-
 @ b99efe77:f3de3616
2025-05-05 09:54:32
@ b99efe77:f3de3616
2025-05-05 09:54:32asfadfadsf
afasdfasdfsadf
Places & Transitions
- Places:
-
Bla bla bla: some text
-
Transitions:
- start: Initializes the system.
- logTask: bla bla bla.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 526bec6a:07c68d13
2025-05-05 07:51:08
@ 526bec6a:07c68d13
2025-05-05 07:51:08Let’s talk about a straightforward betting strategy that’s been around for years, often used by folks who treat horse racing more like a business than a gamble. This method is all about following a clear staking plan to aim for a small, consistent profit per race—without needing to be a racing expert. I’ll break it down step-by-step so it’s easy to understand, even if you’re new to this! The Goal: Small, Steady Wins The idea here is to aim for a target profit (T) of 5 points per race. Think of a "point" as a unit of money you decide on—it could be $50, $1, or whatever you’re comfortable with. For example, I use a starting bank of $200, and I set each point at $1. So, 5 points = $5 profit per race. Important Rule: Once you pick the value of a point, stick with it throughout the entire betting sequence. Don’t change it, no matter what happens! Why This Works (Even If You Know Nothing About Racing) This plan is designed so that you’ll eventually win, even if you’re clueless about horses. The catch? You need to be patient and okay with small profits per point because the stakes (the amount you bet) can grow after each loss. For example: If you set each point at £1 and lose 10 races in a row, your 11th bet would need to recover $55 (your target plus losses). If you set each point at 25p, you’d only need to recover $13.75 after 10 losses. See the difference? Lower point values mean smaller risks, but also smaller profits. Pick a point value that matches the risk you’re willing to take and the profit you want to make. How the Staking Plan Works Here’s the basic idea: you start with a target profit of 5 points per race. If you lose, you add your loss to the next race’s target. If you win, you subtract your gain. The goal is to keep going until you hit your total profit target, then start over. Let’s break down the key terms: T (Target): Your profit goal for the race (starts at 5 points). T + L: Your target plus any losses from previous races (or minus any gains if you won). S (Stake): How much you bet on the race. R (Result): Whether you won (e.g., 2-1 means the horse paid 2-to-1 odds) or lost (L). W (Points Won): How many points you gained from a win. L (Points Lost): How many points you lost from a bet. AWL (Running Total): Your accumulated wins and losses over the sequence. Once you reach your overall profit goal (like 40 points in the example below), you take your winnings and start the sequence over with a 5-point target. Example Sequence: Watch It in Action Here’s a sample sequence to show how this plays out. I’m using a 1-per-point value for simplicity: Race( see image posted for details in url or comment section) https://m.stacker.news/89957 What happened here? In Race 1, I aimed for 5 points but lost my 2-point stake, so my running total is -2. In Race 2, I added my loss (2) to the new target (10), so I’m aiming for 12 points. I lost again, so my running total drops to -6. By Race 8, I finally hit a big win (4-1 odds), gaining 44 points. My running total jumps to +50, which exceeds my overall target of 40 points. I take my profit ($50 if each point is $1) and start over in Race 9 with a 5-point target. How to Calculate Your Stake To figure out how much to bet (your stake), take your T + L (target plus losses) and divide by 3, rounding to the nearest whole number. Why 3? Because you want to bet on horses with odds of 3-1 or higher. A win at those odds will cover all your losses and give you your target profit. For example: In Race 4, my T + L is 33. Divide by 3: 33 ÷ 3 = 11. So, I bet 11 points. My horse wins at 2-1 odds, so I get 22 points back (11 × 2). This clears my losses and gives me a profit. Pro Tip: Stick to odds of evens (1-1) or higher. Many pros avoid “odds-on” bets (like 1-2) because they don’t pay enough to make this system work well. Tips to Make This Work for You Pick Your Races Wisely: You don’t have to bet on every race. Some pros bet on every race at a meeting (e.g., 6 races a day, 36 bets a week), but I recommend being selective. Consider using a professional tipping service for better picks—newspaper tips can be risky (one “expert” once picked 30 losers in a row!). Spread Your Bets: Use 3 or 4 different bookmakers. No single bookie will be happy if you keep winning over time. Account for Betting Tax (If Applicable): If there’s a tax on your bets, add it to your next race’s target. This way, the system covers the tax for you. Be Prepared for Losing Streaks: Even with careful picks, you might hit a string of losses. That’s why you keep your point value low—so your stakes don’t balloon too much. Why This Is a “Business,” Not Gambling People who use this method don’t see it as gambling—they treat racing like a business. The key is patience and discipline. A single win at 3-1 odds or higher will wipe out all your losses and deliver your target profit. It’s a slow grind, but it’s designed to keep you in the game long-term. Final Thoughts This staking plan is all about consistency and managing risk. Start with a small bank (like $200), set a point value you’re comfortable with (like 50 or 1), and stick to the rules. You don’t need to be a racing genius—just follow the system, bet smart, and wait for that big win to clear your slate and put profit in your pocket. Got questions or want to tweak this for your own style? Let me know, and I’ll help you fine-tune your approach! Happy betting!
-
 @ dd664d5e:5633d319
2025-05-05 07:47:50
@ dd664d5e:5633d319
2025-05-05 07:47:50Speak your truth, Nostr
I think that there's a difference in the decisions people make when they're True Believers, and when they've just been hired to do something, or they arrived much later and don't really get the point of the decisions. It's that way with any organization controlled by a protocol, such as a constitution, basic law, canon, or core specification.
The True Believers all eventually look like idiotic fanatics who can't "keep up with the cool kids", but they arrived there because they were looking for a solution to a particular problem that they were having. If you then change the solution, to solve some other problem, while destroying the solution that attracted them to the project, in the first place, then they'll be unhappy about it.
Being cool doesn't automatically make you right about everything, but you can simply have enough might to "change" what is right. Shift the goalposts so that the problem you are trying to solve is The Most Pressing Problem. Everyone still focused on the Original Problem is reduced to protesting and being called "difficult", "unhelpful", "uncooperative", "rude".
Why are they protesting? Why don't they just go with the flow? Look at us, we never protest. We are so nice! We're totally happy with the way things are going. We are always polite and elegant and regal. Only rude people complain.
Good vibes only.
-
 @ 90de72b7:8f68fdc0
2025-05-05 05:50:57
@ 90de72b7:8f68fdc0
2025-05-05 05:50:5705/05 T1 Traffic Light Control System
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
Places & Transitions
- Places:
- greenLight1: Indicates that the first traffic light is green.
- greenLight2: Indicates that the second traffic light is green.
- redLight1: Indicates that the first traffic light is red.
- redLight2: Indicates that the second traffic light is red.
-
queue: Acts as a synchronization mechanism ensuring controlled alternation between the two traffic lights.
-
Transitions:
- start: Initializes the system by placing tokens in greenLight1 and redLight2.
- toRed1: Moves a token from greenLight1 to redLight1, while placing a token in queue.
- toGreen2: Moves a token from redLight2 to greenLight2, requiring queue.
- toGreen1: Moves a token from queue and redLight1 to greenLight1.
- toRed2: Moves a token from greenLight2 to redLight2, placing a token back into queue.
- stop: Terminates the system by removing tokens from redLight1, queue, and redLight2, representing the system's end state.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> ()
-
 @ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05
@ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05A monthly newsletter by The 256 Foundation

May 2025
Introduction:
Welcome to the fifth newsletter produced by The 256 Foundation! April was a jam-packed month for the Foundation with events ranging from launching three grant projects to the first official Ember One release. The 256 Foundation has been laser focused on our mission to dismantle the proprietary mining empire, signing off on a productive month with the one-finger salute to the incumbent mining cartel.
 [IMG-001] Hilarious meme from @CincoDoggos
[IMG-001] Hilarious meme from @CincoDoggosDive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on helping test Hydra Pool, and the current state of the Bitcoin network.
Definitions:
DOJ = Department of Justice
SDNY = Southern District of New York
BTC = Bitcoin
SD = Secure Digital
Th/s = Terahash per second
OSMU = Open Source Miners United
tx = transaction
PSBT = Partially Signed Bitcoin Transaction
FIFO = First In First Out
PPLNS = Pay Per Last N Shares
GB = Gigabyte
RAM = Random Access Memory
ASIC = Application Specific Integrated Circuit
Eh/s = Exahash per second
Ph/s = Petahash per second
News:
April 7: the first of a few notable news items that relate to the Samourai Wallet case, the US Deputy Attorney General, Todd Blanche, issued a memorandum titled “Ending Regulation By Prosecution”. The memo makes the DOJ’s position on the matter crystal clear, stating; “Specifically, the Department will no longer target virtual currency exchanges, mixing and tumbling services, and offline wallets for the acts of their end users or unwitting violations of regulations…”. However, despite the clarity from the DOJ, the SDNY (sometimes referred to as the “Sovereign District” for it’s history of acting independently of the DOJ) has yet to budge on dropping the charges against the Samourai Wallet developers. Many are baffled at the SDNY’s continued defiance of the Trump Administration’s directives, especially in light of the recent suspensions and resignations that swept through the SDNY office in the wake of several attorneys refusing to comply with the DOJ’s directive to drop the charges against New York City Mayor, Eric Adams. There is speculation that the missing piece was Trump’s pick to take the helm at the SDNY, Jay Clayton, who was yet to receive his Senate confirmation and didn’t officially start in his new role until April 22. In light of the Blanche Memo, on April 29, the prosecution and defense jointly filed a letter requesting additional time for the prosecution to determine it’s position on the matter and decide if they are going to do the right thing, comply with the DOJ, and drop the charges. Catch up on what’s at stake in this case with an appearance by Diverter on the Unbounded Podcast from April 24, the one-year anniversary of the Samourai Wallet developer’s arrest. This is the most important case facing Bitcoiners as the precedence set in this matter will have ripple effects that touch all areas of the ecosystem. The logic used by SDNY prosecutors argues that non-custodial wallet developers transfer money in the same way a frying pan transfers heat but does not “control” the heat. Essentially saying that facilitating the transfer of funds on behalf of the public by any means constitutes money transmission and thus requires a money transmitter license. All non-custodial wallets (software or hardware), node operators, and even miners would fall neatly into these dangerously generalized and vague definitions. If the SDNY wins this case, all Bitcoiners lose. Make a contribution to the defense fund here.
April 11: solo miner with ~230Th/s solves Block #891952 on Solo CK Pool, bagging 3.11 BTC in the process. This will never not be exciting to see a regular person with a modest amount of hashrate risk it all and reap all the mining reward. The more solo miners there are out there, the more often this should occur.
April 15: B10C publishes new article on mining centralization. The article analyzes the hashrate share of the currently five biggest pools and presents a Mining Centralization Index. The results demonstrate that only six pools are mining more than 95% of the blocks on the Bitcoin Network. The article goes on to explain that during the period between 2019 and 2022, the top two pools had ~35% of the network hashrate and the top six pools had ~75%. By December 2023 those numbers grew to the top two pools having 55% of the network hashrate and the top six having ~90%. Currently, the top six pools are mining ~95% of the blocks.
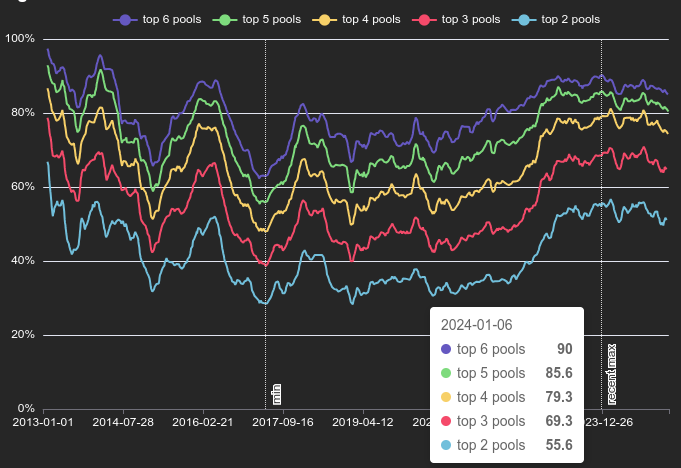 [IMG-002] Mining Centralization Index by @0xB10C
[IMG-002] Mining Centralization Index by @0xB10CB10C concludes the article with a solution that is worth highlighting: “More individuals home-mining with small miners help too, however, the home-mining hashrate is currently still negligible compared to the industrial hashrate.”
April 15: As if miner centralization and proprietary hardware weren’t reason enough to focus on open-source mining solutions, leave it to Bitmain to release an S21+ firmware update that blocks connections to OCEAN and Braiins pools. This is the latest known sketchy development from Bitmain following years of shady behavior like Antbleed where miners would phone home, Covert ASIC Boost where miners could use a cryptographic trick to increase efficiency, the infamous Fork Wars, mining empty blocks, and removing the SD card slots. For a mining business to build it’s entire operation on a fragile foundation like the closed and proprietary Bitmain hardware is asking for trouble. Bitcoin miners need to remain flexible and agile and they need to be able to adapt to changes instantly – the sort of freedoms that only open-source Bitcoin mining solutions are bringing to the table.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open… and then it will get even better. Innovators did not disappoint in April, here are nine note-worthy events:
April 5: 256 Foundation officially launches three more grant projects. These will be covered in detail in the Grant Project Updates section but April 5 was a symbolic day to mark the official start because of the 6102 anniversary. A reminder of the asymmetric advantage freedom tech like Bitcoin empowers individuals with to protect their rights and freedoms, with open-source development being central to those ends.
April 5: Low profile ICE Tower+ for the Bitaxe Gamma 601 introduced by @Pleb_Style featuring four heat pipes, 2 copper shims, and a 60mm Noctua fan resulting in up to 2Th/s. European customers can pick up the complete upgrade kit from the Pleb Style online store for $93.00.
 IMG-003] Pleb Style ICE Tower+ upgrade kit
IMG-003] Pleb Style ICE Tower+ upgrade kitApril 8: Solo Satoshi spells out issues with Bitaxe knockoffs, like Lucky Miner, in a detailed article titled The Hidden Cost of Bitaxe Clones. This concept can be confusing for some people initially, Bitaxe is open-source, right? So anyone can do whatever they want… right? Based on the specific open-source license of the Bitaxe hardware, CERN-OHL-S, and the firmware, GPLv3, derivative works are supposed to make the source available. Respecting the license creates a feed back loop where those who benefit from the open-source work of those who came before them contribute back their own modifications and source files to the open-source community so that others can benefit from the new developments. Unfortunately, when the license is disrespected what ends up happening is that manufacturers make undocumented changes to the components in the hardware and firmware which yields unexpected results creating a number of issues like the Bitaxe overheating, not connecting to WiFi, or flat out failure. This issue gets further compounded when the people who purchased the knockoffs go to a community support forum, like OSMU, for help. There, a number of people rack their brains and spend their valuable time trying to replicate the issues only to find out that they cannot replicate the issues since the person who purchased the knockoff has something different than the known Bitaxe model and the distributor who sold the knockoff did not document those changes. The open-source licenses are maintaining the end-users’ freedom to do what they want but if the license is disrespected then that freedom vanishes along with details about whatever was changed. There is a list maintained on the Bitaxe website of legitimate distributors who uphold the open-source licenses, if you want to buy a Bitaxe, use this list to ensure the open-source community is being supported instead of leeched off of.
April 8: The Mempool Open Source Project v3.2.0 launches with a number of highlights including a new UTXO bubble chart, address poisoning detection, and a tx/PSBT preview feature. The GitHub repo can be found here if you want to self-host an instance from your own node or you can access the website here. The Mempool Open Source Project is a great blockchain explorer with a rich feature set and helpful visualization tools.
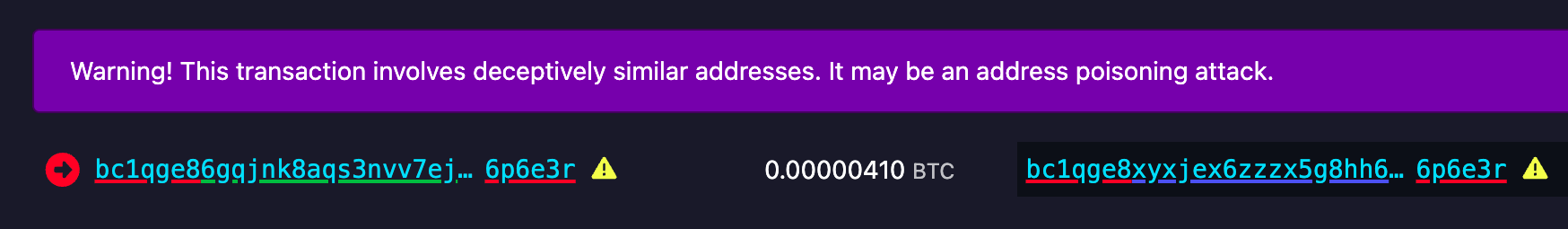 [IMG-004] Address poisoning example
[IMG-004] Address poisoning exampleApril 8: @k1ix publishes bitaxe-raw, a firmware for the ESP32S3 found on Bitaxes which enables the user to send and receive raw bytes over USB serial to and from the Bitaxe. This is a helpful tool for research and development and a tool that is being leveraged at The 256 Foundation for helping with the Mujina miner firmware development. The bitaxe-raw GitHub repo can be found here.
April 14: Rev.Hodl compiles many of his homestead-meets-mining adaptations including how he cooks meat sous-vide style, heats his tap water to 150°F, runs a hashing space heater, and how he upgraded his clothes dryer to use Bitcoin miners. If you are interested in seeing some creative and resourceful home mining integrations, look no further. The fact that Rev.Hodl was able to do all this with closed-source proprietary Bitcoin mining hardware makes a very bullish case for the innovations coming down the pike once the hardware and firmware are open-source and people can gain full control over their mining appliances.
April 21: Hashpool explained on The Home Mining Podcast, an innovative Bitcoin mining pool development that trades mining shares for ecash tokens. The pool issues an “ehash” token for every submitted share, the pool uses ecash epochs to approximate the age of those shares in a FIFO order as they accrue value, a rotating key set is used to eventually expire them, and finally the pool publishes verification proofs for each epoch and each solved block. The ehash is provably not inflatable and payouts are similar to the PPLNS model. In addition to the maturity window where ehash tokens are accruing value, there is also a redemption window where the ehash tokens can be traded in to the mint for bitcoin. There is also a bitcoin++ presentation from earlier this year where @vnprc explains the architecture.
April 26: Boerst adds a new page on stratum.work for block template details, you can click on any mining pool and see the extended details and visualization of their current block template. Updates happen in real-time. The page displays all available template data including the OP_RETURN field and if the pool is merge mining, like with RSK, then that will be displayed too. Stratum dot work is a great project that offers helpful mining insights, be sure to book mark it if you haven’t already.
 [IMG-005] New stratum.work live template page
[IMG-005] New stratum.work live template pageApril 27: Public Pool patches Nerdminer exploit that made it possible to create the impression that a user’s Nerdminer was hashing many times more than it actually was. This exploit was used by scammers trying to convince people that they had a special firmware for the Nerminer that would make it hash much better. In actuality, Public Pool just wasn’t checking to see if submitted shares were duplicates or not. The scammers would just tweak the Nerdminer firmware so that valid shares were getting submitted five times, creating the impression that the miner was hashing at five times the actual hashrate. Thankfully this has been uncovered by the open-source community and Public Pool quickly addressed it on their end.
Grant Project Updates:
Three grant projects were launched on April 5, Mujina Mining Firmware, Hydra Pool, and Libre Board. Ember One was the first fully funded grant and launched in November 2024 for a six month duration.
Ember One:
@skot9000 is the lead engineer on the Ember One and April 30 marked the conclusion of the first grant cycle after six months of development culminating in a standardized hashboard featuring a ~100W power consumption, 12-24v input voltage range, USB-C data communication, on-board temperature sensors, and a 125mm x 125mm formfactor. There are several Ember One versions on the road map, each with a different kind of ASIC chip but staying true to the standardized features listed above. The first Ember One, the 00 version, was built with the Bitmain BM1362 ASIC chips. The first official release of the Ember One, v3, is available here. v4 is already being worked on and will incorporate a few circuit safety mechanisms that are pretty exciting, like protecting the ASIC chips in the event of a power supply failure. The firmware for the USB adaptor is available here. Initial testing firmware for the Ember One 00 can be found here and full firmware support will be coming soon with Mujina. The Ember One does not have an on-board controller so a separate, USB connected, control board is required. Control board support is coming soon with the Libre Board. There is an in-depth schematic review that was recorded with Skot and Ryan, the lead developer for Mujina, you can see that video here. Timing for starting the second Ember One cycle is to be determined but the next version of the Ember One is planned to have the Intel BZM2 ASICs. Learn more at emberone.org
Mujina Mining Firmware:
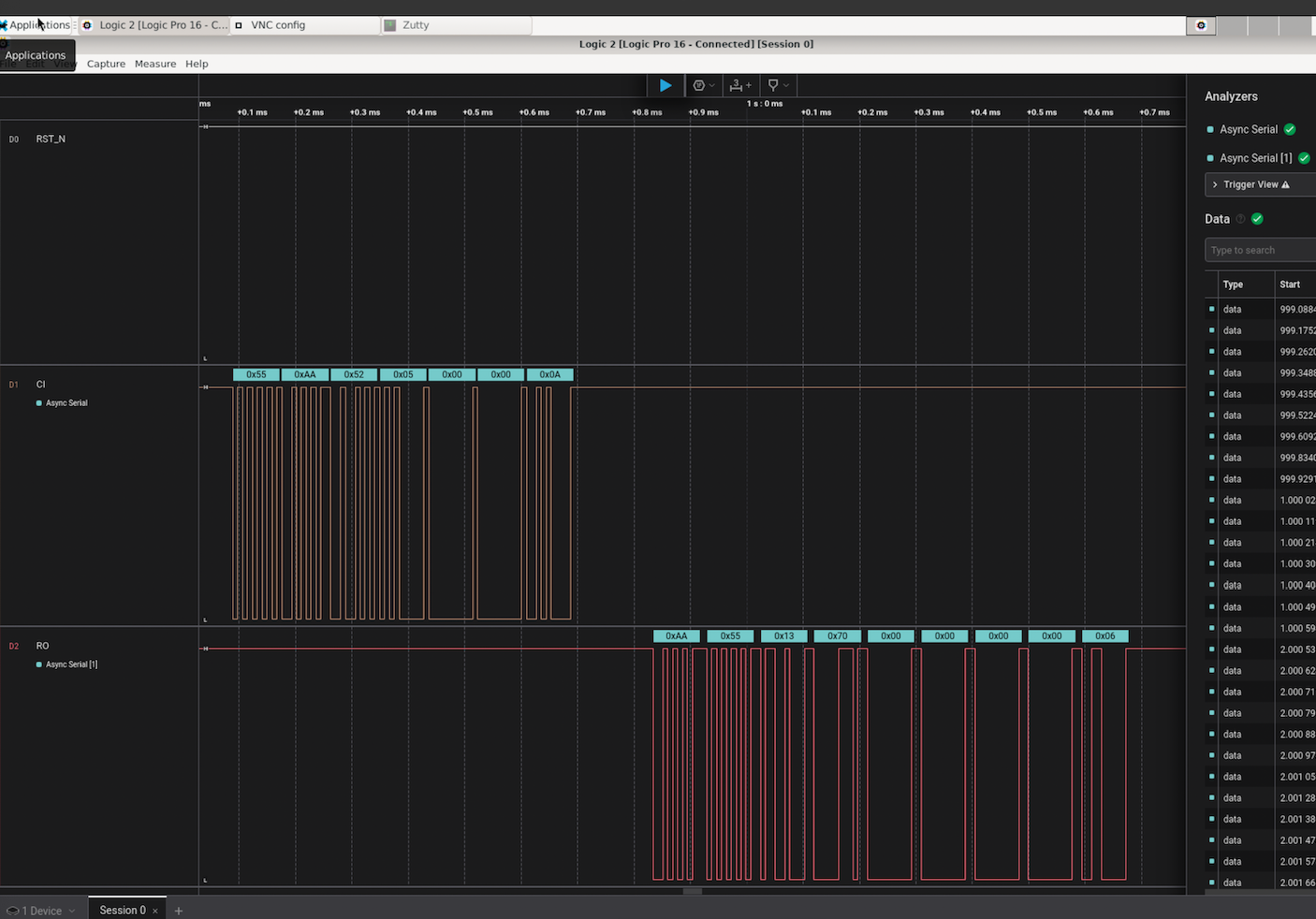
@ryankuester is the lead developer for the Mujina firmware project and since the project launched on April 5, he has been working diligently to build this firmware from scratch in Rust. By using the bitaxe-raw firmware mentioned above, over the last month Ryan has been able to use a Bitaxe to simulate an Ember One so that he can start building the necessary interfaces to communicate with the range of sensors, ASICs, work handling, and API requests that will be necessary. For example, using a logic analyzer, this is what the first signs of life look like when communicating with an ASIC chip, the orange trace is a message being sent to the ASIC and the red trace below it is the ASIC responding [IMG-006]. The next step is to see if work can be sent to the ASIC and results returned. The GitHub repo for Mujina is currently set to private until a solid foundation has been built. Learn more at mujina.org
 [IMG-006] First signs of life from an ASIC
[IMG-006] First signs of life from an ASICLibre Board:
@Schnitzel is the lead engineer for the Libre Board project and over the last month has been modifying the Raspberry Pi Compute Module I/O Board open-source design to fit the requirements for this project. For example, removing one of the two HDMI ports, adding the 40-pin header, and adapting the voltage regulator circuit so that it can accept the same 12-24vdc range as the Ember One hashboards. The GitHub repo can be found here, although there isn’t much to look at yet as the designs are still in the works. If you have feature requests, creating an issue in the GitHub repo would be a good place to start. Learn more at libreboard.org
Hydra Pool:
@jungly is the lead developer for Hydra Pool and over the last month he has developed a working early version of Hydra Pool specifically for the upcoming Telehash #2. Forked from CK Pool, this early version has been modified so that the payout goes to the 256 Foundation bitcoin address automatically. This way, users who are supporting the funderaiser with their hashrate do not need to copy/paste in the bitcoin address, they can just use any vanity username they want. Jungly was also able to get a great looking statistics dashboard forked from CKstats and modify it so that the data is populated from the Hydra Pool server instead of website crawling. After the Telehash, the next steps will be setting up deployment scripts for running Hydra Pool on a cloud server, support for storing shares in a database, and adding PPLNS support. The 256 Foundation is only running a publicly accessible server for the Telehash and the long term goals for Hydra Pool are that the users host their own instance. The 256 Foundation has no plans on becoming a mining pool operator. The following Actionable Advice column shows you how you can help test Hydra Pool. The GitHub repo for Hydra Pool can be found here. Learn more at hydrapool.org
Actionable Advice:
The 256 Foundation is looking for testers to help try out Hydra Pool. The current instance is on a hosted bare metal server in Florida and features 64 cores and 128 GB of RAM. One tester in Europe shared that they were only experiencing ~70ms of latency which is good. If you want to help test Hydra Pool out and give any feedback, you can follow the directions below and join The 256 Foundation public forum on Telegram here.
The first step is to configure your miner so that it is pointed to the Hydra Pool server. This can look different depending on your specific miner but generally speaking, from the settings page you can add the following URL:
stratum+tcp://stratum.hydrapool.org:3333On some miners, you don’t need the “stratum+tcp://” part or the port, “:3333”, in the URL dialog box and there may be separate dialog boxes for the port.
Use any vanity username you want, no need to add a BTC address. The test iteration of Hydra Pool is configured to payout to the 256 Foundation BTC address.
If your miner has a password field, you can just put “x” or “1234”, it doesn’t matter and this field is ignored.
Then save your changes and restart your miner. Here are two examples of what this can look like using a Futurebit Apollo and a Bitaxe:
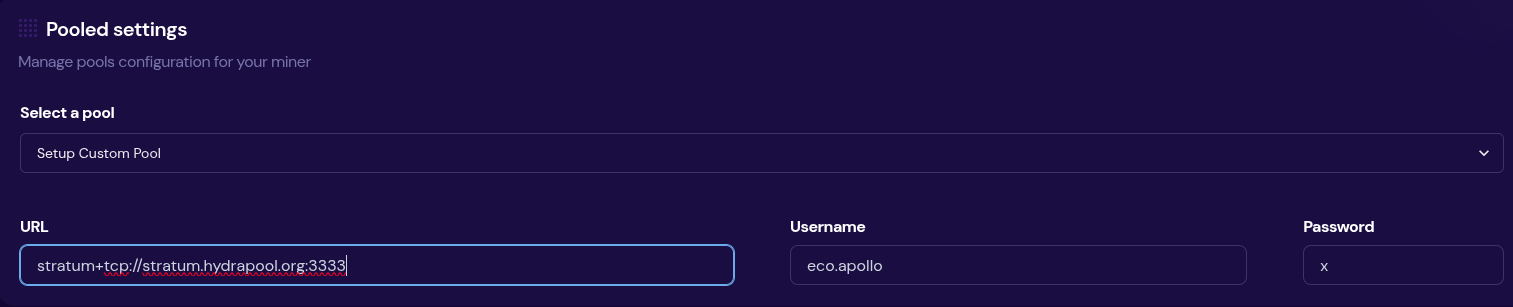 [IMG-007] Apollo configured to Hydra Pool
[IMG-007] Apollo configured to Hydra Pool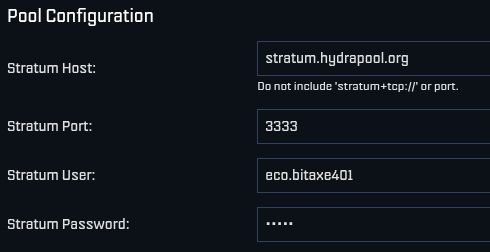 [IMG-008] Bitaxe Configured to Hydra Pool
[IMG-008] Bitaxe Configured to Hydra PoolOnce you get started, be sure to check stats.hydrapool.org to monitor the solo pool statistics.
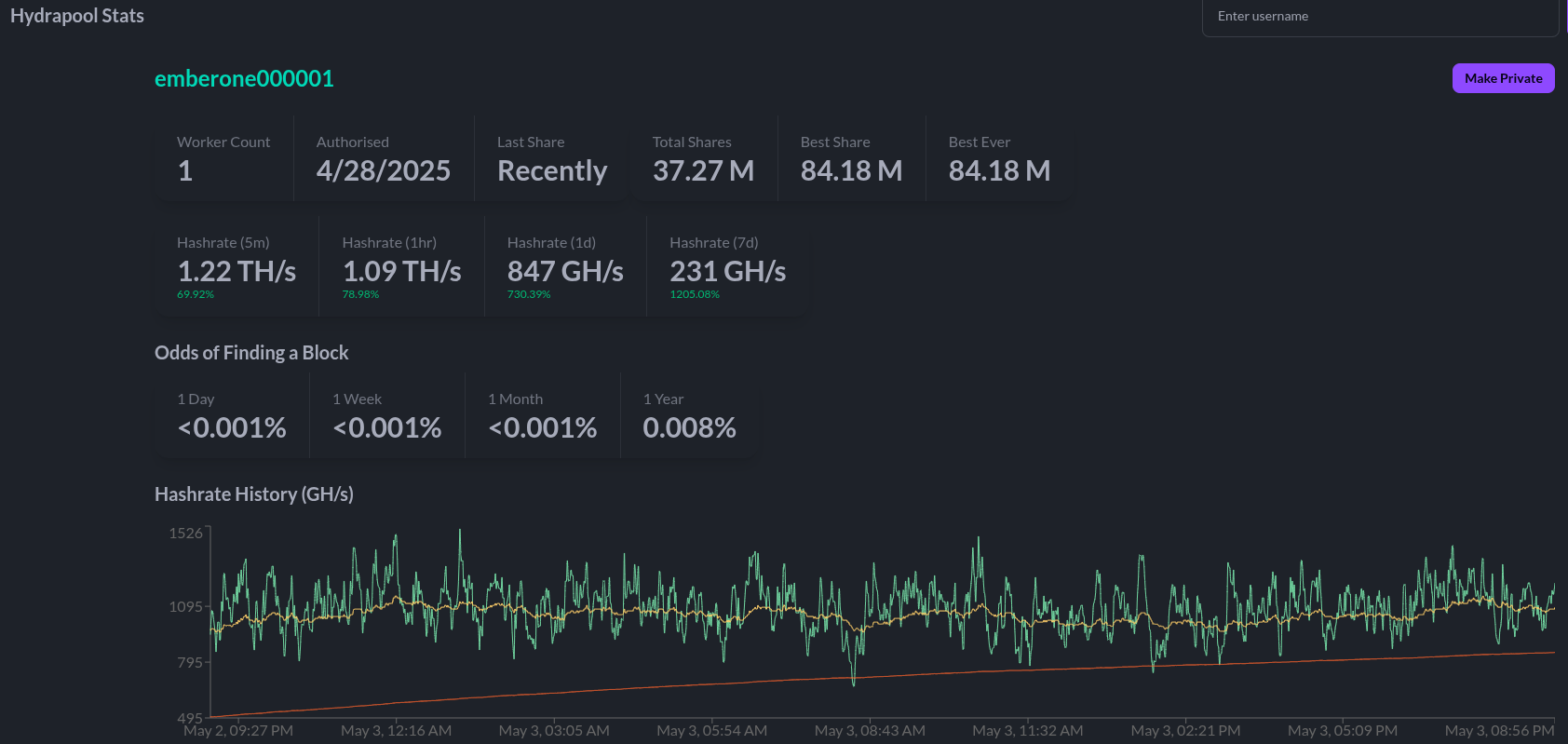 [IMG-009] Ember One hashing to Hydra Pool
[IMG-009] Ember One hashing to Hydra PoolAt the last Telehash there were over 350 entities pointing as much as 1.12Eh/s at the fundraiser at the peak. At the time the block was found there was closer to 800 Ph/s of hashrate. At this next Telehash, The 256 Foundation is looking to beat the previous records across the board. You can find all the Telehash details on the Meetup page here.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~826 Eh/s to a peak of ~907 Eh/s on April 16 before cooling off and finishing the month at ~841 Eh/s, marking ~1.8% growth for the month.
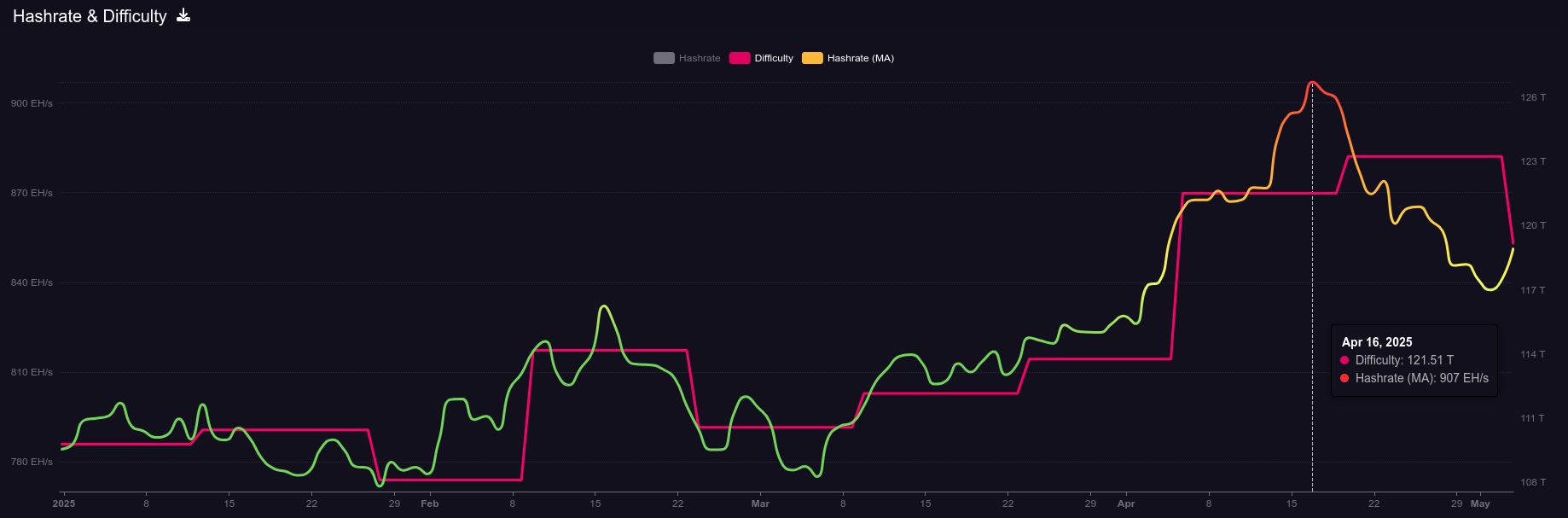 [IMG-010] 2025 hashrate/difficulty chart from mempool.space
[IMG-010] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 113.76T at it’s lowest in April and 123.23T at it’s highest, which is a 8.3% increase for the month. But difficulty dropped with Epoch #444 just after the end of the month on May 3 bringing a -3.3% downward adjustment. All together for 2025 up to Epoch #444, difficulty has gone up ~8.5%.
According to the Hashrate Index, ASIC prices have flat-lined over the last month. The more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
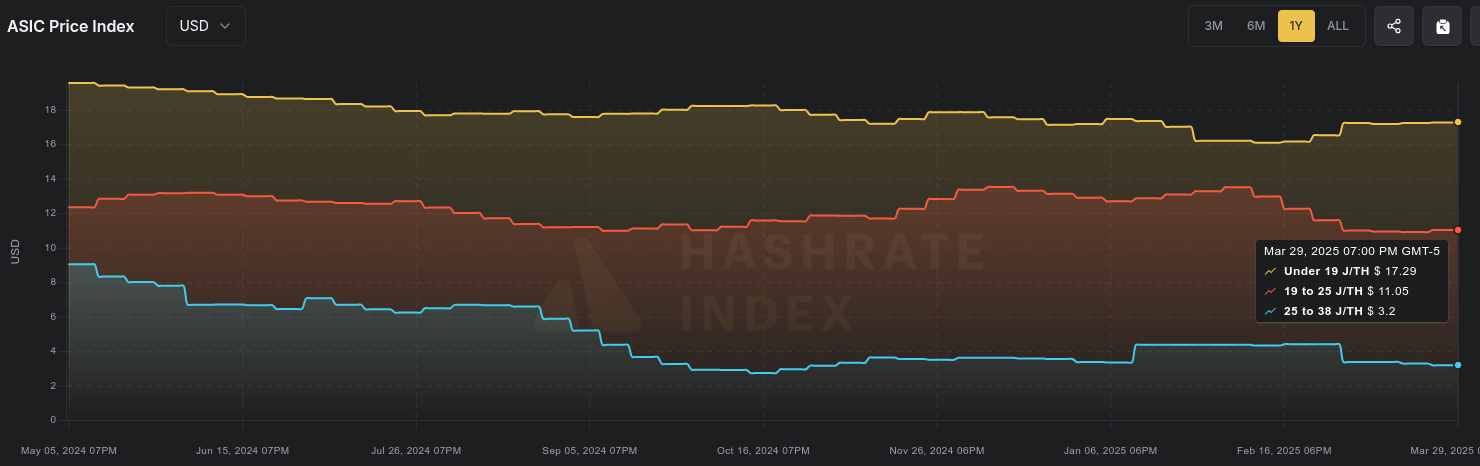 [IMG-011] Miner Prices from Luxor’s Hashrate Index
[IMG-011] Miner Prices from Luxor’s Hashrate IndexHashvalue over the month of April dropped from ~56,000 sats/Ph per day to ~52,000 sats/Ph per day, according to the new and improved Braiins Insights dashboard [IMG-012]. Hashprice started out at $46.00/Ph per day at the beginning of April and climbed to $49.00/Ph per day by the end of the month.
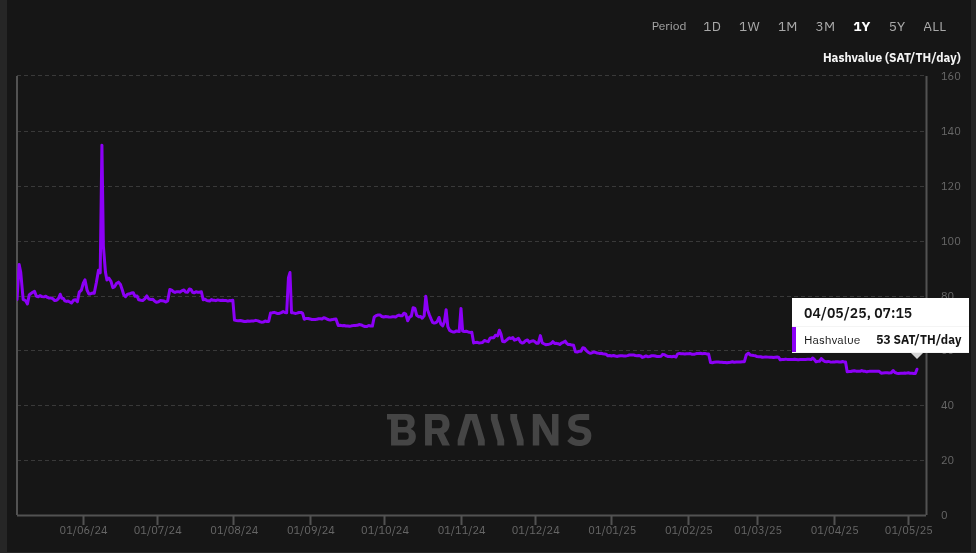 [IMG-012] Hashprice/Hashvalue from Braiins Insights
[IMG-012] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,063 days or in other words ~154,650 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the fifth 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
 [IMG-013] TEMS 2025 flyer
[IMG-013] TEMS 2025 flyer While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
If you are interested in helping The 256 Foundation test Hydra Pool, then hopefully you found all the information you need to configure your miner in this issue.
 [IMG-014] FREE SAMOURAI
[IMG-014] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
Live Free or Die,
-econoalchemist
-
 @ 00033a93:774465e5
2025-05-05 10:40:28
@ 00033a93:774465e5
2025-05-05 10:40:28An Italian artist just announced in the small town of Fornelli a statue of Satoshi, involving the administration in the project and the community of Fornelli in Bitcoin!
Not all heroes wear capes!
Italian article here:
https://bitcoinbeer.events/article/21
originally posted at https://stacker.news/items/971872
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ 51faaa77:2c26615b
2025-05-04 17:52:33
@ 51faaa77:2c26615b
2025-05-04 17:52:33There has been a lot of debate about a recent discussion on the mailing list and a pull request on the Bitcoin Core repository. The main two points are about whether a mempool policy regarding OP_RETURN outputs should be changed, and whether there should be a configuration option for node operators to set their own limit. There has been some controversy about the background and context of these topics and people are looking for more information. Please ask short (preferably one sentence) questions as top comments in this topic. @Murch, and maybe others, will try to answer them in a couple sentences. @Murch and myself have collected a few questions that we have seen being asked to start us off, but please add more as you see fit.
originally posted at https://stacker.news/items/971277
-
 @ efc19139:a370b6a8
2025-05-04 16:42:24
@ efc19139:a370b6a8
2025-05-04 16:42:24Bitcoin has a controversial reputation, but in this essay, I argue that Bitcoin is actually a pretty cool thing; it could even be described as the hippie movement of the digital generations.
Mainstream media often portrays Bitcoin purely as speculation, with headlines focusing on price fluctuations or painting it as an environmental disaster. It has frequently been declared dead and buried, only to rise again—each time, it's labeled as highly risky and suspicious as a whole. Then there are those who find blockchain fascinating in general but dismiss Bitcoin as outdated, claiming it will soon be replaced by a new cryptocurrency (often one controlled by the very author making the argument). Let’s take a moment to consider why Bitcoin is interesting and how it can drive broad societal change, much like the hippie movement once did. Bitcoin is a global decentralized monetary system operating on a peer-to-peer network. Since nearly all of humanity lives within an economic system based on money, it’s easy to see how an overhaul of the financial system could have a profound impact across different aspects of society. Bitcoin differs from traditional money through several unique characteristics: it is scarce, neutral, decentralized, and completely permissionless. There is no central entity—such as a company—that develops and markets Bitcoin, meaning it cannot be corrupted.
Bitcoin is an open digital network, much like the internet. Due to its lack of a central governing entity and its organic origin, Bitcoin can be considered a commodity, whereas other cryptocurrencies resemble securities, comparable to stocks. Bitcoin’s decentralized nature makes it geopolitically neutral. Instead of being controlled by a central authority, it operates under predefined, unchangeable rules. No single entity in the world has the ability to arbitrarily influence decision-making within the Bitcoin network. This characteristic is particularly beneficial in today’s political climate, where global uncertainty is heightened by unpredictable leaders of major powers. The permissionless nature of Bitcoin and its built-in resistance to censorship are crucial for individuals living under unstable conditions. Bitcoin is used to raise funds for politically persecuted activists and for charitable purposes in regions where financial systems have been weaponized against political opponents or used to restrict people's ability to flee a country. These are factors that may not immediately come to mind in Western nations, where such challenges are not commonly faced. Additionally, according to the World Bank, an estimated 1.5 billion people worldwide still lack access to any form of banking services.
Mining is the only way to ensure that no one can seize control of the Bitcoin network or gain a privileged position within it. This keeps Bitcoin neutral as a protocol, meaning a set of rules without leaders. It is not governed in the same way a company is, where ownership of shares dictates control. Miners earn the right to record transactions in Bitcoin’s ledger by continuously proving that they have performed work to obtain that right. This proof-of-work algorithm is also one reason why Bitcoin has spread so organically. If recording new transactions were free, we would face a problem similar to spam: there would be an endless number of competing transactions, making it impossible to reach consensus on which should officially become part of the decentralized ledger. Mining can be seen as an auction for adding the next set of transactions, where the price is the amount of energy expended. Using energy for this purpose is the only way to ensure that mining remains globally decentralized while keeping the system open and permissionless—free from human interference. Bitcoin’s initial distribution was driven by random tech enthusiasts around the world who mined it as a hobby, using student electricity from their bedrooms. This is why Bitcoin’s spread can be considered organic, in contrast to a scenario where it was created by a precisely organized inner circle that typically would have granted itself advantages before the launch.
If energy consumption is considered concerning, the best regulatory approach would be to create optimal conditions for mining in Finland, where over half of energy production already comes from renewable sources. Modern miners are essentially datacenters, but they have a unique characteristic: they can adjust their electricity consumption seamlessly and instantly without delay. This creates synergy with renewable energy production, which often experiences fluctuations in supply. The demand flexibility offered by miners provides strong incentives to invest increasingly in renewable energy facilities. Miners can commit to long-term projects as last-resort consumers, making investments in renewables more predictable and profitable. Additionally, like other datacenters, miners produce heat as a byproduct. As a thought experiment, they could also be considered heating plants, with a secondary function of securing the Bitcoin network. In Finland, heat is naturally needed year-round. This combination of grid balancing and waste heat recovery would be key to Europe's energy self-sufficiency. Wouldn't it be great if the need to bow to fossil fuel powers for energy could be eliminated? Unfortunately, the current government has demonstrated a lack of understanding of these positive externalities by proposing tax increases on electricity. The so-called fiat monetary system also deserves criticism in Western nations, even though its flaws are not as immediately obvious as elsewhere. It is the current financial system in which certain privileged entities control the issuance of money as if by divine decree, which is what the term fiat (command) refers to. The system subtly creates and maintains inequality.
The Cantillon effect is an economic phenomenon in which entities closer to newly created money benefit at the expense of those farther away. Access to the money creation process is determined by credit ratings and loan terms, as fiat money is always debt. The Cantillon effect is a distorted version of the trickle-down theory, where the loss of purchasing power in a common currency gradually moves downward. Due to inflation, hard assets such as real estate, precious metals, and stocks become more expensive, just as food prices rise in stores. This process further enriches the wealthy while deepening poverty. The entire wealth of lower-income individuals is often held in cash or savings, which are eroded by inflation much like a borrowed bottle of Leijona liquor left out too long. Inflation is usually attributed to a specific crisis, but over the long term (spanning decades), monetary inflation—the expansion of the money supply—plays a significant role. Nobel Prize-winning economist Paul Krugman, known for his work on currencies, describes inflation in his book The Accidental Theorist as follows, loosely quoted: "It is really, really difficult to cut nominal wages. Even with low inflation, making labor cheaper would require a large portion of workers to accept wage cuts. Therefore, higher inflation leads to higher employment." Since no one wants to voluntarily give up their salary in nominal terms, the value of wages must be lowered in real terms by weakening the currency in which they are paid. Inflation effectively cuts wages—or, in other words, makes labor cheaper. This is one of the primary reasons why inflation is often said to have a "stimulating" effect on the economy.
It does seem somewhat unfair that employees effectively subsidize their employers’ labor costs to facilitate new hires, doesn’t it? Not to mention the inequities faced by the Global South in the form of neocolonialism, where Cantillon advantages are weaponized through reserve currencies like the US dollar or the French franc. This follows the exact same pattern, just on a larger scale. The Human Rights Foundation (hrf.org) has explored the interconnection between the fiat monetary system and neocolonialism in its publications, advocating for Bitcoin as part of the solution. Inflation can also be criticized from an environmental perspective. Since it raises time preference, it encourages people to make purchases sooner rather than delay them. As Krugman put it in the same book, “Extra money burns in your pocket.” Inflation thus drives consumption while reducing deliberation—it’s the fuel of the economy. If the goal from an environmental standpoint is to moderate economic activity, the first step should be to stop adding fuel to the fire. The impact of inflation on intergenerational inequality and the economic uncertainty faced by younger generations is rarely discussed. Boomers have benefited from the positive effects of the trend sparked by the Nixon shock in 1971, such as wealth accumulation in real estate and inflation-driven economic booms. Zoomers, meanwhile, are left to either fix the problems of the current system or find themselves searching for a lifeboat.
Bitcoin emerged as part of a long developmental continuum within the discussion forums of rebellious programmers known as cypherpunks, or encryption activists. It is an integral part of internet history and specifically a counterculture movement. Around Bitcoin, grassroots activists and self-organized communities still thrive, fostering an atmosphere that is welcoming, inspiring, and—above all—hopeful, which feels rare in today’s world. Although the rush of suits and traditional financial giants into Bitcoin through ETF funds a year ago may have painted it as opportunistic and dull in the headlines, delving into its history and culture reveals ever-fascinating angles and new layers within the Bitcoin sphere. Yet, at its core, Bitcoin is simply money. It possesses all seven characteristics required to meet the definition of money: it is easily divisible, transferable, recognizable, durable, fungible, uniform, and straightforward to receive. It serves as a foundation on which coders, startup enthusiasts, politicians, financial executives, activists, and anarchists alike can build. The only truly common denominator among the broad spectrum of Bitcoin users is curiosity—openness to new ideas. It merely requires the ability to recognize potential in an alternative system and a willingness to embrace fundamental change. Bitcoin itself is the most inclusive system in the world, as it is literally impossible to marginalize or exclude its users. It is a tool for peaceful and voluntary collaboration, designed so that violence and manipulation are rendered impossible in its code.
Pretty punk in the middle of an era of polarization and division, wouldn’t you say?
The original author (not me) is the organizer of the Bitcoin conference held in Helsinki, as well as a founding member and vice chairman of the Finnish Bitcoin Association. More information about the event can be found at: https://btchel.com and https://njump.me/nprofile1qqs89v5v46jcd8uzv3f7dudsvpt8ntdm3927eqypyjy37yx5l6a30fcknw5z5 ps. Zaps and sats will be forwarded to author!
originally posted at https://stacker.news/items/971219
-
 @ 88cc134b:5ae99079
2025-05-05 13:34:22
@ 88cc134b:5ae99079
2025-05-05 13:34:22Hello
-
 @ 56cd780f:cbde8b29
2025-05-05 13:07:53
@ 56cd780f:cbde8b29
2025-05-05 13:07:53A few weeks ago, I ran into an old friend at a coffee shop. We hadn’t spoken in years, and within five minutes, she said something I’ve heard countless times:
“I just feel like I’m so behind.”
Behind who? Behind what?
 There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.
There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.Where did this come from?
Some of it’s cultural, obviously. Social media compresses timelines. You’re 27, doom-scrolling, and suddenly someone from high school just IPO’d their startup and got engaged in Rome. Another just bought a house with a kitchen island the size of a small country. You wonder if you missed a memo.
But beneath that, there’s something deeper. A belief that life is linear. That it should look like a staircase: school, job, marriage, house, kids, success. But real life? It’s a squiggle. A mess. A beautiful disaster.
Here’s the truth: You’re not behind. There’s no schedule. There’s only your path, and the courage it takes to stay on it—even when it looks wildly different from everyone else’s.
I say this as someone who has taken the “scenic route.” I changed careers in my 30s. I moved cities on a hunch. I dropped things that looked great on paper because they felt wrong in my gut. I’ve had seasons of momentum and seasons of stuckness. Both were necessary.
“Catching up” assumes there’s a fixed destination. But what if there isn’t? What if the point isn’t arrival, but presence? Progress that feels real, not performative?
If you need a permission slip to stop comparing, let this be it.
 You’re not late. You’re not early.
You’re not late. You’re not early.
You’re right on time. -
 @ 57d1a264:69f1fee1
2025-05-04 06:37:52
@ 57d1a264:69f1fee1
2025-05-04 06:37:52KOReader is a document viewer for E Ink devices. Supported file formats include EPUB, PDF, DjVu, XPS, CBT, CBZ, FB2, PDB, TXT, HTML, RTF, CHM, DOC, MOBI and ZIP files. It’s available for Kindle, Kobo, PocketBook, Android and desktop Linux.
Download it from https://koreader.rocks Repository: https://github.com/koreader/koreader
originally posted at https://stacker.news/items/970912
-
 @ 56cd780f:cbde8b29
2025-05-05 13:07:51
@ 56cd780f:cbde8b29
2025-05-05 13:07:51There’s something sacred about morning air — the way it carries just enough chill to remind you you’re alive, without pushing you back inside. I’ve been starting my days on the balcony lately. Not because it’s glamorous (it isn’t), or because I have a routine (I don’t), but because it’s the only space in my apartment that feels both open and still.
This morning I made coffee with too much cinnamon and curled up with a blanket that’s seen better days. I watched the city slowly wake up — one barking dog, two joggers, and the clatter of a recycling truck below. It’s odd how these tiny patterns become a kind of comfort.
 I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.
I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.If you’re reading this, maybe you needed that reminder too.
— Natalie
-
 @ 57d1a264:69f1fee1
2025-05-04 06:27:15
@ 57d1a264:69f1fee1
2025-05-04 06:27:15Well, today posts looks are dedicated to STAR WARS. Enjoy!
Today we’re looking at Beat Saber (2019) and why its most essential design element can be used to make great VR games that have nothing to do with music or rhythm.
https://www.youtube.com/watch?v=EoOeO7S9ehw
It’s hard to believe Beat Saber was first released in Early Access seven years ago today. From day one, it was clear the game was something special, but even so we couldn’t have predicted it would become one of VR’s best-selling games of all time—a title it still holds all these years later. In celebration of the game’s lasting legacy we’re re-publishing our episode of Inside XR Design which explores the secret to Beat Saber’s fun, and how it can be applied to VR games which have nothing to do with music.
Read more at https://www.roadtovr.com/beat-saber-instructed-motion-until-you-fall-inside-xr-design/
originally posted at https://stacker.news/items/970909
-
 @ 57d1a264:69f1fee1
2025-05-04 06:16:58
@ 57d1a264:69f1fee1
2025-05-04 06:16:58Found this really fun, so created a few intros for latest SN newsletters https://stacker.news/items/960787/r/Design_r?commentId=970902 and https://stacker.news/items/970459/r/Design_r?commentId=970905
Create your STAR-WARS-like movie intro https://starwarsintrocreator.kassellabs.io/
originally posted at https://stacker.news/items/970906
-
 @ c9badfea:610f861a
2025-05-05 12:55:46
@ c9badfea:610f861a
2025-05-05 12:55:461. Create
bash git bundle create backup.bundle --all2. Verify
bash git bundle verify backup.bundle3. Restore
bash git clone backup.bundleℹ️ Feel free to change the
backup.bundlefile name -
 @ 4fe14ef2:f51992ec
2025-05-04 06:02:38
@ 4fe14ef2:f51992ec
2025-05-04 06:02:38Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: N: https://nostrudel.ninja/#/n/nevent1qvzqqqqqqypzqnlpfme... X: https://x.com/AGORA_SN/status/1918907693516914793
originally posted at https://stacker.news/items/970896
-
 @ 8dac122d:0fc98d37
2025-05-05 12:29:57
@ 8dac122d:0fc98d37
2025-05-05 12:29:57Satoshi Escrow
A Bitcoin non-custodial peer-to-peer dispute resolution using only Nostr keys.
Motivation When a Buyer wants to purchase something for a certain amount of BTC from a Seller but doesn't trust them, they can use our 2-of-2 multisig escrow address. The Buyer and Seller both lock their BTC in a multisig address. Both parties only need their respective Nostr secret keys (nsec) and each other's Nostr public keys (npub).
How it works If the trade is successful: - Both parties sign to release the funds - Buyer receives his BTC back - Seller receives his BTC back
If there's a dispute: - Parties can choose a trusted third party (arbitrator) - Arbitrator can help resolve the dispute after a timelock period - Resolution requires 2-of-3 signatures (Buyer/Seller + Arbitrator)
Technical Implementation We use Pay-to-Taproot (P2TR) multisig script path spends with a verified unknown discrete-log unspendable internal key. The system supports two resolution paths:
Collaborative Resolution 2-of-2 multisig between Buyer and Seller without timelocks.
Dispute Resolution 2-of-3 multisig between either party and the arbitrator with timelock.
Important Security Notice This application can be used offline on an air-gapped computer for maximum security. All transactions can be generated, and signed through the webpage offline.
Getting Started 1. Create Escrow Set up a new escrow address using npubs and specify amounts.
-
Sign Transaction Sign the transaction using your nsec key.
-
Combine Signatures Combine the signatures into a signed transaction.
-
Broadcast Broadcast the signed transaction to the Bitcoin network.
-
Spend Spend from the resolution address derived from your npub using your nsec.
You can learn more and try it n Testnet, Signet and Regtest from https://scrow.exchange/
Github repository https://github.com/storopoli/scrow
originally posted at https://stacker.news/items/971914
-
-
 @ b6524158:8e898a89
2025-05-03 18:11:47
@ b6524158:8e898a89
2025-05-03 18:11:47Steps: 1. Run a node one mynode 2. Upgrade to premium 3. Select your Bitcoin version (to Bitcoin Knots)
originally posted at https://stacker.news/items/970504
-
 @ 41959693:3888319c
2025-05-05 10:58:49
@ 41959693:3888319c
2025-05-05 10:58:49Die Schnelllebigkeit der Moderne tilgt in unserer Wahrnehmung die zeitlichen Abstände von Ereignissen. Es bleibt kaum Gelegenheit ein Thema im Rückspiegel zu erfassen, zu durchdenken, zu rezipieren – schon buhlt der nächste Augenblick um Aufmerksamkeit.
Mögen an die Leipziger Buchmesse Ende März mittlerweile nur noch Visitenkarten und Selfies oder manch signiertes Exemplar im Buchregal erinnern; es lohnt sich doch, die größte deutsche Besuchermesse der Buchbranche nun rückblickend zu betrachten. Gerade da ihr Event-Charakter von Jahr zu Jahr zunimmt, ist die Frage reizvoll, welche beständigen Themen dort wie präsentiert wurden, in diesem Fall natürlich „Frieden“.
An allen vier Messetagen hielt ich die Augen auf, wo sich Autoren, Verlage und allgemeine die Institutionen der Branche dazu äußerten. Vorgreifend muss gesagt werden, dass Krieg und Frieden heute nicht mehr zwingend primäre Themen sind, sondern oft begleitend mitbehandelt werden. Für Zerstörung und Elend scheint dabei immer die große Bühne bereitet zu werden; einvernehmliche Koexistenz wird gewöhnlich mit leiser Klaviatur gespielt. Dennoch fand ich vier Bücher, welche direkt das Thema ansprachen:
- Die norwegische Soziologin und Publizistin Linn Stalsberg stellte ihr Werk „War is contempt for life. An essay on peace“ (ISBN: 978-8282262736, Res Publica, 2024) vor, in welchem sie auf all die Menschen eingeht, die für Pazifismus, Gewaltlosigkeit und Anti-Militarismus einstehen. Ihrer Meinung nach haben wir unzählige Berichte über Kriegs-, kaum jedoch Geschichten von Friedenshelden. Die deutsche Ausgabe soll im schweizerischen Kommode-Verlag im September diesen Jahres erscheinen.
-
„Die Evolution der Gewalt. Warum wir Frieden wollen, aber Kriege führen“, geschrieben von Kai Michel, Harald Meller und Carel van Schaik, wurde für den Preis der Leipziger Buchmesse in der Kategorie Sachbuch/Essayistik nominiert. Die Autoren vertreten u. a. die Thesen, dass Krieg kein essentieller Gesellschaftsprozess ist, wie es einige geflügelte Worte oder ideologische Äußerungen vermuten lassen – und, dass die Erfolge der Bellizisten nur 1 % der Weltgeschichte ausmachen (ISBN: 978-3423284387, dtv, 2024).
-
Der Publizist und taz-Redakteur Pascal Beucker gibt mit „Pazifismus – ein Irrweg?“ (ISBN 978-3170434325, Kohlhammer, 2024) eine Übersicht über die Geschichte des Pazifismus, geht auf in Vergessenheit geratene Hintergründe der einzelnen Motivationen und Bewegungen ein und wagt Zukunftsprognosen über die Erfolgschancen gewaltloser Auseinandersetzungen.
- Neben den Sachbüchern fand sich auch ein Vertreter aus dem Bereich der Belletristik: Rüdiger Heins und Michael Landgraf gaben eine Anthologie mit Friedenstexten, Prosa und Lyrik, heraus: „365 Tage Frieden“ (ISBN: 978-3930758951 Edition Maya, 2025), verspricht der Titel, für den zahlreiche Autoren auf ganz unterschiedliche Art und Weise träumten, sich erinnerten, uns mahnten und weiterhin hoffen.
Ansonsten fanden sich viele kleinere Veranstaltungsformate und Verlage, welche ihr Scherflein beitragen wollten, dabei aber sehr unscharf blieben und beispielsweise im Forum Offene Gesellschaft u. a. Grenzoffenheit, Toleranz und Inklusion behandelten. Inwieweit diese, in jüngster Vergangenheit doch recht stark medial forcierten Themen die zentrale Friedensfrage ergründen und stützen, ist vermutlich Auslegungssache.
Unsere Definition von Frieden mag nicht sonderlich scharf sein; jeder zieht darin andere Grenzen und wird sich situativ nach eigenem Gusto verhalten. Dennoch bewegt uns eine Grundschwingung, führt uns ein Sehnen in eine höhere, gemeinsame Richtung. Diese Erkenntnis ist es wert, durch den Lauf der Geschichte bewahrt zu werden, durch aktuelle Zeugnisse ebenso wie durch die Gedanken derer, die vor uns waren.
Ich habe beschlossen diese Bücher für Sie, werte Leser, in den nächsten Wochen nach und nach zu rezensieren.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Artikel findet man auch auf Telegram unter:
-
 @ 2e8970de:63345c7a
2025-05-03 17:31:07
@ 2e8970de:63345c7a
2025-05-03 17:31:07The figure in this article illustrates exactly how most biology papers are secretly p-hacked. A large number of hypotheses is explored, and only the ones that form a coherent story are reported.
This is actually the main reason behind the replication crisis in biology IMO. (source)
https://www.nature.com/articles/s41587-025-02635-7
originally posted at https://stacker.news/items/970464
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36
@ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36Comments: 3395 (Top Territory!!!) Posts: 306 (3rd) Stacking: 198k (2nd)
We're really bouncing back from the post-Super Bowl lull, with lots of contests and discussion threads. I think we've really found our niche with those two things.
The rest of Stacker News is experiencing declining activity, so our steady growth since February really tells me that we're on the right track.
Thanks for being part of our growing sports community!
originally posted at https://stacker.news/items/970289
-
 @ cb4352cd:a16422d7
2025-05-05 10:08:06
@ cb4352cd:a16422d7
2025-05-05 10:08:06Artificial intelligence is no longer just a buzzword — it’s becoming the quiet powerhouse behind many of the most meaningful changes in financial services. From helping people access credit to stopping fraud in its tracks, AI is making the financial world faster, smarter, and more personal.
Smarter Risk Management
Until recently, getting a loan meant paperwork, credit history checks, and plenty of waiting. But now, AI models can process huge amounts of data — including mobile usage and online behavior — to help lenders better understand a borrower’s real financial picture.
Startups like Upstart and Zest AI are making credit more inclusive by moving beyond legacy scoring models and enabling access to financing for underserved communities.
Personalized Financial Services
Robo-advisors like Betterment and Wealthfront are already using AI to build investment portfolios tailored to individual users. Digital banks use machine learning to analyze spending, offer savings tips, or spot unusual charges.
Meanwhile, virtual assistants and intelligent chatbots help customers manage finances without ever speaking to a human. The result? Financial tools that feel personal — and actually useful.
Fighting Fraud in Real Time
AI is becoming essential in financial security. Firms like Darktrace and Feedzai deploy AI systems that monitor transaction data in real time and flag anything suspicious. They learn from each interaction, making fraud detection faster and more accurate over time.
And in compliance, AI-powered tools can digest dense regulatory texts and help institutions stay within complex legal boundaries.
AI in Trading and Asset Management
In the world of trading, AI is now a key player. Quantitative funds use it to test strategies, scan headlines, and model price movements in seconds. Machine learning enables more nuanced, high-frequency trading — and can even spot trends before humans notice.
The Road Ahead: AI as a Financial Foundation
What once sounded futuristic is now foundational. AI is being woven into nearly every layer of financial services — and the impact is only just beginning.
The Beyond Banking Conference by WeFi will explore what’s next. From ethical AI use to the automation of banking infrastructure, the event will bring together leaders from FinTech, Web3, and AI to map the future of finance.
AI may not replace human judgment — but it’s already changing how we understand money, trust, and access.
-
 @ cefb08d1:f419beff
2025-05-03 11:01:47
@ cefb08d1:f419beff
2025-05-03 11:01:47https://www.youtube.com/watch?v=BOqWgxCo7Kw
The Catch Up Day 1: Bonsoy Gold Coast Pro provides opening day dominance from upper echelon:
https://www.youtube.com/watch?v=B1uM0FnyPvA
Next Round, elimination:
Results of the 1st day, opening round: https://www.worldsurfleague.com/events/2025/ct/325/bonsoy-gold-coast-pro/results
originally posted at https://stacker.news/items/970160
-
 @ cefb08d1:f419beff
2025-05-03 08:57:18
@ cefb08d1:f419beff
2025-05-03 08:57:18There is a well-known legend about pelicans that has been told for centuries: it was believed that pelican parents would wound their own chests with their beaks to feed their young with their blood. In reality, pelicans actually catch fish in their large beaks and then press their beaks to their chicks’ mouths to feed them. The myth likely arose because young pelicans sometimes peck their mother's chest while competing for food, but the mother does not harm herself intentionally.
originally posted at https://stacker.news/items/970123
-
 @ cefb08d1:f419beff
2025-05-03 08:43:37
@ cefb08d1:f419beff
2025-05-03 08:43:37originally posted at https://stacker.news/items/970118
-
 @ 6389be64:ef439d32
2025-05-03 07:17:36
@ 6389be64:ef439d32
2025-05-03 07:17:36In Jewish folklore, the golem—shaped from clay—is brought to life through sacred knowledge. Clay’s negative charge allows it to bind nutrients and water, echoing its mythic function as a vessel of potential.
Biochar in Amazonian terra preta shares this trait: it holds life-sustaining ions and harbors living intention. Both materials, inert alone, become generative through human action. The golem and black earths exist in parallel—one cultural, one ecological—shaping the lifeless into something that serves, protects, and endures.
originally posted at https://stacker.news/items/970089
-
 @ d9a329af:bef580d7
2025-05-03 04:20:42
@ d9a329af:bef580d7
2025-05-03 04:20:42To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ d9a329af:bef580d7
2025-05-03 04:10:03
@ d9a329af:bef580d7
2025-05-03 04:10:03Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones)
To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
- Firefox Forks
This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
- Brave Browser
This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
- Office Suites (If you need to do professional office documents)
- LibreOffice
A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
- OnlyOffice
The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
- Wordgrinder
For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
- Text editors
- Vi, Vim, Neovim and other Vim-like editors
The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
- VSCodium
The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
- Emacs
The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-03 02:29:16
@ 5d4b6c8d:8a1c1ee3
2025-05-03 02:29:16My month long endeavor to be less of a lazibones has concluded.
For the whole month, I fairly consistently did whatever little chores needed to be done, as soon as I noticed they needed to be done. That was mostly laundry, making the bed, and (un)loading the dishwasher, plus lots of random cleaning up after the dog and kid.
Even with focusing less on getting steps, my steps were up about 15% from the previous month (which had nicer weather, btw). These were less empty steps, too. I was actually being productive.
I'm not sure any of the JBP-esque room cleaning type benefits materialized, but it was good for me, so I'll try to carry some new habits forward.
originally posted at https://stacker.news/items/969995
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-02 21:28:12
@ 5d4b6c8d:8a1c1ee3
2025-05-02 21:28:12The top three ~econ posts, by zaprank, in April were
Pleb Economist #6: Analysis of Trump's Reciprocal Tariff Calculations by @SimpleStacker
Remember those goofy tariff and non-tariff barrier numbers? SimpleStacker walks us through the assumptions and formulas that they were derived from. There's a good discussion around how much sense those assumptions make and where they came from.
Twenty One Capital: You Can Just Do Things (Bloomberg, Matt Levine) by @denlillaapan
A commentary on a commentary on the 21 Capital bitcoin strategy. Why are investors willing to pay several multiples of bitcoin's current purchase price to get exposure to it in this form? Let @denlillaapan know in the comments.
The WSJ (kinda) covers the Mar-a-Lago Accords plus Miran's Incredible Speech by @028559d218
Analysis of Steve Miran's speech about "Global Public Goods". Will the rest of the world tell America to "go F itself", as the author repeatedly suggests? Eventually, no doubt they/we will.
Thanks to our great authors and generous zappers!
The top post will be entered into the quarterly top post contest, which we'll hold in July.
originally posted at https://stacker.news/items/969806
-
 @ b099870e:f3ba8f5d
2025-05-05 09:17:11
@ b099870e:f3ba8f5d
2025-05-05 09:17:11IN NOOKS ALL OVER THE EARTH SIT MEN WHO ARE WAITING, SCARCELY KNOWING IN WHAT WAY THEY ARE WAITING, MUCH LESS THAT THEY ARE WAITING IN VAIN. OCCASIONALLY THE CALL THAT AWAKENS-THAT ACCIDENT WHICH GIVES THE "PERMISSION" TO ACT—COMES TOO LATE, WHEN THE BEST YOUTH AND STRENGTH FOR ACTION HAS ALREADY BEEN USED UP BY SITTING STILL; AND MANY HAVE FOUND TO THEIR HORROR WHEN THEY "LEAPED UP" THAT THEIR LIMBS HAD GONE TO SLEEP AND THEIR SPIRIT HAD BECOME TOO HEAVY. "IT IS TOO LATE," THEY SAID TO THEMSELVES, HAVING LOST THEIR FAITH IN THEMSELVES AND HENCEFORTH FOREVER USELESS
Quote by Friedrich Nietzsche, currently reading The 50th Law and came across it
-
 @ cefb08d1:f419beff
2025-05-02 18:49:21
@ cefb08d1:f419beff
2025-05-02 18:49:21I still get some errors on those relays as related in https://stacker.news/items/797226 :
wss://relay.snort.social/, wss://relay.damus.io/, wss://nostr.mutinywallet.com/, wss://relay.mutinywallet.com/
Is it "normal" ?
originally posted at https://stacker.news/items/969662
-
 @ cefb08d1:f419beff
2025-05-02 18:37:13
@ cefb08d1:f419beff
2025-05-02 18:37:13Snapper Rocks surf heralds the start of the Superbank, offering some of the most iconic right barrels in the whole of Australia. If it was good enough for Mick Fanning…
An introduction to Snapper Rocks surf When people talk about Snapper Rocks surf, what they’re really talking about is the first spot in a long line of truly legendary spots that together form the Kirra Superbank. They’ve all garnered endless international attention in the last two decades, since the removal of sand from the Tweed River estuary started building up the engine room for what can only be described as a barrel machine.
Prior to 2001, Snappers was a bit fickle, a touch mushy, but nonetheless a decent left-right break for intermediates. Today, it’s a crowded take-off zone for riders chasing the long peelers that can shift them from the head all the way to Kirra Beach in one interconnected medley of hollow and heavy sections. It’s the land that crafted names like Mick Fanning and it’s understandably awesome stuff.
Location:
https://www.google.com/maps/place/28%C2%B009'41.4%22S+153%C2%B032'58.8%22E/@-28.161507,153.549664,14z/data=!4m4!3m3!8m2!3d-28.161507!4d153.549664?hl=en&entry=ttu&g_ep=EgoyMDI1MDQyOS4wIKXMDSoASAFQAw%3D%3D
To watch it live:
https://www.youtube.com/watch?v=NMnfbXRqe58
originally posted at https://stacker.news/items/969653
-
 @ 526bec6a:07c68d13
2025-05-05 08:20:00
@ 526bec6a:07c68d13
2025-05-05 08:20:0001: Counterfeiting Money002: Credit Card Fraud003: Making Plastic Explosives from Bleach004: Picking Master Locks005: The Arts of Lockpicking I006: The Arts of Lockpicking II007: Solidox Bombs008: High Tech Revenge: The Beigebox (NEW Revision 4.14)009: CO2 Bombs010: Thermite Bombs (NEW Rivision, 4.14)011: Touch Explosives012: Letter Bombs013: Paint Bombs014: Ways to send a car to HELL015: Do ya hate school? (NEW Revision, 4.14)016: Phone related vandalism017: Highway police radar jamming018: Smoke Bombs019: Mail Box Bombs020: Hotwiring cars021: Napalm022: Fertilizer Bomb023: Tennis Ball Bomb024: Diskette Bombs025: Unlisted Phone Numbers (NEW Revision, 4.14)026: Fuses027: How to make Potassium Nitrate028: Exploding Lightbulbs029: Under water igniters030: Home-brew blast cannon031: Chemical Equivalency List032: Phone Taps033: Landmines034: A different kind of Molitov Cocktail035: Phone Systems Tutorial I036: Phone Systems Tutorial II037: Basic Alliance Teleconferencing038: Aqua Box Plans039: Hindenberg Bomb040: How to Kill Someone with your Bare Hands041: Phone Systems Tutorial III042: Black Box Plans043: The Blotto Box044: Blowgun045: Brown Box Plans046: Calcium Carbide Bomb047: More Ways to Send a Car to Hell048: Ripping off Change Machines (NEW Revision, 4.14)049: Clear Box Plans050: CNA Number Listing051: Electronic Terrorism052: How to Start a Conference w/o 2600hz or M-F053: Dynamite054: Auto Exhaust Flame Thower055: How to Break into BBS Express056: Firebomb057: Fuse Bomb058: Generic Bomb059: Green Box Plans060: Portable Grenade Launcher061: Basic Hacking Tutorial I062: Basic Hacking Tutorial II063: Hacking DEC's064: Harmless Bombs 065: Breaking into Houses (NEW Revision, 4.14)066: Hypnotism067: Remote Informer Issue #1068: Jackpotting ATM Machines069: Jug Bomb070: Fun at K-Mart071: Mace Substitute072: How to Grow Marijuana073: Match Head Bomb074: Terrorizing McDonalds075: "Mentor's" Last Words076: The Myth of the 2600hz Detector077: Blue Box Plans (Ye' olde Favorite)078: Napalm II079: Nitroglycerin Recipe080: Operation: Fuckup081: Stealing Calls from Payphones082: Pool Fun (NEW Revision, 4.14)083: Free Postage084: Unstable Explosives085: Weird Drugs086: The Art of Carding087: Recognizing Credit Cards088: How to Get a New Identity089: Remote Informer Issue #2090: Remote Informer Issue #3091: Remote Informer Issue #4092: Remote Informer Issue #5093: Phreaker's Guide to Loop Lines094: Ma-Bell Tutorial095: Getting Money out of Pay Phones096: Computer-based PBX097: PC-Pursuit Port Statistics098: Pearl Box Plans099: The Phreak File100: Red Box Plans101: RemObs102: Scarlet Box Plans103: Silver Box Plans104: Bell Trashing105: Canadian WATS Phonebook106: Hacking TRW107: Hacking VAX & UNIX108: Verification Circuits109: White Box Plans110: The BLAST Box111: Dealing with the Rate & Route Operator112: Cellular Phone Phreaking113: Cheesebox Plans114: How to Start Your Own Conferences115: Gold Box Plans116: The History of ESS117: The Lunch Box118: Olive Box Plans119: The Tron Box120: More TRW Info121: "Phreaker's Phunhouse"122: Phrack Magazine - Vol. 3, Issue 27 (Intro to MIDNET)123: Phrack Magazine - Vol. 3, Issue 27 (The Making of a Hacker)124: Phrack Magazine - Vol. 3, Issue 28 (Network Miscellany)125: Phrack Magazine - Vol. 3, Issue 28 (Pearl Box Schematic)126: Phrack Magazine - Vol. 3, Issue 28 (Snarfing Remote Files)127: Phrack Magazine - Vol. 3, Issue 30 (Western Union, Telex, TWX & Time Service)128: Phrack Magazine - Vol. 3, Issue 30 (Hacking & Tymnet)129: Phrack Magazine - Vol. 3, Issue 30 (The DECWRL Mail Gateway)130: Sodium Chlorate131: Mercury Fulminate132: Improvised Black Powder 133: Nitric Acid134: Dust Bomb Instructions135: Carbon-Tet Explosive136: Making Picric Acid from Aspirin137: Reclamation of RDX from C-4 Explosives138: Egg-based Gelled Flame Fuels139: Clothespin Switch140: Flexible Plate Switch141: Low Signature Systems (Silencers)142: Delay Igniter From Cigarette143: Nicotine144: Dried Seed Timer145: Nail Grenade146: Bell Glossary147: Phone Dial Locks -- How to Beat'em148: Exchange Scanning149: A Short History of Phreaking150: "Secrets of the Little Blue Box" (story)151: The History of British Phreaking152: "Bad as Shit" (story)153: Telenet154: Fucking with the Operator155: Phrack Magazine - Vol. 1, Issue 1 (The Phone Preak's Fry-Um Guide)156: International Country Code Listing157: Infinity Transmitter Schematic and Plans158: LSD159: Bananas160: Yummy Marihuana Recipes161: Peanuts162: Chemical Fire Bottle163: Igniter from Book Matches164: "Red or White Powder" Propellant165: Pipe Hand Grenade166: European Credit Card Fraud (Written by Creditman! A Cookbook IV Recap!!)167: Potassium Bomb168: Your Legal Rights (For adults, or some of us think we are)169: Juvenile Offenders' Rights170: Down The Road Missle171: Fun With ShotGunn Shells172: Surveillance Equipment173: Drip Timer174: Stealing175: Miscellaneous176: Shaving cream bomb177: Ripping off change machines 2178: Lockpicking the EASY way179: Anarchy 'N' Explosives Prelude180: Anarchy 'N' Explosives Vol. 1181: Anarchy 'N' Explosives Vol. 2182: Anarchy 'N' Explosives Vol. 3183: Anarchy 'N' Explosives Vol. 4184: Anarchy 'N' Explosives Vol. 5185: Explosives and Propellants186: Lockpicking 3187: Chemical Equivalent List 2188: Nitroglycerin 2189: Cellulose Nitrate190: Starter Explosives191: Flash Powder192: Exploding Pens193: Revised Pipe Bombs 4.14194: * SAFETY * A MUST READ!195: Ammonium TriIodide196: Sulfuric Acid / Ammonium Nitrate III197: Black Powder 3198: Nitrocellulose199: R.D.X. (Revised 4.14)200: The Black Gate BBS 201: ANFOS202: Picric Acid 2203: Bottled Explosives204: Dry Ice205: Fuses / Ignitors / Delays206: Film Canister Bombs207: Book Bombs208: Phone Bombs209: Special Ammunition210: Rocketry211: Pipe Cannon 2212: Smoke Bombs 4.14213: Firecrackers214: Suppliers II215: Lab-Raid Checklist216: Misc. Anarchy217: LockPicking 4218: Misc. Anarchy II219: -* THERMITE 4 Index of Additions to the Anarchist Cookbook
- Ripping off Coke Machines
- Build an original style zip gun
- Diary of a hacker part one
- Diary of a hacker part two
- How to create a new identity
- Findind Security Holes
- Hacking techniques
- Composite Rocket Fuels
- The Complete Social Engineering faq's
- Association Betting System
- The Beginners Betting System
- The Dream Racing System
- The NetProfits Racing Plan
- The Professional Betting System
- Unix Hacking Tutorial
- Extract from the New York Times
- Unix Hacking Commands
- Home Brew Blast Cannon
- Down The Road Missile
- Internet email security
- Pneumatic spud gun
- The School Stoppers Textbook
- The Big Book of Mischief
- Terror Handbook - 100% bombs and explosives
- Beginners guide to hacking and phreaking
- Easy Grenades/Rockets
- toilet bowl cleaner Bomb
- Blowgun @ f72e682e:c51af867
2025-05-02 18:33:38
@ f72e682e:c51af867
2025-05-02 18:33:38lightning #fees #lnd #node
I'm really tired of bad node operator that do not take advantage of everything we have and expect for the LN network to work properly. If you have a node, please do this.
I recommend having an automatic fee automator like charge-lnd so channels don't become stagnant:
https://github.com/accumulator/charge-lnd
And put some negative inbound fees for channels with no liquidity:
https://docs.lightning.engineering/lightning-network-tools/lnd/inbound-channel-fees
You'll notice you will route A LOT MORE.
Any question I will respond below.
A good starting configuration:
========
``` [encourage-routing]
'autobalance' (lower fees so using outbound is more attractive)
chan.min_ratio = 0.98 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 strategy = static base_fee_msat = 0 fee_ppm = 0
[discourage-routing]
'autobalance' (higher fees so using outbound is less attractive)
chan.max_ratio = 0.2 chan.min_ratio = 0.05 inbound_base_fee_msat = -64 inbound_fee_ppm = -16 strategy = static base_fee_msat = 1_000 fee_ppm = 700
[all-liquidity-is-theirs] chan.max_ratio = 0.00 inbound_base_fee_msat = -128 inbound_fee_ppm = -128 strategy = static base_fee_msat = 100_000 fee_ppm = 5000
[discourage-routing-extreme] chan.max_ratio = 0.05 inbound_base_fee_msat = -128 inbound_fee_ppm = -32 strategy = static base_fee_msat = 10_000 fee_ppm = 2500
[proportional]
'proportional' can also be used to auto balance (lower fee rate when low remote balance & higher rate when higher remote balance)
fee_ppm decreases linearly with the channel balance ratio (min_fee_ppm when ratio is 1, max_fee_ppm when ratio is 0)
chan.min_ratio = 0.2 chan.max_ratio = 0.98 strategy = proportional min_fee_ppm = 8 max_fee_ppm = 160 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 base_fee_msat = 128 min_fee_ppm_delta=16 ```
originally posted at https://stacker.news/items/969651
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-02 16:24:49
@ 5d4b6c8d:8a1c1ee3
2025-05-02 16:24:49The first round is not quite over, with Warriors vs Rockets and Nuggets vs Clippers, still going in the West, But we do know most of who will be playing in the second round, so it's not too early to start thinking about our picks.
This contest is open entry throughout. Just submit a pick for who will win their series and who will be the leading scorer of the entire playoff round. You can select a team or player, up until tipoff of their series.
Matchups (seed)
- Pacers (4) @ Cavs (1)
- Knicks (3) @ Celtics (2)
- Nuggets (4) or Clippers (5) @ Thunder (1)
- T-Wolves (6) @ Rockets (2) or Warriors (7) @ T-Wolves (6)
Scoring
2 Points + seed for picking a winner + 2 points for picking the leading scorer (total points) of the round
Standings
These will change if the Clippers or Warriors advance. Also, if Jokic scores 37 or more, he will catch Brunson (who no one selected) and net a few stackers another point. | Stacker | Points | |---------|--------| | @grayruby | 24| | @Coinsreporter | 19 | | @Carresan | 18 | | @gnilma | 18 | | @Undisciplined | 17 | | @WeAreAllSatoshi | 12 | | @fishious | 11 | | @BlokchainB | 11 | | @Car | 1 |
Prize
10k sats (or total zaps on these posts, whichever is larger)
originally posted at https://stacker.news/items/969492
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-02 15:20:18
@ 5d4b6c8d:8a1c1ee3
2025-05-02 15:20:18After exclusively talking about NFL draft and NBA playoffs last week, we have a lot of ground to make up.
The race for second place in the T20k cricket contest is heating up, but @Coinsreporter has a very commanding hold on 1st. I similarly have a stranglehold on last place in the CricZap contest and, not to brag, I just broke @grayruby's impressive mark for worst single month performance.
We're down to the final two survivors in the UEFA Survivor Pool. C'mon @TNStacker, we're all pulling for you.
The US continues to dominate the rest of the world... in our US vs the world contest.
Our MLB fantasy league (courtesy of @NEEDcreations) is a lot of fun, with tons of daily roster moves and movement in the standings. We should also finally have time for @grayruby to rant about how the American League is the suckiest bunch of sucks who ever sucked (where's that from?).
We do have more playoff basketball to cover. The games this week have been spectacular and we have second round series to start talking about. Shoutout to @WeAreAllSatoshi for hosting discussion threads. I'll get some posts up later summarizing how the bracket challenge is going and taking second round picks in the playoff points challenge.
NHL playoffs are also underway and we've barely talked about them, yet. What are the interesting storylines of round 1? How's the bracket challenge going?
And, of course, we'll talk about our favorite Predyx sports markets.
What else do stackers want to talk about?
originally posted at https://stacker.news/items/969413
-
 @ f1989a96:bcaaf2c1
2025-05-01 15:50:38
@ f1989a96:bcaaf2c1
2025-05-01 15:50:38Good morning, readers!
This week, we bring pressing news from Belarus, where the regime’s central bank is preparing to launch its central bank digital currency in close collaboration with Russia by the end of 2026. Since rigging the 2020 election, President Alexander Lukashenko has ruled through brute force and used financial repression to crush civil society and political opposition. A Central Bank Digital Currency (CBDC) in the hands of such an authoritarian leader is a recipe for greater control over all aspects of financial activity.
Meanwhile, Russia is planning to further restrict Bitcoin access for ordinary citizens. This time, the Central Bank of Russia and the Ministry of Finance announced joint plans to launch a state-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Access would be limited to those meeting previously defined thresholds of $1.2 million in assets or an annual income above $580,000. This is a blatant attempt by the Kremlin to dampen the accessibility and impact of Bitcoin for those who need it most.
In freedom tech news, we spotlight Samiz. This new tool allows users to create a Bluetooth mesh network over nostr, allowing users' messages and posts to pass through nearby devices on the network even while offline. When a post reaches someone with an Internet connection, it is broadcast across the wider network. While early in development, Mesh networks like Samiz hold the potential to disseminate information posted by activists and human rights defenders even when authoritarian regimes in countries like Pakistan, Venezuela, or Burma try to restrict communications and the Internet.
We end with a reading of our very own Financial Freedom Report #67 on the Bitcoin Audible podcast, where host Guy Swann reads the latest news on plunging currencies, CBDCs, and new Bitcoin freedom tools. We encourage our readers to give it a listen and stay tuned for future readings of HRF’s Financial Freedom Report on Bitcoin Audible. We also include an interview with HRF’s global bitcoin adoption lead, Femi Longe, who shares insights on Bitcoin’s growing role as freedom money for those who need it most.
Now, let’s see what’s in store this week!
SUBSCRIBE HERE
GLOBAL NEWS
Belarus | Launching CBDC in Late 2026
Belarus is preparing to launch its CBDC, the digital ruble, into public circulation by late 2026. Roman Golovchenko, the chairman of the National Bank of the Republic of Belarus (and former prime minister), made the regime’s intent clear: “For the state, it is very important to be able to trace how digital money moves along the entire chain.” He added that Belarus was “closely cooperating with Russia regarding the development of the CBDC.” The level of surveillance and central control that the digital ruble would embed into Belarus’s financial system would pose existential threats to what remains of civil society in the country. Since stealing the 2020 election, Belarusian President Alexander Lukashenko has ruled through sheer force, detaining over 35,000 people, labeling dissidents and journalists as “extremists,” and freezing the bank accounts of those who challenge his authority. In this context, a CBDC would not be a modern financial tool — it would be a means of instant oppression, granting the regime real-time insight into every transaction and the ability to act on it directly.
Russia | Proposes Digital Asset Exchange Exclusively for Wealthy Investors
A month after proposing a framework that would restrict the trading of Bitcoin to only the country’s wealthiest individuals (Russians with over $1.2 million in assets or an annual income above $580,000), Russia’s Ministry of Finance and Central Bank have announced plans to launch a government-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Under the plan, only citizens meeting the previously stated wealth and income thresholds (which may be subject to change) would be allowed to trade digital assets on the platform. This would further entrench financial privilege for Russian oligarchs while cutting ordinary Russians off from alternative financial tools and the financial freedom they offer. Finance Minister Anton Siluanov claims this will bring digital asset operations “out of the shadows,” but in reality, it suppresses grassroots financial autonomy while exerting state control over who can access freedom money.
Cuba | Ecash Brings Offline Bitcoin Payments to Island Nation in the Dark
As daily blackouts and internet outages continue across Cuba, a new development is helping Cubans achieve financial freedom: Cashu ecash. Cashu is an ecash protocol — a form of digital cash backed by Bitcoin that enables private, everyday payments that can also be done offline — a powerful feature for Cubans experiencing up to 20-hour daily blackouts. However, ecash users must trust mints (servers operated by individuals or groups that issue and redeem ecash tokens) not to disappear with user funds. To leverage this freedom tech to its fullest, the Cuban Bitcoin community launched its own ecash mint, mint.cubabitcoin.org. This minimizes trust requirements for Cubans to transact with ecash and increases its accessibility by running the mint locally. Cuba Bitcoin also released a dedicated ecash resource page, helping expand accessibility to freedom through financial education. For an island nation where the currency has lost more than 90% of its value, citizens remain locked out of their savings, and remittances are often hijacked by the regime, tools like ecash empower Cubans to preserve their financial privacy, exchange value freely, and resist the financial repression that has left so many impoverished.
Zambia | Introduces Cyber Law to Track and Intercept Digital Communications
Zambia’s government passed two new cyber laws granting officials sweeping powers to track and intercept digital communications while increasing surveillance over Zambians' online activity. Officials insist it will help combat cybercrime. Really, it gives the president absolute control over the direction of a new surveillance agency — a powerful tool to crush dissent. This follows earlier plans to restrict the use of foreign currency in the economy to fight inflation, which effectively trapped Zambians in a financial system centered around the volatile “kwacha” currency (which reached a record low earlier this year with inflation above 16%). For activists, journalists, and everyday Zambians, the new laws over online activity threaten the ability to organize and speak freely while potentially hampering access to freedom tech.
India | Central Bank Deputy Governor Praises CBDC Capabilities
At the Bharat Inclusion Summit in Bengaluru, India, the deputy governor of the Reserve Bank of India (RBI), Rabi Sankar, declared, “I have so far not seen any use case that potentially can solve the problem of cross-border money transfer; only CBDC has the ability to solve it.” Yet — seemingly unbeknownst to Sankar, Bitcoin has served as an effective remittance tool for more than a decade at low cost, fast speed, and with no central point of control. Sankar’s remarks follow a growing push to normalize state-controlled, surveillance-based digital money as a natural progression of currency. The RBI’s digital rupee CBDC, currently in pilot phase, is quickly growing into one of the most advanced CBDCs on the planet. It is being embedded into the government’s UPI payment system and offered through existing financial institutions and platforms. Decentralized alternatives like Bitcoin can achieve financial inclusion and payment efficiency too — but without sacrificing privacy, autonomy, or basic rights over to the state.
Tanzania | Opposition Party Excluded From Election Amid Financial Repression
Last week, the Tanzanian regime banned the use of foreign currency in transactions, leaving Tanzanians to rely solely on the rapidly depreciating Tanzanian shilling. Now, Tanzania's ruling party has taken a decisive step to eliminate political opposition ahead of October’s general elections by barring the CHADEMA party from participation under the pretense of treason against their party leader, Tundu Lissu. Law enforcement arrested Lissu at a public rally where he was calling for electoral reforms. This political repression is not happening in isolation. Last year, the Tanzanian regime blocked access to X, detained hundreds of opposition members, and disappeared dissidents. These developments suggest a broader strategy to silence criticism and electoral competition through arrests, censorship, and economic coercion.
BITCOIN AND FREEDOM TECH NEWS
Samiz | Create a Bluetooth Mesh Network with Nostr
Samiz, an app for creating a Bluetooth mesh network over nostr, is officially available for testing. Mesh networks, where interconnected computers relay data to one another, can provide offline access to nostr if enough users participate. For example, when an individual is offline but has Samiz enabled, their device can connect to other nearby devices through Bluetooth, allowing nostr messages to hop locally from phone to phone until reaching someone with internet access, who can then broadcast the message to the wider nostr network. Mesh networks like this hold powerful implications for activists and communities facing censorship, Internet shutdowns, or surveillance. In places with restricted finances and organization, Samiz, while early in development, can potentially offer a way to distribute information through nostr without relying on infrastructure that authoritarian regimes can shut down.
Spark | New Bitcoin Payments Protocol Now Live
Lightspark, a company building on the Bitcoin Lightning Network, officially released Spark, a new payment protocol built on Bitcoin to make transactions faster, cheaper, and more privacy-protecting. Spark leverages a technology called statechains to enable self-custodial and off-chain Bitcoin transactions for users by transferring the private keys associated with their bitcoin rather than signing and sending a transaction with said keys. Spark also supports stablecoins (digital tokens pegged to fiat currency) and allows users to receive payments while offline. While these are promising developments, in its current state, Spark is not completely trustless; therefore, it is advisable only to hold a small balance of funds on the protocol as this new payment technology gets off the ground. You can learn more about Spark here.
Boltz | Now Supports Nostr Zaps
Boltz, a non-custodial bridge for swapping between different Bitcoin layers, released a new feature called Zap Swaps, enabling users to make Lightning payments as low as 21 satoshis (small units of bitcoin). This feature enables bitcoin microtransactions like nostr zaps, which are use cases that previously required workaround solutions. With the release, users of Boltz-powered Bitcoin wallets like Misty Breez can now leverage their wallets for zaps on nostr. These small, uncensorable bitcoin payments are a powerful tool for supporting activists, journalists, and dissidents — offering a permissionless way to support free speech and financial freedom worldwide. HRF is pleased to see this past HRF grantee add support for the latest freedom tech features.
Coinswap | Adds Support for Coin Selection
Coinswap, an in-development protocol that enables users to privately swap Bitcoin with one another, added support for coin selection, boosting the protocol’s privacy capabilities. Coin selection allows Bitcoin users to choose which of their unspent transaction outputs (UTXOs) to spend, giving them granular control over their transactions and the information they choose to reveal. For activists, journalists, and anyone operating under financial surveillance and repression, this addition (when fully implemented and released) can strengthen Bitcoin’s ability to resist censorship and protect human rights. HRF’s first Bitcoin Development Fund (BDF) grant was to Coinswap, and we are glad to see the continued development of the protocol.
bitcoin++ | Upcoming Bitcoin Developer Conference
The next bitcoin++ conference, a global, bitcoin-only developer series organized by Bitcoin educator Lisa Neigut, will occur in Austin, Texas, from May 7 to 9, 2025. A diverse group of privacy advocates, developers, and freedom tech enthusiasts will convene to learn about the mempool (the queue of pending and unconfirmed transactions in a Bitcoin node). Attendees will learn how Bitcoin transactions are sorted into blocks, mempool policies, and how transactions move through time and space to reach the next block. These events offer an incredible opportunity to connect with the technical Bitcoin community, who are ultimately many of the figures building the freedom tools that are helping individuals preserve their rights and freedoms in the face of censorship. Get your tickets here.
OpenSats | Announces 11th Wave of Nostr Grants
OpenSats, a nonprofit organization supporting open-source software and projects, announced its 11th round of grants for nostr, a decentralized protocol that enables uncensorable communications. Two projects stand out for their potential impact on financial freedom and activism: HAMSTR, which enables nostr messaging over ham radio that keeps information and payments flowing in off-grid or censored environments, and Nostr Double Ratchet, which brings end-to-end encrypted private messaging to nostr clients, safeguarding activists from surveillance. These tools help dissidents stay connected, coordinate securely, and transact privately, making them powerful assets for those resisting authoritarian control. Read the full list of grants here.
Bitcoin Design Community | Organizes Designathon for Open-Source UX Designers
The Bitcoin Design Community is hosting its next Designathon between May 4 and 18, 2025, inviting designers of all levels and backgrounds to creatively explore ideas to advance Bitcoin’s user experience and interface. Unlike traditional hackathons, this event centers specifically on design, encouraging open collaboration on projects that improve usability, accessibility, and innovation in open-source Bitcoin tools. Participants can earn monetary prizes, rewards, and recognition for their work. Anyone can join or start a project. Learn more here.
RECOMMENDED CONTENT
Plunging Currencies, CBDCs, and New Bitcoin Freedom Tools with Guy Swann
In this reading on the Bitcoin Audible podcast, host Guy Swan reads HRF’s Financial Freedom Report #67, offering listeners a front-row view into the latest developments in financial repression and resistance. He unpacks how collapsing currencies, rising inflation, and CBDC rollouts tighten state control in Turkey, Russia, and Nigeria. But he also highlights the tools for pushing back, from the first Stratum V2 mining pool to Cashu’s new Tap-to-Pay ecash feature. If you’re a reader of the Financial Freedom Report, we encourage you to check out the Bitcoin Audible podcast, where Guy Swan will be doing monthly readings of our newsletter. Listen to the full recording here.
Bitcoin Beyond Capital: Freedom Money for the Global South with Femi Longe
In this interview at the 2025 MIT Bitcoin Expo, journalist Frank Corva speaks with Femi Longe, HRF’s global bitcoin lead, who shares insights on Bitcoin’s growing role as freedom money for those living under authoritarian regimes. The conversation highlights the importance of building Bitcoin solutions that center on the specific problems faced by communities rather than the technology itself. Longe commends projects like Tando in Kenya and Bit.Spenda in Ghana, which integrate Bitcoin and Lightning into familiar financial channels, making Bitcoin more practical and accessible for everyday payments and saving. You can watch the interview here and catch the livestreams of the full 2025 MIT Bitcoin Expo here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 502ab02a:a2860397
2025-05-05 07:36:59
@ 502ab02a:a2860397
2025-05-05 07:36:59แค่ลดการ spike แต่ไม่ได้หายไปไหน เฮียขอเล่าเรื่องผับ... ไม่ใช่ผับที่มีไฟสลัว ๆ เสียงเบสแน่น ๆ หรอกนะ แต่เป็น “ผับร่างกาย” ที่เปิดประตูรับแขกชื่อ “น้ำตาล” เข้าไปทุกวันแบบไม่รู้ตัว
ในโลกของสุขภาพ น้ำตาลก็เหมือนวัยรุ่นที่ชอบเข้าไปในผับหลังมืดค่ำทุกคืน ส่วน อินซูลิน ก็คือพีอาร์หน้าผับ มีหน้าที่เปิดประตูให้เด็กพวกนี้เข้าไปในเซลล์ พอวัยรุ่นแห่มาพร้อมกัน อินซูลินก็ต้องเร่งเปิดประตูรัว ๆ นั่นแหละที่เขาเรียกกันว่า insulin spike
หลายคนรู้ว่า spike บ่อย ๆ ไม่ดี เลยพยายามหาวิธี “ลด spike” บางคนดื่มน้ำส้มสายชูแอปเปิ้ล (ACV) บางคนกินผักใยสูงก่อนอาหาร บางคนจัดซุปใส่ไฟเบอร์แบบคุม ๆ มาเสริม เฮียบอกเลยว่า “ดี” อยู่ครับ... แต่ หลายคนเข้าใจว่า การลด spike เท่ากับการลดน้ำตาล จริง ๆ แล้วน้ำตาลไม่ได้หายไปไหนเลย มันแค่ เดินเข้าช้าลงเท่านั้นเอง
ลองนึกภาพตามนะเฮียจะเล่าให้ฟัง...เอาแบบเห็นภาพร่างนะ เปรียบเปรยเปรียบเปรย
ผับเปิด... วัยรุ่นต่อแถว ทุกครั้งที่เรากินคาร์บ โดยเฉพาะแป้งหรือของหวาน ร่างกายก็จะแปลงมันเป็นกลูโคส หรือน้ำตาลในกระแสเลือด เจ้ากลูโคสเหล่านี้ก็จะมาต่อแถวเข้า “ผับเซลล์” พอคนเยอะ อินซูลินก็ต้องออกมาทำงานหนัก พาแต่ละคนเข้าไปจัดสรรให้เรียบร้อย ทีนี้ถ้าน้ำตาลมาก และมาพร้อมกัน อินซูลินก็ต้อง “spike” คือพุ่งขึ้นเพื่อจัดการด่วน ซึ่งถ้าร่างกายทำแบบนี้บ่อย ๆ ไม่ดีเลย เพราะมันทำให้ระบบเสื่อม เกิด ภาวะดื้ออินซูลิน นึภภาพพนักงานทำงานกันแบบ ปาร์ตี้คืนวันสงกรานต์ในผับย่าน อาร์ซีเอ หรือข้าวสาร สุดท้ายก็มักนำไปสู่เบาหวาน ความอ้วน และความเสื่อมแบบค่อยเป็นค่อยไป
ACV, ไฟเบอร์ช่วยไหม? ช่วย แต่ไม่ได้ลดน้ำตาล เทคนิคกินผักก่อน กินน้ำส้มสายชู หรือเพิ่มไฟเบอร์สูง ๆ ก่อนคาร์บ มันช่วย ชะลอการดูดซึม ของน้ำตาลจริง ๆ เหมือนกับมีการ์ดหน้าผับมาตรวจบัตรก่อนเข้าทีละคน แถวมันเลยไม่กรูกันเข้าแบบม็อบ แต่มาเรื่อย ๆ ทีละคน ๆ พีอาร์หน้าประตูก็จัดการระบบได้เบาแรงขึ้น
ฟังดูดีใช่ไหม? ใช่... แต่ ไม่ได้แปลว่าวัยรุ่นเหล่านั้นจะไม่เข้าผับ สุดท้าย พวกเขาก็เข้าไปครบเหมือนเดิมอยู่ดี นั่นคือ ร่างกายก็ยังได้รับน้ำตาลเท่าเดิมนั่นแหละ ... แค่เข้าช้าลงเท่านั้น
แล้วมันดีตรงไหนล่ะ ถ้ามันไม่ได้ลดน้ำตาล? มันดีตรงที่ spike จะไม่พุ่งเร็ว พอชะลอได้ อินซูลินก็ไม่ต้องทำงานแบบโหม ซึ่งในระยะสั้น มันช่วยให้ระดับน้ำตาลในเลือดไม่แกว่งจัดเกินไป ดีต่อสมอง ไม่ทำให้ง่วงหลังมื้ออาหาร
แต่ถ้าเรายังเลือกกินอาหารที่แปลงเป็นน้ำตาลเยอะ ๆ อยู่ดี แม้จะกินช้าลง ยังไงน้ำตาลก็สะสม เหมือนวัยรุ่นที่เข้าผับช้าลง แต่จำนวนก็เท่าเดิม เฮียว่าเราควรหันมาถามตัวเองว่า...
แล้วเราจะเปิดผับให้ใครบ้างดีล่ะ? การจัดการ spike ที่ดีที่สุดไม่ใช่แค่ “ชะลอ” แต่คือ “ลดปริมาณกลูโคสตั้งแต่ต้นทาง” เลือกกินของที่ไม่สร้างน้ำตาลพรึ่บพรั่บ เช่น real food ที่มีไขมันดีและโปรตีนสูง อย่างไข่ เนื้อสัตว์ เครื่องใน น้ำมันสัตว์ น้ำมันสกัดเย็นที่มีทั้งพฤกษเคมีและพลังงานที่ดี ฯลฯ ซึ่งเป็นการบริหารซอย จำกัดจำนวนนักเที่ยวแต่แรก เพราะพวกนี้ไม่พาน้ำตาลมากองหน้าประตูเหมือนขนมปังโพรเซส น้ำหวานจัดๆ หรือเค้กแป้งขัดสีน้ำตาลครีมเยอะๆ
เห็นไหมว่า เฮียไม่ได้บอกให้เลิกกินของอร่อยเลยนะ แต่จะบอกว่า... ถ้าเราเข้าใจว่า การลด spike ไม่ใช่การลดน้ำตาล เราจะวางแผนกินได้ดีกว่าเดิมเยอะ
การลด spike อินซูลินด้วยไฟเบอร์หรือ ACV เป็นวิธี ช่วยผ่อนแรง ให้ร่างกาย แต่ไม่ใช่การ “ลดปริมาณน้ำตาลที่เข้าสู่ร่างกาย” น้ำตาลยังคงเข้าเท่าเดิม และถ้าทำแบบนี้ทุกวัน ทุกมื้อ ก็เหมือนเปิดผับรับวัยรุ่นทุกคืน ต่อให้เข้าช้า แต่ก็ยังเข้าครบอยู่ดี
ถ้าอยากมีสุขภาพดีจริง ๆ ไม่ใช่แค่ใส่การ์ดคอยคุม แต่ต้องคัดตั้งแต่ต้นซอยเลยว่าซอยนี้เข้าได้แค่ไหนตั้งแต่แรก ถ้าแข็งแรงซอยใหญ่แบบทองหล่อทั้งซอย ก็รับนักเที่ยวได้มาก ถ้าป่วย ซอยเล็กแบบซอยแจ่มจันทร์ ก็รับนักเที่ยวได้น้อย ระหว่างนี้ถ้าอยากจะขยายซอยเปิดรับนักเที่ยว คุณจะคุมสารอาหาร ออกกำลังกาย ตากแดด พักผ่อน ยังไงก็เรื่องของคุณแล้ว เลือกตามจริต
เลือกกินแบบรู้ต้นทาง... อินซูลินจะได้พัก ร่างกายจะได้หายใจและสุขภาพเราจะได้แข็งแรงแบบไม่ต้องเหนื่อยกับการควบคุมทีละมื้อทุกวัน และจงจำไว้เสมอว่า ร่างกายนั้นเป็นความสัมพันธ์อันลึกล้ำพัวพันยิ่งกว่า threesome หลายเท่าตัว ยิ่งศึกษาจะยิ่งรู้ว่า การมองเพียงจุดใดจุดหนึ่งคือความผิดพลาดแบบไม่รู้ตัวได้ง่ายๆเลยครับ ดังนั้นจึงเห็นว่า เราควรแยกเรื่องของการ "ลดการ spike" ออกจาก "ลดปริมาณน้ำตาลเข้าร่าง" เพราะมันแค่ชะลอแต่ไม่ได้ทำให้ที่กินเข้าไปหายไปไหน
ร่างกายมันเก่งนะครับ คุณคิดว่าลักไก่มันง่ายขนาดนั้นเลยเหรอ
พักเรื่องน้ำมันไว้วันนึง พอดีมีคนถามต่อเนื่องมาจาก ACV #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูกแค่ลดการ spike แต่ไม่ได้หายไปไหน เฮียขอเล่าเรื่องผับ... ไม่ใช่ผับที่มีไฟสลัว ๆ เสียงเบสแน่น ๆ หรอกนะ แต่เป็น “ผับร่างกาย” ที่เปิดประตูรับแขกชื่อ “น้ำตาล” เข้าไปทุกวันแบบไม่รู้ตัว
ในโลกของสุขภาพ น้ำตาลก็เหมือนวัยรุ่นที่ชอบเข้าไปในผับหลังมืดค่ำทุกคืน ส่วน อินซูลิน ก็คือพีอาร์หน้าผับ มีหน้าที่เปิดประตูให้เด็กพวกนี้เข้าไปในเซลล์ พอวัยรุ่นแห่มาพร้อมกัน อินซูลินก็ต้องเร่งเปิดประตูรัว ๆ นั่นแหละที่เขาเรียกกันว่า insulin spike
หลายคนรู้ว่า spike บ่อย ๆ ไม่ดี เลยพยายามหาวิธี “ลด spike” บางคนดื่มน้ำส้มสายชูแอปเปิ้ล (ACV) บางคนกินผักใยสูงก่อนอาหาร บางคนจัดซุปใส่ไฟเบอร์แบบคุม ๆ มาเสริม เฮียบอกเลยว่า “ดี” อยู่ครับ... แต่ หลายคนเข้าใจว่า การลด spike เท่ากับการลดน้ำตาล จริง ๆ แล้วน้ำตาลไม่ได้หายไปไหนเลย มันแค่ เดินเข้าช้าลงเท่านั้นเอง
ลองนึกภาพตามนะเฮียจะเล่าให้ฟัง...เอาแบบเห็นภาพร่างนะ เปรียบเปรยเปรียบเปรย
ผับเปิด... วัยรุ่นต่อแถว ทุกครั้งที่เรากินคาร์บ โดยเฉพาะแป้งหรือของหวาน ร่างกายก็จะแปลงมันเป็นกลูโคส หรือน้ำตาลในกระแสเลือด เจ้ากลูโคสเหล่านี้ก็จะมาต่อแถวเข้า “ผับเซลล์” พอคนเยอะ อินซูลินก็ต้องออกมาทำงานหนัก พาแต่ละคนเข้าไปจัดสรรให้เรียบร้อย ทีนี้ถ้าน้ำตาลมาก และมาพร้อมกัน อินซูลินก็ต้อง “spike” คือพุ่งขึ้นเพื่อจัดการด่วน ซึ่งถ้าร่างกายทำแบบนี้บ่อย ๆ ไม่ดีเลย เพราะมันทำให้ระบบเสื่อม เกิด ภาวะดื้ออินซูลิน นึภภาพพนักงานทำงานกันแบบ ปาร์ตี้คืนวันสงกรานต์ในผับย่าน อาร์ซีเอ หรือข้าวสาร สุดท้ายก็มักนำไปสู่เบาหวาน ความอ้วน และความเสื่อมแบบค่อยเป็นค่อยไป
ACV, ไฟเบอร์ช่วยไหม? ช่วย แต่ไม่ได้ลดน้ำตาล เทคนิคกินผักก่อน กินน้ำส้มสายชู หรือเพิ่มไฟเบอร์สูง ๆ ก่อนคาร์บ มันช่วย ชะลอการดูดซึม ของน้ำตาลจริง ๆ เหมือนกับมีการ์ดหน้าผับมาตรวจบัตรก่อนเข้าทีละคน แถวมันเลยไม่กรูกันเข้าแบบม็อบ แต่มาเรื่อย ๆ ทีละคน ๆ พีอาร์หน้าประตูก็จัดการระบบได้เบาแรงขึ้น
ฟังดูดีใช่ไหม? ใช่... แต่ ไม่ได้แปลว่าวัยรุ่นเหล่านั้นจะไม่เข้าผับ สุดท้าย พวกเขาก็เข้าไปครบเหมือนเดิมอยู่ดี นั่นคือ ร่างกายก็ยังได้รับน้ำตาลเท่าเดิมนั่นแหละ ... แค่เข้าช้าลงเท่านั้น
แล้วมันดีตรงไหนล่ะ ถ้ามันไม่ได้ลดน้ำตาล? มันดีตรงที่ spike จะไม่พุ่งเร็ว พอชะลอได้ อินซูลินก็ไม่ต้องทำงานแบบโหม ซึ่งในระยะสั้น มันช่วยให้ระดับน้ำตาลในเลือดไม่แกว่งจัดเกินไป ดีต่อสมอง ไม่ทำให้ง่วงหลังมื้ออาหาร
แต่ถ้าเรายังเลือกกินอาหารที่แปลงเป็นน้ำตาลเยอะ ๆ อยู่ดี แม้จะกินช้าลง ยังไงน้ำตาลก็สะสม เหมือนวัยรุ่นที่เข้าผับช้าลง แต่จำนวนก็เท่าเดิม เฮียว่าเราควรหันมาถามตัวเองว่า...
แล้วเราจะเปิดผับให้ใครบ้างดีล่ะ? การจัดการ spike ที่ดีที่สุดไม่ใช่แค่ “ชะลอ” แต่คือ “ลดปริมาณกลูโคสตั้งแต่ต้นทาง” เลือกกินของที่ไม่สร้างน้ำตาลพรึ่บพรั่บ เช่น real food ที่มีไขมันดีและโปรตีนสูง อย่างไข่ เนื้อสัตว์ เครื่องใน น้ำมันสัตว์ น้ำมันสกัดเย็นที่มีทั้งพฤกษเคมีและพลังงานที่ดี ฯลฯ ซึ่งเป็นการบริหารซอย จำกัดจำนวนนักเที่ยวแต่แรก เพราะพวกนี้ไม่พาน้ำตาลมากองหน้าประตูเหมือนขนมปังโพรเซส น้ำหวานจัดๆ หรือเค้กแป้งขัดสีน้ำตาลครีมเยอะๆ
เห็นไหมว่า เฮียไม่ได้บอกให้เลิกกินของอร่อยเลยนะ แต่จะบอกว่า... ถ้าเราเข้าใจว่า การลด spike ไม่ใช่การลดน้ำตาล เราจะวางแผนกินได้ดีกว่าเดิมเยอะ
การลด spike อินซูลินด้วยไฟเบอร์หรือ ACV เป็นวิธี ช่วยผ่อนแรง ให้ร่างกาย แต่ไม่ใช่การ “ลดปริมาณน้ำตาลที่เข้าสู่ร่างกาย” น้ำตาลยังคงเข้าเท่าเดิม และถ้าทำแบบนี้ทุกวัน ทุกมื้อ ก็เหมือนเปิดผับรับวัยรุ่นทุกคืน ต่อให้เข้าช้า แต่ก็ยังเข้าครบอยู่ดี
ถ้าอยากมีสุขภาพดีจริง ๆ ไม่ใช่แค่ใส่การ์ดคอยคุม แต่ต้องคัดตั้งแต่ต้นซอยเลยว่าซอยนี้เข้าได้แค่ไหนตั้งแต่แรก ถ้าแข็งแรงซอยใหญ่แบบทองหล่อทั้งซอย ก็รับนักเที่ยวได้มาก ถ้าป่วย ซอยเล็กแบบซอยแจ่มจันทร์ ก็รับนักเที่ยวได้น้อย ระหว่างนี้ถ้าอยากจะขยายซอยเปิดรับนักเที่ยว คุณจะคุมสารอาหาร ออกกำลังกาย ตากแดด พักผ่อน ยังไงก็เรื่องของคุณแล้ว เลือกตามจริต
เลือกกินแบบรู้ต้นทาง... อินซูลินจะได้พัก ร่างกายจะได้หายใจและสุขภาพเราจะได้แข็งแรงแบบไม่ต้องเหนื่อยกับการควบคุมทีละมื้อทุกวัน และจงจำไว้เสมอว่า ร่างกายนั้นเป็นความสัมพันธ์อันลึกล้ำพัวพันยิ่งกว่า threesome หลายเท่าตัว ยิ่งศึกษาจะยิ่งรู้ว่า การมองเพียงจุดใดจุดหนึ่งคือความผิดพลาดแบบไม่รู้ตัวได้ง่ายๆเลยครับ ดังนั้นจึงเห็นว่า เราควรแยกเรื่องของการ "ลดการ spike" ออกจาก "ลดปริมาณน้ำตาลเข้าร่าง" เพราะมันแค่ชะลอแต่ไม่ได้ทำให้ที่กินเข้าไปหายไปไหน
ร่างกายมันเก่งนะครับ คุณคิดว่าลักไก่มันง่ายขนาดนั้นเลยเหรอ
พักเรื่องน้ำมันไว้วันนึง พอดีมีคนถามต่อเนื่องมาจาก ACV #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ f7d424b5:618c51e8
2025-05-04 19:19:43
@ f7d424b5:618c51e8
2025-05-04 19:19:43Listen to the new episode here!
Finally some good news. Good new games, worthwhile remakes, and bloggers facing the consequences of their actions. Gaming is healing. Let's talk about it!
Stuff cited:
Obligatory:
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ 526bec6a:07c68d13
2025-05-05 08:06:09
@ 526bec6a:07c68d13
2025-05-05 08:06:09Let’s talk about a straightforward betting strategy that’s been around for years, often used by folks who treat horse racing more like a business than a gamble. This method is all about following a clear staking plan to aim for a small, consistent profit per race—without needing to be a racing expert. I’ll break it down step-by-step so it’s easy to understand, even if you’re new to this! The Goal: Small, Steady Wins The idea here is to aim for a target profit (T) of 5 points per race. Think of a "point" as a unit of money you decide on—it could be $50, $1, or whatever you’re comfortable with. For example, I use a starting bank of $200, and I set each point at $1. So, 5 points = $5 profit per race. Important Rule: Once you pick the value of a point, stick with it throughout the entire betting sequence. Don’t change it, no matter what happens! Why This Works (Even If You Know Nothing About Racing) This plan is designed so that you’ll eventually win, even if you’re clueless about horses. The catch? You need to be patient and okay with small profits per point because the stakes (the amount you bet) can grow after each loss. For example: If you set each point at £1 and lose 10 races in a row, your 11th bet would need to recover $55 (your target plus losses). If you set each point at 25p, you’d only need to recover $13.75 after 10 losses. See the difference? Lower point values mean smaller risks, but also smaller profits. Pick a point value that matches the risk you’re willing to take and the profit you want to make. How the Staking Plan Works Here’s the basic idea: you start with a target profit of 5 points per race. If you lose, you add your loss to the next race’s target. If you win, you subtract your gain. The goal is to keep going until you hit your total profit target, then start over. Let’s break down the key terms: T (Target): Your profit goal for the race (starts at 5 points). T + L: Your target plus any losses from previous races (or minus any gains if you won). S (Stake): How much you bet on the race. R (Result): Whether you won (e.g., 2-1 means the horse paid 2-to-1 odds) or lost (L). W (Points Won): How many points you gained from a win. L (Points Lost): How many points you lost from a bet. AWL (Running Total): Your accumulated wins and losses over the sequence. Once you reach your overall profit goal (like 40 points in the example below), you take your winnings and start the sequence over with a 5-point target. Example Sequence: Watch It in Action Here’s a sample sequence to show how this plays out. I’m using a 1-per-point value for simplicity:What happened here? In Race 1, I aimed for 5 points but lost my 2-point stake, so my running total is -2. In Race 2, I added my loss (2) to the new target (10), so I’m aiming for 12 points. I lost again, so my running total drops to -6. By Race 8, I finally hit a big win (4-1 odds), gaining 44 points. My running total jumps to +50, which exceeds my overall target of 40 points. I take my profit ($50 if each point is $1) and start over in Race 9 with a 5-point target. How to Calculate Your Stake To figure out how much to bet (your stake), take your T + L (target plus losses) and divide by 3, rounding to the nearest whole number. Why 3? Because you want to bet on horses with odds of 3-1 or higher. A win at those odds will cover all your losses and give you your target profit. For example: In Race 4, my T + L is 33. Divide by 3: 33 ÷ 3 = 11. So, I bet 11 points. My horse wins at 2-1 odds, so I get 22 points back (11 × 2). This clears my losses and gives me a profit. Pro Tip: Stick to odds of evens (1-1) or higher. Many pros avoid “odds-on” bets (like 1-2) because they don’t pay enough to make this system work well. Tips to Make This Work for You Pick Your Races Wisely: You don’t have to bet on every race. Some pros bet on every race at a meeting (e.g., 6 races a day, 36 bets a week), but I recommend being selective. Consider using a professional tipping service for better picks—newspaper tips can be risky (one “expert” once picked 30 losers in a row!). Spread Your Bets: Use 3 or 4 different bookmakers. No single bookie will be happy if you keep winning over time. Account for Betting Tax (If Applicable): If there’s a tax on your bets, add it to your next race’s target. This way, the system covers the tax for you. Be Prepared for Losing Streaks: Even with careful picks, you might hit a string of losses. That’s why you keep your point value low—so your stakes don’t balloon too much. Why This Is a “Business,” Not Gambling People who use this method don’t see it as gambling—they treat racing like a business. The key is patience and discipline. A single win at 3-1 odds or higher will wipe out all your losses and deliver your target profit. It’s a slow grind, but it’s designed to keep you in the game long-term. Final Thoughts This staking plan is all about consistency and managing risk. Start with a small bank (like $200), set a point value you’re comfortable with (like 50 or 1), and stick to the rules. You don’t need to be a racing genius—just follow the system, bet smart, and wait for that big win to clear your slate and put profit in your pocket. Got questions or want to tweak this for your own style? Let me know, and I’ll help you fine-tune your approach! Happy betting!
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ 005bc4de:ef11e1a2
2025-05-05 07:31:15
@ 005bc4de:ef11e1a2
2025-05-05 07:31:15How does MSTR buy bitcoin without bumping the price?
Michael Saylor buys bitcoin and he has a handy tool to track his purchases, at, well, https://saylortracker.com
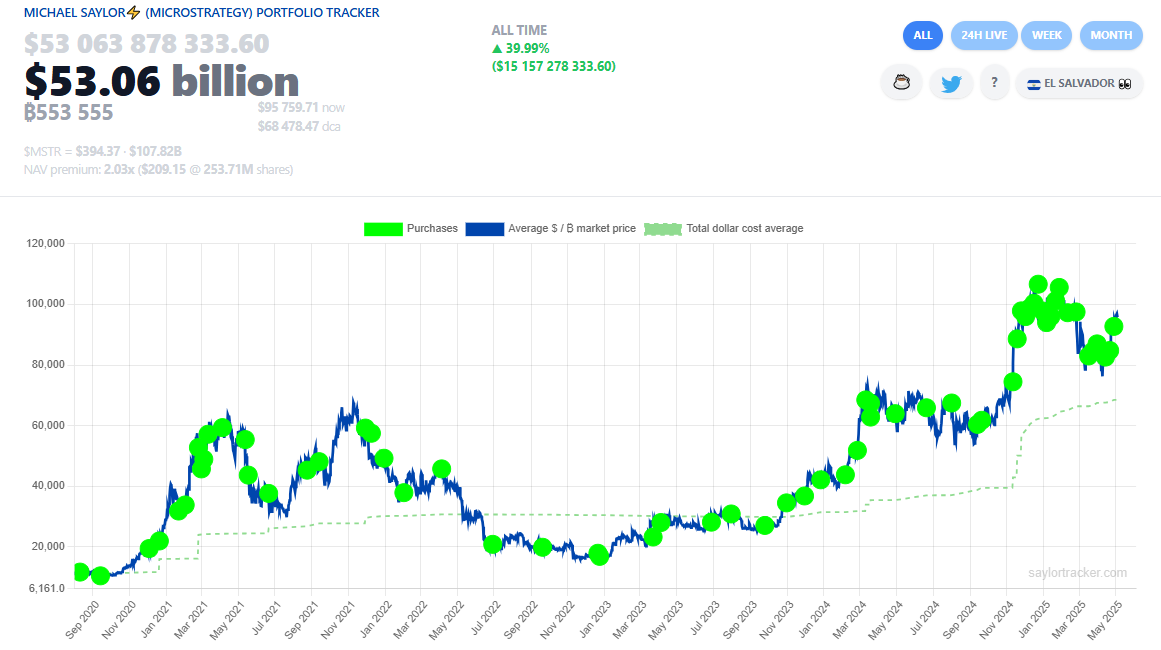
Mondays have been Saylor's buy-days, and rumors are that he may be at it again.
Yet, with all the mega-buying, why does it seem like the price doesn't jump? This is a question that comes to my mind seemingly each week now with the next MSTR buy.
Grok AI seems to imply that even though Saylor's purchases are huge, they're still not big enough to move the market. Average daily volume traded for BTC seems to be in the $15 billion upwards to $60 billion. So, Saylor's 1 to 2 or 4 billion dollar purchases evidently still aren't enough to eat up the order book.
This is a little hard to swallow considering that Grok estimated, "MicroStrategy owns approximately 2.81% of all Bitcoin in circulation and 2.64% of the total Bitcoin supply that will ever exist." I guess that other 97% is just moving their bitcoin around, back-and-forth?
The standard answer I've heard as to why the market doesn't move has been, "Oh, MSTR buys bitcoin over-the-counter, not off of exchanges where the prices come from."
That's a simple elevator-ride one sentence answer that seems plausible. I could meet someone on the street and say, "Hey, you got any bitcoin and do you wanna sell it?" If they said, "Yeah, and sure," then I could hand them some cash and they could send some BTC to me. The exchanges would be unmoved by this over the counter transaction.
Or, I might be interested in buying a Beanie Babie tie-dyed PEACE bear. The market, ebay, seems to list them around $8.99. But, if I buy a hundred of them off that bitcoin guy on the sidewalk, ebay and the price their isn't affected at all. Not are the 79 "watchers" keeping an eye on the PEACE bear.
But still, to me, that one-line OTC answer somehow seems off. Seriously, does Saylor have connections with people who want to sell thousands or tens of thousands of bitcoin? Every week? Who are these people with all that bitcoin to sell? Can Saylor connect me to a seller of 100 tie-dyed PEACE bears?
Maybe Saylor actually does have those kinds of connections to make those kinds of purchases. Or, maybe Grok is right and Saylor's moves aren't as big-fish as they seem. Anyway, I don't know, and those are circles that I don't move in. And, after all, I guess I still really don't know how he buys so much without moving the market.
!HBIT
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ 502ab02a:a2860397
2025-05-05 03:39:58
@ 502ab02a:a2860397
2025-05-05 03:39:58โครงการ “Meat Free Monday” หรือ “จันทร์ไร้เนื้อ” เริ่มต้นในปี 2009 โดยพอล แมคคาร์ทนีย์และลูกสาวสองคนของเขา มีเป้าหมายในการลดการบริโภคเนื้อสัตว์เพื่อสุขภาพของมนุษย์และสุขภาพของโลกอย่างน้อยสัปดาห์ละหนึ่งวัน โดยอ้างถึงเหตุผลด้านสุขภาพและสโครงการ “Meat Free Monday” หรือ “จันทร์ไร้เนื้อ” เริ่มต้นในปี 2009 โดยพอล แมคคาร์ทนีย์และลูกสาวสองคนของเขา มีเป้าหมายในการลดการบริโภคเนื้อสัตว์เพื่อสุขภาพของมนุษย์และสุขภาพของโลกอย่างน้อยสัปดาห์ละหนึ่งวัน โดยอ้างถึงเหตุผลด้านสุขภาพและสิ่งแวดล้อม
https://youtu.be/ulVFWJqXNg0?si=eMs-CxtPE1kjljLD เซอร์พอล แมคคาร์ทนีย์ได้ผลิตภาพยนตร์สั้นเรื่อง "One Day a Week" เพื่อส่งเสริมโครงการ MFM โดยเน้นถึงผลกระทบของการบริโภคเนื้อสัตว์ต่อสิ่งแวดล้อมและสุขภาพของมนุษย์ ภาพยนตร์นี้มีการปรากฏตัวของบุคคลที่มีชื่อเสียง เช่น วูดี้ ฮาร์เรลสัน และเอ็มมา สโตน
MFM ได้รับการสนับสนุนจากโรงเรียนมากกว่า 3,000 แห่งในสหราชอาณาจักร รวมถึงหน่วยงานการศึกษาท้องถิ่น เช่น เอดินบะระและทราฟฟอร์ด โดยมีการจัดทำชุดข้อมูลสำหรับโรงเรียนเพื่อส่งเสริมให้นักเรียนมีสุขภาพดีขึ้นและเป็นพลเมืองที่มีความรับผิดชอบต่อโลก แนวคิดนี้ได้รับการสนับสนุนจากองค์กรต่าง ๆ เช่น ProVeg International ซึ่งมีบทบาทในการส่งเสริมอาหารจากพืชในโรงเรียนผ่านโครงการ “School Plates” โดยให้คำปรึกษาเกี่ยวกับเมนูอาหาร คำแนะนำด้านโภชนาการ และการฝึกอบรมการทำอาหารจากพืช รวมถึงมีการสนับสนุนจากหน่วยงานท้องถิ่นและองค์กรต่างๆ ทั่วโลก เช่น เมืองเกนต์ในเบลเยียมที่มีการจัดวันพฤหัสบดีปลอดเนื้อสัตว์อย่างเป็นทางการ และเมืองเซาเปาโลในบราซิลที่มีการสนับสนุนจากสมาคมมังสวิรัติของบราซิล
อย่างไรก็ตาม มีข้อกังวลเกี่ยวกับการแทรกแซงขององค์กรเหล่านี้ในระบบการศึกษา โดยเฉพาะในโรงเรียนระดับ K-12 ที่มีการนำเสนออาหารจากพืชในวันจันทร์ โดยอ้างถึงประโยชน์ด้านสุขภาพและสิ่งแวดล้อม การดำเนินการดังกล่าวอาจส่งผลต่อการรับรู้ของเด็ก ๆ เกี่ยวกับเนื้อสัตว์ และอาจนำไปสู่การเปลี่ยนแปลงพฤติกรรมการบริโภคในระยะยาว
นอกจากนี้ ยังมีการวิพากษ์วิจารณ์เกี่ยวกับการใช้คำว่า “Meat Free” ซึ่งอาจสื่อถึงการขาดบางสิ่งบางอย่าง ProVeg UK แนะนำให้หลีกเลี่ยงการใช้คำนี้และใช้คำอื่นที่เน้นถึงความเป็นมิตรกับสิ่งแวดล้อมแทน
ในขณะที่การส่งเสริมการบริโภคอาหารจากพืชมีข้อดีในด้านสุขภาพและสิ่งแวดล้อม แต่การดำเนินการที่มีลักษณะเป็นการบังคับหรือแทรกแซงในระบบการศึกษาโดยไม่มีการให้ข้อมูลที่ครบถ้วนและเป็นกลาง อาจนำไปสู่การล้างสมองและการเปลี่ยนแปลงพฤติกรรมการบริโภคโดยไม่รู้ตัว ดังนั้น การส่งเสริมการบริโภคอาหารจากพืชควรเป็นไปอย่างโปร่งใส ให้ข้อมูลที่ครบถ้วน และเคารพสิทธิ์ในการเลือกของแต่ละบุคคล โดยเฉพาะในกลุ่มเด็กและเยาวชน
ProVeg UK ได้เสนอให้เปลี่ยนชื่อจาก “Meat-Free Monday” เป็น “Planet-Friendly Days” โดยให้เหตุผลว่าคำว่า “Meat-Free” อาจสื่อถึงการขาดบางสิ่งบางอย่าง และอาจทำให้ผู้บริโภคมองว่าเมนูดังกล่าวไม่น่าสนใจ การใช้คำว่า “Planet-Friendly” ช่วยเน้นถึงความเป็นมิตรกับสิ่งแวดล้อมและส่งเสริมการบริโภคอาหารจากพืชในแง่บวกมากขึ้น
นอกจากนี้ทาง ProVeg UK ดำเนินโครงการ “School Plates” เพื่อช่วยโรงเรียนในการปรับปรุงเมนูอาหารให้มีความยั่งยืนมากขึ้น โดยให้คำปรึกษาเกี่ยวกับเมนูอาหาร คำแนะนำด้านโภชนาการ และการฝึกอบรมการทำอาหารจากพืช นอกจากนี้ยังมีการจัดกิจกรรมเสริม เช่น การแข่งขันออกแบบโปสเตอร์และชั้นเรียนทำอาหารจากพืช เพื่อส่งเสริมการเรียนรู้เกี่ยวกับระบบอาหารและกระตุ้นให้เด็ก ๆ ลองชิมเมนูใหม่ ๆ
ในส่วนของ ProVeg International ก็ยังสนับสนุนโครงการระดับชาติ เช่น “National School Meals Week” ในปี 2020 โดยให้คำแนะนำแก่โรงเรียนในการจัดเมนูอาหารที่ลดการบริโภคเนื้อสัตว์ และเสนอให้ใช้คำที่เน้นถึงรสชาติหรือส่วนผสมหลักของเมนู เลี่ยงการใช้คำว่า “meat-free” หรือ “vegan” ซึ่งอาจมีผลกระทบต่อการเลือกเมนูของผู้บริโภค แล้วยังมีการส่งเสริมการบริโภคอาหารจากพืชผ่านกิจกรรมต่าง ๆ เช่น “Veggie Challenge” ซึ่งเป็นโปรแกรมออนไลน์ฟรีที่สอนการทำอาหารจากพืช พร้อมให้คำแนะนำและสูตรอาหารรายวัน เพื่อช่วยให้ผู้เข้าร่วมสามารถเปลี่ยนแปลงพฤติกรรมการบริโภคได้อย่างยั่งยืน
จากข้อมูลข้างต้น แสดงให้เห็นว่า ProVeg International มีบทบาทในการส่งเสริมการบริโภคอาหารจากพืชผ่านหลายช่องทาง โดยเฉพาะในระบบการศึกษาและโครงการอาหารโรงเรียน เพื่อสนับสนุนการเปลี่ยนแปลงพฤติกรรมการบริโภคในระยะยาว
คำถามคือ ทำไมต้องเริ่มจากโรงเรียน? ก็เพราะเด็กยังไม่รู้จัก “ฟังร่างกายตัวเอง” ยังเชื่อในสิ่งที่ครู พ่อแม่ หรือคนในทีวีบอก ถ้าเด็กถูกสอนว่า “เนื้อวัวทำลายโลก” และ “ไก่ หมู คือปีศาจ” เด็กคนนั้นจะโตมาโดยมอง “ของจริง” เป็นของแปลก และมอง “ของปลอม” เป็นพระเอก
วันนี้ห้ามกินเนื้อ พรุ่งนี้อาจห้ามพูดถึงเนื้อ และวันหนึ่ง...เขาอาจห้ามเราผลิตเนื้อจริงเลยก็ได้
อย่าเข้าใจผิดว่าเฮียต่อต้านผักนะ เฮียชอบผักที่ขึ้นเองตามธรรมชาติ แต่เฮียไม่ชอบ "ผักที่มากับนโยบาย" ไม่ชอบ "จานอาหารที่ถูกกำหนดด้วยวาระซ่อนเร้น"
Meat Free Monday อาจเป็นแค่หนึ่งวันในสัปดาห์ แต่ถ้าเราไม่ตั้งคำถาม มันอาจกลายเป็นชีวิตทั้งชีวิตที่ถูกออกแบบไว้ล่วงหน้า
ที่น่าสนใจอีกอย่างนึงคือ MFM เป็นองค์กรไม่แสวงหาผลกำไรที่ดำเนินการภายใต้การสนับสนุนของ Charities Aid Foundation (หมายเลขทะเบียนการกุศล 268369) อย่างไรก็ตาม "ไม่มีข้อมูลสาธารณะเกี่ยวกับจำนวนเงินทุนหรือแหล่งเงินทุนที่เฉพาะเจาะจงที่สนับสนุนโครงการนี้"
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 57d1a264:69f1fee1
2025-05-02 06:17:05
@ 57d1a264:69f1fee1
2025-05-02 06:17:05Simple design
For as long as I remember, I’ve believed in simple design as a principle in my practice. It feels fundamental to me when I think about good design.
At the same time, I see many successful examples of complex products in the world. So I decided to ask, what value is simple design really providing me and my work?
Is it nostalgia?
I sometimes wonder if simple design is rooted in nostalgia. An example I like to use is:
Imagine yourself in the year 1981. You just purchased a brand new desk calculator. You are excited because you should be able to do any type of paperwork calculations you can imagine on it.
As you start to use it for the first time, it immediately prompts you to update its software. After using it for a few calculations, it asks you to fill out a survey about your experience. One day in the middle of adding up your checkbook, it interrupts you to tell you about a new leather-bound desk calendar the company just released. Sometimes in the middle of a complex calculation, the calculator will lag and crash. You have to restart it often to fix the issue.
I have a feeling that a person in 1981 would think this is a terrible calculator. They purchased the device to perform their calculations, nothing more. Why is it requiring so much more of their attention and effort?
Focus
I think simple design often refers to a focused product. A product that does a specific task can sometimes do that task really well. Products that try to do many things can offer a lot of value, but rarely do all the things well.
Some people prefer to use specific tools for specific tasks. Others prefer a wide variety of features.
I think the benefits of using fewer products are often a major reason complex products are successful. They may not be focused, they might be lower quality as a result, but people can use them for a wide variety of applications.
You can open a can of beans with a Swiss Army Knife — it will get the job done.
Art and subjectivity
Maybe simple design is valuable for intangible reasons. There is an art to simplicity. There is a beauty to simplicity.
A user can see more of the product's intentionality. The creator chose to leave certain features out. They decided what to include. The product likely exudes more vision and personality.
That might be unnoticed by some, but very valuable to others who care about craft. People who value the experience as much as the result.
Ease of use
I think a true benefit of simple design is the effect it has on ease of use. The less things there are to do in a product, the more obvious the things you can do become.
A simple product requires less of a user. That means a user can stay focused on their own needs and use the product in ways they define. They will encounter boundaries which limit them. These limitations could drive some away, but some might be engaged to find new and creative ways of working.
When to abandon simple design
I think the sad news is simple design is ultimately a limiting factor of a product's growth. I think there are many examples of this throughout the course of history (i.e. Ello vs Facebook, Rdio vs Spotify, Simplenote vs Notion, VSCO vs Instagram, Clear vs Things, Peach vs Twitter, etc). At the same time, I think 'simple design' does provide an entry point to successfully define what a product is.
The biggest challenge is continuing to evoke the benefits of simple design in an established product, while allowing a product to evolve and grow to meet its users' needs. That is a balancing act that very few products have ever achieved, but feels like an ideal that successful products should strive for.
One of Charlie Deets Writings
originally posted at https://stacker.news/items/969089
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ df478568:2a951e67
2025-05-04 20:45:59
@ df478568:2a951e67
2025-05-04 20:45:59So I've worked on this cashu cards idea for a few thousand blocks. The plan is to sell them, while also keeping them open source. I had many of these ideas swarming around in my head for tens of thousands of blocks and fighting with doubt. That's the ultimate final boss. We, bitcoiners have the power to use bitcoin as a
- Store of value
- Medium of exchange
- Unit of account.
Nostr gives us the power to speak feeely. That's an often underlooked aspect of this new protocol. Bitcoin is great for sending value, but it's not tue most efficient way to communicate. There are ways to add messages to the base-chain, but that's not robust enough to build a marketplace. The marketplace consists of people speaking and exchanging value. Nostr provides us this value.
Since we are free to communicate witout censorship on nostr, we are free to use the protocol for almost anything we can imagine. It's a public space without communication restrictions and information verification system with a web of trust and active development. Think of all the bitcoin merch on Etsy. There are posters, T-shirts, coffee cups and more sold on the government/corporate controlled Internet.I'm selling merch on nostr to show them how to sell merch on nostr.
Birthday Cards And Other Stuff
 @ 57d1a264:69f1fee1
2025-05-02 06:04:19
@ 57d1a264:69f1fee1
2025-05-02 06:04:19After being featured in the NY Times and WSJ, New York City officially opens a major addition to Central Park, the Davis Center at the Harlem Meer. Designed by architect Susan T Rodriguez in collaboration with Mitchell Giurgola, the renovation project replaces the old Lasker Rink and pool with a recreational facility that’s built directly into the landscape, restoring nature, reconnecting paths, and creating a year-round space for community activity. At the heart of the new design is a transformative water feature that shifts with the seasons, from a skating rink in winter to a lush green lawn in spring and fall and a pool in the summer.
The center’s new oval-shaped pool sits lower than the old one, surrounded by a gently sloped grassy berm. In winter, the pool becomes an ice-skating rink, making the site a destination in every season. A splash pad at the end of the water feature offers extra water play in the summer. By integrating the design into the natural shape of the land, the architects were able to open up the space around the pool and allow the landscape to flow around it, resulting in a setting that feels like it’s always been there.
Sustainability was a core part of the project. The building is expected to earn LEED Gold certification, thanks to features like passive ventilation, locally sourced stone and wood, energy-efficient systems, and a roof that absorbs rainwater. Bird-safe glass helps protect local wildlife, and recycled materials from the old building were reused during construction. Even more important, the new center supports free and low-cost programming year-round, including education, nature walks, community events, and recreation. It’s designed to welcome all kinds of visitors—from families and school groups to joggers, birdwatchers, and casual parkgoers.
Continue reading: https://www.designboom.com/architecture/giant-pool-new-york-central-park-new-davis-center-susan-t-rodriguez-mitchell-giurgola-04-24-2025/
originally posted at https://stacker.news/items/969086
-
 @ 6830c409:ff17c655
2025-05-04 20:23:30
@ 6830c409:ff17c655
2025-05-04 20:23:30Disclaimer: No artificial intelligence tool has been used to write this article except Grammarly.
There are some things that no one* wants to talk about in a public forum. One of those things is how we clean ourselves after using the toilet. Being a South Asian, I find the bathroom etiquette a bit different from where I am now- in the US. I don't think it is something we have to keep mum about.
[*Mostly]
Earlier, I had read a "Quora WAR" where there was a fierce fight between fellow Western country people vs Indians. Indians advocated using water and the West despised that and advocated using dry wipes/toilet paper. Recently (Yesterday), I remembered this Quora debate and I was curious, when was the commercial production of toilet tissues started? And what were the hygiene methods followed before that.
Obviously, My reading started with Wikipedia. And from there, it was a rabbit-hole. I don't know how, I kept on reading for almost 2 hours. And this piece is out of my understanding of things I read during that mere 2 hours.
We take it for granted today, but toilet paper has a fascinating story spanning thousands of years. From creative ancient solutions to the modern perforated roll, humanity's quest for comfort and cleanliness reveals surprising ingenuity.
Time Before Toilet Paper
Historically, people used whatever they had in their habitat, to clean themselves. This varied from grass, leaves, tree barks, etc. And yes, many civilizations insisted and used water as the main cleaning method. But this was mainly based on the availability of clean water.
Wherever the availability of water was in question, people got creative! Ancient Romans used "tersorium"- basically it is a sea sponge on a stick. They sock it in vinegar or salt water between uses. These were communal.
Greeks preferred smooth pottery fragments with rounded edges. Of course, no one wanted the other end of the digestive tract injured! :D
Early Chinese civilizations wrapped cloth around wooden sticks shaped like spatulas.
Medieval Europeans show their class divisions even in the bathroom! The wealthy used wool, hemp, or even lace. While commoners made do with whatever cloth they had- sometimes, their own sleeves (- today, YUCK!). In the 1700s rural Americas, people turned to nature, using corncobs and seashells.
No matter what we think about these methods, every civilization and every class of people in those valued one thing - Cleanliness.
True Toilet Paper Pioneers
We all know China invented paper somewhere near 100 AD. By the 6th century, Emporer Yandgi's court records show that he used 15,000 sheets of paper annually, just for his personal hygiene!
Early Chinese toilet papers were made from rice straw, hemp, and bamboo. They boiled the material, churned it into a pulp, flattened and dry it, and then cut into shape before using it. By 14th century, the imperial court enjoyed "Perfumed paper sheets". Records show that the royal family alone used almost 0.75 million sheets yearly!!
However, not everyone was happy with this invention. Traveling Muslim merchants described the Chinese practice as "Haraam" (foul), they always preferred using water.
The West Catches Up
Western toilet paper development took longer. Sir John Harrington invented the flushing toilet in 1596, though it would not become common for centuries. By the 1700s, newspapers became a popular bathroom staple.
The commercial breakthrough came only in 1857 when American entrepreneur Joseph Gayetty found a way for the commercial production of toilet papers. But at that time it was sold in another name - "Medicated Paper for Water-Closet". He sold it 500 sheets for 50 cents. Only then the use of "Toilet papers" really arrived in the West.
Rolling into Modern Era
Later in the 19th century, manufacturers found the best and most economical way to produce and store toilet paper - as "Rolls" like we see today. Seth Wheeler of Albany patented perforated wrapping paper in 1871. and the first modern perforated toilet paper roll came out in 1891, making the "tearing" much easier - literally and figuratively! :D
That was the same time home plumbing was improving a lot which resulted in having the toilets inside the home itself. With that, the consumption of toilet paper rose - first as a vanity symbol and later as a common addition to the shopping list.
Big Business in Bathrooms
Brothers - Clarence and Edward Irvin Scott founded Scott Paper Company in Philadelphia in 1879, initially cutting and packaging toilet paper for retailers to sell under their brands. The company grew after 1896 when Arthur Hoyt Scott joined. They started mass-producing their brand of toilet paper. By 1910, they had built the largest paper mill in Chester, marking the industrialization of toilet paper production.
Meanwhile, that old paper made of concoction in China became popular there by the 16th century.
From Luxury to Necessity
We humans always run behind an unknown "comfort". The story of toilet paper is also not so different from that. Imagine using the pottery fragments in place of that "plush quilted ultra-soft scented bathroom tissues". This everyday item we rarely think about represents centuries of innovation and cultural evolution.
Next time you pull a pack of tissue papers from the back aisle of Costco, spare a "thanks" for your ancestors and their corncobs, sea sponges, and pottery fragments.
And maybe soon, you might be "Zapping" to buy tissue papers.
Final Thoughts
The COVID-19 pandemic time gave us some lessons as well as some "FailArmy" videos. One of those videos was people fighting over the last available toilet paper pack in some shop. After the pandemic, there has been a surge in American homes installing Bidet faucets in their bathrooms. A bit late, but the West is now catching up again with the East! :D
Let me know if you liked this article - leave a reaction/comment. Cheers.
-
 @ 866e0139:6a9334e5
2025-05-05 06:18:34
@ 866e0139:6a9334e5
2025-05-05 06:18:34\ \ Autor: Marcel Bühler. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
"Die Ausrufung des Notstands ist der Notstand. Er eröffnet die Möglichkeit eines Endes der Rechtsstaatlichkeit"
Prof. em. Richard K. Sherwin NY Law School
Die von Präsident Donald Trump initiierten Friedensbemühungen zur Beendigung des russisch-ukrainischen Krieges scheinen keinen Erfolg zu bringen. Während Russland darauf beharrt, dass die im Herbst 2022 offiziell in die Russische Föderation aufgenommenenRegionen Lugansk, Donezk, Saporoschje und Cherson von der ukrainischen Armee vollständig geräumt werden, will Präsident Selenskij nicht einmal auf die Krim verzichten und deren Zugehörigkeit zu Russland seit 2014 anerkennen.
Während die Ukraine Sicherheitsgarantien für die Zeit nach einem möglichen Waffenstillstand bzw. Friedensabkommen fordert, besteht Russland weiterhin auf einer weitgehenden Demilitarisierung der ukrainischen Armee und besonders ein Verbot aller ultranationalen bzw. nazistischen Einheiten welche vor allem in der ukrainischen Nationalgarde konzentriert sind.
Nur ein Rohstoffdeal zwischen Washington und Kiew ist offenbar zustande gekommen, da Trump für die vielen Milliarden Dollar, welche in den letzten Jahren in die Ukraine "investiert" wurden, eine Gegenleistung bekommen möchte (nach dem "Ukraine Democracy Defense Lend-Lease Act" vom 19.1.2022 welcher von Präsident Biden am 9.5.2022 unterzeichnet wurde).
Im Rahmen einer Armeereform ist die Ukrainische Nationalgarde auf Anfang April 2025 in 2 Armeekorps mit je fünf Brigaden aufgeteilt worden: das erste Armeekorps wird von der 12. Brigade "Asow", das zweite Armeekorps von der 13. Brigade "Chartia" angeführt welche ursprünglich aus Freiwilligenbataillonen hervorgingen. Insgesamt dürfte es sich bei den 10 Brigaden um ca. 40'000 Mann handeln. Hier eine kurze Selbstdarstellung der Nationalgarde, in der auch der Kommandant, Alexander Pivnenko, zu Wort kommt (leider nur auf ukrainisch):
https://www.youtube.com/watch?v=0fjc6QHumcY
Alexander Syrskij, der aktuelle ukrainische Oberfehlshaber, hat kürzlich den Befehl erlassen, dass die mehr als 100'000 Mann der von der Bevölkerung gefürchteten Rekrutierungstruppe "TZK" ("Територіальний центр комплектування та соціальної підтримки") nun ebenfalls als Kampftruppen an die Front müssen, da die Mobilisierung weiterer ukrainischer Männer weitgehend gescheitert sei. Gleichzeitig wird über die Senkung des Mobilisierungsalters auf 18 Jahre und ein möglicher Einzug von Frauen diskutiert (die bereits als Freiwillige mitkämpfen).

Für die Zeit um den 9. Mai ("Tag des Sieges") hat Russland einen weiteren einseitigen Waffenstillstand ausgerufen, den die Ukrainer vermutlich wie an Ostern für Gegenangriffe an der Front oder Provokationen in Russland (z.B. Anschläge oder Drohnenangriffe in/auf Moskau nutzen werden). Über die Osterfeiertage hatten sich beide Seiten wie üblich gegenseitig beschuldigt, die verkündete Waffenruhe wiederholt gebrochen zu haben.
Die Kämpfe und die Opferung von Abertausenden dürften also bis auf weiteres weitergehen, auch wenn sie den Kriegsverlauf nicht mehr entscheidend ändern werden. Die Verlustrate beträgt aktuell ca. 1:10 zuungunsten der Ukrainer, da die Russen mittlerweile bei allen Waffensystemen überlegen sind, nicht nur bei der Artillerie und der Luftwaffe sondern auch im Bereich der Drohnen und der elektronischen Kriegsführung.
Wie es dazu kommen konnte, dass die Ukraine aus einem zwar hochkorrupten, aber relativ freien Land zu einem totalitären Militärregime wurde, zeigt ein neues Video eines jungen Ukrainers aus Mariupol, der die dortigen Kämpfe im Frühjahr 2022 im Keller überlebte und es aber vorzog, dort zu bleiben und die russische Staatsbürgerschaft anzunehmen. Aus Sicherheitsgründen nennt er seinen ukrainischen Namen nicht. Seine sachliche Darstellung ist weit davon entfernt, russische oder westliche Propaganda zu sein, sondern stellt eine nüchterne und auf persönlicher Erfahrung basierende Analyse der Ereignisse in der Ukraine seit 2014 dar.
Besonders eindrücklich zeigt er mit Filmmaterial auf, wie nach dem rechtswidrigen Putsch in Kiew, welcher von den Rechtsnationalen als "Revolution der Würde" bezeichnet wird und von Kräften aus dem Westen massiv unterstützt wurde (z.B. durch US-AID), besonders die ukrainische Jugend indoktriniert und militarisiert und auf den kommenden Krieg mit Russland vorbereitet wurde. Hier muss man unwillkürlich an die HJ (Hitler Jugend) denken, deren Schicksal am Ende des 2. WK allgemein bekannt sein dürfte. Es lohnt sich, den rund 35minütigen Beitrag zweimal anzusehen, um alles richtig zu verstehen und aufzunehmen (auf englisch mit slawischem Akzent):
https://www.youtube.com/watch?v=ba_NPxVXVyc
Den 1. Mai habe ich dieses Jahr am Stand der Schweizer Friedensbewegung im Areal der ehemaligen Stadt Zürcher Kaserne verbracht und dabei auch für den neu gegründeten Verein "Bewegung für Neutralität" (BENE) geworben. Der bekannte Friedensforscher Daniele Ganser wird diesen und nächsten Monat an den grossen Schweizer Bahnhöfen eine Plakatwerbung für die immerwährende Neutralität der Schweiz starten (siehe Entwurf im Anhang).
Zu Frieden und Völkerverständigung gibt es keine Alternative, dazu gehört auch das Studium und die Analyse des ukrainischen Nationalismus und Faschismus ("Stepan Bandera Ideologie"), dessen Ursprung und Entwicklung in den letzten rund 100 Jahren bis in die heutige Zeit.
Nur die Rüstungslobby kann mit der viel zitierten "Friedensdividende" nichts anfangen!
Marcel Bühler ist freier Mitarbeiter und Rechercheur aus Zürich. Dieser Beitrag erschien zuerst in seinem Newsletter.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
\
-
 @ 57d1a264:69f1fee1
2025-05-02 05:16:39
@ 57d1a264:69f1fee1
2025-05-02 05:16:39Large Language Models (LLMs) have transformed software engineering, but their application to physical engineering domains remains underexplored. This paper evaluates LLMs' capabilities in high-powered rocketry design through RocketBench, a benchmark connecting LLMs to high-fidelity rocket simulations. We test models on two increasingly complex design tasks: target altitude optimization and precision landing challenges. Our findings reveal that while state-of-the-art LLMs demonstrate strong baseline engineering knowledge, they struggle to iterate on their designs when given simulation results and ultimately plateau below human performance levels. However, when enhanced with reinforcement learning (RL), we show that a 7B parameter model outperforms both SoTA foundation models and human experts. This research demonstrates that RL-trained LLMs can serve as effective tools for complex engineering optimization, potentially transforming engineering domains beyond software development.
PDF: https://arxiv.org/pdf/2504.19394
Source: https://arxiv.org/abs/2504.19394
originally posted at https://stacker.news/items/969083
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 000002de:c05780a7
2025-05-01 23:17:11
@ 000002de:c05780a7
2025-05-01 23:17:11A lot of typing has been done comparing various right wing figures and people like Donald Trump and Elon Mush to Fascism and Nazism. It is frankly pretty absurd at this point. I'd be with them if they were just talking about these people being authoritarians. They clearly are in many ways. I'm not a fan.
But very little is said in a "non-partisan" way about the left. This is gonna be short and is meant to peak your curiosity to go and do some research for yourself.
The economist Milton Friedman famously said.
"After the fall of communism, everybody in the world agreed that socialism was a failure. Everybody in the world, more or less, agreed that capitalism was a success. And every capitalist country in the world apparently deduced from that what the West needed was more socialism."
This was said a long time ago and it is still the case. People espouse socialist ideas without even a concern about being called out for it. The same is NOT true of fascism or even traditional American patriotism.
But many of you may not realize just how deep the rot of socialism goes. Most people agree that the USSR committed terrible acts and was a failure. Before the creation of the USSR two socialists movements fought for power and control, the Bolsheviks and Mensheviks. The primary difference between the two groups was how to bring about socialism. The Bolsheviks led by Lenin favored a more radical revolutionary force led by a small group. The Mensheviks, led by Julius Martov, preferred a larger, more democratic rise to power. They supported a more gradual rise of socialism. In October of 1917 the Bolsheviks seized power in Russia in a bloody revolution.
Even to this day there are two different minds around how to bring about socialism. In the US the Menshevik approach is the one more popular. People like Bernie and AOC are this type of socialist. But make no mistake. They want to bring about a socialist utopian society. The type of system we have seen fail time and time again.
A few years ago I heard about another socialist movement and was frankly shocked that I had never heard about it before. In 1890 Britain a group of socialists formed an organization called the Fabian Society. The Fabians were/are socialists. But they believe in gradual incrementalism to bring about socialism. So what did the do you ask? They were at the center of the founding of the Labour party in the UK. Now, you might say. Big deal. But here's the weird thing. The Fabian Society's coat of arms was literally a wolf in sheep's clothing
They sought to bring about socialism covertly through democratic processes by presenting themselves as more moderate politicians. They have worked for decades to bring about socialism in the UK. If you don't count Margret Thatcher's era they've done a pretty great job. The UK is a mess.
So what does this have to do with May Day or Labor day for that matter? Well, socialists are at the center of every labor movement and celebrations like May day. Socialist ideas have been pumped into the government textbooks in the US for decades. Teachers are instructed in Universities full of believers in this wolf in sheep's clothing movement of democratic socialism.
Socialism leads to death and poverty. I'm not here to say that the US economy is the example for what the world should do. I'm a free market guy. We live in a corporatism led economy where the state partners with corporations to screw many in the US as well as the world. But I can tell you this. Socialism would be even worse.
The famous and infamous Russian anarchist Emma Goldman upon returning from her visit to the USSR was broken hearted. She had been a supporter of the revolution, but when she saw it with her own eyes she had a change of heart.
The compassion that seems to be a part of socialism is a lie. You can't institutionalize compassion. It has to come from the people, not a system. We should care for our brothers and sisters. But WE have to do it. We can't take from one group and give to another. We can't surrender our liberties to those that say they will take care of it for us. We have to do it. Capitalism is amoral. The free market is amoral. Both require us to be moral and show the way.
I hope this sparks your interest into looking into the history around socialist movements across the globe. I don't doubt that some have good motives, but the results are disastrous for the masses.
originally posted at https://stacker.news/items/968901
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ b8af284d:f82c91dd
2025-05-05 07:05:46
@ b8af284d:f82c91dd
2025-05-05 07:05:46Vor genau 40 Jahren, unter den Kronleuchtern eines New Yorker Ballsaals, wurde das berüchtigte ‚Plaza Accord‘ unterzeichnet, das eine Finanztsunami auslöste, der den japanischen Yen in nur 16 Monaten um 46 Prozent in die Höhe trieb. Die Exporte brachen ein, und Japans beeindruckendes Wirtschaftswachstum von 5 Prozent schrumpfte zu Staub.“
Xi Jinping am 26. April 2025
Liebe Abonnenten,
2010 kam es zu einer mysteriösen Serie von Selbstmorden in der chinesischen Stadt Shenzhen. Insgesamt nahmen sich zwischen Januar und August 13 Menschen das Leben, in dem sie von Hochhäusern sprangen. Die chinesischen Medien berichteten stets über Einzelfälle. Erst ausländischen Korrespondenten gelang es, die Selbstmorde miteinander in Verbindung zu setzen: Alle waren Angestellte des Apple-Zulieferers Foxconn. Alle waren sogenannte Wanderarbeiter aus den umliegenden Provinzen. Ihr monatliches Gehalt von umgerechnet 110 Euro war auch für chinesische Verhältnisse derart niedrig, dass sie sich gezwungen sahen, Überstunden zu leisten. Trotz der viel gepriesenen chinesischen Fähigkeit 吃苦 „Bitterkeit zu essen“, erschien vielen Angestellten ihr Leben so unerträglich und ausweglos, dass sie sich das Leben nahmen.
Nach einem internationalen Shitstorm reagierte Foxconn: Man erhöhte die Gehälter um 70 bis 100 Prozent und spannte Netze in der „Foxconn-City“ auf, um weitere Selbstmorde zu verhindern.
Gegründet wurde Foxconn 1974 von Terry Gou in Taiwan unter dem Namen „Hon Hai Precision Industry“. Mit der wirtschaftlichen Öffnungspolitik der Volksrepublik expandierte Gou auf das chinesische Festland, wo er Heerscharen von billigen Arbeitskräften fand. Heute beschäftigt Foxconn mehr als eine Million Menschen und fertigt rund 70 Prozent aller iPhones weltweit.
Apple-Zulieferer Foxconn steht wie kaum ein anderes Unternehmen für den wirtschaftlichen Megatrend der vergangenen Jahrzehnte. In den USA entworfene Produkte werden in Asien gefertigt und weltweit verkauft. Komplexe Lieferketten spannen sich um den gesamten Globus. Immer neue Märkte müssen erschlossen werden, um den Rendite-Erwartungen der Anleger gerecht zu werden. Die globale Produktion wandert von Land zu Land, bis die Lohnkosten so dort stark gestiegen sind, dass es Zeit wird weiterzuziehen. Nun ist ein neuer Faktor hinzugekommen: Geopolitik.
Vor wenigen Tagen gab Apple bekannt, dass es einen großen Teil seiner iPhone-Fertigung von China nach Indien verlagern werde.
Sprich: Foxconn zieht um. Der Zulieferer betreibt Werke in Tamil Nadu und Karnataka und plant eine neue Fabrik nahe Bengaluru mit Investitionen von bis zu 2,7 Milliarden US-Dollar. Dort sind zwar die Produktionskosten rund acht Prozent höher als in China, aber Apple will so sein Ziel erreichen, 2026 alle iPhones in Indien fertigen zu lassen. Punktsieg für Trump, Vance und Bessent.
Mehr zum Thema:
Die nächsten 90 Tage
·
11. Apr.
Drei Monate hat die Welt Aufschub vor amerikanischen Zöllen bekommen, 90 Tage, in denen der Handelskrieg mit China tobt. Was Trump in dieser Zeit wirklich vorhat.
Abgekoppelt
·
1. Mai
In den vergangenen Wochen konnte man erleben, wie Bitcoin zum sicheren Hafen wurde. Wie nachhaltig ist die Entwicklung? Der Bling-Report April 2025
"Sie müssen Geld drucken"
·
13. Apr.
Fondsmanager und Investorenlegende Marc Faber über den aktuellen Aktien-Crash, Donald Trump und Gold
Ein Paid-Abo beinhaltet 4 bis 6 Artikel pro Monat (statt 2 bis 4), einen monatlichen Investment-Report samt Musterdepot, Zugang zu allen Artikeln sowie 4 Tutorials über Bitcoin, Gold, ETFs und Altcoins. Ein Test-Abo gibt es schon für sieben Euro im Monat. Bitcoin-Zahler erhalten 20% Rabatt!
Das, was im Zollkrieg zwischen den USA und China gerade stattfindet, ähnelt dem Prinzip des 2500 Jahre alten chinesischen Spiels: im Gegensatz zu Schach, wo es um das Eliminieren des gegnerischen Königs geht, ist Go subtiler. Es gibt kein direktes „Schachmatt“, sondern einen Wettstreit um Raum und Einfluss. Verbündete werden gesucht, um den jeweiligen Gegner zu entwaffnen, bevor es zu einer entscheidenden Schlacht überhaupt kommen kann.
90 Tage Aufschub hat Donald Trump allen Handelspartnern gewährt - bis auf China. Zuvor hatte er am „Liberation Day“ Zölle auf nahezu alle Ländern erhoben, mit denen die USA ein Handelsdefizit aufweisen. Ob hinter der Schaukelpolitik Kalkül steckt, oder ob ihm besonnenere Gemüter in der Regierung dazu geraten haben, nachdem der amerikanische Aktienmarkt in den Keller gerauscht war, bleibt offen für Spekulationen. Auf jeden Fall bleiben den beiden größten Volkswirtschaften der Welt nun noch etwas über zwei Monate, möglichst viele Verbündete zu finden, um den Gegner zu isolieren. „Wir können wahrscheinlich mit unseren Verbündeten einen Deal erreichen“, sagte Finanzminister Scott Bessent. „Und dann können wir gemeinsam als Gruppe auf China zugehen.“ Die USA haben an und für sich viele Argumente auf ihrer Seite:
Hinter der Paywall: Wer hat die besseren Chancen, das Spiel zu gewinnen?
-
 @ dab6c606:51f507b6
2025-04-18 14:59:25
@ dab6c606:51f507b6
2025-04-18 14:59:25Core idea: Use geotagged anonymized Nostr events with Cashu-based points to snitch on cop locations for a more relaxed driving and walking
We all know navigation apps. There's one of them that allows you to report on locations of cops. It's Waze and it's owned by Google. There are perfectly fine navigation apps like Organic Maps, that unfortunately lack the cop-snitching features. In some countries, it is illegal to report cop locations, so it would probably not be a good idea to use your npub to report them. But getting a points Cashu token as a reward and exchanging them from time to time would solve this. You can of course report construction, traffic jams, ...
Proposed solution: Add Nostr client (Copstr) to Organic Maps. Have a button in bottom right allowing you to report traffic situations. Geotagged events are published on Nostr relays, users sending cashu tokens as thank you if the report is valid. Notes have smart expiration times.
Phase 2: Automation: Integration with dashcams and comma.ai allow for automated AI recognition of traffic events such as traffic jams and cops, with automatic touchless reporting.
Result: Drive with most essential information and with full privacy. Collect points to be cool and stay cool.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ a5ee4475:2ca75401
2025-05-04 17:22:36
@ a5ee4475:2ca75401
2025-05-04 17:22:36clients #list #descentralismo #english #article #finalversion
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐🤖🍎💻(🐧🪟🍎)
- Coracle - Super App [source] 🌐
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖
- Primal - Social and wallet [source] 🌐🤖🍎
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana 🤖🍎🌐💻(🐧) [source]
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- Camelus [early access] 🤖 [source]
Communities
- noStrudel - Gamified Experience [info] 🌐
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox comunnity server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
Search
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
Website
App Store
ZapStore - Permitionless App Store [source]
Audio and Video Transmission
- Nostr Nests - Audio Chats 🌐 [info]
- Fountain - Podcast 🤖🍎 [info]
- ZapStream - Live streaming 🌐 [info]
- Corny Chat - Audio Chat 🌐 [info]
Video Streaming
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 (advice: https://zaplinks.lol/ and https://zaplinks.lol/slides/ sites are down)
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
- Keychat - Signal based [🤖🍎 on development] [source]
Reading
- Highlighter - Insights with a highlighted read 🌐 [info]
- Zephyr - Calming to Read 🌐 [info]
- Flycat - Clean and Healthy Feed 🌐 [info]
- Nosta - Check Profiles [on development] 🌐 [info]
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source]
Writing
Lists
- Following - Users list [source] 🌐
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List source 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
AI
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- DEG Mods - Decentralized Game Mods [info] [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🤖🍎🌐
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
- Spring - Browser 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Arcade City - Uber like [on development] ⏱️ [info]
- Nostrlivery - iFood like [on development] ⏱️
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] 🤖🍎
- Wallet of Satoshi [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Exchange
Media Server (Upload Links)
audio, image and video
- Nostr Build - [source] 🌐
- Nostr Check - [info] [source] 🌐
- NostPic - [source] 🌐
- Sovbit 🌐
- Voidcat - [source] 🌐
Without Nip: - Pomf - Upload larger videos [source] - Catbox - [source] - x0 - [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Extensions
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
NOT RELATED TO NOSTR
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ c7aa97dc:0d12c810
2025-05-04 17:06:47
@ c7aa97dc:0d12c810
2025-05-04 17:06:47COLDCARDS’s new Co-Sign feature lets you use a multisig (2 of N) wallet where the second key (policy key) lives inside the same COLDCARD and signs only when a transaction meets the rules you set-for example:
- Maximum amount per send (e.g. 500k Sats)
- Wait time between sends, (e.g 144 blocks = 1 day)
- Only send to approved addresses,
- Only send after you provide a 2FA code
If a payment follows the rules, COLDCARD automatically signs the transaction with 2 keys which makes it feel like a single-sig wallet.
Break a rule and the device only signs with 1 key, so nothing moves unless you sign the transaction with a separate off-site recovery key.
It’s the convenience of singlesig with the guard-rails of multisig.
Use Cases Unlocked
Below you will find an overview of usecases unlocked by this security enhancing feature for everyday bitcoiners, families, and small businesses.

1. Travel Lock-Down Mode
Before you leave, set the wait-time to match the duration of your trip—say 14 days—and cap each spend at 50k sats. If someone finds the COLDCARD while you’re away, they can take only one 50k-sat nibble and then must wait the full two weeks—long after you’re back—to try again. When you notice your device is gone you can quickly restore your wallet with your backup seeds (not in your house of course) and move all the funds to a new wallet.
2. Shared-Safety Wallet for Parents or Friends
Help your parents or friends setup a COLDCARD with Co-Sign, cap each spend at 500 000 sats and enforce a 7-day gap between transactions. Everyday spending sails through; anything larger waits for your co-signature from your key. A thief can’t steal more than the capped amount per week, and your parents retains full sovereignty—if you disappear, they still hold two backup seeds and can either withdraw slowly under the limits or import those seeds into another signer and move everything at once.
3. My First COLDCARD Wallet
Give your kid a COLDCARD, but whitelist only their own addresses and set a 100k sat ceiling. They learn self-custody, yet external spends still need you to co-sign.
4. Weekend-Only Spending Wallet
Cap each withdrawal (e.g., 500k sats) and require a 72-hour gap between sends. You can still top-up Lightning channels or pay bills weekly, but attackers that have access to your device + pin will not be able to drain it immediately.
5. DIY Business Treasury
Finance staff use the COLDCARD to pay routine invoices under 0.1 BTC. Anything larger needs the co-founder’s off-site backup key.
6. Donation / Grant Disbursement Wallet
Publish the deposit address publicly, but allow outgoing payments only to a fixed list of beneficiary addresses. Even if attackers get the device, they can’t redirect funds to themselves—the policy key refuses to sign.
7. Phoenix Lightning Wallet Top-Up
Add a Phoenix Lightning wallet on-chain deposit addresses to the whitelist. The COLDCARD will co-sign only when you’re refilling channels. This is off course not limited to Phoenix wallet and can be used for any Lightning Node.
8. Deep Cold-Storage Bridge
Whitelist one or more addresses from your bitcoin vault. Day-to-day you sweep hot-wallet incoming funds (From a webshop or lightning node) into the COLDCARD, then push funds onward to deep cold storage. If the device is compromised, coins can only land safely in the vault.
9. Company Treasury → Payroll Wallets
List each employee’s salary wallet on the whitelist (watch out for address re-use) and cap the amount per send. Routine payroll runs smoothly, while attackers or rogue insiders can’t reroute funds elsewhere.
10. Phone Spending-Wallet Refills
Whitelist only some deposit addresses of your mobile wallet and set a small per-send cap. You can top up anytime, but an attacker with the device and PIN can’t drain more than the refill limit—and only to your own phone.
I hope these usecase are helpfull and I'm curious to hear what other use cases you think are possible with this co-signing feature.
For deeper technical details on how Co-Sign works, refer to the official documentation on the Coldcard website. https://coldcard.com/docs/coldcard-cosigning/
You can also watch their Video https://www.youtube.com/watch?v=MjMPDUWWegw
coldcard #coinkite #bitcoin #selfcustody #multisig #mk4 #ccq
nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 nostr:npub12ctjk5lhxp6sks8x83gpk9sx3hvk5fz70uz4ze6uplkfs9lwjmsq2rc5ky
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ e968e50b:db2a803a
2025-05-01 16:46:13
@ e968e50b:db2a803a
2025-05-01 16:46:13Hey, are you familiar those scammy sites that will pay you to review companies? The line goes something like, "work from home and review products." Of course, the person is reviewing something online that they might not otherwise care about. When I look for reviews of a company, I'm almost always going to peer to peer type services.
Let's pause for a second for a seeming non-sequitur. Long story short, phone provider that I left has been charging me for an iPad that I accidentally didn't take off the plan. That's not the problem. The problem is that they made it IMPOSSIBLE to cancel this service, including going into a brick and mortar store. I'll spare you the details, but it took more than a full days work to get this thing cancelled. It was obvious that I wasn't even using the service, and it still cost me over a hundred bucks to square up after wasting so much of my life trying to get this thing cancelled on my account that supposedly didn't exist anymore.
Why is this relevant? I'm about to absolutely carpet bomb this company with bad reviews. They legitimately put significantly more work into trying to continue to charge me for this service I didn't want, didn't need, and didn't use, than they ever did trying to give me good service as a customer. When I started looking around online, I found a positive review I did about a flooring company two years ago...and wow! This review had so many great reviews. Beyond being amusingly recursive, it's real bad news for this phone company. I'm like a reviewing celebrity on this medium.
So...it occurred to me, what about a Trustpilot, BBB, or Angie's List type service that is fused with the sn news model? Put some skin in the game to review and put some skin in the game to endorse that review. stacker.reviews maybe?
Obviously, downzapping might not make sense there. Any company with a bad review could really hide their dirty laundry. But if they wanted to boost their good posts, plenty of safety mechanisms might make that costly (percentage of zaps going to website and boosts favored by numbers of zaps). I almost thought a review territory might make sense, but something like this would obviously need to be organized differently than a bulletin board.
I can imagine this being a good way to onboard people to bitcoin. Imagine it:
Wait, I can get some of these satoshi things for shouting to the rooftops about that plumber that saved my family's house?!? Hold my beer.
Wait, I can actually invest in this great review that warns people about that electrician?!?! Hold my warm beer.
idk Just a thought. I'm probably not the first person to think of this. Does it already exist? I got a humdinger of a harangue for it if so.
originally posted at https://stacker.news/items/968624
-
 @ c066aac5:6a41a034
2025-04-27 00:35:38
@ c066aac5:6a41a034
2025-04-27 00:35:38I work in the business world as a salesperson. I am frequently out and about in the community trying to make friends, connect with people who I can help, and ultimately grow my book of business. I have goals set by my employers and I aim to meet those expectations. Because of this, I find myself frequently under pressure to find ways to produce. This often leads to me being disappointed in myself; my sales cycles are long and I lose more deals than I win. My Dad often reminds me that How to Win Friends and Influence People has all the secrets of sales I'll ever need, but I still end up wishing I could find that secret edge to out-do the competition. That's where the watch temptation comes in.
I frequently see a luxurious timepiece on the left wrist of my peers and elder-statesmen closers. Rolex, Omega, Patek, a whole world of $10k minimum machines. It comes across as a power-move, a symbol of status that is hard to ignore. It sends a message that the bearer's time is more valuable than that of other people. It makes me think "if this person is wearing that watch, that means they're great at what they do." The ultimate investment in one's self.
As a newly married man expecting a child, it is hard for me to stomach such a purchase. My wife has supported the idea of me potentially getting such a timepiece; as much as it tickles my fancy, I'd rather put my capital towards things that further my family than my clout. One of the things that struck me was a statement made by an investment advisor in my Kiwanis club: "A watch is a purchase, not an investment."
What a true statement! His words helped me escape my short-lived delusions. That said, I still look at watches sometimes on the internet (The Omega No Time to Die watch is sleek looking). One day, I found myself looking at houses online shortly after looking at watches online. Then it hit me: how many purchases are being marketed as investments in this era? A Rolex is a supposed investment in your career, not just a luxury timepiece. A house is a mechanism for monetary growth, not an attainable home to be enjoyed by a family. A college degree is an investment for your future, not a vehicle for building upon passions.
The Bitcoiners will repeat the phrase "fix the money, fix the world" in harmonious chorus to address the concern I have laid out in this article. Ultimately, I leave you with this reminder: don't let the world pass off things that should be inconsequential purchases as investments with ROIs. I believe the only true investment one can make is into the people around them; that will yield the greatest rewards for the soul.
-
 @ b00a728d:0c16788a
2025-05-01 15:46:13
@ b00a728d:0c16788a
2025-05-01 15:46:13Hey there, racing fans! Let’s talk about a straightforward betting strategy that’s been around for years, often used by folks who treat horse racing more like a business than a gamble. This method is all about following a clear staking plan to aim for a small, consistent profit per race—without needing to be a racing expert. I’ll break it down step-by-step so it’s easy to understand, even if you’re new to this! The Goal: Small, Steady Wins The idea here is to aim for a target profit (T) of 5 points per race. Think of a "point" as a unit of money you decide on—it could be $50, $1, or whatever you’re comfortable with. For example, I use a starting bank of $200, and I set each point at $1. So, 5 points = $5 profit per race. Important Rule: Once you pick the value of a point, stick with it throughout the entire betting sequence. Don’t change it, no matter what happens! Why This Works (Even If You Know Nothing About Racing) This plan is designed so that you’ll eventually win, even if you’re clueless about horses. The catch? You need to be patient and okay with small profits per point because the stakes (the amount you bet) can grow after each loss. For example: If you set each point at £1 and lose 10 races in a row, your 11th bet would need to recover $55 (your target plus losses).
If you set each point at 25p, you’d only need to recover $13.75 after 10 losses.
See the difference? Lower point values mean smaller risks, but also smaller profits. Pick a point value that matches the risk you’re willing to take and the profit you want to make. How the Staking Plan Works Here’s the basic idea: you start with a target profit of 5 points per race. If you lose, you add your loss to the next race’s target. If you win, you subtract your gain. The goal is to keep going until you hit your total profit target, then start over. Let’s break down the key terms: T (Target): Your profit goal for the race (starts at 5 points).
T + L: Your target plus any losses from previous races (or minus any gains if you won).
S (Stake): How much you bet on the race.
R (Result): Whether you won (e.g., 2-1 means the horse paid 2-to-1 odds) or lost (L).
W (Points Won): How many points you gained from a win.
L (Points Lost): How many points you lost from a bet.
AWL (Running Total): Your accumulated wins and losses over the sequence.
Once you reach your overall profit goal (like 40 points in the example below), you take your winnings and start the sequence over with a 5-point target. Example Sequence: Watch It in Action Here’s a sample sequence to show how this plays out. I’m using a 1-per-point value for simplicity: Race( see image posted for details in url or comment section)
What happened here? In Race 1, I aimed for 5 points but lost my 2-point stake, so my running total is -2.
In Race 2, I added my loss (2) to the new target (10), so I’m aiming for 12 points. I lost again, so my running total drops to -6.
By Race 8, I finally hit a big win (4-1 odds), gaining 44 points. My running total jumps to +50, which exceeds my overall target of 40 points.
I take my profit ($50 if each point is $1) and start over in Race 9 with a 5-point target.
How to Calculate Your Stake To figure out how much to bet (your stake), take your T + L (target plus losses) and divide by 3, rounding to the nearest whole number. Why 3? Because you want to bet on horses with odds of 3-1 or higher. A win at those odds will cover all your losses and give you your target profit. For example: In Race 4, my T + L is 33. Divide by 3: 33 ÷ 3 = 11. So, I bet 11 points.
My horse wins at 2-1 odds, so I get 22 points back (11 × 2). This clears my losses and gives me a profit.
Pro Tip: Stick to odds of evens (1-1) or higher. Many pros avoid “odds-on” bets (like 1-2) because they don’t pay enough to make this system work well. Tips to Make This Work for You Pick Your Races Wisely: You don’t have to bet on every race. Some pros bet on every race at a meeting (e.g., 6 races a day, 36 bets a week), but I recommend being selective. Consider using a professional tipping service for better picks—newspaper tips can be risky (one “expert” once picked 30 losers in a row!).
Spread Your Bets: Use 3 or 4 different bookmakers. No single bookie will be happy if you keep winning over time.
Account for Betting Tax (If Applicable): If there’s a tax on your bets, add it to your next race’s target. This way, the system covers the tax for you.
Be Prepared for Losing Streaks: Even with careful picks, you might hit a string of losses. That’s why you keep your point value low—so your stakes don’t balloon too much.
Why This Is a “Business,” Not Gambling People who use this method don’t see it as gambling—they treat racing like a business. The key is patience and discipline. A single win at 3-1 odds or higher will wipe out all your losses and deliver your target profit. It’s a slow grind, but it’s designed to keep you in the game long-term. Final Thoughts This staking plan is all about consistency and managing risk. Start with a small bank (like $200), set a point value you’re comfortable with (like 50 or 1), and stick to the rules. You don’t need to be a racing genius—just follow the system, bet smart, and wait for that big win to clear your slate and put profit in your pocket. Got questions or want to tweak this for your own style? Let me know, and I’ll help you fine-tune your approach! Happy betting!
originally posted at https://stacker.news/items/968545
-
 @ 700c6cbf:a92816fd
2025-05-04 16:34:01
@ 700c6cbf:a92816fd
2025-05-04 16:34:01Technically speaking, I should say blooms because not all of my pictures are of flowers, a lot of them, probably most, are blooming trees - but who cares, right?
It is that time of the year that every timeline on every social media is being flooded by blooms. At least in the Northern Hemisphere. I thought that this year, I wouldn't partake in it but - here I am, I just can't resist the lure of blooms when I'm out walking the neighborhood.
Spring has sprung - aaaachoo, sorry, allergies suck! - and the blooms are beautiful.
Yesterday, we had the warmest day of the year to-date. I went for an early morning walk before breakfast. Beautiful blue skies, no clouds, sunshine and a breeze. Most people turned on their aircons. We did not. We are rebels - hah!
We also had breakfast on the deck which I really enjoy during the weekend. Later I had my first session of the year painting on the deck while listening/watching @thegrinder streaming. Good times.
Today, the weather changed. Last night, we had heavy thunderstorms and rain. This morning, it is overcast with the occasional sunray peaking through or, as it is right now, raindrops falling.
We'll see what the day will bring. For me, it will definitely be: Back to painting. Maybe I'll even share some here later. But for now - this is a photo post, and here are the photos. I hope you enjoy as much as I enjoyed yesterday's walk!
Cheers, OceanBee
!(image)[https://cdn.satellite.earth/cc3fb0fa757c88a6a89823585badf7d67e32dee72b6d4de5dff58acd06d0aa36.jpg] !(image)[https://cdn.satellite.earth/7fe93c27c3bf858202185cb7f42b294b152013ba3c859544950e6c1932ede4d3.jpg] !(image)[https://cdn.satellite.earth/6cbd9fba435dbe3e6732d9a5d1f5ff0403935a4ac9d0d83f6e1d729985220e87.jpg] !(image)[https://cdn.satellite.earth/df94d95381f058860392737d71c62cd9689c45b2ace1c8fc29d108625aabf5d5.jpg] !(image)[https://cdn.satellite.earth/e483e65c3ee451977277e0cfa891ec6b93b39c7c4ea843329db7354fba255e64.jpg] !(image)[https://cdn.satellite.earth/a98fe8e1e0577e3f8218af31f2499c3390ba04dced14c2ae13f7d7435b4000d7.jpg] !(image)[https://cdn.satellite.earth/d83b01915a23eb95c3d12c644713ac47233ce6e022c5df1eeba5ff8952b99d67.jpg] !(image)[https://cdn.satellite.earth/9ee3256882e363680d8ea9bb6ed3baa5979c950cdb6e62b9850a4baea46721f3.jpg] !(image)[https://cdn.satellite.earth/201a036d52f37390d11b76101862a082febb869c8d0e58d6aafe93c72919f578.jpg] !(image)[https://cdn.satellite.earth/cd516d89591a4cf474689b4eb6a67db842991c4bf5987c219fb9083f741ce871.jpg]
-
 @ 0e67f053:cb1d4b93
2025-05-01 14:58:03
@ 0e67f053:cb1d4b93
2025-05-01 14:58:03By Carl Tuckerson, Host of “Feelings Before Finance”
Let’s be clear: May Day isn’t for mattress sales—it’s for smashing economic feudalism with a reusable water bottle and a union card.
Trump? Said he loved workers. Then he golfed while nurses rationed gloves. Elon Musk? Thinks labor laws are a nuisance between him and his next ego-fueled space tantrum. Meanwhile, AOC and Bernie are out here like revolutionary fairy godparents, yelling “TAX THE RICH” while sprinkling universal dignity on the masses.
May Day is for the tired. The overworked. The underpaid. And everyone who's ever been told “we’re a family” by a boss who’d fire them via Slack.
Today we rise. Together. Unionized. Moisturized. Ready to seize the means of basic decency.
✊ Happy May Day from Carl Tuckerson. And remember: No billionaire ever made a sandwich.
originally posted at https://stacker.news/items/968502
-
 @ 9c9d2765:16f8c2c2
2025-05-05 05:16:53
@ 9c9d2765:16f8c2c2
2025-05-05 05:16:53CHAPTER FOURTEEN
"I don't get it... How is James still in charge?" Tracy murmured, her brows furrowed as she stared at her screen. She sat in her office, fingers nervously drumming against her desk.
Across from her, Mark stood with arms folded, pacing slowly. "You mean after all that evidence? After the blacklist, the embezzlement records nothing happened?"
Tracy shook her head. "Nothing. I checked again this morning. He’s still listed as President of JP Enterprises. It’s like the files we found didn’t even exist."
Helen, who had been silent until now, hissed through clenched teeth. "This is ridiculous. Are you sure the information got to the right hands?"
"It did," Tracy insisted. "I sent it directly to the Prime Minister's inbox using a confidential channel. I even received a delivery confirmation. Someone higher up must’ve swept it under the rug or maybe James covered his tracks faster than we imagined."
Mark slumped into the chair, clearly defeated. "He’s not just lucky he’s smart. Smarter than we gave him credit for."
For the first time since they began scheming, their confidence had begun to falter. They had dug into James’s past, unearthed the most damning of records, and yet… nothing. He remained untouched. Unshaken.
James continued to lead JP Enterprises with iron resolve, his status not just preserved, but strengthened. Whatever scandal they tried to ignite had fizzled out before it could burn.
The silence from JP's top board members was loud. No statements. No investigations. Not even a whisper of an internal review. To the outside world, James remained the unshakable President who had pulled a crumbling empire back from the edge.
Mark clenched his jaw. "He must have allies who are protecting him."
Helen nodded slowly. "We underestimated him. That was our biggest mistake."
Tracy remained quiet, her eyes still fixed on the screen as if trying to decipher what had gone wrong. She had risked everything, accessed confidential files, and violated protocols, expecting James to crumble.
Instead, he was thriving.
"Have you heard?" Robert leaned over his desk, eyes wide with interest. "JP Enterprises is about to celebrate their sixteenth anniversary. It’s going to be the biggest corporate event of the year."
Christopher looked up from the documents he was reviewing. "I heard. Mr. and Mrs. JP are returning for it. The entire business world is going to be there including us."
Robert nodded. "Every major company in and out of the city has received an invitation. It’s not just a celebration it’s a power show. A way for JP Enterprises to remind everyone who’s at the top."
Indeed, the buzz around the sixteenth anniversary of JP Enterprises was like nothing the city had seen in years. Massive banners were already being hoisted across the city skyline. High-end hotels were fully booked. Fashion designers, chefs, tech specialists, and media crews from around the world were preparing for the grand occasion. It was more than a business event, it was a spectacle.
At the heart of the preparations was James, the young and surprisingly unshakable President of JP Enterprises. Under his leadership, the company had grown in power and reach, and the anniversary was both a celebration of its legacy and a testament to its transformation.
Meanwhile, at Ray Enterprises, tension brewed behind the scenes. Though they were invited, the Ray family carried mixed feelings about attending the event. Memories of humiliation and disbelief still lingered the day James had revealed himself as the President was still fresh in their minds.
"We have no choice but to attend," Helen muttered in frustration during a board meeting. "If we stay away, we’ll seem petty and afraid. But going there means bowing our heads to him again."
Sarah, the secretary, tried to mask her discomfort. "It’s a corporate event, ma’am. It might be best to appear neutral… diplomatic."
Rita, now reinstated as General Manager, remained quiet but observant. She knew better than anyone how unpredictable James could be when it came to public appearances. She had no idea what to expect from him at the anniversary.
Back at JP Enterprises, preparations continued in full force. The guest list included billionaires, global CEOs, high-ranking politicians, and the most influential figures across industries. Red carpets would roll out, cameras would flash, and speeches would echo through the grand hall like music from an orchestra.
The city, already buzzing with excitement, awaited the grand event.
"I can’t believe it," the young woman muttered as she stared at her phone, her hands trembling with excitement. "James… the same James who used to sleep in front of Mr. Kola’s grocery store? He’s the President of JP Enterprises now?"
Her name was Evelyn. Sharp-tongued, impatient, and fueled by bitter memories, she had known James during his hardest days on the streets days when survival meant fighting for leftovers and sleeping on cold sidewalks. To her, his rise wasn’t a success story to be admired. It was a jackpot she felt entitled to.
Storming into the JP Enterprises headquarters during working hours, Evelyn ignored the receptionist's polite inquiries and pushed her way toward the executive wing.
"I want to see James!" she shouted, causing heads to turn in the busy lobby. "I know he’s here. Tell him Evelyn from the street is here!"
Security was alerted immediately, but by then, Evelyn had already reached the waiting area outside the President’s office.
James, who was in a brief meeting with department heads, heard the commotion and stepped out with a composed expression. As soon as his eyes met Evelyn’s, something shifted. He recognized her instantly.
"Evelyn?" he said, frowning slightly. "What are you doing here?"
"Don’t act like you don’t know me, James," she snapped, crossing her arms. "You owe me. We suffered together. I was there when you were nothing. Now you’re swimming in wealth and you think you can forget the people who once mattered!"
James’s expression hardened.
"This is not the place for this kind of talk. You’re disrupting my company’s operations. If you need help, there are proper channels"
"To hell with proper channels!" she yelled. "I came to get what’s mine!"
That was enough. James turned to the nearby security officer. "Escort her out. And make sure she doesn’t return without a valid appointment."
The security guards moved quickly, but Evelyn didn’t go quietly. She shouted all the way to the exit, throwing insults, struggling, and drawing even more attention.
Among those who witnessed the scene was Tracy. At first, she thought it was just a random case of disturbance some unruly visitor trying to make trouble. But as she watched James’s calm yet stern expression, and the woman’s emotional outburst, something clicked in her cunning mind.
This is gold, she thought, quickly pulling out her phone and snapping a series of pictures from the hallway James arguing with a ragged woman, the woman being dragged out, and James watching in silence. What a perfect way to ruin his reputation.
Tracy, ever the opportunist, reviewed the photos and smirked.
This is it… this will shake him up.
Without hesitation, she sent the pictures to Helen and Mark, attaching a voice note.
"I’ve got something you’ll love. A woman, probably James’s sister from the street came begging for money at JP today. He humiliated her. The whole thing happened in front of staff. Check the photos attached. This could ruin him if we spin it well."
Within minutes, Helen replied: “Excellent. This might be the leverage we’ve been waiting for. Keep digging, Tracy. He can’t escape the past forever.”
Mark responded too, bitter laughter echoing in his voice note: “The mighty always fall. This is just the beginning.”
But what none of them knew was that James had already noticed Tracy's growing interest in him her subtle spying, her conveniently timed questions, and now this bold move to document his personal confrontation. He wasn’t going to act just yet… but he was watching.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 502ab02a:a2860397
2025-05-04 15:48:26
@ 502ab02a:a2860397
2025-05-04 15:48:26วันอาทิตย์ เพื่อนใหม่เยอะพอสมควร น่าจะพอที่จะแนะนำให้รู้จัก โรงบ่มสุขภาพ ขอเล่าผ่านเพลง "บ่ม" เพื่อรวบบทความ #ตัวหนังสือมีเสียง ไว้ด้วยเลยแล้วกันครับ
โรงบ่มสุขภาพ Healthy Hut - โรงบ่มสุขภาพ คือการรวมตัวกันของบุคลากรที่มี content และ ความเชี่ยวชาญ ด้านต่างๆ ทำกิจกรรมหลากหลายรูปแบบ ตั้งแต่แคมป์สุขภาพ พักผ่อนกายใจเรียนรู้การปรับสมดุลร่างกาย, การเรียนรู้พื้นฐาน Nutrition ต่างๆ ลองดูผลงานได้ในเพจครับ และโรงบ่มฯ ก็จะยังคงมีกิจกรรมให้ทุกคนได้เข้าร่วมอยู่เสมอ ดังนั้นไปกดไลค์เพจไว้เพื่อไม่ให้พลาดข้าวสาร เอ้ย ข่าวสาร
โรงบ่มฯนั้น ประกอบด้วย 👨🏻⚕️พี่หมอป๊อบ DietDoctor Thailand ที่เรารู้จักกันดี อาจารย์ของพวกเรา 🏋🏻♀️ 🏅พี่หนึ่ง จาก หนึ่งคีโตแด๊ดดี้ มาเป็น Nueng The One ผมอุปโลกให้ก่อนเลยว่า คนไทยคนแรกที่ทำเนื้อหาการกินคีโต เป็นภาษาไทย แบบมีบันทึกสาธารณะให้ตามศึกษา 👨🏻⚕️หมอเอก หมออ้วนในดงลดน้ำหนัก กับหลักการใช้ชีวิตแบบ IFF สาย Fasting ที่ย้ำว่าหัวใจอีกห้องของ Fasting คือ Feeding กระดุมเม็ดแรกของการฟาส ที่คนมักลืม 🧘🏻♀️ครูบอม เทพโยคะอีกท่านนึงของไทย กับศาสตร์โยคะ Anusara Yoga หนึ่งเดียวในไทย 🧗♂️โค้ชแมท สารานุกรมสุขภาพที่มีชีวิต นิ่งแต่คมกริบ ถ้าเป็นเกมส์ก็สาย สไนเปอร์ ยิงน้อยแต่ Head Shot 🧔🏻แอ๊ดหนวด ฉายา Salt Daddy เจ้าแห่งเกลือแร่ ประจำกลุ่ม IF-Mix Fasting Diet Thailand (Keto # Low Carb # Plant Base # High Fat) 👭👩🏻🤝👨🏼👩🏻🤝👨🏼 รวมถึงทีมงาน กัลยาณมิตรสุขภาพ ที่มีความรู้ในด้านสุขภาพและมากประสบการณ์ 🧑🏻🍳 ผมและตำรับเอ๋เองก็ยินดีมากๆที่ได้ร่วมทีมสุขภาพนี้กับเขาด้วย
จะเห็นได้ว่า แต่ละท่านในโรงบ่มฯ นั้นหล่อหลอมมาจากความต่างเสียด้วยซ้ำไป ตั้งแต่เริ่มก่อร่างโรงบ่ม เราก็ตั้งไว้แล้วว่า ชีวะ ควรมีความหลากหลาย การวางพื้นฐานสุขภาพควรมาจาก "แต่ละคน" ไม่ใช่ one size fit all บันทึกกิจกรรมโรงบ่มผมมีโพสไว้ https://www.facebook.com/share/p/19DUibHrbw/
นั่นเป็นเหตุผลที่ผมเกิดแรงบันดาลใจในการทำเพลง "บ่ม" ขึ้นมาเพื่อเป็น Theme Song ครับ แก่นของเพลงนี้มีไม่กี่อย่างครับ ผมเริ่มคิดจากคำว่า "ความต่าง" เพราะไม่ว่าจะกี่ปีกี่ชาติ วงการสุขภาพ ก็จะมีแนวความคิดประเภท ฉันถูกเธอผิด อยู่ตลอดเวลาเพราะมันเป็นธรรมชาติมนุษย์ครับ มนุษย์เราทุกคนมีอีโก้ การยอมรับในความต่าง การหลอมรวมความต่าง ผมคิดว่ามันเป็นการ "บ่ม" ให้สุกงอมได้
เวลาที่เนื้อหาแบบนี้ ผมก็อดคิดถึงวงที่ผมรักเสมอไม่ได้เลย นั่นคือ เฉลียง แม้ความสามารถจะห่างไกลกันลิบลับ แต่ผมก็อยากทำสไตล์เฉลียงกับเขาบ้างครั้งหนึ่งหรือหลายๆครั้งในชีวิต จึงเลือกแนวเพลงออกมาทาง แจ๊ส สวิง มีเครื่องเป่า คาริเนต เป็นตัวเด่น
ท่อนแรกของเพลงจึงเริ่มด้วย "ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว" เพื่อปูให้คนฟังเริ่มเปิดรับว่า สิ่งที่ต้องการจะสื่อต่อไปคืออะไร
ส่วนคำย้ำนั้นผมแตกมาจาก คำสอนของพระพุทธเจ้า เกี่ยวกับ "คิดเห็นเป็นไป" ซึ่งจริงๆผมเขียนไว้ในโพสนึงแต่ตอนนั้นยังไม่ได้ทำคอลัมน์ #ตัวหนังสือมีเสียง ขอไม่เขียนซ้ำ อ่านได้ที่นี่ครับ https://www.facebook.com/share/p/18tFCFaRLn/ ท่อนที่ว่าจึงเขียนไว้ว่า "บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง" ใช้ความซน สไตล์ rock&roll ผสมแจ๊สนิด ที่เขามักเล่นร้องโต้กับคอรัส นึกถึงยุคทีวีขาวดำ 5555
เนื้อร้องท่อนนี้ เป็นการบอกว่า โรงบ่มคืออะไรทำอะไร เพราะโรงบ่ม เราไม่ได้รักษา เราไม่ได้บังคับไดเอทว่าต้องใช้อะไร เราเปิดตาให้มอง เปิดหูให้ฟัง เปิดปากให้ถาม ถึงธรรมชาติในตัวเรา แล้วบ่มออกไปให้เบ่งบานในเส้นทางของแต่ละคนครับ
แล้วผมก็พยายามอีกครั้งที่จะสื่อถึงการยอมรับความต่าง ให้ติดหูเอาไว้ โดยเฉพาะคำที่ผมพูดบ่อยมากๆ "ชีวะ คือชีวิต" จนมาเป็นท่อน bridge นี้ครับ "อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น"
เพลงนี้สามารถฟังตัวเต็มได้ทุกแพลทฟอร์มเพลงทั้ง youtube music, spotify, apple music, แผ่นเสียง tiktok ⌨️ แค่ค้นชื่อ "Heretong Teera Siri" ครับ
📺 youtube link นี้ https://youtu.be/BvIsTAsG00E?si=MzA-WfCTNQnWy6b1 📻 Spotify link นี้ https://open.spotify.com/album/08HydgrXmUAew6dgXIDNTf?si=7flQOqDAQbGe2bC0hx3T2A
ความลับคือ จริงๆแล้วเพลงนี้มี 3 version ถ้ากดใน spotify แล้วจะเห็นทั้งอัลบั้มครับ
📀เนื้อเพลง "บ่ม"📀 song by : HereTong Teera Siri ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน
หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง
ต่างทั้งลองลิ้ม ต่างทั้งรับรู้ ต่างที่มุมดู ก็ถมไป หนึ่งชีวิต มีความหมาย ที่หลากหลาย ไม่คล้ายกัน แล้วเพราะเหตุใด ใยต้องเป็นเช่นทุกคน
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวิต คือความหลากหลาย เพราะโลกนี้ ไม่เคยห่างหาย อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น บ่มให้เธอชื่น บ่มให้เธอชม ชีวิตรื่นรมย์ ได้สมใจ บ่มให้ยั่งยืน
ตัวหนังสือมีเสียง #pirateketo
โรงบ่มสุขภาพ #siamstr
-
 @ 24462930:3caf03ab
2025-04-25 04:37:25
@ 24462930:3caf03ab
2025-04-25 04:37:25Nostr 中所有的数据都是事件,通过将事件存储在多个中继器上来实现去中心化,通过签名来证明事件的拥有者。但如果你想真正拥有你的事件,你应该运行一个自己的中继器来保存它们。否则一旦你使用的所有中继器出了故障或者刻意删除了你的事件,你将永远丢失它们。
对于大部份人来说,运行一个中继器是复杂的,成本高昂的。为了解决这个问题,我开发了 nostr-relay-tray,这是一款可以很方便在个人电脑上运行的中继器,并且支持通过互联网对其进行访问。
项目地址:https://github.com/CodyTseng/nostr-relay-tray
本文将介绍如何使用 nostr-relay-tray 来运行一个自己的中继器。
下载
从 GitHub Release 页面 下载对应你操作系统的安装包
| 操作系统 | 文件格式 | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | 你们应该知道使用哪个 |安装
因为我没有对这个安装包进行数字签名,所以在安装时会有一些阻碍。安装成功后,菜单栏会出现一个鸵鸟图标。点击鸵鸟图标,你会看到一个菜单,点击 "Dashboard" 选项可以打开中继器的控制面板进行更多的配置。

macOS 用户注意:
- 首次打开时需要前往「系统设置 > 隐私与安全性」点击“仍要打开”按钮。
- 若遇损坏提示,需要在终端执行以下命令解除限制:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows 用户:
- 在安全警告界面点击「更多信息 > 仍要运行」
连接
默认情况下,nostr-relay-tray 只能在本地通过
ws://localhost:4869/进行访问。这让它的用途非常有限,所以我们需要将它暴露到互联网。在控制面板中点击 "Proxy" 选项卡,并打开开关。你将会获得一个 "Public address",你可以使用这个地址在任何地方访问你的中继器。就是这么简单。
接下来,你要将刚刚获得的地址添加到你的中继器列表中。并且要让它在列表中尽可能靠前的位置。因为大部份的客户端会优先连接列表中靠前的中继器,后面的中继器常常会被忽略。

限制
接下来我们需要增加一些限制来防止中继器保存一些与你无关的事件,浪费存储空间。nostr-relay-tray 可以非常灵活精细地设置允许接收哪些事件,但有些复杂,所以不在这里介绍,如果有兴趣可以日后探索。
在这里我先介绍一个很简单有效的策略 —— WoT (Web of Trust)。你可以在 "WoT & PoW" 选项卡中打开这个功能。打开之前你需要先输入你的 pubkey。
这里还有一个非常重要的参数
Depth,它表示某个人与你的关系深度。你关注的人与你的深度为 1,你关注的人关注的人与你的深度为 2,以此类推。- 如果你将这个参数设置为 0,那么你的中继器只会接收你自己的事件。
- 如果你将这个参数设置为 1,那么你的中继器只会接收你和你关注的人的事件。
- 如果你将这个参数设置为 2,那么你的中继器只会接收你和你关注的人的事件,以及你关注的人关注的人的事件。
目前这个参数的最大值只能为 2。

总结
至此,你已经成功运行了一个自己的中继器,并且设置了一个简单的限制来防止中继器保存一些与你无关的事件。
如果你在使用中遇到任何问题,请随时在 GitHub 上提交 issue,我会尽快回复你。
Not your relay, not your events
-
 @ 2e8970de:63345c7a
2025-05-01 14:30:18
@ 2e8970de:63345c7a
2025-05-01 14:30:18Research out of China; they used ice lithography to fabricate 72 nm patterns on living tardigrades. The wild thing isn’t just that they “tattooed” tardigrades. It’s that tardigrades are so resilient, and focused electron beams so precise, that 40% of them survived and went about their lives after the procedure.
https://www.acs.org/pressroom/presspacs/2025/april/scientists-have-found-a-way-to-tattoo-tardigrades.html
originally posted at https://stacker.news/items/968469
-
 @ 57d56d16:458edffd
2025-05-01 13:18:39
@ 57d56d16:458edffd
2025-05-01 13:18:39Kraken
https://www.kraken.com/learn/satoshi-to-usd-converter
CoinCodex
https://coincodex.com/convert/satoshi-sats/usd/1000000/
Coin Guides
https://coinguides.org/satoshi-usd-converter/
BitcoinMagazine
https://bitcoinmagazine.com/satoshi-to-usd-calculator
originally posted at https://stacker.news/items/968362
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ f7d424b5:618c51e8
2025-04-19 22:06:47
@ f7d424b5:618c51e8
2025-04-19 22:06:47It's our podcast and we'll talk about whatever we want. Welcome to a return to normalcy where we cover a variety of subjects instead of just a couple of really long ones. Crack open a beer and chill with us. We're gonna talk about the Galaxy showcase, Marathon, Skyblivion & the leaked Oblivion remake, and a whole bunch more.
In the opening of the episode we get Vic's reaction to a really specific trailer, if you want to follow along, this is the link to that video
Other stuff cited:
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ c066aac5:6a41a034
2025-04-17 00:05:49
@ c066aac5:6a41a034
2025-04-17 00:05:49I am all about fleshing out a fantasy, even if the chances of it coming to reality are fairly slim. Dreams should be written down, meditated on, processed over long periods of time. I don't think of it as manifesting (nor do I condone manifestation); one could argue such practices are Biblical (Habakkuk 2:2).
So I'm going to write this out and make it plain, on the off chance that putting it out there brings somethings to fruition:
Jack Dorsey should take over Mozilla.
Either via an invitation from Mozilla, or via a hostile takeover. I don't really care how it happens, but I believe it should happen and I'll outline why.
The Fallen Hero

Mozilla has been having a bad time. I'm not sure that the organization has done much good since the unceremonious departure of Brenden Eich (there's Rust, but is that really a good thing?).
Firefox is losing its relevance. The FireFox Terms of Service update has sparked outrage, the removal of the promise to never sell your data was a Judas level of betrayal, FireFox currently (at the time this article was penned) makes up less than 3% of the total browser marketshare, their main source of income from Google is in jeopardy, most websites are only optimized for Chromium-based browsers, and the Gecko engine is not very secure.
Mozilla's best product is dying, and what is the organization doing about it? They're working on a plethora of issues their core user base does not care about. They've jumped on the AI hype train, they've bought an advertising company (which is very irrelevant to their user base, especially considering uBlock Orgin exists), they're selling white labeled VPNs (Mullvad), they're selling data removal services (which is powered by a former data broker), they're pushing shopping products, they're forcing features on their users which were never asked for (POCKET!!), it seems that Mozilla is completely out of touch with the people they claim to serve. They've abandoned their first love.
Thunderbird is showing some promise with the recent announcement of Thundermail, but that project will sadly suffer from guilt by association.
We have to remember though: Mozilla used to mean something in the FOSS/Open Source world.

They were the shining city on the hill of the internet. They rose up from the ashes of Netscape. FireFox kicked Internet Explorer's butt; it was a punk rock movement. Thunderbird is still an amazing email client. Rust (despite the arguing programmers) is a significant innovation in the programming language space.
I'm not rooting for the downfall of Mozilla. Sure, in a way I'd be happy about it: I'd like to see poor leadership get what it deserves, but I fear Mozilla as a symbol of FOSS/OS would send a sad signal across the ecosystem. I'm a capitalist at heart so I don't favor bailouts (nor am I calling for one); I truly believe this organization could be turned around with the right leadership. Maybe it could be as simple as going back to their original model of serving the deep pockets of the corporate world with open source tech rather than going for the wallets of the consumer.
Every problem is a leadership problem. Fix the leadership, fix the problems.
The Last Great Open Source Hero?
Sadly FOSS figures tend to die of public crucifixion. As time goes on, we have less and less great figures to point to. Thankfully, Jack hasn't been canceled yet.
Jack Dorsey has a pretty good résumé in the open source world. He jumped right in with Bitcoin. He left BlueSky for NOSTR. He would've made Twitter a protocol if he didn't need to feed himself early in his career. He is currently financing several projects in the Bitcoin and NOSTR world, which is arguably the best open source technology in the world right now.
I do believe that people should stay in their lane of expertise, and maybe Jack should. However, my message to Jack would be that it would be a shame if his passion for open source remained solely in Bitcoin and NOSTR. If his leadership was injected into the Mozilla machine, it could be steered into a magical direction.
Imagine FireFox being the first browser with layer 2 wallet integration (stick it to Brave and their BAT crap [we still love you Brenden Eich flaws and all]). Imagine having a whole world of existing talented developers suddenly interested in contributing their talents to the NOSTR community. Imagine having a browser with an engine that can actually go toe-to-toe with Chromium. Imagine an organization that once again gives FOSS a good name rather than actively eroding public confidence in FOSS.
The True FOSS Heroes

Jack is probably not going to touch Mozilla with a 150 foot pole (or see this article). We all probably need to let the Mozilla dream die in front of us.
Things aren't always black and white. I don't think of Mozilla as an evil organization; just an organization subject to the flaws of fellow humans like you and me. Even the Eye of Sauron, Google, has been a huge blessing to the open source world (Go programming language, Android, all of their open source sponsorships, many more things I could mention).
The beautiful thing about FOSS/OS is that it is a movement of the people. Titans will rise up and fall, but you and I make up the backbone of FOSS. I've had nothing but good interactions with FOSS fanatics. NOSTR's own OceanSlim taught me about Ungoogled Chromium, the Go programming language, and NOSTR relays. When I wanted to get into Linux, I was able to plug in immediately with a group of Linux users here in Nashville. NOSTR devs for the most part are happy to answer my inquiries when I slide into their DMs. I've been in group chats with people openly discussing the best way to make a great lightning wallet.
There's a lot of connection in the Open Source world that I cherish; it's very different from the corporate world most of us are immersed in. The corporate world has gatekeepers; Open Source has collaborators. The corporate world operates in the shadows to maximize profits; Open Source steps into the light for everyone's benefit. The corporate world says you'll never have enough experience/qualifications; Open Source encourages and equips you.
My point is, don't worship any organization. Be thankful for the people around you, try out FOSS programs whenever you can, and have fun with it.
All that said, I wouldn't mind if Jack took over Mozilla. Or if one of his friends took a position (ODELL?). Heck, throw Snowden in while we're at it.
Footnote: "Open Source" and "FOSS/Free and Open Source Software" are used interchangably in this article. Mistakes were made I'm sure, but I hope I got the point across.
-
 @ fd06f542:8d6d54cd
2025-05-05 03:13:13
@ fd06f542:8d6d54cd
2025-05-05 03:13:13“https://following.space/” 是一个围绕Nostr协议打造的社交拓展项目,专注于用户关注列表的管理与分享,其核心功能和特点如下: - 发现优质关注对象:该平台允许用户探索经过精心策划的Nostr用户关注列表。Nostr是一种去中心化的社交网络协议,在这个生态中,用户数量众多且内容繁杂。通过该平台的精选列表,用户能快速定位到可能感兴趣的人,例如找到特定领域的意见领袖、趣味相投的创作者,节省自行筛选关注对象的时间和精力。 - 分享个性化列表:支持用户创建并分享自己的Nostr用户关注列表。这为用户提供了展示个人社交品味和兴趣领域的机会,比如摄影爱好者可创建并分享专注摄影的Nostr用户列表,促进同好间交流,丰富Nostr社交生态的多样性。 - 增强社交连接性:在去中心化的Nostr社交环境里,它起到了连接用户、优化关注体验的作用。借助发现和分享功能,用户能扩大社交圈,找到更多志同道合者,提升社交互动的质量和效率,推动Nostr生态系统的发展与活跃。
-
 @ 4fe14ef2:f51992ec
2025-05-01 12:20:12
@ 4fe14ef2:f51992ec
2025-05-01 12:20:12Hey stackers,
Leave a comment below to share your hustles and wins. Let us know what you've sold this week. Have you sold it for sats or zaps? It doesn't matter how big or small your item is, solid or digital, product or service.
Just share below what you’ve listed, swapped, and sold. Let everyone rave on your latest #deals!
New to ~AGORA? Dive into the marketplace and turn your dusty gears into shiny BTC!
originally posted at https://stacker.news/items/968324
-
 @ a19caaa8:88985eaf
2025-05-05 02:55:57
@ a19caaa8:88985eaf
2025-05-05 02:55:57↓ジャック(twitter創業者)のツイート nostr:nevent1qvzqqqqqqypzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4zqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsqg9cdxf7s7kg8kj70a4v5j94urz8kmel03d5a47tr4v6lx9umu3c95072732
↓それに絡むたゃ nostr:note1hr4m0d2k2cvv0yg5xtmpuma0hsxfpgcs2lxe7vlyhz30mfq8hf8qp8xmau
↓たゃのひとりごと nostr:nevent1qqsdt9p9un2lhsa8n27y7gnr640qdjl5n2sg0dh4kmxpqget9qsufngsvfsln nostr:note14p9prp46utd3j6mpqwv46m3r7u7cz6tah2v7tffjgledg5m4uy9qzfc2zf
↓有識者様の助言 nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqst8w0773wxnkl8sn94tvmd3razcvms0kxjwe00rvgazp9ljjlv0wq0krtvt nostr:nevent1qvzqqqqqqypzpujqe8p9zrpuv0f4ykk3rmgnqa6p6r0lan0t8ewd0ksj89kqcz5xqqsxchzm7s7vn8a82q40yss3a84583chvd9szl9qc3w5ud7pr9ugengcgt9qx
↓たゃ nostr:nevent1qqsp2rxvpax6ks45tuzhzlq94hq6qtm47w69z8p5wepgq9u4txaw88s554jkd
-
 @ 1bc70a01:24f6a411
2025-04-16 13:53:00
@ 1bc70a01:24f6a411
2025-04-16 13:53:00I've been meaning to dogfood my own vibe project for a while so this feels like a good opportunity to use Untype to publish this update and reflect on my vibe coding journey.
New Untype Update
As I write this, I found it a bit annoying dealing with one of the latest features, so I'll need to make some changes right after I'm done. Nonetheless, here are some exciting developments in the Untype article composer:
-
Added inline AI helper! Now you can highlight text and perform all sorts of things like fix grammar, re-write in different styles, and all sorts of other things. This is a bit annoying at the moment because it takes over the other editing functions and I need to fix the UX.
-
Added pushing articles to DMs! This option, when enabled, will send the article to all the subscribers via a NIP-44 DM. (No client has implemented the subscription method yet so technically it won’t work, until one does. I may add this to nrss.app) Also, I have not tested this so it could be broken… will test eventually!
- Added word counts
- Added ability to export as markdown, export as PDF, print.
The biggest flaw I have already discovered is how "I" implemented the highlight functionality. Right now when you highlight some text it automatically pops up the AI helper menu and this makes for an annoying time trying to make any changes to text. I wanted to change this to show a floating clickable icon instead, but for some reason the bot is having a difficult time updating the code to this desired UX.
Speaking of difficult times, it's probably a good idea to reflect a bit upon my vibe coding journey.
Vibe Coding Nostr Projects
First, I think it's important to add some context around my recent batch of nostr vibe projects. I am working on them mostly at night and occasionally on weekends in between park runs with kids, grocery shopping and just bumming around the house. People who see buggy code or less than desired UX should understand that I am not spending days coding this stuff. Some apps are literally as simple as typing one prompt!
That said, its pretty clear by now that one prompt cannot produce a highly polished product. This is why I decided to limit my number of project to a handful that I really wish existed, and slowly update them over time - fixing bugs, adding new features in hopes of making them the best tools - not only on nostr but the internet in general. As you can imagine this is not a small task, especially for sporadic vibe coding.
Fighting the bot
One of my biggest challenges so far besides having very limited time is getting the bot to do what I want it to do. I guess if you've done any vibe coding at all you're probably familiar with what I'm trying to say. You prompt one thing and get a hallucinated response, or worse, a complete mess out the other end that undoes most of the progress you've made. Once the initial thing is created, which barely took any time, now you're faced with making it work a certain way. This is where the challenges arise.
Here's a brief list of issues I've faced when vibe-coding with various tools:
1. Runaway expenses - tools like Cline tend to do a better job directly in VSCode, but they can also add up dramatically. Before leaning into v0 (which is where I do most of my vibe coding now), I would often melt through $10 credit purchases faster than I could get a decent feature out. It was not uncommon for me to spend $20-30 on a weekend just trying to debug a handful of issues. Naturally, I did not wish to pay these fees so I searched for alternatives.
2. File duplication - occasionally, seemingly out of nowhere, the bot will duplicate files by creating an entire new copy and attached "-fixed" to the file name. Clearly, I'm not asking for duplicate files, I just want it to fix the existing file, but it does happen and it's super annoying. Then you are left telling it which version to keep and which one to delete, and sometimes you have to be very precise or it'll delete the wrong thing and you have to roll back to a previous working version.
3. Code duplication - similar to file duplication, occasionally the bot will duplicate code and do things in the most unintuitive way imaginable. This often results in loops and crashes that can take many refreshes just to revert back to a working state, and many more prompts to avoid the duplication entirely - something a seasoned dev never has to deal with (or so I imagine).
4. Misinterpreting your request - occasionally the bot will do something you didn't ask for because it took your request quite literally. This tends to happen when I give it very specific prompts that are targeted at fixing one very specific thing. I've noticed the bots tend to do better with vague asks - hence a pretty good result on the initial prompt.
5. Doing things inefficiently, without considering smarter approaches - this one is the most painful of vibe coding issues. As a person who may not be familiar with some of the smarter ways of handling development, you rely on the bot to do the right thing. But, when the bot does something horribly inefficiently and you are non-the-wiser, it can be tough to diagnose the issue. I often fight myself asking the bot "is this really the best way to handle things? Can't we ... / shouldn't we .../ isn't this supposed to..." etc. I guess one of the nice side effects of this annoyance is being able to prompt better. I learn that I should ask the bot to reflect on its own code more often and seek ways to do things more simply.
A combination of the above, or total chaos - this is a category where all hell breaks loose and you're trying to put out one fire after another. Fix one bug, only to see 10 more pop up. Fix those, to see 10 more and so on. I guess this may sound like typical development, but the bot amplifies issues by acting totally irrationally. This is typically when I will revert to a previous save point and just undo everything, often losing a lot of progress.
Lessons Learned
If I had to give my earlier self some tips on how to be a smarter vibe coder, here's how I'd summarize them:
-
Fork often - in v0 I now fork for any new major feature I'd like to add (such as the AI assistant).
-
Use targeting tools - in v0 you can select elements and describe how you wish to edit them.
-
Refactor often - keeping the code more manageable speeds up the process. Since the bot will go through the entire file, even if it only makes one small change, it's best to keep the files small and refactoring achieves that.
I guess the biggest lesson someone might point out is just to stop vibe coding. It may be easier to learn proper development and do things right. For me it has been a spare time hobby (one that I will admit is taking more of my extra time than I'd like). I don't really have the time to learn proper development. I feel like I've learned a lot just bossing the bot around and have learned a bunch of things in the process. That's not to say that I never will, but for the moment being my heart is still mostly in design. I haven't shared much of anything I have designed recently - mostly so I can remain speaking more freely without it rubbing off on my work.
I'll go ahead and try to publish this to see if it actually works 😂. Here goes nothing... (oh, I guess I could use the latest feature to export as markdown so I don't lose any progress! Yay!
-
-
 @ fd06f542:8d6d54cd
2025-05-05 01:38:09
@ fd06f542:8d6d54cd
2025-05-05 01:38:09https://blossom.band/ 是Nostr.build旗下的Blossom Server服务页面,为Nostr社交媒体平台用户提供媒体上传服务,依托Nostr.build基础设施,具有独特优势和明确规范。 1. 服务背景:由Nostr.build提供支持,借助其经过时间验证、高可用性的基础设施以及全球覆盖的快速CDN网络,每个用户的npub都有专属服务器域名,保证用户数据独立性。 2. 上传限制:单次上传文件大小硬限制为100MiB,上传次数和存储时长不受限。支持常见媒体类型上传,包括图片、音频和视频。若有更大上传尺寸等扩展需求,可查看相关付费计划。所有上传需遵循服务条款。 3. 兼容性与接口:认证方式为签名的nostr事件,支持Nostr文件元数据标签(NIP - 94)BUD - 08等。提供多种接口,如GET、HEAD、DELETE、PUT等用于文件的获取、查看、删除和上传等操作 ,部分接口需认证,不同接口有不同功能和限制。 4. 限制条件:使用PUT /upload或PUT /mirror端点上传时,含GPS元数据的媒体文件会被拒绝。 5. 支持的媒体类型:免费用户可上传常见媒体类型,如.jpg、.png等;付费用户根据不同计划,除免费内容外,还能上传.pdf、.svg和.zip等格式文件。 6. 关于Nostr.build:2022年12月24日开始为Nostr平台提供免费媒体上传服务,旨在推动Nostr生态发展。团队秉持透明、社区化的媒体审核方式和开源理念,致力于打造安全可靠的平台,欢迎用户反馈和建议 。
使用例子:
假设你是Nostr社交媒体平台的用户,想在该平台分享图片、音频或视频等媒体内容,就可以使用
https://blossom.band/提供的服务。下面以分享一张图片和管理已上传媒体为例,介绍其使用方法:- 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用
PUT /upload接口来上传图片。例如,你本地有一张名为example.jpg的图片,通过编程方式(如使用Python的requests库)构造请求:
```python import requests import json
假设你已经获取到签名认证信息
headers = { "Content-Type": "application/json", "Authorization": "Bearer your_signed_nostr_event" } files = { 'file': open('example.jpg', 'rb') } response = requests.put('https://blossom.band/upload', headers=headers, files=files) if response.status_code == 200: print("图片上传成功") else: print(f"上传失败,状态码: {response.status_code}") ```
- 获取上传文件信息:图片上传成功后,会得到一个对应的
sha256哈希值。你可以使用GET /<sha256>接口(假设图片对应的sha256哈希值为your_sha256_value)获取文件信息,例如:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.get(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("获取文件信息成功") else: print(f"获取失败,状态码: {response.status_code}") ```
- 删除上传的图片:如果你想删除已上传的图片,可以使用
DELETE /<sha256>接口。同样以your_sha256_value为例:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } response = requests.delete(f'https://blossom.band/your_sha256_value.jpg', headers=headers) if response.status_code == 200: print("图片删除成功") else: print(f"删除失败,状态码: {response.status_code}") ```
- 查看用户上传列表:使用
GET /list/<pubkey>接口(pubkey为你的Nostr公钥)可以查看你上传的所有媒体文件列表。例如:
```python import requests
headers = { "Authorization": "Bearer your_signed_nostr_event" } pubkey = "your_public_key" response = requests.get(f'https://blossom.band/list/{pubkey}', headers=headers) if response.status_code == 200: print("获取上传列表成功") print(response.json()) else: print(f"获取失败,状态码: {response.status_code}") ```
- 上传图片:你需要先对上传操作进行签名认证(通过Signed nostr event方式)。认证完成后,使用
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00
@ dbc27e2e:b1dd0b0b
2025-04-05 20:44:00This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.

Dose:
20g coffee (Coarse ground coffee) 300mL water (92°C / 197.6°F) Time: 3:30Instructions:
- Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.)
- Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.)
- Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour)
- Pour 4: 2:10 > 60mL
- Pour 5: 2:40 > 60mL
- Remove the V60 at 3:30
-
 @ 8cda1daa:e9e5bdd8
2025-05-01 08:07:48
@ 8cda1daa:e9e5bdd8
2025-05-01 08:07:48
Bitcoin's blockspace is a free market (and a fee market!)
Each byte bids for inclusion according to the fee it carries, whether that byte represents a coffee payment or an encoded inscription protocol. The current debate over expanding OP_RETURN is a reminder that the ledger does not interpret meaning; it only records weight in bytes and payment in bitcoin fees.
There is no value stored on Bitcoin's ledger other than the literal number of bitcoin units recorded in your UTXO.
That means there is no "digital energy" in there, no dollars, no "store of value," nothing except a number in a database.
When you spend bitcoin, for whatever reason, it is your counterparty that decides what those units are worth. They are free to discriminate them, or you, in any way they can get away with.
They can also attribute extra value to them for any reason: a ticker price on their favorite exchange, a JPG forever attached to the output, a USDT anchor, or a private protocol no one even knows about for a VIP club membership.
All value is subjective, so it is impossible to know the trade value of every transaction merely by looking at block data.
Your counterparty also decides when a trade is settled, not the Bitcoin blockchain. They may agree on one confirmation, or three, or zero... They might require a government‑issued ID or even custody of your first‑born child.
Do not confuse Bitcoin "transactions" with trades; they are only score updates in a database. All of the value is decided by people and made competitive by the open market.
Why OP_RETURN Matters Right Now
Bitcoin offers an 80‑byte OP_RETURN field that lets users write data without polluting the UTXO set. As blockspace demand soared with Ordinals, BRC‑20, and Runes, people began hiding data in taproot leaves and bare multisig outputs, which never get spent and therefore swell the UTXO set, driving up node costs.
Relaxing, or even removing, the 80‑byte cap would invite this data back into a provably unspendable, prunable space; the chain stays neutral - every byte either pays or waits.
Is this the right thing to do? Personally, I don't care. Things are working exactly how everyone should have expected.
How to Think About "Spam" vs "Use"
Fee neutrality: If it pays the market fee, it belongs. By design. Hidden context: You can never fully know the value or trade behind the onchain transaction.
UTXO preservation: Favor prunable data (witness & OP_RETURN) over perpetually unspent outputs.
Censorship fragments the mempool: Policy bans force operators to patch their nodes or run alternate relay networks, creating isolated pools, unreliable fee estimates, and extra burden for wallets that must navigate around invisible gaps.
Takeaway
We have no objective tool for classifying "usefulness" on‑chain. The cleanest rule remains: pay the fee, get the block. If you want a lean UTXO set, widen OP_RETURN and let economics, not censorship, do the pruning.
A Meta Recommendation
Bitcoin Core is the de-facto reference implementation, not the policy police. Any subjective rule, whether it targets memes, stablecoins, transaction flags, or inscriptions, can and should be handled in downstream forks, plug‑ins, or user‑level policy. Node operators already tweak mempool size, relay settings, and script limits to match their own risk models. Pretending they cannot already only muddies the debate.
A sure path to minimizing controversy is to keep Bitcoin Core truly core: compact, predictable, and neutral. Every extra rule adds maintenance overhead and widens the surface for accidental forks. By shipping only what consensus requires and leaving higher‑layer policy to the market, Core Devs protect the common base layer we all rely on, and their own sanity.
Bonus Take: 🌶️ Shrink Blocks, or Repeal Taproot
If a transaction looks like spam to you, the blunt but honest remedy is to cut capacity, not to micromanage content. The four‑megabyte block weight and Taproot's flexible script paths are exactly what unlocked today's wave of inscriptions and tokens. If that bothers you, push to shrink the block size or even roll back Taproot and own the trade‑offs. Anything else is selective outrage dressed up as policy.
(NOTE: I do not support any current fork or mempool policy proposals.)
-
 @ 57d1a264:69f1fee1
2025-05-01 05:57:24
@ 57d1a264:69f1fee1
2025-05-01 05:57:24Design and build chemical processes, better. Alkali is creating the world's first AI Process Engineer.
What the future of chemical process design should look like.
Under the hood, APE-0 uses tried-and-true open-source packages to run simulations. You don't have to trust that the LLM predicted the result — you can check out the simulation file it produced, and run it yourself!
Discover more at https://www.alkali-eng.com/blogs/introducing-fel-0
originally posted at https://stacker.news/items/968211
-
 @ a5ee4475:2ca75401
2025-05-04 15:45:12
@ a5ee4475:2ca75401
2025-05-04 15:45:12lists #descentralismo #compilation #english
*Some of these lists are still being updated, so the latest versions of them will only be visible in Amethyst.
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Markdown Uses for Some Clients
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwsppemhxue69uhkummn9ekx7mp0qgsq37tg2603tu0cqdrxs30e2n5t8p87uenf4fvfepdcvr7nllje5zgrqsqqqqqpkdvta4
Other Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ a5ee4475:2ca75401
2025-05-04 15:14:32
@ a5ee4475:2ca75401
2025-05-04 15:14:32lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas e serão traduzidas para português, portanto as versões mais recentes delas só estarão visíveis no Amethyst.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
Comunidades Lusófonas de Bitcoin
nostr:nevent1qqsqnmtverj2fetqwhsv9n2ny8h9ujhyqqrk0fsn4a02w8sf4cqddzqpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyzj7u3r4dz3rwg3x6erszwj4y502clwn026qsp99zgdx8n3v5a2qzqcyqqqqqqgypv6z5
Profissionais Brasileiros no Nostr
nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqylf6kr4
Comunidades em Português no Nostr
nostr:nevent1qqsy47d6z0qzshfqt5sgvtck8jmhdjnsfkyacsvnqe8m7euuvp4nm0gpzpmhxue69uhkummnw3ezumt0d5hsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqsw4vudx
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Games Open Source
nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Formatação de Texto no Amethyst
nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cprpmhxue69uhkummnw3ezuendwsh8w6t69e3xj730qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpd658r3
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 866e0139:6a9334e5
2025-04-05 11:00:25
@ 866e0139:6a9334e5
2025-04-05 11:00:25
Autor: CJ Hopkins. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Dieser Beitrag erschien zuerst auf dem Substack-Blog des Autors.
Er soll andauern, was er auch tut. Genau wie der nie endende Krieg in Orwells 1984 wird er vom Imperium gegen seine eigenen Untertanen geführt, aber nicht nur, um die Struktur der Gesellschaft intakt zu halten, sondern in unserem Fall auch, um die Gesellschaft in eine neo-totalitäre global-kapitalistische Dystopie zu verwandeln.
Bist du nicht vertraut mit dem Krieg gegen was auch immer?
Nun ja, okay, du erinnerst dich an den Krieg gegen den Terror.
Du erinnerst dich daran, als die „Freiheit und Demokratie“ von „den Terroristen“ angegriffen wurden und wir keine andere Wahl hatten, als uns unserer demokratischen Rechte und Prinzipien zu entledigen, einen nationalen „Notstand“ auszurufen, die verfassungsmäßigen Rechte der Menschen auszusetzen, einen Angriffskrieg gegen ein Land im Nahen Osten anzuzetteln, das für uns keinerlei Bedrohung darstellte, und unsere Straßen, Bahnhöfe, Flughäfen und alle anderen Orte mit schwer bewaffneten Soldaten zu füllen, denn sonst hätten „die Terroristen gewonnen“. Du erinnerst dich, als wir ein Offshore-Gulag bauten, um verdächtige Terroristen auf unbestimmte Zeit wegzusperren, die wir zuvor zu CIA-Geheimgefängnissen verschleppt hatten, wo wir sie gefoltert und gedemütigt haben, richtig?
Natürlich erinnerst du dich. Wer könnte das vergessen?
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Erinnerst du dich, als die National Security Agency keine andere Wahl hatte, als ein geheimes „Terroristen-Überwachungsprogramm“ einzurichten, um Amerikaner auszuspionieren, oder sonst „hätten die Terroristen gewonnen“? Oder wie wäre es mit den „Anti-Terror“-Unterleibsuntersuchungen der TSA, der Behörde für Transportsicherheit, die nach über zwanzig Jahren immer noch in Kraft sind?
Und was ist mit dem Krieg gegen den Populismus? An den erinnerst du dich vielleicht nicht so gut.
Ich erinnere mich, denn ich habe zwei Bücher dazu veröffentlicht. Er begann im Sommer 2016, als das Imperium erkannte, dass „rechte Populisten“ die „Freiheit und Demokratie“ in Europa bedrohten und Trump in den USA auf dem Vormarsch war. Also wurde ein weiterer „Notstand“ ausgerufen – diesmal von der Gemeinschaft der Geheimdienste, den Medien, der akademischen Welt und der Kulturindustrie. Ja, genau, es war wieder einmal an der Zeit, unsere demokratischen Prinzipien hintanzustellen, „Hassrede“ in sozialen Medien zu zensieren, die Massen mit lächerlicher offizieller Propaganda über „Russiagate,“ „Hitlergate“ und so weiter zu bombardieren – sonst hätten „die Rechtspopulisten gewonnen.“
Der Krieg gegen den Populismus gipfelte in der Einführung des Neuen Normalen Reichs.

Im Frühjahr 2020 rief das Imperium einen globalen „gesundheitlichen Ausnahmezustand“ aus, als Reaktion auf ein Virus mit einer Überlebensrate von etwa 99,8 Prozent. Das Imperium hatte keine andere Wahl, als ganze Gesellschaften abzuriegeln, jeden dazu zu zwingen, in der Öffentlichkeit medizinisch aussehende Masken zu tragen, die Öffentlichkeit mit Propaganda und Lügen zu bombardieren, die Menschen dazu zu nötigen, sich einer Reihe experimenteller mRNA-„Impfungen“ zu unterziehen, Proteste gegen ihre Dekrete zu verbieten und systematisch diejenigen zu zensieren und zu verfolgen, die es wagten, ihre erfundenen „Fakten“ in Frage zu stellen oder ihr totalitäres Programm zu kritisieren.
Das Imperium hatte keine andere Wahl, als das alles zu tun, denn sonst hätten „die Covid-Leugner, die Impfgegner, die Verschwörungstheoretiker und all die anderen Extremisten gewonnen.“
Ich bin mir ziemlich sicher, dass du dich an all das erinnerst.
Und jetzt … nun, hier sind wir. Ja, du hast es erraten – es ist wieder einmal an der Zeit, kräftig auf die US-Verfassung und die Meinungsfreiheit zu scheißen, Menschen in irgendein salvadorianisches Höllenloch abzuschieben, das wir angemietet haben, weil ein Polizist ihre Tattoos nicht mochte, Universitätsstudenten wegen ihrer Anti-Israel-Proteste festzunehmen und zu verschleppen und natürlich die Massen mit Lügen und offizieller Propaganda zu bombardieren, denn … okay, alle zusammen jetzt: „sonst hätten die antisemitischen Terroristen und venezolanischen Banden gewonnen!“
Fängst du an, ein Muster zu erkennen? Ja? Willkommen beim Krieg gegen-was-auch-immer!
Wenn du die Zusammenhänge noch nicht ganz siehst, okay, lass es mich noch einmal ganz simpel erklären.
Das globale ideologische System, in dem wir alle leben, wird totalitär. (Dieses System ist der globale Kapitalismus, aber nenne es, wie du willst. Es ist mir scheißegal.) Es reißt die Simulation der Demokratie nieder, die es nicht mehr aufrechterhalten muss. Der Kalte Krieg ist vorbei. Der Kommunismus ist tot. Der globale Kapitalismus hat keine externen Feinde mehr. Also muss er die Massen nicht mehr mit demokratischen Rechten und Freiheiten besänftigen. Deshalb entzieht er uns diese Rechte nach und nach und konditioniert uns darauf, ihren Verlust hinzunehmen.
Er tut dies, indem er eine Reihe von „Notständen“ inszeniert, jeder mit einer anderen „Bedrohung“ für die „Demokratie,“ die „Freiheit,“ „Amerika“ oder „den Planeten“ – oder was auch immer. Jeder mit seinen eigenen „Monstern,“ die eine so große Gefahr für die „Freiheit“ oder was auch immer darstellen, dass wir unsere verfassungsmäßigen Rechte aufgeben und die demokratischen Werte ad absurdum führen müssen, denn: sonst „würden die Monster gewinnen.“

Es tut dies, indem es sein Antlitz von „links“ nach „rechts,“ dann zurück nach „links“, und dann zurück nach „rechts,“ dann nach „links“ und so weiter neigt, weil es unsere Kooperation dafür benötigt. Nicht die Kooperation von uns allen auf einmal. Nur eine kooperative demografische Gruppe auf einmal.
Es ist dabei erfolgreich – also das System – indem es unsere Angst und unseren Hass instrumentalisiert. Dem System ist es völlig egal, ob wir uns als „links“ oder „rechts“ identifizieren, aber es braucht uns gespalten in „links“ und „rechts,“ damit es unsere Angst und unseren Hass aufeinander nähren kann … eine Regierung, ein „Notfall,“ ein „Krieg“ nach dem anderen.
Da hast du es. Das ist der Krieg gegen was auch immer. Noch simpler kann ich es nicht erklären.
Oh, und noch eine letzte Sache … wenn du einer meiner ehemaligen Fans bist, wie Rob, die über meine „Einsichten“ oder Loyalitäten oder was auch immer verwirrt sind … nun, der Text, den du gerade gelesen hast, sollte das für dich klären. Ich stehe auf keiner Seite. Überhaupt keiner. Aber ich habe ein paar grundlegende demokratische Prinzipien. Und die richten sich nicht danach, was gerade populär ist oder wer im Weißen Haus sitzt.
Die Sache ist die: Ich muss mich morgens im Spiegel anschauen können ohne dort einen Heuchler oder … du weißt schon, einen Feigling zu sehen.
(Aus dem Amerikanischen übersetzt von René Boyke).
CJ Hopkins ist ein US-amerikanischer Dramatiker, Romanautor und politischer Satiriker. Zu seinen Werken zählen die Stücke Horse Country, Screwmachine/Eyecandy und The Extremists. Er hat sich als profilierter Kritiker des Corona-Regimes profiliert und veröffentlicht regelmäßig auf seinem Substack-Blog.
Sein aktuelles Buch:
https://x.com/CJHopkins_Z23/status/1907795633689264530
Hier in einem aktuellen Gespräch:
https://www.youtube.com/watch?v=wF-G32P0leI
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.)
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 90c656ff:9383fd4e
2025-05-04 17:48:58
@ 90c656ff:9383fd4e
2025-05-04 17:48:58The Bitcoin network was designed to be secure, decentralized, and resistant to censorship. However, as its usage grows, an important challenge arises: scalability. This term refers to the network's ability to manage an increasing number of transactions without affecting performance or security. This challenge has sparked the speed dilemma, which involves balancing transaction speed with the preservation of decentralization and security that the blockchain or timechain provides.
Scalability is the ability of a system to increase its performance to meet higher demands. In the case of Bitcoin, this means processing a greater number of transactions per second (TPS) without compromising the network's core principles.
Currently, the Bitcoin network processes about 7 transactions per second, a number considered low compared to traditional systems, such as credit card networks, which can process thousands of transactions per second. This limit is directly due to the fixed block size (1 MB) and the average 10-minute interval for creating a new block in the blockchain or timechain.
The speed dilemma arises from the need to balance three essential elements: decentralization, security, and speed.
The Timechain/"Blockchain" Trilemma:
01 - Decentralization: The Bitcoin network is composed of thousands of independent nodes that verify and validate transactions. Increasing the block size or making them faster could raise computational requirements, making it harder for smaller nodes to participate and affecting decentralization. 02 - Security: Security comes from the mining process and block validation. Increasing transaction speed could compromise security, as it would reduce the time needed to verify each block, making the network more vulnerable to attacks. 03 - Speed: The need to confirm transactions quickly is crucial for Bitcoin to be used as a payment method in everyday life. However, prioritizing speed could affect both security and decentralization.
This dilemma requires balanced solutions to expand the network without sacrificing its core features.
Solutions to the Scalability Problem
Several solutions have been suggested to address the scalability and speed challenges in the Bitcoin network.
- On-Chain Optimization
01 - Segregated Witness (SegWit): Implemented in 2017, SegWit separates signature data from transactions, allowing more efficient use of space in blocks and increasing capacity without changing the block size. 02 - Increasing Block Size: Some proposals have suggested increasing the block size to allow more transactions per block. However, this could make the system more centralized as it would require greater computational power.
- Off-Chain Solutions
01 - Lightning Network: A second-layer solution that enables fast and low-cost transactions off the main blockchain or timechain. These transactions are later settled on the main network, maintaining security and decentralization. 02 - Payment Channels: Allow direct transactions between two users without the need to record every action on the network, reducing congestion. 03 - Sidechains: Proposals that create parallel networks connected to the main blockchain or timechain, providing more flexibility and processing capacity.
While these solutions bring significant improvements, they also present issues. For example, the Lightning Network depends on payment channels that require initial liquidity, limiting its widespread adoption. Increasing block size could make the system more susceptible to centralization, impacting network security.
Additionally, second-layer solutions may require extra trust between participants, which could weaken the decentralization and resistance to censorship principles that Bitcoin advocates.
Another important point is the need for large-scale adoption. Even with technological advancements, solutions will only be effective if they are widely used and accepted by users and developers.
In summary, scalability and the speed dilemma represent one of the greatest technical challenges for the Bitcoin network. While security and decentralization are essential to maintaining the system's original principles, the need for fast and efficient transactions makes scalability an urgent issue.
Solutions like SegWit and the Lightning Network have shown promising progress, but still face technical and adoption barriers. The balance between speed, security, and decentralization remains a central goal for Bitcoin’s future.
Thus, the continuous pursuit of innovation and improvement is essential for Bitcoin to maintain its relevance as a reliable and efficient network, capable of supporting global growth and adoption without compromising its core values.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 57d1a264:69f1fee1
2025-05-01 05:14:06
@ 57d1a264:69f1fee1
2025-05-01 05:14:06The mystical d attribute in SVG paths is actually a series of small commands. In this guide, we'll take a look at each path command and how we can use them to draw icons. Read more at https://www.nan.fyi/svg-paths
I you'd like to learn Interactive SVG Animations, here a text-based mini-course on making whimsical, playful SVG animations https://www.svg-animations.how/
credits: @nandafyi
originally posted at https://stacker.news/items/968195
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 57d1a264:69f1fee1
2025-05-01 05:01:45
@ 57d1a264:69f1fee1
2025-05-01 05:01:45