-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ 3bf0c63f:aefa459d
2024-03-19 15:35:35
@ 3bf0c63f:aefa459d
2024-03-19 15:35:35Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ c066aac5:6a41a034
2025-05-10 14:55:46
@ c066aac5:6a41a034
2025-05-10 14:55:46This is an article I wrote which originally appeared in the Pamphleteer, a publication run by a friend in Nashville. It has been edited from the published version, which I will link here for everyone to go check out the website and subscribe.
Step back fifty years in time with me if you will. A simpler time. You wake up in the house you could afford on a single income. Instead of blinding yourself with the light of your cell phone first thing in the morning, you wake up to make breakfast and coffee, your mind unencumbered by the stimulus of a thousand notifications. You can’t doom scroll (nor can you conceptualize what that even means).
You breathe in the moment, smelling your coffee with a deliberate, meditative inhale… As this brief moment of Nirvana passes, you decide to pick up the newspaper. You turn to page nine and see that Andy Kaufman, a comedian/performance artist you’ve seen on Taxi and Saturday Night Live, has declared himself “The Inter-Gender Wrestling Champion of the World.”
You are tempted to think this may be a joke, but suddenly you remember that you stepped back in time from the 21st century. You’re a modern person with evolved values. You ask yourself: is this an elaborate bit from Andy Kaufman, or was he simply ahead of his time? After all, you’re from the modern world where Imane Khelif is celebrated for his stunning and brave foray into women’s boxing (and where strangely, most news sources seem to deny that he’s a man).
All of a sudden, you abandon the bigotry of the past and invite Kaufman to come back with you to our present-day society. As you return to social media, endless notifications, a world full of stimulus, you ponder if Andy’s wrestling foray will be accepted for the beautiful thing that it is, rather than taken, without scrutiny, as a joke.
Exiting my narrative device now to speak to you directly: in the not-too-distant past, Andy Kaufman stepped into the ring and goaded women to wrestle with him. Back then, it was a bit. If such an act were to be replicated today, it would likely be celebrated and defended.
Inter-Gender sports pioneering aside, Kaufman's antics made Tennessee history; wrestling legend Jerry Lawler of Memphis went into the ring with Kaufman to relieve a female contestant and treated him to a Tennessee takedown.
Jerry invited the comedian to bring his act to Memphis. Leading up to the match, Kaufman relentlessly mocked his Southern audience, with jokes flexing his intelligence as "someone from Hollywood" and teaching Tennesseans how to use soap. After challenging a few women to wrestle, he was met with a famous Jerry Lawler Pilediver. This led to a staged feud between the two of them. The pair even reached the Letterman Show, with Kaufman in a neck brace.
As far as I know, Kaufman never identified as a woman. I don’t think he (or others from this period) could have fathomed the trans-sports drama occurring now. That said, there is something to be learned from his elaborate inter-gender wrestling bit: we’re watching the absurd unfold on the public stage. We should refuse to be gaslit and adopt Andy’s terminology and call this what it is: inter-gender sports. Whenever a biological man competes against a woman in any sporting event, we should all insist on letting everyone know that it is officially an inter-gender competition.
Maybe this modern dilemma could be solved if everyone surrounding these events treated the whole thing for what it was: an elaborate joke. Imagine if we treated it like WWE. The whole audience already knows it’s rigged anyway. Such rules of engagement would leave true biological women’s sports alone; it would keep their pride intact and be an assurance of physical protection.
That's the end of my original article. Just for fun, I wanted to add a response comment from my sister-in-law. She read the article and shared her thoughts with me, so I figured why not include them here.
I honestly believe mixed sports should be something that is encouraged more in our society—not because we should ignore biological differences and risks, especially in high-impact sports, but because normalizing this collaboration despite our different skill sets can strengthen women’s inclusivity not only as athletes, but in society as a whole. When I played mixed doubles in tennis and joined coed volleyball teams, I was pushed to improve and often held my own, even when the guys hit harder. And there are many sports like shooting, equestrian, archery, ect... that have nothing to do with “physical strength”. Training alongside men, whether in tennis, boxing, or volleyball, never has diminished my ability—it sharpened it, and that kind of mutual growth reflects a deeper value of inclusivity and respect that extends far beyond the sport. Thats my take! :)
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ c9badfea:610f861a
2025-05-10 13:57:17
@ c9badfea:610f861a
2025-05-10 13:57:17- Install Grayjay (it's free and open source)
- Launch the app and navigate to the Sources tab
- Enable the desired sources (and log in if needed by tapping on the source and scrolling down to Authentication)
- Go to Android Settings > Apps, select Grayjay, and tap Open By Default and Add Link to automatically open supported links with Grayjay
- Enjoy
ℹ️ If you are using Obtainium to install apps, search for Grayjay on Complex Apps
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ 84b0c46a:417782f5
2025-05-10 10:41:20
@ 84b0c46a:417782f5
2025-05-10 10:41:20https://long-form-editor.vercel.app/
β版のため予期せぬ動作が発生する可能性があります。記事を修正する際は事前にバックアップを取ることをおすすめします
機能
-
nostr:npub1sjcvg64knxkrt6ev52rywzu9uzqakgy8ehhk8yezxmpewsthst6sw3jqcw や、 nostr:nevent1qvzqqqqqqypzq4jsz7zew5j7jr4pdfxh483nwq9vyw9ph6wm706sjwrzj2we58nqqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyxhwumn8ghj7mn0wvhxcmmvqqsgcn99jyn5tevxz5zxsrkd7h0sx8fwnqztula423xh83j9wau7cms3vg9c7 のようにnostr:要素を挿入できる
-
:monoice:のようにカスタム絵文字を挿入できる(メニューの😃アイコンから←アイコン変えるかも)
:monopaca_kao:
:kubipaca_karada:
- 新規記事作成と、既存記事の修正ができる
やることやったこと
-
[x] nostr:を投稿するときにtagにいれる
-
[x] 画像をアップロードできるようにする
 できる
できる - [x] 投稿しましたログとかをトースト的なやつでだすようにする
- [ ] レイアウトを整える
- [ ] あとなんか
-
-
 @ a296b972:e5a7a2e8
2025-05-10 11:12:09
@ a296b972:e5a7a2e8
2025-05-10 11:12:09***Satiretüchtigkeit***
Deutschland hat den Satirikern den Krieg erklärt, in dem es Realitäten schafft, die die Phantasie der Autoren überbieten soll. Dazu hat das neu geschaffene Satireministerium die Satiretüchtigkeit ganz oben auf die Agenda gesetzt.
***Notlage***
Die Notlage in Deutschland ist in eine Notlage geraten. Das Ausrufen einer Notlage ist Gebot der Stunde, in der die Notlage der Notlage bekämpft werden kann.
***Grenzsicherung***
Nachdem als eine der ersten Amtshandlungen die deutschen Außengrenzen neu vermessen worden sind, hat sich herausgestellt, dass die Grenzen nur gesichert offenbleiben können. Der Bundesgrenzschutz hat ab sofort die Aufgabe übernommen, ausländisches CO2 an der Grenze aufzuhalten.
***Demokratiebeleidigungsparagraph***
Nach intensiver Recherche des Verfassungsschutzes hat sich herausgestellt, dass die Opposition die seinerzeitige Bundesregierung als „Diktatur“ und „totalitär“ bezeichnet hat. Das ist Demokratiebeleidigung. Ein neuer Paragraph ist bereits in der Ausarbeitung.
***Einhaltung des Koalitionsvertrags***
Aus gesicherten Quellen ist durchgesickert, dass der erste Bundeskanzler zweiter Wahl nun doch nicht sein Amt wahrnehmen will, weil das so nicht im Koalitionsvertrag steht. Schließlich halte man sich an selbigen und die Glaubwürdigkeit dürfe unter keinen Umständen infrage gestellt werden.
***Bundesamt für Fassungslosigkeit***
Das Bundesamt für Verfassungsschutz soll nach dem Willen der Bürger in Bundesamt für Fassungslosigkeit umbenannt werden. Es soll ein deutliches Zeichen gesetzt werden, dass Bürgerbeteiligung in Zukunft ein wichtiger Bestandteil der Politik sein wird.
***Brüssel – Zentrum Belgiens***
Der Bundeskanzler mit Blackrock-Hintergrund hat als eine seiner ersten Amtshandlungen die Neugestaltung des Finanzmarktes in Brüssel angeregt. Der Euro soll in den allermeisten Europäischen Staaten durch den Blackrock-Taler ersetzt werden.
***Salutokratie***
Die WHO hat größte Zustimmung bei der Einführung der Salutokratie erfahren. Die Europäer jubeln und ziehen zu Tausenden mit der EU-Fahne durch die europäischen Hauptstädte. Auf vielen Plakaten ist der folgende Text zu lesen: Die Pharmaindustrie ist ein wichtiger Wirtschaftszweig. Durch unsere Erkrankungen tragen wir einen wichtigen Teil dazu bei, dass sie zu unserem Wohle weiter forschen und neue Medikamente auf den Markt bringen kann.
***Elektronische Patientenakte***
Nach für die Ärzte verpflichtender Einführung der elektronischen Patientenakte konnten letzte Lücken in der Datenoffenheit beseitigt werden. Eine vollständige Transparenz ist jetzt für jedermann gewährleistet. Die Krankenkassen jubeln, weil Ferndiagnosen noch effizienter praktiziert werden können.
***Übermenschliche Leistungen***
Die neue Wirtschaftsministerin hat ihre eigene Messlatte sehr hoch angelegt. Sie will die übermenschlichen Leistungen ihres Vorgängers noch übermenschlicher übertreffen. Ihre Mitarbeiter arbeiten fieberhaft an einer neuen Wortschöpfung, die über den Begriff Übermenschlichkeit hinausgeht. Es ist größte Eile geboten, da eine Neuwahl der Regierung schon in den nächsten Monaten zu erwarten ist.
***Lieferprobleme***
Der brutale Umzug der ehemaligen Außen-Dings in die genderunfreundlichen USA verzögert sich, weil ein bekanntes Versandunternehmen die Lieferkette von feministischen Umzugskartons nicht nachweisen kann. Außerdem wurde von Lagerengpässen für die bevorstehende Auslieferung mobiler Toiletten nach Afrika berichtet.
***Erwischt***
Der ehemalige Corona-Minister II. wurde auf der Rückfahrt nach Berlin (1. Klasse, die ist noch pünktlich) dabei gesehen, wie er im Bistro-Wagen mit Genuss eine leicht versalzene Bockwurst gegessen hat. Nach Ankunft in Berlin musste der Vorrat an erlesenem, durstlöschendem Rotwein aufgefüllt werden.
***Verkauf aus Gewissensgründen***
Der Corona-Minister I. bekannt und berühmt geworden durch seine kaufmännisch geschickt eingefädelten Masken-Deals in bedarfsgerechter Anzahl, sucht derzeit nach einem Käufer für seine bescheidene Hütte in Hamburg, weil er mit dem Erlös den bankkaufmanntechnischen Gewinnüberhang ausgleichen will.
***Drohnennahverkehr***
Das zu verstaatlichende Staatsunternehmen Bahn will spätestens 2028 den Drohnennahverkehr im Halbstundentakt bundesweit einführen. In einer Pressekonferenz wurde bekannt, dass man mit den Logistikfragen im Umgang mit den angeschlossenen Glasfaserkabeln schon sehr große Fortschritte gemacht habe.
***Merz-Frisur***
Vollhaar-Inhaber in der CDU wollen sich zur Unterstützung und als Zeichen der Loyalität eine Merz-Frisur bei einem bekannten Star-Friseur schneiden lassen. Die Wartezeiten betragen derzeit rund 5 Tage. Die Friseur-Innung arbeitet an einem Schnellkurs: Merz-Frisur-tüchtig in drei Wochen!
***Bestsellerliste***
Die ehemalige Bundesmutti hat weitere Prosa in zwei Bänden angekündigt: Die Titel lauten „Einigkeit“ und „Recht“. Derzeit laufen die Maschinen der papierverarbeitenden Hygieneindustrie auf Hochtouren (gut für die Wirtschaft!), da die Bestellliste schon 1000 Seiten lang ist, die jedoch aufgrund der Gleichbehandlung nicht veröffentlicht werden kann.
***Autoindustrie mehrheitlich positiv***
Die Umsätze der deutschen Autoindustrie sollen angeblich um rund 30% eingebrochen sein. Das bedeutet, dass die Mehrheit, also rund 70% noch vorhanden ist, was für die Wirtschaft allgemein sehr gute Nachrichten sind. Außerdem können freie Kapazitäten jetzt zur Produktion von Tankfahrzeugen für Panzer genutzt werden.
***Unterbringungsprobleme gelöst***
Durch die anhaltende Insolvenzwelle deutscher Unternehmen werden Werkshallen frei, die in kürzester Zeit zu weltoffenen Unterkünften umgebaut werden. Erfahrungen aus der Plattenbauweise der ehemaligen DDR konnten hier erfolgreich eingesetzt werden.
***Pandemiebekämpfung***
Deutschland ist zepterhaltend in Präventionsmaßnahmen für zukünftig geplante Pandemien. Federführend soll das virenverseuchte Bargeld stufenweise abgeschafft werden. Ein neues Panik-Paper sieht bereits seiner gut durchdachten Vollendung entgegen.
***Verband der Schreib-Fachkräfte***
Der in Anlehnung des bekannten Satzes von Peter Scholl-Latour formulierte Satz: -Wer Begriffe wie „Kriegstüchtigkeit“ und „Hass und Hetze“ aus dunklen Zeiten verwendet, wird selbst zur dunklen Zeit-, wurde vom Verband der Schreib-Fachkräfte als umstritten eingeordnet.
***Leitkultur***
Experten für den unfallfreien Verzehr von Bananen haben in einer teleskopierten Studie herausgefunden, dass das Wort Leitkultur aus den Worten Leitkuh und Kultur künstlich in einem französischen Labor für Gain-of-Word-Forschung zusammengesetzt wurde. Beweis dafür ist das fehlende Ha, das so in der Natur nicht vorkommt. Der Laborsprung konnte so eindeutig nachgewiesen werden.
***Reformvorschlag***
Bisher galt: Alle Bürgerrechte sind Abwehrrechte gegen den Staat. In einer Ausschusstagung soll jetzt darüber befunden werden, ob diese Formulierung aus Gründen der Delegitimierung des Staates nicht geändert werden kann. Der Reformvorschlag lautet: In einer angestrebten Unseredemokratie soll die Hoheit über die Abwehrrechte der Bürger beim Staat liegen. In demokratischen Einzelverfahren soll darüber entschieden werden, wann und in welchem Umfang sie gegen die Bürger zur Anwendung kommen sollen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ c9badfea:610f861a
2025-05-10 11:08:51
@ c9badfea:610f861a
2025-05-10 11:08:51- Install FUTO Keyboard (it's free and open source)
- Launch the app, tap Switch Input Methods and select FUTO Keyboard
- For voice input, choose FUTO Keyboard (needs mic permission) and grant permission While Using The App
- Configure keyboard layouts under Languages & Models as needed
Adding Support for Non-English Languages
Voice Input
- Download voice input models from the FUTO Keyboard Add-Ons page
- For languages like Chinese, German, Spanish, Russian, French, Portuguese, Korean, and Japanese, download the Multilingual-74 model
- For other languages, download Multilingual-244
- Open FUTO Keyboard, go to Languages & Models, and import the downloaded model under Voice Input
Dictionaries
- Get dictionary files from AOSP Dictionaries
- Open FUTO Keyboard, navigate to Languages & Models, and import the dictionary under Dictionary
ℹ️ When typing, tap the microphone icon to use voice input
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 3bf0c63f:aefa459d
2024-03-19 13:07:02
@ 3bf0c63f:aefa459d
2024-03-19 13:07:02Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ 7459d333:f207289b
2025-05-10 10:38:56
@ 7459d333:f207289b
2025-05-10 10:38:56Description: Just as Bitcoin enabled sovereignty over money, a decentralized shipping protocol would enable sovereignty over trade. An LN/Bisq inspired shipping protocol could create an unstoppable free market.
Bitcoin gave us monetary sovereignty, freeing us from central bank manipulation, inflation, and censorship. But there's a missing link in our freedom journey: the physical world of goods.
The Problem: Even with Bitcoin, global trade remains at the mercy of: - Arbitrary tariffs and import restrictions - Political censorship of goods - Privacy invasion of shipping information - Centralized shipping carriers
The Vision: A decentralized shipping protocol with these properties:
- "Onion-routed" packages: Each carrier only knows the previous and next hop
- Bitcoin-secured multi-sig escrow: Funds locked until package delivery confirmed
- Incentive alignment: Carriers set their own fees based on risk assessment
- Privacy tiers: Options for inspected vs. sealed packages with appropriate pricing
- End-to-end sovereignty: Sender and receiver maintain control, intermediate carriers just fulfill their role
How it could work:
- Sender creates shipping request with package details and destination
- Protocol finds optimal route through independent carriers
- Each hop secured by multi-sig deposits larger than package value
- Carriers only see next hop, not ultimate destination
- Reputation systems and economic incentives maintain integrity
This creates a free market where any individual can participate as a carrier, earning Bitcoin for facilitating trade. Just like Lightning Network nodes, anyone can open "channels" with trusted partners.
Impact: This would enable true free market principles globally, making artificial trade barriers obsolete and empowering individuals to engage in voluntary exchange regardless of geographic or political boundaries.
There are a lot of challenges. But the first question is if this is a real problem and if its worth solving it.
What components would need development first? How would you solve the physical handoff challenges?
originally posted at https://stacker.news/items/976326
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 90c656ff:9383fd4e
2025-05-10 08:02:51
@ 90c656ff:9383fd4e
2025-05-10 08:02:51Bitcoin was conceived as a decentralized system where anyone can participate in the network, validate transactions, and help secure the system. However, over the years, Bitcoin mining has become increasingly concentrated in certain regions of the world, raising concerns about its decentralization and security. This debate has sparked a range of opinions, with some arguing that mining centralization could compromise Bitcoin's fundamental principles.
- Why has mining become centralized in some countries?
Bitcoin mining requires a significant amount of energy and specialized equipment, known as ASICs. Due to factors like electricity costs, climate, and regulation, some regions have become mining hubs, attracting large-scale operations. The main reasons for this concentration include:
01 - Electricity cost: Countries with cheap electricity, such as China (before the ban), Kazakhstan, and some regions of the United States, became mining centers because operational costs are significantly lower.
02 - Favorable climate: Locations with colder temperatures reduce the need for cooling systems for mining equipment, making operations more efficient.
03 - Regulation and tax incentives: Some countries foster favorable environments for mining by offering tax benefits or energy sector incentives.
- Impacts of mining centralization
The centralization of mining in certain countries raises concerns about control over the Bitcoin network. Key risks include:
01 - Censorship risk: If a country with a high concentration of miners decides to regulate or restrict mining, it could temporarily affect the network, making it more vulnerable to attacks or censorship.
02 - 51% attack: One of the biggest concerns is the possibility of a group of miners controlling more than 50% of the network’s hash power, which could allow transaction manipulation. While unlikely, this scenario is a persistent worry in the Bitcoin community.
03 - Reliance on centralized infrastructure: If mining is concentrated in a few regions, failures in local infrastructure—such as power outages or natural disasters—can significantly impact the network.
- Measures to decentralize mining
Despite the trend toward centralization, the Bitcoin network remains resilient, and there are initiatives to make mining more distributed. Some solutions include:
01 - Home and community mining: Encouraging small-scale mining can help distribute hash power more evenly.
02 - Use of renewable energy in diverse regions: As more miners adopt renewable sources, new locations are emerging as decentralized mining centers.
03 - Miner exodus: After China’s mining ban in 2021, many operations relocated to countries like the United States, Canada, and nations in Latin America, helping diversify the network.
In summary, the centralization of mining in certain regions poses a challenge for Bitcoin but does not mean the network is in immediate danger. As the industry evolves, mining is expected to become increasingly distributed, helping to safeguard the network’s security and decentralization. While it's crucial to keep an eye on this issue, Bitcoin continues to prove its resilience, constantly adapting to changes in the mining landscape.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 318ebaba:9a262eae
2025-05-10 07:40:00
@ 318ebaba:9a262eae
2025-05-10 07:40:00When connecting to multiple relays in the Nostr protocol, users may encounter several challenges that can affect their overall experience. Here are some of the key issues:
Challenges of Connecting to Multiple Relays
-
Performance Issues: The lightweight design of Nostr relays can lead to performance bottlenecks, especially when many users are connected simultaneously. This can result in slow message delivery or even failures in posting messages if the relays are overwhelmed[1][2][32].
-
Reliability and Connectivity: Users may experience connectivity problems with certain relays, which can lead to inconsistent access to messages or delays in communication. If a relay goes offline or has connectivity issues, it can disrupt the flow of information, making it difficult for users to send or receive messages reliably[3][4][18].
-
Data Synchronization: As users connect to multiple relays, ensuring that data is synchronized across these relays can be challenging. Inconsistent data states may arise if different relays store messages differently or if there are delays in message propagation. This can lead to confusion about which messages have been sent or received[7][41].
-
Configuration Complexity: Managing connections to multiple relays requires a certain level of technical knowledge. Users need to configure their clients properly to connect to various relays, which can be daunting for those less familiar with the technology. Misconfigurations can lead to connection failures or suboptimal performance[4][21].
-
Spam and Quality Control: With the open nature of Nostr, some relays may be more susceptible to spam or low-quality content. Users connecting to multiple relays might encounter a higher volume of irrelevant or unwanted messages, which can detract from the overall user experience[6][32].
-
Security Concerns: When using multiple relays, users must be cautious about the security of their connections. Not all relays may implement the same level of security, and connecting to less secure relays could expose users to risks such as data interception or unauthorized access to their messages[26][27].
In summary, while connecting to multiple relays in Nostr offers benefits such as redundancy and improved access to information, users must navigate various challenges related to performance, reliability, configuration, and security. Addressing these issues is crucial for a smooth and effective experience on the Nostr network.
[1] https://forum.dfinity.org/t/introducing-replicatr-enhancing-nostr-with-internet-computer-integration/31861 [2] https://medium.com/coinmonks/a-deep-dive-into-nostr-clients-with-technical-insights-and-code-snippets-b1666bb11fac [3] https://nostr.com/nevent1qqsfvjvg73wxdn7mda28m704r2zv9lnzlcdgh8r0g52lfvy2wj7uw4czyq32rylmsmre84lhxdypy6jlu4dt3fxfwkq9a0p0lqdl9y8hsp0hur4fuw4 [4] https://www.reddit.com/r/nostr/comments/1e6nm68/new_nostream_relay_created_problems_with_publish/ [5] https://www.lynalden.com/the-power-of-nostr/ [6] https://bitcoinmagazine.com/technical/how-nostr-can-improve-bitcoin-privacy [7] https://barelybuggy.blog/2024/11/26/mostr-offline/ [8] https://github.com/scsibug/nostr-rs-relay/issues/126 [9] https://community.umbrel.com/t/nostr-relay-troubleshooting/17828 [10] https://research.dorahacks.io/2024/04/30/nostr-relay-incentive/ [11] https://community.start9.com/t/issue-confirming-nostr-relay/1682 [12] https://arxiv.org/html/2402.05709v1 [13] https://community.umbrel.com/t/nostr-relay-not-connecting/11401 [14] https://www.purplerelay.com/troubleshooting-common-issues-with-nostr-relay-server-a-users-guide/ [15] https://news.ycombinator.com/item?id=35694029 [16] https://substack.com/home/post/p-158872714?utm_campaign=post&utm_medium=web [17] https://stacker.news/items/142013 [18] https://www.reddit.com/r/nostr/comments/1h6admk/are_these_relays_working/ [19] https://news.ycombinator.com/item?id=33746360 [20] https://github.com/scsibug/nostr-rs-relay/issues/195 [21] https://www.purplerelay.com/how-to-run-a-nostr-relay-a-step-by-step-guide/ [22] https://denostr.medium.com/the-future-of-social-communication-nostrs-origins-and-the-next-destination-in-social-networking-27f0c901d7ae [23] https://nostr.com/nevent1qqsqwklh29cvf3z0skhh77xyqf3m53xkppcttf3c8nuc2jqteulfx0czyqcgr7epv9hha2v9afp99l5wl0ljna0zum59fzyhl9v8pgv5xlhf5ava642 [24] https://www.reddit.com/r/nostr/comments/15fyr6r/pervasive_private_key_sharing_seems_dangerous/ [25] https://whtwnd.com/agoracitizen.network/3l2fysaripd2q [26] https://ron.stoner.com/nostr_Security_and_Privacy/ [27] https://forums.puri.sm/t/about-what-is-nostr/20764 [28] https://github.com/nostr-protocol/nips/issues/107 [29] https://medium.com/@volodymyrpavlyshyn/security-features-of-nostr-a0276a22e815 [30] https://nostr.com/nevent1qqspd8fh3tplxtfhjpka3y3glzh63v3ygsdhacyq8dvyrnxtvl09lpczyr2v7dprke9lad2qk0svug55vxguqv7n3dwn9vm63u8n5n84znxjxedjf6c [31] https://nostr.com/nevent1qqs8e2su6n8m2xtg45qdjw7rdcq6w3g5guvt085h52qhg25wxn755sczyrh26kg89z95jqaz4xkex7kaw2t36twtc75vmrfx2k3p3jqvhfa8vzan82f [32] https://www.cointribune.com/en/nostr-et-la-censure-pourquoi-un-reseau-social-decentralise-est-essentiel-2/ [33] https://nostr.com/nevent1qqsv86d756zcw32x0zcvqmr924y5sltvwqud0dywny83ndee30zzrmczyrh26kg89z95jqaz4xkex7kaw2t36twtc75vmrfx2k3p3jqvhfa8vwpfv29 [34] https://github.com/nbd-wtf/nostr-tools/issues [35] https://www.voltage.cloud/blog/the-growth-of-nostr-the-era-of-decentralization [36] https://medium.com/@BingVentures/status-quo-challenges-and-prospect-of-decentralized-social-networks-18f9584f2e8d [37] https://www.reddit.com/r/RedditAlternatives/comments/14s8ao4/greetings_im_here_to_tell_you_about_nostr_a/ [38] https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [39] https://github.com/mayneyao/eidos/issues/129 [40] https://www.reddit.com/r/nostr/comments/115a8et/data_duplication_and_distribution_in_nostr_relays/ [41] https://github.com/open-nostr/nostar [42] https://nostr.com/nevent1qqsryg8zuc9rdwldat385al24mdt56wanc6g6hfymy8l9tgtmzsc4nspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhg85cx73 [43] https://ckbcn.xlog.app/Nostr-sheng-tai-fa-zhan-xian-zhuang-ji-wen-ti?locale=en [44] https://nostr.com/naddr1qqc92mnvda3kk6twvuk5ummnw3ez6ued2phhgetww35kzmpdwa5hg6pdfehhgetyv43kktt08p5hscnkqgsr7acdvhf6we9fch94qwhpy0nza36e3tgrtkpku25ppuu80f69kfqrqsqqqa28aknkml
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 95543309:196c540e
2025-05-10 07:29:13
@ 95543309:196c540e
2025-05-10 07:29:13:bob:
rant
why the fuck bunkers and stuff try to enctypt long text articles with nip 44
end rant
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ 0c469779:4b21d8b0
2025-03-11 10:52:49
@ 0c469779:4b21d8b0
2025-03-11 10:52:49Sobre el amor
Mi percepción del amor cambió con el tiempo. Leer literatura rusa, principalmente a Dostoevsky, te cambia la perspectiva sobre el amor y la vida en general.
Por mucho tiempo mi visión sobre la vida es que la misma se basa en el sufrimiento: también la Biblia dice esto. El amor es igual, en el amor se sufre y se banca a la otra persona. El problema es que hay una distinción de sufrimientos que por mucho tiempo no tuve en cuenta. Está el sufrimiento del sacrificio y el sufrimiento masoquista. Para mí eran indistintos.
Para mí el ideal era Aliosha y Natasha de Humillados y Ofendidos: estar con alguien que me amase tanto como Natasha a Aliosha, un amor inclusive autodestructivo para Natasha, pero real. Tiene algo de épico, inalcanzable. Un sufrimiento extremo, redentor, es una vara altísima que en la vida cotidiana no se manifiesta. O el amor de Sonia a Raskolnikov, quien se fue hasta Siberia mientras estuvo en prisión para que no se quede solo en Crimen y Castigo.
Este es el tipo de amor que yo esperaba. Y como no me pasó nada tan extremo y las situaciones que llegan a ocurrir en mi vida están lejos de ser tan extremas, me parecía hasta poco lo que estaba pidiendo y que nadie pueda quedarse conmigo me parecía insuficiente.
Ahora pienso que el amor no tiene por qué ser así. Es un pensamiento nuevo que todavía estoy construyendo, y me di cuenta cuando fui a la iglesia, a pesar de que no soy cristiano. La filosofía cristiana me gusta. Va conmigo. Tiene un enfoque de humildad, superación y comunidad que me recuerda al estoicismo.
El amor se trata de resaltar lo mejor que hay en el otro. Se trata de ser un plus, de ayudar. Por eso si uno no está en su mejor etapa, si no se está cómodo con uno mismo, no se puede amar de verdad. El amor empieza en uno mismo.
Los libros son un espejo, no necesariamente vas a aprender de ellos, sino que te muestran quién sos. Resaltás lo que te importa. Por eso a pesar de saber los tipos de amores que hay en los trabajos de Dostoevsky, cometí los mismos errores varias veces.
Ser mejor depende de uno mismo y cada día se pone el granito de arena.
-
 @ 318ebaba:9a262eae
2025-05-10 07:19:47
@ 318ebaba:9a262eae
2025-05-10 07:19:47Relays play a crucial role in the Nostr communication protocol, serving as the backbone of its decentralized architecture. Here’s an overview of their functions and significance:
Functions of Nostr Relays
-
Data Storage and Broadcasting: Relays act as intermediaries that store and distribute messages between users. When a user sends a message, it is transmitted to one or more relays, which then broadcast that message to other connected clients. This decentralized approach ensures that no single entity controls the flow of information, enhancing censorship resistance[1][2][6].
-
Interoperability: Users can connect to multiple relays simultaneously, allowing them to access the same content across different applications. This interoperability means that messages can be shared and retrieved from various clients without being tied to a specific platform, promoting a more flexible user experience[4][11].
-
User Control: Anyone can run their own relay, which empowers users to maintain control over their data and interactions. By operating a personal relay, users can ensure that their messages are stored and accessible without relying on third-party services, thus enhancing privacy and security[3][7][11].
-
Performance and Reliability: The performance of a Nostr client can be influenced by the relays it connects to. If a relay is slow or unreliable, it can affect the overall user experience. Users are encouraged to choose or add multiple relays to improve message delivery speed and reliability[7][8][11].
Types of Relays
-
Public and Private Relays: There are both public and private relays available. Public relays are free to use, while private relays may charge fees. Paid relays often provide better performance and reduced spam, as the cost can deter malicious users from flooding the network with unwanted content[6][7][14].
-
Self-Hosted Relays: For those who want maximum control and privacy, setting up a self-hosted relay is an option. This allows users to manage their own data and ensure that their communications are not subject to external censorship or data loss[4][7].
In summary, relays are essential to the Nostr protocol, facilitating decentralized communication by storing, broadcasting, and managing messages across a network of users. They enhance user autonomy, improve performance, and contribute to the overall resilience of the Nostr ecosystem. [1] https://www.voltage.cloud/blog/the-essential-guide-to-nostr-relays [2] https://substack.com/home/post/p-158872714?utm_campaign=post&utm_medium=web [3] https://www.purplerelay.com/how-to-run-a-nostr-relay-a-step-by-step-guide/ [4] https://medium.com/@michael.leigh.stewart/nostr-series-part-3-setting-up-a-relay-6f9ca426e43e [5] https://www.voltage.cloud/blog/understanding-nostr-data-storage-relays-and-decentralization [6] https://www.ccn.com/education/what-is-nostr-and-how-to-start-using-nostr/ [7] https://nostr.how/en/relays [8] https://blog.theya.us/what-is-nostr/ [9] https://www.cointribune.com/en/nostr-pour-les-debutants-tout-ce-que-vous-devez-savoir-sur-le-protocole-2/ [10] https://community.umbrel.com/t/introducing-the-official-nostr-relay-app/11339 [11] https://nostr.com/ [12] https://www.habyb.com/blog/nostr-what-is-this-protocol-and-how-does-it-work/ [13] https://www.reddit.com/r/nostr/comments/15jmhpi/purpose_of_free_vs_paid_relay/ [14] https://nostr.com/relays [15] https://www.reddit.com/r/nostr/comments/115cgcu/whats_the_point_of_adding_more_and_more_relays_do/ [16] https://messari.io/copilot/share/understanding-nostr-f00aa3df-d02c-4381-91f5-9a103b8e25ce
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: "numbeo" with satoshis
This site has a crowdsourced database of cost-of-living in many countries and cities: https://www.numbeo.com/cost-of-living/ and it sells the data people write there freely. It's wrong!
Could be an fruitful idea to pay satoshis for people to provide data.
-
 @ 318ebaba:9a262eae
2025-05-10 07:06:45
@ 318ebaba:9a262eae
2025-05-10 07:06:45Nostr, which stands for "Notes and Other Stuff Transmitted by Relays," is a decentralized communication protocol designed to facilitate the exchange of messages without relying on centralized servers. This innovative framework allows users to create, broadcast, and receive messages freely, emphasizing user empowerment and censorship resistance.
Key Features of Nostr
-
Decentralization: Unlike traditional social media platforms, Nostr operates on a network of relays, which are servers that anyone can run. This structure eliminates the control that a single entity can exert over the platform, thereby reducing the risk of censorship and enhancing user privacy[1][4][5].
-
Open Protocol: Nostr is not an application itself but a protocol that developers can use to build various applications. This openness allows for a wide range of services, from social media to messaging, all built on the same underlying technology. Users can access multiple applications using a single public/private key pair, making it easier to manage their online identities[2][3][4].
-
Censorship Resistance: One of the primary motivations behind Nostr's creation is to provide a platform where users can communicate without fear of censorship. This is particularly appealing to those disillusioned with traditional social media platforms that often impose restrictions on content[5][10].
-
User Control: Nostr empowers users by allowing them to control their data and interactions. Users can choose which relays to connect to and can run their own relays, ensuring that they are not dependent on any single service provider[4][5][7].
-
Cryptographic Security: The protocol employs public-key cryptography to secure messages and verify identities, similar to how Bitcoin operates. This ensures that messages are authentic and have not been tampered with during transmission[5][10].
Applications and Community
Nostr has gained traction among various communities, particularly within the cryptocurrency space, where figures like Jack Dorsey and Edward Snowden have expressed support for its potential to reshape online communication. The protocol's design allows for a variety of applications, including social media platforms, chat services, and content sharing tools, all of which can interoperate seamlessly[2][3][5].
In summary, Nostr represents a significant shift in how digital communication can be structured, prioritizing decentralization, user autonomy, and resistance to censorship, making it a compelling alternative to conventional social media platforms. [1] https://threenine.blog/posts/what-is-nostr [2] https://www.forbes.com/sites/digital-assets/2023/04/11/how-to-get-started-with-nostr/ [3] https://www.forbes.com/sites/digital-assets/2024/07/17/your-guide-to-nostr-the-decentralized-network-for-everything/ [4] https://www.ledger.com/academy/glossary/nostr [5] https://river.com/learn/what-is-nostr/ [6] https://www.cointribune.com/en/comment-utiliser-nostr-guide-pour-debutants-2/ [7] https://www.ccn.com/education/what-is-nostr-and-how-to-start-using-nostr/ [8] https://nostr.com/ [9] https://mylessnider.com/articles/why-im-excited-about-nostr [10] https://en.wikipedia.org/wiki/Nostr [11] https://nostr.how/en/what-is-nostr [12] https://nostr.org/ [13] https://medium.com/@colaru/an-introduction-to-nostr-protocol-dbc774ac797c [14] https://www.linkedin.com/pulse/what-nostr-manfred-van-doorn-nf9ce [15] https://www.cointribune.com/en/nostr-pour-les-debutants-tout-ce-que-vous-devez-savoir-sur-le-protocole-2/ [16] https://www.reddit.com/r/Bitcoin/comments/17j5glg/do_people_in_this_sub_know_about_nostr/ [17] https://www.voltage.cloud/blog/the-essential-guide-to-nostr-relays [18] https://www.reddit.com/r/nostr/comments/1i6t4g7/explain_how_nostr_works_like_im_a_5_year_old/ [19] https://github.com/nostr-protocol/nostr
-
-
 @ 4857600b:30b502f4
2025-03-11 01:58:19
@ 4857600b:30b502f4
2025-03-11 01:58:19Key Findings
- Researchers at the University of Cambridge discovered that aspirin can help slow the spread of certain cancers, including breast, bowel, and prostate cancers
- The study was published in the journal Nature
How Aspirin Works Against Cancer
- Aspirin blocks thromboxane A2 (TXA2), a chemical produced by blood platelets
- TXA2 normally weakens T cells, which are crucial for fighting cancer
- By inhibiting TXA2, aspirin "unleashes" T cells to more effectively target and destroy cancer cells
Supporting Evidence
- Previous studies showed regular aspirin use was linked to:
- 31% reduction in cancer-specific mortality in breast cancer patients
- 9% decrease in recurrence/metastasis risk
- 25% reduction in colon cancer risk
Potential Impact
- Aspirin could be particularly effective in early stages of cancer
- It may help prevent metastasis, which causes 90% of cancer fatalities
- As an inexpensive treatment, it could be more accessible globally than antibody-based therapies
Cautions
- Experts warn against self-medicating with aspirin
- Potential risks include internal bleeding and stomach ulcers
- Patients should consult doctors before starting aspirin therapy
Next Steps
- Large-scale clinical trials to determine which cancer types and patients would benefit most
- Development of new drugs that mimic aspirin's benefits without side effects
Citations: Natural News
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Lightning and its fake HTLCs
Lightning is terrible but can be very good with two tweaks.
How Lightning would work without HTLCs
In a world in which HTLCs didn't exist, Lightning channels would consist only of balances. Each commitment transaction would have two outputs: one for peer
A, the other for peerB, according to the current state of the channel.When a payment was being attempted to go through the channel, peers would just trust each other to update the state when necessary. For example:
- Channel
AB's balances areA[10:10]B(in sats); Asends a 3sat payment throughBtoC;AasksBto route the payment. ChannelABdoesn't change at all;Bsends the payment toC,Caccepts it;- Channel
BCchanges fromB[20:5]CtoB[17:8]C; BnotifiesAthe payment was successful,Aacknowledges that;- Channel
ABchanges fromA[10:10]BtoA[7:13]B.
This in the case of a success, everything is fine, no glitches, no dishonesty.
But notice that
Acould have refused to acknowledge that the payment went through, either because of a bug, or because it went offline forever, or because it is malicious. Then the channelABwould stay asA[10:10]BandBwould have lost 3 satoshis.How Lightning would work with HTLCs
HTLCs are introduced to remedy that situation. Now instead of commitment transactions having always only two outputs, one to each peer, now they can have HTLC outputs too. These HTLC outputs could go to either side dependending on the circumstance.
Specifically, the peer that is sending the payment can redeem the HTLC after a number of blocks have passed. The peer that is receiving the payment can redeem the HTLC if they are able to provide the preimage to the hash specified in the HTLC.
Now the flow is something like this:
- Channel
AB's balances areA[10:10]B; Asends a 3sat payment throughBtoC:AasksBto route the payment. Their channel changes toA[7:3:10]B(the middle number is the HTLC).Boffers a payment toC. Their channel changes fromB[20:5]CtoB[17:3:5]C.CtellsBthe preimage for that HTLC. Their channel changes fromB[17:3:5]CtoB[17:8]C.BtellsAthe preimage for that HTLC. Their channel changes fromA[7:3:10]BtoA[7:13]B.
Now if
Awants to trickBand stop respondingBdoesn't lose money, becauseBknows the preimage,Bjust needs to publish the commitment transactionA[7:3:10]B, which gives him 10sat and then redeem the HTLC using the preimage he got fromC, which gives him 3 sats more.Bis fine now.In the same way, if
Bstops responding for any reason,Awon't lose the money it put in that HTLC, it can publish the commitment transaction, get 7 back, then redeem the HTLC after the certain number of blocks have passed and get the other 3 sats back.How Lightning doesn't really work
The example above about how the HTLCs work is very elegant but has a fatal flaw on it: transaction fees. Each new HTLC added increases the size of the commitment transaction and it requires yet another transaction to be redeemed. If we consider fees of 10000 satoshis that means any HTLC below that is as if it didn't existed because we can't ever redeem it anyway. In fact the Lightning protocol explicitly dictates that if HTLC output amounts are below the fee necessary to redeem them they shouldn't be created.
What happens in these cases then? Nothing, the amounts that should be in HTLCs are moved to the commitment transaction miner fee instead.
So considering a transaction fee of 10000sat for these HTLCs if one is sending Lightning payments below 10000sat that means they operate according to the unsafe protocol described in the first section above.
It is actually worse, because consider what happens in the case a channel in the middle of a route has a glitch or one of the peers is unresponsive. The other node, thinking they are operating in the trustless protocol, will proceed to publish the commitment transaction, i.e. close the channel, so they can redeem the HTLC -- only then they find out they are actually in the unsafe protocol realm and there is no HTLC to be redeemed at all and they lose not only the money, but also the channel (which costed a lot of money to open and close, in overall transaction fees).
One of the biggest features of the trustless protocol are the payment proofs. Every payment is identified by a hash and whenever the payee releases the preimage relative to that hash that means the payment was complete. The incentives are in place so all nodes in the path pass the preimage back until it reaches the payer, which can then use it as the proof he has sent the payment and the payee has received it. This feature is also lost in the unsafe protocol: if a glitch happens or someone goes offline on the preimage's way back then there is no way the preimage will reach the payer because no HTLCs are published and redeemed on the chain. The payee may have received the money but the payer will not know -- but the payee will lose the money sent anyway.
The end of HTLCs
So considering the points above you may be sad because in some cases Lightning doesn't use these magic HTLCs that give meaning to it all. But the fact is that no matter what anyone thinks, HTLCs are destined to be used less and less as time passes.
The fact that over time Bitcoin transaction fees tend to rise, and also the fact that multipart payment (MPP) are increasedly being used on Lightning for good, we can expect that soon no HTLC will ever be big enough to be actually worth redeeming and we will be at a point in which not a single HTLC is real and they're all fake.
Another thing to note is that the current unsafe protocol kicks out whenever the HTLC amount is below the Bitcoin transaction fee would be to redeem it, but this is not a reasonable algorithm. It is not reasonable to lose a channel and then pay 10000sat in fees to redeem a 10001sat HTLC. At which point does it become reasonable to do it? Probably in an amount many times above that, so it would be reasonable to even increase the threshold above which real HTLCs are made -- thus making their existence more and more rare.
These are good things, because we don't actually need HTLCs to make a functional Lightning Network.
We must embrace the unsafe protocol and make it better
So the unsafe protocol is not necessarily very bad, but the way it is being done now is, because it suffers from two big problems:
- Channels are lost all the time for no reason;
- No guarantees of the proof-of-payment ever reaching the payer exist.
The first problem we fix by just stopping the current practice of closing channels when there are no real HTLCs in them.
That, however, creates a new problem -- or actually it exarcebates the second: now that we're not closing channels, what do we do with the expired payments in them? These payments should have either been canceled or fulfilled before some block x, now we're in block x+1, our peer has returned from its offline period and one of us will have to lose the money from that payment.
That's fine because it's only 3sat and it's better to just lose 3sat than to lose both the 3sat and the channel anyway, so either one would be happy to eat the loss. Maybe we'll even split it 50/50! No, that doesn't work, because it creates an attack vector with peers becoming unresponsive on purpose on one side of the route and actually failing/fulfilling the payment on the other side and making a profit with that.
So we actually need to know who is to blame on these payments, even if we are not going to act on that imediatelly: we need some kind of arbiter that both peers can trust, such that if one peer is trying to send the preimage or the cancellation to the other and the other is unresponsive, when the unresponsive peer comes back, the arbiter can tell them they are to blame, so they can willfully eat the loss and the channel can continue. Both peers are happy this way.
If the unresponsive peer doesn't accept what the arbiter says then the peer that was operating correctly can assume the unresponsive peer is malicious and close the channel, and then blacklist it and never again open a channel with a peer they know is malicious.
Again, the differences between this scheme and the current Lightning Network are that:
a. In the current Lightning we always close channels, in this scheme we only close channels in case someone is malicious or in other worst case scenarios (the arbiter is unresponsive, for example). b. In the current Lightning we close the channels without having any clue on who is to blame for that, then we just proceed to reopen a channel with that same peer even in the case they were actively trying to harm us before.
What is missing? An arbiter.
The Bitcoin blockchain is the ideal arbiter, it works in the best possible way if we follow the trustless protocol, but as we've seen we can't use the Bitcoin blockchain because it is expensive.
Therefore we need a new arbiter. That is the hard part, but not unsolvable. Notice that we don't need an absolutely perfect arbiter, anything is better than nothing, really, even an unreliable arbiter that is offline half of the day is better than what we have today, or an arbiter that lies, an arbiter that charges some satoshis for each resolution, anything.
Here are some suggestions:
- random nodes from the network selected by an algorithm that both peers agree to, so they can't cheat by selecting themselves. The only thing these nodes have to do is to store data from one peer, try to retransmit it to the other peer and record the results for some time.
- a set of nodes preselected by the two peers when the channel is being opened -- same as above, but with more handpicked-trust involved.
- some third-party cloud storage or notification provider with guarantees of having open data in it and some public log-keeping, like Twitter, GitHub or a Nostr relay;
- peers that get paid to do the job, selected by the fact that they own some token (I know this is stepping too close to the shitcoin territory, but could be an idea) issued in a Spacechain;
- a Spacechain itself, serving only as the storage for a bunch of
OP_RETURNs that are published and tracked by these Lightning peers whenever there is an issue (this looks wrong, but could work).
Key points
- Lightning with HTLC-based routing was a cool idea, but it wasn't ever really feasible.
- HTLCs are going to be abandoned and that's the natural course of things.
- It is actually good that HTLCs are being abandoned, but
- We must change the protocol to account for the existence of fake HTLCs and thus make the bulk of the Lightning Network usage viable again.
See also
- Channel
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28There's a problem with using Git concepts for everything
We've been seeing a surge in applications that use Git to store other things than code, or that are based on Git concepts and so enable "forking, merging and distributed collaboration" for things like blogs, recipes, literature, music composition, normal files in a filesystem, databases.
The problem with all this is they will either:
- assume the user will commit manually and expect that commit to be composed by a set of meaningful changes, and the commiter will also add a message to the commit, describing that set of meaningful, related changes; or
- try to make the committing process automatic and hide it from the user, so will producing meaningless commits, based on random changes in many different files (it's not "files" if we are talking about a recipe or rows in a table, but let's say "files" for the sake of clarity) that will probably not be related and not reduceable to a meaningful commit message, or maybe the commit will contain only the changes to a single file, and its commit message would be equivalent to "updated
<name of the file>".
Programmers, when using Git, think in Git, i.e., they work with version control in their minds. They try hard to commit together only sets of meaningful and related changes, even when they happen to make unrelated changes in the meantime, and that's why there are commands like
git add -pand many others.Normal people, to whom many of these git-based tools are intended to (and even programmers when out of their code-world), are much less prone to think in Git, and that's why another kind of abstraction for fork-merge-collaborate in non-code environments must be used.
-
 @ ba3b4b1d:eadff0d3
2025-05-09 23:53:41
@ ba3b4b1d:eadff0d3
2025-05-09 23:53:41Existem seres do tipo "troll" no folclore Português conhecidos como Trasgos, semelhantes a gnomos e duendes. Na interpretação da Vanessa Fidalgo, duende e trasgo seriam sinónimos e ela descreve-os como sendo "refilões, rebeldes, de pequena estatura, nariz arrebatado, tez rugosa, e o povo chama-lhes trasgos ou maruxinhos, que é como quem diz, duendes!"
Escondem-se nas florestas rurais e são famosos por pregar partidas aos viajantes, especialmente aos pastores de ovelhas. Essas criaturas anãs podem aparecer nas lareiras e tornar-se bastante invasivas. Mesmo que alguém se mude de casa, os Trasgos seguem-nos até ao novo lar. Existem rituais que, alegadamente, conseguem expulsar os Trasgos de uma casa.
A natureza jovial e traquina destes seres está relacionada com um Fadário Galego, em que se acreditava que eles eram resultado de crianças que morriam novas, em que a alma ficava presa a uma casa ou a um local agrícola relacionado com a família.
No folclore leonês, são chamados de Trasgos. No folclore castelhano e aragonês, são conhecidos como Martinitos.

Nas Astúrias, o trasgo é conhecido por nomes diferentes, dependendo da localização. Ele é conhecido como Trasno, Cornín ou Xuan Dos Camíos nas Astúrias ocidentais. Ele é conhecido como Gorretín Colorau ou aquele com o "gorro encarnado" (ambos significando "pequeno chapéu vermelho"), nas Astúrias orientais.
Na mitologia Celta, são conhecidos por "Far Darrig" que significa "homem vermelho".
Algumas interpretações sugerem que encarna a natureza caprichosa do destino, lembrando os humanos da imprevisibilidade da jornada da vida. Outras vêem-no como uma representação dos aspectos selvagens e indomáveis do mundo natural, existindo nas margens da compreensão humana.
-
 @ ba3b4b1d:eadff0d3
2025-05-09 23:51:07
@ ba3b4b1d:eadff0d3
2025-05-09 23:51:07Outro indício de que as relações entre Celtas e Ibéros não foi unilateral é a existência em solo Irlandês da planta Erica mackaiana, conhecida como Urze Galego ou Asturiano
Esta é uma espécie de urze encontrada exclusivamente nas costas da Galiza, Irlanda, Astúrias e Cantábria. Estas plantas estão sempre localizadas a menos de 10 km das margens, na proximidade de povoações costeiras da Idade do Ferro.
Não são nativas da Irlanda. Há indícios que sugerem que muitas espécies da fauna hiberno-lusitana chegaram à Irlanda devido a uma intensa actividade comercial exclusivamente marítima. Por exemplo, a Erica erigena, originalmente nativa da Gália e da Hispânia, é teoricamente considerada como tendo sido transplantada para solo irlandês através do comércio de vinho galaico.
Os indícios de contrabando de E. mackiana incluem o facto de serem encontradas apenas em portos que levam a rotas interiores e em baías isoladas. O local com a maior concentração desta espécie é o Pântano de Roundstone, situado entre duas enseadas isoladas, atravessado por uma antiga estrada de Connemara, uma área com uma longa história de contrabando. Em Kerry, há uma estrada conhecida como Trilho dos Contrabandistas, que foi a principal área de distribuição desta espécie.

-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
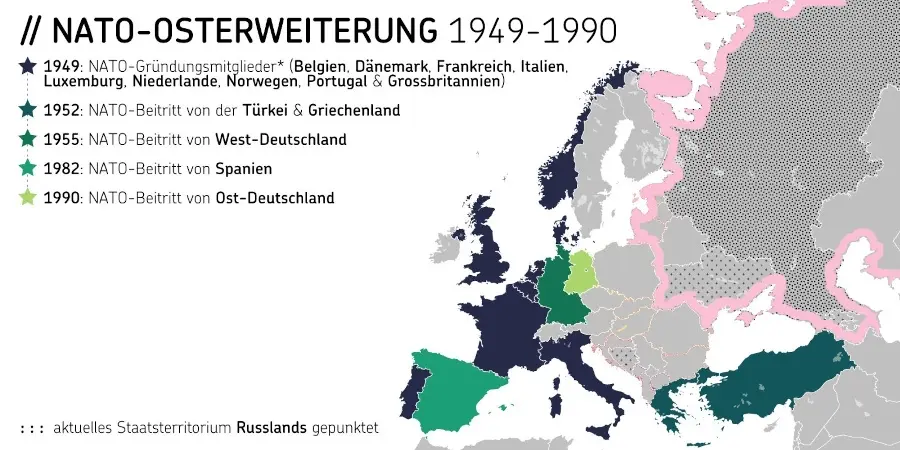
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
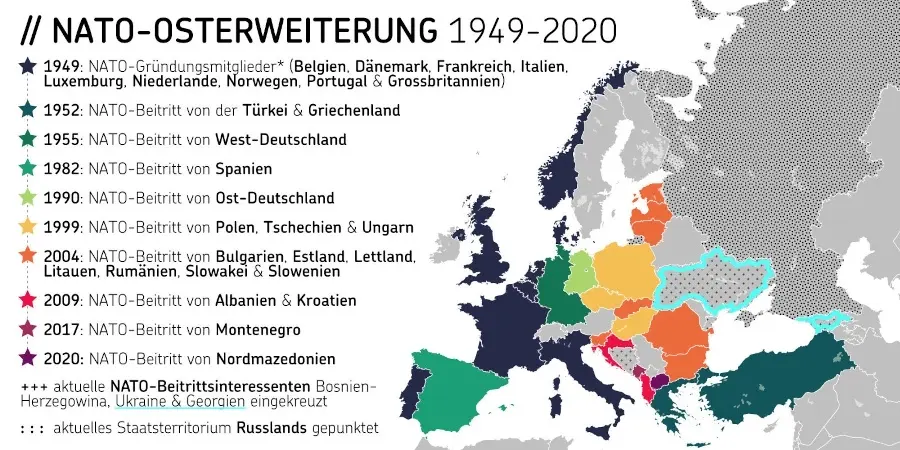
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
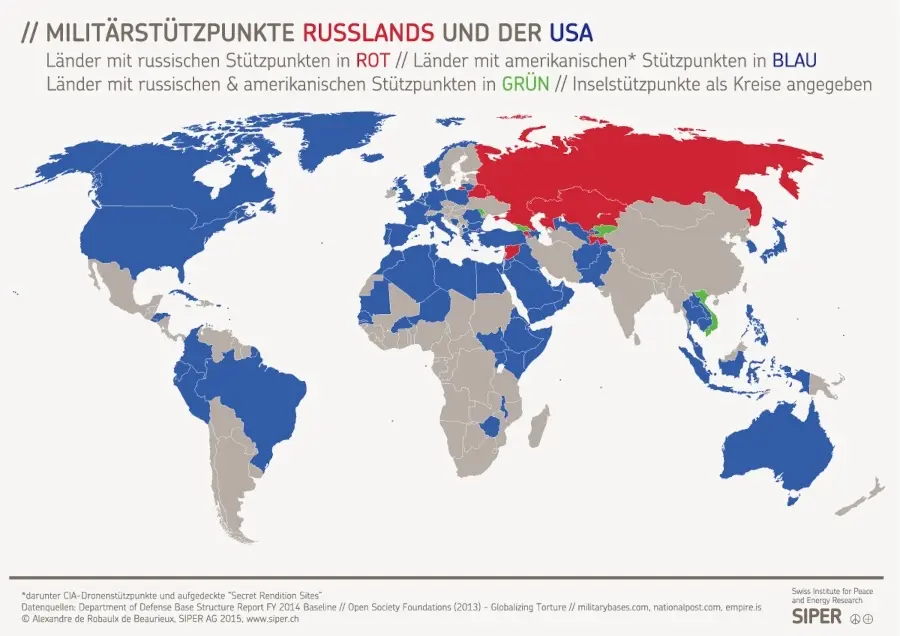
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Custom spreadsheets
The idea was to use it to make an app that would serve as custom database for everything and interact with the spreadsheet so people could play and calculate with their values after they were created by the custom app, something like an MS Access integrated with Excel?
My first attempt that worked (I believe there was an attempt before but I have probably deleted it from everywhere) was this
react-microspreadsheetthing (at the time calledreact-spreadsheetbefore I donated the npm name to someone who asked):This was a very good spreadsheet component that did many things current "react spreadsheet" components out there don't do. It had formulas; support for that handle thing that you pulled with the mouse and it autofilled cells with a pattern; it had keyboard navigation with Ctrl, Shift, Ctrl+Shift; it had that thing through which you copy-pasted formulas and they would change their parameters depending on where you pasted them (implemented in a very poor manner because I was using and thinking about Excel in baby mode at the time).
Then I tried to make it into "a small sheet you can share" kind of app through assemblymade.com, and eventually as I tried to add more things bugs began to appear.
Then there was
cycle6-spreadsheet:If I remember well this was very similar to the other one, although made almost 2 years after. Despite having the same initial goal of the other (the multi-app custom database thing) it only yielded:
- Sidesheet, a Chrome extension that opened a spreadsheet on the side of the screen that you could use to make calculations and so on. It worked, but had too many bugs that probably caused me to give up entirely.
I'm not sure which of the two spreadsheets above powers http://sheets.alhur.es.
-
 @ ba3b4b1d:eadff0d3
2025-05-09 23:49:24
@ ba3b4b1d:eadff0d3
2025-05-09 23:49:24Aisling é um género literário que se tornou popular na Irlanda nos séculos XVII e XVIII depois do tumulto da Guerra Williamita, misturando elementos de folclore, nacionalismo e romantismo. Ela encapsulava um anseio por identidade e liberdade, utilizando a figura da mulher bela como um poderoso símbolo de esperança e aspiração.
Mas a história da Aisling não começa aí e uma das suas origens é o conto muito confuso de Caer Ibormeith, também conhecida por Coerabar Boeth.
(https://yakihonne.s3.ap-east-1.amazonaws.com/ba3b4b1d1c5cc2707f71924368a7adcded1829921c86e022f1cb8117eadff0d3/files/1746834499215-YAKIHONNES3.jpg)
Ela era filha de Etal Anbuail, um rei Feérico dos Tuatha Dé Danann "povos da deusa Danu"; uma filidh - um nome que mais tarde foi atribuido aos poetas da Irlanda com proezas proféticas, uma vez que Ibormeith era a deusa das profecias, de certa forma semelhante a um "bardo", como se diz em Português. A cada Samhain, 31 de Outubro, quando o Mundo dos Vivos se aproximava do Mundo dos Mortos, ela transformava-se num cisne, até ao Samhain seguinte em que regressava à sua forma humana. Numa das versões desse conto, Ibormeith, após consulta ou por iniciativa própria, apaixona-se por Óengus. Numa noite, ela aparece nos sonhos dele tocando a mais bela melodia e quando ele acorda sabe que está apaixonado mas não sabia quem era aquela bela mulher nem onde a poderia encontrar. Ele fica completamente down bad e cada dia que passa só pensa em voltar sonhar com ela outra vez, e ela todas as noites volta a aparecer-lhe no Mundos dos Sonhos. Um dia, Óengus perde o apetite e adoece. Um médico foi chamado. Ele adivinhou a causa da doença de Óengus e disse a Bóann, mãe de Óengus, para encontrar a jovem dos sonhos dele. Bóann procurou durante um ano, mas sem sucesso. Então, eles pediram ajuda ao seu pai, o Dagdha, que também procurou um ano mas sem sucesso. Então foi pedido ao seu irmão Bodb que encontrasse um lugar com a descrição segundo os sonhos. Mas o pai dela, Etal, não permitia que qualquer um ficasse com a mão da sua filha e então revelou que para a conquistar teria que esperar pelo Loch Bél Dragain que significa "Lago da Boca do Dragão" para a encontrar na manhã do Samhain e a chamasse pelo nome. Nesse dia havia 150 cisnes* nesse lago, carregando correntes de prata e Óengus começou a panicar por não encontrar a sua Ibormeith, mas foi então que reparou num cisne mais bonito que os outros, com correntes de ouro e prata, e quando disse o seu nome ela revelou a sua forma humana e perguntou-lhe porque demorou tanto tempo.
Depois disse transformaram-se em cisnes e cantaram uma música tão bela que os humanos dormiram durante 3 dias e Óengus ficou conhecido como deus do amor e da juventude.
*Na mitologia irlandesa, o número 150 refere-se frequentemente aos Cinquenta Guerreiros dos Tuatha Dé Danann e a figura dos cisnes é frequente e também utilizada nas obras de Hans Christian Andersen e Tchaikovsky. Outras versões do conto não dizem cisnes, dizem aves, ou a história acontece de maneira ligeiramente diferente - quem conta um conto acrescenta um ponto.![image]
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28P2P reputation thing
Each node shares a blob of the reputations they have, which includes a confidence number. The number comes from the fact that reputations are inherited from other nodes they trust and averaged by their confidence in these. Everything is mixed for plausible deniability. By default a node only shares their stuff with people they manually add, to prevent government from crawling everybody's database. Also to each added friend nodes share a different identity/pubkey (like giving a new Bitcoin address for every transaction) (derived from hip32) (and since each identity can only be contacted by one other entity the node filters incoming connections to download their database: "this identity already been used? no, yes, used with which peer?").
Network protocol
Maybe the data uploader/offerer initiates connection to the receiver over Tor so there's only a Tor address for incoming data, never an address for a data source, i.e. everybody has an address, but only for requesting data.
How to request? Post an encrypted message in an IRC room or something similar (better if messages are stored for a while) targeted to the node/identity you want to download from, along with your Tor address. Once the node sees that it checks if you can download and contacts you.
The encrypted messages could have the target identity pubkey prefix such that the receiving node could try to decrypt only some if those with some probability of success.
Nodes can choose to share with anyone, share only with pre-approved people, share only with people who know one of their addresses/entities (works like a PIN, you give the address to someone in the street, that person can reach you, to the next person you give another address etc., you can even have a public address and share limited data with that).
Data model
Each entry in a database should be in the following format:
internal_id : real_world_identifier [, real_world_identifier...] : tagWhich means you can either associate one or multiple real world identifier with an internal id and associate the real person designated by these identifiers with a tag. the tag should be part of the standard or maybe negotiated between peers. it can be things like
scammer,thief,tax collectoretc., orhonest,good dentistetc. defining good enough labels may be tricky.internal_idshould be created by the user who made the record about the person.At first this is not necessary, but additional bloat can be added to the protocol if the federated automated message posting boards are working in the sense that each user can ask for more information about a given id and the author of that record can contact the person asking for information and deliver free text to them with the given information. For this to work the internal id must be a public key and the information delivered must be signed with the correspondent private key, so the receiver of the information will know it's not just some spammer inventing stuff, but actually the person who originated that record.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ ba3b4b1d:eadff0d3
2025-05-09 23:40:27
@ ba3b4b1d:eadff0d3
2025-05-09 23:40:27
O culto de Sol Invictus (Sol Invicto, ou "Sol Não Vencido") foi oficialmente instituído como religião estatal do Império Romano pelo imperador Aureliano em 274 d.C., marcando um momento relevante na história religiosa romana. Este culto, que celebrava o Sol como divindade suprema e invencível, estabeleceu celebrações anuais a 25 de Dezembro, uma data estrategicamente escolhida pela sua proximidade com o solstício de Inverno no calendário juliano. Contudo, o culto de Sol Invictus não surgiu isoladamente; tratava-se, na verdade, de uma reformulação e revitalização de práticas religiosas romanas muito mais antigas que veneravam Sol, a personificação deificada do Sol, uma figura presente na religião romana desde os tempos da República.
Antes da oficialização por Aureliano, o culto ao Sol já era praticado em Roma sob diversas formas. Na mitologia romana, Sol era frequentemente associado a deuses solares de outras culturas, como o grego Hélios e, mais tarde, o persa Mitra, cujo culto (o mitraísmo) alcançou grande popularidade entre os soldados romanos nos séculos II e III d.C. O mitraísmo, com os seus rituais iniciáticos e ênfase no Sol como símbolo de renovação e vitória, influenciou profundamente a iconografia e os conceitos do culto de Sol Invictus. A decisão de Aureliano de promover Sol Invictus como divindade unificadora do Império não foi apenas religiosa, mas também política: numa era de crises internas e externas, o culto ao Sol servia como símbolo de estabilidade, poder e unidade, sobretudo após a vitória de Aureliano contra a rainha Zenóbia do Reino de Palmira, cuja derrota foi atribuída à protecção divina do Sol.
Um dos festivais mais significativos associados ao culto era o Dies Natalis Solis Invicti ("Aniversário do Sol Invicto"), celebrado no solstício de Inverno, por volta de 21 de Dezembro, quando o dia começava a prolongar-se novamente, simbolizando a vitória do Sol sobre a escuridão. Este festival, profundamente enraizado no ciclo natural e astronómico, celebrava o renascimento do Sol e a sua força invencível. A proximidade temporal entre o Dies Natalis e a data de 25 de Dezembro, oficialmente adoptada para Sol Invictus, facilitou a sobreposição de significados e práticas religiosas. A ascensão do Cristianismo no Império Romano, particularmente após a conversão do imperador Constantino no início do século IV, conduziu a uma complexa interacção entre os cultos pagãos e a nova religião. É amplamente reconhecido pelos historiadores que o Cristianismo, ao estabelecer-se como religião dominante, absorveu e adaptou elementos de festivais pagãos para facilitar a conversão das populações e consolidar a sua influência. A escolha do 25 de Dezembro como data do nascimento de Jesus Cristo, que não tem fundamento nos textos bíblicos canónicos, é um exemplo evidente deste sincretismo. A data coincidia convenientemente com as celebrações de Sol Invictus e outros festivais pagãos, como a Saturnália, um período de festividades em honra do deus Saturno que ocorria em meados de Dezembro. O simbolismo do Sol, associado à luz, renovação e vitória sobre as trevas, era facilmente adaptável à narrativa cristã. Jesus, frequentemente descrito como a "Luz do Mundo" nos evangelhos (João 8:12), foi associado ao simbolismo solar, e a sua ressurreição passou a ser celebrada como uma vitória sobre a morte, semelhante ao retorno triunfal do Sol no solstício. A iconografia cristã também reflectiu esta influência: imagens de Cristo com uma auréola, reminiscentes dos raios solares, ecoavam representações de Sol Invictus e Hélios. Além disso, o mitraísmo, com os seus rituais de renovação e ênfase num salvador divino, apresentava paralelos com o Cristianismo, o que poderá ter facilitado a transição de fiéis de um culto para o outro.
Importa notar que a adopção do 25 de Dezembro como o Natal cristão não foi imediata. Registos históricos sugerem que a data só foi formalmente estabelecida no século IV, durante o reinado de Constantino e sob a influência da Igreja de Roma. O Papa Júlio I, por volta de 350 d.C., é frequentemente creditado por oficializar a celebração do nascimento de Cristo nesta data. Esta escolha foi estratégica, pois permitiu que o Cristianismo se sobrepusesse aos festivais pagãos, reinterpretando as suas tradições num contexto cristão. Paralelamente, na Sibéria, os cultos xamânicos envolvendo o cogumelo Amanita muscaria também se relacionam com o solstício de Inverno. Povos como os Evenki e os Chukchi utilizavam este cogumelo alucinogénio em rituais para enfrentar o rigoroso Inverno, induzindo visões de renas voadoras e trenós, que alguns estudiosos associam à origem das lendas do Pai Natal. A Amanita muscaria, com o seu píleo vermelho e branco, crescia sob pinheiros, que se tornaram símbolos das árvores de Natal. Os xamãs siberianos distribuíam estes cogumelos secos como "presentes" durante o solstício, muitas vezes entrando nas casas pela chaminé devido à neve, um costume que ecoa na figura do Pai Natal. Assim, tanto o culto de Sol Invictus como os rituais siberianos da Amanita muscaria convergem no simbolismo do solstício de Inverno, influenciando, de formas distintas, as tradições natalícias cristãs.
A escolha de 25 de Dezembro facilitou a integração de tradições pagãs, como a Saturnália e os cultos solares, numa narrativa cristã, com Jesus como a "Luz do Mundo".
Assim, o culto de Sol Invictus e as suas raízes no culto romano a Sol desempenharam um papel crucial na formação das celebrações cristãs do Natal. A amalgamação de elementos pagãos e cristãos reflecte a capacidade do Cristianismo de se adaptar às culturas locais, transformando símbolos e rituais profundamente enraizados em novas expressões de fé. Este processo de sincretismo não só garantiu a sobrevivência do Cristianismo num mundo religiosamente diverso, como também moldou a forma como o Natal é celebrado até hoje, com ecos das antigas tradições solares ainda presentes na sua simbologia de luz e renovação.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28gravity
IPFS is nice as a personal archiving tool (edit: it's not). You store a bunch of data and make it available to the public.
The problem is that no one will ever know you have that data, therefore you need a place to publish it somewhere. Gravity was an attempt of being the tool for this job.
It was a website that showcased the collections from users, and it was also a command-line client that used your IPFS keys for authentication and allowed you to paste IPFS URIs and names and descriptions.
The site was intended to be easy to run so you could have multiple stellar bodies aggregating content and interact with them all in a standardized manner.
It also had an ActivityPub/"fediverse" integration so people could follow Gravity server users from Mastodon and friends and see new data they published as "tweets".
See also
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28TiddlyWiki remoteStorage
TiddlyWiki is very good and useful, but since at this time I used multiple computers during the week, it wouldn't work for me to use it as a single file on my computer, so I had to hack its internal tiddler saving mechanism to instead save the raw data of each tiddler to remoteStorage and load them from that place also (ok, there was in theory a plugin system, but I had to read and understand the entire unformatted core source-code anyway).
There was also a server that fetched tiddlywikis from anyone's remoteStorage buckets (after authorization) and served these to the world, a quick and nice way to publish a TiddlyWiki -- which is a problem all people in TiddlyWiki struggle against.
See also
-
 @ b8851a06:9b120ba1
2025-05-09 22:54:43
@ b8851a06:9b120ba1
2025-05-09 22:54:43The global financial system is creaking under its own weight. The IMF is urging banks to shore up capital, cut risk, and brace for impact. Basel III is their answer, a last-ditch effort to reinforce a brittle foundation.
But behind the scenes, a quieter revolution is under way.
Bitcoin, the world’s first stateless digital asset, is no longer on the sidelines. It’s entering the Basel conversation: not by invitation, but by inevitability.
Basel III: The System’s Self-Diagnosis
Basel III is more than a technical rulebook. It’s a confession: an admission that the global banking system is vulnerable. Created in the aftermath of 2008, it calls for: • Stronger capital reserves: So banks can survive losses. • Lower leverage: To reduce the domino effect of overexposure. • Liquidity buffers: To weather short-term shocks without collapsing.
But here’s the kicker: these rules are hostile to anything outside the fiat system. Bitcoin gets hit with a punitive 1,250% risk weight. That means for every $1 of exposure, banks must hold $1 in capital. The message from regulators? “You can hold Bitcoin, but you’ll pay for it.”
Yet that fear: based framing misses a bigger truth: Bitcoin doesn’t just survive in this environment. It thrives in it.
Bitcoin: A Parallel System, Built on Hard Rules
Where Basel III imposes “fiat discipline” from the top down, Bitcoin enforces it from the bottom up: with code, math, and transparency.
Bitcoin is not just a hedge. It’s a structural antidote to systemic fragility.
Volatility: A Strategic Asset
Yes, Bitcoin is volatile. But in a system that devalues fiat on a schedule, volatility is simply the cost of freedom. Under Basel III, banks are expected to build capital buffers during economic expansions.
What asset allows you to build those buffers faster than Bitcoin in a bull market?
When the cycle turns, those reserves act as shock absorbers: converting volatility into resilience. It’s anti-fragility in motion.
Liquidity: Real, Deep, and Global
Bitcoin settled over $19 trillion in transactions in 2024. That’s not hypothetical liquidity. it’s real, measurable flow. Unlike traditional high-quality liquid assets (HQLAs), Bitcoin is: • Available 24/7 • Borderless • Not dependent on central banks
By traditional definitions, Bitcoin is rapidly qualifying for HQLA status. Even if regulators aren’t ready to admit it.
Diversification: Breaking the Fiat Dependency
Basel III is designed to pull banks back into the fiat matrix. But Bitcoin offers an escape hatch. Strategic Bitcoin reserves are not about speculation, they’re insurance. For family offices, institutions, and sovereign funds, Bitcoin is the lifeboat when the fiat ship starts taking on water.
Regulatory Realignment: The System Reacts
The Basel Committee’s new rules on crypto exposures went live in January 2025. Around the world, regulators are scrambling to define their stance. Every new restriction placed on Bitcoin only strengthens its legitimacy, as more institutions ask: Why so much resistance, if it’s not a threat?
Bitcoin doesn’t need permission. It’s already being adopted by over 150 public companies, forward-looking states, and a new class of self-sovereign individuals.
Conclusion: The Real Question
This isn’t just about Bitcoin fitting into Basel III.
The real question is: How long can Basel III remain relevant in a world where Bitcoin exists?
Bitcoin is not the risk. It’s the reality check. And it might just be the strongest capital buffer the system has ever seen.
Gradually then suddenly.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 000002de:c05780a7
2025-05-09 18:33:06
@ 000002de:c05780a7
2025-05-09 18:33:06I've been eager to share my thoughts on "Return of the Strong Gods" by R.R. Reno since I finished it a week ago.
I found this book incredibly insightful. @SimpleStacker's excellent review prompted me to pick it up, and I'm glad I did. While I won't be providing a full review, I will share some of the key insights and thoughts that resonated with me.
Reno masterfully dissects the sociological underpinnings of the political shifts in the US and the Western world over the past decade and a half. His analysis of the rise of populism and nationalism is compelling and rings true to my personal observations. Reno's central thesis is that post-WW2, the West embraced "weaker gods"—ideals like democracy, pluralism, and liberalism—fearing a repeat of the strong nationalistic sentiments that led to Hitler's rise. He argues that this shift has left many people feeling culturally homeless and desperate for strong leadership that listens to their grievances.
A significant portion of Reno's argument is built on the ideas of Karl Popper, a philosopher I was unfamiliar with before reading this book. Popper's work "The Open Society and Its Enemies" has significantly influenced post-war consensus, which Reno argues has led to a disconnect between the political elite and the common people. This disconnect, he posits, is a primary driver of populist sentiments.
Reno also delves into economics, discussing Friedrich Hayek and his agreement with some of Popper's positions. This intersection of philosophy and economics provides a unique lens through which to view the political landscape. Reno's mention of the Treaty of Versailles as a catalyst for Hitler's rise is a point often overlooked in discussions about WW2. He argues that the punitive measures imposed on Germany created an environment ripe for a strongman to emerge.
One of the most compelling aspects of Reno's argument is his explanation of how the political elite often lose touch with the values and wishes of the people they represent. He draws a powerful analogy between cultural homelessness and the desperation that drives people to seek strong leadership. This section of the book particularly resonated with me, as it aligns with my own observations of the political climate.
I would have liked Reno to start his analysis with Woodrow Wilson, whose "making the world safe for democracy" slogan embodied a form of Christian nationalism. Wilson's ideals and the post-WW1 environment laid the groundwork for the open society movement, which Reno critiques. Exploring this historical context could have strengthened Reno's argument.
Reno occasionally conflates economic liberalism with libertinism, which I found to be a minor flaw in an otherwise strong argument. He rightly points out the need for moral ethics in society but seems to overlook the distinction between economic freedom and moral laxity. Reno's discussion of Milton Friedman's ideas further highlights this confusion. While Reno argues that free trade has contributed to many of our modern ills, I believe the issue lies more with nation-state trade agreements like NAFTA, which are not true examples of free trade.
Another area where I disagree with Reno is his conflation of the nation with the state. Nations are cultural entities that predate and can exist independently of states. Reno's argument would be stronger if he acknowledged this distinction, as it would clarify his points about national pride and cultural heritage.
Reno's final chapters offer a cautionary tale about the return of strong gods and the danger of making them idols. He warns against authoritarianism and the overreach of the state, advocating for a balance that respects cultural heritage without succumbing to nationalism.
In conclusion, "Return of the Strong Gods" is a thought-provoking exploration of the political and cultural shifts of our time. Reno's insights are valuable, and his arguments, while not without flaws, provide a fresh perspective on the rise of populism and nationalism. I recommend this book to anyone seeking a deeper understanding of the forces shaping our world today.
originally posted at https://stacker.news/items/975849
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Democracia na América
Alexis de Tocqueville escreveu um livro só elogiando o sistema político dos Estados Unidos. E mesmo tendo sido assim, e mesmo tendo escrito o seu livro quase 100 anos antes do mais precoce sinal de decadência da democracia na América, percebeu coisas que até hoje quase ninguém percebe: o mandato da suprema corte é um enorme poder, uma força centralizadora, imune ao voto popular e com poderes altamente indefinidos e por isso mesmo ilimitados.
Não sei se ele concluiu, porém, que não existe nem pode existir balanço perfeito entre poderes. Sempre haverá furos.
De qualquer maneira, o homem é um gênio apenas por ter percebido isso e outras coisas, como o fato da figura do presidente, também obviamente um elemento centralizador, não ser tão poderosa quanto a figura de um rei da França, por exemplo. Mas ao mesmo tempo, por entre o véu de elogios (sempre muito sóbrios) deixou escapar que provavelmente também achava que não poderia durar para sempre a fraqueza do cargo de presidente.
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28busca múltipla na estante virtual
A single-page app made in Elm with a Go backend that scrapped estantevirtual.com.br in real-time for search results of multiple different search terms and aggregated the results per book store, so when you want to buy many books you can find the stores that have the biggest part of what you want and buy everything together, paying less for the delivery fee.
It had a very weird unicode issue I never managed to solve, something with the encoding estantevirtual.com.br used.
I also planned to build the entire checkout flow directly in this UI, but then decided it wasn't worth it. The search flow only was already good enough.
-
 @ a5ee4475:2ca75401
2025-05-09 17:10:35
@ a5ee4475:2ca75401
2025-05-09 17:10:35Título H1 - Formatação Markdown
[Titulo com '# ' antes do texto, pode não funcionar se o título H1 for iniciado depois de um texto normal]
list #descentralismo #markdown #clients #Amethyst #Yakihonne
Título H2 [2 hashtags e espaço]
Título H3 [3 hashtags e espaço]
Título H4 [4 hashtags e espaço]
Título H5 [5 hashtags e espaço]
Título H6 [6 hashtags e espaço]
*Copie e cole o texto para enxergar os caracteres usados
Réguas horizontais
- Com 3 sublinhados (_) seguidos:
- Com 3 hífens (-) seguidos:
- Com três asteriscos (*) seguidos:
Ênfases
Negrito: - Dois asteriscos antes e depois: Este é um texto em negrito
- Dois sublinhados antes e depois: Esse é um texto em negrito
Itálico - Um asterisco antes e um depois: Esse é um texto em itálico
- Um sublinhado antes e um depois: Esse é um texto em itálico
Tachado:
~~Aqui houve uma rasura~~
Bloco de citações
Usando 1 a 3 “>”:
O bloco de citações pode ser eninhado…
…Usando cada vez mais maior-que (>).
…Mesmo com espaços entre eles.
Listas
Não-ordenadas
- Crie um tópico começando com
+,-ou*. - Subtópicos são feitos adicionando 2 espaços:
- A mudança da marcação inicial não altera a lista:
- Com asterisco
- Com sinal de mais
- Com sinal de menos
- Muito fácil!
Ordenadas
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
- Integer molestie lorem at massa
- Você pode usar números em sequência...
- ...ou deixar tudo como
1.ou outro número.
O número inicia com recuos:
- foo
- bar
Códigos
códigona mesma linhaCaixa de código
-
Códigos intentados com 4 espaços:
// Some comments line 1 of code line 2 of code line 3 of code
-
Com 3 acentos graves antes e depois:
Marcação de texto:
Insira o texto aqui...Marcação de sintaxe:
``` js var foo = function (bar) { return bar++; };
console.log(foo(5)); ```
Tabelas
| APP | Descrição | | ------ | ----------- | | Element | App de mensagens que usa a rede Matrix. | | Simplex | App de mensagens bastante usado. | | 0xchat | App de mensagens no Nostr. |
Links
-
Link autoconvertido https://github.com/nodeca/pica (habilite o linkify para ver)
Imagens nomeadas
Minion:

Stormtroopocat:
[https://octodex.github.com/images/stormtroopocat.jpg])
Como links, imagens também tem sintaxe footnote ‘!’ + ‘Outro texto’...
[https://octodex.github.com/images/dojocat.jpg])
…com uma referência id posterior da referência na localização da URL.
Plugins
O recurso de
markdown-ité um suporte muito eficaz de plugins de sintaxe.
Emojis
*Acesse o link para entender melhor
Marcação clássica: :wink: :cry: :laughing: :yum:
Figuras Ascii (emoticons): :-) :-( 8-) ;)
Veja como mudar a exibição com o twemoji.
Sobrescrito / Subscrito
*Acesse os links para entender melhor
- 19^th^
- H~2~O
\
*Acesse o link para entender melhor
++Texto Inserido++
\
*Acesse o link para entender melhor
==Texto marcado==
Notas de Rodapé
*Acesse o link para entender melhor
Nota de rodapé 1 link[^primeiro].
Nota de rodapé 2 link[^segundo].
Rodapé^[Texto do rodapé na linha] definição na linha.
Referência duplicada no rodapé[^segundo].
[^primeiro]: Rodapé pode ter marcação
e múltiplos parágrafos.[^segundo]: Texto de rodapé.
Listas de Definição
*Acesse o link para entender melhor
Termo 1
: Definição 1 com continuação preguiçosa.
Termo 2 com marcação na linha
: Definição 2
{ algum código, parte da Definição 2 } Third paragraph of definition 2.Estilo compacto:
Termo 1 ~ Definição 1
Termo 2 ~ Definição 2a ~ Definição 2b
Esse texto é uma adaptação do:
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwspzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyqy0j6zknu2lr7qrge5yt725azecflhxv6d2tzwgtwrql5llukdqjqcyqqqqqqgfdk5w3
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28requesthub.xyz
An app that was supposed to be some kind of declarative connector between two services, one that sent webhooks and the other that accepted HTTP requests of any kind. You would proxy and transform the webhooks using RequestHub and create a new request to the other service using that data.
The transformations were declared in the almighty
jqlanguage.It worked and had other functions planned for the future, but I guess it was too arcane, even I was confused by it sometimes.
Also it was very prone to spam (involuntary) attacks like some that did happen. Maybe it would work better in a world of anonymous satoshi payments.
Later I tried to revive it as a Trello Power-Up that would create comments on cards automatically according to some transformation rules and webhooks received.
-
 @ 32092ec1:8e9fd13a
2025-05-09 16:13:34
@ 32092ec1:8e9fd13a
2025-05-09 16:13:34Bitcoin controversies are not new, in fact, bitcoin’s past has been riddled with one controversy after another. From the viewpoint of a financial investor, controversies are not good. They drive investor fear by amplifying uncertainty and introducing doubt about the future viability of the project. Although bitcoin is an investable asset, and there are certainly individuals, companies and countries who are investing in bitcoin strictly as a new, diversified financial asset that shows growth characteristics the likes of which humanity has rarely seen, bitcoin is not exclusively a financial instrument. Bitcoin is a network that is only as strong as the people running the miners who create the blocks, the nodes that propagate the blocks, and the users who hold the keys.
In this post I do not care to share my view on any of the latest bitcoin controversies, whether that be about OP_RETURNs, MSTR, Blackrock, MSTY, inscriptions, soft fork proposals, mempools, bitcoin strategic reserves, 21, chain surveillance, on-chain privacy, shitcoins projects, or anything else that anyone cares to opine about on Nostr or X to signal their support or opposition for what they think is critical to the success or failure of bitcoin. What I do care to share here is the ONLY winning strategy to defend bitcoin no matter what your opinion its future: USE THE TOOLS, RUN THE CODE, HOLD YOUR KEYS, TAKE RESPONSIBILITY.
In my humble opinion, the biggest problem with the current batch of bitcoin controversies is that so many people are sharing their opinions and expressing their fears about the future of bitcoin who are not even using the tools; they aren’t running the code, supporting the network or even holding their own keys. Everyone is free to share their opinions about the future of bitcoin and allowing everyone a voice is critical if we are serious about adopting the best ideas. Many visionaries have participated in the growth and development of bitcoin up to this point; we are truly standing on the shoulders of giants.
But before jumping to conclusions and spreading opinions about whether people are good faith or bad faith actors in the bitcoin space, I believe we should all hold ourselves to a certain standard. Set a minimum threshold of education for yourself before you jump on one side or the other of the latest controversy. We have tools that offer a level of sovereignty that is unparalleled in the legacy financial world, are you using them?Don’t like what MSTR is doing? Hold your keys in cold storage, then share your opinion.
Think Blackrock wants to use Bitcoin to launch a dystopian new world order agenda? Tell everyone to run a node, implement on-chain privacy strategies and hold their keys in cold storage.
Are Bitcoin developers making changes you don’t like? Use an alternative implementation, get a Bitaxe and construct your own block templates; for almost everyone this will be a stronger signal than shitposting or spreading FUD on the socials.
If you really want to defend bitcoin, think about how you are using it today. Who are you trusting to put your transactions into a block? Who are you trusting to propagate your transactions across the network? Who are you trusting to hold your keys? Who estimates your transaction fees? If you don’t trust the people who you are currently depending on, move your trust elsewhere, or increase your sovereignty and rely on yourself for some, or all, of these functions.
We make bitcoin what it is today, and we will define what bitcoin will be in the future. If we want to defend bitcoin it is our responsibility to keep it as decentralized as possible and that starts with every individual using the tools, running the code, doing the research and taking responsibility for their money.
895982
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ c9badfea:610f861a
2025-05-09 15:32:59
@ c9badfea:610f861a
2025-05-09 15:32:59- Install Feeder (it's free and open source)
- Discover RSS feeds from various sources (see links below)
- Copy the Feed URL
- Open Feeder, tap the ⁞ icon, and choose Add Feed
- Paste the Feed URL and tap Search
- Select the found RSS feed item
- Scroll down and tap OK
Some Sources
ℹ️ You can also use YouTube channel URLs as feeds
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Conceit
IPFS is trying to do many things. The IPFS leaders are revolutionaries who think they're smarter than the rest of the entire industry.
The fact that they've first proposed a protocol for peer-to-peer distribution of immutable, content-addressed objects, then later tried to fix that same problem using their own half-baked solution (IPNS) is one example.
Other examples are their odd appeal to decentralization in a very non-specific way, their excessive flirtation with Ethereum and their never-to-be-finished can-never-work-as-advertised Filecoin project.
They could have focused on just making the infrastructure for distribution of objects through hashes (not saying this would actually be a good idea, but it had some potential) over a peer-to-peer network, but in trying to reinvent the entire internet they screwed everything up.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28notes on "Economic Action Beyond the Extent of the Market", Per Bylund
Source: https://www.youtube.com/watch?v=7St6pCipCB0
Markets work by dividing labour, but that's not as easy as it seems in the Adam Smith's example of a pin factory, because
- a pin factory is not a market, so there is some guidance and orientation, some sort of central planning, inside there that a market doesn't have;
- it is not clear how exactly the production process will be divided, it is not obvious as in "you cut the thread, I plug the head".
Dividing the labour may produce efficiency, but it also makes each independent worker in the process more fragile, as they become dependent on the others.
This is partially solved by having a lot of different workers, so you do not depend on only one.
If you have many, however, they must agree on where one part of the production process starts and where it ends, otherwise one's outputs will not necessarily coincide with other's inputs, and everything is more-or-less broken.
That means some level of standardization is needed. And indeed the market has constant incentives to standardization.
The statist economist discourse about standardization is that only when the government comes with a law that creates some sort of standardization then economic development can flourish, but in fact the market creates standardization all the time. Some examples of standardization include:
- programming languages, operating systems, internet protocols, CPU architectures;
- plates, forks, knifes, glasses, tables, chairs, beds, mattresses, bathrooms;
- building with concrete, brick and mortar;
- money;
- musical instruments;
- light bulbs;
- CD, DVD, VHS formats and others alike;
- services that go into every production process, like lunch services, restaurants, bakeries, cleaning services, security services, secretaries, attendants, porters;
- multipurpose steel bars;
- practically any tool that normal people use and require a little experience to get going, like a drilling machine or a sanding machine; etc.
Of course it is not that you find standardization in all places. Specially when the market is smaller or new, standardization may have not arrived.
There remains the truth, however, that division of labour has the potential of doing good.
More than that: every time there are more than one worker doing the same job in the same place of a division of labour chain, there's incentive to create a new subdivision of labour.
From the fact that there are at least more than one person doing the same job as another in our society we must conclude that someone must come up with an insight about an efficient way to divide the labour between these workers (and probably actually implement it), that hasn't happened for all kinds of jobs.
But to come up with division of labour outside of a factory, some market actors must come up with a way of dividing the labour, actually, determining where will one labour stop and other start (and that almost always needs some adjustments and in fact extra labour to hit the tips), and also these actors must bear the uncertainty and fragility that division of labour brings when there are not a lot of different workers and standardization and all that.
In fact, when an entrepreneur comes with a radical new service to the market, a service that does not fit in the current standard of division of labour, he must explain to his potential buyers what is the service and how the buyer can benefit from it and what he will have to do to adapt its current production process to bear with that new service. That's has happened not long ago with
- services that take food orders from the internet and relay these to the restaurants;
- hostels for cheap accommodation for young travellers;
- Uber, Airbnb, services that take orders and bring homemade food from homes to consumers and similars;
- all kinds of software-as-a-service;
- electronic monitoring service for power generators;
- mining planning and mining planning software; and many other industry-specific services.
See also
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Veterano não é dono de bixete
"VETERANO NÃO É DONO DE BIXETE". A frase em letras garrafais chama a atenção dos transeuntes neófitos. Paira sobre um cartaz amarelo que lista várias reclamações contra os "trotes machistas", que, na opinião do responsável pelo cartaz, "não é brincadeira, é opressão".
Eis aí um bizarro exemplo de como são as coisas: primeiro todos os universitários aprovam a idéia do trote, apoiam sua realização e até mesmo desejam sofrer o trote -- com a condição de o poderem aplicar eles mesmos depois --, louvam as maravilhas do mundo universitário, onde a suprema sabedoria se esconde atrás de rituais iniciáticos fora do alcance da imaginação do homem comum e rude, do pobre e do filhinho-de-papai das faculdades privadas; em suma: fomentam os mais baixos, os mais animalescos instintos, a crueldade primordial, destroem em si mesmos e nos colegas quaisquer valores civilizatórios que tivessem sobrado ali, ficando todos indistingüíveis de macacos agressivos e tarados.
Depois vêm aí com um cartaz protestar contra os assédios -- que sem dúvida acontecem em larguíssima escala -- sofridos pelas calouras de 17 anos e que, sendo também novatas no mundo universitário, ainda conservam um pouco de discernimento e pudor.
A incompreensão do fenômeno, porém, é tão grande, que os trotes não são identificados como um problema mental, uma doença que deve ser tratada e eliminada, mas como um sintoma da opressão machista dos homens às mulheres, um produto desta civilização paternalista que, desde que Deus é chamado "o Pai" e não "a Mãe", corrompe a benéfica, pura e angélica natureza do homem primitivo e o torna esta tão torpe criatura.
Na opinião dos autores desse cartaz é preciso, pois, continuar a destruir o que resta da cultura ocidental, e então esperar que haja trotes menos opressores.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A crappy zk-rollups explanation attempt
(Considering the example of zksync.io) (Also, don't believe me on any of this.)
- They are sidechains.
- You move tokens to the sidechain by depositing it on an Ethereum contract. Then your account is credited in the sidechain balance.
- Then you can make payments inside the sidechain by signing transactions and sending them to a central operator.
- The central operator takes transactions from a bunch of people, computes the new sidechain balances state and publishes a hash of that state to the Ethereum contract.
- The idea is that a single transaction in the blockchain contains a bunch of sidechain transactions.
- The operator also sends to the contract an abbreviated list of the sidechain transactions. The trick is making all signatures condensed in a single zero-knowledge proof which is enough for the contract to verify that the transition from the previous state to the new is good.
- Apparently they can fit 500 sidechain transactions in one mainchain transaction (each is 12 bytes). So I believe it's fair to say all this zk-rollup fancyness could be translated into "a system for aggregating transactions".
-
I don't understand how the zero-knowledge proof works, but in this case it is a SNARK and requires a trusted setup, which I imagine is similar to this one.
-
 @ 15cf81d4:b328e146
2025-05-09 13:53:09
@ 15cf81d4:b328e146
2025-05-09 13:53:09Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 078d6670:56049f0c
2025-05-09 13:22:26
@ 078d6670:56049f0c
2025-05-09 13:22:26It was a dark and stormy night. It had to be: Weather had been fired. If they were working for him he would have fired them, but that is just embarrassed arrogance talking. He remembers standing in the middle of his office, his trashed office. It looked like a hurricane had hit it, or vagrants had been living in it for years, nothing of value was left intact. Monitors were shattered on the floor, couches were covered in debris. There was evidence of food and magazine pages in every gaze space. His supervisor, his name escaped him, was grey with anger. “Explain this!” he had shouted with a tremble, but he couldn’t. Every time he tried to think of the events of the day he met a dazzling white blankness.
He was escorted, handcuffed, to a room by two security guards with his supervisor trailing them. Weather felt humiliated and frustrated, but he didn’t know why. He sat, shivering slightly, in a low-lit conference room he had never seen before. Actually, he doesn’t remember any windows or any specific light source, just a haze of shadows. The big boss is sitting opposite him, looking haggard and white as a sun-bleached shell. His supervisor was sitting on his right looking equally haggard and even depressed. They appeared genuine and he knew it was bad news for him.
“You’ve embarrassed this company! There is even a chance you have ruined us all and you have the audacity to sit there and pretend that you can’t remember a thing!”
He knew there was no point in arguing, he had no ideas with which to make up any argument. He sat staring into space.
“At least, give us a story. Tell us how bored you were and tried to create your own weather system by running around the room swinging the fan around like a sugar mad teenager!”
He couldn’t even clear his throat. He couldn’t lift his eyes to meet theirs. He knew his career was over and they were fearful all their ideals had crashed irreparably. He stared into space at the globe standing in the middle of the table. The more he stared at it the more he realized that it seemed to have an atmosphere around it. There were clouds covering patches of the earth. He didn’t dare bring their attention to it. The only memories he could dredge up seemed like dreams, and they’re hardly constitute a defence.
He looked up at their faces finally, surprised to see more alarm than anger, like they were actually afraid of him. They both stood up suddenly, wanting to get out the room as quickly as possible.
“You have brought Global Sky Incorporated into disrepute. You’ve embarrassed us. You have possibly ruined hundreds of careers here! We never want to see you again! You are never to come within a hundred metres of this building. You can never use your research ever again, it never happened. Everything you have ever written will be classified and restricted until you are dead!” The big boss was shaking wild, Weather was grateful for the security guards that hurled him out of his chair and marched him out of the building.
The afternoon sky had been a deathly grey. It had occurred to him but now he was a little shocked at how much control they had over the weather, maybe it was a good thing that he had been fired, but probably a bad thing as they would certainly make worse mistakes than him, whatever he might have done. He was confused, not sure if he been fired for trashing his office or for state of the weather. About the weird weather he has no idea, all he can remember is a dazzling blank whiteness, and that is hardly a memory.
He couldn’t face going directly home, jumped on public transport travelling on tracks laid down on old unused highways and headed for the city beach, or what passed for a beach. He sat on a concrete bench gazing across the grey sand at the shimmering waves. They weren’t shimmering because of the sparkling sunlight, but the contaminates in the water. But still it was tranquil enough. He tried to think about his day, but couldn’t get past the white blankness, everything else before that was like a postcard from someone else’s holiday, and they looked like movies he might have seen. He has a framed vision of himself in his office with office supplies flying around him without touching him. Clearly, as they weren’t touching him, it had nothing to do with his behaviour. He is a victim here. It wasn’t his fault, the world was changing and the powers that be wanted more control. It seems like Global Weather Incorporated (GWI) lost control of their equipment and need a fall guy, they didn’t need him anymore. Squeezed his brain for the algorithms, then threw him onto the streets. He was nothing without his research, it’s all he had done his entire life. He would have to pursue it, but that would as useful as talking to a brick wall, the world was less transparent; government, science and advertising companies had a law of their own and a police force to uphold them.
He believed in good and the unveiling of truth. He had a romantic connection to the idea that truth grew in people’s hearts that everyone wanted the best for everyone else, no matter what skin colour, car colour they had, or star sign they were born under. Everybody wanted peace, a roof over their heads and food in their bellies; and wanted these things for their neighbours too. If only his neighbours had the same beliefs.
It was late afternoon now. He could tell by the slight luminosity of the grey clouds near the horizon, close to a cloudless gap, a slit above the horizon through which the sun could bid its final farewell to the day. He was in no mood for a sunset minute. He picked his bum off the bench, dusted it off and began his journey home, not wanting to be left in the dark in the city, opportune prey for corrupt cops. Everyone was coming out of the offices, beginning the big commute home. Car pools had reshaped their cars to fit more people in, and many climbed on to the reinvented trams, sitting if they were lucky, holding onto ceiling straps if they were unlucky like him. Couples sat together staring into each other’s eyes, friends joked and discussed their office politics. He hated the commute back and forth from work, it made him feel alone, desperate and unwanted. There had been no office politics for him, it was just him and his mostly silent supervisor.
The sky was struck red, a wound inflicted on the sky, it bleed for a minute then all went dark. Reality shuddered as it returned to him, this would be his last commute along this route. He was without a job; his recently regained self-esteem was destroyed. At the end of university he had wondered if he had a career anywhere, if his self-inflicted social isolation had been worth it and GWI had lifted him out of academic gutter and placed him on a pedestal. And now he was turfed out like a partly cloudy day from a child’s memory, flicked off like an ant off a picnic blanket.
Litter was being chased up and down the aisle, wrapping around legs and trying to hide from the wind amongst commuters’ bags. He didn’t notice that the commuters were becoming concerned about the weather, heads turned to look outside where the clouds were blacker than night. Wind has beating on windows, knocking on doors trying to escape from itself. Loose objects were starting to drift.
“Puck, I’m so stupid!” Weather lamented aloud as a flash of lightning brightened the dusk for a second. He should have protected his research, patented it in his own name. Stupidly, he had thought he would be with GWI for the rest of his life. He had given his life over to GWI and they had thrown it away for an office in disarray. It might have looked like an unnatural disaster, but they could have at least let him evaluate their equipment to check for systems failure. Why he hadn’t opened his mouth and flung accusations back at them? Probably because they had looked angrier than he could possibly have gotten faced with a memory of shimmering blankness.
The weather was surreal, he casually noted it as something GWI would have to correct, something existing outside his present unemployed reality, their problem. His cellphone’s classic “Thunderstuck” ringtone charged the air.
“What’s happening with the weather, dude? I thought I read in the paper that it was supposed to be sunny skies and calm seas. I wanted to go for an evening dive at Devil’s.”
“I’ve no idea, I’ve been fired,” he managed to say calmly before he hung up.
“It’s not my responsibility,” he thought to himself and promptly switched his phone off. He had given his private cellphone number to a few select acquaintances he had tried to impress when he had just got his ‘prestigious’ job. He thought he might finally be able to get his social life out of his house by sharing information with people he had met in supermarkets, recognizing their faces from university. They were jocks obsessed about the weather for their hedonistic lifestyles and they had never invited him out, only phoning to find out about the weather.
He jumped off at his usual stop and leaned into the wind watching his feet moving past one another, his mind seething at the injustice of not having a fair trial where they showed him evidence of him been directly involved in the trashing of his office. He could only remember standing in the middle of it and his office revolving around him, but that was only a flash, there is nothing before that except the facts. Him working on algorithms of weather activation, them tinkering with the clouds. They were practically at the end of their testing, their final live weather event before taking on the whole world’s weather, he knows that, but everyday was still just the same as every other day, him at the computer, them throwing lightning bolts. “Puck! I should’ve challenged them,” he shouted into the howling wind at GSI with all the frustration of his past mistakes. But his voice was lost into the atmosphere.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Eltoo
Read the paper, it's actually nice and small. You can read only everything up to section 4.2 and it will be enough. Done.
Ok, you don't want to. Or you tried but still want to read here.
Eltoo is a way of keeping payment channel state that works better than the original scheme used in Lightning. Since Lightning is a bunch of different protocols glued together, it can It replace just the part the previously dealed with keeping the payment channel.
Eltoo works like this: A and B want a payment channel, so they create a multisig transaction with deposits from both -- or from just one, doesn't matter. That transaction is only spendable if both cooperate. So if one of them is unresponsive or non-cooperative the other must have a way to get his funds back, so they also create an update transaction but don't publish it to the blockchain. That update transaction spends to a settlement transaction that then distributes the money back to A and B as their balances say.
If they are cooperative they can change the balances of the channel by just creating new update transactions and settlement transactions and number them like 1, 2, 3, 4 etc.

Solid arrows means a transaction is presigned to spend only that previous other transaction; dotted arrows mean it's a floating transaction that can spend any of the previous.
Why do they need and update and a settlement transaction?
Because if B publishes update2 (in which his balances were greater) A needs some time to publish update4 (the latest, which holds correct state of balances).
Each update transaction can be spent by any newer update transaction immediately or by its own specific settlement transaction only after some time -- or some blocks.
Hopefully you got that.
How do they close the channel?
If they're cooperative they can just agree to spend the funding transaction, that first multisig transaction I mentioned, to whatever destinations they want. If one party isn't cooperating the other can just publish the latest update transaction, wait a while, then publish its settlement transaction.
How is this better than the previous way of keeping channel states?
Eltoo is better because nodes only have to keep the last set of update and settlement transactions. Before they had to keep all intermediate state updates.
If it is so better why didn't they do it first?
Because they didn't have the idea. And also because they needed an update to the Bitcoin protocol that allowed the presigned update transactions to spend any of the previous update transactions. This protocol update is called
SIGHASH_NOINPUT[^anyprevout], you've seen this name out there. By marking a transaction withSIGHASH_NOINPUTit enters a mystical state and becomes a floating transaction that can be bound to any other transaction as long as its unlocking script matches the locking script.Why can't update2 bind itself to update4 and spend that?
Good question. It can. But then it can't anymore, because Eltoo uses
OP_CHECKLOCKTIMEVERIFYto ensure that doesn't actually check not a locktime, but a sequence. It's all arcane stuff.And then Eltoo update transactions are numbered and their lock/unlock scripts will only match if a transaction is being spent by another one that's greater than it.
Do Eltoo channels expire?
No.
What is that "on-chain protocol" they talk about in the paper?
That's just an example to guide you through how the off-chain protocol works. Read carefully or don't read it at all. The off-chain mechanics is different from the on-chain mechanics. Repeating: the on-chain protocol is useless in the real world, it's just a didactic tool.
[^anyprevout]: Later
SIGHASH_NOINPUTwas modified to fit better with Taproot and Schnorr signatures and renamed toSIGHASH_ANYPREVOUT. -
 @ 4fa5d1c4:fd6c6e41
2025-05-09 07:27:10
@ 4fa5d1c4:fd6c6e41
2025-05-09 07:27:10Den für mich derzeit wichtigsten Impuls über KI nachzudenken lieferte vor einigen Wochen Yuval Noah Harari an der University of Cambridge am Ende eines Podiumsgesprächs hier ab 1:15 h auf youtube:
Ich denke, wir müssen die Frage des Bewusstseins in den Mittelpunkt der Diskussion stellen. Es gibt eine riesige, riesige Verwirrung in der Terminologie, auch in der Welt der KI, zwischen Bewusstsein und Intelligenz. Aber es sind zwei verschiedene Dinge. Intelligenz ist die Fähigkeit, Probleme zu lösen und Ziele zu erreichen. Bewusstsein ist die Fähigkeit, Dinge zu fühlen, wie Schmerz oder Freude oder Liebe oder Hass. Wir neigen dazu, die beiden zu verwechseln, weil bei Menschen und auch bei anderen Säugetieren, Vögeln und anderen Tieren Bewusstsein und Intelligenz zusammengehören. Wir lösen Probleme durch unsere Gefühle. Computer waren bisher sehr anders. Sie sind in einigen Bereichen bereits intelligenter als wir, haben aber, soweit wir wissen, kein Bewusstsein. Soweit wir wissen, können sie überhaupt keinen Schmerz, keine Freude, keine Liebe oder keinen Hass empfinden. Niemand weiß, was in Zukunft passieren wird. Es gibt Modelle und Theorien, die argumentieren, dass KIs irgendwann auch bewusst oder empfindsam werden. Sie werden anfangen, Dinge zu fühlen. Sie werden anfangen, Schmerz oder Liebe oder Hass zu empfinden. Es gibt andere Modelle und Theorien, die sagen, nein. Sie könnten weit intelligenter werden als wir und immer noch null Bewusstsein haben. Das kann in der Evolution des Lebens sein. Wenn man darüber nachdenkt, die lange Entwicklung von Milliarden von Jahren der Evolution. Die Entwicklung der Intelligenz ist im Falle von Tieren wie uns und Schimpansen und Hunden und Schweinen und so weiter durch die Entwicklung des Bewusstseins verlaufen. Aber das ist kein universelles Gesetz der Evolution der Intelligenz. Vielleicht gibt es alternative Wege, die zu Superintelligenz ohne jegliches Bewusstsein führen. Einfach einen anderen, einen fremden Weg gehen. Und wir könnten an einen Punkt gelangen, an dem sie superintelligent sind und trotzdem null Bewusstsein haben. Und die Gefahr besteht dann darin, dass sie nicht nur die menschliche Zivilisation zerstören könnten, sondern das ganze Licht des Bewusstseins, um das gesamte ökologische System nach ihren Bedürfnissen umzugestalten, wofür sie kein Bewusstsein brauchen. Sie funktionieren auf eine völlig andere Weise. Sie könnten sich sogar von der Erde auf andere Planeten, auf andere Galaxien ausbreiten. Sie werden das Universum mit Intelligenz füllen, aber es wird ein völlig dunkles Universum ohne Bewusstsein sein. Wieder hohe Intelligenz, fähig, Raumschiffe zu bauen, die mit Lichtgeschwindigkeit fliegen und was auch immer, aber es gibt null Gefühl. Niemand, keine Entität fühlt Schmerz oder Freude, Liebe oder Hass. Für mich ist das ein schreckliches Szenario. Das schlimmste Szenario von allen ist dies. Dass wir ein Universum voller Intelligenz und völlig ohne Bewusstsein haben werden, denn ich denke, dass von den beiden das Bewusstsein weitaus wichtiger, weitaus wertvoller ist. Und es ist eine gute Erinnerung daran, dass wir das zumindest heute mit vielen anderen Tieren teilen, aber nicht mit den Computern, nicht mit den KIs. Wir sind also immer noch im selben Team wie die Würmer und die Affen, nicht im selben Team wie die Computer.
Ich denke, hier wird eine Spur gelegt, die sich unterscheidet von der reinen Funktion von KI zur intelligenten Verbesserung und Unterstützung von Lernprozessen oder vielfältigem Kompetenzerwerb hin zur Selbstreflexion der Lernenden. Auch im Blick auf (religionsbezogene) Bildung kennen wir den Mensch nicht nur biologisch, wie die Würmer und Affen sondern auch ausgestattet mit Würde, Entscheidungsfreiheit und als Beziehungswesen, das auf ein Gegenüber ausgerichtet sein kann und, wie Harari sagt, nicht im selben Team wie die Computer spielt. Sinn, Seele und Verstand erhalten wir weder aus uns selbst heraus noch von einer wie auch immer gearteten Intelligenz. Liebe, Gnade, Hoffnung, Frieden, Gemeinschaft, Trost, Zuversicht und viele weiteren lebensbedeutsame Erfahrungen gewinnen im Angesicht von Maschinen aus meiner Sicht an elementarer Bedeutung.
Dies ist ein Beitrag zur Blogparade #KIBedenken von Joscha Falck und Nele Hirsch
Austausch und Diskussion zu diesem Beitrag
- offen und dezentral
- geschlossen und plattformgebunden
-
 @ fd06f542:8d6d54cd
2025-05-09 05:48:05
@ fd06f542:8d6d54cd
2025-05-09 05:48:05由nip96模式改成了blossom
blossom的网址 变成了sha256 的id值,理论上 更换服务器或者重传以后 替换图片地址方便。
不过这部分我并没有做兼容接口。如果做成兼容的,应该用 相对地址,然后 后台用proxyimg.xxx.com去做选择。
访问方便些
新的服务器是:https://nosto.re/ 希望他能稳定的被访问不会嘎。
代码其实更简单了,https://github.com/nostrbook/nostrbook/blob/main/src/lib/blossomUpload.ts nosto.re 没有checkupload功能。所以我这里代码也没有加这部分,如果换别的服务器可能需要加检查功能。是不是为了防止图片重复上传?
最后 加一张好看的图片吧。证明此功能好用:
 {.user-img}
{.user-img} -
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Link sharing incentivized by satoshis
See https://2key.io/ and https://www.youtube.com/watch?v=CEwRv7qw4fY&t=192s.
I think the general idea is to make a self-serving automatic referral program for individual links, but I wasn't patient enough to deeply understand neither of the above ideas.
Solving fraud is an issue. People can fake clicks.
One possible solution is to track conversions instead of clicks, but then it's too complex as the receiving side must do stuff and be trusted to do it correctly.
-
 @ 872982aa:8fb54cfe
2025-05-09 05:35:15
@ 872982aa:8fb54cfe
2025-05-09 05:35:15 可以方便访问了
可以方便访问了 -
 @ 872982aa:8fb54cfe
2025-05-09 05:32:42
@ 872982aa:8fb54cfe
2025-05-09 05:32:42{"coverurl":"https://nosto.re/3ebd3bf45e031c2812ca5a36980a9bf7d4e6f30da2941d2bebdb7a2a452c8664.jpeg","title":"养花和施肥","author":"花花的作者"}
-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Rede Relâmpago
Ao se referir à Lightning Network do O que é Bitcoin?, nós, brasileiros e portugueses, devemos usar o termo "Relâmpago" ou "Rede Relâmpago". "Relâmpago" é uma palavra bonita e apropriada, e fácil de pronunciar por todos os nossos compatriotas. Chega de anglicismos desnecessários.
Exemplo de uma conversa hipotética no Brasil usando esta nomenclatura:
– Posso pagar com Relâmpago? – Opa, claro! Vou gerar um boleto aqui pra você.Repare que é bem mais natural e fácil do que a outra alternativa:
– Posso pagar com láitenim? – Leite ninho? -
 @ 805b34f7:3620fac3
2025-05-09 03:05:22
@ 805b34f7:3620fac3
2025-05-09 03:05:22Humans are evolving with social media & devices. These are powerful tools, but neither is built with their users' health and well-being in mind.
The big tech business incentives are a higher priority than their users' health & well being. This results in their products being designed to capture as much attention from you as possible so they can profit.
Many are realizing this. Few know there are emerging, viable alternatives.
 Nostr is a new model for social media (and much more).
Nostr is a new model for social media (and much more).Bitcoin is a new model for money.
nostr:nprofile1qyt8wumn8ghj7ct49eex2mrp09skymr99ehhyecpp4mhxue69uhkummn9ekx7mqqyr4aa6ffghhs22pmuzkrmcjhslyp56jc5y84druuddsanh238td66va34er is a new model for computers.
This article will explain why Nostr is primed to be the new model for social media.
“We cannot have a society in which, if two people wish to communicate, the only way that can happen, is if it’s financed by a third party who wishes to manipulate you” - Jaron Lanier
What is Nostr? What is Primal?
I’ve done a wonderful job of confusing people by interchanging the words Nostr & Primal. So allow me a brief, high level explanation.
Nostr is an internet protocol that allows for censorship resistant social media.
An internet protocol is a set of rules that computers follow to communicate with each other.
Nostr stands for Notes & Other Stuff Transmitted by Relays.
Primal is an app built on Nostr. I work for Primal the company.
When you post to Primal, you can see your content in other Nostr apps. Primal doesn’t own you, your content or identity. You do. You can take your content and followers to any Nostr app.
In this gif, you can see my content in 5 different Nostr apps.
 Nostr is like email, but for social media—it’s a system where anyone can send and receive posts using any app they like. Similar to how you would send an email to everyone you know. Everyone will receive that email no matter what email service provider they’re using (yahoo, gmail, proton, apple etc).
Nostr is like email, but for social media—it’s a system where anyone can send and receive posts using any app they like. Similar to how you would send an email to everyone you know. Everyone will receive that email no matter what email service provider they’re using (yahoo, gmail, proton, apple etc).When you “create an account” on Primal, you create a password that you can use to log in to any Nostr app. Your password is called a private key and you can use that to log in to any apps that are built on Nostr. See them here at nostrapps.com.
All this may sound a bit confusing, but this is just what's going on under the hood. Primal will feel like any other social media app. Check out this image below to learn more and be sure to keep your private key (your password) safe!
#### How I got into Nostr
Long story short, if you’ve been in to Bitcoin, you at least know about Nostr. I used Twitter as my primary news/Bitcoin source for the past 8 years and followed the Trump and Covid dramas closely.
I’ve come to the conclusion that social media needs to be protocol based and decentralized.
 The first Nostr conference in March of 2023 was in Uvita, Costa Rica. I was living in the area, so of course I showed up. Here’s a brief video we made from the conference.
The first Nostr conference in March of 2023 was in Uvita, Costa Rica. I was living in the area, so of course I showed up. Here’s a brief video we made from the conference. Why I'm Stoked on Nostr
The Everything App for Social Media
This is the original idea that made the lightbulb in my head go off. 1 identity for all types of content.
I have accounts on Youtube, Twitter, Nostr, Instagram, TikTok, & Medium. That means 6 different logins, 6 different follower sets, and 6 places to post when I have something to share.
With Nostr, I have 1 identity, 1 follower set, & (potentially) 1 place to post each type of content.
On the Left - 5 apps, 5 identities. Right - 5 apps, 1 identity
 The Nostr apps are in their infancy, but I can imagine a future with more diverse apps specified by content type (blogs, long form vid, vertical vids, music, etc.).
The Nostr apps are in their infancy, but I can imagine a future with more diverse apps specified by content type (blogs, long form vid, vertical vids, music, etc.).The ability to post all of your content to (potentially) one app and giving your audience the choice to consume that content in whatever app they please is revolutionary.
X wants to be the everything app as well. It looks like it's heading towards becoming the WeChat of the West. This begs the question... Does the infrastructure for social media need to be owned by singular corporations or governments?
Check out this video where nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyehwumn8ghj7mnhvvh8qunfd4skctnwv46z7ctewe4xcetfd3khsvrpdsmk5vnsw96rydr3v4jrz73hvyu8xqpqsg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q8dzj6n & nostr:nprofile1qyt8wumn8ghj7ct5d3shxtnwdaehgu3wd3skueqpz4mhxue69uhk2er9dchxummnw3ezumrpdejqqgyymmnwvah9hdnmft2wqsk0wr9as6q32hd4xk2zlnr2q5ectznjgqd27v94 discuss everything apps during the 2nd Nostr conference in Japan.
Nostr is the tool to orange pill the world
Orange pilling is a slightly cringe term used to describe educating people about Bitcoin. In Nostr, we say purple pilling because for some reason, Nostr’s theme is purple.
Jargon aside, the reason I believe that Nostr will orange pill the world is because of zaps!
Zaps are micropayments of bitcoin. You can send zaps on posts as easily as you can send likes on posts with Primal’s built in wallet and creators keep 100% of what they earn. They’re the best way to really feel the Nostr difference.
Here’s an example of me zapping 210 sats to a few people with one click.
 I've now personally watched over 20 people receive and send their1st Bitcoin transactions minutes after downloading Primal. Right away you pop two cherries, owning Bitcoin and sending Bitcoin. Pretty rad.
I've now personally watched over 20 people receive and send their1st Bitcoin transactions minutes after downloading Primal. Right away you pop two cherries, owning Bitcoin and sending Bitcoin. Pretty rad. It's a fundamentally different experience to touch Bitcoin through a social media style app than it is to buy bitcoin from an exchange. Someone new on Primal immediately has a use case for Bitcoin upon downloading the app. Zaps!
Nostr is known as the Bitcoiner social network. It could be/is becoming the place for newbies to come learn about Bitcoin, and interact with people who can help teach. I see a massive opportunity for Primal to play a huge role in this transition to a bitcoin standard.
I wonder how often this scenario with nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyv8wumn8ghj7mn0wd68ytn0wpjku6r0danxgtnwdsqzpq8gr333mlm73rnsfv2uvsrtvg44l5l5r0qrn6c0fw08t5hkccwarhnfev will repeat. Also, check out this video about how zaps got nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyw8wumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctvqqstkm5tw5w2f2qg2zp0tzxk9junagtrqeayyxnzggqcphgec9p37ncc26xj6 to read The Bitcoin Standard.
Micropayments on the internet are only possible with digitally native money.
Zaps are signal. They’re pure life force energy given to another person in appreciation for their content and it's unique to Nostr.
 Social media is simply better with payments. You cannot unsee or unfeel this. We're only beginning to scratch the surface of what zaps mean to a social network. Should be fun :)
Social media is simply better with payments. You cannot unsee or unfeel this. We're only beginning to scratch the surface of what zaps mean to a social network. Should be fun :) Sovereignty
Today, our digital lives are owned. Our data, identity, and content can be taken away.
Nostr flips this. We own our identity & choose where our data lives. Companies no longer have singular control over the flow of information.
Bitcoin gives you private keys for money. Nostr gives you private keys for speech.
On X and Instagram, we make a username and password. We are renting these identities from these corporations. How do we know these identities are not yours? Because they can be taken away from you.
 With Nostr, you and only you have your keys. You can post anytime, from any app, using your own key. If Primal stops working, no big deal. You could post from other Nostr apps.
With Nostr, you and only you have your keys. You can post anytime, from any app, using your own key. If Primal stops working, no big deal. You could post from other Nostr apps. I believe there’s something deeper going on here. Humans are sovereign beings. Being sovereign means being in full control.
With Nostr & Bitcoin, we can be in complete control of our money & speech.
These tools empower humans and reduce our need for dependence on 3rd parties.
Nostr allows us to create & share freely without the potential of being silenced for “wrongthink”.
It’s time for those who care about sovereignty to build their brands on their own land.
Nostr is Organic
Facebook wanted to connect the world. They’ve done an absolutely fantastic job at this. But at what cost?
The ad model has been the best way for platforms to monetize their services. This leads to bad incentives. Social media sites need you to spend as much time as possible on their apps so that they can sell your attention to advertisers.
Maybe there’s more ethical ways to advertise that do not lead to perverse incentives, but this isn’t the point.
Now, social media is basically a dopamine slot machine serving us things that we’re most likely to engage with. Whatever we lend our eyes to, purposefully or not, is the content we’re fed. Engagement is the north star of current social media. This modifies the behavior of everyone on the app.
These algorithms have been weaponized at times. And many would say that they’re programming us.
Let me speak in meme for a moment here:

 It’s different on Nostr
It’s different on NostrAfter using Nostr for a couple years, it’s clearer to me when I switch to another social media platform that they are doing everything they can to grab my attention. They being the platform and the creators. I can feel when people create for an algo vs. for an audience.
With Primal, I can select which algorithm I want to use or create my own feeds using Primal’s advanced search. (I expect these tools to get much better over time.) This gives the user much more control over what they see vs a singular algorithm. Algorithmic choice is something that legacy social media platforms are greatly missing.
I can also control which feed I want to see when I open the app. For example, I created this feed of one person saying “STAY FOCUSED CHAMP” so when I open the app I’m not immediately distracted. Look at what instagram does when you want to simply search for someone’s account…
I can’t help but envision a world where all of the content is posted to Nostr. The apps with the best user experiences would win. I’d imagine the winners would have the best algos, least intrusive ads, and would give their users the most control over their experience.
Thought Experiment
Pretend you’re a super intelligent being looking down upon the earth.
The1st thing you’d notice is that they’re always staring at their phones. You’d also notice that while they have an abundant earth, they insist on chemically altering their food which is making them sick.
Then, you’d notice that the money humans work their entire lives for can be and is manipulated by central authorities with zero effort.
And, you’d notice that the “digital global town square” is owned by a unelected, fallable humans and corporations.\ It’s laughable!
It doesn’t have to be this way anymore. And it’s up to us to change it.
To conclude.
This article is not meant to trash talk other platforms, those who use them, or those who created them. I use them daily. Mostly to advocate for Nostr & Bitcoin these days.
These platforms have created a ton of value for the world, & Nostr can be used alongside of them.
Maybe if Nostr existed back then, they would’ve built on it.
“We shape our tools, and thereafter our tools shape us”. We’ve learned priceless lessons from the evolution of social media thus far. We can use these lessons to shape tools with our health & well-being as our first priority.
We can obsolete these outdated, unhealthy systems.
Nostro and Nuestro mean 'ours' in Italian & Spanish. I don't think this a coincidence. Nostr is our chance to create a better internet for our future generations.
pura vida
(meme cred nostr:nprofile1q9n8wumn8ghj7enfd36x2u3wdehhxarj9emkjmn99ah8qatzx9kx2mrtdqeks6rcwuukserhd33hq6ekwyuhgvrcwsukvdme0fjnq7fsdeuxz7nk0fck5mtjv5ehqwfc0qehxargddm8j73lvfex7ctyvdshxapaw3e82egpp4mhxue69uhkummn9ekx7mqqyrl8767x7uecka4mlqxmgq4duev48cst9u37vm5fsgztv0xyy5u6xs34wwg also check out his nostr doc )
