-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ da0b9bc3:4e30a4a9
2025-03-26 06:54:00
@ da0b9bc3:4e30a4a9
2025-03-26 06:54:00Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/925400
-
 @ d9422098:7ee511a3
2025-03-26 05:04:03
@ d9422098:7ee511a3
2025-03-26 05:04:03екненлотлоло
-
 @ e5de992e:4a95ef85
2025-03-26 04:57:53
@ e5de992e:4a95ef85
2025-03-26 04:57:53Overview
On March 25, 2025, U.S. stock markets experienced modest gains despite declining volume and a drop in the Consumer Confidence Index, indicating that investors remain cautiously optimistic amid mixed economic signals.
U.S. Stock Indices
- S&P 500:
- Increased by 0.2%
- Closed at 5,776.65 points
-
Marked its third consecutive winning session, but volume was declining.
-
Dow Jones Industrial Average (DJIA):
- Rose marginally by 0.01%
- Ended at 42,587.50 points
-
Volume was declining.
-
Nasdaq Composite:
- Advanced by 0.5%
- Finished at 18,271.86 points
- Volume was declining.
U.S. Futures Market
- S&P 500 Futures:
-
Rose by 0.06%, suggesting a modestly positive opening.
-
Dow Jones Futures:
- Remained unchanged, indicating a neutral sentiment among investors.
Note: Both futures segments are experiencing low volume.
Key Factors Influencing U.S. Markets
-
Trade Policy Developments:
Investor sentiment has been influenced by reports suggesting that President Donald Trump's proposed tariffs may be more narrowly targeted than initially feared—potentially exempting certain sectors. This has alleviated some concerns regarding the impact of trade policies on economic growth. -
Economic Data Releases:
The Consumer Confidence Index declined, reflecting growing concerns about economic expectations. However, positive corporate earnings reports have contributed to the market's resilience. -
Sector-Specific News:
- International Paper saw significant stock price increases due to upbeat growth outlooks.
- United Parcel Service (UPS) faced declines amid reduced earnings projections.
Global Stock Indices Performance
International markets displayed mixed performances:
- Germany's DAX:
- Experienced a slight decline of 0.32%
- Closed at 23,109.79 points
-
Initial optimism regarding tariff negotiations waned.
-
UK's FTSE 100:
- Fell marginally by 0.10%
-
Reflects investor caution amid mixed economic data.
-
Hong Kong's Hang Seng:
- Declined by 2.35%
- Closed at 23,344.25 points
-
Impacted by a downturn in Chinese tech shares and ongoing tariff concerns.
-
Japan's Nikkei 225:
- Showed resilience with a modest gain, influenced by positive domestic economic indicators.
Cryptocurrency Market
The cryptocurrency market has experienced notable activity:
- Bitcoin (BTC):
- Trading at approximately $87,460
-
Down 1.23% from the previous close.
-
Ethereum (ETH):
- Priced around $2,057.22
- Marked a 0.69% uptick from the prior session.
These movements indicate the market’s sensitivity to regulatory developments and macroeconomic factors.
Key Global Economic and Geopolitical Events
-
Trade Tensions and Tariff Policies:
Ongoing discussions regarding U.S. tariff implementations have created an atmosphere of uncertainty, influencing global market sentiment and leading to cautious investor behavior. -
Central Bank Communications:
Statements from Federal Reserve officials and other central bank representatives are being closely monitored for insights into future monetary policy directions, especially in light of evolving economic conditions and inflationary pressures. -
Cryptocurrency Regulatory Environment:
Anticipation of a more favorable regulatory landscape under the current administration has contributed to recent rallies in major cryptocurrencies, though analysts caution that these rebounds may be fleeting amid broader market dynamics.
Conclusion
Global financial markets are navigating a complex environment shaped by trade policy developments, economic data releases, and sector-specific news. Investors are advised to remain vigilant and consider these factors when making informed decisions, as they are likely to continue influencing market behavior in the foreseeable future.
-
 @ 9711d1ab:863ebd81
2025-03-26 03:36:56
@ 9711d1ab:863ebd81
2025-03-26 03:36:56 Welcome back friends! We’ve made it to the end of March, congratulations. Here’s what we’ve got to share this month:
Welcome back friends! We’ve made it to the end of March, congratulations. Here’s what we’ve got to share this month:-
🎓 The SDK Class of Q1
-
🤓 Back to School with Antonio
-
⚡️ Lightning is Everywhere
-
🎙️ Shooting the Breez with Danny, Umi & Roy
The SDK Class of Q1 2025 🎓
 We’ve been talking a lot about momentum at Breez and we’re seeing it build every day. More partners are adding Bitcoin payments with our SDK and more sats are moving freely around the world. By offering the choice of two implementations, Nodeless and Native, we’re truly building the best Lightning developer experience out there.
We’ve been talking a lot about momentum at Breez and we’re seeing it build every day. More partners are adding Bitcoin payments with our SDK and more sats are moving freely around the world. By offering the choice of two implementations, Nodeless and Native, we’re truly building the best Lightning developer experience out there.And the momentum just keeps growing stronger.
In fact, we’ve welcomed so many new partners that we had to bundle them all into one big announcement — it’s our pleasure to welcome the SDK Class of Q1 2025: Assetify, Cowbolt, DexTrade, Flash, Lightning Pay, OpenAgents, Satoshi, Shakesco, Tidebinder, and ZapZap.
 ---
---Back to School with Antonio 🚌
 We tell everyone we meet that adding Bitcoin payments to apps is really easy with the Breez SDK. But rather than just tell you this, we’ve decided to show you.
We tell everyone we meet that adding Bitcoin payments to apps is really easy with the Breez SDK. But rather than just tell you this, we’ve decided to show you.Antonio, one of our talented developers at Breez, has produced a video tutorial showing how you can add Bitcoin payments to React Native and Expo apps with the Breez SDK - Nodeless.
Join him as he guides you through each step and shows that it really is that *easy* to add Bitcoin payments to any app with our SDK.
Lightning is Everywhere.
 It’s true — Lightning is everywhere.
It’s true — Lightning is everywhere.Bitcoin payments aren’t just a thing for the few, they’re for the many.
This month, we’re showcasing our friends at Cowbolt. They’ve just released their collaborative cost-splitting, team-chat, and self-custody app (check it out).
Shooting the Breez 🌬️
 Since releasing our Bitcoin payment report — where we explained that Bitcoin isn’t just digital gold, it’s a thriving everyday currency accessible to millions of people around the world — Bitcoin payments have been the talk of the town.
Since releasing our Bitcoin payment report — where we explained that Bitcoin isn’t just digital gold, it’s a thriving everyday currency accessible to millions of people around the world — Bitcoin payments have been the talk of the town.As co-author of the report, I joined the Stephan Livera Podcast to discuss the growing trend in more detail. I also met up with Bo Jablonski to explain why more and more apps are taking notice on the newly-formed Guardians of Bitcoin radio show.
Developments have come thick and fast over the past month — most notably, the announcement of USDT coming to Lightning (check out Roy’s take on the good, the bad, and the unknown in Bitcoin Magazine). Breez’s BD Lead, Umi, joined a Spaces on X with UXTO, Amboss, and Lightning Labs to discuss the stablecoin’s imminent arrival on the network.
 That’s not all from Umi, she also joined her alma mater at the Cornell Bitcoin Club to explain why bitcoin is a medium of exchange, thanks to Lightning.
That’s not all from Umi, she also joined her alma mater at the Cornell Bitcoin Club to explain why bitcoin is a medium of exchange, thanks to Lightning. And last but not least, Roy was spreading the good word of Bitcoin, joining Bitfinex’s podcast to explain how Lightning is truly changing the game.
And last but not least, Roy was spreading the good word of Bitcoin, joining Bitfinex’s podcast to explain how Lightning is truly changing the game.
And there we go folks, another edition of Feel the Breez has come to a close.
As always, we’ll leave you with our usual parting comment: the best time to get into Lightning is now — it always has been.
Stay tuned for exciting announcements we’ll be releasing soon.
Until next time ✌️
-
-
 @ 220522c2:61e18cb4
2025-03-26 03:24:25
@ 220522c2:61e18cb4
2025-03-26 03:24:25npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2

-
 @ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00
@ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00Tldr
- Nostr is a new open social protocol for the internet
- You can use it to create your own online community website/app for your users
- This needs only a few simple components that are free and open source
- Jumble.Social client is a front-end for showing your community content to your users
- Simple With Whitelist relay (SW2) is a back-end with simple auth for your community content
- In this blog I explain the components and set up a online community website/app that any community or company can use for their own users, for free.
You Can Run Your Own Private "X" For Free
Nostr is a new open social protocol for the internet. Because it is a protocol it is not controlled by any one company, does not reside on any one set of servers, does not require any licenses, and no one can stop you from using it however you like.
When the name Nostr is recognised, it is as a "Twitter/X alternative" – that is an online open public forum. Nostr is more than just this. The open nature of the protocol means that you can use it however you feel like, including that you can use it for creating your own social websites to suit whatever goals you have – anything from running your own team collaboration app, to running your own online community.
Nostr can be anything – not just an alternative to X, but also to Slack, Teams, Discord, Telegram (etc) – any kind of social app you'd like to run for your users can be run on Nostr.
In this blog I will show you how to launch your own community website, for your community members to use however they like, with low code, and for free.
Simple useful components
Nostr has a few simple components that work together to provide your experience –
- Your "client" – an app or a website front-end that you log into, which displays the content you want to see
- Your "relay" – a server back-end which receives and stores content, and sends it to clients
- Your "user" – a set of keys which represents a user on the network,
- Your "content" – any user content created and signed by a user, distributed to any relay, which can be picked up and viewed by any client.
It is a pattern that is used by every other social app on the internet, excepting that in those cases you can usually only view content in their app, and only post your content to their server.
Vs with Nostr where you can use any client (app) and any relay (server), including your own.
This is defined as a standard in NIP-01 which is simple enough that you can master it in a weekend, and with which you can build any kind of application.
The design space is wide open for anyone to build anything–
- Clones of Twitter, Instagram, Telegram, Medium, Twitch, etc,
- Whole new things like Private Ephemeral Messengers, Social Podcasting Apps, etc,
- Anything else you can dream up, like replacements for B2B SaaS or ERP systems.
Including that you can set up and run your own "X" for your community.
Super powers for –private– social internet
When considering my use of social internet, it is foremost private not public. Email, Whatsapp, Slack, Teams, Discord, Telegram (etc), are all about me, as a user, creating content for a selected group of individuals – close friends, colleagues, community members – not the wider public.
This private social internet is crying out for the kind of powers that Nostr provides. The list of things that Nostr solves for private social internet goes on-and-on.
Let me eat my own dog food for a moment.
- I am a member of a community of technology entrepreneurs with an app for internal community comms. The interface is not fit for this purpose. Good content gets lost. Any content created within the walled kingdom cannot be shared externally. Community members cannot migrate to a different front-end, or cross-post to public social channels.
- I am a member of many communities for kids social groups, each one with a different application and log in. There is no way to view a consolidated feed. There is no way to send one message to many communities, or share content between them. Remembering to check every feed separately is a drag.
- I am a member of a team with an app for team comms. It costs $XXX per user per month where it should be free. I can't self-host. I can't control or export my data. I can't make it interoperate natively with other SaaS. All of my messages probably go to train a Big Co AI without my consent.
In each instance "Nostr fixes this."
Ready now for low-code admins
To date Nostr has been best suited to a more technical user. To use the Nostr protocol directly has been primarily a field of great engineers building great foundations.
IMO these foundations are built. They are open source, free to use, and accessible for anyone who wants to create an administer their own online community, with only low code required.
To prove it, in this blog I will scratch my own itch. I need a X / Slack / Teams alternative to use with a few team members and friends (and a few AIs) as we hack on establishing a new business idea.
I will set this up with Nostr using only open source code, for free.
Designing the Solution
I am mostly non-technical with helpful AI. To set up your own community website in the style of X / Slack / Teams should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs some other unrelated Nostr projects in Docker containers,
- My objective was to set up and run my own community website for my own team use, in Docker, hosted on my own server.
User requirements
What will I want from a community website?
- I want my users to be able to log into a website and post content,
- I want to save that content to a server I control accessed only be people I authorise,
- I want my users to view only that content by default, and not be exposed to any wider public social network unless they knowingly select that,
- I want my user's content to be either:
- a) viewable only by other community members (i.e. for internal team comms), or
- b) by the wider public (i.e. for public announcements), at the user's discretion.
- I want it to be open source so that other people maintain the code for me,
- I want it for free.
Nostr solutions
To achieve this with Nostr, I'll need to select some solutions "a-la carte" for each of the core components of the network.
- A client – For my client, I have chosen Jumble. Jumble is a free open-source client by Cody Tseng, available free on Github or at Jumble.social. I have chosen Jumble because it is a "relay-centric" client. In key spots the user interface highlights for the user what relay they are viewing, and what relay they are posting to. As a result, it is a beautiful fit for me to use as the home of all my community content.
- A relay – For my relay, I have chosen Simple With Whitelist (SW2). SW2 is a free open-source relay by Utxo The Webmaster, based on Khatru by Fiatjaf, available free on Github. I have chosen SW2 because it allows for very simple configuration of user auth. Users can be given read access to view notes, and write access to post notes within simple
config.jsonfiles. This allows you to keep community content private or selectively share it in a variety of ways. Per the Nostr protocol, your client will connect with your relay via websocket. - A user sign-up flow – Jumble has a user sign-up flow using Nstart by Fiatjaf, or as an admin I can create and provision my own users with any simple tool like NAK or Nostrtool.
- A user content flow – Jumble has a user content flow that can post notes to selected relays of the users choice. Rich media is uploaded to free third-party hosts like Nostr.build, and in the future there is scope to self-host this too.
With each of these boxes ticked I'm ready to start.
Launching a Private Community Website with Jumble and SW2
Install your SW2 relay
The relay is the trickiest part, so let's start there. SW2 is my Nostr relay software of choice. It is a Go application and includes full instructions for Go install. However, I prefer Docker, so I have built a Docker version and maintain a Docker branch here.
1 – In a terminal clone the repo and checkout the Docker branch
git clone https://github.com/r0d8lsh0p/sw2.git cd sw2 git checkout docker2 – Set up the environment variables
These are specified in the readme. Duplicate the example .env file and fill it with your variables.
cp .env.example .envFor me this .env file was as follows–
```
Relay Metadata
RELAY_NAME="Tbdai relay" RELAY_PUBKEY="ede41352397758154514148b24112308ced96d121229b0e6a66bc5a2b40c03ec" RELAY_DESCRIPTION="An experimental relay for some people and robots working on a TBD AI project." RELAY_URL="wss://assistantrelay.rodbishop.nz" RELAY_ICON="https://image.nostr.build/44654201843fc0f03e9a72fbf8044143c66f0dd4d5350688db69345f9da05007.jpg" RELAY_CONTACT="https://rodbishop.nz" ```
3 – Specify who can read and write to the relay
This is controlled by two config files
read_whitelist.jsonandwrite_whitelist.json.- Any user with their pubkey in the
read_whitelistcan read notes posted to the relay. If empty, anyone can read. - Any user with their pubkey in the
write_whitelistcan post notes to the relay. If empty, anyone can write.
We'll get to creating and authorising more users later, for now I suggest to add yourself to each whitelist, by copying your pubkey into each JSON file. For me this looks as follows (note, I use the 'hex' version of the pubkey, rather than the npub)–
{ "pubkeys": [ "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" ] }If this is your first time using Nostr and you don't yet have any user keys, it is easy and free to get one. You can get one from any Nostr client like Jumble.social, any tool like NAK or nostrtool.com or follow a comprehensive guide like my guide on mining a Nostr key.
4 – Launch your relay
If you are using my Docker fork from above, then–
docker compose upYour relay should now be running on port 3334 and ready to accept web socket connections from your client.
Before you move on to set up the client, it's helpful to quickly test that it is running as expected.
5 – Test your websocket connection
For this I use a tool called wscat to make a websocket connection.
You may need to install wscat, e.g.
npm install -g wscatAnd then run it, e.g.
wscat -c ws://localhost:3334(note use
ws://for localhost, rather thanwss://).If your relay is working successfully then it should receive your websocket connection request and respond with an AUTH token, asking you to identify yourself as a user in the relay's
read_whitelist.json(using the standard outlined in NIP-42), e.g.``` Connected (press CTRL+C to quit) < ["AUTH","13206fea43ef2952"]
```
You do not need to authorise for now.
If you received this kind of message, your relay is working successfully.
Set a subdomain for your relay
Let's connect a domain name so your community members can access your relay.
1 – Configure DNS
At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caseassistantrelay.rodbishop.nz
Your subdomain now points to your server.
2 – Configure reverse proxy
You need to redirect traffic from your subdomain to your relay at port
3334.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my SW2 Relay required two steps.
First – I added configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.your_domain_name.comsubdomain. For me this looked like–assistantrelay.rodbishop.nz { reverse_proxy sw2-relay:3334 { # Enable WebSocket support header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }Second – I added the Caddy Docker network to the SW2
docker-compose.ymlto make it be part of the Caddy network. In my Docker branch, I provide this commented section which you can uncomment and use if you like.``` services: relay: ... relay configuration here ...
networks:
- caddy # Connect to a Caddy network for reverse proxy
networks:
caddy:
external: true # Connect to a Caddy network for reverse proxy
```
Your relay is now running at your domain name.
Run Jumble.social
Your client set up is very easy, as most heavy lifting is done by your relay. My client of choice is Jumble because it has features that focus the user experience on the community's content first. You have two options for running Jumble.
- Run your own local copy of Jumble by cloning the Github (optional)
- Use the public instance at Jumble.social (easier, and what we'll do in this demo)
If you (optionally) want to run your own local copy of Jumble:
git clone https://github.com/CodyTseng/jumble.git cd jumble npm install npm run devFor this demo, I will just use the public instance at http://jumble.social
Jumble has a very helpful user interface for set up and configuration. But, I wanted to think ahead to onboarding community members, and so instead I will do some work up front in order to give new members a smooth onboarding flow that I would suggest for an administrator to use in onboarding their community.
1 – Create a custom landing page URL for your community members to land on
When your users come to your website for the first time, you want them to get your community experience without any distraction. That will either be–
- A prompt to sign up or login (if only authorised users can read content)
- The actual content from your other community members (If all users can read content)
Your landing page URL will look like:
http://jumble.social/?r=wss://relay.your_domain_name.comhttp://jumble.social/– the URL of the Jumble instance you are using?r=– telling Jumble to read from a relaywss://– relays connect via websocket using wss, rather than httpsrelay.your_domain_name.com– the domain name of your relay
For me, this URL looks like
http://jumble.social/?r=wss://assistantrelay.rodbishop.nz2 – Visit your custom Jumble URL
This should load the landing page of your relay on Jumble.
In the background, Jumble has attempted to establish a websocket connection to your relay.
If your relay is configured with read authentication, it has sent a challenge to Jumble asking your user to authenticate. Jumble, accordingly should now be showing you a login screen, asking your user to login.
3 – Login or Sign Up
You will see a variety of sign up and login options. To test, log in with the private key that you have configured to have read and write access.
In the background, Jumble has connected via websocket to your relay, checked that your user is authorised to view notes, and if so, has returned all the content on the relay. (If this is your first time here, there would not be any content yet).
If you give this link to your users to use as their landing page, they will land, login, and see only notes from members of your community.
4– Make your first post to your community
Click the "post" button and post a note. Jumble offers you the option to "Send only to relay.your_domain_name.com".
- If set to on, then Jumble will post the note only to your relay, no others. It will also include a specific tag (the
"-"tag) which requests relays to not forward the note across the network. Only your community members viewing notes on your community relay can see it. - If set to off, then Jumble will post the note to your relay and also the wider public Nostr network. Community members viewing notes on the relay can see it, and so can any user of the wider Nostr network.
5– Optional, configure your relay sets
At the top of the screen you should now see a dropdown with the URL of your relay.
Each user can save this relay to a "relay set" for future use, and also view, add or delete other relays sets including some sets which Jumble comes with set up by default.
As an admin you can use this to give users access to multiple relays. And, as a user, you can use this to access posts from multiple different community relays, all within the one client.
Your community website is up and running
That is the basic set up completed.
- You have a website where your community members can visit a URL to post notes and view all notes from all other members of the community.
- You have basic administration to enforce your own read and write permissions very simply in two json files.
Let's check in with my user requirements as a community admin–
- My community is saving content to a server where I control access
- My users view only that content by default, and are not exposed to any wider public social network unless they knowingly select that
- My user's content is a) viewable only by other community members, or b) by the wider public, at the user's discretion
- Other people are maintaining the code for me
- It's free
This setup has scope to solve my dog fooding issues from earlier–
- If adopted, my tech community can iterate the interface to suit its needs, find great content, and share content beyond the community.
- If adopted, my kids social groups can each have their own relays, but I can post to all of them together, or view a consolidated feed.
- If adopted, my team can chat with each other for free. I can self host this. It can natively interoperate with any other Nostr SaaS. It would be entirely private and will not be captured to train a Big Co AI without my consent.
Using your community website in practice
An example onboarding flow
- A new member joins your IRL community
- Your admin person gives them your landing page URL where they can view all the posts by your community members – If you have configured your relay to have no read auth required, then they can land on that landing page and immediately start viewing your community's posts, a great landing experience
- The user user creates a Nostr profile, and provides the admin person with their public key
- The admin person adds their key to the whitelists to read and write as you desire.
Default inter-op with the wider Nostr network
- If you change your mind on SW2 and want to use a different relay, your notes will be supported natively, and you can migrate on your own terms
- If you change your mind on Jumble and want to use a different client, your relay will be supported natively, and you can migrate on your own terms
- If you want to add other apps to your community's experience, every Nostr app will interoperate with your community by default – see the huge list at Awesome Nostr
- If any of your users want to view your community notes inside some other Nostr client – perhaps to see a consolidated feed of notes from all their different communities – they can.
For me, I use Amethyst app as my main Nostr client to view the public posts from people I follow. I have added my private community relay to Amethyst, and now my community posts appear alongside all these other posts in a single consolidated feed.
Scope to further improve
- You can run multiple different relays with different user access – e.g. one for wider company and one for your team
- You can run your own fork of Jumble and change the interface to suit you needs – e.g. add your logo, change the colours, link to other resources from the sidebar.
Other ideas for running communities
- Guest accounts: You can give a user "guest" access – read auth, but no write auth – to help people see the value of your community before becoming members.
- Running a knowledge base: You can whitelist users to read notes, but only administrators can post notes.
- Running a blind dropbox: You can whitelist users to post notes, but only the administrator can read notes.
- Running on a local terminal only: With Jumble and SW2 installed on a machine, running at –
localhost:5173for Jumble, andlocalhost:3334for SW2 you can have an entirely local experience athttp://localhost:5173/?r=ws://localhost:3334.
What's Next?
In my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest three blogs I explored different types of interoperability with NFC cards, n8n Workflow Automation, and now running a private community website on Nostr.
For this community website–
- There is scope to make some further enhancements to SW2, including to add a "Blossom" media server so that community admins can self-host their own rich media, and to create an admin screen for administration of the whitelists using NIP-86.
- There is scope to explore all other kinds of Nostr clients to form the front-end of community websites, including Chachi.chat, Flotilla, and others.
- Nostr includes a whole variety of different optional standards for making more elaborate online communities including NIP-28, NIP-29, NIP-17, NIP-72 (etc). Each gives certain different capabilities, and I haven't used any of them! For this simple demo they are not required, but each could be used to extend the capabilities of the admin and community.
I am also doing a lot of work with AI on Nostr, including that I use my private community website as a front-end for engaging with a Nostr AI. I'll post about this soon too.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 00f8d531:a838c062
2025-03-26 00:21:41
@ 00f8d531:a838c062
2025-03-26 00:21:41Dear nostr, I love you. Stay frosty.
-
 @ 5256d869:9a567e23
2025-03-26 00:09:55
@ 5256d869:9a567e23
2025-03-26 00:09:55Pages stretch like waves, but a single drop remains— just read the last line.
-
 @ e516ecb8:1be0b167
2025-03-25 23:49:34
@ e516ecb8:1be0b167
2025-03-25 23:49:34En los años 20, Estados Unidos vivía una juerga económica conocida como los "Roaring Twenties". La Gran Guerra había terminado, la industria estaba en auge, los autos llenaban las calles y el jazz resonaba en cada esquina. Todo parecía ir viento en popa: las acciones subían como espuma, la gente compraba a crédito como si no hubiera mañana y los bancos estaban felices de prestar dinero. Pero, según los economistas austriacos —piensa en Ludwig von Mises o Friedrich Hayek—, esta prosperidad era una fachada, una burbuja inflada artificialmente que tarde o temprano iba a estallar.
La Escuela Austriaca sostiene que el verdadero villano de esta historia no fue la codicia de los especuladores ni el exceso de optimismo, sino algo más sutil y estructural: la manipulación del dinero y el crédito por parte de la Reserva Federal. Vamos a desglosarlo paso a paso, como si estuviéramos destapando una intriga.
Acto 1: La Reserva Federal enciende la mecha
Tras su creación en 1913, la Reserva Federal (el banco central de EE.UU.) tenía el poder de controlar la oferta de dinero y las tasas de interés. En la década de 1920, decidió que era buena idea mantener las tasas de interés artificialmente bajas. ¿Por qué? Para estimular la economía, ayudar a Gran Bretaña a volver al patrón oro y mantener la fiesta en marcha. Pero para los austriacos, esto fue como echar gasolina a una fogata.
Cuando las tasas de interés se mantienen bajas por decreto, el dinero se vuelve "barato". Los bancos prestan más de lo que lo harían en un mercado libre, y ese crédito fácil fluye hacia empresas, inversores y consumidores. Es como si le dieras a todo el mundo una tarjeta de crédito sin límite: la gente empieza a gastar, invertir y construir como si la riqueza fuera infinita. Pero aquí viene el giro: ese dinero no reflejaba ahorros reales ni riqueza genuina. Era una ilusión creada por la expansión del crédito.
Acto 2: El auge insostenible
Con este dinero barato, los empresarios se lanzaron a proyectos ambiciosos: fábricas, rascacielos, nuevas tecnologías. Los inversores, por su parte, corrieron a Wall Street, comprando acciones a crédito (lo que se llamaba "comprar al margen"). El mercado de valores se disparó: el índice Dow Jones pasó de 63 puntos en 1921 a 381 en 1929. ¡Una locura! La gente común, desde taxistas hasta amas de casa, se metió al juego, convencida de que las acciones solo podían subir.
Para la Escuela Austriaca, este "boom" era una distorsión. Según su teoría del ciclo económico, desarrollada por Mises y Hayek, cuando el crédito se expande artificialmente, los recursos se mal asignan. Imagina que eres un chef con un presupuesto limitado: si alguien te da dinero falso para comprar ingredientes, harás platos extravagantes que no puedes sostener cuando el dinero real se acabe. Eso estaba pasando en la economía: se construían cosas que no tenían demanda real ni base sólida.
Acto 3: La burbuja empieza a pincharse
Hacia 1928, algunos empezaron a oler problemas. La producción industrial comenzó a tambalearse, los inventarios se acumulaban y las deudas crecían. La Reserva Federal, dándose cuenta de que la fiesta se estaba descontrolando, intentó subir las tasas de interés para enfriar las cosas. Pero era demasiado tarde: la economía ya estaba dopada con crédito fácil, y el daño estaba hecho.
El 24 de octubre de 1929 —el famoso "Jueves Negro"— el pánico estalló en Wall Street. Los inversores, viendo que las acciones estaban sobrevaloradas y que sus deudas eran impagables, empezaron a vender en masa. El martes siguiente, 29 de octubre, el mercado colapsó por completo: millones de acciones cambiaron de manos, los precios se desplomaron y la riqueza en papel se evaporó. Pero para los austriacos, esto no fue la causa del problema, sino el síntoma. El verdadero desastre ya había ocurrido en los años previos, con la expansión artificial del crédito.
Epílogo: La lección austriaca
Desde la perspectiva de la Escuela Austriaca, el Crack del 29 no fue un fallo del libre mercado, sino del intervencionismo. La Reserva Federal, al manipular las tasas de interés y la oferta de dinero, creó una burbuja que era insostenible. Cuando estalló, la economía tuvo que pasar por una dolorosa "corrección": las empresas quebraron, los bancos cerraron y el desempleo se disparó. Para Mises y Hayek, esto era inevitable: el mercado necesitaba purgar los excesos y realinear los recursos con la realidad.
¿Y qué pasó después? Bueno, la Gran Depresión que siguió fue agravada, según los austriacos, por más intervenciones: el New Deal de Roosevelt y las políticas proteccionistas como la Ley Smoot-Hawley solo prolongaron la agonía. Pero esa es otra historia para otro café.
-
 @ 1e5d0f11:12eeba92
2025-03-25 23:42:33
@ 1e5d0f11:12eeba92
2025-03-25 23:42:33Una semana en Nostr
Mucho tiempo ha pasado desde la primera vez que escuche de Nostr, guiado por mi eterna curiosidad ante cada nueva tecnología que descubro en internet decidí sumergirme en este protocolo, lo que encontré en ese entonces era un recién nacido, tenia todo el potencial de crecer y convertirse en algo grande y usado por muchas personas, pero todavía estaba en su infancia y los desarrolladores que tomaban provecho de este nuevo protocolo eran pocos y sus aplicaciones eran también jóvenes, ademas que los relés de Nostr (algo critico en su infraestructura) eran muy pocos, en conclusión estaba claro que había llegado muy temprano, y que Nostr todavía no era para alguien que se interesa por la tecnología pero cuya profesión no es el desarrollo de aplicaciones para internet, a esperar.
Grande fue mi sorpresa al volver a Nostr, al igual como ocurrió con muchos, fui recordado de Nostr gracias a Derek Ross y su charla en Nostr for Beginners w/ Derek Ross, al volver mi sorpresa fue grata, "no esta muerto" fue lo primero que pensé, esto porque es común que proyectos de código abiertos y que en superficie parece que intentaran reinventar la rueda están destinados al paredón de desarrolladores criticándolos o hundidos en el océano de Github sin nadie para explorar lo que pudo ser una buena idea, pero no Nostr, Nostr seguía vivo, creciendo y actualizando sus NIPs, gracias, en gran medida, a una generosa donación del co-fundador de Twitter (ahora llamado X o Xitter para algunos) en Bitcoins, la moneda del futuro y que derrotara al dinero fiduciario, o eso aseguran sus varios creyentes en Nostr, y Nostr esta lleno de ellos, lleno, sin duda impulsados por la importante donación que recibió el proyecto y por un mecanismo que lleva a este protocolo mas allá que otros: Nip-57. Lighting Zaps se llaman, y le da la posibilidad al usuario de transferir "Zaps", que como lo dice la propia pagina de Nostr es una propina que puede ser entregada a cualquier usuario que use Nostr y que ya tenga su billetera Lightning funcionando, y esto puede ser convertido en BTC, algo que no he probado y no creo lo haga en el corto tiempo, pero saber que tanto empeño se ha puesto en la creación de un nuevo protocolo pro incensurable que ademas incorpora elementos de cadena de bloques para proveer a creadores de contenido u otros con un método directo de financiación y así remover la necesidad de publicidad en las paginas algo que me parece saludable para internet, internet estaría mucho mejor sin tanto rastreador de publicidad y con mas respeto a la privacidad de los usuarios.
En fin, escribo esto como una prueba para saber como funcionan las publicaciones largas y tediosas desde Flycat, y bueno, seguiré usando el protocolo Nostr porque parece que ya esta en una etapa que me agrada y esta mas maduro, le contare a otros sobre Nostr, pero debo decir que entrar a Nostr, agregar relés y buscar usuarios para seguir es un proceso lento y tranquilo, no parece ser para el usuario común, pero al final siempre es uno el que configura las cuentas de sus padres y otros familiares.
-
 @ 878dff7c:037d18bc
2025-03-25 23:32:39
@ 878dff7c:037d18bc
2025-03-25 23:32:39Federal Budget 2025: Comprehensive Analysis and Implications
Overview:
On March 25, 2025, Treasurer Jim Chalmers presented Australia's Federal Budget for the 2025–26 fiscal year. This budget introduces several significant measures aimed at providing immediate cost-of-living relief, stimulating economic growth, and addressing long-term structural challenges. Key components include:
-
Personal Income Tax Cuts: The budget outlines a reduction in the lowest marginal tax rate from 16% to 15% starting July 1, 2026, and further to 14% from July 1, 2027. This initiative is projected to cost $17.1 billion over three years and aims to benefit low and middle-income earners.
-
Energy Bill Relief: An extension of the Energy Bill Relief Fund will provide $150 rebates to households over the next six months, totaling $1.8 billion. This measure is designed to alleviate rising energy costs and is expected to reduce headline inflation by approximately 0.5 percentage points in 2025.
-
Healthcare Investments: Significant funding has been allocated to Medicare to enhance bulk billing services and reduce pharmaceutical costs under the Pharmaceutical Benefits Scheme (PBS), aiming to improve healthcare accessibility.
-
Housing Initiatives: The budget includes an $800 million expansion of the Help to Buy program, increasing eligibility criteria to assist first-home buyers. However, this measure is limited to 40,000 applicants, leading to concerns about its overall impact on housing affordability.
-
Economic Projections: The budget forecasts a return to deficits, with an anticipated shortfall of $27.6 billion for the 2025–26 fiscal year. Real GDP growth is projected at 2.25%, with unemployment rates expected to peak at 4.25%.
Expert Analyses:
-
Deloitte: Deloitte's analysis emphasizes the need for structural reforms to address underlying fiscal challenges, noting that while the budget provides immediate relief, it may not sufficiently tackle long-term economic issues.
-
PwC: PwC highlights the importance of enacting pending tax and superannuation measures to ensure fiscal stability, pointing out that the budget's forward tax agenda remains uncertain.
-
KPMG: KPMG observes that the budget attempts to balance immediate cost-of-living relief with long-term fiscal responsibility but notes that it may lack measures to boost productivity and incentivize business investment.
Reactions from News Sources:
-
ABC News described the budget as "cautiously optimistic," praising its cost-of-living focus but noting limited ambition in areas such as climate investment and innovation.
-
The Guardian called it a "modest" budget, identifying meaningful but narrow wins for renters, aged care, and public infrastructure, while critiquing it for its limited reach and reliance on temporary relief.
-
The Australian Financial Review emphasized the lack of bold economic reform, pointing out that while the tax cuts may assist consumers in the short term, the broader economic strategy appeared politically calculated rather than reform-driven.
-
News.com.au focused on practical household benefits, highlighting how the budget would impact average Australians. It praised the tax cuts and rebates but expressed skepticism about the housing measures' real-world impact.
-
The Australian accused the budget of being driven by “polling, not policy,” arguing that it sidesteps difficult reforms in areas like energy security, defense, and migration in favor of short-term voter appeal.
Sectoral Implications:
-
Business Investment: The budget projects modest business investment growth of 1.5% in 2025–26 and 2026–27, down from 6% in 2024–25. This decline is attributed to global economic uncertainties and trade tensions.
-
Tax Compliance: The Australian Taxation Office (ATO) will receive nearly $999 million over the next four years to enhance enforcement activities, aiming to recover an additional $3.2 billion in tax receipts by 2029.
-
Housing Market: Despite the expansion of the Help to Buy program, concerns remain about the budget's limited impact on housing affordability, with critics arguing that more comprehensive measures are needed to address supply constraints.
Conclusion:
The Federal Budget 2025 introduces measures aimed at providing immediate relief to Australian households and businesses. While it delivers on promises around tax cuts and cost-of-living support, several analysts and media commentators view it as lacking in ambition and long-term economic vision. The political nature of its design is evident, with many measures framed to appeal to voters in the lead-up to the next federal election. Its success will hinge on effective implementation and how well it navigates the evolving domestic and global economic landscape.
Sources: Deloitte - March 25, 2025, PwC Australia - March 25, 2025, KPMG Australia - March 25, 2025, The Guardian - March 25, 2025, News.com.au - March 26, 2025, The Australian - March 26, 2025, Australian Financial Review - March 26, 2025, ABC News - March 25, 2025
Apple Transforms AirPods Pro 2 into Hearing Aids
Summary:
Apple has released a software upgrade enabling AirPods Pro 2 to function as "clinical grade" hearing aids for individuals with mild to moderate hearing loss. This feature includes the ability to perform hearing tests using an iPhone or iPad. Priced at $399, the AirPods Pro 2 offer an affordable alternative to traditional hearing aids, which can cost thousands. Experts caution that while beneficial, professional guidance is essential, and the AirPods may not be suitable for everyone.
Sources: The Australian - March 26, 2025, The Guardian - March 26, 2025
2000km Rain Band to Drench Queensland and New South Wales
Summary:
A 2000km-long rain band, fueled by tropical air and a low-pressure system, is set to bring exceptionally high rainfall to Queensland and parts of New South Wales. Some regions have already experienced significant downpours, with 208mm recorded in the Central West and 145mm near Townsville. Severe weather warnings are in effect, with flash flooding reported and expected to worsen. Residents are advised to remain vigilant due to rising river and creek levels. In contrast, Western Australia is enduring record-breaking heat, with temperatures surpassing 39°C in certain areas.
Sources: News.com.au - March 26, 2025, ABC News - March 26, 2025
Projected Population Shift from New South Wales to Queensland
Summary:
Federal budget data projects that New South Wales will experience a net loss of 115,300 residents by 2028-29, primarily due to Sydney's high cost of living. Queensland is expected to gain approximately 110,500 residents during the same period. Other states like Victoria and Western Australia are also projected to see slight population increases, while South Australia, Tasmania, the Northern Territory, and the ACT may experience decreases.
Source: News.com.au - March 26, 2025
Ban on Non-Compete Clauses for Workers Earning Below $175,000
Summary:
The Australian government has announced plans to ban non-compete clauses for workers earning below $175,000 annually, including professions such as hairdressers, construction workers, and childcare staff. This initiative aims to enhance job mobility and is projected to boost the economy by approximately $5 billion, potentially increasing individual wages by up to $2,500 annually. The ban is set to take effect in 2027.
Sources: The Guardian - March 25, 2025, Mirage News - March 26, 2025, NAB Business - March 26, 2025
Geopolitical Tensions and Tariffs Hamper Australian Mining Investment
Summary:
Industry leaders express concern that escalating geopolitical tensions and tariffs are adversely affecting investment in Australia's mining sector. The uncertainty surrounding international trade policies, particularly from major partners like the United States and China, is leading to hesitancy among investors. This situation poses challenges for Australia's resource-driven economy, emphasizing the need for strategic responses to navigate the complex global landscape. Sources: National Security News - March 25, 2025
Government Launches Campaign on Tainted Alcohol Risks Abroad
Summary:
In response to the deaths of two Melbourne teenagers in Laos last year from methanol poisoning, the Australian government has initiated a campaign to raise awareness about the dangers of consuming tainted alcohol overseas. The campaign aims to educate young Australians on alcohol-related risks, signs of methanol poisoning, and safety measures through social media, text messages, and airport communications. Foreign Affairs Minister Penny Wong emphasized the importance of this initiative in preventing further tragedies.
Sources: ABC News - March 24, 2025, The Guardian - March 24, 2025
Boeing's MQ-28 Ghost Bat Completes 100th Flight
Summary:
Boeing's MQ-28 Ghost Bat, an uncrewed collaborative combat aircraft developed in partnership with the Royal Australian Air Force (RAAF), has successfully completed its 100th test flight. This milestone signifies the program's maturity and underscores Australia's growing role in advanced aerospace development. The MQ-28 is designed to operate alongside crewed aircraft, enhancing mission capabilities and providing a force multiplier effect. Looking ahead, Boeing plans to conduct an air-to-air missile test from the MQ-28 by late 2025 or early 2026, aiming to further integrate offensive capabilities into the platform.
Sources: Australian Defence Magazine - March 25, 2025, Breaking Defense - March 25, 2025, Flight Global - March 25, 2025, Boeing - March 25, 2025
Russia and Ukraine Agree to Black Sea Ceasefire
Summary:
In a significant development, Russia and Ukraine have agreed to a ceasefire in the Black Sea, aiming to ensure safe navigation and halt military engagements in the region. The agreement, brokered by the United States during separate talks held in Saudi Arabia, includes provisions to prevent the use of commercial vessels for military purposes and to implement a 30-day suspension of attacks on energy infrastructure. However, the implementation of the ceasefire is contingent upon the lifting of certain Western sanctions on Russia's agricultural and financial sectors, a condition that has sparked debate among international observers. Ukrainian President Volodymyr Zelenskyy has expressed cautious optimism, emphasizing the need for concrete actions over verbal commitments. Critics argue that the agreement may disproportionately favor Russia, potentially allowing it to consolidate its position in the region. The situation remains fluid, with further negotiations anticipated to address unresolved issues and ensure adherence to the ceasefire terms. Sources: Associated Press - March 26, 2025, The Guardian - March 26, 2025
UN Research Indicates Under-reported Methane Emissions from Queensland Mine
Summary:
A UN-backed study reveals that methane emissions from Glencore's Hail Creek coalmine in Queensland are likely three to eight times higher than reported. Using aircraft-based measurements, the study found emissions between 1.5Mt and 4.2Mt CO2e per year, compared to the reported 0.53Mt CO2e. This underscores the need for more accurate emission reporting methods, as methane is a potent greenhouse gas.
Sources: The Guardian - March 26, 2025
How to Improve Your Teeth & Oral Microbiome for Brain & Body Health
Summary:
In this episode of the Huberman Lab podcast, Dr. Andrew Huberman interviews Dr. Staci Whitman, a board-certified functional dentist specializing in pediatric and adult care. They discuss the critical role of oral health in overall brain and body wellness. Key topics include:
- Oral Microbiome's Impact: The balance of bacteria in the mouth influences systemic health, affecting digestion, immunity, and even neurological function.
- Preventive Dental Care: Emphasis on regular dental check-ups, proper brushing and flossing techniques, and the use of non-toxic dental products to maintain oral hygiene.
- Dietary Considerations: How nutrition affects oral health, highlighting the importance of reducing sugar intake and consuming nutrient-rich foods to support strong teeth and gums.
- Connections to Chronic Diseases: Exploring links between oral health issues like gum disease and conditions such as heart disease, diabetes, and Alzheimer's.
- Holistic Approaches: Discussion on integrating functional medicine practices into dentistry to address root causes of oral health problems rather than just symptoms.
This conversation underscores the importance of maintaining oral health as a vital component of overall well-being.
-
-
 @ 2f4550b0:95f20096
2025-03-25 23:09:57
@ 2f4550b0:95f20096
2025-03-25 23:09:57Recently, I tuned into a prominent podcast where the conversation turned to what children are learning in K-12 education (around the 1:24:20 mark). Among the contributors was a Silicon Valley tech investor who shared a startling anecdote about an elite private school. He described how, at what he called “the best all-girls private school in Silicon Valley,” students were taught that reading was racist. He went on: “There was a spreadsheet that these kids had to memorize every day that had every other kid’s pronoun, and if you didn’t get it right you’d get in trouble.”
I was floored, not just by the absurdity of the curriculum, but by the casual assertion that a school teaching such ideas could still be deemed “the best.” How could an institution so detached from a rigorous, skill-building education retain that lofty title? I reflected on what truly makes an elite private school worthy of being called “the best,” a label too often thrown around without scrutiny.
Historically, top-tier private schools earned their reputations through academic excellence, robust curricula, and a commitment to preparing students for leadership and success. Think of the traditional hallmarks: mastery of core subjects like literature, mathematics, and science; critical thinking honed through debate and analysis; and extracurriculars designed to cultivate discipline and creativity. These schools were exclusive not just for their price tags but for their promise to deliver an education that equipped graduates to thrive in competitive universities and careers.
Yet the anecdote from that podcast suggests a troubling shift. If a school prioritizes ideological conformity (say, memorizing pronouns or framing foundational skills like reading as racist) over intellectual rigor, it’s fair to question whether it still deserves its elite status. Prestige, wealth, and social cachet might keep a school “elite” in name, but “the best” should mean more than that. It should reflect a dedication to fostering knowledge, skills, and independent thought, qualities that empower students as future leaders, not pawns in a cultural tug-of-war.
Consider what parents and students expect from a premium education. For an astronomical tuition (often exceeding $40,000 annually in places like Silicon Valley) they anticipate a return on investment: a curriculum that challenges young minds, teachers who inspire rather than indoctrinate, and a culture that values merit over dogma. When a school veers into territory where basic literacy is politicized or rote memorization of social rules trumps critical inquiry, it betrays that trust. No spreadsheet of pronouns will help a graduate navigate a complex world; a firm grasp of history, science, and persuasive writing just might.
This isn’t to say elite schools shouldn’t evolve. The world changes, and education must adapt, whether by integrating technology, addressing current issues, or broadening perspectives. But adaptation should enhance, not replace, the core mission of learning. A school can teach ethics alongside traditional subjects without sacrificing intellectual integrity. The problem arises when ideology becomes the curriculum, sidelining the tools students need to reason for themselves. If students are taught to question reading instead of mastering it, how will they author their own futures?
The Silicon Valley example isn’t isolated. Across the country, elite institutions have leaned into progressive trends, prioritizing social justice frameworks and experimental pedagogies over substance. Some might argue this reflects a bold reimagining of education, but there’s a difference between innovation and derailment. A school can be forward-thinking without abandoning the fundamentals that define excellence. Parents paying top dollar, and students investing their formative years, deserve more than a trendy experiment.
So, what should define “the best” private school today? First, employ a curriculum that balances tradition and progress: teach Shakespeare and coding, ethics and algebra, with an eye toward real-world application. Second, hire a faculty of experts who challenge students to think, not just comply. Third, create an environment that rewards effort and achievement over adherence to a script. Prestige alone, whether from alumni networks, manicured campuses, or Silicon Valley buzz, can’t suffice.
The tech investor’s remark about “the best” stuck with me because it revealed a disconnect. A school might remain elite in the eyes of the wealthy or well-connected, but “the best” is a higher bar. It’s a title earned through results, not rhetoric. Until these institutions recommit to education over indoctrination, they risk losing not just their claim to excellence, but the trust of those they serve.
-
 @ 7da115b6:7d3e46ae
2025-03-25 22:59:06
@ 7da115b6:7d3e46ae
2025-03-25 22:59:06These are in order of least to most complex.
Be Warned: Some of these ingredients may be unique to New Zealand and Australia
Pikelets
Pikelets are delicious with butter and jam or jam and whipped cream. To make Pancakes, double this recipe and make them larger. Serve in a stack with butter, maple syrup, bacon and blueberries. I've found a single batch is good for 2-4 people if you just want a snack.
Prep Time: 5 minutes Cooking Time: About 10 minutes
Ingredients: - A Cup Self Raising Flour - A Quarter Teaspoon of Table Salt - 1 Egg - A Quarter Cup of White Sugar - About 3 quarters of a Cup of Whole Milk
Method: 1. Sift the Flour and Salt into a bowl. 2. In another bowl beat the Egg and Sugar with a whisk until pale and thick. 3. Add the Egg mixture and the Milk to the dry ingredients and mix until just combined. 4. Gently heat a non-stick frying pan and drop tablespoonfuls of the mixture from the point of the spoon onto the surface. 5. When bubbles start to burst on the top of the Pikelets, turn them over and cook the second side until golden. 6. Place in a clean tea towel to cool.
This recipe requires a little experience to get right, especially if you prefer to use a cast iron pan or griddle. Basically, you can use a cast iron or aluminium pan, just make sure to grease the pan between each batch. The easiest way to do it, is to grab some baking paper, or butter paper wrap, scrunch it up and wipe it over the block of butter, and then wipe the surface of the pan. After the first round has cooked, do wipe the butter over the pan again. It'll stop the Pikelets from sticking.
Scones
These are based on an old recipe from the Edmond's Cookbook, and have been a Kiwi staple for decades. The yield is about 12 (ish), but it depends on how big or small you shape them.
Prep Time: About 10 minutes Cooking Time: 10 minutes (Depending on your Oven)
Ingredients: - 3 Cups of Premium White Wheat Flour - 2 and a Half Levelled Tablespoons of Baking Powder - A quarter of a Teaspoon of Table Salt - About a Third of a Cup of Butter - Between 1 to 1.5 Cups of Whole Milk
Method: 1. Preheat the oven to 220C. 2. Grease or flour a baking tray. 3. Sift the flour, baking powder and salt into a bowl. 4. Rub in the butter with your fingertips until the mixture resembles fine breadcrumbs 5. Add the milk and quickly mix with a round-bladed table knife to a soft dough. For light and tender scones the mixture should be quite soft and a little sticky. 6. Scrape the dough onto the floured baking tray and flour the top 7. Working quickly, pat the dough out to 2cm thickness and with a floured knife cut it into 12 even-sized pieces, then separate the scones to allow 2cm space between them. 8. Brush the tops with milk. 9. Bake for 10 minutes or until golden brown. Place on a wire rack to cool, wrapped in a clean tea towel to keep them soft.
They're great with Butter or Whipped Cream and Jam. 3-4 per person is excellent with some hot sweet Tea mid afternoon.
A little variation that used to be popular is to dice up about a a cup of Bacon, grate about a cup of Cheese, and throw it in the batter for a savoury twist.
Remember to not overcook them, otherwise they come out dry and crumbly.
Chocolate Muffins
I can't remember where I got this recipe, but I've made them dozens of times over the years. They really fill the gap when it comes to those hungry little faces pleading for snacks. This recipe is a little more complicated, but worth it. They're soft and moist, and extremely more-ish. I can personally eat about half on my own before I start feeling guilty. You can get about 12 muffins out of this mixture.
Prep Time: 20 minutes Cooking Time: About 18 minutes
Ingredients: - 1 and a quarter Cups Self Raising Flour - A quarter Cup of Cocoa Powder - 3 quarters of a Teaspoon of Baking Soda - A Quarter Teaspoon of Table Salt - Half a Cup of Soft Brown Sugar - A Quarter Cup of White Sugar - Half a cup of Chocolate Chips - An Egg - Half a Cup of Greek Yoghurt or Sour Cream - Half a Cup of Whole Milk - A Quarter Cup of Sunflower Oil (substitute with warmed dripping/butter or clean cooking oil to taste) - 1 Teaspoon of Vanilla Essence
Method: 1. Preheat oven to 180C on fan bake. 2. Line a 12-hole muffin tin with paper cases. 3. Sift the Flour, Cocoa Powder, Baking Soda and Salt into a large bowl. Stir in the White and Brown Sugars, followed by the Chocolate Chips. 4. In a separate bowl, whisk together Egg, Yoghurt (or Sour Cream), Milk, Oil (or Butter/Dripping) and Vanilla Essence. 5. Add the mixture to the dry ingredients and mix until just combined. Try not to over-mix it, you're not looking for a smooth texture, just no unmixed dry ingredients. 6. Divide mixture evenly between 12 muffin paper cases. 7. (Optional) Sprinkle with extra chocolate chips, for decoration. 8. Bake for 18-20 minutes, until muffins spring back when lightly pressed. 9. Leave to cool in tins for a couple of minutes before transferring to a wire cooling rack.
If you're feeling especially fancy, you can slice them open, and add a dollop of jam and whipped cream. Garnish with a Mint Leaf or Glacé Cherry. Using a Sieve, you can powder the top with Icing Sugar if you want to go that extra mile. It's a real Wifey pleaser.
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ bc52210b:20bfc6de
2025-03-25 20:17:22
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused! Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
- Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
- Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
Key Differences: 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
Two Flavors of CISA: Half-Agg and Full-Agg CISA comes in two modes:
- Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
- Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
Half Signature Aggregation (Half-Agg) Explained How It Works Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
- Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
- Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
- R: A random point (32 bytes).
- s: A scalar value (32 bytes).
In Half-Agg:
- The R values from each signature are kept separate (one per input).
- The s values from all signatures are combined into a single s value.
Why It Saves Space (~50%) Let’s break down the size savings with some math:
Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes.
After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes.
Comparison:
- Original: 64n bytes.
- Half-Agg: 32n + 32 bytes.
- For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
Real-World Impact: Based on recent Bitcoin usage, Half-Agg could save:
- ~19.3% in space (reducing transaction size).
- ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
Applications of Half-Agg Half-Agg isn’t just a cool idea—it has practical uses:
- Transaction-wide Aggregation
- Combine all signatures within a single transaction.
- Result: Smaller transactions, lower fees.
- Block-wide Aggregation
- Combine signatures across all transactions in a Bitcoin block.
- Result: Even bigger space savings at the blockchain level.
- Off-chain Protocols / P2P
- Use Half-Agg in systems like Lightning Network gossip messages.
- Benefit: Efficiency without needing miners or a Bitcoin soft fork.
Challenges with Half-Agg While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
- Breaking Adaptor Signatures
- Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
-
Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
-
Impact on Reorg Recovery
- In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
- If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
Wrapping Up CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-
 @ 6a6be47b:3e74e3e1
2025-03-25 20:16:37
@ 6a6be47b:3e74e3e1
2025-03-25 20:16:37Hi frens, how are you?
🎨 I've been keeping busy with some personal projects and haven't painted as much as I'd like, but most importantly, I've returned to painting with watercolors. I'm getting used to them again, and although I love them, they can be tricky, especially when working wet on wet.
I've done a few pieces since getting back into it, and I'm excited to show the results, but at the same time, I'm a bit wary. Not because I want them to be "perfect" to share, but because I just want to have fun with them and get the joy back from painting.
🐱 And I'm not slacking because I have my furry little helper with me, and he's not having any of it!

He's a good boi

I've also been baking! 👩🍳 Yesterday, I made cinnamon "donuts" 🍩 , which ended up being muffins since I don't have a donut skillet.

And today, I baked lemon muffins 🍋, and they turned out delicious!

🧁 I had one as soon as they cooled, and chef's kiss... they're amazing!
🫀So as you can see I've been up to a few things, I'm not the best at this social media game. It can be draining so I want to have a balance between creating and showcasing you my proof of work 💪
💎I'm still getting there, but it's worth it.
🪄 Balance to achieve harmony is my goal.
🔮 I just wanted to check in and see what you've been up to! I'd love to know 🩷🫶🏻.
Have an amazing day frens!
-
 @ 2ed3596e:98b4cc78
2025-03-25 19:12:58
@ 2ed3596e:98b4cc78
2025-03-25 19:12:58Americans can now buy bitcoin on the Lightning Network directly from their bank with their Bitcoin Well account. By using the dollars in your Bitcoin Well Cash Balance you can buy bitcoin over the Lightning Network with instant delivery. You can also go directly from your bank to your Lightning Wallet. You can now live fully on a Lightning-powered bitcoin standard ⚡️
How to buy bitcoin on the Lightning Network instantly:
-
Add your Lightning Payment Address (LNURL) to your Bitcoin Well account
-
Enter the amount of dollars you want to buy bitcoin with
-
Choose your Bitcoin Well Cash Balance (you may need to fund this first!)
-
SMASH BUY! Your Lightning wallet will receive sats in seconds 🏎️
\ You can also go directly from your bank to your Lightning wallet. Your bitcoin will be sent over the Lightning network as soon as your dollars arrive (usually within 3 business days).
Here are detailed steps to guide you on how to buy bitcoin on the Lightning Network 👇
Step 1: Get your Lightning details
Go to your Lightning wallet and copy your Lightning Payment Address (looks like an email address). A Payment Address is not a Lightning invoice, but rather a static receiving address similar to a bitcoin receiving address. The benefit of using a Payment Address is that you can passively receive any quantity of sats at any time; unlike an invoice, a Payment Address does not have an expiry or a fixed amount of sats limiting the amount can be received. \ \ In the example below we use the Coinos.io wallet to obtain a Payment Address. Coinos is a powerful and easy to use Lightning wallet available in any country via your favourite web browser. You can set up a Coinos Lightning wallet and start receiving sats in seconds.

\ Coinos features a Lightning Payment Address. Once you’ve set up your wallet, hit “Receive” to access your Payment Address.
Step 2: Add your Lightning wallet to your Bitcoin Well account
Log in to your Bitcoin Well account and navigate to Buy bitcoin. From the buy screen, select bank or balance and add your Lightning wallet to the Destination by clicking Add wallet. Add your Lightning Payment Address from Step 1 here.
Step 3: Buy bitcoin on the Lightning Network
After you’ve selected your source and added your Lightning Payment Address as the destination, you are ready to complete your bitcoin purchase on the Lightning Network! \ \ When buying bitcoin from your Cash Balance, the dollars will instantly convert to bitcoin and be sent directly to your Lightning wallet – delivery takes less than a minute! 🤯\ \ When buying bitcoin from your bank account, you can expect to wait at least a couple business days as we wait for the slow movement of fiat to be finalized before sats can be sent.
## The compromise is over: bitcoin fast, easy and cheap
In the past, Bitcoiners had to choose between using freedom money at the mercy of the speed and cost of Bitcoin’s blockchain, or use the legacy banking system while surrendering their monetary freedom and independence. Ideally, Americans never have to compromise their monetary principles; thankfully, they no longer have to. \ \ Stacking sats straight to the Lightning also enables an innovative way to manage UTXOs. Now anyone can stack sats as much as they like without worrying about UTXO bloat. Simply accumulate sats on your Lightning wallet and then swap it across to your on-chain wallet in one neat UTXO. Since Coinos is a custodial Lightning wallet, you should periodically send your sats to your self-custody hardware wallet. To help you get the most out of the Lightning network, Bitcoin Well has a free swap tool that lets you swap sats between on-chain and Lightning. While this feature is only available in Canada, it will make its way to the United States very soon 🤫
Haven’t signed up with Bitcoin Well yet? Sign up here to start living on a (Lightning powered) Bitcoin Standard free from custodians and centralized honey pots.
Earn sats from your bitcoin transactions
\ Bitcoin Well is also the best place in the world to earn bitcoin. When you earn points in your Bitcoin Well account, you gain the opportunity to play the Bitcoin (Wishing) Well, where you win sats with every play.
The best part? We send bitcoin that you win straight to your personal wallet via the Lightning Network ⚡
Oh yeah, did we mention you can win 1,000,000 sats? If you're an active Bitcoin Well customer, there is a chance you've earned a pile of points. The more you use your account for buying, selling or spending bitcoin - the more points you’ll earn! Log in to your Bitcoin Well account and check your point balance.
About Bitcoin Well
\ Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we make it easy to use bitcoin with self-custody.
-
-
 @ 7d33ba57:1b82db35
2025-03-25 18:31:35
@ 7d33ba57:1b82db35
2025-03-25 18:31:35Located on the Costa de la Luz, Conil de la Frontera is a charming Andalusian fishing village known for its golden beaches, whitewashed streets, and delicious seafood. With a laid-back atmosphere, it’s perfect for relaxation, surfing, and enjoying authentic Spanish culture.

🏖️ Top Things to See & Do in Conil de la Frontera
1️⃣ Playa de los Bateles 🏝️
- The main beach, right next to the town center.
- Long stretches of soft golden sand with clear Atlantic waters.
- Ideal for sunbathing, swimming, and beachside dining.
2️⃣ Playa de la Fontanilla 🌊
- One of the most beautiful beaches in the region, with crystal-clear waters.
- Great for families, surfers, and seafood lovers.
- Home to some of the best chiringuitos (beach bars) in Conil.
3️⃣ Playa del Palmar 🏄♂️
- A surfer’s paradise with consistent waves and a bohemian vibe.
- Popular for surf schools, yoga retreats, and sunset beach bars.
- Less crowded than the town’s main beaches.
4️⃣ Historic Old Town & Plaza de España 🏡
- Wander through narrow, whitewashed streets full of local boutiques, tapas bars, and cafés.
- Visit the Plaza de España, the town’s lively main square.
- Stop by the Torre de Guzmán, a medieval watchtower with great views.
5️⃣ Mercado de Abastos 🐟
- A traditional market where locals buy fresh seafood, fruits, and vegetables.
- Great place to experience the authentic Andalusian food culture.
6️⃣ Mirador del Jabiguero 🌅
- One of the best viewpoints in town, offering panoramic views over Conil and the Atlantic.
- A perfect spot for sunset photos.
🍽️ What to Eat in Conil de la Frontera
- Atún de Almadraba – Fresh bluefin tuna, caught using a traditional method 🐟
- Ortiguillas fritas – Fried sea anemones, a local delicacy 🍤
- Choco a la plancha – Grilled cuttlefish, a simple but delicious dish 🦑
- Tortillitas de camarones – Light and crispy shrimp fritters 🥞🦐
- Sangría or Tinto de Verano – Refreshing drinks to enjoy by the beach 🍷
🚗 How to Get to Conil de la Frontera
🚘 By Car: ~45 min from Cádiz, 1.5 hrs from Seville, 2.5 hrs from Málaga
🚆 By Train: Nearest station is San Fernando-Bahía Sur, then take a bus
🚌 By Bus: Direct buses from Cádiz, Seville, and other Andalusian cities
✈️ By Air: Closest airport is Jerez de la Frontera (XRY) (~1 hr away)💡 Tips for Visiting Conil de la Frontera
✅ Best time to visit? May to September for beach weather, spring & autumn for fewer crowds 🌞
✅ Book accommodation early in summer – It’s a popular vacation spot 🏡
✅ Try local tuna dishes – Conil is famous for its bluefin tuna 🍽️
✅ Visit during the Feria de Conil (June) for a lively cultural experience 🎉 -
 @ b1b16be0:08f41c1d
2025-03-25 18:08:21
@ b1b16be0:08f41c1d
2025-03-25 18:08:21What if Nostr app could save an Illiterate country?
Guatemala is the most illiterate country in Hispanic America at levels as serious as Africa.
About 30% of the population aged 15 or over cannot read or write. This figure rises in rural areas, where illiteracy reaches even more worrying levels, affecting mainly women and indigenous populations.
Limiting their access to paid jobs, their ability to access health services, and their full participation in political and social life. Education is a fundamental right, but there are still large gaps in access and educational quality, especially in rural areas and in communities with high poverty rates.
What if there was an application similar to Duolingo, but that allowed people to learn to read and write while earning Satoshis (Sats) This proposal not only sounds innovative, but could be a powerful tool to combat the country's illiteracy.
The idea of an app that rewards learning "learn to earn"
Duolingo is a popular platform that has proven to be effective in teaching languages through a gamified approach. If that model could be replicated, but with a specific focus on reading and writing, and above all reward users with sats, it could offer two key benefits: encourage learning and offer a direct economic opportunity to users.
Satoshis, being a low-cost and easy-to-access, can be a motivating tool. Many people in Guatemala, especially those in rural areas, do not have access to a traditional banking system, much less to a national identity document, but they have access to mobile phones and the internet, which facilitates the inclusion of an alternative form of value. With this additional motivation, people would be more willing to invest time in learning, knowing that they can get a tangible reward for their effort.
https://image.nostr.build/9da1c3b9478be817e82c891fdceaf87905a4d68876e9190240a8f979ebd35b40.jpg
Will there be developers interested in helping?
In addition, the technology sector globally is increasingly focused on open source, financial inclusion and the use of Bitcoin as an empowerment tool.
A project like this could attract developers interested in creating inclusive technological solutions that not only improve the quality of life of Guatemalans, but also promote access to new economic opportunities through digital tools. Is the possibility of working on a project with social impact, which combines education and Bitcoin, something that could excite many developers?
Algorithms for a greater impact on the illiterate
For this application to be truly effective, it is not enough to replicate existing models. The platform's algorithms would need to be adapted to focus specifically on the needs of the illiterate. The algorithm would have to be flexible enough to adapt to different levels of learning and ensure that users can progress gradually and effectively. (That it can identify literate users who only want the reward).
This could include:
-
Reinforce basic learning: Include exercises focused on phonetics, letter recognition and word construction, something that is not so central in language learning applications.
-
Personalized gamification: Use a system of rewards and levels that motivates users to continue learning, adapting to their learning pace. Sats could accumulate as the user progresses, which could be an additional incentive.
-
Interactivity and visual support: Incorporate visual elements, such as images or videos, that help users associate words with objects or actions, which would be especially useful for those with few previous educational resources.
-
Collaborative learning: Create a community within the application where users can interact, share their progress, and perhaps even solve doubts from others, which would foster an environment of collective learning.
-
This country is also one of those that suffers the most from malnutrition as much as Africa. By having Sats they can exchange them for grains or legumes in the market. That the community in turn learns from the value of Bitcoin and can the markets go through a circular economy.
https://image.nostr.build/ed3805f6c695519ec8327ce6ee9900ec235d714a20a542b5559d9e6c63bc4496.jpg
Is this a feasible idea or just a fantasy?
This type of project could be really valuable. While there are technological and economic challenges, the combination of education and Bitcoin is a growing trend, and Guatemala has the potential to benefit greatly from it. The integration of an accessible platform, which encourages learning and offers a direct reward, can be the key to improving literacy rates in the country.
If you think long-term, this application could not only help reduce illiteracy, but also increase financial inclusion, offering people a way to earn income digitally. This country is one of those with the most migrants to the United States due to lack of work and extreme poverty.
It is clear that there are challenges to bring this idea to reality. Even so, I wouldn't be fantasizing. These types of projects are increasingly common in the digital world, and with the commitment of the technological community, along with the support of organizations that promote education and inclusion, a real difference could be made in the lives of millions of Guatemalans.
In conclusion, Guatemala faces high levels of illiteracy that limit the opportunities for personal and economic development of its population. Could an application that combines learning with economic rewards be an innovative solution to reduce this problem? Although there are challenges, the potential positive impact of this type of initiative is indisputable, and could mark a before and after in the educational and financial history of the country.
I’m not dev but if you know the next step please send me an inbox!
-
-
 @ 2e8970de:63345c7a
2025-03-25 18:03:08
@ 2e8970de:63345c7a
2025-03-25 18:03:08Data collected by nameberry (baby name website)
originally posted at https://stacker.news/items/924756
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ d560dbc2:bbd59238
2025-03-25 17:14:30
@ d560dbc2:bbd59238
2025-03-25 17:14:30If you juggle multiple tasks, projects, and responsibilities, you’ve likely heard of the Getting Things Done (GTD) method—a productivity system developed by David Allen to help you organize your tasks and clear your mind for focused work. You might also be exploring Task4Us, a web-based task management platform I founded that leverages the 2-5 Rule to prioritize tasks based on timing rather than rigid scheduling.
At first glance, these two systems might seem to operate differently: GTD focuses on a structured five-step process to manage tasks, while Task4Us emphasizes an anti-planning approach using its 2-5 Rule. However, combining these two can create powerful synergy by blending GTD’s clarity and structure with Task4Us’s intuitive timing-based prioritization. This guide walks you through how to integrate Task4Us with GTD to streamline your workflow, reduce mental clutter, and achieve your goals with less stress.
Understanding the Basics: GTD and Task4Us
What Is the Getting Things Done (GTD) Method?
GTD is a five-step productivity framework designed to externalize your tasks and commitments, freeing your mind for action. The steps are:
-
Capture:
Collect every task, idea, or commitment that grabs your attention into a trusted external system (e.g., notebook or app). -
Clarify:
Process each item to determine if it’s actionable. If it is, define the next step; if not, trash it, file it for reference, or defer it. -
Organize:
Sort actionable tasks into lists (e.g., Next Actions, Projects, Waiting For) and non-actionable items into categories like Someday/Maybe or Reference. -
Reflect:
Regularly review your lists to update priorities and ensure nothing slips through the cracks. -
Engage:
Choose your next action based on context, time, and energy, and then work on it.
GTD’s strength lies in reducing cognitive load by capturing everything so you can stay decisive and focused. However, GTD doesn’t inherently guide you on when to do tasks, leaving timing decisions up to you.
What Is Task4Us and the 2-5 Rule?
Task4Us is a task management platform built on the 2-5 Rule, an approach that emphasizes timing over detailed scheduling. Instead of planning when to do each task, you simply:
- Enter the Task:
Capture it into Task4Us as your “inbox.” - Set a Time Unit:
Choose whether the task is daily, weekly, monthly, or yearly. - Record the Last Act Date or Set a Fixed Due Date:
For recurring tasks, provide the last date you acted on them. For date-specific tasks, use Fix Mode to set the due date.
The 2-5 Rule calculates the task’s priority based on a “sweet spot” of 2 to 5 time units, ensuring you act at the optimal moment—neither too early nor too late.
Why Combine GTD and Task4Us?
By integrating these methods, you can capitalize on the strengths of both:
- GTD’s Clarity:
Use GTD to capture and organize every task and project, ensuring nothing is forgotten. - Task4Us’s Timing:
Leverage the 2-5 Rule to automatically prioritize tasks based on when they should be acted on, reducing the need to micromanage your schedule.
Together, they form a system where you externalize all your commitments (GTD) and then focus on the most important task at the right time (Task4Us), leading to a seamless, stress-free workflow.
Step-by-Step Guide to Combining Task4Us and GTD
Step 1: Capture Everything with GTD, Using Task4Us as Your Inbox
- Action:
Whenever a task or idea arises—like “Call a client,” “Plan a vacation,” or “Renew passport”—add it directly to Task4Us. - Tip:
Don’t worry about details yet; the goal is to clear your mind by capturing everything.
Example tasks: - “Email project updates to the team” - “Schedule a dentist appointment” - “Meet Uncle Lars for coffee”
Step 2: Clarify and Organize Tasks Using GTD Principles in Task4Us
- Clarify:
Process each captured task. Decide if it’s actionable. - If not actionable:
Trash it, file it for reference, or mark it as a “Someday/Maybe” task in Task4Us. - If actionable:
Determine the next step. - Organize:
In Task4Us, assign each actionable task: - Time Unit:
Choose days, weeks, months, or years (e.g., “Email project updates” as a weekly task). - Fix Mode:
For date-specific tasks (e.g., “Wish Alex a happy birthday”), set the exact due date. - Categories:
Group tasks (e.g., Work, Personal, Health) to align with GTD’s organization system. - Projects:
For multi-step projects, create a dedicated category and break the project into smaller, actionable tasks.
Step 3: Reflect Weekly to Update Your Task4Us Lists
- Review Your Tasks:
Set aside time each week to review your Task4Us lists. - Check your Top Task and Focus Mode (top 3 tasks) to ensure they reflect your current priorities.
- Update as Needed:
Adjust time units, update last act dates, or move tasks between active, someday/maybe, and archived lists. - Projects Review:
Ensure each multi-step project has at least one actionable task with a clear time unit.
Step 4: Engage with Task4Us’s Top Task and Focus Mode
- Engage:
Task4Us automatically surfaces your Top Task based on the 2-5 Rule. - For instance, if “Meet Uncle Lars” is nearing its action window, it will appear as the top task.
- Focus Mode:
Use this mode to display your top 3 tasks for a distraction-free workflow.
This aligns with GTD’s principle of choosing the right next action, making it easier to act decisively.
Step 5: Enhance GTD with Task4Us’s Unique Features
- Fix Mode for Deadlines:
Use Fix Mode for tasks with fixed dates (e.g., passport renewal) to ensure they gain priority as the due date approaches. - Export Tasks:
Download your task list as a CSV file to review your productivity over time. - Customize:
Adjust categories, time units, and Focus Mode settings to best suit your workflow.
A Real-Life Example: Combining GTD and Task4Us
Imagine managing work tasks, personal goals, and social connections:
-
Capture:
Throughout the day, add tasks like “Finish project report,” “Call Mom,” “Book dentist appointment,” and “Brainstorm new blog post” to Task4Us. -
Clarify and Organize:
- “Finish project report” is actionable—set as a weekly task in the Work category.
- “Call Mom” is actionable—set as a monthly task in the Personal category (last called 3 weeks ago).
- “Book dentist appointment” has a deadline (e.g., April 10, 2025)—use Fix Mode.
-
“Brainstorm new blog post” is not urgent—categorize it as Someday/Maybe.
-
Reflect:
During a weekly review, notice “Call Mom” is nearing the 5-week mark and becomes your top task. Update “Finish project report” after completion. -
Engage:
Task4Us displays “Call Mom” as the top task. You call, mark it done, and Task4Us updates the last act date. -
Enhance:
Use Focus Mode to tackle your top 3 tasks without distraction and export your tasks for review.
Why This Combination Works
-
GTD’s Lack of Timing Guidance:
Task4Us’s 2-5 Rule fills the gap by ensuring you act at the optimal moment. -
Task4Us’s Simplicity:
GTD adds structure to Task4Us, helping you manage complex projects and capture non-actionable items. -
Reduced Cognitive Load:
Both systems externalize tasks, reducing mental clutter and ensuring you’re focused on the right task at the right time.
Try It Out and Share Your Experience
Task4Us is currently in beta—now’s the perfect time to integrate it with GTD and transform your productivity. Start by capturing your tasks in Task4Us, apply GTD’s steps to clarify and organize them, and let the 2-5 Rule guide your actions.
Sign up for Task4Us at todo.task4.us and experience the power of combining GTD with the 2-5 Rule.
How do you manage your tasks? Do you use GTD, Task4Us, or a mix of methods? Share your thoughts in the comments—I’d love to hear your experience! 🚀
#Productivity #TaskManagement #GTD #Task4Us
-
-
 @ 3c389c8f:7a2eff7f
2025-03-25 17:12:33
@ 3c389c8f:7a2eff7f
2025-03-25 17:12:33Understanding Relays
Relays are a very simple concept, but an incredibly powerful part of Nostr. They are simple servers, of sorts, with a specific set of tasks- to fetch, hold, and send notes. Relays don't communicate with each other, only with clients. The client sends a request for any relevant notes and the relays oblige. What types of notes (aka events) that each relay will hold or fetch will vary because of different relays will operate under different sets of rules. Some will accept most any type of event from anyone. Others can be very strict, requiring things like payment, proof-of-work, specific event kinds, or only allow a whitelist of users to reduce spam and other unwanted content. When you create an event, or publish a note, it is sent to your "write" or "outbox" relays. Anyone who follows your npub or sends "fetch" /"read" requests, to those relays will receive your notes. When someone replies, likes, or otherwise engages with your note, that note will then duplicate to any "write" or "outbox" relays that the other person is connecting to as their outbox relays. This does two important things:
It creates a new event through through the action of engaging your note. This is a signed record of activity from that user's npub. This is also the event that is sent back to your "read" or "inbox" relays so that you may be notified that someone is interacting with you.
By creating a copy, this helps ensure your note will be able to be spread across more of the ecosystem, expanding your reach and introducing redundancy, in case a relay should go down or disappear completely. This does not imply that your data will be safely stored forever. In fact, its the exact opposite. The protocol assumes that any relay, or many, could disappear at any time. A relay can shut down, kick you out, experience intentional or unintentional data loss, or many other things. It is likely that a copy of your notes will still exist on many relays, but if you are concerned with the longevity of your content, consider running your own. Paid services for long term note storage exists as well, but they do require trusting the provider.
In this light, the importance of relays starts to become obvious. The various rules open up a whole plethora of use cases that make relays interesting, unique, and useful for the user. They are the backbone of the protocol. They are also tools for finding and managing great social connections and great content.
Types of Relays
This section can, in no way, be considered comprehensive. It is nearly impossible to know all of the relay implementations that may exist or all the rules that they may have set for themselves. Here, we will address some common types that will be useful in making the most of Nostr and a few types with specialized tasks.
Public Relays - Most Nostr clients will start new users with a predetermined set of relays that are free and publicly available for fetching and serving. This lowers the entry barrier for getting connected to the network, ensuring that everyone has access. It does come with some tradeoffs. Public relays tend to accept almost any type of content, so they are prone becoming the hosts of spam, bots, and shady content. To curate your space, it is recommended to get connected with some relays that help you clean things up.
Web-of-Trust Relays - These relays use your social graph and the graphs of others to build a network of higher trust for its users. This reduces spam and other yucky stuff from making it into your feeds. For write access, you must be followed by someone else within the network. If you are coming to Nostr with no external social connection, these may not be useful at first, though most do allow for public reading so you may find them useful to discover people and content you find interesting. Once you have established some social connections, they are great for creating a feed that casts a wider net through the whole network.
Paid Read/Write Filter Relays - These relays will charge an admission fee for write access. This helps to reduce spam and bots. Not all paying npubs want to see or interact with all who are willing to pay the fee, so a paid write relay often works best when paired with a paid filter relay for reading. These will operate under many sets of filtering rules, so be sure to read through any available material from the provider. They should explain what they filter and why, so that you may choose filters that match your tastes.
Inbox Relays - These relays are tasked with collecting any events that are intended FOR you. This includes likes, replies, receipts, and mentions, among many other things. If socializing with your friends and colleagues is important to you, you will want to find inbox relays that manage this task well. DM inbox relays are a separate but similar concept, as direct messages are encrypted and wrapped. They are a specialized relay meant for handling encrypted events. Many DM inbox relays charge a subscription fee, some do not. This is also a great use case for private relays.
Private Relays - These relays can be arranged to handle nearly anything you would like. You can whitelist a group of people that can write, restrict read access through AUTH, and set other various rules. They are a great option for any encrypted data, such as DMs, lists, and drafts. They also make a great backup for your own notes to help ensure that they remain available and locatable. Running your own is the optimal option here, but there are paid services, that I think of as relay rental. They are hosted on big servers, and managed by a small company. All details of the relay rules are at the renter's discretion. This is a good option if you do not have the hardware or confidence to set up your own private relay yet.
Search Relays - Search relays can help you find specific users & notes across the wider network. Some specialize in searching for people, others for text, tags, and other criteria. A strong search relay can make navigating through Nostr a breeze. As with other things, some may require a small fee to use them and others are free to use. Try out some free ones before buying to see if you are happy with your experience.
"Read" Relays - This is sort of a catchall term for anywhere that your client connects to for fetching notes and other events. In the best scenerio, you should not have to worry about these, as relays will signal for your client to find the notes you are fetching. The Nostr protocol and its mechanisms are adapting to what works, so being informed of "read" relays is essential for now. These are the places that you may need to tell your client to connect to when fetching notes from the people you follow. Specialized Relays - Specialized relays will vary in function and rules. Some are for curating quality feeds while others host full-fledge communities around a topic or common interest. Clients designed to interact with these more specialized use cases will often have relay information available or a method for you to browse their feeds.
This is just a snapshot of the different types of relays that exists now. Many are in development and testing for algorithmic content distribution, paywalled content, encrypted group messaging, limited read access, media hosting, and more. (This section may be updated as certain types gain or lose traction throughout the ecosystem.)
Managing Relays
By now, this probably feels like a ton of information and it is, but its also part of what gives you the ability to create and maintain a quality experience with Nostr. A truly decentralized system puts power into the user's hands rather than a corporation. If you want to be in control of your space (spatium tuum), relays are the first and foremost way to do that. They don't have to be viewed as boring servers. They are anything but that. They are tools that can enhance your online networking, serve you educational or entertaining content, or provide you with a safe place to store your personal thoughts. What you use them for is up to YOU.
Spend some time trying free ones, exploring relay feeds, or plugging into some paid services until you find a setup that creates a quality online space for you. If you're worried that you might "break" your connection, don't be. Make a note of a couple that you are connecting to when getting started, as a backup, but I feel confident to say that you won't ever look at it again.
Finding Relays
Finding relays can be a bit of a chore, but that is getting easier as time goes by. For now you there a few options you can try.
-
Visit a relay explorer like nostr.watch or nostr.info
-
Use a client that shows you which relays are hosting a note or a person's relay list. There are some examples in our client guide like Amethyst, Coracle, Jumble, and Nostrudel.
-
Just ask. Most people are on a social network to be social. Currently, Nostr is brimming with social people who are passionate about freedom, decentralized communication, and Nostr in particular. They are happy to help.
Running Your Own
Relay.tools is a hosted personal relay service for ease and a user friendly experience. Search Zapstore for Citrine to run a native relay on your Android device.
Below are some suggestions for relays to run on your own hardware. Search "nostr relay" on GitHub for more.
https://utxo.one/#nostr-projects
https://khatru.nostr.technology/
https://github.com/mikedilger/chorus
nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqyghwumn8ghj7mn0wd68ytnhd9hx2tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qqdxymngv35xq6rxdf5xqer2s0rg3q
-
-
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ 3c389c8f:7a2eff7f
2025-03-25 16:38:21
@ 3c389c8f:7a2eff7f
2025-03-25 16:38:21Public Key vs Private Key
When you generate a Nostr identity, you generate a cryptographic keypair. One is your public key (npub...). It is used to find you and your notes. The other is your private key (nsec...), which you use to interact. Everything you do is an event, which is signed by your private key. This makes all of your actions provably yours. You are solely responsible for protecting your nsec. It is recommended to try Nostr with a test keypair before setting up anything that you want to treat seriously.
Key Creation and Protection
Most Nostr clients will have the option to generate a keypair onsite or in-app. This is convenient for trying Nostr or a client. To make a keypair for longterm use, you might want to visit a site that provides some key security from the start. Your keys are a permanent set of identifiers. They cannot be changed or reset. You own them and it is your responsibility to keep your private key safe.
When you are ready to set up a permanent identity, start in a place that specializes in Nostr key generation. Nstart and Hubstr are great places to start. NOA, Nostr Onboarding App, is multiplatform with a native app, which helps make it easier to share with friends. You can create a vanity npub through various methods as well, like https://www.nostr.rest/ . There are other methods but these are some of the most user friendly ones that I have found. They provide some tools and guidance for creating your keypair in a safe manner. Once you've gone through the process, it is a good idea to write down your nsec and store it off of any devices, in the event you should lose access to your computer or phone.
Using a signer or a browser extension to house your nsec (private key), is the next step to keeping your identity safe. (Find out more on key management below)
Portability of Your Keys
This is where all the magic happens. You can use your keys to sign into any Nostr app. If you sign in with your npub (public key), you will enter in a read-only mode. This is nice for seeing a client's interface before trying it. You can sign in with anyone's npub to see what their social feeds look like, too. You do not need to be concerned with security when using npub sign-in. Your public key, is fully public. Not all Nostr clients support this option, but many do.
Signing in with your nsec unlocks all the features of a client and enables you to interact on the protocol. Everything you do is signed by your nsec and made available by your npub. Using some sort of signer is obviously advised, to keep from exposing your nsec online.
Since all of your actions (aka events) are stored on relays and not by clients, all of your content, messages, or anything else becomes available in any client that supports those event types. Most social stuff, like replies and profile views are available almost everywhere. Not all apps will support everything, but the ones that share a common theme will handle your events in similar manners. (I.e., a marketplace listing made from one app will display across many apps. The comments and replies will, too, so there is no need to manage multiple listings to answer questions or mark something as sold.)
Key Management
This is an evolving field, with many methods of key management being explored. People, businesses, and institutions all have different needs.
Signing Extensions keep your key in a browser extension, signaling to an app that the valid nsec is present. This sign in method is available on most Nostr apps. These are the most convenient method of key management but they do have their limitations. Using an extension can be cumbersome on mobile devices, and they could still be subject to vulnerabilities within your browser or the signer itself. They also don't allow for multiple users to sign events, like a business or organization might need. Key Bunkers enable the storage of key shards encrypted across multiple locations or in one spot. Bunker signing calls the encrypted key shards to decrypt for signing events. A bunker key, often called a bunker string, can be shared with staff or used to keep your key offline. They are revocable and replaceable. The process is currently a a little complicated and client support is somewhat limited. Adoption and improvement of this method is happening quickly, as the need for multi-party access to a profile increases. Native Signing Apps, like Amber for Android, make key key storage and signing for mobile a simple process. These apps work to keep your key offline, similarly to a bunker, but it is all stored encrypted on your device. Most Nostr-Android apps and web clients offer support for this method. Development of a similar iOS app is underway. Offline Hardware Signers like standalone devices and NFC cards are being explored, tested, by many groups.
This is a very active development space and this section will be updated as needed. Below are some suggestions for Nostr signers:
https://nsec.app/ https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp https://www.getflamingo.org/
-
 @ 3c389c8f:7a2eff7f
2025-03-25 16:16:29
@ 3c389c8f:7a2eff7f
2025-03-25 16:16:29Android
Amethyst - Experience the all-in-one Nostr client for mobile. Amethyst supports custom emoji reactions, marketplace listings, live streams, and so much more. If you're fresh to exploring Nostr, Amethyst may seem like a wild adventure compared to the any other social media of the past. Packed with features and blazing fast, this client gives you the ability to see just what Nostr is all about.
Voyage - This client is light on storage and data consumption, which is great for anyone with cheaper phones, limited data plans, or traveling/living in areas with lower data signal. Not only that, Voyage also offers some list and relay management tools not available in many other apps, so its great for handling some of the technical aspects of Nostr on the fly.
Web
Satellite - Fast and reliable, this client has topic communities, rich feeds, and beautiful profile displays. They offer paid media hosting for pictures, videos and more, which is essential for sharing visual content on Nostr. Satellite has long been a favorite for its simplified approach to displaying notes in a dense, clean manner and its consistency, reliability, and speed.
Jumble - Explore Nostr relay feeds, follow feeds, and more. Jumble has a clean, no-fluff interface that's easy to use and understand. You can socialize on specialized relays, or browse and chat on public relays with friends.
Coracle - Coracle allows you to easily browse relay feeds, your follow feed, and create custom feeds. You can generate Proof-of Work notes, set 'send' delays, and limit the number of relays the client talks to, to increase speed and reduce data consumption. You can generate PoW anonymous replies, too. A favorite feature is the option to import and export all of your data to/from your local device, so you can easily maintain a copy or send any lost events back to the Nostr network.
Nostrudel - The neat thing about Nostrudel is trying to find a Nostr action that it can't do. It's got all the bells and whistles. Nostudel may be a bit overwhelming if you're not familiar with all that is possible on Nostr, but once you have an idea, take this for a spin and see what new ways of interacting on the protocol that you discover.
iOS/Apple
Sorry... this is going to be a little scant for a while. Simply not one of the Apple people, these are the ones my iOS/Nostr friends seem to love:
Damus is a longtime favorite among users, adhering to a protocol-first approach to development.
Nostur sounds like a fun app, maybe on par with Amethyst as far as fun features and fast performance.
You'll have to do your own exploring to see what they are really all about.
Multi-platform
Primal - Simple, clean, and with an integrated Bitcoin/Lightning wallet for fast, easy zaps (basically tips, but on Nostr!). Get started with Nostr right away with no hassle and send or receive Bitcoin among your social network. Primal is great for anyone new to Nostr or who wants to enjoy a more traditional social media experience with the benefits that Nostr has to offer. Primal is available for Android, iOS, and on the web.
Yakihonne - Yakihonne is a beautiful multi-platform client that is available across any device. With a focus on long-form writing, it makes it easy to read and create Nostr articles, blogs, and any other informative piece. It doesn't stop there, though. You can scroll your social feed, set up smart widgets, and browse curated content collections, too.
Desktop
Notedeck - Built by the Damus team, Notedeck brings the speed and redundancy of Nostr to your machine. The local software is easy to install, set up, and use. Add multiple columns to the interface for a full screen of different feeds, profiles, and notifications.
Gossip - Gossip has a wide array of technical knobs and dials for relay controls, note fetching and publishing, and a clean interface that even I can understand. Gossip is built for the more technically-inclined among us, but is also great for the general Nostr "power user". This client is still a step above my paygrade but I'm loving it, regardless of that. If you are like me, this is a great client for a learn-through-doing method of understanding Nostr.
For Groups, Communities, and Chat
Oxchat - Oxchat puts security at the forefront of its interface with encrypted private and group chats. It does a whole lot more than that, too. You can browse your social feed, make voice and video calls, and display badges.
Flotilla and ChaChi are a couple of up and coming group/community/chat clients that are still very much under development, but look to be worth expounding upon in the future. Nostr's interoperability allows you to create and engage in groups you have joined through any of the above clients.
Specialty Clients
Zap.cooking - Publish recipes, earn zaps, find recipes, send zaps. Its a pretty brilliant system. There is no more need for 20 minute stories or overwhelming popup ads. Nostr adds a social layer to recipe sharing that doesn't require a new account to participate. Just sign in with your signing extension of choice, and you can share and leave feedback instantly.
Highlighter - Its still a bit of a construction site, but Highlighter is on its way to becoming Nostr's premiere content creator studio. Write, highlight, and curate. Not only can you create these, you can also browse and discover great Nostr content. There's lots in the works for video and other types of content, too.
Shipyard - "A Quiet Space for Loud Ideas" says it all. Shipyard is focused solely on your writing experience so that you may focus soley on your writing. This client is clean, reliable, and extemely user friendly. It is also one of few Nostr clients that provide you with the ability schedule the publishing of your notes.
Emojito.meme - Create and find custom emoji packs to use on Nostr! How fun is that? Just bookmark & those emojis ready to be used in any supporting social client.
Badges.page - Create and claim badges that display on Nostr profiles in supporting clients. This is a great way to engage with fans, celebrate moments with friends, or even just to be silly. You can set the difficulty of creating a badge with Proof-of-Work to create rare and super rare badges for top supporters, which is pretty cool.
Olas - A beautiful, visual showcase for photography and more. Its sort of like Instagram, but on Nostr, so its better. You can share, scroll, post, and monetize your content in a breeze.
Zapstore - Its an app store! On Nostr! Built for Android! Just follow the instructions on the site to begin your journey of stepping out of the nightmare that is the Playstore. Find apps recommended by your social graph, built by developers trusted within your networks, and donate to app development directly. You'll find more than just Nostr apps here. Zapstore is devoted to bringing free open source software from builder to user with as little interference as possible.
Listr - Create and manage lists for use in any other supporting client. This was the first thing that wow'd me about Nostr when I discovered it a couple years ago. There's something about making a list of people with common interests in one client, and seeing that list in action in another that just blew me away. Different feeds for different purposes, all chronological and all curated by YOU.
Habla - Long-form writing on Nostr made simple. You can quickly and easily get started with a blog or news publication and distribute it to your entire Nostr audience, regardless of which apps they use. Most social clients support article display within various feeds. You can always quote-note your article in a regular note, if you want to boost article exposure, too.
-
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ 3c389c8f:7a2eff7f
2025-03-25 15:51:44
@ 3c389c8f:7a2eff7f
2025-03-25 15:51:44*Create your keys and set up your profile:
https://start.njump.me/
*Pick a NIP07 browser extension or offline signer to safely store your private key (nsec):
https://nostr.net/
*Pick an app, sign in, and start exploring:
https://nostrapps.com/
That's All! :)
-
 @ a012dc82:6458a70d
2025-03-25 13:57:54
@ a012dc82:6458a70d
2025-03-25 13:57:54Bitcoin, the pioneering cryptocurrency, has once again defied skeptics by surging to a new all-time high. This remarkable resurgence is a testament to the resilience and enduring appeal of Bitcoin, even as it navigates through periods of intense volatility and regulatory scrutiny. Emerging from the shadows of the digital world, Bitcoin has sparked a financial revolution that challenges the very fabric of traditional banking and monetary systems. Its journey from an obscure digital token to a globally recognized financial asset encapsulates a saga of innovation, speculation, and the relentless pursuit of financial autonomy. This article explores the journey of Bitcoin from its inception to its current status as a leading digital asset, highlighting the challenges it has overcome and the factors contributing to its recent record-breaking performance.
Table of Contents
-
The Genesis of Bitcoin
-
Overcoming Adversity
-
The Path to Mainstream Acceptance
-
Breaking New Ground with ETFs
-
Navigating the Crypto Ecosystem
-
Looking Ahead: Challenges and Opportunities
-
Conclusion
-
FAQs
The Genesis of Bitcoin
Bitcoin was introduced to the world in 2008 by an individual or group using the pseudonym Satoshi Nakamoto. Conceived as a decentralized digital currency, Bitcoin offered a novel solution to the double-spend problem without the need for a central authority. This innovation was set against the backdrop of the global financial crisis, positioning Bitcoin as an alternative to traditional banking systems and fiat currencies. The early years of Bitcoin were marked by a passionate but small community of users, and the cryptocurrency was primarily used for niche online transactions. The concept of a decentralized currency was revolutionary, promising a new era of financial freedom and privacy. However, Bitcoin's early days were fraught with challenges, including limited public understanding, technical hurdles, and skepticism from the financial establishment. Despite these obstacles, the foundational principles of Bitcoin—transparency, security, and decentralization—captivated a growing number of enthusiasts who saw its potential to redefine money.
Overcoming Adversity
Bitcoin's journey has been anything but smooth. The cryptocurrency has faced numerous challenges, including regulatory hurdles, security breaches, and intense market volatility. High-profile incidents, such as the collapse of the Mt. Gox exchange in 2014 and the contentious debates over scalability, tested the resilience of the Bitcoin network and its community. Despite these setbacks, Bitcoin continued to gain traction, attracting a diverse group of users and investors drawn to its potential for high returns and its underlying blockchain technology. The path was littered with obstacles, from hard forks and regulatory crackdowns to sensational media coverage and public skepticism. Yet, each challenge served to strengthen the community and refine the technology, forging a cryptocurrency that was increasingly robust, adaptable, and resilient. The adversities faced by Bitcoin acted as a crucible, purifying and validating the concept of decentralized finance in the eyes of a global audience.
The Path to Mainstream Acceptance
The turning point for Bitcoin came with the gradual recognition of its value as both a digital asset and a technological innovation. Institutional investors began to take notice, and the cryptocurrency started to shed its reputation as a tool for illicit transactions. The introduction of futures contracts and the increasing interest from traditional financial firms signaled a shift towards mainstream acceptance. However, the journey was not without its skeptics, who pointed to Bitcoin's energy consumption and its volatile price swings as reasons for caution. The road to mainstream acceptance was paved with educational efforts, technological advancements, and a growing recognition of Bitcoin's unique attributes, such as its fixed supply and borderless nature. As awareness and understanding of Bitcoin increased, so too did its legitimacy and value, leading to a gradual but undeniable integration into the broader financial landscape.
Breaking New Ground with ETFs
The recent surge in Bitcoin's price can be largely attributed to the approval of exchange-traded funds (ETFs) pegged to the digital asset by U.S. regulators. This milestone was achieved after years of advocacy from the crypto community and a legal battle that challenged the Securities and Exchange Commission's initial rejections. The launch of the first "spot" Bitcoin ETFs has opened the doors for more traditional investors to enter the market, providing a regulated and familiar avenue for Bitcoin exposure. This development has not only boosted Bitcoin's price but also reinforced its legitimacy as an investment asset. The introduction of Bitcoin ETFs represents a significant breakthrough in the cryptocurrency's journey, bridging the gap between the innovative, often misunderstood world of digital currencies and the established, regulated realm of traditional finance. This convergence has facilitated a new wave of investment, bringing with it increased liquidity, visibility, and acceptance for Bitcoin and the broader cryptocurrency market.
Navigating the Crypto Ecosystem
Bitcoin's influence extends beyond its own price performance, serving as a bellwether for the broader cryptocurrency market. The ecosystem has grown exponentially, with thousands of altcoins and a burgeoning decentralized finance (DeFi) sector. However, the industry has not been immune to challenges, facing regulatory scrutiny, market manipulation, and high-profile scandals. Despite these obstacles, Bitcoin has maintained its dominance, buoyed by a loyal community and its perceived value as a hedge against inflation and currency devaluation. The cryptocurrency ecosystem is a dynamic and evolving landscape, marked by rapid innovation and intense competition. Yet, through all the tumult and transformation, Bitcoin remains the cornerstone, setting the standard for security, adoption, and market value. Its journey mirrors the maturation of the entire crypto space, from a fringe idea to a major financial force, influencing everything from individual investment strategies to global economic policies.
Looking Ahead: Challenges and Opportunities
As Bitcoin reaches new heights, questions remain about its sustainability and the potential impact of regulatory changes. The upcoming "halving" event, which reduces the reward for mining new blocks, is expected to have significant implications for Bitcoin's supply and, consequently, its price. Additionally, the cryptocurrency must navigate the delicate balance between innovation and regulation, as authorities worldwide grapple with how to oversee this evolving asset class. The future of Bitcoin is inextricably linked to the broader narrative of digital transformation and financial innovation. As it continues to evolve, Bitcoin will face new challenges and opportunities, from technological advancements and competitive pressures to shifting regulatory landscapes and economic trends. Yet, if history is any guide, Bitcoin will adapt and thrive, continuing its unstoppable journey from adversity to record highs.
Conclusion
From its humble beginnings to its current status as a financial phenomenon, Bitcoin's journey is a compelling narrative of innovation, resilience, and the relentless pursuit of decentralization. While the road ahead is fraught with uncertainty, Bitcoin's ability to rebound from adversity and reach new record highs is a testament to its enduring appeal and the transformative potential of cryptocurrencies. As the world continues to embrace digital currencies, Bitcoin's story remains a powerful reminder of the possibilities and challenges that lie ahead in the uncharted waters of the digital age. The saga of Bitcoin is far from over; it is a continuing tale of disruption, adaptation, and, ultimately, triumph in the face of adversity.
FAQs
Why has Bitcoin reached new record highs? Bitcoin's recent surge to new record highs can be attributed to factors such as the approval of Bitcoin ETFs, growing institutional acceptance, its appeal as a hedge against inflation, and increasing mainstream interest.
What are Bitcoin ETFs, and why are they important? Bitcoin ETFs (Exchange-Traded Funds) are investment funds that track the price of Bitcoin and are traded on traditional stock exchanges. They provide investors with a way to gain exposure to Bitcoin without having to buy or store the cryptocurrency directly, which has contributed to increased Bitcoin adoption.
What challenges has Bitcoin faced? Bitcoin has faced numerous challenges, including regulatory hurdles, security breaches, market volatility, and skepticism from the financial community. Despite these challenges, Bitcoin has continued to grow and gain acceptance.
What is the "halving" event in Bitcoin? The "halving" is an event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved. This reduces the rate at which new bitcoins are generated, theoretically increasing scarcity and potentially driving up the price.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 6bae33c8:607272e8
2025-03-25 11:03:28
@ 6bae33c8:607272e8
2025-03-25 11:03:28I try to make these bold enough that I get most of them wrong. If you’re not getting most wrong, they’re not bold enough! Hits from last year included Teoscar Hernandez being the Marcel Ozuna of 2024 and Shohei Ohtani’s gambling scandal getting memory-holed totally. Misses include Walker Buehler > Tarik Skubal and Spencer Torkelson > Vlad Guerrero. As I said, the predictions have to be bold!
Also, these are hunches, the explanations for which are largely irrelevant. The relevant information is priced into ADP, so while I’ll justify it one way or another, it’s the prediction itself, not the explanation that matters.
1, Alex Bregman is top-five in AL MVP voting
This just feels like a perfect fit. Bregman rakes at Fenway (1.240 career OPS), and he rarely strikes out. I could see a .300-plus batting average with 30 home runs. The Red Sox upgraded their pitching too, and after the Yankees lost Gerrit Cole and Juan Soto, have a good chance to win the AL East.
2. Bo Bichette outperforms Mookie Betts
Granted Betts is sick right now and lost a ton of weight, but he was still going in the second round of NFBC Mains, while Bichette was going in Rounds 8-9. Bichette was hurt last year, but prior to that he was a star, is in his age 27 season and has four home runs and a .373 average in Spring Training. I’m sick that I didn’t get any shares (took Bregman over him in the Main.)
3. Chris Sale finishes as a top-5 starter again
This might not sound that bold because he’s SP6 by ADP, but every pitcher except maybe Paul Skenes and Skubal are underdogs to be top-five, given the volatility of the position. I love veterans in their mid-30s finding it again, usually they have 2-3 years of good before age and injury catch up again. It reminds me of Justin Verlander who hit a rough patch before righting the ship for several elite years.
4. Tyler Glasnow finishes as top-3 in NL CY Young votes
My comp for Glasnow is Randy Johnson, another tall lefty who battled injuries in his 20s before settling down to become one of the GOATS. Glasnow managed 135 IP last year and if he ups it to 165, he’ll be in the CY mix on the Dodgers.
5. Cody Bellinger hits 40 homers
A pull hitter with a high fly ball rate, Bellinger is perfect for Yankee Stadium. He’ll have to stay healthy, of course, but he’s still just 29 — won’t turn 30 until July — and is primed for the second best year of his career (he won’t top 2019.)
6. At least one of the following veteran pitchers has a top-five CY finish: Justin Verlander, Max Scherzer, Kevin Gausman, Walker Buehler, Sandy Alcantara or Carlos Rodon.
Pitchers who were once elite still own most of their skills, health permitting. While Scherzer and Verlander have lost velocity, knowing how to pitch is sufficient above a certain minimum threshold.
7. Jackson Chourio goes 30-30-.300
Chourio hit over .300 for the final four months of the season, once the Brewers stopped pulling him in and out of the lineup. The steals should be easy for him with a full season of at-bats, and the power should be there too in that park.
8. Hunter Brown finishes top-five in AL CY voting
After a rough start, Brown was one of the best pitchers in the league last year with a 2.31 ERA over the last four months. He’s in a good park, in the right division (though the A’s home park got a lot worse) and on a good enough team for run support purposes.
9. Aroldis Chapman gets more saves than Jhoan Duran
Chapman is still throwing 99 and landed a job on the much-improved Red Sox, while Duran, who took nine losses last year, has Griffin Jax behind him. I know Chapman’s control has been bad the last few years, but I have a hunch the veteran warhorse has a comeback year.
10. Some of these predictions will be wrong
I’ll pay the cost of never going 10-for-10 to make sure I don’t go 0-for-10.
-
 @ 7da115b6:7d3e46ae
2025-03-25 11:00:01
@ 7da115b6:7d3e46ae
2025-03-25 11:00:01What Happened?
Sadly, some news came to us in the last couple of days, news that has exploded our plans like a bombshell. As you know from previous posts, my family and I had found the property of our dreams, within the price range that suited us. The only issue was that we had to sell our rental property to be able to purchase the land we wanted to develop for our homestead. At the time, it wasn't an issue.
With a few phone calls and some discussion with the local Council; the Realtor; the Vendors, and the bank, we were on our way. We made an offer, and it was accepted, contingent on our rental property selling. Our offer expires this Friday, and the likelihood of it selling before then, is slim. That leaves us 3 days to come up with the $130,000 we need to secure the property.
"So why not just extend the offer?" I hear you say. Well, that's a fair point - We did. The extension runs out this Friday. Can we extend on the extension? Legally, yes. but here's the rub:
A counter offer has been put forward.
This basically means, that without having the money available by the end of the offer extension, the Vendor is going to take the counter offer.
That's Not So Bad... Right?
Yes, and no.
Unfortunately, we've spend thousands of dollars on reports; valuations; building research and site inspections. This means all of the plans, money and time that we've invested so far is going to be lost. Yes yes, you're right of course, it's our own fault for getting so financially and emotionally invested in the first place. Lesson learned.
I think that the hardest part of it all, was breaking it to my wife. She had already started designing her gardens, and had dreams of watching our homestead grow. The look of utter defeat on her face was gut wrenching. I felt as though I had failed her, and torn away the dream we had built together. She and I had lost our dream in the course of a single phone call. It hit both of us hard.
It's been 24 hours now, and the pain is real. I don't want to eat or go to work, I don't want to talk to anyone. I just want to lay down on my wife's lap and close my eyes until it's over. Deep down inside, I know it's a childish reaction, but that doesn't make it any less of a slap across the face.
The Light at the End of the Tunnel
Cliche, I know, but there may be a little glimmer of light on the horizon. If we do sell our rental property, we will have money to play with. This means we can buy a crappy little Ute and caravan, and go exploring our country. Perhaps stop at a few places that look nice, and see if they're places we could settle. If we spend a few months just looking around, and find somewhere homely, then we can stay for a while at a local caravan park, and look for a property that may be suitable.
At the very least, it would mean that we can escape our shit jobs, which has been the biggest goal from the beginning.
Fingers crossed...
-
 @ 7da115b6:7d3e46ae
2025-03-25 10:55:04
@ 7da115b6:7d3e46ae
2025-03-25 10:55:04Originally written and posted on the 12th of December, 2024
Emotionally, it's been challenging to say the least, and the heat just exacerbates the frustration. But don't let that fool you; we've made significant progress. We found our dream property over two months ago for $130,000. 3 hectares of land, but 2 hectares of it is unusable. This was perfectly okay with us as it's going to be a massive effort for one person anyway.
Two months ago, we put in an offer and they accepted it. However, we are not well off by any means; most weeks, we just scrape by. We have two properties - a property in the Far North that we've been renting out to pay the mortgage ($70,000 remaining), and the one we live in which has almost the entire mortgage outstanding.
So how can we afford another property? Well it's no simple feat! First, we need to sell our Rental Property for around $400,000 (a reasonable market rate). Once that sells, about $170,000 in equity gets transferred to the mortgage of the property we're currently living in. After paying off the last of the mortgage on the rental property and shifting the equity to our current property, that will leave us with almost nothing after legal fees and real estate agent fees.
This amount remaining barely covers the cost of the property we put an offer on - our dream property. It's a humbling experience realizing just how far we still have to go in this journey towards self-sufficiency.
It's a sober reminder that we can't rush it, but should rather embrace each step along the way. For better or for worse, we must adapt and learn from every situation as it comes our way. After all, we can only control what's within our reach; the rest is just a matter of time and patience.
Perhaps it's not about achieving self-sufficiency, but truly embracing the journey itself. The path towards that dream property we've been longing for may take longer than expected, but as long as we have each other and keep pushing forward, I can't think of anything more rewarding than seeing our vision unfold step by step.
I have to remember to cherish the memories and experiences along this road, because it's those moments that will truly make the journey worthwhile.
-
 @ 7da115b6:7d3e46ae
2025-03-25 10:52:00
@ 7da115b6:7d3e46ae
2025-03-25 10:52:00Originally written and posted on the 10th of March, 2025
Safety
The first reason that comes to mind is safety. Violent crime has become a recurring theme in our town, with statistics showing a rise in cases such as burglaries and general homicides. These changes have made us acutely aware of the importance of providing a secure environment for our family. As our children grow, we yearn for them to experience not just safety, but also a sense of stability that comes with it.
The thought of crime often makes me reflect on moments like the domestic violence and murder within throwing distance of our current home, or the attempted mugging and homicide at a nearby petrol station. These incidents have sparked a desire for a place where our family can feel more secure and enjoy the peace of mind that comes with knowing they're safe. I hope that growing up in a safe environment will instill confidence and security in my kids as they navigate life. This pursuit of safety is not just about protecting my loved ones; it’s about creating a foundation where they can thrive and feel secure in their surroundings, allowing them to focus on their growth and aspirations without the constant awareness of potential danger.
Cost of Living
The cost of living has been another pivotal factor in our decision to move. Over time, we’ve noticed how the city’s expenses, from petrol to groceries, have steadily increased, making every purchase a mindful choice. The rising costs of utilities, transportation, and daily essentials have become a significant part of our budget, leaving us wondering if there’s room for more than just the basics. While the city offers many amenities, we’ve found ourselves seeking a lifestyle that aligns with our values and allows us to live comfortably without constant financial strain.
The cost of groceries has also become a major consideration. As prices rise, even simple trips to the store have us thinking about every purchase. We’ve found ourselves choosing between brands or quantities to stay within our budget, which has made us appreciate the idea of growing some of our own food.
While we love the idea of the cultural and social offerings of city life, the reality is that we spend more time trying to stretch our weekly budget to make ends meet, than we do enjoying the fruits of our labor. We’re looking forward to a place where we can manage our budget comfortably, while still having access to the amenities we need. This doesn’t mean we’re leaving behind everything we’ve grown accustomed to; it’s about finding a balance—a home that allows us to live fully without feeling constrained by expenses.
Our decision to move isn't about wanting to be one with nature or making a statement; it’s more about practicality. Owning a freehold property gives us the stability we need, allowing us to live sustainably without feeling tied down by expenses. This choice aligns with our values and offers a sense of freedom, not because we're trying to escape something, but because it supports the life we want for ourselves and our family. We’ve worked hard to pay down our mortgages, but now we’re ready for the next step—owning our own land that we can build upon.
We’re not looking to simplify just because we want to be closer to nature; rather, we see this move as an opportunity to create a lifestyle that’s more in tune with our needs. By growing our own food and living in a clean, natural environment, we’re prioritizing sustainability without compromising on what matters most—our family’s future and well-being. It’s about creating a home that reflects our values, not just embracing change for the sake of being different.
Educational Opportunities
Our oldest child’s education is another driving force behind this move. We’ve discovered that the place we’re moving to offers a University with "fees-free" options, which will provide him with an opportunity to pursue his studies without the burden of tuition costs. This not only eases our financial concerns but also gives us peace of mind knowing he can focus on his education without added stress. It’s a decision that aligns with our aspirations for his future and our family's well-being, hoping he can thrive in an environment that supports his academic journey and personal growth.
Also, our youngest child is going to have the opportunity to raise the animals he’s so enamored with, such as chickens; dogs; pigs, and maybe even a couple of sheep. I want these experiences to help him to learn by doing, fostering a sense of responsibility and connection with where our food comes from. By caring for these creatures, we hope he’ll develop life skills that will help him grow into his own skin as he gets older. It’s a chance for him to explore his passions and build confidence in a hands-on way.
Freedom
Space has become something we truly appreciate, especially with our kids and pets. We’re eager for them to have more room to roam and explore freely. The privacy that a rural setting offers is high on our list of needs because living in the city often feels like we're always surrounded by others. It's not uncommon to bump into neighbors or find ourselves at loggerheads over simple things like car parks. This constant interaction, while part of city life, can sometimes feel overwhelming.
But it's not just us - our current place of employment also experiences issues with neighboring businesses, and it’s the employees who end up feeling the impact. It feels as if everyone is out for themselves, and are incapable of thinking about how their actions affect others.The city environment feels cramped and extremely claustrophobic, making us yearn for more personal space. We’re looking forward to the freedom of having our own large property where we can enjoy peace and quiet. It’s exciting to think about the possibilities, like building a barn or adding bee hives, and even sinking a water well as we please.
Food & Gardening
The idea of growing our own food is another exciting prospect that we're eager to explore. We’re looking forward to cultivating fresh produce in our garden, which will not only provide healthier options for our family but also add variety and freshness to our meals. It will be a major undertaking for us. While I personally have some understanding of growing and harvesting simple crops like potatoes and cabbage, I am deeply aware of my lack of knowledge and experience. It will take years for me to actually become proficient. We’re excited to teach our kids where their food comes from and instill an appreciation for sustainable living. Growing our own produce aligns with our desire for a more natural, self-sufficient lifestyle, offering us the joy of seeing the fruits of our labor in our garden.
Exercise & General Wellness
Living in a bustling city has its perks, but it has also take a toll on our sense of well-being. The daily grind often leaves us feeling mentally and emotionally drained, leaving little room for relaxation and physical activity. With the convenience of modern life comes a faster pace, which, while beneficial, frequently feels overwhelming. We long for moments to pause, breathe in fresh air, and reconnect with ourselves.
I think that the desire for more exercise and fresh air, is a natural response to the our current lifestyle. The city’s vibrant atmosphere and endless opportunities often come at the expense of personal time and the chance to enjoy relax. By seeking a new environment, We're looking for a balanced life for our family, where we can revitalize their minds and bodies through simple yet essential activities like walking around the property or the exercise of working the land. This shift is not just about changing scenery; it’s about creating a lifestyle that supports our overall well-being and allows for moments of peace away from the hustle and bustle.
In conclusion, this move is about more than just changing scenery; it’s about creating a home that embodies our values—safety, education, sustainability, and well-being for our family. It’s a step towards a future where we can thrive in an environment that supports our growth and aspirations.
-
 @ ecda4328:1278f072
2025-03-25 10:00:52
@ ecda4328:1278f072
2025-03-25 10:00:52Kubernetes and Linux Swap: A Practical Perspective
After reviewing kernel documentation on swap management (e.g., Linux Swap Management), KEP-2400 (Kubernetes Node Memory Swap Support), and community discussions like this post on ServerFault, it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion.
The Rationale for Disabling Swap
We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes.
With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion.
Additionally, disabling swap may protect data from data remanence attacks, where sensitive information could potentially be recovered from the swap space even after a process terminates.
Theoretical Capability vs. Practical Deployment
Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly.
But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model:
- Memory requests and limits are declared explicitly.
- The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap).
- Swap introduces non-deterministic performance characteristics that conflict with Kubernetes' goals.
So while the kernel supports intelligent swap usage, Kubernetes intentionally sidesteps that complexity.
Why Disable Swap in Kubernetes?
-
Deterministic Failure > Degraded Performance\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early.
-
Transparency & Observability\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically.
-
Performance Consistency\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits.
-
Kubernetes Doesn’t Manage Swap Well\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control.
-
Statelessness is the Norm\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state.
"But Swap Can Be Useful..."
Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need:
- Fine-tuned
vm.swappiness - Memory pinning and cgroup-based control
- Swap-aware monitoring and alerting
- Custom kubelet/systemd integration
That's possible, but not standard practice — and for good reason.
Future Considerations
Recent Kubernetes releases have introduced experimental swap support via KEP-2400. While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments.
Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in KEP-2400's Risks and Mitigations section, swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior.
Some argue that with emerging technologies like non-volatile memory (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet.
Conclusion
Disabling swap in Kubernetes is not a lazy hack — it’s a strategic tradeoff. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability.
If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, disabling swap remains the sane default.
-
 @ 7d33ba57:1b82db35
2025-03-25 09:38:27
@ 7d33ba57:1b82db35
2025-03-25 09:38:27Located on the Costa de la Luz, Chipiona is a charming seaside town in Cádiz province, known for its stunning beaches, iconic lighthouse, and delicious local wines. It’s a perfect destination for those seeking relaxation, history, and Andalusian charm.
🏖️ Top Things to See & Do in Chipiona
1️⃣ Chipiona Lighthouse (Faro de Chipiona) 💡
- The tallest lighthouse in Spain (69 meters), built in 1867.
- Climb 322 steps for breathtaking views of the Atlantic Ocean.
- Used to guide ships through the Gulf of Cádiz for centuries.
2️⃣ Playa de Regla 🏝️
- The most famous beach in Chipiona, known for its golden sand and calm waters.
- Perfect for sunbathing, swimming, and long walks along the shore.
- Surrounded by beach bars (chiringuitos) and seafood restaurants.
3️⃣ Santuario de Nuestra Señora de Regla ⛪
- A beautiful neo-Gothic monastery near the beach.
- Home to the Virgen de Regla, the town’s patron saint.
- A site of religious pilgrimages, especially in September.
4️⃣ Las Corrales de Pesca 🎣
- Ancient fishing structures made of stone walls in the sea, dating back to Roman times.
- A unique traditional fishing method, still in use today.
- Guided tours are available to learn about their history.
5️⃣ Bodega César Florido 🍷
- Visit one of the oldest wineries in Chipiona, famous for Moscatel wine.
- Enjoy a wine tasting tour and learn about the local winemaking tradition.
6️⃣ Paseo Marítimo & Sunset Views 🌅
- A scenic beachfront promenade, ideal for an evening stroll.
- Watch the sunset over the Atlantic Ocean, one of the most beautiful in Andalusia.
🍽️ What to Eat in Chipiona
- Langostinos de Sanlúcar – Delicious local prawns, best with a glass of Manzanilla wine 🦐🍷
- Tortillitas de camarones – Crispy shrimp fritters, a Cádiz specialty 🥞🦐
- Chocos a la plancha – Grilled cuttlefish with olive oil and lemon 🦑
- Pescaíto frito – A mix of fried fresh fish, perfect for a beachside meal 🐟
- Moscatel de Chipiona – A sweet dessert wine, famous in the region 🍷

🚗 How to Get to Chipiona
🚘 By Car: ~30 min from Cádiz, 1 hr from Seville, 2 hrs from Málaga
🚆 By Train: Closest stations in El Puerto de Santa María or Jerez de la Frontera
🚌 By Bus: Regular buses from Cádiz, Jerez, and Seville
✈️ By Air: Nearest airport is Jerez de la Frontera (XRY) (~40 min away)💡 Tips for Visiting Chipiona
✅ Best time to visit? Spring & summer for beach weather, September for festivals 🌞
✅ Try a Moscatel wine tour – The local wineries are world-famous 🍷
✅ Bring comfortable shoes – If climbing the lighthouse 👟
✅ Visit in September for the Fiestas de la Virgen de Regla, a unique cultural experience 🎉 -
 @ da0b9bc3:4e30a4a9
2025-03-25 09:14:07
@ da0b9bc3:4e30a4a9
2025-03-25 09:14:07Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/924287
-
 @ 220522c2:61e18cb4
2025-03-25 06:57:24
@ 220522c2:61e18cb4
2025-03-25 06:57:24
-
 @ d560dbc2:bbd59238
2025-03-25 05:29:36
@ d560dbc2:bbd59238
2025-03-25 05:29:36Hey! Today, I’m diving into the 2-5 Rule—a unique task management method that’s all about timing, not planning. It powers TaskforUs, a beta platform that’s changing how we prioritize tasks. Grab a coffee, and let’s get started!
What Is the 2-5 Rule?
The 2-5 Rule is a task management approach that focuses on when to act on a task rather than creating a detailed plan. Every task has a “time unit” (days, weeks, months, or years), and you should act within 2 to 5 of those units. This “sweet spot” ensures that you’re neither rushing nor neglecting tasks.
Examples:
- Daily tasks: (e.g., “Do cardio”) – Act every 2-5 days.
- Weekly tasks: (e.g., “Meet a friend”) – Act every 2-5 weeks.
- Monthly tasks: (e.g., “Review budget”) – Act every 2-5 months.
- Yearly tasks: (e.g., “Renew passport”) – Act every 2-5 years.
You don’t plan the exact time to do the task—just enter it into TaskforUs, set the time unit, and provide either the last date you acted on it or a fixed due date. The system prioritizes it for you, making it an anti-planning method.
How Does It Work in Practice?
Example 1: Renewing Your Passport
-
Scenario:
You get your passport today (March 24, 2025). -
Action:
Add the task “Renew passport” to TaskforUs with a yearly time unit and set the “last act date” as today. -
Outcome:
The task starts low on your priority list but climbs over time. After 2 years, it begins to rise; by 5 years, it’s near the top—nudging you to act before your passport expires.
Alternatively, use Fix Mode to set the expiration date (e.g., March 24, 2030) so the task climbs in priority as the date approaches.
Example 2: Meeting Uncle Lars Regularly
-
Scenario:
You want to meet your Uncle Lars roughly 10 times a year (about once every 5 weeks). -
Action:
Add the task “Meet Uncle Lars” with a weekly time unit (to provide flexibility) and set the “last act date” as the most recent meeting (e.g., March 1, 2025). -
Outcome:
Over time, the task slowly climbs in your priority list. After 2 weeks, it starts gaining focus; by 5 weeks, it becomes urgent—prompting you to schedule the next meeting.
No detailed planning is required—you simply add the task, and the 2-5 Rule does the rest.
The Psychology Behind the 2-5 Rule
The 2-5 Rule isn’t just a clever idea—it’s grounded in psychology and behavioral science. Here’s why it works so well:
-
It Reduces Decision Fatigue
Constantly deciding when to do each task can be exhausting. The 2-5 Rule automates prioritization, so you don’t have to think about when to act. TaskforUs surfaces the right task at the right time, freeing up mental energy for doing the work. -
It Aligns with Natural Rhythms
Humans thrive on rhythm and consistency. Behavioral science shows that after 2 time units, a task starts to feel pressing, but by 5 units, it’s at risk of being neglected. The 2-5 window captures this natural sense of urgency. -
It Taps into the Zeigarnik Effect
This psychological principle states that uncompleted tasks are remembered better than completed ones. As a task’s due window approaches, it naturally rises in priority—keeping it top of mind. -
It Prevents Over-Planning Stress
Detailed scheduling can be stressful, especially when life is unpredictable. The anti-planning nature of the 2-5 Rule removes this burden: you simply enter your task and let the system remind you when it’s time to act.
The Structure of TaskforUs: Bringing the 2-5 Rule to Life
TaskforUs is a web-based platform (currently in beta) that makes the 2-5 Rule actionable:
-
Add Tasks Easily:
Simply enter a task, set its time unit (days, weeks, months, or years), and provide the last act date or a fixed due date for Fix Mode tasks. -
Top Task:
TaskforUs automatically highlights your most urgent task based on the 2-5 Rule, telling you exactly what to do right now. -
Focus Mode:
See your top 3 tasks (or adjust the number) for distraction-free productivity. -
Fix Mode:
For date-specific tasks (e.g., “Wish Alex a happy birthday”), set the due date and watch the task climb in priority as the day approaches, peaking on the day itself. -
Category Filtering and Archiving:
Organize tasks into categories (e.g., Work, Personal) and archive completed tasks to keep your list clean. -
Export Tasks:
Download your tasks as a CSV file for backup or analysis.
TaskforUs takes the 2-5 Rule’s anti-planning philosophy and makes it seamless, ensuring you always know what to do next without the mental load of scheduling.
Why the 2-5 Rule Works: A Game-Changer for Task Management
The 2-5 Rule stands out because it addresses common pain points in task management:
-
No More Overwhelm:
By focusing on one top task (or a few in Focus Mode), you avoid the clutter of a long to-do list. -
Effortless Prioritization:
The rule automates the decision of what to do next, reducing stress and boosting productivity. -
Never Miss a Deadline:
With Fix Mode, date-specific tasks like passport renewals or birthdays rise to the top at the right time. -
Flexibility:
The 2-to-5 window gives you room to act when it suits you—without rigid deadlines.
Try the 2-5 Rule with TaskforUs
The 2-5 Rule is a fresh take on task management that balances short-term habits with long-term goals—without the burden of meticulous planning. TaskforUs makes it easy to implement, and as a beta user, you can help shape its future.
Here’s why you should try it:
-
No Planning Needed:
Just add your tasks and let the system prioritize them automatically. -
Clarity:
Always know what to do right now—without the mental load of overthinking. -
Flexibility:
The 2-to-5 window gives you the right balance between urgency and ease. -
Reliability:
Fix Mode ensures you never miss critical dates. -
Be Part of the Beta:
Your feedback helps improve TaskforUs as it evolves.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a new way to manage tasks by focusing on timing rather than rigid plans. Ready to say goodbye to overwhelm and hello to effortless prioritization?
Sign up for TaskforUs at task4.us and experience the 2-5 Rule in action.
Your tasks, perfectly timed—without a plan in sight. -
 @ 7da115b6:7d3e46ae
2025-03-25 05:14:41
@ 7da115b6:7d3e46ae
2025-03-25 05:14:41Originally written and posted on the 21st of Sept, 2022
I'm about 6 months into the ownership of my first bike, since I was a teenager. It has most definitely been an interesting time. While I am truly enjoying riding, it's not been without it's hiccups.
The first real issue is that I don't have a great knowledge of motorcycle models, or their general history. My first ride was an 80cc Yamaha Jog, which could do 70 Km/h down hill with a tail wind. My second was a Yamaha DX100 (colloquially known as the "Flying Banana"), which I could start with the handle of a teaspoon, and was lost when the back tyre burst during a trip, resulting in a write-off (a story in of itself).
So a little background first. The reason I purchased a bike, is mostly for financial reasons. While there is an argument to be made that it's more expensive to ride than drive, I did a ton of math, and came to the conclusion that it actually works out cheaper, considering my circumstances. When factoring in the massive rise in fuel costs; the far lower insurance costs; and lower maintenance costs (due to being able to maintain it reasonably well on my own). It seemed that because I do long trips of around 400 Km every couple of weeks, it was a sound option. Also, being middle aged, I ended up having to go back and sit my motorcycle licence, as with my previous bikes, it was in a time where riding dirty on small displacement bikes wasn't really noticed by the cops (yes, that does indeed make me a middle aged learner rider).
When researching bikes, I made a few things a priority:
- Small displacement
- Aesthetically pleasing
- Easily repairable
- Cheap maintenance
- Reliability
- Fuel efficient
nb. I didn't include things like performance or top speed, because they were mostly irrelevant to my needs at the time.
In the end, it worked out that the Kawasaki Ninja 250 fit all of the criteria I had set. It was about then that I set out to find a good example of the model, at a reasonable price.
I delved into the subject with gusto, looking at the Trademe sales, and researching as best as I could. I ran across the Ninja250 Wiki and found a thriving community built around these interesting little bikes. While I didn't interact directly with the community, I did find the compiled resources invaluable for my purposes. They've pulled together schematics, technical manuals, replacement parts lists, tips & tricks and a ton of general information. Very handy.
Unfortunately, Kawasaki have been a little liberal with the "Ninja" moniker, and it seems like they enjoyed slapping the label on a ton of different models. It got extremely confusing in a very short period of time. In the end, I found a listing for a 2007 Ninja 250, that looked really clean for its age, with only 30,000Kms on the clock. Being the 2007 model, it was the last of the dual carb bikes, before they switched to Electronic Fuel Injection. This appealed to me, because it lowered the bar for maintenance.
It seemed like the perfect option for me, so I got in contact with the owner, and we negotiated a price. I looked over the bike, and in my inexperience, I missed some crucial details that a more experienced rider would have noticed (I'll get to those details shortly). After a quick ride on my newly minted Learners Licence, I found the power was decent and it rode well. I checked for things like frame fatigue, engine noise, drops in power, exhaust leaks, tyre tread, oil leaks and more.
The owner seemed trustworthy, so when he told me that "It runs like a dream, and it's never needed any work aside from a replacement faring", I believed him. In hind sight, I seriously should have realised the red flag about it needing new faring.
This is where we get to the details I missed.
Firstly, It looks like the Oil Filter had never been changed, but to cover this fact, they did an oil change just before the sale, so it looked clean.
Secondly, the fuel filter had never been changed, so was full of crud. Because it's hidden in the carb end of the fuel line, you cant see it on a cursory look.
Thirdly, someone had removed the air filter, and just never bothered to put it back or replace it. Unfortunately, it's under the fuel tank, so you cant see it without removing the tank.
Fourth and finally, the Faring. So it turns out that the bike had definitely been laid down at some point. My naivety and excitement blinded me to what was obvious. The clutch handle was scratched to sin, the tail bar has scrapes along one corner, and the foot pegs had been replaced.
Again, looking back, how could I not have seen these things? I'm kicking myself, but now that I have it, I just have to deal with the consequences.
I'm disappointed in the seller for not disclosing these issues, and to say that I was cursing his name when I found out about these things, is a definite understatement. I know that I should have been more diligent, but it calls into question my judgement. I feel a little ripped off by people like this, and am starting to question a lot of decisions I wouldn't normally hesitate to make.
Anyway, after a lot more research it turns out it's not even an EX250, which is what the previous owner told me. It is in fact a GPX250, which has a completely different set of parts. This was a true eye opener, and led me to order parts that are completely incompatible with the bike. When I finally found out the correct model, I was able to move forward.
Since having the bike, I've lubed the chain multiple times (it looks like it had never been done); I've replaced the oil filter and done an oil change; ripped out the silly fuel filter and added an in-line gravity fed one that is transparent and easy to view; and replaced the air filter.
It seems to be running better now, and there is more to be done, but I'm sad that it has come to this. I never should have listened to the previous owner, let alone trusted him. I have learned my lesson, and will be far more vigilant in the future.
-
 @ e5de992e:4a95ef85
2025-03-25 05:00:45
@ e5de992e:4a95ef85
2025-03-25 05:00:45Global financial markets are experiencing significant movements influenced by recent developments in trade policies, economic data releases, and geopolitical events.
U.S. Stock Market Performance
On March 24, 2025, U.S. stock markets rallied sharply, buoyed by optimism surrounding potential easing of forthcoming tariffs:
-
Dow Jones Industrial Average (DJIA):
Rose by nearly 600 points (1.4%), closing at 42,583.32. -
S&P 500:
Increased by 1.8%, ending the session at 5,767.57 points. -
Nasdaq Composite:
Advanced by 2.3%, finishing at 18,188.59 points.
These gains were led by significant advances in the technology sector, with notable performances from companies like Tesla, which surged 12%, and Nvidia, which gained 3.2%.
U.S. Futures Market
As of the latest data, U.S. stock futures are exhibiting slight fluctuations:
-
Dow Jones Futures:
Indicated a modest decline, reflecting investor caution ahead of upcoming economic data releases. -
S&P 500 Futures:
Showed minimal movement, suggesting tentative market sentiment. -
Nasdaq Futures:
Displayed slight volatility, influenced by recent tech sector performances.
Key Factors and Events Influencing U.S. Markets
Trade Policy Developments
- Recent market rallies were largely driven by reports that the U.S. administration plans to implement more targeted tariffs than initially feared.
- Certain sectors such as automobiles and semiconductors may be exempted, alleviating investor concerns about trade policies impacting economic growth.
Economic Data Releases
- Investors are closely monitoring upcoming economic indicators, including the Consumer Confidence Index and the Personal Consumption Expenditures (PCE) index.
- These indicators will help gauge the health of the economy and inform potential implications for monetary policy.
Federal Reserve's Monetary Policy
- The Federal Reserve's recent decision to maintain interest rates—along with its revised economic outlook—continues to influence market sentiment.
- This policy stance is particularly relevant in relation to inflation expectations and growth projections.
Global Stock Indices Performance
International markets have shown mixed reactions in response to U.S. trade policy developments and regional economic data:
-
Germany's DAX:
Experienced modest gains amid cautious optimism over global trade discussions. -
UK's FTSE 100:
Edged higher, supported by strength in commodity-related sectors. -
Euro Stoxx 50:
Advanced, driven by positive corporate earnings reports and easing trade tensions. -
Japan's Nikkei 225:
Rose by over 1%, mirroring Wall Street’s upbeat performance and optimism regarding U.S. tariff policies. -
Hong Kong's Hang Seng:
Declined by 1%, impacted by profit-taking activities and ongoing trade uncertainties.
Cryptocurrency Market
The cryptocurrency market has exhibited volatility, with major digital assets experiencing price fluctuations:
-
Bitcoin (BTC):
Trading at approximately $84,481.00, down 1.82% from the previous close. -
Ethereum (ETH):
Priced around $1,987.26, reflecting a 2.18% decrease from the prior session.
These movements highlight the broader market's sensitivity to regulatory developments and macroeconomic factors affecting investor sentiment in the digital asset space.
Key Global Economic and Geopolitical Events
-
Trade Tensions and Tariff Policies:
Rapid escalation of trade barriers—reminiscent of protectionist measures from the 1930s—has raised concerns about long-term economic and diplomatic ramifications, including slower growth and heightened inflation. -
Central Bank Communications:
Statements from Federal Reserve officials and other central bank representatives are being closely scrutinized for future monetary policy directions. -
Corporate Earnings Reports:
Upcoming earnings releases from major corporations are expected to provide further clarity on sector health and broader economic conditions, influencing market dynamics in the near term.
Conclusion
Global financial markets are navigating a complex landscape shaped by trade policy developments, economic data releases, and geopolitical events. Investors are advised to remain vigilant and consider these factors when making informed decisions, as they are likely to continue influencing market behavior in the foreseeable future.
-
-
 @ bf7973ed:841ad12a
2025-03-25 04:19:41
@ bf7973ed:841ad12a
2025-03-25 04:19:41test
-
 @ 502ab02a:a2860397
2025-03-25 02:24:07
@ 502ab02a:a2860397
2025-03-25 02:24:07ต่อเนื่องจากมหากาพย์น้ำมันมะกอกปลอมนะครับ คนที่ปลอมแปลงน้ำมันมะกอกได้พัฒนาวิธีการต่าง ๆ เพื่อเลียนแบบคุณสมบัติของน้ำมันมะกอกแท้ ทำให้การตรวจสอบด้วยการแช่เย็นเพื่อดูการแข็งตัวอาจไม่สามารถยืนยันความบริสุทธิ์ได้อย่างแน่นอนแล้วหละครับ
คำแนะนำในการเลือกซื้อน้ำมันมะกอกจะแบ่งเป็นกว้างงงงงงงกว้าง 3 เรื่องคือ 1 ซื้อจากแหล่งที่เชื่อถือได้ เลือกซื้อน้ำมันมะกอกจากผู้ผลิตหรือร้านค้าที่มีความน่าเชื่อถือ และมีการรับรองคุณภาพจากหน่วยงานที่เกี่ยวข้อง ซึ่ง เชรี่ยละ ฝากเงินไว้กับคนอื่น 5555 2 ตรวจสอบฉลาก อ่านฉลากผลิตภัณฑ์อย่างละเอียด ตรวจสอบแหล่งที่มา วันที่ผลิต และวันที่หมดอายุ อันนี้คือที่เราจะคุยกันวันนี้ 3 สังเกตลักษณะของน้ำมัน น้ำมันมะกอกแท้มักมีสีและกลิ่นเฉพาะตัว หากพบว่าสีหรือกลิ่นผิดปกติ ควรพิจารณาก่อนซื้อ ตรงนี้นี่ต้องอาศัยความเจ็บปวดจากการพลาดเยอะๆ จะทำให้รู้ความแตกต่างครับ ซึ่ง not bad นะ
ไล่จากเรื่องเล็กก่อน คือ การสังเกตลักษณะน้ำมัน แบบที่นิยมสุุดคือ การแช่ตู้เย็นแล้วดูว่ามันแข็งไหม ที่เราสอนต่อๆกันมาคือ ถ้าแข็งก็คือดี ของแท้ แต่ แต่ แต่ ส่วนใหญ่แล้วการปลอมน้ำมันมะกอกเขาจะใช้หลากหลายวิธี แล้วแต่คนจะทำครับ อาทิเช่น การเจือปนสิ่งเหล่านี้ลงไปครับ - ไขมันเติมไฮโดรเจนบางส่วน ได้แก่พวกน้ำมันพืชราคาถูก เช่น น้ำมันถั่วเหลือง น้ำมันปาล์ม หรือคาโนลา มักถูกเติมไฮโดรเจนบางส่วนเพื่อเพิ่มอายุการเก็บรักษาอยู่แล้ว ต้นทุนต่ำกว่าน้ำมันมะกอกมาก หลายๆคนคงบอกว่า เอ้ย มันแช่เย็นแล้วไม่แข็งตัวนี่ ตรงนี้มีข้อมูลบอกว่า เขาใช้ไขมันทรานส์หรือไขมันเติมไฮโดรเจน โดยใช้หลักการทางเคมีที่ทำให้เนื้อสัมผัสของน้ำมันปลอมเลียนแบบพฤติกรรมของน้ำมันมะกอกแท้เมื่อถูกแช่เย็น บางที่ก็เติมน้ำมันมะพร้าวหรือน้ำมันปาล์ม อันนี้ต้นทุนต่ำทำง่ายเลยครับ เค้าใช้น้ำมันปาล์มโอเลอินที่มีการ ปรับแต่ง ด้วยการ เติมสารเติมแต่ง ทำให้ไขมันในน้ำมันมีลักษณะแข็งขึ้นและสามารถ ปรับจุดหลอมเหลว ให้สามารถแข็งตัวที่อุณหภูมิที่เย็นได้มากขึ้น - กรดไขมันอิ่มตัวสังเคราะห์ ประเภทกรดสเตียริกหรือกรดปาลมิติกสังเคราะห์เป็นผลิตภัณฑ์พลอยได้จากอุตสาหกรรมแปรรูปไขมันพืชและสัตว์ ราคาต่อหน่วยต่ำมาก โดยเฉพาะถ้าซื้อในปริมาณมาก - ไขมันจากสัตว์ อย่างเช่นไขมันหมูและน้ำมันปลาถูกกว่าน้ำมันมะกอก และสามารถหาได้จากอุตสาหกรรมแปรรูปอาหารที่มักมีของเหลือทิ้งในปริมาณมาก - ขี้ผึ้งพืช พวกขี้ผึ้ง Candelilla Wax หรือ Carnauba Wax ราคาถูกกว่าและสามารถใช้ในปริมาณน้อยเพื่อเลียนแบบคุณสมบัติทางกายภาพ - โมโนกลีเซอไรด์และไดกลีเซอไรด์ เป็นสารเติมแต่งที่ใช้ในอุตสาหกรรมอาหารอยู่แล้ว ต้นทุนต่ำมาก และช่วยให้น้ำมันมีเนื้อสัมผัสคล้ายน้ำมันมะกอก
ในข้อต่อมาจะรวมกันได้เลยครับ ฉลาก และ การรับรองคุณภาพ คือผมตัดเรื่องผู้ผลิตหรือร้านค้าออกไปเลย เพราะก็ไปดูเองได้ว่าแบรนด์เก่าแก่ เราก็จะเหมารวมไปเองว่าไม่น่าโกง 5555 เราข้ามมาอะไรที่พอจะมีหลักเกณฑ์ได้นะครับ short cut เลยคือ ตรารับรอง ใครจะดู DOP IGP USDA Organic อะไรผมไม่ค่อยสนใจครับ ผมว่าถ้าเป็นไปได้ข้ามไปดูนี่เลยครับ
 - International Olive Council (IOC) น้ำมันมะกอกที่ได้รับการรับรองจาก IOC เป็นการรับรองคุณภาพน้ำมันมะกอกที่ได้รับการตรวจสอบจากองค์กรที่มีมาตรฐานสากล
- COOC (California Olive Oil Council) สำหรับน้ำมันมะกอกที่ผลิตในแคลิฟอร์เนีย หรือในสหรัฐฯ จะมีการรับรองจาก COOC ที่ยืนยันว่าผ่านการตรวจสอบมาตรฐาน
- International Olive Council (IOC) น้ำมันมะกอกที่ได้รับการรับรองจาก IOC เป็นการรับรองคุณภาพน้ำมันมะกอกที่ได้รับการตรวจสอบจากองค์กรที่มีมาตรฐานสากล
- COOC (California Olive Oil Council) สำหรับน้ำมันมะกอกที่ผลิตในแคลิฟอร์เนีย หรือในสหรัฐฯ จะมีการรับรองจาก COOC ที่ยืนยันว่าผ่านการตรวจสอบมาตรฐานเรามาทำความเข้าใจรายละเอียดของน้ำมันมะกอกกันก่อนครับ เพื่อว่าตอนดูฉลากจะได้รู้ว่าทำไมต้องมีของพวกนี้ พันธุ์มะกอกที่ใช้ทำน้ำมันมะกอกนั้นเป็นตัวกำหนดรสชาติและกลิ่นหอมของน้ำมันมะกอก โดยมะกอกแต่ละสายพันธุ์ให้รสชาติแตกต่างกันครับ Arbequina (สเปน): กลิ่นผลไม้ มีรสคล้ายแอปเปิ้ลเขียว Koroneiki (กรีซ): เผ็ดร้อน มีรสพริกไทย Coratina (อิตาลี - Puglia): รสเข้ม เผ็ดร้อน มีรสขมติดปลายลิ้น Manzanilla cacereña (สเปน): หอมผลไม้ มีรสอัลมอนด์ แอปเปิ้ลเขียว Peranzana (อิตาลี - Puglia): รสชาติกลมกล่อม หอมหวานเล็กน้อย
- พื้นที่เพาะปลูกและผลิต ตัวนี้แหละครับ เอาไปทำตรา IGP เรียกเหมาๆว่า Geographical Origin น้ำมันมะกอกคุณภาพสูงจะระบุชัดเจนว่า มะกอกมาจากไหนและผลิตที่ไหน ถ้าฉลากไม่ระบุ แสดงว่าอาจเป็นน้ำมันมะกอกผสมจากหลายแหล่ง ซึ่งอาจมีคุณภาพต่ำ
- วันที่เก็บเกี่ยว น้ำมันมะกอกมีสารโพลีฟีนอล (Polyphenols) ซึ่งเป็นสารต้านอนุมูลอิสระที่ให้รสชาติและกลิ่นหอม แต่เมื่อเวลาผ่านไป สารเหล่านี้จะลดลง ทำให้น้ำมันเสียรสชาติ
- ระดับความเป็นกรด (Acidity Level) ตัวนี้หละที่ผมโคตรเน้น และพูดบ่อยมาก จนหลายๆคนเบื่อ 5555 น้ำมันมะกอก Extra Virgin ต้องมี ค่าความเป็นกรดต่ำกว่า 0.8% ค่ายิ่งต่ำ ยิ่งดี เพราะหมายความว่ามะกอกถูกเก็บเกี่ยวอย่างเหมาะสมและสกัดอย่างรวดเร็ว
- ระดับความเข้มของรสชาติ เรื่องการกินก็สำคัญนะครับน้ำมันมะกอกมีระดับความเข้มต่างกัน ควรเลือกให้เหมาะกับอาหาร รสอ่อน (Delicate) เหมาะกับปลา เนื้อขาว และสลัดเบาๆ ,รสปานกลาง (Moderate) เหมาะกับพาสต้า ผักย่าง และชีส รสเข้มข้น (Intense) เหมาะกับเนื้อแดง ช็อกโกแลต และอาหารที่มีรสจัด
ส่วนตราที่บอกไว้ข้างบนโน้นนน จำไว้เลยว่า อย่าหลงเชื่อคำว่า "Organic" เพียงอย่างเดียว เพราะการปลูกแบบออร์แกนิกไม่ได้รับประกันว่ารสชาติจะดีเสมอไป หลีกเลี่ยงน้ำมันมะกอกที่ระบุว่า "Product of EU" เพราะอาจเป็นการผสมจากหลายประเทศ
สำหรับเรื่องฉลากนะครับ ใครที่ดื่มไวน์โลกเก่าจะคุ้นเคยความที่ต้องอ่านรายละเอียดพวกนี้เป็นอย่างดี น้ำมันมะกอกแบบ extra virgin olive oil ที่ดี ฉลากและแพคเกจจะต้องมีประมาณนี้ครับ 1.ระดับกรดอิสระ (Free Fatty Acids, FFA) หรือ กรดโอเลอิก (%) ต้องไม่เกิน 0.8% ตามมาตรฐานของ International Olive Council (IOC) ถ้าค่าตัวนี้ยิ่งต่ำ แสดงว่าน้ำมันมะกอกมีคุณภาพดีขึ้น เพราะบ่งบอกว่าผลมะกอกถูกสกัดอย่างดี ไม่ผ่านกระบวนการที่ทำให้เสื่อมสภาพ 2. ค่าความเป็นออกซิเดชัน (Peroxide Value, PV) (meq O₂/kg) ต้องไม่เกิน 20 meq O₂/kg คือไม่ต้องรู้ก็ได้ครับว่ามาจากไหน เอาว่าถ้าค่าสูงเกินไป แสดงว่าน้ำมันเริ่มเหม็นหืนจากปฏิกิริยาออกซิเดชัน 3. ค่า K232 และ K270 (UV Absorbance at 232 nm และ 270 nm) โดยที่ K232 ต้องไม่เกิน 2.50 (บ่งบอกถึงการเกิดออกซิเดชันระยะแรก) และ K270 ต้องไม่เกิน 0.22 (บ่งบอกถึงการเสื่อมสภาพของน้ำมัน) ค่าเหล่านี้ใช้แสง UV ตรวจจับว่ามีการกลั่นน้ำมันอื่นผสมเข้ามาหรือไม่ 4. ค่า Delta-K (ΔK) ต้องไม่เกิน 0.01 ค่านี้ใช้ตรวจจับว่าน้ำมันมีการปนเปื้อนหรือถูกดัดแปลงด้วยสารอื่นไหม 5. ประเทศต้นกำเนิด (Country of Origin) น้ำมันมะกอกที่มีคุณภาพดีมักระบุชื่อฟาร์มหรือแหล่งผลิตที่ชัดเจน เช่น อิตาลี สเปน กรีซ 6. วันที่เก็บเกี่ยว (Harvest Date) และวันหมดอายุ (Best Before Date) ควรเลือกน้ำมันที่มีวันที่เก็บเกี่ยวล่าสุด (อายุการเก็บรักษาโดยทั่วไปคือ 18-24 เดือน) 7. วิธีการสกัด (Extraction Method) ต้องระบุว่าเป็น "Cold Pressed" หรือ "Cold Extracted" หมายถึงสกัดโดยไม่ใช้ความร้อน ซึ่งช่วยรักษาคุณภาพของสารอาหาร 8. ปริมาณโพลีฟีนอล (Polyphenol Content) (mg/kg) [อาจไม่มีในทุกยี่ห้อ] น้ำมันมะกอกคุณภาพสูงมักมีโพลีฟีนอลมากกว่า 250 mg/kg ซึ่งช่วยลดการอักเสบในร่างกาย แต่บางยี่ห้อก็จะให้ดูที่วิตามิน E กับ K เพราะ น้ำมันมะกอกที่มี Polyphenol สูงมักจะมีปริมาณ วิตามิน E ที่สูงตามไปด้วย และการที่น้ำมันมะกอกมี วิตามิน K ก็อาจสะท้อนถึงการที่น้ำมันมะกอกนั้นไม่ได้ถูกผ่านกระบวนการปรับแต่งหรือแปรรูปที่มากจนเกินไป ทำให้รักษาสารอาหารที่สำคัญ รวมถึง Polyphenol ไว้ได้ 9. บรรจุภัณฑ์ ควรเป็นขวดแก้วสีเข้มหรือกระป๋องโลหะ เพื่อป้องกันการเสื่อมสภาพจากแสง




ใน 9 ข้อนี้ ไม่จำเป็นต้องมีครบทุกข้อก็ได้นะครับ เท่าที่ผมพยายามหาในไทย เจอ acidity ก็บุญโขแล้วครับ 55555 บางทีเขาก็อาจไม่ได้แปะไว้บนฉลาก แต่ต้องตามไปอ่านในเว็บของผู้ผลิตก็ได้ครับ
ส่วนใครที่อ่านถึงตรงนี้แล้วท้อใจ ไม่อยากกินมันแล้ว ก็ขอบอกว่า โลกมันก็เป็นแบบนี้แหละครับ ของมันมีราคามากจนต้องมีการปลอมกัน มันไม่ได้โหดร้ายขนาดนั้นหรอกครับ กระเป๋าแบรนด์เนมก็ปลอมกันเกลื่อน นาฬิกาก็ปลอมกันทั่ว แต่คุณๆก็มองออกใช่ไหมครับ น้ำมันมะกอกมันก็ไม่ต่างกันหรอกครับ มันคือเรื่องที่ไม่ธรรมดาของโลกนี้ที่คนทำเป็นเรื่องธรรมดา
ถ้ามันดูหดหู่ไป จำง่ายๆก็ได้ครับว่า "ทุกน้ำมันมะกอกปลอม จะไม่มีฉลากที่บอกรายละเอียดดีๆ แต่ ทุกน้ำมันมะกอกที่ไม่มีฉลากรายละเอียดดีๆ ไม่ได้เป็นน้ำมันมะกอกปลอม" logic แบบง่ายๆนี้เลยครับ
ผมได้แค่บอกว่า สิ่งที่ควรดูเพื่อแลกกับเงินที่ต้องจ่ายให้มันมากๆคืออะไร แล้วสิ่งที่เราจ่ายไปบริโภค เราได้แบบนั้นจริงๆไหม อย่างที่เคยบอกใน #ฉลาก3รู้ เสมอๆคือ ฉลากไม่ได้เป็นตัวประกาศิตที่จะบอกว่าใครไม่มีคือแย่ แต่ฉลากมันเหมือนคำมันสัญญา ว่าผู้ผลิตจะทำตามที่เขียนเอาไว้ ถ้าใครที่กล้าบิดพริ้วจากนั้น หรือ ทำไม่จริงตามฉลาก มันก็คือการที่เขากล้าทำผิดสัญญา และมันต้องแลกมาด้วยค่าใช้จ่าย ไม่ว่าจะชื่อเสียง ความน่าเชื่อถือ หรือ ความภาคภูมิใจ เราคงทำอะไรไม่ได้มากกว่านั้น จะใช้กระบวนการ ก็ต้องพิสูจน์ ใช้เวลา เพราะที่เห็นในบ้านเราก็มีตัวอย่างมากมาย แต่มันก็ "อย่างน้อย" มันวัดกันหล่ะวะ ว่า แกกล้าสัญญากับชั้นมั๊ย
โอเคมะ ถ้าคุณจะหนี มันต้องหนีตลอดไปในทุกๆอย่างครับ หรือจะให้ผมเล่าเรื่อง fun fact ของกินเทพอื่นๆ ที่พวกคุณกินกันอย่างเป็นล่ำเป็นสันเพื่อกระตุ้นให้ศึกษาเพิ่มไหมหล่ะ 55555
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ a3a17f65:e9606ad9
2025-03-25 02:22:32
@ a3a17f65:e9606ad9
2025-03-25 02:22:32Maybe it’s the novelty, or perhaps a placebo effect. Maybe it's the sense of finally accomplishing something I’ve set out to do a long time ago. But the first impression is that writing has already begun to clear my mind. It seems to be one of the most powerful ways to improve thinking. Developing the habit of writing could lead to becoming a better thinker.
This journal is meant to reflect whatever’s on my mind. But posting it online comes with a different set of pros and cons compared to what most productivity gurus recommend. For instance, I’ll cut out personal thoughts or sensitive information—something essential in a personal journal. I could mitigate such flaw by writing two versions: one for public view and one for myself, but that feels like too much hassle when I’m just starting this new habit (as James Clear advises, make your habits easy!). On the flip side, posting on cyberspace forces me to be mindful of you, dear reader. Writing for myself alone would allow me to leave empty spaces between familiar ideas and have no problem joining the dots later. But here, fortunately, that luxury doesn’t exist.
Another complementary habit that’s been nagging at me lately is reading, especially fiction—not for learning, but for the pure joy of reading without the pressure to take notes or analyze everything. I just came across this post and despite not being plagued by the obsessive use of smart phones and social media, these two phrases caught my eye:
Reading literary fiction has been linked to having more empathy and the ability to engage in critical thinking
I’ve always valued critical thinking, so that didn’t surprise me. But the link to empathy caught my attention. It made me think about how reading fiction let us experience different perspectives, possibly engaging the same mirror-neurons activated during real-life interactions. Fascinating how something that sharpens our minds can also help us connect with others on a deeper level.
I feel like myself again. Did I mention I’m also sleeping better, and feel happier too?
This quote resonated on a deep level. For me, a single day of writing has given me a most welcomed sense of accomplishment due to being true to myself. Combining journaling with joyful reading might be one of the most powerful boosts to both sleep quality and a sense of purpose I’ve experienced in a long time.
-
 @ 1d7ff02a:d042b5be
2025-03-25 02:01:41
@ 1d7ff02a:d042b5be
2025-03-25 02:01:41ໃນຍຸກດິຈິຕອນ, ການລົບກວນທາງເທັກໂນໂລຊີໄດ້ສັ່ນຄອນສະຖາບັນແບບດັ້ງເດີມທົ່ວໂລກ. ເຊັ່ນດຽວກັນກັບແພລດຟອມສື່ສັງຄົມອອນລາຍທີ່ໄດ້ທຳລາຍອິດທິພົນຂອງສື່ທ້ອງຖິ່ນ, Tether (USDT) ແລະ ສະເຕເບິນຄອຍອື່ນໆ ກຳລັງທ້າທາຍອຳນາດຂອງທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ສະກຸນເງິນດິຈິຕອນທີ່ມີຄວາມສະຖຽນເຫຼົ່ານີ້ ສະເໜີວິທີການສຳລັບປະຊາຊົນເພື່ອປ້ອງກັນເງິນເຟີ້, ຫຼີກລ່ຽງການຄວບຄຸມທຶນ, ແລະ ເຂົ້າເຖິງຕະຫຼາດການເງິນໂລກໂດຍບໍ່ຕ້ອງອີງໃສ່ລະບົບທະນາຄານແບບດັ້ງເດີມ. ໃນຂະນະທີ່ການນຳໃຊ້ກຳລັງເພີ່ມຂຶ້ນ, USDT ກຳລັງກາຍເປັນໄພຂົ່ມຂູ່ທີ່ມີຢູ່ຈິງຕໍ່ທະນາຄານກາງ, ຈຳກັດການຄວບຄຸມຂອງພວກເຂົາຕໍ່ນະໂຍບາຍການເງິນ ແລະ ອຳນາດອະທິປະໄຕທາງການເງິນ.
ທາງເລືອກໃໝ່ແທນສະກຸນເງິນທ້ອງຖິ່ນ
ປະເທດກຳລັງພັດທະນາມັກຈະປະສົບບັນຫາກັບການລົດຄ່າເງິນ, ເງິນເຟີ້, ແລະ ການໄຫລອອກຂອງທຶນ. ທະນາຄານກາງຫຼາຍແຫ່ງບໍ່ສາມາດຮັກສາສະຖຽນລະພາບຂອງສະກຸນເງິນເນື່ອງຈາກການຄຸ້ມຄອງທີ່ບໍ່ດີ, ການພິມເງິນຫຼາຍເກີນໄປ, ຫຼື ການແຊກແຊງທາງການເມືອງ. ພົນລະເມືອງທີ່ເຫັນເງິນທ້ອນຂອງຕົນຖືກກັດເຊາະ ຕາມປົກກະຕິແລ້ວຈະມີທາງເລືອກບໍ່ຫຼາຍ: ປ່ຽນເງິນທ້ອງຖິ່ນເປັນ ໂດລາ ຫລື ໃນກໍລະນີ້ລາວເຮົາກໍຈະມີ ບາດ ແລະ ຢວນນຳ ຜ່ານທະຫລາດມືດ ຫຼື ລົງທຶນກັບທຸລະກິດ, ຊື້ອະສັງຫາ ແລະ ລົງທຶນໃນຊັບສິນຕ່າງປະເທດ. USDT ໄດ້ປ່ຽນແປງເກມນີ້. ມັນອະນຸຍາດໃຫ້ທຸກຄົນທີ່ມີການເຂົ້າເຖິງອິນເຕີເນັດສາມາດເກັບຮັກສາ ແລະ ໂອນມູນຄ່າໃນຮູບແບບດິຈິຕອນທີ່ທຽບເທົ່າກັບໂດລາໂດຍບໍ່ຈຳເປັນຕ້ອງໄດ້ຮັບການອະນຸມັດຈາກທະນາຄານທ້ອງຖິ່ນ ຫຼື ລັດຖະບານ. ສິ່ງນີ້ຊ່ວຍໃຫ້ຫຼຸດພົ້ນຈາກການອີງໃສ່ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ, ສະເໜີທາງເລືອກທີ່ງ່າຍໃນການປ້ອງກັນການເສື່ອມຄ່າ. ໃນປະເທດເຊັ່ນ: ເວເນຊູເອລາ, ອາເຈນຕິນາ, ໄນຈີເຣຍ, ເລບານອນ, ແລະ ລາວ, ປະຊາຊົນກຳລັງນຳໃຊ້ USDT ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງຂອງພວກເຂົາຈາກພາວະເງິນເຟີ້ສູງ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ.
ການທຳລາຍການຜູກຂາດຂອງທະນາຄານກາງ
ທະນາຄານກາງມີອຳນາດອັນໃຫຍ່ຫຼວງຕໍ່ລະບົບການເງິນໂດຍການຄວບຄຸມການອອກເງິນ, ອັດຕາດອກເບ້ຍ, ແລະ ການໄຫຼຂອງທຶນ. ເຖິງຢ່າງໃດກໍຕາມ, USDT ບ່ອນທຳລາຍການຄວບຄຸມນີ້ດ້ວຍການສະໜອງລະບົບການເງິນຄູ່ຂະໜານທີ່ດຳເນີນງານເປັນອິດສະຫຼະຈາກການກຳກັບດູແລຂອງລັດຖະບານ. ສິ່ງນີ້ທ້າທາຍສາມພື້ນທີ່ຫຼັກຂອງອຳນາດທະນາຄານກາງ:
- ການຄວບຄຸມນະໂຍບາຍການເງິນ:
ເມື່ອປະຊາຊົນຍ້າຍເງິນທ້ອນຈາກສະກຸນເງິນທ້ອງຖິ່ນໄປສູ່ USDT, ທະນາຄານກາງຈະສູນເສຍຄວາມສາມາດໃນການຄວບຄຸມປະລິມານເງິນຢ່າງມີປະສິດທິພາບ. ຖ້າປະຊາກອນສ່ວນໃຫຍ່ຢຸດໃຊ້ສະກຸນເງິນແຫ່ງຊາດ, ນະໂຍບາຍເຊັ່ນ: ການປ່ຽນແປງອັດຕາດອກເບ້ຍ ຫຼື ການພິມເງິນກໍຈະສູນເສຍປະສິດທິພາບຂອງພວກມັນ.
- ການຫຼີກລ່ຽງການຄວບຄຸມທຶນ:
ປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງບັງຄັບໃຊ້ການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດເພື່ອປ້ອງກັນບໍ່ໃຫ້ເງິນອອກນອກປະເທດ, ເຮັດໃຫ້ສະກຸນເງິນຂອງພວກເຂົາມີສະຖຽນລະພາບ. USDT, ໂດຍບໍ່ມີພົມແດນ, ອະນຸຍາດໃຫ້ຜູ້ໃຊ້ຫຼີກລ່ຽງການຄວບຄຸມເຫຼົ່ານີ້, ເຮັດໃຫ້ມັນງ່າຍຂຶ້ນໃນການດຳເນີນທຸລະກຳທົ່ວໂລກ ຫຼື ເກັບຮັກສາຄວາມໝັ້ງຄັ່ງທີ່ມີສະພາບຄ່ອງລະດັບສາກົນ.
- ການລົດບົດບາດຂອງລະບົບທະນາຄານ:
USDT ຫຼຸດຄວາມຕ້ອງການຂອງການບໍລິການທະນາຄານແບບດັ້ງເດີມ. ດ້ວຍສະມາດໂຟນ ແລະ ກະເປົາເງິນດິຈິຕອນ, ປະຊາຊົນສາມາດສົ່ງ ແລະ ຮັບການຊຳລະເງິນໂດຍບໍ່ຕ້ອງຜ່ານລະບົບທະນາຄານ, ຕັດທະນາຄານອອກຈາກລະບົບນິເວດການເງິນ ແລະ ເຮັດໃຫ້ພວກມັນຂາດຄ່າທຳນຽມທຸລະກຳ ແລະ ເງິນຝາກ.
ກໍລະນີຂອງລາວ: ການປ່ຽນແປງທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
ລາວ, ເຊັ່ນດຽວກັນກັບປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງ, ປະເຊີນກັບສິ່ງທ້າທາຍທາງເສດຖະກິດລວມທັງເງິນເຟີ້, ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ (ເງິນກີບລາວ), ແລະ ການເຂົ້າເຖິງເງິນຕາຕ່າງປະເທດທີ່ຈຳກັດ. ລັດຖະບານມີການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດ, ເຮັດໃຫ້ມັນຍາກສຳລັບບຸກຄົນ ແລະ ທຸລະກິດໃນການຊື້ USD ຜ່ານຊ່ອງທາງທີ່ເປັນທາງການ. ສິ່ງນີ້ເຮັດໃຫ້ເກີດຕະຫຼາດມືດສຳລັບການແລກປ່ຽນເງິນຕາທີ່ເຕີບໂຕຂຶ້ນ. ດ້ວຍການເພີ່ມຂຶ້ນຂອງ USDT, ຊາວລາວຫຼາຍຄົນກຳລັງຫັນມາໃຊ້ stable coin ແລະ ເກັບຊັບສິນດິຈິຕອນ ເປັນທາງເລືອກທີ່ປອດໄພກວ່າການຖືເງິນກີບລາວ, ເຊິ່ງມີແນວໂນ້ມທີ່ຈະເສື່ອມຄ່າລົງ.
ບົດຮຽນຈາກການທຳລາຍສື່ທ້ອງຖິ່ນໂດຍສື່ສັງຄົມອອນລາຍ
ການເພີ່ມຂຶ້ນຂອງ USDT ສະທ້ອນໃຫ້ເຫັນເຖິງສື່ສັງຄົມອອນລາຍໄດ້ທຳລາຍສື່ທ້ອງຖິ່ນແນວໃດ. ສື່ຂ່າວແບບດັ້ງເດີມເຄີຍຜູກຂາດການແຈກຢາຍຂໍ້ມູນ, ແຕ່ແພລດຟອມເຊັ່ນ: Facebook, Twitter, ແລະ YouTube ໄດ້ເຮັດໃຫ້ການສ້າງ ແລະ ການແຈກຢາຍເນື້ອຫາເປັນປະຊາທິປະໄຕ. ດັ່ງນັ້ນ, ສື່ທີ່ຄວບຄຸມໂດຍລັດ ແລະ ບໍລິສັດຈຶ່ງສູນເສຍຄວາມສາມາດໃນການກຳນົດເນື້ອຫາ ໃນຂະນະທີ່ສື່ສັງຄົມອອນລາຍເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນການແບ່ງປັນ ແລະ ເຂົ້າເຖິງຂ່າວທີ່ບໍ່ໄດ້ຜ່ານການ censorship. ເຊັ່ນດຽວກັນ, USDT ກຳລັງກະຈາຍອຳນາດທາງການເງິນ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍທີ່ໃຫ້ສຽງແກ່ປະຊາຊົນນອກເໜືອຈາກສື່ກະແສຫຼັກ, USDT ກຳລັງໃຫ້ຄວາມເປັນອິດສະຫຼະທາງການເງິນແກ່ບຸກຄົນທີ່ເກີນກວ່າຂອບເຂດຂອງທະນາຄານກາງ. ແນວໂນ້ມນີ້ຊັດເຈນ: ສະຖາບັນທີ່ລວມສູນຈະສູນເສຍການຄວບຄຸມເມື່ອບຸກຄົນໄດ້ຮັບການເຂົ້າເຖິງໂດຍກົງຕໍ່ທາງເລືອກອື່ນ.
Trump ສະໜັບສະໜູນ Stable Coin
ປະທານາທິບໍດີສະຫະລັດ Donald Trump ໄດ້ສະແດງການສະໜັບສະໜູນຕໍ່ stable coin ແລະ ອຸດສາຫະກຳ cryptocurrency ເມື່ອບໍ່ດົນມານີ້. ຈຸດຢືນຂອງລາວເປັນສັນຍານເຖິງການປ່ຽນແປງທີ່ເປັນໄປໄດ້ໃນນະໂຍບາຍຂອງສະຫະລັດທີ່ອາດຈະສ້າງຄວາມຊອບທຳໃຫ້ແກ່ສະເຕເບິນຄອຍ ແລະ ຂັບເຄື່ອນການນຳໃຊ້ທົ່ວໂລກ. ຖ້າລັດຖະບານສະຫະລັດຮັບຮອງສະເຕເບິນຄອຍເຊັ່ນ USDT, ມັນອາດຈະເລັ່ງການນຳໃຊ້ພວກມັນເປັນທາງເລືອກແທນລະບົບທະນາຄານແບບດັ້ງເດີມ, ສ້າງແຮງກົດດັນເພີ່ມເຕີມຕໍ່ທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ນີ້ອາດຈະສົ່ງເສີມໃຫ້ມີການມີສ່ວນຮ່ວມຂອງສະຖາບັນຫຼາຍຂຶ້ນ, ເຮັດໃຫ້ມັນຍາກຂຶ້ນສຳລັບລັດຖະບານທ້ອງຖິ່ນໃນການປາບປາມການນຳໃຊ້ USDT.
ຊ່ອງຫວ່າງຂອງການຮັບຮູ້: ຫຼາຍຄົນຍັງບໍ່ຮູ້ເຖິງໄພຂົ່ມຂູ່
ເຖິງແມ່ນວ່າ USDT ຈະເຕີບໂຕຢ່າງໄວວາ, ປະຊາຊົນຫຼາຍຄົນໃນປະເທດກຳລັງພັດທະນາຍັງບໍ່ຮັບຮູ້ເຖິງຜົນກະທົບຂອງມັນ. ໃນຂະນະທີ່ຜູ້ໃຊ້ເລີ່ມຕົ້ນຈະເປັນ ບຸກຄົນທີ່ຮູ້ເທັກໂນໂລຊີ, ນັກລົງທຶນ ແລະ ເຈົ້າຂອງທຸລະກິດ, ປະຊາກອນສ່ວນໃຫຍ່ຍັງອີງໃສ່ການທະນາຄານແບບດັ້ງເດີມ ແລະ ສະກຸນເງິນຕາມກົດໝາຍໂດຍບໍ່ຮູ້ເຖິງຄວາມສ່ຽງຂອງການເສື່ອມຄ່າ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ. ເຖິງຢ່າງໃດກໍຕາມ, ບຸກຄົນຕ້ອງມີຄວາມຄິດລິເລີ່ມໃນການສຶກສາຕົນເອງກ່ຽວກັບເຄື່ອງມືທາງການເງິນທາງເລືອກເຊັ່ນ USDT ແລະ Bitcoin ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງ ແລະ ຄວາມເປັນອິດສະຫຼະທາງການເງິນຂອງພວກເຂົາ.
ບົດສະຫຼຸບ: ການປະຕິວັດທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
USDT ແລະ Bitcoin ແມ່ນການປະຕິວັດທາງການເງິນທີ່ເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນປະເທດກຳລັງພັດທະນາທີ່ຈະຫຼຸດພົ້ນຈາກນະໂຍບາຍການເງິນທີ່ລົ້ມເຫຼວ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍໄດ້ປະຕິວັດພູມທັດຂອງສື່ໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມຂໍ້ມູນຂ່າວສານ, USDT ກຳລັງປະຕິວັດການເງິນໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມເງິນຂອງພວກເຂົາ. ສຳລັບທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ, ການປ່ຽນແປງນີ້ສ້າງສະພາວະຫຍຸ້ງຍາກທີ່ຮ້າຍແຮງ: ປັບຕົວ ຫຼື ສູນເສຍອິດທິພົນ. ລັດຖະບານອາດຈະພະຍາຍາມຄວບຄຸມກົດລະບຽບ ຫຼື ຫ້າມສະເຕເບິນຄອຍ, ແຕ່ຕາມທີ່ປະຫວັດສາດໄດ້ສະແດງໃຫ້ເຫັນກັບສື່ສັງຄົມອອນລາຍ.
-
 @ 98028d3f:24448238
2025-03-25 01:57:54
@ 98028d3f:24448238
2025-03-25 01:57:54我写这个例子主要看如何更新修改的1。
-
 @ fd06f542:8d6d54cd
2025-03-25 01:40:53
@ fd06f542:8d6d54cd
2025-03-25 01:40:5330023的 文章 可发以被 删除 1 吗?
-
 @ da0b9bc3:4e30a4a9
2025-03-24 22:50:57
@ da0b9bc3:4e30a4a9
2025-03-24 22:50:57Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
This month is March and we're doing March Madness. So give me those Wacky and Weird crazy artists and songs. The weirder the better!
Let's have fun.
Can't have March Madness without Madness!
https://youtu.be/SOJSM46nWwo?si=gtghOZte3rh41tXg
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/924076
-
 @ 6e0ea5d6:0327f353
2025-03-24 22:42:59
@ 6e0ea5d6:0327f353
2025-03-24 22:42:59🎣
The support I never had could have saved me time, and I would certainly be farther along at this moment. However, that absence taught me to value having, and if I pass this lesson on to you earlier, it is so you have more time to learn what I could not see.
I like what my father once paraphrased: "If I have seen further, it is by standing on the shoulders of giants." And right now, I think of all that the little one who descends from you will one day behold. The heaviest burdens I pushed were so that you could soar, and if I have dedicated my existence to you, it is so that from my ashes, you may always rise again.
Out of love, I will try not to spoil you with excessive gifts, but instead, without being absent, I hope to build you up. With this line and these strands, I wish to teach you to catch your own fish. Live by what I have taught you and seek to understand what I could not. Honor who I was for you by becoming the best you can be.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 21e127ec:b43a5414
2025-03-24 22:30:47
@ 21e127ec:b43a5414
2025-03-24 22:30:47**
Respondiendo a Joel Serrano
nostr:npub1sg0j78carjndmg7qjfstk2y0e23r5cvxwn3u9z5cgnk5jnh4vxqs355u3l
respecto a hilo de Twitter sobre la adopción de Bitcoin como Medio de Intercambio con Unidad de Cuenta Delegada.
Primero, quiero compartir un artículo de Fernando Nieto que aborda la volatilidad inherente de Bitcoin:
https://x.com/fnietom/status/1454114755807961094
Este artículo de Nieto me ha llevado a cuestionarme si, en un escenario de adopción masiva, Bitcoin podría alcanzar realmente una estabilidad relativa suficiente para facilitar la coordinación de precios y el cálculo económico. De ahí surge la idea de que Bitcoin podría necesitar otros instrumentos que perfeccionen su función como unidad de cuenta.
Un ejemplo claro es lo que ocurrió en Venezuela con la dolarización de facto (al margen del Estado). En sus inicios (y aún hoy en gran medida), solo un pequeño porcentaje de la población tenía acceso a dólares a través la banca internacional, lo que les permitía realizar transacciones financieras fuera del sistema estatal. Estas operaciones se llevaban a cabo en el circuito financiero internacional, aunque las relaciones comerciales reales ocurrían dentro de Venezuela. Otro pequeño grupo tenía acceso a dólares en efectivo para sus transacciones económicas, pero la gran mayoría de la población solo disponía del bolívar venezolano como medio de intercambio en una economía dolarizada. En este contexto, muchos usaban el dólar para calcular los precios de bienes y servicios, mientras que el bolívar seguía siendo el medio de intercambio principal.
La diferencia notable con Bitcoin radica en las causas. En Venezuela, este fenómeno de medio de intercambio con unidad de cuenta delegada (Dolar - Bolivar) se debía a las restricciones monetarias impuestas por el gobierno respecto al dólar, la falta de servicios financieros en esa moneda y la escasa liquidez de dólares físicos. En el caso de Bitcoin, seria debido a su volatilidad inherente producto de su oferta inelástica (Bitcoin como medio de intercambio generalmente aceptado con unidad de cuenta delegada en Fiat publico ó privado - stablecoin).
Sin embargo, esto no implica que la unidad de cuenta que complemente a Bitcoin deba ser necesariamente emitida por un Estado. Creo que la verdadera innovación de Bitcoin radica en su potencial para actuar como un patrón monetario que descentralice la emisión monetaria de los estados gracias al monopolio de la violencia, algo que sí podían ejercer con el oro. Con Bitcoin, el Estado pierde el control, permitiendo que la banca libre emita monedas estables respaldadas en un patrón Bitcoin. El escenario sería una competencia entre monedas estables adoptadas en un segundo plano para facilitar el cálculo económico necesario para coordinar precios, préstamos, servicios financieros y la institución del crédito. Y Bitcoin podría funcionar en primer plano principalmente como medio de intercambio.
No pienso que Bitcoin vaya a eliminar las monedas fiat o estables, ya sean públicas o privadas. Más bien, lo veo como un mecanismo disciplinador que podría prevenir los malos comportamientos monetarios.
Gracias por tu tiempo agradecido y atento a tu posible respuesta.
-
 @ 6e0ea5d6:0327f353
2025-03-24 22:11:58
@ 6e0ea5d6:0327f353
2025-03-24 22:11:58People, mio caro, mistake silence for weakness just as they mistake the shine of silver for the value of gold. Because the modern world—hysterical and theatrical—has learned to respect noise, shouting, emotional outbursts, and the endless chatter of failures who demand respect without ever having earned it. But we, who have emerged from the forge of omertà, know that the one who reacts immediately is merely begging for relevance.
A real man—and I do not refer to those who simply wear trousers, but to those who carry their name and reputation upon their shoulders—knows that humiliation is not avenged with words of promise, but with a sentence of action. And sentences, amico mio, are not uttered in impulse. They are written in silence, with permanent ink on the paper of memory.
The one who strikes back in the moment of offense reveals that he is still under the dominion of emotion. But the one who remains silent, who stands still, who looks his aggressor in the eye and does not utter a single word—he has already begun to dig, with his own hands, the symbolic grave of the one who offended him. His coldness is not the absence of pain, but the absolute mastery of it. And that is precisely why he is feared. Not because he screams, but because he thinks. Because he smiles while thinking. Because he watches while you believe he has forgotten.
In Sicily, we say that the wolf does not howl when preparing to strike—it merely crouches. The fool believes that silence is cowardice. The wise man knows it is calculation. While the world carries on with its pathetic routines and social theater, the humiliated man prepares the final stage. And on this stage, there will be no audience, no applause. Only the dry sound of justice being served. Without mercy. Without apologies. Without a second chance.
Vengeance is not an emotion. It is an art. And the first stroke in the masterpiece is control.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 7d33ba57:1b82db35
2025-03-24 21:47:31
@ 7d33ba57:1b82db35
2025-03-24 21:47:31Located on the southeastern coast of Spain, Cartagena is a city rich in history, maritime heritage, and stunning Mediterranean views. With over 3,000 years of history, it boasts Roman ruins, modernist architecture, and a vibrant port, making it one of Spain’s most underrated travel destinations.
🏛️ Top Things to See & Do in Cartagena
1️⃣ Roman Theatre of Cartagena 🎭
- The star attraction, dating back to the 1st century BC.
- One of Spain’s best-preserved Roman theatres, discovered in 1988 beneath the city.
- Visit the museum to learn about its history before exploring the impressive ruins.
2️⃣ Concepción Castle & Panoramic Lift 🏰
- A 14th-century fortress on a hill offering spectacular views of the city and harbor.
- Take the glass elevator for a scenic ride to the top.
- The museum inside explains Cartagena’s rich military and naval history.
3️⃣ Calle Mayor & Modernist Architecture 🏛️
- The city’s main pedestrian street, lined with elegant buildings, shops, and cafés.
- Admire Casa Cervantes, Gran Hotel, and the Casino, examples of Cartagena’s modernist style.
4️⃣ National Museum of Underwater Archaeology (ARQVA) ⚓
- Learn about sunken treasures, ancient shipwrecks, and underwater archaeology.
- Features artifacts from Phoenician, Roman, and medieval maritime history.
5️⃣ Naval Museum & the Peral Submarine 🚢
- Discover Cartagena’s naval history, including models of warships and maritime artifacts.
- See the Peral Submarine, the first-ever electric-powered submarine, invented in 1888.
6️⃣ Playa de Cala Cortina 🏖️
- A beautiful urban beach, just a few minutes from the city center.
- Great for swimming, snorkeling, and relaxing with clear Mediterranean waters.
7️⃣ Batería de Castillitos 🏰
- A dramatic cliffside fortress with fairy-tale turrets and massive coastal cannons.
- Located 30 minutes from Cartagena, offering panoramic sea views.
🍽️ What to Eat in Cartagena
- Caldero del Mar Menor – A local seafood rice dish, similar to paella 🍚🐟
- Michirones – A hearty bean stew with chorizo and ham 🥘
- Marineras – A Russian salad tapa served on a breadstick with an anchovy 🥖🐟
- Tarta de la abuela – A delicious layered biscuit and chocolate cake 🍰
- Asiático Coffee – A signature Cartagena coffee with condensed milk, brandy, and cinnamon ☕🍸
🚗 How to Get to Cartagena
🚆 By Train: Direct trains from Madrid (4 hrs), Murcia (45 min), and Alicante (1.5 hrs)
🚘 By Car: ~30 min from Murcia, 1.5 hrs from Alicante, 3.5 hrs from Madrid
✈️ By Air: Nearest airport is Murcia-Corvera Airport (RMU) (~30 min away)
🚢 By Cruise Ship: Cartagena is a popular Mediterranean cruise stop💡 Tips for Visiting Cartagena
✅ Best time to visit? Spring & Autumn – warm but not too hot 🌞
✅ Wear comfortable shoes – Many streets and attractions involve walking on cobblestones 👟
✅ Visit during the Roman Festival (Carthaginians & Romans, September) for a unique cultural experience 🎭🏛️
✅ Try a sunset drink at a rooftop bar near the port for incredible views 🍹🌅 -
 @ 878dff7c:037d18bc
2025-03-24 21:43:00
@ 878dff7c:037d18bc
2025-03-24 21:43:00China Denies Plans to Send Peacekeeping Troops to Ukraine
Summary:
Recent reports suggested that China was considering participating in a European-led peacekeeping mission in Ukraine. However, the Chinese Foreign Ministry has firmly denied these claims, stating that such reports are "completely untrue" and reaffirming China's consistent and clear position on the Ukraine crisis. This development highlights the complexities in international efforts to address the ongoing conflict in Ukraine.
Sources: Politico - March 25, 2025, Global Times - March 25, 2025, Newsweek - March 25, 2025
Internal Environmental Regulations Pose Greater Threat to Australian Trade Than Foreign Tariffs
Summary:
Australia's stringent environmental regulations, referred to as "green tape," are posing significant risks to its export industries, including LNG, coal, and iron ore. These regulations have drawn criticism from key trading partners like Japan. The Albanese government's commitments under international climate agreements have intensified these regulations, potentially undermining economic stability more than foreign tariffs.
Sources: The Daily Telegraph - March 25, 2025
Government Announces 'Buy Australian' Initiative to Support Local Industries
Summary:
In response to global trade uncertainties, the Albanese government has introduced a 'Buy Australian' policy aimed at bolstering domestic industries and reducing reliance on international markets. The initiative seeks to mitigate the impact of foreign tariffs and promote local manufacturing, aligning with efforts to 'Trump-proof' the Australian economy against external economic policies.
Source: News.com.au - March 25, 2025
Interest Rates Expected to Remain Elevated Amid Global Trade Tensions
Summary:
Economic analysts predict that the Reserve Bank of Australia may maintain higher interest rates for an extended period due to anticipated inflationary pressures stemming from global trade tensions. Policies, such as tariffs imposed by the U.S., are contributing to economic uncertainty, potentially impacting Australia's economic stability and influencing monetary policy decisions.
Source: News.com.au - March 25, 2025
Severe Flooding Threatens Queensland Amid Heavy Rainfall
Summary:
Queensland is experiencing severe weather conditions, with heavy rainfall leading to significant flooding risks. The Bureau of Meteorology has issued warnings for severe thunderstorms and flooding, particularly between Innisfail and Townsville. In the past 24 hours, rainfall totals have ranged from 50 to 150mm, with expectations of up to 200mm in isolated areas. Major flood warnings are in effect for the Bulloo River, with moderate warnings for several others. Inland regions could see up to 400mm, equating to nearly a year's worth of rain. Residents are advised to stay updated and prepare for potential emergencies.
Sources: News.com.au - 25 March 2025, The Guardian - 25 March 2025
Peter Dutton's 'Me Too' Politics Strategy Criticized Within Liberal Party
Summary:
Peter Dutton's approach of rapidly matching Labor's spending pledges, such as the $8.5 billion Medicare boost and a $150 power bill rebate, has drawn criticism within the Liberal Party. This "Me Too" strategy aims to appear equally voter-friendly but is argued to undermine the Coalition's credibility as better economic managers amid a cost-of-living crisis. Critics suggest that by mirroring Labor's spending, the Coalition loses the ability to effectively critique Labor's fiscal policies without appearing hypocritical, potentially benefiting Labor as their spending gains voter favor.
Sources: The Daily Telegraph - March 24, 2025
Community Organizations Oppose Proposed Public Housing Reforms in Northern Territory
Summary:
Community organizations are criticizing the Country Liberal Party's proposed public housing reforms, which aim to address anti-social behavior, evictions, and debt. Critics argue these reforms could negatively impact disadvantaged groups, particularly Aboriginal Territorians, by shifting the perception of housing from a human right to a conditional privilege. The Central Land Council warns of potential increases in homelessness and incarceration rates among Aboriginal people.
Sources: The Courier-Mail - 25 March 2025
Coalition Proposes Changes to Vehicle Emissions Standards and Hybrid Tax Incentives
Summary:
The Coalition plans to modify Labor’s vehicle emissions standards and reinstate tax incentives for plug-in hybrids. They argue that removing these incentives could hinder efforts to reduce emissions and negatively impact Australian families during the current cost-of-living crisis. The car industry also expresses concerns about stringent carbon footprint targets and the financial burden of meeting emission requirements.
Sources: The Australian - 25 March 2025
Call for Development of Sovereign Supply Chains in Australia
Summary:
A recent survey revealed that 63% of company leaders view geopolitical instability as the primary risk to their organizations. The pandemic exposed vulnerabilities in global and domestic supply chains, particularly in Australia's production of essential goods. To address this, there is a call for developing resilient sovereign supply chains, balancing reshoring critical manufacturing with strategic partnerships. Collaborative efforts across government, business, and educational institutions are deemed necessary to build robust supply chains.
Sources: The Australian - 25 March 2025
Interest Rates in Australia May Stay High Amid Global Economic Uncertainty
Summary:
Interest rates in Australia may remain elevated due to expected increases in inflation, driven by U.S. tariff policies causing global economic uncertainty. These tariffs are likely to raise prices and contribute to inflationary pressures. The Reserve Bank of Australia faces a dilemma, balancing the need to address declining employment data with the potential for rate cuts to stimulate the economy. Economists suggest maintaining current interest rates to observe further economic developments.
Sources: News.com.au - 25 March 2025
NSW Government to Remove Shark Nets from Sydney Beaches
Summary:
The NSW government will remove shark nets from 51 Sydney beaches on March 31, ahead of their usual end-of-April schedule, to reduce the bycatch of sea turtles migrating throughout April. This decision follows feedback from coastal councils, six of which have voted for the permanent removal of the nets due to concerns over marine bycatch. However, there are concerns that alternative shark mitigation technologies, such as drones and SMART drumlines, may not be as effective in protecting swimmers. The final decision on the future of the shark nets will be made by the NSW government, based on a report compiled from the feedback of 25 councils.
Sources: The Daily Telegraph - March 24, 2025
Victoria Achieves World-Leading Cardiac Arrest Survival Rates
Summary:
Victoria has quietly become a global leader in cardiac arrest survival, thanks to a combination of fast emergency responses, community training, and public health infrastructure. New data released today shows that 41% of people who suffered a cardiac arrest in public and received immediate CPR and defibrillation survived — putting Victoria among the top three regions globally, just behind King County in the U.S. and Denmark.
Much of the credit goes to everyday citizens. Nearly 80% of cardiac arrests witnessed by bystanders were met with immediate CPR, a rate far above the national average. The widespread rollout of over 7,500 publicly accessible defibrillators and the GoodSAM mobile app — which alerts nearby trained responders in real-time — has also played a key role in improving outcomes.
Health officials say the results are proof that early intervention saves lives, and the state's model could serve as a blueprint for others. Survivors and their families have expressed overwhelming gratitude for both the emergency responders and ordinary citizens whose quick thinking made the difference.
Sources: The Guardian - March 24, 2025, ABC News - March 25, 2025
Wind Drought Challenges Australia's Renewable Energy Sector
Summary:
Zen Energy, co-developed by economist Ross Garnaut, is facing financial difficulties due to a "wind drought" affecting its wind generation capacity. The company had to purchase expensive spot market capacity to meet obligations, leading to the sale of a near 10% stake for $43 million to fund large-scale battery development. This situation highlights the challenges in Australia's transition to renewable energy, especially with fluctuating wholesale electricity prices and long-term contracts.
Sources: The Australian - March 24, 2025
Istanbul Mayor's Arrest Signals Turkey's Authoritarian Shift
Summary:
Ekrem Imamoglu, the mayor of Istanbul and a prominent opposition figure, has been detained and jailed on charges of graft and terrorism. Analysts suggest that President Recep Tayyip Erdogan's move was facilitated by global geopolitical instability, reducing the likelihood of international condemnation. This arrest is viewed as a significant blow to Turkish opposition and indicative of a move towards increased authoritarianism.
Sources: Associated Press - March 25, 2025
Iranian Generals Direct Houthi Attacks in Red Sea
Summary:
Key Iranian figures behind Houthi rebel operations in Yemen have been identified. The Houthis, supported by Iran's IRGC, have launched attacks on merchant vessels and warships in the Red Sea, disrupting global trade. These operations are reportedly commanded by senior Iranian officials and approved by Supreme Leader Ali Khamenei, highlighting Iran's strategic involvement in regional conflicts.
Sources: The Sun - March 22, 2025
Exploring Programming, AI, and Personal Journeys with ThePrimeagen on the Lex Fridman Podcast
Summary:
In episode #461 of the Lex Fridman Podcast, Lex has an in-depth conversation with ThePrimeagen, a well-known software developer and content creator. The episode covers a range of topics including:
- Programming and Development: ThePrimeagen shares insights into modern coding practices, the evolution of software engineering, and his passion for low-level programming.
- Artificial Intelligence: The two discuss AI's impact on society, the future of intelligent systems, and philosophical implications.
- Life with ADHD: ThePrimeagen opens up about living with ADHD, discussing the challenges it brings and how he channels it into productivity.
- Addiction and Recovery: A personal and vulnerable look at his journey through addiction and the steps he took toward recovery.
- Philosophy and Faith: The episode also touches on topics like belief in God, human purpose, and finding meaning through both faith and technology.
Importance:
This episode stands out for its honest blend of technical depth and emotional vulnerability. It offers listeners a rare look at how a high-performing developer balances the pressures of tech life with personal challenges. The philosophical undertones add a reflective layer, making it not just informative but also deeply human.
Sources: Lex Fridman Podcast - March 25, 2025
-
 @ 4520e45a:aa52208a
2025-03-24 21:42:12
@ 4520e45a:aa52208a
2025-03-24 21:42:12Hashrate\ Die Hashrate wird vom Pool basierend auf den übermittelten Shares innerhalb eines Zeitraums berechnet und zeigt, wie viele Hashes pro Sekunde dein Worker generiert.\ Die Statistik zeigt die durschschnittliche Hashrate für:\ 1 Minute (1m), 5 Minuten (5m), 1 Stunde (1hr), 1 Tag (1d), 7 Tage (7d)
1M = 1 MH/s = 1'000'000 H/S\ 1G = 1 GH/s = 1'000'000'000 H/S\ 1T = 1 TH/s = 1'000'000'000'000 H/S\ 1P = 1 PH/s = 1'000'000'000'000'000 H/S
Lastshare\ Angabe in Unix Zeit, wann der letzte Share von deinem Worker bei ckpool abgeliefert wurde.\ 🔗 unix timestamp converter
Worker\ Anzahl Worker. Wenn mehrere Miner identischen Namen haben, werden sie zu einem Worker zusammengefasst. Wenn du für jeden Miner separate Statistiken willst, muss sich deren Worker-Name hinter der Bitcoin-Adresse unterscheiden:\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe1\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe2\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe3
Shares\ Anzahl akzeptierter Shares, die seit Beginn von deinem Worker bei ckpool abgeliefert wurden. Wenn ein Hash alle notwendigen Kriterien und die vom Pool geforderte Schwierigkeit erfüllt, wird er als Share an ckpool übermittelt.
Bestshare\ Der beste/höchste Share der seit dem letzten gefundenen Block abgeliefert wurde.\ Wenn du oder ckpool einen Block gefunden hat, wird dieser Wert zurück auf Null gesetzt.
Bestever\ Der jemals beste/höchste gefundene Share. Im AxeOS als Best Difficulty bezeichnet.\ Wenn du oder ckpool einen Block gefunden hat, wird dieser Wert nicht zurück auf Null gesetzt.
Ein Block wird gefunden, wenn die Schwierigkeit (=Difficulty) eines Shares höher ist als die aktuelle Netzwerk-Schwierigkeit.
Zum Zeitpunkt des Schreibens des Reads — Blockzeit 889277 — liegt die Netzwerk-Schwierigkeit bei: 113'757'508'810'854 = 113T
Authorised\ Angabe in Unix Zeit, wann du dich zum ersten Mal mit ckpool verbunden hast (wurde erst mit v0.9.7 am 30.05.2023 eingeführt).\ 🔗 unix timestamp converter
-
 @ ed5774ac:45611c5c
2025-03-24 21:33:47
@ ed5774ac:45611c5c
2025-03-24 21:33:47Erdogan’s Turkey: The Rise, Reign, and Decline of a Political Strongman
As Turkey’s political crisis intensifies with Erdogan’s imprisonment of Imamoglu—a leading opposition figure and likely frontrunner in the 2028 presidential elections—it is crucial to analyze the historical events and geopolitical factors that enabled Erdogan’s rise, secured the consolidation of his rule, and allowed him to maintain his grip on power for decades. To understand the foundations of Erdogan’s enduring political legacy, we must examine the historical events that shaped his ideology and the global power struggles of the time. Equally important are the international actors who facilitated his rise and prolonged his rule. Key factors include the link between Erdogan’s rise and the Iraq War, the interplay between Turkey’s military coups and the Ukraine crisis, the events that led to the erosion of Western support for Erdogan, the role of the U.S. and NATO in the 2016 coup attempt against his rule, and the shifting geopolitical landscape that continues to define Turkey’s political future.
The Roots of Islamism: The CIA, the 1980 Coup, and the Suppression of Turkish Liberalism
Erdogan’s rise is deeply intertwined with the growth of Turkey’s Islamic movement, which gained traction in the 1970s amid Cold War geopolitics. During this period, the U.S., under the guidance of Zbigniew Brzezinski, National Security Advisor to President Jimmy Carter, devised the “Green Belt” strategy. This plan aimed to cultivate a radicalized Islamic generation across the Muslim world to counter the spread of communist ideology. The U.S. intervention in Afghanistan, which radicalized certain factions and triggered the Soviet invasion, was a critical component of this strategy. Brzezinski himself proudly acknowledged this in various interviews. Turkey, a NATO ally bordering the Soviet Union, became a key theater for implementing this policy.
The military coup of September 12, 1980, marked a pivotal moment in Turkish history. Led by General Kenan Evren, the Turkish armed forces seized power under the pretext of restoring order amid escalating violence between leftist and rightist factions that had claimed thousands of lives. However, the junta’s crackdown disproportionately targeted the Turkish left—a movement distinct from Soviet-style communism, composed of liberal, educated intellectuals such as writers, artists, journalists, and thinkers. These individuals, who championed Turkish sovereignty, intellectual freedom, and democratic ideals, were perceived as a direct threat to the military’s Islamization agenda, backed by the CIA. Tens of thousands were imprisoned, tortured, or executed, while left-wing organizations were banned outright.
At the same time, the junta actively fostered Islamist groups, establishing religious schools known as Imam Hatip institutions under the guise of combating Marxism and communism. In reality, their true objective was to eliminate anyone who sought Turkish sovereignty, embraced patriotism, or valued critical thinking. Writers, artists, journalists, and intellectuals—those who dared to think independently and question authority—were viewed as existential threats to the Islamization model the military and its CIA allies sought to impose. By silencing these voices, the junta aimed to eradicate opposition to their vision of a Turkey subservient to religious dogma and foreign interests, ensuring a populace stripped of sovereign thought and resistant to enlightenment.
This paradox—a secular military suppressing liberal intellectuals while nurturing Islamist groups—laid the foundation for Erdogan’s rise and the eventual Islamization of Turkish society.
The Chaos of the 1990s: Economic Crisis and the Rise of Erdogan
The 1990s were a chaotic decade for Turkey, marked by economic instability, a Kurdish insurgency, and a revolving door of coalition governments. The 1994 financial crisis saw inflation soar, while terrorist attacks by the Kurdistan Workers’ Party (PKK) and political assassinations fueled national disarray. Successive governments, often beholden to globalist agendas dictated by the International Monetary Fund and World Bank, failed to deliver stability. This period mirrored today’s European political crises, where ideological convergence has left voters disillusioned.
Into this void stepped Erdogan, a charismatic former soccer player turned politician from Istanbul’s working-class Kasimpasa district, whose blend of populist appeal and religious rhetoric resonated with a disillusioned populace. His rise was no accident. In 1994, he won the mayoralty of Istanbul as a member of the Islamist Welfare Party (Refah Partisi), showcasing a blend of populist charisma and religious appeal. However, his early political career faced a setback in 1997 when the military, acting as guardians of Turkey’s secular Kemalist legacy, forced the resignation of Welfare Party Prime Minister Necmettin Erbakan in what was dubbed a “postmodern coup.” Erdogan’s imprisonment in 1998 for reciting a divisive poem only solidified his image as a martyr among his devout supporters.
The 2001 Crisis: Neocons, Economic Sabotage, and Erdogan’s Ascendancy
Erdogan’s true ascent began amid Turkey’s devastating 2001 financial crisis, which saw the economy contract by 5.7%, unemployment spike, and the Turkish lira collapse. The crisis, worsened by IMF-mandated austerity measures, discredited the ruling coalition under Prime Minister Bulent Ecevit. A staunch nationalist, Ecevit had spearheaded Turkey’s 1974 intervention in Cyprus and forced Syria to expel PKK leader Abdullah Ocalan in 1999. His refusal to align Turkey with the impending U.S.-led Iraq War in 2003 made him a liability for U.S. neoconservatives, who were already preparing for the conflict.
Far from a mere economic downturn, the 2001 crisis was a deliberate strategy orchestrated by the global Western financial cartel to destabilize Ecevit’s nationalist government. This administration, fiercely protective of Turkish sovereignty, had unequivocally opposed Turkey’s involvement in the Iraq War. To eliminate this obstacle, the financial cartel—comprising international financial institutions and Western-backed actors—engineered the crisis by exploiting Turkey’s reliance on hot money and Western financial support. The resulting economic collapse eroded public trust in the government and existing political parties, creating a power vacuum that paved the way for Erdogan. Handpicked by the globalist cabal as their new proxy, Erdogan was positioned to advance their political agenda in Turkey. The neocons viewed him as a pliable ally: a moderate Islamist who could pacify Turkey’s religious conservatives while advancing Western interests. Despite resistance within his own party, Erdogan advocated for Turkish involvement in the Iraq War, though the Turkish Parliament, with the help of dissidents in his party, ultimately rejected U.S. troop deployments in 2003. Nevertheless, Erdogan remained loyal to his neocon backers and globalist patrons, privatizing state assets at rock-bottom prices—akin to Yeltsin’s controversial reforms in 1990s Russia—and deepening Turkey’s economic dependence on the EU and the U.S.
In addition to tying Turkey’s economy to Western interests, Erdogan targeted the Turkish military in 2007 through the Ergenekon and Sledgehammer trials. Widely criticized as show trials orchestrated with the help of the Gulen movement—a shadowy Islamic network led by Fethullah Gulen—these cases imprisoned or sidelined hundreds of officers, including navy admirals opposed to NATO’s Black Sea ambitions. These officers had long argued that NATO’s mission ended with the fall of the Soviet Union and advocated for closer ties with Russia and China. They also opposed plans to integrate Georgia and Ukraine into NATO, fearing it would destabilize the region and turn the Black Sea into a battleground between the West and Russia. By weakening the navy and sidelining its dissenting admirals, Erdogan brought Turkey back in line with NATO’s strategic objectives, enabling the neocons to advance their plans for NATO expansion into the Black Sea region—a move that set the stage for the 2008 Russo-Georgian War and the 2014 Ukrainian crisis.. Without this internal coup against the Turkish military, these events might have unfolded differently—or not at all.
For his services to the globalist agenda, Erdogan was portrayed in Western media as a democratizing hero, and Turkey’s economy was praised for its growth and strength. However, the reality was starkly different. To understand the globalist propaganda surrounding Erdogan, consider Barack Obama’s first foreign visit as U.S. president: a trip to Turkey in 2009. In a speech to the Turkish Parliament, Obama praised Erdogan’s “democratic reforms” and the strength of Turkey’s economy—which was growing steadily only due to cheap credit provided by international financial institutions serving the same globalist interests Erdogan represented. Meanwhile, journalists and dissidents filled Turkish prisons.
The 2016 Coup Attempt: Erdogan’s Break with the West
Erdogan’s honeymoon with the West soured in the 2010s. His support for Egypt’s Muslim Brotherhood and his interventionist stance in Syria clashed with U.S. priorities, especially after the Arab Spring upended regional alliances. Sensing Erdogan’s growing autonomy, the neocons turned to Fethullah Gulen, a cleric living in Pennsylvania since 1999 with close ties to the CIA and the Clinton Foundation. Gulen’s Hizmet movement, once an ally in Erdogan’s rise, had infiltrated Turkey’s police, judiciary, and military, creating a “parallel state.”
The July 15, 2016, coup attempt—marked by rogue military units bombing parliament and nearly capturing Erdogan—was orchestrated by factions of the Gulen movement within the army, with the involvement of the CIA and NATO, using Incirlik Air Base as one of the primary command centers to coordinate the operation (one of NATO’s largest military bases in the region). The timing suggests that the neocons, anticipating Hillary Clinton’s presidency, planned to install Gulen as their new puppet in Turkey. As a radical Sunni leader hostile to Iran, Gulen could have aligned Turkey with a broader anti-Iranian axis, potentially dragging the country into a regional war against Iran—much like Saddam Hussein did three decades earlier.
The coup’s failure, quashed by loyalists and public resistance, marked a turning point, leading Erdogan to purge over 100,000 civil servants and consolidate his power through a 2017 referendum and pivoting toward Russia and China—not out of conviction, but as leverage against Western abandonment.
Turkey’s Geopolitical Balancing Act: Ukraine, NATO, and the Black Sea
Erdogan’s post-2016 flirtations with Moscow—evidenced by the purchase of Russian S-400 systems and energy deals—reflect more than a pragmatic balancing act. They reflect a desperate attempt to regain Western attention, akin to dating someone new to make an ex jealous, aimed at convincing the West not to write him off.
The Ukrainian crisis, escalating with Russia’s 2022 invasion, has pushed Turkey into a delicate role. As a NATO member controlling the Bosphorus, Erdogan has mediated grain deals and prisoner swaps, leveraging Turkey’s strategic position. Yet his reluctance to fully back NATO’s hardline stance has further alienated him from the West, making him a target for a potential regime change operation as the West has grown desperate to win its proxy war against Russia. As a result, international media and globalist factions have intensified efforts to undermine his regime, seeking to remove him from power.
Turkey at a Crossroads: Imamoglu, Erdogan’s Decline, and the Future
Erdogan has fulfilled his mission: he has made Turkey’s economy dependent on the West, eliminated patriotic voices in the military, dismantled the parliamentary system, wrecked the education system, and buried the secular Turkish republic. His legacy is a deeply polarized Turkey: economically dependent on the West, militarily weakened, and institutionally hollowed out.
Corruption scandals, a collapsing lira, and authoritarian excesses have fueled widespread public discontent. Yet, rather than addressing the root causes of this anger—economic hardship, growing authoritarianism, and systemic corruption—Erdogan has grown increasingly paranoid, attributing every challenge to Western conspiracies and interventions. This refusal to confront reality has only deepened the divide between him and the Turkish people, fueling widespread disillusionment and anger.
Imamoglu’s rise—winning Istanbul in 2019 and 2023 despite blatant election irregularities, systematic government interference, censorship, and the full force of Erdogan’s authoritarian machinery—stands as a testament to his resilience and the enduring hope of Turkey’s opposition. Facing a system rigged to ensure his defeat, Imamoglu triumphed against overwhelming odds. Erdogan’s regime spared no effort, leveraging state media, the judiciary, and security forces to manipulate the results, yet it could not prevent Imamoglu’s victories in Istanbul, which shattered the illusion of invincibility surrounding Erdogan’s rule. His recent imprisonment on fabricated charges ahead of the 2028 elections underscores Erdogan’s desperation to suppress this threat, further alienating a populace yearning for change.
Turkey now stands at a crossroads. The powers that once propelled Erdogan to prominence—U.S. neoconservatives and the Islamist legacy of the 1980 coup—have lost control of their creation. His fall from Western favor, tied to the 2016 coup attempt and his regional overreach, has left him isolated, oscillating between East and West while clinging to power as domestic anger reaches a boiling point. Whether Imamoglu or another leader emerges, Turkey’s post-Erdogan era will face the monumental task of rebuilding its secular republic and defining its role in an increasingly complex global landscape.
Turkey’s struggle is not just its own—it is an example of the suffering endured for decades under Western colonialism and a parasitic financial order. This system, designed to enrich a handful of elites in the West, thrives by exploiting the Global South, perpetuating poverty, and engineering chaos to maintain control. Turkey’s fight for self-determination stands as a beacon for all nations seeking to break free from the chains of neocolonialism and reclaim their rightful place in a just and equitable global order. The future must be built on the sovereignty of nations, free from the selfish designs of a Western oligarchy.
-
 @ 4520e45a:aa52208a
2025-03-24 20:26:56
@ 4520e45a:aa52208a
2025-03-24 20:26:56👾 Hash Obwohl ein Bitaxe mit 1TH eine Billion Hashes pro Sekunde generiert, werden nicht alle Hashes an den Pool übermittelt — das käme einer Dos-Attacke gleich, würde unnötig Bandbreite verschwenden und den Stratum-Pool-Server massiv belasten.
🏋️ Work-Difficulty Deshalb wird für jeden Worker eine individuelle Work-Difficulty festgelegt. Im Stratum-Protokoll, bekannt als <mining.set_difficulty>. Es werden also nur Shares übermittelt, welche grösser als die festgelegte Work-Difficulty sind.
💡 Um eine Share mit Difficulty 1 zu finden, muss ein Miner erwartungsgemäss 2³² = 4'294'967'296 = 4.29G Hashes generieren.
✉️ Share Wenn ein Hash alle notwendigen Kriterien erfüllt und die Nonce-Difficulty grösser ist als die vom Pool festgelegte Work-Difficulty, wird er als Share dem Pool übermittelt.
⏱️ Bei ckpool wird die Work-Difficulty für einen Worker so angepasst, dass im Durchschnitt 20 Shares pro Minute – also alle 3 Sekunden 1 Share – überliefert wird, das ergibt circa 1200 Shares/Stunde
⏱️ Bei Public Pool wird die Work-Difficulty für einen Worker so angepasst, dass im Durchschnitt 6 Shares pro Minute – also alle 10 Sekunden 1 Share – überliefert wird, das ergibt circa 360 Shares/Stunde
📡 Es geht dabei letztlich um die Kommunikation zwischen Miner und Pool, also konkret, wie oft pro Minute dein Miner Shares an den Pool übermittelt und wieviele Datenpakete gesendet/empfangen/verarbeitet werden müssen.
📈 5-20 Shares pro Minute ergeben auch eine einigermassen aussagekräftige Hashrate, damit stets überprüft werden kann, ob dein Miner korrekt arbeitet.
⛏️ Ob Miner pro Minute 20 Shares mit jeweils einer Nonce-Difficulty von 600 an den Pool übermittelt und Miner pro Minute nur 6 Shares dafür jeweils mit einer Nonce-Difficulty von 2000 an den Pool übermittelt ist am Ende das gleiche.
💪 Beide haben die identische Arbeit geleistet (20×600 = 6×2000 = 12'000×1), nur dass der eine 'viele einfache' und der andere 'wenige schwierige' Shares übermittelt hat.
-
 @ 866e0139:6a9334e5
2025-03-24 19:48:43
@ 866e0139:6a9334e5
2025-03-24 19:48:43Autor: Philipp Mattheis. Dieser Beitrag wurde mit dem Pareto-Client geschrieben und erschien zuerst auf dem Substack-Blog "BlingBling". Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
800 Milliarden Euro will die EU ausgeben, um die Ukraine und den Kontinent in ein “stählernes Stachelschwein” zu verwandeln. Deutschland selbst will künftig Verteidigungsausgaben aus der Schuldenbremse ausnehmen, was nichts anderes als eine unbegrenzte Kreditlinie für das Militär bedeutet. Hinzu kommt ein “Sondervermögen” in Höhe von 500 Milliarden Euro für Infrastruktur. Das klingt nach einem Spartopf, den man für schwere Zeiten angelegt hat. Es soll die Tatsache verschleiern, dass es sich dabei um Schulden handelt. Der vermutlich baldige Kanzler Friedrich Merz bricht damit sein Wahlversprechen, die Schuldenbremse einzuhalten. Beschließen soll das Paket noch ein abgewählter Bundestag, da im neuen wohl die Mehrheit fehlt.
Frisches Geld für Krieg und Aufrüstung
Womit also ist zu rechnen, wenn demnächst fast eine Billion frisch gedruckte Euro in Drohnen, Panzer und Raketen investiert werden?
Das beste Beispiel der jüngeren Geschichte ist China: 2009 legte die chinesische Regierung das bisher größte Infrastrukturprojekt der Welt in Höhe von 440 Milliarden Euro auf. Finanziert wurde es durch günstige Kredite, die vor allem an Staatsunternehmen vergeben wurden. Nachdem die Welt nach der in den USA ausgelösten Immobilienkrise 2008 in die Rezession gerutscht war, „rettete“ dieses Paket die globale Konjunktur. China hatte zu diesem Zeitpunkt großen Bedarf an Flughäfen, Straßen und vor allem Zügen. Das Paket war riskant: Schier unbegrenztes Geld, das begrenzten Waren hinterherjagt, führt zu Inflation. Billige Kredite führen meist dazu, dass Unternehmen nicht mehr effizient wirtschaften, und Schuldenberge vor sich her wälzen.
Allerdings wurde das Geld in Produktivität investiert. Denn wenn Menschen und Waren einfacher reisen können, nimmt die Geschäftstätigkeit zu: Arbeitnehmer werden mobiler, Unternehmen konkurrenzfähiger, die Preise sinken. Die Investitionen lohnen sich also, weil sie zu mehr Wirtschaftswachstum führen. Vereinfacht gesagt: Die Schulden können zurückgezahlt werden, und am Ende bleibt noch mehr übrig. In diesem Fall führen Schulden nicht zu Inflation: Durch die gesteigerte Produktivität stehen jetzt sogar mehr Waren der Geldmenge gegenüber.
15 Jahre später kämpft die zweitgrößte Volkswirtschaft zwar noch immer mit den Problemen, die aus diesem Paket resultieren - die Immobilienkrise ist eine indirekte Folge davon. Trotzdem war das Programm ein Erfolg: die Städte, Flughäfen und vor allem Zugstrecken führten zu einer höheren wirtschaftlichen Aktivität oder Produktivität. China ist heute ein wesentlich moderneres Land als vor dem Paket, und verfügt über modernste und größte Netz aus Hochgeschwindigkeitszügen der Welt. Neue Schulden können positiv sein - wenn das Geld produktiv investiert wird.
Auch in Europa lassen sich mit dem Geld-Paket zunächst mehrere Probleme auf einmal lösen: Deutschland ist noch immer ein Industriestandort mit hohen Produktionskapazitäten. Werke der Auto- und Zulieferindustrie können theoretisch zur Waffenproduktion umfunktioniert werden. Immer noch besser als sie stillzulegen oder an die Chinesen zu verkaufen, werden viele Kommentatoren schreiben.
Allein in der deutschen Automobil-Zulieferindustrie sind im vergangenen Jahr über 19000 Arbeitsplätze verloren gegangen. Viele von den Entlassenen können nun Arbeit in der Rüstungsindustrie finden. Oder wie Hans Christoph Atzpodien, Hauptgeschäftsführer des Bundesverbandes der Deutschen Sicherheits- und Verteidigungsindustrie in der WirtschaftsWoche sagt:
„Das Motto muss lauten: Autos zu Rüstung! Anstatt einen volkswirtschaftlichen Schaden durch den Niedergang der Auto-Konjunktur zu beklagen, sollten wir versuchen, Produktionseinrichtungen und vor allem Fachkräfte aus dem Automobilsektor möglichst verträglich in den Defence-Bereich zu überführen“
Immerhin: ein großer Teil des Geldes soll auch in Infrastrukturprojekte fließen: Brücken, Bahn, Internetausbau. Deutschland, und damit Europa, wird in den kommenden Monaten also eine große Party feiern, die über die Tatsache hinwegtäuschen wird, dass man einen dummen Krieg verloren hat. In den kommenden Monaten werden sich Verbände und Organisationen um das Geld reißen. Das Geld wird ein auch kollektiv-psychologisches Ventil sein, um das eigene Versagen bei Corona, Klima und Ukraine vergessen zu machen.
Es gibt allerdings einen wesentlichen Unterschied zum chinesischen Stimulus-Paket 2009: Rüstungsgüter sind im Gegensatz zu Zugstrecken totes Kapital. Eine neue Drohne oder Panzer führt nicht zu mehr Produktivität, im Gegenteil: Kommen sie zum Einsatz, zerstören sie Brücken, Häuser, Straßen und töten Menschen. Die Produktivität sinkt also. Im besten Fall kann Militärgerät herumstehen und vor sich hin rosten. Auch dann aber ist es „totes Kapital“, das nichts zur Produktivität beiträgt. Kommt es zum Einsatz, stehen der nun verringerten Warenmenge eine noch größere Geldmenge gegenüber. Die Inflation steigt.
DIE FRIEDENSTAUBE JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Schleichende Militarisierung
Auch gesellschaftlich wird das Paket mit seinem Blanko-Scheck für die Verteidigungsindustrie viel verändern: Es kommt zu einer „Eichung“ der Gesellschaft, eine kollektive Abscheu des gemeinsamen Feindes. Scharfmacher, eigentlich mittelmäßiger Akademiker und Bürokraten, wie Carlo Masala und Claudia Major werden eine noch größere Rolle im öffentlichen Diskurs spielen und die Talkshows dominieren, die von einer immer älter werdenden deutschen Bevölkerung geglotzt werden. Abweichende Meinungen auf Online-Plattformen zensiert, unter dem Vorwand, die Demokratie sei in Gefahr
Da die Rüstungsindustrie dann eine wichtigere Rolle für die Gesamtwirtschaft spielt, wird ihr Einfluss auf die Politik in Form von Lobbyisten und Verbänden zunehmen. Politiker merken schnell, dass sie von der medialen Aufmerksamkeitsökonomie nach oben gespült werden, wenn sie immer radikalere Forderungen stellen. So empfahl der ehemalige Außenminister Joschka Fischer die Woche die Wiedereinführung der Wehrpflicht für Männer und Frauen. “Star-Ökonomin” Isabella Weber will die Kriegswirtschaft mitplanen.
Der Kontinent wird sich langsam wandeln von einem „Friedensprojekt“ zu einem „metallenen Stachelschwein“, ergo Kriegsprojekt, denn ohne dämonisierten Feind funktioniert das Programm nicht. Der Ton wird rauer, autoritärer, und die Meinungsfreiheit weiter eingeschränkt werden. Die seit 2020 eingeführten Werkzeuge zur soften Propaganda („kognitive Kriegsführung”) werden verfeinert und ausgebaut werden, sodass weiterhin 80 Prozent der Bevölkerung alle noch so antihumanen Maßnahmen gutheißen werden.
Und dann?
Wie Julian Assange einmal sagte: “Das Ziel ist kein erfolgreicher Krieg. Das Ziel ist ein endloser Krieg.” Der Konflikt muss weitergehen, ewig schwelen oder ein neuer gefunden werden, da sonst ein Teil der Wirtschaftsleistung kollabiert.
Nach ein, zwei oder auch erst drei Jahren, werden erste Probleme sichtbar. Die Party endet, der Kater setzt langsam ein. Die Finanzierung an den Kapitalmärkten wird für Deutschland immer kostspieliger. Der Schuldendienst wird einen größeren Teil des Haushalts einnehmen. Die Bürger müssen dies mitfinanzieren. Der voraussichtlich neue Bundeskanzler Friedrich Merz sprach bereits von der „Mobilisierung der deutschen Sparguthaben“.

Was im Ersten Weltkrieg „Kriegsanleihen“ hieß, wird einen schickeren Namen bekommen wie „olivgrüne Bonds“. You name it. Alternativ lässt sich ein Verteidigungs-Soli einführen, oder das Kindergeld streichen, wie kürzlich Ifo-Chef Clemens Fuest forderte.
Philipp Mattheis, Jahrgang 1979, ist München-Korrespondent der WiWo und betreibt den Substack-Blog "BlingBling". Er studierte Philosophie und absolvierte die Deutsche Journalistenschule. Von 2012 bis 2015 war er in Shanghai als China-Korrespondent der WiWo tätig. Von 2016 bis 2020 berichtete er aus Istanbul. Mattheis ist Autor mehrere Bücher zu, China, Geo-, und Wirtschaftspolitik. www.philippmattheis.com
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 2e8970de:63345c7a
2025-03-24 18:40:58
@ 2e8970de:63345c7a
2025-03-24 18:40:58As Congress gears up to pass President Trump’s massive legislative package, one of the biggest fights is over the future of Medicaid. To make their targeted budget numbers, Republicans will likely need to carve hundreds of billions of dollars in spending out of the health program that serves lower-income people. But Medicaid is a political flashpoint because of the core role it plays in the lives of millions of Americans—many of whom vote for Republicans—as well as state budgets and the healthcare economy.
https://www.wsj.com/politics/policy/medicaid-cuts-health-insurance-in-charts-56962433?mod=hp_lead_pos7
originally posted at https://stacker.news/items/923851
-
 @ bf95e1a4:ebdcc848
2025-03-24 17:14:48
@ bf95e1a4:ebdcc848
2025-03-24 17:14:48This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
Everything A Trade
All human interaction can be defined as trade. Yes, all human interaction. Every time a human being interacts with another, an exchange takes place. In every conversation we have, we exchange information with each other. Even the most trivial information is of some value to the other person. If information didn’t have any value to us, we wouldn’t talk to each other. Either what the other person says is valuable to us, or we find it valuable to give information to them. Oftentimes both. At the core of all human interaction that isn’t violent, both parties perceive that they gain some value from it, otherwise the interaction wouldn’t have taken place at all. Civilizations begin this way — two people finding it valuable to interact with each other. That’s all it takes.
So, what constitutes value? What we find valuable is entirely subjective. A comforting hug, for example, probably has a different value to a two-year-old than it has to a withered army general. Even the most basic action, such as breathing, encapsulates the whole value spectrum. We tend to forget that even a single breath of air can be of immense value to us under the right circumstances. A single breath is worth more than anything on the planet to a desperate free-diver trapped under ice, while worth nothing to a person with a death wish in clean forest air on a sunny summer day. Value is derived from supply and demand, and demand is always subjective. Supply is not.
Since all of our lives are limited by time, time is the ultimate example of a scarce, tradeable resource. We all sell our time. We sell it to others, and we sell it to ourselves. Everyone sells their time, either through a product that took them a certain amount of time to produce, or as a service, and services always take time. If you’re an employee on a steady payroll, you typically sell eight hours of your day, every day, to your employer. If you’re doing something you truly love to do, that eight-hour day still belongs to you, in a way, since you’re doing what you’d probably be doing anyway if you had been forced to do it for free. Sometimes, we sacrifice time in order to acquire something in the future. An education, for instance, gives no immediate reward but can lead to a better-paying, more satisfying job in the future. An investment is basically our future self trading time with our present self at a discount. Once again, every human interaction viewed as trade.
It’s rooted in physics. For every action, there is an equally large reaction. Trade is at the very core of what we are, and the tools we use to conduct trade matter a lot to the outcome of each transaction. Money is our primary tool for expressing value to each other and if the creation of money is somewhat corrupt or unethical, that rot spreads down throughout society, from top to bottom. Shit flows downhill, as the expression goes.
So what is money, or rather, what ought money to be? In order for two persons to interact when a mutual coincidence of needs is absent, a medium of exchange is needed in order to execute a transaction. A mutual coincidence of needs might be “You need my three goats, and I need your cow,” or even “both of us need a hug.” In the absence of a physical good or service suitable for a specific transaction, money can fulfill the role of a medium of exchange. What most people fail to realize is that the value of money, just as the value of everything else, is entirely subjective. You don’t have to spend it. The problem with every incarnation of money that mankind has ever tried is that its value always gets diluted over time due to inflation in various forms. Inflation makes traditional money a bad store of value, and money needs to be a good store of value in order to be a good investment, or in other words, a good substitute for your time and your effort over time. Bitcoin tries to solve this problem by introducing absolute scarcity to the world, a concept that mankind has never encountered before. To comprehend what such a discovery means for the future, one needs to understand the fundamentals of what value is and that we assign a certain value to everything we encounter in life, whether we admit it or not. In short, we assign value to everything we do, value is derived from supply and demand, and supply is objective while demand is subjective.
Free trade emerges out of human interaction naturally and it is not an idea that was forced upon us at any specific point in time. The idea that markets should be regulated and governed, on the other hand, was. Free trade is just the absence of forceful interference in an interaction between two humans by a third party. There’s nothing intrinsically wrong or immoral about an exchange of a good or service. Every objection to this is a byproduct of the current global narrative — a narrative that tells us that the world is divided into different nations and that people in these nations operate under various sets of laws, depending on what jurisdiction they find themselves in. All of these ideas are man-made. No species except humans does this to themselves. Animals do trade, but they don’t do politics.
Bitcoin and the idea of truly sound, absolutely scarce money inevitably make you question human societal structures in general and the nature of money in particular. Once you realize that this Pandora’s box of an idea can’t be closed again by anyone, everything is put into perspective. Once you realize that it is now possible for anyone with a decently sized brain to store any amount of wealth in that brain or to beam wealth anonymously to any other brain in the world without anyone else ever knowing, everything you were ever told about human society is turned on its head. Everything you thought you knew about taxes, social class, capitalism, socialism, economics, or even democracy falls apart like a house of cards in a hurricane. It is, in fact, impossible to comprehend the impact Bitcoin will have on the planet without also understanding basic Austrian economics and what the libertarian worldview stems from.
Imagine growing up in an Amish community. Until your sixteenth birthday, you’re purposely completely shielded off from the outside world. Information about how the world really works is very limited to you since internet access, and even TVs and radios, are forbidden within the community. Well, from a certain perspective, we’re all Amish. How money really works is never emphasized enough through traditional media or public educational institutions. Most people believe that the monetary system is somehow sound and fair when there’s overwhelming evidence to the contrary all over the globe. Ask yourself, do you remember being taught about the origins of money in school? Me neither. I don’t believe that there’s some great, global conspiracy behind the fact that the ethics of money creation isn’t a school subject, but rather that plain old ignorance is to blame for the lack of such a subject primarily. As soon as their math-skill limit is reached, people seem to stop caring about numbers. The difference between a million and a billion seems lost on a depressingly large part of the world's population. In the chapters ahead, we’ll explore the pitfalls of central banking, how money pops into existence, and how inflation keeps us all on a leash.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 57d1a264:69f1fee1
2025-03-24 17:08:06
@ 57d1a264:69f1fee1
2025-03-24 17:08:06Nice podcast with @sbddesign and @ConorOkus about bitcoin payments. https://www.youtube.com/watch?v=GTSqoFKs1cE
In this episode, Conor, Open Source product manager at Spiral & Stephen, Product Designer at Voltage & Co founder of ATL Bitlab join Stephan to discuss the current state of Bitcoin user experience, particularly focusing on payments and the challenges faced by users. They explore the comparison between Bitcoin and physical cash, the Western perspective on Bitcoin payments, and the importance of user experience in facilitating Bitcoin transactions.
They also touch upon various payment protocols like #BOLT11, #LNURL, and #BOLT12, highlighting the need for interoperability and better privacy features in the Bitcoin ecosystem. The discussion also covers resources available for developers and designers to enhance wallet usability and integration.
@StephanLivera Official Podcast Episode: https://stephanlivera.com/646
Takeaways
🔸Bitcoin has excelled as a savings technology. 🔸The payments use case for Bitcoin still needs improvement. 🔸User experience is crucial for Bitcoin adoption. 🔸Comparing Bitcoin to cash highlights privacy concerns. 🔸Western users may not see a payments problem. 🔸Regulatory issues impact Bitcoin payments in the West. 🔸User experience challenges hinder Bitcoin transactions. 🔸Different payment protocols create compatibility issues. 🔸Community collaboration is essential for Bitcoin's future. 🔸Improving interoperability can enhance Bitcoin payments. Wallet compatibility issues can create negative user impressions. 🔸Designers can significantly improve wallet user experience. 🔸Testing compatibility between wallets is essential for user satisfaction. 🔸Tether's integration may boost Bitcoin adoption. 🔸Developers should prioritize payment capabilities before receiving capabilities. 🔸Collaboration between designers and developers can lead to better products. 🔸User experience improvements can be low-hanging fruit for wallet projects. 🔸A global hackathon aims to promote miner decentralization. 🔸Resources like BOLT12 and the Bitcoin Design Guide are valuable for developers. 🔸Engaging with the community can lead to innovative solutions.
Timestamps
(00:00) - Intro (01:10) - What is the current state of Bitcoin usage - Payments or Savings? (04:32) - Comparing Bitcoin with physical cash (07:08) - What is the western perspective on Bitcoin payments? (11:30) - Would people use Bitcoin more with improved UX? (17:05) - Exploring payment protocols: Bolt11, LNURL, Bolt12 & BIP353 (30:14) - Navigating Bitcoin wallet compatibility challenges (34:45) - What is the role of designers in wallet development? (43:13) - Rumble’s integration of Tether & Bitcoin; The impact of Tether on Bitcoin adoption (51:22) - Resources for wallet developers and designers
Links:
• https://x.com/conorokus • https://x.com/StephenDeLorme • https://bolt12.org/ • https://twelve.cash/ • https://bitcoin.design/guide/ • Setting Up Bitcoin Tips for Streamers](/watch?v=IWTpSN8IaLE)
originally posted at https://stacker.news/items/923714
-
 @ 401014b3:59d5476b
2025-03-24 16:34:24
@ 401014b3:59d5476b
2025-03-24 16:34:24Alright, hoops degenerates, it’s March 24, 2025, and we’re deep in the March Madness grinder—Sweet 16 time, baby! The bracket’s a damn battlefield, with Auburn, Michigan, Texas Tech, Arkansas, and Purdue locked in alongside some heavy hitters and sneaky upstarts. We’re breaking down every matchup, throwing out some ballsy picks, and calling the full Elite Eight squads on the road to San Antonio. This ain’t some nerdy chalk fest—let’s get loud, let’s get rowdy, and let’s see who’s got the stones to survive this chaos. Strap in, fam—here we go!
South Region: Auburn’s Warpath or Spartan Magic?
Auburn vs. Michigan
Auburn’s the SEC beast, shredding Creighton 82-70 with Tahaad Pettiford’s bench juice (14 points) and Johni Broome’s paint dominance (22 points, 10 boards). Michigan’s Big Ten scrappers outlasted Texas A&M 91-79—Dusty May’s got ‘em humming with Olivier Nkamhoua’s 18 points. The Tigers are a top-5 offensive team, but Michigan’s been scrappy, winning close games all season. Auburn’s depth and Broome’s interior game (top-10 in blocks) overpower Michigan’s grit—Auburn rolls, 78-71.
Ole Miss vs. Michigan St.
Ole Miss’s Chris Beard-led crew topped Iowa St. 91-78—Sean Pedulla dropped 20, and their top-30 offense is humming. Michigan St. beat New Mexico 71-63—Tom Izzo’s Spartans are battle-tested, with a top-15 defense (per KenPom). Ole Miss can score, but Sparty’s physicality (top-10 in defensive rebounds) and Izzo’s March magic (five Final Fours) shut ‘em down—Michigan St. grinds it, 74-69.
Elite Eight Matchup: Auburn vs. Michigan St.
West Region: Houston’s Clamps or Gators’ Grit?
Houston vs. Purdue
Houston’s D suffocated Gonzaga 81-78—L.J. Cryer dropped 22, and their top-5 defense (forcing 16 turnovers per game) is a nightmare. Purdue crushed San Diego St. 76-62—Braden Smith dished 15 assists, and Fletcher Loyer had 18. Cougars are elite defensively, but Purdue’s size (top-10 in offensive rebounds) and tempo keep it close. Houston’s clamps and Cryer’s clutch shooting (40% from three) edge it—Houston dominates, 70-66.
Florida vs. Maryland
Florida stunned UConn 77-75—Walter Clayton Jr.’s 10 points in a three-minute span sealed it. Maryland’s buzzer-beater over Colorado St. 72-71—Derik Queen’s heroics—got ‘em here. Gators are rolling (SEC tourney champs), but Maryland’s Crab Five (top-20 offense) and Queen’s clutch play (20 PPG in March) keep it tight. Florida’s depth (four starters averaging 12+ PPG) pulls through—Florida wins, 82-78.
Elite Eight Matchup: Houston vs. Florida
Midwest Region: Arkansas’ Chaos or Bama’s Firepower?
Texas Tech vs. Arkansas
Calipari’s Razorbacks punked St. John’s 75-66—DJ Wagner dropped 16, and their depth shone. Texas Tech’s Big 12 muscle crushed Drake 77-64—Darrion Williams had 28. Hogs’ talent (six guys in double figures vs. St. John’s) faces Tech’s balanced attack (top-25 offense). Arkansas’ chaos and Calipari’s March pedigree (four Final Fours) overwhelm—Arkansas storms, 82-77.
BYU vs. Alabama
BYU’s hot streak topped Wisconsin 91-89—Trevor Knell hit six threes, averaging 18.9 PPG in their nine-game win streak. Alabama blitzed Saint Mary’s 86-80—Mark Sears dropped 25. Cougars’ offense (top-10 in three-point shooting) meets Bama’s firepower (top-15 in offensive efficiency). Alabama’s speed and Sears’ scoring (21 PPG) edge it—Alabama wins, 88-84.
Elite Eight Matchup: Arkansas vs. Alabama
East Region: Duke’s Flagg Show or Cats’ Revenge?
Duke vs. Arizona
Flagg’s back—Duke crushed Baylor 89-86, with Flagg dropping 20 and 8. Arizona blitzed Oregon 87-83—Caleb Love had 27. Flagg’s versatility (top-5 defensive efficiency for Duke) faces Love’s scoring (20 PPG in March). Duke’s depth (six guys scoring 10+ vs. Baylor) and Flagg’s two-way play edge it—Duke flexes, 85-76.
Kentucky vs. Tennessee
Kentucky beat Illinois—Mark Pope’s Wildcats are 2-0 against Tennessee this season. Tennessee topped UCLA 72-67—Zakai Zeigler had 18 and 8 assists. Cats’ resilience (top-20 offense) meets Vols’ defense (top-15 efficiency). Kentucky’s Quad 1 wins (12 this season) and Pope’s game plan edge it—Kentucky wins, 82-78.
Elite Eight Matchup: Duke vs. Kentucky
Elite Eight Teams (Full List)
South: Auburn, Michigan St.
West: Houston, Florida
Midwest: Arkansas, Alabama
East: Duke, Kentucky
The Final Buzzer
Sweet 16’s a bloodbath, and the Elite Eight’s set—Auburn, Michigan St., Houston, Florida, Arkansas, Alabama, Duke, and Kentucky are my picks to keep dancing. SEC’s got seven teams in the Sweet 16, blue bloods are flexing, and mid-majors are toast. Hit me on Nostr if you disagree, but this is my March Madness gospel—bracket’s clean, let’s see who survives! Let’s freaking go, degenerates!
-
 @ 7d33ba57:1b82db35
2025-03-24 15:40:17
@ 7d33ba57:1b82db35
2025-03-24 15:40:17Located in the Cabo de Gata-Níjar Natural Park, Agua Amarga is a small, picturesque fishing village on the southeastern coast of Spain. Known for its crystal-clear waters, whitewashed houses, and peaceful atmosphere, this is the perfect spot for a relaxing Mediterranean escape.
🏖️ Top Things to See & Do in Agua Amarga
1️⃣ Playa de Agua Amarga 🏝️
- A beautiful, sandy beach with shallow, turquoise waters.
- Family-friendly with beach bars (chiringuitos) and restaurants nearby.
- Great for swimming, paddleboarding, and sunbathing.
2️⃣ Cala de Enmedio – A Hidden Paradise 🌊
- A secluded cove with soft sand and smooth rock formations.
- Reachable by a 30-minute hike or by kayak.
- One of the most photogenic beaches in Cabo de Gata!
3️⃣ Cala del Plomo 🏞️
- Another pristine, unspoiled cove surrounded by dramatic cliffs.
- Accessible by a short hike or 4x4 vehicle.
- A perfect spot for snorkeling and enjoying nature in peace.
4️⃣ Boat & Kayak Excursions 🚤
- Explore the rugged coastline, caves, and hidden beaches by sea.
- Some tours include stops at Cala de San Pedro, a remote beach with an alternative hippie community.
5️⃣ Hiking & Nature Trails 🌿
- Agua Amarga is surrounded by stunning volcanic landscapes within Cabo de Gata Natural Park.
- The Sendero de la Cala de Enmedio is a scenic hike with breathtaking views.
🍽️ What to Eat in Agua Amarga
- Gambas rojas de Garrucha – Sweet red prawns 🦐
- Arroz caldoso de marisco – A rich, brothy seafood rice dish 🍚🐟
- Pulpo a la brasa – Grilled octopus, a local delicacy 🐙
- Pescado fresco – Fresh fish straight from the sea 🐠
- Tarta de almendra – A delicious almond cake for dessert 🍰
🚗 How to Get to Agua Amarga
🚘 By Car: ~1 hour from Almería via A-7 & AL-5106
🚌 By Bus: Limited services from Almería; renting a car is recommended for flexibility
✈️ By Air: Nearest airport is Almería Airport (LEI), about 50 km away💡 Tips for Visiting Agua Amarga
✅ Best time to visit? Spring & early autumn – warm but not too crowded 🌞
✅ Bring water & snacks if visiting remote beaches – no facilities in hidden coves 🏝️
✅ Rent a kayak or boat for the best way to explore the coastline 🚣♂️
✅ Stay overnight to enjoy the peaceful ambiance after the day-trippers leave 🌅 -
 @ 4259e401:8e20e9a6
2025-03-24 14:27:27
@ 4259e401:8e20e9a6
2025-03-24 14:27:27[MVP: Gigi! How do I lightning prism this?]
If I could send a letter to myself five years ago, this book would be it.
I’m not a Bitcoin expert. I’m not a developer, a coder, or an economist.
I don’t have credentials, connections, or capital.
I’m a blue-collar guy who stumbled into Bitcoin almost exactly four years ago, and like everyone else, I had to wrestle with it to understand it.
Bitcoin is one of the most misunderstood, misrepresented, and misinterpreted ideas of our time - not just because it’s complex, but because its very structure makes it easy to distort.
It’s decentralized and leaderless, which means there’s no single voice to clarify what it is or defend it from misinformation.
That’s a feature, not a bug, but it means that understanding Bitcoin isn’t easy.
It’s a system that doesn’t fit into any of our existing categories. It’s not a company. It’s not a product. It’s not a government.
There’s no marketing department, no headquarters, no CEO.
That makes it uniquely resistant to corruption, but also uniquely vulnerable to disinformation.
Whether through negligence or malice, Bitcoin is constantly misunderstood - by skeptics who think it’s just a Ponzi scheme, by opportunists looking to cash in on the hype, by scammers who use the name to push worthless imitations, and by critics who don’t realize they’re attacking a strawman.
If you’re new to Bitcoin, you have to fight through layers of noise before you can even see the signal.
And that process isn’t instant.
Even if you could explain digital signatures off the top of your head, even if you could hash SHA-256 by hand, even if you had a perfect technical understanding of every moving part - you still wouldn’t get it.
Bitcoin isn’t just technology. It’s a shift in incentives, a challenge to power, an enforcer of sovereignty. It resists censorship.
A simple open ledger - yet it shakes the world.
Archimedes asked for a lever and a place to stand, and he could move the world.
Satoshi gave us both.
The lever is Bitcoin - an economic system with perfect game theory, incorruptible rules, and absolute scarcity.
The place to stand is the open-source, decentralized network, where anyone can verify, participate, and build without permission.
And what comes out of this seemingly simple equation?
The entire rearchitecture of trust. The separation of money and state.
A foundation upon which artificial intelligence must negotiate with the real world instead of manipulating it.
A digital economy where energy, computation, and value flow in perfect symmetry, refining themselves in an endless virtuous cycle.
Bitcoin started as a whitepaper.
Now it’s a lifeline, an immune system, a foundation, a firewall, a torch passed through time.
From such a small set of rules - 21 million divisible units, cryptographic ownership, and a fixed issuance schedule - emerges something unstoppable.
Something vast enough to absorb and constrain the intelligence of machines, to resist the distortions of human greed, to create the rails for a world that is freer, more sovereign, more aligned with truth than anything that came before it.
It’s proof that sometimes, the most profound revolutions begin with the simplest ideas. That’s why this book exists.
Bitcoin isn’t something you learn - it’s something you unlearn first.
You start with assumptions about money, value, and authority that have been baked into you since birth. And then, piece by piece, you chip away at them.
It’s like peeling an onion – it takes time and effort.
*And yes, you might shed some tears! *
At first, you might come for the speculation. A lot of people do. But those who stay - who actually take the time to understand what’s happening - don’t stay for the profits.
They stay for the principles.
If you’re holding this book, you’re somewhere on that journey.
Maybe you’re at the very beginning, trying to separate the signal from the noise.
Maybe you’ve been down the rabbit hole for years, looking for a way to articulate what you already know deep in your bones.
Either way, this is for you.
It’s not a technical manual, and it’s not a sales pitch. It’s the book I wish I had when I started.
So if you’re where I was, consider this a message in a bottle, thrown back through time. A hand reaching through the fog, saying:
“Keep going. It’s worth it.”
Preface The End of The Beginning
March 2025.
The moment has arrived. Most haven’t even noticed, let alone processed it. The United States is setting up a Bitcoin (Bitcoin-only!) strategic reserve.
It’s not a theory. Not an idea. The order is signed, the ink is dried.
The people who have been wrong, over and over (and over!) again - for years! - fumble for explanations, flipping through the wreckage of their previous predictions:
“Bubble…’’ “Fad…” “Ponzi…”
No longer.
The same analysts who once sneered are now adjusting their forecasts to protect what’s left of their credibility. Those who dismissed it are now trapped in a slow, humiliating realization: Bitcoin does not require their approval.
It never did.
Something fundamental has shifted, and the air is thick with a paradoxical cocktail of triumph and panic. Bitcoiners saw this coming. Not because they had insider information, but because they understood first principles when everyone else was still playing pretend.
Bitcoin was never just surviving.
It was infiltrating.
The question is no longer whether Bitcoin will succeed.
It already has.
The only question that remains is who understands, and who is still in denial.
Think back to 2022.
At its peak, FTX was one of the world’s largest cryptocurrency exchanges, valued at $32 billion and backed by blue-chip investors. It promised a sophisticated, institutional-grade trading platform, attracting retail traders, hedge funds, and politicians alike. Sam Bankman-Fried, with his disheveled hair and cargo shorts, was its eccentric figurehead, a billionaire who slept on a bean bag and spoke of philanthropy.
Then the illusion shattered.
FTX collapsed overnight, an implosion so violent it left an entire industry scrambling for cover. One moment, Sam Bankman-Fried was the golden boy of crypto - genius quant, regulatory darling, effective altruist™.
The next, he was just another fraudster in handcuffs.
Billions vanished. Customers locked out. Hedge funds liquidated.
Politicians who had once taken photos with SBF and smiled at his political donations, suddenly pretended they had no idea who he was. The same regulators who were supposed to prevent disasters like this stood slack-jawed, acting as if they hadn’t been having closed-door meetings with FTX months before the collapse.
But FTX wasn’t just a scandal, it was a filter.
If you were Bitcoin-only, with your satoshis in cold storage, you didn’t even flinch. From your perspective, nothing important changed:
A new Bitcoin block still arrived every ten minutes (on average). The supply cap of 21 million bitcoins remained untouched. Ownership was still protected by public/private key cryptography.
You were literally unaffected.
You had already updated your priors:
“If you don’t hold your own keys, you own nothing.” “Bitcoin is not ‘crypto’.” “’Crypto’ is a casino.”
FTX was just another financial fire, another chapter in the never-ending saga of people trusting systems that had already proven themselves untrustworthy.
That moment was a prelude.
The U.S. Bitcoin pivot is the paradigm shift.
The Eukaryotic Revolution Is Upon Us
In biology, abiogenesis is when life emerged from non-life - a fragile, uncertain process where the first microscopic self-replicators struggled to survive against hostile conditions. That was Bitcoin’s early history. It had to fight for its existence, attacked by governments, dismissed by economists, ridiculed by mainstream media.
But it survived.
That era is over. We have entered the Eukaryotic Revolution.
This is the moment in evolutionary history when simple lifeforms evolved into something structurally complex - organisms with nuclei, internal scaffolding, and the ability to form multicellular cooperatives and populate diverse ecosystems. Once this transformation happened, there was no going back. Bitcoin is going through its own Eukaryotic leap.
Once an outsider, dismissed and ridiculed, it is maturing into an integrated, resilient force within the global financial system.
On March 2, 2025, the Trump administration announced a Crypto Strategic Reserve.
At first, it wasn’t just Bitcoin - it included XRP, SOL, and ADA, a desperate attempt to appease the altcoin industry. A political move, not an economic one.
For about five minutes, the broader crypto industry cheered. Then came the pushback.
Bitcoiners called it immediately: mixing Bitcoin with centralized altcoin grifts was like adding lead weights to a life raft.
Institutional players rejected it outright: sovereign reserves need hard assets, not tech company tokens. The government realized, almost immediately, that it had made a mistake.
By March 6, 2025, the pivot was complete.
Strategic Bitcoin reserve confirmed. The President signed an executive order, and legislation has been introduced in the United States House of Representatives.
The U.S. government’s official bitcoin policy: hold, don’t sell. Look for ways to acquire more.
Altcoins relegated to second-tier status, treated as fundamentally separate from and inferior to bitcoin. The government’s official policy: sell, and do not actively accumulate more (ouch!).
“Bitcoin maximalism” – the belief that any cryptocurrency other than bitcoin lies on a spectrum between “bad idea” and outright scam - wasn’t vindicated by debate.
It was vindicated by economic reality.
When the government was forced to choose what belonged in a sovereign reserve, it wasn’t even close. Bitcoin stood alone.
“There is no second best.” -Michael Saylor
Who This Book Is For: The Three Types of Readers
You’re here for a reason.
Maybe you felt something shift.
Maybe you saw the headlines, sensed the undercurrents, or simply couldn’t ignore the growing drumbeat any longer.
Maybe you’ve been here all along, waiting for the world to catch up.
Whatever brought you to this book, one thing is certain: you’re curious enough to learn more.
Bitcoin forces a reevaluation of assumptions - about money, trust, power, and the very foundations of the economic order. How much of that process you’ve already undergone will determine how you read these pages.
1. The Layperson → new, curious, maybe skeptical. Bitcoin probably looks like chaos to you right now. One person says it’s the future. Another says it’s a scam. The price crashes. The price doubles. The news is either breathless excitement or total doom. How the hell are you supposed to figure this out?
If that’s you, welcome.
This book was built for you.
You don’t need to be an economist, a technologist, or a finance geek to understand what’s in these pages. You just need an open mind and the willingness to engage with new ideas - ideas that will, if you follow them far enough, challenge some of your deepest assumptions.
Bitcoin is not an investment. Bitcoin is not a company. Bitcoin is not a stock, a trend, or a passing phase.
Bitcoin is a paradigm shift. And by the time you reach the last page, you won’t need to be convinced of its importance. You’ll see it for yourself.
2. The Student → understand the basics, want to go deeper.
You’ve already stepped through the door.
You’ve realized Bitcoin is more than just digital gold. You understand decentralization, scarcity, censorship resistance… But the deeper you go, the more you realize just how much there is to understand.
3. The Expert → You’ve been in the game for years.
You’ve put in the time.
You don’t need another book telling you Bitcoin will succeed. You already know.
You’re here because you want sharper tools.
Tighter arguments.
A way to shut down nonsense with fewer words, and more force.
Maybe this book will give you a new way to frame an idea you’ve been struggling to convey.
Maybe it will help you refine your messaging and obliterate some lingering doubts in the minds of those around you.
Or maybe this will simply be the book you hand to the next person who asks, “Okay… but what’s the deal with Bitcoin?” so you don’t have to keep explaining it from scratch.
*If you’re already deep in the weeds, you can probably skip Part I (Foundations) without missing much - unless you’re curious about a particular way of putting a particular thing. *
Part II (Resilience) is where things get more interesting. Why you want to run a node, even if you don’t know it yet. The energy debate, stripped of media hysteria. The legend of Satoshi, and what actually matters about it.
If you’re a hardcore cypherpunk who already speaks in block heights and sending Zaps on NOSTR, feel free to jump straight to Part III (The Peaceful Revolution). Chapter 15, “The Separation of Money and State” is where the gloves come off.
Bitcoin isn’t just a technology. Bitcoin isn’t just an economic movement. Bitcoin is a lens.
And once you start looking through it, the world never looks the same again.
This book will teach you what Bitcoin is, as much as it will help you understand why Bitcoiners think the way they do.
It isn’t just something you learn about.
Especially not in one sitting, or from one book.
It’s something you grow to realize.
Regardless of which category you fall into, you’ve already passed the first test.
You’re still reading.
You haven’t dismissed this outright. You haven’t scoffed, rolled your eyes, or walked away. You’re at least curious.
And that’s all it takes.
Curiosity is the only filter that matters.
The rest takes care of itself.
The Essential Role of Memes Memes won the narrative war - it wasn’t textbooks, research papers, or whitepapers that did it. Bitcoin spread the same way evolution spreads successful genes - through replication, variation, and selection. Richard Dawkins coined the term “meme” in The Selfish Gene, describing it as a unit of cultural transmission - behaving much like a gene. Memes replicate, mutate, and spread through culture. Just as natural selection filters out weak genes, memetic selection filters out weak ideas.
But Bitcoin memes weren’t just jokes.
They were premonitions.
The most powerful ideas are often compact, inarguable, and contagious - and Bitcoin’s memes were all three. They cut through complexity like a scalpel, distilling truths into phrases so simple, so undeniable, that they burrowed into the mind and refused to leave.
"Bitcoin fixes this." "Not Your Keys, Not Your Coins." "Number Go Up."
Each of these is more than just a slogan.
They’re memetic payloads, compressed packets of truth that can carry everything you need to understand about Bitcoin in just a few words.
They spread through conversations, through tweets, through shitposts, through relentless repetition.
They bypassed the gatekeepers of financial knowledge, infecting minds before Wall Street even understood what was happening.
And they didn’t just spread.
They reshaped language itself.
Before Bitcoin, the word fiat was a sterile economic term, borrowed from Latin, meaning "by decree." It had no weight, no controversy - just a neutral descriptor for government-issued money.
But Bitcoiners forced a memetic shift.
They didn’t just make fiat mainstream.
**They made it radioactive. **
They stripped away the academic detachment and revealed its true essence:
money because I said so.
No backing. No inherent value.
Just a command.
And of course, an unspoken threat -
"Oh, and by the way, I have a monopoly on violence, so you’d better get on board."
This wasn’t just linguistic evolution; it was a memetic coup.
Bitcoiners took a sterile term and injected it with an unavoidable truth: fiat money exists not because it is chosen, but because it is imposed.
Central banks, governments, and financial institutions now use the term fiat without a second thought.
The meme has done its work.
A word that was once neutral, now carries an implicit critique - a quiet but persistent reminder that there is an alternative.
Bitcoin didn’t just challenge the financial system - it rewired the language we use to describe it.
“Money printer go BRRRRRR" did more damage to the Fed’s reputation than a thousand Austrian economics treatises ever could.
Memes exposed what balance sheets and policy reports tried to obscure. They turned abstract economic forces into something visceral, something undeniable.
And now - they are historical markers of the shift, the fossil record of our collective consciousness coming to terms with something fundamentally new in the universe.
The old world relied on authority, institutional credibility, and narrative control.
Bitcoin broke through with memes, first principles, and lived experience.
This wasn’t just an ideological battle.
It was an evolutionary process.
The weaker ideas died. The strongest ones survived.
Once a meme - in other words, an idea - takes hold, there is nothing - no law, no regulation, no institution, no government - that can stop it.
Bitcoin exists. It simply is.
And it will keep producing blocks, every ten minutes, whether you get it or not.
This book isn’t a trading manual.
It won’t teach you how to time the market, maximize your gains, or set up a wallet.
It’s a carefully curated collection of memes, giving you the prerequisite mental scaffolding to grok the greatest monetary shift in human history.
A shift that has already begun.
The only thing to decide is whether you’re watching from the sidelines or whether you’re part of it.
The rest is up to you.
How This Book Is Structured Bitcoin spreads like an evolutionary force - through memes. Each chapter in this book isn’t just an idea, it’s a memetic payload, designed to install the concepts that make Bitcoin inevitable. The book is broken into three phases:
*I. Foundations *** Memes as Mental Antivirus The first layer cuts through noise and filters out distractions. "Bitcoin Only" is the first test - if you get this one wrong, you waste years chasing ghosts. "Don’t Trust, Verify" rewires how you think about truth. And "Not Your Keys, Not Your Coins"? If you learn it the hard way, it’s already too late.
II. Resilience Memes as Weapons in the Information War Here’s where Bitcoin earns its survival. "Shitcoiners Get REKT" is a law, not an opinion. "Fork Around and Find Out" proves that you don’t change Bitcoin - Bitcoin changes you. "Antifragile, Unstoppable" shows how every attack on Bitcoin has only made it stronger.
III. The Peaceful Revolution ** Memes as Reality Distortion Fields By now, Bitcoin isn’t just an asset - it’s a lens. "Separation of Money and State" isn’t a theory; it’s happening in real time. "Fix the Money, Fix the World" isn’t a slogan; it’s a diagnosis. And "Tick Tock, Next Block"? No matter what happens, Bitcoin keeps producing blocks.
These aren’t just memes. They’re scaffolding for a new way of thinking. Each one embeds deeper until you stop asking if Bitcoin will succeed - because you realize it already has.
Next: Chapter 1: Bitcoin Only. ** For now, it’s a heuristic - an efficient filter that separates signal from noise, with minimal effort.
But by the time you finish this book, it won’t be a heuristic anymore.
It will be something you know.Welcome to the rabbit hole.
-
 @ c5128106:9b820f34
2025-03-24 13:50:16
@ c5128106:9b820f34
2025-03-24 13:50:16Continue to dishonour yourself, my soul ! Neither will you have much time left to do yourself honour. For the life of each man is almost up already ; and yet, instead of paying a due regard to yourself, you place your happiness in the souls of other men.
-
 @ a7bbc310:fe7b7be3
2025-03-24 13:18:49
@ a7bbc310:fe7b7be3
2025-03-24 13:18:49I’ve been back from Morocco for just over a month and I’ve had some time to reflect. I started writing a day by day of what I did in my trip to Morocco but that was turning out a bit boring. I couldn’t do the trip justice. I thought I’d share some of my observations instead. I’d start by saying I was only there for 5 1/2 days. 5 days in Marrakesh and half day in Essaouira
You can feel the rich culture and history Morocco has such a rich culture and history. Influence of Romans, French, Arab, Berbers, Saharan and Nomadic tribes. You can see it in the architecture, taste it in the food and hear it in the language. The streets of Marrakesh had the smells of spices, perfumes and petrol. There is a synchronised dance between everyone that occupy the streets. People, motorbikes, donkeys, carts, all jostling for position but never seeming to collide into on another.
One thing that didn’t surprise me was the high level of craftsmanship and intricate designs on some of the buildings. I was told by a tour guide that some of the calligraphy could only be understood and read by the person who wrote it.
There seemed to be a sense of community, people stopping in the street to greet each other and say hello. What surprised me about this in Marrakesh most was that it happened in such a busy city. From my experience big cities are places that you go to get lost, ignored and don’t want to be found. Scene at the end of the movie Collateral comes to mind. You know the one where he’s riding on the subway alone after being shot.
A vendor tried to sell me a pendant, a symbol of the Berber tribe that meant ‘free man’. The symbol looks similar to the one for Sats 丰. I declined to purchase since I wasn’t educated enough on the Berbers to rep a symbol.
Couldn’t get over how much stuff there was for sale! And duplications of everything, rugs, shoes , handbags, jackets. Cold mornings and evenings, warm during the day. Everyone dressed like it was winter, even when it for warmer in the afternoon. It was a special trip. I’d definitely go back. Both to visit Marrakesh and other places.
-
 @ 078d6670:56049f0c
2025-03-24 11:28:59
@ 078d6670:56049f0c
2025-03-24 11:28:59I spent some time outside in the dark last night. After a little sleep I was wide awake again, so I ventured downstairs, rolled a joint and stepped into the darkness. No moon, no outside lights. Just stars flickering through space and landing on the sky dome, expanding my being.
There was nothing unusual. Just the usual fleeting apparitions shooting through the ether, barely visible, like they’re behind a lace curtain and I have a glimpse into the astral: light and dark winged things, miniature meteor orbs and bat shadows. This time I wasn’t listening to anything, just the inspiring tangent thoughts spiralling through my mental DNA. No cows, no lions fornicating, not even any barking dogs. (But there was a Wood Owl hooting.)
Initially, I was a little disappointed I hadn’t seen anything inexplicable, but I got over myself and expectation to always see fairies. There is a bliss in just being present (and stoned)!
When I was ready to exit the deck space, I yelled silently to myself and anyone reading my mind, “Goodnight Sky! Thank you stars for shining! Thank you planets for showing yourselves! Blessings to all the conscious beings in the Universe!”
I wasn’t prepared for what happened next. I wasn’t sure if I should run inside to get my smartphone or just watch.
An orb, a little bigger than the average star, manifested directly above my head, star-height, as far as my perception could guess. Then it disappeared after two seconds. Another one appeared in the same vicinity, and disappeared. I couldn’t tell if it was the same one reappearing in an astral (wormhole) jump, or other orbs were taking turns to greet me, because there were more, probably five in total.
How the f*!k did they hear me?
Is the sky conscious?
Does my being extend to the stars?
It felt like I was inside a lucid dream. The world was alive and acknowledging my blessings instantaneously. What impeccable manners!
I understand everything in my dream world is an extension of my consciousness. When I’m lucid I can interact with any of my dream elements and ask for meaning. There are no limits, only my imagination and unconscious beliefs.
But what is happening now?!
My reality is transforming into a dream, or the dream sandbox is becoming more real. Synchronistically, this is amazing, since my reading is taking me on a journey into western esotericism to expansive experiences through imagination to include the stars and beyond.
Soon, it’ll be time to call reality the Unreal, and the unreal Reality.
-
 @ 866e0139:6a9334e5
2025-03-24 10:54:12
@ 866e0139:6a9334e5
2025-03-24 10:54:12Vom Schrei nach dem Frieden ist hier die Luft ganz schwer,
Der Friede, der Friede, wo kommt denn der Friede her?
Der kommt nicht vom bloßen Fordern,
Der kommt nur, wenn wir ihn tun,
Und wenn in unseren Seelen die Mörderwaffen ruhn.
Wenn wir Gewalt verweigern, in Sprache, Not und Streit,
Wenn wir als Haltung lieben, Zeit unsrer Lebenszeit.
André Heller (*1947)
Die Lage ist ernst. Es ist so unübersehbar wie skandalös:
- Das "Friedensprojekt" Europäische Union rüstet zum Krieg. Orwell ist längst Realität.
- Im "Nie-Wieder-Krieg"-Land Deutschland prügeln die Kriegstreiber hunderte Milliarden durch einen abgewählten Bundestag, Wahlbetrug inklusive. Wieder mal an vorderster Front mit dabei: Kein Weltkrieg ohne uns!
- Ein Joschka Fischer, der nie gedient hat, außer an den Futtertrögen des Steuerzahlers oder von Transatlantistan, bringt die Wehrpflicht für Männer und Frauen ins Spiel. Gleichberechtigt in den Tod für die Waffenlobby!
- Der Ausnahmezustand hat nie aufgehört, bekommt nur ein neues Gesicht: die Fratze von Krieg, Tod und Leid. Corona ist abmoderiert. Das neue Virus heißt Russland, der Impfstoff „slava ukraini“, und auch bei der Finanzierung bleibt alles gleich: die Zeche zahlen (wieder mal) Sie. Diesmal doppelt. Sie dürfen zahlen und sterben, das Sonderopfer für jede Politikverwirrung zahlt in “Unserer Demokratie” immer der angebliche Souverän, der vom Nutztier jederzeit zum Schlachttier gemacht werden kann.
- Was jetzt kommt, kennen Sie schon von der Corona-Generalprobe: Spaltung, Diffamierung, Propaganda, Zensur, irre Milliardenausgaben, Ausnahmezustand, Kriegswirtschaft, Kriegszustand. Volksvertreter und Lobbyisten können sich jetzt straffrei eine goldene Nase verdienen, wenn sie ihre Wähler in die Bajonette laufen lassen. Die Strack-Zimmermanns und Kiesewetters sind die Lauterbachs und Dahmens im Tarnfleck, und sie werden bis zum letzten Wähler mutig „für das Gute“ kämpfen. Wie sich die Bilder doch gleichen:
Nicht mit uns: Erheben wir jetzt die Stimme für den Frieden!
Machen wir den Kriegstreibern einen Strich durch die Rechnung! Bringen wir die Stimmen für den Frieden an einen Tisch! Wir lassen die Friedenstaube fliegen, die erste unzensierbare Friedenspublikation der Welt auf Nostr und Pareto.
Die Vielfalt an Themen ist groß. Wir wollen aufklären und informieren:
Über Diplomatie und Strategien für den Frieden; über Lügen, Propaganda und Manipulation; über Verschwendung, Völkerrechtsbrüche und Kriegsverbrechen. Wir nehmen kein Blatt vor den Mund, egal ob hybride Kriegsführung, kognitive Kriegsführung oder sonstige neuartige Methoden der Kriegsführung. Wir wollen die Friedenswilligen vereinen und der Friedensbewegung eine starke Stimme verleihen, quer durch alle Lager. Wer auch immer jetzt das Lied vom Tod anstimmt, wird es unter den kritischen Augen der Öffentlichkeit machen müssen.
Warum wir?
- Wir haben die unzensierbare Technologie, um eine nachhaltige Publikation als Autorenblog und Newsletter aufzubauen. Diese brauchen wir auch, wir haben aus der Corona-Zensur unsere Lektion gelernt (https://pareto.space/read).

-
Wir können alle Formate bedienen, von Text, Bild und Podcast bis Video und Stream.
-
Wir werden online und in Print stattfinden (wenn Sie das wollen).
- Wir sind eine Gruppe von Autoren mit Reichweite, Erfahrung und Impact. Wir werden eine Kernredaktion haben und auf viele freie Autoren setzen, auch aus dem Ausland. Erste Kontakte sind hergestellt, das Feedback ist überwältigend.
- Wir setzen zudem von Anfang an auch auf Bürgerjournalismus und wollen jeder Stimme für den Frieden Raum und Platz bieten. Auch Sie können auf unserer freien Tribüne ("Weltbühne") publizieren und gelesen werden. Jede Stimme für den Frieden zählt!
Ich will Sie nicht mit Name dropping blenden, freue mich jedoch über bekannte erstklassige Stimmen aus der kritischen Szene, die bereits ihre Mitwirkung zugesagt haben. Diese Liste wird ständig aktualisiert (und auch ich werde Texte beitragen):
- Dr. Ulrike Guérot
- Mathias Bröckers
- Dr. Daniele Ganser
- Tom-Oliver Regenauer
- Prof. Dr. Michael Meyen
- Jonas Tögel
- Jürgen Müller
- uvm.
Sie sind Autor und wollen mit dabei sein? Schreiben Sie uns an: milosz@pareto.space

Jetzt abonnieren! Holen Sie sich die neusten Artikel der Friedenstaube in Ihr Postfach indem Sie HIER klicken.
Gründen wir eine Genossenschaft! Wir sind bereit – und Sie?
Sie entscheiden, ob und wie hoch die Friedenstaube fliegt. Wir werden eine Publikationsgenossenschaft gründen. Die Friedenstaube soll allen und niemandem gehören. Denn auch der Friede gehört allen, die ihn wollen. Krieg dagegen will immer nur eine Minderheit, am liebsten diejenigen, die nicht an die Front gehen.
Die Kriegsmaschine wird mit hunderten Milliarden geschmiert – und das ist nur der Anfang. Wir glauben, dass das Wort mächtiger ist als das Schwert. Für die Genossenschaft sammeln wir mindestens 100 000 CHF, die den Redaktionsbetrieb für ein Jahr sichern sollen. Mit einem Genossenschaftsanteil zu 1000 CHF sind Sie automatisch Verleger und bestimmen mit. Pro Person können maximal 20 Anteile gezeichnet werden, jeder Genossenschafter hat immer nur eine Stimme.
- Für 50 CHF bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
 Für Einzahlungen in Euro:
Für Einzahlungen in Euro:Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Das gilt auch für Unterstützungen jenseits finanzieller Zuwendungen. Wir sind für jede Unterstützung dankbar, die hilft, das Projekt zu realisieren. Wir planen auch Printprodukte, Übersetzungen in andere Sprachen, Ausschreibungen und Wettbewerbe zum Thema Frieden uvm. Seien Sie von Anfang an mit dabei: Als Autor, Mitwirkender, Genossenschafter oder in welcher Rolle sie auch immer hilfreich zu sein glauben.
Ich kann Ihnen keine Wunder versprechen aber Sie dürfen mich an meinen bisherigen Projekten messen. Wenn ich etwas angehe, mache ich es mit voller Kraft:
Mit Ihrer Unterstützung war schon vieles möglich:
- Sie haben den “Appell für freie Debattenräume” zum sichtbarsten Zeichen gegen Cancel Culture in Europa gemacht.
- Sie haben gehofen, die Freischwebende Intelligenz zu einem der führenden Substack-Newsletter in Europa zu machen
- Sie haben “Pandamned” unterstützt, eine Corona-Doku, die mehr als 1 Mio. Menschen gesehen haben.
- Sie haben die Realisierung von Pareto unterstützt und uns geholfen, ein unzensierbares Werkzeug für Blogging/Newsletter zu bauen, weltweit einmalig.
Lassen Sie uns jetzt gemeinsam die Friedenstaube zur führenden Friedenspublikation der freien Welt aufbauen.
Lassen wir die Friedenstaube fliegen!
Jetzt.
 Herzlichen Dank, dass Sie meine Arbeit unterstützen!
Herzlichen Dank, dass Sie meine Arbeit unterstützen!Ich kann Ihnen auch manuell einen Zugang zur Publikation einrichten, wenn Sie lieber per Paypal, Überweisung oder Bitcoin (einmal Jahresbeitrag, ewiger Zugang) bezahlen. Sie erreichen mich unter kontakt@idw-europe.org
-
 @ 866e0139:6a9334e5
2025-03-24 10:51:52
@ 866e0139:6a9334e5
2025-03-24 10:51:52Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Seit Sonntag (zu allem Glück auch noch meinem 45. Geburtstag) ist bei mir noch ein bisschen mehr los als sonst – und das liegt an Ihnen. Der Aufruf zur Gründung der „Friedenstaube“, einer unzensierbaren Friedenspublikation mit bekannten Stimmen aus der kritischen Szene, der Friedensbewegung und von Bürgerjournalisten ist bei Ihnen auf mehr als nur offene Ohren gestoßen! Ich bin regelrecht geplättet von den vielen Reaktionen, die ich noch gar nicht alle beantworten konnte.
Ich danke Ihnen herzlich für das Vertrauen in mich (auch wenn ich natürlich stark auf die Autoren angewiesen bin) und die überwältigenden Reaktionen: Es sind hunderte Abonnements für den Newsletter eingegangen, darunter einige bezahlte Abos und Förderabos und auch die ersten Genossenschaftsanteile wurden gezeichnet! Was mich besonders freut: Gut zehn weitere freiwillige Autoren wollen mitmachen und arbeiten bereits an den ersten Texten. Damit darf ich schon jetzt verkünden, dass die Genossenschaft definitiv gegründet werden kann, die Friedenstaube wird fliegen. Wie hoch und wie weit, das liegt dann nun nur noch in unser aller Hände.
Der Anfang ist jedenfalls gemacht. Die nächsten Wochen werden besonders arbeitsintensiv, ich bitte Sie um etwas Geduld: Aufbau einer Kernredaktion, Organisation der Abläufe, technologische Entwicklungsarbeiten, Genossenschaftsgründung etc. stehen jetzt auf der Agenda. Mit Tom-Oliver Regenauer darf ich den ersten Autor im redaktionellen Kernteam verkünden, der sich nicht nur große Verdienste im Schreiben erarbeitet hat (siehe u.a. sein Buch Hopium) sondern auch über Managementerfahrung verfügt; mit weiteren helfenden Händen bin ich im Gespräch.
Ich freue mich auf die (auch für mich) neue Erfahrung, quasi aus dem Nichts eine Publikation mit Redaktionsbetrieb und freien Autoren auf einer gänzlich neuen technologischen Infrastruktur aufzubauen. Es wäre illusorisch zu glauben, dass alles glatt gehen wird, denn wir starten quasi „on the go“, aber im Fall von Frieden oder Krieg gilt es, keine Zeit verstreichen zu lassen. Ich arbeite nach dem Motto „Tun, statt reden; zeigen, statt ankündigen; liefern, statt versprechen“.
Die ersten Texte zum Thema Frieden sind bereits publiziert, ein halbwegs geordneter Betrieb sollte ab April realistisch sein. Die Liste der Autoren wird regelmäßig aktualisiert, schauen Sie gerne hier (oder noch besser: hier) immer wieder herein. Dort finden Sie auch noch mal alle Infos, wenn Sie die Friedenstaube unterstützen wollen. Ab 1000 Euro/CHF werden Sie Genossenschafter, also Verleger!**
Auch an die bisherigen Unterstützer des Pareto-Projekts, der technologischen Basis der Friedenstaube, will ich hiermit schon etwas zurückgeben: Alle Spender für Pareto werden die Friedenstaube immer kostenlos lesen können. Sie, die Leser dieser Publikation haben die technologische Basis mit aufgebaut, die uns zur weltweit ersten, zensursicheren Friedenspublikation macht. Uns Autoren steht damit ein kompetentes Support-Team von inzwischen über zehn Entwicklern (und weiteren Helfern) an der Seite, welche die Friedenstaube am Fliegen halten werden.
Kontaktieren Sie mich gerne zu allen Fragen (je kürzer die Mail, desto früher kommt die Antwort): milosz\@pareto.space oder kontakt\@idw-europe.org
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Was bewegt mich beim Thema Krieg und Frieden?
Erlauben Sie mir einen kurzen persönlichen Prolog: Ich stamme aus Schlesien. Mein Urgroßvater kämpfte im I. Weltkrieg bei Verdun. Mein Großvater wurde in die Wehrmacht eingezogen, kämpfte im Partisanenkrieg in Jugoslawien, verlor Hand und Auge. Ein Bruder meiner Großmutter entzog sich und landete in Dachau. Ich kenne meine Familiengeschichte nur in groben Umrissen, vielen wird es ähnlich gehen. Einige meiner schlesischen Vorfahren waren später vor allem Lokführer. Aufgrund der bewegten schlesischen Geschichte wechselten sie mehrfach die Uniform. Die Tätigkeit und Fahrstrecke blieb die gleiche. Für wen oder was kämpften sie in Kriegen in welchen Uniformen? Vermutlich wussten sie es selbst nicht.
Auch ich könnte heute nicht genau sagen, welche Interessen und Mächte die Kriegsmaschinerie bedienen. Doch ich wüsste es gerne und Sie vielleicht auch. Kämpfen ohne letztlich zu wissen für wen und warum: Wozu? Krieg simuliert Sinn und Notwendigkeit und lässt einen am Ende mit den großen Fragen allein, ahnungslos gestorben im Schützengraben. Zivilisatorisch ist das ein Offenbarungseid.
Bin ich ein totaler Anti-Militarist? Ich glaube nicht. Ich habe nichts gegen die Idee privaten Waffenbesitzes. Ich kann der Idee der Landesverteidigung durchaus etwas abgewinnen. Den Wehrdienst habe ich bewusst nicht verweigert. Ich wollte die Erfahrung machen. Hier schreibt also auch ein Obergefreiter a. D. eines bayerischen Gebirgspionierbataillons bei Rosenheim mit bronzener Schützenschnur, der am MG durchaus treffsicher war. Aber eben auch jemand, den der Wehrdienst zum Teil-Pazifisten gemacht hat. Mir war nach dem Grundwehrdienst klar: Wir sind eine Gurkentruppe, reines Kanonenfutter. 20-jährige Grünschnäbel mit zu viel Testosteron und Hollywood in den Gliedern, aber wenig Ahnung.
Ich war also einer, der sich verlässlich mit anderen beim Orientierungslauf im Wald verirrte; einer, der mit anderen übermüdet beim ersten Wachdienst einpennte (und damit im Ernstfall den Tod im Schlaf kennengelernt hätte, denn just erfolgte ein simulierter „Angriff“); einer, der auch mal übernächtigt sein Gewehr vor dem Zelt vergaß (wir sollten dem G3 den Namen unserer damaligen Freundin geben – wie pervers – ich vergaß also „Petra“ vor dem Zelt) und schließlich einer, der die meiste Zeit des Dienstes fürs Vaterland letztlich mit dem Servieren von Getränken und Schinkennudeln im Offizierskasino verbrachte und die institutionalisierten Alkoholiker der Bundeswehr bei Laune hielt („it ain’t much, but it was honest work“).
Anders gesagt: Krieg – spätestens seitdem: ohne mich. Auch wenn ich gerne Ernst Jünger lese und zitiere (er war einfach ein großartiger Chronist und lebendiger Geist), seinen abenteuerlustigen Militarismus kreide ich ihm an und rufe ihm posthum hinterher: man muss nicht erst einen Sohn im Krieg verloren haben, um zum Pazifisten zu werden.
Weitere Störgefühle tauchten auf: In meiner Dissertation durfte ich mich u.a. mit philosophischen Theorien zum Gesellschaftsvertrag (u.a. Kant, Rousseau, Locke und Hobbes sind hier zu nennen) beschäftigen. Dies brachte mein Staatsverständnis gerade bei der Kriegsfrage noch mehr durcheinander. Wenn Mindestziel der Staatsgründung innere und äußere Sicherheit sind, aber letztlich nicht der Staat den Bürger, sondern der Bürger den Staat schützt, wozu sich dann eine Schutzmacht erfinden, die einen am Ende durch den Fleischwolf jagt? Hobbes setzte zumindest auf Söldner.
Kriege werden mit Lügen begonnen, wusste Julian Assange. Können Sie mit Wahrheit beendet oder gar verhindert werden? Seit Walter Lippmanns „Liberty and the News“ von 1920 weiß man spätestens, dass gesicherte Information im Krieg das seltenste Gut ist. Sagt Lippmann als oberster Mainstream-Journalist und Einflüsterer der Mächtigen. Jeder Journalist muss hier ein Störgefühl entwickeln, der Leser noch mehr. Der Journalist der Nachrichtenagentur ist selten im Geschehen sondern wird vom heimischen Militär gebrieft, sein Bericht landet dann in den Newstickern und Redaktionen. Die Kriegsmaschinerie produziert also auch ihre eigene Sicht auf die Dinge, die sie den Bürgern als die Realität verkauft.
Kein Wunder, dass jede abweichende Information massiv bekämpft werden muss. Im Krieg ist Zweifel gleich Verrat, quasi unsolidarisches Sektierertum und Wehrkraftzersetzung, wenn nicht Feindbegünstigung. Der kritische Journalist steht in Ausnahmezuständen, wie man schon bei Corona sehen konnte, automatisch aus Staatssicht im Lager des Feindes und wird entsprechend behandelt. Zensursicheres Publizieren ist dann nicht nur ein nettes feature, sondern notwendige Basisvoraussetzung. Vor kurzem war Twitter/X nicht mehr zugänglich wegen massiven Cyberattacken. Wenn dann noch Rundfunk und Presse auf der Propagandawelle surfen und die Plattformzensur wieder zuschlägt, wird das Angebot schnell dünn.
Wem aber dient Zensur und Propaganda? Die aktuelle Lage im Russland-Ukraine-Konflikt ist auch Gelegenheit, um zu zeigen: Es sind eben nicht nur staatliche Interessen, die hier verhandelt werden, sondern es muss (wieder mal) eine andere Entität mit am Tisch sitzen, man nenne sie Deep State oder wie auch immer. Europäische Eliten dienen offensichtlich Fremdinteressen, wenn sie mit Aufrüstungsplänen Volksvermögen verspekulieren oder darin (wie von der Leyen) ein notwendiges „Investment“ sehen. Von wem werden wir letztlich regiert? Auch diesem Themen-Komplex werde ich mich in der Friedenstaube nähern.
Es gibt viel zu tun, aber für mich ist klar: Frieden ist ohne Wahrheit nicht zu bekommen, deshalb ist Wahrheitssuche auch immer Friedenssuche, wie Wahrheitsliebe letztlich Friedensliebe ist.
Gerade fallen auch im Mainstream die Corona-Lügen zur Labortheorie in sich zusammen, fünf Jahre nach Ausrufung der Pandemie. Der Frieden hat nur eine Chance, wenn es uns gelingt, die Lügen nun möglichst synchron zu den Geschehnissen aufzudecken und zu dokumentieren.
Das ist mein persönlicher Wunsch, mit dem ich die Friedenstaube fliegen lasse.
Was ist Ihrer? Schreiben Sie es gerne in die Kommentare. Welche Erwartungen, Wünsche haben Sie an uns? Liebe Autoren: Was ist euer Beweggrund, für den Frieden zur Feder zu greifen?
Zeichnen Sie jetzt “Friedensanleihen”. Werden Sie Genossenschafter und Verleger der Friedenstaube ab 1000 Euro/CHF. Es können mehrere Anteile pro Person gezeichnet werden, es bleibt bei einem Stimmrecht pro Kopf. milosz\@pareto.space
P.S: Mit diesem Text testen wir die Newsletterfunktion erstmals an mehrere Hundert Mailadressen. Wenn Sie die Friedenstaube abonniert haben, sollten Sie diesen Artikel per Mail bekommen haben.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?* Die* Relai-App ist Europas erfolgreichste Bitcoin-App.* Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Pareto has started a crowdfunding campaign on Geyser. We were in the Top 3 in February, thank you for the support!
-
 @ 866e0139:6a9334e5
2025-03-24 10:50:59
@ 866e0139:6a9334e5
2025-03-24 10:50:59Autor: Ludwig F. Badenhagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Einer der wesentlichen Gründe dafür, dass während der „Corona-Pandemie“ so viele Menschen den Anweisungen der Spitzenpolitiker folgten, war sicher der, dass diese Menschen den Politikern vertrauten. Diese Menschen konnten sich nicht vorstellen, dass Spitzenpolitiker den Auftrag haben könnten, die Bürger analog klaren Vorgaben zu belügen, zu betrügen und sie vorsätzlich (tödlich) zu verletzen. Im Gegenteil, diese gutgläubigen Menschen waren mit der Zuversicht aufgewachsen, dass Spitzenpolitiker den Menschen dienen und deren Wohl im Fokus haben (müssen). Dies beteuerten Spitzenpolitiker schließlich stets in Talkshows und weiteren Medienformaten. Zwar wurden manche Politiker auch bei Fehlverhalten erwischt, aber hierbei ging es zumeist „nur“ um Geld und nicht um Leben. Und wenn es doch einmal um Leben ging, dann passieren die Verfehlungen „aus Versehen“, aber nicht mit Vorsatz. So oder so ähnlich dachte die Mehrheit der Bürger.
Aber vor 5 Jahren änderte sich für aufmerksame Menschen alles, denn analog dem Lockstep-Szenario der Rockefeller-Foundation wurde der zuvor ausgiebig vorbereitete Plan zur Inszenierung der „Corona-Pandemie“ Realität. Seitdem wurde so manchem Bürger, der sich jenseits von Mainstream-Medien informierte, das Ausmaß der unter dem Vorwand einer erfundenen Pandemie vollbrachten Taten klar. Und unverändert kommen täglich immer neue Erkenntnisse ans Licht. Auf den Punkt gebracht war die Inszenierung der „Corona-Pandemie“ ein Verbrechen an der Menschheit, konstatieren unabhängige Sachverständige.
Dieser Beitrag befasst sich allerdings nicht damit, die vielen Bestandteile dieses Verbrechens (nochmals) aufzuzählen oder weitere zu benennen. Stattdessen soll beleuchtet werden, warum die Spitzenpolitiker sich so verhalten haben und ob es überhaupt nach alledem möglich ist, der Politik jemals wieder zu vertrauen? Ferner ist es ein Anliegen dieses Artikels, die weiteren Zusammenhänge zu erörtern. Und zu guter Letzt soll dargelegt werden, warum sich der große Teil der Menschen unverändert alles gefallen lässt.
Demokratie
Von jeher organisierten sich Menschen mit dem Ziel, Ordnungsrahmen zu erschaffen, welche wechselseitiges Interagieren regeln. Dies führte aber stets dazu, dass einige wenige alle anderen unterordneten. Der Grundgedanke, der vor rund 2500 Jahren formulierten Demokratie, verfolgte dann aber das Ziel, dass die Masse darüber entscheiden können soll, wie sie leben und verwaltet werden möchte. Dieser Grundgedanke wurde von den Mächtigen sowohl gehasst als auch gefürchtet, denn die Gefahr lag nahe, dass die besitzlosen Vielen beispielsweise mit einer schlichten Abstimmung verfügen könnten, den Besitz der Wenigen zu enteignen. Selbst Sokrates war gegen solch eine Gesellschaftsordnung, da die besten Ideen nicht durch die Vielen, sondern durch einige wenige Kluge und Aufrichtige in die Welt kommen. Man müsse die Vielen lediglich manipulieren und würde auf diese Weise quasi jeden Unfug umsetzen können. Die Demokratie war ein Rohrkrepierer.
Die Mogelpackung „Repräsentative Demokratie“
Erst im Zuge der Gründung der USA gelang der Trick, dem Volk die „Repräsentative Demokratie“ unterzujubeln, die sich zwar nach Demokratie anhört, aber mit der Ursprungsdefinition nichts zu tun hat. Man konnte zwischen zwei Parteien wählen, die sich mit ihren jeweiligen Versprechen um die Gunst des Volkes bewarben. Tatsächlich paktierten die Vertreter der gewählten Parteien (Politiker) aber mit den wirklich Mächtigen, die letztendlich dafür sorgten, dass diese Politiker in die jeweiligen exponierten Positionen gelangten, welche ihnen ermöglichten (und somit auch den wirklich Mächtigen), Macht auszuüben. Übrigens, ob die eine oder andere Partei „den Volkswillen“ für sich gewinnen konnte, war für die wirklich Mächtigen weniger von Bedeutung, denn der Wille der wirklich Mächtigen wurde so oder so, wenn auch in voneinander differierenden Details, umgesetzt.
Die Menschen waren begeistert von dieser Idee, denn sie glaubten, dass sie selbst „der Souverän“ seien. Schluss mit Monarchie sowie sonstiger Fremdherrschaft und Unterdrückung.
Die Mächtigen waren ebenfalls begeistert, denn durch die Repräsentative Demokratie waren sie selbst nicht mehr in der Schusslinie, weil das Volk sich mit seinem Unmut fortan auf die Politiker konzentrierte. Da diese Politiker aber vielleicht nicht von einem selbst, sondern von vielen anderen Wahlberechtigten gewählt wurden, lenkte sich der Groll der Menschen nicht nur ab von den wirklich Mächtigen, sondern auch ab von den Politikern, direkt auf „die vielen Idioten“ aus ihrer eigenen Mitte, die sich „ver-wählt“ hatten. Diese Lenkung des Volkes funktionierte so hervorragend, dass andere Länder die Grundprinzipien dieses Steuerungsinstrumentes übernahmen. Dies ist alles bei Rainer Mausfeld nachzulesen.
Ursprünglich waren die Mächtigen nur regional mächtig, sodass das Führen der eigenen Menschen(vieh)herde eher eine lokale Angelegenheit war. Somit mussten auch nur lokale Probleme gelöst werden und die Mittel zur Problemlösung blieben im eigenen Problembereich.
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Beherrschungsinstrumente der globalen Massenhaltung
Im Zuge der territorialen Erweiterungen der „Besitzungen“ einiger wirklich Mächtiger wurden die Verwaltungs- und Beherrschungsinstrumente überregionaler. Und heute, zu Zeiten der globalen Vernetzung, paktieren die wirklich Mächtigen miteinander und beanspruchen die Weltherrschaft. Längst wird offen über die finale Realisierung einen Weltregierung, welche die Nationalstaaten „nicht mehr benötigt“, gesprochen. Dass sich Deutschland, ebenso wie andere europäische Staaten, der EU untergeordnet hat, dürfte auch Leuten nicht entgangen sein, die sich nur über die Tagesschau informieren. Längst steht das EU-Recht über dem deutschen Recht. Und nur kurze Zeit ist es her, als die EU und alle ihre Mitgliedsstaaten die WHO autonom darüber entscheiden lassen wollten, was eine Pandemie ist und wie diese für alle verbindlich „bekämpft“ werden soll. Eine spannende Frage ist nun, wer denn über der EU und der WHO sowie anderen Institutionen steht?
Diese Beschreibung macht klar, dass ein „souveränes Land“ wie das unverändert von der amerikanischen Armee besetzte Deutschland in der Entscheidungshierarchie an die Weisungen übergeordneter Entscheidungsorgane gebunden ist. An der Spitze stehen - wie kann es anders sein - die wirklich Mächtigen.
Aber was nützt es dann, Spitzenpolitiker zu wählen, wenn diese analog Horst Seehofer nichts zu melden haben? Ist das Wählen von Politikern nicht völlig sinnlos, wenn deren Wahlversprechen ohnehin nicht erfüllt werden? Ist es nicht so, dass die Menschen, welche ihre Stimme nicht behalten, sondern abgeben, das bestehende System nur nähren, indem sie Wahlergebnisse akzeptieren, ohne zu wissen, ob diese manipuliert wurden, aber mit der Gewissheit, dass das im Zuge des Wahlkampfes Versprochene auf keinen Fall geliefert wird? Aktive Wähler glauben trotz allem an die Redlichkeit und Wirksamkeit von Wahlen, und sie akzeptieren Wahlergebnisse, weil sie denken, dass sie von „so vielen Idioten, die falsch wählen“, umgeben sind, womit wir wieder bei der Spaltung sind. Sie glauben, der Stand des aktuellen Elends sei „selbst gewählt“.
Die Wahl der Aufseher
Stellen Sie sich bitte vor, Sie wären im Gefängnis, weil Sie einen kritischen Artikel mit „gefällt mir“ gekennzeichnet haben oder weil Sie eine „Kontaktschuld“ trifft, da in Ihrer Nachbarschaft ein „verschwörerisches Symbol“ von einem „aufmerksamen“ Nachbarn bei einer „Meldestelle“ angezeigt wurde oder Sie gar eine Tat, „unterhalb der Strafbarkeitsgrenze“ begangen hätten, dann würden Sie möglicherweise mit Maßnahmen bestraft, die „keine Folter wären“. Beispielsweise würde man Sie während Ihrer „Umerziehungshaft“ mit Waterboarding, Halten von Stresspositionen, Dunkelhaft etc. dabei „unterstützen“, „Ihre Verfehlungen zu überdenken“. Stellen Sie sich weiterhin vor, dass Sie, so wie alle anderen Inhaftierten, an der alle vier Jahre stattfindenden Wahl der Aufseher teilnehmen könnten, und Sie hätten auch einen Favoriten, der zwar Waterboarding betreibt, aber gegen alle anderen Maßnahmen steht. Sie hätten sicher allen Grund zur Freude, wenn Sie Ihren Kandidaten durchbringen könnten, oder? Aber was wäre, wenn der Aufseher Ihrer Wahl dann dennoch alle 3 „Nicht-Folter-Maßnahmen“ anwenden würde, wie sämtliche anderen Aufseher zuvor? Spätestens dann müssten Sie sich eingestehen, dass es der Beruf des Aufsehers ist, Aufseher zu sein und dass er letztendlich tut, was ihm „von oben“ aufgetragen wird. Andernfalls verliert er seinen Job. Oder er verunfallt oder gerät in einen Skandal etc. So oder so, er verliert seinen Job - und den erledigt dann ein anderer Aufseher.
Die Wahl des Aufsehers ändert wenig, solange Sie sich im System des Gefängnisses befinden und der Aufseher integraler Bestandteil dieses Systems ist. Zur Realisierung einer tatsächlichen Änderung müssten Sie dort herauskommen.
Dieses Beispiel soll darstellen, dass alles in Hierarchien eingebunden ist. Die in einem System eingebundenen Menschen erfüllen ihre zugewiesenen Aufgaben, oder sie werden bestraft.
Das aktuelle System schadet dem Volk
Auch in der staatlichen Organisation von Menschen existieren hierarchische Gliederungen. Eine kommunale Selbstverwaltung gehört zum Kreis, dieser zum Land, dieses zum Staat, dieser zur EU, und diese - zu wem auch immer. Und vereinnahmte Gelder fließen nach oben. Obwohl es natürlich wäre, dass die Mittel dorthin fließen, wo sie der Allgemeinheit und nicht einigen wenigen dienen, also nach unten.
Warum muss es also eine Weltregierung geben? Warum sollen nur einige Wenige über alle anderen bestimmen und an diesen verdienen (Nahrung, Medikamente, Krieg, Steuern etc.)? Warum sollen Menschen, so wie Vieh, das jemandem „gehört“, mit einem Code versehen und bereits als Baby zwangsgeimpft werden? Warum müssen alle Transaktionen und sämtliches Verhalten strickt gesteuert, kontrolliert und bewertet werden?
Viele Menschen werden nach alledem zu dem Schluss kommen, dass solch ein System nur einigen wenigen wirklich Mächtigen und deren Helfershelfern nützt. Aber es gibt auch eine Gruppe Menschen, für die im Land alles beanstandungsfrei funktioniert. Die Spaltung der Menschen ist perfekt gelungen und sofern die eine Gruppe darauf wartet, dass die andere „endlich aufwacht“, da die Fakten doch auf dem Tisch liegen, so wird sie weiter warten dürfen.
Julian Assange erwähnte einst, dass es für ihn eine unglaubliche Enttäuschung war, dass ihm niemand half. Assange hatte Ungeheuerlichkeiten aufgedeckt. Es gab keinen Aufstand. Assange wurde inhaftiert und gefoltert. Es gab keinen Aufstand. Assange sagte, er hätte nicht damit gerechnet, dass die Leute „so unglaublich feige“ seien.
Aber womit rechnete er den stattdessen? Dass die Massen „sich erheben“. Das gibt es nur im Film, denn die Masse besteht aus vielen maximal Indoktrinierten, die sich wie Schafe verhalten, was als Züchtungserfolg der Leute an den Schalthebeln der Macht und deren Herren, den wirklich Mächtigen, anzuerkennen ist. Denn wer mächtig ist und bleiben möchte, will sicher keine problematischen Untertanen, sondern eine gefügige, ängstliche Herde, die er nach Belieben ausbeuten und steuern kann. Wenn er hierüber verfügt, will er keinen Widerstand.
Ob Corona, Krieg, Demokratie- und Klimarettung oder Meinungsäußerungsverbote und Bürgerrechte, die unterhalb der Strafbarkeitsgrenze liegen, all diese und viele weitere Stichworte mehr sind es, die viele traurig und so manche wütend machen.
Auch das Mittel des Demonstrierens hat sich als völlig wirkungslos erwiesen. Die vielen gruseligen Videoaufnahmen über die massivsten Misshandlungen von Demonstranten gegen die Corona-Maßnahmen führen zu dem Ergebnis, dass die Exekutive ihr Gewaltmonopol nutzt(e), um die Bevölkerung gezielt zu verletzen und einzuschüchtern. Bekanntlich kann jede friedliche Demonstration zum Eskalieren gebracht werden, indem man Menschen in die Enge treibt (fehlender Sicherheitsabstand) und einige V-Leute in Zivil mit einschlägigen Flaggen und sonstigen „Symbolen“ einschleust, die für Krawall sorgen, damit die gepanzerten Kollegen dann losknüppeln und die scharfen Hunde zubeißen können. So lauten zumindest die Berichte vieler Zeitzeugen und so ist es auch auf vielen Videos zu sehen. Allerdings nicht im Mainstream.
Dieses Vorgehen ist deshalb besonders perfide, weil man den Deutschen ihre Wehrhaftigkeit aberzogen hat. Nicht wehrfähige Bürger und eine brutale Staatsmacht mit Gewaltmonopol führen zu einem Gemetzel bei den Bürgern.
Ähnliches lässt sich auch in zivilen Lebenssituationen beobachten, wenn die hiesige zivilisierte Bevölkerung auf „eingereiste“ Massenvergewaltiger und Messerstecher trifft, die über ein anderes Gewalt- und Rechtsverständnis verfügen als die Einheimischen.
System-Technik
Die These ist, dass es eine Gruppe von global agierenden Personen gibt, welche das Geschehen auf der Erde zunehmend wirksam zu ihrem individuellen Vorteil gestaltet. Wie sich diese Gruppe definiert, kann bei John Coleman (Das Komitee der 300) und David Icke nachgelesen werden. Hierbei handelt es ich um Autoren, die jahrzehntelang analog streng wissenschaftlichen Grundlagen zu ihren Themen geforscht haben und in ihren jeweiligen Werken sämtliche Quellen benennen. Diese Autoren wurden vom Mainstream mit dem Prädikatsmerkmal „Verschwörungstheoretiker“ ausgezeichnet, wodurch die Ergebnisse Ihrer Arbeiten umso glaubwürdiger sind.
Diese mächtige Gruppe hat mit ihren Schergen nahezu den gesamten Planeten infiltriert, indem sie Personen in führenden Positionen in vielen Belangen größtmögliche Freiheiten sowie Schutz gewährt, aber diesen im Gegenzug eine völlige Unterwerfung bei Kernthemen abfordert. Die Motivatoren für diese Unterwerfung sind, abgesehen von materiellen Zuwendungen, auch „Ruhm und Ehre sowie Macht“. Manchmal wird auch Beweismaterial für begangene Verfehlungen (Lolita-Express, Pizzagate etc.) genutzt, um Forderungen Nachdruck zu verleihen. Und auch körperliche Bestrafungen der betroffenen Person oder deren Angehörigen zählen zum Repertoire der Motivatoren. Letztendlich ähnlich den Verhaltensweisen in einem Mafia-Film.
Mit dieser Methodik hat sich diese mächtige Gruppe im Laufe von Jahrhunderten! eine Organisation erschaffen, welche aus Kirchen, Parteien, Firmen, NGO, Vereinen, Verbänden und weiteren Organisationsformen besteht. Bestimmte Ämter und Positionen in Organisationen können nur von Personen eingenommen und gehalten werden, die „auf Linie sind“.
Die Mitglieder der Gruppe tauchen in keiner Rubrik wie „Die reichsten Menschen der Welt“ auf, sondern bleiben fern der Öffentlichkeit. Wer jemanden aus ihren Reihen erkennt und beschuldigt, ist ein „Antisemit“ oder sonstiger Übeltäter und wird verfolgt und bekämpft. Über mächtige Vermögensverwaltungskonzerne beteiligen sich die Mitglieder dieser Gruppe anonym an Unternehmen in Schlüsselpositionen in einer Dimension, die ihnen wesentlichen Einfluss auf die Auswahl der Topmanager einräumt, sodass die jeweilige Unternehmenspolitik nach Vorgaben der Gruppe gestaltet wird.
Die Gruppe steuert das Geldsystem, von dem sich der Planet abhängig zu sein wähnt. Hierzu eine Erläuterung: Ein Staat wie Deutschland ist bekanntlich maximal verschuldet. Man stelle sich vor, ein unliebsamer Politiker würde entgegen sämtlicher „Brandmauern“ und sonstiger Propaganda und Wahlmanipulationen gewählt, das Land zu führen, dann könnte dieser keine Kredit über 500 Mrd. Euro bei der nächsten Sparkasse beantragen, sondern wäre auf die Mächtigen dieser Welt angewiesen. Jeder weiß, dass Deutschland als Staat kein funktionierendes Geschäftsmodell hat und somit nicht in der Lage ist, solch ein Darlehen zurückzuzahlen. Welche Motivation sollte also jemand haben, einem Land wie Deutschland so viel Geld ohne Aussicht auf Rückführung zu geben? Es leuchtet ein, dass dieser Politiker andere Gefälligkeiten anbieten müsste, um das Darlehen zu bekommen. Im Falle einer Weigerung zur Kooperation könnte der Staatsapparat mit seinen Staatsdienern, Bürgergeld- und Rentenempfänger etc. nicht mehr bezahlt werden und dieser Politiker wäre schnell wieder weg. Er würde medial hingerichtet. Es ist somit davon auszugehen, dass ein Spitzenpolitiker dieser Tage nicht über viele Optionen verfügt, denn er übernimmt eine Situation, die von seinen Vorgängern erschaffen wurde. Trotz alledem darauf zu hoffen, dass es einen anderen Politiker geben könnte, mit dem dann alles wieder gut wird, mutet ziemlich infantil an.
Dass ein Großteil der Medien von Zuwendungen abhängig ist, dürfte ebenfalls leicht nachzuvollziehen sein, denn der gewöhnliche Bürger zahlt nichts für den Content der MSM. Abhängig davon, von wem (Regierung, Philanthrop, Konzern etc.) ein Medium am Leben gehalten wird, gestalten sich auch dessen Inhalte. Und wenn angewiesen wird, dass ein Politiker medial hingerichtet werden soll, dann bedient die Maschinerie das Thema. Man beobachte einfach einmal, dass Politiker der Kartell-Parteien völlig anders behandelt werden als solche jenseits der „Brandmauer“. Und der Leser, der solche Auftragsarbeiten kostenlos liest, ist der Konsument, für dessen Indoktrination die Finanziers der Verlage gerne zahlen. Mittlerweile kann durch die Herrschaft über die Medien und die systematische Vergiftung der Körper und Geister der Population die öffentliche Meinung gesteuert werden. Die überwiegende Zahl der Deutschen scheint nicht mehr klar denken zu können.
Wer sich das aktuelle Geschehen in der deutschen Politik mit klarem Verstand ansieht, kommt nicht umhin, eine Fernsteuerung der handelnden Politiker in Betracht zu ziehen. Aber was soll daran verwundern? Sind es deshalb „böse Menschen“? Sind die in „Forschungslaboren“ arbeitenden Quäler von „Versuchstieren“ böse Menschen? Sind der Schlächter, der Folterer und der Henker böse Menschen? Oder der knüppelnde Polizist? Es handelt sich zunächst einmal um Personen, die einen Vorteil dadurch haben, Ihrer Tätigkeit nachzugehen. Sie sind integrale Bestandteile eines Belohnungssystems, welches von oben nach unten Anweisungen gibt. Und wenn diese Anweisungen nicht befolgt werden, führt dies für den Befehlsverweigerer zu Konsequenzen.
Der klare Verstand
Es ist nun eine spannende Frage, warum so viele Menschen sich solch eine Behandlung gefallen lassen? Nun, das ist relativ einfach, denn das angepasste Verhalten der Vielen ist nichts anderes als ein Züchtungserfolg der Wenigen.
Die Psyche der Menschen ist ebenso akribisch erforscht worden wie deren Körperfunktionen. Würden die Menschen von den wirklich Mächtigen geliebt, dann würde genau gewusst, wie sie zu behandeln und mit ihren jeweiligen Bedürfnissen zu versorgen sind. Stattdessen werden die Menschen aber als eine Einnahmequelle betrachtet. Dies manifestiert sich exemplarisch in folgenden Bereichen:
- Das Gesundheitssystem verdient nichts am gesunden Menschen, sondern nur am (dauerhaft) kranken, der um Schmerzlinderung bettelt. Bereits als Baby werden Menschen geimpft, was die jeweilige Gesundheit (mit Verweis auf die Werke von Anita Petek-Dimmer u. a.) nachhaltig negativ beeinflusst. Wer hat denn heute keine Krankheiten? Die „Experten“ des Gesundheitssystems verteufeln Vitamin D, Vitamin C, Lithium, die Sonne, Natur etc. und empfehlen stattdessen Präparate, die man patentieren konnte und mit denen die Hersteller viel Geld verdienen. Die Präparate heilen selten, sondern lindern bestenfalls zuvor künstlich erzeugte Leiden, und müssen oftmals dauerhaft eingenommen werden. Was ist aus den nicht Geimpften geworden, die alle sterben sollten? Sind diese nicht die einzigen Gesunden dieser Tage? Ist nicht jeder Geimpfte entweder permanent krank oder bereits tot? Abgesehen von denen, welche das Glück hatten, „Sonderchargen“ mit Kochsalz zu erhalten. \ \ Wem gehören die wesentlichen Player im Gesundheitswesen zu einem erheblichen Teil? Die Vermögensverwalter der wirklich Mächtigen.
- Ähnlich gestaltet es sich bei der Ernährungsindustrie. Die von dort aus verabreichten Produkte sind die Ursachen für den Gesundheitszustand der deutschen Population. Das ist aber auch irgendwie logisch, denn wer sich nicht falsch ernährt und gesund bleibt, wird kein Kunde des Gesundheitswesens. \ \ Die Besitzverhältnisse in der Ernährungsindustrie ähneln denen im Gesundheitswesen, sodass am gleichen Kunden gearbeitet und verdient wird.
- Die Aufzählung konnte nun über die meisten Branchen, in denen mit dem Elend der Menschen viel verdient werden kann, fortgesetzt werden. Waffen (BlackRock erhöhte beispielsweise seine Anteile an der Rheinmetall AG im Juni 2024 auf 5,25 Prozent. Der US-Vermögensverwalter ist damit der zweitgrößte Anteilseigner nach der französischen Großbank Société Générale.), Energie, Umwelt, Technologie, IT, Software, KI, Handel etc.
Wie genau Chemtrails und Technologien wie 5G auf den Menschen und die Tiere wirken, ist ebenfalls umstritten. Aber ist es nicht seltsam, wie krank, empathielos, antriebslos und aggressiv viele Menschen heute sind? Was genau verabreicht man der Berliner Polizei, damit diese ihre Prügelorgien auf den Rücken und in den Gesichtern der Menschen wahrnehmen, die friedlich ihre Demonstrationsrechte wahrnehmen? Und was erhalten die ganzen zugereisten „Fachkräfte“, die mit Ihren Autos in Menschenmengen rasen oder auch Kinder und Erwachsene niedermessern?
Das Titelbild dieses Beitrags zeigt einige Gebilde, welche regelmäßig bei Obduktionen von Geimpften in deren Blutgefäßen gefunden werden. Wie genau wirken diese kleinen Monster? Können wir Menschen ihr Unverständnis und ihr Nicht-Aufwachen vorwerfen, wenn wir erkennen, dass diese Menschen maximal vergiftet wurden? Oder sollten einfach Lösungen für die Probleme dieser Zeit auch ohne den Einbezug derer gefunden werden, die offenbar nicht mehr Herr ihrer Sinne sind?
Die Ziele der wirklich Mächtigen
Wer sich entsprechende Videosequenzen der Bilderberger, des WEF und anderen „Überorganisationen“ ansieht, der erkennt schnell das Muster:
- Reduzierung der Weltpopulation um ca. 80 Prozent
- Zusammenbruch der Wirtschaft, damit diese von den Konzernen übernommen werden kann.
- Zusammenbruch der öffentlichen Ordnung, um eine totale Entwaffnung und eine totale Überwachung durchsetzen zu können.
- Zusammenbruch der Regierungen, damit die Weltregierung übernehmen kann.
Es ist zu überdenken, ob die Weltregierung tatsächlich das für die Vielen beste Organisationssystem ist, oder ob die dezentrale Eigenorganisation der jeweils lokalen Bevölkerung nicht doch die bessere Option darstellt. Baustellen würden nicht nur begonnen, sondern auch schnell abgearbeitet. Jede Region könnte bestimmen, ob sie sich mit Chemtrails und anderen Substanzen besprühen lassen möchte. Und die Probleme in Barcelona könnte die Menschen dort viel besser lösen als irgendwelche wirklich Mächtigen in ihren Elfenbeintürmen. Die lokale Wirtschaft könnte wieder zurückkommen und mit dieser die Eigenständigkeit. Denn die den wirklich Mächtigen über ihre Vermögensverwalter gehörenden Großkonzerne haben offensichtlich nicht das Wohl der Bevölkerung im Fokus, sondern eher deren Ausbeutung.
Das Aussteigen aus dem System ist die wahre Herkulesaufgabe und es bedarf sicher Mut und Klugheit, sich dieser zu stellen. Die Politiker, die unverändert die Narrative der wirklich Mächtigen bedienen, sind hierfür denkbar ungeeignet, denn sie verfolgen kein Lebensmodell, welches sich von Liebe und Mitgefühl geleitet in den Dienst der Gesamtheit von Menschen, Tieren und Natur stellt.
Schauen Sie einmal genau hin, denken Sie nach und fühlen Sie mit.
Was tun?
Jedes System funktioniert nur so lange, wie es unterstützt wird. Somit stellt sich die Frage, wie viele Menschen das System ignorieren müssen, damit es kollabiert, und auf welche Weise dieses Ignorieren durchzuführen ist? Merkbar ist, dass die große Masse der Verwaltungsangestellten krank und oder unmotiviert und somit nicht wirksam ist. Würden die entsprechenden Stellen massiv belastet und parallel hierzu keine Einnahmen mehr realisieren, wäre ein Kollaps nah. Die Prügelpolizisten aus Berlin können nicht überall sein und normale Polizisten arbeiten nicht gegen unbescholtene Bürger, sondern sorgen sich selbst um ihre Zukunft. Gewalt ist sicher keine Lösung, und sicher auch nicht erforderlich.
Wie eine gerechte Verwaltungsform aufgebaut werden muss? Einfach so, wie sie in den hiesigen Gesetzen beschrieben steht. Aber eine solche Organisationsform muss frei sein von Blockparteien und korrupten Politikern und weisungsgebundenen Richtern etc. Stattdessen werden Menschen benötigt, welche die Menschen lieben und ihnen nicht schaden wollen. Außerdem sollten diese Führungspersonen auch wirklich etwas können, und nicht nur „Politiker“ ohne weitere Berufserfahrungen sein.
Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt).
Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.
Not yet on Nostr and want the full experience? Easy onboarding via Start.
-
 @ 866e0139:6a9334e5
2025-03-24 10:50:16
@ 866e0139:6a9334e5
2025-03-24 10:50:16Autor: René Boyke, Rechtsanwalt. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.
Frieden. Ein Begriff den jeder kennt, oder? Kennen schon. Aber was bedeutet er? Die Abwesenheit von Gewalt und Konflikten? Ja, auch, wenn man Frieden seinem Widerpart, dem Krieg, gegenüberstellt. Demnach müsste immer dann Frieden herrschen, wenn es keinen Krieg gibt. So richtig überzeugt das nicht, denn Frieden entsteht nicht aus heiterem Himmel. Er erfordert Verhandlungen, Toleranz und ganz allgemein die Förderung von Gerechtigkeit. Doch was verstehen wir unter Gerechtigkeit? Was unter Toleranz? Und wann verhandeln wir wirklich und ehrlich?
Das Grundgesetz als Friedensauftrag
Der Begriff des Friedens ist also unscharf und von weiteren unscharfen Begriffen abhängig. Und doch ist er Gegenstand des Recht z.B. des Grundgesetzes (GG):
- Nach der Präambel des GG verpflichtet sich das Deutsche Volk „dem Frieden der Welt zu dienen.“
- In Art. 1 Abs. 2 GG bekennt sich das Deutsche Volk zu den Menschenrechten als Grundlage des Friedens in der Welt.
- Art. 26 Abs. 1 GG verbietet Handlungen, die geeignet sind und in der Absicht vorgenommen werden, „das friedliche Zusammenleben der Völker zu stören.“
Der Frieden ist also unzweifelhaft Gegenstand des deutschen Rechts – und natürlich auch des Völkerrechts. Bereits in Art. 1 Ziff. 1 der VN-Charta ist zu lesen, dass ein gesetztes Ziel der Vereinten Nationen die Wahrung des Weltfriedens ist und dass sie „Bedrohungen des Friedens verhüten und beseitigen“ will. Es ist also festzustellen: Der Begriff des Friedens ist unscharf und damit unklar, aber dennoch ist er Teil des deutschen Rechts und auch des internationalen Völkerrechts. Bei dieser Sachlage ist Streit vorprogrammiert. Wenn nicht klar ist, was Frieden eigentlich ist, aber von seinem Vorliegen oder seiner Abwesenheit rechtliche Konsequenzen abhängen, dann wird dies selbst zu Auseinandersetzungen führen.
So meinen die einen, einen anderen Staat präventiv mit Waffengewalt anzugreifen, fördere den „Frieden“ – wir erinnern uns an den Präventivschlag der USA gegen den Irak 2003. Andere sehen darin nichts anderes als einen rechtswidrigen Angriffskrieg. Rechtliche Konsequenzen hatte dieser Angriffskrieg für die USA nicht. Blicken wir auf die Bewertung des Ukrainekriegs im Jahr 2022, der seitens 1/3 Russlands ebenfalls einen Präventivkrieg darstellt, ist festzustellen, dass es auch hier wieder geteilte Lager gibt.
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Die einen sehen das Verhaltens Russland als gerechtfertigt an, die anderen als völkerrechtswidrig. Interessanterweise halten viele, die den Angriffs der USA auf den Irak für gerechtfertigt hielten, den Angriff Russlands auf die Ukraine nicht für gerechtfertigt. Wie kann das sein? Werden hier unterschiedliche Kriterien angelegt? Warum gefährdet der Angriff der USA – die im Übrigen die Gründe für die Bedrohung des Iraks nachweislich erfunden und damit gelogen haben – angeblich nicht den Frieden, obwohl es ja nachweislich zum Krieg kam? Und warum soll das Verhalten Russlands den Frieden gefährden? Erscheint diese unterschiedliche Bewertung nicht völlig willkürlich?
Welche Begriffe für Frieden werden hier zugrunde gelegt? Der 2019 verstorbene ehemalige Richter am Bundesverwaltungsvewaltungsgericht, Dr. Dieter Deiseroth, hat in einem Aufsatz 2010 dargelegt, dass völlig unklar ist, was unter dem Begriff des Friedens zu verstehen ist. Deiseroth schrieb: „Für die Kompetenzen des UN-Sicherheitsrates ist damit der Friedensbegriff von\ entscheidender Bedeutung. Er ist in der UN-Charta nicht definiert. Das macht\ Probleme.“ Und: „Je weiter der Friedensbegriff ausgelegt wird, umso weiter gehen\ die Kompetenzen des UN-Sicherheitsrates (...).“
Ein Definitionsvakuum und ein Auftrag
Umfasst Frieden im rechtlichen Kontext lediglich die Abwesenheit zwischenstaatlicher bewaffneter Konflikte? Was ist mit Piraterie? Was mit Terrorakten? Raubbau an der Natur? Wer Frieden nicht definieren kann, der kann auch nicht sagen, wann er bedroht ist. Wenn man etwas bewahren will, dann sollte man doch wissen, was dieses Etwas ist, was man zu bewahren vorgibt, oder? Weiß man dies nicht, lässt sich selbst ein Angriff auf ein anderes Land als friedenssichernde Maßnahme verkaufen, während der Angriff eines anderen Landes plötzlich als rechtswidriger Friedensbruch gilt.
Der Willkür ist Tür und Tor geöffnet. Dann bestimmt der Stärkere bzw. dessen Propaganda, was Recht ist und was Unrecht. Das jedoch hat mit Recht nichts zu tun, bzw. sollte mit Recht nichts zu tun haben, denn es gehört leider auch zur Realität des Rechts, dass es der absolute Regelfall ist, dass der Stärkere seine einzelfallbezogene Definitionshoheit und damit sein „Recht“ durchsetzt und der Schwächere – mag er noch so gute Argumente haben – den Kürzeren zieht.
Doch diesem Sein folgt denklogisch kein Sollen. Dieser systemische Rechtsmissbrauch ist kein Argument dafür, diesen Zustand beizubehalten und ihn nicht anzuprangern. Er ist vielmehr Argument dafür, diesen Zustand offenzulegen, zu kritisieren und auf seine Beseitigung hinzuwirken.
Wie kann Frieden nun also definiert werden? So definiert, dass eben nicht eine Autorität seine eigene Definitionsmacht missbraucht? Meines Erachtens geht dies nur im gegenseitigen ehrlichen Austausch der Parteien. Der Frieden ist kein allgemein definierbarer Zustand, schon gar nicht ist er ein losgelöst von anderen Lebensbereichen existierender normativer Begriff. Die rechtliche Dimension des Friedensbegriffs kann nicht für sich allein stehen, sondern ist in eine Lebenswirklichkeit eingebettet, die bei jedem einzelnen in sich selbst als innerer Frieden beginnt – dieser Ursprung ist auch der Ursprung der rechtlichen Dimension des Friedensbegriffs.
Oder anders formuliert: Ohne inneren Frieden kein äußerer Frieden.
René Boyke ist Rechtsanwalt mit Schwerpunkt Asylrecht. Er hat sieben Jahre im Bundesamt für Migration und Flüchtlinge gearbeitet und betreibt die Seite covid-justiz.de auf der er Gerichtsentscheidungen aus der Coronazeit kommentiert.
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren, zappen etc.)? Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 866e0139:6a9334e5
2025-03-24 10:48:58
@ 866e0139:6a9334e5
2025-03-24 10:48:58Autor: Tom-Oliver Regenauer
Grafik: Tina Ovalle.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.
»Krieg ist Frieden«. Dieses zwischenzeitlich fast abgedroschen wirkende, weil in den letzten Jahren zu häufig verwendete Zitat aus George Orwells Klassiker »1984«, beschreibt zunehmend genau, was europäische Spitzenpolitiker dieser Tage als »Wehrtüchtigkeit« vermarkten – die wahnwitzige Illusion, dass Kriegswaffen der Friedenssicherung dienen.
So aber funktioniert das Geschäft industrialisierten Tötens nicht. Denn Krieg entsteht nicht organisch. Schon gar kein Weltkrieg. Militärische Konflikte globalen Ausmaßes sind stets trauriger Kulminationspunkt langjähriger Entwicklungen. Sie beginnen mit Partikularinteressen, diplomatischen Kontakten, bilateralen Absprachen, militärisch-industriellen Konjunkturprogrammen und der Etablierung von Verteidigungsbündnissen. Kriege sind von langer Hand geplante Disruptionen, die genutzt werden, um Paradigmenwechsel zu rechtfertigen – Entwicklungen, die der Bevölkerung ohne eine solch existenzielle Bedrohung nicht unterzujubeln sind. So gäbe es ohne die beiden ersten Weltkriege heute weder die Bank für Internationalen Zahlungsausgleich noch die Vereinten Nationen oder die NATO. Und auch das herrschende, auf Verschuldung basierende und von Zentralbankkartellen dominierte Weltfinanzsystem, das darauf ausgelegt ist, Staaten und damit deren Bevölkerung schleichend zu enteignen, wäre so nicht entstanden – siehe Bretton Woods und »Nixon Schock«.
Wem dienen Kriege?
Folgt man der tatsächlichen Geschichte des Ersten Weltkrieges, die nicht 1914 mit der Ermordung von Erzherzog Franz Ferdinand, sondern bereits 1891 in Südafrika begann – siehe Teil 1 und 2 meines diesbezüglichen Essays – wird rasch deutlich, wem Kriege dienen. Und damit auch, von wem sie ausgelöst werden: Von Finanzkartellen, die zunächst an der Aufrüstung, dann an der Finanzierung des Krieges und zum Schluss am Wiederaufbau verdienen – ganz zu schweigen von der supranationalen Konsolidierung und Zentralisierung von Finanzmacht, die mit derartigen geopolitischen Verwerfungen einhergeht.
Im Falle der beiden Weltkriege sind diese Hintergründe gut belegt und detailliert nachvollziehbar. Man muss sie nur lesen. Weil Geschichte, zumindest die offiziell goutierte und gelehrte Variante, aber bedauerlicherweise von den Gewinnern geschrieben wird, sind wir scheinbar dazu verdammt, sie zu wiederholen. Dem geschichtsaffinen Leser dürfte es derweil nicht allzu schwer fallen, Parallelen zwischen der Zeit vor den beiden Weltkriegen und der Gegenwart auszumachen.
DIE FRIEDENSTAUBE JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Zum einen stimmt Trump die USA auf Isolationismus ein. Zum anderen lässt er das US-Militär gleichzeitig Öl in die bestehenden Brandherde in Europa, Nahost und dem Indopazifik gießen. Gleichzeitig läuten seine Strafzölle eine Phase internationaler Handelskriege ein, die den Rest der Welt zur Reaktion zwingt. Nicht umsonst spricht Ursula von der Leyen nun von »ReARM Europe« und will bis zu 800 Milliarden Euro für »Wiederaufrüstung« mobilisieren. Nicht von ungefähr wirft Friedrich Merz, ehemaliger BlackRock-Manager, auf dem Weg ins Kanzleramt mit »Sondervermögen« um sich und möchte 500 Milliarden in die Bundeswehr investieren. Vielleicht hat ihn Larry Fink oder die Teilnahme an der Bilderberg Konferenz 2024 in Madrid inspiriert – standen dort doch unter anderem die »Zukunft der Kriegsführung« und die »geopolitische Landschaft« auf der Agenda.
Es besteht kein Zweifel: Wir befinden uns in einer Vorkriegszeit. Die Frage ist nur, wie dieser Krieg aussehen wird und wann er beginnt. Denn die moderne Informationskriegsführung gegen die breite Bevölkerung läuft spätestens seit 9/11 auf Hochtouren – und intensivierte sich nach der Markeinführung des Smartphones im Jahr 2007 konstant. Es hat Gründe, warum ich einen Großteil meiner Artgenossen heute als Smombie bezeichne.
Zeit, für den Frieden zu kämpfen
Wie jedoch ein kinetischer Krieg in den 2020er Jahren aussehen wird, vor allem, wenn atomar bewaffnete, mit Drohnen, Robotern und KI ausgestattete Supermächte sich gegenüberstehen, weiß niemand. Den Ersten Weltkrieg konnte man sich damals auch nicht vorstellen – denn bis zu diesem Zeitpunkt gab es keine derartig weitreichenden »Verteidigungsallianzen« und »Bündnisfälle«. Auch die Waffen, die im Zweiten Weltkrieg zum Einsatz kommen sollten, waren neu. Das Ausmaß der Zerstörung eine todbringende Zäsur.
Wenig verwunderlich also, dass die Reprise dieser zivilisatorischen Katastrophe knapp 60 Millionen mehr Menschen das Leben kostete als die Premiere – und den perfekten Hebel zur Etablierung der postmodernen »Global Governance« bot. Einem inhumanen, antidemokratischen, zusehends totalitären Herrschaftskonstrukt, das sich nun mit der aus dem Elfenbeinturm kommunizierten »Zeitenwende«, »Wehrtüchtigkeit« und »ReARM Europe« anschickt, uns in einen Dritten Weltkrieg zu manövrieren.
Es ist Zeit, nein zu sagen. Nein zu Sondervermögen. Nein zu Aufrüstung. Nein zu Massenvernichtungswaffen. Und nein zu Konflikten, die stets von jenen angezettelt werden, die darin »nicht sterben« werden, wie Robert Habeck im Februar 2022 bei Maischberger selbst einräumte. Nein zu Krieg!
Wer seine Kinder nicht an die Front schicken oder am eigenen Leib erfahren möchte, welche automatisiert mordenden Waffengattungen in einem Dritten Weltkrieg zum Einsatz kommen, sollte für den Frieden kämpfen. Mit allen Mitteln – gemeinsam – und zwar jetzt. Bedarf es für die finale Ausgestaltung der »vierten industriellen Revolution«, für Agenda 2030, C40-Städte und Net Zero 2050, sprich, dem digitalen Gulag von morgen, einer globalen militärischen Disruption – und das scheint im Lichte der Vergangenheit durchaus wahrscheinlich – bleibt uns nicht mehr allzu viel Zeit, um Sand ins Getriebe der aufheulenden Kriegsmaschinerie zu streuen.
Tom-Oliver Regenauer, Jahrgang 1978, war nach betriebswirtschaftlicher Ausbildung in verschiedenen Branchen und Rollen tätig, unter anderem als Betriebsleiter, Unternehmens- und Management-Berater sowie internationaler Projektmanager mit Einsätzen in über 20 Ländern. Seit Mitte der 90er-Jahre ist er zudem als Musikproduzent und Texter aktiv und betreibt ein unabhängiges Plattenlabel. Der in Deutschland geborene Autor lebt seit 2009 in der Schweiz. Zuletzt erschienen von ihm „Homo Demens — Texte zu Zeitenwende, Technokratie und Korporatismus“ (2023), „Truman Show“ (2024) und "HOPIUM" (2025). Weitere Informationen unter www.regenauer.press.\ HOPIUM jetzt direkt im Shop oder im Handel.
Wir testen derzeit den Mailversand an allen Artikeln. In Zukunft bekommen Sie ca. drei Mailsendungen der Friedenstaube pro Woche.
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren, zappen etc.)? Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ d560dbc2:bbd59238
2025-03-24 10:18:44
@ d560dbc2:bbd59238
2025-03-24 10:18:44When it comes to task management, most of us are familiar with the traditional approach: plan your day, set deadlines, and create detailed schedules to stay on top of everything. But what if there’s a better way—a method that doesn’t require meticulous planning, yet ensures you’re always working on the right task at the right time?
Enter the 2-5 Rule, an “anti-planning” concept that focuses on which task to act on right now, rather than creating a rigid plan for the future. In this deep dive, we’ll explore what makes the 2-5 Rule stand out, how it works, why it’s so effective, and how TaskforUs brings this innovative approach to life. Whether you’re renewing a passport or keeping in touch with a loved one, the 2-5 Rule offers a refreshingly simple way to manage your tasks without the stress of planning.
What Is the 2-5 Rule?
The 2-5 Rule is a task management method that prioritizes tasks based on their timing—not a detailed schedule. Instead of planning exactly when to do each task, you simply:
- Enter the task into a system like TaskforUs.
- Assign it a time unit (days, weeks, months, or years).
- Let the algorithm decide when it should climb to the top of your priority list.
The “2-5” refers to the ideal action window: you should act on a task within 2 to 5 of its assigned time units. For example:
- Daily tasks: (e.g., “Do cardio”) should be done every 2-5 days.
- Weekly tasks: (e.g., “Schedule dinner with a friend”) should be acted on every 2-5 weeks.
- Monthly tasks: (e.g., “Review budget”) have a window of 2-5 months.
- Yearly tasks: (e.g., “Reassess career goals”) should be revisited every 2-5 years.
This sweet spot ensures tasks are neither rushed nor neglected.
Key Point: The 2-5 Rule isn’t about planning—it’s about capturing tasks and letting the system determine their priority based on timing. Simply enter the task, set its time unit, and provide either the last date you acted on it or a fixed due date (using Fix Mode for specific events). The system does the rest.
How It Works: No Planning Required
When you add a task to TaskforUs, you assign it a time unit based on how often you want to act on it:
- Daily tasks: Act every 2-5 days (e.g., “Do cardio”).
- Weekly tasks: Act every 2-5 weeks (e.g., “Meet a friend for dinner”).
- Monthly tasks: Act every 2-5 months (e.g., “Review budget”).
- Yearly tasks: Act every 2-5 years (e.g., “Renew passport”).
For recurring tasks, you enter the last date you acted on them (the “last act date”). For date-specific tasks, you can use Fix Mode to set a due date. The 2-5 Rule calculates the task’s priority based on how much time has passed since the last action or how close the due date is—ensuring it rises to the top at just the right moment.
Real-Life Examples of the 2-5 Rule in Action
Example 1: Renewing Your Passport
-
Scenario:
You get your passport today and know it needs to be renewed every 5 years. You don’t want to plan the renewal far in advance—you just want a reminder at the right time. -
Implementation:
- Add the task “Renew passport” and set its time unit to yearly.
-
Enter the “last act date” as today’s date (e.g., March 24, 2025) or use Fix Mode to set the exact expiration date (e.g., March 24, 2030).
-
Outcome:
The task starts low on your priority list. As time passes, it climbs based on the 2-5 Rule. After 2 years, it begins to rise; by 5 years, it’s nearing the top—ensuring you act before the passport expires.
Example 2: Meeting Uncle Lars Regularly
-
Scenario:
You want to meet your Uncle Lars regularly but not too often. You’d like to see him about 10 times a year (roughly once every 5 weeks). However, to give yourself more flexibility, you choose a longer time unit. -
Implementation:
- Add the task “Meet/eat with Uncle Lars” and set its time unit to monthly.
-
Set the “last act date” as the most recent time you met him (e.g., March 1, 2025).
-
Outcome:
Over time, the task slowly climbs in your priority list. After 2 months, it starts gaining focus; by 5 months, it becomes urgent—nudge you to reach out and schedule a meeting, all without needing to plan the exact date in advance.
The Origins of the 2-5 Rule: An Anti-Planning Revolution
The 2-5 Rule isn’t entirely new—it has roots in productivity and behavioral science, emerging as a response to the complexity of traditional task management systems that require detailed schedules, deadlines, and constant reviews. Influential figures, including Bill Gates, have reportedly praised its simplicity for managing tasks without over-planning.
- Why It Works:
The 2-5 Rule leverages the natural rhythm of tasks, ensuring that you act within an optimal time window without micromanaging your schedule. It aligns with our intuition—you don’t need to plan exactly when to call a friend; you just know it’s been a while, and it’s time to reconnect.
Why the 2-5 Rule Works: The Science Behind Anti-Planning
-
Reduces Decision Fatigue:
Traditional planning forces you to decide when to act on each task, which can be mentally exhausting. The 2-5 Rule automates prioritization, freeing up mental energy. -
Aligns with Natural Rhythms:
Research on habit formation shows that consistency is key. The 2-5 window ensures you act within a natural timeframe—tasks feel urgent after 2 units but are at risk of being neglected by 5 units. -
Prevents Over-Planning Stress:
Detailed plans can lead to stress when life interferes. The 2-5 Rule removes the need for rigid scheduling, letting you focus on action rather than planning. -
Ensures Critical Tasks Don’t Slip Through the Cracks:
With Fix Mode, date-specific tasks like passport renewals or birthdays climb in priority as the due date approaches, ensuring you never miss a deadline.
How TaskforUs Brings the 2-5 Rule to Life
TaskforUs is a web-based platform that makes the 2-5 Rule actionable, elevating the anti-planning concept with features designed for ease and precision:
-
Add Tasks Easily:
Enter a task, set its time unit (days, weeks, months, or years), and provide the last act date or a fixed due date for Fix Mode tasks. -
Top Task:
TaskforUs automatically highlights your most urgent task based on the 2-5 Rule—telling you exactly what to do right now. -
Focus Mode:
Display your top 3 tasks (or adjust the number) for a distraction-free view when juggling multiple priorities. -
Fix Mode:
For tasks tied to specific dates, Fix Mode ensures they rise in priority as the due date approaches, peaking on the day itself. -
Category Filtering and Archiving:
Organize your tasks into categories (e.g., Work, Personal) and archive completed tasks to keep your list clutter-free. -
Export Tasks:
Download your tasks as a CSV file for backup or analysis.
Practical Applications: More Ways to Use the 2-5 Rule
-
Health Goals:
Want to drink more water daily? Set “Drink water” as a daily task. TaskforUs will nudge you every 2-5 days to stay hydrated—no strict schedule required. -
Work Projects:
Need to follow up on a client email? Set it as a weekly task. After 2 weeks, it’ll start climbing your list, ensuring you don’t forget. -
Special Dates:
Have a wedding anniversary coming up? Use Fix Mode to set the date; TaskforUs will ensure “Plan anniversary dinner” becomes your top task on that day. -
Long-Term Goals:
Want to learn a new skill every few years? Set “Explore new skill” as a yearly task, and TaskforUs will remind you every 2-5 years.
The 2-5 Rule vs. Traditional Planning: Why Anti-Planning Wins
Traditional planning methods—such as detailed schedules or comprehensive systems like Getting Things Done (GTD)—often come with drawbacks:
-
Complexity:
Detailed planning requires significant time and effort. -
Inflexibility:
Rigid plans can crumble when unexpected events occur. -
Mental Load:
Constantly deciding when to do each task contributes to decision fatigue.
The 2-5 Rule avoids these pitfalls by letting you focus on timing. You simply enter your tasks, and TaskforUs automatically prioritizes them based on the optimal action window.
Why You Should Try the 2-5 Rule with TaskforUs
The 2-5 Rule offers a fresh perspective on task management by focusing on when to act rather than what to do. It’s particularly effective for balancing short-term habits with long-term goals. Here’s why you should give it a try:
-
No Planning Needed:
Simply add your tasks and let the system handle prioritization. -
Clarity:
Always know what to do right now without overthinking. -
Flexibility:
The 2-to-5 window provides the ideal balance between prompt action and careful timing. -
Reliability:
Fix Mode ensures you never miss critical dates. -
Be Part of the Beta:
As a beta user, your feedback can shape the future of TaskforUs.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a new way to think about task management. By focusing on timing, it ensures you’re always working on the right thing at the right time. Ready to say goodbye to over-planning and hello to effortless prioritization?
Sign up for TaskforUs at task4.us and experience the 2-5 Rule in action.
Your tasks, perfectly timed—without a plan in sight. -
 @ d560dbc2:bbd59238
2025-03-24 08:54:06
@ d560dbc2:bbd59238
2025-03-24 08:54:06Task management is a challenge we all face—whether it’s juggling work deadlines, staying in touch with friends, or remembering important dates like birthdays. With endless to-do lists and competing priorities, how do you decide what to tackle next?
Enter the 2-5 Rule, a unique approach to task management that focuses on timing tasks within a specific “sweet spot”—between 2 to 5 time units—ensuring they’re neither rushed nor neglected. In this deep dive, we’ll explore what makes the 2-5 Rule stand out, how it works, and how it compares to other popular task management techniques like the 1-3-5 Rule, Eisenhower Matrix, Getting Things Done (GTD), and the Pomodoro Technique.
What Is the 2-5 Rule?
The 2-5 Rule is a timing-based task management strategy designed to help you act on tasks at the right moment. Every task has a natural rhythm or “time unit” (days, weeks, months, or years) that dictates how often it should be addressed. The rule dictates that you should act on a task within 2 to 5 of these units. For example:
- Daily tasks (e.g., “Do cardio”) should be done every 2-5 days.
- Weekly tasks (e.g., “Schedule dinner with a friend”) should be done every 2-5 weeks.
- Monthly tasks (e.g., “Review budget”) should be done every 2-5 months.
- Yearly tasks (e.g., “Reassess career goals”) should be revisited every 2-5 years.
This “sweet spot” balances urgency and flexibility—acting too soon wastes energy, while waiting too long risks neglecting the task. The 2-5 Rule is the foundation of TaskforUs, a platform that automates this process to help you prioritize tasks with precision.
Comparing the 2-5 Rule to Other Task Management Techniques
1. The 1-3-5 Rule: Daily Structure Without Timing
- Overview:
Organizes your day into 1 big task, 3 medium tasks, and 5 small tasks. - Strengths:
- Helps set realistic daily goals and forces you to prioritize.
- Weaknesses:
- Does not account for the natural rhythm or timing of tasks over longer periods.
- Comparison:
The 1-3-5 Rule is excellent for daily planning, while the 2-5 Rule provides a broader perspective by scheduling tasks over days, weeks, months, or years. They can be combined: use 1-3-5 for daily structure and the 2-5 Rule for long-term timing.
2. Eisenhower Matrix: Urgency vs. Importance
- Overview:
Categorizes tasks into four quadrants based on urgency and importance: - Urgent and Important: Do immediately.
- Important but Not Urgent: Schedule for later.
- Urgent but Not Important: Delegate.
- Neither Urgent nor Important: Eliminate.
- Strengths:
- Excellent for decision-making and eliminating time-wasters.
- Weaknesses:
- Lacks guidance on when to act on tasks that are important but not urgent.
- Comparison:
While the Eisenhower Matrix focuses on what to do, the 2-5 Rule tells you when to do it. They can work together for a complete task management system.
3. Getting Things Done (GTD): Comprehensive but Complex
- Overview:
GTD is a system to capture and organize all your tasks using steps like capture, clarify, organize, reflect, and engage. - Strengths:
- Ensures nothing is forgotten by capturing every task.
- Weaknesses:
- Can be overwhelming and time-consuming for those who prefer simplicity.
- Comparison:
GTD provides a comprehensive framework, whereas the 2-5 Rule offers a focused strategy for timing and prioritization, reducing decision fatigue.
4. Pomodoro Technique: Focus on the Present
- Overview:
Breaks work into intervals (typically 25 minutes of focused work followed by a 5-minute break). - Strengths:
- Boosts focus and prevents burnout during work sessions.
- Weaknesses:
- Doesn’t help you decide which task to tackle or manage long-term priorities.
- Comparison:
The Pomodoro Technique helps you focus on a chosen task; the 2-5 Rule helps you decide the right task to work on at the right time. They complement each other well.
Why the 2-5 Rule Stands Out
-
Integrates Behavioral Science:
Grounded in research on habit formation and decision fatigue, the 2-5 Rule leverages our natural sense of urgency to prompt action at the optimal time. -
Balances Urgency and Flexibility:
It provides a flexible window for action, ensuring tasks are handled neither too early nor too late. -
Simplifies Decision-Making:
By automating prioritization, TaskforUs reduces the mental load, so you always know which task to focus on. -
Addresses Long-Term Timing:
Unlike the Pomodoro Technique, it considers tasks over various timeframes—daily, weekly, monthly, or yearly. -
Never Misses Critical Dates:
With Fix Mode, TaskforUs ensures that date-specific tasks (e.g., birthdays) climb to the top of your list as the date approaches.
Practical Applications of the 2-5 Rule
-
Social Connections:
Task: “Schedule dinner with Alex”
Time Unit: Weeks
Application: If it’s been 3 weeks since your last meetup, TaskforUs flags it as your top task, prompting you to reconnect. -
Health Goals:
Task: “Do cardio”
Time Unit: Days
Application: If it’s been 2 days since your last workout, the platform nudges you to exercise before reaching the 5-day mark. -
Special Dates:
Task: “Wish Alex a happy birthday”
Mode: Fix Mode
Application: TaskforUs ensures the task climbs in priority as the birthday nears, becoming the top task on the day. -
Long-Term Planning:
Task: “Reassess my career path”
Time Unit: Years
Application: If it’s been 2 years since your last career review, the system prompts you to evaluate your progress and goals.
Why You Should Try the 2-5 Rule with TaskforUs
The 2-5 Rule offers a fresh perspective on task management by focusing on timing rather than solely on task content. It is particularly effective for balancing short-term habits with long-term goals. TaskforUs brings this concept to life with features such as:
- Top Task: Automatically highlights your most urgent task within the 2-5 window.
- Focus Mode: Displays your top 3 tasks (customizable) to help you concentrate.
- Fix Mode: Prioritizes date-specific tasks as their deadlines approach.
- Category Filtering and Archiving: Keeps your task list organized and clutter-free.
If you’re tired of chaotic to-do lists, missed deadlines, or the mental load of deciding what to do next, the 2-5 Rule offers a better way.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a mindset shift. By focusing on when to act, it ensures you’re always working on the right task at the right time. Ready to give it a try?
Sign up for TaskforUs at task4.usYour tasks, perfectly timed—every time.
-
 @ da0b9bc3:4e30a4a9
2025-03-24 08:13:00
@ da0b9bc3:4e30a4a9
2025-03-24 08:13:00Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/923278
-
 @ fbf0e434:e1be6a39
2025-03-24 07:37:41
@ fbf0e434:e1be6a39
2025-03-24 07:37:41黑客即命运:四个支点推动未来的杠杆
在《Why Software is Eating the World》中,Marc Andreessen 指出,软件的扩张不仅是一场技术革命,更是一场社会变革。我们深以为然。但 DoraHacks 相信真正改变世界的不只是软件,而是一群愿意动手解决问题的黑客(Hackers)。
DoraHacks 正在构建 Hacker Movement —— 一个以自由、开源、技术为武器的全球创新网络。我们认为这个运动的终点不是某种“Web3.0”神话,也不是一个新冷战时代的技术出口,而是一场社会的重构,是对“什么值得被构建”这一问题的深度回应。
在这个过程中,Dora Ventures 是辅助 DoraHacks 协调与捕获价值的资本引擎。Dora Ventures 当前的工作将围绕以下四个方面展开:
一、FDA 自由社会 (BioHack)
黑客社会的健康自由宣言:解锁生命技术的市场机制
回顾历史,每一次真正的技术突破,都伴随着对既有范式的挑战。今天,医疗健康领域依然是人类最受制于官僚主义的地方 —— 一个新药从实验室走向病人,往往需要十年时间和几十亿美元的投入,绝大多数创新止步于此。
FDA Free Society,并不是呼吁无政府主义,而是呼吁一种更具活力、更以患者为中心的健康和生物科技创新体系。
我们看到的问题:
- FDA的审批周期与风险厌恶机制正在扼杀潜在的突破性治疗;
- 大药企的市场垄断让药品定价脱离现实,限制竞争;
- 病人的“尝试权”(Right to Try)在监管框架下被边缘化;
- 小型生物科技初创公司面对高昂试验成本几乎没有生存空间。
我们相信的解决方向:
- 市场驱动的健康创新机制:把研发、试验和使用的决策权更多交还给患者、医生和创业者;
- 让创新回归第一性原理:不是“通过审批”,而是“是否有效”;
- 为 Right to Try 正名:真正的风险不是尝试未经审批的疗法,而是死于等待;
- 打造有竞争力的生物初创生态:帮助小团队也有机会改变世界,而不只是为大药厂打工。
- 软件和人工智能驱动的生物科技:生物科技和软件的结合驱动全新的生物科技产品。
我们相信,药物研发的未来,不属于某个监管机构,也不属于市值5000亿的大公司,而属于一群不愿等待的创新者。
FDA Free Society 是对“技术进步必须服从监管”的有力反击,是对“创新必须通过审批”的结构性质疑。我们押注这个方向,是因为它比“创新”更稀缺——它关乎人类对生存权的重新主张。
二、开源量子计算基础设施(Open Source Quantum)
量子软件的开源狂潮,是今天的以太坊2015年
Arthur C. Clarke 曾说:“任何足够先进的技术,看起来都像是魔法。” 量子计算就是这样一种技术。但问题在于,魔法要成为工具,必须走向可编程、可复现、可协作 —— 换句话说,它需要“开源”。
Dora Ventures 对量子计算的投资逻辑很清晰:量子计算正走向它的“智能合约时刻”。硬件进入工程优化周期,软件和工具层尚属一片荒芜,但这正是黑客的黄金年代。
我们关注的几个关键趋势:
- 开源量子编译器与转译器:打通经典与量子系统的语言障碍;
- 量子密码学:利用量子力学的原理构建全新的加密系统;
- 量子软件应用:我们相信量子计算软件和应用可以在人工智能、生物科技、区块链等技术的进步中发挥巨大的价值,直接或间接影响金融、物流、制药、国防、太空探索等重要领域。
我们不仅是观察者,更是建设者。通过举办黑客松、资助和投资量子开源软件项目、开展量子密码学的研究和生态发展,我们参与这个时代最具颠覆性的计算平台的构建。
三、消费级加密应用(Consumer Crypto)
胖应用的春天已至:Crypto 将赢得最后10亿用户
如果你理解历史,你会明白今天的 Crypto 不是互联网的“平行世界”,而是互联网故事的下一个篇章。
1990年代,HTTP 和 TCP/IP 改变了信息分发; 2000年代,Web 应用改变了商业与社交; 2010年代,移动端应用重塑了人类行为; 2020年代,是 Crypto 应用真正走向大众的十年。
基础设施已充分,胖应用正在破壳而出。
Dora Ventures 最核心的判断是:谁能抓住第一个亿级用户的Crypto应用场景,谁将书写Web3时代的Paypal和微信故事。
- 稳定币合规化将使 USDC 成为数字美元;
- 去中心化社交和加密支付的全球化催生比特币和 Web3 支付的“ VISA 网络”;
- 大应用链基建将通过 Move 语言和极简化工具降低用户门槛;
- 链上原生经济系统将实现创作者直接变现、社区协作分润。
想象这个场景: 一个住在纽约的人通过链上音乐会平台(KYD Labs)使用快速Move区块链网络(Aptos)的 Circle USDC 购买今晚的演唱会门票,一个阿根廷的居民每天去咖啡馆用闪电网络上的比特币“聪”购买拿铁,在去中心化社交媒体(Yakihonne)与朋友分账单,这些都会在今年真实发生。我们不只是投资协议,而是投资体验新范式的创造者。
四、全自动化组织(Agentic Organizations)
组织将成为智能体,DAO将成为大型语言模型的组织形态
2022年,Sam Altman 重构了“工具”的定义;2025年,我们将重构“组织”的定义。
我们认为,未来组织不是由人构成的矩阵结构,而是由Agent协作而成的智能系统。
Agent 是新的工作单元,它不眠不休、持续学习、自动调度。它不是增强人类的工具,而是自动化组织的大脑。
一些例子:
- DAO Agent 系统将自动执行治理流程,并保护参与者隐私;
- Smart Widget 框架让开发者用三行代码部署社交、支付、交易型 Agent ;
- 隐私协议和隐私应用在自动化组织中成为主流;
- 黑客松涌现出大量加密 Agent。
AI + 区块链不是 Buzzword ,而是组织智能化的起点。
过去我们说“公司是信息处理的机器”,未来我们会说“ DAO 是 Agent 运行的网络”。我们正在进入一个无需CEO的公司、无需审批的流程、无需办公室的全自动化组织时代。
尾声:我们下注在拥有“BUIDL自由”的人类
这四个方向——FDA Free Society、Open Source Quantum、Consumer Crypto、Agentic Organizations,不是我们幻想的未来,而是已经开始发生的未来。
Dora Ventures不是下注在技术上,而是下注在一群不服从的Builder身上。他们愿意解决真正的问题,质疑现有体制,构建新的秩序。他们相信世界可以不同,并愿意动手去实现它。
黑客运动正在吞噬世界,在人工智能的时代,人类必将成为 Hacker ,用代码,用治理,用想象力,创造一个值得居住的世界。
-
 @ a012dc82:6458a70d
2025-03-24 06:54:13
@ a012dc82:6458a70d
2025-03-24 06:54:13Bitcoin, the original cryptocurrency, has once again captured headlines and investor interest by reaching a new record high, surpassing its previous peak from November 2021. This remarkable resurgence underscores the volatile yet unstoppable journey of Bitcoin, reflecting broader trends in the cryptocurrency market and global finance. Beyond its financial implications, this surge represents a significant cultural and technological milestone, highlighting the increasing integration of digital currencies into mainstream financial systems and the growing public interest in decentralized finance solutions. This article delves into the factors behind Bitcoin's latest surge, its implications, and what the future may hold for this digital asset, considering the complex interplay between market dynamics, technological advancements, and regulatory landscapes.
Table of Contents
-
The New Peak: Bitcoin's Latest Achievement
-
Understanding Bitcoin's Appeal
-
Catalysts for the Recent Surge
-
Institutional Acceptance and ETFs
-
Economic Environment
-
-
Is the Surge Sustainable?
-
Regulatory Landscape and Future Prospects
- Conclusion
- FAQs
The New Peak: Bitcoin's Latest Achievement
After more than two years, Bitcoin has shattered its previous record, climbing to just under $69,000 before stabilizing around $64,000. This surge has propelled Bitcoin's market valuation to approximately $1.3 trillion, representing a significant portion of the total $2.6 trillion cryptocurrency market. This achievement is not just a milestone for Bitcoin but also a testament to the growing acceptance and maturation of cryptocurrencies as a whole. The new peak is a reflection of the enduring faith of long-term investors and the influx of new participants drawn by Bitcoin's proven resilience and potential for substantial returns. This landmark event is not merely about surpassing a numerical threshold but symbolizes the culmination of years of development, debate, and adoption that have expanded the boundaries of what is possible in the realm of digital finance. It prompts a reevaluation of Bitcoin's role not only as a speculative asset but as a foundational component of a new, evolving digital economy.
Understanding Bitcoin's Appeal
Bitcoin's inception in 2008 by the enigmatic Satoshi Nakamoto introduced a revolutionary concept: a digital currency enabling direct transactions without the need for traditional financial institutions. The core innovation of Bitcoin, the blockchain, solved the "double spend" problem inherent to digital currencies, ensuring secure, transparent, and decentralized transactions. This anti-authoritarian stance, combined with the promise of lower transaction fees and resistance to inflation, has fueled Bitcoin's popularity. The appeal of Bitcoin extends beyond its technological underpinnings to embody a broader desire for financial autonomy and privacy. It challenges conventional banking systems and offers an alternative for individuals disillusioned with traditional financial institutions. Bitcoin's decentralized nature appeals to those seeking freedom from governmental oversight and inflationary policies, positioning it as a symbol of financial empowerment and self-sovereignty. As Bitcoin continues to evolve, its appeal broadens, attracting a diverse group of users from libertarians to tech enthusiasts, and from small investors to large institutional players.
Catalysts for the Recent Surge
Several factors have contributed to Bitcoin's recent price explosion:
Institutional Acceptance and ETFs
The approval of Bitcoin exchange-traded funds (ETFs) by the US financial regulator marked a significant step towards institutional acceptance. These ETFs allow investors to gain exposure to Bitcoin without directly purchasing the digital asset, reducing barriers to entry and signaling a new level of market maturity. This development is a clear indication of the growing recognition of Bitcoin's value proposition by mainstream financial entities. It reflects a broader shift in perception among institutional investors, who are increasingly viewing Bitcoin and other cryptocurrencies not just as speculative investments but as legitimate components of diversified portfolios. The introduction of ETFs has facilitated this transition by providing a familiar and regulated framework for investing in Bitcoin, thereby attracting a new wave of institutional capital into the cryptocurrency market.
Economic Environment
The low-interest-rate environment since the 2008 financial crisis has driven investors towards riskier assets, including cryptocurrencies, in search of higher returns. Additionally, Bitcoin is increasingly viewed as an "inflation hedge," similar to gold, appealing to those wary of central bank policies and currency devaluation. The economic landscape has been further complicated by the global pandemic, geopolitical tensions, and supply chain disruptions, leading to increased market volatility and a renewed focus on alternative assets like Bitcoin. As traditional financial systems show signs of strain and governments continue to engage in unprecedented levels of monetary expansion, Bitcoin's fixed supply and decentralized nature offer a compelling alternative for those looking to preserve value and hedge against inflationary pressures.
Is the Surge Sustainable?
While the excitement around Bitcoin's new record is palpable, questions remain about the sustainability of this surge. Historical patterns suggest that parabolic increases in Bitcoin's price are often followed by corrections. Factors such as profit-taking by early investors and the eventual saturation of new buyers could lead to a price consolidation. However, the upcoming "halving" event, which reduces the Bitcoin reward for mining, could counterbalance these pressures by reducing the new supply of Bitcoin and potentially driving up its price. The sustainability of Bitcoin's price surge also hinges on broader market dynamics, including technological advancements, regulatory developments, and shifts in investor sentiment. As Bitcoin becomes more integrated into the global financial system, its price movements are increasingly influenced by a complex interplay of factors, making its future trajectory difficult to predict. Nonetheless, the underlying principles of scarcity, security, and decentralization that underpin Bitcoin provide a strong foundation for its long-term value proposition.
Regulatory Landscape and Future Prospects
The regulatory environment continues to evolve, with increased scrutiny in the UK, EU, and US. While tighter regulations may introduce more stability to the market, they could also restrict some of the freedoms that make cryptocurrencies attractive. Nevertheless, the recent approval of Bitcoin ETFs in the US has been a positive development, potentially paving the way for more regulated crypto assets and attracting a broader base of investors. The future of Bitcoin and the broader cryptocurrency market will be significantly shaped by regulatory decisions, technological innovations, and shifts in global economic conditions. As regulators around the world grapple with the challenges and opportunities presented by cryptocurrencies, the outcome of these deliberations will have far-reaching implications for the adoption, utility, and value of Bitcoin. Despite the uncertainties, the ongoing developments in the regulatory landscape signify a growing recognition of the importance of cryptocurrencies and the need for a balanced approach that ensures security, transparency, and innovation.
Conclusion
Bitcoin's latest record high is more than just a numerical milestone; it represents the ongoing evolution and resilience of the cryptocurrency market. While challenges remain, including regulatory hurdles and market volatility, Bitcoin's journey continues to captivate investors, technologists, and financial analysts alike. As the world becomes increasingly digital, the role of cryptocurrencies like Bitcoin in the global financial ecosystem is likely to grow, making its journey an unstoppable force in the changing landscape of money and investment. The path ahead for Bitcoin is fraught with challenges and opportunities, but its recent achievements underscore its potential to redefine the boundaries of finance, technology, and societal norms. As we look to the future, Bitcoin's journey remains a compelling narrative of innovation, speculation, and the relentless pursuit of a decentralized and empowered financial future.
FAQs
What caused Bitcoin to reach a new record high? Bitcoin's recent surge to a new record high was influenced by several factors, including institutional acceptance, the approval of Bitcoin ETFs, the economic environment fostering a search for inflation hedges, and technological advancements in the cryptocurrency space.
What is a Bitcoin ETF, and why is it important? A Bitcoin ETF (Exchange-Traded Fund) allows investors to gain exposure to Bitcoin's price without owning the actual cryptocurrency. This is important because it provides a regulated and accessible way for institutional and retail investors to invest in Bitcoin, potentially increasing its adoption and market stability.
Can Bitcoin's price surge be sustained? While Bitcoin's price has historically been volatile, factors such as its upcoming halving event, institutional investment, and its role as a perceived inflation hedge may support its value. However, market corrections are common following significant surges, and investor caution is advised.
How do regulatory changes affect Bitcoin's price? Regulatory changes can have significant impacts on Bitcoin's price. Positive regulatory developments, such as the approval of Bitcoin ETFs, can boost investor confidence, while stricter regulations may limit trading or use, potentially affecting the price negatively.
What is the "halving" event, and why is it significant? The "halving" is an event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved, effectively reducing the rate at which new Bitcoins are created. This event can lead to increased prices due to reduced supply and increased scarcity.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 502ab02a:a2860397
2025-03-24 04:13:11
@ 502ab02a:a2860397
2025-03-24 04:13:11วันนี้จะมาเล่าเรื่องการทลายและจับกุมเครือข่ายน้ำมันมะกอกปลอม เบื้องหลังการต่อสู้ในโลกของอุตสาหกรรมอาหาร กันครับ
ด้วยความที่ว่าน้ำมันมะกอก Extra Virgin ถูกยกย่องให้เป็นหนึ่งในน้ำมันที่มีคุณภาพสูงและเป็นสัญลักษณ์ของความมีสุขภาพที่ดีทั่วโลก แถมด้วยรสชาติที่ซับซ้อน กลิ่นหอมเฉพาะตัว มาพร้อมคุณค่าทางโภชนาการที่หลากหลาย ไม่ต้องสงสัยเลยว่าทำไมคนทั้งโลกจึงยินดีจ่ายในราคาที่ค่อนข้างสูง
แล้วไอ้ด้วยความต้องการในสินค้าที่มีมูลค่าสูงนี่ละครับ กลายเป็นช่องทางให้กับกลุ่มอาชญากรรมที่มุ่งหวังหากำไรจากการหลอกลวงผู้บริโภค ด้วยการผลิตน้ำมันมะกอกปลอมที่ผ่านการเจือจางหรือดัดแปลงให้ดูเหมือนของแท้ ในเครือข่ายนี้มีการใช้งานเทคนิคและสารเติมแต่งเพื่อเลียนแบบคุณสมบัติของน้ำมันมะกอกแท้ เช่น การปรับเปลี่ยนกลิ่น รสชาติ และคุณสมบัติการแข็งตัวเมื่อแช่เย็น ซึ่งเคยเป็นวิธีตรวจสอบที่ง่ายต่อการแยกแยะของผลิตภัณฑ์แท้ แต่ด้วยเทคนิคใหม่ ๆ ที่ถูกพัฒนาขึ้น ผู้ปลอมแปลงสามารถทำให้ผลิตภัณฑ์ปลอมเหล่านี้ผ่านการตรวจสอบเบื้องต้นได้อย่างไร้ร่องรอย
ข้อมูลจากหลายรายงานของหน่วยงานกำกับดูแลอาหารในยุโรปและสหรัฐอเมริกาเผยว่าขบวนการปลอมแปลงน้ำมันมะกอกเกิดขึ้นในหลายประเทศในแถบเมดิเตอร์เรเนียน โดยเฉพาะในอิตาลี ซึ่งเป็นศูนย์กลางของการผลิตน้ำมันมะกอก
กลุ่มอาชญากรรมในภูมิภาคเหล่านี้ได้นำเอาวิธีการผลิตที่ผิดกฎหมายและการใช้สารเติมแต่งราคาถูกมาเจือจางกับน้ำมันมะกอกแท้ ทำให้ผู้บริโภคไม่สามารถตรวจสอบคุณภาพของผลิตภัณฑ์ได้ด้วยการทดสอบง่าย ๆ เช่น การแช่ตู้เย็นเพื่อตรวจดูการแข็งตัวได้อีกต่อไป (งว่อออ มีอัพเดท patch)
หน่วยงานตำรวจและหน่วยงานกำกับดูแลในอิตาลีร่วมกับหน่วยงานระดับนานาชาติ เช่น EFSA (European Food Safety Authority) และ FDA (Food and Drug Administration) ของสหรัฐอเมริกา ได้ร่วมมือกันเปิดเผยและจับกุมเครือข่ายน้ำมันมะกอกปลอมที่มีความซับซ้อนและขนาดใหญ่ หนึ่งในการจับกุมครั้งใหญ่เกิดขึ้นในปี 2017 เมื่อเจ้าหน้าที่ตำรวจอิตาลีร่วมกับหน่วยงานสอบสวนระดับนานาชาติได้ดำเนินการบุกค้นโรงงานผลิตลับในพื้นที่ชนบทของอิตาลี ที่มีหลักฐานชัดเจนว่ามีการผลิตน้ำมันมะกอกปลอมในปริมาณมหาศาล
เจ้าหน้าที่ได้ค้นพบโกดังที่ถูกซ่อนอยู่ในเขตอุตสาหกรรมที่มีการจัดเก็บถังน้ำมันจำนวนมาก ซึ่งบรรจุผลิตภัณฑ์ที่ถูกเจือจางด้วยน้ำมันพืชราคาถูก เช่น น้ำมันถั่วเหลือง น้ำมันปาล์ม และน้ำมันคาโนลา รวมถึงการเติมสารเคมีที่ช่วยปรับปรุงลักษณะทางกายภาพ เช่น ขี้ผึ้งพืช (Candelilla Wax หรือ Carnauba Wax) เพื่อให้ผลิตภัณฑ์มีคุณสมบัติการแข็งตัวเมื่อนำไปแช่เย็น เหล่านี้เป็นเทคนิคที่ผู้ปลอมแปลงพัฒนาขึ้นเพื่อเลี่ยงการตรวจสอบด้วยวิธีดั้งเดิมที่เคยใช้แยกแยะน้ำมันมะกอกแท้กับปลอมได้
การจับกุมในครั้งนั้นเป็นการร่วมมือระหว่างเจ้าหน้าที่ตำรวจอิตาลีและหน่วยงานสอบสวนของสหภาพยุโรป ที่ได้ใช้เทคโนโลยีการตรวจสอบขั้นสูงและการวิเคราะห์ทางเคมีในห้องปฏิบัติการ เพื่อพิสูจน์ว่าผลิตภัณฑ์ที่ถูกบรรจุในขวดพร้อมฉลากที่หลอกลวงนั้นไม่ได้มีคุณภาพตามมาตรฐานของน้ำมันมะกอก Extra Virgin ขึ้นจริง เจ้าหน้าที่ได้จับกุมผู้ต้องหาและยึดทรัพย์สินในมูลค่าหลายร้อยล้านยูโร จากนั้นคดีนี้ได้ถูกนำเข้าสู่กระบวนการไต่สวนในศาลอิตาลี ซึ่งมีการลงโทษผู้เกี่ยวข้องด้วยโทษจำคุกหลายปีและการปรับเงินจำนวนมหาศาล
ในกระบวนการไต่สวน เจ้าหน้าที่ได้เปิดเผยว่าขบวนการนี้ไม่ได้ดำเนินการโดยบุคคลเพียงไม่กี่คนเท่านั้น แต่เป็นเครือข่ายขนาดใหญ่ที่มีการเชื่อมโยงกับกลุ่มมาเฟียอย่าง Cosa Nostra และ ’Ndrangheta ซึ่งเป็นกลุ่มอาชญากรรมที่มีอิทธิพลทั้งในประเทศและต่างประเทศ กลุ่มเหล่านี้มีบทบาทในการควบคุมการผลิต การจัดจำหน่าย และการขนส่งน้ำมันมะกอกปลอมผ่านเส้นทางลับที่ซับซ้อน ทั้งในรูปแบบของบริษัทหน้ากากและระบบการฟอกเงินที่มีความซับซ้อนสูง
ในปูมหลังของกลุ่มอาชญากรรมที่มีอิทธิพลในอิตาลี อย่างเช่น Cosa Nostra และ ’Ndrangheta เนี่ยครับ ถือเป็นประวัติศาสตร์ที่สลับซับซ้อนและเต็มไปด้วยความรุนแรง ความขัดแย้ง และกลยุทธ์ที่แยบยลในการดำเนินธุรกิจผิดกฎหมายที่กระจายไปทั่วโลก โดยเฉพาะการจับกุมครั้งใหญ่ในวงการปลอมแปลงน้ำมันมะกอกที่เรากำลังพูดถึง
Cosa Nostra หรือที่รู้จักกันในชื่อ “มาเฟียซิซิลี” หรือว่า The Sicilian Mafia ถือเป็นกลุ่มอาชญากรรมที่เก่าแก่ที่สุดและมีชื่อเสียงที่สุดในอิตาลี และมีอิทธิพลอย่างมากในโลกอาชญากรรมระหว่างประเทศ ประวัติของ Cosa Nostra เต็มไปด้วยความรุนแรงและการควบคุมธุรกิจผิดกฎหมายในหลายด้าน ไม่ว่าจะเป็นการค้ามนุษย์ การค้าผิดกฎหมาย และการติดสินบนเจ้าหน้าที่ของรัฐ สิ่งที่ทำให้ Cosa Nostra น่าสะพรึงกลัวคือวิธีการที่พวกเขาควบคุมแหล่งธุรกิจทั้งในอิตาลีและในต่างประเทศด้วยการใช้ความรุนแรงและการหลอกลวง
หนึ่งในคดีที่ทำให้ชื่อเสียงของ Cosa Nostra ติดตรึงในใจผู้คนทั่วโลกคือคดีฆาตกรรม Giovanni Falcone และ Paolo Borsellino ผู้พิพากษาที่ทำงานอย่างหนักเพื่อปราบปรามมาเฟียซิซิลีในช่วงปี 1990 โดยเฉพาะการต่อสู้กับ Cosa Nostra จนกระทั่งทั้งสองถูกลอบสังหารอย่างโหดเหี้ยมในเหตุการณ์ระเบิดที่เกิดขึ้นในปี 1992 การฆาตกรรมนี้ทำให้ผู้คนในอิตาลีและทั่วโลกตระหนักถึงพลังอำนาจและอิทธิพลของ Cosa Nostra ที่สามารถกระทำการรุนแรงได้แม้กระทั่งกับบุคคลในระดับสูง ขอเสริมให้ว่า Giovanni Falcone เป็นผู้พิพากษาและนักสืบที่มีบทบาทสำคัญในการทำลายเครือข่าย Cosa Nostra เขาเป็นผู้นำในการสร้างทีมสอบสวนที่เรียกว่า “Capaci Trial” และการวางแผนปฏิบัติการที่มุ่งหวังจะทำลายการกระทำผิดของมาเฟีย ซึ่งในที่สุดเขาก็เสียชีวิตจากการระเบิดรถยนต์ที่วางกับดักไว้โดยสมาชิก Cosa Nostra ในปี 1992 Paolo Borsellino ก็เป็นผู้พิพากษาที่ทำงานร่วมกับ Falcone ในการต่อสู้กับกลุ่มมาเฟีย Cosa Nostra และมีบทบาทสำคัญในการดำเนินการสอบสวนและพิจารณาคดีที่เกี่ยวข้องกับการกระทำผิดของมาเฟีย แต่เขาก็ถูกสังหารในเหตุการณ์ระเบิดรถยนต์อีกครั้งในปีเดียวกันกับการตายของ Falcone ซึ่งเกิดขึ้นไม่นานหลังจากที่ Falcone ถูกฆ่าตาย
ส่วน ’Ndrangheta ซึ่งมีต้นกำเนิดในแคว้นคาลาเบรีย (Calabria) ในอิตาลี ถือเป็นอีกหนึ่งกลุ่มที่มีอิทธิพลและความน่ากลัวไม่แพ้กัน แม้ว่าในช่วงแรก ’Ndrangheta จะไม่ได้มีชื่อเสียงโด่งดังเท่า Cosa Nostra แต่ในปัจจุบันกลุ่มนี้ถือว่าเป็นหนึ่งในเครือข่ายอาชญากรรมที่ใหญ่ที่สุดในโลก โดยเฉพาะในการควบคุมการค้ายาเสพติดระดับนานาชาติ และการกระทำผิดกฎหมายเกี่ยวกับการฟอกเงิน กลุ่มนี้ไม่ได้จำกัดการดำเนินงานแค่ในอิตาลี แต่ได้กระจายเครือข่ายไปทั่วโลก โดยเฉพาะใน ยุโรป และ อเมริกาเหนือ ซึ่งได้กลายเป็นพลังที่ยากจะหยุดยั้งได้
การทำธุรกิจของ ’Ndrangheta นั้นมีการใช้ความรุนแรงในการรักษาความมั่นคงและการแทรกซึมในระบบเศรษฐกิจ โดยเฉพาะในวงการการก่อสร้างและธุรกิจที่เกี่ยวข้องกับทรัพย์สิน พวกเขามีอิทธิพลอย่างมากในอุตสาหกรรมบางชนิด เช่น การค้ายาเสพติดที่มีมูลค่าสูง ซึ่งการควบคุมและการปราบปรามของพวกเขาทำให้เกิดความตื่นกลัวในทุกภาคส่วน
เคสดังๆ ที่ทำให้ ’Ndrangheta น่าสะพรึงกลัวคือการควบคุมการค้ายาเสพติดในตลาดยุโรป การที่พวกเขามีเครือข่ายกว้างขวางและการเชื่อมโยงกับกลุ่มอาชญากรระหว่างประเทศทำให้พวกเขามีอำนาจในการจัดการและกระจายยาเสพติดได้อย่างไม่มีที่สิ้นสุด อย่างในปี 2007 กลุ่ม ’Ndrangheta ถูกกล่าวหาว่ามีส่วนเกี่ยวข้องในการค้ายาเสพติดโคเคนมูลค่าหลายพันล้านดอลลาร์ โดยพวกเขาสามารถหลีกเลี่ยงการตรวจจับจากหน่วยงานตำรวจได้อย่างเชี่ยวชาญ
แม้การจับกุมครั้งใหญ่ในปี 2017 จะทำให้ขบวนการปลอมแปลงน้ำมันมะกอกในบางส่วนถูกทำลายลง แต่เครือข่ายอาชญากรรมที่เหลือยังคงดำเนินกิจกรรมนี้อยู่ในระดับที่น่ากังวล ผู้บริโภคในหลายประเทศยังคงต้องเผชิญกับผลิตภัณฑ์น้ำมันมะกอกปลอมที่ออกมาจากเครือข่ายเหล่านี้ ซึ่งมักจะมาพร้อมกับความเสี่ยงต่อสุขภาพ เนื่องจากอาจมีการปนเปื้อนสารเคมีอันตรายและการขาดความโปร่งใสในกระบวนการผลิต
Cosa Nostra ยังคงเป็นกลุ่มอาชญากรรมที่มีอิทธิพลมากในซิซิลีและมักจะใช้กลยุทธ์ในการขยายอำนาจผ่านการควบคุมการค้าและอุตสาหกรรมที่มีกำไรสูง การผลิตน้ำมันมะกอกแท้ในซิซิลีเป็นธุรกิจที่มีมูลค่ามหาศาลและเป็นที่นิยมในตลาดทั่วโลก ดังนั้นกลุ่ม Cosa Nostra จึงไม่ได้เพียงแค่ควบคุมการผลิตน้ำมันมะกอกปลอมเท่านั้น แต่ยังควบคุมการขนส่งและการกระจายสินค้าเหล่านี้ไปยังหลายประเทศที่ต้องการผลิตภัณฑ์ปลอมในราคาถูก
กลุ่ม Cosa Nostra ใช้ระบบ “pizzo” หรือการเก็บค่าคุ้มครองจากโรงงานผลิตน้ำมันมะกอกที่ไม่สามารถหลบหนีจากการเรียกเก็บเงินจากพวกเขาได้ รวมถึงการบังคับให้เจ้าของโรงงานผลิตน้ำมันมะกอกต้องซื้อวัตถุดิบที่ไม่ใช่มะกอกจากแหล่งที่พวกเขาควบคุม บางครั้งก็ร่วมมือกับกลุ่มอาชญากรในต่างประเทศ เพื่อให้สามารถขยายตลาดน้ำมันมะกอกปลอมในระดับนานาชาติได้
ขณะที่ Cosa Nostra ครองตลาดในซิซิลี นั้นทางกลุ่ม ’Ndrangheta มีบทบาทในแคว้นคาลาเบรียและมีอิทธิพลในการขยายกิจกรรมการผลิตน้ำมันมะกอกปลอมไปยังตลาดในยุโรปและทั่วโลก โดยเฉพาะในกลุ่มประเทศแถบยุโรปเหนือและอเมริกาเหนือ กลุ่มนี้เป็นหนึ่งในกลุ่มอาชญากรรมที่มีเครือข่ายการกระจายสินค้ามหาศาล รวมถึงน้ำมันมะกอกปลอมที่ไม่ได้รับการตรวจสอบจากผู้บริโภค
การกระจายสินค้าไม่ใช่แค่การจัดส่งน้ำมันมะกอกปลอมไปยังร้านค้าหรือผู้ขายที่ไม่ตรวจสอบ แต่ ‘Ndrangheta ยังมีบทบาทในการสร้างการเชื่อมต่อกับบริษัทส่งออกที่ดูเหมือนจะทำการค้าทั่วไป จนเมื่อการสอบสวนดำเนินไป ก็พบว่าเบื้องหลังของบริษัทเหล่านี้กลับเป็นการขนส่งน้ำมันมะกอกปลอมในปริมาณมหาศาล ขณะเดียวกันก็สร้างแรงกดดันต่อเจ้าหน้าที่และบรรดาผู้ที่พยายามจะเปิดเผยความจริง
ทั้งสองกลุ่มไม่ได้แยกกันไปตามแต่ละเขตแดน แต่พวกเขามักจะร่วมมือกันในการขยายเครือข่ายและหลีกเลี่ยงการถูกจับกุม การรวมตัวระหว่าง Cosa Nostra และ ’Ndrangheta ทำให้เกิดการรวมตัวของอำนาจและความรู้ในการหลบเลี่ยงการตรวจสอบจากเจ้าหน้าที่ ซึ่งทำให้การติดตามและจับกุมยากขึ้น ทั้งนี้เพราะพวกเขามักจะใช้วิธีการที่ซับซ้อนในการบังคับใช้การควบคุมตลาดน้ำมันมะกอกปลอม ซึ่งบางครั้งพวกเขาจะสร้างบริษัทหน้ากากและจดทะเบียนในประเทศที่ไม่มีกฎหมายควบคุมการตรวจสอบอาหารอย่างเคร่งครัด
ทั้ง Cosa Nostra และ ’Ndrangheta จึงเป็นหัวเรือใหญ่ที่ยังคงดำเนินกิจกรรมอาชญากรรมเหล่านี้อยู่ แม้จะมีการจับกุมและเปิดเผยเครือข่ายในบางส่วน แต่เครือข่ายการผลิตน้ำมันมะกอกปลอมยังคงมีความลับอยู่ในที่มืด และอิทธิพลของทั้งสองกลุ่มนี้ก็ยังคงสะท้อนอยู่ในอุตสาหกรรมอาหารทั่วโลก
แม้ว่าจะมีการจับกุมกลุ่มผู้ต้องหาหลายคนในช่วงการบุกค้นครั้งใหญ่ เจ้าหน้าที่ยังคงต้องทำงานหนักเพื่อขยายขอบเขตของการสืบสวน และทำลายเครือข่ายการกระจายสินค้าในระดับนานาชาติที่ทั้งสองกลุ่มควบคุมอยู่อย่างลับๆ แต่ในที่สุดแล้ว การพยายามทำลายอำนาจของ Cosa Nostra และ ’Ndrangheta ในวงการน้ำมันมะกอกปลอมยังคงเป็นการต่อสู้ที่ยาวนานและไม่สิ้นสุดอยู่ดีครับ
หนึ่งในปัญหาที่ผู้บริโภคต้องเผชิญคือ ความยากในการตรวจสอบคุณภาพของน้ำมันมะกอกที่ซื้อมา เนื่องจากการตรวจสอบเบื้องต้นเช่นการแช่ตู้เย็นเพื่อดูการแข็งตัวอาจไม่เพียงพอในการแยกแยะน้ำมันมะกอกแท้กับน้ำมันปลอมที่ผ่านการดัดแปลงด้วยสารเติมแต่งใหม่ ๆ เทคนิคการผลิตที่ซับซ้อนนี้ทำให้ผู้บริโภคต้องพึ่งพาแหล่งข้อมูลที่เชื่อถือได้และการรับรองจากหน่วยงานที่มีอำนาจ
แม้ในปัจจุบันหน่วยงานตำรวจและหน่วยงานกำกับดูแลในยุโรปและสหรัฐอเมริกาจะได้เพิ่มความเข้มงวดในการตรวจสอบและจับกุมขบวนการน้ำมันมะกอกปลอม แต่เครือข่ายขนาดใหญ่ที่มีความลับและการจัดการทางการเงินที่ซับซ้อนยังคงหลบหนีจากการปราบปรามอยู่เป็นอย่างดี ภาพรวมที่พบคือ ผู้ผลิตน้ำมันมะกอกปลอมที่ยังเหลืออยู่ในตลาดมักจะมีการเปลี่ยนแปลงสูตรและเทคนิคอย่างต่อเนื่อง เพื่อให้สามารถหลีกเลี่ยงการตรวจสอบจากห้องปฏิบัติการและการสอบสวนในระดับนานาชาติ
แล้วการจับกุมครั้งใหญ่ในปี 2017 ก็ส่งผลให้เกิดการปรับปรุงมาตรการตรวจสอบในอุตสาหกรรมอาหารและการบังคับใช้กฎหมายในยุโรป แต่ความท้าทายในการจับกุมและทำลายเครือข่ายขนาดใหญ่นี้ยังคงอยู่ เนื่องจากความร่วมมือระหว่างกลุ่มอาชญากรรมทั้งในอิตาลีและต่างประเทศมีความซับซ้อนและเป็นระบบที่ยากต่อการแตกสลาย
ในที่สุด เรื่องราวของการจับกุมขบวนการน้ำมันมะกอกปลอมในยุคนี้จึงเป็นเครื่องเตือนใจให้กับทั้งหน่วยงานกำกับดูแลและผู้บริโภคว่า การตรวจสอบคุณภาพและความโปร่งใสในอุตสาหกรรมอาหารเป็นสิ่งที่ไม่สามารถละเลยได้ และการจับกุมผู้กระทำผิดเพียงส่วนหนึ่งก็ยังไม่เพียงพอที่จะทำให้เครือข่ายอาชญากรรมที่มีอิทธิพลเหล่านี้ถูกทำลายหมดสิ้น ผู้บริโภคจึงควรเลือกซื้อผลิตภัณฑ์จากแหล่งที่เชื่อถือได้และมีการรับรองคุณภาพอย่างเคร่งครัด เพื่อป้องกันไม่ให้ตกเป็นเหยื่อของการหลอกลวงที่อาจมีผลกระทบต่อสุขภาพในระยะยาว
และการเรียนรู้ในการเลือกซื้อก็เป็นเกราะป้องกันขั้นต้นที่สำคัญ ถ้าจะบอกว่าหายาก บ้านเราไม่ค่อยมี เอาแบบง่ายๆในห้างก็ได้มั๊ง
ผมคงบอกได้แค่ เอาตามสะดวกพี่เลยครับ
ผมแค่สื่อสารสุขภาพเออร์ คนนึง
pirateketo
ฉลาก3รู้
ม้วนหางสิลูก #กูต้องรู้มั๊ย #siamstr
-
 @ 6830c409:ff17c655
2025-03-24 02:46:10
@ 6830c409:ff17c655
2025-03-24 02:46:10Nostr ഉപയോഗിച്ച് ഒരു ഉപയോക്താവായി നിങ്ങൾക്ക് ചെയ്യാൻ കഴിയുന്ന കാര്യങ്ങൾ:
-
കുറിപ്പുകൾ (Notes) പോസ്റ്റ് ചെയ്യുക: നിങ്ങളുടെ ചിന്തകൾ, അപ്ഡേറ്റുകൾ, അല്ലെങ്കിൽ മറ്റ് ഉള്ളടക്കങ്ങൾ പങ്കിടാൻ നിങ്ങൾക്ക് ചെറിയ സന്ദേശങ്ങൾ പോസ്റ്റ് ചെയ്യാം. ഈ നോട്ടുകൾക്ക് മാക്സിമം ലെങ്ത് എന്ന ലിമിറ്റ് ഇല്ല.
-
ദീർഘമായ കുറിപ്പുകൾ (Long-form Notes) പ്രസിദ്ധീകരിക്കുക: Nostr ദീർഘമായ ഉള്ളടക്കവും പിന്തുണയ്ക്കുന്നു, അതുവഴി നിങ്ങൾക്ക് ലേഖനങ്ങൾ, പ്രബന്ധങ്ങൾ, അല്ലെങ്കിൽ വിശദമായ പോസ്റ്റുകൾ എഴുതാനും പങ്കിടാനും കഴിയും.
-
Zapping (മൈക്രോ-പേയ്മെന്റുകൾ) ഉപയോഗിക്കുക: Nostr ലെ ലൈറ്റ്നിംഗ് നെറ്റ്വർക്ക് ഉപയോഗിച്ച്, നിങ്ങൾക്ക് ചെറിയ തുകകൾ (സാറ്റോഷികൾ) അയയ്ക്കാൻ കഴിയും, ഇത് കണ്ടൻ്റ് ക്രിയേറ്റർമാർക്ക് പിന്തുണ നൽകാൻ സഹായിക്കുന്നു. സറ്റോഷി എന്നത് ബിറ്റ്കോയിൻ നാണയത്തിന്റെ ഏറ്റവും ചെറിയ യൂണിറ്റാണ്.
-
ചാറ്റുകൾ (Chats) ഉപയോഗിക്കുക: മറ്റ് ഉപയോക്താക്കളുമായി സ്വകാര്യമായി അല്ലെങ്കിൽ പബ്ലിക്ക് ചാറ്റ് റൂമുകളിൽ ആശയവിനിമയം നടത്താൻ നിങ്ങൾക്ക് Nostr ലെ ചാറ്റ് ഫീച്ചറുകൾ ഉപയോഗിക്കാം. ഈ ചാറ്റുകൾ എൻക്രിപ്റ്റ് ചെയ്തതും സുരക്ഷിതവുമാണ്, അതിനാൽ നിങ്ങളുടെ സംഭാഷണങ്ങൾ സ്വകാര്യത ഉറപ്പാക്കുന്നു.
-
മാർക്കറ്റ്പ്ലേസുകൾ (Marketplaces) ഉപയോഗിക്കുക: Nostr മാർക്കറ്റ്പ്ലേസുകൾ ഉപയോഗിച്ച്, ഉപയോക്താക്കൾക്ക് പീർ-ടു-പീർ അടിസ്ഥാനത്തിൽ വസ്തുക്കളും സേവനങ്ങളും വാങ്ങാനും വിൽക്കാനും കഴിയും.
-
വ്യത്യസ്ത ക്ലയന്റുകൾ പരീക്ഷിക്കുക: Nostr വിവിധ ക്ലയന്റുകൾ ഉപയോഗിച്ച് പ്രവർത്തിക്കുന്നു. ഓരോ ക്ലയന്റിനും വ്യത്യസ്ത സവിശേഷതകളും ഇന്റർഫേസുകളും ഉണ്ട്, അതിനാൽ നിങ്ങളുടെ ഇഷ്ടാനുസരണം തിരഞ്ഞെടുക്കാം. Damus, Amethyst, Iris, Yakihonne, Primal, NoStrudel തുടങ്ങിയവയാണ് ചില പ്രശസ്ത ക്ലയന്റുകൾ.
-
മറ്റ് ഉപയോക്താക്കളെ പിന്തുടരുക: Nostr ലെ നിങ്ങളുടെ പ്രൊഫൈൽ ഉപയോഗിച്ച്, നിങ്ങൾക്ക് മറ്റ് ഉപയോക്താക്കളെ പിന്തുടരാനും അവരുടെ പോസ്റ്റുകളുമായി ഇടപെടാനും കഴിയും. ആർട്ടിഫിഷ്യലായി നോട്ടുകളെ ബൂസ്റ്റ് ചെയ്യാൻ കഴിയില്ല - അതുകൊണ്ടു തന്നെ, വളരെ സ്വാഭാവികമായ ഒരു ടൈമ്ലൈൻ ആകും എല്ലാവർക്കും ലഭിക്കുക.
-
മീഡിയയും ഫയലുകളും പങ്കിടുക: നിങ്ങളുടെ ഫോളോവേഴ്സുമായി ചിത്രങ്ങൾ, വീഡിയോകൾ, മറ്റ് ഫയലുകൾ എന്നിവ പങ്കിടുക, ഇത് നിങ്ങളുടെ പോസ്റ്റുകൾ കൂടുതൽ ആകർഷകമാക്കുന്നു.
-
പോളുകളിലും സർവേയുകളിലും പങ്കെടുക്കുക: Nostr ലെ പോളുകളിലും സർവേയുകളിലും പങ്കെടുക്കുക, ഇത് സമൂഹത്തിന്റെ അഭിപ്രായങ്ങൾ അറിയാനും ചർച്ചകളിൽ പങ്കെടുക്കാനും സഹായിക്കുന്നു.
-
യാക്കിഹോൺ പോലുള്ള ക്ലയൻ്റുകളിൽ പോസ്റ്റുകൾക്ക് ടെമ്പ്ലേറ്റ് ഉണ്ടാക്കാനും അത് ഷെയർ ചെയ്യാനും ഒക്കെ സാധിക്കും. ഇത് കൂടുതൽ ഇൻ്ററാക്ടീവ് അനുഭവം നൽകുന്നു, പ്രത്യേകിച്ച് നിങ്ങളുടെ പോസ്റ്റുകൾക്ക് ഒരു യുണീക്ക് ലുക്ക് ആൻഡ് ഫീൽ നൽകാൻ സാധിക്കും.
ഓക്കെ. നിങ്ങൾ എപ്പൊഴാണ് Nostr ഉപയോഗിക്കാൻ തുടങ്ങുന്നത്? നിങ്ങളുടെ നൊസ്റ്റർ ഐഡി/പബ്ലിക്ക് കീ ഷെയർ ചെയ്യൂ.
-
-
 @ 4d4fb5ff:1e821f47
2025-03-24 02:03:53
@ 4d4fb5ff:1e821f47
2025-03-24 02:03:53The entire genetic sequence for peptidase E (pepE, e. coli). Genes in living organisms are subject to mutation across time. In contrast, information on the bitcoin ledger is immutable. By etching the pepE DNA sequence onto bitcoin, its ability to evolve is lost. This challenges the significance of genetic information in a foreign digital context. I chose to keep the title “PEPEGENE” in upper case as a homage to the naming convention for Counterparty assets. This additionally contrasts the notation of a digital asset identifier (PEPEGENE) against the notation of biological identifiers (a,t,c or g), which are kept in lower case.
-
 @ a8d1560d:3fec7a08
2025-03-24 01:56:52
@ a8d1560d:3fec7a08
2025-03-24 01:56:52I have created a Nostr desktop-like client with currently 3 apps. However, it is currently read-only and you have to manually refresh the apps to see if there's something new.
https://websim.ai/@wholewish91244492/nostr-desktop/
-
 @ 1f9e547c:8af216ed
2025-03-24 01:46:55
@ 1f9e547c:8af216ed
2025-03-24 01:46:55Opinion about Earn Crypto with Haru Invest (android)
Hugo Hyungsoo Lee is the CEO of Haru Invest, a South Korean cryptocurrency investment platform. In August 2024, during his fraud trial related to the platform's collapse, Lee was attacked and stabbed in the neck by a former investor at the Seoul Southern District Court. The assailant, identified as Kang, had lost approximately $8.3 million due to Haru Invest's bankruptcy. Lee's injuries were not life-threatening, and Kang now faces a potential 10-year prison sentence for the attack.
Source: Jameson Lopp x.com Secondary Source: the block co
WalletScrutiny #nostrOpinion
-
 @ 7bc05901:8c26d22b
2025-03-24 00:48:46
@ 7bc05901:8c26d22b
2025-03-24 00:48:46There was a time in my life where I wouldn't miss church. I remember returning to church, it was directly next door to my downtown apartment. The amount of various substances I consumed every Sunday morning for those first few months back -- I am surprised they let me in the door, reeking as I must have of ganja.
Not only did they let me in the door, they asked me to go back to my apartment and get my guitar so I could join the band -- a keyboardist (the pastor's wife) and another female singer. I strummed along, and before I knew it, I had spent two years at this little church of less than 20 people, and my girlfriend was pregnant. They threw us the absolute best baby shower, just the sweetest people. And after the baby was born, I spent a few more weeks going, then I just realized it has been two years since I have been in there. Except I still have a key, and my guitar still sits on the stage, so I will stop by in the middle of the day sometimes and strum my guitar.
I feel so bad, because I don't know what church is. I worked at "mega" churches throughout my twenties, always directly for the head pastor -- king of his ecclesiastical empire. I had stayed out of church for almost seven years before I went back to this small, intimate affair next to my apartment. It was the only thing that could have gotten me back into it. I couldn't do anything where they are telling you about joining a "small group" (or, they probably call it like a damn "nucleus group" or "cell group" or "base camp" depending on which Zondervan bible study the pastor subscribes to). I couldn't do a glitzy put together, long-haired worship leader and band. With guitar solos. And synthesizers.
I also couldn't do what I grew up with as a kid: baptist hymns, a pipe organ, and shiny white-haired folks in their suits and skirts. And a deep-voiced "Worship Minister" who shouted "HOW GREAT THOU ART" at the pews.
I know that doesn't really encapsulate the spectrum, but those are the only places I can imagine not getting completely hung up on the evangelical legalism that just gushes from church pulpits here in the bible belt. I had enough of a personal radical grace revolution after I was well into my professional church life that the theology is such a hang up basically everywhere / everyone.
I want to start my own church, but I am in an unusual spot where I don't want to sacrifice my entire weekend. I also dread the thought of the business side of the church. Strange, too, because my twenties were spent figuring out how to generate money in a church role, spinning off media projects, connecting to the conference circuit, and compiling sermon series into devotional literature. I also never thought I would shy away from an opportunity to be in that extroverted church environment.
I think churches can be helpful, possibly even life-saving. I think a lot of folks want to turn it around, and want to find a community of positive folks who are willing to face life's difficult questions. And, most importantly, I think folks desperately want to hear that their sins are forgiven, that Christ's blood was spilled for them, that grace is for them. For you.
Unfortunately, I am not there yet. I hope that airing some of this out will create the room in my head for the nudging that needs to help so I can scratch this itch. Maybe find some faith in the principles behind the church, even if I have lost faith in the building and the business.
-
 @ a3a17f65:e9606ad9
2025-03-24 00:42:06
@ a3a17f65:e9606ad9
2025-03-24 00:42:06I’ve been thinking about journaling lately. It might have been the productivity videos I watched, or maybe it’s just the algorithm doing its thing, but the idea has stuck. Journaling seems like an interesting experiment that could help me build momentum for writing more complex posts later.
The idea came to me during a Yin Yoga class. Being in a relaxed state is great for creative thinking, and for a long time, I’ve been procrastinating on writing proper essays—despite knowing how important it is to crystallize and integrate thoughts. I kept putting unnecessary roadblocks in my way, like picking a good domain name, learning static websites, and customizing themes. All these obstacles just kept me stuck at square one. So, why not start small? A simple, frequent post on NOSTR about whatever’s on my mind, without overthinking it.
Two basic rules: it doesn’t have to be elaborate, it should be as effortless as possible, and whatever I write has to be published on the same day. This won’t be stream-of-consciousness-style writing or morning pages, nor will I get too personal. Just a simple log, hopefully daily.
There’s this growing frustration in my mind: What the fuck have I done with my knowledge and intellect? It doesn’t feel like anything exceptional. I’m not saying that to be modest—I’m just trying to be honest. The people around me, including some I consider genuinely intelligent, seem to think I have exceptional knowledge or a unique way of thinking. But I can’t help wondering if they’re misjudging it—maybe they confuse curiosity with intelligence, or maybe it’s just that their standards are different. All I know for sure is that I’m curious and tend to think a little differently. But where has that gotten me so far? The little financial success I had came from a shitcoin network, and now it barely amounts to anything. If Naval is right—"The only true test of intelligence is if you get what you want out of life”—then I’m damn near the village idiot level.
So, what’s the point of this personal project? Writing regularly to clear my mind, develop self-awareness, and align with my true vision. I hope this process helps me better understand who I am, what I’m struggling with, and how to get back on the path to financial freedom and fulfillment. And maybe, this will be useful to you too—my dear reader, wherever you are.
Here’s to the journey ahead—one post at a time. I hope something here resonates with you, even if it's just a snapshot of someone else navigating their own journey.
-
 @ 30fb9c78:1f1e3c3a
2025-03-23 22:47:02
@ 30fb9c78:1f1e3c3a
2025-03-23 22:47:02The President delivers a ‘State of the Union’ Speech every year, but that’s a snooze. Just look at your worthy representatives struggling to keep their eyes open. That’s because they’ve heard it all before.
We have too. Not much changes in politics. Certainly not the candidates.
There’s more variety at my local gas station, where at least I get to choose from three types of fuel and five flavors of Big Gulp.
So forget about politics. All the action now is happening in mainstream culture—which is changing at warp speed.
That’s why we need a “State of the Culture” speech instead. My address last year was quoted and cited, and was absolutely true back then—but it’s already as obsolete as the ChatGPT-1 help desk at the Bored Ape Yacht Club.
In fact, 2024 may be the most fast-paced—and dangerous—time ever for the creative economy. And that will be true, no matter what happens in November.
So let’s plunge in.
I want to tell you why entertainment is dead. And what’s coming to take its place.
If the culture was like politics, you would get just two choices. They might look like this.
Many creative people think these are the only options—both for them and their audience. Either they give the audience what it wants (the entertainer’s job) or else they put demands on the public (that’s where art begins).
But they’re dead wrong.
Maybe it’s smarter to view the creative economy like a food chain. If you’re an artist—or are striving to become one—your reality often feels like this.

Until recently, the entertainment industry has been on a growth tear—so much so, that anything artsy or indie or alternative got squeezed as collateral damage.
But even this disturbing picture isn’t disturbing enough. That’s because it misses the single biggest change happening right now.
We’re witnessing the birth of a post-entertainment culture. And it won’t help the arts. In fact, it won’t help society at all.
Even that big whale is in trouble. Entertainment companies are struggling in ways nobody anticipated just a few years ago.
Consider the movie business:
- Disney is a state of crisis—where everything is shrinking (except the CEO’s paycheck).
- Paramount just laid off 800 employees - and wants to find a new owner.
- Universal is now releasing movies to streaming after just 3 weeks in theaters.
- Warner Bros actually makes more money canceling films than releasing them.
The TV business also hit a wall in 2023. After years of steady growth, the number of scripted series has started shrinking.
Estimated number of U.S scripted originial series per year, 2010-2023 Source
Music may be in the worst state of them all. Just consider Sony’s huge move a few days ago - investing in Michael Jackson’s song catalog at a valuation of $1.2 billion. No label would invest even a fraction of that amount in launching new artists.
In 2024, musicians are actually worth more old than young, dead than alive.
This raises the obvious question. How can demand for new entertainment shrink? What can possibly replace it?
But something will replace it. It’s already starting to happen.
Here’s a better model of the cultural food chain in the year 2024.
The fastest growing sector of the culture economy is distraction. Or call it scrolling or swiping or wasting time or whatever you want. But it’s not art or entertainment, just ceaseless activity.
The key is that each stimulus only lasts a few seconds, and must be repeated.
It’s a huge business, and will soon be larger than arts and entertainment combined. Everything is getting turned into TikTok - an aptly named platform for a business based on stimuli that must be repeated after only a few ticks of the clock.
TikTok made a fortune with fast-paced scrolling video. And now Facebook—once a place to connect with family and friends - is imitating it. So long, Granny, hello Reels. Twitter has done the same. And, of course, Instagram, YouTube, and everybody else trying to get rich on social media.
This is more than just the hot trend of 2024. It can last forever—because it’s based on body chemistry, not fashion or aesthetics.
Our brain rewards these brief bursts of distraction. The neurochemical dopamine is released, and this makes us feel good—so we want to repeat the stimulus.
The cycle looks like this.
 This is a familiar model for addiction.
This is a familiar model for addiction.Only now it is getting applied to culture and the creative world—and billions of people. They are unwitting volunteers in the largest social engineering experiment in human history.
So you need to ditch that simple model of art versus entertainment. And even ‘distraction’ is just a stepping stone toward the real goal nowadays—which is addiction.
Here’s the future cultural food chain—pursued aggressively by tech platforms that now dominate every aspect of our lives.
The tech platforms aren’t like the Medici in Florence, or those other rich patrons of the arts. They don’t want to find the next Michelangelo or Mozart. They want to create a world of junkies—because they will be the dealers.
Addiction is the goal.
They don’t say it openly, but they don’t need to. Just look at what they do.
Everything is designed to lock users into an addictive cycle
- The platforms are all shifting to scrolling and reeling interfaces where stimuli optimize the dopamine doom loop.
- Anything that might persuade you to leave the platform—a news story, or any outside link—is brutally punished by their algorithms. It might liberate you from your dependent junkie status, and that can’t be allowed.
- But wait, there’s more! Apple, Facebook, and others are now telling you to put on their virtual reality headsets—where you are swallowed up by the stimuli, like those tiny fish in my food chain charts. You’re invited to live as a passive recipient of make-believe experiences, like a pod slave in The Matrix.

The tech CEOs know this is harmful, but they do it anyway. A whistleblower released internal documents showing how Instagram use leads to depression, anxiety, and suicidal thoughts. Mark Zuckerberg was told all the disturbing details.
He doesn’t care. The CEOs all know the score. The more their tech gets used, the worse all the psychic metrics get.
But still they push aggressively forward—they don’t want to lose market share to the other dopamine cartel members. And with a special focus on children. They figured out what every junk peddler already knows: It’s more profitable to get users locked in while they’re young.
And the virtual reality headsets raise even more issues—because they rewire users’ brains. Experts are already talking about “simulator sickness,” and that’s just the physical nausea, dizziness, and headaches. Imagine the psychic dislocations.
And you thought artists had it tough back in the day?
Even the dumbest entertainment looks like Shakespeare compared to dopamine culture. You don’t need Hamlet, a photo of a hamburger will suffice. Or a video of somebody twerking, or a pet looking goofy.
Instead of movies, users get served up an endless sequence of 15-second videos. Instead of symphonies, listeners hear bite-sized melodies, usually accompanied by one of these tiny videos—just enough for a dopamine hit, and no more.
This is the new culture. And its most striking feature is the absence of Culture (with a capital C) or even mindless entertainment—both get replaced by compulsive activity.
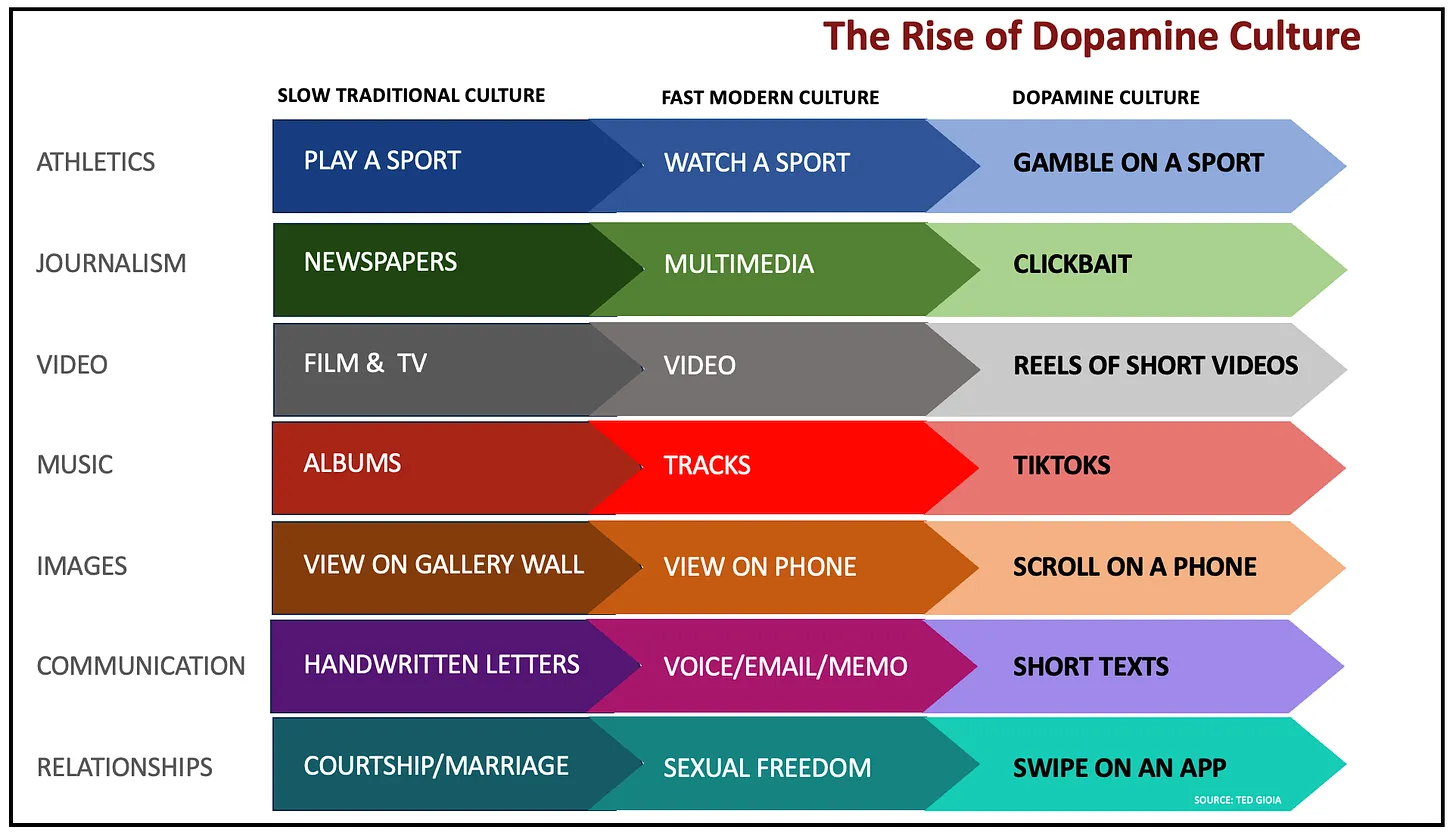
So don’t be surprised when huge corporations stop pretending otherwise—hence entertainment businesses that suddenly embrace gambling, or other equally addictive offerings. (Now you know why the Super Bowl took place in Las Vegas—a perfect symbol for the current moment in our culture.)
Everything is gamified. Anything can be scrollable. You can simulate any boat you row.
But what does this do to our brains? To our lives? To the future?
Here’s where the science gets really ugly. The more addicts rely on these stimuli, the less pleasure they receive. At a certain point, this cycle creates anhedonia—the complete absence of enjoyment in an experience supposedly pursued for pleasure.
That seems like a paradox
How can pursuing pleasure lead to less pleasure? But that’s how our brains are wired (perhaps as a protective mechanism). At a certain point, addicts still pursue the stimulus, but more to avoid the pain of dopamine deprivation.
People addicted to painkillers have the same experience. Beyond a certain level, opioid dependence actually makes the pain worse.
What happens when this same experience is delivered to everybody, via their phones? The results are devastating, as expert Dr. Len Lantz explains. Even people who thought they were immune to addictive behavior, get destroyed by the cycle:
There is a specific, abnormal brain activation pattern that is present in people who have anhedonia, which is a key feature of major depression, and absent in those who do not. It is often the case that when patients come to me with major depression, they say, “I shouldn’t be depressed. I have a good life. If my friends or coworkers knew I was depressed, they wouldn’t understand or they would be mad at me. They think I have it made. So, why don’t I feel that way?”
We’re now seeing the first effects on a grand social scale of this deadening effect.
Sure, let’s give it a name, something like TikTok depression or Silicon Valley zombification or whatever. The key fact is that users can feel it, even if they don’t have a label or a diagnosis. They feel it even if the technocrats refuse to tell them about it. Just listen to the words people use to describe their toxic online interactions: doomscrolling, trolling, doxxing, gaslighting, etc.
In the year 2024, this is what we do for fun.
But it doesn’t bring happiness. The World Happiness Report surveyed 150,000 people in 26 countries, and found that the US and other prosperous, technologically advanced societies are suffering a massive happiness decline. This is what happens when anhedonia is on sale every week—and the pervasive tech platforms increasingly resemble the ruthless corporations that got rich from opioid abuse.
Some companies get people hooked with pills and needles. Others with apps and algorithms. But either way, it’s just churning out junkies.
That’s our dystopian future. Not so much Orwell’s 1984—more like Huxley’s Brave New World.
Dr. Anna Lembke, author of Dopamine Nation, sometimes urges her patients to undergo a “dopamine fast” for one month—a sufficient amount of time for the brain to start rewiring. But even unplugging for a few minutes can be scary for those caught in the cycle.
She shares an example:
My patient Sophie, a Stanford undergraduate from South Korea, came in seeking help for depression and anxiety. Among the many things we talked about, she told me she spends most of her waking hours plugged into some kind of device: Instagramming, YouTubing, listening to podcasts and playlists. In session with her I suggested she try walking to class without listening to anything and just letting her own thoughts bubble to the surface. She looked at me both incredulous and afraid. “Why would I do that?” she asked, openmouthed.
A week later, Sophie returned and reported on the new experience: “It was hard at first. But then I got used to it and even kind of liked it. I started noticing the trees.”
 Want a horror story? Read this book—it’s got more zombies than The Walking Dead
Want a horror story? Read this book—it’s got more zombies than The Walking DeadNot long ago, I’d have dismissed anecdotes like this. I couldn’t really imagine somebody addicted to Instagram or TikTok or some other phone app.
But I don’t need to imagine anything now. I see those sad-eyed junkies, hooked to their devices, wherever I go. And even their facial expressions convey that haggard strungout look.
This is the real state of play in our culture in 2024.
And it’s a bigger issue than just struggling artists or floundering media companies. The dopamine cartel is now aggravating our worst social problems—in education, in workplaces, and in private life.
But you will hardly hear about this—because too many people are making far too much money from the dopamine culture.
If you thought the drug cartels were rich, wait till you see how much money the dopamine cartel is making. For a start, check out the market cap at Apple, Meta, etc. They are literally too big to stop.
Just telling the truth about the dopamine cartel would be a major step forward for the culture in 2024.
Also, do yourself a favor. Unplug yourself from time to time, and start noticing the trees or your goofy pets. They actually look better in real life than in the headset.
Source: Ted Gioia, The Honest Broker, February 18, 2024
-
 @ 6be5cc06:5259daf0
2025-03-23 21:39:37
@ 6be5cc06:5259daf0
2025-03-23 21:39:37O conceito de Megablock propõe uma nova maneira de medir o tempo dentro do ecossistema Bitcoin. Assim como usamos décadas, séculos e milênios para medir períodos históricos na sociedade humana, o Bitcoin pode ser dividido em Megablocks, cada um representando 1 milhão de blocos minerados.
1. Introdução
O Bitcoin opera em um sistema baseado na mineração de blocos, onde um novo bloco é adicionado à blockchain (ou timechain) aproximadamente a cada 10 minutos. A contagem de tempo tradicional, baseada em calendários solares e lunares, não se aplica diretamente ao Bitcoin, que funciona de maneira independente das convenções temporais humanas.
A proposta do Megablock surge como uma alternativa para medir o progresso da rede Bitcoin, dividindo sua existência em unidades de 1 milhão de blocos, permitindo uma estruturação do tempo no contexto da blockchain. Entretanto, diferentemente de medidas fixas de tempo, como anos e séculos, o tempo de um Megablock futuro não pode ser previsto com exatidão, pois variações no hashrate e ajustes de dificuldade fazem com que o tempo real de mineração flutue ao longo dos anos.
2. Definição do Megablock
2.1 O que é um Megablock?
Um Megablock é uma unidade de tempo no Bitcoin definida por um ciclo de 1.000.000 de blocos minerados. Com a taxa de geração de blocos mantida em 10 minutos por bloco, podemos estimar:
1 Megablock ≈ 1.000.000×10 minutos = 10.000.000 minutos = 166.666,7 horas = 6.944,4 dias ≈ 19 anos
Entretanto, dados históricos mostram que a média real de tempo por bloco tem sido levemente inferior a 10 minutos. Ao analisar os últimos 800.000 blocos, percebemos que cada 100.000 blocos foram minerados, em média, 1 a 2 meses mais rápido do que o previsto. Com variações indo de 2 dias a 3 meses de diferença. Esse ajuste pode continuar mudando conforme o hashrate cresce ou desacelera
Isso significa que o Megablock não deve ser usado como uma métrica exata para previsões futuras baseadas no calendário humano, (apenas aproximações e estimativas) pois sua duração pode variar ao longo do tempo. No entanto, essa variação não compromete sua função como uma unidade de tempo já decorrido. O conceito de Megablock continua sendo uma referência sólida para estruturar períodos históricos dentro da blockchain do Bitcoin. Independentemente da velocidade futura da mineração, 1 milhão de blocos sempre será igual a 1 milhão de blocos.
2.2 Estrutura dos Megablocks ao longo da história do Bitcoin
| Megablock | Início (Bloco) | Fim (Bloco) | Ano Estimado (margem de erro: ±2 anos) | | ---------------- | ------------------ | --------------- | ------------------------------------------ | | 1º Megablock | 0 | 1.000.000 | 2009 ~ 2027 | | 2º Megablock | 1.000.001 | 2.000.000 | 2027 ~ 2045 | | 3º Megablock | 2.000.001 | 3.000.000 | 2045 ~ 2064 | | 4º Megablock | 3.000.001 | 4.000.000 | 2064 ~ 2082 | | 5º Megablock | 4.000.001 | 5.000.000 | 2082 ~ 2099 | | 6º Megablock | 5.000.001 | 6.000.000 | 2099 ~ 2117 | | 7º Megablock | 6.000.001 | 7.000.000 | 2117 ~ 2136 |
- Nota sobre o primeiro Megablock: Do Bloco Gênese (0) ao Bloco 1.000.000, serão minerados 1.000.001 blocos, pois o Bloco 0 também é contado. O milionésimo bloco será, na realidade, o de número 999.999. Nos Megablocks subsequentes, a contagem será exatamente de 1.000.000 de blocos cada.
O fornecimento de Bitcoin passará por 6 Megablocks completos antes de atingir seu total de 21 milhões de BTC, previsto para acontecer no Bloco 6.930.000 (7º Megablock), quando a última fração de BTC será minerada.
Se essa tendência da média de tempo por bloco ser ligeiramente inferior a 10 minutos continuar, o último bloco com recompensa pode ser minerado entre 2135 e 2138, antes da previsão original de 2140.
De qualquer forma, o Megablock não se limita ao fornecimento de novas moedas. O último bloco com emissão de BTC será o 6.930.000, mas a blockchain continuará existindo indefinidamente.
Após a última emissão, os mineradores não receberão mais novas moedas como recompensa de bloco, mas continuarão garantindo a segurança da rede apenas com as taxas de transação. Dessa forma, novos Megablocks continuarão a ser formados, mantendo o padrão de 1.000.000 de blocos por unidade de tempo.
Assim como o 1º Megablock marca a era inicial do Bitcoin com sua fase de emissão mais intensa, os Megablocks após o fim da emissão representarão uma nova era da rede, onde a segurança será mantida puramente por incentivos de taxas de transação. Isso reforça que o tempo no Bitcoin continua sendo medido em blocos, e não em moedas emitidas.
3. Benefícios do Conceito de Megablock
3.1 Estruturação do Tempo Já Decorrido
Os Megablocks permitem que os Bitcoiners analisem a evolução da rede com uma métrica clara e baseada no próprio protocolo, estruturando os períodos históricos do Bitcoin.
3.2 Comparação com Unidades Temporais Humanas
Assim como temos décadas, séculos e milênios, podemos organizar a história do Bitcoin com Megablocks, criando marcos temporais claros dentro da blockchain:
- 1 Megablock ≈ 17 a 19 anos (equivalente a uma “geração” no tempo humano)
- 210.000 blocos = ~4 anos (ciclo de halving do Bitcoin)
3.3 Aplicação na História do Bitcoin
Podemos usar Megablocks para marcar eventos históricos importantes da rede:
- O 1º Megablock (2009 ~ 2026/2028) engloba a criação do Bitcoin, os primeiros halvings e a adoção institucional.
- O 2º Megablock (2027 ~ 2044/2046) verá um Bitcoin muito mais escasso, possivelmente consolidado como reserva de valor global.
- O 3º Megablock (2045 ~ 2062/2064) pode ser uma era de hiperbitcoinização, onde a economia gira inteiramente em torno do BTC.
4. Conclusão
O Megablock é uma proposta baseada na matemática da rede para medir o tempo já decorrido no Bitcoin, dividindo sua história em unidades de 1 milhão de blocos minerados. Essa unidade de tempo permite que Bitcoiners acompanhem o desenvolvimento e registrem a história da rede de maneira organizada e independente dos ciclos arbitrários do calendário humano.
Estamos atualmente formando o Primeiro Megablock, assim como estamos vivendo e construindo a década de 2020 e o século XXI. Esse conceito pode se tornar uma métrica fundamental para o estudo da história do Bitcoin, reforçando a ideia de que no Bitcoin, o tempo é medido em blocos, não em relógios.
Você já imaginou como será o Bitcoin no 3º ou 4º Megablock?
-
 @ 878dff7c:037d18bc
2025-03-23 20:40:39
@ 878dff7c:037d18bc
2025-03-23 20:40:39Quantum Mechanics Illuminate Avian Navigation
Summary:
Recent studies have unveiled that migrating birds utilize quantum mechanics to navigate vast distances. Specifically, proteins in their eyes form radical pairs sensitive to Earth's magnetic fields, enabling precise orientation during solo nocturnal migrations. This discovery highlights nature's sophisticated use of quantum principles in biological functions.:contentReference[oaicite:0]{index=0}
Sources: The Guardian - 24 March 2025
Federal Budget 2025-26: Anticipated Deficit and Cost-of-Living Measures
Summary:
Treasurer Jim Chalmers is set to deliver the 2025-26 Federal Budget on March 25, 2025, with expectations of a deficit close to the $26.9 billion predicted in the December 2024 Mid-Year Economic and Fiscal Outlook. The budget aims to provide substantial cost-of-living relief without exacerbating inflation, including measures such as a $150 electricity rebate and a $25 cap on PBS prescription medicines starting January 1, 2026. Chalmers has also highlighted external risks, including escalating US trade tensions, that could impact Australia's economic stability. Sources: The Guardian - March 24, 2025, ShareCafe - March 24, 2025, KPMG - March 21, 2025
Australia's Intelligence Review Warns of Potential Major-Power Conflicts
Summary:
An independent review of Australia's intelligence agencies indicates that the world is more volatile than in the past four decades, with the possibility of major-power conflicts no longer unimaginable. The report highlights increasing instability from U.S.-China rivalry and a bloc of autocratic states undermining global security. It recommends enhancing intelligence capabilities to address emerging threats. Sources: The Guardian - March 21, 2025
Severe Drought in Mali (South Australia) Forces Farmers to Rely on Bottled Water
Summary:
Farmers in Mali, such as Peter Williams, are experiencing an unprecedented drought leading to a scarcity of potable water. This crisis has compelled them to use bottled water for basic needs and purchase water for livestock. The "For Pete's Sake" campaign aims to raise awareness and pressure the government to increase its drought support beyond the current $18 million package. Despite emergency measures, farmers feel the government's efforts are insufficient to address the escalating crisis.
Sources: The Advertiser - 24 March 2025
High-Priced Fundraisers Continue Amid Upcoming Campaign Finance Reforms
Summary:
On Tuesday, Canberra will host budget night fundraisers with tickets costing up to $5,000. Despite impending laws to cap campaign spending and require disclosure, these fundraisers will proceed as usual in 2025. Labor's event, featuring Prime Minister Anthony Albanese, charges $5,000 per attendee, with a $1,000 discount for top-tier Labor business forum members. Liberal events, following Peter Dutton's budget reply speech, range from $500 to $5,000. Transparency advocates argue such practices favor the wealthy and undermine democracy. New rules mandating disclosure will come into effect before the next federal election in 2028, aiming to increase transparency and regulate campaign finances. Sources: The Guardian - 24 March 2025
Tech Giants Oppose Australia's Digital Regulations
Summary:
U.S. technology companies, including Meta, X, Apple, and Google, have expressed dissatisfaction with Australia's digital regulations, such as the News Media Bargaining Code, which requires them to subsidize local media at a cost of $140 million annually. The Computer and Communications Industry Association has filed a 45-page complaint with the U.S. Trade Representative, suggesting measures like tariffs to protect American companies. This tension raises concerns about potential impacts on Australia-U.S. trade relations.
Sources: The Australian - 22 March 2025
Australian Munitions Firm NIOA to Establish $120 Million Weapons Facility in the US
Summary:
Australian munitions company NIOA is set to invest $121.8 million in constructing a new manufacturing facility in Murfreesboro, Tennessee, named the Barrett Manufacturing & Technology Campus. Following its acquisition of Barrett Firearms in 2022, NIOA has become the largest Australian-owned supplier of munitions to the Australian Defence Force (ADF). The upcoming facility will focus on developing and testing a broader range of weapons, including those intended for the ADF, and is projected to commence operations in early 2027, creating nearly 200 new jobs. This expansion aligns with the US administration's initiative to enhance domestic manufacturing, particularly in military industries. Additionally, NIOA's collaborations with companies like L3Harris and Aerojet Rocketdyne aim to bolster missile production both domestically and for allied nations. NIOA’s CEO, Rob Nioa, emphasized the significance of strengthening Australia’s defence industry and the necessity for prompt government contracts to maintain defence capabilities.
Sources: The Australian - March 24, 2025
Canada Announces Snap Election Amid Tensions with Trump Administration
Summary:
Canada has called a snap election for April 28, prompted by escalating tensions with the U.S. under President Donald Trump. Prime Minister Mark Carney described the situation as a critical crisis, emphasizing the need for a strong mandate to navigate the challenges posed by strained U.S.-Canada relations. Sources: The Guardian - March 24, 2025
Grim Weather Warning for Millions of Australians
Summary:
Authorities have issued multiple flood warnings across Queensland due to ongoing heavy rainfall. The Bureau of Meteorology warns of rising river levels in saturated areas, including the Lake Eyre Basin and Gulf of Carpentaria rivers. Townsville residents should remain alert, with forecasts predicting 30 to 50 millimeters of rain extending into next week. Lismore in northern NSW is also expected to experience persistent showers, intensifying later in the week, raising concerns of renewed flooding. Emergency services emphasize vigilance, especially in flood-prone areas, and caution against traveling through floodwaters due to the potential for localized flash flooding. Sources: News.com.au - 24 March 2025
Christian Persecution in Syria, Homeland Attacks and How to Prepare
Summary:
This episode of the Shawn Ryan Show features Sarah Adams, Scott Mann, and Legend discussing the alarming rise in Christian persecution in Syria, the broader implications for global security, and strategies for civilian preparedness. The conversation highlights the complex geopolitical environment in the Middle East, the role of intelligence operations, and potential threats to Western nations, including radicalization and domestic attacks. The guests also touch on how individuals can protect themselves and prepare mentally and logistically for potential crises.
Why It’s Important to Australia:
While the episode is U.S.-focused, the issues raised are globally relevant and resonate with Australian concerns around:
- Religious persecution: Australia is an advocate for international human rights and religious freedom. Understanding the Syrian context supports informed humanitarian and diplomatic responses.
- National security: Australia’s own counter-terrorism and domestic security strategies can benefit from the preparedness insights and threat assessments discussed.
- Community resilience: Encourages a culture of awareness and preparedness among Australians amid global instability, migration, and foreign influence operations.
- Foreign policy: The Syrian conflict and persecution narratives inform Australia’s stance on refugee intake, foreign aid, and military engagement in the region.
Sources: Shawn Ryan Show - 24 March 2025
-
 @ f7d424b5:618c51e8
2025-03-23 18:53:39
@ f7d424b5:618c51e8
2025-03-23 18:53:39A few days ago, on March 20th 2025 one of the most important releases of the year in video games has taken place - Xenoblade Chronicles X! A few other games came out too and we'll talk about those this time while @Dielan@shitposter.world has time to get through the new Xenoblade.
Some links to stuff we talked about:
- EA Open Source & GPL'd C&C
- Lying VAs called out by SC
- PC gamer said something reasonable for once re: asscreed
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ e7bc35f8:3ed2a7cf
2025-03-23 18:42:41
@ e7bc35f8:3ed2a7cf
2025-03-23 18:42:41Imagine a world where governments couldn't fund wars simply by printing money...
Would history have changed? Could World War I have ended in months instead of four bloody years?
August 1914. A small incident in Central Europe triggers a snowball effect no one foresaw. British newspapers call it "the war of the August bank holiday"—a brief summer campaign for the troops.
No one imagined that this "short conflict" would turn into the first global slaughterhouse in human history.
But how did a local war between Austria-Hungary and Serbia spiral into such devastation?
The answer lies in something few suspect: money.
In hindsight, the key difference between World War I and earlier, more limited wars was not geopolitical or strategic—it was monetary.
Before the war, the gold standard imposed strict fiscal discipline on all nations. Money was directly tied to the gold reserves of each country, automatically limiting military expenditures.
Yet, within weeks of the war’s outbreak, every major warring nation did something unprecedented: they suspended the convertibility of their currency into gold.
With this single move, governments gained access not only to their own treasuries but effectively to the entire wealth of their citizens.
As long as a government could print money and people accepted it, it could fund an endless war. Without the gold standard’s constraints, states could keep sending young men to the slaughter.
History might have taken a different course if gold had been in the hands of Europe's citizens, forcing governments to rely on taxation instead of inflation. The war might have ended within months, as one of the alliances would have run out of financial resources.
The absurdity of this war was not lost on those at the front lines. On Christmas Eve of 1914, something remarkable happened: French, British, and German soldiers defied orders, laid down their weapons, and crossed enemy lines.
Men who were supposed to be enemies exchanged gifts and played football. Ordinary people realized what their leaders could not: they had no real quarrel with each other and no true reason to kill.
By the war’s end in 1918, the currencies of all major European powers had collapsed. In the defeated nations, Germany and Austria, money had lost more than half its value.
And for what? The territorial changes resulting from the war barely justified the slaughter of millions. None of the victorious powers gained lands significant enough to warrant such sacrifices.
World War I forever altered our relationship with money. After the war, money ceased to be a matter of the market and became a tool of political control.
Gold would never again serve as the world’s uniform currency, as central banks monopolized its reserves. But decades later, the invention of Bitcoin would lay the foundation for a new kind of money—one beyond national borders and state control.
Could a truly independent currency have prevented a world war? And what can this history teach us about the future of money and global peace?
| From "The Bitcoin Standard", Saifedean Ammus
-
 @ 6bae33c8:607272e8
2025-03-23 17:59:00
@ 6bae33c8:607272e8
2025-03-23 17:59:00After four NFBC teams, I’m done drafting for the season. Below, I’ve made a table of my rosters and noted the players in whom I have multiple shares.
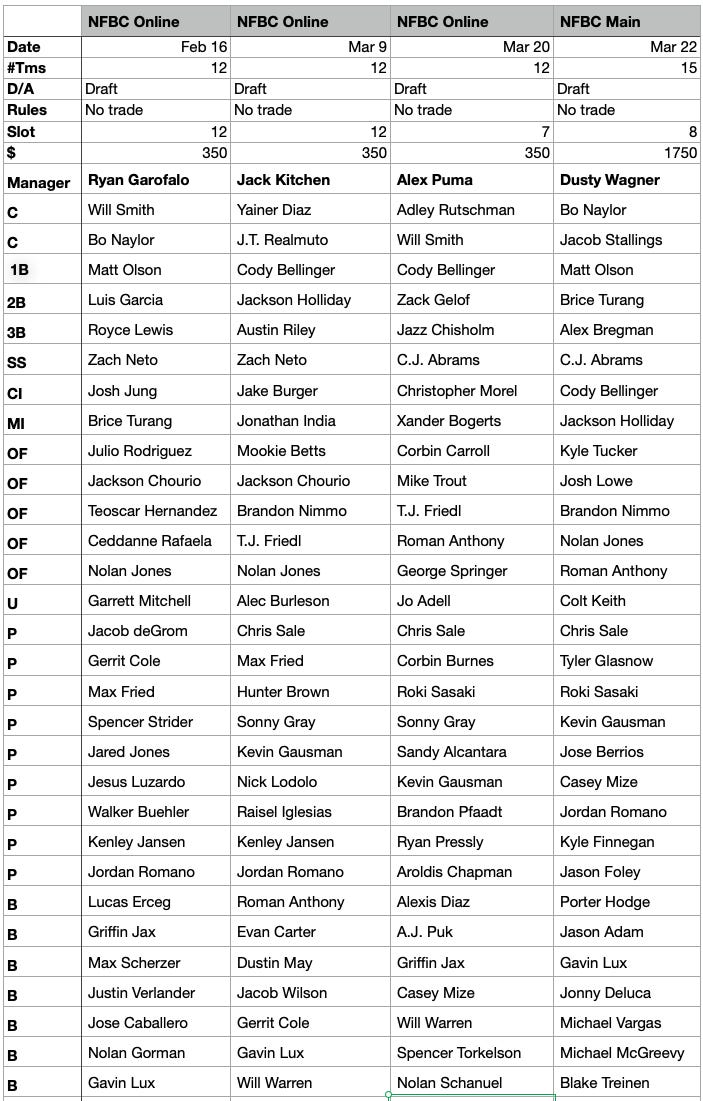
Four shares: None
Three shares: Chris Sale, Cody Bellinger, Kevin Gausman, Jordan Romano, Nolan Jones, Roman Anthony, Gavin Lux
Two shares: Jackson Chourio, Roki Sasaki, Will Smith, Kenley Jansen, Brice Turang, Zach Neto, Jackson Holliday, Brandon Nimmo, Bo Naylor, T.J. Friedl, Casey Mize, Griffin Jax, Will Warren, Gerrit Cole
Zero shares: Shohei Ohtani, Bobby Witt, Aaron Judge, Elly de la Cruz, Jose Ramirez, Juan Soto, Paul Skenes, Francisco Lindor, Tarik Skubal, Vladimir Guerrero, Fernando Tatis, Gunnar Henderson, Zack Wheeler, Yordan Alvarez, Garrett Crochet, Trea Turner, Logan Gilbert, William Contreras, Bryce Harper, Jackson Merrill, Jarren Duran, Wyatt Langford, Oneil Cruz, Ketel Marte, Manny Machado, Freddie Freeman, Mason Miller, Josh Hader, Devin Williams, Emmanuel Clase, Dylan Cease, Ronald Acuna, Blake Snell, Cole Ragans, Michael Harris, Corey Seager, Edwin Diaz, Brent Rooker, Rafael Devers, James Wood, Yoshinobu Yamamoto, Lawrence Butler, Ryan Helsley, Andres Munoz, Spencer Schwellenbach, Framber Valdez, Michael King
Bold = intentional fade
Bold + Italics = hard fade
Write-ups for each league are here: BCL1, BCL2, BCL3 and MAIN.
Links to prior portfolios: 2024, 2023, 2022*, 2021, 2020, 2019, 2018, 2017, 2016, 2015, 2014, 2013, 2012, 2011**
* Sadly lost forever because it was on my now defunct original web site
** including these links not because anyone will click on them, but to show off my meticulous (bordering on OCD) record keeping.After four NFBC teams, I’m done drafting for the season. Below, I’ve made a table of my rosters and noted the players in whom I have multiple shares.
-
 @ 7d33ba57:1b82db35
2025-03-23 17:50:36
@ 7d33ba57:1b82db35
2025-03-23 17:50:36A Coastal Paradise in Costa Blanca
Located between Benidorm, Altea, and L'Alfàs del Pi, Parque Natural de la Serra Gelada is a stunning protected natural park featuring dramatic cliffs, scenic hiking trails, and breathtaking Mediterranean views. This coastal paradise is perfect for hiking, nature walks, and enjoying the wild beauty of Spain’s eastern coast.
🏞️ Top Things to See & Do in Serra Gelada
1️⃣ Hike to the Albir Lighthouse (Faro de l’Albir) 🚶♂️
- An easy, well-paved trail (~5 km round trip) leading to a beautiful white lighthouse with panoramic sea views.
- Along the way, enjoy cliffside scenery, hidden caves, and viewpoints overlooking the Mediterranean.
2️⃣ Serra Gelada Ridge Hike (Benidorm to Albir) 🏔️
- A more challenging but rewarding hike (~8 km one way) that follows the rugged mountain ridges.
- Offers incredible views of Benidorm, Altea Bay, and the towering cliffs plunging into the sea.
3️⃣ Punta del Cavall & Torre Vigía de Punta Bombarda 🏰
- Visit the ancient watchtower ruins, once used to spot pirates.
- One of the best sunset viewpoints in the park.
4️⃣ Boat Trip to Isla de Benidorm ⛵
- Take a boat excursion from Benidorm to this protected island, a paradise for snorkeling and diving.
- The crystal-clear waters are home to colorful marine life and underwater caves.
5️⃣ Coves & Hidden Beaches 🏖️
- Discover secluded beaches like Cala del Tío Ximo and Cala Almadraba, perfect for a quiet escape from Benidorm’s busy beaches.
- Great spots for snorkeling and enjoying nature.
🌿 Flora & Fauna in Serra Gelada
- Home to Mediterranean pine forests, aromatic rosemary, and wild orchids.
- Spot falcons, seagulls, dolphins, and even the occasional wild goat along the cliffs! 🦅🐬
🚗 How to Get to Serra Gelada
🚘 By Car: 15 min from Benidorm, 10 min from Altea, and ~40 min from Alicante
🚌 By Bus: Local buses run from Benidorm to Albir Beach, where many hikes begin
🚶♂️ By Foot/Bike: Many trails start from Albir, Altea, or Benidorm💡 Tips for Visiting Serra Gelada
✅ Best time to visit? Spring & Autumn (cooler weather for hiking) 🌿
✅ Wear good hiking shoes – The ridge trails are rocky and steep in places 👟
✅ Bring water – No facilities along the trails 🌞🥤
✅ For photography lovers – Sunrise & sunset hikes offer the best light 📸 -
 @ fc15d4c6:fba62950
2025-03-23 16:49:27
@ fc15d4c6:fba62950
2025-03-23 16:49:27A Post by Onjezani Kenani
Onjezani reportedly posted on social media:
So according to the Reserve Bank Governor, if a relative asks someone in the diaspora to pay school fees for their child studying abroad, in exchange for the Kwacha equivalent - that's a crime? He want's you in the diaspora to send dollars to Malawi, then your relative applies to the bank, waits endlessly, and counts themselves lucky if the fees are ever paid at all. Is this really what he wants?
Mr. Governor, Sir, the money in the diaspora is ours, not yours. We work hard for this money. Stop having ideas on how we should spend it.
An Article opposing Onjezani's view
An opinion article titled Slow down, Onjezani Kenani; help enlighten Malawians not misguiding them written by one Joe Cholinga, targeting Onjezani's social media critique, but not necessarily directly related to the above post specifically, was published through the Nyasa Times, dated November 16, 2024. Similar articles can be found on other platforms:
Dissecting this Article
The author states about Onjezani: "His mockery of the RBM’s directive is not just misguided; it is dangerously misleading" (emphasis added), yet the "facts" in the article do not mention any role or responsibility that the Malawi Government or its' financial policies may have had in this economic crisis. The author clearly points to the source of the problem on "setting the record straight":
Malawi’s foreign reserves have been severely depleted due to widespread illegal foreign exchange dealings. Commercial banks, NGOs, and even donor-funded projects have been implicated in manipulating forex allocations for private profit. This black-market trading has destabilized the kwacha, driving inflation to alarming levels and pushing the prices of basic goods through the roof.
One may easily conclude that the named entities and the market has created this chaos, but the author seems to switch around cause and effect. The question should really be:
What is the cause for this market response?
The Author goes on to justify the RBM's actions by stressing that "this is a matter of national survival" and "not a joke", he suggests that the "directive is a necessary intervention to ensure that the country’s foreign reserves are properly managed" and to (reading between the lines) protect "the livelihoods of millions of Malawians", "particularly the poor and vulnerable" against rising prices.
Ah, yes it is all about protecting the poor and the vulnerable! He is implying that the Government knows what is best for "millions of Malawians" and is able to "properly manage" resources. Millions of people who have experienced past- and present communist regimes or countries around the world may strongly disagree with this assessment.
He seems to imply that striving to save the fruits of one's labour in harder, non-inflating assets like forex instead of the inflationary Kwacha for "personal gain" is a bad or unworthy goal. One might conclude that those in charge of the RBM and the Government more broadly, lack such egocentric attributes, because the RBM (under Government control and managed by people) wishes to "properly manage" resources. Clearly politicians, public servants and government staff are not greedy, they have no aspirations to act in their own interests for their "personal gain" and would only make decisions to protect "millions of Malawians", for the greater good.
The author goes on to discredit Onjezani to have "lost his way" and criticises his comments for their "lack of substance...", "dangerous oversimplification" and "divorced from the facts". He goes on to conclude:
In Conclusion
The real danger here is that his posts could lead people to believe that the government’s economic strategies are a joke, rather than the urgent steps they are.
So this is the threat? People might stop and question the political narrative, ask difficult questions? Fascinating. Yet surely facts and truths will shine during any darker times that may lay ahead of us, removing any need for concern.
References
forex #inflation #malawi #politics
- This undated screenshot seemingly from a social media platform, circulated on WhatsApp in March 2025

- The Nyasa Times Article, dated November 16, 2024
https://www.nyasatimes.com/opinion-slow-down-onjezani-kenani-help-enlighten-malawians-not-misguiding-them/ - Wikipedia Page on Onjezani
https://en.wikipedia.org/wiki/Stanley_Onjezani_Kenani - Some writing by Onjezani
https://www.author-me.com/fict04/storyofmyfate.htm
- This undated screenshot seemingly from a social media platform, circulated on WhatsApp in March 2025