggle, he managed to turn his life around. Frusciante’s journey to recovery involved intensive therapy and a recommitment to his music, ultimately rejoining the band and contributing to some of the group's most celebrated albums.
Seeking Help
One of the most crucial steps in addressing mental health issues is seeking professional help. Therapy provides a safe space for creative individuals to explore their thoughts, feelings, and behaviors with a trained professional. Therapy can be a lifeline for musicians, who often face unique pressures.
Frusciante’s recovery underscores the importance of professional help. He didn’t just quit drugs cold turkey; he underwent a comprehensive treatment plan that included therapy and support from friends and family. His story is a testament to the power of seeking help and the possibility of recovery, even after hitting rock bottom.
Music as an Outlet
For many musicians, creating music is more than just a career; it’s a vital outlet for expression and coping. Writing, performing, and listening to music can be powerful therapeutic tools. Music allows artists to channel their emotions into something constructive and beautiful, providing a release from their struggles.
Daniel Siegel Alonso takes The Beatles' George Harrison as an example. Harrison turned to Transcendental Meditation (TM) as a means of coping with the pressures of superstardom and personal turmoil. Introduced to TM in the 1960s, Harrison found solace and clarity through the practice, which influenced both his songwriting and his personal life. The song “Within You Without You” reflects his spiritual journey and the peace he found through TM. The recording marked a significant departure from the Beatles' previous work; musically, it evokes the Indian devotional tradition, while the overtly spiritual quality of the lyrics reflects Harrison's absorption in Hindu philosophy.
Mindfulness and Meditation
Mindfulness and meditation have become increasingly popular among musicians seeking to maintain their mental health. These practices help individuals stay grounded, reduce stress, and improve overall well-being. George Harrison’s embrace of TM is a prime example of how mindfulness can transform a creative person's life.
Harrison’s dedication to TM didn’t just help him personally; it also profoundly impacted his music. His incorporation of Indian instruments and philosophical themes into his songs brought a new dimension to The Beatles’ music and left an enduring legacy in the music world. By finding a healthy outlet in meditation, Harrison could navigate the challenges of fame and continue creating impactful music.
The Power of Community
Siegel Alonso notes that another vital aspect of mental health is the strength of community. Like all individuals, musicians need a support system. Whether it’s fellow bandmates, family, friends, or mental health professionals, having people to lean on can make a significant difference.
John Frusciante’s return to the Red Hot Chili Peppers is a testament to the importance of community. His bandmates supported him through his recovery, and their familial bond played a vital role in his comeback. The collaborative nature of music itself fosters a sense of belonging and mutual support, which is critical for mental health.
Moving Forward
The music industry has made strides in recent years to address mental health more openly. Initiatives like MusiCares provide resources and support for musicians dealing with mental health issues. However, there is still much work to be done. Shattering the stigma around mental health and fostering open conversations are key steps toward a healthier industry.
Musicians like John Frusciante and George Harrison show us that recovery and well-being are possible, even though the journey may be challenging. By seeking help, embracing mindfulness, and finding healthy outlets for expression, musicians can navigate their challenges and continue to inspire us with their art.
In conclusion, mental health in the music industry is a complex issue. Still, with the right coping strategies and support systems, Daniel Siegel Alonso posits that it is achievable to overcome the challenges. As fans and listeners, we can also play a role by supporting initiatives promoting mental health and recognizing the humanity behind the music we cherish. After all, the well-being of the artists who create the soundtrack of our lives is just as important as the music itself.
-
 @ fd78c37f:a0ec0833
2025-03-18 10:44:40
@ fd78c37f:a0ec0833
2025-03-18 10:44:40In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology.
YakiHonne: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby?
Tomek K: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways.
During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion.
At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution.
That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin.
YakiHonne: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community?
Tomek K: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this.
As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement.
Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role.
If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path.
YakiHonne: How did the Alby community start, and how did it attract its first members?
Tomek K: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now.
As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere.
We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices.
That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal.
YakiHonne:Were there any notable challenges in the early days that left a strong impression on you?
Tomek K :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged.
Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues.
There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.

YakiHonne:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them?
Tomek K: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing.
You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities.
YakiHonne: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both?
Tomek K: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby.
As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.

YakiHonne: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking?
Tomek K: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together.
The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did.
The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects.
Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it.
YakiHonne:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far?
Tomek K :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work.
YakiHonne:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before?
Tomek K:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join.
Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting.
It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema.
YakiHonne:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation.
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ 75869cfa:76819987
2025-03-18 07:54:38
@ 75869cfa:76819987
2025-03-18 07:54:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 225,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 95%. More than 10 million events have been published, with posts and reposts showing a decrease. Total Zap activity stands at approximately 15 million, marking a 10% decrease.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 463 long-form articles were published, 29% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 225,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 18179 events, with a low of approximately 16093.
The number of new users has decreased significantly. Profiles with a contact list are now around 17,511, reflecting a 95% drop. Profiles with a bio have decreased by 62% compared to the previous period. The only category showing growth is pubkeys writing events, which have increased by 27%.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 14% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.6 million, which is a 6.1% decrease. Both reposts and reactions have decreased by about 10%.
For zap activity, the total zap amount is about 15 million, showing an increase of over 10% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that A bulletin board is a relay-centric system of forums where users can post and reply to others, typically around a specific community. The relay operator controls and moderates who can post and view content. A board is defined by kind:30890. Its naddr representation must provide the community's home relays, from which all posts should be gathered. No other relays should be used.
nostr:npub1xy54p83r6wnpyhs52xjeztd7qyyeu9ghymz8v66yu8kt3jzx75rqhf3urc is proposing a standardized way to represent fitness and workout data in Nostr, including: Exercise Templates (kind: 33401) for storing reusable exercise definitions, Workout Templates (kind: 33402) for defining workout plans, Workout Records (kind: 1301) for recording completed workouts. The format provides structured data for fitness tracking while following Nostr conventions for data representation.Many fitness applications use proprietary formats, locking user data into specific platforms. This NIP enables decentralized fitness tracking, allowing users to control their workout data and history while facilitating social sharing and integration between fitness applications.
nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef is proposing a PR introduces two "1-click" connection flows for setting up initial NWC connections. Rather than having to copy-paste a connection string, the user is presented with an authorization page which they can approve or decline. The secret is generated locally and never leaves the client. HTTP flow - for publicly accessible lightning wallets. Implemented in Alby Hub (my.albyhub.com) and CoinOS (coinos.io). Nostr flow - for mobile-based / self-hosted lightning wallets, very similar to NWA but without a new event type added. Implemented in Alby Go and Alby Hub. Benefits over NWC Deep Links are that it works cross-device, mobile to web, and the client-generated secret never leaves the client. Both flows are also implemented in Alby JS SDK and Bitcoin Connect.
add B0 NIP for Blossom interaction
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 describes a tiny subset of possible Blossom capabilities, but arguably the most important from the point of view of a most basic Nostr client. This NIP specifies how Nostr clients can use Blossom for handling media. Blossom is a set of standards (called BUDs) for dealing with servers that store files addressable by their SHA-256 sums. Nostr clients may make use of all the BUDs for allowing users to upload files, manage their own files and so on, but most importantly Nostr clients SHOULD make use of BUD-03 to fetch kind:10063 lists of servers for each user.
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q defines a standard for creating, managing and publishing to communities by leveraging existing key pairs and relays, introducing the concept of "Communi-keys". This approach allows any existing npub to become a community (identity + manager) while maintaining compatibility with existing relay infrastructure.
A way for relays to be honest about their algos
securitybrahh is proposing a PR introduces NIP-41, a way for relays to be honest about their algos, edits 01.md to account for changes in limit (related #78, #1434, received_at?, #620, #1645) when algo is provided, appends 11.md for relays to advertize whether they are an aggregator or not and their provided algos. solves #522, supersedes #579.
nip31: template-based "alt" tags for known kinds
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that clients hardcoding alt tags are not very trustworthy. alt tags tend to be garbage in a long-enough timeframe.This fixes it with hardcoded rich templates that anyone can implement very easily without having to do it manually for each kind. alt tags can still be used as a fallback.
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a PR addresses 3 main problems of NIP-44v2. First, It has a message size limit of 65Kb, which is unnecessarily small. Second, It forces the encrypting key to be the same as the event's signing key. Which forces multi-sig actors to share their main private key in order to encrypt the payload that would be later signed by the group. Decoupling singing and encryption keys, for both source and destination, is one of the goals of this version. And It offers no way to describe what's inside the encrypted blob before requesting the user's approval to decrypt and send the decrypted info back to the requesting application. This PR adds an alt description to allow decrypting signers to display a message and warn the user of what type of information the requesting application is receiving.
Notable Projects
Damus nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
- Notes in progress will always be persisted and saved automatically. Never lose those banger notes when you aren't quite ready to ship them.
- Make your profile look just right without any fuss. It also optimizes them on upload now to not nuke other people’s phone data bills.
- You won't see the same note more than once in your home feed.
- Fixed note loading when clicking notifications and damus.io links.
- Fixed NWC not working when you first connect a wallet.
- Fixed overly sensitive and mildly infuriating touch gestures in the thread view when scrolling
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for Android build 2.1.9 has been released. * Multi-account support * Deep linking support * "Share via Primal" support * Bug fixes and improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
YakiHonne Wallet just got a fresh new look!
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xchat v1.4.7-beta release * Upgraded the Flutter framework to v3.29.0. * Private chat implementation changed to NIP-104 Nostr MLS. * NIP-17 and NIP-29 messages now support q tags. * You can swipe left to reply to your own messages. * Chat messages now support code block display. * Copy images from the clipboard. * Fixed an issue where underlined text in chat appeared as italic.
GOSSIP 0.14.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * New Features and Improvements * Zappers and amounts are now shown (click on the zap total) * Reactions and who reacted are now shown (click on the reaction numbers) * Multiple search UI/UX improvements * Undo Send works for DMs too * Undo Send now restores the draft * UI: Side panel contains less so it can be thinner. Bottom bar added. * UI: frame count and spinner (optional) * Relay UI: sorting by score puts important relays at the top. * Relay UI: add more filters so all the bits are covered * Image and video loading is much faster (significant lag reduction) * Thread loading fix makes threads load far more reliably * Settings have reset-to-default buttons, so you don't get too lost. * Setting 'limit inbox seeking to inbox relays' may help avoid spam at the expense of possibly * Fix some bugs * And more updates
Nostur v1.18.1 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Floating mini video player * Videos: Save to library, Copy video URL, Add bookmark * Improved video stream / chat view * Top zaps on live chat * Posting to Picture-first * Profile view: Show interactions with you (conversations, reactions, zaps, reposts) * Profile view: Show actual reactions instead of only Likes * Improved search + Bookmark search * Detect nsfw / content-warning in posts * Show more to show reactions outside Web of Trust * Show more to show zaps outside Web of Trust * Support .avif image format * Support .mp3 format * Support .m4v video format * Improved zap verification for changed wallets * Improved outbox support * Show label on restricted posts * Low data mode: load media in app on tap instead of external browser * Many other bug fixes and performance improvements
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Latest two releases of Alby Go, 1.10 and 1.11, brought you lots of goodies: * BTC Map integration for quick access to global bitcoin merchants map * Confirm new NWC connections to your Alby Hub directly in Alby Go! No more copy-pasting or QR code scanning * Support for MoneyBadger Pay Pick n Pay QR payments in over 2000 stores in South Africa
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.0 is now available. This release features the ability to renew channel leases, spin up multiple embedded wallets, Nostr Wallet Connect client support, and more. * Renewable channels * NWC client support * Ability to create multiple Embedded LND 'node in the phone' wallets * Ability to delete Embedded LND wallets * Embedded LND: v0.18.5-beta * New share button (share ZEUS QR images) * Tools: Export Activity CSVs, Developer tools, chantools * Activity: filter by max amount, memo, and note
Long-Form Content Eco
In the past two weeks, more than 463 long-form articles have been published, including over 91 articles on Bitcoin and more than 41 related to Nostr, accounting for 29% of the total content.
These articles about Nostr mainly explore the rise of Nostr as a decentralized platform that is reshaping the future of the internet. They emphasize Nostr's role in providing users with greater freedom, ownership, and fair monetization, particularly in the realm of content creation. The platform is positioned as a counter to centralized social media networks, offering uncensored interactions, enhanced privacy, and direct transactions. Many articles delve into Nostr’s potential to integrate with Bitcoin, creating a Layer 3 solution that promises to end the dominance of old internet structures. Discussions also cover the technical aspects of Nostr, such as the implementation of relays and group functionalities, as well as security concerns like account hacks. Furthermore, there is an exploration of the philosophical and anthropological dimensions of Nostr, with the rise of "Dark Nostr" being portrayed as a deeper expression of decentralized freedom.
The Bitcoin articles discuss the ongoing evolution of Bitcoin and its increasing integration into global financial systems. Many articles focus on the growing adoption of Bitcoin, particularly in areas like Argentina and the U.S., where Bitcoin is being used for rental payments and the establishment of a strategic Bitcoin reserve. Bitcoin is also portrayed as a response to the centralized financial system, with discussions about how it can empower individuals through financial sovereignty, provide a hedge against inflation, and create fairer monetization models for creators. Additionally, the articles explore the challenges and opportunities within the Bitcoin ecosystem, including the rise of Bitcoin ETFs, the development of Bitcoin mining, and the potential impact of AI on Bitcoin adoption. There is also emphasis on Bitcoin's cultural and economic implications, as well as the need for decentralized education and innovation to drive further adoption.
Thank you, nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub17wrn0xxg0hfq7734cfm7gkyx3u82yfrqcdpperzzfqxrjf9n7tes6ra78k nostr:npub1fxq5crl52mre7luhl8uqsa639p50853r3dtl0j0wwvyfkuk4f6ssc5tahv nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2 nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 nostr:npub1uv0m8xc6q4cnj2p0tewmcgkyzg8cnteyhed0zv30ez03w6dzwvnqtu6gwl nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1gqgpfv65dz8whvyup942daagsmwauj0d8gtxv9kpfvgxzkw4ga4s4w9awr nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The first Bitcoin Meetup organized by Mi Primer Bitcoin was successfully held on March 14, 2025, at Texijal Pizza in Apaneca. The event included Bitcoin education, networking, a Q&A session, and merchandise distribution, offering an exciting experience for all participants.
* The Btrust Space discussion was successfully held on March 13, 2024. The event focused on how to support Bitcoin developers, fund open-source contributions, and grow the Bitcoin ecosystem. The speakers included Bitcoin core contributors, Btrust CEO, engineering leads, and other project leaders.Here is the upcoming Nostr event that you might want to check out.
- The Nostr Workshop, organized by YakiHonne and Bitcoin Safari, will take place online via Google Meet on March 17, 2025, at 7:00 PM (GMT+1). The event will introduce the Nostr ecosystem and Bitcoin payments, with participants learning about decentralized technology through YakiHonne and earning rewards. Register and verify your account to claim exclusive rewards, and invite friends to unlock additional rewards.
- The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar will be held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar will be hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (Lawyer specializing in Banking, Corporate, and Financial Law). The session aims to introduce the academic program and explore Bitcoin, the crypto economy, and related legal issues.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. The event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 57d1a264:69f1fee1
2025-05-02 06:17:05
@ 57d1a264:69f1fee1
2025-05-02 06:17:05Simple design
For as long as I remember, I’ve believed in simple design as a principle in my practice. It feels fundamental to me when I think about good design.
At the same time, I see many successful examples of complex products in the world. So I decided to ask, what value is simple design really providing me and my work?
Is it nostalgia?
I sometimes wonder if simple design is rooted in nostalgia. An example I like to use is:
Imagine yourself in the year 1981. You just purchased a brand new desk calculator. You are excited because you should be able to do any type of paperwork calculations you can imagine on it.
As you start to use it for the first time, it immediately prompts you to update its software. After using it for a few calculations, it asks you to fill out a survey about your experience. One day in the middle of adding up your checkbook, it interrupts you to tell you about a new leather-bound desk calendar the company just released. Sometimes in the middle of a complex calculation, the calculator will lag and crash. You have to restart it often to fix the issue.
I have a feeling that a person in 1981 would think this is a terrible calculator. They purchased the device to perform their calculations, nothing more. Why is it requiring so much more of their attention and effort?
Focus
I think simple design often refers to a focused product. A product that does a specific task can sometimes do that task really well. Products that try to do many things can offer a lot of value, but rarely do all the things well.
Some people prefer to use specific tools for specific tasks. Others prefer a wide variety of features.
I think the benefits of using fewer products are often a major reason complex products are successful. They may not be focused, they might be lower quality as a result, but people can use them for a wide variety of applications.
You can open a can of beans with a Swiss Army Knife — it will get the job done.
Art and subjectivity
Maybe simple design is valuable for intangible reasons. There is an art to simplicity. There is a beauty to simplicity.
A user can see more of the product's intentionality. The creator chose to leave certain features out. They decided what to include. The product likely exudes more vision and personality.
That might be unnoticed by some, but very valuable to others who care about craft. People who value the experience as much as the result.
Ease of use
I think a true benefit of simple design is the effect it has on ease of use. The less things there are to do in a product, the more obvious the things you can do become.
A simple product requires less of a user. That means a user can stay focused on their own needs and use the product in ways they define. They will encounter boundaries which limit them. These limitations could drive some away, but some might be engaged to find new and creative ways of working.
When to abandon simple design
I think the sad news is simple design is ultimately a limiting factor of a product's growth. I think there are many examples of this throughout the course of history (i.e. Ello vs Facebook, Rdio vs Spotify, Simplenote vs Notion, VSCO vs Instagram, Clear vs Things, Peach vs Twitter, etc). At the same time, I think 'simple design' does provide an entry point to successfully define what a product is.
The biggest challenge is continuing to evoke the benefits of simple design in an established product, while allowing a product to evolve and grow to meet its users' needs. That is a balancing act that very few products have ever achieved, but feels like an ideal that successful products should strive for.
One of Charlie Deets Writings
originally posted at https://stacker.news/items/969089
-
 @ 75869cfa:76819987
2024-11-25 03:21:20
@ 75869cfa:76819987
2024-11-25 03:21:20GM, Nostriches! The Nostr Review is a biweekly newsletter focused on nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics show over 240,000 daily trusted pubkey events, a 28% increase from the previous period, The daily peak reached 22201, the highest in the past two months.New user profiles with bios have reached around 40,000,profiles with contact lists are around 18000,both showing increases over 20%. More than 11 million events have been published, with posts leading in volume, totaling about 2.1 million. Total Zap activity reached over 19 million, marking a significant 70% increase.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 42 Nostr projects were tracked, with 12 releasing product updates, and over 419 long-form articles were published, 33% focusing on Bitcoin and Nostr. During this period, 1 notable event took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events exceeded 240,000, a 28% increase compared to the previous period (Oct 29-Nov 10). The daily peak reached 22201, the highest in the past two months, with a low of nearly 17682. In terms of new user numbers, profiles with bios are around 40000, up 21% over the past two weeks; profiles with contact lists are around 18697, up 22%. Public writing events exceeded 200,000,The daily peak reached 32480. Regarding event publishing, the total number of note events published has surpassed 11 million, marking a significant increase of approximately 28%. Posts remain the most dominant in volume, totaling about 2.1 million, far exceeding reposts (357,168) and reactions (560,243). For zap activity, the total zap amount has exceeded 19 million, showing a significant increase of over 70% compared to the previous period. In terms of relay usage, the top five relays by user count are: wss://bostr.bitcointxoko.com/,wss://feeds.nostr.band/,wss://realy.nostr.band/,wss://realy.lumina.rocks/,wss://unostr.site/ Data source: https://stats.nostr.band/
NIPs
Break out chat and threads from nip 29 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing that this is a variant of #1589 which attempts to reconcile NIP 29 and flotilla's rooms over chat and thread kinds. This requires no changes of NIP 29 clients, only flotilla will need to be modified,andmove kind 9 and 11 out of NIP 29. The choice of new event kinds was initially made to avoid conflicts with existing implementations. However, it would be beneficial to align the two approaches. For chat and threads, maintaining shallow reply hierarchies rather than arbitrary ones is a key consideration. Moving forward would depend on whether this stipulation is acceptable to the NIP 29 community.
Relay chat nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing an alternative to NIP 29 for several reasons. NIP 29 is overly prescriptive in several ways and encourages group admins to host their groups on a third-party relay. Moving group-like features to relays eliminates the need for separate specifications for each group. Additionally, group metadata is redundant because relays already have a NIP 11 information document and a public key with which they can publish additional information.Admins and moderators can be handled implicitly, out-of-band, or by querying feature support using LIMITS. This approach keeps the base specification small while allowing features like moderator lists to be added as optional extensions. Member lists are managed by the members themselves, enabling them to choose whether to publicly disclose their group membership. This approach facilitates web-of-trust-based community recommendations.
Time-ordered event ids nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that there are a lot of performance benefits to having primary keys with temporal locality.when your database needs to check the uniqueness of IDs, only a small portion of the index needs to be hot (in memory). With the current “random identifiers”, the working set eventually becomes all of the data and your database will be page-faulting continuously. Sequential primary keys also make it easier for the database to place new records in order, minimizing the need to rearrange data or update index structures.This PR makes a simple, but breaking change, to the way we compute event ids. It was inspired by the improvements made by UUIDv7.
NIP-37 - Transport method announcement nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is proposing that Nostr decouples applications completely from the transportation layer, meaning services no longer have to be designed around a single transportation method, but can be accessible through a plethora of ways. This NIP is meant to act as a lookup system that tells a client which transportation methods can be used to access its services.There have been NIP proposals that touch the connection between pubkeys and addresses, example NIP-97 - Nostr Naming System, NIP-66 - Relay Discovery and Liveness Monitoring. NIP-97 is very close to solving the issue of this mapping.However, it attempts to also include human-readable naming into the solution. human-readable naming of pubkeys/services is inherently different from mapping a pubkey to an address where a user can access that pubkey's services, which may or may not map to a legacy domain name.NIP-66 covers discoverability from the client side and can be a very important tool to discern which services are worth connecting to. I think it can act as the feedback mechanism to the proposed event of this NIP. It can be used to build metrics for the various networks a pubkey announces it to be accessible. Things like rtt (round trip time) can also be different for each network and should be measured separately.
nip46: simple public key login using kind:10046 nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that This vastly simplifies the bunker:// flow while also making it easy for the user on every other front possibly -- and brings back NIP-05 login, but in a simpler, more generic way.
Add optional arg to nostr.getPublicKey() Lez is proposing that if login is optional for an application, nostr.getPublicKey({optional: true}) can be used to retrieve the pubkey if the user has already granted permission to the app. This allows the user to view the app’s landing page without being interrupted by a popup window. The user can still press the login button later, which calls nostr.getPublicKey() and prompts for permission.
NIP-62: Collections limina1 is defining a specification for organizing nostr events into collections - ordered, optionally-hierarchical structures like books, journals, or documentation. Currently, there's no standardized way to create versioned collections of content. The closest option is to use lists, but this extends that idea beyond a strictly linear hierarchy. Introducing two new event kinds: kind:30040 - Collection Index and kind:30041 - Collection Section. The Collection Index serves as a table of contents, providing metadata about the collection and listing events in display order. Meanwhile, the Collection Section contains the actual content and supports linking to other content using wikilinks, enabling seamless connectivity within the collection.
Add r to kind 10009 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing adding an "r" field to kind 10009, allowing users can advertise what relays/groups they are members of. Flotilla uses this to recommend relays. These of course should be considered non-canonical because the users publishing them may not actually have access to the relay specified.
Add support for naming unmanaged groups nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing Instead of allowing human-readable ids, it's probably better to just allow users to name groups. I opted for a petnames strategy here instead of recommending sending 9002 events or something. Clients can choose whatever heuristic they want to resolve conflicts.
Add feature detection for unmanaged groups nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn is proposing feature detection for unmanaged groups that has to exist on two levels.On the group level, so that clients can toggle the richer NIP 29 behavior on or off. Feature detection based on NIP 11's supported_nips field isn't sufficient, since a relay implementation might support NIP 29, but the actual relay may not.On the relay level, since clients need to be able to know whether users can post events to groups that don't yet exist, or whether they have to send a create-group event instead.The default (obviously) has to be that unmanaged groups are allowed, so unmanaged group support is opt-out.
kind-scoped follow nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft is proposing kind-scoped follow does NOT (necessarily) replace kind:3, it's a way to do a very simple follow of one or more kinds that might be of interest.This way we also start moving away from huge follow lists that can get wiped at a moment's notice and instead clients are responsible for computing the follow list and updating its local state.This also allows apps to show "followed" notifications without a central source.
Build Your Own Adventure posts nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is defining kind:296 and kind:297 as text notes with options to navigate to the next text notes and continue reading. Kind 296 serves as the root story and 297 for the sections of that story.The idea is to replicate the dynamism of build your own adventure books, where each reader takes their own journey in the story.Story Section events contain an optional title tag and option tags for the next sections.Clients SHOULD render options in a way that users can select and move to that post.
Notable Projects
Primal 2.0 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal now offers a much more comprehensive view of Nostr, with the following additions: * New tab: READS * New tab: EXPLORE * Feed Marketplace * Advanced Search * launched Primal Premium, for $7/month, you can get a Primal Name and Nostr Tools for power users * enable plugging any feed into the sidebar
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Mobile latest updates: * Adjust your home feed with what interests you the most. * Home suggestion box can be enabled and disabled. * Profile preview can be enabled and disabled. * Replies can be previewed and highlighted directly. * Articles, videos and curations can be quoted inside notes for more exposure. * Add the ability to link connected wallets to your profile for zaps receiving. * Thread view is enhanced and well adjusted. * Fix a variety of introduced bugs. * General improvements across the app.
Web latest updates: * A fresh design overhaul for the article, video, and curation pages, enabling seamless browsing and enhanced interaction with content. * Connected threads! A refined notes thread makes following entire discussions more intuitive. * Users can now personalize their home feed by selecting their top interests. * Replies can now be previewed directly from the note card, without needing to open the full note. * Wallets can now be linked to your account directly from the wallet page. * Drafts for notes and replies are now saved, allowing easy edits later. * The suggestions box on the home page can now be hidden. * The on-hover user preview can now be disabled for quicker access to profiles. * Articles, videos and curations can now be quoted and shared as notes. * General improvements. * Bug fixes and optimizations.
ZEUS Pay nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
- All payments will incur no fee for the receiver (previously 2.5-10% depending on amount)
- The minimum amount receivable has been lowered to 1 satoshi (previously 10 satoshis)
TestFlight nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
TestFlight is a program designed for those who want to join the nostr:#damus roadmap, prioritizing improvements to video support and introducing several new features: * Improved video controls * Stability improvements to video support * New image share options on the full screen carousel * Hashtag suggestions * Multi image uploads * A video player that actually works * Share sheet action * Seamless scroll * Added Damus Share Feature * Fixed missing tab bar on navigation * Fixed some issues where profile QR code scanning would not work, and improved UX to make experience more robust
Olas 0.1 nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
Olas is an Instagram-like client for iOS and Android,provides a feed of videos (like those on flare/highlighter/zap.stream), picture events (kind:20, a new kind that no client had implemented yet) and the classical short notes with images attached we are all used to.Some more features already available: * blossom uploads * NIP-22 replies * Reels (still quite buggy though) * Edit your preferred blossom servers * Edit your nutsack mint list * Image download optimization (to be gentle with mobile data plans) Additionally, there are some coming next, including NIP-55 (Amber) Logic,Fix NIP-46 (bunker) login,complete NIP-60 (nutsack) wallet,Add NIP-57/61 zaps + nutzaps,and more.
Gossip 0.12.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
This is a major release with the following major changes: * Bookmarks support (including private bookmarks) * Global feed and per-Relay feeds (with volatile storage, erased when you quit) * Friends-of-friends scores shown in avatar * Improved spam filtering script with more inputs to make decisions on Additionally, there are some minor changes, including updated emoji picker, reworked relay scoring, more efficient background tasks, faster database (less syncing),and more.
Nostur v1.16.0 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
- Nostr Nests integration
- Live video streams and chats
- Relay Autopilot improvements
- VPN detection toggle: only connect to additional relays if VPN is detected
- Relay Connection stats improvements
- Rewrite of feed loading. Faster & more efficient
- Possible imposter label also added on new follower notification and quoted posts
- Improved profile card rendering/animation
- Improved quoted post and inline naddr1 rendering
- Optimized profile gallery loading
- Exclude reposts for new posts notifier
- UI tweaks, more compact, less clutter
- Full width images now go to screen edge
- Reduced data usage for new follower notifications
- Many many bug fixes and other optimizations
Fountain Radio 1.1.8 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
- Add and upvote tracks in the queue
- Support the artist currently playing
- Post in the live chat
- Save tracks to your library
- Listen to Fountain Radio on other apps
- Artist takeovers
Plebeian Progress Update nostr:npub1market6g3zl4mxwx5ugw56hfg0f7dy7jnnw8t380788mvdyrnwuqgep7hd
There are some enhancements and new features: * dialog manager * hide non-working parts of the ui * publish events, we are just signing * Moderation Tools for Admins and Editors * introduce 'editor' role Additionally, a major bug causing errors when creating stalls with more than one shipping method has been fixed, and the “v4v” text has been updated to Community Contribution.
Zapstore 0.16 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8
Zapstore 0.1.6 released now.Some performance issues addressed, reverted installer, fixed themed icon and toasts, and more.
0xchat 1.4.1 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
- Optimized video player UI with support for landscape mode
- Added audio configuration in settings
- Enabled copying of ecash tokens from ecash messages
- Support for media deletion Additionally, some bug fixes,such as the occasional gray screen when sending e-cash,gray screen issue in Hungarian language,“mark all as read” function not working,and more.
DEG Mods update nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x
The updated version introduces a new Web of Trust system and a Blog system, with relevant pages and sections now implemented and updated.And there are some changes: * (technical) nPub user addresses now lead to a user's profile if added through the URL, which would be auto-converted to an nProfile type address. * Reaction (heart/poop) numbers now show a loading indication with 3 dot animation, and you'd only be able to react once loading is finished. * There's now a spinning loader animation for the comments of a post to make sure, as a user, if there are comments or not * There's now a comment loader button that you can press to load newly discovered comments for a mod or blog post * Minor design adjustments for blog posts Additionally, fixed the ordering of the latest mods, ensured profile links in comments (from clicking the name or user address) lead to the correct profile page now, and more.
Long-Form Content Eco
In the past two weeks, more than 419 long-form articles have been published, including over 100 articles on Bitcoin and more than 30 related to Nostr, accounting for 33% of the total content.
These articles about Nostr mainly explore the protocol's development, practical applications, and its role in driving the decentralized social media ecosystem. They cover updates on tools and features like TestFlight and Knox Beta, highlighting innovations such as healthcare micro-apps, privacy enhancements, and NFC integration. Community-driven initiatives, like self-hosted Zap cooking, board member introductions, and the power of collaboration, reflect the growth of the ecosystem. Additionally, the articles discuss challenges such as key management and content moderation, as well as creative contributions like Thanksgiving use cases and cultural content.
The Bitcoin articles discuss the development, adoption, and impact of Bitcoin on the global financial landscape. They cover Bitcoin's market performance, technological advancements, and its role in the broader cryptocurrency ecosystem. The articles also explore Bitcoin's rise, its increasing market cap, and predictions for its future price movements. In addition, they focus on Bitcoin's use in various applications, the challenges faced by Bitcoin mining, and its evolving role in decentralized finance, highlighting Bitcoin's potential to address global issues, from the limitations of fiat currencies to the challenges posed by central banking systems and surveillance. Overall, the articles reflect Bitcoin's growing influence and its potential to drive future technological and financial revolutions.
Thankyou,nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe,nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn,nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft,nostr:npub1t0an3j7nk007fuc7r9zpm89g66dksuc245jsm4xy2674w2uen2nsceqmmp,nostr:npub1klshrs20h2nxf73vrshfjpmmnrq7m8tz7l77sjapwkyaveu22agq5pvxnv,nostr:npub1f7ptem2ztp9x4n7w62n90ddv40z0jrt4490d8lug3uasfwyjsccqkknerm,nostr:npub176zu0wg5l8436nu66qaxwfekx0zz58l66s72dhcu0ur0lvd7q5lq9f66qx,nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and others,for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
- Adopting Bitcoin 2024 took place successfully from November 15 to 16, 2024, in the southern region of El Salvador. The event attracted over a hundred Bitcoin experts, advocates, and innovators from around the world, including nostr:npub14d5399mthprnnur9g2wq877hg0htr5afrdad5dryryeftct885fqtcpuyp, nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m, nostr:npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq, nostr:npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz,and more. Discussions focused on Bitcoin’s potential to reshape global finance, culture, and social structures, with key themes around decentralization, Bitcoin’s challenge to sovereignty, and its impact on education and family life. nostr:npub1ad0ptuzte83alpkpqqctvewlaqj5zq23c83m82xw8apg4t6zlyns6xng2c
Here are the upcoming Nostr events in November that you might want to check out.
-
Btrust Developer Day will take place on Sunday, December 8, 2024, in Nairobi, Kenya, as part of the Africa Bitcoin Conference (ABC 2024). This event aims to provide a platform for African developers to explore Bitcoin technology, learn from industry leaders, and collaborate on projects. The event will feature lightning talks, panel discussions, hands-on workshops, project showcases, and networking opportunities, making it ideal for Bitcoin developers, open-source developers, technologists, and Bitcoin enthusiasts.
-
The Africa Bitcoin Conference 2024 will take place from December 9 to 11, 2024, in Nairobi, Kenya, featuring key programs such as Btrust Developer Day, TBD Hackathon, ABC Social Impact Award, Afro Bitcoin Fellowship, and Africa Bitcoin Day. The event will host nearly 70 distinguished speakers, including nostr:npub1ju2sw9unanr94p5wama3ydv90hcke34wcnmnxedummspaayz55qswlya32, nostr:npub16hssgmdhw9e9j6z8na45lzz4grdsfjqlp5hf8dtcqnp0glseeu3seecguf, nostr:npub1m7uxdt50d2jw35q79zlszlsvy79t7dpdxptz6rfsrsamra7l8ttsq752yl, nostr:npub1gaxapm9t9damh6q2lpc04ptcyeh0ysfdfzzs997agu3ae80ftrns7t985l, and more,focusing on topics such as Bitcoin adoption, regulation, innovation, and security. This conference offers attendees valuable opportunities for in-depth discussions and knowledge sharing.
-
The Asia Bitcoin Tech Unconference is set to take place from February 8 to 10, 2025, in Chiang Mai, Thailand. Organized as a workshop-style event, it will feature a diverse lineup of speakers, including nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef, nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac, nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv, nostr:npub1xtwy7fvu8f7wdtgnpm68wyrf6uxshf49tn5kp7kyusu6872amn8qh06rus, nostr:npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt,and others. The conference will focus on key topics such as scalability, mining, payments, and infrastructure, while also encouraging participants to share unfinished projects or technical challenges. Through hackathons and hands-on discussions, the event aims to foster collaboration and innovation. Highlights include technical talks, pitch competitions, Bitcoin product showcases, and creative and wellness activities such as Thai massages, ice baths, and arts and crafts workshops.nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 57d1a264:69f1fee1
2025-05-02 06:04:19
@ 57d1a264:69f1fee1
2025-05-02 06:04:19After being featured in the NY Times and WSJ, New York City officially opens a major addition to Central Park, the Davis Center at the Harlem Meer. Designed by architect Susan T Rodriguez in collaboration with Mitchell Giurgola, the renovation project replaces the old Lasker Rink and pool with a recreational facility that’s built directly into the landscape, restoring nature, reconnecting paths, and creating a year-round space for community activity. At the heart of the new design is a transformative water feature that shifts with the seasons, from a skating rink in winter to a lush green lawn in spring and fall and a pool in the summer.
The center’s new oval-shaped pool sits lower than the old one, surrounded by a gently sloped grassy berm. In winter, the pool becomes an ice-skating rink, making the site a destination in every season. A splash pad at the end of the water feature offers extra water play in the summer. By integrating the design into the natural shape of the land, the architects were able to open up the space around the pool and allow the landscape to flow around it, resulting in a setting that feels like it’s always been there.
Sustainability was a core part of the project. The building is expected to earn LEED Gold certification, thanks to features like passive ventilation, locally sourced stone and wood, energy-efficient systems, and a roof that absorbs rainwater. Bird-safe glass helps protect local wildlife, and recycled materials from the old building were reused during construction. Even more important, the new center supports free and low-cost programming year-round, including education, nature walks, community events, and recreation. It’s designed to welcome all kinds of visitors—from families and school groups to joggers, birdwatchers, and casual parkgoers.
Continue reading: https://www.designboom.com/architecture/giant-pool-new-york-central-park-new-davis-center-susan-t-rodriguez-mitchell-giurgola-04-24-2025/
originally posted at https://stacker.news/items/969086
-
 @ f18571e7:9da08ff4
2025-03-14 16:43:03
@ f18571e7:9da08ff4
2025-03-14 16:43:03Gostaria de dar-te as boas vindas à essa rede social descentralizada e sem censura. Creio eu que já tenha ouvido falar sobre o que ela é e como funciona parcialmente, caso não, existem dois sites (ao meu conhecimento) com boas informações, se chamam nostr.com e nostr.how, mas darei mais à frente uma explicação básica.
E já te dou um aviso: você precisa saber ler!
Aqui irei tentar ajuntar o máximo de informações que conseguir para que não falte nada para você, e o que faltar, quero que você saiba como pesquisar. Cada parte de como funciona, como acessar, como criar, etc.
Usarei como padrão neste artigo o #Amethyst, pois é o melhor e mais completo client para android, mas muitas das configurações nele podem ser visualizadas em outros clients. E para começar, vamos ver o que são clients.
Clients
Chamamos de clients (ou clientes em português) aqueles sites ou apps que dão acesso ao protocolo Nostr. Assim como para acessar à internet existem vários browsers (ou navegadores), para acessar o Nostr também existem vários clients, cada um voltado a um foco específico.
Amethyst
O melhor e mais completo client para #android, nele você pode ter acesso de tudo um pouco. Lives, comunidades, chats, "vídeos curtos", hashtags, notas populares, e muito mais.
Na versão da Play Store, existe uma funcionalidade de tradução usando o Google tradutor. https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
Em outras lojas de apps e no repositório Github, o apk não possui essa função. https://github.com/vitorpamplona/amethyst
Aqui tem um tutorial do Amethyst: nostr:nevent1qqsgqll63rw7nfn8ltszwx9k6cvycm7uw56e6rjty6lpwy4n9g7pe5qpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqqqqs7yma4t
Outros Clients
Aqui algumas pessoas expondo suas opiniões sobre certos clients: nostr:nevent1qqsdnrqszc2juykv6l2gnfmvhn2durt703ecvvakvmyfpgxju3q2grspzamhxue69uhhyetvv9ujuvrcvd5xzapwvdhk6tczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqghvkced nostr:nevent1qqsvqahwnljqcz3s3t5zjwyad5f67f7xc49lexu7vq5s2fxxskegv4spzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qvg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsxpqqqqqqzeykzw2 Eu mesmo gosto do Amethyst para android e iris.to para web no PC.
Recomendo à você dar uma olhada nesse site: nostrapps.comEle possui todos os clients atuais do Nostr, com uma descrição e links direcionais para você.
Nostr
Agora que você já sabe mais sobre os #clients, você pode acessar o Nostr segundo seu interesse de interface. Vamos ver o que uma IA nos diz sobre o Nostr:
"O #Nostr é um protocolo descentralizado e open source que permite a criação de redes sociais e outros aplicativos sem a necessidade de um servidor central. O nome é um acrônimo para Notes and Other Stuff Transmitted by Relays (Notas e Outras Coisas Transmitidas por Relays). Ele foi projetado para ser resistente à censura, oferecendo uma alternativa às plataformas tradicionais, onde os usuários têm controle total sobre seus dados.
Para que serve?\ O Nostr serve como base para aplicações descentralizadas, como redes sociais, sistemas de pagamento instantâneo em Bitcoin (usando a rede Lightning) e interações diretas entre criadores e consumidores de conteúdo. Ele promove a liberdade de expressão e a privacidade, sem exigir informações pessoais como nome, e-mail ou número de telefone para criar uma conta.
Como funciona?\ O protocolo utiliza dois componentes principais: clientes e relays. Os clientes são aplicações que os usuários usam para interagir com a rede, enquanto os relays são servidores que armazenam e transmitem mensagens. Cada usuário tem uma chave criptográfica única, que garante a autenticidade e a integridade das mensagens. Os relays são independentes, o que significa que, se um relay for bloqueado ou cair, os usuários podem continuar se conectando através de outros.
Em resumo, o Nostr é uma revolução na forma como nos conectamos online, oferecendo liberdade, privacidade e controle aos usuários."
-Perplexity AI
Se você chegou aqui, é porque ouviu em algum lugar ou de alguém, algo parecido com isso. O Nostr é algo moldável, você consegue fazer dele o que quiser, e por aqui você vai encontrar muitas dessas pessoas que o moldam (idealizadores, programadores e desenvolvedores).
Cuide de sua NSEC
Sua Nsec é a chave privada para acesso ao seu perfil, quem a possuir poderá realizar qualquer alteração que queira, comentar, publicar posts e assim por diante. Você deve guardar essa Nsec como se fosse a seed phrase ou chave privada de sua carteira cripto.
Existem alguns modos de guardar e criptografar sua Nsec:
Sem Criptografia
Primeiro de tudo, fique ciente de onde está a sua nsec no client em que acessa o Nostr!
No Amethyst
- Abra o menu de opções
- Selecione "Copia de segurança"
- Clique em "copiar minha chave secreta" Sua nsec será copiada para a àrea de transferência de seu teclado.
Depois de copiar sua nsec, as melhores recomendações que tenho para passar são:
1. Amber
Guarde sua nsec no #Amber, um app assinador de eventos que guarda sua nsec sob criptografia. Após isso, use o mesmo para acessar qualquer client ou site e gerenciar as permissões de cada um. nostr:nevent1qqsvppyfxm87uegv9fpw56akm8e8jlaksxhc6vvlu5s3cmkmz9e0x8cpypmhxue69uhkummnw3ezuampd3kx2ar0veekzar0wd5xjtnrdakj7q3q5wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8cssxpqqqqqqztzjvrd
2. Nos2x-fox
Coloque sua nsec no #Nos2x-fox, um gerenciador de permissões para navegadores a partir do #Firefox. https://addons.mozilla.org/en-US/firefox/addon/nos2x-fox/ E para navegadores da base #chromium existe o #Nos2x do mesmo desenvolvedor. https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
3. Gerenciador de Senhas
Essa é a recomendação mais arriscada, você ainda terá de usar o copiar e colar de sua nsec para acessar o Nostr, a não ser que seu gerenciador reconheça o campo de preenchimento da nsec. Mesmo assim, existem dois gerenciadores que indico; o #Bitwarden e #KeePassDX:
Bitwarden (online)
Play Store: https://play.google.com/store/apps/details?id=com.x8bit.bitwarden Github: https://github.com/bitwarden/mobile
KeePassDX (offline)
Play Store: https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free Github: https://github.com/Kunzisoft/KeePassDX
Com Criptografia
Se tiver interesse em criptografar sua chave, o formato nativo aceito pelos clients é o ncryptsec. O #ncryptsec é uma criptografia por senha (a grosso modo), onde para ser capaz de usá-la nos clients, somente em conjunto com a senha usada na criptografia, fora isso, você não tem acesso. Você consegue encriptar sua nsec e hex para ncryptsec por meios como os abaixo:
1. Amethyst (nsec)
Existe uma função nativa no Amethyst abaixo da opção "copiar chave secreta" onde é só adicionar a sua senha e será criada uma ncryptsec para copiar. Guarde essa nsec encriptada + senha de descriptação em um lugar seguro.
2. Amber (nsec)
No Amber, existe uma função capaz de encriptar sua nsec.
Ao entrar no Amber
- Selecione a engrenagem na parte inferior da tela
- Selecione "backup keys"
- E rolando para baixo existe um campo para digitar sua senha para encriptação da nsec, digite sua senha e copie a ncryptsec. Guarde-as em um lugar seguro.
3. Nostr-Tools (hex)
Foi-me dito que essa ferramenta também encripta o formato nsec, mas eu não consegui fazê-lo, então deixarei para o formato hex. Compile essa ferramenta em seu pc e siga as instruções. Sua chave Hex será encriptada. https://github.com/nbd-wtf/nostr-tools/blob/master/nip49.ts Guarde-as em um lugar seguro.
Relays e Servidores
Relays
Os #Relays (ou relés) são essenciais para receber e enviar informações no Nostr, veja abaixo algumas definições e como utilizar: nostr:nevent1qqsw85k097m8rh5cgqm8glndhnv8lqsm3ajywgkp04mju9je3xje3hcpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqqqqzxvc0le No exemplo é usado o Orbot no Amethyst, você pode escolher usar essa opção, mas houve uma atualização do Amethyst desde a criação deste post, onde foi adicionada a função de "Tor interno".
No Amethyst
- Deslize a tela da esquerda pra direita
- Selecione "Opções de Privacidade"
- Na opção "Motor Tor Ativo" selecione "Interno"
- Para melhor privacidade, na opção "Predefinições Tor/Privacidade" selecione "Privacidade Completa" Todo conteúdo e informação que receber do Nostr passará através da rede Tor, além de que é possível visualizar conteúdos publicados no Nostr exclusivos da rede #Tor com essa configuração. Lembrando que este método é mais veloz que usar o Orbot.
Aqui estão alguns relays Tor: nostr:nevent1qqsqe96a8630tdmcsh759ct8grfsdh0ckma8juamc97c53xvura3etqpxpmhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtmhwden5te0vdhkyunpve6k6cfwvdhk6tmjv4kxz7gzyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgmxr5jk
Servidores de Mídia
Os servidores de mídia são os responsáveis por armazenar seus vídeos e fotos postados no Nostr. No Amethyst já existem alguns por padrão: https://image.nostr.build/8e75323bb428c1e5ef06e37453f56bc3deecd38492a593174c7d141cac1c2677.jpg Mas se você quiser, pode adicionar mais: nostr:nevent1qqster6rm55vy3geqauzzwrm50xwvs2gwa4l27ta2tc65xhpum2pfzcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgv2za2r Fique atento aos limites e regras de cada servidor de mídia. nostr:nevent1qqsq3qchucw49wfu2c4wpsung93ffzg4ktt4uuygnjcs5pldf5alr9c3hsgjr
E aqui vai uma #curiosidade: Caso queira postar uma foto ou vídeo que já postou antes, copie o ID da nota em que ela está e cole no novo post, ou então o URL da mídia. Você pode perceber que após upar uma mídia no Nostr, isso se torna uma URL, sempre que usar essa mesma URL, essa mídia irá aparecer.
Lightning e Zaps
Se você chegou aqui por meio de bitcoinheiros, já deve saber que por aqui, usamos a #Lightning para enviar zaps. Mas o que são zaps?
Zaps são nada mais do que satoshis enviados no Nostr. Um exemplo, eu criei esse artigo, pessoas que querem me apoiar ou agradecer por tal, me enviam alguma quantia em sats, dizemos que essa pessoa me mandou um #zap.
Agora posso falar mais sobre a lightning no Nostr.
Para enviar zaps para usuários no Nostr, você precisa de uma carteira lightning. E a carteira que recomendo criarem para isso é através da #Coinos. Na Coinos, você não precisa criar carteiras com seed phrases nem canais lightning, ela é uma carteira custodial, ou seja, a seed phrase está de posse da Coinos. Basta você acessar coinos.io e criar uma conta com username e senha, você pode configurar um e-mail de resgate, código 2FA, e senha para movimentação de fundos. Se quiser, aqui está o app da Coinos, ainda em fase de testes, mas a maior parte do usual funciona perfeitamente. nostr:nevent1qqspndmkhq2dpfjs5tv7mezz57fqrkmlklp4wrn3vlma93cr57q5xlqpypmhxue69uhkummnw3ezuampd3kx2ar0veekzar0wd5xjtnrdakj7q3q7xzhreevjvzyvuy48mjn7qlx55q2dktk3xm0lnlpehxvl8dq3l6qxpqqqqqqzp4vkne (o app está disponível na #zapstore, baixe a loja para ter acesso) O legal da coinos é que você pode criar um endereço lightning com o nome que você escolher, o meu por exemplo é componente08@coinos.io, basta criar sua conta e poderá enviar e receber zaps no mesmo instante.
Mas para receber de fato um zap usando o Nostr, você precisa configurar seu endereço lightning no seu perfil. Crie sua conta e copie seu endereço lightning.
No Amethyst
- Clique na sua imagem de perfil
- Selecione "Perfil"
- Aperte o botão com um lápis
- Em "Endereço LN" e "LN URL" cole seu endereço lightning Pronto! Agora as pessoas podem te enviar zaps através de suas publicações.
Antes de enviar zaps, configure seus valores no client.
No Amethyst
- Aperte e segure no raio de qualquer publicação
- No campo "novo valor em sats" digite um valor desejado
- Aperte o "x" nos valores que deseja excluir
- Clique em "Salvar"
Agora, você pode clicar no raio e escolher um valor, ao escolher você será direcionado para a sua carteira, confirme a transação e seu zap foi realizado!
Existe outro meio de enviar zaps que é através do #NWC (Nostr Wallet Connect). Siga os mesmos passos do Yakihonne no Amethyst na aba do raio que acessamos anteriormente. nostr:nevent1qqsxrkufrhpxpfe9yty90s8dnal89qz39zrv78ugmg5z2qvyteckfkqpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyr604d4k2mwrx5gaywlcjqjdevtkvtdjq4hmtzswjxjhf6zv2p23qqcyqqqqqqgrw73ux O NWC dá ao client ou app, a permissão de gerenciar sua carteira. Isso te permite enviar zaps sem sair do client ou precisar entrar no app da carteira.
Existem muitas outras carteiras lightning por aí, então além da coinos, deixarei o link de outras duas que utilizo.
WOS (Wallet of Satoshi)
Somente Play Store: https://play.google.com/store/apps/details?id=com.livingroomofsatoshi.wallet
Minibits
Play Store: https://play.google.com/store/apps/details?id=com.minibits_wallet Github: https://github.com/minibits-cash/minibits_wallet
Comunidades
Em uma #comunidade é possível encontrar respostas para suas perguntas, artigos e postagens de seu interesse, links úteis e tutoriais para burlar sistemas, documentos e estudos sem censura, etc. Aqui está um exemplo: nostr:nevent1qqs8qztlq26hhstz9yz2tn02gglzdvl5xhkpzhnpuh8v65mjldtdjlqpzamhxue69uhhyetvv9ujuvrcvd5xzapwvdhk6tczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqqqqgldlvdq Esse usuário recorrentemente atualiza a lista de comunidades brasileiras no Nostr, recomendo seguir o perfil para se manter atualizado caso tenha interesse: nostr:nevent1qqsxkusgt02pmz6mda4emjlnjjyd4y9pa73ux02dcry8vk3wp85aq9cpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqqqqgqq5zn5 Aqui vão algumas #curiosidades para usuários mais avançados: nostr:nevent1qqs246x86gw4zfp70wg65rjklf909n6nppwm0xx6mssl6jgznw4nkjcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgtkt83q Existem alguns clients que podem criar e gerenciar comunidades, caso você não encontrou nada de seu interesse e quer criar uma, os mais populares são:
Satellite.earth e noStrudel.ninja
Chats
Os #chats são espaços voltados a interação por meio de mensagens, aqui estão alguns: nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqqqqpgdaghw Para contatar uma pessoa no privado:
No Amethyst
- Clique no perfil da pessoa
- Clique no ícone de mensagem
- Envie uma mensagem
Caso queira criar um chat, siga os passos:
No Amethyst
- Clique no ícone de mensagens
- Clique no ícone de "+"
- Serão exibidas duas opções; "privado" e "público", escolha privado para um grupo de poucas pessoas e público para qualquer que quiser entrar.
- Adicione as especificações necessárias e seu chat será criado.
Seguidores
Existe uma #ferramenta capaz de identificar quais usuários que você segue estão inativos, ou publicam pouco e a longos hiatos: nostr:nevent1qqsqqqyhmkqz6x5yrsctcufxhsseh3vtku26thawl68z7klwvcyqyzcpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgmfzr67
Mais do Nostr
Existem muitas outras coisas para se explorar no Nostr, e é possível que daqui a uns meses, essas configurações e dicas estejam obsoletas. Explorem e aprendam mais sobre esse protocolo.
Abaixo estão mais algumas coisas que gostaria de compartilhar:
Muitos clients não possuem um sistema de #notificações, isso por conta da natureza #descentralizada dos apps, e para não ceder ao Google para isso, optaram por não ter notificações. O Amethyst por exemplo, só possui notificações ativas para quando você receber zaps. Mas esse problema foi resolvido com o #Pokey: nostr:nevent1qqsyw0m8wkwvzsanwufh6kmu3fkkjsu3x6jxxwxst5fxu3yld7q84cspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3q5wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8cssxpqqqqqqz4d5hj5
Aqui está um post sobre uma #loja de #apps voltada a apps do Nostr: nostr:nevent1qqsrk55p927srd30ukas79qzhlwhm5ls9l07g548y288s5u29najzrqpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg85l2mtv4kuxdg36gal3ypymjchvckmypt0kk9qayd9wn5yc5z4zqpsgqqqqqqskv0pek
Alguns RSS para quem gosta de notícias: nostr:nevent1qqsxctkju0pesrupvwfvzfr8wy3hgqag6r8v4228awgyf2x9htjqa7qpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qvg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsxpqqqqqqzn4acev
Algumas pessoas famosas que estão por aqui: nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqprwcjan
Alguns Nostr clients e outras coisas: nostr:nevent1qqsgx5snqdl2ujxhug5qkmmgkqn5ej6vhwpu4usfz03gt4n24qcfcwspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqp3pf6y2
Outros posts interessantes: nostr:nevent1qqsp6vf8pp6l97ctzq2wp30nfc9eupnu2ytsauyxalp8fe8dda6dvdgpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgtkju3h nostr:nevent1qqs0faflxswn5rg8fe9q3202en927my6kupcf08lt26ry3cg3xuuy3gpzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyzgmafwdjds4qnzqn2h5t9gknz8k3ghu6jp8vt7edxnum3ca73z3cqcyqqqqqqgsyrpkh nostr:nevent1qqspx9t3qfnsuzafxxuc5hyha9n5ul5v97uz57hfac9xdtvk5eygqggpzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qa5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqxpqqqqqqzctx6uf
Funcionalidades do Amethyst
• Reações (noStrudel também aceita)
nostr:nevent1qqst57p0pzw3vsx3n8g7eaa0dlx3kp5ys9rw3t367q5ewhdyw0kd2rspzamhxue69uhkjmnzdauzuct60fsk6mewdejhgtczyz36wgs59y6smv4etwgrygja4pwa69vj53hww0hd0wa38vtu5clzzqcyqqqqqqgpje0yu
• Markdown
nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpekll6f
Espero ter dado alguma direção pela qual seguir por aqui, se tiver dúvidas, pode comentar aqui abaixo e responderemos com o melhor que pudermos. Olhem alguns dos comentários abaixo, terão posts que os veteranos consideram importantes.
Aos veteranos, comentem abaixo caso tenha faltado algo, e complementem aos novatos, grato!
Mais uma vez, seja bem-vindo ao Nostr!
nóspossuímosaweb #awebénostr
-
 @ 57d1a264:69f1fee1
2025-05-02 05:16:39
@ 57d1a264:69f1fee1
2025-05-02 05:16:39Large Language Models (LLMs) have transformed software engineering, but their application to physical engineering domains remains underexplored. This paper evaluates LLMs' capabilities in high-powered rocketry design through RocketBench, a benchmark connecting LLMs to high-fidelity rocket simulations. We test models on two increasingly complex design tasks: target altitude optimization and precision landing challenges. Our findings reveal that while state-of-the-art LLMs demonstrate strong baseline engineering knowledge, they struggle to iterate on their designs when given simulation results and ultimately plateau below human performance levels. However, when enhanced with reinforcement learning (RL), we show that a 7B parameter model outperforms both SoTA foundation models and human experts. This research demonstrates that RL-trained LLMs can serve as effective tools for complex engineering optimization, potentially transforming engineering domains beyond software development.
PDF: https://arxiv.org/pdf/2504.19394
Source: https://arxiv.org/abs/2504.19394
originally posted at https://stacker.news/items/969083
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ b90c3cb7:1be67823
2025-03-14 11:33:12
@ b90c3cb7:1be67823
2025-03-14 11:33:12This guide uses cashu.me and the 0xchat app
First go to cashu.me. Make sure you've added a mint. I suggest mint.0xchat.com (note for newbies like I recently was, it's the number zero and not the letter O). Make sure you have some balance. Then hit SEND and choose ECASH.

Next type in a small amount to send. As always with bleeding-edge stuff accept the token can go poof. Only after you've typed in a number will you see the LOCK button appear next to the SEND button.

Hitting LOCK will reveal the "Receiver public key" field as below. This works for public keys generated within cashu.me (go to cashu.me settings) as well as for Nostr public keys.

Next copy your own public key (or that belonging to whoever you want to test this with) and head over to https://nostrcheck.me/converter/ and paste it in there. This will convert it to hex format, which is needed in this case.

After that go back to cashu.me and paste the hex format key in that field. It'll be in this red color "Invalid public key" state, don't worry.

Add 02 (number zero, number two) in front of the hex key. That'll make it valid. It's just the scheme. You'll see the locked icon appear next to the SEND button.

Then hit SEND and, voila, you now have a Cashu token that only the person in control of the nsec of whatever public key you used just then can redeem. Post it publicly to taunt others. (FYI the P2PK abbreviation there means pay-to-public-key.) Hit COPY to grab the token string.

Last up, open 0xchat. Assuming you're doing this yourself, make sure you're logged in with the nsec of the public key you used to create the test token. Also make sure the token string resides in the clipboard of the device you're using 0xchat on.

Then go to th "Me" tab in 0xchat to open the Cashu wallet. Set it up if you haven't already. Hit "Receive" and then "Redeem Ecash". As long as the token is in your clipboard and you did it all the steps right it should be redeem straight to your Cashu wallet. Well hopefully.
That's it. This guide will self-descrut if it goes out of date or was wrong somehow.
-
 @ 3ffac3a6:2d656657
2025-05-02 03:50:51
@ 3ffac3a6:2d656657
2025-05-02 03:50:51Introduction: Don't Despair—This Can Be Fixed (But Don't Reboot Yet)
Running ZFS on a Raspberry Pi offers powerful features for home servers and personal NAS setups. But with power comes complexity, and in recent months, a quiet pitfall has emerged for Pi users who track kernel updates closely: upgrading to an unsupported kernel version breaks ZFS.
⚠️ Important Warning: If you've just upgraded your kernel and you're using ZFS, do not reboot yet. Rebooting without a working ZFS module can leave your system unbootable—even if you don't have critical partitions on ZFS. The system may hang because it tries to load the missing ZFS kernel module during boot and fails, halting the boot process.
If you're already facing a broken setup or can't boot — don't panic. This guide outlines both the worst-case scenario and the ideal recovery strategy. Whether you're locked out or preparing for a smooth upgrade, we've got you covered.
The Problem: A Kernel Update Too Far
As of ZFS version 2.2.3 (used in Debian-based Raspberry Pi OS), the filesystem supports Linux kernels up to 6.7. However, Raspberry Pi OS backports recently began shipping 6.12.x kernels. If you upgrade to 6.12 without precautions:
- ZFS will fail to compile against the new kernel
- DKMS errors will appear during package updates
- Your ZFS module will be missing after reboot
- Your Raspberry Pi may fail to boot, even without ZFS-mounted root or critical paths, simply due to systemd or boot scripts expecting the kernel module to be present
Example ZFS Compilation Error:
During package updates or installs, you'll see something like:
checking whether bdev_open_by_path() exists... configure: error: *** None of the expected "blkdev_get_by_path()" interfaces were detected. *** This may be because your kernel version is newer than what is *** supported, or you are using a patched custom kernel with *** incompatible modifications. *** *** ZFS Version: zfs-2.2.3-1~bpo12+1~rpt1 *** Compatible Kernels: 3.10 - 6.7This error means ZFS cannot build its kernel module against Linux 6.12.x, making it unusable.
Why This Happens: The Version Trap
The key problem is that ZFS 2.2.3 remains installed even after a kernel upgrade, and it doesn't get upgraded automatically during
apt upgrade. Since ZFS 2.2.3 only supports up to kernel 6.7, it fails to compile against 6.12.x.However, if you remove and then reinstall ZFS, the package manager installs ZFS 2.3.1, which does support Linux kernel 6.12.x. This version transition is what resolves the issue — but only if you explicitly purge and reinstall ZFS.
Worst Case: The System That Wouldn’t Boot
After upgrading the kernel and rebooting, the system failed to boot properly. It showed errors like:
cannot open access to console, the root account is locked
Although the system did not have critical filesystems on ZFS, the boot process still stalled because system services attempted to load the ZFS kernel module, which was no longer available. This resulted in an unrecoverable boot failure.
The only way forward was to reformat and reinstall Raspberry Pi OS. However, the default Raspberry Pi OS image still comes with a 6.6.x kernel, which is incompatible with ZFS 2.3.1 and newer kernels unless upgraded. Therefore, the recovery process requires one crucial step:
- First, perform a full system upgrade:
sudo apt update && sudo apt full-upgradeThis brings the kernel up to 6.12.x.
- Then, reinstall ZFS:
sudo apt install zfs-dkms zfsutils-linuxOnce this is complete, your system will be running kernel 6.12 with ZFS 2.3.1, and you can safely import your pools and resume operations.
Best Case Recovery: Clean Cut, Clean Upgrade
For users who can still log into their system, here's the cleanest and safest sequence to move forward:
- Stop all services using ZFS, including Docker, NFS, Samba, backup tools, etc.
- Export all ZFS pools:
sudo zpool export -a3. Disable swap if it lives on a ZFS vdev:sudo swapoff /dev/sdXn4. Purge ZFS packages:sudo apt purge zfsutils-linux zfs-dkms zfs-zed sudo rm -rf /usr/src/zfs* /var/lib/dkms/zfs5. Update the kernel to the desired version:sudo apt update && sudo apt full-upgrade6. Reboot into the new kernel:sudo reboot7. Reinstall ZFS:sudo apt install zfs-dkms zfsutils-linux8. Import your pool(s):sudo zpool import poolname9. Restart services that depend on ZFS.
Final Notes: Prevention Is Better Than Recovery
To avoid this issue in the future:
- Hold your current working kernel version:
sudo apt-mark hold linux-image-rpi-v8 linux-headers-rpi-v8* Or track ZFS GitHub for kernel compatibility before upgrading * Or test upgrades on a second Pi or cloned SD card before rolling them out to production
Conclusion: A Solvable Trap
ZFS on the Raspberry Pi remains a powerful option, but it demands careful version tracking. If you upgrade responsibly, or recover cleanly as described above, you can continue benefiting from advanced features like snapshots, send/receive, and compression even on this tiny powerhouse.
Don’t let a kernel update ruin your storage plans—with preparation, the Pi + ZFS combo can remain stable and strong.
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ 0461fcbe:35a474dd
2025-03-13 23:10:12
@ 0461fcbe:35a474dd
2025-03-13 23:10:12Background
I will start with a disclaimer: I'm all-in on Nostr. But before that, I spent 4 years building on ActivityPub. Then in Feb 2023 I built a bridge between ActivityPub and Nostr, and in Dec 2024 I built another bridge between Nostr and Bluesky. Most of all I am committed to open source and the decentralized vision. Having experience with all 3 major protocols, I still think Nostr is the best, but Bluesky outshines it in some major areas. The main reason for this blog is to explore the things Bluesky does better than us, and to point out why I still think Nostr is the best solution.
This is a technical blog. For a more high level overview of decentralized protocols, see: https://soapbox.pub/blog/comparing-protocols/
Data Model
Nostr and Bluesky both allow users to store any type of data in a single, unified format. Nostr calls them events. Bluesky calls them records. They are mostly interchangeable ideas, but the way the data is stored and retrieved is very different.
It's worth noting that, like Nostr and ActivityPub, Bluesky is capable of doing anything under the sun. It's a misconception that it can't. You can build whatever Reddit, TikTok, or other stuff clone on Bluesky just fine. It's limited more by the huge knowledge gap you have to overcome than it is by anything about its data model.
NSIDs vs Kinds
Nostr events use a "kind" number, eg
1, to distinguish different type of events. Bluesky records use what they call an "NSID" (namespace identifier), egapp.bsky.feed.post, which is a reverse-DNS string notation.Nostr's
"kind": 1is equivalent to Bluesky's"$type": app.bsky.feed.post.I think Bluesky's system is better, because it allows developers to feel like what they built is "real" without having to get it merged into the NIPs repo, which is basically like an IANA of Nostr kind numbers. I believe this causes significant problems on Nostr, and makes people feel like they are being held back by others. That being said, the counter-argument is that kind numbers encourage interoperability for the very same reasons. The barriers to adding new kinds pushes people to work with what's already there.
Text Content Formatting
Kind 1 events ("plain text notes", ie "Tweets") on Nostr have developed in a haphazard way over time, by many people piling things onto it without taking a step back to assess a unified way to handle it. Some examples include:
- NIP-21
nostr:URIs imetatags- inline media embeds as URLs without
imetatags - unspec'd Markdown rendering by some clients
- legacy specs such as positional mentions (eg,
#[0], mostly gone now)
What we have now is quite a mess, and it's something Bluesky beats us on badly.
Bluesky has a plaintext content field that can be displayed as-is. In addition, it has a "facets" field, which is a structured JSON object, that adds rich-text information such as formatting (bold, italic, etc), links, mentions of users, and whatever else metadata about the text.
This is an extensible system that beats even options like Markdown, due to its ability to include native extension like mentions, and its ability to be parsed by any programming language or software environment.
Bluesky is the winner here.
Syncronization
Nostr and Bluesky are both thought to be descended from Scuttlebutt, an older decentralized protocol.
On Scuttlebutt, a user's whole post history needed to be available for them to make a new post. Scuttlebutt uses a linked list, so each new event would need to reference the one before it. Only linear paths are allowed, so if a "fork" occurred (intentionally or not), only one version would be kept, and the other discarded. This lead to occasional publishing issues, but it allowed readers to assemble a complete view.
Nostr strayed from this draconian approach, removing it entirely and allowing user data to be fragmented. Meanwhile Bluesky, instead of removing it entirely, made it work more like git so that branches could be merged.
Both approaches have tradeoffs. Bluesky's approach has much higher complexity. Also, it's sometimes considered an advantage for events to be fragmented (eg Nostr allows sending DMs to specialized relays for enhanced privacy).
But Bluesky has a true account "sync" mechanism, and Nostr does not. Nostr can send filters to relays to gather events, but it cannot know when to stop looking. Proposals like Negentropy in Nostr do not solve author syncing, and only make typical relay filtering more efficient.
I think it's important to think about Nostr's "outbox" problem as a syncronization problem, and for Nostr to approach syncronization with the goal of syncronizing authors specifically.
I think Bluesky "wins" this one, if only because they have solved a problem that we haven't. Instead of copying their solution, I think Nostr should try to learn from this to recharacterize the "outbox" problem as an author syncing problem, and see if we can come up with a better solution that works for Nostr.
Knowledge Gap
One of the biggest hurdles of Bluesky, and by extension one of the greates appeals of Nostr, is in how easy it is to learn and build on.
Nostr can be understood in a couple of hours. Mastering it is difficult, but limited only by your time and imagination. Hundreds of developers are building new projects on Nostr today. Based on my experience, it seems to me that the Nostr developer community is larger than that of both ActivityPub and Bluesky combined.
Bluesky on the other hand requires a Harvard degree in Blueskyology. I believe that ameteur coders feel a sense of superiority after spending six weeks learning how to commit a post. To learn Bluesky you will have to sift through thousands of technical documents about all kinds of abstractions, especially related to IPFS and IPLD. You will have to master unnecessary technologies like CBOR (which is basically just JSON except it's in binary and takes up the same amount of space). And you will be frequently pointed to academic topics such as "DAG" and "graph theory", all just to say "it's a fucking graph". I will never understand why people will take simple concepts such as a "tree", and then make it harder to understand on purpose by saying it's more than that.
While building on Bluesky, I began to question if the creators did this on purpose. I wondered if they tried to make it complex on purpose, as a sort of IQ test and protective measure to weed out the undeireables. In my view, a truly free and open network must be accessible to all, with the hope that even non-programmers could learn how it works.
Technical complexity is not just an issue of inclusion, but also security. ActivityPub software has been found to be littered with major security holes due to its inherently complex design, while Nostr's simple design makes its attack surface extremely minimal. Bluesky has already had a few mishaps, and it makes me wonder how Bluesky will fare in the long term.
Decentralization
I will keep this short. Bluesky is designed to be decentralized, but isn't. It reminds me of the communist idea about the "withering away of the state". The idea is that you're supposed to first sieze power and become the new state, and then under your rule the state will slowly disappear because you are doing all the right communist things. I think this is basically how Bluesky sees itself (whether they agree with the analogy or not).
Nostr is decentralized, but it is a loaded gun. You're more likely to kill yourself with a gun than someone else. This is on purpose, because it wholly embraces the consequnces of being truly decentralized.
In my view Nostr gets it right. Social media has been done to death by now, so I do not think it's worth the compromise to prioritize UX over decentralization. If that's the case we have not fixed anything. It's best to start with the purist idea and work backwards to UX, rather than start with UX and work backwards to decentralization. Many people have already written extensively about the decentralization of Bluesky, so I'll leave it at that.
- NIP-21
-
 @ dc4cd086:cee77c06
2024-10-18 04:08:33
@ dc4cd086:cee77c06
2024-10-18 04:08:33Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 502ab02a:a2860397
2025-05-02 03:05:18
@ 502ab02a:a2860397
2025-05-02 03:05:18เราได้อ่านเรื่อง EVERY eggwhite ไปแล้วคิดว่าเขาจะหยุดแค่นี้ไหมครับ 555555 ไม่มีทางครับ การคืบคลานต้องมีต่อไป วันนี้จะมาในตอนที่ชื่อว่า
EVERY Egg ไข่ยุคใหม่ที่ไม่ต้องใช้แม่ไก่อีกต่อไป ลองนึกภาพ "ไข่เจียว" ที่ไม่มีแม่ไก่เกี่ยวข้องแม้แต่ขนไก่สักเส้น...ใช่เลยจ้ะ โลกตอนนี้ไปถึงจุดที่ ไข่ สามารถผลิตได้จาก “ยีสต์” ที่ถูกดัดแปลงพันธุกรรม เพื่อให้มันสร้าง “โปรตีนไข่” แบบเดียวกับในธรรมชาติ โดยไม่ต้องผ่านแม่ไก่ ไม่ต้องมีเปลือก และแน่นอน...ไม่มีเสียงขันตอนเช้าอีกต่อไป
ผู้เล่นที่น่าจับตาที่สุดคือบริษัท EVERY Company จาก Silicon Valley เจ้าเดิมที่เปิดตัวผลิตภัณฑ์ใหม่ในชื่อ EVERY Egg ซึ่งเป็น “ของเหลว” ที่หน้าตาเหมือนวิปไข่ไก่ แต่เบื้องหลังคือกระบวนการผลิตระดับไซไฟ! พวกเขาใช้เทคนิคที่เรียกว่า precision fermentation หรือ “การหมักแม่นยำ” เพื่อสั่งให้ยีสต์สร้างโปรตีน ovalbumin (โปรตีนหลักในไข่ขาว) และ lysozyme (สารฆ่าเชื้อแบคทีเรียตามธรรมชาติในไข่) ออกมา จากนั้นก็เอามาผสม เติมแต่ง แต่งกลิ่น เติมสี ใส่สารกันเสียเล็กน้อย...ปิ๊ง! ได้ไข่ที่ไม่มีไข่ ได้ใจประชาชนที่กินสารอาหารแบบคลั่งตัวเลข
จุดขายที่ EVERY Company ใช้ในการนำเสนอ EVERY Egg สลุตมาเป็นตับ ตับ ตับ แบบนี้ครับ 1. High quality egg protein ใช้โปรตีน ovalbumin ที่ได้จากกระบวนการ fermentation ด้วย precision fermentation จากยีสต์สายพันธุ์ Pichia pastoris ซึ่งเป็น โปรตีนหลักในไข่ขาวธรรมชาติและเคลมว่าให้คุณสมบัติเทียบเท่าหรือดีกว่าไข่จากไก่ในเรื่องโครงสร้างโปรตีนและการทำงานในอาหาร เช่น การตีขึ้นฟู (foaming) และการอิมัลซิไฟ คุณเอ๊ยยยย ฟลัฟฟลี่สุดๆ 555 2. No hens used เป็น selling point หลักที่สื่อสารหนักมากในเชิง “ไม่เบียดเบียนสัตว์” ดูมีคุณธรรม จึงถูกจัดเป็นมังสวิรัติ (vegan-friendly) แม้จะได้จากจุลินทรีย์ที่ออกแบบให้ผลิตโปรตีนที่เหมือนจากสัตว์ จุดนี้ล่อใจผู้บริโภควีแกนและกลุ่มที่ต่อต้านฟาร์มอุตสาหกรรมอย่างเต็มๆ พร้อมถวิลหา 3. No cholesterol ยังเป็นจุดขายหลักได้ตลอดกาลกับการครอบงำให้กลัวคอเลสเตอรอล เพราะผลิตจากจุลินทรีย์ ไม่ใช่จากสัตว์จริง ๆ จึงไม่มีคอเลสเตอรอลเลย ซึ่งเป็นข้อได้เปรียบเทียบกับไข่ไก่ที่มีคอเลสเตอรอลตามธรรมชาติ 4. No saturated fat พอๆกันครับ ยังเป็นจุดขู่จุดขายได้ตลอดกาลเช่นเดียวกับคอเลสเตอรอล โปรตีนที่ผลิตจากยีสต์ไม่มีไขมันอิ่มตัวเช่นเดียวกับผลิตภัณฑ์จากสัตว์จริง 5. No artificial flavors แหม่ พยายามสร้างภาพลักษณ์ว่าเป็น clean label ไม่ใช้แต่งกลิ่นหรือสารเติมแต่งรส (แม้จะเป็นผลิตภัณฑ์ที่ผ่านกระบวนการขั้นสูงมากก็ตาม) 6. No salmonella จุดที่คนโคตรกลัวเลยในไข่ สังเกตุไหมว่า จัดหนักจัดเน้นขยี้ความกลัวของคนได้ทุกจุด อย่างอันนี้เนื่องจากไม่มีสัตว์เข้ามาเกี่ยวข้องในการผลิต ทำให้โอกาสปนเปื้อนเชื้อซัลโมเนลลาที่พบบ่อยในไข่สดแทบเป็นศูนย์ เป็นจุดขายด้านความปลอดภัยอาหาร (food safety) ที่เขาเน้นมาก
เท่านี้ยังไม่พอครับ คำถามที่คนต้องสงสัยแน่นอนคือ ชนิดของกรดอมิโนหละครบไหม pain point ของชาววีแกน เนื่องจาก EVERY Company ใช้เทคนิค “Precision Fermentation” โดยใส่ยีนจากไก่ลงไปในยีสต์ เพื่อให้ผลิต ovalbumin ได้เหมือนในธรรมชาติ จึงทำให้โครงสร้างของกรดอะมิโนในโปรตีนนี้ เหมือนไข่จริงแทบ 100% โปรตีน ovalbumin ที่ใช้ผลิต เป็น primary protein จึงถือว่าเป็น โปรตีนมาตรฐาน (reference protein) ในทางโภชนาการ เพราะมี กรดอะมิโนจำเป็นทั้ง 9 ชนิด ในปริมาณที่เพียงพอ ได้แก่ Leucine, Lysine, Valine, Isoleucine, Threonine, Methionine, Phenylalanine, Tryptophan, Histidine
แต่... แม้จะมีกรดอะมิโนครบ ก็ยังมีเรื่องให้คิด โปรตีนนี้ ไม่มาจากธรรมชาติ โดยตรง แต่ผ่านการผลิตจากสิ่งมีชีวิตดัดแปลงพันธุกรรม (GMO yeast) ยังไม่มีข้อมูลชัดเจนเรื่อง bioavailability (การดูดซึม) เมื่อเทียบกับไข่จริง และที่สำคัญ คือการบริโภค “complete protein” ไม่ได้แปลว่า ปลอดภัยในระยะยาว ถ้าพื้นฐานมันคือ GMO จากแลปที่ไม่มีวิวัฒนาการร่วมกับมนุษย์ แน่นอนว่ามันยังต้องการ "ตลาดทดลอง" เพื่อทดลองและเก็บข้อมูลประกอบสินค้าในระยะเวลานึง เข้าใจไหม "หนูๆ"
คำถามคือ โปรตีนแท้...หรือแค่ “เลียนแบบ” EVERY Egg บอกว่าเขาสร้างโปรตีนเหมือนไข่เป๊ะชนิดที่ว่าเชฟชื่อดังยังแยกไม่ออก (ถ้าไม่ดูฉลาก) สามารถนำไปทอด ทำไข่คน ไข่เจียว โอ๊มเล็ต ได้เหมือนไข่จริงทุกประการ แถมยังไม่มีคอเลสเตอรอล ไม่มีไขมันอิ่มตัว มีแต่ “โปรตีนล้วนๆ” แบบคลีนๆ
แต่ตรงนี้แหละที่มันเริ่ม น่าสงสัย เพราะการไม่มีไขมันเลย มันก็คือการตัดเอา matrix ทางโภชนาการ ที่ธรรมชาติออกแบบมาให้เราย่อยง่าย ดูดซึมวิตามินได้ดี และช่วยให้เรารู้สึกอิ่มแบบธรรมชาติ ไข่แท้จากไก่ ไม่ใช่แค่แหล่งโปรตีน แต่มันคือ “ของขวัญจากธรรมชาติ” ที่มีทั้ง choline, lutein, zeaxanthin, วิตามิน A, D, E, B12, โอเมก้า-3, ไขมันดี และเลซิธิน อยู่ครบทุกอนู ช่วยทั้งสมอง ดวงตา และตับ
ในขณะที่ EVERY Egg คือ “ไข่ที่เราอยากให้มันเป็น” มากกว่า “ไข่ที่ธรรมชาติอยากให้เราได้กิน”
บริษัท The EVERY Company ได้ร่วมมือกับเชฟระดับสุดยอดมากมาย ซึ่งการร่วมมือครั้งนี้มีเป้าหมายเพื่อแสดงให้เห็นว่าโปรตีนไข่ที่ผลิตจากกระบวนการ precision fermentation ของ EVERY Egg สามารถตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศได้ เรามาดูตัวอย่างกันครับว่า มีที่ไหนบ้าง
-
Eleven Madison Park โดย เชฟ Daniel Humm (มิชลิน3 ดาว ที่นิวยอร์ก) EVERY Egg เปิดตัวครั้งแรกในปี 2023 ที่ร้าน Eleven Madison Park ซึ่งเป็นร้านอาหารระดับมิชลิน 3 ดาว ในนิวยอร์ก โดยเชฟ Daniel Humm ได้สร้างสรรค์เมนูพิเศษที่ใช้ EVERY Egg เป็นส่วนประกอบหลัก เช่น ออมเล็ต ค็อกเทล และของหวาน เพื่อแสดงถึงความสามารถของผลิตภัณฑ์นี้ในการตอบสนองมาตรฐานสูงสุดของวงการอาหารชั้นเลิศระดับ fine dining มิชลิน
-
Chantal Guillon (ร้านมาการองฝรั่งเศสในซานฟรานซิสโก) EVERY Company ได้ร่วมมือกับร้านขนม Chantal Guillon ในการผลิตมาการองที่ใช้ EVERY EggWhite™ ซึ่งเป็นโปรตีนไข่ขาวที่ผลิตจากกระบวนการ precision fermentation โดยไม่มีการใช้ไข่จากไก่เลย ผลิตภัณฑ์นี้ได้รับการยอมรับว่าให้รสชาติและเนื้อสัมผัสที่เทียบเท่ากับไข่ขาวธรรมชาติ
-
The Vegetarian Butcher เป็นแบรนด์ในเครือ Unilever ตามที่ได้เคยให้ข้อมูลไปแล้ว EVERY Company ได้จับมือกับ The Vegetarian Butcher ซึ่งเป็นแบรนด์อาหารมังสวิรัติในเครือ Unilever เพื่อพัฒนาและผลิตผลิตภัณฑ์ที่ใช้โปรตีนไข่จาก EVERY Egg โดยมีเป้าหมายในการลดการใช้สัตว์ในห่วงโซ่อาหารและส่งเสริมความยั่งยืนในอุตสาหกรรมอาหาร
-
Grupo Palacios ผู้ผลิต Spanish Omelet รายใหญ่ของโลก EVERY Company ได้ร่วมมือกับ Grupo Palacios ซึ่งเป็นผู้ผลิต Spanish Omelet รายใหญ่ของโลก โดยนำ EVERY Egg มาใช้ในผลิตภัณฑ์ของตน เพื่อเป็นทางเลือกที่ปลอดภัยและยั่งยืนต่อไข่ไก่ธรรมชาติ ซึ่งอาจมีปัญหาเรื่องการปนเปื้อนและความไม่แน่นอนในการผลิต
Fiat Egg บนเส้นทางเดียวกับ Fiat Food เฮียชวนให้มองภาพใหญ่เหมือนเวลาเรายืนอยู่บนดาดฟ้าแล้วมองลงไปที่ตลาด... ผลิตภัณฑ์อย่าง EVERY Egg ไม่ใช่แค่การสร้าง “ของใหม่” แต่มันคือการ เปลี่ยนแปลงพื้นฐานของอาหาร ด้วยแนวคิดแบบ “Fiat” เป๊ะ Fiat Food คืออาหารที่ไม่ได้เกิดจากธรรมชาติ แต่ถูก “กำหนดให้มีคุณค่า” โดยอุตสาหกรรม Fiat Money คือเงินที่ไม่ได้มีมูลค่าในตัวเอง แต่รัฐบาลบอกให้เรายอมรับมันเป็นเงิน
ในโลกนี้ ถ้า “ไข่” ไม่ต้องมาจากแม่ไก่ “นม” ไม่ต้องมาจากเต้า และ “เนื้อ” ไม่ต้องมาจากวัว แต่ใช้แค่สารเคมี + ยีสต์ + กราฟ + กลิ่นสังเคราะห์ = “ของกินได้” แล้วมันจะเหลือความเป็น อาหารแท้ (real food) อยู่อีกไหม?
เบื้องหลังที่เราควรถามให้ลึก แม้ว่า EVERY จะอ้างว่าโปรตีนจากยีสต์ของเขา “ปลอดภัยและยั่งยืน” แต่ยังไม่มีข้อมูลด้าน long-term health impact ยังไม่มีข้อมูลว่ายีสต์ GMO ที่ใช้ จะกระตุ้นภูมิแพ้หรือมีสารตกค้างหรือไม่ ยังไม่รู้ว่าสารแต่งกลิ่น รส และตัวพาอื่นๆ ที่ใส่ใน EVERY Egg จะส่งผลอะไรกับ microbiome หรือฮอร์โมนของเราในระยะยาว แต่นั่นก็คงมาพร้อมกับคำตอบหรูๆหล่อๆว่า "ขอให้มั่นใจในกระบวนการผลิตที่ทันสมัยและดีเยี่ยม" . . . ตามเคย
และที่น่าสนใจคือ...ผลิตภัณฑ์ EVERY Egg ยังไม่ได้รับการรับรอง GRAS (Generally Recognized As Safe) อย่างเป็นทางการจาก FDA จึงยังไม่สามารถวางจำหน่ายในร้านค้าปลีกทั่วไปได้ บริษัทกำลังร่วมมือกับบริษัทอาหารข้ามชาติในการเปิดตัวผลิตภัณฑ์ในปีนี้ แต่ยังไม่มีข้อมูลชัดเจนเกี่ยวกับการวางจำหน่ายในร้านค้าปลีกทั่วไป แต่ส่วนตัวเฮียคิดว่าไม่น่ากังวล น่าจะผ่านฉลุยแหละ 5555
ไข่สังเคราะห์ = ความหวัง? หรือกับดักในรูปของนวัตกรรม? เราคงไม่ปฏิเสธว่ามีหลายคนบนโลกที่แพ้ไข่จริง หรือห่วงใยเรื่องสวัสดิภาพสัตว์ รวมถึงต้องการความ "บริสุทธิ์" "สกัด" "เข้มข้น" แต่คำถามคือ...จะดีกว่าไหมถ้าเราหาทางผลิต ไข่จริงจากไก่ที่เลี้ยงแบบธรรมชาติ ในระบบ regenerative farming แทนที่จะพยายามสร้างโปรตีนปลอมขึ้นมาแข่ง? ทุกครั้งที่มีของใหม่ที่ดูดี สะอาด และ “คลีน” เฮียอยากให้ทุกคน ถามกลับในใจว่า “คลีน” แค่ในห้องแล็บ หรือ “คลีน” ในธรรมชาติจริงๆ?
สรุปแบบไม่ต้องตีลังกาคิดได้ว่า EVERY Egg คือก้าวใหม่ของเทคโนโลยีอาหารที่กำลังวิ่งไปข้างหน้าแบบไม่เหลียวหลัง แต่ในฐานะที่เฮียเชื่อใน real food, nutrient density และความฉลาดของธรรมชาติ เราอาจต้องเตือนใจไว้ว่า...การใช้ยีสต์ดัดแปลงพันธุกรรมมาผลิต “ไข่เทียม” ไม่ใช่ความผิด แต่ก็ไม่ใช่ความจำเป็นไหม เพราะแท้จริงแล้ว เรามี “ไข่” ที่สมบูรณ์แบบอยู่ในธรรมชาติแล้ว...แค่ไม่ควรปล่อยให้อุตสาหกรรมทำลายภาพลักษณ์ของมัน เพื่อขายของที่ “เหมือนไข่” แต่ไม่มีชีวิต
คำถามเดิมครับ วันนึงเมื่อถึงจุดที่คุณไม่ได้เลือก แล้วมันมีให้แค่นี้ วันนั้นจะทำอย่างไร วันแห่งความ "บริสุทธิ์" "สกัด" "เข้มข้น" ที่เราถวิลหา ??? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ fd0bcf8c:521f98c0
2025-05-02 02:02:13
@ fd0bcf8c:521f98c0
2025-05-02 02:02:13Bitcoin
It stands alone. Immutable. Unyielding. It records without mercy. Each transaction cuts deep. Some carry wealth. Others just data. The debate rages on.
OP_RETURN
It divides us all. Bloat versus freedom. Money versus use. Simple versus complex.
Nodes
They bear heavy weight. Each byte costs something. Storage grows. Bandwidth drains. Money defenders stand guard.
"Our purpose is clear...Money serves one master." —Mises
Not art.
Not storage.
Not games.
The fee-payers
They disagree. "I paid. I belong." The miners take their cut. The highest fee wins. No questions asked. The protocol allows it.
"Accept what exists."—Marcus Aurelius
The chain is neutral. Always neutral.
What is a transaction?
None agree. Value transfer only? Or any valid data? The white paper speaks. "Electronic cash system." Yet code evolved. It grew teeth. It allows more now.
"Shitcoin"
Cuts both ways. A dangerous word. It keeps focus. It maintains unity. But it wounds creation. Makes builders desperate. They force ideas onto Bitcoin. They use OP_RETURN poorly. They bloat what needs no bloating. Seneca saw this coming...
"Fear makes suffering worse."
Innovation needs proper soil. Not forced transplants.
Money debates sharpen knives. Is Bitcoin gold? Is it currency? Mantras echo loudly.
"Digital gold."
_"Spend dollars, saving Bitcoin." _
"Never sell your Bitcoin."
Bitcoin becomes idol. Not tool. Mises would disapprove, "Money must move." Without exchange, it dies. If none spend, why fight bloat?
Rhetoric
It hurts us. "Shitcoin" closes minds. Forces square pegs round. Drives experiments home. To Bitcoin they return. Bearing misshapen plans.
"Knowledge exists in dispersion," Hayek warns.
Let ideas find homes. Let Bitcoin be Bitcoin.
Fees
They bring new problems. Users flee high costs. They seek cheaper chains. The wealthy still play games. They can afford the bloat. The poor cannot compete. The rich inscribe at will. Rothbard saw this trap, "Markets need equal rules."
Fee markets favor wealth. Always have. Always will.
Nodes must still run. Validators must validate. Decentralized. Resistant. Strong. The burden grows heavier. But principles matter most.
The battle
It continues. Hard words. Hard choices.
Bitcoin endures all. Money or platform? Gold or currency? The answers shift. The chain grows. Block by block. Byte by byte.
We need clearer words. Cleaner definitions. Less pride. More thought. Let Bitcoin be what it is. Not what we demand.
Bitcoin is human.
Not magical. Not divine. Fallible like its makers. A young experiment still. It could fail tomorrow.
"Nothing is too big to fail." —Satoshi
Our rhetoric needs maturity. Our definitions need clarity. Bitcoin needs humility. From all who touch the code.
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13
@ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13Wenn man etwas verkaufen will, muss man eine Geschichte über sein Produkt erzählen. Nur wenige können etwas damit anfangen, wenn du sagst: Unser Produkt enthält 50 Gramm Hafer (hoffentlich gentechnikfrei), 5 mittelgroße Erdbeeren, Spuren von Sesamschalen sowie einen Teelöffel Honig. So funktioniert das nicht. Dein Riegel braucht einen Namen und eine Geschichte.
Wenn wir über Krieg und Frieden sprechen, denn gibt es zumeist Zahlen, Fakten und Meinungen. Tausende von Kindern die in einem Krieg getötet werden sind eine schockierende Anzahl. Nimmst du die Zahlen weg und beschäftigst dich mit jedem einzelnen Schicksal, dann ist das unmöglich zu ertragen. Also kämpfen wir hier vor Ort, in Deutschland, zwar nicht mit Waffen gegeneinander, sondern mittels unserer Meinungen in Kombination mit zu vermittelnden relativen Wahrheiten. Da kommt das Ego ins Spiel. Wir wollen unbedingt Recht haben! Irgendeiner soll in diesem Meinungskampf am Ende als Gewinner dastehen. Weil er die besseren Argumente hat. Schließlich werden Emotionen mit Fakten vermischt und als Totschlagargumente in die Gegenfront geworfen.
Was aber, wenn man eine Geschichte über den Krieg erzählt, die jeden mitnehmen kann, ganz gleich, welche Meinung man zu den aktuell verhandelten Kampfschauplätzen hat? Alles Trennende wird aus der Erzählung herausgenommen und was bleibt, sind die zerstörerische Kraft des Krieges und die Verantwortung jedes einzelnen Menschen zu entscheiden, ob er dieses grausame Monster füttert oder eben nicht. In dem afrikanischen Märchen „Sheikhi“ basieren diese Entscheidungen nicht auf Fakten und Meinungen, sondern auf persönlichen Erfahrungen. Die Protagonisten nehmen uns mit in ihre Welt und lassen uns ihre inneren Kämpfe, Zweifel, Ängste und Hoffnungen miterleben. Wir können uns mit ihnen identifizieren, obwohl wir unter völlig anderen Bedingungen leben und sterben.
Hier kannst du das Buch direkt beim Verlag bestellen
Die alternative Buchmesse Seitenwechsel
Am Ende des Buches konnte ich gar nicht anders, als eine tiefe Sehnsucht nach Frieden und Einigkeit zu verspüren. Diese Sehnsucht basierte aber nicht mehr auf dem Bedürfnis, bessere Argumente als die vermeintliche Gegenseite zu haben, sondern vielmehr darauf, dass dieses verzweifelte Ringen und Hassen endlich zu einem Ende kommt. Nicht nur auf den Schlachtfeldern Asiens und Afrikas, sondern ebenfalls auf Facebook, X, den Straßen unserer Städte und im Krieg jedes Menschen gegen sich selbst. Inzwischen gelingt es mir immer öfter, mir einen bissigen Kommentar zu verkneifen, wenn jemand auf Facebook etwas schreibt, was ich unerträglich finde. Ich weiß, das ich ihn nicht vom Gegenteil überzeugen werde und das mein Kommentar das selbe Monster füttert, dass sich an den Opfern des Krieges satt isst.
Wenn es irgendwo Menschen auf der Welt gibt, die Mord und Folter verzeihen können, dann kann auch ich eine andere Meinung ertragen ohne rechthaberisch, arrogant und destruktiv zu werden. Notfalls gehe ich in den Wald und schreie.
-
 @ 6fc114c7:8f4b1405
2025-05-01 23:57:44
@ 6fc114c7:8f4b1405
2025-05-01 23:57:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 0176967e:1e6f471e
2024-07-27 11:10:06
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.