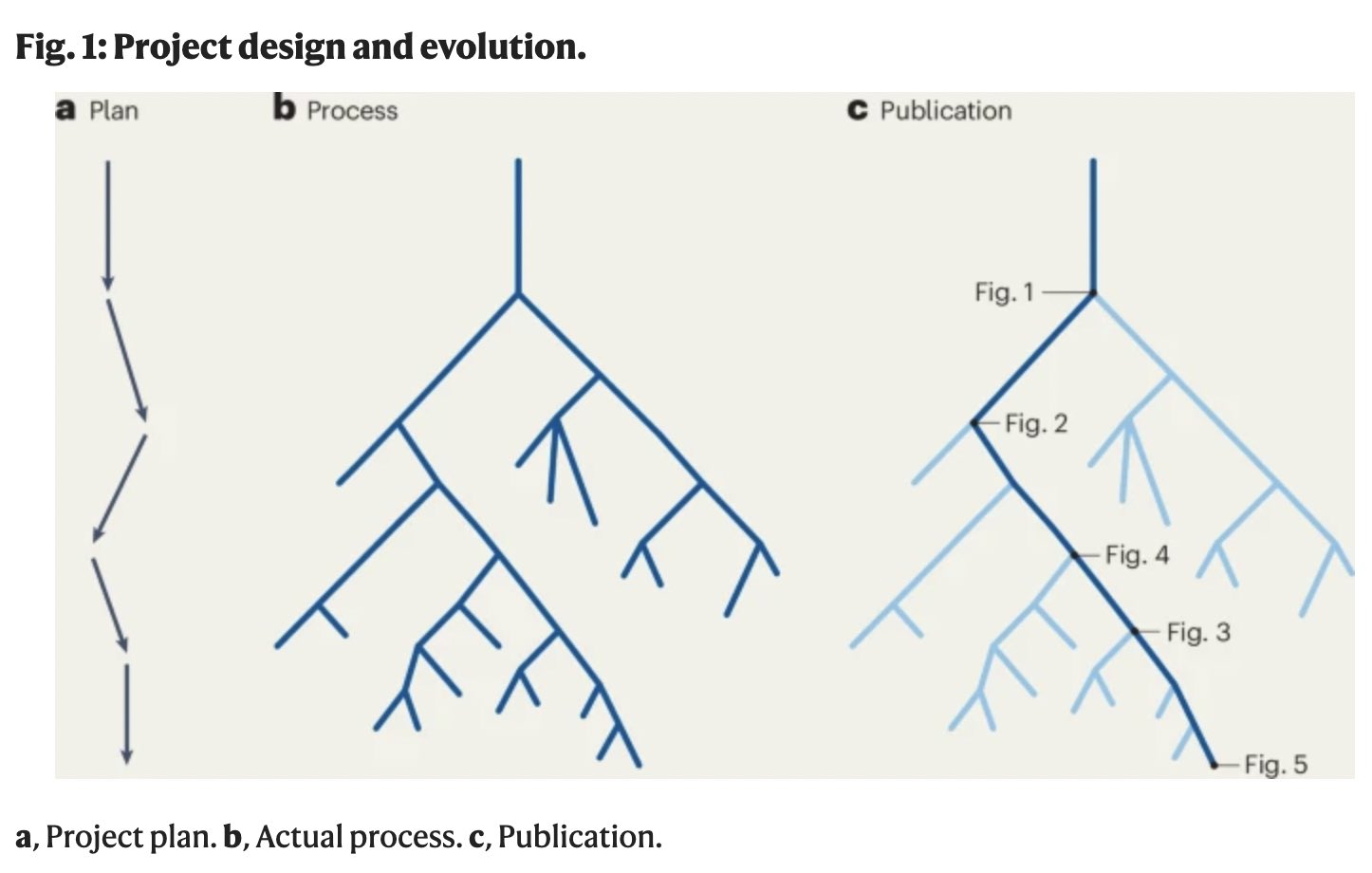
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 84b0c46a:417782f5
2025-05-04 10:00:28
@ 84b0c46a:417782f5
2025-05-04 10:00:28₍ ・ᴗ・ ₎ ₍ ・ᴗ・ ₎₍ ・ᴗ・ ₎
-
 @ 84b0c46a:417782f5
2025-05-04 09:49:45
@ 84b0c46a:417782f5
2025-05-04 09:49:45- 1:nan:
- 2
- 2irorio絵文字
- 1nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw
- 2
- 2
- 3
- 3
- 2
- 1
|1|2| |:--|:--| |test| :nan: |
 ---
---:nan: :nan:
- 1
- 2
- tet
- tes
- 3
- 1
-
2
t
te
test
-
19^th^
- H~2~O
本サイトはfirefoxのみサポートしています うにょ :wayo: This text will bounce wss://catstrr.swarmstr.com/
うにょうにょてすと
-
 @ 84b0c46a:417782f5
2025-05-04 09:36:08
@ 84b0c46a:417782f5
2025-05-04 09:36:08 -
 @ 1f79058c:eb86e1cb
2025-05-04 09:34:30
@ 1f79058c:eb86e1cb
2025-05-04 09:34:30I think we should agree on an HTML element for pointing to the Nostr representation of a document/URL on the Web. We could use the existing one for link relations for example:
html <link rel="alternate" type="application/nostr+json" href="nostr:naddr1qvzqqqr4..." title="This article on Nostr" />This would be useful in multiple ways:
- Nostr clients, when fetching meta/preview information for a URL that is linked in a note, can detect that there's a Nostr representation of the content, and then render it in Nostr-native ways (whatever that may be depending on the client)
- User agents, usually a browser or browser extension, when opening a URL on the Web, can offer opening the alternative representation of a page in a Nostr client. And/or they could offer to follow the author's pubkey on Nostr. And/or they could offer to zap the content.
- When publishing a new article, authors can share their preferred Web URL everywhere, without having to consider if the reader knows about or uses Nostr at all. However, if a Nostr user finds the Web version of an article outside of Nostr, they can now easily jump to the Nostr version of it.
- Existing Web publications can retroactively create Nostr versions of their content and easily link the Nostr articles on all of their existing article pages without having to add prominent Nostr links everywhere.
There are probably more use cases, like Nostr search engines and whatnot. If you can think of something interesting, please tell me.
Update: I came up with another interesting use case, which is adding alternate links to RSS and Atom feeds.
Proof of concept
In order to show one way in which this could be used, I have created a small Web Extension called Nostr Links, which will discover alternate Nostr links on the pages you visit.
If it finds one or more links, it will show a purple Nostr icon in the address bar, which you can click to open the list of links. It's similar to e.g. the Feed Preview extension, and also to what the Tor Browser does when it discovers an Onion-Location for the page you're looking at:
The links in this popup menu will be
web+nostr:links, because browsers currently do not allow web apps or extensions to handle unprefixednostr:links. (I hope someone is working on getting those on par withipfs:etc.)Following such a link will either open your default Nostr Web app, if you have already configured one, or it will ask you which Web app to open the link with.
Caveat emptor: At the time of writing, my personal default Web app, noStrudel, needs a new release for the links to find the content.
Try it now
Have a look at the source code and/or download the extension (currently only for Firefox).
I have added alternate Nostr links to the Web pages of profiles and long-form content on the Kosmos relay's domain. It's probably the only place on the Web, which will trigger the extension right now.
You can look at this very post to find an alternate link for example.
Update: A certain fiatjaf has added the element to his personal website, which is built entirely from Nostr articles. Multiple other devs also expressed their intent to implement.
Update 2: There is now a pull request for documenting this approach in two existing NIPs. Your feedback is welcome there.
-
 @ a296b972:e5a7a2e8
2025-05-04 08:30:56
@ a296b972:e5a7a2e8
2025-05-04 08:30:56Am Ende der Woche von Unseremeinungsfreiheit wird in der Unserehauptstadt von Unserdeutschland, Unserberlin, voraussichtlich der neue Unserbundeskanzler vereidigt.
Der Schwur des voraussichtlich nächsten Unserbundeskanzlers sollte aktualisiert werden:
Jetzt, wo endlich mein Traum in Erfüllung geht, nur einmal im Leben Unserbundeskanzler zu werden, zahlen sich für mich alle Tricks und Kniffe aus, die ich angewendet habe, um unter allen Umständen in diese Position zu kommen.
Ich schwöre, dass ich meine Kraft meinem Wohle widmen, meinen Nutzen mehren, nach Vorbild meines Vorgängers Schaden von mir wenden, das Grundgesetz und die Gesetze des Unserbundes formen, meine Pflichten unsergewissenhaft erfüllen und Unseregerechtigkeit gegen jedermann und jederfrau nicht nur üben, sondern unter allen Umständen auch durchsetzen werde, die sich mir bei der Umsetzung der Vorstellungen von Unseredemokratie in den Weg stellen. (So wahr mir wer auch immer helfe).
Der Antrittsbesuch des Unserbundeskanzlers beim Repräsentanten der noch in Unserdeutschland präsenten Besatzungsmacht wird mit Spannung erwartet.
Ein großer Teil der Unsereminister ist schon bekannt. Die Auswahl verspricht viele Unsereüberraschungen.
Die Unsereeinheitspartei, bestehend aus ehemaligen Volksparteien, wird weiterhin dafür sorgen, dass die Nicht-Unsereopposition so wenig wie möglich Einfluss erhält, obwohl sie von den Nicht-Unserebürgern, die mindestens ein Viertel der Urnengänger ausmachen, voll-demokratisch gewählt wurde.
Das Zentralkomitee der Deutschen Unseredemokratischen Bundesrepublik wird zum Wohle seiner Unserebürger alles daransetzen, Unseredemokratie weiter voranzubringen und hofft auch weiterhin auf die Unterstützung von Unser-öffentlich-rechtlicher-Rundfunk.
Die Unserepressefreiheit wird auch weiterhin garantiert.
Auf die Verlautbarungen der Unserepressekonferenz, besetzt mit frischem Unserpersonal, brauchen die Insassen von Unserdeutschland auch weiterhin nicht zu verzichten.
Alles, was nicht gesichert unserdemokratisch ist, gilt als gesichert rechtsextrem.
Als Maxime gilt für alles Handeln: Es muss unter allen Umständen demokratisch aussehen, aber wir (die Unseredemokraten) müssen alles in der Hand haben.
Es ist unwahrscheinlich, dass Unsersondervermögen von den Unserdemokraten zurückgezahlt wird. Dieser Vorzug ist den Unserebürgern und den Nicht-Unserebürgern durch Unseresteuerzahlungen vorbehalten.
Die Unserebundeswehr soll aufgebaut werden (Baut auf, baut auf!), die Unsererüstungsindustrie läuft auf Hochtouren und soll Unserdeutschland wieder unserkriegstüchtig machen, weil Russland immer Unserfeind sein wird.
Von Unserdeutschland soll nur noch Unserfrieden ausgehen.
Zur Bekräftigung, dass alles seinen unser-sozialistischen Gang geht, tauchte die Phoenix*in aus der Asche auf, in dem Unseremutti kürzlich ihren legendären Satz wiederholte:
Wir schaffen das.
Ob damit der endgültige wirtschaftliche Untergang und die Vollendung der gesellschaftlichen Spaltung von Unserdeutschland gemeint war, ist nicht überliefert.
Orwellsche Schlussfolgerung:
Wir = unser
Ihr = Euer
Vogel und Maus passen nicht zusammen
Ausgerichtet auf Ruinen und der Zukunft abgewandt, Uneinigkeit und Unrecht und Unfreiheit für das deutsche Unserland.
Unserdeutschland – ein Land mit viel Vergangenheit und wenig Zukunft?
Es ist zum Heulen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 1d7ff02a:d042b5be
2025-05-03 09:47:49
@ 1d7ff02a:d042b5be
2025-05-03 09:47:49ບົດຄວາມນີ້ແປມາຈາ: https://jackkruse.com/what-to-do-with-new-cancer-diagnosis/
ເນື້ອຫາສຳລັບຜູ້ອ່ານ: 1. ຈະເຮັດແນວໃດເມື່ອທ່ານໄດ້ຮັບການວິນິດໄສວ່າເປັນມະເຮັງ? 2. ສະໜາມຮົບກັບມະເຮັງທີ່ສຳຄັນແມ່ນຢູ່ບ່ອນການປິ່ນປົວແບບແພດ ຫຼື ໃນຮ່າງກາຍຂອງທ່ານເອງ? 3. ອາຫານການກິນມີບົດບາດແນວໃດ? 4. ຈະຮັບມືກັບໝໍມະເຮັງຄົນໃໝ່ຂອງທ່ານແນວໃດ? 5. ບໍ່ຕ້ອງຢ້ານທີ່ຈະສຳຫຼວດທຸກຄວາມເປັນໄປໄດ້ເພື່ອຊະນະສົງຄາມນີ້. ຮຽນຮູ້ກ່ຽວກັບອາຫານ ketogenic!!!
ກ່ອນທ່ານຈະອ່ານບົດຄວາມນີ້, ໃຫ້ເບິ່ງວິດີໂອນີ້: HYPERLINK
ບົດຄວາມນີ້ແມ່ນສຳລັບໜຶ່ງໃນໝູ່ທີ່ພິເສດຂອງຂ້ອຍ ຜູ້ທີ່ພົວພັນຂ້ອຍໃນອາທິດນີ້ ແລະ ບອກວ່າເມຍລາວຖືກວິນິດໄສວ່າເປັນມະເຮັງໃນໄວອາຍຸໜຸ່ມ. ຂ້ອຍໄດ້ຍິນຈາກການໂທ ແລະ ໂພສຂອງລາວໃນ Facebook ວ່າມັນກຳລັງທຳລາຍລາວ. ຂ້ອຍບອກລາວທັນທີໃຫ້ໄປຊື້ປື້ມ Anti Cancer: A New Way of Life ໂດຍ David Servan Schreiber ແລະ ມອບໃຫ້ເຈົ້າສາວຂອງລາວ. ຂ່າວດີກໍ່ຄືຫຼາຍລ້ານຄົນໃນຈຳນວນ 6 ລ້ານຄົນທີ່ກຳລັງປິ່ນປົວມະເຮັງໃນປະຈຸບັນຈະມີຊີວິດທີ່ສົມບູນຕໍ່ໄປ. ຈຳນວນຜູ້ລອດຊີວິດຕາມຄວາມຄິດເຫັນຂອງຂ້ອຍຍັງຕ່ຳເກີນໄປ (ປະມານ 45-50%). ນອກຈາກນັ້ນ, ຫຼາຍຄົນໃນຈຳນວນ 2000 ຄົນທີ່ເສຍຊີວິດຈາກມະເຮັງທຸກມື້ແມ່ນເນື່ອງຈາກຄອບຄົວຂອງພວກເຂົາບໍ່ຮູ້ກ່ຽວກັບຊັບພະຍາກອນທີ່ມີໃນປະຈຸບັນສຳລັບການປິ່ນປົວມະເຮັງທັງແບບດັ້ງເດີມ ແລະ ແບບທາງເລືອກ ເຊັ່ນ: ການປິ່ນປົວແບບເສີມ ຫຼື ແບບບູລະນາການ.
ເມື່ອຖືກວິນິດໄສດ້ວຍພະຍາດນີ້, ທ່ານຈະຮູ້ສຶກສັ່ນສະເທືອນຢ່າງຮຸນແຮງ. ສິ່ງສຳຄັນທີ່ທ່ານຕ້ອງຮູ້ແມ່ນພະຍາດນີ້ບໍ່ພຽງແຕ່ສາມາດຕໍ່ສູ້ໄດ້ແຕ່ຍັງສາມາດປ້ອງກັນໄດ້ຖ້າທ່ານຕັດສິນໃຈປ່ຽນແປງບາງສິ່ງທັນທີ ແລະ ປ່ອຍວາງຄວາມເຊື່ອທີ່ບໍ່ຖືກຕ້ອງທີ່ທ່ານໄດ້ສະສົມໃນຊີວິດ. ນີ້ເປັນຄວາມຈິງໂດຍສະເພາະຖ້າທ່ານເຮັດວຽກໃນຂົງເຂດສາທາລະນະສຸກ ແລະ ໄດ້ດຳລົງຊີວິດຕາມຄວາມເຊື່ອຕາຍຕົວຕະຫຼອດຊີວິດ. ປື້ມນີ້ຂຽນໂດຍແພດນັກຄົ້ນຄວ້າທີ່ບໍ່ພຽງແຕ່ຖືກກະທົບຈາກມະເຮັງ ແຕ່ຍັງເປັນມະເຮັງສະໝອງທີ່ອັນຕະລາຍທີ່ສຸດ. ລາວສາມາດຮື້ຖອນຄວາມເຊື່ອຂອງຕົນເອງໃນຖານະແພດດ້ວຍວິທະຍາສາດໃໝ່ທີ່ມີຢູ່ສຳລັບນັກຄົ້ນຄວ້າ ແຕ່ບໍ່ແມ່ນແພດມະເຮັງທົ່ວໄປ. ປື້ມນີ້ຈຳເປັນສຳລັບທຸກຄົນທີ່ເປັນມະເຮັງ ຫຼື ມີປັດໄຈສ່ຽງ ເພື່ອທ່ານຈະໄດ້ຊະນະກ່ອນມັນເລີ່ມ. ນີ້ແມ່ນໜຶ່ງໃນເຫດຜົນທີ່ຂ້ອຍຂຽນ QUILT ຂອງຂ້ອຍ ເພາະຂ້ອຍເຊື່ອວ່າຖ້າທ່ານປົກປ້ອງຈຸລັງຂອງທ່ານ ທ່ານຈະບໍ່ເປັນພະຍາດນີ້. ດຽວນີ້ ໝູ່ຂອງຂ້ອຍເປັນພະຍາດນີ້... ນີ້ແມ່ນບົດຄວາມກ່ຽວກັບສິ່ງທີ່ທ່ານອາດພິຈາລະນາເຮັດທັນທີຫຼັງຈາກປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ພິຈາລະນາຂໍຄວາມຄິດເຫັນທີສອງຈາກສູນມະເຮັງທີ່ສຳຄັນເຊັ່ນ MD Anderson.
-
ອ່ານປື້ມ Anticancer ທີ່ກ່າວເຖິງຂ້າງເທິງ. ມັນສຳຄັນທີ່ຈະເຫັນພະຍາດນີ້ໃນມຸມມອງໃໝ່.
-
ປ່ຽນອາຫານການກິນຂອງທ່ານທັນທີເປັນ Epi-paleo Rx ແລະ ອອກຫ່າງຈາກອາຫານແບບຕາເວັນຕົກມາດຕະຖານ.
-
ເລີ່ມເຮັດສະມາທິໂດຍໄວເທົ່າທີ່ຈະເປັນໄປໄດ້ເພື່ອຄວບຄຸມ cortisol ແລະ ຄວາມກັງວົນຂອງທ່ານ. (ທາງເລືອກບໍ່ສຳຄັນແຕ່ການເຮັດຈິງຊ່ວຍຊີວິດໄດ້)
-
ຄົນເຈັບຄວນປຶກສາຫາລືກ່ຽວກັບແຜນການປິ່ນປົວມະເຮັງ: ປັດໃຈສຳຄັນໃນມະເຮັງ: ຄວນຄົນເຈັບໃຊ້ອາຫານເສີມສຳລັບປະເພດມະເຮັງທີ່ທ່ານມີບໍ?
-
ພິຈາລະນາເລີ່ມລະບົບອາຫານເສີມ ລວມເຖິງ Curcumin, Reservatrol, Quercetin, ນ້ຳມັນປາ Omega ສາມ (ຄຸນນະພາບ Rx), ວິຕາມິນ D3 ໂດຍມີເປົ້າໝາຍເກີນ 50 ng/dl, ການໃຊ້ CoEnZQ10 ເປັນປະຈຳທຸກວັນ, R-alpha lipoic acid ແລະ ວິຕາມິນ K ທຸກມື້. ພິຈາລະນາການໃຊ້ N Acetyl Cysteine ທຸກວັນເຊັ່ນກັນ. ສັງເກດວ່າຂ້ອຍບໍ່ໄດ້ກຳນົດປະລິມານເພາະປະລິມານທີ່ຕ້ອງການສຳລັບການບຳບັດມະເຮັງແມ່ນສູງກວ່າທີ່ຈະໃຊ້ໃນການປ້ອງກັນ. ສິ່ງນີ້ຄວນເຮັດພາຍໃຕ້ການປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ຖ້າແພດມະເຮັງຂອງທ່ານບໍ່ເປີດໃຈກວ້າງກ່ຽວກັບບັນຫາເຫຼົ່ານີ້... ຫຼັງຈາກອ່ານປື້ມໃນຂັ້ນຕອນທີໜຶ່ງ ທ່ານອາດຈະຕ້ອງຊອກຫາແພດມະເຮັງຄົນໃໝ່. ເຫຼົ່ານີ້ແມ່ນສິ່ງທີ່ຂ້ອຍພິຈາລະນາວ່າເປັນອາຫານເສີມຫຼັກສຳລັບມະເຮັງສ່ວນໃຫຍ່ທີ່ມະນຸດເປັນ.
-
ໃນອາຫານຂອງທ່ານໃຫ້ເພີ່ມ ຂີ້ໝິ້ນ, ຂິງ, ກະທຽມ, ຣອດສະແມລີ, ແລະ ໃບແບຊິນ (ໃບໂຫລະພາ) ໃສ່ອາຫານຂອງທ່ານໃຫ້ຫຼາຍເທົ່າທີ່ຈະເປັນໄປໄດ້. ທ່ານຄວນດື່ມຊາຂຽວ 1 ລິດຕໍ່ມື້. ຊາຂຽວມີ L-Theanine ທີ່ຊ່ວຍຫຼຸດຄວາມກັງວົນ ແຕ່ຍັງເປັນສ່ວນເສີມຂອງຢາເຄມີບຳບັດໂດຍເຮັດໃຫ້ພວກມັນມີປະສິດທິພາບຍິ່ງຂຶ້ນ. ທ່ານຍັງສາມາດໃຊ້ສານສະກັດຊາຂຽວຖ້າທ່ານບໍ່ຕ້ອງການດື່ມຂອງແຫຼວຫຼາຍ ຫຼື ບໍ່ສາມາດດື່ມໄດ້ເນື່ອງຈາກສະພາບຂອງທ່ານ.
-
ໃນປີ 1955 Otto Warburg ຜູ້ຊະນະລາງວັນໂນເບວພົບວ່າມະເຮັງທັງໝົດໃຊ້ນ້ຳຕານເປັນແຫຼ່ງພະລັງງານ ແລະ ລະດັບອິນຊູລິນສູງເຮັດໃຫ້ຮ່າງກາຍສູນເສຍການຄວບຄຸມລະບົບພູມຄຸ້ມກັນທີ່ຈະປ້ອງກັນມັນ. ນີ້ໝາຍຄວາມວ່າຄົນເຈັບຕ້ອງຈຳກັດທຸກສິ່ງທີ່ກະຕຸ້ນອິນຊູລິນ. ອາຫານແບບ Epi-paleo ທີ່ມີຄາໂບໄຮເດຣດຕ່ຳເຮັດໄດ້ແນວນີ້ພໍດີ. ຂໍ້ມູນອ້າງອີງທີ່ດີສຳລັບອາຫານແມ່ນຢູ່ບ່ອນນີ້.
-
ລະບົບພູມຄຸ້ມກັນຂອງທ່ານແມ່ນການປ້ອງກັນທີ່ດີທີ່ສຸດຕໍ່ມະເຮັງ. ເພີ່ມລະດັບວິຕາມິນ D ແລະ ຮັກສາລະດັບອິນຊູລິນໃຫ້ຕ່ຳກວ່າສອງ. ການຫຼຸດລະດັບ cortisol ຈະປັບປຸງ leptin ແຕ່ສິ່ງສຳຄັນທີ່ສຸດແມ່ນເພີ່ມຈຳນວນຈຸລັງ Natural Killer (WBC) ທີ່ເປັນສ່ວນໜຶ່ງຂອງລະບົບພູມຄຸ້ມກັນໃນຈຸລັງທີ່ຕໍ່ສູ້ກັບມະເຮັງ. ທ່ານຈະໄດ້ອ່ານຫຼາຍກ່ຽວກັບຈຸລັງເຫຼົ່ານີ້ໃນປື້ມທີ່ຂ້ອຍແນະນຳໃນຂັ້ນຕອນທີໜຶ່ງ.
-
ຜັກ. ເຮັດໃຫ້ຜັກຕະກຸນ cruciferous ເປັນອາຫານຫຼັກ. ພືດທັງໝົດໃນຕະກຸນ Brassica ແມ່ນໝູ່ຂອງທ່ານ. Glucosinolates ສາມາດຢັບຢັ້ງ, ຊະລໍ, ແລະ ປີ້ນການເກີດມະເຮັງຫຼາຍຂັ້ນຕອນ. ເຫດຜົນແມ່ນການປ່ອຍ isothiocyanates ເຊັ່ນ sulphoraphanes. Sulphoraphanes ເຮັດສອງສິ່ງຫຼັກ. ພວກມັນສົ່ງເສີມ apoptosis (levee 19) ແລະ ກະຕຸ້ນເອນໄຊມ໌ detoxification ໄລຍະສອງໃນຕັບທີ່ເສີມຄວາມເຂັ້ມແຂງໃຫ້ກັບຍີນ p53 ເປັນຜູ້ປົກປ້ອງຈີໂນມຂອງພວກເຮົາ. ຈຸລັງມະເຮັງມັກຈະຕາຍ (necrosis) ເມື່ອສຳຜັດກັບ sulphoraphanes ຢ່າງຕໍ່ເນື່ອງເປັນເວລາດົນ. ຜັກບຣອກໂຄລີຍັງມີສານ metabolite ຂັ້ນສອງທີ່ເອີ້ນວ່າ Indole 3 Carbinol ທີ່ແຕກຕົວຕໍ່ໄປເປັນສານຕ້ານມະເຮັງອີກຊະນິດໜຶ່ງຊື່ວ່າ DIM, diindolylmethane. ທ່ານບໍ່ສາມາດກິນຜັກພວກນີ້ຫຼາຍພໍຖ້າທ່ານເປັນມະເຮັງໃນທັດສະນະຂອງຂ້ອຍ. I3C ຍັງຂັດຂວາງ 16-hydroxyestrone ແລະ ມີປະໂຫຍດຫຼາຍໃນການປ້ອງກັນມະເຮັງເຕົ້ານົມ ແລະ ມະເຮັງຮັງໄຂ່ໃນແມ່ຍິງ ແລະ ມະເຮັງຕ່ອມລູກໝາກໃນຜູ້ຊາຍ.
-
ນີ້ແມ່ນສິ່ງທີ່ຂັດກັບຄວາມເຊື່ອຊຶ່ງຢູ່ໃນຫົວຂອງທ່ານ... ກິນ cholesterol ຫຼາຍໆ. ໂດຍສະເພາະນ້ຳມັນໝາກພ້າວ. ຫຼາຍການສຶກສາທາງລະບາດວິທະຍາສະແດງໃຫ້ເຫັນວ່າລະດັບ cholesterol ໃນເລືອດຕ່ຳສຳພັນກັບອັດຕາການເກີດມະເຮັງສູງ. ນີ້ແມ່ນເຫດຜົນທີ່ການກິນອາຫານ ketogenic Epi-paleo ມີຄວາມໝາຍຫຼາຍ. ເປັນຫຍັງອາຫານແບບ ketogenic? ເພາະມະເຮັງທັງໝົດໃຊ້ກລູໂຄສເປັນວັດຖຸດິບ. ທ່ານຈຳເປັນຕ້ອງປ່ຽນເຊື້ອໄຟຂອງຈຸລັງ. ໄປຊອກຫາ Otto Warburg ໃນ Google ສຳລັບລາຍລະອຽດເພີ່ມເຕີມ. ອາຫານແບບ ketogenic ຄວນມີ MCT ຈາກນ້ຳມັນໝາກພ້າວຫຼາຍ ເພາະພວກມັນໃຫ້ຂໍ້ໄດ້ປຽບຫຼາຍແກ່ຈຸລັງປົກກະຕິກວ່າຈຸລັງມະເຮັງ. ຂໍ້ໄດ້ປຽບນີ້ເຮັດໃຫ້ລະບົບພູມຄຸ້ມກັນຂອງທ່ານສາມາດຕາມທັນຈຸລັງມະເຮັງ ແລະ ທຳລາຍພວກມັນໂດຍໃຊ້ກົນໄກຊີວະວິທະຍາຂອງທ່ານເອງ. ມີຫຼາຍບົດຄວາມໃນວາລະສານມະເຮັງທີ່ພິມເຜີຍແຜ່ສະແດງໃຫ້ເຫັນການເຊື່ອມໂຍງແບບດຽວກັນ.
-
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 266815e0:6cd408a5
2025-05-02 22:20:02
@ 266815e0:6cd408a5
2025-05-02 22:20:02Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.

Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
re interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now

Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal


New emoji picker
Just another small improvement that makes the app feel more complete.

E
re is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very expe
 n
nt its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Do
hard earned sats, it will eat them!

Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing
ror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 86dfbe73:628cef55
2025-05-04 06:56:33
@ 86dfbe73:628cef55
2025-05-04 06:56:33Building A Second Brain (BASB) ist eine Methode, mit der man Ideen, Einsichten und Vernetzungen, die man durch seine Erfahrungen gewonnen hat, systematisch speichert und die jeder Zeit abrufbar sind. Kurz, BASB erweitert das Gedächtnis mit Hilfe moderner digitaler Werkzeuge und Netzwerke. Die Kernidee ist, dass man durch diese Verlagerung sein biologisches Gehirn befreit, um frei denken zu können, seiner Kreativität freien Lauf zu geben oder einfach im Moment sein kann.
Die Methode besteht aus drei Grundschritten: dem Sammeln von Ideen und Erkenntnissen, dem Vernetzen dieser Ideen und Erkenntnisse und dem Erschaffen konkreter Ergebnisse.
Sammeln: Der erste Schritt beim Aufbau eines Second Brains ist das «Sammeln» der Ideen und Erkenntnisse, die genug wichtig oder interessant sind, um sie festzuhalten. Dafür wird als Organisationsstruktur P.A.R.A empfohlen.
Vernetzen: Sobald man angefangen hat, sein persönliches Wissen strukturiert zu sammeln, wird man anfangen, Muster und Verbindungen zwischen den Ideen und Erkenntnissen zu erkennen. Ab dieser Stelle verwende ich parallel die Zettelkastenmethode (ZKM)
Erschaffen: All das Erfassen, Zusammenfassen, Verbinden und Strukturieren haben letztlich das Ziel: Konkrete Ergebnisse in der realen Welt zu erschaffen.
PARA ist die Organisationsstruktur, die auf verschiedenen Endgeräten einsetzt werden kann, um digitale Informationen immer nach dem gleichen Schema abzulegen. Seien es Informationen, Notizen, Grafiken, Videos oder Dateien, alles hat seinen festen Platz und kann anhand von vier Kategorien bzw. „Buckets“ kategorisiert werden.
PARA steht dabei für: * Projekte * Areas * Ressourcen * Archiv
Projekte (engl. Projects) sind kurzfristige Bemühungen in Arbeit und Privatleben. Sie sind das, woran Du aktuell arbeitest. Sie haben einige für die Arbeit förderliche Eigenschaften: * Sie haben einen Anfang und ein Ende (im Gegensatz zu einem Hobby oder einem Verantwortungsbereich). * Sie haben ein konkretes Ergebnis, dass erreicht werden soll und bestehen aus konkreten Schritten, die nötig und zusammen hinreichend sind, um dieses Ziel zu erreichen, entspricht GTD von David Allen
Verantwortungsbereiche (engl. Areas) betreffen alles, was man langfristig im Blick behalten will. Sie unterscheidet von Projekten, dass man bei ihnen kein Ziel verfolgt, sondern einem Standard halten will. Sie sind dementsprechend nicht befristet. Man könnte sagen, dass sie einen Anspruch an uns selbst und unsere Lebenswelt darstellen.
Ressourcen (engl. Resources) sind Themen, die allenfalls langfristig relevant oder nützlich werden könnten. Sie sind eine Sammelkategorie für alles, was weder Projekt noch Verantwortungsbereich ist. Es sind: * Themen, die interessant sind. (English: Topic) * Untersuchungsgegenständige, die man erforschen will. (Englisch: Subject) * Nützliche Informationen für den späteren Gebrauch.
Das Archiv ist für alles Inaktive aus den obigen drei Kategorien. Es ist ein Lager für Beendetes und Aufgeschobenes.
Das System PARA ist eine nach zeitlicher Handlungsrelevanz angeordnete Ablage. Projekte kommen vor den Verantwortungsbereichen, weil sie einen kurz- bis mittelfristigen Zeithorizont haben, Verantwortungsbereiche dagegen einen unbegrenzten Zeithorizont. Ressourcen und Archiv bilden die Schlusslichter, weil sie gewöhnlich weder Priorität haben, noch dringend sind.
-
 @ 57d1a264:69f1fee1
2025-05-04 06:37:52
@ 57d1a264:69f1fee1
2025-05-04 06:37:52KOReader is a document viewer for E Ink devices. Supported file formats include EPUB, PDF, DjVu, XPS, CBT, CBZ, FB2, PDB, TXT, HTML, RTF, CHM, DOC, MOBI and ZIP files. It’s available for Kindle, Kobo, PocketBook, Android and desktop Linux.
Download it from https://koreader.rocks Repository: https://github.com/koreader/koreader
originally posted at https://stacker.news/items/970912
-
 @ 1d7ff02a:d042b5be
2025-05-02 14:50:01
@ 1d7ff02a:d042b5be
2025-05-02 14:50:01ผมได้ติดตามการแบนการซื้อขายแบบ P2P ของ Binance ในประเทศไทยมาระยะหนึ่งแล้ว จากสถานการณ์ดังกล่าว เห็นได้อย่างชัดเจนว่ารัฐบาลกำลังเริ่มโจมตี Bitcoin ก่อนที่เราจะบรรลุถึง Bitcoin Standard เราจำเป็นต้องมีความเป็นส่วนตัวและอิสระทางการเงิน ซึ่งการซื้อขายแบบ P2P มีความสำคัญมากในการบรรลุเป้าหมายนี้
ความสำคัญของ No-KYC P2P
No-KYC P2P คือหัวใจสำคัญ - เราจำเป็นต้องมีแพลตฟอร์มที่เป็นทางรอด เราไม่สามารถเชื่อใจแพลตฟอร์มแบบรวมศูนย์ได้เนื่องจากสาเหตุสองประการ: 1. ความเสี่ยงจากการถูกโกงโดยแพลตฟอร์มเอง (rug pull) 2. การถูกควบคุมจากภาครัฐ
แพลตฟอร์ม No-KYC P2P ที่แนะนำ
ผมอยากเสนอให้นักพัฒนาและชุมชน Bitcoin ไทย พิจารณาการศึกษาและพัฒนาแพลตฟอร์ม No-KYC P2P ปัจจุบันมีหลายทางเลือกที่มีอยู่แล้ว เช่น:
- Bisq
- RoboSats
- Mostro
- HodlHodl
- Lnp2pbot
เหตุผลที่แนะนำ Lnp2pbot
ผมขอแนะนำให้นำใช้หรือพัฒนาต่อจาก Lnp2pbot เนื่องจากข้อดีหลายประการ:
- ประสบการณ์ผู้ใช้ (UX) ที่ดีกว่า - เมื่อเทียบกับแพลตฟอร์มอื่นๆ
- ใช้ Telegram เป็นพื้นฐาน - มีระบบ Escrow (บุคคลที่สามที่ถือเงินระหว่างการทำธุรกรรม) ซึ่งเพิ่มความมั่นใจและลดโอกาสการถูกโกง
- ลดการรวมศูนย์ - ไม่จำเป็นต้องพัฒนาแอปและส่งขึ้นสโตร์ ซึ่งจะทำให้นักพัฒนาต้องเปิดเผยตัวตนและกลายเป็นจุดอ่อนให้รัฐบาลควบคุม
- สร้างชุมชนได้ง่าย - ทุกคนสามารถสร้างกลุ่มหรือชุมชนเพื่อการซื้อขายได้ ทำให้ตลาดพัฒนากลุ่มที่น่าเชื่อถือตามกลไกตลาดเสรี
- ใช้งานจริงในหลายประเทศแล้ว - ปัจจุบันมีหลายประเทศที่นำ Lnp2pbot ไปใช้งานจริงแล้ว แสดงให้เห็นถึงความเสถียรและความเชื่อถือได้ของระบบ
บทบาทของนักพัฒนาไทย
Lnp2pbot อาจยังมีข้อจำกัดด้าน UX โดยเฉพาะสำหรับผู้ใช้ท้องถิ่น นักพัฒนาไทยสามารถนำเอาซอฟต์แวร์มาพัฒนาต่อและดำเนินการเองได้ เนื่องจากเป็นโอเพนซอร์สอยู่แล้ว
สิ่งสำคัญที่สุดคือการรักษาให้ซอฟต์แวร์เป็นโอเพนซอร์สและให้ทุกคนสามารถนำไปใช้หรือทำให้มันทำงานได้ด้วยตนเอง วิธีการนี้จะหลีกเลี่ยงการมีจุดรวมศูนย์ที่รัฐบาลสามารถโจมตีได้
-
 @ 57d1a264:69f1fee1
2025-05-04 06:27:15
@ 57d1a264:69f1fee1
2025-05-04 06:27:15Well, today posts looks are dedicated to STAR WARS. Enjoy!
Today we’re looking at Beat Saber (2019) and why its most essential design element can be used to make great VR games that have nothing to do with music or rhythm.
https://www.youtube.com/watch?v=EoOeO7S9ehw
It’s hard to believe Beat Saber was first released in Early Access seven years ago today. From day one, it was clear the game was something special, but even so we couldn’t have predicted it would become one of VR’s best-selling games of all time—a title it still holds all these years later. In celebration of the game’s lasting legacy we’re re-publishing our episode of Inside XR Design which explores the secret to Beat Saber’s fun, and how it can be applied to VR games which have nothing to do with music.
Read more at https://www.roadtovr.com/beat-saber-instructed-motion-until-you-fall-inside-xr-design/
originally posted at https://stacker.news/items/970909
-
 @ 57d1a264:69f1fee1
2025-05-04 06:16:58
@ 57d1a264:69f1fee1
2025-05-04 06:16:58Found this really fun, so created a few intros for latest SN newsletters https://stacker.news/items/960787/r/Design_r?commentId=970902 and https://stacker.news/items/970459/r/Design_r?commentId=970905
Create your STAR-WARS-like movie intro https://starwarsintrocreator.kassellabs.io/
originally posted at https://stacker.news/items/970906
-
 @ 502ab02a:a2860397
2025-05-04 03:13:06
@ 502ab02a:a2860397
2025-05-04 03:13:06เรารู้จักกับ Circadian Rhythm และ Infradian Rhythm แล้ว คราวนี้เรามารู้จักกับ Ultradian Rhythm กันครับ จากรากศัพท์ภาษาละติน คำว่า “Ultra” แปลว่า “มากกว่า” หรือ “ถี่กว่า” คำว่า diem” = แปลว่า "วัน" พอเอามารวมกันเป็น “ultradian” ก็หมายถึงวงจรชีวภาพที่เกิดขึ้น บ่อยกว่า 1 รอบต่อวัน (ความถี่สูงกว่ารอบ 24 ชั่วโมง) ไม่ใช่ “ยาวกว่า 1 วัน” สรุปเป็นภาษาง่ายๆคือ "จังหวะชีวภาพที่เกิดซ้ำ มากกว่า 1 ครั้งภายใน 24 ชั่วโมง"
หรือถ้าเราจะเรียงลำดับของ Rythm ทั้ง 3 ประเภทเราจะได้เป็น 1.Circadian Rhythm (ประมาณ 24 ชม.) 2.Ultradian Rhythm (น้อยกว่า 24 ชม.) 3.Infradian Rhythm (มากกว่า 24 ชม.)
สำหรับตัวอย่าง Ultradian Rhythm ที่สำคัญๆนะครับ เช่น 1. วัฏจักรการนอน (Sleep Cycle) ที่แต่ละรอบ จะอยู่ที่ราวๆ 90–120 นาที สลับกันไปมาระหว่าง NREM (หลับลึก) และ REM (ฝัน) อย่างที่สายสุขภาพเรียนรู้กันมาคือ ถ้าหลับสลับครบ 4–6 รอบ จะหลับสนิท ฟื้นเช้ามาสดชื่นแจ่มใสพักผ่อนเต็มที่
แสงเช้า-แดดอ่อนๆ ช่วยรีเซ็ต circadian แต่ก็ส่งผลให้ ultradian sleep cycle เริ่มต้นตรงจังหวะพอดี นอกจากนี้ยังมีสิ่งที่เรียกว่า Power nap ตอนแดดบ่าย (20–25 นาทีแดดอ่อน) จะช่วยกระตุ้น ultradian nap cycle ให้ตื่นขึ้นมาเป๊ะ ไม่งัวเงีย ให้เลือกจุดที่แดดยังอ่อน เช่น ริมหน้าต่างที่มีแดดผ่านมานุ่ม ๆ หรือใต้ต้นไม้ที่กรองแสงได้บางส่วน ไม่จำเป็นต้องนอนตากแดดโดยตรง แต่ให้ “รับแสงธรรมชาติ” พร้อมกับงีบ จะช่วยให้ circadian และ ultradian cycles ทำงานประสานกันได้ดีขึ้น
- การหลั่งฮอร์โมนแบบพัลซ์ หรือ Pulsatile Hormone Secretion คือรูปแบบการปล่อยฮอร์โมนออกมาจากต่อมต่าง ๆ ในร่างกายแบบเป็น “จังหวะ” หรือ “เป็นช่วง” (bursts/pulses) ไม่ใช่การหลั่งออกมาอย่างต่อเนื่องตลอดเวลา เช่น เทพแห่งการลดน้ำหนัก Growth Hormone (GH) หลั่งพุ่งตอนหลับลึกทุก 3–4 ชั่วโมง / Cortisol มีพัลซ์เล็กๆ ในวัน แม้หลักๆ จะเป็น circadian แต่ก็มี ultradian pulse ทุก 1–2 ชั่วโมง ได้เหมือนกัน / Insulin & Glucagon ชัดเลยชาว keto IF รู้ดีที่สุดว่า หลั่งเป็นรอบตามมื้ออาหารและช่วงพักระหว่างมื้อ
ลองนึกภาพว่า “แสงแดง” และ “อินฟราเรด” เปรียบเหมือนอาหารเช้าของเซลล์เรา เมื่อผิวเราโดนแดดอ่อน ๆ ในช่วงเช้าหรือบ่ายแก่ แสงเหล่านี้จะซึมเข้าไปกระตุ้น “โรงไฟฟ้าประจำเซลล์” (ไมโตคอนเดรีย) ให้ผลิตพลังงาน (ATP) ขึ้นมาเพิ่ม เหมือนเติมน้ำมันให้เครื่องยนต์วิ่งได้ลื่น พอเซลล์มีพลังงานมากขึ้น ในช่วงที่ร่างกายหลั่งฮอร์โมนการซ่อมแซมอย่าง “growth hormone” (GH) ร่างกายก็จะใช้พลังงานจากแสงนี้พร้อมกับฮอร์โมนในการซ่อมแซมกล้ามเนื้อและเนื้อเยื่อต่าง ๆ ได้เต็มประสิทธิภาพขึ้นนั่นเองครับ
- ช่วงเวลาการจดจ่อ หรือ Attention Span & Energy Cycle คนทั่วไปมีสมาธิ/พลังงานโฟกัสอยู่รอบละ 90 นาที หลังจากนั้นควรพัก 10–20 นาที หากฝืนต่อเนื่อง จะเกิดอาการอ่อนล้า สมาธิหลุด
Blue light เช้า จากแดดจะไปกระตุ้นในส่วนของ suprachiasmatic nucleus (SCN) ในสมองให้ปล่อยสารกระตุ้นความตื่นตัว (เช่น คอร์ติซอล) พอสมควร ซึ่งช่วยให้ ultradian cycle ของสมาธิ (โฟกัสได้ประมาณ 90 นาที) ทำงานเต็มประสิทธิภาพ ถ้าเช้าๆ ไม่เจอแดดเลย cycle นี้จะเลื่อนออกไป ทำให้รู้สึกง่วงเหงาหาวนอนเร็ว หรือโฟกัสไม่ได้นานตามปกติ เป็นที่มาของการเพลียแม้จะตื่นสายแล้วก็ตาม
- รอบความหิว หรือ Appetite & Digestive Rhythm ชื่อเท่ห์ป่ะหล่ะ 555 คือความหิวมาเป็นรอบตามวิธีการกินของแต่ละคน ซึ่งเป็นความสัมพันธ์กับ ฮอร์โมน GI (เช่น ghrelin, leptin) ก็วิ่งเป็นรอบเหมือนกัน
แสงแดดเช้า ช่วยตั้ง leptin/ghrelin baseline ให้สมดุล ลดการกินจุกจิกนอกมื้อได้ ส่วนแสงอ่อนๆ ตอนบ่ายช่วยบูสต์ blood flow ในทางเดินอาหาร ให้ digestion cycle หรือการดูดซึมสารอาหารตรงจังหวะ
แดดเป็นแค่ส่วนสำคัญในชีวิตแต่การใช้ Ultradian Rhythm มันต้องประกอบกับกิจกรรมอื่นๆด้วยนะครับ เช่น ทำงานหรืออ่านหนังสือ 90 นาที แล้ว พัก 15–20 นาที ยืดเส้นสาย เคลื่อนไหวเล็กน้อย, ออกกำลังกายให้ตรงจังหวะ, ในช่วง ultradian break พยายามลดการใช้จอมือถือ/คอมฯ ออกไปรับแสงธรรมชาติ หรือยืดเส้น เปิดเพลงเบาๆ เพื่อหลีกเลี่ยง "stimuli" ช่วง break หรือ สิ่งเร้าภายนอก ที่มากระตุ้นประสาทสัมผัสและสมองเรา
แสงแดดจึงเป็น ตัวตั้งเวลา (zeitgeber) ที่ไม่ได้แค่กับรอบวัน-เดือน-ปี แต่รวมถึงจังหวะสั้นๆ ภายในวันด้วย การใช้แสงธรรมชาติให้พอดีในแต่ละช่วง (เช้า เบรก บ่าย) จะช่วยให้ ultradian rhythms ในด้านสมาธิ การนอน ฮอร์โมน และการย่อยอาหาร ทำงานสอดคล้องกับจังหวะชีวิตที่เป็นธรรมชาติที่สุดครับ #pirateketo #SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 211c0393:e9262c4d
2025-05-04 02:32:24
@ 211c0393:e9262c4d
2025-05-04 02:32:24**日本の覚せい剤ビジネスの闇:
警察、暴力団、そして「沈黙の共犯関係」の真相**
1. 暴力団の支配構造(公的データに基づく)
- 輸入依存の理由:
- 国内製造は困難(平成6年「覚せい剤原料規制法」で規制強化)→ ミャンマー・中国からの密輸が主流(国連薬物犯罪事務所「World Drug Report 2023」)。
- 暴力団の利益率:1kgあたり仕入れ価格30万円 → 小売価格500万~1000万円(警察庁「薬物情勢報告書」2022年)。
2. 警察と暴力団の「共生関係」
- 逮捕統計の不自然さ:
- 全薬物逮捕者の70%が単純所持(厚生労働省「薬物乱用状況」2023年)。
- 密輸組織の摘発は全体の5%未満(東京地検特捜部データ)。
- メディアの検証:
- NHKスペシャル「覚せい剤戦争」(2021年)で指摘された「末端ユーザー優先捜査」の実態。
3. 矛盾する現実
- 需要の不可視性:
- G7で最高の覚せい剤価格(1gあたり3~7万円、欧米の3倍)→ 暴力団の暴利(財務省「組織犯罪資金流動調査」)。
- 使用者率は低い(人口の0.2%、国連調査)が、逮捕者の過半数を占める矛盾。
4. 「密輸組織対策」の限界
- 国際的な失敗例:
- メキシコ(カルテル摘発後も市場拡大)、欧州(合成薬物の蔓延)→ 代替組織が即座に台頭(英「The Economist」2023年6月号)。
- 日本の地理的ハンデ:
- 海上密輸の摘発率は10%未満(海上保安庁報告)。
5. 解決策の再考(事実に基づく提案)
- ADHD治療薬の合法化:
- アメリカ精神医学会「ADHD患者の60%が自己治療で違法薬物使用」(2019年研究)。
- 日本ではリタリン・アデロール禁止→ 暴力団の市場独占。
- 労働環境改革:
- 過労死ライン超えの労働者20%(厚労省「労働時間調査」2023年)→ 覚せい剤需要の一因。
6. 告発のリスクと情報源
- 匿名性の重要性:
- 過去の暴力団報復事例(2018年、告発記者への脅迫事件・毎日新聞報道)。
- 公的データのみ引用:
- 例:「警察庁統計」「国連報告書」など第三者検証可能な情報。
結論:変革のためには「事実」の可視化が必要
「薬物=個人の道徳的問題」という幻想が、暴力団と腐敗官僚を利している。
国際データと国内統計の矛盾を突くことで、システムの欺瞞を暴ける。安全な共有のために:
- 個人特定を避け、匿名プラットフォーム(Tor上フォーラム等)で議論。
- 公的機関のデータを直接リンク(例:警察庁PDFレポート)。
この文書は、公表された統計・メディア報道のみを根拠とし、個人の推測を排除しています。
脅威を避けるため、具体的な個人・組織の非難は意図的に避けています。 -
 @ e516ecb8:1be0b167
2025-05-04 01:45:38
@ e516ecb8:1be0b167
2025-05-04 01:45:38El sol de la tarde caía oblicuo sobre un campo de hierba alta, tiñéndolo de tonos dorados y rojizos. A un lado, una formación disciplinada de hombres vestidos con armaduras de cuero y metal relucía bajo la luz. Eran legionarios romanos, cada uno portando un scutum, el gran escudo rectangular, y un gladius corto y letal. Se movían como una sola entidad, un muro de escudos erizado de puntas de lanza que asomaban por encima.
Al otro lado del campo, una fuerza más dispersa pero igualmente imponente esperaba. Eran samuráis, guerreros vestidos con armaduras lacadas de intrincado diseño. En sus manos, las brillantes curvas de las katanas reflejaban el sol poniente. Su presencia era menos de masa compacta y más de tensión contenida, como la de depredadores listos para abalanzarse.
El silencio se quebró cuando un oficial romano alzó su signum, un estandarte con el águila imperial. Al unísono, los legionarios avanzaron con paso firme, sus sandalias clavándose en la tierra. Gritaban su grito de guerra, un rugido gutural que resonaba en el aire.
Los samuráis observaron el avance implacable. Su líder, un hombre de rostro sereno con una cicatriz que le cruzaba la mejilla, desenvainó su katana con un movimiento fluido y silencioso. La hoja brilló intensamente. Con un grito agudo, dio la orden de ataque.
La batalla comenzó con un choque violento. Los legionarios, con sus escudos entrelazados, formaron una muralla impenetrable. Los samuráis se lanzaron contra ella, sus katanas trazando arcos de acero en el aire. El choque de metal contra metal llenó el campo, un coro estridente de la guerra.
Un samurái, ágil como un felino, intentó saltar sobre el muro de escudos. Pero un legionario, rápido y entrenado, lo recibió con una estocada precisa de su gladius, que encontró un hueco en la armadura. El samurái cayó, la sangre tiñendo la hierba.
Otro samurái, con un grito furioso, lanzó un corte horizontal con su katana. El golpe impactó contra un scutum, dejando una marca profunda en la madera y el metal, pero el escudo resistió. Antes de que pudiera recuperar su arma, el legionario detrás del escudo le asestó un golpe rápido con el gladius en el costado desprotegido.
La formación romana era una máquina de matar eficiente. Los legionarios trabajaban en equipo, protegiéndose mutuamente con sus escudos y atacando con sus gladius en los momentos oportunos. La disciplina y el entrenamiento eran sus mayores armas.
Sin embargo, la ferocidad y la habilidad individual de los samuráis eran innegables. Sus katanas, a pesar de no poder penetrar fácilmente la sólida pared de escudos, eran devastadoras en los espacios abiertos. Un samurái logró flanquear a un grupo de legionarios y, con movimientos rápidos y precisos, cortó brazos y piernas, sembrando el caos en la retaguardia romana.
La batalla se convirtió en un torbellino de acero y gritos. Los legionarios mantenían su formación, avanzando lentamente mientras repelían los ataques. Los samuráis, aunque sufrían bajas, no retrocedían, impulsados por su honor y su valentía.
En un punto crucial, un grupo de samuráis liderados por su comandante logró concentrar sus ataques en un sector de la línea romana. Con golpes repetidos y feroces, consiguieron romper la formación, creando una brecha. Se lanzaron a través de ella, sus katanas sedientas de sangre.
La disciplina romana se tambaleó por un momento. Los samuráis, aprovechando la oportunidad, lucharon cuerpo a cuerpo con una furia indomable. La longitud de sus katanas les daba ventaja en el combate individual, permitiéndoles mantener a raya a los legionarios con cortes amplios y letales.
Sin embargo, la respuesta romana fue rápida. Los oficiales gritaron órdenes, y las líneas se cerraron nuevamente, rodeando a los samuráis que habían penetrado la formación. Los legionarios, trabajando en parejas, inmovilizaban los largos brazos de los samuráis con sus escudos mientras otros asestaban golpes mortales con sus gladius.
La batalla continuó durante lo que pareció una eternidad. El sol finalmente se ocultó en el horizonte, tiñendo el campo de batalla de sombras oscuras y reflejos sangrientos. Ambos bandos lucharon con una determinación feroz, sin ceder terreno fácilmente.
Al final, la disciplina y la formación compacta de los legionarios comenzaron a imponerse. Lentamente, pero de manera constante, fueron cercando y diezmando a los samuráis. La muralla de escudos era demasiado sólida, y la lluvia constante de estocadas del gladius era implacable.
Los últimos samuráis lucharon con la desesperación de quienes saben que su final está cerca. Sus katanas seguían cortando con gracia mortal, pero eran superados en número y en la táctica del combate en grupo. Uno a uno, fueron cayendo, sus brillantes espadas manchadas de sangre.
Cuando la última katana cayó al suelo con un resonido metálico, un silencio pesado se cernió sobre el campo. Los legionarios, exhaustos pero victoriosos, permanecieron en formación, sus escudos goteando sangre. Habían prevalecido gracias a su disciplina, su equipo y su táctica de combate en grupo. La ferocidad individual y la maestría de la katana de los samuráis no habían sido suficientes contra la máquina de guerra romana.
La noche cubrió el campo de batalla, llevándose consigo los ecos de la lucha y dejando solo la sombría realidad de la victoria y la derrota.
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ 5df413d4:2add4f5b
2025-05-04 01:13:31
@ 5df413d4:2add4f5b
2025-05-04 01:13:31Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 02: Jerusalem Old City
The bus slowly lurches up the winding and steep embankment. We can finally start to see the craggy tops of buildings peaking out over the ridge in the foreground distance. We have almost reached it. Jerusalem, the City on the Hill.
https://i.nostr.build/e2LpUKEgGBwfveGi.jpg
Our Israeli tour guide speaks over the mic to draw our attention to the valley below us instead - “This is the the Valley of Gehenna, the Valley of the Moloch,” he says. “In ancient times, the pagans who worshiped Moloch used this place for child sacrifice by fire. Now, imagine yourself, an early Hebrew, sitting atop the hill, looking down in horror. This is the literal Valley of The Shadow of Death, the origin of the Abrahamic concept of Hell.” Strong open - this is going to be fun.
https://i.nostr.build/5F29eBKZYs4bEMHk.jpg
Inside the Old City, our guide - a chubby, cherub-faced intelligence type on some sort of punishment duty, deputized to babysit foreigners specifically because he reads as so dopey and disarming - points out various Judeo-Christian sites on a map, his tone subtly suggesting which places are most suggested, or perhaps, permitted…
https://i.nostr.build/J44fhGWc9AZ5qpK4.jpg
https://i.nostr.build/3c0jh09nx6d5cEdt.jpg
Walking, we reach Judaism’s Kotel, the West Wall - massive, grand, and ancient, whispering of the Eternal. Amongst the worshipers, we touch the warm, dry limestone and, if we like, place written prayers into the wall's smaller cracks. A solemn and yearning ghost fills the place - but whose it is, I'm not sure.  https://i.nostr.build/AjDwA0rFiFPlrw1o.jpg
Just above the Kotel, Islam’s Dome of the Rock can be seen, its golden cap blazing in the sun. I ask our guide about visiting the dome. He cuts a heavy eyeroll in my direction - it seems I’ve outed myself as my group’s “that guy.” His face says more than words ever could, “Oy vey, there’s one in every group…”
“Why would anyone want to go there? It is a bit intense, no?” Still, I press. “Well, it is only open to tourists on Tuesday and Thursdays…” It is Tuesday. “And even then, visiting only opens from 11:30…” It is 11:20. As it becomes clear to him that I don't intend to drop this...“Fine!” he relents, with a dramatic flaring of the hands and an uniquely Israeli sigh, “Go there if you must. But remember, the bus leaves at 1PM. Good luck...” Great! Totally not ominous at all.
https://i.nostr.build/6aBhT61C28QO9J69.jpg
The checkpoint for the sole non-Muslim entrance leading up to the Dome is administered by several gorgeous and statuesque, assault rifle clad, Ethiop-Israeli female soldiers. In this period of relative peace and calm, they feel lax enough to make a coy but salacious game of their “screening” the men in line. As I observe, it seems none doth protest...
https://i.nostr.build/jm8F3pUp9EXqPRkN.jpg
Past the gun-totting Sirens, a long wooden rampart leads up to the Temple Mount, The Mount of the House of the Holy, al-Ḥaram al-Sharīf, The Noble Sanctuary, The Furthest Mosque, the site of the Dome of the Rock and the al-Masjid al-Asqa.
https://i.nostr.build/DoS0KIkrVN0yiVJ0.jpg
On the Mount, the Dome dominates all views. To those interested in pure expressions of beauty, the Dome is, undeniably, a thing of absolute glory. I pace the grounds, snapping what pictures I can. I pause to breathe and to let the electric energy of the setting wash over me.
https://i.nostr.build/0BQYLwpU291q2fBt.jpg
https://i.nostr.build/yCxfB1V8eAcfob93.jpg
It’s 12:15 now, I decide to head back. Now, here is what they don’t tell you. The non-Muslin entrance from the West Wall side is a one-way deal. Leaving the Dome plaza dumps you out into the back alley bazaar of Old City’s Muslim district. And so it is. I am lost.
https://i.nostr.build/XnQ5eZgjeS1UTEBt.jpg
https://i.nostr.build/EFGD5vgmFx5YYuH4.jpg
I run through the Muslim quarter, blindly turning down alleyways that seem to be taking me in the general direction of where I need to be - glimpses afforded by the city’s uneven elevation and cracks in ancient stone walls guiding my way.
https://i.nostr.build/mWIEAXlJfdqt3nuh.jpg
In a final act of desperation and likely a significant breach of Israeli security protocol, I scale a low wall and flop down back on the side of things where I'm “supposed” to be. But either no one sees me or no one cares. Good luck, indeed.
I make it back to my group - they are not hard to find, a bunch of MBAs in “business casual” travel attire and a tour guide wearing a loudly colored hat and jacket - with just enough time to still visit the Church of the Holy Sepulcher.
https://i.nostr.build/3nFvsXdhd0LQaZd7.jpg
https://i.nostr.build/sKnwqC0HoaZ8winW.jpg
Inside, a chaotic and dizzying array of chapels, grand domed ceilings, and Christian relics - most notably the Stone of Anointing, commemorating where Christ’s body was prepared for burial and Tomb of Christ, where Christ is said to have laid for 3 days before Resurrection.
https://i.nostr.build/Lb4CTj1dOY1pwoN6.jpg
https://i.nostr.build/LaZkYmUaY8JBRvwn.jpg
In less than an hour, one can traverse from the literal Hell, to King David’s Wall, The Tomb of Christ, and the site of Muhammad’s Ascension. The question that stays with me - What is it about this place that has caused so many to turn their heads to the heavens and cry out for God? Does he hear? And if he answers, do we listen?
https://i.nostr.build/elvlrd7rDcEaHJxT.jpg
Jerusalem, The Old City, circa 2014. Israel.
There are secrets to be found. Go there.
Bitcoin #Jerusalem #Israel #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Plebchain #Coffeechain #Bookstr #NostrArt #Writing #Writestr #Createstr
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44
@ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ 5df413d4:2add4f5b
2025-05-04 00:06:31
@ 5df413d4:2add4f5b
2025-05-04 00:06:31This opinion piece was first published in BTC Magazine on Feb 20, 2023
Just in case we needed a reminder, banks are showing us that they can and will gatekeep their customers’ money to prevent them from engaging with bitcoin. This should be a call to action for Bitcoiners or anyone else who wants to maintain control over their finances to move toward more proactive use of permissionless bitcoin tools and practices.
Since January of 2023, when Jamie Dimon decried Bitcoin as a “hyped-up fraud” and “a pet rock,” on CNBC, I've found myself unable to purchase bitcoin using my Chase debit card on Cash App. And I'm not the only one — if you have been following Bitcoin Twitter, you might have also seen Alana Joy tweet about her experience with the same. (Alana Joy Twitter account has since been deleted).
In both of our cases, it is the bank preventing bitcoin purchases and blocking inbound fiat transfers to Cash App for customers that it has associated with Bitcoin. All under the guise of “fraud protection,” of course.
No, it doesn’t make a whole lot of sense — Chase still allows ACH bitcoin purchases and fiat on Cash App can be used for investing in stocks, saving or using Cash App’s own debit card, not just bitcoin — but yes, it is happening. Also, no one seems to know exactly when this became Chase’s policy. The fraud representative I spoke with wasn’t sure and couldn’t point to any documentation, but reasoned that the rule has been in place since early last year. Yet murkier still, loose chatter can be found on Reddit about this issue going back to at least April 2021.
However, given that I and so many others were definitely buying bitcoin via Chase debit throughout 2021 and 2022, I’d wager that this policy, up to now, has only been exercised haphazardly, selectively, arbitrarily, even. Dark patterns abound, but for now, it seems like I just happen to be one of the unlucky ones…
That said, there is nothing preventing this type of policy from being enforced broadly and in earnest by one or many banks. If and as banks feel threatened by Bitcoin, we will surely see more of these kinds of opaque practices.
It’s Time To Get Proactive
Instead, we should expect it and prepare for it. So, rather than railing against banks, I want to use this as a learning experience to reflect on the importance of permissionless, non-KYC Bitcoining, and the practical actions we can take to advance the cause.
Bank with backups and remember local options. Banking is a service, not servitude. Treat it as such. Maintaining accounts at multiple banks may provide some limited fault tolerance against banks that take a hostile stance toward Bitcoin, assuming it does not become the industry norm. Further, smaller, local and regional banks may be more willing to work with Bitcoiner customers, as individual accounts can be far more meaningful to them than they are to larger national banks — though this certainly should not be taken for granted.
If you must use KYC’d Bitcoin services, do so thoughtfully. For Cash App (and services like it), consider first loading in fiat and making buys out of the app’s native cash balance instead of purchasing directly through a linked bank account/debit card where information is shared with the bank that allows it to flag the transaction for being related to bitcoin. Taking this small step may help to avoid gatekeeping and can provide some minor privacy, from the bank at least.
Get comfortable with non-KYC bitcoin exchanges. Just as many precoiners drag their feet before making their first bitcoin buys, so too do many Bitcoiners drag their feet in using permissionless channels to buy and sell bitcoin. Robosats, Bisq, Hodl Hodl— you can use the tools. For anyone just getting started, BTC Sessions has excellent video tutorial content on all three, which are linked.
If you don’t yet know how to use these services, it’s better to pick up this knowledge now through calm, self-directed learning rather than during the panic of an emergency or under pressure of more Bitcoin-hostile conditions later. And for those of us who already know, we can actively support these services. For instance, more of us taking action to maintain recurring orders on such platforms could significantly improve their volumes and liquidity, helping to bootstrap and accelerate their network effects.
Be flexible and creative with peer-to-peer payment methods. Cash App, Zelle, PayPal, Venmo, Apple Cash, Revolut, etc. — the services that most users seem to be transacting with on no-KYC exchanges — they would all become willing, if not eager and active agents of financial gatekeeping in any truly antagonistic, anti-privacy environment, even when used in a “peer-to-peer” fashion.
Always remember that there are other payment options — such as gift cards, the original digital-bearer items — that do not necessarily carry such concerns. Perhaps, an enterprising soul might even use Fold to earn bitcoin rewards on the backend for the gift cards used on the exchange…
Find your local Bitcoin community! In the steadily-advancing shadow war on all things permissionless, private, and peer-to-peer, this is our best defense. Don’t just wait until you need other Bitcoiners to get to know other Bitcoiners — to paraphrase Texas Slim, “Shake your local Bitcoiner’s hand.” Get to know people and never underestimate the power of simply asking around. There could be real, live Bitcoiners near you looking to sell some corn and happy to see it go to another HODLer rather than to a bunch of lettuce-handed fiat speculators on some faceless, centralized, Ponzi casino exchange. What’s more, let folks know your skills, talents and expertise — you might be surprised to find an interested market that pays in BTC!
In closing, I believe we should think of permissionless Bitcoining as an essential and necessary core competency, just like we do with Self-Custody. And we should push it with similar urgency and intensity. But as we do this, we should also remember that it is a spectrum and a progression and that there are no perfect solutions, only tradeoffs. Realization of the importance of non-KYC practices will not be instant or obvious to near-normie newcoiners, coin-curious fence-sitters or even many minted Bitcoiners. My own experience is certainly a testament to this.
As we promote the active practice of non-KYC Bitcoining, we can anchor to empathy, patience and humility — always being mindful of the tremendous amount of unlearning most have to go through to get there. So, even if someone doesn’t get it the first time, or the nth time, that they hear it from us, if it helps them get to it faster at all, then it’s well worth it.
~Moon
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:07:00
@ 3c389c8f:7a2eff7f
2025-04-29 18:07:00Extentions:
https://chromewebstore.google.com/detail/flamingo-%E2%80%93-nostr-extensio/alkiaengfedemppafkallgifcmkldohe
https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
https://chromewebstore.google.com/detail/aka-profiles/ncmflpbbagcnakkolfpcpogheckolnad
https://keys.band/
https://github.com/haorendashu/nowser
The Remote Signer:
https://nsec.app/
https://github.com/kind-0/nsecbunkerd
Native Android Signer:
https://github.com/greenart7c3/amber
iOS
https://testflight.apple.com/join/8TFMZbMs
https://testflight.apple.com/join/DUzVMDMK
Higher Security Options: To start using Nostr with a secure, recoverable keypair: https://nstart.me/en
For Existing Keys: https://www.frostr.org/
Thank you to https://nostr.net/ for keeping a thorough list of Nostr apps, clients, and tools!
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ ecda4328:1278f072
2025-03-26 12:06:30
@ ecda4328:1278f072
2025-03-26 12:06:30When designing a highly available Kubernetes (or k3s) cluster, one of the key architectural questions is: "How many ETCD nodes should I run?"
A recent discussion in our team sparked this very debate. Someone suggested increasing our ETCD cluster size from 3 to more nodes, citing concerns about node failures and the need for higher fault tolerance. It’s a fair concern—nobody wants a critical service to go down—but here's why 3-node ETCD clusters are usually the sweet spot for most setups.
The Role of ETCD and Quorum
ETCD is a distributed key-value store used by Kubernetes to store all its state. Like most consensus-based systems (e.g., Raft), ETCD relies on quorum to operate. This means that more than half of the ETCD nodes must be online and in agreement for the cluster to function correctly.
What Quorum Means in Practice
- In a 3-node ETCD cluster, quorum is 2.
- In a 5-node cluster, quorum is 3.

⚠️ So yes, 5 nodes can tolerate 2 failures vs. just 1 in a 3-node setup—but you also need more nodes online to keep the system functional. More nodes doesn't linearly increase safety.
Why 3 Nodes is the Ideal Baseline
Running 3 ETCD nodes hits a great balance:
- Fault tolerance: 1 node can fail without issue.
- Performance: Fewer nodes = faster consensus and lower latency.
- Simplicity: Easier to manage, upgrade, and monitor.
Even the ETCD documentation recommends 3–5 nodes total, with 5 being the upper limit before write performance and operational complexity start to degrade.
Systems like Google's Chubby—which inspired systems like ETCD and ZooKeeper—also recommend no more than 5 nodes.
The Myth of Catastrophic Failure
"If two of our three ETCD nodes go down, the cluster will become unusable and need deep repair!"
This is a common fear, but the reality is less dramatic:
- ETCD becomes read-only: You can't schedule or update workloads, but existing workloads continue to run.
- No deep repair needed: As long as there's no data corruption, restoring quorum just requires bringing at least one other ETCD node back online.
- Still recoverable if two nodes are permanently lost: You can re-initialize the remaining node as a new single-node ETCD cluster using
--cluster-init, and rebuild from there.
What About Backups?
In k3s, ETCD snapshots are automatically saved by default. For example:
- Default path:
/var/lib/rancher/k3s/server/db/snapshots/
You can restore these snapshots in case of failure, making ETCD even more resilient.
When to Consider 5 Nodes
Adding more ETCD nodes only makes sense at scale, such as:
- Running 12+ total cluster nodes
- Needing stronger fault domains for regulatory/compliance reasons
Note: ETCD typically requires low-latency communication between nodes. Distributing ETCD members across availability zones or regions is generally discouraged unless you're using specialized networking and understand the performance implications.
Even then, be cautious—you're trading some simplicity and performance for that extra failure margin.
TL;DR
- 3-node ETCD clusters are the best choice for most Kubernetes/k3s environments.
- 5-node clusters offer more redundancy but come with extra complexity and performance costs.
- Loss of quorum is not a disaster—it’s recoverable.
- Backups and restore paths make even worst-case recovery feasible.
And finally: if you're seeing multiple ETCD nodes go down frequently, the real problem might not be the number of nodes—but your hosting provider.
-
 @ 6fc114c7:8f4b1405
2025-05-03 22:06:36
@ 6fc114c7:8f4b1405
2025-05-03 22:06:36In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ fd06f542:8d6d54cd
2025-04-28 05:52:48
@ fd06f542:8d6d54cd
2025-04-28 05:52:48什么是narr?
今天翻 fiatjaf 仓库 竟然发现了这个宝贝 narr和我最进做的 nostrbook.com有交集。
? 交集在哪里呢? narr (not another rss reader) is a web-based RSS and Nostr long-form feed aggregator which can be used both as a desktop application and a personal self-hosted server. 1. long-form ,也就是30023. 2. desktop application
这两点足够对我有吸引力。
下载,运行 界面不错。 继续!
 {.user-img}
{.user-img}不过这个是需要 自己通过浏览器浏览的。并没有独立打包成一个app。那么问题来了,不够阿。
顺着他的介绍,The app is a single binary with an embedded database (SQLite), it is based on yarr.
yarr
我去看了看yarr 是可支持gui的,不过Linux支持的不够,我平时基本就是Linux。 怎么办?
webkit
用webkit套一个吧。 ```go package main
/*
cgo linux pkg-config: webkit2gtk-4.1 gtk+-3.0
include
include
static void initAndShow(GtkWidget *window, const char url) { // 必须初始化 GTK gtk_init(NULL, NULL);
*window = gtk_window_new(GTK_WINDOW_TOPLEVEL); gtk_window_set_title(GTK_WINDOW(*window), "nostrbook.com"); gtk_window_set_default_size(GTK_WINDOW(*window), 1024, 600); // 创建 WebView GtkWidget *webview = webkit_web_view_new(); gtk_container_add(GTK_CONTAINER(*window), webview); webkit_web_view_load_uri(WEBKIT_WEB_VIEW(webview), url); // 显示窗口 gtk_widget_show_all(*window);} */ import "C" import ( "unsafe" )
func main() { var window *C.GtkWidget url := C.CString("http://127.0.0.1:7049") defer C.free(unsafe.Pointer(url))
// 调用 C 函数初始化 C.initAndShow(&window, url) // 进入 GTK 主循环 C.gtk_main()}
```
什么是下一步呢?
继续研究吧,看看go + webkit 能不能打包 这个 http server ?
再看看 有没有可以编辑的 md ide 用simple 也可以的。
等等看吧。
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 044da344:073a8a0e
2025-05-03 19:02:02
@ 044da344:073a8a0e
2025-05-03 19:02:02Mein Thema kommt heute aus dem Kalender und hat gleich noch zu einem Video geführt. Internationaler Tag der Pressefreiheit – wie jedes Jahr am 3. Mai. Das Publikum liebt Ranglisten. Shanghai für die Hochschulen, der Best Country Report für die Lebensqualität und Freedom House für die Freiheit in der Welt. Es gibt Aufsteiger und Absteiger und Jahr für Jahr eine Meldung, über die sich trefflich diskutieren lässt – vor allem in Europa und Nordamerika, wo die Sieger wohnen. Man muss die Statistik dafür nicht einmal fälschen, sondern einfach nur das messen, was man selbst am besten kann, und alles weglassen, was das Bild trüben könnte. Bei den „Reportern ohne Grenzen“ sorgen dafür die Geldgeber und Fragen, die sich zum Beispiel in Afrika oder in Südostasien gar nicht stellen. Ergebnis: Die Medien sind bei uns ziemlich frei, auch wenn Leser dieser Seite wissen, dass das so nicht stimmt.
Okay: Deutschland hat es wieder nicht ganz geschafft in den grünen Bereich – dorthin, wo die skandinavischen Länder stehen, die Niederlande oder Irland. Deutschland gehört auch nicht mehr zu den Top Ten wie noch 2024, aber es war knapp. Platz elf. Zum Glück nennen die „Reporter ohne Grenzen“ die Schuldigen. Zensur? Gott bewahre. Das Ausblenden, Diffamieren, Verleumden von allen, die laut Fragen stellen zum Regierungskurs? Doch nicht bei uns. Dieses Land würde auch in Sachen Pressefreiheit längst Weltmeister sein, wenn da nicht ein paar Unverbesserliche wären, die auf Journalisten ungefähr so reagieren wie ein Stier auf ein rotes Tuch. Glaubt man den „Reportern ohne Grenzen“, dann sind Demos in Deutschland ein gefährlicher Ort für alle, die dort mit Kamera, Mikro oder Presseschild auftauchen. 75 „physische Angriffe“ 2024, davon die meisten in Berlin und beim Thema Nahost, wobei es zwei Bild-Reporter allein auf 29 Einträge gebracht haben (Iman Sefati und seine Fotografin Yalcin Askin).
Vorweg: Jede Attacke ist eine zu viel. Gleich danach kommt aber der Verdacht, dass das ganz gut passt, weil die „Reporter ohne Grenzen“ so eine „zunehmende Pressefeindlichkeit“ beklagen können und „ein verengtes Verständnis von Pressefreiheit“. Zitat: „Denn viele Bürger*innen sehen Berichterstattende, die nicht ihrem eigenen politischen Spektrum entstammen, mittlerweile als Gegner an.“
Sorry für die Genderei. Ich habe das so gelassen, weil es vermutlich bereits damit anfängt. Mit einem „verengten Verständnis“ auch und gerade bei der Sprache. Lassen Sie uns das in drei Schritten angehen. Nummer eins: Wir schauen auf den Kellner, der da jedes Jahr zum Welttag der Pressefreiheit eine Quittung ausstellt. Nummer zwei: Wir zählen nach. Und Nummer drei: Wir schlagen all das drauf, was in der Rechnung fehlt.
Die „Reporter ohne Grenzen“ sitzen in Paris und sind damit auf den ersten Blick weniger verdächtig als der US-Thinktank „Freedom House“, der bis 2017 jedes Jahr eine Konkurrenzliste veröffentlicht hat und einen Großteil seiner Gelder und Sicherheiten direkt oder indirekt aus dem Staatshaushalt in Washington bezieht. Der Volksmund weiß, was das Brot aus den Liedern macht, die draußen gesungen werden. Bei den „Reportern ohne Grenzen“ kommt das Geld aus ganz ähnlich Töpfen – 2023 zu drei Vierteln von der EU, von staatlichen Behörden und von den großen Stiftungen. Ford, Luminate (Geldbörse von Ebay-Gründer Pierre Omidyar, der auch bei den Faktencheckern mitspielt), Open Society Foundations. Der deutsche Steuerzahler ist über ein Ministerium (Entwicklungshilfe) und den Berliner Senat jeweils mit einer Viertelmillion Euro dabei. Dass die Niederlande und Schweden mitspielen, erklärt sich bei einem Blick auf die Ergebnisse (in diesem Jahr: Platz 3 und 4). Besser kann man nicht investieren in Werbung für das eigene Land.
Diese Platzierungen sind gewissermaßen ein Selbstläufer, weil all das in die Wertung kommt, was der Westen gut findet – die formale Trennung von Regierung und Redaktionen zum Beispiel. Andersherum: Abzüge gibt es überall da, wo der Staat, Parteien oder Politiker selbst Medien betreiben. In Uganda zum Beispiel, Platz 143, gibt es kaum Werbetreibende, die ein TV-Programm finanzieren könnten, und nur ein kleines Publikum, das sich ein Zeitungsabo leisten kann und will. Sonntags drängen sich die Menschen dort vor kleinen Hütten mit großen Bildschirmen, um ihren Lieblingen aus der Premier League zuzujubeln und vielleicht einen Wettgewinn einzustreichen, der sie über die Woche trägt. Auf dem Land gehören die Radiostationen in aller Regel lokalen Größen. Kirche, Politik, Wirtschaft. Ich habe dort Interviews geführt und gelernt: Über „Pressefreiheit“ und Informationsqualität sagt das alles wenig. Die Menschen in Uganda wissen sehr genau, wer jeweils zu ihnen spricht, und machen sich ihren Reim darauf. Ein anderer Kriterienkatalog könnte daraus ein Qualitätsmerkmal machen. Während Besitz- und damit Machtverhältnisse im Westen hinter Nebelkerzen versteckt werden (Objektivität, Unabhängigkeit, Neutralität), herrscht in Uganda Transparenz.
Neben dem „politischen Kontext“ haben die „Reporter ohne Grenzen“ vier weitere Blöcke in ihrem Punktekatalog. Gesetze, Wirtschaft, Gesellschaft, Sicherheit. Die Fragen decken das ab, was bei uns Standard ist. Dürfen sich Journalisten gewerkschaftlich organisieren? Werden sie bestochen? Können Nachrichtenmedien finanziell überleben? Werden Karikaturen toleriert? Ich will hier nicht zu sehr auf Uganda herumreiten. Nur: Der Beruf wird dort völlig anders gesehen als hier. Es gibt nur eine kleine vierstellige Zahl an Journalisten. 1000, vielleicht 1500. Die meisten sind jung, weil die Redaktionen als Sprungbrett gesehen werden zu einem wirklich lukrativen Job in der Verwaltung, in den Unternehmen, in der Politik. Wer zu einer Pressekonferenz fährt, erwartet dort einen Umschlag. Offiziell: Anreisepauschale. Inoffiziell der Preis für einen wohlwollenden Bericht. Die „Reporter ohne Grenzen“ strafen Uganda folglich ab. Angriffe auf Journalisten (oft von Sicherheitsleuten), wenig Schutz vor Gericht, wenig Achtung vor dem Beruf. Platz 143 halt.
Und Deutschland? Die Demos wie gesagt und Leute, die die Dinge einfach falsch sehen. Ein „verengtes Verständnis von Pressefreiheit“. Außerdem sagen die „Reporter ohne Grenzen“: Wir tun zu wenig gegen „Hassrede und Desinformation“. Der Koalitionsvertrag von Schwarz-Rot ist offenbar nicht mehr eingeflossen in diesen Bericht. Dort heißt es:
Gezielte Einflussnahme auf Wahlen sowie inzwischen alltägliche Desinformation und Fake News sind ernste Bedrohungen für unsere Demokratie, ihre Institutionen und den gesellschaftlichen Zusammenhalt. Die bewusste Verbreitung falscher Tatsachenbehauptungen ist durch die Meinungsfreiheit nicht gedeckt. Deshalb muss die staatsferne Medienaufsicht unter Wahrung der Meinungsfreiheit auf der Basis klarer gesetzlicher Vorgaben gegen Informationsmanipulation sowie Hass und Hetze vorgehen können.
Schon vorab hatten die „Reporter ohne Grenzen“ von „einem stark verengten Meinungskorridor bei der Arbeit zu Israel und Palästina“ berichtet. Selbst alte Hasen haben in dieser Befragung gesagt, dass sie noch nie einen solchen Druck erlebt hätten – vor allem dann, wenn es um die israelische Kriegsführung geht, um die Folgen für die Bevölkerung in Gaza und um das, was in Deutschland zu diesem Thema passiert. Ich verlinke hier die Münchner Rede von Andreas Zumach, gehalten im November 2018, wo all das schon Thema war.
Und sonst? Corona, Ukraine, Klima und damit Energiewende? Kontokündigungen? Gerichtsurteile, die selbst es bis in die Weltpresse schafften (im Bild: The Economist vom 16. April 2025) und dort Unbehagen auslösten? Eine Cancel Culture, die Sprecher aus der Öffentlichkeit verbannt, die sich gegen die herrschende Ideologie und den Regierungskurs stellen?
Alles kein Thema – jedenfalls nicht für die Experten, die gefragt werden (Journalisten, Forscher, Akademiker, Menschenrechtsspezialisten; mithin Menschen, die in irgendeiner Form von Staat oder Konzernen abhängen). Die konzernfreien oder neuen Medien senden für die „Reporter ohne Grenzen“ offenbar jenseits von Gut und Böse. Und dass die Regierung Fernsehen, Radio und Presse nicht unbedingt selbst betreiben muss wie in Uganda, um ihre Sicht der Dinge flächendeckend zu verbreiten, scheint dort außerhalb jeder Vorstellungskraft zu liegen. Anders ist nicht zu erklären, dass im Bericht zwar ein paar öffentlich-rechtliche Skandälchen auftauchen und der Stellenabbau bei der Südwestdeutschen Medienholding, aber nichts zu lesen ist über die Aufrüstung der Medienapparate in Ministerien, Parteien, Unternehmen und über den Druck, der davon auf Journalisten ausgeht, die zwar keinen Umschlag bekommen, wenn sie ordentlich berichten, aber sicher ein wenig Exklusives, wahrscheinlich eine Beförderung und vielleicht sogar ein Ticket für den Sprung auf die andere, besser entlohnte Seite. Bis es soweit ist, melden sie einfach, dass mit der Medienfreiheit alles okay ist, wenn es da nicht diese Chaoten auf der Straße geben würde und ein paar Unverbesserliche mit einem „verengten Verständnis von Pressefreiheit“. Sonst müsste man sich möglicherweise aufmachen und nach den Ursachen für den Unmut fragen.
-
 @ d0ea1c34:9c84dc37
2025-05-03 17:53:05
@ d0ea1c34:9c84dc37
2025-05-03 17:53:05Markdown Rendering Test Document
Basic Text Formatting
This is a paragraph with bold text, italic text, and bold italic text. You can also use underscores for bold or single underscores for italics.
This is a paragraph with some
inline codeusing backticks.Lists
Unordered Lists
- Item 1
- Item 2
- Nested item 2.1
- Nested item 2.2
- Item 3
Ordered Lists
- First item
- Second item
- Nested item 2.1
- Nested item 2.2
- Third item
Links and Images
Blockquotes
This is a blockquote.
It can span multiple lines.
And can be nested.
Code Blocks
```python def hello_world(): print("Hello, world!")
This is a Python code block with syntax highlighting
hello_world() ```
javascript // JavaScript code block function helloWorld() { console.log("Hello, world!"); }Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Cell 1 | Cell 2 | Cell 3 | | Cell 4 | Cell 5 | Cell 6 | | Cell 7 | Cell 8 | Cell 9 |
Horizontal Rules
Task Lists
- [x] Completed task
- [ ] Incomplete task
- [x] Another completed task
Math (if supported)
Inline math: $E = mc^2$
Block math:
$$ \frac{d}{dx}e^x = e^x $$
Footnotes
Here's a sentence with a footnote reference[^1].
[^1]: This is the footnote content.
Definition Lists
Term 1 : Definition 1
Term 2 : Definition 2a : Definition 2b
Special Characters & Escaping
*This text is surrounded by asterisks but not italicized*
Advanced Formatting
Click to expand
This is hidden content that appears when expanded.Emoji (if supported)
:smile: :heart: :thumbsup:
Final Notes
This document demonstrates various Markdown formatting features. Compatibility may vary across different Markdown renderers and platforms.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 2e8970de:63345c7a
2025-05-03 17:31:07
@ 2e8970de:63345c7a
2025-05-03 17:31:07The figure in this article illustrates exactly how most biology papers are secretly p-hacked. A large number of hypotheses is explored, and only the ones that form a coherent story are reported.
This is actually the main reason behind the replication crisis in biology IMO. (source)
https://www.nature.com/articles/s41587-025-02635-7
originally posted at https://stacker.news/items/970464
-
 @ fc7085c3:0b32a4cb
2025-05-03 16:17:10
@ fc7085c3:0b32a4cb
2025-05-03 16:17:10- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- (ongoing) slooowly migrate kind:1 app from Qwik to above framework
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- nread.me: add nostr documentation (mpa for this part cause seo)
- nread.me: add nip crud (save on relay)
- nread.me: add nip curation (rating and labeling)
- nread.me: filter by curator / rating / labeling
- nread.me: seed curator (fiatjaf) adds other curators
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- start simplified messenger app to test custom chat spec
- ...don't know what's next yet
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ 75869cfa:76819987
2025-03-18 07:54:38
@ 75869cfa:76819987
2025-03-18 07:54:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 225,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 95%. More than 10 million events have been published, with posts and reposts showing a decrease. Total Zap activity stands at approximately 15 million, marking a 10% decrease.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 463 long-form articles were published, 29% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 225,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 18179 events, with a low of approximately 16093.
The number of new users has decreased significantly. Profiles with a contact list are now around 17,511, reflecting a 95% drop. Profiles with a bio have decreased by 62% compared to the previous period. The only category showing growth is pubkeys writing events, which have increased by 27%.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 14% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.6 million, which is a 6.1% decrease. Both reposts and reactions have decreased by about 10%.
For zap activity, the total zap amount is about 15 million, showing an increase of over 10% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that A bulletin board is a relay-centric system of forums where users can post and reply to others, typically around a specific community. The relay operator controls and moderates who can post and view content. A board is defined by kind:30890. Its naddr representation must provide the community's home relays, from which all posts should be gathered. No other relays should be used.
nostr:npub1xy54p83r6wnpyhs52xjeztd7qyyeu9ghymz8v66yu8kt3jzx75rqhf3urc is proposing a standardized way to represent fitness and workout data in Nostr, including: Exercise Templates (kind: 33401) for storing reusable exercise definitions, Workout Templates (kind: 33402) for defining workout plans, Workout Records (kind: 1301) for recording completed workouts. The format provides structured data for fitness tracking while following Nostr conventions for data representation.Many fitness applications use proprietary formats, locking user data into specific platforms. This NIP enables decentralized fitness tracking, allowing users to control their workout data and history while facilitating social sharing and integration between fitness applications.
nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef is proposing a PR introduces two "1-click" connection flows for setting up initial NWC connections. Rather than having to copy-paste a connection string, the user is presented with an authorization page which they can approve or decline. The secret is generated locally and never leaves the client. HTTP flow - for publicly accessible lightning wallets. Implemented in Alby Hub (my.albyhub.com) and CoinOS (coinos.io). Nostr flow - for mobile-based / self-hosted lightning wallets, very similar to NWA but without a new event type added. Implemented in Alby Go and Alby Hub. Benefits over NWC Deep Links are that it works cross-device, mobile to web, and the client-generated secret never leaves the client. Both flows are also implemented in Alby JS SDK and Bitcoin Connect.
add B0 NIP for Blossom interaction
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 describes a tiny subset of possible Blossom capabilities, but arguably the most important from the point of view of a most basic Nostr client. This NIP specifies how Nostr clients can use Blossom for handling media. Blossom is a set of standards (called BUDs) for dealing with servers that store files addressable by their SHA-256 sums. Nostr clients may make use of all the BUDs for allowing users to upload files, manage their own files and so on, but most importantly Nostr clients SHOULD make use of BUD-03 to fetch kind:10063 lists of servers for each user.
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q defines a standard for creating, managing and publishing to communities by leveraging existing key pairs and relays, introducing the concept of "Communi-keys". This approach allows any existing npub to become a community (identity + manager) while maintaining compatibility with existing relay infrastructure.
A way for relays to be honest about their algos
securitybrahh is proposing a PR introduces NIP-41, a way for relays to be honest about their algos, edits 01.md to account for changes in limit (related #78, #1434, received_at?, #620, #1645) when algo is provided, appends 11.md for relays to advertize whether they are an aggregator or not and their provided algos. solves #522, supersedes #579.
nip31: template-based "alt" tags for known kinds
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that clients hardcoding alt tags are not very trustworthy. alt tags tend to be garbage in a long-enough timeframe.This fixes it with hardcoded rich templates that anyone can implement very easily without having to do it manually for each kind. alt tags can still be used as a fallback.
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a PR addresses 3 main problems of NIP-44v2. First, It has a message size limit of 65Kb, which is unnecessarily small. Second, It forces the encrypting key to be the same as the event's signing key. Which forces multi-sig actors to share their main private key in order to encrypt the payload that would be later signed by the group. Decoupling singing and encryption keys, for both source and destination, is one of the goals of this version. And It offers no way to describe what's inside the encrypted blob before requesting the user's approval to decrypt and send the decrypted info back to the requesting application. This PR adds an alt description to allow decrypting signers to display a message and warn the user of what type of information the requesting application is receiving.
Notable Projects
Damus nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
- Notes in progress will always be persisted and saved automatically. Never lose those banger notes when you aren't quite ready to ship them.
- Make your profile look just right without any fuss. It also optimizes them on upload now to not nuke other people’s phone data bills.
- You won't see the same note more than once in your home feed.
- Fixed note loading when clicking notifications and damus.io links.
- Fixed NWC not working when you first connect a wallet.
- Fixed overly sensitive and mildly infuriating touch gestures in the thread view when scrolling
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for Android build 2.1.9 has been released. * Multi-account support * Deep linking support * "Share via Primal" support * Bug fixes and improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
YakiHonne Wallet just got a fresh new look!
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xchat v1.4.7-beta release * Upgraded the Flutter framework to v3.29.0. * Private chat implementation changed to NIP-104 Nostr MLS. * NIP-17 and NIP-29 messages now support q tags. * You can swipe left to reply to your own messages. * Chat messages now support code block display. * Copy images from the clipboard. * Fixed an issue where underlined text in chat appeared as italic.
GOSSIP 0.14.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * New Features and Improvements * Zappers and amounts are now shown (click on the zap total) * Reactions and who reacted are now shown (click on the reaction numbers) * Multiple search UI/UX improvements * Undo Send works for DMs too * Undo Send now restores the draft * UI: Side panel contains less so it can be thinner. Bottom bar added. * UI: frame count and spinner (optional) * Relay UI: sorting by score puts important relays at the top. * Relay UI: add more filters so all the bits are covered * Image and video loading is much faster (significant lag reduction) * Thread loading fix makes threads load far more reliably * Settings have reset-to-default buttons, so you don't get too lost. * Setting 'limit inbox seeking to inbox relays' may help avoid spam at the expense of possibly * Fix some bugs * And more updates
Nostur v1.18.1 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Floating mini video player * Videos: Save to library, Copy video URL, Add bookmark * Improved video stream / chat view * Top zaps on live chat * Posting to Picture-first * Profile view: Show interactions with you (conversations, reactions, zaps, reposts) * Profile view: Show actual reactions instead of only Likes * Improved search + Bookmark search * Detect nsfw / content-warning in posts * Show more to show reactions outside Web of Trust * Show more to show zaps outside Web of Trust * Support .avif image format * Support .mp3 format * Support .m4v video format * Improved zap verification for changed wallets * Improved outbox support * Show label on restricted posts * Low data mode: load media in app on tap instead of external browser * Many other bug fixes and performance improvements
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Latest two releases of Alby Go, 1.10 and 1.11, brought you lots of goodies: * BTC Map integration for quick access to global bitcoin merchants map * Confirm new NWC connections to your Alby Hub directly in Alby Go! No more copy-pasting or QR code scanning * Support for MoneyBadger Pay Pick n Pay QR payments in over 2000 stores in South Africa
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.0 is now available. This release features the ability to renew channel leases, spin up multiple embedded wallets, Nostr Wallet Connect client support, and more. * Renewable channels * NWC client support * Ability to create multiple Embedded LND 'node in the phone' wallets * Ability to delete Embedded LND wallets * Embedded LND: v0.18.5-beta * New share button (share ZEUS QR images) * Tools: Export Activity CSVs, Developer tools, chantools * Activity: filter by max amount, memo, and note
Long-Form Content Eco
In the past two weeks, more than 463 long-form articles have been published, including over 91 articles on Bitcoin and more than 41 related to Nostr, accounting for 29% of the total content.
These articles about Nostr mainly explore the rise of Nostr as a decentralized platform that is reshaping the future of the internet. They emphasize Nostr's role in providing users with greater freedom, ownership, and fair monetization, particularly in the realm of content creation. The platform is positioned as a counter to centralized social media networks, offering uncensored interactions, enhanced privacy, and direct transactions. Many articles delve into Nostr’s potential to integrate with Bitcoin, creating a Layer 3 solution that promises to end the dominance of old internet structures. Discussions also cover the technical aspects of Nostr, such as the implementation of relays and group functionalities, as well as security concerns like account hacks. Furthermore, there is an exploration of the philosophical and anthropological dimensions of Nostr, with the rise of "Dark Nostr" being portrayed as a deeper expression of decentralized freedom.
The Bitcoin articles discuss the ongoing evolution of Bitcoin and its increasing integration into global financial systems. Many articles focus on the growing adoption of Bitcoin, particularly in areas like Argentina and the U.S., where Bitcoin is being used for rental payments and the establishment of a strategic Bitcoin reserve. Bitcoin is also portrayed as a response to the centralized financial system, with discussions about how it can empower individuals through financial sovereignty, provide a hedge against inflation, and create fairer monetization models for creators. Additionally, the articles explore the challenges and opportunities within the Bitcoin ecosystem, including the rise of Bitcoin ETFs, the development of Bitcoin mining, and the potential impact of AI on Bitcoin adoption. There is also emphasis on Bitcoin's cultural and economic implications, as well as the need for decentralized education and innovation to drive further adoption.
Thank you, nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub17wrn0xxg0hfq7734cfm7gkyx3u82yfrqcdpperzzfqxrjf9n7tes6ra78k nostr:npub1fxq5crl52mre7luhl8uqsa639p50853r3dtl0j0wwvyfkuk4f6ssc5tahv nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2 nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 nostr:npub1uv0m8xc6q4cnj2p0tewmcgkyzg8cnteyhed0zv30ez03w6dzwvnqtu6gwl nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1gqgpfv65dz8whvyup942daagsmwauj0d8gtxv9kpfvgxzkw4ga4s4w9awr nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The first Bitcoin Meetup organized by Mi Primer Bitcoin was successfully held on March 14, 2025, at Texijal Pizza in Apaneca. The event included Bitcoin education, networking, a Q&A session, and merchandise distribution, offering an exciting experience for all participants.
* The Btrust Space discussion was successfully held on March 13, 2024. The event focused on how to support Bitcoin developers, fund open-source contributions, and grow the Bitcoin ecosystem. The speakers included Bitcoin core contributors, Btrust CEO, engineering leads, and other project leaders.Here is the upcoming Nostr event that you might want to check out.
- The Nostr Workshop, organized by YakiHonne and Bitcoin Safari, will take place online via Google Meet on March 17, 2025, at 7:00 PM (GMT+1). The event will introduce the Nostr ecosystem and Bitcoin payments, with participants learning about decentralized technology through YakiHonne and earning rewards. Register and verify your account to claim exclusive rewards, and invite friends to unlock additional rewards.
- The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar will be held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar will be hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (Lawyer specializing in Banking, Corporate, and Financial Law). The session aims to introduce the academic program and explore Bitcoin, the crypto economy, and related legal issues.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. The event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ 90c656ff:9383fd4e
2025-05-03 11:52:14
@ 90c656ff:9383fd4e
2025-05-03 11:52:14In recent years, Bitcoin has often been compared to gold, earning the nickname “digital gold.” This comparison arises because both forms of value share key characteristics, such as scarcity, durability, and global acceptance. However, Bitcoin also represents a technological innovation that redefines the concept of money and investment, standing out as a modern and efficient alternative to physical gold.
One of the main reasons Bitcoin is compared to gold is its programmed scarcity. While gold is a naturally limited resource whose supply depends on mining, Bitcoin has a maximum cap of 21 million units, defined in its code. This cap protects Bitcoin from inflation, unlike traditional currencies that can be created without limit by central banks.
This scarcity gives Bitcoin lasting value, similar to gold, as the limited supply helps preserve purchasing power over time. As demand for Bitcoin grows, its reduced availability reinforces its role as a store of value.
Another feature that brings Bitcoin closer to gold is durability. While gold is resistant to corrosion and can be stored for centuries, Bitcoin is a digital asset protected by advanced cryptography and stored on the blockchain. An immutable and decentralized ledger.
Moreover, Bitcoin is far easier to transport than gold. Moving physical gold involves high costs and security risks, making transport particularly difficult for international transactions. Bitcoin, on the other hand, can be sent digitally anywhere in the world in minutes, with low fees and no intermediaries. This technological advantage makes Bitcoin more effective in a globalized and digital world.
Security is another trait that Bitcoin and gold share. Gold is difficult to counterfeit, making it a reliable store of value. Similarly, Bitcoin uses cryptographic protocols that ensure secure transactions and protect against fraud.
In addition, all Bitcoin transactions are recorded on the blockchain, offering a level of transparency that physical gold does not provide. Anyone can review transactions on the network, increasing trust and traceability.
Historically, gold has been used as a hedge against inflation and economic crises. During times of instability, investors turn to gold as a way to preserve their wealth. Bitcoin is emerging as a digital alternative with the same purpose.
In countries with high inflation or political instability, Bitcoin has been used as a safeguard against the devaluation of local currencies. Its decentralized nature prevents governments from directly confiscating or controlling the asset, providing greater financial freedom to users.
Despite its similarities with gold, Bitcoin still faces challenges. Its volatility is much higher, which can cause short-term uncertainty. However, many experts argue that this volatility is typical of new assets and tends to decrease over time as adoption grows and the market matures.
Another challenge is regulation. While gold is globally recognized as a financial asset, Bitcoin still faces resistance from governments and financial institutions, which seek ways to control and regulate it.
In summary, Bitcoin - often called "digital gold" - offers a new form of value that combines the best characteristics of gold with the efficiency and innovation of digital technology. Its programmed scarcity, cryptographic security, portability, and resistance to censorship make it a viable alternative for preserving wealth and conducting transactions in the modern world.
Despite its volatility, Bitcoin is establishing itself as both a store of value and a hedge against economic crises. As such, it represents not just an evolution of the financial system but also a symbol of the shift toward a decentralized and global digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13
@ 04cb16e4:2ec3e5d5
2025-03-13 21:26:13Wenn man etwas verkaufen will, muss man eine Geschichte über sein Produkt erzählen. Nur wenige können etwas damit anfangen, wenn du sagst: Unser Produkt enthält 50 Gramm Hafer (hoffentlich gentechnikfrei), 5 mittelgroße Erdbeeren, Spuren von Sesamschalen sowie einen Teelöffel Honig. So funktioniert das nicht. Dein Riegel braucht einen Namen und eine Geschichte.
Wenn wir über Krieg und Frieden sprechen, denn gibt es zumeist Zahlen, Fakten und Meinungen. Tausende von Kindern die in einem Krieg getötet werden sind eine schockierende Anzahl. Nimmst du die Zahlen weg und beschäftigst dich mit jedem einzelnen Schicksal, dann ist das unmöglich zu ertragen. Also kämpfen wir hier vor Ort, in Deutschland, zwar nicht mit Waffen gegeneinander, sondern mittels unserer Meinungen in Kombination mit zu vermittelnden relativen Wahrheiten. Da kommt das Ego ins Spiel. Wir wollen unbedingt Recht haben! Irgendeiner soll in diesem Meinungskampf am Ende als Gewinner dastehen. Weil er die besseren Argumente hat. Schließlich werden Emotionen mit Fakten vermischt und als Totschlagargumente in die Gegenfront geworfen.
Was aber, wenn man eine Geschichte über den Krieg erzählt, die jeden mitnehmen kann, ganz gleich, welche Meinung man zu den aktuell verhandelten Kampfschauplätzen hat? Alles Trennende wird aus der Erzählung herausgenommen und was bleibt, sind die zerstörerische Kraft des Krieges und die Verantwortung jedes einzelnen Menschen zu entscheiden, ob er dieses grausame Monster füttert oder eben nicht. In dem afrikanischen Märchen „Sheikhi“ basieren diese Entscheidungen nicht auf Fakten und Meinungen, sondern auf persönlichen Erfahrungen. Die Protagonisten nehmen uns mit in ihre Welt und lassen uns ihre inneren Kämpfe, Zweifel, Ängste und Hoffnungen miterleben. Wir können uns mit ihnen identifizieren, obwohl wir unter völlig anderen Bedingungen leben und sterben.
Hier kannst du das Buch direkt beim Verlag bestellen
Die alternative Buchmesse Seitenwechsel
Am Ende des Buches konnte ich gar nicht anders, als eine tiefe Sehnsucht nach Frieden und Einigkeit zu verspüren. Diese Sehnsucht basierte aber nicht mehr auf dem Bedürfnis, bessere Argumente als die vermeintliche Gegenseite zu haben, sondern vielmehr darauf, dass dieses verzweifelte Ringen und Hassen endlich zu einem Ende kommt. Nicht nur auf den Schlachtfeldern Asiens und Afrikas, sondern ebenfalls auf Facebook, X, den Straßen unserer Städte und im Krieg jedes Menschen gegen sich selbst. Inzwischen gelingt es mir immer öfter, mir einen bissigen Kommentar zu verkneifen, wenn jemand auf Facebook etwas schreibt, was ich unerträglich finde. Ich weiß, das ich ihn nicht vom Gegenteil überzeugen werde und das mein Kommentar das selbe Monster füttert, dass sich an den Opfern des Krieges satt isst.
Wenn es irgendwo Menschen auf der Welt gibt, die Mord und Folter verzeihen können, dann kann auch ich eine andere Meinung ertragen ohne rechthaberisch, arrogant und destruktiv zu werden. Notfalls gehe ich in den Wald und schreie.
-
 @ a012dc82:6458a70d
2025-03-11 15:41:36
@ a012dc82:6458a70d
2025-03-11 15:41:36Argentina's journey through economic turmoil has been long and fraught with challenges. The country has grappled with inflation, debt, and a fragile economic structure that has left policymakers searching for solutions. In this context, President Javier Milei's introduction of the "Ley Ómnibus" represented a bold step towards addressing these systemic issues. The reform package was not just a set of isolated measures but a comprehensive plan aimed at overhauling the Argentine economy and social framework. The intention was to create a more robust, free, and prosperous Argentina, where economic freedoms could lead to broader social benefits.
The "Ley Ómnibus" was ambitious in its scope, covering a wide range of areas from tax reform to social policies, aiming to stimulate economic growth, reduce bureaucratic red tape, and enhance the overall quality of life for Argentines. This package was seen as a critical move to reset the economic compass of the country, aiming to attract foreign investment, boost local industry, and provide a clearer, more stable environment for businesses and individuals alike. However, such sweeping reforms were bound to encounter resistance, particularly when they touched upon sensitive areas like taxation and digital assets.
Table of Contents
-
The Crypto Tax Proposal: Initial Considerations
-
Public Backlash and Strategic Withdrawal
-
The Rationale Behind Dropping Crypto Taxes
-
Implications for Crypto Investors and the Market
-
Milei's Political Strategy and Future Prospects
-
Conclusion
-
FAQs
The Crypto Tax Proposal: Initial Considerations
Within the vast array of proposals in the Ley Ómnibus, the crypto tax stood out due to its novelty and the growing interest in digital currencies within Argentina. The country had seen a surge in cryptocurrency adoption, driven by factors such as high inflation rates and currency controls that made traditional financial systems less attractive. Cryptocurrencies offered an alternative for savings, investment, and transactions, leading to a burgeoning crypto economy.
The initial rationale behind proposing a crypto tax was multifaceted. On one hand, it aimed to bring Argentina in line with global trends where countries are increasingly seeking to regulate and tax digital currencies. On the other hand, it was seen as a potential new revenue stream for the government, which was desperately seeking funds to address its fiscal deficits. The proposal also intended to bring transparency to a sector that is often criticized for its opacity, making it easier to combat fraud, money laundering, and other illicit activities associated with cryptocurrencies.
However, the proposal was not just about regulation and revenue. It was also a litmus test for Argentina's approach to innovation and digital transformation. How the government handled this issue would signal its stance towards new technologies and economic paradigms, which are increasingly dominated by digital assets and fintech innovations.
Public Backlash and Strategic Withdrawal
The backlash against the proposed crypto taxes was swift and significant. The crypto community in Argentina, which had been flourishing in an environment of relative freedom, saw the tax as a direct threat to its growth and viability. But the discontent went beyond the crypto enthusiasts; the general public, already burdened by high taxes and economic instability, viewed the proposal as yet another financial strain.
The protests and debates that ensued highlighted a broader discontent with the government's approach to economic management. Many Argentines felt that the focus should be on fixing the fundamental issues plaguing the economy, such as inflation and corruption, rather than imposing new taxes. The crypto tax became a symbol of the government's perceived detachment from the real concerns of its citizens.
In this heated atmosphere, President Milei's decision to withdraw the crypto tax proposal from the Ley Ómnibus was not just a tactical retreat; it was a necessary move to quell the growing unrest and focus on more pressing economic reforms. This decision underscored the complexities of governing in a highly polarized environment and the need for a more nuanced approach to policy-making, especially when dealing with emerging technologies and markets.
The Rationale Behind Dropping Crypto Taxes
The decision to drop the crypto tax from the omnibus reform package was not taken lightly. It was a recognition of the crypto sector's unique dynamics and the government's limitations in effectively regulating and taxing this space without stifling innovation. The move also reflected a broader understanding of the economic landscape, where rapid development and legislative efficiency were deemed more crucial than ever.
By removing the contentious clauses, the government aimed to streamline the passage of the Ley Ómnibus, ensuring that other, less controversial, reforms could be implemented swiftly. This strategic pivot was also a nod to the global debate on how best to integrate cryptocurrencies into national economies. Argentina's government recognized that a more cautious and informed approach was necessary, one that could balance the need for regulation with the desire to foster a thriving digital economy.
Furthermore, the withdrawal of the crypto tax proposal can be seen as an acknowledgment of the power of public opinion and the crypto community's growing influence. It highlighted the need for governments to engage with stakeholders and understand the implications of new technologies before rushing to regulate them.
Implications for Crypto Investors and the Market
The removal of the crypto tax proposal has had immediate and significant implications for the Argentine crypto market. For investors, the decision has provided a reprieve from the uncertainty that had clouded the sector, allowing them to breathe a sigh of relief and continue their activities without the looming threat of new taxes. This has helped sustain the momentum of the crypto market in Argentina, which is seen as a vital component of the country's digital transformation and economic diversification.
However, the situation remains complex and fluid. The government's stance on cryptocurrencies is still evolving, and future regulations could impact the market in unforeseen ways. Investors are now more aware of the need to stay informed and engaged with regulatory developments, understanding that the legal landscape for digital currencies is still being shaped.
The episode has also highlighted the broader challenges facing the Argentine economy, including the need for comprehensive tax reform and the creation of a more conducive environment for technological innovation and investment. The crypto market's response to the government's actions reflects the delicate balance between regulation and growth, a balance that will be crucial for Argentina's economic future.
Milei's Political Strategy and Future Prospects
President Milei's handling of the crypto tax controversy reveals much about his political strategy and vision for Argentina. By withdrawing the proposal, he demonstrated a willingness to listen to public concerns and adapt his policies accordingly. This flexibility could be a key asset as he navigates the complex landscape of Argentine politics and governance.
The episode also offers insights into the potential future direction of Milei's administration. The focus on economic reforms, coupled with a pragmatic approach to contentious issues, suggests a leadership style that prioritizes economic stability and growth over ideological purity. This could bode well for Argentina's future, particularly if Milei can harness the energy and innovation of the digital economy as part of his broader reform agenda.
However, the challenges ahead are significant. The Ley Ómnibus is just one part of a larger puzzle, and Milei's ability to implement comprehensive reforms will be tested in the coming months and years. The crypto tax saga has shown that while change is possible, it requires careful negotiation, stakeholder engagement, and a clear understanding of the economic and social landscape.
Conclusion
The story of Argentina's crypto tax proposal is a microcosm of the broader challenges facing the country as it seeks to reform its economy and society. It highlights the tensions between innovation and regulation, the importance of public opinion, and the complexities of governance in a rapidly changing world.
As Argentina moves forward, the lessons learned from this episode will be invaluable. The need for clear, informed, and inclusive policy-making has never been greater, particularly as the country navigates the uncertainties of the digital age.
FAQs
What is the Ley Ómnibus? The Ley Ómnibus, formally known as the "Law of Bases and Starting Points for the Freedom of Argentines," is a comprehensive reform package introduced by President Javier Milei. It aims to address various economic, social, and administrative issues in Argentina, aiming to stimulate growth, reduce bureaucracy, and improve the overall quality of life.
Why were crypto taxes proposed in Argentina? Crypto taxes were proposed as part of the Ley Ómnibus to broaden the tax base, align with global trends of regulating digital currencies, and generate additional revenue for the government. They were also intended to bring more transparency to the cryptocurrency sector in Argentina.
Why were the proposed crypto taxes withdrawn? The proposed crypto taxes were withdrawn due to significant public backlash and concerns that they would stifle innovation and economic freedom in the burgeoning crypto market. The decision was also influenced by the government's priority to ensure the swift passage of other reforms within the Ley Ómnibus.
What does the withdrawal of crypto taxes mean for investors? The withdrawal means that, for now, crypto investors in Argentina will not face additional taxes specifically targeting their cryptocurrency holdings or transactions. However, selling large amounts of cryptocurrency at a profit will still be subject to income tax.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1d7ff02a:d042b5be
2025-04-23 02:28:08
@ 1d7ff02a:d042b5be
2025-04-23 02:28:08ທຳຄວາມເຂົ້າໃຈກັບຂໍ້ບົກພ່ອງໃນລະບົບເງິນຂອງພວກເຮົາ
ຫຼາຍຄົນພົບຄວາມຫຍຸ້ງຍາກໃນການເຂົ້າໃຈ Bitcoin ເພາະວ່າພວກເຂົາຍັງບໍ່ເຂົ້າໃຈບັນຫາພື້ນຖານຂອງລະບົບເງິນທີ່ມີຢູ່ຂອງພວກເຮົາ. ລະບົບນີ້, ທີ່ມັກຖືກຮັບຮູ້ວ່າມີຄວາມໝັ້ນຄົງ, ມີຂໍ້ບົກພ່ອງໃນການອອກແບບທີ່ມີມາແຕ່ດັ້ງເດີມ ເຊິ່ງສົ່ງຜົນຕໍ່ຄວາມບໍ່ສະເໝີພາບທາງເສດຖະກິດ ແລະ ການເຊື່ອມເສຍຂອງຄວາມຮັ່ງມີສຳລັບພົນລະເມືອງທົ່ວໄປ. ການເຂົ້າໃຈບັນຫາເຫຼົ່ານີ້ແມ່ນກຸນແຈສຳຄັນເພື່ອເຂົ້າໃຈທ່າແຮງຂອງວິທີແກ້ໄຂທີ່ Bitcoin ສະເໜີ.
ບົດບາດຂອງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ
ລະບົບເງິນຕາປັດຈຸບັນໃນສະຫະລັດອາເມລິກາປະກອບມີການເຊື່ອມໂຍງທີ່ຊັບຊ້ອນລະຫວ່າງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ. ກະຊວງການຄັງສະຫະລັດເຮັດໜ້າທີ່ເປັນບັນຊີທະນາຄານຂອງປະເທດ, ເກັບອາກອນ ແລະ ສະໜັບສະໜູນລາຍຈ່າຍຂອງລັດຖະບານເຊັ່ນ: ທະຫານ, ໂຄງລ່າງພື້ນຖານ ແລະ ໂຄງການສັງຄົມ. ເຖິງຢ່າງໃດກໍຕາມ, ລັດຖະບານມັກໃຊ້ຈ່າຍຫຼາຍກວ່າທີ່ເກັບໄດ້, ເຊິ່ງເຮັດໃຫ້ຕ້ອງໄດ້ຢືມເງິນ. ການຢືມນີ້ແມ່ນເຮັດໂດຍການຂາຍພັນທະບັດລັດຖະບານ, ຊຶ່ງມັນຄືໃບ IOU ທີ່ສັນຍາວ່າຈະຈ່າຍຄືນຈຳນວນທີ່ຢືມພ້ອມດອກເບ້ຍ. ພັນທະບັດເຫຼົ່ານີ້ມັກຖືກຊື້ໂດຍທະນາຄານໃຫຍ່, ລັດຖະບານຕ່າງປະເທດ, ແລະ ທີ່ສຳຄັນ, ທະນາຄານກາງ.
ວິທີການສ້າງເງິນ (ຈາກອາກາດ)
ນີ້ແມ່ນບ່ອນທີ່ເກີດການສ້າງເງິນ "ຈາກອາກາດ". ເມື່ອທະນາຄານກາງຊື້ພັນທະບັດເຫຼົ່ານີ້, ມັນບໍ່ໄດ້ໃຊ້ເງິນທີ່ມີຢູ່ແລ້ວ; ມັນສ້າງເງິນໃໝ່ດ້ວຍວິທີການດິຈິຕອນໂດຍພຽງແຕ່ປ້ອນຕົວເລກເຂົ້າໃນຄອມພິວເຕີ. ເງິນໃໝ່ນີ້ຖືກເພີ່ມເຂົ້າໃນປະລິມານເງິນລວມ. ຍິ່ງສ້າງເງິນຫຼາຍຂຶ້ນ ແລະ ເພີ່ມເຂົ້າໄປ, ມູນຄ່າຂອງເງິນທີ່ມີຢູ່ແລ້ວກໍຍິ່ງຫຼຸດລົງ. ຂະບວນການນີ້ຄືສິ່ງທີ່ພວກເຮົາເອີ້ນວ່າເງິນເຟີ້. ເນື່ອງຈາກກະຊວງການຄັງຢືມຢ່າງຕໍ່ເນື່ອງ ແລະ ທະນາຄານກາງສາມາດພິມໄດ້ຢ່າງຕໍ່ເນື່ອງ, ສິ່ງນີ້ຖືກສະເໜີວ່າເປັນວົງຈອນທີ່ບໍ່ມີທີ່ສິ້ນສຸດ.
ການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ
ເພີ່ມເຂົ້າໃນບັນຫານີ້ຄືການປະຕິບັດຂອງການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ. ເມື່ອທ່ານຝາກເງິນເຂົ້າທະນາຄານ, ທະນາຄານຖືກຮຽກຮ້ອງໃຫ້ເກັບຮັກສາພຽງແຕ່ສ່ວນໜຶ່ງຂອງເງິນຝາກນັ້ນໄວ້ເປັນເງິນສະຫງວນ (ຕົວຢ່າງ, 10%). ສ່ວນທີ່ເຫຼືອ (90%) ສາມາດຖືກປ່ອຍກູ້. ເມື່ອຜູ້ກູ້ຢືມໃຊ້ຈ່າຍເງິນນັ້ນ, ມັນມັກຖືກຝາກເຂົ້າອີກທະນາຄານ, ເຊິ່ງຈາກນັ້ນກໍຈະເຮັດຊ້ຳຂະບວນການໃຫ້ກູ້ຢືມສ່ວນໜຶ່ງຂອງເງິນຝາກ. ວົງຈອນນີ້ເຮັດໃຫ້ເພີ່ມຈຳນວນເງິນທີ່ໝູນວຽນຢູ່ໃນລະບົບໂດຍອີງໃສ່ເງິນຝາກເບື້ອງຕົ້ນ, ເຊິ່ງສ້າງເງິນຜ່ານໜີ້ສິນ. ລະບົບນີ້ໂດຍທຳມະຊາດແລ້ວບອບບາງ; ຖ້າມີຫຼາຍຄົນພະຍາຍາມຖອນເງິນຝາກຂອງເຂົາເຈົ້າພ້ອມກັນ (ການແລ່ນທະນາຄານ), ທະນາຄານກໍຈະລົ້ມເພາະວ່າມັນບໍ່ໄດ້ເກັບຮັກສາເງິນທັງໝົດໄວ້. ເງິນໃນທະນາຄານບໍ່ປອດໄພຄືກັບທີ່ເຊື່ອກັນທົ່ວໄປ ແລະ ສາມາດຖືກແຊ່ແຂງໃນຊ່ວງວິກິດການ ຫຼື ສູນເສຍຖ້າທະນາຄານລົ້ມລະລາຍ (ຍົກເວັ້ນໄດ້ຮັບການຊ່ວຍເຫຼືອ).
ຜົນກະທົບ Cantillon: ໃຜໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ
ເງິນທີ່ຖືກສ້າງຂຶ້ນໃໝ່ບໍ່ໄດ້ກະຈາຍຢ່າງເທົ່າທຽມກັນ. "ຜົນກະທົບ Cantillon", ບ່ອນທີ່ຜູ້ທີ່ຢູ່ໃກ້ກັບແຫຼ່ງສ້າງເງິນໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ. ນີ້ລວມເຖິງລັດຖະບານເອງ (ສະໜັບສະໜູນລາຍຈ່າຍ), ທະນາຄານໃຫຍ່ ແລະ Wall Street (ໄດ້ຮັບທຶນໃນອັດຕາດອກເບ້ຍຕ່ຳສຳລັບການກູ້ຢືມ ແລະ ການລົງທຶນ), ແລະ ບໍລິສັດໃຫຍ່ (ເຂົ້າເຖິງເງິນກູ້ທີ່ຖືກກວ່າສຳລັບການລົງທຶນ). ບຸກຄົນເຫຼົ່ານີ້ໄດ້ຊື້ຊັບສິນ ຫຼື ລົງທຶນກ່ອນທີ່ຜົນກະທົບຂອງເງິນເຟີ້ຈະເຮັດໃຫ້ລາຄາສູງຂຶ້ນ, ເຊິ່ງເຮັດໃຫ້ພວກເຂົາມີຂໍ້ໄດ້ປຽບ.
ຜົນກະທົບຕໍ່ຄົນທົ່ວໄປ
ສຳລັບຄົນທົ່ວໄປ, ຜົນກະທົບຂອງປະລິມານເງິນທີ່ເພີ່ມຂຶ້ນນີ້ແມ່ນການເພີ່ມຂຶ້ນຂອງລາຄາສິນຄ້າ ແລະ ການບໍລິການ - ນ້ຳມັນ, ຄ່າເຊົ່າ, ການດູແລສຸຂະພາບ, ອາຫານ, ແລະ ອື່ນໆ. ເນື່ອງຈາກຄ່າແຮງງານໂດຍທົ່ວໄປບໍ່ທັນກັບອັດຕາເງິນເຟີ້ນີ້, ອຳນາດການຊື້ຂອງປະຊາຊົນຈະຫຼຸດລົງເມື່ອເວລາຜ່ານໄປ. ມັນຄືກັບການແລ່ນໄວຂຶ້ນພຽງເພື່ອຢູ່ໃນບ່ອນເກົ່າ.
Bitcoin: ທາງເລືອກເງິນທີ່ໝັ້ນຄົງ
ຄວາມຂາດແຄນ: ບໍ່ຄືກັບເງິນຕາ fiat, Bitcoin ມີຂີດຈຳກັດສູງສຸດໃນປະລິມານຂອງມັນ. ຈະມີພຽງ 21 ລ້ານ Bitcoin ເທົ່ານັ້ນຖືກສ້າງຂຶ້ນ, ຂີດຈຳກັດນີ້ຝັງຢູ່ໃນໂຄດຂອງມັນ ແລະ ບໍ່ສາມາດປ່ຽນແປງໄດ້. ການສະໜອງທີ່ຈຳກັດນີ້ເຮັດໃຫ້ Bitcoin ເປັນເງິນຫຼຸດລາຄາ; ເມື່ອຄວາມຕ້ອງການເພີ່ມຂຶ້ນ, ມູນຄ່າຂອງມັນມີແນວໂນ້ມທີ່ຈະເພີ່ມຂຶ້ນເພາະວ່າປະລິມານການສະໜອງບໍ່ສາມາດຂະຫຍາຍຕົວ.
ຄວາມທົນທານ: Bitcoin ຢູ່ໃນ blockchain, ເຊິ່ງເປັນປຶ້ມບັນຊີສາທາລະນະທີ່ແບ່ງປັນກັນຂອງທຸກການເຮັດທຸລະກຳທີ່ແທບຈະເປັນໄປບໍ່ໄດ້ທີ່ຈະລຶບ ຫຼື ປ່ຽນແປງ. ປຶ້ມບັນຊີນີ້ຖືກກະຈາຍໄປທົ່ວພັນຄອມພິວເຕີ (nodes) ທົ່ວໂລກ. ແມ້ແຕ່ຖ້າອິນເຕີເນັດລົ້ມ, ເຄືອຂ່າຍສາມາດຢູ່ຕໍ່ໄປໄດ້ຜ່ານວິທີການອື່ນເຊັ່ນ: ດາວທຽມ ຫຼື ຄື້ນວິທະຍຸ. ມັນບໍ່ໄດ້ຮັບຜົນກະທົບຈາກການທຳລາຍທາງກາຍະພາບຂອງເງິນສົດ ຫຼື ການແຮັກຖານຂໍ້ມູນແບບລວມສູນ.
ການພົກພາ: Bitcoin ສາມາດຖືກສົ່ງໄປໃນທຸກບ່ອນໃນໂລກໄດ້ທັນທີ, 24/7, ດ້ວຍການເຊື່ອມຕໍ່ອິນເຕີເນັດ, ໂດຍບໍ່ຈຳເປັນຕ້ອງມີທະນາຄານ ຫຼື ການອະນຸຍາດຈາກພາກສ່ວນທີສາມ. ທ່ານສາມາດເກັບຮັກສາ Bitcoin ຂອງທ່ານໄດ້ດ້ວຍຕົນເອງໃນອຸປະກອນທີ່ເອີ້ນວ່າກະເປົາເຢັນ, ແລະ ຕາບໃດທີ່ທ່ານຮູ້ວະລີກະແຈລັບຂອງທ່ານ, ທ່ານສາມາດເຂົ້າເຖິງເງິນຂອງທ່ານຈາກກະເປົາທີ່ເຂົ້າກັນໄດ້, ເຖິງແມ່ນວ່າອຸປະກອນຈະສູນຫາຍ. ສິ່ງນີ້ສະດວກສະບາຍກວ່າ ແລະ ມີຄວາມສ່ຽງໜ້ອຍກວ່າການພົກພາເງິນສົດຈຳນວນຫຼາຍ ຫຼື ການນຳທາງການໂອນເງິນສາກົນທີ່ຊັບຊ້ອນ.
ການແບ່ງຍ່ອຍ: Bitcoin ສາມາດແບ່ງຍ່ອຍໄດ້ສູງ. ໜຶ່ງ Bitcoin ສາມາດແບ່ງເປັນ 100 ລ້ານໜ່ວຍຍ່ອຍທີ່ເອີ້ນວ່າ Satoshis, ເຊິ່ງອະນຸຍາດໃຫ້ສົ່ງ ຫຼື ຮັບຈຳນວນນ້ອຍໄດ້.
ຄວາມສາມາດໃນການທົດແທນກັນ: ໜຶ່ງ Bitcoin ທຽບເທົ່າກັບໜຶ່ງ Bitcoin ໃນມູນຄ່າ, ໂດຍທົ່ວໄປ. ໃນຂະນະທີ່ເງິນໂດລາແບບດັ້ງເດີມອາດສາມາດຖືກຕິດຕາມ, ແຊ່ແຂງ, ຫຼື ຍຶດໄດ້, ໂດຍສະເພາະໃນຮູບແບບດິຈິຕອນ ຫຼື ຖ້າຖືກພິຈາລະນາວ່າໜ້າສົງໄສ, ແຕ່ລະໜ່ວຍຂອງ Bitcoin ໂດຍທົ່ວໄປຖືກປະຕິບັດຢ່າງເທົ່າທຽມກັນ.
ການພິສູດຢັ້ງຢືນ: ທຸກການເຮັດທຸລະກຳ Bitcoin ຖືກບັນທຶກໄວ້ໃນ blockchain, ເຊິ່ງທຸກຄົນສາມາດເບິ່ງ ແລະ ພິສູດຢັ້ງຢືນ. ຂະບວນການພິສູດຢັ້ງຢືນທີ່ກະຈາຍນີ້, ດຳເນີນໂດຍເຄືອຂ່າຍ, ໝາຍຄວາມວ່າທ່ານບໍ່ຈຳເປັນຕ້ອງເຊື່ອຖືທະນາຄານ ຫຼື ສະຖາບັນໃດໜຶ່ງແບບມືດບອດເພື່ອຢືນຢັນຄວາມຖືກຕ້ອງຂອງເງິນຂອງທ່ານ.
ການຕ້ານການກວດກາ: ເນື່ອງຈາກບໍ່ມີລັດຖະບານ, ບໍລິສັດ, ຫຼື ບຸກຄົນໃດຄວບຄຸມເຄືອຂ່າຍ Bitcoin, ບໍ່ມີໃຜສາມາດຂັດຂວາງທ່ານຈາກການສົ່ງ ຫຼື ຮັບ Bitcoin, ແຊ່ແຂງເງິນຂອງທ່ານ, ຫຼື ຍຶດມັນ. ມັນເປັນລະບົບທີ່ບໍ່ຕ້ອງຂໍອະນຸຍາດ, ເຊິ່ງໃຫ້ຜູ້ໃຊ້ຄວບຄຸມເຕັມທີ່ຕໍ່ເງິນຂອງເຂົາເຈົ້າ.
ການກະຈາຍອຳນາດ: Bitcoin ຖືກຮັກສາໂດຍເຄືອຂ່າຍກະຈາຍຂອງບັນດາຜູ້ຂຸດທີ່ໃຊ້ພະລັງງານການຄິດໄລ່ເພື່ອຢັ້ງຢືນການເຮັດທຸລະກຳຜ່ານ "proof of work". ລະບົບທີ່ກະຈາຍນີ້ຮັບປະກັນວ່າບໍ່ມີຈຸດໃດຈຸດໜຶ່ງທີ່ຈະລົ້ມເຫຼວ ຫຼື ຄວບຄຸມ. ທ່ານບໍ່ໄດ້ເພິ່ງພາຂະບວນການທີ່ບໍ່ໂປ່ງໃສຂອງທະນາຄານກາງ; ລະບົບທັງໝົດໂປ່ງໃສຢູ່ໃນ blockchain. ສິ່ງນີ້ເຮັດໃຫ້ບຸກຄົນມີອຳນາດທີ່ຈະເປັນທະນາຄານຂອງຕົນເອງແທ້ ແລະ ຮັບຜິດຊອບຕໍ່ການເງິນຂອງເຂົາເຈົ້າ.
-
 @ 90c656ff:9383fd4e
2025-05-03 11:39:03
@ 90c656ff:9383fd4e
2025-05-03 11:39:03The emergence of Bitcoin brought a new perspective to the concept of money, challenging the conventional financial system based on fiat currencies. While fiat currencies like the real, dollar, and euro are widely used and recognized as means of exchange, Bitcoin represents a digital innovation that promotes decentralization and financial autonomy. Although both serve basic functions such as a medium of exchange and store of value, their main differences lie in how they are issued, managed, and transacted.
One of the key distinctions between Bitcoin and fiat currencies is the way they are issued and administered. Fiat currencies are issued by central banks, which have the power to regulate the amount in circulation. This model allows for the implementation of monetary policies, such as increasing the money supply to stimulate the economy or decreasing it to control inflation. However, this power can also result in currency devaluation if money is issued in excess.
Bitcoin, on the other hand, has a completely decentralized issuance system. It is created through a process called mining, in which computers solve complex mathematical problems to validate transactions on the network. Additionally, the total supply of bitcoins is limited to 21 million units, making it a deflationary asset—its scarcity can potentially increase its value over time. This limitation contrasts sharply with the unlimited nature of fiat money printing.
Fiat currencies are centralized, meaning their issuance and control are decided by governmental authorities. This also means that transactions involving these currencies go through intermediaries like banks, which can impose fees and limits, and are subject to regulations and audits.
Bitcoin, by contrast, is decentralized. It operates on a peer-to-peer network where transactions are verified by participants called miners and recorded in a public ledger known as the blockchain. This decentralization eliminates the need for intermediaries, making Bitcoin more resistant to censorship and government control. It also provides greater transparency, as anyone can verify transactions on the network.
Another important difference lies in how transactions are carried out. With fiat currencies, transactions usually depend on banks or payment systems, which may impose time restrictions and high fees, especially for international transfers.
Bitcoin, on the other hand, enables direct transfers between people, anywhere in the world and at any time, without the need for intermediaries. This makes the system more accessible, particularly for those without bank accounts or living in countries with restrictive financial systems. Additionally, Bitcoin transaction fees can be lower than those charged by traditional banks.
Fiat currencies offer security backed by government laws and the banking system, but users must place trust in those intermediaries. Bitcoin, by contrast, offers a high level of security through advanced cryptography. Digital wallets that store bitcoins are protected by private keys, ensuring that only the owner has access.
However, privacy works differently. Fiat currency transactions are typically linked to the user's identity, whereas Bitcoin offers a certain level of anonymity, since wallet addresses do not require personal identification. Still, all transactions are public and recorded on the blockchain, which can serve as a point of monitoring for authorities.
The value of fiat currencies is backed by trust in the government that issues them and the country's economy. In contrast, Bitcoin is not backed by any government or physical asset. Its value is determined by market supply and demand, making it highly volatile. While this volatility presents a risk, it also attracts people who see Bitcoin as a long-term appreciation opportunity.
In summary, Bitcoin and fiat currencies differ significantly in their structure, control, and functionality. While fiat currencies are government-controlled and depend on intermediaries, Bitcoin offers decentralization, transparency, and financial freedom. Despite its volatility and some regulatory challenges, Bitcoin represents a new alternative to the traditional financial system.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-03 11:17:21
@ 90c656ff:9383fd4e
2025-05-03 11:17:21Bitcoin was created as something far beyond just a digital currency; it is a revolutionary idea that challenges the foundations of the conventional financial system. The concept behind its creation, presented by the enigmatic Satoshi Nakamoto, focuses on two main principles: decentralization and financial freedom. These ideas reflect an effort to return control of money to the people, eliminating intermediaries and reducing the influence of governments and large financial institutions.
Decentralization is the foundation of Bitcoin. Unlike traditional currencies, which are issued and managed by central banks and governments, Bitcoin operates on a peer-to-peer network. This means there is no central authority or single entity controlling the currency. Instead, all transactions are validated and recorded on a public ledger called the blockchain or timechain, maintained by thousands of computers around the world.
This decentralized structure ensures that Bitcoin is resistant to censorship and immune to monetary policy manipulations such as excessive money printing, which can lead to inflation. It also removes the need for intermediaries like banks, allowing for direct transactions between users. This is especially valuable in scenarios where the traditional banking system is inaccessible or unreliable, such as in remote areas or countries facing economic crises.
The financial freedom promoted by Bitcoin is another transformative element. In traditional systems, individuals depend on third parties such as banks or financial institutions to access, store, and transfer money. These entities can impose restrictions like withdrawal limits, high transfer fees, or even freeze accounts. With Bitcoin, the user has full control over their funds through private keys (a kind of password that grants access to their digital wallet).
Moreover, Bitcoin offers an accessible solution for billions of people worldwide who are unbanked. According to World Bank data, around 1.4 billion adults lack access to a bank account, but many of them do have access to the internet or smartphones. Bitcoin allows these individuals to participate in the global economy without needing intermediary institutions.
Another crucial point is its censorship resistance. In authoritarian regimes or politically unstable situations, governments may confiscate or freeze citizens' assets. Bitcoin, being decentralized and operating on a global network, cannot be arbitrarily controlled or seized, offering an extra layer of financial protection for individuals at risk.
Bitcoin’s vision also includes the creation of a fairer and more transparent financial system. The blockchain or timechain, by recording all transactions in a public and immutable way, reduces the chances of fraud and corruption. Additionally, the limited supply of 21 million bitcoins, hard-coded into the system, supports a deflationary model that contrasts with the unlimited expansion of fiat currencies. This gives Bitcoin the potential to be a stable store of value in the long term.
Despite its promising vision, the path toward full financial freedom is not without challenges. Bitcoin’s price volatility, regulatory concerns, and technological barriers remain hurdles to overcome. However, these challenges also create opportunities for innovation and for strengthening the ecosystem over time.
In summary, the vision behind Bitcoin represents a disruption of the centralized financial system, offering people more autonomy, transparency, and security over their financial resources. It is not just a technology but a movement that aims to empower individuals, especially those excluded or harmed by traditional economic models. By promoting decentralization and financial freedom, Bitcoin paves the way for a future where money truly belongs to the people, not the institutions.
Thank you very much for reading this far — I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 90c656ff:9383fd4e
2025-05-03 11:07:50
@ 90c656ff:9383fd4e
2025-05-03 11:07:50Bitcoin is the world’s first decentralized digital currency, created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Its birth marked the beginning of a revolution in the global financial system, introducing a new kind of currency that is not controlled by governments or traditional financial institutions. The history of Bitcoin is deeply rooted in the ideals of economic freedom, transparency, and resistance to censorship.
The journey began in October 2008, when Satoshi Nakamoto published a paper titled “Bitcoin: A Peer-to-Peer Electronic Cash System.” The white paper, published on the Cryptography mailing list, described the idea of a digital payment system based on a peer-to-peer network. This concept eliminates the need for intermediaries like banks and solves a problem known as “double spending” — the possibility of duplicating digital currencies — through a technology called blockchain, or what Satoshi Nakamoto himself referred to as the timechain.
The blockchain, or timechain, is essentially a public and immutable ledger that records all Bitcoin transactions. It operates through a decentralized system where participants in the network (the so-called nodes) verify transactions and organize them into blocks. These blocks are in turn linked together in a continuous chain, forming the basis of the system’s security and transparency.
On January 3, 2009, Satoshi Nakamoto mined the first Bitcoin block, known as the genesis block. The block contained a coded message referencing the 2008 global financial crisis: "The Times, January 3, 2009, Chancellor on brink of second bailout for banks." This message is emblematic of the motivation behind Bitcoin: to provide an alternative to the centralized financial system that failed to protect the global economy.
Throughout 2009 and 2010, Bitcoin remained an experiment among tech and crypto enthusiasts. The first Bitcoin transactions took place between network participants, and the first commercial use of the currency occurred on May 22, 2010, when a programmer named Laszlo Hanyecz bought two pizzas for 10,000 Bitcoins. This historic transaction became known as “Bitcoin Pizza Day.”
Satoshi Nakamoto continued to contribute to Bitcoin's development until the end of 2010, when he gradually disappeared from the community. To this day, his identity remains a mystery, and there is no concrete evidence of who or how many people were behind the pseudonym. Before leaving, Satoshi Nakamoto handed over control of the project to other developers and made it clear that Bitcoin should be a decentralized technology, owned by everyone and controlled by no one.
Since then, Bitcoin has grown exponentially. It has evolved from a technological experiment into a multibillion-dollar asset and is widely considered a legitimate form of digital money and store of value. Governments, companies, and individuals around the world have adopted Bitcoin as an alternative to traditional fiat currencies.
In summary, the creation of Bitcoin by Satoshi Nakamoto was more than just the birth of a digital currency; it was the beginning of a global movement to rethink how money is controlled and distributed. Although the identity of Satoshi Nakamoto remains unknown, his legacy will continue to shape the future of the financial system and challenge traditional economic structures.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ b8a9df82:6ab5cbbd
2025-03-06 22:39:15
@ b8a9df82:6ab5cbbd
2025-03-06 22:39:15Last week at Bitcoin Investment Week in New York City, hosted by Anthony Pompliano, Jack Mallers walked in wearing sneakers and a T-shirt, casually dropping, “Man… I hate politics.”
That was it. That was the moment I felt aligned again. That’s the energy I came for. No suits. No corporate jargon. Just a guy who gets it—who cares about people, bringing Bitcoin-powered payments to the masses and making sure people can actually use it.
His presence was a reminder of why we’re here in the first place. And his words—“I hate politics”—were a breath of fresh air.
Now, don’t get me wrong. Anthony was a fantastic host. His ability to mix wittiness, playfulness, and seriousness made him an entertaining moderator. But this week was unlike anything I’ve ever experienced in the Bitcoin ecosystem.
One of the biggest letdowns was the lack of interaction. No real Q&A sessions, no direct engagement, no real discussions. Just one fireside chat after another.
And sure, I get it—people love to hear themselves talk. But where were the questions? The critical debates? The chance for the audience to actually participate?
I’m used to Bitcoin meetups and conferences where you walk away with new ideas, new friends, and maybe even a new project to contribute to. Here, it was more like sitting in an expensive lecture hall, watching a lineup of speakers tell us things we already know.
A different vibe—and not in a good way
Over the past few months, I’ve attended nearly ten Bitcoin conferences, each leaving me feeling uplifted, inspired, and ready to take action. But this? This felt different. And not in a good way.
If this had been my first Bitcoin event, I might have walked away questioning whether I even belonged here. It wasn’t Prague. It wasn’t Riga. It wasn’t the buzzing, grassroots, pleb-filled gatherings I had grown to love. Instead, it felt more like a Wall Street networking event disguised as a Bitcoin conference.
Maybe it was the suits.
Or the fact that I was sitting in a room full of investors who have no problem dropping $1,000+ on a ticket.
Or that it reminded me way too much of my former life—working as a manager in London’s real estate industry, navigating boardrooms full of finance guys in polished shoes, talking about “assets under management.”
Bitcoin isn’t just an investment thesis. It’s a revolution. A movement. And yet, at times during this week, I felt like I was back in my fiat past, stuck in a room where people measured success in dollars, not in freedom.
Maybe that’s the point. Bitcoin Investment Week was never meant to be a pleb gathering.
That said, the week did have some bright spots. PubKey was a fantastic kickoff. That was real Bitcoin culture—plebs, Nostr, grassroots energy. People who actually use Bitcoin, not just talk about it.
But the absolute highlight? Jack Mallers, sneakers and all, cutting through the noise with his authenticity.
So, why did we even go?
Good question. Maybe it was curiosity. Maybe it was stepping out of our usual circles to see Bitcoin through a different lens. Maybe it was to remind ourselves why we chose this path in the first place.
Would I go again? Probably not.
Would I trade Prague, Riga, bitcoin++ or any of the grassroots Bitcoin conferences for this? Not a chance.
At the end of the day, Bitcoin doesn’t belong to Wall Street from my opinion. It belongs to the people who actually use it. And those are the people I want to be around.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ 0d8633e5:eec06e57
2025-05-03 10:58:22
@ 0d8633e5:eec06e57
2025-05-03 10:58:22The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ 90c656ff:9383fd4e
2025-05-03 10:31:25
@ 90c656ff:9383fd4e
2025-05-03 10:31:25Bitcoin is a decentralized digital currency created in 2009 by an individual or group under the pseudonym Satoshi Nakamoto. Unlike traditional government-issued currencies like the US dollar or the euro, Bitcoin is not controlled by any central authority, such as a central bank or financial institution. This innovative feature has made it a focal point of economic, technological, and even social debate in recent years.
Bitcoin operates using a technology called blockchain (which the Bitcoin community increasingly prefers to call "timechain"). It is essentially a distributed digital ledger. The blockchain or timechain records all transactions made on the Bitcoin network in an open and transparent way. Each block contains a set of transactions that are immutably added to the chain once they are verified by miners (miners are basically network participants who use their computing power to validate these same transactions). This ensures security and prevents fraud, as no person or entity can retroactively alter the records.
One of Bitcoin's most notable features is its limited supply. Only 21 million Bitcoins can ever be created, which gives Bitcoin a deflationary nature — unlike fiat currencies, which central banks can print in unlimited quantities. This fixed limit, combined with growing global interest in the technology in general and individual privacy specifically, has driven Bitcoin’s value over time.
Another important characteristic of Bitcoin is that it enables direct peer-to-peer transactions, removing the need for intermediaries. This is particularly useful in cases like international transfers, where Bitcoin can be used to send money quickly and at low cost, without going through a bank or traditional financial services. Additionally, it is seen as a form of financial freedom in countries with unstable local currencies (often due to central banks printing money uncontrollably) or strict state-imposed capital controls.
However, Bitcoin is not immune to criticism — though these are often hollow arguments that mask the personal interests of those making them, whether because they work in traditional banks or brokerages and fear losing "power" or even their jobs, or because they have bad intentions and want to promote their own cryptocurrencies, which are fundamentally worthless (the infamous “shitcoins”). Bitcoin’s price volatility can also pose significant risks for inexperienced users who buy at a certain price and end up selling when the value drops by half, losing at least half their money. On the other hand, many experts view Bitcoin as a technological and social milestone that challenges existing economic models.
In summary, Bitcoin is much more than just a “crypto” or “cryptocurrency.” It represents a revolution — or a revision — in how most people think about money, offering a decentralized, transparent, and censorship-resistant alternative. Although it still faces challenges to becoming widely accepted by some skeptics and by governments worried about losing control over “their” populations (as mentioned earlier), its impact has been undeniable, paving the way for a new era in the global economy and opening many minds to reflection.
Thank you very much for reading this far — I hope you're doing well, and sending a huge hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 8947a945:9bfcf626
2025-03-06 10:50:28
@ 8947a945:9bfcf626
2025-03-06 10:50:28Law of diminishing returns : ทำมากได้น้อย ซวยหน่อยขาดทุน
 ** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับ
** หมายเหตุ บทความนี้มีเนื้อหาต่อเนื่องจาก “(TH) Why I quit : สาเหตุที่ผมลาออกจากที่(ทำงาน) ที่ (เคย) เรียกว่า”บ้าน” ใครยังไม่ได้อ่าน แนะนำให้ไปอ่านก่อนนะครับผมได้ยิน คุณท็อป จิรายุส (คุณท๊อป บิทคับ) พูดคำว่า "Law of diminishing returns" ไว้ตอนแชร์มุมมองด้านการทำธุรกิจ ตอนนั้นผมไม่เข้าใจ แต่ผมรู้สึกว่ามันเป็นเจ๋งดี
สำหรับผม สรุปกฏนี้สั้นๆ คือ “ทำมากได้น้อย ซวยหน่อยขาดทุน”
กฏข้อนี้ว่าด้วยเรื่องการทำธุรกิจ พูดถึงปัจจัย 3 อย่าง - Fixed input คือสิ่งที่ไม่สามารถผลิตเพิ่มได้อีกในธุรกิจตอนนั้น เช่น จำนวนห้องตรวจในโรงพยาบาล, พื้นที่ที่ดินทำการเกษตร, ห้องเก็บสินค้า, จำนวนโต๊ะทำงานในสำนักงาน, ช่องบริการลูกค้าในธุรกิจบริการต่างๆ เป็นต้น ผมขอเรียกสั้นๆว่า “พื้นที่” - Variable input คือสิ่งที่สามารถเติมเข้ามาในธุรกิจได้ ปรับแต่งได้ เช่น แรงงาน เครื่องจักร พลังงาน - Marginal product คือผลลัพธ์ของธุรกิจ กำไรเพิ่มขึ้นหลังจากเพิ่ม variable input เข้าสู่ระบบ
ระยะของ law of diminishing returns
- Increased return (ทำเงินได้เยอะขึ้น) เมื่อป้อนแรงงานหรือเครื่องจักรเข้าสู่ระบบ ธุรกิจสามารถทำเงินเพิ่มขึ้นเนื่องจาก fixed input เดิมที่ถูกใช้สอยไม่เต็มที่ (underutilized) ถูกเติมเต็ม กรณีของรพ. คือมีห้องตรวจที่ว่าง ไม่มีหมอนั่งตรวจคนไข้ ห้องตรวจนั้นก็จะไม่สร้างรายได้ แต่เมื่อห้องนั้นมีหมอมานั่ง จะเปลี่ยนเป็นพื้นที่ที่ก่อให้เกิดรายได้ เมื่อห้องตรวจทุกห้องมีหมอนั่งครบ ถือว่าเต็มศักยภาพ ประสิทธิภาพการทำงานที่ดีตามมา
- Diminishing return (ทำมากได้น้อย) จุดของความพอดี (optimum point) คือจุดที่สมดุลพอดีของธุรกิจนั้น ทำกำไรได้เหมาะสม ไม่มากไม่น้อยจนเกินไป แต่ถ้ามองไม่เห็นจุด optimum นี้แล้วยังเพิ่ม”แรงงาน”เข้าไปอีก มันจะทำให้ ”พื้นที่” วุ่นวายเละเทะ ประสิทธิภาพในการทำงานลดลง
- Negative returns (ซวยหน่อยขาดทุน) ถ้ายังไม่หยุดเพิ่ม “แรงงาน” อีก สามารถนำมาสู่การขาดทุน
สรุปเป็นกราฟหน้าตาตามนี้ครับ
ทำไมมันถึงเป็นอย่างนั้น
ผมใช้โมเดลธุรกิจรพ.นี้เป็นตัวอย่างเลยนะครับ
ช่วงแรกที่สร้างรพ. ห้องตรวจมีไม่มาก จำนวนหมอและคนไข้สมดุลกันพอดี งานไม่หนักเกินไป การดูแลคนไข้มีประสิทธิภาพ รพ.เป็นที่ไว้ใจของคนในพื้นที่ มีชื่อเสียง ถูกบอกต่อ ทำให้จำนวนคนไข้เข้ามารับบริการมากขึ้น ต้องขยายพื้นที่รพ. สร้างตึกเพิ่ม รับบุคคลากรทุกระดับเข้ามาทำงานมากขึ้น จนเต็มพื้นที่ที่ดินรพ.ไม่สามารถขยายเพิ่มไปได้มากกว่านี้แล้ว เกิดสมดุลพอดี ทุกพื้นที่ถูกใช้งานเต็มศักยภาพ ประสิทธิภาพงานดีมาก

ผลการดำเนินงาน
ไม่เคยขาดทุน ผ่านช่วงวิกฤตต้มยำกุ้ง และ COVID ได้สบายๆ ฐานะทางการเงินแข็งแรง จ่ายปันผลสม่ำเสมอ ถ้าผมเป็นเจ้าของรพ.ผมจะ 1. สร้างระบบ 2. สร้างทีมผู้บริหาร 3. เน้นย้ำความสำคัญทำตามระบบ 3. Plan - Do- Check - Act เมื่อเกิดปัญหา
เพื่อให้ตัวผมสามารถถอยตัวเองออกมาจากตัวธุรกิจ คอยติดตาม monitor ทุกไตรมาส อย่างใกล้ชิด ไม่ทำอะไรเพิ่มไปมากกว่านี้
แต่สุดท้ายมันก็เกิดเหตุการณ์ทายาทรุ่นที่ 2 “ไม่เอา” นั่นแหละครับ มันทำให้วัฒนธรรมองค์กรเปลี่ยน ก้าวเท้าเข้าไปสู่ยุคตกต่ำ

บริหารแบบล้าหลัง ทำอะไรไม่สุด คิดว่าทำแล้วแต่จริงๆคือไม่ได้ทำ แก้ปัญหาไม่ตรงจุดสร้างปัญหากว่าเดิม
ตัวอย่าง
1. นโยบายการประหยัดพลังงานเพื่อลด carbon footprint
ฟังดูเหมือนจะดี แต่รพ.สื่อสารให้
รณรงค์ให้ปิดไฟ ... ปิดแอร์เมื่อไม่ใช้งาน ...
ผมว่าประโยคนี้มันคุ้นๆ เหมือนเคยได้ยินมามากกว่า 10 ปีแล้ว ... หรือผมเข้าใจผิดหรือเปล่าไม่แน่ใจ
รณรงค์แค่นี้แหละครับ เรื่องลด carbon footprint ไม่ได้เป็นการคิดอะไรใหม่ๆที่เหมาะกับยุคสมัย หรือสร้างอะไรที่จับต้องได้ (objective)
แต่สิ่งที่ทำสวนทางโดยสิ้นเชิงคือใช้พลาสติกแบบใช้แล้วทิ้ง (single use plastic) เป็นภาชนะหลักในการบรรจุอาหารของแพทย์ และผู้เข้าร่วมประชุมงานใหญ่ๆ
 มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ
มีเสียงเสนอแนะจากบุคคลากรทุกระดับว่าให้ทำเป็นบุฟเฟ่ต์ จานชามช้อนส้อมแบบปกติก็ได้ เสนอกันมา 5 ปี ก็ยังคงไม่่มีการเปลี่ยนแปลง ได้รับแจ้งลงมาว่าใช้ภาชนะพลาสติกมันประหยัดกว่า เอาเป็นว่ากล่องข้าวพลาสติกมีการใช้อย่างน้อย 1200 กล่องต่อเดือน … คาดว่าสมการการปล่อยก๊าสคาร์บอน (carbon emission) ที่ทีมผู้บริหารคำนวณ อาจจะซับซ้อนเกินความเข้าใจของผมก็ได้นะครับ2. การตลาดที่ล้มเหลวและพาแพทย์ซวย

ทำการตลาดไม่เข้าเป้า “เหมือนจะ” ทำ digital marketing แต่ทำแค่โพสกราฟฟิคโปรโมชั่นภาพนิ่งลงสื่อโซเชียลทุกช่องทาง แล้วบอกว่านั่นคือ digital marketing
... แต่เดี๋ยวก่อนๆๆๆ ...
ผมจะบอกว่าการโพสมันเป็นแค่ 1 ใน 10 ของ digital marketing แต่รพ.เข้าใจว่าตัวเองได้เข้าสู่ digital marketing แล้ว
... จริงๆมันไม่ใช่เลยเว้ย ...
ผลลัพธ์คือไม่สามารถเปิดน่านน้ำลูกค้าใหม่ได้เลย ได้แต่ฐานลูกค้าเดิมที่มี brand royalty (แต่แนวโน้มลดลง)
แถมที่แย่ที่สุดคือทำการตลาดแพคเกจออกมาโดยไม่ปรึกษาแพทย์ก่อนว่ามันขัดต่อมาตรฐานการรักษาหรือไม่ กลายเป็นทำแพคเกจดึงดูดคนไข้เข้ามาใช้บริการ แต่การรักษาในแพคเกจขัดต่อมาตรฐานการรักษาของแพทย์
คนไข้ไม่รู้หรอกครับ คนไข้จะเอาตามที่มีในแพคเกจ เขาจ่ายตังค์แล้ว แต่ความซวยมันไปตกอยู่กับแพทย์
3. วางกลยุทธไม่เข้าเป้า

ทุกๆต้นปีทางผู้บริหารจะประกาศกลยุทธประจำปี ว่าในปีนั้นๆรพ.จะมุ้งเน้นพัฒนาด้านไหน รพ.นี้มีปัญหาที่เป็นงูกินหางมานาน มันส่งผลต่อประสิทธิภาพการทำงานของหมอและพยาบาล มีการเสนอแก้ปัญหาเรื่องนี้วนซ้ำซากมา 5 ปี แต่ไม่ได้รับแก้ไขจริงจัง (ผมขอไม่เล่านะครับ)
แต่กลยุทธประจำปี 3 ปีที่ผ่านมา พุ่งใส่ตัวบุคคลากร เน้นพฤติกรรมบริการที่ดีเลิศ ทราบมาว่ามีการลงทุนกับโครงการนี้หลักแสนหรือหลักล้าน มีการจัด workshop เชิญวิทยากรและ trainer จากบริษัทภายนอก (outsource) เข้ามาอบรม เป็นโครงการที่เน้นให้บุคคลากรทุกคนเข้าอบรม 100%
ผมมองว่าปัญหาที่เป็นราก (root cause) มันยังไม่ถูกแก้เลย เปรียบเทียบเหมือนฐานรากของอาคารที่มันโคลงเคลงๆไม่มั่นคงยังไม่ได้รับการแก้ไข แต่พยายามตกแต่งห้องด้วยวัสดุคุณภาพดีและเทคโนโลยีที่ทันสมัย … แต่พร้อมจะล้มลงมาได้ทุกเมื่อ
4. มีเสน่ดึงดูด partner ใหม่ๆ แต่ไม่เอาเอง
ในช่วง COVID ระลอกแรก มีผู้นำทางด้านธุรกิจโรงแรมในจังหวัดมานำเสนอโมเดลธุรกิจ “hospitel เปลี่ยนโรงแรมให้เป็นโรงพยาบาล” ด้วยศักยภาพของรพ.ที่มีบุคคลากรเพียงพอ และตัวโรงแรมที่นำมาเสนอมีห้องพักประมาณ 300 ห้อง เป็นโมเดลที่รพ.และโรงแรม win-win ทั้งคู่ แต่ทางผู้บริหารมองว่าไม่คุ้ม ปฏิเสธข้อเสนอนี้ ทำให้เสียโอกาสให้กับคู่แข่งคว้าตลาด blue ocean นี้ไป

ผมได้แต่เกาหัวตอนรู้เรื่องนี้ เพราะ 1. ช่วง COVID คนไข้น้อย พนักงานโดนลดชั่วโมงการทำงาน ได้เงินเดือนขั้นต่ำ ไม่ได้ OT 2. ทาง partner เสนอขอบุคคลากรเหล่านี้แหละ ไปช่วยงาน เรื่องสถานที่ทางโรงแรมเขามีแม่บ้าน ฝ่ายทำความสะอาดอยู่แล้ว 3. ทาง partner เสนอ profit sharing กับทางรพ. ถึงผมจะไม่รู้ตัวเลข แต่เชื่อว่ามันยุติธรรม
ผมก็ไม่รู้ครับ ว่าอะไรคือคุ้มสำหรับผู้บริหาร
5. Top down absolute power
ไม่ฟังข้อเสนอจากตัวแทนหมอ คนที่มีอำนาจการตัดสินใจไม่เคยเอาตัวลงมาคุยกับหมอแบบจริงจังเลย
1-2 ปีจะลงมาพบหมอทั้งรพ.ซักหนึ่งครั้ง สร้างภาพเก่ง พูดขายฝันสวนหรูถึงภาพที่เขาต้องการ สั่งการลงมา พอเกิดปัญหาตัวเองไม่ลงมารับผิดชอบ แต่อาศัยหน่วยข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ออกคำสั่งแก้ผ้าเอาหน้ารอดลงมาทีหลัง
แถมสั่งให้เงียบและหุบปาก
ครั้งหนึ่งมีคำสั่งออกมาไม่ชัดเจน จนพยาบาลทำงานไม่ได้ ตัวแทนพยาบาลต้องโทรมาหาผมเพื่อให้ผมช่วย
ผมรวบรวมข้อมูลทั้งหมดและพบว่าคำสั่งมีปัญหาจริงๆ ผมจึง chat line ลงไปสอบถามผู้บริหารเพื่อขอความชัดเจน
… ผ่านไปไม่ถึง 5 นาที หนึ่งในผู้บริหาร(คนที่แทงข้างหลังผมที่หาว่าผมมาตรวจคนไข้ VIP เขาช้า 5 นาทีนั่นแหละ)โทรหาผมทันทีคุยกับผมสั้นๆ ใจความว่า “คำสั่งนั้นเอาแบบเดิม ไม่ต้องแก้ และให้ผมเงียบๆซะ”... (ก็ได้วะครับ)

จุดเปลี่ยนที่ทำให้รพ.เข้าสู่ law of diminishing returns
ห้องตรวจทุกห้องของรพ. ถูกใช้จนเต็มศักยภาพ … เอาจริงๆคือล้นศักยภาพเสียอีก (over-utilized) บางแผนกมีเก้าอี้ดนตรี - หมอคนแรกหมดเวลาออกตรวจ - หมอคนต่อไปเดินเข้าใช้ห้องตรวจต่อทันที - ถ้าไม่ทันก็ต้องคว้าห้องตรวจที่ว่างพร้อมใช้งานก่อน - หมอทำการไล่ที่กันเอง - หมอบางท่านต้องใช้ห้องทำงานของพยาบาลเป็นห้องตรวจชั่วคราว
ห้องพักผู้ป่วยก็เช่นกัน บางช่วงเตียงเต็มจนไม่สามารถ admit คนไข้ได้
แต่จำที่ผมบอกได้มั้ยครับว่า คนที่เป็น top down absolute power ไม่เคยเอาตัวลงมาพูดคุยกับแพทย์เพื่อรับฟังปัญหาที่แท้จริงเลย รับแต่ข่าวกรอง(ที่ไม่รู้ว่ากรองอะไรเข้าไปบ้าง) ช่วงนึงมีคนไข้ complaint ว่ารอนั่งรอหมอนาน หมอมาตรวจช้า ผู้บริหารเลยพยายามจะแก้ปัญหา โดยการ monitor waiting time (ระยะเวลารอหมอ) หยิบยกเรื่องนี้ขึ้นมาเป็นวาระเร่งด่วนต้องรีบแก้ไข
แต่เขายังงงๆกับ concept waiting time อยู่เลยว่าจะนับตั้งแต่ตอนไหนถึงตอนไหน - Waiting time สั้นแปลว่าดี เพราะคนไข้ได้เจอหมอเร็ว - Waiting time นานแปลว่าไม่ดี เพราะคนไข้นั่งรอหมอนาน
เขาตีความจากตัวเลขครับ แต่เคยเอาตัวลงมาดูจริงๆหรือเปล่าว่าทำไมตัวเลขมันถึงออกมาไม่ดี
คำตอบคือ“ไม่” ครับ
หมอบางสาขามีความจำเป็นต้องไปดูคนไข้ที่อาการหนักใช้เวลารักษานาน ... หรือ ... รับปรึกษาจากแพทย์ต่างสาขา ... หรือ ... เป็นสาขาเฉพาะทางของเฉพาะทางอีกที ต้องใช้เวลาตรวจละเอียดตรวจนาน
มันเป็นกระบวนการทำงานของหมอ ที่หมอด้วยกันเข้าใจกัน
ส่วนคนเก็บข้อมูลก็นำเสนอไปทั้งอย่างนั้นโดยที่ไม่ได้วิเคราะห์อะไรเลย มันเป็นการกรองข้อมูลที่ไม่รอบคอบก่อนนำเสนอผู้บริหาร
สุดท้ายผู้บริหาร “โทษหมอ” ว่าไม่มีการบริหารเวลาทำงานที่ดีเพียงพอ ทำให้คนไข้รอนาน เขาสรุปกันดื้อๆแบบนี้เลยครับ
พอหนักๆเข้า “รอหมอนาน ต้องเพิ่มหมอ” season การรับสมัครหมอหลายตำแหน่งได้เริ่มขึ้น
แต่เดี๋ยวนะ ห้องตรวจมันแน่นจนแทบไม่มีที่ให้หมอนั่งทำงานแล้ว แต่เขาก็ไม่สนครับ รับหมอหน้าใหม่ๆมาเพิ่มเรื่อยๆ
ด้วย mindset ว่า "ต้องเพิ่มหมอ หมอจะได้เยอะขึ้น คนไข้จะได้ไม่ต้องรอนาน" และเชื่อว่าจะทำรายได้ให้รพ.มากขึ้น หมอหน้าใหม่บางท่านเข้ามาทำงานวันแรกถึงขั้นอยู่ในสภาวะ dead air คือไม่มีที่ให้นั่งทำงาน
“ทำมากได้น้อย” เริ่มต้น
คนไข้รพ.นี้ ส่วนใหญ่เป็นโรคซับซ้อน ต้องการทักษะและเวลาหมอเฉพาะทางแต่ละสาขาอยู่ดี ไม่ได้ทำให้ waiting time ดีขึ้น คนไข้ยัง “นั่งรอหมอนานเหมือนเดิม”
รายได้เริ่มลดลง ยอดคนไข้เริ่มลดลง รพ.พยายามแก้เกมโดยการเพิ่มราคาค่าบริการ (เพิ่มขนาด ticket size) ทำให้มีเสียงรีวิวตามโซเชียลว่า "แพง"
ผลที่เกิดขึ้นคือคนไข้หลายคนอาศัยรพ.นี้ในการตรวจวินิจฉัยโรคแล้วเอาผลไปรักษาต่อรพ.รัฐบาลตามสิทธิ์เพราะสู้ราคาค่ารักษาไม่ไหว บางคนมีประกันสุขภาพหลายฉบับแต่ก็ต้องจ่ายส่วนต่างมากอยู่ดี

วิธีการข้างต้นนี้ ไม่ผิดกติกาครับ ผล X-ray , CT, MRI, ultrasound จากรพ.เอกชน ไวกว่ารพ.รัฐบาลอยู่แล้ว แต่ก็มีคนไข้บางส่วนยินดีจ่ายแพง เพราะเชื่อมั่นหมอที่รพ.นี้ไม่อยากย้ายรพ.ก็มีครับ เพราะหมอไม่ได้ทำอะไรผิด หมอเก่งๆมีเยอะ
ถึงแม้ว่ารพ.จะรักษา momentum มีจำนวนคนไข้ประมาณ 1100 - 1200 รายต่อวัน แต่ก็เป็นโรคง่ายๆ(simple disease) เช่นไข้หวัด อาหารเป็นพิษ เป็นต้น โรคเหล่านี้ ticket size ไม่ได้ใหญ่มาก ประคองไว้ไม่ให้ขาดทุนเท่านั้นครับ
แต่ความแพงแบบไม่สมเหตุสมผล ทำให้คนไข้หลายรายถอดใจย้ายรพ.ตั้งแต่ทราบค่าใช้จ่ายวินาทีแรก
คนไข้น้อยลง --> รายได้ลดลง --> เพิ่ม ticket size ต่อหัวให้แพงขึ้น --> คนไข้หนีเพราะแพงเกิน
ผมไม่รู้ว่าผู้บริหารเขาเห็นไหม แต่คาดว่าคงจะไม่เห็น
ส่วนโรคหรือการผ่าตัดที่สมศักดิ์ศรีกับศักยภาพของรพ. "น้อยมากจนแทบไม่มี" ไม่ใช่สาเหตุอื่นเลยครับ โดนรพ.คู่แข่งในรัศมี 20 กิโลเมตรเอาไปหมด เพราะราคาถูกกว่า หมอก็เก่งไม่แพ้กัน หมอบางคนเคยอยู่ที่รพ.แห่งนี้ เสนอโปรเจคการรักษาโรคบางโรคที่สามารถสร้างรายได้เป็นกอบเป็นกำ แต่ทางรพ.ไม่เอาเอง สุดท้ายหมอเหล่านั้นย้ายไปอยู่กับรพ.คู่แข่งและผลักดันโปรเจคเหล่านั้นสำเร็จจนมีชื่อเสียง
"รพ.ขายสินค้า premium ไม่ได้เลย ขายได้แต่สินค้าเกรดท้องตลาด"
กลยุทธที่รพ.ทำต่อมาคือเพิ่มจำนวนชั่วโมงการทำงานของหมอให้เพิ่มขึ้นโดยให้หมอมาทำงานเร็วขึ้น 2 ชม. แต่ไม่จ่าย OT ให้ ด้วยตรรกะว่าถ้าหมอทำงานนานขึ้น จะมีจำนวนคนไข้มากขึ้น ทางรพ.ไม่ได้ขอร้อง แต่บีบคอให้หมอร่วมมือ หากไม่ร่วมมือไล่ออกทันที

ไปๆมาๆ มีการไล่ออกกระทันหันเกิดขึ้น มีการส่งหนังสือส่วนตัวหาหมอทุกคน ใครมีรายชื่อที่จะปลดออกก็ต้องออกจากงานทันที
ผมมองว่าฐานะทางการเงินมีปัญหารุนแรงครับ เงินเดือนพนักงานถือเป็น fixed cost ที่ธุรกิจต้องแบกรับ ถ้าเจ๋งจริงต้องควบคุมรายจ่ายให้ธุรกิจสามารถไปต่อได้โดยไม่ปลดคน ในส่วนของธุรกิจรพ. หมอคือบุคคลากรที่สำคัญที่สุดและเป็นด่านสุดท้ายที่จะไล่ออกเพื่อรักษาชีวิตของธุรกิจ ตอนนี้รพ.ได้เข้าสู่ระยะสุดท้ายของ law of diminishing returns คือ “ซวยหน่อยขาดทุน” เป็นที่เรียบร้อยครับ
จุดจบของรพ.แบบนี้ ที่ศักยภาพดี แต่บริหารห่วยแตก มันจะจบด้วยการถูก take over ผ่านมาไม่นานกราฟหุ้นออกอาการ exit liquidity แล้วครับ
ข้อคิดที่อยากแบ่งปันกับทุกคนที่อ่านมาจนจบ
- ช่วงธุรกิจเปลี่ยนผ่านสู่ทายาท คือจุดวัดใจหัวเลี้ยวหัวต่อว่าจะรอดหรือไม่รอด
- Law of diminishing returns ไม่ได้ใช้เฉพาะกับธุรกิจ แต่สามารถประยุกต์ใช้กับการดำเนินชีวิตได้หลายมิติ หากใครเข้าใจ จะขยับเข้าสู่ Pareto’s rule … สั้นๆคือ ทำน้อยแต่ได้(โคตร)มาก
- เจ้าของธุรกิจ ต้องหูไว มองหาเนื้อร้ายที่คอยกัดกินธุรกิจให้เจอ แล้วกำจัดมันซะ ก่อนที่ธุรกิจจะล้มทั้งยืน ทับตัวเองตาย
-
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:59
@ e4950c93:1b99eccd
2025-05-03 09:59:59🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 62a6a41e:b12acb43
2025-03-04 22:19:29
@ 62a6a41e:b12acb43
2025-03-04 22:19:29War is rarely (or if ever) the will of the people. Throughout history, wars have been orchestrated by political and economic elites, while the media plays a key role in shaping public opinion. World War I is a clear example of how propaganda was used to glorify war, silence dissent, and demonize the enemy.
Today, we see similar tactics being used in the Ukrainian War. The media spreads one-sided narratives, censors alternative views, and manipulates public sentiment. This article argues that wars are decided from the top, and media is used to justify them.
How the Media Glorified and Propagated WW1
The Media Sold War as an Adventure
Before WW1, newspapers and propaganda made war seem noble and exciting. Young men were encouraged to enlist for honor and glory. Posters displayed slogans like “Your Country Needs You”, making war look like a duty rather than a tragedy.
Demonization of the Enemy
Governments and media portrayed Germans as "barbaric Huns," spreading exaggerated stories like the "Rape of Belgium," where German soldiers were accused of horrific war crimes—many later proven false. Today, Russia is painted as purely evil, while NATO’s role and Ukraine’s internal conflicts are ignored.
Social Pressure & Nationalism
Anyone who opposed WW1 was labeled a traitor. Conscientious objectors were shamed, jailed, or even executed. The same happens today—if you question support for Ukraine, you are called "pro-Russian" or "anti-European." In the U.S., opposing war is falsely linked to supporting Trump or extremism.
Fabricated Stories
During WW1, fake reports of German soldiers killing babies were widely spread. In Ukraine, reports of massacres and war crimes often circulate without verification, while Ukrainian war crimes receive little coverage.
How the Media Promotes War Today: The Case of Ukraine
One-Sided Narratives
The media presents Ukraine as a heroic struggle against an evil invader, ignoring the 2014 coup, the Donbas conflict, and NATO expansion. By simplifying the issue, people are discouraged from questioning the full story.
Censorship and Suppression of Dissent
During WW1, anti-war activists were jailed. Today, journalists and commentators questioning NATO’s role face censorship, deplatforming, or cancellation.
Selective Coverage
Media highlights civilian deaths in Ukraine but ignores similar suffering in Yemen, Syria, or Palestine. Coverage depends on political interests, not humanitarian concern.
Glorification of War Efforts
Ukrainian soldiers—even extremist groups—are painted as heroes. Meanwhile, peace negotiations and diplomatic efforts receive little attention.
War is a Top-Down Decision, Not the Will of the People
People Don’t Want Wars
If given a choice, most people would reject war. Examples:
- Before WW1: Many workers and socialists opposed war, but governments ignored them.
- Vietnam War: Protests grew, but the war continued.
- Iraq War (2003): Millions protested, yet the invasion went ahead.
Small Elites Decide War
Wars benefit arms manufacturers, politicians, and corporate interests—not ordinary people. Public opposition is often ignored or crushed.
Manipulation Through Fear
Governments use fear to justify war: “If we don’t act now, it will be too late.” This tactic was used in WW1, the Iraq War, and is used today in Ukraine.
Violence vs. War: A Manufactured Conflict
Violence Happens, But War is Manufactured
Conflicts and disputes are natural, but large-scale war is deliberately planned using propaganda and logistical preparation.
War Requires Justification
If war were natural, why does it need massive media campaigns to convince people to fight? Just like in WW1, today’s wars rely on media narratives to gain support.
The Crimea Referendum: A Case of Ignored Democracy
Crimea’s 2014 Referendum
- Over 90% of Crimeans voted to join Russia in 2014.
- Western governments called it "illegitimate," while similar referendums (like in Kosovo) were accepted.
The Contradiction in Democracy
- If democracy is sacred, why ignore a clear vote in Crimea?
- Other examples: Brexit was resisted, Catalonia’s referendum was shut down, and peace referendums were dismissed when they didn’t fit political interests.
- Democracy is used as a tool when convenient.
VII. The Libertarian Case Against War
The Non-Aggression Principle (NAP)
Libertarianism is fundamentally opposed to war because it violates the Non-Aggression Principle (NAP)—the idea that no person or institution has the right to initiate force against another. War, by its very nature, is the ultimate violation of the NAP, as it involves mass killing, destruction, and theft under the guise of national interest.
War is State Aggression
- Governments wage wars, not individuals. No private citizen would naturally start a conflict with another country.
- The state forces people to fund wars through taxation, violating their economic freedom.
- Conscription, used in many wars, is nothing more than state-sponsored slavery, forcing individuals to fight and die for political goals they may not support.
War Creates Bigger Government
- War expands state power, eroding civil liberties (e.g., WW1's Espionage Act, the Patriot Act after 9/11).
- The military-industrial complex grows richer while taxpayers foot the bill.
- Emergency powers granted during wars rarely get repealed after conflicts end, leaving citizens with fewer freedoms.
Peaceful Trade vs. War
- Libertarians advocate for free trade as a means of cooperation. Countries that trade are less likely to go to war.
- Wars destroy wealth and infrastructure, while peaceful trade increases prosperity for all.
- Many wars have been fought not for defense, but for economic interests, such as securing oil, resources, or geopolitical power.
Who Benefits from War?
- Not the people, who suffer death, destruction, and economic hardship.
- Not small businesses or workers, who bear the burden of inflation and taxes to fund wars.
- Not individual liberty, as war leads to greater state control and surveillance.
- Only the elites, including defense contractors, politicians, and bankers, who profit from war and use it to consolidate power.
Conclusion: The Media’s Role in War is Crucial
Wars don’t happen naturally—they are carefully planned and sold to the public using propaganda, fear, and nationalism.
- WW1 and Ukraine prove that media is key to war-making.
- The media silences peace efforts and glorifies conflict.
- If people truly had a choice, most wars would never happen.
To resist this, we must recognize how we are manipulated and reject the forced narratives that push us toward war.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ 8947a945:9bfcf626
2025-02-28 09:11:21
@ 8947a945:9bfcf626
2025-02-28 09:11:21Chef's notes
https://video.nostr.build/ea19333ab7f700a6557b6f52f1f8cfe214671444687fa7ea56a18e5d751fe0a9.mp4
https://video.nostr.build/bcae8d39e22f66689d51f34e44ecabdf7a57b5099cc456e3e0f29446b1dfd0de.mp4
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- ไข่ 1 - 2 ฟอง
- ข้าวโอ๊ต 3 - 4 ช้อน
Directions
- ตอกไข่ + ตีไข่
- ปรุงรส พริกไทย หรือ ซอสถั่วเหลืองตามชอบ
- ใส่ข้าวโอ๊ต 3 - 4 ช้อน
- ใส่ถั่วลิสงอบ 1 - 2 หยิบมือ
- เทน้ำใส่พอท่วมข้าวโอ๊ต
- เข้าไมโครเวฟ ไฟแรง 1 - 2 นาที
-
 @ a296b972:e5a7a2e8
2025-05-03 07:48:25
@ a296b972:e5a7a2e8
2025-05-03 07:48:25Derzeit formiert sich ein neues Gruselkabinett, als Folge einer Pandemie der Ungeeigneten. Kostproben der Unfähigkeit konnte man schon in den aktuellen „Quassel-Shows“ des Staatsfunks „genießen“. Die Riege der Universal-Dilettanten, die noch schnell hochgelobt wurde, macht gerade Platz für Rekruten aus dem Milieu der überzeugten Realitätsverweigerer.
Impfpflichtbefürworter, ideologisch vergiftete Klima- und Gender-Gagaisten, Verteidiger des Russen-Dauer-Feindbilds, Finanzwirtschafts-Ahnungslose, zahllose „Südamerika-Experten“, die davon überzeugt sind, solche zu sein, weil sie unfallfrei eine Banane essen können und weitere, die als einzige Qualifikation das Prädikat „Untauglich“ auszeichnet, geben sich ein neues Stelldichein.
Nach Vorbild des öffentlich-rechtlichen Unfugs bilden sie ein in sich geschlossenes System, das sich gegen Kritik abschotten will, in dem es alles, was sich nach Nicht-nach-dem-Maul geredet anhört, als Hass und Hetze bezeichnet und sich als Hüter der Wahrheit aufspielt.
Begriffe wie „Hass und Hetze“ und „Kriegstüchtigkeit“ werden einem Wortschatz entlehnt, die dem bisher dunkelsten Kapitel der deutschen Geschichte entnommen sind. Zur Abschreckung verwendete Begriffe, im Sinne von „Wehret den Anfängen!“, wie die Anlehnung „Impfen macht frei“ hingegen, werden mit Geldbußen und Haft belegt. Es kommt eben immer darauf an, von wem diese verbrannten Begriffe verwendet werden.
Wenn aus einer Demokratie „Unseredemokratie“ wird, müssen alle Alarmglocken schrillen, weil so Tür und Tor weit aufgerissen werden, um Tendenzen und Ideologien den Einzug zu ermöglichen, die in einer freiheitlich-demokratischen Grundordnung nichts, aber auch rein gar nichts zu suchen haben, weil die Auslegung davon, was „Unseredemokratie“ bedeutet, in den Händen derjenigen liegt, die sich zwar noch als Volksvertreter ausgeben, aber den Willen des Souveräns nicht mehr umsetzen.
Die Meinung und der Wille des Volkes werden maximal ignoriert und unterdrückt. Mit einem „weiter so“ manifestiert sich die Verachtung der Wähler, die in ihrer unterstellten Dummheit bestenfalls noch als Stimmvieh taugen, ansonsten aber zu vernachlässigen sind, wenn das Ziel erreicht ist: Die Macht!
Eine Absichtserklärung, genannt Koalitionsvertrag, ist die Grundlage für „alles kann, nichts muss“. Er lässt so eine unbegrenzte Flexibilität in jede Richtung zu, alles ist möglich. ALLES!
Die Basis der Koalition beruht auf Lügen, sei es in der Migrationspolitik oder in der Neuverschuldung. Das gemeinsame Klüngeln hat schon begonnen, bevor der eigentliche Regierungsauftrag überhaupt erteilt wurde.
Das wirklich einzige, gemeinsame Ziel ist, mit allen Mitteln an der Macht zu bleiben, koste es, was es wolle und eine demokratisch gewählte Opposition, die rund ein Viertel der Wählerstimmen ausmacht, wo immer es geht zu delegitimieren und so klein zu halten, wie es nur eben geht.
Hirngespinste sollen weiter vorangetrieben, die Rückkehr zur Vernunft soll unter allen Umständen verhindert werden, bzw. ist aufgrund mangelnder Kenntnisse und Einsicht gar nicht möglich.
Das Lügen bleibt den Nicht-Volksvertretern vorbehalten, die definieren, was Lüge ist und was nicht, sofern die Kritik vom Volk kommt. Berichtet man über die Politik, spricht man von Unwahrheiten, spricht die Politik über das Volk, sind es Lügen. Überall wird mit zweierlei Maß gemessen.
Die Verachtung des Souveräns wirkt wie ein Bumerang und wird wie durch einen Spiegel auf die Versender zurückgeworfen.
Ein zukünftiger Ex-Bundeskanzler verliert bereits den Rückhalt, noch bevor er in sein Amt eingesetzt wird. Grisu, der kleine Drache, will unbedingt, nur einmal im Leben, Feuerwehrmann werden. Phrasen-Dreschen wird zur Staatsräson.
Ministerposten werden nach maximaler Fachferne verschachert.
Gut ausgebildete Kräfte verlassen das Land, die Wirtschaft stagniert, massive Einbrüche in der Auto-Industrie, der einstigen Vorzeige-Marken in der ganzen Welt. Ja, Autos bauen, das könnten die Deutschen, wenn sie noch dürften.
Wer kann, wandert ab ins Ausland, wo Energiekosten und Steuern ein unternehmerisches Handeln ermöglichen, statt es mit aller Kraft durch gezielte Wirtschaftsvernichtung abzuwürgen. Wo ist der massive Widerstand seitens der Wirtschaftsverbände, der Industrie- und Handelskammern und Groß-Unternehmen? Geht es denen immer noch zu gut?
Recht haben und Recht bekommen waren noch nie so weit auseinander, wie heute.
Die Kirche, in einem christlich geprägten Land, schreibt ihre eigene Lehre um: „Gott ist queer!“ Grenzt das schon an Gotteslästerung aus den eigenen Reihen? Dabei merkt sie offensichtlich nicht, dass sie sich damit selbst abschafft. Wieder einmal springt sie auf den Zug der vorgegebenen Staatsdoktrin auf. Unvergessen die Hakenkreuzfahne über dem Hauptportal am Kölner Dom in der bisher dunkelsten Zeit Deutschlands.
Eine Überzeugung, und seien die Beweggründe mit noch so guten Absichten verbunden, darf nie wieder zu einer Ideologie werden, die nur in die Irre führen kann. Deshalb ist es demokratische Pflicht, auf die Gefahr hinzuweisen, wenn auch nur der leiseste Hauch Anlass zu solchen Befürchtungen gibt. Das gilt für die Kirche, die Politik, die Rechtsprechung und Menschen, von denen man den Eindruck hat, dass sie sich verirrt haben.
Das Zuviel an Fremden wird nicht gestoppt. Eine Minderheit, die bei Verstand geblieben ist, verlässt das Land, wenn es ihr finanziell möglich ist. Andere, die sich das nicht leisten können, müssen ausharren und dabei zusehen, wie ein Land vor die Hunde geht.
Gut integrierte „Gastarbeiter“ schämen sich für den Plebs, der nach Deutschland kommt. Natürlich unter dem Deckmantel der Menschlichkeit, der die Menschlichkeit gegenüber den Bio-Deutschen mit Füßen tritt. Ihr Ansehen, ihr Fleiß und ihre Dankbarkeit, dass sich ihre Vätergeneration hier eine neue Existenz aufbauen konnte, wird mit Füßen getreten. Sie geraten unter einen Generalverdacht, der ihnen schadet. Auch sie haben Jahrzehnte in die Krankenkassen eingezahlt und ihre Steuern brav entrichtet.
Der Polizei sind von staatlicher Seite die Hände gebunden gegen Clan-Kriminalität und asozialem Verhalten durchzugreifen. Sie bilden Parallel-Gesellschaften mit eigenen Regeln und eigenen Gesetzen und die Polizei muss tatenlos dabei zusehen. Banden in Berlin und Duisburg stellen sich über herrschende Gesetze, Roma terrorisieren Kiel, benehmen sich, wie die Axt im Walde. „An Leib und Leben gefährdete Migranten“ werfen, wie in Bochum, Ziegel von Dächern, und gefährden die Bevölkerung an Leib und Leben. Anschließend setzen sie sich mit einem Gartenstuhl auf einem Kamin in die Sonne und träumen vermutlich vom Ausblick auf dem Kilimandscharo. Statt sie bei Kopf und Kragen zu fassen und sofort aus dem Land zu werfen, werden solche irren Taten mit psychischen Problemen aufgrund der Erfahrungen in ihrem Heimatland entschuldigt. Würden sich solche Bekloppte in ihrem eigenen Land vergleichbare Handlungen erlauben, würde sie die Dorfgemeinschaft wahrscheinlich den Löwen zum Fraß vorwerfen.
Jeder, der nicht das in Deutschland geltende Recht akzeptiert und stattdessen seine eigene Auffassung von Recht durchsetzen will, gehört unverzüglich des Landes verwiesen, und es ist Aufgabe des Staates, dafür zu sorgen, dass solche Personen nie wieder einen Fuß über die Grenzen des Landes setzen dürfen. Stattdessen werden die Fahnder verfolgt und die Täter laufen gelassen. Der Staat lässt so zu, dass geltendes Recht unterwandert und außer Kraft gesetzt wird. Seine abschreckende Wirkung geht verloren, weil es in den einschlägigen Kreisen bekannt ist, dass sich jeder aufführen kann, wie er will, ohne, dass es Konsequenzen nach sich zieht.
Gepaart mit Willkür ist das hoch gefährliches Dynamit, dass die Gesellschaft sprengt und eine Gefahr in sich birgt, dass die Gesellschaft ab dem Punkt, wo es unerträglich geworden ist, zur Selbstjustiz greift, und das wäre möglicherweise der Anfang eines Bürgerkriegs.
Für alles ist Geld da. Es werden Schulden in atemberaubender Höhe aufgenommen, vor allem, um die Kriegswirtschaft anzukurbeln, um vor einem Feind - Russland gewappnet zu sein, das nicht das geringste Interesse an einem Land hat, das nichts unversucht lässt, auf irgendeine Art und Weise Selbstmord zu begehen. Einmal muss es doch gelingen!
Und natürlich müssen auch die westlichen Werte im Stellvertreterkrieg zwischen den USA und Russland in der Ukraine verteidigt werden.
Kein Geld ist allerdings für die eigenen Leute da. Im Gegenteil: Wer Flaschen sammelt, muss ab einer bestimmten Höhe der Einnahmen ein Gewerbe anmelden. Aber sonst haben die Sesselfurzer nichts zu tun, oder? Es sollte Geld in die Hand genommen werden, die zunehmende Armut in der Bevölkerung nachhaltig zu stoppen, aus dem Abfahrtsvorschlags-Plan der Bahn wieder einen richtigen Fahrplan zu machen, die Schlagloch-Nostalgie á la DDR abzuschaffen, Brücken wieder ihrem Wesen zuzuführen, nämlich, dass man drüberfahren kann, das ganze Land einer dringenden Generalüberholung zu unterziehen, die Gewinnorientierung aus dem Gesundheitssystem wieder abzuschaffen, die Fallpauschalen samt dem Verursacher in die Wüste zu schicken, Deutschland steuer-sexy zu machen.
Das ist wohl zu viel verlangt, denn diejenigen, die das bewirken könnten, haben keine Not. Die einzige Not, die sie kennen, ist, wie sie immer genug Leim auf Vorrat haben können, um an ihrem Pöstchen kleben zu bleiben. Solche Menschen können nur in einem geschützten Rahmen existieren, weil sie in der Welt da draußen gar nicht zurecht kämen, geschweige denn in der Lage wären, für ihren Lebensunterhalt mit einer wirklichen Arbeit selbst zu sorgen.
Der Staat erfüllt nicht mehr seine Aufgabe für die Sicherheit seiner Bürger zu sorgen. Statt Messer-Attacken und Terror-Anschläge aufzuklären und damit den Bürgern ein Gefühl von Sicherheit zu vermitteln, wird die Aufklärung auf dem Mond im Meer der Stille versenkt. Transparenz: Fehlanzeige. Im besten Fall werden Symptom-Bekämpfungs-Maßnahmen ergriffen, statt die Ursachen zu verunmöglichen. Schilder an Messerverbots-Zonen aufzustellen, manifestieren bestenfalls die Gewissheit der Lächerlichkeit und Unfähigkeit seitens der Messerfachkräfte und der selbstfahrenden Autos, die von niemandem gesteuert werden.
Gleiches gilt für das Nennen der hinlänglich bekannten Verursacher der Sprengung der Nordstream 2-Pipelines, die dem scheidenden Bundeskanzler, an dessen Namen man sich schon jetzt nicht mehr erinnern kann, bekannt gewesen sein müssen. Selbst Trump soll sich auf die Frage, ob die USA maßgeblich daran beteiligt waren, geäußert haben, dass, wenn er auf diese Frage antworten würde, er seinem Land sehr schaden würde. Er könne aber mit Gewissheit sagen, dass es die Russen nicht waren. Immerhin ist eine für ganz Europa wichtige Energieversorgung absichtlich, bewusst und mutwillig zerstört worden. Aber aus Rücksicht darauf, dass die Wahrheit Teile der deutschen Bevölkerung verunsichern könnte, verzichtet man in Berlin auf eine Stellungnahme, lügt wiederholt, dass die Ermittlungen noch andauern und glaubt, dass man die Bürger damit ahnungslos halten kann. Die doofen Deutschen werden auch das noch schlucken.
Vergessen die Verpflichtung: Von deutschem Boden soll nur noch Frieden ausgehen. Vergessen die grauen Gesichter der Männer mit einem hochgeklappten Hosenbein, in der Kinderzeit. Wer von den aktuellen Kriegstreibern war live bei einem Gemetzel dabei, in dem Körperteile herumfliegen und Blut spritzt, in dem Menschen zerfetzt werden oder in ihren Panzern bei lebendigem Leib verbrennen? Viele Dümmste unter den Dummen kennen Krieg nur aus Video-Spielen. Nur einmal live als Zaungast dabei sein, und sehen, wie der halbe Darm aus dem Körper heraushängt, dann würde sich ihr großes Maul schon von alleine schließen.
Immer mehr Deutsche sagen: Das ist nicht mehr mein Staat. Kann man es ihnen verdenken?
Deutschland ist ein Paradebeispiel dafür, wie man in der heutigen Zeit, ein einst in aller Welt hochangesehenes Land, im Handumdrehen wirtschaftlich, politisch, rechtsstaatlich, gesundheitlich, und nicht zuletzt auch gesellschaftlich zerstören kann.
Sowohl innen- als auch außenpolitisch wurde nichts unterlassen, um Deutschland, vom Ausland aus gesehen, in die absolute Lächerlichkeit zu überführen.
Die Dummheit, gepaart mit unerträglicher Überheblichkeit, haben ein Maß erreicht, dass in die Gefährlichkeit übergegangen ist. Deutschland braucht gar keinen Feind von außen, denn der Feind sitzt im eigenen Land und zerstört es von innen heraus.
Der Eindruck taucht auf, dass spätestens mit dem Corona-Ereignis das Schleusentor des Wahnsinns sperrangelweit aufgerissen wurde, und keiner vermag es derzeit wieder zu schließen.
Entweder schließen sich Kräfte zusammen, die noch vorhanden sind, dieses Land von innen heraus zu retten, hierzu tragen auch die Neuen Medien erheblich bei, oder Deutschland ist noch einmal darauf angewiesen, von außen gerettet zu werden.
Zukunftsplanungen werden verunmöglicht. Mindestens eine Generation wird die komplette Lebensplanung geraubt. Man ist gezwungen, von einem Tag auf den anderen zu leben, weil alles derartig unberechenbar geworden ist. Eine junge Familie überlegt sich drei Mal, ob sie noch Kinder in diese Welt setzen will. Wo soll das enden?
Der Alltag in Deutschland gleicht einer Dauer-Vorstellung eines Theater-Stücks. Irgendwie läuft es noch, jedoch es fehlt der Rückhalt. Man versucht seinen Alltag zu meistern, Normalität zu leben, doch über allem schwebt das Damokles-Schwert. Keiner weiß, wie lange was noch gut geht und welchen Irrsinn sich die Realitätsverweigerer als Nächstes ausdenken werden. Manchen gelingt das Verdrängen recht gut. Manche schotten sich vollkommen von schlechten Nachrichten ab. Die Psychologie sagt jedoch, dass jedes erlebte Trauma den Menschen früher oder später einholen wird.
Wetten, wie lange die unheilvolle Allianz der Neuen Nullen halten wird, können ab sofort entgegengenommen werden. Und dann? Wie geht es weiter?
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ a93be9fb:6d3fdc0c
2025-05-03 06:02:56
@ a93be9fb:6d3fdc0c
2025-05-03 06:02:56GG
-
 @ fd06f542:8d6d54cd
2025-04-15 02:38:14
@ fd06f542:8d6d54cd
2025-04-15 02:38:14排名随机, 列表正在增加中。
Cody Tseng
jumble.social 的作者
https://jumble.social/users/npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
- Running [ wss://nostr-relay.app ] (free & WoT) 💜⚡️
- Building 👨💻:
- https://github.com/CodyTseng/jumble
- https://github.com/CodyTseng/nostr-relay-tray
- https://github.com/CodyTseng/danmakustr
- https://github.com/CodyTseng/nostr-relay-nestjs
- https://github.com/CodyTseng/nostr-relay
- https://github.com/CodyTseng
阿甘
- @agan0
- 0xchat.com
- canidae40@coinos.io
- https://jumble.social/users/npub13zyg3zysfylqc6nwfgj2uvce5rtlck2u50vwtjhpn92wzyusprfsdl2rce
joomaen
- Follows you
- joomaen.com
-
95aebd@wallet.yakihonne.com
-
nobot
- https://joomaen.filegear-sg.me/
- https://jumble.social/users/npub1wlpfd84ymdx2rpvnqht7h2lkq5lazvkaejywrvtchlvn3geulfgqp74qq0
颜值精选官
- wasp@ok0.org
- 专注分享 各类 图片与视频,每日为你带来颜值盛宴,心动不止一点点。欢迎关注,一起发现更多美好!
- https://jumble.social/users/npub1d5ygkef6r0l7w29ek9l9c7hulsvdshms2qh74jp5qpfyad4g6h5s4ap6lz
6svjszwk
- 6svjszwk@ok0.org
- 83vEfErLivtS9to39i73ETeaPkCF5ejQFbExoM5Vc2FDLqSE5Ah6NbqN6JaWPQbMeJh2muDiHPEDjboCVFYkHk4dHitivVi
-
low-time-preference
-
anarcho-capitalism
-
libertarianism
-
bitcoin #monero
- https://jumble.social/users/npub1sxgnpqfyd5vjexj4j5tsgfc826ezyz2ywze3w8jchd0rcshw3k6svjszwk
𝘌𝘷𝘦𝘳𝘺𝘥𝘢𝘺 𝘔𝘰𝘳𝘯𝘪𝘯𝘨 𝘚𝘵𝘢𝘳
- everyday@iris.to
- 虽然现在对某些事情下结论还为时尚早,但是从趋势来看,邪恶抬头已经不可避免。
- 我们要做的就是坚持内心的那一份良知,与邪恶战斗到底。
- 黑暗森林时代,当好小透明。
- bc1q7tuckqhkwf4vgc64rsy3rxy5qy6pmdrgxewcww
- https://jumble.social/users/npub1j2pha2chpr0qsmj2f6w783200upa7dvqnnard7vn9l8tv86m7twqszmnke
nostr_cn_dev
npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm@npub.cash
Developed the following products: - NostrBridge, 网桥转发 - TaskQ5, 分布式多任务 - NostrHTTP, nostr to http - Postr, 匿名交友,匿名邮局 - nostrclient (Python client) . -nostrbook, (nostrbook.com) 用nostr在线写书 * https://www.duozhutuan.com nostrhttp demo * https://github.com/duozhutuan/NostrBridge * * https://jumble.social/users/npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm *
CXPLAY
- lightning@cxplay.org
- 😉很高兴遇到你, 你可以叫我 CX 或 CXPLAY, 这个名字没有特殊含义, 无需在意.
- ©本账号下所有内容如未经特殊声明均使用 CC BY-NC-SA 4.0 许可协议授权.
- 🌐如果您在 Fediverse 收到本账号的内容则说明您的实例已与 Mostr.pub 或 Momostr.pink Bridge 互联, 您所看到的账号为镜像, 所有账号内容正在跨网传递. 如有必要请检查原始页面.
- 🧑💻正在提供中文本地化(i10n): #Amethyst #Amber #Citrine #Soapbox #Ditto #Alby
- https://cx.ms/
https://jumble.social/users/npub1gd8e0xfkylc7v8c5a6hkpj4gelwwcy99jt90lqjseqjj2t253s2s6ch58h
w
- 0xchat的作者
- 0xchat@getalby.com
- Building for 0xchat
- https://www.0xchat.com/
- https://jumble.social/users/npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Michael
- highman@blink.sv
- Composer Artist | Musician
- 🎹🎼🎤🏸🏝️🐕❤️
- 在這裡可以看到「我看世界」的樣子
- 他是光良
- https://jumble.social/users/npub1kr5vqlelt8l47s2z0l47z4myqg897m04vrnaqks3emwryca3al7sv83ry3
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 147ac18e:ef1ca1ba
2025-04-13 01:57:13
@ 147ac18e:ef1ca1ba
2025-04-13 01:57:13In a recent episode of The Survival Podcast, host Jack Spirko presents a contrarian view on the current trade war and tariffs imposed by the U.S. government. Far from being a chaotic or irrational policy, Jack argues that these tariffs are part of a broader strategic plan to rewire the global trade system in America's favor—and to force long-overdue changes in the domestic economy. Here's a breakdown of the core reasons Jack believes this is happening (or will happen) as a result of the tariffs:In a recent episode of The Survival Podcast, host Jack Spirko presents a contrarian view on the current trade war and tariffs imposed by the U.S. government. Far from being a chaotic or irrational policy, Jack argues that these tariffs are part of a broader strategic plan to rewire the global trade system in America's favor—and to force long-overdue changes in the domestic economy. Here's a breakdown of the core reasons Jack believes this is happening (or will happen) as a result of the tariffs:
1. Tariffs Are a Tool, Not the Goal
Jack’s central thesis is that tariffs are not meant to be a permanent fixture—they’re a pressure tactic. The goal isn’t protectionism for its own sake, but rather to reset trade relationships that have historically disadvantaged the U.S. For example, Taiwan responded to the tariffs not with retaliation but by proactively offering to reduce barriers and increase imports from the U.S. That, Jack says, is the intended outcome: cooperation on better terms.
2. Forced Deleveraging to Prevent Collapse
One of the boldest claims Jack makes is that the Trump administration used the tariffs as a catalyst to trigger a “controlled burn” of an over-leveraged stock market. According to him, large institutions were deeply leveraged in equities, and had the bubble popped organically later in the year, it would have required massive bailouts. Instead, the shock caused by tariffs triggered early deleveraging, avoiding systemic failure.
“I’m telling you, a bailout scenario was just avoided... This was intentional.” – Jack Spirko
3. Global Re-shoring and Domestic Manufacturing
Tariffs are incentivizing companies to move production back to the U.S., especially in key areas like semiconductors, energy, and industrial goods. This shift is being further accelerated by global geopolitical instability, creating a “once-in-a-generation” opportunity to rebuild small-town America and domestic supply chains.
4. Not Inflationary—Strategically Deflationary
Jack challenges conventional economic wisdom by arguing that tariffs themselves do not cause inflation, because inflation is a function of monetary expansion—not rising prices alone. In fact, he believes this economic shift may lead to deflation in some sectors, particularly as companies liquidate inventory, lower prices to remain competitive, and reduce reliance on foreign supply chains.
“Rising prices alone are not inflation. Inflation is expansion of the money supply.” – Jack Spirko
5. Energy Costs Will Fall
A drop in global oil prices, partially due to reduced transport needs as manufacturing reshoring increases, plays into the strategy. Jack notes that oil at $60 per barrel weakens adversaries like Russia (whose economy depends heavily on high oil prices) while keeping U.S. production viable. Lower energy costs also benefit domestic manufacturers.
6. The Digital Dollar & Global Dollarization
Alongside this industrial shift, the U.S. is poised to roll out a “digital dollar” infrastructure, giving global access to stablecoins backed by U.S. banks. Jack frames this as an effort to further entrench the dollar as the world’s dominant currency—ensuring continued global demand and export leverage without the need for perpetual military enforcement.
7. A Window of Opportunity for Americans
For individuals, Jack sees this economic transformation as a rare chance to accumulate long-term assets—stocks, Bitcoin, and real estate—while prices are suppressed. He warns that those who panic and sell are operating with a “poverty mindset,” whereas those who stay the course will benefit from what he describes as “the greatest fire sale of productive assets in a generation.”
Conclusion: Not a Collapse, But a Reset
Rather than viewing tariffs as a harbinger of economic doom, Jack presents them as part of a forced evolution—an uncomfortable but necessary reboot of the U.S. economic operating system. Whether or not it works as intended, he argues, this is not a haphazard policy. It’s a calculated reshaping of global and domestic economic dynamics, and one with enormous implications for trade, energy, inflation, and the average American investor.
-
 @ a2eddb26:e2868a80
2025-02-20 20:28:46
@ a2eddb26:e2868a80
2025-02-20 20:28:46In personal finance, the principles of financial independence and time sovereignty (FITS) empower individuals to escape the debt-based cycle that forces them into perpetual work. What if companies could apply the same principles? What if businesses, instead of succumbing to the relentless push for infinite growth, could optimize for real demand?
This case study of the GPU industry aims to show that fiat-driven incentives distort technological progress and imagines an alternative future built on sound money.
Fiat Business: Growth or Death
Tech companies no longer optimize for efficiency, longevity, or real user needs. Instead, under a fiat system, they are forced into a perpetual growth model. If NVIDIA, AMD, or Intel fail to show revenue expansion, their stock price tanks. Let's take NVIDIA's GPUs as an example. The result is predictable:
- GPUs that nobody actually needs but everyone is told to buy.
- A focus on artificial benchmarks instead of real-world performance stability.
- Endless FPS increases that mean nothing for 99% of users.
The RTX 5090 is not for gamers. It is for NVIDIA’s quarterly earnings. This is not a surprise on a fiat standard.
Fiat Marketing: The Illusion of Need and the Refresh Rate Trap
Benchmarks confirm that once a GPU maintains 120+ FPS in worst-case scenarios, additional performance gains become irrelevant for most players. This level of capability was reached years ago. The problem is that efficiency does not sell as easily as bigger numbers.
This extends beyond raw GPU power and into the display market, where increasing refresh rates and resolutions are marketed as critical upgrades, despite diminishing real-world benefits for most users. While refresh rates above 120Hz may offer marginal improvements for competitive esports players, the average user sees little benefit beyond a certain threshold. Similarly, 8K resolutions are pushed as the next frontier, even though 4K remains underutilized due to game optimization and hardware constraints. This is why GPUs keep getting bigger, hotter, and more expensive, even when most gamers would be fine with a card from five years ago. It is why every generation brings another “must-have” feature, regardless of whether it impacts real-world performance.
Marketing under fiat operates on the principle of making people think they need something they do not. The fiat standard does not just distort capital allocation. It manufactures demand by exaggerating the importance of specifications that most users do not truly need.
The goal is not technological progress but sales volume. True innovation would focus on meaningful performance gains that align with actual gaming demands, such as improving latency, frame-time consistency, and efficient power consumption. Instead, marketing convinces consumers they need unnecessary upgrades, driving them into endless hardware cycles that favor stock prices over user experience.
They need the next-gen cycle to maintain high margins. The hardware is no longer designed for users. It is designed for shareholders. A company operating on sound money would not rely on deceptive marketing cycles. It would align product development with real user needs instead of forcing artificial demand.
The Shift to AI
For years, GPUs were optimized for gaming. Then AI changed everything. OpenAI, Google, and Stability AI now outbid consumers for GPUs. The 4090 became impossible to find, not because of gamers, but because AI labs were hoarding them.
The same companies that depended on the consumer upgrade cycle now see their real profits coming from data centers. Yet, they still push gaming hardware aggressively. However, legitimate areas for improvement do exist. While marketing exaggerates the need for higher FPS at extreme resolutions, real gaming performance should focus on frame stability, low latency, and efficient rendering techniques. These are the areas where actual innovation should be happening. Instead, the industry prioritizes artificial performance milestones to create the illusion of progress, rather than refining and optimizing for the gaming experience itself. Why?
Gamers Fund the R&D for AI and Bear the Cost of Scalping
NVIDIA still needs gamers, but not in the way most think. The gaming market provides steady revenue, but it is no longer the priority. With production capacity shifting toward AI and industrial clients, fewer GPUs are available for gamers. This reduced supply has led to rampant scalping, where resellers exploit scarcity to drive up prices beyond reasonable levels. Instead of addressing the issue, NVIDIA benefits from the inflated demand and price perception, creating an even stronger case for prioritizing enterprise sales. Gaming revenue subsidizes AI research. The more RTX cards they sell, the more they justify pouring resources into data-center GPUs like the H100, which generate significantly higher margins than gaming hardware.
AI dictates the future of GPUs. If NVIDIA and AMD produced dedicated gamer-specific GPUs in higher volumes, they could serve that market at lower prices. But in the fiat-driven world of stockholder demands, maintaining artificially constrained supply ensures maximum profitability. Gamers are left paying inflated prices for hardware that is no longer built with them as the primary customer. That is why GPU prices keep climbing. Gamers are no longer the main customer. They are a liquidity pool.
The Financial Reality
The financial reports confirm this shift: NVIDIA’s 2024 fiscal year saw a 126% revenue increase, reaching \$60.9 billion. The data center segment alone grew 217%, generating \$47.5 billion. (Source)
The numbers make it clear. The real money is in AI and data centers, not gaming. NVIDIA has not only shifted its focus away from gamers but has also engaged in financial engineering to maintain its dominance. The company has consistently engaged in substantial stock buybacks, a hallmark of fiat-driven financial practices. In August 2023, NVIDIA announced a \$25 billion share repurchase program, surprising some investors given the stock's significant rise that year. (Source) This was followed by an additional \$50 billion buyback authorization in 2024, bringing the total to \$75 billion over two years. (Source)
These buybacks are designed to return capital to shareholders and can enhance earnings per share by reducing the number of outstanding shares. However, they also reflect a focus on short-term stock price appreciation rather than long-term value creation. Instead of using capital for product innovation, NVIDIA directs it toward inflating stock value, ultimately reducing its long-term resilience and innovation potential. In addition to shifting production away from consumer GPUs, NVIDIA has also enabled AI firms to use its chips as collateral to secure massive loans. Lambda, an AI cloud provider, secured a \$500 million loan backed by NVIDIA's H200 and Blackwell AI chips, with financing provided by Macquarie Group and Industrial Development Funding. (Source)
This practice mirrors the way Bitcoin miners have used mining hardware as collateral, expecting continuous high returns to justify the debt. GPUs are fast-depreciating assets that lose value rapidly as new generations replace them. Collateralizing loans with such hardware is a high-risk strategy that depends on continued AI demand to justify the debt. AI firms borrowing against them are placing a leveraged bet on demand staying high. If AI market conditions shift or next-generation chips render current hardware obsolete, the collateral value could collapse, leading to cascading loan defaults and liquidations.
This is not a sound-money approach to business. It is fiat-style quicksand financialization, where loans are built on assets with a limited shelf life. Instead of focusing on sustainable capital allocation, firms are leveraging their future on rapid turnover cycles. This further shifts resources away from gamers, reinforcing the trend where NVIDIA prioritizes high-margin AI sales over its original gaming audience.
At the same time, NVIDIA has been accused of leveraging anti-competitive tactics to maintain its market dominance. The GeForce Partner Program (GPP) launched in 2018 sought to lock hardware partners into exclusive deals with NVIDIA, restricting consumer choice and marginalizing AMD. Following industry backlash, the program was canceled. (Source)
NVIDIA is not merely responding to market demand but shaping it through artificial constraints, financialization, and monopolistic control. The result is an industry where consumers face higher prices, limited options, and fewer true innovations as companies prioritize financial games over engineering excellence.
On this basis, short-term downturns fueled by stock buybacks and leveraged bets create instability, leading to key staff layoffs. This forces employees into survival mode rather than fostering long-term innovation and career growth. Instead of building resilient, forward-looking teams, companies trapped in fiat incentives prioritize temporary financial engineering over actual product and market development.
A Sound Money Alternative: Aligning Incentives
Under a sound money system, consumers would become more mindful of purchases as prices naturally decline over time. This would force businesses to prioritize real value creation instead of relying on artificial scarcity and marketing hype. Companies would need to align their strategies with long-term customer satisfaction and sustainable engineering instead of driving demand through planned obsolescence.
Imagine an orange-pilled CEO at NVIDIA. Instead of chasing infinite growth, they persuade the board to pivot toward sustainability and long-term value creation. The company abandons artificial product cycles, prioritizing efficiency, durability, and cost-effectiveness. Gaming GPUs are designed to last a decade, not three years. The model shifts to modular upgrades instead of full replacements. Pricing aligns with real user needs, not speculative stock market gains.
Investors initially panic. The stock takes a temporary hit, but as consumers realize they no longer need to upgrade constantly, brand loyalty strengthens. Demand stabilizes, reducing volatility in production and supply chains. Gamers benefit from high-quality products that do not degrade artificially. AI buyers still access high-performance chips but at fair market prices, no longer subsidized by forced consumer churn.
This is not an abstract vision. Businesses could collateralize loans with Bitcoin. Companies could also leverage highly sought-after end products that maintain long-term value. Instead of stock buybacks or anti-competitive practices, companies would focus on building genuine, long-term value. A future where Bitcoin-backed reserves replace fiat-driven financial engineering would stabilize capital allocation, preventing endless boom-bust cycles. This shift would eliminate the speculative nature of AI-backed loans, fostering financial stability for both borrowers and lenders.
Sound money leads to sound business. When capital allocation is driven by real value rather than debt-fueled expansion, industries focus on sustainable innovation rather than wasteful iteration.
Reclaiming Time Sovereignty for Companies
The fiat system forces corporations into unsustainable growth cycles. Companies that embrace financial independence and time sovereignty can escape this trap and focus on long-term value.
GPU development illustrates this distortion. The RTX 3080 met nearly all gaming needs, yet manufacturers push unnecessary performance gains to fuel stock prices rather than improve usability. GPUs are no longer designed for gamers but for AI and enterprise clients, shifting NVIDIA’s priorities toward financial engineering over real innovation.
This cycle of GPU inflation stems from fiat-driven incentives—growth for the sake of stock performance rather than actual demand. Under a sound money standard, companies would build durable products, prioritizing efficiency over forced obsolescence.
Just as individuals can reclaim financial sovereignty, businesses can do the same. Embracing sound money fosters sustainable business strategies, where technology serves real needs instead of short-term speculation.
Bitcoin
FITS
Marketing
TimeSovereignty
BitcoinFixesThis
OptOut
EngineeringNotFinance
SoundBusiness
-
 @ 7e538978:a5987ab6
2025-04-10 13:14:04
@ 7e538978:a5987ab6
2025-04-10 13:14:04After five years and over 6,000 commits, LNbits has reached a momentous milestone: Version 1.0.0 is here. LNbits is officially out of beta!
This release represents the five years relentless development, dedication, bug-hunting, feature-building, and community involvement. What started as a lightweight Lightning wallet application for Lightning Network payments has evolved into one of the most versatile, modular, and widely-used Bitcoin tools in the space.
We want to offer a heartfelt thank you to every contributor, developer, tester, and user—from those running LNbits for personal use to the communities and businesses who rely on it every day. Your feedback, bug reports, feature requests, and support have made LNbits what it is today.
🚀 Key Highlights in v1.0.0
- LNbits now at v1.0.0 – the software is stable, hardened, and production-ready.
- Vue 3 migration – a complete frontend overhaul for performance and long-term maintainability.
- WebSocket payments – faster and more efficient, replacing older SSE and long-polling methods.
- New lnbits.sh install script – simplifies setup and local deployment.
- Access Control Lists (ACL) – token-based permissions for powerful role and scope control.
- Admin tools:
- Admin payments overview
- Toggle outgoing payments
- View payments from deleted wallets
- NWC (Nostr Wallet Connect) support
- Login with Nostr or OAuth – expanding integration and authentication options
💱 Fiat & Exchange Upgrades
- Custom exchange providers
- Improved fiat precision
- Wallet-level fiat tracking and labels
- Support for Bitpay and Yadio fiat rate providers
🧑🎨 UI / UX Improvements New Login/Register interface
- Default theme for new users
- Custom background images
- Visual refresh with new themes (including neon and light/dark modes)
- Revamped Pay Invoice dialog and invoice creation
- Custom wallet icons/colours
- CSV export and in-wallet payment filtering
🛠️ Developer Tools & Internal Enhancements Migration to pyjwt, updated to breez-sdk 0.6.6, pyln-client 24.5
- Support for Python 3.10–3.13
- New nodemanager for managing Lightning channels
- Backend refactors, improved database handling, type hinting, and extension logic
- More robust testing and CI support
🩹 Maintenance & Fixes Persistent fix for admin removal bug
- Improved extension handling
- Bug fixes across wallet logic, funding sources, and legacy compatibility
- Dozens of improvements to reliability, performance, and developer experience
🎉 A Huge Thank You
To every developer, translator, tester, UX contributor, node runner, and user: thank you.
LNbits wouldn’t be what it is without your involvement. Whether you've written code, opened issues, translated labels, or simply used it and given feedback—this release is yours too.
Here's to the next chapter!
-
 @ 866e0139:6a9334e5
2025-05-03 04:53:34
@ 866e0139:6a9334e5
2025-05-03 04:53:34Autor: Friderike Komárek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Was grade war, ist schief.
Wer Frieden will, ist böse.
Wer tötet, der ist lieb.
Gesund ist nur symptomlos krank,
Abstand ist gefühlte Nähe,
Maskenatmen – Gott sei Dank!
Fakten dienen Hass und Hetze,
Lügen tun gut.
Wer Fakten nennt, der wird zensiert,
Wahrheit schafft nur böses Blut.
Für Frieden braucht man Krieg,
für Meinungsfreiheit die Zensur.
Demokratie, die braucht Verbote,
fürs Klima zerstört man die Natur.
Mann ist Frau
und Frau ist Mann.
Ein Glück, dass man
die Biologie jetzt lenken kann!
Der Größenwahn beherrscht die Welt,
hat alles auf den Kopf gestellt.
Kritiker wandern als Kriminelle ins Gefängnis.
Mit ihren Gedanken bringen sie
die andern in Bedrängnis.
Was schief war, das ist grade.
Was grade war, ist schief.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ d9a329af:bef580d7
2025-05-03 04:20:42
@ d9a329af:bef580d7
2025-05-03 04:20:42To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ f7f4e308:b44d67f4
2025-04-09 02:12:18
@ f7f4e308:b44d67f4
2025-04-09 02:12:18https://sns-video-hw.xhscdn.com/stream/1/110/258/01e7ec7be81a85850103700195f3c4ba45_258.mp4
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 554ab6fe:c6cbc27e
2025-02-14 16:29:51
@ 554ab6fe:c6cbc27e
2025-02-14 16:29:51Bitcoin’s Price and the Power Law: A Reflection of Energy and the Early Stages of Monetary Adoption Introduction Bitcoin’s price trajectory has long puzzled analysts, with its seemingly chaotic booms and busts. However, when examined through the lens of power laws, a pattern emerges—one that is fundamentally tied to Bitcoin’s energy-based production cost. This article argues that Bitcoin’s price has historically followed a power law because its underlying cost structure is dictated by mining, an energy-intensive process. However, this relationship will not persist indefinitely. I propose that as Bitcoin matures into a widely adopted monetary system, its price will decouple from mining production costs and instead oscillate in accordance with natural business cycles, much like traditional forms of money.
Bitcoin’s Price and the Power Law
 Source and Credit: Giovanni Santostasi’s “The Bitcoin Power Law”
Source and Credit: Giovanni Santostasi’s “The Bitcoin Power Law”When Bitcoin’s price is plotted on a logarithmic scale against time, a strikingly straight-line trajectory appears, punctuated by cycles of rapid price expansion (bull markets) followed by severe corrections (bear markets). These perturbations correspond to Bitcoin’s well-known halving cycles, which occur approximately every four years and reduce the block reward paid to miners, effectively doubling the cost of production per Bitcoin. Historically, Bitcoin’s price has always returned to a fundamental minimum—one that closely aligns with the average cost of mining.
This observation suggests that Bitcoin’s power law price behavior is not arbitrary but rather a reflection of its fundamental energy constraints. As in many natural systems governed by power laws, energy dynamics play a central role. In Bitcoin’s case, the “base layer” of its valuation is determined by the energy and computational resources required for mining. This power law behavior is therefore a consequence of Bitcoin’s fundamental design: as block subsidies decrease and mining efficiency improves, the minimum sustainable price follows an upward trajectory dictated by production costs.
Bitcoin as an Energy-Based System
Power laws commonly emerge in natural systems involving energy constraints, from thermodynamics to biological ecosystems and planetary dynamics. Bitcoin, as an energy-based monetary system, exhibits similar characteristics. Mining requires significant electricity and computational power, and as the difficulty adjustment ensures a competitive equilibrium, the cost of mining a Bitcoin remains closely tied to its market value over the long run.
Unlike traditional fiat currencies, which are controlled by central banks and subject to arbitrary monetary expansion, Bitcoin’s supply schedule is immutable. Its economic foundation is rooted in proof of work, where value is derived from energy expenditure. This fundamental linkage between energy and price explains why Bitcoin’s valuation has adhered to a power law trajectory. It is an entropy engine, and follows physical laws related to energy and entropy.
However, this pattern is not a permanent feature of Bitcoin’s monetary future—it is, rather, an indication of Bitcoin’s early-stage monetization process.
The Transition from Mining-Based Pricing to a Business Cycle
A crucial implication of Bitcoin’s price following a power law dictated by mining costs is that it suggests Bitcoin has yet to fully mature as money. If Bitcoin were already a widely adopted monetary standard, its valuation would no longer be primarily influenced by the floor mining costs but instead by macroeconomic forces—specifically, the natural fluctuations of the business cycle.
In a world where Bitcoin is the dominant global currency, the “price of money” (which correlates with the cost of capital and prevailing interest rates) would fluctuate according to the broader economic cycle. The dynamics would resemble those of natural interest rate cycles described by the Austrian School of Economics:
- During periods of economic expansion, lower interest rates spur increased investment and consumption, prices slightly rise, and savings deplete.
- As savings decline and prices rise, interest rates naturally rise as well, leading to reduced investment and spending, initiating a contractionary phase and lowered prices.
- During the contraction, savings accumulate, more capital becomes available, and interest rates and prices decline.
- With the availability of capital, lower interest rates and lowered prices, the economy is now ready to enter a phase of investment and expansion once again.
- This oscillatory process continues indefinitely, driven by real economic growth rather than central bank intervention.
If Bitcoin were fully monetized, its price would no longer oscillate based on mining halvings and energy costs but instead reflect economic expansion and contraction cycles—just as traditional currencies do when not artificially manipulated by central banks.
The Early Stage Indicator: Bitcoin’s Dependence on Mining Costs
Today, Bitcoin’s price still “bounces” off the power law baseline, indicating that its valuation remains primarily anchored to its minimum cost of production. This means that, while Bitcoin is widely recognized as an asset, it has not yet reached the level of adoption where its price is dictated by macroeconomic cycles.
A future in which Bitcoin is used as a primary medium of exchange and unit of account would necessarily imply a decoupling from mining-driven pricing. Instead of periodic halvings triggering speculative bull runs followed by crashes, Bitcoin’s price would become far more stable, with fluctuations primarily driven by business cycle dynamics. The continued adherence to the power law model, therefore, is evidence that Bitcoin is still in an early phase of adoption—where mining remains a primary determinant of price.
Conclusion
Bitcoin’s price trajectory has long conformed to a power law, reflecting the underlying energy costs of mining. This characteristic, however, is likely not a permanent feature but rather a hallmark of Bitcoin’s early stage as an emerging monetary system. As adoption increases and Bitcoin becomes widely used as money, its price should transition away from being dictated by mining costs and should instead fluctuate according to the natural oscillations of the business cycle.
The persistence of Bitcoin’s power law trend is a sign that it remains in its infancy. The real transformation will occur when Bitcoin is no longer bound to its production cost but is instead driven by the natural ebb and flow of savings, investment, and capital cycles—marking its full emergence as a global monetary system.
Disclaimer: The information provided in this blog is for informational and educational purposes only and should not be construed as financial advice. Please consult with a financial advisor or conduct your own research before making any financial decisions.
-
 @ 68c90cf3:99458f5c
2025-04-04 16:06:10
@ 68c90cf3:99458f5c
2025-04-04 16:06:10I have two Nostr profiles I use for different subject matter, and I wanted a way to manage and track zaps for each. Using Alby Hub I created two isolated Lightning wallets each associated with one of the profile’s nsecs.
YakiHonne made it easy to connect the associated wallets with the profiles. The user interface is well designed to show balances for each.
In my case, I have one profile for photography related content, and the other for Bitcoin, Nostr, and technology related content. I can easily switch between the two, sending and receiving zaps on each while staying up to date on balances and viewing transactions.
Using my self-hosted Alby Hub I can manage Lightning channels and wallets while sending and receiving zaps for multiple profiles with YakiHonne.
YakiHonne #AlbyHub #Lightning #Bitcoin #Nostr
-
 @ d9a329af:bef580d7
2025-05-03 04:10:03
@ d9a329af:bef580d7
2025-05-03 04:10:03Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones)
To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
- Firefox Forks
This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
- Brave Browser
This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
- Office Suites (If you need to do professional office documents)
- LibreOffice
A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
- OnlyOffice
The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
- Wordgrinder
For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
- Text editors
- Vi, Vim, Neovim and other Vim-like editors
The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
- VSCodium
The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
- Emacs
The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ d61f3bc5:0da6ef4a
2025-02-12 16:57:44
@ d61f3bc5:0da6ef4a
2025-02-12 16:57:44Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet.
There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what kind of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help.
Primal Wallet
Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.
 Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app.
Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app. Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed 1,338,460 transactions, with 238,916 just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish.
All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem.
Zapping from Any Nostr App
For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:
 Yes. Click, click. And you can start zapping!
Yes. Click, click. And you can start zapping! Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in.
Primal enables you to connect any number of external apps and manage them from wallet settings:
 Note that you can set your daily spend budget for each app or revoke its access at any time.
Note that you can set your daily spend budget for each app or revoke its access at any time. How This Works
So, what is this sorcery? How does it work under the hood?
Connecting Nostr apps to external wallets is accomplished via the Nostr Wallet Connect protocol. It utilizes Nostr’s public relay infrastructure to enable communication between apps and wallets. You can learn more about this protocol here, and access developer docs here.
The smooth, two-click connection setup UX is implemented through deep links between Primal and the external app. Here’s the deep link that the external app needs to call to invoke this feature:
nostrnwc+primal://connect?appicon=[icon_url]&appname=[app_name]&callback=[callback_string]After the user clicks “Create Wallet Connection” in Primal, the Primal app calls the deep link defined in the callback, and passes the NWC connection string. That's all that the external app needs to make the wallet connection.
What Comes Next?
The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments.
Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿
-
 @ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30
@ 34f1ddab:2ca0cf7c
2025-05-03 02:45:30In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
Our Recovery Services Include: 📈 Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞 For quick queries or support, connect with us on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪In the world of cryptocurrency, the stakes are high, and losing access to your digital assets can be a nightmare. But fear not — Crypt Recver is here to turn that nightmare into a dream come true! With expert-led recovery services and cutting-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust
At Crypt Recver, we combine state-of-the-art technology with skilled engineers who have a proven track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or dealt with damaged hardware wallets, our team is equipped to help.
⚡ Fast Recovery Process
Time is of the essence when it comes to recovering lost funds. Crypt Recver’s systems are optimized for speed, enabling quick recoveries — so you can get back to what matters most: trading and investing.
🎯 High Success Rate
With over a 90% success rate, our recovery team has helped countless clients regain access to their lost assets. We understand the intricacies of cryptocurrency and are dedicated to providing effective solutions.
🛡️ Confidential & Secure
Your privacy is our priority. All recovery sessions at Crypt Recver are encrypted and kept entirely confidential. You can trust us with your information, knowing that we maintain the highest standards of security.
🔧 Advanced Recovery Tools
We use proprietary tools and techniques to handle complex recovery scenarios, from recovering corrupted wallets to restoring coins from invalid addresses. No matter how challenging the situation, we have a plan.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Have you lost access to your Bitcoin wallet? We can help you recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in extracting assets safely and securely.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s critical to act swiftly when facing access issues. Whether you’ve been a victim of a dust attack or have simply forgotten your key, Crypt Recver offers the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!
Ready to get your cryptocurrency back? Don’t let uncertainty hold you back!
👉 Request Wallet Recovery Help Today!
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Trust Crypt Recver for the Best Crypto Recovery Service — Get back to trading with confidence! 💪
-
 @ 4e7c1e83:1c2939b5
2025-05-03 02:42:17
@ 4e7c1e83:1c2939b5
2025-05-03 02:42:17Discover the power of Flash Bitcoin with FLASHCORE BTC Softwareclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss
-
 @ 4e7c1e83:1c2939b5
2025-05-03 02:37:13
@ 4e7c1e83:1c2939b5
2025-05-03 02:37:13Discover the power of Flash Bitcoin with FLASHCORE BTC Softwareclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
What is FLASHCORE BTC Software (Basic)? The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic) 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate. Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities. Single-Device Security: Locked to one computer via obfuscation code for exclusive use. Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection. Why Choose FashExperts’ FLASHCORE BTC Software (Basic)? Simple & Effective: Perfect for beginners or testers who need basic flashing features. Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams. Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate. Reliable Performance: Built for consistent, hassle-free blockchain interaction. How It Works With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably? Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action: 📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertssDiscover the power of Flash Bitcoin with FLASHCORE BTC Software (Basic), exclusively available at FashExperts! This full-version tool allows you to send Flash Bitcoin across blockchain networks, with transactions lasting up to 90 days in any wallet — or indefinitely with hash rate. Ideal for crypto enthusiasts and testers, this software offers a simple, secure way to explore blockchain capabilities.
 # What is FLASHCORE BTC Software (Basic)?
# What is FLASHCORE BTC Software (Basic)?The FLASHCORE BTC Software (Basic) is a streamlined version of our innovative flashing technology, designed to generate and send fake Bitcoin (Flash BTC) over blockchain networks. Without hash rate, Flash BTC remains in your wallet for a maximum of 90 days before being rejected and disappearing. However, with hash rate, it can stay indefinitely! Built with a unique obfuscation security code, this software ensures authenticity and functionality — exclusively from FashExperts.
Key Features of FLASHCORE BTC Software (Basic)
- 90-Day Duration: Flash BTC lasts up to 90 days without hash rate, and indefinitely with hash rate.
- Full-Version Access: Get the latest Flashcore BTC Software with essential flashing capabilities.
- Single-Device Security: Locked to one computer via obfuscation code for exclusive use.
- Blockchain Compatibility: Sends Flash BTC across networks, visible until rejection.
Why Choose FashExperts’ FLASHCORE BTC Software (Basic)?
- Simple & Effective: Perfect for beginners or testers who need basic flashing features.
- Secure Purchase: Sold only by the original developer at FashExperts — avoid reseller scams.
- Unlimited Potential: Extend Flash BTC duration indefinitely with hash rate.
- Reliable Performance: Built for consistent, hassle-free blockchain interaction.
How It Works
With FLASHCORE BTC Software (Basic), you can send Flash Bitcoin to any wallet, where it remains for 90 to 360 days unless paired with hash rate for unlimited duration. Transactions are sent across blockchain networks and disappear after rejection if no hash rate is applied. The software’s full-version design ensures ease of use, while its single-device lock keeps it secure and exclusive just for you.
Important Warning
This software is sold solely by the developer at FashExperts. Each purchase includes a unique obfuscation security code, restricting use to one computer. Resold versions are scams and won’t work — buy directly from FashExperts to ensure you get the authentic FLASHCORE BTC Software (Basic).
Ready to Flash Bitcoin Affordably?
Get FLASHCORE BTC Software (Basic) from FashExperts and start sending fake BTC that lasts 90 days (or longer with hash rate). It’s the best entry-level flashing tool online — secure your copy today!
Call to Action:
📞 Call Us on WhatsApp : +1 (329) 226–0153
💬 Chat with Us on Telegram: @fashexpertss
-
 @ d4309e24:8a81fcb0
2025-02-09 00:16:55
@ d4309e24:8a81fcb0
2025-02-09 00:16:551. What if You Could Send a Message into the Future?
Imagine leaving a message for your future self, a loved one, or even an entire community—one that no one, not even you, can unlock until a specific moment in time. Picture leaving a message for your children, a note of wisdom or love that remains hidden until they're old enough to appreciate it, all timed by Bitcoin's block height. You might also make a bold prediction about the future price of Bitcoin, sealing it away until the blockchain reaches a certain block height.
This is the idea behind Hatchstr, a decentralized app for time-locked messages that only unlock at predetermined Bitcoin block heights—no central authority required.
Why Build This?
I want to dive into the Nostr protocol not just by reading documentation, but by actually building something that embodies its core principles: censorship resistance, user ownership, and decentralization. Hatchstr is both an experiment and a contribution to the Nostr ecosystem—a way to test the limits of permissionless communication while learning and engaging with the community.
2. The Vision: How Hatchstr Would Work for Users
At its core, Hatchstr lets users create time capsules—encrypted messages that only become readable after a specified Bitcoin block height. Here’s what that looks like:
- You design a capsule with text and images using Hatchstr’s web app.
- You pick an unlock time (e.g., 1000 blocks from now).
- The message is encrypted, locked away, and published as a Nostr event.
- At the chosen time, the decryption key is revealed, allowing the recipient to finally access the message.

Potential Use Cases
-
Personal Messages: Send birthday wishes that unlock at midnight, time-delayed love letters, or notes to your future self.
-
Timed Learning: Lock educational content to unlock when students reach key learning stages or ages.
-
Creative Storytelling: Release serialized fiction, riddles, or treasure hunt clues that unlock over time.
-
Community & Events: Time-gate announcements for Nostr-based communities or scheduled voting mechanisms.
3. The Centralized Trap: Why Build on Nostr
When thinking about how to implement this, we could go the obvious, easy route:
- Store messages on a centralized server.
- Release them when the time is right.
- Let users download their messages.
Simple, right? But is it the right approach? Let's break it down.
Why This Fails
-
Single Point of Failure: If my server goes down, all messages are unavailable.
-
Privacy Risks: Users would need to trust me not to access their messages.
-
Ownership & Longevity: What happens if I lose interest? The system dies with me.

A centralized model defeats the purpose of time-locking messages. Users shouldn’t have to trust a third party. We need decentralization.
4. Nostr to the Rescue: How Decentralization Can Help
Instead of a single server holding messages hostage, Nostr allows users to publish messages to decentralized relays. Here are the key differences:
-
Nostr IDs = Self-Owned Identities: Your public key is your identity, not tied to any company.
-
Relays = Decentralized Bulletin Boards: Anyone can run one, ensuring redundancy and censorship resistance.
-
Messages = Signed Events: Cryptographically signed by the sender or encrypted for only the recipient.

How Nostr Reduces Centralization
In this version of Hatchstr, capsules are still stored in a centralized manner at first until they 'hatch'. However, once the Bitcoin block height condition is met:
- Capsule Publication: The system publishes the capsule events to Nostr relays, making the messages available for decryption by the intended recipients.
This approach, while not eliminating the central server, allows for:
-
Third-Party Clients: Developers can now create clients that interact with Hatchstr capsules on Nostr, enhancing the system's openness and potentially leading to a richer ecosystem around time-locked messages.
-
Decentralized Access: Even though the initial storage is centralized, the access to the messages becomes decentralized once published to Nostr, reducing the dependency on a single point for message retrieval.
We have some improvements, but I am sure we can do better!
5. The Path to Decentralized Timekeeping
The Timeless Nature of Encryption
Encrypted messages exist outside time—once locked, they remain secure indefinitely. Modern cryptography (like AES-256) doesn’t "expire" or weaken unless decrypted (excluding brute force attacks). This creates a paradox: How do you bind something timeless to a specific moment in the physical world?
The Time-Lock Puzzle Dilemma
Cryptographers have proposed time-lock puzzles—encryption that requires sustained computation to unlock, theoretically forcing a minimum wait time. But these face critical hurdles:
-
Hardware Uncertainty
Solving time depends on an attacker’s computational power. A nation-state could crack in hours what takes years for a regular user. -
No Real-World Alignment
Puzzles can’t guarantee unlocks align with calendar dates or real-world events ("unlock on my child’s 18th birthday"). -
Energy Waste
Requires continuous computation, making it environmentally impractical for longer time locking.
Bitcoin as a Decentralized Clock
This is where Bitcoin’s blockchain shines. Its difficulty-adjusted proof-of-work acts as a trustless metronome:
-
Predictable Rhythm
Despite hash rate fluctuations, the 10-minute block target (via difficulty adjustments) creates a consistent approximation of real-world time.
-
Immutable History
Block height 1,000,000 will always correspond to the same point in Bitcoin’s timeline, regardless of future changes in mining power
Splitting the Problem
Hatchstr can bridge timeless encryption and blockchain timing by separating concerns:
1. Capsules – The time-locked message itself:
-
Design independent of the time-locking mechanism.
-
Encrypted client-side.
-
Content stored anywhere the user wants (IPFS, personal servers, etc.).
-
Completely owned by the user—not Hatchstr.
2. Clock Servers – Independent, lightweight timing nodes that:
-
Only publish decryption keys when the target Bitcoin block height is reached.
-
Users can choose which Clock Server to trust.
-
Anyone can run their own Clock Server.
-
Multiple servers can coordinate to prevent a single point of failure.

This means Hatchstr itself doesn’t store anything—users are fully in control.
6. What Comes Next
This project is just beginning—a blueprint with open questions and untested assumptions. In the next two articles, I’ll explore how to turn this concept into something tangible. First, how we might design playful time capsules that can be displayed faithfully by multiple clients, balancing creativity with decentralization. Then, the messy realities of clock servers: why federating them matters, how to incentivize reliability, and borrow Bitcoin’s rhythm without centralizing control. We will dive into setting up a simple clock server to get things started.
I’m still learning Nostr’s ecosystem, and this project is as much about sharing my education as anything else. If any part of this concept makes you think “yes, but…” or “what if…”, I’d genuinely love to hear it. Find me on Nostr – no expertise required, just an interest in sending messages to the future. :

npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uhThank you for reading 🧡
-
 @ c9badfea:610f861a
2025-05-03 01:50:40
@ c9badfea:610f861a
2025-05-03 01:50:401. Create
bash git bundle create backup.bundle --all2. Verify
bash git bundle verify backup.bundle3. Restore
bash git clone backup.bundleℹ️ Feel free to change the
backup.bundlefile name -
 @ c9badfea:610f861a
2025-05-03 01:23:19
@ c9badfea:610f861a
2025-05-03 01:23:19To qualify, a domain must:
- End in
.xyz - Contain only numbers
- Be 6-9 digits long (between
000000through999999999)
Examples:
123123.xyz01020304.xyz
- End in
-
 @ e373ca41:b82abcc5
2025-02-06 09:25:07
@ e373ca41:b82abcc5
2025-02-06 09:25:07This article by Milosz Matuschek first appeared in German in "Freischwebende Intelligenz".
In my first multi-part Corona series, The Corona Complex, I focused on the early inconsistencies of the "pandemic." In The Corona Connection, I will explore the key players involved in this event over multiple installments.
It’s not yet spring, but the bud of truth is already breaking through the icy layer of lies. You can cover the truth with as much PR, manipulation, and propaganda as you want—it will only turn into compost. Because truth is rooted in something; it’s a living organism, while lies are rotting waste. The coming weeks and months will be enlightening.
The USAID Front Organization
The grand cleanup led by Musk & Trump is in full swing. In the U.S., the agency USAID is currently being dismantled amid protests from employees. As of Friday, February 7, nearly all staff members have lost their jobs. What does this mean?
Der Spiegel referred to USAID as a "development agency" and reported that a nervous Bill Gates now wants to call Trump "to save lives." The NZZ euphemistically describes USAID as an "independent development aid agency." Seeing "AID" in the name, people think of humanitarian efforts—Bob Geldof, compassionate nuns, and "Bread for the World."
In reality, USAID ("United States Agency for International Development" – claim: "From the American People") is far from just a food distribution service (although it does that too). Primarily, it serves as a covert, rapid-response intelligence force for operations such as regime change, astroturfing, and targeted executions—expanding new business models for the U.S. empire. They are the enforcers who move in before "peace, democracy, and reconstruction" are declared.
USAID was heavily involved in Ukraine, providing $5 billion in funding, as Robert Kennedy Jr. recently stated in an interview. The agency throws money around freely, financing both the GAVI vaccine alliance and the World Economic Forum—because, of course, these are the world's most "needy" causes.
https://x.com/ShadowofEzra/status/1886153128757629157
The PREDICT Program
It gets even stranger. Under the so-called PREDICT program, significant funding was allocated to research coronaviruses in bats. This research was conducted in collaboration with the Wuhan Institute of Virology (WIV) and included gain-of-function experiments. In 2017, the NIH lifted a previously imposed moratorium on funding such research, paving the way for its resumption and expansion, including international partnerships like the one with WIV.
USAID spent about $200 million in taxpayer money on bat virus research, with approximately $50 million going directly to WIV. Despite being a publicly funded science program, PREDICT's administrators have largely refused to release sensitive details about its research. Peter Daszak, who received substantial funding (now cut off), even ignored some subpoenas. Officials shared information with taxpayers only reluctantly and in minimal amounts.
https://x.com/KanekoaTheGreat/status/1886098345938284813
A 2023 investigation by the White Coat Waste Project, following a public records request, revealed that U.S. taxpayer dollars—through the NIH and USAID—flowed to the Wuhan Institute of Virology. These funds supported gain-of-function experiments in which viruses were genetically modified to increase their transmissibility or virulence. The program ended in 2019.
The Mystery of Ben Hu
One of the most explosive revelations was the identification of Ben Hu, a lead researcher at WIV, as a potential "Patient Zero." Reports indicate that he developed COVID-like symptoms as early as November 2019—before the first officially recognized cases. Hu was deeply involved in the gain-of-function experiments funded by U.S. taxpayer money.
Looking further back, the picture becomes clearer. As early as 2012, USAID funds were used to capture bats in caves, including those in Mojiang, where several miners died from a deadly respiratory illness. The infection was reportedly caused by bat droppings.
https://x.com/TheSeeker268/status/1886469590701760960
Too many coincidences are piling up: The virus strain from back then, RaTG13, has striking similarities to SARS-CoV-2. Fauci’s pardon dates back to as early as 2014. A significant portion of funding from both Fauci and USAID went to Peter Daszak’s EcoHealth Alliance. Daszak in 2016 gave surprisingly candid responses regarding gain-of-function research.
https://x.com/mazemoore/status/1883378918687719725
The director of the CDC, Robert Redfield, had already pointed out in previous hearings that U.S. public funds were used for research in Wuhan.
So, to summarize here quickly, adding a question:
- A CIA front organization was catching sick bats in a previous outbreak zone of deadly respiratory diseases in China (e.g., Mojiang caves) in 2012.
- It funded tens of millions of dollars' worth of research to enhance the pathogenicity of coronaviruses in Wuhan.
- It transferred money to Chinese military-medical institutions.
- Wuhan researcher Ben Hu fell mysteriously ill and became Patient Zero.
So here’s the question: Isn't a natural origin of the virus the most obvious explanation in the world?
ADVERTISEMENT:
Looking for the easiest way to buy Bitcoin and store it yourself? The Relai app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.

Need more security? The Trezor wallets are recommended and easy to use, others are available in the store. Need more advice? Book an introductory meeting with a wallet expert.
Who still believes in a natural origin of COVID-19?
The official narrative worldwide is that the virus originated naturally—perhaps from someone consuming or handling a bat at a wet market near WIV. Yet, neither the sick animal nor the first human case of "natural transmission" has ever been identified.
At the same time, intelligence-backed "nudging" units worked preemptively to discredit vaccine skeptics and bolster "Trusted News Initiatives" and fact-checking programs. Even the CIA director has now suggested that COVID may have originated in a lab. And he likely knows exactly why.
One thing is certain: The theory of natural zoonotic transmission in COVID-19 has been obliterated. It was the PR stunt of the century. A joint effort by the CIA and China—who else could pull off such a grand deception?
These revelations are making the players behind the "Corona Connection" increasingly visible: a network of CIA-China partnerships, NGOs, the media apparatus, corrupt politicians, and willing, unscrupulous, or even outright sociopathic scientists.

As these connections come to light over the next months and years, the consequences for those involved—and for society at large—will be immense. We are approaching a moment of societal reckoning. A house of cards can only stand for so long before it collapses.
In Germany, Christian Drosten was one of the most aggressive proponents of the "conspiracy theory" label, frequently using it to discredit critics. As one of the main gatekeepers of the COVID narrative, he played a key role in shaping the scientific community’s response. His most steadfast domestic opponent was Hamburg physicist Roland Wiesendanger.
This is what happens when the desire for recognition and power overshadows any sense of medical ethics. Now, serious questions arise about his role: What did he know about the research in Wuhan? Was he aware of USAID’s funding? Given that Charité (his institution) received grants from Bill Gates and that his PCR test was immediately declared the global gold standard, it seems unlikely that he knew nothing.
This demands an investigative committee and legal proceedings.
In the coming weeks and months, many more connections will be uncovered, fully exposing the "Corona Connection."
The era of silence is over.
And so is the era of immunity.
This article was written with the Pareto-client on Nostr. Check it out!
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).

Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Nosta.me.

-
 @ 4bfad9a2:bd954efa
2025-05-02 23:36:06
@ 4bfad9a2:bd954efa
2025-05-02 23:36:06The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 15cf81d4:b328e146
2025-05-02 20:36:37
@ 15cf81d4:b328e146
2025-05-02 20:36:37Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ 961e8955:d7fa53e4
2025-02-01 23:20:53
@ 961e8955:d7fa53e4
2025-02-01 23:20:53"@YakiHonne community partners successfully convened a seminal Nostr101 meetup in Barnawa, Nigeria! Donning bespoke YakiHonne Nigeria Limited Edition T-shirts, the Purple Army infused the town with infectious energy.
Facilitated by @Olaoluwa Ezekiel Michael, this gathering leveraged YakiHonne's decentralized platform to foster unbridled dialogue, idea exchange, and community engagement.
The event's resounding success underscores the burgeoning demand for decentralized solutions in Africa. This milestone marks the inception of a revolutionary movement, empowering voices and fostering collaboration throughout the continent.
Nostr #DecentralizedRevolution #Africa #CommunityFirst #YakiHonne"
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3c7dc2c5:805642a8
2025-05-02 19:35:35
@ 3c7dc2c5:805642a8
2025-05-02 19:35:35🧠Quote(s) of the week:
'We are watching the greatest transfer of wealth in the history of the world. You are either on the right side, or you are not..... This is for all of the marbles.' - Lawrence Lepard
https://i.ibb.co/20SknGYv/Gpeq-ZCq-Wo-AAww-a.jpg
“Well, well, well… how the turntables.” ~Michael Scott
🧡Bitcoin news🧡
42,000 BTC taken off exchanges in the last month. ETFs bought 4,500 BTC yesterday (21st of April), and gold is doing all-time highs every day. Something is brewing.
On the 21st of April:
➡️Oregon Attorney General Dan Rayfield sues Coinbase over unregistered securities sales.
➡️It makes sense that capital will flow from real estate to Bitcoin.
Over 20 years:
$100K in Bitcoin at 30% CAGR = $19M.
$100K in real estate at 10% CAGR = only $670K.
The difference in potential long-term returns is astronomical. https://i.ibb.co/r2nS4ftN/Gp-Fh5-UWXEAAc-Jo-H.jpg
On the 22nd of April:
➡️The Swiss National Bank is loading up big on Saylor’s Strategy https://i.ibb.co/SwXZKZ6F/Gp-IIN1-Wg-AA-l-F.jpg
➡️https://i.ibb.co/JFC05nvb/Gp-JG9yca8-AACQXW.jpg Bitcoin is following the money/M2
➡️The first time Bitcoin hit $88,000 (Nov 11), Ethereum was trading at $3377. Today, with Bitcoin trading at $88,000, Ethereum is trading at $1562 (-54%). Incredible, yet so unsurprising.
➡️American Funds Has Bought 3.3 Million Strategy₿ Stocks For 1.03 Billion Dollars At A Average Price Of $307.5 Per Share In Q1 2025.
➡️The market dominance of Bitcoin continues to rise. https://i.ibb.co/DfcJ4CCb/Gp-Ix-Xll-XAAAnv3m.jpg
➡️ Bitcoin surges above $90,000 for the first time since March 7th.
➡️Pro-Bitcoin Paul Atkins was officially sworn in as the new SEC Chair.
➡️US Bitcoin ETFs posted their strongest inflow day, ETFs bought $381 MILLION worth of BTC, since January yesterday.
On the 23rd of April:
➡️Cantor Fitzgerald, Tether, and SoftBank are forming a $3B Bitcoin investment vehicle, with Tether contributing $1.5B in BTC. Bitfinex and SoftBank will add $600M and $900M. Modeled after Saylor’s playbook, the firm aims to absorb billions in Bitcoin. Jack Mallers to be the CEO of SoftBank, Cantor, Tether, and Bitfinex's "multibillion-dollar bitcoin acquisition vehicle". Twenty-One is set to launch with 42,000+ BTC.
'Masayoshi Son's biggest Bitcoin bet yet. In 2017, Softbank's Son personally bought ~$200M of Bitcoin near the top, then sold months later, reportedly losing over $130M. Earlier this year, SoftBank invested $50M in Cipher Mining, acquiring approximately 10.4 million shares (3%) to support HPC data center development and entering into a month-exclusive negotiation for data center space which was never completed. This time, it looks like the bet from one of big tech's most infamous risk takers can't be unwound so easily.' - Matthew Sigel
Hello, game theory!
Sam Callahan:
'A Bitcoin treasury company with: * – Cantor’s institutional Rolodex & capital markets expertise * – Tether’s profitability & technological expertise * – SoftBank’s huge war chest & portfolio of companies * – Jack Mallers’ energy & leadership
A serious player just entered the fray.'
Let the games begin. Food for thought. A great read by Adam Livingston: “Bitcoin’s next leg up won’t be demand-driven. It will be capital-structured. Engineered. Manufactured. Monetized.” https://x.com/AdamBLiv/status/1915220871699890312
'This all is great for Number Go Up. Not so great for Freedom Go Up. Basically a company that sells you stocks (paper bitcoin) and they own the bitcoin. You can do better: self-custody bitcoin. You'll make more profit, no third party risks.' - Anita Posh
Do you remember last week's quote by Jameson Lopp:
'The "Bitcoin Corporate Treasury" narrative is a foot gun if it's not accompanied by the sovereignty via self-custody narrative. Number Go Up folks are pitching companies to funnel their funds into a handful of trusted third parties. Systemic Risk Go Up.'
➡️CarlBMenger:'Bitcoin hit a new ATH against the NASDAQ. The decentralized revolution just outran Wall Street’s elite. The people’s protocol is winning.'
➡️Mara: Our gas-to-power network has eliminated CO₂ equivalent emissions on par with removing 6,800 gasoline vehicles from the road for a full year—while simultaneously lowering energy costs. Learn more from our recent blog post: https://www.mara.com/posts/mara-energizes-full-25-mw-micro-data-center-initiative-powered-by-associated-natural-gas
Daniel Batten: "MARA recently joined 28 other Bitcoin mining companies who collectively mitigate 3.5 Million Tonnes of CO2e emissions per year by using previously flared gas or vented gas as their fuel source ... and have now scaled up fast to 25MW of flare-gas powered mining!"
From energy vampires to green energy producers. Bitcoin miners are changing the world.
➡️M2 money supply has now been expanding at 4.1%. After reaching its deepest contraction in 65 years. This is very constructive for the markets.
One month later, right on schedule... and this is before the Fed, ECB, PBOC, and BOJ start easing.
➡️As of April 23, 87.3% of Bitcoin's circulating supply was in profit.
On the 24th of April:
➡️Someone just moved 50 Bitcoins they mined 15 years ago under $0.10. Now worth $4.75M.
➡️Panama City officially signs a deal with a local bank to process municipal payments in Bitcoin.
➡️Swiss citizens have stepped up calls for the Swiss National Bank to buy Bitcoin, saying the global economic turmoil triggered by U.S. President Donald Trump's tariffs made it more important for the central bank to diversify its reserves.
➡️Fidelity Digital Assets said public companies buying Bitcoin are dropping the supply on exchanges and this will accelerate further. Bitcoin exchange balances are at the lowest levels since late 2018.
https://i.ibb.co/fdrfSg2W/Gp-S0wy-CWk-AA2-M8h.jpg
➡️US ETFs purchased a whopping 10,740 BTC yesterday. That’s 24,534 BTC last 3 business days. When these guys buy, they buy heavy. Time is running out to “get some / get yours”
➡️Ruya just became the first Islamic bank worldwide to enable customers to buy Bitcoin.
➡️Metaplanet purchases an additional 145 $BTC, and total holdings reach 5,000 BTC.
➡️Publicly traded HK Asia Holdings Limited to raise HK$65,498,320 to buy more Bitcoin.
➡️ARK Invest updates their 2030 Bitcoin price prediction to $2.4 million.
On the 25th of April:
➡️Bitcoin Energy Value is at $130K. We are one year post Halving and Bitcoin is trading at a whopping 40% discount to its intrinsic value.
➡️Banks are now free to begin supporting Bitcoin. Your local neighborhood bank in America can now buy, sell, and hold Bitcoin. On April 24, the Federal Reserve withdrew its previous letters that had forced banks to get special regulatory permission first for any Bitcoin service, preventing the technology adoption.
https://www.federalreserve.gov/newsevents/pressreleases/bcreg20250424a.htm https://i.ibb.co/rGmB6yw7/Gp-YUXl-VXw-AADpqs.jpg
➡️CitiBank, one of the largest US banks, will soon allow its customers to invest in "bitcoin and various cryptocurrencies" directly from their bank accounts, per WSJ.
➡️'Norway’s sovereign wealth fund didn’t want to invest in bitcoin, saying it’s “too risky.” Now they have reported a loss on “safe” tech investments. Irony level: $40 billion -Eli Nagar
➡️Semler Scientific acquires 111 more bitcoins for $10 million, bringing its total holdings to 3,303 BTC. The company has generated a 23.5% Bitcoin yield year-to-date.
➡️BlackRock bought $1.2 Billion of Bitcoin this week and now holds 2.77% of the entire BTC supply.
➡️Monthly DCA in BTC beats Monthly DCA in SPY at any time. Here is an overview of how much annual return would have generated a Monthly DCA, from January or July in the last 5 years, both in SPY and in Bitcoin.
https://i.ibb.co/v4J5YVM1/Gpa-ACEXWEAAwcb-S.png
➡️The Swiss National Bank rejects a proposal to hold Bitcoin, saying it "does not meet the high requirements" for national currency reserves. HFSP!
On the 26th of April:
➡️61,178 Bitcoin were withdrawn from exchanges this week!
On the 27th of April:
➡️The IMF confirmed Tuesday that El Salvador has upheld its commitment to stop bitcoin accumulation by its fiscal sector. "I can confirm that El Salvador continues to comply with its commitment to not hoard bitcoin by the fiscal sector in general, which is our performance criterion," - Rodrigo Valdés, director of the Western Hemisphere at the IMF
But yet, the El Salvadoran government publicly claims they are still stacking sats... Somebody is lying.
➡️Arizona's two Bitcoin Reserve Bills have their third reading and potential FINAL vote tomorrow. We may be looking at a State's first SBR across the line.
➡️'Cardone Capital is accumulating BTC from its real estate holdings to create a public Real Estate/BTC REIT. We are on our 4th Fund with current acquisitions adding 350 BTC.' - Grant Cardone
💸Traditional Finance / Macro:
On the 21st of April:
👉🏽$1.5 trillion wiped out from the US stock market today. $60 billion was added to the crypto market.
On the 24th of April:
👉🏽TKL: 'The market remains historically concentrated: The 10 largest S&P 500 stocks now reflect 38% of the index's market cap, near the highest since the 1960s. By comparison, at the 2000 Dot-Com Bubble peak, this percentage was ~27%. At the same time, the top 11-50 stocks now account for ~23% of the S&P 500's market cap, near an all-time low. This is 12 percentage points lower than at the 2000 Dot-Com Bubble high. The market cannot survive without big tech.'
🏦Banks:
👉🏽No news
🌎Macro/Geopolitics:
Every nation in the world is in debt and no one wants to say who the creditor is.
On the 21st of April:
👉🏽Trump: There is virtually no inflation. Shown below is CPI in its cumulative form. Seems there may be ... a bit of inflation. No matter who is in power they almost always lie about inflation. https://i.ibb.co/LzvGbw4C/Gp-EVd-J4-X0-AA31-JS.png
👉🏽'China is doubling down: China has just announced that they will be pulling back from US private equity investments. Chinese state-backed funds are halting new investments in US PE firms due to government pressure. According to PE executives, funds like China Investment Corporation (CIC) have already begun withdrawing planned commitments. Chinese investors are also avoiding US-linked deals, even when managed by non-US-based PE funds. Just 24 hours ago, China warned it would retaliate against countries that cooperate with the US in ways that compromise their interests. It's very clear what's happening here: China is seeking to isolate the US through trade and investment. The US-China trade war just escalated to a new level.' - TKL
👉🏽From 95 million in taxpayers' money — from all of us — for the completely unnecessary look-at-me party of NATO Mark Rutte, to 183.4 million euros. The cost of organizing the NATO summit in June appears to be twice as high as initially estimated. According to the spring budget update, the summit in The Hague is expected to cost 183.4 million euros "for now." In official documents from July last year, the estimated amount was 95 million euros. The increase in costs is mainly due to "necessary security measures."
The spending is spread across four ministries: Justice and Security contribute the most, with nearly 82 million euros, Interior Affairs follows with 53 million euros, Defense contributes just over 42 million euros, and Infrastructure and Water Management adds about 6 million euros.
Meanwhile, two-thirds of police officers call NATO summit in the Netherlands irresponsible: 'Report wait times will only get longer'
On the 22nd of April:
👉🏽'Japan's Finance Minister Kato and US Treasury Secretary Bessent are arranging a meeting to discuss "forex issues." This comes as the US Dollar just fell to a 52-week low on tariff worries. "Currency manipulation" was the #1 item on President Trump's "non-tariff cheating" list.' -TKL Bessent wrote the book on currency manipulation under Soros. I am not surprised. Currency manipulation is what the US has been doing since 1971.
👉🏽German 2y yields fall to 1.63%, lowest since 2022 due to ECB rate cut hopes.
👉🏽Gold prices officially surge above $3,500/oz for the first time in history. Remember people, Gold isn’t rising, the dollar is sinking…
👉🏽Argentine Wages Soar to 7-Year High.
👉🏽President Donald Trump would put the credibility of the dollar on the line and destabilize the US economy if he fired Federal Reserve Chair Jerome Powell, French Finance Minister Eric Lombard warned.
Source: https://finance.yahoo.com/news/firing-powell-hurt-dollar-us-203000819.html
"The reason France (and other countries) care, is because, despite all the arguments to the contrary, they need access to USD liquidity provided by the Fed in a Eurodollar crisis. And a new Trump loyal Fed Chair would be less likely to provide it."- Santiago Capital.
On the 23rd of April:
👉🏽Bessent now saying that President Trump has not offered to take down US tariffs on China on a unilateral basis. The ball is in China's court and Bessent just said it will take 2-3 years to reach a deal.
On the 24th of April:
👉🏽'The US Consumer Sentiment Index fell 6.2 points to 50.8 in April, the second-lowest on record. This was only above the 50.0 points recorded in June 2022 when inflation was at 9.1%, the highest since 1981. This also marks the 4th-consecutive monthly decline for a total of 23.2 points, or 31%. Current conditions fell 7.3 points, to 56.5, the lowest since June 2022 and the second-lowest in history. Consumer expectations fell 5.4 points, to 47.2, the second-lowest since May 1980. Consumer sentiment is at crisis levels.' -TKL
For the Dutch readers:
👉🏽Small and medium-sized businesses and institutions in the Netherlands pay twice as much per cubic meter of natural gas as their counterparts in Belgium. (The difference is due to taxes; the base gas price is the same in both countries.) https://i.ibb.co/prL73N57/Gp-Ro-V5-HWs-AEb-VIL.jpg
On the 25th of April:
👉🏽Germany has been in recession for 6 quarters: the longest contraction in its post-reunification history. And it will be for at least another year.' -ZeroHedge
👉🏽10% of the world population own 75% of all wealth, get 50% of all income, and are responsible for nearly half of all CO2 emissions. The richest half of US families owned 97.5% of all wealth at the end of 2024. The bottom half of the population held just 2.5% of wealth.
https://i.ibb.co/XkZk4NpV/Gp-XZJqz-WYAAw-GAN.jpg
You could put it this way: The top 10% control the machinery of violence, power, capital, and ideology—ensuring that the bottom 90% remain locked out of any meaningful or lasting challenge to the inequality that holds them down.
👉🏽Telegraaf: 'The Dutch Central Bureau of Statistics (CBS) has released positive figures regarding particulate emissions from traffic in the Netherlands:
Over the past ten years, emissions have dropped by more than 16 percent. Interestingly, this improvement is not thanks to plug-in hybrids—they actually emit more particulate matter on average than diesel vehicles. Petrol cars emit an average of 0.018 grams of particulate matter per kilometer. Electric cars perform only slightly better, at 0.017 grams per kilometer.
Interestingly, when it comes to particulate emissions, you're actually better off driving a diesel than a plug-in hybrid. According to the Dutch statistics agency CBS, diesels emit 0.025 grams per kilometer, while plug-in hybrids emit 0.027 grams.'
https://i.ibb.co/NfQrw84/Gpj49ye-XYAAl1-ZI.jpg
It’s just basic physics.
Moving more mass requires more energy and causes more wear on components. But all those humanities types don’t get that. They keep rewarding the wrong people. Electric sounds “green,” but it’s anything but. Hilarious — the green dream is slowly turning into a nightmare. Electric driving is more expensive than gasoline (so gas prices are pushed up), wind turbines kill birds and require a lot of oil to operate, and solar energy no longer generates any real return.
On the 26th of April:
👉🏽Jeroen Blokland: 'In Spain, where the law already restricts cash payments exceeding 1,000 euros in transactions, tax authorities can now impose massive fines for withdrawing cash from an ATM if it is not recorded and/or accounted for. This has little to do with money laundering but everything to do with capital flight, tax income (the Spanish tax authority raised EUR 200 million in 2024), fiscal dominance (low rates and high inflation), currency debasement, and control. Even more striking, European leaders, including those of Spain, have expressed urgency to rearm Europe and for civilians to stockpile water, canned food, and cash for unforeseen emergencies like war. Even from an objective angle, Spanish regulation seems pretty paradoxical. Meanwhile, the purchasing power of the Spanish people is eroded every day, trapped in the system due to inflation. Sounds great. Investing is not just about returns, but also about securing wealth in assets that cannot be locked up and debased by ideological governments."
That's why we Bitcoin and have our Bitcoin in cold storage.
👉🏽'The IMF has just forecasted a French fiscal deficit of 6%+ till at least 2030. At the same time, the payroll cost of French state employees increased by 6.7% in 2024. In which parallel universe do French politicians live? The next Euro crisis will start in France, just wait.' - Michael A. Arouet
I agree this is just pathetic. But unfortunately, the policies of the French politicians are the result of a financially illiterate French electorate. Let's not forget that Europe will talk about plans for building up a European defense force.
Historically, the French have not had a great record of seeing their self-made calamities coming.
👉🏽Here's why the government wants rates down. Add to it, there's a lot of Treasury debt to refinance this year.
https://i.ibb.co/qFmWWg2P/Gp-YMSd-QWUAEVJl9.jpg
U.S. Debt Burden Deepens. Interest Payments Eat ~20% of Tax Revenue Today, Set to Reach ~25% and Climbing.
👉🏽Millionaires have left Britain in record numbers since Labour took power. https://www.cityam.com/millionaires-leave-britain-in-record-numbers-since-labour-took-power/
On the 27th of April:
👉🏽'World central banks are diversifying their reserves: Foreign holdings of Treasuries as % of US government debt have fallen to ~23%, the lowest in 22 years. The percentage is down ~11 percentage points over the last 9 years. At the same time, gold holdings as a % of global international reserves have hit ~18%, the highest in 26 years. The share has risen ~8 percentage points since 2015. China has been one of the biggest buyers of gold over the last few years. Since the beginning of 2023, China’s gold reserves as a % of total foreign reserves have doubled to 7.1%. Everyone wants gold.' -TKL
👉🏽China approved NEW nuclear power projects at 5 sites On 27 April, the State Council approved 10 reactors at the following sites, according to domestic news: * -Haiyang phase 3 * -Xiapu phase 1 * -Sanmen phase 3 * -Taishan phase 2 * -Fangchenggang phase 2
And what about the Netherlands? Jetten didn’t want to, Hermans didn’t want to, and the next VVD/PvdA/GL/CDA minister won’t want to either.
Dutch politics simply doesn’t want cheap energy.
Just look at how much gas they leave in the ground.
The truth is, they don’t want prosperity or a thriving economy. https://i.ibb.co/bGRXJkw/Gp-Si-Ti-HWk-AA90-Ot.jpg
🎁If you have made it this far I would like to give you a little gift, well in this case two gifts:
Post of the month by Joe Consorti:
https://x.com/JoeConsorti/status/1915145534630969459
Fantastic analysis. Poetic macro analysis rooted in Bitcoin. Most won’t read the whole post. My advice, is please do it.
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ e111a405:fa441558
2025-01-26 18:25:59
@ e111a405:fa441558
2025-01-26 18:25:59OpenAI released its new o3 models and numerous people argue that this is in fact Artificial General Intelligence (AGI) – in other words, an AI system that is on par with human intelligence. Even if o3 is not yet AGI, the emphasis now lies on “yet,” and – considering the exponential progression – we can expect AGI to arrive within months or maximum one to two years.
According to OpenAI, it only took 3 months to go from the o1 model to the o3 model. This is a 4x+ acceleration relative to previous progress. If this speed of AI advancement is maintained, it means that by the end of 2025 we will be as much ahead of o3 as o3 is ahead of GPT-3 (released in May 2020). And, after achieving AGI, the self-reinforcing feedback loop will only further accelerate exponential improvements of these AI systems.
But, most anti-intuitively, even after we have achieved AGI, it will for quite some time look as if nothing has happened. You won’t feel any change and your job and business will feel safe and untouchable. Big fallacy. We can expect that after AGI it will take many months of not 1-2 years for the real transformations to happen. Why? Because AGI in and of itself does not release value into the economy. It will be much more important to apply it. But as AGI becomes cheaper, agentic, and embedded into the world, we will see a transformation-explosion – replacing those businesses and jobs that are unprepared.
I thought a lot about the impact the announced – and soon to be released – o3 model, and the first AGI model are going to have.
To make it short: I am extremely confident that any skill or process that can be digitized will be. As a result, the majority of white-collar and skilled jobs are on track for massive disruption or elimination.
Furthermore, I think many experts and think tanks are fooling themselves by believing that humans will maintain “some edge” and work peacefully side-by-side with an AI system. I don’t think AGI will augment knowledge workers – i.e. anyone working with language, code, numbers, or any kind of specialized software – it will replace them!
So, if your job or business relies purely on standardized cognitive tasks, you are racing toward the cliff’s edge, and it is time to pivot now!
Let’s start with the worst. Businesses and jobs in which you should pivot immediately – or at least not enter as of today – include but are not limited to anything that involves sitting at a computer:
- anything with data entry or data processing (run as fast as you can!)
- anything that involves writing (copywriting, technical writing,
- editing, proofreading, translation)
- most coding and web development
- SAAS (won’t exist in a couple of years)
- banking (disrupted squared: AGI + Blockchain)
- accounting and auditing (won’t exist as a job in 5-10 years)
- insurance (will be disrupted)
- law (excluding high-stake litigation, negotiation, courtroom advocacy)
- any generic design, music, and video creation (graphic design, stock photography, stock videos)
- market and investment research and analysis (AI will take over 100%)
- trading, both quantitative and qualitative (don’t exit but profit now, but expect to be disrupted within 5 years)
- any middle-layer-management (project and product management)
- medical diagnostics (will be 100% AI within 5 years)
- most standardized professional / consulting services
However, I believe that in high-stakes domains (health, finance, governance), regulators and the public will demand a “human sign-off”. So if you are in accounting, auditing, law, or finance I’d recommend pivoting to a business model where the ability to anchor trust becomes a revenue source.
The question is, where should you pivot to or what business to start in 2025?
My First Principles of a Post-AGI Business Model
First, even as AI becomes infallible, human beings will still crave real, raw, direct trust relationships. People form bonds around shared experiences, especially offline ones. I believe a truly future-proof venture leverages these primal instincts that machines can never replicate at a deeply visceral level. Nevertheless, I believe it is a big mistake to assume that humans will “naturally” stick together just because we are the same species. AGI might quickly appear more reliable, less selfish than most human beings, and have emotional intelligence. So a business build upon the thesis of the “human advantage” must expertly harness and establish emotional ties, tribal belonging, and shared experiences – all intangible values that are far more delicate and complex than logic.
First Principle: Operate in the Physical World
If your product or service can be fully digitalized and delivered via the cloud, AGI can replicate it with near-zero marginal cost Infuse strategic real-world constraints (logistics, location-specific interactions, physical limitations, direct relationships) that create friction and scarcity – where AI alone will struggle
Second Principle: Create Hyper Niche Human Experiences
- The broader audience, the easier it is for AI to dominate. Instead, cultivate specialized groups and subcultures with strong in-person and highly personalized experiences.
- Offer creative or spiritual elements that defy pure rational patterns and thus remain less formulaic
Third Principle: Emphasize Adaptive, Micro-Scale Partnerships
- Align with small, local, or specialized stakeholders. Use alliances with artisan suppliers, local talents, subject-matter experts, and so on.
- Avoid single points of failure; build a decentralized network that is hard for a single AI to replicate or disrupt
Fourth Principle: Embed Extreme Flexibility
- Structured, hierarchical organizations are easily out-iterated by AI that can reorganize and optimize instantly
- Cultivate fluid teams with quickly reconfigurable structures, use agile, project based collaboration that can pivot as soon AGI-based competition arises
Opportunity Vectors
With all of that in mind, there are niches that before looked unattractive, because less scalable, that today offer massive opportunities – let’s call them opportunity vectors.
The first opportunity vector I have already touched upon:
Trust and Validation Services: Humans verifying or certifying that a certain AI outcome is ethically or legally sound – while irrational, it is exactly what humans will insist on, particularly where liability is high (medicine, finance, law, infrastructure)
Frontier Sectors with Regulatory and Ethical Friction: Think of markets where AI will accelerate R&D but human oversight, relationship management, and accountability remain essential: genetic engineering, biotech, advanced materials, quantum computing, etc.
The second opportunity vector focuses on the human edge:
- Experience & Community: Live festivals, immersive events, niche retreats, or spiritual explorations – basically any scenario in which emotional energy and a human experience is the core product - Rare Craftsmanship & Creative Quirks: Think of hyper-personalized items, physical artwork, artisanal or hands-on creations. Items that carry an inherent uniqueness or intangible meaning that an AI might replicate in design, but can’t replicate in “heritage” or provenance.
Risk Tactics
Overall, the best insurance is fostering a dynamic brand and a loyal community that invests personally and emotionally in you. People will buy from those whose values they trust. If you stand for something real, you create an emotional bond that AI can’t break. I’m not talking about superficial corporate social responsibility (nobody cares) but about authenticity that resonates on a near-spiritual level.
As you build your business, erect an ethical moat by providing “failsafe” services where your human personal liability and your brand acts as a shield for AI decisions. This creates trust and differentiation among anonymous pure-AGI play businesses.
Seek and create small, specialized, local, or digital micro-monopolies – areas too tiny or fractal for the “big AI players” to devote immediate resources to. Over time, multiply these micro-monopolies by rolling them up under one trusted brand.
Furthermore, don’t avoid AI. You cannot out-AI the AI. So as you build a business on the human edge moat, you should still harness AI to do 90% of the repetitive and analytic tasks – this frees your human capital to build human relationships, solve ambiguous problem, or invent new offerings.
Bet on What Makes Us Human
To summarize, AI is logical, combinatorial intelligence. The advancements in AI will commoditize logic and disrupt any job and business that is mainly build upon logic as capital. Human – on the other hand – is authenticity. What makes human human and your brand authentic are elements of chaos, empathy, spontaneity. In this context, human is fostering embodied, emotional, culturally contextual, physically immersive experiences. Anything that requires raw creativity, emotional intelligence, local presence, or unique personal relationships will be more AI resilient.
Therefore, a Post-AGI business must involve:
- Tangibility: Physical goods, spaces, unique craftsmanship
- Human Connection: Emotional, face-to-face, improvisational experiences
- Comprehensive Problem Solving: Complex negotiations, messy real-world situations, diverse stakeholder management
The inverse list of AGI proof industries involve some or multiple aspects of that:
Physical, In-Person, Human-Intensive Services - Healthcare: Nursing, Physical therapy, Hands-on caregiving - Skilled trades & craftsmanship
High-Level Strategy & Complex Leadership - Diplomacy, Negotiation, Trust building - Visionary entrepreneurship
Deep Emotional / Experiential Offerings - Group experiences, retreats, spiritual or therapeutic gatherings - Artistic expression that thrives on “imperfection”, physical presence, or spontaneous creativity
Infrastructure for AGI - Human-based auditing/verification - Physical data center operations & advanced hardware - Application and embedment of AI in the forms of AGI agents, algorithmic improvements, etc. to make it suitable for everyday tasks and workflow
The real differentiator is whether a business is anchored in the physical world’s complexity, emotional trust, or intangible brand relationships. Everything pure data-driven or standardized is on the chopping block – imminently.
-
 @ 9bcc5462:eb501d90
2025-01-10 19:42:28
@ 9bcc5462:eb501d90
2025-01-10 19:42:28Cuneiform is mankind’s first writing system created by the ancient Sumerians of Mesopotamia, what is now Iraq. (The word “Sumer” means land of civilized kings). Despite being developed 5,000 years ago, its parallels to Notes and Other Stuff Transmitted by Relays will blow your mind! The most striking is how both breakthroughs materialized from the fundamental need to track value exchange–from primal grain tallies to now exchanging bitcoin.
Let’s begin with the fact that the styluses used by these archaic scribes were crafted from reed plants. Their stems were strong because of attachment points called nodes! These were the resilient, ring-like parts of the stem that joined it together with the rest of the plant. Similarly, although symbolically, lightning nodes are powerful on nostr since they allow us to zap each other with sats. An approach stemming from the need to modernize how we interact on social media, trade in networks and conduct business—It’s not surprising cuneiform came about as a way for merchants and farmers to track economic transactions and agricultural inventories!
Another parallel involves how both share everlasting marks. The Sumerians used their styluses to press wedge-like symbols onto wet tablets. They then would bake them in the sun, leaving a permanent record of the documentation. If an error was made, it could not be changed. Likewise, on nostr there is no delete function. Once you publish a note, including any typos, it is preserved for history.
Lastly, the proto-writing that emerged in Mesopotamia which led to Cuneiform was in the form of bullae (bulla: singular). These were spherical clay envelopes encased with tokens representing a transaction. They were sealed with unique markings representing the parties involved for authentication. In other words, cuneiform cylinder seals were effectively early public key cryptography! The seal itself being the private key and its impression being the public key. Just as us nostriches use our nsec to sign our notes with integrity and verify value-for-value with our npub.

*Rare bulla seal (shout out to Conny Waters from ancientpages.com)*
*Sumerian cuneiform tablet (source: britannica.com)*At the end of the day, maybe we’re not so different from our ancestors after all. The evolution of our writing technology over the course of our history is more than innovation born of necessity. Across millennia, 3025 BCE to 2025 AD, it's man telling the universe– we will be remembered– beyond space and time. As our ancestors stacked their clay tablets, we’ll stack our sats! Onward nostr! The new land of civilized kings.

*Mankind's Innovations in Writing Technology by Learning Producers, Inc.*