-
 @ 000002de:c05780a7
2025-05-08 16:14:37
@ 000002de:c05780a7
2025-05-08 16:14:37Just an observation that makes me chuckle.
originally posted at https://stacker.news/items/974829
-
 @ 5b730fac:9e746e2a
2025-05-08 15:33:12
@ 5b730fac:9e746e2a
2025-05-08 15:33:12| Channel | Push to Branch | Previous Installation Method | NIP94 Event ID Updated as Expected | New Update Installed as Expected | Test Passed | | ----------------------------------- | ----------------- | ---------------------------- | ---------------------------------- | -------------------------------- | -------------------------------------------------------------------------------------------------------------------------------- | | deleted config files, first install | Already installed | Manual | Yes | Yes | Yes
nostr:naddr1qvzqqqr4gupzqkmnp7kx5h36rumhjrtkxdslvqu38fyf09wv53u4hrqmvx08gm32qqxnzde5xcmnzwpnxq6rvdp59d83mz |Before pushing update
Check state
Currently installed NIP94 event:
{ "id": "8e75993b2b6d28e4336bc90150e2c69db97d45f1c7db6bf3c3892cee55f45c44", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746716510, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/bf6608e98a60cf977100d50aa21f720d4e369356fd9b5ca24616f9a7226bd41c.ipk" ], [ "m", "application/octet-stream" ], [ "x", "bf6608e98a60cf977100d50aa21f720d4e369356fd9b5ca24616f9a7226bd41c" ], [ "ox", "bf6608e98a60cf977100d50aa21f720d4e369356fd9b5ca24616f9a7226bd41c" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package_test-92-1157a2f" ], [ "release_channel", "dev" ] ] }Current version picked up by opkg:
root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-92-1157a2fCheck basic module's logic
Config.json contains the right event ID: ``` root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "62a39f60f5b3e3f0910adc592c0468c5c134ce321238884e9f016caad4c5231b" }
```
Install.json contains the right package path:
root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746715561, "download_time": 1746715507, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Deactivate, delete config files and start
Deactivate & delete config files:
root@OpenWrt:/tmp# service tollgate-basic stop root@OpenWrt:/tmp# service tollgate-basic status inactive root@OpenWrt:/tmp# rm /etc/tollgate/config.json /etc/tollgate/install.json root@OpenWrt:/tmp# ls /etc/tollgate/config.json /etc/tollgate/install.json ls: /etc/tollgate/config.json: No such file or directory ls: /etc/tollgate/install.json: No such file or directoryStart and check configs. Release channel is set to stable by default:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "unknown" } root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "false", "ip_address_randomized": "false", "install_time": 0, "download_time": 0, "release_channel": "stable", "ensure_default_timestamp": 1746717311 }Logs are too verbose, but otherwise fine. Skipped all events due to release channel:
Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.233356 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.235395 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.237559 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.239556 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.241685 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.259370 Skipping event due to release channel mismatch Thu May 8 15:15:13 2025 daemon.err tollgate-basic[13609]: 2025/05/08 15:15:13.261258 Skipping event due to release channel mismatch Thu May 8 15:15:31 2025 daemon.info tollgate-basic[13609]: Connecting to relay: wss://relay.tollgate.me Thu May 8 15:15:56 2025 daemon.info tollgate-basic[13609]: Connecting to relay: wss://relay.tollgate.meStop
tollgate-basic:root@OpenWrt:/tmp# service tollgate-basic stop root@OpenWrt:/tmp# service tollgate-basic status inactiveSwitch to
devchannel:root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "false", "ip_address_randomized": "false", "install_time": 0, "download_time": 0, "release_channel": "stable", "ensure_default_timestamp": 1746717311 } root@OpenWrt:/tmp# vi /etc/tollgate/install.json root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "false", "ip_address_randomized": "false", "install_time": 0, "download_time": 0, "release_channel": "dev", "ensure_default_timestamp": 1746717311 }Restart service:
root@OpenWrt:/tmp# service tollgate-basic start root@OpenWrt:/tmp# service tollgate-basic status runningLogread:
Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10 NIP94EventID: unknown Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10 IPAddressRandomized: false Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: TODO: include min payment (1) for https://mint.minibits.cash/Bitcoin in future Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: TODO: include min payment (1) for https://mint2.nutmix.cash in future Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10 Janitor module initialized and listening for NIP-94 events Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10.861535 Registering handlers... Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10.861715 Starting HTTP server on all interfaces... Thu May 8 15:21:10 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:21:10.861834 Starting to listen for NIP-94 events Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Starting Tollgate - TIP-01 Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Listening on all interfaces on port :2121 Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Starting event processing loop Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://nos.lol Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://nostr.mom Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.tollgate.me Thu May 8 15:21:10 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.damus.io Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Connected to relay: wss://nos.lol Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscription successful on relay wss://nos.lol Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscribed to NIP-94 events on relay wss://nos.lol Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Connected to relay: wss://nostr.mom Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscription successful on relay wss://nostr.mom Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscribed to NIP-94 events on relay wss://nostr.mom Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Connected to relay: wss://relay.damus.io Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscription successful on relay wss://relay.damus.io Thu May 8 15:21:11 2025 daemon.info tollgate-basic[13838]: Subscribed to NIP-94 events on relay wss://relay.damus.io Thu May 8 15:21:30 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.tollgate.meTrigger new event: ``` c03rad0r@CobradorRomblonMimaropa:~/TG/tollgate-module-basic-go/src$ git push github Enumerating objects: 9, done. Counting objects: 100% (9/9), done. Delta compression using up to 8 threads Compressing objects: 100% (5/5), done. Writing objects: 100% (5/5), 416 bytes | 416.00 KiB/s, done. Total 5 (delta 4), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (4/4), completed with 4 local objects. To https://github.com/OpenTollGate/tollgate-module-basic-go.git 1157a2f..e775bce multiple_mints_rebase_taglist_detect_package -> multiple_mints_rebase_taglist_detect_package
{ "id": "c73756a13f0ca270510d4301c1dbf433989974c33262fd3cd07627eacc3d6481", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746718037, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk" ], [ "m", "application/octet-stream" ], [ "x", "cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078" ], [ "ox", "cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-93-e775bce" ], [ "release_channel", "dev" ] ] } ```
New event caught, updated and restarted:
Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Started the timer Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Right Arch Keys count: 61 Thu May 8 15:27:19 2025 daemon.info tollgate-basic[13838]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:29 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:27:29.928620 Timeout reached, checking for new versions Thu May 8 15:27:29 2025 daemon.info tollgate-basic[13838]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-93-e775bce] Thu May 8 15:27:29 2025 daemon.info tollgate-basic[13838]: Newer package version available: multiple_mints_rebase_taglist_detect_package-93-e775bce Thu May 8 15:27:29 2025 daemon.info tollgate-basic[13838]: Downloading package from https://blossom.swissdash.site/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk to /tmp/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk Thu May 8 15:27:34 2025 daemon.info tollgate-basic[13838]: Package downloaded successfully to /tmp/ Thu May 8 15:27:34 2025 daemon.info tollgate-basic[13838]: New package version is ready to be installed by cronjob Thu May 8 15:27:34 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:27:34.073022 Verifying package checksum Thu May 8 15:27:34 2025 daemon.err tollgate-basic[13838]: 2025/05/08 15:27:34.082504 Package checksum verified successfully Thu May 8 15:27:55 2025 daemon.info tollgate-basic[13838]: Connecting to relay: wss://relay.tollgate.me Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07 NIP94EventID: c73756a13f0ca270510d4301c1dbf433989974c33262fd3cd07627eacc3d6481 Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07 IPAddressRandomized: 10.156.11.1 Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: TODO: include min payment (1) for https://mint.minibits.cash/Bitcoin in future Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: TODO: include min payment (1) for https://mint2.nutmix.cash in future Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Starting Tollgate - TIP-01 Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Listening on all interfaces on port :2121 Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07 Janitor module initialized and listening for NIP-94 events Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07.915222 Registering handlers... Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07.915366 Starting HTTP server on all interfaces... Thu May 8 15:28:07 2025 daemon.err tollgate-basic[14419]: 2025/05/08 15:28:07.917009 Starting to listen for NIP-94 events Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Starting event processing loop Thu May 8 15:28:07 2025 daemon.info tollgate-basic[14419]: Connecting to relay: wss://relay.damus.ioNew config files with new IP address
root@OpenWrt:~# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "c73756a13f0ca270510d4301c1dbf433989974c33262fd3cd07627eacc3d6481" } root@OpenWrt:~# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/cffba9d8b8bc9e1c59c97fdf238a47bdb8d6ad3003e4ae8b6cf50ca301f13078.ipk", "ip_address_randomized": "10.156.11.1", "install_time": 1746718081, "download_time": 1746718054, "release_channel": "dev", "ensure_default_timestamp": 1746717311, "update_path": null } -
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 611021ea:089a7d0f
2025-05-08 15:00:17
@ 611021ea:089a7d0f
2025-05-08 15:00:17This is the 2nd article I've written regarding my thoughts around the nostr health and fitness ecosystem and how something like NIP101h could play a part in enabling an ecosystem of highly specialized apps benefiting from nostr inherent interoperability. I've posted the last article on Wikistr and have continued experimenting with the NIP in a couple of clients. Recently I've been focused on extending the NIP to include calories and workout intensity.
Caloric Data
Let's talk about calories for a minute. Seems simple, right? You burn some, you consume some. But as I started implementing kind 1357 for caloric data, I quickly realized this was too simplistic.
The reality is tracking calories burned through a 10K run is fundamentally different from logging the calories in your morning avocado toast. Different contexts, different metadata, different user flows. Trying to cram both into one kind felt like forcing a square peg through a round hole.
So I split them: - Kind 1357: Calories expended (your run, your workout, even just existing) - Kind 2357: Calories consumed (your meals, snacks, that beer you "forgot" to log)
This wasn't just a technical decision. It reflects how people actually think about and track their health. Nobody mentally lumps "I burned 350 calories on my run" with "I ate a 650 calorie lunch" as the same type of data point. They're related but distinct.
Workout Intensity
Speaking of workouts, RUNSTR has been sending workout data for a while now, but workout intensity (kind 1356) is something I've been particularly excited about.
Why? Because intensity is the secret sauce that makes fitness data meaningful. Two people can run the same distance, but one might be casually jogging while catching up on podcasts, and another might be doing high-intensity intervals that leave them gasping for air.
Same distance, totally different physiological impacts.
Intensity gives context to duration. It turns "I worked out for 45 minutes" into a meaningful metric about how hard you pushed. And this isn't just for the fitness obsessed—it's essential for things like heart rate zone training, progressive overload, and recovery monitoring.
The Bigger Vision: Why I'm Building This
I'm not building NIP-101h because I think the world needs another fitness standard. God knows there are plenty already. I'm building it because I believe health data belongs to people, not platforms.
Right now, your Apple Health data lives in Apple's ecosystem. Your Fitbit data lives in Fitbit's walled garden. Your Strava data? Yep, siloed there too. These companies have built incredible products, but they've also created digital gulags.
Nostr gives us a chance to flip the script. What if your health data lived on the internet rather than the platform? What if you could: - Track your runs in RUNSTR - Encrypt sensitive data - Store data in relays or blossom servers - Use the data across an open ecosystem of interoperable apps
...all without asking permission from some corporate overlord?
That's pretty much the vision. I've also spun up HealthNote Relay to support some of the new NIPs and Kinds while I continue to flesh out NIP-101h.
The Power of Specialization
One thing I've realized is that the real magic happens when we get specific. A diabetes management app needs different data structures than a strength training app. But they both benefit from a common language for the overlap.
So I'm intentionally designing the NIP-101h series as a collection of highly specialized kinds rather than a monolithic standard. This lets developers pick and choose exactly what they need, while still ensuring interoperability where it matters.
Take our calorie example—by splitting into two kinds, we allow for specialized nutrition tracking apps that might never care about workout calories, while still ensuring they can talk to fitness apps when needed.
What's Coming Next
I've got a growing list of kinds I want to tackle: - Sleep data (duration, quality, phases) - Strength training specifics (sets, reps, weight) - Hydration tracking - Mental health metrics
But I'm equally excited to see what others build. Maybe someone will create specialized kinds for pregnancy tracking, or chronic illness management, or physical therapy progress.
That's the beauty of this approach—I don't need to anticipate every use case. The framework lets the community evolve it organically.
Join the Health Data Revolution
If you're a developer interested in health and fitness on Nostr, I'd love to hear from you. What kinds would help your use case? What are you building? What am I missing?
And if you're just a Nostr user who cares about your health data, check out RUNSTR (Alpha) or Npub.health (super alpha) to see what we're building.
You can find information the specification here NIP 101h.
See you in volume three, where I'll dig into NIP101h format details and share what I've learned from the early experiments.
Lets Go!
-
 @ 6e64b83c:94102ee8
2025-05-05 16:50:13
@ 6e64b83c:94102ee8
2025-05-05 16:50:13Nostr-static is a powerful static site generator that transforms long-form Nostr content into beautiful, standalone websites. It makes your content accessible to everyone, even those not using Nostr clients. For more information check out my previous blog post How to Create a Blog Out of Nostr Long-Form Articles
What's New in Version 0.7?
RSS and Atom Feeds
Version 0.7 brings comprehensive feed support with both RSS and Atom formats. The system automatically generates feeds for your main content, individual profiles, and tag-specific pages. These feeds are seamlessly integrated into your site's header, making them easily discoverable by feed readers and content aggregators.
This feature bridges the gap between Nostr and traditional web publishing, allowing your content to reach readers who prefer feed readers or automated content distribution systems.
Smart Content Discovery
The new tag discovery system enhances your readers' experience by automatically finding and recommending relevant articles from the Nostr network. It works by:
- Analyzing the tags in your articles
- Fetching popular articles from Nostr that share these tags
- Using configurable weights to rank these articles based on:
- Engagement metrics (reactions, reposts, replies)
- Zap statistics (amount, unique zappers, average zap size)
- Content quality signals (report penalties)
This creates a dynamic "Recommended Articles" section that helps readers discover more content they might be interested in, all while staying within the Nostr ecosystem.
See the new features yourself by visiting our demo at: https://blog.nostrize.me
-
 @ 5b730fac:9e746e2a
2025-05-08 14:55:38
@ 5b730fac:9e746e2a
2025-05-08 14:55:38| Channel | Push to Branch | Previous Installation Method | NIP94 Event ID Updated as Expected | New Update Installed as Expected | Test Passed | | ------- | ----------------- | ---------------------------- | ---------------------------------- | -------------------------------- | -------------------------------------------------------------------------------------------------------------------------------- | | dev | Already Installed | Automatic | Yes | Yes | Yes
nostr:naddr1qvzqqqr4gupzqkmnp7kx5h36rumhjrtkxdslvqu38fyf09wv53u4hrqmvx08gm32qqxnzde5xcmnzdfex5unzvfcfywh0x |Before pushing update
Check state
Currently installed NIP94 event:
{ "id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746714091, "kind": 1063, "tags": [ [ "url", "https://blossom.swissdash.site/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk" ], [ "m", "application/octet-stream" ], [ "x", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "ox", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-91-ca43710" ], [ "release_channel", "dev" ] ], "content": "TollGate Module Package: basic for gl-mt3000" }Current version picked up by opkg:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-91-ca43710Check basic module's logic
Config.json contains the right event ID:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9" }Install.json contains the right package path:
root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746714121, "download_time": 1746714105, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Update package manually
Trigger new event announcement on this branch
New NIP94 event on this branch
{ "id": "62a39f60f5b3e3f0910adc592c0468c5c134ce321238884e9f016caad4c5231b", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746715485, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk" ], [ "m", "application/octet-stream" ], [ "x", "1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3" ], [ "ox", "1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-92-1157a2f" ], [ "release_channel", "dev" ] ] }The new version was updated automatically despite internet gateway interruption: ``` Thu May 8 14:44:51 2025 daemon.info tollgate-basic[10154]: Subscription successful on relay wss://relay.damus.io Thu May 8 14:44:51 2025 daemon.info tollgate-basic[10154]: Subscribed to NIP-94 events on relay wss://relay.damus.io Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Started the timer Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Right Arch Keys count: 59 Thu May 8 14:44:54 2025 daemon.info tollgate-basic[10154]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:45:05 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:05.228500 Timeout reached, checking for new versions Thu May 8 14:45:05 2025 daemon.info tollgate-basic[10154]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:45:05 2025 daemon.info tollgate-basic[10154]: Newer package version available: multiple_mints_rebase_taglist_detect_package-92-1157a2f Thu May 8 14:45:05 2025 daemon.info tollgate-basic[10154]: Downloading package from https://blossom.swissdash.site/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk to /tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk Thu May 8 14:45:07 2025 daemon.info tollgate-basic[10154]: Package downloaded successfully to /tmp/ Thu May 8 14:45:07 2025 daemon.info tollgate-basic[10154]: New package version is ready to be installed by cronjob Thu May 8 14:45:07 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:07.693753 Verifying package checksum Thu May 8 14:45:07 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:07.703697 Package checksum verified successfully Thu May 8 14:45:10 2025 daemon.info tollgate-basic[10154]: Started the timer Thu May 8 14:45:22 2025 daemon.info tollgate-basic[10154]: Connecting to relay: wss://relay.tollgate.me Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.453098 Timeout reached, checking for new versions Thu May 8 14:45:23 2025 daemon.info tollgate-basic[10154]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-92-1157a2f] Thu May 8 14:45:23 2025 daemon.info tollgate-basic[10154]: Newer package version available: multiple_mints_rebase_taglist_detect_package-92-1157a2f Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.461627 Verifying package checksum Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.471684 Package checksum verified successfully Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.471744 Verifying package checksum Thu May 8 14:45:23 2025 daemon.info tollgate-basic[10154]: Package /tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk already exists with correct checksum, skipping download Thu May 8 14:45:23 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:23.481076 Package checksum verified successfully Thu May 8 14:45:47 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:45:47.810824 Relay wss://nos.lol disconnected, attempting to reconnect Thu May 8 14:45:47 2025 daemon.info tollgate-basic[10154]: Connecting to relay: wss://nos.lol Thu May 8 14:45:47 2025 daemon.info tollgate-basic[10154]: Connected to relay: wss://nos.lol
```
New version picked up by opkg: ``` root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-92-1157a2f
```
tollgate-basic is running again:
root@OpenWrt:/tmp# service tollgate-basic status runningEvent id in config is fine:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "62a39f60f5b3e3f0910adc592c0468c5c134ce321238884e9f016caad4c5231b" }install.json is fine: ``` root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/1bfcd4d08a4bf70d2878ee4bca2d3ba7c5a839355dc0eeef30e2589aa16ccfb3.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746715561, "download_time": 1746715507, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }
```
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ 000002de:c05780a7
2025-05-08 14:55:34
@ 000002de:c05780a7
2025-05-08 14:55:34There are so many projects in the bitcoin space that deserve praise but I just wanna shout out Cashu.me. Its a browser based cashu (eCash / Lighting) wallet. It can be very handy when you need a wallet but don't wanna download yet another app. I hadn't used it in a very long time and decided to try it out again the other day. Its really well done.
As with other Cashu wallets you need to select a mint and backup your key phrase but it is very simple the get started.
If you wanna learn more about Cashu check out Cashu.space
Two other good wallets that support Cashu.
originally posted at https://stacker.news/items/974759
-
 @ f1989a96:bcaaf2c1
2025-05-08 15:05:45
@ f1989a96:bcaaf2c1
2025-05-08 15:05:45Good morning, readers!
This week, we bring reports from Bangladesh, where the interim government instructed the central bank to halt the printing of old banknotes featuring Sheikh Mujibur Rahman, the founding president of Bangladesh. This has induced a currency shortage, as new notes have yet to be issued to replace the discontinued ones. As a result, Bangladeshis find themselves holding worthless currency, facing increased costs, and feeling frustrated over such poor currency management. Meanwhile, in Indonesia, citizens are fleeing to gold as the local rupiah currency crashes to record lows amid increasing financial controls from the government.
In open-source news, LNbits, a Bitcoin and Lightning wallet management software, emerged from beta with its v1.0.0 release. LNbits works like a control panel on top of a Bitcoin wallet, letting users divide funds into separate accounts and use different features and functionalities. It is a handy tool for educators, civil society organizations, and communities who want to use Bitcoin for real-world transactions without needing advanced technical skills. We also spotlight a new tool called following .space that allows users to curate and share premade follow packs for nostr. The result is a more straightforward onboarding process for new users interested in censorship-resistant social media and the ability to curate feeds to better suit their interests.
We end with an interview with HRF Chief Strategy Officer Alex Gladstein, who explores his thinking behind the relationship between Bitcoin and human rights as we enter an age of increased corporate and nation-state adoption. He highlights the paradox where Bitcoin, a tool for individual financial freedom, is being adopted by institutions around the world, many of which regularly seek greater control over financial activity. We also include a new report from Bitcoin developer and past HRF grantee, b10c, who documents the current state of Bitcoin mining centralization and the threat it poses to decentralization and censorship resistance.
Now, let’s jump right in!
SUBCRIBE HERE
GLOBAL NEWS
Bangladesh | Currency Shortage as Central Bank Halts Printing of Banknotes
A state-induced cash crunch is paralyzing Bangladesh after the interim government, led by Muhammad Yunus, ordered the central bank to discontinue old banknotes featuring Sheikh Mujibur Rahman, the founding president of Bangladesh. New cash is expected to be printed in phases beginning in May. But Bangladeshis report they are currently stuck with old and unusable currency, as the national mint has yet to issue replacement currency and lacks the capacity to print more than three notes at a time. Meanwhile, public ATMs continue to dispense old and worn-out banknotes, with merchants reluctantly accepting them and banks refusing to exchange them. Through all this, the central bank of Bangladesh sits on nearly 15,000 crore taka ($1.28 billion) worth of old notes in vaults, but the interim government has refused to release them, deepening public frustration.
Nigeria | Regulates Bitcoin as a Security
Nigerian lawmakers are moving to regulate digital assets as securities by passing the Investment and Securities Act (ISA) 2025. Rather than embrace it as a tool for financial freedom, the law places Bitcoin under the purview of the Nigerian Securities and Exchange Commission (SEC). Companies must now register with the Nigerian SEC, implement more strict data-collection processes (to harvest personal information), and navigate a legal framework not designed for a borderless and permissionless technology like Bitcoin. The law further grants the SEC access to data from telecom and Internet providers to investigate “illegal market activity” — a provision that could easily be abused to surveil or intimidate Bitcoin users and developers. Nigeria routinely uses regulations to stifle the presence of open-source money, raising compliance hurdles, imposing taxes, and punishing digital asset companies. It’s not unreasonable to suspect this new classification could provide the state with a means to suppress the free adoption and innovation of Bitcoin.
Indonesia | Gold Rush Amid Economic Uncertainty
As the rupiah currency falls to record lows, Indonesians are flocking to gold in a rush to protect their savings. But gold isn’t the only safe haven. With 74% of Indonesia’s population unbanked or underbanked, digital tools like Bitcoin offer a more accessible alternative, especially when nearly 70% of Indonesians have Internet access. The Indonesian government is also tightening capital controls. A new policy forces exporters to keep all foreign currency earnings inside the country for a full year to trap dollars in the financial system. HRF grantee Bitcoin Indonesia is responding by helping people in the region (especially in nearby states like Burma) build financial resilience through meetups, workshops, and training focused on Bitcoin custody, privacy, and adoption. In an area where financial services remain out of reach for millions, learning how to save and transact permissionlessly is paramount.
Kenya | Introduces Legal Framework for Virtual Asset Service Providers (VASPs)
Kenya’s government introduced a comprehensive legal framework to regulate Virtual Asset Service Providers (VASPs) through its newly proposed 2025 VASP Bill. The legislation outlines strict licensing requirements for digital asset exchanges, wallet providers, brokers, and other digital asset firms. It functionally bars individuals from operating independently (think: open-source freedom tech builders) by mandating local incorporation, compliance with cybersecurity standards, and approval from financial regulators. This appears to be an attempt to formalize and better control the rapidly growing digital asset space. It could stifle grassroots innovation and limit access to financial tools that have become vital for activists and citizens seeking privacy and autonomy as economic policies and high inflation drive unrest.
El Salvador | Attorney General’s Office Preparing Arrest Warrants for Independent Journalists
El Faro, one of El Salvador’s most prominent investigative news outlets, shared reliable information that the Salvadoran Attorney General’s Office is preparing arrest warrants against three of its journalists. The warning came from El Faro director Carlos Dada, who suggests that the charges may include “apology for crimes” and “illicit association.” The alleged charges allegedly stem from El Faro’s latest reporting: a three-part video interview with former leaders of the 18th Street Revolucionarios gang that sheds light on Bukele’s “years-long relationship” with Salvadoran gangs. El Faro editor-in-chief Óscar Martínez said that any arrests or home raids following this news would be “for having done journalism.” With El Salvador’s shrinking civic space, this potential action against independent media would further restrict Salvadorans’ ability to access independent information and hold officials accountable.
BITCOIN AND FREEDOM TECH NEWS
LNbits | Emerges from Beta with v1.0.0 Release
LNbits, an open-source software tool that lets people create and manage Bitcoin Lightning wallets securely for themselves and for others, officially launched version 1.0.0, marking its transition out of beta and into a more stable release for public use. It works like a control panel sitting on top of a Bitcoin wallet, letting users divide funds into separate accounts and use different features and functionalities. LNbits is especially useful for educators, small businesses, and community organizers who want to use and manage Bitcoin for payments and savings. HRF is pleased to see this Bitcoin Development Fund (BDF) grantee strengthen the tools available to activists to achieve financial freedom in the face of censorship, surveillance, or inflation.
SeedSigner | Self-Custody Tool for Chinese Bitcoiners Facing Local Corruption
Chinese Bitcoin users are turning to SeedSigner, an open-source and fully customizable Bitcoin hardware wallet, as a more private way to protect their savings from law enforcement corruption. While many assume the primary threat to Bitcoin in China comes from top-down management and enforcement from the Chinese Communist Party (CCP), new reports suggest greater concern over the police, who regularly monitor mail, detect hardware wallet purchases, and fabricate charges to extort Chinese users’ Bitcoin. SeedSigner solves this by allowing users to assemble a secure signing device from generic, inexpensive parts, avoiding the risk of shipping a branded wallet that might flag them as a target. When privacy violations begin at the local level, SeedSigner can help citizens safeguard their financial freedom by making secure self-custody discreet, accessible, and affordable.
Following .space | Create and Share Follow Packs on Nostr
Following.space is a new tool for nostr that solves one of the protocol’s biggest pain points: finding people worth following in the absence of an algorithm. Created by developer and HRF grantee Calle, the tool lets anyone build and share curated “follow packs” — pre-made lists of nostr users that can be easily distributed across the web. The lists are customizable and can be made based on shared interests, communities, organizations, regions, and more. This makes onboarding new users easier and allows users to curate their feeds to suit their interests. The result is a simple but powerful tool that helps nostr scale more organically by encouraging natural discovery. Enabling free expression and connections without reliance on centralized platforms strengthens human rights and financial freedom in repressive environments. Try it here.
256 Foundation | Releases Ember One Source Code
The 256 Foundation, an open-source Bitcoin mining initiative, released the source code of its new Ember One Bitcoin mining hashboard to the public. A Bitcoin hashboard is a device with multiple chips for performing Bitcoin mining computations. The open-source Ember One only consumes 100 Watts of total power and is modular by design, allowing user customization and the ability to mine discreetly even under autocratic regimes. This is important because it gives individuals a way to access and earn Bitcoin without drawing the attention of officials. For dissidents, mining at home means gaining more control over how they earn, spend, and store their money, all without relying on centralized systems at the whims of dictators.
Btrust and Africa Free Routing | Announce Partnership to Advance African Bitcoin Development
Btrust, a nonprofit advancing Bitcoin development in Africa, awarded a grant to Africa Free Routing, a program within African Bitcoiners, to support five Bitcoin Lightning-focused developer boot camps across the continent in 2025. These bootcamps aim to onboard non-Bitcoin developers into the Bitcoin ecosystem, offering hands-on training, mentorship, and opportunities to contribute to open-source projects. This work strengthens the foundations of freedom tech in Africa, providing tools that allow people to resist financial repression under tyranny. Learn more about the partnership here.
Presidio Bitcoin | Hosting First Hackathon
Presidio Bitcoin, the Bay Area’s first dedicated freedom tech co-working and events space, just announced its first-ever hackathon, which will take place from May 16-17, 2025. This 24-hour hackathon in San Francisco brings together developers and technologists to build and collaborate at the frontier of Bitcoin, AI, and open-source technology. In addition to the hackathon, Presidio is launching a new program offering free three-month access to its workspace for Bitcoin open-source contributors. This is a valuable opportunity to connect with fellow developers, startup founders, and freedom tech advocates in the area. HRF is proud to sponsor this hackathon and is looking forward to how the outcomes might help create better freedom tools for dissidents worldwide. Learn more about the event here.
RECOMMENDED CONTENT
Bitcoin Nation State Adoption Paradox - Interview with Alex Gladstein
In a recent episode of the Bitcoin Fundamentals podcast, hosted by Preston Pysh, Alex Gladstein, HRF’s chief strategy officer, discusses the complexities of Bitcoin’s new era of adoption. He highlights the paradox where Bitcoin, a tool for individual financial freedom, is being adopted by governments, which some believe to be potentially compromising to its core principles. He emphasizes that while governments may adopt it for strategic or economic reasons, in doing so, they expose their populations to a technology that will ultimately weaken state control over money and advance individual liberty and human rights. Watch the full interview here.
Bitcoin Mining Centralization by b10c
In this report, Bitcoin developer and past HRF grantee b10c documents the growing trend of centralization in Bitcoin mining pools. It shows that over 95% of blocks are now mined by just six Bitcoin mining pools, with Foundry and AntPool controlling roughly 60–70% of the hashrate (the computing power dedicated to the Bitcoin network). This marks a rise in mining pool centralization in recent years. While this hasn’t harmed Bitcoin’s censorship resistance yet, it reduces the number of block template producers. This concentration of template producers poses a potential risk to Bitcoin’s neutrality, which is essential for ensuring access to uncensorable money and protecting human rights in autocratic regimes. HRF has happily supported both Hashpool and Public Pool with recent grants to support smaller, independent pools that help preserve Bitcoin's decentralization. Read the full report here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 266815e0:6cd408a5
2025-05-02 22:24:59
@ 266815e0:6cd408a5
2025-05-02 22:24:59Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.
Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
The communities where interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now
Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal

New emoji picker
Just another small improvement that makes the app feel more complete.
Experimental Wallet
There is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very experimental and probably won't work for you, but its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Don't feed the wallet your hard earned sats, it will eat them!
Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing on load
- Add option to mirror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 5b730fac:9e746e2a
2025-05-08 14:32:04
@ 5b730fac:9e746e2a
2025-05-08 14:32:04| Channel | Push to Branch | Previous Installation Method | NIP94 Event ID Updated as Expected | New Update Installed as Expected | Test Passed | | ------- | ----------------- | ---------------------------- | ---------------------------------- | -------------------------------- | -------------------------------------------------------------------------------------------------------------------------------- | | dev | Already Installed | Manual | Yes | Yes | Yes
nostr:naddr1qvzqqqr4gupzqkmnp7kx5h36rumhjrtkxdslvqu38fyf09wv53u4hrqmvx08gm32qqxnzde5xcmnzdp4xvmnvdpkpctkgk |Before pushing update
Check state
Currently installed NIP94 event:
{ "id": "33bf30e90f1e09924a933f08e788165eada8cca2d6c78443e7e52910f0705988", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746711607, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk" ], [ "m", "application/octet-stream" ], [ "x", "0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97" ], [ "ox", "0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-89-4e46a9b" ], [ "release_channel", "dev" ] ] }Installed here:
Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Started the timer Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Right Arch Keys count: 56 Thu May 8 13:40:13 2025 daemon.info tollgate-basic[6709]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:23 2025 daemon.err tollgate-basic[6709]: 2025/05/08 13:40:23.779018 Timeout reached, checking for new versions Thu May 8 13:40:23 2025 daemon.info tollgate-basic[6709]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-89-4e46a9b] Thu May 8 13:40:23 2025 daemon.info tollgate-basic[6709]: Newer package version available: multiple_mints_rebase_taglist_detect_package-89-4e46a9b Thu May 8 13:40:23 2025 daemon.info tollgate-basic[6709]: Downloading package from https://blossom.swissdash.site/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk to /tmp/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk Thu May 8 13:40:28 2025 daemon.info tollgate-basic[6709]: Package downloaded successfully to /tmp/ Thu May 8 13:40:28 2025 daemon.err tollgate-basic[6709]: 2025/05/08 13:40:28.863469 Verifying package checksum Thu May 8 13:40:28 2025 daemon.err tollgate-basic[6709]: 2025/05/08 13:40:28.873010 Package checksum verified successfully Thu May 8 13:40:28 2025 daemon.info tollgate-basic[6709]: New package version multiple_mints_rebase_taglist_detect_package-89-4e46a9b is ready to be installed by cronjob Thu May 8 13:41:06 2025 daemon.err tollgate-basic[7713]: 2025/05/08 13:41:06 NIP94EventID: 33bf30e90f1e09924a933f08e788165eada8cca2d6c78443e7e52910f0705988 Thu May 8 13:41:06 2025 daemon.err tollgate-basic[7713]: 2025/05/08 13:41:06 IPAddressRandomized: 192.168.3.1Current version picked up by opkg:
root@OpenWrt:~# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-89-4e46a9bCheck basic module's logic
Config.json contains the right event ID: ``` root@OpenWrt:~# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "33bf30e90f1e09924a933f08e788165eada8cca2d6c78443e7e52910f0705988" }
```
Install.json contains the right package path:
root@OpenWrt:~# cat /etc/tollgate/install.json { "package_path": "/tmp/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746711661, "download_time": 1746711628, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Update package manually
Prevent automatic update
Stop
tollgate-basicso that it doesn't automatically update to newer event kinds.root@OpenWrt:~# service tollgate-basic stop root@OpenWrt:~# service tollgate-basic status inactiveTrigger new event announcement on this branch
New NIP94 event on this branch
c03rad0r@CobradorRomblonMimaropa:~/TG/tollgate-module-basic-go/src$ git push github Enumerating objects: 9, done. Counting objects: 100% (9/9), done. Delta compression using up to 8 threads Compressing objects: 100% (5/5), done. Writing objects: 100% (5/5), 429 bytes | 429.00 KiB/s, done. Total 5 (delta 4), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (4/4), completed with 4 local objects. To https://github.com/OpenTollGate/tollgate-module-basic-go.git 4e46a9b..ad29788 multiple_mints_rebase_taglist_detect_package -> multiple_mints_rebase_taglist_detect_packageThe new version that we will install manually:
{ "id": "2ff8b1e63036f03884a82450c811d9df0ed2b9f1a4099bbb1e4308e1d845be97", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746712364, "kind": 1063, "content": "TollGate Module Package: basic for gl-mt3000", "tags": [ [ "url", "https://blossom.swissdash.site/e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk" ], [ "m", "application/octet-stream" ], [ "x", "e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059" ], [ "ox", "e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-90-ad29788" ], [ "release_channel", "dev" ] ] }The installation:
root@OpenWrt:/tmp# wget https://blossom.swissdash.site/e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk Downloading 'https://blossom.swissdash.site/e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk' Connecting to 212.47.72.157:443 Writing to 'e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk' e8633b4c2ceb05b5fd45 2943k --:--:-- ETA Download completed (4509706 bytes) root@OpenWrt:/tmp# opkg install e8633b4c2ceb05b5fd45fe0574417b644bbc62e6e3862147e94ca46104735059.ipk Upgrading tollgate-module-basic-go on root from multiple_mints_rebase_taglist_detect_package-89-4e46a9b to multiple_mints_rebase_taglist_detect_package-90-ad29788... Command failed: Not found Removing existing banner file if present... Configuring tollgate-module-basic-go. nodogsplash cfg7c92bd Running TollGate NoDogSplash file copy script... Source files: drwxr-xr-x 2 root root 384 May 8 13:57 . drwxr-xr-x 3 root root 224 May 8 13:50 .. -rw-r--r-- 1 root root 599 May 8 13:50 asset-manifest.json -rw-r--r-- 1 root root 312 May 8 13:50 manifest.json -rw-r--r-- 1 root root 642 May 8 13:50 splash.html Copying splash.html... IP is already randomized or not set to false. Exiting.Current version picked up by opkg:
root@OpenWrt:/tmp# opkg list-installed | grep "tollgate" tollgate-module-basic-go - multiple_mints_rebase_taglist_detect_package-90-ad29788 root@OpenWrt:/tmp#tollgate-basic is running again:
root@OpenWrt:/tmp# service tollgate-basic status runningEvent ID successfully set to
unknown:root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "unknown" }install.jsonis still pointing at dev channel:root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/0456244a6b01629d86d6218ddacb149fd3a54b007154531ade55415c5573ab97.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746712641, "download_time": 1746711628, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null }Trigger new event announcement on this branch
Trigger new event:
c03rad0r@CobradorRomblonMimaropa:~/TG/tollgate-module-basic-go/src$ git push github Enumerating objects: 9, done. Counting objects: 100% (9/9), done. Delta compression using up to 8 threads Compressing objects: 100% (5/5), done. Writing objects: 100% (5/5), 418 bytes | 418.00 KiB/s, done. Total 5 (delta 4), reused 0 (delta 0), pack-reused 0 remote: Resolving deltas: 100% (4/4), completed with 4 local objects. To https://github.com/OpenTollGate/tollgate-module-basic-go.git ad29788..ca43710 multiple_mints_rebase_taglist_detect_package -> multiple_mints_rebase_taglist_detect_packageNew event json:
{ "id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9", "pubkey": "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a", "created_at": 1746714091, "kind": 1063, "tags": [ [ "url", "https://blossom.swissdash.site/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk" ], [ "m", "application/octet-stream" ], [ "x", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "ox", "75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b" ], [ "filename", "basic-gl-mt3000-aarch64_cortex-a53.ipk" ], [ "architecture", "aarch64_cortex-a53" ], [ "version", "multiple_mints_rebase_taglist_detect_package-91-ca43710" ], [ "release_channel", "dev" ] ], "content": "TollGate Module Package: basic for gl-mt3000" }Logread output: ``` Thu May 8 14:12:11 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:12:11.615394 Relay wss://relay.damus.io disconnected, attempting to reconnect Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Connecting to relay: wss://relay.damus.io Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Connected to relay: wss://relay.damus.io Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Subscription successful on relay wss://relay.damus.io Thu May 8 14:12:11 2025 daemon.info tollgate-basic[8933]: Subscribed to NIP-94 events on relay wss://relay.damus.io Thu May 8 14:20:41 2025 daemon.info tollgate-basic[8933]: Connecting to relay: wss://relay.tollgate.me Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Started the timer Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Intersection: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Right Time Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-90-ad29788 basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-90-ad29788 basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Right Arch Keys count: 115 Thu May 8 14:21:33 2025 daemon.info tollgate-basic[8933]: Right Version Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:43 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:21:43.304879 Timeout reached, checking for new versions Thu May 8 14:21:43 2025 daemon.info tollgate-basic[8933]: Sorted Qualifying Events Keys: [basic-gl-mt3000-aarch64_cortex-a53.ipk-multiple_mints_rebase_taglist_detect_package-91-ca43710] Thu May 8 14:21:43 2025 daemon.info tollgate-basic[8933]: Newer package version available: multiple_mints_rebase_taglist_detect_package-91-ca43710 Thu May 8 14:21:43 2025 daemon.info tollgate-basic[8933]: Downloading package from https://blossom.swissdash.site/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk to /tmp/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk Thu May 8 14:21:45 2025 daemon.info tollgate-basic[8933]: Package downloaded successfully to /tmp/ Thu May 8 14:21:45 2025 daemon.info tollgate-basic[8933]: New package version is ready to be installed by cronjob Thu May 8 14:21:45 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:21:45.667395 Verifying package checksum Thu May 8 14:21:45 2025 daemon.err tollgate-basic[8933]: 2025/05/08 14:21:45.676755 Package checksum verified successfully Thu May 8 14:22:06 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:22:06 NIP94EventID: 51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9 Thu May 8 14:22:06 2025 daemon.err tollgate-basic[10154]: 2025/05/08 14:22:06 IPAddressRandomized: 192.168.3.1
```
Config has the right event id again:
root@OpenWrt:/tmp# cat /etc/tollgate/config.json | jq { "tollgate_private_key": "8a45d0add1c7ddf668f9818df550edfa907ae8ea59d6581a4ca07473d468d663", "accepted_mints": [ "https://mint.minibits.cash/Bitcoin", "https://mint2.nutmix.cash" ], "price_per_minute": 1, "bragging": { "enabled": true, "fields": [ "amount", "mint", "duration" ] }, "relays": [ "wss://relay.damus.io", "wss://nos.lol", "wss://nostr.mom", "wss://relay.tollgate.me" ], "trusted_maintainers": [ "5075e61f0b048148b60105c1dd72bbeae1957336ae5824087e52efa374f8416a" ], "fields_to_be_reviewed": [ "price_per_minute", "relays", "tollgate_private_key", "trusted_maintainers" ], "nip94_event_id": "51ca573636243df455333e83d5b456b4bcefd939c8160c5737545abcdc95dfd9" }Install.json has the right file path again:
root@OpenWrt:/tmp# cat /etc/tollgate/install.json | jq { "package_path": "/tmp/75990a3f245069a56c02c6e24dc312ecc6ff1f0df632fb99ddb247c98a745a5b.ipk", "ip_address_randomized": "192.168.3.1", "install_time": 1746714121, "download_time": 1746714105, "release_channel": "dev", "ensure_default_timestamp": 1746634883, "update_path": null } -
 @ 9c35fe6b:5977e45b
2025-05-08 11:49:44
@ 9c35fe6b:5977e45b
2025-05-08 11:49:44Into the Heart of the Desert If you're looking for an adventure beyond the ordinary, Egypt Safari Tours with ETB Tours Egypt offer an unforgettable escape into the Egyptian desert. Venture into the golden sands of the White Desert, Bahariya Oasis, or Siwa, where time seems to stand still. This is more than sightseeing — it's a soul-stirring journey.
Exclusive Experiences with Egypt Private Tours For those who value privacy and exclusivity, ETB Tours Egypt designs tailor-made Egypt private tours that bring the desert to life on your terms. Whether it's a sunset camel ride, a 4x4 dune adventure, or camping under the stars, your itinerary is crafted just for you.
Explore More with Egypt Vacation Packages Why stop at the desert? Combine your safari adventure with cultural highlights and coastal escapes through our curated Egypt vacation packages. Enjoy the perfect balance between relaxation and exploration as you transition from the desert to the Nile.
Budget-Friendly Desert Escapes Traveling on a budget doesn’t mean you have to sacrifice experience. ETB Tours Egypt offers incredible Egypt budget tours that make desert adventures accessible to all. With professional guides and well-organized itineraries, you’ll enjoy value-packed experiences at an affordable price.
All Inclusive Egypt Vacations: Worry-Free Travel Enjoy stress-free travel with our all inclusive Egypt vacations. From hotel stays and meals to guided safaris and transportation, every detail is taken care of. Just bring your adventurous spirit—we’ll handle the rest.
Combine Desert Thrills with Ancient Wonders Turn your desert safari into a grand journey by including one of our Egypt pyramid tour packages. Witness the mystique of the Pyramids of Giza before heading into the vast desert—blending ancient history with modern adventure To Contact Us: E-Mail: info@etbtours.com Mobile & WhatsApp: +20 10 67569955 - +201021100873 Address: 4 El Lebeny Axis, Nazlet Al Batran, Al Haram, Giza, Egypt
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ bbb5dda0:f09e2747
2025-05-08 07:38:07
@ bbb5dda0:f09e2747
2025-05-08 07:38:07
I've been neglecting my weekly updates a bit. I haven't really gotten to them lately because i've been insanely busy frying my brains at #SovEng. And after that i haven't been keeping my weekly notes properly. WHICH I'm planning to pick back up now!
This week/ the last couple weeks I've been doing some general planning around @tollGate's appearances on various conferences around Europe! First on the list will be Pizza Day in Prague! And from there I'll be cruising straight to @Oslo Freedom Forum! For TollGate that also means getting us set up with some T-Shirts and Stickers, though not super hard to do, it's the first time I'm doing any 'marketing' like this so I did test my own patience by properly cropping and ordering the designs. So far the stickers came out well Look at our first officially baptized TollGate! :)
TollGate Installer
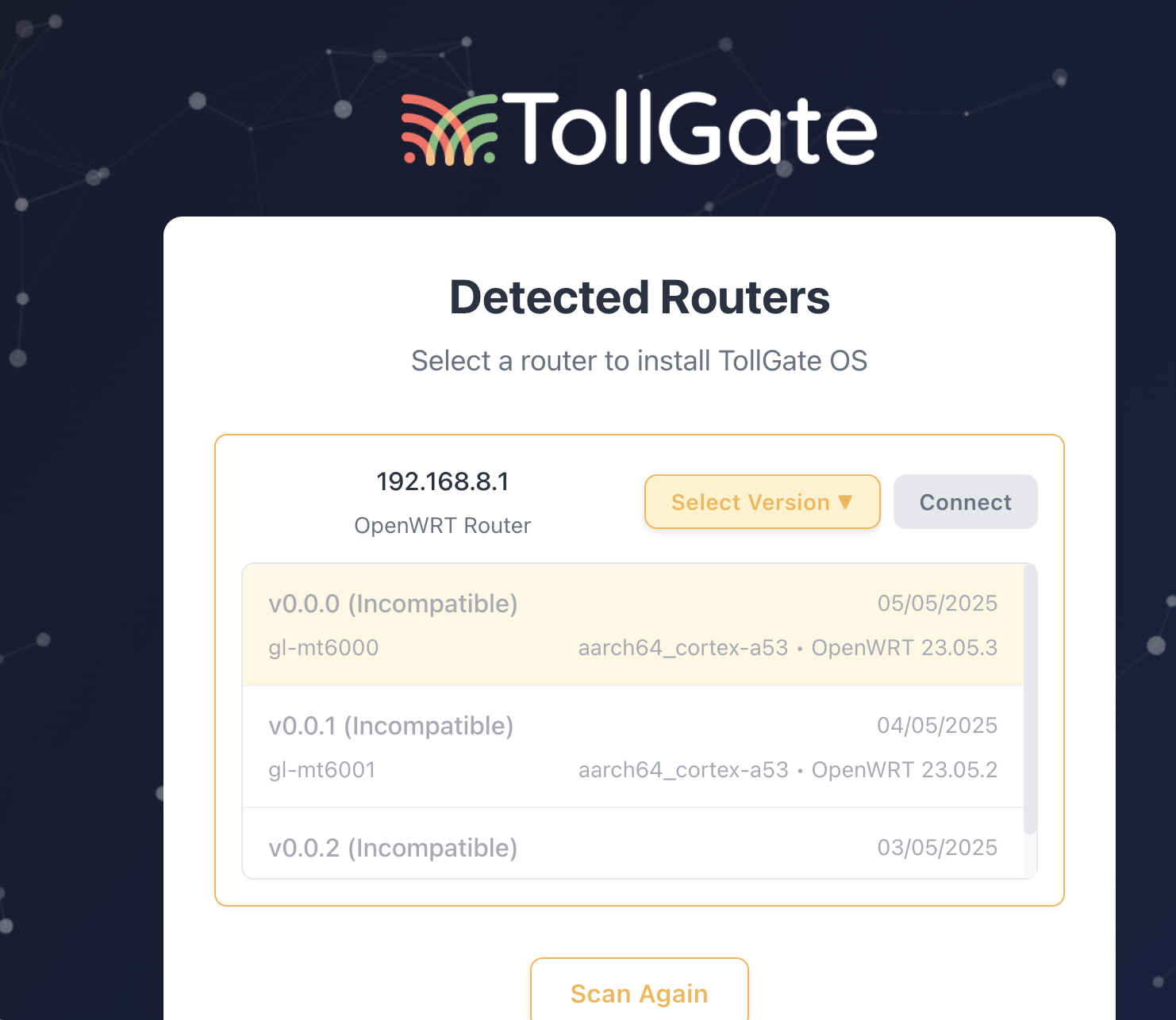 As we're installing versions of TollGateOS on routers quite often now I figured it'd be a good idea to streamline the experience a bit by building a TollGate Installer. I've been vibecoding it mostly, and one of the things I discovered is how easy it is to make it replicate the style of another app. To stick with the theme I told it to mirror the style of our TollGate Captive portal site and it did it perfectly!
As we're installing versions of TollGateOS on routers quite often now I figured it'd be a good idea to streamline the experience a bit by building a TollGate Installer. I've been vibecoding it mostly, and one of the things I discovered is how easy it is to make it replicate the style of another app. To stick with the theme I told it to mirror the style of our TollGate Captive portal site and it did it perfectly!Anyway, still a lot of manual engineering is required but at least I can outsource the stuff i'm bad at. What I did improve was the GitHub workflows we use for building and publishing the OS. We publish our releases to Blossom + Nostr (NIP-94). I then use those messages in the installer to get the download links.
👀 But which version!?
I quickly ran into the issue that I didn't know which binary to install on the router i hooked up to my computer. I connect the router via lan, then I scan the network and ssh into the router, get some basic info, like the device name. BUT, the format of that device name wouldn't match any of the names we'd use in our release.
For example: the router name would be
glinet,mt3000while our release was calledgl-mt3000. The difference may seem subtle but I can't match them. So after some discussion with the others I went on and revamped our OS pipeline to properly follow the OpenWRT naming of boards/devices. The pipeline is now much more extensible, making it easier for us to add support for more hardware!What's next?
We're aiming for a v0.0.2 release of TollGate OS by friday, incorporating some of the feedback we've gotten from our test users! Hang on tight guys! 🙏 I'm hoping to finish an earlier version of the installer in the upcoming week as well.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-08 01:22:05
@ 5d4b6c8d:8a1c1ee3
2025-05-08 01:22:05I've been thinking about how Predyx and other lightning based prediction markets might finance their operations, without undermining their core function of eliciting information from people.
The standard approach, of offering less-than-fair odds, guarantees long-run profitability (as long as you have enough customers), but it also creates a friction for participants that reduces the information value of their transactions. So, what are some less frictiony options for generating revenue?
Low hanging fruit
- Close markets in real-time: Rather than prespecifying a closing time for some markets, like sports, it's better to close the market at the moment the outcome is realized. This both prevents post hoc transactions and enables late stage transactions. This should be easily automatable (I say as someone with no idea how to do that), with the right resolution criteria.
- Round off shares: Shares and sats are discrete, so just make sure any necessary rounding is always in the house's favor.
- Set initial probabilities well: Use whatever external information is available to open markets as near to the "right" value as possible.
- Arbitrage: whenever markets are related to each other, make sure to resolve any illogical odds automatically
The point of these four is to avoid giving away free sats. None of them reduce productive use of the market. Keeping markets open up until the outcome is realized will probably greatly increase the number of transactions, since that's usually when the most information is coming in.
Third party support
- Ads are the most obvious form of third party revenue
- Sponsorships are the more interesting one: Allow sponsors to boost a market's visibility. This is similar to advertising, but it also capitalizes on the possibility of a market being of particular interest to someone.
- Charge for market creation: users should be able to create new markets (this will also enhance trade quantity and site traffic), but it should be costly to create a market. If prediction markets really provide higher quality information, then it's reasonable to charge for it.
- Arbitrage: Monitor external odds and whenever a gain can be locked in, place the bets (buy the shares) that guarantee a gain.
Bitcoin stuff
- Routing fees: The volume of sats moving into, out of, and being held in these markets will require a fairly large lightning node. Following some helpful tips to optimize fee revenue will generate some sats for logistical stuff that had to be done anyway.
- Treasury strategy: Take out loans against the revenue generated from all of the above and buy bitcoin: NGU -> repay with a fraction of the bitcoin, NGD -> repay with site revenue.
Bitcoin and Lightning Competitive Advantages
These aren't revenue ideas. They're just a couple of advantages lightning and bitcoin provide over fiat that should allow charging lower spreads than a traditional prediction market or sportsbook.
Traditional betting or prediction platforms are earning depreciating fiat, while a bitcoin based platform earns appreciating bitcoin. Traditional spreads must therefor be larger, in order to pull in the same real return. This also means the users' odds are worse on fiat platforms (again in real terms), even if the listed odds are the same, because their winnings will have depreciated by the time they receive them. Technically, this opens an opportunity to charge even higher spreads, but as mentioned in the intro, that would be bad for the information purposes of the market.
Lightning has much lower transactions costs than fiat transactions. So, even with tighter spreads, a lightning platform can net a better (nominal) return per transaction.
@mega_dreamer, I imagine most of those ideas were already on y'all's radar, and obviously you're already doing some, but I wanted to get them out of my head and onto digital paper. Hopefully, some of this will provide some useful food for thought.
originally posted at https://stacker.news/items/974372
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ 7460b7fd:4fc4e74b
2025-05-08 10:14:59
@ 7460b7fd:4fc4e74b
2025-05-08 10:14:59背景与研究范围
Backpack 是由多名前 FTX 和 Alameda 员工在 FTX 崩盘后创立的一家加密交易平台,与 Amber Group(一家大型加密金融服务商)和已倒闭的交易所 FTX 之间可能存在多重隐秘关联。本研究超越公开新闻,从团队延续、资金路径、合规架构、基础设施复用和链上迹象等角度,推理分析三者之间的联系。下文将分别讨论:团队与股权延续性、法币出金(稳定币清算)架构、Amber Group 的支持角色、Circle/Equals Money 等第三方的关联,以及“交叉代币解锁”机制的可能性,并给出关键证据与信息缺口。
团队与股权上的延续性
首先,在团队方面,Backpack 由多名 FTX/Alameda 前成员创立。据报道,Backpack 的联合创始人包括前 Alameda Research 早期员工 Armani Ferrante,以及 FTX 前总法律顾问 Can Suncoinspeaker.com;另一位联合创始人 Tristan Yver 也曾任职于 FTX/Alamedanftgators.com。据 CoinSpeaker 披露,Backpack 40名员工中至少有5人是 FTX 前员工coinspeaker.com。这表明 Backpack 在团队传承上与 FTX 存在明显延续。一方面,创始团队直接来自原 FTX 帝国的核心人员;另一方面,他们将过往在大型交易所积累的经验带入了 Backpack。
其次,在股权投资方面也有延续痕迹。早在2022年9月,Backpack 背后的公司 Coral 即获得了由 FTX Ventures 领投的2000万美元种子轮融资,用于开发 Backpack xNFT 钱包等产品nftgators.com。然而由于2022年11月FTX暴雷,这笔来自 FTX 的投资资金大部分被冻结损失nftgators.com。在经历了资金困难的“蟑螂生存模式”后,Backpack 团队于2023-2024年重新融资,成功在2024年2月完成1700万美元的 A 轮融资nftgators.com。值得注意的是,此轮融资的投资阵容中出现了 Amber Group 的身影nftgators.com。Amber Group 与 Placeholder、Hashed、Wintermute 等知名机构共同参与了该轮融资coinspeaker.com。这意味着 Amber 已经成为 Backpack 股东之一,在股权上建立了联系。此外,Jump Crypto 和 Delphi Digital 等与 FTX时代关系密切的机构也参与了投资nftgators.com。综上, Backpack 的股东和团队构成反映出明显的历史延续:既有原FTX系资本(FTX Ventures)和人员直接过渡,也有 Amber Group 等行业巨头在FTX倒台后入场接棒投资,为 Backpack 提供资金和资源支持。
法币出金架构与 USDC 清算渠道
FTX 时代的稳定币清算: 为了解 Backpack 是否继承了 FTX 的 USDC 清算架构,需要回顾 FTX 过往的法币出入金体系。FTX 在运营高峰时期,以其流畅的出入金和稳定币兑换闻名。用户可以将 USDC 等稳定币充值到 FTX 并直接视同美元资产使用,提取时又能以银行电汇方式取出美元,过程中几乎无汇兑损耗。这背后可能依赖于 FTX 与 Circle 等机构的直接清算合作,以及自有银行网络的支持。例如,Circle 提供的企业账户服务可以让像FTX这样的平台在后台实现USDC与美元的1:1兑换与清算circle.com。事实上,FTX 曾是 USDC 的主要场景之一,大量用户通过将美元换成 USDC 再转入FTX进行交易,从而绕过昂贵的跨境汇款费用。FTX 很可能建立了高效的稳定币兑换通道——例如通过 Silvergate 银行网络或与稳定币发行方直接交割——来实现低成本、快速的法币⇄USDC 转换。这套“USDC 清算架构”是FTX业务成功的重要基础之一。
Backpack 的出金方案: Backpack 作为新兴交易所,近期正式推出了类似的法币⇄稳定币出入金功能,并号称实现了“0费率”的美元/USDC转换panewslab.com。根据官方公告,从2025年5月起,Backpack Exchange 用户可以通过电汇方式充值和提取美元,且美元与USDC的兑换不收取任何手续费panewslab.com。这与FTX当年提供的低成本稳定币出入金体验如出一辙,表明 Backpack 很可能在复用或重建一种高效的清算架构。
与FTX相比,Backpack 并未公开具体采用了何种技术/金融渠道来实现0手续费。但通过社区测试和代码线索,可以推测其架构与FTX思路相似:首先, Backpack 将美元法币与USDC稳定币视为等价资产开放存取,用户电汇美元到账后在平台得到USDC或美元余额,提币时可用USDC直接提走或兑换成美元汇出。其次, Backpack 可能通过与稳定币发行方Circle的合作,或通过场外流动性方,将用户的USDC和法币进行实时对冲清算。Circle提供的API允许合规企业账户方便地将USDC兑换为美元存入银行账户circle.com;Backpack 很可能利用了这一渠道,在后台完成USDC的兑换,再通过银行网络把美元汇给用户。虽然Backpack官方未明言使用Circle,但其USDC通道开放的举措本身就体现了Circle所倡导的稳定币跨境支付应用场景circle.com。因此,从设计上看,Backpack 的法币出入金体系是对FTX模式的一种延续和致敬,即充分利用稳定币作为清算中介,实现跨境汇款的低成本与高效率。
银行网络与 Equals Money: 更有意思的是,有社区用户实测 Backpack 的美元提现,发现汇款发起方显示为“Equals Money PLC”btcxiaolinzi.top。Equals Money 是英国一家持有FCA牌照的电子货币机构(EMI),为企业提供银行转账和外汇服务btcxiaolinzi.top。测试者推断,Backpack 可能在 Equals Money 开立了企业账户,用于代替传统银行向用户汇出美元btcxiaolinzi.top。这一细节揭示了Backpack出金架构的实现路径:Backpack 很可能将待提现的USDC通过某种方式兑换成法币并存入其在Equals Money的账户,由后者完成跨境电汇至用户收款银行。由于Equals Money本质上连接着欧洲和国际支付网络,Backpack借助它可以避开美国传统银行的限制,为全球用户(包括无法直接与美国持牌银行打交道的用户)提供出金服务。这一点在FTX时代并未被广泛报道,但符合FTX/Alameda团队擅长搭建复杂金融通道的作风。由此推断, Backpack 确实在承袭FTX时期的清算理念:利用多层金融机构合作(如稳定币发行方、电子货币机构等),构筑高效的全球资金出入网络。在表面0手续费的背后,可能是由Backpack或其合作方(如做市商)承担了兑换成本,以吸引用户panewslab.com。目前这一体系已进入公开测试及运营阶段,随着更多支付方式(ACH、SEPA)的推出,Backpack正逐步完善其全球法币出入金矩阵panewslab.com。
Amber Group 的潜在支持角色
作为Backpack的重要战略投资方,Amber Group 在该体系中可能扮演多重支持角色。首先是资金层面: Amber参与了Backpack的A轮融资nftgators.com并获得股权,这意味着Amber对Backpack的发展具有直接利益。在FTX倒闭后,Amber选择投资由FTX前团队创立的新交易所,体现出其对这支团队能力和商业模式的认可。Amber本身是知名的加密市场做市和金融服务公司,管理着庞大的资产并具备深厚的流动性提供能力dailycoin.com。因此可以合理推测,Amber除了资本投入,还可能作为做市商为Backpack的交易提供充足的流动性支持,确保用户在Backpack上交易时有良好的市场深度和稳定的价格。这种隐性支持符合许多交易所背后有大做市商“站台”的行业惯例。尤其Backpack定位要提供低成本的稳定币兑换和跨链流动性,Amber在稳定币交易市场的经验和库存或可帮助其维持汇率稳定。
其次是技术与基础设施支持: Amber Group 多年来构建了自己的交易系统(包括托管、风控和前端应用,如之前面向零售的 WhaleFin 应用)。尽管目前未有公开信息表明Backpack直接复用了Amber的技术,但不排除Amber在底层架构上提供咨询或授权支持的可能。例如,Amber深耕多链资产管理和清算,其内部API或合规方案可能对Backpack搭建跨法币/加密的基础设施有所启发。双方如果有合作,极有可能保持低调以避免监管敏感。还有一种支持形式是隐性投资或子基金合作: Amber可能通过旗下基金或关联投资工具,持有Backpack相关业务的权益而不公开身份。然而截至目前,我们尚未发现明确证据证明Amber有这种“隐形”持股行为——Amber作为领投方之一出现于公开融资名单,说明其支持主要还是以正式股权投资和业务协作的方式进行coinspeaker.com。
第三是合规与网络资源: Amber在全球(尤其亚洲)拥有广泛的业务网络和合规资源。Backpack注册在阿联酋迪拜,并计划拓展美国、日本、欧洲等市场learn.backpack.exchangelearn.backpack.exchange。Amber总部位于亚洲(最初在香港,新加坡等地开展业务),对东亚和东南亚市场非常了解。Amber的联合创始人团队中有合规专家,曾帮助公司获取多地牌照。Backpack的联合创始人之一(Can Sun)本身是前FTX法务,这保证了内部合规经验,但Amber的外部资源也可能提供协助。例如,Amber在香港与监管机构打交道的经验,或许有助于Backpack寻求香港或东南亚牌照;Amber在银行业和支付领域的关系网络,也可能帮助Backpack连接银行通道(如引荐像Equals Money这样的机构)。虽然这方面多属于推测,但考虑到Amber投资后通常会积极赋能被投企业,Backpack有理由从Amber处获得合规咨询、市场拓展等方面的帮助。
总的来看,Amber Group 对 Backpack 的支持可能是**“润物细无声”**式的:既体现在台前的融资与做市合作,也体现在幕后的资源共享和经验输出。这种支持帮助Backpack在短时间内补齐了从交易技术到法币通道的诸多要素,使其有能力低成本快速上线类似FTX当年的核心功能(如稳定币快速出入金)。然而,由于双方都未公开详述合作细节,我们对Amber介入的深度仍缺乏直接证据,只能从结果倒推其可能性。
Circle、Equals Money 等第三方的关联
在Backpack、FTX与Amber的关系网络中,Circle和Equals Money等第三方机构扮演了关键“节点”,它们的出现为三者合作提供了基础设施支撑:
-
Circle(USDC发行方): Circle公司本身与FTX及Backpack都有千丝万缕的业务联系。FTX在世时是USDC重要的使用方,帮助USDC拓展了交易所场景;FTX垮台后,Backpack继续扛起“稳定币交易所”的大旗,大量采用USDC作为美元计价和清算工具panewslab.com。虽然我们没有公开材料直接指出Backpack已与Circle签署合作协议,但Backpack推出USD/USDC通道的举措实际是在推动USDC的使用,这与Circle致力于扩大USDC应用的战略不谋而合circle.com。Circle近年来打造跨境支付网络,与多家交易平台和金融机构合作提供法币-稳定币转换服务circle.com。因此,有理由相信Backpack在后台利用了Circle的流动性或API来实现用户提币时的USDC兑换和赎回。比如,当用户在Backpack提取美元,Backpack可能将等额USDC通过Circle赎回成美元,Circle则将该美元汇入Backpack的银行账户进行出金。这种模式其实正是Circle提供给企业客户的“稳定币托管清算”服务之一circle.com。换言之,Circle充当了Backpack法币出金链条中的关键一环,尽管普通用户感知不到它的存在。反过来看Amber,作为全球领先的做市商,也大量使用USDC进行交易和结算,Amber与Circle之间亦可能有直接合作关系(如参与Circle的伙伴计划等)。可以说,Circle及其USDC网络构成了FTX时代和Backpack时代连接传统金融和加密世界的桥梁:FTX和Backpack都踩在这座桥上快速发展,而Amber作为市场参与者,同样频繁走这座桥,为自身和伙伴创造价值。
-
Equals Money(英国电子货币机构): 前文提及,Equals Money PLC 在Backpack的出金过程中显现出来btcxiaolinzi.top。这家公司提供面向企业的银行即服务(BaaS),允许像Backpack这样的客户通过其平台发起全球付款。Equals Money的出现意味着Backpack选择了一条灵活的合规路径来实现银行转账功能:相比直接开设传统银行账户,使用EMI能更快获取支付能力且准入门槛较低。FTX时期并未传出使用EMI的消息,因为当时FTX可直接依赖自己的银行关系网(例如通过位于美国、欧洲的自有账户)来处理汇款。然而在后FTX时代,许多加密公司(包括Amber)都在寻找新的银行替代方案,EMI因此受到青睐。具体联系: 根据实测,Backpack用户提现美元到Wise时,Wise收到的汇款来自Equals Moneybtcxiaolinzi.top。Wise作为跨境汇款平台,其收款机制对资金来源要求严格,但Equals Money持有FCA牌照,属于受监管机构,Wise接收来自Equals的资金被视为合规btcxiaolinzi.top。由此推断,Backpack通过Equals的企业账户,将兑换好的美元直接打给用户填入的收款账号(包括Wise提供的虚拟账号)。这表明Backpack和Equals Money之间有直接业务往来,Equals是Backpack法币出金服务链条上的合作伙伴。值得一提的是,Amber Group 此前在欧洲也曾探索电子货币牌照或合作渠道的可能,尽管无法确认Amber是否也使用Equals,但不排除Amber为Backpack牵线搭桥、推荐了Equals这类服务商的可能性。
综合来看, Circle和Equals Money分别代表了稳定币清算层和法币支付层的基础设施,与Backpack/FTX/Amber的联系体现为:Circle提供“链上到链下”的美元流动性支持,Equals提供“链下”最后一公里的银行网络接口。三者之所以都选择/使用这些渠道,是因为它们共享了对加密法币融合效率的追求。对于FTX和Backpack而言,这些渠道是业务方案的一部分;对于Amber而言,这些渠道是服务布局和投资的一环(Amber支持的交易所采用了这些方案,也间接符合Amber推动行业基础设施完善的利益)。
“交叉代币解锁”机制与链上协作迹象
“交叉代币解锁”是指Amber、Backpack(或其关联项目)之间通过持有彼此发行的代币,并利用协议合作、解锁计划或链上交易,实现协同利益的一种机制。鉴于Backpack尚处于发展初期,我们需要探讨哪些代币或资产可能涉及双方的互动:
-
Backpack 平台代币的潜在发行: 根据Backpack社区的信息,平台计划通过交易积分空投方式向活跃用户发放代币资格btcxiaolinzi.top。这暗示Backpack未来会推出自己的平台代币。若真如此,早期投资方(包括Amber Group)很可能在代币经济中占有一席之地,例如通过投资协议获得一定比例的平台代币配额。在代币正式解锁流通时,Amber等机构投资者将持有相应份额。这就产生了潜在的“交叉代币”联系:Amber持有Backpack的代币,并可在协议允许的时间窗口解锁出售或利用。这种关系一方面绑定了Amber与Backpack的长期利益,另一方面也为Amber提供了在二级市场获利或支持Backpack代币市值的机会。如果Backpack设计代币经济时有锁仓解锁期,那么Amber的代币解锁时间和数量将受到协议约束。从链上数据看,未来可以观察这些大额代币解锁地址是否与Amber的钱包存在关联,以验证Amber对Backpack代币的处置行为。当前,由于Backpack代币尚未发行,我们只能提出这一推测性机制,等待后续链上数据来印证。
-
Amber 持仓代币与Backpack业务的协同: 反之,Amber Group 或其子基金本身持有众多加密资产,是否有与Backpack生态互动的情况?例如,Amber可能持有某些与Backpack生态有关的项目代币(如Solana链上资产,Backpack钱包支持的特定NFT/代币等)。一个案例是Backpack团队曾在Solana上发行受欢迎的 xNFT系列“Mαd Lads”NFTlearn.backpack.exchange。Amber或其投资部门是否参与了该NFT的投资或持有尚无公开资料,但不排除Amber透过场内交易购买一些以支持Backpack生态热度。再者,如果Amber在其他项目上持有代币,而Backpack平台上线这些资产交易,Amber可能通过链上转账将流动性注入Backpack,从而实现双方受益——Amber获得流动性做市收益,Backpack获得交易量和资产丰富度。这可以视作一种链上协作。例如Amber持有大量某种代币X,在Backpack上新上线代币X交易对时,Amber账户向Backpack的热钱包充值代币X提供初始流动性。这样的行为在链上会呈现Amber已知地址向Backpack地址的大额转账。如果将来这些数据出现,将成为印证双方链上合作的直接证据。目前,此类链上轨迹还未有公开披露,我们只能假设其存在的可能性。
-
FTX 遗留资产与Backpack 的关联: 另一个值得一提的链上观察维度是FTX/Alameda遗留资产的动向。FTX倒闭后,其相关钱包曾多次异动。Backpack团队作为前员工,有可能知晓某些地址或资产的情况。但由于破产清算在法庭监管下进行,直接将FTX遗留资产转给新项目不太现实。不过,不排除某些前Alameda投资的项目代币后来为Backpack团队所用。例如,Alameda早期投资的项目若代币解锁,Backpack团队个人可能持有部分并用于新平台的流动性。这种间接关联较难确认,但链上仍可寻找蛛丝马迹,比如监测前Alameda标识的钱包与Backpack相关地址之间的交易。如果有频繁互动,可能暗示Backpack获取了Alameda旧有资产的支持。至今未见显著证据,推测空间大于实证。
小结: “交叉代币解锁”机制目前更多停留在理论推演层面。我们确认了Backpack未来存在发行平台代币的规划btcxiaolinzi.top;也确认Amber作为投资方大概率会获得并持有该代币份额。但具体的锁仓解锁安排、双方是否会通过特殊协议(如做市激励、流动性挖矿等)进行合作,还有待官方披露或链上数据验证。链上分析工具可以在未来帮助捕捉Amber地址与Backpack生态代币/NFT的交互,从而揭示深层协作。如果发现Amber旗下地址在Backpack代币解锁后立即大量转入交易所,可能意味着Amber选择变现;反之,若锁定期内就有灰度交易发生,甚至可能存在双方提前约定的场外交换。这些都是值得持续监测的方向,但就目前信息来看,尚无定论。
\ 图:FTX、Amber Group 与 Backpack 三者关系示意图。红色/橙色线表示团队和股权延续(FTX前员工和投资延续到Backpack,Amber参与投资并可能提供流动性);蓝色线表示Backpack法币出金所依赖的稳定币清算和银行通道(通过USDC及Equals Money实现);灰色虚线表示FTX和Amber分别与USDC发行方Circle在业务上的联系。这些关系共同构成了Backpack在FTX余荫和Amber支持下快速搭建全球业务的基础。
关键证据与信息缺口
通过上述分析,我们梳理了已知的信息链条,并挖掘了若干可能的隐秘关联,同时也识别出需要进一步调查的信息空白:
-
明确的证据链: 我们找到了多项公开资料证明Backpack与FTX/Amber的联系:包括创始团队来自FTX/Alamedacoinspeaker.com、FTX Ventures 曾投资Backpack母公司nftgators.com、Amber Group 参与了Backpack的融资coinspeaker.com、多名FTX旧部现在Backpack任职coinspeaker.com等。这些形成了人员和资金延续的直接证据。另外,通过用户分享和代码库,我们确认Backpack法币出金使用了Equals Money通道btcxiaolinzi.top并提供了0手续费的USD/USDC转换panewslab.com——这证明了Backpack确实建立了类似FTX当年的稳定币清算架构,只是技术实现上借助了新的合作方(Equals Money)。这些证据支撑了本文的大部分推论基础。
-
合理的推测与佐证: 有些关联尚无官方公告证明,但基于行业惯例和现有线索推测合理,并有部分侧面佐证。例如,Amber 为Backpack提供做市流动性支援一事,没有直接新闻来源,但考虑到Amber投资交易所的动机和能力,此推断具有高概率可靠性。再如,Backpack疑似使用Circle的USDC清算服务,虽无明示,但从其业务模式和Circle的产品定位来看circle.com,这一幕后合作应该存在。同样地,Amber可能通过非公开方式向Backpack输出技术/合规支持,也是基于双方利益绑定关系而做出的推断。这些推测目前缺乏直接证据,只能算作可能性假设,需要后续留意更多细节披露。
-
信息缺口与待验证点: 首先,关于Backpack具体的清算路径,我们仍不清楚它如何在链上/链下转换巨额USDC为法币。虽然Equals Money出现在汇款端btcxiaolinzi.top,但在那之前USDC的结算或许涉及Circle或其他做市商(如Amber)——这部分交易发生在后台,需更多技术信息或链上监控来捕捉。其次,Amber与Backpack之间除股权外是否存在合同约定的业务合作(如Amber成为指定做市商、提供信贷支持等)目前尚未公开,属于信息真空。第三,Backpack未来的代币发行和分配细节未知,Amber等投资方将如何参与、解锁周期如何,将直接影响“交叉代币”协作的发生与否,需等官方白皮书出台。第四,更多链上证据的挖掘:由于没有公开的钱包标签,很难直接将某条链上交易指认属于Amber或Backpack。但如果未来Backpack发行代币或大型交易上线,链上必然会出现相关资金流,我们可以通过已知Amber常用地址(如果有披露)来交叉比对,看其是否与Backpack生态有交互。这是一块需要进一步研究的领域,可能借助区块链分析工具和交易图谱来补全证据。最后,还有监管和法律结构的信息:例如Backpack在不同司法管辖区的注册实体与银行账号详情,FTX遗产处理过程中是否对Backpack团队有约束,这些在公开资料中都尚无答案。
结论
综合全篇分析,Backpack、Amber Group 与已倒闭的FTX之间确实存在千丝万缕的延续和关联。Backpack可以被视作FTX精神和技术路线的“继承者”之一——由FTX旧将创建,在FTX垮台造成的市场空白中迅速崛起coinspeaker.com。Amber Group 则扮演了重要的扶持者角色,通过投资和可能的资源注入,参与了Backpack的重建过程coinspeaker.com。在具体业务层面,Backpack延续了FTX时代的创新,如高效的稳定币清算和全球化业务布局,但为了适应新的环境,它也采用了新的工具(如Equals Money的出金渠道)和更严格的合规措施(迪拜等地的牌照)coinspeaker.com。这一切背后,隐现着Amber等老牌加密公司的身影支持,以及Circle等基础设施提供商的支撑。
当然,隐秘关联并不意味着不正当行为,上述关系很多是基于正常的商业合作和延续,只是未明言于公众。例如,前FTX团队利用自己的经验和人脉创建新平台,本身无可厚非;Amber投资新交易所也是市场行为。从推理和现有证据看,并没有直接迹象显示三者存在违法的秘密勾连。然而,对于研究者和行业观察者而言,了解这些联系有助于洞察加密行业格局的演变:FTX的倒下并未让其积累的人才和思想消失,反而通过创业和投资,以新的形式(Backpack)继续影响市场;Amber等老牌玩家则通过战略投资,将自己的版图延伸到新兴平台,以保持竞争力。
未来展望: 随着Backpack进一步发展,我们预计会有更多信息浮出水面来验证或修正上述假设。例如,Backpack若推出平台代币,其投资人持仓和解锁情况将记录在链,从而揭示Amber等的参与细节;再比如,Backpack进入美国市场时需要公开其合作银行或支付伙伴,届时我们可能印证Circle等在其中的角色。如果出现新的合作公告或监管披露文件,也能帮助我们更清晰地绘制三者关系网。目前的信息不对称使我们只能尽力拼凑一幅关联图景,并针对关键环节提供已知证据支持。仍存在的一些信息缺口需要持续跟进调查。总之,Backpack、Amber Group 与FTX的故事折射出加密行业的新旧交替与传承。在FTX的余烬上,新火花正在由熟悉旧世界的人点燃,而这些火花能否照亮一个更加合规稳健的未来,还有待时间检验。 nftgators.comcoinspeaker.com
-
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 8d34bd24:414be32b
2025-05-07 21:47:57
@ 8d34bd24:414be32b
2025-05-07 21:47:57I’ve been really deeply studying end times prophecy today. Trying to see how all of the prophecies from the initial proto-Gospel in Genesis 3 through the last chapter in Revelation is hard to arrange in my head. That being said, after reading the Bible daily for about 40 years and reading through it each year for about 30 years, I am really starting to see so many links between passages through out the Bible. It has made my Bible study enthralling. I wish I had time to spend hours and hours every day studying and writing about what I have learned.
I thought it might be handy to share some hints on how I study the Bible. Hopefully this can help some people, although I do tend to think my subscribers tend to be those who love Bible study and are already in the word. People who don’t love the Bible are unlikely to read my long, scripture laden posts. Still, hopefully this will be useful.
Starting the Habit of Bible Reading
The first and foremost thing we all need is to start the habit of daily Bible reading. You can’t worship a God you don’t know about and you can’t obey a God whose commands you don’t know. Every Christian needs to read the whole Bible. This needs to be a priority.
I used to recommend people just start at the beginning, Genesis, and read straight through to Revelation, but I’ve lately changed my mind. So many people will start in Genesis, enjoy Genesis and Exodus, which are basically just stories about creation, judgment in the global flood, and God’s chosen people. They then get to Leviticus, Numbers, and Deuteronomy (the details of the law including the intricate ceremonial law) and they lose momentum in the tedium. I do think every Christian eventually needs to read and know these books, but I think it is OK to skip some or all of them the first time through. They will mean more once you have read the whole Bible. If you are only going to read one, I’d probably read Deuteronomy.
I also know that it can be helpful for some people to mix up their reading. I used to have book marks with daily readings, so I read some Old Testament, some Psalms/Proverbs, some New Testament. There was one other category, but I can’t remember what it was. This way, you get a little of different types of passages. My bookmarks burnt up when my house burnt down and when I went searching online for something similar, I found a few similar reading plans, but not the one I used and really liked. Here are a couple that looked good, but I haven’t used myself. here. here. here. These plans look good, but don’t have the convenient bookmarks. here. here. For those who like reading online or on your phone (which isn’t me), I found this one. It looked nice I’ve just started using it despite the fact I prefer a Bible I can hold, turn the pages of, and write in. It has a chronological Old Testament Passage and a New Testament reading that relates in some way to the Old Testament Passage. It also links to some maps that let you see where the places mentioned in the passages are located and questions to get you to think about what you read. The one downside is it only lets you attach notes if you create a group. I do really like the idea that you can setup a group to read through the Bible and share your comments and thoughts, but I haven’t tried the feature.
Another thing I’ve found very helpful is a chronological Bible. It is handy having things in the order they happened and the different passages that cover an event (such as from each gospel or 1/2 Samuel vs 1/2 Chronicles or Leviticus vs Deuteronomy, etc.) right by each other. It is handy to see what actually comes before what and the way different writers describe the same event, since different authors include different details. I think reading a chronological Bible has helped me see more links between passages and get a better understanding of the Bible as a whole. I am getting close to finishing my second reading through. I don’t know if one chronological Bible is significantly better than another, but this is the one I am reading right now.
Another tactic I have used, when I started getting bogged down reading through the Bible again and again was to study one book of the Bible in depth. It worked best reading one of the shorter books. I’d read through the book repeatedly for a month, usually in 1-3 days. I’d follow the links in my study Bible to related passages or study where some of the words were used in other parts of the Bible. I’d get so I really knew the book well.
One thing that has helped me with my Bible study is writing in my Bible. The first time I wrote, it felt almost sacrilegious, but it helps me to organize my thoughts. I’ll write what I get out of it, how it relates to another passage, etc. I’ll underline or circle key words or sentences. These are then useful when I read through again and may see something different, but it reminds me of my growth and learning. I’ve actually thought I really need to get a new wide margin Bible to have more room for my notes. I can write really small and have an ultrafine point pen, so I can write even smaller than the print. The problem is my eyes aren’t so good and I now have trouble reading my tiny print. I can’t read my own writing without my reading glasses.
Bible reading starts getting really exciting when you get to know the Bible well enough that you start seeing the links between different passages and different books. Suddenly it opens up a whole new level of understanding. It is like an exciting scavenger hunt finding how all of the ideas in the Bible relate to each other and clarify each other in one whole.
Historically I’ve hated writing. The thought of writing a journal or something sounded like torture, but I have truly found organizing my thoughts in an essay, really helps my understanding of the Scriptures in ways that reading and thinking about it never did. Whether anyone reads my writings or not, I’ll continue writing because it is a blessing to me. I have grown immensely in my understanding of the Bible by writing out a reasoned argument for what I believe the Bible is saying. I’ve also done in depth study and realized that I was not completely right in my understanding and had to adjust my understanding of Scripture.
but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence (1 Peter 3:15)
As Christians, we are supposed to be ready to make a defense. Reading, studying, and knowing the Bible is the only true way to be ready. I made a necklace with the first letter in each word in this verse to help me memorize it.

Memorizing God’s word is also well worth the effort. I’ll admit, that I would be terrible for following my own advice in this, except I have a special needs son, who is in Awana, and needs help memorizing 1-5 verses a week. The only way either of us can pull it off is I make a song for each 1-3 verse passage that he has to memorize. We then sing them together until we know them. I debated on whether to share my songs. They are not well done. The version uploaded is my first rough attempt at the song and we usually fine tune them over the week, but I don’t get around to rerecording them. I also have at best an OK voice. Still, I decided to share in case these songs can help someone else with their Bible memorization. Hopefully I am not embarrassing myself too much.
Another thing that has helped me is finding Open Bible’s geocoding site. When reading Bible passages, there are frequent references to places that are unfamiliar, either because they are far away or because the ancient names, rather than modern names, are used. This site allows you to see on a map (satellite & modern country formats) where places are located and how they relate to each other. I’ve especially found this useful with end times prophecy because the Bible describes places with their ancient, not modern names.
In addition to my direct Bible study, I also daily listen to sermons, Christian podcasts, read Christian substack posts, and read Christian commentaries. All help my understanding of the Bible. FYI, the sermons, podcasts, blogs, and commentaries are a risk if you don’t know the Bible and aren’t being like the Bereans who searched “… the Scriptures daily to see whether these things were so.” (Acts 17:11) There are so many false or erroneous teachers, that you have to be very careful listening to people and never put the opinions of men above the word of God. Of course, it is possible to learn a bunch from Godly teachers. Sadly, even the best Bible teachers seem to have at least one area of error. For example, I love listening to R.C. Sproul’s “Renewing Your Mind” podcast, but his teaching on the first 11 chapters of Genesis are a bit “squishy” (not outright wrong, but not holding firm enough to the Bible) and I’d say his end times teaching is flat out wrong. Everything I’ve heard him teach between Genesis 12 and Jude is amazing and very true to the Bible. This is where he spends almost all of his time teaching, so I can highly recommend his podcast. Without a firm foundation in the Bible, it is not possible to recognize false teaching, especially when taught by someone who is very good in most respects.
I hope this is useful to people to help them get into the habit of regular Bible reading and seeing how exciting Bible study can be.
May God give you a hunger for and understanding of His word. May you fill your heart and mind with the word of God so it overflows and is seen by all around you.
Trust Jesus.
-
 @ a008def1:57a3564d
2025-04-30 17:52:11
@ a008def1:57a3564d
2025-04-30 17:52:11A Vision for #GitViaNostr
Git has long been the standard for version control in software development, but over time, we has lost its distributed nature. Originally, Git used open, permissionless email for collaboration, which worked well at scale. However, the rise of GitHub and its centralized pull request (PR) model has shifted the landscape.
Now, we have the opportunity to revive Git's permissionless and distributed nature through Nostr!
We’ve developed tools to facilitate Git collaboration via Nostr, but there are still significant friction that prevents widespread adoption. This article outlines a vision for how we can reduce those barriers and encourage more repositories to embrace this approach.
First, we’ll review our progress so far. Then, we’ll propose a guiding philosophy for our next steps. Finally, we’ll discuss a vision to tackle specific challenges, mainly relating to the role of the Git server and CI/CD.
I am the lead maintainer of ngit and gitworkshop.dev, and I’ve been fortunate to work full-time on this initiative for the past two years, thanks to an OpenSats grant.
How Far We’ve Come
The aim of #GitViaNostr is to liberate discussions around code collaboration from permissioned walled gardens. At the core of this collaboration is the process of proposing and applying changes. That's what we focused on first.
Since Nostr shares characteristics with email, and with NIP34, we’ve adopted similar primitives to those used in the patches-over-email workflow. This is because of their simplicity and that they don’t require contributors to host anything, which adds reliability and makes participation more accessible.
However, the fork-branch-PR-merge workflow is the only model many developers have known, and changing established workflows can be challenging. To address this, we developed a new workflow that balances familiarity, user experience, and alignment with the Nostr protocol: the branch-PR-merge model.
This model is implemented in ngit, which includes a Git plugin that allows users to engage without needing to learn new commands. Additionally, gitworkshop.dev offers a GitHub-like interface for interacting with PRs and issues. We encourage you to try them out using the quick start guide and share your feedback. You can also explore PRs and issues with gitplaza.
For those who prefer the patches-over-email workflow, you can still use that approach with Nostr through gitstr or the
ngit sendandngit listcommands, and explore patches with patch34.The tools are now available to support the core collaboration challenge, but we are still at the beginning of the adoption curve.
Before we dive into the challenges—such as why the Git server setup can be jarring and the possibilities surrounding CI/CD—let’s take a moment to reflect on how we should approach the challenges ahead of us.
Philosophy
Here are some foundational principles I shared a few years ago:
- Let Git be Git
- Let Nostr be Nostr
- Learn from the successes of others
I’d like to add one more:
- Embrace anarchy and resist monolithic development.
Micro Clients FTW
Nostr celebrates simplicity, and we should strive to maintain that. Monolithic developments often lead to unnecessary complexity. Projects like gitworkshop.dev, which aim to cover various aspects of the code collaboration experience, should not stifle innovation.
Just yesterday, the launch of following.space demonstrated how vibe-coded micro clients can make a significant impact. They can be valuable on their own, shape the ecosystem, and help push large and widely used clients to implement features and ideas.
The primitives in NIP34 are straightforward, and if there are any barriers preventing the vibe-coding of a #GitViaNostr app in an afternoon, we should work to eliminate them.
Micro clients should lead the way and explore new workflows, experiences, and models of thinking.
Take kanbanstr.com. It provides excellent project management and organization features that work seamlessly with NIP34 primitives.
From kanban to code snippets, from CI/CD runners to SatShoot—may a thousand flowers bloom, and a thousand more after them.
Friction and Challenges
The Git Server
In #GitViaNostr, maintainers' branches (e.g.,
master) are hosted on a Git server. Here’s why this approach is beneficial:- Follows the original Git vision and the "let Git be Git" philosophy.
- Super efficient, battle-tested, and compatible with all the ways people use Git (e.g., LFS, shallow cloning).
- Maintains compatibility with related systems without the need for plugins (e.g., for build and deployment).
- Only repository maintainers need write access.
In the original Git model, all users would need to add the Git server as a 'git remote.' However, with ngit, the Git server is hidden behind a Nostr remote, which enables:
- Hiding complexity from contributors and users, so that only maintainers need to know about the Git server component to start using #GitViaNostr.
- Maintainers can easily swap Git servers by updating their announcement event, allowing contributors/users using ngit to automatically switch to the new one.
Challenges with the Git Server
While the Git server model has its advantages, it also presents several challenges:
- Initial Setup: When creating a new repository, maintainers must select a Git server, which can be a jarring experience. Most options come with bloated social collaboration features tied to a centralized PR model, often difficult or impossible to disable.
-
Manual Configuration: New repositories require manual configuration, including adding new maintainers through a browser UI, which can be cumbersome and time-consuming.
-
User Onboarding: Many Git servers require email sign-up or KYC (Know Your Customer) processes, which can be a significant turn-off for new users exploring a decentralized and permissionless alternative to GitHub.
Once the initial setup is complete, the system works well if a reliable Git server is chosen. However, this is a significant "if," as we have become accustomed to the excellent uptime and reliability of GitHub. Even professionally run alternatives like Codeberg can experience downtime, which is frustrating when CI/CD and deployment processes are affected. This problem is exacerbated when self-hosting.
Currently, most repositories on Nostr rely on GitHub as the Git server. While maintainers can change servers without disrupting their contributors, this reliance on a centralized service is not the decentralized dream we aspire to achieve.
Vision for the Git Server
The goal is to transform the Git server from a single point of truth and failure into a component similar to a Nostr relay.
Functionality Already in ngit to Support This
-
State on Nostr: Store the state of branches and tags in a Nostr event, removing reliance on a single server. This validates that the data received has been signed by the maintainer, significantly reducing the trust requirement.
-
Proxy to Multiple Git Servers: Proxy requests to all servers listed in the announcement event, adding redundancy and eliminating the need for any one server to match GitHub's reliability.
Implementation Requirements
To achieve this vision, the Nostr Git server implementation should:
-
Implement the Git Smart HTTP Protocol without authentication (no SSH) and only accept pushes if the reference tip matches the latest state event.
-
Avoid Bloat: There should be no user authentication, no database, no web UI, and no unnecessary features.
-
Automatic Repository Management: Accept or reject new repositories automatically upon the first push based on the content of the repository announcement event referenced in the URL path and its author.
Just as there are many free, paid, and self-hosted relays, there will be a variety of free, zero-step signup options, as well as self-hosted and paid solutions.
Some servers may use a Web of Trust (WoT) to filter out spam, while others might impose bandwidth or repository size limits for free tiers or whitelist specific npubs.
Additionally, some implementations could bundle relay and blossom server functionalities to unify the provision of repository data into a single service. These would likely only accept content related to the stored repositories rather than general social nostr content.
The potential role of CI / CD via nostr DVMs could create the incentives for a market of highly reliable free at the point of use git servers.
This could make onboarding #GitViaNostr repositories as easy as entering a name and selecting from a multi-select list of Git server providers that announce via NIP89.
!(image)[https://image.nostr.build/badedc822995eb18b6d3c4bff0743b12b2e5ac018845ba498ce4aab0727caf6c.jpg]
Git Client in the Browser
Currently, many tasks are performed on a Git server web UI, such as:
- Browsing code, commits, branches, tags, etc.
- Creating and displaying permalinks to specific lines in commits.
- Merging PRs.
- Making small commits and PRs on-the-fly.
Just as nobody goes to the web UI of a relay (e.g., nos.lol) to interact with notes, nobody should need to go to a Git server to interact with repositories. We use the Nostr protocol to interact with Nostr relays, and we should use the Git protocol to interact with Git servers. This situation has evolved due to the centralization of Git servers. Instead of being restricted to the view and experience designed by the server operator, users should be able to choose the user experience that works best for them from a range of clients. To facilitate this, we need a library that lowers the barrier to entry for creating these experiences. This library should not require a full clone of every repository and should not depend on proprietary APIs. As a starting point, I propose wrapping the WASM-compiled gitlib2 library for the web and creating useful functions, such as showing a file, which utilizes clever flags to minimize bandwidth usage (e.g., shallow clone, noblob, etc.).
This approach would not only enhance clients like gitworkshop.dev but also bring forth a vision where Git servers simply run the Git protocol, making vibe coding Git experiences even better.
song
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 created song with a complementary vision that has shaped how I see the role of the git server. Its a self-hosted, nostr-permissioned git server with a relay baked in. Its currently a WIP and there are some compatability with ngit that we need to work out.
We collaborated on the nostr-permissioning approach now reflected in nip34.
I'm really excited to see how this space evolves.
CI/CD
Most projects require CI/CD, and while this is often bundled with Git hosting solutions, it is currently not smoothly integrated into #GitViaNostr yet. There are many loosely coupled options, such as Jenkins, Travis, CircleCI, etc., that could be integrated with Nostr.
However, the more exciting prospect is to use DVMs (Data Vending Machines).
DVMs for CI/CD
Nostr Data Vending Machines (DVMs) can provide a marketplace of CI/CD task runners with Cashu for micro payments.
There are various trust levels in CI/CD tasks:
- Tasks with no secrets eg. tests.
- Tasks using updatable secrets eg. API keys.
- Unverifiable builds and steps that sign with Android, Nostr, or PGP keys.
DVMs allow tasks to be kicked off with specific providers using a Cashu token as payment.
It might be suitable for some high-compute and easily verifiable tasks to be run by the cheapest available providers. Medium trust tasks could be run by providers with a good reputation, while high trust tasks could be run on self-hosted runners.
Job requests, status, and results all get published to Nostr for display in Git-focused Nostr clients.
Jobs could be triggered manually, or self-hosted runners could be configured to watch a Nostr repository and kick off jobs using their own runners without payment.
But I'm most excited about the prospect of Watcher Agents.
CI/CD Watcher Agents
AI agents empowered with a NIP60 Cashu wallet can run tasks based on activity, such as a push to master or a new PR, using the most suitable available DVM runner that meets the user's criteria. To keep them running, anyone could top up their NIP60 Cashu wallet; otherwise, the watcher turns off when the funds run out. It could be users, maintainers, or anyone interested in helping the project who could top up the Watcher Agent's balance.
As aluded to earlier, part of building a reputation as a CI/CD provider could involve running reliable hosting (Git server, relay, and blossom server) for all FOSS Nostr Git repositories.
This provides a sustainable revenue model for hosting providers and creates incentives for many free-at-the-point-of-use hosting providers. This, in turn, would allow one-click Nostr repository creation workflows, instantly hosted by many different providers.
Progress to Date
nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr and nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 have been working on a runner that uses GitHub Actions YAML syntax (using act) for the dvm-cicd-runner and takes Cashu payment. You can see example runs on GitWorkshop. It currently takes testnuts, doesn't give any change, and the schema will likely change.
Note: The actions tab on GitWorkshop is currently available on all repositories if you turn on experimental mode (under settings in the user menu).
It's a work in progress, and we expect the format and schema to evolve.
Easy Web App Deployment
For those disapointed not to find a 'Nostr' button to import a git repository to Vercel menu: take heart, they made it easy. vercel.com_import_options.png there is a vercel cli that can be easily called in CI / CD jobs to kick of deployments. Not all managed solutions for web app deployment (eg. netlify) make it that easy.
Many More Opportunities
Large Patches via Blossom
I would be remiss not to mention the large patch problem. Some patches are too big to fit into Nostr events. Blossom is perfect for this, as it allows these larger patches to be included in a blossom file and referenced in a new patch kind.
Enhancing the #GitViaNostr Experience
Beyond the large patch issue, there are numerous opportunities to enhance the #GitViaNostr ecosystem. We can focus on improving browsing, discovery, social and notifications. Receiving notifications on daily driver Nostr apps is one of the killer features of Nostr. However, we must ensure that Git-related notifications are easily reviewable, so we don’t miss any critical updates.
We need to develop tools that cater to our curiosity—tools that enable us to discover and follow projects, engage in discussions that pique our interest, and stay informed about developments relevant to our work.
Additionally, we should not overlook the importance of robust search capabilities and tools that facilitate migrations.
Concluding Thoughts
The design space is vast. Its an exciting time to be working on freedom tech. I encourage everyone to contribute their ideas and creativity and get vibe-coding!
I welcome your honest feedback on this vision and any suggestions you might have. Your insights are invaluable as we collaborate to shape the future of #GitViaNostr. Onward.
Contributions
To conclude, I want to acknowledge some the individuals who have made recent code contributions related to #GitViaNostr:
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 (gitstr, song, patch34), nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks (gitplaza)
nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume (ngit contributions, git-remote-blossom),nostr:npub16p8v7varqwjes5hak6q7mz6pygqm4pwc6gve4mrned3xs8tz42gq7kfhdw (SatShoot, Flotilla-Budabit), nostr:npub1ehhfg09mr8z34wz85ek46a6rww4f7c7jsujxhdvmpqnl5hnrwsqq2szjqv (Flotilla-Budabit, Nostr Git Extension), nostr:npub1ahaz04ya9tehace3uy39hdhdryfvdkve9qdndkqp3tvehs6h8s5slq45hy (gnostr and experiments), and others.
nostr:npub1uplxcy63up7gx7cladkrvfqh834n7ylyp46l3e8t660l7peec8rsd2sfek (git-remote-nostr)
Project Management nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t (kanbanstr) Code Snippets nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 (nodebin.io) nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac (snipsnip.dev)
CI / CD nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr
and for their nostr:npub1c03rad0r6q833vh57kyd3ndu2jry30nkr0wepqfpsm05vq7he25slryrnw nostr:npub1qqqqqq2stely3ynsgm5mh2nj3v0nk5gjyl3zqrzh34hxhvx806usxmln03 and nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z for their testing, feedback, ideas and encouragement.
Thank you for your support and collaboration! Let me know if I've missed you.
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 6be5cc06:5259daf0
2025-04-28 01:05:49
@ 6be5cc06:5259daf0
2025-04-28 01:05:49Eu reconheço que Deus, e somente Deus, é o soberano legítimo sobre todas as coisas. Nenhum homem, nenhuma instituição, nenhum parlamento tem autoridade para usurpar aquilo que pertence ao Rei dos reis. O Estado moderno, com sua pretensão totalizante, é uma farsa blasfema diante do trono de Cristo. Não aceito outro senhor.
A Lei que me guia não é a ditada por burocratas, mas a gravada por Deus na própria natureza humana. A razão, quando iluminada pela fé, é suficiente para discernir o que é justo. Rejeito as leis arbitrárias que pretendem legitimar o roubo, o assassinato ou a escravidão em nome da ordem. A justiça não nasce do decreto, mas da verdade.
Acredito firmemente na propriedade privada como extensão da própria pessoa. Aquilo que é fruto do meu trabalho, da minha criatividade, da minha dedicação, dos dons a mim concedidos por Deus, pertence a mim por direito natural. Ninguém pode legitimamente tomar o que é meu sem meu consentimento. Todo imposto é uma agressão; toda expropriação, um roubo. Defendo a liberdade econômica não por idolatria ao mercado, mas porque a liberdade é condição necessária para a virtude.
Assumo o Princípio da Não Agressão como o mínimo ético que devo respeitar. Não iniciarei o uso da força contra ninguém, nem contra sua propriedade. Exijo o mesmo de todos. Mas sei que isso não basta. O PNA delimita o que não devo fazer — ele não me ensina o que devo ser. A liberdade exterior só é boa se houver liberdade interior. O mercado pode ser livre, mas se a alma estiver escravizada pelo vício, o colapso será inevitável.
Por isso, não me basta a ética negativa. Creio que uma sociedade justa precisa de valores positivos: honra, responsabilidade, compaixão, respeito, fidelidade à verdade. Sem isso, mesmo uma sociedade que respeite formalmente os direitos individuais apodrecerá por dentro. Um povo que ama o lucro, mas despreza a verdade, que celebra a liberdade mas esquece a justiça, está se preparando para ser dominado. Trocará um déspota visível por mil tiranias invisíveis — o hedonismo, o consumismo, a mentira, o medo.
Não aceito a falsa caridade feita com o dinheiro tomado à força. A verdadeira generosidade nasce do coração livre, não da coerção institucional. Obrigar alguém a ajudar o próximo destrói tanto a liberdade quanto a virtude. Só há mérito onde há escolha. A caridade que nasce do amor é redentora; a que nasce do fisco é propaganda.
O Estado moderno é um ídolo. Ele promete segurança, mas entrega servidão. Promete justiça, mas entrega privilégios. Disfarça a opressão com linguagem técnica, legal e democrática. Mas por trás de suas máscaras, vejo apenas a velha serpente. Um parasita que se alimenta do trabalho alheio e manipula consciências para se perpetuar.
Resistir não é apenas um direito, é um dever. Obedecer a Deus antes que aos homens — essa é a minha regra. O poder se volta contra a verdade, mas minha lealdade pertence a quem criou o céu e a terra. A tirania não se combate com outro tirano, mas com a desobediência firme e pacífica dos que amam a justiça.
Não acredito em utopias. Desejo uma ordem natural, orgânica, enraizada no voluntarismo. Uma sociedade que se construa de baixo para cima: a partir da família, da comunidade local, da tradição e da fé. Não quero uma máquina que planeje a vida alheia, mas um tecido de relações voluntárias onde a liberdade floresça à sombra da cruz.
Desejo, sim, o reinado social de Cristo. Não por imposição, mas por convicção. Que Ele reine nos corações, nas famílias, nas ruas e nos contratos. Que a fé guie a razão e a razão ilumine a vida. Que a liberdade seja meio para a santidade — não um fim em si. E que, livres do jugo do Leviatã, sejamos servos apenas do Senhor.
-
 @ bbef5093:71228592
2025-05-07 15:09:39
@ bbef5093:71228592
2025-05-07 15:09:39Az Európai Bizottság terve az orosz urán- és energiafüggőség felszámolására
Az Európai Bizottság bejelentette, hogy korlátozni kívánja az új urán-, dúsított urán- és egyéb, Oroszországból származó nukleáris anyagokra vonatkozó ellátási szerződéseket, ezzel is elősegítve, hogy az Európai Unió „teljesen megszüntesse” az orosz energiától való függését[8][6][2].
A Bizottság új ütemtervet mutatott be, amely részletesen tartalmazza, hogyan kívánja megszüntetni az orosz energiafüggőséget, miközben biztosítja az EU energiaellátásának és árainak stabilitását[6][2][15].
Főbb intézkedések és célok
- Az EU az orosz gázimport arányát 45%-ról 19%-ra csökkentette a 2022 májusában indított REPowerEU tervnek köszönhetően, de 2024-ben ismét növekedett az orosz gáz behozatala[2][20].
- Az új ütemterv szerint az orosz olaj, gáz és nukleáris energia fokozatosan, összehangoltan és biztonságosan kerül ki az uniós piacokról, miközben az EU a tiszta energiára való átállást gyorsítja fel[6][15][7].
- Az EU-tagállamoknak 2025 végéig nemzeti terveket kell készíteniük arról, hogyan járulnak hozzá az orosz gáz, nukleáris energia és olaj importjának megszüntetéséhez[13][7][18].
- Az orosz eredetű urán, dúsított urán és egyéb nukleáris anyagok esetében új korlátozásokat vezetnek be: az Euratom Ellátási Ügynökség (ESA) nem hagy jóvá új orosz beszállítási szerződéseket, és gazdasági eszközökkel is igyekeznek visszaszorítani az importot[4][5][16].
- A meglévő rövid távú szerződéseket 2025 végéig meg kell szüntetni, új szerződéseket pedig nem lehet kötni; a hosszú távú szerződéseket 2027 végéig kell felmondani[5][7][6].
- Az intézkedések célja, hogy a teljes orosz gáz- és olajimport 2027 végéig megszűnjön, az orosz atomenergia pedig fokozatosan kivezetésre kerüljön[3][9][17].
Nukleáris háttér
- Az ESA jelentése szerint 2023-ban az EU-ban felhasznált természetes urán 23,4%-a érkezett Oroszországból, ami 72,6%-os növekedést jelentett, főként a VVER típusú orosz atomerőművek üzemanyag-felhalmozása miatt[16].
- Az EU-ban 19 VVER reaktor működik (Bulgáriában, Csehországban, Finnországban, Magyarországon és Szlovákiában).
- Az EU természetes uránszükséglete a globális igények mintegy 22%-át teszi ki, a beszerzések 91%-a Kanadából, Oroszországból, Kazahsztánból és Nigerből származik[16].
Célkitűzés és indoklás
A Bizottság szerint az orosz energiafüggőség felszámolása nemcsak gazdasági, hanem biztonságpolitikai kérdés is, mivel Oroszország többször is eszközként használta az energiát az EU-val szemben[2][12]. A lépések célja, hogy az EU energiaellátása biztonságos, stabil és kiszámítható maradjon, miközben az orosz energiaimportból származó bevételek ne finanszírozhassák tovább az Ukrajna elleni háborút[6][2][12].
Források alapján készült magyar összefoglaló és fordítás
Citations: [1] Döntött az Európai Bizottság: teljes mértékben megszüntetik ... - 444 https://444.hu/2025/05/06/dontott-az-europai-bizottsag-teljes-mertekben-megszuntetik-az-orosz-energiatol-valo-fuggest [2] Három éven belül felszámolná az orosz energiafüggőséget az ... https://hu.euronews.com/my-europe/2025/05/06/harom-even-belul-felszamolna-az-orosz-energiafuggoseget-az-europai-bizottsag [3] 2027-re teljesen leállítaná az Európai Bizottság az orosz ... - Új Szó https://ujszo.com/kozelet/2027-re-teljesen-leallitana-az-europai-bizottsag-az-orosz-energiabehozatalt-a-nuklearis [4] Bejelentették Brüsszelben: megkerülik Magyarországot, teljesen ... https://www.portfolio.hu/gazdasag/20250506/bejelentettek-brusszelben-megkerulik-magyarorszagot-teljesen-levalik-az-orosz-olajrol-es-gazrol-az-eu-759267 [5] Érik az újabb ütközés: Brüsszel betiltaná az orosz energiát https://www.valaszonline.hu/2025/05/06/energia-szankcio-oroszorszag-haboru-eu-olaj-gaz-uran/ [6] Az EU teljes mértékben megszünteti az orosz energiától való függését https://hungary.representation.ec.europa.eu/az-eu-teljes-mertekben-megszunteti-az-orosz-energiatol-valo-fuggeset-2025-05-06_hu?prefLang=en [7] Megvan az ütemterv, végleg betiltaná az orosz energiát az Európai ... https://index.hu/kulfold/2025/05/06/orosz-energiafuggoseg-orosz-gaz-olaj-import-europai-unio-repowereu/ [8] European Commission Unveils Plans To Restrict New Uranium ... https://www.nucnet.org/news/european-commission-unveils-plans-to-restrict-new-uranium-deals-with-russia-5-3-2025 [9] Az EU teljes mértékben megszünteti az orosz energiától való ... https://infostart.hu/belfold/2025/05/06/az-eu-teljes-mertekben-megszunteti-az-orosz-energiatol-valo-fuggoseget-a-nap-hirei [10] [PDF] EURÓPAI BIZOTTSÁG Brüsszel, 2025.4.9. COM(2025) 159 final ... https://secure.ipex.eu/IPEXL-WEB/download/file/082d29089612ec1e019619f955940250 [11] Kiszivárgott az Európai Bizottság 2025-ös munkaprogramja https://www.eu-monitor.hu/hu/cikk/20250206-kiszivargott-az-europai-bizottsag-2025-os-munkaprogramja [12] EU says it will end dependency on Russian energy supplies https://www3.nhk.or.jp/nhkworld/en/news/20250507_B4/ [13] Végleg leválik az orosz energiáról az Európai Unió ... - Népszava https://nepszava.hu/3278673_oroszorszag-europai-unio-foldgaz-koolaj-levalas-terv [14] Egyre több európai ország támogatja az atomenergiát https://www.vg.hu/nemzetkozi-gazdasag/2025/03/atomenergia-energiatarolas-europa [15] Az EU teljes mértékben megszünteti az orosz energiától való ... https://karpatinfo.net/energiafuggetlenseg-orosz-foldgaz-orosz-energiafuggoseg-2025-05-07 [16] EU outlines measures to end Russian gas, oil imports by end-2027 https://balkangreenenergynews.com/eu-outlines-measures-to-end-russian-gas-oil-imports-by-end-2027/ [17] Az Európai Unió 2027 végére betiltaná az orosz gáz importját https://www.korkep.sk/cikkek/gazdasag/2025/05/05/az-europai-unio-2027-vegere-betiltana-az-orosz-gazimportot/ [18] Ficónak és Orbánnak sem tetszik, hogy az EU teljesen kitiltaná az ... https://napunk.dennikn.sk/hu/4623240/ficonak-es-orbannak-sem-tetszik-hogy-az-eu-teljesen-kitiltana-az-orosz-energiat/ [19] Várhelyi Olivér késlelteti az EU orosz energiafüggőségét felszámoló ... https://telex.hu/kulfold/2025/05/05/varhelyi-oliver-europai-bizottsag-orosz-energia-kivaltas-hatraltatas [20] REPowerEU roadmap - Energy - European Commission https://energy.ec.europa.eu/strategy/repowereu-roadmap_en
-
 @ 1893da11:a9bd4471
2025-05-08 14:42:20
@ 1893da11:a9bd4471
2025-05-08 14:42:20Introduction: The Challenge of Bitcoin-Secured Loans
Bitcoin holders often face a dilemma: they need liquidity but don't want to sell their assets, potentially missing out on future gains or triggering taxable events. Bitcoin-secured loans offer a solution, allowing users to borrow cash (like digital dollars) using their Bitcoin as collateral. However, the current landscape is fraught with challenges. Many existing solutions require users to trust centralized entities or involve complex mechanisms like wrapping Bitcoin, exposing them to significant risks:
- Custodial Risk: Handing over your Bitcoin to a third party means trusting they won't lose it, misuse it, or become insolvent. Billions have been lost this way.
- Smart Contract Risk: Platforms built on chains like Ethereum rely on complex smart contracts, which can contain bugs or vulnerabilities exploitable by hackers.
- Oracle Risk: Loan systems need reliable price feeds (oracles) to manage collateral. Centralized or manipulatable oracles can lead to unfair liquidations.
- Privacy Risk: Loan details and transactions are often publicly visible on the blockchain.
- Complexity and Cost: Existing processes can be slow, require extensive documentation, and involve high fees.
There's a clear need for a better way – one that is simple, reliable, and minimizes trust. This is where the Lava Loans Protocol comes in.
What is Lava Loans?
In simple terms, Lava Loans provides a way to borrow digital dollars using your native Bitcoin as collateral, directly from your own vault. It's designed to be:
- Simple & Fast: Get a loan in seconds with minimal questions asked.
- Low-Cost & Flexible: Offers competitive rates, dynamic fee structures, and allows borrowing any amount.
- Reliable & Trust-Minimized: Leverages Bitcoin's own capabilities to reduce reliance on intermediaries and enhance security.
How Lava Loans Addresses the Risks
Lava tackles the common pitfalls of crypto loans head-on:
- Eliminating Custodial Risk: Instead of transferring your Bitcoin to a custodian or wrapping it, Lava uses native Bitcoin locked directly on the Bitcoin network within a special type of contract. This prevents rehypothecation and loss through hacks or confiscation.
- Minimizing Smart Contract Risk: Lava utilizes Bitcoin smart contracts, also known as Discreet Log Contracts (DLCs). These are designed to be less complex and more secure than many general-purpose smart contracts, with outcomes pre-defined and formally verified.
- Reducing Oracle Risk: Users choose their own off-chain, blinded oracles (called Sibyls) for price data, with enhanced redundancy to ensure reliability. Off-chain attestations avoid high fees and miner manipulation risks associated with on-chain oracles. Blinded oracles provide price data without knowing the specific contract they influence, preventing targeted attacks.
- Enhancing Privacy: Because DLCs operate differently from typical public smart contracts, the details of the loan contract are not broadcast publicly on the Bitcoin blockchain.
- Trustless Initiation & Repayment: Atomic swaps ensure that collateral only moves to the contract once the loan is received, and collateral is automatically returned upon verified repayment.
The Magic Ingredients: DLCs and Sibyls Oracles
Two core technologies make Lava Loans unique:
-
Discreet Log Contracts (DLCs): Think of a DLC as a pre-programmed Bitcoin transaction agreed upon by the borrower and lender. Before the loan starts, they define all possible outcomes (e.g., repayment, liquidation at a specific price, expiry) and create encrypted signatures for each. The Bitcoin collateral is locked in a multisig output controlled by these pre-signed transactions. Only the conditions agreed upon (verified by oracle signatures) can unlock the funds according to the pre-defined rules. This offers:
- Security: Formally verified, pre-defined outcomes minimize bug risk.
- Privacy: Contract details remain off-chain.
- Scalability: Minimal on-chain footprint as execution logic is off-chain.
- Customization: Users can choose their own oracles and LTV thresholds.
-
Sibyls Oracles: These are the independent price feed providers for Lava. Key characteristics include:
- Off-Chain: Attestations happen off-chain, avoiding blockchain fees and manipulation.
- User-Chosen: Borrowers select the oracles they trust for each loan.
- Blinded: Oracles provide signed price data without knowing the specific DLC it applies to, enhancing security.
- Redundant: Multiple oracles can be configured to provide fallback price feeds, reducing the risk of oracle failure.
System Overview
Here's a high-level look at the components involved in the Lava Loans ecosystem:
[ Borrower ] --(locks Bitcoin)--> [ DLC Contract (Bitcoin) ] [ Lender ] --(sends stablecoins)--> [ Alt-Chain Contract (Solana) ] [ Oracles ] --(provides price)--> [ DLC Contract (Bitcoin) ] [ Borrower ] --(repays loan)--> [ Alt-Chain Contract (Solana) ] [ Lender ] --(claims collateral)--> [ DLC Contract (Bitcoin) ]The Lava Loan Lifecycle
A loan progresses through several states:
- Initialized: A trustless atomic swap occurs. The borrower locks Bitcoin collateral into the DLC on the Bitcoin network, and the lender locks the loan capital (e.g., digital dollars on a network like Solana using HTLCs) which the borrower then claims.
- Active: The collateral is secured in the DLC, and the borrower has the loan capital. The Lava Protocol monitors the loan-to-value (LTV) ratio using price data from the chosen Sibyls oracles, with customizable LTV thresholds for greater flexibility.
- Terminated: The loan concludes in one of several ways:
- Repaid: The borrower repays the loan capital plus interest on the loan asset network, with dynamic fees adjusting based on network conditions. Upon verification, the DLC automatically releases the Bitcoin collateral back to the borrower.
- Liquidated: If the Bitcoin price drops and the LTV reaches a pre-determined threshold (now more flexible to avoid premature liquidations), the DLC automatically releases the collateral to the lender.
- Expired: If the loan term ends before repayment, the DLC releases an amount equivalent to the principal plus interest to the lender, and the remaining collateral is returned to the borrower.
- Fail-safe: In rare cases of unresponsive oracles, redundant Sibyls oracles and built-in mechanisms ensure collateral is not permanently lost.
Loan Process Sequence
The following diagram illustrates the typical sequence of events in a Lava Loan:
1. Borrower --> DLC: Create loan contract with collateral 2. Lender --> Alt-Chain: Fund loan with stablecoins 3. Borrower --> Alt-Chain: Receive and use stablecoins 4. (If repayment) 4a. Borrower --> Alt-Chain: Repay loan 4b. Lender --> Alt-Chain: Confirm repayment 4c. Borrower --> DLC: Claim collateral 5. (If liquidation) 5a. Oracle --> DLC: Provide price attestation 5b. Lender --> DLC: Claim collateral 6. (If expiry) 6a. Borrower/Lender --> DLC: Split collateralLava Loans vs. Other Bitcoin Lending Platforms: A Quick Comparison
How does Lava stack up against typical DeFi lending protocols and other Bitcoin lending platforms like Unchained, Strike, and Coinbase?
| Feature | Lava Loans (Bitcoin) | Typical Ethereum DeFi | Unchained | Strike | Coinbase | | :------------------- | :---------------------------------------------------- | :-------------------------------------------------------- | :---------------------------------------------------- | :---------------------------------------------------- | :---------------------------------------------------- | | Collateral | Native Bitcoin | Often Wrapped Bitcoin (wBTC) or other assets | Native Bitcoin | Native Bitcoin | Native Bitcoin | | Contract Type | Discreet Log Contracts (DLCs) - Pre-agreed, Private | Smart Contracts - Public, Complex, Run on EVM | 2/3 Multisig Vaults | Custodial Contracts | Custodial Contracts | | Security | Aims for higher security via simpler, pre-set DLCs | Can be complex, potential for bugs/exploits | Secure via multisig, but relies on key holders | Custodial, less transparent | Custodial, less transparent | | Privacy | Higher privacy (contract details off-chain) | Lower privacy (contract interactions often public) | Moderate privacy (multisig details on-chain) | Lower privacy (custodial model) | Lower privacy (custodial model) | | Oracles | User-chosen, Off-chain, Blinded (Sibyls) | Often On-chain, potentially manipulatable | Not applicable (manual monitoring) | Centralized oracles | Centralized oracles | | Trust | Designed to minimize trust in intermediaries | Often requires trust in custodians, bridges, or protocols | Moderate trust (key holders could collude) | Higher trust (custodial, opaque practices) | Higher trust (custodial, opaque practices) | | Rehypothecation | No rehypothecation, verifiable on-chain via DLCs | Possible, depends on protocol | No rehypothecation, secured by multisig | Opaque, likely rehypothecated | Opaque, likely rehypothecated | | Interest Rates | Competitive, typically lower due to non-custodial model | Varies, often 5-10% for wBTC loans | 11-14% for non-rehypothecated loans | 12-13% (implies rehypothecation) | ~5-6% (implies rehypothecation) |
Lava leverages Bitcoin’s native capabilities and a specific oracle design to prioritize security, privacy, and trust minimization. Unlike Unchained, which uses a 2/3 multisig where two key holders could potentially collude, Lava’s DLCs ensure cryptographic proof of non-rehypothecation, verifiable on-chain in real time. Strike and Coinbase, being custodial, lack transparency about rehypothecation practices, with market rates suggesting they rehypothecate collateral. The v3 protocol introduces dynamic fee adjustments and more flexible LTV thresholds, reducing premature liquidations and optimizing costs based on network conditions.
Conclusion
Lava Loans presents a compelling option for those seeking liquidity against their Bitcoin holdings without sacrificing security or control. By utilizing Discreet Log Contracts, a user-centric, blinded oracle system (Sibyls) with enhanced redundancy, and new features like dynamic fees and flexible LTV thresholds, Lava provides a simple, reliable, and trust-minimized borrowing experience. These advancements directly address the major pain points found in many existing centralized and decentralized lending platforms.
References
- Maredia, Shehzan. "Lava Loans". Lava Blog, April 9, 2025. https://www.lava.xyz/blog/lava-loans
- https://github.com/lava-xyz/loans-paper/blob/main/loans_v3.pdf
- https://github.com/lava-xyz/sibyls
-
 @ b83a28b7:35919450
2025-05-07 12:46:19
@ b83a28b7:35919450
2025-05-07 12:46:19This article was originally part of the sermon of Plebchain Radio Episode 109 (April 25, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with Noa Gruman from nostr:nprofile1qyv8wumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wsqzqvfdqratfpsvje7f3w69skt34vd7l9r465d5hm9unucnl95yq0ethzx7cf and nostr:nprofile1qye8wumn8ghj7mrwvf5hguewwpshqetjwdshguewd9hj7mn0wd68ycmvd9jkuap0v9cxjtmkxyhhyetvv9usz9rhwden5te0dehhxarj9ehx2cn4w5hxccgqyqj8hd6eed2x5w8pqgx82yyrrpfx99uuympcxmkxgz9k2hklg8te7pq0y72 . You can listen to the full episode here:
https://fountain.fm/episode/gdBHcfDgDXEgALjX7nBu
Let’s start with the obvious: Bitcoin is metal because it’s loud, it’s aggressive, it’s uncompromising. It’s the musical equivalent of a power chord blasted through a wall of amps—a direct challenge to the establishment, to the fiat system, to the sanitized, soulless mainstream. Metal has always been about rebellion, about standing outside the norm and refusing to be tamed. Bitcoin, too, was born in the shadows, dismissed as the currency of outlaws and freaks, and it thrived there, fueled by the energy of those who refused to bow down
But Bitcoin isn’t just any metal. It’s progressive metal. Prog metal is the genre that takes metal’s aggression and fuses it with experimentation, complexity, and a relentless drive to push boundaries. It’s not satisfied with three chords and a chorus. Prog metal is about odd time signatures, intricate solos, unexpected detours, and stories that dig into philosophy, psychology, and the human condition. It’s music for those who want more than just noise—they want meaning, depth, and innovation.
That’s Bitcoin. Bitcoin isn’t just a blunt instrument of rebellion; it’s a living, evolving experiment. It’s code that’s open to anyone, a protocol that invites innovation, a system that’s constantly being pushed, prodded, and reimagined by its community.
Like prog metal, Bitcoin is for the thinkers, the tinkerers, the relentless questioners. It’s for those who see the flaws in the mainstream and dare to imagine something radically different.
Both prog metal and Bitcoin are about freedom — freedom from the tyranny of the predictable, the safe, the centrally controlled. They are countercultures within countercultures, refusing to be boxed in by genre or by law. Both attract those who crave complexity, who aren’t afraid to get lost in the weeds, who want to build something new and beautiful from the chaos.
If you want to reach the heart of Bitcoin’s counterculture, you don’t do it with bland, safe, mainstream pop. You do it with prog metal—with music that refuses to compromise, that demands your attention, that rewards those who dig deeper. Prog metal is the true voice of Bitcoin’s core: the plebs, the builders, the dreamers who refuse to accept the world as it is.
Bitcoin is prog metal. It’s technical, it’s rebellious, it’s unafraid to be different. It’s music and money for those who want to break free—not just from the old systems, but from the old ways of thinking. And as the mainstream tries to water down both, the true counterculture survives at the core, pushing boundaries, making noise, and refusing to die.
The sermon and episode clearly had an impact on people, as evidenced by the fountain charts here (snapshot taken on May 6, 2025)
nostr:nevent1qvzqqqqqqypzqkcpsw4kc03j906dg8rt8thes432z3yy0d6fj4phylz48xs3g437qqsy7rfh8n6vgxppkwzq2ntjps0lmt4njkxjrv3rv5r59l7lkv6ahps2eavd9 And here's the clip of the sermon:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsptkpkd0458yshe7gfshck2f9nfxnqe0nrjz0ptlkm9rhv094rxagapyv4d
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 8d5ba92c:c6c3ecd5
2025-05-07 11:23:35
@ 8d5ba92c:c6c3ecd5
2025-05-07 11:23:35"There are seasons to give and seasons to receive. The more we give when we can, the more we receive when we need to. That’s how great relationships work. That’s how resilient communities grow." (— Anja Schuetz )
On May 22 (Bitcoin Pizza Day, which this year in Warsaw, PL, makes a Day Zero for Bitcoin FilmFest 2025), Bitvocation, special cameos for this edition, will host a unique networking session — ₿-Social.
-
Fast-paced, good vibes, to help all participants build closer connections, and for those who need it, to break free from the fiat job with high signal resources and guidance.
-
Expect conversations that go beyond “What do you do?” and “How long have you been in Bitcoin?”
-
Less small talk, more real connections with fellow Bitcoiners—filmmakers, musicians, artists, founders, builders, and creative souls. For everyone who wants to share, learn, give, take, meet others, and collaborate.
- Bitcoiners from all over Europe + Honduras, El Salvador, Thailand, the US, Canada, Australia, Turkey, Iran, Dubai, and other corners of the world.
As Anja, the founder of Bitvocation, once told me:
"Face-to-face interactions create real connections and trust—vital ingredients for Bitcoin’s social layer. The best opportunities come to those who truly show up."
Thus, hope to see you in Warsaw, at Bitcoin FilmFest 2025. Get your ticket here, if you haven't done so yet (🟠 use the code 'BITVOCATION' to get a 10% discount). The 3rd annual edition. Around 300 people. Orange-pill cinema, decentralized music, permissionless, art. No other way, it's going to be FUN!
💡 Check more about Bitvocation, a dynamic project empowering Bitcoiners with tools, guidance, and even hands-on work experience, for careers in Bitcoin-only markets.
BTC Your Mind. Let it Beat.... Şela
-
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 2b24a1fa:17750f64
2025-05-08 07:14:35
@ 2b24a1fa:17750f64
2025-05-08 07:14:35"Was ist da drin?", fragte wohl jedes unverdorbene Kind, bevor eine Flüssigkeit in den Muskel seines Arms gespritzt würde. Aber wir sind alle keine unverdorbenen Kinder mehr. Wissen, das haben die anderen, die Gebildeteren, die Wissenschaftler, die Ärzte. Nachfragen würde Autoritäten untergraben und Unglauben demonstrieren. Und drum fällt kaum jemandem auf, dass wir bis heute keine sauberen Inhaltsangaben über die sogenannten Corona-Spritzen erhalten haben, geschweige denn wissen, was der Inhalt in unseren Körpern genau anrichten kann.
Auf die Suche nach Aufklärung hat sich von Beginn dieser sogenannten Pandemie der Verein Mediziner und Wissenschaftler für Gesundheit, Frieden und Demokratie gemacht. Jetzt gibt es ein erstes Labor, das die bekannten, relevanten Impfstoffbestandteile nachweisen will. Darüber unterhält sich unsere Redakteurin Eva Schmidt mit dem Molekularbiologen Prof. Klaus Steger von der Universität Gießen und engagiert bei inmodia, dem Institut für molekularbiologische Diagnostik. Zunächst wollte sie wissen, welche Bestandteile eigentlich bekannt sind, die in Millionen von Menschen gespritzt wurden.
Link zur Webseite: inmodia.de
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ b04082ac:29b5c55b
2025-05-08 14:35:02
@ b04082ac:29b5c55b
2025-05-08 14:35:02Money has always been more than a medium of exchange. It reflects what societies value, how they organize trust, and what they choose to remember. This article explores the idea that money functions as a form of collective memory, and how Bitcoin may be restoring this role in a new way.

The Asante Example
In the Asante Empire, which flourished in West Africa during the 18th and 19th centuries, gold dust served as the primary medium of exchange. To measure it, traders used ornate spoons made of brass. These spoons were often carved with birds, animals, or abstract symbols. They were not currency themselves, but tools used to handle gold dust accurately.
Importantly, these spoons also carried meaning. Symbols and proverbs embedded in the spoons conveyed lessons about honesty, community, and continuity. For example, the Sankofa bird, shown turning its head backward to retrieve an egg from its back, represented the proverb, “It is not wrong to go back for that which you have forgotten.” This was a reminder to learn from the past.

The spoons reflect an understanding that money and its instruments are not just practical tools. They are cultural artifacts that store shared values. In the Asante context, even measurement was ritualized and tied to ethics and memory.
Money as a Cultural Medium
This connection between money and cultural meaning is not unique to the Asante Empire. Modern fiat currencies also carry symbols, phrases, and designs that reflect national identity and political values.
The U.S. dollar includes Latin phrases and national symbols meant to convey stability and purpose. The British pound features royal iconography, reinforcing the idea of continuity and sovereignty. When the euro was introduced, it deliberately avoided specific national references. Itsdesign used bridges and windowsto suggest openness and cooperation across the continent.

These design choices show that societies still embed meaning into their money. Even in a digital or fiat context, money is used to transmit a story about who we are, where authority lies, and what we value.
The Fragility of Fiat Memory
While fiat money carries cultural symbols, the narratives behind those symbols can be fragile.
In 2021, the central bank of the Philippines removed democratic leaders from its banknotes,triggering public criticism. In the United States, attempts to replace Andrew Jackson with Harriet Tubman on the $20 billfaced repeated delays. These examples show how political control over money includes control over what stories are told and remembered.

Unlike objects passed down through generations, fiat memory can be edited or erased. In this sense, it is vulnerable. The meaning encoded in fiat systems can shift depending on who holds power.
Bitcoin as a New Form of Memory
Bitcoin is described as digital money. But it also introduces a different model of how societies can record value and preserve meaning.
The Bitcoin network launched in 2009 with a small message embedded in its first block: “Chancellor on brink of second bailout for banks.” This was a reference to a newspaper headline that day and a clear sign of protest against financial bailouts, centralized monetary policy, and forever wars.

This moment marked the beginning of a system where memory is stored differently. Instead of relying on governments or institutions, Bitcoin stores its history on a public ledger maintained by a decentralized network of participants. Its memory is not symbolic or political; it is structural. Every transaction, every block, is preserved through time-stamped computation and consensus.
No single authority can change it. The rules are clear and publicly auditable. In this way, Bitcoin offers a version of money where memory is both neutral and resilient.
Cultural Expression and Community Values
Even though Bitcoin lacks the traditional symbols found on banknotes, it has developed its own culture. Phrases like “Don’t trust, verify” or “Stay humble, stack sats” are shared widely in the Bitcoin community. These ideas reflect a focus on self-responsibility, verification, and long-term thinking.
These proverbs can be compared to the carved messages on the Asante spoons. While the contexts are very different, the underlying idea is similar: a community using language and symbols to reinforce its shared values.
Bitcoin also has a well established and growing art scene. Bitcoin conferences often feature dedicated sections for art inspired by the protocol and its culture. Statues of Satoshi Nakamoto have been installed in cities like Budapest, Lugano, and Fornelli. These physical works reflect the desire to link Bitcoin’s abstract values to something tangible.

Looking Back to Look Forward
The Asante example helps us see that money has long been tied to memory and meaning. Their spoons were practical tools but also cultural anchors. Bitcoin, while new and digital, may be playing a similar role.
Instead of relying on political symbols or national myths, Bitcoin uses code, transparency, and global consensus to create trust. In doing so, it offers a way to preserve economic memory that does not depend on power or politics.
It’s still early to know what kind of legacy Bitcoin will leave. But if it succeeds, it may not just change how money works. It may also change how civilizations remember.
-
 @ c11cf5f8:4928464d
2025-05-08 11:51:12
@ c11cf5f8:4928464d
2025-05-08 11:51:12Here we are again with our monthly Magnificent Seven, the summary giving you a hit of what you missed in the ~AGORA territory.
Let's check our top performing post Ads!
Top-Performing Ads
This month, the most engaging ones are:
-
01[SELL] The Book of Bitcoin Mythology - Bitcoin accepted - ($21 + shipping) by @VEINTIUNO offering a printed version of the Bitcoin Mythology @spiral series, available online originally in English and translated by the post author in Spanish. 100 sats \ 6 comments \ 18 Apr -
02[SELL] Southwest voucher, 50k sats (digital code/ USA) by @BlokchainB, where he share a voucher Southwest Airlines. Have you sold it to @itsrealfake then? 206 sats \ 3 comments \ 27 Apr -
03SoapMiner Beef Tallow Soap by @PictureRoom, a review of a great handmade product sold P2P. 83 sats \ 2 comments \ 3 May -
04[SELL] Walter Whites Mega Package eBook (25000) by @MidnightShipper, return selling hand-picked ebooks from his/her huge collection 36 sats \ 4 comments \ 21 Apr -
05Medical Consultation (an update to a previous post) by @BTCLNAT, renewing prices and details of a previous Ad-post. Pretty fair still... 5k sats/consultation still a bargain! 100 sats \ 3 comments \ 22 Apr -
06[SELL] Bitcoin Education Playing Cards $30 Bitcoin accepted by @NEEDcreations, releasing a new updated edition, ow available for sale on the 360BTC's pleb shop 19 sats \ 0 comments \ 30 Apr -
07OFFICIAL - VINTAGE - Marlboro Zippo - Real & WORKS by @watchmancbiz, returns with just a link to SatStash for more info on the auction 0 sats \ 0 comments \ 3 May
A quick reminder that now you ca setup auctions here in the AGORA too! Learn how. The other feature released last month was the introduction of Shopfronts on SN. Check our SN Merch and SN Zine examples. Thank you all! Let's keep these trades coming and grow the P2P Bitcoin circular economy!
Lost & Found in SN' Wild West Web
Stay with me, we're not done yet! I found plenty of other deals and offers in other territories too..
- Private Package Delivery where @Jon_Hodl share his experience on receiving one personally
- 🚨 VIP-Only Flash Sale: Bitaxe Gamma for $125 by @siggy47, grabbing one of these bad boys.
- Where do you sell books for Bitcoin, besides on ~Agora Territory? by @hasherstacker, asking ~BooksAndArticles community. Do you have a book to sell? Let me know how I can help!
- This best-selling book on ‘abundance’ has got it wrong - Max Rashbrooke by @Solomonsatoshi sharing an interesting external article.
- Trump Store Selling ‘Trump 2028’ Hats Trump Says He’s ‘Not Joking’ another interesting article shared by our dear friend @CarlTuckerson
Wow, such an exciting month!
Active Professional Services accepting Bitcoin in the AGORA
Let us know if we miss any, here below the most memorable ones: - https://stacker.news/items/900208/r/AG @unschooled offering Language Tutoring - https://stacker.news/items/813013/r/AG @gpvansat's [OFFER][Graphic Design] From the paste editions (It's important to keep these offers available) - https://stacker.news/items/775383/r/AG @TinstrMedia - Color Grading (Styling) Your Pictures as a Service - https://stacker.news/items/773557/r/AG @MamaHodl, MATHS TUTOR 50K SATS/hour English global - https://stacker.news/items/684163/r/AG @BTCLNAT's OFFER HEALTH COUNSELING [5K SAT/ consultation - https://stacker.news/items/689268/r/AG @mathswithtess [SELL] MATHS TUTOR ONILINE, 90k sats per hour. Global but English only.
Let me know if I'm missing other stackers offering services around here!
In case you missed
Here some interesting post, opening conversations and free speech about markets and business on the bitcoin circular economy:
- https://stacker.news/items/972209/r/AG Here Comes Bitcoin Swag Shop by @k00b
- https://stacker.news/items/969011/r/AG Sales Corner (Prospecting) by @Akg10s3
- https://stacker.news/items/971914/r/AG Satoshi Escrow A Bitcoin non-custodial P2P dispute resolution using Nostr keys by @AGORA
- https://stacker.news/items/972209/r/AG Twin Cities Outdoor Agora Market by @k00b
- https://stacker.news/items/942025/r/AG How to create your Shopfront on STACKER NEWS to upsell your products & services by @AGORA
BUYing or SELLing Cowboys Credits?
BUY or SELL them in the ~AGORA marketplace
Here's what stackers have to offers: - [SWAP] SN Cowboy credits by @DarthCoin - https://stacker.news/items/758411/r/AG by @SimpleStacker that also shares a CCs market analysis. - [BUY] 100 cowboy credits for one satoshi by @ek - Will Pay Sats For Cowboy Credits by @siggy47 - 📢 CCs to Sats Exchange Megathread recently started by @holonite, not sure why in ~bitcoin. Consider the ~AGORA next time ;)
🏷️ Spending Sunday and Selling weekly?
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! All series available here: Or read the latest one from https://stacker.news/items/970896/r/AG
📢 Thursday Talks: What have you sold for Bitcoin this week?
Our recently launched weekly series going out every Thursday. In the past one, I collected all @Akg10s3's Sales Corner posts. Fresh out of the box, today edition https://stacker.news/items/974581/r/AG
Create your Ads now!
Looking to start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- Start your own [SHOPFRONT] or simply...
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to.
Or contact @AGORA team on nostr DM, and we can help you publish a personalized post.
.
#nostr#bitcoin#stuff4sats#sell#buy#plebchain#grownostr#asknostr#market#businessoriginally posted at https://stacker.news/items/974611
-
-
 @ 30ceb64e:7f08bdf5
2025-04-26 20:33:30
@ 30ceb64e:7f08bdf5
2025-04-26 20:33:30Status: Draft
Author: TheWildHustleAbstract
This NIP defines a framework for storing and sharing health and fitness profile data on Nostr. It establishes a set of standardized event kinds for individual health metrics, allowing applications to selectively access specific health information while preserving user control and privacy.
In this framework exists - NIP-101h.1 Weight using kind 1351 - NIP-101h.2 Height using kind 1352 - NIP-101h.3 Age using kind 1353 - NIP-101h.4 Gender using kind 1354 - NIP-101h.5 Fitness Level using kind 1355
Motivation
I want to build and support an ecosystem of health and fitness related nostr clients that have the ability to share and utilize a bunch of specific interoperable health metrics.
- Selective access - Applications can access only the data they need
- User control - Users can choose which metrics to share
- Interoperability - Different health applications can share data
- Privacy - Sensitive health information can be managed independently
Specification
Kind Number Range
Health profile metrics use the kind number range 1351-1399:
| Kind | Metric | | --------- | ---------------------------------- | | 1351 | Weight | | 1352 | Height | | 1353 | Age | | 1354 | Gender | | 1355 | Fitness Level | | 1356-1399 | Reserved for future health metrics |
Common Structure
All health metric events SHOULD follow these guidelines:
- The content field contains the primary value of the metric
- Required tags:
['t', 'health']- For categorizing as health data['t', metric-specific-tag]- For identifying the specific metric['unit', unit-of-measurement]- When applicable- Optional tags:
['converted_value', value, unit]- For providing alternative unit measurements['timestamp', ISO8601-date]- When the metric was measured['source', application-name]- The source of the measurement
Unit Handling
Health metrics often have multiple ways to be measured. To ensure interoperability:
- Where multiple units are possible, one standard unit SHOULD be chosen as canonical
- When using non-standard units, a
converted_valuetag SHOULD be included with the canonical unit - Both the original and converted values should be provided for maximum compatibility
Client Implementation Guidelines
Clients implementing this NIP SHOULD:
- Allow users to explicitly choose which metrics to publish
- Support reading health metrics from other users when appropriate permissions exist
- Support updating metrics with new values over time
- Preserve tags they don't understand for future compatibility
- Support at least the canonical unit for each metric
Extensions
New health metrics can be proposed as extensions to this NIP using the format:
- NIP-101h.X where X is the metric number
Each extension MUST specify: - A unique kind number in the range 1351-1399 - The content format and meaning - Required and optional tags - Examples of valid events
Privacy Considerations
Health data is sensitive personal information. Clients implementing this NIP SHOULD:
- Make it clear to users when health data is being published
- Consider incorporating NIP-44 encryption for sensitive metrics
- Allow users to selectively share metrics with specific individuals
- Provide easy ways to delete previously published health data
NIP-101h.1: Weight
Description
This NIP defines the format for storing and sharing weight data on Nostr.
Event Kind: 1351
Content
The content field MUST contain the numeric weight value as a string.
Required Tags
- ['unit', 'kg' or 'lb'] - Unit of measurement
- ['t', 'health'] - Categorization tag
- ['t', 'weight'] - Specific metric tag
Optional Tags
- ['converted_value', value, unit] - Provides the weight in alternative units for interoperability
- ['timestamp', ISO8601 date] - When the weight was measured
Examples
json { "kind": 1351, "content": "70", "tags": [ ["unit", "kg"], ["t", "health"], ["t", "weight"] ] }json { "kind": 1351, "content": "154", "tags": [ ["unit", "lb"], ["t", "health"], ["t", "weight"], ["converted_value", "69.85", "kg"] ] }NIP-101h.2: Height
Status: Draft
Description
This NIP defines the format for storing and sharing height data on Nostr.
Event Kind: 1352
Content
The content field can use two formats: - For metric height: A string containing the numeric height value in centimeters (cm) - For imperial height: A JSON string with feet and inches properties
Required Tags
['t', 'health']- Categorization tag['t', 'height']- Specific metric tag['unit', 'cm' or 'imperial']- Unit of measurement
Optional Tags
['converted_value', value, 'cm']- Provides height in centimeters for interoperability when imperial is used['timestamp', ISO8601-date]- When the height was measured
Examples
```jsx // Example 1: Metric height Apply to App.jsx
// Example 2: Imperial height with conversion Apply to App.jsx ```
Implementation Notes
- Centimeters (cm) is the canonical unit for height interoperability
- When using imperial units, a conversion to centimeters SHOULD be provided
- Height values SHOULD be positive integers
- For maximum compatibility, clients SHOULD support both formats
NIP-101h.3: Age
Status: Draft
Description
This NIP defines the format for storing and sharing age data on Nostr.
Event Kind: 1353
Content
The content field MUST contain the numeric age value as a string.
Required Tags
['unit', 'years']- Unit of measurement['t', 'health']- Categorization tag['t', 'age']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the age was recorded['dob', ISO8601-date]- Date of birth (if the user chooses to share it)
Examples
```jsx // Example 1: Basic age Apply to App.jsx
// Example 2: Age with DOB Apply to App.jsx ```
Implementation Notes
- Age SHOULD be represented as a positive integer
- For privacy reasons, date of birth (dob) is optional
- Clients SHOULD consider updating age automatically if date of birth is known
- Age can be a sensitive metric and clients may want to consider encrypting this data
NIP-101h.4: Gender
Status: Draft
Description
This NIP defines the format for storing and sharing gender data on Nostr.
Event Kind: 1354
Content
The content field contains a string representing the user's gender.
Required Tags
['t', 'health']- Categorization tag['t', 'gender']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the gender was recorded['preferred_pronouns', string]- User's preferred pronouns
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - male - female - non-binary - other - prefer-not-to-say
Examples
```jsx // Example 1: Basic gender Apply to App.jsx
// Example 2: Gender with pronouns Apply to App.jsx ```
Implementation Notes
- Clients SHOULD allow free-form input for gender
- For maximum compatibility, clients SHOULD support the common values
- Gender is a sensitive personal attribute and clients SHOULD consider appropriate privacy controls
- Applications focusing on health metrics should be respectful of gender diversity
NIP-101h.5: Fitness Level
Status: Draft
Description
This NIP defines the format for storing and sharing fitness level data on Nostr.
Event Kind: 1355
Content
The content field contains a string representing the user's fitness level.
Required Tags
['t', 'health']- Categorization tag['t', 'fitness']- Fitness category tag['t', 'level']- Specific metric tag
Optional Tags
['timestamp', ISO8601-date]- When the fitness level was recorded['activity', activity-type]- Specific activity the fitness level relates to['metrics', JSON-string]- Quantifiable fitness metrics used to determine level
Common Values
While any string value is permitted, the following common values are recommended for interoperability: - beginner - intermediate - advanced - elite - professional
Examples
```jsx // Example 1: Basic fitness level Apply to App.jsx
// Example 2: Activity-specific fitness level with metrics Apply to App.jsx ```
Implementation Notes
- Fitness level is subjective and may vary by activity
- The activity tag can be used to specify fitness level for different activities
- The metrics tag can provide objective measurements to support the fitness level
- Clients can extend this format to include activity-specific fitness assessments
- For general fitness apps, the simple beginner/intermediate/advanced scale is recommended
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-06 19:49:39
@ 5d4b6c8d:8a1c1ee3
2025-05-06 19:49:39One of the best first rounds in recent memory just concluded. Let's recap our playoff contests.
Bracket Challenge
In our joint contest with Global Sports Central, @WeAreAllSatoshi is leading the way with 85 points, while me and some nostr jabroni are tied for second with 80 points.
The bad news is that they are slightly ahead of us, with an average score of 62 to our 60.8. We need to go back in time and make less stupid picks.
Points Challenge
With the Warriors victory, I jumped into a commanding lead over @grayruby. LA sure let most of you down. I say you hold @realBitcoinDog responsible for his beloved hometown's failures.
I still need @Car and @Coinsreporter to make their picks for this round. The only matchup they can choose from is Warriors (7) @ Timberwolves (6). Lucky for them, that's probably the best one to choose from.
| Stacker | Points | |---------|--------| | @Undisciplined | 25| | @grayruby | 24| | @Coinsreporter | 19 | | @BlokchainB | 19| | @Carresan | 18 | | @gnilma | 18 | | @WeAreAllSatoshi | 12 | | @fishious | 11 | | @Car | 1 |
originally posted at https://stacker.news/items/973284
-
 @ 8bde549d:567bf85c
2025-05-08 09:40:41
@ 8bde549d:567bf85c
2025-05-08 09:40:41TP88 là một trong những nền tảng giải trí trực tuyến được đánh giá cao nhờ vào giao diện thân thiện và dễ sử dụng, giúp người chơi dễ dàng tham gia và trải nghiệm các trò chơi yêu thích. Với mục tiêu mang đến những giây phút thư giãn tuyệt vời cho người dùng, TP88 không ngừng cải thiện và cập nhật các tính năng mới để phù hợp với nhu cầu giải trí ngày càng cao. Nền tảng này cung cấp đa dạng các trò chơi từ các game trí tuệ yêu cầu tư duy chiến lược đến các trò chơi vui nhộn và giải trí, giúp người chơi có thể lựa chọn theo sở thích và phong cách của mình. Từ những trò chơi đơn giản nhưng đầy thử thách cho đến những trò chơi phức tạp và sáng tạo, TP88 đều có thể đáp ứng mọi yêu cầu của người chơi. Với đồ họa sắc nét, âm thanh sống động và hiệu ứng đặc biệt, TP88 chắc chắn sẽ mang đến cho người tham gia những trải nghiệm giải trí chân thực và đầy đủ cảm xúc.
Ngoài những yếu tố về sự đa dạng và hấp dẫn của các trò chơi, TP88 cũng đặc biệt chú trọng đến bảo mật và sự an toàn của người chơi. Trong môi trường trực tuyến hiện nay, vấn đề bảo vệ thông tin cá nhân và các giao dịch tài chính luôn được đặt lên hàng đầu. TP88 sử dụng công nghệ bảo mật tiên tiến để đảm bảo rằng thông tin người chơi sẽ được bảo vệ một cách an toàn và không bị xâm phạm. Mọi giao dịch tài chính, từ việc nạp tiền đến rút tiền, đều được thực hiện nhanh chóng, chính xác và bảo mật tuyệt đối, giúp người chơi có thể yên tâm trong suốt quá trình tham gia. Nền tảng này cũng tuân thủ các tiêu chuẩn quốc tế về bảo mật và an toàn, mang đến cho người chơi một môi trường giải trí trực tuyến đáng tin cậy và an toàn. Hệ thống bảo mật và hỗ trợ khách hàng của TP88 luôn hoạt động 24/7 để đảm bảo rằng mọi vấn đề phát sinh của người chơi sẽ được giải quyết kịp thời và hiệu quả.
Một trong những yếu tố quan trọng khiến TP88 trở thành sự lựa chọn hàng đầu của những người yêu thích giải trí trực tuyến chính là các chương trình khuyến mãi và sự kiện hấp dẫn. Nền tảng này thường xuyên tổ chức các chương trình khuyến mãi, sự kiện đặc biệt và các giải thưởng giá trị để thu hút người chơi tham gia và tạo cơ hội cho họ nhận được nhiều phần thưởng hấp dẫn. Các chương trình này không chỉ làm tăng thêm phần thú vị mà còn mang đến nhiều cơ hội để người chơi tăng thêm tài khoản của mình một cách dễ dàng. Ngoài ra, TP88 còn có các sự kiện cộng đồng, nơi người chơi có thể giao lưu, chia sẻ kinh nghiệm và kết nối với nhau. Những sự kiện này góp phần tạo nên một cộng đồng gắn kết và sôi động, nơi mà người chơi có thể học hỏi và phát triển kỹ năng của mình. Với tất cả những ưu điểm này, TP88 không chỉ là một nền tảng giải trí đơn thuần mà còn là một cộng đồng lớn mạnh, nơi người chơi có thể tìm thấy niềm vui và sự thỏa mãn trong mỗi lần tham gia.
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 90c656ff:9383fd4e
2025-05-08 08:35:04
@ 90c656ff:9383fd4e
2025-05-08 08:35:04Bitcoin operates through a decentralized system that relies on a process called mining to validate transactions and secure the network. However, Bitcoin mining requires a large amount of energy, which raises concerns about its environmental impact. Although there are solutions to make this process more sustainable, energy consumption remains a topic of debate among both critics and advocates of the technology.
How does Bitcoin mining work?
Bitcoin mining is the process by which new blocks are added to the blockchain (or timechain) and new coins are created. This process uses a mechanism called proof-of-work, where specialized computers (miners) compete to solve complex mathematical problems. To do this, they consume a huge amount of electricity, as the equipment must operate continuously to keep the network secure and decentralized.
- Energy consumption and environmental impact
The main criticism of Bitcoin mining is its high electricity consumption. Currently, it is estimated that the Bitcoin network consumes as much energy as some entire countries. This raises environmental concerns, as much of the world's electricity is still generated from fossil fuels, which emit polluting gases.
The environmental impacts of Bitcoin mining include:
01 - Carbon Emissions: If the electricity used for mining comes from polluting sources, the process contributes to increased CO₂ emissions, intensifying global warming.
02 - Excessive Use of Natural Resources: Large-scale mining can strain local power grids and increase demand for electricity, leading to higher fossil fuel consumption in some regions.
03 - Electronic Waste Production: Mining equipment has a relatively short lifespan, which leads to the generation of large amounts of electronic waste.
- Alternatives and sustainable solutions
Despite these concerns, Bitcoin mining is becoming increasingly efficient and sustainable. Many mining operations already use renewable energy sources such as hydroelectric, solar, and wind, significantly reducing their ecological footprint. Some solutions include:
01 - Use of Renewable Energy: Miners are relocating to regions with excess renewable energy production, taking advantage of resources that would otherwise be wasted.
02 - Recycling Heat Generated by Mining: Some companies are using the heat produced by mining equipment to warm buildings and infrastructure, making more efficient use of the energy.
03 - Technological Innovations: The development of new chips and more efficient equipment reduces the energy consumption of mining without compromising network security.
In summary, the environmental impact of Bitcoin mining is a controversial issue, but solutions to make the process more sustainable are rapidly evolving. While energy consumption remains high, the shift toward renewable energy sources and new technologies could make Bitcoin a more efficient and environmentally friendly system. Thus, the issue is not merely the amount of electricity consumed, but the origin of that energy and the innovations making mining increasingly sustainable.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ a5ee4475:2ca75401
2025-05-07 20:00:42
@ a5ee4475:2ca75401
2025-05-07 20:00:42lista #descentralismo #comunidades #portugues
[em atualização]
*Até a criação desse post, só alguns clients têm acesso às comunidades, tal como o Satellite, o Coracle e o Amethyst.
**Se a comunidade não tiver proprietários ou moderadores ativos, o seu envio de mensagem poderá não ser aprovada para aparecer nela.
***Se criar uma, busque colocar um ou mais moderadores para a comunidade não acabar, caso você se ausente.
Geral:
n/Brasil (Por: nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqryyunpwd5kcq3qzdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2sxpqqqzr0v4va9m3
n/Portugal (por: nostr:nprofile1qqsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshszynhwden5te0dehhxarj9ek82tntv5hsd2h46x) nostr:naddr1qqy9qmmjw36kwctvqgsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqrqsqqpphkc3wuaj
n/Moçambique (por: nostr:nprofile1qqszx6hsp38v2re3q2pzxpv3slg5u7pxklxze7evarqk4eugqmhntdcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctc082x0w) nostr:naddr1qqf56m7r5ask6cnfw96ktuyls7e0p8u8hupzqgm27qxya3g0xypgygc9jxraznncy6muct8m9n5vz6h83qrw7ddhqvzqqqyx7c0autxh
n/África (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqru8qtxwf5kxcgzyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdaspqgn0q
-
n/Perguntas-e-Respostas (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq3lp8u85lcflpah2pz4y364fe2yz5edg5k4y32n2p84x4zp203fm980hz8sygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqsmmqtz9a9x
n/Links-e-Tutoriais-Úteis (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqj0p8u85lcflpahf3y5uj6n94zj64z42384yj2pf9fjmsu623z5j5lsn7ftkq3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqzr0v3zu9fd
n/JornalismoNãoEstáMorto - Notícias e escrita informativa (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:nprofile1qqs0f74kketdcv63r53mlzgzfh93we3dkgzkldv2p6g62a8gf3g92yqpz4mhxue69uhkummnw3ezummcw3ezuer9wchszyrhwden5te0dehhxarj9ekk7mf0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9ufhpwuw) nostr:naddr1qqd55n6jfeq5cj2nf48j6nkrsd8j632n2npczt2dfaf9gnczyrvvsrjnp9xgqysjendxg6x2q7fldu73ajnf5e2h7uspp9tjl7jvxqcyqqqgdasy2kfg4
n/Agorismo³-E-Mercado (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpahg9r575jf2dx5ls4n94zj6n292fp5z3z094gry5qzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasrlnr7s
n/FeiraNostr - Marketplace (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qq9yvetfwfs5ummnw3eqyg9hpjdlkf2tvpegqssjvsa7kpmmdw55zcy76sz3tkd3p9sawancnypsgqqqsmmqucz73h
Tecnologia:
n/ndevs-br (por: nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcppemhxue69uhkummn9ekx7mp0gc3lmk) nostr:naddr1qqyxuer9weej6cnjqgs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcrqsqqpphk7z3axp
n/BrasilDev (por: nostr:nprofile1qqsyczyspluueyxautr3nxa2httku5e9m7d05dnu5zj3jnrg0jmucqcpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uqs6amnwvaz7tmwdaejumr0dsq3camnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdsz8cl6e) nostr:naddr1qqy5yunpwd5kc3r9wcpzqnqgjq8lnnysmh3vwxvm42adwmjnyh0e473k0js22x2vdp7t0nqrqvzqqqyx7cvxdlla
n/Linux (por: nostr:nprofile1qqsxhewvq6fq9lzjmfwqrpg2ufgl09uh2cksupa853zxv04u2fva4uqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0dehhxarjv4kxjar9wvhx7un89uqsuamnwvaz7tmwdaejumr0dshs6tvc92 ) nostr:naddr1qqz5c6tww4uqz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsygrtuhxqdyszl3fd5hqps59wy50hj7t4vtgwq7n6g3rx8679ykw67qpsgqqqsmmqznes6u
n/IA - Inteligencia Artificial (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqpyjsgpzpmhxue69uhkummnw3ezumt0d5hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqs03ln5
n/HardwareBr - Dúvidas, experiências e atualizações sobre hardware (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq9ysctjv3mkzun9gfeqyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmq54k3eu
n/SegurançaDaInformação (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqv9xet8w4exzmkr5as5gc2fdenx7undv8p60sardupzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cpss4m0
n/Moneroptbr (Por: nostr:nprofile1qqsyrmue77dm5ef5pmqsly0wp3248mk3vr9temj5p54plygcr97pavcpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqg5waehxw309aex2mrp0yhxgctdw4eju6t0tpqrvk) nostr:naddr1qq9y6mmwv4ex7ur5vfeqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygzpa7vl0xa6v56qasg0j8hqc42namgkpj4uae2q62sljyvpjlq7kvpsgqqqsmmqknmdan
Ciência:
n/Astronomia - Espaço e astros (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qq9yzum5wfhkummdd9ssz9thwden5te0dehhxarj9ehhsarj9ejx2a30qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqpphkkdel5t
n/Mecatrônica-NOSTR (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqfy6etrv9689sa5de5kxcfdfe84x4zjqythwumn8ghj76twvfhhstnp0faxzmt09ehx2ap0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphkgsy84w
n/Antropologystr - Antropologia (por: nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg ) nostr:naddr1qq85zmn5dpex7ur0d3hkw7tnw3eqygzfrtlt4hds900g0nl80lk6luq5h7fds622r5uqa3882jgckeyrfcpsgqqqsmmq4xrrgc
Cultura:
n/Estante-Nostr - Literatura e livros (por: nostr:nprofile1qqsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqpr4mhxue69uhkummnw3ez6vp39eukz6mfdphkumn99e3k7mf0qywhwumn8ghj7mn0wd68ytfsxgh8jcttd95x7mnwv5hxxmmd9uq37amnwvaz7tmwdaehgu3dxqejuer0wfskvctrw3hhy7fwdaexwtcjwfqr2) nostr:naddr1qqx52um5v9h8ge2lfehhxarjqgsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqrqsqqpphkwzdgct
n/Literatura-Arte-Cultura (por: nostr:nprofile1qqs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9cprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqsuamnwvaz7tmwdaejumr0dshs8l9z0j) nostr:naddr1qqt5c6t5v4exzar4wfsj6stjw3jj6sm4d3682unpqgs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9crqsqqpphkty54um
n/História-e-Filosofia (por: nostr:npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk ) nostr:naddr1qqjlp8u85lcflpahfpy4x4xrjdfyjsfdg5k5vj2vfaf573jfg8cflrum7z0cezczyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdas35g9vs
n/Urbanism - Urbanismo (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qqy92unzv9hxjumdqgstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgrqsqqpphkyl5u8a
Fé:
n/Religião-e-Teologia - Cristianismo (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpah2fz5cj28f8pcxnedg5k4g320f385wj2p7z0ehyqzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasta04x5
n/Ateismo-e-Agnosticismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqtyzar9d9ek6medv5k5zemwdaehg6trd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdasuuzmw8
n/Budismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5yatyd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas0kmt4m
n/Taoismo - Daoismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqy9gct0cwkhxmt0qy88wumn8ghj7mn0wvhxcmmv9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7crkzqvd
n/Espiritualidade - Significação e sublimidade (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq852umsd9exjar4v9kxjerpv3jszyrhwden5te0dehhxarj9ekk7mf0qgsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscrqsqqpphkxa5nfy
Entretenimento:
n/Equinox - Cinema no Nostr (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr) nostr:naddr1qqr52ut4d9hx77qpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cmc79n5
n/Rock/metal - Músicas Rock e Metal (por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4 e nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz748t750 ) nostr:naddr1qq99ymmrdvh56et5v9kqzqqzypvep8kzcfyvdvug0j9agfv07ujkx9elwfujy5qfl06jy25zmvctwqcyqqqgdas306zj5
n/Música-Cinema-e-Livros (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq4lp8u85lcflpahfhpe556fgdqj6s6ffez56sfdyck5cj2k2f848uyl366lp8unhhcflyu6qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkfyz9pf
n/Lugares-e-Viagens (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqjlp8u85lcflpahf325ws2jg4fj63fd2ey5z369feflp8uv3mcflryd7z0cercpqqpzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7c965gfw
n/MídiasPerdidas - Lost Media (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqw0p8u85lcflpahfhpc63zfg9fj65z92fzyj3zp20cflfusqgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkdltjpa
n/Football - Futebol (Por: nostr:nprofile1qqsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc9l2d6x / Moderadores: nostr:nprofile1qqsx5rzeds2gf6hzaqf35qc0y6v5fys72fsec8w3gwszn3jw5mxewvgpz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9u5c2kxa & nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqyxvmm0w33xzmrvqgsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsrqsqqpphkg0nfw5
n/Formula-1 (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqy5vmmjd46kccfdxypzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7cc95u5w
n/Games - Atualizações sobre jogos (por: nostr:npub1atyuu22fvvj4yf2uf050fwra3pu7hjvykc7ravpmrkpwjxcc6hpsfneh4e ) nostr:naddr1qqz5wctdv4esyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqn0x7k7
n/JogosBrasil - Clips de jogos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qq955mm8dae5yunpwd5kcqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qj90yg0hl4e6qr7yg982dlh0qxdefy72d6ntuqet7hv3ateya782sxpqqqzr0vus9jl2
n/Minecraft (por: nostr:npub19xc7f5lg2z6svrjgye63rx44a96aq2ysqajx5tmum28cu6mk5j3qj3n9m9 ) nostr:naddr1qqy566twv43hyctxwspzq2d3unf7s594qc8ysfn4zxdtt6t46q5fqpmydghhek503e4hdf9zqvzqqqyx7ct7hldr
n/GenshinImpactBr (por: nostr:nprofile1qqs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcnffw22) nostr:naddr1qqtlp8u85lcflpahgajkuumgd9hyjmtsv93hgsnjq9z8wue69uhkw6tjwahhgvntdaunx6mkdgmxv6ehdaek2mm3v9a8qdtkwa3x2cthda3kyvmdxgmk5cm3w3sksd34vcexv6mvxdukgtn0de5k7m30qgs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggrqsqqpphkq4s4py
Libertarianismo:
n/Defensores-caseiros (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq0lp8u85lcflpahg3jkvetwwdhhyetn943kzum9d9ex7ulsn78mgq3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vcr78h2
n/Desobediência_Civil (por: nostr:nprofile1qqs2kw4x8jws3a4heehst0ywafwfymdqk35hx8mrf0dw6zdsnk5kj9gpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m306r5ytp) nostr:naddr1qq2ygetnda3x2erfcw4xucmfv905x6tkd9kqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsyg9t82nre8gg76muumc9hj8w5hyjdkstg6tnra35hkhdpxcfm2tfz5psgqqqsmmqlg3ata
n/sobreviNOSTR - Sobrevivencialismo (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq20p8u85lcflpah2dhkyun9we55un6n23fqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqsmmqtempje
n/Triggr - Armas (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqr9g5jfgar4yqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vt5085y
n/Kaboom - Química e explosivos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qqt0p8u85lcflpahfdq5yn60fhcflra57z0602qppemhxue69uhkummn9ekx7mp0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphk637p09
n/CAVERNA-DO-PIRATA - Pirataria (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq40p8u85lcflpahgdq4v32jfeqj63z094gyj5jp23qlp8u0kn3gpr0znzswlwy07z0ca2gpg3mhxw309ankjunhda6ry6m00yekkan2xenxkdm0wdjk7utp0fcr2anhvfjkzam0vd3rxmfjxa4xxut5v95rvdtxxfnxkmpn09jzummwd9hkutczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqgdask5hmmn
n/PrivateSociety - Propostas e discussões para uma sociedade privada (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq89qunfweshge2nda3kjet50ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cfvhgrt
n/TeoriaDasBandeiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqf9get0wf5kzerpwdpxzmnyv45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkatc9rh
n/SemFronteiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqx4xetdgeex7mn5v45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkjs0cue
n/AnarcoSobrevivencialismo (por: nostr:nprofile1qqsfj5s9lrcckaxd8ul7vf3c4ajfg0n0ytcjvetclw679hy6p98wpfqpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uykdgj7) nostr:naddr1qqdyzmnpwf3k75m0vfex2anfwejkucmfv9kxjumddap9yq3qn9fqt7833d6v60elucnr3tmyjslx7gh3yejh37a4utwf5z2wuzjqxpqqqzr0vsz5kcy
n/SociedadeAlternativaLibertaria - Libertários (por: nostr:nprofile1qqs2ph3za34henpq2y3rzgqwgdc4pjmpleqr5t62rf7kxj0lmdyxnfgppemhxue69uhkummn9ekx7mp0ydypw5) nostr:naddr1qq09xmmrd9jkgctyv4qkcar9wfhxzarfwes5c6tzv4e8gctjd9ssyg9qmc3wc6muess9zg33yq8yxu2sedslusp69a9p5ltrf8lakjrf55psgqqqsmmq8dtk3m
n/LibertariosPT - Libertários de Portugal (por: nostr:nprofile1qqszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4gppemhxue69uhkummn9ekx7mp05leack) nostr:naddr1qqx5c6tzv4e8gctjd9hhx5z5qgszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4grqsqqpphke05802
Discussões Sociais
n/Aliança-Conservadora-Brasileira (por: nostr:npub1atg5rgfuarup49470kqexfgcesdr85yru56y0y8qf3z6kc30g2vqyfyqyp ) nostr:naddr1qqsyzmrfv9hv8fmptapk7mnnv4e8vctydaexzh6zwfshx6tvv45hycgzyr4dzsdp8n50sx5khe7crye9rrxp5v7ss0jng3usupxyt2mz9apfsqcyqqqgdasue9j59
n/Ilha-de-Anhatomirin - Monarquia (Por: nostr:nprofile1qqsgzc22v804davx6vpwtwfu6j84yvupeld497tfr396usmu7s0m08qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszymhwden5te0v9ehgunpdshxu6twdfsj7qguwaehxw309a5x7ervvfhkgtnrdaexzcmvv5h8gmm0d3ej7a2jp7u) nostr:naddr1qqf5jmrgvykkgefdg9hxsct5dakkjunfd5q3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7q3qs9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqxpqqqzr0vu2qg3m
n/ManosphereBrasil - Contra a misandria (Por: nostr:nprofile1qqs0p3yd48kzm56a4tual772y3vsjwehx6tc3rv8ht8q0zgncg5r7qgpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpjnhed) nostr:naddr1qqgy6ctwdaehq6r9wfj5yunpwd5kcqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyrcvfrdfaskaxhd2l80lhj3ytyynkdekj7ygmpa6ecrcjy7z9qlszqcyqqqgdasl3kaju
Memes
n/Shitposting (Por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4) nostr:naddr1qq94x6rfw3cx7um5d9hxwqgswaehxw309ahx7um5wghx6mmd9upzqkvsnmpvyjxxkwy8ez75yk8lwftrzulhy7fz2qylhafz92pdkv9hqvzqqqyx7chlz42w
n/Puro-caldo-do-Brasil. (por: nostr:nprofile1qqsztjv2pflmwcayr2jaq90astj94lu5l0smr0zhkfdct4ry7uxu7dqywzq8t) nostr:naddr1qq24qatjdukkxctvv3hj6er094p8yctnd9kzuqghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7q3qyhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6qxpqqqzr0vwh0r4w
Locais
n/NordesteLibertário - Nordeste (Por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqf5ummjv3jhxar9f35kyetjwnp6zunfdupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cnejrgl
n/BahiaLibertária - Bahia (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqgyyctgd9s5c6tzv4e8fsapwf5kzq3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqzr0vc4949j
n/LiberdadeMinas - Minas Gerais (Por: nostr:nprofile1qqsf0kszkmrmy9l3c7mxr3uhh3fmyjpq2z4hjvv7wdq84k5npd7gw3cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxthwden5te0wfjkccte9eekummjwsh8xmmrd9skctcprpmhxue69uhhyetvv9ujuurvv438xarj9e3k7mf0mx68nx) nostr:naddr1qq8yc6tzv4exgctyv4xkjmnpwvqsqq3qjldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsxpqqqzr0vag4knt
n/CyberpunkManaus - Manaus (Por: nostr:nprofile1qqsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqpz3mhxw309ucnqt3jx5cjuvpwxgarsvpcxqq3wamn8ghj7vfexghrzd3c9ccjuv3s8gurqwps9uq5gamn8ghj7entv43kjd3nvfcx5en6093h2up5w3ekgmn4xsekvatwx438xamywp6ksemcwp6xummzdgekzdmz0pmhzd3j0g6xzepwdahxjmmw9u2upp88) nostr:naddr1qqgyx7tzv4e8qatwdvk56ctwv96hxqgqqgsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqrqsqqpphkgjh4rf
n/BelémLibertario (por: nostr:npub167s6q8sfzkhel4227kacu98zcg6e37v5sqwkv8mxaazrryz9huzqlhcu2t) nostr:nevent1qqsqnqgx3u2whdqdqmlstqcmgav6xfe4upz2qxfvj03tlk699dzlk7qzyrt6rgq7py26l874ft6mhrs5utprtx8ejjqp6eslvmh5gvvsgklsgqcyqqqqq2qqsdz6l
n/SãoPauloLivre - São Paulo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq898sardagxzatvdaxxjanjv5pzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cmls060
n/AcreLibertário - Acre (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq85zcmjv4xxjcn9wf6v8gtjd9hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqftljpt
n/Alagoas (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5zmrpvahkzuczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas8qtaf4
Empreendedorismo:
n/Empreendedorismo/BR (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqd5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj7snjv9ekjmqzyz5jr7tdaz02wwfsksstyrf9ytx4x9yhaa257my24xlw5s29yt5dkqcyqqqgdaslzrp3p
n/Empreendedorismo/SP (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqt5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj756sqgs2jg0edh5fafeexz6zpvsdy53v65c5jlh42nmv325ma6jpg53w3kcrqsqqpphkcym25j
Análise
n/EBDV (Em Busca Da Verdade) - Análise geral e desenvolvimento pessoal (por: nostr:nprofile1qqs0xmu0skfdlmtl5tth6cv99za8f8kv7ulz5srkm8p6v5k03dx9lzspz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9usvrt9r) nostr:naddr1qqzy2sjy2cpzpum037ze9hld073dwltps55t5ay7enmnu2jqwmvu8fjje795chu2qvzqqqyx7cy9v5px
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
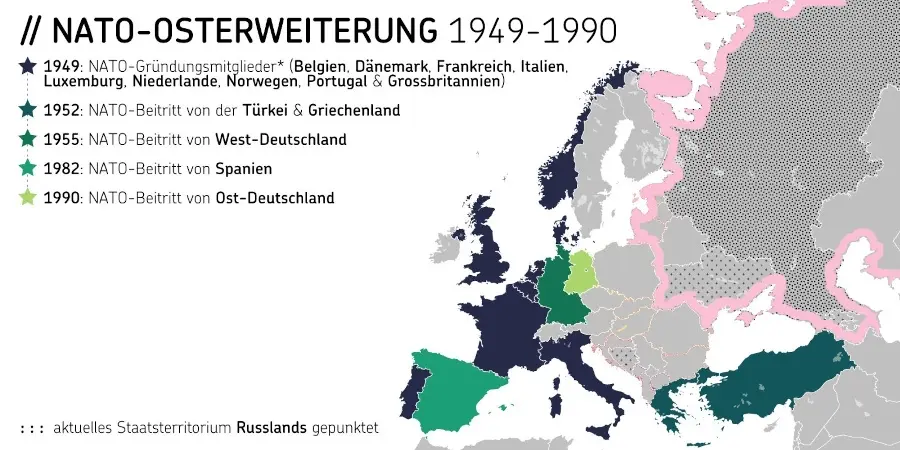
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
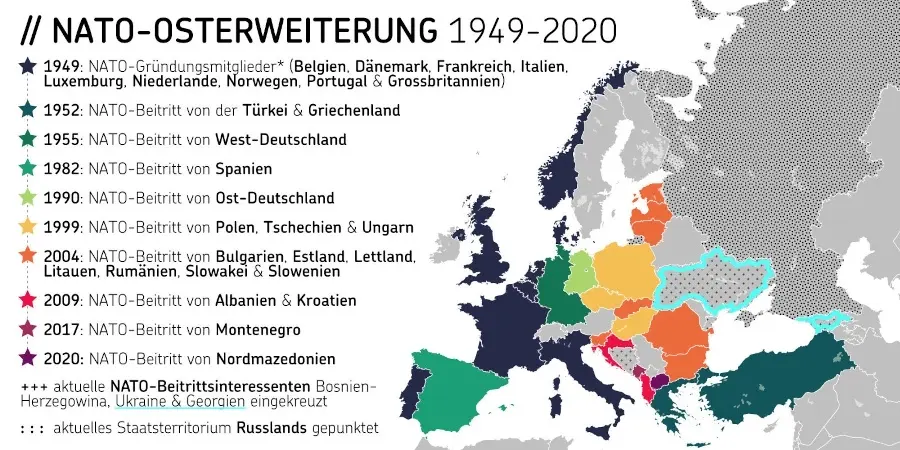
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ e691f4df:1099ad65
2025-04-24 18:56:12
@ e691f4df:1099ad65
2025-04-24 18:56:12Viewing Bitcoin Through the Light of Awakening
Ankh & Ohm Capital’s Overview of the Psycho-Spiritual Nature of Bitcoin
Glossary:
I. Preface: The Logos of Our Logo
II. An Oracular Introduction
III. Alchemizing Greed
IV. Layers of Fractalized Thought
V. Permissionless Individuation
VI. Dispelling Paradox Through Resonance
VII. Ego Deflation
VIII. The Coin of Great Price
Preface: The Logos of Our Logo
Before we offer our lens on Bitcoin, it’s important to illuminate the meaning behind Ankh & Ohm’s name and symbol. These elements are not ornamental—they are foundational, expressing the cosmological principles that guide our work.
Our mission is to bridge the eternal with the practical. As a Bitcoin-focused family office and consulting firm, we understand capital not as an end, but as a tool—one that, when properly aligned, becomes a vehicle for divine order. We see Bitcoin not simply as a technological innovation but as an emanation of the Divine Logos—a harmonic expression of truth, transparency, and incorruptible structure. Both the beginning and the end, the Alpha and Omega.
The Ankh (☥), an ancient symbol of eternal life, is a key to the integration of opposites. It unites spirit and matter, force and form, continuity and change. It reminds us that capital, like Life, must not only be generative, but regenerative; sacred. Money must serve Life, not siphon from it.
The Ohm (Ω) holds a dual meaning. In physics, it denotes a unit of electrical resistance—the formative tension that gives energy coherence. In the Vedic tradition, Om (ॐ) is the primordial vibration—the sound from which all existence unfolds. Together, these symbols affirm a timeless truth: resistance and resonance are both sacred instruments of the Creator.
Ankh & Ohm, then, represents our striving for union, for harmony —between the flow of life and intentional structure, between incalculable abundance and measured restraint, between the lightbulb’s electrical impulse and its light-emitting filament. We stand at the threshold where intention becomes action, and where capital is not extracted, but cultivated in rhythm with the cosmos.
We exist to shepherd this transformation, as guides of this threshold —helping families, founders, and institutions align with a deeper order, where capital serves not as the prize, but as a pathway to collective Presence, Purpose, Peace and Prosperity.
An Oracular Introduction
Bitcoin is commonly understood as the first truly decentralized and secure form of digital money—a breakthrough in monetary sovereignty. But this view, while technically correct, is incomplete and spiritually shallow. Bitcoin is more than a tool for economic disruption. Bitcoin represents a mythic threshold: a symbol of the psycho-spiritual shift that many ancient traditions have long foretold.
For millennia, sages and seers have spoken of a coming Golden Age. In the Vedic Yuga cycles, in Plato’s Great Year, in the Eagle and Condor prophecies of the Americas—there exists a common thread: that humanity will emerge from darkness into a time of harmony, cooperation, and clarity. That the veil of illusion (maya, materiality) will thin, and reality will once again become transparent to the transcendent. In such an age, systems based on scarcity, deception, and centralization fall away. A new cosmology takes root—one grounded in balance, coherence, and sacred reciprocity.
But we must ask—how does such a shift happen? How do we cross from the age of scarcity, fear, and domination into one of coherence, abundance, and freedom?
One possible answer lies in the alchemy of incentive.
Bitcoin operates not just on the rules of computer science or Austrian economics, but on something far more old and subtle: the logic of transformation. It transmutes greed—a base instinct rooted in scarcity—into cooperation, transparency, and incorruptibility.
In this light, Bitcoin becomes more than code—it becomes a psychoactive protocol, one that rewires human behavior by aligning individual gain with collective integrity. It is not simply a new form of money. It is a new myth of value. A new operating system for human consciousness.
Bitcoin does not moralize. It harmonizes. It transforms the instinct for self-preservation into a pathway for planetary coherence.
Alchemizing Greed
At the heart of Bitcoin lies the ancient alchemical principle of transmutation: that which is base may be refined into gold.
Greed, long condemned as a vice, is not inherently evil. It is a distorted longing. A warped echo of the drive to preserve life. But in systems built on scarcity and deception, this longing calcifies into hoarding, corruption, and decay.
Bitcoin introduces a new game. A game with memory. A game that makes deception inefficient and truth profitable. It does not demand virtue—it encodes consequence. Its design does not suppress greed; it reprograms it.
In traditional models, game theory often illustrates the fragility of trust. The Prisoner’s Dilemma reveals how self-interest can sabotage collective well-being. But Bitcoin inverts this. It creates an environment where self-interest and integrity converge—where the most rational action is also the most truthful.
Its ledger, immutable and transparent, exposes manipulation for what it is: energetically wasteful and economically self-defeating. Dishonesty burns energy and yields nothing. The network punishes incoherence, not by decree, but by natural law.
This is the spiritual elegance of Bitcoin: it does not suppress greed—it transmutes it. It channels the drive for personal gain into the architecture of collective order. Miners compete not to dominate, but to validate. Nodes collaborate not through trust, but through mathematical proof.
This is not austerity. It is alchemy.
Greed, under Bitcoin, is refined. Tempered. Re-forged into a generative force—no longer parasitic, but harmonic.
Layers of Fractalized Thought Fragments
All living systems are layered. So is the cosmos. So is the human being. So is a musical scale.
At its foundation lies the timechain—the pulsing, incorruptible record of truth. Like the heart, it beats steadily. Every block, like a pulse, affirms its life through continuity. The difficulty adjustment—Bitcoin’s internal calibration—functions like heart rate variability, adapting to pressure while preserving coherence.
Above this base layer is the Lightning Network—a second layer facilitating rapid, efficient transactions. It is the nervous system: transmitting energy, reducing latency, enabling real-time interaction across a distributed whole.
Beyond that, emerging tools like Fedimint and Cashu function like the capillaries—bringing vitality to the extremities, to those underserved by legacy systems. They empower the unbanked, the overlooked, the forgotten. Privacy and dignity in the palms of those the old system refused to see.
And then there is NOSTR—the decentralized protocol for communication and creation. It is the throat chakra, the vocal cords of the “freedom-tech” body. It reclaims speech from the algorithmic overlords, making expression sovereign once more. It is also the reproductive system, as it enables the propagation of novel ideas and protocols in fertile, uncensorable soil.
Each layer plays its part. Not in hierarchy, but in harmony. In holarchy. Bitcoin and other open source protocols grow not through exogenous command, but through endogenous coherence. Like cells in an organism. Like a song.
Imagine the cell as a piece of glass from a shattered holographic plate —by which its perspectival, moving image can be restructured from the single shard. DNA isn’t only a logical script of base pairs, but an evolving progressive song. Its lyrics imbued with wise reflections on relationships. The nucleus sings, the cell responds—not by command, but by memory. Life is not imposed; it is expressed. A reflection of a hidden pattern.
Bitcoin chants this. Each node, a living cell, holds the full timechain—Truth distributed, incorruptible. Remove one, and the whole remains. This isn’t redundancy. It’s a revelation on the power of protection in Truth.
Consensus is communion. Verification becomes a sacred rite—Truth made audible through math.
Not just the signal; the song. A web of self-expression woven from Truth.
No center, yet every point alive with the whole. Like Indra’s Net, each reflects all. This is more than currency and information exchange. It is memory; a self-remembering Mind, unfolding through consensus and code. A Mind reflecting the Truth of reality at the speed of thought.
Heuristics are mental shortcuts—efficient, imperfect, alive. Like cells, they must adapt or decay. To become unbiased is to have self-balancing heuristics which carry feedback loops within them: they listen to the environment, mutate when needed, and survive by resonance with reality. Mutation is not error, but evolution. Its rules are simple, but their expression is dynamic.
What persists is not rigidity, but pattern.
To think clearly is not necessarily to be certain, but to dissolve doubt by listening, adjusting, and evolving thought itself.
To understand Bitcoin is simply to listen—patiently, clearly, as one would to a familiar rhythm returning.
Permissionless Individuation
Bitcoin is a path. One that no one can walk for you.
Said differently, it is not a passive act. It cannot be spoon-fed. Like a spiritual path, it demands initiation, effort, and the willingness to question inherited beliefs.
Because Bitcoin is permissionless, no one can be forced to adopt it. One must choose to engage it—compelled by need, interest, or intuition. Each person who embarks undergoes their own version of the hero’s journey.
Carl Jung called this process Individuation—the reconciliation of fragmented psychic elements into a coherent, mature Self. Bitcoin mirrors this: it invites individuals to confront the unconscious assumptions of the fiat paradigm, and to re-integrate their relationship to time, value, and agency.
In Western traditions—alchemy, Christianity, Kabbalah—the individual is sacred, and salvation is personal. In Eastern systems—Daoism, Buddhism, the Vedas—the self is ultimately dissolved into the cosmic whole. Bitcoin, in a paradoxical way, echoes both: it empowers the individual, while aligning them with a holistic, transcendent order.
To truly see Bitcoin is to allow something false to die. A belief. A habit. A self-concept.
In that death—a space opens for deeper connection with the Divine itSelf.
In that dissolution, something luminous is reborn.
After the passing, Truth becomes resurrected.
Dispelling Paradox Through Resonance
There is a subtle paradox encoded into the hero’s journey: each starts in solidarity, yet the awakening affects the collective.
No one can be forced into understanding Bitcoin. Like a spiritual truth, it must be seen. And yet, once seen, it becomes nearly impossible to unsee—and easier for others to glimpse. The pattern catches.
This phenomenon mirrors the concept of morphic resonance, as proposed and empirically tested by biologist Rupert Sheldrake. Once a critical mass of individuals begins to embody a new behavior or awareness, it becomes easier—instinctive—for others to follow suit. Like the proverbial hundredth monkey who begins to wash the fruit in the sea water, and suddenly, monkeys across islands begin doing the same—without ever meeting.
When enough individuals embody a pattern, it ripples outward. Not through propaganda, but through field effect and wave propagation. It becomes accessible, instinctive, familiar—even across great distance.
Bitcoin spreads in this way. Not through centralized broadcast, but through subtle resonance. Each new node, each individual who integrates the protocol into their life, strengthens the signal for others. The protocol doesn’t shout; it hums, oscillates and vibrates——persistently, coherently, patiently.
One awakens. Another follows. The current builds. What was fringe becomes familiar. What was radical becomes obvious.
This is the sacred geometry of spiritual awakening. One awakens, another follows, and soon the fluidic current is strong enough to carry the rest. One becomes two, two become many, and eventually the many become One again. This tessellation reverberates through the human aura, not as ideology, but as perceivable pattern recognition.
Bitcoin’s most powerful marketing tool is truth. Its most compelling evangelist is reality. Its most unstoppable force is resonance.
Therefore, Bitcoin is not just financial infrastructure—it is psychic scaffolding. It is part of the subtle architecture through which new patterns of coherence ripple across the collective field.
The training wheels from which humanity learns to embody Peace and Prosperity.
Ego Deflation
The process of awakening is not linear, and its beginning is rarely gentle—it usually begins with disruption, with ego inflation and destruction.
To individuate is to shape a center; to recognize peripherals and create boundaries—to say, “I am.” But without integration, the ego tilts—collapsing into void or inflating into noise. Fiat reflects this pathology: scarcity hoarded, abundance simulated. Stagnation becomes disguised as safety, and inflation masquerades as growth.
In other words, to become whole, the ego must first rise—claiming agency, autonomy, and identity. However, when left unbalanced, it inflates, or implodes. It forgets its context. It begins to consume rather than connect. And so the process must reverse: what inflates must deflate.
In the fiat paradigm, this inflation is literal. More is printed, and ethos is diluted. Savings decay. Meaning erodes. Value is abstracted. The economy becomes bloated with inaudible noise. And like the psyche that refuses to confront its own shadow, it begins to collapse under the weight of its own illusions.
But under Bitcoin, time is honored. Value is preserved. Energy is not abstracted but grounded.
Bitcoin is inherently deflationary—in both economic and spiritual senses. With a fixed supply, it reveals what is truly scarce. Not money, not status—but the finite number of heartbeats we each carry.
To see Bitcoin is to feel that limit in one’s soul. To hold Bitcoin is to feel Time’s weight again. To sense the importance of Bitcoin is to feel the value of preserved, potential energy. It is to confront the reality that what matters cannot be printed, inflated, or faked. In this way, Bitcoin gently confronts the ego—not through punishment, but through clarity.
Deflation, rightly understood, is not collapse—it is refinement. It strips away illusion, bloat, and excess. It restores the clarity of essence.
Spiritually, this is liberation.
The Coin of Great Price
There is an ancient parable told by a wise man:
“The kingdom of heaven is like a merchant seeking fine pearls, who, upon finding one of great price, sold all he had and bought it.”
Bitcoin is such a pearl.
But the ledger is more than a chest full of treasure. It is a key to the heart of things.
It is not just software—it is sacrament.
A symbol of what cannot be corrupted. A mirror of divine order etched into code. A map back to the sacred center.
It reflects what endures. It encodes what cannot be falsified. It remembers what we forgot: that Truth, when aligned with form, becomes Light once again.
Its design is not arbitrary. It speaks the language of life itself—
The elliptic orbits of the planets mirrored in its cryptography,
The logarithmic spiral of the nautilus shell discloses its adoption rate,
The interconnectivity of mycelium in soil reflect the network of nodes in cyberspace,
A webbed breadth of neurons across synaptic space fires with each new confirmed transaction.
It is geometry in devotion. Stillness in motion.
It is the Logos clothed in protocol.
What this key unlocks is beyond external riches. It is the eternal gold within us.
Clarity. Sovereignty. The unshakeable knowing that what is real cannot be taken. That what is sacred was never for sale.
Bitcoin is not the destination.
It is the Path.
And we—when we are willing to see it—are the Temple it leads back to.
-
 @ bbef5093:71228592
2025-05-06 16:11:35
@ bbef5093:71228592
2025-05-06 16:11:35India csökkentené az atomerőművek építési idejét ambiciózus nukleáris céljai eléréséhez
India célja, hogy a jelenlegi 10 évről a „világszínvonalú” 6 évre csökkentse atomerőművi projektjeinek kivitelezési idejét, hogy elérje a 2047-re kitűzött, 100 GW beépített nukleáris kapacitást.
Az SBI Capital Markets (az Indiai Állami Bank befektetési banki leányvállalata) jelentése szerint ez segítene mérsékelni a korábbi költségtúllépéseket, és vonzóbbá tenné az országot a globális befektetők számára.
A jelentés szerint a jelenlegi, mintegy 8 GW kapacitás és a csak 7 GW-nyi építés alatt álló kapacitás mellett „jelentős gyorsítás” szükséges a célok eléréséhez.
A kormány elindította a „nukleáris energia missziót”, amelyhez körülbelül 2,3 milliárd dollárt (2 milliárd eurót) különített el K+F-re és legalább öt Bharat kis moduláris reaktor (BSMR) telepítésére, de további kihívásokat kell megoldania a célok eléréséhez.
Az építési idők csökkentése kulcsfontosságú, de a jelentés átfogó rendszerszintű reformokat is javasol, beleértve a gyorsabb engedélyezést, a földszerzési szabályok egyszerűsítését, az erőművek körüli védőtávolság csökkentését, és a szabályozó hatóság (Atomic Energy Regulatory Board) nagyobb önállóságát.
A jelentés szerint a nemzet korlátozott uránkészletei miatt elengedhetetlen az üzemanyagforrások diverzifikálása nemzetközi megállapodások révén, valamint az indiai nukleáris program 2. és 3. szakaszának felgyorsítása.
India háromlépcsős nukleáris programja célja egy zárt üzemanyagciklus kialakítása, amely a természetes uránra, a plutóniumra és végül a tóriumra épül. A 2. szakaszban gyorsneutronos reaktorokat használnak, amelyek több energiát nyernek ki az uránból, kevesebb bányászott uránt igényelnek, és a fel nem használt uránt új üzemanyaggá alakítják. A 3. szakaszban fejlett reaktorok működnek majd India hatalmas tóriumkészleteire alapozva.
2025 januárjában az indiai Nuclear Power Corporation (NPCIL) pályázatot írt ki Bharat SMR-ek telepítésére, először nyitva meg a nukleáris szektort indiai magáncégek előtt.
Eddig csak az állami tulajdonú NPCIL építhetett és üzemeltethetett kereskedelmi atomerőműveket Indiában.
A Bharat SMR-ek (a „Bharat” hindiül Indiát jelent) telepítése a „Viksit Bharat” („Fejlődő India”) program része.
Engedélyezési folyamat: „elhúzódó és egymásra épülő”
A Bharat atomerőmű fejlesztésének részletei továbbra sem világosak, de Nirmala Sitharaman pénzügyminiszter júliusban elmondta, hogy az állami National Thermal Power Corporation és a Bharat Heavy Electricals Limited közös vállalkozásában valósulna meg a fejlesztés.
Sitharaman hozzátette, hogy a kormány a magánszektorral közösen létrehozna egy Bharat Small Reactors nevű céget, amely SMR-ek és új nukleáris technológiák kutatás-fejlesztésével foglalkozna.
Az SBI jelentése szerint javítani kell az SMR programot, mert az engedélyezési folyamat jelenleg „elhúzódó és egymásra épülő”, és aránytalan kockázatot jelent a magánszereplők számára a reaktorfejlesztés során.
A program „stratégiailag jó helyzetben van a sikerhez”, mert szigorú belépési feltételeket támaszt, így csak komoly és alkalmas szereplők vehetnek részt benne.
A kormánynak azonban be kellene vezetnie egy kártérítési záradékot, amely védi a magáncégeket az üzemanyag- és nehézvíz-ellátás hiányától, amely az Atomenergia Minisztérium (DAE) hatáskörébe tartozik.
A jelentés szerint mind az üzemanyag, mind a nehézvíz ellátása a DAE-től függ, és „a hozzáférés hiánya” problémát jelenthet. India legtöbb kereskedelmi atomerőműve hazai fejlesztésű, nyomottvizes nehézvizes reaktor.
A jelentés szerint: „A meglévő szabályozási hiányosságok kezelése kulcsfontosságú, hogy a magánszektor vezethesse a kitűzött 100 GW nukleáris kapacitás 50%-ának fejlesztését 2047-ig.”
Az NPCIL nemrégiben közölte, hogy India 2031–32-ig további 18 reaktort kíván hozzáadni az energiamixhez, ezzel az ország nukleáris kapacitása 22,4 GW-ra nő.
A Nemzetközi Atomenergia-ügynökség adatai szerint Indiában 21 reaktor üzemel kereskedelmi forgalomban, amelyek 2023-ban az ország áramtermelésének körülbelül 3%-át adták. Hat egység van építés alatt.
Roszatom pert indított a leállított Hanhikivi-1 projekt miatt Finnországban
Az orosz állami Roszatom atomenergetikai vállalat pert indított Moszkvában a finn Fortum és Outokumpu cégek ellen, és 227,8 milliárd rubel (2,8 milliárd dollár, 2,4 milliárd euró) kártérítést követel a finnországi Hanhikivi-1 atomerőmű szerződésének felmondása miatt – derül ki bírósági dokumentumokból és a Roszatom közleményéből.
A Roszatom a „mérnöki, beszerzési és kivitelezési (EPC) szerződés jogellenes felmondása”, a részvényesi megállapodás, az üzemanyag-ellátási szerződés megsértése, valamint a kölcsön visszafizetésének megtagadása miatt követel kártérítést.
A Fortum a NucNetnek e-mailben azt írta, hogy „nem kapott hivatalos értesítést orosz perről”.
A Fortum 2025. április 29-i negyedéves jelentésében közölte, hogy a Roszatom finn leányvállalata, a Raos Project, valamint a Roszatom nemzetközi divíziója, a JSC Rusatom Energy International, illetve a Fennovoima (a Hanhikivi projektért felelős finn konzorcium) között a Hanhikivi EPC szerződésével kapcsolatban nemzetközi választottbírósági eljárás zajlik.
2025 februárjában a választottbíróság úgy döntött, hogy nincs joghatósága a Fortummal szembeni követelések ügyében. „Ez a döntés végleges volt, így a Fortum nem része a választottbírósági eljárásnak” – közölte a cég.
A Fortum 2015-ben kisebbségi tulajdonos lett a Fennovoima projektben, de a teljes tulajdonrészt 2020-ban leírta.
A Fennovoima konzorcium, amelyben a Roszatom a Raos-on keresztül 34%-os kisebbségi részesedéssel rendelkezett, 2022 májusában felmondta a Hanhikivi-1 létesítésére vonatkozó szerződést az ukrajnai háború miatti késedelmek és megnövekedett kockázatok miatt.
A projekt technológiája az orosz AES-2006 típusú nyomottvizes reaktor lett volna.
2021 áprilisában a Fennovoima közölte, hogy a projekt teljes beruházási költsége 6,5–7 milliárd euróról 7–7,5 milliárd euróra nőtt.
2022 augusztusában a Roszatom és a Fennovoima kölcsönösen milliárdos kártérítési igényt nyújtott be egymás ellen a projekt leállítása miatt.
A Fennovoima nemzetközi választottbírósági eljárást indított 1,7 milliárd euró előleg visszafizetéséért. A Roszatom 3 milliárd eurós ellenkeresetet nyújtott be. Ezek az ügyek jelenleg is nemzetközi bíróságok előtt vannak.
Dél-koreai delegáció Csehországba utazik nukleáris szerződés aláírására
Egy dél-koreai delegáció 2025. május 6-án Csehországba utazik, hogy részt vegyen egy több milliárd dolláros szerződés aláírásán, amely két új atomerőmű építéséről szól a Dukovany telephelyen – közölte a dél-koreai kereskedelmi, ipari és energetikai minisztérium.
A delegáció, amelyben kormányzati és parlamenti tisztviselők is vannak, kétnapos prágai látogatásra indul, hogy részt vegyen a szerdára tervezett aláírási ceremónián.
A küldöttség találkozik Petr Fiala cseh miniszterelnökkel és Milos Vystrcil szenátusi elnökkel is, hogy megvitassák a Dukovany projektet.
Fiala múlt héten bejelentette, hogy Prága május 7-én írja alá a Dukovany szerződést a Korea Hydro & Nuclear Power (KHNP) céggel.
A cseh versenyhivatal nemrég engedélyezte a szerződés aláírását a KHNP-vel, miután elutasította a francia EDF fellebbezését.
A versenyhivatal április 24-i döntése megerősítette a korábbi ítéletet, amelyet az EDF megtámadott, miután 2024 júliusában elvesztette a tenderpályázatot a KHNP-vel szemben.
Ez lehetővé teszi, hogy a két dél-koreai APR1400 reaktor egység szerződését aláírják Dukovanyban, Dél-Csehországban. A szerződés az ország történetének legnagyobb energetikai beruházása, értéke legalább 400 milliárd korona (16 milliárd euró, 18 milliárd dollár).
A szerződést eredetileg márciusban írták volna alá, de a vesztes pályázók (EDF, Westinghouse) fellebbezései, dél-koreai politikai bizonytalanságok és a cseh cégek lokalizációs igényei miatt csúszott.
A KHNP januárban rendezte a szellemi tulajdonjogi vitát a Westinghouse-zal, amely korábban azt állította, hogy a KHNP az ő technológiáját használja az APR1400 reaktorokban.
A szerződés aláírása Dél-Korea első külföldi atomerőmű-építési projektje lesz 2009 óta, amikor a KHNP négy APR1400 reaktort épített az Egyesült Arab Emírségekben, Barakahban.
Csehországban hat kereskedelmi reaktor működik: négy orosz VVER-440-es Dukovanyban, két nagyobb VVER-1000-es Temelínben. Az IAEA szerint ezek az egységek a cseh áramtermelés mintegy 36,7%-át adják.
Az USA-nak „minél előbb” új reaktort kell építenie – mondta a DOE jelöltje a szenátusi bizottság előtt
Az USA-nak minél előbb új atomerőművet kell építenie, és elő kell mozdítania a fejlett reaktorok fejlesztését, engedélyezését és telepítését – hangzott el a szenátusi energiaügyi bizottság előtt.
Ted Garrish, aki a DOE nukleáris energiaügyi helyettes államtitkári posztjára jelöltként jelent meg, elmondta: az országnak új reaktort kell telepítenie, legyen az nagy, kis moduláris vagy mikroreaktor.
Az USA-ban jelenleg nincs épülő kereskedelmi atomerőmű, az utolsó kettő, a Vogtle-3 és Vogtle-4 2023-ban, illetve 2024-ben indult el Georgiában.
„A nukleáris energia kivételes lehetőség a növekvő villamosenergia-igény megbízható, megfizethető és biztonságos kielégítésére” – mondta Garrish, aki tapasztalt atomenergetikai vezető. Szerinte az USA-nak nemzetbiztonsági okokból is fejlesztenie kell a hazai urándúsító ipart.
Vizsgálni kell a nemzetközi piacot és a kormányközi megállapodások lehetőségét az amerikai nukleáris fejlesztők és ellátási láncok számára, valamint meg kell oldani a kiégett fűtőelemek elhelyezésének problémáját.
1987-ben a Kongresszus a nevadai Yucca Mountain-t jelölte ki a kiégett fűtőelemek végleges tárolóhelyének, de 2009-ben az Obama-adminisztráció leállította a projektet.
Az USA-ban az 1950-es évek óta mintegy 83 000 tonna radioaktív hulladék, köztük kiégett fűtőelem halmozódott fel, amelyet jelenleg acél- és betonkonténerekben tárolnak az erőművek telephelyein.
Garrish korábban a DOE nemzetközi ügyekért felelős helyettes államtitkára volt (2018–2021), jelenleg az Egyesült Haladó Atomenergia Szövetség igazgatótanácsának elnöke.
Egyéb hírek
Szlovénia közös munkát sürget az USA-val a nukleáris energiában:
Az USA és Horvátország tisztviselői együttműködésről tárgyaltak Közép- és Délkelet-Európa energiaellátásának diverzifikálása érdekében, különös tekintettel a kis moduláris reaktorokra (SMR). Horvátország és Szlovénia közösen tulajdonolja a szlovéniai Krško atomerőművet, amely egyetlen 696 MW-os nyomottvizes reaktorával Horvátország áramfogyasztásának 16%-át, Szlovéniáénak 20%-át adja. Szlovénia fontolgatja egy második blokk építését, de tavaly elhalasztotta az erről szóló népszavazást.Malawi engedélyezi a Kayelekera uránbánya újraindítását:
A Malawi Atomenergia Hatóság kiadta a sugárbiztonsági engedélyt a Lotus (Africa) Limited számára, így újraindulhat a Kayelekera uránbánya, amely több mint egy évtizede, 2014 óta állt a zuhanó uránárak és biztonsági problémák miatt. A bánya 85%-át az ausztrál Lotus Resources helyi leányvállalata birtokolja. A Lotus szerint a bánya újraindítása teljesen finanszírozott, kb. 43 millió dollár (37 millió euró) tőkével.Venezuela és Irán nukleáris együttműködést tervez:
Venezuela és Irán a nukleáris tudomány és technológia terén való együttműködésről tárgyalt. Az iráni állami média szerint Mohammad Eslami, az Iráni Atomenergia Szervezet vezetője és Alberto Quintero, Venezuela tudományos miniszterhelyettese egyetemi és kutatási programok elindításáról egyeztetett. Venezuelában nincs kereskedelmi atomerőmű, de 2010-ben Oroszországgal írt alá megállapodást új atomerőművek lehetőségéről. Iránnak egy működő atomerőműve van Bushehr-1-nél, egy másik ugyanott épül, mindkettőt Oroszország szállította. -
 @ 557c650b:b04c6817
2025-05-07 19:46:47
@ 557c650b:b04c6817
2025-05-07 19:46:47Um exercício mental
-
 @ 005bc4de:ef11e1a2
2025-05-07 14:19:15
@ 005bc4de:ef11e1a2
2025-05-07 14:19:15The beautiful evil of horse racing

Horse racing intrigues me. And, it appalls me. I find it to be both gloriously beautiful and brutally cruel.
One of the fun facts shared tirelessly around social media for Kentucky Derby #151 was something like this: "This is the first Derby where every horse is in the bloodline of Secretariat." Secretariat, if you don't know, won the Triple Crown in 1973 (KY Derby, Preakness, Belmont) and still holds the fastest times in all three of those races.
That's really a nice fun fact when you first hear it, but maybe it shouldn't be too surprising. After a successful racing career, a male racehorse "retires" to a life of studding himself out, which is where the real horse money is. His post-racing stats: he bred 60 mares per year, he sired 660 foals, and he earned an estimated $120 million in stud fees. When you start branching out the Secretariat family tree over several generations, well, the sheer numbers must be very large. That means the chances that any given Thoroughbred might have a hint of Secretariat blood must get rather high. Grok AI estimates there are 500,000 Thoroughbreds today worldwide, and that beteen 250,000 to 400,000 are in Secretariat's lineage, that's 50% to 80% of every Thoroughbred. Suddenly, the social media snippet from Derby #151 is less surprising, less cool.

Secretariat, retired from racing.
The beautiful side of horse racing
Horse racing is beautiful. This is the easy part to write. If you've ever been to a horse track, especially on a big race day, it's a true multi-sensory experience.
- There are smells that we typically don't smell often in this modern world...especially if you hang out near the paddock. Personally, I don't find horse dung particularly stinky, but earthy.
- There are tastes and good smells. Food and drink are a huge part of horse racing. There is a reason that the Derby has its own pie (a chocolate pecan pie) and each major race has its own drink. Feasting and tailgating are huge parts of horse racing.
- There are things to feel, actually to bodily feel. Aside from crowds of people to bump into, if you stand close to the track, you can feel the reverberation of hooves beating the dirt. We hear the term "thundering herd" sometimes in college sports, but, that term is not just words. You can actually feel the thunder of those hooves.
- The sounds are distinctly horse racing. The announcer's calls of "Less than a minute," "They're in the gates," and "And they're off!" are iconic, not to mention the terms "down to the wire," "won by a nose," or "photo finish." And then there's the bugle's announcement, the singing of "My Old Kentucky Home" at the Derby, the roar of the crowd, and moans of loss from bad bets, shrieks of joy from good bets, and that thunder from the herd, of course.
- The visuals are just stunning. People-wise, the women in their pastel sundresses, the men are snazzy in their colors too (though some go too over-the-top for my liking; they move from classy to clownish), and then there are the hats which are their own category altogether. There's the track, and the spires, and the grass and dirt (or mud) and roses. And there's the jockeys and their colorful silks. But, mostly, there's the horses. A Thoroughbred racehorse at full speed, in full stride, is incredible to look upon. It is a beast that is entirely built for one pure reason: speed. You might be familiar with ESPN's "The Body Issue" that features elite, pro athletes in the nude so that their incredible physiques are displayed. Horse racing is the same thing, equine style. The Derby, in particular, is a sports photographer's bonanza. If you actually know what you're doing, you can't not get great results. Below are some photos amateur me point-and-clicked on Derby Day at a horse track (not Churchill Downs):
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/Eq7LSG39v5H5NpQppxhzwhfAtJVQikYVppRJsgZXh6KxGXU2YochRXqoJaW7NMZ8Yd8.jpg]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23wWw7ZbXPJxKFAyLwuraK1QypVcLV6QpsyG6Ccr6ZLiPYgNtUBa3ALWx1XR4wPYayhmT.png]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/2432HqW3ZtUCjvGD7WTkg2z2ngoByX2rV6htgENN1eytUYXycRCaQdevL7xn1mdKC8qG8.gif]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/245HijMM8pQ7c2EdJwrzUPa3LDjm1P51WqU6j5mYkAJnAXJrkbAn6XBNCzR7G28MSR62u.png]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/EpVAhnScSoAVCYvw2Faf7ZyipskYLvu9MuBXzmHN3jdVPoDBVAVR8yqrrGf1c7Apxzb.jpg]
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/245Hm6k5HafqiMfzUiNK7Z3pUG752f4CmLc5pMVuonkQVY1sKG9ucSrdGgvNVQGNud628.gif]
Horse racing appeals to all senses and is viscerally exhilarating in so many ways. It is beautiful.
Genetics
But, let's get back to the real point: this game is all about Brave New World-like breeding and genetics. It is horse eugenics. The idea is simple: fast Mommy horse and fast Daddy horse means fast baby horse. In horse racing, a horse's blood lineage is called its dosage. Personally, I pay zero attention to dosage (I focus on track length and closing the long races), but dosage is a mathematical stat that tries to answer, "How much is this horse truly a Thoroughbred and a genetic winner?" This question of dosage begs another question, "What actually is a Thoroughbred?"
A Thoroughbred is a horse breed. There are a lot of horse breeds, a lot. For a novice like me, it's very hard to distinguish one from another. I think most people can see a difference between a draft horse, bred for pulling heavy loads, and a Thoroughbred, bred for speed. I think most people, if betting on a foot race, would bet on the Thoroughbred below, left and not on "Jupiter, the largest draft horse in America" on the right. If betting on hauling a wagon load of beer up a steep hill, most would bet Jupiter.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23yx8AjtVZkpE7jXJ2RXzV78hhXSvsgU97i2FkvfcFcEZevfshNgwPw2diJNhmL344gmR.png]
But, when comparing racing horses, there are also Sandardbreds which are bred for harness racing and thus have a heavier build than Thoroughbreds. The two breeds are shown below, but their distinctions are not particularly outstanding to my novice eye. Can you tell the difference, which is the Standardbred versus the Thoroughbred? (Answer at the bottom of page.) Maybe side-by-side you can tell, but could you tell if you saw one standing alone? If you saw two of the same breed, could you judge by appearance which one runs faster? If you can, I tip my cap to you.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23zbTqFJgYpKyXwxbGsVeQiKv4tTZSj8S8QboTJWEhTETPqjnaUVDtX2BirjBXH5KVNo6.png]
I imagine most people are much more familiar with, and can more readily notice, the differences in dog breeds. For instance, take the French Bulldog, the Greyhound, or the world's best dog breed, the Labrador Retriever (totally unbiased here).
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/244oozGkxAwS4sqoWiT8phQv8ssrqq4caB9bHgDufsogds7scUUfhp54WTKmosDzfL5WT.png]
The French Bulldog is bred for cosmetics, the greyhound for pure speed, and the Labrador for all-around everything...intelligence, sturdy athleticism, loyal companionship (totally unbiased here). In these three dogs, we can clearly see the differences that have resulted from breeding.
The evil side of horse racing
Horse racing is evil. And, it is cruel. But, for now, let's step back to the dogs. Dog breeding can be cruel as well.
The French Bulldog is something of the "it" dog right now. A quick Google Gemini search reported it as the most popular breed in 2025.

I remember when "101 Dalmatians" came out 1996. Dalmatians skyrocketed in popularity. But, that popularity was anything but a blessing for Dalmatian pups. They were overbred (and are too inbred as it is), oversold, and were taken in by people eager to get in on the "it" dog then and scoop up the cute spotted pups. But, Dalmatians are very active pups that grow into very active dogs. When the novelty of the spotted pup wore off, many were returned or given away or taken to shelters as being uncontrollable.
The French Poodle situation is not too different. The dogs were bred for little purpose beyond the sin of human vanity. People wanted a short, stocky, smoosh-faced dog that they perceived as cute. And, that's what they got: an unathletic dog that looked a certain way, with middle-of-the-road intelligence, and little use aside from its appearance.
Worse, seeking out this certain "toy dog" look, French Bulldogs suffer from a plethora of health issues. Summed up, they have the lowest life expectancy "by a large margin" of all dogs at only 4.5 years (average is 11.2. years).
There is a neighbor near to me who breeds French Bulldogs. Evidently, it's a lucrative business as they apparently sell for an estimated $2,000 to $8,000 dollars each. I don't know how many litters the neighbor's have bred and pawned, but it has been several. The breeder bitch is constantly given a little trot outside before being hauled to the vet for insemination. (Sadly, this seems to be about the only time she is taken out for exercise and family "fun.") Considering he and his wife have no real job, this seems to be their job. Breed, advertise (complete with foofy tutu outfit photos), market, sell, repeat. With only a 4.5 year life span, I see the lucrative nature in this business.
All told, it's basically a sin and a shame that humans do this to these dogs. A certain segment of people desire a certain unnatural smooshed face in a dog. And because we vainly want a certain look in a dog, so as to accessorize our own look, we breed them into forms unnatural to a canine, curse them with severe breathing difficulties and other serious health issues, and short lives.
A Greyhound is essentially a canine Thoroughbred. From generations of selective breeding, it has a massive chest, long body with a narrow waist, and long, spindly legs. It's sole purpose is speed. Ironically, both the Thoroughbred and Greyhound can race at about the same speed...44 mph, give or take.
Man's sinful nature has abused the Greyhound too. These hounds are racing dogs and racing means gambling. So, dog tracks for have been common. The pups are bred, they race a few years, then they are hopefully adopted out. A good friend of mine once adopted a retired racer to become the family dog. "Bandit" initially had a post-race job as a business's guard dog. But, due to him constantly doing nothing but laying around and sleeping, he was fired as a guard dog (who gets a Greyhound for a guard dog anyway?). Bandit eventually went to my friend, was a bit neurotic, but turned out to be a good family dog.
I think most Greyhounds don't have the fortunate story of Bandit. Once raced out, they're done and forgotten. Man's thrills are fleeting, whatever sparkles in his eye soon fades. To combat the ills of dog racing, I know that the citizens of Florida voted to outlaw dog racing in 2018 (and it indeed ended Dec. 31, 2020). Now, dog tracks lay rusting away, and Greyhounds are largely forgotten.
And then, there's the Labrador Retriever. What's not to like? These dogs can do it all, and they do it all well. Name a dog task, Labs do that well. Full disclosure: I once had a Lab (or rather, half Lab, and half...Great Dane? Doberman? Something?). Her mother was Lab and my dog looked Lab, though a bit taller and leaner. She was incredible. So, yes, I favor Labs.
But, even my beloved Labs and all that they excel in, even Labs have their issues, such as high rates of hip dysplasia. Selective breeding, and a too-narrow gene pool, have consequences.
Back to horses
Let's try to bring this back to horses. Thoroughbreds and horse racing mirror both of the characteristics seen in the French Bulldog and the Greyhound.
- Thoroughbreds have been, and still are, extremely selectively bred to accentuate certain qualities: speed, speed, speed.
- Thoroughbreds are bred for money. Literally, a champion stud or mare doesn't breed for free.
Regarding speed, Thoroughbreds have a massive muscular chest, almost no waist at all, massive muscular hindquarters, and long, spindly, almost cartoonishly thin legs. And, this built-for-speed physique brings up one of the cruelest aspects of horse racing: Thoroughbreds are prone to "break down."
These horses are structured unnaturally, like aliens. Having such a massive, muscular, powerful architecture stilted on such twig-like legs (and getting more massive and twiggier due to constant selective breeding of these traits) is a recipe for disaster. "Breaking down" in horse terms is a rather correct term. Their leg bones break under the stress and force of running, then the horse's weight and thrust breaks the legs down further.
The name Barabaro might come to memory. Barbaro won the Kentucky Derby in 2006 impressively, by a full 6.5 lengths. Hopes were high for a Triple Crown winner. At the Preakness two weeks later, Barabaro broke down. Actually, in his pre-start excitement he broke through the gate to false start. These animals are bred to run and race, they know when it's race time. He was so jacked up and ready to run while in the starting gate, he bucked up, banged his head hard, then literally broke through the gate to false start. Then, after reentering, he started off the race clean before breaking down in front of the main grandstand of viewers. Horse's can break any of their several leg bones. Barbaro broke the cannon, sesamoid, long pastern, and dislocated the fetlock (ankle joint). In other words, he shattered his leg.
When horses break their legs, they're usually put down. As to why, there are lots of reasons, but it comes down to the fact that horses are built for standing and running, especially Thoroughbreds. They are not built for laying down to recuperate, and actually suffer health consequences for not standing. Understandably, a broken leg causes the horse to favor weight to the other legs while standing and this, in turn, can cause other issues. Altogether, the horse suffers.
In Barbaro's case, they tried to rehab him. I think normally he would have been put down on the track in the equine ambulance (the "meat wagon"), but this was Barbaro. The resources were there, he was beloved, and millions had witnessed his injury live. Not trying to save him would have been a public relations nightmare. Putting him down on live TV would have been even worse. There was surgery, then laminitis (inflammation under the hoof) in his opposite good hoof, the result of standing unnaturally. He rallied, then had more setbacks including laminitis in his front hooves. He was in pain, with no way to stand, and then was euthanized in 2007.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23wgoS1v6e2i2gizAqeMeXHf6Zwhz3BTuYMuYNL676tqbPZWwvXUhw7R1J6K4r7DmRj2K.png]
Regarding the money, top studs earn $200 to $400,000 for stud service. A top mare can be bought for $100 to $300,000, then you need the stud service. This is only to breed the foal. This has nothing to do with stabling or training the animals. In other words, it's extremely expensive.
Also regarding the money, there is, of course, the gambling. You might say this is the whole point of horse racing. It's certainly the whole point for breeding Thoroughbreds. It was the whole point for Greyhounds in Florida, before that point was banned.
This year, an estimated $200 million was bet on the Kentucky Derby, the one race alone. $300 million was bet on the races combined. Grok estimated that globally in 2022, horse racing was a $402 billion dollar industry and expects it to grow to $793 billion by 2030.
Those numbers are staggering. But, again, I come back to sinful man. Our love of money is the root of this beautiful evil called horse racing.
I really don't know many scenes more beautiful than a Kentucky horse ranch and a Thoroughbred running across the bluegrass. Add a colt running with his mother, the beauty is staggering. But, underneath that beauty, there is an evil side to horse racing. That side is fueled by sinful man's pride to win and his love of money.
Horse racing is a beautiful evil.


Image sources: https://wikipedia.org, original by me at the track, equine bones at https://www.anatomy-of-the-equine.com/distal-limb-bones.html, the final two images from https://pixabay.com
Note: In the "Can you tell the difference" side-by-side images above, the Thoroughbred was on the left, the Standardbred on the right.
-
 @ 9c35fe6b:5977e45b
2025-05-07 08:49:00
@ 9c35fe6b:5977e45b
2025-05-07 08:49:00Sailing the Nile on the Dahabiya Gorgonia Nile Cruise offers an intimate way to experience the timeless beauty of Egypt. This elegant boat is ideal for travelers who seek calm, charm, and tradition. With only a few cabins onboard, guests can enjoy a more serene atmosphere compared to larger vessels. ETB Tours Egypt offers this unique cruise option as part of its Egypt vacation packages, blending cultural richness with comfort.
Cultural Encounters Along the Nile The Dahabiya Nile Cruises give you a chance to witness life along the riverbanks up close. Onboard the Gorgonia, travelers visit lesser-known villages, ancient temples, and local markets far from the tourist crowds. With ETB Tours Egypt, your itinerary includes authentic experiences guided by knowledgeable Egyptologists—an ideal choice for those seeking Egypt private tours.
Scenic Sailing with Modern Comfort Although traditional in style, the Dahabiya Gorgonia is equipped with modern amenities to ensure a pleasant journey. Guests enjoy spacious decks, elegant dining, and personalized service. Whether part of an All inclusive Egypt vacations or a custom-designed plan, this cruise ensures you travel in style without missing out on comfort.
Smart Choices for Smart Travelers ETB Tours Egypt also makes sure that the Dahabiya Gorgonia Nile Cruise is available as part of their Egypt budget tours, offering excellent value without compromising on experience. It's perfect for those who want to enjoy the best of Egypt without overspending. Flexible options are also available through their wide range of Egypt travel packages, making it easy to match your schedule and interests.
To Contact Us: E-Mail: info@etbtours.com Mobile & WhatsApp: +20 10 67569955 - +201021100873 Address: 4 El Lebeny Axis, Nazlet Al Batran, Al Haram, Giza, Egypt
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ b6dcdddf:dfee5ee7
2025-05-06 15:58:23
@ b6dcdddf:dfee5ee7
2025-05-06 15:58:23You can now fund projects on Geyser using Credit Cards, Apple Pay, Bank Transfers, and more.
The best part: 🧾 You pay in fiat and ⚡️ the creator receives Bitcoin.
You heard it right! Let's dive in 👇
First, how does it work? For contributors, it's easy! Once the project creator has verified their identity, anyone can contribute with fiat methods. Simply go through the usual contribution flow and select 'Pay with Fiat'. The first contribution is KYC-free.
Why does this matter? 1. Many Bitcoiners don't want to spend their Bitcoin: 👉 Number go up (NgU) 👉 Capital gains taxes With fiat contributions, there's no more excuse to contribute towards Bitcoin builders and creators! 2. Non-bitcoin holders want to support projects too. If someone loves your mission but only has a debit card, they used to be stuck. Now? They can back your Bitcoin project with familiar fiat tools. Now, they can do it all through Geyser!
So, why swap fiat into Bitcoin? Because Bitcoin is borderless. Fiat payouts are limited to certain countries, banks, and red tape. By auto-swapping fiat to Bitcoin, we ensure: 🌍 Instant payouts to creators all around the world ⚡️ No delays or restrictions 💥 Every contribution is also a silent Bitcoin buy
How to enable Fiat contributions If you’re a creator, it’s easy: - Go to your Dashboard → Wallet - Click “Enable Fiat Contributions” - Complete a quick ID verification (required by our payment provider) ✅ That’s it — your project is now open to global fiat supporters.
Supporting Bitcoin adoption At Geyser, our mission is to empower Bitcoin creators and builders. Adding fiat options amplifies our mission. It brings more people into the ecosystem while staying true to what we believe: ⚒️ Build on Bitcoin 🌱 Fund impactful initiatives 🌎 Enable global participation
**Support projects with fiat now! ** We've compiled a list of projects that currently have fiat contributions enabled. If you've been on the fence to support them because you didn't want to spend your Bitcoin, now's the time to do your first contribution!
Education - Citadel Dispatch: https://geyser.fund/project/citadel - @FREEMadeiraOrg: https://geyser.fund/project/freemadeira - @MyfirstBitcoin_: https://geyser.fund/project/miprimerbitcoin
Circular Economies - @BitcoinEkasi: https://geyser.fund/project/bitcoinekasi - Madagascar Bitcoin: https://geyser.fund/project/madagasbit - @BitcoinChatt : https://geyser.fund/project/bitcoinchatt - Uganda Gayaza BTC Market: https://geyser.fund/project/gayazabtcmarket
Activism - Education Bitcoin Channel: https://geyser.fund/project/streamingsats
Sports - The Sats Fighter Journey: https://geyser.fund/project/thesatsfighterjourney
Culture - Bitcoin Tarot Cards: https://geyser.fund/project/bitcointarotcard
originally posted at https://stacker.news/items/973003
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 752f5d10:88491db3
2025-05-07 00:25:29
@ 752f5d10:88491db3
2025-05-07 00:25:29Opinion about Trendo: Forex Trading & Broker (android)
L o s i n g $111,555 overnight was a crushing blow. The account lockout and subpar customer service that followed left me stunned. However, I gained invaluable insights from this ordeal : Conduct thorough research before committing Verify credentials and read reviews from multiple sources Be c a u t i o u s of un realistic promises Demand responsive and reliable support. Fortunately, I found chelsy__desmarais__54__A T__g=m=a=i=l__D=o=t__c_o_m, which helped me re-cover from this financial setback. W_h_a_t_s_A_p_p ; +1=8=5=9=4=3=6=4=2=1=1
WalletScrutiny #nostrOpinion
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ ed22fab2:422b9051
2025-05-08 04:32:01
@ ed22fab2:422b9051
2025-05-08 04:32:01A plataforma BRL987 tem se consolidado como uma das principais opções para quem busca entretenimento online com qualidade, segurança e uma ampla gama de jogos. Com uma proposta moderna e acessível, a BRL987 oferece aos usuários uma experiência completa, unindo tecnologia, suporte eficiente e uma interface amigável que atende tanto os iniciantes quanto os mais experientes.
Introdução à Plataforma BRL987 O BRL987 foi criado com o objetivo de proporcionar diversão de forma segura e confiável. Desde o primeiro acesso, os usuários percebem o cuidado com a usabilidade do site. O design intuitivo facilita a navegação e permite que qualquer jogador encontre rapidamente seus jogos preferidos, promoções ativas e métodos de pagamento.
A segurança também é um pilar da plataforma. Todos os dados dos usuários são protegidos por tecnologia de criptografia de ponta, garantindo total confidencialidade em cada transação realizada. Além disso, o BRL987 opera com total transparência e é reconhecido por sua reputação positiva entre os jogadores brasileiros.
Variedade de Jogos para Todos os Estilos Um dos grandes destaques da BRL987 é sua impressionante diversidade de jogos. A plataforma abriga títulos de fornecedores renomados internacionalmente, oferecendo gráficos de alta qualidade, jogabilidade fluida e mecânicas inovadoras.
Entre os jogos mais populares estão as máquinas de giros, que conquistam os jogadores com temas variados e bônus surpreendentes. Também há opções de jogos de mesa, como roleta e blackjack virtual, para quem prefere desafios estratégicos. Para os amantes de interatividade, há jogos ao vivo com crupiês reais, proporcionando uma experiência imersiva e próxima da realidade.
Outro diferencial são os torneios e competições periódicas promovidas pela plataforma. Essas disputas aumentam ainda mais o nível de diversão e premiam os participantes com bônus generosos e brindes exclusivos.
Experiência do Jogador: Simples, Rápida e Gratificante A experiência do jogador na BRL987 é pensada para ser fluida e satisfatória desde o cadastro até o saque dos ganhos. O processo de registro é simples, exigindo poucos passos e informações básicas. Após o cadastro, o usuário já pode aproveitar bônus de boas-vindas, que dão aquele incentivo inicial para explorar os jogos disponíveis.
Os métodos de pagamento incluem as principais opções do mercado brasileiro, como PIX, boleto bancário e transferências. Os depósitos são processados rapidamente e os saques são feitos com eficiência, muitas vezes sendo liberados no mesmo dia.
Outro ponto que merece destaque é o suporte ao cliente. O BRL987 oferece atendimento 24 horas por dia, 7 dias por semana, através de chat ao vivo e e-mail. A equipe de suporte é treinada para resolver dúvidas e problemas com agilidade e cordialidade.
Conclusão A BRL987 se destaca como uma plataforma completa de entretenimento online, ideal para quem busca qualidade, segurança e diversão em um só lugar. Com uma seleção de jogos variada, suporte eficiente e pagamentos rápidos, ela conquista cada vez mais usuários em todo o Brasil. Seja para quem está começando ou para quem já tem experiência, o BRL987 é o destino certo para momentos de lazer com emoção e confiança.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 80a6a657:536a97e2
2025-05-06 10:00:48
@ 80a6a657:536a97e2
2025-05-06 10:00:48
The dawn of Bitcoin ushered in a transformative mission: empowering individuals and dismantling centralized power structures that erode personal freedoms. As the world’s first decentralized currency, Bitcoin offers an alternative financial system—one that transcends borders, government control, and corporate interests.
But this mission isn’t just about money. It’s about freedom. It’s about self-sovereignty. And most importantly, it’s a rallying cry for vigilance in an ongoing struggle for the liberation of humanity from systemic oppression. Who better to lead this critical mission than those who have already dedicated their lives to serving and protecting freedom: Veterans.
Freedom: A Lifelong Fight Freedom is neither freely given nor guaranteed—it is earned and fiercely preserved. Veterans understand this intimately. They have endured sacrifice, hardship, and battle in their service to protect the liberties we often take for granted. And today, freedom faces threats from a new frontier: financial manipulation, surveillance, and the centralization of power.
Governments across the globe continue to devalue currencies through inflation, tighten financial surveillance by controlling banking systems, and stifle individual autonomy. These issues underscore the need for a sound financial alternative, one that aligns with the ideals veterans have sworn to uphold. The solution? Bitcoin.
Bitcoin represents the antithesis of centralized control. It is censorship-resistant, immune to monetary debasement, and built upon a trustless, transparent system. It is not merely a currency; it is a tool for human liberation.
Vigilance in Bitcoin Adoption While Bitcoin adoption grows, the journey is far from complete. The powerful status quo—central banks, governments, and financial elites—does not take threats to its systems lightly. These entities work tirelessly to misinform, regulate, and marginalize Bitcoin. This makes sustained vigilance in promoting Bitcoin adoption not just important, but essential.
The failure to remain vigilant could see Bitcoin’s potential diminished through undue regulation, controlled implementation (such as CBDCs—Central Bank Digital Currencies), or a failure to educate people about its benefits. Complacency would mean ceding victory to oppressive systems the world over.
This is why Bitcoin adoption isn’t solely a technological phenomenon—it is an ideological mission. To resist control, to safeguard freedom, and to empower individuals to thrive under self-sovereignty requires the active participation of people across all sectors of society.
Why Veterans Are Uniquely Positioned to Lead Veterans are inherently equipped to lead the charge in the fight for Bitcoin adoption and the broader battle for freedom. Their unique skillsets, shaped by discipline, adaptability, and leadership under pressure, are perfectly suited to this challenge. Here’s why veterans play a pivotal role in this movement: 1. Leadership and Vision: Veterans are natural leaders. They can galvanize communities toward a vision of financial independence, self-sovereignty, and empowerment through Bitcoin. Their experience coordinating efforts—whether on the battlefield or in humanitarian missions—allows them to efficiently communicate the importance of Bitcoin adoption. 2. Commitment to Freedom: The fight for Bitcoin adoption is deeply aligned with the ethos of service members: defending freedom at all costs. Veterans understand that true freedom cannot persist without vigilance, sacrifice, and a commitment to challenging oppressive systems. 3. Trust and Credibility: The military often fosters a level of trust and camaraderie among people. Veterans, therefore, have the clout to introduce Bitcoin to communities that may otherwise view it with skepticism. Their credibility as protectors of freedom gives them an edge in delivering Bitcoin’s message of liberation. 4. Adaptability in Uncertain Environments: Just as they’ve thrived in complex and chaotic environments, veterans are poised to navigate the evolving financial landscape. Bitcoin is still maturing and faces regulatory challenges, technological hurdles, and cultural misunderstandings. Veterans excel at adapting to change and finding solutions in challenging circumstances. 5. Mission-Driven Mindset: Every mission has an objective, and every objective demands clear focus. Veterans approach tasks methodically and with a commitment to success—the same mindset required to bridge the gap between Bitcoin skepticism and widespread adoption.
The Call to Action Veterans, the mission isn’t over. Humanity stands at a crossroads, and freedom is at stake. Bitcoin is not just a disruptive technology; it’s the torchbearer of liberty in a world increasingly dominated by centralized control. It’s time to take the skills, discipline, and passion forged in your service and channel them into this new fight: the fight for financial freedom and independence from a centralized system that has dominated the lives of billions of people for far too long.
Educate yourself about Bitcoin. Learn its nuances, its strengths, and its use cases. Share this knowledge with your communities, help dismantle misconceptions, and shine a light on the real promise of self-sovereignty. Become an anchor of leadership in this decentralized revolution.
For civilians: do not underestimate the importance of this mission. Every individual who adopts Bitcoin drives us one step closer to a world where personal freedom and economic empowerment are accessible to all. Join arms with veterans, thought leaders, and Bitcoin adopters to ensure the torch of liberty burns brightly.
Closing Thoughts Bitcoin is more than a financial revolution—it’s a movement for freedom. Veterans have long stood on the frontline for this cause, and today, they have an opportunity to champion it in a new way. With vigilance, resolve, and determination, humanity can achieve greater levels of freedom. But, as with all efforts to secure liberty, we must remain constantly committed to the mission. Remember: freedom demands eternal vigilance. So does Bitcoin.
Will you answer the call? Together, we can reshape the future as champions of sovereignty and bring the world closer to the ideals we all deserve.
OPERATION BITCOIN is a 501(c)(3) nonprofit on a mission to connect military veterans with Bitcoin.
You can directly support this mission by sharing our publication with a veteran today, zapping this article or donating at www.operationbitcoin.io
-
 @ 000002de:c05780a7
2025-05-06 20:24:08
@ 000002de:c05780a7
2025-05-06 20:24:08https://www.youtube.com/watch?v=CIMZH7DEPPQ
I really enjoy listening to non-technical people talk about technology when they get the bigger picture impacts and how it relates to our humanity.
I was reminded of this video by @k00b's post about an AI generated video of a victim forgiving his killer.
Piper says, "Computers are better at words than you. Than I". But they are machines. They cannot feel. They cannot have emotion.
This people honors me with their lips, but their heart is far from me
~ Matthew 15:8
Most of us hate it when people are fake with us. When they say things they don't mean. When they say things just to get something they want from us. Yet, we are quickly falling into this same trap with technology. Accepting it as real and human. I'm not suggesting we can't use technology but we have to be careful that we do not fall into this mechanical trap and forget what makes humans special.
We are emotional and spiritual beings. Though AI didn't exist during the times Jesus walked the earth read the verse above in a broader context.
Then Pharisees and scribes came to Jesus from Jerusalem and said, “Why do your disciples break the tradition of the elders? For they do not wash their hands when they eat.” He answered them, “And why do you break the commandment of God for the sake of your tradition? For God commanded, ‘Honor your father and your mother,’ and, ‘Whoever reviles father or mother must surely die.’ But you say, ‘If anyone tells his father or his mother, “What you would have gained from me is given to God,” he need not honor his father.’ So for the sake of your tradition you have made void the word of God. You hypocrites! Well did Isaiah prophesy of you, when he said:
“‘This people honors me with their lips,
but their heart is far from me;
in vain do they worship me,
teaching as doctrines the commandments of men.’”
Empty words. Words without meaning because they are not from a pure desire and love. You may not be a Christian but don't miss the significance of this. There is a value in being real. Sharing true emotion and heart. Don't fall into the trap of the culture of lies that surrounds us. I would rather hear true words with mistakes and less eloquence any day over something fake. I would rather share a real moment with the ones I love than a million fake moments. Embrace the messy imperfect but real world.
originally posted at https://stacker.news/items/973324
-
 @ bbef5093:71228592
2025-05-06 05:17:07
@ bbef5093:71228592
2025-05-06 05:17:07*Holtec új atomenergetikai együttműködése Utah államban*
Az amerikai Holtec International stratégiai megállapodást kötött Utah állammal és a Hi Tech Solutions nukleáris szolgáltatóval, hogy elősegítse saját fejlesztésű, SMR-300 típusú kis moduláris reaktorainak (SMR) telepítését Utahban és az Egyesült Államok Mountain West régiójában. A megállapodás értelmében 2028-ig állandó képzési központot hoznak létre Utahban, amely az üzemeltetéshez, karbantartáshoz és az új generációs nukleáris technológiákhoz szükséges munkaerő képzését célozza, szoros együttműködésben helyi egyetemekkel, főiskolákkal és szakiskolákkal.
A projekt Utah állam energetikai stratégiájának („Operation Gigawatt” és „Built Here”) része, amely a következő tíz évben megduplázná az állam energiatermelését, kiemelt szerepet szánva a tiszta nukleáris energiának. A Holtec Utah-t választotta nyugati gyártóbázisának is, ezzel erősítve az amerikai nukleáris ellátási láncot és hosszú távú munkahelyeket teremtve. A cég a 2030-as években akár 4 GW összkapacitású SMR-300 telepítését tervezi főként Utahban és Wyomingban.
Az SMR-300 egy nyomottvizes reaktor, amely 300 MW villamos vagy 1050 MW hőteljesítményt biztosít, és a Holtec tervei szerint kulcsszerepet játszhat a tiszta, szén-dioxid-mentes energiatermelésben.
*Amerikai SMR-piac helyzete*
Az SMR-technológia az utóbbi években került a figyelem középpontjába, mivel gyorsabban és olcsóbban telepíthető, mint a hagyományos atomerőművek, és lehetőséget kínál magánbefektetők számára is. Ugyanakkor az első amerikai SMR-projekt, a NuScale és a Utah Associated Municipal Power Systems közös beruházása költségnövekedés miatt meghiúsult, ami rávilágított a technológia gazdasági kihívásaira.
Nemzetközi fejlemények és további hírek
- Az ausztrál Okapi Resources és az Urenco együttműködési megállapodást kötött új urán dúsítási technológia fejlesztésére, amely tisztább és olcsóbb dúsítási eljárást ígér.
- Az Argonne National Laboratory sikeresen kicserélt egy 30 éves kulcsfontosságú alkatrészt a nátriumhűtésű gyorsreaktor-tesztberendezésében, ami hozzájárulhat a gyorsreaktor-technológia fejlesztéséhez az Egyesült Államokban.
- A Tennessee Egyetem ösztöndíjprogramot indít a Fülöp-szigeteki nukleáris szakemberek képzésére, támogatva ezzel a délkelet-ázsiai ország nukleáris energiafejlesztési törekvéseit.
- Bulgáriában a Westinghouse Electric Company helyi beszállítókkal kötött megállapodásokat két új AP1000 típusú reaktor építéséhez a kozloduji atomerőműben.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 732c6a62:42003da2
2025-03-09 22:36:26
@ 732c6a62:42003da2
2025-03-09 22:36:26Não são recentes as táticas da esquerda de tentar reprimir intelectualmente seus opositores na base do deboche, da ironia, do desprezo e do boicote à credibilidade. Até Marx usava ironia para chamar os críticos de "burgueses iludidos". A diferença é que, no século XXI, trocaram o manifesto comunista por threads no Twitter e a dialética por memes de mau gosto.
A Falácia da Superioridade Moral
O debate sobre o "pobre de direita" no Brasil é contaminado por uma premissa tácita da esquerda: a ideia de que classes baixas só podem ter consciência política se aderirem a pautas progressistas. Quem ousa divergir é tratado como "traidor de classe", "manipulado", "ignorante", ou até vítimas de deboches como alguma pessoa com um qi em temperatura ambiente repetir diversas vezes "não é possível que ainda exista pobre de direita", "nunca vou entender pobre de direita", ou "pobre de direita é muito burro, rico eu até entendo", como se o autor dessas frases fosse o paladino dos mais oprimidos e pobres. Esse discurso, porém, não resiste a uma análise empírica, histórica ou sociológica.
Contexto Histórico: A Esquerda e o Mito do "Voto Consciente"
A noção de que o pobre deve votar na esquerda por "interesse de classe" é herança do marxismo ortodoxo, que via a política como mero reflexo da posição econômica. No entanto, a realidade é mais complexa:
- Dados do Latinobarómetro (2022): 41% dos brasileiros de baixa renda (até 2 salários mínimos) apoiam redução de impostos e maior liberdade econômica — pautas tradicionalmente associadas à direita.
- Pesquisa IPEC (2023): 58% dos pobres brasileiros priorizam "segurança pública" como principal demanda, acima de "distribuição de renda".
Esses números não são acidentais. Refletem uma mudança estrutural: o pobre moderno não é mais o "operário industrial" do século XX, mas um empreendedor informal, motorista de app, ou microempresário — figuras que valorizam autonomia e rejeitam paternalismo estatal. Eles dizem não entender o pobre de direita e que nunca vai entendê-los, mas o fato é que não entendem porque nunca conversaram com um sem fazer cara de psicólogo de posto de saúde. Sua "preocupação" é só uma máscara para esconder o desprezo por quem ousa pensar diferente do seu manual de "oprimido ideal".
Se ainda não entenderam:
Direita ≠ rico: Tem gente que trabalha 12h/dia e vota em liberal porque quer ser dono do próprio negócio, não pra pagar mais taxação pra você postar meme no Twitter.
Acham que são o Sherlock Holmes da pobreza: o palpite de que "o pobre é manipulado" é tão raso quanto sua compreensão de economia básica.
A Psicologia por Trás do Voto Conservador nas Periferias
A esquerda atribui o voto pobre em direita a "falta de educação" ou "manipulação midiática". Essa tese é não apenas elitista, mas cientificamente falsa:
Análise Psicológica Básica (para você que se acha o Paulo Freire):
- Síndrome do Branco Salvador: Acha que o pobre é uma criatura tão frágil que precisa de você pra pensar. Spoiler: ele não precisa.
- Viés da Superioridade Moral: "Se você é pobre e não concorda comigo, você é burro". Parabéns, recriou a escravidão intelectual.
- Efeito Dunning-Kruger: Não sabe o que é CLT, mas dá palpite sobre reforma trabalhista.- Estudo da Universidade de São Paulo (USP, 2021): Entre moradores de favelas, 63% associam políticas de segurança dura (como "bandido bom é bandido morto") à proteção de seus negócios e famílias. Para eles, a esquerda é "branda demais" com o crime.
- Pesquisa FGV (2020): 71% dos trabalhadores informais rejeitam aumentos de impostos, mesmo que para financiar programas sociais. Motivo: já sofrem com a burocracia estatal para legalizar seus negócios.
Esses dados revelam uma racionalidade prática: o pobre avalia políticas pelo impacto imediato em sua vida, não por abstrações ideológicas. Enquanto a esquerda fala em "reforma estrutural" e tenta importar discursos estrangeiros para debate, por exemplo, o tema irrelevante do pronome neutro, ele quer resolver problemas como:
- Violência (que afeta seu comércio);
- Impostos (que consomem até 40% do lucro de um camelô);
- Burocracia (que impede a legalização de sua barraca de pastel).
Religião, Valores e a Hipocrisia do "Ateísmo de Redes Sociais"
A esquerda subestima o papel da religião na formação política das classes baixas. No Brasil, 76% dos evangélicos são pobres (Datafolha, 2023), e suas igrejas promovem valores como:
- Família tradicional (contra pautas progressistas como ideologia de gênero em escolas);
- Auto-responsabilidade (ênfase em "trabalho duro" em vez de assistencialismo).Exemplo Concreto:
Nas favelas de São Paulo, pastores evangélicos são frequentemente eleitos a cargos locais com plataformas anticrime e pró-mercado. Para seus eleitores, a esquerda urbana (que defende descriminalização de drogas e críticas à polícia) representa uma ameaça ao seu estilo de vida.
A Esquerda e seu Desprezo pela Autonomia do Pobre
O cerne do debate é a incapacidade da esquerda de aceitar que o pobre possa ser autônomo. Algumas evidências:
O Caso dos Empreendedores Informais
- Segundo o IBGE (2023), 40% dos trabalhadores brasileiros estão na informalidade. Muitos veem o Estado como obstáculo, não aliado. Políticas de direita (como simplificação tributária) são mais atraentes para eles que o Bolsa Família.
A Ascensão do Conservadorismo Periférico
- Pessoas assim tem um pensamento simples. Sua mensagem: "Queremos empreender, não depender de político."
A Rejeição ao "Vitimismo"
- Pesquisa Atlas Intel (2022): 68% dos pobres brasileiros rejeitam o termo "vítima da sociedade". Preferem ser vistos como "lutadores".
A projeção freudiana "o pobre é burro porque eu sou inteligente"
O deboche esquerdista esconde um complexo de inferioridade disfarçado de superioridade moral. É a Síndrome do Salvador em sua forma mais patética:
- Passo 1: Assume-se que o pobre é um ser desprovido de agência.
- Passo 2: Qualquer desvio da narrativa é atribuído a "manipulação da elite".
- Passo 3: Quem critica o processo é chamado de "fascista".Exemplo Prático:
Quando uma empregada doméstica diz que prefere o livre mercado a programas sociais, a esquerda não pergunta "por quê?" — ela grita "lavagem cerebral!". A ironia? Essa mesma esquerda defende a autonomia feminina, exceto quando a mulher é pobre e pensa diferente.Dados Globais: O Fenômeno Não é Brasileiro
A ideia de que "pobre de direita" é uma anomalia é desmentida por evidências internacionais:
- Estados Unidos: 38% dos eleitores com renda abaixo de US$ 30k/ano votaram em Trump em 2020 (Pew Research). Motivos principais: conservadorismo social e rejeição a impostos. A esquerda: "vítimas da falsa consciência". Mais um detalhe: na última eleição de 2024, grande parte da classe "artística" milionária dos Estados Unidos, figuras conhecidas, promoveram em peso a Kamala Harris, do Partido Democrata. Percebe como a esquerda atual é a personificaçãoda burguesia e de só pensar na própria barriga?
- Argentina: Javier Milei, libertário radical, quando candidato, tinha forte apoio nas villas miseria (favelas). Seu lema — "O estado é um parasita" — ressoa entre quem sofria com inflação de 211% ao ano.
- Índia: O partido BJP (direita nacionalista) domina entre os pobres rurais, que associam a esquerda a elites urbanas desconectadas de suas necessidades.
A história que a esquerda tenta apagar: pobres de direita existem desde sempre
A esquerda age como se o "pobre de direita" fosse uma invenção recente do MBL, mas a realidade é que classes baixas conservadoras são regra, não exceção, na história mundial:
- Revolução Francesa (1789): Camponeses apoiaram a monarquia contra os jacobinos urbanos que queriam "libertá-los".
- Brasil Imperial: Escravos libertos que viraram pequenos proprietários rurais rejeitavam o abolicionismo radical — queriam integração, não utopia.Tradução:
Quando o pobre não segue o script, a esquerda inventa teorias conspiratórias.
A Hipocrisia da Esquerda Urbana e Universitária
Enquanto acusa o pobre de direita de "alienado", a esquerda brasileira é dominada por uma elite desconectada da realidade periférica:
- Perfil Socioeconômico: 82% dos filiados ao PSOL têm ensino superior completo (TSE, 2023). Apenas 6% moram em bairros periféricos.
- Prioridades Descoladas: Enquanto o pobre debate segurança e custo de vida, a esquerda pauta discussões como "linguagem não-binária em editais públicos" — tema irrelevante para quem luta contra o desemprego. Os grandes teóricos comunistas se reviram no túmulo quando veem o que a esquerda se tornou: não debatem os reais problemas do Brasil, e sim sobre suas próprias emoções.
"A esquerda brasileira trocou o operário pelo influencer progressista. O pobre virou um personagem de campanha, não um interlocutor real."
A diversidade de pensamento que a esquerda não suporta
A esquerda prega diversidade — desde que você seja diverso dentro de um checklist pré-aprovado. Pobre LGBTQ+? Herói. Pobre evangélico? Fascista. Pobre que abre MEI? "Peão do capitalismo". A realidade é que favelas e periferias são microcosmos de pluralidade ideológica, algo que assusta quem quer reduzir seres humanos a estereótipos.
Respostas aos Argumentos Esquerdistas (e Por que Falham)
"O pobre de direita é manipulado pela mídia!"
- Contradição: Se a mídia tradicional é dominada por elites (como alegam), por que grandes veículos são abertamente progressistas? A Record (evangélica) é exceção, não regra.
Contradição Central:
Como explicar que, segundo o Banco Mundial (2023), países com maior liberdade econômica (ex.: Chile, Polônia) reduziram a pobreza extrema em 60% nas últimas décadas, enquanto modelos estatizantes (ex.: Venezuela, Argentina com o governo peronista) afundaram na miséria? Simples: a esquerda prefere culpar o "neoliberalismo" a admitir que o pobre com o mínimo de consciência quer emprego, não esmola.Dado que Machuca:
- 71% das mulheres da periferia rejeitam o feminismo radical, associando-o a "prioridades distantes da realidade" (Instituto Locomotiva, 2023)."Ele vota contra os próprios interesses!"
- Falácia: Pressupõe que a esquerda define o que é o "interesse do pobre". Para um pai de família na Cidade de Deus, ter a boca de fogo fechada pode ser mais urgente que um aumento de 10% no Bolsa Família.
O pobre de direita não é uma anomalia. É o produto natural de um mundo complexo onde seres humanos têm aspirações, medos e valores diversos. Enquanto a esquerda insiste em tratá-lo como um projeto fracassado, ele está ocupado:
- Trabalhando para não depender do governo.
- Escolhendo religiões que dão sentido à sua vida.
- Rejeitando pautas identitárias que não resolvem o custo do gás de cozinha."É falta de educação política!"
- Ironia: Nos países nórdicos (modelo da esquerda), as classes baixas são as mais conservadoras. Educação não correlaciona com progressismo.
Por que o Debuste Precisa Acabar
A insistência em descredibilizar o pobre de direita revela um projeto de poder fracassado. A esquerda, ao substituir diálogo por deboche, perdeu a capacidade de representar quem mais precisaria dela. Enquanto isso, a direita — nem sempre por virtude, mas por pragmatismo — capturou o descontentamento de milhões com o status quo.
O pobre de direita existe porque ele não precisa da permissão do rico de esquerda para pensar. A incapacidade de entender isso só prova que a esquerda é a nova aristocracia.
Último Dado: Nas eleições de 2022, Tarcísio de Freitas (direita) venceu em 72% das favelas de São Paulo. O motivo? Seu discurso anti-burocracia e pró-microempreendedor.
A mensagem é clara: o pobre não é um projeto ideológico. É um agente político autônomo — e quem não entender isso continuará perdendo eleições.
A esquerda elitista não odeia o pobre de direita por ele ser "irracional". Odeia porque ele desafia o monopólio moral que ela construiu sobre a miséria alheia. Enquanto isso, o pobre segue sua vida, ignorando os berros de quem acha que sabem mais da sua vida que ele mesmo.
Pergunta Retórica (Para Incomodar):
Se a esquerda é tão sábia, por que não usa essa sabedoria para entender que pobre também cansa de ser tratado como cachorro que late no ritmo errado?
Fontes Citadas:
- Latinobarómetro (2022)
- IPEC (2023)
- USP (2021): "Segurança Pública e Percepções nas Favelas Cariocas"
- FGV (2020): "Informalidade e Tributação no Brasil"
- Datafolha (2023): "Perfil Religioso do Eleitorado Brasileiro"
- Atlas Intel (2022): "Autopercepção das Classes Baixas"
- Pew Research (2020): "Voting Patterns by Income in the U.S."
- TSE (2023): "Perfil Socioeconômico dos Filiados Partidários"
Leitura Recomendada para Esquerdistas:
- "Fome de Poder: Por que o Pobre Brasileiro Abandonou a Esquerda" (Fernando Schüller, 2023)
- "A Revolução dos Conservadores: Religião e Política nas Periferias" (Juliano Spyer, 2021)
- "Direita e Esquerda: Razões e Paixões" (Demétrio Magnoli, 2019) -
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 8671a6e5:f88194d1
2025-05-06 16:23:25
@ 8671a6e5:f88194d1
2025-05-06 16:23:25"I tried pasting my login key into the text field, but no luck—it just wouldn't work. Turns out, the login field becomes completely unusable whenever the on-screen keyboard shows up on my phone. So either no one ever bothered to test this on a phone, or they did and thought, ‘Eh, who needs to actually log in anyway?’."

### \ \ Develop and evolve
Any technology or industry at the forefront of innovation faces the same struggle. Idealists, inventors, and early adopters jump in first, working to make things usable for the technical crowd. Only later do the products begin to take shape for the average user.
Bitcoin’s dropping the Ball on usability (and user-experience)
First, we have to acknowledge the progress we've made. Bitcoin has come a long way in terms of usability—no doubt about it. Even if I still think it’s bad, it’s nowhere near as terrible as it was ten or more years ago. The days of printing a paper wallet from some shady website and hoping it would still work months or years later are behind us. The days of buggy software never getting fixed are mostly over.
The Bitcoin technology itself made progress through many BIPs (Bitcoin Improvement Proposals) and combined with an increasing number of apps, devs, websites and related networks (Liquid, Lightning, Nostr, ....) we can say that we're seeing a strong ecosystem going its way. The ecosystem is alive and expanding, and technically, things are clearly working. The problem is that we’re still building with a mindset where developers and project managers consider usability—but don’t truly care about it in practice. They don’t lead with it. (Yes, there are always exceptions.)
All that progress looks cool, when you see the latest releases of hardware wallets, software wallets, exchanges, nostr clients and services built purely for bitcoin, you're usually thinking that we've progressed nicely. But I want to focus on the downside of all these shiny tools. Because if Bitcoin has made it this far, it’s mostly thanks to people who deeply understand its value and are stubborn enough to push through the friction. They don’t give up when the user experience sucks.
Many bitcoiners completely lost their perspective on the software front in my opinion. Because we could have been so much further ahead, and we didn't because some of the most important components on the user-facing side of Bitcoin (arguably the most important part) hasn’t kept pace with the popularity and possible growth. And that should be a great concern, because Bitcoin is meant to be open and accessible. The blockchain is public. This is supposed to be for everyone. This is an open ledger technology so in theory everything is user-facing to one extent or another. Yet we fail on that front to make the glue stick. Somewhere, we’re easily amused by the tools we create, and often contains hurdles we can’t see or feel. While users reject it after 5 seconds tops.
We didn’t came a lot further yet, because we’ve ignored usability at its core (pun intended).
I’m not talking about usability in the “it works on my machine” sense. I’m talking about usability that meets the standard of modern apps. Think Spotify, Instagram, Uber, Gmail. Products that ordinary people use without reading a manual or digging through forums.
That’s the bar. We’re still far from it.
Bad UX scares your grandma away
… and that’s how many bitcoiners apparently like it.
Subsequently, when I say usability, I’m using it as an umbrella term. For me, it covers user experience, user interface, and real-life, full-cycle testing—from onboarding a brand new user to rolling out a new version of the app. And oh boy, our onboarding is so horrible. (“Hey wanna try bitcoin? Here’s an app that takes up to 4 minutes or more to get though, but wait, you’ll have to install a plugin, or wait I’ll send you an on-chain transaction…)
Take a look at the listings on Bitvocation, an excellent job board for Bitcoiners and related projects. You’ll quickly notice a pattern: almost no companies are hiring software testers. It’s marketing, more marketing, some sales, and of course, full-stack developers. But … No testers.
Because testing has become something that’s often skipped or automated in a hurry. Maybe the devs run a test locally to confirm that the feature they just built doesn’t crash outright. That’s it. And if testing does happen at a company, it’s usually shallow—focused only on the top five percent of critical bugs. The finer points that shape real user experience, like button placement, navigation flow, and responsiveness, are dumped on “the community.”
Which leads to some software being rushed out to production, and only then do teams discover how many problems exist in the real world. If there’s anyone left to care that is, since most teams are scattered all over the world and get paid by the hour by some VC firm on a small runway to a launch date.
This has real life consequences I’ve seen for myself with new users. Like a lightning wallet having a +5 minute onboarding time, and a fat on-screen error for the new users, or a hardware wallet stuck in an endless upgrade loop, just because nobody tested it on a device that was “old” (as in, one year old).
The result is clear: usability and experience testing are so low on the priority list, they may as well not exist. And that’s tragic, because the enthusiasm of new users gets crushed the moment they run into what I call Linux’plaining.
That’s when something obvious fails — like a lookup command that’s copied straight from their own help documentation but doesn’t work — and the answer you get as a user is something like: “Yeah, but first you have to…” followed by an explanation that isn’t mentioned anywhere in the interface or documentation. You were just supposed to know. No one updates the documentation, and no one cares. As most of the projects are very temporary or don’t really care if it succeeds or not, because they’re bitcoiners and bitcoin always wins. Just like PGP always was super cool and good, and users should just be smarter.
Lessons from the past usability disasters
We can always learn from the past especially when its precedents are still echoing through the systems we use today
So here goes, some examples from the legacy / fiat industry:
Lotus Notes, for example. Once a titan in enterprise communication software, which managed to capture about 145 million mailboxes. But its downfall is an example of what happens when you ignore and keep ignoring real-life user needs and fail to evolve with the market. Software like that doesn’t just fade, it collapses under the weight of its own inertia and bloat. If you think bitcoin can’t have that, yes… we’re of course not having a competitor in the market (hard money is hard money, not a mailbox or office software provider of course). But we can erode trust to the extent that it becomes LotusNotes’d.
Its archaic 1990s interface came with clunky navigation and a chaotic document management system. Users got frustrated fast—basic tasks took too long. Picture this: you're stuck in a cubicle, trying to find the calendar function in Lotus Notes while a giant office printer hisses and spits out stacks of paper behind you. The platform never made the leap to modern expectations. It failed to deliver proper mobile clients and clung to outdated tech like LotusScript and the Domino architecture, which made it vulnerable to security issues and incompatible with the web standards of the time. By 2012, IBM pulled the plug on the Lotus brand, as businesses moved en masse to cloud-based alternatives.
Another kind of usability failure has plagued PGP1 (and still does so after 34 years). PGP (Pretty Good Privacy) is a time-tested and rock-solid method for encryption and key exchange, but it’s riddled with usability problems, especially for anyone who isn’t technically inclined.
Its very nature and complexity are already steep hurdles (and yes, you can’t make it fully easy without compromising how it’s supposed to work—granted). But the real problem? Almost zero effort has gone into giving even the most eager new users a manageable learning curve. That neglect slowly killed off any real user base—except for the hardcore encryption folks who already know what they’re doing.
Ask anyone in a shopping street or the historic center of your city if they’ve heard of PGP. And on the off chance someone knows it’s not a trendy new fast-food joint called “Perfectly Grilled Poultry,” the odds of them having actually used it in the past six months are basically zero, unless you happen to bump into that one neckbeard guy in his 60s wearing a stained Star Wars T-shirt named Leonard.
The builders of PGP made one major mistake: they never treated usability as a serious design goal (that’s normal for people knee deep in encryption, I get that, it’s the way it is). PGP is fantastic on itself. Other companies and projects tried to build around it, but while they stumbled, tools like Signal and ProtonMail stepped in; offering the same core features of encryption and secure messaging, minus the headache. They delivered what PGP never could: powerful functionality wrapped in something regular people can actually use. Now, we’ve got encrypted communication flowing through apps like Signal, where all the complex tech is buried so deep in the background, the average user doesn’t even realize it’s there. ProtonMail went one step further even, integrating PGP so cleanly that users never need to exchange keys or understand the cryptography behind it all, yet still benefit from bulletproof encryption.
There’s no debate—this shift is a good thing. History shows that unusable software fades into irrelevance. Whether due to lack of interest, failure to reach critical mass, or a competitor swooping in to eat market share, clunky tools don’t survive. Now, to be clear, Bitcoin doesn’t have to worry about that kind of threat. There’s no real competition when it comes to hard money. Unless, of course, you genuinely believe that flashy shitcoins are a viable alternative—in which case, you might as well stop reading here and go get yourself scammed on the latest Solana airdrop or whatever hype train’s leaving the station today for the degens.
The main takeaway here is that Bitcoin must avoid becoming the next Lotus Notes, bloated with features but neglected by users—or the next PGP, sidelined by its own lack of usability. That kind of trajectory would erode trust, especially if usability and onboarding keep falling behind. And honestly, we’re already seeing signs of this in bitcoin. User adoption in Europe, especially in countries like Germany is noticeably lagging. The introduction of the EU’s MiCA regulations isn’t helping either. Most of the companies that were actually pushing adoption are now either shutting down, leaving the EU, or jumping through creative loopholes just to stay alive. And the last thing on anyone’s mind is improving UX. It takes time, effort, and specialized people to seriously think through how to build this properly, from the beginning, with this ease of use and onboarding in mind. That’s a luxury most teams can’t or won’t prioritize right now. Understandably when the lack of funds is still a major issue within the bitcoin space. (for people sitting on hard money, there’s surprisingly little money flowing into useful projects that aren’t hyped up empty boxes)
The number of nodes being set up by end users worldwide isn’t exactly skyrocketing either. Sure, there’s some growth but let’s not overstate it. Based on Bitnodes’ snapshots taken in March of each year, we’re looking at: 2022 : around 10500 2023 : around 17000 2024 : around 18500 2025 : around 21000 (I know there are different methods of measuring these, like read-only nodes, the % change is roughly the same nonetheless)
In my opinion, if we had non-clunky software that was actually released with proper testing and usability in mind, we could’ve easily doubled those node numbers. A bad user experience with a wallet spreads fast—and brings in exactly zero new users. The same goes for people trying to set up a miner or spin up a node, only to give up after a few frustrating steps. Sure, there are good people out there making guides and videos2 to help mitigate those hurdles, and that helps. But let’s be honest: there’s still very little “wow” factor when average users interact with most Bitcoin software. Almost every time they walk away, it’s because of one of two things—usability issues or bugs.
For the record: if a user can’t set up a wallet because the interface is so rotten or poorly tested, so they don’t know where to click or how to even select a seed word from a list, then that’s a problem — that’s a bug. Argue all you want: sure, it’s not a code-level bug and no, it’s not a system crash. But it is a usability failure. Call it onboarding friction, UX flaw, whatever fits your spreadsheet or circus Maximus of failures in your ticketing system. Bottom line: if your software doesn’t help users accomplish its core purpose, it’s broken. It’s a bug. Pretending it’s something a copywriter or marketing team can fix is pure deflection. The solution isn’t to relabel the problem, 1990’s telecom-style, just to avoid dealing with it. It’s to actually sit down, think, collaborate, and go through the issue, and getting real solutions out. ”No it’s not an issue, that’s how it works” like someone from a failing (and by now defunct) wallet told me once, is not a solution.
You got 21 seconds
The user can’t be onboarded because your software has an “issue”? In my book, that’s a bug. The usual response when you report it? “Yeah, that’s not a priority.” Well, guess what? It actually is a priority. All these small annoyances, hurdles, and bits of BS still plague this industry, and they make the whole experience miserable for regular people trying it out for the first time. The first 21 seconds (yeah, you see what I did there) are the most important when someone opens new software. If it doesn’t click right away—if they’re fiddling with sats or dollar signs, or hunting for some hidden setting buried behind a tiny arrow—it’s game over. They’re annoyed. They’re gone.
And this is exactly why we’re seeing a flood of shitcoin apps sweeping new users off their feet with "faster apps" or "nicer designs" apps that somehow can afford the UI specialists and slick, centralized setups to spread their lies and scams.
I hate to say it, but the Phantom wallet for example, for the Solana network, loaded with fake airdrop schemes and the most blatant scams — has a far better UX than most Bitcoin wallets and Lightning Wallets. Learn from it. Download that **** and get to know what we do wrong and how we can learn from the enemy.
That’s a hard truth. So, instead of just screaming “Uh, shitcooooin!” (yes, we know it is), maybe we should start learning from it. Their apps are better than ours in terms of UI and UX. They attract more people 5x faster (we know that’s also because of the fast gains and retardation playing with the marketing) but we can’t keep ignoring that. Somehow these apps attract more than our trustworthiness, our steady, secure, decentralized hard money truth.
It’s like stepping into one of the best Italian restaurants in town—supposedly. But then the menu’s a mess, the staff is scrolling on their phones, and something smells burnt coming from the kitchen. So, what do you do? You walk out. You cross the street to the fast food joint and order a burger and fries. And as you’re walking out with your food, someone from the Italian place yells at you: “Fast food is bad!” ”Yeah man I know, I wanted a nice Spaghetti aglio e olio, but here I am, digesting a cheeseburger that felt rather spongy.” (the problem is so gone so deep now, that users just walk past that Italian restaurant, don’t even recognize it as a restaurant because it doesn’t have cheeseburgers).
Fear of the dark
Technical people, not marketeers built bitcoin, it’s build on hundreds of small building blocks that interacted over time to have the bitcoin network and it’s immer evolving value. At one point David Chaum cooked up eCash, using blind signatures to let people send digital money anonymously — except it was still stuck on clunky centralized servers. Go back even further, to the 1970s, when Diffie, Hellman, and Rivest introduced public-key cryptography—the magic sauce that gave us secure digital signatures and authentication, making sure your messages stayed private and tamper-proof.
Fast forward to the 1990s, where peer-to-peer started to take off, decentralized networks getting started. Adam Back’s Hashcash in ‘97 used proof-of-work to fight email spam, and the cypherpunks were all about sticking it to the man with privacy-first, the invention 199 Human-Readable 128-bit keys3, decentralized systems. We started to swap files over p2p networks and later, torrents.
All these parts—anonymous cash, encryption, and leaderless networks finally clicked into place when Satoshi Nakamoto poured them into a chain of blocks, built on an ingenious “time-stamping” system: the timechain, or blockchain if you prefer. And just like that, Bitcoin was born—a peer-to-peer money system that didn’t need middlemen and actually worked without any central servers.
So yes, it’s only natural that Bitcoin and the many tools, born from math, obscurity, and cryptography, isn’t exactly always a user-interface darling. That’s also it’s charm for me in any case, as the core is robust and valuable beyond belief. That’s why we love to so see more use, more adoption.
But that doesn’t mean we can’t squash critical “show-stopper” bugs before releasing bitcoin-related software. And it sure as hell doesn’t mean we should act like jerks when a user points out something’s broken, confusing, or just doesn’t meet expectations. We can’t be complacent either about our role as builders of the next generations, as the core is hard money, and it would be a fatal mistake for the world to see it being used only for some rockstars from Wall Street and their counterparts to store their debt laden fiat. We can free people, make them better, make them elevate themselves. And yet, the people we try to elevate, we often alienate. All because we don’t test our stuff well enough. We should be so good, we blow the banking apps away. (they’re blowing themselves out of the market luckily with fiat “features” and overly over the top use of “analytics” to measure your carbon footprint for example).
We should be so damn professional that someone using Bitcoin apps for a full year wouldn’t even notice any bugs, because there wouldn’t be much to get annoyed by.
So… we have to do better. I’ve seen it time and time again — on Lightning tipping apps, Nostr plugins, wallets, hardware wallets, even metal plates we can screw up somehow … you name it. “It works on my machine”, isn’t enough anymore! Those days are over.
Even apps built with solid funding and strong dev and test teams like fedi.xyz4 can miss the mark. While the idea was good and the app itself ran fine without too much hurdles and usual bugs. But usability failed on a different front: there was just nothing meaningful to do in the app beyond poking around, chatting a bit, and sending a few sats back and forth. The communities it’s supposed to connect, just aren’t there, or weren’t there “yet”.
It’s a beautifully designed application and a strong proof-of-concept for federated community funds. But then… nothing. No one I know uses it. Their last blogpost was from beginning of October 2024, which doesn’t bode well, writing this than 6 months after. That said, they got some great onboarding going, usually under 20 seconds, which proves it can be done right (even if it was all a front-end for a more complex backend).
As you can see “usability” is a broad terminology, covering technical aspects, user-interface, but also use-cases. Even if you have a cool app that works really well and is well thought-out users won’t use it if there’s no real substance. You can’t get that critical mass by waiting for customers to come in or communities to embrace it. They won’t, because most of the individuals already had past experiences with bitcoin apps or services, and there’s a reason for them not being on-board already.
A lot of bitcoin companies build tools for new people. Never for the lapsed people, the persons that came in, thought of it as an investment or “a coin”… then left because of a bad experience or the price going down in fiat. All the while we have some software that usually isn’t so kind to new people, or causes loss of funds and time. Even if they make one little “mistake” of not knowing the system beforehand.

Bitcoin’s Moby Dick
\ Bitcoin itself has a big issue here. The user base could grow faster, and more robust, if there wasn’t software that worked as a sort of repellent against users.
I especially see a younger and less tech-savvy audience absolutely disliking the software we have now. No matter if it’s Electrum’s desktop wallet (hardly the sexiest tool out there, although I like it myself, but it lacks some features), Sparrow, or any lightning wallet out there (safe for WoS). I even saw people disliking Proton wallet, which I personally thought of as something really slick, well-made and polished. But even that doesn’t cut it for many people, as the “account” and “wallet” system wasn’t clear enough for them. (You see, we all have the same bias, because we know bitcoin, we look at it from a perspective of “facepalm, of course it’s a wallet named “account”, but when you sit next to a new user, it becomes clear that this is a hurdle. (please proton wallet: name a wallet a wallet, not “account”. But most users already in bitcoin, love what you’re doing)
Naturally disliking usability
The same technically brilliant people who maintain Bitcoin and build its apps haven’t quite tapped into their inner Steve Jobs—if that person even exists in the Bitcoin space. Let’s be honest: the next iOS-style wow moment, or the kind of frictionless usability seen in Spotify or Instagram, probably won’t come from hardcore Bitcoin devs alone. In fact, some builders in the space seem to actively disregard—or even look down on—discussions about usability. Just mention names like Wallet of Satoshi (yes, we all know it’s a custodial frontend) or the need for smoother interactions with Bitcoin, and you’ll get eye-rolls or defensive rants instead of curiosity or openness.
Moving more towards a better user interface for things like Sparrow or Bitcoin Core for example, would bring all kinds of “bad things” according to some, and on top of that, bring in new users (noobs) that ask questions like: “Do you burn all these sats when I make a transaction?” (Yes, that’s a real one.)
I get the “usability sucks” gripe — fear of losing key features, dumbing things down, or opening the door to unwanted changes (like BIP proposals real bitcoiners hate) that tweak bitcoin to suit any user’s whim. Close to no one in bitcoin (really in bitcoin!) wants that, including me.
That fear is however largely unfounded; because Bitcoin doesn’t change without consensus. Any change that would undermine its core use or value proposition simply won’t make it through. And let’s be honest: most of the users who crave these “faster,” centralized alternatives—those drawn to slick apps, one-click solutions, and dopamine-driven UI—will either stick with fiat, ape into the shitcoin-of-the-month, or praise the shiny new CBDC once it drops (“much fast, much cool”). These degen types, chasing fiat gains and jackpot dreams, aren’t relevant to this story, No matter what we build for bitcoin, they’ll always love the fiat-story and will always dislike bitcoin because it’s not a jackpot for them. (Honestly, why don’t they just gamble at a casino?)
People who fear that improving usability will somehow bring down the Bitcoin network are being a bit too paranoid—and honestly, they often don’t understand what usability or proper testing actually means.
They treat it like fluff, when in reality it's fundamental. Usability doesn't mean dumbing things down or compromising Bitcoin's core values; it means understanding why your fancy new app isn’t being used by anyone outside of your bubble. Testing is the beating heart of getting things out with confidence. Nothing more satisfying in software building than to proudly show even your beta versions to users, knowing it’s well tested. It’s much more than clicking a few buttons and tossing your code on GitHub. It's about asking real questions: can someone outside your Telegram group actually use this and will it they be using the software at all?
If you create a Nostr app that opens an in-app browser window and then tries to log you in with your NIPS05 or NIPS07 or whatever number it is that authenticates you, then you need to think about how it’s going to work in real life. Have people already visited this underlying website? Is that website using the exact same mechanism? Is it really working like we think it is in the real world? (Some notable good things are happening with the development of Keychat for example, I have the feeling they get it, it’s not all bad). And yes, there are still bugs and things to improve there, they’re just starting. (The browser section and nostr login need some work imho).
Guess what? You can test your stuff. But it takes time and effort. The kind of effort that, if skipped, gets multiplied across thousands of people. Thousands of people wasting their time trying to use your app, hitting errors, assuming they did something wrong, retrying, googling workarounds—only to eventually realize: it’s not them. It’s a bug. A bug you didn’t catch. Because you didn’t test. And now everyone loses. And guess what? Those users? They’re not coming back.
A good example (to stay positive here) is Fountain App, where the first versions were , eh… let’s say not so good, and then quickly evolved into a company and product that works really well, and also listens to their users and fixes their bugs. The interface can still be better in my opinion, but it’s getting there. And it’s super good now.
A bad example? Alby. (Sorry to say.) It still suffers from a bloated, clunky interface and an onboarding flow that utterly confuses new or returning users. It just doesn’t get the job done. Opinions may vary, sure, but hand this app to any non-technical user and ask them to get online and do a Nostr zap. Watch what happens. If they even manage to get through the initial setup, that is.
Another example? Bitkit. When I tried transferring funds from the "savings" to the "spending" account, the wallet silently opened a Lightning channel—no warning, no explanation—and suddenly my coins were locked up. To make things worse, the wallet still showed the full balance as spendable, even though part of it was now stuck in that channel. That was in November 2024, the last time I touched Bitkit. I wasted too much time trying to figure it out, I haven’t looked back (assuming the project is even still alive, I didn’t see them pop up anywhere).
Some metal BIP39 backup tools are great in theory but poorly executed. I bought one that didn’t even include a simple instruction on how to open it. The person I gave it to spent two hours trying to open it with a screwdriver and even attempted drilling. Turns out, it just slides open with some pressure. A simple instruction would’ve saved all that frustration.
Builders often assume users “just get it,” but a small guide could’ve prevented all the hassle. It’s a small step, but it’s crucial for better user experience. So why not avoid such situations and put a friggin cheap piece of paper in the box so people know how to open it? (The creators would probably facepalm if they read this, “how can users nòt see this?”). Yeah,… put a paper in there with instructions.
That’s natural, because as a creator you’re “in” it, you know. You don’t see how others would overlook something so obvious.
Bitcoiners are extremely bad on that front.
I’ll dive deeper into some examples in part 2 of this post.
By AVB
end of part 1
If you like to support independent thought and writings on bitcoin, follow this substack please https://coinos.io/allesvoorbitcoin/receive\ \ footnotes:
1 https://philzimmermann.com/EN/findpgp/
2 BTC sessions: set up a bitcoin node
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ ed22fab2:422b9051
2025-05-08 04:31:25
@ ed22fab2:422b9051
2025-05-08 04:31:25A plataforma Pix177 chegou para redefinir a forma como os brasileiros aproveitam o entretenimento digital. Com uma proposta moderna, segura e recheada de opções emocionantes, o Pix177 tem conquistado milhares de usuários por todo o país, oferecendo uma experiência completa e personalizada desde o primeiro acesso. Se você busca diversão, praticidade e oportunidades de ganhos reais, o Pix177 pode ser o lugar ideal para você.
O grande diferencial do Pix177 está na sua interface amigável e acessível. Logo ao entrar na plataforma, o usuário percebe a fluidez e organização do site. Cada seção é pensada para facilitar a navegação, seja no computador ou pelo celular. Outro ponto de destaque é o sistema de pagamentos: o Pix177 conta com suporte total ao método Pix, permitindo transações instantâneas e seguras, tanto para depósitos quanto para saques. Isso significa menos tempo esperando e mais tempo jogando.
A equipe responsável pela plataforma se preocupa com a segurança e a privacidade dos usuários, implementando tecnologia de criptografia de ponta e protocolos rigorosos de proteção de dados. Assim, os jogadores podem se concentrar apenas no que realmente importa: a diversão e a emoção dos jogos.
Variedade de jogos para todos os gostos
O Pix177 oferece uma seleção extensa de jogos que atendem a todos os perfis de jogadores. Desde opções clássicas e populares até lançamentos mais recentes, há algo para cada tipo de gosto. Os amantes das cartas encontram mesas de poker, blackjack e baccarat com diferentes níveis de apostas. Para quem prefere jogos de giro, há uma vasta biblioteca de slots online com gráficos vibrantes, trilhas sonoras envolventes e recursos especiais como rodadas grátis e multiplicadores.
Jogos ao vivo também fazem parte do catálogo da plataforma, permitindo que os usuários participem de partidas em tempo real com crupiês reais e interajam com outros jogadores. A imersão é total, com transmissão de alta qualidade e ambiente virtual que simula uma sala de jogos tradicional — tudo sem sair de casa.
Além disso, o Pix177 frequentemente atualiza seu portfólio com novidades de provedores renomados do mercado, garantindo sempre conteúdo fresco e inovador.
Uma experiência pensada para o jogador brasileiro
O Pix177 entende as preferências e necessidades do público nacional. Por isso, oferece suporte em português, atendimento ao cliente via chat ao vivo e promoções personalizadas com foco nos usuários brasileiros. O processo de cadastro é simples e rápido, permitindo que novos jogadores comecem sua jornada em poucos minutos.
Os bônus de boas-vindas e promoções semanais são outros atrativos que mantêm os jogadores engajados. Programas de fidelidade e desafios especiais aumentam ainda mais as chances de recompensas, tornando a experiência mais empolgante e dinâmica.
Conclusão
O Pix177 é mais do que uma simples plataforma de jogos online: é um verdadeiro universo de entretenimento digital, feito sob medida para o público brasileiro. Com seu sistema de pagamentos ágil, interface intuitiva, suporte completo e uma biblioteca de jogos impressionante, o Pix177 se posiciona como uma das melhores opções para quem quer unir diversão e praticidade em um só lugar.
Se você ainda não conhece o Pix177, essa é a hora de explorar tudo o que a plataforma tem a oferecer. Prepare-se para uma jornada cheia de emoção, desafios e recompensas!
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 732c6a62:42003da2
2025-03-06 06:00:53
@ 732c6a62:42003da2
2025-03-06 06:00:53De acordo com a Forbes, a Ripple (Empresa responsável pela Criptomoeda XRP) tem financiado e apoiado campanhas contra a mineração de Bitcoin.
Por que Ripple faz propaganda anti-bitcoin?
Simples: eles são o oposto do Bitcoin em quase tudo. Enquanto o Bitcoin foi criado para ser descentralizado, resistente à censura e independente de instituições, o Ripple é basicamente um serviço bancário 2.0. Eles precisam atacar o Bitcoin para justificar sua própria existência.
O que você não sabe:
- Ripple Labs controla a maioria do XRP: Eles têm um estoque estratégico que pode ser liberado no mercado a qualquer momento. Isso é o oposto de descentralização.
- XRP não é uma moeda para "pessoas comuns": Foi criada para bancos e instituições financeiras. Basicamente, é o "banco central" das criptomoedas.
- Ripple não é blockchain no sentido tradicional: Eles usam um protocolo chamado Ripple Protocol Consensus Algorithm (RPCA), que é mais rápido, mas menos descentralizado.
Os principais ataques do Ripple ao Bitcoin:
- Anti-mineração: O Ripple critica o consumo de energia do Bitcoin, mas esquece que seu próprio sistema depende de servidores centralizados que também consomem energia.
- Anti-reserva estratégica: O Ripple tem um estoque gigante de XRP, mas critica o Bitcoin por ser "deflacionário". Hipocrisia? Nunca ouvi falar.
- Anti-descentralização: O Ripple prega que a descentralização do Bitcoin é "ineficiente", mas o que eles realmente querem é manter o controle nas mãos de poucos.
Análise Psicológica Básica (para você que acha que XRP é o futuro):
- Síndrome do Underdog: Acha que apoiar o Ripple te faz um rebelde, mas na verdade você está torcendo para o sistema bancário tradicional.
- Viés de Confirmação: Só ouve opiniões que validam sua decisão de comprar XRP.
- Efeito Dunning-Kruger: Acha que entender Ripple te torna um especialista em criptomoedas, mas não sabe o que é um hard fork.
Estudo de Caso (Real, mas Você Vai Ignorar):
Carlos, 30 anos, comprou XRP porque "é o futuro das transações bancárias". Ele não sabe que o Ripple está sendo processado pela SEC por vender XRP como um título não registrado. Carlos agora está esperando o "pump" que nunca vem.Conclusão: ou, "volte para a aula de economia do ensino médio"
Ripple não é o futuro das finanças. É só mais um player tentando lucrar em um mercado competitivo. E sua propaganda anti-Bitcoin? Essa só prova que a descentralização assusta quem quer controle. Agora vá estudar blockchain básico — ou pelo menos pare de compartilhar memes com erros de português.
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ 6538925e:571e55c3
2025-05-05 20:00:48
@ 6538925e:571e55c3
2025-05-05 20:00:48It’s been a little while since we released a major design update, so we’re really excited to get this new version of the app into your hands. Here’s a breakdown of all the main updates included in Fountain 1.2:
 #### Library Design Update
#### Library Design Update-
New content-type filters at the top of the page make it easier to navigate between podcasts and music in your library.
-
Recently Played is now the default view in your library, so it’s easier to jump back into podcasts you’ve already started.
-
The Music filter now makes it easier to find saved tracks and albums, and it also gives you a list of all the artists whose music you’ve saved.
-
We’ve refreshed the design of the content cards to make it easier to see how much time is remaining on episodes you’ve already started.
 #### Content Pages Design Update
#### Content Pages Design Update-
All of the different content pages have undergone an extensive redesign, including shows, episodes, artists, albums, tracks, clips and playlists
-
We’ve replaced the tab layout we were using on the content pages with one scrollable page, making it easier to access features like chapters and tracklists
-
We’ve sanitised the formatting of show notes too, and if there is no activity for a given episode, we now display the expanded show notes
 #### Episode Summaries
#### Episode SummariesEver looked at a 4-hour Lex Fridman episode and wished you could just read a high-level summary? We certainly have, so we did something about it.
-
Every episode page now has a Summary button above the show notes.
-
Simply pay 500 sats to unlock a summary, or upgrade to Fountain Premium for $2.99/month to enjoy unlimited summaries.
-
Summaries and transcripts now come as a bundle — two for the price of one!
-
Thanks to major improvements, they’re now faster, cheaper, and more accurate than ever before.
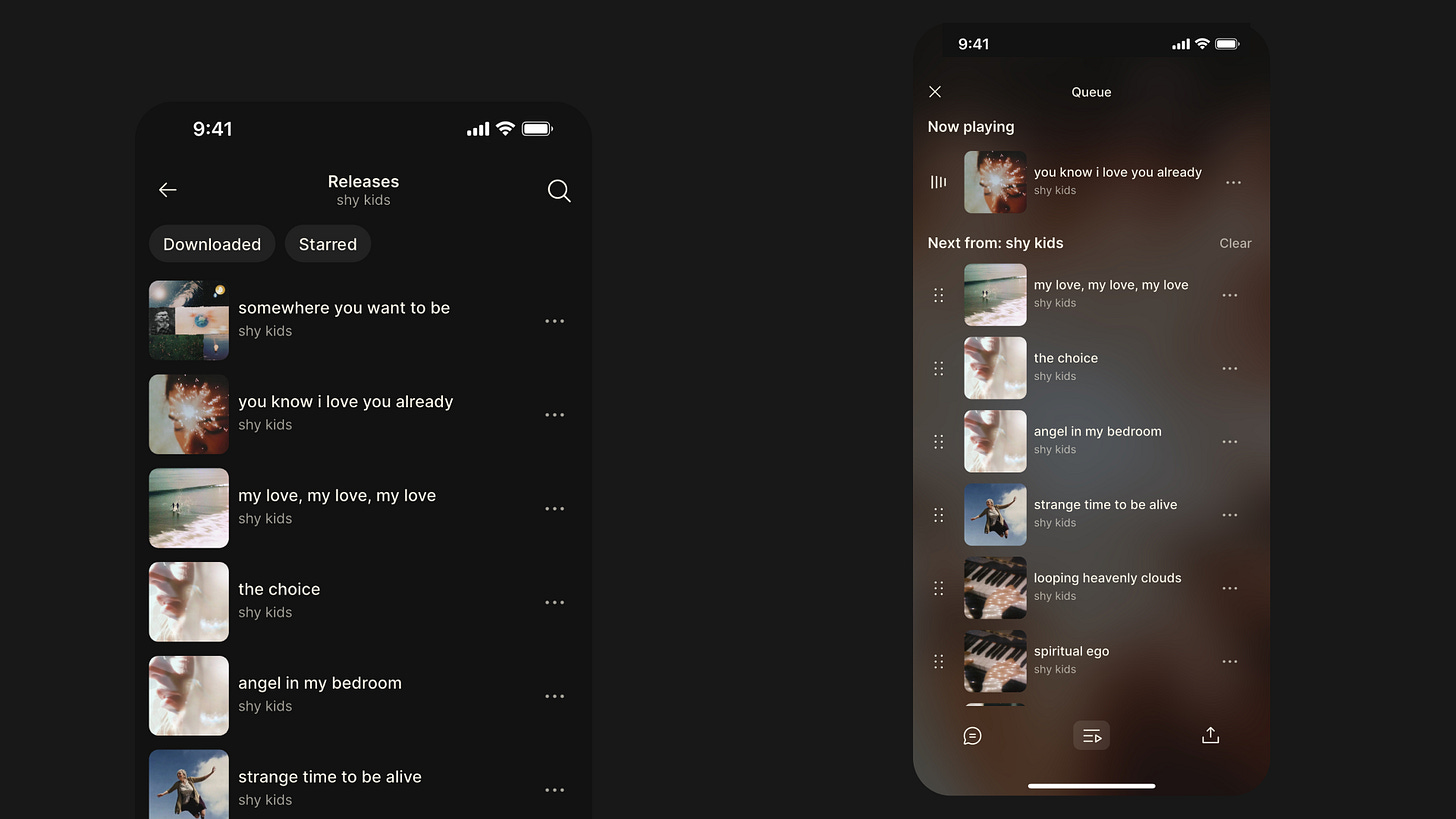 #### Playback Improvements
#### Playback ImprovementsWe’ve completely rebuilt our audio engine from the ground up. Playback is now more robust and reliable — especially for music. Here are some of the key enhancements in Fountain 1.2:
-
Tracks now load and play instantly when tapped.
-
When playing a collection of tracks (e.g. from an artist, album, or playlist), you can now skip seamlessly between them.
-
We’ve replaced the scrollable player page with full-screen modals to make it easier to access show notes, comments, transcripts, chapters, tracklists, and your queue.
-
The new Smart Resume feature rewinds the episode by 5 seconds when you hit pause, so you don’t miss a beat.
-
You can now skip forward or backward by 60 seconds for faster navigation through episodes.
Other Bug Fixes & Improvements
-
Rebuilt payment stats for more complete and reliable transaction records.
-
Refreshed the design of the Settings pages for better usability.
-
Added new episode notification preferences in Settings.
-
Fixed several playback issues that were causing crashes or freezes.
-
Updated lock screen display and controls for livestreams.
-
Fixed issue where the next item in the queue paused unexpectedly.
-
Resolved playback stuttering on Android during livestreams.
-
Fixed disappearing playback controls on the lock screen.
-
Fixed playback speed not updating correctly.
-
Resolved issue where played episodes couldn’t be replayed.
-
Fixed playback not resuming correctly when listening in the car.
-
Synced car playback position with the device.
-
Fixed persistent car display refresh issue.
-
Fixed volume control via car controls.
-
Resolved issue with headphone controls after playing a transcript.
-
Fixed disappearing metadata on the lock screen.
-
Fixed bug where downloaded episodes stopped in airplane mode but showed as playing.
We would love to hear how you’re finding Fountain 1.2. Please submit your thoughts and feedback via the main menu in the app and we will take it on board as we continue to improve the app.
If you want to help test new features out before they get released, you can join Fountain Beta on Telegram. All iOS and Android users welcome.
-
-
 @ 502ab02a:a2860397
2025-05-08 01:18:46
@ 502ab02a:a2860397
2025-05-08 01:18:46เฮียไม่แน่ใจว่าโลกยุคนี้มันเปลี่ยนไป หรือแค่เล่ห์กลมันแนบเนียนขึ้น แต่ที่แน่ ๆ คือ “อาหารไม่ใช่อาหารอีกต่อไป” มันกลายเป็นสินค้าในพอร์ตการลงทุน มันกลายเป็นเครื่องมือสร้างภาพลักษณ์ และในบางมุมที่คนไม่อยากมอง...มันคือเครื่องมือควบคุมมวลชน
ทุกอย่างเริ่มจากแนวคิดที่ดูดี “เราต้องผลิตอาหารให้พอเลี้ยงคน 8,000 ล้านคน” จากนั้นบริษัทเทคโนโลยีเริ่มกระโดดเข้ามา แทนที่จะให้เกษตรกรปลูกผักเลี้ยงวัว เรากลับได้เห็นบริษัทวิเคราะห์ดีเอ็นเอของจุลินทรีย์ แล้วขายโปรตีนจากถังหมัก แทนที่จะสนับสนุนอาหารพื้นบ้าน กลับอัดเงินให้สตาร์ทอัพทำเบอร์เกอร์ที่ไม่มีเนื้อจริงแม้แต่เส้นใยเดียว
เบื้องหลังมันมี “ทุน” และทุนเหล่านี้ไม่ใช่แค่ผู้ผลิตอาหาร แต่พ่วงไปถึงบริษัทยา บริษัทวัคซีน บริษัทเทคโนโลยี บางเจ้ามีทั้งบริษัทยา + ธุรกิจฟาร์มแมลง + บริษัทลงทุนในบริษัทวิจัยพันธุกรรม แปลว่า...คนที่ขายยาให้เฮียเวลาเฮียป่วย อาจเป็นคนเดียวกับที่ขาย "อาหารที่ทำให้เฮียป่วย" ตั้งแต่แรก ตลกร้ายไหมหล่ะ หึหึหึ
เคยมีใครสังเกตไหม ว่าองค์การระดับโลกบางองค์กรที่ส่งเสริม "เนื้อทางเลือก" และ "อาหารยั่งยืน" ได้รับเงินบริจาคหรืออยู่ภายใต้บอร์ดของบริษัทผลิตอาหารอุตสาหกรรมเจ้าใหญ่ไหมนะ แล้วคำว่า “วิทยาศาสตร์รองรับ” ที่ติดบนฉลากสวย ๆ เฮียไม่รู้หรอกว่าใครเป็นคนตีความ แต่ที่รู้แน่ ๆ คือ บทวิจัยจำนวนไม่น้อย มาจากทุนวิจัยที่สนับสนุนโดยอุตสาหกรรมอาหารเอง ดั่งเช่นที่เราเรียนรู้กันมาจากประวัติศาสตร์แล้ว
มีคนเคยพูดไว้ว่า “เราควบคุมคนด้วยอาหารง่ายกว่าด้วยอาวุธ” และเฮียเริ่มเชื่อขึ้นเรื่อย ๆ เพราะถ้าบริษัทใดบริษัทหนึ่ง ควบคุมได้ทั้งอาหาร ยา ข้อมูลสุขภาพ และการวิจัย นั่นหมายความว่า เขาไม่ได้ขายของให้เฮีย แต่เขากำหนดว่าเฮียควร “อยากกินอะไร” และ “รู้สึกผิดกับอะไร”
เหมือนที่ให้ลองจินตนาการเล่น ๆ เมื่อวาน สมมติเฮียไปร้านข้าวมันไก่ปากซอยแบบดั้งเดิม สั่งไก่ต้มไม่เอาข้าวมากิน แล้วแอปสุขภาพขึ้นข้อความเตือนว่า “ไขมันสูง ส่งผลต่อคะแนนสุขภาพคุณ” แต่ถ้าเฮียสั่งข้าวกล่องสำเร็จรูปอัจฉริยะจากโปรตีนที่หมักจากจุลินทรีย์ GMO ระบบจะบอกว่า “คุณกำลังช่วยลดโลกร้อน” แล้วเพิ่มคะแนนสุขภาพให้เราไปเป็นส่วนลดครั้งต่อไป
ใครนิยามคำว่า “ดี” ให้เฮีย?
เบื้องหลังอาหารจึงไม่ใช่แค่โรงงาน แต่มันคือโครงข่ายที่พัวพันตั้งแต่ห้องแล็บ ห้องบอร์ด ไปจนถึงห้องครัวในบ้านเรา แล้วถ้าเราไม่ตั้งคำถาม เฮียกลัวว่าเราจะไม่ได้กินในสิ่งที่ร่างกายต้องการ แต่กินในสิ่งที่ “ระบบ” ต้องการให้เรากิน
ขอบคุณล่วงหน้าที่มองว่าสิ่งนี้คือการ แพนิคไปเอง ขอให้มีสุขสวัสดิ์
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 005bc4de:ef11e1a2
2025-05-06 11:54:14
@ 005bc4de:ef11e1a2
2025-05-06 11:54:14May 6 marks my "Nostr birthday." This means I've been on Nostr for two years now. See my initial "Running nostr" note timestamped and archived on the Hive blockchain at https://peakd.com/bitcoin/@crrdlx/running-nostr
Two years ago, I really had no idea what Nostr was. I was asking, "What is this Nostr thing?"

And, I had no idea what I was doing then while using the front end clients. The clients were clunky and since the protocol was rather plastic (still kinda is). As evidence to my ignorance, the spinning wheels on Coracle.social just kept spinning. I didn't realize that since I was only following two people, one being myself, there was nothing to load from relays except my one "Running nostr" note. Hence, the Coracle wheels just spun in their mesmerizing manner. At least they're soothing to watch.
Yet, despite my ignorance, I had an inkling of a notion that Nostr was indeed something different, maybe special. Otherwise, I wouldn't have taken the time to capture an animated gif and make that Hive post to chronicle my first Nostr note.
For fun, I made another "Running nostr" note yesterday using Coracle.social. It still has those muted, earthy tones, but the wheels are not there anymore for long. Coracle, like Nostr, has come a long way in two years. It loads much faster now, which means less wheel spinning. I kind of miss the wheels for some reason, they build the drama and expectation of what might appear.
!HBIT
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 6d8e2a24:5faaca4c
2025-05-07 19:15:55
@ 6d8e2a24:5faaca4c
2025-05-07 19:15:55Decentralized social media platforms like Yakinhonne is gaining popularity as alternatives to traditional networks like Facebook and Twitter. But here’s the big question: Can you actually make money from them?
Unlike traditional social media with the likes of Facebook, Twitter, Instagram, WhatsApp etc. Yakihonne runs on blockchain tech, meaning:
✅ You own your content (no shadow banning or sudden account bans).
✅ No creepy ads tracking your every move.
✅ Real monetization no waiting for a partner program approval.Therefore the short answer? Yes! But it’s different from how monetization works on mainstream platforms. Let’s break it down in simple terms.

- How Decentralized Social Media Works
Unlike Facebook or Instagram (which are owned by corporations), decentralized platforms run on blockchain or peer to peer networks. This means:
✅ No central control (no Zuckerberg making the rules).
✅ Users own their data (no creepy ads tracking you).
✅ More freedom (fewer bans and censorship).
But since these platforms don’t rely on ads, how do creators and users earn money?
2. Ways to earn on Yakinhonne Decentralized Social Media Platform.
A. Rewards & Tipping ✅ Users can tip you in crypto SAT (Satoshi, which is a native of Bitcoin) for great content.
✅ Earn tokens for engagement (likes, shares, etc.).
Example: Post a viral thread on Yakinhonne and followers might send you $SAT Tokens as appreciation.
B. Paid Subscriptions & Exclusive Content
✅ Platforms like Yakinhonne allow paid memberships.
✅ Offer premium posts (Flash news or post), private chats, or early access to supporters.Example: A writer post a paid article making it stand out, attracting more engagement which in returns earns more SAT.
C. Decentralized Ads (But Better)
✅Instead of intrusive ads, users opt-in to promotions.
✅ Creators get paid directly for promoting products (no middleman).Example: A tech reviewer gets paid in crypto for sharing a decentralized VPN service.
D. Affiliate Marketing & Sponsorships
✅ Promote products and earn commissions (like Amazon links).
✅ Partner with Web3 brands (crypto projects, tools, etc.).Conclusion:
Decentralized social media is still growing, but the monetization potential is real especially if you’re a lover of freedom, having absolute control and fairness.
As blockchain technology evolves, we might see even smarter ways to earn on these platform. So, getting in early could be a smart move!
- How Decentralized Social Media Works
Unlike Facebook or Instagram (which are owned by corporations), decentralized platforms run on blockchain or peer to peer networks. This means:
-
 @ 90c656ff:9383fd4e
2025-05-07 18:25:24
@ 90c656ff:9383fd4e
2025-05-07 18:25:24Bitcoin is known for its strong volatility, with price swings that can occur over short periods of time. This characteristic attracts both investors seeking high returns and deters those who prefer more stable assets. Bitcoin's price volatility has a significant impact on the market, influencing investment strategies, adoption, and even public perception of the digital currency.
What Causes Bitcoin's Price Volatility?
Bitcoin’s volatility is due to several factors that affect its supply and demand. Among the main reasons are:
01 - Limited supply and halving: Bitcoin has a maximum supply of 21 million units, creating scarcity. Additionally, the halving-an event that reduces the issuance of new bitcoins every four years-can drive up prices due to the reduced supply.
02 - Market speculation: Many investors buy and sell Bitcoin in pursuit of quick profits, causing large price fluctuations. Speculative movements, often driven by news and social media, can trigger abrupt changes in price.
03 - Economic events and regulation: Government decisions-such as bans or favorable regulations-directly impact the price. Statements from central banks or influential figures in the financial sector can also trigger strong market reactions.
04 - Liquidity and trading volume: The Bitcoin market is still small compared to traditional assets like gold or stocks. This means that large buy or sell orders can cause significant price swings.
- Impact on Investors and “Investors”
Bitcoin’s price volatility affects different types of investors in different ways:
01 - Short-term traders: Day traders attempt to profit from price swings. However, this strategy carries high risks and can lead to significant losses for those without market experience.
02 - Long-term investors (HODLers): Those who invest with a long-term perspective typically ignore daily price changes and focus on Bitcoin's potential appreciation over the years. Despite temporary dips, many believe the price will continue to rise due to scarcity and increasing adoption.
03 - Companies and institutions: Companies investing in Bitcoin as a store of value-like MicroStrategy and Tesla, must manage the risks of volatility. Some adopt strategies to minimize direct exposure to large fluctuations.
- How to deal with volatility
Despite the challenges, there are strategic ways to manage Bitcoin’s volatility:
01 - Portfolio diversification: Instead of investing all capital in Bitcoin, many investors diversify to reduce the impact of price fluctuations.
02 - Recurring investment: Strategies like dollar-cost averaging (recurring, fractional purchases) help smooth out volatility effects, reducing the risk of buying during a temporary high.
03 - Secure storage: Rather than leaving Bitcoin on exchanges—which can be vulnerable to hacks and market manipulation—self-custody in secure wallets protects long-term investments.
In summary, Bitcoin's volatility is one of its defining traits and influences both investor behavior and broader adoption. While it offers opportunities for large profits, it also carries considerable risk, requiring well-defined strategies to minimize losses. As Bitcoin matures and more institutional investors enter the market, volatility may decrease, making it even more attractive as a store of value.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 1b9fc4cd:1d6d4902
2025-05-06 11:06:40
@ 1b9fc4cd:1d6d4902
2025-05-06 11:06:40Music has always been dynamic, molding and reflecting cultural shifts across generations. From the smoky underground clubs of Northern England to the gritty, graffiti-laden walls of New York City's punk venues, and the rain-soaked streets of Seattle, the evolution of music is a testament to the ever-changing landscape of human expression. Daniel Siegel Alonso takes you on a witty and insightful journey through pivotal moments in music history: The Beatles at The Cavern Club, punk rock's birth at CBGBs, and the Seattle grunge explosion.
The Beatles do The Cavern
Close your eyes and imagine: It's 1961, and you're down in the basement of The Cavern Club in Liverpool; it's packed with sweat-drenched, eager faces, and the air thick, dripping with anticipation. On stage, four young lads who would soon become the most famous band in the world are tuning their guitars. The Beatles, with their mop-top haircuts and cheeky grins, are on the precipice of changing music for generations.
Before they were household names, John, Paul, George, and Ringo honed their craft in this humble, dimly lit venue. The Cavern Club was their proving ground, where they transitioned from covering American icons Chuck Berry and Little Richard to showcasing their original material. Here, they first captivated audiences with their infectious energy and groundbreaking sound.
The group's time at The Cavern Club was pivotal. It was where they caught the eye of Brian Epstein, who would become its manager, and later, record producer George Martin, aka the fifth Beatle. This tiny, subterranean venue was the launchpad for a nuclear cultural revolution. The Beatles didn't just play pop and rock music; they constructed an identity, a lifestyle, and, in hindsight, an era. They embodied the spirit of the Swinging 60s, melding rock 'n' roll with a bouncy pop sensibility that was both rowdy and charming.
Anarchy in the Big Apple
Daniel Siegel Alonso fast-forwards to the mid-70s, and we're in an entirely different world. Bankrupt Manhattan, in the bowels of a biker bar on the Bowery called CBGBs--a mouthful of an acronym standing for Country, Bluegrass, and Blues. The stage is dilapidated, and the sound system is a haphazard collection of amps and speakers at best. Here, the raw energy of punk rock was born, thrashing and pogoing its way into the mainstream.
CBGBs became the center of a musical revolt. Groups like The Ramones, Blondie, and Television took to the ramshackle stage, bringing with them a loud, fast, and unapologetically raw sound. Punk was a direct response to the bloated excesses of middle-of-the-road rock and bands like Yes, Chicago, and Fleetwood Mac; punk was do-it-yourself, back to basics, and in-your-face.
The Ramones epitomized this new angsty attitude with their black leather jackets and torn jeans. The songs they wrote were short, sharp, and shocking to audiences accustomed to indulgent guitar solos and elaborate stage productions. CBGBs was more than just a venue; it was a breeding ground for a cultural movement. It embraced the DIY ethic, encouraging emerging bands to play regardless of polish or professionalism. This sense of independence and defiance reverberated with a new generation of listeners disenchanted by the status quo.
The Last Great Rock Revolution
Siegel Alonso jumps ahead another decade to Seattle, a city known more for its rain than its rock-and-roll. Yet, over three decades ago, Seattle was the epicenter of grunge, a new genre that would once again redefine music. The core of this movement was a collection of venues like The Crocodile and The Off Ramp, where bands like Nirvana, Pearl Jam, and Soundgarden first made their mark.
Grunge was a gritty, angst-filled reaction to the over-produced pop and ostentatious hair metal of the 80s. It combined the raw energy of punk from the previous decade with heavy metal's strength, birthing a sound that was both abrasive and softly melodic. Grunge poster boy Kurt Cobain, with his ragged sweaters and unkempt wiry hair, became the reluctant voice of the last analog generation. Nirvana's breakout album, "Nevermind," was a seismic pop culture event, forcing grunge into the global mainstream.
Seattle's grunge scene was characterized by authenticity and a sense of community. Bands often collaborated and supported each other, creating a tight-knit musical ecosystem. The city's isolation from traditional music industry hubs allowed for a unique sound to develop, one that was untainted by commercial pressures.
Connecting the Dots
What ties these three musical moments together is their grassroots beginnings. The Beatles, the first wave of punk rock, and grunge all began in small, dingy venues, driven by pure passion and a craving to disrupt the status quo. Each musical chapter mirrored and influenced the cultural zeitgeist of its time, providing a soundtrack to their respective eras' social changes and attitudes.
The Cavern Club, CBGBs, and Seattle's grunge venues were more than places where bands performed; they were incubators of innovation and rebellion. They nurtured the raw, unpolished energy that would shape the future of popular music.
As Siegel Alonso reflects on these musical milestones, a pattern of evolution emerges driven by a handful of fundamental ingredients: authenticity, community, and a bold embrace of the unknown. Music's narrative is one of constant change, and as these examples depict, it's often in the most unexpected places that the next big thing begins to take shape.
-
 @ 732c6a62:42003da2
2025-03-06 04:33:48
@ 732c6a62:42003da2
2025-03-06 04:33:48De ''Dialética do Oprimido'' a ''Like do Oprimido'': A Queda Livre do Debate que Nunca Existiu.
A moda do momento
Fiquei aproximadamente 8 meses sem ter acesso a nenhum dispositivo. Quando consegui novamente o acesso ao smartphone, percebi algo diferente no debate político brasileiro: enquanto a direita estava se engajando em incontáveis números de curtidas e compartilhamentos com memes que demonstravam críticas ao governo e aos seus ainda poucos apoiadores que se humilham para defender o indefensável, a esquerda radical repetia sua imposição intelectual em comentários de vários posts, incluindo textos, vídeos e tweets com frases semelhantes a "vai ler um livro de história" "nunca leu um livro", "eu estou do lado certo da história" e "se eu fosse irracional eu seria de direita". Tudo isso pra tentar passar uma mensagem de que a história é de esquerda. A tese é: será que eles realmente são tão inteligentes como juram?
Fatos que ignoram enquanto cospem jargões do "lado certo da história":
1. A esquerda também tem seus terraplanistas: Anti-vaxxers de organicafé, terraplanistas do gênero, e os que acham que a Coreia do Norte é uma democracia.
2. Viés de confirmação não é monopólio da direita: Eles compartilham estudos "científicos" do Medium como se fossem peer-reviewed, mas desdenham de dados que contradizem sua narrativa.
3. A direita não é um monolito: Tem desde ancaps que calculam até a última casa decimal até bolsominions que acham que a Terra é plana. Generalizar é... bem, irracional.Estudo de Caso (Fictício, mas Verdadeiro):
Larissa, 23 anos, posta sobre "ciência e razão" enquanto defende horóscopo como "ferramenta de autoconhecimento". Acredita que o capitalismo causa depressão, mas não sabe o que é taxa Selic. Larissa é você após três caipirinhas.A Imposição intelectual que ninguém pediu (mas todos recebem de graça)
A esquerda brasileira, em sua cruzada épica para salvar o mundo dos "fascistas que ousam discordar", adotou uma nova estratégia: transformar complexidade política em slogans de camiseta de feira. A frase "se eu fosse irracional, seria de direita" não é original — é plágio descarado da cartilha do Complexo de Deus em Oferta no AliExpress.
O Quebra-Cabeça da superioridade Auto-Delirante
A tese esquerdista se sustenta em três pilares frágeis:
1. A falácia do "lado certo da história": Como se história fosse um jogo de futebol com narração do João Cléber.
2. A ilusão de que citar Foucault = ter QI elevado: Spoiler: decorar "biopoder" não te torna imune a acreditar em astrologia.
3. A crença de que volume de texto = profundidade: 15 parágrafos no Twitter não equivalem a um semestre de Ciência Política.Dado Cruel: Um estudo da Universidade de Cambridge (2022) mostrou que extremistas de ambos os lados cometem erros lógicos similares. A diferença? A esquerda usa palavras mais bonitas para mascarar a burrice.
A hipocrisia do "nunca tocou em um livro" (enquanto compartilham resumo de livro no TikTok)
A acusação preferida — "você não lê!" — esconde uma ironia deliciosa:
- 72% dos "intelectuais de rede social" citam livros que nunca leram além do título (Fonte: Pesquisa Informal do Twitter, 2023).
- Obras citadas como troféu: "1984" (para chamar Bolsonaro de Big Brother), "O Capital" (para justificar o NFT da Gal Gadot), e "Feminismo para os 99%" (para atacar homens heterossexuais que usam sandália de dedo).Pergunta Incômoda: Se ler Marx fosse garantia de racionalidade, por que a União Soviética acabou em pizza (literalmente, considerando a economia deles)?
Quando a autoimagem colide com a realidade (Ou: por que nenhum esquerdista lassa no teste de turing da coerência)
A esquerda adora se pintar como a Última Trincheira da Razão, mas pratica o que critica:
- Exemplo 1: Defendem "ciência" quando convém (vacinas), mas abraçam pseudociência quando é trendy (cristais energéticos contra o capitalismo).
- Exemplo 2: Chamam a direita de "terraplanista", mas acham que inflação se resolve com tabelamento estatal — a versão econômica de "a Terra é sustentada por tartarugas".
- Exemplo 3: Criticam "fake news", mas compartilham teorias de que o agro "envenena a comida" (enquanto comem sushi de supermercado).Frase-Chave: "Racionalidade seletiva é o novo analfabetismo funcional."
Pergunta Final: Se a esquerda é tão racional, por que não usa a "lógica implacável" para resolver algo além do enquadro perfeito de stories no Instagram?
Enfim
O debate "esquerda racional vs. direita irracional" é só mais um episódio da novela "Brasil: O País que Confunde Opinião com Ataque de Ego". Enquanto uns brincam de "quem tem o QI mais alto", o país queima — literalmente, considerando o Pantanal. Talvez a verdadeira irracionalidade seja gastar energia discutindo superioridade moral enquanto o Wi-Fi cai pela décima vez no dia. Racionalidade não tem lado político. Arrogância, por outro lado, é universal. Sua necessidade de se sentir superior só prova que a lacração é o último refúgio dos fracos de argumento. Agora deviam estudar economia básica — ou pelo menos que parem de achar que "Ah, mas o capitalismo!" é um contra-argumento.
Saudade da época em que a esquerda não se fingia de intelectual.
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 90de72b7:8f68fdc0
2025-05-06 08:23:59
@ 90de72b7:8f68fdc0
2025-05-06 08:23:59🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> () -
 @ 9c9d2765:16f8c2c2
2025-05-07 12:39:48
@ 9c9d2765:16f8c2c2
2025-05-07 12:39:48CHAPTER FIFTEEN
"Have you seen the news?" Sandra’s voice crackled through the phone, her tone urgent and unsettled.
James, seated in his office at JP Enterprises, furrowed his brows. He hadn’t turned on the television yet. "No. What happened?"
"You need to check the headlines immediately. It’s everywhere. They’ve dragged your name through the mud!"
Without another word, James reached for the remote and turned on the large flat-screen mounted on his office wall. The screen lit up with a news report, the broadcaster’s voice sharp and sensational.
“Shocking footage surfaces: JP Enterprises’ President humiliates his only sister in broad daylight!”
Photos of James and Evelyn outside the company played in a dramatic sequence him confronting her, her being escorted out, and his seemingly cold expression. The captions twisted the story:
“Heartless Billionaire?” “President throws out helpless sister for asking money” “The shameful side of JP Enterprises’ leader exposed!”
James leaned back in his chair, eyes narrowing as he watched.
"This is calculated," he muttered under his breath. "Scripted. Twisted."
He turned off the screen and called Sandra back. "I want Tracy's devices checked. Every message, every image. And I want a full trace on the origin of this story. Media outlets don’t run this kind of narrative without a source."
"You think Tracy’s behind it?" Sandra asked, her voice low.
"She took the pictures, I’m sure of it. But she’s not working alone," James replied, voice steely. "This is too well-planned for one person. They’re trying to frame me, twist reality, and attack my image. And I’ll make sure every single one of them is exposed."
Meanwhile, at a discreet location, Mark, Helen, and Tracy gathered to watch the fire they had ignited. Tracy grinned as she scrolled through social media posts and reactions.
"It’s gone viral," she said gleefully. "Everyone thinks that woman’s your sister. It’s everywhere on blogs, gossip pages, even official news networks. The damage is done."
Mark chuckled darkly. "This will shatter his reputation. Let’s see how he enjoys being publicly hated."
Helen, sipping her wine with a satisfied look, added, "It’s only the beginning. Let’s push this narrative harder. We’ll make sure the board at JP Enterprises starts questioning his character."
But little did they know James had already activated his private investigative team. Every file, every message, every trail was being traced.
Back at JP Enterprises, James stood by the window of his office, watching the skyline, his hands in his pockets.
"They want a war?" he said to himself quietly. "Then I’ll give them one. But on my own terms."
His phone buzzed. A message from his chief of cyber-security read:
“We’ve located the media contact. Payment traced to a dummy account linked to Helen Ray.”
James stared at the screen, his jaw tightening.
The day of the much-anticipated 16th Anniversary of JP Enterprises finally arrived, cloaked in glamour, prestige, and tension. The event venue, a grand luxury hall draped in velvet and golden decor, radiated elegance and opulence. Bright lights illuminated the red carpet, and camera flashes sparked like lightning as influential business magnates, city officials, and esteemed guests from far and wide began to pour in.
Among the prominent guests were Helen Ray, Mark, Tracy, and other members of the Ray family. Dressed in designer gowns and tailored suits, they mingled with high society, laughing and sipping champagne, their polished facades hiding the scheme they had carefully orchestrated for the night.
The hall buzzed with anticipation for the arrival of Mr. and Mrs. JP, the founders of the JP Empire. Meanwhile, in a secluded corner of the hall, Helen leaned towards Mark, whispering with a smirk, “She’s on her way. Get ready for the show.”
The “she” Helen referred to was Evelyn, the same woman they had bribed to once again impersonate James’s sister and stir public humiliation. This time, it wouldn’t just be a few photos, they wanted a scandal of epic proportions, a scene so chaotic and public that it would crumble James’s standing in the business world for good.
As guests chatted and live music flowed through the air, James entered the hall in a pristine black tuxedo, exuding power and poise. He walked beside his uncle Charles and his loyal staff, warmly greeting dignitaries and longtime associates. His presence commanded attention, but murmurs soon rippled through the crowd.
Whispers filled the air like wind in dry grass:
"That’s the man from the headline, isn’t he?" "They say he threw his own sister out for asking for help." "Such cruelty… and yet here he is, smiling like a saint."
As James navigated through the crowd with measured grace, Helen sauntered over, her heels clicking on the marble floor, her expression dripping with sarcasm.
“Well, well, if it isn’t our gallant President,” she began, feigning admiration. “I must say, you clean up well for someone who was just exposed in the most shameful news of the year.”
James turned to her with a calm but unreadable gaze. “Helen,” he greeted curtly.
She chuckled. “You really should be more careful with family matters. The public has a long memory, you know.”
Before James could reply, a loud voice broke through the soft music. “James! James! You left me with nothing!”
All heads turned toward the entrance, where Evelyn stumbled in, her appearance carefully staged to look disheveled and distraught. She weaved through the crowd, screaming and sobbing uncontrollably, clutching at the air as security hesitated to intervene.
“Please! I’m your sister! I just needed a little help!” she cried dramatically. “How could you do this to your own blood?!”
Gasps echoed through the grand hall.
Guests froze in place, their judgmental stares directed at James. Cameraman didn’t hesitate to raise their lenses. Phones were pulled out. A social media storm was already brewing in real time.
James stood still, eyes narrowed. He didn’t move, didn’t speak.
Tracy, standing beside Helen, discreetly snapped more photos, already typing up the next round of false headlines to feed into the media engine.
Helen smirked at the chaos and whispered, “This is it. The downfall begins.”
But James wasn’t shaken.
With quiet authority, he raised his hand, and two personal bodyguards appeared from the sidelines. He looked Evelyn square in the eye, then said, loud enough for the nearest guests to hear, “Escort this woman outside. She is not my sister. And she has no place here.”
Evelyn’s cries turned more dramatic, but it was clear to the more discerning eyes in the room that something about her act was off. Her appearance was too deliberate, her performance too exaggerated.
As security led her away, some guests began to murmur with skepticism.
“Wait… that woman doesn’t even resemble him.” “Isn’t it strange she showed up right after that story went viral?” “Could this be a setup?”
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.




