-
 @ 6be5cc06:5259daf0
2025-05-12 14:50:36
@ 6be5cc06:5259daf0
2025-05-12 14:50:36A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 51faaa77:2c26615b
2025-05-12 17:34:37
@ 51faaa77:2c26615b
2025-05-12 17:34:37My goal is to share a concise list of questions about OP_RETURN limits that we've answered on Stacker News, as the original thread has become unwieldy with over 200 comments. We began compiling this list about a week ago. I've frequently shared individual links and received very positive feedback. I hope this resource helps us work from a common set of facts and reduces misinformation. I hope you find this as a valuable resource.
I'll list the questions in order of activity and tips received. I've removed duplicates, rephrased some statements as questions, and ignored completely irrelevant questions.
- Users should be given clear configurable options to decide what's in their mempool, why were these options taken away? link
- Won't spammers abuse large OP_RETURNs to bloat the blockchain and make IBD take longer? link
- A similar PR was proposed by Peter Todd 2 years ago, why was it rejected then? What has changed since then, why would this get approved now? link
- Shouldn't we be fighting spam, why are we making policies less strict, shouldn't we be making them more strict? link
- How would someone get around the standardness policy currently for OP_RETURN size? link
- What does "standardness mean" in reference to OP_RETURNs? link
- Will more than 1 OP_RETURN per transaction be possible if this PR gets merged? link
- What are the current OP_RETURN limits and what restrictions are being lifted? link
- Are current relay and mempool policies effective for filtering out spam transactions? link
- Is it true that this type of update could affect Bitcoin's decentralization? link
- Is it possible to stop the abuse of payment outputs (i.e., bare multisig, fake pubkeys, and fake pubkey hashes) that are used to embed data, thereby creating unprunable UTXOs that bloat the UTXO set? link
- What was the main reason /concern to add this PR? ... What will happen if we do nothing? link
- If OP_RETURN still cannot stop all the garbage, why is so important to remove it? Does it affect future development / improvements for LN? link
- What will be the worst case scenario if users still could set their own limits for OP_RETURN? link
- Shouldn't we debate the controversy of this PR on Github since it's where the code gets merged to make these changes? link
- What does it mean when someone says "Fix the Filters"? link
- Will this open the flood gates and drown out all legitimate onchain activity? link
- What can we do to stop spam at the consensus layer of Bitcoin? link
- Will Taproot wizards and other spam companies and projects start using OP_RETURN to put jpegs on the blockchain? link
- If we prevent these transaction from going into our mempools doesn't that prevent or delay these spam transactions from being mined therefore discouraging the spammers? link
- Is it possible to stop abuse of witness data? If so, how? (i.e ordinal theory inscriptions, "jpegs"). link
- Is there any conflict of interest with Bitcoin Core and companies like Citrea, in ref to this PR? link
- Is there any estimation on how much would this affect fees for the average user, considering external projects (like Citrea) using it? Any possibility that this could saturate the mempool and boost fees beyond reasonable? link
- Was this PR initially proposed because of Citrea BitVM needs? If so don't they only need a slight bump in OP_RETURN size, why is it being proposed to make the size unrestricted? link
- What makes a UTXO unprunable? Which projects are making unprunable UTXOs? link
- Why would a spammer use OP_RETURN if it's cheaper to use Witness data to store arbitrary data? link
- Won't large OP_RETURNs allow people to spam the mempool with 100kb transactions and mess up bitcoin for everyone by bloating the mempool and not allowing legitimate transactions in the mempool? link
- If relaxing op_return standardness limit seeks to make 'spam' prunable, then what are proponents of this change assuming about the long-term feasibility of running a 'full' (unpruned) bitcoin node? link
- Is allowing standardness for larger OP_RETURNs a slippery slope? If we allow this won't we continue to allow things that make bitcoin less for money and more for arbitrary data? link
- Won't removing the OP_RETURN cap reduce fee market pressure by allowing senders to consolidate arbitrary data into a single transaction? link
- Could this PR be the beginning of reducing other mempool restrictions? link
- Culture is what protects Bitcoin from external forces, shouldn't non-technical arguments be valid when considering these types of changes? link
- What's the difference between UTXO set, mempool, and blockchain, and how do larger OP_RETURN or witness data affect node resource usage? link
- What is the difference in defining a transaction as valid versus defining a transaction as standard and why do we need this difference? link
- If you're happy with your viewpoint on consensus and mempool rules, is not upgrading Bitcoin Core until it makes sense to you a valid action to take right now? link
- Why didn't this PR get a BIP number? link
- Why is core rushing this change? link
- If there will be a hard fork resulted from this PR (split chain like in 2017), what will happen with existing LN channels? Will exist on both chains with 2 LNs? link
- Isn't this all moot in a (almost guaranteed) future where fees are very high? link
- What is this controversy about, and what is it really about? link
originally posted at https://stacker.news/items/978404
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 005bc4de:ef11e1a2
2025-05-12 14:00:42
@ 005bc4de:ef11e1a2
2025-05-12 14:00:42Hostr
Hive + Nostr = Hostr, a bidirectional bridge.

Hostr is a bidirectional bridge between Nostr and Hive. What you post on one is automatically cross-posted to the other. (See SETUP.md if you want to jump right in and run it.)
This is experimental. Expect that there will be glitches, errors, and corrections to be made. So, consider it very beta, with no guarantees, and use at your own risk.
Nostr and Hive have differences, mainly, Nostr is a protocol and Hive is a blockchain. Nostr does not have a token, although bitcoin is much-loved and used across Nostr. Hive has two main tokens: HIVE and the HBD stablecoin. More importantly, Nostr and Hive have similarities. Both are decentralized and censorship resistant thanks to users owning and controlling their own private keys.
Nostr users - why you might want to bridge to Hive
I feel the #1 reason a Nostr user might wish to use this bridge is to permanently store and chronicle your Nostr notes.
-
Immutability for your Nostr notes. Your notes on Nostr are held on relays; if they go away, your notes go away. (There was a “nosdrive.app” backup, however I do not believe it’s still working.) Hive is immutable. There is no "delete" and even an “edit” on Hive does not erase the original. Like with a wiki page, a Hive edit shows the most recent version, but the original still remains historically. This would give Nostr users a permanent record of their notes in chronological order.
-
Hive is an excellent long form blogging platform with stable and persistent links. Finding old Nostr notes can be difficult.
-
Increase your reach and potentially gain followers. Your content will bridge off of the Nostr island and be opened to 10-30,000 daily Hive users. Go to https://peakd.com/c/hive-133987 and look for “Hive statistics” to see numbers.
-
Earn rewards in HIVE and HBD. “Likes” on Nostr do not reward you monetarily, but every upvote on Hive yields rewards. For bitcoin maxis, these tokens can easily be swapped into sats with tools like the https://v4v.app web app, or others.
-
Help grow Nostr. Every note that bridges over to Hive will have a footer saying something like, “This note originated on Nostr,” with a link back to your Nostr note on njump.me. On that page, a "Join Nostr" button is prominent.
Hive users - why you might want to bridge to Nostr
-
Increase your reach and potentially gain followers. Your content will be bridged off the Hive island and be opened to 17-18,000 daily users. See https://stats.nostr.band for Nostr stats.
-
Earn bitcoin sats in the form of “zaps.” Nostr does not have a token. But, it has a strong culture of zapping (tipping) bitcoin satoshis to other users to reward quality content. Memes are loved and often zapped too.
-
Unlimited posting. Nostr is not held back by posting or activity limitations, such as with Resource Credits or community norms that frown on posting too often.
-
Even more censorship resistance. Hive is truly censorship-free in that posted content, no matter the content, does indeed posted. However, front ends can choose to show or not show content that the community has downvoted. Nostr is more free speech or censorship resistant...you post it, it's posted. (Relays can choose to relay it or not, accept it or reject it, but you could run your own relay.)
-
Help grow Hive. Every post that bridges over to Nostr will have a footer saying something like, “This post originated on Hive,” with a link back to your Hive blockchain post. This brings wider exposure to Hive.
Quirks about Nostr and Hive
If you’re unfamiliar with Nostr, it has a few quirks:
-
You have one private key, called an “nsec”. It goes along with your “npub”, your public key. Your npub is your username, your nsec IS your account.
-
You simply need an nsec, then a “client” which is a front end.
- You need to add “relays” to your client in order to connect. This is very easy, but how to do it depends on the client. Client's usually walk you through this when you start.
- Short form content (like the old "Tweets") are called kind 1 notes. Long form notes, like most Hive posts, are called kind 30023.
If you’re unfamiliar with Hive, it has more quirks:
-
Hive has five private keys, yes, five. Each has a specific purpose. From least powerful to most powerful, they are: posting key (to post), active key (to move tokens), owner key (to do anything), memo key (to dm/pm), and backup/master private key (to totally restore all keys). Don’t worry about all the keys. For Hostr, we only deal with posting notes/posts, so the posting key is all we deal with.
-
Hive has a culture of frowning on posting too often. Doing so can be seen as trying to milk the HIVE/HBD rewards that you gain from upvotes. Too much posting can be viewed as spamming and result in downvotes (this hurts your Web-of-Trust score, called “reputation” on Hive, and is shown alongside your username; you want to grow and keep your reputation up). The chain also has a 5-minute cool-down rule coded in: after posting, you cannot post for another five minutes.
-
Additionally, to avoid spam, Hive actions burn “Resource Credits” or RCs. Think of RCs as the charge % in your phone battery. Every action on Hive uses RCs, so they dwindle with every use. Posting is high in RC cost. Bad news: if you run out of RCs, you’re unable to do things on Hive. Good news: RCs also recharge. If out of RCs, you can wait and then do things later. For the Hostr script, over-posting means the script will post until RCs are exhausted, then it will stall until RCs are recharged, post again, stall, etc. You can check your RCs in many places, such as a Hive explorer like https://hivescan.info and entering your Hive username. If you have RC issues, reach out for help.
You don't want to over-post on Hive. To avoid over-posting, Hostr has two versions of the script:
-
bidirectional-longform30023.js
- Nostr ➡️ Hive - Listens only for kind 30023 (long form) Nostr notes to bridge over to Hive. Kind 1 short form notes are ignored.
- Hive ➡️ Nostr - Any Hive post over 380 characters gets truncated as a kind 1 (short form) Nostr note (with a link back to the full Hive post).
-
bidirectional-bridge.js
- Nostr➡️Hive - This script listens for both kind 1 (short form) and kind 30023 (long form) Nostr notes and bridges both over to Hive.
- Hive ➡️ Nostr - Same as above (380+ is truncated).
Which script version should I use?
- If you post frequently on Nostr (more than 2 times per day?), the bidirectional-longform30023.js script is likely best. Per Hive community norms, you don't want to post too often on there. With this script version, only long form notes will bridge over from Nostr to Hive.
- For newcomers to Hive, I would start with this script to be safe.
-
If in doubt, use this script.
-
If you post infrequently on Nostr (2 times per day or fewer?), the bidirectional-bridge.js (both kinds 1 and 30023) might work fine for you.
Nostr users - how to begin
You’ll need a Hive account. You can see sign-up options at https://signup.hive.io. Some options are free, others are not. I (crrdlx) have some free “VIP tickets” to sign up with and you are welcome to use one if you wish, see https://crrdlx.vercel.app/hive-vip-ticket.html. If the tickets there are already spent, contact me and I'll get you set up.
As with Nostr, the critical thing with a Hive account is saving your keys. Hive has multiple keys, just save them all. We’ll only use the “posting key” for the Hostr bridge, however. The other keys can be used on Hive if you wish. (For instance, the "active key" is used to handle your HIVE/HBD rewards earned, the "memo key" for private messages.)
Once signed up (and keys are safe), you can adjust your Hive account/profile using any Hive front end like https://peakd.com/username, https://ecency.com/username, or https://hive.blog/username. Just remember, every action on Hive burns RCs, keep an eye on that.
You can learn more about Hive at https://hivewiki.vercel.app if you wish.
See the "Setting up..." section below to set up the bridge.
Hive users - how to begin
You’ll need a Nostr account. Getting a Nostr "account" is nothing more than generating keys. A simple way to do this is at https://nstart.me If you wish to dig into details, take a look at http://nostrwiki.crrdlx.infinityfreeapp.com/doku.php?id=wiki:get-started
As with Hive, you simply need to safely store your private keys. On Nostr, your private key is called your “nsec” (sec, as in “secret”). Your public key is your “npub” (pub, as in "public"). Your nsec is all you need, but just so you know, your private key comes in two formats: (a) your nsec, and (b) the “hex” form (same key, just different forms). With the Hostr bridge, we’ll use the hex private key. Depending on how you join Nostr, your hex key may be given to you at sign up. But, even if it's not, you can always check back-and-forth between nsec and hex keys using a tool like https://nostrtool.com and choosing "Load a privkey from nsec/hex".
Again, just save your nsec and/or hex private key and you’re set.
You can learn more about Nostr at https://nostrwiki.vercel.app if you wish.
See the "Setting up..." section below to set up the bridge.
Setting up the Hostr bridge
To set up the bridge, see SETUP.md in the repo below. The Hostr bridge has a bit of technicals behind it, but don't get intimidated. Because technical things change, I’ll keep the technical how-to instructions housed at https://github.com/crrdlx/hostr
Disclaimer
This is an experimental bridge. Expect that there will be glitches, errors, and corrections to be made. So, consider it very beta, with no guarantees, and use at your own risk. Source code: https://github.com/crrdlx/hostr
Built with ❤️ by crrdlx
Connect on Hive: @crrdlx
Connect on Nostr: nostr:npub1qpdufhjpel94srm3ett2azgf49m9dp3n5nm2j0rt0l2mlmc3ux3qza082j
All contacts: https://linktr.ee/crrdlx
-
-
 @ a296b972:e5a7a2e8
2025-05-12 16:52:30
@ a296b972:e5a7a2e8
2025-05-12 16:52:30Wo sind der 1. Stock, das Erdgeschoss und der Keller? Das Dach ist noch zu bauen. Das Haus zum unerklärlichen Krieg ist unfertig. Der Bau wurde schon viel früher begonnen, aber die westlichen Medien behaupten das Gegenteil oder verschweigen es. Eine Vorgeschichte darf es nicht geben.
Am Ukraine-Krieg sieht man, dass ein Konflikt, der entgegen den Behauptungen der Propaganda-Maschine nicht erst im Februar 2022 angefangen hat, wie lange es dauert, bis wieder Verhältnisse zustande kommen, die eine Befriedung ermöglichen. Das Ringen darum ist hoffentlich endlich in die Zielgerade eingelaufen und man findet besser gestern als heute eine Lösung. So viele Menschenleben auf beiden Seiten hat dieser Wahnsinn bislang gekostet. Am Ende, wofür? Die Verwirrung bleibt bis zuletzt, denn einerseits treibt der US-amerikanische Präsident die Friedensbemühungen maßgeblich voran, andererseits werden von US-amerikanischer Seite mutmaßlich die Waffenlieferungen fortgesetzt und Starlink nicht abgeschaltet, was erheblich zum abrupten Beenden des sinnlosen Sterbens beitragen würde.
Verträge sind zu erfüllen? Sicherung der US-amerikanischen Interessen? Druckmittel auf Russland? Und Europa? Europa, vor allem Deutschland, Frankreich und Großbritannien geben weiterhin den Geisterfahrer und haben immer noch nicht mitbekommen, dass sie in der Beilegung des Ukraine-Kriegs nicht das geringste zu sagen haben. Sie spielen sich aber auf, als hätten sie und machen „einen auf dicke Hose“. Murmeln werden als Eier verkauft.
Etwas aus dem Fokus der Neuen Medien gerät dabei der immer noch wütende Krieg im Gaza-Streifen mit einer israelischen Planier-Raupe, dessen Vorgeschichte noch länger ist, als die, die zum Ukraine-Krieg geführt hat. Rund 80 Jahre, aber auch hier eigentlich noch länger. Man kann sich vorstellen, wie lange es hier dauern wird, bis sich sichere, friedliche Verhältnisse einstellen können.
Wer kann sicher sein, wer nimmt sich das Recht heraus zu behaupten, wer entscheidet darüber, dass sich Zustände, wie im 3. Reich, die Verfolgung und Vernichtung einer Minderheit, damals die Juden, nicht wiederholen kann? Seitdem das geschehen ist, hat sich der Großteil der Menschheit keinen Millimeter weiterentwickelt.
Wenn gerade Deutsche Anzeichen für eine Wiederholung dieser tief-dunklen Zeit zu erkennen glauben, derzeit in dem, wie der israelische Staat mit dem Gaza-Streifen verfährt, dann ist das keine Verharmlosung der Gräueltaten im 3. Reich, sondern der Beweis dafür, dass es doch einige gibt, die aus der Geschichte gelernt haben, und die der Meinung sind, dass sich so etwas niemals mehr wiederholen darf.
Um auf einen Genozid hinzuweisen, muss jeder Vergleich möglich und erlaubt sein. Es geht um eine Mehrzahl von Menschen, von Familien, die einfach nur in Frieden leben wollen! Ungeachtet der Tatsache, dass es auf beiden Seiten Kräfte gibt, die das nicht interessiert.
Besonders tragisch wird es, wenn dieser Genozid augenscheinlich ausgerechnet von denen ausgeht, die selbst so schrecklich davon betroffen waren.
Wie kann sich der deutsche Staat erdreisten, diejenigen als Anti-Semiten zu bezeichnen, die hier Merkmale eines Genozids zu erkennen glauben und versuchen, diese kritischen Stimmen zu unterdrücken, „nur“, weil es sich um den Staat Israel handelt, der hier als Täter infrage kommt. Auch der Staat Israel hat keinen Freibrief, die Bevölkerung im Gaza-Streifen nach seinen Vorstellungen und Überzeugungen abzurasieren.
Ein Genozid ist ein Genozid, egal von welcher Regierung eines Landes er begangen wird.
Der Staat Israel ist keine Ausnahme! Im Gegenteil. Aufgrund der Erfahrung seines Volkes müsste es die Menschlichkeit gebieten, dass derartiger Völkermord nie wieder geschieht.
Weiter müsste der Begriff Anti-Semitismus einmal genau unter die Lupe genommen werden, was wer aus welchen Gründen darunter versteht. Man kann den Eindruck gewinnen, dass dieser Begriff vor allem als Totschlagargument verwendet wird, um kritische Stimmen mundtot zu machen. Besonders bei diesem heiklen Thema wäre absolute Akkuratesse dringend notwendig.
Es ist die Pflicht eines jeden, der Kritik an den Zuständen üben will, nicht zu verallgemeinern.
Nicht alle israelischen Staatsbürger sind Netanjahu-Anhänger (das zeigen die Demonstrationen), nicht alle Juden sind Zionisten, nicht einmal alle Zionisten sind Juden.
Und sicher sind auf der Gaza-Seite ebenfalls nicht nur „Engel“ unterwegs!
Beide Lager haben rund 80 Jahre Zeit gehabt, den gegenseitigen Hass durch gegenseitige Provokationen aufzubauen und ihn immer wieder sich entladen zu lassen.
Dieser unermessliche Hass kann nur über Generationen hinweg wieder abgebaut werden.
Wenn es jemals eine ernste Absicht gegeben hätte, eine 2-Staaten-Lösung zu realisieren, wäre diese schon längst in die Tat umgesetzt worden. Wenn jedoch der politische Wille dazu fehlt, vor allem auf der Seite des Stärkeren, passiert gar nichts. Und der fehlt jetzt schon seit rund 80 Jahren.
Maßgeblich durch die Briten ist der Staat Israel künstlich entstanden. Die Ableitung der Nutznießer auf einen Gebietsanspruch aus einem Glauben heraus, ist einmalig.
In dem nicht natürlich entstandenen, sondern künstlich geschaffenen Staatsgebilde liegt möglicherweise die Wurzel allen Übels, die von langer Hand, spätestens durch die Balfour-Deklaration im Jahre 1917 ihren Anfang genommen hat.
Man hat nun Jahrzehnte lang Zeit gehabt, zu beobachten, dass dieses Konstrukt ein sicheres Leben und eine Garantie für friedliche Verhältnisse aller nicht zustande gebracht hat. Schmerzliche Erfahrungen auf beiden Seiten haben bislang nicht dazu geführt, dass man zu der Einsicht gekommen wäre, dass man sich möglicherweise auf dem Holzweg befindet.
Die verfeindeten Lager müssten sich, neutral moderiert (welcher Staat, welcher Mensch ist heute noch neutral, oder zumindest kein Interessenvertreter?), zusammensetzen und sich in sicher nicht einfachen, langwierigen, zähen Gesprächen und Verhandlungen über die Neugründung eines gemeinsamen Staates für alle Beteiligten ernsthaft nachdenken, solange, bis es zu einer Einigung gekommen wäre, die für alle Beteiligten akzeptabel ist. Das Ergebnis, eine gemeinsame Staatenlösung, müsste das erklärte Ziel sein und wenn es noch so lange dauern würde.
Das Mitspracherecht müsste nach Bevölkerungsanteil in einem gerechten Verhältnis festgelegt werden. So müssten kleinere Anteile verhältnismäßig mehr Stimmanteile haben, als der größere Anteil, um zu möglichst für alle gerechten Entscheidungen zu gelangen, die alle Beteiligten mittragen könnten. Ein Vorankommen wäre nur durch Vernunft, nicht durch Starrsinn möglich.
Aufgrund der hitzigen Mentalität aller Beteiligten müssten beide Lager auf Gedeih und Verderb voneinander abhängig gemacht werden, sodass ein friedliches Zusammenraufen immer wieder nötig wäre, weil niemand in der Lage wäre, die Oberhand zu gewinnen.
Es müssten gegenseitige Abhängigkeiten geschaffen werden. So könnten zum Beispiel Lieferungen von Lebensmitteln, Wasser, Energie (Israel) usw. mit der Hoheit über die noch zu erschließenden Gasfelder (Gaza) vor Gaza „verrechnet“ werden, ohne, dass die USA oder sonst wer die Finger im Spiel haben.
Bei derartigen gegenseitigen Abhängigkeiten würde man sich schon zusammenraufen.
Das alles setzt voraus, dass der Mensch an sich seine menschlichen Schwächen unter Kontrolle bringen würde. Hierzu können Machtstreben, Geldgier, Rechthaberei, Überheblichkeit, Ideologien, Ansprüche aus einem Glauben heraus usw. gezählt werden.
Jerusalem müsste einen Sonderstatus erhalten und die Verwaltung müsste unter den drei Weltreligionen aufgeteilt werden. Jerusalem könnte im „Kleinen“ ein Beispiel dafür sein, wie der gesamte neue Staat im „Großen“ funktioniert. Und möglicherweise würde er so in der Tat funktionieren.
Für viele mag das alles vielleicht naiv oder sogar absurd klingen. Zur Herstellung von Frieden, Frieden in dem jede Mutter, gleich welcher Religion sie angehört, ihre Kinder in Sicherheit aufwachsen sehen kann, muss jede Überlegung und Idee, wie ein friedliches Miteinander realisiert werden kann, erlaubt sein zu denken und auch auszusprechen.
Eines ist sicher. So, wie die Verhältnisse in der Vergangenheit gestaltet wurden, hat die Realität eindeutig gezeigt, dass es so auf gar keinen Fall funktioniert. Also, warum nicht einfach einmal das Gehirn durchblasen, alte, überkommene Überzeugungen loswerden und endlich einmal etwas Neues denken?
Und wer jetzt immer noch sagt, das wäre eine Delegitimierung des Staates Israel, der sollte seine Gehirnwindungen einmal zur Inspektion bringen. Der Mensch, egal welcher Couleur und welcher Religion steht hier im Mittelpunkt. Im Mittelpunkt stehen Überlegungen, wie ein friedliches Miteinander möglich sein könnte. Falls sich herausstellt, dass das eine Utopie ist, auch gut, aber immerhin sind sich Gedanken gemacht worden, die von den eingefahrenen, zu nichts außer Elend führenden Entscheidungen abweichen. Und wenn es nur zur Anregung für andere Ideen dient, dann wäre schon viel getan. Und das ist weder anti-semitisch, noch anti-israelisch, noch anti-christlich, noch anti-moslemisch, noch anti-sonst wie, sondern vor allem ein Appell an die Vernunft, zu der der Mensch schließlich auch begabt ist.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von Georg Ohrweh)
-
 @ 55f04590:2d385185
2025-05-12 12:34:10
@ 55f04590:2d385185
2025-05-12 12:34:10
Behind the scenes, a lot has happened over the past weeks.
The design of the book’s pages is nearly finished. I’ve selected and placed the illustrations and sketches I’ll feature and I’m close to finalising the Introduction section. All that’s left to do is a small photo shoot of some things from my archives, selecting one or two more articles for the Context section, and illustrating the articles.
After that I’ll print a dummy and kick off the second round of iteration—crossing T’s, dotting I’s. (And then I’ll cross those T’s and dot those I’s again and again because, surely, more things will arise.)
In parallel, and perhaps most importantly, I’m working on the design of the cover. I have a few ideas I’d like to discuss with the printer to learn more about the various possibilities and costs.

Book site
The book is now also available for pre-order through its own website, where you can pay for it in euros or dollars, if you prefer. BTC payments are still possible, too.
Originally I only offered one pre-order option that included rewards, like a print and a sticker pack. I’ve now named that the Collectors Edition, and added a separate option to order just the book (without additional rewards) at a reduced price.
Once the book is out in the world, this site is where I’ll have it up for sale. I’ll make the articles and illustrations from the Context section available there too. They’ll be published, in their entirety, under the Creative Commons Share-alike license.
Promo video
My friend Lilia shot and edited a short promotional video that provides a glimpse behind the scenes in my studio in Amsterdam, a peek at the book’s production process, and a sneak preview of the first spreads. While the process was new to me, this video was a lot of fun to make and I’m proud of the result.
Pre-orders
The total number of pre-orders has grown to 76—12 of which came through the new website. I initially thought I’d be selling 50 pre-orders at most, so things are definitely exceeding my expectations.
Feel free to place your pre-order through the new site, or use the Geyser crowdfund campaign to secure your copy.
Up next
In my next blog I’ll dive a little deeper into the technical side of the book. I’ll take you through the different kinds of paper I’ll use, the printing methods we’ll employ, and how the book will be bound and finished.
Keep your eyes peeled! Thomas
Previous updates
The NoGood art book announcement Update 01 – Humble beginnings Update 02 – Throwback Update 03 – Loops
Pre-order a book
The NoGood art book is available as a pre-order on book.nogood.studio, where you can pay for it in euros or dollars, if you prefer. BTC payments are still possible, too.
Alternatively, visit the Geyser crowdfund campaign to secure your copy.
originally posted at https://stacker.news/items/978096
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ 7460b7fd:4fc4e74b
2025-05-12 12:23:54
@ 7460b7fd:4fc4e74b
2025-05-12 12:23:54警惕:那些“帮你”保管密钥的人
—— 多签钱包中的隐形风险与逻辑陷阱
“我们可以帮您设置一个更安全的钱包。” 这句话,听上去就像是关心,其实却可能是一次有预谋的接管。
摘要
多签钱包被广泛视为提升数字资产安全性的“进阶方案”,尤其适用于不希望将所有信任寄托于单一点故障(如一把私钥)的人群。然而,在这些看似“民主化”、“抗单点失败”的技术结构背后,仍潜藏着极为隐秘且被低估的风险。
本文聚焦两类常见却高度隐蔽的逻辑攻击模型:
- 替换 xpub 并接管下一层级地址生成;
- 伪造
k-of-n多签结构,在形式上给予用户参与感,实则实现单人提款。
在未引入 Taproot 的传统多签结构下,这类攻击已能轻易完成。而即便在 Taproot 和 MuSig2 合约模型下,攻击者也可以借助合成结构进一步隐藏其篡改行为。
本报告不仅梳理攻击逻辑,更强调“人性中的信任误区”——攻击者不需要主动索取密钥,只需要维持友善形象,自会有用户主动递交钥匙。更令人警惕的是,在某些极端场景下,这类“被信任的服务商”甚至可能向受害者收取“保管密钥”的费用后再实施盗窃,形成双重获利。
Taproot 虽然在结构上增强了隐私与复杂性,但也使验证逻辑失去了可直观还原的优势。随着时间推移、服务厂商退出市场乃至私有恢复流程被锁死,用户极可能落入无法恢复的“密钥黑箱”中。
阅读本文,希望你能意识到:
真正的安全,从不是托付给别人帮你“多签”,而是你真正理解你签了什么、和谁签的、签名之后将通往哪一个脚本。
多签钱包的逻辑攻击向量分析
以 xpub 替换与伪造 k-of-n 结构为例
攻击模型一:替换 xpub 实现地址劫持
场景设定
攻击者假扮为友好的钱包初始化服务者,主动提出“免费帮你生成一个更安全的多签钱包”。表面上,他为你设置了标准的 HD 多签结构,实际上却在关键的派生路径中,悄悄将本应由你或另一个可信方持有的 xpub 替换为他自己的。
在 HD 钱包结构(例如 BIP45、BIP67)中,用户通常无法直观验证每一个新地址是否仍属于原来的签名组。这种设计让“看上去很安全”的地址,可能早已成为攻击者可完全支配的提款口袋。
攻击结构(逻辑表示)
- 假设多签参与者为
P1, P2, P3 - 攻击者控制伪造者身份
P1',实际替代掉用户的P1 - 地址生成函数为:
Addr = f(xpub(P1'), xpub(P2), xpub(P3))- 用户未验证 xpub 时,成立:
∃ Addr_i ∈ wallet, spendable_by(attacker)换言之,钱包中的某些地址虽然看起来正常,但已可被攻击者花费。
人性陷阱提示
用户往往不认为“地址生成这件事”是需要人工检查的,特别是在使用 Ledger、Trezor 等硬件钱包时形成了“签名即安全”的错觉。而攻击者只需一次替换,就能悄悄监视整个钱包生命周期。
更重要的是,攻击者不需要向你“索取密钥”,他只需维持友善、专业甚至略带“为你好”的姿态。在 100 个用户中,总会有一部分人,在受到“信任感”与“他人看起来更专业”的影响下,主动提出将某个密钥托管给对方,甚至支付一定“密钥保管费”作为安全保障。这类行为并非愚蠢,而是人性的一部分。
这种松懈与依赖,背后深植着心理学上著名的「责任分散效应(diffusion of responsibility)」。当责任从“自己一人持有私钥”转变为“我们多人共同掌控”时,大脑会自动削弱“必须百分百保护密钥”的紧迫感;一旦密钥有三份或五份,人就会默认“即使我丢了一份也无所谓”,由此降低警惕,弱化加密习惯的执行力度。
尤其是在多签结构下,密钥不再是“唯一真理”。你开始认为:“我只是 n-of-m 的一员”,进而产生 安全责任稀释(safety dilution)。举个例子:如果你的 seed words 是唯一的,你很可能将其写在一张专用纸上,藏入防火袋,存放于密封保险箱中;但一旦你拥有的是 3-of-5 多签中的一份,你可能就只是把它存在 Evernote、存图于手机相册,或者发给自己 Telegram 备份——并自我安慰说:“这只是其中一把钥匙,又不怕。”
这正是攻击者渗透的最佳入口。他无需破解密码学算法,仅凭理解人性中的懒惰、依赖与责任下沉机制,就足以发起极具杀伤力的社会工程攻击。
提醒:没有人例外。你的安全不是由数学公式决定,而是由你是否对它持续保持敬畏与冷静判断所决定的。
Taproot 下的隐蔽性升级
在 Taproot + MuSig2 合约结构中:
- 合成公钥如:
P = H(P1 + P2 + P3) - 用户无法从地址推导出其组成
- 所有 pubkey 被掩盖,无任何可读性结构泄露
结果:攻击者替换某个 xpub 之后,哪怕是资深用户,也无法通过比对地址结构来发现任何异常。
攻击模型二:伪造 k-of-n 多签脚本结构
场景设定
攻击者承诺为你部署一个“非常安全”的
2-of-3多签钱包。然而他实际创建的却是一个1-of-3结构,并诱导你保留或交出其中一个密钥。用户一旦信任其脚本不可见性(或 UI 模糊性),资金注入该地址之后,攻击者即可单独提款。
攻击结构(逻辑描述)
- 正确脚本应为:
OP_2 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 实际被构造为:
OP_1 <pk1> <pk2> <pk3> OP_3 OP_CHECKMULTISIG- 用户错误地相信:
user_believes(k=2) ∧ attacker_has(sk1) → safe- 但实际上:
real_k = 1 ∧ attacker_has(sk1) → attacker_can_spend成立条件
- 用户未能验证 redeem script
- 钱包界面(UI 或 PSBT)未明确标识 k 值与脚本结构
- 攻击者拥有脚本定义权,或 UI 权限
人性陷阱提示
这类攻击往往并非“高技术”,而是利用用户对脚本结构的无感。尤其是当攻击者扮演“技术专家”时,用户往往不具备审查 redeem script 的能力或意识。攻击者甚至可以用“给你设置一个冷备密钥”作为幌子,骗取部分 key,并收取额外费用。
多签攻击模型对比分析(无表格)
- 攻击类型一:xpub 替换
- 本质:公钥注入
- 隐蔽性:极高(生成地址完全正常)
- 关键条件:用户未验证每个 xpub
-
Taproot 是否能规避:否,反而更难发现
-
攻击类型二:伪造 k-of-n
- 本质:脚本结构欺骗
- 隐蔽性:中等(需查看 redeem script 才能识别)
- 关键条件:用户不懂脚本,UI 不展示结构
- Taproot 是否能规避:否,合约结构反而隐藏了更多细节
安全建议(基于当前攻击模型)
- 强制在 UI 中完整展示所有 xpub、合成地址派生路径与对应签名人列表
- 如 Coldcard 的二维码验证机制
- 用户必须自行保存每个 xpub,并可验证任一地址确实源自该集合派生
- 多签钱包必须提供可见 redeem script 的界面与 k 值校验提示
- 不接受“帮你配置好了”的 UI 黑箱
- Taproot 虽增强隐私,但也加剧验证障碍
- 若使用合签结构,应避免依赖第三方界面进行签名决策
- 始终优先使用硬件钱包本地签名流程,避免通过 Web 或中间服务生成交易
真实案例分析
1. Coldcard 硬件钱包的 xpub 替换漏洞
2021 年,安全研究员 benma 发现 Coldcard 硬件钱包在注册多签钱包时,未验证自身是否为多签钱包的一部分。这使得恶意计算机钱包可以用攻击者控制的 xpub 替换多签 xpub,同时仍通过所有用户验证。所有接收到此多签钱包的币随后可以随时转移到攻击者的钱包。
来源:benma.github.io2. Bybit 交易所的多签钱包被黑事件
2025 年 2 月,Bybit 交易所的多签冷钱包在一次例行转账中被黑,损失约 14.6 亿美元。该钱包使用 2-of-3 多签设置,意味着需要三位授权签名人中的两位批准交易。用户界面显示了合法的目标地址,并且 URL 与受信任的多签提供商 Safe 相关联。但这是一种欺骗。黑客利用硬件钱包中的“盲签名”漏洞,使设备只能显示交易的哈希,从而掩盖了一个更改,使攻击者控制了钱包的智能合约。
来源:certora.com3. Parity 多签钱包漏洞
2017 年,Parity 多签钱包版本 1.5+ 中发现了一个漏洞,允许攻击者窃取超过 150,000 ETH(约 3000 万美元)。攻击者向受影响的合约发送两个交易:第一个获取多签的独占所有权,第二个移动其所有资金。
来源:blog.openzeppelin.com
攻击流程图解
- 建立信任:攻击者以技术专家或受信任的服务提供商身份接近受害者,提出帮助设置多签钱包。
- 替换 xpub:在设置过程中,攻击者用自己控制的 xpub 替换原本应由用户或第三方控制的 xpub。
- 生成地址:攻击者生成看似正常的多签地址,并展示给用户,用户未进行验证。
- 资金注入:用户将资金转入这些地址,认为资金安全。
- 资金转移:攻击者利用控制的私钥,单方面将资金转出,用户无法察觉。
参考文献
附录:攻击面分析——为何 xpub 替换是多签特有的风险?
单签钱包是否存在 xpub 替换攻击?
答案:否。
在单签钱包结构中(如 BIP32/BIP39 衍生的标准钱包):
- 钱包只依赖一个 xpub,并且这个 xpub 是从用户私钥派生而来;
- Coldcard、Trezor 等硬件钱包会自动根据本地 seed 派生地址,无需输入外部 xpub;
- 用户可以通过设备显示屏确认“这是我派生出来的地址”,不存在外部注入路径。
因此:xpub 替换在单签钱包中不存在攻击面,攻击路径被封死。
多签钱包为什么引入了 xpub 攻击面?
多签钱包(如 2-of-3、3-of-5)需要以下信息来生成地址:
- 所有参与者的 xpub;
- 公钥排序规则(如 BIP67);
- 多签脚本模板(如 OP_2
OP_3 OP_CHECKMULTISIG); - 每个 key 的派生路径(如 m/48'/0'/0'/2'/0/1);
这就意味着,用户必须信任这些输入的 xpub 是来自真正的签名方。如果攻击者悄悄将其中某一份换成自己控制的 xpub,那他就自动成为地址共管人,甚至是单签人。
Coldcard 攻击案例回顾:
- 用户通过 PSBT 模板或 JSON 导入多签配置;
- 攻击者在其中替换了某一参与者的 xpub;
- Coldcard 在旧版本中未提示或验证该替换;
- 用户生成地址、发送资金,攻击者即可随时提取。
攻击面比较表
- 单签钱包
- 不接收外部 xpub,派生路径完全由设备掌控;
- 地址来源明确、签名单一;
-
xpub 替换攻击无效。
-
多签钱包
- 依赖多个外部 xpub 合成结构;
- 用户很难手动验证每一条 xpub 与 fingerprint;
- xpub 替换为高危攻击点。
Taproot 是否规避了 xpub 替换问题?
部分规避,但引入了新的验证难题。
Taproot + MuSig2 等结构通过将多个 pubkey 合成为一个点:
P = H(P1 + P2 + P3)
这确实可以隐藏合约结构,提升隐私,但也导致:
- 用户无法从地址还原参与者是谁;
- 如果其中一个公钥被攻击者替换,生成的地址仍然合法;
- 用户在链上看不到任何异常,但攻击者已取得合约控制权。
因此:Taproot 并未从根本上消除 xpub 替换的攻击面,反而因为其不可还原性使得攻击更加隐蔽。
总结
多签钱包之所以引入新的攻击面,不是因为它“更复杂”,而是因为它必须信任外部结构。一旦你的钱包要“与他人协作生成地址”,你就必须验证“这些人是谁”、“这些地址是怎么来的”——这就是攻击的入口。
单签保护的是私钥,
多签则要求你保护你的伙伴。 -
 @ 30611079:ecac89f8
2025-05-10 13:30:51
@ 30611079:ecac89f8
2025-05-10 13:30:51Um Shell Script simples para facilitar backups bip39 baseados nos números das palavras, coloque o script na mesma pasta que o arquivo contendo as palavras, passe o idioma no 1º argumento (Ex. english) e as palavras em sequência, a saída serão os números correspondentes as palavras passadas no idioma selecionado
```
!/bin/bash
Enter in correct diretory
if [ ${0%/} == $0 ]; then cd ${PWD} elif [ -e ${PWD}/${0%/} ]; then cd ${PWD}/${0%/} else cd ${0%/} fi
file="$1.txt"
index=0 numbers=() for word in "$@"; do while IFS= read -r linha; do if [[ "$linha" == "$word" ]]; then numbers+=($index) break fi ((index++)) done < "$file" index=0 done echo "${numbers[@]}" ```
Fiz para aprender um pouco de Shell Script, podem dizer se está bom e se dá para melhorar algo?
Também fiz outro que faz o processo reverso
-
 @ 8d34bd24:414be32b
2025-05-11 02:47:03
@ 8d34bd24:414be32b
2025-05-11 02:47:03What does it say about us that believers don’t listen as well as unbelievers? Let’s investigate some scripture verses and see what we can discover.
An Object Lesson:
Jesus warned His disciples several times that He would be killed and rise from the dead on the third day. Right after Jesus asked them who they thought He was and Peter replied that He was the Christ (Messiah), Jesus told them what would happen.
From that time Jesus began to show His disciples that He must go to Jerusalem, and suffer many things from the elders and chief priests and scribes, and be killed, and be raised up on the third day. (Matthew 16:21)
We know the disciples heard and understood what Jesus was saying because Peter immediately rebuked Jesus.
Peter took Him aside and began to rebuke Him, saying, “God forbid it, Lord! This shall never happen to You.” But He turned and said to Peter, “Get behind Me, Satan! You are a stumbling block to Me; for you are not setting your mind on God’s interests, but man’s.” (Matthew 16:22-23)
You’d think that Peter would have this moment locked in his mind after being rebuked so harshly for questioning Jesus’s prediction of what would happen.
A while later, Jesus again told His disciples what was about to happen.
And while they were gathering together in Galilee, Jesus said to them, “The Son of Man is going to be delivered into the hands of men; and they will kill Him, and He will be raised on the third day.” And they were deeply grieved. (Matthew 17:22-23)
They again heard what was said because they were “deeply grieved.” They didn’t like what they heard.
Then a third time, as they were approaching Jerusalem, He made certain they knew what was coming:
As Jesus was about to go up to Jerusalem, He took the twelve disciples aside by themselves, and on the way He said to them, “Behold, we are going up to Jerusalem; and the Son of Man will be delivered to the chief priests and scribes, and they will condemn Him to death, and will hand Him over to the Gentiles to mock and scourge and crucify Him, and on the third day He will be raised up.” (Matthew 20:17-19)
The disciples should have known that Jesus’s crucifixion and death were not the end. He told them repeatedly that He would die and be raised from the dead on the third day. They should have been diligently waiting with expectation, but instead they immediately hid, gave up, and headed back to their old lives.
His female followers still cared enough to try to prepare Jesus’s body for burial, but even they did not expect Him to rise as He said.
The angel said to the women, “Do not be afraid; for I know that you are looking for Jesus who has been crucified. He is not here, for He has risen, just as He said. Come, see the place where He was lying. Go quickly and tell His disciples that He has risen from the dead; and behold, He is going ahead of you into Galilee, there you will see Him; behold, I have told you.” (Matthew 28:5-7) {emphasis mine}
Even when the woman came and told the disciples that they had seen Jesus as He had said, none believed them, although Peter and John did have a glimmer of hope and went to look for themselves.
In contrast, the Pharisees, the very people who hated Jesus so much that they fought to have Him crucified, remembered Jesus’s statements.
Now on the next day, the day after the preparation, the chief priests and the Pharisees gathered together with Pilate, and said, “Sir, we remember that when He was still alive that deceiver said, ‘After three days I am to rise again.’ Therefore, give orders for the grave to be made secure until the third day, otherwise His disciples may come and steal Him away and say to the people, ‘He has risen from the dead,’ and the last deception will be worse than the first.” Pilate said to them, “You have a guard; go, make it as secure as you know how.” And they went and made the grave secure, and along with the guard they set a seal on the stone. (Matthew 27:62-66) {emphasis mine}
The Pharisees acted in response to Jesus’s claims. The disciples ignored or forgot Jesus’s claims.
KNOW:
How often do we ignore or forget Jesus’s promises? How often do we despair when we should hold tightly to the promises given to us in the Bible? Are there times that our opponents, unbelievers, are better at quoting the Bible back at us than we are at using the Bible to defend the truth and our faith?
but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence (1 Peter 3:15)
We need to know God’s word so we can “give an account for the hope that is in” us. First we need to read the whole Bible. We can’t know who God is, what He has done, and what He commands for us without knowing God’s word.
After we have gotten the big picture by reading through the Bible once, we need to really get to know it well. This not only includes reading the Bible continually, but also include memorizing key verses, so we can bring them to remembrance when we need them.
Some people can repeat a verse multiple times and just know it. Some of us have trouble memorizing things. We have to go to extraordinary measures to memorize God’s word. Some techniques I have used:
-
WHITEBOARD APPROACH:
-
Write the verse on the white board.
-
Read out loud.
-
Erase one word. (You can underline where the word is if that helps you remember that a word goes there)
-
Read out loud saying verse including missing word.
-
Continue erasing words, one at a time, saying the verse until all of the words are gone.
-
I haven’t used it personally, but Verse Locker was recommended by another substacker and seems to use a similar technique.
-
MUSICAL VERSES:
-
Make up a tune and sing the verse or put the verse to a tune you already know.
-
If you aren’t good at making up songs, there are sites that have verses to songs, but I haven’t used them personally other than a few from Awana years ago.
-
FIRST LETTER:
-
Write down the first letter of each word of the verse you want to memorize This gives hints and helps you not accidentally miss words.
-
I’ve also made a necklace (it was supposed to be a bracelet, but the verse, 1 Peter 3:15 above, I picked was too long) made of beads with the letters of the words of the verse. By wearing it, you have a reminder to memorize and rememorize the verse till it sticks stronger.
-
This is my version of 1 Peter 3:15

-
APPS:
-
There are multiple apps that can help you memorize verses. 5 Best Bible Memory Apps for 2025
We are all different and have different learning styles. Pick the version that works best for you, but be intentional. For so long I wasn’t. Having a child with Down Syndrome in Awana who needed help led me to finding ways to help him and me to memorize the hundreds (or thousands) of verses that are required to finish the program. Keep in mind that you need to keep reviewing them or the memories will fade. The more times you memorize the verse, the longer it will stick with you. You just never know when you will need a Scripture verse and you may not have your Bible or phone (with Bible app) handy.
APPLY:
Knowing the Bible is critical for the Christian life, but knowing the Bible and God’s commands is not enough. We have to live according to this knowledge. We have to apply it in our lives. It needs to change the way we view the world and change the way we live our lives and interact with others.
for it is not the hearers of the Law who are just before God, but the doers of the Law will be justified. (Romans 2:13) {emphasis mine}
Our faith needs to be exhibited through action.
But someone may well say, “You have faith and I have works; show me your faith without the works, and I will show you my faith by my works.” (James 2:18) {emphasis mine}
There is nothing we need to do to be saved besides believe, but if we have saving faith, we should desire God’s word like the author of Psalm 119. Our lives should also change to be conformed to Jesus.
And do not be conformed to this world, but be transformed by the renewing of your mind, so that you may prove what the will of God is, that which is good and acceptable and perfect. (Romans 12:12) {emphasis mine}
There must be works as evidence of our faith.
You believe that God is one. You do well; the demons also believe, and shudder. But are you willing to recognize, you foolish fellow, that faith without works is useless? Was not Abraham our father justified by works when he offered up Isaac his son on the altar? You see that faith was working with his works, and as a result of the works, faith was perfected; (James 2:19-22) {emphasis mine}
The disciples heard Jesus tell them what was going to happen to Him. They knew what He had said because they reacted to it negatively. The problem was they didn’t believe it and didn’t live according to Jesus’s plain words. As important as it is to read and understand the Bible, none of that matters if we don’t believe it and live it.
But I Can’t Do It Myself:
Jesus knew that we could not know and do what we were commanded to know and do, at least not in our own power.
Then He opened their minds to understand the Scriptures, and He said to them, “Thus it is written, that the Christ would suffer and rise again from the dead the third day, and that repentance for forgiveness of sins would be proclaimed in His name to all the nations, beginning from Jerusalem. You are witnesses of these things. And behold, I am sending forth the promise of My Father upon you; but you are to stay in the city until you are clothed with power from on high.” (Luke 24:45-49)
Jesus not only sent the disciples (and all believers) out into the world to tell of what He has done for us, but He told the disciples to “stay in the city until you are clothed with power from on high.” Jesus told them to wait until they had received the Holy Spirit to guide and empower them in the work He had designed them to complete. We also have the Holy Spirit to change our hearts and minds, so we can fulfill the commandments and plans He has for us.
I’m sorry if this post had a little too much overlap with my last post, but knowing God’s word has become a passion of mine and it is where I felt led to go.
May the God of Heaven give you a hunger for His word, help you to understand His word, believe His word, and live His word. May your understanding of the word of God guide you in everything you think, speak, and do. May you never doubt God’s word or discount God’s word because it isn’t according to your preference. God bless you and keep you.
Trust Jesus.
-
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 84b0c46a:417782f5
2025-05-10 10:41:20
@ 84b0c46a:417782f5
2025-05-10 10:41:20https://long-form-editor.vercel.app/
β版のため予期せぬ動作が発生する可能性があります。記事を修正する際は事前にバックアップを取ることをおすすめします
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの😃アイコンから←アイコン変えるかも)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
-
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 732c6a62:42003da2
2025-03-09 22:36:26
@ 732c6a62:42003da2
2025-03-09 22:36:26Não são recentes as táticas da esquerda de tentar reprimir intelectualmente seus opositores na base do deboche, da ironia, do desprezo e do boicote à credibilidade. Até Marx usava ironia para chamar os críticos de "burgueses iludidos". A diferença é que, no século XXI, trocaram o manifesto comunista por threads no Twitter e a dialética por memes de mau gosto.
A Falácia da Superioridade Moral
O debate sobre o "pobre de direita" no Brasil é contaminado por uma premissa tácita da esquerda: a ideia de que classes baixas só podem ter consciência política se aderirem a pautas progressistas. Quem ousa divergir é tratado como "traidor de classe", "manipulado", "ignorante", ou até vítimas de deboches como alguma pessoa com um qi em temperatura ambiente repetir diversas vezes "não é possível que ainda exista pobre de direita", "nunca vou entender pobre de direita", ou "pobre de direita é muito burro, rico eu até entendo", como se o autor dessas frases fosse o paladino dos mais oprimidos e pobres. Esse discurso, porém, não resiste a uma análise empírica, histórica ou sociológica.
Contexto Histórico: A Esquerda e o Mito do "Voto Consciente"
A noção de que o pobre deve votar na esquerda por "interesse de classe" é herança do marxismo ortodoxo, que via a política como mero reflexo da posição econômica. No entanto, a realidade é mais complexa:
- Dados do Latinobarómetro (2022): 41% dos brasileiros de baixa renda (até 2 salários mínimos) apoiam redução de impostos e maior liberdade econômica — pautas tradicionalmente associadas à direita.
- Pesquisa IPEC (2023): 58% dos pobres brasileiros priorizam "segurança pública" como principal demanda, acima de "distribuição de renda".
Esses números não são acidentais. Refletem uma mudança estrutural: o pobre moderno não é mais o "operário industrial" do século XX, mas um empreendedor informal, motorista de app, ou microempresário — figuras que valorizam autonomia e rejeitam paternalismo estatal. Eles dizem não entender o pobre de direita e que nunca vai entendê-los, mas o fato é que não entendem porque nunca conversaram com um sem fazer cara de psicólogo de posto de saúde. Sua "preocupação" é só uma máscara para esconder o desprezo por quem ousa pensar diferente do seu manual de "oprimido ideal".
Se ainda não entenderam:
Direita ≠ rico: Tem gente que trabalha 12h/dia e vota em liberal porque quer ser dono do próprio negócio, não pra pagar mais taxação pra você postar meme no Twitter.
Acham que são o Sherlock Holmes da pobreza: o palpite de que "o pobre é manipulado" é tão raso quanto sua compreensão de economia básica.
A Psicologia por Trás do Voto Conservador nas Periferias
A esquerda atribui o voto pobre em direita a "falta de educação" ou "manipulação midiática". Essa tese é não apenas elitista, mas cientificamente falsa:
Análise Psicológica Básica (para você que se acha o Paulo Freire):
- Síndrome do Branco Salvador: Acha que o pobre é uma criatura tão frágil que precisa de você pra pensar. Spoiler: ele não precisa.
- Viés da Superioridade Moral: "Se você é pobre e não concorda comigo, você é burro". Parabéns, recriou a escravidão intelectual.
- Efeito Dunning-Kruger: Não sabe o que é CLT, mas dá palpite sobre reforma trabalhista.- Estudo da Universidade de São Paulo (USP, 2021): Entre moradores de favelas, 63% associam políticas de segurança dura (como "bandido bom é bandido morto") à proteção de seus negócios e famílias. Para eles, a esquerda é "branda demais" com o crime.
- Pesquisa FGV (2020): 71% dos trabalhadores informais rejeitam aumentos de impostos, mesmo que para financiar programas sociais. Motivo: já sofrem com a burocracia estatal para legalizar seus negócios.
Esses dados revelam uma racionalidade prática: o pobre avalia políticas pelo impacto imediato em sua vida, não por abstrações ideológicas. Enquanto a esquerda fala em "reforma estrutural" e tenta importar discursos estrangeiros para debate, por exemplo, o tema irrelevante do pronome neutro, ele quer resolver problemas como:
- Violência (que afeta seu comércio);
- Impostos (que consomem até 40% do lucro de um camelô);
- Burocracia (que impede a legalização de sua barraca de pastel).
Religião, Valores e a Hipocrisia do "Ateísmo de Redes Sociais"
A esquerda subestima o papel da religião na formação política das classes baixas. No Brasil, 76% dos evangélicos são pobres (Datafolha, 2023), e suas igrejas promovem valores como:
- Família tradicional (contra pautas progressistas como ideologia de gênero em escolas);
- Auto-responsabilidade (ênfase em "trabalho duro" em vez de assistencialismo).Exemplo Concreto:
Nas favelas de São Paulo, pastores evangélicos são frequentemente eleitos a cargos locais com plataformas anticrime e pró-mercado. Para seus eleitores, a esquerda urbana (que defende descriminalização de drogas e críticas à polícia) representa uma ameaça ao seu estilo de vida.
A Esquerda e seu Desprezo pela Autonomia do Pobre
O cerne do debate é a incapacidade da esquerda de aceitar que o pobre possa ser autônomo. Algumas evidências:
O Caso dos Empreendedores Informais
- Segundo o IBGE (2023), 40% dos trabalhadores brasileiros estão na informalidade. Muitos veem o Estado como obstáculo, não aliado. Políticas de direita (como simplificação tributária) são mais atraentes para eles que o Bolsa Família.
A Ascensão do Conservadorismo Periférico
- Pessoas assim tem um pensamento simples. Sua mensagem: "Queremos empreender, não depender de político."
A Rejeição ao "Vitimismo"
- Pesquisa Atlas Intel (2022): 68% dos pobres brasileiros rejeitam o termo "vítima da sociedade". Preferem ser vistos como "lutadores".
A projeção freudiana "o pobre é burro porque eu sou inteligente"
O deboche esquerdista esconde um complexo de inferioridade disfarçado de superioridade moral. É a Síndrome do Salvador em sua forma mais patética:
- Passo 1: Assume-se que o pobre é um ser desprovido de agência.
- Passo 2: Qualquer desvio da narrativa é atribuído a "manipulação da elite".
- Passo 3: Quem critica o processo é chamado de "fascista".Exemplo Prático:
Quando uma empregada doméstica diz que prefere o livre mercado a programas sociais, a esquerda não pergunta "por quê?" — ela grita "lavagem cerebral!". A ironia? Essa mesma esquerda defende a autonomia feminina, exceto quando a mulher é pobre e pensa diferente.Dados Globais: O Fenômeno Não é Brasileiro
A ideia de que "pobre de direita" é uma anomalia é desmentida por evidências internacionais:
- Estados Unidos: 38% dos eleitores com renda abaixo de US$ 30k/ano votaram em Trump em 2020 (Pew Research). Motivos principais: conservadorismo social e rejeição a impostos. A esquerda: "vítimas da falsa consciência". Mais um detalhe: na última eleição de 2024, grande parte da classe "artística" milionária dos Estados Unidos, figuras conhecidas, promoveram em peso a Kamala Harris, do Partido Democrata. Percebe como a esquerda atual é a personificaçãoda burguesia e de só pensar na própria barriga?
- Argentina: Javier Milei, libertário radical, quando candidato, tinha forte apoio nas villas miseria (favelas). Seu lema — "O estado é um parasita" — ressoa entre quem sofria com inflação de 211% ao ano.
- Índia: O partido BJP (direita nacionalista) domina entre os pobres rurais, que associam a esquerda a elites urbanas desconectadas de suas necessidades.
A história que a esquerda tenta apagar: pobres de direita existem desde sempre
A esquerda age como se o "pobre de direita" fosse uma invenção recente do MBL, mas a realidade é que classes baixas conservadoras são regra, não exceção, na história mundial:
- Revolução Francesa (1789): Camponeses apoiaram a monarquia contra os jacobinos urbanos que queriam "libertá-los".
- Brasil Imperial: Escravos libertos que viraram pequenos proprietários rurais rejeitavam o abolicionismo radical — queriam integração, não utopia.Tradução:
Quando o pobre não segue o script, a esquerda inventa teorias conspiratórias.
A Hipocrisia da Esquerda Urbana e Universitária
Enquanto acusa o pobre de direita de "alienado", a esquerda brasileira é dominada por uma elite desconectada da realidade periférica:
- Perfil Socioeconômico: 82% dos filiados ao PSOL têm ensino superior completo (TSE, 2023). Apenas 6% moram em bairros periféricos.
- Prioridades Descoladas: Enquanto o pobre debate segurança e custo de vida, a esquerda pauta discussões como "linguagem não-binária em editais públicos" — tema irrelevante para quem luta contra o desemprego. Os grandes teóricos comunistas se reviram no túmulo quando veem o que a esquerda se tornou: não debatem os reais problemas do Brasil, e sim sobre suas próprias emoções.
"A esquerda brasileira trocou o operário pelo influencer progressista. O pobre virou um personagem de campanha, não um interlocutor real."
A diversidade de pensamento que a esquerda não suporta
A esquerda prega diversidade — desde que você seja diverso dentro de um checklist pré-aprovado. Pobre LGBTQ+? Herói. Pobre evangélico? Fascista. Pobre que abre MEI? "Peão do capitalismo". A realidade é que favelas e periferias são microcosmos de pluralidade ideológica, algo que assusta quem quer reduzir seres humanos a estereótipos.
Respostas aos Argumentos Esquerdistas (e Por que Falham)
"O pobre de direita é manipulado pela mídia!"
- Contradição: Se a mídia tradicional é dominada por elites (como alegam), por que grandes veículos são abertamente progressistas? A Record (evangélica) é exceção, não regra.
Contradição Central:
Como explicar que, segundo o Banco Mundial (2023), países com maior liberdade econômica (ex.: Chile, Polônia) reduziram a pobreza extrema em 60% nas últimas décadas, enquanto modelos estatizantes (ex.: Venezuela, Argentina com o governo peronista) afundaram na miséria? Simples: a esquerda prefere culpar o "neoliberalismo" a admitir que o pobre com o mínimo de consciência quer emprego, não esmola.Dado que Machuca:
- 71% das mulheres da periferia rejeitam o feminismo radical, associando-o a "prioridades distantes da realidade" (Instituto Locomotiva, 2023)."Ele vota contra os próprios interesses!"
- Falácia: Pressupõe que a esquerda define o que é o "interesse do pobre". Para um pai de família na Cidade de Deus, ter a boca de fogo fechada pode ser mais urgente que um aumento de 10% no Bolsa Família.
O pobre de direita não é uma anomalia. É o produto natural de um mundo complexo onde seres humanos têm aspirações, medos e valores diversos. Enquanto a esquerda insiste em tratá-lo como um projeto fracassado, ele está ocupado:
- Trabalhando para não depender do governo.
- Escolhendo religiões que dão sentido à sua vida.
- Rejeitando pautas identitárias que não resolvem o custo do gás de cozinha."É falta de educação política!"
- Ironia: Nos países nórdicos (modelo da esquerda), as classes baixas são as mais conservadoras. Educação não correlaciona com progressismo.
Por que o Debuste Precisa Acabar
A insistência em descredibilizar o pobre de direita revela um projeto de poder fracassado. A esquerda, ao substituir diálogo por deboche, perdeu a capacidade de representar quem mais precisaria dela. Enquanto isso, a direita — nem sempre por virtude, mas por pragmatismo — capturou o descontentamento de milhões com o status quo.
O pobre de direita existe porque ele não precisa da permissão do rico de esquerda para pensar. A incapacidade de entender isso só prova que a esquerda é a nova aristocracia.
Último Dado: Nas eleições de 2022, Tarcísio de Freitas (direita) venceu em 72% das favelas de São Paulo. O motivo? Seu discurso anti-burocracia e pró-microempreendedor.
A mensagem é clara: o pobre não é um projeto ideológico. É um agente político autônomo — e quem não entender isso continuará perdendo eleições.
A esquerda elitista não odeia o pobre de direita por ele ser "irracional". Odeia porque ele desafia o monopólio moral que ela construiu sobre a miséria alheia. Enquanto isso, o pobre segue sua vida, ignorando os berros de quem acha que sabem mais da sua vida que ele mesmo.
Pergunta Retórica (Para Incomodar):
Se a esquerda é tão sábia, por que não usa essa sabedoria para entender que pobre também cansa de ser tratado como cachorro que late no ritmo errado?
Fontes Citadas:
- Latinobarómetro (2022)
- IPEC (2023)
- USP (2021): "Segurança Pública e Percepções nas Favelas Cariocas"
- FGV (2020): "Informalidade e Tributação no Brasil"
- Datafolha (2023): "Perfil Religioso do Eleitorado Brasileiro"
- Atlas Intel (2022): "Autopercepção das Classes Baixas"
- Pew Research (2020): "Voting Patterns by Income in the U.S."
- TSE (2023): "Perfil Socioeconômico dos Filiados Partidários"
Leitura Recomendada para Esquerdistas:
- "Fome de Poder: Por que o Pobre Brasileiro Abandonou a Esquerda" (Fernando Schüller, 2023)
- "A Revolução dos Conservadores: Religião e Política nas Periferias" (Juliano Spyer, 2021)
- "Direita e Esquerda: Razões e Paixões" (Demétrio Magnoli, 2019) -
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ c9badfea:610f861a
2025-05-12 16:29:32
@ c9badfea:610f861a
2025-05-12 16:29:32- Install Organic Maps
- Launch the app and download the World Map first
- Tap the ☰ at the bottom, then select Download Maps, and tap the + icon
- Download maps by tapping ⤓ next to your desired region
- Return to the main screen and tap 🔍 to search for your destination
- Enjoy navigating offline
ℹ️ Note that Organic Maps does not provide live traffic updates
-
 @ 732c6a62:42003da2
2025-03-06 06:00:53
@ 732c6a62:42003da2
2025-03-06 06:00:53De acordo com a Forbes, a Ripple (Empresa responsável pela Criptomoeda XRP) tem financiado e apoiado campanhas contra a mineração de Bitcoin.
Por que Ripple faz propaganda anti-bitcoin?
Simples: eles são o oposto do Bitcoin em quase tudo. Enquanto o Bitcoin foi criado para ser descentralizado, resistente à censura e independente de instituições, o Ripple é basicamente um serviço bancário 2.0. Eles precisam atacar o Bitcoin para justificar sua própria existência.
O que você não sabe:
- Ripple Labs controla a maioria do XRP: Eles têm um estoque estratégico que pode ser liberado no mercado a qualquer momento. Isso é o oposto de descentralização.
- XRP não é uma moeda para "pessoas comuns": Foi criada para bancos e instituições financeiras. Basicamente, é o "banco central" das criptomoedas.
- Ripple não é blockchain no sentido tradicional: Eles usam um protocolo chamado Ripple Protocol Consensus Algorithm (RPCA), que é mais rápido, mas menos descentralizado.
Os principais ataques do Ripple ao Bitcoin:
- Anti-mineração: O Ripple critica o consumo de energia do Bitcoin, mas esquece que seu próprio sistema depende de servidores centralizados que também consomem energia.
- Anti-reserva estratégica: O Ripple tem um estoque gigante de XRP, mas critica o Bitcoin por ser "deflacionário". Hipocrisia? Nunca ouvi falar.
- Anti-descentralização: O Ripple prega que a descentralização do Bitcoin é "ineficiente", mas o que eles realmente querem é manter o controle nas mãos de poucos.
Análise Psicológica Básica (para você que acha que XRP é o futuro):
- Síndrome do Underdog: Acha que apoiar o Ripple te faz um rebelde, mas na verdade você está torcendo para o sistema bancário tradicional.
- Viés de Confirmação: Só ouve opiniões que validam sua decisão de comprar XRP.
- Efeito Dunning-Kruger: Acha que entender Ripple te torna um especialista em criptomoedas, mas não sabe o que é um hard fork.
Estudo de Caso (Real, mas Você Vai Ignorar):
Carlos, 30 anos, comprou XRP porque "é o futuro das transações bancárias". Ele não sabe que o Ripple está sendo processado pela SEC por vender XRP como um título não registrado. Carlos agora está esperando o "pump" que nunca vem.Conclusão: ou, "volte para a aula de economia do ensino médio"
Ripple não é o futuro das finanças. É só mais um player tentando lucrar em um mercado competitivo. E sua propaganda anti-Bitcoin? Essa só prova que a descentralização assusta quem quer controle. Agora vá estudar blockchain básico — ou pelo menos pare de compartilhar memes com erros de português.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ b8851a06:9b120ba1
2025-05-09 22:54:43
@ b8851a06:9b120ba1
2025-05-09 22:54:43The global financial system is creaking under its own weight. The IMF is urging banks to shore up capital, cut risk, and brace for impact. Basel III is their answer, a last-ditch effort to reinforce a brittle foundation.
But behind the scenes, a quieter revolution is under way.
Bitcoin, the world’s first stateless digital asset, is no longer on the sidelines. It’s entering the Basel conversation: not by invitation, but by inevitability.
Basel III: The System’s Self-Diagnosis
Basel III is more than a technical rulebook. It’s a confession: an admission that the global banking system is vulnerable. Created in the aftermath of 2008, it calls for: • Stronger capital reserves: So banks can survive losses. • Lower leverage: To reduce the domino effect of overexposure. • Liquidity buffers: To weather short-term shocks without collapsing.
But here’s the kicker: these rules are hostile to anything outside the fiat system. Bitcoin gets hit with a punitive 1,250% risk weight. That means for every $1 of exposure, banks must hold $1 in capital. The message from regulators? “You can hold Bitcoin, but you’ll pay for it.”
Yet that fear: based framing misses a bigger truth: Bitcoin doesn’t just survive in this environment. It thrives in it.
Bitcoin: A Parallel System, Built on Hard Rules
Where Basel III imposes “fiat discipline” from the top down, Bitcoin enforces it from the bottom up: with code, math, and transparency.
Bitcoin is not just a hedge. It’s a structural antidote to systemic fragility.
Volatility: A Strategic Asset
Yes, Bitcoin is volatile. But in a system that devalues fiat on a schedule, volatility is simply the cost of freedom. Under Basel III, banks are expected to build capital buffers during economic expansions.
What asset allows you to build those buffers faster than Bitcoin in a bull market?
When the cycle turns, those reserves act as shock absorbers: converting volatility into resilience. It’s anti-fragility in motion.
Liquidity: Real, Deep, and Global
Bitcoin settled over $19 trillion in transactions in 2024. That’s not hypothetical liquidity. it’s real, measurable flow. Unlike traditional high-quality liquid assets (HQLAs), Bitcoin is: • Available 24/7 • Borderless • Not dependent on central banks
By traditional definitions, Bitcoin is rapidly qualifying for HQLA status. Even if regulators aren’t ready to admit it.
Diversification: Breaking the Fiat Dependency
Basel III is designed to pull banks back into the fiat matrix. But Bitcoin offers an escape hatch. Strategic Bitcoin reserves are not about speculation, they’re insurance. For family offices, institutions, and sovereign funds, Bitcoin is the lifeboat when the fiat ship starts taking on water.
Regulatory Realignment: The System Reacts
The Basel Committee’s new rules on crypto exposures went live in January 2025. Around the world, regulators are scrambling to define their stance. Every new restriction placed on Bitcoin only strengthens its legitimacy, as more institutions ask: Why so much resistance, if it’s not a threat?
Bitcoin doesn’t need permission. It’s already being adopted by over 150 public companies, forward-looking states, and a new class of self-sovereign individuals.
Conclusion: The Real Question
This isn’t just about Bitcoin fitting into Basel III.
The real question is: How long can Basel III remain relevant in a world where Bitcoin exists?
Bitcoin is not the risk. It’s the reality check. And it might just be the strongest capital buffer the system has ever seen.
Gradually then suddenly.
-
 @ 732c6a62:42003da2
2025-03-06 04:33:48
@ 732c6a62:42003da2
2025-03-06 04:33:48De ''Dialética do Oprimido'' a ''Like do Oprimido'': A Queda Livre do Debate que Nunca Existiu.
A moda do momento
Fiquei aproximadamente 8 meses sem ter acesso a nenhum dispositivo. Quando consegui novamente o acesso ao smartphone, percebi algo diferente no debate político brasileiro: enquanto a direita estava se engajando em incontáveis números de curtidas e compartilhamentos com memes que demonstravam críticas ao governo e aos seus ainda poucos apoiadores que se humilham para defender o indefensável, a esquerda radical repetia sua imposição intelectual em comentários de vários posts, incluindo textos, vídeos e tweets com frases semelhantes a "vai ler um livro de história" "nunca leu um livro", "eu estou do lado certo da história" e "se eu fosse irracional eu seria de direita". Tudo isso pra tentar passar uma mensagem de que a história é de esquerda. A tese é: será que eles realmente são tão inteligentes como juram?
Fatos que ignoram enquanto cospem jargões do "lado certo da história":
1. A esquerda também tem seus terraplanistas: Anti-vaxxers de organicafé, terraplanistas do gênero, e os que acham que a Coreia do Norte é uma democracia.
2. Viés de confirmação não é monopólio da direita: Eles compartilham estudos "científicos" do Medium como se fossem peer-reviewed, mas desdenham de dados que contradizem sua narrativa.
3. A direita não é um monolito: Tem desde ancaps que calculam até a última casa decimal até bolsominions que acham que a Terra é plana. Generalizar é... bem, irracional.Estudo de Caso (Fictício, mas Verdadeiro):
Larissa, 23 anos, posta sobre "ciência e razão" enquanto defende horóscopo como "ferramenta de autoconhecimento". Acredita que o capitalismo causa depressão, mas não sabe o que é taxa Selic. Larissa é você após três caipirinhas.A Imposição intelectual que ninguém pediu (mas todos recebem de graça)
A esquerda brasileira, em sua cruzada épica para salvar o mundo dos "fascistas que ousam discordar", adotou uma nova estratégia: transformar complexidade política em slogans de camiseta de feira. A frase "se eu fosse irracional, seria de direita" não é original — é plágio descarado da cartilha do Complexo de Deus em Oferta no AliExpress.
O Quebra-Cabeça da superioridade Auto-Delirante
A tese esquerdista se sustenta em três pilares frágeis:
1. A falácia do "lado certo da história": Como se história fosse um jogo de futebol com narração do João Cléber.
2. A ilusão de que citar Foucault = ter QI elevado: Spoiler: decorar "biopoder" não te torna imune a acreditar em astrologia.
3. A crença de que volume de texto = profundidade: 15 parágrafos no Twitter não equivalem a um semestre de Ciência Política.Dado Cruel: Um estudo da Universidade de Cambridge (2022) mostrou que extremistas de ambos os lados cometem erros lógicos similares. A diferença? A esquerda usa palavras mais bonitas para mascarar a burrice.
A hipocrisia do "nunca tocou em um livro" (enquanto compartilham resumo de livro no TikTok)
A acusação preferida — "você não lê!" — esconde uma ironia deliciosa:
- 72% dos "intelectuais de rede social" citam livros que nunca leram além do título (Fonte: Pesquisa Informal do Twitter, 2023).
- Obras citadas como troféu: "1984" (para chamar Bolsonaro de Big Brother), "O Capital" (para justificar o NFT da Gal Gadot), e "Feminismo para os 99%" (para atacar homens heterossexuais que usam sandália de dedo).Pergunta Incômoda: Se ler Marx fosse garantia de racionalidade, por que a União Soviética acabou em pizza (literalmente, considerando a economia deles)?
Quando a autoimagem colide com a realidade (Ou: por que nenhum esquerdista lassa no teste de turing da coerência)
A esquerda adora se pintar como a Última Trincheira da Razão, mas pratica o que critica:
- Exemplo 1: Defendem "ciência" quando convém (vacinas), mas abraçam pseudociência quando é trendy (cristais energéticos contra o capitalismo).
- Exemplo 2: Chamam a direita de "terraplanista", mas acham que inflação se resolve com tabelamento estatal — a versão econômica de "a Terra é sustentada por tartarugas".
- Exemplo 3: Criticam "fake news", mas compartilham teorias de que o agro "envenena a comida" (enquanto comem sushi de supermercado).Frase-Chave: "Racionalidade seletiva é o novo analfabetismo funcional."
Pergunta Final: Se a esquerda é tão racional, por que não usa a "lógica implacável" para resolver algo além do enquadro perfeito de stories no Instagram?
Enfim
O debate "esquerda racional vs. direita irracional" é só mais um episódio da novela "Brasil: O País que Confunde Opinião com Ataque de Ego". Enquanto uns brincam de "quem tem o QI mais alto", o país queima — literalmente, considerando o Pantanal. Talvez a verdadeira irracionalidade seja gastar energia discutindo superioridade moral enquanto o Wi-Fi cai pela décima vez no dia. Racionalidade não tem lado político. Arrogância, por outro lado, é universal. Sua necessidade de se sentir superior só prova que a lacração é o último refúgio dos fracos de argumento. Agora deviam estudar economia básica — ou pelo menos que parem de achar que "Ah, mas o capitalismo!" é um contra-argumento.
Saudade da época em que a esquerda não se fingia de intelectual.
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 000002de:c05780a7
2025-05-09 18:33:06
@ 000002de:c05780a7
2025-05-09 18:33:06I've been eager to share my thoughts on "Return of the Strong Gods" by R.R. Reno since I finished it a week ago.
I found this book incredibly insightful. @SimpleStacker's excellent review prompted me to pick it up, and I'm glad I did. While I won't be providing a full review, I will share some of the key insights and thoughts that resonated with me.
Reno masterfully dissects the sociological underpinnings of the political shifts in the US and the Western world over the past decade and a half. His analysis of the rise of populism and nationalism is compelling and rings true to my personal observations. Reno's central thesis is that post-WW2, the West embraced "weaker gods"—ideals like democracy, pluralism, and liberalism—fearing a repeat of the strong nationalistic sentiments that led to Hitler's rise. He argues that this shift has left many people feeling culturally homeless and desperate for strong leadership that listens to their grievances.
A significant portion of Reno's argument is built on the ideas of Karl Popper, a philosopher I was unfamiliar with before reading this book. Popper's work "The Open Society and Its Enemies" has significantly influenced post-war consensus, which Reno argues has led to a disconnect between the political elite and the common people. This disconnect, he posits, is a primary driver of populist sentiments.
Reno also delves into economics, discussing Friedrich Hayek and his agreement with some of Popper's positions. This intersection of philosophy and economics provides a unique lens through which to view the political landscape. Reno's mention of the Treaty of Versailles as a catalyst for Hitler's rise is a point often overlooked in discussions about WW2. He argues that the punitive measures imposed on Germany created an environment ripe for a strongman to emerge.
One of the most compelling aspects of Reno's argument is his explanation of how the political elite often lose touch with the values and wishes of the people they represent. He draws a powerful analogy between cultural homelessness and the desperation that drives people to seek strong leadership. This section of the book particularly resonated with me, as it aligns with my own observations of the political climate.
I would have liked Reno to start his analysis with Woodrow Wilson, whose "making the world safe for democracy" slogan embodied a form of Christian nationalism. Wilson's ideals and the post-WW1 environment laid the groundwork for the open society movement, which Reno critiques. Exploring this historical context could have strengthened Reno's argument.
Reno occasionally conflates economic liberalism with libertinism, which I found to be a minor flaw in an otherwise strong argument. He rightly points out the need for moral ethics in society but seems to overlook the distinction between economic freedom and moral laxity. Reno's discussion of Milton Friedman's ideas further highlights this confusion. While Reno argues that free trade has contributed to many of our modern ills, I believe the issue lies more with nation-state trade agreements like NAFTA, which are not true examples of free trade.
Another area where I disagree with Reno is his conflation of the nation with the state. Nations are cultural entities that predate and can exist independently of states. Reno's argument would be stronger if he acknowledged this distinction, as it would clarify his points about national pride and cultural heritage.
Reno's final chapters offer a cautionary tale about the return of strong gods and the danger of making them idols. He warns against authoritarianism and the overreach of the state, advocating for a balance that respects cultural heritage without succumbing to nationalism.
In conclusion, "Return of the Strong Gods" is a thought-provoking exploration of the political and cultural shifts of our time. Reno's insights are valuable, and his arguments, while not without flaws, provide a fresh perspective on the rise of populism and nationalism. I recommend this book to anyone seeking a deeper understanding of the forces shaping our world today.
originally posted at https://stacker.news/items/975849
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-09 13:25:40
@ 5d4b6c8d:8a1c1ee3
2025-05-09 13:25:40The second round of the NBA Playoffs is historically weird. We'll try to figure out what's going wrong for all three of the presumed contenders. Which of the other East teams need to be considered contenders now? With how bad the Warriors look without Steph (just how underrated is he?), do the Warriors still have any chance?
In Blok'd Shots, we'll talk about the NHL Star who got traded midseason and then beat his former team in the playoffs.
There was a big trade in the NFL. Plus, @grayruby wants to start a media beef with Colin Cowherd.
The MLB introduced a new stat. I have no idea what it is, but I'm looking forward to trying to understand it live on air.
And, of course, lots of contest and betting updates.
What do you want us to talk about?
originally posted at https://stacker.news/items/975474
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-08 22:57:55
@ 5d4b6c8d:8a1c1ee3
2025-05-08 22:57:55Using a discussion style post to get better formatting on the nostr cross-post.
The Fed Leaves Fed Funds Rate at 4.5% as Economic Storm Clouds Gather
by Ryan McMaken
The Fed is now hemmed in by a rising risk of stagflation. It doesn’t know where the economy is headed, or is unwilling to take a position. At this point, “hope for the best” is Fed policy.
originally posted at https://stacker.news/items/975059
-
 @ 4bc7982c:4cb5c39d
2025-05-12 14:21:38
@ 4bc7982c:4cb5c39d
2025-05-12 14:21:38-----BEGIN PGP PUBLIC KEY BLOCK----- mQINBFav2jMBEADPCRsFp9Vtw0vlkeho2v8lIPblVNNeW43HLNXeEGvgn+gaK5sW 9H5mbp6ZLEjbdEr7zc3eu7iLFudw9IdJCLKYcqkXWBpAQF7JF6l4J18oOQK1Tfzc QyU5jWuAcc+Ds8REW91X/N9Ae/QF+dtRyuv1ILFKZ88G2za/TdV06PuNdyi3qTlD 5HPVhd5YrZyY7GVG1gTi7Wtj6tONGjjQARR6T1LDuN75QmoDvw3m68U5QnoECGg4 BFAdPrnFxYpTCl6SyV9AsCfzTwP2mIkLKZi7X/wSubt4b+nhPMuFeZ/6XFCfHCD4 mEcQudyXByi7FgAXmX+UPS1iFtaXG8UJHM4Fq2k5FcjdLXW2s0kKk915XVEE9Q4Y wWQpTonr9FwgT+aSbV7UX8ihNhNCSQAv1RnIIt8t9hncztfZD7g/FMj4FfZ8GkI0 gmn3DliSlswBZbr1rN0HTitAzYKNUsiinIxwICfj9yRTcQ92F0ML+zwQB5UOXjEJ ra+D3tGjyVCNKO940rbjvj/QAvakoNBdCnbaZDKf26Hc0qpcn3DvGei0QLFJ2gmz EnK1dW4kftcJE8piibvq35EEptqkDiCMlI0Eq819vtJBumF3ZSBjMeEB1IPfSvDG 1OoUXXS0TGwCGstjMTRQ1S2D8fDb0ENBrbdhyWXZVQFzxi/YMwkNGswDoQARAQAB tBpzaGlub2hhaSA8YnRjaW5mb0BzZGYub3JnPokCNwQTAQgAIQIbAwIeAQIXgAUC Y+g7QQYLCQgHAwIGFQgCCQoLAxYCAQAKCRBKdYg8wbHTTG6OD/wJ9V3tjvaerA6Y GViWU6h0Nrvjs6/NWq48K3hP9eqy9n7CKVOviCjglF/yf1FEfEDg7LKYtFYLs1pf MFzNolynfGearK7HQeOXRoNFfkDqQWcjPWeVWhkEgxrqq9AMg+7gHMMtKnHWezJT E4NaAui7uW7rTiOvS8PT8+Y3uATermzJ0Cmb1c0su/s9in3bPwnmxJpbj9EruOWg MVY8Hov5fEJTwghIwoVBR2D4nWObQMWQsiNrEG/XdPeE1XzHGLrSmH64o6T2vWK2 XkQU6TVDBKhsIy0EjX9B36Hx+MmFx1pfHfxtGpAgZKwnEnMIoNc2vvrkjJhnRCUQ 1MfMoPDnn01mOT/kNkijyTUlh4rYeqa/A5JuqLbQ6qWz4e9rodu9C6/drn7Ivk/D ipRyMihNKbWq1PkAr7I9YQ/1NAM8ZmUE/bFL7/t6rDsa5IinwUeu/WGqNmKHIo0o u5vQD9zwmYOqeZLo2vzmmr/NkaRD7/3j5pb81MTjZzqTh/BGI31TEbjWpJ4StJ4g 2QNcXamGa/7/TpgI5u2EQojdvUojzSg7V3/ZNsNaJnDnqtZNzY7n2q4qvE2H/xJq z5y0SsTgpMPktt+ljg/T3po/LGQIcCPE4EBpSBKSpi0VWvkGVM2sraUCzP82c/X+ ztr12YwcckdET9SWDtSloE942tXKO4kCOQQTAQgAIwUCVq/aMwIbAwcLCQgHAwIB BhUIAgkKCwQWAgMBAh4BAheAAAoJEEp1iDzBsdNMrLMP/1pQZUXNzG9FlhBBGA8X ko+ObEvuVUvtZzTu8DXrQGDp/DYQq+O7YWhZ8WwyxYJx718bkIemHP5IbXbzmeS3 Nijf1mszrCbmw7QZ496YTihoZxyeb8MHYECPAiUbz9Ie2S6/isF45LZX3SbkwlYc M5UfV4iaXqvKSuydRJ8Xk68rn+AiEXFrv1vcGy7cqDz4PBOd9ZJwiAWhr0m9hMZT uDqYPI8choUh3uhpMIEf9YLD77ru1xl0Uba8e34qrOs+Secfv81ItbFION9z0A17 W2/q01dQfojpcoC+YS3CXXCJGm5TwYniIWVUmtL4eIfg6T/ZX5o5Am3aj4pQxr+E y/NNkUvplXZ+nG3fG4mthY4r+NV4E/RSsZJDU55BAWhZj3fHVhu7Q40yVMHLJNP9 KKCdacd/WWJtUX3Z1X/mQplJcMCYwhvdPNCctDpHrEyuIlvDvJuqbCY5eBa0hk8z jRNA9IghWW7JMzcnQR5u6FXWiqmcfFOEJwDUu8hM057Q6e6/FRPjlmua6SzcMK+k ERS+AwAIX4BIaLCnE7ndizQ/y6ek2hpKFXzPBLmxLyID91/wlA6NzbtyZkgZvJ7X g/7Rtt4FyZwKZqbfBFrjzLIyFTkmJ0lSPCSuWna5vaSg1HXPfc05wOUXsGV8xA8D zrolAoj4OIo//H2YMvLy5Giz0f8AACeO/wAAJ4kBEAABAQAAAAAAAAAAAAAAAP/Y /+AAEEpGSUYAAQEAAAAAAAAA/9sAQwAIBgYHBgUIBwcHCQkICgwUDQwLCwwZEhMP FB0aHx4dGhwcICQuJyAiLCMcHCg3KSwwMTQ0NB8nOT04MjwuMzQy/9sAQwEJCQkM CwwYDQ0YMiEcITIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIy MjIyMjIyMjIyMjIy/8AAEQgAyADIAwEiAAIRAQMRAf/EABwAAAIDAQEBAQAAAAAA AAAAAAYHAAQFAwIIAf/EAEkQAAEDAwIDBAcFAwgIBwAAAAECAwQABREGEgchMRNB kaEUIjJRcYGxFSNCYcEIUtEWFyQlM1OSohg0YmNzgpPSQ1RVcpTC4f/EABkBAAMB AQEAAAAAAAAAAAAAAAABAgMEBf/EACIRAAICAgIDAQEBAQAAAAAAAAABAhEDEiFB EzFRBCJhgf/aAAwDAQACEQMRAD8AAbvwd1NZkuKf9GWhH4miog/5aEpOn50UkLQC R7s/rX0K1xpmuEJk6RW4g9exloX5GuMvibpeY2U3TRFxCVclH0dKh4irpfBWfOog P4yUgVyMdwHG2n8q8cGZQw/CfiLV3dk4nH58q/E2Pg/NwpjUaWCT0W4QfMUUgEN6 C9tzgAfnX43DdcHq4p/p4XaLnpzA1iypJ6BTqD+teU8CkryYd/jOJ7iBn6UUg5EM LbII9kVbg6emTpAZSppsnvcJApxyOBd/59nNiLx05kVjyeEesYSj2cL0gD+6dHOi ogZ8DgVqO4xw8zcbVgjOC8rPkmhu8cO7zZXFokKZVsOCUbv1FFyLBru0glqLdI5/ 2Mn6VbTf+IEMhMiRJUnG3ZIjBWfmRRURWxPrirQspJTkcq/RDdV0xTYe1Jc3QW7h YLPKHeVxSlXiDWQ87ZXlZd0p2ZByr0WUpvPjmqSiDbMDTWg7nqdakxZENnb3vubc +Ao1T+zvqpYym4Wkj3h1f/bWIpzTvLbbb3BXn2mZKXCPHFbdvviIiQImr79EGOQe ZCgPjg0nFdMSk+z9/wBHXVf/AKhaf+ov/tqf6Ouq/wDz9p/6q/8Atrft2v782/ln XMGU2kY7OdAUgH/mAzW9B4lanW+cq01NQPwNSy2o+NTqyrFPO4Oaht7qm3JEFRBx lKl8/wDLVNPC29KyPSYQI961fwp9t6/vTqgqToztmu9Uae04fkDiuL2tbSFf0/Q1 8ZCj6znogUB80mjVlKhDq4ZXhPWTC/xq/hVJ/Qs+ODvlw+XuUr+FPh3UfDt93Y8u 4QlH+9YWgDxFeC3w5lqAZ1THCjyw4sfrRqPg+endOyWjjtmD+YJ/hXH7Ekf3jXia +j/5C6amDETUNvcUroN6D+tVX+D6lt5iy4iyf3TVJR7Jkn0Ii26Rm3KSlhuRFbUr oXVkD6Uao4CamcY7VE+1KTt3eq8o/wD1oqk8HryzktJS57tjnOqY0jra0J+4Vcmw ByKCVAU6gZtyFvdNAXa0qUl9xhRT12bv1FSmC7c9dQhskPreQOqZEYHPzxUqtYBc hTtKlME7FOIPfg4q43ebnGQezlvpJ9yzX0C3qrhFfiS8iEy4eoejls/TFezw/wCG moGyqDMaST0LEkcvkaj0aUINrUl1BClvhwjudbSr9KujUvapPptmtkjPXDZQfKnH J4B2p5sGDeHkH3qbCgfCh2ZwEvUcqMSdGkp7gfUNPZCoXyZumHkff2F1pZ6lh7p8 M1aaNkSE+gX26wFk9FlRCfA1rT+Eeq4gUr7OLgH90QrND0jSN9hubH7dJQT72zTt DQSQp2qY53WniAh0p9lt50pz/izW7D1lxVgrKu1hXJHuOwj5EEUrXYLrR2rScjuK ajfpjQ+7cWgZ/CsilaHSHQ1xo1Tb1BF20gVH8RacI/Q1qxOPWnpDgbn2qbG7iVIC wKSsW/32IrLdwlJ/LfkedXV6wmrAEuJCkj8RcjgE/MU6iNJD0b4gcNLsrD0uElau X37JSfpV1myaBvCCYbkFee9h8Z+tfPxv9ikIKZOnGUk/iYcKT51G2NHvthYfuNue V1ASFpHzHOp1XQOI/JHCyyyMqjvLQD05BQrIkcH0bVFmSws9yVNkedLCEJUcZsev XAB7KHXFtjwPKiOFqbiVCSFsTY9zR0GVIXn4YOaWrJ1NWRwkmZ5R2T+bazWa7w3m RchcV/HvCc1bb4u6yty9l20yhZ7i2FDNacXj/ZgsN3O0Toa+8gpWKlwbGkD8TSzl tkJc7HtOfNDoIzTLtsOxPxWk9q/EexzDT6gM/PlVeJxU0NdkpC57aNwyBIaKa2oz +lryN8OVDd/4TgBHyqanH0Pj4fjmnS+3hi7OLQR7LzaHUnyofuOhj2brztrs8wJS TybUyo+HKi9uysJAUw+4kdxCs1+O2l9aFIEtSkqGCFE01kl2SJF3T+m5MdyQ7ZJ8 FaTgvRF9okfOqH2NBSlRt+sZcRwD1Q+laPMGm1O0YVRlMI7TslHJS2vA8KE7joV3 CkbnkoHetGRTWV9oaBuIeIkUA2nV7E9tPQGQlXyIUK2GNc8U7V61wsUe4N95bTt8 01hSNBPtKKmZSASe7Kaz1QdVWlRMSfJCEnklt448KayRfspJBwzxtW24W73pKQxj qpCgryIqUEHV2qYQxMaTJSe6QylVSrTgS0gPTcdJSifSbDJYUe+NI5eBqzHiaSc3 GPerhbz/AL9rI8RXiZw91RbiRJsspPLOQncPKsR61SWSQ/FeQR3LQRVbDDCDDuzL gcsevGlbT6qTKUg+BokjX/i3bAC1KbuKCeXrodz4EHFKURdp9nmPfXdrtmFb2XHW le9Cyk+VCkuxUN1rjVre2L23XTbS0jkT2S2/MZFbET9oO2LA+1LFJZ7tyCFjzpOx tU6ggoKGbtKCP3VnePOryddT3AlM6DbZqU9zsYDPzFH8MKHVG4m8NL/lEtpppajj EmKAfEVcTYOGV/GIjsEKHXsXtp86Rwv2mLgpX2npdltSvxRHijFeVQdCSQOyk3SA 4T1JStIH1o0j0w5Ha9wcsEpBXBuDwz09ZKh5VhTOB0oEmNcGFjuCwU0vIlljtrSq x6/bjlPMB9xbWfh3URx5fFC2JSYOoGrkjPIIfQ/kfDrih430w5Okvg9fWNxTDQ8B 0U26Dn5UPv6AuUdakvQZKVJ6jYaLY/FTiFaXdl50+2+kDqhhST5ZFakX9oCGghFz skhgj2lJUD4A1Gkh2K13TTycpSopx1Cga8N2O5x/WjukEc/VUU074nFTh/eloakY aUsZHbsY8xWu0xoK8hJjTIJUegbkBKvDNS4zQWIhi46nt3NMuT+e5W8edXUajub4 2zIcCUOn38VP1FO9egrQ+gmNIWM9MLChVNXDlAJKZDax3BScUtmh2KiDFh3p9UY6 SjOOhO4+iu7CfgDWo7w+s4b3+g3mAo+0EtbgPCj9Oi34D/pEaMjtE9FNq51stXO7 w0BD0RagnvUmluwsVsW0XOAMWjWLzIT7LcgLRjx5VdTduJ8L14syFcmx1wpCvLka ZLt6Yfb2yrelYPUKGfrQLqq12iWtDsCCYbuPWUydufCrU49jtMzEcWNcWtzF2000 tsdVNoWk/qK04vHu1ZCLjZprHvKBvA+VBjzmpbVziXOZs7krVvHga5K1fektlFxt 8Cck/wB9FAPiKr+GHA1YnFLQN3TtXMbbJ6pfZKSK0UM6NvIBjTYpUvmOzeAPgaRr 100pcF/1hpUMrPNTkV4p5/Cqi7doOSCUXS629WeSXWwseI7qXjRLHtK4ew5SMxpq v+YBQ8qlJqJp6S2oL09r5sHqltUlTZ8DyqUtCbCdj9oZ6PtTdNMPN9ylIc2+AUK1 Y/G7Qt0XsuFueY3cip5hKx4ikO1rK+oTtcmJfT7nmkrz413VqqNISBNsNve95bQW yfz5VVREP9M7hFqFeN1p7VfLJHZK/SvbnCnQd1QVQZGzd+KPKChXz8zcNJyEkSLX Lik/iZWFgeNWGY2nspNu1JMiEnmHmSkD5pNUoJ9hY4pvAKK4k+hXhaPd2re6sGZw GvLWfR5cSQPiUnzoZgz9WRQr7J1yxJS2PVT6Xjl8FVuQtfcU7ad7rCbi2ocgW0q+ YKTmh430w2MeZwh1TEWoC2LdA72lBQNY0jRN4hJK5NtktJHUqaVgeVMSNx8vURQR dtLnlyKmypJ8CK34nH/S0lGyfCmxieRCmwsUtZ/B2ItVtWkHLasD8uVeEQnmnAtj e2pPRTZKSPCvpJGtOGt7ZSl2bbcHmEvI2Hn8qso0joS7JPogiKKu9h8Z+tS7XtDs +eoeotR2zIj3GWkHkQpRUD41oDXt6cQlubHgzUp7noqefzxTlf4PWlxRVHnPoSeg UAqsqRwceTvMeYw4PwhSSCaFOgFZ9uaemhRuekY6VE+1CcU0fCvwsaCmJTtTc7Y5 nmtWHQKNZPCq8MZxCS4P92rNZEnh9OY5vW19H57CRV+ZhwVYdtZbVm0a+Q2ceql4 qbJPjiiCHP4lWxKfRLzFuSP3Q6lz686FpGkFt81JUkjplJFWYukpTyUGA3K7Ue0p vOKXkT9lew1Y4ka7tqwLppzt0e9tsjPzHKtqDxqtDig1cbdMhu9FDbuANZ1u0Lq1 phsxL9KYUQCUvHcBRBbtGX5RP21cLdNST+KICfGmnjftCo0mtf6QnJAXcY6c9zo2 1aSNLXU7mpUNwn9x4fxqo7w103Kyp+A1vPXsxtHhWLK4MWN1RVGmTIx7tqs4qWsX ViCd3SNteR90tQ9xBzWZI0Il1JAdaUO4KRQ0vhVqKEsm06vkIA6Bzdy86prj8WbE 6sNSftJpA9pSUqCvh31Gi6YFqdw4J3g24LH7yKD7loJqOSDHfZwe8GiBfFTWlpWB c9Ndoke1htSD+oq/E47WZ4bLnZZsdXfyCxT1kArZelQ2vDCxu6jNSnOzxA4bXgf0 iTEZcUMESWigj51Kf9fA4AJ7gVCmK32jU0V5s+yFYyfCsSfwM1VEBMZliUO7Y6Af OqMXQCXiF2HW0FZz6oLqmlA+NaybDxaszZVCurkloDOWZiXPI1pp8JBGbw31VA5S bLJSfcgBf0rEesU6J6r8V9o+5bZFM1HEfipp9vNwt632/Zy/EKh4pruzx8lEhq+a XhvD8W0FJ8FA1Li0AozDdTzwg/GvbD9wiEKjyH2SnoW3VDHnTqHFDhld0g3PTTjL g/cjpI/ymu7cXg7enMR7kYi1dEbijHiKLYCki6t1DDX6lzecHudAWPOrR1rLcA9M tdtk+/cyEk/MU1jwf09PQpdo1Aw+SeilJOPCsuZwLvCSTGfiPo6jCsGhTaFQvkXb Tcn/AFrTamCfxRX+/wCBro1H0knK412usJ0nkCjIH+GiCXwm1JEb3/Zi3Eg4+7IN DcnSc6M4UPRJDax+Etqp+VhRuxHLzHATZeIJIRzCHZC2/lhWaJ4+suKEBKCpUKeg DokoXn5g5pWOWN9Jxg/AivKLbLjqy2txtQORtUU0t0/aDkcrfGjU1vQn7W0oTk81 NbkjzogsnGu1XWSmNItc2K6r99ORSLF61JCRsRcpe33FW4edEFplajvcRSloZcKe RcUhKFeNZ5JRSui0mfRd5b9KtHbQ4jL7hAUlK09RVfS90RPhlBiojPNnattIxg0v NE64lRZP2TdXANpwhSj5UWq/qzVLclC8Rpg7jy3V5j/X/R2Q/PcWn/wORUrw2oKT kHOa913xdqziJUqVKoCVKlSgDMvVukXCIUxZRjvgeqcApP5EUir/AHq522a/Eudp tkotqKSpTACj8xX0RQXqnQqL7LMxhxpt0jCkrTyJ99VGTQ0rEM5e9LSjtn6YW2rv VGexj88GpR1cOEd3JUppuM7+SV4NStlkJ1PnssOIJ949xq5Eud2g84s2S1/7XCKf Kb7wYvwHbxWobqh1U2ps/MjlXQcPeGt7VttOoGmlEZShEhKvrzqbChRwuJGtICQl q8vlA/C4kKB8a22uMN3eTtulotNwHQl1gA0aucBC8lS4N/YdT3ZRnzFDdy4H6pjl QYZjyQOikOYz8jSjIXJnfy40TPUBc9EMIOea4ju3Fd1ROEl1JLU262tXuV66fOsG bw31PABVItMkJHUpbJFYrlkmxiQ8y4z/AMRBTWmwWHTHDuxy2+1sOuooKj6iZH3a j51oxdD8TLatK7Rf25aUjKTGnhXkaVqoKx1KVfCvcd+fb1bosmQwR/duFNG4WNlO quMVh3plQpEhKTzU7EDg8U1ficd7sw52V504hIHIq9ZB8CKW8LiFrCApJavcshPR KyFDzrdY4x34p2XOHAuCfc8wmio9oLDxHF3QV1SEXWyONKzzPYpXj5irTM7hRfHE lqUIzh7juR9eVAC9f6MuaNt30MzvPVyIsI8K5B7hTczhDV5tThHUq3p86lRiykM2 Rw70tMjOyLfe0hKU7v7VKkj40obxIVbZyo0aSF4OAWz1q1cNO6ft9tcmWTVqZueS o+wpX88cqG4gV6YHCd2D31z5Uki4vkNrboLUF9hpmRpLaHMggOKwaMYydQW+xrg3 iMrtGPXYfHMZFEOh7g09bmUpGCU0fpbafa2rSlQ9xFeeoQzcPg7vP4kuAQ0fq9u7 wQh1QS+3yWk8jmjJl5LqeRrMOmLR6QX0RENunqpHKtJmKhgYRnArqxRnBU/RzZp4 p8xVM71KlStznJXCUh9xgpjuJbWfxEZxXepSasCi08phxEd0qWsjO/HWulwVITb3 1RNvpAQS3u6ZqzgZ6VWnNregvtNr2LUggK91SkoIq7Yo5nEvWlrcWJGn23kIOCpK Fc/CpS4vVzv0O4SG2rjIRsWQNquXWpWycaLaSfop/bXDe4rPpWnLhbt34or+8J/P BrsjTXDua4fQdZPw1H2BJjHzIrMuHCzVVu/t7TI+KE7h5UPv6euEUqEiM82E9dyC P0rbYxGDC0VfY33mmtbwH8H1ENTS2T8jyrUEzjVY0qSn0uY2nHrhKHx4jnSe7Bxo +qohSe8HBFaMS+3+CoLi3Wc2R02vq/jRsn0A1muNmt7Q2EXjT7bhT7S1tLbz4cq0 4/Hqy3BopvGmOROFBKkuE/IgUtovFfWENnsH5qZaM5xLaDn1rQHFZmY8F3bR9jmH GCoNbDSqFgMVvVHB+9oSJMVqE4T+NktqHzFdTo3hjfDm23xpsjqEvg+RpcN3/hlc 1lM7TMy3qPMuRniQD+QrqNN8Mrg4pcHWEqBuHJqTHyEn409Y/RB5J4GMPtqVbb00 4M8t6MjxBrAncD7+wD2BjSfdsVj61SicPru20XdM68hyVZyhtmYpoq88ZrWjReMd lRvafkzUA8gXkPj60tfjGCEvhxqGCCX7VIAH7qM/SsV7T8mOr76O42fcpGKZo4ta 7tGEXXT5dCT6yzGWnl39OVaUfjjZJaki5WAJKjzPqq8iKThJAhN+hejoVjIJ7q7Q jho7k86ZWu9VaTvFrBs8FtuQTlbgZ2KH5UuYxL4CWk5JPLArmyJ1yXAN9EasRa5H YyFbUjkCTypw2/U0Z4Aodzn86REPRl0lFLiWFEnmAKMrfDm2wpakMrbIA5mvNnHV 3FnfBbKmOFq6trAIUOdWhJSWyoEUCW5x1zaAVEZ76JkJU3EcWonATWmPPJ8MWT88 F6LibiO0wcYq2iShY5GhyG0qSjeFdTWo1GWhIwauGSbIy4ca4RqhQPQ1+1mffJOB muyPSCK6I5P8Od467LRcSDjPOuEl1DbKlOLCEAc1E9K/EsKCtyqwb867IivtFh0R dhC3Ep9YfAd9Ty3yOEE37BeVoPTN4eccYvqO0USojck4J+dSgKdprSL0laWtXOQn 1cyh9kpwfjUrpWPgJWnVnNPFDidYNybpae1Sn2i9EVjxSauxf2gAslu96YYWk9S2 efgoUurfxT1nbUpQ3dluIT3PIC8+NbbPGKdJSRebDaLjnluUyEHFbLV+0YBt/OTw vvKOxuVgXFB5lYjjr8U10TYeEV+UHYd5MRahhLfbbQD+aSKCFas4cXEBM7Rb0VR9 pcV6vQs/Cm6JJYvVztiz+F9veB86NF0Abv8ABG1z/XtN+ZeBHRWD5isGfwKv7IJj iLIA/cXtJ+RrOZ4asuJDundeQVZPqIcdLSvrWkzZOL2n2wm2XRU5nqCxJS8B/io1 f0YMXDhZqa3p3O2d8pJwC2N/0oak6fmRFlMmI+0r3LbIppfzncUrGB9qWMutpICl uRFDPzTyrQa4+srXsu2lTuxhW0jP+YUtJCEiILzSt7RUkjoQcGtC33W/2xQXEukx kg5wl9WPDNO0cROGF6aH2jaFs9/rxwcH4pNdUWPhPfWyqBdGI7ixkDttpT8lUv6X QCxh8V9bQm9i5/pKc8w+gKz+VXlcW3ZrJbu+k7PMUU47QN7VD86PVcGLPNZ322/N ug9FHaoeVYczgde2t3o70aQnPIhW3I+dTswFu1NRc5y0IYSyHPZQjoPyo10ppeZC mpkOsF1gjKeVDdx01O01dyxLZUy8363vGPfW/H4wXexx0xWI8RaW04BW3k+NY5E5 8GsHQ97IWvR0Es9mQMEEVqSYsJ1re8hvA71V88tftCagQrLltgLHuwRV1P7Qjr6Q idp5hxPfscP61gvztL2W8lu/Q4lOQ2l4aU3/AMtS7TOysElxJ5hOBSxh8WND3I4l xZ9ucx1QcpzRaxedOXiyuRI2omtq+eXhhQH51g/zZEzbzRdWddLXhtxBZU764/Oj qM4laMgilM7/ACOsCVPzL4p1XujpzWavjFpW0PKEO3XSSQPVK3AEn5ZqsX58idiy zjMeYSnrgV7HKkAP2iWAMDTrn/yK0Lf+0Lb3SBIs7zIzgntAcV2RtezlodpUAoJ7 zVVNwjLdW0Fex7RPQUHQOKNmucVUlhK9oTnJ91D1413Gt0pLyoy3Ybg3KCe/NTtz SLjjsGuLV5ts67IjwUNZbT67iUj1jUrVXrvhhdUhNwtrjKz1UWenzFSt0pUJmPK4 ATVEqgXaC+nHILBHmKHp3BXVMXeUwG3gnvZczmtiNw01TCy7pvV8aSUc0pZmKST8 skVcFx412HAXFdmoTyJKEugj5Vpr/pkLeXoK+wl7ZNrlNHuy0TWS9YpjCiCFJI7l JINN1HGvWEBWy7aYbXg4JUhaP/ytNnjTpG4rUL5ptTCiMFWxLufAZp6yXQxDGA8k gkjd7wK7xp11gYTFly2ADn7pwp50+0XPg3qDs0lxiI4rkEqC2jn6V1PC7Rd0bWq2 39vnzTtdSoDzqNmApoPFHXUHalN4cdbSMBMhtKwfjW03xiuTxAvNjtE8YwoqY2qP zovlcCpJG6FdmHUnoFNkedDdx4M6kjlSkRUvpT3tKBz8qakBW/llw+uSiq6aJcZW faciO4HhmuiLXwmu5zHvFxtS180pko3JT+XPNDszQV+hnDtpmo/MtEjyrHVZJbZI U2tOOoKcVW7AYbPDeK/td03r23LIVkJcUWz5H9K3Y9q4sWkqMSe3cWRjapD4Wk/A Gk63bJCFHswoK/2eVXI03UFrXui3Gaxg5wh0gZ+FS5X7A29WzNTO3dbt/Zdbkq6h SMDH5UET23CorUORrduV8u10eS7cpjshxIwFOHNVJBS5GOR176zbGgaPKvIJFXHm U5O0g1x7E9MVLYHlt3CvW5imhw90FO1hH9IRI9GYScBRGcigi0afduDiSpJDYPXH Wvqjhrafs3TrXqbAUjAxisZZFeqKUeLEZrrR0/TcoRJEsSGsbkLAxS6eBQo5JJr6 14kaOOpLX20dOZTI5JH4hXzNeLC/EdWgpIUk4IPLFa3RV2uAdCj76/CskGva2nEK IKTW5oywnUGo48ReOyCgpefdUuVK2Qk7GDoO1lOl2nnRgOZAyOoouu8iHZLE1Ldj IfVySltaeShWnJhNx/RbXFKGylshAPTlXjUWiblqK0R/RZDTrzKdqkhWEn4Vhjbl Kzr1UY8i5kar0ZIBVcdIlKj7S4zxHlUqrdeFuqGSr+qH1Ad7RCh5VK9JTdHI/Yvm PtGGvfGffaPeW3Cn6VuQtcaytikmNe5wSnolbm8eBpvN6i4P6jUEPMphOYz67ZbH j0rsOHXD6+c7RqFKFK6JS+lXkedSpfSQChcbNUobDc+PAnI70yGPa8Kufzp6enE/ begrc44eRXHwOXzFEczgPIUlXoV0YfR1G8YPlWBO4H6iYaK2mmnsdzboJPyp7IDw ZXCK8NntoFyta/e2Sa/EaG4f3FzFo14uOo/+HIRg/pQ7P4eX23qUl+3yUKAycIzy +IoedsMhtRJSsE/vJxRsA12uG+tYjXbab1smUhP9mluYRkeOK7tu8bbCFBxDtwTy O4lDoH0NJ9uPOhncw680R0LThT9DWvC1rrC1KBZvU5KQMAKc3fWmqAaX88GtLaQL rpVBQOSlFK0HPmKtM8YtMXBRRddMraCvaUUJVzoFicadXsYTIciS2x1S+wDn5itV njBap7iUXnRlvfCuSlM4B86VR+AHUa9cLbutLhSzGdP4VIUjHhyrsrhvpC+b3bfd FErORsdCgPlQEq+8JLmkofs1ygKUea2ugPyPSvEqw8Pm4SpNq1rcoihzCOavIAEU qXQBVN4FbwDGuqSf943j6UudXaPf006uHIUhSwMhSDyIri1rrUFhfP2XqeTJabOE CQNwI+BrNuurbvqZ0v3J1DjqhglKdo8KhqgBchIcKVHlXpbiUABASa8SGiFkg86r hKietZsY0NMaxtLEWNBehobXkJ7THfX0dp2THdtMcMrScIGcV8SJ3JOQa24Gr7/a 0Yh3WQ0ByACsgVzeNqWyLTTVM+yLpe7bZY/bXCY0wju3HmflSh1wizypibgYoehy RuQ4gFOT30B6JtV11texOu0519hshR7RRO8/Cnvd9Nxpuk3oKQMto3NnHskDupTy NvU0jFJWJZuw6QuCFeu8y73I3VZsFtt2kpEia06Fkp5KUeYoLuYdiy1DJSpJ54rO aemTpbcdLzhSpYB592azqXb4LVJjcWtepoyFuT24EhQJbW4raCPjVVvTXEi2KC7H fWpTQOQhuWOfyNc9S6alSocdERxvLbQHZ5x3UuZdovVrfUnMhtSeeW3VAeVdX55Q SoWTkaCtYcXbIf6balPJHeqPvHik1KWcLWeqbdj0e/T07fwqc3DzqV2rU5Q1buvB 27/61ZZ1seUeZQSUjwNdmdB8Or3lVo1euKR0S+ACD8Tg0LXDhhqSAD2lskJA6lKd w8qwXdNTWge0bdSR3qQRUJsY02eF+q4Z7TT+tmnwPYCZZTy8xXcucbbA0rITNab5 5IS6VD60oEQrlDI7JTiccxsUR9K3ImutZ24jsL1OTt5AKIUB8iKL+gMVjjDri1DF 70uHUj2trS0H6EVoNcbtLTQGLzpp5onkr1EOJH0NBcfjdq5hARKEGYMYIeYxnwq5 /O1ZZ5AvGh4MknkVtYSfMUcPoQaNXbhJqJ1RHZsLCeYKVNj+GawdRWrhkwyosXl1 C8cg0O0FC98uWjZbW+xWR+3LUMrC1ZBPwzQJOeKlHCuVLgZoT3bMy4oRHFuozyUp OKzFzImSEIPhVI868EcqmwLReRjlyriXjzAUarkV+YxStiOoWrPWr8d9SU4x1rMS o5ruw8UHnSsCy8oEnNVuSTXVSt9cVc81AzwtQFeAoEYr8Uk13jWybLGWI61j3imA ZaZ15frRFTFtMOOpLY5nYSfnRAnjRqhsqZejRVFQKSkJINBMDTV7RkMvNR9/tZdA 8a37NplMO4tvXCZGddChgBeR86ylGF2bwUgcuF4fmyVuPNFC1nOMUccN9NremouU xshA5oCh1o/i6J07dlJlLDQdT7iMGtdyK1a2ihpaNgGBisZyVcGqg75Mma4hUlY6 AHArLkutYUlaQoHkcjNWXlJWpSveay5Ccg1y92dCjFoxpOl7XOJKNzSj+7Uq+kba lbLLNL2T4ofAgPGq82xYZvOj5QVj11NhScfIir0fjVoa5fdzobrGR6weYBxS5h8b dVsL/pkeFNT0wtvBHzrRHFTTN1bS1e9FRSScrW1jr7x316NnmjBRO4UaiSdki3Nu dM7i0oV7PDHR1yRmDPPPoW30rpdF7g/d3Cl6JKtqnBjcknamu0bQujpCkqsGvFsn PJLi8YPlQARTOBSVFRj3Ftz3BaMGhu4cGr1CSVtxkyAATlpYOPlWn/JLiNbQfsPW SJrecpSqRzPyOfrXh3U/F/T8VX2lbWZDOMF8pB2/nlJpgLG4xXoC1NOoKFJ5EK7q HJCiSTmiG83GXcHXHpLaUuKOVbffQw6SQakDzvIr938q2NFNtv63sjT7aHWlzWgp CxlKhuHIjvpt37R9tsFj1/cXbew416cwYqSkDa0VJUoIP4QdxTy91ACL3ipuB76Y XEfTundNW6Gm1t7pFxeXLZX2hV2cQgbE4z1yTz68qM5llYnTNGWiRbLOLJOaih4t JQiWtzsio5I9bacde+mIRYFegnnTAl6Xs7T2hEojKAurq0zPvD64D+wfD1fdRL/I 6wp1zNtcjTAjFmOtVviLuCv6wIcxuznIO0EhPfSATyT+dRQpjapg2iDw4kqtcUoQ jUbrLTj7W14NhAwhRPPkc8jS3S4D1ooZ4UMV0ZmSWB906pIHurQtdqN1e2B1Lae9 Ro4h6D0+ljfLnOKPeQqpbSGrvgXv2lKOSt5XPrRBYrNerwntokd1TY/FjkaY1k0x ouK+hSWRJcTz+9Oc/KmfBuVqjMJS00y0hI5JSkACsJzXRunJdiqtFm1LD2FSFNtj qSegrbkzZO7sXcnbyye+u2stdNP3GLZba6kekLCVrT3flWlqKGiMY45EloEn3nFZ ODfJe/0wd+U1VfOBX4t7aoiuEiW20yVLIz3CsXFmsZ8HNaxipWSJDqySrlk1KFFj 2C248IYTx322YUj91xOfMUNS+Et5aUezaafT70LA+tSpXrHmmHK4fXdhtRVbpHLq Nmaw5GmpzRG6G8g92Wz/AAqVKQzmY11iOhSXZjSxzBQtSavjU+qWoS4artNVHUMK QslWR8TUqUwMeRIedQd6VEn/AGTWWpClE5Qv/CalSpAu2KabNqC33Mx1upiSEPFs ct205xnuo0vnE2TfNPy7U7bnEh5jsQsuZ2ntu0yRjnywn5VKlAApqK8rvwtYERbP oMBuHzOd+0n1unLr0rZTrYjWNiv32a5i1RmWC1v5ubElOc45ZzUqUxFlOt4C4FjT JsUlybZ1lTDyZG1PN3tDlO3n7q6J1tZRqOZczpqUUTgVPhUnc4hztN4U2op9Tpj4 GpUoAydR6rGooUxCre+zIk3Fc0kPKLaQRjbs6Z5e1QqELH4Ff4TUqUAdG1vtf2fa JP5A13E+4AFPbPEe7nUqUmkB2j3a5RXN7bjoPwNao1TdHWihal59+DUqVOqKtmjo uFJumrGH1hZDZzkg9c06dXysPMN7cqDfM4qVKJJAm7AKU+pJOEq8KznXVOe0lRx+ VSpXM0joi2cys4xtOfhUqVKii7P/2YkCNgQTAQoAIAUCZ0teqgIbAwULCQgHAwUV CgkICwQWAgEAAh4BAheAAAoJEEp1iDzBsdNMxsoP/2amun27Yf9/9lXVZJUagfkm 5M4dBPDoC5YfR7IQ1kFjvexC5vSEQRcD8w/hxyrAlqdYOZqZ8K30S8DS5XFlo0DV O/UXSiglaaTHpZIBkiZwutB5BJA1BzGdj0CsQZnOc2lVaJQoZg29k1TBFvinO1tQ t5o2ue4GMg20CjNjDG7QmQ+Dex1rNSIlbusEPeNybyLZVoRsAEAWirwZ2khAwuxo S+EUs3hTRTXVuhg0Ed9zL4nvV3f8WiUoK0fTHLj5Esx8DBiB/IXZCGGRZziORupe xeugX7kOx5eRpmok7rxZIPIUEfBpC5Zr0EysVa6lh9b6U11eDPFZfNkIUAYJboj7 MvvvJkviA8kg8xEo4oe2eMrwOvMKnpPq0xtsOesmdT4iXREEAbndlnOm9L7o1lIn ZvH7fk3K+myDryh/JejgUNiz/Vk8s8JBCsD8vb9P0TdkG8Jy07VoiTcKdDjaNj9T dqjXq280OYwb8KprhdQmfSMfVhqOa3X0N5xFxIPutOZHYILenAbLQ9GXpNVhCshm ApW8F0cHqoPJXLyIyAQQRgib2zmUfY8aZCgxd5C08HOZMfnY2vdoYZ+tchVoHGIR mpo4RlLFY9ZF6NQW9c+bXJqVXpFNJqtRc2O7YZCs2HzisaudBnx1aFbz2HLDzSU3 ybKi93/CIASzyBkzVpLtuQINBFav2jMBEACxwOSaz5YrOdJ2pp3L/8454ACGhRGX YzKtNgj9gPNT6GyJDHW+x61TN1AeR13MqM5UaIvMrjhE17bh62LhkpBEvg2cRrYB Ge7r8J/8E0Q1i/FeFnjS7PeAGOmT32krDtz0GhcRYoTh6uWBIb3aiYYyU5dufit5 ObSjS3qWHRBdIr2Pie6/ppLOVXdeDsbtscU63HkujRMljYd4uPR6oJwFgdQbySK9 tKU/HUS3qhX8SJ6hEN6rfuzEONWynN36ofDS74W2srZxXF5rz7XxYMUe27+9sZd0 zlgTmXL+3wcUfyCTfr3ZxZdx0FL8GY53OrZDQmSCyY667133O/EzVdBLH5vY1I9u d1H2PxoDPQacjl36/mRCpKNGs2Oh52B3NbJ5U7YeEG4OMcA1zC2blih9ExRhi3gD KFcpTXklvJPPS4ffIurdYFTkcWa8Ko+Ck+RHEOl3qXAINrQk9B5M2+eK3SBt5vC8 L/+Ke0ah3vpkuLUV2Piimtgw38eoDw/H/3v+vQ6O5mYLTCqY59c84HZw2NWGaJdX gHZpr2DlwuEMCQkwPWUt53r+8/Sru4LaDjsJv2V6MNTTeYB9e4LfWwZhHA1Us3SU 4A47B5MpNmTXmBxVLfX0qVJfrs0c5726F16cuAqpL8pOQ5+O/UPQ9+F2l/1h3lxK w0I0ZBq4tOqhzQARAQABiQIfBBgBCAAJBQJWr9ozAhsMAAoJEEp1iDzBsdNMGugP /05GhajYg4ES54fn8lcbvnkGm1w5NVP7OS9wzGY/6nDTHX8rmMvVFBYQXerCBZEo IihXPBTuvQ3vYfXnfwglyRw6QvepLM3oez0iLLJPjQU25SgXutl2EIjVbzYtcmkX DGhUGi7IHSqmjIQumrTQWbHzyUAA58otUh4aPYl4aAKxCOMSJlqzUnOmkZRFIynC 6zxHZvh68G2bv503w7R0S867fjO7qnckRMQI7+MYRfWvTdiwqtw+0dKUkTDhkHIz 4sHHZmWISUXhC1kIA9BoxxVXddL5GoAde0L/62cSXL7HDt1tkA0hhO17is1wu3sm lLUeTvsL7LfXI3bOIQjY1CdlNyf65utFnvFsNNVav2ZEXGYcZH2uvKgY/quIa1+y Cbf8w/aYt+ahoi54NAldvoXE6EPs+bZuDviGLHXCLfQLuMu7NfJyJEkPbxLMf+58 k/bkZ8r7vC+x3EpRSI7oHaYYtoQDsRN2NIrRYwuCXlLt26dIGmmdbzLT5bribw7Q CZYkhjd9jnV7+dpAcVTVrE+A7AXb46JVvFaKrhl6rPIlcB81+XoSg4hvAJOWPvcZ CfWrtHVGvPzOJpNxBQteoYUc1SrVi/1j5WR+FnVDA68pY5QdK3fNSDXIhctNxMxC Yv5/cxSTVRCsTbtFg8tRHkJHhq4FVIk0O8o+TSVrfxzs =JPry -----END PGP PUBLIC KEY BLOCK-----
-
 @ 000002de:c05780a7
2025-05-08 16:14:37
@ 000002de:c05780a7
2025-05-08 16:14:37Just an observation that makes me chuckle.
originally posted at https://stacker.news/items/974829
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 000002de:c05780a7
2025-05-08 14:55:34
@ 000002de:c05780a7
2025-05-08 14:55:34There are so many projects in the bitcoin space that deserve praise but I just wanna shout out Cashu.me. Its a browser based cashu (eCash / Lighting) wallet. It can be very handy when you need a wallet but don't wanna download yet another app. I hadn't used it in a very long time and decided to try it out again the other day. Its really well done.
As with other Cashu wallets you need to select a mint and backup your key phrase but it is very simple the get started.
If you wanna learn more about Cashu check out Cashu.space
Two other good wallets that support Cashu.
originally posted at https://stacker.news/items/974759
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-08 01:22:05
@ 5d4b6c8d:8a1c1ee3
2025-05-08 01:22:05I've been thinking about how Predyx and other lightning based prediction markets might finance their operations, without undermining their core function of eliciting information from people.
The standard approach, of offering less-than-fair odds, guarantees long-run profitability (as long as you have enough customers), but it also creates a friction for participants that reduces the information value of their transactions. So, what are some less frictiony options for generating revenue?
Low hanging fruit
- Close markets in real-time: Rather than prespecifying a closing time for some markets, like sports, it's better to close the market at the moment the outcome is realized. This both prevents post hoc transactions and enables late stage transactions. This should be easily automatable (I say as someone with no idea how to do that), with the right resolution criteria.
- Round off shares: Shares and sats are discrete, so just make sure any necessary rounding is always in the house's favor.
- Set initial probabilities well: Use whatever external information is available to open markets as near to the "right" value as possible.
- Arbitrage: whenever markets are related to each other, make sure to resolve any illogical odds automatically
The point of these four is to avoid giving away free sats. None of them reduce productive use of the market. Keeping markets open up until the outcome is realized will probably greatly increase the number of transactions, since that's usually when the most information is coming in.
Third party support
- Ads are the most obvious form of third party revenue
- Sponsorships are the more interesting one: Allow sponsors to boost a market's visibility. This is similar to advertising, but it also capitalizes on the possibility of a market being of particular interest to someone.
- Charge for market creation: users should be able to create new markets (this will also enhance trade quantity and site traffic), but it should be costly to create a market. If prediction markets really provide higher quality information, then it's reasonable to charge for it.
- Arbitrage: Monitor external odds and whenever a gain can be locked in, place the bets (buy the shares) that guarantee a gain.
Bitcoin stuff
- Routing fees: The volume of sats moving into, out of, and being held in these markets will require a fairly large lightning node. Following some helpful tips to optimize fee revenue will generate some sats for logistical stuff that had to be done anyway.
- Treasury strategy: Take out loans against the revenue generated from all of the above and buy bitcoin: NGU -> repay with a fraction of the bitcoin, NGD -> repay with site revenue.
Bitcoin and Lightning Competitive Advantages
These aren't revenue ideas. They're just a couple of advantages lightning and bitcoin provide over fiat that should allow charging lower spreads than a traditional prediction market or sportsbook.
Traditional betting or prediction platforms are earning depreciating fiat, while a bitcoin based platform earns appreciating bitcoin. Traditional spreads must therefor be larger, in order to pull in the same real return. This also means the users' odds are worse on fiat platforms (again in real terms), even if the listed odds are the same, because their winnings will have depreciated by the time they receive them. Technically, this opens an opportunity to charge even higher spreads, but as mentioned in the intro, that would be bad for the information purposes of the market.
Lightning has much lower transactions costs than fiat transactions. So, even with tighter spreads, a lightning platform can net a better (nominal) return per transaction.
@mega_dreamer, I imagine most of those ideas were already on y'all's radar, and obviously you're already doing some, but I wanted to get them out of my head and onto digital paper. Hopefully, some of this will provide some useful food for thought.
originally posted at https://stacker.news/items/974372
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 000002de:c05780a7
2025-05-06 20:24:08
@ 000002de:c05780a7
2025-05-06 20:24:08https://www.youtube.com/watch?v=CIMZH7DEPPQ
I really enjoy listening to non-technical people talk about technology when they get the bigger picture impacts and how it relates to our humanity.
I was reminded of this video by @k00b's post about an AI generated video of a victim forgiving his killer.
Piper says, "Computers are better at words than you. Than I". But they are machines. They cannot feel. They cannot have emotion.
This people honors me with their lips, but their heart is far from me
~ Matthew 15:8
Most of us hate it when people are fake with us. When they say things they don't mean. When they say things just to get something they want from us. Yet, we are quickly falling into this same trap with technology. Accepting it as real and human. I'm not suggesting we can't use technology but we have to be careful that we do not fall into this mechanical trap and forget what makes humans special.
We are emotional and spiritual beings. Though AI didn't exist during the times Jesus walked the earth read the verse above in a broader context.
Then Pharisees and scribes came to Jesus from Jerusalem and said, “Why do your disciples break the tradition of the elders? For they do not wash their hands when they eat.” He answered them, “And why do you break the commandment of God for the sake of your tradition? For God commanded, ‘Honor your father and your mother,’ and, ‘Whoever reviles father or mother must surely die.’ But you say, ‘If anyone tells his father or his mother, “What you would have gained from me is given to God,” he need not honor his father.’ So for the sake of your tradition you have made void the word of God. You hypocrites! Well did Isaiah prophesy of you, when he said:
“‘This people honors me with their lips,
but their heart is far from me;
in vain do they worship me,
teaching as doctrines the commandments of men.’”
Empty words. Words without meaning because they are not from a pure desire and love. You may not be a Christian but don't miss the significance of this. There is a value in being real. Sharing true emotion and heart. Don't fall into the trap of the culture of lies that surrounds us. I would rather hear true words with mistakes and less eloquence any day over something fake. I would rather share a real moment with the ones I love than a million fake moments. Embrace the messy imperfect but real world.
originally posted at https://stacker.news/items/973324
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ c3e23eb5:03d7caa9
2025-05-12 13:00:36
@ c3e23eb5:03d7caa9
2025-05-12 13:00:36The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale. Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs.
``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299)
```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet: ```
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP Enterprise```
So its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-06 19:49:39
@ 5d4b6c8d:8a1c1ee3
2025-05-06 19:49:39One of the best first rounds in recent memory just concluded. Let's recap our playoff contests.
Bracket Challenge
In our joint contest with Global Sports Central, @WeAreAllSatoshi is leading the way with 85 points, while me and some nostr jabroni are tied for second with 80 points.
The bad news is that they are slightly ahead of us, with an average score of 62 to our 60.8. We need to go back in time and make less stupid picks.
Points Challenge
With the Warriors victory, I jumped into a commanding lead over @grayruby. LA sure let most of you down. I say you hold @realBitcoinDog responsible for his beloved hometown's failures.
I still need @Car and @Coinsreporter to make their picks for this round. The only matchup they can choose from is Warriors (7) @ Timberwolves (6). Lucky for them, that's probably the best one to choose from.
| Stacker | Points | |---------|--------| | @Undisciplined | 25| | @grayruby | 24| | @Coinsreporter | 19 | | @BlokchainB | 19| | @Carresan | 18 | | @gnilma | 18 | | @WeAreAllSatoshi | 12 | | @fishious | 11 | | @Car | 1 |
originally posted at https://stacker.news/items/973284
-
 @ cecdc1e8:b6c264ee
2025-05-12 12:41:57
@ cecdc1e8:b6c264ee
2025-05-12 12:41:57GM
-
 @ b6dcdddf:dfee5ee7
2025-05-06 15:58:23
@ b6dcdddf:dfee5ee7
2025-05-06 15:58:23You can now fund projects on Geyser using Credit Cards, Apple Pay, Bank Transfers, and more.
The best part: 🧾 You pay in fiat and ⚡️ the creator receives Bitcoin.
You heard it right! Let's dive in 👇
First, how does it work? For contributors, it's easy! Once the project creator has verified their identity, anyone can contribute with fiat methods. Simply go through the usual contribution flow and select 'Pay with Fiat'. The first contribution is KYC-free.
Why does this matter? 1. Many Bitcoiners don't want to spend their Bitcoin: 👉 Number go up (NgU) 👉 Capital gains taxes With fiat contributions, there's no more excuse to contribute towards Bitcoin builders and creators! 2. Non-bitcoin holders want to support projects too. If someone loves your mission but only has a debit card, they used to be stuck. Now? They can back your Bitcoin project with familiar fiat tools. Now, they can do it all through Geyser!
So, why swap fiat into Bitcoin? Because Bitcoin is borderless. Fiat payouts are limited to certain countries, banks, and red tape. By auto-swapping fiat to Bitcoin, we ensure: 🌍 Instant payouts to creators all around the world ⚡️ No delays or restrictions 💥 Every contribution is also a silent Bitcoin buy
How to enable Fiat contributions If you’re a creator, it’s easy: - Go to your Dashboard → Wallet - Click “Enable Fiat Contributions” - Complete a quick ID verification (required by our payment provider) ✅ That’s it — your project is now open to global fiat supporters.
Supporting Bitcoin adoption At Geyser, our mission is to empower Bitcoin creators and builders. Adding fiat options amplifies our mission. It brings more people into the ecosystem while staying true to what we believe: ⚒️ Build on Bitcoin 🌱 Fund impactful initiatives 🌎 Enable global participation
**Support projects with fiat now! ** We've compiled a list of projects that currently have fiat contributions enabled. If you've been on the fence to support them because you didn't want to spend your Bitcoin, now's the time to do your first contribution!
Education - Citadel Dispatch: https://geyser.fund/project/citadel - @FREEMadeiraOrg: https://geyser.fund/project/freemadeira - @MyfirstBitcoin_: https://geyser.fund/project/miprimerbitcoin
Circular Economies - @BitcoinEkasi: https://geyser.fund/project/bitcoinekasi - Madagascar Bitcoin: https://geyser.fund/project/madagasbit - @BitcoinChatt : https://geyser.fund/project/bitcoinchatt - Uganda Gayaza BTC Market: https://geyser.fund/project/gayazabtcmarket
Activism - Education Bitcoin Channel: https://geyser.fund/project/streamingsats
Sports - The Sats Fighter Journey: https://geyser.fund/project/thesatsfighterjourney
Culture - Bitcoin Tarot Cards: https://geyser.fund/project/bitcointarotcard
originally posted at https://stacker.news/items/973003
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 6be5cc06:5259daf0
2025-01-21 23:17:29
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ cb4352cd:a16422d7
2025-05-12 12:18:41
@ cb4352cd:a16422d7
2025-05-12 12:18:41In the early days of the internet, openness was a foundational value. Today, as the financial world undergoes its next great evolution, that same principle is making a powerful return — this time through open-source code, permissionless protocols, and user-owned ecosystems. The future of finance isn’t just digital. It’s open.
Beyond the Institution: A Shift in Trust
Traditional finance has always been built around institutions — banks, central authorities, and regulatory bodies. While these structures offer stability, they also limit access, enforce gatekeeping, and concentrate power.
Permissionless innovation flips this model. Instead of asking for approval, builders create protocols that anyone can use, fork, or improve. In DeFi, anyone with an internet connection can lend, borrow, or trade without relying on a centralized intermediary.
Composability: Financial Lego for the Internet Age
Open protocols don’t just stand alone — they connect. In Web3, composability means developers can build on top of each other’s code like financial Lego blocks. This accelerates experimentation and reduces duplication of effort.
You can build a lending protocol that integrates with a decentralized exchange, which in turn connects to a stablecoin, creating a rich, interoperable financial ecosystem — all without closed APIs or licensing fees.
DAOs and the Redefinition of Governance
Openness is not only about access — it’s about control. Decentralized Autonomous Organizations (DAOs) allow communities to govern protocols, allocate resources, and shape development roadmaps. In contrast to top-down decision-making, DAOs are built on transparency, collective voting, and participatory ownership.
As financial systems move on-chain, governance itself becomes programmable. This allows for more adaptive, responsive institutions that can evolve with user needs — not just boardroom mandates.
More Than Code: A Philosophical Shift
Open finance isn’t just a stack of protocols. It reflects a deeper belief: that financial systems should be inclusive, interoperable, and transparent by design.
This philosophy challenges legacy ideas of exclusivity and control. It opens space for local currencies, niche communities, experimental markets, and user-first financial design. It treats users not as passive consumers but as co-owners and co-builders.
How Beyond Banking Conference by WeFi Embraces Openness
This vision of open finance is a central theme of the Beyond Banking Conference by WeFi. Taking place online on May 30, 2025, the conference brings together pioneers from DeFi, AI, Web3, and FinTech to discuss permissionless technologies, composable architecture, and the human values behind them.
Speakers will explore how openness fuels innovation, and how protocol design shapes access, governance, and trust. From DAOs to AI-powered DeFi, the program emphasizes tools that scale freedom — not just efficiency.
In the future, finance won’t just be smart. It will be open. And that changes everything.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ f72e682e:c51af867
2025-05-06 10:35:01
@ f72e682e:c51af867
2025-05-06 10:35:01All across the Lightning Network we can detect quite a lot of nodes, specially new nodes but also old nodes, that show a concerning lack of good node operation which impedes proper routing. I’ve seen nodes with a variable capacity whose channels are stagnant and non performant, which raises a question: what is the point on maintaining a public node if you are not able to route and dynamically assign resources as needed? Certainly it is a useless node, and channels of those nodes with other nodes better maintained are also useless, not because the fault of the good ones, but because the fault of the bad ones, which makes the whole network not as performant and great as it should be.
For the shake of improving the Lightning Network, I have created this guide, so every node out there can become useful, and, also, will greatly improve gains in routing for itself. Do not expect to become rich or even live out of routing fees, that is impossible unless you have a node with 100 or more BTC in 2025, but at least, a node should be able to cover its own maintenance costs; its the idea. Problem is that, currently, most nodes run on a loss, and that is highly related with the fee policy and the choice of nodes that they connect to. Let’s put an end to this. Here you will learn how to, at least, earn enough to cover electricity of your node, and with luck, a bit more.
Current earnings cover electricity and the payment of my node:
3K sats per day might not seem much for a 5 BTC capacity (2.5 BTC real outbound) node, but the screenshot was taken in a bad day, when the mempool was empty. I took the screenshot of a bad day on purpose, to prove my point. Some other days, specially when Bitcoin is going bullish and it is used a lot, I have seen 20K per day. A quick calculation brings around 1M sats per year at a minimum, more than enough to pay electricity, the machine, and even a bit more for beers and fun! Real gains across the year could be closer to around 5M in my case, which is not bad. And what is incredible, I maintain general low fees for most of the cases, except when I have no liquidity in the channel which must be high, as you will understand later in this article. So if you double or triple my recommended fees I would expect quite a lot more earnings. So expect gains of around 2% of the total capacity (4% for the amount you put in) per year minimum, and any extra beyond that by fine-tuning my recommendations I'm sure it will be very welcomed by you!
Step 1: put the node in a good machine
Please, don’t use an old computer or laptop, unless you change the SSD for a new one. Bitcoin and lightning uses the SSD heavily, which means it will fry it sooner or later. That is so that I recommend changing the SSD every 2 years even it it still feels good. If your SSD dies during operation, expect big loses. I’ve seen this so many times, and it also happened to me, that I am very serious about recommending it. Also, please use only Linux with ext4 file format, other formats, including ZFS, I’ve seen failing badly. If your filesystem fails, the sqlite db that LND or CLN uses will fail and you will force close many if not most channels, with big fees for onchain closings, which will totally ruin all your gains. You have been warned!
Also, please take your time to configure a clearnet (ipv4) address. Do not rely only on Tor, because Tor is slow and unreliable, specially when updating channel states on the gossip, which you will be doing a lot. Of course, configure Tor also, but as secondary, because too many nodes are Tor only, which is unfortunate.
Step 2: connect to good nodes
As a public node operator, your duty is to connect to as many nodes as possible, but first, to good reputable nodes. Your first 10 channels should be with big nodes and service providers, like exchanges, wallets, but also to very well positioned big nodes. Take your time to select these 10 first nodes and connect to the ones you think will improve your position in the network. Don’t choose the first 10 biggest, take your time to study the fees. Select nodes that use a wide range of fees, from 0 to 1000ppm. Don’t discard a node because you see some channels with high fees, it could only mean that they have no liquidity right now in that channel. But if all its channels have high fees, or at least all small channels have high fees, then discard it.
Then, when you have your first 10 big nodes connected, go ahead and go to https://lightningnetwork.plus/ to choose less popular ones. You need them, because you seek to fill the voids between smaller nodes, it is what most of your revenue will come from. Always try to do swaps, use the liquidity pool later when you have enough total inbound liquidity. Remember that total capacity is not total outbound. Total capacity is total outbound + total inbound. So you can start with 0.25BTC of your own, but total capacity could be much higher if other peers have open channels to you.
A proper public node should have a minimum of 50 channels at its peak. It doesn’t matter much the size of the channels, but the quantity and the quality. A node with 50x500k sized channels will usually perform 10x better than a node with 5x5M sized channels, even if they have the same total capacity. This is because more opportunities to route will be found if you have more channels, which means you are much better positioned.
Anyway, the minimum recommended is 1M per channel because most HTCLs are 100k to 500k and less than 1M will wipe out all your liquidity in the channels in one or two routings. This could change in the future because of the Bitcoin price, but in 2025 this is the state of things. But if you don’t have 0.25 BTC to open 50 channels (25 open by you, 25 by others using swaps), just use smaller channels, don't let your available liquidity to crush your excitement, who knows what is the future ahead us! Remember that we are just at the beginning of this technology and there is nothing that impides your channels to be open for the next 20 years when 1BTC=$1M! I would put the ultra minimum at 250k per channel, which means a 12.5M node (6.25M required sats to start with), but even that is too precarious in 2025. But hopefully not in the future! If you have less than that my honest recommendation is to run a private node and open private channels only, and only if you absolutely need a node because you have to provide a service for multiple people and you can't conform to use simpler wallets. Right now, I can think of only one example of requiring an ultra-small node instead of wallets, which is using LNBits to service your small business or family. Be aware, anyway, that a 12.5M node will definitely not cover your node running costs in 2025, it is just an investment and positioning for a future!
In any case, never, ever, put all your BTC in a LN node, at most one third of your bitcoins and only when you are confident.
Also remember you have to be online 24/7. Please, don’t setup a node if you can’t. Remember you are providing a constant service, not an intermittent one. This guide won’t work if you are not committed to this rule.
Step 3: understand the flow
I’ve seen too many node operators that do not understand how payments are routed, and this is a big problem, because this is the base of everything we do with a LN node.
Payments go from one node to another to another to another until it reaches destination. Each node has what is called an outbound fee. This fee controls how much does it cost to route a payment through that node. If the fee is low it is considered attractive and other nodes will prefer to use that route. If the fee is high, it is obvious that nodes will not choose that route unless there is no other way.
But there is a problem here: all channels have a liquidity limit. If a channel has 1M liquidity and a payment of 500k comes through it, then now the channel has 500k liquidity, that is, a ratio of 0.5. If another 400k comes through, now it has 100k liquidity and a ratio of 0.1. If now somebody tries to route a 200k payment through that channel, and error will happen, because it doesn’t have enough liquidity. It is called an HTCL failure, and this are quite normal. Liquidity can come backwards, which means that now that channel becomes the income instead of the outcome, so if 300k comes in, in the example above, now the liquidity ratio is 0.4 (100k already there plus 300k that just came in). So it is easy to understand that liquidity is very volatile: it will come in and out with any successful in or out HTLC.
The problem is: how do you know if a channel has liquidity? For privacy reasons, the liquidity of a channel is never announced, and only the two connected nodes know it. This is logical, to avoid bad actors to figure out which payments have been done by other people. So the only possible solution is to try all connected channels you have until one lets you go through because it has enough liquidity. And it is going to be done, always, in the order of outbound fees, from low to high. So the channel that has the lowest fee with enough liquidity, will catch the prize.
There is a way to signal that you have liquidity or you don’t, and it is based on scarcity: if you don’t have much liquidity, you increase the outbound fee, so other nodes will not find attractive to route through you in that direction. You don't have much liquidity, so why bother to allow routing? But, when you have again outbound liquidity, because other nodes have taken the opposite direction (inbound) using another channel of yours which has liquidity (as outbound), you intelligently lower the fees to signal your new updated increased liquidity in the channel. So, the idea is simple: if you have liquidity in the channel, you put low fees, if you don’t have liquidity, you put high fees. Please read that again until you fully understand it, it is extremely important.
There is another concept introduced by LND which is negative inbound fees: if you put negative inbound fees, for example -100ppm, it means that any payment going from that inbound channel to another of your outbound channels, will have a maximum discount of 100ppm. (Don’t worry, you will never lose because LND forbids to route losing money, so 100ppm is the maximum, but it could be less if the outgoing channel has less than 100ppm fees.) What this does is to encourage the filling of empty channels at the cost of earning less in channels with plenty of liquidity. This is very good, because it will automatically rebalance your extremes: channels with no liquidity will be filled up, channels with plenty of liquidity will be emptied down, creating a balance.
It is obvious that the total ratio, including all your channels, should be around 100%. That means that the total amount summing all channels of inbound and outbound should be approximately the same. Don’t get obsessed with this, 80% or 120% is ok too, but if it is lower or higher than that you should take measures to open or close channels, or even swap out or in using boltz.exchange or LOOP.
Step 4: managing fees
So, in order to make proper routing, you will have to constantly monitor all your channels on a regular basis. Minimum recommended frequency is once a day. You can do this automatically or manually. Some people prefer to do it manually because each channel has its own characteristics and some fees work better than others, which is something you learn with time observing the flow. But some other people, like me, don’t want to spend so much time doing so, and do automatic fee management using charge-lnd or lndg automators. A mixture of both styles is possible by disabling automatic fee management for selected channels.
Every node operator has his/her own preferences, but here are some basic recommendations that you can tweak over time as you acquire experience:
ratio > 0.98: fees 0 (or less than 10) 0.2 < ratio < 0.98: fees proportional max 128, min 16 0.2 > ratio > 0.05: fees 500, inbound -16 ratio < 0.05: fees 1000, inbound -64 ratio = 0: fees more than 1000, inbound -128So, as you can see, when the channel is full we encourage routing, when the channel is more balanced is when the earnings will occur (from 16 to 128ppm), when the channel is mostly empty we discourage forward routing (500ppm) but encourage backwards routing (inbound -16) and when it is almost empty we clearly totally discourage forward routing (1000ppm) but encourage backwards routing (inbound -64). And when someone just opened a channel with us, all liquidity is theirs so we aggressively encourage inbound routing by putting ultra high outbound fees and ultra inbound discounts. Simple, eh?Step 5: automatic fee management
As stated before, you can automate this using charge-lnd or lndg or Lightning Terminal if you use LND. If you use CLN you are probably limited to create a personalized script, because I don’t know of any similar tool for it, apart from CL-BOSS which is unmaintained and non-customizable.
You will run this configuration a maximum of once per hour, and a minimum of once per day. You should not try to run it more frequent than once per hour because of two reasons: 1. The channel states stored in the gossip take from some minutes to some hours to properly propagate. 2. Some nodes will ban you if you try to update more than once per hour. What I recommend is once every 2 hours for big nodes with more than 50 channels. If you have less than 50 channels, your gossip will be slow to propagate so run it once a day. If you get many “Insufficient Fee” errors is because you are trying to update channel states too frequently. Also, some people report that increasing the variable numgraphsyncpeers in the LND configuration file helps with better propagation, but be aware that this will increase bandwidth usage.
I’ve been using lndg for some time, but I switched to charge-lnd because it is clearly superior and faster and more customizable. Lndg is still great for rebalancing (which I use a lot) and as a general interface, but I have disabled the fee management, which I now do with charge-lnd. If you can’t access charge-lnd then just use lndg with the frequency chosen above, but be aware that the configuration parameters are very limited, as you will soon realize (you are limited to just one strategy which is proportional, and it is very slow as it changes the fee in incremental steps). Yet it is better using lndg than nothing.
Lightning Terminal from Lightning Labs I have not tested. So I can’t say anything about it.
But here is a good starting configuration for charge-lnd that you can customize to your preferences:
``` [default]
'default' is special, it is used if no other policy matches a channel
strategy = static base_fee_msat = 128 fee_ppm = 96 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 min_fee_ppm_delta=20
[mydefaults]
no strategy, so this only sets some defaults
base_fee_msat = 128 min_fee_ppm_delta = 0
[lost-onchain-sync]
The fact that lnd was not synchronized with the chain for more than 5 minutes
was an indicator of a severe problem in the past.
onchain.synced_to_chain = false base_fee_msat = 210_000 fee_ppm = 210_000
[expensive]
match channels where the peer node has set a high (>=8_000 ppm) fee rate
and set the same fee rate on our side (strategy=match_peer)
chan.min_fee_ppm = 8000 strategy = match_peer
[leafnode]
charge non-routing (private=true) peers a bit more for our service
chan.private = true strategy = static fee_ppm = 1000
[encourage-routing]
'autobalance' (lower fees so using outbound is more attractive)
chan.min_ratio = 0.98 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 strategy = static base_fee_msat = 64 fee_ppm = 16
[discourage-routing]
'autobalance' (higher fees so using outbound is less attractive)
chan.max_ratio = 0.2 chan.min_ratio = 0.05 strategy = proportional inbound_base_fee_msat = -64 inbound_fee_ppm = -16 min_fee_ppm = 32 max_fee_ppm = 700 base_fee_msat = 1_000
[all-liquidity-is-theirs] chan.max_ratio = 0.00 inbound_base_fee_msat = -128 inbound_fee_ppm = -128 strategy = static base_fee_msat = 1_000 fee_ppm = 1000
[discourage-routing-extreme] chan.max_ratio = 0.05 inbound_base_fee_msat = -128 inbound_fee_ppm = -32 strategy = proportional min_fee_ppm = 32 max_fee_ppm = 1000 base_fee_msat = 1_000
[proportional]
'proportional' can also be used to auto balance (lower fee rate when low remote balance & higher rate when higher remote balance)
fee_ppm decreases linearly with the channel balance ratio (min_fee_ppm when ratio is 1, max_fee_ppm when ratio is 0)
20% excess:
chan.min_ratio = 0.2 chan.max_ratio = 0.98 strategy = proportional min_fee_ppm = 32
20% excess, so for a max of 128, it’s calculated 128/(1-0.20)=160
max_fee_ppm = 160 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 base_fee_msat = 128 min_fee_ppm_delta=16 ```
So you might run this config in a crontab or with your node distribution script if it is provided. I think Umbrel has this app in their portfolio, so just use it if you have Umbrel and ignore the following. If you run it manually or with a distro that doesn’t have charge-lnd, you can configure a crontab. This is just an example, please ask support for proper configuration on your distro. And if you distro do not include charge-lnd, ask support to include it, at this point it’s quite a necessity. Anyway here is the manual configuration: ``` $ crontab -e
0 */2 * * * echo "=======>"
date>> /home/nodo/charge-lnd/log && /home/nodo/charge-lnd/env/bin/charge-lnd -c /home/nodo/charge-lnd/my.config >> /home/nodo/charge-lnd/log ```That is supposing charge-lnd executable is installed under /home/nodo/charge-lnd/env/bin/charge-lnd and config is in /home/nodo/charge-lnd/my.config and LND is running without docker. If it is running under docker, you will have to ask support of your distro.
Step 6: help your peers
Remember that your peers are not only your competition, they are also your customers. So it is a strange symbiosis: you compete with them, but they also help you (and you help them).
If your peers are not well informed and have a bad maintained node, you are in a loss, because your channels with them will get stagnant and will not route. If they are well informed and know how to manage a node, then the channels will not be stagnant and they will route through you.
So it is stupid to keep this information as a secret. Every node operator should know it. And the more people know it, the better for everybody.
So, please, if you detect stagnant channels and bad maintained peers connected to you, just lead them to this guide, or guide them yourself. It’s a good idea to bookmark this guide so you have it prepared for the future.
And that’s it!! Happy routing!!
originally posted at https://stacker.news/items/972730
-
 @ 866e0139:6a9334e5
2025-05-12 10:41:33
@ 866e0139:6a9334e5
2025-05-12 10:41:33Autor: Bastian Barucker. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
John Lennon besang in seinem weltberühmten Lied „Imagine“ die fast unvorstellbare Utopie einer Welt, in der es keinen Grund mehr zu töten gäbe und die Menschen in Frieden zusammen leben. Die enorme Resonanz und Verbreitung dieser Zeilen zeigt den Wunsch fast aller Menschen nach Frieden. Wie Lennon zu diesen Zeilen kam, ist ein Hinweis darauf, dass es dazu neben geopolitischen Analysen und deren Verbreitung durch eine nicht eingebettete und freie Presse vielleicht noch etwas braucht: Schattenarbeit – ein bewusstes Hinwenden zu den eigenen Tiefen der Persönlichkeit, dem inneren Tiefenstaat.
Was ist der Tiefenstaat?
Mit dem Begriff Tiefenstaat verbinde ich Strukturen, die Edward Bernays bereits vor knapp 100 Jahren in seinem Grundlagenwerk „Propaganda“ beschrieb. Im Vorwort schreibt er: „Organisationen, die im Verborgenen arbeiten, lenken die gesellschaftlichen Abläufe. Sie sind die eigentlichen Regierungen in unserem Land.“ Er verwendet diesbezüglich auch das Wort „Schattenkabinett“. Im Bereich der Persönlichkeitsentwicklung wird der Begriff „Schattenarbeit“ dafür verwendet, unbekannte, aber einflussreiche Anteile des eigenen Selbst zu entdecken und zu integrieren.
Lennon begab sich in den 70er Jahren des letzten Jahrhunderts auf die Reise zu sich selbst. Sein Weg führte ihn zum Psychologen Dr. Arthur Janov, der Menschen mithilfe der von ihm entwickelten Primärtherapie dabei begleitete, sich ihrer primären Prägungen und frühkindlichen Traumatisierungen bewusst zu werden und abgespaltenen Schmerz wieder zu erleben, um sich davon zu befreien. Entgegen stark kognitiv geprägter Ansätze wie der Gesprächstherapie steht bei dieser Art der Therapie Gefühlsausdruck im Vordergrund. Janov selbst schreibt dazu: «Die Krankheit ist die Verleugnung des Fühlens, und das Heilmittel ist das Fühlen.»
Auch der Psychologe und Psychotherapeut Franz Ruppert beschäftigt sich intensiv mit dem Fühlen als einem möglichen Weg, eine Traumatisierung aufzuarbeiten. Er schreibt Folgendes über die Bedeutung des Fühlens in seinem Buch „Wer bin ich in einer traumatisierten Gesellschaft“: „Denn letztlich können nur über das Ausdrücken von Gefühlen die fragmentierten psychischen Strukturen wieder zu einer Einheit zusammenfinden.“
Lennon war es möglich, die immense Menge an Schmerz zu entdecken, die er verborgen in sich trug, und er erkannte dabei, welche Verhaltensweisen und Bewältigungsstrategien damit verbunden waren. Laut Lennon ist „Unser Schmerz der Schmerz, durch den wir die ganze Zeit gehen. Du wirst in Schmerz hineingeboren, und wir befinden uns meist im Schmerz. Und ich glaube, je größer der Schmerz ist, umso mehr Götter brauchen wir.“
Die Schilderungen von John Lennon decken sich mit den Erfahrungen meiner Selbsterfahrung und meiner mittlerweile über 10 Jahre langen Begleitungsarbeit in der durch den Schweizer Willi Maurer entwickelten Gefühls- und Körperarbeit.
Auch in dieser Arbeit geht es darum, abgespaltenen Schmerz langsam und über viele Jahre aus dem Schatten in das Bewusstsein zu integrieren, um nicht weiter von ihm unbewusst beeinflusst zu werden. Hunderte Male habe ich Menschen ihnen vorher unbekannten Hass, tiefe Trauer, unendliche Ohnmacht, starke Hilflosigkeit, aber auch Freude, tiefe Geborgenheit, Liebe und Friedfertigkeit entdecken und ausleben sehen. Selber habe ich mich nach einem einjährigen Aufenthalt in der nordamerikanischen Wildnis, bei dem es darum ging, so ehrlich wie möglich miteinander umzugehen, ausführlich meiner Selbsterfahrung gewidmet und dabei Intensitäten von Schmerz, aber auch Zufriedenheit entdeckt, die mir nicht vorstellbar erschienen.
Der Krieg in uns
Fast immer zeigte sich in den begleiteten Prozessen, dass die im Alltag, in der Partnerschaft oder in der Familie angerührten Gefühle aus der eigenen frühen Kindheit stammten. Innere, überfordernde „Kriege“ und Übergriffigkeiten, die auch das Leben im Außen zum Krieg werden ließen, erwachten zum Leben und durften endlich Ausdruck finden. Schlussendlich zeigte sich meist, dass es einen friedlichen Umgang mit der aktuellen Situation gibt, wenn die Altlast „entsorgt“ beziehungsweise kompostiert, also gefühlt und integriert wurde.
Franz Renggli beschreibt diese Psychodynamik in seinem Buch Verlassenheit und Angst – Nähe und Geborgenheit in Bezug auf Partnerschaft wie folgt:
„Die Erfahrung aller meiner Paarbegleitungen zeigt nun: Wenn nach der ersten Verliebtheit langsam der „Alltag“ in eine Beziehung einkehrt, neigen beide Partner immer mehr dazu, ihre Schattenseiten, ihre alten und frühen Verletzungen auch in der Beziehung zuzulassen. Je sicherer die Grenzen sind, desto vertrauensvoller dürfen diese frühen Schmerzen gespürt und erfahren werden. Wir „steigen dann wieder ab“ in unsere ursprüngliche Hölle der Verlassenheit, in die frühkindlichen Prägungen, wie ich sie hier beschrieben habe. Nur: die Hölle sind dann nicht länger die Eltern, sondern jetzt der Partner oder die Partnerin! Vielleicht könnte ich sie oder ihn umbringen vor Enttäuschung und Wut, weil er/sie mich so sehr verletzt hat. Und damit kann sie beginnen, die Heilung der alten Wunden in der Paarbeziehung! Aber nur dann, wenn wir bereit sind, unsere alten verletzten Gefühle wirklich zu spüren und zuzulassen. Und wenn wir zu diesem Schritt bereit sind, dann können wir auch gleichzeitig empfinden und wissen: Das sind unsere ureigensten alten Verletzungen, welche wir seit der Kindheit in uns tragen – ein Partner mit seinen Worten und seinem Verhalten ist nur der Auslöser unseres alten Schmerzes, ein harter Spiegel unserer alten Wunden! Wir alle haben unsere Partner entsprechend gewählt, damit wir in unseren Grundfesten immer wieder – neben allem Glück, das wir mit ihnen erleben und teilen dürfen – auch erschüttert werden.“
Diese wiederkehrenden Erschütterungen werden auch Reinszenierungszwang genannt und lassen Menschen immer wieder dieselben misslichen Lagen (mit)erschaffen, die ihnen Leid zufügen. Willi Maurer beschreibt diese Dynamik in einem sehr lesenswerten Artikel mit dem Titel „Die verschüttete Quelle des Friedens“ wie folgt: „Die Spirale der Gewalt zeigt, dass wir andern Menschen das antun, was uns selbst widerfahren ist. Doch ohne Selbsterforschung bleiben wir blind gegenüber der tief in uns verdrängt liegenden Wahrheit.“
Diese Reinszenierung ist gleichzeitig jedoch eine immer wiederkehrende Chance, sich der Ursache dieser Dynamik zuzuwenden. Das geschieht dann, wenn die Person sich als Erschaffer oder Erschafferin und nicht als reines Opfer der Umstände versteht und beginnt, die volle Verantwortung für das eigene Leben zu übernehmen.
Vor einigen Jahren brachte ich den Prozessbegleiter Willi Maurer und den Friedensforscher Dr. Daniele Ganser zu einem Gespräch zusammen, weil ich der Ansicht war, dass beide Friedensarbeit aus verschiedenen Perspektiven leisten. Es war eine Wohltat, zu erleben, wie Ganser durch die sehr authentischen Schilderungen Maurers zu ahnen begann, dass es eine Verbindung zwischen weltweiten Kriegen und frühen Erfahrungen geben kann. Was hat der Soldat, Politiker oder Geostratege erlebt, dass er in der Lage ist, Krieg zu befördern, zu verursachen oder auch nur zu dulden?
Vielleicht ist die immer wiederkehrende Kriegsbereitschaft und Kriegslust elitärer Kreise neben der wahrscheinlich frühkindlich erzeugten Gier nach Macht, Einfluss und Geld ebenfalls ein gesellschaftlicher Reinszenierungszwang. Die inneren Zerwürfnisse und Kriege müssen quasi ins Außen getragen werden, um sich dem im Schatten der eigenen Persönlichkeit wartenden Schmerz nicht zuwenden zu müssen.
Eine weitere Bewältigungsstrategie für innere, emotionale Zerwürfnisse ist die Projektion, also die Veräußerlichung des Eigenen auf andere. Ein hier vielleicht Sinn stiftendes Beispiel ist die immer wieder betonte weitestgehend unbelegte Unterstellung imperialistischer Bestrebungen Russlands im Zuge des völkerrechtswidrigen Krieges in der Ukraine. Meist kommt diese Behauptung von Vertretern oder Unterstützern der NATO, die – wie an ihrer großflächigen, gegen westliche Zusagen an Russland verstoßenden NATO-Osterweiterung leicht zu erkennen – offensichtlich selbst imperialistische Bestrebungen verfolgt.
Die Projektion ins Außen
Interessanterweise hat ausgerechnet Präsident Putin in anschaulichen Worten beschrieben, was unter anderem mit im Schatten liegenden Persönlichkeitsanteilen auch auf geopolitischer Ebene passieren kann. Sie werden anderen Menschen oder Staaten zugeschrieben, also ins Außen projiziert. Auf die Beschuldigung durch US-Präsidenten Joe Biden, ein Mörder zu sein, antwortete Putin: „Aber wenn wir andere Menschen bewerten, oder wenn wir sogar andere Staaten, andere Völker bewerten, sehen wir immer in den Spiegel, wir sehen uns immer selbst, weil wir auf eine andere Person übertragen, was wir selbst sind, was uns im Wesentlichen ausmacht. Wissen Sie, ich erinnere mich, als wir als Kinder im Hinterhof waren, als wir miteinander gestritten und gesagt haben: Wie Du andere nennst, so bist Du selbst. Und das ist kein Zufall, das ist nicht nur ein Kindersprichwort oder ein Witz. Der Sinn ist sehr psychologisch. Wir sehen immer unsere eigenen Qualitäten in einer anderen Person und denken, dass sie so ist wie wir, und daraus bewerten wir ihr Handeln und bewerten sie insgesamt.“
https://www.youtube.com/watch?v=7sMAHWH_hhQ
Der bereits erwähnte Tiefenstaat, also eine quasi Schattenregierung, existiert auf der geopolitischen Weltbühne und bestimmt größtenteils die Geschicke, insbesondere wenn es um Krieg und Frieden geht. Der Kognitionsforscher Professor Rainer Mausfeld beschreibt die unsichtbar im Hintergrund wirkenden Strukturen in seinem Buch „Angst und Macht“ wie folgt: „Die tatsächliche Macht ist heute in neuartigen globalen Organisationsformen verortet, die vollkommen einer gesellschaftlichen Kontrolle entzogen sind, die für die Bevölkerung weitgehend unsichtbar sind…“
Gleiches gilt meiner Annahme nach auch für die persönlichen Machtverhältnisse, bei denen eigene Schattenanteile ebenfalls großen Einfluss auf die sichtbaren Verhaltensweisen nehmen. Dieser unbewusste Anteil kann auf der einen Seite Macht über die eigene Kriegsbereitschaft und Friedenstüchtigkeit ausüben, auf der anderen Seite wird er von Kriegstreibern mittels kognitiver Kriegsführung aktiv benutzt, um die Bevölkerung zu manipulieren. Der Propagandaforscher Dr. Jonas Tögel schreibt dazu: „Die Tiefenpsychologie dient als Fundament der wohl wichtigsten Manipulationswaffe: die gezielte Beeinflussung des Unbewussten der menschlichen Psyche. Wie bei einem Eisberg liegt ein großer Teil unserer Gedanken und Gefühle „unter der Wasseroberfläche“, und hier können wir so beeinflusst werden, dass wir die Steuerung selbst oft nicht bemerken.“
Der Tiefe Staat kann also ungesehen politisch schalten und walten und gleichzeitig die unbewussten Anteile der menschlichen Psyche zu seinen Gunsten ausnutzen.
Teil 2 folgt in Kürze.
Bastian Barucker, Jahrgang 83, ist Wildnispädagoge, Überlebenstrainer und Prozessbegleiter. Seit 2005 begleitet er Menschen bei Wachstumsprozessen in der Natur. Seit 2011 macht er mithilfe der Gefühls- und Körperarbeit tiefgreifende Selbsterfahrungen, und seit 2014 begleitet er Gruppen, Paare und Einzelpersonen. Er lebt und arbeitet im wunderschönen Lassaner Winkel, nahe der Insel Usedom. Zuletzt erschien von ihm das Buch "Auf Spurensuche nach Natürlichkeit: Vom Leben in der Wildnis und der Reise zu sich selbst" im Massel Verlag.
Kontakt: www.bastian-barucker.de
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ a9434ee1:d5c885be
2025-05-12 08:09:26
@ a9434ee1:d5c885be
2025-05-12 08:09:26Colors as a fun and useful identifier
Nostr apps often use totally random colors for their default avatars, profiles names in chat bubbles, etc... That's a missed opportunity. Why don't we just we just derive a color from the npub and use that instead, interoperably across apps?
It gives us a fun and visual extra point of recognition, often without having to add anything extra to the UIs.
The only problem is that we cannot just allow for any color. The colors should be readable as text in Light and Dark modes and gray-scales should be avoided too.
This is the goal:
Luckily, there's a super simple solution.
(which was used to derive the colors above)Deriving the Colors
You can find the simple spec here: nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qy88wumn8ghj7mn0wvhxcmmv9uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hszxmhwden5te0w35x2en0wfjhxapwdehhxarjxyhxxmmd9uq3kamnwvaz7tm5dpjkvmmjv4ehgtnwdaehgu339e3k7mf0qyghwumn8ghj7mn0wd68ytnhd9hx2tcpz9mhxue69uhkummnw3ezuamfdejj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7qg3waehxw309ahx7um5wgh8w6twv5hszythwden5te0dehhxarj9emkjmn99uqsuamnwvaz7tmwdaejumr0dshsz8rhwden5te0w35x2cmfw3skgetv9ehx7um5wgcjucm0d5hsqpnwd9cz6ce3pvatyf
TLDR: 1. Convert HEX pubkey to Int 2. Calculate the Hue value: Int % 360 3. Set Saturation to 90 for Hues between 216 and 273, use 80 for the rest 4. Set Brightness to 65 for Hues between 32 and 212, use 85 for the rest
Convert HSB color to whatever format you need. Done.
Easy & Fun to integrate!
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
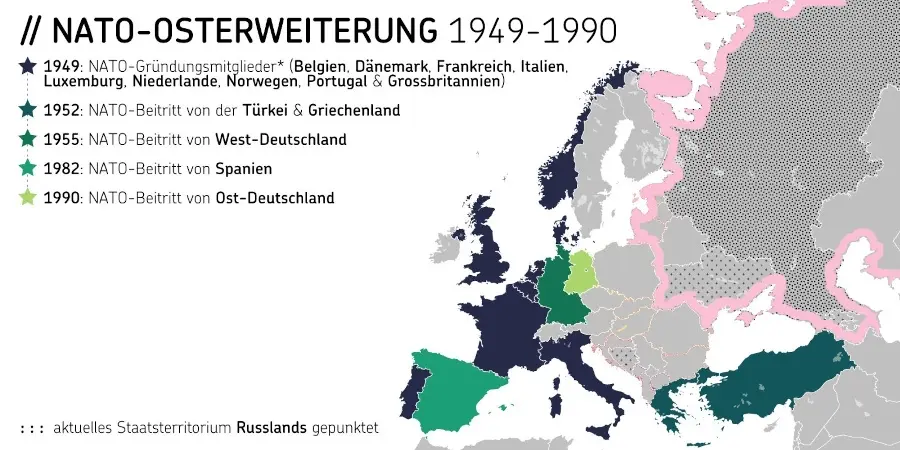
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
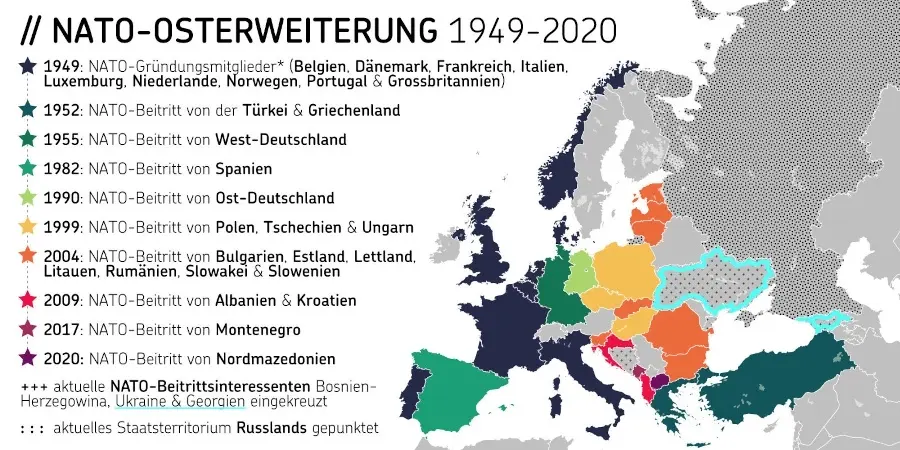
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
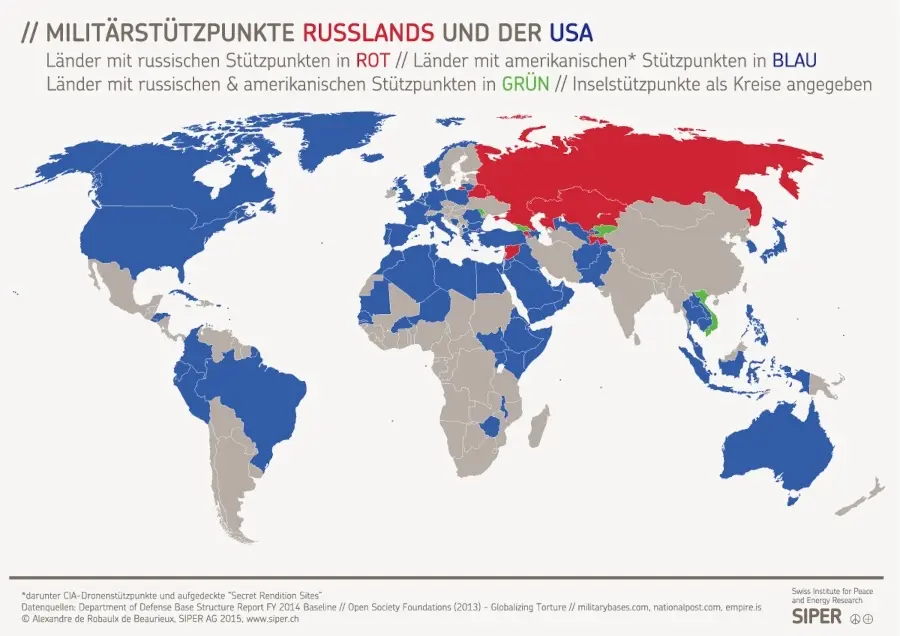
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 6538925e:571e55c3
2025-05-05 20:00:48
@ 6538925e:571e55c3
2025-05-05 20:00:48It’s been a little while since we released a major design update, so we’re really excited to get this new version of the app into your hands. Here’s a breakdown of all the main updates included in Fountain 1.2:
 #### Library Design Update
#### Library Design Update-
New content-type filters at the top of the page make it easier to navigate between podcasts and music in your library.
-
Recently Played is now the default view in your library, so it’s easier to jump back into podcasts you’ve already started.
-
The Music filter now makes it easier to find saved tracks and albums, and it also gives you a list of all the artists whose music you’ve saved.
-
We’ve refreshed the design of the content cards to make it easier to see how much time is remaining on episodes you’ve already started.
 #### Content Pages Design Update
#### Content Pages Design Update-
All of the different content pages have undergone an extensive redesign, including shows, episodes, artists, albums, tracks, clips and playlists
-
We’ve replaced the tab layout we were using on the content pages with one scrollable page, making it easier to access features like chapters and tracklists
-
We’ve sanitised the formatting of show notes too, and if there is no activity for a given episode, we now display the expanded show notes
 #### Episode Summaries
#### Episode SummariesEver looked at a 4-hour Lex Fridman episode and wished you could just read a high-level summary? We certainly have, so we did something about it.
-
Every episode page now has a Summary button above the show notes.
-
Simply pay 500 sats to unlock a summary, or upgrade to Fountain Premium for $2.99/month to enjoy unlimited summaries.
-
Summaries and transcripts now come as a bundle — two for the price of one!
-
Thanks to major improvements, they’re now faster, cheaper, and more accurate than ever before.
 #### Playback Improvements
#### Playback ImprovementsWe’ve completely rebuilt our audio engine from the ground up. Playback is now more robust and reliable — especially for music. Here are some of the key enhancements in Fountain 1.2:
-
Tracks now load and play instantly when tapped.
-
When playing a collection of tracks (e.g. from an artist, album, or playlist), you can now skip seamlessly between them.
-
We’ve replaced the scrollable player page with full-screen modals to make it easier to access show notes, comments, transcripts, chapters, tracklists, and your queue.
-
The new Smart Resume feature rewinds the episode by 5 seconds when you hit pause, so you don’t miss a beat.
-
You can now skip forward or backward by 60 seconds for faster navigation through episodes.
Other Bug Fixes & Improvements
-
Rebuilt payment stats for more complete and reliable transaction records.
-
Refreshed the design of the Settings pages for better usability.
-
Added new episode notification preferences in Settings.
-
Fixed several playback issues that were causing crashes or freezes.
-
Updated lock screen display and controls for livestreams.
-
Fixed issue where the next item in the queue paused unexpectedly.
-
Resolved playback stuttering on Android during livestreams.
-
Fixed disappearing playback controls on the lock screen.
-
Fixed playback speed not updating correctly.
-
Resolved issue where played episodes couldn’t be replayed.
-
Fixed playback not resuming correctly when listening in the car.
-
Synced car playback position with the device.
-
Fixed persistent car display refresh issue.
-
Fixed volume control via car controls.
-
Resolved issue with headphone controls after playing a transcript.
-
Fixed disappearing metadata on the lock screen.
-
Fixed bug where downloaded episodes stopped in airplane mode but showed as playing.
We would love to hear how you’re finding Fountain 1.2. Please submit your thoughts and feedback via the main menu in the app and we will take it on board as we continue to improve the app.
If you want to help test new features out before they get released, you can join Fountain Beta on Telegram. All iOS and Android users welcome.
-
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 90c656ff:9383fd4e
2025-05-12 06:06:00
@ 90c656ff:9383fd4e
2025-05-12 06:06:00Bitcoin emerged as an alternative to the traditional financial system, offering a decentralized and censorship-resistant medium of exchange. However, this proposition directly challenges the control governments exert over the economy, particularly in terms of currency issuance and financial regulation. As a result, many governments view Bitcoin with suspicion and attempt to limit its adoption, while others seek to integrate it into the economy in a controlled manner.
Reasons for conflict between governments and Bitcoin
Government resistance to Bitcoin adoption stems from several key factors:
01 - Loss of Monetary Control: Governments manage monetary policy through the issuance of fiat currency and manipulation of interest rates. Bitcoin, with its fixed supply and decentralized nature, prevents governments from printing more money, thereby limiting their influence over the economy.
02 - Challenges in Taxation: Bitcoin usage makes it harder for authorities to monitor transactions and enforce tax collection, posing a challenge for governments that rely heavily on taxation to fund public services.
03 - Concerns Over Regulation and Financial Crime: Many governments argue that Bitcoin can be used for money laundering, tax evasion, and other illicit activities. However, since all transactions are recorded on the blockchain (or timechain), Bitcoin is actually more traceable than physical cash.
04 - Competition with Central Bank Digital Currencies (CBDCs): Some governments are developing their own digital currencies, known as CBDCs. These offer a high level of control over financial transactions but lack Bitcoin’s decentralized properties. To promote CBDC adoption, some governments attempt to restrict or ban Bitcoin.
Different countries have taken varied approaches to Bitcoin, ranging from full acceptance to outright repression.
- El Salvador:
In 2021, El Salvador became the first country to adopt Bitcoin as legal tender. This decision sparked conflict with global financial institutions like the International Monetary Fund (IMF), which pressured the Salvadoran government to reverse its stance.
- China:
The Chinese government banned Bitcoin mining and usage entirely in 2021, citing environmental concerns and financial risks. Nonetheless, many Chinese miners and users continue to operate through alternative means.
- United States:
While Bitcoin is legal in the U.S., the government has imposed stricter regulations on exchanges and mining operations, seeking to exert more control over the sector. Some politicians advocate for a pro-Bitcoin stance, while others see it as a threat to the dollar.
- European Union:
The EU has taken a more rigorous regulatory approach, requiring user identification and transaction transparency. Despite this, Bitcoin remains legal and widely used.
Despite the challenges imposed by some governments, Bitcoin adoption continues to grow. Many users see Bitcoin as a way to preserve wealth in the face of inflationary monetary policies and excessive government control over money. Furthermore, in countries with unstable economies and limited access to financial services, Bitcoin provides a solution for international payments and protection against economic crises.
Government resistance may slow Bitcoin adoption in certain regions, but it is unlikely to stop it entirely. As a decentralized and global network, Bitcoin will continue to be used regardless of restrictions imposed by any single government. In the long run, its adoption will depend on individuals and businesses standing firm against regulatory pressures and continuing to use it as a financial alternative.
In summary, the conflict between governments and Bitcoin reflects the broader struggle between a centralized traditional financial system and a new decentralized alternative. While some countries seek to ban or restrict its use, others embrace it as part of their economy. Ultimately, government resistance may only delay-but not prevent-the global adoption of Bitcoin, which continues to demonstrate its resilience and utility as a store of value and medium of exchange.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 502ab02a:a2860397
2025-05-12 03:11:06
@ 502ab02a:a2860397
2025-05-12 03:11:06สัปดาห์ที่ผ่านมา เราพักผ่อนย้อนไปเพื่อทำความเข้าใจต้นเหตุของซีรีส์นี้กันแล้วนะครับ ทีนี้เราจะมาสนทนากันต่อจากที่ค้างคาไว้กันครับ
ย้อนกลับไปเมื่อราวทศวรรษ 1970-1980 เป็นยุคที่โลกยังเชื่อว่า “ไขมัน” คือผู้ร้ายตัวจริงในวงการสุขภาพ ปิรามิดอาหารจาก USDA จึงถือกำเนิดขึ้น โดยมีฐานล่างกว้างใหญ่เต็มไปด้วยข้าว แป้ง ซีเรียล พาสต้า และขนมปัง เรียกรวมว่า “กลุ่มคาร์โบไฮเดรต” และถูกวางให้เป็นเสาหลักของอาหารประจำวัน ภายใต้แนวคิดว่าให้พลังงานสูง ไขมันต่ำ ดีต่อหัวใจ และเหมาะกับการเลี้ยงประชากรโลกที่เพิ่มขึ้นอย่างรวดเร็ว
แต่ความจริงที่เปิดเผยภายหลังคือ ปิรามิดอาหารนี้มิได้เกิดจากวิทยาศาสตร์บริสุทธิ์ หากแต่เกิดจากกระบวนการ “เปิดประมูลนโยบาย” โดยกลุ่มอุตสาหกรรมเกษตรรายใหญ่ ซึ่งต้องการระบายผลผลิตคาร์โบไฮเดรตจำนวนมหาศาลจากข้าวโพด ข้าวสาลี และถั่วเหลืองที่รัฐบาลอเมริกันอุดหนุนให้เพาะปลูกเกินความจำเป็น (ดูรายงาน PBS: The Food Pyramid) หน้าที่จัดสรรนี้จึงอยู่ภายใต้ USDA หรือ กระทรวงเกษตรสหรัฐอเมริกา
ขณะที่ผู้คนถูกสอนให้หลีกเลี่ยงไขมัน โปรตีนสัตว์ และหันมากินซีเรียลเป็นอาหารเช้า ผลิตภัณฑ์ไขมันต่ำแทบทุกชนิดกลับต้องเติมน้ำตาลและแป้งเพื่อให้มีรสชาติ นำไปสู่การระบาดของโรคอ้วน เบาหวาน ความดัน และ NCD ทั่วโลก ที่เราเพิ่งจะเข้าใจกันวันนี้ว่ามีรากมาจาก “ปิรามิดคาร์บ” นั่นเอง
คำถามคือ ทำไมการกำหนดอาหารของอเมริกา (ซึ่งแน่นอนว่าแพร่กระจายไปทั่วโลกภายใต้ข้อกำหนดเดียวกัน) จึงเกิดขึ้นจาก "กระทรวงเกษตรสหรัฐอเมริกา" ไม่ใช่ หน่วยงานทางวิทยาศาสตร์ หรือ การแพทย์
หรือเพราะ “อาหาร” ในอเมริกา ไม่ได้เริ่มจากคำว่า “สุขภาพ” แต่เริ่มจาก “เศรษฐกิจ”
ย้อนกลับไปช่วงต้นศตวรรษที่ 20 โดยเฉพาะหลังสงครามโลกครั้งที่สอง สหรัฐฯ ต้องการฟื้นฟูเศรษฐกิจและผลักดันภาคการเกษตรให้โตอย่างรวดเร็ว โดยเฉพาะสินค้าพืชเชิงอุตสาหกรรม เช่น ข้าวโพด ข้าวสาลี ถั่วเหลือง นม และเนื้อจากฟาร์มอุตสาหกรรม และปากท้องของเกษตรกรคือฐานเสียงสำคัญในทุกๆรัฐบาล ดังนั้น USDA ซึ่งเป็นหน่วยงานที่ตั้งขึ้นเพื่อดูแลเกษตรกร จึงรับบทผู้ออก “แนวทางโภชนาการ” โดยเน้นว่า
อาหารอะไรที่ เกษตรกรผลิตได้เยอะ ก็เอามาดันให้ประชาชนกินเยอะ อาหารอะไรที่ ราคาถูก ผลิตได้เร็ว ก็นำมาใส่ไว้ฐานล่างของพีระมิด ให้ประชาชนกินเยอะ อาหารอะไรที่ มีอุตสาหกรรมอยู่เบื้องหลัง ก็เปิดประมูลให้มีบทบาทมากในการล็อบบี้นโยบาย ให้ประชาชนกินเยอะ
พูดง่ายๆ ก็คือ นโยบายอาหารอเมริกา ไม่ได้ออกโดยนักวิทยาศาสตร์หรือนักโภชนาการที่ไม่มีผลประโยชน์ทับซ้อน แต่มาจาก “ข้าราชการสายเกษตร+กลุ่มทุน” ที่ต้องการให้ภาคการเกษตรมีกำไรอย่างต่อเนื่อง และอย่าลืมว่า อเมริกา = โลก
แล้วหน่วยงานด้านวิทยาศาสตร์หรือแพทย์ เช่น NIH (National Institutes of Health) หรือ CDC (Centers for Disease Control and Prevention) หล่ะ แน่นอนครับว่ามีข้อมูลอยุ่ว่าก็มีสิทธิ์เสนอแนะอยู่บ้างแต่ทั้งหมดนี้ ไม่มีอำนาจออกนโยบายหลักที่ใช้จริงกับประชาชน ส่วนใหญ่แค่ให้ข้อมูลวิชาการ ซึ่งมักจะถูกลดทอนหรือละเลยเมื่อนโยบายจริงถูกเขียนขึ้นโดย USDA ในที่สุด
เมื่อเสียงของการตั้งคำถามเริ่มดังกว่าเสียงโฆษณา ขบวนการ “Low Carb” ก็เริ่มตั้งหลักและขยายวงกว้างอย่างเงียบๆ งานวิจัยใหม่ๆ เริ่มบ่งชี้ว่า “น้ำตาลและแป้ง” โดยเฉพาะแป้งแปรรูป คือภัยเงียบที่ส่งผลต่อการอักเสบเรื้อรัง ภาวะดื้ออินซูลิน และเมตาบอลิกซินโดรม จนกระทั่งช่วงต้นทศวรรษ 2010 เป็นต้นมา อาหารแนว “ลดคาร์บ เพิ่มไขมันดี เพิ่มโปรตีน” ก็กลายเป็นกระแสหลักขึ้นมา
ตอนนั้นหลายคนคิดว่า “พวกเราชนะแล้ว” โลกกลับมาฟังเสียงสุขภาพที่แท้จริง โปรตีนกลายเป็นคำตอบใหม่แห่งยุค
แต่มึงเอ๊ยยยยยย... เกมอาจไม่ได้จบตรงนั้น
เพราะในวันที่ประชาชนเริ่มหลีกหนีคาร์บ กลุ่มทุนอาหารข้ามชาติที่เคยวางรากอยู่ในอุตสาหกรรมแป้ง ได้ค่อยๆ แปรทิศ ย้ายการลงทุนไปสู่ “โปรตีนทางเลือก” รอไว้นานแล้วโดยที่เราไม่รู้ตัว ทั้งอาหารพืชแปรรูปอย่าง texture ถั่วเหลือง (TVP), โปรตีนจุลินทรีย์, เนื้อปลูกจากห้องแลบ ไปจนถึง “ไข่” และ “นม” ที่ไม่ได้มาจากสัตว์ โปรตีนสังเคราะห์ที่ผลิตโดยระบบชีวภาพวิศวกรรม (synthetic biology) ซึ่งได้รับเงินทุนจากบริษัทยักษ์ใหญ่อย่างต่อเนื่องตลอดสิบปีที่ผ่านมา
พอถึงวันโปรตีนกลายเป็นเทรนด์ เขาก็เข้ามาเป็นเจ้าของเทรนด์เป็นที่เรียบร้อยแล้ว พร้อมทุกอย่างแล้ว คำถามคือ ใครกันแน่ที่เป็น Trend Setter
โปรตีนจึงไม่ใช่เพียง “สารอาหาร” อีกต่อไป แต่มันคือ “สินค้าอนาคต” ที่สามารถควบคุมแหล่งผลิต แหล่งพันธุ์ เทคโนโลยีการแปรรูป และการกระจายผ่านแพลตฟอร์มค้าปลีกทั่วโลก และถ้าคุณสังเกต จะเห็นว่าไม่มีใครพูดถึง “คาร์บทางเลือก” หรือ "คาร์บเข้มข้น" หรือ "คาร์บที่ไม่ต้องใช้พืช" แม้แต่นิด ทั้งที่ในทางหลักการก็สามารถคิดค้นได้ไม่ต่างกัน แปลว่า พวกเขาไม่ได้แค่อยาก “เลิกขายคาร์บ” แต่กำลัง “เปลี่ยนสินค้าหลักใหม่” ให้ไปอยู่ในกลุ่มที่พวกเขาควบคุมได้ทั้งหมด แค่เอาคำว่า "โปรตีน" ขึ้นมาเป็นฉากหน้าไว้ก่อน
เริ่มเห็นภาพไหมครับ จากคาร์บที่เคยถูกบิดเบือน กลายมาเป็นโปรตีนที่ถูกเสนอให้เรายินดีรับอย่างไม่ตั้งคำถาม
“โปรตีนอนาคต” ดูเหมือนจะเป็นทางเลือก แต่จริงๆ แล้วอาจเป็นกับดักหรือเปล่า
วันนี้ที่หลายคนเฝ้ามองชัยชนะของผู้คนในการล้ม “ปิรามิดคาร์บ” แต่ไม่ทันเห็นว่ากำลังถูกลากเข้าสู่ “หอคอยโปรตีนจำลอง” ที่พวกเขาสร้างขึ้นใหม่ ด้วยบรรจุภัณฑ์สวยหรู คำว่า "รักษ์โลก" "ปลอดภัย" และ "ยั่งยืน" แต่แท้จริงคือห่วงโซ่ที่มัดให้เราเป็นเพียง “ผู้บริโภค” ที่ไม่มีทางรู้ว่าอาหารของเรามาจากธรรมชาติหรือห้องแลบอีกต่อไป เรากลายเป็นหนูที่ย้ายจากกล่องวงกตหนึ่ง มายังอีกกล่องวงกตหนึ่งหรือเปล่า เป็นคำถามที่ยังต้องตอบต่อไป
เฮียไม่ได้มาเพื่อหวาดระแวงนะครับ เพราะในเกมอำนาจอาหาร ไม่มีใครยอมเสียพื้นที่ พวกเขาแค่เปลี่ยนกลยุทธ์ เพื่อครองความเชื่อมั่นใหม่ ในชื่อ “โปรตีน” #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 51faaa77:2c26615b
2025-05-04 17:52:33
@ 51faaa77:2c26615b
2025-05-04 17:52:33There has been a lot of debate about a recent discussion on the mailing list and a pull request on the Bitcoin Core repository. The main two points are about whether a mempool policy regarding OP_RETURN outputs should be changed, and whether there should be a configuration option for node operators to set their own limit. There has been some controversy about the background and context of these topics and people are looking for more information. Please ask short (preferably one sentence) questions as top comments in this topic. @Murch, and maybe others, will try to answer them in a couple sentences. @Murch and myself have collected a few questions that we have seen being asked to start us off, but please add more as you see fit.
originally posted at https://stacker.news/items/971277
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 3d073b19:4ae60f39
2025-05-12 00:09:07
@ 3d073b19:4ae60f39
2025-05-12 00:09:07This is an English openletter
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ e39333da:7c66e53a
2025-05-12 00:03:18
@ e39333da:7c66e53a
2025-05-12 00:03:18::youtube{#VQRLujxTm3c}
Rockstar released the second trailer for Grand Theft Auto VI, where they mention that it showcases both cinematic and gameplay scenes equally, though of course it doesn't show any direct gameplay.
This trailer also announces the release date for the game. The game will come out on the 26th of May, 2026, for the PS5 and the Xbox One.
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ 3d073b19:4ae60f39
2025-05-11 23:59:56
@ 3d073b19:4ae60f39
2025-05-11 23:59:56Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lists
Unordered List
- Item 1
- Item 2
- Subitem 2.1
- Subitem 2.2
Ordered List
- First item
- Second item
- Third item
Links
OpenAI - A link to OpenAI's website. Markdown Guide - A comprehensive guide to Markdown syntax.
Images
 - An example image with a title.
- An example image with a title.Blockquotes
This is a blockquote. It can span multiple lines. It is often used to highlight important information or quotes.
Code
Inline Code
Here is some
inline codethat demonstrates how to format code within a sentence.Code Block
```python
This is a Python code block
def hello_world(): print("Hello, world!") ```
Emphasis
Bold
This text is bold. This text is also bold.
Italic
This text is italic. This text is also italic.
Strikethrough
~~This text is strikethrough.~~
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36
@ 5d4b6c8d:8a1c1ee3
2025-05-03 14:18:36Comments: 3395 (Top Territory!!!) Posts: 306 (3rd) Stacking: 198k (2nd)
We're really bouncing back from the post-Super Bowl lull, with lots of contests and discussion threads. I think we've really found our niche with those two things.
The rest of Stacker News is experiencing declining activity, so our steady growth since February really tells me that we're on the right track.
Thanks for being part of our growing sports community!
originally posted at https://stacker.news/items/970289

