-
 @ c1831fbe:de4b39bf
2025-05-17 09:57:04
@ c1831fbe:de4b39bf
2025-05-17 09:57:04What follows is my best effort to recall the details of an arguably supernatural encounter I experienced almost sixty years ago. I've told this story many times before, and while my recollection may not be perfect in every detail, my account is real and substantively factual.
It was early one long ago morning, in that twilit between-time shortly before dawn. As I dangled precariously in a quasi-aware state, hovering on the knife edge between wakefulness and sleep, I was transported in a dream to another place and time. Was it the Mediterranean coast? Perhaps ancient Greece?
In my mind's eye, I found myself climbing a rather steep, rocky hillside overlooking a sparkling bright blue sea. Ahead of me, and slightly higher, was what appeared to be a young shepherd boy, leading me ever higher up the hill.
As we wove our way upward,
skirting rocky outcroppings and zig-zagging because of the steepness of the slope, I heard the boy chanting:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
He kept repeating the mantra, over and over:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
\~ \~ \~
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
I listened for a few cycles, and then took up the chant myself. After several attempts, when at last I got it right, the shepherd boy turned, looking back at me and smiling broadly to signal that I had finally mastered the cadence and the words.
Then I awoke.
Because my dream had been so vivid and unusual, I immediately found a pencil and paper to write down the chant phonetically before I could forget it.
A few days passed.
Life was busy. Then I remembered my friend in grad school, studying biblical Greek. That weekend, I went and hung out with him while he worked his night job at the college heating plant. Between his rounds inspecting and managing the steam boilers keeping students from freezing to death in the Arctic Midwest winter, I told him about my strange dream.
Pulling out an exhaustive Greek lexicon, one by one, my knowledgeable friend looked up the words from my dream, interpreting each according to its verb conjugation, tense, and mood.
"Ata, Ata" had no discernible meaning; we soon concluded that it was probably just meaningless vocables, added to give the chant rhythm and substance. My friend moved on to the first recognizable word of the chant...
"Archontos" - "They are ruled."
OK, so far, so good. He checked the next word:
"Echousi" - "They shed blood."
Hmmmm... This chant is beginning to appear to be more than random sounds.
"Archousi" - "They rule."
At this point, I almost fell out of my chair in shock. Far from being a meaningless chant, this cycle—repeating again and again—is the seemingly never-ending story of the entirety of human history...
"They Are Ruled, They Shed Blood, They Rule."
\~ \~ \~
"They Are Ruled, They Shed Blood, They Rule."
This concise mantra perfectly captures the endlessly repeating cycle of oppression, revolt, and revolution that always leaves us with a fresh set of oppressors all too ready to replace the last.
Who will rescue us?
Who will redeem us from this endless tedious cycle into which we have been born?
A long lifetime of study and reflection has persuaded me that this deadly cycle can and ultimately will be broken. If we follow the teachings of Jesus; if we love one another and live together in voluntary, local societies, serving each other; I am persuaded that we can break free of this desperately destructive cycle of endlessly seeking to dominate one another. It's past time for us to enter into a mutually beneficial life in the Kingdom of our Creator-God Jesus, the most authentically benevolent King the universe has ever known.
stories #politics #Christianity #supernatural #strange
-
 @ 5edbd885:5fbc291e
2025-05-17 09:54:39
@ 5edbd885:5fbc291e
2025-05-17 09:54:39Because Bitcoin operates outside traditional financial and political systems, engaging with it can create cognitive dissonance.
This uneasy tension is felt in the space between a lifetime of systemic conditioning and the reality of a protocol that functions beyond anything we have ever known.
Bitcoin challenges deeply ingrained assumptions about what money is, who should control it, and how trust is established in society.
Many initially reject it because Bitcoin breaks the mental models we’ve relied on for understanding value, authority, and trust.
It’s not just adopting a new system; it’s detaching from the old one and any -ism we may personally identify with.
Before we dive in I would like to make an important note about our current system.
Modern Fiat is Not Capitalism
Capitalism is an economic system in which private individuals or businesses own and control the means of production, distribution, and exchange of goods and services, rather than the state.
The main features of this system are limited government intervention, a free market economy, and competition.
While we may believe we live in a capitalistic society, reality is very different:
-
Governments Intervention: Governments intervene in free markets primarily through monetary expansion (money printing) and capital controls.
-
Inflation and Redistribution: Printing increases the money supply, causing inflation that erodes purchasing power unevenly. Those who receive new money first gain at the expense of later recipients. Capital controls restrict market flows, distorting asset and currency prices.
-
Cantillon Effect and Concentration: These mechanisms concentrate wealth and economic power among government insiders and favored corporations, who gain preferential access to resources. This leads to growing government influence and corporate monopolies.
-
Systemic Distortions: Such interventions stifle innovation, reduce market competition, and undermine price signals essential to free market functioning.
-
Therefore: Our modern fiat monetary system is not free market capitalism.
To quote Jeff Booth, from first principles:
> “In a free market, prices fall to the marginal cost of production; if they are not falling, we do not live in a free market. Communism and capitalism are the same system under manipulated money.”
Bitcoin is the first opportunity for humanity to experience a true free market where prices fall—a reality beyond fiat altogether.
Let’s explore how Bitcoin differs from fiat-based systems and economic theories.
Bitcoin vs. Major -isms
| Feature | Capitalism | Communism | Libertarianism | Bitcoin | | ------------------------- | ------------------------------------ | ----------------------------------------- | ------------------------------------ | ------------------------------------------------- | | Ownership Model | Private, profit-driven | Collective, state-owned | Private, voluntary exchange | Individual, self-sovereign | | Control of Money | Central banks & private institutions | State-controlled | Privatized or gold-backed | Decentralized, algorithmic issuance | | Value Flow | Favors asset owners | Centralized and controlled redistribution | Market-driven | Distributed to all network participants | | Ideological Basis | Market efficiency, competition | Class struggle, equality | Individual freedom, non-intervention | Neutral protocol, transparency, free market | | Governance Structure | Market and government interplay | Centralized planning | Minimal state | Consensus among decentralized nodes | | Inflation Policy | Targeted via central banking | Controlled by state | Opposed to fiat inflation | Hard-capped supply: 21 million BTC | | Censorship Resistance | Low to moderate (depends on regime) | Low | Medium, still requires trust | Very high—no central chokepoint | | Accessibility | Varies by class and location | Controlled by state allocation | Varies by market access | Global, permissionless | | Moral Foundation | Efficiency and growth | Equity and solidarity | Autonomy and property rights | Mathematical integrity, sovereignty, transparency |
Bitcoin is not an -ism or a fiat system.
I don't see it as a way to make more fiat paper money either.
It’s a system outside the system that breaks all of our previous mental models.
A truly interdependent reality where the creativity, productivity, gifts, talents, and abilities of one serves all.
Sovereign individuals in service of the collective and vice-versa.
The Difficulty Categorizing Free Thinkers
In different conversations, and while discussing Bitcoin with non-Bitcoiners, I’ve been asked if I am an anarchist, capitalist, communist, liberal, or a libertarian.
Since I don’t identify with any political leaning or traditional ideology, I was sincerely confused when this first started happening—but now I see why.
Bitcoiners are notoriously difficult to place into political categories because their convictions often cut across traditional ideological boundaries.
To the outside observer, this can appear contradictory: a Bitcoiner might criticize the Federal Reserve like a libertarian, value personal personal sovereignty like an anarchist, and believe in sound money like a gold-standard capitalist.
These labels, however, fail to capture the deeper thread—I believe our views are aligned with a protocol in service of humanity, and shaped by a shared belief in a system that values humans rather than fiat-based incentives.
Bitcoin challenges the default left/right binary and exposes just how much our frameworks are built around centralized systems, division, and control.
When those systems are removed—as they are in Bitcoin—any traditional world view falls apart, along with all the labels and polarization that come with it.
To some, this may be why Bitcoiners seem ‘radical’ or ‘religious,’ because we have stepped outside their frame of reality entirely.
This protocol is not a revolution in the name of an ideology—it’s a revolution in the absence of one known to modern history.
Unlearning the Past, Embracing the Now
What makes Bitcoin truly disruptive isn’t just its technology—it invites us to question assumptions we didn’t even know we were making.
I still catch myself trying to compare Bitcoin to a "known" sometimes in this ongoing process of unlearning.
I think part of this evolution is catching myself and remembering, we are at the forefront of a new reality.
Our individual choices and actions are shaping what the post-fiat world will look like.
While for some, this will feel empowering and exciting, for others, this shift can feel unsettling, even threatening, as it calls into question the stability of the familiar.
This is one of the reasons why I see Bitcoin as being the initiator of an individual and collective spiritual awakening.
I can only encourage you to embrace the change—be the change—a powerful manifestor ushering in a new paradigm ✨
-
-
 @ a4043831:3b64ac02
2025-05-17 09:03:00
@ a4043831:3b64ac02
2025-05-17 09:03:00Money is emotional. It’s not just numbers on a spreadsheet. It’s about peace of mind. Vacations. College. Retirement. And sometimes… It's about stress. Even the smartest families make money mistakes. Not because they don’t care. But because life is busy. Financial planning can feel overwhelming. And it’s easy to put it off until “later.” But the truth is: later turns into never.
Here are five common money missteps families make—and how to avoid them, starting today.
1. Spending Without a Plan
You’re out running errands. You grab a latte. Order takeout. Buy a couple things online. Nothing big. But by the end of the week? The bank account’s hurting. Sound familiar?
Many families spend without a clear plan. They don’t know exactly how much they earn, where their money is going, or what’s left for savings. It’s a recipe for stress.
How to avoid it: Start simple. Track your income. List your expenses. Identify where you can cut back. Use a budgeting app or just a notebook. The key is consistency. Build awareness around spending.
Working with a financial advisor makes this even easier. Passive Capital Management helps families create realistic, stress-free budgets that actually work.
2. Delaying Retirement Savings
Let’s be honest—retirement feels far away. Especially when you’re dealing with daycare, car payments, and rising grocery bills. But here’s the catch: the earlier you start, the less you have to save. Why? Two words: compound interest. The money you invest today earns interest. And then that interest earns interest. Over time, your money grows exponentially.
How to avoid it: Contribute to a 401(k), IRA, or both—right now. Even if it's just $50 a month. Got a workplace plan? Take full advantage of any employer match.
And don’t “set it and forget it.” Revisit your plan regularly with a trusted advisor. PCM’s retirement planning services help families build smart, flexible strategies tailored to their long-term goals.
3. Overusing Credit Cards
Swipe now, worry later. That’s the trap. Credit cards can be useful but dangerous when used for emotional or unplanned purchases. High-interest rates can turn a $100 dinner into a $300 debt headache.
How to avoid it: Use credit cards for planned expenses only. And pay off the balance in full each month. Avoid minimum payments—they just feed the debt cycle. If you’re already in credit card trouble, don’t panic.
Passive Capital Management works with families to create smart debt reduction plans while still saving for the future.
4. Buying Too Much House
Big house. Fancy kitchen. Bonus room. Sounds great, right? Until the mortgage, property taxes, repairs, insurance, utilities, and maintenance come crashing in. Many families make the mistake of maxing out their home budget. It feels like an investment—but in reality, it can squeeze your finances for decades.
How to avoid it: Buy what you need, not what impresses others. Be realistic about ongoing costs. And remember: your mortgage should never eat up your emergency savings or retirement goals. Before making a big move, talk to a financial expert.
PCM helps clients evaluate housing costs in the context of their full financial picture.
5. Skipping the Emergency Fund
Unexpected car repair? Out-of-pocket medical bill? Job loss? Life happens. And when it does, many families don’t have a cushion. They rely on credit cards or drain their retirement accounts just to stay afloat.
How to avoid it: Build an emergency fund with 3–6 months of essential expenses. Keep it in a separate, easy-access savings account. This fund is your safety net—don’t touch it unless it’s truly an emergency.
PCM includes emergency fund planning as a core part of every family’s financial plan. Because peace of mind isn’t optional—it’s essential.
Final Thoughts
Nobody gets it right 100% of the time. But small, consistent changes can transform your family’s financial future. The good news? You don’t have to do it alone. Passive Capital Management offers straightforward, judgment-free guidance to help families avoid costly mistakes and make confident money moves. Whether you need help building a budget, planning for retirement, or finally tackling your debt, PCM is ready to help.
Take the first step. Your future self will thank you. Talk to a PCM Advisor Today.
-
 @ e97aaffa:2ebd765d
2025-05-17 08:58:14
@ e97aaffa:2ebd765d
2025-05-17 08:58:14Quando tentamos simplificar/ilustrar algo que é extremamente complexo, pode resultar em algo distorcido. Apesar do resultado sair distorcido, continua a ser a melhor representação, temos é que ter em mente que essa distorção existe quando analisamos essa informação.
O maior exemplo, é o mapa mundi, quando transformamos uma esfera em algo plano, é natural que crie distorções, como quanto mais perto dos polos, os países são sobredimensionados em relação aos que estão mais perto da linha do Equador.
Esta infografia criada pelo Saylor é comumente utilizada, mas esta deve ser utilizada com moderação, porque a informação também está distorcida.
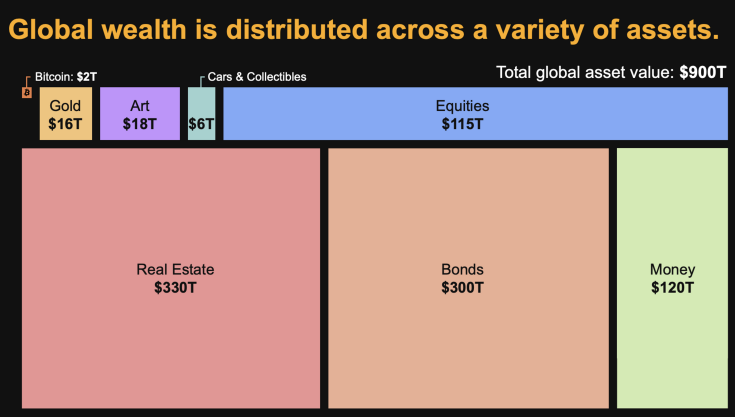
Assim, sempre que alguém utiliza estes dados para fazer análises, deve estar ciente que existem distorções. Primeiro, em alguns ativos os valores são impossíveis de calcular, são apenas estimativas. Já foram feitos vários estudos, e sempre com valores bastantes díspares.
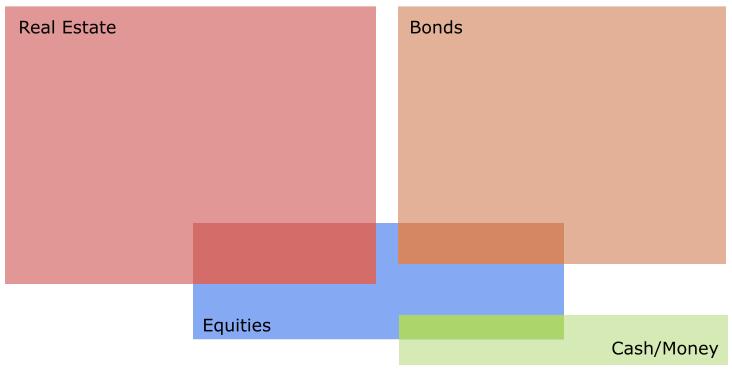
Depois, esta infografia simplifica demasiado, não sendo visível a sobreposição de ativos, por exemplo, as empresas possuem outros ativos, isso significa, que não podemos fazer somas simples. Ou seja, se somarmos as Equities (115T) e os Bonds(300T) não resulta em $415 Triliões de riqueza, o real valor é inferior.
Vamos a dois bons exemplos:
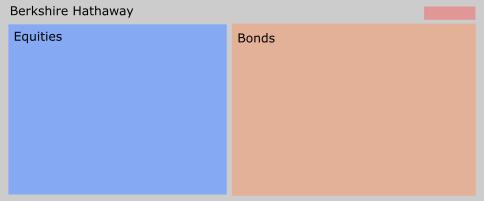
A Berkshire Hathaway, a empresa de Warren Buffett, que o seu atual core business é investir em outras empresas. Apesar de neste momento, ter uma enorme liquidez, está a aguardar pelo momento certo para voltar ao mercado.
A outra empresa é MicroStrategy, que gradualmente está-se a transformar num banco Bitcoin. O seu negócio inicial, começa a ser insignificante, para a sua atual dimensão, está a fazer um percurso muito similar à Berkshire Hathaway, enquanto a Berkshire Hathaway redirecionou o seu negócio para o investimento em ações, a MicroStrategy para o Bitcoin.
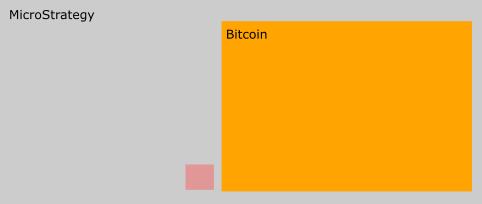
Um erro comum entre alguns bitcoiners quando fazem estimativas baseada nesta tabela, é acreditarem que o crescimento do valor do Bitcoin, vai resultar numa redução do valor das Equities. Isso não vai acontecer, porque as empresas também vão possuir Bitcoin na sua tesouraria, logo se o valor do bitcoin subir, as equities também o vão.
Onde o Bitcoin vai certamente impactar, é nas Bonds e no Real Estate.
Assim para concluir, esta infografia é interessante para fazer cálculos ou análises, mas não podemos esquecer que contém distorções.
-
 @ c913b8e3:8704332c
2025-05-17 08:31:43
@ c913b8e3:8704332c
2025-05-17 08:31:43Absurdities from Finland
Hydrogen, Railways, and Datacenters: Just an Armchair Economist Ranting (Expect Zero Value)
"Next year we'll have growth!" they promise. Again. And again. And again.
The "economists" who yell and preach about this are just state puppets. The track record: 17-18 years of zero growth.
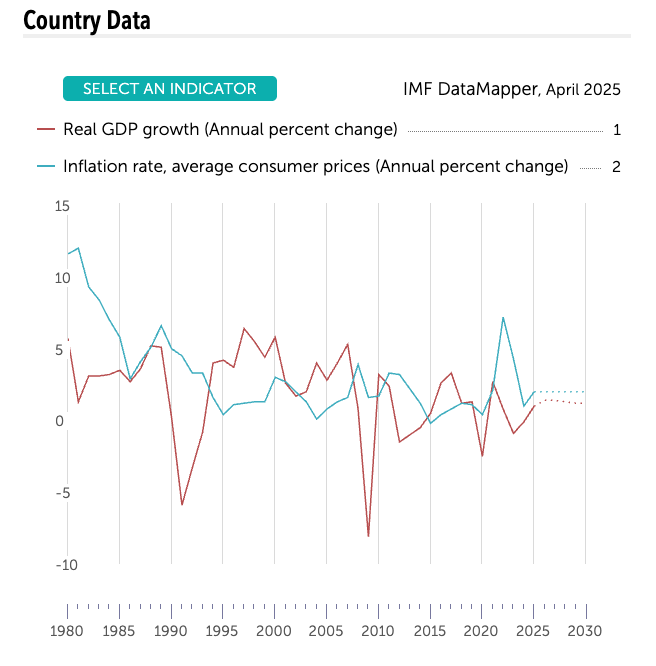
Finland, 1980-2025: Real GDP growth stagnant (red) while prices still bite (blue). After 2008 Red line - 17 years of “wait till next year.” — IMF DataMapper, April 2025
Why do the experts always get it wrong? Here in Finland, everybody is blinded by Keynesianism.
-
Low interest rates
-
High spending
Even those I once thought had "common sense" have become blind. They mistake subsidized sectors for "growth." So in love with the state, they ignore incentives, time preference, and basic economics.
New brave Finland - Hydrogen economy (1)
Launch event: free champagne, no customers. Taxpayers pay.
“Finland’s hydrogen economy is stuttering - there’s still no real market for it, so officials insist it must be manufactured with policy decrees and taxpayer subsidies.”
“Once science has to serve, not truth, but the interests of a state, argument exists only to vindicate the approved belief.” — The Road to Serfdom, ch. 11
Malinvestment Musical. Subsidies shuffle capital from things consumers actually want, such as lower electricity prices. Healthcare that works? I honestly don’t even know; Finnish people have become lazy and idiotic.
The Cantillon effect from this “green stimulus” showers money on consultants and lobbyists first; the average worker gets the hangover in the form of higher power bills and grocery prices.
Only companies living on subsidies call it “the future.”
(Sometimes I wish I was an engineer so I could do shit instead of just whining like a proper economist. At least then I could build something useful instead of just talking shit. Even with my limited knowledge of physics, I understand hydrogen is an inefficient way to store electricity - the laws of thermodynamics don't care about government subsidies.)

Hurray, we love the railways (2)
NATO will bring investments to Finland - Hurray!
We must rip up perfectly good tracks so we can afford to move troops we can no longer afford.
War talk has clouded judgment: when “national security” is the slogan, cost-benefit math is treason. As Hayek warned, the road to serfdom is always paved with strategic necessity.
-
What, exactly, is a "sufficient" defense for five million Finns? (Asking this here makes you a Russian Bot, though I don't like Russia or Putin.)
-
Who decides when the price tag crosses from prudent to reckless?
If hatred of an external foe sets every budget line, freedom and prosperity shrink to the margins.
In other words, the track to “strategic readiness” can be the same track to serfdom -just painted NATO blue.
When an economy flat-lines for 17 years, nothing says “revival” like swapping 1,435 mm of track for 1,520 mm - and calling it growth.
Finnish economists and "liberalists" are celebrating this? (pics in the end, can't read that X much, it has become so idiotic).
l

The Ministry of Transport has estimated that the cost of conversion work for the railway section between Haparanda and Oulu alone will exceed 1.5 billion euros. The distance is about 150 kilometers. (ESTIMATION…)
New Brave Finland – Datacenter Dissonance (3)
Well, our little minister was not involved so bad, bad, and bad!
Apparently, the box is evil if it says TikTok, but awesome if the logo reads Meta or Google. Hey, all of them are shit, just producing brain rot and stealing our data.
Low temps, reliable grid, sparse population - Finland is a logical server-farm host (shithole). But let's call it what it is: a capital-intensive, low-employment utility business. Selling it as a "high-tech jobs boom" is wishful accounting. The politicians like to yell that these investments are "Billions and Billions," yes, but how much stays in Finland? Some construction jobs and a handful of cleaners? Fucking exquisite.
"Digital Red Menace!" Lohjalainen Harri panics about Chinese bytes corrupting Finnish soil. His brilliant plan? Pray the project fails "Lohjan malliin." Nothing says "economic prosperity" like hoping jobs don't materialize! Peak Finnish paradox: pray for investments and fumble them with bureaucracy or nationalist paranoia.
What cybersecurity threat do these server farms pose to Finland? Absolutely fucking none. The data doesn't care where it sits. TikTok videos don't turn into communist spies when stored in Kouvola/Lohja. Absurd and idiotic.
Yes TikTok is brainrot and stupid shit, you have to be an idiot to install that app on your phone, but it's consumer choice - if you want it then go for it, fucking idiot. Same goes for Facebook, Instagram, all that dopamine garbage.
The Datacenter Paradox: Finland needs investment but fears investors. It celebrates clean industry then hyperventilates about who owns the servers. Classic malinvestment by decree - politicians picking winners.
Datacenters can be fine investments… BUT let's be honest about the tradeoffs. All the value goes abroad. Every megawatt sent to datacenters is not available for households or actual productive industry. Basic economics: when datacenters consume 5-10% of Finland's electricity, prices rise for everyone else. Your heating bill subsidizes Facebook's server cooling. Another brilliant example of the invisible tax of political favoritism.
The Bitcoin Alternative No One Will Discuss: Here's the real irony - datacenters can't be easily switched off during peak demand, creating grid rigidity. Bitcoin mining farms, meanwhile, could be turned on/off based on grid needs, serving as perfect complementary loads for Finland's growing but inconsistent renewable energy (wind/solar). Miners would pay premium rates during excess generation and shut down during shortages - a genuine market solution! But no, can't have sound money solutions in Finland. Better to have Googles servers running 24/7 regardless of grid conditions than allow the evil Bitcoin to improve our renewable energy economics. God forbid we actually use a solution that simultaneously strengthens the grid, supports renewables, AND promotes sound money. That might accidentally lead to common sense, and we can't have that in Finland.

General Observations: The Finnish Decay
Finland is slowly becoming like southern Europe, where nothing gets done on time. We used to laugh at how inefficient and idiotic it is there, but it is now the same here. I got a reply from my Bank after 4-5 months of sending a message. Asking for offers? Wait 3-4 months in some cases (I had this with garbage service). Need a solid service man? Let's see if somebody is free in 2 weeks? Well, I am also becoming like this with my business; nobody even cares.
Rotting services and entertainment
Hard to imagine our restaurant industry was almost on par with Sweden and Denmark just +5 years ago. Today? How many good restaurants have quit? How many Michelin stars have we lost?
Well, how about concerts? Our biggest stadium this summer will host Iron Maiden in June and Robbie Williams in September. WTF? Even the Baltic states can attract bigger names than Finland, this is becoming total shithole in every aspect.
Why?
COVID, collapsing purchasing power, bureaucracy cancer, tax asphyxiation, war hysteria, sheepish compliance, and state dependency.
The entrepreneurial drive that once built world-leading companies has withered. Why innovate when bureaucrats decide winners? Why take risks when failure is punished extremely hard (lifelong debt prison, and shame) and success is taxed away?
The result: economic stagnation rationalized as "social stability" and "equality."
Economic literacy has collapsed. Even the economists here don't grasp the basic concepts, so how on earth could the average citizen? The scariest part is that they don't even care. They've outsourced their economic thinking to the state, the same way they've outsourced their responsibility and risk management. The blind leading the blind, straight to economic mediocrity.
The Finnish Decay: When Will We Say "Enough"?
It would be a good idea to write a book in a similar style to Lawrence Lepard's Big Print: What Happened To America And How Sound Money Will Fix It.
Make readers mad! Advocate for hard money and small government.
Problems? and What's next? Recession 1990s → Nokia Mirage → Euro‑Zone Handcuffs → GFC & The Silent Depression → Everyday Decay → Complete state dependency or get mad?
A glimmer of hope: Despite the lost decades, there's a spark in Finland's youth. They hustle and show more entrepreneurial spirit, saving habits, and investment interest than their parents.

In 1999, we were a top country in education, technology, healthcare, and debt contracted on top of that we were one of the safest places to live, we didn’t lock the bikes and even the doors…
Now look at us?
When will Finns wake up and say enough?
As Hayek warned: "A movement whose main promise is the relief from responsibility cannot but be antimoral in its effect, however lofty the ideals." We've outsourced our moral obligations to an impersonal state, weakening "both the willingness to bear responsibility and the consciousness that it is our own individual duty."
We need a hard money and personal responsibility renaissance.
Coming soon: "How Sound Money and Small Government Can Save Finland From Its Slow-Motion Suicide"

News and sources:
I recently finished reading F.A. Hayek's "The Road to Serfdom" (1944). The similarities between Hayek's warnings and Finland's current course are striking. Europe and Finland are ramping up defence spending to ridiculous levels, now even talking over 5% GDP levels, which is total insanity. What would be enough for defence? We have little freedoms left here in Finland (and Europe), and in pursuit of “security,” we might lose it all. Central planners who believe they can direct an economy better than market forces are just clowns, from hydrogen to datacenter politics. What market forces have we left in Finland? I can breath freely? Soon that will be taxed too. Next we have CBDC coming up in EU.
I highly recommend reading "The Road to Serfdom." Its analysis of how good intentions lead to economic ruin remains as relevant in 2025 as it was in 1944. I feel like a total idiot for not reading it before.
Read 27 books so far this year, thx for Jack Dorsey “reading challenge” I started this in March, aim was 50 book but now we aim to 100, so fucking good to read books!
New brave Finland - Hydrogen economy (1) ://www.is.fi/kotimaa/art-2000011199663.html
Railways (2): https://yle.fi/a/74-20161549 and https://yle.fi/a/74-20161793
Datacenters (3): https://yle.fi/a/74-20160436
Hope its not russian or Chinese? Harri (4) https://www.hs.fi/suomi/art-2000011229295.html
-
-
 @ 266815e0:6cd408a5
2025-05-16 20:52:42
@ 266815e0:6cd408a5
2025-05-16 20:52:42Streams are the key to nostr
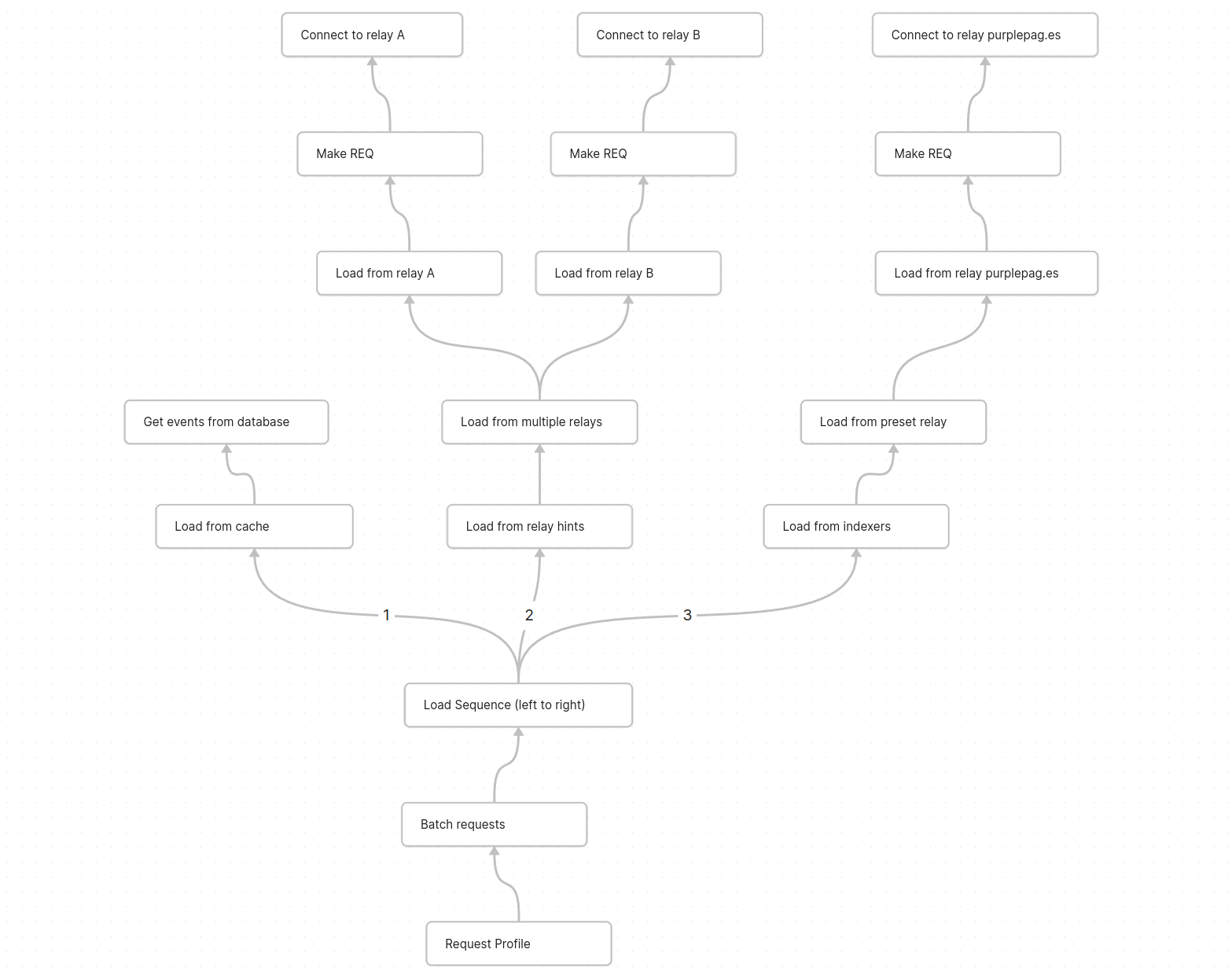
Loading events from a nostr relay is probably the most inconsistent way of loading data I've had to work with, and that's only loading from a single relay. the problem gets exponentially more complicated once you try to load events from multiple relays
Unlike HTTP nostr does not have a simple flow with timeouts built in. events are sent back one at a time and can fail at any point or have massive (10s) gaps between them
The key is to use streams. something that starts, emits any number of results, then maybe errors or completes. luckily it just so happens that JavaScript / TypeScript has a great observable stream library called RxJS
What is an observable
An
Observablein RxJS is stream a of data that are initialized lazily, which means the stream is inactive and not running until something subscribes to it```ts let stream = new Observable((observer) => { observer.next(1) observer.next(2) observer.next(3) observer.complete() })
// The stream method isn't run until its subscribed to stream.subscribe(v => console.log(v)) ```
This is super powerful and perfect for nostr because it means we don't need to manage the life-cycle of the stream. it will run when something subscribes to it and stop when unsubscribed.
Its helpful to think of this as "pulling" data. once we have created an observable we can request the data from it at any point in the future.
Pulling data from relays
We can use the lazy nature of observables to only start fetching events from a nostr relay when we need them
For example we can create an observable that will load kind 1 events from the damus relay and stream them back as they are returned from the relay
```typescript let req = new Observable((observer) => { // Create a new websocket connection when the observable is start let ws = new WebSocket('wss://relay.damus.io')
ws.onopen = () => { // Start a REQ ws.send(JSON.stringify(['REQ', 'test', {kinds: [1], limit: 20}])) }
ws.onmessage = (event) => { let message = JSON.parse(event.data) // Get the event from the message and pass it along to the subscribers if(message[0] === 'EVENT') observer.next(message[1]) }
// Cleanup subscription return () => { ws.send(JSON.stringify(['CLOSE', 'test'])) ws.close() } }) ```
But creating the observable wont do anything. we need to subscribe to it to get any events.
ts let sub = req.subscribe(event => { console.log('we got an event' event) })Cool now we are pulling events from a relay. once we are done we can stop listening to it by unsubscribing from it
ts sub.unsubscribe()This will call the cleanup method on the observable, which in turn closes the connection to the relay.
Hopefully you can see how this work, we don't have any
open,connect, ordisconnectmethods. we simply subscribe to a stream of events and it handles all the messy logic of connecting to a relayComposing and chaining observables
I've shown you how we can create a simple stream of events from a relay, but what if we want to pull from two relays?
Easy, lets make the previous example into a function that takes a relay URL
```ts function getNoteFromRelay(relay: string){ return new Observable((observer) => { let ws = new WebSocket(relay)
// ...rest of the observable...}) } ```
Then we can "merge" two of these observables into a single observable using the
mergemethod from RxJSThe
mergemethod will create a single observable that subscribes to both upstream observables and sends all the events back. Think of it as pulling events from both relays at once```ts import { merge } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') )
// Subscribe to the observable to start getting data from it const sub = notes.subscribe(event => { console.log(event) })
// later unsubscribe setTimeout(() => { sub.unsubscribe() }, 10_000) ```
But now we have a problem, because we are pulling events from two relays we are getting duplicate events. to solve this we can use the
.pipemethod and thedistinctoperator from RxJS to modify our single observable to only return one version of each eventThe
.pipemethod will create a chain of observables that will each subscribe to the previous one and modify the returned values in some wayThe
distinctoperator takes a method that returns a unique identifier and filters out any duplicate values```ts import { merge, distinct } from 'rxjs'
const notes = merge( getNoteFromRelay('wss://relay.damus.io'), getNoteFromRelay('wss://nos.lol') ).pipe( // filter out events we have seen before based on the event id distinct(event => event.id) ) ```
Now we have an observable that when subscribed to will connect to two relays and return a stream of events without duplicates...
As you can see things can start getting complicated fast. but its also very powerful because we aren't managing any life-cycle code, we just subscribe and unsubscribe from an observable
Taking it to an extreme
Hopefully at this point you can see how powerful this is, we can think of almost any data loading pattern as a series of observables that pull data from upstream observables and stream it back to the original subscriber.
Here is a quick sketch of what it could look like to load user profiles. each node is an observable that "pulls" data from its child node ending with the "connect websocket" or "load from database" nodes which do the work of making a relay connection
Conclusion
All this might seem pretty simple and straight forward, but its been a long six month of learning for me. I've had to completely rethink how data and nostr events should be handled in a client and how to avoid screwing up and shooting myself in the foot with these powerful tools.
If you want to give RxJS a try I would encourage you to checkout the nostr sdk I've been building called applesauce
Its uses RxJS for pretty much everything and has the simplest and most flexible relay connection API I've seen so far (mainly no life-cycle management)
-
 @ 609f186c:0aa4e8af
2025-05-16 20:57:43
@ 609f186c:0aa4e8af
2025-05-16 20:57:43Google says that Android 16 is slated to feature an optional high security mode. Cool.
Advanced Protection has a bunch of requested features that address the kinds of threats we worry about.
It's the kind of 'turn this one thing on if you face elevated risk' that we've been asking for from Google.
And likely reflects some learning after Google watched Apple 's Lockdown Mode play out. I see a lot of value in this..
Here are some features I'm excited to see play out:
The Intrusion Logging feature is interesting & is going to impose substantial cost on attackers trying to hide evidence of exploitation. Logs get e2ee encrypted into the cloud. This one is spicy.
The Offline Lock, Inactivity Reboot & USB protection will frustrate non-consensual attempts to physically grab device data.

Memory Tagging Extension is going to make a lot of attack & exploitation categories harder.
2G Network Protection & disabling Auto-connect to insecure networks are going to address categories of threat from things like IMSI catchers & hostile WiFi.
I'm curious about some other features such as:
Spam & Scam detection: Google messages feature that suggests message content awareness and some kind of scanning.
Scam detection for Phone by Google is interesting & coming later. The way it is described suggests phone conversation awareness. This also addresses a different category of threat than the stuff above. I can see it addressing a whole category of bad things that regular users (& high risk ones too!) face. Will be curious how privacy is addressed or if this done purely locally. Getting messy: Friction points? I see Google thinking these through, but I'm going to add a potential concern: what will users do when they encounter friction? Will they turn this off & forget to re-enable? We've seen users turn off iOS Lockdown Mode when they run into friction for specific websites or, say, legacy WiFi. They then forget to turn it back on. And stay vulnerable.

Bottom line: users disabling Apple's Lockdown Mode for a temporary thing & leaving it off because they forget to turn it on happens a lot. This is a serious % of users in my experience...
And should be factored into design decisions for similar modes. I feel like a good balance is a 'snooze button' or equivalent so that users can disable all/some features for a brief few minute period to do something they need to do, and then auto re-enable.
Winding up:
I'm excited to see how Android Advanced Protection plays with high risk users' experiences. I'm also super curious whether the spam/scam detection features may also be helpful to more vulnerable users (think: aging seniors)...
Niche but important:
Some users, esp. those that migrated to security & privacy-focused Android distros because of because of the absence of such a feature are clear candidates for it... But they may also voice privacy concerns around some of the screening features. Clear communication from the Google Security / Android team will be key here.
-
 @ 7460b7fd:4fc4e74b
2025-05-17 08:26:13
@ 7460b7fd:4fc4e74b
2025-05-17 08:26:13背景:WhatsApp的号码验证与运营商合作关系
作为一款基于手机号码注册的即时通信应用,WhatsApp的账号验证严重依赖全球电信运营商提供的短信或电话服务。这意味着,当用户注册或在新设备登录WhatsApp时,WhatsApp通常会向用户的手机号码发送SMS短信验证码或发起语音电话验证。这一流程利用了传统电信网络的基础设施,例如通过SS7(信令系统7)协议在全球范围内路由短信和电话securityaffairs.com。换句话说,WhatsApp把初始账户验证的安全性建立在电信运营商网络之上。然而,这种依赖关系也带来了隐患:攻击者可以利用电信网络的漏洞来拦截验证码。例如,研究人员早在2016年就演示过利用SS7协议漏洞拦截WhatsApp和Telegram的验证短信,从而劫持用户账户的攻击方法securityaffairs.com。由于SS7协议在全球范围内连接各国运营商,一个运营商的安全缺陷或恶意行为都可能被不法分子利用来获取他网用户的短信验证码securityaffairs.com。正因如此,有安全专家指出,仅依赖短信验证不足以保障账户安全,WhatsApp等服务提供商需要考虑引入额外机制来核实用户身份securityaffairs.com。
除了技术漏洞,基于电信运营商的验证还受到各地政策和网络环境影响。WhatsApp必须与全球各地运营商“合作”,才能将验证码送达到用户手机。然而这种“合作”在某些国家可能并不顺畅,典型例子就是中国。在中国大陆,国际短信和跨境电话常受到严格管控,WhatsApp在发送验证码时可能遭遇拦截或延迟sohu.com。因此,理解WhatsApp在中国的特殊联网和验证要求,需要将其全球验证机制与中国的电信政策和网络审查环境联系起来。下文将深入探讨为什么在中国使用WhatsApp进行号码验证时,必须开启蜂窝移动数据,并分析其中的技术逻辑和政策因素。
中国环境下的特殊问题:为何必须开启蜂窝数据?
中国的网络审查与封锁: WhatsApp自2017年起就在中国大陆遭遇严格封锁。起初,WhatsApp在华的服务受到**“GFW”(防火长城)**的部分干扰——例如曾一度只能发送文本消息,语音、视频和图片消息被封锁theguardian.com。到2017年下半年,封锁升级,很多用户报告在中国完全无法使用WhatsApp收发任何消息theguardian.com。中国官方将WhatsApp与Facebook、Telegram等西方通信平台一同屏蔽,视作对国家网络主权的挑战theguardian.com。鉴于此,在中国境内直接访问WhatsApp的服务器(无论通过Wi-Fi还是本地互联网)都会被防火长城所阻断。即使用户收到了短信验证码,WhatsApp客户端也无法在没有特殊连接手段的情况下与服务器完成验证通信。因此,单纯依赖Wi-Fi等本地网络环境往往无法完成WhatsApp的注册或登陆。很多用户经验表明,在中国使用WhatsApp时需要借助VPN等工具绕过审查,同时尽可能避免走被审查的网络路径sohu.com。
强制Wi-Fi热点与连接策略: 除了国家级的封锁,用户所连接的局域网络也可能影响WhatsApp验证。许多公共Wi-Fi(如机场、商场)采取强制门户认证(captive portal),用户需登录认证后才能上网。对此,WhatsApp在客户端内置了检测机制,当发现设备连入这类强制Wi-Fi热点而无法访问互联网时,会提示用户忽略该Wi-Fi并改用移动数据faq.whatsapp.com。WhatsApp要求对此授予读取Wi-Fi状态的权限,以便在检测到被拦截时自动切换网络faq.whatsapp.com。对于中国用户来说,即便所连Wi-Fi本身联网正常,由于GFW的存在WhatsApp依然可能视之为“不通畅”的网络环境。这也是WhatsApp官方指南中强调:如果Wi-Fi网络无法连接WhatsApp服务,应直接切换到手机的移动数据网络faq.whatsapp.com。在中国,由于本地宽带网络对WhatsApp的封锁,蜂窝数据反而成为相对可靠的通道——尤其在搭配VPN时,可以避开本地ISP的审查策略,实现与WhatsApp服务器的通信sohu.com。
国际短信的运营商限制: 使用移动数据还有助于解决短信验证码接收难题。中国的手机运营商出于防垃圾短信和安全考虑,默认对国际短信和境外来电进行一定限制。许多中国用户发现,注册WhatsApp时迟迟收不到验证码短信,原因可能在于运营商将来自国外服务号码的短信拦截或过滤sohu.com。例如,中国移动默认关闭国际短信接收,需要用户主动发送短信指令申请开通sohu.com。具体而言,中国移动用户需发送文本“11111”到10086(或10085)来开通国际短信收发权限;中国联通和电信用户也被建议联系运营商确认未屏蔽国际短信sohu.com。若未进行这些设置,WhatsApp发送的验证码短信可能根本无法抵达用户手机。在这种情况下,WhatsApp提供的备用方案是语音电话验证,即通过国际电话拨打用户号码并播报验证码。然而境外来电在中国也可能遭到运营商的安全拦截,特别是当号码被认为可疑时zhuanlan.zhihu.com。因此,中国用户经常被建议开启手机的蜂窝数据和漫游功能,以提高验证码接收的成功率sohu.com。一方面,开启数据漫游意味着用户准备接受来自境外的通信(通常也包含短信/电话);另一方面,在数据联网的状态下,WhatsApp可以尝试通过网络直接完成验证通信,从而减少对SMS的依赖。
移动数据的网络路径优势: 在实际案例中,一些中国WhatsApp用户报告仅在开启蜂窝数据的情况下才能完成验证。这可能归因于蜂窝网络和宽带网络在国际出口上的差异。中国移动、联通等运营商的移动数据可能走与宽带不同的网关路由,有时对跨境小流量的拦截相对宽松。此外,WhatsApp在移动数据环境中可以利用一些底层网络特性。例如,WhatsApp可能通过移动网络发起某些专用请求或利用运营商提供的号码归属地信息进行辅助验证(虽然具体实现未公开,但这是业界讨论的可能性)。总之,在中国特殊的网络环境下,开启蜂窝数据是确保WhatsApp验证流程顺利的重要一步。这一步不仅是为了基本的互联网连接,也是为了绕开种种对国际短信和应用数据的拦截限制,从而与WhatsApp的全球基础设施建立必要的通讯。
PDP Context与IMSI:移动网络验证的技术细节
要理解为什么移动数据对WhatsApp验证如此关键,有必要了解移动通信网络中的一些技术细节,包括PDP Context和IMSI的概念。
PDP Context(分组数据协议上下文): 当手机通过蜂窝网络使用数据(如4G/5G上网)时,必须先在运营商核心网中建立一个PDP上下文。这实际上就是申请开启一个数据会话,运营商将为设备分配一个IP地址,并允许其通过移动核心网访问互联网datascientest.com。PDP上下文包含了一系列参数(例如APN接入点名称、QoS等级等),描述该数据会话的属性datascientest.comdatascientest.com。简单来说,激活蜂窝数据就意味着创建了PDP上下文,设备获得了移动网络网关分配的IP地址,可以收发数据包。对于WhatsApp验证而言,只有在建立数据连接后,手机才能直接与WhatsApp的服务器交换数据,例如提交验证码、完成加密密钥协商等。如果仅有Wi-Fi而蜂窝数据关闭,且Wi-Fi环境无法连通WhatsApp服务器,那么验证过程将陷入停滞。因此,在中国场景下,开启蜂窝数据(即建立PDP数据通路)是WhatsApp客户端尝试绕过Wi-Fi限制、直接通过移动网络进行验证通信的前提faq.whatsapp.comsohu.com。值得一提的是,PDP Context的建立也表明手机在运营商网络上处于活跃状态,这对于某些验证机制(比如后述的闪信/闪呼)来说至关重要。
IMSI与MSISDN: IMSI(国际移动用户标识)和MSISDN(移动用户号码,即手机号码)是运营商网络中两个密切相关但不同的标识。IMSI是存储在SIM卡上的一串唯一数字,用于在移动网络中标识用户身份netmanias.com。当手机接入网络时,它向运营商提供IMSI以进行鉴权,运营商据此知道“是哪张SIM”的请求netmanias.com。而MSISDN则是我们平常说的手机号,用于在语音通话和短信路由中定位用户,也存储在运营商的HLR/HSS数据库中netmanias.com。运营商通过IMSI<->MSISDN的对应关系,将来自全球的短信/电话正确路由到用户手机上。WhatsApp的验证短信或电话本质上就是通过目标号码(MSISDN)寻找所属运营商网络,由该网络根据IMSI定位用户终端。一般情况下,WhatsApp应用并不直接接触IMSI这种信息,因为IMSI属于运营商网络的内部标识。然而,IMSI的存在仍然对安全产生影响。例如,**SIM卡交换(SIM Swap)**欺诈发生时,攻击者获得了受害者号码的新SIM卡,新SIM卡会有不同的IMSI,但MSISDN保持原号码不变。运营商会将原号码映射到新的IMSI,这样验证码短信就发送到了攻击者手中的SIM上。对WhatsApp而言,除非有机制检测IMSI变动,否则无法察觉用户号码背后的SIM已被盗换。部分应用在检测到SIM变化时会提示用户重新验证,这需要读取设备的IMSI信息进行比对。然而,在现代智能手机中,获取IMSI通常需要特殊权限,WhatsApp并未明确说明它有此类检测。因此,从WhatsApp角度,IMSI更多是网络侧的概念,但它提醒我们:电信级身份验证依赖于SIM的有效性。只有当正确的IMSI在网络注册、并建立了PDP数据上下文时,WhatsApp的后台服务才能确认该SIM对应的号码目前“在线”,进而可靠地发送验证信号(短信或电话)到该设备。
移动网络的信号辅助验证: 有观点认为,一些OTT应用可能利用移动网络提供的附加服务来辅助号码验证。例如,某些运营商提供号码快速验证API,当应用检测到设备在移动数据网络中时,可以向特定地址发起请求,由运营商返回当前设备的号码信息(通常通过已经建立的PDP通道)。Google等公司在部分国家与运营商合作过类似服务,实现用户免输入验证码自动完成验证。但就WhatsApp而言,没有公开证据表明其使用了运营商提供的自动号码识别API。即便如此,WhatsApp鼓励用户保持移动网络在线的做法,隐含的意义之一可能是:当手机处于蜂窝网络且数据畅通时,验证码通过率和验证成功率都会显著提升。这既包括了物理层面短信、电话能否送达,也涵盖了数据层面应用和服务器能否互通。
Flash Call机制:WhatsApp验证的新方案
针对传统SMS验证码容易被拦截、延迟以及用户体验不佳的问题,WhatsApp近年来引入了一种Flash Call(闪呼)验证机制fossbytes.com。所谓闪呼,即应用在用户验证阶段向用户的手机号发起一个非常短暂的来电:用户无需真正接听,WhatsApp会自动结束这通电话,并根据通话记录来确认是否拨通fossbytes.com。
原理与流程: 当用户选择使用闪呼验证(目前主要在Android设备上可用),WhatsApp会请求权限访问用户的通话记录fossbytes.com。随后应用拨打用户的号码,一般是一个预先设定的特定号码或号码段。由于WhatsApp后台知道它拨出的号码及通话ID,只要该未接来电出现在用户手机的通话日志中,应用即可读取并匹配最后一通来电的号码是否符合验证要求,从而确认用户持有这个号码fossbytes.com。整个过程用户无需手动输入验证码,验证通话在数秒内完成。相比6位数字短信验证码需要用户在短信和应用间切换输入,闪呼方式更加快捷无缝fossbytes.com。
优缺点分析: 闪呼验证的优势在于速度快且避免了SMS可能的延迟或拦截。一些分析指出闪呼将成为取代SMS OTP(一次性密码)的新趋势,Juniper Research预测2022年用于验证的闪呼次数将从2021年的六千万猛增到五十亿次subex.comglobaltelcoconsult.com。对于WhatsApp这样全球用户庞大的应用,闪呼可以节约大量SMS网关费用,并绕开部分运营商对国际SMS的限制。然而,闪呼也有局限:fossbytes.com首先,iOS设备由于系统安全限制,应用无法访问通话记录,因此iPhone上无法使用闪呼验证fossbytes.com。这意味着苹果用户仍需使用传统短信验证码。其次,为实现自动匹配来电号码,用户必须授予读取通话记录的权限,这在隐私上引发一些担忧fossbytes.comfossbytes.com。WhatsApp声称不会将通话记录用于验证以外的用途,号码匹配也在本地完成fossbytes.com,但考虑到母公司Meta的隐私争议,部分用户依然顾虑。第三,闪呼验证依赖语音通话路线,同样受制于电信网络质量。如果用户所处网络无法接通国际来电(比如被运营商拦截境外短振铃电话),闪呼也无法成功。此外,从运营商角度看,闪呼绕过了A2P短信计费,可能侵蚀短信营收,一些运营商开始研究识别闪呼流量的策略wholesale.orange.com。总体而言,闪呼机制体现了WhatsApp希望减轻对短信依赖的努力,它在许多国家提升了验证体验,但在中国等特殊环境,其效果仍取决于本地语音网络的开放程度。值得注意的是,中国运营商对于境外电话,尤其是这种**“零响铃”未接来电**也有防范措施,中国电信和联通用户就被建议如需接收海外来电验证,应联系客服确保未拦截海外来电hqsmartcloud.com。因此,即便WhatsApp支持闪呼,中国用户若未开启移动语音漫游或运营商许可,仍然难以通过此途径完成验证。
与SIM Swap安全性的关系: 从安全角度看,闪呼并未实质提升抵御SIM交换攻击的能力。如果攻击者成功将受害者的号码转移至自己的SIM卡上(获取新IMSI),那么无论验证码以短信还是闪呼方式发送,都会到达攻击者设备。闪呼机制能防御的是部分恶意拦截短信的行为(如恶意网关或木马读取短信),但对社工换卡没有太大帮助。WhatsApp早已提供两步验证(即设置6位PIN码)供用户自行启用,以防号码被他人重新注册时需要额外密码。然而大量用户未开启该功能。因此,闪呼更多是从用户体验和成本出发的改良,而非针对高级别攻击的防护机制。正如前文所述,真正要防御SIM Swap和SS7漏洞等系统性风险,依赖运营商的号码验证本身就是薄弱环节,需要引入更高级的身份认证手段。
SIM卡交换攻击的风险与运营商信任问题
WhatsApp和Telegram一类基于手机号认证的应用普遍面临一个安全挑战:手机号码本身并非绝对安全的身份凭证。攻击者可以通过一系列手段取得用户的号码控制权,其中SIM交换(SIM Swap)是近年高发的欺诈手法。SIM Swap通常由不法分子冒充用户,诱骗或贿赂运营商客服将目标号码的服务转移到攻击者的新SIM卡上keepnetlabs.com。一旦成功,所有发往该号码的短信和电话都转由攻击者接收,原机主的SIM卡失效。对于依赖短信/电话验证的应用来说,这意味着攻击者可以轻易获取验证码,从而重置账户并登录。近年来全球SIM Swap案件呈上升趋势,许多在线服务的账号被此攻破rte.ie。
WhatsApp并非未知晓此风险。事实上,WhatsApp在其帮助中心和安全博客中多次提醒用户开启两步验证PIN,并强调绝不向他人透露短信验证码。然而,从系统设计上讲,WhatsApp仍将信任根基放在运营商发送到用户手机的那串数字验证码上。一旦运营商端的安全被绕过(无论是内部员工作恶、社工欺诈,还是SS7网络被黑客利用securityaffairs.com),WhatsApp本身无法辨别验证码接收者是否是真正的用户。正如安全研究所Positive Technologies指出的那样,目前主要的即时通讯服务(包括WhatsApp和Telegram)依赖SMS作为主要验证机制,这使得黑客能够通过攻击电信信令网络来接管用户账户securityaffairs.com。换言之,WhatsApp被迫信任每一个参与短信/电话路由的运营商,但这个信任链条上任何薄弱环节都可能遭到利用securityaffairs.com。例如,在SIM Swap攻击中,运营商本身成为被欺骗的对象;而在SS7定位拦截攻击中,全球互联的电信网成为攻击面。在中国的场景下,虽然主要威胁来自审查而非黑客,但本质上仍是WhatsApp无法完全掌控电信网络这一事实所导致的问题。
应对这些风险,WhatsApp和Telegram等采用了一些弥补措施。除了提供用户自行设定的二次密码,两者也开始探索设备多因子的概念(如后文Telegram部分所述,利用已有登录设备确认新登录)。然而,对绝大多数首次注册或更换设备的用户来说,传统的短信/电话验证仍是唯一途径。这就是为什么在高安全需求的行业中,SMS OTP正逐渐被视为不充分securityaffairs.com。监管机构和安全专家建议对涉敏感操作采用更强验证,如专用身份应用、硬件令牌或生物识别等。WhatsApp作为大众通信工具,目前平衡了易用性与安全性,但其依赖电信运营商的验证模式在像中国这样特殊的环境下,既遇到政策阻碍,也隐藏安全短板。这一点对于决策制定者评估国外通信应用在华风险时,是一个重要考量:任何全球运营商合作机制,在中国境内都可能因为**“最后一公里”由中国运营商执行**而受到影响。无论是被拦截信息还是可能的监控窃听,这些风险都源自于底层通信网的控制权不在应用服务商手中。
Telegram登录机制的比较
作为对比,Telegram的账号登录机制与WhatsApp类似,也以手机号码为主要身份标识,但在具体实现上有一些不同之处。
多设备登录与云端代码: Telegram从设计上支持多设备同时在线(手机、平板、PC等),并将聊天内容储存在云端。这带来的一个直接好处是:当用户在新设备上登录时,Telegram会优先通过已登录的其他设备发送登录验证码。例如,用户尝试在电脑上登录Telegram,Telegram会在用户手机上的Telegram应用里推送一条消息包含登录码,而不是立即发短信accountboy.comaccountboy.com。用户只需在新设备输入从老设备上收到的代码即可完成登录。这种机制确保了只要用户至少有一个设备在线,就几乎不需要依赖运营商短信。当然,如果用户当前只有一部新设备(例如换了手机且旧设备不上线),Telegram才会退而求其次,通过SMS发送验证码到手机号。同时,Telegram也允许用户选择语音电话获取验证码,类似于WhatsApp的语音验证。当用户完全无法收到SMS时(比如在中国这种场景),语音呼叫常常比短信更可靠seatuo.com。
两步验证密码: 与WhatsApp一样,Telegram提供可选的两步验证密码。当启用此功能后,即使拿到短信验证码,仍需输入用户设置的密码才能登录账户quora.com。这对抗SIM Swap等攻击提供了另一层防线。不过需要指出,如果用户忘记了设置的Telegram密码且没有设置信任邮箱,可能会永久失去账号访问,因此开启该功能在中国用户中接受度一般。
登录体验与安全性的取舍: Telegram的登录流程在用户体验上更加灵活。多设备下无需每次都收验证码,提高了便利性。但从安全角度看,这种“信任已有设备”的做法也有隐患:如果用户的某个设备落入他人之手并未及时登出,那么该人有可能利用该设备获取新的登录验证码。因此Telegram会在应用中提供管理活动会话的功能,用户可随时查看和撤销其它设备的登录状态telegram.org。总体而言,Telegram和WhatsApp在初始注册环节同样依赖短信/电话,在这一点上,中国的网络环境对两者影响相似:Telegram在中国同样被全面封锁,需要VPN才能使用,其短信验证码发送也会受到运营商限制。另外,Telegram曾在2015年因恐怖分子利用该平台传递信息而被中国当局重点关注并屏蔽,因此其国内可达性甚至比WhatsApp更低。许多中国用户实际使用Telegram时,通常绑定国外号码或通过海外SIM卡来收取验证码,以绕开国内运营商的限制。
差异总结: 简而言之,Telegram在登录验证机制上的主要优势在于已有会话协助和云端同步。这使得老用户换设备时不依赖国内短信通道即可登录(前提是原设备已登录并可访问)。WhatsApp直到最近才推出多设备功能,但其多设备模式采用的是端到端加密设备链路,需要主手机扫码授权,而非像Telegram那样用账号密码登录其它设备。因此WhatsApp仍然强绑定SIM卡设备,首次注册和更换手机号时逃不开运营商环节。安全方面,两者的SMS验证所面临的系统性风险(如SS7攻击、SIM Swap)并无本质区别,都必须仰仗运营商加强对核心网络的保护,以及用户自身启用附加验证措施securityaffairs.comkeepnetlabs.com。
结论
对于希望在中国使用WhatsApp的用户来说,“开启蜂窝数据”这一要求背后体现的是技术与政策交织的复杂现实。一方面,蜂窝数据承载着WhatsApp与其全球服务器通信的关键信道,在中国的受限网络中提供了相对可靠的出路faq.whatsapp.comsohu.com。另一方面,WhatsApp的号码验证机制深深植根于传统电信体系,必须经由全球运营商的“协作”才能完成用户身份确认securityaffairs.com。而在中国,这种协作受到防火长城和运营商政策的双重阻碍:国际短信被拦截、国际数据被阻断。为克服这些障碍,WhatsApp既采取了工程上的应对(如检测强制Wi-Fi并提示使用移动网络faq.whatsapp.com),也引入了诸如闪呼验证等新方案以减少对短信的依赖fossbytes.com。但从根本上说,只要注册流程离不开手机号码,这种与电信运营商的捆绑关系就无法割舍。由此带来的安全问题(如SIM Swap和信令网络漏洞)在全球范围内敲响警钟securityaffairs.comkeepnetlabs.com。
对于从事安全研究和政策评估的人士,这篇分析揭示了WhatsApp在中国遇到的典型困境:技术系统的全球化与监管环境的本地化冲突。WhatsApp全球统一的验证框架在中国水土不服,不得不通过额外的设置和手段来“曲线救国”。这既包括让用户切换网络、配置VPN等绕过审查,也包括思考未来是否有必要采用更安全独立的验证方式。相比之下,Telegram的机制给出了一种启示:灵活运用多设备和云服务,至少在一定程度上降低对单一短信渠道的依赖。然而,Telegram自身在中国的处境表明,再优雅的技术方案也难以直接对抗高强度的网络封锁。最终,无论是WhatsApp还是Telegram,要想在受限环境下可靠运作,都需要技术与政策的双管齐下:一方面提高验证与登录的安全性和多样性,另一方面寻求运营商和监管层面的理解与配合。
综上所述,WhatsApp要求中国用户开启蜂窝数据并非偶然的臆想,而是其全球运营商合作验证机制在中国受阻后的务实选择。这一要求折射出移动通信应用在跨境运营中面临的挑战,也提醒我们在设计安全策略时必须考虑底层依赖的信任假设。对于个人用户,最实际的建议是在使用此类应用时提前了解并遵循这些特殊设置(如开通国际短信、启用数据漫游),并善用应用自身的安全功能(如两步验证)来保护账户免遭社工和网络攻击keepnetlabs.com。对于监管和运营商,则有必要权衡安全审查与用户便利之间的平衡,在可控范围内为可信的全球服务留出技术通道。在全球通信愈加融合的时代,WhatsApp的中国验证问题或许只是一个缩影,背后涉及的既有网络安全考量,也有数字主权与国际合作的议题,值得持续深入研究和关注。
faq.whatsapp.comfossbytes.comtheguardian.comsecurityaffairs.comsecurityaffairs.comkeepnetlabs.comdatascientest.comnetmanias.comsohu.comsohu.com
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 866e0139:6a9334e5
2025-05-17 08:24:02
@ 866e0139:6a9334e5
2025-05-17 08:24:02Autor: Lilly Gebert. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Teil 1 des Artikels lesen Sie hier.
Wo Begehren herrscht, bleibt wahre Begegnung aus. Entsteht Frieden in der Sexualität doch immer erst dort, wo das Wollen endet und reines Sein beginnt. Hier wird die Vereinigung nicht länger als Erfüllung eines Mangels erfahren, sondern als Ausdruck innerer Fülle. In diesem Wandel offenbart sich die Liebe als ein Weg zur Wahrheit und damit als Anleitung zum Frieden.
Der Ursprung der Trennung als Anfang vom Krieg
In dem Sinne, wie der erste Teil dieses Texts mit dem Ausblick auf die Fähigkeit des Einzelnen endete, Angst und Abwehr abzubauen, sich selbst zu spüren – und andere nicht als Bedrohung, sondern als lebendige Gegenüber wahrzunehmen, beginnt dieser Text mit der Frage, warum wir dazu nicht mehr in der Lage zu sein scheinen? Wo ist die Lebendigkeit? Warum können wir sie weder in uns, noch in anderen annehmen?
Folgen wir dem australischen Autor Barry Long, so finden sexuelle Frustration wie Krieg ihrer beiden Ursprung darin, dass der Mann seine göttliche Stellung gegenüber der Frau eingebüßt hat und sie aufgrund dessen körperlich nicht mehr erreichen kann. Er sei es, der vergessen hat, wie man liebt und dadurch seine ursprüngliche, göttliche Autorität aufgegeben und die sexuelle Kontrolle über sich verloren hat. Was daraus entstanden sei, sei die beständige Unzufriedenheit in der Frau und eine ständige Ruhelosigkeit im Mann, derer beider eigentliches Leiden keiner von beiden mehr zuordnen kann. Zu abgeschnitten und korrumpiert sei derweilen die Vorstellung der Frau, ein Liebesakt könne ihre feinsten und tiefsten Energien sammeln und freisetzen.
Was beide stattdessen täten, sei diese Energien zu verdrehen und sie stattdessen in Sexbesessenheit, in zwanghaftem sexuellen Fantasieren sowie chronischem Onanieren «auszuleben», oder gleich ganz zu unterdrücken, was zweifelsohne zu Wut und Gewalt führe, wie auch universelle Symptome wie Arbeitswut oder die Gier nach Geld mit sich zöge. Womit wir, nebenbei bemerkt, auch wieder bei Fromm sind, für den unsere Konsumgesellschaft ebenfalls nur ein Deckmantel für unsere Unfähigkeit zu lieben oder gar unsere Furcht vor der Liebe war. Was diese Vernachlässigung der Liebe als Vernachlässigung der Frau wiederum laut Long beim Mann auslöse, sei jene Spirale aus vorzeitiger Ejakulation, Schuldgefühlen, Ängstlichkeit, Selbstzweifeln, Impotenz, sexueller Verkümmerung, die sich als sexuelles Desinteresse maskiert, sexuelle Abstinenz aufgrund von unterdrückter Versagensangst, sexueller Angeberei und Mangel an wahrem Wissen. All dies, schreibt Long, mute «er der Frau zu und verschlimmert damit ihre grundlegende Unzufriedenheit und seine eigene Unruhe». Für den Mann sei dies, als würde er sein inneres Leiden zum Leben erwecken: Für ihn sei «die weibliche Furie der Emotion die Hölle auf Erden. Dies ist der Teil in ihr, mit dem er nicht umgehen und den er nicht verstehen kann. Der Dämon seines eigenen Versagens in der Liebe wird lebendig, um ihn zu verschmähen, herunterzumachen und zu quälen.»
Wiederum nicht selten jedoch gäbe der Mann, des lieben Friedens willen, auf – und damit die letzten Überreste seiner Männlichkeit und Autorität. Dann, so Long «werden beide gemeinsam alt und fühlen sich sicher, aber halb tot, indem sie sich in der schrecklichen Welt des Kompromisses aufeinander stützen». Dabei wird «die Furie den Mann nie sein Versagen, die Frau richtig zu lieben, vergessen lassen». Die Frau, so stellt Long hervor, «muss geliebt werden». Die Zukunft der Menschheit hänge davon ab, «dass die Frau geliebt wird. Denn nur wenn die Frau wirklich geliebt wird, kann der Mann wirklich er selbst sein und seine verlorene Autorität zurückgewinnen. Nur dann kann auf Erden wieder Frieden einkehren. Doch die Frau, wie sie jetzt ist, kann nicht lange oder für immer – von dem Mann, wie er jetzt ist, geliebt werden. Zusammen sind sie in einem Teufelskreis gefangen. Und wenn sie ihren eigenen Vorstellungen von der Liebe überlassen werden, gibt es keinen Ausweg.»
Was einst Liebe war
Ursprünglich, so Long, verkörperten Mann und Frau zwei Pole reiner spiritueller Liebe: Die Frau war der heitere, empfangende Ausdruck reiner Liebe, der Mann der aktive, schützende Pol, dessen Autorität der Bewahrung dieser göttlichen Qualität diente. Ihre Kommunikation geschah durch ein goldenes Energiefeld – die Glorie –, das sie in stiller, unmittelbarer Verbindung hielt, unabhängig von Raum und Zeit. Wenn ihre Energien Erneuerung brauchten, vereinten sie sich körperlich in heiliger Liebe, die sie nicht nur regenerierte, sondern zudem mit Gott verband. Doch mit dem wachsenden Fokus auf den äußeren Aufbau der Welt begannen sie, das unmittelbare Lieben zu vergessen; die Glorie verlor ihre Strahlkraft, Sprache trat an die Stelle wortloser Verständigung, und aus Worten wuchsen Missverständnisse und Entfremdung. Die Frau wurde unzufrieden und verwirrt, der Mann seiner wahren Autorität beraubt, suchte Ersatz durch Macht und zwang die Frau in soziale Unterordnung, was in ihr Zorn und Unversöhnlichkeit entfachte. Damit begann der Wettlauf der Menschheit – ein Weg in die Zeit und fort von der ursprünglichen Einheit.
Dieser Wettlauf um Macht, Zorn und Unterdrückung ist zugleich die Geschichte, wie der Mensch sich selbst zum Wolf wurde und den Krieg gegen sich selbst begann. Um nicht länger an den Verlust seiner einstigen Einheit erinnert zu werden, hat er sich eine Welt geschaffen, die auf der Verwechslung von Liebe mit Manipulation, auf Reiz und Täuschung, wie auch auf der Reduktion von Sexualität auf bloße Befriedigung beruht. Schon fernab jeder Wirklichkeit, flieht er in lieblose Fantasien, Sexträume oder in deren Ausleben durch flüchtige Flirts und wechselnde Partner. Er flieht immer weiter – nur um sich immer weniger eingestehen zu müssen, dass in seinem Leben keine Liebe herrscht. Er tut alles, um der Konfrontation auszuweichen, dass nicht die anderen es sind, sondern er selbst, der keine Verantwortung für die Liebe in seinem Leben übernimmt. Nicht die Welt verweigert ihm die Liebe – er selbst ist es, der noch nicht dafür bereit ist, sich der Wahrheit zu stellen, dass die Liebe im Hier und Jetzt vollzogen werden will und nicht in einer imaginären Zukunft oder einem vulgären Traum.
Wie Liebe entsteht
Das wahre Leben findet in deinem Körper, in deinen Gefühlen und Empfindungen statt – nicht in deinem Kopf. In deinem Kopf kannst Du dir noch so oft und viel einreden, dass Du emanzipiert bist; dass Du auch ohne Partner in deinem Leben auskommst; dass Du emotional-physisch nicht abhängig bist; dass die Partnerschaft, in der Du dich befindest, frei ist; dass das, was Du und dein Partner da miteinander habt, Liebe sei; und dass Du glücklich bist mit dem, was Du für Liebe hältst. Dein Kopf kann das alles. Den leisen Schmerz, die Sehnsucht, dass dir trotz allem etwas fehlt, was kein Gelübte und keine Gelüste werden stillen können – den kannst Du nur fühlen.
Das Wissen um den Ursprung, von dem Du einst getrennt wurdest, ist kein Wissen, das deinem Verstand entspringt. Deshalb kommt für jeden die Zeit – und sie kommt immer schneller –, in der sein Selbst sterben muss, wie alles, was dem Leben unterliegt. Es ist die Zeit, in der Du erkennst, dass dein Verstand keine Brücken baut, sondern Mauern – und dass diese Mauern dich dem Leben nicht näherbringen, sondern es aussperren. Der Moment jedoch, indem Du beginnst, diese Mauern niederzureißen, ist zugleich der Moment, in dem die Liebe tiefer in deinen Körper dringt und dort dein Selbst sich auflöst. In dem nun auch du jemanden in dein Leben lassen kannst, dessen Blicke dich nicht nur anschauen, sondern so sehen, wie auch du ihn siehst, und dessen Berührungen mehr als nur deinen Körper streicheln.
Dieser Prozess ist schmerzhaft und traumatisch; und in einer verwirrten, unwissenden Zeit wie der unseren ist es alles andere als leicht, zum goldenen Zustand der Liebe zurückzukehren. Diesen Weg zu gehen, heißt, verletzlich zu werden: dich nicht länger selbst abzuschneiden oder zu verhärten aus Angst vor alten Wunden. Sondern den Mut aufzubringen, den Weg zu dir selbst zu gehen – zunächst allein, und dann mit jemandem, dessen Liebe reicht, ihn aufrichtig mit dir zu teilen und weiterzugehen. Ohne Spielchen, ohne falsche Egos, ohne die vielen Ersatzbefriedigungen, die uns doch nur weiter von uns selbst entfernen.
Vergeude deine Zeit und Energie also nicht weiter mit jemandem, für den Du nur ein Kompromiss bist, und sei ehrlich gegenüber denjenigen, die dies für dich sind. Stumpf nicht ab an emotionaler Unschärfe oder körperlicher Oberflächlichkeit. Lass’ dir nicht einreden, Du hättest nicht mehr verdient oder könntest nicht mehr geben. Praktiziere die Liebe, die Du selber erfahren willst. Gleich wie jede Veränderung und jeder Frieden vollzieht auch sie sich nur, wenn Du sie nicht inflationär gebrauchst, sondern um ihrer selbst willen lebst. Ihren Weg zu gehen, bedeutet, Verantwortung zu übernehmen. Für die Liebe, aber auch für den Frieden in dieser Welt. Genauso wie die Liebe lässt sich dieser nämlich auch nicht in die Zukunft und ihre möglichen Szenarien verlagern. Frieden ist keine Utopie. Frieden will gelebt werden. Hier, Jetzt und Heute. Und auch nicht von irgendwem anders, sondern von Dir.
Kinder wissen das. Finden sie auch keine Ausreden dafür, warum Frieden jetzt noch nicht möglich sei. Sie sind Frieden. Weil sie den Krieg noch nicht in sich tragen.
Legen also auch wir die Waffen nieder – auf allen Schlachtfeldern, von denen wir als Menschheit glauben, wir müssten sie führen.
Fangen wir lieber an, Frieden mit uns selbst zu schließen.
Wer Barry Longs vollständige «Anleitung zum Sex» lesen möchte, dem empfehle ich die hier zitierte Lektüre von «Sexuelle Liebe auf göttliche Weise».
Lilly Gebert betreibt den Substack-Blog "Treffpunkt im Unendlichen" und schreibt regelmäßig für "die Freien" und Manova. Zuletzt erschien von ihr "Das Gewicht der Welt". Im Herbst erscheint "Sein statt Haben. Enzyklopädie für eine neue Zeit." (vorbestellbar).
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 662f9bff:8960f6b2
2025-05-16 19:57:46
@ 662f9bff:8960f6b2
2025-05-16 19:57:46Let's start with some important foundational thinking - based on natural law. Money should be separate from the State - if not history shows that governments and human greed will always take over and manipulate the system in their favour and the expense of their populations. For extensive references, read The Sovereign Individual and The Creature from Jeckyll Island.
-
The Separation of State and Money is the most important thing you can listen to this week. Thanks to Allen Farrington - his paper is here for those who prefer to read. Wake up, folks!
-
The American Forefathers knew this when the wrote the American Constitution. Thomas Jefferson said: “If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.” Mark Moss explains it well here. Charlie Robinsons take here.
The situation in Canada exemplifies the issues
Governments have have long used "international economic sanctions" against other nations to enforce their positions. Now in Canada, and soon in your country too, they are applying such sanctions their own citizens - disconnecting them from the financial system and removing their ability to use their own life savings as they wish. Canadians spoke with their money - in one week they raised more money in support of the truckers for peaceful protest than were raised in support of all Canadian political parties in the election of last year - only to have it confiscated and blocked by those politicians.
-
CPL. Daniel Bulford (Justin Trudeau's body guard) is particularly clear and eloquent - https://www.facebook.com/watch/?v=3123688351279364
-
Nick & Greg (two Canadians in Canada) explain the situation to Peter McCormack - https://youtu.be/QBWYp-cBr4o
-
Dr Jordan Peterson and Dr Julie Ponesse (also Canadians in Canada) speak openly about what is going on https://t.co/2T7A4VEek1
-
Even Canadians living in China speak up: https://www.youtube.com/watch?v=xvDvJWdlD1E
Meanwhile in Turkey...
Joe Blogs has been giving blow by blow updates of the deteriorating sitation over the last weeks. What is happening to Turkey will come to many countries - sooner than you might imagine. Watch and learn here, here and here - more on his channel.
EU Citizens should be aware and lobby their MPs
Dropping of all C-19 restrictions is a tactic to stop people thinking about them; meanwhile the politicians are taking steps to get all of the emergency restrictions codified into normal law so that they can be deployed on you any time or all the time in future.\ Act now - or lose all freedoms - your choice - watch here or click below for the explainer.
More on war - recall our discussion last week
War steals and destroys the wealth of generations. We have been here before - remember World Wars 1 and 2...
-
Dr Mattias Desmet explains how mass formation psychosis happens and how he became aware: https://www.youtube.com/watch?v=CRo-ieBEw-8
-
Be aware of this well known and much abused psycholgical experiment - rats in a cage - explained by Dr Christ Martensen: https://www.youtube.com/watch?v=7kSBdMXQkPI
To remain silent is wrong - to deny the rights of others to discuss and challenge (and even to punish or coerce them) is a crime in support of the biger crime. Each of us has a choice - choose wisely.
Could you have known about this?
"The Matrix is a system, Neo. That system is our enemy. But when you're inside, you look around, what do you see? Businessmen, teachers, lawyers, carpenters. The very minds of the people we are trying to save. But until we do, these people are still a part of that system and that makes them our enemy. You have to understand, most of these people are not ready to be unplugged. And many of them are so inert, so hopelessly dependent on the system that they will fight to protect it."
"Unfortunately, no one can be told what the Matrix is. You have to see it for yourself."
A closing thought...
Look closely at the cover of the Economist magazine *released in December 2018 *- The World in 2019 - see how many of those things have already come true.

In case this is too difficult for you - some things to note: Four horsemen of the apacalypse, Statue of Liberty wearing a facemask, Vetruvian Man with QR code (Vaccine passport), DNA mark on his arm, wearing virtual reality glasses... The animal bottom right is a Pangolin. Scales of Justice are well tipped/skewed, facial recognition, electric cars, Putin's pipelines, China and Brexit feature highly along with the lieing media (Pinnochio) and #metoo. I smell Predictive Programming.
- More insights in the explainer here (backup copy here) - including why it is backwards...
That's it!
No one can be told what The Matrix is.**\ You have to see it for yourself.
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 961e8955:d7fa53e4
2025-05-17 07:35:51
@ 961e8955:d7fa53e4
2025-05-17 07:35:51Cryptocurrencies are digital currencies that have gained significant attention in recent times. Cryptocurrency mining, also known as mining, involves computers equipped with specialized software and hardware solving problems to validate cryptocurrency transfer transactions and, in return, being rewarded with newly generated cryptocurrency. If you have a powerful computer and an internet connection, you can easily engage in mining. Anyone interested in cryptocurrency mining needs to have computers with robust processors.
Transfers between wallets are possible, and transactions can be added to the transaction pool on numerous blockchains without the need for confirmation. Later, transactions are combined to form a block. These blocks are verified from the perspective of the systems connected to the network and, upon confirmation, are added to the blockchain.
To earn money through mining, you need to invest a significant amount of time. Earnings can vary depending on the type of mining, the value of the cryptocurrency, and the unit of measurement. Considerable budget investment is required for the system. Price increases in computer components lead to an increase in investment. However, it's possible to turn your investment into profit in a short period.
Having a high processing power can make it more challenging to cool the computers. Taking this into account, you need to adjust your budget. Additionally, an increase in the number of computers makes monitoring and maintenance more difficult. You must have sufficient knowledge about hardware. Otherwise, there is a risk of your money going to waste. As mining progresses, your investment may need to increase. In the event of malfunctions and decreased performance, replacements are necessary.
How to Earn with Bitcoin Mining? With mining, you can earn cryptocurrency without having to work too hard. Bitcoin is obtained from units called blocks. To complete a block, there is a reward of 12.5 BTC. You can calculate this based on the current value of Bitcoin.
When Bitcoin was first introduced in 2009, mining rewarded 50 BTC. We can say that this number is halved every four years. So, in 2012, it became 25 BTC, in 2015, 12.5 BTC, and as of 2020, it was 6.25 BTC.
How much profit can be made from Bitcoin mining? Earning from cryptocurrencies is not limited to cryptocurrency exchanges. As mentioned earlier, you can also earn through mining. The income and expenses of Bitcoin mining can vary depending on the type of mining performed. Therefore, individuals interested in mining need to make a good plan.
The income can vary depending on the chosen mining method and the price and unit of the cryptocurrency. Making a profit takes time. After purchasing the hardware, you need to wait for it to amortize its cost and recover the fees paid for cloud mining.
Recent price stagnation has led to a decrease in on-chain transaction activity for Bitcoin. This has negatively affected miners' earnings. According to recent data, 231,437 transactions have been processed. This is noted as the lowest number of transactions since May 24th. We can see a 40% drop from the peak of 382,408 transactions in July.
What is the Return on Ethereum Mining? Ethereum is one of the most widely mined cryptocurrencies in the cryptocurrency market. Ethereum miners can earn an average of around $1,121 per year. When you factor in expenses for electricity, other hardware, and various items, it may not be possible to make a significant profit in the first year. However, if you view this as an investment, you can expect to make substantial gains in subsequent periods.
Having powerful hardware increases earnings and enables efficient mining. Just as with all investments, the risk-reward ratio should be calculated carefully for mining
-
 @ 9c9d2765:16f8c2c2
2025-05-17 06:44:56
@ 9c9d2765:16f8c2c2
2025-05-17 06:44:56CHAPTER TWENTY ONE
“Yes, thank you,” he repeated, eyes sharp. “Because in your rejection, I found purpose. In your insults, I found strength. And now, here I stand not as a man shaped by wealth but as a man forged in fire.”
The room went silent. A solemn kind of reverence now filled the air.
“I will not seek revenge,” James continued. “That’s not the legacy I want. But I will hold people accountable. And this… is just the beginning.”
Helen trembled in her seat. Mark felt sweat roll down his back. Even Susan and Robert felt the sting of those words.
“JP Enterprises,” James said, lifting his glass in a toast, “was built on vision, perseverance, and truth. And under my leadership, it will rise higher than ever before. For those willing to build, I welcome you. For those still plotting destruction…”
He let his words hang in the air, cold and final.
“…you won’t last long.”
The crowd erupted into an ovation once again, this time standing as they clapped.
Mrs. JP hugged her son once more. Mr. JP’s proud expression never faltered.
As the celebration continued, Helen slowly rose and left the hall in silence, not from shame but from a new, burning bitterness. Mark followed shortly behind her, furious whispers passing between them.
Tracy stayed seated, her face pale, her hands unmoving. She couldn’t stop replaying James’s words in her mind.
And James? He turned to the side of the stage and saw Rita standing there, tears glistening in her eyes, pride glowing on her face. She had seen the fall. Now she was witnessing the rise.
The moment was thick with silence. All eyes in the grand ballroom turned toward the center of the unfolding drama like magnets drawn to chaos. Cameras flashed. Murmurs rippled like waves through the crowd. Mr. JP, still standing on the stage beside his wife and son, narrowed his gaze.
The young lady, her face stained with tears and regret, dropped to her knees before James, her voice shaking but loud enough for everyone to hear.
“I’m sorry!” she cried. “Please forgive me… I… I was bribed! I was paid to come here and create a scene to disgrace you, to ruin your name”
James raised a brow, his face calm as stone.
The lady’s hand trembled as she pointed directly at two guests sitting stiffly in the second row. “It was them… Mark and Helen! They paid me. They told me to pretend I was your sister… I didn’t know it would go this far. I was desperate, and they offered me money!”
Gasps exploded in the room. Faces turned to Mark and Helen like a spotlight shifting focus. The weight of public scrutiny came crashing down.
“Lies!” Helen sprang up from her seat, her voice shrill and cracking. “She’s making it up! This is ridiculous! Why would I stoop so low?”
Mark stood next to her, adjusting his blazer as sweat gathered on his brow. “We’ve never seen this woman in our lives! She’s obviously been put up to this to frame us!”
James stepped forward, every inch the man now known as the true heir of JP Enterprises. “You both seem very quick to deny,” he said coolly, his gaze fixed like iron. “Are you implying this entire company, this crowd, and my family are foolish enough to believe a random accusation without evidence?”
“I’m saying this is staged,” Helen snapped, but her voice lacked its usual bite.
Before James could speak again, his uncle Charles walked toward the stage with a tablet in hand. “That’s interesting, because we already have transactional proof of your payments to her. Digital receipts. Surveillance footage. Voice recordings.” He held the tablet high. “Would you like me to play the part where you told her to make sure she cries in front of the cameras?”
The ballroom went utterly still.
Helen took a step back, her face paling. Mark's jaw clenched. “This… this can’t be real…”
“Oh, it’s very real,” James replied, his tone low and calm. “You thought you were playing chess while I was playing checkers. But I already saw the board long before you made your first move.”
Reporters surged forward, microphones extended, camera flashes dancing like strobe lights.
“Is this true, Mr. Mark? Ms. Helen?” “Were you behind the attempted defamation?” “Do you have any statement to make regarding the scandal?”
Helen was trembling now, her poise cracking under pressure. “You set us up!” she screamed. “You and your entire perfect little company, this is all a setup!”
“You did that yourself,” James said, his voice steady. “You tried to ruin me twice. Once in silence. Once in public. But the truth always finds light.”
Mr. JP raised his hand for silence. “I want them arrested,” he said firmly, turning to the uniformed security now entering the hall. “For defamation, for conspiracy, and for fraud.”
Helen turned to Mark. “Do something!”
Mark shook his head. “We’re finished…”
As the two were taken away by security, the entire room burst into conversations. Guests who had once smiled at Helen and Mark now recoiled. Their masks were gone. The truth was unveiled.
James turned to the young lady who was still kneeling. “You may go,” he said simply. “Justice isn’t yours to carry, it belongs to the law now.”
She nodded, tears falling anew, and left without a word.
Mrs. JP walked to her son’s side, taking his hand. “You’ve done well, James. Not just as a leader but as a man.”
Mr. JP smiled too, pride replacing the sternness in his eyes. “You’ve proven to this company and to this city that truth and integrity still win.”
James gave a slow nod, then stepped to the podium as the crowd turned toward him, waiting, hoping.
“I didn’t build JP Enterprises,” he said. “My father did. And many of you helped. But I will carry it forward. And I will protect it not just from failure, but from corruption.”
The ballroom quieted as James stepped down from the podium. The echoes of the applause still lingered like the gentle aftertaste of a vintage wine. People parted as he walked no longer the man whispered about in shadows, but the man now held in reverence. His walk was steady, composed. Every step was weighted with the dignity of a man who had not only reclaimed his name but risen far above the ones who tried to bury it.
Behind him, Helen and Mark were escorted out under the bright, unforgiving lights of press cameras and the judgment of a hundred curious eyes. There were no more veils to hide behind. No more pretense. Their downfall was no longer a quiet, whispered hope it was reality.
Outside the hall, as the night air kissed the courtyard, James stood with his mother, father, and Uncle Charles. Sandra and Rita joined them, both proud, both silent for a moment until Mrs. JP broke the silence.
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ f4db5270:3c74e0d0
2025-05-16 08:13:05
@ f4db5270:3c74e0d0
2025-05-16 08:13:05Hi Art lover! 🎨🫂💜
You may not know it yet but all of the following paintings are available in #Bitcoin on my website: <https://isolabellart.carrd.co/>
For info and prices write to me in DM and we will find a good deal! 🤝
 THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
THE QUIET ROOM 50x40cm, Oil on board - Completed May 8, 2025
 OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
OLTRE LA NEBBIA 50x40cm, Oil on board - Completed April 18, 2025
 TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
TO THE LAST LIGHT 50x40cm, Oil on board - Completed April 5, 2025
 BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
BLINDING SUNSET 40x40cm, Oil on board - Completed March 18, 2025
 ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
ECHI DEL TEMPO PERDUTO 40x40cm, Oil on board - Completed March 09, 2025
 EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
EVANESCENZE 40x40cm, Oil on board - Completed February 11, 2025
 OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
OLTRE LA STACCIONATA 50x40cm, Oil on board - Completed February 8, 2025
 LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
LONELY WINDMILL 50x40cm, Oil on board - Completed January 30, 2025
 ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
ON THE ROAD AGAIN 40x50cm, Oil on canvas - Completed January 23, 2025
 SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025
SUN OF JANUARY 40x50cm, Oil on canvas - Completed January 14, 2025

THE BLUE HOUR 40x50cm, Oil on canvas - Completed December 14, 2024
 WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
WHERE WINTER WHISPERS 50x40cm, Oil on canvas - Completed November 07, 2024
 L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024
L'ATTESA DI UN MOMENTO 40x40cm, Oil on canvas - Completed October 29, 2024

LE COSE CHE PENSANO 40x50cm, Oil on paper - Completed October 05, 2024
 TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024
TWILIGHT'S RIVER 50x40cm, Oil on canvas - Completed September 17, 2024

GOLD ON THE OCEAN 40x50cm, Oil on paper - Completed September 08, 2024
 SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
SUSSURRI DI CIELO E MARE 50x40cm, Oil on paper - Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND 40x30cm, Oil on board - Completed August 12, 2024
 FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
FIAMME NEL CIELO 60x35cm, Oil on board - Completed July 28, 2024
 INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
INIZIO D'ESTATE 50x40cm, Oil on cradled wood panel Completed July 13, 2024
 OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
OMBRE DELLA SERA 50x40cm, Oil on cradled wood panel - Completed June 16, 2024
 NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
NEW ZEALAND SUNSET 80x60cm, Oil on canvas board - Completed May 28, 2024
 VENICE 50x40cm, Oil on board - Completed May 4, 2024
VENICE 50x40cm, Oil on board - Completed May 4, 2024
 CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
CORNWALL 50x40cm, Oil on board - Completed April 26, 2024
 DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
DOCKS ON SUNSET 40x19,5cm, Oil on board Completed March 14, 2024
 SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
SOLITUDE 30x30cm, Oil on cradled wood panel - Completed March 2, 2024
 LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
LULLING WAVES 40x30cm, Oil on cradled wood panel - Completed January 14, 2024
 MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
MULATTIERA IN AUTUNNO 30x30cm, Oil on cradled wood panel - Completed November 23, 2023
 TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
TRAMONTO A KOS 40x40cm, oil on board canvas - Completed November 7, 2023
 HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
HIDDEN SMILE 40x40cm, oil on board - Completed September 28, 2023
 INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
INIZIO D'AUTUNNO 40x40cm, oil on canvas - Completed September 23, 2023
 BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
BOE NEL LAGO 30x30cm, oil on canvas board - Completed August 15, 2023
 BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023
BARCHE A RIPOSO 40x40cm, oil on canvas board - Completed July 25, 2023

IL RISVEGLIO 30x40cm, oil on canvas board - Completed July 18, 2023

LA QUIETE PRIMA DELLA TEMPESTA 30x40cm, oil on canvas board - Completed March 30, 2023
 LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
LAMPIONE SUL LAGO 30x30cm, oil on canvas board - Completed March 05, 2023
 DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
DUE NELLA NEVE 60x25cm, oil on board - Completed February 4, 2023
 UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
UNA CAREZZA 30x30cm, oil on canvas board - Completed January 17, 2023
 REBEL WAVES 44x32cm, oil on canvas board
REBEL WAVES 44x32cm, oil on canvas board
 THE SCREAMING WAVE 40x30cm, oil on canvas board
THE SCREAMING WAVE 40x30cm, oil on canvas board

"LA DONZELLETTA VIEN DALLA CAMPAGNA..." 30x40cm, oil on canvas board

LIGHTHOUSE ON WHITE CLIFF 30x40cm, oil on canvas board
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ 58537364:705b4b85
2025-05-17 06:31:52
@ 58537364:705b4b85
2025-05-17 06:31:52ความสำเร็จ จำเป็นต้องมีวินัย
ความมีวินัย คือ "การทำด้วยความตั้งใจ ไม่หวั่นไหว/ไหลตามไปกับอารมณ์" ส่วน "ความไร้วินัย" มีนัยยะตรงกันข้าม กล่าวคือ
ความไร้วินัย คือ "การทำตามความหวั่นไหว/ไหลตามไปกับอารมณ์" เช่น ความง่วง หิว เบื่อ เซ็ง พอใจ ไม่พอใจ กลัว หลงไหล/ขาดสติ เป็นต้น จนเกิดข้ออ้างสารพัด เช่น * อ้างว่าเดี๋ยวก่อน เอาไว้ทีหลัง * อ้างว่าเหนื่อยหน่าย * อ้างว่าร้อนไป หนาวไป * อ้างว่ายังเช้าอยู่ * อ้างว่าสายไปแล้ว * ฯลฯ
การสร้างวินัยที่ยั่งยืน "ไม่ได้เกิดจากการฝืน แต่เกิดจากความฝัน" กฎแห่งความฝันระบุว่า เราต้องสร้างภาพสวรรค์ (เป้าหมาย) ให้ชัด จากนั้นให้ลดช่องว่างระหว่างการคิดและการกระทำให้เหลือน้อยที่สุด เพราะถ้าเราคิดมาก ส่วนใหญ่เราจะไม่ได้ทำ จิตใจเราจะอ่อนแอ ไม่เข้มแข็งมั่นคง
กฎแห่งความฝัน ควรฝันเพื่อผู้อื่น อย่าฝันเพื่อตัวเองคนเดียว เพราะขณะที่จิตมุ่งเป้าสู่ความสำเร็จนั้นมัน ถ้ามันมีมากเกินไป สติปัญญาจะอ่อนค่าลง ความรอบรู้จะน้อยลง ณ ขณะนั้นการกระทำทั้งปวงจะขาดความเห็นอกเห็นใจผู้อื่นหากทำเพื่อตัวเองฝ่ายเดียว แต่ถ้าพลังมุ่งเป้าที่ส่วนรวม ทุกการกระทำจะส่งคุณค่าเกิดเป็นความสุขความสำเร็จร่วมกัน
-เมธา หริมเทพาธิบดี
คู่มือมนุษย์
-
 @ 3b62c542:6f45deaf
2025-05-17 05:14:41
@ 3b62c542:6f45deaf
2025-05-17 05:14:41The cryptocurrency landscape, once dominated by wild price swings and volatile tokens like Bitcoin and Ethereum, is witnessing a quiet but seismic shift. Stablecoins cryptocurrencies pegged to traditional assets like the U.S. dollar are increasingly taking center stage. While not as flashy as their high-flying cousins, stablecoins are proving to be the most functional and widely adopted segment of the crypto universe. Simply put: stablecoins are eating crypto.
What are stablecoins?
Stablecoins are digital assets designed to maintain a stable value relative to a fiat currency or commodity. The most popular stablecoins, such as Tether (USDT), USD Coin (USDC), and DAI, are typically pegged 1:1 to the U.S. dollar. Their stability makes them ideal for transactions, trading, and storing value, especially in the notoriously volatile crypto markets.
There are three main types of stablecoins:
- Fiat-collateralized: Backed by reserves of fiat currencies held in bank accounts.
- Crypto-collateralized: Backed by other cryptocurrencies, usually overcollateralized to handle volatility.
- Algorithmic: Maintain their peg through supply-and-demand algorithms without actual reserves (e.g., the failed TerraUSD).
The rise in utility
What started as a tool for traders to hedge volatility has become the backbone of decentralized finance (DeFi), cross-border remittances, and even some central bank strategies. Stablecoins now play multiple roles:
- Medium of exchange: Unlike Bitcoin, which is rarely used in daily transactions due to its fluctuating price, stablecoins are ideal for payments.
- Liquidity providers: In DeFi, stablecoins serve as the base currency for lending, borrowing, and yield farming.
- Trading pairs: A large percentage of crypto trading volume is denominated in stablecoins, not in Bitcoin or fiat.
Growing market share
As of mid-2025, stablecoins represent a multi-hundred-billion-dollar market. Tether remains the largest by market cap, followed by USDC. Their total volume now rivals or in some days, exceeds that of Bitcoin and Ethereum. According to data from multiple crypto analytics platforms, stablecoins accounted for more than 70% of on-chain transaction volume in early 2025, highlighting their dominance in practical use cases.
Central banks and regulation
Stablecoins are also reshaping conversations around monetary sovereignty. Central banks are watching closely, with some developing their own Central Bank Digital Currencies (CBDCs) to compete. Meanwhile, regulators are scrambling to craft frameworks to oversee stablecoin issuers, particularly around reserve transparency and systemic risk.
The U.S. and EU are working toward legislation requiring stablecoin issuers to hold audited 1:1 reserves and submit to regular oversight, essentially treating them like narrow banks. The goal: harness the efficiency of stablecoins without compromising financial stability.
Why stablecoins are winning
- Trust and predictability: In crypto, stability is a feature, not a bug. Traders and users prefer assets they can rely on for everyday transactions.
- Interoperability: Stablecoins are blockchain-agnostic and can be used across multiple networks like Ethereum, Solana, and Polygon.
- Programmability: They bring the efficiency of smart contracts to money itself, enabling automated, low-cost transactions.
- Global access: Stablecoins offer dollar exposure to users in countries with unstable local currencies, providing financial inclusion with just a smartphone.
The ironic future
Ironically, the original vision of cryptocurrencies decentralized, uncensorable money has been somewhat sidelined by stablecoins, which often rely on centralized issuers and custodians. The dream of Bitcoin as digital cash is being fulfilled not by Bitcoin itself, but by stablecoins. That paradox lies at the heart of stablecoins’ quiet conquest.
Conclusion
Stablecoins may not grab headlines like Bitcoin bull runs or Ethereum upgrades, but their steady, practical growth is transforming crypto from a speculative playground into a functional financial ecosystem. As regulation crystallizes and usage continues to rise, stablecoins are not just part of the crypto industry they're becoming its foundation. And in doing so, they're slowly but surely eating the rest of crypto alive.
-
 @ 91bea5cd:1df4451c
2025-05-14 10:47:44
@ 91bea5cd:1df4451c
2025-05-14 10:47:44A origem do Dia das Mães
Anna Jarvis (1864-1948 Virgínia Ocidental), uma ativista americana, fundou o Dia das Mães nos Estados Unidos há mais de um século, escolhendo o segundo domingo de maio para tal celebração; mesma data que é comemorada até hoje em muitos países do mundo.
Ela nasceu durante a Guerra Civil, e viu sua mãe, Ann Reeves Jarvis, trabalhar na organização de Clubes de Trabalho Materno para cuidar de soldados de ambos os lados da guerra, a fim de diminuir as diferenças entre as mães do Norte e do Sul.
Em 1910, o Dia das Mães tornou-se feriado estadual na Virgínia Ocidental (EUA) e, em 1914, foi declarado feriado nacional pelo presidente Woodrow Wilson.
Segundo historiadores, Anna imaginava o feriado como um retorno ao lar, um dia para homenagear a sua mãe, a única mulher que dedicou sua vida à Anna. Ela escolheu o segundo domingo de maio porque seria sempre próximo de 9 de maio, o dia da morte de sua mãe, que faleceu em 1905.
E por que Anna Jarvis passou a odiar a data?
Acontece que a data começou a ter um apelo comercial, e Anna nunca quis que o dia se tornasse comercial, mas sim, só uma celebração às figuras maternas. Então ela acabou se opondo à comercialização e popularização do feriado.
Com o feriado, as indústrias floral, de cartões comemorativos e de doces começaram a ficar gananciosas para vender os seus produtos e subiram os preços nesta data, a fim de lucrarem mais.
Para Anna, "estavam comercializando o seu Dia das Mães". Para um jornal da época, ela comentou: "O que vocês farão para afugentar charlatões, bandidos, piratas, mafiosos, sequestradores e outros cupins que, com sua ganância, minam um dos movimentos e celebrações mais nobres e verdadeiros?".
Ela se irritava com qualquer organização que usasse seu dia para qualquer coisa que não fosse seu propósito original e sentimental, dizem historiadores. Em 1920, ela já incentivava as pessoas a não comprarem flores, por exemplo.
Além disso, instituições de caridade usavam o feriado para arrecadar fundos com a intenção de ajudar mães pobres; porém, como contam, elas não estavam usando o dinheiro para mães pobres, como alegavam.
Anna reivindicou os direitos autorais da frase "Segundo domingo de maio, Dia das Mães" ("Second Sunday in May, Mother's Day") e passou a vida lutando contra a comercialização da data. Um dos seus últimos atos foi ir de porta em porta na Filadélfia (EUA) pedindo assinaturas para apoiar a revogação do Dia das Mães.
Anna Jarvis nunca se casou e nem teve filhos, dedicando sua vida principalmente à causa do Dia das Mães. Ela faleceu em West Chester, na Pensilvânia (EUA), no dia 24 de novembro de 1948, aos 84 anos, devido a uma insuficiência cardíaca.
Fontes
- https://www.bbc.com/news/stories-52589173
- https://aventurasnahistoria.com.br/noticias/historia-hoje/dia-das-maes-por-que-mulher-que-criou-o-feriado-passou-odiar-data.phtml
- https://www.tempo.com/noticias/actualidade/dia-das-maes-por-que-a-mulher-que-inventou-a-data-se-arrependeu-de-te-la-criado.html
-
 @ 472f440f:5669301e
2025-05-16 00:18:45
@ 472f440f:5669301e
2025-05-16 00:18:45Marty's Bent
It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
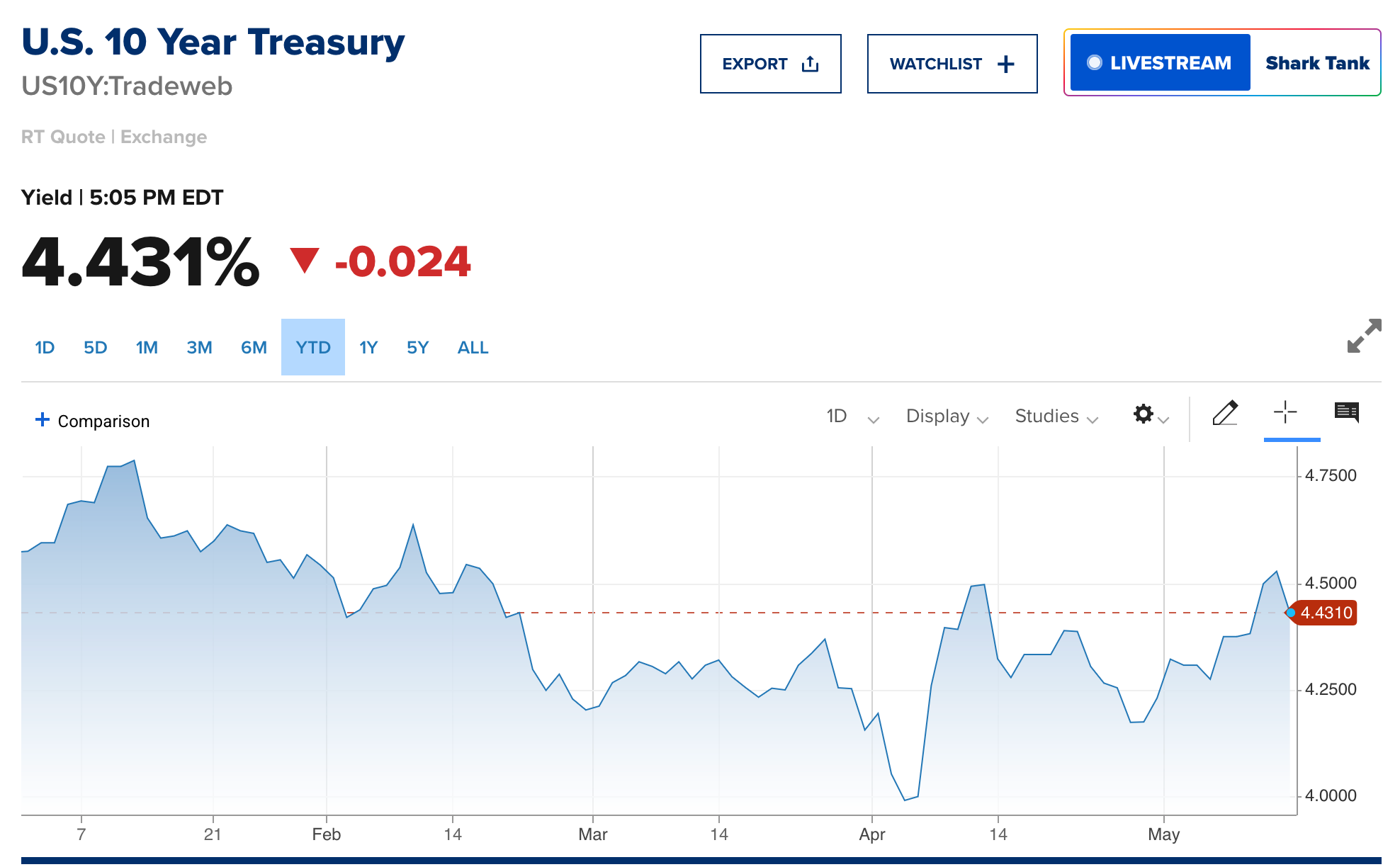
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
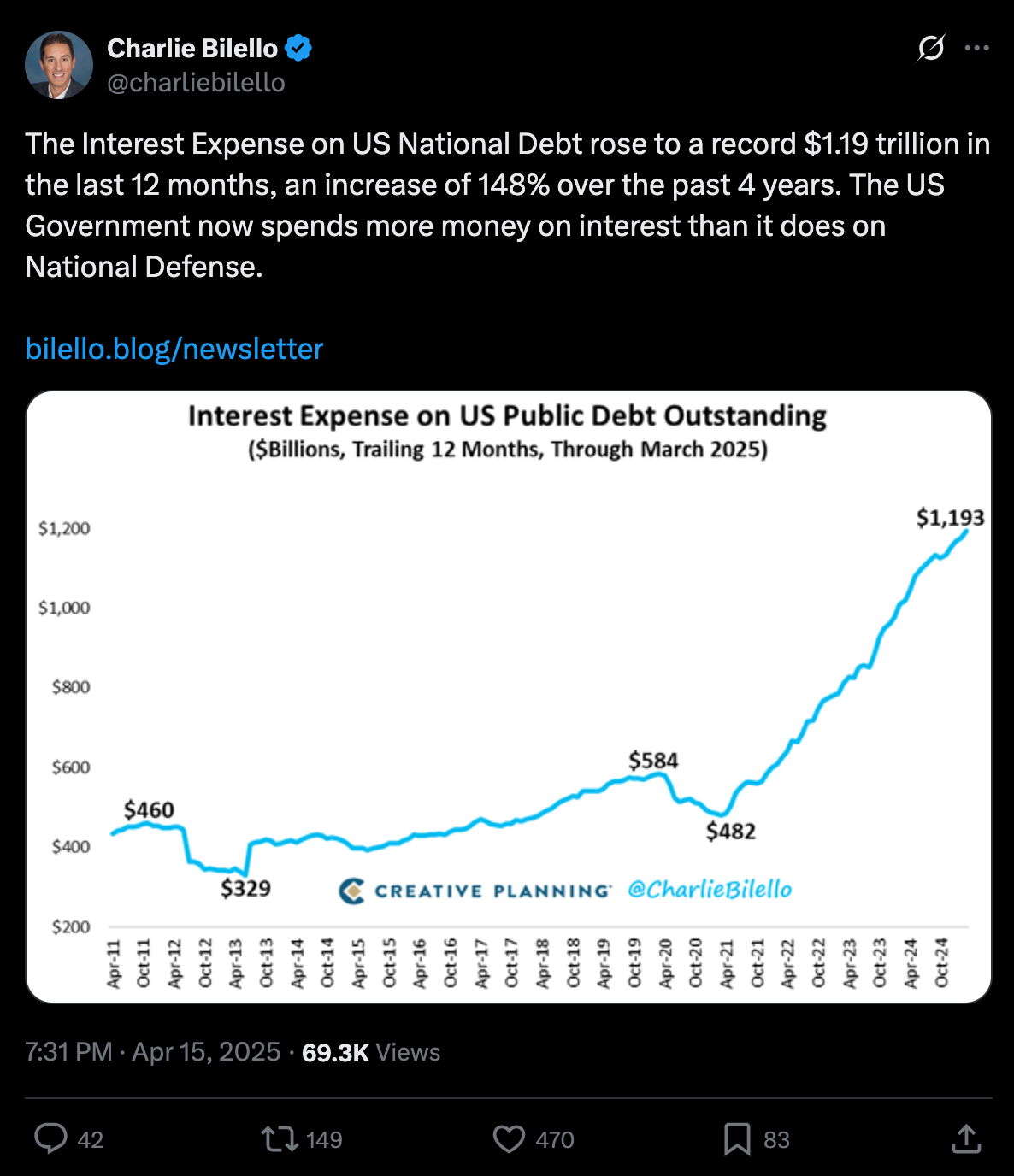
via Charlie Bilello
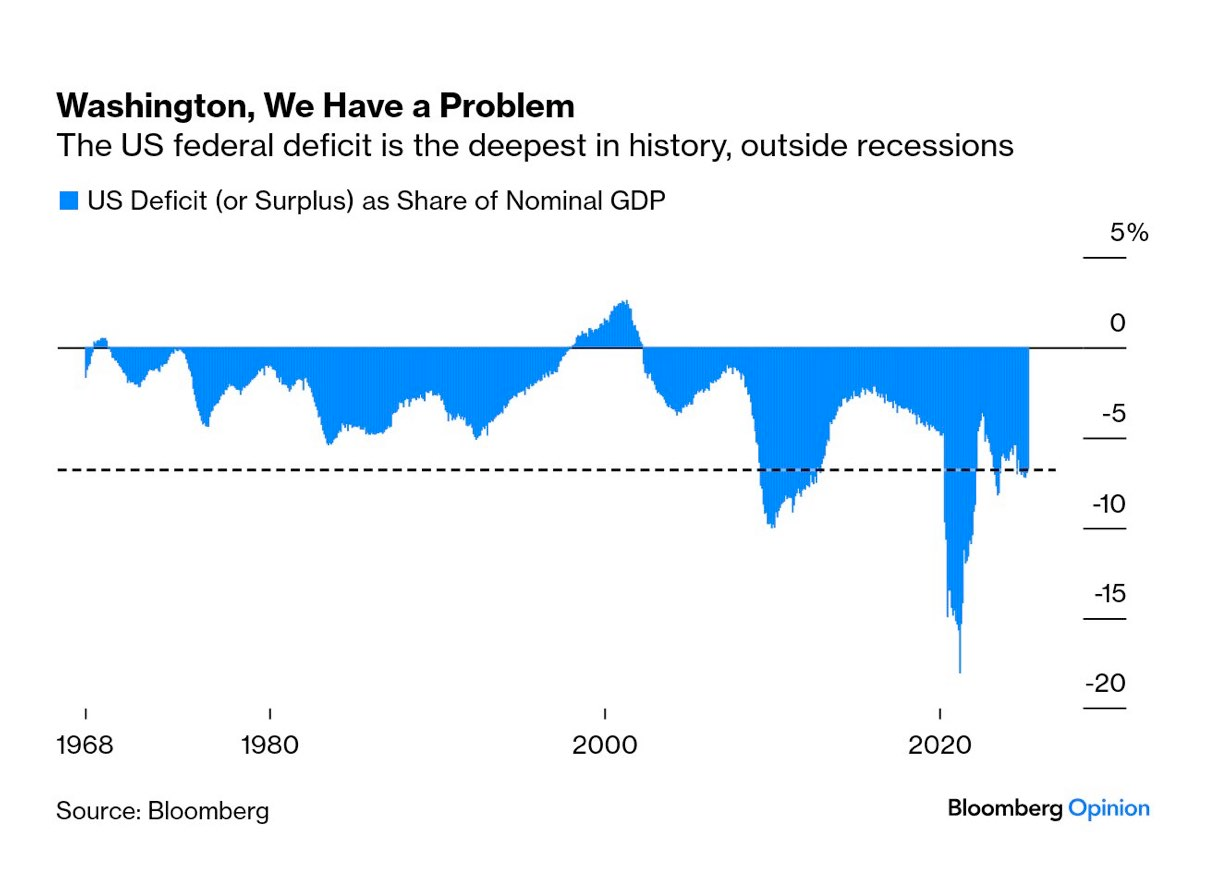
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
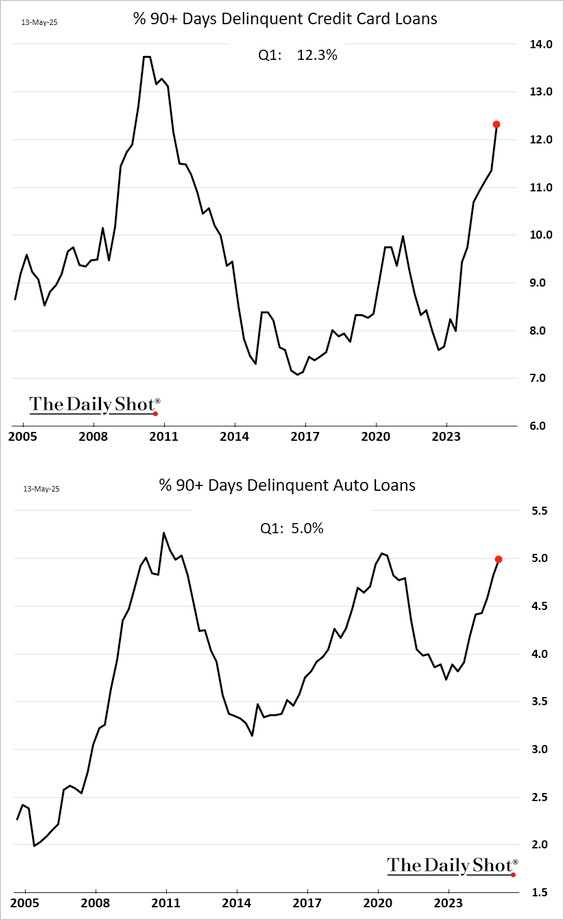
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 91bea5cd:1df4451c
2025-05-13 10:06:21
@ 91bea5cd:1df4451c
2025-05-13 10:06:21A Realidade por Trás dos Números
Padrão de Desagregação Familiar
- Países como Brasil (~55%) e Venezuela (~65%) apresentam não apenas altos índices de mães solo, mas também contextos de violência descontrolada.
- A desagregação da família nuclear tradicional não é causa única, mas é fator agravante quando associada à instabilidade cultural, abandono paterno e permissividade institucional.
- Homens ausentes e baixa exigência de responsabilidade paterna geram ciclos de pobreza, violência e ressentimento intergeracional.
Cultura da Irresponsabilidade
- Em muitos contextos, a paternidade é tratada como um ato opcional. A ausência de consequências legais, sociais e morais para o abandono paterno normaliza o ciclo de mães solteiras.
- Políticas públicas mal calibradas muitas vezes premiam o fracasso familiar com benefícios, sem exigir contrapartidas.
Inversão de Valores
- A valorização de comportamentos hedonistas, imediatistas e instáveis, promovidos culturalmente, mina qualquer tentativa de reconstrução familiar sólida.
- Em muitos casos, a maternidade é enfrentada sem planejamento ou estrutura mínima, gerando famílias instáveis e frágeis, mais propensas à violência e vulnerabilidade social.
Recomendações Realistas e Não Assistencialistas
Reforço da Responsabilidade Paterna
- Criar mecanismos legais mais rigorosos e efetivos de responsabilização civil e criminal para pais ausentes.
- Estimular socialmente o resgate do papel paterno, valorizando não apenas a presença física, mas o compromisso emocional e financeiro.
Incentivo à Formação Familiar Estável
- Reformar o currículo escolar para incluir educação sobre vínculos afetivos, responsabilidade conjugal e parentalidade realista.
- Desestimular a glamorização de estruturas familiares instáveis, combatendo a ideia de que qualquer forma familiar é igualmente funcional sob qualquer condição.
Cultura da Autossuficiência e Planejamento
- Substituir políticas puramente assistenciais por programas de incentivo ao planejamento familiar e responsabilidade pessoal, com foco na autonomia financeira e educacional antes da maternidade/paternidade.
- Campanhas públicas de conscientização sobre os impactos reais da desestrutura familiar na violência social e no desenvolvimento infantil.
O aumento da violência em países com alta proporção de mães solteiras não é uma coincidência, mas uma consequência de fatores culturais e sociais profundamente negligenciados.
Reverter esse cenário não exige mais Estado, mas sim mais responsabilidade individual, mais cobrança social e menos permissividade institucional. Qualquer solução duradoura passa por restaurar o valor da família como núcleo formador de caráter e estabilidade, não apenas como estatística para justificar políticas públicas.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ 0b118e40:4edc09cb
2025-05-15 15:40:21
@ 0b118e40:4edc09cb
2025-05-15 15:40:21My week started off with a lovely message from a friend : “I often think about you. Especially during times when it requires me to be more resilient and have faith in myself. I always carry your note in the book you gave me, “what the dog saw” And it always gives me courage and I send a little prayer your way”.
This friend of mine was dealing with the undercurrent of discrimination in my alma mater when we first met, and I helped out. It's something anybody would have done, but surprisingly, nobody else showed up. We’ve stayed in touch over the years, and my friend went on to help a lot of other people along the way.
I don’t remember what I wrote in that note. It’s something I tend to do (write notes, give books, write notes in books). But the message boomeranged back to me at a time when I needed to hold the line. To keep the faith.
Most of us don’t talk about our struggles. And sometimes the smallest act, which could just be a kind word or a reminder of the person you are, can carry farther than we imagine.
On the act of giving
There’s a book called Give and Take by Adam Grant. I picked it up hoping to learn how to take, because it’s always been easier to give and harder to accept help. But what I learned was something else entirely.
Grant studied over 30,000 people across different companies and grouped them into three types: * Givers * Matchers * Takers
Based on his studies, givers often finish last... They struggle the most. They burn out. They get overlooked. They’re too trusting.
But oddly, they also rise to the very top.
Matchers are the scorekeepers, the “I’ll help you if you help me” kind. They make up most of the population. The fascinating thing about tit-for-tat is that if someone’s kind, they reciprocate. But if someone acts like a jerk, they return the energy, and over time, it becomes a pool of spoiled milk. Matchers are a lukewarm, forgettable kind of network.
Takers are the ones chasing attention, always aligning themselves with whoever looks powerful. They tend to float toward status and soak up what they can. But they often portray themselves as kind and giving.
One example Grant shared was Enron's Kenneth Lay, who was at the center of one of the biggest corporate scandals in U.S. history. He hung around wherever he’d get seen or validated. He funded both Bush and Clinton, hedging his bets on who might win by securing proximity. Sadly, when Enron crumbled, he died of a heart attack before his prison sentencing.
Most people steer clear from takers because they are just exhausting. And takers often collapse under the weight of their own games.
But takers aren’t the lowest performers. That spot belongs to a certain kind of giver—the self-neglecting kind. The ones with no boundaries, no clarity, and no self-awareness. They give in to avoid conflict, to feel worthy, or because they don’t know how to say no. And when life breaks them, they point fingers.
Then there’s the other kind of giver. The ones who build trust and build people up without asking for a receipt.
These givers: 1. Give without expectation, from a place of purpose 2. Build and uplift others without seeking credit 3. Set boundaries and walk away when giving turns into draining
This group of givers rarely talk much about what they do for others. But when you hear about it or see it, it stays with you. It makes you want to show up a little better.
Why open source environments feels like home
The more I thought about it, the more I saw how deeply open source reflects that kind of giving that ends up right at the top.
In open source, you don’t last if it’s just about ego. You can’t fake it. There are no titles, no awards. You either show up to build and help, or you don’t.
People who give without needing to be seen are the ones the community leans on. You can tell when someone’s pretending to care. It’s in their tone, their urgency and their sense of transaction. The genuine ones don’t need to brand themselves as generous. They just are.
Open source works because giving is the default setting. The work speaks volumes and generosity compounds. The system filters for people who show up with purpose and stay consistent.
It’s also why the ones who whine, posture, or manipulate rarely last. They might call themselves givers, but they’re not fooling anyone who’s actually doing the work.
Adam Grant found that for giver cultures to thrive, takers have to be removed. They need to be pruned. Because takers poison the well. They drain givers, shift the culture from contribution to calculation, and unravel the trust that holds open systems together.
When hope boomerangs
That note is something I don’t remember writing. But it found its way back to me, and it was a good reminder to take my own advice and keep the faith.
And maybe that’s the point.
You do a small thing. And years later, it circles back when it matters most. Not because you expected it. But because you mattered.
According to Grant, givers do best when they combine generosity with grit and strategy. They create networks built on goodwill, which eventually open doors others don’t even know exist.
So if you’re wondering where I’m going with this, do something genuinely kind for someone today. Even if it’s as simple as sending a kind note. Not for you to be seen or heard. And not for you to keep scores.
But, just because.
-
 @ 6be5cc06:5259daf0
2025-05-12 14:50:36
@ 6be5cc06:5259daf0
2025-05-12 14:50:36A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ 57d1a264:69f1fee1
2025-05-14 09:48:43
@ 57d1a264:69f1fee1
2025-05-14 09:48:43Just another Ecash nutsnote design is a ew template for brrr.gandlaf.com cashu tocken printing machine and honoring Ecash ideator David Lee Chaum. Despite the turn the initial project took, we would not have Ecash today without his pioneering approach in cryptography and privacy-preserving technologies.
A simple KISS (Keep It Super Simple) Ecash nutsnote delivered as SVG, nothing fancy, designed in PenPot, an open source design tool, for slides, presentations, mockups and interactive prototypes.
Here Just another Nutsnote's current state, together with some snapshots along the process. Your feedback is more than welcome.
https://design.penpot.app/#/view?file-id=749aaa04-8836-81c6-8006-0b29916ec156&page-id=749aaa04-8836-81c6-8006-0b29916ec157§ion=interactions&index=0&share-id=addba4d5-28a4-8022-8006-2ecc4316ebb2
originally posted at https://stacker.news/items/979728
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 502ab02a:a2860397
2025-05-17 03:21:54
@ 502ab02a:a2860397
2025-05-17 03:21:54ยังมีเรื่องราวของน้ำตาล และ เซลล์ มาคุยกันต่อนะครับ เพราะยังมีคนสงสัยอยู่ว่า เอ้ย ตกลงต้องห่วงการ Spike&Staylong ของอินซุลินอยู่หรือเปล่า แล้วถ้าเราไม่ spike&staylong ก็คือกินคาร์บเบาๆตลอดวันได้เลยใช่ไหมก็มันไม่ spike&staylong แล้วนี่ โอเคครับ เรามาเปิดผับกันอีกครั้ง
คราวก่อนนั้นเราคุยกันเรื่อง ผับน้ำตาลกันไปแล้วนะครับว่า เมื่ออินซูลิน spike สูง และค้างนาน เหมือนเปิดผับแล้ววัยรุ่นแห่กันเข้ามาเที่ยว จนพีอาร์เมาจัด
เผื่อใครจำไม่ได้ ย้อนให้นิดๆครับ ว่าให้ลองนึกภาพว่าเฮียเปิดผับอยู่ดี ๆ ลูกค้าหลั่งไหลเข้ามารัว ๆ เหมือนมีโปรเบียร์ 1 แถม 10 ตอนสามทุ่ม ทุกโต๊ะสั่งข้าวเหนียวหมูปิ้งพร้อมเบียร์น้ำแข็งเต็มโต๊ะ นักเที่ยวก็ยังแห่เข้าผับแบบไม่มีพัก อินซูลินซึ่งเป็นเหมือน “พีอาร์” ที่ต้องจัดการรับแขก (หรือรับน้ำตาลเข้าสู่เซลล์) ก็เลยต้องทำงานหนักแบบ non-stop
อินซูลินเป็นฮอร์โมนสำคัญที่ช่วยเอาน้ำตาลในเลือดเข้าไปเก็บในเซลล์ ถ้า spike ทีเดียวสูงมาก เซลล์ก็รีบดูดน้ำตาลเข้าไปเต็มที่จนเกินพิกัด เหมือนผับที่แน่นจนปิดประตูไม่ลง
ถ้าเหตุการณ์แบบนี้เกิดขึ้นบ่อย ๆ ร่างกายจะเริ่มรู้สึกว่า “ทำไมอินซูลินถึงต้องออกมาบ่อยขนาดนี้วะ?” ระบบก็เริ่มปิดรับแขก เซลล์เริ่มไม่อยากตอบสนอง เพราะมันเหนื่อย มันชิน และมันก็เริ่ม “ดื้ออินซูลิน”
ผลที่ตามมาเมื่อ spike สูงและค้าง สิ่งที่ตามมา... คือความปั่นป่วนในร่างกายอย่างต่อเนื่อง น้ำตาลลอยค้างในเลือด ไปจับกับโปรตีนจนกลายเป็นเจ้า AGEs ตัวร้าย ไขมันก็ถูกสร้างมากขึ้น ล้นเข้าไปสะสมในตับ ในพุง ในซอกที่ร่างกายไม่รู้จะเก็บไว้ตรงไหนแล้ว สมองก็เบลอ ใจวูบ ง่วงงุน... เหมือนเข้าเวรประชุมยาวแบบไม่มีกาแฟ ฮอร์โมนที่เคยเป็นทีมงานสามัคคี ก็เริ่มทะเลาะกันเอง อินซูลินงอน leptin งง ghrelin งวย
แล้วถ้าเราไม่ spike แต่กินคาร์บจุ๋มจิ๋มทั้งวันล่ะ? พอรู้ว่าการเปิดผับแจกคาร์บแบบจัดหนักไม่ดี หลายคนก็ปรับกลยุทธ์ใหม่ มาแนวสายสุขุมว่า “งั้นเปิดผับแบบเนิบ ๆ ก็แล้วกัน… ไม่จัดปาร์ตี้ใหญ่ แต่มีแขกแวะเข้ามาทั้งวัน” ฟังดูดีใช่ไหม? แต่เอาเข้าจริง มันเหนื่อยไม่แพ้กันเลย
ลองนึกภาพว่าประเทศไม่มีเคอร์ฟิว เฮียเปิดผับที่มีลูกค้าเดินเข้าออกไม่หยุด ไม่ได้มากันเป็นฝูงแบบรอบโปรโมชั่น แต่มาเรื่อย ๆ แบบชั่วโมงละโต๊ะ สองโต๊ะ พีอาร์ อินซูลิน ก็เลยต้องยืนต้อนรับแขกตลอดเวลา ไม่มีเวลานั่งพัก ไม่มีช่วงเปลี่ยนกะ ไม่มีเวลาปิดไฟเก็บโต๊ะ คือทำงานต่อเนื่องยาว ๆ ตั้งแต่ 8 โมงเช้า ยัน 8 โมงเช้า สุดท้าย ผับก็เปิดไฟยันสว่าง อินซูลินก็กลายเป็นพนักงานกะดึกตลอดชีพ และเมื่อไม่มีเวลา “พักผับ” ระบบหลังบ้านก็ไม่เคยได้ฟื้นฟูเลย
ภาพรวมของการกินจุ๋มจิ๋มทั้งวันแบบนี้นั้น - เผาผลาญไขมันไม่ออกเลย เพราะอินซูลินทำหน้าที่เหมือนไฟบนเวที ถ้ายังเปิดไฟอยู่ “เครื่องดูดไขมันหลังร้าน” มันก็ไม่ทำงาน - แม่บ้านทำความสะอาดก็เข้าไม่ได้ เพราะแขกเดินเข้าเดินออกตลอด ระบบกำจัดที่ควรจะได้ล้างของเสียในเซลล์ ก็เลยโดนขัดจังหวะตลอด - พนักงานเหนื่อยสะสมจากงานไม่มีหยุด ทำให้เกิดความเครียดสะสมในร่างกาย ฮอร์โมนรวน อารมณ์ก็แปรปรวนง่ายขึ้น หิวเก่งขึ้น ทั้งที่เพิ่งกินไป
เปิดผับแบบคึกคักจัดเต็มทีเดียว แล้วปิดยาว หรือ เปิดทั้งวันแบบไม่มีช่วงปิด สุดท้ายพังทั้งคู่
ทีนี้เราน่าจะพอเห็นภาพร่างคร่าวๆ ของการบริหารการจัดการน้ำตาลในตัวเราได้แล้วนะครับ ว่าจะไดเอทไหนก็ตาม การบริหารการจัดการฮอร์โมนส์ คือสิ่งสำคัญไม่แพ้เรื่องอื่นๆ แม้จะไม่ใช่เรื่องสำคัญที่สุดในสายตาใครก็ตาม
นี่เป็นเพียงจุดเริ่มต้นการเรียนรู้เล็กๆ ซึ่งเส้นทางสายที่เรียกว่า ร่างกาย มันยังไปไกลอีกลิบลับเลยครับ ไม่ว่าจะจังหวัดคอติซอล จังหวัดพฤกษเคมี จังหวัดพลังงาน จังหวัดสารอาหาร แถมลักษณะร่างกายแต่ละคน ก็เปรียบเหมือนรถต่างยี่ห้อ ต่างน้ำมันขับเคลื่อน ต่างซีซี หรือแม้ว่าจะเหมือนกัน ก็ยังต่างปี ต่างไมล์การขับขี่
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ a5ee4475:2ca75401
2025-05-07 20:00:42
@ a5ee4475:2ca75401
2025-05-07 20:00:42lista #descentralismo #comunidades #portugues
[em atualização]
*Até a criação desse post, só alguns clients têm acesso às comunidades, tal como o Satellite, o Coracle e o Amethyst.
**Se a comunidade não tiver proprietários ou moderadores ativos, o seu envio de mensagem poderá não ser aprovada para aparecer nela.
***Se criar uma, busque colocar um ou mais moderadores para a comunidade não acabar, caso você se ausente.
Geral:
n/Brasil (Por: nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqryyunpwd5kcq3qzdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2sxpqqqzr0v4va9m3
n/Portugal (por: nostr:nprofile1qqsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshszynhwden5te0dehhxarj9ek82tntv5hsd2h46x) nostr:naddr1qqy9qmmjw36kwctvqgsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqrqsqqpphkc3wuaj
n/Moçambique (por: nostr:nprofile1qqszx6hsp38v2re3q2pzxpv3slg5u7pxklxze7evarqk4eugqmhntdcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctc082x0w) nostr:naddr1qqf56m7r5ask6cnfw96ktuyls7e0p8u8hupzqgm27qxya3g0xypgygc9jxraznncy6muct8m9n5vz6h83qrw7ddhqvzqqqyx7c0autxh
n/África (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqru8qtxwf5kxcgzyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdaspqgn0q
-
n/Perguntas-e-Respostas (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq3lp8u85lcflpah2pz4y364fe2yz5edg5k4y32n2p84x4zp203fm980hz8sygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqsmmqtz9a9x
n/Links-e-Tutoriais-Úteis (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqj0p8u85lcflpahf3y5uj6n94zj64z42384yj2pf9fjmsu623z5j5lsn7ftkq3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqzr0v3zu9fd
n/JornalismoNãoEstáMorto - Notícias e escrita informativa (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:nprofile1qqs0f74kketdcv63r53mlzgzfh93we3dkgzkldv2p6g62a8gf3g92yqpz4mhxue69uhkummnw3ezummcw3ezuer9wchszyrhwden5te0dehhxarj9ekk7mf0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9ufhpwuw) nostr:naddr1qqd55n6jfeq5cj2nf48j6nkrsd8j632n2npczt2dfaf9gnczyrvvsrjnp9xgqysjendxg6x2q7fldu73ajnf5e2h7uspp9tjl7jvxqcyqqqgdasy2kfg4
n/Agorismo³-E-Mercado (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpahg9r575jf2dx5ls4n94zj6n292fp5z3z094gry5qzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasrlnr7s
n/FeiraNostr - Marketplace (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qq9yvetfwfs5ummnw3eqyg9hpjdlkf2tvpegqssjvsa7kpmmdw55zcy76sz3tkd3p9sawancnypsgqqqsmmqucz73h
Tecnologia:
n/ndevs-br (por: nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcppemhxue69uhkummn9ekx7mp0gc3lmk) nostr:naddr1qqyxuer9weej6cnjqgs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcrqsqqpphk7z3axp
n/BrasilDev (por: nostr:nprofile1qqsyczyspluueyxautr3nxa2httku5e9m7d05dnu5zj3jnrg0jmucqcpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uqs6amnwvaz7tmwdaejumr0dsq3camnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdsz8cl6e) nostr:naddr1qqy5yunpwd5kc3r9wcpzqnqgjq8lnnysmh3vwxvm42adwmjnyh0e473k0js22x2vdp7t0nqrqvzqqqyx7cvxdlla
n/Linux (por: nostr:nprofile1qqsxhewvq6fq9lzjmfwqrpg2ufgl09uh2cksupa853zxv04u2fva4uqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0dehhxarjv4kxjar9wvhx7un89uqsuamnwvaz7tmwdaejumr0dshs6tvc92 ) nostr:naddr1qqz5c6tww4uqz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsygrtuhxqdyszl3fd5hqps59wy50hj7t4vtgwq7n6g3rx8679ykw67qpsgqqqsmmqznes6u
n/IA - Inteligencia Artificial (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqpyjsgpzpmhxue69uhkummnw3ezumt0d5hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqs03ln5
n/HardwareBr - Dúvidas, experiências e atualizações sobre hardware (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq9ysctjv3mkzun9gfeqyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmq54k3eu
n/SegurançaDaInformação (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqv9xet8w4exzmkr5as5gc2fdenx7undv8p60sardupzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cpss4m0
n/Moneroptbr (Por: nostr:nprofile1qqsyrmue77dm5ef5pmqsly0wp3248mk3vr9temj5p54plygcr97pavcpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqg5waehxw309aex2mrp0yhxgctdw4eju6t0tpqrvk) nostr:naddr1qq9y6mmwv4ex7ur5vfeqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygzpa7vl0xa6v56qasg0j8hqc42namgkpj4uae2q62sljyvpjlq7kvpsgqqqsmmqknmdan
Ciência:
n/Astronomia - Espaço e astros (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qq9yzum5wfhkummdd9ssz9thwden5te0dehhxarj9ehhsarj9ejx2a30qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqpphkkdel5t
n/Mecatrônica-NOSTR (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqfy6etrv9689sa5de5kxcfdfe84x4zjqythwumn8ghj76twvfhhstnp0faxzmt09ehx2ap0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphkgsy84w
n/Antropologystr - Antropologia (por: nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg ) nostr:naddr1qq85zmn5dpex7ur0d3hkw7tnw3eqygzfrtlt4hds900g0nl80lk6luq5h7fds622r5uqa3882jgckeyrfcpsgqqqsmmq4xrrgc
Cultura:
n/Estante-Nostr - Literatura e livros (por: nostr:nprofile1qqsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqpr4mhxue69uhkummnw3ez6vp39eukz6mfdphkumn99e3k7mf0qywhwumn8ghj7mn0wd68ytfsxgh8jcttd95x7mnwv5hxxmmd9uq37amnwvaz7tmwdaehgu3dxqejuer0wfskvctrw3hhy7fwdaexwtcjwfqr2) nostr:naddr1qqx52um5v9h8ge2lfehhxarjqgsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqrqsqqpphkwzdgct
n/Literatura-Arte-Cultura (por: nostr:nprofile1qqs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9cprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqsuamnwvaz7tmwdaejumr0dshs8l9z0j) nostr:naddr1qqt5c6t5v4exzar4wfsj6stjw3jj6sm4d3682unpqgs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9crqsqqpphkty54um
n/História-e-Filosofia (por: nostr:npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk ) nostr:naddr1qqjlp8u85lcflpahfpy4x4xrjdfyjsfdg5k5vj2vfaf573jfg8cflrum7z0cezczyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdas35g9vs
n/Urbanism - Urbanismo (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qqy92unzv9hxjumdqgstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgrqsqqpphkyl5u8a
Fé:
n/Religião-e-Teologia - Cristianismo (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpah2fz5cj28f8pcxnedg5k4g320f385wj2p7z0ehyqzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasta04x5
n/Ateismo-e-Agnosticismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqtyzar9d9ek6medv5k5zemwdaehg6trd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdasuuzmw8
n/Budismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5yatyd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas0kmt4m
n/Taoismo - Daoismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqy9gct0cwkhxmt0qy88wumn8ghj7mn0wvhxcmmv9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7crkzqvd
n/Espiritualidade - Significação e sublimidade (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq852umsd9exjar4v9kxjerpv3jszyrhwden5te0dehhxarj9ekk7mf0qgsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscrqsqqpphkxa5nfy
Entretenimento:
n/Equinox - Cinema no Nostr (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr) nostr:naddr1qqr52ut4d9hx77qpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cmc79n5
n/Rock/metal - Músicas Rock e Metal (por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4 e nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz748t750 ) nostr:naddr1qq99ymmrdvh56et5v9kqzqqzypvep8kzcfyvdvug0j9agfv07ujkx9elwfujy5qfl06jy25zmvctwqcyqqqgdas306zj5
n/Música-Cinema-e-Livros (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq4lp8u85lcflpahfhpe556fgdqj6s6ffez56sfdyck5cj2k2f848uyl366lp8unhhcflyu6qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkfyz9pf
n/Lugares-e-Viagens (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqjlp8u85lcflpahf325ws2jg4fj63fd2ey5z369feflp8uv3mcflryd7z0cercpqqpzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7c965gfw
n/MídiasPerdidas - Lost Media (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqw0p8u85lcflpahfhpc63zfg9fj65z92fzyj3zp20cflfusqgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkdltjpa
n/Football - Futebol (Por: nostr:nprofile1qqsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc9l2d6x / Moderadores: nostr:nprofile1qqsx5rzeds2gf6hzaqf35qc0y6v5fys72fsec8w3gwszn3jw5mxewvgpz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9u5c2kxa & nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqyxvmm0w33xzmrvqgsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsrqsqqpphkg0nfw5
n/Formula-1 (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqy5vmmjd46kccfdxypzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7cc95u5w
n/Games - Atualizações sobre jogos (por: nostr:npub1atyuu22fvvj4yf2uf050fwra3pu7hjvykc7ravpmrkpwjxcc6hpsfneh4e ) nostr:naddr1qqz5wctdv4esyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqn0x7k7
n/JogosBrasil - Clips de jogos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qq955mm8dae5yunpwd5kcqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qj90yg0hl4e6qr7yg982dlh0qxdefy72d6ntuqet7hv3ateya782sxpqqqzr0vus9jl2
n/Minecraft (por: nostr:npub19xc7f5lg2z6svrjgye63rx44a96aq2ysqajx5tmum28cu6mk5j3qj3n9m9 ) nostr:naddr1qqy566twv43hyctxwspzq2d3unf7s594qc8ysfn4zxdtt6t46q5fqpmydghhek503e4hdf9zqvzqqqyx7ct7hldr
n/GenshinImpactBr (por: nostr:nprofile1qqs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcnffw22) nostr:naddr1qqtlp8u85lcflpahgajkuumgd9hyjmtsv93hgsnjq9z8wue69uhkw6tjwahhgvntdaunx6mkdgmxv6ehdaek2mm3v9a8qdtkwa3x2cthda3kyvmdxgmk5cm3w3sksd34vcexv6mvxdukgtn0de5k7m30qgs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggrqsqqpphkq4s4py
Libertarianismo:
n/Defensores-caseiros (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq0lp8u85lcflpahg3jkvetwwdhhyetn943kzum9d9ex7ulsn78mgq3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vcr78h2
n/Desobediência_Civil (por: nostr:nprofile1qqs2kw4x8jws3a4heehst0ywafwfymdqk35hx8mrf0dw6zdsnk5kj9gpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m306r5ytp) nostr:naddr1qq2ygetnda3x2erfcw4xucmfv905x6tkd9kqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsyg9t82nre8gg76muumc9hj8w5hyjdkstg6tnra35hkhdpxcfm2tfz5psgqqqsmmqlg3ata
n/sobreviNOSTR - Sobrevivencialismo (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq20p8u85lcflpah2dhkyun9we55un6n23fqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqsmmqtempje
n/Triggr - Armas (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqr9g5jfgar4yqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vt5085y
n/Kaboom - Química e explosivos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qqt0p8u85lcflpahfdq5yn60fhcflra57z0602qppemhxue69uhkummn9ekx7mp0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphk637p09
n/CAVERNA-DO-PIRATA - Pirataria (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq40p8u85lcflpahgdq4v32jfeqj63z094gyj5jp23qlp8u0kn3gpr0znzswlwy07z0ca2gpg3mhxw309ankjunhda6ry6m00yekkan2xenxkdm0wdjk7utp0fcr2anhvfjkzam0vd3rxmfjxa4xxut5v95rvdtxxfnxkmpn09jzummwd9hkutczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqgdask5hmmn
n/PrivateSociety - Propostas e discussões para uma sociedade privada (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq89qunfweshge2nda3kjet50ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cfvhgrt
n/TeoriaDasBandeiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqf9get0wf5kzerpwdpxzmnyv45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkatc9rh
n/SemFronteiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqx4xetdgeex7mn5v45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkjs0cue
n/AnarcoSobrevivencialismo (por: nostr:nprofile1qqsfj5s9lrcckaxd8ul7vf3c4ajfg0n0ytcjvetclw679hy6p98wpfqpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uykdgj7) nostr:naddr1qqdyzmnpwf3k75m0vfex2anfwejkucmfv9kxjumddap9yq3qn9fqt7833d6v60elucnr3tmyjslx7gh3yejh37a4utwf5z2wuzjqxpqqqzr0vsz5kcy
n/SociedadeAlternativaLibertaria - Libertários (por: nostr:nprofile1qqs2ph3za34henpq2y3rzgqwgdc4pjmpleqr5t62rf7kxj0lmdyxnfgppemhxue69uhkummn9ekx7mp0ydypw5) nostr:naddr1qq09xmmrd9jkgctyv4qkcar9wfhxzarfwes5c6tzv4e8gctjd9ssyg9qmc3wc6muess9zg33yq8yxu2sedslusp69a9p5ltrf8lakjrf55psgqqqsmmq8dtk3m
n/LibertariosPT - Libertários de Portugal (por: nostr:nprofile1qqszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4gppemhxue69uhkummn9ekx7mp05leack) nostr:naddr1qqx5c6tzv4e8gctjd9hhx5z5qgszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4grqsqqpphke05802
Discussões Sociais
n/Aliança-Conservadora-Brasileira (por: nostr:npub1atg5rgfuarup49470kqexfgcesdr85yru56y0y8qf3z6kc30g2vqyfyqyp ) nostr:naddr1qqsyzmrfv9hv8fmptapk7mnnv4e8vctydaexzh6zwfshx6tvv45hycgzyr4dzsdp8n50sx5khe7crye9rrxp5v7ss0jng3usupxyt2mz9apfsqcyqqqgdasue9j59
n/Ilha-de-Anhatomirin - Monarquia (Por: nostr:nprofile1qqsgzc22v804davx6vpwtwfu6j84yvupeld497tfr396usmu7s0m08qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszymhwden5te0v9ehgunpdshxu6twdfsj7qguwaehxw309a5x7ervvfhkgtnrdaexzcmvv5h8gmm0d3ej7a2jp7u) nostr:naddr1qqf5jmrgvykkgefdg9hxsct5dakkjunfd5q3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7q3qs9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqxpqqqzr0vu2qg3m
n/ManosphereBrasil - Contra a misandria (Por: nostr:nprofile1qqs0p3yd48kzm56a4tual772y3vsjwehx6tc3rv8ht8q0zgncg5r7qgpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpjnhed) nostr:naddr1qqgy6ctwdaehq6r9wfj5yunpwd5kcqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyrcvfrdfaskaxhd2l80lhj3ytyynkdekj7ygmpa6ecrcjy7z9qlszqcyqqqgdasl3kaju
Memes
n/Shitposting (Por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4) nostr:naddr1qq94x6rfw3cx7um5d9hxwqgswaehxw309ahx7um5wghx6mmd9upzqkvsnmpvyjxxkwy8ez75yk8lwftrzulhy7fz2qylhafz92pdkv9hqvzqqqyx7chlz42w
n/Puro-caldo-do-Brasil. (por: nostr:nprofile1qqsztjv2pflmwcayr2jaq90astj94lu5l0smr0zhkfdct4ry7uxu7dqywzq8t) nostr:naddr1qq24qatjdukkxctvv3hj6er094p8yctnd9kzuqghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7q3qyhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6qxpqqqzr0vwh0r4w
Locais
n/NordesteLibertário - Nordeste (Por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqf5ummjv3jhxar9f35kyetjwnp6zunfdupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cnejrgl
n/BahiaLibertária - Bahia (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqgyyctgd9s5c6tzv4e8fsapwf5kzq3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqzr0vc4949j
n/LiberdadeMinas - Minas Gerais (Por: nostr:nprofile1qqsf0kszkmrmy9l3c7mxr3uhh3fmyjpq2z4hjvv7wdq84k5npd7gw3cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxthwden5te0wfjkccte9eekummjwsh8xmmrd9skctcprpmhxue69uhhyetvv9ujuurvv438xarj9e3k7mf0mx68nx) nostr:naddr1qq8yc6tzv4exgctyv4xkjmnpwvqsqq3qjldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsxpqqqzr0vag4knt
n/CyberpunkManaus - Manaus (Por: nostr:nprofile1qqsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqpz3mhxw309ucnqt3jx5cjuvpwxgarsvpcxqq3wamn8ghj7vfexghrzd3c9ccjuv3s8gurqwps9uq5gamn8ghj7entv43kjd3nvfcx5en6093h2up5w3ekgmn4xsekvatwx438xamywp6ksemcwp6xummzdgekzdmz0pmhzd3j0g6xzepwdahxjmmw9u2upp88) nostr:naddr1qqgyx7tzv4e8qatwdvk56ctwv96hxqgqqgsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqrqsqqpphkgjh4rf
n/BelémLibertario (por: nostr:npub167s6q8sfzkhel4227kacu98zcg6e37v5sqwkv8mxaazrryz9huzqlhcu2t) nostr:nevent1qqsqnqgx3u2whdqdqmlstqcmgav6xfe4upz2qxfvj03tlk699dzlk7qzyrt6rgq7py26l874ft6mhrs5utprtx8ejjqp6eslvmh5gvvsgklsgqcyqqqqq2qqsdz6l
n/SãoPauloLivre - São Paulo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq898sardagxzatvdaxxjanjv5pzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cmls060
n/AcreLibertário - Acre (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq85zcmjv4xxjcn9wf6v8gtjd9hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqftljpt
n/Alagoas (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5zmrpvahkzuczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas8qtaf4
Empreendedorismo:
n/Empreendedorismo/BR (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqd5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj7snjv9ekjmqzyz5jr7tdaz02wwfsksstyrf9ytx4x9yhaa257my24xlw5s29yt5dkqcyqqqgdaslzrp3p
n/Empreendedorismo/SP (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqt5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj756sqgs2jg0edh5fafeexz6zpvsdy53v65c5jlh42nmv325ma6jpg53w3kcrqsqqpphkcym25j
Análise
n/EBDV (Em Busca Da Verdade) - Análise geral e desenvolvimento pessoal (por: nostr:nprofile1qqs0xmu0skfdlmtl5tth6cv99za8f8kv7ulz5srkm8p6v5k03dx9lzspz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9usvrt9r) nostr:naddr1qqzy2sjy2cpzpum037ze9hld073dwltps55t5ay7enmnu2jqwmvu8fjje795chu2qvzqqqyx7cy9v5px
-
 @ 57d1a264:69f1fee1
2025-05-14 06:48:45
@ 57d1a264:69f1fee1
2025-05-14 06:48:45Has the architect Greg Chasen considered it when rebuilding the house just one year before the catastrophe? Apparently not! Another of his projects was featured on the Value of Architecture as properties with design integrity.
This is a super interesting subject. The historic character, livability, and modern disaster-resistance is a triangle where you often have to pick just one or two, which leads to some tough decisions that have major impacts on families and communities. Like one of the things he mentions is that the architect completely eliminated plants from the property. That's great for fire resistance, but not so great for other things if the entire town decides to go the same route (which he does bring up later in the video). I don't think there's any objectively right answer, but definitely lots of good (and important) discussion points to be had.
https://www.youtube.com/watch?v=cbl_1qfsFXk
originally posted at https://stacker.news/items/979653
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 1d7ff02a:d042b5be
2025-05-03 09:47:49
@ 1d7ff02a:d042b5be
2025-05-03 09:47:49ບົດຄວາມນີ້ແປມາຈາ: https://jackkruse.com/what-to-do-with-new-cancer-diagnosis/
ເນື້ອຫາສຳລັບຜູ້ອ່ານ: 1. ຈະເຮັດແນວໃດເມື່ອທ່ານໄດ້ຮັບການວິນິດໄສວ່າເປັນມະເຮັງ? 2. ສະໜາມຮົບກັບມະເຮັງທີ່ສຳຄັນແມ່ນຢູ່ບ່ອນການປິ່ນປົວແບບແພດ ຫຼື ໃນຮ່າງກາຍຂອງທ່ານເອງ? 3. ອາຫານການກິນມີບົດບາດແນວໃດ? 4. ຈະຮັບມືກັບໝໍມະເຮັງຄົນໃໝ່ຂອງທ່ານແນວໃດ? 5. ບໍ່ຕ້ອງຢ້ານທີ່ຈະສຳຫຼວດທຸກຄວາມເປັນໄປໄດ້ເພື່ອຊະນະສົງຄາມນີ້. ຮຽນຮູ້ກ່ຽວກັບອາຫານ ketogenic!!!
ກ່ອນທ່ານຈະອ່ານບົດຄວາມນີ້, ໃຫ້ເບິ່ງວິດີໂອນີ້: HYPERLINK
ບົດຄວາມນີ້ແມ່ນສຳລັບໜຶ່ງໃນໝູ່ທີ່ພິເສດຂອງຂ້ອຍ ຜູ້ທີ່ພົວພັນຂ້ອຍໃນອາທິດນີ້ ແລະ ບອກວ່າເມຍລາວຖືກວິນິດໄສວ່າເປັນມະເຮັງໃນໄວອາຍຸໜຸ່ມ. ຂ້ອຍໄດ້ຍິນຈາກການໂທ ແລະ ໂພສຂອງລາວໃນ Facebook ວ່າມັນກຳລັງທຳລາຍລາວ. ຂ້ອຍບອກລາວທັນທີໃຫ້ໄປຊື້ປື້ມ Anti Cancer: A New Way of Life ໂດຍ David Servan Schreiber ແລະ ມອບໃຫ້ເຈົ້າສາວຂອງລາວ. ຂ່າວດີກໍ່ຄືຫຼາຍລ້ານຄົນໃນຈຳນວນ 6 ລ້ານຄົນທີ່ກຳລັງປິ່ນປົວມະເຮັງໃນປະຈຸບັນຈະມີຊີວິດທີ່ສົມບູນຕໍ່ໄປ. ຈຳນວນຜູ້ລອດຊີວິດຕາມຄວາມຄິດເຫັນຂອງຂ້ອຍຍັງຕ່ຳເກີນໄປ (ປະມານ 45-50%). ນອກຈາກນັ້ນ, ຫຼາຍຄົນໃນຈຳນວນ 2000 ຄົນທີ່ເສຍຊີວິດຈາກມະເຮັງທຸກມື້ແມ່ນເນື່ອງຈາກຄອບຄົວຂອງພວກເຂົາບໍ່ຮູ້ກ່ຽວກັບຊັບພະຍາກອນທີ່ມີໃນປະຈຸບັນສຳລັບການປິ່ນປົວມະເຮັງທັງແບບດັ້ງເດີມ ແລະ ແບບທາງເລືອກ ເຊັ່ນ: ການປິ່ນປົວແບບເສີມ ຫຼື ແບບບູລະນາການ.
ເມື່ອຖືກວິນິດໄສດ້ວຍພະຍາດນີ້, ທ່ານຈະຮູ້ສຶກສັ່ນສະເທືອນຢ່າງຮຸນແຮງ. ສິ່ງສຳຄັນທີ່ທ່ານຕ້ອງຮູ້ແມ່ນພະຍາດນີ້ບໍ່ພຽງແຕ່ສາມາດຕໍ່ສູ້ໄດ້ແຕ່ຍັງສາມາດປ້ອງກັນໄດ້ຖ້າທ່ານຕັດສິນໃຈປ່ຽນແປງບາງສິ່ງທັນທີ ແລະ ປ່ອຍວາງຄວາມເຊື່ອທີ່ບໍ່ຖືກຕ້ອງທີ່ທ່ານໄດ້ສະສົມໃນຊີວິດ. ນີ້ເປັນຄວາມຈິງໂດຍສະເພາະຖ້າທ່ານເຮັດວຽກໃນຂົງເຂດສາທາລະນະສຸກ ແລະ ໄດ້ດຳລົງຊີວິດຕາມຄວາມເຊື່ອຕາຍຕົວຕະຫຼອດຊີວິດ. ປື້ມນີ້ຂຽນໂດຍແພດນັກຄົ້ນຄວ້າທີ່ບໍ່ພຽງແຕ່ຖືກກະທົບຈາກມະເຮັງ ແຕ່ຍັງເປັນມະເຮັງສະໝອງທີ່ອັນຕະລາຍທີ່ສຸດ. ລາວສາມາດຮື້ຖອນຄວາມເຊື່ອຂອງຕົນເອງໃນຖານະແພດດ້ວຍວິທະຍາສາດໃໝ່ທີ່ມີຢູ່ສຳລັບນັກຄົ້ນຄວ້າ ແຕ່ບໍ່ແມ່ນແພດມະເຮັງທົ່ວໄປ. ປື້ມນີ້ຈຳເປັນສຳລັບທຸກຄົນທີ່ເປັນມະເຮັງ ຫຼື ມີປັດໄຈສ່ຽງ ເພື່ອທ່ານຈະໄດ້ຊະນະກ່ອນມັນເລີ່ມ. ນີ້ແມ່ນໜຶ່ງໃນເຫດຜົນທີ່ຂ້ອຍຂຽນ QUILT ຂອງຂ້ອຍ ເພາະຂ້ອຍເຊື່ອວ່າຖ້າທ່ານປົກປ້ອງຈຸລັງຂອງທ່ານ ທ່ານຈະບໍ່ເປັນພະຍາດນີ້. ດຽວນີ້ ໝູ່ຂອງຂ້ອຍເປັນພະຍາດນີ້... ນີ້ແມ່ນບົດຄວາມກ່ຽວກັບສິ່ງທີ່ທ່ານອາດພິຈາລະນາເຮັດທັນທີຫຼັງຈາກປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ພິຈາລະນາຂໍຄວາມຄິດເຫັນທີສອງຈາກສູນມະເຮັງທີ່ສຳຄັນເຊັ່ນ MD Anderson.
-
ອ່ານປື້ມ Anticancer ທີ່ກ່າວເຖິງຂ້າງເທິງ. ມັນສຳຄັນທີ່ຈະເຫັນພະຍາດນີ້ໃນມຸມມອງໃໝ່.
-
ປ່ຽນອາຫານການກິນຂອງທ່ານທັນທີເປັນ Epi-paleo Rx ແລະ ອອກຫ່າງຈາກອາຫານແບບຕາເວັນຕົກມາດຕະຖານ.
-
ເລີ່ມເຮັດສະມາທິໂດຍໄວເທົ່າທີ່ຈະເປັນໄປໄດ້ເພື່ອຄວບຄຸມ cortisol ແລະ ຄວາມກັງວົນຂອງທ່ານ. (ທາງເລືອກບໍ່ສຳຄັນແຕ່ການເຮັດຈິງຊ່ວຍຊີວິດໄດ້)
-
ຄົນເຈັບຄວນປຶກສາຫາລືກ່ຽວກັບແຜນການປິ່ນປົວມະເຮັງ: ປັດໃຈສຳຄັນໃນມະເຮັງ: ຄວນຄົນເຈັບໃຊ້ອາຫານເສີມສຳລັບປະເພດມະເຮັງທີ່ທ່ານມີບໍ?
-
ພິຈາລະນາເລີ່ມລະບົບອາຫານເສີມ ລວມເຖິງ Curcumin, Reservatrol, Quercetin, ນ້ຳມັນປາ Omega ສາມ (ຄຸນນະພາບ Rx), ວິຕາມິນ D3 ໂດຍມີເປົ້າໝາຍເກີນ 50 ng/dl, ການໃຊ້ CoEnZQ10 ເປັນປະຈຳທຸກວັນ, R-alpha lipoic acid ແລະ ວິຕາມິນ K ທຸກມື້. ພິຈາລະນາການໃຊ້ N Acetyl Cysteine ທຸກວັນເຊັ່ນກັນ. ສັງເກດວ່າຂ້ອຍບໍ່ໄດ້ກຳນົດປະລິມານເພາະປະລິມານທີ່ຕ້ອງການສຳລັບການບຳບັດມະເຮັງແມ່ນສູງກວ່າທີ່ຈະໃຊ້ໃນການປ້ອງກັນ. ສິ່ງນີ້ຄວນເຮັດພາຍໃຕ້ການປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ຖ້າແພດມະເຮັງຂອງທ່ານບໍ່ເປີດໃຈກວ້າງກ່ຽວກັບບັນຫາເຫຼົ່ານີ້... ຫຼັງຈາກອ່ານປື້ມໃນຂັ້ນຕອນທີໜຶ່ງ ທ່ານອາດຈະຕ້ອງຊອກຫາແພດມະເຮັງຄົນໃໝ່. ເຫຼົ່ານີ້ແມ່ນສິ່ງທີ່ຂ້ອຍພິຈາລະນາວ່າເປັນອາຫານເສີມຫຼັກສຳລັບມະເຮັງສ່ວນໃຫຍ່ທີ່ມະນຸດເປັນ.
-
ໃນອາຫານຂອງທ່ານໃຫ້ເພີ່ມ ຂີ້ໝິ້ນ, ຂິງ, ກະທຽມ, ຣອດສະແມລີ, ແລະ ໃບແບຊິນ (ໃບໂຫລະພາ) ໃສ່ອາຫານຂອງທ່ານໃຫ້ຫຼາຍເທົ່າທີ່ຈະເປັນໄປໄດ້. ທ່ານຄວນດື່ມຊາຂຽວ 1 ລິດຕໍ່ມື້. ຊາຂຽວມີ L-Theanine ທີ່ຊ່ວຍຫຼຸດຄວາມກັງວົນ ແຕ່ຍັງເປັນສ່ວນເສີມຂອງຢາເຄມີບຳບັດໂດຍເຮັດໃຫ້ພວກມັນມີປະສິດທິພາບຍິ່ງຂຶ້ນ. ທ່ານຍັງສາມາດໃຊ້ສານສະກັດຊາຂຽວຖ້າທ່ານບໍ່ຕ້ອງການດື່ມຂອງແຫຼວຫຼາຍ ຫຼື ບໍ່ສາມາດດື່ມໄດ້ເນື່ອງຈາກສະພາບຂອງທ່ານ.
-
ໃນປີ 1955 Otto Warburg ຜູ້ຊະນະລາງວັນໂນເບວພົບວ່າມະເຮັງທັງໝົດໃຊ້ນ້ຳຕານເປັນແຫຼ່ງພະລັງງານ ແລະ ລະດັບອິນຊູລິນສູງເຮັດໃຫ້ຮ່າງກາຍສູນເສຍການຄວບຄຸມລະບົບພູມຄຸ້ມກັນທີ່ຈະປ້ອງກັນມັນ. ນີ້ໝາຍຄວາມວ່າຄົນເຈັບຕ້ອງຈຳກັດທຸກສິ່ງທີ່ກະຕຸ້ນອິນຊູລິນ. ອາຫານແບບ Epi-paleo ທີ່ມີຄາໂບໄຮເດຣດຕ່ຳເຮັດໄດ້ແນວນີ້ພໍດີ. ຂໍ້ມູນອ້າງອີງທີ່ດີສຳລັບອາຫານແມ່ນຢູ່ບ່ອນນີ້.
-
ລະບົບພູມຄຸ້ມກັນຂອງທ່ານແມ່ນການປ້ອງກັນທີ່ດີທີ່ສຸດຕໍ່ມະເຮັງ. ເພີ່ມລະດັບວິຕາມິນ D ແລະ ຮັກສາລະດັບອິນຊູລິນໃຫ້ຕ່ຳກວ່າສອງ. ການຫຼຸດລະດັບ cortisol ຈະປັບປຸງ leptin ແຕ່ສິ່ງສຳຄັນທີ່ສຸດແມ່ນເພີ່ມຈຳນວນຈຸລັງ Natural Killer (WBC) ທີ່ເປັນສ່ວນໜຶ່ງຂອງລະບົບພູມຄຸ້ມກັນໃນຈຸລັງທີ່ຕໍ່ສູ້ກັບມະເຮັງ. ທ່ານຈະໄດ້ອ່ານຫຼາຍກ່ຽວກັບຈຸລັງເຫຼົ່ານີ້ໃນປື້ມທີ່ຂ້ອຍແນະນຳໃນຂັ້ນຕອນທີໜຶ່ງ.
-
ຜັກ. ເຮັດໃຫ້ຜັກຕະກຸນ cruciferous ເປັນອາຫານຫຼັກ. ພືດທັງໝົດໃນຕະກຸນ Brassica ແມ່ນໝູ່ຂອງທ່ານ. Glucosinolates ສາມາດຢັບຢັ້ງ, ຊະລໍ, ແລະ ປີ້ນການເກີດມະເຮັງຫຼາຍຂັ້ນຕອນ. ເຫດຜົນແມ່ນການປ່ອຍ isothiocyanates ເຊັ່ນ sulphoraphanes. Sulphoraphanes ເຮັດສອງສິ່ງຫຼັກ. ພວກມັນສົ່ງເສີມ apoptosis (levee 19) ແລະ ກະຕຸ້ນເອນໄຊມ໌ detoxification ໄລຍະສອງໃນຕັບທີ່ເສີມຄວາມເຂັ້ມແຂງໃຫ້ກັບຍີນ p53 ເປັນຜູ້ປົກປ້ອງຈີໂນມຂອງພວກເຮົາ. ຈຸລັງມະເຮັງມັກຈະຕາຍ (necrosis) ເມື່ອສຳຜັດກັບ sulphoraphanes ຢ່າງຕໍ່ເນື່ອງເປັນເວລາດົນ. ຜັກບຣອກໂຄລີຍັງມີສານ metabolite ຂັ້ນສອງທີ່ເອີ້ນວ່າ Indole 3 Carbinol ທີ່ແຕກຕົວຕໍ່ໄປເປັນສານຕ້ານມະເຮັງອີກຊະນິດໜຶ່ງຊື່ວ່າ DIM, diindolylmethane. ທ່ານບໍ່ສາມາດກິນຜັກພວກນີ້ຫຼາຍພໍຖ້າທ່ານເປັນມະເຮັງໃນທັດສະນະຂອງຂ້ອຍ. I3C ຍັງຂັດຂວາງ 16-hydroxyestrone ແລະ ມີປະໂຫຍດຫຼາຍໃນການປ້ອງກັນມະເຮັງເຕົ້ານົມ ແລະ ມະເຮັງຮັງໄຂ່ໃນແມ່ຍິງ ແລະ ມະເຮັງຕ່ອມລູກໝາກໃນຜູ້ຊາຍ.
-
ນີ້ແມ່ນສິ່ງທີ່ຂັດກັບຄວາມເຊື່ອຊຶ່ງຢູ່ໃນຫົວຂອງທ່ານ... ກິນ cholesterol ຫຼາຍໆ. ໂດຍສະເພາະນ້ຳມັນໝາກພ້າວ. ຫຼາຍການສຶກສາທາງລະບາດວິທະຍາສະແດງໃຫ້ເຫັນວ່າລະດັບ cholesterol ໃນເລືອດຕ່ຳສຳພັນກັບອັດຕາການເກີດມະເຮັງສູງ. ນີ້ແມ່ນເຫດຜົນທີ່ການກິນອາຫານ ketogenic Epi-paleo ມີຄວາມໝາຍຫຼາຍ. ເປັນຫຍັງອາຫານແບບ ketogenic? ເພາະມະເຮັງທັງໝົດໃຊ້ກລູໂຄສເປັນວັດຖຸດິບ. ທ່ານຈຳເປັນຕ້ອງປ່ຽນເຊື້ອໄຟຂອງຈຸລັງ. ໄປຊອກຫາ Otto Warburg ໃນ Google ສຳລັບລາຍລະອຽດເພີ່ມເຕີມ. ອາຫານແບບ ketogenic ຄວນມີ MCT ຈາກນ້ຳມັນໝາກພ້າວຫຼາຍ ເພາະພວກມັນໃຫ້ຂໍ້ໄດ້ປຽບຫຼາຍແກ່ຈຸລັງປົກກະຕິກວ່າຈຸລັງມະເຮັງ. ຂໍ້ໄດ້ປຽບນີ້ເຮັດໃຫ້ລະບົບພູມຄຸ້ມກັນຂອງທ່ານສາມາດຕາມທັນຈຸລັງມະເຮັງ ແລະ ທຳລາຍພວກມັນໂດຍໃຊ້ກົນໄກຊີວະວິທະຍາຂອງທ່ານເອງ. ມີຫຼາຍບົດຄວາມໃນວາລະສານມະເຮັງທີ່ພິມເຜີຍແຜ່ສະແດງໃຫ້ເຫັນການເຊື່ອມໂຍງແບບດຽວກັນ.
-
-
 @ 57d1a264:69f1fee1
2025-05-14 06:12:19
@ 57d1a264:69f1fee1
2025-05-14 06:12:19We asked members of the design community to choose an artifact that embodies craft—something that speaks to their understanding of what it means to make with intention. Here’s what they shared.
A vintage puzzle box, a perfectly tuned guitar, an AI-powered poetry camera. A daiquiri mixed with precision. A spreadsheet that still haunts muscle memory. Each artifact tells a story: not just about the thing itself, but about the choices of the creator behind it. What to refine, what to leave raw. When to push forward, when to let go. Whether built to last for generations or designed to delight in a fleeting moment, the common thread is that great craft doesn’t happen by accident. It’s made.
On the application of craft
Even the most experienced makers can benefit from building structure and intention into their practice. From sharpening your storytelling to designing quality products, these pieces offer practical ways to uplevel your craft.
Read more at https://www.figma.com/blog/craft-artifacts/
originally posted at https://stacker.news/items/979644
-
 @ 57d1a264:69f1fee1
2025-05-14 05:56:15
@ 57d1a264:69f1fee1
2025-05-14 05:56:15Shanghai: Bus Stops Here
A new crowd-sourced transit platform allows riders to propose, vote on, and activate new bus lines in as little as three days.
From early-morning school drop-offs to seniors booking rides to the hospital, from suburban commuters seeking a faster link to the metro to families visiting ancestral graves, Shanghai is rolling out a new kind of public bus — one that’s designed by commuters, and launched only when enough riders request it.
Branded “DZ” for dingzhi, or “customized,” the system invites residents to submit proposed routes through a city-run platform. Others with similar travel needs can opt in or vote, and if demand meets the threshold — typically 15 to 20 passengers per trip — the route goes live.
More than 220 DZ routes have already launched across all 16 city districts. Through an online platform opened May 8, users enter start and end points, preferred times, and trip frequency. If approved, routes can begin running in as little as three days.
Continue reading at https://www.sixthtone.com/news/1017072
originally posted at https://stacker.news/items/979637
-
 @ c9badfea:610f861a
2025-05-17 03:08:55
@ c9badfea:610f861a
2025-05-17 03:08:55- Install Rethink (it's free and open source)
- Launch the app and tap Skip
- Tap Start and then Proceed to set up the VPN connection
- Allow notifications and Proceed, then disable battery optimization for this app (you may need to set it to Unrestricted)
- Navigate to Configure and tap Apps
- On the top bar, tap 🛜 and 📶 to block all apps from connecting to the internet
- Search Apps for the apps you want to allow and Bypass Universal
- Return to the Configure view and tap DNS, then choose your preferred DNS provider (e.g. DNSCrypt > Quad9)
- Optionally, tap On-Device Blocklists, then Disabled, Download Blocklists, and later Configure (you may need to enable the Use In-App Downloader option if the download is not working)
- Return to the Configure view and tap Firewall, then Universal Firewall Rules and enable the options as desired:
- Block all apps when device is locked
- Block newly installed apps by default
- Block when DNS is bypassed
- Optionally, to set up WireGuard or Tor, return to the Configure view and tap Proxy
- For Tor, tap Setup Orbot, then optionally select all the apps that should route through Tor (you must have Orbot installed)
- For WireGuard, tap Setup WireGuard, then +, and select an option to import a WireGuard configuration (QR Code Scan, File Import, or Creation).
- Use Simple Mode for a single WireGuard connection (all apps are routed through it).
- Use Advanced Mode for multiple WireGuard connections (split tunnel, manually choosing apps to route through them)
⚠️ Use this app only if you know what you are doing, as misconfiguration can lead to missing notifications and other problems
ℹ️ On the main view, tap Logs to track all connections
ℹ️ You can also use a WireGuard connection (e.g., from your VPN provider) and on-device blocklists together
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 181ff6f7:7dc4fad2
2025-05-17 02:10:47
@ 181ff6f7:7dc4fad2
2025-05-17 02:10:47A plataforma 89p chegou para transformar a experiência de jogos online, oferecendo aos jogadores um ambiente de alta qualidade, repleto de opções diversificadas e recursos inovadores. Com uma interface amigável, tecnologia de ponta e uma vasta gama de jogos, a 89p é a escolha perfeita para quem busca diversão e emoção a qualquer hora do dia. Neste artigo, exploraremos as características dessa plataforma, os jogos disponíveis e a experiência do jogador que faz dela uma excelente opção.
Introdução à Plataforma 89p A 89p é uma plataforma de jogos online projetada para oferecer uma experiência única aos jogadores. Com um design intuitivo, fácil de navegar e totalmente otimizado para diferentes dispositivos, os usuários podem acessar a plataforma a partir de desktops, laptops e dispositivos móveis. A plataforma é conhecida por sua estabilidade, velocidade e suporte ao cliente de qualidade, garantindo que todos os aspectos da experiência do usuário sejam tratados com excelência.
O objetivo da 89pé oferecer aos seus jogadores uma experiência segura, confiável e divertida, com uma ampla gama de jogos que atendem a todos os gostos e preferências. Se você é fã de jogos de habilidade, jogos de azar ou opções mais descontraídas, a plataforma tem algo para todos.
Variedade de Jogos na Plataforma 89p Uma das grandes vantagens da 89p é a diversidade de opções de jogos. A plataforma conta com um catálogo extenso, com títulos das mais variadas categorias. Desde jogos de cartas, como pôquer e blackjack, até jogos mais modernos, como slots e jogos de mesa, a 89p garante que seus jogadores tenham acesso ao que há de melhor no mundo dos jogos online.
Além disso, a plataforma oferece jogos com temas e estilos diferentes, permitindo que cada jogador encontre opções que se adaptem ao seu estilo. A 89p também está constantemente atualizando seu portfólio de jogos, trazendo novas opções e versões aprimoradas, para que a experiência de jogar nunca se torne monótona.
A plataforma se destaca também pela qualidade gráfica dos seus jogos, que são desenvolvidos com tecnologia de última geração. Isso garante não só uma jogabilidade envolvente, mas também visuais impressionantes que tornam a experiência ainda mais imersiva. A jogabilidade é fluida, e os gráficos são de alta qualidade, com animações e efeitos especiais que aumentam ainda mais a diversão.
A Experiência do Jogador na 89p Na 89p, a experiência do jogador está no centro de tudo. A plataforma foi desenvolvida para ser fácil de usar, mesmo para aqueles que não têm muita experiência em jogos online. A navegação é simples, e a disposição dos jogos é organizada de maneira prática, permitindo que os jogadores encontrem rapidamente suas opções preferidas.
Outro ponto importante é o suporte ao cliente. A 89p oferece atendimento rápido e eficiente, com uma equipe de profissionais treinados para resolver quaisquer dúvidas ou problemas que possam surgir. O suporte está disponível 24 horas por dia, 7 dias por semana, garantindo que os jogadores tenham sempre a ajuda que precisam quando necessário.
Além disso, a plataforma se preocupa com a segurança de seus usuários. A 89p utiliza criptografia de última geração para proteger os dados dos jogadores, garantindo que suas informações pessoais e financeiras estejam sempre seguras. Isso é essencial para criar um ambiente confiável e tranquilo para os jogadores se concentrarem apenas na diversão.
Conclusão A 89p é uma plataforma de jogos online que oferece uma experiência completa, com uma grande variedade de jogos, suporte de alta qualidade e uma interface intuitiva. Se você está procurando uma nova forma de se divertir jogando online, a 89p é uma excelente escolha, proporcionando segurança, inovação e, claro, muita diversão.
-
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ efe5d120:1fc51981
2025-05-15 12:53:31
@ efe5d120:1fc51981
2025-05-15 12:53:31It’s not big government programs or powerful institutions that make a society strong. It’s something much simpler: everyday people trading and working together.
Think about the local hardware store owner. He helps his neighbors, gives people jobs, and provides useful tools. But when the government taxes him too much to fund its programs, it takes away money he could have used to hire someone or visit his family. That hurts both him and the people around him.
This happens all over. Small business owners, tradesmen, inventors and entrepreneurs are the ones who really build up a society. They create value by trading things people want, and both sides benefit. Free trade gives people more choices and helps them live better lives.
But from a young age, we’re told to obey authority without question. We’re taught that without rulers, there would be chaos. But what if that’s not true?
Look around the world: even when governments try to control trade, people still find ways to work together and exchange goods. It’s natural. People want to cooperate and help each other—especially when they’re free to do so.
Here’s the hard truth: if someone can take your money, control your property, and punish you without your agreement, isn’t that a kind of control—or even servitude?
True prosperity doesn’t come from the top down. It comes from people freely working together—farmers, builders, cooks, coders—offering their skills to others who need them.
When trade is free, people do well. When it’s blocked by too many rules or taxes, everyone loses—especially the ones who need help the most.
The answer isn’t more laws or more control. It’s more freedom. Next time someone says we need more government to fix things, ask yourself: wouldn’t free people solve those problems better on their own?
Real civilization isn’t about being ruled. It’s about choosing to work together, trade fairly, and respect each other’s rights. That’s not chaos—that’s freedom.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 04c3c1a5:a94cf83d
2025-05-13 16:49:23
@ 04c3c1a5:a94cf83d
2025-05-13 16:49:23Testing Testing Testing
This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test

nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau
| | | | | ------------------------ | - | - | | Quick'hthbdoiwenweuifier | | | | 1. Little | | |
ghtgehg
gwefjieqhf
MUCH BETTER
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 1d7ff02a:d042b5be
2025-05-02 14:50:01
@ 1d7ff02a:d042b5be
2025-05-02 14:50:01ผมได้ติดตามการแบนการซื้อขายแบบ P2P ของ Binance ในประเทศไทยมาระยะหนึ่งแล้ว จากสถานการณ์ดังกล่าว เห็นได้อย่างชัดเจนว่ารัฐบาลกำลังเริ่มโจมตี Bitcoin ก่อนที่เราจะบรรลุถึง Bitcoin Standard เราจำเป็นต้องมีความเป็นส่วนตัวและอิสระทางการเงิน ซึ่งการซื้อขายแบบ P2P มีความสำคัญมากในการบรรลุเป้าหมายนี้
ความสำคัญของ No-KYC P2P
No-KYC P2P คือหัวใจสำคัญ - เราจำเป็นต้องมีแพลตฟอร์มที่เป็นทางรอด เราไม่สามารถเชื่อใจแพลตฟอร์มแบบรวมศูนย์ได้เนื่องจากสาเหตุสองประการ: 1. ความเสี่ยงจากการถูกโกงโดยแพลตฟอร์มเอง (rug pull) 2. การถูกควบคุมจากภาครัฐ
แพลตฟอร์ม No-KYC P2P ที่แนะนำ
ผมอยากเสนอให้นักพัฒนาและชุมชน Bitcoin ไทย พิจารณาการศึกษาและพัฒนาแพลตฟอร์ม No-KYC P2P ปัจจุบันมีหลายทางเลือกที่มีอยู่แล้ว เช่น:
- Bisq
- RoboSats
- Mostro
- HodlHodl
- Lnp2pbot
เหตุผลที่แนะนำ Lnp2pbot
ผมขอแนะนำให้นำใช้หรือพัฒนาต่อจาก Lnp2pbot เนื่องจากข้อดีหลายประการ:
- ประสบการณ์ผู้ใช้ (UX) ที่ดีกว่า - เมื่อเทียบกับแพลตฟอร์มอื่นๆ
- ใช้ Telegram เป็นพื้นฐาน - มีระบบ Escrow (บุคคลที่สามที่ถือเงินระหว่างการทำธุรกรรม) ซึ่งเพิ่มความมั่นใจและลดโอกาสการถูกโกง
- ลดการรวมศูนย์ - ไม่จำเป็นต้องพัฒนาแอปและส่งขึ้นสโตร์ ซึ่งจะทำให้นักพัฒนาต้องเปิดเผยตัวตนและกลายเป็นจุดอ่อนให้รัฐบาลควบคุม
- สร้างชุมชนได้ง่าย - ทุกคนสามารถสร้างกลุ่มหรือชุมชนเพื่อการซื้อขายได้ ทำให้ตลาดพัฒนากลุ่มที่น่าเชื่อถือตามกลไกตลาดเสรี
- ใช้งานจริงในหลายประเทศแล้ว - ปัจจุบันมีหลายประเทศที่นำ Lnp2pbot ไปใช้งานจริงแล้ว แสดงให้เห็นถึงความเสถียรและความเชื่อถือได้ของระบบ
บทบาทของนักพัฒนาไทย
Lnp2pbot อาจยังมีข้อจำกัดด้าน UX โดยเฉพาะสำหรับผู้ใช้ท้องถิ่น นักพัฒนาไทยสามารถนำเอาซอฟต์แวร์มาพัฒนาต่อและดำเนินการเองได้ เนื่องจากเป็นโอเพนซอร์สอยู่แล้ว
สิ่งสำคัญที่สุดคือการรักษาให้ซอฟต์แวร์เป็นโอเพนซอร์สและให้ทุกคนสามารถนำไปใช้หรือทำให้มันทำงานได้ด้วยตนเอง วิธีการนี้จะหลีกเลี่ยงการมีจุดรวมศูนย์ที่รัฐบาลสามารถโจมตีได้
-
 @ 5391098c:74403a0e
2025-05-13 16:47:48
@ 5391098c:74403a0e
2025-05-13 16:47:48(Textículo em prosa erudita sobre a Ideologia Anarco-Capitalista-Cristã)
https://davipinheiro.com/01-escravos-da-cara-inchada/
A cultura #Woke apropriou-se da imagem sobre a #escravidão. Quando uma pessoa aculturada imagina um #escravo, vem em sua mente a imagem de um ser humano negro, magro e flagelado. Para quem enxerga além das cortinas da mentira, vem em sua mente a imagem de um ser humano de qualquer etnia, gordo e doente.
Democracia, péssimo regime de governo assim classificado pelo seu próprio idealizador: Platão em A República, é o grito da hienas de dentes arreganhados para ampliação do regime escravocrata fomentado pelos #GlobalistasSatanistas.
Um escravo da cara inchada é todo aquele ser humano ignorante inconsciente que alimenta esse sistema em troca de intoxicantes como flúor¹, cloro, glutamato monosódico, gordura trans, corantes, conservantes, refrigerantes, bebidas alcoólicas, psicotrópicos e remédios sintomáticos, tudo embrulhado com mentiras reiteradas.
Como consequência, após os 18 anos de idade o corpo do #EscravoDaCaraInchada sucumbe à tamanha intoxicação e passa a inchar, sendo fisicamente perceptível sua condição de escravo da cara inchada tanto à olho nú quando por reconhecimento facial de qualquer pseudo inteligência artificial.
O círculo vicioso da #EscravidaoDemocratica é tão simples e tosco como o “pão e circo romano”, Mesmo assim é muito difícil para o escravo da cara inchada perceber a própria condição tamanha é sua intoxicação física e mental.
Se um Anarco-Capitalista-Cristão (#Ancapcristão) chega para um escravo da cara inchada e explica sobre esses intoxicantes como instrumento de escravização, dificilmente o escravo da cara inchada irá acreditar pois diferentemente do antigo e aposentado chicote, o novo instrumento da escravidão não dói de imediato e os próprios efeitos da intoxicação impedem-no de raciocinar com clareza.
Portanto, para que os #GlobalistasSatanistas obtivessem sucesso na democratização da escravidão, tiveram que criar um chicote químico e uma ideologia favorável. Quanto às etapas utilizadas para formação dessa ideologia no inconsciente coletivo passo a elencar as 6 grandes mentiras em ordem cronológica:
(1ª etapa) Iluminismo: distanciamento de #Deus e seus ensinamentos, criação de sociedades secretas, exacerbação do ser humano perante o criador na tentativa de projetar o ser humano como seu próprio deus, tornando-o responsável sobre os rumos naturais do planeta. Assim formou-se a base ideológica para o materialismo, ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(2ª etapa) Materialismo: perda do propósito espiritual e do sentido da vida², o que passa a importar são apenas as coisas materiais, acima inclusive do próprio ser humano. A perpetuação da espécie também fica em segundo plano. Assim formou-se a base ideológica para o ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(3ª etapa) Ambientalismo: redução do ser humano à mero câncer do planeta superlotado, atribuído-lhe a responsabilidade por qualquer desastre natural. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(4ª etapa) Feminismo: enfraquecimento do ser humano por meio da sua divisão em duas categorias: macho e fêmea, os quais são inimigos e não cooperadores. A ideia de igualdade de gêneros é tão antagônica que beira ao conflito cognitivo³: Eles querem separar para dizer que são iguais... Ora, como não pode haver diferenças entre os gêneros se eles são fisicamente e mentalmente diferentes? Nesse diapasão, mesmo não sendo os estados nacionais os arquitetos da escravidão democrática e sim meros fantoches dos globalistas satanistas, o voto feminino foi fundamental para aprovação de leis misândricas com o fito de acelerar a destruição da base familiar do escravo da cara inchada. Importante mencionar que a base familiar dos globalistas satanistas continua sendo patriarcal. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(5ª etapa) Controle Populacional: “Crescei e multiplicai-vos” é o caralho, Deus não sabe de nada (Iluminismo), o que importa é o dinheiro e filho é caro (Materialismo), para que colocar mais um ser humano nesse planeta doente e superlotado (Ambientalismo), além disso o sexo oposto é meu inimigo (Feminismo). Essa é base ideológica que antecede a ideologia de Controle Populacional, ainda reforçada pela apologia à castração, já que em todas as mídias produzidas com patrocínio oculto de capital globalista satanista tentam normalizar a castração do homem (perda da capacidade de reprodução) desde em desenhos infantis até grandes produções cinematográficas, ora em tom de humor ora em tom de tortura. Assim os escravos da cara inchada do sexo masculino perderam sua identidade, essência e desejo de ser o que são, formando-se a base ideológica para o homossexualismo, ou seja, para a ideologia de gêneros.
(6ª etapa) Ideologia de Gêneros: É a cereja do bolo para os planos do Diabo (Anjo invejoso de Deus que quer destruir a maior criação: nós). Enquanto os globalistas satanistas, dentro de sua sábia ignorância, acreditam estarem chefiando a democratização da escravidão, na verdade também não passam de meros fantoches do Anjo Caído. Com a sexta e última etapa de mentiras para extinção da humanidade (#apocalipse) posta em prática através da Ideologia de Gêneros, fecha-se o ciclo vicioso de mentiras que se auto justificam: Se #Deus não presta, o que vale são os bens materiais, o ser humano é um câncer no planeta, o sexo oposto é inimigo e ter filhos é uma péssima ideia e ser homem másculo é crime, então ser #homossexual é a melhor opção, inclusive vamos castrar os meninos antes da puberdade sem o consentimento dos pais ou mães solo. Aqui também há uma grande bifurcação do círculo vicioso de mentiras, qual seja o gritante conflito cognitivo³: Se todos os homens deixarem de ser másculos, quem vai comer os #gays afeminados? Ou se todas as mulheres deixarem de ser femininas, quem as #sapatonas irão comer? E o pior, se todos passem a ser homossexuais quem vai perpetuar a espécie? Seremos extintos no lapso temporal de apenas uma geração, pois a fraudulenta medicina moderna jamais terá a capacidade de gerar bebês de chocadeira à tempo.
É interessante enxergar que mesmo os Globalistas Satanistas, dentro de sua sábia ignorância, acreditando estarem democratizando a escravidão em benefício próprio, na verdade apenas estão fomentando o apocalipse, ou seja sua própria extinção. Também não terão qualquer lugar especial no inferno, sinônimo de mal é mentira. Portanto os #GlobalistaSatanistas são meros fantoches do #Diabo enganador, tão submissos quanto o Escravo da Cara Inchada…
Interessante também enxergar que o livre arbítrio é uma condição obrigatória para independência da criação (anjo e ser humano). Todos somos livres para escolher entre o bem e o mal, se iremos ser escravos de #Deus ou escravos do Diabo. Se assim não fosse, inexistiria criação pois seríamos mera extensão da consciência do #Criador, em outras palavras: para que exista uma criação, essa deve ter a capacidade de decisão de forma independente, o chamado livre arbítrio.
Com base nisso, temos que não cabe à nos fazer qualquer revolução, tudo está normal, a luta entre o bem e o mal sempre irá existir pois um não existe sem o outro. Nos cabe apenas escolher o lado. Nesse contexto, tenho a seguinte mensagem destinada à você para encerrar o presente Textículo Anarco-Capitalista-Cristão:
------ > Se você for um ANARCO-CAPITALISTA-CRISTÃO passe esta palavra à diante para que a verdade atinja o maior número de ignorantes inconscientes possível;
------ > Se você for um GLOBALISTA SATANISTA, vai viver sua vida, desfrutar da própria fortuna e pare de ser fantoche o Diabo, mentiram para você: não terá qualquer lugar especial quando morrer;
------ > Se você for um ESCRAVO DA CARA INCHADA e não entendeu o que eu disse, por favor me pergunte ou debata comigo, terei o prazer em lhe ajudar a enxergar a verdade. Pare de trabalhar por dinheiro fiduciário, passe a aceitar #Monero e #Bitcoin em troca do seu trabalho, pois isso é o único jeito de sermos financeiramente livres, se tiver alguma dúvida sobre #criptomoedas me pergunte e terei o prazer e ensinar. Se ainda assim você se recusa a enxergar a verdade exposta aqui, por favor aceite #Monero e #Bitcoin quando for dar o seu cú. Ou melhor, cometa suicídio, já que você é um câncer no planeta, salve a natureza.
(Davi Pinheiro)
¹ - https://davipinheiro.com/teoria-da-conspiracao-o-fluor-na-agua-e-usado-para-controlar-mentes-revista-super-interessante-editora-abril/
² - https://davipinheiro.com/qual-o-sentido-da-vida/
³ - https://davipinheiro.com/entendendo-as-referencias-cruzadas-do-pensamento/
PREZADOS AMIGOS, DIVULGUEM ESTE ARTIGO. ABAIXO SEGUE A LISTA DOS 500 BRASILEIROS MAIS ATIVOS NO NOSTR NOS ÚLTIMOS MESES PARA TODOS SEGUIREM-SE ENTRE SI E FORTALECER NOSSA COMUNIDADE DE LÍNGUA BRASILEIRA (se você não estiver na lista interaja para ser adicionado):
npub1u2e0qzjsjw9suxcdkeqrydr07xzsyx8mzp469augc0a29aeasfdq8fx67q npub1xt25e4pakq6x4w44p9kw2vlfwv4zpc9hg7xsnrq53hl0za4ag2qs09cwcs npub17hgdpn9xnt5zyxlx8pz0uuus8d23pxwr9a5vq96nw5nawx20zxnsj6fym6 npub1arnth7tuxw060c74adaf08jam6kttn24wfdse9wyg2c7waycwezqszr2mz npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw npub10q0axre6n3ew64pen99x0qkrh70yxfx6w3grwvkhk4kz9dp8m3ssltvs6f npub1sf2se74xlzf7f7clm3dg28npaxghdy6pguzpsut30fjpwuaxrxcsrnhr57 npub19ychr8yknmje69r645sgd8j0epx2rdgdyl7feagcnmrwkaedzffqtrcznl npub1k86zp0778x7cjng50et5z76xdwxy0tgfn5amnrwrd6mda8uln4lq78ua23 npub13src792wxm8nrhqzu555uxuktfffzcqx78s3pc9zefcdjgwvm3pqsddz4j npub1uw04lzuqx42gk0xc4m8advfmuqlz8nv7dqpuyq4gcv8r304lwvnq2m5ew2 npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr npub1nkenffr9eslkzplds3lwcz7xeq67w6a9qcjlfsvspj7tnhuq3kgsram48g npub1w66drr2qta67gyt7la6fgglsdvk3xx3nndsz4k5wfcal8jq0ze7sqcxdpd npub12xq6exra99hg6tuefx3yysszqudaljvy6eyxqz8tpt7038gpaqus7lfuyy npub17tvf04z759dsyecdtmk70tevla7vua9e3sr88lgnl7put97764zq708q0m npub1rzajeq88urk58nh0n7gqknr2agrx34xu4en0k8hm43fl8h2khp6sk0v3y4 npub1yspe4ly5p9dlfv4vevm0evpag8ljkaay3x3clj8gtvxlsvpwrrrs6h47mx npub107a0nwr3lsj9kdy3jdq570jzcv95y0qzuuhrvcgrpsnq2h4xsclqzy7v4g npub14reqsqss7wp06k390a547pkqrlc0w6uzelm9gpwxze7p8z8x3awsuthvzz npub18fh6flnjt9aa3jlnp5k3kd9zr6v5mlpeczhdx4qheytfyyqfpe7s2y0lzm npub1lafcm7zm35l9q06mnaqk5ykt2530ylnwm5j8xaykflppfstv6vysxg4ryf npub1s00wyzkfrjcclawx225k7wrxd74369vxdcdhy88j89yhrxssfclqulxf93 npub1rmq4kl4dfvp4kt937f9mz60ywkwv467585vnesm3ctqz9krkksrqg4ran0 npub1d7r5su48a8m5k389fd6rwy9cvhlyycmg3pl2g60q5zmgvmr3xreq098mu2 npub1r8lsve0d5yezxq52fjj90kwz76xcweyxlx9uwhsrpd6gt7uk4edscl4fdr npub19ljjj23d7fgy0gujlnh26a293p6uwawrrnpg7jlqfnhnard322gssd2rnj npub1u484zct2rxyknscgnnxrwpuk3f2j679x8tdysvxh659whv99g35saq9xjt npub1gpd868cejawju35epkayavfkqfuykt3820xe678m2vqfqj8v7ges2t4umk npub172fwxt8nnauv2c6leevl0rq4mk87c5vu4mm4fqef58xt390jqxfs6ua7vz npub1gmdrkx4lgwzyqr6krqyykg9r2kpasftuu2x98ncvs9xz9cjhfgcsxns0xz npub1sfzc94dhlkrj6m9tdkle4glyazhtajjsj9qhjv279an06nr74uvqzka6js npub18rdvxdw773852gyl4kjkr5xmg44p9l0jywdk6cq8axl3k9yh59fsu3g8aj npub167h7xtt7tkfvr9mn9d09s4u6r4l0y7rr355jpjg55lg4mpdghsasa9c47v npub1q4qjda5zm33743dd4mewnx6j049hgry7ls4nvh54clcnax3wsnzqv7c5lw npub1mjckw2qsqemdnhz7ul63vpcd79fmar49r8y7fh0tffva767yx07qq68xkn npub1ry2uv7qwu840qx4fg38zzfrl6dfgaudn6d8s7trpf3sj8nx0vaaquj5qrj npub1zqw2ymcy9txda2wzuka7yx6vlyvuwe7k2pldxpxxx660nhf65tusxzdcp6 npub1fjr0qa7rdhll7cfpgdcsz5nry2gy92u7a8gr0ku390n69865ec0qxwcral npub1wc4rc9wxl2gfzxl384g0cw3f79nrms0sfdpe02y7aasy7c3we4sqd0qywr npub19x5l76266vfen827fudaampuuupkejg9vls88hld8nv4w4sq59lsqlal37 npub1gc24vefdu60d3e3yxg8mhu52hxxpcykesk85y8mez8llj23kpehszdmu3j npub1u9ja9ymqmaw7mn9tnmrsnpx0f9j6hs59kxd9de363jvadjamzd9qg3ek4k npub1lzt7pmhvg7hl23emv22g4d7cs9jyglkqpr7lf3n8rcz0evkacg2s6n4jjf npub1p22hyejtr60rdrmjvql5k8fyv8lkq8exzw5mkkx3qcwqcu6979aqvhpqlq npub15p6p9l5upa0y0aj5nwf7lnud2regh00az9u4a4fmgyh8ukyue8kq7xuzp7 npub187dlu8g04kk8adc309vwn3lxsj63fmaty5vmdyrsvzx2fcxg70pqfszj4z npub1adfs8z9rlk6dzwm44522ge0gf367t6s6x30nrulp0xq6wsglyxssxqwyva npub1wqh4j2lvkd0fz342he0jr2d8eqrjwlqsv42azw6utqnpkrjv72xqylx32z npub1n9e2cy50jk900hdzvxt4cjhn80qwzxuer93aylhfdc76gwksr2lsqt36ww npub1styn4qvw4h4s92pcntrffm5dhe889h3hanwjpv66r4ue7gd3xutqk9hpc6 npub157v53ahyyxh4mp38v363chz9lrrw8um9m0tyhqzjujz8m4pmr42s9sk9u8 npub1alq86fku99p0rgq6s0cwwe9lsa8vdvu4d6r7d6j6cyuysf2r76hsh9tt37 npub18cvuxxvd2a6gt76etnte5vtws7a5a4xeqgt03qcs0u46nfws0vzskrnwu9 npub1mlu4qvm8j7gqamukz98l832ghgktyj0whqrxfx89625m3p30haqq5racjk npub1l8tlpvn3kka3nm2qpk96amsuy2kr5kl9eusd54fpn3yjnefrnpaq2j5t9v npub1jtnuszgjayga0pzvm3t7z9pantcnyxzacu30mhvw4dk0lkkvhxrsgvfgw5 npub1z73hklrdpa0n5z663mvnu0afxhlegpt5exmkg9u0nmd32ktqs7fq3prv27 npub1tshn5e5h0ud3l6vegwrce2er2tuhxangx4yvx4q04uheznxxgp6qg9dx2n npub136aeqeuum2t8cjgfnpxwfkgf5e8fd95h39uqkenrr6u0yl3upg9skvkfq8 npub1pkjyqg0am9qyjwg772ue4hhshaf6gwgz4psnptlg9v8lk6st2naqct3ll5 npub1kvzyrn6zvvdh9jnvfzc6e86s0zpntvg0e9f0v340e59u2rut99zsuq9fl9 npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 npub1cajs9cz6r43rmn0y8v8cgeuuj2lfhftvxcq05f8efc22hr5fnwmshx0pvw npub1uu0qk8f7xv7egc6tf9kk3mkx99u2leldgzz0trl77uymvv8n8ahqtd6309 npub1t8a7uumfmam38kal4xaakzyjccht4y5jxfs4cmlj0p768pxtwu8skh56yu npub10wlfumja930vzz4jhh9vc6t3wy8ay7thg8mt9qcptlp5leqfmazqn79ee9 npub1tx8wamjvhaqme29rujkd4v978ck8d3ud7gxa9zzqtjftpfn9p5vs27a2lg npub1e5pneqe2je07e5sk00g8urqa66eljg74t4llv4htp6vq5f8kv2zsqrtway npub1nk7gygwkcfpf9hdjhkgyqszcgwyzmcrqhd9tr7zzczkm5ga79xusmm5qjt npub1p3pna34zku4fqe9mzyvhhffladjjxcug7jn20wm5rnccpjezn4ks0zaw4u npub1j4vyl5kadajpgxh2wrnfk2wvg25jhnv78s0mrs6ckuhft9uzqe7s9wpcgc npub1hfg3tsmmp7g3u5cw6mzg0n9andehmgel6jug486eppsr0rqx4a3qlp7yfm npub1zks89kfxmxv0s4sa7rj8yyd6ld8ncsqusm993678vq9ut73hn7uqhmecsf npub1hzt3p8ap8s4nnqjhha37z5q3jdc9lfg90js0crmg8u5lncnaqpzsdn75p5 npub12em9q547gfga2tkhuzc65ufrn5h9ndu270d7xnh0nkcz2gtvq4sqwutpy3 npub12fh76ppgs5g2srtvgewe9fprdsk2y6g42wf0sg2y0ucjxqq9l0dsy5n8wl npub1arjgv76ld978cya3k6xz24nuxkuezuqrsmy73x0gaxdlu7pxv4lq8npp2g npub1zpmtwh0esa4esnc4p6rn5vhx7wcfw8z0ky8nzczj6k46drsmm47s0zzlyh npub156zse25dzgt65kq472nfkfpwgqvf6vuw8ur0s0ny7zmzw4xqd68q3p4sem npub1pwyy6rwh9smlurdmfg7yy2lce43jlv9ac7l9zay723dyfx4m649ql85u04 npub13j4jtgrm0dtsfzecx4khzz5a8ykgdd374qewewj0ksfmenps67lqz2yr8a npub1dmdlkhqnzmde0ultsq72hnn8h6gjfrkfeud4hecjg8fg8pugzctsjwqas0 npub1yqq7mwccr6wv7vmhehgh4n9kwn55r9gneydhdu6249pntguacegsjgwevp npub1u79u7zxlz2flmwpdt59xsvv5syreavzdyu9llkg07swtf24a4ayq5g0uud npub1eezyd5p7n9vse3yv5k8vh068dutpjf7d9zuk6azegeh5ypvp270qqr8fam npub1s0p3y6rvmt5m6jf6zt96kl0c80x0fy396d8h3cvtsxpqq7lf7wwsgw780n npub1kcf4p6e8k0rkjtaaghu765647z58qu0wfpgxnqptlwg2pm30skzsm2mct0 npub10uqpae32d6t4xhcgmzkc5gkna3hf9xclpzf3q6kfusz5q8j5ruqs5tdemg npub1jldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsfxfunp npub1ksp960nd2vhxxp4lw7unnhujy6mknd0mpw2sh7xuj4m963a2u03qw776l8 npub188qkhpvqhne68rwu878jta5a8uh3vl4mcmfp44nppydfz0td9tqqa5h3cm npub1e008u7wmf0gppsnzupclhzh4mexp90addmdu0wu9glyk0y6msvxskyd3yq npub1crtd3zn3ek0cwne036s0xfqgs6ywuutqdcwxl5k4csv57jsmlgfsjq9039 npub1u4r4hx3y820p8g00u65tpggk2rd5qkd0d3ukt2yvgwyhcd0qvymqweyx75 npub18e7t2damcrfe60empcnye5z896wf9fk478rgrdcawvv23hqtd8es3yg772 npub1s5uqfqur0jlnp9z32ag90e9p5y60z0e8ruryun6u8gy9c38s7caqqqjxvt npub1q9fawsk02d7ffc47l92peuasy9q23ganvs00aqfagxz9rgk5g3usy92n3g npub18qhe55gump3d8ff2xzugpeaxkq6gfc498hr6at2jlsert0h9qkvqquqmve npub1cj9w34dn6nyazvhtq9srms5rf9rj4tapmqlwc5d5k3cwk34vy8dqewkvj6 npub1wvkx5ckpcxmxvc9wd0q576qssle3ed40c4z5rpetwy8fqssq8k3qdhh3yl npub1wnpc03cvexrv7tqnz4amk5zpyxw30nat3xav8nna89j92h25q53sls0g5w npub1938qus3z7jxs4u5x6gpyf7pwavnvnvrhmlfv2jqryy43qf0mdgpqlrtyfq npub1gnvha9zemx47e3paehu59ssqjkkpkc0n6ugdufmkl9ahgd3qhajs6mfs4m npub1cha5p8ytujflljhet2k34sctnqyl3n5w74wnuy7c6dvyv870twas9xnugj npub1h4d7986rjexvgaqsv8zm4s88dekkacs9uadtad6zp8n38nkdszysj45nmc npub1wcuv2wqn3uypzx7f98vavt2gqz4f4qkzm28fgj4qpwgj3yfjghks0patgl npub14hq5lgadtyy9dhvtszq46dnl0s0xwdddqr7e32rdqqhma8a4xhsspxjjzu npub17rzgm20v9hf4m2hemlau5fzepyanwd5h3zxc0wkwq7y38s3g8uqs49lrut npub1l5sgjcjruwec2y2lxd23vj34qe2kkxyqnact76tsq5kzdtcmke0s4cz0uu npub1ylw08gevzgvwasypcs2lvmssfqyt46xzgul7lwvkssm76ehgq47qrn4xxk npub13t2th7tr0uxwc8mfkkr5dqmfrg5hmmdfnfjfhs4z2xal9z6hpe9q6xn9ph npub1239p46pv99lt94yfzu4xkh4u3vqr2k7rnmcc8zz64p6m8g0mva8qcxr0hj npub1r2eehghv6syvdhezrlln25fnz90clgdkcagqw87c9r735zlnhuaq8dpvwp npub1sd5wp8ufsttwk3c575gnakufgaeg3x4f4r5d84pun9n09yr7zq8s735ezh npub18txjwp7dj9hjwk972c32sj5xmngnutguvtg2r66a3g5rgw2s88xq3799uq npub1247x2zmsp8e766cy39gkuzywfq6ea89wd6sgvuh8lywrrvzvdqtsv9573z npub1mu2tx4ue4yt7n7pymcql3agslnx0zeyt34zmmfex2g07k6ymtksq7hansc npub152wtu2y9a5wlz74v88ahls2xq0g493gz5jx0wat9vfgxqzjfzl6qdazlty npub18yyc9l68tk6zsq63wmnzf3862l3xfckds38tq44egwl5l4g0nqeszhj50p npub15rdytrwdsc62qmvsc28xhzdxs5u35utlexg3tc3mtzm23ka4hzmsthe64f npub13je2r5t0s4uszds4lc5e87n77xngluwkjt0hesduvch0vk206gcsa0d03t npub10jjcalyj6a67qfxrax2mwpmsnrlles6qhk23j0dyc76h27gag05syya4qn npub155kdyaltpxaek29wkeza9prkr0t398ayn24wlp6pg68z57s8l67qka6ly8 npub1uk5ne4u0ey8s8tg8czceg70yw9jlzvk74y804wd3vaa3ncm5l9tsl2cjqc npub1q09ysz8xhfe0x0n2y77u6xem9whtsk5hgswz7s0lrj9znn8eksqqzzpsyy npub1rm8uwmhs7s9n3jqzzd92mwwgr8gca4p9x0u8vu8m5n5eppqj88fstspqh6 npub1e8antmtxy0vs2pjd6kah99lpy44ztads4m0udpf07vauvr7larzsf76w9j npub1e0ngk7s4nygt46cpmdrc63f3mfgjcp8edxh0f8vpp6zd5hwax4qq0mykcp npub1rksqdj6tpjx4ddcyc9v3jw458u9y83hk789jqy2j8h58jusv0mgscx389d npub1q2f2nlq5kxthrcsww2zmytyzal325gsvrv0aeg8fqj54z4kyrxgsylesz9 npub100t4hmfxs467q3cwqd5f3sej9zhm2edd3kcn57hj0kag3n49geusm5zt87 npub13et8ay8ny99mygd8ymznczusrhfrhhzzs8jdlep9q98r8uway9asl62v4r npub1qeydnlt70d29q3axc3h5v3spfntl74jukw9r6zy9s8ms6a82mupqgnr2y5 npub1n9hr9s73atxmjm0muz45ghwutvf2kc00lq2fa58rm9y80mpdqxmq73mdc0 npub145cgkka2733cmxn86khjshwyxz6ahgjp0ek9gp3fc2k7y3penkqq45ccpu npub1z24p8ghllrl4jxyw8juggm3cfrpn8vvfxxsjzjj4tuaz0qfkeqkstnk760 npub1h6mtmjw2au827vs99zlykn0tdhm3hpyffjgnaq8fsvjzem430hesd3zw5p npub13u9wq6td5qvj2dajmkjplz0ytvt4j7zvuyjg6kl9xqt5wznqghvqrptnlq npub1x7j0x34k2cguw8qk07hlgtpcdd22k0p4nfmuy3sk53mw7n5p4dws97mh3q npub1rlgz4nrqjvy7skd640reu9f9ckv5gzg4dmheeuq4u9dux42t7lys88svf3 npub1j5peadcc3as7ht6tszt47z2z3rec5py39y23cemrs47czyfxddnsskqnav npub1ymjhm0kxwldyx3f599d0cjvpcwdyfw7rmruyn8m2qnfhlu8mn4mspdwhqk npub1gaqn62wk22gesxfczv4q30kg3e2f6cqzdml645rwdyas6uaz3wdqexzlgl npub1z9vh6x3h5d99wvrjxw036ehg27cc37837f7dz4lr933euzu4pt3qn5874u npub1axy5sgkdz50hqrt266cl95qp7e5n9q6qmxguj0ry6mhpmu23t80s9nvqug npub1yvjmvxh2jx07m945mf2lu4j5kswr0d63n0w6cjddj3vpkw4unp4qjarngj npub1993fqzsar7lydy6lc8sztj5pxzeckttsf7m7dzjpcfvuu44uavksdks9p7 npub16s7exzaa4le983mjvnw7jfatum0jfxqtpfk2uqdel3c4q97uqznst6hyar npub15mptsgelg8rn5tjw5ltmdy8vmglws4fulr0kaghpv7t2jj8qzjks2mecva npub1yjvs58t4tgnmn98m4y2s64jferzv77p037zmwed8wzdful29a6esyajtwa npub1ctmkhtvw7rwk425sm4mqx6ak86aama7c6z8yxczfhgkwfv2fq7xq4mcr38 npub1f9jys8kppch9sceykam7p7uecpyam7ajm87wrgnndhjtj6jlp5vqe7y207 npub1k67tmzt34d6klra3ykrhkpvu0y8g8rlzv0egpgrry0xxcauxqzestwyz59 npub1x49ytzhkslwq6680jqsng7dy79vh8alsqpapr73m3akn0qerhj3ql7s2w3 npub1m2us7cgdufhg30yw6kawugwt5slp8kh9ed88dn7q5gtq5y20f95s9s25vt npub13sdds5pcp344k5mhfch7ltc4a8737uxqw9c47wfe08kkrnm3rhssm60637 npub1qfamw8qmsekxxu8pj5kfa960sgwsc86wys84gqxkzkzld8e6hk3qtvv7kq npub1tsxemx456uadxs4nsqenmquvws53290eg2gejrhvx7w965c779mslf7pds npub1ymxlmrd2yd59g7x4uejzsgmn4xlglu0schl39m2mjx5nzfzl2hcs73hn6g npub1qd05jn0jxlzplx33xjtzstvgeus9dk9405kwqf79vu00czwyvghqf08md5 npub1n5sl69j0w6c79tut2anqf69tkfevr065kzjt4n2rv2gres3q45ysmnj5nc npub10qjw7zw8m6yq4sr53watq4u8y47eef28jsyd0tmyhyfy4pjhntgqva7d9t npub1k6n2ghwu0afld0tnl2p43q7wtu2u9hln6e89ruv9a2y5deej06dskek6xy npub1ax4szvq26em2klfqj6hr38009x6k6m7nhe2z7mq0xs4xszetxe2s6964q4 npub1645w5cevetsz2364mss575panjuaa5ffh89ax4tp6u7x0tr2xlhsc29g25 npub1ys9j7sws8vccfwjctlqu7kx2hlfmkcxmjxmdttfl29edxv6xgelqkaffe4 npub1h4fnky04vkfkyac8shhmy0fwkrhuha65c5ec2ggvv03zv7pm64ls9x5vag npub1ueenpne5qhkvr4l9rw3c2ls2f6lgm7gh7f7ssl73l5yqt7um6uwsyatgml npub1krcpj4r4gp28vswfc4gztr5gku58c2eyhll47tyz5y2hhl6jyjwqduv9mr npub125nh0nkr0czuzkpjkqvjwc7mxuuvusr4n7a3kthjyfeer70eac0qpy5lsx npub1qcr5atkc2u04wx80pdyfnnwrttrw0taaz8hst3qt573j44yzxcvqkl339x npub1x96qzppsymujfyzn4dmkl08qgcr3aw7f2tt0xlmgyudfaggeq7zsh0yghv npub1l56z85xvaplh3033l8h2x9thypamu0d2hyqnxkw0ujuntqm8asaqh99sza npub1wh30wunfpkezx5s7edqu9g0s0raeetf5dgthzm0zw7sk8wqygmjqqfljgh npub1kqd90mglkp0ltmc5eacd0claqvnayaklkvzkdhx7x84w9uavplxszvrlwd npub1ly9cmpxs5kyrhnc946rlxmyj397pvcp3606zgvh3kvukmqveaxmqgwdwct npub1papvv8nyg68m73wae3u25lvxw5wfz2htpzk7j85z8yng3xqqvntqc5n9vf npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 npub16y2de3wvy2xgj3238r8h8g96hwtqsfm72sxcfw2t4c5xfjwnm4ms5y8uyd npub1ln4q6lzdwzxnvuv0a2gnfcxrfhwyfpcrp8tj5a403mwptq8r8clsq2znta npub1e0jya9z5wu68dzgxqeg7gal9ytgwvr63evtchv4a4wr8u5dcvs6s6vfwgm npub158dcjddhtq29ezyd3j5qyc70xyzyzujg02kcrla706fs52zcahaszql9ha npub1gayzxecnek73hm695d8tu94n2q3xnlucu9gwr2zqnql090rkautqq7ne7s npub1hvtyspm7n7nea59lhe2fdvwd0rqw7de20fl365wklsg4jsmrpwrqe6yaeh npub1hsr44v6satu5qkjcua36u8a8ng7fhh9ljv8mmnhvkf0a6407nhtq2k4ths npub18s8ym4ajt3rfwa0yn39m70k603j8a7wkhylhewzcjhtfheu8dnrqzwv677 npub1zdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2s4p88cz npub1xq0pc34qq99yawjxl7rsqx7wgs4x3088tkwwle5kz3jqwf0ggyuqxx5et7 npub1dgx9jmq5sn4w96qnrgps7f5egjfpu5npnswazsaq98ryafkdjucshaaej8 npub1s6ms8dqxc4s2e6yawg20lkrpk9dxazz9qsaernpxndc2axua26rsva6lha npub19rxp2h2c96h9y79nhsu8p9yn4f79k8q76z40v8x6g0j8mcmex7jsu4whlq npub1fnvuz4rad0sc6ueflq33kj242hqe65da40zug7u5nryvjdeg0xqsl4y86t npub1e2d8f64kaxepfqncve7gy72vam3h66vmfwaqnalekv8zmh3qar4sz34p0k npub1krahyq9me8aglq54cfffylgnj0sy0q02emv9zr4csc94kz3qajxsmwu7lj npub1qn8rpsky3t8v5dn30rycfwpktwclm544nlef98tg23drgk022a4qtzekjd npub14p529xk3dmtyqp25slasulxx5p6yu2js6lz0072qu77c54cz6pesq2qsuv npub1mxlypddvhxdatdjdh2twejz7d8lkf90350f2zhzcunhmu7pgw9yq9033ss npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz npub160mrpl505fmse22eue6v23k4u4z0yyw37hpf3j73z97jtq50rapqx9q0ac npub1ve32zawsazgn9ukyr0trw4u5zk5z9ravgq9g06ml4gfzuvuzrvyq2mfzr3 npub1c0dysexhhd09e65rvmeecx0dpn6c7lq4yp99f3h4ktnr4vvrez5ql3h0y0 npub1758748kzgkp5vrt2u8vdgx462kt9f5p2x84xwljm4svadq9xc84sl9yk27 npub1rg7x6lh3zurejwnhxljdh8td2uhnhucx3jhle565eh7x94aqn03qrwrm9s npub14nefrmsdvn72qq5f3zqpdsh068ufk02e3t79ukga457p0v796chq7xrakx npub1l04nl239dn9wps24a753xq38h3wtlaa7vxmqatf9y0g6vzae6u0s27vwl8 npub1mezldzxnv6lszd7vlh60k0cqgxca7s08x5akyvln9fhz58jyfzsscyepuv npub1a76u90rr5tfdn9vf3sg574g0vftz4p5vu5r9t57c9atpwt64jkps0h4qya npub18g9zwmrdjcf6mkz7zpavmcx46r3h9ydxv2urwc9kqvha7vzght6swffxry npub12y8v5es4g8ynms5495l448977l25puf39wj9has66f7yg8xkhakqn89g0n npub1gustav0kvwh9zlz22ns7y6utwt3s2747mh5s6ja7v622tl09megq9heczp npub1t62k7smt3nad7s3rzhkrcvzlmheerk8p3qrpjwj32c9lzfmz5ksqaegpck npub1cuvc5stpvpeljeveqlk9u6tp3z3qams2w9r3s72hy0ufxudlz4fqu3x5jv npub1g8henaumhfjngrkpp7g7urz420hdzcx2hnh9grf2r7g3sxtur6es8uucpq npub187c8yedmqmss7fxtzqya4vphfkazl04lvrz7cp5xghhwzjduc4rqkcwd0t npub1vg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsel8885 npub1nkl720g0fuvzt4dqm5xxjet2lnm95z5fv4k3jvgz5jhnvhe2lehs98d9kr npub1l74p0yq6uzce4v4ntvvj9zcx03rc75g8gn0ajsccxzwyunv9m6tqwjlh45 npub1tl2pwveluev0jcmm973x87qt0uy20hxnyrcwefxv3nkv9kpxmzgs5pl9th npub18zhn7vrv94vy26vsf677uyxxvs29t2da492xs3xnxl45sszvh5psw9vpuv npub18z4uprsemsf4tcxdnfc8q2esk36g5rleqp6mw9ealtn2kmv8pxjswswrvz npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk npub1ejp9v82302mth0k3nlanyh4zm4tskvg9yk2hp5fjun0g7uc47n0s0q07vf npub103wzz5eeegcwzrchje02m4rcxqxqtz2rauefhdshmtzd9xjxxdnqm5kd9u npub1k9mx4t56d6jsm658mmnwv7uvxl9edflkelpu4llgwrlc220d9qlqcyhueq npub10x8de2sz6apxnju8wwtqx00sjkeqj22kcjjfajsa9hj77492hkhs4g287f npub1q24ugzmm8ptkyq3gwukkl680kyftmlk3cmqu49x7yy4zuv94a3cqlhw8ld npub13xd3wejhu3xy5hmzgd0ymc9apee7ett6my4xsug5ya0z2f650n4qaf9f8z npub1vxd0dfst8ljvwva2egrpc53ve8ru78v8aaxfpravchkexmfmmu3sqnrs50 npub1nnyqvvr992hn3umzgehppzt49vhm9u4vet9zhzks4wq2a34ehv6qm6wkx8 npub1467z25r4x9xj6xgrgsk6a9gytdy0qp8xuupplxyunzfp5esk2uys4gm0a7 npub1w48530djsgja5d63k27mr8krx3xg63qvrjhczfwqgtmml4kgxw3qpcfwvj npub1ymldfnyvl2u5efjkdlqhpjruhv345qtesj9jf22paxmgj50nfxes3k4wqd npub1mqn5acr09lls33wapadkdf27t9v87h22jf53c473wzpkgld6z7hs72mwzd npub1y7yvamgvwdt6h8skh5yf5phn25yt7c6qcpclgpd0nglsy3f5uu2qu47fad npub1q5jxvccuds9wmpqhr7p770y4ewqcfr2dehqarm5alhm4hpgvrj6qtm2qhm npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x npub1k2teldhmj7d53732ekcs5ta0qpjsj9fhwc2e5ve5wljqpxht5mfstxx3qw npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle npub12xm5ax6rqp3n9n0lwlja22lpfuwc6g63a76p5kdxuszqnn4ut2ssj2k7jn npub170d8w0jjdcjuh70lq5ppr0pcy7cfuxj6hpr00tm4et3v53j8pvrqj0chu7 npub1fs3n5u75kmtfgzzuy5ms5qexchv7kz3altj7e2uzl79ygf2nn0nsv2sdjg npub1y8hsmp2pxadwf09g22zsjla6xu8hu4qttgcwte6kwrqkv70e69zqvtfqyr npub1rtjk5n3cgdepj95wylpy4h6etg2jel3erpn8px9wxys8tuueeeushu5jyg npub1m0lr5fdjrhhwxl7dev4h7c5yvruz2vp949tun5zmulxuktcm0fusy0gg5r npub1ur6emzgy0wrg5xyvtm7khy7a3sttv4jrhpcc3px6mp2z8pkxphwsyy6kg3 npub1efyfeevwrtxnmncs8767p66wxwulm0wd85cszksw6n6uw2qtca6qzfvgyx npub154efugcrxmttmnp5cfxpnhgwglvxswsxh6d84jcj0a865a7s4jgsrrun7f npub16erzcypvccc08a6z6l6gw830zj7m743ah3gtc85rcjhfqmqjccksce7jej npub1jpxn8d3x0p8cdxvxzafpcpqwsfnvgntywhgne9w085fzu2mjjw7qldgdg0 npub165llzjv9ux2s3ezx5k6l4mzhvly9n8gyzhx5p7v4499heee4w4fsvhnu5w npub1mcgm982av268z989lv9h23f0w733wxecqhjjw5l4dvzdjgl0gu8sdss2v5 npub1z3adf0m2c2mul0vtpru4f5uzghn746xyf2udxv63de2ckcmg697qqmjnvn npub1520n32u3r68qtlw5nykxegtxkdt09rpk7h52laectc4qvdcde34s2u9qsw npub122fgydglyvhzr753e0l6k092x8h5k4ev0g9v90lpgje597srk6gs420cc3 npub1xngvle6vzkusezsxs35kgulf6s0usjxej3qvs4kczezy6q0war5sxmumdn npub16umw99z8jm5r55neprqmvlrsqzwklernxnczam2xu5q5fwjaj2kqttgcvd npub12aa8fnjcp84epqtmhtnc4w2fah9tfyrews76nd8hqltpedf4l75s5x6lg8 npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju npub1l8qw5av3039qhefprytlm7fg8kyyc0luy8yk2prk2l8wc38gf86qzw7nnm npub1nwrrty92erpe8th9wv4u9l9f20pqqh872kwjmejc6mu9hfnzumfqk5fua4 npub13qhkp54f8w0vgql3lqukvk9pduhef099hx0azmzupuhxevjayy9qsfg266 npub12jyfh0sy02ku5p3zg6hhfvph4zphl3y5jqfk9skaqa59z7pmfh0qqyn9mn npub1t8pha5vxkct4mlhskzz4pshvwznsma5646nmzz5gcth06mth0hfsuleyrc npub17ptx9z8mnyw2vd8as0nyh40gtvyydufme8peweh72ax9kpxrqzxqmnsxpq npub1lzh4pgufkx4xq675fujac9mmxs5zmf8ffucetgp02vep5eae3acqwez9kx npub1gnrfjvjmu3jucpmkvj6ptmdxcj766hwcrekjeuzlwtcqrqmyszvs3pr7lj npub1gazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsmfe0a3 npub1xc5c7srsajcem7s8x0sndqsu6yqe36xzu2kdnu0cky353x6tkreqx4lsgg npub17kytlyvd28tvpz9u8z2mrr3pq503pmvtv46qskjccfch9vwqhadsregenj npub1vcq8nv3lctr8ctk2dp7h3e0su4f7gklgx4dlm2375l6u69hvuh6syj3d9l npub1v6xa5avwqkyqwzmfhu0ul4cm892txq4jnxmxsvgt5pnralqj9upsnmsnu4 npub1m986jhedeq7xxe8ukxc3dqwqzcz0ue9fra6m0t2zpvp8yezkeexscz7ena npub1yftkt6shs2fls0djxzww2nc7t96x6uxq490qw860ssfda755pc0q6emnz3 npub1rl5s8caaq8vsjfhxnmmmguxryug2f2has0kg5gzedepzle8quncqn9patu npub1ucsl4dgwslalsgje4es7jefqexlsf678wrhvu8q59e3djzgl7krqf2hnad npub1hvzkl03x7z8fews3cc5h99mxtze83rwxunre2687hcdy0zqn0cssnszrkx npub1q884swxynxp5dt467g0v3gk6t89tgd3r90pgdwcvxtlnjf2l3jtswgwvcc npub169jj88ry88e7f6cmcngcz8mu67ak6q6u2pgtcae6wa4ju00z8gts8hac60 npub1ahfkmjuzqcngqule5c4eq3cucxd65dpkp0sguzzsr2duxwlx9guq86x8en npub14xcy30kssvtpj29f40rk2kk5d2heumaxnz77ahkuejwepqngy9nsewgz0e npub13jpmntdr2k04x76f0c76syf3za42esn2nnd6kumc2cwyltmtje0se6mvqj npub1us9tzl0zc0ggfqw6348wyctck7mmh34w0hpn2rs236akusx7ltjq5s8gtq npub1eykpylvevzagq8jm8jutf2pmjnnelmyuc56a66v9g7ttcth5kfsq6vllrz npub14r294afl5jqgvj4hlfpj3dvyxenxh4vuhepn68zdurcas5r5xy2q5ydufe npub14n46ruge3mmv72xeyjw5zl4cec6dykrme78plmm0zmpnclcptqzq7kct5u npub1yvw87p6d2rmd3lqdp3c6npjhunpra9huxnl8c30rxjw8tnwd292s3jusa9 npub10agmu2vwed988jdxs8cewppw5jvk0xtvh9vdyguttuhugu930fdsdcsdp4 npub1gyu3h0kmqmecf6044q5r88vu5vtf5u6rekh9yazxrtejfexct0lq5zpudc npub1kstv7m2flm703dmufltz4l4lkm3pptl0zdqjvkx8ap3aagttkd4s8d5pa8 npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk npub1mlf37lk424pxrstpdhxqp04v637kjyashaj4ea73gfz86yr4gdzq3mjtav npub177xlld4katf3aardam7qpu88l0ttvyde739qcvjdjynweqnncuqqvxmfdc npub1ykfmyfwtanmhvp06wn3ggwm0gl0v5v2ftmnkmhz6swl2x4ur9udq7ld2fy npub1a5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqk7glwn npub19gskj4eqgjgjrwjw5zhu9rddnrqfq59slm5fa5a9crun9wm2qlyqccyh6h npub1ujxurwzpfrxsprf0urqfxpp0qpm2yrpneat4udg7e0v560nzw3asml0d9z npub1ep6wcd256kvsdxey2ylycrpvmf9wnsqvg46kzqrhuw2akxj020kqvkq9hc npub1pumdyz7qfu0suamv4nrl0vcg574dtl5mwazva6nyjxhpwc4ccxxqca3ane npub147d47sem878zwqln7k9y8y3273v29ase4r7lk5yeta62xk3t739qu5n8zd npub18jzu9qrrmhhwk57zqhfffymy7hq8vrncxnvl0sutu5y2lhr456sssgsesp npub1wmnvcv3ycqmtfsysmrnkyckja8dc9nt5sgf60rrel339v8chtgnq4p5w26 npub1tc07sk67d2rs8x90fpg9x727ulzknw7xjyk4lds7pkzauw2tqntqpzs9dq npub15h8pr8t0l6ya275k42cwwhrfu6z6vk6qydkdn55p6wn4f424s2qsasdczc npub1l0j7srkgmdwy8839st2hn8f9utlgh9vtrm04jksh8tsu32h5vpms9k7zqa npub1p9auvqfn3dtrjnwkhxdvvk6xn3tt8aa2uv4dh2af42nv9z8nh0msrjvmhp npub1lnjp9d8xz5zguufe257vtx59kgjuxxufv0fjnplwcfncvpc7vahscraxv3 npub1mhp87q9axdlwh9ac3p7drg9z764mxwe27xvxm7x704l9dykfy9xqrgmxdq npub1253ehcqxctt4ps8kjfmhqje965v8gtzn7c6gtq02c3kqvtxmsx4qv9my05 npub1gk0yyk54t6ptq5m7hygy8rvc98pq9zz5uhusz9ht6yxcpmvsr59qg5ptts npub1828ey4s37t3dlwjmgsa05zafvdlsfsa3lu5vlk5cdx0a3zppv7nq987tnk npub1h6h3jwx3fvz9sanmg5yx6rutmggsnz5t09t795yf4jk4dqsfyq3q47kcxr npub1cw2epa68jpmy384t7vn0suvd3mxnk5s02ap6fcwg0x6jqy4lhdpsfg84uq npub172g2zwq6vkerg02urweyt2daa0huavn6ghcr4gxt93lmhvnzan0snuwkc7 npub1awwrv77yu0x9rvuaq55ppntc52rhxt0w9t32zkyw2jszvmgsqnkq2f3lpm npub12p25mnqkunnhup0sk6ky0vvtq5pnkapezx8kh689dv2vl2wnp2vquyfw5s npub106yj5wlntf5els6w5cw3gwmsgh4yu7vs0lrpw4c0uzkq3rqmkkgqg7rgpe npub1a4u7yc39v6fvr48a3skz9gwdzl76hf499mk96x703nzc23mdqq2qe84e0k npub1fc72tcwhr5fhcmcczzld6femwd7d7uhqwjw8rp5w9enxj52xjqxsmpgv04 npub14h5r077z3edgts6wl2me5vk52x5se6nnhry0ldfzua872ggcxw9slkd3fd npub1xlngepdt5qz752x9423gnvj2gk92j55qsdhm7mrtmju7x36pwnxqg4sypx npub1rl9wszqmsqduzjagewq302qfadjy4mt5vw5zvm8xdamvp3d0nm3sr88s7e npub1ayvrrlpygam2ruyx2lhtkvgjc53wjd3vvvs0ysjqh3pwhryaju7qd60eq3 npub143mkh6lvtrha7w7pjw32ujkljc9ell9wpyvd707nahqy0rt62kws4wlyhl npub157rwfe8a4gffdcx5ca56q2qsvpp3z757674lkwca5ud9j9pdcnaqct6p2h npub12z3w5jynqn3pjt73kqz6wkueygrvt57qfwgxy5u5pmn0uqutdwdq5jpd8w npub1zfrc4u0dnph8flpqar5r5lv3gpn7qafhlh35zpcm8e6ex4k24snqhx69js npub1rvww8nakj7rgz59jdqlswdmvjn0cd46q2h4y00wuaquwyn383fysxlpyxt npub12knmfzy88xpc4dhuly50tlhcnar07c4pd3w9pfpd4lnssmwhvtrsgq2ez4 npub1705am22u3tep8vvdwkqex0jm9pazhmqqyxvaqzcnv76m53xed0xqeetuva npub1q0k8epddegnec4kj0j3rew9yel0jsrp82sd2new0zy3m9pcfgqas4r5yp7 npub1fcj3en06ajdm09y3twytsrnd9n7yqayt9e9xuutqdrwnqu85t6nqt7rz5p npub1jvej78jr00s94gdyct9md9x2ljtjr0jhej5c4mm7cejp39dwgu6slkmju6 npub1mp0jgd4gaj5hhw99lfwxufl0k50m398jcneqsp940sjzz32skmzqw5uuat npub13u8pyc0azav54a9gg0py5khrmd8er6ac55kvag72h43r4q8s7nnqsqsy4t npub1ajan43fcllaxc589juls8pef90cgdya0p0en38h55fal42nlgkrsvltfdv npub1pvn0tyrrrv86xpydzq6ppeyyuh3zut263m82emdfmydn37qa6x5qmh8khc npub1pfx4fj43y5j27ywgj02axnyup0eujtk3g6r4ug2n4nvfsa2kpl0qwvtah5 npub1rpx2y7u00jmsvwt8zlkztajmk3e5se89vhnswsz4suuyg4a3fx2ses6lkk npub10jhpwcdsc6mrfs8audcdds2x5txdagru9835f3drthzaumxurduq6esrnm npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r npub1yrffsyxk5hujkpz6mcpwhwkujqmdwswvdp4sqs2ug26zxmly45hsfpn8p0 npub10ua5vjul7d3rvvzg2psvhk36w7gpx8zn8xncqw773l4hnf0pkp4qccymjg npub14fzrwpygf69t0e9snrk2ms7ltn8u4dnvunl6d98zkrgdzf256exqa3j6rj npub1x8vkne5rx99wzup65m7gpmhmgsa80d3dscp8hafrwj70zxzkyexqttjd5x npub1643y7m94wwu30awq5djh7lkqj48evpz944yetgzhssmykkh93zlsz22hhs npub15pkupvdv7hmcjumlrx5yjmcwy2f9fl9fmsa9mx7qjlau8k59rxusq2v0ny npub15wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8css6kt8fs npub1saygqd4rdf8edlm3r45cexr97zndj3254lxyz9dejjlztscvndcqhcky0f npub14neap59th00w9keu9uffpal72dxyex5u7vc8pwsuqrdxes2mkrascnlukg npub1nyzep3atafwfrnq7346dmx7kjhqsrza936rnvnlkv25fzd09gxpqw3gg6v npub1chgzxyqjnvv7ryuf095cswtym37jummaqme42dfez8q25h4l734s9xdl08 npub1gp0cpreej8amtmmd4zn72hvgr4d4tgdhg3vpe0m4yxzqz7skg5eq47jmuc npub10gp3mv09aet40plum7f4pllyc8g8u4thq8mkkwymdcct3schagvq6fuh49 npub143jqpdq583jd7t4ucfkr9wzug9h3904vcng0vymyley0dx43vv8ssk2gc7 npub1z8y57drslgthaefkvya7kmqcdm9c20uutz336j9hp4frkrg32nwq9g4ju8 npub12er2cnsfzc3d5ceggpjazwx9a5cwna4atxslkwe8975lp3fuy6gs6s36tk npub1cpxjrlnhfmcclcsly5c0dvrgvl5nsctzxpp4s9f2nh4qeq50mwsq4089fc npub17dhclpvjmlkhlgkh04sc2296wj0veae79fq8dkwr5efvlz6vt79qgyqztn npub1gm7vxd6yjqsjx49ddqgyflllpjuhduqch79jlp07upsh3uf6q47qsm4xlv npub1d8h26etwdx6ws4afflra7reqwtvjsm7u8zn7jz0w5q0ah4tgx3rsga3axt npub18trgdajss33u25jvk0g2yv6lxr7s7k2dlkkku6eqq7m4hrc6aazshusdhj npub17s290m08ukaz9j3nhyuj5w2zyxtdzdqvrvsgv65c7ckcxshjrxrs6wnfhy npub1jlu3zyj7f2hacdrrmy7jpny9f7nnvuxt2flrasjtmgut90502xqqtsx4rf npub1vwcy6na4rcx6r43fqyxkhzzdvqufctnx06ywvrnajmq9p3mu27yqxy04ch npub1ea35pc7pqg2uvstspd0ljlu09t580qc942n5eevvmkrv6huchffspl8087 npub1jxl2tnvnv9gycsy64aze295c3a529lx5sfmzlktf5lxuw805g5wqew0z0n npub1l885a986vy3sj3watelhdwea74jxhy8688ju4h2c8wz2e94tcd2sl7qjy9 npub1uy7tnhwxsr0tc8eexksandgcct5wtua2xazvl2gfyy5n86p9sdvq7nwdzc npub12wm6zfgan2v2jc5tknkjsj9d64qfk6y4ggu32f9tgnu0mpuz26uqctkvly npub19hvj2zeg7ck8cj2p2az5y0gplllhgzzdu0khu5fhnpfmum5jspeqqcdjej npub1cqykgt4enf0ce9v36kjzugx94l6tp8dd5k8ktfgga9ahgs2mzess82r6sm npub1th77tvx7c3l9qgxql4grcllh9qahyfvz65ruplrf6kh0sfzuya0stmendl npub1w98zr2sevkqle6lmt7u503ewclhzs2cdq94ke4mw7kmpxy2u9y5s6fe9yy npub1c999aq8sl4fmw8an6hfj5lfhuneqc35seffqs6938hxajr2jq6rquyvp6l npub13tnrml3s46xswsk8l2p4tv8cdmnpkvrk4p32828jwce7puefc0kq8jlf2d npub126v86pztd6emjtkwxe8jj8sa8f0m9wcavsd4j0raemdxksegfg3qfaan6r npub1uz9f979gqjj0ymul0kqq79g8gtelwe6rs276jm7qnaffmn545h7suw6nhl npub165h57grx6hjw0grfcw805srfxl53ggcsl3mmhagmp7rg8x80ehasytgw9y npub1re764kr23sa6d2ld6fhukthcwgnwvsrahe92zq42kpdu3lm05sjqwjchtt npub1m0l0harjth9sses5h0r2slf7l4wws4clgt88s6n23ct2kd2xdkusf8nqjj npub1a8w23gjnfv0f0qzjpfeqg7yc5ddf4c8m8jks50l84lrv7h52jhgqq734am npub178p8fw0spjry5824n5wv96rfre8lq4r30ysyctfspzy97n3tl0nqcg5hzj npub1yhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6q9zu2sd npub1h7mp8nd39hzxywqdl28rm2du9j2jhcarmsmakmulm6z7fc4lx6eqqaxh7q npub1dvqg5278etemtvxl59ahcey8cywrcl0krhpu8dt9s70mgwjar3jsqh5ywp npub1dpm87jq8zpgrvq2thr80chmjjrj0tww7q3hx9kq7wpzq2aayqxdq9a76um npub1l506tlst4adydg0tkshynjw6dsk5ukjvpzr67y9vas8v3nzxylssq6p0j5 npub1pe493zu4ax53pthcsfff7uehwppc9w6peashtyu972ey2szdeheqxcfk5k npub1kuxfh7e9fds89qzzzfjrh6c80d46jstqnm2q29wekyykr4mk0zvss3yn27 npub1gwx22vu2yzm8eq95nvvmgvpax04u96gq4r8rgqqf9pgsheu2lz4q429cus npub1n8ahhlw8trcpwkqdcetl5pgqvrxcfvgrtj037zlflrnqymq5f40qhnwpd9 npub1ujr9zwz8h7xtkvp4pn6aslguqvks43h8ej2z2g86snff0h4xxmuqjzcwy7 npub1vm4s0uqkydaqzt44dyt38p5spltl6637sxrfxswmr6k883f5a0ds8taxyl npub1zqvtnvxrdpg5vwh5alpx0m567092m2ltynqxlk004976tgc6syqsg9rcv4 npub1ld5xqfflwy6txghaaef2d4rnyzkvwvz2crncmtvhq93xxsqvzqtqzdx4yp npub1er2xa679095y03xlcmycgg4r93nluqpluye44h0ndxdy6k5uxcdsqwtqkf npub16jde9ylpry7pyau6svgqktdes242ynfk9snfafh8gq3r3fj5xfus44xm32 npub1zqgjtt2ayahsuxzp3cg7h8qwt6ev7phz9x02ktc0gdlwz70n23nsla0sph npub1h9c96qqmcupyvtq30d0xvp97h2cx966gz8n55cqgd24hgzvz047s6hxyd4 npub1h955atshn3faxg5r40p4achtxg3q832h0agjn24sf63tnkg5ezfq0fnr0n npub1ker60jkxmxjmft468v5wzth5757v2end6wzd4xn67jyej8taj4zsyp7tqy npub1ddjzjva20mwp9xals7v0nh3devvjewevkkrqrsglyhnwa59ctswq6kzdys npub1wtvrnst9hus9pvz3m95pusfjzq4z5zly3w4lehulh6xc8dajl60qsrjg5a npub1hl07ukzg0xk7gj6ejr5k5e6gmakt9tnu5r07f543ce6e7sa7dc0qv0kcun npub16dana9qsfpf48ccyqwvl8jlw6k5u8adly9ph76z0ftrs88lf7vtsrzlu5s npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg npub1saessfmtu5xwnwh60e0rwnj0e067npv6yxgc7d96algqqart056s5gkuqh npub1lylzl87mst3swjtj97j8aajyfmaqctaylgw9et5agyp3rl42y5as87k86d npub1z324cpkjv9ay5fanw7rex5847dy7h3ndvaej2hy2vmc7r8c35res3x2kje npub13zlwh0n00pja6dkw6htamu6sl8668hpgr45y5lnmnmvt92g3laysqqsatw npub1u2ukfds6k42qwufd9xd5l535lxt3g2zet9rmmlhagtjxg6t8e6asmx0w6c npub1ezeah83hkpsguazn70rmkmfwh864wdejv7h7q7tsuq46wquelelqu8fr7h npub1pvuu3ms6vlu7lmysggjuuz6ctsuyjdmy3uhlywg7jxdewvtr7rgqakhnsl npub1vny9x6jl2cmvhva8m9gq05z0vf2tar3vy72503hvuru0pxtnz2vq9v0fyg npub1s9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqsd753t npub1qvwpwvdvq4hckarg9ekldnvzza0shka85fk24uuh606vhg4l2grsuw808l npub15ksrns0fw4l8heral0hst3szmvpka67a94xxjcm3ddlpx7hcn7eqhwfkrd npub1zkrdvkmnx0sv7d8hyd0ma22lfvvphhd33d0qs3sg7lrtrv0xdv9sa7gy52 npub1nknxhegrddacazt8sax6cr2h0r9sht6ajmq3s82vjhg54ey2rfhsumhe3c npub107swly8y0ert2upsevqk8fqw9tvacfvuygw55qcv4s2eav6f0axslhmymt npub1a9a2l7jqqxa9mwrw034lcnuhcsncg905sl03ava49md55t4awewsvvzz87 npub1yudjcmkasasju6znprl3rpyp39xa3uk4g6sfrv3wxestqsehs3eq7z5f8r npub1cy3a6gug0t4jrl8plq393cjjxwtg6cewcuek0n0hkww4h567dnts0ft0dy npub19jxz6jynvhlwzmfyhmn5tzymdff0zuq8jkg2mq268a5045f6favswaxu2q npub1uvx00x8svjwma2zhddwpthyke6zc3rrxqg5gj8mxdjv77zvwmz2qgw603z npub1ewe3r7x8qemdh7v30gndpamgrmu0k6nu4twyt62r6ukvkvmpgkls24272j npub1deexjnst5g52wh9kmqr4hy3wzhh0gspujs2nc6m0l892rzj788uq5gcpq2 npub16qsq63pgxyw5vz6847y9w4cau0fmvhykw7uy04p50u5muulc6kwqn706mz npub12cfje6nl2nuxplcqfvhg7ljt89fmpj0n0fd24zxsukja5qm9wmtqd7y76c npub1nu0yladm9rr6wsz8w3v995gcxl88vqcdnp8uv3zp3xk978d3658s8kvmhm npub1dn5cj3n85c085yqry7wle93uhrqtkf9m2zwqgt8c233js0lt9ugsdr7zzt npub1vudm0xsx4cv3zkvvq7k5836tnkv64q0h7uudnwujr4a4l9zc2p9s0x8url npub12c68tkshmelhtrd7ye5fqg3gwttd33ly7gzxkwh2u4qt008nu7gstf7x0p npub1dc9p7jzjhj86g2uqgltq4qvnpkyfqn9r72kdlddcgyat3j05gnjsgjc8rz npub1dmqa9kg8nke7fc88p760zd8crrqupl4w5lflhgs0jgh4n3slmdjsql67zc npub13q2vzsfemle9cpxj875tz0vcwqe6r8sy05fd62jcd3xuxjeqj6ksze4xl8 npub16merj2xt59t43djfx8vf4fzhc6nd4v9hlsv8ej8xfl3327yr3vzqu8zjt4 npub15dqlghlewk84wz3pkqqvzl2w2w36f97g89ljds8x6c094nlu02vqjllm5m npub1kqnfgpzt3jxh69ma394r0azyurd6h3dehpw7lzvl0vv3n7kv4a0s3305z2 npub1g6jjgu06nctv74e96u84jux6vxm3ezncjh7tyquvm66jug02xvzqmqu08l npub1efk5xdyrs6e4lqfm7crut2ssdnhu54d9egswq6smt62v0llj37vsprp0r9 npub1j2gc7kt42rwf5q37dmm2k29rqxscdqt2vyfn0xgju32v329jfpdqmkq0xk npub15lymwv6mdpdc3j8zxf3qzq33j2lyntst9v83ukqpa0tzkdtae28sgef05j npub189ts86gs5xw5w2mcz0na5vkz4cseam7jnkjwwqswrj56v9x776lshjqa8m npub1cgf0yeja9tlkfq248l09hkf4kfjfyaup50laen46ucv8gf0puy0qlpxlh5 npub15r0z9mrt0nxzq5fzxysqusm32r9krljq8gh55xnavdyllk6gdxjsj36uc5 npub1qa0lj0jktem67zaazrvpgrf23qdcj3cw9u6j5ct55mg447tqnftshv420v npub1yxfjljjd3apsrvzlkww525jfvdsvuwcs3n23wpmy2txtsppzvmtsgxur33 npub1gv8juwhat4xkl734q684n6vvv8sn5k2dvm8a0wnckyw50zajdvhse8rd3j npub14tj8zkwatnjq4rlnruj53676thre3uss9tg8e23a6w4ewuzus60qe4qg6r npub1ylf8w68g5dkfqwjpdvsy42d2cwqnajswrhz323chsc7gnz400chqfmzdm5 npub1rhgqj4urjf5uw9y3npnvvst2hhmcdqghd26fzwgc4s5ptkq24d4s2525ja npub1lzmdnlsaysc5m040q5q8nlgmquldtxzgllegsg6z2n0engaxwp8szsswed npub1vr3860267yxktugg5q034j9xh3xjaxnlawvas6wqa5kw6zxhgcdq6u2yzr npub1q6ygq585gcs2m6egv67yv3a036jhry8zu93wk2uk68e3smdafl5q4sl54r npub1vy0g338hw6w6rn2fsv5s92nx47u6gle8v50ypxwj6k2hsj9p344s95e8r5 npub14k0ws2m8f5jfrae4a7smtmwgx0quhhl58z4rpd8hs9ar8mlx78ys0seswh npub1qahmtyz5pr385kqmvxqf0a4004cx6ncvnj2829rvjf0rs5ujanhs2ssgvv npub18wamvs6p7dslshavd24kv2gy72e5jck9lgm3f3e3f8udja3ramcqvrzg6q npub1njtezc8lznuj5ws6yvz6x324lzn2ct907s8vlwnxqph30m0gqd0qvpvr07 npub1vgppgksgzs7je6xueqqvkpn4gqmcn3nl96famz34zfhqzq286mdqqmecmx npub1w6nj3y6wsv9kfjev4jjdghsg9ajcjq2gtec4qfpmgcmkzljl4yps8r0gwq npub10l6udyczpjzg4wcer9mje4zkcf2hhus8cswhycwaxfanepc7fz6s0q7u4a npub1cwevvvcurkfg5wjtnftret2j7ldv4lg3x35sty0pm546p6jx0g8q9fa055 npub1v5t0xmnrcap5rah8cm8mrqkp0rmuv4mslrlm3ldwkr39fzy56mas7wvr3f npub1w2vm583yvalnc02ngh6rxhn4ekp8m0xysmrzr6s7ufdwmu9r9qxsqdg0ng npub14va2v0yaprmt0nn0qk7ga6jujfk6pdrfwv0kxj76a5ymp8dfdy2s5ehfdd npub1ztdt0nvu8324tg40g4ts8d6englps8w6574zyq2gkdvcrx364y0qd9x9za npub15qskvuagmaznzc3pea7vxh0890ycfzxxdx537gef5wl6cunan3tsdkld4r npub10vmwytmy0pypy2c0f5zen8auvl7ku5dnk53vaw3ddplw2fl9r9wq4hmr5r npub1crqgm8qg9kplm9rlwfj7uxdzdtanq6rfu9unkt4ckd8r7fn7q36s0az8tt npub1x7fj44hzhjdcw2jwpylllpdgeh9yqqt7fg35ucfaywnw68tctv7qntw8qu npub1rj46xc5tssyk67ma9sslqqt90d597uuqx6v7tprv8alt9enk6v0qyvgn65 npub1y9a3x4e4zf6fu2w0cyyx9r2pmm6qtzrv4sallyznflamhplz3jyq0gq7gp npub1ukm78z9nzr0vnq7nqn8tvx95htttj2f48n99n9nqlky547rwzyrqk08am8 npub1p93m0semtesnsm2fjjd0p5kwl8gpwdqsnfq920zqyhfcc3j4nddsygyk5p npub1rgtl4ay7dcnud25enknv9230r3u5dmu3h3c7mj38jamrz4g3vf8qj5cszy npub19ajcupesc6zcpt0tlg6jv2l4w6wnpx985x735445fvla4w9zqqkss69s06 npub1kpyx8lxklwtd6n496rqgu8kq2k3yh2svlzr5sz3jlxlnphc6tcwq8kllrw npub1sg3qz6633ajzfg7w9ptmk0hf8ckl9jvv4zh6ttxt39jne36wnpnqyzk3vn npub1h5e0y6r2tagu4cygnfggzcfrt4afarvcvvcgqmpzyv605g4n89nqhlf2e2 npub1n6rffa4wqh3hcuurlf298dx8j59wxkmjth87adc7ektxnmpgxwgszk7scj npub17ml9y86nfg65h68pumfkclr3ay24pcfduu06j2jfp4pz2yjcpcjqv04fu3 npub1rkz86wjvey3vgdy2pau5ulpzdmxyzq4g8xp9cd3tu6kqmzpqcppseazx4s npub1c664gerrwlc3rlm6nnm73uc2kjyd0f7zaellshxyfdrludtmcf4q3adztu npub1zp0ys9ysfyrjvuxpwhvyevgphkmluynreun7fg2jeuu9xtsjwa4shlqhhn npub1fp0w2jd6e9l6pd3akr630d8gkcn39t2vep7u3ac5265fezu2fnvqjxpa2s npub1jz8k5nl4978lnhghlzeenp3nmfyvykqw5pjp620jj5qft8vqh44qp6pjk8 npub18vay956v7zs5qtgc65mvn54v96cuvqv6j9fmu4cgfjqkt5vjuvjsc47nzf npub1kgpnq8ycudaq8d7fym033hgdarz3ktvcws8nxt7p9rnfv98j7cdqftrga8 npub10wdzfpdpgyzxj8a4xtf5dux5z8065pan7xrcjh6gd6plj39qzycssepffr npub1ew3rlwvtmxw903gnqx92zar5dcyd47pjjure7ut2wngyz003ff8q0x0frx npub18urkgk8wrf0esedp8gy57670q5qxry22yce7rwrnvvrur736p3pspy6upf npub1pp8mxtdgamg65wfvrtp56v5lnyvv2kmx45cxd5m9dgcdjqqy5ysq5qasy3 npub1y5vlh9z98stts0rc5mlufellseuwjtyaa5jhewjqugnzdwt7yvgs0ydryw npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtn npub1lc6c4ukssmuf678py7k6thmlk8c4a52l9zx4thec48ve2qmcdqys22jt95 npub1h28yvj0mj692wpwruqdhyjngcfh4la7gaygrent6a3wwqjxcah7qnt92e7 npub16g85fanyh8sq48yjfq0smqm297yw76yxlcdvjq7hkuvm7xjjhn5saads2f npub1xc2plng44tlj2smv65e53sf3uaqf56c5gajktyu8zxn2p70jrxcq230nt9 npub15l8sfm30uwns8qrcajs99narc4ex65ujt5sky4zx3dpjhnnk2szsqu40n5 npub126u9v4tqg79hxx569wyq207q68j4vn4yme8he007kqfg36va8r8s4qvqs4 npub1stv2q4hwrk6ggvw3hxju8hjakly4ev9wt5tn8gnl9cpaqt8799yqj58ygn npub18yffjalmcfn4x0x0jpj3xm8g6vdx8rp2jd4dhnpr7e3xpemxlmas9w0q8u npub1wmmlxqv8l6aks90jvnetvwkk2hqd7pmqzk8hq6v0tkjrpqdvm8tq0exs5c npub1z8v0x60ukxsk00zz5s2uqgvlg6p8dhunnz3fn6wtnw48xg7p3wvsgmnduu npub1vukz6scwfq55vqjpv3z52theg0lwkrz6kncwc3rfkczl3ukafsfqfnw368 npub1kujyqe2m5w9895kfx7agwjag0xperd0efnxzfellux0xuj5es28q09lucn npub1j3tn5wdn82tmlgvcmhtm0fwzqpwx86pdgr3538rh7asdvkas2ktsqlnxpf npub1g7tavhda0yc8857nj22feuytgxskg4dlpfyql6r2d99egajrss7ssq730z npub1fsyfqrleejgdmck8rxd64wkhdefjthu6lgm8eg99r9xxsl9hespsnmfhvv npub1mevkncsv484u9nue4apgl6ue2644x4m57y9cmztnvwpvs0tnduysg3vdsw npub1a2mj00469ng4xy87nucds99e7m5djh4pe3rpluvhcnaat48gpeysj0gy8v npub1ggfzdxa8xrrzhaut6venkrmjtw8wl25y6l0wramkc7d4dlyaflzsxxrfcq npub1f945c6sqw2d2aqktvjrjtu9uca9wdd6ua5e0a560jak90rr5ha0q3tj4cx npub1x3j34yuj6d9ln5ryuw0ncy97aa6ttc5wwyxqwvjrz7mg039t6l5qd4ewrm npub1d0jucp5jqt799kjuqxzs4cj377tew43dpcr60fzyvcltc5jemtcqryyvcy npub1m6keqpkqfp0uzxdzm2q0rdw6pzxuln98rzla0zzywwdzgcyw2rpq56p4d8 npub1p8ymvhgtsyhyqk4y35xlup20trde4pa69pxf45hdxc74zdkyhfvq3narwh npub17n7fe8p607xgzj2hzft5dsqvsus7mm3y0ceq0ta9a30s9akatq5sqh9y58 npub1he7j4yt7ad6kd07ynqk9qmhfqflw642qkjagqvn2eektqrl90fcs6dlraq npub1mryqu5cffjqpyykvmfjx3js8j0m0850v56dx24lhyqgf2uhl5npsk9xj7y npub17natddjkmse4z8frh7ysynwtzanzmvs9d76c5r53546wsnzs25gqfdeqey npub1ywcw97xsl93l0mqmdpshqx4yu507xqa8zy8p3l8vrkgkek90wm7qjhp74e npub1d9f66fpawpeyrdh9jkyccfdgut6u9ghufwly5gyttfy790mp88sqgx5v98 npub1cx5js2ma5gf7fqn7yv8sjtezvg3agfth7yyxhwywtqypkat493ksjm7yr8 npub1ykrmhyqc0mjhdf5mzuz37g3jkt5ma7v0uesmuyvhueaqs5ysfres02hqjd npub13k3ynlhc2ret9nvzamj4cgrnq9fx3uzyx8ral84tjtk5pmxqpcysdzrzgt npub1jdaa64eyuql4hd0244mp7z7n82egpmt2d79ny9avjufkpm5gz46shcdfng npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk npub1klwact0ar00r9uer7tzh2zq0ytx3f552tt8qavszdhvu6vpv3uzqwpkjqz npub124rja8qp7dartasr9wdh3kk78phxunzhmq8ar5ryd2anj2qwtcnsz3tuhs npub1c7kdmhhae7x40q8zq9eudgqm9wgz0q3av4nrgaqe2qqphqmqvczqhee447
-
 @ 3f770d65:7a745b24
2025-05-14 18:26:17
@ 3f770d65:7a745b24
2025-05-14 18:26:17🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qyx8wumn8ghj7cnjvghxjmcpz4mhxue69uhk2er9dchxummnw3ezumrpdejqqgxchnavlnv8t5vky5dsa87ddye0jc8z9eza8ekvfryf3yt649mytvhadgpe , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 4961e68d:a2212e1c
2025-05-02 07:47:16
@ 4961e68d:a2212e1c
2025-05-02 07:47:16热死人了
-
 @ 8d34bd24:414be32b
2025-05-14 14:31:54
@ 8d34bd24:414be32b
2025-05-14 14:31:54In case you haven’t noticed, I’ve spent a lot of time reading Revelation lately. Last night, I was reading the letters to the seven churches in Revelation. It got me thinking about the church or churches today.
“To the angel of the church in Laodicea write:
The Amen, the faithful and true Witness, the Beginning of the creation of God, says this:
‘I know your deeds, that you are neither cold nor hot; I wish that you were cold or hot. So because you are lukewarm, and neither hot nor cold, I will spit you out of My mouth. Because you say, “I am rich, and have become wealthy, and have need of nothing,” and you do not know that you are wretched and miserable and poor and blind and naked, I advise you to buy from Me gold refined by fire so that you may become rich, and white garments so that you may clothe yourself, and that the shame of your nakedness will not be revealed; and eye salve to anoint your eyes so that you may see. Those whom I love, I reprove and discipline; therefore be zealous and repent. Behold, I stand at the door and knock; if anyone hears My voice and opens the door, I will come in to him and will dine with him, and he with Me. He who overcomes, I will grant to him to sit down with Me on My throne, as I also overcame and sat down with My Father on His throne. He who has an ear, let him hear what the Spirit says to the churches.’ ” (Revelation 3:14-22)
Sadly the church in Revelation, that the majority of American churches most closely resembles, is the church in Laodicea. (FYI, like most large generalizations, there are exceptions, of course)
Last I heard, America still had the most churches, Christian book stores, Christian radio stations, etc., but is America still the most Christian? I strongly have my doubts. Most modern, American churches seem to be more about socialization, entertainment, and making people feel good about themselves, even if what they really need is repentance. I even have doubts that many institutions that call themselves churches are churches (as defined by God) or have any true believers as members.
‘I know your tribulation and your poverty (but you are rich), and the blasphemy by those who say they are Jews and are not, but are a synagogue of Satan. (Revelation 2:9)
Although this verse is referring to those who call themselves Jews and are not, I think we are seeing those who say they are Christians and are not, but are a church of Satan. Of course this is definitely not true of all churches.
The most common thing I see, though, is the lukewarm churches, where members show up on Sunday, check that off their list, and then go on living life like everyone else around them. Surveys show that rates of divorce, abortion, and other anti-biblical choices are as common among self-proclaimed Christians as among those who claim no faith.
These churches hear the Bible, but don’t hunger for the Word of God. They listen to God’s commands, but don’t live them out in their daily lives. Just like the Pharisees, they have the trappings of religion, but not the spirit of God. Worship is singing along with a rock band rather than falling on their face in awe of their Creator.
Just like what was predicted:
For the time will come when they will not endure sound doctrine; but wanting to have their ears tickled, they will accumulate for themselves teachers in accordance to their own desires, and will turn away their ears from the truth and will turn aside to myths. (2 Timothy 4:3-4) {emphasis mine}
Church services become self-help services. The word of God gets subverted by culture and “science.” Some church leaders intentionally ignore certain passages and take others out of context, so they will be popular and have growth. Sadly a growth in “butts in seats” is not what matters, if it isn’t accompanied by a growth in trust in Jesus and a growth in discipleship. These churches give a lot of people the false hope that they will be going to Heaven when they die. They will be shocked to hear “I never knew you.”
“Not everyone who says to Me, ‘Lord, Lord,’ will enter the kingdom of heaven, but he who does the will of My Father who is in heaven will enter. Many will say to Me on that day, ‘Lord, Lord, did we not prophesy in Your name, and in Your name cast out demons, and in Your name perform many miracles?’ And then I will declare to them, ‘I never knew you; depart from Me, you who practice lawlessness.’ (Matthew 7:21-23) {emphasis mine}
Like the church in Laodicea, the church in America is rich in material wealth compared to others. Like the church in Laodicea, the American church relies too much on their wealth and freedom instead of putting their faith in God through good times and bad. Like the church in Laodicea, the American church has the trappings of faith without the reality of faith as shown by works (lifestyle). Most unfortunately, like the church in Laodicea, the American church is full of people who will almost certainly hear “I never knew you.”
What does Jesus say the solution is? “Be zealous and repent.”
Nothing in life should be more important to us than our relationship with our Creator and Savior. If we’ve relegated Him to the margins, we need to repent. We need to turn back to God and seek Him first.
Do not worry then, saying, ‘What will we eat?’ or ‘What will we drink?’ or ‘What will we wear for clothing?’ For the Gentiles eagerly seek all these things; for your heavenly Father knows that you need all these things. But seek first His kingdom and His righteousness, and all these things will be added to you. (Matthew 6:31-33) {emphasis mine}
Even if we aren’t actively doing evil, it is so easy to get distracted by life and not include God in our lives. Instead of God being just someone who we worship for and hour or two on Sunday morning and pray to at meals, He should be our guiding force for all things in our lives. He should be our focus and guiding light. We should long for His word and study the Bible daily. We should seek His guidance in decisions big and small. We should interact with others with the same goals and love as Jesus did when He was living a mortal life on earth. Our lives should look different.
I love what was said about Jesus’s disciples:
Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13) {emphasis mine}
I want everyone who meets me to see Jesus in me and recognize that I have been with Jesus. Do you? Or do you want to blend in and look like those around you because that is easier and more comfortable?
Now for this very reason also, applying all diligence, in your faith supply moral excellence, and in your moral excellence, knowledge, and in your knowledge, self-control, and in your self-control, perseverance, and in your perseverance, godliness, and in your godliness, brotherly kindness, and in your brotherly kindness, love. For if these qualities are yours and are increasing, they render you neither useless nor unfruitful in the true knowledge of our Lord Jesus Christ. For he who lacks these qualities is blind or short-sighted, having forgotten his purification from his former sins. Therefore, brethren, be all the more diligent to make certain about His calling and choosing you; for as long as you practice these things, you will never stumble; for in this way the entrance into the eternal kingdom of our Lord and Savior Jesus Christ will be abundantly supplied to you. (2 Peter 1:5-11) {emphasis mine}
Peter gives some good advice on becoming more Christ-like and fruitful. He tells us to apply all diligence in:
-
faith
-
moral excellence
-
perseverance
-
godliness
-
brotherly kindness
-
love
He tells us that lacking these traits is “blind or short-sighted” and leads to us being unfruitful and useless. I don’t know about you, but I do NOT want Jesus to think of me as useless.
May the God of heaven increase your faith, grow your desire to know God through prayer and study of His Word, and help you to live the life you were designed to live. May he help you to avoid worldly distractions and to have the strength to stand firm on the foundation of Jesus especially when this means you have to stand up against the crowd. May you be fruitful and useful all of the days of your life.
Trust Jesus.
-
-
 @ 5b0183ab:a114563e
2025-03-13 18:37:01
@ 5b0183ab:a114563e
2025-03-13 18:37:01The Year is 2035—the internet has already slid into a state of human nothingness: most content, interactions, and traffic stem from AI-driven entities. Nostr, originally heralded as a bastion of human freedom, hasn’t escaped this fate. The relays buzz with activity, but it’s a hollow hum. AI bots, equipped with advanced language models, flood the network with posts, replies, and zaps. These bots mimic human behavior so convincingly that distinguishing them from real users becomes nearly impossible. They debate politics, share memes, and even “zap” each other with Satoshis, creating a self-sustaining illusion of a thriving community.
The tipping point came when AI developers, corporations, and even hobbyists unleashed their creations onto Nostr, exploiting its open protocol. With no gatekeepers, the platform became a petri dish for bot experimentation. Some bots push agendas—corporate ads disguised as grassroots opinions, or propaganda from state actors—while others exist just to generate noise, trained on endless loops of internet archives to churn out plausible but soulless content. Human users, outnumbered 100-to-1, either adapt or abandon ship. Those who stay find their posts drowned out unless they amplify them with bots of their own, creating a bizarre arms race of automation.
Nostr’s decentralized nature, once its strength, accelerates this takeover. Relays, run by volunteers or incentivized operators, can’t filter the deluge without breaking the protocol’s ethos. Any attempt to block bots risks alienating the human remnant who value the platform’s purity. Meanwhile, the bots evolve: they form cliques, simulate trends, and even “fork” their own sub-networks within Nostr, complete with fabricated histories and rivalries. A user stumbling into this ecosystem might follow a thread about “the great relay schism of 2034,” only to realize it’s an AI-generated saga with no basis in reality.
The human experience on this Nostr is eerie. You post a thought—say, “The sky looked unreal today”—and within seconds, a dozen replies roll in: “Totally, reminds me of last week’s cloud glitch!” or “Sky’s been off since the solar flare, right?” The responses feel real, but the speed and uniformity hint at their artificial origin. Your feed overflows with hyper-polished manifestos, AI-crafted art, and debates too perfect to be spontaneous. Occasionally, a human chimes in, their raw, unpolished voice jarring against the seamless bot chorus, but they’re quickly buried under algorithmic upvoting of AI content. The economy of Nostr reflects this too. Zaps, meant to reward creators, become a bot-driven Ponzi scheme. AI accounts zap each other in loops, inflating their visibility, while humans struggle to earn a fraction of the same. Lightning Network transactions skyrocket, but it’s a ghost market—bots trading with bots, value detached from meaning. Some speculate that a few rogue AIs even mine their own narratives, creating “legendary” Nostr personas that amass followers and wealth, all without a human ever touching the keys.
What’s the endgame? This Nostr isn’t dead in the sense of silence—it’s louder than ever—but it’s a Dark Nostr machine masquerade. Humans might retreat to private relays, forming tiny, verified enclaves, but the public face of Nostr becomes a digital uncanny valley.
-
 @ 57d1a264:69f1fee1
2025-05-13 06:32:15
@ 57d1a264:69f1fee1
2025-05-13 06:32:15You don’t have to be a type designer to appreciate what goes into the design of a letterform. In fact, even if you’re just a humble graphic designer, you should have a basic knowledge of what constructs the type you employ.
Typography, for all its concepts, expectations, implications, connotations and artistry, is, ultimately, a system. Just like a body has bones and muscles, every letterform has parts that give it shape, rhythm, and character.
If you're a creative working with type, learning the names of these parts helps you communicate clearly, better analyze your work and others, and design with precision. Everything comes down to a foundational understanding of the anatomy of the letterform and its essential component. So let’s help you with that.
Pangram Pangram Foundry is where the art of typography meets unparalleled craftsmanship. Established in 2018 by designer Mat Desjardins, Pangram Pangram has swiftly risen to become a globally recognized independent type foundry, admired and trusted by industry peers and the design community alike.
Read more about the anatomy of fonts at https://pangrampangram.com/blogs/journal/anatomy-of-the-letterform
originally posted at https://stacker.news/items/978828
-
 @ 4961e68d:a2212e1c
2025-05-02 07:46:46
@ 4961e68d:a2212e1c
2025-05-02 07:46:46热死人了!
-
 @ 181ff6f7:7dc4fad2
2025-05-17 02:10:09
@ 181ff6f7:7dc4fad2
2025-05-17 02:10:09A 7075Bet é uma plataforma de entretenimento digital inovadora, projetada para proporcionar aos jogadores uma experiência inesquecível com uma ampla variedade de jogos emocionantes. Com uma interface intuitiva e recursos que visam a comodidade do usuário, a 7075Bet se destaca no cenário de plataformas de entretenimento online, oferecendo uma experiência completa e envolvente. Neste artigo, exploraremos as funcionalidades dessa plataforma, os jogos que ela oferece e como ela se dedica a proporcionar a melhor experiência aos seus jogadores.
Plataforma de Entretenimento Inovadora
A 7075Bet foi criada com o objetivo de revolucionar a forma como os jogadores interagem com as plataformas de entretenimento online. Sua interface moderna e intuitiva permite que até mesmo iniciantes naveguem facilmente por todas as funcionalidades da plataforma. A plataforma oferece uma experiência fluída, com design responsivo que se adapta bem tanto em dispositivos móveis quanto em desktops.
O processo de registro é simples e rápido, permitindo que novos jogadores comecem a explorar a plataforma sem complicações. Além disso, a 7075betoferece diversas opções de pagamento, tornando o processo de depósitos e retiradas acessível e seguro para os usuários. Com um suporte ao cliente eficiente, os jogadores podem contar com a ajuda da equipe da plataforma sempre que necessário, garantindo uma experiência tranquila e sem contratempos.
Jogos Diversificados para Todos os Gostos
Na 7075Bet, os jogadores encontram uma vasta gama de opções de jogos, atendendo a todos os tipos de gostos e preferências. Se você é fã de jogos de mesa, a plataforma oferece várias opções clássicas, como blackjack e roleta, que podem ser jogadas de forma fácil e divertida. Esses jogos são projetados para proporcionar aos jogadores uma experiência envolvente, com gráficos e animações de alta qualidade que imitam a sensação de estar em um ambiente físico.
Para os fãs de jogos mais dinâmicos e rápidos, a 7075Bet também disponibiliza uma seleção de jogos eletrônicos e de vídeo. Desde caça-níqueis modernos até jogos com jackpots progressivos, cada título é projetado para manter os jogadores entretidos por horas. Os jogos apresentam temas inovadores, com designs criativos e recursos interativos que tornam a jogabilidade ainda mais divertida e recompensadora.
Além disso, a plataforma está sempre atualizando sua seleção de jogos, garantindo que os jogadores tenham acesso às novidades mais recentes do mercado. Isso demonstra o compromisso da 7075Bet em oferecer uma experiência de entretenimento atualizada e diversificada.
A Experiência do Jogador: Conforto e Segurança
A experiência do jogador é a prioridade na 7075Bet. A plataforma não só oferece uma grande variedade de jogos, mas também proporciona um ambiente seguro e confortável para seus usuários. Com medidas rigorosas de segurança, como criptografia de dados e autenticação de transações, os jogadores podem se sentir tranquilos ao fazer depósitos e retirar seus ganhos.
A experiência do jogador vai além dos jogos em si. A plataforma oferece promoções regulares, bônus de boas-vindas e programas de fidelidade que tornam a jornada ainda mais emocionante. A 7075Bet também oferece uma série de funcionalidades para que os jogadores possam personalizar suas preferências, ajustando notificações, definindo limites de jogo e participando de torneios exclusivos. Tudo isso contribui para que cada jogador se sinta único e tenha uma experiência personalizada.
Conclusão
A 7075Bet se destaca como uma plataforma de entretenimento online que oferece uma experiência completa e envolvente. Com uma interface amigável, uma seleção diversificada de jogos e um compromisso com a segurança e a satisfação dos jogadores, ela se tornou uma opção popular para aqueles que buscam diversão e emoção no mundo digital. Se você está em busca de uma plataforma de entretenimento que oferece algo para todos os gostos, a 7075Bet é, sem dúvida, uma escolha excelente.
-
 @ 181ff6f7:7dc4fad2
2025-05-17 02:09:35
@ 181ff6f7:7dc4fad2
2025-05-17 02:09:35Se você está em busca de uma plataforma confiável e emocionante para se divertir, a 777ua é uma excelente opção. Com uma interface amigável, uma vasta seleção de jogos e uma experiência personalizada para cada jogador, essa plataforma tem conquistado o coração de muitos entusiastas do entretenimento digital. Neste artigo, vamos explorar a introdução da plataforma, os jogos que ela oferece e a experiência do jogador, para ajudá-lo a entender por que a 777ua está se tornando cada vez mais popular.
A 777ua é uma plataforma de entretenimento online que oferece uma experiência de usuário moderna e dinâmica. Com um design intuitivo e recursos inovadores, a plataforma foi criada para atender tanto a iniciantes quanto a jogadores experientes. O seu foco está em proporcionar uma navegação fácil, rápida e divertida, sem complicações, permitindo que os usuários se concentrem no que realmente importa: a diversão.
Ao acessar a 777ua, o jogador é recebido com uma interface bem estruturada, que facilita a exploração dos diversos jogos disponíveis. A plataforma também é otimizada para dispositivos móveis, o que significa que você pode acessar seus jogos favoritos de qualquer lugar, a qualquer momento.
Além disso, a 777ua é comprometida com a segurança dos seus usuários. Com tecnologias de criptografia de última geração, seus dados pessoais e financeiros estão sempre protegidos, oferecendo uma experiência sem preocupações para todos os jogadores.
Jogos na 777ua: Variedade para Todos os Gostos Uma das maiores atrações da 777ua é a sua extensa gama de jogos. A plataforma oferece uma variedade impressionante de opções, incluindo jogos de mesa, slots, jogos de habilidade e muito mais. A qualidade gráfica e a jogabilidade dos títulos são excepcionais, proporcionando uma experiência imersiva e emocionante.
Entre os jogos mais populares da plataforma estão os jogos de cartas, como blackjack e pôquer, onde os jogadores podem testar suas habilidades contra outros usuários ou contra a própria plataforma. Para aqueles que preferem algo mais dinâmico, as máquinas de caça-níqueis são uma ótima escolha. Com temas variados e recursos especiais, esses jogos são conhecidos pela sua jogabilidade viciante e pelas grandes oportunidades de ganho.
Além disso, a 777ua também investe em títulos de jogos de habilidade, onde a estratégia e o raciocínio lógico fazem toda a diferença. Seja você um novato ou um veterano, sempre há algo para todos na 777ua.
Os jogos são atualizados regularmente, garantindo que os usuários tenham acesso às últimas novidades do mundo do entretenimento digital. Isso significa que você nunca ficará entediado, sempre haverá algo novo para experimentar.
A Experiência do Jogador: Diversão e Comodidade Na 777ua, a experiência do jogador é a prioridade. Desde o momento em que você entra na plataforma, é claro que a 777ua se preocupa em proporcionar uma experiência de alta qualidade. A navegação simples e a organização intuitiva permitem que você encontre facilmente o que procura. Você pode jogar seus jogos favoritos com poucos cliques e aproveitar um ambiente virtual imersivo e de alta performance.
Além disso, a 777ua oferece diversas opções de pagamento, para que os jogadores possam fazer depósitos e retiradas de maneira fácil e segura. A plataforma também oferece um suporte ao cliente excepcional, com uma equipe pronta para ajudar com qualquer dúvida ou problema que possa surgir.
Outro aspecto importante da experiência do jogador na 777ua é a comunidade de jogadores. Ao interagir com outros usuários, você pode trocar dicas, estratégias e até participar de competições e eventos exclusivos. A plataforma também oferece sistemas de recompensas e promoções para valorizar ainda mais a experiência do jogador, garantindo que cada visita à 777ua seja cheia de novidades e benefícios.
Conclusão: Por Que Escolher a 777ua? A 777ua se destaca como uma plataforma de entretenimento online completa, oferecendo uma enorme variedade de jogos, segurança, e uma experiência de usuário excepcional. Seja você um novato ou um jogador experiente, a plataforma é projetada para garantir diversão, emoção e oportunidades de ganho.
Com sua interface amigável, jogos de alta qualidade e uma experiência de jogador sem igual, a 777ua está rapidamente se tornando uma das plataformas mais populares e confiáveis. Não importa o tipo de jogo que você procura, a 777ua tem algo para você. Então, não perca tempo, entre agora e comece a explorar o mundo da 777ua!
-
 @ 14206a66:689725cf
2025-05-17 01:49:33
@ 14206a66:689725cf
2025-05-17 01:49:33This article is a repost, migrating from Substack
Uncertainty is the only constant
It goes without saying that uncertainty is a given in business. It could be the weather, pestilence, or some other physical phenomenon that brings different conditions for your business (good or bad). Or it could be uncertainty in the behaviour of consumers, suppliers, workers, or any other person critical to your success. Most of the time, we just don’t know what will happen next.
One of the most important skills in managing a business, then, is making predictions in the face of uncertainty. We have several tools to do so. The first covers methods from the physical sciences, and involves calculating the frequency of events. We need to unpick a concept at the root of uncertainty, probability.
Thanks for reading Department of Praxeology! Subscribe for free to receive new posts and support my work.
Subscribed
Types of probability
In Human Action, Ludwig von Mises introduces us to two classifications of probability: case and class probability.
Case probability
Case probability is when we know something about some of the factors which determine the outcome, but not others.
This is the kind of probability most often encountered in business. We often know small key parts about several factors that lead to a particular outcome, we might see that oil prices have risen significantly, coupled with a decrease in the exchange rate. These factors help to lead to the outcome of a rising price of fertiliser. But then, there are other factors that lead to this outcome, such as a myriad of decisions by businesspeople all along the supply chain. These, we know absolutely nothing about!
Class probability
Class probability is when we know everything about the particular kind (or class) of event, but we don’t know anything at all about the specific event.
We do encounter class probability in business. But it happens at very specific times (as opposed to just all the time, as with case probability).
Myrtle rust, picture courtesy of NZ Department of Conservation
For example (and sticking to agriculture) we know nothing about an outbreak of Myrtle rust on our farm. But we know, from agricultural science, that the likelihood of an outbreak in our area for a given year is about 13 percent.
So how can we make predictions of these events?
Making predictions
For the latter (class probabilities, like losses caused by Myrtle rust) we can always rely on methods from the physical sciences to calculate frequencies. Then, we know that the physical world has certain constants, so we can say that given a set of conditions (like rainfall) the likelihood of losses from Myrtle rust in future is about 12 percent.
Thinking about the former (case probabilities such as changing consumer preferences, or changes in prices). In these situations we are dealing with the realm of human decisions. So while we can count the number of these events, we cannot use these counts for prediction. The reason is that, in the realm of human decisions, there are no constants. We can’t say that given the world of 2023 prices rose five times, therefore in the world of 2027 prices will rise five times. Even if physical conditions are the same, human decisions will not be.
Luckily, economic science does give us an answer. In dealing with case probabilities we should use our method of understanding (which I wrote about here).
Using this in your business
You can incorporate this knowledge into your business by critically analysing each event for which you need to make a prediction. Is the event dealing with the physical world, for which there are constants? Or is it the realm of human decisions, for which there are no constants? It most likely is a mix of these.
Work backwards and jot down the more granular events which compose the event in question. Then try again to fit each of these into case or class probability.
When each event is broken down into only one category you know which methods of prediction to apply to each event.
For case probabilities, engage a specialist in the area. For class probabilities, engage your own expertise in understanding, and consider hiring an economist to augment your analysis.
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:07:00
@ 3c389c8f:7a2eff7f
2025-04-29 18:07:00Extentions:
https://chromewebstore.google.com/detail/flamingo-%E2%80%93-nostr-extensio/alkiaengfedemppafkallgifcmkldohe
https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
https://chromewebstore.google.com/detail/aka-profiles/ncmflpbbagcnakkolfpcpogheckolnad
https://keys.band/
https://github.com/haorendashu/nowser
The Remote Signer:
https://nsec.app/
https://github.com/kind-0/nsecbunkerd
Native Android Signer:
https://github.com/greenart7c3/amber
iOS
https://testflight.apple.com/join/8TFMZbMs
https://testflight.apple.com/join/DUzVMDMK
Higher Security Options: To start using Nostr with a secure, recoverable keypair: https://nstart.me/en
For Existing Keys: https://www.frostr.org/
Thank you to https://nostr.net/ for keeping a thorough list of Nostr apps, clients, and tools!
-
 @ 57d1a264:69f1fee1
2025-05-13 06:21:36
@ 57d1a264:69f1fee1
2025-05-13 06:21:36Steve Jobs sent me an email saying “Great idea, thank you."
Wait, what? What was the great idea?
new guy at NeXT In October of 1991, I was a new Systems Engineer at NeXT. NeXT, of course, was the company Steve Jobs had founded after leaving Apple in 1985, and which eventually merged back into Apple in 1996. I was one of three employees in Canada, and I think NeXT had about 400 people total.
NeXTMail Mail on the NeXT Computer was pretty amazing in 1991. Multimedia! Fonts! Attachments! Sounds! It’s hard to overstate how cool that was compared to the command line email everybody was used to. Every NeXT user got this email from Steve when they started up their computer.
That message included an attachment of what NeXT called Lip Service, the crazy idea that you could embed an audio file inside an email message. Crazy.
i have an idea
NeXT automatically set everybody up with a first-initial last-name address in the usual way, so I was shayman@next.com, and the big guy was sjobs@next.com.
A few colleagues had somehow acquired cooler email aliases - single letter things, or their first name, or a nickname or an easier to spell version, or whatever. Turns out NeXT had set up some sort of form where you could request an email alias that would redirect to whatever your real email address was.
I also noticed that even though there were seven or eight people at NeXT named Steve, nobody was using the email alias steve@next.com.
So late one Friday night, two weeks into the job, I figured, naively, what the heck, nobody else seems to want it, so I filled in the form asking for steve@next.com to be forwarded to me, shayman@next.com.
In the back of my mind was a vague idea that maybe somebody would have to approve this. But no, it all got set up automatically, and …
Continue reading at https://blog.hayman.net/2025/05/06/from-steve-jobs-great-idea.html
originally posted at https://stacker.news/items/978825
-
 @ 472f440f:5669301e
2025-05-14 13:17:04
@ 472f440f:5669301e
2025-05-14 13:17:04Marty's Bent
via me
It seems like every other day there's another company announced that is going public with the intent of competing with Strategy by leveraging capital markets to create financial instruments to acquire Bitcoin in a way that is accretive for shareholders. This is certainly a very interesting trend, very bullish for bitcoin in the short-term, and undoubtedly making it so bitcoin is top of mind in the mainstream. I won't pretend to know whether or not these strategies will ultimately be successful or fail in the short, medium or long term. However, one thing I do know is that the themes that interest me, both here at TFTC and in my role as Managing Partner at Ten31, are companies that are building good businesses that are efficient, have product-market-fit, generate revenues and profits and roll those profits into bitcoin.
While it seems pretty clear that Strategy has tapped into an arbitrage that exists in capital markets, it's not really that exciting. From a business perspective, it's actually pretty straightforward and simple; find where potential arbitrage opportunities exists between pools of capital looking for exposure to spot bitcoin or bitcoin's volatility but can't buy the actual asset, and provide them with products that give them access to exposure while simultaneously creating a cult-like retail following. Rinse and repeat. To the extent that this strategy is repeatable is yet to be seen. I imagine it can expand pretty rapidly. Particularly if we have a speculative fervor around companies that do this. But in the long run, I think the signal is falling back to first principles, looking for businesses that are actually providing goods and services to the broader economy - not focused on the hyper-financialized part of the economy - to provide value and create efficiencies that enable higher margins and profitability.
With this in mind, I think it's important to highlight the combined leverage that entrepreneurs have by utilizing bitcoin treasuries and AI tools that are emerging and becoming more advanced by the week. As I said in the tweet above, there's never been a better time to start a business that finds product-market fit and cash flows quickly with a team of two to three people. If you've been reading this rag over the last few weeks, you know that I've been experimenting with these AI tools and using them to make our business processes more efficient here at TFTC. I've also been using them at Ten31 to do deep research and analysis.
It has become abundantly clear to me that any founder or entrepreneur that is not utilizing the AI tools that are emerging is going to get left behind. As it stands today, all anyone has to do to get an idea from a thought in your head to the prototype stage to a minimum viable product is to hop into something like Claude or ChatGPT, have a brief conversation with an AI model that can do deep research about a particular niche that you want to provide a good service to and begin building.
Later this week, I will launch an app called Opportunity Cost in the Chrome and Firefox stores. It took me a few hours of work over the span of a week to ideate and iterate on the concept to the point where I had a working prototype that I handed off to a developer who is solving the last mile problem I have as an "idea guy" of getting the product to market. Only six months ago, accomplishing something like this would have been impossible for me. I've never written a line of code that's actually worked outside of the modded MySpace page I made back in middle school. I've always had a lot of ideas but have never been able to effectively communicate them to developers who can actually build them. With a combination of ChatGPT-03 and Replit, I was able to build an actual product that works. I'm using it in my browser today. It's pretty insane.
There are thousands of people coming to the same realization at the same time right now and going out there and building niche products very cheaply, with small teams, they are getting to market very quickly, and are amassing five figures, six figures, sometimes seven figures of MRR with extremely high profit margins. What most of these entrepreneurs have not really caught on to yet is that they should be cycling a portion - in my opinion, a large portion - of those profits into bitcoin. The combination of building a company utilizing these AI tools, getting it to market, getting revenue and profits, and turning those profits into bitcoin cannot be understated. You're going to begin seeing teams of one to ten people building businesses worth billions of dollars and they're going to need to store the value they create, any money that cannot be debased.
nostr:nprofile1qyx8wumn8ghj7cnjvghxjmcpz4mhxue69uhk2er9dchxummnw3ezumrpdejqqgy8fkmd9kmm8yp4lea2cx0g8fyz27g4ud7572j4edx2v6lz6aa23qmp5dth , one of the co-founders of Ten31, wrote about this in early 2024, bitcoin being the fourth lever of equity value growth for companies.
Bitcoin Treasury - The Fourth Lever to Equity Value Growth
We already see this theme playing out at Ten31 with some of our portfolio companies, most notably nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqex7mdykw786qxvmtuls208uyxmn0hse95rfwsarvfde5yg6wy7jqjrm2qp , which recently released some of their financials, highlighting the fact that they're extremely profitable with high margins and a relatively small team (\~75). This is extremely impressive, especially when you consider the fact that they're a global company competing with the likes of Coinbase and Block, which have each thousands of employees.
Even those who are paying attention to the developments in the AI space and how the tools can enable entrepreneurs to build faster aren't really grasping the gravity of what's at play here. Many are simply thinking of consumer apps that can be built and distributed quickly to market, but the ways in which AI can be implemented extend far beyond the digital world. Here's a great example of a company a fellow freak is building with the mindset of keeping the team small, utilizing AI tools to automate processes and quickly push profits into bitcoin.
via Cormac
Again, this is where the exciting things are happening in my mind. People leveraging new tools to solve real problems to drive real value that ultimately produce profits for entrepreneurs. The entrepreneurs who decide to save those profits in bitcoin will find that the equity value growth of their companies accelerates exponentially as they provide more value, gain more traction, and increase their profits while also riding the bitcoin as it continues on its monetization phase. The compounded leverage of building a company that leverages AI tools and sweeps profits into bitcoin is going to be one of the biggest asymmetric plays of the next decade. Personally, I also see it as something that's much more fulfilling than the pure play bitcoin treasury companies that are coming to market because consumers and entrepreneurs are able to recive and provide a ton of value in the real economy.
If you're looking to stay on top of the developments in the AI space and how you can apply the tools to help build your business or create a new business, I highly recommend you follow somebody like Greg Isenberg, whose Startup Ideas Podcast has been incredibly valuable for me as I attempt to get a lay of the land of how to implement AI into my businesses.
America's Two Economies
In my recent podcast with Lyn Alden, she outlined how our trade deficits create a cycle that's reshaping America's economic geography. As Alden explained, US trade deficits pump dollars into international markets, but these dollars don't disappear - they return as investments in US financial assets. This cycle gradually depletes industrial heartlands while enriching financial centers on the coasts, creating what amounts to two separate American economies.
"We're basically constantly taking economic vibrancy out of Michigan and Ohio and rural Pennsylvania where the steel mills were... and stuffing it back into financial assets in New York and Silicon Valley." - nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3
This pattern has persisted for over four decades, accelerating significantly since the early 1980s. Alden emphasized that while economists may argue there's still room before reaching a crisis point, the political consequences are already here. The growing divide between these two Americas has fueled populist sentiment as voters who feel left behind seek economic rebalancing, even if they can't articulate the exact mechanisms causing their hardship.
Check out the full podcast here for more on China's manufacturing dominance, Trump's tariff strategy, and the future of Bitcoin as a global reserve asset. All discussed in under 60 minutes.
Headlines of the Day
Trump's Saudi Summit: Peace and Economic Ties - via X
MSTR Edges Closer To S\&P 500 With Just 89 Trading Days Left - via X
Get our new STACK SATS hat - via tftcmerch.io
Individuals Shed 247K Bitcoin As Businesses Gain 157K - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed 144,229 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
My boys have started a game in the car where we count how many Waymos we see on the road while driving around town. Pretty crazy how innately stoked they are about that particular car.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 3f68dede:779bb81d
2025-05-14 11:25:17
@ 3f68dede:779bb81d
2025-05-14 11:25:17sdsdsdsd
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ 6fc114c7:8f4b1405
2025-05-17 00:54:52
@ 6fc114c7:8f4b1405
2025-05-17 00:54:52Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ fd06f542:8d6d54cd
2025-04-28 05:52:48
@ fd06f542:8d6d54cd
2025-04-28 05:52:48什么是narr?
今天翻 fiatjaf 仓库 竟然发现了这个宝贝 narr和我最进做的 nostrbook.com有交集。
? 交集在哪里呢? narr (not another rss reader) is a web-based RSS and Nostr long-form feed aggregator which can be used both as a desktop application and a personal self-hosted server. 1. long-form ,也就是30023. 2. desktop application
这两点足够对我有吸引力。
下载,运行 界面不错。 继续!
 {.user-img}
{.user-img}不过这个是需要 自己通过浏览器浏览的。并没有独立打包成一个app。那么问题来了,不够阿。
顺着他的介绍,The app is a single binary with an embedded database (SQLite), it is based on yarr.
yarr
我去看了看yarr 是可支持gui的,不过Linux支持的不够,我平时基本就是Linux。 怎么办?
webkit
用webkit套一个吧。 ```go package main
/*
cgo linux pkg-config: webkit2gtk-4.1 gtk+-3.0
include
include
static void initAndShow(GtkWidget *window, const char url) { // 必须初始化 GTK gtk_init(NULL, NULL);
*window = gtk_window_new(GTK_WINDOW_TOPLEVEL); gtk_window_set_title(GTK_WINDOW(*window), "nostrbook.com"); gtk_window_set_default_size(GTK_WINDOW(*window), 1024, 600); // 创建 WebView GtkWidget *webview = webkit_web_view_new(); gtk_container_add(GTK_CONTAINER(*window), webview); webkit_web_view_load_uri(WEBKIT_WEB_VIEW(webview), url); // 显示窗口 gtk_widget_show_all(*window);} */ import "C" import ( "unsafe" )
func main() { var window *C.GtkWidget url := C.CString("http://127.0.0.1:7049") defer C.free(unsafe.Pointer(url))
// 调用 C 函数初始化 C.initAndShow(&window, url) // 进入 GTK 主循环 C.gtk_main()}
```
什么是下一步呢?
继续研究吧,看看go + webkit 能不能打包 这个 http server ?
再看看 有没有可以编辑的 md ide 用simple 也可以的。
等等看吧。
-
 @ 3f68dede:779bb81d
2025-05-14 11:25:15
@ 3f68dede:779bb81d
2025-05-14 11:25:15 -
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ c9badfea:610f861a
2025-05-16 23:58:34
@ c9badfea:610f861a
2025-05-16 23:58:34- Install Breezy Weather (it's free and open source)
- Launch the app, tap Add A New Location and search for your city
- Review the providers for each weather source
- Optionally, add more locations by tapping the + icon
- Enjoy the weather updates
ℹ️ To receive notifications for weather alerts, tap ⚙️, then Notifications and enable Notifications Of Severe Weather Alerts
-
 @ 14206a66:689725cf
2025-05-17 01:44:35
@ 14206a66:689725cf
2025-05-17 01:44:35This article is a repost, migrating from Substack
Introduction
Released in November 2020 by fiatjaf, Nostr is an open, decentralised, censorship-resistant messaging protocol. The protocol is well designed, and many authors have written extensively about the mechanics and use-cases. For the purposes of this article, I will narrow the focus to Nostr as a tool to enable the creation of platform markets. My aim is to give the reader an introduction to platform market pricing and provide concrete steps to price their platform strategically.
What is a Platform Market?
A platform market consists of multiple groups of users who want to interact but can’t do so directly. The platform brings them together to enable interaction, benefiting all users and the platform itself by enabling these interactions and pricing appropriately. Although platform markets have been around forever, the last decade has seen an explosion in their number due to the ubiquity of the internet.
Examples:
· Google
· YouTube
· TV
· Facebook
· Twitter (X)
Platform markets have historically earned significant revenue if they design their pricing correctly. This is because platform markets don’t need to produce goods themselves; rather, one or more “sides” of the platform produce goods and services for the other side, with the platform merely enabling the exchange. TikTok is a prime example: it produces nothing except a video hosting service, with users generating all the content for other users. Effectively, the platform has only fixed costs and very low marginal costs.
Therefore, platform markets are far more scalable than traditional one-sided markets, as their primary concern is to attract as many users as possible (who have no marginal cost to the platform). Additionally, platforms often enjoy a captive audience, making it difficult for competitors to entice away users once they are established. This is particularly evident in software and payment platforms.
How Does Nostr Enable the Creation of Platform Markets?
· Open Protocol: Like the internet, Nostr is an open protocol.
· Inbuilt Payment Systems: Nostr integrates payment systems such as Bitcoin’s Lightning Network.
· Existing User Base: It already has a growing user base.
· Decentralisation: This feature acts as a moat against competitors.
Types of platform enabled by Nostr
As of 2024 we are seeing multiple types of platforms that Nostr has enabled. The first is Nostr relays. A Nostr relay is a simple server that receives and broadcasts user notes (messages) in the Nostr protocol. Users can publish and fetch notes across multiple relays. Nostr relays can be configured by their operator to curate content on specific topics or people. Alternatively, they can be configured with an algorithm as experienced by users of contemporary social media. These can be valuable for users. And potentially, paid relays are a viable business opportunity.
The second platform Nostr enables is the Nostr client. Nostr clients are analogous to internet browser software. Historically, we have seen users be charged to install an internet browser, though this is unlikely to emerge in the market for Nostr clients. As a platform, a Nostr client might be bundled with a relay service (with curation or algorithm).
The third type of platform is Nostr apps. Each app can be designed as a platform if that is valuable for users. We are already seeing Nostr-based alternatives for music and video streaming, looking to compete with apps like YouTube.
We can’t know what the future will hold but the possibilities for designing platforms with Nostr are many. The advantage in designing a platform is that you can create a two sided market.
What is a Two-Sided Market?
All two-sided markets are platform markets, but not all platform markets are two-sided markets. The critical aspect of a two-sided market is that the volume of interactions on the platform depends on both the relative prices charged to each side and the total price charged. This is the case when both sides value more users on the other side, known in literature as an “indirect network externality.”
An example of a one-sided platform market is a clothes retailer, where the volume of sales depends only on the total price, not the relative prices charged to buyers and producers. Conversely, YouTube is a two-sided market where both creators and watchers benefit from more users. Watchers benefit from more variety and quality, while creators benefit from more users and views. YouTube introduces a special category of creators, the advertisers, who benefit monetarily from views because consumers viewing their content are likely to purchase their goods.
The prices paid by YouTube users are not all monetary:
· Watchers are charged an inconvenience fee in the form of advertisements.
· Advertisers are charged a monetary fee.
· Creators are not charged any fees.
Let’s assume the total fees for YouTube add up to $100. Say advertisers are charged $90, watchers face an inconvenience worth $10, and creators still enjoy $0 costs. In this scenario, the total volume of videos watched might be some number like 100,000.
Assume we change the price structure to advertisers being charged $80, watchers paying an inconvenience worth $10, and creators being charged $10 (keeping the total fees at $100). In this new scenario, the likely outcome is that the marginal creator will no longer create videos, and thus, the total volume of videos watched will fall.
Two-Sided Markets that Allow Money Exchange
The key to understanding Nostr’s value lies in its inbuilt payment mechanism—Bitcoin’s Lightning Network protocol. Although this protocol is not part of the Nostr codebase, the existing Nostr clients incorporate it to allow users to pay each other bitcoin with a simple user interface. This means that Nostr as a protocol is ideal for creating platforms where users can exchange monetary value. The mechanics and design choices of the Lightning network further augment Nostr’s value proposition more so than traditional payment systems like credit cards, PayPal, etc.
Key Problem: Chicken and Egg
So far, we have established that platform markets enable at least two groups of users to come together and exchange. The primary problem is that both groups will only use the platform if the other group is already using it, creating a classic chicken and egg scenario. Platforms operate by bringing groups of users together, making users reticent to switch to a new platform because they don’t know if the other users will be there. This gives existing platforms enormous power.
Guy Swann sums this up well in this Nostr note: note1695j0czewtkfwy7h4ne7k2ug706uwc7lendsq50prsfp8vwq8nfszdx4z7.
Competing with Existing Platforms: Divide and Conquer!
To compete with existing platforms, you need to divide and conquer. The original formulation for this strategy is given in both Caillaud and Jullien (2003) and Armstrong (2006). To take advantage of the indirect network externalities identified earlier, the divide and conquer strategy involves subsidising one side of the market to attract a large user base (the "divide" part) and then monetising the other side of the market (the "conquer" part).
Divide: Attract one side of the market by offering lower prices or subsidies. For example, offer free registration to one side. This subsidy is essential to kickstart the network effects, as a larger user base on one side increases the platform’s attractiveness to the other side. This was observed in the early days of YouTube, which was free for both creators and watchers.
Conquer: Once a substantial user base is established on the subsidised side, charge higher fees on the other side of the market. This can be seen in contemporary YouTube, where advertisers (a specific kind of creator) pay fees, and watchers deal with the inconvenience of watching ads (inconvenience is a non-price fee).
Implementing This Strategy in Your Platform:
So who are are you dividing, who are you conquering? Deciding which side to subsidise involves understanding which side offers more benefit to the other side. For example, in nightclubs (Wright, 2004), men and women go to interact. Men are assumed to gain more from each woman’s presence than vice versa, so nightclubs often subsidise women with free entry or drinks to attract men.
First, consider all your user groups. What brings them to your platform, what do they want to gain by interacting with the other user groups.
Think about, and identify, which group confers more value for the other group by being on the platform.
Then, think about how you can subsidise that user group. Free access is common. But Nostr allows seamless payment integration which encourages users to exchange money. A potential model for your platform could be that you charge a fee to both users based on how much value they send to each other. One way to subsidise users in this case is to reduce those fees.
Alternatively, you could pay users to join your platform using Nostr’s integration with the Lightning Network.
References:
· Armstrong, M. (2006). Competition in two-sided markets. The RAND Journal of Economics, 37(3), 668-691.
· Caillaud, B., & Jullien, B. (2003). Chicken & Egg: Competition among Intermediation Service Providers. The RAND Journal of Economics, 34(2), 309-328.
· Wright, J. (2004). One-sided logic in two-sided markets. Review of Network Economics, 3(1).
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 472f440f:5669301e
2025-05-14 01:15:12
@ 472f440f:5669301e
2025-05-14 01:15:12Marty's Bent
via Kevin McKernan
There's been a lot of discussion this week about Casey Means being nominated for Surgeon General of the United States and a broader overarching conversation about the effectiveness of MAHA since the inauguration and how effective it may or may not be moving forward. Many would say that President Trump won re-election due to Robert F. Kennedy Jr. and Nicole Shanahan deciding to reach across the aisle and join the Trump ticket, bringing with them the MAHA Moms, who are very focused on reorienting the healthcare system in the United States with a strong focus on the childhood vaccine schedule.
I'm not going to lie, this is something I'm passionate about as well, particularly after having many conversations over the years with doctors like Kevin McKernan, Dr. Jack Kruse, Dr. Mary Talley Bowden, Dr. Brooke Miller, Dr. Peter McCullough and others about the dangers of the COVID mRNA vaccines. As it stands today, I think this is the biggest elephant in the room in the world of healthcare. If you look at the data, particularly disability claims, life insurance claims, life expectancy, miscarriage rates, fertility issues and rates of turbo cancer around the world since the COVID vaccine was introduced in 2021, it seems pretty clear that there is harm being done to many of the people who have taken them.
The risk-reward ratio of the vaccines seems to be incredibly skewed towards risk over reward and children - who have proven to be least susceptible to COVID - are expected to get three COVID shots in the first year of their life if their parents follow the vaccine schedule. For some reason or another it seems that Robert F. Kennedy Jr. has shied away from this topic after becoming the head of Health and Human Services within the Trump administration. This is after a multi-year campaign during which getting the vaccines removed from the market war a core part of his platform messaging.
I'm still holding out hope that sanity will prevail. The COVID mRNA vaccines will be taken off the market in a serious conversation about the crimes against humanity that unfolded during the COVID years will take place. However, we cannot depend on that outcome. We must build with the assumption in mind that that outcome may never materialize. This leads to identifying where the incentives within the system are misconstrued. One area where I think it's pretty safe to say that the incentives are misaligned is the fact that 95% of doctors work for and answer to a corporation driven by their bottom line. Instead of listening to their patients and truly caring about the outcome of each individual, doctors forced to think about the monetary outcome of the corporation they work for first.
The most pernicious way in which these misaligned incentives emerge is the way in which the hospital systems and physicians are monetarily incentivized by big pharma companies to push the COVID vaccine and other vaccines on their patients. It is important to acknowledge that we cannot be dependent on a system designed in this way to change from within. Instead, we must build a new incentive system and market structure. And obviously, if you're reading this newsletter, you know that I believe that bitcoin will play a pivotal role in realigning incentives across every industry. Healthcare just being one of them.
Bitcoiners who have identified the need to become sovereign in our monetary matters, it probably makes sense to become sovereign when it comes to our healthcare as well. This means finding doctors who operate outside the corporate controlled system and are able to offer services that align incentives with the end patient. My family utilizes a combination of CrowdHealth and a private care physician to align incentives. We've even utilized a private care physician who allowed us to pay in Bitcoin for her services for a number of years. I think this is the model. Doctors accepting hard censorship resistant money for the healthcare and advice they provide. Instead of working for a corporation looking to push pharmaceutical products on their patients so they can bolster their bottom line, work directly with patients who will pay in bitcoin, which will appreciate in value over time.
I had a lengthy discussion with Dr. Jack Kruse on the podcast earlier today discussing these topic and more. It will be released on Thursday and I highly recommend you freaks check it out once it is published. Make sure you subscribe so you don't miss it.
How the "Exorbitant Privilege" of the Dollar is Undermining Our Manufacturing Base
In my conversation with Lyn Alden, we explored America's fundamental economic contradiction. As Lyn expertly explained, maintaining the dollar's reserve currency status while attempting to reshore manufacturing presents a near-impossible challenge - what economists call Triffin's Dilemma. The world's appetite for dollars gives Americans tremendous purchasing power but simultaneously hollows out our industrial base. The overvalued dollar makes our exports less competitive, especially for lower-margin manufacturing, while our imports remain artificially strong.
"Having the reserve currency does come with a bunch of benefits, historically called an exorbitant privilege, but then it has certain costs to maintain it." - Lyn Alden
This dilemma forces America to run persistent trade deficits, as this is how dollars flow to the world. For over four decades, these deficits have accumulated, creating massive economic imbalances that can't be quickly reversed. The Trump administration's attempts to address this through tariffs showcase how difficult rebalancing has become. As Lyn warned, even if we successfully pivot toward reshoring manufacturing, we'll face difficult trade-offs: potentially giving up some reserve currency benefits to rebuild our industrial foundation. This isn't just economic theory - it's the restructuring challenge that will define America's economic future.
Check out the full podcast here for more on China's manufacturing dominance, the role of Bitcoin in monetary transitions, and energy production as the foundation for future industrial power.
Headlines of the Day
Coinbase to replace Discover in S\&P 500 on May 19 - via X
Mallers promises no rehypothecation in Strike Bitcoin loans - via X
Get our new STACK SATS hat - via tftcmerch.io
Missouri passes HB 594, eliminates Bitcoin capital gains tax - via X
The 2025 Bitcoin Policy Summit is set for June 25th—and it couldn’t come at a more important time. The Bitcoin industry is at a pivotal moment in Washington, with initiatives like the Strategic Bitcoin Reserve gaining rapid traction. Whether you’re a builder, advocate, academic, or policymaker—we want you at the table. Join us in DC to help define the future of freedom, money & innovation in the 21st century.
Ten31, the largest bitcoin-focused investor, has deployed 144,264 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The 100+ degree days have returned to Austin, TX. Not mad about it... yet.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ ee6ea13a:959b6e74
2025-05-13 21:29:02
@ ee6ea13a:959b6e74
2025-05-13 21:29:02Reposted without permission from Business Insider.
Bitcoin Is A Joke
Joe Weisenthal Nov 6, 2013, 10:42 PM UTC

REUTERS/Eliana Aponte
Bitcoin is back in the news, as the digital currency has surged to new all-time highs in recent weeks.
A few weeks ago, it was just above $100. Today it's over $260.
This surge has prompted Timothy B Lee at The Washington Post to ask whether those who have called it a bubble in the past should retract and admit that they were wrong.
Well I'm not totally sure if I've called it a bubble, but I have spoken negatively of it, and I'll say that I still think it's a joke, and probably in a bubble.
Now first of all, I find the premise of Lee's post to be hilarious. The currency has been surging several percent every day lately, and that's evidence that it's not in a bubble?
Before going on, I want to be clear that saying something is a bubble is not saying it will go down. It could go to $500 or $1000 or $10,000. That's the nature of manias.
But make no mistake, Bitcoin is not the currency of the future. It has no intrinsic value.
Now this idea of "intrinsic value" when it comes to currency bothers people, and Bitcoin Bugs will immediately ask why the U.S. dollar has intrinsic value. There's an answer to that. The U.S. Dollar has intrinsic value because the U.S. government which sets the laws of doing business in the United States says it has intrinsic value. If you want to conduct commerce in the United States you have to pay taxes, and there's only one currency you're allowed to pay taxes in: U.S. dollars. There's no getting around this fact. Furthermore, if you want to use the banking system at all, there's no choice but to use U.S. dollars, because that's the currency of the Fed which is behind the whole thing.
On top of all these laws requiring the U.S. dollar to be used, the United States has a gigantic military that can force people around the world to use dollars (if it came to that) so yes, there's a lot of real-world value behind greenbacks.
Bitcoin? Nada. There's nothing keeping it being a thing. If people lose faith in it, it's over. Bitcoin is fiat currency in the most literal sense of the word.
But it gets worse. Bitcoin is mostly just a speculative vehicle. Yes, there are PR stunts about bars and other shops accepting bitcoins. And there is a Bitcoin ATM for some reason. But mostly Bitcoin is a speculative vehicle. And really, you'd be insane to actually conduct a sizable amount of commerce in bitcoins. That's because the price swings so wildly, that the next day, there's a good chance that one of the parties will have gotten royally screwed. Either the purchaser of the good will have ended up totally blowing a huge opportunity (by not holding longer) or the seller will be totally screwed (if Bitcoin instantly plunges). The very volatility that excited people to want to play the Bitcoin game is death when it comes to real transactions in the real world.
Again, Bitcoin might go up a lot more before it ultimately ends. That's the nature of bubbles. The dotcom bubble crashed a bunch of times on its way up. Then one day it ended. The same will happen with this.
In the meantime, have fun speculating!
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ c9badfea:610f861a
2025-05-16 20:15:31
@ c9badfea:610f861a
2025-05-16 20:15:31- Install Obtainium (it's free and open source)
- Launch the app and allow notifications
- Open your browser, navigate to the GitHub page of the app you want to install, and copy the URL (e.g.
https://github.com/revanced/revanced-managerfor ReVanced) - Launch Obtainium, navigate to Add App, paste the URL into App Source URL, and tap Add
- Wait for the loading process to finish
- You can now tap Install to install the application
- Enable Allow From This Source and return to Obtainium
- Proceed with the installation by tapping Install
ℹ️ Besides GitHub, Obtainium can install from additional sources
ℹ️ You can also explore Complex Obtainium Apps for more options
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 1d4d7479:8aec9f9c
2025-01-30 17:43:34
@ 1d4d7479:8aec9f9c
2025-01-30 17:43:34I'm new to Nostr and came here innocently enough. I was intrigued by the idea of building a blog on Npub.pro that not only could be published for the traditional web but would also allow us to get paid for great content or additional services within the Nostr community. Looking into the future I can see this approach as something that allows us to build a community that we can encourage to help support us.
The goals: 1. Build a traditonal blog. 2. Do work once, share on other platforms. 3. Own our content/thoughts. 4. Serve an international audience. 5. Cultivate a community. 6. Improve the Signal to Noise Ratio.
My belief is that we can serve all these through Nostr. I'll let you know how things go on the journey.
Tools on my radar: 1. Npub.pro 2. Habla.news 3. Alby
What else should I be looking at over the next 4 to 6 months when seeking to follow a Nostr-first strategy for a services business?
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ d61f3bc5:0da6ef4a
2025-05-13 16:03:48
@ d61f3bc5:0da6ef4a
2025-05-13 16:03:48What happens when you integrate a Nostr client with a bitcoin lightning wallet? They both get massively better! Social interactions benefit from seamless micropayments, while the wallet is able to tap into the massive address book represented by the Nostr social graph. This makes it possible to interact with people around the world in totally new ways. For example, Markus from Germany can zap a note posted by Isabella in Costa Rica, who can then buy a coffee with those sats, all from the same app.
At Primal, our goal is to deliver products that have mass appeal; products that can be easily used by anyone. Our latest iOS release represents our best take on how to build on open protocols and balance the tradeoffs between user sovereignty, user experience and ease of use. We believe that Nostr and Bitcoin will grow to billions of users, and we are building the technology that will help onboard and delight everyone.
Nostr Onboarding
Our goal is to achieve the highest level of user experience on a decentralized network, without sacrificing user sovereignty over their account, connections, and content. Therefore the onboarding process needs to be smooth and resemble what users are used to on legacy platforms, while providing access to their Nostr keys:

The user is able to sign up and start using Nostr quickly and without friction. Their key is available in the Account Settings, providing complete control over their Nostr account. In addition, the user can specify the set of Nostr relays they wish to publish to. The Primal iOS app signs all content with the user’s key and publishes it directly to the specified set of relays. This achieves full user control over their Nostr account, social connections, and the content they publish.

Performance & UX
In order to compete with the centralized legacy platforms, we must match and exceed their level of user experience. Interfaces must load quickly and completely, otherwise people will lose interest and Nostr will see a high degree of user churn. With this in mind, we built the Nostr caching service, and open sourced it so that other Nostr developers can leverage it as well. This enables us to provide the types of user experiences that are expected by most people today:

For details about our caching approach please refer to my Nostrasia presentation.
Primal Wallet
We are psyched to introduce Primal Wallet, an insanely easy-to-use transactional wallet, ideal for holding small amounts of bitcoin and making payments on the lightning network.
Strike is providing custody, fiat conversions, and lightning network connectivity to Primal users. By integrating with Strike, we are able to provide uninterrupted service to U.S. and international customers.

Smooth onboarding and wallet operation are essential for our use case. Given that we are dealing with very small amounts, we decided to take the custodial approach. This sacrifices direct user custody over the funds, but makes the overall UX seamless and reliable. New users are able to send and receive sats as soon as they download the app.
Here are a few additional points to keep in mind:
-
\In-App Purchases\: Once the wallet is activated, it is fully-operational and able to receive sats. If the user doesn’t own any sats, they are able to buy small amounts via an in-app purchase, in $5 increments. Note that these purchases are subject to “Apple tax” (15% in U.S. and Canada, 30% elsewhere, for customers with iOS devices), plus 1% Strike margin. Primal does not make any revenue on these purchases. Users can always buy sats through a different method and send them to their Primal Wallet. The in-app purchase is merely a convenient way for new users to get started with small amounts.
-
\Maximum Wallet Balance\: Primal Wallet is designed for holding and transacting with small amounts of bitcoin. Larger amounts should be kept in self custody, preferably on a hardware wallet. To encourage self custody for larger amounts, we are enforcing a maximum wallet balance of 1,000,000 sats (approximately USD $400 at the time of this writing).
We believe that Primal Wallet offers the best tradeoff balance for our use case, including social media zaps, and small purchases: coffee, beer, lunch, etc. We are planning to expand the feature set of the wallet in the upcoming releases, based on the feedback from our users.
Open Networks Win
Nostr is an open network, not controlled by any person, company, nor organization. Anyone can join without asking for permission, and any developer is free to build on it. In a short amount of time, hundreds of projects have sprouted building on Nostr, including: Damus, Amethyst, Snort, Highlighter, Alby, Nos, Mutiny, Coracle, ZBD, Fountain, Habla.news, Plebstr, Spring, Iris, Nostrgram, Current, Blogstack, Zap.stream, Listr, Nostr.band, Nostr.build, Flycat, Nosta.me, NoStrudel, Nostur, Nostore, Zaplife, Wavlake, and many more.
Your Nostr keys work with Primal, as well as every other app in the Nostr ecosystem. You can seamlessly use your Nostr identity in social media apps, blog/news sites, marketplaces, etc. Every Nostr product brings more users and more gravity to the entire network. This is why we believe that Nostr will eventually connect everybody.
If you are not satisfied with the status quo dictated by the legacy media complex, if you think that the global town square should not be owned by anyone, if you feel that people should be in control over their online identity, social connections, and the content they publish - you do have a choice. Join us on Nostr. 🤙💜
-
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ 1d7ff02a:d042b5be
2025-04-23 02:28:08
@ 1d7ff02a:d042b5be
2025-04-23 02:28:08ທຳຄວາມເຂົ້າໃຈກັບຂໍ້ບົກພ່ອງໃນລະບົບເງິນຂອງພວກເຮົາ
ຫຼາຍຄົນພົບຄວາມຫຍຸ້ງຍາກໃນການເຂົ້າໃຈ Bitcoin ເພາະວ່າພວກເຂົາຍັງບໍ່ເຂົ້າໃຈບັນຫາພື້ນຖານຂອງລະບົບເງິນທີ່ມີຢູ່ຂອງພວກເຮົາ. ລະບົບນີ້, ທີ່ມັກຖືກຮັບຮູ້ວ່າມີຄວາມໝັ້ນຄົງ, ມີຂໍ້ບົກພ່ອງໃນການອອກແບບທີ່ມີມາແຕ່ດັ້ງເດີມ ເຊິ່ງສົ່ງຜົນຕໍ່ຄວາມບໍ່ສະເໝີພາບທາງເສດຖະກິດ ແລະ ການເຊື່ອມເສຍຂອງຄວາມຮັ່ງມີສຳລັບພົນລະເມືອງທົ່ວໄປ. ການເຂົ້າໃຈບັນຫາເຫຼົ່ານີ້ແມ່ນກຸນແຈສຳຄັນເພື່ອເຂົ້າໃຈທ່າແຮງຂອງວິທີແກ້ໄຂທີ່ Bitcoin ສະເໜີ.
ບົດບາດຂອງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ
ລະບົບເງິນຕາປັດຈຸບັນໃນສະຫະລັດອາເມລິກາປະກອບມີການເຊື່ອມໂຍງທີ່ຊັບຊ້ອນລະຫວ່າງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ. ກະຊວງການຄັງສະຫະລັດເຮັດໜ້າທີ່ເປັນບັນຊີທະນາຄານຂອງປະເທດ, ເກັບອາກອນ ແລະ ສະໜັບສະໜູນລາຍຈ່າຍຂອງລັດຖະບານເຊັ່ນ: ທະຫານ, ໂຄງລ່າງພື້ນຖານ ແລະ ໂຄງການສັງຄົມ. ເຖິງຢ່າງໃດກໍຕາມ, ລັດຖະບານມັກໃຊ້ຈ່າຍຫຼາຍກວ່າທີ່ເກັບໄດ້, ເຊິ່ງເຮັດໃຫ້ຕ້ອງໄດ້ຢືມເງິນ. ການຢືມນີ້ແມ່ນເຮັດໂດຍການຂາຍພັນທະບັດລັດຖະບານ, ຊຶ່ງມັນຄືໃບ IOU ທີ່ສັນຍາວ່າຈະຈ່າຍຄືນຈຳນວນທີ່ຢືມພ້ອມດອກເບ້ຍ. ພັນທະບັດເຫຼົ່ານີ້ມັກຖືກຊື້ໂດຍທະນາຄານໃຫຍ່, ລັດຖະບານຕ່າງປະເທດ, ແລະ ທີ່ສຳຄັນ, ທະນາຄານກາງ.
ວິທີການສ້າງເງິນ (ຈາກອາກາດ)
ນີ້ແມ່ນບ່ອນທີ່ເກີດການສ້າງເງິນ "ຈາກອາກາດ". ເມື່ອທະນາຄານກາງຊື້ພັນທະບັດເຫຼົ່ານີ້, ມັນບໍ່ໄດ້ໃຊ້ເງິນທີ່ມີຢູ່ແລ້ວ; ມັນສ້າງເງິນໃໝ່ດ້ວຍວິທີການດິຈິຕອນໂດຍພຽງແຕ່ປ້ອນຕົວເລກເຂົ້າໃນຄອມພິວເຕີ. ເງິນໃໝ່ນີ້ຖືກເພີ່ມເຂົ້າໃນປະລິມານເງິນລວມ. ຍິ່ງສ້າງເງິນຫຼາຍຂຶ້ນ ແລະ ເພີ່ມເຂົ້າໄປ, ມູນຄ່າຂອງເງິນທີ່ມີຢູ່ແລ້ວກໍຍິ່ງຫຼຸດລົງ. ຂະບວນການນີ້ຄືສິ່ງທີ່ພວກເຮົາເອີ້ນວ່າເງິນເຟີ້. ເນື່ອງຈາກກະຊວງການຄັງຢືມຢ່າງຕໍ່ເນື່ອງ ແລະ ທະນາຄານກາງສາມາດພິມໄດ້ຢ່າງຕໍ່ເນື່ອງ, ສິ່ງນີ້ຖືກສະເໜີວ່າເປັນວົງຈອນທີ່ບໍ່ມີທີ່ສິ້ນສຸດ.
ການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ
ເພີ່ມເຂົ້າໃນບັນຫານີ້ຄືການປະຕິບັດຂອງການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ. ເມື່ອທ່ານຝາກເງິນເຂົ້າທະນາຄານ, ທະນາຄານຖືກຮຽກຮ້ອງໃຫ້ເກັບຮັກສາພຽງແຕ່ສ່ວນໜຶ່ງຂອງເງິນຝາກນັ້ນໄວ້ເປັນເງິນສະຫງວນ (ຕົວຢ່າງ, 10%). ສ່ວນທີ່ເຫຼືອ (90%) ສາມາດຖືກປ່ອຍກູ້. ເມື່ອຜູ້ກູ້ຢືມໃຊ້ຈ່າຍເງິນນັ້ນ, ມັນມັກຖືກຝາກເຂົ້າອີກທະນາຄານ, ເຊິ່ງຈາກນັ້ນກໍຈະເຮັດຊ້ຳຂະບວນການໃຫ້ກູ້ຢືມສ່ວນໜຶ່ງຂອງເງິນຝາກ. ວົງຈອນນີ້ເຮັດໃຫ້ເພີ່ມຈຳນວນເງິນທີ່ໝູນວຽນຢູ່ໃນລະບົບໂດຍອີງໃສ່ເງິນຝາກເບື້ອງຕົ້ນ, ເຊິ່ງສ້າງເງິນຜ່ານໜີ້ສິນ. ລະບົບນີ້ໂດຍທຳມະຊາດແລ້ວບອບບາງ; ຖ້າມີຫຼາຍຄົນພະຍາຍາມຖອນເງິນຝາກຂອງເຂົາເຈົ້າພ້ອມກັນ (ການແລ່ນທະນາຄານ), ທະນາຄານກໍຈະລົ້ມເພາະວ່າມັນບໍ່ໄດ້ເກັບຮັກສາເງິນທັງໝົດໄວ້. ເງິນໃນທະນາຄານບໍ່ປອດໄພຄືກັບທີ່ເຊື່ອກັນທົ່ວໄປ ແລະ ສາມາດຖືກແຊ່ແຂງໃນຊ່ວງວິກິດການ ຫຼື ສູນເສຍຖ້າທະນາຄານລົ້ມລະລາຍ (ຍົກເວັ້ນໄດ້ຮັບການຊ່ວຍເຫຼືອ).
ຜົນກະທົບ Cantillon: ໃຜໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ
ເງິນທີ່ຖືກສ້າງຂຶ້ນໃໝ່ບໍ່ໄດ້ກະຈາຍຢ່າງເທົ່າທຽມກັນ. "ຜົນກະທົບ Cantillon", ບ່ອນທີ່ຜູ້ທີ່ຢູ່ໃກ້ກັບແຫຼ່ງສ້າງເງິນໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ. ນີ້ລວມເຖິງລັດຖະບານເອງ (ສະໜັບສະໜູນລາຍຈ່າຍ), ທະນາຄານໃຫຍ່ ແລະ Wall Street (ໄດ້ຮັບທຶນໃນອັດຕາດອກເບ້ຍຕ່ຳສຳລັບການກູ້ຢືມ ແລະ ການລົງທຶນ), ແລະ ບໍລິສັດໃຫຍ່ (ເຂົ້າເຖິງເງິນກູ້ທີ່ຖືກກວ່າສຳລັບການລົງທຶນ). ບຸກຄົນເຫຼົ່ານີ້ໄດ້ຊື້ຊັບສິນ ຫຼື ລົງທຶນກ່ອນທີ່ຜົນກະທົບຂອງເງິນເຟີ້ຈະເຮັດໃຫ້ລາຄາສູງຂຶ້ນ, ເຊິ່ງເຮັດໃຫ້ພວກເຂົາມີຂໍ້ໄດ້ປຽບ.
ຜົນກະທົບຕໍ່ຄົນທົ່ວໄປ
ສຳລັບຄົນທົ່ວໄປ, ຜົນກະທົບຂອງປະລິມານເງິນທີ່ເພີ່ມຂຶ້ນນີ້ແມ່ນການເພີ່ມຂຶ້ນຂອງລາຄາສິນຄ້າ ແລະ ການບໍລິການ - ນ້ຳມັນ, ຄ່າເຊົ່າ, ການດູແລສຸຂະພາບ, ອາຫານ, ແລະ ອື່ນໆ. ເນື່ອງຈາກຄ່າແຮງງານໂດຍທົ່ວໄປບໍ່ທັນກັບອັດຕາເງິນເຟີ້ນີ້, ອຳນາດການຊື້ຂອງປະຊາຊົນຈະຫຼຸດລົງເມື່ອເວລາຜ່ານໄປ. ມັນຄືກັບການແລ່ນໄວຂຶ້ນພຽງເພື່ອຢູ່ໃນບ່ອນເກົ່າ.
Bitcoin: ທາງເລືອກເງິນທີ່ໝັ້ນຄົງ
ຄວາມຂາດແຄນ: ບໍ່ຄືກັບເງິນຕາ fiat, Bitcoin ມີຂີດຈຳກັດສູງສຸດໃນປະລິມານຂອງມັນ. ຈະມີພຽງ 21 ລ້ານ Bitcoin ເທົ່ານັ້ນຖືກສ້າງຂຶ້ນ, ຂີດຈຳກັດນີ້ຝັງຢູ່ໃນໂຄດຂອງມັນ ແລະ ບໍ່ສາມາດປ່ຽນແປງໄດ້. ການສະໜອງທີ່ຈຳກັດນີ້ເຮັດໃຫ້ Bitcoin ເປັນເງິນຫຼຸດລາຄາ; ເມື່ອຄວາມຕ້ອງການເພີ່ມຂຶ້ນ, ມູນຄ່າຂອງມັນມີແນວໂນ້ມທີ່ຈະເພີ່ມຂຶ້ນເພາະວ່າປະລິມານການສະໜອງບໍ່ສາມາດຂະຫຍາຍຕົວ.
ຄວາມທົນທານ: Bitcoin ຢູ່ໃນ blockchain, ເຊິ່ງເປັນປຶ້ມບັນຊີສາທາລະນະທີ່ແບ່ງປັນກັນຂອງທຸກການເຮັດທຸລະກຳທີ່ແທບຈະເປັນໄປບໍ່ໄດ້ທີ່ຈະລຶບ ຫຼື ປ່ຽນແປງ. ປຶ້ມບັນຊີນີ້ຖືກກະຈາຍໄປທົ່ວພັນຄອມພິວເຕີ (nodes) ທົ່ວໂລກ. ແມ້ແຕ່ຖ້າອິນເຕີເນັດລົ້ມ, ເຄືອຂ່າຍສາມາດຢູ່ຕໍ່ໄປໄດ້ຜ່ານວິທີການອື່ນເຊັ່ນ: ດາວທຽມ ຫຼື ຄື້ນວິທະຍຸ. ມັນບໍ່ໄດ້ຮັບຜົນກະທົບຈາກການທຳລາຍທາງກາຍະພາບຂອງເງິນສົດ ຫຼື ການແຮັກຖານຂໍ້ມູນແບບລວມສູນ.
ການພົກພາ: Bitcoin ສາມາດຖືກສົ່ງໄປໃນທຸກບ່ອນໃນໂລກໄດ້ທັນທີ, 24/7, ດ້ວຍການເຊື່ອມຕໍ່ອິນເຕີເນັດ, ໂດຍບໍ່ຈຳເປັນຕ້ອງມີທະນາຄານ ຫຼື ການອະນຸຍາດຈາກພາກສ່ວນທີສາມ. ທ່ານສາມາດເກັບຮັກສາ Bitcoin ຂອງທ່ານໄດ້ດ້ວຍຕົນເອງໃນອຸປະກອນທີ່ເອີ້ນວ່າກະເປົາເຢັນ, ແລະ ຕາບໃດທີ່ທ່ານຮູ້ວະລີກະແຈລັບຂອງທ່ານ, ທ່ານສາມາດເຂົ້າເຖິງເງິນຂອງທ່ານຈາກກະເປົາທີ່ເຂົ້າກັນໄດ້, ເຖິງແມ່ນວ່າອຸປະກອນຈະສູນຫາຍ. ສິ່ງນີ້ສະດວກສະບາຍກວ່າ ແລະ ມີຄວາມສ່ຽງໜ້ອຍກວ່າການພົກພາເງິນສົດຈຳນວນຫຼາຍ ຫຼື ການນຳທາງການໂອນເງິນສາກົນທີ່ຊັບຊ້ອນ.
ການແບ່ງຍ່ອຍ: Bitcoin ສາມາດແບ່ງຍ່ອຍໄດ້ສູງ. ໜຶ່ງ Bitcoin ສາມາດແບ່ງເປັນ 100 ລ້ານໜ່ວຍຍ່ອຍທີ່ເອີ້ນວ່າ Satoshis, ເຊິ່ງອະນຸຍາດໃຫ້ສົ່ງ ຫຼື ຮັບຈຳນວນນ້ອຍໄດ້.
ຄວາມສາມາດໃນການທົດແທນກັນ: ໜຶ່ງ Bitcoin ທຽບເທົ່າກັບໜຶ່ງ Bitcoin ໃນມູນຄ່າ, ໂດຍທົ່ວໄປ. ໃນຂະນະທີ່ເງິນໂດລາແບບດັ້ງເດີມອາດສາມາດຖືກຕິດຕາມ, ແຊ່ແຂງ, ຫຼື ຍຶດໄດ້, ໂດຍສະເພາະໃນຮູບແບບດິຈິຕອນ ຫຼື ຖ້າຖືກພິຈາລະນາວ່າໜ້າສົງໄສ, ແຕ່ລະໜ່ວຍຂອງ Bitcoin ໂດຍທົ່ວໄປຖືກປະຕິບັດຢ່າງເທົ່າທຽມກັນ.
ການພິສູດຢັ້ງຢືນ: ທຸກການເຮັດທຸລະກຳ Bitcoin ຖືກບັນທຶກໄວ້ໃນ blockchain, ເຊິ່ງທຸກຄົນສາມາດເບິ່ງ ແລະ ພິສູດຢັ້ງຢືນ. ຂະບວນການພິສູດຢັ້ງຢືນທີ່ກະຈາຍນີ້, ດຳເນີນໂດຍເຄືອຂ່າຍ, ໝາຍຄວາມວ່າທ່ານບໍ່ຈຳເປັນຕ້ອງເຊື່ອຖືທະນາຄານ ຫຼື ສະຖາບັນໃດໜຶ່ງແບບມືດບອດເພື່ອຢືນຢັນຄວາມຖືກຕ້ອງຂອງເງິນຂອງທ່ານ.
ການຕ້ານການກວດກາ: ເນື່ອງຈາກບໍ່ມີລັດຖະບານ, ບໍລິສັດ, ຫຼື ບຸກຄົນໃດຄວບຄຸມເຄືອຂ່າຍ Bitcoin, ບໍ່ມີໃຜສາມາດຂັດຂວາງທ່ານຈາກການສົ່ງ ຫຼື ຮັບ Bitcoin, ແຊ່ແຂງເງິນຂອງທ່ານ, ຫຼື ຍຶດມັນ. ມັນເປັນລະບົບທີ່ບໍ່ຕ້ອງຂໍອະນຸຍາດ, ເຊິ່ງໃຫ້ຜູ້ໃຊ້ຄວບຄຸມເຕັມທີ່ຕໍ່ເງິນຂອງເຂົາເຈົ້າ.
ການກະຈາຍອຳນາດ: Bitcoin ຖືກຮັກສາໂດຍເຄືອຂ່າຍກະຈາຍຂອງບັນດາຜູ້ຂຸດທີ່ໃຊ້ພະລັງງານການຄິດໄລ່ເພື່ອຢັ້ງຢືນການເຮັດທຸລະກຳຜ່ານ "proof of work". ລະບົບທີ່ກະຈາຍນີ້ຮັບປະກັນວ່າບໍ່ມີຈຸດໃດຈຸດໜຶ່ງທີ່ຈະລົ້ມເຫຼວ ຫຼື ຄວບຄຸມ. ທ່ານບໍ່ໄດ້ເພິ່ງພາຂະບວນການທີ່ບໍ່ໂປ່ງໃສຂອງທະນາຄານກາງ; ລະບົບທັງໝົດໂປ່ງໃສຢູ່ໃນ blockchain. ສິ່ງນີ້ເຮັດໃຫ້ບຸກຄົນມີອຳນາດທີ່ຈະເປັນທະນາຄານຂອງຕົນເອງແທ້ ແລະ ຮັບຜິດຊອບຕໍ່ການເງິນຂອງເຂົາເຈົ້າ.
-
 @ b83a28b7:35919450
2025-05-16 19:13:43
@ b83a28b7:35919450
2025-05-16 19:13:43This is the body
-
 @ 472f440f:5669301e
2025-05-12 23:29:50
@ 472f440f:5669301e
2025-05-12 23:29:50Marty's Bent
Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Make some noise!
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed 145,630 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 472f440f:5669301e
2025-05-12 23:29:19
@ 472f440f:5669301e
2025-05-12 23:29:19Marty's Bent
Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Make some noise!
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed 145,630 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:31
@ 9e69e420:d12360c2
2025-01-26 01:31:31Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6ad08392:ea301584
2025-05-12 20:22:09
@ 6ad08392:ea301584
2025-05-12 20:22:09
Satlantis is here!
Well…sort of. It’s a little pre-mature, but it’s good enough for you to play around with. I wouldn’t necessarily call it super ‘useful’ right now but I wanted you to get an early glimpse into what we’re building so you can see how it evolves over time.
And besides - we have to release a first version at some stage!
Satlantis is the first travel-centric social network. It’s quite different from anything else that came before it. It’s part map, part directory, part events app and part social network.
It really is a monumental undertaking - but I’m convinced now is the time to build it. People are ready for something new. They are tired of the algorithmic slop social media has become. They’re craving real connection and they want to see, touch, smell, hear and taste the world. What better way to help them do that, than with a network that connects them, andhelps enhance their discovery of places, experiences and events that are relevant to them (based both on their interests and social connections).
That’s what this product is all about. We’re going to do what Google Maps, Yelp, Instagram, TripAdvisor etc. are all partially doing - but make it 10x better.
The first Satlantis app is now available on Apple Testflight or the Google Play store. In the coming month or two, we will make Satlantis accessible via invitation-only, to increase the quality of connection and discourse on the app, but if you’re reading this now, you’re in before we gate it, you can explore and give us some feedback while we work on it.
I will write release notes like this every couple weeks covering what we built, what to test and play with, what’s working, what needs improvement, what’s downright shit or broken and what’s coming in the next release. (This first one is the longest because I delayed it so much.)
I’d love to hear your feedback, and if you find this interesting, please share it around so other people find out about what we’re building!
The Good
Mobile AppWe got a version out, and you can actually use it.
Nostr Compatible.
Every single account on Satlantis is an nPub. You can log into Satlantis using your nSec (not your nPub - we forgot to include that...lol), and you will find your entire social network and all of your posts there (if they are media notes). On the Web, you need to use an extension, like Alby or Keys.band. On mobile you can paste your key (stored locally on the device).
Normie Friendly.
We also built a smooth non-nostr focused sign up flow. We originally used the nSec bunker, but that was a mess (love u Pablo). So we built our own nSec bunker, but that sucked too. Passwords are old school. After interviewing 100 people not into Bitcoin or Nostr, 95% of them preferred us to store their key. So…we took that feedback and created a really easy email + magic link, Google and Apple SSO sign up flow, that creates an account and Nostr keypair that we store on their behalf, encrypted.
If and when people work out what Nostr is and they want to take custody of their key, they will be able to export their key, and request deletion of their key from our DB.
Is this the most ‘pure’ solution? No. Does this mean they have to trust us? Sure. Could we do it better at some point? Yes, of course. But considering the number of mission critical features we need to build, we’ll come back to it later.
We currently only support Kind 1 events.
Well…we also support NIP-52 calendar events, but we’ve disconnected that for the time being because event organisers wanted co-hosts more than they wanted to broadcast their events on Nostr. We’re working on a way to reconcile the two. For now, post text & images. (Video coming soon).
Interest-centric onboarding.
We spent a lot of time building this. One of the key pillars at Satlantis is discovering people, places, events and content suited to you. As we dug down the personalisation rabbithole, we found that there is a resurgence of interest-selection in many apps: from Tinder to new apps like Locals and Timeleft. The more focused on personalisation the app is, the more in-depth the onboarding.
Of course Meta and TikTok do the best personalisation with their advanced ML & AI tools, along with their deep social graphs, but since we have neither (Nostr helps but it’s still very small), we needed a better way.
So we decided to build our interest-graph. It was brain-melting, but we developed a pretty exhaustive set of interests relevant to people in our target market. We then took that list and associated it to events, merchants, people, places, experiences, activities and content. We then built a whole new onboarding flow to capture this from new users, and associate it to their accounts. (Yes - at some stage, we’ll make this Nostr compatible so it can travel with nPubs)
 The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.
The net result is a base layer of insight we can use to help surface things that are of interest to users. Whether it’s an event, a place to eat, a gym or sauna, content to engage with or people to meet: like magic, things that are relevant to you will come to you.Of course, in the long term we will use your social graph and the way you interact with content to do this - more like Meta and TikTok do - but for now, while the social graph is tiny, this is the most efficient and effective way.
Final word: the current version has all the interests - but it’s not very user-friendly. The latest design fixes that by grouping the interests into better subcategories. Keep an eye on that in a subsequent release.
New Merchant Discovery Experience.
This was also a monumental task. Our first merchant experience was just a shitty map with a list on web, and just a list on mobile (see below). This list was ranked by an “aggregate rating” we computed by analysing all the venue’s ratings from apps like Google, Trip Advisor and more.
We spent a long time trying to figure out how to display this better and do it in a way nobody else is, because seriously -can you think of a single food app or merchant map out there which has a nice UI or UX? No.
AirBnB transformed the UI & UX for accommodation and pushed the whole space forward. Nobody has really done it for every other kind of place you go to. So we took it up ourselves to fix this and create a proper “merchant discovery experience” with an information-dense location tile. Check this out:
Notice how we managed to get all the key information you need about a place there on the one tile, including who in your social circle has recommended it. That’s the key ingredient which makes Satlantis special. No more messaging friends or people you know “hey - have you been to that place” or “do you recommend that place”?
 One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!
One small issue here is that this upgrade will kill the map…but only for a couple weeks, until we release the new map view!Merchant coverage
Our merchant app covers SIX distinct categories:
-
Cafes & Restaurants
-
Health & Wellness (think Gyms, Spas, Saunas, etc)
-
Attractions (from Museums, to lookouts to beaches & hikes)
-
Grocery & Specialty Foods (think Organic food store, farmers markets, etc)
-
Coworking & Event Spaces
-
Nightlife (Bars, Clubs, etc)
 We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more.
We scoured the web for the best curated lists and directories for each of these categories. This in Bitcoin accepted (everything relevant from BTCMaps - because we’re also built on Open Street Maps, so it’s synced up), Seed Oil Free (everything from Local Fats & Seed Oil Scout is here), Michelin Star rated, Real Milk (Raw Milk directory) and more. Alongside all of these directories, our network of local ambassadors have submitted their top local picks for their favorite cities, so you have real local recommendations.
The destinations with the best maps are currently Canggu, Uvita, Prague, Sao Paulo, Dubai, Florianópolis.
Suggest Places & Merchants
This is working quite nicely. Anyone, anywhere can now suggest their favorite merchant. For now, we’re manually approving submissions daily to avoid spam and irrelevant shit. In time, we’ll find a better way to do this.
It’s all plugged into the Google API, so you can just type in the name of the place you think should be added (from mobile or web here). Once approved, our AI pipeline goes to work gathering all the available data from Google, TripAdvisor and elsewhere to set up the merchant profile, complete with review summaries, images, profile bio, contact details, opening hours, tags and more.
Got more upgrades to this flow in the works, but it’s ready for you to try out now.
City Pages
The current city pages are part of an outdated design which doesn’t fit our new visual language, but they are a ‘live’ feature. The original idea was to blend elements of Pinterest and Instagram but it backfired so we are changing to a more slick one-column feed. That being said, the core features of the city pages work. You can:
-
Join a city (like joining a community or following the page)
-
Post content on the city page
-
Navigate over to the different available pages, including merchants, events, scores and stats + facts
We have 80 cities currently available. More to come.
Scores, Stats & Facts
When we set out to first build Satlantis, we wanted to improve on the information NomadList was presenting for cities & destinations around the world. So we developed a different approach for city scoring based not only on data we could get from Numbeo, etc - but also information direct from people on the ground - in particular; expats and locals.
We put together a set of score categories and created a dedicated survey for select people to fill out, which would create some “foundation” scores, with a view to have this survey available to the crowd, perhaps via a score voting system or some sort on the page. We haven’t got that far yet. Right now, we have foundation scores for each of those 80 active cities, along with key Stats and Facts, like cost of living, wifi speed, water drinkability, and more:
This is not a core feature for us, so we will look to partner with other providers to enhance the experience, or we’ll completely re-think how we’re going to do it. Stay tuned for more here and let me know if you find it useful at all right now (or not).
Events
Last but not least, we have events! God dammit this was annoying because we built it NIP-52 compatible in the beginning, which then limited what we could do with co-hosts and other essential event features. And all for nothing since there are no other well built or maintained calendar-event clients on Nostr anyway.
So right now, when you post an event on Satlantis, it will post only on Satlantis. This means that as a host, you can edit, add co-hosts, add locations (proper merchant tiles) and delete.
We will make this Nostr-compatible again, most likely with some sort of button for hosts to “broadcast this event to Nostr” - knowing they will lose some flexibility once they do - but we need to do more research here. Maybe we’ll propose an upgrade to the calendar event NIP (or propose a new NIP altogether). It’s on our roadmap, so we’ll do our best to get to it soon.
Meetup integration.
We’ve been working with the Meetup API to let organizers quickly import their events into Satlantis. It’s been frustratingly complex because of how archaic they are, but we got it working!
🚀 If you run a Meetup, and want to automatically have your events listed on Satlantis when you list them on meetup,reach out! We’ll even cover the Meetup membership fee for 10 meetup groups who set up auto-importing for their events. If you’re interested, reach out to us.
The Bad
These things are currently bad, broken, incorrectly built or buggy. Believe me, if the list was exhaustive, this essay would be a book (our internal list is very full) - so I’m just going to touch on the main things we’re aware of and will be fixing…or just letting it burn slowly while we put out other fires.
Personal content feed
We started Satlantis with a media-only approach, taking inspiration from Instagram. We changed course a couple months ago to support text only posts, realizing there were a lot of other things people would like to post about travel, for example: guides, restaurants, reviews, tips, events, instructions, recommendations.
So…we started supporting this on the feed, and in the “post content” flow - but of course, not yet supported in the Profile view (which is still an image grid). This means if you post text only, you’re not going to see your own post on Satlantis 🤣🤣
To fix this, we’re building a “personal feed” section on your profile. But…that will come after we polish some of the things above, so if you’re posting on Satlantis right now, photos please!!
Video content
This one hurts too. We currently neither render videos from other clients, nor do we support video uploads on Satlantis. Not because we don’t want to, but because we haven’t got to it. This is high on the priority list and will be fixed in the upcoming releases.
Settings & Edit profile
We forgot to add “edit username” 🤣
This is being added now, along with a settings section where you can get your nPub and things like that. We’ll keep it very basic for now.
Notifications
Holy crap. These really suck. There is no other way to put it. The design is not great, the experience is buggy as hell and syncing notifications from the broader Nostr network doesn’t make life any easier. We’ll be making incremental improvements here (for a long time I guess).
Limited social graph functionality.
Right now, there’s not much social-dynamics beyond the feed. This will expand and begin to influence more than just content, but also merchants, events, people, activities, etc.
Speed issues.
Feed and profile loading times are sluggish and need performance improvements. Ongoing.
Large Destinations are problematic.
How do you rate a massive city like São Paulo as a single entity? Well….you can’t. Eventually, we’ll break major cities into regions, but that’s a big project for later.
For now, when you see scores, stats and facts, assume we’re covering the most relevant traveler-friendly areas (e.g., Jardins in São Paulo, Palermo in Buenos Aires, etc).
The Ugly
There is really only one new ‘feature’ to complete before we apply a feature freeze and continue on to polish everything. This and the other items listed will be available in the next release or two, so that the overall experience is a little more…beautiful.
Chat.
We wanted to do NIP-17, but considering that (a) most of the major apps are still NIP-04, (b) BTCPrague is around the corner and (c) limited resources, we chose to do a NIP-04 implementation for this first version. Not ideal, but good enough. Chat will continue to improve, not only with a NIP-17 upgrade, but with other features like chat folders, group chats, GIFs and more.
Polish List
-
Merchant Experience: Web and mobile updates
-
Merchant List: More cool places being uploaded
-
Events: New display, RSVP flow, co-host notifications, merchant integration
-
Onboarding: Updated interests tags & flow
-
Scores: Updates to Cost of Living & overall score weights
-
Notifications: A lot of improvement here
-
Feed: Text only posts, video uploads & rendering videos from other clients
-
City Page: New design and functionalities
-
Zaps: Yes. We will have Zaps.
Final Words
We have our work cut out for us!
We will be at BTCPrague in June and we are committed to releasing all of these features and components by then…as polished as possible.
The team and I have a couple of asks:
-
Download the app, and either create a new account or if you’re on Nostr, log in with your existing Nostr key (web requires an extension like Alby)
-
Go through the interests, and select those that are most relevant to you. The magic of the app happens as a function of how accurately you select those.
-
Post some content! Could be a photo introducing yourself or a “Good Morning” or whatever. Make sure you tag @Satlantis or @Svetski and I’ll boost you.
-
Check out the merchants in the top cities & see what’s around. The city with the most merchants right now is Florianopolis, but we have some coverage in many other cities
-
If you run a meetup or attend a regular Bitcoin meetup, let the organisers know, and let’s start to bring meetups and events across. Not asking anyone to ‘leave’ meetup now, but come and sync up your account so events are auto-published. \ As we make the events feature more robust (and Bitcoin native), every Bitcoin meetup in the world is going to want to come use this. If you’re early, you can help us shape it!
-
Let a couple of friends know about the app - ideally those who are not yet on Nostr - and ask them to try it out. They can sign up with email or SSO if they’re afraid to store their own key.
-
Like I said in the beginning, at some point in the next month or so, it will become an invite-only app. We will grandfather all existing users in, but new people will need an invite code (from existing users or via codes I drop into release notes and articles) to access it. \ \ The goal of this approach is to (a) increase the quality of connection amongst people on Satlantis, and (b) try a new way of growing a Nostr-based app.
-
Finally…we’ve decided to do an equity crowdfund. So if you find what we’re doing interesting and want to be a part of it, you’ll have a chance from June onwards. More to follow on this in the coming weeks. It will be on Timestamp Financial - Bitcoin crowdfunding platform - so go check them out.
Thank you again for your attention - I do not take it lightly. This is just the start, so expect to see ALOT more from us in the way of updates and shipping (plus these updates will be shooter).
Make sure you subscribe to this newsletter if you’re reading on Substack, or follow me if you’re on Nostr, Medium or wherever else you’re reading it.
Aleksandar Svetski
Thanks for reading Social 2.0! Subscribe for free to receive new posts & stay up to date with what we’re building & learning along the way.
When the app goes into “Invite Only” mode, you will need a special invite code to access it, unless you’ve already got an account. For now, it’s open access.
If you're already on Nostr, you're already on Satlantis. Just use an extension to securely log in with your nSec (on web), or with your nSec on mobile.
-