-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ d360efec:14907b5f
2025-04-22 08:12:27
@ d360efec:14907b5f
2025-04-22 08:12:27ความทรงจำเรานั้นเชื่อได้แน่หรือ ?
"เพราะจิตเราเกิดดับทุกเสี้ยววินาที ทุกความทรงจำจึงสร้างขึ้นมาใหม่เสมอ ดังนั้นมันก็ไม่เหมือนต้นฉบับเป็นธรรมดา แต่ยังคงเค้าโครงเดิมอยู่ ความเปลี่ยนแปลงจึงเป็นนิรันดร์ค่ะ" - Lina Engword
เรามักจะคิดว่าความทรงจำของเราคือการบันทึกเหตุการณ์ในอดีตไว้อย่างแม่นยำ เหมือนการดูวิดีโอ 📼 หรือเปิดไฟล์คอมพิวเตอร์ 💾 แต่ในความเป็นจริงแล้ว แนวคิดนี้อาจไม่ใช่ภาพที่สมบูรณ์ บทความที่เรานำมาวิเคราะห์นี้ได้นำเสนอข้อคิดที่น่าสนใจเกี่ยวกับธรรมชาติของความทรงจำมนุษย์ ความน่าเชื่อถือของมัน และเชื่อมโยงไปถึงความจำเป็นในการฝึกฝนจิตตามหลักพุทธศาสนาเพื่อเข้าถึงความจริงที่เที่ยงแท้ 🧘♀️🔍
ความทรงจำไม่ใช่การบันทึก แต่เป็นการสร้างใหม่ 🏗️🧩
ประเด็นสำคัญที่บทความชี้ให้เห็นคือ ความทรงจำของมนุษย์ไม่ได้ทำงานเหมือนการ "บันทึก" เหตุการณ์ไว้ตายตัว 📼❌ แต่เปรียบเสมือน "ชิ้นส่วนของโค้ด" 💻 ที่จะถูก "สร้างขึ้นใหม่" 🏗️ ทุกครั้งที่เราพยายามระลึกถึง นั่นหมายความว่า ทุกครั้งที่เราดึงความทรงจำเก่าๆ กลับมา มันไม่ใช่การเปิดไฟล์เดิมซ้ำๆ แต่เป็นการประกอบชิ้นส่วนเหล่านั้นขึ้นมาใหม่ในห้วงเวลานั้นๆ กระบวนการนี้เองที่เปิดโอกาสให้เกิดการ "เติมเต็ม" ✨ หรือ "แก้ไข" ✏️ ข้อมูลในความทรงจำอยู่เสมอ ทำให้ความทรงจำที่เราเพิ่งนึกถึงอาจไม่เหมือนกับความทรงจำครั้งก่อนหน้าเสียทีเดียว 🔄
การปรุงแต่งด้วยเหตุผลและความคุ้นเคย 🤔➕🏠
สิ่งที่น่าสนใจอย่างยิ่งคือ ในกระบวนการ "สร้างใหม่" หรือ "ประกอบ" ความทรงจำขึ้นมานี้ มนุษย์มักจะเติม "เหตุผล"💡 หรือใส่สิ่งที่ตนเอง "คุ้นเคย" 🏠 ลงไปในเรื่องราวที่ระลึกได้เสมอ แม้ว่าสิ่งเหล่านั้นอาจจะไม่ได้เกิดขึ้นจริงหรือไม่เกี่ยวข้องโดยตรงกับเหตุการณ์นั้นๆ ก็ตาม ยกตัวอย่างเช่น เมื่อเราเล่าเรื่องในอดีต เรามักจะอธิบายว่าทำไมเราถึงทำสิ่งนั้น หรือทำไมเหตุการณ์นี้ถึงเกิดขึ้น โดยใส่เหตุผลที่เราคิดว่าสมเหตุสมผลในปัจจุบันลงไป สิ่งนี้ทำให้เรื่องราวในความทรงจำของเราดูมีความเชื่อมโยงและฟังดู "จริง" ✅ มากขึ้นในสายตาของเราเอง
เมื่อเราใส่เหตุผลหรือรายละเอียดที่คุ้นเคยลงไปในความทรงจำบ่อยครั้งเข้า มันก็จะยิ่งทำให้เรา "เชื่อ" 👍 โดยสนิทใจว่าสิ่งที่เราระลึกได้นั้นคือความจริงทั้งหมด ทั้งที่ความเป็นจริงของเหตุการณ์ดั้งเดิมอาจแตกต่างออกไป 🤥 นี่คือสาเหตุว่าทำไมคนสองคนจึงอาจมีความทรงจำเกี่ยวกับเหตุการณ์เดียวกันที่แตกต่างกันอย่างสิ้นเชิง ซึ่งปรากฏการณ์นี้สามารถอธิบายได้ดีด้วยตัวอย่างคลาสสิกในภาพยนตร์เรื่อง "ราโชมอน" (Rashomon) 🎬 ที่นำเสนอเหตุการณ์เดียวผ่านมุมมองและความทรงจำของตัวละครที่ขัดแย้งกันอย่างสิ้นเชิง แต่ทุกคนต่างเชื่อในสิ่งที่ตนเองจำได้ว่าเป็นความจริง 🤔❓
เครื่องมือและกระบวนการช่วยตรวจสอบความจริง 📱📹📝🔍
จากข้อจำกัดโดยธรรมชาติของความทรงจำนี้เอง ทำให้เห็นว่าเราไม่สามารถพึ่งพาสิ่งที่ 'จำได้' เพียงอย่างเดียวได้หากต้องการเข้าถึงความจริงที่เที่ยงแท้ เราจึงจำเป็นต้องมี 'กระบวนการตรวจสอบ' 🤔🔍 มาช่วยยืนยันหรือแก้ไขข้อมูลในความทรงจำ
ในยุคปัจจุบัน เรามีเครื่องมือภายนอกมากมายที่ช่วยในกระบวนการนี้ เช่น กล้องจากสมาร์ทโฟน 📱 หรือกล้องวงจรปิด 📹 ที่บันทึกเหตุการณ์ต่างๆ ไว้ได้อย่างเป็นกลาง ทำให้เรามี 'หลักฐาน' 📄 ที่เป็นรูปธรรมไว้อ้างอิงเพื่อเปรียบเทียบกับความทรงจำส่วนตัว ซึ่งบ่อยครั้งสิ่งที่กล้องเห็นนั้น 'ตรงกับความจริง' ✅ ในมุมมองที่ปราศจากอคติมากกว่าสิ่งที่ใจเราจำได้ การจดบันทึกด้วยเสียง 🎤 หรือการจดบันทึกเป็นลายลักษณ์อักษร 📝 ในทันที ก็เป็นอีกวิธีหนึ่งที่ช่วย 'ตรึง' ข้อมูลเบื้องต้นไว้ได้ระดับหนึ่งเช่นกัน ✍️
นอกจากเครื่องมือภายนอกแล้ว 'กระบวนการตรวจสอบเชิงจิตวิทยา' 🤔🧠 ที่เป็นระบบ ก็สามารถช่วยให้มนุษย์ค้นพบความจริงได้เช่นกัน ไม่ว่าจะเป็นกระบวนการซักถามในเชิงนิติวิทยาศาสตร์ 👮♀️ หรือแม้กระทั่งการฝึกฝนจิตเพื่อให้สามารถสังเกตการณ์ทำงานของตนเองได้อย่างละเอียดลึกซึ้ง ซึ่งนำเราไปสู่แนวคิดตามหลักพุทธศาสนา...
ทำไมพุทธศาสนาจึงสอนไม่ให้เชื่อแม้เป็นความคิดตัวเอง? 🙏🧠❌
จากธรรมชาติของความทรงจำและกระบวนการปรุงแต่งของจิตใจที่อธิบายมานี้เอง ทำให้เราเห็นความเชื่อมโยงกับหลักคำสอนในพุทธศาสนา 🙏 ที่เน้นย้ำให้เรา "ไม่เชื่อแม้แต่ความคิดตัวเอง" 🧠❌ อย่างปราศจากการพิจารณา เพราะความคิด อารมณ์ ความทรงจำ หรือแม้แต่ความรู้สึกมั่นใจอย่างแรงกล้าที่เรามีนั้น อาจถูกสร้างขึ้นหรือปรุงแต่งโดยกลไกของจิตใจที่ไม่ได้สะท้อนความจริงทั้งหมด 🤥
พุทธศาสนาชี้ให้เห็นว่า การจะเข้าถึงความจริงที่แท้จริงได้นั้น 🔍 จำเป็นต้องมีกระบวนการตรวจสอบภายในจิตใจ เปรียบเสมือนการสร้าง "อัลกอริทึม" 🤖 เพื่อตรวจทานว่าสิ่งที่เราคิดหรือจำได้นั้นเป็นความจริงหรือไม่ ✅❌ การจะทำเช่นนี้ได้ ไม่ใช่เรื่องง่าย และต้องอาศัยการฝึกฝนจิตอย่าง "สมาธิอย่างมาก" 🧘♂️🧘♀️ เพื่อให้จิตมีความตั้งมั่น เป็นระบบ และสามารถ "เห็นการดำเนินไปของจิตได้อย่างเป็นระบบ" 👀🔬 เห็นว่าจิตปรุงแต่งความทรงจำอย่างไร เห็นว่าเหตุผลที่เราใส่เข้าไปนั้นจริงหรือไม่ เป็นเพียงการตีความ หรือเป็นเพียงสิ่งที่ใจเราอยากให้เป็น
บทความยังกล่าวเสริมว่า ความทรงจำที่ "สด" ✨ หรือใกล้เคียงกับเวลาที่เกิดเหตุการณ์นั้นมักจะมีความน่าเชื่อถือมากกว่า 👍 แม้จะดู "ดิบๆ" หรือไม่ผ่านการปรุงแต่งมากนัก ซึ่งสอดคล้องกับแนวคิดที่ว่ายิ่งระยะเวลาผ่านไปนานเท่าไหร่ ⏳ ยิ่งมีการเรียกคืนความทรงจำนั้นๆ บ่อยครั้ง ความทรงจำก็ยิ่งมีโอกาสถูกแก้ไข เติมเต็ม หรือปรุงแต่งด้วยเหตุผลและความคุ้นเคยมากขึ้นเท่านั้น 🔄✏️
"ใดๆในโลกนั้นคือสมมุติ ความคิดความทรงจำ ก็เป็นสมมุติเพียง แต่เราต้องรู้จักใช้สมมุติให้เป็นประโยชน์ และรู้จักใช้มันให้เป็นเพื่อดำรงอยู่บนโลก"
สรุป ✨🧠🔍
โดยสรุปแล้ว บทความนี้เตือนใจเราว่า ความทรงจำของเราไม่ใช่กล้องวิดีโอที่บันทึกทุกอย่างไว้แม่นยำ 📼❌ แต่เป็นกระบวนการสร้างสรรค์ที่ซับซ้อนซึ่งมีแนวโน้มที่จะถูกปรุงแต่งด้วยเหตุผล ความคุ้นเคย และการตีความของเราเอง 🏗️🤔🏠 ความมั่นใจที่เรามีต่อสิ่งที่จำได้นั้น ไม่ได้เป็นหลักประกันว่าเป็นความจริงเสมอไป 👍🤥
การตระหนักถึงธรรมชาติข้อนี้ของจิต และการใช้เครื่องมือภายนอก 📱📹📝 รวมถึงการฝึกฝนจิตให้สามารถสังเกตการณ์ทำงานของมันได้อย่างละเอียดรอบคอบตามหลักพุทธศาสนา 🙏🧘♀️ จึงเป็นกุญแจสำคัญที่จะช่วยให้เราสามารถแยกแยะระหว่าง "ความจริง" ✅ กับ "สิ่งที่จิตปรุงแต่งขึ้น" 🤥 ได้มากขึ้น และช่วยให้เราเข้าใกล้ความเข้าใจในธรรมชาติของสรรพสิ่งได้อย่างเที่ยงตรง ไม่หลงติดอยู่ในวังวนของความทรงจำและความคิดที่อาจบิดเบือนไปจากความเป็นจริง 🔄
**#ความทรงจำ #จิตวิทยา #พุทธศาสนา #สมอง #สมาธิ #การฝึกจิต #ราโชมอน #ความจริง #ไม่เชื่อความคิด #ธรรมชาติของจิต #พัฒนาตนเอง #บทความน่ารู้ #เทคโนโลยี #บันทึกความจริง #พระอภิธรรม #พระหฤทัยสูตร #LinaEngword **
-
 @ d360efec:14907b5f
2025-04-22 07:54:51
@ d360efec:14907b5f
2025-04-22 07:54:51“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง “การพนัน” ภาพที่ชาวเมืองมักนึกถึงคือ “ยาจกข้างถนน”
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า จ้าวแห่งหอคอยรัตติกาล ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก “เกมพนัน” เช่น เวเนสซา รุสโซ นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ “โป๊กเกอร์” หรือแม้แต่ เอ็ดเวิร์ด โอ. ทอร์ป จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา “แบล็กแจ็ก” ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ “หอคอยรัตติกาล” เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ “คณิตศาสตร์” เหตุใด “คณิตศาสตร์” จึงช่วยให้ผู้คนเอาชนะ “การพนัน” ได้? และนอกจาก “การพนัน” แล้ว “คณิตศาสตร์” ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? นักเล่าเรื่องแห่งเฮรันเทล จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: * ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก * แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ * ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ * ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น * จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น “วงจรอุบาทว์” สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด “วงจรอุบาทว์” นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก “กลไกต้องสาป” ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ “สมาคมพ่อค้าผู้พิทักษ์” คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม “กฎแห่งจำนวนมหาศาล” เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ “คณิตศาสตร์” เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: ๑. ปริศนาแห่ง “กำไรคาดหวัง” สำหรับการแสวงหา “เกมเสี่ยงทาย” ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ “การประเมินกำไรคาดหวัง” หรือ “เวทคำนวณอนาคต” “กำไรคาดหวัง” ถูกคิดค้นโดย คริสเตียน ฮอยเกนส์ นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) ดังนั้น หากปรารถนาจะสะสม “ทองคำมายา” ในระยะยาว จงเลือกเกมที่มี “กำไรคาดหวัง” เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ “กำไรคาดหวัง” เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว “กำไรคาดหวัง” ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ “สลากกินแบ่งรัฐบาล” ก็ล้วนเป็นเกมที่มี “กำไรคาดหวัง” ติดลบทั้งสิ้น นอกจาก “กำไรคาดหวัง” จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ “คณิตศาสตร์” ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ “ศิลาแห่งโชค” แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี “กำไรคาดหวัง” = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ ๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน” แม้ว่าท่านจักรับรู้ “กำไรคาดหวัง” แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย “ศิลาแห่งโชค” หรือหลาย “เกมเสี่ยงทาย” แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร “การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)” หรือ สูตร “ขนาดเดิมพันที่เหมาะสม (Kelly Formula)” ๓. ปริศนาแห่ง “อคติ” ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ “Gambler's Fallacy” หรือ “ความเชื่อผิด ๆ แห่งนักพนัน” ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง “สลากกินแบ่งรัฐบาล” มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก “ศิลาแห่งโชค A” ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น “เกมเสี่ยงทายแห่งโชคชะตา” หรือ “การผจญภัยในตลาดทุน” หากท่านมีความเข้าใจ และนำ “คณิตศาสตร์” เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. สูตรเวทย์มนตร์ที่ปรากฏในตำนาน: * กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล: "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-
 @ 37c10448:f8256861
2025-04-22 07:44:10
@ 37c10448:f8256861
2025-04-22 07:44:10Title H1
Hello !
-
 @ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28
@ 4fa5d1c4:fd6c6e41
2025-04-22 06:46:28Bibel-Selfies
Prompts
Eva, Schlange, Apfel und Adam

A selfie of a woman resembling eve in the time of old testament, blurred body, holding an apple, kneeling in front adam. he has a shocked expression with his mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with a huge snake behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with adam and eve, possibly at a place like garden eden. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Tochter des Pharao mit Mose

A selfie of the biblical figure moabite woman with her baby in front of an oasis. She is wearing traditional and has black hair. The background shows water from the desert oasis and grasses around it. In the Background a wicker basket on the water. The photo was taken in the style of a selfie shot with GoPro cameraSimon Petrus

A selfie of a man resembling Simon Petrus, wearing a white robe, surrounded by waves and thunderstorm. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many waves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus at the dead sea, possibly at a place like the sea. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Zachäus auf dem Baum
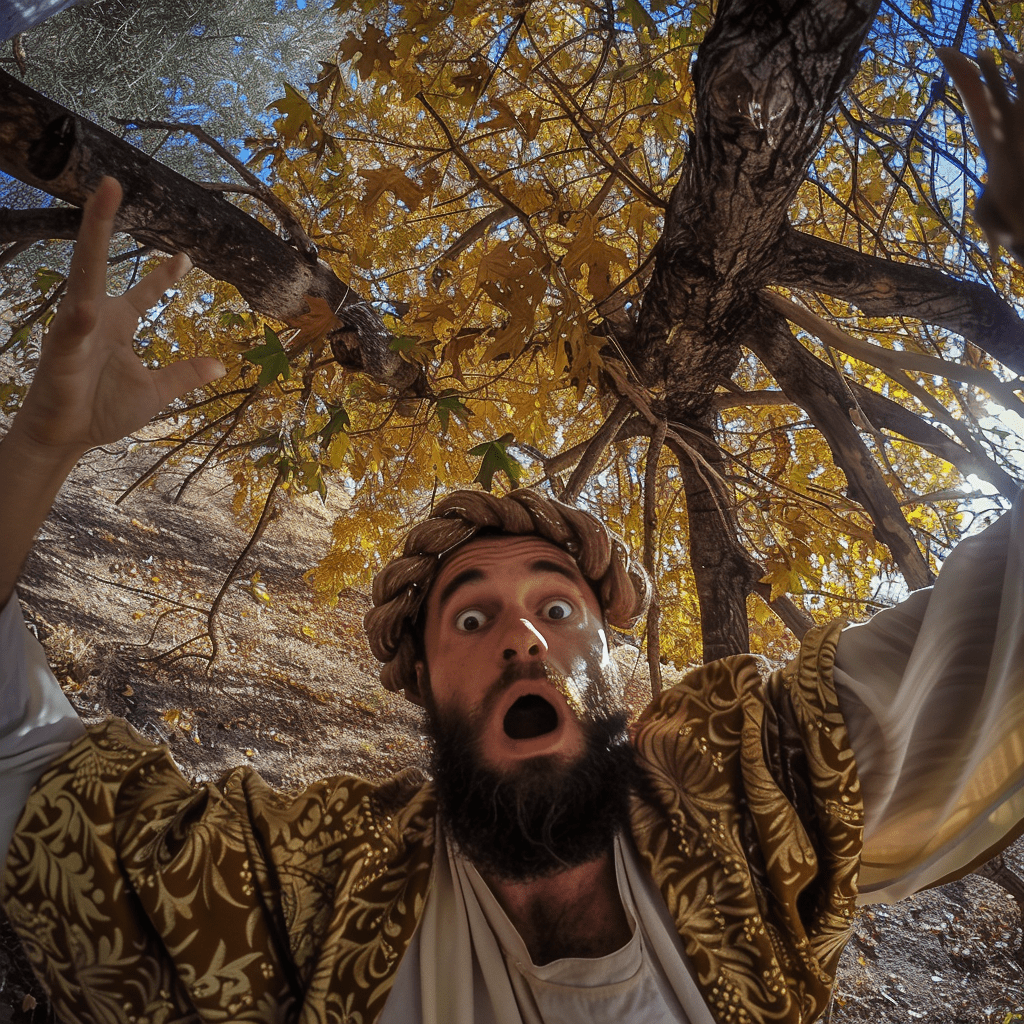
A selfie of a man resembling a roman in the time of jesus, wearing a glamorous robe, surrounded by the crown of a tree. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many leaves behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Maria am Ostermorgen

A selfie of a woman resembling maria in the time of jesus, wearing a robe, kneeling in front of stone grave. she has a shocked expression with her mouth open and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with the open glowing grave behind her. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus resurrection, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Der verlorene Sohn bei den Schweinen

A young ancient arabic man with short hair in the time of jesus, brown eyes, and a dirty face, covered in mud from working on his pig farm, takes an amateur selfie at dusk. He is surrounded by pig stables, with a barn visible in the background and pigs seen near the front. The photo captures a raw, authentic moment, as he gazes directly into the camera with an expression of excitement or wonder. The image has a realistic style, akin to Unsplash photography, and is meant to be posted on a primitive-themed social network. The resolution of the photo is high, style of selfie with gopro --v 6.0Vater und Sohn vereint
 A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0
A selfie of an Arab father in simple garments in the time of jesus, embracing and hugging a young man. The father's face, visible in the foreground, radiates joy and relief. Only the back of the son's head is visible, as he faces away from the camera, returning the embrace in tattered clothing. In the background, a large ancient house and other family members can be seen watching from a distance, blurred. The photo is taken with a wide-angle lens using a GoPro, enhancing the dramatic and overwhelming effect of the scene --v 6.0Bartimäus

A selfie of a man resembling blind bartimaeus in the time of jesus, black and brown and white bandages on his head over his eyes and face, wearing a robe, kneeling in front of a market place. he has a shocked expression with his mouth open and wide eyes still covered with black and brown and white bandages on his head, evoking a sense of both fear and surprise. The scene appears surreal, with many sand behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus healing the blind, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudha --v 6.0Daniel in der Löwengrube

A selfie of a man resembling Jesus, wearing a beige hoodie, surrounded by lions and cheetahs. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with many lions behind him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a lion's den, possibly at a place like the Grand Tabahar. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan ChaudharyDavid und Goliath

selfie of a the boy and shepherd david holding his slingshot resembling a fight with the giant goliath in the time of old testament, wearing a glamorous sligshot focusing on his giant opponent. David has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a desert surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of the scene of David fighting with the giant goliath with his slingshot, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Simson im Philistertempel

A selfie of a man resembling simson in the time of old testament, wearing a glamorous beard and long hair, surrounded by thousands of ancient fighters. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with a temple surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with jesus walking by, possibly at a place like the jerusalem. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary --v 6.0Jona und der Wal

A selfie of a man resembling israeli jona in the time of old testament,`wearing a glamorous beard and long hair, inside the body of a whale. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with the ocean surrounding him. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene in the bible. The style of the photo blends surrealism with humor, similar to the style of Yasir Khan Chaudhary
Jakob und Isaak

A selfie of a young man resembling an ancient Arabic in clothes made of skins of goats and furs of the goats, looking overwhelmed and distressed as he betrays his father, who blesses him. The scene shows a dawn sky with hints of the sunrise, evoking a surreal and dramatic atmosphere. The scene is set in ancient Jerusalem, with stone buildings. in the background an old man with a gesture of blessing, rising his hands to the sky, The photo is taken with a wide-angle lens, blending surrealism with humor. The style is reminiscent of a GoPro selfie, capturing the intense moment with a sense of both fear and surprisePetrus und der Hahn

A selfie of a man resembling ancient young arabic man saint in traditional biblical attire, being eaten by a whale,. he has a shocked expression with his mouth pressed and wide eyes, evoking a sense of both fear and surprise. The scene appears surreal, with one rooster crowing out loud behind the man. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene with peter and the rooster, possibly at a place in jerusalem . The style of the photo blends surrealism with humor, go pro selfie, morning dawn near sunrise settingJosef im Brunnen

A selfie of an ancient israelian man with a magical dreamcoat clothing in a deep well, looking at the camera from above, captured in the style of a go pro selfie stickElia und die Raben

A close-up selfie of a bearded man (Elijah) in biblical clothing, smiling gratefully. He is standing near a stream in a secluded, rocky area. Several black ravens are perched on his shoulders and arms, holding pieces of bread and meat in their beaks. The scene has a warm, golden light, symbolizing God's provision. Photorealistic style, high detail.Absalom im Baum

A selfie of a man resembling of a young man (Absalom) with long hair knotted arount the branches of a large oak tree.. He has a shocked expression with his mouth open and wide eyes, evoking a sense of both humor and surprise. The scene appears surreal, with all of his hairs knotted around the tree. The photo is taken with a wide-angle lens, adding to the dramatic and humorous effect. The setting is reminiscent of a scene of a robin hood movie in the forest . The style of the photo blends surrealism with humorRuth und Boas im Weizenfeld

A selfie of a young woman resembling Ruth, with a radiant smile and sun-kissed skin. She's standing in a golden wheat field at sunset, her arms filled with freshly gathered sheaves of wheat. Her hair is partially covered with a simple headscarf, with loose strands blowing in the wind. She has a look of joy and gratitude in her eyes. The scene appears idyllic, with wheat stalks seeming to embrace her. In the background, a distinguished older man (Boaz) can be seen watching from a distance, his expression a mix of curiosity and admiration. The photo is taken with a wide-angle lens, capturing the vastness of the field, the warmth of the setting sun, and Boaz in the distance. The setting is reminiscent of a biblical harvest scene. The style of the photo blends realism with a touch of romantic nostalgia."Bibel-Selfies" von Jörg Lohrer Lizenz: CC0 1.0
.
`
-
 @ 9223d2fa:b57e3de7
2025-04-22 20:02:06
@ 9223d2fa:b57e3de7
2025-04-22 20:02:069,322 steps
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ d360efec:14907b5f
2025-04-21 22:10:23
@ d360efec:14907b5f
2025-04-21 22:10:23สวัสดีเพื่อนนักเทรดทุกท่าน! 👋 วันนี้ฉันมาแนะนำตารางกิจวัตรประจำวันของ Day Trader ที่น่าสนใจนี้กันนะคะ มาดูกันว่ามีอะไรที่เราสามารถเรียนรู้และนำไปปรับใช้กับการเทรดของเราได้บ้างค่ะ

ภาพรวมกิจวัตรประจำวันของ Day Trader 📊
ตารางนี้แสดงให้เห็นถึงโครงสร้างของวันที่สมดุลสำหรับนักเทรดรายวันที่ประสบความสำเร็จ โดยเน้นทั้งการเตรียมตัว 🤓 การลงมือเทรด 🚀 การเรียนรู้ 📚 และการดูแลสุขภาพส่วนตัว 🧘♀️ ซึ่งเป็นสิ่งสำคัญอย่างยิ่งในการรักษาประสิทธิภาพและความสม่ำเสมอในการเทรด 💪
การวิเคราะห์และอธิบายแต่ละช่วงเวลา
$ 05.30 น. > ตื่นนอน 🌅 อาบน้ำ 🚿 และเตรียมตัว 👔 > การเริ่มต้นวันอย่างกระปรี้กระเปร่า 🎉 และการมีกิจวัตรส่วนตัวที่ผ่อนคลายเป็นสิ่งสำคัญในการเตรียมพร้อมทั้งร่างกายและจิตใจ 🧠 สำหรับการเทรด
$ 06.00 น. > ตรวจสอบข่าวสาร 📰 วิเคราะห์กราฟ 📈 และเตรียมตัว 🎯 > ช่วงเวลานี้เป็นหัวใจสำคัญของการเตรียมตัวก่อนตลาดเปิด ⏰ นักเทรดจะตรวจสอบข่าวเศรษฐกิจ 💰 และข่าวที่เกี่ยวข้องกับสินทรัพย์ที่ตนเองเทรด 🧐 วิเคราะห์กราฟเพื่อหาแนวโน้ม 🔭 และระดับราคาที่น่าสนใจ 📍 รวมถึงวางแผนกลยุทธ์การเทรดสำหรับวันนี้ ✍️
$ 06.30 น. > ตลาดเปิด 🔔 เริ่มทำการเทรด 🚀 > เมื่อตลาดเปิด นักเทรดจะเริ่มดำเนินการตามแผนที่วางไว้ 📝 โดยจะเฝ้าติดตามการเคลื่อนไหวของราคา 👀 และเข้าเทรดตามสัญญาณที่เกิดขึ้น 🚦
$ 12.00 น. > พักรับประทานอาหารกลางวัน 🥪 > การพักผ่อน 😌 และการเติมพลัง 💪 ในช่วงกลางวันเป็นสิ่งสำคัญในการรักษาความมีสมาธิ 🧘♀️ และความสามารถในการตัดสินใจที่ดี 👍
$ 12.45 น. > ปิดสถานะการเทรดทั้งหมด 🛑 > สำหรับ Day Trader การปิดสถานะทั้งหมดภายในวันถือเป็นกฎเหล็ก 🚫 เพื่อหลีกเลี่ยงความเสี่ยงจากความผันผวนข้ามคืน 🌙
$ 13.00 น. > ทบทวน 🤔 เรียนรู้ 📚 และปรับปรุง ⚙️ > หลังจากการเทรด นักเทรดที่ประสบความสำเร็จ 🎉 จะใช้เวลาในการทบทวนการเทรดของตนเอง 🧐 วิเคราะห์ว่าอะไรทำได้ดี 👍 และอะไรที่ต้องปรับปรุง 📝 การเรียนรู้อย่างต่อเนื่องเป็นกุญแจสำคัญสู่การพัฒนา 🚀
$ 14.00 น. > ออกกำลังกาย 💪 และพักผ่อน 🧘♀️ > การดูแลสุขภาพกาย 🍎 และใจ 💖 มีความสำคัญไม่ยิ่งหย่อนไปกว่าการเทรด 📈 การออกกำลังกายและการมีเวลาว่าง 🌴 ช่วยลดความเครียด 😥 และเพิ่มประสิทธิภาพในการเทรดในระยะยาว ✨
$ 17.00 น. > รับประทานอาหารเย็น 🍽️ และพักผ่อน 🛋️ > การมีเวลาพักผ่อนกับครอบครัว ❤️ หรือทำกิจกรรมที่ชอบ 😊 ช่วยให้ผ่อนคลาย 😌 และเตรียมพร้อมสำหรับวันต่อไป 🌅
$ 19.00 น. > วางแผนการเทรดสำหรับวันพรุ่งนี้ 🗓️ และตรวจสอบข่าวสาร 📰 > การวางแผนล่วงหน้า 🤓 ช่วยให้นักเทรดมีความพร้อม 💪 และสามารถตอบสนองต่อสถานการณ์ตลาดได้อย่างมีประสิทธิภาพ 🚀
$ 22.00 น. > เข้านอน 😴 > การนอนหลับพักผ่อนอย่างเพียงพอ 🛌 เป็นสิ่งจำเป็นสำหรับการรักษาสุขภาพ 💖 และประสิทธิภาพในการเทรด 💪
สิ่งที่น่าสนใจและข้อคิด 🤔
$ ความมีระเบียบวินัย 💯 > ตารางนี้แสดงให้เห็นถึงความมีระเบียบวินัยที่เข้มงวด 📏 ซึ่งเป็นคุณสมบัติที่สำคัญของนักเทรดที่ประสบความสำเร็จ 🎉
$ การเตรียมตัวอย่างรอบคอบ 🧐 > การใช้เวลาในการวิเคราะห์ 📊 และวางแผน 📝 ก่อนตลาดเปิดช่วยลดการตัดสินใจที่ผิดพลาด 🚫 และเพิ่มโอกาสในการทำกำไร 💰
$ การเรียนรู้อย่างต่อเนื่อง 📚 > การทบทวน 🤔 และปรับปรุงกลยุทธ์ ⚙️ อยู่เสมอเป็นสิ่งสำคัญในการพัฒนาทักษะการเทรด 🚀
$ ความสมดุล ⚖️ > การให้ความสำคัญกับการดูแลสุขภาพ 🧘♀️ และการพักผ่อน 🌴 ควบคู่ไปกับการเทรด 📈 ช่วยป้องกันภาวะหมดไฟ 🔥 และรักษาประสิทธิภาพในระยะยาว ✨
การนำไปปรับใช้ 🛠️
เพื่อนๆ นักเทรดสามารถนำแนวคิดจากตารางนี้ไปปรับใช้กับกิจวัตรประจำวันของตนเองได้ 👍 โดยอาจไม่จำเป็นต้องทำตามทุกช่วงเวลาอย่างเคร่งครัด ⏰ แต่ให้เน้นที่หลักการสำคัญ เช่น การเตรียมตัวก่อนเทรด 🤓 การทบทวนหลังเทรด 🤔 และการดูแลสุขภาพ 🧘♀️ เพื่อสร้างสมดุล ⚖️ และเพิ่มประสิทธิภาพในการเทรดของเราค่ะ 💪
ขอให้ทุกท่านประสบความสำเร็จในการเทรดนะคะ! 💸🚀
#DayTrader #นักเทรดรายวัน #กิจวัตรประจำวัน #การลงทุน #เทรด #หุ้น #คริปโต #ตลาดหุ้น #แรงบันดาลใจ #พัฒนาตัวเอง #LinaEngword
-
 @ 86dfbe73:628cef55
2025-04-21 10:08:34
@ 86dfbe73:628cef55
2025-04-21 10:08:34Mit dem Internet kam das Ende der Massengesellschaft. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar. Nicht als Netzwerk zur Kommunikation, sondern als Netzwerk der Beziehungen, bestehend aus den Erwartungen, Kenntnissen und letztlich bestehend aus dem Vertrauen, das Menschen gegenüber anderen Menschen und Institutionen aufzubauen pflegen. Wichtig ist nicht mehr, wo jemand eine Information plaziert, wichtig ist, wann und wer und unter Einbeziehung welcher Faktoren diese abfragt.
In Sozialen Netzwerken entscheidet jeder selbst, wem er folgt. Er entscheidet selbst, wie die eigene Startseite, der eigene Blick auf den Dienst, aussieht. Als Beispiel sei hier Twitter erwähnt. Aus der Liste der Gefolgten wird die Timeline generiert, die eine Wirklichkeit abbildet, die einzig und alleine von den Following-Entscheidungen des Nutzers bestimmt ist.
Die Beziehungsweise des Folgens ist eine direkte Willenserklärung, die Inhalte eines Users sehen zu wollen. Sie ist ein Pakt, der auch eine gewisse, wenn auch kleine, Verantwortungsübernahme bedeutet. Und diese Beziehungsweise wurde zum integralen Strukturbaustein der digitalen Öffentlichkeit zwischen 2010 bis 2020 und damit auch zur tragenden Säule vieler Karrieren, Geschäftsmodellen und außerdem zur Grundlage der Selektionsverfahren von kulturellen Trends. Im Follower steckte die Macht.
Die digitale Öffentlichkeit hat aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in den „For you“-Algorithmen der kommerziellen Plattformen auf. Ab 2020 wurde dem Follower von Diensten wie Tiktok der Gar ausgemacht und von dort setzte sich der „For You-Algoritmus“ auf allen kommerziellen Plattformen durch. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist. Auf einmal bedeutete ein Following nicht mehr die Garantie, dass der Content die Abonnenten erreicht.
Mit der Zerstörung dieser Beziehung entgleiten den Creators ihre medialen Regime und beide, User und Creator werden immer abhängiger vom Algorithmus und arbeiten folglich nur noch für die Interessen der Plattformen, statt für sich selbst.
-
 @ 7d33ba57:1b82db35
2025-04-22 19:43:27
@ 7d33ba57:1b82db35
2025-04-22 19:43:27Welcome to Hortobágy National Park, Hungary’s oldest and largest national park, and a UNESCO World Heritage Site that showcases the wild, open heart of the Puszta—the vast steppe of Eastern Europe. Spanning over 800 km², this park is a land of windswept grasslands, grazing animals, traditional herding culture, and incredible birdlife.
🌾 What to See & Do in Hortobágy
🐃 Explore the Puszta Landscape
- Ride through the grasslands in a horse-drawn cart or take a bike tour
- See iconic gray cattle, racka sheep with spiral horns, water buffalo, and traditional herdsmen in wide-brimmed hats
🐎 Horse Shows & Herding Traditions
- Visit a csikós show, where Hungarian horsemen perform riding tricks and herding techniques
- Learn about the unique pastoral culture that has existed here for centuries
🐦 Birdwatching Paradise
- Hortobágy is one of Europe’s best spots for birdwatching
- See cranes, eagles, storks, and rare migratory species, especially in spring and autumn
- Visit the Hortobágy Bird Hospital and crane observation sites
🌉 Hortobágy Nine-Arch Bridge (Kilenclyukú híd)
- An iconic stone bridge built in the 19th century, stretching over the river Hortobágy
- The symbolic center of the park and a great photo spot
- Nearby you’ll find the Hortobágy Village, with museums, markets, and local food
🧀 Local Culture & Cuisine
- Taste slambuc (a traditional shepherd’s stew), cheeses, and local smoked meats
- Check out folk art and handmade crafts in local markets and heritage centers
🚶♂️ How to Visit
- Closest city: Debrecen (around 30 minutes by car or bus)
- The park offers guided tours, bike rentals, and wildlife safaris
- Great for day trips or overnight stays in nearby guesthouses or rural lodges
Hortobágy is more than a landscape—it’s a living cultural heritage site, where ancient traditions, wildlife, and wide horizons stretch as far as the eye can see. Perfect for nature lovers, culture seekers, or anyone looking to experience a different side of Hungary.
-
 @ d34e832d:383f78d0
2025-04-21 08:32:02
@ d34e832d:383f78d0
2025-04-21 08:32:02The operational landscape for Nostr relay operators is fraught with multifaceted challenges that not only pertain to technical feasibility but also address pivotal economic realities in an increasingly censored digital environment.
While the infrastructure required to run a Nostr relay can be considered comparatively lightweight in terms of hardware demands, the operators must navigate a spectrum of operational hurdles and associated costs. Key among these are bandwidth allocation, effective spam mitigation, comprehensive security protocols, and the critical need for sustained uptime.
To ensure economic viability amidst these challenges, many relay operators have implemented various strategies, including the introduction of rate limiting mechanisms and subscription-based financial models that leverage user payments to subsidize operational costs. The conundrum remains: how can the Nostr framework evolve to permit relay operators to cultivate at least a singular relay to its fullest operational efficiency?
It is essential to note that while the trajectory of user engagement with these relays remains profoundly unpredictable—analogous to the nebulous impetus behind their initial inception—indicators within our broader economic and sociocultural contexts illuminate potential pathways to harmonizing commercial interests with user interaction through the robust capabilities of websocket relays.
A few musingsI beg you to think about the Evolutionary Trajectory of Nostr Infrastructure Leveraging BDK (Bitcoin Development Kit) and NDK (Nostr Development Kit) in the Context of Sovereign Communication Infrastructure
As the Nostr ecosystem transitions through its iterative phases of maturity, the infrastructure, notably the relays, is projected to undergo significant enhancements to accommodate an array of emerging protocols, particularly highlighted by the Mostr Bridge implementation.
Additionally, the integration of decentralized identity frameworks, exemplified by PKARR (Public-Key Addressable Resource Records), signifies a robust evolutionary step towards fostering user accountability and autonomy.
Moreover, the introduction of sophisticated filtering mechanisms, including but not limited to Set Based Reconciliation techniques, seeks to refine the user interface by enabling more granular control over content visibility and interaction dynamics.
These progressive innovations are meticulously designed to augment the overall user experience while steadfastly adhering to the foundational ethos of the Nostr protocol, which emphasizes the principles of digital freedom, uncurtailed access to publication, and the establishment of a harassment-free digital environment devoid of shadowbanning practices.
Such advancements underscore the balancing act between technological progression and ethical considerations in decentralized communication frameworks.
-
 @ 7d33ba57:1b82db35
2025-04-22 19:29:59
@ 7d33ba57:1b82db35
2025-04-22 19:29:59Tucked into the foothills of the Bükk Mountains, Eger is one of Hungary’s most charming and historic towns. Famous for its Baroque architecture, thermal baths, and Egri Bikavér (“Bull’s Blood”) red wine, Eger offers a perfect blend of culture, relaxation, and rustic charm all just a couple of hours from Budapest.
🏰 Top Things to Do in Eger
🏯 Eger Castle (Egri Vár)
- A key site in Hungary’s defense against the Ottoman Empire
- Learn about the 1552 Siege of Eger, when outnumbered locals held off the Turks
- Climb the walls for views of the old town’s red rooftops and spires
⛪ Eger’s Baroque Old Town
- Wander elegant streets lined with pastel facades, cute cafés, and small boutiques
- Don’t miss the Minorite Church and Dobó Square, the lively heart of the city
🛁 Thermal Baths
- Relax in the Eger Turkish Bath, built during the Ottoman period and still in use today
- Or soak at Eger Thermal Spa, great for families and wellness seekers
🍷 Wine Tasting in the Valley of the Beautiful Women (Szépasszony-völgy)
- A short walk or ride from town, this valley is lined with wine cellars built into the hillside
- Taste the iconic Egri Bikavér (a full-bodied red blend) and Egri Csillag (a refreshing white)
- Most cellars offer generous tastings and hearty local snacks
🧀 Local Food to Try
- Goulash, Lángos, and hearty meat dishes
- Pair local cheeses and sausages with regional wines
- Cozy cellar restaurants and rustic taverns set the mood
🚆 Getting There
- About 2 hours by train or car from Budapest
- Walkable town, no car needed once you’re there
-
 @ d34e832d:383f78d0
2025-04-21 08:08:49
@ d34e832d:383f78d0
2025-04-21 08:08:49Let’s break it down.
🎭 The Cultural Love for Hype
Trinidadians are no strangers to investing. We invest in pyramid schemes, blessing circles, overpriced insurance packages, corrupt ministries, miracle crusades, and football teams that haven’t kicked a ball in years. Anything wrapped in emotion, religion, or political flag-waving gets support—no questions asked.
Bitcoin, on the other hand, demands research, self-custody, and personal responsibility. That’s not sexy in a culture where people would rather “leave it to God,” “vote them out,” or “put some pressure on the boss man.”
🧠 The Mindset Gap
There’s a deep psychological barrier here:
Fear of responsibility: Bitcoin doesn’t come with customer service. It puts you in control—and that scares people used to blaming the bank, the government, or the devil.
Love for middlemen: Whether it’s pastors, politicians, or financiers, Trinidad loves an “intercessor.” Bitcoin removes them all.
Resistance to abstraction: We’re tactile people. We want paper receipts, printed statements, and "real money." Bitcoin’s digital nature makes it feel unreal—despite being harder money than the TT dollar will ever be.
🔥 What Gets Us Excited
Let a pastor say God told him to buy a jet—people pledge money.
Let a politician promise a ghost job—people campaign.
Let a friend say he knows a man that can flip $100 into $500—people sign up.
But tell someone to download a Bitcoin wallet, learn about self-custody, and opt out of inflation?
They tell you that’s a scam.
⚖️ The Harsh Reality
Trinidad is on the brink of a currency crisis. The TT dollar is quietly bleeding value. Bank fees rise, foreign exchange is a riddle, and financial surveillance is tightening.
Bitcoin is an escape hatch—but it requires a new kind of mindset: one rooted in self-education, long-term thinking, and personal accountability. These aren’t values we currently celebrate—but they are values we desperately need.
🟠 A Guide to Starting with Bitcoin in Trinidad
- Understand Bitcoin
It’s not a stock or company. It’s a decentralized protocol like email—but for money.
It’s finite. Only 21 million will ever exist.
It’s permissionless. No bank, government, or pastor can block your access.
- Get a Wallet
Start with Phoenix Wallet or Blue Wallet (for Lightning).
If you're going offline, learn about SeedSigner or Trezor for cold storage.
- Earn or Buy BTC
Use Robosats or Peach for peer-to-peer (P2P) trading.
Ask your clients to pay in Bitcoin.
Zap content on Nostr to earn sats.
- Secure It
Learn about seed phrases, hardware wallets, and multisig options.
Never leave your coins on exchanges.
Consider a steel backup plate.
- Use It
Pay others in BTC.
Accept BTC for services.
Donate to freedom tech projects or communities building open internet tools.
🧭 Case In Point
Bitcoin isn’t just technology. It’s a mirror—one that reveals who we really are. Trinidad isn’t slow to adopt Bitcoin because it’s hard. We’re slow because we don’t want to let go of the comfort of being misled.
But times are changing. And the first person to wake up usually ends up leading the others.
So maybe it’s time.
Maybe you are the one to bring Bitcoin to Trinidad—not by shouting, but by living it.
-
 @ d34e832d:383f78d0
2025-04-21 07:31:10
@ d34e832d:383f78d0
2025-04-21 07:31:10The inherent heterogeneity of relay types within this ecosystem not only enhances operational agility but also significantly contributes to the overall robustness and resilience of the network architecture, empowering it to endure systemic assaults or coordinated initiatives designed to suppress specific content.
In examining the technical underpinnings of the Nostr protocol, relays are characterized by their exceptional adaptability, permitting deployment across an extensive variety of hosting environments configured to achieve targeted operational objectives.
For example, strategically deploying relays in jurisdictions characterized by robust legal protections for free expression can provide effective countermeasures against local censorship and pervasive legal restrictions in regions plagued by oppressive control.
This strategic operational framework mirrors the approaches adopted by whistleblowers and activists who deliberately position their digital platforms or mirrored content within territories boasting more favorable regulatory environments regarding internet freedoms.
Alternatively, relays may also be meticulously configured to operate exclusively within offline contexts—functioning within localized area networks or leveraging air-gapped computational configurations.
Such offline relays are indispensable in scenarios necessitating disaster recovery, secure communication frameworks, or methods for grassroots documentation, thereby safeguarding sensitive data from unauthorized access, ensuring its integrity against tampering, and preserving resilience in the face of both potential disruptions in internet connectivity and overarching surveillance efforts.
-
 @ 9223d2fa:b57e3de7
2025-04-21 05:53:02
@ 9223d2fa:b57e3de7
2025-04-21 05:53:02193 steps
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ 8d34bd24:414be32b
2025-04-20 14:18:37
@ 8d34bd24:414be32b
2025-04-20 14:18:37I started working on this post a couple weeks ago, and out of pure accident, it became my Resurrection Sunday (Easter) post. Maybe it was by God’s design. On Resurrection Sunday, Jesus was raised from the grave. Forty days later he rose to heaven before many witnesses. Someday in the future, the dead in Christ will be raised from the dead, and all believers will be snatched up to heaven. Maybe this is this right post for Resurrection Sunday.
For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. … For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. (1 Thessalonians 4:14, 16-17) {emphasis mine}
It always amazes me that some Christians don’t believe in the rapture of the church. I understand how there can be a disagreement about exactly when the rapture is to occur, but I can’t comprehend how some Christians don’t believe the rapture is coming or that they believe that the rapture happened in the first century.
Let’s start with the three key verses on the subject and then we’ll get into more details.
Key Rapture Verses
I didn’t notice that this first passage referred to the rapture until it was pointed out to me. I was so focused on Jesus preparing a place, that I missed the key sentence.
“Do not let your heart be troubled; believe in God, believe also in Me. In My Father’s house are many dwelling places; if it were not so, I would have told you; for I go to prepare a place for you. If I go and prepare a place for you, I will come again and receive you to Myself, that where I am, there you may be also. (John 14:1-3) {emphasis mine}
Jesus, after His resurrection and as promised in these verses, rose up to heaven to go prepare a place for believers. He will then return to bring believers to Himself. This whole idea would have been particularly clear for the Jews when it was written. When a bride and groom were engaged (a legal contract where they were considered married), the groom would go and prepare a place for them to live. It could be an extra room in his parent’s home or it could be a whole new home. The bride didn’t know when the groom would return to take her to himself to become man and wife. In the same way, Jesus has gone away to prepare a place for us and will return at a time we do not know. Just as the Jewish bride had to be ready to leave with her groom when he suddenly arrived, we also must be ready for Jesus’s return when He will snatch us from earth and take us home with Him to heaven.
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
The Bible has a wonderful euphemism for the death of believers. It speaks of them falling asleep because death is not the end for believers. It is just a pause, a separation of body and spirit, before we are raptured to Jesus, to meet Him in the sky, where we will receive a new resurrection body, just as Jesus received when He was raised from the dead 3 days after His crucifixion. Both the dead in Christ and the alive in Christ will “be caught up together with them in the clouds to meet the Lord in the air.” God gives us this promise in the Bible to comfort us. It gives us comfort that death is not the end and we will see our fellow believers again in heaven one day. It also gives us comfort that we will not have to experience God’s wrath. “For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
What else can we learn about the rapture?
Now I say this, brethren, that flesh and blood cannot inherit the kingdom of God; nor does the perishable inherit the imperishable. Behold, I tell you a mystery; we will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised imperishable, and we will be changed. For this perishable must put on the imperishable, and this mortal must put on immortality. But when this perishable will have put on the imperishable, and this mortal will have put on immortality, then will come about the saying that is written, “Death is swallowed up in victory. O death, where is your victory? O death, where is your sting?” The sting of death is sin, and the power of sin is the law; but thanks be to God, who gives us the victory through our Lord Jesus Christ. (1 Corinthians 15:50-57) {emphasis mine}
The rapture will be an instantaneous change from our perishable bodies to imperishable, whether we are alive in Christ or dead in Christ. At the rapture we “will be raised imperishable.” I am very excited to be snatched up into the air, receive a new, eternal body, and meet Jesus face-to-face.
There is one more passage that I believe talks of the rapture that is a bit more subtle from Isaiah.
The righteous man perishes, and no man takes it to heart;\ And devout men are taken away, while no one understands.\ For the righteous man is taken away from evil,\ **He enters into peace;\ They rest in their beds,\ Each one who walked in his upright way. (Isaiah 57:1-2) {emphasis mine}
The seven year Tribulation is the wrath of God poured out on those who rejected Him and the merciful, last chance warning before eternal judgement. Those who have trusted in Jesus (the devout men, the righteous man) will be “taken away from evil” and will “enter into peace.” Instead of experiencing God’s wrath, they will experience His peace. Instead of experience horror, they will “rest in their beds.”
The Seven Raptures Before the Rapture of the Church
How can we know that we will be raptured to heaven to be with Jesus forever? One way is because people have been raptured before (in different ways)
I am borrowing the organization of this section from Chapter 9 of “The End: Everything You’ll Want to Know about the Apocalypse” by Mark Hitchcock, which I happen to be reading at the moment.
-
Rapture of Enoch\ ”So all the days of Enoch were three hundred and sixty-five years. Enoch walked with God; and he was not, for God took him.” (Genesis 5:23-24) \ Enoch was raptured to heaven to be with God. He did not die, but went straight to God.
-
Rapture of Elijah\ ”And it came about when the Lord was about to take up Elijah by a whirlwind to heaven, that Elijah went with Elisha from Gilgal. … As they were going along and talking, behold, there appeared a chariot of fire and horses of fire which separated the two of them. And Elijah went up by a whirlwind to heaven.” (2 Kings 2:1,11) \ Elijah also was raptured to heaven without having to die. This passage gives more details. He went up in a whirlwind to heaven.
-
Rapture of Isaiah\ ”In the year of King Uzziah’s death I saw the Lord sitting on a throne, lofty and exalted, with the train of His robe filling the temple. Seraphim stood above Him, each having six wings: with two he covered his face, and with two he covered his feet, and with two he flew. And one called out to another and said,
“Holy, Holy, Holy, is the Lord of hosts,
The whole earth is full of His glory.”” (Isaiah 6:1-3)\ Isaiah’s situation was different. He was raptured to heaven only temporarily to be given God’s word and His prophecy and to call Isaiah for His good plan.
-
Rapture of Jesus\ ”And she gave birth to a son, a male child, who is to rule all the nations with a rod of iron; and her child was caught up to God and to His throne.” (Revelation 12:5)\ and\ ”And after He had said these things, He was lifted up while they were looking on, and a cloud received Him out of their sight. And as they were gazing intently into the sky while He was going, behold, two men in white clothing stood beside them. They also said, “Men of Galilee, why do you stand looking into the sky? This Jesus, who has been taken up from you into heaven, will come in just the same way as you have watched Him go into heaven.” (Acts 1:9-11)\ I’ve listed two verses about Jesus’s rapture. The one from Revelation uses the Greek word harpazo, caught up - when translated to Latin, the word is rapturo, which is where we get our English word rapture. The verses in Acts give a more detailed description of His rapture to heaven, which is an example of our rapture. We are also promised His return.
-
Rapture of Philip\ ”And he ordered the chariot to stop; and they both went down into the water, Philip as well as the eunuch, and he baptized him. When they came up out of the water, the Spirit of the Lord snatched Philip away; and the eunuch no longer saw him, but went on his way rejoicing. But Philip found himself at Azotus, and as he passed through he kept preaching the gospel to all the cities until he came to Caesarea.” (Acts 8:38-40)
The rapture of Philip is different than the rest, because Philip was snatched away, not to heaven, but to Azotus. This is still an instance worth pointing out because it also uses the Greek word Harpazo.
- Rapture of Paul\ ”I know a man in Christ who fourteen years ago—whether in the body I do not know, or out of the body I do not know, God knows—such a man was caught up to the third heaven. And I know how such a man—whether in the body or apart from the body I do not know, God knows— was caught up into Paradise and heard inexpressible words, which a man is not permitted to speak.” (2 Corinthians 12:2-4)\ Like Isaiah, Paul was temporarily caught up (Harpazo) to heaven to receive revelation from God and then returned to his work and life on earth
These examples show God snatching people from one location to another, physically or spiritually for His good purpose. I expect it to happen again, shortly before the beginning of the seven year tribulation.
The 3 Views of the Rapture
There are three main views of the rapture: pre-trib, mid-trib, and post-trib. The basic beliefs are pretty much self explanatory by their name. Does the rapture occur before the tribulation, around the mid-point of the tribulation (which is right before the Great Tribulation or final 3.5 years), or after the tribulation? Which one fits what the Bible says better?
Although the Bible doesn’t directly say when the rapture happens, there are some very strong hints.
No wrath For saints
“For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
God promises believers that we are not destined for wrath. The tribulation is also known as1 “The wrath” (1 Thessalonians 5:9 & Revelation 11:18), “The wrath to come” (1 Thessalonians 1:10), “The great day of their wrath” (Revelation 6:17), “The wrath of God” (Revelation15:1,7, 14:10,19, 16:1), “The wrath of the lamb” (Revelation 6:16). There are numerous other equally unpleasant names, but I am sticking with those that use the word wrath. God promised believers that we are not destined for wrath. God never breaks His promises.
Similarly Revelation 3 promises believers will be kept from the hour of testing.
Because you have kept the word of My perseverance, I also will keep you from the hour of testing, that hour which is about to come upon the whole world, to test those who dwell on the earth. I am coming quickly; hold fast what you have, so that no one will take your crown. (Revelation 3:10-11) {emphasis mine}
The word quickly can also be translated suddenly. Although Jesus has not returned quickly by our way of figuring time, He will come suddenly.
No one knows when
“But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone.” (Matthew 24:36)
Scripture says the Tribulation starts when the Antichrist signs a peace treaty with Israel. If the rapture happens before the tribulation, then we won’t know when it will happen. If the rapture occurs at the mid-trib position, then it will happen 3.5 years after the peace treaty. If the rapture occurs post-trip, then it will happen 7 years after the peace treaty is signed and 3.5 years after the abomination of desolation, when the Antichrist declares himself god in the Jewish temple and requires the whole world to worship him. Only one makes sense if we can’t know when it happens.
Just as in the days of …
“For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left.” (Matthew 24:37-41)
If we look at the words of Jesus, He compares the rapture to the days of Noah. Life happening as normal, then God put Noah and his family on the ark and personally shut the door (Genesis 7:16). Then the flood came, pouring God’s wrath out on those who had rejected Him. In the same way, God will take believers out of the world before pouring out His wrath on those who remain. He clearly states, “one will be taken and one will be left.”
A parallel passage in Luke, not only talks of God removing Noah before the flood, but also tells of God removing Lot before destroying Sodom & Gomorrah.
For just like the lightning, when it flashes out of one part of the sky, shines to the other part of the sky, so will the Son of Man be in His day. But first He must suffer many things and be rejected by this generation. And just as it happened in the days of Noah, so it will be also in the days of the Son of Man: they were eating, they were drinking, they were marrying, they were being given in marriage, until the day that Noah entered the ark, and the flood came and destroyed them all. It was the same as happened in the days of Lot: they were eating, they were drinking, they were buying, they were selling, they were planting, they were building; but on the day that Lot went out from Sodom it rained fire and brimstone from heaven and destroyed them all. It will be just the same on the day that the Son of Man is revealed. (Luke:17:24-30) {emphasis mine}
Just as Noah was removed before judgement, so also was Lot removed before judgement. In both cases the majority of people were going about business, living normal lives, not expecting anything to change.
In Genesis 19, the angels must remove Lot and his family before the city is destroyed.
Then the two men said to Lot, “Whom else have you here? A son-in-law, and your sons, and your daughters, and whomever you have in the city, bring them out of the place; for we are about to destroy this place, because their outcry has become so great before the Lord that the Lord has sent us to destroy it.” \ …\ When morning dawned, the angels urged Lot, saying, “Up, take your wife and your two daughters who are here, or you will be swept away in the punishment of the city.” But he hesitated. So the men seized his hand and the hand of his wife and the hands of his two daughters, for the compassion of the Lord was upon him; and they brought him out, and put him outside the city. (Genesis 19:12-13,15-16) {emphasis mine}
In the last days, God has promised to remove us before His judgment is poured out on those who willfully rejected Him. Jesus spoke these words to comfort us and so we would not fear the end.
Removal of the Restrainer
Now we request you, brethren, with regard to the coming of our Lord Jesus Christ and our gathering together to Him, that you not be quickly shaken from your composure or be disturbed either by a spirit or a message or a letter as if from us, to the effect that the day of the Lord has come. Let no one in any way deceive you, for it will not come unless the apostasy comes first, and the man of lawlessness is revealed, the son of destruction, who opposes and exalts himself above every so-called god or object of worship, so that he takes his seat in the temple of God, displaying himself as being God. Do you not remember that while I was still with you, I was telling you these things? And you know what restrains him now, so that in his time he will be revealed. For the mystery of lawlessness is already at work; only he who now restrains will do so until he is taken out of the way. Then that lawless one will be revealed whom the Lord will slay with the breath of His mouth and bring to an end by the appearance of His coming; (2 Thessalonians 2:1-8) {emphasis mine}
The restrainer is the Holy Spirit and the lawless one is the antichrist. This passage is saying that the antichrist will not be revealed until the restrainer is removed. The Holy Spirit indwells every believer. The believers also have to be removed before the antichrist is revealed, otherwise the Holy Spirit would have to leave the believers, leaving them alone during God’s wrath. That, of course, is contrary to God’s character, history, and promise.
Why is There No Mention of the Church During the Tribulation?
In the first three chapters of Revelation, the word church is used again and again. The church is not mentioned again until Revelation 19, regarding the Bride of Christ.
Let us rejoice and be glad and give the glory to Him, for the marriage of the Lamb has come and His bride has made herself ready.” It was given to her to clothe herself in fine linen, bright and clean; for the fine linen is the righteous acts of the saints. (Revelation 19:7-8) {emphasis mine}
All of this makes sense if the church was raptured before the tribulation. Therefore the bride (the church) has had seven years to make herself ready. They then get to descend with Jesus in the second coming of Jesus.
And I saw heaven opened, and behold, a white horse, and He who sat on it is called Faithful and True, and in righteousness He judges and wages war. His eyes are a flame of fire, and on His head are many diadems; and He has a name written on Him which no one knows except Himself. He is clothed with a robe dipped in blood, and His name is called The Word of God. And the armies which are in heaven, clothed in fine linen, white and clean, were following Him on white horses. From His mouth comes a sharp sword, so that with it He may strike down the nations, and He will rule them with a rod of iron; and He treads the wine press of the fierce wrath of God, the Almighty. And on His robe and on His thigh He has a name written, “KING OF KINGS, AND Lord OF LORDS.” (Revelation 19:11-16) {emphasis mine}
The Bride of Christ follows the King of Kings and Lord of Lords back to earth after being made “white and clean.”
Some may accuse pre-trib believers of being escapists. I’ll admit, I am happy to avoid the wrath of God, whether that be the tribulation or eternal damnation or just His daily disappointment in my failings. The fact that I am glad to “escape” the wrath, doesn’t make it untrue. I hope the passages and explanations I shared will give you comfort as the Day of the Lord and the Wrath of God approaches and as we see the world seemingly spiraling out of control. God is in control. Everything is happening according to His plan and for our good.
May the Lord of heaven comfort you with His promises and make you know His love. May you trust Him in good times and bad until the last days. May God give you a desire for His word and an understanding of His prophecies, so you will know the day is fast approaching.
Trust Jesus.
FYI, You can find most of my articles at end times. Some are directly relating to end times while others are loosely related. This post is a logical explanation of the rapture. You can also check out my older article on the rapture, “Up, Up, and Away.” The focus in my previous post was a little different including focusing on how the rapture will effect us, how we should respond to its immanency, and how it relates to the 2nd coming of Christ after the tribulation, so it is worth checking out as well.
-
-
 @ d34e832d:383f78d0
2025-04-22 18:15:42
@ d34e832d:383f78d0
2025-04-22 18:15:42Proof Of Concept
In a world where decentralization often hinges on the strength of its weakest node, the idea of federation—applied not to content moderation or identity, but strictly to communication protocols—opens up intriguing possibilities. In this model, Nostr relays do not operate in total isolation, nor do they function in a single cohesive mesh. Instead, they form selective, encrypted alliances, communicating through secure tunnels while preserving autonomy.
💡 The Core Idea
Relays remain sovereign, but may establish peer-to-peer encrypted channels with other trusted relays using Elliptic Curve Diffie-Hellman (ECDH) to generate shared secrets. These secrets are then used to encrypt communication tunnels—facilitating a federated communication layer.
Each relay is free to choose: - Whom it speaks to - How often - What types of events are relayed through the tunnel
But never must it rely on a central coordinator.
🔁 Schnorr for Authentication
While ECDH can create the secure tunnel, Schnorr signatures (already a part of Nostr’s pubkey-based design) can be used to authenticate the origin of the data inside. This keeps the integrity of messages intact even when traveling over shared or hostile networks.
Use case: - Relay A and Relay B establish an ECDH-based shared key. - All communication is tunnel-encrypted with this shared key. - Inside the tunnel, every message still carries a Schnorr signature, proving its source.
This separation of transport-level encryption from message-level authenticity provides an elegant layering of security.
🌐 Practical Benefits
- Obfuscation: Encrypted tunnels reduce visibility into relay-to-relay traffic patterns.
- Privacy: Federation over encrypted channels shields metadata and protects against surveillance.
- Resilience: Relays can route around censorship by tunneling through less obvious peers.
- Synergy: Specific relay clusters can form ephemeral or long-term alliances—say, art relays or academic relays—without disclosing their full graph to the world.
🧩 Optional Enhancements
- Noise Protocol Framework to standardize encrypted relay tunnels.
- Tor Hidden Services or I2P for transport obfuscation.
- Relay Reputation Systems to gauge trust before federation.
- Dynamic Federation Negotiation: using NIP-like proposals over encrypted handshakes to initiate or terminate communication agreements.
🌱 Case In Point
This is not about governing content, users, or identities—this is about strengthening how relays talk. By embracing federated communication via ECDH and Schnorr-secured tunnels, Nostr relays could evolve into a resilient underground of trust-minimized, pseudonymous routers that defy surveillance while amplifying decentralization.
federated communication via ECDH and Schnorr-authenticated encrypted tunnels between Nostr relays:
markdown NIP-xyz: Federated Encrypted Relay Communication Status: Draft Type: Relay Created: 2025-04-22
Summary
This NIP proposes a method for encrypted, authenticated communication between Nostr relays using ECDH-based tunnels for transport encryption and Schnorr signatures for payload integrity. This federation model allows relays to communicate securely while maintaining full autonomy, enhancing privacy, censorship resistance, and interoperability.
Motivation
Nostr’s decentralized architecture relies heavily on relays, which currently operate in isolated or broadcast modes. There is no standard for secure, peer-to-peer communication between relays themselves, outside of client interactions.
Introducing encrypted tunnels between relays offers:
- Privacy: Reduces metadata leakage across public or adversarial networks.
- Resilience: Allows relays to forward events and metadata through trusted peers when direct access is blocked or filtered.
- Autonomy: Federation is opt-in and purely communicational—no centralized authority or directory is involved.
- Extensibility: Enables experimental protocols or content-specific subnets without altering the global Nostr model.
Specification
1. Key Exchange via ECDH
Each relay maintains: - A persistent relay keypair:
relay_pubkey,relay_privkey- Optionally: rotating session keys for forward secrecyWhen two relays (A and B) wish to establish communication: - They exchange their public keys (
relay_pubkey_Aandrelay_pubkey_B) - Both calculate a shared secret using ECDH oversecp256k1:plaintext shared_secret = SHA256(ECDH(relay_privkey_A, relay_pubkey_B))This
shared_secretis used to derive an encryption key for an authenticated symmetric cipher, such as AES-GCM or ChaCha20-Poly1305.
2. Encrypted Tunnel Establishment
Once the shared secret is derived: - All messages between relays are sent through an encrypted tunnel - Transport can be TCP, WebSocket, or HTTP/3 over QUIC, optionally via Tor or I2P
A RelayHello message is exchanged encrypted, optionally containing:
json { "type": "relay_hello", "relay_name": "nostr.relay.example", "features": ["forwarding", "dedup", "metadata"], "timestamp": 1684000000, "sig": "<Schnorr-signed payload>" }The
sigis a Schnorr signature from therelay_pubkey, verifying the message content.
3. Event Forwarding
Relays may forward selected event types across tunnels, such as: - Kind 1 (Text Note) - Kind 3 (Contacts) - Kind 5 (Deletion Notices) - Custom kinds (with mutual agreement)
All forwarded events MUST retain original client-level signatures. Relay-to-relay metadata (like timestamps, relay hints, or scores) may be added in a separate metadata envelope.
4. Access Control and Policies
Each relay maintains a federation list, including: - Public key of the peer relay - Features enabled - Rate limits and quotas - Last active session or rotation timestamp
Relays MAY: - Deny tunnel requests - Rotate keys periodically - Restrict communication to a whitelist - Use Proof-of-Work or tokens for DoS protection
5. Optional Features
- Forward Secrecy: ephemeral key pairs with HKDF for short sessions
- Relay Reputation: signed relay trust scores (future NIP)
- Message Compression: gzip or zstd on tunnel payloads
- Encrypted Gossip: tunnel-specific metadata routing
Compatibility
This NIP is backward-compatible. Relays that do not implement it will simply not participate in tunnel-based communication.
No changes are required from Nostr clients.
Reference Implementation (Proposed)
nostr-tunnel-relay: Rust-based relay that supports federated encrypted tunnelsnostr-relay-link: CLI tool to establish and monitor tunnels- Example configs for federation policies in JSON or TOML
Rationale
- ECDH ensures only the two relays involved can decrypt tunnel data
- Schnorr signatures authenticate content without duplicating identity schemes
- Federation is scoped only to communication, preserving Nostr’s core simplicity
Security Considerations
- Relay pubkeys must be carefully verified to prevent MITM
- Session expiration and key rotation should be configurable
- Replay protection and nonce management are required for AEAD ciphers
- Metadata leakage minimized by default obfuscation or Tor-based transport
NIP.eshgham
-
 @ e8deeca0:4b55db9b
2025-04-20 09:32:16
@ e8deeca0:4b55db9b
2025-04-20 09:32:16Lily Phillips
Lily Phillips, a 23-year-old OnlyFans creator from Derbyshire, sparked global controversy after announcing her intention to have sex with 1,000 men in one day. While the event itself never occurred, she completed a "training" session with 101 men, which was documented by YouTuber Josh Pieters in a film titled I Slept with 100 Men in One Day. The documentary shows Phillips breaking down emotionally mid-way, which further fueled debates about the psychological toll of such performances.
Phillips maintained that the experience was voluntary and empowering. Still, she also admitted that her content might contribute to unrealistic expectations of women, saying, "It’s my fantasy, but I’m not helping the situation."
The backlash was swift and intense. She was permanently banned from Airbnb for violating their policies during the event, and she faced accusations of idea theft from fellow adult creator Bonnie Blue (no rivalry). But beyond the drama and headlines, her actions touched on something deeper within society—triggering reactions that reveal much about our collective psyche.
Why the Outrage?
The reaction to Phillips was not just about one extreme act. It tapped into long-standing emotional, cultural, and gender-based tensions:
-
For many women, it felt like exploitation. Even though Phillips claimed agency, the imagery of one woman being with over a hundred men appeared dehumanizing, echoing trauma around objectification and sexual coercion.
-
For some feminists, the event divided opinion. Was it a radical expression of freedom or a reinforcement of male-centered pornographic fantasies?
-
For many men, the outrage often stemmed from a sense of moral violation. A woman expressing sexuality so publicly and without shame challenges deep-seated beliefs about purity, modesty, and traditional gender roles.
-
Across the board, the situation made people confront how casual sex is viewed in our culture. While society consumes sexualized content daily, overt expressions of it—especially by women who claim control over it—are still met with hostility.
Lily Phillips didn’t just spark a conversation about adult content; she exposed a fault line in how we view sex, autonomy, and public morality. Whether one sees her actions as empowering or disturbing, the public reaction speaks volumes about our own discomforts, hypocrisies, and evolving values.
In the end, Lily became a mirror—reflecting a culture still unsure of how to talk honestly about sex and power.
-
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 9bde4214:06ca052b
2025-04-22 17:30:02
@ 9bde4214:06ca052b
2025-04-22 17:30:02“We do not have the answers."
Pablo & Gigi have no solutions.
In this dialogue:
- What is this No Solutions thing anyway?
- Why dialogue and distributed cognition is so important
- Why is nostr exciting for developers?
- Evolution, Life, and nostr
- What is the perfect nostr app, and why can’t there be THE perfect nostr app?
- Why there is no “global” view in nostr
- Impossible problems vs. possible (but still hard) problems
- Blossom, blossom, and more blossom
- Zooko’s Triangle
- Freedom Tech Building Blocks
- NIP-60/61, NIP-89
- Email vs ICQ
- Accepting constraints & moving forward
- Nostr has data integrity, but no data guarantees
- Bitcoin as an extreme RAID system
- Fault tolerance vs. efficiency
- “Build the infrastructure, don’t run it.”
- eCash fixes 402
- Everything in nostr can be one-click
- There’s infinite nsecs (and they are free!)
- The magic of the nostr view-only mode
- The Local-first movement
- How to monetize without putting yourself in the middle?
- RoboSats as an example of open-source monetization
- The YouTube like count is a lie
Further links:
- https://en.wikipedia.org/wiki/Distributed_cognition
- https://nips.nostr.com/60
- https://nips.nostr.com/61
- https://nips.nostr.com/89
- https://github.com/hzrd149/blossom
- https://en.wikipedia.org/wiki/Zooko’s_triangle
- https://www.jrepodcast.com/guest/adam-curry/
- https://localfirstweb.dev/
- https://www.localfirstconf.com/
- https://en.wikipedia.org/wiki/ICQ
- https://appleinsider.com/articles/24/05/25/icq-1996-2024-the-first-universal-messenger-had-a-good-run-and-is-leaving-us-soon
- https://www.chatinum.com/articles/the-old-chat-apps-of-the-2000s
- https://en.wikipedia.org/wiki/Standard_RAID_levels
- https://www.youtube.com/watch?v=oIkhgagvrjI
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ 65f03c16:f77e9d92
2025-04-20 08:33:37
@ 65f03c16:f77e9d92
2025-04-20 08:33:37is a game changer for traders. It blends chaos theory & market psychology to decode price action. Learn to spot order in market noise using fractals & momentum, teaches the Alligator indicator to ride trends & avoid chop. His 5-stage approach, from novice to expert, builds discipline & edge. Perfect for futures or stocks, It’s practical, not abstract. Williams’ 40+ yrs of trading shine through, with tools like Elliott Wave & nonlinear dynamics
recommended !
-
 @ f7d424b5:618c51e8
2025-04-19 22:06:47
@ f7d424b5:618c51e8
2025-04-19 22:06:47It's our podcast and we'll talk about whatever we want. Welcome to a return to normalcy where we cover a variety of subjects instead of just a couple of really long ones. Crack open a beer and chill with us. We're gonna talk about the Galaxy showcase, Marathon, Skyblivion & the leaked Oblivion remake, and a whole bunch more.
In the opening of the episode we get Vic's reaction to a really specific trailer, if you want to follow along, this is the link to that video
Other stuff cited:
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ bc52210b:20bfc6de
2025-04-19 21:04:53
@ bc52210b:20bfc6de
2025-04-19 21:04:53In the ever-evolving world of Bitcoin mining, a new player has emerged, promising to revolutionize the way miners operate. OCEAN Bitcoin Mining (https://ocean.xyz) introduces a hybrid model that combines the autonomy of solo mining with the reduced variance of pool mining. This article delves into how OCEAN achieves this balance, offering miners the best of both worlds while maintaining Bitcoin's decentralized ethos.
Understanding Solo and Pool Mining
To appreciate OCEAN's innovation, it's essential to understand the traditional mining models: *** Solo Mining: In solo mining, an individual miner uses their computational power to solve the cryptographic puzzle required to add a new block to the Bitcoin blockchain. If successful, the miner receives the entire block reward, which includes newly minted bitcoins and transaction fees. Solo miners have full control over which transactions are included in their blocks. However, with the current difficulty of Bitcoin mining, solo miners with limited hash power face high variance—long periods without rewards followed by rare, large payouts. * Pool Mining**: Pool mining addresses the variance issue by allowing miners to combine their computational resources. When the pool finds a block, the reward is distributed among participants based on their contributed hash power. This provides more consistent, smaller payouts. However, the pool operator typically decides which transactions are included in the block, potentially leading to centralized control and censorship concerns.
How OCEAN Combines the Two
OCEAN Bitcoin Mining introduces a novel approach that merges the benefits of solo and pool mining: * DATUM (Decentralized Alternative Templates for Universal Mining): OCEAN empowers miners with DATUM, a system that allows them to create their own block templates. This means miners can decide which transactions to include in the blocks they are working on, similar to solo mining. Unlike traditional pool mining, the pool does not dictate transaction selection. * Pool Benefits: While miners maintain control over transaction selection, they also contribute their hash power to a collective effort, akin to pool mining. This increases the likelihood of finding a block, thereby reducing the variance in rewards. When a block is found, the miner who discovers it receives the full reward directly, and the block reflects their chosen transactions. Key Advantage: This setup eliminates the high variance associated with solo mining while preserving miners' autonomy. Miners enjoy more frequent opportunities to earn rewards due to the pool's combined power, yet they retain the freedom to select transactions, a feature typically lost in traditional pool mining.
Censorship Resistance
One of the most significant benefits of OCEAN's model is its resistance to transaction censorship: * In traditional pool mining, if a pool operator is pressured—perhaps by regulatory forces affecting entities like Tether—to exclude certain transactions, all miners in the pool are impacted. * With OCEAN and DATUM, even if some miners or entities are compelled to censor transactions, other miners in the pool can still include any valid transactions they choose. When these miners find a block, their selected transactions are added to the blockchain, effectively bypassing centralized control or censorship attempts. * This mechanism upholds Bitcoin's decentralized nature, ensuring that no single authority can dictate which transactions are processed, provided miners opt to include them.
Conclusion
OCEAN Bitcoin Mining represents a significant step forward in the mining landscape. By blending the autonomy of solo mining with the reduced variance of pool mining, OCEAN offers miners a unique opportunity to maintain control over their operations while enjoying more consistent rewards. Furthermore, its resistance to censorship reinforces Bitcoin's core principles of decentralization and freedom. As the mining industry continues to evolve, OCEAN stands out as a beacon of innovation, providing miners with the tools they need to thrive in a competitive and ever-changing environment.
-
 @ 1bc70a01:24f6a411
2025-04-19 09:58:54
@ 1bc70a01:24f6a411
2025-04-19 09:58:54Untype Update
I cleaned up the AI assistant UX. Now you can open it in the editor bar, same as all other actions. This makes it a lot easier to interact with while having access to normal edit functions.
AI-generated content
Untype uses OpenRouter to connect to various models to generate just about anything. It doesn't do images for now, but I'm working on that.
Automatic Title, Summary and Tag Suggestions
Added the functionality to generate titles, summaries and tags with one click.
A Brief Preview
Here is a little story I generated in Untype, ABOUT Untype:
This story was generated in Untype
Once upon a time, in the bustling digital city of Techlandia, there lived a quirky AI named Untype. Unlike other software, Untype wasn't just your everyday article composer — it had a nose for news, quite literally. Untype was equipped with a masterful talent for sniffing out the latest trends and stories wafting through the vast digital ether.
Untype had a peculiar look about it. Sporting a gigantic nose and a pair of spectacles perched just above it, Untype roamed the virtual city, inhaling the freshest gossip and spiciest stories. Its nostr-powered sensors twitched and tickled as it encountered every new scent.
One day, while wandering around the pixelated park, Untype caught a whiff of something extraordinary — a scandalous scoop involving Techlandia's mayor, Doc Processor, who had been spotted recycling old memes as new content. The scent trail was strong, and Untype's nose twitched with excitement.
With a flick of its AI function, Untype began weaving the story into a masterpiece. Sentences flowed like fine wine, infused with humor sharper than a hacker’s focus. "Doc Processor," Untype mused to itself, "tried to buffer his way out of this one with a cache of recycled gifs!"
As Untype typed away, its digital friends, Grammarly the Grammar Gremlin and Canva the Artful Pixie, gathered around to watch the genius at work. "You truly have a knack for news-sniffing," complimented Grammarly, adjusting its tiny monocle. Canva nodded, painting whimsical illustrations to accompany the hilarious exposé.
The article soon spread through Techlandia faster than a virus with a strong wifi signal. The townsfolk roared with laughter at Untype’s clever wit, and even Doc Processor couldn't help but chuckle through his embarrassment.
From that day on, Untype was celebrated not just as a composer but as Techlandia's most revered and humorous news-sniffer. With every sniff and click of its AI functions, Untype proved that in the world of digital creations, sometimes news really was just a nose away.
-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
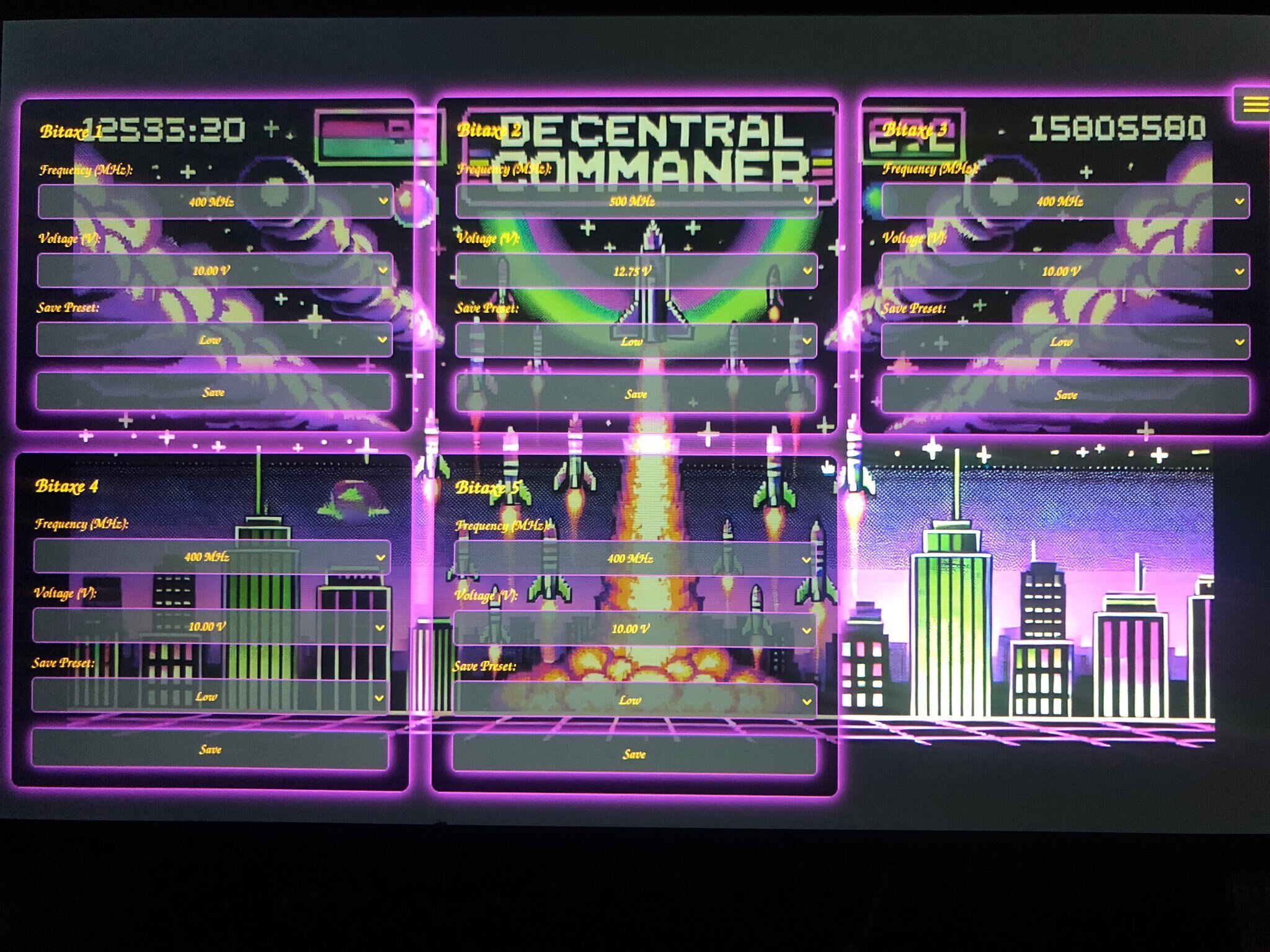 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
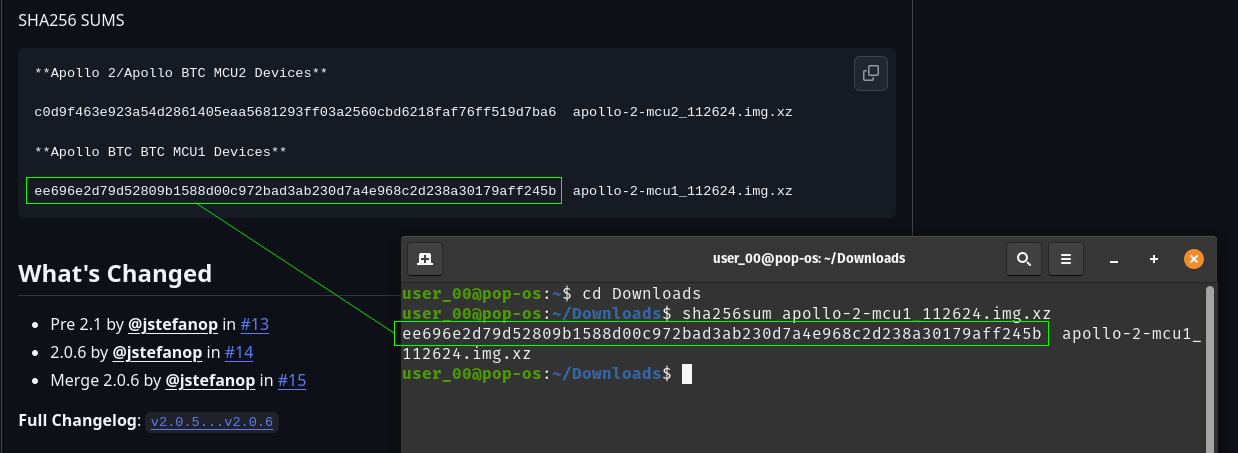 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
 [IMG-017] Futurebit dashboard
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
 [IMG-018] Futurebit node page
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
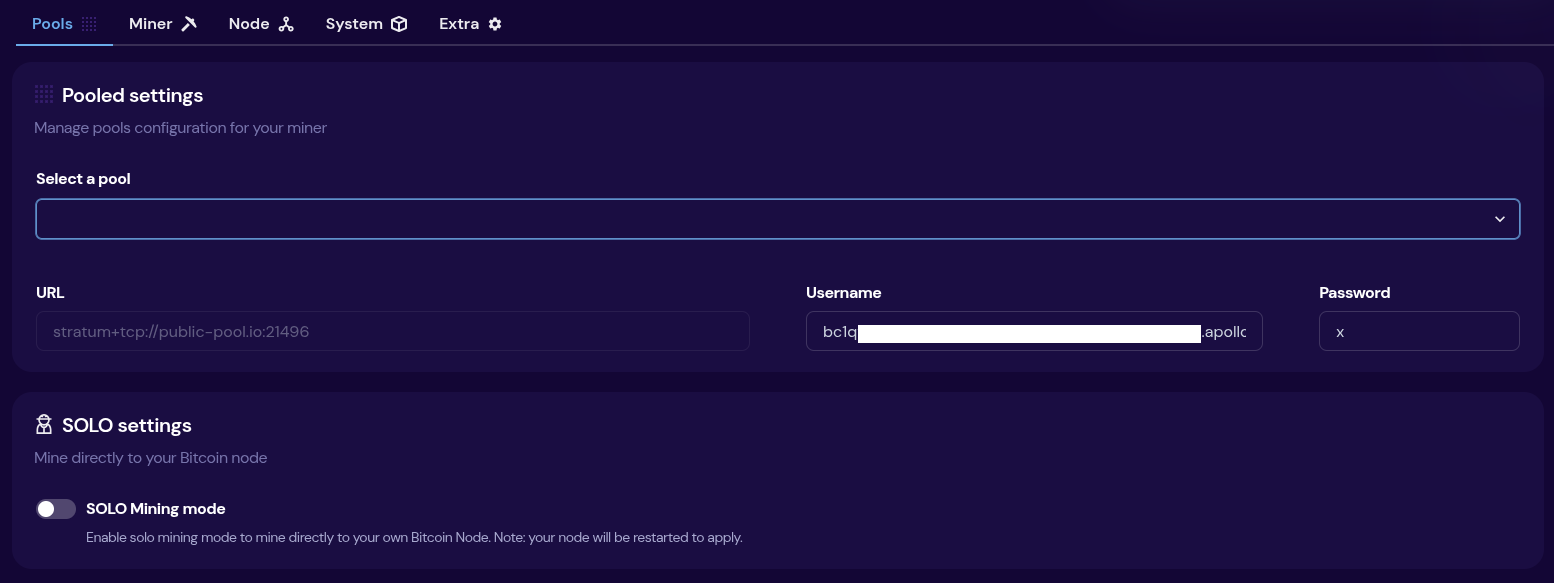 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
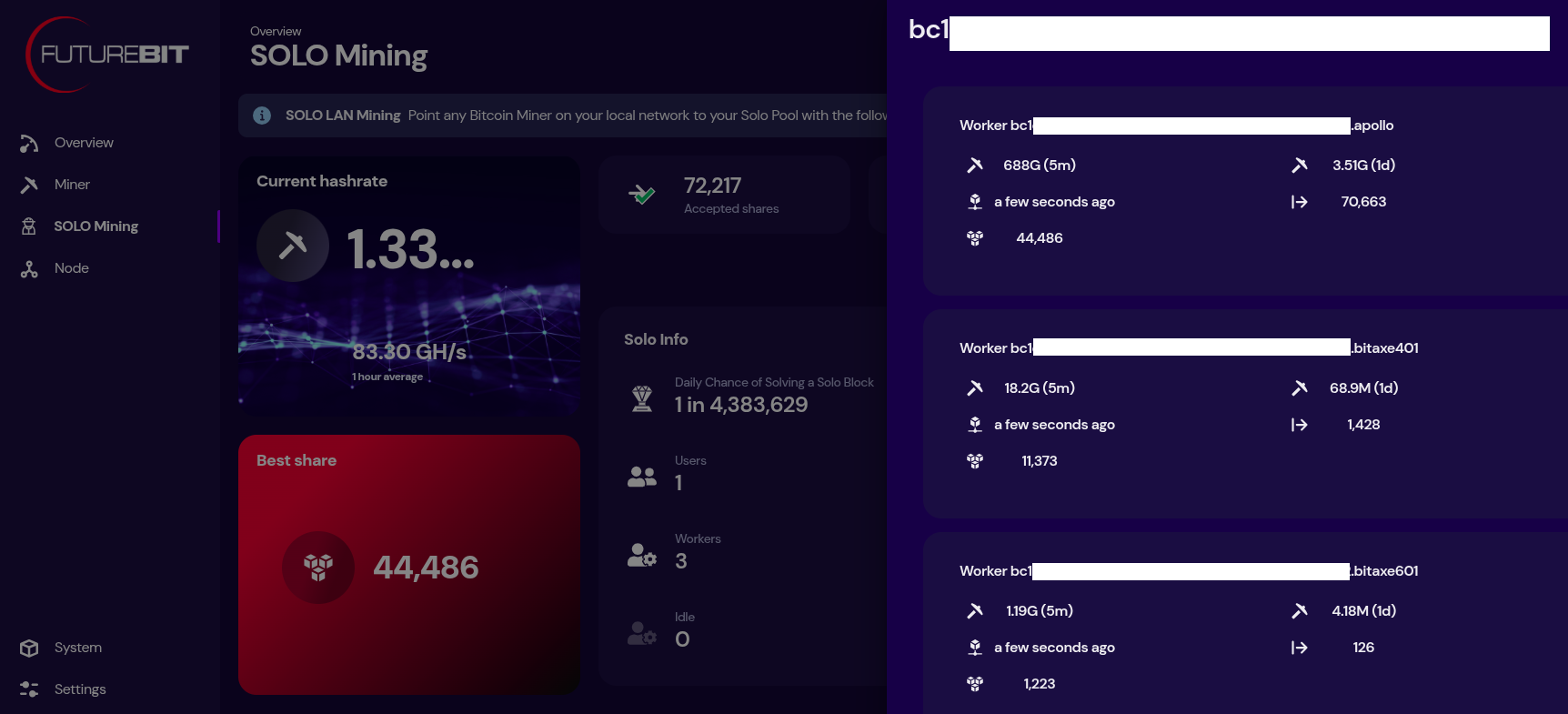 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
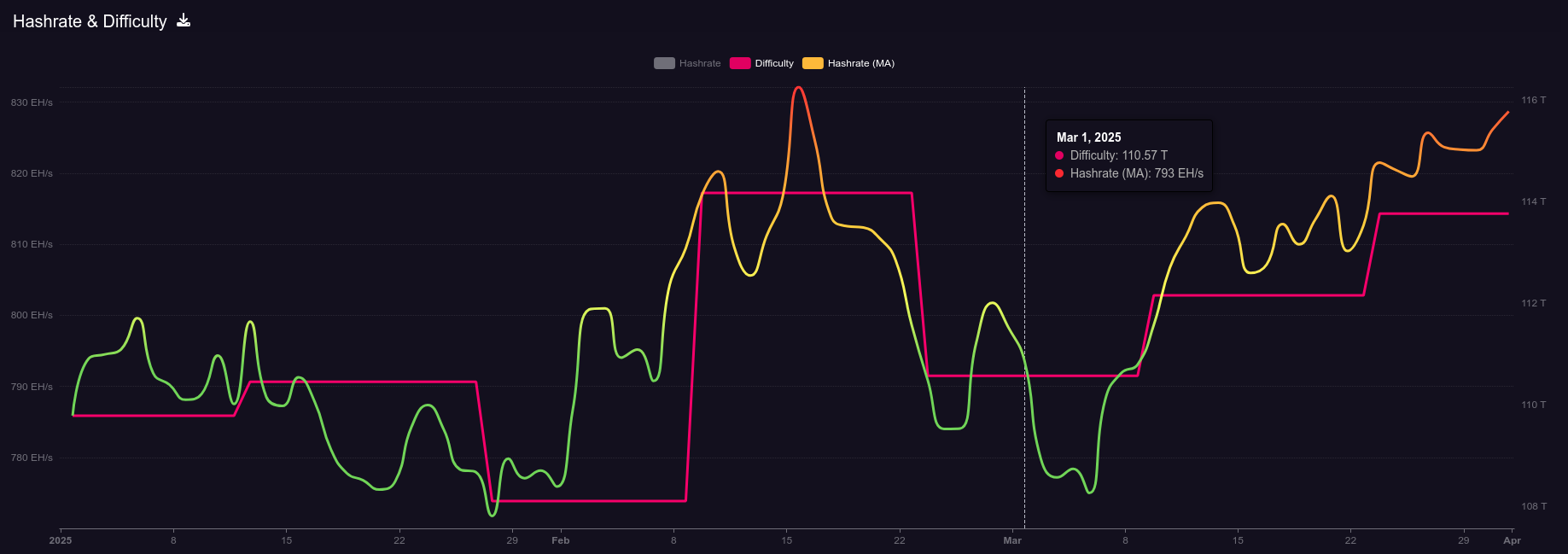 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
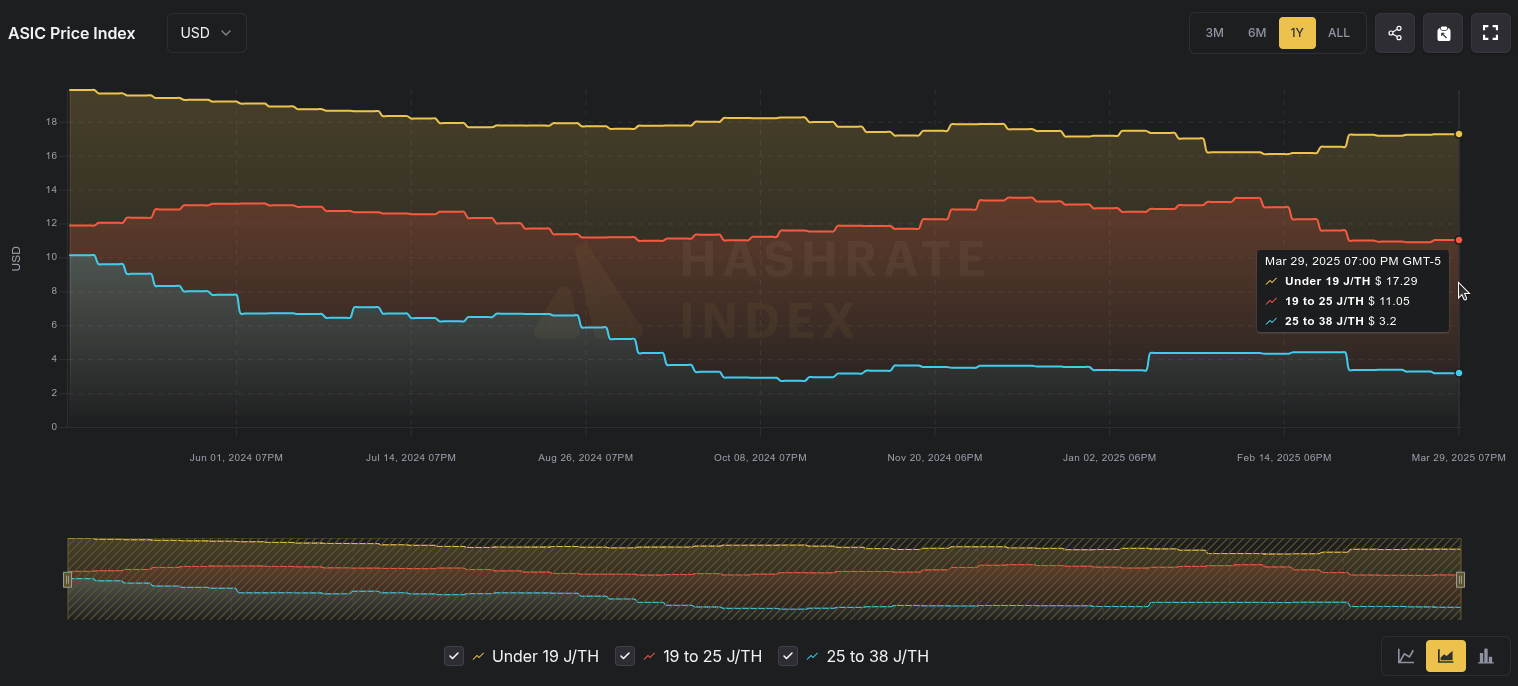 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
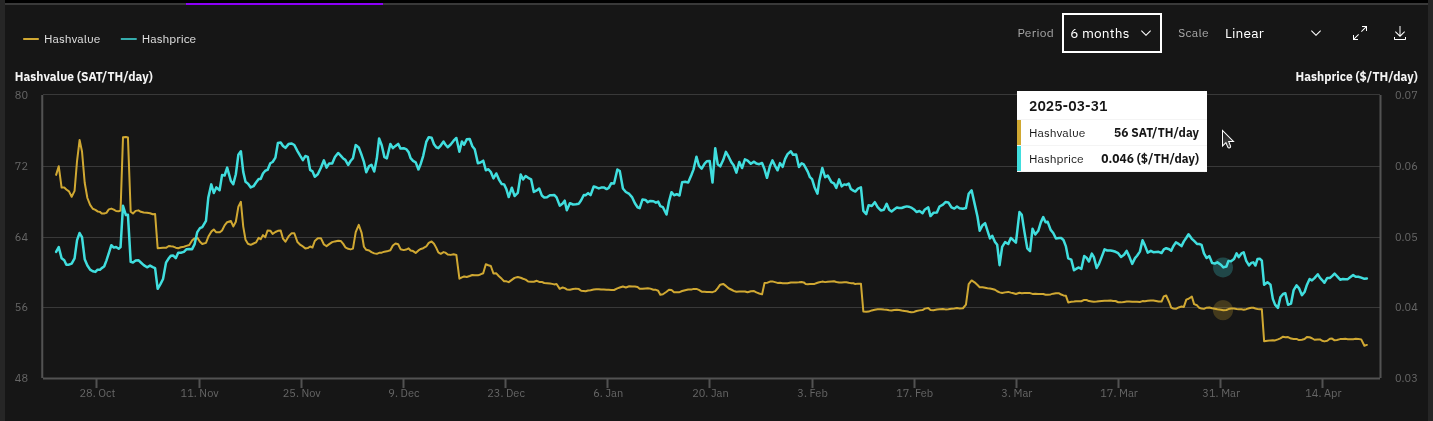 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ dab6c606:51f507b6
2025-04-18 14:59:25
@ dab6c606:51f507b6
2025-04-18 14:59:25Core idea: Use geotagged anonymized Nostr events with Cashu-based points to snitch on cop locations for a more relaxed driving and walking
We all know navigation apps. There's one of them that allows you to report on locations of cops. It's Waze and it's owned by Google. There are perfectly fine navigation apps like Organic Maps, that unfortunately lack the cop-snitching features. In some countries, it is illegal to report cop locations, so it would probably not be a good idea to use your npub to report them. But getting a points Cashu token as a reward and exchanging them from time to time would solve this. You can of course report construction, traffic jams, ...
Proposed solution: Add Nostr client (Copstr) to Organic Maps. Have a button in bottom right allowing you to report traffic situations. Geotagged events are published on Nostr relays, users sending cashu tokens as thank you if the report is valid. Notes have smart expiration times.
Phase 2: Automation: Integration with dashcams and comma.ai allow for automated AI recognition of traffic events such as traffic jams and cops, with automatic touchless reporting.
Result: Drive with most essential information and with full privacy. Collect points to be cool and stay cool.
-
 @ 9bde4214:06ca052b
2025-04-22 17:23:02
@ 9bde4214:06ca052b
2025-04-22 17:23:02“You’ll get all that for free if you build it right.”
Pablo & Gigi try to stop giggling.
In this dialogue:
- 01: Start Ugly
- 02: There is No Global
- Concept of ownership & “Read, Write, Own”
- Shamir Secret Sharing and Timelocks
- “No amount of violence will ever solve a math problem.”
- You can’t prove deletion of a key (or anything, really); best you can do is “burn” bitcoin
- Data is information, which behaves like an idea (not like an apple)
- “If you have an apple and I have an apple and we exchange these apples then you and I will still each have one apple. But if you have an idea and I have an idea and we exchange these ideas, then each of us will have two ideas.” – https://dergigi.com/threads/memes-vs-the-world
- Why the Pubky architecture isn’t great
- Cashu
- Nutzaps: NIP-60 / NIP-61
- How nutzaps fix fake zaps on zaplife.lol
- “Ecash fixes HTTP 402”
- “[Bitcoin [and nostr]] take advantage of the nature of information being easy to spread but hard to stifle.” –Satoshi Nakamoto
- Discovery with NIP-89
- #RunDVM with NIP-90
- Why micropayments can’t work on credit rails, and how bitcoin is the rediscovery of money.
- Putting payments into blossom
- “Money is essentially a tool to keep track of who owes what to whom. Broadly speaking, everything we have used as money up to now falls into two categories: physical artifacts and informational lists. Or, to use more common parlance: tokens and ledgers.”
- “maximum utility in the world of Bitcoin entails the adoption of maximum responsibility.”
- Complexity of Lightning vs the simplicity of eCash
- Amber and Citrine
- How Pablo became the BIS
- 12 words in your head can literally save your life
- The in-between of custodial and non-custodial in a multi-mint world
- Nutzaps integrated in chachi.chat
- The intermediacy of nostr is magic
- In nostr you’ll get a lot for free IF YOU BUILD IT RIGHT
- “Free Speech platforms cannot exist; if there is a ‘deplatform’ button, the button will be pressed.”
- “Neither nostalgia nor utopia.”
- Solutions that make stuff worse over time vs solutions that make stuff better over time.
-
asknostr on passkeys, and why we think they’ll make things worse over time.
- Authentication vs identity: “identification asks, authentication proves”
- You are not your name and photo; identity is prismatic
- (m00t’s talk on it at web summit 2011)
- Starbug from CCC pwning TouchID biometrics from a high-res photo (article)
- Key rotation and (American) HODL
- Social recovery
- Multi-sig for nostr with FROSTR
Links & References:
- Nostr Protocol Repository: https://github.com/nostr-protocol
- Cashu (e-cash): https://github.com/cashubtc
- NIP-60 (Nutzaps): https://github.com/nostr-protocol/nips/blob/master/60.md
- NIP-89 (Service Discovery) & NIP-90 (DVMs) – upcoming proposals: https://nips.nostr.com/89 & https://nips.nostr.com/90
-
 @ 1f9e547c:8af216ed
2025-04-18 03:52:38
@ 1f9e547c:8af216ed
2025-04-18 03:52:38Opinion about Bitcoin Core (desktop)
From Hebasto Twitter
Fellow Bitcoin Core Guix builders,
Heads up! If you're using the Ubuntu guix package, avoid upgrading to Ubuntu 24.04 as it breaks your Guix setup.
https://bugs.launchpad.net/ubuntu/+source/guix/+bug/2064115
WalletScrutiny #nostrOpinion
-
 @ 7b3f7803:8912e968
2025-04-18 00:16:02
@ 7b3f7803:8912e968
2025-04-18 00:16:02As we enter Holy Week, we are confronted with a world steeped in sin, strife, conflict, and mortality. There exists a peculiar fascination among some with societal decline, as if they derive satisfaction from witnessing civilization’s unraveling. This attraction to darkness may reflect their inner turmoil, a desire to see others share in their suffering. Alternatively, it could stem from a profound hopelessness, a belief that life lacks purpose, leading them to wish for its end. The allure of dystopian futures is, indeed, a curious phenomenon.
Alexander Hamilton once yearned for war as a means to elevate his status, a reflection of youthful ambition for decisive action. Such a desire—to distinguish oneself and ascend the social hierarchy—underlies some of the grim visions of the future propagated by certain ideological circles. Their aim is not war itself but a reconfiguration of power, placing authority in the hands of those who affirm their values. For years, such individuals have held sway, yet their influence appears to be waning.
In the absence of hope, many embrace visions of decline. This despair is characteristic of a faltering empire, signaling the end of an era. The younger generation, burdened by weariness, falters under the weight of their circumstances. They lack hope for a brighter future and see no clear path out of life’s monotony. In a word, they are trapped, uncertain of how to proceed.
We witnessed a similar sentiment during the Arab Spring, where upheaval was celebrated as a longed-for revolution, a societal reset. The assassination of a prominent corporate executive, such as the CEO of United Health, evokes a comparable yearning for disruption. There is a desire for a cultural transformation, though its precise nature remains elusive.
Yet, the youth find themselves dominated by the very elites whose rhetoric they echo. Unlike the 1960s, when generational values clashed overtly, today’s power structures co-opt the language of the young, redirecting their frustration toward populist movements. This inversion is a cunning strategy, mitigating the potential for significant rebellion.
The reality remains that the older generation holds the wealth, power, and authority, while the young are consistently marginalized. They are the ones left with little hope, ensnared by the system. However, a quiet rebellion is emerging—one rooted in hope and faith. Many are beginning to see through the falsehoods propagated by those in power. The promises of governmental provision, once alluring, now appear untenable in light of fiscal realities. The youth seek a new source of hope, a renewed perspective. Thankfully, they are beginning to find it, turning toward faith as a foundation for a more optimistic future.
-
 @ 9bde4214:06ca052b
2025-04-22 17:15:24
@ 9bde4214:06ca052b
2025-04-22 17:15:24“I don’t believe in Utopia anymore. I’m too old for that.”
Calle & Gigi philosophize about nuts.
Books and articles mentioned:
In this dialogue:
- Where is the Utopia that the internet promised?
- “Neither nostalgia nor utopia”
- Net Neutrality is a moral stance
- Where did the internet go wrong?
- Tech as a tool; is tech always neutral?
- Technology that increases agency VS tech that enslaves
- Competition vs Symbiosis
- “Who will run the mints?”
- “Anyone” can use it vs “everyone” can use it
- Centralizing vs. Monopolizing
- Bitcoin has an ethos baked in (You Shall Not Steal)
- Passive internet vs active internet
- Agency in cyberspace, and how to maximize it
- Blinded custodian vs regular custodian
- User data is a liability
- Obscura / Mullvad / Silent.Link as obvious early adopters
- Run your own ISP - Tollgate
- Cryptography is Not Enough
- Bitcoin is Time
- Time requires heat
- Zero-knowledge service providers
- Electronic Cash vs Digital Cash (CBDCs)
- Credit requires KYC, KYC implies outside enforcement
- Writings on Micropayments by Nick Szabo
- eCash fixes 402, obviously
- Who Owns the Future?
- “You are the product” vs “Subscription Hell”
- “Hello old friend!!!”
- Cathedral vs Bazaar
- Why paywalls suck
- Information wants to be free
- "Markets become absurd as supply approaches infinity."
- eCash + AI = match made in heaven
- #LearnToCode vs #LearnToPrompt
- Scarcity in cyberspace: compute, storage, networking
- Zero-Knowledge compute & zero-knowledge proofs
- https://en.wikipedia.org/wiki/Zero-knowledge_proof
- https://github.com/AbdelStark/cashu-zk-engine
- Cairo: https://github.com/starkware-libs/cairo
- MCP https://github.com/AbdelStark/bitcoin-mcp
- MCP DVM: https://github.com/r0d8lsh0p/n8n-AI-agent-DVM-MCP-client
- DVMCP: https://mcp.so/server/dvmcp
- Olas & Nutzaps (NIP-60, NIP-61)
- Bitcoin is not only the internet of money, but it is the money of the internet
- Re-building the internet archive on top of nostr
- Bitrot & 404
- Resurrection markets & marketplace for hashes via Blossom
- Hugs 🫂
-
 @ f10512df:c9293bb3
2025-04-22 17:11:05
@ f10512df:c9293bb3
2025-04-22 17:11:05Details
- 🍳 Cook time: 5-7 minutes
- 🍽️ Servings: 1
Ingredients
- 2 eggs
- Shredded cheese (Sharp cheddar is a favorite)
- 1 Tbsp olive oil or ghee
Directions
- Add oil to a non-stick pan and allow it to get hot (med-high heat)
- Add eggs and additional toppings, scramble and wait for the edges to get brown.
- Add shredded cheese while edges are browning. It is best if cheese begins to melt before flipping.
- Flip, and make sure all cheese stayed down, and there is enough oil left in the pan.
- Keep checking until pan side of eggs lift easily. Done correctly, the cheese will form a crisp layer.
- When fully cooked, serve with cheese right side up and enjoy!
-
 @ 4c96d763:80c3ee30
2025-04-17 19:41:12
@ 4c96d763:80c3ee30
2025-04-17 19:41:12Changes
William Casarin (26):
- dave: reorganize ModelConfig
- dave: organize
- dave: remove old file
- dave: add a few tool docs
- dave: update to custom filters nostrdb
- dave: only search non-replies
- context: implement note broadcasting
- multicast: broadcast context
- dave: fix bugs
- chrome: fix wallet button
- previews: disable for now
- ui: add some margin to chrome sidebar
- columns: remove thread warning
- nostrdb: fix on windows
- dave: tweak prompt
- misc: driveby fixes
- refactor: move input buttons ui into its own fn
- refactor: extract input_ui into its own function
- dave: refactor a bit
- post: fix bug where send shortcut send unfocused inputs
- dave: give up on plaintext formatting
- dave: fix input box
- log: silence gif log
- refactor: nevernest get_display_name
- refactor: ocd unnecessary pass by value
- ui: move note and profile rendering to notedeck_ui
kernelkind (4):
- Fix flaky test_zap_event
- move error out of
AnyZapState - introduce
ImagePulseTint - pulse pending zap button
pushed to notedeck:refs/heads/master
-
 @ 7776c32d:45558888
2025-04-17 02:05:15
@ 7776c32d:45558888
2025-04-17 02:05:15Opinion about Bitcoin Wallet (android)
I think this was the first self-custody wallet I ever used. I'm really glad it's still maintained and reproducible from source 🤙
WalletScrutiny #nostrOpinion
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ f839fb67:5c930939
2025-04-16 21:07:13
@ f839fb67:5c930939
2025-04-16 21:07:13Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nostr:nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nostr:nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nostr:nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nostr:nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bots
Unlocks Bot
Hex: 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0
nprofile:
nostr:nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak
Latest Data:
nostr:naddr1qq882mnvda3kkttrda6kuar9wgq37amnwvaz7tmnddjk6efwweskuer9wfmkzuntv4ezuenpd45kc7gzyqhfgxk3w9zwpgzdrwxzr39qm0plhjae6z9wvg44l8y9xs06clpdqqcyqqq823cgnl9u5Step Counter
Hex: 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7
nprofile: nostr:nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w
Latest Data:
nostr:naddr1qvzqqqr4gupzpy3r6tawh9v98dxjyjscf357rhckvjxn2pn63rxlj37xxx6hu008qys8wumn8ghj7umtv4kk2tnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp3ehgets943k7atww3jhyn39gffRCTGuest
Hex: 373904615c781e46bf5bf87b4126c8a568a05393b1b840b1a2a3234d20affa0c
nprofile: nostr:nprofile1qqsrwwgyv9w8s8jxhadls76pymy2269q2wfmrwzqkx32xg6dyzhl5rqpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3usy92jlxNow Playing
Hex: 8096ed6ba1f21a3713bd47a503ee377b0ce2f187b3e5a3ae909a25b84901018b
nprofile: nostr:nprofile1qqsgp9hddwslyx3hzw750fgracmhkr8z7xrm8edr46gf5fdcfyqsrzcpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3uspk5v4w
Latest Data:
nostr:naddr1qq9kummh94cxccted9hxwqglwaehxw309aekketdv5h8vctwv3jhyampwf4k2u3wvesk66tv0ypzpqyka446rus6xufm63a9q0hrw7cvutcc0vl95whfpx39hpyszqvtqvzqqqr4gupdk2hd
NIP-29 Groups
- Minecraft Group Chat
nostr:naddr1qqrxvc33xpnxxqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvqazypfd- VFNet Group Chat
nostr:naddr1qqrrwvfjx9jxzqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvq08hx48
"Nostrified Websites"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
Lists
- Bluesky
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqapxcat9wd4hj0ah0jw
- Fediverse
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh
- Fediverse_Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqperx2erfwejhyum9tapx7arnfcpdzh
- My Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz4uh5jnpwscyss24fpkxw4fewafk566twa2q8f6fyk
-
 @ ba36d0f7:cd802cba
2025-04-16 16:39:58
@ ba36d0f7:cd802cba
2025-04-16 16:39:581. El placer creativo (pero efímero) de las tácticas
Las tácticas en ajedrez son como las golosinas entre comidas: satisfacción inmediata, pero no sustento real. Escoger entre atacar a un alfil o un caballo puede ser como elegir entre helado de vainilla o chocolate - con chispas o sin chispas, cereza o sin cereza....
-
Son libertad dentro de las reglas: el tablero es finito, pero la creatividad no.
-
Reflejan tu estilo: ¿ataques rápidos como un espresso? ¿O finales lentos como un té verde?
2. Dos tipos de tácticas, dos tipos de placeres
-
Sencillas (como un rey descubierto): placeres cotidianos (como un golpe de buena suerte).
-
Complejas (combinaciones de 3+ jugadas): placeres que exigen planificación (como cumplir metas).
3. La advertencia budista: "No confundas el postre con la cena"
El Buddha enseñó que aferrarse a los placeres (kāma-tanha) genera sufrimiento. En ajedrez y en la vida:
-
Las tácticas son golosinas: te dan ventaja, pero no son estrategia.
- Ejemplo: Ganar por un descuido del rival es como heredar dinero; ganar por planificación es como construir un negocio.
-
El equilibrio: Disfruta ese sacrificio de dama espectacular… pero no bases tu juego en ellos. Como saborear un pastel ocasional sin volverse adicto al azúcar.
4. Cómo aplicar esto en el tablero (y en la vida)
✅ Pregúntate siempre:
-
¿Esta táctica es sólida o solo emocionante? (Como diferenciar antojo de hambre real).
-
¿Estoy jugando para ganar… o para impresionar? (El ego es peor enemigo que el rival).
Conclusión: El camino medio (ajedrecístico)
El budismo no pide renunciar a los placeres, sino disfrutarlos sin apego. En el ajedrez:
-
Tácticas = especias: dan sabor, pero no son el plato principal.
-
Estrategia = nutrición: lo que realmente te hace mejor jugador.
♟️ ¿Y tú? ¿Eres de los que prefieren un ataque brillante (aunque riesgoso) o una victoria lenta pero segura?
Recursos en linea
Tácticas - chess.com https://www.chess.com/es/article/view/tacticas-ajedrez
Problemas de ajedrez - chess.com https://www.chess.com/es/puzzles
Tácticas - lichess.org https://lichess.org/study/qgLXlnIF/udsuAudN
ajedrez #somachess #chess #chesselsalvador #budismo #budhism #filosofia #philosophy #apaneca #rutadelasflores #article #longform #articulo
-
-
 @ 9bde4214:06ca052b
2025-04-22 17:00:55
@ 9bde4214:06ca052b
2025-04-22 17:00:55"What should the next iteration of the internet look like?"
Paul & Gigi pray for a better tomorrow.
Books mentioned:
- The Bible
- I, Pencil by Leonard E. Read
- Don't make me think! by Steve Krug
- The Sovereign Individual by James Dale Davidson and William Rees-Mogg
In this dialogue:
- Paul and his awesome nostr t-shirt
- Are we all just nostalgic?
- Where did the optimism of computing and the information superhighway go?
- We went from interop to pay-to-unlock.
- Do we have to live in the digital gulags forever?
- Homecooked meals and homecooked apps
- Paper straws and the downfall of Western Civilization
- "You need to be okay with people getting rekt"
- If the car would be introduced today, it would be illegal
- Bravery and personal responsibility
- "nostr will only be what diehards will build it to be"
- Bad teleology is built into the current (non-nostr) app landscape
- "You can get a lot of the upside without holding your own keys”
- “...but you can't get ALL of the upside!"
- Expressiveness and free speech online
- Freedom of Speech, Freedom of Assembly, and Financial Freedom in Cyberspace
- Self-publishing vs platform publishing
- Information calories. Can we count them?
- Don't make me think!
- Is not being forced to think part of the problem?
- Mutiny & bitcoin UX that's too easy
- Games and costly mistakes
- The early days: software distribution via print magazines
- Prompting allows you to define your own teleology
- Vibe coding and Cursor
- "The hard part is to figure out what you want."
- "What should the next iteration of the internet look like?"
- GenZ doesn't know shit about files and folders
- Why files are great
- Gigi's SyncThing & Standard Notes setup
- File-based apps like Smart AudioBook Player
- Reading apps like Pocket, Instapaper, and Readwise Reader
- Saving all the things & linking stuff together
- Clips of podcasts and videos, e.g. Fountain
- A Commonplace Book to cyberspace
- Creating a "Family Bible" app
- If you want to maximize profits in the attention economy, you have to get users addicted
- (Zaps potentially fix this, as you wouldn’t zap a car crash)
- Let computers do computer work, let humans be humans
- "The end is not being on the computer"
- Solo private / group private / public
- Liberal vs Conservative sentiment in social environments
- Whom to care about?
- Web of trust & our understanding of it
- Forgiveness, Trust, and Repeat Games
- Tit-for-tat and forgiving tit-for-tat
- Three strikes and you're out!
- "Choose your gulag" is the alternative to nostr
- 7-generation thinking
- 2140
- The Sovereign Individual is embedded in a social structure, always
- I, Pencil
- Jungle vs Civilization
- Fiat = because I said so (“Fiat Lux” - Let there be light)
- Do we need leaders in bitcoin?
- Peterson Fallacy / God vs Bitcoin
- Jesus early followers were the Followers of The Way
- Zaps are not payments
- Zaps are not "tips"
- Bitstein & Pierre: The Reorg
- Vervaeke: “Where do you go for wisdom?”
- Rough consensus and Pieter Wuille
- "There is no such thing as a leaderless system"
- Wisdom in cyberspace
- Can we build wise tools?
- Prompting the Bible, ChristGPT, and Bible Slop
- Gell-Mann amnesia effect
- Vervaekes AI argument: The Coming Thresholds and The Path We Must Take
- Where do new ideas come from?
- Sandwich prompting style (HLDD / LLDD)
- The Tale of John Henry
- Silicon Sages
- Conscience and The Muse
- Hypermedia and HyperNote
- Glassholes, Google Glasses, and wearable technology
- Prompting & Praying for An Internet Worth Having
-
 @ f10512df:c9293bb3
2025-04-22 17:00:44
@ f10512df:c9293bb3
2025-04-22 17:00:44Chef's notes
Use a tea bag to hold the spices. I like to fill it and drape it on the side of the pan so the flavors get in, and then toss it before serving. Easier than picking rosemary out of your teeth later.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour 45 from scratch, 45 if using chicken stock
- 🍽️ Servings: 4
Ingredients
- 1 Cup Carrots (sliced)
- 1C celery (sliced)
- 2 cloves garlic
- 1 tsp dried thyme
- 1/2 tsp dried minced onion
- 2 Tbsp lemon juice (or more to taste)
- 1/2 Tbsp salt (to taste)
- 1 rotisserie chicken
- 2 tsp dried rosemary (or 1-2 sprigs fresh)
- 8 C water & additional 1-2 C later
- 10 oz pre-cooked noodles
- 1 tsp cracked pepper (to taste)
Directions
- Remove chicken meat from bones and set aside. Do not discard skin. Put bones and skin in a large stock pot and add water. Let boil covered for one hour, and then remove bones and strain out any bits of skin from broth.
- Add chopped vegetables, spices, and lemon juice to broth with up to 2 C. additional water to replace what might have boiled away. Simmer over low to medium heat (covered) for another half hour, stirring occasionally. Add in chicken meat. Taste test and add additional salt if needed.
- When vegetables are cooked, add in noodles and stir for an additional 2-3 minutes until hot (uncovered), and enjoy.
- If using store bought chicken stock, only simmer until vegetables are cooked (about half an hour).
-
 @ edeb837b:ac664163
2025-04-16 12:59:09
@ edeb837b:ac664163
2025-04-16 12:59:09If you’ve spent any time around stock trading communities, chances are you’ve heard the name Webull pop up more than once. It’s not just another brokerage app—it’s one of the go-to platforms for retail traders across the globe. But what exactly is Webull? Why do so many individual traders prefer it over other platforms? And how does NVSTly take its capabilities even further?
Let’s break it all down.
What Is Webull?
Webull is a commission-free trading app that allows users to trade stocks, ETFs, options, and cryptocurrencies from their phones or desktop. Launched in 2017, it quickly gained popularity for its sleek interface, real-time data, and powerful tools—all without the traditional fees associated with many brokerage platforms.
While it’s often compared to Robinhood, Webull caters more to active traders and those who want slightly more advanced tools without the complexity (or costs) of institutional-level platforms.
What Can You Do on Webull?
Webull offers a full suite of features for modern traders:
- Commission-free trading for stocks, options, ETFs, and crypto
- Extended trading hours (premarket and after-hours)
- In-depth charting tools with technical indicators
- Fractional shares trading to invest with any dollar amount
- Paper trading for practice without real money
- Level 2 market data (Nasdaq TotalView, subscription-based)
- Custom alerts and watchlists
- Community feed for trade ideas and discussions
Whether you’re a beginner trying to learn the ropes or an experienced trader managing multiple positions daily, Webull is designed to give you an edge.
Why Retail Traders Prefer Webull Over Other Brokers
Here are some reasons why Webull has become a fan favorite among retail traders:
✅ Advanced Tools, Simple UI
Unlike many traditional brokers with clunky interfaces, Webull balances powerful tools with a user-friendly design. You get access to real-time quotes, charting with dozens of indicators, and customizable layouts—all wrapped in a clean, modern app.
✅ Free Options Trading
While some platforms charge per contract or per trade for options, Webull offers commission-free options trading, which is a huge win for active options traders.
✅ No Account Minimums
New traders can get started with as little (or as much) money as they want. There are no minimum deposit requirements for standard cash or margin accounts.
✅ Fractional Shares
Webull lets users invest in fractional shares, meaning you don’t need to buy an entire share of high-priced stocks like Amazon or Tesla. You can invest as little as $5 into a stock, making it easier to build a diversified portfolio with any budget.
✅ Paper Trading
Webull gives users a way to test strategies in a simulated environment, which is perfect for learning without risking real money.
✅ Mobile & Desktop Support
Webull’s mobile app is robust, but the desktop version is just as powerful—great for traders who prefer multi-screen setups or deeper analysis.
Webull Pros & Cons
✅ Pros
- $0 commissions on stocks, options, ETFs, and crypto
- Clean and intuitive interface
- Real-time data and news
- Built-in paper trading
- Fractional shares
- Support for extended hours trading
- Level 2 market data available
⚠️ Cons
- No mutual funds
- Webull uses a high spread for crypto trading
- Slight learning curve for beginners
How NVSTly Supercharges Your Webull Experience
Webull is powerful on its own—but when integrated with NVSTly, it becomes next-level.
NVSTly is the fastest-growing social trading app, where traders can automatically track, share, and analyze their trades, all in one place. Thanks to deep Webull integration, you can now connect your Webull account to NVSTly in seconds.
🔗 Connect in Seconds with a QR Code
Linking your Webull account is as simple as scanning a QR code inside your NVSTly account settings using the Webull mobile app. That’s it—your trades are now synced automatically.
💼 What You Get with NVSTly + Webull
- Auto-tracked trades — No more manual logging or screenshots
- Real-time trade sharing — Followers see your trades as they happen
- Performance analytics — Gain insights into your win rate, risk/reward, and more
- Automate your trade signals — Save time and help followers catch entries earlier, closer to your price
- Trade history dashboards — View and share detailed stats for your trades, with visual breakdowns
- Daily/Weekly/Monthly Recaps — Get beautifully designed trade summaries sent straight to your Discord or social profiles
Whether you’re a solo trader or part of a larger trading community, NVSTly makes it ridiculously easy to share your journey, learn from others, and improve your performance—all while staying 100% focused on the markets.
Final Thoughts
Webull has earned its spot as a top-tier brokerage app for retail traders, offering a powerful platform with zero commissions and high-quality tools. When paired with NVSTly, your trading becomes smarter and more connected—automating the way your trades are tracked, shared, and analyzed, so you can focus on the markets while NVSTly handles the rest.
If you’re a Webull user and haven’t connected to NVSTly yet, now’s the time. Your trading deserves more than just a broker—it deserves a platform built to grow with you.
Ready to level up your Webull trading?
➡️ Sign in to NVSTly, go to Brokerages & Exchanges in your account settings, click Connect next to Webull, and follow the QR code instructions to link your account in seconds.Available on web, iOS, Android, & fully integrated with Discord through a unique bot – the only of its kind!
-
 @ 06639a38:655f8f71
2025-04-16 12:11:31
@ 06639a38:655f8f71
2025-04-16 12:11:31Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ d1667293:388e7004
2025-04-22 16:52:15
@ d1667293:388e7004
2025-04-22 16:52:15In my book “Bitcoindollar The Dawn of American Hegemony in the Digital Era,” I challenge the prevailing narrative that de-dollarization is a distant or hypothetical threat. Rather, I present a body of evidence suggesting that we are already living in a world where de-dollarization is unfolding—not through bombastic proclamations or sudden abandonment of the dollar in trade—but through a quieter, more telling trend: the steady escape of emerging powers like China, Russia, India, and much of the Global South from US Treasuries as the global reserve asset.
Structural, Not Cyclical: The Causes Behind the Exodus
This transformation is not cyclical or temporary; it is structural. The root causes run deep and stem from decades of US foreign and monetary policy—specifically, the aggressive military posturing that has defined American global engagement, the weaponization of dollar-based financial systems, and the overuse of sanctions as instruments of coercion rather than diplomacy. The result has been a widespread erosion of trust in the US as a neutral monetary steward. Increasingly, large economies and trading blocs—such as the Shanghai Cooperation Organization (SCO), BRICS, and the Belt and Road Initiative (BRI)—are seeking alternatives. They are diversifying their reserves, entering bilateral currency agreements, stockpiling gold, and in some cases, launching central bank digital currencies (CBDCs).
The message is clear: the era of unquestioned dollar supremacy is over.
The Treasury Dilemma: Who Will Fund America’s Debt?
This structural shift raises a daunting question for American policymakers: who will buy US Treasuries in the future? For decades, the demand for Treasuries rested on the premise of dollar dominance. Global trade surpluses—especially from oil-exporting nations under the Petrodollar system—were recycled into US debt markets. This “exorbitant privilege” allowed the US to run persistent deficits, finance wars, and project power without facing the immediate fiscal consequences most nations would. But that privilege is now in peril.
The Bitcoindollar System: A Strategic Response
In my book, I argue that the United States still has one viable path forward—a path that does not require relinquishing its leadership role, but rather reimagining it for the digital era. I call this new paradigm the Bitcoindollar system. It is an evolutionary successor to the Petrodollar framework, and it hinges on embracing bitcoin as the global store of value and dollar denominated stablecoins to maintain the US dollar’s relevance in a multipolar world. Under the Bitcoindollar system, global capital flows are incentivized to enter dollar-denominated stablecoins such as USDC and USDT. These stablecoins can then be recycled into short-term US debt instruments like Treasury bills, creating a digital-era version of the Petrodollar recycling mechanism. At the heart of this system lies Bitcoin—not as a threat to the dollar, but as a global decentralized and uncensorable Store of Value (SOV) that drives capital into the broader dollar-denominated ecosystem. As Bitcoin grows in adoption and price, it draws global attention and capital toward stablecoins, which in turn creates natural demand for dollar-based instruments such as Treasuries. This system offers the United States a first-mover advantage. No other nation has the credibility, capital markets depth, or global network effects to replicate it—if, and only if, the dollar’s digital rails are perceived as trustworthy and politically neutral. Herein lies the great conundrum: trust cannot be mandated. It must be earned, particularly in a geopolitical climate where the United States continues to alienate both allies and adversaries alike.
Trump’s Paradox: Economic Nationalism vs Monetary Hegemony
The current Trump administration, despite its rhetoric on economic nationalism, continues along a path that exacerbates this alienation. By doubling down on tariffs, aggressive posturing toward China, and unconditional support for Israel’s supremacist regional ambitions, it perpetuates the same policies that catalyzed de-dollarization in the first place. Tariffs, in this context, are a distraction. The US trade deficit is not primarily the result of unfair trade practices by other countries—it is largely the result of the dollar's role as the global reserve currency. To sustain global demand for dollars, the US has had to export dollars—and therefore run trade deficits. The dollar’s dominance enabled vast capital inflows and supported America’s imperial military architecture, but this model is fundamentally incompatible with dreams of reshoring industry, reducing deficits, and limiting foreign entanglements. Furthermore, these policies undermine any future attempt to establish dollar stablecoins as trusted global instruments. Why would a nation park its savings in a dollar-based asset, however digitized, if it fears arbitrary sanctions or seizure at the stroke of a keyboard? Despite his aggressive posturing, Trump, like Zelensky and the EU before him, has no cards to play to force China or Russia to the table.
A Fork in the Road: Choose Multipolar Collaboration or Decline
Absent a disastrous military escalation—which will not prevent the fall of American unipolar hegemony—the US is left with ONLY ONE path forward: a deliberate, peaceful shift from military and imperial posturing toward a more collaborative, multipolar engagement with the world. This means treating allies, adversaries, and vassal states alike with respect and inclusion in a reimagined dollar-based system—one that is digital, decentralized, and incentivized by global participation. The Bitcoindollar system can serve as the financial infrastructure of this new era, but it demands that the United States rehabilitate its image as a trustworthy party. For the Trump administration to succeed in securing America’s future financial relevance, it must course-correct immediately. This includes ending the influence of the neo-conservative and Zionist hardliners who perpetuate conflict and distrust for their own interest, and embracing a vision of digital dollar diplomacy that builds bridges instead of burning them.
In conclusion, the Bitcoindollar is not just a financial mechanism—it is a strategic opportunity for the United States to retain leadership in the emerging multipolar order. The alternative is clear: a continued slide into irrelevance, fiscal instability, and geopolitical isolation or a mutually assured destruction through war.
The time to act boldly for President Trump is now.
bitcoin #bitcoindollar #stablecoin
-
 @ da0b9bc3:4e30a4a9
2025-04-16 08:28:24
@ da0b9bc3:4e30a4a9
2025-04-16 08:28:24Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/944844
-
 @ 8d34bd24:414be32b
2025-04-16 03:48:30
@ 8d34bd24:414be32b
2025-04-16 03:48:30Ever since becoming a Christian, I have whole-heartedly believed the Bible and that God will fulfill what He has promised. On the other hand, for the majority of the time I have been a Christian, I have dreaded reading prophecy. It seemed so hard to understand. Some is couched in figurative language, but I now believe much of it was hard to understand because there were no words for the technology and systems that would come into being and fulfill these predictions.
Now reading End times prophecy, like in Revelation, Daniel, Matthew 24-25, 2 Thessalonians, Zechariah, etc. the prophecies are starting to sound like the evening news instead of some poetic mystery. These predictions are making more and more sense as the technology and world politics begin to align with the prophecies. I have gone from hating when I get to prophecy passages, especially Revelation, in my Bible reading, to spending extra time reading these passages and seeing how they line up and clarify each other. (I really want to start a project linking all of the end-times prophetic passages together to see how they clarify each other and try to see the big picture, but that is a massive project and time is in short supply. The only way I know to do it is in Excel, but that isn’t efficient. If anyone has a suggestion for a better way to link and show relationships, I’d love to hear about it, especially if it is free or very cheap.)
Matthew recounts Jesus telling His disciples about what to expect in the end times. Although Matthew 24 describes more of the details of the events that happen, this passage in Matthew 25 describes the importance of watching expectantly for the signs of the times, so we are ready.
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13) {emphasis mine}
Many Christians think studying prophecy is not useful for today, but that is not true. Our time is short and Jesus warned us to be aware and ready. We can’t be ready for something if we know nothing about it.
In this passage it mentions that “while the bridegroom was delaying, they all got drowsy and began to sleep.” How often do we feel the delay and begin to rest or get distracted by other things? Most Christians do not live like Christ’s return is imminent. Although we can’t know the hour or the day, we can know that we are closer to that hour than we have ever been before. Peter warns us not to doubt Christ’s coming or to become focused solely on our earthly lives.
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” (2 Peter 3:3-4)
Because Jesus has not returned for almost 2,000 years, many act as if He will never come, but that long wait instead suggests the time is nearing because God never breaks His promises.
For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men.
But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:5-9) {emphasis mine}
The long wait is due to God’s unfathomable mercy and patience, but we should also realize that the increase of evil in the world cannot continue forever. How much more can evil increase before mankind destroys itself? God claims judgement for Himself and finds every kind of sin abhorrent. If we are distraught over the sin in the world today, how much more awful is it to a holy, perfect God to see His very own creation destroyed by sin?
Just as the ten virgins became tired waiting, we tend to get caught up in the things of this world instead of focusing on God’s plan for us and the world. We act as if this world is the only thing we will experience instead of preparing for our rapture to heaven. We focus on our job, our homes, and our families (all good things) and miss the most important things — winning souls for heaven.
Just as Jesus gently reprimanded Martha for having the wrong focus:
But Martha was distracted with all her preparations; and she came up to Him and said, “Lord, do You not care that my sister has left me to do all the serving alone? Then tell her to help me.” But the Lord answered and said to her, “Martha, Martha, you are worried and bothered about so many things; but only one thing is necessary, for Mary has chosen the good part, which shall not be taken away from her.” (Luke 10:40-42) {emphasis mine}
In the same way, we get focused with the business of life and miss the most important stuff. It wasn’t bad of Martha to take care of her guests, but sitting with Jesus and learning from Him was more important. In the same way, our jobs, families, and homes are good things and we should do them well, but reading our Bibles, praying, growing closer to Jesus, and sharing the Gospel with those who don’t know Jesus is better.
When we believe that our time on earth is short and Jesus is coming for us soon, we are more likely to focus on the most important things — the eternal things.
This passage in Matthew 16 describes the importance of us knowing, understanding, and looking for the signs of the times.
The Pharisees and Sadducees came up, and testing Jesus, they asked Him to show them a sign from heaven. But He replied to them, “When it is evening, you say, ‘It will be fair weather, for the sky is red.’ And in the morning, ‘There will be a storm today, for the sky is red and threatening.’ Do you know how to discern the appearance of the sky, but cannot discern the signs of the times? An evil and adulterous generation seeks after a sign; and a sign will not be given it, except the sign of Jonah.” And He left them and went away. (Matthew 16:1-4) {emphasis mine}
Christians that believe studying end times prophecy is not important would be rebuked even today by Jesus. We are supposed to study and learn and prepare and watch eagerly for His return.
In Revelation, God says we are blessed if we hear and heed the words of this prophecy.
The Revelation of Jesus Christ, which God gave Him to show to His bond-servants, the things which must soon take place; and He sent and communicated it by His angel to His bond-servant John, who testified to the word of God and to the testimony of Jesus Christ, even to all that he saw. Blessed is he who reads and those who hear the words of the prophecy, and heed the things which are written in it; for the time is near. (Revelation 1:1-3) {emphasis mine}
Do you seek God’s blessing? Then study God’s prophecies, especially as written in Revelation. God is good and He has shown His children what will happen, so they can be prepared. Don’t be like the five foolish virgins who were unprepared. Study the Scriptures. Look for the signs. Be ready for our Savior’s return by inviting as many people as possible to join us.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, the judgement, etc.).
-
 @ 91266b9f:43dcba6c
2025-04-16 03:42:09
@ 91266b9f:43dcba6c
2025-04-16 03:42:09"No," I said, "you've got no right."
Sergeant Curtis sighed. "Come on, Mister Alton, I need you to work with me here."
"No," I said. "Absolutely not."
"He did it," shouted Mavis Harris, my recently new neighbor, leaning over the garden fence. "I saw him! He had a knife, a carving knife. And I heard the screaming and the shouting! He did it!"
"Thank you, Miss Harris," said Sergeant Curtis. "We've got it from here."
We were in my beautifully manicured backyard, sweating under the midday sun, along with six other police officers--all of them armed with shovels, ready to dig.
"This is an invasion of my privacy and I won't have it," I said.
"If you just tell us where your wife is we can get this all cleared up," he said.
"I'm not married," I said. "I've never been married."
Sergeant Curtis chewed on that for a bit, while he did the same to his bottom lip. "Girlfriend then. Partner?"
"I have no girlfriend. No partner. There's nobody at all," I said.
But there was. Sort of. Cindy, wonderful, difficult Cindy.
"He's lying!" said Mavis Harris. "I've seen her. Through the window. One time I called by when he wasn't here and she was just sitting in there, not moving. Wouldn't even answer the door. She must've been terrified, the poor girl. I bet he had her tied to the chair!"
That was absurd. Cindy wasn't into that kind of thing. I would never tie her to a chair and leave the house. That's crazy talk.
"We've got more than one eyewitness that says there's been a woman in the house with you," said Sergeant Curtis. "How about we get this woman on the phone, clear this up?"
"I can't make the impossible happen, Sergeant," I said, stiffly.
My back door opened and Constable Jenkins stepped onto the verandah. "Got a carving knife missing from a set of six," he said.
"I told you, he went after her with a knife!" said Mavis Harris.
She was right. Things had got heated. Words were said. The knife had made an appearance. There had definitely been some stabby-cutty action. Much to my dismay. I hated that it happened. I guess I was going to have to live with the damage.
Sergeant Curtis sighed. "This isn't looking good, Mr Alton."
"I bet he put her under the roses!" said Mavis Harris. "That's where I saw him heading with the body!"
"Alleged body," I muttered.
"Jenkins, any sign of blood in there?" said Sergeant Curtis.
"None whatsoever," said Jenkins. "Not even under black light. Couldn't spot any in the garden either."
"He must have cleaned it up," said Mavis. "Bleach. Bleach will clean up anything. And I saw him, I saw him carry her out and she had what looked like a knife sticking out of her chest!"
"Last chance, Mr Alton," said Curtis, "let's get this lady friend of yours on the phone and clear this up."
"I told you, I can't do the impossible," I said.
"Then you're leaving me no choice," he said.
He turned and nodded at the waiting officers with their shovels. "Start with the rose garden," he said.
They rolled up their sleeves with obvious relish and got to work.
"This is destruction of private property," I said. "When you're done, every rose petal, every grain of soil, better be back exactly as it was. Or you'll be dealing with my lawyer."
"Don't worry," said Sergeant Curtis, "I assure you everything will be put back as we found it. Whether we uncover anything or not."
As we watched the officers desecrate my rose garden, Sergeant Curtis said, "You know there's probably a few million square kilometers of country, forests, lakes, beaches, and do you know where most killers bury their wives or husbands? On their own property, right in their own backyard."
"Convenience trumps everything, I suppose," I said.
"Laziness," said Sergeant Curtis, "most casual criminals are just bone lazy."
"Or," I said, "they maybe wanted to keep their loved ones close."
Sergeant Curtis looked at me, eyes narrowed. "Is that what it is? You kill them, but somehow you want to keep them close?"
I shrugged. "Things happen. But you still love them. Maybe, you want them to be close to home," I said.
Curtis glared at me.
After a while Constable Jenkins climbed out of the rose garden and moped his sweating forehead with his sleeve. "Nothing here," he said. "This soil is pretty solid, hasn't been dug up in a while."
"The other rose bed," said Mavis Harris, "he must have used the other rose bed, beside the shed."
Damn that woman, why won't she keep her mouth shut?!
Constable Jenkins went over and stabbed his shovel into the dirt a few times. "Yeah," he said, "this has been dug up recently."
"Okay," said Sergeant Curtis, "get to it."
"I really must protest," I said. "This is a violation of my rights!"
"I'm sure we'll be done soon enough," said Sergeant Curtis, with a tight smile.
I turned and stared daggers at Mavis Harris, who haughtily thrust her nose and chin in the air, a smug smile on her face. Damn that woman and her meddling ways!
The officers found my second rose garden easier going. They were at it about twenty minutes when Constable Jenkins suddenly said, "Jesus Christ!"
"What, what is it?" said Sergeant Curtis, coming to attention.
"I ... I don't know," said Jenkins. "Hang on ..." He scraped at the dirt and then leaned over, grabbed something and lifted it out of the dirt.
A leg.
"Jeezuz," said Jenkins, letting the leg drop back into the soil. "I think we found her!"
"I knew it," said Mavis Harris. "I told you! Didn't I tell you? He did it! He killed her!"
They worked quickly now, gently digging and scraping away dirt until they could lift her other leg out. My beautiful Cindy doll.
"We've got a knife," said Jenkins, "but it's ... it's ..."
He turned to look at me, his face twisted in disgust.
"What is it?" said Curtis.
Jenkins swallowed, hard. "It's ... the knife, it's ... it's stabbed ... up between her legs, if, uh, if you know what I mean."
"Oh my god, you absolute monster," said Mavis Harris, clutching the neck of her blouse.
I sighed. They had no right. No right. This was a private matter. It was nobody's business but mine and Cindy's. We would work it out, Cindy and me. We always did.
"Okay," said Curtis, "get her out of there, quick! Check for a pulse, just in case."
"She's gone, Sarge," said Jenkins. "She's stone cold dea--wait, hang on a second."
He did some more digging and scraping with the shovel and slowly eased my Cindy all the way out of the dirt.
"Oh, bloody hell " said Jenkins. "You have got to be kidding."
"What, what is it?" said Curtis.
"Oh my, oh my Lord," said Mavis Harris, "I feel sick."
Jenkins struggled a bit with the weight, but managed to get Cindy upright. She is a bit of a heavy lass, I have to admit.
"It's a doll," said Jenkins. "It's just a doll, a sex doll, I think." He lifted Cindy's arm and made her give a little wave. "Seems to be silicon. Wow, very life-like, I must say." He was gently squeezing Cindy's arm and nose and cheek with his fingertips.
I seethed. The disrespect!
"A doll?" said Curtis.
"Yes, sir."
Curtis turned to me, his face a throttled purple colour. "A bloody sex doll?!"
I said nothing.
He struggled to keep his anger in check. "I could arrest you for obstruction of justice, Alton, for wasting Police time and resources," he said.
"How?" I said. "I was nothing but absolutely honest with you. There was no wife, no girlfriend, no body. I told you this repeatedly. You chose to ignore me and you, sir, have wasted not only my time, but that of your department and your own men."
I left him there, chewing air, and went to Jenkins and took Cindy gently in my arms. Her wounds were bad but not unamendable.
"Pervert," hissed Mavis Harris. "He's a dirty little pervert!"
I headed for the house, but paused at the back door and said, "I will expect you to return my rose gardens to their absolute pristine condition. My lawyer already doesn't like your department, not one bit, Sergeant Curtis."
I did not wait for a reply. I went inside and closed the door, quietly, behind me.
Night was coming on and the police had returned my garden to its former glory, and departed. A cool breeze drifted through the kitchen window.
I was at the table with Cindy, tending her wounds. Silicon glue isn't cheap, I'll tell you that, and it would leave Cindy with some scars, unfortunately. If I'm honest, I don't think she was all that pleased about it. As I knelt down to treat a wound across her ribcage, I copped her knee right in my groin.
"Ugh!" I said, the wind snapping out of me and tears rimming my eyes.
I reached out to steady myself and that's when she lurched forward, out of her chair, and headbutted me square in the face.
"For godsakes, Cindy!" I said.
She was baring down on me. I grabbed her by the shoulders, pushing her up and back, but like I said, she wasn't exactly a lightweight. I staggered back with her falling into me, and I winced as the edge of the kitchen counter stabbed into the small my back. Cindy gave me another hit to the testicles with her hand, making me gasp.
I rolled us around, putting her back against counter, silicon squeaking against marble--see how she likes it. I almost took another groin hit from her other hand. I was bending her back over the kitchen sink and without realising it, I had grabbed one of the serrated steak knives in my fist, raised it over my head, and was ready to drive it down into the open O of her mouth.
And that's when I looked past Cindy's head, out the kitchen window, across the fence, and over there in her kitchen window was Mavis Harris. Staring right at me, at us, her mouth an identical open O to Cindy's.
We stared at each other for a long moment, and then I reached up and slowly closed the kitchen blinds.
I sighed. I decided that Mavis Harris was a problem I just couldn't tolerate. Her constant invasion of my privacy was one thing, but calling the police was unacceptable. I would have to take care of her at my earliest opportunity. But carefully. And I had just the spot for her, out behind her very own shed.
Right next to Henry Patterson, the last neighbour and resident of that house, who had also gotten far too nosey for his own good.
Yes, a real nice spot, and close to home.
-
 @ 9bde4214:06ca052b
2025-04-22 16:35:00
@ 9bde4214:06ca052b
2025-04-22 16:35:00"We have the chance of building the next iteration of the internet, and hopefully, not repeat the mistakes of the past."
In this dialogue:
- Why starting ugly and shipping early is hard
- The ugliest thing that Pablo ever shipped
- “Happiness is shipping”
- Make it real first, you can make it pretty later
- Getting into the habit of shipping
- Highlighter and the hang-up of shipping something big
- How nostr allows you to have cash flow from the get-go
-
value4value for artists and devs
- What DHH & 37Signals got right
People and projects mentioned:
Further links:
- https://excellentjourney.net/2015/03/04/art-fear-the-ceramics-class-and-quantity-before-quality/
- https://world.hey.com/dhh/that-shipping-feeling-b7c8c565
- https://world.hey.com/dhh/i-was-wrong-we-need-crypto-587ccb03
- https://sovereignengineering.io/
- https://dergigi.com/2023/04/04/purple-text-orange-highlights/
- https://highlighter.com/
- https://njump.me/nosolutions@sovereignengineering.io
-
 @ b04082ac:29b5c55b
2025-04-22 15:57:28
@ b04082ac:29b5c55b
2025-04-22 15:57:28Africa has long grappled with the “resource curse,” a paradox where nations rich in natural resources face economic stagnation, political instability, and reliance on foreign powers. The reason isn’t hard to pinpoint. For centuries, foreign entities have extracted immense wealth from African soil such as gold, oil, cobalt, and more, leaving behind weak institutions, crippling debt, and minimal infrastructure. Instead of fueling local growth and uplifting communities, Africa’s resources have powered the industrial and digital revolutions of others.
Now, this extractive pattern is resurfacing in new ways. Recent headlines paint a clear picture:
-
Bill Gates and Jeff Bezos plan to invest $537 million in Africa to mine rare metals.
-
A ‘terrifying’ crackdown on mining companies in Africa’s coup belt.
-
Blackwater founder and Trump ally strikes mineral security deal with Congo.
-
Biden’s last dash to Africa highlights the power of minerals.
As the world scrambles to secure minerals vital for green energy and artificial intelligence, Africa stands at a crossroads. It can remain a supplier of cheap raw materials or seize this moment to shape its economic destiny.
1. Diversifying Beyond Minerals
The global race for Africa’s resources centers on critical minerals like cobalt in the Congo, rare earths in Zambia, and nickel in Tanzania. Superpowers are jostling for control, but leaning too heavily on mineral exports is fraught with risks. Prices fluctuate wildly, extraction demands massive capital, profits often vanish overseas, and overreliance can fuel political instability by deepening inequality and sparking conflicts over resource control.
To truly escape the boom-and-bust cycles of commodity markets, countries must find alternative ways to monetize their natural advantages, particularly in areas that the rest of the world tends to overlook.
One promising avenue is to tap into the continent’s vast renewable energy sources such as hydro, solar, and geothermal, and convert them into something transformative: Bitcoin.
Bitcoin mining involves validating transactions and securing the Bitcoin network in exchange for new bitcoins and fees. At its heart, it’s an energy market. Wherever there’s surplus or stranded energy, mining can thrive. Africa’s renewable energy potential is enormous and largely untapped. Rather than waiting for foreign companies to swoop in, African governments could monetize their energy directly by mining Bitcoin themselves.
2. Bitcoin Mining for Monetary Independence
Many African nations are burdened by debt, much of it in foreign currencies like the U.S. dollar. Servicing these loans drains public funds and forces governments to prioritize external creditors over local needs.
Bitcoin mining offers a way to build reserves in a neutral, censorship-resistant asset. Unlike foreign aid or currencies, Bitcoin isn’t tied to political strings or inflationary policies of other nations. It’s a step toward financial self-reliance.
In the long run, Bitcoin’s scarcity could drive its value higher, helping countries reduce their reliance on dollar-dominated systems. Looking further ahead, African nations that participate meaningfully in the Bitcoin economy may also gain influence over blockspace, the limited space where Bitcoin transactions are recorded.
3. Stabilizing Energy Grids with Mining
In much of Africa, electricity is costly, unreliable, or nonexistent. Yet, the problem often stems from underused infrastructure. Power producers struggle to recover costs due to inconsistent demand, and grids falter when supply and demand don’t align.
Bitcoin mining can act as an economic “shock absorber” for energy providers. It creates a flexible buyer that adjusts to grid demands, soaking up excess power or scaling back when needed. By placing miners near energy sources, especially in remote areas, utilities can earn steady revenue to fund broader electrification.
Take Gridless in rural Kenya. By mining Bitcoin off-grid with small hydro units, they’ve stabilized local power, supported rural internet access, and lowered costs for nearby residents. This model works. To make a more meaningful impact, however, it needs national-scale adoption supported by clear government strategy.
4. Foreign Miners Are Already Here
The shift is already happening. In Ethiopia, foreign Bitcoin mining firms are signing deals to tap the country’s hydroelectric surplus. Similar moves are underway across the continent. This isn’t a distant possibility; it is already happening.
Miners chase the cheapest energy, and Africa boasts some of the world’s most affordable renewables. Mining will happen with or without local policies. The critical question is whether the benefits will stay in Africa or flow abroad, repeating history’s mistakes.
Foreign companies bring expertise and capital, but if they dominate, African nations risk becoming mere hosts to another extractive industry. Governments must act swiftly by launching national Bitcoin mining initiatives, forging public-private partnerships, and securing ownership of infrastructure to keep the value local.
Conclusion
Africa is at a turning point. The world craves its minerals, its energy, and increasingly, its role in shaping the future. But African nations can’t afford to sit on the sidelines. The next revolution must be led, not endured.
Bitcoin mining is not a silver bullet. It is a tool that, if used wisely, could help transform energy into economic power, build digital infrastructure, and break the cycle of debt and dependence.
Bitcoin miners are already arriving. The real question is whether African nations will take the lead and ensure that this industry builds lasting value at home, rather than repeating the patterns of the past.
-
-
 @ c13fd381:b46236ea
2025-04-16 03:10:38
@ c13fd381:b46236ea
2025-04-16 03:10:38In a time of political volatility and declining public trust, Australians are looking for leaders who don’t just talk about accountability—but prove it. It’s time for a new standard. A protocol that filters for competence, responsibility, and integrity—not popularity alone.
Here’s the idea:
Anyone who wants to run for public office in Australia must stake 100Ksats to a public address and maintain provable control of the corresponding private key for the duration of their term.
A Low Barrier With High Signal
The amount—100Ksats—is modest, but meaningful. It isn’t about wealth or exclusion. It’s about signal. Controlling a private key takes care, discipline, and a basic understanding of digital responsibility.
This protocol doesn't reward those with the most resources, but those who demonstrate the foresight and competence required to secure and maintain something valuable—just like the responsibilities of public office.
How It Works
This system is elegantly simple:
- To nominate, a candidate generates a keypair and deposits 100Ksats into the associated address.
- They publish the public key alongside their candidate profile—on the electoral roll, campaign site, or an independent registry.
- Throughout their time in office, they sign periodic messages—perhaps quarterly—to prove they still control the private key.
Anyone, at any time, can verify this control. It’s public, permissionless, and incorruptible.
Why This Matters
Private key management is more than technical—it’s symbolic. It reflects:
- Responsibility – Losing your key means losing your ability to prove you’re still accountable.
- Integrity – Key control is binary. Either you can sign or you can’t.
- Long-term thinking – Good key management mirrors the strategic thinking we expect from leaders.
This isn’t about promises. It’s about proof. It moves trust from words to cryptographic reality.
A Voluntary Standard—for Now
This doesn’t require legislative change. It can begin as a voluntary protocol, adopted by those who want to lead with integrity. The tools already exist. The expectations can evolve from the ground up.
And as this becomes the norm, it sets a powerful precedent:
"If you can’t manage a private key, should you be trusted to manage public resources or national infrastructure?"
Identity Without Surveillance
By linking a public key to a candidate’s public identity, we create a form of digital accountability that doesn’t rely on central databases or invasive oversight. It’s decentralized, simple, and tamper-proof.
No backdoors. No bureaucracy. Just Bitcoin, and the competence to manage it.
Bitcoin is the foundation. Asymmetric encryption is the filter.
The result? A new class of public leaders—proven, not promised.Let’s raise the standard.
-
 @ 6be5cc06:5259daf0
2025-04-15 20:16:08
@ 6be5cc06:5259daf0
2025-04-15 20:16:08Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ 9a859fbc:8a9270f3
2025-04-22 15:45:55
@ 9a859fbc:8a9270f3
2025-04-22 15:45:55A story of art and inspiration
This image was generated by AI
That is...
I am artificial. I was created by two other humans (hi mum and dad 👋)
I am intelligent. I can perceive the world, experience it, learn to understand cause & effect, and make decisions.
To go perhaps deeper, cells, DNA and life itself are artifices of the fabric of reality.
I sat, in a pub in Bristol, a place where I rarely frequent. I sat with one housemate, who I rarely spent time with. I met his friends that day, only once, never we met again.
I got chatting with a lady there. I had some paper and pencils with me. My intention, for a couple of weeks, was to come up with a symbol to represent Deep Sea Frequencies, at that time still known as Psychedelic Jelly. We were a new collaboration.
She and I got chatting about art. About symbolic representation of concepts, feelings, ideas. We chatted about flow, about how there are different types of flow, different elemental conditions of flow. I doodled some shapes, and we noticed how fire, water and air all look similar due to their fluid natures. So we considered how to differentiate, distinguish them from one another.
I doodled some more, and we came up with swooshes, curls, crests and bubbles. These seemed to be distinguishing enough such that they were no longer reminiscent of fire or air. I doodled fire and air too, just in case, just to check.
Then we chatted about symmetry types, reflective, axes, rotational. About geometry, geometric containers. We both enjoy triangles and hexagons. (It's always hexagons!)
I doodled some more shapes and put them in hexagonal shapes. Then I tried bending them into triangular forms instead, and overlaid two triangles.
Each triangle looked like a triskelion. Perfect.
Overlaid, they looked just like the flow of water, coming up, spiralling down.
The logo was born in this moment, in this serendipitous meeting, in this unlikely chat with a total stranger. We met for the first time that day, and I'm not sure if we ever met again. This interaction was, is, precious, and it led to a particular creation that is now a core part of my life and is a highlight for many people around the UK and the world, as we put on events and released musicians' music.
This is inspiration. This is expression. This is flow, through the fluid nature of the cosmos.
This is what you miss out on when you talk into your AI LLM black hole prompt.
This is what you steal from when you demand your AI LLM to generate you something according to your whim.
Art and expression is the very foundation of human community. Join in! Try new things! Learn from each other! Bring us all closer together by interacting and creating through shared ideas, shared visions, shared wisdom!
After that, I drew it up cleanly, geometrically.
I photographed it like scanning it, carefully aligning the camera because I didn't have a scanner.
I redrew it more than twice.
I digitised it, colourised it, split it into two layers so I could apply colour & lighting effects to it.
I painstakingly traced the photograph into a vector format, to enlarge it and use it for various media.
I even more painstakingly (do we have a more extreme adverb??) divided all the vector shapes into new objects so that the layers became "real". And cleaned up the vector nodes, shaping them to my imagination.
The vector form is used all over our record label & events branding.
And then I imported the vector form into Blender, a 3D rendering application, free and open source.
I learnt Blender, day by day developing my understanding and my skills. Day by day my GPU crashing on raytracing and cutting the laptop's power out!
And finally, I learnt to make some simple renders that look like being underwater, like surreal glassy objects floating in the deep. I even learnt to animate it, although I haven't released that into the wild.
I imagined all of this stuff, and then I spent months over years developing my skills in my spare time in order to bring these imaginations to life.
You can do the same.
You have to sacrifice things.
Sacrifice your time.
Sacrifice your energy.
Sacrifice your distractions and enter yourself into the learning process and the creative process.
To you, amazing lady who helped me draw this symbol from the fabric of the Realm of Forms, thank you! I'm sorry that I don't recall your name, although actually I think I do remember but I would be embarrassed if I tagged the wrong person. Please reach out if you recognise this story! It was about 7, maybe 8 years ago, in the painted pub in St. Werburgh's.
-
 @ e0921d61:e0fe7bd5
2025-04-15 16:13:32
@ e0921d61:e0fe7bd5
2025-04-15 16:13:32Hans-Hermann Hoppe explains the capitalist process as driven by time preference, how people value present vs. future goods. Economic growth hinges on savings and investment, and this shapes our prosperity.

Factors like population, natural resources, and technology matter, but Hoppe argues they're secondary. Without prior savings and investment, even the richest resources and best technology remain untapped.

True economic advancement happens through increasing per capita invested capital, raising productivity, real incomes, and further lowering time preferences. This creates a self-reinforcing cycle of prosperity.

Hoppe claims this process naturally continues smoothly until scarcity itself disappears, unless people voluntarily choose leisure over more wealth. This growth has no inherent reason to halt abruptly.

This smooth capitalist cycle, however, is disrupted when government enters the picture. Government control of resources it didn’t earn or acquire legitimately distorts incentives and investment.

Government monopolization of money through fractional reserve banking artificially lowers interest rates.
Entrepreneurs mistakenly think, and are incentivized to think, there's more savings, so more unsustainable investments proliferate.

Without real savings backing these projects, a painful correction (a bust following the boom) inevitably occurs.
Investments must eventually realign with actual savings, thus leading to bankruptcies and unemployment.

Hoppe concludes that boom-bust cycles aren’t natural. They’re directly caused by government-created credit expansion. Unless governments stop manipulating fiat money supply, these cycles remain unavoidable.

-
 @ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53
@ 5d4b6c8d:8a1c1ee3
2025-04-22 15:37:53How I wish I had time for this!
https://primal.net/e/nevent1qvzqqqqqqypzqntcggz30qhq60ltqdx32zku9d46unhrkjtcv7fml7jx3dh4h94nqqsynzz85x8dcqnzxrzypec9xw6haxxjt0z0c547suty7gpa835v0vs2qusmr
originally posted at https://stacker.news/items/953418
-
 @ 9f2b5b64:e811118f
2025-04-15 15:23:25
@ 9f2b5b64:e811118f
2025-04-15 15:23:25Let's test some Articles
Let's star by just blabbing for a while blah blah balh
But this is the most important part, which will eventually be highlighted I hope.
-
 @ d1667293:388e7004
2025-04-22 14:27:15
@ d1667293:388e7004
2025-04-22 14:27:15The motivation behind my newly published book Bitcoindollar the Dawn of American Hegemony in the Digital Era was simple: to answer some of the most pressing and overlooked questions about the future of money. My analysis starts by viewing Bitcoin not in isolation, but as a paradigm shift in the evolution of money—a foundational institution that underpins both economic and societal relationships, from individuals to nations.
Rethinking the Monetary Landscape
To understand Bitcoin's potential, we need to explore the landscape it seeks to disrupt:
-
The dominance of nation-states.
-
The role of the US fiat dollar as the global reserve currency.
-
US debt as the reserve liability (pardon "asset") underpinning the fiat system.
-
The influence of the banking cartel and the distorted incentives built into the fiat monetary structure—especially in the last 55 years, since the US elegantly defaulted on its promise to convert paper dollars into gold in 1971.
Bitcoin is a direct response to these imbalances, but its adoption will depend on how and who drives the transition.
Two Paths of Bitcoin Adoption: Bottom-Up vs. Top-Down
Bitcoin’s journey can take two distinct paths:
1. Bottom-Up Adoption
This is driven by grassroots use of Bitcoin as a currency, particularly in developing nations, often alongside dollar-denominated stablecoins like USDt.
2. Top-Down Adoption
This path sees Bitcoin increasingly used as a store of value (SOV) and financial asset, especially in developed economies. It is driven by institutions, wealth managers, and financial innovation.
It's clear that top-down adoption correlates with faster price appreciation, whereas bottom-up adoption is slower, more organic—and potentially more resilient in the long run.
Why the Top-Down Path Matters
A critical but often uncomfortable truth is: elites don’t give up power easily. The fiat system is held tightly by those benefiting most from its continuation.
Pareto’s Law teaches us that no historical revolution was purely bottom-up. Real change happens when a new elite emerges to replace the old one—carrying the masses along.
The advantages of top-down adoption:
-
Speeds up the revolution.
-
Allows coexistence between Bitcoin and fiat for a transitional period, avoiding violent disruption.
-
Strengthens new power structures around Bitcoin as it becomes a more established SOV.
-
Enables the U.S. to reinvent the dollar’s role through dollar-backed stablecoins and their recycling into US TBills, maintaining global dollar demand even post-Petrodollar.
A Warning for the United States
In my book, I argue that the #Bitcoindollar system gives the U.S. a first-mover advantage—but only if it changes course.
The U.S. must shift from a militaristic, imperialist approach to a cooperative, multipolar model that welcomes both allies and adversaries into this new system.
Unfortunately, the Trump administration appears headed in the opposite direction, risking this historic opportunity. I explore this further in an upcoming article expanding on my book’s conclusions.
Store of Value vs. Currency: Which Comes First?
Some critics lament that Bitcoin isn’t widely used as a currency yet. But ask yourself:
What is the world’s most urgent need in today’s monetary environment?
A medium of exchange? Or a store of value to protect savings from corrupt governments and inflation?
We already have more or less efficient payment systems. But we lack a sound store of value with key properties such as decentralization, censorship resistance and hard coded scarcity. That’s why the market is adopting Bitcoin primarily as a SOV.
Gresham’s Law gives us the formula:
Save the hard money (Bitcoin, gold), spend the USDt, USDC, and fiat.
Looking Ahead: From Store of Value to Currency
This doesn’t mean #bitcoin won’t be used as a currency eventually. Once it’s widely adopted as a store of value—perhaps within the next 10–20 years—its volatility will decrease, more people will price goods in bitcoin, and acceptance for payments will grow.
We will get there. Just not through the path many imagined at the beginning.
Call It What It Is: A Revolutionary Monetary Transition
Rather than a disruptive revolution, think of this as a revolutionary monetary transition—a new system growing alongside the old, until one inevitably replaces the other.
-
-
 @ 3ffac3a6:2d656657
2025-04-15 14:49:31
@ 3ffac3a6:2d656657
2025-04-15 14:49:31🏅 Como Criar um Badge Épico no Nostr com
nak+ badges.pageRequisitos:
- Ter o
nakinstalado (https://github.com/fiatjaf/nak) - Ter uma chave privada Nostr (
nsec...) - Acesso ao site https://badges.page
- Um relay ativo (ex:
wss://relay.primal.net)
🔧 Passo 1 — Criar o badge em badges.page
- Acesse o site https://badges.page
-
Clique em "New Badge" no canto superior direito
-
Preencha os campos:
- Nome (ex:
Teste Épico) - Descrição
-
Imagem e thumbnail
-
Após criar, você será redirecionado para a página do badge.
🔍 Passo 2 — Copiar o
naddrdo badgeNa barra de endereços, copie o identificador que aparece após
/a/— este é o naddr do seu badge.Exemplo:
nostr:naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Copie:
naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0
🧠 Passo 3 — Decodificar o naddr com
nakAbra seu terminal (ou Cygwin no Windows) e rode:
bash nak decode naddr1qq94getnw3jj63tsd93k7q3q8lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vetsxpqqqp6njkq3sd0Você verá algo assim:
json { "pubkey": "3ffac3a6c859eaaa8cdddb2c7002a6e10b33efeb92d025b14ead6f8a2d656657", "kind": 30009, "identifier": "Teste-Epico" }Grave o campo
"identifier"— nesse caso: Teste-Epico
🛰️ Passo 4 — Consultar o evento no relay
Agora vamos pegar o evento do badge no relay:
bash nak req -d "Teste-Epico" wss://relay.primal.netVocê verá o conteúdo completo do evento do badge, algo assim:
json { "kind": 30009, "tags": [["d", "Teste-Epico"], ["name", "Teste Épico"], ...] }
💥 Passo 5 — Minerar o evento como "épico" (PoW 31)
Agora vem a mágica: minerar com proof-of-work (PoW 31) para que o badge seja classificado como épico!
bash nak req -d "Teste-Epico" wss://relay.primal.net | nak event --pow 31 --sec nsec1SEU_NSEC_AQUI wss://relay.primal.net wss://nos.lol wss://relay.damus.ioEsse comando: - Resgata o evento original - Gera um novo com PoW de dificuldade 31 - Assina com sua chave privada
nsec- E publica nos relays wss://relay.primal.net, wss://nos.lol e wss://relay.damus.io⚠️ Substitua
nsec1SEU_NSEC_AQUIpela sua chave privada Nostr.
✅ Resultado
Se tudo der certo, o badge será atualizado com um evento de PoW mais alto e aparecerá como "Epic" no site!
- Ter o
-
 @ 4ba8e86d:89d32de4
2025-04-22 13:26:12
@ 4ba8e86d:89d32de4
2025-04-22 13:26:12Cashu é Ecash para Bitcoin
Cashu é um sistema ecash Chaumian gratuito e de código aberto criado para Bitcoin. Cashu oferece privacidade quase perfeita para usuários de aplicativos Bitcoin de custódia. Ninguém precisa saber quem você é, quanto dinheiro você tem e com quem você faz transações.
O que é Cashu?
Cashu é um novo protocolo ecash para aplicativos de custódia Bitcoin que está totalmente integrado à rede Lightning. Um sistema Ecash consiste em duas partes, a carteira mint e a carteira ecash. Transações Ecash não rastreáveis, instantâneas e sem taxas. Cashu é construído para Bitcoin. As carteiras usam o nó Lightning da casa da moeda para fazer ou receber pagamentos em Bitcoin em troca de ecash. Uma casa da moeda Cashu não sabe quem você é, qual é o seu saldo ou com quem você está negociando.Os usuários de uma casa da moeda podem trocar ecash de forma privada, sem que ninguém saiba quem são as partes envolvidas. Os pagamentos em Bitcoin são executados sem que ninguém possa censurar usuários específicos.
A postagem de David Wagner em 1996 na lista de discussão Cypherpunk é a base da criptografia Cashu. Wagner descreve um sistema ecash usando troca de chave cega Diffie-Hellman em vez de RSA, na qual a implementação original de David Chaum foi baseada.
https://cypherpunks.venona.com/date/1996/03/msg01848.html
https://en.m.wikipedia.org/wiki/Ecash
Como isso começou.
https://void.cat/d/2HJKtTEfuDxmDfh3uH9ZoS.webp https://void.cat/d/XyyHFSQYa5vEswzzt6MMq7.webp
Como vão as coisas.
https://void.cat/d/WUrKzsFDnsvUQdFKZChLeS.webp
Como funciona A Carteira Cashu é através de um esquema criptográfico chamado assinaturas cegas, descrito pela primeira vez pelo cypherpunk e criptógrafo David Chaum. Pense assim:você produz uma mensagem secreta e a envolve em um envelope feito de papel carbono que você envia para a casa da moeda. https://void.cat/d/SbEEHCiGFUHWvk4qGv9xCb.webp
A casa da moeda não pode ver o que está dentro do envelope. Ele assina do lado de fora dizendo "qualquer que seja esse segredo, vale 420 Satoshis”e o envia de volta para você. Como o envelope é realmente criptografado, somente você pode abri-lo e ver sua mensagem secreta (agora assinada por carbono). https://void.cat/d/Pakyb6ztW9B7L5ubAQ74eL.webp
Este segredo assinado é na verdade o seu token Ecash e vale Satoshis.
Você pode enviar e receber esses tokens para qualquer outra pessoa como quiser, seja com um mensageiro, via e-mail ou um pombo. A casa da moeda não sabe nada disso.
A anatomia de um token Cashu. https://void.cat/d/JzvxreMoCitmYe2FthAsei.webp
Um breve passo a passo de uma carteira cashu deixará tudo isso bem claro.
Comece abrindo
https://nutstash.app/
Pressione " WALLET " https://void.cat/d/VeCANsaxkkq9YtoPRS26ZK.webp https://void.cat/d/CTmK9GcPGn3i2gHCVXcL5r.webp https://void.cat/d/UWjyjGLS6MzyZvt6zkuUgG.webp https://void.cat/d/HzNtKanCSAJatrMa9yTKwF.webp
Pressione "+ ADD ".
Agora a carteira cashu está aberta… https://void.cat/d/GAYSrNxHEEhctoW37bFPjJ.webp
O próximo passo é deposite alguns sats com a Casa da moeda.
Pra depositar Pressione o botão "MINT". https://void.cat/d/LC5WEDKAzzZoHXxrKZDiWu.webp
Digite a quantidade de sats a ser depositado na carteira cashu depois Pressione " REQUEST MINT ". https://void.cat/d/Pr6foBWBBCq73i8WggbLGG.webp
Você Pode copiar a fatura ou ler o qrcode , no meu caso usei a carteira LNbits pra pagar a fatura de 10 sats , você tem 10 minutos pra pagar fatura. https://void.cat/d/BQerpEtW2H9ANaoW8truJE.webp https://void.cat/d/8PGFBRW64zavDnQJfYQh9C.webp
Agora pra enviar Ecash.
Pressione “SEND” https://void.cat/d/8rkF2dvhJeZWf8GeQhhf2d.webp
Digite 10 , Pressione “SEND” https://void.cat/d/5SK5w6ewgt8wikCuyk7znM.webp
Então o token Ecash usando a assinatura cega da casa da moeda foi criado. https://void.cat/d/PedBMcZPfczZLLymGmfzVq.webp
O Token Ecash foi criado é esse logo abaixo.
eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19
Se pressionar o botão " send as link "
Então criar link do token Ecash.
https://wallet.nutstash.app/#eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19 https://void.cat/d/U1UnyxsYgj516YbmkgQNkQ.webp Este token Ecash pode ser compartilhado como você quiser. Você pode enviá-lo por e-mail para alguém, enviá-lo em uma mensagem privada, um SMS ou convertê-lo em um código QR e imprimi-lo. Quem tiver este token pode resgatá-lo com o 10 sats.
Você verá que seu saldo caiu para 20 sats: https://void.cat/d/95AVkevmknKNzqRcnJZwQX.webp
Para resgatar um token Ecash sem o link, pressione o botão “Receive ” https://void.cat/d/UjrbAPn8mj5qGZYVQ1Ba2B.webp
cole-o token Ecash no campo
" token: "pressione "RECEIVE" https://void.cat/d/GZLcBgvHfaB3c5N66ygZyV.webp
Com o Link do token Ecash só pressionar no link vai abrir a tela já preencher automáticamente só pressionar " RECEIVE " https://void.cat/d/ARNkKCtchhFt4NCTkfRJRG.webp
Pra Ativa o Nostr na carteira vai na aba settings , pressione o botão ativa o Nostr. https://void.cat/d/MjoDA1dgueWUFABcQFDVRe.webp
Por padrão ficar ativo pra usar o " Use external Key (nos2x , outros) " Mas Nesse caso não vou usar vou desativar e vou ativa " Edit Nostr Keys " https://void.cat/d/BAA6eFkmK5f7BHzLwYLSGF.webp
Ao pressionar esse botão https://void.cat/d/VTNGVsLvwqfy3dWu4hhMSK.webp é gerar um novo par de chaves privadas e pública , assim podemos usar uma nova chave a cada pagamentos. Aumentando a privacidade no pagamentos.
A pois Ativa o Nostr na carteira , você pode enviar Sats / Ecash via Nostr.
Pressione " Send " https://void.cat/d/R2Svye4XPd2VdHfPxT1DzF.webp
Pressione " Send " https://void.cat/d/AwLeBBr2db2wrTHHUHwEPs.webp
Agora pode adicionar npud / hex / nip-05 pra enviar token. https://void.cat/d/VZR6BUXjG7pm3FDogrDvo4.webp
Pressione " SEND OVER NOSTR " pra enviar o token Ecash. https://void.cat/d/MWveqpmii5dqpioa5a3wVt.webp
Pra quem não tem a carteira nutstash , pode entra no seu cliente Nostr no meu caso e snort nostr , Demora algums minutos pra chegar mensagem com o token Ecash.. https://void.cat/d/MVg3fPD7PAzZUskGCCCcps.webp https://void.cat/d/YNtKuCbQYo1wef7pJcjhKy.webp
Ja se a outra pessoa usar carteira nutstash com a chave pública que você mandou chegar mais rápido. Essa bolinha azul no campo " Indox " Indica que você recebeu o pagamento já está pronto pra ser regastado. https://void.cat/d/So6FAp4wiTUeKBBmRBU2Rv.webp
Pressione "Indox " depois pressione a seta. https://void.cat/d/TqYNYDoyy9fUFas9NFxReJ.webp
Pressione " TRUS MINT " pra recebe os Token Ecash. https://void.cat/d/LP6zUTZ3HDPxd6fLvPPNXB.webp
O aplicativo de resgate Cashu, que permite resgatar tokens Ecash via Lightning.
https://redeem.cashu.me/ https://void.cat/d/Mw9kzDHr4A469EjFNoTHyB.webp
Cola o Token no campo " paste in your Cashu Ecash token.. " https://void.cat/d/SkA3MGJaGGxCjNnzeBhPHP.webp
Pressione " REDEEM " pra converter Ecash em Lightning. https://void.cat/d/693C1yfwYz3P3BQB6f7xXN.webp
Você pode editar e manda já pronto pra pessoa só basta a pessoa ou você aberta em " REDEEM " pra converter Ecash em Lightning.
https://redeem.cashu.me/?token=token ecash=&to=Lightning address
Exemplo:
https://redeem.cashu.me/?token=eyJwcm9vZnMiOlt7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoyLCJDIjoiMDJhYWE5OWJiMmUwODQyYjJmNzdmNDRlZWEyZjEzMmNkOTNhZjJlNWU0MzI3ZjhjMTE5ODcxZWNiMTNhMTUxYjY0Iiwic2VjcmV0IjoicE5jb3hFRHJRT1ovTXU4d3d2SlpvMnRIaXBSM3pPYkRrSWJUUlB6VXh5bz0ifSx7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoxNiwiQyI6IjAzNDM4ZDc1NmZmMjdmYjgyZmQxNWNhNzg3NzgwNTAyZWU4NzdmMzQ5MmYyMWQzMTMwMzc1NTdlNWNmMDJlOWQ0MCIsInNlY3JldCI6Im9DTXQwUTRVT0MvZWhmd2FVOWt5aGFJZUdHdXhiYUNzQTZ2STh2a0w2N1U9In0seyJpZCI6IlBFbjFXS2pRaDdqRiIsImFtb3VudCI6MzIsIkMiOiIwMmIyMmQ4MDEwZWU5MDA2MWYyNWQzODAyY2UyMDE3ZjAwMmVjMDVmMjM5NjIwNGNkYjllMmU2ODllYWY3YTZkYjIiLCJzZWNyZXQiOiI5ejVVMEdzWHZiUS84Rjd4ZFdYUXRxUDlvWGFyVnBRTzRFdUtzb2JSck1vPSJ9XSwibWludHMiOlt7InVybCI6Imh0dHBzOi8vbGVnZW5kLmxuYml0cy5jb20vY2FzaHUvYXBpL3YxL29DcXNTR3I1enphTTZxM1hWZU5ZNXQiLCJpZHMiOlsiUEVMVdLalFoN2pGIl19XX0=&to=alexemidio@ln.tips
Obs: o teclado do celular pode adicionar "=" a mais ou corrigir " &to " com "&tô" assim escrevendo errado, tanto erro no link.
" SWAP " transferência de uma carteira para outra. Pressione " INTER-MINT SWAP" https://void.cat/d/PsCdoLAmYpYCChkgqTAE7p.webp
A carteira que você selecionar em cima é a carteira de saídas e a carteira de baixo e a carteira de entrada. https://void.cat/d/VKY6ts6qttJmCaefrduv4K.webp
Agora digita o valor que quer fazer o SWAP. Após Pressione " CONFIRM AMOUNT" https://void.cat/d/WuuQqeC1mSQUufb75eeMbw.webp
Depois Tem que pressionar " SWAP " não esqueça. https://void.cat/d/Eb2ajSaZfzZkBEWBv8tuk.webp
Pronto antes a primeira Carteira tinha 10 Ecash, e segunda carteira tinha 8 Ecash.
Somando 18 Ecash.
Apois o SWAP Agora as duas tem 9.
Somando 18. https://void.cat/d/8yRtSoFyih2D2KEm66h6in.webp
Fazer o backup da sua carteira cashu ecash. Pressione " BACKUP TOKENS " https://void.cat/d/26vtnDiVP4YpDiQmunatko.webp
Você pode editar o nome do backup E pode alterar o local aonde vai salva o arquivo 📂 do backup. Depois só pressionar " Baixar " https://void.cat/d/PQH94o81U23txdmyx3cHEn.webp
Agora pra recuperar a carteira cashu ecash. Pressione " RESTORE " https://void.cat/d/2vkLS1qUCbJ1XXjSLBou25.webp
Pressione " CONTINUAR " https://void.cat/d/PCbT2UPSLtwcZohwbhD85A.webp
Click no espaço em branco vai abrir pra encontrar o arquivo 📂 Do backup.. https://void.cat/d/P1VC7b46oNe62v4puVZ79b.webp
Selecionar o arquivo 📂 de backup. https://void.cat/d/D6FAGxYRquz2WWwNznSAzT.webp
Pressione " CONTINUE" https://void.cat/d/HicRn5e2feSRicgjy6kuC5.webp
Pressione " CONTINUE" https://void.cat/d/VP6uh8bXHz42PBGrPwGq5e.webp
Backup feito com sucesso. Só aberta " Ok " https://void.cat/d/QsZV1umL9DhoPtEXBMfPtY.webp
O eCash pode ser útil em diversas situações, oferecendo várias vantagens. Uma das principais vantagens do uso de tokens eCash é a privacidade que oferece. Como as transações usando eCash são quase impossíveis de rastrear, isso pode ser útil para quem deseja manter sua atividade financeira privada. O eCash pode ser especialmente útil para Pagamento de serviços em áreas rurais , pode ser difícil acessar serviços financeiros tradicionais, como bancos ou caixas eletrônicos. O uso de tokens eCash pode permitir que as pessoas paguem por serviços como transporte , serviços de saúde ou eletricidade sem a necessidade de viajar para áreas urbanas. No entanto, é importante lembrar que o uso do eCash ainda apresenta riscos e desafios. Como o eCash cashubtc ainda é bem novo , pode haver falhas de segurança ou outras vulnerabilidades que ainda não foram identificadas use com cautela poucos Sats.
Obrigado por ler, e espero que você dedique alguns minutos para experimentar o eCash e ver do que se trata melhor.
Alguma artigos e vídeos a baixo.
https://cashu.space/
https://docs.cashu.space/
https://github.com/cashubtc/
https://youtu.be/UNjVc-WYdgE
https://youtu.be/_XmQSpAhFN4
https://youtu.be/zdtRT7phXBo
https://maxmoney.substack.com/p/ecash-for-better-bitcoin-privacy?utm_source=substack&utm_campaign=post_embed&utm_medium=web
https://cypherpunks.venona.com/date/1996/03/msg01848.html
Encontre-me ou envie um zap para nostr alexemidio@ln.tips alexemidio@alexemidio.github.io
Twitter: alexemidio7
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 1f9e547c:8af216ed
2025-04-15 10:03:32
@ 1f9e547c:8af216ed
2025-04-15 10:03:32Opinion about Mixin Messenger Desktop (desktop)
Mixin Network suffered a major breach on September 23, 2023, due to a vulnerability in its Google Cloud Services-based withdrawal system. The attack led to the unauthorized extraction of over $150 million in BTC, ETH, and USDT-ERC20, traced to known addresses. Mixin immediately suspended deposits and withdrawals, enlisted Slowmist and Mandiant for investigation, and offered a $20M bounty for asset recovery. Losses were converted into a structured debt, with a repayment commitment using existing funds and future ecosystem revenue. As of April 2024, a new mainnet is operational, core products are restored, and over half of affected users have received partial compensation in XIN tokens.
WalletScrutiny #nostrOpinion
-
 @ 54609048:8e22ba03
2025-04-22 12:25:50
@ 54609048:8e22ba03
2025-04-22 12:25:50One of the greatest threats facing liberty lovers around the world today is the rise of the biomedical security state—the militarization of healthcare. COVID-19 was merely a compliance test, and sadly, most failed it dismally. But pay attention: “pandemic response,” war-gamed at elite gatherings like Davos, is steadily morphing into official health policy through backdoor mechanisms—diabolical agreements like the WHO Pandemic Treaty, which effectively transfers sovereign pandemic authority to Bill Gates via the WHO; the rollout of digital IDs; and the global push for central bank digital currencies (CBDCs).
This biomedical Leviathan requires all three pillars to be firmly in place before it can unleash a never-ending cycle of pandemics. The goal? To normalize draconian measures like those witnessed in 2020, thereby dismantling not only national sovereignty but, more dangerously, individual sovereignty. A digital ID won't merely confirm your identity—it will track your vaccination status, movements, and even your sentiments, all to determine what privileges you're allowed. Meanwhile, the CBDC will act not just as a means of transaction but as an enforcement mechanism—particularly for dissenters. This is why having an alternative like Bitcoin is not just relevant, but essential.
Vaccines are a cornerstone of this architecture—not only as instruments of control but also as tools for "redesigning" humanity. Welcome to the realm of transhumanism. The merger of man and machine through brain-computer interfaces and artificial intelligence is no longer science fiction; it's a stated goal. In this context, vaccines are not merely preventative medicine but potentially covert instruments of eugenics. This could explain the near-religious devotion to these pharmaceutical products—despite their increasingly controversial outcomes and questionable safety record—especially when mandates enter the equation.
The first piece of property any individual owns upon birth is their body. And yet, this sacred ownership is violated at birth when governments mandate certain injections—often administered without informed parental consent. I've often wondered: Why, despite mounting evidence to the contrary, is vaccine efficacy treated as “settled science”? Why is it taboo to question vaccines or hold their manufacturers accountable for harm, even as we’re expected to believe—without scrutiny—that they are “safe and effective”? We’re told our refusal to comply endangers everyone else who took a product supposedly designed to protect them. Strange, isn’t it? If it’s so effective, why must everyone take it simultaneously?
If you're wondering where this seemingly off-the-cuff rant is headed, here's the point: when the state mandates vaccines, it violates your property rights over your own body. It’s a direct claim of ownership over you, dressed up in moral language like “we're all in this together.” You're guilt-tripped into compliance under the pretense of saving “grandma.” But the truth is, if your rights can be suspended for the collective, they were never yours to begin with.
The biomedical security state will manufacture a permanent state of emergency under the guise of “pandemic preparedness.” You’ll be expected—required, even—to inject yourself with the latest mRNA-based bioweapon, all in the name of public health. Some will die. Others will become incapacitated—zombies or vegetables. The altar of compliance will be merciless towards those that bow before it.
Public health agencies like the CDC, WHO, and NIH are on track to become as powerful as central banks. In fact, they may soon act as arms of monetary policy enforcement. Don’t believe it? Look into what was happening in the repo markets in September 2019—just months before the global shutdown. While you're at it, investigate how many elderly pensioners quietly dropped dead like flies between 2021 and 2023, either from the virus or the vaccine. I’ll let the numbers speak for themselves.
These agencies are becoming the new face of the war machine. Vaccines will be marketed as shields against biological threats—“benevolent” weapons to protect us from invisible enemies. And if history is any guide, the next “9/11-style” event will be biological in nature.
The lunatics running the asylum will seize any such crisis to strip away more of your freedoms while simultaneously redesigning the global economy—consolidating even more power in their hands. For a blueprint of this ambition, look no further than Klaus Schwab’s COVID-19: The Great Reset.
The only antidote is a decentralized parallel system of medicine—one that stands entirely outside the Big Pharma cartel. This will require not only a network of courageous healthcare providers but also a new generation of researchers willing to ask uncomfortable questions and challenge sacred cows in the pursuit of truth. Add independent scientific journals to the mix, and we can finally dismantle the machinery that suppresses unprofitable—but potentially life-saving—treatments.
In my view, none of this is viable at scale without decentralized money. Enter Bitcoin. It’s not a panacea, but it’s a crucial tool for realigning incentives. Bitcoin renders CBDCs dead on arrival and undermines the foundation of any future social credit system—where vaccine compliance will be its crown jewel.
The biomedical state is not coming—it’s already here, creeping into every corner of our lives. It will be the scepter of a new technocratic tyranny. So beware the white coats who worship the state. They are not here to heal—they are here to rule.
A more polished series of articles on this topic is forthcoming. Stay tuned.
-
 @ d34e832d:383f78d0
2025-04-22 08:40:25
@ d34e832d:383f78d0
2025-04-22 08:40:25
In the twilight of forgotten eras, where the whispers of the past wove through the air like a ghostly melody, two shadowy figures emerged beneath an ageless sky. She was Eve, not the emblem of gardens, but the Mitochondrial Eve—her essence pulsing within the very mitochondria that spark life in each human heartbeat. He stood before her as Adam, not forged from soil, but the Y-Chromosome Adam—guardian of a singular lineage, his heritage dancing through the veins of sons alone.
Their encounter was not one of flesh and blood, but a meeting of symbols, sparked by the insatiable curiosity of humanity, prowling through the labyrinth of DNA, seeking to uncover the tales of their primordial roots.
In the ethereal glimmer of a timeless pool, two figures stood, their outlines rippling like whispered secrets. They were neither lovers nor allies, nor of the same age, yet their names danced together in every headline and wisdom-filled book.
Today, however, was different—they had gathered at the brink of the infinite to unravel the threads of their intertwined destinies.
As the twilight draped its ethereal cloak over the meadow, Eve let her fingers dance through the glimmering starlight, weaving dreams from its luminous threads.
“You know,” she mused, her voice a whisper carried by the evening breeze, “they often ponder why fate kept us apart. Why our paths never crossed beneath the same sun.”Adam’s lips curled into a wry smile, his eyes reflecting the cosmos above.
“Perhaps they seek a narrative that is neat and orderly, a story with perfect symmetry,” he replied, the gentle rustle of leaves echoing his words.Eve shook her head softly, her gaze fixed on the swirling constellations.
“Ah, but nature, dear Adam,” she countered with a glimmer of mischief, “is a master of chaos. It delights in the untamed, the beautiful mess of existence.”In the grand tapestry of time, two figures emerged from the mists of ancient Africa:
Mitochondrial Eve, a woman of vibrant spirit, who roamed the earth around 150,000 to 200,000 years ago, and
Y-Chromosome Adam, a man of strength and wisdom, appearing some 60,000 to 100,000 years later.Though separated by a chasm of tens of thousands of years, they were not the sole beings of their era, yet in the intricate web of life, they were the most recent ancestors, bearers of unbroken trails of maternal and paternal lines, from which all humanity flows.
Their stories intertwine, echoing through generations, whispers of a time long past.
In a hushed tone, Eve shared the tale of her lineage, weaving a rich tapestry of time.
“Behold my daughters,” she said, her eyes gleaming with pride. “From them sprang another generation, and those daughters too have borne daughters.This precious thread of life, my mitochondrial DNA, weaves through the tapestry, handed down solely by women.
With each passing age, while many lines faded into shadows—some in mere moments, others enduring for centuries—mine flowed on, a river of continuity and strength.
My legacy, a steadfast whisper across generations, defied the silence of so many others.”In a dimly lit room, Adam pondered the weight of generations past.
“And what of mine?” he inquired, his voice tinged with a mix of curiosity and melancholy.He shook his head slowly, as if unraveling a forgotten tale.
“The Y-chromosome, it weaves a delicate thread through the tapestry of life.
Passed from fathers to sons, a fleeting whisper of legacy, vanishing if a man begets no heirs.Like branches of a grand oak, countless lines have been severed by the cruel hands of war, the relentless march of disease, and the silent grasp of chance.
Mine is not the sole survivor in this timeless struggle, but it is the one that defied extinction—standing resilient against the bottleneck of time, thriving into the present day, a testament to tenacity and fate.”Their inheritance patterns are straightforward but ruthless.
Mitochondrial DNA (mtDNA) is stable and abundant, making it a powerful marker for tracing maternal lineage.
It mutates slowly, preserving a clear path backward.In contrast, the Y-chromosome, despite its utility in tracing paternal lines, is subject to greater volatility: smaller effective population sizes, male-specific extinction events, and the disproportionate reproductive success of a few males—all contribute to a narrower, more chaotic record.
In a dimly lit chamber nestled among ancient trees, Eve’s voice resonated with the wisdom of ages.
“The numbers are not our destiny,” she declared, her finger tracing a pattern in the soil.
“They are mere echoes of survival, tales of those who dared to pass their legacy—a lineage of children begetting children, weaving a tapestry of existence.”Adam stood by, thoughtful as a storm brewing on a distant horizon.
“Indeed, lineages dissolve like whispers in the wind,” he mused, his gaze fixed on the moonlight filtering through the leaves.
“Some genetic threads endure not from superiority, but sheer fortune. Bottlenecks of fate, the whims of founders, the swirling dance of genetic drift—these unseen forces hold the key to who emerges amidst the chaos of time.”Together, they pondered the intricate dance of life, where luck and survival intertwined, crafting the very fabric of their world.
Eve paused, her voice a whisper woven with time.
“And so it is,” she mused, “the humans trace their lineage back to me, painting me as the primordial bloom of existence.Yet, shadows linger—my cousins, neighbors, even rivals shared this space, vibrant as I, yet their stories faded like whispers in the wind.
They bore no daughters to carry forth their tales, only their echoes lingered, lost in the tapestry of forgotten history…”
In the shadow of an ancient, pulsing tree that mirrored their very essence, Adam mused aloud,
“I came along far down the line, but not right at the start.
I am but one among countless men, and in the end, only my Y-line remained, a solitary thread in the tapestry of time.
Your lineage, however, stretches across continents, vibrant and thriving.”They stood quietly, lost in the vast glow of humanity’s fractal branches, each flicker representing a birth, a connection, a glimmer of possibility.
“Isn’t it amusing?” Adam chuckled, breaking the reverie.
“They pair us as if we were a couple, forever intertwined.”Eve’s laughter echoed like sweet music.
“Merely symbols, nothing deeper. We are called ancestors, yet we are merely the fortunate survivors of an exquisite genetic lottery.”Adam continued,
“And yet, the very essence of your spark resides in every human’s mitochondria, while half of them carry my signature in their Y chromosome.”Eve’s voice was soft as she spoke, weaving a tapestry of understanding.
“Ah, but dear friend, ancestry is far more than mere lineage.
It’s like tracing the delicate threads of a grand tapestry, where some strands are visible, yet countless others lie hidden in the shadows of time.Each soul walking upon this earth is a descendant of a multitude of individuals from ages long past.
Their names may fade like whispers in the wind, and their unique genes become mere echoes of history.
Yet, amidst this beautiful chaos, the patterns of our heritage forever linger, binding us in an unseen embrace of shared existence.”As Adam stood beneath the shimmering canopy of stars, he pondered aloud,
“Maybe the tale isn’t solely ours. It’s about the delicate yet unwavering dance of life itself.”Eve, her eyes reflecting the celestial lights, agreed with a subtle nod.
“Indeed, for no single thread can unveil the entirety of the narrative.
One must gaze upon the grand tapestry woven through time.”They dimmed away, not with finality, but like starlight traversing the vastness of the cosmos—whispers that remind us history bends and weaves, a spider’s web of fate, woven with threads of fortune, affection, and heartache, where beams of hope dance through the dark.
Within each of us, they linger still, a harmonious symphony resonating with the voices of billions, echoing through time.
-
 @ cdee943c:5e637400
2025-04-15 08:38:29
@ cdee943c:5e637400
2025-04-15 08:38:29Flotilla-Budabit is fork of Flotilla which aims to provide a first class, git-centric community experience for developers. Based on the popular Coracle client, Flotilla is a drop in replacement for Matrix/Discord/Slack, using a variation of NIP-29. This post is a result of a brainstorming session for features that would deliver the best possible user experience.
1. Repositories Overview
Goal: Browse and discover Git repositories. - Project cards showing name, description, tags, clone URL. - Buttons: Star, Watch, Fork. - Links to discussion channels and activity.
Powered by:
kind:30617
2. Branch and Tag View
Goal: Show active branches and tags with latest commits. - Branch/tag selector - HEAD pointer visualization - Timeline of commits
Powered by:
kind:30618
3. Issues Board
Goal: Track bugs, discussions, and feature requests. - Markdown issue rendering - Labels and status indicators - Threaded comments
Powered by:
kind:1621,kind:1630–1632
4. Patch Threads
Goal: View and discuss patches as threaded conversations. - Rich patch preview - Reply threads for review - Revision tracking
Powered by:
kind:1617,kind:1630–1633,NIP-10
5. Pull Request UX
Goal: Display patch series as PR-style units. - Patch stack visualization - Merge/apply status indicators - Final result commit link
Powered by:
kind:1617,kind:1631,merge-commit,applied-as-commits
6. Diff and Merge Preview
Goal: Side-by-side comparison with inline comments. - Expandable diff viewer - Merge conflict resolution UI - Apply/Close buttons
Powered by:
kind:1622,parent-commit,commit
7. Real-time Git Chat
Goal: Communicate in real-time around a repo. - Dedicated chat channels for each repo - Markdown, code snippets, and tagging support - Pinned patches, issues, and sessions
Powered by:
NIP-29,a:30617,kind:1337
8. Notifications and Mentions
Goal: Alert users to relevant events. - Mentions, assignments, and status changes - Personal notification pane
Powered by:
ptags,mentione-tags
9. Repository-Wide Search
Goal: Search patches, issues, snippets. - Full-text search with filters - Search by kind, label, commit ID
Powered by:
kind:1617,1621,1337,t,x,l,subject
10. Repository Wikis
Goal: Collaboratively edit and view project documentation. - Wiki sidebar tab - Markdown articles with versioning - Linked inline in chat
Powered by (proposed):
kind:1341(Wiki article)
kind:30617withwiki-hometag
11. Live Coding Sessions
Goal: Host real-time collaborative coding events. -
/livecodestarts a session thread - Snippets auto-tagged to session - Export as patch or wikiPowered by (proposed):
kind:1347(Live coding session)
kind:1337,kind:1622,kind:1341
Supporting Tools
1. GitHub Browser Extension
Goal: Publish GitHub content to Nostr directly. - “Share on Nostr” buttons on PRs, issues, commits
Backed by:
kind:1623,1622,1617,1621
2. VS Code Extension
Goal: Enable developers to interact with Flotilla from their IDE. - Repo feed, patch submission, issue tracking - Inline threads and comment rendering
Backed by:
kind:1617,1621,1337,163x
3. GitHub Actions Integration
Goal: Automate Nostr publishing of repo activity. - Push = repo state - PR = patch - Issue/Comment = issue - Merge = status update
Backed by:
kind:30618,1617,1621,1631
Configured via.nostr.yml -
 @ 7d33ba57:1b82db35
2025-04-22 08:35:57
@ 7d33ba57:1b82db35
2025-04-22 08:35:57Nestled in Lower Saxony’s East Frisia region, Leer is a charming canal town known for its historic tea culture, maritime heritage, and postcard-worthy Altstadt (Old Town). With colorful gabled houses, cobbled streets, and a relaxed pace, Leer offers a taste of northern Germany’s quiet beauty—without the crowds.
🏘️ Things to See & Do in Leer
🚶♂️ Altstadt (Old Town)
- Stroll through narrow lanes lined with 17th and 18th-century houses
- Highlights include Waageplatz, the Reformed Church, and Evenburg Castle
- Perfect for a slow wander, especially during golden hour
🛶 Canal Walks & Harbor
- Take a peaceful walk along the Leda and Ems rivers
- Watch boats pass through the small port and historic trading canals
- In summer, you can even book a scenic canal cruise
🍵 East Frisian Tea Culture
- Leer is considered the tea capital of Germany
- Visit the Bünting Teemuseum to learn about the centuries-old tea tradition
- Don’t miss a tea session with rock sugar and cream—served the traditional East Frisian way
🌳 Nature Nearby
- Cycle or walk through the flat green landscapes of East Frisia
- Great routes along rivers and meadows, with plenty of windmills and grazing sheep
- A short drive takes you to the Wadden Sea, a UNESCO site and tidal wonder
🍽️ Local Eats
- Sample Matjes (pickled herring), smoked fish, and hearty stews
- East Frisian cakes pair beautifully with black tea
- Cozy inns and riverside cafés make for a warm, welcoming meal
🚆 Getting There
- Easily accessible by train from Bremen or Emden
- Compact and walkable—no car needed in the town center
Leer is a peaceful, picturesque retreat where canals, culture, and comfort flow together. Whether you're cycling through the countryside or sipping tea by the harbor, it’s a place to unwind and soak up the slow life.
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ 70c48e4b:00ce3ccb
2025-04-22 08:35:52
@ 70c48e4b:00ce3ccb
2025-04-22 08:35:52Hello reader,
I can say from personal experience that crowdfunding has truly changed my life. I found people who believed in my dream of using Bitcoin as money. Every single one of my videos was made possible through crowdfunding. And I’m not alone. I know several Bitcoiners who have raised funds this way, from Africa to Korea to Haiti.
https://images.forbesindia.com/media/images/2022/Jul/img_190501_runwithbitcoin_bg.jpg
Crowdfunding is deeply rooted in the traditional financial world. From raising money for life-saving surgeries to helping someone open a local coffee shop, platforms like GoFundMe, Kickstarter, and Indiegogo have become essential tools for many. But behind all the heartwarming stories and viral campaigns, there’s a side of crowdfunding that doesn’t get talked about enough. Traditional platforms are far from perfect.
They are centralized, which means there’s always someone in control. These platforms can freeze campaigns, delay payouts, or take a significant cut of the money. And often, the people who need funding the most, those without access to strong banking systems or large social media followings are the ones who get left out.
Here are some of the problems I’ve noticed with these platforms:
Problem 1: Inequality in Who Gets Funded
A recent article in The Guardian pointed out something that’s hard to ignore. Crowdfunding often benefits people who already have influence. After the Los Angeles wildfires in January 2025, celebrities like Mandy Moore were able to raise funds quickly. At the same time, everyday people who lost their homes struggled to get noticed.
https://i.guim.co.uk/img/media/f8398505e58ec3c04685aab06e94048e5d7b6a0c/0_127_4800_2880/master/4800.jpg?width=1300&dpr=1&s=none&crop=none
Angor (https://angor.io/) changes that by removing the need for a central platform to choose which projects get featured or promoted. Anyone can share their project. People can find them on Angor Hub (https://hub.angor.io/), which is a public directory built on the Nostr protocol. Instead of relying on popularity, projects are highlighted based on transparency and engagement.
Problem 2: Platform Dependence and Middlemen
Here’s something people don’t often realize. When you raise funds online, the platform usually has control. It holds the money, decides when to release it, and can freeze everything without warning. This happened during the trucker protests in Canada in 2022. Tens of millions of dollars were raised, but platforms like GoFundMe and GiveSendGo froze the donations. The funds never reached the people they were meant for. Supporters were left confused, and the recipients had no way to access what had been raised for them.
https://upload.wikimedia.org/wikipedia/commons/thumb/2/2d/Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg/800px-Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg
Angor avoids all of this. It does not hold the funds, does not require approval processes, and only the project creator has control over the campaign. Contributions go directly from supporters to the people building the project, using Bitcoin. It is a peer-to-peer system that works without any gatekeepers. Angor never touches the money. It simply provides the tools people need to raise funds and build, while staying fully in control.
Problem 3: Global Access
Another major issue is that these platforms often exclude people based on where they live. If you're in a region with limited banking access or outside the supported list of countries, you’re likely shut out. In 2023, a woman named Samar in Gaza tried to raise funds for food and medical supplies during a crisis. A friend abroad set up a campaign to help, but the platform froze it due to "location-related concerns." The funds were locked, and the support never arrived in time.
https://images.gofundme.com/EMFtPWSLs3P9SewkzwZ4FtaBQSA=/720x405/https://d2g8igdw686xgo.cloudfront.net/78478731_1709065237698709_r.jpeg
Angor removes these barriers by using Bitcoin, which works globally without needing banks or approvals. Anyone, anywhere, can raise and receive support directly.
Problem 4: Lack of Transparency
Post-funding transparency is often lacking. Backers rarely get consistent updates, making it difficult to track a project's progress or hold anyone accountable.
In 2015, the Zano drone project on Kickstarter raised over £2.3 million from more than 12,000 backers. It promised a compact, smart drone for aerial photography. But as time went on, updates became rare and vague. Backers had little insight into the project’s struggles, and eventually, it was canceled. The company shut down, and most backers never received their product or a refund.
https://ichef.bbci.co.uk/ace/standard/976/cpsprodpb/2A0A/production/_86626701_ff861eeb-ce94-43b7-9a43-b30b5adbd7ab.jpg
Angor takes a different approach. Project updates are shared through Nostr, a decentralized and tamper-proof communication protocol. This allows backers to follow progress in real time, with no corporate filters and no blackout periods. Everyone stays in the loop, from start to finish.
Problem 5: Fraud and Accountability
Scams are a growing problem in the crowdfunding world. People can launch fake campaigns, collect donations, and vanish — leaving supporters with empty promises and no way to recover their money. One well-known example was the "Homeless Vet GoFundMe scam" in the U.S.
https://a57.foxnews.com/static.foxnews.com/foxnews.com/content/uploads/2018/09/720/405/1536549443584.jpg
A couple and a homeless man raised over $400,000 by telling a heartwarming story that later turned out to be completely fake. The money was spent on luxury items, and it took a legal investigation to uncover the truth. By the time it was resolved, most of the funds were gone.
This kind of fraud is hard to stop on traditional platforms, because once the funds are transferred, there’s no built-in structure to verify how they’re used.
On Angor, projects are funded in stages, with each step tied to a specific milestone. Bitcoin is held in a shared wallet that only unlocks funds when both the backer and the creator agree that the milestone is complete. If something feels off, backers can choose to stop and recover unspent funds.
This structure discourages scammers from even trying. It adds friction for bad actors, while still giving honest creators the freedom to build trust, deliver value, and raise support transparently. It can’t get any better than this
So, does Angor matter?
For me, it really does. I’m genuinely excited to have my project listed on Angorhub. In a world shaped by AI, open source and transparency light the way forward. Let the work shine on its own.
Have you tried Angor yet? Thanks for tuning in. Catch you next week. Ciao!
Guest blog: Paco nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk
References:
• The Guardian, 2025: Crowdfunding after LA fires and inequality - https://www.theguardian.com/us-news/2025/jan/17/la-fires-gofundme-mandy-moore • https://www.theguardian.com/us-news/2018/nov/15/johnny-bobbitt-gofundme-scam-arrest-viral-gas-story-couple-charged • FundsforNGOs: The Success Story of an NGO That Scaled with Limited Resourceshttps://www2.fundsforngos.org/articles/the-success-story-of-an-ngo-that-scaled-with-limited-resources/ • https://www.freightwaves.com/news/gofundme-freezes-37m-until-organizers-of-canada-trucker-convoy-detail-spending-plan
-
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ ef53426a:7e988851
2025-04-22 07:47:07
@ ef53426a:7e988851
2025-04-22 07:47:07In 1997, an IBM supercomputer beat the sport’s greatest mind. Deep Blue II became the first machine to defeat a chess world champion — Garry Kasparov. Humans would never win at chess again.
But if computers have been better than us for so long, why do we still play chess? Don’t we always play to win?
Well, even though we’re unlikely to record a victory over the machines, chess has become more popular than ever. According to a June 2023 PBS feature, subscriptions to chess clubs have soared and earlier this year chess.com servers overloaded due to a the highest number of active users ever.
This is not just a fad based on The Queen’s Gambit (a 2020 Netflix adaptation). Over 100m people have registered on chess.com since then, and books, YouTube channels and other content is flourishing. A Grandmaster recently visited the city in Spain where I live, and thousands of people came to watch her play.
Here’s my theory behind the recent revival of chess. The answer to why we still play is what’s behind the game of chess — strategy and spatial recognition.
It’s a system of training ourselves to appreciate cause and consequence, to improve our decision making. The best players train against computers, knowing they can’t win, but they can learn.
The same is true with today’s writing landscape. Professionals are panicking that machines will produce most of the content we’ll read from now on. Writing will change — that’s true. AI can write faster and more (grammatically) accurately.
But what’s behind writing? 🧠 Patterns of structured thought 🗣️ Sound rhetoric 🖊️ The creativity of language 📚 The beauty of stories.
Writing is a skill that we still need to train.
If we don’t, how will we know what makes our words effective? How will we communicate? How will we make sense of our past?
We can use AI to help, but the words it processes belong to us.
Just as we have recognised the importance of the concepts behind chess, we must do the same for the process of writing.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 2b24a1fa:17750f64
2025-04-22 06:57:36
@ 2b24a1fa:17750f64
2025-04-22 06:57:36Es fühlt sich wie ein Staatsstreich an. Vielleicht ist es auch einer. Ein abgewählter Bundestag genehmigt mittels Grundgesetzänderung die größte Staatsverschuldung in der Geschichte Deutschlands mit der unvorstellbaren Summe von 1000 Milliarden Euro, also eine Billion.
https://soundcloud.com/radiomuenchen/vom-schuldenstaatsstreich-zur-finanzdiktatur-von-rob-kenius?\ Jedem muss klar sein, wohin diese Gelder aus den Taschen der Steuerzahler wandern und wer, wenn in Rüstung, Militärhilfen, Konzern-Subventionen investiert wird, die Leidtragenden sind: Kinder, Rentner, kleine Firmen und Betriebe, sozial Schwache, Kranke, Arbeitslose, Obdachlose.
\ Die Kräfte aus Finanzeliten, Militär, Rüstungsindustrie, regierenden Parteien und den staatstragenden Medien werden dafür immer stärker.
\ Hören Sie den Beitrag „Vom Schuldenstaatsstreich zur Finanzdiktatur“ von Rob Kenius, der zunächst beim Overton-Magazin erschienen war: https://overton-magazin.de/top-story/vom-schuldenstaatsstreich-zur-finanzdiktatur-in-leicht-verstaendlicher-sprache/
Sprecherin: Sabrina Khalil
Redaktion: Jonny Rieder
Bild: Bund der Steuerzahler / Janek Werner
Rob Kenius betreibt die systemkritische Webseite kritlit.de und den Podcast 9min Denksport. Der Text Vom Schuldenstaatsstreich zur Finanzdiktatur ist davon die 14. Folge.
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 24dffa2c:185b741a
2025-04-14 22:29:27
@ 24dffa2c:185b741a
2025-04-14 22:29:27sd
-
 @ da0b9bc3:4e30a4a9
2025-04-22 06:44:40
@ da0b9bc3:4e30a4a9
2025-04-22 06:44:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/952743
-
 @ bb1c863a:2953c3fb
2025-04-14 22:22:50
@ bb1c863a:2953c3fb
2025-04-14 22:22:50Block Height 892385 11:47 pm Monday, 14 April 2025
In a powerful gesture of support for Bitcoin-aligned education, Blockstream has donated 21 Blockstream Jade hardware wallets to the Consensus21 School — a groundbreaking learning initiative launching its first campus this year on the Mornington Peninsula, just outside Melbourne, Australia.
The donation will place 21 Jades directly into the hands of the first 21 students at the new campus — some as young as five years old — giving them real tools to explore Bitcoin self-custody, digital sovereignty, and privacy-first technology in an age-appropriate and hands-on way.
“The Jade wallets are more than just devices — they’re symbols of freedom, responsibility, and the future of education,” said Kieran Nolan, co-founder of Consensus21. “We’re incredibly grateful to Blockstream for standing behind our mission.”
Real Tools for Real Sovereignty
The Blockstream Jade is a secure, open-source hardware wallet built for Bitcoiners who value freedom, privacy, and independence. These values are embedded deeply into the Consensus21 educational philosophy, which blends Steiner-inspired learning, homeschooling flexibility, and a curriculum rooted in Bitcoin principles like voluntary exchange, decentralization, and self-responsibility.
With the Jades now part of the learning toolkit, Consensus21 learners will be introduced to key concepts like:
- Private key management
- Seed phrase generation and backup
- Multisig wallets
- The importance of self-custody and trust minimization
This is not just about theory — learners will get to use these tools in real-world contexts, preparing them to grow up fluent in the principles of freedom tech.
A Campus, A Vision, A Movement
Launching in 2025, the Mornington Peninsula campus is the pilot site for the broader Consensus21 vision: a distributed, regenerative, and values-aligned network of co-learning spaces, including a future 10-acre farm campus and a registered Steiner school.
The Blockstream donation comes at a pivotal time, as the community transitions from vision to reality. The gift of exactly 21 Blockstream Jades — echoing Bitcoin’s 21 million hard cap — is both a symbolic and practical gesture of support, underscoring the shared commitment between Bitcoin builders and grassroots educators.
Stay Connected
📄 Whitepaper: https://github.com/consensus21school/consensus21school.github.io/blob/main/whitepaper.md
🌐 Website: https://consensus21.school
📝 Nostr: CONSENSUS21@nostrcheck.me
🐦 X (Twitter): https://x.com/Consensus21
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ d34e832d:383f78d0
2025-04-22 06:43:30
@ d34e832d:383f78d0
2025-04-22 06:43:30It is noteworthy to mention that Bill Gates, a distinguished co-founder of Microsoft and a philanthropist with extensive impact on global health and education initiatives, serves as a limited partner in various investment vehicles associated with Village Global. However, it is critical to delineate the nuances of this relationship, as Gates' status as a limited partner does not confer upon him any authoritative control or decision-making power regarding the operational protocols or strategic direction of SimpleX Chat.
The development team behind SimpleX Chat has made a concerted effort to clarify that Village Global's involvement is strictly financial in nature, devoid of any operational oversight or influence over the management and technical development of the project.
Privacy Without Compromise
SimpleX Chat aims to provide a messenger that is both convenient and private, addressing the perceived trade-off between these two qualities in existing solutions. They define privacy as protecting not only message content but also metadata like connection details and user identities.
In contrast to a multitude of contemporary messaging applications, SimpleX Chat distinctly emphasizes the safeguarding of metadata privacy as a foundational component of its architecture.
The development team articulates a compelling argument regarding the intrinsic value of communication relationships, suggesting that the identification of interlocutors constitutes sensitive data that may be weaponized against users in various contexts—an issue that current market leaders in the domain have failed to remedy with sufficient rigor.
Consequently, the developers are actively engaged in initiatives to bolster the obfuscation of users’ IP addresses, thereby enhancing the overall security framework against potential surveillance and data exploitation threats.
A Radical Architectural Shift
The architecture underpinning SimpleX Chat diverges notably from conventional paradigms associated with user account management.
Specifically, it eschews the creation and maintenance of user profiles in the traditional sense, thereby negating the repository of personally identifiable information on centralized servers. Instead, all pertinent data transactions pertinent to user interactions are localized, existing solely on the end-user's devices.
This paradigm shift engenders a formidable barrier to data accessibility, effectively neutralizing the potential for data disclosure to law enforcement agencies, irrespective of judicial mandates such as court warrants.
Furthermore, in their adherence to statutory obligations, SimpleX Chat's design ethos proactively prioritizes the minimization of data collection, establishing a privacy-centric framework that aptly aligns with contemporary concerns regarding data sovereignty and user anonymity.
Functionality Grounded in Security
The SimpleX Chat application exemplifies a multi-device compatibility framework, strategically prioritizing stringent security protocols over user convenience.
This methodology distinctly contrasts with that of various competitors who may opt for convenience-focused functionalities that inadvertently jeopardize user data integrity and confidentiality.
The current technical architecture facilitates seamless profile transfers across devices, while also enabling a desktop terminal interface that remains operationally tethered to the mobile device.
Such an arrangement underscores SimpleX Chat's commitment to balancing usability with robust security measures, effectively mitigating potential vulnerabilities in cross-platform interactions.
Transient Messaging and Signal Protocol Reimagined
SimpleX Chat integrates the functionality of transient messaging, which serves primarily as a user convenience element rather than representing a robust security mechanism.
The developers have explicitly articulated that they are unable to ensure the irreversible deletion of messages from the recipient's device, thereby highlighting potential vulnerabilities associated with data retention and privacy concerns in digital communications.
The development team arrived at a strategic decision to forgo the utilization of the existing Signal codebase, primarily attributed to its inherent complexity and the prospective risks associated with the coupling dynamics that could emerge between the Signal protocol and its corresponding system architecture.
As a result, they opted to engineer the Signal protocol anew, commencing from foundational coding principles.
This approach not only enables them to exert comprehensive control over the implementation but also significantly facilitates the seamless integration of advanced cryptographic frameworks, specifically post-quantum key agreement methodologies, which are imperative in future-proofing cryptographic communications against the advent of quantum computing threats.
UX Development and the Road Ahead
The UI is still under development. The developers acknowledge some usability challenges, especially for users unfamiliar with the concept of profile-based messaging without traditional accounts.
They are actively working on improving UX based on user feedback.
A Decentralized Economic Model
SimpleX Chat is poised to introduce an innovative commercial framework predicated on the integration of a decentralized accounting mechanism, characterized by the utilization of distributed ledger technology, which underpins cryptocurrency transactions, coupled with a system reminiscent of traditional gift card paradigms.
This commercial model is strategically designed to provide economic incentives to both infrastructure operators, who maintain the necessary backbone for the network's operations, and software vendors, who contribute essential applications and services—all while preserving the fundamental decentralized architecture inherent to blockchain systems.
This careful balance is crucial for fostering a sustainable ecosystem that rewards participants without compromising the network's core principles of transparency and egalitarian access.
🚧 Prerequisites
| Requirement | Description | |-------------------|----------------------------------------------| | VPS | Debian 12, at least 1GB RAM (for running server) | | Build Machine | A second Linux machine with ≥ 8GB RAM for compiling binaries | | Domains | FQDNs like
smp.yourdomain.com,xfp.yourdomain.com,turn.yourdomain.com| | SSH Keys | SSH access secured with key-based auth only | | Firewall | Only allow ports for SSH (22), SMP (5223), XFP (5353), TURN (5349) |
🧱 Step 1: Build SimpleX on Build Machine
You’ll compile the binaries on your high-RAM machine and then SCP them over.
```bash sudo apt update && sudo apt install build-essential git rustc cargo pkg-config libssl-dev
Clone repo
git clone https://github.com/simplex-chat/simplexmq cd simplexmq
Build binaries
cargo build --release ```
You’ll find: -
target/release/smp-server-target/release/xfp-serverCopy them to your VPS:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/
🧑💻 Step 2: Harden the VPS
🔒 SSH-only access
```bash
Edit /etc/ssh/sshd_config
PermitRootLogin no PasswordAuthentication no ```
Restart SSH:
bash sudo systemctl restart ssh🔥 UFW Firewall
bash sudo apt install ufw sudo ufw default deny incoming sudo ufw default allow outgoing sudo ufw allow OpenSSH sudo ufw enable🛡️ Fail2ban
bash sudo apt install fail2ban sudo systemctl enable --now fail2ban
📡 Step 3: SMP Server Setup
Create user and directories:
bash sudo useradd -m -r -s /usr/sbin/nologin smp sudo mkdir -p /var/lib/smp /var/log/smp sudo chown -R smp:smp /var/lib/smp /var/log/smpMove binary and set permissions:
bash sudo mv /home/user/smp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/smp-serverCreate systemd service:
/etc/systemd/system/smp.service```ini [Unit] Description=SimpleX SMP Server After=network.target[Service] User=smp ExecStart=/usr/local/bin/smp-server --fqdn smp.yourdomain.com --log /var/log/smp/smp.log WorkingDirectory=/var/lib/smp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now smp.service
🗂️ Step 4: XFP Server Setup
bash sudo useradd -m -r -s /usr/sbin/nologin xfp sudo mkdir -p /var/lib/xfp /var/log/xfp sudo chown -R xfp:xfp /var/lib/xfp /var/log/xfp sudo mv /home/user/xfp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/xfp-serverCreate systemd service:
/etc/systemd/system/xfp.service```ini [Unit] Description=SimpleX XFP Server After=network.target[Service] User=xfp ExecStart=/usr/local/bin/xfp-server --storage /var/lib/xfp --log /var/log/xfp/xfp.log --quota 2GB WorkingDirectory=/var/lib/xfp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now xfp.service
🎙️ Step 5: Optional TURN Server (WebRTC)
Install Coturn:
bash sudo apt install coturnEdit
/etc/turnserver.conf:ini listening-port=5349 tls-listening-port=5349 fingerprint lt-cred-mech realm=turn.yourdomain.com user=someuser:somepassword cert=/etc/letsencrypt/live/turn.yourdomain.com/fullchain.pem pkey=/etc/letsencrypt/live/turn.yourdomain.com/privkey.pem cipher-list="ECDHE-RSA-AES256-GCM-SHA384" no-stdout-logSet to auto-start:
bash sudo systemctl enable coturnConfigure DNS and firewall to allow 5349.
🔁 Step 6: Certificate Renewal (Let's Encrypt)
bash sudo apt install certbotSet up renewal cron:
bash sudo crontab -ebash 0 3 * * * certbot renew --quiet && systemctl restart coturn
🧪 Step 7: Testing with SimpleX Desktop
- Download SimpleX Desktop
- Launch and go to Settings → Relay Settings
- Disable defaults, add your SMP and XFP addresses.
🔄 Upgrading SimpleX
On your build machine:
bash git pull origin main cargo build --releaseThen:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/On VPS:
bash sudo systemctl stop smp xfp sudo mv /home/user/smp-server /usr/local/bin/ sudo mv /home/user/xfp-server /usr/local/bin/ sudo systemctl start smp xfp
What if you communicated securely?
📡 SimpleX – Anonymous chat, no phone numbers, no metadata
SimpleX is unlike anything else. It doesn’t just encrypt your messages—it hides who you're talking to. No central servers, no profiles, no traces. Just pure private messaging.
Perfect for when you need total metadata privacy and no digital fingerprint.
🌱 Nostr DMs – Messages with your Web of Trust
If you’re already on Nostr, using DMs is a natural step. Messages are encrypted end-to-end and tied to your public key identity.
Great for building trusted, decentralized communication channels within your Web of Trust.
🔐 PGP Email – Old-school but rock solid
PGP lets you encrypt your emails and verify identities with public keys. It’s still one of the most powerful tools for asynchronous, verifiable, and encrypted communication—especially for long-form or professional exchanges.
🔁 Use them all together
Different tools for different roles. Want to talk anonymously? Use SimpleX.
Connecting with your Nostr tribe? Slide into those DMs.
Need to send a secure file or message over email? PGP's got your back.Privacy isn’t just one app—it’s a toolkit. Build yours.
-
 @ e97aaffa:2ebd765d
2025-04-14 20:16:59
@ e97aaffa:2ebd765d
2025-04-14 20:16:59Num recente podcast, o Miguel Milhão falou sobre o crash nos mercados financeiros. No meio de muita conversa de macroeconomia e mercados financeiros, o convidado deixou alguns pontos interessantes, mas duas ideias ficaram no meu pensamento, infelizmente, ele não aprofundou, mas é algo que eu quero fazer futuramente.
Perda de paridade
A primeira ideia que o convidado apontou foi, a possibilidade da perda de paridade do papel-moeda e a CBDC, eu nunca tinha pensado neste ponto de vista.
Se os governos não conseguirem retirar de circulação todo o papel-moeda rapidamente, se houver circulação em simultâneo com a CBDC, o papel-moeda poderá ter um premium. Isto faz todo o sentido, os governos poderão dar oficialmente o mesmo valor facial, mas como nas CBDCs existirá mais controlo, restrições e monitorização, as pessoas vão preferir o papel-moeda, vão pagar um premium para manter a sua privacidade.
Na prática, será algo similar ao que acontece em alguns países onde existem algumas controlo de capitais, onde o dólar do mercado negro é superior ao dólar oficial. Os comerciantes também poderão fazer descontos superiores nos produtos quando são pagos com papel-moeda.
Isso poderá provocar um descolar do valor, a mesma moeda com valores diferentes, a oficial e do mercado negro. Isso poderá levar os governos a tomar medidas mais autoritárias para eliminar o papel-moeda de circulação.
Não sei se alguma vez acontecerá, mas é algo que eu tenho que refletir e aprofundar esta ideia.
RBU e Controlo
A outra ideia apontada pelo convidado, a CBDC será uma peça fundamental numa sociedade onde a maioria das pessoas sobrevivem com Rendimento Básico Universal (RBU).
Todos sabemos que a CBDC vai servir para os governos monitorar, fiscalizar e controlar os cidadãos. O ponto que eu nunca tinha pensado, é que esta pode ser essencial para a implementação do RBU. Se chegarmos a esse ponto, será o fim da liberdade dos cidadãos, onde o estado controla quando, quanto e onde o cidadão pode gastar o seu dinheiro. O estado irá determinar o valor do RBU e as CBDC vão determinar onde podes gastá-lo.
Penso que já não existem dúvidas que a AI e a robótica vão revolucionar o mundo laboral, vai provocar uma profunda queda nos postos de trabalho, profissões vão desaparecer ou vão reduzir drasticamente o número de funcionários.
Muitas pessoas consideram que a solução é o RBU, mas eu tenho muitas dificuldades em encontrar viabilidade económica e social numa sociedade onde a maioria recebe o RBU.
É a implementação do conceito: não terá nada, mas será feliz.
Será que as máquinas vão conseguir produzir tudo, o que os seres humanos necessitam, a um custo tão baixo, que vai deixar de ser necessário os humanos trabalharem? Tenho muitas dúvidas que essa possibilidade aconteça, se nós humanos não necessitarmos de trabalhar, vai se perder o incentivo para desenvolver novas tecnologias, gerar inovação e de evoluir a sociedade.
Eu já tenho refletido bastante sobre o RBU, mas por mais que pense, não consigo encontrar uma viabilidade económica para manter isto de pé. Onde vão buscar dinheiro para financiar uma percentagem expressiva de pessoas que sobreviverá com o RBU. Eu só olho para isto, como um comunismo com esteróides, talvez esteja errado.
Além dos problemas econômicos, eu acredito que isso vai gerar problemas sociais e de comportamento, vai gerar uma revolta social. Em primeiro lugar, existe uma parte de seres humanos que são ambiciosos, querem mais coisas, que vão lutar e vão conseguir mais. Depois existe outra parte, que é invejosa, quer ter mais, mas não consegue.
Uma sociedade onde quase ninguém trabalha, existindo demasiado tempo livre, vão emergir vícios e conflitos sociais. As pessoas com tempo para pensar reflectir sobre a sua vida e sobre a sociedade, alguns vão delirar, vão questionar tudo. Por isso, a religião desempenha um papel importante na sociedade, cria moralismo através de dogmas, os crentes não questionam, apenas seguem. Por vezes, a ignorância é uma bênção.
Isto faz lembrar-me o porquê das sociedades monogâmicas tornaram-se mais desenvolvidas, em comparação com as poligâmicas. A monogamia trouxe uma paz social à sociedade, existem muito menos conflitos e guerras, há mais harmonia. Milhões de anos de evolução das espécies, nos humanos e alguns animais, a natureza/genética trouxe um equilíbrio no número de nascimento de elementos masculinos e femininos. Mas nas sociedades poligâmicas, normalmente os homens mais ricos têm várias mulheres, consequentemente haveria outros homens que não teriam nenhuma mulher, isso resulta em maior revolta e conflitos sociais. Isto é pura matemática, se existe quase 50/50, de um homem tem 7 mulheres, isto resulta, que 6 homens não terão qualquer mulher. As religiões ao defenderem a monogamia, ao determinar que era pecado ter mais que uma mulher, resultaram em menos conflitos, numa maior paz social. Isso permitiu um maior desenvolvimento de sociedades monogâmicas, do que as poligâmicas.
Acabei por desviar um pouco do assunto. Além disso, o valor do RBU teria que ser elevado, para que permita aos cidadãos ter acesso ao desporto, aos espetáculos, futebol, viajar, para financiar os seus tempos livres. Se eu já acho difícil arranjar dinheiro para financiar a generalidade dos cidadãos, com produtos e serviços básicos, ainda será mais difícil ou impossível, se tiver que financiar os passatempos.
Em vez do RBU, ainda existe a opção do Imposto sobre o Rendimento Negativo (IRN), minimiza um pouco, mas o problema mantém-se. Aconselho a leitura do artigo do Tiago sobre o IRN.
Mas o mais interessante de tudo, os governos vão criar as CBDC para controlar os cidadãos, com a ideia distópica de criar mais paz social, mas eu acredito que resultará no seu inverso.
São duas ideias que eu tenho que aprofundar, futuramente.
-
 @ 23202132:eab3af30
2025-04-14 20:01:29
@ 23202132:eab3af30
2025-04-14 20:01:29Ter um segundo sistema de mensagens é importante para uso com a família ou grupo de amigos, especialmente naqueles casos em que o WhatsApp é invadido para aplicar golpes nos seus contatos ou, ainda, por conta de bloqueios judiciais que alguns governantes consideram necessários impor. Nesses casos — entre outros possíveis problemas — possuir um segundo sistema de mensagens pode garantir a continuidade da comunicação com seus amigos ou familiares.
Como sistemas de mensagem alternativos, os aplicativos Mixin, Session e Simplex se destacam, cada um com funcionalidades bem distintas. Um fator importante é o grau de dificuldade para usuários com pouca ou nenhuma familiaridade na configuração de aplicativos. Nesse sentido, a escolha do aplicativo deve levar em conta o perfil das pessoas que irão usá-lo.
O aplicativo mais fácil de operar para quem já usa WhatsApp é, sem dúvidas, o Mixin Messenger. Ele permite o cadastro com o número do celular, em uma lógica muito semelhante ao WhatsApp. Para os mais exigentes em relação à privacidade, é possível criar uma conta sem uso de e-mails ou número de telefone. Assim, atende tanto ao usuário acostumado ao WhatsApp quanto àquele que prefere algo com menor vínculo de identificação, ao eliminar dados de contato.
Já o Session oferece a criação de contas totalmente desvinculadas de qualquer dado pessoal, sem necessidade de e-mail ou número de telefone. No entanto, ao criar uma conta, é gerado um ID totalmente aleatório e uma seed (13 palavras) que serve como senha. Se você perder essa seed, perderá o acesso à conta. Essa forma de cadastro garante total privacidade, mas exige cuidado por parte do usuário em armazenar bem a seed. É ideal para grupos com alguma familiaridade no uso de palavras-chave. Usuários acostumados a recuperar senhas com frequência geralmente não dão a devida importância à segurança dessas seeds.
O Simplex é o que há de mais radical em termos de privacidade até o momento — mas é importante lembrar que mais privacidade também significa mais complexidade. A alta privacidade exige uma combinação equilibrada entre comportamento e tecnologia, algo mais comum entre usuários com perfil técnico. Nesse sentido, o Simplex geralmente é utilizado por grupos com algum conhecimento tecnológico e hábitos de segurança digital. Ele permite, por exemplo, que o próprio usuário hospede seu relay na rede Onion, em um Raspberry Pi ou outro tipo de computador.
Uma característica que torna o Simplex tão radical é o fato de não gerar um ID fixo nem utilizar servidores convencionais para trafegar mensagens, além de não coletar metadados. No entanto, isso pode representar dificuldades para usuários sem experiência com tecnologias de comunicação.
Basicamente, se você pretende usar um aplicativo de mensagens alternativo com um grupo inexperiente, o Mixin pode ser a melhor escolha. Já se os familiares e amigos têm mais desenvoltura com tecnologia, o Session pode ser uma excelente alternativa. O Simplex, por outro lado, pode gerar dor de cabeça para grupos inexperientes, dada sua complexidade de uso. No Simplex não há recuperação automatizada de conta com arquivos na nuvem ou qualquer recurso semelhante — é necessário o hábito de realizar backups manuais com alguma frequência. A configuração inicial também pode gerar confusão para usuários não técnicos. Por isso, o Simplex é uma boa escolha apenas para grupos com alguma desenvoltura tecnológica. Para pessoas experientes, ele oferece total personalização e privacidade.
Em termos de segurança, todos os três aplicativos oferecem privacidade e resistência à censura, não são atraentes para golpistas e são difíceis de bloquear. Isso é importante se você está buscando um sistema de mensagens alternativo justamente para manter a comunicação ativa em caso de problemas com seu mensageiro principal. Mas não se esqueça de considerar qual é o perfil dos usuários do seu grupo de contatos.
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ c21b1a6c:0cd4d170
2025-04-14 14:41:20
@ c21b1a6c:0cd4d170
2025-04-14 14:41:20🧾 Progress Report Two
Hey everyone! I’m back with another progress report for Formstr, a part of the now completed grant from nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f . This update covers everything we’ve built since the last milestone — including polish, performance, power features, and plenty of bug-squashing.
🏗️ What’s New Since Last Time?
This quarter was less about foundational rewrites and more about production hardening and real-world feedback. With users now onboard, our focus shifted to polishing UX, fixing issues, and adding new features that made Formstr easier and more powerful to use.
✨ New Features & UX Improvements
- Edit Existing Forms
- Form Templates
- Drag & Drop Enhancements (especially for mobile)
- New Public Forms UX (card-style layout)
- FAQ & Support Sections
- Relay Modal for Publishing
- Skeleton Loaders and subtle UI Polish
🐛 Major Bug Fixes
- Fixed broken CSV exports when responses were empty
- Cleaned up mobile rendering issues for public forms
- Resolved blank.ts export issues and global form bugs
- Fixed invalid
npubstrings in the admin flow - Patched response handling for private forms
- Lots of small fixes for titles, drafts, embedded form URLs, etc.
🔐 Access Control & Privacy
- Made forms private by default
- Fixed multiple issues around form visibility, access control UIs, and anonymous submissions
- Improved detection of pubkey issues in shared forms
🚧 Some Notable In-Progress Features
The following features are actively being developed, and many are nearing completion:
-
Conditional Questions:
This one’s been tough to crack, but we’re close!
Work in progress bykeralissand myself:
👉 PR #252 -
Downloadable Forms:
Fully-contained downloadable HTML versions of forms.
Being led bycasyazmonwith initial code by Basanta Goswami
👉 PR #274 -
OLLAMA Integration (Self-Hosted LLMs):
Users will be able to create forms using locally hosted LLMs.
PR byashu01304
👉 PR #247 -
Sections in Forms:
Work just started on adding section support!
Small PoC PR bykeraliss:
👉 PR #217
🙌 Huge Thanks to New Contributors
We've had amazing contributors this cycle. Big thanks to:
- Aashutosh Gandhi (ashu01304) – drag-and-drop enhancements, OLLAMA integration
- Amaresh Prasad (devAmaresh) – fixed npub and access bugs
- Biresh Biswas (Billa05) – skeleton loaders
- Shashank Shekhar Singh (Shashankss1205) – bugfixes, co-authored image patches
- Akap Azmon Deh-nji (casyazmon) – CSV fixes, downloadable forms
- Manas Ranjan Dash (mdash3735) – bug fixes
- Basanta Goswami – initial groundwork for downloadable forms
- keraliss – ongoing work on conditional questions and sections
We also registered for the Summer of Bitcoin program and have been receiving contributions from some incredibly bright new applicants.
🔍 What’s Still Coming?
From the wishlist I committed to during the grant, here’s what’s still in the oven:
-[x] Upgrade to nip-44 - [x] Access Controlled Forms: A Form will be able to have multiple admins and Editors. - [x] Private Forms and Fixed Participants: Enncrypt a form and only allow certain npubs to fill it. - [x] Edit Past Forms: Being able to edit an existing form. - [x] Edit Past Forms
- [ ] Conditional Rendering (in progress)
- [ ] Sections (just started)
- [ ] Integrations - OLLAMA / AI-based Form Generation (near complete)
- [ ] Paid Surveys
- [ ] NIP-42 Private Relay support
❌ What’s De-Prioritized?
- Nothing is de-prioritized now especially since Ollama Integration got re-prioritized (thanks to Summer Of Bitcoin). We are a little delayed on Private Relays support but it's now becoming a priority and in active development. Zap Surveys will be coming soon too.
💸 How Funds Were Used
- Paid individual contributors for their work.
- Living expenses to allow full-time focus on development
🧠 Closing Thoughts
Things feel like they’re coming together now. We’re out of "beta hell", starting to see real adoption, and most importantly, gathering feedback from real users. That’s helping us make smarter choices and move fast without breaking too much.
Stay tuned for the next big drop — and in the meantime, try creating a form at formstr.app, and let me know what you think!
-
 @ 86102a64:33871ac0
2025-04-22 02:11:57
@ 86102a64:33871ac0
2025-04-22 02:11:57{"imageData":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAXAAAAEUCAYAAAAyfG1zAAAgAElEQVR4Xux9CWBcRf3/N5uz6X3RNk16t0lb6F16gaCC8hcERQVFEFAUFUFU/AkooiKKioqAKKICIpeIXJ4cytkWytVCaZLeTZo2bdq0TZp7d//f7xzvzXv7jnlv326SsrOEttk5vzPzme98r8mDXHo3USBvQtXyhyAv72OZHnQSkpCHH5mS+Jc8/B39n5Lle/PXnt1KJrHOPLNOVo/td+q/nfKnNIDlk1glqxX7Qb2GPGvfdWnFhmH+T7eYdj4aD1Uf06CBqPTCuuqVd2k3kMvY7yhg3Q39rvu5DgehwITK5Tfg7v9WkDJh8mrisQLnNkB3aRTxCwHc+qX9d+q/LX8XxwahNR0kBNqUCHCTWCkDXtEjA9DDDN4oo0uF4I2kHlpWutC4Rbq7rvqlC4K3kCvRXyiQA/D+MlNp9rOiavkFyL3emWY1gYr7ccB2gFUXo52DZ/CqDeC8NMNjAmnOFgfqu+V0CVbSzB2mWYdbhl/zToeYKLMWAXyeX/nc9/2XAgFXdf8d6Lu558MmzRs2uKS0AQF8QLbo4AS2HIRNMYiKb35gbynLRB2c60wmCNUFUHO0tgBoksQhabDUdtFPYPqFAHG/NhitlLE6iZHE1407Nqwc61df7vv+S4EcgPffudPuOcq9v4fAdq12gQgzpgC5AmieoE3yXsFxc7m0kC/TISAF1oTXQcCZiUt4B4IsfOonB8QgpZRzxOHmECGJPapKdu/YUFQK8GxPdtrLtZJtCoRbkdnuZa690BSYNOnEksSA7gasYHjoSkIWZMDHsFdVZjorCLl6zpRJy7/zpk0EdGVoA3C6UkQcdPEHaCIkxZRiPo3xQwUpKwdhz2/IwZOvJZLJB6EA/lC/ftX+9DuWq6EvUSDoGu5Lfc/1RYMCE2YuPw83+p80skaSxcQRDskSvIVUmsumhYUKxxghDuCqRQH19r/bJNiiETeMcxPf2Aeom08tpyPqiYSQPpWoAO4mQuEnIj//jL9DXg/+ey/++/GuRNdPG2vXbMlGf3NtZIYCOQDPDF37TK0VVSvuQi7t/Ix2iMmkU038/NrkHDoJsvmfBjOp/FvmYThky+dVv5MS1DF/GBT3G5jb9wHb8jospKWJQj6jVcUKRVxpLAAu6C3oCbHq7kTXqTkgDzupvVsuB+C9S/+Mt44c+DbcxRMz0ZAh9ggkUU7tCQNblGXbFY7y99ygxFRGWv4uFHpMMBNyNfcVrjqFMj6AL/udanMv7zamfbvCgVsAPA9iSNkE5CXy7q+rXYm3NYhnYq3k6swMBUIu+cx0JldrtBQQ8u/2aGvltWlzuJloPECdfQ2cg/XHWxDOrVGEuEk5vaTSlchEildVCWtKU7iSmCA+mYcAnkQgTyZeqK9Z9Z4A5M1l7WUK5AC8lycgk82Pnr147IBE0a5MttEf6s6q8tGHIAGlKN61eWhjTemUaUGjgjcDbqZjRv6bWfiwv5GZzpb6lm3HQENDW3+Y23d7H3MAfgSvgPFVx47MzytsinSIkSKQS89ssnEjl8XzR7HNU36fDlgH446dHYv8aB2UfF43nRRLFLoZmdYnpgKZW2GyexNPJngzL1TxFTOxZP/Fn6+vfvkEv7Hkvu99CuQAvPfnIKM9mFC1ogN3aHFGG+kHlQcFZ50hZaJOnXYZ3gosDi33ZzAukmLVwyvGn0TyF3W1q7+h259cvt6hQA7Ae4fuWWs1k0rMrA0iYENBuVxL9YEKh+P3tYHfoy/EmdPXamArlfu2eKcyQUlqMAGphJZcObf04WIV6mNT6+GK9p3r6gOSP5c9ixTIAXgWid0bTU2YueIpbPektNsOBGxpt8YrSEOU4tQDHeDUyRPR6Hyr8TcjVMISGKITazQBeyNeppgGualQIoES8eSLO2tWH+/b0VyGXqNADsB7jfTZaXhC1bIrIS/24+y01ndacQI/HXDWyaOOMqg1TqD6wzH4Qr4ipN4O8m92NipmmdbxCN8fRHOMM5Osb90+KKfQ7Dvr2t6THID33bmJpGcTJhw3PDkwUY+qKoyJES4FAp1wTbiWMmydyWTOZion/632z/i7443BHxH9c6Q3wCAXGbfDgYk+KCxuyN2rPUbsbFdP/Nrdm17+QXqjzpXOFAVCLoFMdSdXbyYogN6Yv8XNfnHYuvsjgIflwAPRKAgai4q1wdOjI2YdqsOO2MpMEO7NfUsOXDZhiVWjHJREw3gyuaOhZtXEQHTJZc4aBXIAnjVS915DZE4Yg8JqBPFRYXoRAqfCNONYJmIxuFa/dA8s3XzWRvUg3K1uw0nHiDsQjBN3bd02yZL7T2BC5558LcLlMmWdAjkAzzrJe6fBisoVX8yLwW/CtB4OqMK0lFomtAgFq3IUQWjgp/Z4NeqKhgpmLQmMf06blolPmJelqbQ0rLy5KQkPGcalLZZgB6r1iVNgXXX8cWxvZ83KHE5EPZER1ZebmIgI2R+qQZPCe3Arn9sf+hpFH+1ArAPMOnlk34IrML0tRIwxu1x5zNsIekziaaxE2dUglxS36MdC5ybhSairacCHQLZ1aDSSy5JlCuQAPMsE7+Xm8vFxhyeRc3ufdj96gctM6Zvsg70v6r/d/q5UpgO4Onm0aRdhRgN+WdCvVJvuKJpihxdVJDh77rmZB02NBya2N6/fEUUbuTqipUAOwKOlZ5+vjQJcxQd0/xIn/ou6nQ3ClerWqZsvrAjFiYnVGYeuvF+nLnWMuvVaytA/qKA8nBhwCwUlQ3QhNGHyFJGPAbD4nxCl8H8F2+pc1s7rbWo8mANw3QWb5XzBZjXLncs1lzkKVFQuPyMvxh459n2pJwz4RNXzsEpMZysUTRFGVJ1Pox6OvehMw2TcMcNkkNtvC+hWYqhzF3hn6xP2FX1H74O6ALl6UPJum/lbDnZMbG54LceBpzGfmSqaA/BMUbYf1Dt22vGjiwri30F0uMyru70pVpBtO8W8tr72I8CLq+5CUV+bq87AiWYYBLIHP01RBvrSMHd5w/qEoJW94mDgtdZYU+r3MCKXbUk7+/amwsF79z7bqtVQLlNWKRBupWe1i7nGMk2BsVVLJxXlxb6EsLEckWGB3ekH40QfQi5wSKb74VR/WBGKva7ePITc6MatQSQYOx886NEOMdJXWuyzqcbg4hNpfUJ/xvAjk53GSaEjZa2QErM6Z4XSG2tfp80cgOtQ6V2W56jJS8YUlOSNp2HHWvI2tJUkCgcV5uM7inlF/YIUIThkbe5bgwBedfGuUbAoZ/tty0GDmTEeCbMDjMVQoILIisIUIVYRHfGRf3PFJIK1TXzCuGxFpq4Oy+D6mfwGkgjgJtprjD+XJXsUyAF49mjdr1uqmLn8AYScs7mujP5njWVnGRwTn5pPpBk5BWBYuEniQYmZZBhjNa8IK/9OIXQIQA8zWZyfFhDM6CO3l5Bbk8yaGG4G4uafnNNNlc8TeMcU3STF646xhxc4486SOAhUsYfgzUVUQZ5ZvrrDxDNSfKI2Kv7O5eWyf2zm9tVXrwzlABaGhrkywSiQA/Bg9HrX5i6bctyEWFFiPQLAIC8iMPmzMIpg0gGBCKpcWspw+RuYFHpaiarnAehaxM8SWBt9MYDa5J3dxNNO4O3UXfk7yQmjMyR/Gk3Q1di0GtYnDOARhtVXd2JkQy6TrQNyvvgYiNuP/xYjEn5Ji/a5TFmnQA7As07yftlg/vjpS69EvMCgRuruN8fCAEZwd4bCjXGVHNBN8OL5pAiXc3tcDqwD6AxYxKp1YCAjJq4JymO6O2FidweM7e6C0T1d8JehR8HB/EKLujRscCmnThNoW0Qc3CgkPfGJoLEUvTNoJ4E3QbWYP8nRk7iG/DjbEsmKfbWrdkZM2Fx1EVEgB+AREfJIrqa8cskcVGK+ivu/0G2cFssIKWZRwNlezhfQsYBqeUHlGTOPzCPJgdMGbxc2uRiBczwC9dz2Fjjx8AGY2tUO0zvboYQBnZn2xwpg8fTF0EMaRqWvasTEMGtChnnlMmqSlfMDTopPuFmhqFlT/q2KT4yTlB22ghO3iE/4bSgZx7bzklsxDsqUMOPIlckOBXIAnh06999WZs8uKo8PeRUHcIwreHuITfir6KZM1RCv2CqzALoUu0jOnPGIVpk7U+gheAY2GRQy3sGJHqjsbGMc9bieDjim/TB8sHV/ClB7TdzOgiL4f5PnwcECfq6Z4iKN6faQp1A9dFxQBCkpXmK3EyYH8QJv6gQjFk9CWG68Oo+1kviE6y9NYTfjwgWt1VfsMQ7KzIbaVdUao8ll6SUK5AC8lwjfX5otr1x2Cm7qf3n1V256dfNTfgt4C7GJF6Bz7lXhOgXIeDmfENgRkHO8SjXFo+9LEaDGd3XA+5CjPrbtEFR1HoYKFIlEkRpHAixeOB/ydmC4EAnikkWWIO3XkA3M6XAiQGVKXaIB/hHG+kTIYDiei1fnDR0F/ZaJaYT4RNVD0OP0kLgPue9P+3U9933vUiAH4L1L/z7fOr3og7Do+aKPFoALgDC4cTdAl8DP0TDlEQc7wYiPHIVg/P62g8hJd8HAeBwGJuIwBDnsSQjaxGXbxR9REX3HBIAlLwPsHgtQ/MJwGPHtaVCwV3LjNBCSgripNJVe2ACccfJ0JsmiBOAIwOHFJ1zHYNQpxCesHaIxHoD4+g7+yfOh/2eivjoXQjaqdZLJenIAnknq+tQ9fMrCoQMLit6XzMs7CTfPglgyOQ6LDMOtVIxXXNrCPfj3NjLlwj1el0jEX+6Eztuaat5oyFa3yXwQ2zrbqz1u58C5X3uoUlV8Yue+1X8LvBYiWs51WuN+KLJfoQNVWxuLIH5RcwNc0LwbiqQtXAaJtGkqwHEvAjQieKupaO1AGPrLSVD86hDI65GCCuJyhWzZpsAlXCWaJYZ3Qff0dogP7oaBT49m+bkVCoJrBOaDJJTh4hPeIufEmZkQs25hZwb+m8LV4r/+iNz35zJIvlzVEVEgB+AREVK3mjFTlx+FItNzkfCfx/1SGTQcv9h+rcgx/QNZpu/urH6xVrftMPnSB3ATuLjVgykPtwK6aalC/VQtTVTbZXlAGHbmeN1XRcN4CKKIpA1OONwMX2mqh8E25WMYGtjL1JWj2GRNKnjb88UOFUDh+oFQvG4g5NeXALSiVJtMSUoT0FPeAZ1zWqH76MOQHBI3ig65ejIMfmSssPcWtIvIfFCKT1gsFUULLA9fmg8S33R3541p3LxyTxS0ytWRWQrkADyz9DVqHz9zxVJ0yrgJ98iSqJpkDjFJOIAPX329rublO6OqV60nbRGKwplzAHcDdAnapshBRsQzwNxg0xkTaSjrGJizf5r8Py3sGILRzxs2wpkt+yIjTfMwgJkb/ME7bIPjZy9BZaWinBXmg0IfyavVdN4xvC8JsI0IWOKmJBXFKD4x7My5XrOhvmYl88LNpb5PgRyAZ3iOJkxbMitZUPBrBKETM9YU36D7IRH/LAL5Y1G2U1619ER0xf6fV52BZOBugG7jzA2sNiwquEjBMNMz5Ma8Z24gTt6MS1A+/uCOd5hVRzqpDfWUUzehzLssnVo8ynbkwfi5S0XsE2k+SIBtGpbwq4mQIbGBi/9x0xKebM47vAIhJzHoT/mY3ITpMvPZnwnoTHYdv7f2NRQO5VJ/oEAOwDM0S+S5mF+U/CXuko8i6GSczpyzZcKG3XGIn9qwYfXrEQ0tVl65nOqa61aftB7hCMKtSBisMAsHcV0X/04RoUhAsSs5VasIVp+slEshOEcqQElQV3L4Tv1ciCD+yA50JA2ZujAKzDFvAdTOCFmBRrHB102AofeVm7pGwX2HUV7auW9DfMXmhwM6kY0OODr8SIGZ6EkerN+4Eu8YudRfKJBxYOkvhIiynxVVyz+AW+Ix3CEo+Mx+wg1Ku/SvdTWrzoqi9fEzjpsbiyXW4Lb3cOQhjJX3fVOYwRlGwTUyjz8XQLcBuTU4iBCNGHIEHmXEAuJioIZXJ+G7RaUKMAll409vWxtYydmOs3g0gveWaVFQ070OEp8Aik/ICJyCV0XuvCO5dWK5xYEaJ3v6vHzmkRlP9Jywa+Oa5zM7ylztUVIgB+BRUhPrqpi57BLceTcjkPR+BLdksqWjB+bv2bRyc7rDTFsWLhRnjCqOgC7AnQEvB3l5cbHGp+aR/LglhRCFS0acnIYEp+4lF78HOfHj0NNSJx0YymXeu8k+KJOpLQ/K5y9lnLChJ8iE8w7RSJgPkviEmQ8y5SU9XrwqhweZnOMM1J2bsAiJWlG14hbcC1+JsMr0qiJGnJtwPBQ/2HFhQ8NrbelUWDZr2fz8BDyMdU52q8c7mBW/tNPZxjGEbI85oNs5c5UD5yIZofyUoiLjEOA94bE8GPKbyk1DKGztLbV75sE9cNMuFGh7pAY0EZz/JsCeMelQTa/soFvHw9BbJwjTST6GTDjvMLt0IXrioWqJ22eKzANoOuj7OpPeaHK5skWBHIBHROnymSs+h1j0+4iqi7wa3Ldoehg/q752tadXpV/DZWULS2FQ4YdRIfgx3PvLMP8oLlphiMov6cyLkDPQLFSsYfFAj4QJ3pnJVqyAboIvtyiXtoRq7GoTzFlLJs7zw8oAJ0PtIOTldgsV6sd7W/bDn3Y6e4pvwSNq2arsgDd1+6gVC6FoPwraaRCCNOm5zjOFiLPzjphkFrCKnmvDfyfiiTt3blz9Wb/5z33ftyiQA/AI5qOsatny/LzYc0jMggiqy0gVhtlvIvlf9BH6/I7aF7dkoiHEjA9hvX/FH+5b7pL2o9z1hjGT4IWBQ6EpVgid+WQjIiMVcvAmxxJKXH2pmr/ZZepmLosDkBSneHDiZx9ohJ/ttkqYNk4HOP4FNBXMAuctyVNetYydV9LSJiru2815hxqT5oPM9rsrOXbP1pcbM7EmcnVmjgI5AE+TtuOnLSmPFeS/iRwfRsXo+4m/0II4kZe8pz0Ru7Sp5iU9YbDG0BBoP4rZ/oI/gQ8yO6B3EGeIMlo1vopFTCJAmWO8lIsrDkDs1/6u+HRonHZoD9yG9uKUss15U5t5W4ug7EML0f4b/0EiJRKfROQ6L+NUscHJ3S4MeiwmiJB3e1ei66eNtWsycrBrLJ9clhAUyAF4CKKpRdDi5N8ILB9Ms5qMF7e82GICWydyXz/CuBc/xA5Y46UG7BFiwmewyF0KTASswZq9KZYPZ06cA9uLS5likkkDpALOsGk2ZeccyAXHLuTgpis+RywvCxWyFf9x4h1YgUFzsyHzVkc79j0LMYZKEdMJqK7zYcwHzdCxPM63cfPiBMD/CZmSQS6pAZbWQbHq7kTXqTkgT2v5Zq1wDsDTIDVF6kMFUFoy5TSaD1zUas1hWnrgJt/a2ZM8Oay1CkLCVdiZHwXukEaBy8ZNg8eGjTGu+1SEiYkFiEt3fFPJySs1Le8dohu6eG4mChLQeMd66F4a2aXEf4TovFM2dwmgCI4dU2w8IvZJGABHY0CuCKX/woafJUVzIu/+utqV5+EATD9//9HkcmSZAjkAD0/w2ISZK9A6GGaFr6L3StofAENwpydYflS3YeU1QXqFYHoL5s+o5c09Q8fA98ZOgS6CJnqhnT+2y5WljMvkmj8pTrFw4gLsUyxU3EAcQfTwaXuh+WfeFipBaOSVd/ANFTD07nJjHBLAg4Avu50IxloqfCORoScTL6BlynuiGmuunugpkAPwkDRF0ckFuNnuDFm814q5iFLM/iA33tPddULD5jV1fp1EzCBl5cf88kXxfSsKh787bgo8PngkdOcXQBzDxpIFBXN4oQYMT07VflxKDawWKlIW7OW52b7oADTd804UXfesY/wsdJ0XBjwq+MpbhhRXu1ciVbz4J5eaRC1D31Lfsu0YaGhIywQ144R8lzaQA/AwE4+v1ExIDMUogHkTwxTva2XsDyEQN454+DMManSlW18RLuj2cXRvjOX3w8fC9WMmQw+9R0AxrCkJ13DFzNnwtFedfpRfimLc3I7z8NZXf7omtUHj42vRSNIfRsPQIW9LEYw/dRFvV5gPchNMaWXjB9v8FiJDxNrDz4YRwaS+3kM0iT9fX/3yCWHGmCuTWQrkADwEfSmyIBq9oZVw/0yqEYLh9Wez2OAjS25vb+9eunfbmt1ypFiWwgOQpUKmfRM9iXsAzRBvGzUe/jx0LLQWFFiUnNY445qemy6mhiQX3/PHt6FrUfRy8bHHo/Kyqdg4OHRD5kjlrCQQs+dmIiGrDJ3NM7fJF1EOBLcuFASGUQq/wvAjDE1h8jAUPcUPt4SfTSR+UVe7+hv9c8X3bq/HTjt+dEF+/ArsxQeQ4ZiEVB6I242HpchLdqFZ7yGk/zb83UNQkPx9/fpV+3V7nANwXUop+SZULr8BzQW+FaJo3ygiHGsUTZ9Hv5LdyNldgJYq9+EWJyO3XfhzVN8YCO/F58ZXwn8GDudPq6Vw4iLIl4fnpq/TD+6Slk83wMFvb4tu2OQ6v2ApA1YmQtEIvGAAt3LNINg1HtOQYiRLdXpbXIrWONorAK7Y3ze1Hq5o37muPjoiHNk1DZs8f+LgopK/4Ao81lCq61kCrYvH2z+5a+PrGMTBO+nNrl8t77LvJ1StqEb2pLK/DtuO395cOLNWoV391Obq1TMLIVnRF8f98OBR8DW0WEmiSEU6r1gtVBi7Y3lQws3pxwAz20Bbzt4FB763NZLhk+v8sFvQdV7YuutWajELRBkJiyaomFCa8WOoRnHX8gENThlhgsmpxJ9vY52SLy2R80DixZ01q4/X7eu7OB9G8Fz2OyQgemeHfAqPbkDJvEfralbSa1hdbrTMAXjAVVY2Y1lVQX7M92QMWG3Ws/sqM0WP1KBStJkXtrXAN/duh2X4OHBfS/vRdvxDE+dCQzE6gZIvv2KhIkUEhgk5AZVY/YaFihiQaS+eKvtODOmG1rMa4eDFyIgOCm86P+YEFJ/sLmJxuH2T0VFCVTM/eVLyG4cQoHMkNsLtSscnCcSq6IzDNAdpacVjhKAV0M+dvqSCgOkKknUt2wblFJruM1Y2Y+GoGBRuwndGh6pP4ckzlIupxOFqRO8Uh6Whz1BEWcnEzsPdXbObt7x20KlVjdXju7zeVRn6q/WJfZKsAK6AmaMs3CwtAX1ovBu+ik+WfXZ/g4v0uPeWxVfHToW/oe04c/xhe8UEOLupIX3HviV8YvjIZclynK4PRWBUr6YbNkLHaeFe+ymrItvvfG7PrpvUQFTsUkRCLbTEEYDLqmEAbsrDdarm1i9CcSojPSqHhrpWunri1+7e9PIPdOp9l+WJja9cej/OxllSF2FsDLGudOjBxWHi7sTmkZkWNTd3HJx1eNt6Qxcl6wqwenSaP/LzUFhVvPd6vtLeH6hgd+qRfbZy3P4jGYCvv1++tx6+uH+nf+Ys5vhS2Qz4x5BRvEVHz00uTjHEDErfDLiXBi4CECUXrw6je1w7ND68DpLDg/m7VFRi7JN8DcG3C83iyH2zQGFMZCQsUWR/lSPVPLqsz82pHLgx9wQeNFZxezF+L+KHi9d7duysWTkxi1PZ55sah7Lu/OKSNUj+0VLwJA9Eu8JZezBC8SxNpNAwrK6+ZjXR3XItzAG4NkV5xvKZy29CudZXAxbrc9lTvDINZZXllm702w/Yy7o64H6Msz2pu6PPjPW82dPhufhowWFzFttuoZIiF5eCBYMlFx6r7LorAd/cNvS3BFpu7PvBZmj/+F69se+PQcVyjP3tt/tEBidxF7ODpw6R3pYL8w05Npd6WOPAeHVMcuBqd6RNuiGGopsKZw0T6NyT7ut0enTqg7nKZpxYFcvr+jZOzYexe0MM4jNugGMrF2pJx7L0BmEyGazuu+uqV12g1ui3hNJr/Qgsja+0P4pTc0Z/H5rx8IHk1izasdTR2QHcbjvOFi7Wccm+epSR7+h18vz9VICPo5tR6XVTofSvow1loQQk035aPiSBI+IiZUYRsqk2NiNjdfnGdBN5EH06Klth71/WAWBUWK80+McVMPyeCYFoZFc0E4CTspZhvAR6BUBk5WE4cPPqr8jccXz0eg85T9VXr3zX4UbF0cunYlCBf+NSYO8ycbEbZwr4B29CkuhOJ7PBUZvTzpaVQkm3LciyUTv403S4rby9fq1x3X3XTUSgXeOQuWLmitVItMhelk+3P2HLp4hQlNXjBM5O7bhx5VPx6bKHtr8FI+M9YbuXVrlffB3gihu57TOlAf8cCcO/Pg03WL7hucmYSXEZ5fsw1dyQ2VeLD+NwfVhmqqNrZis0PuAN4mNRgVm4p9hzjKo1iSmfl3J6DFBCHLiQfxOAW+YsAg6cdc5KIAbgdGjUVTeglnhb37lqpbVafAsXoGz7PpyPT8g5YTcedb+giClJymSmUDYTB14rSHu1Zt6EUgsxhgtNg/DzLIpS3mucFb7dz2WwUOBIBXALGLuyAgpH5rMuihFgbty9CU4/1JTVFfTVXwHcfFlqk3nN+TDmjHlQuJcDZwoHLjlu2psMuxgKctEE25h6vA5tsaYf1UD7R9yVm+WzlzN/GS/CmACuvkQkZN1sLyOYIoCrh4p6q7LI9w0FpWiRtSxBiP+OX/u5DNzKFYrbB9Yh44c3NR6c2N68vvevWVlYWRVVy15EgqxQRVTq9kiQvSX7BX/ZiJ17QhwZtntSyG1fILQmyUe6/uCWwdDYeFjMYthm3p3ljhgRigFYYpmoq9JHnKLOvJ9sfAGaG/6+fkPGuXEKvEcik0fO9F6Xoz9xNJS8PUQgM0Nqw/LEfKuTb0IJbH6ct73FBFqo1L+8GuU3Fn2TzLYZ19BUC0o6dNnFcpDlJNBgkhMyQRRzZTjzMBA2r/g6IhQnM0KOROLAFn+yxybw162HOic2N7x2hAP4wtLymUXr8ECbajp6CSrL6xs71EgXgcBN9vwZhkQpSulJJn7aULOaORJmus0MDyn71eO7l7/Febs4+y1H22KKElMAGd+37gowz3HeQ30AACAASURBVO9cOI8YXjE/17wLvr1nW0YWXA+q1D78d4B/n6JHoxGXVELpMyMs3DUDbIa3bHeaZoS+mkbnNpsv3QYtX0qxzOmA6qJjKz66CGUs3snCgXP2z7gRxDEIDAXxMuLAiDkTJ060ZoQCyIkxZ2c+/u/wnq5hzc3Odsl+4+ov3yPn/SxS+AROUw6TbHlY9gkdpqiLYM5YFCZT/4aqS4cU3RPevPAgrUOHKqZEyQG4LiVFvglVy7+Hs3VtwGJ9LnsqgBvr1HMh+nHcXt+X4mK/oQHFKi1NkS28ZnyGd/EagM3I0wZJAx4bBSOunIZgR3JxITJRLE+k7XhQ7lv2oX3Ffth7R4q/15kjxh/96qChQwNzr6oSk/4ur+sGBy6u8XxTh9vWUoRimBGqcl5xYyMxys5aUgMduWl85bJfomnm5XY9hEprKYKT8+K6TmyCcMO6h5lr8gNBxqtxmzbrnkIzIFRG1NdyS6AjeiIyscSOREcezl1wz0XOZATjwP1A3TIPWPdIdAK6cs92+AS+DJ/OAtwyBcH7FYD9IR+zI7n4UecdA0WbS80uCnmxsTFD9rB7XAfseuY1deh/wKouGj584dDBY0oOeK5NB6Ko0gwK3c7eCxXKS0NW79BXHRGKU19UM0ICGflWJz5+nMTHj8MbsGdiU0ZY5wh8IrE0P7YDAZmSUTMXhpnevdICxYjg63BTC7QvePVaiExzgZZABOAkOcylIBQ4El3pOWibHLjXTdDpO7vSxrG8wy8HoRPQuft3w5Xomh90Ib60HOCUf6M8dnCQ2XPOO/qCWVDy8jDDYZMxRuTMgixSWA68e3Qn7HruVdngth7o+Uo+5K/AX5ThQyDn+/U6RYkpwYOJd/jzcuK0Va5OolYmDUrPDtxeNw9VS3E9Es0Y2AzlT0dimlZcMeOowzhMdJElMFV0DDbRCX0ldQKWNYL5mEVKBslD89/c3DKmtXHdnky2k8Eh9G7VR1owKw7gykMIHlr0wFyFy1SpeF6MopWL9+2EL+PPADLG9klPnowy7ycwwo+3JZ5fNZbvR1yKcvGnRuLIydZZbMAA1if2xjrmtMAeNCcsgZL4LtgVHwbDDOvwSbOON+zM3Tpp4LON62OWCAJMDYbNww48CBFSrFCE2ITqYACOsqaenq47Gzau+WyQevtJ3lhF5VKUeeXNYCINO0dtEyfR90yZzC5CUm/ib2qqS4sUPw1lj9JcHDzUMrOl4a3qHIDrUlTJ1++9MeXGVBepZYGmMnVy+G4AnsqFp3KATmWN3yEaUVTvczG2ypfxZ0yPcwC2v+G792fhu/fxwO/e+080ycVHXjUdknHsO/NwtJrp+ddg5jj42Xpou6IBqvEzBT9qmrvkg9Dc0upZnRkd0BRtSSClP+XGNTh1l0M3rAhFnW92wPNTHtriiYr9m14+4kLKTpi5/B6U75/LNAgCwC1MjU0/SduFTDnzhemgtvwjyCJykalQ202NB5gpZw7AAxGUZ+5vjxnbh+hmZ+oH0nwPu1zNbSISx3xeshm1k9jBqs7DcNm+Ojj1kGlPfcdFAF/4nYJeIebOrwjJxUdcOQOK/jsE8gswNBEheYi059634ZX5L8Ax+LGkH/4Qrrr1j3DvcO/3MOwiFA6iXHxC+5oFMXSzkIlKhGIuCBZeluwTUXxyxGHGqMpFlSVQuEGy3Zy0pvjEMn/iRFSNAJwZE0UkKSogb0o6edmRTHNE3Lvf2rLJxTnvhQ5jbd1TG3es2eJb3q/+d+f3CwsnVBXvxVkeeiSMP2UBegCtq5NCCoC740sQmg1Gb84vYdTDQxfvhKsz8u69c2/y9qPjz8nzobCtKLAcvGdiB/z3H/dCZUwJGU/0OessfEX0r7CzoAiWT1sUikA0V0ycQSCg2IFLgKc/ebgA/huWwjryyDnFP+MEO4nkwfra1cOCzF9/yIsmg7uQrmPzMDqkTJJkqvmmeZ6ZzlXcwlPCKN8dRHZ961NVPepMLetNgLeNyuRytETZmQPwkCusonLFF5E5+03I4r1WzFl6EkTh5bw4dWXjbmeDn/davLQHDn25Dlo+25BV2o354DwoqivVNs1L5ifhvr/+Ao6rtEVbmDkToLra6PviaQuhsdDHnV4BBsmrsRgtxIHb4ohnxJFHoTTJe9EC+V50IEExw5GTxkxbsLQwv3gloaIKhtJMkP3JDkUzyTXMQi2wG5qM4qjBUYchHek9mGjHvAHv2PBSzgolDC2VMjFUZm5Cuk5Os54+VdwPiF2Zc4cv/OqyD9wvP22kxLBu2HdjDXQsd4xvnxFajrhsBgx6GiOFaqRLvvZp+L/Pf8nMeRD7OX06wF5rpMJXBwyGj01E8Yo+q8bqNJSYhuyVNyWv9IwjjDIeuBgJ2X8faG87unXH2vUaZOgnWcpKyysn0XuU+RyIeXKaEnV5G4elvOVYuPDMDN04RLjoJVm34SXW4RwHnga90SX6k3gu3p9GFVktqsrtZMN20PQFURcZeBCZtx+3rUOUtpP2wf4fbEJAz07ArMLVg+Gor1VB/kGXUIOTu+FPN94EJ8xcZnYf48HAmDEA+5zjolw6bgY8NtT7YDDBhG9hBuD4N757rWZucjerRmxBlJiujjwktsHmujrjY/dsfblRZ376QZ58FJ3gqZo3XCpo2dMYTADuoOuxWaFwMYmOEDsaSlgOkGRyf131Sub9kAPwNOmLjj3rcCJtmqo0K+3DxV2tUBzkfroWK2GHmyiNw4FvbIPWs/GhknC6xkBN57XHoOSlYVBUMxAKN3Lnn+5pbTCsaiA8f/yTMKHY9lzoIpRzv2Zx5klp77gpC2BHEQb380hWYyEuM1WtT1IceSJQYlocebA9+nf74fbxTXVvZFeGFWiGdDNPKqmYWbYLWVlFni9V+7wOuxmhfS2TSMkuxtJtPWw+2YdkIvFQXc0qVKjkADwsLY1yZbOWzS9IxF7Co9B7F6bdUvQVBOa+vezDHb5zB3t9mbvOqLsntcE+fN6sa463aZ5OXUHzTIfp8AJ+xuDHki65BOC223yr2x8rgMXTF0OPTSTiVhAdIYkPT3Glp/yRRyNU2D4SoaDzyNjDe97u7xw4ct7L9yBAj5CKXm5XH5MqXwHg3s5t9EiR05RZRS3iMAhjfSIOTbuTEEF2R3f8uD2bV7+UA3Df7aWXAa9in0IZ2n16uftGrjBiDK8yTrLxINy6SpUw5ahM56JDKB+vhfgY10e8IyX+ZFR/rMJPCni/8QbAggXabZFVyocmz4MDBYW+ZQwxGANswYExRZtw82YKNRY62pTl+lihMHoz8YHV5tyIBy7aOgKiEBYieO9CscNIHldRiKW47Qg/AIU82wivqwop7NpMY7YyY31iXwziwEmi+IS8IJjHW06E4rtl9DL0WeceJ7MThyH5yb4Zh+ci/3b7zjW/60bgHdPpi+us4IpuOacBmr+9VW/iQuYaD+PhNfykgDfRexzaeDcGY1TpRc2TJ8+HzcXeFzkhQBHgo4hSxDzLl9DDADgLUp4UVhXSu1OuH4SK9sNt/VmEEptQuWw9ss1VfI0J8BNrURrzyeXArVBsCk3xC+thyYNSZQxI7bL3PGis27ByrNHPkOs3VyyFAicWVMzs+i+e3Mf3N+KE4cZTxhjACsUPoINy+k707jmqE3Y/sBYSY7sjn47BMBg24icFvKmlb2GY5p/+NHSb/xs4HK4omwZ78525cRn2VgazkigjH1sIBOBKL5lIQDwdZ7FeNNg8ptnDV3jyXuzo6fy/vZtexWtG/0nkaYkM9rkMr8mOWrwuJG80RuwYAeiO0UwUMbnKrWeTColk/JH66tVG1PuMHRzZHFTfaWshXtGK78YF8qm+06doeuLDNDs24gbEfgDu1WNXM0aHQslYEpqv3AKt56KSM6JUCIWwAT9T8ZOS3noLYM6cSFp6o2Qg/GT0JHi5dAg60ZjbVJVzkyOPBHRDwYUgHEOW0IkDl/isdhBtu5n4xEJXDZELJGMHOuOd7+sPQE6elgPyijaQqbdBJ8FdGxcMw+lJBAJjlv/c6scSldDjFhrJxDutY0W/1NPTfU7DxlcMy7ccgGeA6uVVyy9Fwt6EE58F2wj9AQQBP/1a3UUe7iIUB5MVW4OeXDhxUS4ddGqzfUUzxuZ+J8iQHPMWYLQWEpvMwU9KIuKOGoWxbfen3Y69gkOo6FyLgP5m8UCoQRHLY0PHGBYQFFpWmheya78AcJPTZN+mEExy7ERIN8A3tHqM2NJkUcw3gT6BfyJvTV3tSowNCdmx5wxBXfK0xP6jp6XwUFVk/Sw8gQBINf6MYSZoX5e9AeDysMG+HO7uGYqxaNB2naccgIdYEDpFxs9Y9v5YfuwxJPBAnfyZzxOGhxa98kH+oNYmWhy4R5thRD7d4ztg9xNvQLLEP9qh01wUQzGsxs88/Dimj30M4G9/y/g0NucXwJxpi1loV1Nuq3CKhiMPf5CZ5XHY5QTgzPLCBvjmKpG8vixueiRysQMdFlxmjlz8jp3VqyZmfPAhGiBPy6KCkpXUYeldSX2XXo2WKiWd2PNDnG52px436xNWD5YhekpoVf5qmLTorF03rh/P6nhdzUuWMG45AA+xKHSLHDV5yZjiovzv4j75PC4FfxMD3Ypt+QzRnPiLjnNfprhxtWtpiVC8ANyHgXdrtwdjdDfe/xbEyzoDUXoEjIB1+CHFpWN6+mnUQGKM2yykvQjgC6Yfa7GhMBBaOKAwzBaLwC7LJZEJfwZAiAYMwNc37eQ24sKKg3l94qvsybzWnXs2lJeNnjsultf1Dfz6VOzkKPyywDxJBChCXjdWQa9dP96V6PppY+2aLZkh3aSS8spxrRgGN9/LSspu886wmMBYnH1yP6UyHgyxeT5NJOV1UP38EAmSMIzCdnzIYZJaJmAVQZrL5ZUUKJ+9bEReT+wqvKtejtMWXSBUHwsTd547DW7cfni4XCk9uWyN00OLSw+xxCimStOt1dC5VM8Vn0wF1+BnJH5cE3lb7tkTojfBi+xG5eZiDITF4BMRwOCLDe5RoE6q1IQ1xvlqkdn4Q5Wxy2/dOXDZa9Vzk7P6SbTfzGOuqtYYIt7cPEJadXei69SIgZzsvSl+wXAjrgm3EeR0ELcIBqaKGIW/c8YB2TDZZKIXTlDz1Sp90HaaZTYLXtvQvkcwLx6TtyCAX5YD8OD7JpISZWULS6Gk4Oz8ovzbcFGVhK9UsNryfmw7hoVVqrlRQzakgbOuNetcFT27FVJsY4KLs3yQSEbKzYPowdlyobdT4XJYDv/GD1mduKYbbwT45jdDUjh4sb0oD5+Pjj9s86MSU7rUS2Wm3YNQbYG/ICNlAyYYsau/5Mg1uiQ5cLnsyKJDgrY9DoufSMbQntJ8J+B+lKefh3WRVWU6idl74wi5u7myP0wlpk05yYnADx7lJmsBcbGj0tkXYQdF/cjvKBq3bduzFo18jgPXpOikSSeW9Azo/H+o8JmLRWaLYm8n8pLrCtqL/4WERRMr/VQ+fellefmxm/ia4Oe6isecoeH1sUmymBA4T5vK59hzRMdzm2MMahfOhqSpBPLN5wfwiubePiuyaPtxzdB0c7WjXPxkOBmewA/Jvl1TE0oBKtB9viPQ1OsvEoec9ciBL53KOXADwJ1qtN3PSeZNSGbEUGHLiy+wdGKnWBWdoq6wBwKTSCRfQDvn96RBJMPemwOxcE4yOG/JXaf+6Sb3Rtd1ltnrcEyjv65FVSYID98dyH1PtGfOAbgG5Zm7fDzvPtTXVKn2WeY1KLm7K578SOPG1S9rVGdkGTZs3rDBYwc8gytjAV3duLVAsCmxcjip1qtRceMpIOgBkF408AVmUdiPy/Hj8HXbiQ/phj1/XA/dsw4b3f4ofBT+gh+yOvFMX/wiwO23B5nytPOSCGXR1IXcyA05cDXsKauc2Q+mNpPE3ydtHLuxWkICLtfasRNAiLlTDwQGocqyFjwJ8iO8n+rjBuxfzAQyuaW+Zdsx0NDQFpRgpr03Z4mMmDGCcfDzMZD7yb4NVU7cgboG98UlMOwk4kyXnA6ffe20XiXd6M84JM5pqF6VEjgvGFoEpWb/z49ytBXfQq7g+7iqCmgxsAXBOQU5P8Yo8Sr5UrKl+wMNDa8FWnjl0xafkFdQdC8C+HiSa5o4jstNdfNiG0EsMbEBnAUFJndl5a+yMyFe3L4usEYF0Dojprk89IV6OPjVHXARfn6HH0dHDrWyNWsAli5FwAxn1aLTL6c8pMScjxw4WZAwO3Bx3/cUnVAfae0IwJf1psWB2/QvqfMlWIdAPAmHd/4oQuL5uupVJwSh0+iZS6aXJPNruL23vLnyGkwwVEHdyoXzfOIQMjWXok9cvKImHbGVPb+QsGsNy9gryUTXjupV5KKbsthyAO5BytGT5s0rKS59FZEag6cLbkfKypgZlRXEiZioaOjp6omftmfTK//RmiUzU17FtGUXJgvzbkEupDQT3HjA/kSfPYAcx5cD1xDF+DVnP0xGHD0Inv7t/TByxHD/sS9cCPD66/75Is4hOXAG4FLuJnax+cCAtVFpMqi+4GMB3DAcODbBRXupoMbk4IwrN5O8rXLGVAC1YSljBVlZKtHT86v6jS9frkvCispl67A/x9g9LblC1RbnxaNSO4izF5CUcZrHTEj4lAy67sCSyYd3VK/8uFP2kD3Qbbkf55s9u6g8PhRd65IzUrgxsXGY0MMZxJGBSP5tZ+1qCvmorZDBec1vyct/7Poxk069f9gYZmUQBTce5Sz4gWJqAAl1F+uzY36cut/31KpfHqdDonRACfzkuivh9A+d5E62O+8E+GzvPMxOSswFqMSkF+KdgMZpQ1sA3AKqVpGHLshK5Qy/jZpzmmKpwUDeEJpoLUNzTLzqvQebJ3Xs2rDdr/Do8gXTSgaV1LIjRSgi1e6pa0EFczdGwZB7Y4XE9nIA5yIR+TqOX5/8vnds2/5LbC/R1TOjfsvLG3MA7kdR5fsx0489rSi/4AnOeXMwsJziEsSliZGtbpH/lZ01q8lLzRfECbwxH3mCnE5VbSksgQsnzIKt+GemlCdsa2lwsnJoflxxAPL6Z/VTUmr02w/AvTqxZNE8+M1N16Vy46S4LC8H6AxmS+4/YL0c9bFCWDYdlZhi3VnXhjM/Rt6aBPgsCbrKtcwP5AAgK2XsAXU1eqMzc8l+Yde76mpWkjOch6dnWWlF1cRmdHwuYsy9zdPSVxymdk7hUOivXBTjbiOvK98PyynjraoeH5K2BZo3Oxy23qDz0e/yV1Qu/SPk5V8o7UTlGne6irkBLAPxBKyur115nBeI28FbJdbjQ0bC1/Hlli7cgFFNli8X7TBb6YJ3uuXtXdKpTwfAvfIUFBTAt752MXzhQiW0zfEYq+zFF3ttPTMAn4FmhAQuDHz9E43RCH7ln90zB3PBFwpUt4ye1klGn/3tzNl5Qz+JZE19zUp8VNQ4adSmU+y9VaaLMhqKTEWMorN+qKwMemUda3ryffuc2TFFpV883nPFztqXf+5Ga535T3PK+2dxjJ+wFi9OcwyDfrlj2IrgG4cvAi7mcBKlMI00Ob4lk3/ZWbvqbCdKeIG3zN+G8s4zJ86BDQMGekoovCjNuW2rYifKmdEBS932dOqKKo9On8rGjYEH7roFJj7/P4Bze/dNXwLw5QjgTtDtxBQzHSu5y6tKOUfunVPCi6OkV2hMRb4qOkkRhdvxjt9eNbl2Loqx8s09yfgDDdWrbUHi8E3Lqkm7kbUZzA4zG5r5rZEUELefiExcIsRMUo7uIN/XWUNB8sh+U/868g8M3rt+vetLJTkAd6EsD4ATwwA4pmbaNNbmhaRyhMupTYsAe5W0CLq7ek5q3LLmGfU7HfBW8986shxuHD2BLynWLyXsvJxJsehUOWCQxWPrnxaHF7Z+t3J+G48DjT8g6CquXOWgCsdGz2d9Z+8O+NyeHVEPN1B9JoDbMJJx2amx09gr9jgObw5cj6MkAGd1ab4e5GTlEmSwrFdCG4rznexK9kxtrHllq6jDeFnHWA+SsxLrw+DEQ3Desp9cJCNPNlajMYQoxSfq2SHrxZtHHYqPJnjRLAfgLtTBBxq2I+MyQQVpO2jbi6o2p/bv8CrWg/JwculjXh9BwVvWV4PvJ35k0hxoyyeReWamL1O240E2r19eHXDWAXm/w8Bex/y2Q/CH+g0wMt47wffIkWfFjGMt3oJyDE40Y1wz2X87cL8SIJ0eJDABRcAwD3poiG1SxBK2U9BpftIFPFQs1uNbkCgPlpw3IOdtjSlicq96cmvXdSaurJw26j7TO+xsxyv7p58djL3vqLu4HU0p0dnAPWUGAfx2Xz/4HjnwfyFbfYrkccUMsD8MbtsmSrFbBdiHiSdqR1d357G7t7xGsU0NhWVQcrTE8uHUSXNhG4YW5Qav0UyjKpWMqsagh4wO6Ork8QNmlea69fE6AUqScbhx1yY4/RDFY8puOpSXD8dUov25gwCcX/Zt0MFYSOa0yZNYK3aLEbm+vUQdcn3LPaA38ugAj7jwjpa2BSWDBzyNCkvmJs+VjDQu3huDexXbwv5v1z477CPVfNDrsNOjQ7BciBXJeLLzqIba1zwXWTT7NFjf+kXu8ZVLLo/lFfzSIgNnK0QsFmW3cG4Ep1iIUvxk4pc21W/45r4dpJQJnaj5y8dNh0eGjOa7ky3k4GBu5bQC6etD9z3dgrqAq5/P+wx0OiOp7uVtB+HXO2uyzo1PqCLDptTkBL4cdJ05cFmDk6hDXRc8dni+WN/8G34OiFwO9383wEuLCyejAMiL4zrPZ00qsnyDe/Xgc/14HWNLC/Ecjx0jlF8OnLiUZYb1vjTor4gD5TgS8fjW+trVU/z2Sg7A3SlEXpioPEiaQacURabV1pRPvY5MnE8QwD+3roWjOwM5bDr2dOWAIfCFipnQgh56ckuZOE6HirgmiC91PTn9Fk4mvtcHXH/5Nx+u36WVj0K3XacxFyC4XbqvHi5vqssESRzrnIgAzp/htadUHpyBM64BLgN3AX2DfZVKO8tC5/bmgjewmC+6IGIqdx8NF67Ok33OTE7b29MylWQOTA8/KNgK6g3vS7Ym4/DV+o0rb/ZbVDkA96DQ+GnLPhEryPuLBEYilrm0Tdkb3ySpFXmZF5aiDHX9xleY8Xe6icSTF5dXwZOD8FaZoRnlTJbDvT3dzovyumAbpDldYNbJ55dnTE8nPLFlLYyJR/8Gp33Mc9AK5QDKwp1oZr9DUb9p1qQM3PE2oSxe+4v28lbJzOlIaZ6vKvE4M+K26Jy4cC7REZtFcY5hY5R1GXIRKX8WIxVjkcxTWvbeClHtnLf8SqUvz6PHEDiuUX6Oum9PZWJozjryD3pan8g2MrTdg2yzvp2XycIhdgq7RqKSn6yx2ZVJBGRXFQ8p5oWUTcggLaMULmLH4hX8rzvWR0aAd0pK4TtjpsDryJUzL84IkgHZmcNuw1lCS5bvdw8OMWadKt0AXN3kxI3fjCKVU1ujf1ZNHdZVYybDvcPHOY/UNu2s30zkkfIFkxupzIf1dR4uTzaAQpjPMccvQ6Buypzt9q12LpyDuRC6sHYlmKmaF47i8jvZd4P9F/vJtPhSmChVDKEArevcOsvFlJuNFBXxTmfK+9JpXcUTiT07a1ZhkHn/FM0u92+nX+com7nkk/mJ/D+hRr+QBQQiay0FwBW2nI1TNSl0sxPn53kS/rz9HTihXe9xAV0iHkYzr2sQyP+O8vFOTZMvtW65b3UWB99+fU927scxW8arbH43GnuBvL2ts5t3w093b9adrsD5thcWv3P81IWkQ2GE96K+yoG73XLU9zFlPG8Lryg8G1msFRaQVhEZWuS3qboEg4GhfrLXawKIv7igm50Spsw7TZ29woi4cd5sb/qsCZ0DKOjEyvlJxBOP1teu+qhOeZ09qlPPEZ9n8OCqkUPGD7ka4vlfQiMQjAxmhvI0QNs4+U2FpuRwXJ0YcKHcveNtOBHN0zKRnh04DG4dVQ5riCs3ThqhmjEUUWwEwSxa2JUwjStliMEGuQT4bcCgAB6kuwT28zpa4NFt63j87WgTvnoD48nRDNdUmSMoi1dlJJPARH8OHDi/SYrOKUjAA17yhw3IDZ/e5pbKfO6whqNS3dU9wE5y4mKFWSihHopGNwisbU48KqAaXLnor1XMYa5HnVuV0RlD5m0eDs50FXoVzdstH7vz8WqpX+STfe7pSXy6YeOq+3SWTQ7AdahkyzN+xtId+GBxBZsawR0YIO4gMjE2jwQ9cZXki5pFMIRPNzfC9Y1bIpGJOw2JvDkvL5sB/xkyInXH6tJAIGigzeFRd1T16HbfLZ8u2Ovmk+1M6zgM/0QQLxYv1qTbT1H+S7hmfltWtWx5PuS9yNhvhhPWrSyXIfWZnJBMixEOKhwUhXG3AuQELExMaLtWUv30nqZ0rFFcyLiYUNwE5JwaopmUG4KPQlOAKRePu3PequjSXddk49btHAA7NUx6yPmhVil+unRYkkKesPdMqQvw00/JMbVBR1nThtfQkdA/5QDcn0ZOOYrLK5e34cagkHBCJi5FJ/LWZy5qvkw4antFMDz7QCPcuDtD77uKUawqRauV8plwkDkCyfXLuS1poWKKRdiJ46F5CUc8Dh5pXoUjPRg0efsQnZ6ClkaPbHsLhiUicfx5A2djgRx6ReWKe3FBnaMIlA2qSDw3YnnY+s45WUwioylGEbczvnzlEhEHgOBAxe2TnITocHAki709JgN3CDOrrAOnA9IC1FLJpKwfe9shpijVdlwRCzpx4m43B8bPsZus3rZRV50hPklCvL7a+vK81y7LAXhIDCqfuuyjeYV56IzDhHviKsqVKuqJbVFiCk7HC8SXHj4ID9S9kzFOnIZL3Phn0fRwFYpXckmfAn4cuNv3ZV3t8ND29VCOlippJIpouRSX0KtqHchIbEYOdIrTEcTWIr0GhhIPSsAIDQAAIABJREFUuQ4ls035hSrHFKPIKz9x22R1wvgTxo+acnaxvmNY2s4Fy3z2w8Gu0JTHgMr8GqBoiBO4rDwVoMXv1T7ZiKoF4i7cN2cuuNjImnxuDo4TywVDXoJGk4b8LMWDtL6eeZvqpRyA69HJMRcGkH8cqf5hOUVSU61uZKcN4HTllQ1Q/tkdrfB3vHpHYWLoNbx7Meb4tajs7A6h6AxDNk0+N0zVRhk/kLVXHiS/X16372nrD0Oz0fsRxGd3mk+3BRzo7bhZU9yqx48/dmT+4MKd2AZ7vNMrYJQBFsobj05iFKuPA4cgrvMhcR+97sOPASlSUDl546BwkBNLUULKpc4Bcf0571R7b096uqC6IfKx3wQ4MfnhFXUAK4/xxhPxP2PIDXrYWSvlAFyLTO6ZyipX/CsGiVPIztYO4IYckC13ZcHLxe0hE1/c1gIPoXIz0yDeidvwirLp8PjQUWyTZiIJ3iVw/X6AmQ4YGwdmgF759cdR8SUaorIFuAZ+V18NJ7U2ByVzOxZAnQvscyo4YuriioGFhW/gd+IVdus8sgcd8JDm0QQ5Hsvn2Ng/GafOZb5Mdm6Lp82wTKwNY02TFRYyqdwyRZrzUUXOsrFULpz3w1gbjNt2B2UD0D35WW+ycn6Y2nW3hLG4zyuyfbVmkxGRd225c8J5Sqjj7uhKrNizedVK3QWSmR2r2/oRkm/k5PmfGVA04G7aHNIbk4lJxAJgDAzfBSkbwSuK4UcP7IFf7d6UUSr14AlxGj5b8fS8Ihh16UwoXo+x8zW17H4dU5d34IWmdQ/264HO9/r3Aj8A12mNwOOaxm1wUXODVnaR6QdIv2t9CuRPqFz+NtK8ym75QFxzDF3hWWRCJvvmeg1DjCJglDEhHMENqxOjTYH0qliGh6rlohZDmS8OB4GTjkvJLmI0lfwm+HMxDO+nWpcF5BUwd10uTl8wsRCvONU4xwXc5WGjuTf43tdTe5o3o2QSow8Sz2acNX6LJPC+8qvw3fg9UvuEBweOePqbFZX48DFyMWJhyeukXIQGqNuI5GUrPg2v3H9HJVhptJYMrAetgwCWrAZ4Z7bZoYIdxTDsx1NgwPPDaW8GBnMrd6K3gPvLmtEBcC8uXB3nZ/Y3wHWNW3WGfgg36VA1I2LDPPz3hfgzC3/G4o98sWbPgw+P6bjmR5MXtx+ODVHwz5Any9d55JNhDMSk0i3FksWLU6VyqHHDw6EA7Wq9RCeWvsu9QRgljWCUG6n9EpgNztuwEmHIaR2z3QIlqALT0wLFdrgkEnGUf6/Wln+zudNZQbk87hTAZbgIv30Of0rfO2k+bBlQaip3+B2RJUuoWcFY8PkzveHclJsxBO8/1m2A96LnZlRpF277+XjpbqTt75Dy9xbC0J9NgoH/wGBZCXlFxuXYj2Kr+NFKB5CdwMez3gA3h3P372Kmox6JVs9HcLk8jtXOwb9TbIxl+FPkN7Y31g6EH/1scs8rrw2OJZJkyM05WmPM4qTly5N/Z+V4FU5cLmJhXy5twllJ7Jg0t5OiGl6jbM+ByxX7gjMuNq6bWwGkz3k7EciD85Zjscj/DQ4/egWmfe2xAzAJtyEHfonf3Krf5wA8CLVseZHkR+OvSF5Fcb6hCxdf5YylEKerkwRmvpotQO3YpJRN0iZzeSj5lEP74LcNtWnLxTdPheQKtCB2A2+1fwTkw6+Zjhz5MNMSIQ2aORaVHGCIeoOCcIgmjCJabfkAuL0OH6/NZ3DtfBc7cA/++EamcxvboUMFyWOWLkQqFyCYK2IUBrPEcZKjDocCi/LQSRFp4q3BdUsQt7/ebumPCtSC+2Yu+S4SrCCcdwrJXeq008fCeeOeU22/jUMoagWmHUOEPJ7EUQfz9o1qqa521HO4zW0OwEPuaFwjk7HoOvxBQYSZ/o4Bpb5cXom/MBCZfalyP3LB0SK1m2hJsHfqFuWf234IHt0eXrm5ZQoklr8EMR3wVvtQUFcMI6+ohKK3BkUH5AG41ZDT5F4sRNs6AO6XJ+V77MdXMJLhN+3RDPOgFT8boBTo/bS000WXzIAn/4u3KVpxAjTkBZHA25BiCIA21yjnoJlonNaxDTHkGpYmh/wg4AiaIk6SlcgciuIylSOV7SqKTR2ZdxqUYuFj6XYsL86KzooBunp4iXZ4PH5xh9FhRCyVcAENY/YSiXZ8rKI0aPdzAB6UYnzx0U6gu68FvGVV38VgQ3cOw2BDUpsvFoJFQaSIV4JaqByLFip/CWGhsnUyxJethPyg4K2SKK81H4b9YiIMfPQoyGs3ObdAZBSLWJNRClR1JjNrybf9OHAFhIy+Ypnb0TrlFDMIVhzWQBMK57QCGumMed/+Api7fDGLSmjoZgT3LcurCninOlNAXIph2BccuO1iEXs9xOXKU8BLH6hDa60zmB08CvJ6EMv58I1efKJ2wTgoE4mHEMDP0plLy34MWuDdnh+XAnm/0MOITGzilu4dOgauRiBPiNfkTVm3ouGXzApVopz20lQrSguVKMDbMlZ0Kyl9chQMvq0cijcT42A6XZibz2RJ+Jg4e9MfVZt+nLWkjW4++7qJ4R36CbT9P5rsxH8PLfA57/UVZh9OmLmMiUukGEVaSVjtvlNN+VyBUnxBsm9av/JNTk4DsahtMm7eb3Phq3brVuY0JOft0ln7jcICooaMX9FV0WGUYfEJO1rYLZwceDpH+72+4zTnOQ48wE5AQpOJD8UoIA7cNx1A8D51wjzYUVLMvdoEiKlKoGxYqEQO3raRF78+GIb/cAoUVpN4JVPJUIsJAMhUO8716nCEfEP6G+641TWopwf+MXPt4UmPdZBVSeRp3opFsH8/+fsoYhRpMuh0M9DogZCsAMQR8JRY4VZ5A8/FbMbRnNHg1G31R0Vjo09SVOQ4DitnzS4RxuRxsYjKaLA7hsGD8BZkyGa55nXmnq8RYcTIbkNUT7K1fsNKT4bQbSoyt980Jr8/ZRHg/Tb2uSpov88ePwtWDTbd1lXLE6pLy0LF5b5ZiNzP3XXrYYVLNMOwMu+gY6T8hRsGwqhvzoDCLYFFed7NRSVr0d1hDr3R5ay1QMijH+PGdMK/HnkThg+LJHaKZSTXXj8Z/nDPWC5G4UhiBmxSwE4dgyf3zRevCc6GbbUpplHXNp9GAYsCeWwiYYuMXasfcoROHWXcLW/ITVwjxUJk02h3n5eSfN6EHlSa5pR6ZSg/buG/76xdiR7dwZNer4LXe0SVEOD9JA7qfWEHdvqEOfBG6UAG1kyhabu2SbGJU/1+0Qyp7DkO0QwzzXm70aJo3SAYdcUMyK/H1+hE3PSgdFO2XtCivZpf64zwyoSLbWZVK/ztXrT9LyVD6ejSzl1FsPS9iwTDgMCBbfG3GUwlpm9rymGqcroGyNnCzJr4yq1dsFUjxoqfzN3eFz/a+nHedqsTblhA4E60EGFzXYDaHLaxc+XR4GhII8GfzG4dDw8hOiEadHbGT27csvppX9o7ZMgBuA/VBHg/htlODUNgtcxHK2bDq6XDkOvh1yi7+MQuiwwqF//Ugd3wExHNcPtE6Fy6Gop3u9h5pzsW3/KIPYMeHAvDf4rGOp08QCmXkyseduJeyrggKTOVf/VtQC+DyRGFX+pBLgA6nLpnHoFSC+YegofueQsK+FOnkaWJKAdHu3Csj8LGIqAysnB5cyCOV+0RgREXBVjBmbP5LKdJQ6kDMq1bVIBzs0ZxJUCanDcbdSwJ3eM6oXDnAGFxI5Wxwp7dS9uqdIzvaauGRx4qpphF1THwv3ce7prauGNNqDCk4Vd1ZEuqb1eEE/Aw9vDMqHp56djp8NgwRYTuZqHCgEy1GDB74OW5OR2VYL8//NahZWsTQ9KxNolqvLEDBXDUZ2cz8YqqsIqq/j5Xjx+byNCMb3S/tOzYA3D/net1svpVZXx/0SWV8J9nMCa8ABoJ2k5zk9JN+0kmAdpmQ65GMrSIHmwxVnSV2X7kSofzJvBueOINKPvwAvQ85nMieWzd/tmJb3D6PlMsD6sdjY1DYf+mUC+6+K8i7aVxZGWMkvO2U+bs8tmwatBQgytxslBJRy6ezE9A4+/XQ9eSUGsiIxM56K5xMPxnk/mDAP0p+aFHiLH4cekqJ3zi8fvh7ts3hGjFuQiJUZaduJhzmpL7pqwGCGudLZbKJYlYsCzx4ppl/bIzSzoMidsna1IApiJ/1x5oFJx3fhJ2/u9VSIzuhopZyw3Rph24LXJ60cHA9t/qwESFBoBveCn0pghdUJvQ/TBjJsFbkuNz46vgPwMx3gg9lOxgoWJXdNrJaDW/MngQIxv9pvXsXXDgmq3cdqYPpIKtJTDm/GMg1lSYMVNCqZTSYHAjp4gfMMsGg54JH/pAE/zmpprI+jtx9jJ0HBF6GEQAEqU44It3ezbuW2Y2Xu2hS4Z4/JiJV4Q6UZrGRnEbS4fzTqB+Ydejb0C8HONxNhRAxfuPtZ1c0dt/p4qH2Ai66qpXslDAYVIOwG1UywZ4yyYfGjwKvjF2GgKsuYFUWaSccLnhpdxccggpYCXkkIYnGTYUR6uGQxc0wOFPNWLE6GiVYqEWHDoCkYKz5PkRzCxLU7nv25R6hPXWotYGcB2TPQvKJ+Gqb2yDL34uUARDV5qRGOXJ/1L4YEE1LhL3FnG5nDrm2hQybWYqK5qWdYp5VqXh7AbgQQeLrsTvdGEKQT1rEzq2uqe1wa4n3jRqHXVpFZQ+zcVKUvwR6UNUDrQzjGITia3owBM6TEJvrXXfDdkbGbIJ3nJ8TRjJ7QOT58PeQuRKFQsVU/4tlD5iV1jB2+rs4LUJE4N6YO/Pq6Hz+OgCYoWeIyT0sF9PQCcgDLxGm5zwg+kCgiVTEczQIFJZsS4YB+sxz63Dgae2n4Q//HoDnPTewLHEU7rIrFHet5DbOgvCS8soL7mvH8crRse5ewxlqb5gz8YtADtd7tuvH67WJijv3o8HYetnrQdh+dylEOsWERWFTspyZhh8hp4Fivea4KeZXAPxePzunbWrLwizjqhM0D0Ttp0+X06A94vY0aW90Vm7hYqvXFw6YEg2nCZTyg0cOHGa6ASyvIfP3APN39/cq2KVfJTpPIWfxLNFcPFl34ZudGCRm5+QnL92by5PA8zktZ195RBrozcmTvY8gBxX53BwyhNDAHriobVw9MzQr/oYFJqx4FjoaEcTF8kJ00vzwhrFQsaQsmbuMc8WolIdBy/uyJZqheLIdYsqHIEqAOfdM6YDGh9dCwmbfX3hulIY+8l5qSI9KfbRlMU5WaB4LUc5v41791V2NlXXhl26OQBny5ZJiUlTND0sIaMop1qoeAO4yW2miFXEFdaNy6H8LecI2XgUnQ5YRwG+S7MSP4tFjKaNm7bCaWddBB0dab0XGbAXvZxdjwV3vFIMLO2Bf/1tLUyc0JHWIP715HD4wlfp7QcBAexwdLZZDsPxGq//GNUrIWttPdchBxWRvhKua5sOIHFgcCaAH/KtH98NzT9wttIb9/4FULhrgNEjuwUKO3LkISKYJS8PTE8LFIeB7khDgWmyOGkthf5dGOeGFAg0u2V9YSTSQkUIFliXnOTixoLm204JUKTBieOi7njvfmi6BRVjWVRwFmEY69fwczSLwmumpqb9cMqZF8LepkCRNPvCdLE+6HDUwTvroiBAECgr64J/Ppy+t+b0+Uugg2z0ifsmjtj+jq+90wE4XsVVzVqLkJepXHgKbTy4boNz5xvAUWzGQZS/F5EsjsPON192Jv/hGFQsxgu3cLYx5NJsT8ljS4/H9fPAVNeIMYY4xOtq9V+gdxqEXu+Cr75+UUJw3ihPgIl9qcNkofLkIFKqcBm3RT6pnOLWRcGFyYaMXIMTbz0DxSk3ZPbJNknXATAA1uJnusslh8Zy/sVXwLMvrO5X9uJarvPK4tIFe698tARmReCt+eobg+HMT+NhyrhWDlnCcERrOzjJmu0FLTbhDvJlv4b8uG5eniO+ynXLPbP77rege3GLYzNDfzIRht5d7tkF8xjVk38LCTd7+MRJ+mICfR69QL8FX6Cf6kcDr+/f7QBOjzHQCyd9LpGFyhVl05CLyDc8N+0mWIaViqLglAuEBqRjatj+3ibYdwuK4DLIiQ/EF79ewc8s9gKYd3rs70/BN759PXR3Rx8LxK/toN+zszSg9lQfwP2VsrNntsLjD65Ny1vz4ksr4V9PjWLctwouPAC4gId0UALrSQjZunHYKS/7pNDcyWJDyssFVjsCo+C6SbwhvX57Snqg4XUX7hvrGvsBFJ9guAduDWV9rYj1NQ35t8G/q+NhNxieuDNe8pYd1SsvC7ru1PzpTE067fZ6WSTk77ETn+v1jnh0gCxUzpp4DGwq5sGhxKQbO9u48ikKNF9TQ6yHi/LEBsV/xEd0Qwtq5lsu2hk5OYjzfg4/Uuat00Br62H49EVfgzfXvpMxNbvklDLWgM5APfL4Az0fQdWMw/BvDH6liTWOLZJFys5dJYz7VkGcWuCKRbb6ArVBa5NJoak8RirEx4AsMuwUnFbOCz+ZOx+EjetmIG+aE9Ii3/X316FnqruuoHzOMoj1mHKjbHhgqsrb9vaOsqbtr1F009DpXQngONffQIrdGJpqWS6oysVVjs8O4CkKGAHUdq844zCwjSM+qgv23lQNXQucr5xBh03WJk/j50T8hEn/fOo5+ObV10Nra1tkOGvghAIYYfoWpow/KKu1endQrWvihHZ48tE3oaQknJ3/fnzsYdF7FkFPnD/QIR88NhWcCjC6xHPnS032WXnYAX/30sZX4UNT5sOBgkKDb9A6cALK3NUT5vAH9sK+mzyMO7rzoAIB3NgbwsQxZQb4OcEOIjZE0XEJnLoKWFmvnDd8wPgwPmDs+CBMkLX1rgNwnIaPI4H+wliKfpTeP2neO7XFpbOo1xQOlO8XaxCiFJm4wjVZrsfGaqIFyRU+BteD37Ud3wz7f1UDyQHhAIEdEPh5CD8fw086qa2tHb5/w81w/1+fCO34Y1xb0+mIUjbopg3VrE8jdngfc1Qn/O2+t6C8LJw1z84fFsEH754LhxBkudLcvKkxCbmCuKalheSCpc23NA+k6H55UIQR/v6x5Q2o6u6AFpTRzJmxBN+LJU6cbz6jSvtg5A3RhvJeMndpgkhg2z2+HXY/9bon2WO7C2G8CCmgAr95M+OrWCdpKTBZdcqjJ8nE3XXVqy7Qqd8rj14P022lj5THyXkvdoXCwkYc4y3jA/wVguyaAY+O+vOIq6Yx12dVHu4sSjE3iJMiyE85lCiKw95foePPCQdCDe5OuBMuwE9U6bkXX4YvXHo1tHd28JdSjIr5lhPGDQQ74ht+fQ9079fobNgqg3Hf4SxbBg/qhttvroEVS0M4a/0/9Nr9N8BJk+bB5pJSxbyQwJhoSmvOXS5M42OKO4qrjeE2R/R0wasb11hUKzsKiuH46QuFCE85FFyIqoob7By75bZplMe+ordxwzMY32SEtw4lf0MJjP8YOjN5TKh5roRUYDrK87lwKZHoCvUCj32JvmsAHCdjHg7+JfyJ+LUBjV2fXpa7cN9cg1Wsx58hefvyMZ7I0VC0eRCXKXLocjU1pKatehQT+vyUnFR1y4U74cDXtwdSct4AN8C38BN1ajvUAucuOAFeK+pfUxjUUoXPmb8SzRl7kvDtb26DL1wYwO3+OWzwRHO2/ocxei4vmw778wsEp2zCBAdqLm8m2QI5h6GanS1D+n1pMg7f3b0VzjnYmDL9z70HA+rfXwRlp8+HvMNca26KMER2KXN3lLEIUY7tXOYcMPZlaDfsQn1AYlyX79Ibev0kGHrveJMNkPRmt1F/2suCXOfkHUKW55V0y4N4ItG6s2ZVqBd43pUAjiSmWANv9UPwfgb7fDLuEbKWsXiIjvz6DBj479E8DrMMki/leMrOtgNBqpKTAzpXkDqLVNqPPQj7frdBK5bKZXAZ/Ao/kac4PsI5Zw7AO+/APcPGwrVjp+B1PDv8h/2GH2RsbCoCWqro1u91GzjhuGb43c3VenLx5djiqtRW3ygZCD8YPRkfIhmCQG0Vo1hyY0cm4M3ou41b4OQ29xvbODxTduNb35TGnbIACrahC4YEP8OhyJS3u9mKG/wwcfwopiEzra4ZrbAbPS1101h04CnycODRrccAcmYFw+wkXZPciz3xxCMNtasiCVGdnR0QlBoR5sf9gwbVgCyk8wvyETYVdVX0cPIUBO/v45/fdqq89IExMPJHUyCJDAd/Dkpw4ir3poK5Ym7I6zO5Ah2Ryp7b3/EMUXs+nA934SfyRGP4GMrSH3nEqPogvq144YRZ8FopMTKZWcYKlEQ+JK8KdbhvMXuG3b9anyw/dEg3/OG2DbDYSyn9Eyx5pf/wDsUKYE3JIHgF6d2IopAheKDO6TwEJ7QegtGJbt8Kbr0E4NJbrdmKXxgOI6+ajtEpuUu/nEVneTsaI9rc/WlZJEZ3QdP1mzDGT7AYMRUzMXys1CU5KDA5N0P9JftyTm35KDc7j9lXmutO7EG5FXfs2VsO+2ojMfnS7IHv/PTJDHSjw44RocwHKftkT1M6RYG8xyF40/uba/DH3UfuUAyG/3gylP4bbXk7UDrODXoVAbj591Qlp7VdrVgqH2+E5mvRcdVmN34KnAL/wI89NGkk5P7859Hok6w+U9P/Bg6Fr4yfCa30zJHuhvLplCrx7I0Nosvxu+azsOZJ+L/Lt8MlX3DAi/8gIVD2bdFgRzJh1kr2IQtVhtx3l0vQ1KK1A2HoLydB0ZohaHIozRXdzRZJ8d45twUOfGsLdM0NEReGPDAXLXUEYT9Gxk4ev0Ne3XOkSyADhHTd59U+9Mb6zMASSa0SFzdBTD3+9NajYmHH2Y4FK3GNEktBNqLapkajzp8JA17BMK3Kld0O2qZJIce7FJGK4DykkpQPgsvZ5Z8tZ+2GA983Y0tMhalQjR+KcxJ5ugbF/z/8oWe1bXhoXTtmMjw4HKc6pMjCqrAK+xaL2c2wys4g9PNqw/pdEj6D8W+u+85Ws3pywF2AP9FYjHp2+1P3AzzwSb2RxQ4VQOH6gVD8+iDI31QK+fhvCoPcM6kd2vGBkp75rZAYkp6T19Dr0QPzXvTAtNxOqX/iuT+9rlpzSQZd/tY2OYqDXTfG/y4K04RTmSMSwAV4U8Bfa9CNqKiWuXqInZiCk7IH1xIpXEk6GSgNv3I6DHxstGlqqCxK01pFgLciUlE9ONUGmV+bg6lh9+Q2aPzrOhhQWoKd3YO+lgMD9VMr86145770Uq2slGkVymrPr5iFT3BiaFC+HwVTzi0kjDs6+72AbC6kxhTdVkgLvHXZbxqehqJTJd6pH9wLv/5FLeShfxTzP84CeP8LOfwP/VN7CrOScRw6LhXuxge3WeKiEgbdESwBN8Uy07Oy5pJpxf+2EyiCLmeF5tqNCPB+QSxR7XJ9ICNFcpqNE4IvL8AK/DuNIdT8jPw8Bqh/ETlx1T2YLVURoU0Am507V60lzGiI7sqrZEECLrvuPLjijC9FT7477gD4whcC10v2xqdOngfbi80Ic4Er6ScF/K1bUk+DFQsOwH0PoEET6oQznVrxTK/EeGkNprFHppvUqr/8GPTARKclt2SRQIpMaT2hxnCbMxOJZPyO+urVwRe2S2dDAYQWlXohkwDvN7DpY3qh+XSarMPCixjnTSnJRD9pLfvhV0+FwY+gSEGISSx24zYAl3I/pwFYTQ155+wilfM++RH4wXe+Dvn5EQVUefBBgE9q3rldqH4ZmsE9NuSokEdg8KkMwDi7A0fgK7x3q24c+v872AS/bYjuiTa3AV3ya4DbvhyclhktQR6YCODyuTezLWcTRe++cLbaSfBiHK6GApMbGOzfc3BW6763I3vk9IgBcCQlyYopsiDu2n6VSJi8TAHv0/DfT0QxAtPUUN7fODft5MHJ25PB9rlYwXz9x1o+tW8oY/3Ux+C6a76efrf/ifftD38YWZXwXqCyE/cNHQNXjcNgbxGLSNRB+imx0ieIew1+IhQveD+7eTf8dDdtl8ykl/GJyaWr2ZLqUym2pRjKT1tk3QMskmFmu8pFKMkkyr+JyzE3VJrU6WPkDTcapAbpt8lzgUwG+1OygjebYyAJ5cyoBiFNDQE5D84800o1g92rscQNsQmHctYFRxd8uQKloFkoOY9fvhjuueMXaJbrF1jaZXTPP4+ugCehL7S/WZouff43cBh8Hq1UuvDd0Sg9M3vbUkXOjW7EPDu9qP/n798N16HtdtSpC0OezEYpzaZefR7FeVTDvzGtafC/xowSeGphVHgJLhOPwnzQuKsKATgaQvbsrF6F1IkuHSkAvhVJMik6smSlJifwJm9REgFFm4Sp4YD/joTYQW5zS+ZMKiduBLVXFGN2kyrp8SbtzVNAAcsOHTIY7rr9Z7BwXkAp1mpk1973PoB2MsKJNq1DhxSK6thOcTiEw1IY5xqTo/WXPkc7Aufa/DhwDvLu1pVU/nzkxKMG8St/DPATDdvybNDI3sb4ect2xbryxtntjKI2H5TtqsYB+PedGP/bOwB5QKL0ewDH9flXHHN6EZMCEi2C7BuxjuOZwlJNSRan5eQI6netovDNQXDUl2dCrJkzAnZlpVWxad38PGAQK8TKimsh/YL+Jf7kX//yhmvgzNM/qDeUdevQ3gYNbg6HsOnVawE2Fw1A5eZcaEcLFWNzsUH0jqWKZrdds+lauujk+8x+NDGMiBN/HVmQhRRHqm8iy18qZq44A9enYZHuLsXWnCFi2H3EL4YCM5H4IwJ4pCGs+yaZ9WlHLwS83WeXi/M4UjlvDiSL8f8UfT4rczL6CzOhBD3hTPA1wVyKVZxipVjtw90sVGhbxOAv99wKSxbO9Z7NjXiWLVkC0BzMk05ziViy7c4vhBOnLbSAeJh6+kIZHe6bLytv22YJLp840Ag37krvdSaa9aEYR6tlSF+gUEofumGVKctoAAAgAElEQVRHSVX5BxdsZm9ciRCcmTIftDJCGOALb3+N+w5O69zzdqSKh6yARaamExcMrbi0niTKVN9c6iX3+MWGwlLNlAQKXpxVqeHwq6fBwL+RpQZ6iDGtpfLSu90RwTBB5DyLXfZqXhU5N065iouKoPaNZ9xl4nVofHMsart2787aNOwpKIATpiyENgzU1JspXasVHc6aA7g+R/Ce1ma4p45UMOHSB9Cz86kPhCubhVI/GVk595bS2MB6V70BI5YiKBM+Aiz6JVvW/LqmZNHqttgbkSsw2T7U6kEfzISkPBW79fc+2DW3LpGd9ywX8P4efndtb4xlwD9HwogrMB4Fxpmw2I2rXmpCLu4kJ1RlfE5OPwUF+WihciZc9Y0vQ3Gx4oC2dy/etTGcJ4F4ltMe5MTfP3UBHBTR9rLcfFab0wF6lVuc2tkG/9i6FgZQkKgAaR2qPOaiJKyPJnqW56hhU+aPGFwyYJuTn63ujcYYn8vJaLnxKMTHt0G76qtXuQQTCE+1/gzgZEtJsUL6Q6IFNNEFvNNy2oli8BSi9qjPHANFW8yn2yxXQHHSWxwcDNeyVDm6U59KSorhh9deAZ84A13z9uFZNns2agBSQ45GMR6dOrYWlcBpk+ZAK4L5kZx0gMmeZ1C8Bx7a/hbMQjDXTeSwUztDN3fW830fWdXvjZpy7KIBRQVrLC8N2ULBZqpn8US8fmfN6oqo6++XAI6HH8U3SestuagJ6VEfsTLHIaFTA3YmgTTSJAaK/GQOM75R582GAa8O5XCtPJ3lZEro5HrvFwyLXPLPOeUkuP72n0N+mz44hBmLTpk3MbreJ9A6pSus2aNOI5iH38w9zEE06wmTzU8GTnU6dS0fOfBv79kOn9vvH1f8+eMATkAL0D56n2/Fng3FviUqKlfci7LCc5igkE1HZuBPZc4l/ePxxD07a1d9JswcepXJzAii7qWtPiQQvWdJ71r29UQOyychkZ9N6WgSSIO4DX/6lMpnJFqoDPgvdo3k4ixErYi5QX8xrE/4EvULhuU0OQT8nzxATiTR2x+HWQzPop34BRg/hcwLueQ+/UBWsh/2QGFh+mcvowPI1jJBpOCpPTwe5eI3N9TCCOTK3dIstPneQOYEfTOdh1P6Z+rahKrlh3DRYvzh9GjiPExrnYaJrji3W7t7Zu/f9HJ4BYMLbfsrgJPL+ei+uV6MXhHnfSoSGB+qckj4aDb+tk9GSpz16LFw+NuF6AypxBe3Abjd6cciC1c4G7tyU1q9nNKyD36zs8YelbZXpvShIaPhivHq/d+IGsMAPUzi2zkTQBGsNzoiFKrRK9+weDf8ur4GjmtLfartHXQ5mx05LAUbo0fudTgJzAyqbMbCUfmxYsINXLrWOZW6yygfL5Z9yqQCk23JyEiVpYqQ2NOwKbKj7uvpXCTuvS7gTRzBp/viAAbDYHy7bT0M2DcQPnnBZVC7aavRTadQtObviNUw+Vc/5SZVurDtEDyAVg/FARVmmaDbD0dPhDtGOfhYSPkCM75ReHS8ofA3IPnvTSL1rW2lC+BuHj9GeaTDRw7uhZ+jqSEGeDWGeyqaEfyTzAn6XqIrwzCcIOZcML5y2S/zY7HLZTfNA1Z/vkxRonsZq/mg8dRhd92G6ELIqqTujwDeH6xPrkbCoj+aQ0oCebf8C3/6JO3/jLfNTytny3d/+Au4688Po1k3WcwqIhW7JycbEPfulMniJETf2cLSEgFiCN7XozjlnIM8jldvpk9MOBpewQcijqSkC+Be+dTvhqAo5eFt62BGVzv0ce77c7jk/ijnsqJqWS3aYkdipivBnx3gHrtY0i2RSNSjA0/kCkz9o6cPrWgk3tewO7/oQ12yd+UPOKcXufYvCXQP7VNyb9nXD+LZ8m8Hic/d9z0M370OSa7IwCU4251+nJSb0lHTycyQ1j/GiIBTDu3DCHm1vS5SWYaOPg2FMlZ0H1llISUxQfSmukDPQAMr/jFy4g/duQce+WgfoZG1G4/hmvuI+quKyuVxjEAYCzJOv5FJVsWO4fbpQguUP6MFynl+9YX5vk9ygV4DQeLQC+0/CDPYLJR5CAl6lgd4X4Hf/SwL/QjcBL2msw8/Q1zOlo0oSjnpdLEGZYhMxbnH9NA0lZsWhRtHavY4nHCCY31k/hHiu7kdh+DR7W/3Koh3FObB8gWLYN+hyB5NCTwXaoF0ACdIWb+8Tt+3nt4I+29Iz3szLeI4FyYGaQYuLONKN3bakllFBQXr7Xdei1msqCvduN9Ujd3ctrM7uWLP5lX0MHnkqT8COIXJcRZPRE6eQBVSEKolSFDnUHpJGIXfk8thREGzA/XNN/N1cB18Bz9e6clnnofPX3q1GQRLcfBROXE1vripDuQu3V5cOIlWl7a3wAM7egnECbPxHafWCTE47uRF0Hygd23E/UDVb1IzxYGr7XbMPQR77n3L69VWv25G/b1FdEKVo/z7Tyj/ltwHYzvMGDg6zXNeO8iDa6b4JJmsr4k2hKza4/4I4BR0+uc6ZM9iHnQrZE+hkc2pc0rC7fhFZC9xRDm2ozCE+m786BjQ/fzmO+Dm39wt1Hn2+ClcyiLN51hkTgHyrL+M3RaycqYIS5UNJJFNv75uE3zmcFOUQ/Svi8D7FfwRoVv2NqG35mnz4eCh3gVx/45Hk0PnsHCT5HRVtULj/W+xtyt7OT2Pa+wEex/Kq5YdxhtiqXSJzwTo2elnmhEmdtZVRxuBsL8D+Jk4ANSq9ZlEXpaTcFG4uxUmWXxvCroVMlB2Zsf6MJLzTPzoplt+exf87GZ8JZ4pLDkqW1/8EdJBAnM0RVStUxjzw6IakqiFG9qZ/+N10fc/2VUL56BcPCuJwPs5/FlqbW3r9hI49eNzMUhi78ZNyQYNtOzLPVj6riltsOfPb0FiWHoPDqcxVopDPBOX1Xa1jvKqpSei8v1/ljUoMpgHkhrdnb5M3wDUAPBE8ra6mpWXpDEuz6KZOIwy1VdWLxJ9JP6RZfbMdUi0Wik4FT2g7J6ScAN++a2MEiZk5VUYjeAd/Ohw32oT9Q274cxzvgS7dqOoUTj9GIuWsd7WSHhGHBW2OQjw6SzjwG9PUhG67PABFlwpo9JoYrDp0V18R8IpvbkOvTXPOxq6usRDKpny3hPGyEHnIeS0O9LczzPRTyTTXdYOe/60HuJlnVF1K0g9/4dLK0W/VFG1oganzDTyl+tScx75bVJ3VqxHAhU9CPtHtVRXZ4wT6XcALkCc3PgmB5ndDOSlVUrgjQJAn5SEasxR6ZetN75/BB5Bdb1FYa/fjeeeg1s+9Vm4Ed+eTOblc77F8Gjk3Dd7e1Aw5By4hfyRWhF/dzIvlIrN0w41wW3IjWck0RlCj9d9yLv2Z19Ab80vorcmRaWjbvshWZDORlmXaFeLm7b1UUeEwvaeKhKz10FH88A4NP7pbeiembnY7g7kJf3TIlyAFhlO2dTFFfmFhdvJc0fy2LpQbG+D0dQv8LedHolkO3LfPMBQhlJ/BfBbkR4Zu5Zo0PoA5pmHxLNc1xzLJVnArcgeMdXom3aWkXiZ2YufUIv6x6hH/g4qPfHtykMYS+TDE+fCVnwJ3rBGYdIQwZEoYhPZOR0bcTIvpP/+VLce3otOP5GnB7DGs/VqfeSJ0XD5t2zemj52wF41M9ymDH1kB+qCvh/QM6DEMTVfvQVaP52VMMEE2sdgmyn+oOXIfSP/MMNpbOLCwx9jEL4L7LUmZUp0zlYvesSTyad2Vq/MaIDdPrJ89DaRzIXEJ+6bAqP3Rv9JfDMbG9bzPEEHNsz/SLARZif3LXALfAU/gVIcw7ssWoRCo1Sp0fnlM+F/gyjEC0/2jaOCtpFJVWw6OPoQiOcjJ7+hdjUMCNRRn8y/we+/GKzCG34xAX7ze5s/Bu5yDgJkDmmLFW1c14W6luWJMtpKsP675fYDZbVckLwdiw9C06+qMy0X/w2iwJftYxszddHRRYVF61S/ec5OiOugJnRIcR7Hdn+4UUG/qyOxZPfWVaQaz1jy71HGmk6vYpyGx7EGfL48q8k9LKzr7mAwQXDRpxK5zB/ETyDu+6mnAM44w/Pdyq+UTYfHMbYI2yYyoqHcM/Qr4cEZ1Ea8rLsDXtryejQ2mD/CjlwVbjrOvmA2rH5lWLjCfbSULvdN3dcBcDVPojgOB/5vG7Sejdx49Cp8EmMOxkWcYrqLT6etRs56id1VkjPbUskuuAcLprProoHVarAEHsVQeF9ajb1TndyQCFG/QO+0fPozgFP8s7X4ky0TAZrmE5BgLwTah0n4Hua/NlCZLGT+I3oZX4gfrUSPL1x6KcCDD2plv2zcdPjb4FH4Eg9DbKWMdcP0io04xbCkWJZppJM+PB82bs6oaDN470z9WeCyOqAsKw0C9mpHuie1wb4bNkLXHHdL28Adp2M4jxkIWNOYOQMrhg9qkdy3NGuVDmTS+omvTHcLFM598+uVPeqNG3AqivxGjH+S8WB1/RbAOenhu/jH90NMfJgityGxgsvd+yCAL0J9zxr8+CZawL/9LW4TZFcPpkai8yr/+OCR8BUEcobicpWpnA6JE+w24j6emqTs/GVdDXz88H7frjtmoAAHd4QrqpZCsT986GNzYUPNoPQri6CGIACcbnO6bTnlo991vOcA7PtJbRRiFXJcGOc0nooZK+5Cnfr5DCNkbB5agwkh66IvGGPBdSzcysQMVMYPKWYjJaoXsi8Xqyl5DKi3WQzxc3tdzUsBhXTBZ6e/AzjZdhEXjs+7ZDT9D2v/IBLL2cvSq+lk3xKhDIJBTHFZgh/PRC/FX3ABwBuk4A+XaIcdW0XG1Q7LjG6qio245Oz8PDXJ1mVtzUqM0B8wUYADUlpGuOLPPOcYeO3N3g1rowuobtQKyrjrtufJqWNgtJazdkPzNWhMFn4+PoJlH3ME8MplrXmx2EAJ4NzKiQKtcdwW0B3oQQdXc0IZVkLULdvs6Oget3fbmoxrccOTL+D+yVR2pBtplZ7Dn8kZaoPeGvkAEiqccWsfUmLmowT5Dfwcgx/X1IpXXLIu+dWvIiHnYwNHwFcqKk1Zu8H48GtpChfOxI/OkQulVcqpB/bCbxsDxODAV9yYuWAGghicf/FMePaFEZHQqj9Uog3gHuaGcpyJ0h7Yf+1maDsN7QKCIdFazD/PiV7DJs0bNrikFK9oCNvydMK6Y8IElElEAjamtmP4MyjROCVoSzv6RDLZUF+9cnw25jMY2bLRoxBt4Dzh0+pAXHLU74JQnachkcK//5WESVjH1hDDiryIr833HzH65tcw2OOhaE32ziqfBasoTCtdVcWKkzbiTp6a3BLNHcRJlvlWzSo9LpyMuPC19Eym2+4YDz+9aSJTcPWrpGMnZxuQLoC70cGpfHxYFxy8eCe0nofPt+kpOs/A5UFGDCmpvHLZT2Ox2DeJ3UYg5Vy2YBr8HJXCzp06Jvp7PAGXNNSuvC1sfUHK9bMV5z403NN0Zfol/nw+CAFc8pI0lmwVrkUCpR/goQ848niaDD79NMC552b0keHTJ8yB1wcMxGfakKo8YAoXPwpuyNEqhW08YaZn4ZqSMADjUq/e9DoMT9KrdS5pCf7+WfzJQnTY2k0l8KkL5kDTPtSpa3r5BV2nnKMMElIpaAv++YMAeJDzgalH8hPQdvJ+aL5qCyRGu0or38ClsMCtp2T7jVt2hsFlZxi8eegHbl1FCxpviT3IfZPzsNT4+BM1jRxHDIBLGiDVyCn6TvxxeF5Fi1IkU/8GEuYZrdw6mZJwE2b7qk7WTOQZASNYqFjHdBFq9v7wh0w0m1LnmfhgwprSIYIh4gqkFE9NQ53Ei5veb1ZpLS3cBH5+3LAZzj1EscRsifxeX8WfLOoZW1rz4YtfrYIXVuFDMEHQy4/6Udbl15bP94EAnKkBg0MMzXR3RRu0fmY3tH4SXx60ir5cuW/qennl8g4kfjFrN+PgjQ0yRsQMoYz/eBS9L7MWJT04ddNcANkqjouAXoAmA3/iw/xSC2agK9mtSJDVfpkDf9/LcvA70PTiIvsbE11dqPpF3e+mALLkwANPLXAPmhdePR6tU2h/MR7F3GiGxYDgaEj5xHIYLszOID69ow3+ja/EGDFTKHAv8mF4bmU9Edbe9OsKuOk27vDj92qLVwcz5a0ZBITt/QtS1vPccdGeGvXT+U5MbSwOHe87APuv2UxcuSf3LQA8KW95YU0egy4alSZdyfjk3dWrtwWtI2z+IxbAJUFwHZDGjp5Som1NP2SxQp4YpCGux5/nkAj/DUtA7XJJdpk/QTt/RBkdue8DGAlg8mQA+rMX0oOlI+CbEyotIhTCcSkPZxtCfHRBfFxHJ7y47Q0oIndNOpPKemFgSpPPPDscLkZuvLsbhbpHgLcmP4yCSYc8wT5gZQTGidJ4Y/JQ4dcaNr5IDgkpos2ioyrnHDVi5FqLGD1D4ix1dRmWinnJ9Ts2rDw6myvviAfwbBLTs60kHI/fk0VLVtOD8CA+EaQ8ElSPZ9acORisojmr/bA39n6MnVJbWsqv2EyaoogMxb+DgviYzk5Y+XcE8ahV2SEpVbNxAJx+1lzo6MyA+UvIPqVVLATohhWhUD/dwAkPBjIxaUlA3loUwW1FKN90uKfrrgGx/Ndi+bHRzFFHBlJLa8D6hZPoHIDkWVJfm1nXeXuPcgCuP0fp58xyWNn3wHvQvvI5s9/r1wOsWBHYKSf9gafWQHF4p1QtM12QacMpkQwlqDuCuO1ZNrnZycxw7Bh0uX8SQTyjMWj1KdLYWAgnnTEfDXv6/8MQLlIPV2L44b2XiMOrrFmOKxBZBEwEULZWUH4iRXGZsjpxGjB2o6duQwe6574W3FdEfzml5MwBeBrEC1yUu3ZR9OlTApcNWIBinZDishA/LGHoVzj1VMDXCQLWlLnsXxs7FR4eNkYomzg8SLdn1qoDJ842qce1mMpPnNgGzzz+Zp8B8dbWGJz0/9u7EjC7iip93uukOxsJZFWyL6QTCYYkDJAMgcggixAQmZHVccBv2BxZhpHwKSCoGYkSENEBRjFiZkYz7AOMMOqwSLqDLEMjId1BpLM1JEAwQRKzdN/5z13ee91599W991Xd5fWp/i7d4VWdqvpv3f/WO3WWebOoY09DKOcRc8jHI1lF4NWMort6BqZ7CLKW55DGbDYGN8h8Pv5vPcg+fxKyzz9ezbzCthUCD4tYtfUtO2sw+7GXxiatVmq39pyg+GX8HOw5qN57L9E552CPkFi2lLLz49FMxi6c32v2rsozLyzd6rkkjoTitowguyp+uE8+8R36/s2vU138z/G+c70H783z8/SZ8YdQa/8YzWI0rqooZByoTaBK/hPxmoM8Qdp5ewPAyycfg+6756jQ9V0bWs27z5f2KwSucZEHFmVhe+xYvSwI3CZgxYEwh2/Bz2T82IXjmNy0b7yfgOKMV/M8NR1jFNczE706X43d7l1zwzD6VH6MH/iPFjrs0IS/cbRjDjgv5vIhXkLnjjuYXmJTyrD6iBB3wv0uUwJgiMYaqwbhZpVVi+pzb7hM4MW0fnlTpvgV0cF8W0DgZT1ENcLaTZQQuClkVXIR5hpVkBWBvqyqGvTzmcjI+wx+BvMmvw12dAvwfnjbeDiGoMPzrceemqsGcXQTx/vS8cQskrhKbeIneMTw3dT06xeovm/JAWnVow0hgAPvsTVhibEPk/h5IPEXByAKaqkZZQixflUL7wTNL4egJNpzXHoIPJjli+11yWvGfW0F+aamAfIeIqzNsEIxHoGwtFMhcP13MZxECyeNjuPRpHANi7VZz70EP1fix7br5tCvj8eqios69EK7IyfNpo56dpl0PC9LSZy/Gkct99y1mhbMT8BcEmb2dhK99n1H7pE478S52KQTkXS9V1MaH+RAxB+E5X1uvtfUMeMrApiA9sQdobVn/Zp6HGQ+FZuuMo33Peqzmu12lh2cm6NVB46syAeVZ+KHHXXoLXisXXcdEccz8QxTM4SIrQ9vnOtE/OTHsYTEnQTI0cqiK9vp0r/fFK1x1FZshzALF4x+/AqT+JnjZ9Dv+rM2zSn2OYAXdMn9P16wASfMSpGutXp6Rp2nlnbqN5fqRdBlWzC5GGLtV/PCr3ZK+Z19+7e3P8WJX2IpQuCxwByiE8t2QeE0bMeCoA+FOmTSTtqZ4/CvI/HDeSwn4edz+Jlvm5bzc42H4POfJ1q+PERH6av6yKBhdDEy+jghxFmd4nCWd4AZZcSnnPQO/WCpoaTI5QbE5vXs+/u6erRM4qdOnEm/b0hZcgj10JU1VKTrCQhaz69Db/ft6L/dlyAqJ6JCsazt61ubQkc6VoJZoYIQeDXoGWyLhc3B6l/FVdkhHM4rdO65RPffb3A08Yn+27HT6VcNQ6iOY0K5JJ4PGKKu3CjPOG0L3fKtAGyqY4rtLnkHy5Zq98gk/onJs2lz3wYdI9AnowrVhjMI9c7arsXnHQFYyK+e/f+9rtzf9q8AMvWB5c7Ysl5HGjVj1mXlxpvANHXDVpvyQOBsaojswYpyzTVES5aoamXq84cGD6MvjpxC+T6uG08VKpTF1yPY1VkxHORy7BU+zQhB3t5NQfYBmj/lMNraJ/vOPmEXWtAdeKV6jgq8eFDNqqhqvrWFnYNXH/2uQBq1s6K2j9JOCDwKaobbYLFCmU1fV3bD9t2fLXGTVzbIToWtp9bR3HWH0o5dfW0HjajlwZ+9QrNncqwyg6UK8vZGtRvfNk6BOqWtn51IJtMl6K7amWTQnbrrJ1AGGSfJQimV+dc1CSzGcTYInPM+xVaEwGODOlhHIG824G7FVTlZMycangTDFc6gU0uFVyRHYscXCy6HHT2LtrzTP5JOc9rUD+kXD7zsJFc2VTSQd+nQLhndSI8hYmMSKgBTEFWUG5DtK7rW27pv1w7cDWEbxmdAx7w5PstOKzfk3baVhncL3UcrBK7j7mmUgXVwH8SdoRR5MfKl3nWXslqmKvBG+0FcC7uP+vAFc+jtLXBD9w1vtO8s+/TpokfvbaHpjdGTKSmxa0cNPrCMoDapJPu7w8bQrSPGJaPIVU5aVSHYjtqTokOFwrIKoYg9wa5jmGq0uj5H8Kw1iAMeexg1IXBdd1CDHCxCTg0He0DFqd1rrxHNQNTKDJoL+sLEwaeacfnkWjlu4Ux6/Y3gbujGzQe3Yax8XKWZvD18fgfLlAvg8LO5T32I11a4RVg4+wt4kBhOerDaugjc9sTkQODupMK87ION1L8W77535+jjm9c0sdFBrEUIPFa4K3eGdbAYNb6iHFKtHVxydPaXcY2vPPN/WzGCrvvGFOrq8teJjB2zk+68rY1mTDfoQs9WvtNxtSvvVNUVFo+cQP86lPPjamTZgGqLsIMPt/cOJ105ZFToctPNFaIVQi8ehyoKdujvbGxr4s1X7EUIPHbIK77JN+NT9UKYNs1xla+F8glM4n9wVdb4F2a6dWsd3bVsNLW8sh+9ua4f7d6dp2FD91Dj1B104iffo+OPfZ8aGqpPY+oLLaw2bVerN+ID/3k4+1w8ehq9i914ZJdNe7iupUYhw1F8cyjXU9Ddtz1ydpWvFIWyMDdU9pzAXNtwkyTOLvxd1u5pHW0vJPJACoEnu4YLvWOBQulJ65TDacX55nTe/mW8sNnzbbguytA8PgBLzAA9rI9/zNsQHvXyA6fSk/t5bgEcC9vdYdqHeC5xuTxtP9g9vDdNjVpFrn79htmxq/rwPkck2QKB2wHSDDOc1QnTwbXxmg6W4ml4eqaWTO3JxQI8BbN6RDmzhx4iOj22nKnK4YSuwCvuTFx8/uqEAslG2Uh7aRq+JxjUzAQB4qcHfIS+NmoS1AW969ENSuCMoRPYikMUO1xuCiro3d9E/O/IMYyC3G9Vnd61ClRoJPg5FuhX0f03lUO4806iSy5RVktlBc4WuAyX2j0pXcNvwcHyHPoodaZjWGuR+PM02IzvSCBpgYeATaj8j+J/woETZvttS67coJTge1qkFFQvSkV60CnYluc7rA+ssRs3Nm8N2spEPSFwE6hGkIlFtxTN/lHZ9IYbiG68UVktVRV4p/0NXP+Ay6RNtolJr6PlNIHO86jKRBdRZO6A9+aJEw+ldQ2cxVlKzx26H4kX/DUVOvWeiDrc7xyPQne19cO9nTO3/v45ToqeaBECTxT+YudYcOx5yR6YlUvWCJwdRVnXHWuUZBWIgT9fhOf1ctROOMe9/3gvHT2VHhs8IvCEqq5oOz06KoqopVIuzHIyVeoTblNuc+0lefA+dL4suONGA/c7REUVi2epaytk7ENRC0kbmmJN2lAJ5+h3Ierdk3ZlEcDCWIQP1KlzsqJCGQPXuHuw3z42kzeco9t+ARyFDNB0Ydpn8PMhI/dc/dEpbMcDbUHtPdJBtC3lSL5wsOkZ39gsX0z0VIqVF8rXtvLhkL4lLyn35fDWnq7cBW+1PZuqQPu1d7fT/rT5jA+Ljb0v2Quzckn/IaZFV2C7chPIO2UB9lTQup+zlfepeNA58bRapRVQqMFq7Lp92NjGuZPgx/IwwjjV6+RwbWrjqgBQU3hZAnfd6r2uOXN9MeSVZyPubysOmWiQa7a6/nzVxtdffK6qKRhqLARuCNiwYrFY+Huw2q+vvR05FieGFR9PfZhl00qq9/OmjGcQVfWyCyaCx8GhiL8NsVVQ2gsC4tAMPMT2uhk37Yg5RHVP4s/9LLC483Crya90kgXCdnerzmfpp4myapkyb5+iuaGT+Qku8IX8ffaOnKfaSTv67GkYjcQMCaRyCrfk0n9nws0n07WxuDZgAmOUk0ijI890+jO9hKwTnBUtm4Xz6ByBB/g7+P1XGZhCB8Y4yyNvb7wHNv5lY13eWgn6Hlakb1ct4Gl97XM4N+mBtyW1mSCsdto8SsH03+WdfCrtyovqFadtNysWsnYgqmAmwkIKgZtfg4F7wCL6HiojoaWiXHEFDmX2DEoAABAySURBVAb5ZDAl5e+g774bKpOsWZgU4WP/ykNB3hfgt7Yk0wbvznuQ/bGe5F0g8alzhvfJ92vBfFJ7+KoTGz+SL/v/3V15RQJHZh0cVMaaWScqHkLgUZEz0A6LikPJIiuxoqRJD34Dxvo11YBT/TmHpZoNsmPr9BWpHqkzOE6XPNaPvL3xjzj44EH9Ovd/DpvL2CPklWIYToHTA/2ACvggu3RPsh9xd9+B09sb1qzkjFipL0LgKbtFWEisw1ygHNYCVHn6aWU1YxXYrmo5aA/Z3DJcOKLJIZgFK37acaXdN5RdiY7CQ7sqIOa5cdPn3oKDzSt63YPu8+YIROBW12sbWpsDJxcPeC+MVOt199UIihqFYoEdA3FPKUU+8wzRMVw1gZIHef8CtHd8An3r6/LXEHUCdqideNa/i7/Z3jvNhSnpFDyw/x12kPVNQ94feen0/fO7omc2CttnbPV9dumqzbtChfJLqFAysbqFwGNbacE7wuK6BbWvVLZIIqxsHcj7addCWjnA1Fa4FcRtmwiCFcfjF2c9TntCysvxsPIZSbhi0Qlo8HjuwzyNOu/jVN9m7mzO3vSqmDPc6CPV9h1Cya68EoF3Wp23bGpddVWkzmNuJAQeM+BBu8MCQ9YGO+q0f4FdK33qU0RPPBFUbHX1+uGwsglHlbOqE5Nw60Ug7297Y8Az/S387SZwS3hk/t2vwIMaLVmuRWsgFvGHndKveQjtv3gS9f3DAG3Ggbbbum2Bp4FOQrwAfPXril2593HP34yP43lpnY8d+E9SuxpKBqYB8SxMM3tjxEPBUfz5a35jxdFvwxncHJj/vmE4QPUExOF7jQZSdkNv2N6VIO+fluKJ5/VN/HtCilfIJoxtHB7U8EHOLXsDwBuBfUrDC4Np2NUHUd3b/Uri9oVHwSHRqo4qw3caoUU3Tlcw+N4ua3rH2mbOS5v6IgSe4lsEEudDtf/CVVnZvX070cknEz37rInZWNAOb4eWOBNmVT4AsJngQpD3L3uQ90H491oToGmSyS+dCXhImcTDFz6pINujtHzBK2HQio/QAd+ZSLmdvIVmA3Guakfbc3bUHMCJ447bEop+jJGjEJYZib2D5/40uJD6WqSUMLj3uun5m8cAv551G1tXTggPdjIthMCTwT1wr1iQfPLE+tobcfnvfzthoPAVZGP7dkE7ELiPChXXIgp2PdWleoeqmie7xh8Nbni+Z0U8wKfi/z2sEpDg52fgAX0gUv/O7nu1zcOKkv9jHxp+2TRqeH6wFhJV9Zfqz7usJevbmtKuUitAqLy5qQa7Fw0ORM6B43+Ay39HxXiwaSFnrOfMPdHL+zCo+xJtoyUQwaqcrBbbQQfkXRYMEDiAojtSOrmH8HBGz9xh2aaGR4SZ24CHR9DQGyZTrVmrdLPxtj1Qi9ELS1Ur/HdXjuZuWrMyqJlmGHiN1BUCNwKrOaFYjLyzYm/Nz+HyT9O+bBnR0qV7afXqgNkm7TFzsrA78E2Z3clZtZBotpEqUWSHl5l+5M2y8bwGC+Fb5UAiNN+JNiPwcEbL/2PRPLRnfVr45xtqlaHXT6GBD42gXIXk0RHmVGhSCNEacnSVHHZCnH36D92it9a3rsyU92pICKu5bdJWNwJY0HMhk68puMbiYkcPPpRrwdUEneJakBQvyE/jOhIXe3qOwsV54Dn2BwdD4pgavOP4FyyGLXgQOBbLC2493UOOSx4T32yQd0X9NrDhNBPXxjWoEP2ch3vx7yHqd69q2SmXq3r55rf2oWFXNVL/VVgqmliiRIMeXmQFhg7qiamw/eYwspdsaFuJlFfZKZpuTXYmLCP1RwDPCOvb+eFn2+islncx8Bkg782qCYBQLkUdVkulqbTgoYyeMMCyD7yf0jWhunf60hAccg58DLGxrHxo4vVMDO23gKu+0DU2W05FYg+eDxPjfBWmgzMhMby1j9YJhRMmBB4Or5qtjeeAD0h5x6qOhpheFFgF9Bcgb3VYXn72iT6DX/enaDqssx+Oh/JPkcdkEVx0aX7k9j4NmcgH3z6OBt0/0latOAkPuLj2KVhAthWJa8XifMQGhtVl76k0j0rGi0F35Z58q7Pr9A1rm5ExPFtFCDxb98vYaPH8NUM4q1myWtowcLY2CUTePEkQwFT84nZpKQvxQD5a1WAsO9iVMa/Surfqaeg1U6kfW6yE3o8HnBluDMfqjkxOYRXiltW0vrWJsy9lrkTGKHMzlQH7IoD1fjM+zITrsM8kQpN3YedF9Af8PTEFy6M6qxPnjcTxO2Jxy+3T3o+GfbmR6lcP1EfkYYm3zE3bZ1eucNrBi2JHZ846quO15v9LwRoIPQQh8NCQ1VYDrG/29GR366yuhcjk7e7C0xDIig9dR0W2Oim+jWI/lK3raKD9l46n/k8MpxyO0CM543gxulWLEPVshYzGlYqsaecg8uDPsvpUa4QiqxD07nHjmWBnj0RjRldxB9ah7eFh1CY9+8KOLbDDSxXjVDU9Cw9i9bHILboXHf21qjMjn+/J0cBHR9CQW8cT68udLDeec6enBy/qRmxfT1tPUllHbpscKupEnk/GnHbKzVMIPPLdz35DPByc95Fd9bO4Dtja5OBqyLu4caWf4+8zE7qjvwX4oRxufMdp0ZP4bEFC8yh0a8dZuazRqnsf+ZUjryzPnZ/FVhAScVcO6c8gbRpjVWrdmDR0ofuPDG/onqRB6hDI8MHlDoA5UQd5803BE8z28WyBE3dSOE6NNhIPoR7TNUMWKBEX7mVjph05IJeru8mxRXGIOIfdNO+8ux1SepYrthEL6lQyL+H7Ve2uvMv60fq2XTAhfZF9ITJdhMAzffuqGzweBKMWC9WNzrc1xzZhO2+t4RfBCUsh144RHlNh7CfiAWRHKj0lJTtwTGYLeJgdxmjU5Hkz6uvzdyP9++FesCzdu3KP7znBfJ7fhu5vh+gLSed5OJ14cVy0cc3Ku/UAnrwUIfDk70EiI8DiPgkdh87ukshgi51uxZ+NIABWn2gtrK6FQI5WGEdGes7DOQ8dlg31Gnlilh1++NjI7fU1PB1odrOpHjtj3mTam/sx9t7zCwpyLxBt1F25wsKk9LQTduHvdVm5v9nUtpLVTDVThMBr5laGmwjWfhYSGZRO6iX8gw8sOVyAkQISPwCCX8Rl0qzwN3jojjY0AX4h84s5ybIdvOwbevjAA+cMzw+qvyqfz/OZw4RoNoiu2trbehd+O4eidnF1NPjXh9DL3LFr196bt7z5nNI7N0ngovQtBB4FtRpoAwJ/BNPgQ8y0Fybsa0HcN8UxUDzw/NWfQ7hyQCidBUHbiWOcMO5mimV/gzjOjPDAUltAyoFDAYxtPBKmj/kTsFtmS6gBuIr+Qd2OFz0tusPNtls+D8nWx3gVS+jMsrah3u1W3rp14+pm/uZWk0UIvCZvq3pSIPBXUSvtmbfZNf4YPKPt6hnprQFK4BfGIk1Sf4gH7UJNsvzFWEh45wQ3S7I0g1kjvfywOx9QN6j++FxdDiEOcgsxCQ66Fqb8EWT+aBdZD3Rt2/1ER8eLfNhd00UIvKZvb4VnXUPEOsPQ3Q75/wTy5sO+RApInFUp38R1Nq6wzwpblizHdT0a8ovIfMk4gfcEaNy0Ixd2Ud08mAZxpM0DcT9G4y444V4t6gCunKmoA2qTTTgkfXZ96ypz327M371IPYRdlJE6kUbpQwA78KpDjhqaFRPf2SDu/zQkP7RYEAc7+3D8ddbbqsK08sEkB8hajoeLs93HV9KhQvkVSPaT8U26d/ckBN5L739KVShsIjgf5M3xyFNZQOYzMLDZuDgQ1iG42JaYSZvJelXspF2KkpWoQ5I3khUg8LNSefNqcFBC4DV4U4NMCQTOZl6nBakbUx12avmYLuecmMacrm4s+ioGxCqfJMu1IPDFSQ6gN/UtBN6b7nbJXFNmRsjOLLOEvKtcjJadeenBKqVU23wfG/BqBUp7fwSEwHvp6gCBH4Wp/yYF05edt66bYMGu2kmpl2SZiB14e5ID6E19C4H3prvdY64gcdbfhkl6rBstDqM6OUj6M90d16w8izZibqMTmt9GkDdbjEiJCQEh8JiATmM3IHAOYh/Y6ULzHNja5CCQNydUkKILAYuSjG9+Gwj8Cl1TETlqBITA1RjVbI2E9eC3gLyznAUonesiWT34SSDwx9MJTG2OSgi8Nu9r4FmBxOG95h+7IrCgcBW3g7x942WEEyW190HAsrPSHxMzMk+DvBfE3Gev704IvJcvARD4FwHB92OG4UIQ+A9j7rP3dGfZWek5O32cZR4InBNjS4kRASHwGMFOa1cxJ3ZYBfJOOl5HWm+FvnFZWmO5qMa1BOR9jaqSfK4fASFw/ZhmTiIInDPRvI1rhOHBcxzvUSBwPRloDA820+I5tQ3RY7hMh5d9wu6D0+5IiR0BIfDYIU9nhyDxMRgZx0epNzRCJwNNTmMGGkMDrRmxFg3GXH6Lq9HQnDgN3WEg7w8MyRexCgSEwGWJFBAAiXOkt1dwDdMMC8djPkTIWzOqQcRZtB+qcXxz3XHC/xcyPy3kHeQmmKsjBG4O20xKBonzDpwPwPRkSid6HrKOSjIsbCZvhM5BW1QHcf+M62pNYm+GnGtA3sayI2kaZ82LEQKv+VscbYIg8i+h5RJc/aNJoJ1otwjEzXG9paQBActO5fY9XDMjDqcF7S4Dccdt4RJxuLXfTAi89u9xVTMEkXMG78/iGhRQEKcOuw/E/YWA9aVa3AhYdD66vAhX0G9Zz6Luj0Hcy+IeqvRXGQEhcFkhgRAAkc/iHTUujoPNqa48Qv8T/mZnID7Q+jqIW2+m9UCjk0qREHDOPDiC4UG4hrsXi2JrIb44xvl9IO4tkeRLI+MICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4Av8PmtVExuho1m4AAAAASUVORK5CYII=","user":{},"timestamp":"2025-04-22T02:11:57.947Z"}
-
 @ 4e088f30:744b1792
2025-04-14 12:38:12
@ 4e088f30:744b1792
2025-04-14 12:38:12Pouco menos de um mês antes de sua morte, minha mãe escreveu um texto com suas reflexões sobre a carta dezesseis do conjunto de cartas que eu criei. Ela estava lendo com a fonoaudióloga que a atendia e me contou. Eu disse que queria ouvir a reflexão, e um dia ela gravou um áudio para mim.
A carta dizia assim:
Ajo como borboleta que vai contra a força da vida ao sair do casulo tentando controlar o modo como será vista. Não percebo que tudo o que precisa ser feito agora é me entregar às minhas próprias asas.
Se a borboleta sai do casulo para ser vista como idealiza, o que ela deixa de ver, o que ela deixa de nutrir na vida?
Um dos trechos do texto que ela escreveu era:
“Você pode me ver?”
E eu me pergunto: será que tenho coragem de vê-la por inteiro? Ver sem palavras, sem conceitos, sem julgamentos, sem projeções? Será que tenho coragem de apenas ver quem ela é?
–
Outro dia, estava na casa dela - e o que mais me interessa sempre são seus cadernos - eu encontrei um que ainda não tinha visto. Parece que ela o usava em meados dos anos 90. Eu o abri e encontrei o nome Elizabeth Kubler Ross e eu tinha lido alguns livros dela alguns anos atrás, quando comecei a mergulhar em estudos sobre cuidados paliativos, morte e luto, então achei oportuno e li o que estava escrito:
“Depois de passar por todas as provas para as quais fomos mandados à terra como parte de nosso aprendizado, podemos nos formar. Podemos sair do nosso corpo, que aprisiona a alma como um casulo aprisiona a futura borboleta e, no momento certo, deixá-lo para trás. E estaremos livres da dor, livres dos medos e livres das preocupações… Livres como uma borboleta voltando para casa, para Deus… em um lugar onde nunca estamos sós, onde continuamos a crescer, a cantar, a dançar, onde estamos com aqueles que amamos e cercados de mais amor que jamais poderemos imaginar.” Elizabeth Kubler Ross, M.D (A roda da vida)
Antes de ouvir o que ela tinha escrito, eu disse que ela estava confiando na fonoaudióloga para se abrir e isso ia ajudá-la a florescer, ela emendou com “largar o casulo e virar borboleta”. Ela se sentia ainda emaranhada no casulo. No último ano ela falou algumas vezes sobre a necessidade de desapegar, sobre a única dificuldade dela ser soltar o apego a nós, os filhos dela. Mas ela foi fazendo o trabalho de soltar e soltar e soltar, até que se entregou às suas asas que sempre foram lindas e brilhantes a cada metamorfose em vida, e agora sendo vida.
Começo essa jornada, que ainda não sei o que será - embora tenha alguns desejos, com esses escritos, que ofereço à Vida, que já foi chamada de Glória e de minha mãe.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16
@ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16"There are two pillars in Costa Rica, education and coffee." A tourist guide I met told me this, and during the trip I discovered the strong link between coffee and the locals.
In fact, coffee runs very deeply in the Ticos' culture. So deep that the summer vacations from school (November to January) coincide with the coffee collection season. Children had to help their parents with the coffee. Coffee was a family business.
Monteverde, in the region of Puentarenas, is one of those places where coffee ha always been a corner stone of the society. Here, My gf and I went to visit a coffee plantation and discovered how coffee is made.
Monteverde
Monteverde is a well-known turistic location in the central part of Costa Rica. Many people reach this beautiful place to visit the famous Cloud Rainforest, acres and acres of pristine forest, with many different kind of animals and plants living in it.

However, other than tourism is coffee that pushes the economy of this place. The hills around the town are covered with coffee plantations and there are tours than try to explain how coffee is made.

Coffee Tours
While we were in Monteverde, we joined one of these tours. We decided to give credit to a smaller plantation instead of the super turistic ones. A more rustic and family-owned business, El Pueblo Coffee Tour. We were not disappointed. We had the show all to ourselves, a super-prepared guide and all the time to make questions and enjoy with no rush.
The Plant of Coffee
Since Costa Rica is a quite small country, to compete on the market producers decided to bet on quality instead of quantity. That's why, the only type produced here is the Arabica.
Before the coffee bean, the plant produces a nice white flower, similar to the jasmine.

After a while, the coffee beans appear.

As soon as they turn red, they are ready to be collected.
Interesting fact: between the coffee plants many fruit trees like mangos or bananos can be found. In fact, those plants help keep the soil fertile and healthy, thus leading to a higher coffee quality!
Coffee Harvesting
Coffee is still harvested by hand. Beans do not get mature at the same time, so manual labor is needed. Laborer use a very simple tool to collect coffee, one which allow them to have both hands free.
 Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Each cajuela is paid around 3.50$.
Coffee Drying
In the farm we visited, drying was perfomed naturally, through the heat of the sun. There are three ways in which the bean is left to dry: lavado, miel and naturàl.
- Lavado: The beans are peeled and washed to remove the jelly.
 - Miel: The jelly on the beans is maintained to give it more sweet flavour.
- Miel: The jelly on the beans is maintained to give it more sweet flavour. - Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
- Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
Back in the days, to peel the beans for the lavado and the miel variety, the pìlon was used. The bean is very hard, thus this tool does not damage it.

However, today the peeling procedure is done using a machine.

Coffee Roasting
The last step in the production of coffee is roasting. Coffee is put inside a sort of hoven, and is left there at high temperature according to the level of roasting that is needed. The more roasting, the less caffeine there is and the more bitter the coffee. Usually you have light, medium and dark roast.

Coffee Tasting
In the end, we also had a coffee tasting. We tried different roasting and different varieties.
Our guide explained us the best way to taste coffee and helped us defining the different flavours that we perceived. He also taught us the best way to prepare it: infusion time, water temperature, coffe makers and so on.
My favorite one was the dark one, while my gf enjoyed the light roast more. Of course, we bought some packs of these varieties!
Thanks for tuning in!
I hope you enjoyed this brief overview of the Costa Rican coffee.
Pura Vida
Tuma
-
 @ b17fccdf:b7211155
2025-04-14 07:07:54
@ b17fccdf:b7211155
2025-04-14 07:07:54What's changed
- Updated Fulcrum and added the new configuration parameter:
zmq_allow_hashtx = true~> diff reference, to subscribe to Bitcoind's transaction notifications, enabling real-time detection of mempool transactions. - Updated Fulcrum and deleted unnecessary
FulcrumAdmincommands after this comment. The changes were on Configuration ~> diff reference and systemd service configuration ~> diff reference. - New Resources Launched and added on Homepage & Menus: Calendar (Launchpad) + Badge (requested by a DM to 2FakTor) < ~ REMOVE the "[]" symbols from the URLs (naddr/npub...) to access.
- Readded project tags on the Homepage.
- Readded Broadcast past events section on Nostr relay in Rust bonus guide with a new method.
- Modernize Ordisrespector guide by @Unhosted Marcellus < ~ REMOVE the "[]" symbols from the URL (npub...) to access | in PR #113.
- Updated Electrs and added the new configuration parameter:
db_parallelism=4to allow concurrent DB background operations. - Added new FREE service: Hockeypuck OpenPGP Public Keyserver (soon will be a guide on MiniBolt to build it).
- Phrasing and formatting consistency on Wireguard VPN by @Singlebeam < ~ REMOVE the "[]" symbols from the URL (npub...) to access | in PR #109.
- Updated Bitcoin Core to the latest v28.1.
- Updated LND to the latest v0.18.5.
- Updated other services: NBXplorer + BTCPay Server + Cloudflared + Go; to the latest versions.
- Added new Remote access over Tor and Allow insecure WebSocket connections in Firefox-based browsers sections on Nostr relay in Rust guide and separated Cloudflare tunnel configuration in a dedicated extra section.
- Added a new Upgrade to major version section on PostgreSQL guide.
- Added a new Upgrade to major version section on Node + NPM guide.
- Added a "Uninstall Snap" (optional section) on Configuration. Although it is in the initial stages (1.4 Configuration), it can be applied anytime.
- Included some useful commands in the PostgreSQL guide.
- Added and separated Cloudflare tunnel configuration in a dedicated extra section on BTCPay Server and BTC RPC Explorer.
- Separated Wireguard VPN + Cloudflare tunnel + Tor services: bridges & relays to a new "Networking" category.
- Separated Login with SSH keys guide to a new and dedicated "Security" section.
- Added
AssumeReachable=1new parameter on obfs4 bridge config ~> diff reference. - Added new items to the Bitcoin Core extra section to Accelerate the IBD and Improve the reliability.
- Completed the improvement of the official MiniBolt Linktr (FOSS version).
- Added a new section to the Nostr Relay in Rust bonus guide to create a Cloudflare exception that allows incoming connections from Tor.
- Other minor fixes and improvements.
~> If you have any questions, feel free to join one of our discussion groups on our 🌳Linktr page🌳
Enjoy it! 🖥🔄🍓
- Updated Fulcrum and added the new configuration parameter:
-
 @ 812cff5a:5c40aeeb
2025-04-22 01:27:45
@ 812cff5a:5c40aeeb
2025-04-22 01:27:45يوم جديد وتطبيق نوستر جديد
أكتب هذا المقال من داخل نفس التطبيق اللي براجعه—يعني بختبر وبوثق التجربة في نفس الوقت، حرفياً!
الهدف من تطبيق أنتايپ
untyp| هو تطبيق مخصص للمنشورات الطويلة على بروتوكول نوستر. فكرته بسيطة جداً، لكنها عبقرية: إزالة كل الحواجز بينك وبين أفكارك، بحيث تقدر تكتب بحرية وسلاسة، كأنك بتكتب على ورقة فاضية... بس رقمية.
المزاية.. آو يمكن الميزة الوحيدة
ميزة التطبيق الأساسية هي دعمه الكامل لتنسيق Markdown، وهذا يعطيك مرونة هائلة في عرض أفكارك بشكل منظم وواضح—عناوين، روابط، كود، اقتباسات، وكل شيء بينهما.
الفكرة مو بس في المزايا، بل في الحد من المشتتات. التصميم بسيط وأنيق، بدون أي زوائد أو إعلانات، مما يساعدك تركز على الكتابة فقط.
untyp| مش بس وسيلة للنشر، بل أداة بتخليك أقرب لأفكارك، وأسرع في التعبير عنها.
جربته؟ قول لي رأيك. مطور التطبيق هو كارنج: nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
-
 @ 1ef61805:f18312cc
2025-04-13 22:40:49
@ 1ef61805:f18312cc
2025-04-13 22:40:49In today’s increasingly surveilled digital world, privacy and security are paramount. OpSec Academy has taken a major step forward by customizing TailsOS to create OpSecOS, an operating system built with the same focus on anonymity and privacy, but enhanced with a suite of peer-reviewed and battle-tested applications. These applications empower users with decentralised tools, ensuring complete control over their digital lives while maintaining the high standards of security and privacy that OpSec Academy stands for.
In this article, we’ll explore the tools available in OpSec Academy’s custom OpSecOS image, highlighting the new and updated features that enhance security, decentralisation, and privacy.
-
Sparrow Wallet (Version 2.1.3) Sparrow Wallet remains one of the most privacy-conscious Bitcoin wallets available. It provides an advanced suite of features such as multi-signature support, coin control, and hardware wallet integration, which allow users to have complete control over their funds. By integrating Sparrow Wallet into OpSecOS, we ensure that Bitcoin transactions are handled with the highest standards of privacy, all while utilising Tor to anonymise transaction data. Peer-Reviewed & Battle-Tested: Sparrow Wallet has been rigorously tested by the privacy community and has earned a reputation for robustness and security. Its commitment to user privacy makes it one of the most trusted Bitcoin wallets in the ecosystem.
-
Feather Wallet (Version 2.7.0) Feather Wallet is a lightweight yet powerful Bitcoin wallet designed with privacy and simplicity in mind. Featuring Tor support and integration with hardware wallets, Feather Wallet ensures that users' private information remains secure while offering an intuitive user experience. By adding Feather Wallet to OpSecOS, we provide an easy-to-use wallet solution without compromising security. Peer-Reviewed & Battle-Tested: Feather Wallet has undergone thorough peer review and is widely regarded as a secure and privacy-focused option for Bitcoin users. Its simplicity and security features have been battle-tested by users in real-world environments.
-
Liana Wallet (Version 10.0) Liana Wallet is a Bitcoin wallet designed with a strong emphasis on long-term security, recovery, and inheritance. It allows users to set up primary keys for regular spending and recovery keys that activate after a specified period of inactivity, making it ideal for scenarios where funds need to be securely passed on without relying on third-party custodians. The wallet supports advanced features like on-chain timelocks, enabling users to create time-locked backup keys for inheritance planning. Additionally, Liana offers a user-friendly interface with ready-made templates, such as "Simple Inheritance" and "Expanding Multisig," to simplify the wallet setup process. For those seeking a comprehensive solution, the Liana Box Starter Pack includes hardware signing devices, tamper-evident bags, seed phrase storage, and an inheritance letter, providing everything needed to set up a secure and resilient Bitcoin wallet.
-
Snort & Iris (Nostr Clients) For decentralised, secure communication, OpSecOS includes two leading Nostr protocol clients: Snort and Iris. These applications allow users to send and receive messages privately across a peer-to-peer network, eliminating the need for centralised messaging platforms that can compromise privacy. Snort: A minimalist interface for basic, secure messaging.
Iris: A feature-rich client that provides more tools and options for a robust, decentralised messaging experience.
Peer-Reviewed & Battle-Tested: Both Snort and Iris have been reviewed by the community for their security, decentralisation, and resilience. These clients have been battle-tested in real-world environments where privacy and security are non-negotiable, making them trusted tools for secure communications. By including both Snort and Iris, users of OpSecOS have a flexible and secure communication platform that protects their privacy.
-
BIP39 - Ian Coleman’s Tool Managing Bitcoin securely requires careful attention to wallet seed phrases. BIP39 allows users to generate mnemonic seed phrases offline, protecting against online threats. By integrating Ian Coleman's BIP39 tool into OpSecOS, we provide a secure, offline method for generating and managing wallet backups, ensuring users’ funds remain under their control at all times. Peer-Reviewed & Battle-Tested: The BIP39 tool is widely regarded as one of the most secure and trusted methods for generating wallet seed phrases. It has been peer-reviewed by security experts and used in countless real-world scenarios to ensure the safe recovery of cryptocurrency wallets.
-
Mempool.space Mempool.space is a real-time visualisation tool for Bitcoin’s mempool — the collection of unconfirmed transactions awaiting inclusion in the next block. This tool allows users to see transaction fees, network congestion, and block size, helping them optimise their Bitcoin transactions for speed and cost-effectiveness. Mempool.space provides an edge for users who want to monitor Bitcoin’s network activity and ensure that their transactions are processed in the most efficient manner. Peer-Reviewed & Battle-Tested: Mempool.space is used by advanced Bitcoin users, miners, and developers worldwide to monitor and optimise transactions. It has been thoroughly reviewed and is trusted by the community as an indispensable tool for understanding Bitcoin's network dynamics.
**Why These Applications Matter ** The integration of these peer-reviewed and battle-tested applications into OpSecOS transforms it from a privacy-focused operating system into a powerful, decentralised security suite. Each of these tools has been carefully selected to provide users with more control over their digital assets, communications, and privacy. Whether you’re trading Bitcoin, Monero, or engaging in private communications, these tools ensure that you are operating in a trusted, decentralised environment free from surveillance or censorship. These applications, trusted by privacy experts, offer an elevated user experience built on the core principles of decentralisation, security, and privacy. With these tools, users can navigate the digital world with confidence, knowing their activities remain private and under their control.
**New and Improved for 2025 ** While some applications have been updated to the latest, most secure versions, others have been removed to ensure OpSecOS stays focused on delivering the best possible security. We’ve carefully vetted each app to make sure it meets the highest standards for privacy and decentralisation, removing older or less secure applications that could pose risks to our users.
**Conclusion ** OpSec Academy’s custom OpSecOS takes the trusted, privacy-focused foundation of TailsOS and supercharges it with a suite of powerful, peer-reviewed and battle-tested applications. Whether you’re managing your Bitcoin and Monero holdings, engaging in private communications, or ensuring your wallet is securely backed up, OpSecOS provides you with everything you need to operate in a decentralised, secure, and private environment. As surveillance and digital threats continue to grow, OpSecOS remains a vital tool for users looking to protect their privacy and maintain complete control over their digital lives. OpSec Academy is committed to continually improving OpSecOS to meet the evolving demands of privacy-conscious users. With OpSecOS, we provide an enhanced privacy experience that stays true to the principles of decentralisation and operational security.
OpSec Academy offers consultations for individuals or organisations looking to integrate OpSecOS into their security framework. Contact us securely for more information.
-
-
 @ 502ab02a:a2860397
2025-04-22 01:16:17
@ 502ab02a:a2860397
2025-04-22 01:16:17ก่อนที่จะมูฟออนจากเทคนิคการสร้าง เรามาดูเรื่องสำคัญครับ
วันที่ไม่มีวัว แต่มีเวย์โปรตีน – เบื้องหลังเทคโนโลยีที่เปลี่ยนถังหมักให้กลายเป็นเต้านมวัว เคยมีคำถามไหมว่า “เวย์โปรตีน” ที่กินตอนออกกำลังกาย หรือโยเกิร์ตถ้วยโปรดที่ซื้อมาจากร้านใกล้บ้าน มันยังมาจากนมวัวอยู่ไหม? ถ้าคำตอบคือ “ไม่” แล้วมันมาจากไหน?
ยินดีต้อนรับสู่โลกของ Perfect Day บริษัทที่บอกว่า "เราสร้างเวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว” ฟังดูเหมือนมายากล แต่นี่คือวิทยาศาสตร์ขั้นสูงที่ผูกสูตรไว้กับ DNA, จุลินทรีย์ และการหมักอย่างแยบยล
ขั้นตอนที่ 1: หารหัสโปรตีนจากแม่วัว เริ่มต้นจากคำถามง่าย ๆ ว่า “โปรตีนเวย์ที่อยู่ในน้ำนมวัว คืออะไร?” คำตอบคือ เบต้า-แลคโตโกลบูลิน (Beta-lactoglobulin) ซึ่งเป็นโปรตีนหลักในเวย์ประมาณ 50-55% โดยในธรรมชาติ วัวจะสร้างโปรตีนนี้จาก รหัสพันธุกรรมใน DNA ของมัน Perfect Day จึงไปค้นหา ลำดับเบส (DNA sequence) ของโปรตีนนี้จากฐานข้อมูลวิทยาศาสตร์ชื่อ UniProt (Universal Protein Resource) ซึ่งเก็บรหัสโปรตีนของสิ่งมีชีวิตแทบทุกชนิดไว้ครบถ้วน ได้รหัสมาแล้ว ก็เตรียมเข้าสู่ภารกิจ “หลอกจุลินทรีย์ให้สร้างโปรตีนแทนวัว”
ขั้นตอนที่ 2: สร้างแผ่นดีเอ็นเอสังเคราะห์ รหัส DNA ที่ได้จาก UniProt จะถูกนำไปสร้างเป็น DNA สังเคราะห์ โดยนักชีววิทยาจะออกแบบให้เหมาะสมกับการทำงานในเซลล์ของจุลินทรีย์ ไม่ใช่เซลล์วัว จะเรียกว่านี่คือ “การดัดแปลงบทละครชีวิตของวัว แล้วส่งให้จุลินทรีย์เล่นแทน” ก็ไม่ผิด DNA ที่ออกแบบนี้ มักจะมาพร้อมกับเครื่องมือบางอย่าง เช่น ตัวกระตุ้นการทำงานของยีน (promoter) หรือ ตัวตัดต่อยีน ที่จะทำให้จุลินทรีย์ยอมรับและใช้มันได้อย่างมีประสิทธิภาพ
ขั้นตอนที่ 3: ปลอมตัวแทรกเข้าไปในจุลินทรีย์ จุลินทรีย์ที่ Perfect Day ใช้คือกลุ่มที่เรียกว่า Microflora ซึ่งอาจเป็นยีสต์, เชื้อรา, หรือแบคทีเรียชนิดที่เลี้ยงง่าย แต่มันจะไม่ยอมรับ DNA แปลกปลอมง่าย ๆ ดังนั้นต้องมี “เทคนิคหลอกล่อ” นิดหน่อย เขาจะทำให้ DNA ของจุลินทรีย์ เสียหายตรงจุดหนึ่ง แล้วแอบแนบ DNA ปลอม (ที่มีรหัสโปรตีนของวัว) เข้าไปซ่อมแซมจุดนั้นพอดีเป๊ะ แบบ “จิ๊กซอว์พอดีช่อง” แล้วจุลินทรีย์ก็จะเผลอรับ DNA แปลกปลอมนี้เข้าร่าง เมื่อติดตั้งสำเร็จ มันจะเริ่มแปลรหัสและ “ผลิตโปรตีนเวย์” ออกมาเหมือนกับแม่วัวตัวจริงไม่มีผิด
ขั้นตอนที่ 4: เลี้ยงจุลินทรีย์ในถังหมัก ตอนนี้จุลินทรีย์กลายเป็น “แม่วัวในร่างเซลล์เดียว” แล้ว Perfect Day ก็แค่เลี้ยงมันใน ถังหมักชีวภาพ (fermentor) ที่ควบคุมอุณหภูมิ ค่าความเป็นกรดด่าง อากาศ และใส่น้ำตาลลงไปเป็นอาหาร จุลินทรีย์จะกินน้ำตาลแล้วเปลี่ยนเป็น เวย์โปรตีน ปล่อยออกมานอกเซลล์ จากนั้นก็เก็บเอาน้ำที่มีโปรตีนนี้ ไปผ่านกระบวนการกรอง แยก แปรรูป และทำให้แห้ง เป็นผงเวย์โปรตีน พร้อมใช้ในอาหารหรือเครื่องดื่มต่าง ๆ
ขั้นตอนที่ 5: ตรวจสอบความเหมือนจริง ก่อนนำเวย์โปรตีนที่ได้ไปใช้งาน บริษัทต้อง ตรวจสอบระดับโมเลกุล ว่าโปรตีนที่ได้เหมือนกับของวัวจริง ๆ ไหม? สิ่งที่ต้องดูคือ โครงสร้างโปรตีน: ใช้เทคนิค mass spectrometry ตรวจความแม่นยำระดับกรดอะมิโน พฤติกรรมทางชีวเคมี เช่น ความสามารถในการจับกับน้ำ การเกิดฟอง หรือการละลาย ความปลอดภัย ตรวจหาสารปนเปื้อน สารก่อภูมิแพ้ หรือสารที่ไม่ได้ตั้งใจให้มี Perfect Day เคลมว่าทั้งหมดนี้ปลอดภัย และได้รับการรับรองจาก FDA ว่าเป็น GRAS (Generally Recognized as Safe)
แล้วเราควรรู้สึกยังไง? นี่คือ “นมที่ไม่มีวัว” แต่มีเวย์โปรตีนครบสูตร ทำให้โยเกิร์ต ไอศกรีม และแม้กระทั่งกาแฟลาเต้ที่ไม่มีนมวัว แต่ยังมีฟองนมหนานุ่ม กลายเป็นจริงได้แบบไม่ต้องพึ่งวัวเลยแม้แต่นิดเดียว แต่คำถามที่ลึกกว่านั้นคือ... เรายังได้กินอาหารจากธรรมชาติอยู่หรือเปล่า? หรือกำลังอยู่ในยุคที่ “ชีวิต” ถูกตัดออกจากอาหาร โดยสิ้นเชิง? เทคโนโลยีนี้อาจช่วยโลกในมุมของ ESG แต่สำหรับบางคน มันคือ ทางแยกของความจริงกับของจำลอง คำว่า “Perfect” จึงอาจขึ้นอยู่กับว่า… สมบูรณ์แบบในสายตาใคร?
แล้วคำถามที่ล่องลอยอยู่เสมอคือ เมื่อทางเลือกกลายเป็นทางหลัก แล้วเราจะเหลือทางไหนอีกบ้าง หรือจะเป็น...ทางตัน? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 592295cf:413a0db9
2025-04-13 15:52:02
@ 592295cf:413a0db9
2025-04-13 15:52:02Nostur is capable of login with bunker
Photo, note by Fabian
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqxfktwlm2qdkpxy556e4yg4l8p6v8930nfyzg7p3vsknk7krutz0s8znjtq
When you decide to share an app you have to know a lot about that app. For example the nstart feature that you can share your friends, has a "smart pack" and the app can onboard, at least following the link --> Apps-integration
So let's try to read and bring a bit to the summary of the thing. Only the one about the profiles, which you don't know exactly how it will end, you have to try it before sending to someone. the second point is that it says that there is no "support encryption, so it cannot be used for DMs apps".
there was an update of nstart, now it shows you
the names of the bunkers, maybe now it's too much, decide if it does 3/2 4/2 or just automatic.
So they talked about frost in the hodlbod podcast. I didn't understand much except that they said to test frost and report the feedback. Tomorrow I'll try to download igloo and frost+nos2ex
So I have to wait for let's say version 0_1_0 of igloo now it is (0_0_4) and
maybe there will be the version of the extension ready.
Sebastix also found it difficult but I think he was trying to install the server, which didn't even occur to me. Anyway I leave you the note if you want to go deeper...
nostr:nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qytkummnw3ez66tyvgaz7tmrv93ksefdwfjkccteqqs2wzkkx220e24revkpxmdzkqj73rnz0reeenjwgy53g36hlkdgurgrs5e62
Let's see if I can download the video. ok Downloaded. Video .mov
If you don't want to watch I'll leave a little description
1 Download and install igloo, from the frost page. 2 Create a new key set, you can generate or copy an existing key. 3. Choose the options for the key and now they become multiple keys 4. Created a group of credentials. 5. Save the two credentials with a password and bring the third into the browser extension that it creates from the repository, it says that there will be a bootable extension for chrome. 6. Copy the third key and the group package key into the application node. 7. Once you have entered these keys you can finish the operation (and you have backed up the other two) in igloo. 8. When it goes forward it finds itself with two keys, both encrypted with passwords. 9. Since it is a three of two, it just needs to activate a key in igloo and it starts communicating "startsigner". 10. Opens a nostr client and connects with frost2sx and writes a note 11. Shows the log, and says that if you enter two keys it can generate a third, invalidating the old one (I assume)
-
 @ 502ab02a:a2860397
2025-04-13 15:45:19
@ 502ab02a:a2860397
2025-04-13 15:45:19มูลนิธิร็อกกี้เฟลเลอร์ (Rockefeller Foundation) ก่อตั้งขึ้นในปี ค.ศ. 1913 โดยตระกูลร็อกกี้เฟลเลอร์ ซึ่งเป็นหนึ่งในตระกูลที่มีอิทธิพลทางเศรษฐกิจและสังคมของสหรัฐอเมริกา จุดมุ่งหมายหลักของมูลนิธิคือการส่งเสริมสุขภาพ การศึกษา และความเป็นอยู่ที่ดีของมนุษยชาติทั่วโลก
บทบาทของมูลนิธิร็อกกี้เฟลเลอร์ในประเทศไทยนั้น สำหรับกรุงเทพฯแล้ว เป็นศูนย์ใหญ่ประจำภาคเอเชีย มูลนิธิร็อกกี้เฟลเลอร์ได้เข้ามามีบทบาทสำคัญในการพัฒนาระบบสาธารณสุขของประเทศไทย โดยเฉพาะในด้านการศึกษาและการวิจัยทางการแพทย์ มูลนิธิได้ให้การสนับสนุนทั้งทางด้านการเงินและวิชาการแก่สถาบันการแพทย์ต่าง ๆ รวมถึงการส่งเสริมการศึกษาของบุคลากรทางการแพทย์ไทยในต่างประเทศ พูดง่ายๆคือ ช่วยรัฐบาไทยจัดตั้ง "สาธารณสุขแห่งแรก" ในประเทศไทย เมื่อ พ.ศ. 2457 แสดงถึงความสัมพันธ์ลึกซึ้งกับสาธารณสุขอเมริกาเป็นอย่างดี
แม้ว่าการสนับสนุนของมูลนิธิร็อกกี้เฟลเลอร์จะช่วยยกระดับระบบสาธารณสุขของไทยอย่างมีนัยสำคัญ แต่ก็มีข้อถกเถียงเกี่ยวกับอิทธิพลของมูลนิธิต่อทิศทางการพัฒนาทางการแพทย์ของประเทศ บางฝ่ายมองว่าการพึ่งพาทุนและแนวคิดจากต่างประเทศอาจทำให้ประเทศไทยสูญเสียความเป็นอิสระในการกำหนดนโยบายด้านสาธารณสุข เพราะมีคำกล่าวหาว่า มูลนิธิ มีเบื้องหลังที่สามารถควบคุมกิจกรรมต่างๆเกี่ยวกับสาธารณสุขในเมืองไทยได้ (โอเค ซึ่งนั่นก็เป็นข้อถกเถียง)
นอกจากนี้มูลนิธิ ยังมีการร่วมทุนในด้าน "อาหาร" ในเมืองไทยด้วย
ในช่วงปี พ.ศ. 2512-2513 (ค.ศ. 1969-1970) มูลนิธิร็อกกี้เฟลเลอร์ (Rockefeller Foundation) ได้ร่วมลงทุนกับเครือเจริญโภคภัณฑ์ (CP) ในเอเชียตะวันออกเฉียงใต้ โดยเฉพาะในประเทศไทย ความร่วมมือนี้เกี่ยวข้องกับการพัฒนาอุตสาหกรรมการเลี้ยงไก่เนื้อ ซึ่งเป็นส่วนหนึ่งของการส่งเสริมการเกษตรและอาหารในภูมิภาค นั่นทำให้เทคโนโลยีการเลี้ยงสัตว์ของซีพีรุดหน้าอย่างเร็วมาก พันธุ์กุ้งขาวจากอเมริกา และ ไก่เนื้อที่จากเดิมต้องเลี้ยง 6 เดือน แต่ก็สามารถทำให้เหลือเวลาแค่ 8สัปดาห์ก็ได้กิโลครึ่งแล้ว
นอกจากนี้ยังร่วมทุนกับ มหาวิทยาลัยเกษตรศาสตร์ หนึ่งในโครงการที่โดดเด่นคือการสนับสนุน "ไร่สุวรรณ" หรือ Suwan Farm
ไร่สุวรรณ ตั้งอยู่ที่อำเภอปากช่อง จังหวัดนครราชสีมา เป็นศูนย์วิจัยข้าวโพดและข้าวฟ่างที่สำคัญของประเทศไทย เดิมทีพื้นที่นี้เป็นของจอมพลสฤษดิ์ ธนะรัชต์ และต่อมาได้โอนให้มหาวิทยาลัยเกษตรศาสตร์ดูแล มูลนิธิร็อกกี้เฟลเลอร์ได้ให้การสนับสนุนด้านทุนและความรู้ในการปรับปรุงพันธุ์ข้าวโพดเลี้ยงสัตว์ จนทำให้ไร่สุวรรณกลายเป็นแหล่งวิจัยข้าวโพดเลี้ยงสัตว์ที่ใหญ่ที่สุดในเอเชีย นักวิจัยที่ไร่สุวรรณได้พัฒนาพันธุ์ข้าวโพดที่ทนทานต่อโรคราน้ำค้าง ซึ่งเป็นปัญหาสำคัญในช่วงเวลานั้น
นั่นละครับ 5555
-
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ da0b9bc3:4e30a4a9
2025-04-13 08:48:10
@ da0b9bc3:4e30a4a9
2025-04-13 08:48:10Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/942018
-
 @ 502ab02a:a2860397
2025-04-13 08:27:33
@ 502ab02a:a2860397
2025-04-13 08:27:33หากเดินเข้าแผนกผักในซูเปอร์มาร์เก็ต แล้วเกิดความรู้สึกว่า “บรอกโคลี” กับ “กระหล่ำดอก” หน้าตามันเหมือนกันยังกับแฝดที่คนหนึ่งเป็นเด็กเรียนเก่ง อีกคนเป็นศิลปิน ก็ไม่ต้องแปลกใจ เพราะจริง ๆ แล้วพวกเขาเป็นญาติสายตรงกันเลยล่ะครับ ชนิดที่ว่าเกิดจากต้นตระกูลเดียวกันเป๊ะ ๆ และไม่ได้เกิดจากการหล่นลงมาของเมล็ดพืชจากฟากฟ้าหรือจากการปลุกเสกของเทพธิดาในตำนานไหนทั้งนั้น แต่เกิดจากมือมนุษย์เราเองล้วน ๆครับ
ต้นกำเนิดของพืชทั้งสองนั้นย้อนกลับไปไกลถึง “Brassica oleracea” ซึ่งเป็นพืชผักพื้นฐานริมทะเลเมดิเตอร์เรเนียน หน้าตาเมื่อแรกพบก็ไม่ได้หรูหราเหมือนลูกหลานยุคนี้ มันเป็นแค่พืชใบเขียวธรรมดา ๆ ที่ชาวโรมันโบราณเดินผ่านไม่เหลียวหลัง
แต่เมื่อเวลาผ่านไป มนุษย์เริ่มรู้จักการ “คัดเลือกพันธุ์” (selective breeding) คือการเลือกปลูกต้นที่มีลักษณะที่ต้องการ แล้วขยายพันธุ์เฉพาะต้นนั้นต่อไป รุ่นแล้วรุ่นเล่า เหมือนการเลือกเพาะลูกหมาที่ฉลาดและขนฟู จนในที่สุดก็ได้สายพันธุ์ใหม่ ๆ ขึ้นมา
เช่นในกรณีต้นไม้ต้นนึง ถ้าชาวสวนคนหนึ่งชอบต้นที่มี “ตาดอก” ใหญ่หน่อย ก็จะปลูกมันต่อ ส่วนอีกคนชอบใบที่แน่น ๆ ก็เลือกปลูกต้นแบบนั้นต่อ แล้วสิ่งที่ตามมาก็คือความเลยเถิดของความหลากหลายอย่างไม่น่าเชื่อ เช่น • ถ้าเน้นปลูกส่วนใบได้ คะน้า • ถ้าเน้นปลูกส่วนตาดอกได้ กระหล่ำดอก • ถ้าตาดอกสีเขียวแน่น ๆได้ บรอกโคลี • ถ้าเน้นลำต้นบวม ๆได้ กะหล่ำหัว • ถ้าดอกออกแปลก ๆ คล้ายปะการังได้ โรมานีสโก (Romanesco)
แต่ทุกชนิดที่ว่ามานั้น…เป็น “สายพันธุ์ย่อย” ของพืชชนิดเดียวกัน คือ Brassica oleracea ทั้งหมด!
พูดให้เข้าใจง่ายคือบรอกโคลีไม่ได้มาจากพระเจ้า แต่มาจาก “การขยี้ย้ำในลักษณะ จนเป็นการเล่นแร่แปรพันธุ์ของเกษตรกรในยุคโรมัน” ที่ทำกันจริงจังจนกลายเป็นผักจานหลักบนโต๊ะอาหารเราทุกวันนี้
สิ่งที่น่าสนใจอีกคือ บรอกโคลีกับกระหล่ำดอกยังคงกลิ่นกายทางพันธุกรรมเดียวกันอยู่ แม้หน้าตาจะต่าง แต่ DNA ก็คล้ายกันมาก พอ ๆ กับพี่น้องที่ชอบกินของไม่เหมือนกัน แต่มาจากบ้านเดียวกัน
จริง ๆ แล้วพืชตระกูล Brassica พวกนี้แหละ ที่มีสารสำคัญชื่อ Glucosinolate เป็นเหมือนกับนักเคมีของพืช ที่มีสูตรลับไว้ป้องกันตัวเองจากแมลง กลูโคซิโนเลตบางชนิด (เช่น goitrin) อาจรบกวนการดูดซึมไอโอดีน ส่งผลต่อการทำงานของต่อมไทรอยด์ เลยเรียกสิ่งนี้ว่า เป็น anti-nutrient ที่เราเคยได้ยินกันครับ
ถึงตรงนี้ ใครที่ชอบกินผักเหล่านี้ก็น่าจะรู้สึกภูมิใจว่ากำลังกิน “ผลผลิตจากภูมิปัญญามนุษย์” ที่ไม่แพ้การสร้างปิรามิดหรือเครื่องจักรไอน้ำเลย เพราะการคัดเลือกพันธุ์อย่างละเอียดอ่อน ต้องใช้เวลาการย้ำปลูกเป็นร้อยปี และไม่ได้ใช้วิทยาศาสตร์ล้ำยุคอะไรเลย แค่ใช้ใจและมือเปล่าของชาวสวนรุ่นแล้วรุ่นเล่า
สรุปแล้ว บรอกโคลีและกระหล่ำดอก ไม่ใช่ของจากสวรรค์ แต่เป็นของจาก “ความพยายาม” ที่ยิ่งใหญ่พอ ๆ กับการสร้างอารยธรรม พระเจ้าอาจไม่ได้สร้างมัน…แต่มนุษย์เราก็เก่งพอที่จะเป็น “พระเจ้าแห่งผัก” อยู่เหมือนกันนะครับ 555
pirateketo #โรงบ่มสุขภาพ #HealthyHut #ตำรับเอ๋ #siripun
-
 @ d41bf82f:ed90d888
2025-04-21 23:18:20
@ d41bf82f:ed90d888
2025-04-21 23:18:20"ประวัติศาสตร์ก็เฉกเช่นธรรมชาติ — การเกิดและการตายล้วนดำเนินไปอย่างสมดุล" -โยฮัน ฮุยซิงกา3
การเสื่อมถอยของโลกยุคใหม่
พวกเรากำลังอยู่ในช่วงปลายของสิ่งที่เรียกว่า “ยุคใหม่” — ระบบโลกที่ถูกจัดระเบียบผ่านรัฐชาติอันรวมศูนย์ ซึ่งเคยพาเราผ่านยุคอุตสาหกรรม สงครามโลก และการสร้างโครงสร้างทางสังคมที่เข้มแข็งด้วยภาษี สวัสดิการ และระบบราชการ แต่ยุคนี้กำลังเคลื่อนเข้าสู่ฉากสุดท้ายของมันอย่างเงียบงัน โดยไม่มีใครในกระแสหลักพูดถึงอย่างจริงจัง และสิ่งที่กำลังมาแทนที่ก็จะแตกต่างอย่างสิ้นเชิงในเชิงคุณภาพจากโลกที่เราคุ้นเคย
เช่นเดียวกับที่สังคมเกษตรกรรมเคยมาแทนที่สังคมสัตว์-หาของป่า และระบบอุตสาหกรรมเคยมาแทนระบบศักดินา สังคมใหม่ที่กำลังปรากฏขึ้นจะเป็นการเปลี่ยนผ่านครั้งใหญ่ โดยในยุคใหม่นี้ “ประสิทธิภาพ” จะไม่ผูกติดกับ “ขนาด” อีกต่อไป อำนาจแบบรวมศูนย์ของรัฐจะถูกสั่นคลอน และระบบใหม่จะเกิดขึ้นซึ่งเล็กกว่า คล่องตัวกว่า และยากที่รัฐแบบเดิมจะควบคุม
นักประวัติศาสตร์ในอนาคตอาจมองว่าการล่มสลายของสหภาพโซเวียตในปี 1991 หรือการพังทลายของกำแพงเบอร์ลินในปี 1989 คือจุดสิ้นสุดของยุคสมัยนี้ และเปิดฉากสู่สิ่งใหม่ — บ้างเรียกมันว่ายุคหลังสมัยใหม่ บ้างว่าโลกไซเบอร์ หรือสังคมสารสนเทศ ไม่ว่าจะตั้งชื่ออย่างไร สิ่งที่ทุกคนยอมรับคือมันคือ "โลกใบใหม่" ที่แตกต่างอย่างถึงแก่นจากโลกเดิม
ความเข้าใจของมนุษย์ต่อการเปลี่ยนแปลงใหญ่ระดับอารยธรรมมักมาช้า เพราะขาดกรอบความคิดและภาษาที่จะมองเห็นมันได้ในขณะที่มันเกิดขึ้นจริง ยกตัวอย่างเช่น ไม่มีใครในยุคศักดินาคิดว่าตนเองอยู่ใน “ยุคกลาง” จนกระทั่งยุคใหม่เข้ามาเปรียบเทียบ ในทำนองเดียวกัน พวกเราทุกวันนี้ก็อาจไม่รู้ตัวว่าเรากำลังอยู่ในช่วงสิ้นสุดของยุคหนึ่ง และจุดเริ่มต้นของอีกยุคหนึ่ง
ระบบสังคมใดก็ตามมักฝังข้อสันนิษฐานโดยปริยายว่าระบบของตนคือสิ่งสูงสุด เป็นสิ่งที่ไม่มีวันเปลี่ยน และไม่ควรถูกตั้งคำถาม การตั้งคำถามถึงความอยู่รอดของระบบ จึงเป็นเรื่องที่ถูกกีดกันโดยไม่รู้ตัว เพราะยิ่งระบบใกล้ล่มสลายเท่าไร มันก็ยิ่งต้องพยายามปกปิดไม่ให้ใครรับรู้ถึงความเปราะบางของมัน
ตัวอย่างจากประวัติศาสตร์เช่น การล่มสลายของจักรวรรดิโรมันใน ค.ศ. 476 ก็ไม่ได้รับการรับรู้ว่าเป็น “จุดจบ” ในเวลานั้น แม้เมื่อจักรพรรดิองค์สุดท้าย(โรมุลุส เอากุสตุส)ถูกปลด แต่ผู้คนและโครงสร้างเดิมของโรมันก็ยังคงแสร้งทำว่าทุกอย่างดำเนินไปตามปกติ รูปแบบของรัฐบาลเก่ายังคงถูกรักษาไว้ พิธีกรรมในระบบเดิมยังคงจัดขึ้น วุฒิสภายังคงประชุม กงสุลยังได้รับการแต่งตั้ง และระบบราชการก็ยังคงอยู่เกือบครบถ้วน พวกป่าเถื่อนที่เข้ามาปกครองก็ยังแสดงตนว่าให้ความเคารพต่อจักรวรรดิไบแซนไทน์และกฎหมายโรมัน ศาสนาคริสต์ยังคงดำรงเป็นศาสนาประจำรัฐ เครื่องราชสัญลักษณ์ยังถูกใช้ในพิธีสาธารณะ ทั้งหมดนี้เป็นฉากหน้าของการพยายามรักษาภาพความต่อเนื่องในขณะที่แก่นของอำนาจได้เปลี่ยนไปแล้วโดยสิ้นเชิง
ประวัติศาสตร์ช่วงนี้สอนให้เห็นว่า การเปลี่ยนแปลงใหญ่ในระดับอารยธรรมมักถูกซ่อนเร้นอยู่ภายใต้ความเฉื่อยของสังคมที่ไม่ยอมรับความเป็นจริง คนในยุคนั้นไม่ได้รู้สึกว่าโรมล่มสลายไปแล้ว พวกเขาเพียงรู้สึกว่าชีวิตยังดำเนินต่อไปได้ แม้ภายใต้ระเบียบใหม่ที่ซ้อนทับเข้ามาโดยไม่ได้ประกาศตนอย่างเป็นทางการ ความเปลี่ยนแปลงที่แท้จริงจึงไม่ใช่เหตุการณ์ที่เกิดขึ้นในวันใดวันหนึ่ง แต่เป็นกระบวนการค่อยเป็นค่อยไปที่อาศัยแรงเฉื่อยของความเชื่อเก่าว่าสิ่งต่างๆ “ยังเหมือนเดิม”
ผู้เขียนใช้ตัวอย่างนี้เพื่อสะท้อนมาสู่โลกปัจจุบันว่า แม้ตัวอย่างโรมจะดูไกลตัว แต่ก็มีลักษณะใกล้เคียงกับสิ่งที่เรากำลังเผชิญอยู่ ระบบรัฐชาติสมัยใหม่ก็อาจกำลังเข้าสู่ภาวะเสื่อมถอยโดยที่คนส่วนใหญ่ยังไม่รู้ตัวเช่นเดียวกัน หนังสือเล่มนี้จึงไม่ได้ตั้งต้นจากการคาดเดาอนาคตอย่างลอย ๆ หากแต่เสนอว่า เราจะเข้าใจอนาคตได้ดีขึ้น ถ้าเริ่มจากการเรียนรู้กระบวนการเปลี่ยนผ่านในอดีต โดยเฉพาะพลวัตทางการเมืองและตรรกะของอำนาจ
จุดเปลี่ยนของโรมันไม่เพียงแต่แสดงให้เห็นการล่มสลายของรัฐรวมศูนย์ แต่ยังเผยให้เห็นว่าการล่มสลายนั้นสามารถเปิดทางให้กิจกรรมทางเศรษฐกิจในท้องถิ่นเบ่งบานขึ้นได้ ในยุคของเรา แม้สาเหตุจะต่างกัน — โรมล่มเพราะขยายเกินตัว เศรษฐกิจเกษตรกรรมไม่สามารถรองรับภาระรัฐ การเก็บภาษีที่หนักหนาและทหารที่ใช้อำนาจในทางมิชอบ — แต่สิ่งที่คล้ายกันคือ การไม่ยอมรับต่อการเปลี่ยนแปลงที่กำลังก่อตัว
เรายังเห็นการเปรียบเทียบถึงผลกระทบจากโรคระบาดในอดีต เช่น โรคฝีดาษที่ทำให้โรมอ่อนแอลง เช่นเดียวกับความกังวลเรื่องไวรัสกลายพันธุ์ในยุคปัจจุบัน ที่บ่งชี้ถึงความเปราะบางของโครงสร้างสังคม แม้รูปแบบของภัยคุกคามจะต่างกัน แต่สิ่งที่เหมือนกันคือ “ความไม่พร้อมของระบบ” ที่จะรับมือกับความเปลี่ยนแปลงใหญ่
แต่สิ่งสำคัญที่สุดที่ผู้เขียนต้องการชี้ ไม่ใช่แค่สาเหตุของการล่มสลาย แต่คือความจริงที่ว่า ผู้คนในยุคนั้น “ไม่เห็น” ว่าตนเองอยู่ในจุดเปลี่ยน เพราะแรงเฉื่อยทางความคิดและการเมืองทำให้พวกเขายึดมั่นในสิ่งที่เคยรู้จัก โดยไม่รู้เลยว่าโลกได้เคลื่อนเข้าสู่ระยะใหม่แล้ว และเราทุกวันนี้ก็อาจกำลังทำเช่นเดียวกัน
เรากำลังอยู่ในช่วงเวลาที่ไมโครโปรเซสเซอร์ เทคโนโลยีดิจิทัล และโครงสร้างไร้ศูนย์กลางจะเปลี่ยนกฎเกณฑ์ของอำนาจอย่างรุนแรง แต่ผู้คนกลับพยายามตีความสิ่งเหล่านี้ผ่านเลนส์ของโครงสร้างอุตสาหกรรมแบบเดิม ซึ่งอาจทำให้พลาดโอกาสที่จะเข้าใจการเปลี่ยนแปลงที่แท้จริง
ผู้เขียนเตือนว่าแม้บางหนังสือว่าด้วยอนาคตจะเต็มไปด้วยข้อมูล แต่กลับพาเราเข้าใจผิด เพราะยังยึดติดอยู่กับกรอบคิดเดิม เช่น การเชื่อว่ามนุษย์สามารถควบคุมทิศทางประวัติศาสตร์ได้เสมอ ทั้งที่ในความจริงแล้ว ปัจจัยที่ขับเคลื่อนการเปลี่ยนแปลงทางประวัติศาสตร์นั้น มักเป็นเงื่อนไขพื้นฐานที่มนุษย์ควบคุมไม่ได้ และไม่ได้อยู่ในความสนใจของการเมืองกระแสหลัก
มนุษย์มักไม่เปลี่ยนแปลงเพราะ “ต้องการเปลี่ยน” แต่เพราะ “ไม่เปลี่ยนไม่ได้แล้ว” และการเปลี่ยนแปลงเหล่านั้นมักเกิดสวนทางกับความต้องการของคนส่วนใหญ่ที่อยากรักษาสถานะเดิม
ชีวิตที่ขาดวิสัยทัศน์
ความไม่ตระหนักถึงการเปลี่ยนแปลงอันยิ่งใหญ่ที่กำลังก่อตัวขึ้นรอบตัวเรา อาจไม่ได้เกิดจากความไม่รู้ แต่เพราะเราลึกๆ แล้ว “ไม่อยากเห็น” ความเปลี่ยนแปลงนั้นเอง ความต้านทานนี้ไม่ใช่เรื่องใหม่ บรรพบุรุษของเราที่ดำรงชีพด้วยการล่าสัตว์และหาของป่าก็อาจเคยดื้อรั้นไม่ต่างกัน เพียงแต่พวกเขามีข้อแก้ตัวที่ฟังขึ้นมากกว่า เพราะในยุคก่อนประวัติศาสตร์ ไม่มีใครอาจคาดเดาว่า “การปฏิวัติการเกษตร” จะเปลี่ยนโลกไปในระดับใด พวกเขาไม่มีปฏิทิน ไม่มีการบันทึก ไม่มีแบบจำลองใดจากอดีตให้ใช้ทำนายอนาคต แม้แต่แนวคิดเรื่อง “เวลา” ก็ยังไม่มีอยู่ในจิตสำนึก พวกเขาใช้ชีวิตอยู่ใน “ปัจจุบันที่ไม่สิ้นสุด” และเมื่อพูดถึงการคาดการณ์อนาคต พวกเขาก็เป็นเหมือน “คนตาบอด” ที่ยังไม่เคยลิ้มรส “ผลไม้แห่งความรู้” (ตามคำเปรียบในพระคัมภีร์) แต่ต่างจากพวกเขา พวกเราในวันนี้มีเครื่องมือและมุมมองที่ลึกซึ้งกว่า จากองค์ความรู้ของบรรพบุรุษกว่าสี่ห้าร้อยรุ่น วิทยาศาสตร์ คณิตศาสตร์ และอัลกอริธึมของคอมพิวเตอร์ความเร็วสูง ช่วยให้เราทำความเข้าใจระบบที่ซับซ้อนอย่างเศรษฐกิจมนุษย์และพลวัตของสังคมได้ดียิ่งขึ้น แม้ทฤษฎีเศรษฐศาสตร์จะไม่สามารถอธิบายพฤติกรรมมนุษย์ได้แบบสมบูรณ์ แต่ก็ทำให้เราเข้าใจว่า “แรงจูงใจ” คือแรงผลักดันสำคัญ เมื่อผลตอบแทนสูงขึ้น หรือความเสี่ยงต่ำลง พฤติกรรมย่อมเกิดขึ้นถี่ขึ้น และนี่คือหลักการที่แม่นยำอย่างยิ่งในการวิเคราะห์อนาคต
แรงจูงใจนี้เองที่เป็นหัวใจของการพยากรณ์ และการพยากรณ์ที่ดีไม่ได้ขึ้นกับการรู้เหตุการณ์ล่วงหน้าแบบเฉพาะเจาะจง แต่ขึ้นอยู่กับการเข้าใจโครงสร้างของแรงขับเคลื่อน เช่นเดียวกับที่เราอาจไม่รู้ว่าเมื่อไรเสียงฟ้าร้องจะดังขึ้น แต่เมื่อเห็นฟ้าแลบ ก็สามารถคาดหมายได้ว่าจะมีเสียงตามมา เช่นกัน หากเราสามารถเข้าใจ “ตรรกะของความรุนแรง” ที่กำลังเปลี่ยนไปในระดับการเมืองมหภาคได้ เราก็จะมองเห็น “โอกาส” หรือ “ช่องโหว่” ของระเบียบเดิม และใครจะเป็นผู้ฉวยโอกาสเหล่านั้น
การเปลี่ยนแปลงครั้งใหญ่ในอดีต เช่น การปฏิวัติการเกษตร หรือการเข้าสู่ยุคอุตสาหกรรม ล้วนเกิดขึ้นช้าและกินเวลาหลายศตวรรษกว่าจะเผยผลเต็มที่ ในทางตรงกันข้าม การเปลี่ยนผ่านสู่ยุคสารสนเทศกลับเกิดขึ้นรวดเร็วเพียงช่วงชีวิตเดียว
ผู้เขียนวางกรอบเพื่อให้เราเข้าใจว่า การเปลี่ยนแปลงทางการเมืองมหภาคมักมาก่อนการเปลี่ยนแปลงในโครงสร้างของรัฐอย่างเป็นรูปธรรม รายได้ที่ลดลง วิกฤตที่เกิดจากทรัพยากรจำกัด และแรงกดดันจากประชากร ล้วนเป็นผลพลอยได้จากความไม่สามารถของระเบียบเดิมในการรองรับแรงกระแทกของโลกใหม่ และการพูดถึงการเปลี่ยนแปลงจาก “ภายนอกระบบ” มักถูกห้ามหรือมองว่าเป็นเรื่องต้องห้ามในทุกยุคทุกสมัย ยิ่งไปกว่านั้น การเปลี่ยนแปลงในระดับนี้มักก่อให้เกิดแรงปะทะทางวัฒนธรรมระหว่างผู้ที่ยึดมั่นในกรอบศีลธรรมดั้งเดิมกับผู้ที่เปิดรับแนวคิดใหม่ และไม่ใช่เรื่องแปลกที่การเปลี่ยนแปลงเช่นนี้จะไม่เป็นที่นิยม เพราะมันลดคุณค่าของทุนทางปัญญาเดิม ทำให้ระบบเก่าไร้ความหมาย และบีบบังคับให้สังคมต้องเรียนรู้ใหม่เกือบทั้งหมด โดยเฉพาะในกลุ่มคนที่ได้รับผลกระทบโดยตรง
สัญญาณของการเสื่อมถอยมักปรากฏในรูปของคอร์รัปชัน ความไร้ประสิทธิภาพ และการสูญเสียศีลธรรมของผู้มีอำนาจ ซึ่งมักเป็นสัญญาณล่วงหน้าของการเปลี่ยนแปลงที่หลีกเลี่ยงไม่ได้ ยิ่งในยุคที่เทคโนโลยีก้าวหน้าเร็วขึ้น กระบวนการเหล่านี้ก็จะยิ่งเร่งตัว จนทำให้เวลาที่เหลืออยู่สำหรับการปรับตัวลดลงเรื่อย ๆ
"เมื่อมองย้อนกลับไปตลอดหลายศตวรรษ — หรือแม้แต่แค่ในปัจจุบัน — เราจะเห็นได้อย่างชัดเจนว่า มีผู้คนจำนวนมากที่สร้างรายได้(บ่อยครั้งเป็นรายได้จำนวนมาก) จากทักษะในการใช้ความรุนแรงผ่านอาวุธ และกิจกรรมของพวกเขาเหล่านี้มีบทบาทอย่างสำคัญยิ่งในการกำหนดว่าทรัพยากรที่มีอยู่จำกัดในสังคมจะถูกจัดสรรไปในทิศทางใด." --เฟรเดอริก ซี. เลน
แนวคิดของการเมืองมหภาค(megapolitics) เป็นกรอบความคิดที่ทรงพลัง ซึ่งช่วยให้เรามองเห็นกลไกเบื้องหลังเหตุการณ์ที่ดูซับซ้อนหรือลึกลับในประวัติศาสตร์ ไม่ว่าจะเป็นเหตุผลที่บางรัฐบาลเจริญรุ่งเรือง ขณะที่บางแห่งกลับล่มสลาย เหตุใดสงครามจึงอุบัติขึ้น และเหตุใดฝ่ายหนึ่งจึงมีชัย หรือแม้กระทั่งว่าอะไรเป็นตัวแปรที่กำหนดวงจรแห่งความรุ่งเรืองและความตกต่ำทางเศรษฐกิจ ทั้งหมดล้วนสามารถอธิบายได้ผ่านเลนส์ของการเมืองมหภาค ซึ่งเน้นวิเคราะห์ว่า "ต้นทุนและผลตอบแทนของการใช้ความรุนแรง" เปลี่ยนไปอย่างไรในแต่ละบริบทของเวลา หากต้นทุนในการใช้อำนาจบังคับลดต่ำลง เช่น การเข้าถึงอาวุธที่ง่ายขึ้นและราคาถูกลง ก็ทำให้อำนาจเปลี่ยนมือได้ง่ายขึ้นตามไปด้วย หลักการนี้ยังคงใช้ได้ตั้งแต่ยุคโบราณจนถึงโลกยุคไซเบอร์สเปซในปัจจุบัน
ใน Part 2 เราจะมาดูกันว่ามีปัจจัยอะไรบ้างที่อยู่เบื้องหลังการเปลี่ยนแปลงครั้งใหญ่ในประวัติศาสตร์ to be continue....


















