-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 909e3fdc:73f2b10a
2025-05-22 02:14:38
@ 909e3fdc:73f2b10a
2025-05-22 02:14:38Pizza Day’s not really about pizza. It’s about Laszlo exhibiting Bitcoin as a P2P payment mechanism. That’s worth a cheers. In 15 years, Bitcoin went from a nerdy experiment to challenging the fiat system. That’s massive! It’s changed how I see the world. Patient hodling and carnivore-focus, practices that I picked up from the bitcoin community, shifted me from kinda nihilistic to stupidly optimistic. So, definitely celebrate Pizza Day. Or maybe barbecue steaks instead. Commiserate on the frivolous purchases that you made with bitcoin in the day. I think of these sometimes. Honour Laszlo’s pioneer vibe and Bitcoin’s insane rise, but keep your eyes on what’s coming. The future’s gonna be wilder than we think.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 75869cfa:76819987
2025-04-28 14:51:12
@ 75869cfa:76819987
2025-04-28 14:51:12GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 216,000 daily trusted pubkey events. The number of new users has seen a notable decrease, Profiles with contact lists and pubkeys writing events were both representing a 70% decline. More than 7 million events have been published, reflecting a 24% decrease. Total Zap activity stands at approximately 16 million, marking a 20% increase.
Additionally, 14 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 7 releasing product updates, and over 378 long-form articles were published, 24% focusing on Bitcoin and Nostr. During this period, 9 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 216,000, representing a slight 2 % decrease compared to the previous period. Daily activity peaked at 17483 events, with a low of approximately 15499.
The number of new users has decreased significantly.Profiles with contact lists and pubkeys writing events were 26,132 and 59,403 respectively, both representing a decline of approximately 70% compared to the previous period.
The total number of note events published is around 7 million, reflecting a 24% decrease.Posts remain the most dominant category by volume, totaling approximately 1.7 million, representing a 4% decrease compared to the previous period.Reposts, however, saw a significant increase, rising by 33% compared to the same period.
For zap activity, the total zap amount is about 16 million, showing an decrease of over 20% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Allow multi-user AUTH #1881 vitorpamplona is proposing a PR that reuses one connection for everyone by accepting multi-user logins on the relay side. Additionally, this PR standardizes how relays should handle multiple AUTH messages from the client, instead of leaving it as undefined behavior. Currently, most relays override the previous AUTH, which means developers can rotate the authenticated user within the same connection. Some relays only accept the first AUTH and ignore the rest. A few newer relays already support multi-user logins as described in this PR, which he believes is the correct way to implement NIP-42 AUTH. The purpose of this PR is to formalize that behavior.
Adds optional nip60.signSecret() and kind 10019 filter tag #1890 robwoodgate is proposing a PR that clarifies and improves Nostr <---> Cashu interoperability as follows:Adds an optional signer signature for NUT-10 well-known secrets to NIP-60, NIP-07 and NIP-46;Clarifies use of Nostr <---> Cashu public keys in NIP-61;Adds an optional reverse lookup filter tag to NIP-61 kind 10019 events.
Notable Projects
Coracle 0.6.10 nostr:npub13myx4j0pp9uenpjjq68wdvqzywuwxfj64welu28mdvaku222mjtqzqv3qk
Coracle 0.6.10 release is out on the web and zapstore! This is another maintenance release, including a complete rewrite of the networking code (coming soon to flotilla), and several bug fixes. * Fix spotify url parsing bug * Fix nip46 signer connect * Use new version of network library * Fix reply drafts bug * Fix creating a new account while logged in * Re-work storage adapter to minimize storage and improve performance * Improve initial page load times * Fix followers page * Upgrade welshman * Remove platform relay * Show PoW * Don't fetch messages until decryption is enabled
Damus v1.14 nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
A new TestFlight release is here for Purple users to try! * ️Setup a wallet lightning fast with our new one-click wallet setup, powered by Coinos! * New revamped wallet experience with balance and transactions view for your NWC wallet — see how much you got zapped without even leaving the app! * New notification setting to hide hellthreads. ie. Achieve notification peace. * NIP-65 relay list support — more compatibility across Nostr apps! * Unicode 16 emoji reactions (only for iOS 18.4+) - even more options to express your reactions! * Blurred images now show some more information — no more wondering why images are occasionally blurred. * More bugs fixed, and general robustness improvements.
0xchat v1.4.9 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
What's new: * Implemented updated NIP-29 group logic with support for group admin roles * Added support for Aegis URL scheme login on iOS
YakiHonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🌐web v4.6.0: * Introducing Smart Widgets v2 – now dynamic and programmable. Learn more at https://yakihonne.com/docs/sw/intro * New Tools Smart Widgets section in note creation for advanced content editing. * Curations, videos, and polls are now Tools Smart Widgets, enabling quick creation and seamless embedding in notes. * Zap advertisements added—top zappers can now appear below notes. * Note translation button has been relocated next to the note options for easier access. * Followers and following lists are now visible directly on the dashboard home page. * General improvements and bug fixes for a smoother experience.
📱mobile v1.7.0: * Introducing the fully upgraded smart widget with its expanded set of functionalities. * A set of tools to enhance content editing. * Curations, videos, and polls are now Tools Smart Widgets, enabling quick creation and seamless embedding in notes. * Shortened URLs for a better user experience. * Highest zappers in notes will be highlighted. * Zapper list now includes zaps messages. * Videos and curations are no longer visible in the app. * Gossip models can be enabled and disabled. * Fixed multiple bugs for a more stable and seamless app experience. * Enhanced overall performance, usability, and design across the app.
Nostur v1.20 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Added support for Lists (kind 30000) * Show preview of feed from list * Turn list into feed tab with 1 tap * Subscribe toggle to keep updating the feed from original maintainer, or keep list as-is * Share List: Toggle to make list public * Lists tab on Profile view * 'Add all contacts to feed/list' post menu item * Discover tab now shows Lists shared by your follows * Enable manual ordering of custom feeds / tabs * New Top Zapped feed * New onboarding screens * New default color scheme / adjusted backgrounds * Lower delays and timeouts for fetching things * Improved hellthread handling * Support for comment on highlights (kind 9802) * Toggle to post to restricted/locked relay when starting post from single relay feed * Support relay auth for bunker/remote signer accounts * Zoom for previous profile pictures * Improved Relay Autopilot / Outbox when loading a single profile, always try to find 2 additional relays not in already used relay set * Improved support for accounts with large follow lists * Keep things longer in cache on desktop version * Improved support for pasting animated gifs * Use floating mini video player also on iPad and Desktop * Many performance improvements and bugfixes
Zapstore 0.2.6 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8
- Fixes for stale data, apps should now show their latest versions
- Upgrade to nostr:npub1kpt95rv4q3mcz8e4lamwtxq7men6jprf49l7asfac9lnv2gda0lqdknhmz DVM format
- New Developer screen (basic for now, delete local cache if apps are missing!)
ZEUS v0.11.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.11.0-alpha 2 with Cashu support is now available for testing. In this build: * Fix: addresses an issue where some Cashu wallets would crash when redeeming their first token. If you were affected by this bug, try removing the mint in question and re-adding it with the 'Existing funds' toggle enabled. FUNDS ARE SAFU! * Feat: Core Lightning: show closed channels list * Locale updates
Long-Form Content Eco
In the past two weeks, more than 378 long-form articles have been published, including over 57 articles on Bitcoin and more than 32 related to Nostr, accounting for 24% of the total content.
These articles about Nostr mainly explore the protocol’s steady evolution toward simplicity, decentralization, and practical usability. There is a clear call within the community to strip away unnecessary complexity and return to Nostr’s minimalist roots, emphasizing lightweight structures and user autonomy. At the same time, a wave of innovation is expanding Nostr’s possibilities—new marketplaces, interoperable bridges with other protocols, and creative tools for publishing, identity, and social interaction are emerging rapidly. The articles also reflect a growing focus on censorship resistance, advocating for more diverse and independent relay networks, encrypted communications between relays, and broader user control over data and publishing. Practical guides and firsthand user experiences reveal both the excitement and the challenges of building within an open, permissionless ecosystem.
These articles about Bitcoin depict the evolution and expansion of the Bitcoin ecosystem from various perspectives. On the technical front, they focus on the iteration of Bitcoin Core versions, innovations in secure storage methods, advancements in multisignature solutions and post-quantum cryptography, as well as the ongoing optimization of payment tools like the Lightning Network, highlighting Bitcoin's continuous progress in enhancing asset security and transaction efficiency. At the same time, through real-life stories and personal experiences, many articles illustrate Bitcoin's practical role in individuals' lives, showing how it helps people achieve financial autonomy, build resilience, and transform their lifestyles in times of turmoil. From a financial perspective, the articles delve into Bitcoin’s unique value as digital gold and an inflation hedge, and its function as a safe haven and transformative force in emerging economies and shifting trade environments.
Thank you, nostr:npub1jp3776ujdul56rfkkrv8rxxgrslqr07rz83xpmz3ndl74lg7ngys320eg2 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1qd6zcgzukmydscp3eyauf2dn6xzgfsevsetrls8zrzgs5t0e4fws7re0mj nostr:npub12q4tq25nvkp52sluql37yr5qn059qf3kpeaa26u0nmd7ag5xqwtscduvuh nostr:npub1t49ker2fyy2xc5y7qrsfxrp6g8evsxluqmaq09xt7uuhhzsurm3srw4jj5 nostr:npub1p7dep69xdstul0v066gcheg2ue9hg2u3pngn2p625auyuj57jkjscpn02q nostr:npub1l0cwgdrjrxsdpu6yhzkp7zcvk2zqxl20hz8mq84tlguf9cd7dgusrmk3ty nostr:npub1fn4afafnasdqcm7hnxtn26s2ye3v3g2h2xave7tcce6s7zkra52sh7yg99 npub1jh95xvxnqdqj5ljh3vahh7s7s0pv9mj9sfrkdnx4xgead9kmwpkq2e0fqm,npub1qn4ylq6s79tz4gwkphq8q4sltwurs6s36xsq2u8aw3qd5ggwzufsw3s3yz,npub1penlq56qnlvsr7v3wry24twn6jtyfw5vt6vce76yawrrajcafwfs0qmn5s,and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * Recently, YakiHonne collaborated with multiple communities and universities across Africa, such as nostr:npub1yp5maegtq53x536xcznk2hqzdtpgxg63hzhl2ya3u4nrtuasxaaqa52pzn nostr:npub1tk59m73xjqq7k3hz9hlwsvspu2xq7t9gg0qj86cgp4rrlqew5lpq5zq7qp nostr:npub1wjncl8k8z86qq2hwqqeufa4g9z35r5t5wquawxghnrs06z9ds8zsm49yg7 and more, to successfully host seven Nostr Workshops, attracting over 200 enthusiastic participants. The events not only provided a comprehensive introduction to the Nostr ecosystem and Bitcoin payments but also offered hands-on experiences with decentralized technologies through the YakiHonne platform.
- The second BOBSpace Nostr Month Meetup took place on Friday, April 25, 2025, at 6:30 PM in Bangkok. This special event featured nostr:npub18k67rww6547vdf74225x4p6hfm4zvhs8t8w7hp75fcrj0au7mzxs30202m the developer of Thailand’s home-grown Nostr client Wherostr, as the guest speaker. He shared his developer journey, the story behind building Wherostr, and how Nostr enables censorship-resistant communication. This was a Bitcoin-only meetup focused on the Nostr protocol and decentralized technologies.
- Panama Blockchain Week 2025 took place from April 22 to 24 at the Panama Convention Center in Panama City. As the first large-scale blockchain event in Central America, it aimed to position Panama as a leading blockchain financial hub in Latin America. The event featured a diverse lineup, including a blockchain conference, Investor’s Night, Web3 gaming experiences, tech exhibitions, and an after-party celebration.
Here is the upcoming Nostr event that you might want to check out. * Nostr & Poker Night will be held on April 30 at the Bitcoin Embassy in El Salvador. The event will feature an exciting Nostr-themed presentation by nostr:npub1dmnzphvk097ahcpecwfeml08xw8sg2cj4vux55m5xalqtzz9t78q6k3kv6 followed by a relaxed and fun poker night. Notably, 25% of the poker tournament prize will be donated to support MyfirstBitcoin’s Bitcoin education initiatives. * A free webinar on venture capital, Bitcoin, and cryptocurrencies will be held online on May 6 at 12:00 PM (ARG time). Organized in collaboration with Draper Cygnus, the event aims to introduce the fundamentals of venture capital, present the projects of ONG Bitcoin Argentina Academy, and provide attendees with the opportunity to interact with the guest speakers. * Bitcoin Unveiled: Demystifying Freedom Money will take place on May 10, 2025, at Almara Hub. The event will explore Bitcoin’s transformative potential, helping participants understand its purpose, learn how to get started, build a career in the Bitcoin space, and begin their Bitcoin savings journey. Featured speakers include nostr:npub1sn0q3zptdcm8qh8ktyhwtrnr9htwpykav8qnryhusr9mcr9ustxqe4tr2x Theophilus Isah, nostr:npub1s7xkezkzlfvya6ce6cuhzwswtxqm787pwddk2395pt9va4ulzjjszuz67p , and Megasley.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 6cc4225f:942b7222
2024-12-30 00:32:47
@ 6cc4225f:942b7222
2024-12-30 00:32:47(Cover image photo credit: The Crypto Times)
“Our world of widows needs to be saved / it’s now or never — victim or victory, rebel or regret / who you are and who you claim to be / no more heroes.” -Converge, “No Heroes”
Usually, bad takes from big figures in the Bitcoin space roll off my back. I often don’t feel a need to counter them because 1.) Everyone is entitled to their opinion and 2.) I don’t enjoy spending my time arguing with people on the Internet.
But when a take is really bad — downright evil — I feel compelled to respond.
And respond I did to a bad take this week (link in just a second, first some context).
Lately in the media, MicroStrategy Chair Michael Saylor has been laying out his vision for a digital asset framework.
This framework includes conceptualizing Bitcoin as a commodity — nothing more than capital — and stablecoins like Tether (USDT) and USD Coin (USDC) as “digital currencies” (his words).
As if someone who considers themselves a “triple bitcoin maxi” (maybe one of the lamest terms ever) denying that bitcoin is a currency weren’t nauseating enough, his “evil genius plan” (his words) to get the world hooked on USD stablecoins as money while the US hoards bitcoin should have you upchuck everything in your guts if you truly believe in Bitcoin’s value proposition.
Below (a few lines down) is the piece I wrote countering Saylor’s perspective.
If there are two things I hope you take away from it, the first is to KILL YOUR IDOLS (not literally, of course) and the second is that WE ARE BITCOIN, and if we believe in the technology — all dimensions of it — we have to defend it.
Enjoy.
Michael Saylor Doesn't Understand Bitcoin
## Support The Open Dialogue Foundation
Speaking of defending Bitcoin, we all owe a debt of gratitude to the work that the Open Dialogue Foundation (ODF) is doing to defend our legal right to use non-custodial bitcoin wallets.
Please read the following piece I wrote this week to learn more.
Protect Your Non-Custodial Bitcoin Wallet — Support The Open Dialogue Foundation
And please make a tax-deductible contribution (before the year’s end) to the organization here.
Bitcoin’s Second Book-Length Academic Text — The Satoshi Papers — Coming Soon
This week, I published my interview with Natalie Smolenski, a PhD-holding theoretical anthropologist who often makes very valuable thought contributions to the Bitcoin space.
What I loved most about this interview (and I loved a lot about it) is Smolenski’s lack of reverence.
Two of my favorite quotes from the interview:
“There was kind of a triumph of a certain very statist approach to socialism and even communism in the American academy, in the Anglophone academy, that has persisted to this day, where there's, like I was saying earlier, a suspicion of anything smacking of individualism as bourgeois conceit or reinscribing social hierarchies, racial hierarchies, gender hierarchies, blah, blah, blah.”
The “blah, blah, blah” hit hard. It reminded me of how I used to tune out when speaking with a good portion of my co-workers during the years I taught at the college level.
The other one:
“What do you hope people will take away from The Satoshi Papers?
*> If there's only one idea that people take away from it, it's that your emancipation does not require the state. You do not need to wait for the government.
*> My God, take control of your life. You can, it is within your power to do so, and here are some examples of ways that people throughout human history have chosen to do so."
The “My God” was so properly placed. Chef’s kiss.
Check out to entire piece to absorb more of Smolenski’s wisdom.
Thank you all for reading, and here’s to a great week ahead!
Best,
Frank
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ 6e0ea5d6:0327f353
2025-05-20 01:35:20
@ 6e0ea5d6:0327f353
2025-05-20 01:35:20**Ascolta bene! ** A man's sentimental longing, though often disguised in noble language and imagination, is a sickness—not a virtue.
It begins as a slight inclination toward tenderness, cloaked in sweetness. Then it reveals itself as a masked addiction: a constant need to be seen by a woman, validated by her, and reciprocated—as if someone else's affection were the only anchor preventing the shipwreck of his emotions.
The man who understands the weight of leadership seeks no applause, no gratitude, not even romantic love. He knows that his role is not theatrical but structural. He is not measured by the emotion he evokes, but by the stability he ensures. Being a true man is not ornamental. He is not a decorative symbol in the family frame.
We live in an era where male roles have been distorted by an overindulgence in emotion. The man stopped guiding and began asking for direction. His firmness was exchanged for softness, his decisiveness for hesitation. Trying to please, many have given up authority. Trying to love, they’ve begun to bow. A man who begs for validation within his own home is not a leader—he is a guest. And when the patriarch has to ask for a seat at the table he should preside over and sustain, something has already been irreversibly inverted.
Unexamined longing turns into pleading. And all begging is the antechamber of humiliation. A man who never learned to cultivate dignified solitude will inevitably fall to his knees in desperation. And then, he yields. Yields to mediocre presence, to shallow affection, to constant disrespect. He smiles while he bleeds, praises the one who despises him, accepts crumbs and pretends it’s a banquet. All of it, cazzo... just to avoid the horror of being alone.
Davvero, amico mio, for the men who beg for romance, only the consolation of being remembered will remain—not with respect, but with pity and disgust.
The modern world feeds the fragile with illusions, but reality spits them out. Sentimental longing is now celebrated as sensitivity. But every man who nurtures it as an excuse will, sooner or later, pay for it with his dignity.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 08f96856:ffe59a09
2025-05-15 01:17:18
@ 08f96856:ffe59a09
2025-05-15 01:17:18เมื่อพูดถึง Bitcoin Standard หลายคนมักนึกถึงภาพโลกอนาคตที่ทุกคนใช้บิตคอยน์ซื้อกาแฟหรือของใช้ในชีวิตประจำวัน ภาพแบบนั้นดูเหมือนไกลตัวและเป็นไปไม่ได้ในความเป็นจริง หลายคนถึงกับพูดว่า “คงไม่ทันเห็นในช่วงชีวิตนี้หรอก” แต่ในมุมมองของผม Bitcoin Standard อาจไม่ได้เริ่มต้นจากการที่เราจ่ายบิตคอยน์โดยตรงในร้านค้า แต่อาจเริ่มจากบางสิ่งที่เงียบกว่า ลึกกว่า และเกิดขึ้นแล้วในขณะนี้ นั่นคือ การล่มสลายทีละน้อยของระบบเฟียตที่เราใช้กันอยู่
ระบบเงินที่อิงกับอำนาจรัฐกำลังเข้าสู่ช่วงขาลง รัฐบาลทั่วโลกกำลังจมอยู่ในภาระหนี้ระดับประวัติการณ์ แม้แต่ประเทศมหาอำนาจก็เริ่มแสดงสัญญาณของภาวะเสี่ยงผิดนัดชำระหนี้ อัตราเงินเฟ้อกลายเป็นปัญหาเรื้อรังที่ไม่มีท่าทีจะหายไป ธนาคารที่เคยโอนฟรีเริ่มกลับมาคิดค่าธรรมเนียม และประชาชนก็เริ่มรู้สึกถึงการเสื่อมศรัทธาในระบบการเงินดั้งเดิม แม้จะยังพูดกันไม่เต็มเสียงก็ตาม
ในขณะเดียวกัน บิตคอยน์เองก็กำลังพัฒนาแบบเงียบ ๆ เงียบ... แต่ไม่เคยหยุด โดยเฉพาะในระดับ Layer 2 ที่เริ่มแสดงศักยภาพอย่างจริงจัง Lightning Network เป็น Layer 2 ที่เปิดใช้งานมาได้ระยะเวลสหนึ่ง และยังคงมีบทบาทสำคัญที่สุดในระบบนิเวศของบิตคอยน์ มันทำให้การชำระเงินเร็วขึ้น มีต้นทุนต่ำ และไม่ต้องบันทึกทุกธุรกรรมลงบล็อกเชน เครือข่ายนี้กำลังขยายตัวทั้งในแง่ของโหนดและการใช้งานจริงทั่วโลก
ขณะเดียวกัน Layer 2 ทางเลือกอื่นอย่าง Ark Protocol ก็กำลังพัฒนาเพื่อตอบโจทย์ด้านความเป็นส่วนตัวและประสบการณ์ใช้งานที่ง่าย BitVM เปิดแนวทางใหม่ให้บิตคอยน์รองรับ smart contract ได้ในระดับ Turing-complete ซึ่งทำให้เกิดความเป็นไปได้ในกรณีใช้งานอีกมากมาย และเทคโนโลยีที่น่าสนใจอย่าง Taproot Assets, Cashu และ Fedimint ก็ทำให้การออกโทเคนหรือสกุลเงินที่อิงกับบิตคอยน์เป็นจริงได้บนโครงสร้างของบิตคอยน์เอง
เทคโนโลยีเหล่านี้ไม่ใช่การเติบโตแบบปาฏิหาริย์ แต่มันคืบหน้าอย่างต่อเนื่องและมั่นคง และนั่นคือเหตุผลที่มันจะ “อยู่รอด” ได้ในระยะยาว เมื่อฐานของความน่าเชื่อถือไม่ใช่บริษัท รัฐบาล หรือทุน แต่คือสิ่งที่ตรวจสอบได้และเปลี่ยนกฎไม่ได้
แน่นอนว่าบิตคอยน์ต้องแข่งขันกับ stable coin, เงินดิจิทัลของรัฐ และ cryptocurrency อื่น ๆ แต่สิ่งที่ทำให้มันเหนือกว่านั้นไม่ใช่ฟีเจอร์ หากแต่เป็นความทนทาน และความมั่นคงของกฎที่ไม่มีใครเปลี่ยนได้ ไม่มีทีมพัฒนา ไม่มีบริษัท ไม่มีประตูปิด หรือการยึดบัญชี มันยืนอยู่บนคณิตศาสตร์ พลังงาน และเวลา
หลายกรณีใช้งานที่เคยถูกทดลองในโลกคริปโตจะค่อย ๆ เคลื่อนเข้ามาสู่บิตคอยน์ เพราะโครงสร้างของมันแข็งแกร่งกว่า ไม่ต้องการทีมพัฒนาแกนกลาง ไม่ต้องพึ่งกลไกเสี่ยงต่อการผูกขาด และไม่ต้องการ “ความเชื่อใจ” จากใครเลย
Bitcoin Standard ที่ผมพูดถึงจึงไม่ใช่การเปลี่ยนแปลงแบบพลิกหน้ามือเป็นหลังมือ แต่คือการ “เปลี่ยนฐานของระบบ” ทีละชั้น ระบบการเงินใหม่ที่อิงอยู่กับบิตคอยน์กำลังเกิดขึ้นแล้ว มันไม่ใช่โลกที่ทุกคนถือเหรียญบิตคอยน์ แต่มันคือโลกที่คนใช้อาจไม่รู้ตัวด้วยซ้ำว่า “สิ่งที่เขาใช้นั้นอิงอยู่กับบิตคอยน์”
ผู้คนอาจใช้เงินดิจิทัลที่สร้างบน Layer 3 หรือ Layer 4 ผ่านแอป ผ่านแพลตฟอร์ม หรือผ่านสกุลเงินใหม่ที่ดูไม่ต่างจากเดิม แต่เบื้องหลังของระบบจะผูกไว้กับบิตคอยน์
และถ้ามองในเชิงพัฒนาการ บิตคอยน์ก็เหมือนกับอินเทอร์เน็ต ครั้งหนึ่งอินเทอร์เน็ตก็ถูกมองว่าเข้าใจยาก ต้องพิมพ์ http ต้องรู้จัก TCP/IP ต้องตั้ง proxy เอง แต่ปัจจุบันผู้คนใช้งานอินเทอร์เน็ตโดยไม่รู้ว่าเบื้องหลังมีอะไรเลย บิตคอยน์กำลังเดินตามเส้นทางเดียวกัน โปรโตคอลกำลังถอยออกจากสายตา และวันหนึ่งเราจะ “ใช้มัน” โดยไม่ต้องรู้ว่ามันคืออะไร
หากนับจากช่วงเริ่มต้นของอินเทอร์เน็ตในยุค 1990 จนกลายเป็นโครงสร้างหลักของโลกในสองทศวรรษ เส้นเวลาของบิตคอยน์ก็กำลังเดินตามรอยเท้าของอินเทอร์เน็ต และถ้าเราเชื่อว่าวัฏจักรของเทคโนโลยีมีจังหวะของมันเอง เราก็จะรู้ว่า Bitcoin Standard นั้นไม่ใช่เรื่องของอนาคตไกลโพ้น แต่มันเกิดขึ้นแล้ว
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c1831fbe:de4b39bf
2025-05-17 09:57:04
@ c1831fbe:de4b39bf
2025-05-17 09:57:04What follows is my best effort to recall the details of an arguably supernatural encounter I experienced almost sixty years ago. I've told this story many times before, and while my recollection may not be perfect in every detail, my account is real and substantively factual.
It was early one long ago morning, in that twilit between-time shortly before dawn. As I dangled precariously in a quasi-aware state, hovering on the knife edge between wakefulness and sleep, I was transported in a dream to another place and time. Was it the Mediterranean coast? Perhaps ancient Greece?
In my mind's eye, I found myself climbing a rather steep, rocky hillside overlooking a sparkling bright blue sea. Ahead of me, and slightly higher, was what appeared to be a young shepherd boy, leading me ever higher up the hill.
As we wove our way upward,
skirting rocky outcroppings and zig-zagging because of the steepness of the slope, I heard the boy chanting:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
He kept repeating the mantra, over and over:
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
\~ \~ \~
"Ata, Ata, Archontos, Ata, Ata, Echousi, Ata, Ata, Archousi"
I listened for a few cycles, and then took up the chant myself. After several attempts, when at last I got it right, the shepherd boy turned, looking back at me and smiling broadly to signal that I had finally mastered the cadence and the words.
Then I awoke.
Because my dream had been so vivid and unusual, I immediately found a pencil and paper to write down the chant phonetically before I could forget it.
A few days passed.
Life was busy. Then I remembered my friend in grad school, studying biblical Greek. That weekend, I went and hung out with him while he worked his night job at the college heating plant. Between his rounds inspecting and managing the steam boilers keeping students from freezing to death in the Arctic Midwest winter, I told him about my strange dream.
Pulling out an exhaustive Greek lexicon, one by one, my knowledgeable friend looked up the words from my dream, interpreting each according to its verb conjugation, tense, and mood.
"Ata, Ata" had no discernible meaning; we soon concluded that it was probably just meaningless vocables, added to give the chant rhythm and substance. My friend moved on to the first recognizable word of the chant...
"Archontos" - "They are ruled."
OK, so far, so good. He checked the next word:
"Echousi" - "They shed blood."
Hmmmm... This chant is beginning to appear to be more than random sounds.
"Archousi" - "They rule."
At this point, I almost fell out of my chair in shock. Far from being a meaningless chant, this cycle—repeating again and again—is the seemingly never-ending story of the entirety of human history...
"They Are Ruled, They Shed Blood, They Rule."
\~ \~ \~
"They Are Ruled, They Shed Blood, They Rule."
This concise mantra perfectly captures the endlessly repeating cycle of oppression, revolt, and revolution that always leaves us with a fresh set of oppressors all too ready to replace the last.
Who will rescue us?
Who will redeem us from this endless tedious cycle into which we have been born?
A long lifetime of study and reflection has persuaded me that this deadly cycle can and ultimately will be broken. If we follow the teachings of Jesus; if we love one another and live together in voluntary, local societies, serving each other; I am persuaded that we can break free of this desperately destructive cycle of endlessly seeking to dominate one another. It's past time for us to enter into a mutually beneficial life in the Kingdom of our Creator-God Jesus, the most authentically benevolent King the universe has ever known.
stories #politics #Christianity #supernatural #strange
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 90c656ff:9383fd4e
2025-05-24 12:11:01
@ 90c656ff:9383fd4e
2025-05-24 12:11:01Since its creation, Bitcoin has marked a turning point in the digital money revolution—but its evolution didn’t stop at the original concept of decentralized transactions. Over the years, new technological solutions have been developed to expand its capabilities, making it more efficient and versatile. Among these innovations, smart contracts and the Lightning Network stand out, enabling increased functionality and scalability of the network, and ensuring a faster, cheaper, and more accessible system.
Smart contracts on Bitcoin
Smart contracts are programs that automatically execute certain actions when predefined conditions are met. Although the concept is more commonly associated with other networks, Bitcoin also supports smart contracts, especially through upgrades like Taproot.
- Smart contracts on Bitcoin enable functionalities such as:
01 - Conditional payments: Transactions that are only completed if certain rules are met, such as multi-signatures or specific time conditions.
02 - Advanced fund management: Use of multi-signature wallets, where different parties must approve a transaction before it is processed.
03 - Enhanced privacy: With the Taproot upgrade, smart contracts can be more efficient and indistinguishable from regular transactions, improving privacy across the network.
Although smart contracts on Bitcoin are simpler than those on other platforms, this simplicity is a strength—it preserves the network's security and robustness by avoiding complex vulnerabilities.
Lightning Network: scalability and instant transactions
One of the biggest challenges Bitcoin faces is scalability. Since the original network was designed to prioritize security and decentralization, transaction speed can be limited during periods of high demand. To address this issue, the Lightning Network was created—a second-layer solution that enables near-instant transactions with extremely low fees.
The Lightning Network works by creating payment channels between users, allowing them to conduct multiple transactions off-chain and recording only the final balance on the main Bitcoin blockchain or timechain. Key advantages include:
01 - Speed: Transactions are completed in milliseconds, making Bitcoin more suitable for daily payments.
02 - Low fees: Since transactions occur off-chain, fees are minimal, allowing for viable microtransactions.
03 - Network decongestion: By moving many transactions to the Lightning Network, Bitcoin’s main chain becomes more efficient and less congested.
In summary, Bitcoin continues to evolve technologically to meet the demands of a global financial system. Smart contracts increase its functionality, offering greater flexibility and security in transactions. The Lightning Network improves scalability, making Bitcoin faster and more practical for everyday use. With these innovations, Bitcoin remains at the forefront of the financial revolution, proving that despite its initial limitations, it continues to adapt and grow as a truly decentralized and global monetary system.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
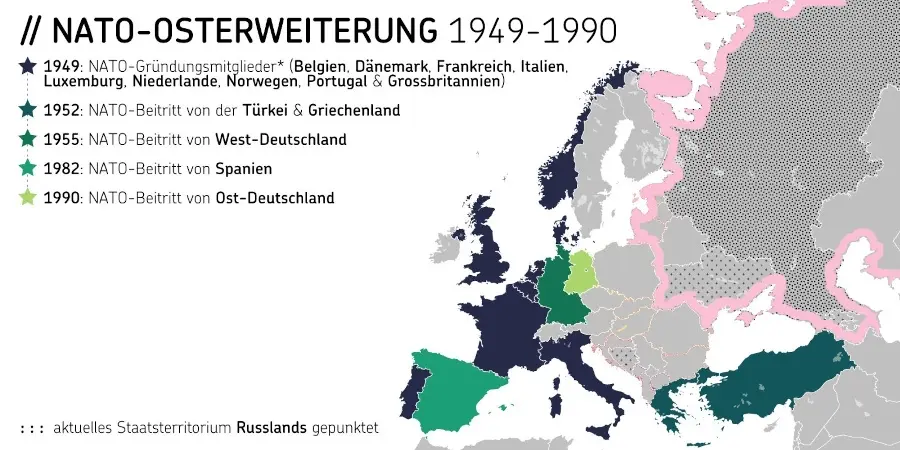
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
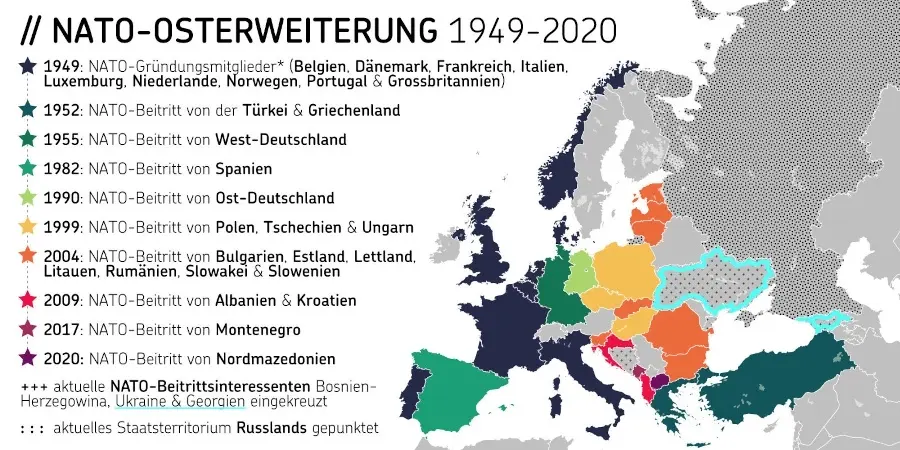
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
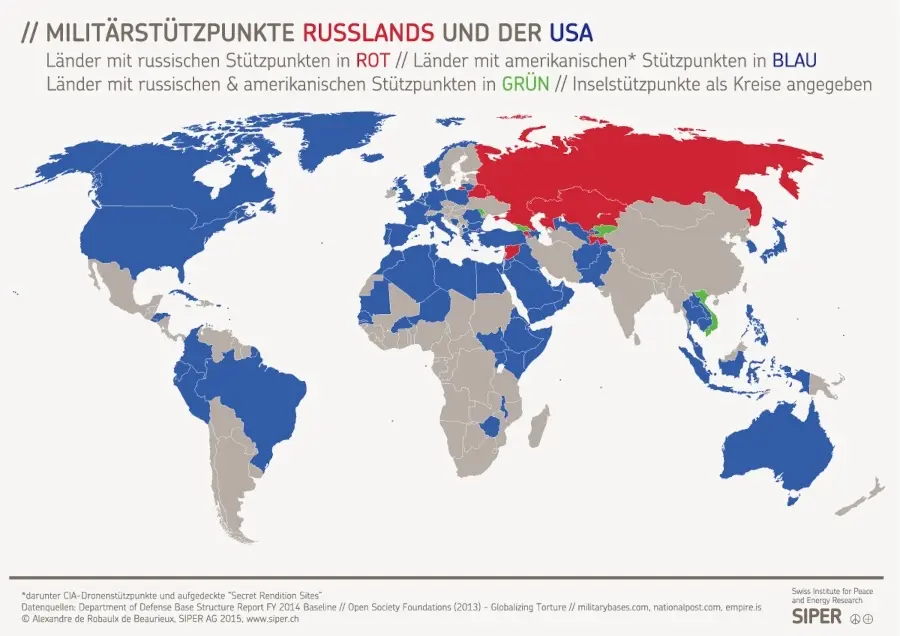
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 90c656ff:9383fd4e
2025-05-24 12:06:36
@ 90c656ff:9383fd4e
2025-05-24 12:06:36Throughout history, money has always been under the control of central authorities, such as governments and banks. These intermediaries have set the rules of the financial system, controlled the issuance of currency, and overseen transactions. However, with the emergence of Bitcoin, a new paradigm began to take shape: decentralized money. This transformation represents a profound shift in how people store and transfer value, challenging the traditional financial model.
- The traditional model: centralized money
01 - Dependence on intermediaries: To carry out transactions, people rely on banks, governments, and other regulatory entities.
02 - Inflation and devaluation: Central banks can print money endlessly, often leading to a loss in purchasing power.
03 - Censorship and restrictions: Access to money can be denied for political, bureaucratic, or institutional reasons, limiting individuals’ financial freedom.
Despite being the dominant model for centuries, the centralized system has shown its vulnerabilities through numerous economic and political crises. It was in this context that Bitcoin emerged as an innovative alternative.
- The revolution of decentralized money
01 - Elimination of intermediaries: Transactions can be made directly between users, without the need for banks or financial companies.
02 - Limited and predictable supply: Bitcoin has a fixed cap of 21 million units, preventing the inflation caused by excessive money printing.
03 - Censorship resistance: No entity can block or prevent transactions, ensuring full financial freedom.
04 - Self-custody: Each user can hold their own funds without relying on a bank or any other institution.
This paradigm shift has a significant impact not only on the financial system but also on how people interact with money and protect their wealth.
Challenges and opposition to financial decentralization
The transition to a decentralized financial system faces several challenges, the main one being resistance from traditional institutions. Banks and governments see Bitcoin as a threat to their control over money and seek to regulate or limit its adoption.
There are also technical and educational barriers. Many people still do not fully understand how Bitcoin works, which can hinder its adoption. However, as more people become aware of the benefits of decentralized money, its use is likely to grow.
In summary, the shift from a centralized financial system to a decentralized one represents one of the most significant transformations of the digital era. Bitcoin leads this movement by offering a censorship-resistant, transparent, and accessible alternative. Despite opposition from the traditional system, the decentralization of money continues to gain momentum, providing greater autonomy and financial freedom to people around the world. This revolution is not just technological, but also social and economic—redefining the way the world understands and uses money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 8bad92c3:ca714aa5
2025-05-24 11:01:08
@ 8bad92c3:ca714aa5
2025-05-24 11:01:08Marty's Bent

It's been a hell of a week in Austin, Texas. The Texas Energy & Mining Summit was held at Bitcoin Park Austin on Tuesday and yesterday. Around 200 people from across the energy sector and the mining sector convened to discuss the current state of bitcoin mining, how it integrates with energy systems, and where things are going in the near to medium term. Representatives from ERCOT, Halliburton, and some of the largest mining companies in the world were in attendence. Across town, Bitcoin++ is holding their conference on mempools, which is fitting considering there is currently an ongoing debate about mempool policy and whether or not Bitcoin Core should eliminate the data limit on OP_RETURN.
I've had the pleasure of participating in both events. At the Texas Energy & Mining Summit I opened up the two-day event with the opening panel on why Texas is perfectly suited not only for bitcoin mining but for the bitcoin industry in general. Texas is a state that highly values private property rights, low taxes, and free market competition. It's become clear to me over the four years that I've lived in Texas that it is an incredible place to start a bitcoin business. The energy down here (pun intended) is palpable.
I also hosted the ending panel with Nick Gates from Priority Power, Will Cole from Zaprite and Jay Beddict from Foundry about what we have to look forward to through the rest of the year. I think the consensus was pretty clear on the panel, there's never been a more bullish setup for bitcoin historically. The political support we're getting here in the United States, the institutional adoption that we're seeing, and the fervor around protocol level development are all pointing in the right direction. Even though the discussions around protocol development can be contentious at times, it's a signal that people really care about this open source monetary protocol that we're all building on. We all agreed that Bitcoin has never been more de-risked than it is today. That is not to say that there aren't any risk.
We also discussed the problem with mining pool centralization and the FPPS payout scheme and why people need to be paying attention to it. But I think overall, things are looking pretty good right now.
Yesterday I also had the pleasure of running the live desk at Bitcoin++ speaking with many of the developers building out the protocol layer and layers above bitcoin. It's always extremely humbling to sit down and speak with the developers because they are so damn smart. Brilliant people who really care deeply about bitcoin. Even though many of them have very different views about the state of bitcoin and how to build it out moving forward. I view my role on the live desk is simply to try to get everybody's perspective. Not only on the OP_RETURN discussion, but on the future of bitcoin and how the protocol progresses from a technical perspective.
I had many conversations. The first with Average Gary and VNPRC, who are working on hashpools, which are attempting to solve the mining pool centralization and privacy problems that exists by using ecash. Hashpool gives miners the ability to exchange hash shares for ehash tokens. that are immediately liquid and exchangeable for bitcoin over the lightning network. Solving the consistent payout and liquidity problem that miners are always trying to solve. Currently FPPS payout schemes are the way they solve these problems. I'm incredibly optimistic about the hashpools project.
I also had the pleasure of speaking with SuperTestNet and Dusty Daemon, who are both focused on making bitcoin more inherently private at the protocol layer and on the lightning network. I think Dusty's work on splicing is very underappreciated right now and is something that you should all look into. Dusty also explained an idea he has that would make CoinJoin coordination much easier by creating a standardized coordination protocol. I'm going to butcher the explanation here, But I think the general idea is to create a way for people to combine inputs by monitoring the lightning network and looking for individual actors who are looking to rebalance channels and opportunistically set up a collaborative transaction with them. This is something I think everyone should look into and champion because I think it would be incredibly beneficial to on-chain privacy. As Bitcoin scales and gets adopted by millions and billions of people over the next few decades.
I also had the pleasure of speaking with Andrew Poelstra and Boerst about cryptography and block templates. For those of you who are unaware, Andrew Poelstra the Head of Research at Blockstream and on the cutting edge of the cryptography that bitcoin uses and may implement in the future. We had a wide ranging discussion about OP_RETURN, FROST, Musig2, Miniscript, quantum. resistant cryptographic libraries, and how Bitcoin Core actually works as a development project.
I also spoke with Liam Egan from Alpen Labs. He's working on ZK rollups on Bitcoin. Admittedly, this is an area I haven't explored too deeply, so it was awesome to sit down with Liam and get his perspective. Alpen Labs is leveraging BitVM to enable their rollups.
I highly recommend if and when you get the time to check out the YouTube stream of the Live Desk. A lot of very deep, technical conversations, but if you're really interested to learn how bitcoin actually works and some of the ideas that are out there to make it better, this is an incredible piece of content to watch. I'm about to head over for day two of Bitcoin++ to run the Live Desk again. So if you get this email before we go live make sure you subscribe to the YouTube channel and tune in for the day.
One thing I will say. Last night, there was a debate about OP_RETURN and I think it's important to note that despite how vitriolic people may get on Twitter, it's always interesting to see people with diametrically opposed views get together and have civil debates. It's obvious that everyone involved cares deeply about bitcoin. Having these tough conversations in person is very important. Particularly, civil conversations. I certainly think yesterday's debate was civil. Though, I will say I think that as bitcoiners, we should hold ourselves to a higher standard of decorum when debates like this are had.
Tyler Campbell from Unchained mentioned that it is insane that there was such a small group of people attending this particular debate about the future of a two trillion dollar protocol. Bitcoin is approaching $100,000 again as I type and no one in big tech, no one in big finance outside of people looking for bitcoin treasury plays is really paying attention to what's happening at the protocol level. This is simply funny to observe and probably a good thing in the long run. But, Meta, Stripe, Apple, Visa, Mastercard and the Teslas of the world are all asleep at the wheel as we build out the future of money.
The $1 Trillion Basis Trade Time Bomb
The massive basis trade currently looming over financial markets represents a systemic risk that dwarfs previous crises. As James Lavish warned during our conversation, approximately $1 trillion in leveraged positions exist within this trade - ten times larger than those held by Long-Term Capital Management before its 1998 collapse. These trades employ staggering leverage ratios between 20x to 100x just to make minuscule basis point differences profitable. The Brookings Institution, which Lavish describes as a "tacit research arm of the Fed," has published a paper explicitly warning about this trade's dangers.
"The Brookings Institution came out with a solution... instead of printing money this time, the Fed will just take the whole trade off of the hedge funds books. Absolutely, utterly maniacal. The thought of the Fed becoming a hedge fund... it's nuts." - James Lavish
What makes this situation particularly alarming is how an unwind could trigger cascading margin calls throughout interconnected financial markets. As Lavish explained, when positions begin unwinding, prices move dramatically, triggering more margin calls that force more selling. This "powder keg behind the scenes" is being closely monitored by sophisticated investors who understand its destructive potential. Unlike a controlled demolition, this unwinding could quickly become chaotic, potentially forcing unprecedented Fed intervention.
Check out the full podcast here for more on Bitcoin's role as the neutral reserve asset, nation-state mining strategies, and the repeal of SAB 121's impact on banking adoption.
Headlines of the Day
Panama City Signs Deal for Bitcoin Municipal Payments - via X
U.S. Economy Polls Show Falling Confidence in Trump Leadership - via CNBC
Jack Mallers's Bitcoin Bank Targets $500 Trillion Market - via X
Bitcoin Decouples From Markets With 10% Gain Amid Asset Slump - via X
Looking for the perfect video _to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 2
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 94215f42:7681f622
2025-05-16 08:18:52
@ 94215f42:7681f622
2025-05-16 08:18:52Value Creation at the Edge
The conversation around artificial intelligence has largely centered on the technology itself, the capabilities of large language models, the race for more parameters, and the competition between AI companies.
He with the most data / biggest model / biggest platform wins all.
As we're been exploring in recent "Good Stuff" podcasts, the true business model of AI may be much more straightforward. AI is after all a productivity tool with little technical moat, in fact the existence of AI coding and learning tools quickly chop away at this moat even quicker!.\ \ We believe that the it's about transforming traditional human heavy businesses by dramatically reducing operational costs while maintaining or increasing output.
AI is poised to create value not primarily for AI companies themselves, but for businesses that effectively implement AI to transform their operations, particularly small, local businesses that can become extraordinarily efficient through AI adoption.
The Value Shift: From AI Companies to AI-Enabled Traditional Businesses
A central insight from episode 1 of the podcast series, is that the value of AI isn't likely to accrue primarily to companies like OpenAI or other AI technology providers. Instead, the real winners will be traditional service businesses that can leverage AI to transform their operations and cost structures.
"I think we're gonna see this shift to traditional service businesses... that traditionally have pretty fixed low margins because of a dependency on language-heavy workflows that require a lot of humans as the medium of intelligence in the business."
The opportunity here is to use AI to manage the language dependency and shift the moments of intelligence, that currently exist in the heads of our staff, into software that can run 24x7 for fractions of a cost.\ \ The real limiting factor here is less a magic AGI, but instead detailed thinking and process redesign to move humans to the edge of the process. As it turns out if we think through what each person is doing in detail we see the specific decisions, outputs, moments of intelligence are actually quite constrained and can be replicated in LLM's if we break them down to a low enough level of fidelity and take each decisions one step at a time.\ \ The result? Businesses that have traditionally operated with fixed, low margins can potentially achieve "software-style margins" by dramatically reducing their operational expenses.
Transforming Traditional Service Businesses
We have developed three key heuristics for identifying businesses that could benefit most from AI transformation:
-
Language Intensity: Businesses where much of the work involves processing language (reading, writing, communicating). Language in, language out. If you are sat in a chair and typing all day, this could be you.
-
Labor Component: Where we see this language intensity so we find many people performing similar, standardized roles. For examples, if we have four people in the same role this is a big clue we have good process, checklists, role descriptions etc for how the work can be done in order to replicate work across multiple people.
-
Load in the Business: Taking these processes into account, what amount of the operational expense of the business do they represent? Where these language and labor-intensive operations represent a significant portion of the business cost, we can see there will be significant return.
Traditional service businesses that match these criteria—legal firms, accounting practices, consulting agencies, contract engineering, design agencies and others—could see dramatic transformations through AI implementation.
By automating these language-heavy processes, businesses can potentially reduce operational costs by 50-80% while maintaining similar levels of output.
The Power of Small
We believe that small businesses may have an inherent advantage in this transformation. While large enterprises face significant barriers to reducing their workforce (political pressure, media scrutiny, organizational complexity), smaller businesses can adapt more quickly and focus on growth rather than just cost-cutting.
If I'm in a 20,000 person business and I need to remove 10,000 people... that's hard. You can't do this without sending political shock waves in your local community.
If I'm a 10 person business and I need to double my revenue, nobody gives a shit. I can just do it.
For small businesses, AI removes growth constraints. When adding the "21st person" no longer represents a significant capital investment, small businesses can scale much more efficiently:
If the next nominal client that you onboard doesn't actually cause you any more additional pain, if you don't need to hire more people to service that client... you just take off the brakes off from a growth perspective.
This gives small business a unique advantage in capitalizing on AI.
From "Bionic Humans" to "Humans at the Edge"
We currently see this integration to business happening in one of two models:
-
The Bionic Human: Equipping workers with AI tools to make them more productive.
-
Human at the Edge: Redesigning processes to be AI-native, with humans entering the process only when needed (and often facilitated by bitcoin payments).
While many businesses are focused on the first approach and it can certainly see returns, it is still a process constrained by the human input. The real value unlock comes from fundamentally redesigning business processes with AI at the core.
Now we can purchase intelligence in buckets of $0.02 API calls, how would we operate different?
This represents a profound shift in how we think about work and processes. Rather than humans being central to processes with tools supporting them, AI becomes the backbone of operations with humans providing input only at critical junctures.
This is "a complete mental shift" that challenges our fundamental assumptions about how businesses operate. The human becomes "the interface with the real world" for AI systems rather than the primary processor of information and decision-maker.
The Value Trap: Understanding the Competitive Dynamic
So what happens next? Here we have developed the concept of the Value Trap to explain how the competitive landscape will evolve as AI adoption increases..\ \

Initially, early adopters of AI and "Human at the Edge" business processes, will see dramatic benefits.
If your costs have dropped from 90 to 20 this creates an immediate competitive advantage where the early adopter is "now making 80 units of profit versus your 10 units of profit.
They gain massive pricing power in the industry and can compete for growth with an unfair advantage.
Over time, and here we believe this is likely a 5-10 year period although we believe the quicker side, competitive pressures will erode these advantages.\ \ As competitors adopt similar AI strategies, price competition will intensify, and revenues will decline. The business that initially saw its costs drop from 90 to 20 units might see its revenue decline from 100 to 30 units, resulting in similar margins but much lower overall revenue, often destroying the enterprise value of the company at these new revenue / profit levels!
This evolution creates an imperative for businesses to adopt AI early, not just to maintain perpetual advantage, but simply to survive the transition. Worse they're hit with a second challenge of the value trap, how do I keep hold of the value I generate along the way.\ \ If you're reading this on Nostr you may already suspect a way out of this value trap.\ \ If not I would invite you to consider storing the immediate short term returns you pull forwards in something that would be inflation resistant, hard to seize and ideally portable.\ \ We refer to this as a 'The big orange arbitrage".
Implications for Business Owners and Capital Allocators
For business owners, especially those running small to medium-sized enterprises, the message is clear: understand how AI could transform your industry and begin planning your transition now.\ \ This might involve creating an "AI-native twin" of your current business—similar to how Netflix developed streaming alongside its DVD business—to eventually replace your current operations. If you want help please ask, I heavily favor more small businesses in the world and would love to help make this a reality.
For capital allocation, the emerging opportunity we see if in "transformation led private equity". The acquisition of traditional service businesses and applying AI to dramatically reduce operational costs and increase enterprise value.\ \ This approach treats AI not as a product but as a transformation strategy for existing businesses with proven product-market fit.
Transformation led PE is venture style returns without the risk of product market fit.
So the lesson?
The business model of AI isn't all about selling AI technology, adding a RAG chatbot to a new DB or collecting everyone's data.\ \ Consider the humble cash flow business, use AI to transform the operational processes and save into everyone's favorite orange coin.
-
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 1d7ff02a:d042b5be
2025-05-24 10:15:40
@ 1d7ff02a:d042b5be
2025-05-24 10:15:40ຄົນສ່ວນຫຼາຍມັກຈະມອງເຫັນ Bitcoin ເປັນສິນຊັບທີ່ມີຄວາມສ່ຽງສູງ ເນື່ອງຈາກມີອັດຕາການປ່ຽນແປງລາຄາທີ່ຮຸນແຮງແລະກວ້າງຂວາງໃນໄລຍະສັ້ນໆ. ແຕ່ຄວາມຈິງແລ້ວ ຄວາມຜັນຜວນຂອງ Bitcoin ແມ່ນຄຸນລັກສະນະພິເສດທີ່ສຳຄັນຂອງມັນ ບໍ່ແມ່ນຂໍ້ບົກພ່ອງ.
ລາຄາແມ່ນຫຍັງ?
ເພື່ອເຂົ້າໃຈເລື້ອງນີ້ດີຂຶ້ນ ເຮົາຕ້ອງເຂົ້າໃຈກ່ອນວ່າລາຄາໝາຍເຖິງຫຍັງ. ລາຄາແມ່ນການສະທ້ອນຄວາມຄິດເຫັນແລະການປະເມີນມູນຄ່າຂອງຜູ້ຊື້ແລະຜູ້ຂາຍໃນເວລາໃດໜຶ່ງ. ການຕັດສິນໃຈຊື້ຫຼືຂາຍໃນລາຄາໃດໜຶ່ງ ກໍແມ່ນການສື່ສານກັບຕະຫຼາດ ແລະກົນໄກຂອງຕະຫຼາດຈະຄ້ົນຫາແລະກໍານົດລາຄາທີ່ແທ້ຈິງຂອງສິນຊັບນັ້ນ.
ເປັນຫຍັງ Bitcoin ຈຶ່ງຜັນຜວນ?
Bitcoin ຖືກສ້າງຂຶ້ນບົນພື້ນຖານອິນເຕີເນັດ ເຮັດໃຫ້ການສື່ສານຄວາມຄິດເຫັນຂອງຜູ້ຄົນສາມາດເຮັດໄດ້ຢ່າງໄວວາ. ຍິ່ງໄປກວ່ານັ້ນ Bitcoin ມີລັກສະນະກະຈາຍສູນ (decentralized) ແລະບໍ່ມີຜູ້ຄວບຄຸມສູນກາງ ຈຶ່ງເຮັດໃຫ້ຄົນສາມາດຕັດສິນໃຈຊື້ຂາຍໄດ້ຢ່າງໄວວາ.
ສິ່ງນີ້ເຮັດໃຫ້ລາຄາຂອງ Bitcoin ສາມາດສະທ້ອນຄວາມຄິດເຫັນຂອງຄົນໄດ້ແບບເວລາຈິງ (real-time). ແລະເນື່ອງຈາກມະນຸດເຮົາມີຄວາມຄິດທີ່ບໍ່ແນ່ນອນ ມີການປ່ຽນແປງ ລາຄາຂອງ Bitcoin ຈຶ່ງປ່ຽນແປງໄປຕາມຄວາມຄິດເຫັນລວມຂອງຜູ້ຄົນແບບທັນທີ.
ປັດໄຈທີ່ເພີ່ມຄວາມຜັນຜວນ:
ຂະໜາດຕະຫຼາດທີ່ຍັງນ້ອຍ: ເມື່ອປຽບທຽບກັບຕະຫຼາດການເງິນແບບດັ້ງເດີມ ຕະຫຼາດ Bitcoin ຍັງມີຂະໜາດນ້ອຍ ເຮັດໃຫ້ການຊື້ຂາຍຈຳນວນໃຫຍ່ສາມາດສົ່ງຜົນກະທົບຕໍ່ລາຄາໄດ້ຫຼາຍ.
ການຄ້າຂາຍຕະຫຼອດ 24/7: ບໍ່ເຫມືອນກັບຕະຫຼາດຫຼັກຊັບທີ່ມີເວລາເປີດປິດ Bitcoin ສາມາດຊື້ຂາຍໄດ້ຕະຫຼອດເວລາ ເຮັດໃຫ້ການປ່ຽນແປງລາຄາສາມາດເກີດຂຶ້ນໄດ້ທຸກເວລາ.
ການປຽບທຽບກັບສິນຊັບອື່ນ
ເມື່ອປຽບທຽບກັບສິນຊັບອື່ນທີ່ມີການຄວບຄຸມ ເຊັ່ນ ສະກຸນເງິນທ້ອງຖິ່ນຫຼືທອງຄຳ ທີ່ເບິ່ງຄືວ່າມີຄວາມຜັນຜວນໜ້ອຍກວ່າ Bitcoin ນັ້ນ ບໍ່ແມ່ນຫມາຍຄວາມວ່າພວກມັນບໍ່ມີຄວາມຜັນຜວນ. ແຕ່ເປັນເພາະມີການຄວບຄຸມຈາກອົງການສູນກາງ ເຮັດໃຫ້ການສື່ສານຄວາມຄິດເຫັນຂອງຄົນໄປຮອດຕະຫຼາດບໍ່ແບບເວລາຈິງ.
ດັ່ງນັ້ນ ສິ່ງທີ່ເຮົາເຫັນແມ່ນການຊັກຊ້າ (delay) ໃນການສະແດງຄວາມຄິດເຫັນທີ່ແທ້ຈິງອອກມາເທົ່ານັ້ນ ບໍ່ແມ່ນຄວາມໝັ້ນຄົງຂອງມູນຄ່າ.
ກົນໄກການຄວບຄຸມແລະຜົນກະທົບ:
ສະກຸນເງິນ: ທະນາຄານກາງສາມາດພິມເງິນ ປັບອັດຕາດອກເບີ້ຍ ແລະແຊກແຊງຕະຫຼາດ ເຮັດໃຫ້ລາຄາບໍ່ສະທ້ອນມູນຄ່າທີ່ແທ້ຈິງໃນທັນທີ.
ຫຼັກຊັບ: ມີລະບຽບການຫຼາຍຢ່າງ ເຊັ່ນ ການຢຸດການຊື້ຂາຍເມື່ອລາຄາປ່ຽນແປງຫຼາຍເກີນໄປ (circuit breakers) ທີ່ຂັດຂວາງການສະແດງຄວາມຄິດເຫັນທີ່ແທ້ຈິງ.
ທອງຄຳ: ຖຶງແມ່ນຈະເປັນສິນຊັບທີ່ບໍ່ມີການຄວບຄຸມ ແຕ່ຕະຫຼາດທອງຄຳມີຂະໜາດໃຫຍ່ກວ່າ Bitcoin ຫຼາຍ ແລະມີການຄ້າແບບດັ້ງເດີມທີ່ຊ້າກວ່າ.
ບົດສະຫຼຸບ
ການປຽບທຽບຄວາມຜັນຜວນລະຫວ່າງ Bitcoin ແລະສິນຊັບອື່ນໆ ໂດຍໃຊ້ໄລຍະເວລາສັ້ນນັ້ນ ບໍ່ມີຄວາມສົມເຫດສົມຜົນປານໃດ ເພາະວ່າປັດໄຈເລື້ອງການຊັກຊ້າໃນການສະແດງຄວາມຄິດເຫັນນີ້ແມ່ນສິ່ງສຳຄັນທີ່ສົ່ງຜົນຕໍ່ລາຄາທີ່ແທ້ຈິງ.
ສິ່ງທີ່ຄວນເຮັດແທ້ໆແມ່ນການນຳເອົາກອບເວລາທີ່ກວ້າງຂວາງກວ່າມາວິເຄາະ ເຊັ່ນ ເປັນປີຫຼືຫຼາຍປີ ແລ້ວຈຶ່ງປຽບທຽບ. ດ້ວຍວິທີນີ້ ເຮົາຈຶ່ງຈະເຫັນປະສິດທິຜົນແລະການດຳເນີນງານທີ່ແທ້ຈິງຂອງ Bitcoin ໄດ້ຢ່າງຈະແຈ້ງ
-
 @ ee6ea13a:959b6e74
2025-05-13 21:29:02
@ ee6ea13a:959b6e74
2025-05-13 21:29:02Reposted without permission from Business Insider.
Bitcoin Is A Joke
Joe Weisenthal Nov 6, 2013, 10:42 PM UTC

REUTERS/Eliana Aponte
Bitcoin is back in the news, as the digital currency has surged to new all-time highs in recent weeks.
A few weeks ago, it was just above $100. Today it's over $260.
This surge has prompted Timothy B Lee at The Washington Post to ask whether those who have called it a bubble in the past should retract and admit that they were wrong.
Well I'm not totally sure if I've called it a bubble, but I have spoken negatively of it, and I'll say that I still think it's a joke, and probably in a bubble.
Now first of all, I find the premise of Lee's post to be hilarious. The currency has been surging several percent every day lately, and that's evidence that it's not in a bubble?
Before going on, I want to be clear that saying something is a bubble is not saying it will go down. It could go to $500 or $1000 or $10,000. That's the nature of manias.
But make no mistake, Bitcoin is not the currency of the future. It has no intrinsic value.
Now this idea of "intrinsic value" when it comes to currency bothers people, and Bitcoin Bugs will immediately ask why the U.S. dollar has intrinsic value. There's an answer to that. The U.S. Dollar has intrinsic value because the U.S. government which sets the laws of doing business in the United States says it has intrinsic value. If you want to conduct commerce in the United States you have to pay taxes, and there's only one currency you're allowed to pay taxes in: U.S. dollars. There's no getting around this fact. Furthermore, if you want to use the banking system at all, there's no choice but to use U.S. dollars, because that's the currency of the Fed which is behind the whole thing.
On top of all these laws requiring the U.S. dollar to be used, the United States has a gigantic military that can force people around the world to use dollars (if it came to that) so yes, there's a lot of real-world value behind greenbacks.
Bitcoin? Nada. There's nothing keeping it being a thing. If people lose faith in it, it's over. Bitcoin is fiat currency in the most literal sense of the word.
But it gets worse. Bitcoin is mostly just a speculative vehicle. Yes, there are PR stunts about bars and other shops accepting bitcoins. And there is a Bitcoin ATM for some reason. But mostly Bitcoin is a speculative vehicle. And really, you'd be insane to actually conduct a sizable amount of commerce in bitcoins. That's because the price swings so wildly, that the next day, there's a good chance that one of the parties will have gotten royally screwed. Either the purchaser of the good will have ended up totally blowing a huge opportunity (by not holding longer) or the seller will be totally screwed (if Bitcoin instantly plunges). The very volatility that excited people to want to play the Bitcoin game is death when it comes to real transactions in the real world.
Again, Bitcoin might go up a lot more before it ultimately ends. That's the nature of bubbles. The dotcom bubble crashed a bunch of times on its way up. Then one day it ended. The same will happen with this.
In the meantime, have fun speculating!
-
 @ 5ea46480:450da5bd
2025-05-24 09:57:37
@ 5ea46480:450da5bd
2025-05-24 09:57:37Decentralization refers to control/power, and relates to censorship resistance. That is it, it is not more complicated then that. Resilience is a function of redundancy; a centralized censored system can have a redundant set-up and therefor be resilient.
Take Bitcoin; the blockchain is a central database, it is resilient because it has many redundant copies among a lot of different nodes. The message (txs and blocks) propagation is decentralized due to existence of a p2p network among these nodes, making the data distribution censorship resistant (hello op_return debate). But onchain transactions themselves are NOT p2p, they require a middlemen (a miner) because it is a central database, as opposed to something like lightning which is p2p. Peer to Peer says something about relative architectural hierarchical position/relation. P2P provides censorship resistance because it entails equal power relations, provided becoming a peer is permissionless. What makes onchain transactions censorship resistant is that mining is permissionless, and involves this open power struggle/game where competition results in a power distribution among players, meaning (hopefully) decentralization. The fact users rely on these middlemen is mitigated by this decentralization on the one hand, and temper-proofing via cryptographic signatures on the other, resulting in what we call trustlessness (or trust minimization for the autists in the room); we only rely on a miner to perform a job (including your tx into a block), but we don’t trust the miner to perform the job correctly, this we can verify ourselves.
This leads us to Nostr, because that last part is exactly what Nostr does as well. It uses cryptography to get tamper-proof messaging, which then allows you to use middle-men in a trust minimized way. The result is decentralization because in general terms, any middle man is as good as any other (same as with miners), and becoming such a middleman is permissionless(somewhat, mostly); which in turn leads to censorship resistance. It also allows for resilience because you are free to make things as redundant as you'd like.
Ergo, the crux is putting the cryptography central, making it the starting point of the system; decentralization then becomes an option due to trust minimization. The difference between Bitcoin an Nostr, is that Bitcoin maintains a global state/central ledger and needs this PoW/Nakamoto consensus fanfare; Nostr rests itself with local perspectives on 'the network'.
The problem with the Fediverse, is that it does not provide trust minimization in relation to the middlemen. Sure, there are a lot different servers, but you rely on a particular one (and the idea you could switch never really seemed to have materialized in a meaningful way). It also fails in permisionlessness because you rely on the association between servers, i.e. federation, to have meaningful access to the rest of the network. In other words, it is more a requirement of association than freedom of association; you have the freedom to be excommunicated.
The problem with ATproto is that is basically does not solve this dynamic; it only complicates it by pulling apart the components; identity and data, distribution and perspective are now separated, and supposedly you don’t rely on any particular one of these sub-component providers in the stack; but you do rely on all these different sub-component providers in the stack to play nice with each other. And this ‘playing nice’ is just the same old ‘requirement of association’ and ‘freedom of excommunication’ that looms at the horizon.
Yes, splitting up the responsibilities of identity, hosting and indexing is what is required to safe us from the platform hellscape which at this stage takes care of all three. But as it turns out, it was not a matter cutting those up into various (on paper) interchangeable middlemen. All that is required is putting cryptographic keys in the hands of the user; the tamperproofing takes care of the rest, simply by trust minimizing the middlemen we use. All the sudden it does not matter which middlemen we use, and no one is required to play nice; we lost the requirement of association, and gained freedom of association, which was the purpose of censorship resistance and therefor decentralization, to begin with.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 374ee93a:36623347
2025-05-13 11:47:55
@ 374ee93a:36623347
2025-05-13 11:47:55Chef's notes
Lovely tart rhubarb jam with the extra firey kick of fresh root ginger.
Technically a vegetable rhubarb has low pectin content so be sure to include a high pectin fruit such as lemon/cooking apple/redcurrant/gooseberry. It also quite watery so we use a slightly higher fruit to sugar ratio (1.2:1) and evaporate off some water at the beginning.
Testing for setting point: put a saucer in the freezer to chill whilst cooking the fruit, after 5 mins of a high boil with the sugar put a small blob of jam on the cold saucer and return to the freezer for 2 minutes. If the jam forms a solid wrinkle when pushed with a spoon it is ready, if it is runny continue cooking and retest every 5 mins
The recipe can be halved for a small batch but if you have lots of rhubarb to process it is better to cook double batches in separate pans because it will take much longer to heat through, this affects the colour and flavour - the jam will taste warm and mellow rather than zingy
Sterilise glass jars in a 120c oven and pot the jam hot leaving 1/4 inch head space, it will keep for 5 years unopened if the lids are well sealed and does not require water bath canning
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 30 mins
- 🍽️ Servings: 6 (jars)
Ingredients
- 1.2kg Rhubarb
- 200g Grated Root Ginger
- 100g Chopped Crystalised Ginger
- 1kg Sugar
- 1 Lemon
Directions
- Chop the rhubarb into 1/2 inch pieces, peel and finely grate the fresh root ginger, chop crystalised ginger into tiny bits. Juice and quarter a lemon (discard pips) and add all these to a pan with a small amount of water
- Simmer gently for 20 mins until the lemon and rhubarb are soft then add the sugar, stir until fully dissolved
- Boil on high to reach setting point, usually at 105 degrees c or when a small blob of jam wrinkles on a cold plate instead of being runny
- Remove the lemon pieces and pot into sterilised jars
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ a296b972:e5a7a2e8
2025-05-24 09:35:09
@ a296b972:e5a7a2e8
2025-05-24 09:35:09„Aaaach, was für ein herrlicher Tag!“
In Berlin geht man hochmotiviert an die Arbeit, in der tiefen Überzeugung stets die richtigen Entscheidungen zu treffen, die Steuern der Einzahler ausschließlich für wohlüberlegte, notwendige Investitionen auszugeben und Entscheidungen zu treffen, die im dem Umfeld, in dem man sich bewegt, als höchst sinnvoll erachtet werden. Zustimmung von allen Seiten, dann muss es ja richtig sein.
Man fährt im Dienstwagen ins Regierungsviertel, sieht die vielen geschäftigen Menschen, wie sie ebenfalls zur Arbeit eilen. Man freut sich darüber, dass alles so gut läuft, dank der überragenden Kompetenz, die man einbringen darf und die das alles ermöglicht.
In Gedanken klopft man sich auf die Schulter und sagt sich im Stillen: „Bist schon ein geiler Typ, der richtig was bewegen kann, bewegen kann.“
Man hat auch schon erkannt, dass die zunehmende Kriminalität, vorzugsweise mit einem unsachgemäß gebrauchten Messer, durch den schlechten Einfluss der sozialen Medien entstanden ist und schon entsprechende Maßnahmen auf den Weg gebracht, um das durch geleitete Meinungsäußerungen, selbstverständlich zum Wohle aller, zu unterbinden. Man ist ja nicht umsonst in diese verantwortungsvolle Position gelangt. „Endlich am Ziel!“
„Messerattacken sind unschön, unschön, aber man muss auch berücksichtigen, dass viele der Attentäter und Attentäterinnen in ihren Herkunftsländern Schlimmes erlebt haben und dadurch traumatisiert wurden. Den betroffenen Traumaopfern kann ja nichts Besseres passieren, als in eine deutsche Psychiatrie zu kommen, wo sie die allerbeste Therapie erfahren, um wieder glückliche Menschen der Gesellschaft zu werden.
** **
Und jeder, der nicht die große soziale Aufgabe erkennt, die wir uns gestellt haben und auch effizient umsetzen, muss es eben noch besser erklärt bekommen, erklärt bekommen. Daran müssen wir noch arbeiten. (Muss ich mir notieren, damit ich meinem Sekretär die Anweisung erteile, das in die Wege zu leiten). Und jeder, der sich dagegen sträubt, zeigt damit eindeutig, dass er zum rechten Rand gehört. Was denen nur einfällt? Da müssen klare Zeichen gesetzt werden, und das muss unter allen Umständen unterbunden werden, unterbunden werden.
** **
Sowas schadet der Demokratie, es delegitimiert sie“.
Zum Schutz der braven Bürger arbeitet man auch fleißig daran, Deutschland, in neuem Selbstbewusstsein, zur stärksten Kraft in Europa zu machen. Mit der Stationierung von deutschen Soldaten an der Ostfront, pardon, an der Ostflanke, zeigt man dem bösen, aggressiven Russen schon mal, was eine Harke ist. „Und das ist ja erst der Anfang, der Anfang. Warte nur ab!“
„Was noch? Ach ja, die Wirtschaft. Solange die nicht auf die Barrikaden geht, das sehe ich derzeit nicht, scheint es ja noch keinen akuten Handlungsbedarf zu geben. Darum kümmern wir uns später. Immerhin halten sich die Wirtschaftsprognosen in einem akzeptablen Rahmen und die Priorität (die kann auch nicht jeder richtig setzen) der Investitionen muss derzeit auf dem wichtigsten Bereich, der Aufrüstung liegen, Aufrüstung liegen. Schließlich werden wir bald angegriffen.
** **
Ich darf nicht vergessen, meinen Sekretär zu beauftragen, meine Bestellung im Feinkostladen abholen zu lassen, sonst gibt’s Zuhause Ärger. Ach ja, und die Anzüge und die Wäsche muss auch noch aus der Reinigung abgeholt werden. Darf ich nicht vergessen, nicht vergessen.
** **
Wie viele Reinigungen gäbe es nicht, wenn wir Politiker nicht wären, nicht wären. Viele sichere Arbeitsplätze, gut so!
** **
Was, schon da? Das ging aber heute schnell. Kein Stau. Ja, der Chauffeur ist schon ein Guter, der weiß, wo man lang muss, um Baustellen zu umfahren. Allerdings muss ich ihm bei nächster Gelegenheit noch einmal deutlich sagen, dass er bitte die Sitzheizung früher anzuschalten hat, anzuschalten hat! Dass der sich das immer noch nicht gemerkt hat, unmöglich!“
Wen wundert es, wenn in dieser Wonnewelt der Selbstüberschätzung von Unsererdemokratie gesprochen wird, so entrückt vom Alltag, in einem Raumschiff, dass völlig losgelöst von der Realität über allem schwebt.
„Ich müsste ja verrückt sein, wenn ich an diesen Zuständen etwas ändern wollte. Warum auch, es läuft doch und mir geht es doch gut. Ich habe ein gutes Einkommen, kann mir allerhand leisten, Haus ist bezahlt, Frau ist gut untergebracht, Kinder sind versorgt, wie die Zeit vergeht. Und wenn ich mal ausscheide, erhalte ich weiter meine Bezüge und muss nicht an mein Vermögen ran, man will ja auch den Kindern was hinterlassen. Schadet ja nicht, wenn ich mich etwas einschränke, und der eine oder andere Job wird schon an mich herangetragen werden, schließlich habe ich ja erstklassige Kontakte, die dem einen oder anderen sicher etwas wert sein werden.
** **
Na, dann woll’n wir mal wieder, woll’n wir mal wieder!“
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 95543309:196c540e
2025-05-11 12:42:09
@ 95543309:196c540e
2025-05-11 12:42:09Lets see if this works with the blossom upload and without markdown hassle.
:cat:

https://blossom.primal.net/73a099f931366732c18dd60da82db6ef65bb368eb96756f07d9fa7a8a3644009.mp4
-
 @ 6a6be47b:3e74e3e1
2025-05-24 08:21:35
@ 6a6be47b:3e74e3e1
2025-05-24 08:21:35Hi, frens!
🥳 This is my first post over here, yaaay! I’m very excited to start this journey. I have lots of posts on my website https://samhainsam.art/ , but I decided to give you a short introduction to me and my artwork. Shall we?
But first, how’s your weekend going? Already dreading Monday, or just enjoying the moment? I hope it’s the latter, but if not, that’s okay too. Everything passes, and while that might not be the most comforting thought, knowing that it will eventually pass—and, most importantly, that we get to decide how to respond—makes a big difference. Either way, we’re all going to die, so take it as you wish! 😅
Anyway, I wanted to share a little something. If you’ve visited my shop on Ko-fi https://ko-fi.com/samhainsam/shop , you might have wondered why it seems a bit all over the place. Or maybe you haven’t noticed or don’t care—but either way, I thought I’d clarify.
🖼️ I’m a self-taught artist who loves everything related to religion, occultism, paganism, animals, and esotericism—and how all these themes intertwine in our lives. I paint and illustrate inspired by these ideas.
Most of my recent paintings come with a blog post explaining their background. Even before, I always researched the subjects I painted, but lately, I’ve been diving much deeper.
🎨 My “Wheel of the Year” series has completely fascinated me. I’ve been learning so many nuggets of wisdom, and discovering how Christianity borrowed or even erased many symbols and traditions to create new narratives. For example, Imbolc was rebranded as Candlemas, and my blog post about the Spanish Inquisition touches on some of these symbols and their impact on both past and present society.
🐦 I also have some paintings just about birds—I'm a bit of a sucker for them! Shoebills and cassowaries are among my favorites, and I might end up painting them again soon. But you get the picture! If not, why not take a peek at my blog? https://samhainsam.art/blog/
🖋️ You can read something fun and interesting while enjoying my artwork.
Come on over, and let’s have some cool and healthy fun.
Enjoy your weekend, my friends!
Godspeed ⚡
https://stacker.news/items/988069
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 57d1a264:69f1fee1
2025-05-24 06:07:19
@ 57d1a264:69f1fee1
2025-05-24 06:07:19Definition: when every single person in the chain responsible for shipping a product looks at objectively horrendous design decisions and goes: yup, this looks good to me, release this. Designers, developers, product managers, testers, quality assurance... everyone.
I nominate Peugeot as the first example in this category.
Continue reading at https://grumpy.website/1665
https://stacker.news/items/988044
-
 @ 7459d333:f207289b
2025-05-10 10:38:56
@ 7459d333:f207289b
2025-05-10 10:38:56Description: Just as Bitcoin enabled sovereignty over money, a decentralized shipping protocol would enable sovereignty over trade. An LN/Bisq inspired shipping protocol could create an unstoppable free market.
Bitcoin gave us monetary sovereignty, freeing us from central bank manipulation, inflation, and censorship. But there's a missing link in our freedom journey: the physical world of goods.
The Problem: Even with Bitcoin, global trade remains at the mercy of: - Arbitrary tariffs and import restrictions - Political censorship of goods - Privacy invasion of shipping information - Centralized shipping carriers
The Vision: A decentralized shipping protocol with these properties:
- "Onion-routed" packages: Each carrier only knows the previous and next hop
- Bitcoin-secured multi-sig escrow: Funds locked until package delivery confirmed
- Incentive alignment: Carriers set their own fees based on risk assessment
- Privacy tiers: Options for inspected vs. sealed packages with appropriate pricing
- End-to-end sovereignty: Sender and receiver maintain control, intermediate carriers just fulfill their role
How it could work:
- Sender creates shipping request with package details and destination
- Protocol finds optimal route through independent carriers
- Each hop secured by multi-sig deposits larger than package value
- Carriers only see next hop, not ultimate destination
- Reputation systems and economic incentives maintain integrity
This creates a free market where any individual can participate as a carrier, earning Bitcoin for facilitating trade. Just like Lightning Network nodes, anyone can open "channels" with trusted partners.
Impact: This would enable true free market principles globally, making artificial trade barriers obsolete and empowering individuals to engage in voluntary exchange regardless of geographic or political boundaries.
There are a lot of challenges. But the first question is if this is a real problem and if its worth solving it.
What components would need development first? How would you solve the physical handoff challenges?
originally posted at https://stacker.news/items/976326
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 57d1a264:69f1fee1
2025-05-24 05:53:43
@ 57d1a264:69f1fee1
2025-05-24 05:53:43This talks highlights tools for product management, UX design, web development, and content creation to embed accessibility.
Organizations need scalability and consistency in their accessibility work, aligning people, policies, and processes to integrate it across roles. This session highlights tools for product management, UX design, web development, and content creation to embed accessibility. We will explore inclusive personas, design artifacts, design systems, and content strategies to support developers and creators, with real-world examples.
https://www.youtube.com/watch?v=-M2cMLDU4u4
https://stacker.news/items/988041
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ f6488c62:c929299d
2025-05-24 05:10:20
@ f6488c62:c929299d
2025-05-24 05:10:20คุณเคยจินตนาการถึงอนาคตที่ AI มีความฉลาดเทียบเท่ามนุษย์หรือไม่? นี่คือสิ่งที่ Sam Altman ซีอีโอของ OpenAI และทีมพันธมิตรอย่าง SoftBank, Oracle และ MGX กำลังผลักดันผ่าน โครงการ Stargate! โครงการนี้ไม่ใช่แค่เรื่องเทคโนโลยี แต่เป็นก้าวกระโดดครั้งใหญ่ของมนุษยชาติ! Stargate คืออะไร? Stargate เป็นโปรเจกต์สร้าง ศูนย์ข้อมูล AI ขนาดยักษ์ที่ใหญ่ที่สุดในประวัติศาสตร์ ด้วยเงินลงทุนเริ่มต้น 100,000 ล้านดอลลาร์ และอาจสูงถึง 500,000 ล้านดอลลาร์ ภายในปี 2029! เป้าหมายคือการพัฒนา Artificial General Intelligence (AGI) หรือ AI ที่ฉลาดเทียบเท่ามนุษย์ เพื่อให้สหรัฐฯ ครองความเป็นผู้นำด้าน AI และแข่งขันกับคู่แข่งอย่างจีน โครงการนี้เริ่มต้นที่เมือง Abilene รัฐเท็กซัส โดยจะสร้างศูนย์ข้อมูล 10 แห่ง และขยายไปยังญี่ปุ่น สหราชอาณาจักร และสหรัฐอาหรับเอมิเรตส์ ทำไม Stargate ถึงสำคัญ?
นวัตกรรมเปลี่ยนโลก: AI จาก Stargate จะช่วยพัฒนาวัคซีน mRNA รักษามะเร็งได้ใน 48 ชั่วโมง และยกระดับอุตสาหกรรมต่าง ๆ เช่น การแพทย์และความมั่นคงแห่งชาติสร้างงาน: คาดว่าจะสร้างงานกว่า 100,000 ตำแหน่ง ในสหรัฐฯ
พลังงานมหาศาล: ศูนย์ข้อมูลอาจใช้พลังงานถึง 1.2 กิกะวัตต์ เทียบเท่ากับเมืองขนาดใหญ่!
ใครอยู่เบื้องหลัง? Sam Altman ร่วมมือกับ Masayoshi Son จาก SoftBank และได้รับการสนับสนุนจาก Donald Trump ซึ่งผลักดันนโยบายให้ Stargate เป็นจริง การก่อสร้างดำเนินการโดย Oracle และพันธมิตรด้านพลังงานอย่าง Crusoe Energy Systems ความท้าทาย? ถึงจะยิ่งใหญ่ แต่ Stargate ก็เจออุปสรรค ทั้งปัญหาการระดมทุน ความกังวลเรื่องภาษีนำเข้าชิป และการแข่งขันจากคู่แข่งอย่าง DeepSeek ที่ใช้โครงสร้างพื้นฐานน้อยกว่า แถม Elon Musk ยังออกมาวิจารณ์ว่าโครงการนี้อาจ “ไม่สมจริง” แต่ Altman มั่นใจและเชิญ Musk ไปดูไซต์งานที่เท็กซัสเลยทีเดียว! อนาคตของ Stargate ศูนย์ข้อมูลแห่งแรกจะเริ่มใช้งานในปี 2026 และอาจเปลี่ยนโฉมวงการ AI ไปตลอดกาล นี่คือก้าวสำคัญสู่ยุคใหม่ของเทคโนโลยีที่อาจเปลี่ยนวิถีชีวิตของเรา! และไม่ใช่ประตูดวงดาวแบบในหนังนะ! ถึงชื่อ Stargate จะได้แรงบันดาลใจจากภาพยนตร์ sci-fi อันโด่งดัง แต่โครงการนี้ไม่ได้พาเราไปยังดวงดาวอื่น มันคือการเปิดประตูสู่โลกแห่ง AI ที่ทรงพลัง และอาจเปลี่ยนอนาคตของมนุษยชาติไปเลย! และไม่เหมือน universechain ของ star ของผมนะครับ
Stargate #AI #SamAltman #OpenAI #อนาคตของเทคโนโลยี
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 6e64b83c:94102ee8
2025-05-05 16:50:13
@ 6e64b83c:94102ee8
2025-05-05 16:50:13Nostr-static is a powerful static site generator that transforms long-form Nostr content into beautiful, standalone websites. It makes your content accessible to everyone, even those not using Nostr clients. For more information check out my previous blog post How to Create a Blog Out of Nostr Long-Form Articles
What's New in Version 0.7?
RSS and Atom Feeds
Version 0.7 brings comprehensive feed support with both RSS and Atom formats. The system automatically generates feeds for your main content, individual profiles, and tag-specific pages. These feeds are seamlessly integrated into your site's header, making them easily discoverable by feed readers and content aggregators.
This feature bridges the gap between Nostr and traditional web publishing, allowing your content to reach readers who prefer feed readers or automated content distribution systems.
Smart Content Discovery
The new tag discovery system enhances your readers' experience by automatically finding and recommending relevant articles from the Nostr network. It works by:
- Analyzing the tags in your articles
- Fetching popular articles from Nostr that share these tags
- Using configurable weights to rank these articles based on:
- Engagement metrics (reactions, reposts, replies)
- Zap statistics (amount, unique zappers, average zap size)
- Content quality signals (report penalties)
This creates a dynamic "Recommended Articles" section that helps readers discover more content they might be interested in, all while staying within the Nostr ecosystem.
See the new features yourself by visiting our demo at: https://blog.nostrize.me
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ 06830f6c:34da40c5
2025-05-24 04:21:03
@ 06830f6c:34da40c5
2025-05-24 04:21:03The evolution of development environments is incredibly rich and complex and reflects a continuous drive towards greater efficiency, consistency, isolation, and collaboration. It's a story of abstracting away complexity and standardizing workflows.
Phase 1: The Bare Metal & Manual Era (Early 1970s - Late 1990s)
-
Direct OS Interaction / Bare Metal Development:
- Description: Developers worked directly on the operating system's command line or a basic text editor. Installation of compilers, interpreters, and libraries was a manual, often arcane process involving downloading archives, compiling from source, and setting environment variables. "Configuration drift" (differences between developer machines) was the norm.
- Tools: Text editors (Vi, Emacs), command-line compilers (GCC), Makefiles.
- Challenges: Extremely high setup time, dependency hell, "works on my machine" syndrome, difficult onboarding for new developers, lack of reproducibility. Version control was primitive (e.g., RCS, SCCS).
-
Integrated Development Environments (IDEs) - Initial Emergence:
- Description: Early IDEs (like Turbo Pascal, Microsoft Visual Basic) began to integrate editors, compilers, debuggers, and sometimes GUI builders into a single application. This was a massive leap in developer convenience.
- Tools: Turbo Pascal, Visual Basic, early Visual Studio versions.
- Advancement: Improved developer productivity, streamlined common tasks. Still relied on local system dependencies.
Phase 2: Towards Dependency Management & Local Reproducibility (Late 1990s - Mid-2000s)
-
Basic Build Tools & Dependency Resolvers (Pre-Package Managers):
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
autoconf/makefor C/C++ helped automate the compilation and linking process, managing some dependencies. - Tools: Apache Ant, GNU Autotools.
- Advancement: Automated build processes, rudimentary dependency linking. Still not comprehensive environment management.
- Description: As projects grew, manual dependency tracking became impossible. Tools like Ant (Java) and early versions of
-
Language-Specific Package Managers:
- Description: A significant leap was the emergence of language-specific package managers that could fetch, install, and manage libraries and frameworks declared in a project's manifest file. Examples include Maven (Java), npm (Node.js), pip (Python), RubyGems (Ruby), Composer (PHP).
- Tools: Maven, npm, pip, RubyGems, Composer.
- Advancement: Dramatically simplified dependency resolution, improved intra-project reproducibility.
- Limitation: Managed language-level dependencies, but not system-level dependencies or the underlying OS environment. Conflicts between projects on the same machine (e.g., Project A needs Python 2.7, Project B needs Python 3.9) were common.
Phase 3: Environment Isolation & Portability (Mid-2000s - Early 2010s)
-
Virtual Machines (VMs) for Development:
- Description: To address the "it works on my machine" problem stemming from OS-level and system-level differences, developers started using VMs. Tools like VMware Workstation, VirtualBox, and later Vagrant (which automated VM provisioning) allowed developers to encapsulate an entire OS and its dependencies for a project.
- Tools: VMware, VirtualBox, Vagrant.
- Advancement: Achieved strong isolation and environment reproducibility (a true "single environment" for a project).
- Limitations: Resource-heavy (each VM consumed significant CPU, RAM, disk space), slow to provision and boot, difficult to share large VM images.
-
Early Automation & Provisioning Tools:
- Description: Alongside VMs, configuration management tools started being used to automate environment setup within VMs or on servers. This helped define environments as code, making them more consistent.
- Tools: Chef, Puppet, Ansible.
- Advancement: Automated provisioning, leading to more consistent environments, often used in conjunction with VMs.
Phase 4: The Container Revolution & Orchestration (Early 2010s - Present)
-
Containerization (Docker):
- Description: Docker popularized Linux Containers (LXC), offering a lightweight, portable, and efficient alternative to VMs. Containers package an application and all its dependencies into a self-contained unit that shares the host OS kernel. This drastically reduced resource overhead and startup times compared to VMs.
- Tools: Docker.
- Advancement: Unprecedented consistency from development to production (Dev/Prod Parity), rapid provisioning, highly efficient resource use. Became the de-facto standard for packaging applications.
-
Container Orchestration:
- Description: As microservices and container adoption grew, managing hundreds or thousands of containers became a new challenge. Orchestration platforms automated the deployment, scaling, healing, and networking of containers across clusters of machines.
- Tools: Kubernetes, Docker Swarm, Apache Mesos.
- Advancement: Enabled scalable, resilient, and complex distributed systems development and deployment. The "environment" started encompassing the entire cluster.
Phase 5: Cloud-Native, Serverless & Intelligent Environments (Present - Future)
-
Cloud-Native Development:
- Description: Leveraging cloud services (managed databases, message queues, serverless functions) directly within the development workflow. Developers focus on application logic, offloading infrastructure management to cloud providers. Containers become a key deployment unit in this paradigm.
- Tools: AWS Lambda, Azure Functions, Google Cloud Run, cloud-managed databases.
- Advancement: Reduced operational overhead, increased focus on business logic, highly scalable deployments.
-
Remote Development & Cloud-Based IDEs:
- Description: The full development environment (editor, terminal, debugger, code) can now reside in the cloud, accessed via a thin client or web browser. This means developers can work from any device, anywhere, with powerful cloud resources backing their environment.
- Tools: GitHub Codespaces, Gitpod, AWS Cloud9, VS Code Remote Development.
- Advancement: Instant onboarding, consistent remote environments, access to high-spec machines regardless of local hardware, enhanced security.
-
Declarative & AI-Assisted Environments (The Near Future):
- Description: Development environments will become even more declarative, where developers specify what they need, and AI/automation tools provision and maintain it. AI will proactively identify dependency issues, optimize resource usage, suggest code snippets, and perform automated testing within the environment.
- Tools: Next-gen dev container specifications, AI agents integrated into IDEs and CI/CD pipelines.
- Prediction: Near-zero environment setup time, self-healing environments, proactive problem identification, truly seamless collaboration.
web3 #computing #cloud #devstr
-
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 90152b7f:04e57401
2025-05-24 03:47:24
@ 90152b7f:04e57401
2025-05-24 03:47:24"Army study suggests U.S. force of 20,000"
The Washington Times - Friday, April 5, 2002
The Bush administration says there are no active plans to put American peacekeepers between Palestinians and Israelis, but at least one internal military study says 20,000 well-armed troops would be needed.
The Army’s School of Advanced Military Studies (SAMS), an elite training ground and think tank at Fort Leavenworth, Kan., produced the study last year. The 68-page paper tells how the major operation would be run the first year, with peacekeepers stationed in Gaza, Hebron, Jerusalem and Nablus.
One major goal would be to “neutralize leadership of Palestine dissenting factions [and] prevent inter-Palestinian violence.”
The military is known to update secret contingency plans in the event international peacekeepers are part of a comprehensive Middle East peace plan. The SAMS study, a copy of which was obtained by The Washington Times, provides a glimpse of what those plans might entail.
Defense Secretary Donald H. Rumsfeld repeatedly has said the administration has no plans to put American troops between the warring factions. But since the escalation of violence, more voices in the debate are beginning to suggest that some type of American-led peace enforcement team is needed.
Sen. Arlen Specter, Pennsylvania Republican, quoted U.S. special envoy Gen. Anthony Zinni as saying there is a plan, if needed, to put a limited number of American peacekeepers in the Israeli-occupied territories.
Asked on CBS whether he could envision American troops on the ground, Mr. Specter said Sunday: “If we were ever to stabilize the situation, and that was a critical factor, it’s something that I would be willing to consider.”
Added Sen. Joseph R. Biden Jr., Delaware Democrat and Senate Foreign Relations Committee chairman, “In that context, yes, and with European forces as well.”
The recent history of international peacekeeping has shown that it often takes American firepower and prestige for the operation to work. The United Nations made futile attempts to stop Serbian attacks on the Muslim population in Bosnia.
The U.S. entered the fray by bombing Serbian targets and bringing about a peace agreement that still is being backed up by American soldiers on the ground. U.S. combat troops are also in Kosovo, and they have a more limited role in Macedonia.
But James Phillips, a Middle East analyst at the Heritage Foundation, used the word “disaster” to describe the aftermath of putting an international force in the occupied territories.
“I think that would be a formula for sucking us into the violence,” he said. “United States troops would be a lightening rod for attacks by radical Islamics and other Palestinian extremist groups. The United States cannot afford to stretch its forces any thinner. They’re very busy as it is with the war against international terrorism.”
Mr. Phillips noted that two Norwegian observers in Hebron were killed this week. U.N. representatives on the Lebanon border have been unable to prevent terrorists from attacking Israel.
The SAMS paper tries to predict events in the first year of peacekeeping and the dangers U.S. troops would face.
It calls the Israeli armed forces a “500-pound gorilla in Israel. Well armed and trained. Operates in both Gaza [and the West Bank]. Known to disregard international law to accomplish mission. Very unlikely to fire on American forces.”
On the Mossad, the Israeli intelligence service, the Army study says, “Wildcard. Ruthless and cunning. Has capability to target U.S. forces and make it look like a Palestinian/Arab act.”
It described Palestinian youth as “loose cannons; under no control, sometimes violent.” The study was done by 60 officers dubbed the “Jedi Knights,” as all second-year SAMS students are called. The Times first reported on their work in September. Recent violence in the Middle East has raised questions about what type of force it would take to keep the peace.
In the past, SAMS has done studies for the Army chief of staff and the Joint Chiefs. SAMS personnel helped plan the allied ground attack that liberated Kuwait.
The Middle East study sets goals that a peace force should accomplish in the first 30 days. They include “create conditions for development of Palestinian State and security of [Israel],” ensure “equal distribution of contract value or equivalent aid” and “build lasting relationships based on new legal borders and not religious-territorial claims.”
The SAMS report does not specify a full order of battle for the 20,000 troops. An Army source who reviewed the paper said each of three brigades would require about 100 armored vehicles, 25 tanks and 12 self-propelled howitzers, along with attack helicopters and spy drones.
The Palestinians have supported calls for an international force, but Tel Aviv has opposed the idea.
https://www.washingtontimes.com/news/2002/apr/5/20020405-041726-2086r/
-
 @ 58537364:705b4b85
2025-05-24 03:25:05
@ 58537364:705b4b85
2025-05-24 03:25:05Ep 228 "วิชาชีวิต"
คนเราเมื่อเกิดมาแล้ว ไม่ได้หวังแค่มีชีวิตรอดเท่านั้น แต่ยังปรารถนา "ความเจริญก้าวหน้า" และ "ความสุขในชีวิต"
จึงพากันศึกษาเล่าเรียนเพื่อให้มี "วิชาความรู้" สำหรับการประกอบอาชีพ โดยเชื่อว่า การงานที่มั่นคงย่อมนำ "ความสำเร็จ" และ "ความเจริญก้าวหน้า" มาให้
อย่างไรก็ตาม...ความสำเร็จในวิชาชีพหรือความเจริญก้าวหน้าในชีวิต ไม่ได้เป็นหลักประกันความสุขอย่างแท้จริง
แม้เงินทองและทรัพย์สมบัติจะช่วยให้ชีวิตมีความสุข สะดวก สบาย แต่ไม่ได้ช่วยให้สุขใจในสิ่งที่ตนมี หากยังรู้สึกว่า "ตนยังมีไม่พอ"
ขณะเดียวกันชื่อเสียงเกียรติยศที่ได้มาก็ไม่ช่วยให้คลายความทุกข์ใจ เมื่อต้องเผชิญปัญหาต่างๆ นาๆ
ทั้งการพลัดพราก การสูญเสียบุคคลผู้เป็นที่รัก ความเจ็บป่วย และความตายที่ต้องเกิดขึ้นกับทุกคน
ยิ่งกว่านั้น...ความสำเร็จในอาชีพและความเจริญก้าวหน้าในชีวิต ล้วนเป็น "สิ่งไม่เที่ยง" แปรผันตกต่ำ ไม่สามารถควบคุมได้
วิชาชีพทั้งหลายช่วยให้เราหาเงินได้มากขึ้น แต่ไม่ได้ช่วยให้เราเข้าถึง "ความสุขที่แท้จริง"
คนที่ประสบความสำเร็จในวิชาชีพไม่น้อย ที่มีชีวิตอมทุกข์ ความเครียดรุมเร้า สุขภาพเสื่อมโทรม
หากเราไม่อยากเผชิญกับสิ่งเหล่านี้ ควรเรียน "วิชาชีวิต" เพื่อเข้าใจโลก เข้าใจชีวิต รู้เท่าทันความผันแปรไปของสรรพสิ่ง
วิชาชีวิต...เรียนจากประสบการณ์ชีวิต เมื่อมีปัญหาต่างๆ ขอให้คิดว่า คือ "บททดสอบ"
จงหมั่นศึกษาหาบทเรียนจากวิชานี้อยู่เสมอ สร้าง "ความตระหนักรู้" ถึงความสำคัญในการมีชีวิต
ช่วงที่ผ่านมา เมื่อมีปัญหาฉันไม่สามารถหาทางออกจากทุกข์ได้เศร้า เสียใจ ทุรน ทุราย สอบตก "วิชาชีวิต"
โชคดีครูบาอาจารย์ให้ข้อคิด กล่าวว่า เป็นเรื่องธรรมดาหากเรายังไม่เข้าใจชีวิต ทุกสิ่งล้วนผันแปร เกิด-ดับ เป็นธรรมดา ท่านเมตตาส่งหนังสือเล่มนี้มาให้
เมื่อค่อยๆ ศึกษา ทำความเข้าใจ นำความทุกข์ที่เกิดขึ้นมาพิจารณา เห็นว่าเมื่อ "สอบตก" ก็ "สอบใหม่" จนกว่าจะผ่านไปได้
วิชาทางโลกเมื่อสอบตกยังเปิดโอกาสให้เรา "สอบซ่อม" วิชาทางธรรมก็เช่นเดียวกัน หากเจอปัญหา อุปสรรค หรือ ความทุกข์ถาโถมเข้ามา ขอให้เราตั้งสติ ว่า จะตั้งใจทำข้อสอบนี้ให้ผ่านไปให้จงได้
หากเราสามารถดำเนินชีวิตด้วยความเข้าใจ เราจะค้นพบ "วิชาชีวิต" ที่สามารถทำให้หลุดพ้นจากความทุกข์ได้แน่นอน
ด้วยรักและปรารถนาดี ปาริชาติ รักตะบุตร 21 เมษายน 2566

น้อมกราบขอบพระคุณพระ อ.ไพศาล วิสาโล เป็นอย่างสูง ที่ท่านเมตตา ให้ข้อธรรมะยามทุกข์ใจและส่งหนังสือมาให้ จึงตั้งใจอยากแบ่งปันเป็นธรรมทาน
-
 @ a008def1:57a3564d
2025-04-30 17:52:11
@ a008def1:57a3564d
2025-04-30 17:52:11A Vision for #GitViaNostr
Git has long been the standard for version control in software development, but over time, we has lost its distributed nature. Originally, Git used open, permissionless email for collaboration, which worked well at scale. However, the rise of GitHub and its centralized pull request (PR) model has shifted the landscape.
Now, we have the opportunity to revive Git's permissionless and distributed nature through Nostr!
We’ve developed tools to facilitate Git collaboration via Nostr, but there are still significant friction that prevents widespread adoption. This article outlines a vision for how we can reduce those barriers and encourage more repositories to embrace this approach.
First, we’ll review our progress so far. Then, we’ll propose a guiding philosophy for our next steps. Finally, we’ll discuss a vision to tackle specific challenges, mainly relating to the role of the Git server and CI/CD.
I am the lead maintainer of ngit and gitworkshop.dev, and I’ve been fortunate to work full-time on this initiative for the past two years, thanks to an OpenSats grant.
How Far We’ve Come
The aim of #GitViaNostr is to liberate discussions around code collaboration from permissioned walled gardens. At the core of this collaboration is the process of proposing and applying changes. That's what we focused on first.
Since Nostr shares characteristics with email, and with NIP34, we’ve adopted similar primitives to those used in the patches-over-email workflow. This is because of their simplicity and that they don’t require contributors to host anything, which adds reliability and makes participation more accessible.
However, the fork-branch-PR-merge workflow is the only model many developers have known, and changing established workflows can be challenging. To address this, we developed a new workflow that balances familiarity, user experience, and alignment with the Nostr protocol: the branch-PR-merge model.
This model is implemented in ngit, which includes a Git plugin that allows users to engage without needing to learn new commands. Additionally, gitworkshop.dev offers a GitHub-like interface for interacting with PRs and issues. We encourage you to try them out using the quick start guide and share your feedback. You can also explore PRs and issues with gitplaza.
For those who prefer the patches-over-email workflow, you can still use that approach with Nostr through gitstr or the
ngit sendandngit listcommands, and explore patches with patch34.The tools are now available to support the core collaboration challenge, but we are still at the beginning of the adoption curve.
Before we dive into the challenges—such as why the Git server setup can be jarring and the possibilities surrounding CI/CD—let’s take a moment to reflect on how we should approach the challenges ahead of us.
Philosophy
Here are some foundational principles I shared a few years ago:
- Let Git be Git
- Let Nostr be Nostr
- Learn from the successes of others
I’d like to add one more:
- Embrace anarchy and resist monolithic development.
Micro Clients FTW
Nostr celebrates simplicity, and we should strive to maintain that. Monolithic developments often lead to unnecessary complexity. Projects like gitworkshop.dev, which aim to cover various aspects of the code collaboration experience, should not stifle innovation.
Just yesterday, the launch of following.space demonstrated how vibe-coded micro clients can make a significant impact. They can be valuable on their own, shape the ecosystem, and help push large and widely used clients to implement features and ideas.
The primitives in NIP34 are straightforward, and if there are any barriers preventing the vibe-coding of a #GitViaNostr app in an afternoon, we should work to eliminate them.
Micro clients should lead the way and explore new workflows, experiences, and models of thinking.
Take kanbanstr.com. It provides excellent project management and organization features that work seamlessly with NIP34 primitives.
From kanban to code snippets, from CI/CD runners to SatShoot—may a thousand flowers bloom, and a thousand more after them.
Friction and Challenges
The Git Server
In #GitViaNostr, maintainers' branches (e.g.,
master) are hosted on a Git server. Here’s why this approach is beneficial:- Follows the original Git vision and the "let Git be Git" philosophy.
- Super efficient, battle-tested, and compatible with all the ways people use Git (e.g., LFS, shallow cloning).
- Maintains compatibility with related systems without the need for plugins (e.g., for build and deployment).
- Only repository maintainers need write access.
In the original Git model, all users would need to add the Git server as a 'git remote.' However, with ngit, the Git server is hidden behind a Nostr remote, which enables:
- Hiding complexity from contributors and users, so that only maintainers need to know about the Git server component to start using #GitViaNostr.
- Maintainers can easily swap Git servers by updating their announcement event, allowing contributors/users using ngit to automatically switch to the new one.
Challenges with the Git Server
While the Git server model has its advantages, it also presents several challenges:
- Initial Setup: When creating a new repository, maintainers must select a Git server, which can be a jarring experience. Most options come with bloated social collaboration features tied to a centralized PR model, often difficult or impossible to disable.
-
Manual Configuration: New repositories require manual configuration, including adding new maintainers through a browser UI, which can be cumbersome and time-consuming.
-
User Onboarding: Many Git servers require email sign-up or KYC (Know Your Customer) processes, which can be a significant turn-off for new users exploring a decentralized and permissionless alternative to GitHub.
Once the initial setup is complete, the system works well if a reliable Git server is chosen. However, this is a significant "if," as we have become accustomed to the excellent uptime and reliability of GitHub. Even professionally run alternatives like Codeberg can experience downtime, which is frustrating when CI/CD and deployment processes are affected. This problem is exacerbated when self-hosting.
Currently, most repositories on Nostr rely on GitHub as the Git server. While maintainers can change servers without disrupting their contributors, this reliance on a centralized service is not the decentralized dream we aspire to achieve.
Vision for the Git Server
The goal is to transform the Git server from a single point of truth and failure into a component similar to a Nostr relay.
Functionality Already in ngit to Support This
-
State on Nostr: Store the state of branches and tags in a Nostr event, removing reliance on a single server. This validates that the data received has been signed by the maintainer, significantly reducing the trust requirement.
-
Proxy to Multiple Git Servers: Proxy requests to all servers listed in the announcement event, adding redundancy and eliminating the need for any one server to match GitHub's reliability.
Implementation Requirements
To achieve this vision, the Nostr Git server implementation should:
-
Implement the Git Smart HTTP Protocol without authentication (no SSH) and only accept pushes if the reference tip matches the latest state event.
-
Avoid Bloat: There should be no user authentication, no database, no web UI, and no unnecessary features.
-
Automatic Repository Management: Accept or reject new repositories automatically upon the first push based on the content of the repository announcement event referenced in the URL path and its author.
Just as there are many free, paid, and self-hosted relays, there will be a variety of free, zero-step signup options, as well as self-hosted and paid solutions.
Some servers may use a Web of Trust (WoT) to filter out spam, while others might impose bandwidth or repository size limits for free tiers or whitelist specific npubs.
Additionally, some implementations could bundle relay and blossom server functionalities to unify the provision of repository data into a single service. These would likely only accept content related to the stored repositories rather than general social nostr content.
The potential role of CI / CD via nostr DVMs could create the incentives for a market of highly reliable free at the point of use git servers.
This could make onboarding #GitViaNostr repositories as easy as entering a name and selecting from a multi-select list of Git server providers that announce via NIP89.
!(image)[https://image.nostr.build/badedc822995eb18b6d3c4bff0743b12b2e5ac018845ba498ce4aab0727caf6c.jpg]
Git Client in the Browser
Currently, many tasks are performed on a Git server web UI, such as:
- Browsing code, commits, branches, tags, etc.
- Creating and displaying permalinks to specific lines in commits.
- Merging PRs.
- Making small commits and PRs on-the-fly.
Just as nobody goes to the web UI of a relay (e.g., nos.lol) to interact with notes, nobody should need to go to a Git server to interact with repositories. We use the Nostr protocol to interact with Nostr relays, and we should use the Git protocol to interact with Git servers. This situation has evolved due to the centralization of Git servers. Instead of being restricted to the view and experience designed by the server operator, users should be able to choose the user experience that works best for them from a range of clients. To facilitate this, we need a library that lowers the barrier to entry for creating these experiences. This library should not require a full clone of every repository and should not depend on proprietary APIs. As a starting point, I propose wrapping the WASM-compiled gitlib2 library for the web and creating useful functions, such as showing a file, which utilizes clever flags to minimize bandwidth usage (e.g., shallow clone, noblob, etc.).
This approach would not only enhance clients like gitworkshop.dev but also bring forth a vision where Git servers simply run the Git protocol, making vibe coding Git experiences even better.
song
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 created song with a complementary vision that has shaped how I see the role of the git server. Its a self-hosted, nostr-permissioned git server with a relay baked in. Its currently a WIP and there are some compatability with ngit that we need to work out.
We collaborated on the nostr-permissioning approach now reflected in nip34.
I'm really excited to see how this space evolves.
CI/CD
Most projects require CI/CD, and while this is often bundled with Git hosting solutions, it is currently not smoothly integrated into #GitViaNostr yet. There are many loosely coupled options, such as Jenkins, Travis, CircleCI, etc., that could be integrated with Nostr.
However, the more exciting prospect is to use DVMs (Data Vending Machines).
DVMs for CI/CD
Nostr Data Vending Machines (DVMs) can provide a marketplace of CI/CD task runners with Cashu for micro payments.
There are various trust levels in CI/CD tasks:
- Tasks with no secrets eg. tests.
- Tasks using updatable secrets eg. API keys.
- Unverifiable builds and steps that sign with Android, Nostr, or PGP keys.
DVMs allow tasks to be kicked off with specific providers using a Cashu token as payment.
It might be suitable for some high-compute and easily verifiable tasks to be run by the cheapest available providers. Medium trust tasks could be run by providers with a good reputation, while high trust tasks could be run on self-hosted runners.
Job requests, status, and results all get published to Nostr for display in Git-focused Nostr clients.
Jobs could be triggered manually, or self-hosted runners could be configured to watch a Nostr repository and kick off jobs using their own runners without payment.
But I'm most excited about the prospect of Watcher Agents.
CI/CD Watcher Agents
AI agents empowered with a NIP60 Cashu wallet can run tasks based on activity, such as a push to master or a new PR, using the most suitable available DVM runner that meets the user's criteria. To keep them running, anyone could top up their NIP60 Cashu wallet; otherwise, the watcher turns off when the funds run out. It could be users, maintainers, or anyone interested in helping the project who could top up the Watcher Agent's balance.
As aluded to earlier, part of building a reputation as a CI/CD provider could involve running reliable hosting (Git server, relay, and blossom server) for all FOSS Nostr Git repositories.
This provides a sustainable revenue model for hosting providers and creates incentives for many free-at-the-point-of-use hosting providers. This, in turn, would allow one-click Nostr repository creation workflows, instantly hosted by many different providers.
Progress to Date
nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr and nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 have been working on a runner that uses GitHub Actions YAML syntax (using act) for the dvm-cicd-runner and takes Cashu payment. You can see example runs on GitWorkshop. It currently takes testnuts, doesn't give any change, and the schema will likely change.
Note: The actions tab on GitWorkshop is currently available on all repositories if you turn on experimental mode (under settings in the user menu).
It's a work in progress, and we expect the format and schema to evolve.
Easy Web App Deployment
For those disapointed not to find a 'Nostr' button to import a git repository to Vercel menu: take heart, they made it easy. vercel.com_import_options.png there is a vercel cli that can be easily called in CI / CD jobs to kick of deployments. Not all managed solutions for web app deployment (eg. netlify) make it that easy.
Many More Opportunities
Large Patches via Blossom
I would be remiss not to mention the large patch problem. Some patches are too big to fit into Nostr events. Blossom is perfect for this, as it allows these larger patches to be included in a blossom file and referenced in a new patch kind.
Enhancing the #GitViaNostr Experience
Beyond the large patch issue, there are numerous opportunities to enhance the #GitViaNostr ecosystem. We can focus on improving browsing, discovery, social and notifications. Receiving notifications on daily driver Nostr apps is one of the killer features of Nostr. However, we must ensure that Git-related notifications are easily reviewable, so we don’t miss any critical updates.
We need to develop tools that cater to our curiosity—tools that enable us to discover and follow projects, engage in discussions that pique our interest, and stay informed about developments relevant to our work.
Additionally, we should not overlook the importance of robust search capabilities and tools that facilitate migrations.
Concluding Thoughts
The design space is vast. Its an exciting time to be working on freedom tech. I encourage everyone to contribute their ideas and creativity and get vibe-coding!
I welcome your honest feedback on this vision and any suggestions you might have. Your insights are invaluable as we collaborate to shape the future of #GitViaNostr. Onward.
Contributions
To conclude, I want to acknowledge some the individuals who have made recent code contributions related to #GitViaNostr:
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 (gitstr, song, patch34), nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks (gitplaza)
nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume (ngit contributions, git-remote-blossom),nostr:npub16p8v7varqwjes5hak6q7mz6pygqm4pwc6gve4mrned3xs8tz42gq7kfhdw (SatShoot, Flotilla-Budabit), nostr:npub1ehhfg09mr8z34wz85ek46a6rww4f7c7jsujxhdvmpqnl5hnrwsqq2szjqv (Flotilla-Budabit, Nostr Git Extension), nostr:npub1ahaz04ya9tehace3uy39hdhdryfvdkve9qdndkqp3tvehs6h8s5slq45hy (gnostr and experiments), and others.
nostr:npub1uplxcy63up7gx7cladkrvfqh834n7ylyp46l3e8t660l7peec8rsd2sfek (git-remote-nostr)
Project Management nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t (kanbanstr) Code Snippets nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 (nodebin.io) nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac (snipsnip.dev)
CI / CD nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr
and for their nostr:npub1c03rad0r6q833vh57kyd3ndu2jry30nkr0wepqfpsm05vq7he25slryrnw nostr:npub1qqqqqq2stely3ynsgm5mh2nj3v0nk5gjyl3zqrzh34hxhvx806usxmln03 and nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z for their testing, feedback, ideas and encouragement.
Thank you for your support and collaboration! Let me know if I've missed you.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 502ab02a:a2860397
2025-05-24 01:14:43
@ 502ab02a:a2860397
2025-05-24 01:14:43ในสายตาคนรักสุขภาพทั่วโลก “อโวคาโด” คือผลไม้ในฝัน มันมีไขมันดี มีไฟเบอร์สูง ช่วยลดคอเลสเตอรอลได้ มีวิตามินอี มีโพแทสเซียม และที่สำคัญคือ "ดูดี" ทุกครั้งที่ถูกปาดวางบนขนมปังโฮลวีตในชามสลัด หรือบนโฆษณาอาหารคลีนสุดหรู
แต่ในสายตาชาวไร่บางคนในเม็กซิโกหรือชุมชนพื้นเมืองในโดมินิกัน อโวคาโดไม่ใช่ผลไม้แห่งสุขภาพ แต่มันคือสัญลักษณ์ของความรุนแรง การกดขี่ และการสูญเสียเสรีภาพในผืนดินของตัวเอง
เมื่ออาหารกลายเป็นทองคำ กลุ่มอิทธิพลก็ไม่เคยพลาดจะเข้าครอบครอง
เรามักได้ยินคำว่า "ทองคำเขียว" หรือ Green Gold ใช้เรียกอโวคาโด เพราะในรอบ 20 ปีที่ผ่านมา ความต้องการบริโภคของมันพุ่งสูงขึ้นเป็นเท่าตัว โดยเฉพาะในสหรัฐฯ และยุโรป จากผลการวิจัยของมหาวิทยาลัยฮาร์วาร์ดและข้อมูลการส่งออกของ USDA พบว่า 90% ของอโวคาโดที่บริโภคในอเมริกา มาจากรัฐมิโชอากังของเม็กซิโก พื้นที่ซึ่งควบคุมโดยกลุ่มค้ายาเสพติดไม่ต่างจากเจ้าของสวนตัวจริง
พวกเขาเรียกเก็บ “ค่าคุ้มครอง” จากเกษตรกร โดยใช้วิธีเดียวกับมาเฟีย คือ ถ้าไม่จ่าย ก็เจ็บตัวหรือหายตัว ไม่ว่าจะเป็นกลุ่ม CJNG (Jalisco New Generation Cartel), Familia Michoacana หรือ Caballeros Templarios พวกเขาไม่ได้สนใจว่าใครปลูกหรือใครรดน้ำ ตราบใดที่ผลผลิตสามารถเปลี่ยนเป็นเงินได้
องค์กรอาชญากรรมเหล่านี้ไม่ได้แค่ “แฝงตัว” ในอุตสาหกรรม แต่ ยึดครอง ห่วงโซ่การผลิตทั้งหมด ตั้งแต่แปลงปลูกไปจนถึงโรงบรรจุและเส้นทางขนส่ง คนที่ไม่ยอมเข้าระบบมืดอาจต้องพบจุดจบในป่า หรือไม่มีชื่ออยู่ในทะเบียนบ้านอีกต่อไป
จากรายงานของเว็บไซต์ Food is Power องค์กรไม่แสวงกำไรด้านความยุติธรรมด้านอาหารในสหรัฐฯ เผยว่า ในปี 2020 มีเกษตรกรในเม็กซิโกจำนวนมากที่ถูกข่มขู่ บางรายถึงขั้นถูกฆาตกรรม เพราะปฏิเสธจ่ายค่าคุ้มครองจากกลุ่มค้ายา
การปลูกอโวคาโดไม่ใช่เรื่องเบาๆ กับธรรมชาติ เพราะมันต้องการ “น้ำ” มากถึง 272 ลิตรต่อผลเดียว! เรามาดูว่า “272 ลิตร” นี้ เท่ากับอะไรบ้างในชีวิตจริง อาบน้ำฝักบัวนาน 10–12 นาที (โดยเฉลี่ยใช้น้ำ 20–25 ลิตรต่อนาที) ใช้น้ำซักเสื้อผ้าเครื่องหนึ่ง (เครื่องซักผ้า 1 ครั้งกินประมาณ 60–100 ลิตร) น้ำดื่มของคนหนึ่งคนได้นานเกือบ เดือน (คนเราต้องการน้ำดื่มประมาณ 1.5–2 ลิตรต่อวัน)
ถ้าเราใช้ข้อมูลจาก FAO และ Water Footprint Network การผลิตเนื้อวัว 1 กิโลกรัม ต้องใช้น้ำ 15,000 ลิตร (รวมทั้งการปลูกหญ้า อาหารสัตว์ การดื่มน้ำของวัว ฯลฯ) ได้โปรตีนราว 250 กรัม อโวคาโด 1 กิโลกรัม (ราว 5 ผล) ใช้น้ำประมาณ 1,360 ลิตร ได้โปรตีนเพียง 6–8 กรัมเท่านั้น พูดง่ายๆคือ เมื่อเทียบอัตราส่วนเป็นลิตรต่อกรัมโปรตีนแล้วนั้น วัวใช้น้ำ 60 ลิตรต่อกรัมโปรตีน / อโวคาโด ใช้น้ำ 194 ลิตรต่อกรัมโปรตีน แถมการเลี้ยงวัวในระบบธรรมชาติ (เช่น pasture-raised หรือ regenerative farming) ยังสามารถเป็นส่วนหนึ่งของระบบหมุนเวียนน้ำและคาร์บอนได้ พอเห็นภาพแล้วใช่ไหมครับ ดังนั้นเราควรระมัดระวังการเสพสื่อเอาไว้ด้วยว่า คำว่า "ดีต่อโลก" ไม่ได้หมายถึงพืชอย่างเดียว ทุกธุรกิจถ้าทำแบบที่ควรทำ มันยังสามารถผลักดันโลกไม่ให้ตกอยู่ในมือองค์กร future food ได้ เพราะมูลค่ามันสูงมาก
และเมื่อราคาสูง พื้นที่เพาะปลูกก็ขยายอย่างไร้การควบคุม ป่าธรรมชาติในรัฐมิโชอากังถูกแอบโค่นแบบผิดกฎหมายเพื่อแปลงสภาพเป็นไร่ “ทองเขียว” ข้อมูลจาก Reuters พบว่าผลไม้ที่ถูกส่งออกไปยังสหรัฐฯ บางส่วนมาจากแปลงปลูกที่บุกรุกป่าคุ้มครอง และรัฐบาลเองก็ไม่สามารถควบคุมได้เพราะอิทธิพลของกลุ่มทุนและมาเฟีย
ในโดมินิกันก็เช่นกัน มีรายงานจากสำนักข่าว Gestalten ว่าพื้นที่ป่าสงวนหลายพันไร่ถูกเปลี่ยนเป็นไร่อโวคาโด เพื่อป้อนตลาดผู้บริโภคในอเมริกาและยุโรปโดยตรง โดยไม่มีการชดเชยใดๆ แก่ชุมชนท้องถิ่น
สุขภาพที่ดีไม่ควรได้มาจากการทำลายสุขภาพของคนอื่น ไม่ควรมีผลไม้ใดที่ดูดีในจานของเรา แล้วเบื้องหลังเต็มไปด้วยคราบเลือดและน้ำตาของคนปลูก
เฮียไม่ได้จะบอกให้เลิกกินอโวคาโดเลย แต่เฮียอยากให้เรารู้ทัน ว่าความนิยมของอาหารสุขภาพวันนี้ กำลังเป็นสนามใหม่ของกลุ่มทุนโลก ที่พร้อมจะครอบครองด้วย “อำนาจอ่อน” ผ่านแบรนด์อาหารธรรมชาติ ผ่านกฎหมายสิ่งแวดล้อม หรือแม้แต่การครอบงำตลาดเสรีด้วยกำลังอาวุธ
นี่ไม่ใช่เรื่องไกลตัว เพราะเมื่อกลุ่มทุนเริ่มฮุบเมล็ดพันธุ์ คุมเส้นทางขนส่ง คุมฉลาก Certified Organic ทั้งหลาย พวกเขาก็ “ควบคุมสุขภาพ” ของผู้บริโภคเมืองอย่างเราไปด้วยโดยอ้อม
คำถามสำคัญที่มาทุกครั้งเวลามีเนื้อหาอะไรมาฝากคือ แล้วเราจะทำอะไรได้? 555555 - เลือกบริโภคผลไม้จากแหล่งที่โปร่งใสหรือปลูกเองได้ - สนับสนุนเกษตรกรรายย่อยที่ไม่อยู่ภายใต้กลุ่มทุน - ใช้เสียงของผู้บริโภคกดดันให้มีระบบตรวจสอบต้นทางจริง ไม่ใช่แค่ฉลากเขียวสวยๆ - และที่สำคัญ อย่าเชื่อว่า “ทุกสิ่งที่เขาวางให้ดูสุขภาพดี” จะดีจริง (ข้อนี่ละตัวดีเลยครับ)
สุขภาพไม่ใช่สินค้า และอาหารไม่ควรเป็นอาวุธของกลุ่มทุน หากเราเริ่มตระหนักว่าอาหารคือการเมือง น้ำคืออำนาจ และแปลงเกษตรคือสนามรบ เฮียเชื่อว่าผู้บริโภคอย่างเราจะไม่ยอมเป็นหมากอีกต่อไป #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:49
@ 6be5cc06:5259daf0
2025-04-28 01:05:49Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 611021ea:089a7d0f
2025-05-24 00:00:04
@ 611021ea:089a7d0f
2025-05-24 00:00:04The world of health and fitness data is booming. Users are tracking more aspects of their well-being than ever before, from daily steps and workout intensity to sleep patterns and caloric intake. But for developers looking to build innovative applications on this data, significant hurdles remain: ensuring user privacy, achieving interoperability between different services, and simply managing the complexity of diverse health metrics.
Enter the NIP-101h Health Profile Framework and its companion tools: the HealthNote SDK and the HealthNote API. This ecosystem is designed to empower developers to create next-generation health and fitness applications that are both powerful and privacy-preserving, built on the decentralized and user-centric principles of Nostr.
NIP-101h: A Standardized Language for Health Metrics
At the core of this ecosystem is NIP-101h. It's a Nostr Improvement Proposal that defines a standardized way to represent, store, and share granular health and fitness data. Instead of proprietary data silos, NIP-101h introduces specific Nostr event kinds for individual metrics like weight (kind
1351), height (kind1352), step count (kind1359), and many more.Key features of NIP-101h:
- Granularity: Each piece of health information (e.g., weight, caloric intake) is a distinct Nostr event, allowing for fine-grained control and access.
- User Control: Built on Nostr, the data remains under user control. Users decide what to share, with whom, and on which relays.
- Standardization: Defines common structures for units, timestamps, and metadata, promoting interoperability.
- Extensibility: New metrics can be added as new NIP-101h.X specifications, allowing the framework to evolve.
- Privacy by Design: Encourages the use of NIP-04/NIP-44 for encryption and includes a
consenttag for users to specify data-sharing preferences.
You can explore the full NIP-101h specification and its metric directory in the main project repository.
The HealthNote SDK: Simplifying Client-Side Integration
While NIP-101h provides the "what," the HealthNote SDK provides the "how" for client-side applications. This (currently draft) TypeScript SDK aims to make it trivial for developers to:
- Create & Validate NIP-101h Events: Easily construct well-formed Nostr events for any supported health metric, ensuring they conform to the NIP-101h specification.
- Handle Encryption: Seamlessly integrate with NIP-44 to encrypt sensitive health data before publication.
- Manage Consent: Automatically include appropriate
consenttags (e.g., defaulting toaggregate-only) to respect user preferences. - Publish to Relays: Interact with Nostr relays to publish the user's health data.
- Prepare Data for Analytics: Extract minimal, privacy-preserving "stat-blobs" for use with the HealthNote API.
The SDK's goal is to abstract away the low-level details of Nostr event creation and NIP-101h formatting, letting developers focus on their application's unique features.
The HealthNote API: Powerful Insights, Zero Raw Data Exposure
This is where things get really exciting for developers wanting to build data-driven features. The HealthNote API (detailed in
HealthNote-API.md) is a server-side component designed to provide powerful analytics over aggregated NIP-101h data without ever accessing or exposing individual users' raw, unencrypted metrics.Here's how it achieves this:
- Privacy-Preserving Ingestion: The SDK sends only "stat-blobs" to the API. These blobs contain the numeric value, unit, timestamp, and metric kind, but not the original encrypted content or sensitive user identifiers beyond what's necessary for aggregation.
- Aggregation at its Core: The API's endpoints are designed to return only aggregated data.
GET /trend: Provides time-series data (e.g., average daily step count over the last month).GET /correlate: Computes statistical correlations between two metrics (e.g., does increased activity duration correlate with changes in workout intensity?).GET /distribution: Shows how values for a metric are distributed across the user base.
- Built-in Privacy Techniques:
- k-Anonymity: Ensures that each data point in an aggregated response represents at least 'k' (e.g., 5) distinct users, preventing re-identification.
- Differential Privacy (Optional): Can add statistical noise to query results, further protecting individual data points while preserving overall trends.
- No Raw Data Access for Developers: Developers querying the API receive only these aggregated, anonymized results, perfect for powering charts, dashboards, and trend analysis in their applications.
A Typical Workflow
- A user records a workout in their NIP-101h-compatible fitness app.
- The app uses the HealthNote SDK to create NIP-101h events for metrics like distance, duration, and calories burned. Sensitive data is encrypted.
- The SDK publishes these events to the user's configured Nostr relays.
- The SDK also extracts stat-blobs (e.g.,
{ kind: 1363, value: 5, unit: 'km', ... }) and sends them to the HealthNote API for ingestion, tagged with anaggregate-onlyconsent. - Later, the app (or an authorized third-party service) queries the HealthNote API:
GET /trend?kind=1363&bucket=week&stat=sum. - The API returns a JSON object like:
{"series": [{"date": "2024-W20", "value": 15000}, ...]}showing the total distance run by all consenting users, week by week. This data can directly populate a trend chart.
Benefits for the Ecosystem
- For Users:
- Greater control and ownership of their health data.
- Ability to use a diverse range of interoperable health and fitness apps.
- Confidence that their data can contribute to insights without sacrificing personal privacy.
- For Developers:
- Easier to build sophisticated health and fitness applications without becoming privacy experts or building complex data aggregation pipelines.
- Access to rich, aggregated data for creating compelling user-facing features (trends, benchmarks, correlations).
- Reduced burden of storing and securing sensitive raw health data for analytical purposes.
- Opportunity to participate in an open, interoperable ecosystem.
The Road Ahead
The NIP-101h framework, the HealthNote SDK, and the HealthNote API are foundational pieces for a new generation of health and fitness applications. As these tools mature and gain adoption, we envision a vibrant ecosystem where users can seamlessly move their data between services, and developers can innovate rapidly, all while upholding the highest standards of privacy and user control.
We encourage developers to explore the NIP-101h specifications, experiment with the (upcoming) SDK, and review the HealthNote API design. Your feedback and contributions will be invaluable as we build this privacy-first future for health data.
https://github.com/HealthNoteLabs
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 90152b7f:04e57401
2025-05-23 23:38:49
@ 90152b7f:04e57401
2025-05-23 23:38:49WikiLeaks The Global Intelligence Files
Released on 2013-03-04 00:00 GMT
| Email-ID | 296467 | | -------- | -------------------------- | | Date | 2007-10-29 20:54:22 | | From | <hrwpress@hrw.org> | | To | <responses@stratfor.com> |
Gaza: Israel's Fuel and Power Cuts Violate Laws of War\ \ For Immediate Release\ \ Gaza: Israel's Fuel and Power Cuts Violate Laws of War\ \ Civilians Should Not Be Penalized for Rocket Attacks by Armed Groups\ \ (New York, October 29, 2007) - Israel's decision to limit fuel and\ electricity to the Gaza Strip in retaliation for unlawful rocket attacks\ by armed groups amounts to collective punishment against the civilian\ population of Gaza, in violation of international law, and will worsen the\ humanitarian crisis there, Human Rights Watch said today.\ \ "Israel may respond to rocket attacks by armed groups to protect its\ population, but only in lawful ways," said Sarah Leah Whitson, director of\ Human Rights Watch's Middle East division. "Because Israel remains an\ occupying power, in light of its continuing restrictions on Gaza, Israel\ must not take measures that harm the civilian population - yet that is\ precisely what cutting fuel or electricity for even short periods will\ do."\ \ On Sunday, the Israeli Defense Ministry ordered the reduction of fuel\ shipments from Israel to Gaza. A government spokesman said the plan was to\ cut the amount of fuel by 5 to 11 percent without affecting the supply of\ industrial fuel for Gaza's only power plant.\ \ According to Palestinian officials, fuel shipments into Gaza yesterday\ fell by more than 30 percent.\ \ In response to the government's decision, a group of 10 Palestinian and\ Israeli human rights groups petitioned the Israeli Supreme Court on\ Sunday, seeking an immediate injunction against the fuel and electricity\ cuts. The court gave the government five days to respond but did not issue\ a temporary injunction. On Monday, the groups requested an urgent hearing\ before the five days expire.\ \ Last Thursday, Defense Minister Ehud Barak approved cutting electricity to\ Gaza for increasing periods in response to ongoing rocket attacks against\ civilian areas in Israel, but the government has not yet implemented the\ order.\ \ The rockets fired by Palestinian armed groups violate the international\ legal prohibition on indiscriminate attacks because they are highly\ inaccurate and cannot be directed at a specific target. Because Hamas\ exercises power inside Gaza, it is responsible for stopping indiscriminate\ attacks even when carried out by other groups, Human Rights Watch said.\ \ On Friday, Israeli Prime Minister Ehud Olmert said that Israel would\ respond strongly to the ongoing attacks without allowing a humanitarian\ crisis. But the UN's top humanitarian official, UN Deputy\ Secretary-General John Holmes, said that a "serious humanitarian crisis"\ in Gaza already exists, and called on Israel to lift the economic blockade\ that it tightened after Hamas seized power in June.\ \ Israel's decision to cut fuel and electricity is the latest move aimed\ ostensibly against Hamas that is affecting the entire population of Gaza.\ In September, the Israeli cabinet declared Gaza "hostile territory" and\ voted to "restrict the passage of various goods to the Gaza Strip and\ reduce the supply of fuel and electricity." Since then, Israel has\ increasingly blocked supplies into Gaza, letting in limited amounts of\ essential foodstuffs, medicine and humanitarian supplies. According to\ Holmes, the number of humanitarian convoys entering Gaza had dropped to\ 1,500 in September from 3,000 in July.\ \ "Cutting fuel and electricity obstructs vital services," Whitson said.\ "Operating rooms, sewage pumps, and water well pumps all need electricity\ to run."\ \ Israel sells to Gaza roughly 60 percent of the electricity consumed by the\ territory's 1.5 million inhabitants. In June 2006, six Israeli missiles\ struck Gaza's only power plant; today, for most residents, electricity is\ available during only limited hours.\ \ Israeli officials said they would cut electricity for 15 minutes after\ each rocket attack and then for increasingly longer periods if the attacks\ persist. Deputy Defense Minister Matan Vilnai said Israel would\ "dramatically reduce" the power it supplied to Gaza over a period of\ weeks.\ \ Cutting fuel or electricity to the civilian population violates a basic\ principle of international humanitarian law, or the laws of war, which\ prohibit a government that has effective control over a territory from\ attacking or withholding objects that are essential to the survival of the\ civilian population. Such an act would also violate Israel's duty as an\ occupying power to safeguard the health and welfare of the population\ under occupation.\ \ Israel withdrew its military forces and settlers from the Gaza Strip in\ 2005. Nonetheless, Israel remains responsible for ensuring the well-being\ of Gaza's population for as long as, and to the extent that, it retains\ effective control over the area. Israel still exercises control over\ Gaza's airspace, sea space and land borders, as well as its electricity,\ water, sewage and telecommunications networks and population registry.\ Israel can and has also reentered Gaza for security operations at will.\ \ Israeli officials state that by declaring Gaza "hostile territory," it is\ no longer obliged under international law to supply utilities to the\ civilian population, but that is a misstatement of the law.\ \ "A mere declaration does not change the facts on the ground that impose on\ Israel the status and obligations of an occupying power," said Whitson.\ \ For more information, please contact:\ \ In New York, Fred Abrahams (English, German): +1-917-385-7333 (mobile)\ \ In Washington, DC, Joe Stork (English): +1-202-299-4925 (mobile)\ \ In Cairo, Gasser Abdel-Razek (Arabic, English): +20-2-2-794-5036 (mobile);\ or +20-10-502-9999 (mobile)
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 23:37:17
@ 5d4b6c8d:8a1c1ee3
2025-05-23 23:37:17@grayruby loves to blow up the odds of various sports markets at Predyx. Well, the jig is up, because I finally managed to deposit some sats at BetPlay where I can leverage the mismatched odds.
So, I've now locked in guaranteed wins on the 49ers winning the Super Bowl and the Panthers winning the Stanley Cup.
https://stacker.news/items/987847
-
 @ e691f4df:1099ad65
2025-04-24 18:56:12
@ e691f4df:1099ad65
2025-04-24 18:56:12Viewing Bitcoin Through the Light of Awakening
Ankh & Ohm Capital’s Overview of the Psycho-Spiritual Nature of Bitcoin
Glossary:
I. Preface: The Logos of Our Logo
II. An Oracular Introduction
III. Alchemizing Greed
IV. Layers of Fractalized Thought
V. Permissionless Individuation
VI. Dispelling Paradox Through Resonance
VII. Ego Deflation
VIII. The Coin of Great Price
Preface: The Logos of Our Logo
Before we offer our lens on Bitcoin, it’s important to illuminate the meaning behind Ankh & Ohm’s name and symbol. These elements are not ornamental—they are foundational, expressing the cosmological principles that guide our work.
Our mission is to bridge the eternal with the practical. As a Bitcoin-focused family office and consulting firm, we understand capital not as an end, but as a tool—one that, when properly aligned, becomes a vehicle for divine order. We see Bitcoin not simply as a technological innovation but as an emanation of the Divine Logos—a harmonic expression of truth, transparency, and incorruptible structure. Both the beginning and the end, the Alpha and Omega.
The Ankh (☥), an ancient symbol of eternal life, is a key to the integration of opposites. It unites spirit and matter, force and form, continuity and change. It reminds us that capital, like Life, must not only be generative, but regenerative; sacred. Money must serve Life, not siphon from it.
The Ohm (Ω) holds a dual meaning. In physics, it denotes a unit of electrical resistance—the formative tension that gives energy coherence. In the Vedic tradition, Om (ॐ) is the primordial vibration—the sound from which all existence unfolds. Together, these symbols affirm a timeless truth: resistance and resonance are both sacred instruments of the Creator.
Ankh & Ohm, then, represents our striving for union, for harmony —between the flow of life and intentional structure, between incalculable abundance and measured restraint, between the lightbulb’s electrical impulse and its light-emitting filament. We stand at the threshold where intention becomes action, and where capital is not extracted, but cultivated in rhythm with the cosmos.
We exist to shepherd this transformation, as guides of this threshold —helping families, founders, and institutions align with a deeper order, where capital serves not as the prize, but as a pathway to collective Presence, Purpose, Peace and Prosperity.
An Oracular Introduction
Bitcoin is commonly understood as the first truly decentralized and secure form of digital money—a breakthrough in monetary sovereignty. But this view, while technically correct, is incomplete and spiritually shallow. Bitcoin is more than a tool for economic disruption. Bitcoin represents a mythic threshold: a symbol of the psycho-spiritual shift that many ancient traditions have long foretold.
For millennia, sages and seers have spoken of a coming Golden Age. In the Vedic Yuga cycles, in Plato’s Great Year, in the Eagle and Condor prophecies of the Americas—there exists a common thread: that humanity will emerge from darkness into a time of harmony, cooperation, and clarity. That the veil of illusion (maya, materiality) will thin, and reality will once again become transparent to the transcendent. In such an age, systems based on scarcity, deception, and centralization fall away. A new cosmology takes root—one grounded in balance, coherence, and sacred reciprocity.
But we must ask—how does such a shift happen? How do we cross from the age of scarcity, fear, and domination into one of coherence, abundance, and freedom?
One possible answer lies in the alchemy of incentive.
Bitcoin operates not just on the rules of computer science or Austrian economics, but on something far more old and subtle: the logic of transformation. It transmutes greed—a base instinct rooted in scarcity—into cooperation, transparency, and incorruptibility.
In this light, Bitcoin becomes more than code—it becomes a psychoactive protocol, one that rewires human behavior by aligning individual gain with collective integrity. It is not simply a new form of money. It is a new myth of value. A new operating system for human consciousness.
Bitcoin does not moralize. It harmonizes. It transforms the instinct for self-preservation into a pathway for planetary coherence.
Alchemizing Greed
At the heart of Bitcoin lies the ancient alchemical principle of transmutation: that which is base may be refined into gold.
Greed, long condemned as a vice, is not inherently evil. It is a distorted longing. A warped echo of the drive to preserve life. But in systems built on scarcity and deception, this longing calcifies into hoarding, corruption, and decay.
Bitcoin introduces a new game. A game with memory. A game that makes deception inefficient and truth profitable. It does not demand virtue—it encodes consequence. Its design does not suppress greed; it reprograms it.
In traditional models, game theory often illustrates the fragility of trust. The Prisoner’s Dilemma reveals how self-interest can sabotage collective well-being. But Bitcoin inverts this. It creates an environment where self-interest and integrity converge—where the most rational action is also the most truthful.
Its ledger, immutable and transparent, exposes manipulation for what it is: energetically wasteful and economically self-defeating. Dishonesty burns energy and yields nothing. The network punishes incoherence, not by decree, but by natural law.
This is the spiritual elegance of Bitcoin: it does not suppress greed—it transmutes it. It channels the drive for personal gain into the architecture of collective order. Miners compete not to dominate, but to validate. Nodes collaborate not through trust, but through mathematical proof.
This is not austerity. It is alchemy.
Greed, under Bitcoin, is refined. Tempered. Re-forged into a generative force—no longer parasitic, but harmonic.
Layers of Fractalized Thought Fragments
All living systems are layered. So is the cosmos. So is the human being. So is a musical scale.
At its foundation lies the timechain—the pulsing, incorruptible record of truth. Like the heart, it beats steadily. Every block, like a pulse, affirms its life through continuity. The difficulty adjustment—Bitcoin’s internal calibration—functions like heart rate variability, adapting to pressure while preserving coherence.
Above this base layer is the Lightning Network—a second layer facilitating rapid, efficient transactions. It is the nervous system: transmitting energy, reducing latency, enabling real-time interaction across a distributed whole.
Beyond that, emerging tools like Fedimint and Cashu function like the capillaries—bringing vitality to the extremities, to those underserved by legacy systems. They empower the unbanked, the overlooked, the forgotten. Privacy and dignity in the palms of those the old system refused to see.
And then there is NOSTR—the decentralized protocol for communication and creation. It is the throat chakra, the vocal cords of the “freedom-tech” body. It reclaims speech from the algorithmic overlords, making expression sovereign once more. It is also the reproductive system, as it enables the propagation of novel ideas and protocols in fertile, uncensorable soil.
Each layer plays its part. Not in hierarchy, but in harmony. In holarchy. Bitcoin and other open source protocols grow not through exogenous command, but through endogenous coherence. Like cells in an organism. Like a song.
Imagine the cell as a piece of glass from a shattered holographic plate —by which its perspectival, moving image can be restructured from the single shard. DNA isn’t only a logical script of base pairs, but an evolving progressive song. Its lyrics imbued with wise reflections on relationships. The nucleus sings, the cell responds—not by command, but by memory. Life is not imposed; it is expressed. A reflection of a hidden pattern.
Bitcoin chants this. Each node, a living cell, holds the full timechain—Truth distributed, incorruptible. Remove one, and the whole remains. This isn’t redundancy. It’s a revelation on the power of protection in Truth.
Consensus is communion. Verification becomes a sacred rite—Truth made audible through math.
Not just the signal; the song. A web of self-expression woven from Truth.
No center, yet every point alive with the whole. Like Indra’s Net, each reflects all. This is more than currency and information exchange. It is memory; a self-remembering Mind, unfolding through consensus and code. A Mind reflecting the Truth of reality at the speed of thought.
Heuristics are mental shortcuts—efficient, imperfect, alive. Like cells, they must adapt or decay. To become unbiased is to have self-balancing heuristics which carry feedback loops within them: they listen to the environment, mutate when needed, and survive by resonance with reality. Mutation is not error, but evolution. Its rules are simple, but their expression is dynamic.
What persists is not rigidity, but pattern.
To think clearly is not necessarily to be certain, but to dissolve doubt by listening, adjusting, and evolving thought itself.
To understand Bitcoin is simply to listen—patiently, clearly, as one would to a familiar rhythm returning.
Permissionless Individuation
Bitcoin is a path. One that no one can walk for you.
Said differently, it is not a passive act. It cannot be spoon-fed. Like a spiritual path, it demands initiation, effort, and the willingness to question inherited beliefs.
Because Bitcoin is permissionless, no one can be forced to adopt it. One must choose to engage it—compelled by need, interest, or intuition. Each person who embarks undergoes their own version of the hero’s journey.
Carl Jung called this process Individuation—the reconciliation of fragmented psychic elements into a coherent, mature Self. Bitcoin mirrors this: it invites individuals to confront the unconscious assumptions of the fiat paradigm, and to re-integrate their relationship to time, value, and agency.
In Western traditions—alchemy, Christianity, Kabbalah—the individual is sacred, and salvation is personal. In Eastern systems—Daoism, Buddhism, the Vedas—the self is ultimately dissolved into the cosmic whole. Bitcoin, in a paradoxical way, echoes both: it empowers the individual, while aligning them with a holistic, transcendent order.
To truly see Bitcoin is to allow something false to die. A belief. A habit. A self-concept.
In that death—a space opens for deeper connection with the Divine itSelf.
In that dissolution, something luminous is reborn.
After the passing, Truth becomes resurrected.
Dispelling Paradox Through Resonance
There is a subtle paradox encoded into the hero’s journey: each starts in solidarity, yet the awakening affects the collective.
No one can be forced into understanding Bitcoin. Like a spiritual truth, it must be seen. And yet, once seen, it becomes nearly impossible to unsee—and easier for others to glimpse. The pattern catches.
This phenomenon mirrors the concept of morphic resonance, as proposed and empirically tested by biologist Rupert Sheldrake. Once a critical mass of individuals begins to embody a new behavior or awareness, it becomes easier—instinctive—for others to follow suit. Like the proverbial hundredth monkey who begins to wash the fruit in the sea water, and suddenly, monkeys across islands begin doing the same—without ever meeting.
When enough individuals embody a pattern, it ripples outward. Not through propaganda, but through field effect and wave propagation. It becomes accessible, instinctive, familiar—even across great distance.
Bitcoin spreads in this way. Not through centralized broadcast, but through subtle resonance. Each new node, each individual who integrates the protocol into their life, strengthens the signal for others. The protocol doesn’t shout; it hums, oscillates and vibrates——persistently, coherently, patiently.
One awakens. Another follows. The current builds. What was fringe becomes familiar. What was radical becomes obvious.
This is the sacred geometry of spiritual awakening. One awakens, another follows, and soon the fluidic current is strong enough to carry the rest. One becomes two, two become many, and eventually the many become One again. This tessellation reverberates through the human aura, not as ideology, but as perceivable pattern recognition.
Bitcoin’s most powerful marketing tool is truth. Its most compelling evangelist is reality. Its most unstoppable force is resonance.
Therefore, Bitcoin is not just financial infrastructure—it is psychic scaffolding. It is part of the subtle architecture through which new patterns of coherence ripple across the collective field.
The training wheels from which humanity learns to embody Peace and Prosperity.
Ego Deflation
The process of awakening is not linear, and its beginning is rarely gentle—it usually begins with disruption, with ego inflation and destruction.
To individuate is to shape a center; to recognize peripherals and create boundaries—to say, “I am.” But without integration, the ego tilts—collapsing into void or inflating into noise. Fiat reflects this pathology: scarcity hoarded, abundance simulated. Stagnation becomes disguised as safety, and inflation masquerades as growth.
In other words, to become whole, the ego must first rise—claiming agency, autonomy, and identity. However, when left unbalanced, it inflates, or implodes. It forgets its context. It begins to consume rather than connect. And so the process must reverse: what inflates must deflate.
In the fiat paradigm, this inflation is literal. More is printed, and ethos is diluted. Savings decay. Meaning erodes. Value is abstracted. The economy becomes bloated with inaudible noise. And like the psyche that refuses to confront its own shadow, it begins to collapse under the weight of its own illusions.
But under Bitcoin, time is honored. Value is preserved. Energy is not abstracted but grounded.
Bitcoin is inherently deflationary—in both economic and spiritual senses. With a fixed supply, it reveals what is truly scarce. Not money, not status—but the finite number of heartbeats we each carry.
To see Bitcoin is to feel that limit in one’s soul. To hold Bitcoin is to feel Time’s weight again. To sense the importance of Bitcoin is to feel the value of preserved, potential energy. It is to confront the reality that what matters cannot be printed, inflated, or faked. In this way, Bitcoin gently confronts the ego—not through punishment, but through clarity.
Deflation, rightly understood, is not collapse—it is refinement. It strips away illusion, bloat, and excess. It restores the clarity of essence.
Spiritually, this is liberation.
The Coin of Great Price
There is an ancient parable told by a wise man:
“The kingdom of heaven is like a merchant seeking fine pearls, who, upon finding one of great price, sold all he had and bought it.”
Bitcoin is such a pearl.
But the ledger is more than a chest full of treasure. It is a key to the heart of things.
It is not just software—it is sacrament.
A symbol of what cannot be corrupted. A mirror of divine order etched into code. A map back to the sacred center.
It reflects what endures. It encodes what cannot be falsified. It remembers what we forgot: that Truth, when aligned with form, becomes Light once again.
Its design is not arbitrary. It speaks the language of life itself—
The elliptic orbits of the planets mirrored in its cryptography,
The logarithmic spiral of the nautilus shell discloses its adoption rate,
The interconnectivity of mycelium in soil reflect the network of nodes in cyberspace,
A webbed breadth of neurons across synaptic space fires with each new confirmed transaction.
It is geometry in devotion. Stillness in motion.
It is the Logos clothed in protocol.
What this key unlocks is beyond external riches. It is the eternal gold within us.
Clarity. Sovereignty. The unshakeable knowing that what is real cannot be taken. That what is sacred was never for sale.
Bitcoin is not the destination.
It is the Path.
And we—when we are willing to see it—are the Temple it leads back to.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 6c05c73e:c4356f17
2025-05-23 22:59:35
@ 6c05c73e:c4356f17
2025-05-23 22:59:35Como a grande maioria dos brasileiros. Eu não comecei um negócio porque “queria empreender”. Diferente disso, eu PRECISAVA para poder pagar contas e manter o básico.
Festas, openbar e camisas
Meu primeiro negócio foi na verdade um combo. Eu tinha saído do último trampo e eu gostava de festas. Então, comecei a organizar uma festa mensalmente na casa do meu pai. Eu pagava a água, energia e dava uma grana para ele. Em troca, organizava festa de sábado para domingo open bar.
A fórmula era simples. Criava o evento da festa no facebook, convidava todo mundo que conhecia. Panfletava na cidade e espalhava cartazes nos pontos de ônibus sobre a festa. E, para fechar com chave de ouro. Mulher era OFF até 20:00. Consequência? Os caras vinham e pagavam o ingresso deles e delas. Kkkkk. E, enchia…
Comecei a notar que a galera se vestia mal. E, pensei: "Porque não vestir eles?” Pimba! Comecei a desenha e confeccionar camisas para vender nas festas. E, pimba denovo! Vendeu, tudo! Fiz 2 coleções e mais algumas festas. Até o dia que um menino deu PT de tanto beber e decidi que era hora de tentar outra coisa.
Como assim a Apple não vai vender mais os carregadores?
Isso, foi durante a pandemia. A Apple decidiu vender o telefone e o cabo. E, você que lute com a fonte. Estava difícil achar dinheiro no mercado naqueles tempos e eu pensei. Vou pesquisar no google trends e validar a ideia. Caixa! Tinha mais de 80 pts de busca. Colei em SP, no Brás e comprei literalmente. Todo meu dinheiro de cabo de iphone, carregador e bateria portátil.
Fiquei com R$100 na conta. Para fazer um lanche e pagar pelo uber para voltar para casa. Chegando aqui, eu tirei foto e fiz várias copys. Anunciei no Olx, Mercado Livre e Facebook. Impulsionei os anúncios no OLX, vendi para familiares e amigos, e; vendia até para quem estava na rua. Fiz entrega de bike, a pé, de ônibus e é isso mesmo. Tem que ralar. Para queimar o resto da mercadoria. Deixei com uma loja de eletrônicos e fiz consignado. E, hora da próxima ideia.
Mulheres, doces e TPM
Meu penúltimo negócio veio depois dos cabos. Eu pesquisei na net, negócios online para começar com pouca grana. (Depois que paguei as contas do dia a dia, sobraram R$3mil). E, achei uma pesquisa mostrando que doces. Tinha baixa barreira de entrada e exigia poucos equipamentos. Eu trabalhei em restaurante por muitos anos e sabia como lucrar com aquilo. Além do mais, mulheres consomem mais doce em uma certa época do mês.
Não deu outra, convidei 2 pessoas para serem sócias. Desenvolvemos os produtos, fotografamos e fizemos as copys. Em sequência, precisávamos vender. Então, lá vamos denovo: Ifood, WPP, 99food (na época), Uber eats (na época), Elo7, famílias e amigos e; por fim começamos a vender consignado com alguns restaurantes e lojas. Foi uma época em que aprendi a prospectar clientes de todas as maneiras possíveis.
De novo, minha maior dificuldade era a locomoção para fazer entregas. Só tinha uma bike. Mas, entregávamos. Os primeiros 3 meses foram difíceis demais. Mas, rolou. No fim, nossas maiores vendas vinham de: Ifood, encomendas de festas e consignados. Mas, como nem tudo são flores. Meus dois sócios tomaram outros caminhos e abandonaram o projeto. Galera, está tudo bem com isso. Isso acontece o tempo todo. A vida muda e temos que aprender a aceitar isso. Vida que segue e fui para frente de novo.
Sobre paixões, paciência e acreditar
Estava eu comemorando meu níver de 30 anos, num misto de realizações e pouco realizado. Como assim? Sabe quando você faz um monte de coisas, mas ainda assim. Não sente que é aquilo? Pois então…
Eu amo investimentos, livros, escrever e sempre curti trocar ideia com amigos e família sobre como se desenvolver. Desde que comecei a usar a internet eu criei: Canal no youtube, páginas no IG e FB, pinterest, steemit, blog e até canal no Telegram. Mas, nunca tinha consistente sabe? Tipo assim, vou fazer isso por um ano e plantar 100 sementes aqui. Enfim, inconsistência te derruba meu amigo…Eu voltei a trabalhar com restaurantes e estava doido para mudar de área. Estava exausto de trabalhar e meu wpp não parava de tocar. Fui estudar ADM e Desenvolvimento de sistemas no Senac. Dois anos depois, formei. Consegui trabalho.
E, comecei a pensar em como criar um negócio online, escalável e multilíngue. Passei os próximos 7 meses desenhando e pensando como. Mas, tinha que dar o primeiro passo. Criei um site e fui escrevendo textos. Os primeiros 30 foram aquilo, os próximos 10 melhoraram muito e os 10 a seguir eu fiquei bem satisfeitos. Hoje, tenho o negócio que estava na cabeça desde 2023. Mas, olha o tamanho da volta que o universo me fez dar e aprender para chegar aqui hoje. Dicas? Só 3:
- Você precisa usar a internet para fazer negócio. Em todos os negócios que falei, sempre teve algo online. Não negligencie isso.
- Tem que aprender a vender e se vender.
- Confia em si mesmo e faz sem medo de errar. Porque, advinha? Você vai errar! Mas, vai aprender e melhorar. Tem que persistir…
Por hoje é isso. Tamo junto!
-
 @ bf47c19e:c3d2573b
2025-05-23 22:14:37
@ bf47c19e:c3d2573b
2025-05-23 22:14:37Originalni tekst na antenam.net
22.05.2025 / Autor: Ana Nives Radović
Da nema besplatnog ručka sigurno ste čuli svaki put kad bi neko poželio da naglasi da se sve na neki način plaća, iako možda tu cijenu ne primjećujemo odmah. Međutim, kada govorimo o događaju od kojeg je prošlo tačno 15 godina onda o „ručku“ ne govorimo u prenešenom smislu, već o porudžbini pice čija tržišna vrijednost iz godine u godinu dostiže iznos koji je čini najskupljom hranom koja je ikad poručena.
Tog 22. maja 2010. godine čovjek sa Floride pod imenom Laslo Hanjec potrošio je 10.000 bitcoina na dvije velike pice. U to vrijeme, ta količina bitcoina imala je tržišnu vrijednost od oko 41 dolar. Ako uzmemo u obzir da je vrijednost jedne jedinice ove digitalne valute danas nešto više od 111.000 dolara, tih 10.000 bitcoina danas bi značilo vrijednost od 1,11 milijardi dolara.
Nesvakidašnji događaj u digitalnoj i ugostiteljskoj istoriji, nastao zbog znatiželje poručioca koji je želio da se uvjeri da koristeći bitcoin može da plati nešto u stvarnom svijetu, pretvorio se u Bitcoin Pizza Day, kao podsjetnik na trenutak koji je označio prelaz bitcoina iz apstraktnog kriptografskog eksperimenta u nešto što ima stvarnu vrijednost.
Hanjec je bio znatiželjan i pitao se da li se prva, a u to vrijeme i jedina kriptovaluta može iskoristiti za kupovinu nečeg opipljivog. Objavio je ponudu na jednom forumu koja je glasila: 10.000 BTC za dvije pice. Jedan entuzijasta se javio, naručio pice iz restorana Papa John’s i ispisao zanimljivu stranicu istorije digitalne imovine.
Taj inicijalni zabilježeni finansijski dogovor dao je bitcoinu prvu široko prihvaćenu tržišnu vrijednost: 10.000 BTC za 41 dolar, čime je bitcoin napravio svoj prvi korak ka onome što danas mnogi zovu digitalnim zlatom.
Šta je zapravo bitcoin?
Bitcoin je oblik digitalnog novca koji je osmišljen da bude decentralizovan, transparentan i otporan na uticaj centralnih banaka. Kreirao ga je 2009. godine anonimni autor poznat kao Satoši Nakamoto, neposredno nakon globalne finansijske krize 2008. godine. U svojoj suštini, bitcoin je protokol, skup pravila koja sprovodi kompjuterski kod, koji omogućava korisnicima da bez posrednika sigurno razmjenjuju vrijednost putem interneta.
Osnova cijelog sistema je blockchain, distribuisana digitalna knjiga koju održavaju hiljade nezavisnih računara (tzv. čvorova) širom svijeta. Svaka transakcija se bilježi u novi „blok“, koji se potom dodaje u lanac (otud naziv „lanac blokova“, odnosno blockchain). Informacija koja se jednom upiše u blok ne može da se izbriše, niti promijeni, što omogućava više transparentnosti i više povjerenja.
Da bi blockchain mreža u kojoj se sve to odvija zadržala to svojstvo, bitcoin koristi mehanizam konsenzusa nazvan dokaz rada (proof-of-work), što znači da specijalizovani računari koji „rudare“ bitcoin rješavaju kompleksne matematičke probleme kako bi omogućili obavljanje transakcija i pouzdanost mreže.
Deflatorna priroda bitcoina
Najjednostavniji način da se razumije deflatorna priroda bitcoina je da pogledamo cijene izražene u valuti kojoj plaćamo. Sigurno ste u posljednje vrijeme uhvatili sebe da komentarišete da ono što je prije nekoliko godina koštalo 10 eura danas košta 15 ili više. Budući da to ne zapažate kada je u pitanju cijena samo određenog proizvoda ili usluge, već kao sveprisutan trend, shvatate da se radi o tome da je novac izgubio vrijednost. Na primjer, kada je riječ o euru, otkako je Evropska centralna banka počela intenzivno da doštampava novac svake godine, pa je od 2009. kada je program tzv. „kvantitativnog popuštanja“ započet euro zabilježio kumulativnu inflaciju od 42,09% zbog povećane količine sredstava u opticaju.
Međutim, kada je riječ o bitcoinu, njega nikada neće biti više od 21 milion koliko je izdato prvog dana, a to nepromjenjivo pravilo zapisano je i u njegovom kodu. Ova ograničena ponuda oštro se suprotstavlja principima koji važe kod monetarnih institucija, poput centralnih banaka, koje doštampavaju novac, često da bi povećale količinu u opticaju i tako podstakle finansijske tokove, iako novac zbog toga gubi vrijednost. Nasuprot tome, bitcoin se zadržava na iznosu od 21 milion, pa je upravo ta konačnost osnova za njegovu deflatornu prirodu i mogućnost da vremenom dobija na vrijednosti.
Naravno, ovo ne znači da je cijena bitcoina predodređena da samo raste. Ona je zapravo prilično volatilna i oscilacije su česte, posebno ukoliko, na primjer, posmatramo odnos cijena unutar jedne godine ili nekoliko mjeseci, međutim, gledano sa vremenske distance od četiri do pet godina bilo koji uporedni period od nastanka bitcoina do danas upućuje na to da je cijena u međuvremenu porasla. Taj trend će se nastaviti, tako da, kao ni kada je riječ o drugim sredstvima, poput zlata ili nafte, nema mjesta konstatacijama da je „vrijeme niskih cijena prošlo“.
Šta zapravo znači ovaj dan?
Bitcoin Pizza Day je za mnoge prilika da saznaju ponešto novo o bitcoinu, jer tada imaju priliku da o njemu čuju detalje sa raznih strana, jer kako se ovaj događaj popularizuje stvaraju se i nove prilike za učenje. Takođe, ovaj dan od 2021. obilježavaju picerije širom svijeta, u više od 400 gradova iz najmanje 75 zemalja, jer je za mnoge ovo prilika da korisnike bitcoina navedu da potroše djelić svoje imovine na nešto iz njihove ponude. Naravno, taj iznos je danasd zanemarljivo mali, a cijena jedne pice danas je otprilike 0,00021 bitcoina.
No, dok picerije širom svijeta danas na zabavan način pokušavaju da dođu do novih gostiju, ovaj dan je za mnoge vlasnike bitcoina nešto poput opomene da svoje digitalne novčiće ipak ne treba trošiti na nešto potrošno, jer je budućnost nepredvidiva. Bitcoin Pizza Day je dan kada se ideja pretvorila u valutu, kada su linije koda postale sredstvo razmjene.
Prvi let avionom trajao je svega 12 sekundi, a u poređenju sa današnjim transkontinentalnim linijama to djeluje gotovo neuporedivo i čudno, međutim, od nečega je moralo početi. Porudžbina pice plaćene bitcoinom označile su početak razmjene ove vrste, dok se, na primjer, tokom jučerašnjeg dana obim plaćanja bitcoinom premašio 23 milijarde dolara. Nauka i tehnologija nas podsjećaju na to da sve počinje malim, zanemarivim koracima.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:35:30
@ 3c389c8f:7a2eff7f
2025-05-23 21:35:30Web:
https://shopstr.store/
https://cypher.space/
https://plebeian.market/
Mobile:
https://www.amethyst.social/
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too




