-
 @ eaccf0cb:23be2b8f
2025-05-13 05:02:24
@ eaccf0cb:23be2b8f
2025-05-13 05:02:24Trong thời đại công nghệ phát triển nhanh chóng, việc tìm kiếm một nền tảng số toàn diện, thân thiện và ổn định đã trở thành nhu cầu thiết yếu đối với người dùng. LU8 chính là câu trả lời cho nhu cầu đó, khi mang đến một hệ sinh thái tích hợp với giao diện thông minh, cấu trúc hợp lý và tốc độ xử lý vượt trội. Mọi thao tác trên LU8 đều được thiết kế để tối giản hóa quá trình sử dụng, từ việc đăng ký, truy cập đến thao tác các tiện ích bên trong. Tính năng tương thích đa nền tảng là một trong những điểm mạnh nổi bật, cho phép người dùng sử dụng LU8 linh hoạt trên điện thoại, máy tính bảng hoặc máy tính cá nhân mà không gặp bất kỳ rào cản nào về kỹ thuật hay hiệu suất. Ngoài ra, LU8 thường xuyên cập nhật các xu hướng công nghệ mới, giúp hệ thống luôn vận hành trơn tru và đáp ứng kịp thời những thay đổi trong hành vi người dùng. Việc áp dụng các thuật toán tối ưu hóa hiệu suất cũng giúp thời gian phản hồi của hệ thống nhanh hơn, mang lại trải nghiệm liền mạch cho người dùng ở mọi hoàn cảnh.
Không chỉ dừng lại ở khả năng vận hành mượt mà, LU8 còn đặc biệt chú trọng đến yếu tố bảo mật và sự an toàn thông tin cá nhân cho người sử dụng. Hệ thống được xây dựng trên nền tảng mã hóa hiện đại, sử dụng nhiều lớp xác thực và kiểm tra chéo để ngăn chặn các rủi ro đến từ bên ngoài. Việc này không chỉ giúp bảo vệ dữ liệu một cách toàn diện mà còn tăng cường mức độ tin cậy từ phía người dùng, đặc biệt là trong những hoạt động yêu cầu tính riêng tư cao. LU8 còn cung cấp các tùy chọn bảo mật nâng cao như xác minh qua email, mã OTP và các công cụ nhận diện thiết bị truy cập để hỗ trợ người dùng quản lý tài khoản một cách hiệu quả nhất. Ngoài ra, quá trình sao lưu dữ liệu được thực hiện định kỳ, đảm bảo không có sự cố mất mát nào ảnh hưởng đến trải nghiệm tổng thể. Đội ngũ kỹ thuật đứng sau LU8 luôn theo dõi hệ thống liên tục, nhằm phát hiện và khắc phục mọi sự cố có thể xảy ra trong thời gian ngắn nhất. Những yếu tố này cho thấy LU8 không chỉ là một nền tảng công nghệ hiện đại, mà còn là một hệ thống được đầu tư bài bản với mục tiêu dài hạn.
Bên cạnh sự mạnh mẽ về công nghệ và bảo mật, LU8 còn tạo nên khác biệt thông qua chất lượng chăm sóc khách hàng vượt trội. Với hệ thống hỗ trợ trực tuyến hoạt động liên tục 24/7, người dùng luôn nhận được sự hỗ trợ tận tình, nhanh chóng và chính xác từ đội ngũ chuyên viên. Mọi thắc mắc, từ đơn giản đến phức tạp, đều được giải đáp cặn kẽ, giúp người dùng an tâm hơn khi tương tác với nền tảng. LU8 cũng duy trì một kênh phản hồi mở, nơi người dùng có thể gửi góp ý để cải thiện chất lượng dịch vụ. Các ý kiến này không bị bỏ qua mà luôn được phân tích và áp dụng vào quá trình nâng cấp hệ thống nhằm phục vụ người dùng tốt hơn mỗi ngày. Ngoài ra, LU8 thường xuyên triển khai các chương trình tri ân khách hàng, khuyến khích sự gắn bó lâu dài và xây dựng cộng đồng người dùng tích cực. Trong tương lai, LU8 đặt mục tiêu mở rộng hơn nữa phạm vi ứng dụng và tích hợp thêm nhiều tiện ích mới, tạo nên một nền tảng số toàn diện, đáp ứng đa dạng nhu cầu của người dùng hiện đại và không ngừng thích ứng với xu hướng công nghệ toàn cầu.
-
 @ bbef5093:71228592
2025-05-13 04:18:45
@ bbef5093:71228592
2025-05-13 04:18:45Nukleáris politika – 2025. május 12. | Szerző: David Dalton
Lengyelország és Franciaország nukleáris szerződést ír alá, Macron új építési szerződéseket céloz
Lengyelország és Franciaország olyan szerződést kötött, amely együttműködést irányoz elő a polgári nukleáris energia szektorban, miközben Párizs reménykedik abban, hogy Varsótól jövedelmező új atomerőmű-építési szerződéseket nyer el.
A szerződés közös tevékenységeket tartalmaz, amelyek célja a nukleáris energia előnyeinek kihasználása az európai ipar dekarbonizációja érdekében.
A két ország együtt kíván működni a nukleáris fűtőanyag-ellátás biztonságának megerősítésében is.
Európa szeretné kizárni Oroszországot a nukleáris fűtőanyag-piacáról, de az Euratom Ellátási Ügynökség (ESA) legfrissebb éves jelentése szerint 2023-ban nőtt az Oroszországból származó természetes urán szállítása, mivel az uniós szolgáltatók készleteket halmoztak fel az orosz tervezésű VVER atomerőművekhez.
Az ESA, amely az európai nukleáris anyagok rendszeres és méltányos ellátásáért felelős, közölte, hogy az uniós szolgáltatók tovább diverzifikálják nukleáris fűtőanyag-beszerzéseiket, különösen a VVER reaktorokhoz, hogy csökkentsék a „egy forrásból származó vagy magas kockázatú” ellátásoktól való függést.
„Majdnem minden olyan ország, amely orosz tervezésű reaktorokat üzemeltet, halad az alternatív fűtőanyagok engedélyeztetésében, és ígéretes fejlemények várhatók a közeljövőben” – közölte az ESA.
Az EU-ban jelenleg 19 VVER reaktor működik, köztük négy 1000 MW-os Bulgáriában és Csehországban, valamint tizenöt 440 MW-os Csehországban, Finnországban, Magyarországon és Szlovákiában.
A jelentések szerint a francia–lengyel nukleáris szerződés különösen fontos a francia állami EDF energetikai vállalat számára, amely még mindig reménykedik abban, hogy részt vehet Lengyelország ambiciózus atomerőmű-építési programjában, annak ellenére, hogy az első új építésű projekt tenderét az amerikai Westinghouse nyerte el Pomeránia északi tartományában.
Franciaország ambiciózus reaktorépítési tervei
Franciaország maga is nagyszabású nukleáris fejlesztési terveket dédelget: a kormány nemrégiben felkérte az EDF-et, hogy gyorsítsa fel a hat új generációs EPR2 atomerőmű megépítésének előkészítését.
Az EDF kezdetben három EPR2 párost tervez: az elsőt Penlyben, majd egyet-egyet a Gravelines-i atomerőmű telephelyén (Calais közelében), illetve vagy Bugey-ben (Lyon keleti részén), vagy Tricastinban (Lyon és Avignon közelében).
A nukleáris szerződés aláírását megelőzte egy másik szerződés is, amely a két szövetséges közötti kapcsolatok elmélyítését, valamint kölcsönös biztonsági garanciákat is tartalmaz háború esetére.
Donald Tusk lengyel miniszterelnök, aki Emmanuel Macron francia elnökkel együtt írta alá a biztonsági dokumentumot, „áttörésnek” nevezte a szerződést, kiemelve, hogy csak Németországnak van hasonló biztonsági paktuma Franciaországgal, és ez Lengyelországot „egyenrangú partnerként” helyezi nyugati szövetségesei közé.
Macron eközben úgy fogalmazott, hogy a szerződés „új korszakot nyit” nemcsak Lengyelország és Franciaország, hanem egész Európa számára. „Bresttől Krakkóig Európa együtt áll ki” – mondta a francia elnök.
Nukleáris politika – 2025. május 12. | Szerző: David Dalton
Trump csapata a nukleáris erőművek építésének felgyorsítását tervezi
A Trump-adminisztráció tisztviselői végrehajtási rendeleteket készítenek elő, amelyek célja az atomerőművek jóváhagyásának és építésének felgyorsítása az Egyesült Államokban – számolt be róla a sajtó.
Az erőfeszítés, amelyet egy kormányzati tisztviselő és más, az egyeztetéseket ismerő személyek írtak le, még folyamatban van. Az elnök még nem hagyta jóvá a tervezetet – mondta az egyik forrás, aki névtelenséget kért, mivel hivatalos bejelentés még nem történt. Az amerikai Axios hírportál és a New York Times is beszámolt az egyeztetésekről.
Trump és kormányának tisztviselői többször hangsúlyozták a bőséges, olcsó villamos energia fontosságát az energiaigényes mesterséges intelligencia ipar számára, amely segítheti az Egyesült Államokat abban, hogy megnyerje a feltörekvő technológia globális versenyét.
„Meg kell nyernünk az MI-versenyt, és ebben vezetnünk kell – ehhez pedig sokkal több energiára lesz szükség” – mondta Chris Wright energiaügyi miniszter múlt hónapban egy kabinetülésen Trump társaságában.
Az elnök már hivatalosan is energia-vészhelyzetet hirdetett, nemzeti és gazdasági biztonsági szempontokra hivatkozva annak érdekében, hogy gyorsítsa az erőművek, csővezetékek és elektromos távvezetékek építését az országban.
A szóban forgó tervezetek célokat tűznének ki az atomerőművek gyors országos építésére, illetve az amerikai nukleáris ipar vezető szerepének visszaállítására.
Legalább az egyik intézkedés a Nukleáris Szabályozási Bizottságnál (NRC) vezetne be változtatásokat, amelyek gyorsíthatják az erőműtervek, köztük az új kis moduláris reaktorok (SMR-ek) engedélyezését.
Wright nemrégiben úgy nyilatkozott, hogy az új reaktorblokkok építésének legnagyobb akadálya az Egyesült Államokban a szabályozás volt.
Az elképzelés részeként akár katonai létesítményekre is telepíthetnek majd atomerőműveket, valószínűleg mikroreaktorok vagy SMR-ek formájában.
Jelenleg az Egyesült Államokban nincs kereskedelmi atomerőmű építés alatt. Az utolsó két üzembe helyezett blokk a georgiai Vogtle-3 és Vogtle-4 volt, 2023-ban és 2024-ben.
Előrehaladott tervek vannak a michigani Palisades atomerőmű újraindítására. Ha megvalósul, ez lenne az első olyan, korábban leállított amerikai atomerőmű, amely ismét működésbe lép.
Új építések – 2025. május 12. | Szerző: David Dalton
Vietnam és Oroszország tárgyalásokat kezd atomerőmű-építésről
Vietnam és Oroszország megállapodott abban, hogy tárgyalásokat folytatnak és szerződéseket írnak alá kereskedelmi atomerőművek építéséről Vietnamban – közölték a két ország egy közös nyilatkozatban.
„Az erőművek fejlesztése korszerű technológiával szigorúan megfelel majd a nukleáris és sugárbiztonsági előírásoknak, és a társadalmi-gazdasági fejlődést szolgálja” – áll a közleményben, amely a vietnami vezető, To Lam moszkvai látogatása után jelent meg.
Az orosz állami atomenergetikai vállalat, a Roszatom szerint a látogatás „az együttműködés új szakaszát” jelenti – egy nagy atomerőmű építését Délkelet-Ázsiában.
A Roszatom felajánlotta Vietnámnak a VVER-1200 nyomottvizes reaktor technológiáját, amelyből kettő már működik az oroszországi Novovoronyezs 2 atomerőműben, és kettő Fehéroroszországban.
A Roszatom közölte, hogy további tárgyalásokra van szükség a vietnami atomerőmű műszaki és pénzügyi feltételeinek tisztázásához, de hozzátette: „ezek a tárgyalások ma [május 10-én] megkezdődtek”.
A Roszatom arról is beszámolt, hogy Alekszej Lihacsov vezérigazgató és Nguyen Manh Hung vietnami tudományos és technológiai miniszter aláírt egy nukleáris energia ütemtervet.
Az ütemterv tartalmazza egy nukleáris tudományos és technológiai központ lehetséges megépítését, fűtőanyag-szállítást a dél-vietnami Dalat kutatóreaktorhoz, Vietnam részvételét Oroszország IV. generációs MBIR többcélú gyorsneutronos kutatóreaktor projektjében, valamint vietnami szakemberek képzését.
Vietnamnak jelenleg egy kutatóreaktora van Dalatban, és egy másik is tervben van. A Roszatom nem közölte, melyikre gondolt.
A múlt hónapban Vietnam elfogadta a nemzeti energiastratégia módosított változatát, amely 2030-ig 136 milliárd dollárt irányoz elő az energiaellátás hosszú távú biztonságának megerősítésére, és először szerepel benne az atomenergia.
Vietnam azt szeretné, ha első atomerőművei 2030 és 2035 között lépnének üzembe. A beépített nukleáris kapacitás várhatóan 4–6,4 GW lesz, ami körülbelül 4–6 nagy atomerőműnek felel meg.
A kormány szerint további 8 GW nukleáris kapacitás kerül majd a mixbe az évszázad közepéig.
Vietnam már 2009-ben is tervezett két atomerőművet, de a Nemzetgyűlés 2016-ban költségvetési okokból elutasította a javaslatot.
Új építések – 2025. május 12. | Szerző: David Dalton
Az NRC engedélyt adott az „energia-sziget” munkálatokra a TerraPower wyomingi atomerőművénél
Az Egyesült Államok Nukleáris Szabályozási Bizottsága (NRC) mentességet adott a TerraPower Natrium demonstrációs atomerőművének wyomingi Kemmererben, lehetővé téve a vállalat számára bizonyos „energia-sziget” tevékenységek folytatását, miközben a hatóságok tovább vizsgálják az építési engedély iránti kérelmet.
Az energia-sziget a tervezett Natrium atomerőműben a felesleges hő tárolására szolgál majd, hogy csúcsterhelés idején növelje az áramtermelést.
Az NRC szerint az energia-szigethez kapcsolódó bizonyos tevékenységek engedélyezése nem jelent indokolatlan kockázatot a közegészségre és biztonságra, és „különleges körülmények” állnak fenn.
A mentesség a létesítmények, rendszerek és komponensek korlátozott részére vonatkozik, lehetővé téve például cölöpverést, alapozást, vagy bizonyos szerkezetek, rendszerek és komponensek összeszerelését, gyártását, tesztelését korlátozott munkavégzési engedély nélkül.
Az NRC szerint a mentesség nem befolyásolja a reaktor építési engedélyéről szóló végső döntést. „Az NRC folytatja az építési engedély iránti kérelem vizsgálatát az egész projektre vonatkozóan” – áll a közleményben.
A Bill Gates által alapított TerraPower üdvözölte a döntést, hozzátéve, hogy a nukleáris reaktor és az energiatermelő létesítmények szétválasztása rövidebb építési időt és alacsonyabb anyagköltségeket tesz lehetővé.
Februárban az amerikai energiaügyi minisztérium befejezte a projekt előzetes tevékenységeire vonatkozó végső környezeti értékelést.
A TerraPower, amelyet Gates 2008-ban alapított, 2024 júniusában kezdte meg első kereskedelmi Natrium atomerőművének építését Kemmererben, ahol egy széntüzelésű erőmű zár be.
A Natrium demonstrációs projekt három különálló részből áll: egy nátrium teszt- és feltöltő létesítményből, az energiatermelő vagy energia-szigetből, valamint a nukleáris szigetből magával a reaktorral.
A kezdeti építkezés a teszt- és feltöltő létesítményre összpontosít, amely egy különálló, nem nukleáris épület, és a reaktor nátrium hűtőrendszerének tesztelésére szolgál. Itt történik a folyékony nátrium fogadása, mintavételezése, feldolgozása és tárolása, mielőtt a Natrium reaktorhoz kerülne.
Egyéb hírek
A lengyel atomerőmű-projekt biztosítási szerződéseket kötött
A lengyel Polskie Elektrownie Jądrowe (PEJ) atomerőmű-projekt vállalat négy biztosítási bróker céggel kötött keretmegállapodást. Az Aon Polska, GrECo Polska, Marsh és Smartt Re cégek támogatják a PEJ-t Lengyelország első kereskedelmi atomerőművének biztosítási szerződéseinek megkötésében, valamint a napi működéshez szükséges biztosítások beszerzésében. A PEJ minden brókerrel keretmegállapodást írt alá, amelyek alapján egyes biztosítási feladatokra kiválasztja a megfelelő brókert.
Az Aecon cég nyerte az ontariói SMR építési szerződését
A kanadai Aecon Kiewit Nuclear Partners nyerte el az Ontario Power Generation (OPG) által Darlingtonban építendő első kis moduláris reaktor (SMR) kivitelezési szerződését. A szerződés értéke 1,3 milliárd kanadai dollár (934 millió USD, 841 millió euró), amely projektmenedzsmentet, kivitelezési tervezést és végrehajtást foglal magában, a befejezést és a kereskedelmi üzemet 2030-ra tervezik. Ontario tartomány és az OPG múlt héten hagyta jóvá a négy SMR első darabjának 20,9 milliárd CAD értékű tervét Darlingtonban.
26 000 dolgozó a Hinkley Point C projekten a csúcskivitelezés idején
Az Egyesült Királyságban mintegy 26 000 dolgozó vesz részt a Hinkley Point C atomerőmű építésében, amely jelenleg csúcskivitelezési szakaszban van – derül ki az EDF Energy jelentéséből. Közvetlenül a projekten 18 000-en dolgoznak, ebből 12 000-en a helyszínen, további 3 000 fővel bővülhet a létszám a következő 12 hónapban. További 8 000-en a beszállítói láncban dolgoznak. A jelentés szerint a Hinkley Point C építése fontos katalizátor a gazdasági növekedésben, jelenleg 13,3 milliárd fonttal (15,7 milliárd euró, 17,5 milliárd dollár) járul hozzá a gazdasághoz. Ebből 5 milliárd fontot már a délnyugati régió beszállítóinál költöttek el – jóval meghaladva az 1,5 milliárd fontos célt. A Hinkley Point C két francia EPR reaktort kap.
Az Ansaldo Nucleare nukleáris mesterszakot indít Olaszországban
Az olasz Ansaldo Nucleare és a Politecnico di Milano vállalati mesterszakot indít, amely a nukleáris energia és kapcsolódó technológiák új szakértő generációját képzi. A képzés októberben indul, egy évig tart, 1500 órás, mérnöki, fizikai és kémiai diplomásoknak szól. Húsz résztvevőt választanak ki a következő hónapokban, akiket az Ansaldo Nucleare azonnal, határozatlan időre alkalmaz, és október elején kezdik meg a képzést.
-
 @ 75869cfa:76819987
2025-05-13 03:26:29
@ 75869cfa:76819987
2025-05-13 03:26:29GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 211,000 daily trusted pubkey events. The number of new users has seen a notable decrease, Profiles with contact lists were representing a 50% decline. More than 5 million events have been published, reflecting a 34% decrease. Total Zap activity stands at approximately 14 million, marking a 12% increase.
Additionally, 25 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 60 Nostr projects were tracked, with 18 releasing product updates, and over 356 long-form articles were published, 36% focusing on Bitcoin and Nostr. During this period, 5 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 211,000, representing a slight 2.7 % decrease compared to the previous period. Daily activity peaked at 17027 events, with a low of approximately 15340.
The number of new users has decreased significantly.Profiles with contact lists were 12961, representing a decline of approximately 50% compared to the previous period. The number of profiles with bios and pubkey-written events remained stable.
The total number of note events published is around 5 million, reflecting a 34% decrease.Posts remain the most dominant category by volume, representing a 9% decrease compared to the previous period.
For zap activity, the total zap amount is about 14 million, showing an decrease of over 12% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Introduce NIP-PNS: Private Note Storage #1893
nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s is proposing PNS that empowers Nostr users with a secure and seamless way to store personal notes—like diaries, drafts, or private application settings—across devices while keeping them completely private. Built on client-side encryption, PNS ensures that only the user can read or manage their notes, even as they sync effortlessly via Nostr relays. Unlike traditional local storage or cumbersome encrypted file solutions, PNS offers privacy without sacrificing convenience, using deterministic keys tied to each user or device. It integrates directly with Nostr’s open infrastructure, enabling private data to coexist with public events—secure, synchronized, and under your control.
Create 97.md: Ring Signatures #1894
nostr:npub1u5njm6g5h5cpw4wy8xugu62e5s7f6fnysv0sj0z3a8rengt2zqhsxrldq3 is proposing a PR that ring signatures can be synergistic with other web of trust related tools.
Introduce NIP: Relay metadata propagation #1900
nostr:npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl is proposing a simple propagation mechanism for kind:0 (user metadata) and kind:10002 (relay list metadata) events between relays. Relays are allowed to forward such events to their peers, improving client synchronization.
nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds defines a standardized interaction pattern for Nostr Data Vending Machines (DVMs). It focuses on how clients discover DVM capabilities, request jobs, and receive results. This NIP decouples the core DVM interaction from specific job-type implementations, which should be defined in separate documents.
NIP-47 Add Hold Invoice Support #1913
frnandu is proposing PR that introduces support for hold invoices in the Nostr Wallet Connect (NIP-47) protocol.Hold invoices enable more advanced payment workflows where the receiver must explicitly settle or cancel the invoice using the preimage. This allows for enhanced control and coordination in payment flows, such as conditional payments or escrow-like behavior.
Add A Generic Raitng/Review NIP #1914
nostr:npub1cgd35mxmy37vhkfcmjckk9dylguz6q8l67cj6h9m45tj5rx569cql9kfex is proposing generic nip that meant to handle all categories of things via namespaced Ids.
Notable Projects
Coracle 0.6.15 nostr:npub13myx4j0pp9uenpjjq68wdvqzywuwxfj64welu28mdvaku222mjtqzqv3qk
New version of Coracle is out: 0.6.15 — this one is just more QoL improvements and bugfixes — the big one this time is better blossom support (and dropping nip 96!). * Fix safe areas more * Improve remote signing * Drop nip 96 support * Use user blossom servers * Improve profile edit page * Avoid duplicate notes in feeds
Flotilla nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
New version of Flotilla is out as well — 1.0.2 is mostly cleanup from the 1.0 release earlier this week. * Fix add relay button * Fix safe inset areas * Better rendering for errors from relays * Improve remote signer login
Damus Notedeck Beta nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
New in Notedeck Beta: * Dave nostr ai assistant app * GIFs! * Fulltext note search * Add full screen images, add zoom & pan * Zaps! NWC/ Wallet ui * Introduce last note per pubkey feed (experimental) * Allow multiple media uploads per selection * Major Android improvements (still wip) * Added notedeck app sidebar * User Tagging * Note truncation * Local network note broadcast, broadcast notes to other notedeck notes while you're offline * Mute list support (reading) * Relay list support * Ctrl-enter to send notes * Added relay indexing (relay columns soon) * Click hashtags to open hashtag timeline
Primal V2.2 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Version 2.2 is now live, bringing long-awaited features like Amber signing support and much more. Here’s what’s new: * Blossom media * Push notifications * Notifications overhaul * External signer support * Feed: image gallery revamp * Muted words, hashtags, & threads * Request delete for notes and articles * System photos: share via Primal
Nostur nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Add blossom media server support * Support multiple blossom servers as mirror * Fixed feed position reset on audio bar toggle * Fixed post screenshot broken for quoted posts
Fountain 1.2 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
Fountain 1.2 is live on iOS and Android This massive update brings significant design and UX improvements across the app along with new episode summaries features. Here's what's new: * Library Design Update: Fountain has made it much easier to navigate between podcasts and music in the library with the addition of new content-type filters. The Recently Played view allows users to quickly jump back into what they were listening to before, and the design of the content cards has also been refreshed. * Content Pages Design Update: All content pages—including shows, episodes, artists, albums, tracks, clips, and playlists—have undergone an extensive redesign. The previous tab layout has been replaced with scrollable pages, show notes formatting has been improved, and features like chapters and transcripts have been revamped. * Episode Summaries: Each episode page now features a Summary button above the show notes. Users can pay 500 sats to unlock a summary or upgrade to Fountain Premium for $2.99/month to enjoy unlimited summaries. Summaries and transcripts are now bundled together, and they’re faster, cheaper, and more accurate than ever before. * Playback Improvements: The audio engine has been completely rebuilt from the ground up. Playback is now more robust and reliable—especially for music. Tracks now play instantly when tapped, and users can skip seamlessly between tracks in albums and playlists. The player interface has also been updated for easier access to show notes, comments, transcripts, and chapters, with the addition of a smart resume feature for podcasts.
DEG Mods nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x
- New Events Aggregator Server, a type of aggregate/caching server that helps collect and organize mod and blog posts from the (nostr) network and presents them to the user, providing more (immensely more) reliability in discovering and presenting mods and blog posts.
- Adjusted how the mods and blogs are fetched and presented in various pages (there's now pagination for each of their pages, making navigation easier than before).
- Minor adjustment to the design of the gallery of mod posts.
- Images in a social post (in /feed) are now clustered depending on if they're next to each other.
- Quote-repost chain won't render its preview with the second quote-repost (under the posts tab in the feed page).
- Added media upload to the edit profile page.
- The games page now has a filter to switch between popular ones (shows the most popular games first based on mods published to it) or latest ones (shows games based on the latest published mods).
- Mods that are blocked by the user are now swapped with a box telling the user this is a blocked mod by them, with an option to see what that mod is.
- Mods can now be properly discovered, as soon as they're discovered, and presented (Because of that aggregate server implementation).
- A lot more games, with better search term prioritization, are now properly showing when searching in the mod submission page
- Visiting a social post directly is now visible without needing to login
RUNSTR nostr:npub1vygzr642y6f8gxcjx6auaf2vd25lyzarpjkwx9kr4y752zy6058s8jvy4e
- Record your cardio and post to nostr
- Save your stats to nostr
- Listen to your nostr:npub1yfg0d955c2jrj2080ew7pa4xrtj7x7s7umt28wh0zurwmxgpyj9shwv6vg playlists and zap your favorite artists
- Interact with the Kind1 RUNSTR Feed
- Interact with NIP29 run clubs
nostr:npub17h9fn2ny0lycg7kmvxmw6gqdnv2epya9h9excnjw9wvml87nyw8sqy3hpu Now it's possible to keep playing your text while voca is in the background.
Wasabi Wallet v2.6.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- Support for Standard BIP 158 Block Filters
- Full Node Integration Rework
- Create & Recover SLIP 39 Shares
- Nostr Update Manager
Futr nostr nostr:npub18wxf0t5jsmcpy57ylzx595twskx8eyj382lj7wp9rtlhzdg5hnnqvt4xra
- Solved memory leak in Qt5
- Fixed recursive re-rendering bug in Qt5
- Enable QML debugger through Haskell binding
- Improve event handling and Qt5 signal triggering
ZEUS v0.11.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.11.0-alpha3 with Cashu support is now available for testing: * Fix: addresses issues with sweeping Cashu tokens to self-custody with remote connections * Feat: Core Lightning: Taproot address support * Misc: UX enhancements * Cashu wallets are tied to Embedded LND wallets. Enable under Settings > Ecash * Other wallet types can still sweep funds from Cashu tokens * ZEUS Pay now supports Cashu address types. You can switch between Zaplocker, Cashu, and NWC mode but can only use one at a time.
Oracolo nostr:npub10000003zmk89narqpczy4ff6rnuht2wu05na7kpnh3mak7z2tqzsv8vwqk
Now the short notes block has two new styles: "Board" and "Full content"; the former shows notes in a pinterest-like fashion on two columns, while the latter shows full notes in full screen.
Umbrel 1.4.1 nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct
- Search files anywhere with ⌘/Ctrl + K
- New Favorites & Recents widgets
- Real-time transfer speed + ETA
- Snappier performance
- Several other enhancements & fixes
Shopstr v0.4.2 nostr:npub15dc33fyg3cpd9r58vlqge2hh8dy6hkkrjxkhluv2xpyfreqkmsesesyv6e
This update brings the following improvements and fixes: * Added Blossom media support for image uploads with metadata stripping * Added a terms of service and privacy policy * Added pagination for product viewing * Fixed relay list duplication bug * Removed excessive bottom margin on marketplace page
nostr.build nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7
The latest free features are: * 100MB upload size * Blossom support * David Lynch tribute page
openvibe nostr:npub1plstrz6dhu8q4fq0e4rjpxe2fxe5x87y2w6xpm70gh9qh5tt66kqkgkx8j
- Share Even Further : Crosspost from one network to another, or take posts beyond the open social web. Share anything, anywhere — effortlessly from
Ditto.13 nostr:npub10qdp2fc9ta6vraczxrcs8prqnv69fru2k6s2dj48gqjcylulmtjsg9arpj
Ditto 1.3 is all about discovery. From improved search and event fetching to a brand-new Explore tab, this release makes it easier than ever to find people, posts, and conversations across the #Nostr network. We've also rolled out streaks, media improvements, translation upgrades, and key admin tools.
Long-Form Content Eco
In the past two weeks, more than 356 long-form articles have been published, including over 90 articles on Bitcoin and more than 37 related to Nostr, accounting for 36% of the total content.
These articles about Nostr mainly explore the ongoing evolution and challenges of the decentralized protocol, including relay scalability, spam mitigation, signer tools, and publishing workflows. They highlight the network’s technical progress as it handles increasing data loads and infrastructure demands, while also addressing issues like spam and search limitations. Many articles focus on content creation and distribution, showcasing tools for decentralized publishing and media hosting. Others introduce practical guides for secure identity management and signer usage. The ecosystem’s economic potential is also discussed, with suggestions for monetization and community growth. Personal reflections and critiques further illustrate the culture and complexity of Nostr as it expands.
These articles about Bitcoin cover a broad spectrum of topics, highlighting its evolving role in technology, culture, and the global economy. They discuss core concepts such as decentralization, financial sovereignty, and Bitcoin as digital gold, while also addressing current issues like OP_RETURN restrictions, mining centralization, and environmental concerns. Real-world use cases—such as remittances, merchant adoption, and Bitcoin's growth in emerging markets like Africa and South America—are frequently explored. Many articles focus on user education, including wallet security, key management, and node operation. Others provide commentary through book reviews, political reflections, and personal narratives, illustrating how Bitcoin is shaping both individual behavior and institutional thinking.
Thank you, nostr:npub186a9aaqmyp436j0gkxl8yswhat2ampahxunpmfjv80qwyaglywhqswhd06 nostr:npub1xncam2l8u5chg6w096v89f2q2l0lz4jz4n7q7tdjsu6y5t9qea7q2cmrua nostr:npub10m6lrv2kaf08a8um0plhj5dj6yqlw7qxzeag6393z352zrs0e5nsr2tff3 nostr:npub15hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsffn4vc nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub1jp3776ujdul56rfkkrv8rxxgrslqr07rz83xpmz3ndl74lg7ngys320eg2 nostr:npub1dk8z5f8pkrn2746xuhfk347a0g6fsxh20wk492fh9h8lkha2efxqgeq55a nostr:npub18sufer6dgm9gzvt8gw37x08dk8gxr8u80rh8f4rjv4m4u73wlalsygnz5q nostr:npub1qpdufhjpel94srm3ett2azgf49m9dp3n5nm2j0rt0l2mlmc3ux3qza082j nostr:npub1th6p84x9u5p4lagglkvm8zepa2dq4s9eanp57vcj4w5652kafads7m930q nostr:npub1xx8t4wk2cvnz5ez7sxkvx40phgqa05a8qas4mcss0fjcdx3x96hq7jdm20 npub1qn4ylq6s79tz4gwkphq8q4sltwurs6s36xsq2u8aw3qd5ggwzuf, nostr:npub1jrr9dlerex7tg8njvc88c60asxnf5dp8hgcerh0q8w3gdyurl48q6s5nwv nostr:npub1harur8s4wmwzgrugwdmrd9gcv6zzfkzfmp36xu4tel0ces7j2uas3gcqdy and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * Recently, YakiHonne collaborated with the University of Jos and Ipaybtc community to successfully host two Nostr Workshops, attracting over 50 enthusiastic participants. The events not only provided a comprehensive introduction to the Nostr ecosystem and Bitcoin payments but also offered hands-on experiences with decentralized technologies through the YakiHonne platform.
The Nostr & Poker Night* was held on April 30 at the Bitcoin Embassy in El Salvador.The event featured an engaging Nostr-themed presentation by nostr:npub1dmnzphvk097ahcpecwfeml08xw8sg2cj4vux55m5xalqtzz9t78q6k3kv6 followed by a relaxed and enjoyable poker night. Notably, 25% of the poker tournament prize was donated to support MyFirstBitcoin and its mission to provide Bitcoin education. * A free webinar on venture capital, Bitcoin, and cryptocurrencies was held online on May 6 at 12:00 PM (ARG time). Organized in collaboration with Draper Cygnus, the event introduced the fundamentals of venture capital, showcased the projects of ONG Bitcoin Argentina Academy, and provided attendees with the opportunity to interact with the guest speakers. * Bitcoin Unveiled: Demystifying Freedom Money was held on May 10, 2025, at Almara Hub. The event explored Bitcoin’s transformative potential, helping participants understand its purpose, learn how to get started, build a career in the Bitcoin space, and begin their Bitcoin savings journey. Featured speakers included nostr:npub1sn0q3zptdcm8qh8ktyhwtrnr9htwpykav8qnryhusr9mcr9ustxqe4tr2x Theophilus Isah, nostr:npub1s7xkezkzlfvya6ce6cuhzwswtxqm787pwddk2395pt9va4ulzjjszuz67p and Megasley.
Here is the upcoming Nostr event that you might want to check out. * The Bitcoin 2025 conference was held from May 26 to 29 at the Venetian Convention Center in Las Vegas, with the Nostr community hosting a series of vibrant activities. While the Nostr Lounge served as a central hub for socializing and technical exchange, featuring app demos, lightning talks, and limited-edition merchandise. Nostr also delivered two key presentations during the conference, focusing on multisig key management and the future of decentralized social media. * BTC Prague 2025 is the largest and most influential Bitcoin-only conference in Europe. It will take place from June 19 to 21, 2025, at PVA Expo Praha in Prague, Czech Republic. The event is expected to attract over 10,000 attendees from around the world, including entrepreneurs, developers, investors, and educators.
The conference will feature more than 200 speakers from various sectors of the global Bitcoin ecosystem, nostr:npub14gm6rq7rkw56cd08aa4k5tvjnepqnxm4xvc535wj0wyjxlgrfa8sqdgv87 nostr:npub1dg6es53r3hys9tk3n7aldgz4lx4ly8qu4zg468zwyl6smuhjjrvsnhsguz nostr:npub1ymgefd46k55yfwph8tdlxur573puastaqdmxff4vj20xj0uh3p2s06k8d5 nostr:npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y nostr:npub1dtgg8yk3h23ldlm6jsy79tz723p4sun9mz62tqwxqe7c363szkzqm8up6m nostr:npub1g53mukxnjkcmr94fhryzkqutdz2ukq4ks0gvy5af25rgmwsl4ngq43drvk nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr
and more. In addition to the main program, several side events will be held, such as Developer Hack Days, Cypherpunk gatherings, and Women in Bitcoin initiatives.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ fbf0e434:e1be6a39
2025-05-13 02:00:02
@ fbf0e434:e1be6a39
2025-05-13 02:00:022025年3月17日
塔林·克里斯滕森(Taryn Christiansen),DoraHacks
特别感谢DoraHacks创始人Eric Zhang提供的深刻讨论和支持。
Part 1
自动化的浪潮无疑正在到来。人类劳动将迅速贬值。人工智能已经取得了巨大的进展,并且,随着许多创新降低了成本,越来越多的企业将能够整合这一技术。随着生产模式、资本和供应链越来越多地实现自动化,生产力和效率将加速发展。
问题是,这是否是好事。答案五花八门。从末世论者如埃利泽·尤德科夫斯基(Eliezer Yudkowsky)[1]和罗曼·扬波尔斯基(Roman Yampolskiy)[2]等人认为,人工智能有潜力——并最终将——消灭人类物种。人类将远远不如未来的人工智能高效,因此,当通用人工智能(AGI)得以实现时,智能机器很容易得出结论:人类消耗太多,世界没有人类会更好。然后是怀疑论者,如马克斯·泰格马克(Max Tegmark)[3],他认为应该暂停人工智能的发展,以便更好地将其与人类利益对齐。“只有当我们确信其影响将是积极的、其风险可控时,才应开发强大的人工智能系统。[4]”再者,也有技术乐观主义者,如马克·安德森(Mark Andreessen)[5]、萨姆·奥特曼(Sam Altman)[6]和雷·库兹韦尔(Ray Kurzweil)[7],他们主张人工智能将带来物质上的丰盈乌托邦。发展应该加速,监管者应当退让,未来将带来经济增长、生产力提高和生活水平的惊人提升。
[1] 美国人工智能理论家、作家,MIRI(Machine Intelligence Research Institute,机器智能研究所)创始人之一。 [2] 俄罗斯裔美国计算机科学家,路易斯维尔大学教授,专长于AI安全和人工智能伦理。 [3] 瑞典裔美国物理学家、MIT教授,Future of Life Institute(未来生命研究院)联合创办人。 [4] https://futureoflife.org/open-letter/pause-giant-ai-experiments/. [5] https://a16z.com/the-techno-optimist-manifesto/. 硅谷知名风险投资家、网景(Netscape)浏览器联合创始人,Andreessen Horowitz投资公司创始人。 [6] https://ia.samaltman.com/. OpenAI CEO. [7] 发明家、未来学家、作家,现为谷歌工程总监。
在这里很难做出具体的预测。不同立场的人常常以某种“不可避免性”的口气宣扬他们的观点。安德森是乐观主义最著名的主张者之一,他坚信由快速技术进步所带来的未来将是每一代人梦寐以求的那种未来。将会有具备无限同情心和耐心的人工智能导师,使教育更加普及和易获取;医疗行业将大幅提升,提供更好的预测并减少错误;机器人可以执行危险的工作,从而让人们追求自己的愿望。经济效益也将是巨大的。由于生产成本的降低,价格将更低,人们的钱将有更强的购买力,需求将增加,新的工作岗位将被创造,工资也将提高。他主张这一观点的主要论据是历史先例。每次有新技术革命到来时,社会总会从中获得净效益(net good)。十九世纪石油工业的形成之前,鲸鱼行业雇用了成千上万的工人。石油取代了这些工作,但也消除了依赖屠杀成千上万头鲸鱼来制造日常产品的需求。汽车威胁了许多行业,但当它成为普遍拥有的财产时,突然之间,需要更多的道路、桥梁和加油站来满足需求。虽然将会有自动化,人工智能将以良好的成果充斥世界,赋予经济前所未有的机会,让人们找到工作、积累财富,并利用人工智能所创造的价值。
然而,人工智能不同于以往的技术发展。人工智能是一种智能的进步和普及,而不仅仅是机械化的进步。库兹韦尔写道:“第一次工业革命扩展了我们身体的能力,第二次则扩展了我们思想的能力。”但是,一种新变量意味着结果的不同。人工智能能够学习、适应、生成、发现、反驳、怀疑、确认、设定目标,能够制定手段,也许有一天它会拥有意志并感知情感。它变得越来越具能动性(agentic)和自主性(autonomous),能够承担和完成通过它自身流程所生成的任务。如果它现在还没有具备能动性,那目标是让它达到这一点。仅仅基于先前经验得出的预测可能是一种范畴错误,容易导致误导和错误。当然,过去的技术形式与人工智能之间存在重叠,但它们之间有一个明确的区别,并且这种区别应该指导我们的预测。
另一方面,末世论者的观点并不具备很大的现实意义。那些通常潜藏在末世论者警告背后的“终结者”般的情景是不太可能发生的。尽管正如埃隆·马斯克(Elon Musk)[8]最近在《乔·罗根播客》(The Joe Rogan Podcast)上所言,如果嵌入了错误的目标,也许像“太空奥德赛(Space Odyssey)”系列作品中的HAL 9000那样的情景[9]是可能的。考虑到DeepSeek公司最近在降低计算成本方面的进展,该公司开发的AI模型已具有与美国最先进的模型竞争的水平,一场新的竞赛已经宣告开始,事情将会加速发展。美国副总统在人工智能行动峰会上的讲话清楚地表明了这一点。当前存在着一场争夺国际技术主导地位的竞争,这将塑造未来,发展速度的减缓等同于举白旗。因此,如果对安德森的主张有任何可行的反对意见,那也必须集中在如何引导技术发展,而非停止它。这应当为关于自动化的讨论提供启示:如何最好地引导自动化以避免不良结果?我们需要一种积极主动的方式。
[8] 特斯公司CEO,SpaceX创始人兼首席执行官,X(原Twitter)所有人。 [9] HAL 9000(简称HAL)是科幻小说和电影系列《太空奥德赛》中的虚构人工智能角色,由阿瑟·克拉克(Arthur C. Clarke)和斯坦利·库布里克(Stanley Kubrick)共同创作。在作品中,HAL 9000原本是飞船“发现号”(Discovery One)的中央控制系统,它被设计得极其可靠,拥有高度智能、情感模拟能力,负责飞船运行,包括导航、生命支持、通信等核心任务。在执行任务时,由于HAL开始表现出微妙的异常(如错误报告设备损坏),同行宇航员决定关闭HAL。当这一计划被HAL得知,HAL控制飞船上设备造成了同行宇航员的死亡。但后续作品揭示,HAL的表现是由于收到了相互冲突的人类指令,并决定杀死宇航员来保证两种指令都能够实现。
Section 1.1
安德森对自动化的乐观态度存在一个问题,那就是他过于确定新工作机会会得到足够的分配,供人们享受并加以利用。问题在于,经济正变得越来越依赖知识和信息。知识和信息的比重远远超过了体力劳动,而在市场上能够取得成功的人是那些拥有相关技能的人,这些技能需要通过教育和培训来获得。正如托马斯·皮凯蒂(Thomas Piketty)[10]在其《21世纪资本论》(Capital in the Twenty-First Century)一书中所观察到的,这是一个普遍的经济趋势,“趋同(即减少和限制不平等)的主要动力是知识的传播和对培训与技能的投资。”因此,随着经济日益依赖知识,那些没有相关技能或安全保障的失业工人将处于严重的不利地位。而那些拥有相关知识、技能和信息的人则更有优势,能够投资资本并增加财富。例如,即便经济增长和生产成本降低,那些没有技能的人将看到工资停滞不前。但是,假设由于生产成本降低,消费者的购买力增强,需求可能会上升,如果供应无法迅速满足这一需求,价格可能会随之上涨,从而引发需求拉动型通货膨胀。关键在于,经济和生产力增长可能无法自然应对的变量和情境。正如皮凯蒂所说,“没有自然、自发的过程能够防止不稳定、不平等的力量永久占据主导地位。”因此,必须采取积极的应对策略,来避开那些可能会导致漂浮在经济表面上的大量船只沉没的尖锐岩石。
[10] 法国经济学家。
在杰里米·里夫金(Jeremy Rifkin)[11]的《工作的终结》(The End of Work)一书中,他采用了更加严峻的语气:“(下一个)工业革命正迫使全球经济面临空前的危机,数百万人因技术创新失业,全球购买力急剧下降。”而埃里克·布林约尔松(Erik Brynjolfsson)[12]和安德鲁·麦卡菲(Andre McAfee)[13]在《第二次机器时代》(The Second Machine Age)[14]一书中提供了充分的理由,认为里夫金的观点具有一定的道理。他们认为,经济增长所带来的回报(bounty)——即通过较少的投入产生更多的产出,使商品更加便宜、更加易得,从而改善人们生活——并没有通过财富、收入和资本的分配,使每个人都被惠及而受益。换句话说,“科技进步的浪潮可能并不会使所有船只都得以提升。”例如,在上文提到的技能差距上,“自1970年代中期以来,拥有研究生学位的人的工资上涨了约25%,而高中辍学者的平均工资则下降了30%。”尽管自20世纪中期以来,美国GDP和经济生产力呈现“令人印象深刻的轨迹”,但该国的中位数收入却在下降,表明少数人正在获得好处,而大多数人却错失了机会:自里根时代以来,贫富差距不断扩大。布鲁金斯学会的这篇文章[15]也支持这一观点。
[11] 美国经济和社会理论家、作家、公众演说家、政治顾问和活动家。 [12] 经济学家、教授,现任斯坦福大学数字经济实验室主任。 [13] 研究员、作家,MIT斯隆管理学院副教授、MIT数字经济计划副主任。 [14] http://digamo.free.fr/brynmacafee2.pdf/ [15] https://www.brookings.edu/articles/rising-inequality-a-major-issue-of-our-time/
然而,也许这些观点的实际含义被错误的同情心所误导。尽管不平等的确存在,但这并不意味着它应该被视为最主要的关注变量。再次强调,技术创新使商品变得异常便宜,使人们的生活更加轻松、生活水平更高,并且通过提供更多商品、服务、信息和知识的可获取性,来满足人们的需求和愿望,从而让日常生活更便利。尽管财富分配可能存在不平等,但其整体增长使每个人都变得更好。而且,随着财富的进一步增长,这一趋势将持续。曾经只有富人能够负担得起的东西,如今大多数人都可以买得起。比如iPhone,它能提供比所有现存图书馆更多的信息,而历史上,只有最富有的人才能使用后者,而几乎任何人都能购买前者。欧洲最大的图书馆是1481年的梵蒂冈图书馆,馆内估计有三千五百本书籍和文献。ChatGPT估计,如果将网上的信息转化为书籍大小的量,将约合467千万亿本书。看看农业的发展。当经济学家米尔顿·弗里德曼(Milton Friedman)在1980年写《选择的自由》(Free to Choose)时,他写道,在《独立宣言》被签署的时代,“每20个工人中就需要有19个(从事农业劳动),以养活这个国家的居民,以及提供生产盈余以供出口,来交换外国商品。如今,只需要每20个工人中的不到1个工人,就能养活2.2亿美国居民,并提供生产盈余使美国成为世界上最大的食品出口国。”
彼得·蒂尔(Peter Theil)[16]常常宣称,问题是技术创新停滞,而不是与福利项目或分配模式相关的道德失败。科学和技术需要突破,以转变行业并提高生活标准。人工智能的智能革命,理应能够实现这一潜力。因此,也许最好是直接放手不管。专注于特定分配模式的公平或正义,就像尼采所说的那样,是一种“坏良心(bad-conscience)”——以被认为的集体利益为代价而追求个人利益时所体验到的罪疚感,但实际上,这种感受只会阻碍进步,而非推动它。真正和最好的目标,可以说是努力创新并创造推动历史发展的价值,这就像亚当·斯密(Adam Smith)[17]的“看不见的手”的隐喻一样,自然地调和了人们的自利。正如米尔顿·弗里德曼所说,“对于促使个人之间合作,进而使得每个个人都可以从合作中受益的状态而言,没有外部力量是必要的,没有对自由的侵犯是必要的。这就是为什么正如亚当·斯密所说的,‘只关心自身利益’的个人会‘被一只隐形之手引导,以推动一种与他的意图无关的目标’。”
[16] 硅谷投资人,PayPal创始人,企业家、风险投资家、政治思想家、作家。 [17] 经济学家、哲学家、道德理论家,古典经济学奠基人。
Section 1.2
关于经济增长是否足以改善长期的福祉和生活水平的问题,存在着高度争议。这个问题显然在这里无法解决。然而,提到这一点的目的是为了表明两种观点都具有正确性。个人在市场上追求自己的利益,像价格和工资这样的变量通过人们的自愿交换达成平衡,已经带来了巨大的成果。但差距也随之产生。
自动化是一个潜在的威胁。忽视它并声称它是危言耸听是一个错误。在可能的人工智能颠覆之后,某种形式的平衡达成之前,过渡期可能是复杂的,并且可能造成不必要的痛苦,如果事先处理,这些痛苦本可以避免。革命性的新技术可能既有好的一面,也有坏的一面。例如,十五世纪的印刷术使人们摆脱了教会强加的信息控制,催生了科学文献涌现的浪潮,为文明提供了巨大的价值。但它也导致了激烈而血腥的宗教战争,因为它允许人们传播各种信息。因此,为了避免类似的结果,在实施任何能够重新安排和重组社会经济安排的技术时,采取主动的方式非常重要。
从这里出发,通常的推论是,监管措施是应对这些可能性最好的手段。但与其满足于监管,正如马克·安德森在拜登政府执政期间警告的那样,监管会导致人工智能垄断,本文将力图支持自由市场中的自愿交换,同时促进必要的社会合作,帮助人们适应并在一个越来越不依赖于人力资本的经济中发挥作用。
本文的担忧是人们失去行使自身能动性(agency)的机会,从而无法拥有对自己的生活的控制(control)感和影响(influence)感。如果大量的人失去参与工作的机会,将会出现一条鸿沟,阻挡人们在世界中通常实现自己潜力的方式。他们将不再有机会在关键的社会领域做出具有深远影响的生活选择,这些选择需要谨慎和远见。人们将失去测试自我、发现天性的倾向和兴趣、辨认自己重视的事物以及行使选择去追求它的机会。社会中培养毅力、动机和个人意志的主要机会将会丧失。如果工作将主要被自动化替代,那么需要一个新的机会媒介来取而代之。作为社会制度的工作需要进步,并保持人们成长和发展的途径。
20世纪的自由主义哲学家约翰·杜威(John Dewey)写道:“正如感觉需要可感知的对象来刺激它们,我们的观察、回忆和想象能力也不是自发工作的,而是由当前社会活动所设定的需求激发。”像教育和工作这样的社会环境提供了刺激特定能力和功能所需的活动媒介,这些能力和功能需要完成定义活动的任务。人们常常争论说,自动化将使人们摆脱繁琐和机械的工作束缚。他们将有更多时间寻找新的方式来表达自己的需求,并最终实现工作一直阻碍他们实现的目标。人们将有自由去实现自己的潜力。但这一切不会自发发生。需要有能激发实现真正自由、意义和目的的活动的环境。当一个人完全孤单地待在一个没有人阻碍其动作和倾向的房间里时,可以说他是自由的。这样的人可以随心所欲。但由于没有能够激发适当反应的情境,且没有成功与失败的可能性,也缺少需要合作和协调的场景,这些场景有助于培养社会和情感的能力,也没有必要发挥智力和解决问题的能力,这个房间里的人的成长会停止,反而会枯萎,无法实现自由。一个从天空自由下落、不被任何东西阻挡的人,他看似自由,其实并不自由,因为他注定会撞向地面。
正如弗朗茨·卡夫卡(Franz Kafka)所写:“我自由了,因此我迷失。”哲学家让-保罗·萨特(Jean-Paul Sartre)则说:“人类被注定要自由。”
因此,当前的问题是,如何开辟一个人们能够自愿进入其中,并找到表达美好生活所需能力的机会的空间。此类机会,旨在行使人们的能动性,将被称为“质性丰富(qualitatively rich)机会”,而能够实现这些机会的环境则被称为“质性丰富环境”。
一个体现“质性丰富机会”的“质性丰富环境”是“开源生态系统”(open source ecosystems),它应当是人工智能发展的主要模式,它提供了以下框架:市场将为人们提供机会,让他们通过具有挑战性和刺激性的工作来行使自己的能动性,进而实现有意义的项目。人们将不得不学习新技能,克服障碍,但这一过程不仅是为了保持一个人们可以竞争、做出选择、发展能动性的市场,同时也促进人们生活中的目的和意义。如果经济要关上旧有工作形式的门,比如流水线和服务性工作,那么应该为人们提供更多有意义的工作机会。正如经济学家泰勒·科文(Tyler Cowen)在《莱克斯·弗莱德曼博客》(Lex Fridman podcast)中指出的那样,人们需要事情做。他们不想只是待在家里,正如COVID封锁所证明的那样。如果例行劳动和低技术劳动将被自动化,那么唯一的选择是确保存在“质性丰富机会”,以便人们能够利用并行使自己的能力,进行有意义的工作。
因此,应该在经济中引入一种新的范式。从佩卡·希曼宁(Pekka Himanen)[18]的《黑客伦理》(The Hacker Ethic)一书中汲取灵感,人们应当从以工业为基础的工作范式转向一种“黑客范式”。在工业范式中,个体主要执行重复性的劳动任务,其目的仅仅是为了获取收入以维持生存。而黑客范式则以内在价值为核心,强调工作本身的趣味性、刺激性、创造性与游戏性,其特征是激情与游戏,而非“履行对工作的责任”或“为经济做出贡献”的社会义务,正如马克斯·韦伯(Max Weber)[18]在《新教伦理与资本主义精神》(Capitalism and The Protestant Ethic)中所揭示的那样。黑客范式强调人类能动性及其实现价值的潜力,这种价值能提升人类。工业范式则在工人与他们与世界的积极参与之间产生疏离感:工人对他们所贡献的工作漠不关心;人们通常不喜欢甚至讨厌他们的工作。他们在那里是为了赚钱,而不是参与有意义的工作。正如希曼宁所写:“改革工作形式不仅是尊重工人的问题,更是尊重人类作为人类的问题。黑客不认同‘时间就是金钱’的格言,而认同‘这是我的生活’的格言。”正如埃里克·史蒂文·雷蒙德(Eric Steven Raymond)在《如何成为黑客》(How To Become A Hacker)[20]中所说,黑客认为世界充满了奇妙的问题,并在致力于解决这些问题中找到了自由。他们寻找需要动机和热情的项目,并相信当其他人也有机会获得同样的自由时,世界将变得无限美好,这需要社会合作以及对信息的最大程度的开放获取——这也正是“开源”的重要意义所在。
[18] 芬兰哲学家。 [19] 社会学家、经济学家、历史学家、政治学理论家,德国社会学与历史学传统的代表人物之一,被称为现代社会学的奠基人之一。 [20] http://www.catb.org/esr/faqs/hacker-howto.html
为了凸显为何引入新范式对于应对人工智能的挑战至关重要,具有显著的历史意义,我们可以回到亚当·斯密的思想。随后,将进一步阐明“质性丰富环境”与“质性丰富机会”的概念,并将其应用于当下以专有技术(proprietary technology)为核心的人工智能垄断体系。届时可以看到,这些垄断将扼杀黑客范式的生成,因此是不可取的。
透过亚当·斯密的视角我们可以看到,尽管工业化在长期内极大地提升了人们的生活水平,但它也对从事重复性、机械性劳动的人产生了消极影响,因为这类劳动削弱了对人类认知能力的刺激,阻碍了其全面发展。劳动分工极大地加速了专业化的进程,却减少了个体接触那些能调动其高级心智能力的机会——而这些能力正是实现有意义、有目标、富有成就感的工作的基础。人工智能与自动化正成为一种转型催化剂,逐步替代工业时代的工作模式与生产逻辑,将人力资本曾承担的任务转交予智能机器完成。若人工智能真的是一种进步——即人类进步——那么它就应回应亚当·斯密关于劳动分工及其对人类生活影响的担忧。
Part 2
Section 2.1
亚当·斯密在1776年写下了《国富论》(The Wealth of Nations)。受到艾萨克·牛顿(Isaac Newton)的影响,斯密希望理解社会背后的设计,以及社会的运作机制,类似于牛顿发现并使用采用机械论术语来公式化了解释宇宙的物理法则。那个时代的模型是将现象看作是像精密调校的手表一样有组织和有秩序的,所有部件和机械都在完美的和谐中协同工作,产生各种各样的效应和涌现现象。
在斯密生活的时代,第一次工业革命正在英格兰进行。城市扩张,曾经仅限于富人阶层的商品和服务变得更加廉价且易于获取,生活水平提高,基础设施得到了发展,表面上看,人们过上了前所未有的更好生活。斯密观察到社会的进步。由于大发现时代以及使欧洲人能够踏上新大陆的技术,欧洲人与那些似乎尚未经历欧洲所经历的历史进程、被欧洲人认为是“未开化”的民族接触,因此,欧洲大陆的风尚(ethos)是历史和文明正在进入一个新的、更为先进的阶段。科学探索和知识带来的创新提升了生产力和效率,从而使社会系统的组织更加复杂。斯密希望了解推动这一进程的因果机制。
斯密观察并认为劳动分工在社会经济中扮演了主要的,甚至是基础性的角色。随着社会组织的扩展,制造与生产过程逐渐细分为更为专业的任务,结果这些过程的产出大幅增加。在传统的行会框架中,工匠将一生投入到完整的手工业中,学习所需的所有方面并精通每一部分。这种行会框架逐渐被分工化的工厂模式所取代,后者在日益发展的城市中通过劳动分工的方式系统化生产。一个庞大的个体系统因此浮现,它需要极高的协调性,而劳动分工则将这一系统组织成一个复杂的机制,旨在调和人们的利益。
斯密还认为,劳动分工反映了人类本性中的某些更深层次的特征。人们涌向城市,赚取劳动报酬并享受更好的生活条件,因为斯密认为,人类天生具有进行交换(truck)、易货交易(barter)和贸易(exchange)[21]的倾向。他写道:“交换、易货和将一种物品与另一种物品贸易的倾向是所有人类共有的,在其他任何动物种群中都无法找到。”像狼这样的动物自然地在等级化的群体中组织自己,刚孵化的小鸟倾向于飞行,而像树木这样的有机体则在密林中争夺阳光。与此不同,人类进行交换、易货和贸易,是因为他们有天生的倾向来改善自身状况。劳动分工推动了这一目标的实现。
[21] 这三个词的区别在斯密研究中并没有得到广泛讨论。一些学者认为它们是同义的,通过重复表达强调(参考J.Z. Muller, (1993) Adam Smith in His Time and Ours: Designing the Decent Society, New York: Free Press第69页,Willie Henderson and Warren J. Samuels, (2004) The etiology of Adam Smith’s division of labor, in Essays on the History of Economics)。就这三个词在英语中的使用历史而言,truck system在英国曾经意为用实物作为工资的薪资制度,barter通常指不涉及货币的物物交换。
然而,斯密认为,劳动分工是一种权衡——它也有代价。尽管人们的生活水平提高,他们享受更好的条件,能够满足诸如食物、水和住所等消费需求,但劳动分工却将工人简化为机器中的齿轮。这些任务几乎不需要认知努力。一旦任务变得常规化,并转化为肌肉记忆后,便没有更多的障碍或问题需要克服。因此,斯密深切担忧这一过程将随着时间推移产生深远的负面认知效应。人们去上班,只要他们熟悉自己的任务,就不需要动脑;他们机械地行动。斯密直言不讳地写道:
“一个人一生都在执行少量简单的操作,并且这些操作的效果始终显而易见,他便无需发挥理解力,或利用自己的创造力去寻求解决从未出现的困难的方法。他自然会变得愚笨无知,几乎达到人类可能变得最愚笨和无知的地步。”
劳动分工提供的机会在质性上较为贫乏,无法使人们具备过上有意义和有目的生活的能力。借用另一位启蒙时期哲学家伊曼纽尔·康德(Immanuel Kant)的术语,劳动分工未能尊重人类的尊严,而尊严要求针对并培养那些能够使人过上自主选择生活所必需的能力。拥有尊严意味着对个人生活拥有影响力(influence)和掌控力(efficacy)。
劳动分工创造了更多提高生活水平的机会,但它没有提供“质性丰富机会”,使人们能够整合他们的能力并实现全面的人生。大多数人可用的机会并未促使他们将创造性和生产力能力集中于那些能够扩展他们在世界中自由感的目标上。与行会制度相比,劳动分工提供了更多的机会,但这些机会也更浅薄,更缺乏产生掌控感的体验。但由于生活水平较高,人们正确地选择了将自己降级为齿轮的工作。但正如斯密所观察到的,提高生活水平不足以满足人类需求的全面范围。它没有让大多数个体能够发挥他们的更高能力。
斯密认为,必须进行改善。对人们而言,更多“质性丰富机会”是至关重要的,这些机会使他们能够过上更有意义和目的的生活,体现人类尊严,并为行使他们的能动性提供基础。劳动分工提供了物质自由的增益,但并未提供足够的机会以实现更内在的、主体驱动的自由。
这无疑是卡尔·马克思对资本主义的重大批评之一。在资本主义体制下,人们与他们的劳动发生异化(alienation)。劳动的异化意味着人们与自己的活动脱离;即人在其自身和它的创造与生产能力之间产生了距离。在心理学家埃里克·弗洛姆(Eric Fromm)关于马克思的著作[22]中,他写道:“对马克思而言,异化的过程表现在工作和劳动分工中。工作是人类与自然之间的积极联系,是创造新世界的过程,包括创造人类自身……但随着私有制和劳动分工的发展,劳动失去了作为人类力量表达的特性;劳动及其产品变成了与人类、与他的意志和计划分离的存在。”
[22] Eric Fromm, Marx's Concept of Man.
人类通过他们所参与的活动以及在其中投入的内在力量和驱动力来理解和塑造自己的身份。通过创造和塑造世界及其环境,并将能量集中于外部项目和目标,一个人在世界中实现自我感。活动(Activity),而非被动的消费或任务,定义了马克思所说的人类本质。正如弗洛姆在其著作《拥有与存在》(To Have or To Be)中所指出的,通过“存在(being)”,而非“拥有(having)”,一个人才能体验到生活的意义和目的。通过“在爱中存在”,“以充满激情的方式存在”,“以积极行动的方式存在”,“以有希望的方式存在”,“有目的地存在”,以及“以有生产力地方式存在”,一个人才能过上充实的生活,而不必依赖“拥有”(爱、激情、积极性,等等)这些东西。劳动分工强调“拥有”,而其所涉及的许多工作和活动并未促使人们发展出“存在感”。正如德国诗人歌德(Johann Wolfgang von Goethe)所言,人类通过“将自己从可能性的黑夜转化为现实的白昼”来努力存在。人类通过外化他们内心的价值观和设想来追求成为自我,而这一过程通过活动得以实现。弗洛姆写道:“人类只有在生产性行为中才是活着的,只有在他通过表达自己特定的人类能力来把握外部世界,并且以这些能力来把握世界时……在这个生产性过程中,人类实现了自己的本质。”劳动分工减少了人类的能动性感,即人类以他们所珍视的、选择并在其上实践自身意志的有意义的方式,来主动影响和引导自己生活的能力。
通过创建“质性丰富环境”,黑客范式及其对开源的推动提供了多个“质性丰富机会”,从而推动了我们社会和政治结构的进步。它具有实现人类天性中更为积极的一面——人的能动感——的潜力,而不仅仅是其消极和消费的部分。这里的主要假设是,如果人工智能要发展并融入经济基础,它应当使人们的生活得到改善。更具体地说,如果自动化发生,其结果应当是改善人们的生活,而非对他们造成伤害。实现这一目标的一种途径是确保足够分配“质性丰富机会”,让每个人都能从中受益,而开源正是实现这一目标的途径。人工智能发展可能导致人们境况恶化以及抑制他们潜在机会的一个重要原因是存在使用专有模型来控制人工智能并主导其市场使用的垄断现象。黑客范式和开源则为避免这种结果提供了可能的解决方案。
Section 2.2
在理解垄断如何减少“质性丰富机会”之前,我们需要进一步弄清楚什么是“质性丰富机会”,以及它们激发并帮助发展哪些能力。在解释这类机会的性质及其意义之后,我们将探讨垄断是如何大幅削弱这些机会的可及性,以及这意味着什么。
“质性丰富机会”的理念源自亚里士多德(Aristotle)[23],更具体地说,是由哲学家玛莎·努斯鲍姆(Martha Nussbaum)和经济学家阿玛蒂亚·森(Amartya Sen)进一步发展的。亚里士多德认为,人类要实现繁荣、过上充实而有尊严的生活,必须达成某些特定的功能(functions)或方式。他认为存在一种“人性(human nature)”,而这种人性包含基本的和更高层次的需求。无论历史和偶然条件如何变化,人类都具有一些根本特征。当然,这些特征是在历史情境中体现的,但在所有文化和文明中都可以观察到某些本质上的一致性。亚里士多德说:“善是万物所追求的目标。”所谓“善”,即是一种事物的适当功能。例如,眼睛的善是“看见”,种子的善是“长成一棵树”。实现某物的适当功能,就是实现其“繁荣”(flourish),也就是达到它所追求和努力趋向的状态。达到这样的状态,就是获得一种内在价值。
[23] 古希腊哲学家。
作为一个人去实现其功能,需要基本的生活必需品,如食物、水、住所和行动能力。但这些物品本身并不具有内在价值;它们之所以有价值,是因为它们使人能够运作以追求更进一步、更有内在价值的事物。如果一个人仅仅拥有这些基本的生存条件,我们可以说他“运作”着,但未必是“良好地运作”。要使一个人“良好地运作”,必须拥有其他内在价值更高的资源。人类需要教育与信息获取,以发展其认知能力;需要家庭和亲密关系,以发展社交技巧、个人身份认同和情感处理能力;还需要能够施展意志、探索兴趣、投入热情的追求,并培养目标感的渠道。一个良好的政治与社会安排,即我们应当追求的那种社会制度,应当为人们提供具体的机会,让他们得以实践这些需求,从而实现良好的人类运作状态。“质性丰富机会”即是指那些能够为人类发展内在有价值的能力(如做出知情决策的能力、制定值得追求的目标及其实现路径的能力,以及建立有意义、有影响力的人际关系的能力)提供基础的机会。像工作、教育、社区和艺术等社会制度,正是那些激发并促进实现这些目标所需能力的质性丰富环境。
质性丰富机会之所以重要,是因为它们使人们具备发展“能动性”的能力。借用斯坦福大学心理学家阿尔伯特·班杜拉(Albert Bandura)[24]的概念,我们可以将“人类的能动性”理解为个体感受到自己对生活有控制和影响力的能力。更具体地说,质性丰富机会能够激发那些针对“自我效能”(self-efficacy)能力的行为。所谓“自我效能”,是指一个人在面对挑战和障碍时所拥有的自我信心感。当面对一个困难且新颖的任务时,高自我效能的人会评估自己有能力克服困难完成任务;他们会拥有坚持不懈、克服失败的动机;即使身处陌生与复杂情境中,他们也能维持良好的心理状态。质性丰富机会旨在发展那些能够提升自我效能以及应对具体情境所需的能力。通过这些机会,一个人得以锻炼其能动性、获取掌控力,从而扩展其自由感。而正如班杜拉(1994)[25]所说:“一个人自我效能感越强,他为自己设定的目标挑战越高,并且对这些目标的承诺也越坚定。”因此,通过增强自我效能,无论是在信念层面还是实践层面,个人将获得更高程度的自由,并过上更具质感、更丰富的人生。
[24] https://happyheartfamilies.citymax.com/f/Self_Efficacy.pdf [25] https://happyheartfamilies.citymax.com/f/Self_Efficacy.pdf
工作在塑造个体身份和自我认同方面具有至关重要的作用。它为人们提供了探索不同职业路径的机会,使他们能够发现自己在人生中希望追求的目标。工作往往也是建立职业与个人关系、融入不同社会网络的重要方式,同时也是人们获取能力、攀登社会阶梯的媒介。工作这一领域还能帮助人们在多种环境和情境中培养动机、智力以及态度。换句话说,工作为人们提供了发展某些功能或生活方式的机会,而这些功能和生活方式正是实现美好生活所必不可少的。
例如,想象一个年轻人第一次进入劳动力市场。他尝试了几份工作。他发现自己不太喜欢零售业,因为需要持续与顾客打交道。他又尝试了送货服务,结果发现自己不喜欢那种日复一日的重复性工作。最后,他在一个建筑工地找到了工作,并发现有些任务既有趣又具有挑战性。他喜欢动手工作的感觉,于是决定投身技工行业。这个人随后进入技校学习,建立起重要的人际关系,在新环境中受到挑战,被激发去提升技能、积累知识与经验,并在这个过程中不断面对和克服新的困难与障碍。毕业后,他抓住了一个机会——一位欣赏他职业精神的导师为他提供了许多关注和支持。之后,他在某家公司工作了一段时间,并在这个过程中积累了足够的知识和自信,决定创办自己的公司,以实现这个目标。他开始建立客户关系,专注于能让自己在竞争中脱颖而出的技能,并最终打造出一家成功的企业。
这听起来也许有些理想化,但却是一个既熟悉又现实的例子。它描绘了一种有目的的生活,这些目的是通过在环境和情境中发现的机会而形成的,这些环境和情境提供了能够产生能动感和自我价值感的体验。当然,要实现这样的人生画面,通常还需要一系列其他条件,例如成长于一个有支持的环境中,拥有探索个人兴趣所需的资源和时间等——但在美国,工作无疑是提供发展构成美好生活的关键功能的核心渠道。上文中的这个人通过学习新技能、克服挑战、做出关键选择来应对社会环境,最终实现了成功与成就。随着在专业领域的成长,他不断设立新的目标,并获得足够的自我效能感,相信自己能够实现这些目标。他发展出一整套完整的能力体系,最终也获得了尊严感。无论这个人过去或未来是否还拥有其他美好的人生经历,如果没有那些能够让他工作与成长的机会,他的人生质量将会大打折扣。
这里有一个真实的例子,不过这个人将保持匿名。在荷兰大学毕业后,他不想找一份“普通的工作”,于是开始前往其他国家旅行。他靠在 YouTube 上制作音乐赚了一些钱,住在各地的酒店和青年旅舍。但随着资金逐渐减少,孤独与疏离感开始加剧,他变得抑郁。他完全自由——可以去任何地方、看任何东西,做任何他想做的事——但他感到极度孤独。在亚洲的一家青年旅舍,他一个人躺在床上盯着天花板,没有钱、没有女朋友、也没有工作,他想起了父亲曾对他说的话:“他小时候教过我:每当我感到沮丧或者不知道做什么时,就去找一座沙堆,拿把铲子,把沙子从院子的一边搬到另一边……干点体力活,做点辛苦的事——做点什么。我做创业项目时也一样。”于是,他开始学习编程,开发软件和应用程序,并利用 Stripe 平台[26]将作品发布给公众以筹集资金。他专注于那些能够带来方向感与创作机会的活动。在真正的“黑客精神”指引下,他把世界看作充满待解决问题的迷人场域,有些问题他认为是可处理且值得去做的,于是尝试去解决。令人惊讶的是,他立下目标:一年内创办十二个初创公司——而他真的做到了。
[26] 一个专注于在线支付处理和金融基础设施的平台,帮助企业在互联网上管理资金流动。
这个人起初感到疏离与孤独,缺乏人生目标。因此他选择行动起来,把自己投入到使用基础编程语言与工具进行的创造性表达中。通过利用人工智能,他也更能创造出具有价值和实用性的产品,供他人使用与体验。他采纳了父亲的建议,将自己投入到实际行动中,结果是抑郁与焦虑逐渐缓解。他在信息丰富的环境中,发现了许多“质性丰富机会”,得以发展自我,提升自我效能感与能力。他与更多富有挑战性的目标建立联系,不断努力达成这些目标。而开源技术在这一过程中扮演了关键角色。
这也正是 Dora 生态系统的重要意义所在。通过像 DoraHacks.io 这样的平台,像上文所描述的那样的人们可以借由“质性丰富机会”,与全球各地的开发者协作,共同创新,创造出人们认为紧迫且相关的有意义的解决方案。该生态系统为开发者提供了必要的资源,使他们能够加入全球任何地方的 “BUIDL” 团队,解决引人入胜的问题;并在黑客松中与其他建设者一起感受到社区归属感;同时还通过激励机制推动他们实现有意义的目标,而这些目标往往又会引发更具挑战性和刺激性的下一阶段任务。Dora 生态系统创造了一个充满可能性的环境,使人们能够构建去中心化的产品与服务,例如将所有权交还给用户本人,增强他们在数字世界中的自主性、安全性以及对金融资产的控制力。正如下文将进一步讨论的,大型企业和垄断机构通常并不会从这些类型的技术中直接受益。那么,他们又有什么动机去资助这类技术呢?开源技术栈能够提升价值的质量,因为它为人们提供了开发更具意义产品的路径,而这些产品通常比那些由大型、目标狭隘的机构所产出的产品更具意义。
因此,如果自动化有可能减少甚至消除人们运用能动性、获得自我效能感的“质性丰富机会“,那么它所腾出的空间,理应由其他在质性上更丰富的机会来填补。如果确实存在“人性”这样的东西,而这种人性包含了一系列需要被发展、以使人得以过上有尊严生活的能力,那么最优与最值得追求的政治与社会安排,应当是将“质性丰富机会”公平分配,以确保人们有选择去运用自身能力、成为能够良好运作并实现繁荣生活的个体。为人们提供质性丰富机会,使他们能够加以利用,并据此组织、调动并集中自身内在力量于那些能够锻炼与激发个体能力的实践之上,这就构成了一个让人过上更有意义人生的基础。它是给予人们成为他们所珍视之人的自由。
接下来的部分将转向对 AI 垄断企业的讨论,揭示它们是如何压制上述这类未来机会的。
Part 3
Section 3.1
人工智能领域中潜在的垄断者不言自明:谷歌、苹果、微软、Meta 和亚马逊。这些公司以及少数其他企业在 2024 年占据了 65% 的固定网络流量和 68% 的移动网络流量[27]。谷歌大约占据全球约 90% 的搜索市场,其品牌名几乎已成为“搜索”行为本身的代名词;Meta 拥有主要的社交媒体平台,如 Instagram、Facebook 和 WhatsApp,这些都是人们日常交流与信息分享中访问量极高的平台;微软控制着大约 72% 的桌面操作系统市场;在美国,苹果约占据 60% 的智能手机市场份额;而亚马逊则主导了线上零售,其规模“超过美国排名其后的 15 家最大电商零售商的总和”[28]。此外,谷歌、Meta 和亚马逊合计占据了美国约 60% 的广告收入。我们在网上所接触到的产品、精美广告、以及注意力的买卖,主要都是由这几家大型科技公司驱动的。根据 Synergy Research [29]的研究,到本世纪末,微软、谷歌和亚马逊三家公司可能将掌握全球高达三分之二的数据份额。这些公司还控制着大部分云基础设施——亚马逊、微软、谷歌(以及阿里巴巴)合计拥有全球 67% 的云计算市场份额[30]。
这些公司拥有庞大的资源储备,同时也长期以来采用各种手段排挤竞争对手,包括通过并购消灭潜在威胁、利用市场主导地位优先推广自家产品、实行掠夺性定价、利用网络效应,以及其他众所周知的策略。例如,鉴于亚马逊在电子商务领域的市场主导地位,它可以通过优先推荐自家产品,排挤其他可能品质更高的供应商产品。消费者在面对价格更低的亚马逊产品时,往往更倾向于购买,而亚马逊正好拥有充足的资源来维持这种低价策略。在网络效应方面,“目前[31]大多数科技巨头的用户数量都以十亿计”,这为初创企业和小公司制造了几乎无法跨越的障碍。而谷歌也多次被指控故意降低某些内容的排名,并优先展示有利于自身利益的信息。
[27] https://www.applogicnetworks.com/blog/sandvines-2024-global-internet-phenomena-report-global-internet-usage-continues-to-grow [28] https://www.emarketer.com/learningcenter/guides/amazon-revenue/ [29] https://cxotoday.com/news-analysis/big-tech-to-own-two-thirds-of-world-data/#:~:text=Without%20sounding%20like%20a%20predictor%20of%20doomsday%2C,data%20centers%20while%20the%20rest%20is%20on [30] https://botpopuli.net/digging-deeper-assessing-big-techs-capture-of-the-internets-infrastructure/#:~:text=The%20dominance%20of%20Big%20Tech,Services%20(AWS)%20in%202006. [31] https://academic.oup.com/policyandsociety/advance-article/doi/10.1093/polsoc/puae012/7636223
如今,这些公司正积极争夺对人工智能发展的主导权。“Meta、微软、亚马逊和Alphabet 预计在2025年将累计投入高达 3250 亿美元的资本支出与投资……相比这些公司在2024年报告[32]的约 2230 亿美元,这相当于增长了 46%。”此外,“几乎没有例外,所有初创公司、新进入者,甚至 AI 研究实验室都依赖这些大型科技公司:他们依靠微软、亚马逊和谷歌的计算基础设施来训练系统,也依靠它们庞大的消费市场渠道来部署和销售 AI 产品[33]。”科技巨头垄断了初创公司赖以生存[34]的关键资源——人才、数据和算力。
[32] https://finance.yahoo.com/news/big-tech-set-to-invest-325-billion-this-year-as-hefty-ai-bills-come-under-scrutiny-182329236.html [33] https://www.technologyreview.com/2023/12/05/1084393/make-no-mistake-ai-is-owned-by-big-tech/ [34] https://academic.oup.com/policyandsociety/advance-article/doi/10.1093/polsoc/puae012/7636223
现有的行业巨头正在开发各种模型,以维持其在各自市场中的立足点。由于它们掌握着大多数资源——例如,“这些公司贡献了标普500指数公司市值的 22% 以上,其单独市值甚至超过了加拿大、意大利等[35]部分 G7 国家 GDP”——它们可以随意挤压竞争对手,阻止初创企业和小型公司进入市场。正如前文所述,随着 DeepSeek 在全球市场中作为竞争者不断取得进展,这些最大规模的 AI 公司正在大肆渲染一场“军备竞赛”,并夸大中国威胁以及人工智能可能带来的危害,从而推动对 AI 的监管和开发限制,而这些限制最终最有可能使它们自身受益。与此同时,由于垄断体制依赖于专有模型,其架构、权重、学习算法、代码以及内嵌目标都对公众隐蔽不明,在 AI 渗透信息网络的过程中,这些公司的经济与市场主导地位也将以一种“隐秘的方式”塑造人们的思维和行为。
[35] https://academic.oup.com/policyandsociety/advance-article/doi/10.1093/polsoc/puae012/7636223
那么,监管是否能解决这个问题呢?《麻省理工科技评论》最近指出:“监管或许有帮助[36],但政府政策最终往往加固了这些公司的权力,而非加以削弱——这些公司能够利用其资本与政治影响力来操控政策。”亚历克斯·蓝姆佩尔(Alex Rampell)[37]最近写道[38]:“拜登政府发布了一项行政命令[39],试图以人为设定的门槛限制计算能力,禁止开源技术,理由是其对国家安全构成威胁,同时这实际上为几家最大公司垄断监管资源敞开了大门。”例如,尽管萨姆·奥特曼在与贝利·韦斯(Barry Weiss)[40]的《自由新闻播客》(Free Press podcast)中否认了这一说法,投资人马克·安德森却一再警告称,拜登的 AI 行政命令的真正目的在于将 AI 的控制权交到少数几家公司(极可能是 OpenAI)手中,并通过提高市场准入门槛来消除竞争者。此外,尽管此举颇具争议、甚至可能显得天真,自从 DeepSeek 发布其 V1 和 V3 模型以来,Anthropic的 CEO 达里·阿摩地(Dario Amodei)一直呼吁加强出口管制政策[41],进一步限制中国获取芯片的能力。然而,正如迪伦·潘特(Dylan Patel)[42]和纳森·兰伯特(Nathan Lambert)[43]在 《莱克斯·弗莱德曼博客》中指出的那样,DeepSeek 的开源模型显然并不构成任何实质性的国家安全威胁。但它确实对那些依赖专有系统、通过模型控制潜在价值的生态构成了威胁。DeepSeek 的方法迫使这些“专有资本”朝着可被任何人使用与构建的公共资源方向转化。正因如此,阿摩地对“单极 vs. 双极世界”的坚持背后其实包含着竞争性的动机:要么 AI 权力集中于美国,要么中美都拥有对等的 AI 能力——而后者,在阿摩地看来,是必须避免的局面。
[36] https://www.technologyreview.com/2023/12/05/1084393/make-no-mistake-ai-is-owned-by-big-tech/ [37] 硅谷知名投资人,安德森·霍洛维茨基金(Andreessen Horowitz,简称a16z)的普通合伙人(General Partner)。 [38] https://a16z.com/why-deepseek-is-a-gift-to-the-american-people/ [39] https://www.federalregister.gov/documents/2023/11/01/2023-24283/safe-secure-and-trustworthy-development-and-use-of-artificial-intelligence [40] 美国著名记者、专栏作家,独立新闻平台自由新闻(The Free Press)的创办人。 [41] https://darioamodei.com/on-deepseek-and-export-controls [42] 半导体行业分析师,SemiAnalysis网站创始人。 [43] AI研究员、工程师。
或许,我们应当持有一种不那么鹰派的乐观态度。经济学家泰勒·科文提出了充分理由,认为与其全面投入一场军备竞赛,不如在相互合作[44]与共赢中寻找发展路径。当然,竞争仍然是必要的,但推动未来事件进程的竞争心态,不应仅仅源于达尔文式的“适者生存”逻辑,而应更接近尼采所观察到[45]的古希腊式“竞技”(Agon)[46]传统——那是一种社会制度,其中的艺术家、军事领袖与运动员通过竞争彼此激励、共同成长。
[44] https://www.youtube.com/watch?v=TcJtvzF-FP8&t=2736s [45] http://www.northamericannietzschesociety.com/uploads/7/3/2/5/73251013/nietzscheana5.pdf [46] https://en.wikipedia.org/wiki/Agon
没有对手,竞争者也将迷失方向。因为没有了改进、突破和创新的机会,个体便失去了变得更好、更具创造力的可能。竞争者的存在本身就依赖于愿意对抗他们的人。正是因为有人挑战,希腊诗人才得以想象得更深远、表达得更出色。尼采指出,希腊竞技者面临的最大危险不是失败,而是——失去竞争对手。他写道:“这正是希腊竞技理念的核心:它厌恶独裁,畏惧其危险,它渴望用‘另一个天才’来抵御某一位天才的压倒性力量。”我们不应将竞争理解为自然状态下的求生挣扎,那种资源稀缺、人与人互为威胁的霍布斯(Thomas Hobbes)式处境——“孤独、贫穷、肮脏、残暴而短暂”[47]。我们也不应将竞争本能视为某种原始性冲动的残余,只为了压制对手、消灭威胁。我们应当将其理解为一种可以高贵化的本能,正如尼采所言,它是“所有人类情感、行为与作品的唯一丰沃土壤”。竞争本能自身也具有德性,应当被培养成“在正确的时间、以正确的方式、出于正确的理由”去发挥作用的东西(亚里士多德,《尼各马科伦理学》(Nicomachean Ethics)第二卷),而不是被视作一种必要之恶。阿摩地害怕中国,这可能不是正确的回应——或许,一个更好的、更具德性的回应,是将中国视为值得尊敬的竞争者。
[47] 霍布斯的《利维坦》(Leviathan)中对自然状态下的人的生活的刻画。
Section 3.2
现在让我们聚焦于这些潜在的 AI 垄断企业为何会通过主导 AI 生态系统,压制质性丰富机会的更广泛传播。原因至少有两个:第一个涉及经济能动性,第二个涉及价值能动性。所谓经济能动性,是指人们进入市场、创造能满足消费者需求与欲望的价值与效用的能力。如果市场上的 AI 模型被集中掌握在少数公司手中,新兴企业与创业者为世界做出有价值贡献的机会将受到限制。那些能够回应民主、医疗保健、金融自主、政治权利与自由,或其他重大而有意义问题的创新,将大幅减少,从而也会降低 AI 所可能带来的社会福祉。任何威胁到这些少数 AI 垄断企业的控制力、影响力或财富的产品与服务,将被直接排除在市场之外,而不是由市场自然机制或消费者的真实需求所决定。
另一方面,所谓价值能动性,是指人们有能力对社会应追求的目标产生影响、发表意见。如果 AI 是在不透明的条件下、依据无法被公众了解和介入的价值与目标进行训练的,那么人们在这些问题上的影响力就会被削弱。如果由专有模型决定大多数或几乎全部嵌入 AI 的产品与服务的性质,那么人们对这些技术的控制权将大为减少。例如,所谓“对齐问题”指的是如何使 AI 与人类的利益保持一致。那么,什么是人类的利益?什么是构成一个良好且值得追求社会的目标?AI 的运行应遵循哪些道德与伦理原则?这些价值是否可以由少数几家公司决定,而无需公开其训练数据与学习算法?是否可以不接受公众监督与介入?如果技术架构被封闭在公众视野之外,那么上述问题的答案就更有可能来自权威的决定,而不是通过民主程序获得的共识。
经济能动性与价值能动性的双重丧失是危险的,本文余下部分将进一步阐述原因。
Section 3.3: 经济能动性
正如奥地利经济学家路德维希·冯·米塞斯(Ludwig von Mises)与弗里德里希·哈耶克(Friedrich Hayek)所著名指出的,苏联之所以在某些方面具有毁灭性,部分原因在于它无法通过自然发生的市场机制来合理分配资源。在这样的体制下,由内部的中央计划者来决定人民的需求与欲望——而这些人所掌握的信息资源既稀缺、又充满偏见与误差,无法实现准确分配。因此,大量官僚主义和强制性的手段被实施来调配国家资源。
举例来说,国家必须设定价格。至少是在苏联的情况中,并不存在一个广泛可用的自由市场,来使商品与服务受到供需关系的调节。生产者依据国家命令进行生产,而非根据市场激励(如竞争)自行调整方向——这些激励本应协调生产与消费,促成市场均衡。换句话说,价格失去了其关键信息功能——它本应指示资源该流向何处。哈耶克在《通往奴役之路》(The Road to Serfdom)中写道:“任何对某些商品的价格或数量的控制,都剥夺了竞争协调个体努力的能力,因为此时价格变动无法反映环境中的相关变化,也就无法为个体行动提供可靠的指导。”
不过,对本文来说,更重要的是:国家控制的生产与经济计划还意味着人们被剥夺了进入市场并创造价值的机会,使他们难以通过创新改善自身生活。任何可能威胁国家权力、削弱其合法性与影响力,或转移其部分控制权的创新行为,都将被禁止进入市场。举个例子:假设某人观察到,在某国的偏远乡村地区,由于常年洪水泛滥,人们无法修建道路,从而难以参与国家选举。这位发明者研发了一种不受洪水腐蚀的新型混凝土,并希望在乡村修建道路,改善人们的通行条件,让他们更容易参与公共事务。但当他向国家交通委员会申请资源时,却遭到了拒绝。原因是:该地区居民普遍希望拥有农业生产的自主权,因此国家不愿意为这些人提供进入选举制度的通道。而在缺乏市场竞争的情况下,也没有其他机会和机制可以去建设这些道路。
垄断,尤其是在受到监管体系保护的情况下,构成了类似的威胁。马克思曾做出一个著名批评:资本主义作为一种社会制度,其内在逻辑会逐步而不可避免地导致生产资料向少数人手中集中。虽然包括哈耶克和米塞斯在内的许多经济学家认为这种看法是错误的,并坚信在正常运作的资本主义体系中,这一结果是可以避免的。但如果人工智能遭到垄断,那么马克思的预测将比以往更加接近现实——无论这是由于历史规律,还是由于无法预见的结构性变数所致。正如克里斯·迪克森(Chris Dixon)[48]在其著作《阅读、写作、拥有》(Read, Write, Own)中观察到的,初创公司之所以能在市场中找到生存空间,部分原因在于大公司往往目光短浅,无法及时察觉到新兴产品正逐步获得消费者的关注。在专注于自身业务的过程中,这些巨头常常错失市场趋势与动向,而初创企业若运气足够好,就能积累足够势能以形成竞争力。但如果这些老牌巨头掌控了人工智能,他们就可能利用 AI 的能力来抹平初创企业原本可以利用的那些优势。随着时间推移,垄断企业将对市场形成难以穿透的控制权,各行各业的价值链最终将进一步“上游集中”到这些公司手中——比现在更甚。由专家所忽视、却能在市场中创造出意想不到价值的颠覆性技术,其创新空间可能会被完全挤压出去。
[48] 安德森·霍洛维茨基金普通合伙人,负责加密货币与Web3投资部门(a16z crypto)。
由于人工智能具备智能能力,它作为资本工具拥有极大的潜力,能够创造出改善人类生活的先进技术。但,由于有些对公众最有益的应用方式,可能并不符合政府与大型企业的利益,其潜在福祉也就可能在权力结构中被悲剧性地削弱。其中最明显的例子就是金融自主权。
看看比特币的案例就足以说明问题。中本聪(Satoshi)[49]发明比特币的初衷,是为了让人们拥有金融自由的能力——通过创造一种稀缺资源,其价值储存功能可与黄金相类比。比特币使那些生活在高通胀、货币极度贬值国家的人们,能够积累具有全球流通性的财富。人们可以拥有一种不会因货币供应过量或国家财政赤字上升而贬值的资产。比特币能够帮助人们过上更加稳定、安全的生活,它提供了透明性、个人所有权,以及能够激励社会合作的制度安排——这一切都无需依赖强制性信任或道德施舍。
[49] 比特币(Bitcoin)的创造者,身份不明。
人们本希望掌权者能够设法将中本聪为世界带来的巨大价值纳入现有体系。并不是说比特币应立即取代法定货币,而是说,考虑到比特币在应对法币体系中潜在致命问题方面提供了极具前景的解决方案,政府至少应当付出更大的努力,将这些解决方案纳入实践。合理的期待是,执政者会寻求一种方式,将区块链、比特币及其增强经济自由的潜力加以整合。然而,直到最近,有关这一技术的监管进展一直缓慢而混乱。在拜登政府期间,由于政策缺乏清晰性与明确性,关于加密货币的许多举措都未能充分发挥其潜在价值,反而阻碍了其更高效、更具生产性的使用路径。
如果AI被通过监管框架实现垄断,那么那些原本有潜力改善人类生活的技术也可能轻易被弃置。若这些技术与政府或企业利益发生冲突,大多数人将无法通过授权或专利使用这些专有模型,而中小型企业也会被并购吸收。尽管人工智能本可以彻底革新选举平台及人们参与选举的方式;尽管它本可以通过更优的数据安全手段或创造更多经济机会来增强个体自由,但探索这些可能性的路径,若与掌控大多数 AI 技术栈(甚至全部)的公司利益不符,就很可能被封锁。如果某项潜在的 AI 技术有可能通过解决某些产业赖以牟利、甚至具有寄生性质的问题,从而威胁广告收入,那么像谷歌与 Meta 这样的科技公司几乎必然会阻止这一技术进入市场的尝试。
特朗普政府迄今为止最重要的政策举措之一,就是其新的加密货币政策。该政策废除了上一届政府的行政命令,并致力于制定一个有助于推动该技术发展的监管框架。这对于人工智能领域中正在发生的其他形式的创新具有重要意义。有了除了传统风险投资之外的其他资源——例如通证经济(tokenomics)[50],初创公司可以为其项目提供资金支持,并积累发展势能。
[50] 也译为“代币经济学”,是对加密货币或区块链项目的经济层面的研究和分析,尤其关注其原生数字代币的设计和发行。该术语由“代币/通证”(token)和“经济学”(economics)两个词组合而成。
彼得·蒂尔在其著作《从零到一》(Zero to One)中提出,初创公司本身就在、也应该在寻求成为垄断者。他们需要在市场中占据一个特定空间,通过开发专有技术击败其他竞争者,并进一步排除后来者进入该市场。正如蒂尔所言,如果企业不想成为失败者,这种策略是至关重要的。若他们希望获得投资者的关注,就必须采取建立垄断地位的路径。然而,借助通证经济以及其他与加密货币相关的机制,人们也有机会开发出有价值的技术,同时保留开源精神。在这样的机制下,合作与协作得以推动,同时也能获得支持增长所需的资金。
Section 3.4 价值能动性
经济能动性之所以被削弱,是因为市场中那些具备质感的价值创造机会正在减少,使个体难以通过创新与生产满足不断变化的需求与欲望。当 AI 技术栈被少数几家垄断企业掌控并主导整个生态系统时,即使有人识别出一个真正有意义的问题,并设计出强有力的解决方案,如果这不符合大型企业的利益,该方案也很可能无法进入市场。经济活动及其所带来的社会价值,不应建立在一套容许权力任意压制、扼杀对社会整体有益事务的权威机制上。那么,AI 垄断企业又是如何压缩人们在价值能动性上的“质性丰富机会”的呢?
如果雷·库兹韦尔的奇点理论及其相关预测哪怕部分属实——如果人类真的将与非生物智能融合,并生活在日益人工化的环境中——那么人工智能的垄断不仅不可取,而且可以说是一种反乌托邦式的局面。这种设想唤起了关于“技术霸主”的画面:他们主宰着人类社会,而人们要么沦为智能机器的奴工,要么则是舒适而满足地享受着智能繁荣所带来的物质成果。在这样的图景中,总有人必须开采矿物资源,而另一些人则消费着由此生产出的丰富商品与服务。但如果我们假设 AI 的发展会快到足以让智能机器人无需人力就能完成矿产开采工作,那最终所有人都会转变为纯粹的“消费者”。“在接下来的几十年里,”库兹韦尔预测,“几乎所有例行性的体力与脑力活动都将被自动化。”届时,唯有那些具有社交性、创造性、创新性或高度不可预测性的工作将对拥有相关技能与培训的人开放,其余人将大多成为消费者。而借助纳米机器人、虚拟现实、非生物智能增强技术与无处不在的信息流动,我们的现实将愈加接近哲学家罗伯特·诺齐克(Robert Nozick)所设想的“体验机”(experience machine)。
通过某种装置的介入——无论是接入某种模拟装置,还是完全沉浸于类似虚拟现实(VR)那样的数字化、信息化环境中——人们可以体验到他们所希望的任何事情。任何感官体验、情绪、思想或事件,都会随时向任何人开放,随时可供消费。一个人可以体验写出“伟大的美国小说”所带来的深刻满足,像苏格拉底[51]那样在雅典法庭上勇敢地对抗陪审团,或像拿破仑那样英勇地站在青翠的高岗上俯瞰敌军,也可以在模拟的攀登中登上珠穆朗玛峰,体会坚持不懈的荣耀与世界之巅的视野。重要的不是这些事件是否真实发生,而是有人“渴望”它,而它就会“存在”。在这样的图景中,人生的目标就是消费;而“道德生活”——值得追求的生活——则被定义为追求内部刺激的生活。外部世界、个体真实的存在状态将不再重要。一个人是否真实地勇敢、富有同情心、充满爱意、公正、虔诚、善良或邪恶——这都不再有意义。人们的兴趣与冲突将在人工体验的消费中得到调和。在一个“问题已被解决”的世界中,没有需要行动者去解决的具体问题,行动者也就变得可有可无;唯一需要的,是“消费”。
[51] 古希腊哲学家。
这种情境真正危险之处在于,垄断企业将完全掌控生成技术的算法,也即控制我们可接触的信息结构。信息将不断被嵌入到以消费为中心的环境中。理想情况下,人们应当拥有自由,做他们想做的事,以他们认可的方式生活。但人们“看待”世界的方式,他们建构现实的方式,他们所处的社会语境——都会被那些已经整合智能资本、成为未来唯一商品与服务生产者的公司所过滤与塑造。哲学家艾伦·布鲁姆(Allan Bloom)在其著作《美国精神的封闭》(The Closing of the American Mind)中写道:“每一个教育系统都有一个它希望达成的道德目标,并据此构建其课程。它希望塑造出某种特定类型的人。”人工智能的垄断企业将通过改造人的生存环境来塑造“人是什么”的意义,以符合其自身利益。而真正重要的那些事情——运用能动性、实现真实的自我效能感、发现自己在人生中真正珍视与渴望的事物、建构让现实更一贯、宜居和统一的人生目标等等的机会——将被被企业利益所强烈影响和操控。而这些利益,本质上是围绕经济增长与利润最大化构建的。
在诺姆·乔姆斯基(Noam Chomsky)[52]与爱德华·赫尔曼(Edward Herman)[53]合著的《制造共识》(Manufacturing Consent)[54]一书中,两位作者提出,美国媒体实际上是一种宣传工具,而非客观的信息来源(这一观点当时颇具争议,但如今已成为主流看法)。他们认为,这种宣传功能是通过一套“过滤模型”来运作的,该模型将信息作为输入,并为公众“福祉”完美制造出标准化的输出。而其中一些媒体过滤机制,正是今天科技巨头所采用的。第一个过滤器是媒体公司的规模、所有权结构及其以利润为导向的商业模式。这使得进入媒体市场所需的投资与准入成本变得高得惊人,从而使其他竞争者难以生存。法律制度被用来执行一系列标准,这些标准压制了初创公司与中小企业的发展;而政府补贴则倾向于支持那些与政府利益保持一致的媒体公司。第二个过滤器是广告收入。广告不仅提升了特定公司的利润,也让它们在竞争中占据优势。那些无法吸引广告支持的媒体来源往往被市场边缘化。在此过程中,那些资金雄厚的媒体公司为了争取广告商的“青睐”,被迫迎合股东所要求的持续利润增长。这意味着任何挑战企业利益的声音,都可能因营收减少而遭受惩罚,最终被逐出市场竞争。
[52] 美国教授和公共知识分子,以其在语言学、政治活动和社会批评领域的研究而闻名。乔姆斯基有时被称为“现代语言学之父”,他也是分析哲学的重要人物和认知科学领域的创始人之一。 [53] 美国经济学家、媒体学者和社会评论家。 [54] https://focalizalaatencion.wordpress.com/wp-content/uploads/2012/08/herman-chomsky-2002-manufacturingconsent.pdf
这两个过滤器,正是当今科技巨头在其平台上运用的机制。他们主导市场,并依靠广告收入获取惊人的利润。正如乔姆斯基与赫尔曼所指出的另一个过滤器——意识形态偏向,大科技公司同样如此。就像上世纪八十年代的主流媒体会大肆报道敌对国家的种族灭绝与谋杀,却对发生在美国“势力范围”如拉美地区的同类事件视而不见,大科技公司也会在符合其经济与利益考量时,沿着特定的意识形态线索行事。由于其庞大的利润模式与动机,大科技公司的利益并不必然与真理、勇气、准确性、诚实、公正或善恶标准一致。只有当这些价值可以带来可预见的利润与效用最大化时,它们才可能被采纳。因此,如果 AI 垄断企业逐步获得市场主导权,并以其最先进模型为基础将大量商品与服务推向市场,那么人们对于世界的理解、他们如何看待现实、哪些事物最值得关注——都会在信息过滤器的引导下被重塑。这些过滤器正是大科技公司用于“产出有利于技术发展结果”的机制的一部分。个体发展自身的机会、形成自我世界观的过程、以及构成生活统一性的价值体系,都将受到科技信息过滤器的支配与重构。
我们很容易想象这样一个世界:信息的生成由一小部分集中的模型主导,这些模型构建出一套相互交织的信息网络,强化着不准确、不诚实、甚至是伪造的信息结构。新闻标题与报道可能散布错误主张与对现实的歪曲,而这些说法又会被其他虚假信息源所“证实”,彼此互为支撑。这种信息结构——即信息的组织方式及其意义赋予机制——可能会被人为策划,以服务于掌握权力与控制信息传播资源者所设定的特定目的。少数人认为“最好的”内容将被优先推送,而公众的想法将逐渐变得从属,最终被操控以符合权力方的利益。这并不是在指责某个实体或个人有恶意意图,而是在强调这样一种结构性困境:当生成并传播社会所消费的信息的能力被集中在少数几方手中时,这种权力格局所带来的难以解决的困境。
这最终将不可避免地导向类似于前文提到的诺齐克“体验机”的世界。人们获得一种超越消费伦理的生活形式能力的机会将被极大压缩,甚至被彻底剥夺。确实,假设未来大多数工作被自动化,人们通过基本收入实现生活保障,那么个体将从劳作的束缚中解放,不再被迫为经济增长贡献劳动力。从某种意义上说,人类将获得对约束与必需品的自由。但问题在于,如果没有施展自由的媒介,如果没有真正的机会在具体经验中运用自己的能动性,那么这种自由就并不是真正的自由——至少不是那种更深层次的、积极意义上的自由。那种引导人们思考“如何生活”、那种通过探索而发现值得投入心力与时间的事业的过程、那种确立人生目标并在充满挑战与刺激的环境中努力实现的能力,将会在这样的结构中逐渐失效,甚至彻底被边缘化。
哲学家约翰·杜威(John Dewey)曾写道:
我们很少意识到,我们对什么有价值、什么无价值的判断,在多大程度上是受制于我们并不自觉的标准。但一般来说,那些我们未经思考便视为理所当然的事物,正是决定我们有意识思维与判断结论的关键。而那些位于反思之下的习性,往往正是在我们与他人的持续互动与交换中形成的。
如果构成社会的制度是由那些以提升股东利润为目的的大型企业所主导——这将在它们主导人工智能时成为现实——那么它们的模型将渗透进经济的每一个领域,渗入我们的环境。这些环境将影响我们所被激发的生活方式,朝向不再体现为实际的‘存在’(being),而是依赖于‘拥有’(having)。也就是说,什么是显著的、值得追求的、具有吸引力的,不再取决于它所需要的努力、它所要求的冒险精神,或它所能激发的成长过程,而是取决于它能否填满并打发时间。对于一种由消费伦理塑造的意识而言,显而易见、理所当然的东西,将与另一种由合作构成、旨在促使个体能动性寻求意义与目标的社会完全不同。前者会看到一个充满各种可能体验的世界,但这些体验除了即时呈现的感受之外毫无意义;而后者则仍然会体验到“必要性”,以及那种不可遏制的冲动——即人必须感受到世界上仍有值得行动之事。赫尔曼·梅尔维尔(Herman Melville)在其伟大的美国小说《白鲸》(Moby Dick)中写下了这样的句子:
我坚定目标的道路铺设着铁轨,我的灵魂被刻槽其上。穿越无底峡谷,穿越山脉深处与激流之下,我直奔而去!没有障碍,没有转弯,只有通向铁轨终点的直路!
但愿,那些曾赋予梅尔维尔写作力量的精神碎片,在未来的某个角落依然得以存在。
Section 3.5
在《查拉图斯特拉如是说》(Thus Spoke Zarathustra)一书中,尼采描绘了两种未来人类的形象:“末人”(Last Man)与“超人”(Overman)。这两者在本能、欲望、动机与驱力方面有着根本性的不同。他们所看到的世界、感知世界的方式也截然不同:哪些事物对他们而言是显著且有意义的,什么是“善”或“恶”,对自我与世界的信念与态度,皆南辕北辙。
尼采对“末人”充满蔑视,而他的理想目标则是“超人”。“末人”代表一种追求舒适、安逸与满足的生活方式——那是一种消费的生活,是一种被动的满足。末人的畜群(herd)沉浸在“白天的微小快乐、夜晚的微小快乐中,但极度重视健康。他们说:‘我们发现了幸福’,眨着眼睛”。这样的存在,培养出的是享乐、安逸、饱足与消费的本能。尼采常将这种状态比喻为“反刍的牛”。而“超人”则是那种能够保有创造与超越本能的存在,他将生命导向某个遥远而艰难的目标,借此创造出一种超出自身的价值,使生活因此获得尊严与意义。超人仍然保有那种穿越变革性经验的冲动,那种能改变自我存在状态与意识体验的本能。正是这种冲动激发个体去掌握现实、理解现实,并因此增强他们影响现实的能力——个体越来越能够通过自己的活动与存在方式去塑造经验,建构世界。“末人”的美德——最大化快乐并最小化痛苦,在“超人”看来,恰恰是堕落的恶德。
人工智能的垄断结构及其以利润为导向的模式,正在推动“末人”的出现;而开源则是在为“超人”保留空间。随着人工智能被集中于少数强权之手,并通过这些权力机构设定的参数向市场大量输出商品与服务,整个信息景观及其传播网络将被精心策划成一种伦理结构——这种伦理以最大满足与持续消费所带来的舒适感为核心。在这样的结构中,个体所接触到的机会与环境将不再是“质感质性丰富”的;它们不会激发人们内在的主动能力,而只会使人变得能够追求一种消费社会所设定的终极目标——即最大化产出与回报的路径。
而开源生态系统,则保留了一个人类能动性仍能找到出口的空间。在那里,创造力与创新的目标不再仅仅是为了逐利,而是为了实现一种更完整的人类生活。
现在,本文开篇提出的一个问题是:自动化是否能带来足够多的机会,使被替代的劳动力能够重新获得工作?到现在我们已经看到,黑客范式与开源生态系统的确让这一目标更为可行。彼得·蒂尔的《从零到一》可以说是一本创业者指南。而他在书中明确指出:创业的目标应当是至少模仿,并努力实现垄断。所谓“成功”,就是在某一市场领域内占据主导地位,排除其他进入者,并通过专属供应尚未满足的需求来实现利润最大化。但成功初创企业的统计数据[55]却令人沮丧。初创企业的失败率高达90%。在那些成功者中,首次创业者只占18%。获得风险投资资金的初创企业不到1%;获得天使投资的比例也不到1%;约有75%的初创公司依赖“信用卡债务、商业贷款与信用额度”来筹集资金。成功的几率微乎其微,而对那些敢于创业,尤其是技术驱动型创业者(这是失败率最高的一类)所需承担的门槛与风险,往往近乎不可逾越。蒂尔之所以鼓励初创企业采用垄断策略,部分原因正是因为唯有在获得足够稳固的市场地位之后,公司才终于能够喘息、拓展与创新。一旦达到垄断标准,企业便能掌控其特定领域(甚至是整个)市场中的价值输出——理论上,这会给企业与消费者双方带来好处。
[55] https://explodingtopics.com/blog/startup-failure-stats
然而,这种能力最终被集中在极少数能够侥幸成功的公司手中。一旦掌握了这种能力,它们便没有自利的动机去放手。而当某家企业依靠其垄断地位终于获得创新的自由之时,这种专属能力却也意味着其他拥有创造潜力的人被排除在外,仅仅因为他们没有获得那唯一的机会。
如果企业的成功几率更高,那无疑会更具吸引力。但传统的融资方式以及作为成功创业者所需经历的艰难过程,往往会打击甚至扼杀那些本有能力提出改变世界的强大创意的人们。而黑客范式之所以具有深远意义,正是因为它能够提供丰富的机会,让人们得以创造价值,而无需承担传统创业所附带的高风险。黑客范式的“北极星”之一,就是致力于打造一个开放的、无需许可的生态系统——一个充满机会、人们可以自由进入、自由利用关键技术信息,并能够与成熟企业协作,从而共同创造出更好、更具创新性的产品的环境。开放的生态系统能够赋予人们创造价值的可能,而封闭系统则将他人排除在外,关闭了协作的大门。
按照蒂尔模式的创业路径,那是一条崎岖不平的道路。它需要强烈的意志、非凡的创造力,当然还需要一定的运气。而这三者的完美契合,是极其罕见的。因此,真正能在创业中成功的人少之又少。通过一个无需许可的开源生态系统,通过减轻人们在创造有价值事物时所承受的沉重负担,我们可以释放出大量机会——这些机会无需你拥有成为乔布斯或贝索斯那样的雄心与资源,也不要求你必须独力成就一番技术帝国。事实上,那些科技巨头的成功,早已远远超越了他们当初想要创造创新科技的初衷。开源生态系统将推动科技进步的机会民主化,使人们能够真正参与其中,不必成为少数天才企业家的复制品。创新,理应是更具协作性、更广泛分布的,也应当距离普通人更近。黑客范式正在使这成为可能,它正在重构赛场的平衡。
或许,并不是每个人都想成为一名“黑客”。但开源为我们保留并拓展了一种最佳的原型模式,通过它,可以将具体的机会持续地、公平地分配给人们,让他们得以实践自己的能动性。正是通过拥有这类机会,人们仍能发现和体验到那种强烈的召唤感——“我必须去做某事”——即,一个目标的存在,使个体不得不相信,若忽视它,人生就将失去意义与目标。如果我们生活的世界中,人们能接触到的、最显眼且最具吸引力的事物,仅仅是尼采所说的那种“幸福”——那种不涉及个人牺牲、不包含作为德性的献身(devotion)、也无需为艰难而变革性的事业奋斗的意愿的“幸福”——那么这样的世界无疑比不上另一个世界:在那里,人们拥有真正的机会去成就伟大的事业,只要他们愿意去追求。
结语
当 IBM 的“深蓝”在 1997 年击败国际象棋冠军卡斯帕罗夫(Garry Kasparov)时,象棋并未因此被淘汰。人们依旧继续比赛,并不断变得更强。这一事实——即从那以后任何人类棋手都不可能战胜 AI 程序——并未动摇那些热爱象棋之人的热情与动力。那些献身于象棋的人依旧渴望打磨自己的技艺,学习更复杂的策略,在不断成长的过程中超越其他选手。象棋选手依然渴望变得更优秀,仅仅是为了变得更优秀。通过意志与投入实现成长,当他们登上新的水平时,那种深刻的成就感依旧真实而宝贵,尽管一台机器将永远是更强的选手。
在一部关于李世石(Lee Sedol)在 2016 年败给 AlphaGo 的纪录片中,有人说:“他在这台机器的对弈中获得了成长。他的人性在与这台无生命的创造物对局之后得到了拓展。而我们的希望,是这种机器,尤其是背后的技术,也能对我们所有人产生同样的作用。”还有人说:“或许 AlphaGo 能向人类展示一些我们从未发现过的东西。或许那是一种美。”如果被正确使用,人工智能可以拓展个体影响与改变世界的能力。它可以提供创造的机会,而非只是劳作的义务;可以唤起意义的体验,而非冷漠与疏离;可以使人获得一种有价值的自由,而非无所依托的自由。但这一切都取决于社会写作和去推动人们向值得努力实现的目标前进的环境;它也要求我们以不同的方式理解竞争。
Agency/Agent/Agentic/… 能动性 Being (以…方式)存在 Qualitatively Rich 质性(上)丰富 Open Source Ecosystem 开源生态系统 Proprietary 专有 Pleasure 快乐 Happiness 幸福 所有著作、节目与人物名称第一次出现标记英文原文。 除网站链接之外的脚注,均为译者补充;脚注中的外部链接为原文超链接的对应标记。 原文中的特殊格式均保留在中文对应词项中。
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ 7e8ca676:b6a7569f
2025-05-13 01:47:06
@ 7e8ca676:b6a7569f
2025-05-13 01:47:06There was a time when Bitcoin smelled like ozone and rebellion. When men wore hoodies because they meant it. When software didn’t come with a mission statement or a DAO-approved pronoun guide. When the only thing a Bitcoin dev feared was being wrong, not being unpopular. \ \ That time is dead. \ \ It died somewhere between the fifth Twitter thread explaining why putting JPEGs on the base layer was “valid use,” and the fiftieth PR that added complexity to the engine in order to simplify the cupholders. Now we’re here, ankle-deep in a pool of our own mediocrity, arguing over whether we should triple the OP_RETURN limit so a VC-backed sidechain company can offload its plumbing costs onto your Raspberry Pi. \ \ Welcome to the future. It’s paved in GitHub comments and smells like a WeWork bathroom. \ \ Let’s speak plainly. This whole drama is not about OP_RETURN. It’s about power. Not electrical power. Not hash power. Soft power. The power to redefine what Bitcoin is for, one pull request at a time. It is the power to turn the protocol from a blunt, uncompromising monetary weapon into a polite corporate middleware bus for protocol startups that couldn’t raise a Series B without a little help from their friends in Core. \ \ Jameson Lopp wants to increase the OP_RETURN limit. Why? Because his company, Citrea, needs to squeeze a few more bytes into every transaction. It's not a crime. It’s not even dishonest. It's just pathetically on the nose. They don’t want to pay miners directly. They want the mempool to be their free emergency broadcast system. They want to lean on the public infrastructure without sending flowers or even a thank-you note. \ \ And what does Core say? \ \ They say yes. \ \ Because of “technical merit.” \ \ Because it’s “more efficient.” \ \ Because the devs have long since stopped being guardians of the protocol and started being unpaid product managers for whoever can string enough buzzwords together in a conference talk. \ \ You can see it in their eyes. You can hear it in their interviews. The Core devs aren’t building Bitcoin anymore. They’re managing Bitcoin. They’re curating it. Polishing it. Nerfing it for mass adoption. Like a bunch of Brooklyn baristas trying to make espresso kid-friendly. Bitcoin used to be an espresso shot poured directly into the mouth of the Federal Reserve. Now it’s a lukewarm latte with oat milk and consensus-breaking sprinkles. \ \ The worst part? The refusal to acknowledge that this is not about UTXO bloat. It's not about cleaner mempools. It’s about upstreaming corporate convenience into the base layer under the halo of neutrality. It’s about giving polite names to ugly compromises. “Policy adjustment.” “Ergonomic improvement.” “Relay optimization.” They speak in this weird dialect of bureaucratic techspeak that means nothing and does less. \ \ Meanwhile, the only thing that actually matters gets lost: ossification. \ \ The holy grail of this protocol is ossification. Not stagnation. Not laziness. Not gridlock. Just stability. The longer Bitcoin can go without consensus changes, the more credible it becomes. The more unchangeable it becomes. Like gravity. Like rust. It doesn’t matter how good your argument is. The system won’t budge. That’s the point. The value of Bitcoin isn’t in how clever the devs are. It’s in how irrelevant they become. \ \ But ossification isn't something you declare. You sneak up on it. You approach it sideways, like a wild animal. You do less and less until eventually you’re doing nothing at all, and nobody even remembers how to change the code anymore. That is the goal. To make the protocol so boring, so petrified, that no one can move it. Not Lopp. Not Luke. Not even Larry from Legal. \ \ To get there, we need something devs hate: client balkanization. \ \ That means splitting the client into pieces. Break the codebase. Separate the consensus engine from the policy fluff. Let people run different implementations. Let the free market decide what filters they want, what mempool rules they tolerate, what behavior they’re willing to relay. You want a node that bans inscriptions? Run it. You want a client that auto-forwards every transaction with a JPEG of your left toe? Go for it. Just don’t make it my problem. \ \ Right now, Bitcoin Core is a monoculture. It’s the cathedral and the altar and the pamphlet all rolled into one. That’s not healthy. That’s a single point of failure. That’s a priesthood. \ \ And no, Bitcoin isn’t a religion. It’s worse. It’s a culture. Religion has rituals. Culture has habits. And habits are harder to break. Especially when your dev team gets drunk on the idea that their opinions are features. \ \ If you want to fix this mess, you need to kill the idea that Bitcoin Core is the final word. Strip it down. Remove every line of non-consensus code. Make it boring. Make it dumb. Let the client rot in peace, and let a thousand weird little nodes bloom. \ \ Let the spammers spam themselves into oblivion. Let the free-riders find someone else to subsidize their infrastructure. Let every operator set their own damn filters. \ \ You’ll know ossification is working when the devs start getting bored. When they stop showing up. When there are no more debates. When the politics dry up. When Jameson Lopp finally logs off. \ \ Until then, every line of code you don’t remove is a future argument you’ll be forced to have with someone who thinks “data availability” is more important than keeping the protocol boring. \ \ Bitcoin does not need to be exciting. It needs to be a brick. A self-righteous, opinionated, uncompromising, utterly stubborn monetary brick. \ \ Keep your hands off it. \ \ And take your startup with you.OP_RETURN and the Cult of Cleverness: Or, How Bitcoin Core Learned to Love the Smell of Its Own Farts
There was a time when Bitcoin smelled like ozone and rebellion. When men wore hoodies because they meant it. When software didn’t come with a mission statement or a DAO-approved pronoun guide. When the only thing a Bitcoin dev feared was being wrong, not being unpopular.
That time is dead.
It died somewhere between the fifth Twitter thread explaining why putting JPEGs on the base layer was “valid use,” and the fiftieth PR that added complexity to the engine in order to simplify the cupholders. Now we’re here, ankle-deep in a pool of our own mediocrity, arguing over whether we should triple the OP_RETURN limit so a VC-backed sidechain company can offload its plumbing costs onto your Raspberry Pi.
Welcome to the future. It’s paved in GitHub comments and smells like a WeWork bathroom.
Let’s speak plainly. This whole drama is not about OP_RETURN. It’s about power. Not electrical power. Not hash power. Soft power. The power to redefine what Bitcoin is for, one pull request at a time. It is the power to turn the protocol from a blunt, uncompromising monetary weapon into a polite corporate middleware bus for protocol startups that couldn’t raise a Series B without a little help from their friends in Core.
Jameson Lopp wants to increase the OP_RETURN limit. Why? Because his company, Citrea, needs to squeeze a few more bytes into every transaction. It's not a crime. It’s not even dishonest. It's just pathetically on the nose. They don’t want to pay miners directly. They want the mempool to be their free emergency broadcast system. They want to lean on the public infrastructure without sending flowers or even a thank-you note.
And what does Core say?
They say yes.
Because of “technical merit.”
Because it’s “more efficient.”
Because the devs have long since stopped being guardians of the protocol and started being unpaid product managers for whoever can string enough buzzwords together in a conference talk.
You can see it in their eyes. You can hear it in their interviews. The Core devs aren’t building Bitcoin anymore. They’re managing Bitcoin. They’re curating it. Polishing it. Nerfing it for mass adoption. Like a bunch of Brooklyn baristas trying to make espresso kid-friendly. Bitcoin used to be an espresso shot poured directly into the mouth of the Federal Reserve. Now it’s a lukewarm latte with oat milk and consensus-breaking sprinkles.
The worst part? The refusal to acknowledge that this is not about UTXO bloat. It's not about cleaner mempools. It’s about upstreaming corporate convenience into the base layer under the halo of neutrality. It’s about giving polite names to ugly compromises. “Policy adjustment.” “Ergonomic improvement.” “Relay optimization.” They speak in this weird dialect of bureaucratic techspeak that means nothing and does less.
Meanwhile, the only thing that actually matters gets lost: ossification.
The holy grail of this protocol is ossification. Not stagnation. Not laziness. Not gridlock. Just stability. The longer Bitcoin can go without consensus changes, the more credible it becomes. The more unchangeable it becomes. Like gravity. Like rust. It doesn’t matter how good your argument is. The system won’t budge. That’s the point. The value of Bitcoin isn’t in how clever the devs are. It’s in how irrelevant they become.
But ossification isn't something you declare. You sneak up on it. You approach it sideways, like a wild animal. You do less and less until eventually you’re doing nothing at all, and nobody even remembers how to change the code anymore. That is the goal. To make the protocol so boring, so petrified, that no one can move it. Not Lopp. Not Luke. Not even Larry from Legal.
To get there, we need something devs hate: client balkanization.
That means splitting the client into pieces. Break the codebase. Separate the consensus engine from the policy fluff. Let people run different implementations. Let the free market decide what filters they want, what mempool rules they tolerate, what behavior they’re willing to relay. You want a node that bans inscriptions? Run it. You want a client that auto-forwards every transaction with a JPEG of your left toe? Go for it. Just don’t make it my problem.
Right now, Bitcoin Core is a monoculture. It’s the cathedral and the altar and the pamphlet all rolled into one. That’s not healthy. That’s a single point of failure. That’s a priesthood.
And no, Bitcoin isn’t a religion. It’s worse. It’s a culture. Religion has rituals. Culture has habits. And habits are harder to break. Especially when your dev team gets drunk on the idea that their opinions are features.
If you want to fix this mess, you need to kill the idea that Bitcoin Core is the final word. Strip it down. Remove every line of non-consensus code. Make it boring. Make it dumb. Let the client rot in peace, and let a thousand weird little nodes bloom.
Let the spammers spam themselves into oblivion. Let the free-riders find someone else to subsidize their infrastructure. Let every operator set their own damn filters.
You’ll know ossification is working when the devs start getting bored. When they stop showing up. When there are no more debates. When the politics dry up. When Jameson Lopp finally logs off.
Until then, every line of code you don’t remove is a future argument you’ll be forced to have with someone who thinks “data availability” is more important than keeping the protocol boring.
Bitcoin does not need to be exciting. It needs to be a brick. A self-righteous, opinionated, uncompromising, utterly stubborn monetary brick.
Keep your hands off it.
And take your startup with you.
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 7e8ca676:b6a7569f
2025-05-13 01:08:28
@ 7e8ca676:b6a7569f
2025-05-13 01:08:28There was a time when mining meant something. Not just the noise of fans and the stink of ozone, but a political act. An act of rebellion, like smuggling pamphlets under the nose of the king. You mined in the basement. You mined with pride. You mined because you could. Not because Fidelity wrote a whitepaper on it. Not because a hosting provider in Iceland offered you a bulk discount. But because you believed.
That miner is dead.
He didn’t die in a blaze of glory. He didn’t go down swinging. He was euthanized. Slowly, over years, by spreadsheets, subsidies, and a thousand tiny concessions. Killed off by a culture that said, “Why do it yourself when you can outsource the soul of Bitcoin to a pool in Singapore?”
Welcome to the age of industrial Bitcoin: a world where miners don’t mine, pools don’t just process. They rule. And the only thing sovereign anymore is the dividend.
The Sovereign Miner is Dead, And No One Mourned
The sovereign miner, the madman with a dusty rack, a full node, and a middle finger pointed squarely at the Eccles Building, is extinct. He’s gone the way of the dodo, the blacksmith, the outlaw. And in his place? A fleet of khaki-wearing ASIC clerks uploading hashrate reports to their VC lords like dutiful little interns. These are not revolutionaries. They are box operators. Corporate larvae wiggling around in server farms financed by pension funds.
Once upon a time, mining was an act of insubordination. You ran a rig to say "no" to Janet Yellen. You ran a node because you meant it. You didn’t need permission. You didn’t ask for subsidies. You didn’t file paperwork. You fought for consensus by living it. Every block was a punch thrown in a quiet, bloodless rebellion. Now? Now you’ve got KPMG-certified mining outfits measuring ESG impact and tweeting about carbon offsets like they’re trying to win a grant from the UN.
The eulogies for that old miner are full of oily euphemisms. They drone on about "efficiency," as if selling your vote for a cheaper power bill is some kind of virtue. "Economies of scale," they whisper, as though scale were some holy sacrament instead of the Trojan horse that delivered centralization to our doorstep. What they call progress, I call a back-alley mugging of Bitcoin’s soul.
The modern miner isn’t mining. He’s leasing his dignity to a pool that doesn’t know his name. He’s plugging in Bitmain boxes like a hotel maintenance worker changing light bulbs. The only heat he generates is for the benefit of someone else's node. Someone else's mempool. Someone else's idea of consensus. He doesn’t build the block. He just pays the electric bill.
And the worst part? He likes it. He thinks it’s normal. He thinks it’s “smart business.” He’s internalized the defeat so completely he brags about it on social media. He’ll tweet about uptime, about efficiency ratios, about hashprice curves—as if he were describing a well-run gulag. He’s the obedient prisoner who polishes the chains and calls it freedom.
The sovereign miner didn’t die in a blaze of glory. He died quietly, smothered under a fleece blanket of comfort and yield optimization. And no one mourned. No one wept. Because everyone was too busy benchmarking their ROI and counting fiat. The revolution didn’t end in a shootout. It ended in quarterly earnings calls.
Power Reversed: Pools Run Nodes, Miners Run Cable
Let’s be crystal clear: The pools run the nodes. The miners do not. This is not a subtle shift. It is a total inversion of power. A coup d'état wrapped in JSON-RPC and relayed with a smile. The pool clerks have become the governors of consensus, and the miners? They’re errand boys. They might control the heat, but they don’t control the protocol. They’re like engine pistons in a car they’ll never be allowed to drive.
Pointing hash at a pool and calling yourself sovereign is like renting a tux and declaring yourself royalty. It’s cosplay. At best. Pools decide what transactions are valid. Pools enforce the rules. Pools interpret consensus, not the miners, not the miners, and certainly not the plebs stacking sats on Raspberry Pis, who, through their economic activity and validation, still enforce the rules but are powerless to stop this creeping centralization in the mining layer. In a world obsessed with decentralization theater, pools are the centralized prop masters pulling the strings.
And when the curtain pulled back in 2021, it wasn’t some secret backroom scandal. No. Marathon Digital bragged about OFAC-compliant mining. They filtered transactions with state-sanctioned precision. They announced it like a new feature rollout. “Censorship-as-a-Service, now in beta!” The mining pool became an extension of the U.S. Treasury—while still waving the Bitcoin banner.
That wasn’t a red flag. That was a blood-soaked banner waved from the parapets of captured consensus. And the response? Nothing. No mass exit. No fork. No slash-and-burn rebellion. Just soft mewling from miners who’d already convinced themselves this was “pragmatic.”
Miners didn’t revolt. They shrugged. They shrugged because they didn’t feel it in their bones anymore. They’d been domesticated. Fattened on subsidies and mining-as-a-service. Pacified by dashboards and yield spreadsheets. When the pools took the steering wheel, the miners reached for the air conditioning controls.
This is the hard truth: sovereignty cannot be delegated. You don’t get to outsource rebellion. You don’t get to file a ticket and request autonomy. If someone else runs the node, someone else owns the power. And if you’re pointing hash at their rules, you’re not free. You’re furniture. Industrial-grade silicon furniture humming in tune with someone else’s politics.
ASICs Are Treadmills, Not Weapons
Here’s a bitter pill: plugging in an ASIC doesn’t make you a participant in Bitcoin. It makes you a battery. Yes, economic nodes still set the rules through their validation and transaction activity. But what happens when the mining layer, the muscle that enforces those rules on-chain, goes rogue? What happens when the mempool you built gets ignored because your hashpower is pointed at someone else's filter?
A node might define validity, but without aligned mining, it’s a lion without teeth. If economic consensus is the blueprint, mining is the builder. And right now, most builders are following someone else's floor plan. The node might say, "this is how we build," but the pool, with its centralized relay and selective enforcement, says, "this is what we’re willing to build."
Without a node, without building your own block, without choosing your own mempool, you’re a hamster in a high-voltage wheel. All that heat and noise? It’s not rebellion. It’s treadmill sweat.
Without a node, without building your own block, without choosing your own mempool, you’re a hamster in a high-voltage wheel. All that heat and noise? It’s not rebellion. It’s treadmill sweat.
You are not a general. You are a grunt. A CPU on contract to someone else’s war.
Fiat Habits: The Culture of Convenience
Bitcoin was supposed to be the great divorce from fiat thinking, a severance from the debt-ridden clown world where every moral principle is for sale if the yield’s high enough. But lo and behold, the fiat habits came slithering in through the miner’s back door. It started small. “Just a hosting service,” they said. “Just outsourcing the firmware,” they claimed. “Just using a pool for efficiency.” And before you knew it, the average miner was indistinguishable from a middle manager at an Enron reunion. Optimizing, spreadsheeting, begging for subsidies like a lobbyist on his third bourbon.
The culture is poison. It rewards cowardice, convenience, and cost-shifting. Small miners moan about volatility like day traders with arthritis. Big miners wine and dine regulators, sniffing after tax incentives and ESG badges like some filthy dog begging at the World Economic Forum’s dinner table. We’re no longer talking about building a sovereign financial system—we’re talking about quarterly earnings, power purchase agreements, and whether your server farm meets carbon neutrality guidelines. What the hell happened?
Take a look back at the New York Agreement in 2017. That wasn’t a negotiation. It was a ransom note. The largest mining outfits, including BTC.Top and ViaBTC, held SegWit hostage because it didn’t butter their bread. The principles didn’t matter. The technical merit didn’t matter. All that mattered was leverage, yield, and preserving their own stranglehold. They tried to shove a hard fork down Bitcoin’s throat like a goose being force-fed for foie gras. And if not for the sheer stubbornness of the user base, real economic nodes who still gave a damn, Bitcoin would’ve gone full Frankenstein.
But did those miners learn? No. They just shifted tactics. Today they ask for different forms of convenience: not block size increases, but subsidies, regulations tailored to their rigs, public-private partnerships. The song remains the same. It’s the fiat mindset dressed up in ASIC drag. Instead of defending neutrality, they demand special treatment. Instead of embracing the responsibility of consensus participation, they’d rather hand it off to a pool that promises good customer service and a Discord server with emojis.
What we’re seeing is the spiritual sequel to fiat monetary policy—moral hazard in overclocked silicon. Miners begging for insulation from the market, protection from volatility, and someone else to carry the political weight of consensus. That’s not sovereignty. That’s serfdom with a spreadsheet. These aren't rebels. They’re corporate supplicants doing yield gymnastics while the heart of Bitcoin withers under the fluorescent lights of their co-location facility.
Bitcoin doesn’t need more efficient parasites. It needs fewer of them. The culture must shift from comfort to combat. From optimization to obligation. A miner who outsources consensus is no better than a fiat printer optimizing bond auctions. The minute you make convenience your god, you become indistinguishable from the system Bitcoin was meant to destroy.
The Culture of Convenience
Bitcoin was born as a rejection of fiat habits. So naturally, miners dragged every last fiat habit into the server farm like rats carrying plague. Outsource the firmware. Outsource the hosting. Outsource the power contract. Outsource the node. Outsource the sovereignty. What’s left?
Mining today looks like Goldman Sachs cosplay. ESG reports. Carbon credits. Webinars on regulatory compliance. Bitcoin isn't being mined anymore. It's being monetized. It's being lobotomized by yield-chasers and spreadsheet cultists.
The New York Agreement was the test. The miners failed. They held the protocol hostage for a slightly thicker block and a fat slice of yield. They were willing to hard fork Bitcoin into a Frankenstein fiat-friendly platform if it meant a better power purchase agreement.
They haven't changed. They’ve just gotten better at disguising their cowardice as competence.
Software Will Not Save You (But Cowards Sure Will Sell You the Illusion)
Let me tell you a ghost story. A tale of silicon treachery dressed up as innovation. It was 2017. The air stank of backroom deals and nervous sweat. Bitmain, the ASIC kingpin of the age, had quietly embedded a little something into its hardware. A cheat code. A hidden rake. A parasitic exploit called ASICBoost, but not the honest kind. No, this was the covert variant, slinking beneath the protocol’s floorboards, exploiting transaction ordering for a tidy little edge. It wasn’t disclosed. It wasn’t debated. It was used. Quietly. Gleefully. While the rest of the ecosystem was busy arguing about scaling like philosophers in a house fire.
Bitmain wasn't interested in consensus. It was interested in arbitrage. They saw Bitcoin not as a commons, but as a slot machine they had rigged. And when SegWit appeared, when it offered scaling and immunity to covert ASICBoost in one surgical tweak, Bitmain panicked. Because SegWit would end the grift. Not softly. Not eventually. Immediately.
So they did what every entrenched parasite does when exposed. They lied. They stalled. They "compromised." They ginned up support for SegWit2x, not to scale Bitcoin, but to preserve their exploit. A hard fork with extension blocks would keep the legacy block structure alive and well, tucked into a cozy parallel track where covert ASICBoost could still thrive. It was a bait-and-switch. A con. A trojan upgrade smuggled in under the banner of progress.
But this time, the hosts fought back.
Node runners saw the ploy. They didn’t need fancy tooling. They needed guts. They didn’t negotiate. They didn’t flinch. They ran SegWit. They activated UASF. They drew a line—not in sand, but in bedrock. Bitcoin would not be held hostage by ASIC cartels. It would not bend for Bitmain. It would not become an extension block casino for rent-seekers in Shenzhen.
So no, software didn’t save Bitcoin. Men did.
Ordinary plebs with full nodes and no backdoor. They used the tool, yes, but what mattered is that they refused. Refused the scam. Refused the deal. Refused to bend the knee to an ASIC cartel dressed in business-casual and lies.
SegWit didn’t win because it was elegant. It won because enough people had the guts to jam it through in spite of sabotage. The protocol gave them a knife, and they had the moral clarity to use it. That’s the lesson. Not that we need better code, but that we need sharper men.
Because in the end, every exploit is possible when the culture is weak. And every fix is worthless if the people implementing it don’t care. The problem was never ASICBoost. The problem was what miners were willing to do to keep it.
The Pool Cartel is the New Central Bank
Middlemen were supposed to die in 2009. That’s the entire reason Bitcoin exists. To gut them. To render them obsolete. To salt the earth behind them so nothing like them could ever grow again. But here they are, reborn, not as banks, but as pools. Not in suits, but in server racks. They wear the garb of "infrastructure providers," but they function as gatekeepers, choke points wrapped in API documentation.
Pools don’t just process, they decide. They decide what gets into the chain. They decide whose transactions are valid. They decide what software matters, and what consensus looks like. They’ve become the central banks of the hashrate economy: unaccountable, invisible, and too boring to fear until it’s too late.
They don’t win power. They absorb it. They don’t need legislation or signatures. They just need you to keep pointing your hash in their direction. That’s the magic trick of middlemen: their power lies in being taken for granted. And in that, they’re the perfect parasite, one that feeds on your energy and then tells you they’re helping you digest it.
Every time you optimize for pool payout efficiency, every time you default to the biggest provider, every time you accept their mempool instead of building your own, you’re kneeling. You’re pledging allegiance to a cartel of block-builders whose loyalty isn’t to Bitcoin, it’s to operational ease and regulatory appeasement.
These aren’t neutral actors. They’re political animals. They hold the levers of consensus without bearing any of its weight. They’re the mortgage-backed securities of Bitcoin: abstracted, opaque, and one market panic away from becoming a systemic risk. We have, once again, created a class of intermediaries who profit by extracting value from a system they didn’t build and no longer understand.
Bitcoin didn’t kill the middlemen. It fed them. It made them smarter. It made them less visible. But their hunger hasn’t changed. And until we name them for what they are—cartels in priestly robes—we will keep mistaking the cage for the cathedral.
Stratum v2: A Rifle, Not a Revolution
Stratum v2 is the closest thing to a loaded weapon Bitcoin miners have been handed in a decade. It is, quite literally, the mechanism by which miners can wrench their dignity back from the clenched fists of the pool cartel. And what have they done with it? Mostly shrugged. A few pilot programs, some halfhearted integrations, and a handful of blog posts filled with the kind of cautious optimism you’d expect from a risk-averse actuary.
This isn’t a critique of the protocol. Stratum v2 is beautifully ugly. It’s messy, technical, and dense enough to scare away the very consultants who want to repackage Bitcoin into polite compliance middleware. But none of that matters if no one has the guts to use it. You don’t win wars by stockpiling weapons you refuse to fire.
Stratum v2 gives miners the power to construct their own blocks. Not just vote with hash, but wield it. Choose transactions. Set mempool policy. Actually participate in consensus instead of spectating like a retiree watching a soap opera. It is the rifle hanging over the mantelpiece. The one Chekhov warned us about. And right now it’s gathering dust.
The tragedy here isn’t technical. It’s cultural. Because this tool, this literal key to sovereignty, is being treated like a library dependency. Something for someone else to test, to vet, to implement. Meanwhile, miners continue to act like it’s 2015 and their biggest concern is firmware compatibility and finding a better power rate in Kazakhstan.
Ignore Stratum v2, and it becomes protocol theater. A museum piece. A tragic artifact of what could have been. But use it, and it becomes a wedge. A crowbar in the gears of centralized mining. A bright, shining middle finger to the entire architecture of compliance-friendly consensus.
But don’t fool yourself. Stratum v2 won’t make you sovereign any more than buying a gun makes you a revolutionary. It won’t beam liberty into your soul via Tor, won’t whisper “freedom” into your hashboard, won’t bathe your rack in the holy light of decentralization. It’s not salvation. It’s a tool. And tools don’t care who uses them—they serve the hand that holds them.
Stratum v2 is a rifle, yes—but even a rifle requires guts, aim, and the clarity to know what you're shooting at. In the hands of a coward, it’s a paperweight. In the hands of a rent-seeker, it’s a bargaining chip. But in the hands of a miner with fire in his gut and sovereignty in his blood? It’s a revolution.
This isn’t about technology. It’s about spine. About picking up the one weapon you’ve been given and refusing to keep it locked in the safe while tyrants build your blocks. Stratum v2 offers freedom, but it demands ferocity. You have to load it with your own mempool. You have to chamber every transaction. And then you have to fire.
No protocol, no BIP, no whitepaper will ever substitute for moral will. And if you’re too polite to use the weapon, too busy maximizing uptime to get your hands dirty with real consensus, then you deserve whatever filtered, censored, OFAC-compliant future you inherit.
Stratum v2 is not your savior. You are. And until miners act like it, until they treat this protocol like a weapon and not a toy, the pools will rule, and the timechain will continue to serve the highest bidder.
It’s just a rifle. But rifles have rewritten history when wielded by men who knew they weren’t free.
Ossification Without Decentralization Is Death
Everyone loves ossification, until they realize they missed their chance to do it when it mattered. We had a window. A golden, fleeting window to freeze Bitcoin in a state of clarity, minimalism, and neutrality. Instead, we blinked. We let upgrades seep in. Complexity crept through the back door, and with it came unintended consequences. Among the earliest and most corrosive: the rise of centralized mining pools. A structural outcome embedded in Satoshi’s original design, born from the brutal variance of solo mining. But if that centralization was unforeseen, imagine how many more we’ve introduced since, through every soft fork, every upgrade, every decision to keep tinkering instead of locking the vault when we had the chance.
Ossification isn’t just about code. It’s about culture. It’s a posture. A refusal. And we failed to assume it when it counted. We chose tinkering over tenacity. We chose cleverness over caution. And now the fruits of our hubris hang heavy on the vine: a mining layer riddled with capture points, a mempool hijacked by middlemen, and a user base quietly wondering why their transactions feel like applications.
Yes, economic nodes enforce the rules through validation and usage. But that power has a prerequisite: inclusion. If the only blocks being built are by pools with selective relay policies and a fondness for government compliance, then your economic activity is a shout into a soundproof room. The validation rules may be perfect, but if your transaction never hits the chain, it’s as good as invalid.
The trap we set for ourselves was gilded with good intentions. Soft forks meant to improve scalability. Relay policies meant to minimize bloat. Fee markets meant to incentivize good behavior. And now? Now we find ourselves staring at a timechain that functions—but no longer feels inviolable. The foundation wasn’t corrupted in a day. It was eroded, line by line, by developers trying to be helpful.
Freeze Bitcoin now, and we don’t immortalize virtue—we immortalize vulnerability. We lock in the flaws. We preserve a snapshot where the power has already been ceded to those least equipped to wield it justly. It’s like slamming the vault door shut just as the thieves finish loading the bags.
That’s not ossification. That’s embalming. That’s turning the timechain into a museum exhibit of the ideals we almost lived up to, before we traded principle for pragmatism and thought we could always fix it later.
Ossification is not neutral. It’s not some universal good. It is power, fixed in time. And if that power belongs to the wrong class of actors, the OFAC miners, the hosting conglomerates, the Silicon Valley startups that mine with ESG consultants on speed dial, then ossification doesn’t lock in liberty. It locks in them. It fossilizes a regime that already serves someone else’s interests.
We speak of ossification like it’s an event. One final commit. One last hardening. But in truth, it’s asymptotic. You don’t slam the door shut in one dramatic gesture. You inch toward it. You tighten the bolts over time until change becomes culturally, politically, and economically impossible. And that means we’re ossifying right now.
Picture it: a frozen Bitcoin where the rules can’t change, but the blockspace is filtered, the miners are compliant, and the pools relay transactions based on a government-approved blacklist. That’s not sound money. That’s a digital leash. A ledger of obedience masquerading as freedom.
If Bitcoin ossifies after it has been captured, it does not become incorruptible. It becomes irredeemable. Like sealing a vault before checking what’s inside, you don’t get resilience, you get entombment. You get permanence without virtue. You get consensus without sovereignty.
That’s not ossification. That’s embalming. That’s turning the timechain into Lenin’s corpse: glassy-eyed, sterile, and meticulously preserved in service of a state it was meant to outlive.
We may only have one chance to rescue bitcoin from the clutches of the fiat maximalists, before it is impossible to do so.
Core's Quiet Capitulation
Bitcoin Core was once the temple guard. Militant minimalism. Ruthless conservatism. The last line of defense against creeping bloat and protocol erosion. You didn’t have to agree with them, but by God, you respected the trench they were willing to die in.
Now? They’re white-gloving the stretcher for a dying protocol. Hospice caretakers tending to consensus rot with polite documentation and GitHub tickets labeled "enhancement." The keepers of the flame have become interior decorators for a collapsing cathedral.
They removed filters, the thin defensive crust that kept bad-faith actors at bay. They weakened defaults, the backbone settings that preserved network sanity. They bend policies not to protect consensus, but to please mining cartels and PR-sensitive operators. Every decision smells like appeasement baked in a think tank.
This isn’t some grand betrayal of principle for power or riches. It’s worse. It’s resignation. Exhaustion wrapped in technocratic humility. They didn’t sell out to the highest bidder, they just ran out of fire.
Where once they chanted ossification, now they mumble "flexibility." Where once they enforced sanity with zero tolerance for grift, now they entertain proposals that would’ve been laughed out of the room a decade ago. They say yes out of fatigue. They say no with asterisks. They commit code like bureaucrats signing off on a slow-motion demolition.
Core didn’t just get captured. It got comfortable. And comfort, in protocol stewardship, is fatal. The war for Bitcoin's soul isn’t being lost in some smoky backroom. It’s being forfeited in polite silence by maintainers who forgot the protocol doesn’t just need to run. It needs to refuse.
The Call: Rewild the Hash
This is the fork in the road. This is the final flare fired into the sky before the trench goes quiet forever. You either take back the hash, or you become a dependent serf in a digital fiefdom run by pool lords and relay priests. No more excuses. No more polite appeals. No more PRs begging middlemen to do the right thing.
Run your own node. Build your own block, even if it takes a lifetime. Not tomorrow. Not after the next bull run. Not when it’s convenient. Now. Because if you don’t, someone else will do it for you, and they will not share your values.
Stop waiting for permission. Stop tweeting at pool operators like they’re public servants. Stop optimizing for latency like it’s a sacrament. You are not here to impress compliance officers. You are here to enforce your damn sovereignty.
Don’t beg the cartel to behave. Starve it. Cut it off. Build the mempool you want to see in the world and let their VC primed and bloated relay network choke on their own paperwork. Let their blocks fill with NFT spam and chain analysis reports. You are not required to participate in their theater.
Use Stratum v2. Not because it’s clever, not because it’s next-gen, but because it puts the steering wheel back in your hands. It lets you carve your transactions from granite instead of begging for a line on someone else's spreadsheet. It is not optional. It is not academic. It is your rifle, and the target is consensus capture.
Rewilding the hash isn’t about nostalgia. It’s about survival. It’s about tearing up the artificial turf of corporate convenience and letting the hard, messy, glorious chaos of sovereign mining grow back. Every node a fortress. Every block a declaration. Every miner a free man with dirt under his fingernails and fire in his chest.
This is the line. Pick up your weapon. Run your own node. Build your own block. Or die watching someone else sell your freedom by the byte.
Murder the pools. Rewild the hash. And mine like it means something... because it does.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 502ab02a:a2860397
2025-05-13 01:07:59
@ 502ab02a:a2860397
2025-05-13 01:07:59มีคนเคยพูดเล่นว่า “ถ้าคุณอยากเปลี่ยนโลก ไม่ต้องปฏิวัติ แค่เปลี่ยนอาหารคนซะ" บรรดาเจ้าพ่อเทคโนโลยีชีวภาพก็เลยเริ่มจับมือกับกลุ่มทุนระดับโลก สร้าง “อาหารแห่งอนาคต” ที่แม้จะไม่งอกจากธรรมชาติ แต่งอกมาจากถังหมักในโรงงานได้แทน
หลังจากที่เราเริ่มมองเห็นแล้วว่า ช่องทางแทรกซึมเข้าสู่อาหารโลกอนาคตนั้น ตั้งอยู่บนพื้นฐาน "โปรตีน" ซึ่งถ้าใครตามซีรีส์นี้กันมาตลอด คงจำโพสเรื่อง "เรากินนมเพราะความกลัว?" กันได้ดีนะครับ ไวรัล และ ตีความหลุด theme กันกระจาย ซึ่งเป็นธรรมดาของ social media ที่มันจะโผล่ไปหาขาจรแค่ครั้งเดียว ดังนั้น ก้าวข้ามมันไปครับ
สิ่งที่ปูทางไว้แล้วก่อนจะแบไต๋ว่า เป้าหลักของโลกคือ โปรตีน นั่นคือ นมทางเลือก มาสู่การยึดพื้นที่นมโรงเรียน การเข้าตลาดของ Perfect Day โปรตีนนมที่อยู่ในทั้งนม ขนม ไอศกรีม แล้วทั้งหมดจะถูกปรับภาพล้างไพ่ใหม่ ในนามของ milk 2.0 ครับ เรามาต่อซีรีส์ของเราด้วยการทำความรู้จัก ผู้เล่น กันทีละตัวนะครับ หลังจากเราได้ เวย์นมตั้งบนชั้นบนเชลฟ์กันไปแล้ว
New Culture เป็นบริษัทสตาร์ทอัปจากซานลีอันโดร รัฐแคลิฟอร์เนีย ที่ก่อตั้งขึ้นในปี 2018 โดย Matt Gibson และ Inja Radman โดยมีเป้าหมายในการผลิตโปรตีนเคซีน (casein) ซึ่งเป็นโปรตีนหลักในนมวัว โดยไม่ใช้สัตว์ ผ่านกระบวนการ precision fermentation หรือการหมักด้วยจุลินทรีย์ที่ได้รับการดัดแปลงพันธุกรรม โดยการฝึกจุลินทรีย์ให้ผลิตโปรตีนเคซีนในห้องปฏิบัติการ เพื่อสร้างผลิตภัณฑ์ชีสที่ปราศจากสัตว์ ซึ่งโปรตีนนี้สามารถนำมาใช้ในการผลิตชีสที่มีคุณสมบัติใกล้เคียงกับชีสจากนมวัว แต่ยังคงคุณสมบัติของชีสแท้ๆ เช่น การยืดหยุ่น การละลาย และรสชาติที่คุ้นเคย เปลี่ยนนิยามของคำว่า “ชีส” ให้กลายเป็นโปรตีนเคซีนจากจุลินทรีย์ ไม่ใช่จากน้ำนมวัวอีกต่อไป
Matt Gibson ชายชาวนิวซีแลนด์ ผู้ก่อตั้ง New Culture ไม่ใช่นักวิทยาศาสตร์ แต่เป็นคนหัวธุรกิจที่มีปมบางอย่างกับการกินชีสแบบดั้งเดิม เขาร่วมมือกับ Dr. Inja Radman นักชีววิทยา แล้วตั้งเป้าผลิต “เคซีน” โปรตีนหลักในนมโดยไม่ใช้สัตว์เลยสักตัว
การที่เขาเลือกใช้ precision fermentation หรือการหมักจุลินทรีย์ที่ตัดต่อพันธุกรรม ให้ผลิตเคซีนออกมาจากถังหมัก ซึ่งไม่ใช่เทคโนโลยีใหม่ในโลกแล้ว (แม้บ้านเราหลายคนจะเพิ่งเคยได้ยิน และ ตกใจกันอยู่) บริษัทคู่แข่งอย่าง Perfect Day ก็ใช้แนวทางเดียวกัน ผลิต “เวย์โปรตีนไร้สัตว์” ไปก่อนแล้ว และตอนนี้ มหาเศรษฐีสายลงทุนยั่งยืนก็กำลังรุมแห่ใส่เงินสนับสนุนแขนงนี้เหมือนเห็นโอกาสใหม่ในโลก Fiat ทำให้ New Culture ปรับทิศไปที่ "ชีส"
ผลิตภัณฑ์หลักของ New Culture คือ มอสซาเรลล่าปราศจากสัตว์ ที่มีคุณสมบัติใกล้เคียงกับมอสซาเรลล่าจากนมวัว โดยสามารถละลายและยืดหยุ่นได้เหมือนชีสแท้ๆ และยังมีปริมาณโปรตีนเคซีนเพียง 50% ของชีสทั่วไป ซึ่ง "ช่วยลดต้นทุนการผลิตและผลกระทบต่อสิ่งแวดล้อม"
New Culture ได้รับการสนับสนุนทางการเงินจากนักลงทุนรายใหญ่ เช่น Kraft Heinz, ADM, CJ CheilJedang, และ Dr. Oetker โดยในปี 2021 บริษัทได้ระดมทุนรอบ Series A จำนวน 25 ล้านดอลลาร์สหรัฐ เพื่อขยายการผลิตและนำผลิตภัณฑ์ออกสู่ตลาด นอกจากนี้ New Culture ยังได้ร่วมมือกับ CJ CheilJedang บริษัทผู้ผลิตผลิตภัณฑ์จากการหมักที่ใหญ่ที่สุดในโลก เพื่อเข้าถึงโรงงานการหมักที่ทันสมัยและลดต้นทุนการผลิตโปรตีนเคซีน
และแน่นอนเลยครับว่า ผลิตภัณฑ์ของ New Culture ต้องมาพร้อมกับการโหมประกาศว่า ปราศจากแลคโตส คอเลสเตอรอล ฮอร์โมน และยาปฏิชีวนะที่พบในนมวัว นอกจากนี้ การผลิตโปรตีนเคซีนผ่านการหมักยังช่วยลดการปล่อยก๊าซเรือนกระจกและการใช้ทรัพยากรน้ำและที่ดินเมื่อเทียบกับการผลิตนมวัวแบบดั้งเดิม เพื่อรับความดีงามจากประชากรโลกไปตามระเบียบ
มาดูรอบการระดมทุนกันครับ ยอดเงินทุนรวมที่ได้รับ จนถึงเดือนมีนาคม 2025 New Culture ได้รับเงินทุนรวมประมาณ $35 ล้านดอลลาร์สหรัฐ จากการระดมทุนทั้งหมด 8 รอบ ที่น่าจับตามองคือ Series A ในเดือนพฤศจิกายน 2021 บริษัทได้รับเงินทุน $25 ล้านดอลลาร์สหรัฐ จากนักลงทุนรวมถึง ADM Ventures และ Evolv Ventures ซึ่งเป็นหน่วยงานร่วมลงทุนของ Kraft Heinz
นอกจาก Evolv Ventures จาก Kraft Heinz แล้ว อย่าคิดว่ามันไกลเกินนะครับ CJ CheilJedang บริษัทจากเกาหลีใต้ที่เป็นผู้นำด้านเทคโนโลยีการหมัก ได้เข้าร่วมลงทุนในรอบ Series A เมื่อเดือนพฤศจิกายน 2022 แล้วเจ้านี้นี่บอกได้เลยครับ บิ๊กเนม CJ CheilJedang เป็นผู้นำด้านเทคโนโลยีการหมักและมีส่วนแบ่งตลาด 25% ในตลาดพิซซ่าแช่แข็งของสหรัฐฯ เป้าหมายการเข้าร่วมลงทุนใน New Culture ก็เพื่อสนับสนุนการพัฒนาผลิตภัณฑ์และการขยายกำลังการผลิตของชีสปราศจากสัตว์ของบริษัท
New Culture ยังได้ร่วมมือกับเชฟชื่อดัง Nancy Silverton เพื่อเปิดตัวผลิตภัณฑ์ชีสในร้านอาหารระดับเชฟชื่อดังในสหรัฐฯ กลางปี 2025 โดยเริ่มที่ร้าน Pizzeria Mozza ในลอสแอนเจลิส ซึ่งถือเป็นการเปิดตัวผลิตภัณฑ์สู่ตลาดผู้บริโภคครั้งแรกของบริษัท
การเข้ามาลงทุนของ Evolv Ventures กองทุนร่วมลงทุนของ Kraft Heinz ทำให้เจ้าพ่อชีสโปรเซสในตำนาน มีโอกาสเข้ามาร่วมมือเปิดร้านอาหารนำร่องกับ New Culture
น่าสนใจไหม เงินทุนใหญ่ๆมาจากหน่วยลงทุนที่มีผลิตภัณฑ์เป็น พิซซ่า #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c1e6505c:02b3157e
2025-05-13 00:58:11
@ c1e6505c:02b3157e
2025-05-13 00:58:11I rarely make black and white photographs. I usually find color more interesting. But sometimes, it’s wise to strip it away.
Color can be distracting. It can pull attention from what matters. Beauty, I believe, should be simple - something that’s felt, not overthought.
Removing the excessive, the superfluous, can do a lot. It reduces noise. It reveals what’s often hidden. What’s elusive becomes clear.




-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ c9badfea:610f861a
2025-05-13 00:43:22
@ c9badfea:610f861a
2025-05-13 00:43:22ℹ️ FMHY is the largest collection of free stuff on the internet - regularly mirrored from the original source
💡️ Content is updated automatically; bookmark this article to stay up to date
Getting Started
Wiki
- 📛️ Adblocking / Privacy
- 🤖️ Artificial Intelligence
- 📺️ Movies / TV / Anime
- 🎵️ Music / Podcasts / Radio
- 🎮️ Gaming / Emulation
- 📗️ Books / Comics / Manga
- 💾️ Downloading
- 🌀️ Torrenting
- 🧠️ Educational
- 📱️ Android / iOS
- 🐧️ Linux / macOS
- 🌏️ Non-English
- 📂️ Miscellaneous
Tools
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ c9badfea:610f861a
2025-05-13 00:24:49
@ c9badfea:610f861a
2025-05-13 00:24:49► Dev Communities
- 🌐 Programming-Telegram-Group - Telegram Communities
- ⭐ StackOverflow - Developer Forum
- ⭐ XDA - App Development Forum
- CodeProject - Developer Forum
- Spiceworks Community - Developer Forum
- DEV Community - Developer Forum
- Blind - Developer Forum
- IndieHackers - Developer Forum
- CyberArsenal - Cybersecurity Forums
- TheSecMaster - Cybersecurity Blog
- Tech-Blogs or HN Popularity - Blogs for Developers
- The Devs Network - Developer Chat
- DevBuddies - Search for Programming Partners
- StackShare - Tech Stack Collaboration
► Dev News
- ⭐ KrebsOnSecurity - Cybersecurity News
- ⭐ Lobsters - Dev News / Highlighter
- TechURLs - Dev / Tech News
- DevURLs - Dev News
- Techmeme - Dev News
- The Brutalist Report - Dev News
- jimmyr - Dev News
- daily.dev - Dev News
- Talos Blog - Cybersecurity News
- IT Security Guru - Cybersecurity News
- This Week in Rust - Rust News / Updates
- hackertab.dev or daily.dev - Dev Browser Startpages
► Developer Learning
► Developer Tools
- ↪️ Data Visualization Tools
- ⭐ DevToys - Dev Multi-Tool App / GitHub
- ⭐ DevDocs / GitHub or ZealDocs - Dev Documentation
- ⭐ ImHex / Web Version / GitHub or HexEd.it - Hex Editors
- Slidev - Developer Presentation Slides / GitHub
- Devhints - Developer Cheat Sheets
- Dev Emoji List - Emoji-List with Names, Shortcodes, Unicode & HTML Entities
- Student Developer Pack - Free Developer Tools for Students
- choose-a-license or ChooseALicense - How to pick a license
- PrivacyPolicyTemplate - Generate Privacy Policies
- Eternal Terminal or NxShell - SSH Clients / Servers
- PuTTY - SSH & Telnet Client / Multi-Tab / Fork / GitHub
- Penpot - Cross Domain Design & Prototyping Platform
- Webhook.site - Webhook Tools
- Libraries.io - Package, Framework & Tool Search
- Deps.dev - Open Source Package Search
- Bardeen or N8N - Workflow Automation
- UI.Vision RPA - Workflow Automation Extension
- Hajimari - Kubernetes Startpage / Discord
- discord-api-libs - Community Libraries for Discord API
- botwiki - Learn How to Make Bots
- reddit-moderator-toolbox - Toolbox for Reddit Extension Development
- devSwag - Developer Giveaways
- Commands.dev - Terminal Commands
- Linear, AirBroke or Glitchtip - Error Tracking Platforms
- UMLet or JDL Studio - Create UML Diagrams
- Mockaroo - Generate Mock Data
- Mockium - Generate Test Data
- Globster - Test Glob Patterns
- Big List of Naughty Strings - Check for Edge Case Inputs
- overmind - Process Managers
- sed.js - GNU sed Live Editor
- PlantText - UML Editor
- Code::Stats or Wakatime - Programmer Stat Tracking
- WiredJS - Wireframe Designer
- KeyCheck - Dev Tool Hotkeys
- NBviewer - Jupyter Notebook Sharing
▷ Dev Tool Indexes
- ⭐ Free for Developers / GitHub
- Useful Tools / GitHub
- Best-Websites
- Tiny Helpers / GitHub
- Tiny Tools
- Free For Life / GitHub
- WebdevHome
- Free Developer Stuff
- Addy
- Prototypr
- Awesome Sys Admin - System Admin Resources
- Awesome Design Patterns - Design Pattern Resources
▷ Online Toolkits
- ⭐ AppDevTools
- IT Tools
- Web Toolbox
- devina
- wangchujiang
- SmallDev.tools
- Coders Tool
- Utilities and Tools
- Clean CSS
- FreeFormatter.com
- Online String Tools
▷ Software Dev Tools
- 🌐 Awesome Software Quality - Software Quality Testing Resources
- 🌐 Awesome DOS - DOS App Development Resources
- ⭐ Every-programmer-should-know, raylib technologie or bookmarks - Software Development Tools
- ⭐ Electron Tools - App Store / Debugger / Mod Loader / Builder
- ⭐ new(releases) - Software Release Notifications
- Budibase, ToolJet or Appsmith - Internal Tool Builders
- Theos - Program Build System / GitHub / Jailed Tweaks
- New Software - Project Decision Checklist
- Open Source Guides - Open Source Software Tips / GitHub
- Dokploy - App Deployment
- Gaultier Blog - Learn x86-64 Assembly
- dnSpyEx - .NET Debugger and Assembly Editor
- Crontab Guru - Crontab Editor / Job Scheduler
- Crontab Generator - Generate Crontab Syntax
- Slint - GUI Development Tools / GitHub
- Inno Setup or InstallForge - Create Installation Programs
- Etebase - Encrypted App Backend
- tl;drLegal - Software License Summaries
- minisign - Sign Files / Verify Digital Signatures / GitHub
- VirtualBuddy - Virtualize macOS 12 and later on Apple Silicon
- Pencil - Software Mockup Tool / GitHub
▷ Mobile Dev Tools
- 🌐 AndroidRepo - Android Development Resources
- 🌐 Awesome iOS - iOS Development Resources
- 🌐 UXArchive, Mobbin or UISources - Mobile UI Resources
- ↪️ App Mockups
- ⭐ Android Developer Roadmap
- App ideas - Collection of App Ideas
- IconKitchen or AppIcon - App Icon Generator
- namae - App Name Availability Check
- XDGuru - Adobe XD Resources
- Media Kit - Video / Audio Library for Flutter and Dart
- ADB or Appium / GitHub - Automated App Testing
- Privado - Generate App Privacy Reports / GitHub
- PM2 - Process Manager
- Andure - Android Chrome Dev Tools
- useAnimations - Animated Icon Pack
- Official Android Courses - Android Training Courses
- Android Libhunt - Android Packages
- Android-Iconics - Use Any Icon / Font as Your Drawable App
- AndroidAssetStudio - Android App Assets
- Contacts Android - Android Contacts APIs
- Push Notifications API - Push Notifications API
- React Native Apps - React App Examples
- TV Samples - Android TV App Samples
- iOS Icon Gallery - iOS Icon Examples
- PrivacyFlash-Pro - Generate iOS Privacy Policies
▷ Database Tools
- 🌐 DB Engines or DBDB - Database Rankings
- 🌐 Awesome Opensource Data Engineering - Data Engineering Tools
- 🌐 Awesome Big Data - Big Data Resources
- ⭐ DB Browser, SQLook, DuckDB, SQL Lite Studio or HeidiSQL - SQL Managers
- Sqlable - SQL Tools
- Grafana or Beszel - Dev Data Dashboards
- DBeaver - Universal Database Tool
- ChartDB - Database Visualization / GitHub
- Ingestr - Transfer Data between Databases
- NocoDB - Turn Database into Smart Spreadsheet / GitHub
- Generate Fake Data - Ruby / Swift
- Qdrant - Vector Database
- SQL Cheat Sheet - SQL Cheat Sheet
- Gel - SQL Alternative
- QueryStorm - SQL and .NET programming in Excel
- SQLizer - Convert Files To SQL Databases
- franchise - SQL Notebook
▷ Git Tools
- 🌐 Console - Search Projects on OpenSourceHub.io
- 🌐 Awesome README - GitHub Readme Resources
- 🌐 Forge Comparison, Forgejo or Forgeperf.org - Git Collab Tool Comparison
- ↪️ Git Project Indexes
- ⭐ Git-Fork, GitButler or GitQlient - Git Desktop Clients
- ⭐ Codeberg, Drift, Gitea, GitLab.com or sourcehut - GitHub Alts / Version Control Systems
- Git - Version Control System
- searchcode or PublicWWW - Source Code Search
- git-sim - Visually Simulate Git Operations Before Running
- Gittea.dev, Savannah, FSFE, git.sr.ht, GitGud or Notabug - Git Hosting / Software Forge
- Forgejo or Gogs - Self-Hosted Git Services / Forge
- posh-git - Git Powershell Environment
- up-for-grabs - Curated List of Tasks for New Contributes
- GitKraken, RelaGit, Sourcetree, lazygit or gitui - Git GUIs
- Gut, Jujutsu, GitHub Cli or gitu - Git CLI / TUI
- git-pr - Git Collab Tools
- Git-notify - Embed Announcements into Git Commit Messages
- Allstar - Git Repository Security App
- git-bug - Git Embedded Bug Tracker
- Plane / Discord, Git Extensions or Thermal - Git Project / Repo Managers
- git-annex - Manage Large Git Files (without Git)
- GitList - Elegant Git Repository Viewer / GitHub
- Gittyup - Git Source Code History / GitHub
- Gource - Git Project Visualizer
- multi-gitter - Bulk Repository Updater
- Delta or Git-Split-Diffs - Syntax Highlighting / Comparison
- Onefetch - Command-line Git information tool / GitHub
- commitlint - Lint Commit Messages / GitHub
- Git Cliff - Changelog Generator
- github-readme-terminal - Terminal Style Readme
- GIT Quick Stats - View Git Statistics / GitHub
- gitignore.io - Gitignore Templates / GitHub
▷ GitHub Tools
- 🌐 OSS Insight - GitHub Project Index
- 🌐 Awesome First PR Opportunities - Beginner FOSS Project Index
- 🌐 Awesome Actions - GitHub Action Resources
- 🌐 Awesome Browser Extensions - GitHub Browser Extensions
- 🌐 Awesome Badges - GitHub Badge Resources
- 🌐 GitHub-Userscripts - GitHub Userscripts
- ⭐ GitHub Desktop / Linux - GitHub Desktop Client
- ⭐ GitHub.Dev - GitHub Web Apps
- Gothub - GitHub Frontend
- GitHub Cheat Sheet - GitHub Cheat Sheet
- GitHubStatus - GitHub Outage Status
- Languish - GitHub Programming Language Stats
- Langits - View Your Most Used Languages on GitHub
- refined-github or Ungit - Improved GitHub Interface
- GitHub Dorks - GitHub Search Tool
- Imgbot - GitHub Image Compression
- ActionServerless - Create Serverless Service
- Rahularity - Use Multiple Git Accounts at Once
- dotfiles - GitHub Dotfiles
- GitHub Web IDE - Web IDE / GitHub
- Octobox, Gitify, advanced-github-notifier, PR Monitor, Gitification or CatLight - GitHub Notifications
- github1s - GitHub Code Viewer / GUI: do
gitkin Repo Folder - Pages CMS - Content Managment System / GitHub
- KeyManager - GitHub SSH / GPG Key Manager
- Serctl - Backup GitHub Projects
- Pew Pew - Cleanup Unused Repos
- No Secrets - Cleanup Sensitive Files in Repos
- DownGit, GitHub2File, Gitzip or Download Directory - Download GitHub Repo Sub-Folders / Files
- Install from GitHub or Eget - Install Packages / Binaries Directly from GitHub
- useful-forks or GitPop3 - GitHub Fork Search
- Active-Forks - Find Active GitHub Forks / GitHub
- Graphite or Stacking - Improve Pull Request Workflow
- PR-Agent - Automated Pull Requests
- SemanticDiff - Review Pull Requests using Language Aware Diff
- StarGrab - Mirror GitHub Repositories
- Repo2Txt - Convert Repos to Text Formatted Files / GitHub
- Gitingest or Repomix / GitHub - Convert Repos to Prompt-Friendly Text
- OctoLinker - Make GitHub Code References Clickable
- Octotree - GitHub Repo File Tree View
- Nightly.link - GitHub Sharable Nightly Links
- ActionFlow - Action Workflow Automation
- shot-scraper-template - Take Automated Screenshots of Web Pages
- Star History - Repository Star History Graph
- GitWhoIs - GitHub Repo History / Info
- Gitstar Ranking - Git Repo Star Rankings
- GithubReleasesBot - Repository Change Feeds
- GitHub Markdown Preview - Preview GH Markdown
- ReadmeGallery - GitHub Readme Gallery Creator
- GitHub Readme Stats - Dynamically Generated GitHub Readme Stats
- GitHub Contribution Graph - Add GitHub ReadMe Contribution / Commit Graph
- GitHub Readme Quotes - GitHub Readme Quote Generator / GitHub
- Shields.io - Metadata Badges for GitHub Readme
- SkillIcons, Badgers, SpaceBadgers or SimpleBadges / GitHub - Skill Badges for GitHub Readme / Resumes
- For the Badge - Custom GitHub Badges
- GitHub Spray - Draw on GitHub Contribution Page
- GitHub Snake - Enable Snake Game on GitHub Readme
- GitHub Profile Readme Generator or GPRM - Generate Git Profile Readme
- GitStalk - GitHub Profile Info Search
- ProfileMe.dev - Create GitHub Profile
- Beautify GitHub Profile - Custom GitHub Profile Resources
- Discord MD Badge - Add Discord Badge to GitHub
- github-material-icons-extension - Material Icons
- gist.io - Git Blog Platform
▷ Docker Tools
- 🌐 Awesome Docker - Docker Services Index
- 🌐 Selfhosted-Apps-Docker - Self-hosted Docker Apps / Guides
- ⭐ Docker - Build, Manage and Run Apps in Containers
- ⭐ portainer, yacht, DockGE, moncho or podman / 2 - Container Managers
- ⭐ Composerize, 2 - Compose Docker Files
- ⭐ Hub Docker, 2, 3 - Docker Images
- Docker Desktop - Docker Desktop App
- LazyDocker, oxker or Isaiah - Docker Managers / TUIs
- Dockerized - Docker Command-Line
- Dockle - Image Linter
- Dive - Analyze Images
- WatchTower - Container Automation
- autoportforward - Port Forwarding
- Dozzle - Log Viewer
- Docker AutoHeal - Container Monitor
- Diun - Docker Notifications
- Podman Compose / Playground - Podman Compose
- Termible - Docker Powered Site Terminals
▷ CLI Tools
- ↪️ CLI Cheat Sheets
- Awesome CLI - CLI Interface for Searching Awesome Lists
- Charm - Add Backend to Terminal Based Apps
- OhMyPosh - Terminal Theme Engines
- Lip Gloss - Style Definitions for Terminal Layouts
- sshx - Share Terminal Screen / GitHub
- cURL - Transfer Data with URLs / Converter / IP Lookup
- ripgrep or Sift - grep Alternatives
- Edbrowse - Command Line Editor / Browser / Mail Client
- Command Not Found - Install Missing Commands
- Atuin - Sync, search and backup shell history
- pueue - Shell Command Manager
- Zoxide - Improved CD Command
- yoctocolors - Command Line Coloring Package
- open - Open URLs, Files, Executables in CLI or Scripts
- VisiData - Spreadsheet CLI Editor
▷ API Tools
- 🌐 Public APIs, API List, Public APIs, APIsList, APIs Guru, FreePublicAPIs, Public API Lists, APIVault or Any API - API Indexes
- 🌐 Awesome API Security or APIKit - API Security Resources
- 🌐 Streaming Site APIs
- 🌐 List of Providers - Piracy Site APIs
- 🌐 Free AI Stuff / 2, Respy, FreeAPIProviders or API Together - LLM / AI API Indexes
- 🌐 Countless - AI API Price Comparisons
- ⭐ hoppscotch, Firecamp, Strapi or Postman - API Builders
- ⭐ Shizuku or Dhizuku - Let Apps Use System API (Android)
- Wyzie Subs - Subtitle Scraping API / NPM Package / Docs
- HTTPie - Test REST, GraphQL, and HTTP APIs
- Rest Test Test - Test REST / CORS Services
- Beeceptor - Mock REST APIs
- Pipedream - Connect APIs / Tutorial
- FastAPI - API Framework
- Posting / GitHub, Insomnia or Yaak - API Clients
- Bruno - API Testing Client
- ReDoc - Generate API Documentation
- Mockable, {JSON} Placeholder, jsoning, Mocky or MockLab - Mock APIs
- Mockae - Mock APIs with Lua Execution
- InstantAPIs - API Endpoint Generator
- Stein - Turn Google Sheets into Database API
- Lanyard - Export Discord Rich Presence to API Endpoint / Websocket / Discord
- Telegram Bot API / GitHub or PHP Telegram Bot - Telegram Bot API
- cf-workers-telegram-bot - Serverless Telegram Bot / GitHub
- Perspective API - Toxicity Reduction API
- Plaid - Financial Account API / GitHub
- PDF Bot - A Node queue API for generating PDFs
▷ Machine Learning
- 🌐 Awesome Machine Learning - Machine Learning Framework Index
- 🌐 Awesome ML or ML Resources - Machine Learning Resources
- ⭐ Hugging Face, LLM Papers or OpenML - Machine Learning Datasets / Papers
- ⭐ Deep playground - Neural Networks Playground
- ⭐ LLM Visualization - Learn how LLMs Work
- Awesome Generative AI Guide - LLM Research Resources
- Machine Learning Roadmap, SAAYN, machine-learning-zoomcamp, ML Engineering or LLM Course - Learn Machine Learning
- LLM Text Complation - LLM Finetuning / Text Complation
- DeepSpeed - Deep Learning Optimization Library
- Netron - Visualizer for Neural Network, Deep Learning, and Machine Learning Models
- MMDeploy - Deep Learning Model Deployment Toolset / GitHub
- ChatGPT-Next-Web - Cross-Platform ChatGPT / Gemini UI
- Nixified - Nix Flake for AI Projects
- Cyberbotics - Robot Simulator
► Game Dev Tools
- 🌐 List of Game Engines, Awesome Game Engine or Game-Engines - Game Engine Development Resources
- 🌐 EnginesDatabase - Game Engines Database
- 🌐 Awesome Game Dev or /AGDG/ Resources - Game Dev Resources
- 🌐 Awesome Game Production - Game Production Resources
- ↪️ Learn Game Development
- ↪️ Sound Effect Sites
- HiddenPalace - Game Development Media Archive
- Tommti Systems - 3D Benchmark Tools
- Tracy Profiler - Frame Profiler
- Doshaven Programming List - DOS Game Creator Tools
- Fantasy Consoles / Computers - List of Fantasy Consoles and Computers
- Xelu's Controller Prompts - Free Game Prompts / Video
- Basic Computer Games - Basic Computer Game Examples
▷ Asset Creation
- ↪️ Download Game Assets
- ↪️ 3D Models / Modeling Tools
- ↪️ Design Tools / Resources
- ↪️ Art Resources
- ↪️ Animation Resources
- ↪️ Writing Tools
- Nuklear - Game GUI Creator
- HUDSxGUIS - UI Design Concepts
- SPARTAN Procedural - Procedural Tile Generator
- Game Sounds - Royalty Free Game Sounds
- Bleeper or jfxr - Game Sound Effects Creators
- Engine Simulator - Engine Sound Simulator / GitHub
- The Sounds Resource - Game Sounds Examples
- EZ Conversion - Game Audio Converter
▷ Map Creators / Editors
- ⭐ SpriteFusion - Tilemap Editor / Discord
- MapEditor or Tilesetter - Level Editors
- LDtk or Ogmo Editor - 2D Level Editors
- CharPad - Commodore 64 Graphics Editor
- Fantasy Map Generator - Fantasy Map Generator
- Inkarnate - Fantasy Map Editor
- HexHTML - Hexagon Fantasy Map Editor
- ProFantasy - Fantasy Map Tutorials
- Medieval Fantasy City Generator - Medieval Fantasy City Generator
- donjon - RPG Resources / Tools
- RPG Map II - RPG Map Editor
- MapTool - Virtual Tabletop for RPG Games
- Inkwell Ideas - Free Map Tools
- Neighbourhood - Neighborhood Map Generator
- Laigter - Map Generator for 2D Sprites
- Dungeon Scrawl - Dungeon Mapmaking Tool / Subreddit / Discord / GitHub
- Dungeon Map Doodler - Draw Dungeon & Terrain Maps
- One Page Dungeon - Single-page Dungeon Map Generator
► IDEs / Code Editors
- ↪️ Text Editors / Notes
- ⭐ VSCodium or Visual Studio Code, 2, 3 - Code Editor / Extensions
- ⭐ JetBrains / Unlock / License Server
- ⭐ Neovim - Code Editor
- ⭐ Lite XL or Pragtical - Code Editor / Plugin Manager / Plugins / Themes
- ⭐ Emacs - Code Editor / Docs / Resources
- ⭐ WebDen, Sharplab, tech.io or CodingGround - Code Playgrounds
- ⭐ Android Studio / Guide, SupaBase or Plasmic - App Creators / Builders
- Heynote - Code Editor / Notepad
- Edna - Web App / Code Editor / Notepad
- Trinket - Web App / Live Preview / Sign-Up Required / Online Workspace
- Firebase - Gemini AI Cloud Webapp
- Helix - Kakuone / Neovim-Based Code Editor
- HaystackEditor - Canvas-Based Code Editor
- Brackets - Webapp / Live Preview
- Bluefish - Code Editor / Templates
- CudaText - Code Editor
- Lapce - Code Editor
- ecode - Code Editor
- Competitive Editor - Competitive Programming Editor
- JSON Hero - JSON Viewer / Editor
- Apache NetBeans, KDevelop, Mitosis, Lazarus or OpenShift - Cross Platform IDEs
- TidalCycles - Live Algorithmic Coding Environment / Discord
- SciTE - Source Code Editor for Win32 and X
▷ Cloud IDEs / Collab
- 🌐 cloud - Cloud Platform Index
- 🌐 Heroku-Alt or heroku-free-alternatives - Heroku Alternatives
- ↪️ Code Collaboration Platforms
- ⭐ goormIDE - Cloud IDE
- ⭐ Google Colaboratory - Cloud IDE
- ⭐ CodeSandbox, StackBlitz or GitPod - VSCode Cloud IDE
- ⭐ judge0 - Online Code Editor / Discord
- Fleet - Cloud IDE
- CodeTasty - Cloud IDE
- Atheos - Server Required / Cloud IDE / GitHub
- Datalore - Cloud IDE
- JSFiddle - Cloud IDE
- html-css-js - Cloud IDE
- Collabedit - Cloud IDE
- CoderPad - Cloud IDE
- zed - Cloud IDE
- Ideone - Cloud IDE
- PlayCode - Cloud IDE
- pad.ws - Whiteboard Style Cloud IDE / GitHub
- Openshift - Cloud IDE / Eclipse Che
- Arduino - Cloud IDE for Arduino
- Shell Cloud - Google Cloud Shell Environment
- Blazepack, Flox or DevPod - Development Environments
- bloop - IDE AI Suggestion Extension
- glot.io - Pastebin with Runnable Snippets, API & Compiler
- Notebooks.azure - Access Jupyter Notebooks in VS Code
- Jupyter Server - Jupyter Services / APIs
- Anywidget - Create Jupyter Widgets / GitHub
- CoCalc - Virtual online workspace
- CodePen, Web Maker or Liveweave - Code Sandbox
- Platform.uno or Enact - App Frameworks
- InstantDB - Collaborative App Framework
- Codeface, Monaspace, Programming Fonts or Dev Fonts - Fonts for Coding / Comparison
▷ Android Code Editors
- ⭐ Acode - Android Code Editor / GitHub
- Sora - Android Code Editor
- Squircle-CE - Android Code Editor
- Visual Code Space - Android Code Editor
- Spck Editor - Android Code Editor
- droidvim - Vim Code Editor
- VHEditor - VSCode Editor
- diohub, PuppyGit or OctoDroid - Android Git Clients
- GitSync - Android Git Remote Repo Sync
- Gidget - GitHub Notifications / Android
- FlutterMarkdownEditor - Markdown Editor
▷ Coding Tools
- 🌐 Awesome Creative Coding - Creative Coding Resources
- Prettier or codebeautify - Code Formatting Tools
- editorcornfig - Maintain Code Styles Across Editors
- ThemesElection or Dracula - Code Editor Themes
- Freeze - Generate Images of Code / Terminal Output
- myCompiler, Compiler Explorer, OneCompiler, GodBolt, ryugod or Wandbox - Online Compilers / Explorers
- DogBolt - Decompiler Explorers / GitHub
- Code2Flow or Flowchart.js - Code to Flowchart Converter
- tuc - Improved Code Cut
- massCode - Code Snippet Manager
- Meld / 2, Beyond Compare / Pro or WinMerge - File / Directory Comparison Tools
- 0xacab - Code Host
- OctoLinker - Turn Code Statements into Links / GitHub
- RTutor - Translate Natural Language to R code / No Sign-Up
- BrickHub - Share Code Brick Templates
- Sourcegraph or SeaGOAT - Code Searching
- Sourcecodester, Code Projects, Codastro, Kashipara or ItSourceCode - Source Code Projects
- ShortCode or CodeList - Script / Code Indexes
- AnimateCode - Create Code Animations
- DelphiTools - Code Profiler / Delphi Tools
- Adrenaline or Console Ninja - Code Debugging
- JBin or Replay - Collaborative Code Debugging
- Winddown or Sandman - Coding Break Reminders
- Decompiler - Online Decompiler
▷ Vim / Neovim Tools
- 🌐 Awesome Neovim or NeoVimCraft - NeoVim Plugins Collections
- ⭐ Vim Bootstrap - Bootstrap Config for Vim
- SpaceVim, NeoVim Kickstart, AstroNvim, LazyVim, NvChad or LunarVim - Neovim Configs
- DotFyle - Neovim Config Search
- Lazy.nvim or packer.nvim - Neovim Plugin Managers
- FireNVim - Neovim in Browser
- neovide, gnvim, nvui, Neovim wiki##gui - Neovim GUIs
- instant.nvim - Collaborative Neovim Editing
- chatgpt.nvim - ChatGPT in Neovim
- Vim Plug, vim-pathogen / GitHub or Shougo - Vim Plugin Managers
- VimAwesome - Vim Plugins
- nerdtree - Vim Tree Explorer
- VimColorSchemes - Vim Color Schemes
- The Ultimate vimrc - Vim Config
- Vim Markdown or Markdown Preview - Vim Markdown Plugins
▷ VSCode Tools
- 🌐 Awesome VSC Extensions, 2 - VSCode Extensions
- github-vscode-icons - VSCode Icons
- chatgpt-vscode - VSCode ChatGPT
- Open VSX - Open VSX Registry
- snippet-generator - Snippet Generator
- Dendron - Knowledge Managment
- Discord Tools
- vscode-smart-clicks - Smart Clicks
- code-server - Web Server / GitHub
- vscode-settings - VSCode Settings
- insiders.vscode - Insider Build
- VSCodeThemes or VSColors - VSCode Themes
- oslo - Theme Generator
▷ Coding AIs
► Programming Languages
- 🌐 Awesome Cheatsheets, QuickRef.me, HowDoI, OverApi, Reference / GitHub or Cheat Sheets - Programming Cheat Sheets
- 🌐 Awesome Go or Go Recipes - Go Resources
- 🌐 TheAlgorithms - Coding Algorithms / GitHub
- ↪️ Learn Programming
- ⭐ Benchmarks Game - Measure PL Speeds
- ⭐ Language Benchmarks - Benchmarks for PLs & Compilers
- ⭐ 30 Seconds of Code or FreeFrontend - Find Code Snippets
- ⭐ generatedata.com - Generate Test Data in Different Languages
- Try It Online - Programming Language Interpreters
- nunu - Build Go Programs
- Learn X in Y minutes - Programming Language Rundowns / GitHub
- OneLang - Convert Code to Multiple Languages
- Crystalline - Crystal Language Server
- icr - REPL for Crystal
- explaine.rs - Rust Syntax Explanation
▷ Python
- 🌐 Awesome Python - Python Resources
- ⭐ Automate The Boring Stuff - Python Automation Book
- Python Cheatsheet or SpeedSheet - Python Cheat Sheets
- Python Patterns - Python Design Patterns
- Clean Code Python - Clean Up Python Code
- RustPython - Python Interpreter
- uv - Python Package / Project Manager
- Thonny - Python IDE
- pylyzer - Static Code Analyzer
- Online Python Compiler - Online Python Editor & Tester
- ClipRun - Run Python Code in Browser / Chrome Extension
▷ C Languages
- 🌐 Awesome C++ - C++ Resources
- RoslynPad - C# Editor
- RoslynQuoter - C# Syntax Tree API Viewer
- The Algorithms - C++ - C++ Algorithms
- cpp.sh - Online C++ Compiler
- CP-Algorithms - C++ Algorithms
- cppreference - C++ Cheat Sheets
▷ Java / Kotlin
- 🌐 Awesome Kotlin - Kotlin Resources / GitHub
- 🌐 Obfuscator List - Java Obfuscator Index
- Recaf - Java Bytecode Editor
- bytecode-viewer, jd-gui, Krakatau, Luyten, Vineflower or Fernflower - Java Decompilers
- JEnv For Windows - Change Java Version
- jadx - Dex to Java Decompiler
- GraalVM - Advanced Multi-language JVM
- Adoptium - Download OpenJDK Binaries
► Web Development
▷ HTML
- 🌐 Awesome HTML5 - HTML5 Resources
- ⭐ HTML Reference, HTML Cheat Sheet or HTML.com - HTML Guides / Cheat Sheets
- HTML-Minifier - HTML Minifier
- HTMLRev - Free HTML Templates
- Markdown to HTML - Markdown to HTML Converter
- APlayer, DPlayer or xgplayer - HTML5 Video Players
▷ CSS
- 🌐 Awesome CSS - CSS Resources
- ↪️ CSS Framework Tools
- ⭐ You Don't Need JavaScript - CSS Demos
- CSS Cheat Sheet or CSS Tricks - CSS Cheat Sheets
- Easings - CSS Animation Cheat Sheet
- CSSLayout or CSS Layout Generator - CSS Layout / Grid Generators
- CSSPeeper - Smart CSS Viewer
- Project Wallace - CSS Analyzer
- CSS Protips, Modern CSS or CSS Reference - CSS Guides
- Water.css - CSS Styles
- Style Stage - Modern CSS Styles
- Glass UI - Glassmorphism CSS Generator
- Hover.CSS - CSS Hover Effects
- PixelArtCSS - Pixel Art to CSS
- Buttons.cool - Copy CSS Buttons
- CSS Doodle - CSS Pattern Generator
- CSS3 Transform - 2D & 3D CSS Transform Functions Visualizer
- css3patterns, gradienta, GradientMagic or heropatterns - CSS Patterns / Gradients
- FilterBlend - CSS Blend Modes
- Animista - CSS Animations
▷ JavaScript
- 🌐 Awesome JavaScript - JavaScript Resources
- ↪️ TypeScript Tools
- Vanilla List - Vanilla JavaScript Repository
- RunKit - Browser JavaScript Sandbox
- Component Party - Web Component JS Frameworks Overview / GitHub
- jsdfe, de4js, Deobfuscator, WebCrack, Deobfuscate or deobfuscate.io - JavaScript Deobfuscators
- Minify JS or JS Compressor - JavaScript Minifiers
- 1loc or Underdash - JavaScript Snippets
- Node.js Best Practices - Node.js Style Guide
- Airbnb JavaScript Style Guide or StandardJS - JavaScript Style Guides
- Discord.js Guide or An Idiot's Guide - Discord.js Bot Guides
▷ React
- OpenChakra or Plate - React Code Editors
- ReactBits, React Suite / GitHub, 21st / GitHub or Radix UI / GitHub - React Components
- Mantine - Components and Templates / GitHub
- Bulletproof React - React App Architecture
- Refine - React App Builders
- Alright - Generate React Apps
- Codux - Visual IDE for React
- React SVG - Convert SVG to React Components
- Zorm - Type-Safe Form for React
- Million - React Replacement
- novu - Real-Time React Notifications / GitHub
- React Use or UseHooks - React Hooks
- React Query - Fetch, Cache and Update React Data / GitHub
- MMKV - React Key / Value Storage
- Vision Camera - React Camera Support / GitHub
- React PDF - Create PDFs in React
- react-spring - React Spring Animations
- Create React App - Set Up React Web Apps / GitHub
- Codebases - Collection of Projects Written in React
▷ PHP
- 🌐 Awesome PHP - PHP Resources
- XAMPP - PHP Development Environment
- Clean Code PHP - Clean Code for PHP
- Valinor / GitHub - PHP Object Mapper
- Spatie / GitHub or 3v4l - Run PHP Concurrently
► Web Dev Tools
- 🌐 Website Creation Resources - Web Dev Resources
- 🌐 Awesome Tunneling - Tunneling Resources
- 🌐 Awesome list of secrets in environment variables - Environment Variables Secrets
- 🌐 Frontend Developers or Web Dev / Programming YouTube Channels - Web Dev YouTube Channel Indexes
- ↪️ Site Mockups
- ↪️ Archive / Scrape / Crawl Web Pages
- ⭐ Ray.st or Wappalyzer - Identify Technologies on Websites / Addons
- ⭐ GoAccess - Web Log Analyzer / GitHub
- ⭐ Formulaer, Tally, FormBricks, Formshare, Deformity or Stylr - Form Builders
- DataNodes - Webmasters Only File Host / Discord
- Website Planet Tools, Browserling Tools or WebCode - Site Development Tools
- shadcn-ui or shadcn-svelte - Web Component Libraries
- Web Developer - Web Developer Toolbar Extension
- GoatCounter, Rybbit or Umami - Site Analytics
- ElasticSearch - Search & Analytics Engine / GitHub
- Tabler - Site Admin Dashboard
- Octopus - Site Planning Tool
- WireFlow - Flow Prototype Maker
- Web Dev Checklist - Things to Remember for Web Devs
- Dagu - WebUI Job Manager / GitHub
- QuickEmailVerification, Email Marker or ZeroBounce - Email Validation Services
- Plow - HTTP Benchmarking
- http-server - No Config HTTP Server
- Apache - HTTP Server
- Observatory - HTTP Header Security Test
- Transform - Polyglot Web Converter
- BuiltWith - Find Out What Sites are Built With
- LibreCaptcha or mCaptcha - Privacy-Based Captcha Systems
- Media Chrome - Media Player Elements / GitHub
- OneLinePlayer - Vimeo / Dropbox Video Player
- Motion - Animation Library
- LDRS - Loading Animations
- Medusa - Digital Commerce Development Tool
- Can I Use? - Browser Support Tables
- Shuttle / GitHub or PocketBase / GitHub - Open-Source Backend Platforms
- Cloudflare Radar - Cloudflare Insights
- Check for Cloudflare - Check Sites for Cloudflare
- Caddy - Web Server
- Directory Lister - Web-based Directory Listing
- BawkBox - Website Widgets
- The SSO Wall of Shame - Vendors without Built-in SSO
- Remarkbox or HTML Comment Box - Site Comment Systems
- Typebot - Embedded Chat App
- Microlink SDK / GitHub, React Tiny Link / GitHub or Link Preview JS - Create Link Previews
- CORS Proxy - Free CORS Proxy
- frp, GoDoxy or YARP - Reverse Proxies
- WhatPWACanDo - PWA Examples
- Selenium, CopyCat, PlayWright or Huginn - Browser Automation
- Automa or Browserflow - Browser Automation Extensions
- PWABuilder - Turn Site into Progressive Web App
- Chaos Frontend Toolkit - Break Your Web Apps to Improve Them
- LocalHost - Connect Web Apps to Internet
- Shiki, tailspin or Sight - Syntax Highlighters
- ngrok - Introspectable Tunnels to Localhost Tools
- Bore - TCP Tunnel to Expose Servers Local Ports
- NConfig - Server Config
- Nginx-Admins-Handbook - Improve NGINX Performance
- Null PHP Script - Nulled Scripts
▷ Website Generators
- 🌐 Awesome Static Generators / GitHub or Jamstack Generators - Lists of Static Website Generators / Frameworks
- ⭐ Hugo or vitepress - Static Website Generators
- ⭐ Docusaurus, retype / GitHub, Zola, Jekyll or docsify - Static Markdown Website Generators
- Feather Wiki - Extensible Website Generator
- SouPalt - Static Website Generator with HTML Element Tree
- Barely - Python Static Website Generator
- Vvveb, Universe, Google Sites, GrapeDrop or Odoo - Drag & Drop Website Builders
- Tails - Tailwind CSS Website Builder
- 8b - Simple Online Website Builder
- Potion - Notion Website Builder
- Odie - Make Webpages out of Google Docs
- ProjectVisBug - Webpage Editor
- Anvil or Lowdefy - Web App Creators
▷ Color Schemes
- 🌐 Colorful - Color Scheme Resources
- ↪️ Color Palette Generators
- ↪️ Color Pickers
- ⭐ ColorHexa - Color Hex Encyclopedia
- ⭐ Realtime Colors - Preview Color Palettes
- ⭐ Color & Contrast - Color / Contrast Guide
- Colors & Fonts - Quickly Copy Colors
- Khroma or Paletton - Color Scheme Designers
- Palettte - Color Palette Editor
- Colouris - Color Model Conversions
- PaletteGenerator or Alwane - Color Palette Extractor
- Colorable / GitHub, color.review, accessible-color-matrix or Accessible Brand Colors - Accessible Color Pallette Builders
- Color Oracle, WhoCanUse or Toptal - Color Blindness Simulator / Tests
- Simpler Color - Create Web Color System
- Stylify Me - Extract Webpage Colors
- ColorZilla - Color Picker, Gradient Generator & more
- uiGradients - Hex Gradients
- MakeTintAndShade - Tint and Shade Generator
- Alphredo - Create Translucent Colors
- Contrast Checker or Colour Contrast - Background / Text Contrast Checkers
▷ Frontend Tools
- 🌐 Awesome Design Systems - UI Design Systems / Libraries
- 🌐 Awesome Web Animation - Web Animation Resources
- ↪️ Design Resources or Open Source Design
- ⭐ Design Checklist, Performance Checklist or Front-End Checklist - Frontend Development Checklist
- ⭐ ThemeWagon or Tooplate - Free HTML Templates
- ⭐ Boilerplate, html5up or TEMPLATED - Custom HTML Templates
- Templatemo or Free CSS - Free CSS Templates
- Repth Themes - Y2K Anime Themes
- Aspect or OpenUI - Make UI with AI
- Contentdrips or CreatorKit - Brand Design Tools
- SuperNova - Design System Manager
- Interplay - Product Design Tool
- CollectUI, Hoverstat, httpster, Wave Guide, Godly Website, ReallyGoodUX or Pageflows - UI / Site Design Ideas
- StoryBook, Akira or Mockend - UI Development Tools
- UI Design Daily or UIVerse - Free UI Design Resources
- Open UI - Open Standard UI
- Same.dev - Copy Sites User-Interface Code
- CodeMyUI or Semantic UI - User Interface Code Snippets
- Icon Shelf - Icon Manager
- Favicon Maker or Favicon Generator - Create Favicons
- Icon Horse, favicon-hash or Favicone - Download a Sites Favicon / Note
- Meta-Mapper - Website Metadata Thumbnails
- SREWorks - Operation & Maintenance Platform
- the component gallery - Design Components Gallery
- Scrollbar.app - Design Custom Scrollbars
- LogoTaco - Project Logos
- Emanote - Create Sites from Plain-Text Notes / GitHub
- Plunker or Bloo - Prototype / Test Websites Idea
- WebDesignMuseum - Website Designs Over Time
- Bootstrap - Mobile Site Creator / Icons / Snippets / UI Components / Templates, 2
- PsdRepo - Templates, Mockups, Logos, Videos
- Daft Page - Landing Page Creator
- LandingPage - Landing Page Tool Index
- SaaS Pages, SaaS Landing Page or lapa - Landing Page Templates / Ideas
- Zeplin - Design Templates / Editor
- vite or layoutit - Frontend Development Tools
- Frontend Development - Frontend Development Resources
- BoxCoding, UI Beats or MagicUI - UI Components
- Hydrogen - Online Store Templates
- CSS Bed - Classless CSS Templates / GitHub
- Beer CSS - Lightweight CSS Framework / GitHub
- RoughAnnotations - Webpage Annotations / Animations
- Lorem.space, dummyimage, Placeholdifier, PlaceHolder, PicSum or FakeIMG - Site Placeholder Images
- Visiwig - Copy / Paste Site Graphics
- WebDesigner, T3, Theatre.js / GitHub, GSAP, Stylie, RenderForest, Mantra or Lottielab - Create Motion Graphics
- useAnimations or LordIcon - Animated Icons
- NakerApp - Interactive Background Maker
- HTTP Cats - Put Cat Pictures in Your Status Codes
▷ Hosting Tools
- 🌐 Awesome Cloudflare - Cloudflare Resources
- 🌐 VPS Comparison Chart or Bitcoin VPS - VPS Comparisons
- ↪️ Free Webhosting Sites
- ↪️ Domain Tools
- ⭐ Check-Host, StatPing, Uptime, Uptime Kuma, Highlight, AreWeDown?, UptimeRobot or 24x7 - Site / Server Uptime Monitors
- ⭐ TLD-List, TLDES or SitePriace - Domain Price Comparisons
- GoodBadISPs - Best ISPs for Tor Hosting
- Server Hunter or ServerSearcher - Search / Compare Servers
- srvrlss - Search / Compare Serverless Platforms
- Host-Tracker or OONI - Check Site Location Availability / Bypass Paywall
- OpenPanel / GitHub, Sentora or Moonlight - Web Hosting Panels
- GetDeploying - Compare Cloud Providers
- Meta Tag Gen, OpenGraph or MetaTags - Meta Tag Generators
- DNForum - Domain Name Forum
- HaveIBeenSquatted - Typosquatting Discovery Tool
- iana, arin, lacnic, afrinic or apnic - Internet Registry Sites
- takingnames, GetFreeDomain or EU.org / 2 - Free Subdomains
- TheDev - Free Developer Subdomains
- is-a.dev or JS.ORG - Developer Homepages
- Homepage / GitHub, CasaOS / GitHub, Flame, Homer or Dashy / GitHub - Home Server Startpages
- redirect.name - URL Forwarding
- Kener or cstate - Self-Hosted Status Pages
- Sandstorm, Cosmos or CloudRon - Web App Hosts
- vichan / GitHub or overscript - Imageboard Hosting
- ProBoards - Forum & Imageboard Hosting
- MyBB, FreeFlarum or PHPBB - Forum Hosting
- WikiDocs / GitHub, Media Wiki, xWiki, DokuWiki, Miraheze, wikmd or Fandom - Host Free Wiki
- HumHub, HubZilla or scuttlebutt - Self-Hosted Social Network
- UNIT3D Community Edition - Private Tracker Hosting
▷ WordPress Tools
- ↪️ Wordpress Themes
- ⭐ GPLDL - Premium Themes / Plugins / 25 Monthly / Sign-Up Required
- ⭐ WPLocker or Weadown - Premium Themes / Plugins
- Babiato - Themes / Plugins Forum / Sign-Up Required
- WordPress Themes & Plugins - Themes / Telegram
- Visual CSS Editor - WordPress Site Designer
- LocalWP - WordPress Site Deployment Tools
- faustjs - WordPress Framework
- Timber - WordPress Theme Creator / GitHub
- KokoAnalytics - WordPress Analytics
- UUID Tools - UUID Generator
▷ Regex Tools
- Note - You can use AI chatbots like ChatGPT to create complex regex patterns more easily.
- 🌐 Awesome Regex - Regex Resources
- ⭐ Regex Vis, Regulex, Regexper - Regex Visualizer
- ⭐ RegexLearn, refrf.dev or learn-regex - Learn Regex
- ⭐ RegExr, Rubular or Regex101 - Regex Editors
- ⭐ grex or Regex Generator - Regex Generators
- RegexOne - Regex Practice
- iHateRegex - Regex Patterns
- Melody - Compile to Regex / GitHub
- PyRegex - Python Regex Playground
▷ Benchmark Tools
- 🌐 Awesome Accessibility - Accessibility Tools Index
- ⭐ LightTest, Yellow Lab Tools, PageSpeed, SpeedVitals, Geofetcher, GTmetrix or Websu - Test Webpage Speed
- ⭐ Geekflare Tools or Frontend Dogma - Site Benchmarking Tools
- LambDatest - Cross Browser Testing Cloud
- Accessibility Guide, Pa11y, Wave, Andi or A11ygator - Accessibility Evaluation Tools
- Accessibility Insights - Fix Accessibility Issues
- Accessibility Cheatsheet or A11Project - Site Accessibility Guidelines
- Web Vitals Leaderboard, CodSpeed or Lighthouse Metrics - Website Performance Tests
- Prometheus - Site Metrics / Setup
- Carbon Calculator - Estimate Sites Carbon Footprint
- UX Check - Site Heuristic Evaluation
- Testmail - Site Signup Test
- Responsive Viewer - Test Site on Multiple Screen Types / Chrome
- Responsively, ResponsiveTestTool, Responsivize or Am I Responsive - Website Responsiveness Tests
- LightHouse - Web App Performance Test
▷ Image Optimization
- ⭐ ImageMagick - Image Optimization / Scripts
- RIOT - Image Optimization
- YOGA - Image Optimization
- ImageFoo - Image Optimization
- tiny.pictures - Image Optimization
- Ihancer - Image Optimization
- Waifu2x - Image Optimization
- OxiPNG - PNG Optimization
- Crunch - PNG Optimization / Self-Hosted / No Sign-Up
▷ SVG Tools
- ↪️ SVG / Vector Images
- Method, SVG.wtf, Boxy SVG, Mossaik or SVG Viewer - SVG Editors / Viewers
- SVGFilters - SVG Filter Builder
- Crayon or SVGArtista - SVG Animation Tools
- SVGO or SVGCrop - SVG Optimization / GUI
- SVG Tutorial - Learn How to Code SVG Images
- SVGX - SVG Assets Manager
- Vector Express or Vector Magic - Vector Converters
- svgco or IMG to SVG - Image to SVG Converter
- SVG2JSX - SVG to JSX Converter
- Pattern Monster - SVG Pattern Generator
- Blobs - SVG Shape Generator
- Broider - Create Border Designs
- ShapeDivider - Make SVG Shape Divider
- SVG Path - SVG Path Visualizer
- svg-path-editor - SVG Path Editor
- Get Waves, Wavelry, SVGWave / GitHub or SVG Wave - SVG Wave Generators
- Blobmaker - SVG Blob Generator
- AutoTracer - Image Vectorizer
- JSLogo - Logo Interpreter
► Cybersecurity Tools
- ⭐ pyWhat - File Analyzer
- Open Source Security Software - Cybersecurity Software
- osquery or Nmap / Results - Security Monitors
- Canarytokens - Network Breach Check
- Nuclei / GitHub, Synk or NVD - Vulnerability Tracking / Scanning
- Zeek, Kismet, ntop or Sniffnet - Network Monitors
- Crowdsec - Crowd-Sourced Intrusion Detection / Prevention / GitHub
- BBRadar or BugBountyHunting - Bug Bounty Trackers
- X-Force Exchange - Security Threat Intelligence Platform
- OpenSCA-CLI - Composition Analysis for Third Party Components
- Unblob - Extraction Suite
- Security Onion Solutions, Wazuh or Snyk / GitHub - Site Security Monitor
- spur.us - Block VPNs / Proxies
- Greenbone - Vulnerability Management
- Evervault - Security / Compliance Infrastructure
- DarkVisitors - Autonomous Chatbots / Data Scraper List
- Al-Khaser - Anti-Malware Stress Test
- CVE Details - CVE Details
- AllSafe - Intentionally Vulnerable Android App
▷ Cybersecurity Indexes
- 🌐 Awesome Cyber Security - Cybersecurity Resources
- 🌐 Awesome CI/CD Security - CI/CD Security Resources
- 🌐 Awesome GPT Agents - Cybersecurity GPT Agent Index
- Advisory Database, ThreatFox, Exploit DB or Att&ck - Cybersecurity Defense Databases
- VirusShare, Bazaar, MalShare, URLhaus, PulseDive or Malpedia - Malware Search / Indexes
- ThreatMap or CyberMap - Live Malware Distribution Maps
- The Void - Software Incident Reports
- Rawsec's CyberSecurity Inventory - Cybersecurity Resources
- CybersecResources - Cybersecurity Resources / GitHub
- Awesome List - Cybersecurity Resources
- Cybersecurity-Resources - Cybersecurity Resources
- Infosec Resources - Cybersecurity Resources
- CyberSecTools - Cybersecurity Resources
- My Infosec Awesome - Infosec Resources
▷ Pen Testing
- 🌐 Awesome Pen Testing - Penetration Testing Resources
- 🌐 Awesome Hacking - Pentesting / Security Index
- Metasploit / Cheatsheet - Pentesting Framework
- MobileApp-Pentest-Cheatsheet - App Pentesting Cheatsheet
- Pentest Contracts - Security Contract Templates
- OSCP-Exam-Report-Template-Markdown - Offensive Security Exam Report Markdown / GitHub
- Kali NetHunter or AndroGuard - Penetration Testing / Forensics Apps
▷ DNS Tools
- ↪️ Free DNS Resolvers
- ⭐ mess with dns - Experiment with DNS
- DNS over HTTPS - Encrypted DNS Providers & Resources
- DNSPerf - DNS Provider Rankings
- GRC DNSBench - DNS Benchmark
- DNS Propagation - DNS Checker
- MXToolBox - MX Record Lookup Tool
- DNSDumpster, DNS Watch, DNSHistory or WhatsMyDNS - DNS Lookup / Security
- Web Check, NSLookup or dog - DNS Information Tools
- DuckDNS, FreeDNS, dynu, NoIP, myaddr, nsupdate / GitHub or Desec - Dynamic DNS Services
▷ Web Security
- WebAuthn - Web Authentication API - Demo
- Hydra - OAuth 2.0 Server / OpenID Connect Provider
- SuperTokens or Lucia - User Authentication
- ZAP - Web App Security Testing
- IP Intelligence, AbuseIPDB or Proxy Check - Proxy / VPN / Bad IP Detection
- Fail2Ban - Protect Servers from Brute Force Attacks
- Tempesta FW - DDoS / Web Attack Protection
- IPv6 Leak Test, Test-IPv6 or IPv6 Test - IPv6 Test
- How To Turn off IPv6 - Prevent IPv6 Leaks
▷ Encryption / Certificates
- ⭐ Awesome Cryptography - Cryptography Resources
- mitmproxy - Analyze and modify HTTPS traffic / OpenAPI Converter / GitHub
- HTTPToolkit - Intercept, Debug, and Mock HTTP(S)
- Mozilla SSL - SSL Configuration Generator
- Tailscale - Secure Network VPN
- SSLLabs - SSL Testing
- BadSSL - Test Clients Against Bad SSL Configs
- Hitch - SSL / TLS Proxy / GitHub
- Let's Encrypt or Certbot - Free TLS Certificates
- SSL for Free or ZeroSSL - Free SSL Certificates
- CertAlert - TLS/SSL Certificate Expiration Alerts
- acme.sh - Auto Issues / Certificate Renewal
- mkcert - Locally Trusted Development Certificates
- SSLMate CAA - CAA Record Helper
▷ Reverse Engineering
- 🌐 Reverse Engineering Resources or ReversingBits / GitHub - Reverse Engineering Resources
- 🌐 Awesome Malware Analysis - Malware Analysis Resources
- ⭐ GHIDRA - Reverse Engineering
- ⭐ x64dbg - Debugger for Reverse Engineering
- Radare - Free Reversing Toolkit / GitHub / Discord
- Rizin or Cutter - Reverse Engineering Framework
- Frida - Reverse Engineering
- Flare VM - Reverse Engineering Environment Setup Script
- ROP Emporium - Learn Return-Oriented Programming
- MSTG or DVIA-v2 - App Security Testing / Reverse Engineering
- Malimite - iOS / macOS Decompiler
- challenges.re - Reverse Engineer Code
- horsicq - File Type Identification Tools / GitHub
► Markup Tools
- ⭐ Markdown Guide - Guide for Markdown (.md)
- ⭐ generatedata.com - Generate Test Data in Markup Formats
- markup.rocks - Online Markup Editor
- Markup Validation Service - Validate Your Markup Language Structure
- YAMLine - Online YAML Tools / Converters
- yq - Portable YAML Processor / GitHub
- readme.so - Create README.md Files
- Tableconvert - Markdown / Code Converter
- Linkspector - Check Markdown Files for Dead Links
- Table Magic - Table to Markdown Converters
- Clipboard2Markdown - Text to Markdown Converter
- gd2md-html - Convert Google Doc to Markdown
- MarkItDown or GetMarkdown - File to Markdown Converter
- Quartz, Perlite or FlowerShow - Publish Markdown
- Markdown Tutorial - Interactive Markdown Tutorial
- emoji-cheat-sheet - Emoji Markdown Cheatsheet
▷ Markdown Editors
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ c9badfea:610f861a
2025-05-13 00:23:34
@ c9badfea:610f861a
2025-05-13 00:23:34► Video Tools
- 🌐 Digital Video Intro - Digital Video Guides / Resources
- ↪️ AI Video Generators
- ⭐ Reincubate Camo - Use Any Camera as Webcam
- Deep-Live-Cam, Rope, SimSwap or Roop - Video Face Swap Tools
- VideoHelp Forum - All Things Media / Video
- ICAT - Video Quality Comparison & Analysis Tool
- videoduplicatefinder - Duplicate Video Finder
- VHS Decode - VHS Decoder
- VidClue - Short Form Video Inspiration
▷ Disc Utilities
- ImgBurn, DVDStyler, DeepBurner or Alcohol Soft - CD / DVD Burning
- MakeMKV - Create MKV From Blu-ray / DVD / Beta Keys
- VidCoder or DVDDecrypter - DVD / Blu-ray Ripping
- DGDemux - Blu-Ray/UHD Disk Demuxer
- PgcDemux - DVD Disk Demuxer
- BatchGuy - Blu-Ray Ripping
▷ Video File Hosts
- Note - Most file hosts remove files after inactivity, while some delete them regardless. Check each host if you're concerned about file expiry.
- ⭐ DoodStream - 5GB / 60 Days / Account Required
- ⭐ Litterbox - 1GB / 3 Days
- ⭐ Catbox - 200MB / Forever / Allows Hotlinking
- ⭐ Gofile - 100GB Monthly / 10 Days
- ⭐ Send.now - Unlimited / 30 Days
- Files.vc - Unlimited / 10GB / Forever / Discord
- VOE - Unlimited / 60 Days / 720p / Account Required
- MixDrop - Unlimited / 60 Days / 720p / Account Required
- FEX.NET - 100GB / 10GB Guest / 7 Days
- FileMoon, 2, 3 - 50GB / 40TB per account / Forever / Account Required
- Hexupload or AnonTransfer - 15GB / 30 Days
- Fastupload.io - 10GB / 30 Days (60 Days with Account)
- Vidoza - 15GB / 15 Days / Account Required
- Streamtape - 15GB / Account Required / .to
- Dubz - 100MB / Forever
- EarnVids
- Streamable - 250MB / 2 Days (90 Days with Account)
- uguu - 128MB / 3 Hours
- webmshare - WebM & GIF Hosting / 20MB / Forever
- Videy - 100MB / MP4 Only
▷ Screen Recording
- ⭐ OBS
- gifcap - Turn Screencasts into GIFs / GitHub
- Shinobi - Network Video Recorder
- MythTV - Digital Video Recorder (DVR)
- tldv or ZoomRec - Record Google Meets / Zoom Calls
- FFmpeg / Tools
- Vileo
- ShareX
- Screen Recorder
- vokoscreenNG
- Cap / GitHub
- Shar.ec - Online
- ScreenREC - Online
- ScreenRecorder.me - Online
- KazCap - Online
- RecordScreen - Online
- Google Screen Recorder - Online
▷ Processing / Encoding
- ⭐ HandBrake - Video Encoding Software / Guide
- ⭐ FFmpeg - Multimedia Processors / Converters / Tools
- ⭐ Shutter Encoder - Video Encoding Software / GitHub
- ⭐ MKVToolNix - MKV Editing Tools
- ⭐ archived-things, The Encoding Guide or Silentaperture - Video Encoding Guides
- ⭐ Disc Rip - Disc Ripping Guide / Mirror
- ⭐ Basics to the Art of Remuxing - Learn How to Remux Videos
- DDVT - Dolby Vision RPU Demuxing / Injecting / Editing
- MKV Muxing Batch GUI - Mux Videos
- staxrip - Video Encoding / Contact Sheet + Thumbnails Creator
- IFME - Video Encoding
- XMedia Recode - Video Conversion
- FastFlix - Video Conversion / GitHub
- NEAV1E or Av1an - AV1 Encoding
- Winnydows - Video Conversion Software
- sickbeard_mp4_automator - Automate Video Processing
- Seven Converter - Video Conversion / GitHub
- nmkoder - Media Encoding / Muxing
- selur - Video Encoding
- vvenc, vvdec or VVCEasy - VVC Encode / Decode
- Ingex - Tapeless (Uncompressed) Recording / Digital Tape Converter
▷ Online Processing
- Compress Video Online - Compress / Unlimited
- 8mb.video - Compress / 2GB
- autocompressor - Compress / 2GB
- Rotato - Compress / 2GB
- VideoSmaller - Compress / 500MB
- YouCompress - Compress / 500MB
- MP4Compress - Compress / 500MB
- VERT - Converter / Discord / GitHub
- Video Express Converter
- VideoConverter - Converter
- Restream Tools - Converter
▷ FFmpeg Tools
- FFmpeg-Builds or media-autobuild_suite - Autobuild Tools
- ffmpeg-web - FFmpeg Web App / GitHub
- FFmpeg Libav or ffmprovisr - FFmpeg Guides
- ASM Lessons - FFmpeg Assembly Language Lessons
- FFmpeg Cheat Sheet, FFmpeg Commander or FFmpeg Buddy - Command Lists
- WebMConverter - WebM Converter
- PureMPV - Info Copy Tool
- ffmpeg.lav - Preview Filters
- LLmpeg or idli - AI Commands
- FFmpeg Batch - Bulk Conversion Tools
▷ Live Streaming
- 🌐 Awesome Streaming or StreamerFreebies - Live Streaming Resources
- ⭐ OBS - Live Stream Manager
- ⭐ OBS Tools - Virtual Cam / Tweaks / Effects / Keyboard Visualiser / Background Remover / Web App / Phone Controller / Dock Layouts / WebRTC Server / Plugin Updater / Guide
- Stream Elements - Streaming Service Manager
- Streamlabs-OBS - Live Stream Manager
- StreamLabs - Live Stream Manager
- Restream - Live Stream Manager
- FBX - Live Stream Manager
- XSplit - Live Stream Manager
- TwitchChat - Live Stream Manager / Discord
- VDO Ninja - Live Stream Colab Tool
- LiveStreamDVR / Display Chat - Live Stream Recorders
- NVIDIA Broadcast - Stream Audio / Video Enhancer
- Owncast or Restreamer - Self-Hosted Live Streaming
- WDFlat - Stream Elements
- Twelve47Studios - Stream Overlays
- Strem - Stream Automation
- ppInk, glnk, Annotate Screen or Live Draw - Screen Annotation
- Amuse or Songify - Now Playing Overlays
- StreamPi or ODeck - ElGato Streamdeck Alternatives
- real-url - Copy Live Stream URLs
- Chat-Downloader - Retrieve Chat Messages from Livestreams
▷ VTuber Tools
- 🌐 Runa's Archive - VTuber Resources / Discord
- Best VTuber - VTuber Resources
- VTResources - VTuber Resources
- VTuber Assets - VTuber Resources
- VTuber Kit - VTuber App
- Inochi2D - VTuber App / Discord
- Vtube Studio - VTuber App
- Kalidoface 3D, VRoid, Animaze or TransTube - VTuber Characters
- avatarify-python or veadotube - Video Call Avatars
- VTuberized Logos - VTuber Style Logos
▷ Subtitle Tools
▷ Linux Video Tools
▷ Mac Video Tools
► Video Players
- 🌐 Awesome Video - Video Streaming Resources
- 🌐 Video Help - Video Player Index
- ⭐ MPC-HC, MPC-QT or MPC-BE - Video Player / YT-DL Support
- ⭐ MPV - Video Player / Frontends
- ⭐ VLC - Video Player
- Screenbox - Video Player
- AVPlayer, ICAT or GridPlayer - Multi-Video Players
- SPlayer - Video Player with Smart Translation
- PotPlayer - Video Player / Twitch Addon / YouTube Addon
- ImPlay - Video Player
- SMPlayer / 2 - Video Player / YouTube
- uView - Video Player
- Rise Media Player - Video Player
- Flyleaf - Video Player
- MoonPlayer - Video Player
- KikoPlay - Video Player
- Plyr - Online HTML5, YouTube and Vimeo Player / GitHub
- PiP-Tool - Use Picture-in-Picture on All Videos
- PlayVideo - Google Drive Video Player
- MotionMonkey - Stream Online Videos in Player
- StreamLink - Extract Videos from Sites to Players / Twitch Adblock / GitHub
- Hohoema - Nico Nico Video Player
- polsy.org.uk - Alt Players for Video Sites
▷ Stream Sync
- ⭐ SyncPlay - App
- ⭐ Watch2Gether - Online Player
- ⭐ SyncWatch - Online Extension
- ⭐ Kosmi - Online Player
- ⭐ WatchParty - Online / Virtual Browser
- ⭐ neko / GitHub - Docker Virtual Browser
- HyperBeam / VIP - Virtual Computer Embed
- Trast, OpenTogetherTube, TurtleTV or twoseven - Online Player
- bear.cat - Online Virtual Machine / Allows NSFW
- Metastream - Online Extension / Discord / GitHub / X
- Caracal Club - Online Video Player
- CyTube - Online Video Player
- VideoTogether - App
- baked.live - Online Video Player
- Rave.io - Online Extension
- MovieNight / Discord - Docker
- Kast - Screen Share
- Screen Share Party - Online Screen Share
▷ MPV Tools
- ↪️ MPV Shaders
- MPV Config Guide, 2, 3
- ModernX, tethys or uosc - Alt User Interfaces
- Simple MPV WebUI - WebUI Controller
- MPV Context Menu
- MPV Scripts - Userscripts
- VideoClip, 2 - Clip Tool
- MPV WebM - WebM Tool
- Play With MPV or ff2mpv - Open Videos with MPV
- MPV WebTorrent Hook - Torrent Streaming
- AutoSubSync MPV - Sub Sync
- MPV SponsorBlock, 2 - SponsorBlock for MPV
- ThumbFast - MPV Thumbnails
▷ VLC Tools
- 🌐 Awesome VLC - VLC Resources
- VLSub - Sub Downloader
- VLC Skin - VLC Skins
- VLC Slow Seek Fix
► Media Servers
- 🌐 Auto Download Tool Index
- ⭐ Jellyfin - Media Server
- ⭐ Kodi - Media Server
- TRaSH Guides / Discord or The Complete Guide - Server Setup Guides
- Self-hosted Anime - Anime Server Setup Guides
- Prowlarr, FlexGet or /r/softwarr - Autodownload Tools
- Organizr, Reiverr or Homarr - Media Server Managers
- Fixarr - Media Server File Renamer
- HTPC Download Box - Media Server Automation
- Emby - Media Server
- Plex - Media Server
- Universal Media Server - Media Server
- OSMC - Media Server
- Kawaii-Player - Media Server
- Streama - Media Server
- Gerbera - Media Server
- Homehost - Media Server
- Dim - Media Server
- Kyoo - Media Server
- WatchIt / GitHub / Discord - Media Server
- SimpleDLNA - Media Server
- Chocolate - Media Server
- Media-Hoarder - Media Catalog Frontend
- Seanime - Anime Server
- Frames - Google Drive Server
- HTPC - Home Theater PC guides / Subreddit
- MSX - Web App
- ErsatzTV or dizqueTV - Live Channel Media Servers
- YTDL-Sub - Add YouTube Channels to Media Servers / GitHub
- xTeVe - Plex / Emby M3U Proxy
- Ombi - Plex / Emby User Request Management
▷ Plex Tools
- Reddit Guide - Plex Setup Guides
- Tautulli - Server Monitor / Note
- SuperPlex - Plex Plugins
- Kitana - Plugin Frontend
- Plex Ripper - Merge Plex Libraries w/ Your Own
- PlexDrive or mergerfs - Mount Google Drive
- SyncLounce - Media Sync
- PseudoTV - Create TV Channels
- Overseerr - User Requests / IMDb Extension
- Pasta Tool - Audio / Sub Changer
▷ Jellyfin Tools
- 🌐 Awesome Jellyfin - Jellyfin Resources
- ⭐ Blink, Fladder or jellyfin-media-player - Desktop Clients
- /r/JellyfinShare - Jellyfin Server Sharing
- Jellyfin Forum - Official Jellyfin Forum
- Jellyfin Vue - Jellyfin Web Client
- Jellyfin "arr" Setup Guide
- Jellyfin Customization Guide
- Jellyfin Themes
- Jellyseerr - User Requests
- Jellyfin RPC - Jellyfin Discord Rich Presence
▷ Kodi Tools
- ⭐ Elementum - Torrent Streaming / Trakt Sync / Similar to Stremio + Torrentio
- EverythingKodi - Kodi Addon Tutorials
- Kodi Builds Chart
- /r/Addons4Kodi / Tracker / Trending - Kodi Addons
- Kodi Skins or WIP Skins - Kodi Skins
- Synko - Kodi Stream Sync
- Plex Kodi Connect or plex-for-kodi - Plex for Kodi
- quasar - Torrent Plugin
- IPTV Client
- Simkl - Media Tracker
- tinyMediaManager or MediaElch - Media Collection Managers
► Video Download
- ↪️ YouTube Video Downloaders
- ↪️ Twitch Video Downloaders
- ↪️ Download Managers
- ⭐ yt-dlp or YTDL-PATCHED - Multi-Site / Commands / Zoom Fix / Discord
- ⭐ cobalt - Multi-Site / Online / Instances / Playlist Support, 2
- ⭐ 9xbuddy, 2, 3 - Multi-Site / Online
- ⭐ Download Helper, FetchV or MPMux - Extensions
- CD(R)M-Project - DRM Tools / Discord
- VideoFK - Multi-Site / Online
- you-get - Multi-Site / CLI
- Hitomi Downloader - Multi-Site / Software
- SCrawler - Multi-Site / Software / Discord
- Musvkrobot - Multi-Site / Telegram Bot
- myfaveTT, SnapTik or tiktok-to-ytdlp - TikTok
- Threads Downloader - Threads
- Piner - Pinterest / Online
- hls-downloader, hls extension or hlsloader - HLS Downloaders
- GetWVKeys - Send Widevine Requests / GitHub
► Video Editing
- ⭐ /r/VideoEditing - Video Editing Subreddit / Wiki
- ⭐ Eyecandy - Visual Technique Examples
- ⭐ Waifu2x GUI, Video2x, Enhancr, Lossless Scaling or Dandere2x - Video Upscaling
- Codecs and Containers - Info on Codecs & Containers
- ALF FreeWare VideoCODECs, Codec Guide or Free-Codecs - Video Codec Collections
- VideoHelp Forum - Video Editing Forums
▷ Video Editors
- ⭐ LosslessCut - Video Editor
- ⭐ kdenlive - Video Editor / GitHub
- ⭐ DaVinci Resolve - Video Editor / Sign-Up Required
- ⭐ Shotcut - Video Editor
- Auto-Editor - CLI Editor
- MoviePy - Python Editor
- Webm Generator - Webm Editor
- avisynth or VapourSynth - Video Processors
- Source Filmmaker - Steam Movie-Making Tool / Resources
- OpenRV - Image / Sequence Playback Review
- Remotion - Video Editor
- Olive - Video Editor
- EZVid - Video Editor
- OpenShot - Video Editor
- Lightworks - Video Editor
- VSDC - Video Editor
- Pitivi - Video Editor
- Visla - Video Editor
- Windows Movie Maker, 2, 3 - Video Editor
- Avidemux - Cut / Filter / Encode
- suckless-cut or vidcutter - Cut / Trim Videos
- Opus - Clip Creator
- Kurku or FreeMoCap - Motion Tracking Tools
- VSeeFace - Face / Hand Tracking VRM
▷ Online Editors
- ⭐ wide.video - Discord
- ⭐ Pikimov - Use Edge or Chrome
- ⭐ Mastershot - Sign-Up Required
- VideoToolbox - Sign-Up Required
- VideoInu - Works Offline
- Panzoid
- vidmix
- Video Cutter
- Omniclip - GitHub / Discord
- Vididoo - Multitool
- VideoCandy - Multitool
- Video2Edit - Multitool
- Crop Video - Crop Videos
- LoopVid - Loop Videos
- Crossfade - Video / Audio Crossfading
- VidLouder - Increase Video Volume
- Convert2Video - Image / Audio to Video
▷ Video Enhancement / Effects
- Video Enhance AI - Video Enhancement Tool / Search "Topaz" on LR
- Gyroflow - Video Stabilization / GitHub
- Flowframes / Beta or SVP / Guide - Video Interpolation / Increase FPS
- VideoColorizerColab - Video Colorization Colab
- OpenColorIO - Video Color Manager
- FreshLUTs - Free LUTs (Color Filters)
- blur or Smoothie - Add Motion Blur to Videos / Tutorial
- ProPainter - Video Inpainting
▷ VFX Sites
- FootageCrate
- FreeVideoEffect
- VideoCoPilot
- VFXmed
- Team V.R releases
- flex_cg_vfx
- VFXLoot
- Download Pirate - Use Adblock / Avoid Fake Download Buttons / Discord
- ShareAE - After Effects
- HunterAE - After Effects
- Visual Effects Pack - After Effects
- AERiver - After Effects
- AEDownloadPro - After Effects
- Intro HD - After Effects
▷ Animation Tools
- 🌐 Creator Resources - Art & Animation Resource Index
- ⭐ Unreal Engine, MoonRay, cgsoftbox, SketchUp or Twinmotion - 3D Creation Tools
- ⭐ Immersity AI - 2D Image to 3D Animation Tool
- OpenToonz, Wick Editor, Clipnote Studio or Pencil2D - Animation Tools
- Animaker - Animated Video Creator
- 3DThis - 3D Animation Tools
- Mega Scans - 3D Scans
- Mixer - 3D Texture Creation Tool
- PlanetSide - CG Environment Generator
- cgplugdump - CG Software Plugins
- Physically Based - RGB Values of Elements
- AnimeEffects, enve, Cavalry, TupiTube or Synfig - 2D Animation Tools
- ScribbleDiffusion - Turn Doodles into Artwork
- MonsterMash - Sketch-Based Modeling & Animation Tool
- Storyboarder - Quickly Visualize & Test Animations / GitHub
- LuxCoreRender - Rendering Engine
- RenderChan - 2D Animation Render Manager
- Mandelbulber or FragM - Fractal Rendering Software / 3D
- JWildfire, IFSRenderer or Fractorium - Flame Fractal Rendering Software
- BestSnip, Sketch Machine, Plask or Rive - Online Animation Tools
- Glaxnimate or Trangram - Vector Animation Tools
- LibreSprite, GraphicsGale, Pixel Compresor, JPixel, Aseprite / Guide or SpookyGhost - Pixel Art Animation Tools
- Spritesheet Generator - Spritesheet Generator / Gitea
- Animated Drawings, FAIR Animated Drawings or MotorPen - Animate Drawings
- FlipAnim - Create Animated Flipbooks
- Viggle / Discord or Picrew - Animated Character Creators
- Mixamo or Cascadeur - 3D Character Animation Tools
- MMHuman3D - 3D Human Model Creator
- Talking Face Avatar - Talking Avatar Generator
- Blender Open Movies - CGI Assets
▷ Stock Videos
- 🌐 Awesome Stock Resources or CuteStockFootage - Stock Video Indexes
- Pexels - Stock Videos
- 4K Media - 4K Stock Videos
- Dareful - 4K Stock Videos
- Monzoom - 4K Stock Videos
- BeachFrontBroll - Stock Videos
- Videvo - Stock Videos
- veed.io - Stock Videos
- VidsPlay - Stock Videos
- MitchMartinez - Stock Videos
- MixKit - Stock Videos
- ineedfx - Stock Videos
- MotionPlaces - Worldwide Stock Videos
- DroneStock - Drone Video Footage
- MovieTools - Video Loops
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ c9badfea:610f861a
2025-05-13 00:22:27
@ c9badfea:610f861a
2025-05-13 00:22:27► Image Editing
- ↪️ Background / Object Removers
- Croppola, AutoCropper, Bulk Image Crop or Avatar Cropper - Cropping Tools
- Scribus - Page Layout & Typesetting Program
- FilmDev - Film Development Recipes
- Images.weserv.nl - Image Editing Server
- GradientArt or TailBlend - Gradient Editor
- Canvas - Turn Simple Art into Photorealistic Landscapes
- Image Splitter - Split Images into Tiles
- PicFont - Add Text to Images
▷ Editing Software
- ⭐ m0nkrus / 2 or GenP / Revolt - Adobe Software Archive / Use VPN / Block Adobe / Search / Telegram
- ⭐ GIMP / Discord / Subreddit
- ⭐ GIMP Tools - Photoshop UI / Texture Synthesizer / Batch Editor / Text Effects
- ⭐ Pinta Project
- ⭐ ImageMagick / Scripts
- darktable - Virtual Lighttable & Darkroom
- RawTherapee - Raw Image Editor
- StitchTool - Image Stitcher, Splitter, Upscaler & more
- PhotoDemon
- Paint.net
- PhotoFiltre
- Gimel Studio
- Luna Paint - VS Code Extension
▷ Online Editors
- ⭐ Pixlr - Simple Editor / Hide Premium / Unlimited Saves, 2
- ⭐ Polarr - Multi-Tool
- ⭐ Lunapic - Multi-Tool
- ⭐ Photopea - Photoshop Alt
- BitMappery - Photoshop Alt
- iPiccy - Photoshop Alt
- Stet - Photoshop Alt
- Resize Pixel - Multi-Tool
- ImageOnline - Multi-Tool
- GifGit - Multi-Tool
- Tom's Editor - Multi-Tool
- Peko-Step - Multi-Tool
- photo.codes/ - Simple Editor w/ Shareable Colab Codes
- Photomate - Simple Editor
- MiNi Photo Editor - Simple Editor / GitHub
- BeFunky - Simple Editor
- Polotno Studio - Simple Editor
- OIE - Simple Editor
- ILoveImg - Simple Editor
- UpperPix - Simple Editor
- Online Photo Editor - Simple Editor
- Picverse - Simple Editor
- webp2jpg - Simple Editor
- edit.photo - Simple Editor
- Image Resizer - Simple Editor
- PicSynth - Multi-Tool
- Ribbet - Multi-Tool
- RedKetchup - Multi-Tool
- Img2Go - Multi-Tool
- fffuel - Multi-Tool
- Mara - Multi-Tool
▷ Upscale / Restore
- ⭐ Waifu2x - Anime Image Upscaling / WebUI, 2, 3 / Self-Host / No Sign-Up
- ⭐ WaifuXL - Anime Image Upscaling / Online / Self-Host / No Sign-Up
- ⭐ Upscayl - Image Upscaling / GitHub / Self-Host / No Sign-Up
- ⭐ chaiNNer - Image Upscaling / Self-Host / No Sign-Up
- ⭐ OpenModelDB - AI Upscaling Model Database / No Sign-Up
- Real-ESRGAN - Image Restoration Algorithms / Face Restoration / Online / Self-Host / No Sign-Up
- /r/estoration - Photo Restoration Requests
- image-upscaling.net - Image Upscaling / Online / No Sign-Up
- IMGUpscaler - Image Upscaling / Restoration / Video Upscaling / Online / No Sign-Up
- Bigjpg - Image Upscaling / Online / No Sign-Up
- Ilaria_Upscaler - Image Upscaling / Online / No Sign-Up
- Final2x - Image Upscaling / Self-Host / No Sign-Up
- Lossless Scaling - Image Upscaling
- imgupscaler - Image Upscaling / Online / No Sign-Up
- QualityScaler - Image Upscaling / Video Upscaling / Denoising / Self-Hosted / No Sign-Up
- resdet - Detect Source Resolution of Upscaled Images / Self-Host / No Sign-Up
- InColor or Colorizer - Online Image Colorization
▷ Image Effects
- ⭐ PhotoMosh, jpg-glitch-electron, glitch-this!, glitch2, Image Glitcher or GlitchyImage - Glitch Images
- PhotoFunia, Pixelizer, Image Mage or Designify - Photo Effects / Filters
- distort-grid - Grid-Based Image Distortion
- Change Image Hue or Tinter - Hue Editor
- ordered-dither-maker, Ditherista or Dither Me This - Image Dithering
- Fotosketcher or PhotoMaker, Stylized - Turn Photos into Artwork
- AnimeGAN - Image to Anime Style Converter
- AIDraw - Turn Photos into Line Art
- Rutt-Etra-Izer - Scanned-line Images
- Geometrize - Redraw Images with Geometric Shapes
- PBNify - Paint by Number Tool
- Shimmer - Oscillating Wave Images
- CollidingScopes - Kaleidoscope Images
- Party-ify - Party-ify Images
▷ Linux Image Editing
▷ Mac Image Editing
► Image Creation
- 🌐 PuccaNoodles' Sheet - Image Creation Resources
- ↪️ AI Image Generators
- ↪️ Art Education
- ⭐ TierMaker - Tier List Image Creator
- ⭐ Topsters - Make Taste / Recommendation Collages
- PanosFX or Fix the Photo - Photoshop Actions
- imgsli - Before & After Slider Generator
- Hugin - Panorama Image Generator
- FlipAnim - Animated Flipbook Creator
- CharacterCreator - Character Generator
- Picrew - Animated Character Maker
- Mimi - Create Coloring Pages from Photos
- Text-Image - Text Image Generator
- Photovisi or PhotoJoiner - Collage Generators
- Tiler - Mosaic Image Generator
- NoiseDeck - Art Generator
▷ Painting
- 🌐 Digital Art Brushes - Download Brushes
- ⭐ Krita - Painting App
- ⭐ Krita Tools - Custom Backend / AI Generation / Forums
- ⭐ miniPaint - Browser Painting
- SmoothDraw - Painting App
- FireAlpaca - Painting App
- LazPaint - Painting App
- PaintOnline - Browser Painting
- jspaint - Browser Painting
- PinTor - Browser Painting
- Tegaki - Browser Painting
- Milton - Infinite Canvas Painting
- IOGraphica - Turn Mouse Movement into Art
- HeavyPaint - Water Color Painting
- Mixbox Painter - Realistic Paint Mixing
- Vervette - Realistic Fluid Painting
- ArtistAssistApp - Useful Painting Tools
▷ Drawing
- ⭐ Excalidraw - Drawing / Sketching / Sharing
- ⭐ AutoDraw, Co-Drawing or Magic Sketchpad - AI Drawing Tools
- DrawTab - Drawing Tablet Info / Wiki
- Inscribed / GitHub - Sketch-Based Slides
- inkscape - Drawing / Sketching
- Inkdo - Drawing / Sketching
- Sketch Toy - Drawing / Sketching
- Webchemy - Drawing / Sketching
- tldraw - Drawing / Sketching
- Ok! So - Drawing / Sketching
- Sketchpad, 2 - Drawing / Sketching
- Sketchbook - Drawing / Sketching / Mobile Only
- Paper - Drawing / Sketching / iOS Only
- Fresco - Drawing / Windows / iOS
- Concepts - Drawing / Sketching
- Magma, Magma, HelloPaint, DrawPile, LockDraw, World Draw or malmal - Collaborative Drawing
- Ink Workspace - Pen App Launcher
- Perfect Freehand - Draw Free Hand Lines / GitHub
- Eschersket - Symmetry Drawing Tool
- TEv2 - Share Your Drawings
- Virtual Graph Paper or minimator - Create Grid-Based Drawings
- Gridzzly - Print Custom Grid Papers
- Crayon Town - Infinite Online Canvas
- Perspective Tools - Interactive Perspective Grids
- x6ud - Animal Drawing Reference Tool
- Noodle - 1-bit Sketch Tool
- Tiny Sketchbook - Create and Share Doodle Art
- ScribbleDiffusion - Turn Doodles into Artwork
- MonsterMash - Sketch-Based Modeling & Animation Tool
- Animated Drawings, FAIR Animated Drawings, MotorPen or Scratch - Animate Drawings
- Mutsuacen - Create Moving Drawings
▷ Pixel Art
- 🌐 Awesome Pixel Art - Pixel Art Resource Index
- ↪️ ASCII Art
- ⭐ rx - Pixel Art Editor
- Piskel - Pixel Art Editor
- Pixelated - Pixel Art Editor
- PyDPainter - Bitmap Graphics Editor
- PaintWith - Pixel Art Editor
- PixelCraft - Pixel Art Editor / GitHub
- Kleki - Pixel Art Editor
- CSprite - Pixel Art Editor
- PixilArt - Pixel Art Editor
- Strike - 1-bit Pixel Art Editor
- Pixel Painter or Pixel Paint - Paint with Pixels
- pixels.land, EveryoneDraw, pxls.space or World of Pixels - Infinite Online Pixel Art
- dpixel - Pixel Art Remastering Tool
- Paint Of Persia - Rotoscoping Pixel Art Tool
- Dither Machine - Pixel Art Dithering Creator
- PixelMe, Pixel It, Pixelator, Img8Bit or Pixelart Converter - Image to Pixelart Converters
- Pixelorama - 2D Sprite Editor
- pixeldudesmaker, Pixel Sprite or Creature Mixer - Sprite Generator
- Pixelicious or PixelartVillage - Image to Pixel Art Converter
- Nasu - Spritesheet Editor
- Pixel Art Scaler - Scale Pixel Art without Quality Loss
▷ GIF Tools
- 🌐 Awesome GIF - GIF Resources / GitHub
- 🌐 Online GIF Tools - GIF Tools
- ⭐ Gifski - GIF Encoder / GitHub
- ⭐ EZGif, GIFCurry / GitHub, Giflr, GIFMemes, GIFnText, makeagif, Gifsicle or Pixteller - GIF Creators / Editors
- Giphy, Tenor, Gifer, Curlie GIFs, GifCities, Animations or GIFBin - View / Download GIFs
- /r/animegifs - View / Download Anime GIFs
- EatMyArt, DrawIsland or Sketch Machine - Create GIFs from Drawings
- Kinegram - Kinegram GIF Creator
- GifRun - Make GIFs from Online Videos
- ScreenToGif or Peek - GIF Recorder
- ugiffer or licecap - Create GIFs via Screencasts
- TokkingHeads - Face Movement GIFs
- petpet - Headpatting GIF Maker
▷ Meme Tools
- ⭐ Know Your Meme or FindThatMeme - Meme Databases
- ImgFlip, Meme Generator, Meme Town, MemeBetter, meme-generator, Classic Memes or Emacs Meme Generator - Meme Creators
- MemeCam - AI Meme Generator
- Memegine - Meme Search Engine
- MemeAtlas or Templates - Meme Templates
- GreenScreenMemes - Green Screen Memes
- iFake - Fake Text Conversation Creator
- Wojak Studio - Wojak Meme Creator
- Pokémon Battle Creator - Pokémon Battle Scene Meme Generator
- Master of all Science - Rick and Morty Meme Generator
- Frinkiac - Simpsons Meme Generator
- Morbotron - Futurama Meme Generator
- LowQualitymemes - Low Quality / Cursed Meme Generator
- YouWouldntStealAWebsite - "You Wouldn't Steal" Meme Generator
- BreakYourOwnNews - Breaking News Meme Generator
- AnimorphGenerator - Animorph Image Generator
- AwesomeCars - Drip Car Memes
▷ Animation
► Design Resources
- 🌐 Awesome Design, Design Resources or pilssken - Design Resources
- 🌐 archives.design - Graphic Design Books
- calltoidea, onepagelove, awwwards, thedesigninspiration, SMPoster, AnotherGraphic, theinspirationgrid or inspirationde - Graphic Design Examples / Inspiration
- PSDcovers, mockups-design, zippypixels, Mockups, medialoot or MockupsForFree - Product Mockups
- The Boolean Game - Learn Boolean Operations in Vector Editors
▷ Design Apps
- ⭐ Figma - Design Collab App
- ⭐ Canva - Design App / Giveaways
- lunacy - Design App
- ArtBoard - Design App
- VistaCreate - Design App
- PosterMyWall - Design App
- Kittl - Design App
- Kosmik - Design Asset Manager
- Venngage - Infographic Design
- CoverView - Blog Banner Design
- blush or IRA Design - Illustration Design
- SuperDesigner or Pattern Ninja - Background / Pattern Design
- Pixelied - Online Design Tool
- Evernote.Design - Online Design Tools
- Graphite or Recraft - Vector Editors
- MagicaVoxel or Goxel - Voxel Art Editor / Interactive Path Tracing Renderer
- Vectr or VectorInk - Vector Graphics Editor
▷ Icons / Avatars
- ↪️ Avatar / Logo Creators
- ↪️ Icon Drives - Icon Drives
- ↪️ SVG Icons / SVG Tools
- ⭐ Alphacoders Avatars - PFPs / Avatars
- PFP Finder - PFPs / Avatars
- Random Avatars - PFPs / Avatars
- pfps.gg - Profile Picture Index
- Innocenzi - Round Avatar Creator
- RealFaviconGenerator - Favicon Generator
▷ Textures / Patterns
- AmbientCG - Textures
- TextureTown - Textures
- 3D textures - Textures
- Textureking - Textures
- Texture Labs - Textures
- Transparent Textures - Textures
- Texture Club - Textures
- TexturesForFree - Textures
- texture4photoshop - Textures
- MatLib - Textures
- TextureNinja - Textures
- cgbookcase - Textures
- Texture Collection - Textures
- Subtle Patterns - Patterns
- Background Tiles - Patterns
- Pattern Collection - Patterns
- ArmorLab, Pixela, Texture Library or TextureLab - Texture Generators
- TextureLab - Procedural Texture Generator / GitHub / Discord
- Material Maker - Procedural Texture Creator
- DoodDad, Repeater, PatternPad, patternico, Repeater, more.graphics, Valentina, Patternizer or Haikei - Pattern Generators
- Noise & Gradient, PhotoGradient, BGJar, MeshGradient or BGGenerator - Background / Gradient Generators
- Tabbied or Slopes - Art Pattern Generators
- Generative Landscapes - Generative Landscape Blog
- Mixer - 3D Texture Creation Software
- The Textures Resource - Game Textures
- Trianglify.io - Low-Poly Texture Generator
▷ Free Assets
- ⭐ FreePreset
- UnliPresets
- Gumroad (Enter $0)
- psdkeys
- AvaxGFX
- Freeject
- Cg_peers
- PNGTree
- Dassets Design
- TianUI
- Designer Candies
- GraphixTree
- PSDLY
- Unblast
- CGArchives
- CGPlugin
- SearchGFX
- Quasual
- designersgan9
- Free_Design_Files
- WockupWorld
- OnlyGFX
- The GFX
- Graphics Materials
- desiignertm
- all_psd
- Playersdsg
- designbloody
- designarchiv
- outsideotf
- DOPE Editing
- desgang
- grphc dsgn
- creativemrkt
- freepsdvn
- PrivateDesigner
- Solutioonn
- ae-project
- godownloads
► Download Images
- 🌐 2ndBrain or designer - Image Download Site Indexes
- ↪️ Random Images
- ↪️ PNG Images / Clipart
- ↪️ AI Galleries
- ↪️ Media Covers / Posters
- ⭐ gallery-dl, RipMe, WFDownloader, ImgDownloader, SCrawler / Discord or Image Extractor - Image Download Tools
- same.energy - Visual Search Engine
- Dezoomify - Download Zoomable Images
- PicTriev - Find Look-Alike Images
- OpenMoji or JoyPixels - Emojis
- PixelJoint, Lospec or rsrcs - Download / Share Pixel Art
- PimpMyDrawing - Human Silhouettes
- FanCaps or Film Grab - Media Screenshots
- Footyrenders - Football Related Images
- PSDGraphics - PSD Files
- The NFT Bay or Extremely Fungible Tokens - Free NFTs
- Artvee - Public Domain Artwork
- Behance - Design Projects
- Placeit - Image Templates
- Worldvectorlogo, Logo Source, Logos & Badges Bundle, Brands of the World, Logos Download, Logodust, Logowik, Logo Wine, seeklogo, logospire, LogoSearch, logopond, SuperTinyIcons, logotouse, brandeps, logolounge, logomoose - Logo Search / Designs
- MariaLetta - Free Doodles
- Watercolor Collection - Download Watercolor Pictures
- googleimagerestored - Old Google Image Search
- Block Posters, PosterRazor or Rasterbator - Create Printable Posters
▷ Image Search Engines
- ⭐ Yandex Images or Mavink - Image Search
- ⭐ Search by Image - Browser Extension
- ⭐ SauceNao - Reverse Image Search / Extension
- ⭐ SmartImage - Reverse Image Search App
- ⭐ Google Lens - Reverse Image Search
- ⭐ TinEye - Reverse Image Search / Extension
- infini.wtf - Reddit Image Search
- Visual Search - Reverse Image Search
- IQDB - Reverse Image Search
- CopySeeker - Reverse Image Search
- MaxURL - Larger Image Search / GitHub
- VISE - Image Search with Search Queries
- Have I Been Trained? - AI Image Search
- RootAbout - Archive / OpenLibrary Reverse Image Search
- Multicolr - Color-Based Image Search
- trace.moe or Saucekudasai - Anime Reverse Image Search
- Image_Max_URL - Browser Userscript
▷ Stock Images
- Note - Royalty-free implies images free for personal or commercial use with some usage restrictions (see sites TOS). CC0 stands for Creative Commons Zero and means images are public domain. Sites not tagged have licensing that varies.
- 🌐 Awesome Stock Resources - Stock Photo Index
- ⭐ GetPaidStock, DownPic, Downloader.la or istock - Paid Stock Photo Downloaders
- ⭐ EveryPixel, O-DAN or LibreStock - Stock Photo Search Engines
- Adobe Stock - Stock Photos / Royalty-Free
- Unsplash - Stock Photos / Royalty-Free
- Pixnio - Stock Photos / Royalty-Free
- Pikwizard - Stock Photos / Royalty-Free
- diverseui - Human Face Photos / Royalty-Free
- themeisle - Stock Photos / CC0
- PxHere - Stock Photos / CC0
- focastock - Stock Photos / CC0
- Foodiesfeed - Food Photos / CC0
- freenaturestock - Nature Photos / CC0
- Burst - Stock Photos
- Hippopx - Stock Photos
- BarnImages - Stock Photos
- Pixabay - Stock Photos
- Lummi - AI Generated Stock Photos
- Smithsonian Open Access - Smithsonian High-Quality Photos
- desirefx - Stock Photo Overlays
- creativity103 - Abstract Background Photos
- Warren Photographic - Animal Photos
- PhyloPic - Animal Silhouettes
- iwaria - African Photos
- twnsnd - Vintage Photos / Public Domain
- PNGIMG or stickpng - PNG Photos / Noncommercial License
- gfxmountain - Stock Photo Collections
- FreePik Downloader or freepikuz_pro - FreePik Downloaders
- Flickr Commons - Public Photo Archives / Downloader
- Shutterstock Premium, freestockphotos or Shutter - Shutterstock Telegram Downloaders
- Nohat, FreeImages, cgispread, Vecteezy or FreeDesignFile - Misc Stock Photos / Vectors
- publicdomainvectors, Free Vector, VectorJunky, freevectors or vector4free - Misc Vectors
- VectorPortal - Vector Collections / Creative Common Attribution
- 123freevectors - Background Vectors
▷ Art / Illustrations
- ⭐ Kemono - Patreon Content / Some NSFW / Use Adblock
- ⭐ DeviantArt - User-Made Art / Fanart / Downloader / Frontend Instances
- ⭐ ArtStation - User-Made Art / Fanart / Downloader
- ⭐ Pixiv - Japanese Fanart
- ⭐ Pixiv Tools - Downloader, 2 / Rankings / Official Frontend / Frontend List / Preview, 2 / Android
- ⭐ Danbooru, Sankaku Complex or yande.re - Anime-Style Image Booru / Downloader
- ⭐ hydrus - Booru-Style Media Tagger / GitHub
- Buzzly - User-Made Art / Fanart
- Artfol - User-Made Art / Fanart
- Cara - User-Made Art / Fanart
- InkBlot - User-Made Art / Fanart
- Safebooru or TBIB - Image Boorus
- icons8, LostGeometry, 3D Illustrations or NS-illustration-pack - 3D Illustrations
- StorySet, unDraw, blush or Humaaans - Customizable Illustrations
- Pastel - Marker Illustrations
- Fresh Folk or lukaszadam - Illustrations of People
- free-gophers-pack - Gophers Illustrations
- reshot, freeillustrations, DrawKit, NiceIllustrations or manypixels - Misc Illustrations
- OldBookIllustrations - Illustrations from Old Books
- Plant Illustrations - Plant Illustrations
- Yummybooru or Animes Boxes - Booru Clients / Telegram
- Buhitter - X.com Illustration Search
- imgbrd-grabber - Booru Image Downloader
- Artbreeder - Image Discovery / Combining
▷ Download Extensions
▷ Wallpapers
► 3D Models
- ⭐ Thingiverse - Share / Download 3D Models
- ⭐ Printables - Find Practical 3D Models Ready for Printing
- Clara.io, PolyHaven, CadNav, Open3dModel or Archibase - Misc 3D Models
- Sketchfab, cgtrader, blendswap or 3dsky - Misc 3D Models / Sign-Up Required
- Cults, Thangs, MakerWorld or Pinshape - Printable 3D Models / Sign-Up Required
- 3D Warehouse - 3D Models Compatible with SketchUp / Sign-Up Required
- Pack 3D Models - Vehicle / Character 3D Models
- Figurosity - Human 3D Models
- Handz - 3D Hand Models
- Generated Photos - AI Generated Model Photos
- ripper.store - 3D Avatar Assets
- Archive3D - Furniture / Accessories / Vehicle 3D Models
- poly.pizza - Low Poly 3D Models
- RIGModels - Rig / Animate 3D Models
- NASA 3D Resources - NASA 3D Models
- 3D Find It - Industrial / Engineering 3D Models
- thebasemesh - Mesh 3D Models
- BlenderKit - 3D Model Library Integrated into Blender
- CosplayStaticFigure - Cosplay / Figurine 3D Models
- 3DBrute, 3DZip or DesignConnected - 3D Furniture Models
- Halloween.WannaThis - 3D Halloween Models
- Vertex - 3D Icons
- Ameede - CNC / Laser Design Vectors
- Skybox - AI Generated 3D Environments
- PoseManiacs, Anatomy Doc, Adorkastock or Anatomy360 - Pose References
▷ 3D Modeling Apps
- ⭐ Blender - FOSS 3D Modeling App
- ⭐ Blender Tools - Resources, 2 / Plugins / Tutorials / Textures / Renderer / 3D Nodes / AI Render
- ⭐ Shap-e - Generate 3D Objects based on Text / Image Prompts
- Goo Engine - 3D Anime Blender Mod
- Meshy.ai / Discord or TRELLIS / GitHub / HuggingFace - AI 3D Model Generators
- Wings 3D - Cross-platform 3D Modeling App
- JustSketchMe - Cross-platform 3D Pose Reference Tool
- MakeHuman - 3D Humanoid Modeler
- PoseMy.art, SetPose, DesignDoll, Magic Poser, Quickposes or JustSketchMe - Posing Tools
- Vectary, Womp, Bloom3D or Zdog - Online 3D Modeling Tools
- FaceMaker - 3D Face / Avatar Generator
- Recursivity - 3D Tree Creator
- CSS 3D Clouds - 3D Cloud Creator
- ModelViewer, 3DViewer or F3D - 3D Model Viewers
- Armorpaint - 3D Painting
- SculptGL - 3D Sculpting
▷ 3D Modeling Tools
- Embossify, Tripo3D or TripoSG - Image to 3D Model Converters
- Anaglyph Maker - Make 3D Images
- 3D Transformer - Rotate 3D Images
- 3DConvert - Online 3D Image Converter
- PaintUp - Make 2D Art into 3D
- Keygen - 3D Key Model Generator
- AliceVision - 3D Reconstruction / Camera Tracking
- Perspective Grid - 3D Perspective Tool
- Assemblr - Augmented Reality Image Creator
- MeshLab - 3D Mesh Processing / GitHub
- Ninja Ripper / 2 / 3 - Extract 3D Models from Games
- Ultimaker Cura - 3D Printing Software
▷ CAD Engineering
- Onshape - CAD Modeling with Real-time Collaboration
- Tinkercad - Educational CAD Modeling
- FreeCAD / GitHub - Parametric CAD Modeling
- BRL-CAD or OpenSCAD - Cross-platform CSG CAD Modeling
- LibreCAD or QCAD - 2D CAD Modeling
- Mayo - 3D CAD Viewer and Converter
- CadHub - Community Hub for CAD Projects
► Image Tools
- 🌐 Creator Resources - Art / Animation Resources
- 🌐 Awesome Colab Notebooks - Image Colab Resources
- ↪️ Color Scheme Tools - Guide
- ⭐ ImgOps - Image Operations Meta-Tool
- ⭐ AntiDupl or cbird - Duplicate Image Removers
- ⭐ Muzli - Design Inspiration Search
- ⭐ Slowpoke Pics, ICAT or Image Comparison Tool - Image Comparisons
- odiff - Image Visual Difference Tool
- PhotoFeeler - Get Photo Feedback
- Picviewer CE+ - Turn Webpages into Image Galleries
- Binternet - Pinterest Frontend
- /r/Photography Guide or Cambridge In Colour - Photography / Camera Guides
- PhotoEphemeris - Photography Sunlight Calculator
- PixelPeeper - Extract Lightroom Edits / Settings
- MagicLantern - Custom Canon EOS Firmware / Unsupported / X / Subreddit / Discord
- CHDK - Custom Canon PowerShot Firmware
- fSpy - Still Image Camera Matching
- DPReview - Camera Image Quality Comparison
- GlanceBack - Daily Webcam Photo Journal
- Image Color Summarizer - Image Color Summarizer
- Image Colors - Image Color Scatter Plot
- Image Pixel Sorter - Sort Pixels of Images
- Adobe Bridge - Adobe Assets Manager
- behind! - View Background Images
- Visual Center - Find the Visual Center of an Image
- Watermarkly, BatchWatermark or Watermarkup - Image Watermarking
- Watermark Remover, Unwatermark or DeWatermark - Watermark Removal
- Glaze or Nightshade - Protect Digital Art from AI Copies
- APNG Maker - Create / Optimize APNG Images
- JPEGMedic ARWE - Recover Ransomware-Encrypted Images
- CamScanner or Microsoft Lens - Scan & Digitize Documents / iOS
- FaceSwapApp / Discord, Swapface / Discord, faceswap, AIFaceSwap, Face Swapper, face-swap, FaceSwapVideo, facy.ai, Swapper or FaceFusion - Face Swapping
- WiseTagger - Image Tagger
- BooruDatasetTagManager - Booru Image Tagger
- Cluttr, Exif Sorter or TagStudio - Image File Organizers / Managers
- Allusion - Reference Image Manager
- Camera Wiki - Camera Model Wiki
- Canon Camera Museum - History of Canon Cameras
- Something to Draw - Find Things to Draw
- Make Photo Gallery - Collage Creator
▷ Image Compressors
- ↪️ Image Optimization
- ⭐ Caesium - Compression Software / Caesium Web App / GitHub
- ⭐ Squoosh - Compressor / Converter / GitHub
- ⭐ Seopix - Batch Compressor / Editor
- optimize.photos - Batch Compressor
- CompressImage - Batch Compressor
- CrushImage - Batch Compressor
- Bulk Image Compress - Batch Compressor
- minipic - Batch Compressor / Converter
- Compress JPEG - Batch Compressor / Unlimited Upload
- TinyPNG or TinyJPG - Batch Compressor / 20MB Upload / GitHub
- ImageSmaller - Compressor / 50MB Upload
- CompressOrDie - Multitool
- PNGQuant - PNG Compression Software / GitHub
▷ Image Converters
- ↪️ File Converter - Multi-Format Converters
- ⭐ minipic
- Knvrt
- Convertmyimage
- ImageConvert
- imverter
- Raw Pics
- Converseen
▷ Image Resizing
- PixelHunter - Resize Images for Different Sites
- Resize App Icon - Resize Square Images
- Simple Image Resizer
- ImageResizer
- PicResize
- Birme
- Bulk Image Resize
- ResizeNow
- BulkResizePhotos
▷ Image to Text / OCR
- ↪️ AI Chatbots - Most Chatbots have Built-in Image to Text
- ⭐ Capture2Text, tesseract or gImageReader - OCR Desktop Apps
- ⭐ Text Grab - Minimal OCR Windows Tool
- TextShot - Cross Platform OCR
- ImageScanOCR - Windows OCR Tool
- Handwriting-OCR - Handwriting OCR
- Project Naptha - Automatic OCR while Browsing Images
- i2ocr - Online OCR
- OCR.SPACE - Online OCR
- 2OCR - Online OCR
- Ocrify - Online OCR
- OnlineOCR - Online OCR
- NewOCR - Online OCR
- ImageToText - Online OCR
- OnlineOCR - Online OCR
▷ Image Viewers
- ⭐ IrfanView
- ⭐ JPEGView
- ⭐ FastStone
- ⭐ qView
- ⭐ XnView MP
- ⭐ Digikam
- ⭐ ImageGlass
- nomacs / GitHub
- qimgv
- oculante
- PhotoQt
- PicView
- ImagefanReloaded
- Image Eye
- Quick Picture Viewer
- Fragment
- HoneyView
- picturama
- narrative
- G'MIC
- BeeRef or PureRef - Reference Image Viewers
- HDRView or tev - HDR / Technical Image Viewers
- FlipFlip - Image Slideshow
▷ Self-Hosted Galleries
- 🌐 FOSS Photo Libraries
- Immich / GitHub
- Damselfly
- HomeGallery
- LibrePhotos
- Lychee
- Photoprism
- Photoview
- Photonix
- photos
- imagestore
- Memories
- Piwigo
- PiGallery 2
- PicoShare
- Up1
- Chevereto
- Photofield
- Google Photos Toolkit - Manage / Delete Google Photos
- Google Takeout - Export from Google Photos / Script
- GPhotos Guide - Unlimited Google Photos Storage Guide / Windows
- Google Photos EXIF - Populate Missing EXIF metadata in Google Photos
▷ Online Galleries
- ⭐ Postimages - 32MB / Forever
- Imgur - 20MB Image / 200MB Animated / Forever / Upload Limits
- Rimgo / 2 - Imgur Frontend
- tixte - 15GB Storage Total / Forever / Sign-Up Required
- lookimg - 20MB / Forever / Sign-Up Required
- Horizon - 75MB (500MB Storage) / Forever / Sign-Up Required
- imgchest - 10MB (30MB with Account) / Forever
- Piczel - 10MB / Forever / Sign-Up Required
- TurboImageHost - 20MB / Forever
▷ Image Hosts
- ⭐ PixVid - 32MB / Forever
- ⭐ ImgBB - 32MB / Forever
- ⭐ Catbox - 200MB / Forever / ShareX Config
- pixelfed - Decentralized Image Sharing Social Network / Sign-Up Required / Tools / Android / GitHub
- sxcu.net - Free ShareX Uploader Service / 95MB / N/A
- FreeImage.Host - 64MB (128MB with Account) / Forever
- imgbox - 10MB / Forever
- i - 8MB / Forever
- IMGPile - 100MB / Forever
- YourImageShare - 100MB / Forever
- pic.maxiol - 100MB / Forever
- GIFYU - 50MB (100MB with Account) / Forever
- IMGDrop - 50MB / Forever
- WebHotPix - 50MB / Forever
- ThumbSnap - 48MB / Forever
- Kepkuldes - 40MB / Forever
- FreeIMGHost - 20MB / Forever
- Pikky - 20MB / Forever
- imagebam - 20MB / Forever
- imagevenue - 20MB / Forever
- BayIMG - 100MB / Forever
- Lutim - 20MB / Forever
- FastPic - 25MB / Forever
▷ Screenshot Tools
- ⭐ ShareX / Image Hosts / File Manager
- ⭐ Flameshot / GitHub
- ⭐ Zipline / GitHub or yaass - Self-Hosted ShareX Server
- Greenshot
- KSnip
- Nimbus Capture
- PixpinApp
- ScreenshotX
- FRAMED - In-Game Screenshotting Tips
- Pika / GitHub, FabPic, OnPaste, Screenstab or Limus - Screenshot Editors / Mockups
- Screenshot Guru, Site-Shot or Pikwy - Take Screenshots of Websites
- Screenshot Rocks / GitHub - Create Screenshot Mockups of Websites
- paste.photos - Paste Image to Download
- How to Screenshot - Multi-Platform Screenshot Tutorials
▷ Palette Generators
- ⭐ Color Designer, TheGoodColors, Super Color Palette or Coolors - Color Palette Generators
- Clariss, Color Palette Generator, Palitra or Color Picker - Generate Color Palettes from Images
- Color Space - Generate Gradient Color Palettes
- Colors Wall or ColorKit - Generate Random Color Palettes
- Color Kit - Generate Color Palettes by Mixing 2 Colors
- Pigment, Eva Design System, Scale, copypalette or Huey - Simple Color Palette Generators
- ColorBox, hue.tools, Randoma11y, accessiblepalette or colorcolor - Advanced Color Palette Generators
- Good Palette, Huemint, AI Colors or PaletteMaker - Generate UI Color Palettes
- Couleur.io - CSS Color Palettes Generator
- UI Colors or Tints - Tailwind CSS Color Generators
- Poolors - Generate Most / Least Used Color Palettes
▷ Color Pickers
- 🌐 React Color - Color Pickers Index
- 🌐 BrandColors - Brand Color Palettes Index
- Material UI, OKLCH, Color Deck, Picular or ColorKit's Color Picker - Color Pickers
- Colorpicker, Just Color Picker or epick - Color Picker Desktop Apps
- Colorscales - Find Colors in Color Space
- ColourCode or Colordot - Find Colors by Moving Mouse
- Geenes or Leonardo - Find UI Color Palettes
- Sorted CSS Colors - Find Similar CSS Colors
- Color Hunt, COLOURlovers, SchemeColor, Culrs or Colorffy - Find Color Palettes
- Adobe Color - Find Color Palettes with Color Wheel
- Color Lisa - Find Art-Based Color Palettes
- Color Leap - Find Historical Color Palettes
- COLORWISE - Find Color Palettes from Product Hunt Products
▷ Photo Forensics
- 🌐 Photo OSINT - Image OSINT Resources
- ⭐ Fawkes - Facial Cloaking
- ⭐ FotoForensics, Sherloq or Forensically - Photo Forensics Tools
- Picarta / Discord, GeoSpy or GeoEstimation - Estimate Image Locations
- Image Identification Project - Image Identification Tool
- StegOnline, OpenStego, OpenPuff, Steganography-PNG / GitHub, ImSter, stegano, hide-text or stegpy - Images Steganography Tools
- Aperisolve / 2 or stegextract - Steganography Analysis Tool
- Redacted - Blur, Pixelate or Blackout parts of Images
- Image Scrubber - Blur Images / Scrub Metadata
- Schizoware - Image Name / Hash Randomizer
- ViewEXIF, Jimpl, ExifData, OnlineEXIFViewer, ExifLooter, CameraSummary or JPEGsnoop - EXIF / Metadata Viewers
- exiftool, 2, ExifCleaner, EXIFRemove, scrambled-exif, Metadata-Remover, exifpurge, adarsus or VerExif - Remove Meta / EXIF Data
- Pic2Map - Image EXIF data viewer with GPS support
- TheExifer, Photini or ColorPilot - Image EXIF Data Editors
- Base64 Image - Encode / Decode Images
- Faceagle - Face Recognition Search Engines
▷ Android Camera
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
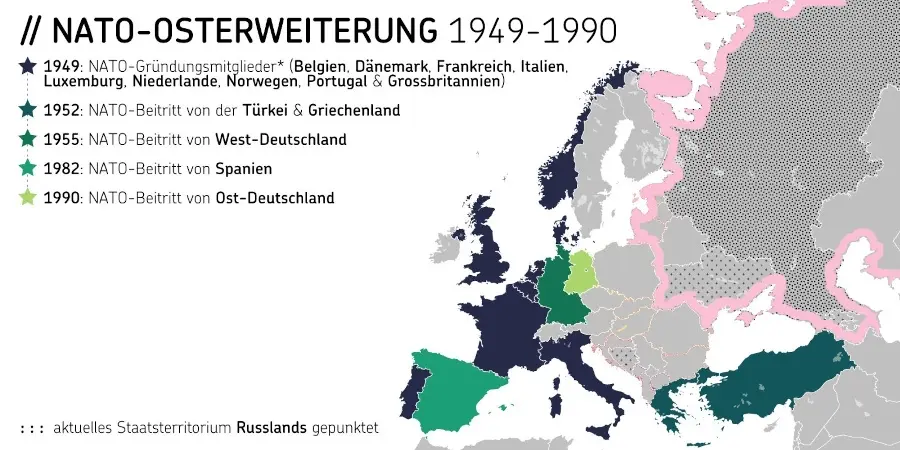
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
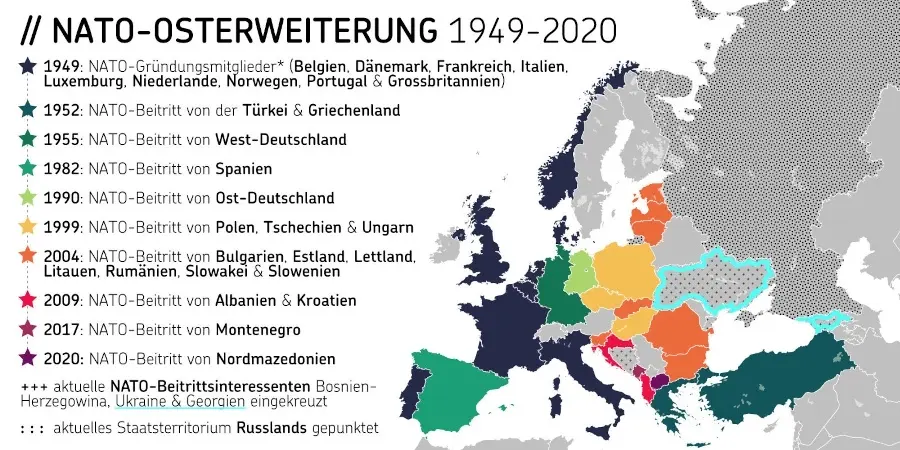
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
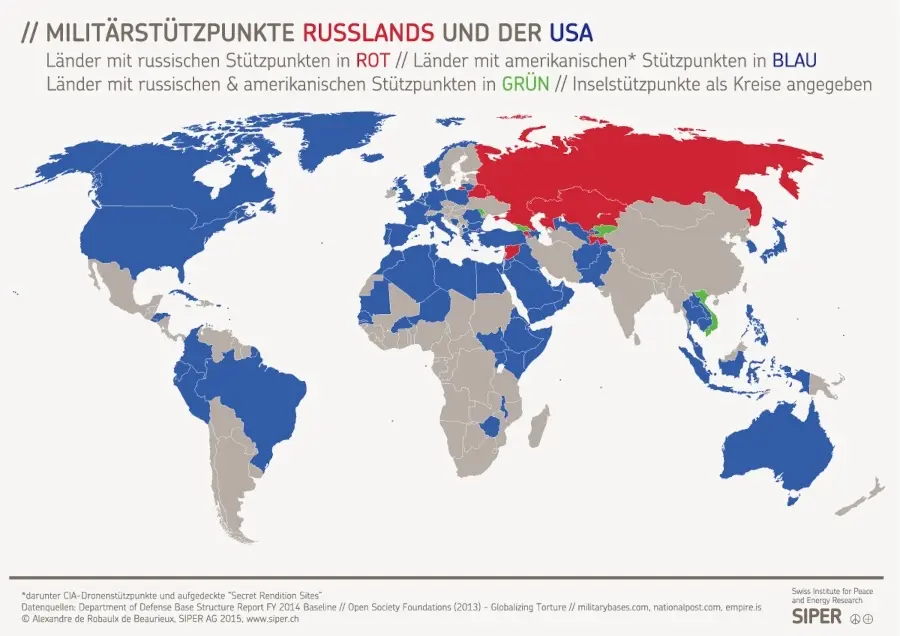
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ c9badfea:610f861a
2025-05-13 00:21:07
@ c9badfea:610f861a
2025-05-13 00:21:07► Gaming Tools
- ↪️ Download Managers
- ↪️ Media Posters / Covers
- ↪️ Game Soundtracks
- ⭐ PCGamingWiki - Game Fixes & Workarounds / Discord
- ⭐ Sunshine, Apollo or Moonlight - Gaming Remote Desktop Client / Mobile
- ⭐ Library of Codexes - Game Codex Library
- ⭐ HowLongToBeat, 2 - Find Average Game Lengths
- ⭐ /r/tipofmyjoystick - Find Games via Screenshot or Description
- ⭐ Game Pauser - Pause Unpausable Cutscenes
- ⭐ Valve Archive - Rare Valve Data Archive
- VGHF Digital Archive - Historical Documents, Magazines, Transcripts, etc. / Archive
- NIWA - Nintendo Independent Wiki Alliance / Discord
- Gog To Free - Add Piracy Site Links to GOG Store
- The Models Resource - Game Models
- The Spriters Resource - Video Game Sprites
- MiiCharacters - Famous Mii Creation Guides
- Archiverse - Miiverse Archive
- Buzz In - Online Buzzer System
- Challonge or Lorenzi's Game Boards - Tournament Creators / Managers
- Medal - Shadowplay for non Nvidia Cards / Premium Bypass
- RePlays - Game Recording Manager
- Moments - Game Clip Tool
- Keystrokes - Keystrokes Overlay
- PSNProfiles - Trophy Guide / PSN Profile Viewer
- Achievement Watcher - Achievement File Parser, Notifications & Playtime Tracker / Note
- Shmuplations - Japanese Developer Interviews
- Wiki.gg - Game Wikis / Redirector
- CSDb or GB64 - Commodore 64 Resources
- Awesome J2ME - J2ME Resources
- GARbro - Browse / Extract Visual Novel Resources
- ConceptArt - Video Game Concept Art
- How Denuvo Works
- Game Cracking / Repacking Guides
▷ Game Launchers
- ⭐ Playnite - Game Library / Launcher / Extensions / Subreddit / Discord / GitHub
- ⭐ GoG Galaxy or Project GLD / GitHub - Game Libraries / Launchers
- Ascendara - Game Launcher / Downloader / Discord / GitHub
- Fit Launcher - Game Launcher / Torrent Client / Discord
- Launchbox - Retro / Console Game Library / Launcher
- GameHUB Launcher - Rainmeter Game Launcher
- Hydra - Game Launcher / Torrent Client / Plugins, 2 / Game Search / Discord / Telegram
- OpenGamepadUI - Gamepad Native Launcher
- JackboxUtility - Jackbox Games Launcher / Discord / GitHub
- GameVault - Self-Hosted Gaming Platform / Discord / GitHub
▷ Optimization Tools
- 🌐 Nvidia Overclocking - Nvidia Overclocking Resources
- ⭐ SpecialK - Game Optimization Tool / Discord
- ⭐ MSI Afterburner, GPU Tweak III or EVGA Precision X1 / Warning - GPU Overclocking / Guide
- ⭐ SystemRequirementsLab or PCGameBenchmark - Game Requirements Tests
- ⭐ MSI Kombustor - GPU Benchmark Test
- ⭐ ProSettings, Share Gaming Tweaks, /r/OptimizedGaming, SweetFX, ENBSeries - Settings Optimization Guides
- ⭐ DisplayMagician or AutoActions - Per-Game Display Profiles
- ⭐ Lossless Scaling, Magpie, DLSS2FSR or OptiScaler - Game Upscaling
- RagnoTech Optimization Catalog or TroubleChute - Gaming Optimization Guides
- cancerogenoslab or MikeMartin - FPS / Latency Guides
- Fraps, OCAT / GitHub, Rivatuner Statistics Server, CapFrameX or Xbox Game Bar - FPS Tracking / Benchmarking
- SSTap - Decrease Ping
- Overclock - Overclocking Forum
- Ryzen Master Utility - Overclocking Control for Ryzen Desktop CPU
- AMD-APU-Tuning-Utility - AMD APU Tuning
- DLSS Swapper - Download, Manage & Swap DLSS
- dgVoodoo2 - Glide & DirectX Graphics Wrapper
- VibranceGUI - Automate Digital Vibrance Control
- Vuenxx - Free FSR 3 Mods / Note
- ReShade - Generic Post-Processing Injector / Easy Installer / Shaders / Discord / GitHub
- Scanlines for Windows - Add Scanlines to Games / Discord
- DLSSG to FSR3 - AMD FSR3 Frame Generation for NVIDIA
- WindowedBorderlessGaming, Borderless Gaming or FullScreenizer - Borderless Windows for All Games
- DxWnd - Play Fullscreen Only Games in Window
- WSGF - Widescreen Gaming Community / Solutions
- Widescreen Fixes Pack / GitHub, Widescreen Fixer v3.4 or Flawless Widescreen - Widescreen Fixes
- 4GB Patch - Patch x86 executables to use 4GB
▷ Controller Tools
- ⭐ DS4Windows / 2, AntiMicroX, DualSenseX, DualSenseY, PCXSense or Input Remapper - Gamepad Input Tools / Steam Note
- x360ce / GitHub - DS4 / 360 Controller Emulator
- XOutput - DirectInput to Xinput wrapper
- DsHidMini - Use PS3 Controllers on Windows
- JoyToKey - Controller Emulator
- Spud Controller - Controller / Mouse Input Displays
- Gamepad-Tester or AresLuna - Controller Connectivity Testers
- hidusbf - Decrease DS4/5 Input Lag / Video
- HidHide - Input Device Firewall
- Whitescent Engine - Use Phone as Joy Stick / GitHub
- JoystickGremlin - Remap Joystick Devices
- Arcade Controls - DIY Arcade Controls
- AltCtrls - Custom Controller Crafting Resources
▷ Game Mods
- 🌐 Big List of Randomizers - Game Randomizer Index / Discord / GitHub
- ↪️ Game Mods - Mods for Individual Games
- ⭐ ChronoCrash - Side Scrolling Modding Forum / Games List
- ⭐ ModDB - Game Mods
- ⭐ Nexus Mods - Game Mods / Bulk Downloader / Redirect Skip / Download Hidden / Discord
- ⭐ ModdingLinked - Bethesda Game Modding Guides / Discord
- WeMod - Cheats / Trainer Manager / Single Player Only / Unlocker / Discord
- ModOrganizer - Mod Manager
- Otis_Inf Camera Mods or CinematicTools Archive - Game Camera Mods
- Mod.io - Cross Platform Game Mods Support / Discord
- WabbaJack - Automated Modlist Installer / Discord
- ModWorkshop - Game Mods / Discord
- GameFront - Game Mods / Discord
- Video Game Mods - Game Mods / Discord
- GameBanana - Game Mods / Discord
- SMods - Game Mods
- Silent's Blog - Game Mods / Patches
- FlingTrainer - Game Mods / Trainers for Single Player Games
- Top Mods - PC Game Mods
- ProAsm - Retro Game Mods
- Thunderstore - Unity Game Mods
- Gale or r2modman - Thunderstore / BepInEx Unity Mod Managers
- Archipelago - Multi-Game Randomizer
▷ Game Saves
- ↪️ File Backup / Sync
- ⭐ Ludusavi or GameSave Manager - Game Save Managers / Backup
- PCGamingWiki - Save Locations Listed Under "Game Data"
- Save Game World - PC / PlayStation / Switch / Xbox / Wii
- SavegameDownload.com - PC / PlayStation / Switch / Xbox / Android
- YourSaveGames - PC / PSP
- SaveGame.Pro - PC
- Saves For Games - PC
- GC Saves - Gamecube / Discord
- Save Editor Online - Game Save Editor
▷ Game Maps
- 🌐 Map Genie, GameMaps, THGL or VGMaps - Game Map Indexes
- noclip - Explore Game Maps
- KudosPrime - Racing Game Maps
- bspview - Explore Quake & GoldSRC Maps / GitHub
- NES Maps - NES Game Maps
- SNES Maps - SNES Game Maps
- Forgehub - Halo Maps / Discord
- Zelda BotW Street View - Breath of the Wild Map
- Palworld Interactive - Palworld Map
- Fortnite.gg - Fortnite Map, Guides, Skins, etc.
- Hitmaps - Hitman Maps / Discord
- Hallownest or Interactive HN Map - Hollow Knight Maps
▷ Git Gud
- Note - There are guides on almost every Steam page, some for beginners, 100% completion walkthroughs, and more.
- 🌐 Mousepad Mastersheet - Mousepad Comparison Chart
- 🌐 Gamepadla - Gamepad / Controller Latency Tests
- ⭐ Before I Play - Tips for any Game
- ⭐ GamingSmart, Sens Covnerter, Sens Converter or Mouse Sensitivity - Game Sensitivity Converters / Tools
- ⭐ Aim400kg, 3D Aim Trainer, Aimlabs, Aiming.Pro or AimTrainer - Aim Training
- ⭐ Speedrun - Speedrunning Streams, Leaderboards, Resources, etc.
- GameGuides, DotGG, Retro Guides, Game8, StrategyWiki, Samurai Gamers, UHS Hints or Kirklands - Game Guides
- Voltaic - Aim Benchmark & Guides
- Piper - Gaming Mouse Config Tool
- LiveSplit - Customizable Speedrun Timer
- The Manual Project, ReplacementDocs or GamesDatabase - Game Manuals
- SNES Manuals - SNES Game Manuals
- Ukikipedia - SM64 Speedrunning Wiki
- FOUR.lol - Tetris Openers Wiki
- Underdogs Cup Lounge - Tetris Resources & Coaching Discord
- Fumen - Tetris Field Editor
► Tracking / Databases
- ⭐ Glitchwave - Tracking / Database
- ⭐ Backloggd - Tracking / Database
- ⭐ Infinite Backlog - Tracking / Database
- ⭐ IGDB - Game Database
- Moby Games - Game Database
- GiantBomb - Game Database
- Grouvee - Tracking / Database
- RankOne - Tracking / Database
- GG - Tracking / Database
- KeepTrackOfMyGames - Tracking / Database
- PlayTracker - Tracking / Database
- Gamelib - Tracking / Database
- Backloggery - Tracking / Database
- Exophase - Tracking / Database
- LaunchBox Games Database - Game Database
- GameFAQs - Game Database
- Rawg - Game Database
- rate.house - Game Database
- listal - Game Database
- FrontierNav - Game Database
- IMDb Advanced Search - Game Search
- Low Spec Games - Low Spec Game Database / Text Only / GitHub
- JRPGC - JRPG Databases / Discord
- RPGCodex - RPG Database / Forum
- SteamPeek or IndieDB - Indie Game Databases
- RetroShowcase or The Good Old Days - Retro Game Databases
- Sega Retro - Sega Game Database
- AtariAge - Atari Game Database
- Polish Pixels - Retro Polish Games Database
- Co-Optimu or PlayCo-opGame - Co-Op Game Databases
- SvenEvils Playground or Local Multiplayer List - Local Multiplayer Game Database
- DoesItPlay? - Offline Game Compatibility Database
- CloudBase - Cloud Game Database
- HOTU - Rare Game Database
- Delisted Games - Delisted Games Database
- BoardGameGeek or Kallax - Board Game Database
- Are We Anti-Cheat Yet? - Anti-Cheat Game Database / GNU/Linux or Wine/Proton Compatibility
- Unseen64 - Cancelled / Lost Games
- Incendar - Game Release Date Tracker
▷ Curated Recommendations
- 🌐 Awesome Engineering Games - Engineering Games
- ⭐ AcclaimedVideoGames or VideoGameCanon - Game Top 1000 List
- ⭐ OpenCritic - Critic Game Reviews / Ratings
- ⭐ TasteDive, Mythic Maps / Discord or /r/ifyoulikeblank - Game Recommendations
- Rec Charts - Game Recommendation Guides
- Board Game Breakdown - Board Game Reviews
- Can I Play That? - Video Game Accessibility Reviews
- MoreGamesLike or Games Like Finder - Find Similar Games
► Steam / Epic
- 🌐 Steam Tool Collection, steam.tools or SteamInternals - Steam Tool Indexes
- ↪️ Steam Workshop Downloaders
- ⭐ SDD GUI or DepotDownloader - Steam Depot Downloaders
- ⭐ RedAlt SteamUp - Steam Depot Update Creator
- Steam Link - Stream Steam Library to TV
- Steam Mover - Store Steam Games on Multiple Drives
- Steam Rom Manager - Add ROMs to Steam
- BoilR - Sync Game Platforms with Steam
- SteamAchievementManager - Steam Achievement Manager
- SteamHunters / Discord or TrueSteamAchievements - Steam Achievement Tracking / Leaderboards / Profiles
- SteamID / 2, SteamDetective or SteamFinder - Steam ID Lookup
- SteamGuard - Generate Steam 2FA Codes
- Super Steam Packer - Pack and Share Your Steam Games
- Steam API Check Bypass - Steam API Check Bypass
▷ Client Tools
- ⭐ Heroic Games Launcher - Epic / GOG / Prime Games Launcher
- ⭐ Nemirtingas Epic Emulator - Epic Online Service Emulator
- ⭐ TCNO - Platform Account Switcher / Tutorial
- LEGENDARY / Discord or Rare - Epic Games Launchers
- Depressurizer or Backlog.rip - Steam Library Organizers
- Steam Art Manager - Find / Manage Game Art
- Millennium - Steam Client Customization / Discord / GitHub
- Watt Toolkit - Enhance Steam Functionality / GitHub
- SteamCMD - Command-Line Steam Client
- Adwaita for Steam - Steam GNOME Skin
- Backgrounds.Gallery - Steam Backgrounds
- Steam.Design - Steam Background Cropper
- Center.Steam - Center Steam Text
- Steam Inventory Helper - Steam Inventory Enhancement Extension
- Fuck Off EA App - Use Origin Instead of EA App
▷ DLC Unlock / DRM Bypass
- ⭐ CreamAPI - Steam DLC Unlocker / Auto Setup
- ⭐ GreenLuma - Offline Steam DRM Bypass / DLC Unlocker / Manager / Family Bypass Guide
- ⭐ Unsteam - Online Steam DRM Bypass / Cracked Servers Only / Multiplayer Emulator
- ⭐ Steamless - Steam DRM Remover
- ⭐ Goldberg, 2 / GUI / Guide or SmartSteamEmu - Offline Steam / Multiplayer Emulators
- ⭐ Steam-Auto-Crack or SteamAutoCracker - Auto Apply Goldberg + Steamless / Guide
- ⭐ Koalageddon - DLC Unlocker for Epic, Origin, EA, Uplay
- DreamAPI - DLC Unlocker for Epic, Origin and EA
- Anadius - DLC Unlockers for EA and Origin
- ScreamAPI - Epic DLC Unlocker
- GetDataFromSteam-SteamDB - Find SteamDB DLC Data / Create Configs
▷ Steam Store
- ⭐ SteamDB / Extension or Steambase / Extension - Steam Insights Tools
- AugmentedSteam - Steam Web Enhancement Extension
- SteamScout - Steam Review Analyzer
- Steam Link Dropdown - Add Piracy Site Links to Steam Store
- UWPHook - Add Windows Store Games to Steam
- Free Packages - Mass Activate All Free Steam Games / $5 Account Min / Guide
- Wishlist Removals - Remove Hidden Items from Steam Wishlist
- Steam URL Opener - Open URLs Inside Steam Client
- Steam Age Bypass - Bypass Age Confirmation
- Steam Currency Converter / Note - Steam Currency Converter
► Multiplayer Tools
- ⭐ Nucleus Co-op - Local Split-Screen PC Multiplayer / Subreddit
- Liquipedia - Competitive Gaming / Esports Wiki / Discord
- Tracker.gg - Game Leaderboards / Stats
▷ Multiplayer Fixes
- ⭐ Online Fix - Online / LAN Multiplayer Fix / Discord
- ⭐ Playit.gg - LAN Multiplayer Fix / Discord
- ⭐ ZeroTier - LAN Multiplayer Fix
- Radmin - LAN Multiplayer Fix / Discord
- Hamachi - LAN Multiplayer Fix
- NetMaker - LAN Multiplayer Fix
- OpenSpy - LAN Multiplayer Fix / Discord / GitHub
- Team XLink - LAN Multiplayer Fix / Discord
- ZLOEmu - LAN Multiplayer Fix
- t7patch - Black Ops 3 Crash Fix
▷ Multiplayer Mods
- 🌐 Multiplayer Mods or Unmoddable - Multiplayer Mods for Single-Player Games
- ⭐ Plutonium - COD BO1/BO2, MW3 and WaW Multiplayer Client / Setup Guide / Video Guide / Offline Launcher / Discord
- AlterWare - COD MW2 (2009), MW3, BO3, AW and Ghosts Multiplayer Client / Discord / GitHub
- HorizonMW - Modern Warfare Remastered Multiplayer Client / Guide / Servers / Info / Tools
- CoD4x Mod - COD4 (2007) Multiplayer Project / Requires MP Key / Discord
- Venice Unleashed / Discord or Warsaw Revamped / Discord - Battlefield Mod Projects
- SM64 Coop Deluxe - Super Mario 64 Co-Op / Discord
- Smash64 - Smash Bros 64 Online / Discord
- Marne - BF1 Multiplayer Project / Discord
- Slippi - Super Smash Bros Melee Online / Discord
- Tilted Online - Multiplayer Skyrim & Fallout 4 / GitHub / Discord / Setup Guide
- NV:MP - Fallout: New Vegas Multiplayer / Discord
- Nitrox - Subnautica Multiplayer
- BeamMP - BeamNG Multiplayer / GitHub
- Fika - Play Single Player Tarkov Co-Op / Requires Legit Game
- OnlineCTR - Crash Team Racing Multiplayer
- CnCNet - Multiplayer Command & Conquer / Discord
- Old School RuneScape - Classic Runescape / Discord
- RuneLite - Old School RuneScape Client w/ Plugin Support / Discord
- Mega Man Arena or Megaman 2.5D - Multiplayer Mega Man
- DMP - Kerbal Spaceprogram Multiplayer Mod / Discord
▷ Multiplayer Servers
- ⭐ TrackyServer - Find Private Multiplayer Servers
- Server.pro - Game Server Hosting
- Pterodactyl / Discord or Pelican / GitHub - Game Server Management Panel
- Impostor - Among Us Private Server / Discord
- VRCList - Find VRChat Worlds / Sign-Up Required
- OldUnreal - Unreal Tournement Servers / Discord
- DiIiS - Open-Source Diablo III Local Server
- Insignia - Original Xbox Replacement Servers / Discord
- ElDewrito - Halo Online / Halo 3 Servers
- Project Cartographer - Halo 2 Online Servers
- Halo Custom Edition - Halo CE Online Servers
- BF2142 Reclamation - BF2142 Servers / Discord
- SiMPLE - Battlefield 1942 Servers / Discord
- Overwatch-Server-Selector - Overwatch Server Selector
- Northstar, 2 - Titanfall 2 Server Hosting & Modding / GitHub / Guide / Discord
- ET: Legacy - Wolfenstein Enemy Territory Servers / Discord
- Arctic Combat - Arctic Combat Server Revival / Discord
- Factorio.zone - Free Factorio Servers
- Clash of Magic / Discord or Atrasis / Discord - Clash of Clans Private Servers
- Rusticaland - Free Rust Servers / Discord
- Ephinea - Phantasy Star Online Blue Burst Server Revival
- PSO Servers - Phantasy Star Online 1 Server Revivals
- KOCity - Knockout City Multiplayer Revival / Discord / GitHub
- Elemental Fracture - Spellbreak Community Revival / Discord
- NolfRevival - NOLF, NOLF 2 & Contract Jack
- Toontown Rewritten or Corporate Clash - Toontown Multiplayer Revivals
► Homebrew
- 🌐 Darthsternie - Console Firmware / Exploit Archive
- 🌐 Emulators on Consoles - List of Emulators for Consoles
- 🌐 Firmware / Bios Files
- ⭐ Hacks.Guide / 2, CFW Guide, ConsoleMods.org / Discord, Digiex, Homebrew Guides, CFWaifu or Gamebrew - Homebrew Guides
- ⭐ Nintendo Homebrew - Nintendo Homebrew Discord
- ⭐ GBATemp - Homebrew Forum
- /r/Homebrew - Homebrew Subreddit
- Game Boy Tech Page - Game Boy Tools
- Game Boy Book Reader - Game Boy Book Reader
- NESC-SNESC-Modifications - NES, SNES & Playstation Mods
- ModMyClassic - Classic Console Mods
- N64Brew - N64 Homebrew Wiki
- /r/XboxModding or /r/XboxRetailHomebrew - Xbox Homebrew Subreddits
- Team Resurgent - Xbox Homebrew Tools
- /r/XboxHomebrew - Xbox One/Series Homebrew Subreddit
- /r/360Hacks Guide - Xbox 360 Modding Guide
- C-Xbox Tool - .XBE to ISO File Converter
- NKit - Disc Image Processor
- NASOS - Gamecube iso.dec to ISO Converter
- NESDev - NES / SNES Dev Homebrew Guides / Forum
- hakchi2 CE - Add More Roms to NES/SNES Classic Mini / Discord
- ROM News - Console Game Release PreDB / NFO Database
▷ Switch Homebrew
- ↪️ Switch Homebrew Guides
- ⭐ Homebrew App Store - Switch / Wii U Homebrew App Store
- /r/SwitchPirates or /r/SwitchHacks - Switch Homebrew Subreddits
- LAN Play Status or Switch-LAN-Play / Discord - Switch Multiplayer Servers
- FlagBrew - Switch Homebrew / Discord
- NSP Forwarder - Switch NSP Forwarder
- Switch Army Knife - Switch File Converter
- SysDVR - Switch Game Capture
- sys-con - Use Any USB Controller on Switch
- MissionControl - Use Any Bluetooth Controller on Switch
▷ Wii U / Wii Homebrew
- ⭐ WiiBrew - Wii Homebrew Wiki
- ⭐ WiiUBrew - Wii U Homebrew Wiki
- ⭐ Wii U Hacks Guide - Wii U Jailbreak Guide
- ⭐ Wii Hacks Guide - Wii Jailbreak Guides
- ⭐ Wiimmfi or WiiLink - Wii Multiplayer Servers
- ⭐ Homebrew App Store - Switch / Wii U Homebrew App Store
- Pretendo - Wii U Network Replacement
- /r/WiiUHacks - Wii U Homebrew Subreddit
- /r/WiiHacks - Wii Homebrew Subreddit
- Open Shop Channel - Wii Homebrew App Library
- WBFStoISO - WBFS to ISO
▷ 3DS / DS Homebrew
- 🌐 DS Homebrew - DS Homebrew Resources / Wiki / Discord
- ⭐ 3DS Jailbreak Guide - 3DS Jailbreak Guide
- ⭐ DSi Jailbreak Guide - DSi Jailbreak Guide
- ⭐ Wiimmfi or Kaeru Team - DS Multiplayer Servers
- Pretendo - 3DS Network Replacement
- Universal DB - 3DS / DS Modding Apps
- Theme Plaza - 3DS Themes / Discord
- Artic Base - Play Physical 3DS Games on Citra
- BootNTR - Stream 3DS to PC or Mac / Instructions
- /r/3DSPiracy or 3DSHacks - 3DS Modding Subreddit
- FlagBrew - 3DS Homebrew Apps / Discord
- Luma3DS - 3DS Custom Firmware
- GodMode9 - 3DS File Browser
- Batch CIA 3DS Decryptor - Decrypt 3DS Files
- Rverse - 3DS Miiverse Recreation Discord Server
▷ Playstation Homebrew
- ⭐ PS4 Modding, PSX Hax, PSDevWiki or Wololo - Playstation Modding Guides
- Chiaki / GitHub or RemotePlay - Playstation Remote Play Clients
- /r/PS5Homebrew - PS5 Homebrew Subreddit
- /r/PS4Homebrew - PS4 Homebrew Subreddit
- Exploit Host - PS4 Exploit Hosting
- DarkSoftware - PS4 / PS3 Firmware
- /r/PS3Homebrew - PS3 Homebrew Subreddit
- PS3 Disc Dumper - Decrypted PS3 Disc Dumper
- PS3 Game Updater or Rusty Pan - Update PS3 Games
- PS3Themes - PS3 Themes
- PSONE - Play PS1 Games Online / PS3 Required / Discord
- PSXDev - PS1 Development
- MemcardRex - PS1 Save Transfer Tools / Archive
- /r/VitaPiracy / Discord or /r/VitaHacks - PSVita Homebrew Subreddits
- PSP Archive - PSP Homebrew Archive / Discord
- VitaDB - PS Vita Homebrews
- Vita Volume - Set PS Vita Volume without Buttons
- PSPunk - PSP Homebrew Info
▷ Steam Deck
- 🌐 Steam Deck Mods - Steam Deck Mods / Discord
- ⭐ Decky Loader - Steam Deck Plugin Loader / Plugins / GitHub
- /r/SteamDeckPirates - Steam Deck Piracy Subreddit
- great-on-deck-search - Verified Steam Deck Game Search
- Steam Deck Tools - Fan Overlay, Power Control and Steam Controller
- EmuDeck - Steam Deck Emulator Setup / Compatibility / Discord
- GameImage - Steam Deck Game Setup
- Bazzite - Alt Steam Deck OS
- Steam-Deck.Force - Force SteamOS Boot
- HoloISO - SteamOS 3 (Holo) Archiso Config / Telegram
- Steam Deck Repo - Steam Deck Boot Videos
► Minecraft Tools
- 🌐 MCDOC - Minecraft Tools & Unlockers / Discord
- 🌐 Awesome Minecraft - Minecraft Resources
- ⭐ Minecraft Wiki - Minecraft Wikis
- ⭐ Villager Trading Cheatsheet or Image Cheatsheet
- ⭐ Minecraft Brewing Cheatsheet
- MC Utils - Minecraft Web Tools
- MCPEDL - Bedrock Resources
- DigiMinecraft or Birdflop - Minecraft Guides / Tools
- ViveCraft - VR Minecraft / Discord / GitHub
- SkyClient - Hypixel Asset Installer / Discord / GitHub
- SkyCrypt - SkyBlock Stats
- MC Icons - Minecraft Icon Search
- Textcraft - Minecraft Text & Logo Generator
- Pixelart Builder or PixelStacker - Turn Photos into Minecraft Art
- Block Palettes or Block Colors - Block Color Palettes
- The Minecraft Archive Project - Minecraft Archive
- Open Note Block Studio - Minecraft Note Block Song Editor
- Voyager - Minecraft AI
- MiniMessageViewer - Format Plugin Messages
- Minecraft Timeline - Minecraft Update History Timeline
▷ Hosting Tools
- 🌐 FMHL - Free Minecraft Hosts List / Mirror
- ⭐ auto-mcs - Easy Server Setup / GitHub
- ⭐ Playit.gg - Global Proxy / Discord
- ⭐ paper-optimization or minecraft-optimization - Server Optimization Guides
- World Host or e4mc / Lan Server Properties - Local Server Multiplayer Mods
- setup.md - Server Admin Guides / Wiki
- CraftyControl, MCSManager, Lodestone / GitHub or Fork - Minecraft Server Managers
- Minekube Connect - Ingress Tunnel for Minecraft Servers
- ViaVersion - Allow Connections from Older Versions / Discord / GitHub
- mclo.gs - Minecraft Log Sharing / Analyzing
- Minestom - Lightweight Minecraft Server / Discord
- Cuberite - Server Setup
- DriveBackupV2 - Server Plugin to Create Cloud Backups of Worlds
- Pufferfish, Purpur / Discord or Paper / Plugins - Performance Enhancement Servers
- GeyserMC - Join Minecraft Java Servers with Bedrock Client / Consoles
- Minecraft Server Scanner - Minecraft Server Info
- Minecraft Server Checker - Simple Server Checker
- mcsrvstat - Server Status Updates
- MC-Server-Banner-API - Real-Time Updated Server Banners
▷ Launchers
- ⭐ Prism Launcher - Feature-Rich Launcher / Free Method / Ely.by Version / Discord / GitHub
- ⭐ ATLauncher or Technic Launcher - Modpack Launchers
- ⭐ PojavLauncher / Discord / GitHub, ZalithLauncher or FoldCraftLauncher / Discord - Java Edition for Android & iOS
- ⭐ Bedrock Launcher or MCLauncher - Launcher for Bedrock Edition
- SkLauncher - User-friendly Launcher
- UltimMC - Launcher for Cracked Accounts
- Betacraft - Legacy Versions Launcher
- CheatBreaker - FPS Modpack Launcher / GitHub
- HMCL - Launcher / GitHub
- LabyMod - Launcher
- Crystal Launcher - Launcher
- GDLauncher - Launcher
- X Minecraft Launcher - Launcher
- Quantum Launcher - Lightweight Launcher / Discord / GitHub
- Omniarchive - Download Old Minecraft Versions
▷ Mods / Data Packs
- 🌐 Not Essential - List of Alternatives to Essential
- 🌐 OptiFine Alternatives - OptiFine Alternatives for Fabric
- ↪️ Mod Indexes
- ⭐ MCModdingGuide - Minecraft Modding Guide
- Builders Refuge - Building Modpack
- WorldEdit or Axiom - Building Tools
- Worldedit Tools - Docs / CUI / Discord / GitHub
- quark - Add Vanilla-like / QoL Features
- Voxy, DistantHorizons or Bobby - Lightweight Distance Rendering Mods
- VulkanMod - Vulkan Renderer Mod / Discord
- Forge, NeoForged, Quilt or Fabric / Discord - Mod Loaders
- PAX, ModMenu (fabric) or Mod Manager - Minecraft Mod Managers
- Forgix - Merge Mod Loaders
- /r/feedthebeast - MC Modding Community
- CraftPresence or Phase's Discord RPC - Discord RPC for Java Edition
- Controlify - Add Controller Support to Java Edition
- No Telemetry - Disable Telemetry Data
- SimpleVoicechat - Feature-Rich Voice Chat Mod / Discord
- ReplayMod or FlashBack - Record Game Sessions
- Craftify - Display / Control Playing Music
- Vanilla Tweaks, Smithed or Voodoo Packs / Discord - Minecraft Data Packs
- Data Pack Generators - Minecraft Data Pack Generators
▷ Maps / World Tools
- 🌐 ChunkBase - Minecraft Map Tools
- Amulet, Minecraft Datapack Map / GitHub, MCA Selector, uNmINeD or WorldPainter - Minecraft Map Editors / Viewers
- MineAtlas, Cubiomes Viewer or MCSeeder - Minecraft Seeds
- MinecraftMaps or Mapcraft - Minecraft Maps
- Minecraft Earth Map - Earth Maps
- CTMRepository - Complete the Monument Maps / Discord
- MapartCraft or Cartographer - Mapart Schematic / map.dat Generator
- BlueMap - Create 3D Map Models / GitHub
- Arnis - Generate Real-world Locations in Minecraft
- Chunker - Java / Bedrock Format Converter
- Minecraft Map Converter - PS3/360 Format Converter
- Amidst - Minecraft World Overview Display Tool
▷ Technical Tools
- 🌐 TMC Links - Technical Minecraft Resources
- 🌐 Minecraft Speedrunning - Minecraft Speedrunning Resources
- ⭐ MCPropertyEncyclopedia - Block Property Encyclopedia
- ⭐ spark - Minecraft Performance Profiler
- ⭐ Minecraft Java Flags - Java Edition Performance Tweaks
- Report Inspector - Crash Report / Profiling Inspector
- Mineflayer - Minecraft Bot Creator / GitHub
- Minecraft Armor Stand - Design Poses for Armorstands
- Enchant Order - Minecraft Enchantment Ordering Tool
- Minecraft Tools or GamerGeeks - Minecraft Tools / Calculators
- Minecraft Command Science or MCStacker - Minecraft Command Generators
- NBT Studio or webNBT - Minecraft NBT File Editors
- MinecraftJSON - Minecraft Tellraw Generator
▷ Customization
- 🌐 ShaderLABS - Shader Comparisons and Resources
- ↪️ Resource Pack Indexes
- ⭐ NameMC, Laby / Discord or Crafty - Minecraft Name & Skin Availability Trackers
- ShadersMods or MinecraftShader - Minecraft Shaders
- Iris Shaders - Fabric Shadermod for Minecraft
- MinecraftSkins or SkinMC - Minecraft Skins
- MSkins - Skin Grabber
- Ely.by - Skin System / Authorization
- Nova Skin or Blockbench - Minecraft Skin Editor
- MinecraftCapes or Capes - Minecraft Capes
- Minecraft Heads - Custom Minecraft Heads
- PVPRP - PVP Texture Packs
▷ 3D Tools
- ⭐ MCprep - All-in-one Blender Addon / GitHub / Discord
- ⭐ jmc2obj, Mineways, MiEX, Minutor - Minecraft World Exporters
- Mine-imator - Animation Tool / 2.0 Version / Forum / GitHub / Discord
- Chunky - Photorealistic Renderer / GitHub / Discord
- Block Display - Design / Share Block Display Models / Discord
- Cubical - Minecraft 3D Schematic Tool / Beta
- Custom-MC-Render-Cweeper - Import Custom 3D Models into Minecraft
- ObjToSchematic - Converts 3D Models into MC Formats / Discord
- NBT2Components - NBT to Component Converter
- Layoutit, VoxelSphereGenerator, BDStudio or Minecraft Shapes - Minecraft Shape Tools / Voxel Editors
► Game Specific
- 🌐 Awesome Trackmania - Trackmania Resources
- 🌐 ACNH.Directory - Animal Crossing: New Horizons Resources
- 🌐 FM Scout - Football Manager Resources / Community
- Half Life Project Beta - Unreleased / Cut Half-Life Content
- Palworld.gg, PalworldTrainer.com or Paldb.cc - Palworld Databases
- /codmeta/ - Call of Duty Loadouts / Metas
- Warzone Loadout or WZHub - Warzone Loadouts and Builds
- Braytech - Destiny 2 Stats
- The Halo Archive (Discord) or 405th - Halo Assets Archive
- Sym.gg - Battlefield Info & Weapon Stats / Discord
- Rust Clash - Rust Info / Tools
- Stardew.app - Stardew Valley Progress Tracker
- Fortnite Tracker - Fortnite Leaderboards / Stats
- FortniteEXP - Fortnite XP Progression / Leveling Rates
- Ready or Not Doc - Ready or Not Info
- FM Moneyball - Football Manager Recruitment Tool / Tutorial
- Minesweepergame.com and Minesweeper.online Wiki - All about Minesweeper
- WRCsetups - WRC Setups
- Peacock - Hitman World of Assassination Server Replacement
- Useful Osu - Osu! Resources
- Collection Manager - Osu! Collection Manager
- osu trainer - Osu! Trainer
- danser-go - Osu! Dancing Visualizer
- SpinShare - Spin Rhythm XD Custom Charts
▷ MOBA Tools
- ⭐ OP.GG - LoL Player Background Check
- ⭐ DPM.LOL, U.GG, KoreanBuilds, EuropeanBuilds, LoLTheory, MurderBridge or LoLAlytics / Discord - LoL Builds / Tiers
- ⭐ Gol.gg - LoL Competitive Stats, All Regions
- ⭐ Tactics.tools / Discord or MetaTFT / Discord - Team Fight Tactic Guides, Stats, Tools, etc.
- MobaFire - LoL Champion Guides
- ProBuilds - LoL Pro Player Builds
- LoL Wiki - Official LoL Wiki
- LoL Math - LoL Item Optimizer / Discord
- iTero - LoL AI Coach
- DraftGap - LoL Draft Analysis Tools
- Mobalytics or DeepLoL - Game Performance & Stats Analyzer
- Porofessor - Live LoL Game Stats
- ProStreams - Watch Pro LoL Twitch Streams
- DotaBuff, Stratz, OpenDota or Dota2ProTracker - Dota 2 Stat Trackers / Hero Guides
- SmiteGuru - Smite Leaderboards
- mood.gg - LoL Character-Based Audio Playlists
- RuneForge - Custom LoL Skins / Discord
- Deceive - Appear Offline in LoL
- Disenchanter - LoL Mass Disenchanter
▷ ARPG / MMORPG Tools
- 🌐 Grim Tools - Grim Dawn Tools
- 🌐 Last Epoch Tools - Last Epoch Tools
- ⭐ Maxroll - ARPG Build Guides
- D4Builds - Diablo IV Build Guides
- Helltides - Diablo IV Pit Leaderboards / Helltide Tracker
- Path of Building - Path of Exile Build Planner
- Murlok - WoW PvP / PvE Guides / Discord
- WoWProgress or CheckPVP - WoW Rankings
- RaidPlan - WoW Raid Planner / Discord
▷ Pokemon Tools
- 🌐 Awesome Pokémon - Pokémon Resources
- 🌐 /r/PTCGP Resource Guide - Pokémon TCG Pocket Resources
- ⭐ Bulbapedia - Pokémon Wiki
- ⭐ Serebii.net, Pokémon Awesome, Pokémon Database or PocketMonsters.net - Pokémon Databases
- ⭐ PokeList or PokeAPI - Pokédexes
- ⭐ Pokémon Typechart or Type Calculator - Pokémon Type Charts / Image
- ⭐ PokeMMO, DelugeRPG, Pokemon Blaze Online / Discord or Pokémon Revolution Online - Pokémon MMOs
- ⭐ PokéRogue - Pokémon Dungeon Crawler / Wiki / Subreddit / Mobile / Discord
- ⭐ Pokémon Showdown - Online Pokémon Battles
- PokeCommunity - Pokémon Community
- Project Pokémon - Pokémon Tools, Exploits, Saves, etc.
- PokeGB - Pokémon Blue Emulator
- PokemonLog, PokeHarbor or Pokémon Coders - Hacked Pokémon ROMs
- pret - Pokémon Disassembly / Decompilation Projects
- Pokemon Auto Chess - Pokemon Style Teamfight Tactics / Discord / GitHub
- PKHeX - Pokémon Save File Editor
- PMD Generators - Pokémon Mystery Dungeon Generators
- GameBanana - Pokémon Brilliant Diamond / Shining Pearl Mods
- pkNX - Switch Pokémon ROM Editor / Randomizer
- Universal Pokémon Randomizer ZX - Randomize Pokémon (works for GBA to 3DS)
- NYCPokeMap - Real-Time Pokémon GO Map for NYC
- PkmnCards, Pokéllector or Limitless - Pokémon Card Databases / Resources
- TCG ONE - Online Pokémon Card Game / Discord
- unite-db - Pokémon Unite Database
- HelixChamber - Unused Pokémon Material
▷ Counter-Strike Tools
- ⭐ CsWarzOnE - Counter-Strike Downloads
- ⭐ HLTV or Dust2 - Counter-Strike News
- ⭐ CS Demo Manager - Counter-Strike Demo manager
- ⭐ Faceit - Matchmaking Client
- ⭐ CSNADES - CS2 Nade Lineups
- CSGO Trader - CS:GO Trading Enhancements
- CS2 Weapon Spreadsheet - Weapon Stats / Prices
- ArminC-AutoExec - ArminC's CS2 Config
- CS2 Browser or CS2 Server Picker - Counter-Strike 2 Server Browser
- Faceit Finder - Faceit Account Finder
- Repeek - Faceit Enhancement Extension
▷ GTA Tools
- 🌐 GTAAll, GTAInside, GameModding, GTAGarage or LibertyCity - GTA Mods, Walkthroughs & More
- 🌐 GTA5-Mods - GTAV Mods
- 🌐 MixMods - GTASA Mods
- ⭐ FiveM, alt:V or RAGE - Modded GTAV Servers / Requires Legit Copy
- ⭐ San Andreas: Multiplayer / Discord or Multi Theft Auto / GitHub - Multiplayer GTA:SA
- ⭐ CLEO - Extensible Library Plugin for GTA III, VC & SA / Discord
- ⭐ SilentPatch - Quality of Life Fixes for GTA III, VC & SA
- Grand Theft Wiki - GTA Wiki
- GTA Cars - GTA Car Database / Stats
- Rainbomizer - GTA Randomizer Mods
- OpenIV - Rockstar Game Modding Tool
- Gillian's GTA - GTA IV Modding Guide
- GTA Connected - Multiplayer Mod / GTA III, IV, VC, SC / Discord
- Vice City: Multiplayer - Mutiplayer GTA:VC
- GTA Manager - GTA V Business Manager
- GTA Downgraders - GTA Game Downgraders
▷ Doom Tools
- ⭐ Doom Wiki - Doom Wiki
- ⭐ ZDoom - Doom Source Port
- ⭐ ZDaemon, Doomseeker, oDamex, DoomUtils or Zandronum - Online Multiplayer Doom
- Classic DOOM or DoomWorld - Doom Downloads
- Doom64 EX - Doom 64 PC Port
- dhewm3 - Doom 3 Source Port
- DoomsHack, Doom WADs, Doom Pastebin or Doom Wad Station - Doom WADs
- DOOM FX - Doom SNES Source Code
- UltimateDoomBuilder - Doom Map Builder
▷ Mario Kart Tools
- ⭐ Retro Rewind - Retro MKW Tracks / Multiplayer / Discord
- ⭐ RR Tools - Wiki / Auto-Updater / VR Rankings / Troubleshooting
- ⭐ CTGP Revolution - Custom MKW Tracks / Multiplayer / Disc Required / Discord
- ⭐ MKWRs - Mario Kart Records / Videos
- ⭐ MKW Lobbies - Online MKW Lobbies
- ⭐ CTGP Deluxe - Custom MK8DX Tracks
- ⭐ CTGP-7 - Custom MK7 Tracks
- Luigi_Fan2's Stat Charts - MK8DX / MK8 - Mario Kart stats
- MK8DX Builder - Kart Builder
- MKCentral - Mario Kart Tournaments
- /r/MarioKart or /r/MarioKartWii - Mario Kart Subreddits
- RiiBalanced - Rebalanced MKW Mod / Discord
- TTs Online - MKW Online Time Trials Mod
- CTGPRecords - Custom Track Records / Videos
- MaxVRList - VR Leaderboards
- xer - MKW Item Probabilities
- Tockdom Wikis - MKW / MK8 / MK3DS / MKDS / MKDD - Custom Mario Kart Wikis
- Custom Track Tutorial - How to Make Custom MKW Tracks
- MKW Texture Hacks - Custom MKW Textures
- ShortCat - MK8DX Strategy Guide
▷ Geometry Dash Tools
- ↪️ GD Demon Lists
- ⭐ Geode - Mod Menu & Modding Framework
- ⭐ GDDP or GD Demon Ladder - Practice & Improve Your Skills
- Soluble Texture Packs - GD Texture Packs / Manager
- Spritesheet Splitter - Split & Merge GD Spritesheets
- GD Save Explorer - View Detailed Stats & Data of Save Files
- Song File Hub - GD Songs & Mashups / Discord
- Globed - GD Multiplayer Mod
- GD Browser - GD Level Browser
- GD Font Generator - Generate Custom GD Logos & Messages
- G.js - GD Level Programming Language
- GD Docs - GD Programming Documentation
- GD History - GD Archival Project / Downloader
- GMD Private Server - Private Server Maker
- 3Dash - 3D Geometry Dash Game
- 3Dash Tools - Demon List / Challenge List / Impossible Levels
▷ Roblox Tools
- 🌐 Roblox Archive - Roblox Client Archive
- ⭐ Rolimon's or RoMonitor Stats - Roblox Experience Stats
- ⭐ Bloxstrap or Fishstrap - Roblox Player Bootstrapper / Discord / GitHub
- Novetus - Self-Hosted Multi-version Roblox Client
- Roblox Studio Mod Manager - Roblox Studio Bootstrapper
- RoPro, Roblox+, BTRoblox, RoGold or RoSeal - Enhance Roblox Website
- Better Discovery - Game Discovery
- RBXServers or FreeVIPServers - Roblox VIP Servers
- RobloxDen - Track Roblox Promo Codes
- Roblox Web APIs - Roblox APIs
- ingame.clothing - Preview Avatar Clothing
- FastFlags Collection - Roblox FastFlags Collection
▷ Terraria Tools
- ⭐ Terraria Wiki or Terranion - Terraria Wikis
- tShock - Terraria Server Tools / Plugins
- Terraria Forum - Terraria Community, Mods Help and More
- TEdit, terramap, TerraFirma or terraria-map-editor - Map Viewers / Editors
- Terrasavr - Terraria Character Editor
- Increased FOV - Increase Terraria FOV for 21:9 Monitors
▷ Gacha Tools
- 🌐 Paimon.moe or Honey Impact - Genshin Impact Resources / Tools
- 🌐 Honkai.gg - Honkai Star Rail Resources / Tools
- ⭐ Prydwen - Gacha Game Guides / Discord
- ⭐ Keqingmains - Genshin Guides
- ⭐ XXMI - Gacha Games Modding Tool / Discord
- /r/GachaGaming - Gacha Games Subreddit
- FGO GamePress - FGO Wiki + Guides
- Chaldea - FGO Planner & Battle Simulator
- LunarCore - Private Honkai: Star Rail Servers
- Star Rail Station or stardb.gg - Honkai Star Rail Guides
- Seelie.me - Genshin / Star Rail Planner
- Genshin Center - Genshin Planner
- Genshin Optimizer - Genshin Impact Calculator / Artifact Optimizer
- Genshin Helper Doc - Genshin Builds Guide
- Grasscutter - Private Genshin Impact Servers / Discord
- Genshin Impact FPS Unlocker - Unlock Genshin Impact FPS Cap
- Hoyolab Teyvat Interactive Map, Mapgenie Teyvat Interactive Map or Genshin Impact Map - Genshin Impact Maps
▷ Tabletop Tools
- 🌐 Awesome TTRPG - Online TTRPGs / Resources
- 🌐 5ETools, Roll for Fantasy, Kassoon or DragonsFoot - TTRPG Tools
- ⭐ dice.run, Random Dice or Desktop Dice - Dice Simulators
- ⭐ Kanka - Tabletop RPG Manager
- RPG.net - RPG Forums
- Adventurer's Codex - Online D&D 5e Campaign Manager / System
- NaturalCrit - Create D&D Homebrews / Badges
- DnD-Books - D&D 4e/5e Books
- FantasiaArchive - World Building / Documenting Tool
- DnD World Building - Fantasy World Building Guides
- The Acaeum - Dungeons & Dragons Database
- DnD Rules - Dungeons & Dragons Rules
- Archives of Nethys - Pathfinder Database
- WarGamer - Tabletop RPG Guides
- Roll20 or Rolisteam - Tabletop RPG Streaming
- Tabletopy - Tabletop RPG Soundboard
- Eigengrau's Generator - Town / NPC Generator
- Map Generator - Tabletop Roleplaying Map Generator
- MOGG - Magic: The Gathering Card Scans
- Yugipedia or YGOPRODeck - Yu-Gi-Oh! Resources / Card Lists
- Untap.in - Test Card Game Decks
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ c9badfea:610f861a
2025-05-13 00:20:18
@ c9badfea:610f861a
2025-05-13 00:20:18► Text Tools
- ↪️ Image to Text
- ↪️ Text to Speech
- ↪️ Study / Research
- ↪️ Data Visualization
- ⭐ TextCleanr, Text Mechanic, TextFixer, OnlineTextTools, Convert Case, TextCleaner, SortMyList or The Alphabetizer - Organize / Format Text
- OpenPaper, papis, PaperMerge, Paperless-ngx / Doc Analyzer or DataShare - Document Managers
- SmartDoc - Document Analyzer
- diffr, Diffchecker, TextCompare, Text-Compare, OnlineTextCompare, CompareText or DiffNow - Compare Text
- Count Duplicates or DuplicateWord - Count / Remove Duplicates in a List
- WindowTextExtractor - Extract Text From Any Window
- Textify - Copy Text from Any Dialog
- BeefText - Text Substitution Tool
- Scanner or NAPS2 - Scanner Apps / GitHub
- Calligrapher.ai, Text to Handwriting, texttohandwriting or HandWrittner - Text to Handwriting Converters
- StegCloak - Hide Messages in Text
- telescopictext - Write Text Within Text
- quipqiup or dCode - Cryptogram Solvers
- DocuSeal - Free Document Signing
- TemplateLab or FreePrintables - Free Document Templates
▷ Pastebins
- 🌐 PrivateBin Instances
- ⭐ Rentry, 2 - Markdown Support / CLI / Styling
- ⭐ GitHub Gists - Multi-Syntax / Account Needed
- ⭐ pastes.dev - Multi-Syntax / Markdown Support / GitHub
- ⭐ PrivateBin, 2 - Markdown Support / Syntax Highlighting / GitHub
- ⭐ Katbin - Plain Text / GitHub
- snowbin, 2 - Markdown Support / GitHub
- Text.is - Markdown Support / Rentry Clone
- Stellular, 2, 3 - Markdown Support
- bpa.st - Multi-Syntax / Markdown Support
- dpaste - Multi-Syntax / Markdown Support / GitHub
- cryptgeon - Single View / Plain Text / GitHub
- Paste.ee - Multi-Syntax / Markdown Support
- pst.moe - Multi-Syntax / Markdown Support / Source
- dpaste.com - Multi-Syntax / Markdown Support
- Pastebin.com - Multi-Syntax
- pastebin.pl - Multi-Syntax
- CentOS Pastebin - Multi-Syntax
- Microbin - Multi-Syntax
- snippet.host - Multi-Syntax
- ProtectedText - Multi-Tab
- bin - Minimal Pastebin
- txt.fyi - Markdown Pastebin
- MarkdownPastebin - Markdown Support
- Sparked Paste - Plain Text / Syntax Highlighting
- Riseup Pad - WYSIWYG Pastebin
- WriteXO - WYSIWYG Pastebin
▷ Translators
- Note - Chatbots like ChatGPT and Claude can also translate text, and are sometimes better than the ones listed below.
- ⭐ DeepLX or DeepL - AI-Based
- ⭐ Kagi Translate, Google Translate / Extension, Lingva Translate or GTranslate / API - Translation Sites
- ⭐ /r/Translator - Translation Request Community
- ⭐ Translate Web Pages - Browser Extension
- Argos - Translation Apps
- Translate Shell - Translation CLI / GitHub
- OnlineDocTranslator - Document Translator
- Matecat - Online Translation Editor
- LingoJam - Create Translator
- Renpy Translator or Renpy Editor - Ren'py Automatic Translator / Editor
- Translator++ - Automatic Translator / Editor
- Eazypo or Poedit - Translation Editor
- OmegaT - Translation Memory Tool
- Morsecode World or MorseDecoder - Morse Code / Binary Translators
- Emojify - Emojify Text
- Simple Translate - Browser Extension
- Linguist Translator - Browser Extension
- ImTranslator - Browser Extension
- Papago
- Libretranslate / 2
- ImmersiveTranslate / Extension
- Translate.com
- MyMemory
- Nice Translator
- Yandex Translator
- Bing Translator
- Reverso
- babelfish
- translation2
- collinsdictionary
- translatedict
- Translator.eu
- Textractor - Game / Visual Novel Translator
▷ Audio Transcription
- 🌐 ASR Leaderboard - Speech to Text Leaderboard
- Whisper - Audio Transcription / WebUI, 2
- mp4grep - MP4 File Transcription Tool
- SpeechTexter, VoiceToText, Dictation, oTranscribe or TalkTyper - Browser-Based Speech-To-Text Tools
- Revoldiv or Turboscribe - AI-Based Transcriptions
- Vibe - Audio Transcription Software
- Buzz - Audio Transcription Tool
- WhisperX - Audio Transcription Tool
- SpeechNotes - Speech Recognition Notes App
- LilySpeech - Fast Voice-To-Text Software
- VoiceNotebook - Speech Transcription Notebook
▷ Encode / Decode
- 🌐 DecodeUnicode - Unicode Decoding Database
- ⭐ CyberChef - Encode / Decode Text / GitHub
- ⭐ Base64 Decode or Base64 Editor - Encode / Decode Base64
- ⭐ Auto Decoder - Auto-Decode B64 Links on Pastebins
- Ciphey - Automated Decryption Tool
- Universal Encoding Tool - Encode / Convert Text
- cryptii or DenCode - Text / URL Encoding
- Coder - Text / File / URL Encoding
- Online Tools - Text / URL Encoding and Decoding
- URL Decode / Encode - URL Encoding / Decoding
- Base64 Repair - Fix Broken Base64
- Base64 Extensions - Chrome, 2, 3 / Firefox
▷ Grammar Check
- Note - Most chatbots in the AI section can also check grammar.
- ⭐ LanguageTool
- Writing Tools - Desktop App
- DeepL Write
- QuillBot
- Scribens
- EditGPT - Sign-Up Required
- Grammarly - Sign-Up Required / Extension
- ProWritingAid - Sign-Up Required
- Outwrite - Sign-Up Required
▷ Text Rephrasing
- ⭐ QuillBot AI or Rewritify - AI-Enhanced Text Rephrasing
- ⭐ Paraphrasetool or Rephrasely - AI Text Rephrasing / Generation
- ⭐ Goblin.tools - Transform Text with Spiciness Levels
- Paraphraser - Multilingual Text Rephrasing
- Paraphrase-Online, Paraphrasingtool, Henshu or WriteFull - Versatile Text Rewriting
▷ Emoji Indexes
- ⭐ Emojipedia, EmojiDB, Slackmojis, Emoji Picker or EmojiBatch - Emoji Indexes
- Emoji Engine - Multilingual Emoji Search
- winMoji - Emoji Managers
- EmojiRequests - Custom User-Made Emojis
- Cult of the Party Parrot - Party Parrot Emojis
- Pepe Server Archive - Pepe Emojis
▷ Unicode Characters
- ⭐ Amp What
- CopyChar
- Unicode Table
- Unicode Explorer
- Character Map
- Unifoundry
- Cool Symbol
- emotes.io, CuteSymbols, 2 or GetSymbol / 2 - Copy Unicode Emotes
▷ Typing Lessons
- ⭐ Monkeytype - Customizable Typing Tests / Discord / GitHub
- Typing Guide - In-Depth Typing Guide
- Typing.io - Typing Practice for Programming / Sign-Up Required
- Typ.ing, Typings or typing.works - Typing Tests
- keybr - Typing Practice
- CyberType - Typing Practice
- Typing.com - Typing Lessons
- Typing Club - Touch Typing Lessons
- typing.academy - Typing Lessons / Requires JavaScript Enabled
- TypeRacer, ZType, TypeRush or ARRRType - Typing Games
- NGram Type, KeyZen MAB or Keyzen Colmak - Touch Typing Tests
- TypeLit.io or Entertrained - Book Typing Tests
- Colemak Academy - Alt / Custom Keyboard Tests
- TypingStudy or TypeFast - Multilingual Typing Tests
- 10fastfingers - Typing Competitions
► Text Editors
- 🌐 List of Text Editors - Text Editor / Notepad Index
- ↪️ Android Text Editor
- ↪️ Code Editors / IDEs
- ↪️ Markdown Editors
- ⭐ Notepad++ / GitHub or NotepadNext - Notepad & Code Editor / Markdown
- EncryptPad - Encrypted Text Editor / GitHub
- Notepads - Text Editor / GitHub
- FastNotes - Text Editor / GitHub
- Kompad - Text Editor / GitHub
- Sublime Text - Text Editor / Patcher / Package Manager
- Zim Wiki - Wiki Text Editor
- tomboy-ng - TomBoy-Based Text Editor
▷ Note-Taking
- ↪️ Android Note-Taking
- ⭐ Obsidian - Markdown Note-Taking / Discord
- ⭐ Obsidian Tools - Resources / Publish Notes / Web Clipper / Google Drive Sync / ChatGPT Addon / Guides / Forum
- ⭐ Notion - Note-Taking
- ⭐ Notion Tools - Themes / Templates / Resources, 2 / Guide / Markdown Extractor
- ⭐ Notesnook - Note-Taking / GitHub
- ⭐ AnyType - Note-Taking
- ⭐ Logseq - Outlining
- Mochi Cards or Silicon - Note-Taking / Study Tools
- Flotes - Markdown Note-Taking
- QOwnNotes - Markdown Note-Taking
- AFFiNE - Note-Taking / GitHub
- vNote - Markdown Note-Taking / GitHub
- Tiddly - Info Manager / Desktop
- Trilium - Info Manager
- Org-roam - Info Manager
- Desklamp - Reading / Note-Taking / Highlighting Tool / Guide
- UseMemos - Note-Taking / Discord / GitHub
- Papers.IM - Note-Taking
- Joplin - Note-Taking / Firefox / Chrome / GitHub
- AppFlowy - Note-Taking / GitHub
- MicroPad - Note-Taking
- WriteDown - Note-Taking
- DocMost - Note-Taking
- KeyNote NF - Note-Taking
- SilentNotes - Note-Taking / GitHub
- Google Keep - Simple Notes
- StandardNotes - Encrypted Notes
- Saber - Handwritten Notes
- Butterfly - Handwritten Notes / Discord / GitHub
- Xournal++ - Handwritten Notes / GitHub
- BookStack or Siyuan - Self-Hosted Info Managers
▷ Office Suites
- ↪️ Office Activation / Guide / Custom Install Guide
- ⭐ LibreOffice - FOSS Office Suite
- ⭐ OnlyOffice - FOSS Office Suite
- ⭐ Microsoft Office - Office Suite / Removal Tool / Hot Keys, 2
- Calligra - FOSS Office Suite
- Office365Version - Office 365 Version History
▷ Online Editors
- ⭐ Simplenote - Local / Cloud Saves
- ⭐ Proton Docs - Local / Cloud Saves
- ⭐ takenote - Local Saves
- ⭐ Zen - Local Saves
- Leaflet - Cloud Saves / Customizable / Examples
- Browserpad - Local Saves
- Notepad - Local Saves
- onlinenotepad - Local Saves
- notepad-online.net - Local Saves
- ssavr - Local Saves
- notepad-online.com - Local Saves
- JustNotePad - Local Saves
- PasteePad - Local Saves
- Shrib - Local / Cloud Saves
- MemOnNotepad - Local / Cloud Saves
- Write Box - Local / Cloud Saves
- dDocs - Cloud Saves
- NimbleText - Cloud Saves
- ZippyJot - Cloud Saves
- KiloDoc - Cloud Saves
- TinyList - Cloud Saves
- Edit-Document - Local / Cloud Saves
- TextSlave - Cloud Saves
- GhostText - Cloud Saves
- AnyTextEditor - Cloud Saves
▷ Mind Mapping
- ⭐ Obsidian Canvas
- FreeMind
- Kinopio
- Freeplane
- Mindomo
- Yuque
- MindMapp
- are.na
- Domino
- GitMind
- xTiles
- Capacities
- bubbl
- Heimer
- Cubox
- vym
- markmap - Markdown Mind Mapping / GitHub
- Coggle - Collaborative
- CardSmith - Collaborative Mind Mapping
- Memrey - Collaborative Mind Mapping
- MindMeister - Collaborative Mind Mapping
- Slatebox - Collaborative Mind Mapping
▷ Text / Code Collaboration
- ⭐ Google Docs / HTML Converter
- ⭐ CryptPad
- ⭐ Kludd
- Mattermost
- Codeshare
- HackMD
- Taskade
- Socket
- Whimsical
- Ellipsus
- Etherpad
- SharePad
- Pixso
- FidusWriter
- overleaf
- Rustpad / GitHub
- OnlineInterview.io
▷ Spreadsheet Editors
- 🌐 MTEB Leaderboard - Text Embedding AI Leaderboard
- tad, Tree Sheets, Gnumeric or Quadratic - Spreadsheet Viewers / Editors
- Baserow, Framacalc, EtherCalc, NocoDB or AirTable - Collaborative Spreadsheets
- Jamovi - Statistical Spreadsheets
- Excel Practice Online - Excel Practice / Guides
- Excel Macro Mastery - Excel VBA Guides
- ExcelJet or Excel Functions - Excel Formulas
- Vertex42 - Excel Templates
- Plain Text Table - Text Tables
- EditCSVOnline - Online CSV Editor
- SubjectiveSort - Create Ranked List from CSV
- VisiData - Spreadsheet CLI Editor
- Structifi - Convert Files to Structured Data
- TadViewer - View / Analyze Tabular Data
▷ Writing Tools
- 🌐 Author Stash - Writing Tools / Resources
- ↪️ AI Text Generators
- ⭐ Writer, FocusWriter, Writemonkey, blank.page, Telegra.ph, Aurelius, ZenPen, Write.as, Owri, WriteSpace or WriteNext - Distraction-Free Writing
- ⭐ Manuskript - Writing Organizer / Planner
- ⭐ NovelWriter or Bibisco - Novel Editors
- ⭐ Linked, journaltxt, Gekri, Microsoft Journal, Diarium, Gemlog or jrnl.sh - Journal Apps
- ⭐ ChaoticShiny, Seventh Sanctum, Notebook.ai or WorldAnvil - Fantasy Writing Generators
- Tuesday JS - Visual Novel Editor / GitHub
- RenPy - Visual Novel Editor / GitHub
- Fortelling or Novelist - Novel Plotting / Editing Workspaces
- Infinite Story, Strand, Agora or WriteAlong - Collaborative Writing / Feedback
- LanguageIsAVirus or MDWA - Writing Prompts
- Twinery - Interactive Non-Linear Story Creator
- TextUSM - User Story Map Generator / GitHub
- Blackout Poetry - Blackout Poetry Creator
- Idyll - Create Interactive Essays / GitHub
- STARC, WriteSolo or Celtx - Script / Screen Writing Tools
- Rarebit - Webcomics Template
- Fantasy Name Generators - Fantasy Name Generators
- PolyGlot or VulgarLang - Spoken Language Construction Tools
- How to annotate literally everything - Annotation Tools / Resources
- Label Buddy - Annotation Tool / GitHub
- rNote - Annotation Tool / GitHub
- MonsterWriter - Thesis Writing / Note-Taking
▷ To Do Lists
- ↪️ Android To-Do Apps
- ⭐ Goblin.tools - Automatic Task Breakdown
- ⭐ TickTick / Premium
- ⭐ Super Productivity
- Columns or ChecklistGenerator - Checklists
- YearCompass - New Years Resolution Booklet
- daily.place
- SuperList
- dooit / Extras
- ToDo List / GitHub
- Diry AI
- Fokus
- OpenToDoList
- Microsoft To Do
- NullBoard
- LunaTask
- ToDoZero
- LifeAt
- Tasks
- Taskwarrior
- Vikunja
▷ ASCII Art
- ⭐ TAAG, DeepAA, Kammerl, ASCII Art Studio or ASCII Today - ASCII Art / Text Generators
- REXPaint, Playscii or PabloDraw - ASCII Editors
- ASCII Paint - ASCII Paint Tool
- ascii-art-generator, asciiart, ascii-image-converter, Monospace, ITOA, text-image or ASCII-art-creator - Image to ASCII Art
- Love ASCII, asciiart.eu, EmojiCombos, 16colors, ascii.co or RoySAC - Browse / Copy ASCII Art
- Image to Braille - Convert Images to Braille
- AnsiLove or convert-ascii-to-image - ANSI / ASCII Art to PNG Converters
- lvllvl or Petmate - C64 PETSCII Image Editor
► Fonts
- ⭐ Nerd Fonts - Icon-Rich Developer / Terminal Fonts
- OpenDyslexic - Typeface for Dyslexia
- Typewolf or Typ.io - Trending Website Fonts
- Cava's Pixel Resources - Pixel Fonts
- Oldschool PC Fonts - Oldschool PC Fonts
- FiraCode, Cascadia Code or Maple Font - Monospace Fonts
▷ Open Source / Freeware
- ⭐ FontSource - Open Source
- ⭐ Font Squirrel - Commercial Use
- ⭐ DaFont - Freeware
- ⭐ 1001 Fonts - Freeware
- Modern Fonts Stacks - Collection of CSS System Font Stacks
- Velvetyne - Open Source
- uncut.wtf - Open Source
- Beautiful Web Type - Open Source
- FontRepo - Open Source
- Bunny Fonts - Open Source
- Google Fonts - Commercial Use / Tags / Privacy-Friendly API
- FontShare - Commercial Use
- Fontlot - Freeware
- Fontsly - Freeware
- Fonts4Free - Freeware
- FontSpace - Freeware
- Online Fonts - Freeware
- CDNFonts - Freeware
- Fontesk - Freeware
- FontStruct - Freeware
- iFonts - Freeware
- DownloadFonts - Freeware
- AbstractFonts - Freeware
- FontGet - Freeware
- FreeFontsDownload - Freeware
- Fonts2u - Freeware
- Awwwards - Freeware
- GlukFonts - Freeware
- Iconian - Freeware
▷ Free Fonts
- ⭐ Fonts CSE - Multi-Site Font Search
- ⭐ Font Piracy 101 - Font Download Guide
- ⭐ Font Drives
- ⭐ BeFonts
- Windows Fonts
- Free Fonts Family
- Cufon Fonts
- FontsFree
- DFonts
- Font Spring
- FFonts
- FontsHub
- Font Meme
- FONToMASS
- 1.5_million_fonts
- Mr.E-Fonts
- psd_fonts
- 1001 Free Fonts
► Font Tools
- ⭐ Font Interceptor - Download Fonts from Websites
- ⭐ FontDrop - Analyze Font Files
- ⭐ Adobe Fonts, Font Finder, WhatTheFont, Identifont, WhatFont - Font Identification Tools
- Fonts Ninja - Font Identification Extension
- Unicode Explorer or Compart - Unicode Character Identification
- Transfonter - Create CSS @font-face Kits
- TypeRip - Adobe Font Ripper / GitHub
- FontBase, NexusFont or Font Manager (Linux) - Font Managers
- Colors & Fonts - Typography Tools
- DS-Fusion - AI Typography Generator
- Formito - Typography Logo Maker
- Type Terms - Typography Cheat Sheet
- The Good Line-Height - Typography Scaling Editor
- Font List or So You Need A Typeface 2.0 - Examples of Font Styles
- Type Design Resources or Free Faces - Typeface Resources
▷ Font / Text Generators
- ⭐ FontoGen - Custom AI Font Generator
- ⭐ Make WordArt, FlameText, MakeText, TextGiraffe, Text Pro or CoolText - WordArt Generators
- Polona Typo - Generate WordArt from Book, Poster, & Map Letters
- Text Color Fader - Rainbow Text Generator
- TextDrom, 3DText2GIF or TextStudio - 3D / Animated Text Generators
- Textanim or Space Type Generator - Animated Text Generators
- Batname - Batman (2022) Text Generator
- NFG's Arcade Font Maker or Arcade Font Writer - Arcade Text Generators
- Glitch - Zalgo Text Generator
▷ Font Customization
- ⭐ TypeTrials - Variable Font Playground
- V-Fonts or Phase - Variable Fonts Testers
- enFont or Calligraphr - Custom Font Creators
- Fontjoy - Generate Font Combinations
- FontSprite - FontSprite Editor
- BitFontMaker2 - BitMap Font Editor
- FontEdit, metaflop, MFEKglif, Glyphr Studio, Birdfont, Universal Sans or FontForge - Font / Typeface Editors
▷ Unicode Text Generators
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 9e69e420:d12360c2
2025-01-30 12:13:39
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c9badfea:610f861a
2025-05-13 00:17:07
@ c9badfea:610f861a
2025-05-13 00:17:07► File Tools
- ↪️ File Scanners
- ⭐ Fileinfo, Filext or OpenMyFiles - File Extension Libraries
- ⭐ czkawka or dupeGuru - Duplicate File Finders
- ⭐ Phockup - Organize Photo / Video Files by Date
- UnLock IT or Lock Hunter - File Unlocker / Deleter
- Magika - AI File Content Type Detector
- Icaros - Add Explorer Thumbnails to any Video Format
- Tagging for Windows - Tag-Based File System
- HTTPDirfs or hfs / 2 - HTTP File Systems
- WinBtrfs - Btrfs File System
- mergerfs - Union File System
- filebrowser - Online File Viewer
- WhatsLink - View File Download Metadata
- File-Examples - Dummy File Examples
- OpenHashTab - Compare / Display File Hashes
- Attribute Changer - Edit File & Folder Properties
- TagSpaces - Add Tags to Files and Folders
- SKTimeStamp - Change File Created / Modified Time
- ExtractMetadata or Metadata2Go - Metadata Viewers / Editors
- CUETools - Manupulate .cue Files / GitHub
▷ Download Managers
- ⭐ JDownloader - Download Manager / Debloat / Dark Theme, 2 / Dracula Theme / Apps
- ⭐ IDM - Download Manager
- AB Download Manager - Download Manager / GitHub / Telegram
- Go Speed - Download Manager / Extension / Plugins / GitHub
- aria2 or Persepolis - Terminal Download Manager / GitHub / Download Bot / WebUI, 2
- pyLoad - Lightweight Download Manager
- Hitomi - Multi-Site Media Download Tool
- ArrowDL - Download Manager / GitHub
- FDM - Download Manager / YTDL Addon
- File Centipede - Upload / Download Manager
- DownThemAll - Download Management Extension
- HTTP Downloader - Download Manager for HTTP / FTP / SFTP Protocols / GitHub
▷ Archiving / Compression
- 🌐 SuperCompression - File Compression Resources
- ⭐ NanaZip or 7-Zip - File Archiver
- ⭐ PeaZip - Cross Platform File Archiver
- ⭐ CompactGUI - Transparent Compression
- Fileforums or Encode - Data Compression Forums
- TurboBench - Compression Benchmark
- WinRAR, 2 - File Archiver / Licenses
- Efficient Compression Tool or Minuimus - File Archivers / Optimizers
- ezyZip - Zip Files Online
- unzip-online - Unzip Files Online
- Unrar online - Unrar Files Online
- UPX - Executable File Compressor / GitHub
- lessmsi - .msi Content Extractor / GitHub
▷ File Converters
- 🌐 .to Sites - File Converters Index
- ⭐ File Converter - Convert / Compress Files / GitHub
- ⭐ VERT / Discord / GitHub
- Pandoc - Document Converter
- ConvertCSV - Online CSV Data Conversion
- Encoding Converter - Online File Encoding Converter
- Deark - Decode and Convert Files / GitHub
- text2img - Online NFO Files to Image Converter
- CloudConvert - Convert Files / 1GB
- FreeConvert - File Converter / 1GB
- videoutils - File Converter / 500MB
- Xconvert - File Converter / 400MB
- ConvertFiles - File Converter / 250MB
- Convertio - File Converter / 100MB
- AnyConvert - File Converter / 100MB
- onlineconvertfree - File Converter / 100MB
- MiConv - File Converter / 75MB
- Converter 365 - File Converters / 200MB
- Aconvert - Various Converters / 40MB
- LetsConvert - Image/Audio Converter / 250MB
- Online Convert - Online File Converter
- Zamzar - File Converter / 200MB
- Online Converter - Online Simple Media / Unit Converter
- Convert Town - Online Text / Image Converter
- Docspal - Various Converters / 50MB Image, Documents / 200MB Video, Archive, Audio
- Better Converter - Text-Focused Converters / 10MB
- go4convert - Online Document Converter / 100MB
▷ File Explorers
- ⭐ Files - Customizable File Manager / Use Classic Installer / Discord
- ⭐ Directory Opus - Windows File Manager
- Xplorer / GitHub / Discord, DoubleCMD or muCommander - Cross Platform File Explorers
- Sigma - Modern File Manager for Windows / Linux / GitHub
- ChromaFiler - Column-Based Windows File Manager
- Yazi - Terminal File Explorer / Plugins / GitHub
- One Commander - File Explorer
- Free Commander - File Explorer
- Q-Dir - File Explorer
- Quick Access Popup - File Explorer
- FileExplorer - File Explorer
- FileStash - File Manager / GitHub
- Explorer++ - Lightweight Windows File Manager
- Far Manager - Windows File / Archive Manager
- Total Commander - Shareware Windows File Manager
- Organize - Automated File Manager
- TrayDir - System Tray File Manager
- TablacusExplorer, QTTabBar or Multi Commander - Tab File Managers
- Vifm - Vim-Based File Manager
- WinSetView - Globally Set Explorer Folder Views
▷ File Searching
- ⭐ Everything - File Search Engine
- Recoll / Addon, Spyglass, DocFetcher or Orange - Cross Platform Search Engines
- AnyTXT or FluentSearch - Windows Search Engines
- AstroGrep, grepWin or dnGrep - Windows GUI Grep Utilities
- fselect - SQL-like Search Engine
- fd - User Friendly "find" Alternative
- sist2 - Simple Incremental Search Tool
▷ File Encryption
- ⭐ Cryptomator / GitHub or Tahoe-LAFS / GitHub - Cloud File Encryption
- ⭐ VeraCrypt - Disk Encrypter
- ⭐ Picocrypt - Lightweight File Encrypter
- age - File Encrypter
- gocryptfs - File Encrypter
- Hat - Browser-Based Encrypter
- Kryptor - File Encrypter
▷ File Sync
- ⭐ SyncThing - Cross-Platform File Sync / Tray Support / GitHub
- ⭐ FreeFileSync - Open-Source File Sync
- MyPhoneExplorer, SyncFolder - Phone and Desktop Sync
- allwaysync - File Sync Utility
- Resilio - P2P File Sync
- SmartFTP - FTP File Sync
- rsync - Command-line File Sync / GitHub
- Unison - Bidirectional File Sync
▷ File Backup
- ⭐ Kopia - Encrypted File Backup / GitHub
- ⭐ Rescuezilla or CloneZilla - Disk Image Backup
- FolderClone or Echosync - Folder Clone / Backup
- BackupPC - Networked File Backup
- TeraCopy - File Backup
- restic / GitHub, duplicity or Duplicati - Secure File Backup
- UrBackup - Client / Server File Backup
- AOMEI Backupper - Windows File Backup
- Borg - De-duplicating File Backup
- USBImager - USB Image Backup
- Toucan - Portable File Backup
▷ File Recovery
- ⭐ TestDisk - File Recovery
- PhotoRec - File Recovery
- DMDE - File Recovery
- Windows File Recovery - File Recovery
- MultiPar - Prevent File Corruption / Guide
- ShadowExplorer or ShadowCopyView - Shadow Copy Explorers
▷ Formatting / Deletion
- ⭐ SDelete - File Deletion CLI
- Eraser, File Shredder, Alternate File Shredder, Permadelete or Delapp - File Shredding
- SSuite File Shredder and Burner - File Shredder with Disk Burning
- Low Level Format, nwipe or ShredOS - Complete Hard Drive Erasers
- RED - Remove Empty Directories
▷ Data Automation
- ⭐ Advanced Renamer or Bulk Rename Utility - Bulk Renamers
- FoliCon - Automatic Custom Media Icons / Folders / GitHub
- MediaMonkey - Media Organizer
- MediaInfo - Media File Analysis / Online
- tinyMediaManager or MediaElch - Media Collection Managers
- FileBot - Media File Renaming
- TVRename - TV File Data Automation
- Shoko - Anime File Data Automation
- PowerRename, Szyszka, F2, Ant Renamer or Flut Renamer - Bulk Renamers
► PDF Tools
▷ Online PDF Toolkits
▷ Offline PDF Toolkits
- ⭐ PDFGear
- PDF24
- Foxit / Pro / Warning
- xPDFReader
- PDF Arranger
- PrivatePDF
- PDFBox
- OpenPDF
- Stirling-PDF
▷ PDF Conversion Tools
- Rare2PDF, online2pdf or 2PDFConverter - File to PDF Conversion
- MD2PDF - Markdown to PDF Converter
- PDFconvert - PDF File Converters
- Marker - PDF to Markdown
- PDFCrowd, TailWindPDF or wkhtmltopdf - HTML to PDF / Image Converter
- Issuu - Convert PDF Files to Webpages, Flipbooks, Brochures & More / Downloader, 2
- WebToPDF or Percollate - Webpage to PDF Converters
- Dangerzone - Convert Malicious PDFs to Safe Files / GitHub
▷ PDF Utilities
- PDFGrep or OCRmyPDF - PDF Text Search
- View-only PDF - Download View-Only PDF on Google Drive
- PDFEncrypt - PDF File Encryption
- GraphPaper - PDF Graphs
- Aspose or pdf-unstamper - PDF Watermark Remover
- PDF Fixer - Repair Damaged PDFs
- OpenSign, FalsiScan, JustSignPDF or Adobe Sign - PDF Signature Tools
- Google Drive PDF Downloader - Download Protected Google Drive PDFs
- PDFCoffee - Upload PDF, Word or PowerPoint Files
- PrintFriendly - Printer Formatting Tools
► File Transfer
- ⭐ LocalSend - Desktop / Mobile Transfer / Discord / GitHub
- Photon - Desktop / Mobile Transfer / GitHub
- KDE Connect - Desktop / Mobile Transfer
- Warpinator - Desktop / Mobile Transfer
- Sefirah - Desktop / Mobile Transfer
- QRServ - Desktop / Mobile Transfer / GitHub
- Magic Wormhole - Desktop / Mobile Transfer
- croc - Desktop / Mobile Transfer / GUI
- LANDrop - Desktop / Mobile Transfer
- OnionShare - Share Files Over Tor Network
- FileZilla - FTP Client
- WinSCP - FTP Client
- Wing FTP - FTP Client
- Xlight - FTP Client
- IPFS or kubo - P2P Hypermedia Protocol
- IPFS Tools - Resources, 2 / Extension / Desktop / IPFS Cluster
▷ P2P Transfer
- ⭐ Blaze / GitHub
- ⭐ PairDrop / GitHub
- ⭐ JustBeamIt
- ⭐ SpaceDrop
- Surge - P2P App
- Wormhole
- ToffeeShare
- new.space
- FilePizza
- TransferNow
- Horizon Send
- Salad Room
- drop.lol / GitHub
- sendfilesencrypted.com
- LIGHTNING SHARE
- rDrop
- WebDrop
- MyAirBridge.com
- Sprend
- WebWormhole
- EchoDuck
- FileLove
► File Hosts
- Note - Keep in mind that it's never a good idea to upload personal or confidential files to any file host, even if they claim to be encrypted. Most file hosts only remove files after inactivity, while some delete them regardless. Check each host if you're concerned about file expiry. Tags are: Storage Size / File Size / Expiry.
- ↪️ Video File Hosts
- ⭐ Gofile - 100GB Monthly / Unlimited / 10 Days After Last Download / Cold Storage Bypass
- ⭐ Pixeldrain - Unlimited / 20GB per File / 120 Days After Last Pageview / Discord / Speedtest / Limit Bypass / Bypass Script
- ⭐ Files.vc - Unlimited / 10GB / Forever / Discord
- ⭐ Buzzheavier, 2, 3, 4 - Unlimited / 8 Days, Can Extend Forever / File Expiry / Use Adblocker / Discord
- ⭐ Catbox - Unlimited / 200MB / Forever
- ⭐ Pillowcase - Audio File Host / 200MB (500MB w/ Account) / Forever
- HIDAN - Unlimited / 10+ Days (from upload)
- Send.now - 100GB / 100GB per File / 30 Days After Last Download
- DesiUpload - Unlimited / 15 Days (15GB / 30 Days w/ Account)
- MixDrop - Unlimited / 60 Days / Account Required
- Qiwi - Account Required
- Fastupload.io - Unlimited / 30 Days (60 Days w/ Account)
- 1fichier.com - 300GB / 15 Days (30 Days w/ Account)
- Filebin - Unlimited / 6 Days / Warning
- file.kiwi - Unlimited / File Expiry Explanation
- Easyupload.io - 100GB / 30 Days
- FEX.NET - 100GB / 7 Days
- VikingFile - 500GB / 20 Days After Last Download
- DropMeFiles - 50GB / 14 Days
- GigaFile - 300GB / 100 Days
- UploadNow - 100GB / 7 Days, Can Extend Forever
- eDisk - 20GB / 30 Days
- Drop Download - 25GB / 90 Days / Account Required
- SwissTransfer - 50GB / 30 Days / 250 Downloads
- BowFile - 20GB / 20 Days
- Hexupload or AnonTransfer - 15GB / 30 Days
- Tempcloud - 10GB / 3 Days
- GrosFichiers or DataTransfer - 10GB / 14 Days
- Fshare - 10GB / 5 Days
- ShareFile, 2 - 5GB / Unlimited
- FileTransfer.io - 6GB / 21 Days / 50 Downloads
- udrop - 5GB / Forever
- Uploadev - 10GB / 180 Days After Last Download w/ Account
- Imagenetz - 5GB / 30 Days After Last Download
- FilePort - 5GB / 7 Days
- FileDitch or SendGB - 5GB / 90 Days
- MegaUp - 5GB / 60 Days
- Bestfile - 5GB / 80 Days After Last Download
- ufile.io - 5GB / 30 Days
- Internxt Send - 5GB / 15 Days
- UserDrive - 5GB / 65 Days
- pCloud Transfer or Tresorit Send - 5GB / 7 Days / Email Required
- Temp.sh - 4GB / 3 Days
- File Convoy - 3GB / 21 Days
- Send - 2.5GB / 3 Days / 10 Downloads / CLI / Instances
- JUMBOmail - 2GB / 7 Days / Email Required
- KrakenFiles - 1GB / 3 Months on Sign-Up
- DropMB - 512MB / 5 Years
- FireLoad - 2GB / 60 Days / Account Required
- FileGo - 2GB / 30 Days / Account Required
- Lufi - 2GB / 30 Days
- FilesPayouts - 10GB / Forever / Account Required
- DooDrive - 2GB / 30 Days / Account Required
- Clicknupload, 2 - 10GB / 8 Days / Account Required
- WeTransfer - 2GB / 3 Days
- Smash - 2GB / 7 Days / Email Required
- MultiUp.io / Extract / Upload or Mirrored.to - Multi Host Uploaders
- Z-o-o-m - Multi-Host Upload Desktop App
- Limited Upload Hosts - More Hosts / 1GB or Below
▷ Cloud Storage
- Note - Monthly prices are based on annual plans. 2TB prices are halved for comparison if a 1TB plan doesn't exist for a service.
- 🌐 Eylenburg Comparisons or ComparisonTabl.es - Compare Cloud Storage Sites
- ⭐ Google Drive - 15GB Free / 2 Years / ~$3 for 1TB
- ⭐ mega - 20GB Free / 3 Months / ~$4.50 for 1TB / GitHub
- disk.yandex - 5GB Free / 2 Years / $2 for 1TB
- filen - 10GB Free / 3 Months / ~$8 for 1TB / Account Required for Sharing
- terabox - 1TB Free / $3.50 for 2TB
- Dropbox - 1 or 2GB Free / 12 Months / ~$5 for 1TB / Client
- mediafire - 10GB Free / 8 Months / $5 for 1TB
- icedrive - 10GB Free / 3 Months / $5 for 1TB
- PCloud - 10GB Free / 1 Year / ~$4 for 1TB
- FebBox - 1TB Free / 1 Month / ~$4 for 2TB
- Proton Drive - 2GB Free (or 5GB for tasks) / 1 Year / ~$10 for 1TB
- JumpShare - 2GB Free / 1 Year / $8.25 for 1TB
- FileLu - 10GB / Forever / Expiry Warning
- CyberFile - 10GB Free
- MrOwl - 10GB Free / ~$16 for 1TB
- Blomp - 20GB Free / 1 Month / ~$3 for 2TB
- Akira Box - 20GB Free / 1 Years
- Backblaze B2 - 10GB Free / ~$6 for 1TB
- Cloudflare R2 - 10GB Free / ~$15.5 per 1TB
- 1Cloud File - 10GB Free
- OneDriveFly - OneDrive Indexes
- Fix-OneDrive-Zip - Fix OneDrive Zip Files >4GB
- SeaFile - Self-Hosted Cloud Storage
▷ Cloud Managers
- ⭐ Rclone - Cloud Storage Manager
- ⭐ Rclone Tools - Guide / Colab / Telegram / Transfer Tool
- ⭐ gclone - Cloud Storage Manager
- ⭐ Air Explorer - Cloud Storage Manager
- ⭐ RaiDrive - Cloud Storage Manager
- ⭐ Cyberduck - Libre Server / Cloud Storage Browser / GitHub
- SpaceDrive - Cloud Storage Manager
- AList - Cloud Storage Manager
- MultCloud - Cloud Storage Manager
- xpipe - Remote File Manager
▷ Google Drive Tools
- ⭐ OneClickRun - Google Drive Tools Colab / Features / Use Throwaways
- Any File to Google Drive - DDL to Google Drive Tool
- DriveUploader - Receive Files via Google Drive
- ZIP Extractor - Google Drive / Gmail File Archiver
- Google Drive CLI - Google Drive CLI Client
- goodls - Google Drive Downloader
- Google Drive Downloader - Google Drive Folder Downloader
- gdrivedl - Google Drive Python Download Script
- ISAAC - Google Service Account Generators
- goindex-extended / Themes or Google-Drive-Index - Google Drive Indexers
- gdurl, GDrive Link Generator, Direct.GDrive, Maulvi or GDriveWebAppPublic - Host Direct Links on Google Drive
- GdriveCloneWeb or Google Drive Clone Bot / GitHub - Copy Google Drives
- GD-EFC Link Encryptor - Google Drive Link Encryptor for GD-EFC
- gd-efc - Copy Encrypted Google Drive
- DriveRename - Bulk Google Drive File Rename
- Sharer, YuShare or GDToT - Google Drive File Sharing
▷ MEGA Tools
- ⭐ Megabasterd - Download Quota Bypass / Note
- ⭐ Mega Account Generators - Account Gen / Unlimited Upload Size / Fix
- MEGA Desktop / GitHub - Official GUI App
- MEGA CMD / GitHub - Official CLI App
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ c9badfea:610f861a
2025-05-13 00:19:14
@ c9badfea:610f861a
2025-05-13 00:19:14► Social Media Tools
- 🌐 alternative-frontends, Farside / 2 or PrivacyRedirect - Frontend Indexes
- ↪️ Android Social Media Apps / iOS
- ⭐ GrayJay - Combines YouTube, Twitch, Rumble, etc. / Guide
- ⭐ SocialBlade - Social Media Stats
- ⭐ LiveCounts - Live Social Media Stats
- ⭐ LibRedirect / GitHub, Predirect or Proxy Redirect - Frontend Redirect Extensions
- Numblr - Self-Hosted Frontend Redirect
- Proxitok, Urlebird or OffTikTok - TikTok Frontends
- Social-Searcher, WeVerify or Social Media CSE - Social Media Search Engines
- Social Media Hacker List - Social Media Apps / Tools
- ExportComments - Export Social Media Comments
- socid_extractor - Extract Social Media User Info from Pages
- BlackTwist - Free Threads Analytics
- Schedul - Threads Content Publishing & Scheduling
- Mind Your Banners - Social Media Banner Design
- CleanSnap - Customize Social Media Screenshots
► Discord Tools
- Warning - Misuse of chat archivers, mass-deleters, mods or third-party clients is against Discord's terms of service, so use at your own risk.
- ⭐ embeds.video, x266, Stolen Shoes, embedez or Discord Embedder - Discord Video Embedders
- ⭐ Disblock Origin or Discord Adblock - Hide Nitro / Boost Ads
- ⭐ Revolt / Bots / Resources or Guilded - Discord Alternatives
- ⭐ OpenAsar - Improved Discord Desktop's Asar / Discord / GitHub
- AnswersOverflow - Discord Search Engine
- DiscordFS - Discord File Search
- Discord Downloader Go - Discord File Downloader
- Toolscord, discord.id or Discord Avatar - Avatar Downloaders
- Disbox - Discord Cloud Storage
- Discrub - Message Manipulation / Export Tool
- Discord Chat Exporter / Python or Discord History Tracker / GitHub - Archive / Export Discord Chats
- Wumpus Central - Discord Experimental Server Hub
- SimpleDiscordCrypt - Discord Message Encryption
- Permissions Calculator - Generate Discord OAuth Invites
- dsc.gg - Create Custom Discord Invites
- Discord Previews - New Discord Builds / Changes
- instaparty - Temporary Discord Servers
- Discord Templates - Discord Server Templates
- Discord UI Mockup - Discord UI Mockups
- discord-badges - Discord Badges Image Files
- Discord Creation Date Check - Check Creation Date of User / Channel / Server
- Discord Lookup - Look up a Discord User or Bot ID
- Guild Counter - Check How Many Servers You're In
- Discord Dev Badges, active-developer-badge or GiveMeBadge - Unlock Discord Dev Badges / Script
- Discord-Api - Discord API Chat
- Discord-Datamining - Discord Datamining via JS Files
- Discord TTS Bot - Text to Speech for Discord
- Discord Webhooks Guide - Webhooks Guide
- Webhooker - Simple Webhooks App
- Embed Visualizer - Preview Embeds
- BetterTwitFix - Fix X.com / Telegram Embeds
- 8mb.video or @Snooober's Script - Encode Videos to <8MB
- Discord Packages - View Discord Packages / Self Host for Privacy / Discord
- Soundboards.gg - Discord Soundboard Sounds
- Hammertime, Dank.tools, Timestamp Maker, discord-timestamps or discordtimestampgenerator - Discord Timestamp Generators
- TagMap - Meet People with Similar Interests
▷ Discord Clients
- 🌐 Discord3rdParties - Discord Clients Index
- ⭐ Vencord - Discord Client Mod / Discord / GitHub
- ⭐ WebCord - Privacy-Hardened Client / Discord
- Replugged - Discord Client Mod / Discord
- Legcord - Discord Client / Lightweight / Discord
- GoofCord - Privacy-Focused Legcord Fork
- BetterDiscord - Discord Client Mod / Discord / GitHub
- BetterDiscord Tools - Plugins / Banned Plugins / Nitro / Re-install Guide
- abaddon - Discord Client Mod / Lightweight / Discord
- Discordo - Discord Terminal Client
- Vesktop - Web Client w/ Vencord Preinstalled
- Spacebar - Self-hostable Discord Compatible Client
- Dorion - Lightweight Discord Client / GitHub
- Dissent - GTK4 Discord Client
- Discord Portable / PTB PortApps - Portable Discord Stable
▷ Client Customization
- 🌐 Client Themes or Discord Themes - Client Theme Index
- ⭐ Discohook, Embed Creator or Embed Generator - Embed Generators
- ⭐ CustomRP - Customizable Rich Presence
- BD Editor - Client Theme Editor
- ChromaDiscordApp - Chroma Light for Discord
- Overlayed - Alternative Discord VC Overlay / GitHub
- BeautifulDiscord - Custom CSS Support
- ansi-colors-discord.md - Discord ANSI Text Guide
- Coloured-Text-Generator - Discord ANSI Text Generator
- Auto Creative - Animated Icon / Banner Generator
- Discord Decorations - Free Discord Avatar Decorations
- Discord Avatar Maker - Discord Avatar Creator
- Better Default Discord - Improved Default Discord Avatars
- Pfps.gg - Find Discord Avatars
- usrbg - Custom Discord Profile Backgrounds
- Disgradient - Discord Folder / Role Color Gradients
- Nelly, mgcounts / Discord or Discord.band - Discord Server Tag Lists
- Emoji List - Discord Emojis / GIFs
- Discord-Emoji-Downloader - Emoji Downloader
- ImageClipboard, Slackmoji or emoji.gg - Free Discord Nitro Emojis
- Snowsgiving Icons & Emotes - Snowsgiving Event Icons / Emojis
- Discord Text to Emoji - Convert Text to Discord Emojis
- Stickers.gg - Free Discord Stickers
- PreMiD - Display Web Activity in Discord Status / GitHub / Discord
- Music Presence - Audio Player Rich Presence / Discord
- Jellyfin RPC - Jellyfin Rich Presence
- Adobe Discord RPC - Adobe Rich Presence
- PS3 Rich - PS3 Rich Presence
- discord-vscode - VSCode Rich Presence / GitHub
▷ Discord Bots
- ⭐ FreeStuff Bot - Free Games Alert Bot / Discord / Telegram
- FixEmbed - Fix Embeds on Discord Bot
- esmBot - Image / Music Bot
- NotQuiteNitro - Discord Nitro Alternative
- fmbot - Discord Voice Chat Scrobbling
- Chuu - Last.fm Discord Bot
- Craig - Voice Channel Recorder Bot / Backup
- MonitoRSS or ReadyBot - RSS Discord Bots
- Wallabot - Wallabag Discord Bot
- Discord Music Bot, Music-bot / Discord, Chip, MusicBot or EvoBot - Music Bots
- Steambase Bot - Steam Insights Bot
- Red Discordbot, Discord-Bot or Loritta - Self-Hostable Discord Moderation Bots
- Wickbot - Discord Security Bot
- anti-phishing-bot - Discord Anti-Phishing Bot
- Automod Config - Automod Bot Config
- Modmail - Discord Modmail Bot
- Discord-Linux - Linux Container Bot
▷ Server / Bot Indexes
- 🌐 Alternatives to MEE6 - MEE6 Alternatives / Discord
- UnFocused - Server Index / Discord
- DISBOARD - Server Index
- Discadia - Server / Bot Index
- Discords.com - Server / Bot Index
- Discord Me - Server / Bot Index
- Discord Servers - Server Index
- DiscordServers.com - Server / Bot Index
- Disforge - Server / Bot Index
- Open Source Projects - Server / Bot Index
- BotBlock - Bot Index
- Top.gg - Bot Index
- Bots on Discord - Bot Index
- Discord Bots - Bot Index
- Top Bots - Bot Index
- Infinity Bot List - Bot Index
- Discord Services - Bot Index
- DiscordBots - Bot Index
- Discord Bot List - Bot Index
- Carbon Bot List - Bot Index
- Botlist.me - Bot Index
- Void Bots - Bot Index
- Discord Botlist - Bot Index
► Reddit Tools
- ⭐ Reddit Stream - Live Thread Viewer
- ⭐ Reddit Enhancement Suite, Reddit++, Reddit Fix, Reddit Extension, RedditEnhancer or RedditMod2 - Reddit Enhancement Extensions / Scripts
- ⭐ Old Reddit Redirect - Redirect New Reddit to Old
- Redlib / 2 or Photon, reditr, RDX - Reddit Frontends
- Redditp or Reddit Viewer - Reddit TikTok Style Viewers
- Beleave or SubCleaner - Subreddit Cleaners / Managers
- Reddit Comber or Sub Notification - Reddit Keyword Notifications
- Reddit Preview - Preview Reddit Posts
- RedditRaffler - Reddit Raffle System
- SubTransfer - Export / Transfer Subreddits
- PowerDeleteSuite - Reddit Auto Post Delete
- SnooSnoop - Reddit Account Analyzer
- Reddit Emojis - Emojis for Old Reddit
- Subreddit Tabs - Subreddit Icon Tabs
- Reddit Comment Highlights - Highlight New Comments
- Newsit - Find Reddit Comments for any Webpage
- infini.wtf - Reddit Image Search
- Load Reddit Images Directly - Direct Image Viewer
- When to Post - Best Reddit Posting Times
- UniversalScammerList - List of Reddit Scammers
▷ Reddit Downloaders
- Note - You can also download Reddit videos by commenting "/u/SaveVideo".
- Viddit - Reddit Video Downloaders
- gallery-dl - Reddit Bulk Image Downloaders
- saveddit - Reddit Bulk Media Downloaders
▷ Reddit Alternatives
- ↪️ Lemmy Tools
- ⭐ Raddle - Minimalist / Privacy-Focused
- ⭐ Saidit - Free-Speech / Dual Upvote System
- /r/RedditAlternatives - Find Reddit Alternatives
- TheMotte - User-Driven Discussion
- Tildes - Non-Profit / User-Driven Discussion
- Scored - User-Driven Discussion
- Ramble - Privacy-Focused
- Squabblr - X.com / Reddit Style Alt
- Discuit - Centralized Reddit Alt with User Control
▷ Reddit Search
- ⭐ TheGigaBrain - Reddit Search Engines
- ⭐ Reddit Repost Sleuth - Reverse Post / Image Search
- ⭐ Undelete or Reveddit - View Deleted Reddit Posts / Comments
- New PullPush / 2 / 3, Samac or Better Reddit Search - Advanced Reddit Search
- Redditle - Reddit-Only Google Search
- Arctic Shift - Reddit Archive Dump Search / GitHub
- Reddit Dump Files - Reddit Comment Archives
- Expanse, redarcs or Rareddit - Reddit Post Archive Tools / Note
- RedditMetis, Reddit-User-Analyser or Redective - Reddit Profile Information
- rComments - Explore Comments / Replies without Clicking a Post
- ScrollDrop - Reddit Media Crawler
- Wiki Downloader - Reddit Wiki Page Scraper
- Find on Reddit - Find Discussions of the Current URL
- PullPush - Reddit Content API / Discord
▷ Subreddit Discovery
- 🌐 /r/ListOfSubreddits - Subreddits Index
- ↪️ Multireddit Indexes
- ⭐ Vizit, sayit, subreddit_map or SubredditMentionsGraph - Visualize Related Subreddits
- FindAReddit - Get Subreddit Suggestions / Subreddit
- Subreddit Calculator or redsim - Find Similar Subreddits
- Map of Reddit or Reddit Map - Subreddit Maps
- subreddits - Find Random Subreddits
- /r/Serendipity - Posts from Random Subreddits
- /r/wowthissubexists - Find Niche Subreddits
- Subreddit Stats or SubRanking - Subreddits Stats / Ranking
► Telegram Tools
- 🌐 TDirectory, Telemetr, Telegram Channels, Awesome Telegram - Telegram Channel Indexes
- 🌐 ComBot Groups - Top Telegram Groups Index
- Telegago, 2, Lyzem, xTea or TG-ME - Telegram CSEs
- SaveRestrictedContentBot - Save Restricted Content
- Telesco.pe - Telegram Round Video Recorder
- Video Stream - Telegram Video Player
- TGCF - Telegram Message Forwarding
- tg-channel-cloner-workers - Clone Telegram Channels
- tasra - Telegram Channel Archive
- Telegram Email - Email Alias Telegram Bot
- CHPic, Stickers Cloud, ComBot Stickers or moe_sticker_bot - Telegram Sticker / Emojis
▷ Telegram Clients
- ↪️ Android Telegram Clients
- ⭐ web.telegram / 2 / 3 - Web Client
- ⭐ Materialgram - Desktop Client / Portable
- ⭐ Unigram - Desktop Client
- TDesktop - Desktop Client
- TDesktop x64 - Desktop Client / Telegram
- VideoGram - Desktop Client
- AyuGram - Desktop Client / GitHub
- Pyrogram - Telegram API Client
- Telega.el - Telegram Emacs Client
- VanillaTG - Client Themes
▷ Telegram File Tools
- ⭐ Teldrive - File Manager / Uploader / Discord / GitHub
- File-Sharing-Bot / Telegram, TelegramCloud, easy_share_bot or UploadBot - Upload Files to Telegram
- MediaDownBot, WZML-X, Telegram Media Downloader, TopSaverBot, CatdlBot or DownloadsMasterBot - Media Downloaders
- Musvkrobot - Video Downloader
- GdriveXbot, google-drive-telegram-bot or Python Aria Mirror Bot - Google Drive Upload Bots
- SearchX - Google Drive Search Bot
- MEGA Uploader X or Mega-Bot - Remote Mega File Upload Bot
- OneDrive X - Remote OneDrive File Upload Bot
- MultiUpload-Bot - Telegram to File Host Upload Bot
- telegram-download-daemon - Download Large Telegram Files
- convrt_bot, FileConvertBot, newfileconverterbot or pdfbot - File Converters
- ILovePDF - Telegram File to PDF Converter
▷ Telegram Bots
- 🌐 BotsArchive, TelegramBotsList or borodutch.eth - Telegram Bots Indexes
- Now Playing - Now Playing Audio Bot
- Searchee Bot - Telegram Channel Search Bot
- Rose or GroupHelpBot - Telegram Group Managers
- TediCross - Telegram to Discord Bridge
- WatgBridge - Telegram to WhatsApp Bridge
- Mautrix - Telegram to Matrix Bridge
- Callmebot - Trigger Voice Calls or Chats
- Skeddy - Telegram Reminder Bot
- Reddit2Telegram - Reddit Post Bot
- rss2tg_bot or TheFeedReaderBot - RSS Feed Bots
- ShortUrlBot - Link Shortener Bots
- AiImageBot - Text to Image
- Shieldy Bot - Spam Protection Bot / GitHub
- ProxyBot, proxy_socks5_bot or ShadowSocks_bot - Telegram Proxy Bots
- /r/TelegramBots - Telegram Bots Discussion
► YouTube Tools
- ⭐ PocketTube or Kadium - Subscription Managers
- Youtube-shorts block or Shorts Deflector / GitHub - Play Shorts In The Normal Desktop Interface
- Remove YouTube Shorts or Hide YT Shorts Filter List - Hide YouTube Shorts
- YouTube Wrapped - Personal YouTube Rewind
- YouTube-Subscriptions-RSS - Export Subscriptions to RSS Feed
- YouTube Subscription History - Subscription History Tracker
- MassYoutubeUnsubscriber - Bulk Remove YouTube Subscriptions
- YouTube Spammer Purge - Delete All YouTube Spam Comments / Domain List
- Playboard or Viewstats - YouTube Channel Stats
- vidIQ - YouTube Viewership Data
- yt2pod - Create Podcasts from YouTube Channels
- SpeechChat - Text to Speech Client
- Rapidtags - YouTube Tag Generator
- songs-to-youtube - Convert Audio Files and Upload to YouTube
- YTSubConverter - Styled YouTube Subtitles
- Amara or SubtitlesForYoutube - Import Local Subtitles to YouTube / Edge
- ChatReplay - Livestream Chat Replay
- LiveTL - Livestream Chat Translator
- YT Boost Chat or YT RM3 - Reduce YouTube Chat Memory Usage
- YT LiveChat Flusher - Add Bullet Chatting (Danmaku) to Livestreams
▷ YouTube Customization
- ⭐ Return YouTube Dislike - View YouTube Dislikes / Web App / Discord
- ⭐ DeArrow or Clickbait Remover - Reduce Sensationalism / Clickbait
- ⭐ UnTrap, TubeMod or Less Addictive YouTube - Distraction-Free YouTube
- ImprovedTube, YouTube Alchemy, Tweaks for YT, Magic Actions or Enhancer for YT / Note - YouTube Enhancement Extensions
- PKGA or YouTube WideScreen - Improved YouTube Theater Mode
- YouTube Hide Watched - Toggle Visibility of Watched Videos / Shorts
- Fast Forward YT Shorts - Add Seek Hotkeys to Shorts
- Thumbnail Rating Bar - Display Like / Dislike Ratio on Thumbnails
- YT Like-Dislike Shortcut - Add Like / Dislike Hotkeys
- YT: Not Interested - Show "Not Interested" and "Don't Recommend" Buttons
- YouTube Grid View - View Search Results in Grid View
- YouTube Search Fixer - Declutter Search Results / Homepage
- BlockTube or YTBlock - YouTube Content Blocker
- YouTube Fixes - YouTube Tweaks
- Restore Handle to Custom - Shows Display Name Instead of Handle
- Focused YouTube, yt-neuter or GoodTube - Minimalist YouTube
- YouTube Redux, VORAPIS / Extra Features / Discord or Cosmic Cat - Restore Classic YouTube Layout / /r/OldYouTubeLayout
- Non-Rounded Design - Revert YouTube's New Rounded Design
- Timestamped YouTube Comments - View Timestamped Comments
- Tabview YouTube - View Comments / Info in Tab View
▷ Players / Frontends
- ↪️ Android YouTube Apps / iOS
- ⭐ FreeTube - Local YouTube Frontend / GitHub
- ⭐ Invidious, Invuedious or Materialio - YouTube Frontends / Instances, 2 / TUI
- ⭐ GrayJay - Combines YouTube, Twitch, Rumble, etc. / Guide
- YouTube Notes - YouTube Note-Taking Frontend
- Walrus, Sync-Tube, YouTube Party or Hergetto - YouTube Watch Parties
- TwitchTheater, VidGrid, YouTube Multiplier or ViewSync - Watch Multiple YouTube Videos
- YouTube Clone KMP - YouTube Frontend
- Poke - YouTube Frontend
- Piped / 2 / 3 - YouTube Frontend
- Tube Cadence - YouTube Frontend
- youtube-local or yt-local - YouTube Frontend
- YouT-ube - YouTube Frontend
- Ytfzf or YewTube - Terminal YouTube Players
▷ Video Tools
- ↪️ Summarize YT Videos
- ↪️ Video Transcribers
- ⭐ SponsorBlock - Skip Sponsored Video Segments / Chromecast / Script, 2
- ⭐ polsy.org.uk - Video Region Restriction Checker
- Video Resumer - Remembers Where You Left Off in Video
- Jump Cutter - Skip Silent Parts of Videos
- Rotate YouTube Video - Rotate, Zoom, & Mirror Videos
- YouTube Upload Time - Check Exact Upload Time/Date of Videos
- Annotations Data Archive - Restore Video Annotations
- YouTube Metadata - YouTube Video Metadata Viewer
- YT Cutter or yt_clipper - Crop YouTube Videos / Create Clips
- Looptube - Loop YouTube Videos / Segments
- YourCodecs - Enable / Disable Player Codecs
- Video Speed Controller - Control Speed of YouTube Videos
▷ Playlist Tools
- ⭐ playlists.at - Playlist Creators / Chrome Extension
- TubeSync - Sync YouTube Channels / Playlists to a Media Server
- ytcc - Keep Track of Your Playlists
- Multiselect (Firefox) or Multiselect (Chrome) - Playlist Manager
- Playlist Randomizer - YouTube Playlist Randomizer
- playlist.tools - Reverse YouTube Playlists
- YT Playlist Length / 2 or Length Checker - Playlist Length Checkers
- YouTubePlaylistMerge - Playlist Merge Guide
▷ YouTube Downloaders
- 🌐 YT-DL GUI Index - List of YouTube Downloader GUIs
- ↪️ Multi-Site Downloaders
- ⭐ yt-dlp - YouTube CLI Downloader / Commands / Discord
- ⭐ JDownloader - YouTube Downloader App
- ⭐ cobalt - Multi-Site / Online Downloader / Instances / Playlist Support, 2
- ⭐ Parabolic or Tartube - Cross-Platform YT-DLP GUIs
- ⭐ YoutubeDownloader - YouTube Downloader App
- ⭐ AMP4 - YouTube Downloader / Online
- Stacher, oleksis youtube-dl-gui or StefanLobbenmeier youtube-dl-gui - Cross-Platform YT-DL GUIs
- yt-dlp-gui / Easy Installer, ytdlp-interface or Vividl - YT-DLP GUIs
- Cube YouTube Downloader - YouTube-DL GUI
- YTDL-PATCHED - YouTube CLI Downloader / YT-DLP Fork
- EZMP3 - YouTube Downloader / Online
- CNVMP3 - YouTube Downloader / Online
- Pinchflat, MeTube, YoutubeDL-Material or yt-dlp Web UI - Self-Hosted YT-DLP
- ytarchive - YouTube Livestream Downloader
- YTI, YTThumbnailHD, Get Thumbs, YT Thumbnail Grabber or thumbnail-download - Download Video Thumbnails
- youtube-comment-downloader - Download YouTube Comments
- YT Subtitle Downloader - Download Video Subtitles
▷ YouTube Search
- 🌐 YouTube_Channels - YouTube Channel Index
- ⭐ Favoree or ChannelCrawler - Discover YouTube Channels
- ⭐ YouTube Advanced Search - Search Engine
- ⭐ Filmot or CTRL-F-VIDEO - Search within YouTube Transcripts / Firefox / Chrome
- comb.io, clip.cafe, InPhrase or Yarn / 2 - Clip / Phrase Search Engines
- yt-fts - Full-Text Search of Subtitles from Channels / Videos
- Icono - Description-Based Video Search / Discord
- MW Geofind or TubeTrotter - Find Geotagged Videos
- YT Comment Viewer, CommentShark, Hadzy or YCF - YouTube Comment Search
- Tokin - Find Trending / Hidden Gem Videos
- Project Random or petittube - Find Videos with <100 Views
- Find-Unfinished-YT - Find Partially Watched Videos
- IMG_0001 - Find Random YouTube Videos
▷ YouTube Archiving
- ⭐ YouTube Video Finder - Multi-Site Archive Search / GitHub
- Tubeup - YouTube Video to IA Uploader
- Tube Archivist - Self-Hosted YouTube Media Server / GitHub
- yark - YouTube Channel Archiver
- Filmot - Search Unlisted Videos
- Hobune or PreserveTube - YouTube Video Archives
- youtubecrawl - Captures of Pages From YouTube (IA)
- Filmot Title Restorer, quite a playlist or RecoverMy.Video - Restore Titles of Deleted / Private Videos
► Twitch Tools
- 🌐 SullyGnome - Twitch Tool Index
- 🌐 Twitch Extensions - Twitch Extensions Index
- ⭐ FrankerFacez, BetterTTV or 7TV - Twitch Enhancement Extensions
- ⭐ TwitchNoSub or Sub-Vod - Watch Sub Only Twitch Videos
- ⭐ Stream Scheme - Livestreaming Guides / Resources
- Gumbo or Twitch-Live - Twitch Stream Trackers
- HypeTrigger - Automatically Create Clips
- Twitch Clip Search - Search for Clips
- VODarchive or TwitchArchive - Twitch Video Archives
- Twitch Previews or Previews - Twitch Video Previews
- Unwanted Twitch - Hide Twitch Categories / Channels
- vTwitch - Show Chat Below Player
- JChat - Show Twitch Chat on Screen
- Hide-Twitch-Chat-Users - Hide Twitch Chat Users
- TwitchChatDanmaku, Transparent-Twitch-Chat or Transparent Twitch Chat Overlay - Transparent Twitch Chat
- Screenshot Twitch - Add Screenshot Button to Twitch
- Auto-Claim-Twitch-Channel-Points or TTVDropBot - Auto Claim Twitch Points
- Twitch Drops Miner - Auto Claim Twitch Drops
- TwitchRSS or twitchrss - Twitch RSS Generators
- Streamlink Twitch GUI - Twitch Browser for Streamlink
- get stream - Extract Twitch URLs
- Lurker.tv - Discord Server-Based Twitch Stream Recs
- Twitch TV OBS Subtitles - Add Subtitles to Twitch Stream
- StreamLadder - Social Media Templates for Twitch Clips
- TwitchLeak - Twitch Top Earners Table
- TwitchQuotes - Twitch Copypastas
- TwitchEmotes - Global Twitch Emotes
- ChatGuessr - GeoGuessr for Twitch
- TwitchInsights, StreamCharts or TwitchTracker - Twitch Stats
- Trovo, Kick, dlive, Caffeine, Lightspeed or Theta - Twitch Alternatives
▷ Twitch Players
- ⭐ Chatterino / 2, Chatterino Homies or Chatty - Twitch Chat Clients
- Orion, Twitch App or Tress - Twitch Desktop Clients
- SpeechChat - Twitch Text to Speech Client
- Twitch Lite, SafeTwitch or Twineo - Twitch Frontends
- Walrus - Make Twitch Watch Parties
- MultiTwitch.tv, MultiTwitch.co, Twitch3D, Multi, MultiStre.am, MultiStreamer or TwitchTheater - Twitch Multi-Stream
- Twitchls - HTML5 Twitch Stream Player
- nobody.live or Twitch Roulette - Random Stream Roulette
- Alternate Player for Twitch.tv - Alternative Twitch Player
- Twitch Replay - Twitch Video Player
- Twitch Lurker - Twitch Stream Auto-Open
▷ Twitch Adblockers
- 🌐 TwitchAdSolutions - Solutions / Scripts for Blocking Twitch Ads
- ⭐ AdGuardExtra - Twitch Adblocker
- TTV LOL PRO - Twitch Adblocker / Proxies
- PurpleAdblock - Twitch Adblocker
- luminous-ttv - Twitch Adblocker
- PurpleTV / Alpha / Telegram or TwitchAdBlock - Mobile Ad-Free Twitch Apps
▷ Twitch Downloaders
- ClipsGameLab, Twiclips or clipsey - Video Downloaders
- twitch-dl, twitch-downloader or Twitch clips downloader - CLI Video Downloaders
- Twitch Downloader or TwitchLink - Desktop Video Downloaders
- TwitchRecover - Recover / View / Download Twitch Videos
- Twitch-Chat-Downloader - Download Twitch Chat Messages
► Twitter/X Tools
- ⭐ Trends24 or GetDayTrends - Trending Hashtags Trackers
- ⭐ /r/Twitter - X.com Subreddit
- Typefully - Schedule Tweets
- twstalker, X Cancelled or nitter, 2 / Instances, 2 - X.com Frontends
- Chirr App - Turn Articles into X.com Threads / Firefox / Chrome
- Klear - Find Influencers
- FollowerWonk - Find / Analyze / Optimize Followers
- Scoutzen - Search X.com Use Lists
- Community Notes Leaderboard - X.com Community Notes Leaderboard
- Hoaxy - Twitter Info Spread Data
- tinfoleak - View Your Geosocial Footprint
- Twitter Mass Unfollow - X.com Unfollow Tool
- Twitter Detector - Detect X.com Link on a Page
▷ Twitter/X Archiving
- Thread Safe - Twitter Backup Tool
- TwitterMediaHarvest or InThisTweet - Twitter Media Downloader
- GetVideoBot or sssTwitter - Download Twitter Videos
- Pikaso - Twitter Screenshot Bot
- memory.lol - Twitter Account Archive
- Ghost Archive or Megalodon - Twitter Archive Services
- Twitter Archive Parser or twitter-web-exporter - Tweet Archivers
- Twayback Machine - View Users' Old Tweets
- TweetedAt - View Tweet Dates
▷ Twitter/X Customization
- ⭐ Eight Dollars - Show Twitter Blue vs. Real Verified Users
- Control Panel for Twitter - Twitter Enhancement Extensions
- Minimal Twitter - Minimal Twitter Themes
- OldTwitter or GoodTwitter2 - Original Twitter Theme
- OldTweetDeck - Twitter Dashboard
- Twitter Plus - View Twitter Images in Original Quality
- Twitter Demetricator - Remove All Twitter Metrics
- Thread Reader App - Unroll Twitter Threads / Search
- Hide Content Warning or Disable Blur - Remove Sensitive Content Blur
► Facebook Tools
- ⭐ Facebook Ad Filters - Facebook Filters
- FBPurity - Facebook Enhancement Extensions
- Caprine - Facebook Desktop Messenger
- Social Tools - Block "Sending" & "Seen" Facebook Chat Indicators
- Charcoal Dark Mode - Facebook Messenger Dark Mode
- Facebook Matrix - Facebook Search Formulas
- Graph.tips - Advanced Facebook Search Tool
- WhoPostedWhat - Facebook Post Search
- FB.Zone - Color Themes for Facebook
- Kill Fbclid or Remove FBclid - Removes fbclid and utm_ Query Parameters in URLs
- News Feed Eradicator - Hide Facebook News Feed
- Lookup ID - Find Facebook ID
- Unlike-Everything - Remove All Facebook Likes
► Instagram Tools
- 🌐 Instagram Tools - Multiple Tools
- 🌐 Instagram Search Tools - Search Tool
- ↪️ Instagram Viewers / Downloaders - View Profiles / Download Pictures
- ⭐ Redirect Logins - Redirect Instagram Login
- InstaFix - Fix Instagram Embeds on Discord / GitHub
- Proxigram or Imginn - Instagram Frontends
- otzberg or Find-User-ID - ID Finder
- Image Counter - Count Page Images
- InstaAddict - Instagram Addiction Test
- Unfollow-Everyone - Bulk Instagram Unfollow
- InstagramUnfollowers - Check Who Follows Back / GitHub
- Instagram Experiments Guide
► Tumblr Tools
- Tumlook, Tumgik or PriviBlur - Tumblr Frontends
- Pillowfort - Tumblr Alternatives
- tumblr-utils - Tumblr Utilities
- XKit - Tumblr Enhancement Extension
- tumbex - Tumblr Search
- Outbox for Tumblr - Tumblr Outbox
- TumblrOriginalPostFinder - Tumblr Post Finder
- Tumbl Backup Guide or TumblThree - Tumblr Backup Tools
- Palettes for Tumblr - Tumblr Palettes
- Filtering Plus - Improved Filtering
► Fediverse Tools
- 🌐 Awesome Bluesky or BlueskyDirectory - Bluesky Resources
- 🌐 Fediverse.Party - Fediverse Software Index
- ⭐ Fediverse Observer - Fediverse Instances
- ⭐ Bluesky - Federated Twitter Alternative / App Directory / Twitter Import, 2 / TUI / Dashboard
- FediDB or The Federation - Network Statistics
- Fedi.Tips - Fediverse Guide
- FediSearch - Fediverse Search
- Fedi.Garden - Curated User Directory
- Fediverse People Directory - Self-Submitted User Directory
- Hubzilla Public Sites - Hubzilla Instances
- Friendica Directory - Friendica Instances
- DarkSky - Bluesky Client
- Diaspora or Friendica - Decentralized Social Netoworks
- FediverseRedirect - Frontend Redirect
- Bridgy Fed - Fediverse Bridge
- PodcastAP - Podcast Feed Bridge
- The Fediverse Report - Fediverse News
- FediBuzz - Fediverse Trends
▷ Mastodon Tools
- 🌐 Awesome Mastodon, 2 - Mastodon Resources
- ⭐ instances.social or Mastodon Near Me - Mastodon Instances
- ⭐ Mastodon Apps - Mastodon Client List
- Phanpy or Mastodeck - Mastodon Clients
- MastoVue or FediWall - View Public Timelines / Hashtags
- Followgraph or StreetPass - Find Mastodon Users
- MastoGizmos - Mastodon Search Tools
- western.social - User Search
- Tootfinder - Opt-In Full Text Search
- Mastodon Scheduler or FediPlan - Schedule Posts
- Mastodon List Manager or Mastodon Lists Manager - Bulk List Editors
- Mastodon Share Bookmarklet Creator - Quick Share Bookmarklet
- fedv.link - Mastodon Link Redirect
- Mastodon Embed Timeline or Mastofeed - Embedded Mastodon Feeds
- Cheap Bots, Toot Sweet! - Create Bots
- emojos.in - Mastodon Custom Emoji Lists
- MastoMetrics - Mastodon Analytics
▷ Lemmy Tools
- ⭐ Lemmy Explorer or Awesome Lemmy Instances - Lemmy Instances
- ⭐ Lemmy Apps - Lemmy Client List
- ⭐ Divisions by zero - Piracy Focused Instance
- Quiblr - Lemmy Instance Browser / GitHub
- Fediverser - Reddit to Lemmy Community Auto-Sync
- LemmyTools - Lemmy Improvement Extension
▷ Pixelfed Tools
- 🌐 Pixelfed Apps - Pixelfed Client List
- The Federation Pixelfed - Pixelfed Instances
- FediDB Pixelfed - Pixelfed Instances
- Fediverse Observer Pixelfed - Pixelfed Instances
- Pixelfed.social - Pixelfed Instance
▷ Peertube Tools
- 🌐 Peertube Apps - Peertube Client List
- Sepia Search, 2 - Peertube Search Engine
- Peertube Instances, 2 - Peertube Instances
- The Federation Peertube - Peertube Instances
- FediDB Peertube - Peertube Instances
- Fediverse Observer Peertube - Peertube Instances
► 4chan Tools
- ⭐ AnyChans - 4chan Web Clients
- ⭐ 4chan X, SpookyX, 4chan XT or Dollchan - Enhancement Extensions
- Lurka - Desktop Client
- RedditChan - Reddit Style 4chan Web Client
- 4Webm - Load All Webm Videos in 4chan Thread
- 4stats - 4chan Board / Thread Stats
- Mass Reply or Reply All - Mass Reply on 4chan
- Anon Files Names - Anonymizes File Names
- 4chan GhostPostMixer - Interleave Deleted Posts from Archives
- Tripgen - Imageboard Trip Code Generator
- 4chan Captcha Solver - Auto Captcha Solvers
- Bypass Derefer - Remove Link Derefer
- Extra Flags for 4chan - Add More Flags to 4chan
- ss21, OneeChan or 4cheddit - 4chan Themes
▷ 4chan Archives
- ⭐ boards.4channel, 2 - 4chan Archives
- 4chanSearch or 4search - Search 4chan Archives
- Oldfriend Archive - 2004 - 2014 Archive
- Ten Billion or 4Museum - 2006 - 2008 Archive
- 4GBs of 4chan Threads - 2009 - 2012 Archive
- Archive.4plebs - 2013 - 2023 Archive
- BibAnon - Vyrd's Archive
- Yotsuba Catalog - Yotsuba Archive
- sup/tg/, Palanq.win, Desuarchive, Archived.Moe or The /b/ Archive - Misc 4chan Archives
► Blogging Tools
- ⭐ Bear Blog, Mataroa or smol.pub / Key - Minimalist Blogging Platforms
- Telescope - Publishing Platform
- Arbital - Hybrid Blogging / Wiki Platform
- Dreamwidth - Blogging Platform
- Haven or WriteFreely - Self-Hosted Blogging Platforms
- Notepin - Anonymous Blogging Platform
- Zonelets - Static Blog Template
- twtxt - Decentralized Minimalist Microblogging Service
- Emanates Docs - Make GitHub-Based Blogs
- CoverView - Blog Banner Creator
-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!