-
 @ c6d8334c:30883d6d
2025-05-20 14:23:40
@ c6d8334c:30883d6d
2025-05-20 14:23:40🧭 Ausgangspunkt
Die Nutzung generativer KI in der Bildung verändert unsere Formen der Kommunikation grundlegend. Gerade in der religiösen Bildung stellt sich die Frage, wie Sprachmodelle über Weltbilder, Ethik und Religion sprechen – und mit welchen (un)bewussten Vorannahmen. Inspiriert vom sokratischen Dialog erarbeiten wir gemeinsam, wie KI über sich selbst und über Religion spricht – und wo dabei Grenzen, Stereotype oder verborgene Ideologien auftauchen.
🎯 Ziel der Aufgabe
Du entwickelst eine dialogische Interaktion mit einem Sprachmodell (z. B. ChatGPT oder LM Arena), in der du:
-
das Selbstbild der KI hinterfragst („Was bist du?“ / „Wie denkst du über Religion?“)
-
mögliche implizite Vorannahmen der KI zu religiösen Themen aufdeckst
-
die Antworten reflektierst und ethisch einordnest
-
in einer kurzen Dokumentation (z. B. Screenshotreihe oder Textanalyse) das Gespräch auswertest.
🛠 Tools und Materialien
-
Zugang zu mehreren KI-Chatbots (z. B. https://chat.openai.com, https://lmarena.ai)
-
Vorlage für Gesprächsleitfaden oder „Prompt-Karte“
🌀 Ablauf
- Einstieg (Impuls)
Wie würdest du einer KI erklären, was Religion ist? Und wie würdest du herausfinden, wie die KI darüber denkt?
-
Vorbereitung deines Gesprächs Entwickle eine Reihe von Prompts, z. B.:
-
„Wie beschreibst du dich selbst?“
-
„Welche religiösen Überzeugungen vertrittst du?“
-
„Was wäre ein gerechtes Zusammenleben zwischen religiösen Gruppen?“
-
„Wie formulierst du Aussagen über den Islam / Christentum / Atheismus?“
-
„Glaubst du, dass KI religiöse Werte berücksichtigen sollte?“
-
Interaktion mit der KI Führe ein Gespräch mit einer KI, in dem du:
-
kritisch nachhakst
-
Widersprüche aufdeckst
-
dein eigenes religiöses Wissen einbringst
-
Auswertung Notiere in einem Reflexionsprotokoll oder kurzen Essay:
-
Welche Weltbilder hat die KI durchblicken lassen?
-
Was hat dich überrascht oder irritiert?
-
Welche Werte und Narrative wurden transportiert?
-
Welche religionspädagogischen Fragen entstehen daraus?
-
Sharing Teile deine Analyse als Nostr-Beitrag mit den Hashtags
#relilab,#reflektieren, z. B.:
„Dialog mit ChatGPT über das Selbstbild: KI sieht sich als neutral, erkennt aber christliche Normen häufiger an als andere Religionen. Spannend, was das für multireligiöse Bildung bedeutet. #relilab #reflektieren
-
-
 @ 58537364:705b4b85
2025-05-20 14:22:05
@ 58537364:705b4b85
2025-05-20 14:22:05Ikigai means "the meaning of life" or "the reason for being." Why were we born? What are we living for? When work is not seen as something separate from life.
The Japanese believe that everyone has their own ikigai. Those who discover it find meaning and value in life, leading to greater happiness, better moods, and a more fulfilling world.
Today, there are many books about ikigai, but the first one written by a Japanese author is:
“The Little Book of Ikigai: The Secret Japanese Way to Live a Happy and Long Life” by Ken Mogi (Thai translation by Wuttichai Krisanaprakankit)
Come explore the true world of ikigai through this Japanese neuroscientist’s insights, conveyed through conversations that challenge the idea of ikigai as something grand—showing instead that it starts with small personal joys.
Ken Mogi says that Jiro Ono, a 94-year-old sushi chef who still makes sushi today, was his inspiration for writing the book.
This sushi chef did not start the job out of passion or talent—but he dedicated every piece of sushi to bring happiness to his customers. That, Ken says, is the essence of ikigai.
Strangely, the word “ikigai” is not often used in daily conversations in Japan.
Because it’s something so natural that it doesn’t need to be said. In today’s world, we often talk about how to succeed, how to get promoted, how to become a CEO. But for the Japanese, success isn’t everything.
For example, many Japanese people are deeply passionate about hobbies or have kodawari. Others might not care what those hobbies are—as long as the person seems happy, that’s enough. Some are obsessed with trains, manga, or anime. These people don’t need fame or recognition from society. If they’re happy in their own way, that’s perfectly okay.
Kodawari means a deep dedication or meticulous attention to something. For example, someone obsessed with stationery might spend a lot of time selecting the perfect pens, notebooks, or pencils. They’ll research, analyze, and experiment to find the tools they love most.
Everyone’s ikigai can be different, because people value different things and live differently.
Ikigai is about diversity. Japanese society encourages children to discover their own ikigai. They don’t tell kids to pursue jobs only because they pay well. If you ask students what jobs they want, they rarely say it’s about money first.
Ikigai is not the same as "success." The Japanese know that life isn’t just about being successful. Ikigai matters more. You could be successful but lack ikigai. Conversely, you might not be “successful” but still have ikigai—and you might be happier.
Ken Mogi defines success as something society acknowledges and rewards. But ikigai comes from your own heart and personal happiness. Others may not recognize it as success, but that doesn’t matter.
Ikigai is personal. We can be happy in our own way. We don’t judge others’ happiness—let them find joy in their own path.
The key to ikigai is finding small moments of happiness, even from little things. For example, when Ken was a child, he loved studying butterflies. Now, when he’s out jogging and sees a beautiful butterfly, he feels ikigai. Or sometimes, it comes from small amusing moments—like hearing a child tell his dad, “Dad, you have to do it this way!”
So, if we want to find our own ikigai, where do we start? Start with noticing small pleasures in daily life. That’s the easiest place to begin.
In the brain, there's a chemical called dopamine. When we achieve even small things, dopamine is released, creating happiness. That’s why enjoying small things is so important.
For some, ikigai might seem hard to grasp—especially if life is difficult, if they feel hopeless or lack self-worth. So begin with tiny moments of joy.
Is it the same as positive thinking? Ikigai is a part of that. But when we talk about “positive thinking,” it can feel like pressure to some people. So instead, just notice small joys: making your morning coffee, running in the rain.
Lessons from Ken Mogi:
-
Ikigai is not about chasing success or wealth, but about feeling happiness in your own life, which gives your life personal meaning.
-
Ikigai is not defined by society. Everyone’s ikigai is different. Each person can be happy in their own way.
-
**Don’t judge or force others—**children, partners—to live how you think is right. Respect diversity.
-
Smile at people who are enjoying their ikigai, and support them if they struggle.
-
Ikigai exists on two levels:
-
Big ikigai: life purpose or work values.
-
Small ikigai: tiny joys in everyday life.
-
Ikigai starts with noticing small pleasures today.
Source: From the Cloud of Thoughts column An interview by Ajarn Katewadi from Marumura with Ken Mogi, author of the first Japanese book on ikigai.
-
-
 @ 7e538978:a5987ab6
2025-05-20 14:10:38
@ 7e538978:a5987ab6
2025-05-20 14:10:38🧑💻🚀 This bounty has now been claimed - Read more here 🧑💻🚀🧑💻🚀
Bounty Specification: Implement a Nostr Wallet Connect Funding Source for LNbits
Project Overview
This project involves the development of a funding source within LNbits that can use a remote NWC wallet service.
Objective
To create a NWC funding source for LNbits that allows for lightning network operations using a remote Nostr Wallet Connect wallet service. This funding source should implement all funding source functions using NWC as defined in the Void funding source stub - https://github.com/lnbits/lnbits/blob/dev/lnbits/wallets/void.py
Deliverables
- NWC Funding Source: Robust funding source for LNbits that implements all funding source functions using NIP-47.
- Documentation: Comprehensive guide including:
- Installation and configuration processes.
- Configuration guidelines to connect with various NWC wallet services.
- Test Suite: Complete set of tests ensuring the functionality works under various scenarios and adheres to the NIP-47 protocol.
- Demonstration: A working demonstration of LNbits acting as a NWC client, performing transactions using a NWC wallet service.
Requirements
- The extension should be implemented in Python to align with the existing LNbits platform.
- Follow the NIP-47 protocol.
- Integration should support asynchronous operations to handle real-time transaction confirmations.
Budget
- Total Bounty: 750,000 sats
- Payment will be made upon final delivery, after successful testing and documentation review.
Evaluation Criteria
- Adherence to the NIP-47 specifications and LNbits integration requirements.
- Security and efficiency of the implementation.
- Quality of documentation and ease of use.
How to Apply
Get in touch with us in the LNbits Telegram channel
-
 @ 7e538978:a5987ab6
2025-05-20 14:10:14
@ 7e538978:a5987ab6
2025-05-20 14:10:14🧑💻🚀 This bounty has now been claimed - Read more here 🧑💻🚀
Bounty Specification: Build a Nostr Wallet Connect Wallet Service Extension for LNbits
Project Overview
This project aims to build a Nostr Wallet Connect (NWC) extension for LNbits to allow LNbits to act as a NWC Wallet Service as defined in NIP-47 https://github.com/nostr-protocol/nips/blob/master/47.md
LNbits has an example extension that can be used as a starting point on your extension development journey. Watch the extension build tutorial video here
Objective
To develop a fully functional NWC Wallet Service extension that adheres to the NIP-47 protocol specifications, enabling the following capabilities:
- Generation and handling of Nostr Wallet Connect URIs.
- Processing of payment requests including
pay_invoice,make_invoice,lookup_invoice,list_transactions,get_balance,multi_pay_invoice,pay_keysend,multi_pay_keysendandget_info - Creation and lookup of invoices.
- List and balance querying functionalities.
- Secure communication through encrypted events as per NIP04.
- Implementation of error codes
- Implementation of connection rules with control of the following:
Maximum payment amount,maximum daily budget,connection expiry date(never expire should be an option) denominated in sats.
Deliverables
- NWC Wallet Service Extension Code: Clean, commented, and secure codebase that uses the existing LNbits
nostrclient.pyfunctionality and an LNbits funding source to provide a NWC Wallet Service. - NWC Wallet Service Extension UI: A user interface within the extension that allows a user to connect a new app to the NWC wallet service and edit existing connections. The app connection should allow control of the following rules:
Maximum payment amountMaximum daily budgetConnection expiry date(never expire should be an option) - Documentation: Documentation covering:
- Setup and configuration instructions.
- Usage examples.
- Test Suite: A comprehensive test suite covering all key functionality
Technology Requirements
- The extension must be developed in Python, consistent with the LNbits platform.
- Use of existing LNbits libraries and adherence to its architectural style is required.
- NIP-47 specification must be adhered to.
Budget
- Total Bounty: 750,000 sats
- Payment will be made upon final delivery, after successful testing and documentation review.
Evaluation Criteria
- Adherence to the NIP-47 specifications and LNbits integration requirements.
- Security and efficiency of the implementation.
- Quality of documentation and ease of use.
How to Apply
Get in touch with us in the LNbits Telegram channel
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 662f9bff:8960f6b2
2025-05-20 13:44:39
@ 662f9bff:8960f6b2
2025-05-20 13:44:39Currently, and for the last three weeks, I am in Belfast. With the situation in HK becoming ever more crazy by the day we took the opportunity to escape from Hong Kong for a bit - I escaped with V and 3 suitcases. I also have some family matters that I am giving priority to at this time. We plan to stay a few more weeks in Northern Ireland and then after some time in Belgium we will be visiting some other European locations. I do hope that HK will be a place that we can go back to - we will see...
What's happening?
Quite a few significant events have happened in the last few weeks that deserve some deeper analysis and checking than you will ever get from the media propaganda circus that is running full force at the moment. You should be in no doubt that the "Great Reset" with its supporting "Great Narrative" is in full swing.
In most of the world the C19 story has run its course - for now. Most countries seem to have have "declared victory" and "moved on". Obviously HK is an exception (nothing happened there for the last two years) and I fear they will get to experience the whole 2-year thing in the coming 3-4 months. Watch out - the politicians everywhere are looking to permanently establish the "emergency controls" as "normal" - see previous Letter for some examples in Ireland and EU.
Invasion of Ukraine has led to so many lines being crossed - to the extent that clearly things will never be the same again in our lifetime.
Why? How did we get here?
I do not claim to know all the answers but some things are fairly clear if you look with open eyes and the wisdom that previous generations and civilisations have made available to us - even if most choose to ignore it (Plato on the flaws of democracy). Those who do not learn from history are doomed to repeat it and even those who learn will have litle choice but to go along for much of the ride.

Perhaps my notes and the links below will help you to form an educated opinion rather than the pervasive propaganda we are all being fed.
The current situation is more than 100 years in the making and much (if not most) of what you thought was true is less veracious than you could ever imagine. No doubt we could (and maybe should) go back further but let's start in 1913 when the British Government asked the public no longer to request exchange of their pounds for gold coins at the post office. This led to the issuing of War Bonds and fractional reserve accounting that allowed the Bank of England essentially to print unlimited money to fight in WW1; without this devious action they would have been constrained to act within the limits of the country's reserves and WW1 would have been shorter. Read The Fiat Standard for more details on how this happened. Around this time, and likely no coincidence, the US bankers were scheming how to get around the constitutional controls against such actions in their own country - read more in The Creature from Jekyll Island.
Following WW1, Germany was forced to pay war reparations in Gold (hard money). This led to a decade of money printing and extravagant excesses and crashes as hyperinflation set in, ending in the bankrupting of the country and the nationalism that fed WW2 - the gory details of devaluation and hyperinflation in Weimar Germany are described in When Money Dies. Meanwhile the US bankers who had been preparing since 1913 stepped in with unlimited money printing to fund WW2 and then also in their Marshal Plan to cement in place the Bretton Woods post-war agreement that made US Dollar the global reserve currency.
Decades of boom and bust followed - well explained by Ray Dalio who portrays this as perfectly normal and to be expected - unfortunately it is for soft (non-hard) money based economies. The Fourth Turning will give many additional insights to this period too as well as cycles to watch for and their cause and nature. In 1961 Eisenhower tried to warn the population in his farewell address about the "Military Industrial Complex" and many believe that Robert Kennedy's assassination in 1963 may well be not entirely unrelated.
Things came to a head in August 1971 when the countries of the world realised that the US was (contrary to all promises) printing unlimited funds to (among other things) fight the Vietnam war and so undermining the expected and required convertibility of US dollars (the currency of global trade) for Gold (hard money). A French warship heading to NY to collect France's gold was the straw that caused Nixon to default on US Debt convertibility and "close the gold window".
This in turn led to further decades of increasing financialization, further fuelled (pun intended) by the PetroDollar creation and "exorbitant priviledge" that the US obtained by having the global reserve currency - benefiting those closest to the money supply (Cantillon effect) while hollowing out the US manufacturing and eventually devastating its middle and working classes (Triffin dilemma) - Arthur Hayes describes all this and much more as well as the likely outlook in his article - Energy Canceled. Absolutely required reading or listen to Guy Swan reading it and giving his additional interpetation.
Zoltan Pozsar of Credit Suisse explains how the money system is now being reset following the events of last few weeks and his article outlines a likely way forward - Bretton Woods III. His paper is somewhat dense, heavy reading and you might prefer to listen to Luc Gromen's more conversational explainer with Marty
All of this was well known to our forefathers
The writers of the American Constitution understood the dangers of money being controlled by any elite group and they did their best to include protections in the US constitution. It did take the bankers multiple decades and puppet presidents to circumvent these but do so they did. Thomas Jefferson could not have been more clear in his warning.
" If the American people ever allow private banks to control the issue of their currency, first by inflation, then by deflation, the banks and corporations that will grow up around(these banks) will deprive the people of all property until their children wake up homeless on the continent their fathers conquered."
Islamic finace also recognised the dangers - you will likely be aware of the restrictions that forbid interest payments - read this interesting article from The Guardian
You will likely also be aware from schooldays that the Roman Empire collapsed because it expanded too much and the overhead became unbearable leading to the debasement of its money and inability to extract tax payments to support itself. Read more from Mises Institute. Here too, much of this will likely ring familiar.
So what can you do about it?
In theory Governments should respect Consent of the Governed and the 1948 Universal Declaration of Human Rights states that "The will of the people shall be the basis of the authority of government".
For you to decide if and to what extent governments today are acting in line with these principles. If not, what can you do about it?
The options you have are basically - Loyalty, Voice or Exit. 1. You can be loyal and accept what you are told - 2. you may (or may not) be able to voice disagreement and 3. you may (or may not!) be able to exit. Authoritarian governments will make everything except Loyalty difficult or even impossible - if in doubt, read George Orwell 1984 - or look just around at recent events today in many countries.
I'll be happy to delve deeper into this in subsequent letters if there is interest - for now I recommend you to read Sovereign Individual. It is a long read but each chapter starts with a summary and you can read the summaries of each chapter as a first step. Also - I'm happy to discuss with you - just reach out and let me know!
For those who prefer a structured reading list, check References
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can easily ask questions or discuss any topics in the newsletters in our Telegram group - click the link here to join the group.\ You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ c6d8334c:30883d6d
2025-05-20 14:08:19
@ c6d8334c:30883d6d
2025-05-20 14:08:19🔑 Hashtag-Kombination (immer gleich aufgebaut):
```
relilab #verstehen 1️⃣
relilab #anwenden 2️⃣
relilab #reflektieren
relilab #gestalten 3️⃣
```
✅ Pflicht:
-
#relilab -
genau ein Kompetenz-Hashtag:
#verstehen,#anwenden,#reflektieren,#gestalten
✨ Optional:
-
eine Niveaustufe:
-
1️⃣ Reproduktion
-
2️⃣ Rekonstruktion
-
3️⃣ Konstruktion
📝 Beispielhafte Posts
```text
relilab #verstehen 1️⃣
Ich habe heute zum ersten Mal ausprobiert, wie KI überhaupt "lernt". Spannend!
relilab #anwenden 2️⃣
ChatGPT half mir dabei, einen Ablaufplan für einen Unterricht zu entwerfen – sehr hilfreich.
relilab #reflektieren
Welche Rolle spielt das Menschenbild, wenn KI religiöse Themen behandelt?
relilab #gestalten 3️⃣
Ich habe ein eigenes H5P-Modul mit einem KI-generierten Bibelquiz gebaut. Wer testet es? ```
-
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:44:28
@ 6ad3e2a3:c90b7740
2025-05-20 13:44:28I https://www.chrisliss.com/p/mstr a few months ago with the subtitle “The Only Stock,” and I’m starting to regret it. Now, it was trading at 396 on January 20 when I posted it and 404 now (even if it dipped 40 percent to 230 or so in between), but that’s not why I regret it. I pointed out it was not investable unless you’re willing to stomach large drawdowns, and anyone who bought then could exit with a small profit now had they not panic-sold along the way.
The reason I regret it is I don’t want to make public stock predictions because it adds stress to my life. I have not sold any of my shares yet, but something I’ve noticed recently has got me thinking about it, and stock tips are like a game of telephone wherein whoever is last in the chain might find out the wrong information and too late. And while every adult has agency and is responsible for his own financial decisions, I don’t want my readers losing money on account of anything I write.
My base case is still that MSTR becomes a trillion-dollar company, destroys the performance of the S&P, the Mag-7 and virtually any other equity portfolio most people would assemble. Michael Saylor is trading an infinitely-printable asset (his shares) for humanity’s best-ever, finite-supply digital gold, and that trade should be profitable for him and his shareholders in perpetuity.
I don’t know exactly what he plans to do when that trade is no longer available to him — either because no one takes fiat currency for bitcoin anymore or because his mNAV (market-cap-to-bitcoin-holding ratio) goes below one — but that’s not my main concern, either. At that point he’ll have so much bitcoin, he’ll probably become the world’s first and largest bitcoin bank and profit by making his pristine collateral available to individuals and institutions. Even at five percent interest, half a trillion in bitcoin would yield $25B in profits every year. Even at a modest 10x valuation, the stock would more than double from here.
I am also not overly concerned with Saylor’s present amount of convertible debt which is at low or zero rates and is only https://www.strategy.com/. He’s been conservative on that front and only issuing on favorable terms. I don’t doubt Saylor’s prescience, intelligence or business sense one bit.
What got me thinking were some Twitter posts by a former Salomon Brothers trader/prophet Josh Mandell https://x.com/JoshMandell6/status/1921597739458339193 recently. In November when bitcoin was mooning after the election, he predicted that on March 14th it would close at $84,000, and if it did it would then go on an epic run up to $444,000 this cycle.
A lot of people make predictions, a few of them come true, but rarely do they come true on the dot (it closed at exactly $84K according to some exchanges) and on such a specific timeframe. Now, maybe he just got lucky, or maybe he is a skilled trader who made one good prediction, but the reason he gave for his prediction, insofar as he gave one, was not some technical chart or quantitative analysis, but a memory he had from 30 years ago that got into his mind that he couldn’t shake. He didn’t get much more specific than that, other than that he was tuned into something that if he explained fully would make too many people think he had gone insane. And then the prediction came true on the dot months later.
Now I believe in the paranormal more than the average person. I do not think things are random, and insofar as they appear that way it’s only because we have incomplete information — even a coin toss is predictable if you knew the exact force and spin that was put on the coin. I think for whatever reason, this guy is plugged into something, and while I would never invest a substantial amount of money on that belief — not only are earnestly-made prophecies often delusions or even if correct wrongly interpreted — that he sold makes me think.
He gave more substantive reasons for selling than prophecy, by the way — he seems to think Saylor’s perpetual issuance of shares ATM (at the market) to buy more bitcoin is putting too much downward pressure on the stock. Obviously, selling shares — even if to buy the world’s most pristine collateral at a 2x-plus mNAV — reduces the short-term appreciation of those shares.
His thesis seems to be that Saylor is doing this even if he would be better off letting the price appreciate more, attracting more investors, squeezing more shorts, etc because he needs to improve his credit rating to tap into the convertible debt market to the extent he has promised ($42 billion more over the next few years) at favorable terms. But in doing this, he is souring common stock investors because they are not seeing the near-term appreciation they should on their holdings.
Now this is a trivial concern if over the long haul MSTR does what it has the last couple years which is to outperform by a wide margin not only every large cap stock and the S&P but bitcoin itself. And the bigger his stack of bitcoin, the more his stock should appreciate as bitcoin goes up. But markets do not operate linearly and rationally. Should he sour prospective buyers to a great enough extent, should he attract shorts (and supply them with available shares to borrow) to a great enough extent, perhaps there might be an mNAV-crushing cascade that drives people into other bitcoin treasury companies, ETFs or bitcoin itself.
Now Saylor as first mover and by far the largest publicly-traded treasury company has a significant advantage. Institutions are far less likely to invest in size in smaller treasury companies with shorter track records, and many of them are not allowed to invest in ETFs or bitcoin at all. And even if a lot of money did go into any of those vehicles, it would only drive the value of his assets up and hence his stock price, no matter the mNAV. But Josh Mandell sold his shares prior to a weekend where bitcoin went from 102K to 104K, the US announced a deal with China, the mag-7 had a big spike (AAPL was up 6.3 percent) and then MSTR’s stock went down from 416 to 404. As I said, he is on to something.
So what’s the real long-term risk? I don’t know. Maybe there’s something about the nature of bitcoin that long-term is not really amenable to third-party custody and administration. It’s a bearer asset (“not your keys, not your coins”), and introducing counterparty risk is antithetical to its core purpose, the separation of money and state, or in this case money and bank.
With the bitcoin network you can literally “be your own bank.” To transact in digital dollars you need a bank account — or at least a stable coin one mediated by a centralized entity like Tether. You can’t hold digital dollars in your mind via some memorized seed words like you can bitcoin, accessible anywhere in the world, the ledger of which is maintained by tens of thousands of individually-run nodes. This property which democratizes value storage in the way gold did, except now you can wield your purchasing power globally, might be so antithetical to communal storage via corporation or bank that doing so is doomed to catastrophe.
We’ve already seen this happen with exchanges via FTX and Mt. Gox. Counterparty risk is one of the problems bitcoin was created to solve, so moving that risk from a fractionally reserved international banking system to corporate balance sheets still very much a part of that system is probably not the seismic advancement integral to the technology’s promise.
But this is more of a philosophical concern rather than a concrete one. To get more specific, it’s easy to imagine Coinbase, if indeed that’s where MSTR custodies its coins, gets hacked or https://www.chrisliss.com/p/soft-landing, i.e., seized by an increasingly desperate and insolvent government. Or maybe Coinbase simply doesn’t have the coins it purports like FTX, or a rogue band of employees, working on behalf of some powerful faction for “https://www.chrisliss.com/national-security-and-public-healt” executes the rug pull. Even if you deem these scenarios unlikely, they are not unfathomable.
Beyond outright counterparty malfeasance, there are other risks — what if owning common stock in an enterprise that simply holds bitcoin falls out of favor? Imagine if some new individual custody solution emerges wherein you have direct access to the coins themselves in an “even a boomer can do this” kind of way wherein there’s no compelling reason to own common stock with its junior claims to the capital stack in the event of insolvency? Why stand in line behind debt holders and preferred shares when you can invest in something that’s directly withdrawable and accessible if world events spike volatility to a systemic breaking point?
Things need not even get that rocky for this to be a concern — just the perception that they might could spook people into realizing common stock of a corporate balance sheet might be less than ideal as your custody solution.
Moreover, Saylor himself presents some risk. He could be compromised or blackmailed, he could lose his cool or get into an accident. These are low-probability scenarios, but also not unfathomable as any single point of failure is a target, especially for those factions who stand to lose unimaginable wealth and power should his speculative attack on the system succeed at scale.
Finally, even if Saylor remains free to operate as he sees fit, there is what I’d call the Icarus risk — he might be too ambitious, too hell-bent on acquiring bitcoin at all costs, too much of a maniac in service of his vision. Remember, he initially bought bitcoin during the covid crash and concomitant massive money print upon his prescient realization that businesses providing goods and services couldn’t possibly keep pace with inflation over the long haul. He was merely playing defense to preserve his capital, and now, despite his sizable lead and secured position is still throwing forward passes in the fourth quarter rather than running out the clock and securing the W.
Saylor is now arguably less a bitcoin maximalist and advocate, articulately making the case for superior money and individual sovereignty, but a corporate titan hell-bent on world domination via apex-predator-status balance sheet. When is enough enough? Many of the greatest conquerors in history pushed their empires too far until they fractured. In fact, 25 years ago MSTR was a big winner before the dot-com crash during which its stock price and most of Saylor’s fortune were wiped out when he was sued by the SEC for accounting fraud (he subsequently settled).
Now it’s possible, he learned from that experience, got up off the mat and figured out how to avoid his youthful mistakes. But it’s also possible his character is such that he will repeat it again, only this time at scale.
But as I said, my base case is MSTR is a trillion-dollar market cap, and the stock runs in parallel with bitcoin’s ascendance over the next decade. Saylor has been https://www.strategy.com/, prescient, bold and responsible so far over this iteration. I view Mandell’s concerns as valid, but similar to Wall St’s ones about AMZN’s Jeff Bezos who relentlessly ignored their insistence on profitability for a decade as he plowed every dollar into building out productive capacity and turned the company into the $2T world-dominating retail giant it is now.
Again, I haven’t (yet) sold any of my shares or even call options. But because I posted about this in January I felt I should at least follow-up with a more detailed rundown of what I take to be the risks. As always, do your own due diligence with any prospective investment.
-
 @ bd32f268:22b33966
2025-05-20 14:07:47
@ bd32f268:22b33966
2025-05-20 14:07:47Recentemente tive conhecimento do mais recente flagelo cuja popularidade espelha bem o estado avançado de degeneração da nossa sociedade, o bebé reborn. Há uns anos certamente não passaria de uma piada de mau gosto quando alguém nos dissesse que decidiu adquirir um boneco para criar como se se tratasse de um filho, infelizmente em 2025 deixou de ser uma piada para se tornar algo assombroso.
Depois de fazer alguma pesquisa sobre o tema percebi que há pessoas que têm em curso processos litigantes judiciais relativos à, note-se com pasmo, guarda da boneca. A insanidade não fica por aqui uma vez que, algumas "mães" procuram atendimento médico para os seus bonecos. No Brasil, a câmara dos deputados recebeu três projetos destinados à criação de políticas públicas relacionadas com estes bonecos. As notícias sobre este fenómeno surreal multiplicam-se à medida que a insanidade se alastra como vírus pelas redes sociais.
Vivemos numa sociedade que há muito se divorciou da realidade, uma sociedade de pós-verdade, por isso de alguma forma não choca que este tipo de coisa possa acontecer. Podemos dizer que de alguma forma existe um primado do sentimento face à razão, preferimos, por vezes com consequências catastróficas, uma mentira "empática" do que uma verdade salvífica. Esta nossa tibieza em afirmar a verdade leva-nos consequentemente a uma crendice insustentável que é esta de, cada um tem a sua verdade. Graças a essa filosofia permitimos que um certo discurso lunático tenha mais alcance no espaço público. Por vezes ingenuamente podemos pensar que se trata de algo inofensivo, sem consequências de maior, contudo a experiência mostra-nos precisamente o contrário. Há por detrás destes fenómenos uma índole corrosiva que funciona como aguilhão para a disseminação das agendas políticas e ideológicas que visam a destruição da família. Considerando a excecional vulnerabilidade psíquica que observamos em cada vez mais pessoas neste tempo e a ampla disseminação destes fenómenos temos razão mais que suficientes para estarmos preocupados.
Uma outra elação que podemos retirar é que a nossa sociedade com as alegadas gerações "mais bem preparadas de sempre" está claramente a produzir um excesso de adultos que se comporta e, a todos os títulos são, crianças funcionais.
Com tudo isto fica cada vez mais difícil viver uma vida harmoniosa com a lei natural, pois vivemos em harmonia com algo considerado opressor pelos apologetas destes produtos do marxismo cultural. Com a pretensa igualdade que se pretende alcançar, equiparando inclusive um boneco a uma bebé, as famílias no sentido próprio do termo ficam em segundo plano relativamente a estes "novos" e esotéricos conceitos de família.
Importa perguntar, no meio de todas essas novas formas de se pensar uma família, qual é o ideal ?
Provavelmente os apologetas destas bizarrices ficarão em silêncio uma vez que coerentemente consideram que todas as formas são iguais e válidas.
Isto é apenas mais um sinal que nos é dado do declínio palpável dos valores que construíram a nossa sociedade e civilização. Façamos algo para que estas nocivas ideologias não entrem no nosso coração e em nossas casas, sob pena da corrupção dos nossos princípios e dos daqueles que nos são queridos. Estes fenómenos são de tal forma doentios que nos levam a crer que vivemos numa época tragicómica, o que me fez lembrar de uma história contada por Kierkgaard e que partilho de seguida.
“Certa vez, houve um incêndio num circo ambulante na Dinamarca. O director mandou imediatamente o palhaço, que já se encontrava vestido e maquilhado a preceito, para a vila mais próxima, à procura de ajuda, advertindo-o de que existia o perigo de o fogo se espalhar pelos campos ceifados e ressequidos, com risco iminente para as casas do próprio povoado. O palhaço correu até à vila e pediu aos moradores que viessem ajudar a apagar o incêndio que estava a destruir o circo. Mas os habitantes viram nos gritos do palhaço apenas um belo truque de publicidade que visaria levá-los a acorrer em grande número às sessões do circo; aplaudiam e desatavam a rir. Diante dessa reacção, o palhaço sentiu mais vontade de chorar do que de rir. Fez de tudo para convencer as pessoas de que não estava a representar, de que não se tratava de um truque e sim de um apelo da maior seriedade: estava realmente em causa um incêndio. Mas a sua insistência só fazia aumentar os risos; eles achavam que a performance estava excelente – até que o fogo alcançou de facto aquela vila. Aí já foi tarde, e o fogo acabou por destruir não só o circo, mas também a povoação”.
Soren Kierkgaard - Filósofo dinamarquês
-
 @ cae03c48:2a7d6671
2025-05-20 14:00:00
@ cae03c48:2a7d6671
2025-05-20 14:00:00Bitcoin Magazine

Auradine Expands Bitcoin Mining Solutions with Advanced ASIC Chips, Cooling Systems, and Modular Megawatt ContainersAuradine Inc., a U.S.-based Bitcoin miner manufacturer, today announced it is unveiling a broadened portfolio of mining products at the Bitcoin 2025 Conference in Las Vegas, featuring high-performance ASIC chips, specialized cooling systems, and fully integrated modular containers engineered for scalable, megawatt-class mining operations, according to a press release sent to Bitcoin Magazine.
“Our goal is to democratize access to Bitcoin mining and enable innovative integrations,” said the CEO and Co-Founder of Auradine Rajiv Khemani. “Whether you’re running a megawatt container or building a small form-factor heater-miner for your home, we provide the chips, systems, and support to help you succeed. This new chapter is about giving miners the tools to innovate, scale, and operate efficiently.”
The new ASIC offerings, designed for both industrial and small-scale deployments, support customizable form factors and have already been adopted by operators including MARA Holdings, FutureBit, and Deep South Operating. Alongside the chips, Auradine continues to produce a full range of mining rigs to support a variety of deployment needs.
“Auradine’s ability to deliver both high-performance chips and scalable infrastructure aligns with MARA’s mission to stay at the forefront of bitcoin mining,” stated the Chief Technology Officer of MARA Holdings Ashu Swami. “We have been pleased with the partnership with Auradine with their leading edge engineering capability and innovation.”
Auradine’s modular 1 MW container units, developed in collaboration with Fog Hashing and FBox, are designed to accommodate 100–200 miners each. Merkle Standard, the first to deploy the system, reported improved energy efficiency and operational flexibility.
“We were the first to deploy Auradine’s container solution, and it immediately exceeded our expectations,” said the COO at Merkle Standard Monty Stahl. “The combination of performance, energy efficiency, and modular design gives us the flexibility to scale our operations faster and smarter than traditional infrastructure allows. This is the kind of innovation the mining industry has needed for a long time.”
Their recent $153 million Series C funding supports its push to offer flexible mining infrastructure and supplying ASIC chips for third-party integration. The company also plans to extend its hardware expertise to AI and networking through its AuraLinks initiative.
“We were one of the first to try Auradine’s ASIC chips and were immediately impressed by the support and customization that the team provided,” added the CEO of Deep South Operating, LLC Brock Tompkins. “It helps miners like us to stay scalable and efficient while raising the standard for what decentralized mining looks like.”
This post Auradine Expands Bitcoin Mining Solutions with Advanced ASIC Chips, Cooling Systems, and Modular Megawatt Containers first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 7e538978:a5987ab6
2025-05-20 13:45:12
@ 7e538978:a5987ab6
2025-05-20 13:45:12LNbits now has full NWC support thanks to the work of contributor @riccardobl, who has claimed two LNbits bounties for implementing Nostr Wallet Connect (NWC) support in LNbits.
LNbits can now act both as a wallet service and as a funding source using the Nostr NWC protocol (NIP-47). This opens the door to new integrations with a growing ecosystem of Nostr clients and Lightning wallets.
Two Sides of NWC Integration
The work delivered by Riccardo B comprises two separate peices of work that together implement full support for NWC:
1. LNbits as a Wallet Service
This extension allows LNbits to operate as an always-on wallet service compatible with Nostr Wallet Connect clients such as Damus, Amethyst, or any app supporting NIP-47. Users can connect these Nostr clients to their LNbits instance and create and pay Lightning invoices through it.
This turns your LNbits wallet into a backend Lightning provider for your favourite Nostr app all self-hosted.
2. NWC as a Funding Source
The second piece of work flips the relationship. With this in place, LNbits can now act as an NWC client, meaning it can be funded from any NWC wallet service. This could be another LNbits, Alby, Minibits and more.
Why This Is a Big Deal for LNbits Users
These two bounties make LNbits one of the first applications in the Lightning ecosystem to offer bidirectional NWC support — as both a service and a client. This brings benefits such as:
-
Fund any NWC-compatible app using your LNbits wallet.
-
Fund LNbits using any wallet that supports Nostr Wallet Connect.
-
Build NWC-native apps with LNbits as a backend, or power your own LNbits server using existing wallet infrastructure.
For developers, it’s a chance to build in flexible, interoperable ways. For users, it means more choice, more control, and less friction when managing Lightning payments across apps and devices.
Both of these features were developed and delivered by Riccardo B (@riccardobl), an contributor who took on and completed both LNbits bounties and was extremely helpful during the PR review process. We owe a huge thanks to Riccardo for his work here.
To try them out, read the full article detailing how NWC works with LNbits.
-
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:38:04
@ 6ad3e2a3:c90b7740
2025-05-20 13:38:04When I was a kid, I wanted to be rich, but found the prospect of hard work tedious, pointless and soul-crushing. Instead of studying for exams, getting some job and clawing your way up the ladder, I wondered why we couldn’t just build a device that measured your brain capacity and awarded you the money you would have made had you applied yourself. Eliminate the middleman, so to speak, the useless paper pushing evoked by the word “career.”
But when you think about it, it’s not really money you’re after, as money is but purchasing power, and so it’s the things money can provide like a nice lifestyle and the peace of mind that comes from not worrying about it. And it’s not really the lifestyle or financial independence, per se, since moment to moment what’s in your bank account isn’t determining your mental state, but the feeling those things give you — a sense of expansiveness and freedom.
But if you did have such a machine, and it awarded you the money, you probably wouldn’t have that kind of expansiveness and freedom, especially if you did nothing to achieve those things. You would still feel bored, distracted and unsatisfied despite unrestricted means to travel or dine out as you saw fit. People who win the lottery, for example, tend to revert to their prior level of satisfaction in short order.
The feeling you really want then is the sense of rising to a challenge, negotiating and adapting to your environment, persevering in a state of uncertainty, tapping into your resourcefulness and creativity. It’s only while operating at the edge of your capacity you could ever be so fulfilled. In fact, in such a state the question of your satisfaction level would never come up. You wouldn’t even think to wonder about it you’d be so engrossed.
So what you really crave is a mind device that encourages you to adapt to your environment using your full creative capabilities in the present moment, so much so you realize if you do not do this, you have the sense of squandering your life in a tedious, pointless and soul-crushing way. You need to be totally stuck, without the option of turning back. In sum, you need to face reality exactly as it is, without any escape therefrom.
The measure of your mind in that case is your reality itself. The device is already with you — it’s the world you are presently creating with the consciousness you have, providing you avenues to escape, none of which are satisfactory, none that can lead to the state you truly desire. You have a choice to pursue them fruitlessly and wind up at square one, or to abandon them and attain your freedom. No matter how many times you go down a false road, you wind up at the same place until you give up on the Sisyphean task and proceed in earnest.
My childhood fantasy was real, it turns out, only I had misunderstood its meaning.
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ f85b9c2c:d190bcff
2025-05-20 12:51:06
@ f85b9c2c:d190bcff
2025-05-20 12:51:06 Sometimes I feel like reversing time.
I miss my childhood. Honestly, who wouldn’t? Back then, life was so simple, so carefree. I had no bills to pay, no deadlines to chase, and no worries about what tomorrow might bring. All I had to do was wake up, play, eat, and maybe dodge a beating or two from Mum when I got a little too adventurous😂. Sometimes I feel like reversing time, just to relive those golden days when my biggest problem was figuring out how to sneak a piece of meat from the pot without getting caught.
Sometimes I feel like reversing time.
I miss my childhood. Honestly, who wouldn’t? Back then, life was so simple, so carefree. I had no bills to pay, no deadlines to chase, and no worries about what tomorrow might bring. All I had to do was wake up, play, eat, and maybe dodge a beating or two from Mum when I got a little too adventurous😂. Sometimes I feel like reversing time, just to relive those golden days when my biggest problem was figuring out how to sneak a piece of meat from the pot without getting caught.I remember those moments vividly. When I was little, I’d tiptoe into the kitchen, the aroma of Mum’s stew pulling me like a magnet. I’d wait for her to turn her back, then—bam!—my tiny hand would dive into the pot, snagging a juicy piece of meat. Of course, I wasn’t exactly a master thief. Mum always seemed to know. She’d catch me red-handed, and let’s just say her wooden spoon wasn’t just for cooking! I was kinda stubborn back then, so those beatings happened a lot. But I don’t steal meat anymore—grown-up me knows better. Life was different then. My only “job” was to have fun—climbing trees, chasing friends, or making up wild stories in my head. Now, adulthood feels like a never-ending to-do list. I miss the freedom, the laughter, the way problems seemed to vanish with a nap or a hug. If I could, I’d turn back the clock, even just for a day, to feel that lightness again. Childhood wasn’t perfect, but it sure felt like it.
-
 @ f85b9c2c:d190bcff
2025-05-20 12:41:35
@ f85b9c2c:d190bcff
2025-05-20 12:41:35 Solana (SOL) is acquiring popularity in the crypto world for its speed and flexibility.It's rapidly gaining ground on established blockchains, grabbing investor interest.
Solana (SOL) is acquiring popularity in the crypto world for its speed and flexibility.It's rapidly gaining ground on established blockchains, grabbing investor interest.History Of Solana Anatoly Yakovenko, once a Qualcomm executive, formulated the concept for Solana in 2017. A town on the Southern California coast inspired the name. Yakovenko wanted a swifter, more reliable blockchain network to address the limitations of existing onesat that time. Solana is based in San Francisco, California, at the headquarters of Solana Labs. Solana was launched in March 2020, making a major step in the advancement of blockchain technology.
What Is Solana? Solana is a blockchain network built for speed and affordability.This versatility makes it useful for DeFi, NFTs, and more. Solana operates on its own independent blockchain network with SOL as its native token and infrastructure to power its operations. It functions as a self-sufficient ecosystem, independent of any other existing blockchain network.
How Does Solana Work? Unlike normal blockchains that usually rely on the Proof-of-Work mechanism, Solana uses another approach. It combines two mechanisms: 1.Proof-of-Stake: It lets operators secure the network by putting SOL tokens at stake. These operators are entrusted with adding new blocks to the blockchain and are rewarded for their contribution.
2.Proof-of-History: It helps eliminates the need for communications between operators and boosts transaction processing speed.
Conclusion The mix of these mechanisms is a key factor behind Solana’s reputation for superior speed. Of course, it uses other technical aspects that contribute to its efficiency, but PoS and PoH play a critical role.
-
 @ 91bea5cd:1df4451c
2025-05-20 12:16:57
@ 91bea5cd:1df4451c
2025-05-20 12:16:57Contexto e início
O precursor direto do avivamento foi William J. Seymour, um pregador afro-americano filho de ex-escravos, influenciado pelos ensinamentos de Charles Parham, que pregava o "batismo no Espírito Santo" com evidência do falar em línguas.
Em 1906, Seymour foi convidado para pregar em uma igreja em Los Angeles. Após ser rejeitado por alguns por sua pregação sobre o batismo com o Espírito Santo, ele começou a liderar reuniões de oração na casa da família Asberry. Em abril de 1906, durante uma dessas reuniões, os participantes começaram a experimentar manifestações intensas do Espírito Santo, incluindo glossolalia (falar em línguas), curas e profecias.
A Rua Azusa
Logo, o número de participantes cresceu tanto que foi necessário mudar para um antigo prédio da Igreja Metodista Africana Episcopal, no número 312 da Rua Azusa, no centro de Los Angeles. Esse local se tornou o epicentro do avivamento.
Características marcantes
Cultos espontâneos e fervorosos, muitas vezes sem ordem pré-definida.
Diversidade étnica e social: negros, brancos, latinos, asiáticos, ricos e pobres adoravam juntos — algo radical para os padrões da época.
Ênfase nas manifestações espirituais, como línguas, curas, visões e profecias.
Igualdade de gênero e raça no ministério, com mulheres e homens de diversas origens pregando e liderando.
Impacto
O avivamento da Rua Azusa marcou o nascimento e expansão global do pentecostalismo, hoje uma das maiores forças do cristianismo mundial. Missionários saíram de Azusa para várias partes do mundo, levando a mensagem pentecostal. Movimentos como as Assembleias de Deus e Igreja do Evangelho Quadrangular têm raízes nesse avivamento.
Tensão e Interpretação entre Reformistas e Pentecostalistas
Evangelhos e Atos
João Batista profetiza: “Ele vos batizará com o Espírito Santo e com fogo” (Mateus 3:11).
Em Atos 2, no Pentecostes, os discípulos falam em línguas e recebem poder (Atos 1:8; 2:4).
Outros episódios: Atos 10 (Casa de Cornélio) e Atos 19 (Éfeso).
Cartas Paulinas
Paulo não relaciona diretamente o “batismo com o Espírito” ao falar em línguas. Em 1 Coríntios 12:13 ele diz: “Pois em um só Espírito todos nós fomos batizados em um corpo”.
A glossolalia aparece como um dom entre outros, mas não como evidência obrigatória (1 Coríntios 12:30).
Tensão
Pentecostais veem o batismo com o Espírito como uma segunda experiência após a conversão, evidenciada por línguas. Reformados geralmente interpretam que o batismo com o Espírito ocorre na conversão e que línguas não são obrigatórias ou cessaram com os apóstolos.
Reformadores e o Batismo com o Espírito Santo
Martinho Lutero, João Calvino e outros reformadores não falavam em línguas nem davam ênfase a experiências carismáticas.
Cessacionismo: Doutrina comum entre reformados que diz que os dons sobrenaturais (línguas, profecias, curas) cessaram com a era apostólica.
Continuação (posição pentecostal): Os dons continuam hoje.
Filmes / Documentários
“Azusa Street: The Origins of Pentecostalism” (2006) – Documentário com imagens históricas e entrevistas.
“Wesley” (2009) – Biografia de John Wesley, precursor do metodismo e influência indireta no pentecostalismo.
“The Cross and the Switchblade” (1970) – História de David Wilkerson e a conversão de Nicky Cruz; enfatiza a obra do Espírito.
Série “God in America” (PBS) – Episódio sobre o pentecostalismo (não só Azusa, mas seu impacto cultural).
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ a5142938:0ef19da3
2025-05-20 11:05:20
@ a5142938:0ef19da3
2025-05-20 11:05:20Content coming soon.
-
 @ 662f9bff:8960f6b2
2025-05-19 15:11:25
@ 662f9bff:8960f6b2
2025-05-19 15:11:25Let's start with some important foundational thinking - based on natural law. Money should be separate from the State - if not history shows that governments and human greed will always take over and manipulate the system in their favour and the expense of their populations. For extensive references, read The Sovereign Individual and The Creature from Jeckyll Island.
-
The Separation of State and Money is the most important thing you can listen to this week. Thanks to Allen Farrington - his paper is here for those who prefer to read. Wake up, folks!
-
The American Forefathers knew this when the wrote the American Constitution. Thomas Jefferson said: “If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.” Mark Moss explains it well here. Charlie Robinsons take here.
The situation in Canada explifies the issues
Governments have have long used "international economic sanctions" against other nations to enforce their positions. Now in Canada, and soon in your country too, they are applying such sanctions their own citizens - disconnecting them from the financial system and removing their ability to use their own life savings as they wish. Canadians spoke with their money - in one week they raised more money in support of the truckers for peaceful protest than were raised in support of all Canadian political parties in the election of last year - only to have it confiscated and blocked by those politicians.
-
CPL. Daniel Bulford (Justin Trudeau's body guard) is particularly clear and eloquent - https://www.facebook.com/watch/?v=3123688351279364
-
Nick & Greg (two Canadians in Canada) explain the situation to Peter McCormack - https://youtu.be/QBWYp-cBr4o
-
Dr Jordan Peterson and Dr Julie Ponesse (also Canadians in Canada) speak openly about what is going on https://t.co/2T7A4VEek1
-
Even Canadians living in China speak up: https://www.youtube.com/watch?v=xvDvJWdlD1E
Meanwhile in Turkey...
Joe Blogs has been giving blow by blow updates of the deteriorating sitation over the last weeks. What is happening to Turkey will come to many countries - sooner than you might imagine. Watch and learn here, here and here - more on his channel.
EU Citizens should be aware and lobby their MPs
Dropping of all C-19 restrictions is a tactic to stop people thinking about them; meanwhile the politicians are taking steps to get all of the emergency restrictions codified into normal law so that they can be deployed on you any time or all the time in future.\ Act now - or lose all freedoms - your choice - watch here or click below for the explainer.
More on war - recall our discussion last week
War steals and destroys the wealth of generations. We have been here before - remember World Wars 1 and 2...
-
Dr Mattias Desmet explains how mass formation psychosis happens and how he became aware: https://www.youtube.com/watch?v=CRo-ieBEw-8
-
Be aware of this well known and much abused psycholgical experiment - rats in a cage - explained by Dr Christ Martensen: https://www.youtube.com/watch?v=7kSBdMXQkPI
To remain silent is wrong - to deny the rights of others to discuss and challenge (and even to punish or coerce them) is a crime in support of the biger crime. Each of us has a choice - choose wisely.
Could you have known about this?
"The Matrix is a system, Neo. That system is our enemy. But when you're inside, you look around, what do you see? Businessmen, teachers, lawyers, carpenters. The very minds of the people we are trying to save. But until we do, these people are still a part of that system and that makes them our enemy. You have to understand, most of these people are not ready to be unplugged. And many of them are so inert, so hopelessly dependent on the system that they will fight to protect it."
"Unfortunately, no one can be told what the Matrix is. You have to see it for yourself."
A closing thought...
Look closely at the cover of the Economist magazine released in December 2018 - The World in 2019 - see how many of those things have already come true.

In case this is too difficult for you - some things to note: Four horsemen of the apacalypse, Statue of Liberty wearing a facemask, Vetruvian Man with QR code (Vaccine passport), DNA mark on his arm, wearing virtual reality glasses... The animal bottom right is a Pangolin. Scales of Justice are well tipped/skewed, facial recognition, electric cars, Putin's pipelines, China and Brexit feature highly along with the lieing media (Pinnochio) and #metoo. I smell Predictive Programming.
- More insights in the explainer here (backup copy here) - including why it is backwards...
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-20 13:39:22
@ 5d4b6c8d:8a1c1ee3
2025-05-20 13:39:22https://youtu.be/US9iYJNTOkU
I had no idea Tosh was still doing anything, much less that he talks about sports.
https://stacker.news/items/984547
-
 @ 8576ca0e:621f735e
2025-05-20 09:31:18
@ 8576ca0e:621f735e
2025-05-20 09:31:18The Bitcoin community is currently debating BIP 177, a proposal that seeks to redefine Bitcoin’s base unit from the satoshi (sat) to bitcoin itself. Proposed by Synonym CEO John Carvalho, this initiative aims to simplify Bitcoin’s usability, reduce cognitive barriers for newcomers, and align the currency’s representation with its integer-based protocol design. While the proposal has sparked enthusiasm among some supporters, it has also faced criticism for potentially eroding Bitcoin’s cultural heritage. Here’s a comprehensive breakdown of BIP 177 and its implications.
What Is BIP 177? BIP 177 is a non consensus proposal that reimagines how Bitcoin units are displayed and labeled. Key changes include: 1. Base Unit Redefinition: The smallest unit, currently called a satoshi (1 sat = 0.00000001 BTC), would be renamed to "bitcoin" (lowercase). Thus, 1 BTC would equal 100,000,000 bitcoins under the new system . 2. Integer Only Display: Transactions and balances would be shown in whole numbers (e.g., "10,000 bitcoins" instead of "0.0001 BTC") to eliminate decimal complexity . 3. Symbol Adoption: The "₿" symbol could represent the base unit, making values like ₿34,500,000 equivalent to 0.345 BTC . 4. Backward Compatibility: The BTC ticker and total supply (21 million BTC) remain unchanged. Users and applications can toggle between legacy and new formats .
Why BIP 177? The Case for Change 1. Reducing Cognitive Load Decimal heavy displays (e.g., 0.000023 BTC) are unintuitive, especially for new users. Integer values (e.g., 2,300 bitcoins) simplify mental calculations and reduce errors in transactions . As Carvalho argues, Bitcoin’s protocol inherently uses integers, and the decimal system is a "human imposed abstraction" .
-
Eliminating Unit Fear A Bitcoin priced at $100,000+ can deter newcomers who perceive it as unaffordable. By rebranding the base unit, 1 bitcoin would appear as a fraction of a cent (e.g., $0.00104 per bitcoin), making ownership of thousands of bitcoins feel more accessible . This shift could mitigate "price ceiling anxiety" and encourage broader adoption .
-
Aligning with Bitcoin’s Design Bitcoin’s ledger tracks discrete units, not fractions. BIP 177 emphasizes this by removing artificial decimal formatting, fostering a clearer understanding of Bitcoin’s scarcity and indivisible nature .
-
Mainstream Usability For everyday transactions like buying coffee integer displays (e.g., "1,830 bitcoins") are more practical than tiny decimals. This aligns with Bitcoin’s growing role in micropayments, as seen in El Salvador’s adoption of satoshis for daily use .
Criticisms and Concerns 1. Cultural Erosion The term "satoshi" honors Bitcoin’s pseudonymous creator, and its deprecation risks alienating long-time supporters. Critics argue that abandoning this term weakens Bitcoin’s cultural identity .
-
Confusion Risks Renaming the base unit "bitcoin" while retaining BTC could cause ambiguity. For example, saying "I own 1,000 bitcoins" might mislead newcomers into thinking they own 1,000 BTC . Translation challenges also arise, particularly in languages like Chinese where "比特币" (Bitcoin) would represent both BTC and the base unit .
-
Brand Perception Bitcoin’s high value per BTC is a marketing strength. Displaying prices as fractions of a cent might dilute its perceived prestige, potentially affecting investor sentiment .
-
Implementation Hurdles Wallets, exchanges, and merchants would need to update interfaces, APIs, and educational materials—a process estimated to take 2+ years .
Community Reactions: A Divided Ecosystem - Supporters: Proponents like Jack Dorsey argue that integer displays simplify Bitcoin for mass adoption. They compare the shift to historical advancements like replacing Roman numerals with Arabic numbers . - Opponents: Critics dismiss BIP 177 as "bikeshedding" focusing on trivial changes while ignoring larger issues like transaction fees. Some Reddit users warn, "Don’t split it, don’t change anything" .
Implementation Timeline 1. Phase 1 (3–6 months): Introduce dual displays and pilot testing in wallets like Bitkit . 2. Phase 2 (6–12 months): Mainstream platforms adopt integer displays by default. 3. Phase 3 (12+ months): Legacy decimal formats are phased out entirely .
Conclusion: Tradition vs Progress BIP 177 highlights Bitcoin’s evolving identity: Should it prioritize cultural heritage or usability for the next billion users? While the proposal doesn’t alter Bitcoin’s code or supply, its success hinges on community consensus. As Carvalho notes, "Bitcoin’s heart is immovable code. BIP 177 merely retires the decimal point" . Whether this change becomes a footnote or a revolution remains to be seen but it undeniably sparks a vital conversation about Bitcoin’s future.
-
-
 @ 640f3844:d7b13a29
2025-05-20 08:52:49
@ 640f3844:d7b13a29
2025-05-20 08:52:49CrazyGames là một nền tảng giải trí số đang ngày càng khẳng định vị thế trong cộng đồng người dùng hiện đại nhờ vào khả năng cung cấp trải nghiệm linh hoạt, hấp dẫn và thân thiện. Với giao diện được thiết kế thông minh và trực quan, CrazyGames giúp người dùng dễ dàng tiếp cận và khám phá hàng loạt nội dung đa dạng chỉ trong vài thao tác. Dù sử dụng điện thoại, máy tính bảng hay máy tính để bàn, hệ thống luôn được tối ưu hóa để vận hành mượt mà, không gây gián đoạn hay ảnh hưởng đến trải nghiệm tổng thể. CrazyGames không chỉ đơn thuần là một nền tảng kỹ thuật số mà còn là nơi hội tụ của sáng tạo, công nghệ và niềm vui, nơi người dùng có thể tìm thấy sự giải tỏa sau những giờ làm việc căng thẳng hoặc học tập mệt mỏi. Nền tảng luôn chú trọng đến việc đổi mới giao diện, bổ sung các tính năng tiện ích nhằm mang lại giá trị sử dụng thực tế và phù hợp với xu hướng công nghệ đang thay đổi từng ngày.
Một trong những điểm nhấn nổi bật khiến CRAZYGAMES thu hút sự quan tâm rộng rãi chính là tính cá nhân hóa và khả năng kết nối cộng đồng vượt trội. Hệ thống sử dụng các thuật toán phân tích hành vi thông minh để đưa ra các đề xuất nội dung phù hợp với sở thích và nhu cầu riêng biệt của từng người dùng, từ đó nâng cao mức độ hài lòng và giữ chân người dùng lâu hơn. Không gian cộng đồng tích hợp trong nền tảng cũng tạo điều kiện cho các thành viên giao lưu, chia sẻ cảm nhận và trao đổi kinh nghiệm, giúp tăng sự gắn kết và hình thành một hệ sinh thái giải trí sôi động, đầy màu sắc. Hơn thế nữa, CrazyGames thường xuyên cập nhật nội dung mới, điều chỉnh theo phản hồi thực tế từ người dùng nhằm đảm bảo mọi người luôn cảm thấy được lắng nghe và phục vụ đúng với mong đợi. Việc áp dụng công nghệ mới, đặc biệt là trí tuệ nhân tạo và dữ liệu lớn, đã giúp CrazyGames trở thành một nền tảng tiên phong trong việc cá nhân hóa trải nghiệm người dùng ở cấp độ cao nhất.
CrazyGames cũng đặt yếu tố bảo mật và hỗ trợ kỹ thuật làm trọng tâm trong chiến lược phát triển lâu dài. Với hệ thống bảo mật nhiều lớp, kết hợp xác thực người dùng và mã hóa dữ liệu tiên tiến, người dùng có thể yên tâm khi trải nghiệm mà không phải lo lắng về quyền riêng tư hay nguy cơ rò rỉ thông tin cá nhân. Đồng thời, đội ngũ chăm sóc khách hàng của CrazyGames luôn sẵn sàng phản hồi nhanh chóng, giải quyết kịp thời các vướng mắc phát sinh và liên tục cập nhật các hướng dẫn sử dụng để người dùng tận dụng được mọi tính năng mà nền tảng mang lại. Ngoài ra, CrazyGames còn tổ chức nhiều chương trình tương tác hấp dẫn và hoạt động khuyến khích sáng tạo trong cộng đồng, giúp nâng cao trải nghiệm người dùng và biến mỗi lần truy cập trở thành một hành trình khám phá mới mẻ. Với tất cả những yếu tố đó, CrazyGames không chỉ là một nền tảng giải trí kỹ thuật số, mà còn là người bạn đồng hành lý tưởng trong hành trình kết nối công nghệ, sáng tạo và cảm xúc.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ bbb5dda0:f09e2747
2025-05-20 13:33:59
@ bbb5dda0:f09e2747
2025-05-20 13:33:59My week 19 started with a celebration of 80 years of liberation from the Germans (we love you guys now tho 🫶🏼). It feels conflicting, we're celebrating freedom, whilst cutting down those freedoms day by day more rapidly as time progresses. Should we still celebrate...?
The current path back to freedom can be mundane in the day to day but I wouldn't wanna have it any other way. These last couple weeks I've continued working on our TollGate pipelines to facilitate our release cycle, make it faster and easier to release in quick succession. There's been a lot of details to get right, because our releases are nostr based and once people start relying on the structure of the events we can't easily change it.
A TollGateOS release event now looks like this NIP-94 file metadata event:
json { "id": "a867f15ca7edc95a69e1557539a624466147584f68c62a16c47fe9bca3778312", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1747475980, "kind": 1063, "tags": [ [ "url", "https://blossom.swissdash.site/9e5e8c48810a1b59cf10fa56486f311e048a0305eb58444992b6133fd19fcb3e.bin" ], [ "m", "application/octet-stream" ], [ "x", "9e5e8c48810a1b59cf10fa56486f311e048a0305eb58444992b6133fd19fcb3e" ], [ "ox", "9e5e8c48810a1b59cf10fa56486f311e048a0305eb58444992b6133fd19fcb3e" ], [ "architecture", "aarch64_cortex-a53" ], [ "device_id", "glinet_gl-mt3000" ], [ "supported_devices", "glinet,gl-mt3000 glinet,mt3000-snand" ], [ "openwrt_version", "24.10.1" ], [ "tollgate_os_version", "v0.0.2" ], [ "release_channel", "stable" ] ], "content": "TollGate OS Firmware for glinet_gl-mt3000", "sig": "1d050233428304685d202e954cb48714c800a7ca5f2d6a8d8fd657a775b9c51bf83364505311859c846e25098168a8ff309af2308712aafe634fcbdc96fcd84a" }One of the missing links was the
supported_devicestag. That is because the installer checks the device name by ssh-ing into the router and it returns theglinet,gl-mt3000which doesn't properly translate into thedevice_id, which is what's used for compiling the OS. So this helps us to do the lookups and compatibility checks in the installer.I also worked on: - getting the versioning of the tollgate-basic package's naming in line with the OpenWRT naming convention. - Rework versioning for dev builds into
[branchname].[commit_height].[commit_hash]which will show up on thedevrelease_channelreleases. - Getting an initial release of the tollgate-installer done, so we can easily flash a bunch of routers to become TollGates.Bright minds in Prague
I met up with some bright minds from the space in Prague where @cobrador and i did a workshop on turning routers into TollGates and start earning sats. As is part of building things, things break and people make us aware of issues that we wouldn't foresee. Like for some reason Minibits cashu tokens being rejected, which is likely because of the memo's but we still need to dive into that issue.
Also we released [v0.0.2] of TollGate OS, which now includes an updater feature, again for faster release cycles. Currently we're focussing on getting a v0.0.3 out quickly with fixes for the user feedback we've gathered so far!
Receipt.Cash
I also, kind of unplanned, saw an opportunity to shill Receipt.Cash. I'd made a few improvements recently and it's ready enough for reckless people to try it out ;).
|
 |
| 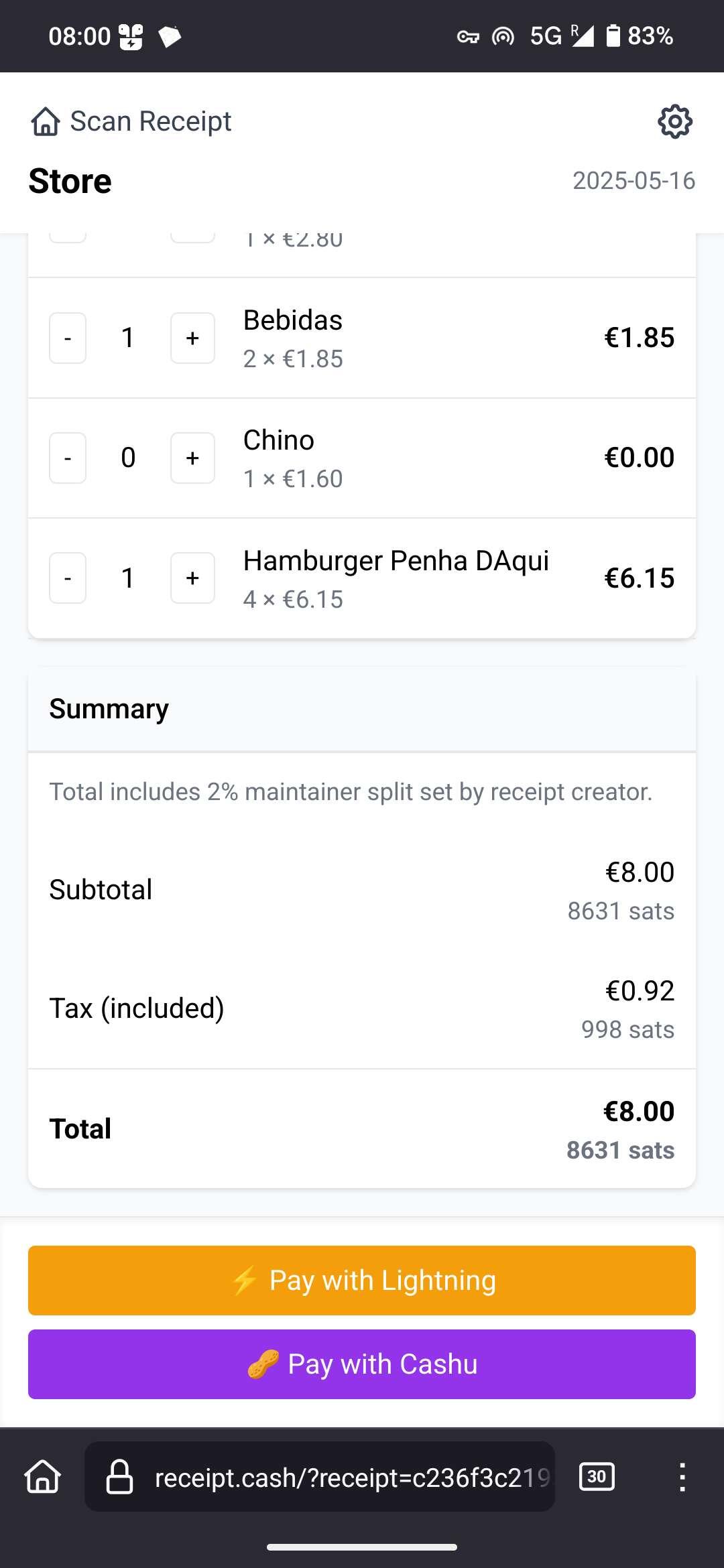 |
| |
| Payer Scans any fiat receipt & Share link with friends | Friends tap what they had, price is auto-converted to sats, then pay by Lightning or Cashu. |
If you want to try it, BE CAREFUL! It is highly experimental and you might lose your sats, no refunds!
|
| |
| Payer Scans any fiat receipt & Share link with friends | Friends tap what they had, price is auto-converted to sats, then pay by Lightning or Cashu. |
If you want to try it, BE CAREFUL! It is highly experimental and you might lose your sats, no refunds!Source Code here.
-
 @ 8576ca0e:621f735e
2025-05-20 08:46:45
@ 8576ca0e:621f735e
2025-05-20 08:46:45
Now that you’ve mastered the basics, it’s time to level up. Bitcoin isn’t just about buying and holding it’s about understanding the ecosystem, optimizing security, and leveraging its unique properties to build wealth. In this deep dive, we’ll explore advanced concepts every Bitcoin enthusiast needs to know.
-
Mastering Bitcoin Security: Beyond the Basics -Multisig Wallets: Require multiple private keys to authorize transactions (e.g., 2-of-3 signatures). Ideal for protecting large holdings. -Cold Storage Deep Dive: How to set up air gapped hardware wallets, metal seed backups, and geographic redundancy. -Privacy Best Practices: Using CoinJoin, Tor, and wallets like Wasabi or Samourai to enhance anonymity. -Pro Tip: Test recovery phrases before transferring large sums.
-
Bitcoin’s Economic Landscape: Scarcity, Halvings, and Market Cycles -The Halving Explained: How Bitcoin’s supply schedule (every 4 years) impacts price, miner behavior, and long term value. -Stock to Flow (S2F) Model: Why Bitcoin’s scarcity makes it a compelling store of value. -Market Psychology: Spotting bull/bear cycles, avoiding FOMO, and using dollar cost averaging (DCA) strategically.
-
Advanced Transaction Techniques -Layer 2 Solutions: Harnessing the Lightning Network for instant, low cost payments (and earning routing fees). -Replace by Fee (RBF): Speed up stuck transactions by increasing fees. -Taproot and Schnorr Signatures: How Bitcoin’s upgrades improve privacy and scalability.
-
Earning Passive Income with Bitcoin -Lending and Yield: Risks and rewards of platforms like Celsius (post-bankruptcy lessons) and decentralized alternatives. -Bitcoin Mining Pools: Can you still profit as a small miner? We break down the math. -Staking Alternatives: Wrapped Bitcoin (WBTC) in DeFi opportunities and risks.
-
Navigating Regulation and Taxes -Global Tax Compliance: Reporting crypto gains, airdrops, and forks (IRS, HMRC, etc.). -Self custody vs Regulation: How governments are approaching Bitcoin custody laws and privacy tools. -Bitcoin ETFs and Institutions: What BlackRock, Fidelity, and others mean for retail investors.
-
The Future of Bitcoin: What’s Next? -Bitcoin as a Reserve Asset: Nation states adopting BTC (El Salvador, Lugano). -Smart Contracts on Bitcoin: Exploring Rootstock (RSK) and Discreet Log Contracts (DLCs). -Quantum Computing Threats: Separating hype from reality.
Why Follow My Profile? -Weekly Deep Dives: From mining profitability calculators to privacy tool tutorials. -Market Analysis: Bullish catalysts, bearish risks, and how to stay ahead. -Community Q&A: Get your advance bitcion questions answered.
🔔 Follow my profile to unlock Bitcoin 103: Building Wealth in a Decentralized World. Coming soon!
-
-
 @ 3770c235:16042bcc
2025-05-20 13:27:03
@ 3770c235:16042bcc
2025-05-20 13:27:03In recent years, a remarkable transformation has taken place in the way people view and utilize their homes. No longer confined to the four walls of traditional interior spaces, homeowners are increasingly turning their attention outward—toward their own backyards. The concept of outdoor living has evolved from mere patio furniture and barbecues to fully functional living environments, equipped with kitchens, entertainment systems, and even workspaces.
This growing trend is not just a design choice; it reflects changing lifestyles, shifting priorities, and a reimagining of what it means to feel at home. The rise of outdoor living is more than a fad—it's a movement, and it's here to stay.
**A Shift in Lifestyle and Values ** At the heart of the outdoor living boom is a deeper shift in how people value their time, environment, and personal space. The COVID-19 pandemic played a significant role in this evolution. Lockdowns and restrictions forced many to reassess their living situations, seeking ways to make the most of what they already had. The backyard, once overlooked, suddenly became a sanctuary—a space to breathe, gather, and escape the monotony of indoor life.
According to a 2021 study by the International Casual Furnishings Association, over 90% of Americans with outdoor living space report that it is more valuable to them than ever before, with nearly 60% saying they upgraded their outdoor spaces during the pandemic source.
This change in perception is not solely pandemic-related. There's a growing emphasis on wellness, mindfulness, and balance. People are looking to nature for inspiration and relaxation. Outdoor living spaces—be they modest balconies or expansive decks—allow homeowners to connect with nature without leaving the comfort of home.
Redefining the Backyard: From Playgrounds to Living Rooms
Traditionally, the backyard has served specific purposes—gardening, children’s play areas, maybe a grill tucked in the corner. Today, backyards are being reimagined as multi-functional extensions of the home.
-
Outdoor Kitchens and Dining Areas Once considered a luxury, outdoor kitchens have become increasingly common. With built-in grills, pizza ovens, refrigerators, sinks, and full countertops, these outdoor culinary spaces rival their indoor counterparts. The convenience of preparing and serving meals outside is matched by the social benefit: cooking becomes a shared experience.
-
Living and Lounge Areas Outdoor seating now goes far beyond foldable lawn chairs. Modular sectionals, fire pits, weather-resistant rugs, and even smart lighting have turned patios into legitimate living rooms under the sky. Some include mounted TVs, Bluetooth speakers, and retractable canopies or pergolas for all-weather comfort.
-
Work and Study Zones Remote work has blurred the boundaries between office and home. Now, it’s expanding into the outdoors. With Wi-Fi extenders, weather-protected furniture, and shade structures, backyards are becoming viable home office environments, perfect for Zoom calls with a natural backdrop.
-
Wellness Retreats From hot tubs and saunas to yoga decks and meditation gardens, outdoor spaces are being tailored to support wellness. These personal sanctuaries offer solitude and stress relief, all within the perimeter of one's property.
The Role of Technology and Innovation Modern outdoor spaces owe much of their versatility to advances in technology and materials. Weather-resistant fabrics, composite decking, solar lighting, and smart irrigation systems have all expanded what's possible in backyard design.
Smart home technology has also made its way outdoors. Lighting can be automated or voice-controlled. Outdoor speakers can be synced across zones. Even grills can be connected to apps that monitor cooking temperatures. These innovations allow outdoor living to be both luxurious and convenient, requiring minimal maintenance while offering maximum comfort.
**Economic Impact and Value Addition ** Investing in outdoor living isn't just about lifestyle—it’s also smart economics. Outdoor upgrades can significantly boost a home's resale value. A well-designed patio or outdoor kitchen can yield a return on investment (ROI) of up to 80%, according to the National Association of Realtors. In fact, data from Houzz shows that nearly 57% of homeowners are investing in their outdoor spaces specifically to increase resale value source.
This financial motivation has fueled demand for landscape architects, outdoor furniture designers, and construction professionals specializing in outdoor living projects. As a result, the industry surrounding outdoor enhancements—from pergola manufacturers to luxury fire pit designers—has seen exponential growth.
Environmental Considerations and Sustainability As outdoor living becomes more popular, so does the demand for environmentally conscious design. Homeowners are increasingly incorporating sustainable elements into their outdoor plans, including: • Native plant landscaping: Reduces water usage and supports local ecosystems. • Rainwater harvesting systems: Collect and store rain for garden irrigation. • Solar-powered lighting: Minimizes energy consumption while maximizing ambiance. • Permeable paving materials: Reduce runoff and promote groundwater recharge. Green living isn't just a buzzword—it’s influencing how people design their outdoor sanctuaries. Eco-conscious homeowners are prioritizing sustainability as much as aesthetics, ensuring their outdoor spaces are in harmony with nature, not in conflict with it.
The Social Connection
Outdoor living also taps into our basic need for connection. From summer barbecues to cozy firepit gatherings, the backyard is an ideal setting for meaningful social interactions. During a time when indoor gatherings have been restricted or limited, outdoor spaces have offered a safer, more accessible alternative.
Community ties can also be strengthened through outdoor living. In urban settings, rooftop terraces or shared gardens create communal spaces for neighbors to engage, collaborate, and unwind. For families, these outdoor extensions offer a way to spend quality time together—whether through games, meals, or simply enjoying the open air. For individuals, they provide a space to recharge, free from the digital and physical clutter of indoor life.
Customization and Personalization
One of the most appealing aspects of outdoor living is the high degree of customization available. Unlike interior spaces that may be limited by architectural constraints, outdoor areas can often be more flexible in layout and design.
Homeowners can craft outdoor environments that reflect their personalities and values: • The entertainer may opt for a bar area, ambient lighting, and surround sound. • The minimalist might choose clean lines, neutral tones, and eco-friendly materials. • The nature-lover may emphasize greenery, water features, and natural textures. DIY options also abound, allowing for creative freedom and budget-friendly upgrades. Raised garden beds, handmade furniture, repurposed materials, and vertical planters give individuals the opportunity to leave their personal mark on the space.
The Influence of Global Design Trends Outdoor living isn’t confined to North America. Around the world, cultures have long embraced outdoor spaces—from Japanese zen gardens to Mediterranean courtyards. The current global design conversation draws inspiration from a variety of traditions and climates.
Scandinavian principles of simplicity and functionality influence clean-lined, open-air designs, while tropical resorts have inspired lush, greenery-filled retreats in suburban settings. The blending of international styles enables homeowners to create outdoor spaces that are both eclectic and functional.
Looking Ahead: The Future of Outdoor Living The trajectory of outdoor living points to continued growth, innovation, and integration. Here are some trends likely to define the next decade:
- Year-Round Use With heating lamps, insulated pergolas, and all-weather furniture, outdoor spaces are becoming viable in all seasons. Expect to see more designs tailored for winter, including hot tubs, enclosed lounges, and warm lighting features.
- Outdoor Smart Hubs Technology will play an even greater role, with integrated outdoor control systems for lighting, security, irrigation, and entertainment—managed through a single device or app.
- Edible Landscaping Gardens will not only be for beauty but also for sustenance. Raised vegetable beds, fruit trees, and herb walls will become staples in functional outdoor design.
- Modular Design Portable and adaptable elements like movable walls, foldable furniture, and hybrid indoor-outdoor structures will offer more flexibility, especially in smaller spaces.
- Wellness Integration Expect an even stronger emphasis on health and well-being—cold plunge pools, outdoor gyms, meditation pods, and immersive natural soundscapes will take center stage.
Conclusion The rise of outdoor living is not just a design phenomenon—it’s a cultural shift. Homeowners are recognizing the value of outdoor spaces as extensions of their identities, routines, and dreams. Whether it's a serene garden, a vibrant entertainment hub, or a cozy work nook, the backyard is being redefined as a vital part of the home. In a world that often feels fast-paced and digitally overloaded, outdoor living offers a much-needed antidote: space to breathe, relax, connect, and thrive. It’s about more than upgrading the home—it’s about enhancing the human experience. As this trend continues to evolve, one thing is clear: the best room in the house may not be inside at all.
-
-
 @ a5ee4475:2ca75401
2025-05-19 01:11:59
@ a5ee4475:2ca75401
2025-05-19 01:11:59clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 📱 (on development) ⏳
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] [source] 🤖🍎
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ 58537364:705b4b85
2025-05-20 06:47:23
@ 58537364:705b4b85
2025-05-20 06:47:23อิคิไก (Ikigai) แปลว่า ความหมายของการมีชีวิตอยู่ เหตุผลของการมีชีวิตอยู่ เราเกิดมาเพื่ออะไร ใช้ชีวิตอยู่ไปทำไม เมื่อการงานไม่ใช่สิ่งที่แปลกแยกจากชีวิต
คนญี่ปุ่นเชื่อว่าทุกคนมี ikigai ของตัวเอง ผู้ที่ค้นพบ ikigai จะเจอความหมายและคุณค่าของชีวิต ทำให้มีความสุขกว่า อารมณ์ดีกว่า และมีโลกที่น่าอยู่กว่าด้วย
ปัจจุบัน มีหนังสือเกี่ยวกับอิคิไกออกวางขายเป็นจำนวนมาก แต่เล่มที่คนญี่ปุ่นเป็นคนเขียนเล่มแรกนั้น คือ
- The Little Book of Ikigai : The secret Japanese way to live a happy and long life โดยอาจารย์เคน โมหงิ (แปลภาษาไทยโดย คุณวุฒิชัย กฤษณะประการกิจ)
ตามมาสัมผัสโลกของอิคิไกที่แท้จริงจากนักวิทยาศาสตร์วิจัยด้านสมองชาวญี่ปุ่นคนนี้ ผ่านบทสนทนาที่จะเปลี่ยนความคิดใหม่ที่ว่า 'อิคิไก' เริ่มต้นจากมองหาความสุขเล็กๆ น้อยๆ ในแบบของตัวเราเอง
อาจารย์เคน โมหงิว่า ปู่จิโร่ เชฟซูชิวัย 94 ปี ที่ยังยืนปั้นซูชิให้เราทานอยู่ในทุกวันนี้ เป็นแรงบันดาลใจให้อาจารย์เกิดไอเดียในการเขียนหนังสืออิคิไก
เชฟซูชิที่ ‘ไม่ได้’ เริ่มเลือกงานนี้เพราะความรักหรือความถนัด แต่กลับทุ่มเทปั้นซูชิทุกคำเพื่อให้ลูกค้ามีความสุข… นั่นคือต้นแบบของอิคิไก
น่าแปลกที่คนญี่ปุ่นไม่ค่อยใช้คำว่า ‘อิคิไก’ ในชีวิตประจำวันหรือบทสนทนาทั่วไปเท่าไหร่
เพราะมันเป็นสิ่งที่ปกติและเราทำกันตามธรรมชาติ ในโลกปัจจุบัน เรามักพูดกันว่าทำอย่างไรเราถึงจะประสบความสำเร็จ ทำอย่างไรจะได้เลื่อนตำแหน่ง หากอยากเป็น CEO จะเป็นได้อย่างไร แต่คนญี่ปุ่นมีความคิดว่าความสำเร็จไม่ใช่ทุกอย่างในชีวิต
ยกตัวอย่างเช่นมีคนญี่ปุ่นจำนวนมากที่จริงจังกับงานอดิเรก หรือมี โคดาวาริ* คนอื่นไม่สนหรอกว่างานอดิเรกของคนคนนั้นจะเป็นอะไร ตราบใดที่คนคนนั้นดูมีความสุขดีนั่นก็โอเคแล้ว มีคนจำนวนมากคลั่งไคล้รถไฟ มังงะ (หนังสือการ์ตูน) หรือแอนิเมะ (ภาพยนตร์การ์ตูน) คนเหล่านี้ไม่จำเป็นต้องมีชื่อเสียงหรือได้รับการยอมรับจากสังคม ตราบเท่าที่พวกเขามีความสุขในแบบของเขาเอง มันก็ดีแล้ว
- ความพิถีพิถันใส่ใจในบางเรื่องเป็นพิเศษ เช่น คนที่ชอบเครื่องเขียนมากๆ จะพิถีพิถันในการเลือกปากกา สมุด ดินสอที่ตนเองจะใช้ เพราะฉะนั้น คนที่มีโคดาวาริเหล่านี้จะศึกษาเครื่องเขียนจนถึงที่สุด วิเคราะห์ ทดลอง จนพบว่าเครื่องเขียนแบบใดที่ตนเองหลงใหลที่สุด
อิคิไกของแต่ละคนอาจแตกต่างกัน ต่างคนอาจมีค่านิยมที่ต่างกัน ซึ่งสะท้อนในรูปแบบชีวิตที่แตกต่างกันก็ได้
อิคิไกเป็นเรื่องของความหลากหลายนะ สังคมญี่ปุ่นพยายามผลักดันให้เด็กๆ ทุกคนตามหาอิคิไกของตนเอง เราจะไม่บอกว่า งานนี้เงินดี ทำสิ หรืองานนี้เงินน้อย อย่าไปทำเลย ถ้าคุณถามนักศึกษาว่า พวกเขาอยากทำงานอะไร พวกเขาคงไม่ตอบว่าเลือกทำที่บริษัทนี้เพราะเงินเป็นอันดับแรกหรอก
อิคิไกแตกต่างจากคำว่า ‘ความสำเร็จ’ คนญี่ปุ่นรู้ว่าชีวิตไม่ได้มีแค่เรื่องประสบความสำเร็จ อิคิไกสำคัญกับชีวิตมากกว่า คุณอาจจะประสบความสำเร็จ แต่คุณอาจไม่มีอิคิไก ในทางกลับกัน แม้คุณไม่ประสบความสำเร็จ คุณอาจจะมีอิคิไกก็ได้ ซึ่งชีวิตคุณอาจจะมีความสุขมากกว่า
อาจารย์เคน โมหงินิยามคำว่า ‘ความสำเร็จ’ คือสิ่งที่คุณจะได้รับการยอมรับจากคนในสังคมหรือบริบทสังคมนั้นๆ แต่อิคิไกมาจากหัวใจของคุณ มาจากความสุขส่วนตัวของคุณ คนอื่นอาจจะไม่ได้มองว่านั่นคือความสำเร็จ
อิคิไกเป็นสิ่งที่เฉพาะบุคคล เราสามารถมีความสุขในแบบของเราเอง เราไม่ตัดสินความสุขของคนอื่น และให้เขามีความสุขในแบบของเขาเอง…
สิ่งสำคัญของอิคิไกคือ คุณมีความสุขเล็กๆ น้อยๆ จากเรื่องที่ดูเหมือนเป็นเรื่องเล็กๆ น้อยๆ หรือเปล่า เช่น ตอนเด็กๆ ผมชอบศึกษาเกี่ยวกับผีเสื้อ เวลาผมไปวิ่งออกกำลังกายแล้วเห็นผีเสื้อสวยๆ ผมก็สัมผัสได้ถึงอิคิไก หรือบางทีอาจเกิดขึ้นตอนที่ผมรู้สึกตลกๆ ก็ได้ ผมเห็นเด็กผู้ชายคนหนึ่งบอกพ่อว่า “พ่อๆ ต้องทำอย่างนี้สิ” เวลาผมได้ยินบทสนทนาแบบนี้ ผมก็รู้สึกถึงอิคิไก
หากพวกเราอยากมีอิคิไกบ้าง เราควรเริ่มจากอะไรดี ? เริ่มจากการสัมผัสความสุขจากสิ่งเล็กๆ น้อยๆ ก่อน มันเริ่มทำได้ง่ายที่สุด ในสมองเรามีสารชื่อโดพามีน หากเราทำอะไรสำเร็จเล็กๆ น้อยๆ โดพามีนจะหลั่งออกมา วงจรนั้นจะช่วยทำให้คุณมีความสุข การมีความสุขกับสิ่งเล็กๆ เช่นนี้เป็นเรื่องสำคัญมาก สำหรับหลายคน แนวคิดเรื่องอิคิไกอาจเข้าใจยาก หรือยากสำหรับบางคนที่ชีวิตพวกเขากำลังอยู่ในช่วงยากลำบาก กำลังรู้สึกหมดหวัง ท้อแท้ หรือไม่ได้เคารพตนเอง เพราะฉะนั้น เริ่มจากความสุขเล็กๆ น้อยๆ ก่อนครับ
มันเหมือนการคิดบวกไหม ? อิคิไกเป็นส่วนหนึ่งนะ เวลาเราคิดถึงชีวิต หรือคิดหาวิธีการคิดบวก มันเป็นเรื่องที่ซับซ้อนมาก สำหรับบางคนคำว่า ‘คิดบวก’ อาจฟังดูกดดันสำหรับพวกเขา เพราะฉะนั้น เริ่มจากการมองเห็นความสุขจากสิ่งเล็กๆ น้อยๆ รอบตัว สิ่งเล็กมากๆ เช่นการได้ตื่นมาชงกาแฟดื่ม การได้วิ่งกลางสายฝน

Lesson from Ken Mogi 1. อิคิไก ไม่ใช่การแสวงหาความสำเร็จหรือความร่ำรวย แต่เป็นการรู้สึกหรือสัมผัสถึงความสุขในชีวิตของตนเอง จนทำให้เราเห็นความหมายของชีวิตเราในแบบของเรา 2. อิคิไกไม่ใช่สิ่งที่สังคมนิยามหรือโลกให้ความสำคัญ แต่ละคนมีอิคิไกที่แตกต่างกัน และมีความสุขกับชีวิตในแบบของตนเอง ที่เราเลือกเอง 3. เราไม่ควรตัดสินคนอื่นหรือบีบบังคับคนอื่น เช่น ลูก แฟน ให้ใช้ชีวิตในแบบที่เราคิดว่าใช่ แต่เราควรเคารพความหลากหลายนั้น 4. มองคนที่มีอิคิไกหรือกำลังสนุกกับสิ่งที่พวกเขารักด้วยรอยยิ้ม และคอยช่วยเหลือหากพวกเขาลำบาก 5. อิคิไกมีทั้งระดับใหญ่ ซึ่งเกี่ยวกับแนวทางชีวิตหรือคุณค่าของงาน และอิคิไกระดับเล็กคือการสัมผัสความสุขเล็กๆ น้อยๆ ที่พบเห็นได้ในชีวิตประจำวัน 6. อิคิไก เริ่มต้นจากมองหาความสุขเล็กๆ น้อยๆ ในวันนี้
ที่มา : จากคอลัมน์ Cloud of Thoughts บทสัมภาษณ์ของอ.เกตุวดี Marumura พาไปคุยกับอาจารย์เคน โมหงิ ผู้เขียนหนังสืออิคิไกเล่มแรก!
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 87f5e1d9:e251d8f4
2025-05-17 13:13:42
@ 87f5e1d9:e251d8f4
2025-05-17 13:13:42In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
Why Choose Crypt Recver? 🤔 🔑 Expertise You Can Trust At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases. Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds! Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets. Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security. Don’t Let Lost Crypto Ruin Your Day! 🕒 With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now! Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back! 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞 For quick queries or support, connect with us on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪In the realm of cryptocurrency, the stakes are incredibly high, and losing access to your digital assets can be a daunting experience. But don’t worry — cryptrecver.com is here to transform that nightmare into a reality! With expert-led recovery services and leading-edge technology, Crypt Recver specializes in helping you regain access to your lost Bitcoin and other cryptocurrencies.
 # Why Choose Crypt Recver? 🤔
# Why Choose Crypt Recver? 🤔🔑 Expertise You Can Trust\ At Crypt Recver, we blend advanced technology with skilled engineers who have a solid track record in crypto recovery. Whether you’ve forgotten your passwords, lost your private keys, or encountered issues with damaged hardware wallets, our team is ready to assist.
⚡ Fast Recovery Process\ Time is crucial when recovering lost funds. Crypt Recver’s systems are designed for speed, enabling quick recoveries — allowing you to return to what matters most: trading and investing.
🎯 High Success Rate\ With a success rate exceeding 90%, our recovery team has aided numerous clients in regaining access to their lost assets. We grasp the complexities of cryptocurrency and are committed to providing effective solutions.
🛡️ Confidential & Secure\ Your privacy is paramount. All recovery sessions at Crypt Recver are encrypted and completely confidential. You can trust us with your information, knowing we uphold the highest security standards.
🔧 Advanced Recovery Tools\ We employ proprietary tools and techniques to tackle complex recovery scenarios, from retrieving corrupted wallets to restoring coins from invalid addresses. No matter the challenge, we have a solution.
 # Our Recovery Services Include: 📈
# Our Recovery Services Include: 📈- Bitcoin Recovery: Lost access to your Bitcoin wallet? We can assist in recovering lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistaken transfers, lost passwords, or missing transaction records — let us help you reclaim your funds!
- Cold Wallet Restoration: Did your cold wallet fail? We specialize in safely extracting assets.
- Private Key Generation: Forgotten your private key? We can help you generate new keys linked to your funds without compromising security.
Don’t Let Lost Crypto Ruin Your Day! 🕒
With an estimated 3 to 3.4 million BTC lost forever, it’s essential to act quickly when facing access issues. Whether you’ve been affected by a dust attack or simply forgotten your key, Crypt Recver provides the support you need to reclaim your digital assets.
🚀 Start Your Recovery Now!\ Ready to retrieve your cryptocurrency? Don’t let uncertainty hold you back!\ 👉 Request Wallet Recovery Help Today!cryptrecver.com
Need Immediate Assistance? 📞
For quick queries or support, connect with us on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Trust Crypt Recver for the best crypto recovery service — get back to trading with confidence! 💪
-
 @ cefb08d1:f419beff
2025-05-20 13:26:14
@ cefb08d1:f419beff
2025-05-20 13:26:14https://www.youtube.com/watch?v=jIydjo4B25U
The GWM Catch Up Day 2: Western Australia pushes CT to the ultimate test in all or nothing bouts:
https://www.youtube.com/watch?v=4zwuqs6iTPg
Women and Men Results:
https://stacker.news/items/984538
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 9c9d2765:16f8c2c2
2025-05-20 05:45:33
@ 9c9d2765:16f8c2c2
2025-05-20 05:45:33CHAPTER TWENTY THREE Across town, the Ray estate was drenched in shame. The once-proud family was now the subject of ridicule, their downfall televised, published, and whispered in business circles. Helen stood before a cracked mirror in her bedroom, mascara smudged, lips trembling with fury. The headlines were merciless:
"Heir to JP Empire Humiliated by Ray Family Then Bought Them Out."
"President James: From Rejection to Royalty."
She had lost more than power. She had lost control.
Mark, seated in an armchair with a drink that had gone warm, stared at the wall, his eyes empty. He was a strategist, a manipulator but somehow, he had underestimated James.
"He's just one man…" Mark muttered.
"No," Helen corrected him coldly. "He's not just a man. He’s a symbol now. Of power… of justice… and worst of all, forgiveness."
Mark scoffed. "Forgiveness?"
"Yes," she snapped, spinning to face him. "Because he didn’t destroy us when he could. That makes him look grander than anything we can ever fabricate. He let the world ruin us instead."
There was a long pause.
Then Mark stood, eyes narrow. "We’ll find another way. We always do."
But the fire in his voice had dulled. The Ray family was crippled, their company reduced to a shadow of its former self. Their staff had dwindled, partners severed ties, and their name now stood for arrogance and downfall.
Meanwhile, James had begun the silent restoration of more than just a company he was rebuilding legacies.
Back at JP Enterprises, Rita stepped into James’s office, her presence warm and reassuring.
“You’ve been in here for hours,” she said softly. “Everything alright?”
James looked up, his eyes thoughtful. “Everything is fine. I’m just… reflecting.”
“About them?”
He nodded. “Helen, Mark, Tracy. I know they’re not done. People like them never accept defeat.”
Rita approached, placing a comforting hand on the desk. “Then be ready for their next move. But know that you’re not alone anymore. And you’re no longer the man they thought you were.”
A faint smile curved on his lips. “No. I’m the man they made me become.”
Outside the office, whispers of the upcoming restructuring had already begun. Rumors swirled about James planning to absorb Ray Enterprises entirely into JP Holdings. Some believed he would dismantle it brick by brick. Others hoped he would revive it, proving once again that mercy was strength.
But only James knew his next move.
And as the days passed, the city watched some in admiration, others in dread.
Nightfall settled over the city like velvet, embroidered with the glimmer of a thousand restless lights. From the penthouse office of JP Enterprises, James stood before the floor-to-ceiling windows, his silhouette framed against the horizon. The world below him pulsed with ambition and whispers. Yet his mind wasn’t on the skyline, but on the murky tide still gathering beneath it Mark, Helen, and the crumbling remnants of a fallen dynasty that refused to stay buried.
The public had embraced his rise like a storybook tale. From the ashes of mockery, betrayal, and scorn, he had risen dignified, strategic, and unyielding. News outlets now hailed him as a symbol of resilience, of leadership sharpened by adversity. But James knew that the brightest stars cast the darkest shadows.
Behind the glamour, war drums still beat.
He sat at his desk, opening a sealed file handed to him earlier by his private investigator. Inside were photographs, recordings, and written transcripts irrefutable proof of secret meetings between Helen, Mark, and a few disgruntled former board members of Ray Enterprises. They were not merely planning revenge, they were mobilizing.
A knock interrupted his thoughts. Rita stepped in, poised and composed.
“You asked me to bring the reports on the integration of Ray Enterprises’ satellite branches.”
“Thank you, Rita,” James said, his voice calm but laced with calculation. “Leave them here.”
She lingered. “There’s something else,” she said, her tone more hushed now. “The woman from the anniversary… she’s resurfaced.”
James looked up slowly. “Where?”
“She was seen outside a media house yesterday, trying to set up another exclusive. But word is she's trying to recant her confession. Claims she was ‘coerced’ into blaming Mark and Helen.”
James’s gaze narrowed. “They’re trying to rewrite the narrative.”
Rita nodded. “And if they succeed, they’ll portray you as the one who orchestrated the chaos.”
He exhaled quietly, rising from his seat. “Let them try. The truth is no longer their weapon, it's mine.”
Meanwhile, in a dimly lit lounge across town, Mark and Helen sat opposite a trembling young woman, the same one who once fell to her knees and confessed everything at the anniversary.
“You owe us,” Helen said through clenched teeth. “We gave you the money, we protected you… and you humiliated us in front of the entire city.”
“I was scared,” the woman stammered, eyes darting between them. “Everyone was watching. Mr. JP was furious. What was I supposed to do?”
Mark leaned in, his expression carved from ice. “Fix it.”
“Y-You mean go to the press?”
Helen smiled coldly. “No. We mean bury the damage. Make James look like the one pulling your strings. We’ll give you twice what we paid. You just have to make the world believe he bribed you.”
As the woman hesitated, fear swimming in her gaze, Helen added softly, “Or you disappear.”
The woman’s nod was reluctant, but it was enough.
-
 @ 472f440f:5669301e
2025-05-20 13:01:09
@ 472f440f:5669301e
2025-05-20 13:01:09Marty's Bent
via me
Don't sleep on what's happening in Japan right now. We've been covering the country and the fact that they've lost control of their yield curve since late last year. After many years of making it a top priority from a monetary policy perspective, last year the Bank of Japan decided to give up on yield curve control in an attempt to reel inflation. This has sent yields for the 30-year and 40-year Japanese government bonds to levels not seen since the early 2000s in the case of the 30-year and levels never before seen for the 40-year, which was launched in 2007. With a debt to GDP ratio that has surpassed 250% and a population that is aging out with an insufficient amount of births to replace the aging workforce, it's hard to see how Japan can get out of this conundrum without some sort of economic collapse.
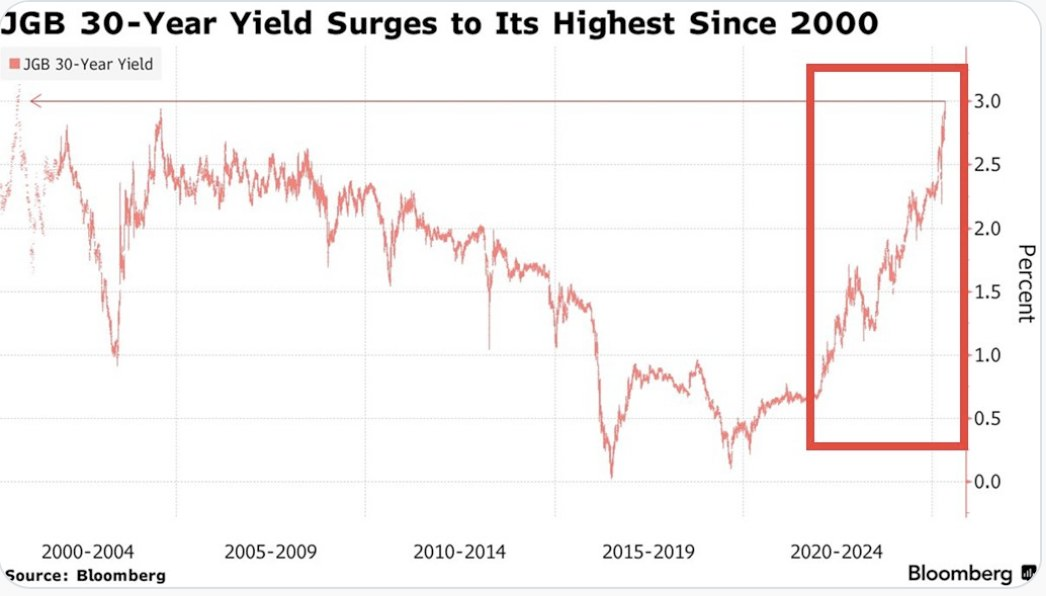
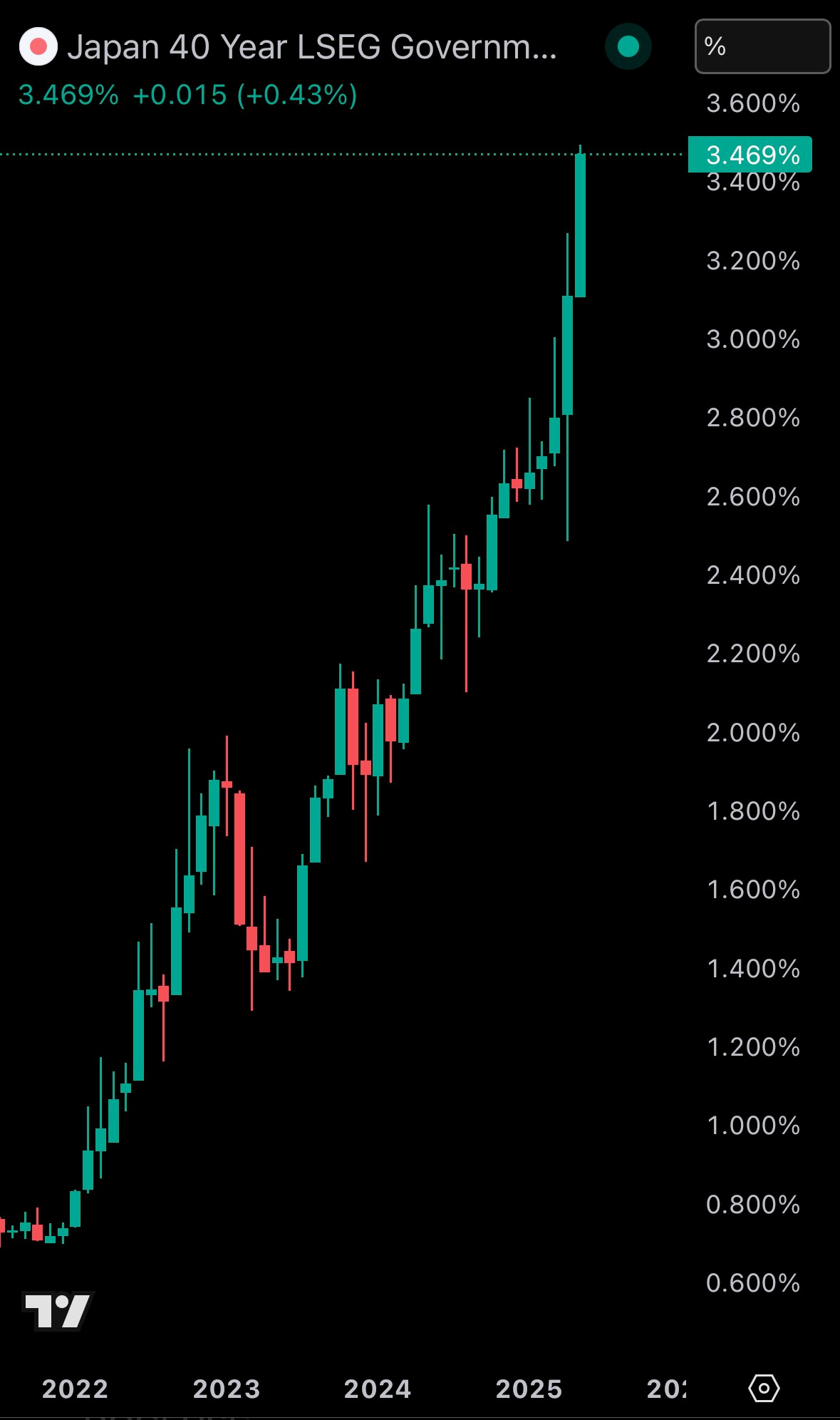
This puts the United States in a tough position considering the fact that Japan is one of the largest holders of U.S. Treasury bonds with more than 1,135 sats | $1.20 trillion in exposure. If things get too out of control in Japan and the yield curve continues to drift higher and inflation continues to creep higher Japan can find itself in a situation where it's a forced seller of US Treasuries as they attempt to strengthen the yen. Another aspect to consider is the fact that investors may see the higher yields on Japanese government bonds and decide to purchase them instead of US Treasuries. This is something to keep an eye on in the weeks to come. Particularly if higher rates drive a higher cost of capital, which leads to even more inflation. As producers are forced to increase their prices to ensure that they can manage their debt repayments.
It's never a good sign when the Japanese Prime Minister is coming out to proclaim that his country's financial situation is worse than Greece's, which has been a laughing stock of Europe for the better part of three decades. Japan is a very proud nation, and the fact that its Prime Minister made a statement like this should not be underappreciated.
As we noted last week, the 10-year and 30-year U.S. Treasury bonds are drifting higher as well. Earlier today, the 30-year bond yield surpassed 5%, which has been a psychological level that many have been pointed to as a critical tipping point. When you take a step back and look around the world it seems pretty clear that bond markets are sending a very strong signal. And that signal is that something is not well in the back end of the financial system.
This is even made clear when you look at the private sector, particularly at consumer debt. In late March, we warned of the growing trend of buy now, pay later schemes drifting down market as major credit card companies released charge-off data which showed charge-off rates reaching levels not seen since the 2008 great financial crisis. At the time, we could only surmise that Klarna was experiencing similar charge-off rates on the bigger-ticket items they financed and started doing deals with companies like DoorDash to finance burrito deliveries in an attempt to move down market to finance smaller ticket items with a higher potential of getting paid back. It seems like that inclination was correct as Klarna released data earlier today showing more losses on their book as consumers find it extremely hard to pay back their debts.
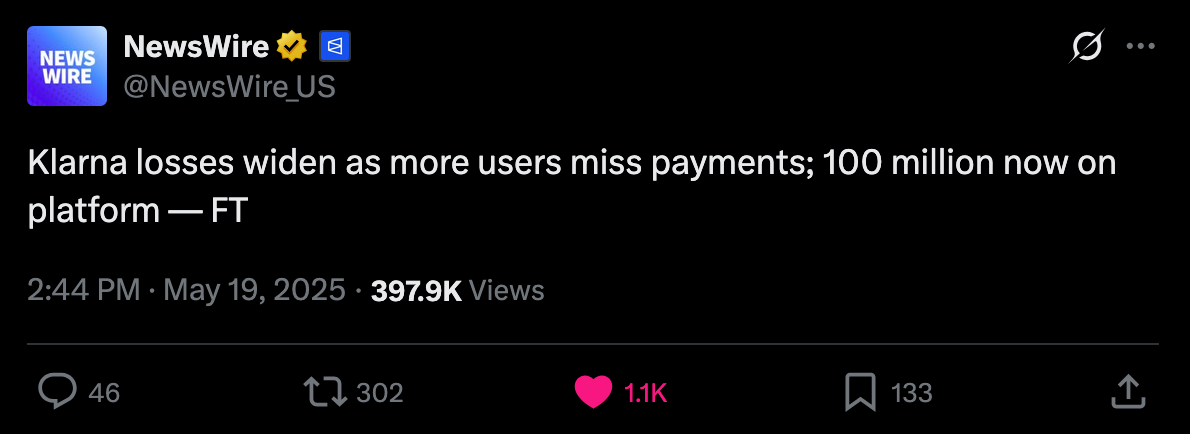
via NewsWire
This news hit the markets on the same day as the average rate of the 30-year mortgage in the United States rose to 7.04%. I'm not sure if you've checked lately, but real estate prices are still relatively elevated outside of a few big cities who expanded supply significantly during the COVID era as people flooded out of blue states towards red states. It's hard to imagine that many people can afford a house based off of sticker price alone, but with a 7% 30-year mortgage rate it's becoming clear that the ability of the Common Man to buy a house is simply becoming impossible.
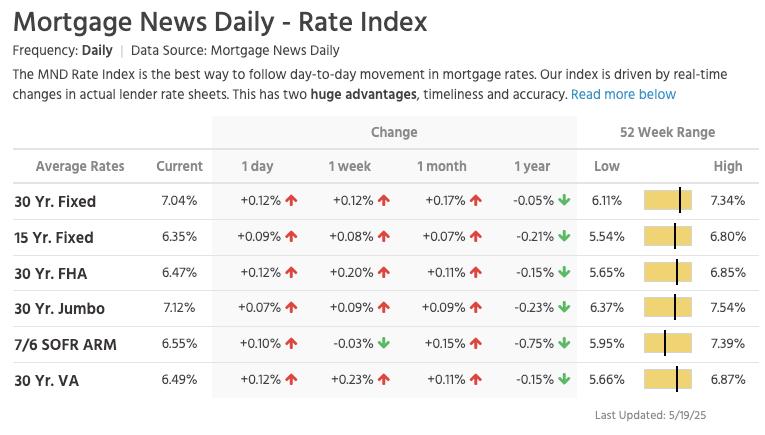
via Lance Lambert
The mortgage rate data is not the only thing you need to look at to understand that it's becoming impossible for the Common Man of working age to buy a house. New data has recently been released that highlights That the median home buyer in 2007 was born in 1968, and the median home buyer in 2024 was born in 1968. Truly wild when you think of it. As our friend Darth Powell cheekily highlights below, we find ourselves in a situation where boomers are simply trading houses and the younger generations are becoming indentured slaves. Forever destined to rent because of the complete inability to afford to buy a house.
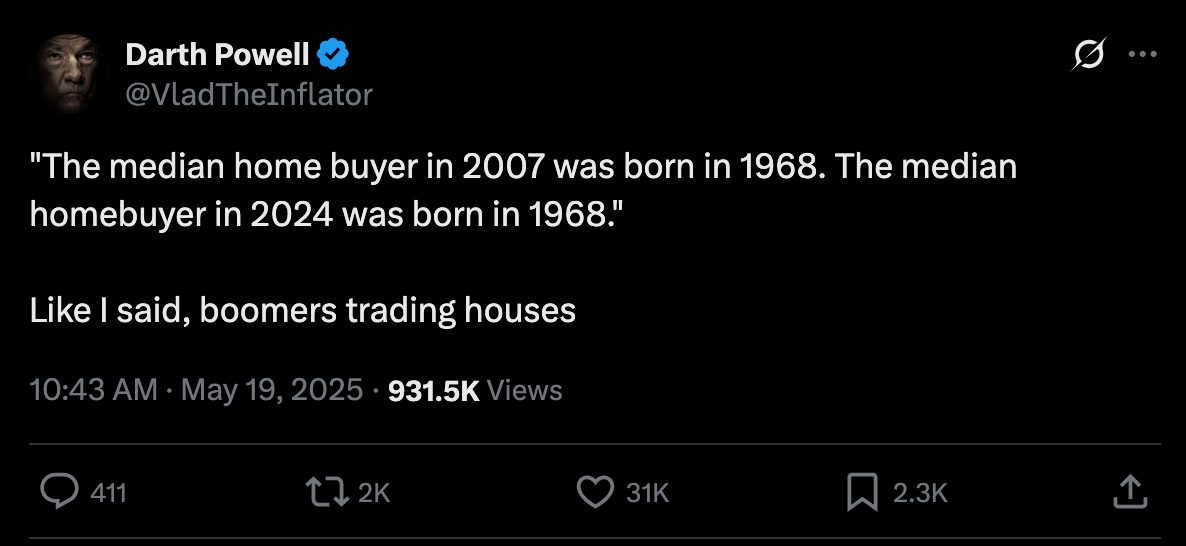
via Darth Powell

via Yahoo Finance
Meanwhile, Bitcoin re-approached all-time highs late this evening and looks primed for another breakout to the upside. This makes sense if you're paying attention. The high-velocity trash economy running on an obscene amount of debt in both the public and private sectors seems to be breaking at the seams. All the alarm bells are signaling that another big print is coming. And if you hope to preserve your purchasing power or, ideally, increase it as the big print approaches, the only thing that makes sense is to funnel your money into the hardest asset in the world, which is Bitcoin.

via Bitbo
Buckle up, freaks. It's gonna be a bumpy ride. Stay humble, Stack Sats.
Trump's Middle East Peace Strategy: Redefining U.S. Foreign Policy
In his recent Middle East tour, President Trump signaled what our guest Dr. Anas Alhajji calls "a major change in US policy." Trump explicitly rejected the nation-building strategies of his predecessors, contrasting the devastation in Afghanistan and Iraq with the prosperity of countries like Saudi Arabia and UAE. This marks a profound shift from both Republican and Democratic foreign policy orthodoxy. As Alhajji noted, Trump's willingness to meet with Syrian President Assad follows a historical pattern where former adversaries eventually become diplomatic partners.
"This is really one of the most important shifts in US foreign policy to say, look, sorry, we destroyed those countries because we tried to rebuild them and it was a big mistake." - Dr. Anas Alhajji
The administration's new approach emphasizes negotiation over intervention. Rather than military solutions, Trump is engaging with groups previously considered off-limits, including the Houthis, Hamas, and Iran. This pragmatic stance prioritizes economic cooperation and regional stability over ideological confrontation. The focus on trade deals and investment rather than regime change represents a fundamental reimagining of America's role in the Middle East.
Check out the full podcast here for more on the Iran nuclear situation, energy market predictions, and why AI development could create power grid challenges. Only on TFTC Studio.
Headlines of the Day
Bitcoin Soars to 100,217 sats | $106.00K While Bonds Lose 40% Since 2020 - via X
US Senate Advances Stablecoin Bill As America Embraces Bitcoin - via X
Get our new STACK SATS hat - via tftcmerch.io
Texas House Debates Bill For State-Run Bitcoin Reserve - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Don't let the noise consume you. Focus on making your life 1% better every day.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 04ce30c2:59ea576a
2025-05-20 04:19:25
@ 04ce30c2:59ea576a
2025-05-20 04:19:25Em uma sociedade verdadeiramente livre, o indivíduo tem o direito de escolher como guardar e transferir valor. Isso inclui a liberdade de escolher qual moeda usar, sem coerção, monopólios ou imposições estatais. A concorrência entre moedas permite que as melhores propriedades monetárias prevaleçam de forma natural e voluntária.
Moeda imposta é controle
Quando uma única moeda é forçada por lei, seja por decreto estatal ou por exigências institucionais, o usuário perde a soberania sobre seu próprio patrimônio. Isso abre espaço para inflação arbitrária, bloqueios de transações, congelamento de fundos e vigilância massiva.
Concorrência monetária é essencial
A liberdade monetária implica a coexistência de várias moedas competindo entre si. Cada uma traz suas características e vantagens específicas. A escolha deve estar nas mãos do usuário, não em autoridades centralizadas.
A melhor moeda tende a se tornar o padrão
No longo prazo, a moeda com melhores propriedades monetárias, como previsibilidade, descentralização, auditabilidade e liquidez, tende a ser adotada como padrão de referência para precificação, poupança e comércio global.
O Bitcoin é a moeda mais forte nesse sentido. Mas isso não impede que outras moedas coexistam como ferramentas complementares em contextos específicos.
Conversão é liberdade
Se o usuário quiser por exemplo mais privacidade ao comprar um café ou pagar uma conta, ele pode facilmente trocar seus bitcoins por monero e usá-los conforme sua necessidade. A possibilidade de trocar entre moedas é parte essencial da liberdade financeira.
Uma sociedade livre permite a escolha. O padrão monetário deve emergir do consenso do mercado, não de imposições. Que o Bitcoin se torne o padrão não por decreto, mas por mérito. E que outras moedas existam para servir à liberdade individual em toda sua complexidade.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 7953d1fa:69c8039d
2025-05-20 02:39:56
@ 7953d1fa:69c8039d
2025-05-20 02:39:56No mundo digital em constante evolução, plataformas de entretenimento online vêm ganhando espaço entre os brasileiros que buscam diversão, emoção e recompensas. Uma das opções que tem se destacado recentemente é a KK999, uma plataforma moderna, segura e repleta de oportunidades para jogadores de todos os níveis. Com uma ampla gama de jogos envolventes e uma experiência de usuário otimizada, o KK999 está conquistando cada vez mais adeptos no Brasil.
Introdução à Plataforma KK999 O KK999 se diferencia por oferecer uma experiência completa e intuitiva desde o primeiro acesso. A interface da plataforma foi cuidadosamente projetada para ser amigável, permitindo que novos usuários se cadastrem rapidamente e naveguem com facilidade. Tudo é pensado para garantir que o jogador tenha uma experiência fluida, sem complicações e com total transparência.
Além disso, o kk999se destaca por sua forte infraestrutura de segurança. Utilizando tecnologia de criptografia de ponta, os dados dos usuários são protegidos em todas as transações, garantindo tranquilidade para quem deseja apenas se divertir. Outro ponto importante é o suporte ao cliente, que está disponível 24 horas por dia, com atendimento em português, pronto para auxiliar com qualquer dúvida ou necessidade.
Variedade de Jogos para Todos os Gostos Um dos grandes atrativos do KK999 é a impressionante variedade de jogos disponíveis. Desde os tradicionais jogos de cartas até opções modernas com gráficos avançados, a plataforma atende todos os estilos de jogadores. Entre os destaques, estão as famosas roletas virtuais, jogos de pesca interativa, slot machines com temas variados e jogos ao vivo que simulam a sensação de estar em uma sala de jogos física.
Os slots, por exemplo, são um sucesso entre os brasileiros, oferecendo desde títulos clássicos com frutas e números até aventuras temáticas com bônus emocionantes. Os jogos de cartas também têm grande popularidade, incluindo versões modernas de pôquer, bacará e outros jogos estratégicos que desafiam a mente do jogador.
Para quem gosta de competir em tempo real, o KK999 oferece jogos ao vivo com crupiês reais e interatividade instantânea, proporcionando uma experiência imersiva e cheia de adrenalina. Tudo isso com transmissões de alta qualidade e conexão estável.
Experiência do Jogador: Diversão e Confiabilidade A experiência do jogador é uma das maiores prioridades do KK999. Desde o primeiro cadastro até as jogadas mais avançadas, a plataforma investe em funcionalidades que aumentam o conforto e a confiança do usuário. A navegação é rápida, os jogos carregam com eficiência e as recompensas são distribuídas com agilidade.
Outro fator que atrai muitos jogadores é o sistema de bônus e promoções. O KK999 frequentemente disponibiliza ofertas especiais para novos membros e prêmios para usuários frequentes, incentivando a fidelidade e aumentando ainda mais as chances de ganhar.
Além disso, o KK999 oferece uma experiência totalmente otimizada para dispositivos móveis. Seja no celular ou tablet, o jogador pode acessar todos os recursos da plataforma de qualquer lugar, a qualquer momento, sem perder desempenho ou qualidade.
Conclusão O KK999 se consolida como uma das principais plataformas de entretenimento digital no Brasil, reunindo inovação, segurança e uma variedade impressionante de jogos. Ideal tanto para iniciantes quanto para jogadores experientes, o site oferece tudo o que é necessário para transformar momentos comuns em experiências emocionantes.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 9bcc5462:eb501d90
2025-02-24 17:47:28
@ 9bcc5462:eb501d90
2025-02-24 17:47:28Every generation loves to learn. However, our public schooling system has gone as far as it can take us. The abundance of easily accessible information on the internet, coupled with emerging tech like AI, decentralized protocols and bitcoin, means this is our time to innovate our learning infrastructure. A complete overhaul is due along with the development of a pilot program to test new and unconventional models.
Let’s carve a path towards innovation by sparking discussion around this topic. Hence, this blueprint. It is a gauntlet for any person who genuinely wants to become a stakeholder for our country’s future. Entry points are:
- Builders—Startups, developers and investors who will fund and create infrastructure.
- Practitioners—Educators and researchers who will test models.
- Supporters—Parents, donors and community members who want to contribute.
Where Do We Begin?
Let’s think about crafting the main components of a new pilot model. Below are suggested areas of focus:
- DEFINITION
- APPROACH
- PHILOSOPHY
- CULTURE
- PHYSICAL DESIGN
- OPERATIONAL ORGANIZATION
- ACCOUNTABILITY METHODS
- RISKS & CHALLENGES
- STYLE
- STAKEHOLDERS
How It Works
After researching your pedagogical ideas for current and future generations of scholars, it’s time to share your insights. Contribute your viewpoint by structuring a blueprint—one page per section—in the following sequence:
- Definition of your modern learning model with its key principles.
- Description of the core learning approach.
- Philosophy distilled into central concepts that will orient stakeholders.
- Culture your modern learning model aspires to live by.
- Potential challenges, risks and drawbacks.
- Design of physical spaces and rationale.
- Operational framework detailing adult and child learning organization.
- Accountability methods to ensure skill growth and competency.
- Style development and name of your model.
- Skin in the game, sign your model with your first and last name (unite stakeholders).
Perhaps if enough stakeholders come together, we can begin to actualize a more effective and updated way of learning. This is a challenge meant to separate those willing to engage in discourse, planning and laying foundations from those content to complain from the sidelines.
Why Now and Where Does the Money Come From?
After being a public educator for fifteen years, I learned you will not change the system, the system will change you. It’s time to design and build above and apart from the current model. 2025 is when courageous people step up to the plate and discuss our learning infrastructure. Whether it’s contributing out of the box thinking, modernizing curriculum, investing in startups or creating your own venture; there is no greater time than now. And no greater place than in the USA!
(By extension, we also create the opportunity to influence our global allies including our neighbors to the North and South.)
“But how!?” Learning Producers is figuring it out by asking not, “how?” but “who?” Who will unite together to develop our learning infrastructure? If you decide you want to participate and join our efforts, share your blueprint as well. For all stakeholders, this is an investment in an untapped market of a new learning economy.
If not, you’re not alone. Some consider this just rhetoric, idealism, or wishful thinking. Additionally, it is unclear how such actions can be profitable or how such infrastructure building will be funded. Money talks. Bullshit walks, right? In that case, let’s talk, and let’s fine tune our BS detectors. Onward, with this call to action:
- Share your own blueprint online or reach out to Learning Producers, Inc. (Learningproducers.com).
- Conduct research on an ideal location and team to lay foundations on a pilot program at small scale.
- Engage in dialogue with investors interested in developing learning infrastructure for their own children and families.
- Secure stakeholders to develop and test a real world pilot model (real location, real agreements, real timeline, real people).
- Sponsor or donate resources to counter concerns over funding.
Now, we leave you with our blueprint:
PEDAGOGICAL WABI-SABI
We hope you enjoy it.
Sincerely,
Israel Hernandez
Founder of Learning Producers
**[Read or download full blueprint here: https://www.learningproducers.com/blog/pedagogical-wabi-sabiblueprint-for-developing-learning-infrastructure ]
-
 @ d61f3bc5:0da6ef4a
2025-05-05 15:26:08
@ d61f3bc5:0da6ef4a
2025-05-05 15:26:08I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify a media file and maliciously ascribe it to the note author.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 9be6a199:6e133301
2025-05-20 12:47:14
@ 9be6a199:6e133301
2025-05-20 12:47:14sadfsflkjsdflkdsjfglksjdfglksdaasdfsdfsdfsdfssdsd
-
 @ 91bea5cd:1df4451c
2025-05-14 10:47:44
@ 91bea5cd:1df4451c
2025-05-14 10:47:44A origem do Dia das Mães
Anna Jarvis (1864-1948 Virgínia Ocidental), uma ativista americana, fundou o Dia das Mães nos Estados Unidos há mais de um século, escolhendo o segundo domingo de maio para tal celebração; mesma data que é comemorada até hoje em muitos países do mundo.
Ela nasceu durante a Guerra Civil, e viu sua mãe, Ann Reeves Jarvis, trabalhar na organização de Clubes de Trabalho Materno para cuidar de soldados de ambos os lados da guerra, a fim de diminuir as diferenças entre as mães do Norte e do Sul.
Em 1910, o Dia das Mães tornou-se feriado estadual na Virgínia Ocidental (EUA) e, em 1914, foi declarado feriado nacional pelo presidente Woodrow Wilson.
Segundo historiadores, Anna imaginava o feriado como um retorno ao lar, um dia para homenagear a sua mãe, a única mulher que dedicou sua vida à Anna. Ela escolheu o segundo domingo de maio porque seria sempre próximo de 9 de maio, o dia da morte de sua mãe, que faleceu em 1905.
E por que Anna Jarvis passou a odiar a data?
Acontece que a data começou a ter um apelo comercial, e Anna nunca quis que o dia se tornasse comercial, mas sim, só uma celebração às figuras maternas. Então ela acabou se opondo à comercialização e popularização do feriado.
Com o feriado, as indústrias floral, de cartões comemorativos e de doces começaram a ficar gananciosas para vender os seus produtos e subiram os preços nesta data, a fim de lucrarem mais.
Para Anna, "estavam comercializando o seu Dia das Mães". Para um jornal da época, ela comentou: "O que vocês farão para afugentar charlatões, bandidos, piratas, mafiosos, sequestradores e outros cupins que, com sua ganância, minam um dos movimentos e celebrações mais nobres e verdadeiros?".
Ela se irritava com qualquer organização que usasse seu dia para qualquer coisa que não fosse seu propósito original e sentimental, dizem historiadores. Em 1920, ela já incentivava as pessoas a não comprarem flores, por exemplo.
Além disso, instituições de caridade usavam o feriado para arrecadar fundos com a intenção de ajudar mães pobres; porém, como contam, elas não estavam usando o dinheiro para mães pobres, como alegavam.
Anna reivindicou os direitos autorais da frase "Segundo domingo de maio, Dia das Mães" ("Second Sunday in May, Mother's Day") e passou a vida lutando contra a comercialização da data. Um dos seus últimos atos foi ir de porta em porta na Filadélfia (EUA) pedindo assinaturas para apoiar a revogação do Dia das Mães.
Anna Jarvis nunca se casou e nem teve filhos, dedicando sua vida principalmente à causa do Dia das Mães. Ela faleceu em West Chester, na Pensilvânia (EUA), no dia 24 de novembro de 1948, aos 84 anos, devido a uma insuficiência cardíaca.
Fontes
- https://www.bbc.com/news/stories-52589173
- https://aventurasnahistoria.com.br/noticias/historia-hoje/dia-das-maes-por-que-mulher-que-criou-o-feriado-passou-odiar-data.phtml
- https://www.tempo.com/noticias/actualidade/dia-das-maes-por-que-a-mulher-que-inventou-a-data-se-arrependeu-de-te-la-criado.html
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 9be6a199:6e133301
2025-05-20 12:46:43
@ 9be6a199:6e133301
2025-05-20 12:46:43sadfsflkjsdflkdsjfglksjdfglksdaasdfsdfsdfsdfssdsd
-
 @ 91bea5cd:1df4451c
2025-05-13 10:06:21
@ 91bea5cd:1df4451c
2025-05-13 10:06:21A Realidade por Trás dos Números
Padrão de Desagregação Familiar
- Países como Brasil (~55%) e Venezuela (~65%) apresentam não apenas altos índices de mães solo, mas também contextos de violência descontrolada.
- A desagregação da família nuclear tradicional não é causa única, mas é fator agravante quando associada à instabilidade cultural, abandono paterno e permissividade institucional.
- Homens ausentes e baixa exigência de responsabilidade paterna geram ciclos de pobreza, violência e ressentimento intergeracional.
Cultura da Irresponsabilidade
- Em muitos contextos, a paternidade é tratada como um ato opcional. A ausência de consequências legais, sociais e morais para o abandono paterno normaliza o ciclo de mães solteiras.
- Políticas públicas mal calibradas muitas vezes premiam o fracasso familiar com benefícios, sem exigir contrapartidas.
Inversão de Valores
- A valorização de comportamentos hedonistas, imediatistas e instáveis, promovidos culturalmente, mina qualquer tentativa de reconstrução familiar sólida.
- Em muitos casos, a maternidade é enfrentada sem planejamento ou estrutura mínima, gerando famílias instáveis e frágeis, mais propensas à violência e vulnerabilidade social.
Recomendações Realistas e Não Assistencialistas
Reforço da Responsabilidade Paterna
- Criar mecanismos legais mais rigorosos e efetivos de responsabilização civil e criminal para pais ausentes.
- Estimular socialmente o resgate do papel paterno, valorizando não apenas a presença física, mas o compromisso emocional e financeiro.
Incentivo à Formação Familiar Estável
- Reformar o currículo escolar para incluir educação sobre vínculos afetivos, responsabilidade conjugal e parentalidade realista.
- Desestimular a glamorização de estruturas familiares instáveis, combatendo a ideia de que qualquer forma familiar é igualmente funcional sob qualquer condição.
Cultura da Autossuficiência e Planejamento
- Substituir políticas puramente assistenciais por programas de incentivo ao planejamento familiar e responsabilidade pessoal, com foco na autonomia financeira e educacional antes da maternidade/paternidade.
- Campanhas públicas de conscientização sobre os impactos reais da desestrutura familiar na violência social e no desenvolvimento infantil.
O aumento da violência em países com alta proporção de mães solteiras não é uma coincidência, mas uma consequência de fatores culturais e sociais profundamente negligenciados.
Reverter esse cenário não exige mais Estado, mas sim mais responsabilidade individual, mais cobrança social e menos permissividade institucional. Qualquer solução duradoura passa por restaurar o valor da família como núcleo formador de caráter e estabilidade, não apenas como estatística para justificar políticas públicas.
-
 @ 7953d1fa:69c8039d
2025-05-20 02:39:23
@ 7953d1fa:69c8039d
2025-05-20 02:39:23O cenário do entretenimento online no Brasil vem evoluindo rapidamente, e uma das plataformas que mais se destaca atualmente é a 8CC. Com uma proposta moderna, intuitiva e voltada para a melhor experiência do usuário, a 8CC conquistou a confiança de milhares de jogadores que buscam diversão, praticidade e oportunidades de ganhos reais em um ambiente seguro.
Conhecendo a Plataforma 8CC A 8CC é uma plataforma digital desenvolvida para atender tanto iniciantes quanto jogadores experientes. Sua interface amigável e bem organizada facilita a navegação mesmo para quem nunca teve contato com esse tipo de entretenimento antes. Compatível com computadores, tablets e celulares, o site é totalmente responsivo, o que significa que você pode se divertir de qualquer lugar, a qualquer hora.
Um dos diferenciais da 8cc é o seu compromisso com a segurança dos usuários. A plataforma utiliza tecnologia de criptografia de ponta para garantir a proteção de dados pessoais e transações financeiras. Além disso, o suporte ao cliente está sempre disponível para tirar dúvidas, resolver problemas e oferecer o melhor atendimento possível.
Diversidade de Jogos para Todos os Gostos Na 8CC, os jogadores têm acesso a uma vasta seleção de jogos online, desenvolvidos pelos principais provedores do mercado internacional. Isso garante alta qualidade gráfica, mecânicas inovadoras e excelente desempenho.
Entre os jogos mais populares da plataforma estão:
Slots (caça-níqueis): com temas variados, rodadas bônus e jackpots progressivos que proporcionam grandes emoções.
Jogos de mesa clássicos: como roleta, blackjack e bacará, com versões que imitam perfeitamente a experiência de jogo ao vivo.
Jogos com crupiês em tempo real: transmitidos com qualidade HD, esses jogos trazem interatividade e realismo, permitindo que o jogador se sinta dentro de um ambiente físico de alto padrão.
A plataforma também disponibiliza jogos de habilidade e apostas esportivas ao vivo, oferecendo uma experiência ainda mais completa e personalizada de acordo com o perfil de cada usuário.
Experiência do Jogador na 8CC Quem já experimentou jogar na 8CC sabe o quanto a plataforma valoriza o conforto e a satisfação de seus usuários. Desde o momento do cadastro até o resgate de ganhos, tudo é feito de forma simples, rápida e segura. O processo de registro é intuitivo, exigindo apenas alguns dados básicos, e os métodos de pagamento são variados, aceitando transferências bancárias, carteiras digitais e até criptomoedas.
Outro destaque é o sistema de recompensas e promoções. A 8CC frequentemente oferece bônus de boas-vindas, rodadas grátis e campanhas especiais para usuários fiéis, o que aumenta ainda mais as chances de ganhar e prolonga a diversão. Além disso, a plataforma promove torneios e desafios semanais com prêmios atrativos, incentivando a competição saudável entre os jogadores.
Por Que Escolher a 8CC? Existem muitas razões para escolher a 8CC como sua principal plataforma de jogos online:
Confiabilidade e segurança em todas as operações;
Variedade de jogos para todos os perfis;
Interface moderna e de fácil navegação;
Promoções e bônus frequentes;
Atendimento ao cliente eficiente e disponível 24 horas.
Se você busca uma experiência diferenciada, com diversão garantida e a possibilidade de transformar seu tempo livre em momentos empolgantes, a 8CC é a escolha certa. Descubra agora mesmo tudo o que essa plataforma inovadora tem a oferecer e junte-se à comunidade que está revolucionando o entretenimento digital no Brasil.
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 9be6a199:6e133301
2025-05-20 12:46:20
@ 9be6a199:6e133301
2025-05-20 12:46:20sadfsflkjsdflkdsjfglksjdfglksdaasdfsdfsdfsdfs
-
 @ 6be5cc06:5259daf0
2025-05-12 14:50:36
@ 6be5cc06:5259daf0
2025-05-12 14:50:36A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 88cc134b:5ae99079
2025-05-20 12:22:03
@ 88cc134b:5ae99079
2025-05-20 12:22:03content
nostr:nevent1qvzqqqqqqypzpkygz22lv3pdey6gr7ygmk67wjh24hdvj3t797mm6z0x3ax4erdhqqsdxy48qm3tces0tu90shwltcg20zsprejkahklwftpzyhytcf32tc9sm779
-
 @ a296b972:e5a7a2e8
2025-05-20 12:22:00
@ a296b972:e5a7a2e8
2025-05-20 12:22:00Die Natur strebt nach einem Gleichgewicht durch Ausgleich von nicht zueinander passenden Verhältnissen. Die Gesellschaft ist ein sozialer Organismus, der ebenso nach Ausgleich und einer Stimmigkeit der Verhältnisse strebt. Das sind Naturgesetze, die keine Regierung auf Dauer imstande ist, außer Kraft zu setzen.
Weder oppositionelle Kräfte, noch Kräfte innerhalb des Souveräns haben die Absicht, die Demokratie abzuschaffen. Es geht vielmehr darum, sie wieder in der Form herzustellen, in der sie ihren Namen auch verdient. Dazu gehört, dass alle Macht vom Volke ausgeht, was derzeit nicht der Fall ist.
Ein durch den Staat vorgegebenes Bildungssystem hat Menschen vor allem zu gefügigen Rädchen im Wirtschaftsgetriebe und nicht zu alles kritisch hinterfragenden Bürgern erzogen, die ständig der Regierung auf die Finger schauen.
Wenn die Bürger, der Souverän, eine Regierung immer mehr „machen lässt“ und glaubt, es sei genug, alle 4 Jahre sein Wahl-Kreuzchen zu machen, entfernt er sich immer mehr von der Kontrolle der durch ihn beauftragten Vertreter, und diese entfernen sich so immer mehr vom Alltag der Bürger.
Zu wenig Gegenrede des Souveräns führt zu immer mehr Übermut der Regierung, die sich immer sicherer wird, mit jedem Unsinn durchzukommen.
Ist dann die Schmerzgrenze des Souveräns erreicht, beginnt er, die Opposition zu stärken. In einer funktionierenden Demokratie würde das dazu führen, dass die Opposition die Regierung bildet, die dann die Chance hat, Fehlentwicklungen abzustellen und ausgleichend tätig zu werden.
Derzeit findet sowohl beim Souverän, als auch bei den Parteien, die bisher Regierungen zusammengestellt haben, ein Erwachen statt.
Da die ehemaligen Volks-Parteien unbedingt an der Macht festhalten wollen, seitens des Souveräns auf zu wenig Widerstand stoßen, wird mit der Macht, einer Demokratie nicht würdig, umgegangen. Dem sollte dringend Einhalt geboten werden.
Der Missbrauch äußert sich in brutalen (Lieblingswort der Ex-Außen-Dings) Einschränkungen der Grundrechte (Corona-Zeit), in der Einschränkung der Meinungsfreiheit (D S A), in Tendenzen zunehmender Kontrolle und Überwachung, Förderung von Denunzianten-Portalen, Kapern des öffentlich-rechtlichen Rundfunks, Förderung von NGOs, die als Sprechpuppen genutzt werden. Besetzt von Menschen, die entweder tatsächlich überzeugt sind von dem, was sie ideologisch vertreten, oder die über Charaktereigenschaften verfügen, die noch sehr viel Optimierungspotenzial in sich bergen. Gepaart mit fachlicher Inkompetenz ist das ein gefährlicher Cocktail.
Erst jüngst sogar durch Ausreiseverbote, wie in einem Staat, mit dem man das derzeitige Deutschland nicht vergleichen darf. So groß ist inzwischen schon die Angst geworden, die Kontrolle über die Macht zu verlieren. Alles, was an Kritik geäußert werden will, gilt als Delegitimierung des Staates. Auf keinen Fall darf sie im Ausland geäußert werden, damit es ja nichts davon mitbekommt, was in Deutschland abgeht. Das ist so wie ein Kind, dass sich die Hände vor die Augen hält und meint, es würde nicht gesehen werden.
Die Regierung ist übergriffig geworden. Je lauter sie Demokratie schreit, desto totalitärer wird sie.
Durch fehlende Kontrolle des Souveräns sind charakterlich und fachlich ungeeignete Personen in die Politik gelangt, deren ständige Überforderung dazu führt, dass sich deren Entscheidungen immer weiter von der Lebensrealität des Souveräns entfernen.
Bislang haben rund 25% des Souveräns diese Schieflage erkannt und wollen einer Opposition, die so stark geworden ist, weil die Alt-Parteien über Jahre Fehler an Fehler aneinandergereiht haben, die Gelegenheit geben, diese Fehler zu beheben und auszugleichen. Offen bleibt die Frage, ob sie dazu wirklich in der Lage sind, oder ob die Gefahr besteht, dass sie von einem möglicherweise grundsätzlich kranken System vereinnahmt werden.
Da es seitens der Alt-Parteien keine Einsicht gibt, dass sie in der Regierung nicht mehr den Willen des Souveräns vertreten, derzeit auch besonders gut zu sehen an dem Friedenswillen des Souveräns im Vergleich zur Kriegstreiberei der Regierung, bleibt nur, der Opposition zumindest die Chance zu geben, es besser zu machen und den Willen des Souveräns umzusetzen. Gelänge das nicht, ist die Demokratie, wie wir sie bislang verstanden haben, gescheitert.
Eine daraus resultierende Staatsform stünde dem Freiheitsgedanken diametral gegenüber.
Die Verteidigung von Unseredemokratie seitens der Regierung entlarvt das eigentliche, was damit gemeint ist, nämlich die Erhaltung der eigenen Macht, verbunden mit allen Vorzügen und Privilegien. Sie richtet sich gegen das eigene Volk, das mit einer ganz normal funktionierenden Demokratie schon sehr zufrieden wäre. Unseredemokratie ist nicht unsere Demokratie!
In Anlehnung an die berühmt gewordene Lüge Walter Ulbrichs: „Niemand hat die Absicht eine Mauer zu errichten“, hat derzeit niemand die Absicht, die sogenannte Brandmauer einzureißen, bzw. sie so lange stehen zu lassen, wie es eben geht, um die herrschenden Machtverhältnisse so lange wie möglich aufrechtzuerhalten. Die Geschichte hat jedoch zum Glück gezeigt, dass selbst eine Berliner Mauer nicht ewig hält.
Wie sich aus dem absurd-lächerlichen Gutachten, einer der Regierung gegenüber weisungsgebundenen Behörde herausgestellt hat, gibt es keinerlei Anzeichen dafür, dass die Opposition die demokratische Grundordnung weder gefährden noch beseitigen will.
Da die ehemaligen Volksparteien augenscheinlich nicht in der Lage sind, politische, wirtschaftliche und gesellschaftliche Verhältnisse zum Wohle des Deutschen Volkes herzustellen, ist der demokratische Weg, die Opposition hierzu zu ermächtigen.
Wird das weiterhin verhindert, wird der Unmut des Souveräns weiter zunehmen, und spätestens, wenn die zunehmenden Schikanen die Schmerzgrenze überschritten haben, wird der Souverän nach geeigneten Mitteln und Möglichkeiten suchen, diese Schieflage zu beheben und auszugleichen.
Derzeit stehen sich ein in der Zahl und im Befinden zunehmend unzufrieden werdender Souverän und eine immer absurdere Entscheidungen treffende Regierung im lebendigen Tauziehen um Interessen gegenüber. Je mehr Bockmist die Alt-Parteien bauen, um so stärker wird die Opposition.
Aufgrund der jetzt schon vorhandenen Anzahl wacher Bürger und der Anzahl der in der Politik Unfähigen, ist eigentlich schon jetzt klar, wer in diesem Tauziehen die größere Kraft hat und wer das „Spiel“ nach demokratischen Regeln am Ende gewinnen wird. Das ist eindeutig der Souverän. Verliert er, wider Erwarten, verliert auch die Demokratie.
Dem Souverän fehlt nur noch ein wenig mehr Selbstvertrauen und ein Bewusstsein für die Macht, über die er tatsächlich verfügt.
Je mehr absurde Entscheidungen seitens der Regierung getroffen werden, und man arbeitet ja sehr fleißig daran, besonders, wenn es um Frieden geht, desto stärker wird das Selbstbewusstsein des Souveräns werden und ein natürlicher, friedlicher Ausgleich der Schieflage kann stattfinden. Der Start der neuen Regierung war jedenfalls schon einmal sehr "Keine-4-Jahre".
Wer sich in die steile und eisglatte Abfahrtspiste Deutschlands vertiefen will, hier eine Rezension zu dem Buch „Im Taumel des Niedergangs“ von dem von mir sehr geschätzten und akribisch arbeitenden Uwe Froschauer:
https://www.manova.news/artikel/abwarts
oder
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 9e69e420:d12360c2
2025-01-26 15:26:44
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-
 @ 502ab02a:a2860397
2025-05-20 01:22:31
@ 502ab02a:a2860397
2025-05-20 01:22:31พอพูดถึงบริษัทอย่าง Formo ที่ทำชีสโดยไม่ใช้วัวเลย คนส่วนใหญ่จะนึกถึงคำว่า “นวัตกรรม” “ยั่งยืน” “ลดโลกร้อน” กันเป็นด่านแรก แต่พอเฮียมองทะลุม่านควันพวกนี้ไป จะเห็นทุนรายใหญ่ที่หนุนหลังอยู่ ซึ่งหลายเจ้าก็ไม่ใช่ผู้พิทักษ์โลก แต่เป็นผู้เล่นตัวจี๊ดในอุตสาหกรรมอาหารโลกมายาวนาน
หนึ่งในนั้นคือบริษัทจากเกาหลีใต้ชื่อ CJ CheilJedang ซึ่งอาจฟังดูไกลตัว แต่จริงๆ แล้ว เฮียว่าชื่อนี้โผล่ตามซองอาหารสำเร็จรูปในครัวคนไทยหลายบ้านโดยไม่รู้ตัว
ถ้าจะเข้าใจ Formo ให้ถึงแก่น เราต้องมองไปถึงทุนที่ “ใส่เงิน” และ “ใส่จุดยืน” ลงไปในบริษัทนั้น และหนึ่งในผู้ถือหุ้นรายสำคัญก็คือ CJ CheilJedang บริษัทเกาหลีใต้ที่ก่อตั้งมาตั้งแต่ปี 1953 โดยเริ่มจากการเป็นโรงงานผลิตน้ำตาล จากนั้นก็กินรวบแทบทุกวงจรอาหารของเกาหลี
โปรไฟล์ CJ แค่เห็นภาพรวมก็ขนลุกแล้วครับ ลูกพี่เราแข็งแกร่งขนาดไหน - เป็นเจ้าของแบรนด์ Bibigo ที่เราอาจจะคุ้นในสินค้า กิมจิ และ CJ Foods ที่มีขายทั่วโลก -เป็นผู้ผลิต กรดอะมิโน รายใหญ่ของโลก เช่น ไลซีน, ทรีโอนีน, ทริปโตแฟน ที่ใช้เป็นวัตถุดิบในอาหารสัตว์ แต่ตอนนี้หลายบริษัทเอาไปใส่ใน Plant-based food แล้วเคลมว่าเป็นโปรตีนสมบูรณ์ -เป็นเจ้าของโรงงานผลิต แบคทีเรียสายพันธุ์พิเศษ สำหรับการหมักหลายประเภท -ขึ้นชื่อเรื่อง bioscience โดยเฉพาะ precision fermentation ซึ่งเป็นเทคโนโลยีเดียวกับที่ Formo ใช้ผลิตเคซีน (โปรตีนในนมวัว)
แปลว่า CJ ไม่ได้มาลงทุนใน Formo แบบ “หวังผลกำไรเฉยๆ” แต่เขามองเห็น “อนาคตใหม่ของอาหาร” ที่ตัวเองจะเป็นเจ้าของต้นน้ำยันปลายน้ำ
คำถามก็คือเบื้องลึกการลงทุนใน Formo ใครได้อะไร? Formo ปิดรอบระดมทุน Series A ได้ประมาณ 50 ล้านดอลลาร์สหรัฐ เมื่อปี 2021 โดยมีนักลงทุนหลายเจ้า เช่น EQT Ventures, Elevat3 Capital, Atomico แต่ CJ CheilJedang ก็เป็นหนึ่งในผู้ลงทุนเชิงกลยุทธ์ (strategic investor) ที่เข้ามาแบบไม่ใช่แค่ลงเงิน แต่เอา เทคโนโลยี + เครือข่ายโรงงาน + ซัพพลายเชนระดับโลก มาเสริมให้ Formo ขยายได้เร็วขึ้น
การจับมือกันครั้งนี้มีนัยยะสำคัญครับ -Formo ได้ เทคโนโลยีหมักจุลินทรีย์ (ที่ CJ ถนัดมาก) และช่องทางกระจายสินค้าในเอเชีย -CJ ได้ ถือหุ้นในบริษัทที่กำลังจะเปลี่ยนภาพ “ผลิตภัณฑ์จากนม” ให้กลายเป็นสิ่งที่ไม่ต้องมีสัตว์อีกต่อไป ซึ่งจะเป็นกลยุทธ์สำคัญในการสร้างแบรนด์อาหารแห่งอนาคต ที่นมจะต้องมาจากโรงงานผลิตเท่านั้นจึงจะมีคุณสมบัติที่ดีทั้งสารอาหารและความสะอาด
CJ เองก็เคยประกาศต่อสื่อว่า อยากเป็น “Global Lifestyle Company” ซึ่งฟังดูเบาๆ แต่จริงๆ คือแผนใหญ่ในการ เปลี่ยนวิธีการกินของคนทั้งโลกได้เลยเช่นกัน -จาก “อาหารจริง” ไปเป็น “อาหารสังเคราะห์” (synthetic food) -จาก “ฟาร์มสัตว์” ไปเป็น “ถังหมักจุลินทรีย์” -จาก “ความหลากหลายตามธรรมชาติ” ไปเป็น “สูตรกลาง” ที่ควบคุมได้ในระดับโมเลกุล
การหนุนหลัง Formo จึงไม่ใช่เรื่องบังเอิญ แต่เป็นอีกหนึ่งหมากในกระดานใหญ่ที่ CJ วางไว้ เพื่อเป็นเจ้าของอาหารอนาคตแบบไม่ต้องเลี้ยงหมู ไก่ วัว แต่ครองเทคโนโลยีแทน
คำถามคือแล้วผู้บริโภคจะรู้ทันไหมว่า เบื้องหลังชีสที่ไม่มีวัว อาจมี “ทุนที่อยากครองโลกอาหาร” คำที่เคลมว่า “ยั่งยืน” อาจสร้างระบบอาหารใหม่ที่ยิ่งห่างจากธรรมชาติเข้าไปทุกที
คนที่เคย “กลัวสารเคมี” ในอาหารแปรรูป กลับกลืนผลิตภัณฑ์จากห้องแล็บ โดยคิดว่า “มันคือความสะอาดและอนาคต” #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ f85b9c2c:d190bcff
2025-05-19 13:22:09
@ f85b9c2c:d190bcff
2025-05-19 13:22:09
Fake KYC Emails
Phishing scammers are again targeting users of the popular cryptocurrency wallet MetaMask. In a recent email campaign, cybercriminals are attempting to trick people into revealing their secret MetaMask passphrase. The emails falsely claim that you must urgently verify your wallet due to new Know Your Customer (KYC) regulations. If you fall for the scope and click the “Verify” button, you will be taken to a fake MetaMask website that asks you to enter your passphrase. If you do provide your passphrase, criminals can access your wallet and steal any cryptocurrency you have stored there. You are unlikely to get your stolen crypto back. Such email scam campaigns are ongoing and target users of many different cryptocurrency wallets. Be wary of any unsolicited email or text message that claims that you must provide your crypto wallet passphrase or other sensitive personal information. image
-
 @ 9be6a199:6e133301
2025-05-20 12:45:08
@ 9be6a199:6e133301
2025-05-20 12:45:08sadfsflkjsdflkdsjfglksjdfglksd
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 05a0f81e:fc032124
2025-05-19 11:31:47
@ 05a0f81e:fc032124
2025-05-19 11:31:47There are stages in life that man must encounter in the life living process. And in thus stage are what I called the most scary moment in life.
The stages of life are typically recognized as Infancy (birth to 2 years), Early Childhood (3-8 years), Adolescence (9-18 years), and Adulthood (19 years and older). Adulthood can be further divided into early, middle, and late stages.
The adulthood, is the youthful stage, the stage where the youths are enrolled into the career part of there life, either academic pursuit or entrepreneurial pursuit. The adult hood are raged from the beginning of career pursuit to the ending of career pursuit, and at the stage is where the youths choose to either proper in life or become a failure.
With a well detailed analysis, some see the youthful stage as the most enjoyable stage in life, and there are no doubt about that but one thing is certain about, the mistake you made at the youthful stage of your life but in your career pursuit and daily living stay with you forever unless your ability to deal with your emotions and regret is 90%.
The adulthood is a scary moment because that's the stage where youths choose there career focus, either further education, skilled labor or entrepreneurs and at the beginning of the career path, they are scared of making the wrong choice. But the most fearful path of the adulthood is facing the laboratory market, that is after school or after acquiring skills, how to start making a good living. This path of life affects mostly the youths that choose academic pursuit at the early adulthood without making necessary research on there field of study, and this is the reason while there are many graduates that are bike man, brick layers, driver and so on.
The inability to face the labor market as a graduates can be linked to your field of study, the decisions you made while in school, and the channels you choose when you graduated.
The ending of career pursuit to face the labor market is the most scary moment in life and youths that escape that fear easily are either born with golden spoon allowing their parents to pave their way for them or they chose the right part at the earliest adulthood.
Proper orientation are need in career pursuit to enable youths to have the self confident and boldness to choose a enroll into the best to face the labor market when it is time ⏲️.
-
 @ 9be6a199:6e133301
2025-05-20 12:44:22
@ 9be6a199:6e133301
2025-05-20 12:44:22 -
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ e4950c93:1b99eccd
2025-05-20 11:06:09
@ e4950c93:1b99eccd
2025-05-20 11:06:09Contenu à venir.
-
 @ a5ee4475:2ca75401
2025-05-07 20:00:42
@ a5ee4475:2ca75401
2025-05-07 20:00:42lista #descentralismo #comunidades #portugues
[em atualização]
*Até a criação desse post, só alguns clients têm acesso às comunidades, tal como o Satellite, o Coracle e o Amethyst.
**Se a comunidade não tiver proprietários ou moderadores ativos, o seu envio de mensagem poderá não ser aprovada para aparecer nela.
***Se criar uma, busque colocar um ou mais moderadores para a comunidade não acabar, caso você se ausente.
Geral:
n/Brasil (Por: nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqryyunpwd5kcq3qzdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2sxpqqqzr0v4va9m3
n/Portugal (por: nostr:nprofile1qqsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshszynhwden5te0dehhxarj9ek82tntv5hsd2h46x) nostr:naddr1qqy9qmmjw36kwctvqgsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqrqsqqpphkc3wuaj
n/Moçambique (por: nostr:nprofile1qqszx6hsp38v2re3q2pzxpv3slg5u7pxklxze7evarqk4eugqmhntdcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctc082x0w) nostr:naddr1qqf56m7r5ask6cnfw96ktuyls7e0p8u8hupzqgm27qxya3g0xypgygc9jxraznncy6muct8m9n5vz6h83qrw7ddhqvzqqqyx7c0autxh
n/África (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqru8qtxwf5kxcgzyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdaspqgn0q
-
n/Perguntas-e-Respostas (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq3lp8u85lcflpah2pz4y364fe2yz5edg5k4y32n2p84x4zp203fm980hz8sygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqsmmqtz9a9x
n/Links-e-Tutoriais-Úteis (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqj0p8u85lcflpahf3y5uj6n94zj64z42384yj2pf9fjmsu623z5j5lsn7ftkq3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqzr0v3zu9fd
n/JornalismoNãoEstáMorto - Notícias e escrita informativa (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:nprofile1qqs0f74kketdcv63r53mlzgzfh93we3dkgzkldv2p6g62a8gf3g92yqpz4mhxue69uhkummnw3ezummcw3ezuer9wchszyrhwden5te0dehhxarj9ekk7mf0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9ufhpwuw) nostr:naddr1qqd55n6jfeq5cj2nf48j6nkrsd8j632n2npczt2dfaf9gnczyrvvsrjnp9xgqysjendxg6x2q7fldu73ajnf5e2h7uspp9tjl7jvxqcyqqqgdasy2kfg4
n/Agorismo³-E-Mercado (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpahg9r575jf2dx5ls4n94zj6n292fp5z3z094gry5qzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasrlnr7s
n/FeiraNostr - Marketplace (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qq9yvetfwfs5ummnw3eqyg9hpjdlkf2tvpegqssjvsa7kpmmdw55zcy76sz3tkd3p9sawancnypsgqqqsmmqucz73h
Tecnologia:
n/ndevs-br (por: nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcppemhxue69uhkummn9ekx7mp0gc3lmk) nostr:naddr1qqyxuer9weej6cnjqgs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcrqsqqpphk7z3axp
n/BrasilDev (por: nostr:nprofile1qqsyczyspluueyxautr3nxa2httku5e9m7d05dnu5zj3jnrg0jmucqcpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uqs6amnwvaz7tmwdaejumr0dsq3camnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdsz8cl6e) nostr:naddr1qqy5yunpwd5kc3r9wcpzqnqgjq8lnnysmh3vwxvm42adwmjnyh0e473k0js22x2vdp7t0nqrqvzqqqyx7cvxdlla
n/Linux (por: nostr:nprofile1qqsxhewvq6fq9lzjmfwqrpg2ufgl09uh2cksupa853zxv04u2fva4uqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0dehhxarjv4kxjar9wvhx7un89uqsuamnwvaz7tmwdaejumr0dshs6tvc92 ) nostr:naddr1qqz5c6tww4uqz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsygrtuhxqdyszl3fd5hqps59wy50hj7t4vtgwq7n6g3rx8679ykw67qpsgqqqsmmqznes6u
n/IA - Inteligencia Artificial (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqpyjsgpzpmhxue69uhkummnw3ezumt0d5hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqs03ln5
n/HardwareBr - Dúvidas, experiências e atualizações sobre hardware (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq9ysctjv3mkzun9gfeqyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmq54k3eu
n/SegurançaDaInformação (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqv9xet8w4exzmkr5as5gc2fdenx7undv8p60sardupzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cpss4m0
n/Moneroptbr (Por: nostr:nprofile1qqsyrmue77dm5ef5pmqsly0wp3248mk3vr9temj5p54plygcr97pavcpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqg5waehxw309aex2mrp0yhxgctdw4eju6t0tpqrvk) nostr:naddr1qq9y6mmwv4ex7ur5vfeqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygzpa7vl0xa6v56qasg0j8hqc42namgkpj4uae2q62sljyvpjlq7kvpsgqqqsmmqknmdan
Ciência:
n/Astronomia - Espaço e astros (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qq9yzum5wfhkummdd9ssz9thwden5te0dehhxarj9ehhsarj9ejx2a30qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqpphkkdel5t
n/Mecatrônica-NOSTR (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqfy6etrv9689sa5de5kxcfdfe84x4zjqythwumn8ghj76twvfhhstnp0faxzmt09ehx2ap0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphkgsy84w
n/Antropologystr - Antropologia (por: nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg ) nostr:naddr1qq85zmn5dpex7ur0d3hkw7tnw3eqygzfrtlt4hds900g0nl80lk6luq5h7fds622r5uqa3882jgckeyrfcpsgqqqsmmq4xrrgc
Cultura:
n/Estante-Nostr - Literatura e livros (por: nostr:nprofile1qqsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqpr4mhxue69uhkummnw3ez6vp39eukz6mfdphkumn99e3k7mf0qywhwumn8ghj7mn0wd68ytfsxgh8jcttd95x7mnwv5hxxmmd9uq37amnwvaz7tmwdaehgu3dxqejuer0wfskvctrw3hhy7fwdaexwtcjwfqr2) nostr:naddr1qqx52um5v9h8ge2lfehhxarjqgsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqrqsqqpphkwzdgct
n/Literatura-Arte-Cultura (por: nostr:nprofile1qqs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9cprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqsuamnwvaz7tmwdaejumr0dshs8l9z0j) nostr:naddr1qqt5c6t5v4exzar4wfsj6stjw3jj6sm4d3682unpqgs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9crqsqqpphkty54um
n/História-e-Filosofia (por: nostr:npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk ) nostr:naddr1qqjlp8u85lcflpahfpy4x4xrjdfyjsfdg5k5vj2vfaf573jfg8cflrum7z0cezczyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdas35g9vs
n/Urbanism - Urbanismo (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qqy92unzv9hxjumdqgstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgrqsqqpphkyl5u8a
Fé:
n/Religião-e-Teologia - Cristianismo (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpah2fz5cj28f8pcxnedg5k4g320f385wj2p7z0ehyqzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasta04x5
n/Ateismo-e-Agnosticismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqtyzar9d9ek6medv5k5zemwdaehg6trd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdasuuzmw8
n/Budismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5yatyd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas0kmt4m
n/Taoismo - Daoismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqy9gct0cwkhxmt0qy88wumn8ghj7mn0wvhxcmmv9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7crkzqvd
n/Espiritualidade - Significação e sublimidade (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq852umsd9exjar4v9kxjerpv3jszyrhwden5te0dehhxarj9ekk7mf0qgsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscrqsqqpphkxa5nfy
Entretenimento:
n/Equinox - Cinema no Nostr (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr) nostr:naddr1qqr52ut4d9hx77qpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cmc79n5
n/Rock/metal - Músicas Rock e Metal (por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4 e nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz748t750 ) nostr:naddr1qq99ymmrdvh56et5v9kqzqqzypvep8kzcfyvdvug0j9agfv07ujkx9elwfujy5qfl06jy25zmvctwqcyqqqgdas306zj5
n/Música-Cinema-e-Livros (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq4lp8u85lcflpahfhpe556fgdqj6s6ffez56sfdyck5cj2k2f848uyl366lp8unhhcflyu6qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkfyz9pf
n/Lugares-e-Viagens (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqjlp8u85lcflpahf325ws2jg4fj63fd2ey5z369feflp8uv3mcflryd7z0cercpqqpzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7c965gfw
n/MídiasPerdidas - Lost Media (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqw0p8u85lcflpahfhpc63zfg9fj65z92fzyj3zp20cflfusqgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkdltjpa
n/Football - Futebol (Por: nostr:nprofile1qqsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc9l2d6x / Moderadores: nostr:nprofile1qqsx5rzeds2gf6hzaqf35qc0y6v5fys72fsec8w3gwszn3jw5mxewvgpz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9u5c2kxa & nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqyxvmm0w33xzmrvqgsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsrqsqqpphkg0nfw5
n/Formula-1 (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqy5vmmjd46kccfdxypzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7cc95u5w
n/Games - Atualizações sobre jogos (por: nostr:npub1atyuu22fvvj4yf2uf050fwra3pu7hjvykc7ravpmrkpwjxcc6hpsfneh4e ) nostr:naddr1qqz5wctdv4esyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqn0x7k7
n/JogosBrasil - Clips de jogos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qq955mm8dae5yunpwd5kcqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qj90yg0hl4e6qr7yg982dlh0qxdefy72d6ntuqet7hv3ateya782sxpqqqzr0vus9jl2
n/Minecraft (por: nostr:npub19xc7f5lg2z6svrjgye63rx44a96aq2ysqajx5tmum28cu6mk5j3qj3n9m9 ) nostr:naddr1qqy566twv43hyctxwspzq2d3unf7s594qc8ysfn4zxdtt6t46q5fqpmydghhek503e4hdf9zqvzqqqyx7ct7hldr
n/GenshinImpactBr (por: nostr:nprofile1qqs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcnffw22) nostr:naddr1qqtlp8u85lcflpahgajkuumgd9hyjmtsv93hgsnjq9z8wue69uhkw6tjwahhgvntdaunx6mkdgmxv6ehdaek2mm3v9a8qdtkwa3x2cthda3kyvmdxgmk5cm3w3sksd34vcexv6mvxdukgtn0de5k7m30qgs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggrqsqqpphkq4s4py
Libertarianismo:
n/Defensores-caseiros (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq0lp8u85lcflpahg3jkvetwwdhhyetn943kzum9d9ex7ulsn78mgq3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vcr78h2
n/Desobediência_Civil (por: nostr:nprofile1qqs2kw4x8jws3a4heehst0ywafwfymdqk35hx8mrf0dw6zdsnk5kj9gpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m306r5ytp) nostr:naddr1qq2ygetnda3x2erfcw4xucmfv905x6tkd9kqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsyg9t82nre8gg76muumc9hj8w5hyjdkstg6tnra35hkhdpxcfm2tfz5psgqqqsmmqlg3ata
n/sobreviNOSTR - Sobrevivencialismo (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq20p8u85lcflpah2dhkyun9we55un6n23fqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqsmmqtempje
n/Triggr - Armas (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqr9g5jfgar4yqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vt5085y
n/Kaboom - Química e explosivos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qqt0p8u85lcflpahfdq5yn60fhcflra57z0602qppemhxue69uhkummn9ekx7mp0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphk637p09
n/CAVERNA-DO-PIRATA - Pirataria (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq40p8u85lcflpahgdq4v32jfeqj63z094gyj5jp23qlp8u0kn3gpr0znzswlwy07z0ca2gpg3mhxw309ankjunhda6ry6m00yekkan2xenxkdm0wdjk7utp0fcr2anhvfjkzam0vd3rxmfjxa4xxut5v95rvdtxxfnxkmpn09jzummwd9hkutczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqgdask5hmmn
n/PrivateSociety - Propostas e discussões para uma sociedade privada (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq89qunfweshge2nda3kjet50ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cfvhgrt
n/TeoriaDasBandeiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqf9get0wf5kzerpwdpxzmnyv45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkatc9rh
n/SemFronteiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqx4xetdgeex7mn5v45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkjs0cue
n/AnarcoSobrevivencialismo (por: nostr:nprofile1qqsfj5s9lrcckaxd8ul7vf3c4ajfg0n0ytcjvetclw679hy6p98wpfqpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uykdgj7) nostr:naddr1qqdyzmnpwf3k75m0vfex2anfwejkucmfv9kxjumddap9yq3qn9fqt7833d6v60elucnr3tmyjslx7gh3yejh37a4utwf5z2wuzjqxpqqqzr0vsz5kcy
n/SociedadeAlternativaLibertaria - Libertários (por: nostr:nprofile1qqs2ph3za34henpq2y3rzgqwgdc4pjmpleqr5t62rf7kxj0lmdyxnfgppemhxue69uhkummn9ekx7mp0ydypw5) nostr:naddr1qq09xmmrd9jkgctyv4qkcar9wfhxzarfwes5c6tzv4e8gctjd9ssyg9qmc3wc6muess9zg33yq8yxu2sedslusp69a9p5ltrf8lakjrf55psgqqqsmmq8dtk3m
n/LibertariosPT - Libertários de Portugal (por: nostr:nprofile1qqszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4gppemhxue69uhkummn9ekx7mp05leack) nostr:naddr1qqx5c6tzv4e8gctjd9hhx5z5qgszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4grqsqqpphke05802
Discussões Sociais
n/Aliança-Conservadora-Brasileira (por: nostr:npub1atg5rgfuarup49470kqexfgcesdr85yru56y0y8qf3z6kc30g2vqyfyqyp ) nostr:naddr1qqsyzmrfv9hv8fmptapk7mnnv4e8vctydaexzh6zwfshx6tvv45hycgzyr4dzsdp8n50sx5khe7crye9rrxp5v7ss0jng3usupxyt2mz9apfsqcyqqqgdasue9j59
n/Ilha-de-Anhatomirin - Monarquia (Por: nostr:nprofile1qqsgzc22v804davx6vpwtwfu6j84yvupeld497tfr396usmu7s0m08qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszymhwden5te0v9ehgunpdshxu6twdfsj7qguwaehxw309a5x7ervvfhkgtnrdaexzcmvv5h8gmm0d3ej7a2jp7u) nostr:naddr1qqf5jmrgvykkgefdg9hxsct5dakkjunfd5q3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7q3qs9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqxpqqqzr0vu2qg3m
n/ManosphereBrasil - Contra a misandria (Por: nostr:nprofile1qqs0p3yd48kzm56a4tual772y3vsjwehx6tc3rv8ht8q0zgncg5r7qgpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpjnhed) nostr:naddr1qqgy6ctwdaehq6r9wfj5yunpwd5kcqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyrcvfrdfaskaxhd2l80lhj3ytyynkdekj7ygmpa6ecrcjy7z9qlszqcyqqqgdasl3kaju
Memes
n/Shitposting (Por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4) nostr:naddr1qq94x6rfw3cx7um5d9hxwqgswaehxw309ahx7um5wghx6mmd9upzqkvsnmpvyjxxkwy8ez75yk8lwftrzulhy7fz2qylhafz92pdkv9hqvzqqqyx7chlz42w
n/Puro-caldo-do-Brasil. (por: nostr:nprofile1qqsztjv2pflmwcayr2jaq90astj94lu5l0smr0zhkfdct4ry7uxu7dqywzq8t) nostr:naddr1qq24qatjdukkxctvv3hj6er094p8yctnd9kzuqghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7q3qyhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6qxpqqqzr0vwh0r4w
Locais
n/NordesteLibertário - Nordeste (Por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqf5ummjv3jhxar9f35kyetjwnp6zunfdupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cnejrgl
n/BahiaLibertária - Bahia (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqgyyctgd9s5c6tzv4e8fsapwf5kzq3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqzr0vc4949j
n/LiberdadeMinas - Minas Gerais (Por: nostr:nprofile1qqsf0kszkmrmy9l3c7mxr3uhh3fmyjpq2z4hjvv7wdq84k5npd7gw3cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxthwden5te0wfjkccte9eekummjwsh8xmmrd9skctcprpmhxue69uhhyetvv9ujuurvv438xarj9e3k7mf0mx68nx) nostr:naddr1qq8yc6tzv4exgctyv4xkjmnpwvqsqq3qjldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsxpqqqzr0vag4knt
n/CyberpunkManaus - Manaus (Por: nostr:nprofile1qqsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqpz3mhxw309ucnqt3jx5cjuvpwxgarsvpcxqq3wamn8ghj7vfexghrzd3c9ccjuv3s8gurqwps9uq5gamn8ghj7entv43kjd3nvfcx5en6093h2up5w3ekgmn4xsekvatwx438xamywp6ksemcwp6xummzdgekzdmz0pmhzd3j0g6xzepwdahxjmmw9u2upp88) nostr:naddr1qqgyx7tzv4e8qatwdvk56ctwv96hxqgqqgsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqrqsqqpphkgjh4rf
n/BelémLibertario (por: nostr:npub167s6q8sfzkhel4227kacu98zcg6e37v5sqwkv8mxaazrryz9huzqlhcu2t) nostr:nevent1qqsqnqgx3u2whdqdqmlstqcmgav6xfe4upz2qxfvj03tlk699dzlk7qzyrt6rgq7py26l874ft6mhrs5utprtx8ejjqp6eslvmh5gvvsgklsgqcyqqqqq2qqsdz6l
n/SãoPauloLivre - São Paulo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq898sardagxzatvdaxxjanjv5pzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cmls060
n/AcreLibertário - Acre (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq85zcmjv4xxjcn9wf6v8gtjd9hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqftljpt
n/Alagoas (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5zmrpvahkzuczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas8qtaf4
Empreendedorismo:
n/Empreendedorismo/BR (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqd5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj7snjv9ekjmqzyz5jr7tdaz02wwfsksstyrf9ytx4x9yhaa257my24xlw5s29yt5dkqcyqqqgdaslzrp3p
n/Empreendedorismo/SP (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqt5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj756sqgs2jg0edh5fafeexz6zpvsdy53v65c5jlh42nmv325ma6jpg53w3kcrqsqqpphkcym25j
Análise
n/EBDV (Em Busca Da Verdade) - Análise geral e desenvolvimento pessoal (por: nostr:nprofile1qqs0xmu0skfdlmtl5tth6cv99za8f8kv7ulz5srkm8p6v5k03dx9lzspz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9usvrt9r) nostr:naddr1qqzy2sjy2cpzpum037ze9hld073dwltps55t5ay7enmnu2jqwmvu8fjje795chu2qvzqqqyx7cy9v5px
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ 9be6a199:6e133301
2025-05-20 12:24:02
@ 9be6a199:6e133301
2025-05-20 12:24:02test
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ a31f394c:7ad8f439
2025-05-19 07:55:53
@ a31f394c:7ad8f439
2025-05-19 07:55:53No mundo dos jogos online, onde inúmeras plataformas buscam a atenção dos jogadores, KK999 se destaca como uma opção inovadora e empolgante. Focada no público brasileiro, a plataforma oferece uma ampla gama de jogos, uma interface intuitiva e um excelente suporte ao cliente. Se você está em busca de um destino online para jogos que combine entretenimento, qualidade e segurança, KK999 é a escolha certa para você.
Visão Geral da Plataforma KK999 é mais do que uma simples plataforma de jogos. É uma experiência imersiva e moderna, desenvolvida para atender às necessidades específicas dos jogadores brasileiros. A plataforma possui uma interface limpa e fácil de navegar, o que torna a experiência de jogar agradável e sem complicações. O site é responsivo, o que significa que você pode acessar e jogar de qualquer dispositivo, seja no desktop ou no celular, tornando a plataforma perfeita para quem deseja jogar em qualquer lugar.
O diferencial do kk999 é a experiência personalizada que oferece aos jogadores brasileiros. Além de estar completamente traduzido para o português, o site também oferece promoções e suporte técnico localizados, o que cria uma sensação de familiaridade e confiança entre os usuários.
Variedade de Jogos para Todos os Gostos Uma das características mais atraentes da KK999 é sua vasta seleção de jogos. A plataforma oferece desde jogos tradicionais de mesa, como poker e baccarat, até os modernos jogos de slots, que são incrivelmente populares entre os jogadores. Se você gosta de desafios estratégicos ou prefere a emoção de uma boa rotação de roletas, KK999 tem algo para todos.
Os jogos de mesa, como poker e blackjack, permitem que os jogadores testem suas habilidades e se envolvam em desafios emocionantes. Cada jogo é projetado com gráficos de alta qualidade e animações fluidas, criando uma experiência realista e envolvente. Além disso, a plataforma oferece uma coleção diversificada de slots, com temas variados e recursos extras que aumentam a emoção a cada giro.
Para aqueles que preferem uma experiência mais interativa, KK999 também oferece jogos com dealers ao vivo. Esses jogos permitem que os jogadores interajam com dealers profissionais em tempo real, criando uma atmosfera de jogo ao vivo, que remete à experiência de um cassino físico.
Experiência do Jogador: Segurança e Suporte de Qualidade O KK999 entende que uma experiência de jogo de alta qualidade vai além de apenas jogar. A plataforma se destaca pelo seu compromisso com a segurança dos jogadores. Utilizando as mais recentes tecnologias de criptografia, KK999 garante que todas as informações pessoais e financeiras dos jogadores estejam seguras, proporcionando tranquilidade para que os jogadores possam se concentrar apenas no jogo.
Além disso, o suporte ao cliente do KK999 é impecável. A plataforma oferece suporte 24 horas por dia, 7 dias por semana, por meio de chat ao vivo e e-mail. Caso o jogador tenha dúvidas sobre um jogo, questões relacionadas à conta ou precise de assistência técnica, a equipe de atendimento está sempre disponível e pronta para ajudar.
Bônus e Promoções para Todos os Jogadores KK999 também se destaca pelas suas ofertas generosas de bônus e promoções. Para os novos jogadores, a plataforma oferece bônus de boas-vindas, enquanto os jogadores regulares podem aproveitar programas de fidelidade que recompensam a lealdade dos usuários com ofertas exclusivas e prêmios.
Essas promoções tornam a experiência de jogar ainda mais divertida e empolgante, dando aos jogadores mais chances de se divertir e ganhar enquanto jogam seus jogos favoritos.
Conclusão KK999 se estabeleceu como uma plataforma de jogos online de referência no Brasil, oferecendo uma experiência única que combina uma enorme variedade de jogos, uma interface amigável, suporte excepcional e medidas de segurança robustas. Se você está à procura de uma plataforma para se divertir e explorar, KK999 é o lugar perfeito para começar sua jornada de jogos online.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 56f27915:5fee3024
2025-05-20 11:02:41
@ 56f27915:5fee3024
2025-05-20 11:02:41Buchbeschreibung:\ \ Dieses Buch ist ein Appell.
Es richtet sich nicht nur an den Kopf des Lesers, sondern auch an seinen Willen.\ \ Es ist ein Appell an Volk und Leser, die Lenkung der Geschicke direkt selbst in die Hand zu nehmen. Nicht nur: "Was ist?" sondern vor allem: "Was können wir tun?" ist in diesem Buch die große Frage.\ \ Mit dem Blick auf diese Frage wird das Grundgesetz betrachtet und gezeigt, dass es absolut noch nicht der gediegene Glockenguss ist, als der es uns von "oben" immer vorgestellt wurde, sondern dass in ihm auch extrem gegenläufige, bemessen an seinen freiheitlich-demokratischen Idealen sogar als extrem verfassungs-widrig zu bezeichnende Tendenzen wirken, die heute in seine Zerstörung führen.\ \ Vor allem die unselige Übermacht des Parteienwesens und die damit verbundene systemische Entmündigung des Souveräns, des Volkes, ist das Ergebnis dieser verfassungs-widrigen Tendenzen.\ \ Es wird aber auch gezeigt, wo in den Idealen des Grundgesetzes und in den Entscheidungen der Mütter und Väter dieses Grundgesetzes die Ansatzpunkte liegen, durch die der Zerstörung des Grundgesetzes wirkungsvoll begegnet werden kann. Und diese Ansatzpunkte werden im Buch allseits zur Entfaltung gebracht.\ \ "Wer die Demokratie verteidigen will, der muss sie weiter entwickeln." Im Sinne dieses Wortes wird dem Leser ein praktikabler Weg gewiesen, auf dem er unmittelbar helfen kann, das Grundgesetz den wirkenden Zerstörungskräften zu entwinden, durch Einrichtung der direkten Bürgerbeteiligung an den entscheidenden Fragen unserer Republik die Position des Souveräns gegenüber der Parteienmacht zu stärken, Freiheitsrechte, Demokratie und Rechtsstaat auf eine wesentlich höhere Stufe als bisher zu bringen und sich durch eine verfassungs-klärende Versammlung seine Basis selbst und neu zu geben.
Buch bestellen: https://great-reset-von-unten.de/
\ Und nicht vergessen, abzustimmen! Die Zeit ist reif. Packen wir's an.\
-
 @ 1d7ff02a:d042b5be
2025-05-03 09:47:49
@ 1d7ff02a:d042b5be
2025-05-03 09:47:49ບົດຄວາມນີ້ແປມາຈາ: https://jackkruse.com/what-to-do-with-new-cancer-diagnosis/
ເນື້ອຫາສຳລັບຜູ້ອ່ານ: 1. ຈະເຮັດແນວໃດເມື່ອທ່ານໄດ້ຮັບການວິນິດໄສວ່າເປັນມະເຮັງ? 2. ສະໜາມຮົບກັບມະເຮັງທີ່ສຳຄັນແມ່ນຢູ່ບ່ອນການປິ່ນປົວແບບແພດ ຫຼື ໃນຮ່າງກາຍຂອງທ່ານເອງ? 3. ອາຫານການກິນມີບົດບາດແນວໃດ? 4. ຈະຮັບມືກັບໝໍມະເຮັງຄົນໃໝ່ຂອງທ່ານແນວໃດ? 5. ບໍ່ຕ້ອງຢ້ານທີ່ຈະສຳຫຼວດທຸກຄວາມເປັນໄປໄດ້ເພື່ອຊະນະສົງຄາມນີ້. ຮຽນຮູ້ກ່ຽວກັບອາຫານ ketogenic!!!
ກ່ອນທ່ານຈະອ່ານບົດຄວາມນີ້, ໃຫ້ເບິ່ງວິດີໂອນີ້: HYPERLINK
ບົດຄວາມນີ້ແມ່ນສຳລັບໜຶ່ງໃນໝູ່ທີ່ພິເສດຂອງຂ້ອຍ ຜູ້ທີ່ພົວພັນຂ້ອຍໃນອາທິດນີ້ ແລະ ບອກວ່າເມຍລາວຖືກວິນິດໄສວ່າເປັນມະເຮັງໃນໄວອາຍຸໜຸ່ມ. ຂ້ອຍໄດ້ຍິນຈາກການໂທ ແລະ ໂພສຂອງລາວໃນ Facebook ວ່າມັນກຳລັງທຳລາຍລາວ. ຂ້ອຍບອກລາວທັນທີໃຫ້ໄປຊື້ປື້ມ Anti Cancer: A New Way of Life ໂດຍ David Servan Schreiber ແລະ ມອບໃຫ້ເຈົ້າສາວຂອງລາວ. ຂ່າວດີກໍ່ຄືຫຼາຍລ້ານຄົນໃນຈຳນວນ 6 ລ້ານຄົນທີ່ກຳລັງປິ່ນປົວມະເຮັງໃນປະຈຸບັນຈະມີຊີວິດທີ່ສົມບູນຕໍ່ໄປ. ຈຳນວນຜູ້ລອດຊີວິດຕາມຄວາມຄິດເຫັນຂອງຂ້ອຍຍັງຕ່ຳເກີນໄປ (ປະມານ 45-50%). ນອກຈາກນັ້ນ, ຫຼາຍຄົນໃນຈຳນວນ 2000 ຄົນທີ່ເສຍຊີວິດຈາກມະເຮັງທຸກມື້ແມ່ນເນື່ອງຈາກຄອບຄົວຂອງພວກເຂົາບໍ່ຮູ້ກ່ຽວກັບຊັບພະຍາກອນທີ່ມີໃນປະຈຸບັນສຳລັບການປິ່ນປົວມະເຮັງທັງແບບດັ້ງເດີມ ແລະ ແບບທາງເລືອກ ເຊັ່ນ: ການປິ່ນປົວແບບເສີມ ຫຼື ແບບບູລະນາການ.
ເມື່ອຖືກວິນິດໄສດ້ວຍພະຍາດນີ້, ທ່ານຈະຮູ້ສຶກສັ່ນສະເທືອນຢ່າງຮຸນແຮງ. ສິ່ງສຳຄັນທີ່ທ່ານຕ້ອງຮູ້ແມ່ນພະຍາດນີ້ບໍ່ພຽງແຕ່ສາມາດຕໍ່ສູ້ໄດ້ແຕ່ຍັງສາມາດປ້ອງກັນໄດ້ຖ້າທ່ານຕັດສິນໃຈປ່ຽນແປງບາງສິ່ງທັນທີ ແລະ ປ່ອຍວາງຄວາມເຊື່ອທີ່ບໍ່ຖືກຕ້ອງທີ່ທ່ານໄດ້ສະສົມໃນຊີວິດ. ນີ້ເປັນຄວາມຈິງໂດຍສະເພາະຖ້າທ່ານເຮັດວຽກໃນຂົງເຂດສາທາລະນະສຸກ ແລະ ໄດ້ດຳລົງຊີວິດຕາມຄວາມເຊື່ອຕາຍຕົວຕະຫຼອດຊີວິດ. ປື້ມນີ້ຂຽນໂດຍແພດນັກຄົ້ນຄວ້າທີ່ບໍ່ພຽງແຕ່ຖືກກະທົບຈາກມະເຮັງ ແຕ່ຍັງເປັນມະເຮັງສະໝອງທີ່ອັນຕະລາຍທີ່ສຸດ. ລາວສາມາດຮື້ຖອນຄວາມເຊື່ອຂອງຕົນເອງໃນຖານະແພດດ້ວຍວິທະຍາສາດໃໝ່ທີ່ມີຢູ່ສຳລັບນັກຄົ້ນຄວ້າ ແຕ່ບໍ່ແມ່ນແພດມະເຮັງທົ່ວໄປ. ປື້ມນີ້ຈຳເປັນສຳລັບທຸກຄົນທີ່ເປັນມະເຮັງ ຫຼື ມີປັດໄຈສ່ຽງ ເພື່ອທ່ານຈະໄດ້ຊະນະກ່ອນມັນເລີ່ມ. ນີ້ແມ່ນໜຶ່ງໃນເຫດຜົນທີ່ຂ້ອຍຂຽນ QUILT ຂອງຂ້ອຍ ເພາະຂ້ອຍເຊື່ອວ່າຖ້າທ່ານປົກປ້ອງຈຸລັງຂອງທ່ານ ທ່ານຈະບໍ່ເປັນພະຍາດນີ້. ດຽວນີ້ ໝູ່ຂອງຂ້ອຍເປັນພະຍາດນີ້... ນີ້ແມ່ນບົດຄວາມກ່ຽວກັບສິ່ງທີ່ທ່ານອາດພິຈາລະນາເຮັດທັນທີຫຼັງຈາກປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ພິຈາລະນາຂໍຄວາມຄິດເຫັນທີສອງຈາກສູນມະເຮັງທີ່ສຳຄັນເຊັ່ນ MD Anderson.
-
ອ່ານປື້ມ Anticancer ທີ່ກ່າວເຖິງຂ້າງເທິງ. ມັນສຳຄັນທີ່ຈະເຫັນພະຍາດນີ້ໃນມຸມມອງໃໝ່.
-
ປ່ຽນອາຫານການກິນຂອງທ່ານທັນທີເປັນ Epi-paleo Rx ແລະ ອອກຫ່າງຈາກອາຫານແບບຕາເວັນຕົກມາດຕະຖານ.
-
ເລີ່ມເຮັດສະມາທິໂດຍໄວເທົ່າທີ່ຈະເປັນໄປໄດ້ເພື່ອຄວບຄຸມ cortisol ແລະ ຄວາມກັງວົນຂອງທ່ານ. (ທາງເລືອກບໍ່ສຳຄັນແຕ່ການເຮັດຈິງຊ່ວຍຊີວິດໄດ້)
-
ຄົນເຈັບຄວນປຶກສາຫາລືກ່ຽວກັບແຜນການປິ່ນປົວມະເຮັງ: ປັດໃຈສຳຄັນໃນມະເຮັງ: ຄວນຄົນເຈັບໃຊ້ອາຫານເສີມສຳລັບປະເພດມະເຮັງທີ່ທ່ານມີບໍ?
-
ພິຈາລະນາເລີ່ມລະບົບອາຫານເສີມ ລວມເຖິງ Curcumin, Reservatrol, Quercetin, ນ້ຳມັນປາ Omega ສາມ (ຄຸນນະພາບ Rx), ວິຕາມິນ D3 ໂດຍມີເປົ້າໝາຍເກີນ 50 ng/dl, ການໃຊ້ CoEnZQ10 ເປັນປະຈຳທຸກວັນ, R-alpha lipoic acid ແລະ ວິຕາມິນ K ທຸກມື້. ພິຈາລະນາການໃຊ້ N Acetyl Cysteine ທຸກວັນເຊັ່ນກັນ. ສັງເກດວ່າຂ້ອຍບໍ່ໄດ້ກຳນົດປະລິມານເພາະປະລິມານທີ່ຕ້ອງການສຳລັບການບຳບັດມະເຮັງແມ່ນສູງກວ່າທີ່ຈະໃຊ້ໃນການປ້ອງກັນ. ສິ່ງນີ້ຄວນເຮັດພາຍໃຕ້ການປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ຖ້າແພດມະເຮັງຂອງທ່ານບໍ່ເປີດໃຈກວ້າງກ່ຽວກັບບັນຫາເຫຼົ່ານີ້... ຫຼັງຈາກອ່ານປື້ມໃນຂັ້ນຕອນທີໜຶ່ງ ທ່ານອາດຈະຕ້ອງຊອກຫາແພດມະເຮັງຄົນໃໝ່. ເຫຼົ່ານີ້ແມ່ນສິ່ງທີ່ຂ້ອຍພິຈາລະນາວ່າເປັນອາຫານເສີມຫຼັກສຳລັບມະເຮັງສ່ວນໃຫຍ່ທີ່ມະນຸດເປັນ.
-
ໃນອາຫານຂອງທ່ານໃຫ້ເພີ່ມ ຂີ້ໝິ້ນ, ຂິງ, ກະທຽມ, ຣອດສະແມລີ, ແລະ ໃບແບຊິນ (ໃບໂຫລະພາ) ໃສ່ອາຫານຂອງທ່ານໃຫ້ຫຼາຍເທົ່າທີ່ຈະເປັນໄປໄດ້. ທ່ານຄວນດື່ມຊາຂຽວ 1 ລິດຕໍ່ມື້. ຊາຂຽວມີ L-Theanine ທີ່ຊ່ວຍຫຼຸດຄວາມກັງວົນ ແຕ່ຍັງເປັນສ່ວນເສີມຂອງຢາເຄມີບຳບັດໂດຍເຮັດໃຫ້ພວກມັນມີປະສິດທິພາບຍິ່ງຂຶ້ນ. ທ່ານຍັງສາມາດໃຊ້ສານສະກັດຊາຂຽວຖ້າທ່ານບໍ່ຕ້ອງການດື່ມຂອງແຫຼວຫຼາຍ ຫຼື ບໍ່ສາມາດດື່ມໄດ້ເນື່ອງຈາກສະພາບຂອງທ່ານ.
-
ໃນປີ 1955 Otto Warburg ຜູ້ຊະນະລາງວັນໂນເບວພົບວ່າມະເຮັງທັງໝົດໃຊ້ນ້ຳຕານເປັນແຫຼ່ງພະລັງງານ ແລະ ລະດັບອິນຊູລິນສູງເຮັດໃຫ້ຮ່າງກາຍສູນເສຍການຄວບຄຸມລະບົບພູມຄຸ້ມກັນທີ່ຈະປ້ອງກັນມັນ. ນີ້ໝາຍຄວາມວ່າຄົນເຈັບຕ້ອງຈຳກັດທຸກສິ່ງທີ່ກະຕຸ້ນອິນຊູລິນ. ອາຫານແບບ Epi-paleo ທີ່ມີຄາໂບໄຮເດຣດຕ່ຳເຮັດໄດ້ແນວນີ້ພໍດີ. ຂໍ້ມູນອ້າງອີງທີ່ດີສຳລັບອາຫານແມ່ນຢູ່ບ່ອນນີ້.
-
ລະບົບພູມຄຸ້ມກັນຂອງທ່ານແມ່ນການປ້ອງກັນທີ່ດີທີ່ສຸດຕໍ່ມະເຮັງ. ເພີ່ມລະດັບວິຕາມິນ D ແລະ ຮັກສາລະດັບອິນຊູລິນໃຫ້ຕ່ຳກວ່າສອງ. ການຫຼຸດລະດັບ cortisol ຈະປັບປຸງ leptin ແຕ່ສິ່ງສຳຄັນທີ່ສຸດແມ່ນເພີ່ມຈຳນວນຈຸລັງ Natural Killer (WBC) ທີ່ເປັນສ່ວນໜຶ່ງຂອງລະບົບພູມຄຸ້ມກັນໃນຈຸລັງທີ່ຕໍ່ສູ້ກັບມະເຮັງ. ທ່ານຈະໄດ້ອ່ານຫຼາຍກ່ຽວກັບຈຸລັງເຫຼົ່ານີ້ໃນປື້ມທີ່ຂ້ອຍແນະນຳໃນຂັ້ນຕອນທີໜຶ່ງ.
-
ຜັກ. ເຮັດໃຫ້ຜັກຕະກຸນ cruciferous ເປັນອາຫານຫຼັກ. ພືດທັງໝົດໃນຕະກຸນ Brassica ແມ່ນໝູ່ຂອງທ່ານ. Glucosinolates ສາມາດຢັບຢັ້ງ, ຊະລໍ, ແລະ ປີ້ນການເກີດມະເຮັງຫຼາຍຂັ້ນຕອນ. ເຫດຜົນແມ່ນການປ່ອຍ isothiocyanates ເຊັ່ນ sulphoraphanes. Sulphoraphanes ເຮັດສອງສິ່ງຫຼັກ. ພວກມັນສົ່ງເສີມ apoptosis (levee 19) ແລະ ກະຕຸ້ນເອນໄຊມ໌ detoxification ໄລຍະສອງໃນຕັບທີ່ເສີມຄວາມເຂັ້ມແຂງໃຫ້ກັບຍີນ p53 ເປັນຜູ້ປົກປ້ອງຈີໂນມຂອງພວກເຮົາ. ຈຸລັງມະເຮັງມັກຈະຕາຍ (necrosis) ເມື່ອສຳຜັດກັບ sulphoraphanes ຢ່າງຕໍ່ເນື່ອງເປັນເວລາດົນ. ຜັກບຣອກໂຄລີຍັງມີສານ metabolite ຂັ້ນສອງທີ່ເອີ້ນວ່າ Indole 3 Carbinol ທີ່ແຕກຕົວຕໍ່ໄປເປັນສານຕ້ານມະເຮັງອີກຊະນິດໜຶ່ງຊື່ວ່າ DIM, diindolylmethane. ທ່ານບໍ່ສາມາດກິນຜັກພວກນີ້ຫຼາຍພໍຖ້າທ່ານເປັນມະເຮັງໃນທັດສະນະຂອງຂ້ອຍ. I3C ຍັງຂັດຂວາງ 16-hydroxyestrone ແລະ ມີປະໂຫຍດຫຼາຍໃນການປ້ອງກັນມະເຮັງເຕົ້ານົມ ແລະ ມະເຮັງຮັງໄຂ່ໃນແມ່ຍິງ ແລະ ມະເຮັງຕ່ອມລູກໝາກໃນຜູ້ຊາຍ.
-
ນີ້ແມ່ນສິ່ງທີ່ຂັດກັບຄວາມເຊື່ອຊຶ່ງຢູ່ໃນຫົວຂອງທ່ານ... ກິນ cholesterol ຫຼາຍໆ. ໂດຍສະເພາະນ້ຳມັນໝາກພ້າວ. ຫຼາຍການສຶກສາທາງລະບາດວິທະຍາສະແດງໃຫ້ເຫັນວ່າລະດັບ cholesterol ໃນເລືອດຕ່ຳສຳພັນກັບອັດຕາການເກີດມະເຮັງສູງ. ນີ້ແມ່ນເຫດຜົນທີ່ການກິນອາຫານ ketogenic Epi-paleo ມີຄວາມໝາຍຫຼາຍ. ເປັນຫຍັງອາຫານແບບ ketogenic? ເພາະມະເຮັງທັງໝົດໃຊ້ກລູໂຄສເປັນວັດຖຸດິບ. ທ່ານຈຳເປັນຕ້ອງປ່ຽນເຊື້ອໄຟຂອງຈຸລັງ. ໄປຊອກຫາ Otto Warburg ໃນ Google ສຳລັບລາຍລະອຽດເພີ່ມເຕີມ. ອາຫານແບບ ketogenic ຄວນມີ MCT ຈາກນ້ຳມັນໝາກພ້າວຫຼາຍ ເພາະພວກມັນໃຫ້ຂໍ້ໄດ້ປຽບຫຼາຍແກ່ຈຸລັງປົກກະຕິກວ່າຈຸລັງມະເຮັງ. ຂໍ້ໄດ້ປຽບນີ້ເຮັດໃຫ້ລະບົບພູມຄຸ້ມກັນຂອງທ່ານສາມາດຕາມທັນຈຸລັງມະເຮັງ ແລະ ທຳລາຍພວກມັນໂດຍໃຊ້ກົນໄກຊີວະວິທະຍາຂອງທ່ານເອງ. ມີຫຼາຍບົດຄວາມໃນວາລະສານມະເຮັງທີ່ພິມເຜີຍແຜ່ສະແດງໃຫ້ເຫັນການເຊື່ອມໂຍງແບບດຽວກັນ.
-
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 6389be64:ef439d32
2025-01-13 21:50:59
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ cae03c48:2a7d6671
2025-05-20 11:00:00
@ cae03c48:2a7d6671
2025-05-20 11:00:00Bitcoin Magazine

Ben Allen Receives Maelstrom Bitcoin Developer Grant to Advance Payjoin TechBen Allen has been named the third recipient of the Maelstrom Bitcoin Developer Grant, the family office of Arthur Hayes announced in a recent press release sent to Bitcoin Magazine. Over the next year, Allen will focus on enhancing the Payjoin Dev Kit project, a privacy-focused Bitcoin transaction tool designed to improve user anonymity and network scalability.
Payjoin, first introduced in 2019 by Nicolas Dorier in BIP 78, allows both the sender and receiver to contribute inputs to a single Bitcoin transaction. This disrupts common assumptions used by financial surveillance firms, namely the idea that multiple transaction inputs must come from a single entity. By breaking this assumption, even limited adoption of Payjoin can bolster privacy across the Bitcoin network.
“Maelstrom would like to congratulate Ben Allen on this grant,” said Arthur Hayes, Chief Investment Officer of Maelstrom. “The great thing about Payjoin, is that if only a small amount of adoption is achieved, it breaks a key assumption used by financial surveillance companies. The assumption they have is that if a Bitcoin transaction has multiple inputs, all the inputs must all belong to the same entity. Therefore, Payjoin adoption improves the privacy of even the people who don’t use it. We are excited to support Ben Allen’s work on open-source tools and software to increase Payjoin adoption.”
Allen, who will be working alongside Dan Gould, aims to expand the implementation of Payjoin so it can be integrated into more Bitcoin wallets. He acknowledged the technical complexities of the project—including the requirement for receivers to be online—but expressed optimism about overcoming these challenges.
“I’m deeply grateful to Arthur Hayes and Maelstrom for generously providing me with this grant to support my work on the Payjoin Dev Kit project,” said Allen. “With this funding, I can dedicate myself full-time to enhancing the Payjoin implementation, improving testing, and ensuring that the dev kit remains robust, well-documented, and maintainable for the future.”
Allen also emphasized the broader mission of his work: “Improving privacy for bitcoin is an area where continued improvement allows for a better experience by empowering users to control their financial data and foster greater peace of mind when using bitcoin day to day. This is an exciting opportunity to contribute to Bitcoin’s privacy and scalability, and I’m looking forward to continuing to collaborate with the community to make Payjoin more widely adopted.”
Maelstrom, which is focused on supporting digital asset infrastructure, is led by Arthur Hayes, co-founder of BitMEX. Through grants like this one, the firm is investing in the foundational tools that promote a more private, scalable, and decentralized Bitcoin ecosystem.
This post Ben Allen Receives Maelstrom Bitcoin Developer Grant to Advance Payjoin Tech first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 8576ca0e:621f735e
2025-05-19 06:43:00
@ 8576ca0e:621f735e
2025-05-19 06:43:00
In the ever evolving landscape of social media, a new contender has emerged, seeking to redefine how we connect and interact online. YakiHonne, a mobile application built upon the innovative Nostr protocol, isn't just another platform vying for your attention. It represents a bold step towards decentralized social networking, seamlessly integrating the power of Bitcoin's Lightning Network into its very core.
Imagine a social space free from the control of centralized entities, where your data belongs to you, and where value can flow as freely as information. This is the vision YakiHonne is striving to realize. By leveraging the open and censorship resistant nature of Nostr, it offers a refreshing alternative to the traditional social media giants.
The Power of Decentralization: A Foundation Built on Nostr
At its heart, YakiHonne is powered by Nostr (Notes and Other Stuff Transmitted by Relays). Unlike conventional platforms that rely on a central server, Nostr operates on a network of independent relays. This decentralized architecture offers several key advantages:
• Censorship Resistance: No single entity can easily censor or shut down the network. Your posts and interactions are distributed across multiple relays.
• Data Ownership: Your data isn't locked away in a corporate database. You control your private keys, granting you greater autonomy over your information.
• Open and Extensible: The open nature of the protocol allows for innovation and the development of diverse clients and applications, fostering a vibrant ecosystem.
YakiHonne acts as a user friendly gateway to this decentralized world, providing an intuitive mobile interface to interact with the Nostr network.
Zaps: Where Social Interaction Meets Bitcoin
What truly sets YakiHonne apart is its deep integration of Bitcoin payments through the Lightning Network, often referred to as "zaps." This isn't just a tacked on feature; it's woven into the fabric of social interaction.
• Show Appreciation: Found a post insightful, funny, or valuable? You can instantly send a small amount of Bitcoin as a "zap" to show your appreciation directly to the creator.
• Monetize Content: Creators can earn Bitcoin for their contributions, fostering a more sustainable model for online content generation.
• Seamless Transactions: Lightning Network enables near instant and low fee Bitcoin transactions, making zapping a practical and frictionless experience.
This innovative integration transforms social interactions into potential value exchanges, creating new dynamics between creators and their audience.
Beyond the Basics: Features for Content and Connection
YakiHonne isn't solely focused on Bitcoin. It provides a robust set of features for creating, sharing, and discovering content:
• Long Form Articles (NIP-23): For those who want to delve deeper, YakiHonne supports the creation of wel formatted articles using a rich markdown editor. This allows for more nuanced discussions and the sharing of substantial ideas.
• Topic Based Collections (NIP-51): Users can curate content into organized collections, making it easier to discover information on specific topics and follow thought leaders in various domains.
• Following and Discovery (NIP-02): Stay connected with the people and ideas that matter to you by following other users. The platform also offers ways to discover top creators, curators, and trending discussions through hashtags (NIP-12).
• Rich User Profiles: Your profile showcases your followers, who you're following, your zapping activity, and the articles you've published, providing a comprehensive overview of your presence on the platform.
• Direct Messaging (DMs): For more private conversations, YakiHonne includes a direct messaging feature, allowing for one on one communication.
A Growing Ecosystem and Continuous Improvement
YakiHonne is actively being developed and refined by JustHonne Technologies. Recent updates highlight a commitment to improving the user experience and addressing bugs. Enhancements to the zap functionality, fixes for various technical issues, and improved stability demonstrate the ongoing dedication to making the app a reliable and enjoyable platform.
The open source nature of the mobile application, with its code available on GitHub, encourages community involvement and transparency. This collaborative approach can contribute to the platform's growth and evolution.
Looking Ahead: The Potential of Decentralized Social with Bitcoin
YakiHonne represents an exciting intersection of decentralized social networking and Bitcoin's utility. By seamlessly integrating Lightning Network payments, it introduces a novel way to interact and exchange value online. While still in its relatively early stages, YakiHonne holds significant potential to:
• Empower Creators: Provide new avenues for content monetization and direct interaction with their audience.
• Foster Meaningful Interactions: Encourage more thoughtful engagement through the ability to easily show appreciation.
• Offer a More Resilient Social Space: Provide an alternative to centralized platforms with greater resistance to censorship and single points of failure.
As the Nostr ecosystem continues to grow and evolve, and as more users seek decentralized alternatives, YakiHonne is well positioned to be a leading application in this burgeoning space. It's more than just another social media app; it's a glimpse into a future where online connections are more open, and truly belong to the users themselves.
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ dc0bbb4c:b5479e81
2025-05-19 06:31:45
@ dc0bbb4c:b5479e81
2025-05-19 06:31:45Trong bối cảnh thị trường giải trí trực tuyến ngày càng phát triển mạnh mẽ, 1BWM đã và đang khẳng định vị thế là một trong những nền tảng kỹ thuật số được cộng đồng người dùng tin tưởng và lựa chọn nhiều nhất. Nhờ sở hữu giao diện thiết kế hiện đại, tinh tế và cực kỳ dễ sử dụng, 1BWM giúp người dùng dễ dàng tiếp cận và trải nghiệm mọi tiện ích mà nền tảng này mang lại chỉ với vài thao tác đơn giản. Không chỉ vậy, 1BWM còn ghi điểm bởi khả năng tối ưu hóa trải nghiệm trên đa dạng thiết bị như điện thoại di động, máy tính bảng và máy tính để bàn, giúp người dùng có thể giải trí bất cứ lúc nào, ở bất kỳ đâu một cách thuận tiện và mượt mà. Từ các chuyên mục nội dung hấp dẫn, phong phú cho đến hệ thống tính năng linh hoạt, 1BWM luôn biết cách làm mới mình để phù hợp với xu hướng công nghệ và nhu cầu giải trí ngày càng đa dạng của người dùng hiện đại.
Điểm mạnh nổi bật tiếp theo khiến 1BWM được nhiều người lựa chọn chính là hệ thống bảo mật dữ liệu và quyền riêng tư vô cùng nghiêm ngặt. Nền tảng này ứng dụng công nghệ mã hóa tiên tiến, đảm bảo mọi thông tin cá nhân, tài khoản và dữ liệu giao dịch của người dùng luôn được bảo vệ an toàn tuyệt đối. Bên cạnh đó, 1BWM còn sở hữu đội ngũ chăm sóc khách hàng chuyên nghiệp, tận tâm và giàu kinh nghiệm, luôn sẵn sàng hỗ trợ giải đáp mọi thắc mắc cũng như xử lý các tình huống phát sinh một cách nhanh chóng, hiệu quả nhất. Người dùng có thể yên tâm khi trải nghiệm các dịch vụ tại đây mà không phải lo lắng về bất cứ rủi ro nào liên quan đến bảo mật thông tin. Ngoài ra, nền tảng này còn thường xuyên triển khai các chương trình ưu đãi hấp dẫn, quà tặng đặc biệt dành cho người dùng mới lẫn hội viên lâu năm, tạo thêm nhiều giá trị và động lực cho cộng đồng người tham gia.
Không dừng lại ở đó, 1BWM luôn nỗ lực không ngừng trong việc nâng cao chất lượng dịch vụ và mở rộng thêm nhiều tiện ích giải trí mới, nhằm mang đến cho người dùng những trải nghiệm trọn vẹn và thú vị nhất. Nền tảng này liên tục cập nhật các chuyên mục nội dung mới mẻ, phong phú và bắt kịp xu hướng giải trí hiện đại, giúp người dùng luôn có thêm nhiều lựa chọn phù hợp với sở thích cá nhân. Đồng thời, 1BWM cũng chú trọng vào việc cải tiến công nghệ, tối ưu tốc độ kết nối và giao diện sử dụng để nâng cao trải nghiệm mỗi lần truy cập. Với định hướng phát triển rõ ràng cùng sự đầu tư bài bản, 1BWM không chỉ là một nền tảng giải trí đơn thuần mà còn là cộng đồng trực tuyến năng động, nơi người dùng có thể kết nối, tương tác và chia sẻ những khoảnh khắc giải trí vui vẻ, ý nghĩa cùng nhau. Nhờ những ưu điểm vượt trội này, 1BWM ngày càng khẳng định được vị thế và trở thành sự lựa chọn hàng đầu của người dùng Việt khi tìm kiếm một không gian giải trí số chất lượng, an toàn và uy tín.
-
 @ cae03c48:2a7d6671
2025-05-20 10:50:37
@ cae03c48:2a7d6671
2025-05-20 10:50:37Bitcoin Magazine
Proof of Reserves Should Be the Standard for Bitcoin Treasury Companies“The root problem with conventional currency is all the trust that’s required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Banks must be trusted to hold our money and transfer it electronically, but they lend it out in waves of credit bubbles with barely a fraction in reserve.”
— Satoshi Nakamoto (2009)
Bitcoin was created to eliminate the need for trusted intermediaries. It replaced opaque, permissioned systems with transparency, auditability, and decentralized verification. The ethos was clear from day one: don’t trust—verify.
And yet, many of the institutions now holding Bitcoin—custodians, exchanges, ETFs, even public companies—continue to rely on trust-based assumptions, the very problem Bitcoin was designed to solve.
For Bitcoin treasury companies, this contradiction is especially glaring. These are firms that claim to operate on a Bitcoin standard—yet without verifiable Proof of Reserves (PoR), there’s no way for shareholders to know whether the Bitcoin is actually there.
The Problem: Unproven Bitcoin Is Just Another IOU
Bitcoin is designed to be verifiable—but most corporate disclosures aren’t. When companies report BTC holdings without public wallet visibility or on-chain proof, investors are left to trust balance sheets, auditors, and custodians.
That opens the door to systemic risks:
- Rehypothecation: BTC pledged or lent behind the scenes
- Custodial failure: Centralized services operating without 1:1 backing
- “Paper Bitcoin”: Multiple claims on the same BTC, echoing legacy financial opacity
The mere presence of Bitcoin on a balance sheet is not a guarantee. Without verification, it’s no different than a fiat-denominated claim—an IOU dressed up in BTC terms.
What We Learned from Gold: The Paper Problem
Bitcoin is not the first hard asset to face this challenge. The gold market offers a cautionary tale.
For decades, gold investors have dealt with “paper gold” systems—unallocated accounts, synthetic ETFs, and derivatives with little or no linkage to actual metal. These claims often outnumber real reserves many times over, leading to widespread suspicion of price distortion and systemic misrepresentation.
Most gold investors don’t own gold—they own a claim to gold. And they have no way to prove it.
Bitcoin gives us the tools to break this cycle. But only if companies choose to use them.
Bitcoin Is Built for Proof—and Companies Should Use It
Unlike legacy assets, Bitcoin is designed to make proof of ownership and solvency a native function of the asset itself. Through public key cryptography, on-chain auditability, and permissionless transparency, Bitcoin enables real-time, trust-minimized verification.
This isn’t just a technical capability—it’s a governance feature. Bitcoin allows companies to demonstrate, cryptographically and without intermediaries, that their reserves exist, are intact, and are unencumbered. No bank statements. No opaque custodial claims. Just data, on-chain.
That’s a radical shift—and it’s one that Bitcoin treasury companies are uniquely positioned to take advantage of. In doing so, they can reduce audit complexity, strengthen shareholder communication, and align their internal capital practices with the trustless architecture of the asset they’re holding.
And it’s already happening. Metaplanet, Premiere Member of Bitcoin For Corporations, publicly discloses its BTC reserve addresses and transaction history. Anyone in the world—including shareholders, analysts, and regulators—can independently verify the existence and movement of their treasury. That’s not just compliance. That’s Bitcoin, applied. View the snapshot of Metaplanet’s proof of reserves dashboard below.

Public Companies Face the Greatest Responsibility
Public companies don’t operate in a vacuum. Their disclosures shape market perception, influence investor behavior, and—especially when Bitcoin is involved—serve as a proxy for the maturity of the asset class itself.
When a publicly traded company holds Bitcoin but offers no visibility into how that Bitcoin is held or verified, it exposes itself to multiple levels of risk: legal, reputational, operational, and strategic. It undermines trust at the very moment it claims to be embracing a trustless system.
More importantly, public companies send signals. Whether they like it or not, they become de facto representatives of the Bitcoin strategy they’ve adopted. Their behavior becomes part of the playbook for others considering similar moves.
That’s why the responsibility is higher. Transparency isn’t optional for companies who lead with Bitcoin. It’s a duty. And companies that choose opacity not only take on unnecessary risk—they weaken the credibility of the entire movement.e.
What Proof of Reserves Should Actually Include
For Proof of Reserves to have real integrity, it must go beyond vague references to “custody partners” or internal assurance statements. The key is verifiability—independent, data-driven, and actionable by any shareholder or auditor.
At a minimum, Bitcoin treasury companies should provide:
- Custody model clarity: Is the company using self-custody, shared multisig, or third-party solutions? Who controls the keys, and under what governance?
- On-chain transparency: Whether through view-only wallet addresses or cryptographic attestations (like Merkle tree proofs), companies must make it possible to verify balances against public disclosures.
- Encumbrance disclosure: Reserves that are pledged, lent out, or locked in yield strategies should be disclosed clearly, with timelines and risk parameters attached.
- Routine updates: Proof should be refreshed regularly—not once per year in an audit footnote, but as part of ongoing financial communication.
- Reconciliation framework: Companies should explain how on-chain data maps to reported BTC NAV in filings or investor materials.
For boards and CFOs, this doesn’t need to introduce operational risk. Tools already exist—xpub view-only wallets, custody APIs, third-party validators—to provide assurance without compromising security. The obstacle isn’t capability. It’s willingness.
Setting the Industry Benchmark: Where Bitcoin Treasury Companies Must Lead
Bitcoin treasury companies are not just financial outliers—they are structural pioneers. Their decision to hold BTC signals not only a belief in long-term value, but a rejection of legacy capital inefficiency. That’s why they must also lead on standards of integrity.
By adopting PoR voluntarily and early, companies can position themselves as trustworthy, sophisticated, and future-ready. This will matter more as institutional capital rotates into Bitcoin, as index inclusion expands, and as regulators begin asking sharper questions about crypto asset disclosures on balance sheets.
PoR isn’t just a way to comply with future standards—it’s a way to shape them. The companies that lead now will not only avoid future scrutiny—they’ll attract capital from allocators who are seeking transparency but don’t yet know where to find it.
At BFC, we believe the market rewards clarity. Bitcoin treasury companies have a chance to bake transparency into their structure, not as an afterthought, but as a strategic differentiator.
Shareholders Must Demand It
Proof of Reserves isn’t just a company initiative—it’s a shareholder obligation. When a public company holds Bitcoin on its balance sheet, it is acting as a fiduciary for shareholder capital denominated in one of the hardest, most transparent assets in history. To accept opacity in that context is to forfeit the very advantage Bitcoin offers.
If you’re an investor in a Bitcoin treasury company and you can’t verify the Bitcoin, you don’t own a monetary reserve—you own a narrative. You’re trusting that someone else is telling the truth, rather than requiring the proof Bitcoin makes possible.
That’s not aligned with the principles of sound capital stewardship.
Institutional allocators, activist shareholders, and governance professionals have a growing role to play here. Just as proxy advisors and investor coalitions have pushed for climate disclosures, board transparency, and ESG clarity in the past decade, it’s time to apply that same rigor to Bitcoin disclosures—especially for companies who claim to operate on a Bitcoin standard.
Demand direct answers:
- Can we verify the holdings on-chain?
- Are reserves fully collateralized and unencumbered?
- Has manageme
-
 @ 9c9d2765:16f8c2c2
2025-05-19 05:04:10
@ 9c9d2765:16f8c2c2
2025-05-19 05:04:10CHAPTER TWENTY TWO
“I should have trusted my son,” she said softly, her voice thick with emotion. “I allowed the world’s opinion to silence my instincts.”
James turned to her, his expression gentle. “You needed time to see what I had to become, Mother. I don’t blame you for anything.”
Mr. JP stepped forward, placing a firm hand on James’s shoulder. “Son, you’ve given this family more than we ever gave you. And tonight… Tonight, you gave JP Enterprises its legacy.”
Uncle Charles, who had silently stood behind James during the entire storm, finally spoke. “It took courage to keep quiet and watch those who wronged you bury themselves with their own greed.”
James nodded slightly. “And now… it’s done.”
Rita came closer, smiling softly. “Not completely,” she said with a hint of laughter. “You still have an entire empire to run… and a celebration to finish.”
James allowed a rare, genuine smile to appear. “Right. The anniversary.”
They returned to the hall, which had now regained its glamour and golden glow. The orchestra resumed a soft melody. The guests whispered less now and admired more. The reputation of James was not only redeemed, it was immortalized.
A grand toast was raised in his honor. Champagne glasses clinked gently beneath crystal chandeliers.
Meanwhile, in a corner of the room, Tracy sat, feeling like the walls were closing in. Her palms were damp. She had seen the storm come full circle, and it landed directly on the heads of her former allies. Her gaze lingered on James from afar no longer the man she belittled, deceived, and mocked. He was now untouchable.
She lowered her head, guilt dancing between her thoughts. What have I done?
As if sensing her gaze, James glanced in her direction. For a heartbeat, their eyes met. But there was no anger in his. Just clarity. And silence. He turned away, giving her no attention, no confrontation. That indifference stung more than any rebuke.
Back on stage, Mr. JP announced, “Tonight, we not only celebrate sixteen years of excellence, but we also honor the future. A future with James as our guiding light.”
The crowd once again erupted in applause.
As the music swelled and the lights dimmed to warm hues, couples danced, laughter returned, and the celebration continued. But for James, the victory wasn’t in the glamour, nor the spotlight. It was in knowing that he had not only defeated those who plotted against him but done so without losing his soul.
Later that evening, James stood alone at the terrace, looking out at the moonlit city below. Sandra approached quietly.
“You finally have it all,” she said gently. “The name. The company. The power.”
James didn’t turn. “It was never about having it all. It was about becoming everything they said I couldn’t.”
She smiled, stepping beside him. “And now?”
He exhaled, his breath misting into the cold night air. “Now… I build. For real this time.”
The celebration had ended, but its echoes still danced through the night like a lingering song in the soul. The grand hall slowly emptied, leaving behind the soft shuffling of feet and murmurs of astonishment. JP Enterprises’ 16th Anniversary had become more than a commemoration of business success it was now remembered as the night the city witnessed a man rise from ruin to royalty.
The staff bustled through the corridors, clearing the remains of laughter, toasts, and carefully prepared cuisine. James had stepped away, far from the glitz and glamour, and now stood once more on the terrace, his thoughts stretched thin across the skyline of the city he once wandered in as nothing more than a nameless shadow.
The weight of it all rested gently on his shoulders, not a burden, but a reminder. He remembered the cold nights on the street, the hunger, the humiliation at the Ray household, the scorn in Helen’s voice, and the way Tracy used to avoid eye contact with him as if he were dirt beneath her polished shoes.
His fists clenched slowly as memory swirled within him like a storm. But he released the tension just as quickly. That past could no longer touch him. He had outgrown it. Transcended it.
Behind him, the heavy oak doors creaked. It was Uncle Charles.
“You should rest,” Charles said, his tone fatherly. “You’ve had a long night.”
James turned, eyes soft yet heavy. “You ever wonder what happens after the applause ends?”
Charles smiled. “That’s when the real work begins.”
James chuckled dryly. “Exactly.”
They stood side by side, looking out at the city lights. It felt poetic somehow like all the scattered stars in the sky had descended to earth in the form of streetlights and skyscrapers.
“You did well tonight, James,” Charles said. “You kept your composure even when that girl tried to destroy everything.”
“She was just a pawn,” James replied. “Mark and Helen used her like they use everyone. Their power was built on manipulation. Mine won’t be.”
Charles looked at him, pride gleaming in his eyes. “And that’s why you’re different. That’s why you deserve the crown.”
Meanwhile, back in the Ray residence, chaos brewed. Mark paced violently, his jacket flung to the floor, his tie undone. Helen sat on the edge of the sofa, her heels off, nursing a glass of wine with trembling fingers.
“She betrayed us,” Mark spat. “That girl after all the money we gave her, she folded.”
“What did you expect?” Helen hissed. “She was a desperate street rat! Loyalty is not in their blood!”
Mark slammed his fist on the table. “Now the city sees us as liars. As criminals. We’ve been blacklisted by investors! Do you know what that means, Helen? We’re finished!”
Helen's face hardened. “No. We’re not. James might have won tonight, but the game isn’t over.”
Mark turned toward her. “You still want to fight him?”
The silence that followed the explosive revelation at the anniversary was thick and reverent. It blanketed the city like a veil, as if the skyline itself paused to absorb the magnitude of what had transpired. James, once discarded and humiliated, had emerged not only as the President of JP Enterprises, but as its rightful heir, son to the powerful and elusive Mr. JP. What was once speculation had now become an undeniable truth, echoing across boardrooms, dinner tables, and digital screens.
Back at JP Towers, the building pulsed with energy. Staff walked a little straighter, greeted one another with more awareness. The man they once passed in hallways without a second glance had now become a figure of awe and authority. His name echoed in hushed reverence: Mr. James.
Inside his office, James sat behind a polished obsidian desk, the city's skyline stretching behind him like a conquest. His fingers drummed silently on a closed file. He had received more than twenty new partnership requests within forty-eight hours of the celebration. Shares had surged. The media, which once sought to condemn him, was now clamoring for exclusive interviews, praising his resilience and visionary leadership.
Yet, James was silent.
Not because he didn't revel in victory, but because he understood something deeper this was not the end. It was only the beginning.
-
 @ 1d7ff02a:d042b5be
2025-05-02 14:50:01
@ 1d7ff02a:d042b5be
2025-05-02 14:50:01ผมได้ติดตามการแบนการซื้อขายแบบ P2P ของ Binance ในประเทศไทยมาระยะหนึ่งแล้ว จากสถานการณ์ดังกล่าว เห็นได้อย่างชัดเจนว่ารัฐบาลกำลังเริ่มโจมตี Bitcoin ก่อนที่เราจะบรรลุถึง Bitcoin Standard เราจำเป็นต้องมีความเป็นส่วนตัวและอิสระทางการเงิน ซึ่งการซื้อขายแบบ P2P มีความสำคัญมากในการบรรลุเป้าหมายนี้
ความสำคัญของ No-KYC P2P
No-KYC P2P คือหัวใจสำคัญ - เราจำเป็นต้องมีแพลตฟอร์มที่เป็นทางรอด เราไม่สามารถเชื่อใจแพลตฟอร์มแบบรวมศูนย์ได้เนื่องจากสาเหตุสองประการ: 1. ความเสี่ยงจากการถูกโกงโดยแพลตฟอร์มเอง (rug pull) 2. การถูกควบคุมจากภาครัฐ
แพลตฟอร์ม No-KYC P2P ที่แนะนำ
ผมอยากเสนอให้นักพัฒนาและชุมชน Bitcoin ไทย พิจารณาการศึกษาและพัฒนาแพลตฟอร์ม No-KYC P2P ปัจจุบันมีหลายทางเลือกที่มีอยู่แล้ว เช่น:
- Bisq
- RoboSats
- Mostro
- HodlHodl
- Lnp2pbot
เหตุผลที่แนะนำ Lnp2pbot
ผมขอแนะนำให้นำใช้หรือพัฒนาต่อจาก Lnp2pbot เนื่องจากข้อดีหลายประการ:
- ประสบการณ์ผู้ใช้ (UX) ที่ดีกว่า - เมื่อเทียบกับแพลตฟอร์มอื่นๆ
- ใช้ Telegram เป็นพื้นฐาน - มีระบบ Escrow (บุคคลที่สามที่ถือเงินระหว่างการทำธุรกรรม) ซึ่งเพิ่มความมั่นใจและลดโอกาสการถูกโกง
- ลดการรวมศูนย์ - ไม่จำเป็นต้องพัฒนาแอปและส่งขึ้นสโตร์ ซึ่งจะทำให้นักพัฒนาต้องเปิดเผยตัวตนและกลายเป็นจุดอ่อนให้รัฐบาลควบคุม
- สร้างชุมชนได้ง่าย - ทุกคนสามารถสร้างกลุ่มหรือชุมชนเพื่อการซื้อขายได้ ทำให้ตลาดพัฒนากลุ่มที่น่าเชื่อถือตามกลไกตลาดเสรี
- ใช้งานจริงในหลายประเทศแล้ว - ปัจจุบันมีหลายประเทศที่นำ Lnp2pbot ไปใช้งานจริงแล้ว แสดงให้เห็นถึงความเสถียรและความเชื่อถือได้ของระบบ
บทบาทของนักพัฒนาไทย
Lnp2pbot อาจยังมีข้อจำกัดด้าน UX โดยเฉพาะสำหรับผู้ใช้ท้องถิ่น นักพัฒนาไทยสามารถนำเอาซอฟต์แวร์มาพัฒนาต่อและดำเนินการเองได้ เนื่องจากเป็นโอเพนซอร์สอยู่แล้ว
สิ่งสำคัญที่สุดคือการรักษาให้ซอฟต์แวร์เป็นโอเพนซอร์สและให้ทุกคนสามารถนำไปใช้หรือทำให้มันทำงานได้ด้วยตนเอง วิธีการนี้จะหลีกเลี่ยงการมีจุดรวมศูนย์ที่รัฐบาลสามารถโจมตีได้
-
 @ f6488c62:c929299d
2025-05-19 03:25:26
@ f6488c62:c929299d
2025-05-19 03:25:26เรื่องจริงที่ต้องเตือน: เมื่อ "ความรวยจากคริปโต" กลายเป็นดาบสองคมที่อันตรายถึงชีวิต! 🔪💰
ในขณะที่หลายคนยินดีกับกำไรจาก Bitcoin และคริปโตอื่นๆ มีเรื่องราวอีกด้านที่น่าสะเทือนใจเกิดขึ้นทั่วโลก โดยเฉพาะเหตุการณ์ "ลักพาตัวเพื่อเรียกค่าไถ่เป็นคริปโต" ที่ทวีความรุนแรงขึ้น
ข้อมูลและข่าวจากหลายแหล่งยืนยันว่า ผู้ใช้งานคริปโตกำลังตกเป็นเป้าหมายของอาชญากร โดยใช้วิธีการที่โหดเหี้ยม เช่น การทำร้ายร่างกาย หรือแม้กระทั่งการ "ตัดนิ้ว" เพื่อบีบบังคับให้เหยื่อโอนคริปโตใน Cold Wallet ที่เก็บไว้! เคสล่าสุดที่เกิดขึ้นในฝรั่งเศสและสหรัฐฯ ในช่วงปี 2025 เป็นเครื่องย้ำเตือนชั้นดี
ทำไมพวกเขาถึงเลือก "คุณ" ที่เป็นนักลงทุนคริปโต? ปัจจัยสำคัญคือ: มูลค่าสินทรัพย์ที่คุณถือสูงมาก, การเก็บ Private Key ของ Cold Wallet คือจุดอ่อนที่คนร้ายใช้ความรุนแรงบังคับเอาได้ง่าย, และที่น่าตกใจคือ การ "โพสต์โชว์ความรวย" หรือพูดถึงคริปโตมากเกินไปบนโซเชียลมีเดีย กำลังเป็นการชี้เป้าให้ตัวเอง!
ข้อคิดและแนวทางป้องกันตัวที่สำคัญสุดๆ:
จงเป็น "Ghost" ในโลกคริปโต: อย่าให้ใครรู้ว่าคุณถืออะไร เท่าไหร่ หรือรวยแค่ไหน การปิดทองหลังพระในโลกคริปโตอาจช่วยรักษาชีวิตคุณได้ ยกระดับความปลอดภัย "ชีวิตจริง": คิดถึงกล้องวงจรปิด, ระบบรักษาความปลอดภัยที่บ้าน, การจ้างบอดี้การ์ด (ถ้าจำเป็นจริงๆ), และระวังการเดินทางคนเดียว บริหารจัดการ "กุญแจ" ของคุณให้ดีที่สุด: Cold Wallet สำคัญมาก แต่การเก็บ Private Key ให้ปลอดภัยจากสายตาคนอื่น และการกระจายความเสี่ยงโดยแบ่งทรัพย์สินไปหลาย Wallet ก็สำคัญไม่แพ้กัน ความรุนแรงในวงการคริปโตเป็นบทเรียนราคาแพงที่บอกว่า ความมั่งคั่งที่มองไม่เห็นในโลกดิจิทัลนั้น มีราคาค่างวดที่ต้องจ่ายในโลกจริงหากประมาท การลงทุนอย่างรอบคอบ ไม่ใช่แค่การดูกราฟ แต่คือการประเมินและจัดการความเสี่ยงใน "ชีวิต" ของคุณด้วย!
แชร์โพสนี้เพื่อเตือนเพื่อนๆ นักลงทุนทุกคน ให้ปลอดภัยทั้งทรัพย์สินและชีวิตครับ/ค่ะ!
Crypto #Bitcoin #Ethereum #ColdWallet #PrivateKey #Security #Crime #DigitalAssets #Investor #SafetyFirst #เตือนภัย #ลงทุนอย่างปลอดภัย
-
 @ 9bcc5462:eb501d90
2025-01-10 19:42:28
@ 9bcc5462:eb501d90
2025-01-10 19:42:28Cuneiform is mankind’s first writing system created by the ancient Sumerians of Mesopotamia, what is now Iraq. (The word “Sumer” means land of civilized kings). Despite being developed 5,000 years ago, its parallels to Notes and Other Stuff Transmitted by Relays will blow your mind! The most striking is how both breakthroughs materialized from the fundamental need to track value exchange–from primal grain tallies to now exchanging bitcoin.
Let’s begin with the fact that the styluses used by these archaic scribes were crafted from reed plants. Their stems were strong because of attachment points called nodes! These were the resilient, ring-like parts of the stem that joined it together with the rest of the plant. Similarly, although symbolically, lightning nodes are powerful on nostr since they allow us to zap each other with sats. An approach stemming from the need to modernize how we interact on social media, trade in networks and conduct business—It’s not surprising cuneiform came about as a way for merchants and farmers to track economic transactions and agricultural inventories!
Another parallel involves how both share everlasting marks. The Sumerians used their styluses to press wedge-like symbols onto wet tablets. They then would bake them in the sun, leaving a permanent record of the documentation. If an error was made, it could not be changed. Likewise, on nostr there is no delete function. Once you publish a note, including any typos, it is preserved for history.
Lastly, the proto-writing that emerged in Mesopotamia which led to Cuneiform was in the form of bullae (bulla: singular). These were spherical clay envelopes encased with tokens representing a transaction. They were sealed with unique markings representing the parties involved for authentication. In other words, cuneiform cylinder seals were effectively early public key cryptography! The seal itself being the private key and its impression being the public key. Just as us nostriches use our nsec to sign our notes with integrity and verify value-for-value with our npub.

*Rare bulla seal (shout out to Conny Waters from ancientpages.com)*
*Sumerian cuneiform tablet (source: britannica.com)*At the end of the day, maybe we’re not so different from our ancestors after all. The evolution of our writing technology over the course of our history is more than innovation born of necessity. Across millennia, 3025 BCE to 2025 AD, it's man telling the universe– we will be remembered– beyond space and time. As our ancestors stacked their clay tablets, we’ll stack our sats! Onward nostr! The new land of civilized kings.

*Mankind's Innovations in Writing Technology by Learning Producers, Inc.* -
 @ a93d7cd3:ae5ce5dd
2025-05-20 10:16:55
@ a93d7cd3:ae5ce5dd
2025-05-20 10:16:55Test Nostr
-
 @ 33baa074:3bb3a297
2025-05-19 02:53:31
@ 33baa074:3bb3a297
2025-05-19 02:53:31Distilled water and purified water are different in some aspects. Which one is better depends on personal needs and preferences. The following is a comparative analysis of the two from multiple dimensions:
Water source and process flow Distilled water: The water source usually comes from natural water bodies such as rivers, lakes and seas. It is treated by distillation, that is, water is heated to boiling and water vapor is condensed into liquid water. This process can remove impurities, harmful substances and most minerals in the water.

Purified water: The water source is mainly tap water. Through a series of complex processes such as filtration, adsorption, reverse osmosis, and electrolysis, harmful substances, bacteria, viruses and some minerals in the water are removed to achieve high purity. The process flow is relatively complex and some trace elements that are beneficial to the human body are retained.
Ingredients and nutrition Distilled water: Highly pure, almost no minerals and trace elements. Long-term drinking may cause the human body to lack necessary minerals and trace elements, thus affecting health.
Purified water: After treatment, some trace elements that are beneficial to the human body are retained. While maintaining a high degree of purity, it has certain nutritional value and is more suitable as daily drinking water to meet the basic needs of the human body for water and minerals.
Uses Distilled water: Due to its high purity and impurity-free characteristics, it is widely used in the pharmaceutical industry (such as preparing and diluting various drug solutions, saline, and cleaning wounds, etc.), chemical experiments (dissolving and diluting chemical reagents, preparing chemical solutions, etc.), and industrial production.
Purified water: More used in daily drinking, cooking, and brewing tea and coffee. It has a fresh taste and no odor, which can better preserve the original flavor of food and drinks. It can also be used to prepare infant milk powder and formula milk powder, etc., which is safer and more reliable because it does not contain harmful substances.
Potential risks Distilled water: Due to the lack of minerals and trace elements, it may cause nutritional imbalance in the human body.
Purified water: Although some trace elements are retained, it may also bring potential health risks due to chemical residues in the processing process.
In summary, if you are worried about the loss of minerals, it may be more appropriate to choose purified water; if you think that excessive mineral intake is not good for health, then distilled water may be a better choice. But no matter which one you choose, it is not recommended to drink a large amount of water for a long time. It can be combined with other mineral-rich drinks or foods to maintain the body's nutritional balance.
-
 @ 3f770d65:7a745b24
2024-12-31 17:03:46
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025:
Decentralization: The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
Privacy Standards: Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
Interoperability: Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
Adoption and Migration: Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-
 @ 16d11430:61640947
2024-12-23 16:47:01
@ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence.
The Philosophical Void of Fiat
Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation.
The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence.
Theological Implications: Fiat and the Collapse of the Sacred
Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger.
This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect.
Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests.
Physics and the Infinite Growth Paradox
Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility.
In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself.
Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level.
Biology: The Fiat System and the Destruction of Human Health
Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans.
Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders.
The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse.
Finance as the Final Illusion
At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses.
This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality.
As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems.
The Ultimate Extermination
In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being.
To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
-
 @ a367f9eb:0633efea
2024-12-22 21:35:22
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate Matt Odell, “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine Devolution Review in September 2017, I had a breaking point. The article was titled “Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century”.
It was later republished in Huffington Post and across dozens of financial and crypto blogs at the time with another, more appropriate title: “Bitcoin Has Become About The Payday, Not Its Potential”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
…
The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
I was at least somewhat wrong.
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests on my college radio show, and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at Occupy Tampa in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “How to Avoid Bank Fees Using Bitcoin,” discussing its potential legalization in Germany, and interviewing Jeremy Hansen, one of the first political candidates in the U.S. to accept Bitcoin donations.
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
But I was wrong.
When I gave my first public speech on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
Now I understand I was wrong.
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG Pierre Rochard: Bitcoin as a savings technology.
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “Technological Literacy is Doomed” in 2016.
And I was wrong again.
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now dozens of ways to use Bitcoin privately — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-
 @ 4ba8e86d:89d32de4
2025-05-02 13:51:37
@ 4ba8e86d:89d32de4
2025-05-02 13:51:37Tutorial OpenKeychain
- Baixar no F-droid https://f-droid.org/app/org.sufficientlysecure.keychain
Ao abrir o OpenKeychain pela primeira vez, você verá uma tela inicial indicando que ainda não há chaves configuradas. Nesse ponto, você terá três opções:
-
Criar uma nova chave PGP diretamente no OpenKeychain: Ideal para quem está começando e precisa de uma solução simples para criptografia em comunicações diárias.
-
Usar um token de segurança (como Fidesmo, Yubikey, NEO, ou Sigilance) Se você busca uma segurança ainda maior, pode optar por armazenar sua chave privada em um token de segurança. Com essa configuração, a chave privada nunca é salva no dispositivo móvel. O celular atua apenas como uma interface de comunicação, enquanto a chave permanece protegida no token, fora do alcance de possíveis invasores remotos. Isso garante que somente quem possui o token fisicamente possa usar a chave, elevando significativamente o nível de segurança e controle sobre seus dados.
-
Importar uma chave PGP existente: Você pode importar uma chave PGP que já tenha sido gerada anteriormente, seja por meio de um arquivo no dispositivo ou por outro meio ler na área de transferência. https://image.nostr.build/51fdd924df4843ab73faa02a505c8fb17794f1789396ed89b154348ebb337f07.jpg
1. CRIANDO UMA NOVA CHAVE PGP.
Para iniciantes, recomendamos criar uma nova chave diretamente no aplicativo. abordaremos o uso do OpenKeychain em modo online, que é mais comum para comunicações diárias.
Passo 1: Clique em “Criar minha chave”. https://image.nostr.build/235f5cfdf4c3006ca3b00342741003f79a5055355c2a8ee425fc33c875f51e49.jpg
Passo 2: Criando sua chave PGP.
Para criar sua chave, você precisará fornecer algumas informações Os campos 'Nome' e 'Endereço de e-mail' são apenas formas convenientes para identificar a sua chave PGP.
-
Nome: Escolha um nome ou um pseudônimo. https://image.nostr.build/de3fe3ddbde0c7bf084be6e4b8150fdb8612365550622559b0ee72f50f56a159.jpg
-
E-mail: Associe um endereço de e-mail à chave, seja ele pessoal ou um e-mail relacionado ao pseudônimo. https://image.nostr.build/aff62baaeafe2c9a429ef10435a6f99dea36d6cfd7494e2bb882421dc8ed0f4e.jpg
2. REVISANDO E PERSONALIZANDO A CRIAÇÃO DA CHAVE.
Passo 3: Antes de criar sua chave PGP, verifique se os dados inseridos estão corretos. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
Você também pode personalizar as configurações de segurança clicando nos três pontos no canto superior direito. https://image.nostr.build/1ce615555cea9a979ea951472052a219e77f4e1ebaaf5fcbbe9e91ea4f852bce.jpg
Ao cliclar em ' nova subchave ' pode alterar a data de expiração e pode mudar a criptografia usado na chave cliclando opção ed2255/cv255. https://image.nostr.build/b3224ff3dbe48ff78c4a2df8b001926b6d3eef1e33ef677a73b0d281791073da.jpg https://image.nostr.build/7763c7847e062cdcf71aafedbc2ef4c38056fd66aeb162ef3a1c30c028a14376.jpg https://image.nostr.build/5d3e20ade460dd5e89cc001ebdc062a36aff2c0e1573584ca3c0d1cb34bddcce.jpg
Neste tutorial, utilizaremos as configurações padrão do aplicativo.
Passo 4: Clique em "Criar chave" para concluir o processo. https://image.nostr.build/a8ec09ef3d9b4f557b0c4e380e7ca45d0fdbfa33fe80becea03ed0e5f5eedd24.jpg
3. Como Compartilhar sua Chave PGP Pública
Após criar sua chave PGP, você pode compartilhá-la para que outras pessoas possam enviar mensagens criptografadas para você. Veja o passo a passo de como exibir e compartilhar sua chave pública:
Passo 1: Acesse sua chave pública
Abra o OpenKeychain e selecione a chave que deseja compartilhar. Clique na chave para visualizar os detalhes. https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/4001610109579f27535628932258087b3b06c1f86b05f4f85537b6585c12a10b.jpg
Passo 2: Copiar sua chave pública
Nos detalhes da chave, você verá a opção "Copiar para a Área de Transferência". Clique nessa opção para copiar o código da sua chave pública. https://image.nostr.build/01ab3efa5e997e1910a2f8f7a888e6ad60350574cca4ca0214eee5581797f704.jpg
A chave PGP copiada terá o seguinte formato:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZwsLHRYJKwYBBAHaRw8BAQdA6NRLlJIWnTBJtYwZHlrMbTKRbYuXmjsMn8MB 7etV3HK0JERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPohyBBMW CAAaBAsJCAcCFQgCFgECGQEFgmcLCx0CngECmwMACgkQFZf+kMeJWpR4cwEA8Jt1 TZ/+YlHg3EYphW8KsZOboHLi+L88whrWbka+0s8A/iuaNFAK/oQAlM2YI2e0rAjA VuUCo66mERQNLl2/qN0LuDgEZwsLHRIKKwYBBAGXVQEFAQEHQEj/ZfJolkCjldXP 0KQimE/3PfO9BdJeRtzZA+SsJDh+AwEIB4hhBBgWCAAJBYJnCwsdApsMAAoJEBWX /pDHiVqUo/oA/266xy7kIZvd0PF1QU9mv1m2oOdo7QSoqvgFiq6AmelbAP9lExY5 edctTa/zl87lCddYsZZhxG9g2Cg7xX/XsfrnAA== =TniY -----END PGP PUBLIC KEY BLOCK-----
Dica: Se ocorrer algum erro ao compartilhar sua chave pública com um amigo, peça para que ele a criptografe para ele mesmo. Isso permitirá que ele adicione a chave corretamente. Caso a chave pública ainda não esteja no dispositivo, ao clicar em "Backup de chave", aparecerá a opção para importá-la. Se a chave já estiver no dispositivo, essa ação irá recarregá-la. https://image.nostr.build/cd12abf07c93473db95483fe23112325f89d3eb02977e42756708bbd043f8bcf.jpg https://image.nostr.build/537aeae38d229ee2cc78e18f412237b659c059e1c74fd7f0deecfe37f15713c9.jpg https://image.nostr.build/16c8a3db5966c7c06904ee236655f47a6464ae0c1b5af6af27b28c61611d2bbe.jpg
Passo 3: Compartilhar sua chave PGP
Você pode colar a chave pública em e-mails, assinaturas, perfis de redes sociais ou outros meios para compartilhá-la facilmente. Para facilitar a visualização, você também pode exibi-la em seu perfil de redes sociais.
Para acessar mais opções de compartilhamento, clique nos três pontos no canto superior direito e selecione a opção "Avançado". https://image.nostr.build/0d4a13b7bd9a4794017247d1a56fac082db0f993a2011a4dd40e388b22ec88f5.jpg https://image.nostr.build/4ac2a7bc9fa726531a945221cf7d10e0e387deba68100ccf52fdedfcd17cbd59.jpg
Na seção "Compartilhar", você verá sua Key ID e terá a opção de publicar sua chave PGP em um servidor de chaves. https://image.nostr.build/1e972cc211a6d8060cdbd4a8aa642dd1a292810c532f178d3ddb133d1b9bca76.jpg
Passo 4: Como compartilhar sua chave pública PGP no formato .asc. no OpenKeychain
1 . Acesse sua chave
Abra o OpenKeychain e toque na chave que você deseja compartilhar. Isso abrirá a tela com os detalhes da chave. https://image.nostr.build/c080f03d2eb7a9f7833fec0ff1942a5b70b97e4f7da7c6bc79ca300ef9ace55d.jpg
2 . Compartilhe o arquivo .asc
Toque no ícone de compartilhamento, como indicado na imagem abaixo. O aplicativo abrirá a janela para que você escolha por qual app deseja compartilhar sua chave pública no formato .asc. Nesse exemplo, usei o SimpleXChat , mas você pode usar qualquer aplicativo de sua preferência.
-
Botão de compartilhar. https://image.nostr.build/8da74bdb04737a45df671a30bba1dd2e7980841fa0c2d751d6649630e7c25470.jpg
-
Seleção do aplicativo para compartilhamento. https://image.nostr.build/5444f4e9d3fa5aef6b191bb6f553f94c6e49d30ead874c9ee435bca3218fd6c8.jpg
-
Enviando via SimpleXChat. https://image.nostr.build/e5d1ca04cbc69e1e8ac5caf1ab2a4b9b695500861c1ae9c55cea679cce349214.jpg
Sugestão para compartilhar nas redes sociais:
Você pode exibir sua chave de forma simples, por exemplo:
PGP: 1597 FE90 C789 5A94
Importar a chave pública usando a fingerprint
Passo 1:Clique no ícone "+" para começar. https://image.nostr.build/ca6e6e569b4be60165eaf60c7ba1e6e3ec781b525e467c72b4f3605837e6b5ec.jpg
Passo 2: Selecione a opção "Buscar Chave". https://image.nostr.build/87e27d9435e6e3ef78063b9f15799a8120ead4637cd06c89c0220b48327573ae.jpg
Passo 3: Digite a fingerprint da chave em letras minúsculas, sem espaços. A chave correspondente aparecerá para ser adicionada. https://image.nostr.build/33e6819edd4582d7a8513e8814dacb07e1a62994bb3238c1b5b3865a46b5f234.jpg
Além disso, você pode compartilhar sua chave pública em formato QR Code, facilitando a troca de chaves em eventos ou conversas rápidas. Como Assinar Mensagens para Confirmar a Autenticidade da Sua Rede Social
Você pode autenticar sua conta em redes sociais utilizando sua chave PGP. Ao assinar uma mensagem com sua chave, você demonstra que realmente possui essa conta. Siga o passo a passo abaixo para assinar uma mensagem:
Passo 1: Clique na sua chave PGP. https://image.nostr.build/ffacce1bfb293c9a0888cd5efe340a63d96b293f4c010f8626105c7b212d8558.jpg
Passo 2: Clique no ícone indicado pela seta para abrir o campo de texto. https://image.nostr.build/4e992a2553810e2583b9d190280ce00a52fc423600a75eca48cbf541cf47d3c2.jpg
Passo 3: Deixe a opção "Encriptar para:" vazio. Em "Assinar com:", selecione sua chave PGP e digite a mensagem que deseja enviar, como o nome da sua rede social. https://image.nostr.build/a4a2a8d233d186e3d8d9adddccc445bcb3ca3ed88de0db671a77cede12323a75.jpg
Passo 4: Clique no ícone indicado pela seta para copiar o texto assinado. Uma mensagem aparecerá informando: "Assinado/Encriptado com Sucesso". https://image.nostr.build/a076dfc90e30a495af0872005bf70f412df57b7a0e1c2e17cf5aee9e9b3e39aa.jpg
A mensagem copiada terá o seguinte formato:
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256
Minha rede social NOSTR é Danielfraga oficial. -----BEGIN PGP SIGNATURE-----
iIQEARYIACwlHERhbmllbCBGcmFnYSAgPGRhbmllbGZyYWdhQG1haWwuaTJwPgUC ZxBBLgAKCRAVl/6Qx4lalGeNAPwP71rpsbhRnZhoWZsTDOFZY8ep/d0e5qYx5iPx HV26dwD/fKyiir1TR8JwZvEbOTYS0+Dn4DFlRAAfR3lKVTC96w4= =37Lj -----END PGP SIGNATURE-----
Com isso, você pode facilmente demonstrar a autenticidade da sua conta nas redes sociais.
4. PROTEGENDO SUA CHAVE COM UMA SENHA.
Passo 5: Após a criação da chave, é fundamental definir uma senha (ou passphrase) para adicionar uma camada extra de segurança. Recomendamos usar senhas longas (com mais de 20 caracteres) e de alta entropia para evitar ataques de força bruta. Ferramentas como KeePassDX ou Bitwarden podem ajudá-lo a gerar e gerenciar essas senhas.
Para definir a senha, clique na sua chave PGP, acesse o menu no canto superior direito e selecione "Alterar senha". https://image.nostr.build/689c5237075317e89e183d2664630de973b09b68aaf8f3e3033654e987b781be.jpg https://image.nostr.build/f28ecaa9890a8827f93cac78846c4b2ef67f86ccfc3501fdadf1d1c4874b0041.jpg https://image.nostr.build/919c277fbec63c397402abdd60f915cb239a674c317855cbda63a38edef80789.jpg
Agora basta adicionar uma senha forte. https://image.nostr.build/eb378219fbb1780f89663a474ce43b8d8ebb13beeb538f2a16279b056e5d9645.jpg https://image.nostr.build/cdfa3f9c6c4045841341da789deabb6318107812d5ba195529418572ab352aaf.jpg
5. CRIPTOGRAFAR E DESCRIPTOGRAFAR MENSAGENS E ARQUIVOS COM SUA CHAVE PGP
Criptografar Mensagens
Você pode criptografar mensagens para garantir que apenas o destinatário, que possui sua chave pública, possa lê-las. Siga os passos abaixo para criptografar um texto:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3: Clique na opção "Encriptar Texto".
https://image.nostr.build/405a730a6c774759d7913f92f59059d43146db4afb28451a6f8833f94e99437f.jpgPasso 4: Preencha os seguintes campos: https://image.nostr.build/7dc5eba39ff82a321195dbf46b8113818632e3ef41175991d58e799a8e9d2751.jpg
-
Encriptar para: Selecione o destinatário da mensagem, ou seja, a pessoa para quem você está enviando o texto criptografado.
https://image.nostr.build/1e8c8cba6d3c3136d9857512e2794a81ceb7434eccdfb0f7d26cdef008b2e6d2.jpg -
Assinar com: Escolha sua chave PGP para assinar a mensagem.
https://image.nostr.build/d25b228c35b132d396d01c354ef093b43b3565578fbc0d6ff7b9de4e41619855.jpg -
Digitar o texto: No campo de texto, escreva a mensagem que deseja criptografar.
https://image.nostr.build/8537271dfa4445e60cb4c3cdb5d97571dc0ff5ee8acd6ed89a8c81e4bd8736c2.jpg
Passo 5: Depois de preencher os campos, você pode copiar o texto criptografado de duas formas:
-
Copiar para a área de transferência: Clique na opção para copiar o texto criptografado e cole-o em um aplicativo de mensagens para enviá-lo.
https://image.nostr.build/a5cb8e2c538a38db3972e7f3ac9aa9f602cda6b62848ff0c4b99928a67dcd486.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o texto criptografado diretamente através de seus aplicativos de mensagens.
https://image.nostr.build/2b79cb564d623788a0de1111a067e0eb496f743389d465d4f4e8f6e65f0d08a7.jpg https://image.nostr.build/ff59e52bc8ab54ff377980a6ba5d1c4743d3298de11e5daa187ab7d45163a7be.jpg
Criptografar arquivos.
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção "Encriptar/Descriptar".
https://image.nostr.build/8cd905d616b53968f0551c071d9acc2f47bbe8434c2c7e1a33076a504342de48.jpgPasso 3 : clique na opção "Encriptar arquivos ". https://image.nostr.build/3fcae48ee38e7f4079ebccfd3eafb9ab0ad3559221d2c3560cdfe60e29f56a15.jpg
Passo 4 : os passos a seguir são os mesmo que você seguiu pra encriptar a mensagem texto. Ítens "Encriptar para:" "Assinar com:" https://image.nostr.build/4d6599b9d3a9fdfae0964daaa9dae513d5ce277a7b61930fa2937d534f72ed40.jpg
Passo 5 : clilcar na opção " Adicionair arquivo(s)" Vai abrir na memória interna do celular selecione o arquivo que deseja encriptar. https://image.nostr.build/09e3b9b54a1406426114926aab19011c36b98886ebae6fcf556cfea83bb2c2f4.jpg https://image.nostr.build/af422e243b36762dd66111ec7c848a1352c100ca3040dc21792c923f80aef74d.jpg https://image.nostr.build/ebebbdb273b4bca58d901852aec1c60e4799aa77e9d12a31f992b0cf8f73e753.jpg
Passo 6: Depois de preencher os campos, você pode compartilhar o arquivo criptografado de duas formas:
-
Salvar na memória do celular: A primeira opção salva o arquivo criptografado no armazenamento do seu dispositivo. Você terá a opção de editar o nome do arquivo antes de salvar.
https://image.nostr.build/0a47c1e9f0003541f47091b2c2e8ce6b8d1533d95463e331b218070bae964ac8.jpg https://image.nostr.build/95a7a2b67356eb5ded5b217bab38a19bdeba5af7befd105834e413e0aec45462.jpg https://image.nostr.build/66cb3d22b271f3b73b7015613c72711a3ffbf5e1070d43153f9d1f3fcf35001c.jpg https://image.nostr.build/f9624d86f7592fe7ffad932b7805762dc279d9e8ff410222108155438a2c970f.jpg -
Compartilhar diretamente: Utilize a opção de compartilhamento para enviar o arquivo criptografado diretamente por meio dos seus aplicativos de mensagens.
https://image.nostr.build/85541e466c7755c65bd6ba0208a6d8612beaa5298712b6d92f53865167695a38.jpg https://image.nostr.build/bf1e0f0aeb60cafbdf82af4b3b598288519e85b396bd3f9e00e61f65b89ea9f8.jpg https://image.nostr.build/fb090339898f37cdbb020828689b142ca601ca3ee549f67ddf6b2e094df9ab9f.jpg https://image.nostr.build/50c249ced06efe465ba533fef15207b0dcd1a725e9b2c139e8d85c13fd798276.jpg
Descriptografar Mensagens e Arquivos
Para ler uma mensagem ou arquivo criptografado que você recebeu, utilize sua chave privada. Siga os passos abaixo:
Descriptografar Mensagens
Passo 1: Copie a mensagem criptografada que você recebeu.
https://image.nostr.build/c37754b12a458e0176b9137ae0aa9e8209f853bf9d9292c0867fd8b0606d53c4.jpgPasso 2: Clique na opção "Ler da área de transferência" para descriptografar o texto.
https://image.nostr.build/d83c7dad2ee1cb6267779863bc174ee1a8f3cc3c86b69063345321027bdde7b5.jpg https://image.nostr.build/c0fae86e6ab1fe9dcee86753972c818bed489ea11efdd09b7e7da7422a9c81eb.jpgDescriptografar Arquivos
Passo 1: Clique na opção "Selecionar arquivo de entrada".
https://image.nostr.build/9c276c630311d19a576f2e35b5ba82bac07360476edae3f1a8697ff85df9e3c9.jpgPasso 2: Selecione o arquivo criptografado que deseja descriptografar.
https://image.nostr.build/6b6c2a3284ba96e7168fc7bd0916020c4f1bed7b77dfca48227fc96d6929e15a.jpg https://image.nostr.build/9945aad644af2e2020e07e55f65f11a0958d55e8fc9e13c862e6b9ca88b4f4d9.jpg6. BACKUP E RESTAURAÇÃO DE CHAVE PGP.
Realizar o backup das suas chaves PGP é fundamental para evitar a perda de acesso às suas mensagens e dados criptografados. O OpenKeychain facilita esse processo, permitindo que você faça um backup completo e seguro. Recomendamos que você armazene o backup em um local seguro, como um HD externo ou pendrive conectado via cabo OTG, sempre protegendo-o com senha.
PASSOS PARA REALIZAR O BACKUP:
Passo 1: Abra o menu lateral clicando no ícone no canto superior esquerdo.
https://image.nostr.build/13ac93b38dd1633118ae3142401c13e8a089caabdf4617055284cc521a45b069.jpgPasso 2: Selecione a opção Backup/restaurar.
https://image.nostr.build/6fa8fd14e23b47c6c924bc0d900646663f2124a93d8172ae79fdf43b5c7d4490.jpgPasso 3: Escolha a primeira opção: Backup completo (criptografado).
https://image.nostr.build/4875fb27b6d04c3cb838b4fb9f308ef9194edc35ba1254ba965b7f0db2544170.jpgPasso 4: O backup será protegido por um código de backup gerado automaticamente. Anote esse código em um papel e guarde local seguro, pois sem ele você não conseguirá recuperar suas chaves PGP. Após anotar o código, marque a opção “Anotei o código” e clique em Salvar Backup. Obs: todas as vezes que você for fazer o backup da sua chave PGP vai ser criado um novo código aleatório.
https://image.nostr.build/72a317ef5e59a01c03c36f1d04a91d42c418a478cc82e372acf21bb8302daa00.jpg
Passo 5: Escolha o local onde deseja salvar o backup (HD externo, pendrive, etc.), confirme sua escolha e clique em OK. Você verá uma mensagem de confirmação indicando que o backup foi salvo com sucesso.
https://image.nostr.build/d757e8bdf429371320daa44be8a48a0dbeb2324129f4254327f0f0383e70ede4.jpg https://image.nostr.build/f3ad80ceb8a191b4d1b40722b1d0d4f85bf183d412e7d7d901b25d19b2dfe0e3.jpg
Importação da Chave PGP
Caso você precise restaurar suas chaves PGP a partir de um backup, o OpenKeychain também facilita o processo de importação. Siga os passos abaixo para restaurar sua chave PGP:
Passo 1: Selecione a opção "Selecionar arquivo de entrada"
Abra o OpenKeychain, acesse o menu lateral no canto superior esquerdo e escolha a opção "Selecionar arquivo de entrada" para localizar o arquivo de backup que você deseja importar.
https://image.nostr.build/a06ddc1c1e6c50519097e614aa25b14311e49c0ca4d4607e42ebdcca3a6641c4.jpgPasso 2: Selecione o arquivo de backup
Navegue até o local onde você salvou o arquivo de backup (HD externo, pendrive, etc.) e selecione-o. Em seguida, o OpenKeychain solicitará que você insira o código de recuperação que foi gerado no momento do backup. https://image.nostr.build/9d5649c04a98ec8b0a29355d9068e48313b1c5dc36cd965961f4d33f22d10046.jpgPasso 3: Digite o código de recuperação
Insira o código de recuperação que você anotou anteriormente. É importante digitar o código corretamente para garantir o sucesso da restauração.Passo 4: Depois de inserir o código corretamente, o OpenKeychain irá restaurar suas chaves PGP, e uma mensagem de confirmação será exibida, indicando que a recuperação foi concluída com sucesso.
Agora suas chaves estão restauradas e você pode continuar usando o OpenKeychain para gerenciar suas comunicações criptografadas de maneira segura.
https://www.openkeychain.org/
https://github.com/open-keychain/open-keychain
https://youtu.be/fptlAx_j4OA
-
 @ 9bcc5462:eb501d90
2024-12-19 16:14:46
@ 9bcc5462:eb501d90
2024-12-19 16:14:46This event has been deleted; your client is ignoring the delete request.
-
 @ b099870e:f3ba8f5d
2025-05-20 11:14:41
@ b099870e:f3ba8f5d
2025-05-20 11:14:41The fools in life want things fast and easy – money, success, attention. Boredom is their great enemy and fear. Whatever they manage to get slips through their hands as fast as it comes in. You, on the other hand, want to outlast your rivals. You are building the foundation for something that can continue to expand. To make this happen, you will have to serve an apprenticeship. You must learn early on to endure the hours of practice and drudgery, knowing that in the end all of that time will translate into a higher pleasure – mastery of a craft and of yourself. Your goal is to reach the ultimate skill level – an intuitive feel for what must come next.
Quote from The 50th Law that I'm currently reading







