-
 @ cd17b2d6:8cc53332
2025-05-20 10:15:09
@ cd17b2d6:8cc53332
2025-05-20 10:15:09🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs 🔥 Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
🌐 Visit cryptoflashingtool.com for complete details.
🌟 Why Choose Our Crypto Flashing Service? Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
🎯 Our Crypto Flashing Features: ✅ Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
🔒 Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
🖥️ Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
📅 Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
🔄 Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
💱 Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
📊 Proven Track Record: ✅ Over 79 Billion flash transactions completed. ✅ 3000+ satisfied customers worldwide. ✅ 42 active blockchain nodes for fast, reliable transactions. 📌 Simple Step-by-Step Flashing Process: Step 1️⃣: Enter Transaction Details
Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20) Specify amount & flash duration Provide wallet address (validated automatically) Step 2️⃣: Complete Payment & Verification
Pay using the cryptocurrency you wish to flash Scan the QR code or paste the payment address Upload payment proof (transaction hash & screenshot) Step 3️⃣: Initiate Flash Transaction
Our technology simulates blockchain confirmations instantly Flash transaction appears authentic within seconds Step 4️⃣: Verify & Spend Immediately
Access your flashed crypto instantly Easily verify transactions via provided blockchain explorer links 🛡️ Why Our Technology is Trusted: 🔗 Race/Finney Attack Logic: Creates realistic blockchain headers. 🖥️ Private iNode Cluster: Guarantees fast synchronization and reliable transactions. ⏰ Live Timer System: Ensures fresh wallet addresses and transaction legitimacy. 🔍 Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash ❓ Frequently Asked Questions: Is flashing secure? ✅ Yes, encrypted with full VPN/proxy support. Can I flash from multiple devices? ✅ Yes, up to 5 Windows PCs per license. Are chargebacks possible? ❌ No, flash transactions are irreversible. How long are flash coins spendable? ✅ From 60–360 days, based on your chosen plan. Verification after expiry? ❌ Transactions can’t be verified after the expiry. Support available? ✅ Yes, 24/7 support via Telegram & WhatsApp.
🔐 Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
📲 Get in Touch Now: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Start?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs
Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
Visit cryptoflashingtool.com for complete details.
Why Choose Our Crypto Flashing Service?
Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
Our Crypto Flashing Features:
Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
Proven Track Record:
- Over 79 Billion flash transactions completed.
- 3000+ satisfied customers worldwide.
- 42 active blockchain nodes for fast, reliable transactions.
Simple Step-by-Step Flashing Process:
Step : Enter Transaction Details
- Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20)
- Specify amount & flash duration
- Provide wallet address (validated automatically)
Step : Complete Payment & Verification
- Pay using the cryptocurrency you wish to flash
- Scan the QR code or paste the payment address
- Upload payment proof (transaction hash & screenshot)
Step : Initiate Flash Transaction
- Our technology simulates blockchain confirmations instantly
- Flash transaction appears authentic within seconds
Step : Verify & Spend Immediately
- Access your flashed crypto instantly
- Easily verify transactions via provided blockchain explorer links
Why Our Technology is Trusted:
- Race/Finney Attack Logic: Creates realistic blockchain headers.
- Private iNode Cluster: Guarantees fast synchronization and reliable transactions.
- Live Timer System: Ensures fresh wallet addresses and transaction legitimacy.
- Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash
Frequently Asked Questions:
- Is flashing secure?
Yes, encrypted with full VPN/proxy support. - Can I flash from multiple devices?
Yes, up to 5 Windows PCs per license. - Are chargebacks possible?
No, flash transactions are irreversible. - How long are flash coins spendable?
From 60–360 days, based on your chosen plan. - Verification after expiry?
Transactions can’t be verified after the expiry.
Support available?
Yes, 24/7 support via Telegram & WhatsApp.
Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
Get in Touch Now:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Start?
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
-
 @ dfc7c785:4c3c6174
2025-05-20 09:55:44
@ dfc7c785:4c3c6174
2025-05-20 09:55:44![[0B745064-2D34-4A3C-8393-AD033910E6D7.jpeg]]![[0C3FA837-E1BA-497F-8D44-9EC1CD723970.jpeg]]
-
 @ 8576ca0e:621f735e
2025-05-20 09:31:18
@ 8576ca0e:621f735e
2025-05-20 09:31:18The Bitcoin community is currently debating BIP 177, a proposal that seeks to redefine Bitcoin’s base unit from the satoshi (sat) to bitcoin itself. Proposed by Synonym CEO John Carvalho, this initiative aims to simplify Bitcoin’s usability, reduce cognitive barriers for newcomers, and align the currency’s representation with its integer-based protocol design. While the proposal has sparked enthusiasm among some supporters, it has also faced criticism for potentially eroding Bitcoin’s cultural heritage. Here’s a comprehensive breakdown of BIP 177 and its implications.
What Is BIP 177? BIP 177 is a non consensus proposal that reimagines how Bitcoin units are displayed and labeled. Key changes include: 1. Base Unit Redefinition: The smallest unit, currently called a satoshi (1 sat = 0.00000001 BTC), would be renamed to "bitcoin" (lowercase). Thus, 1 BTC would equal 100,000,000 bitcoins under the new system . 2. Integer Only Display: Transactions and balances would be shown in whole numbers (e.g., "10,000 bitcoins" instead of "0.0001 BTC") to eliminate decimal complexity . 3. Symbol Adoption: The "₿" symbol could represent the base unit, making values like ₿34,500,000 equivalent to 0.345 BTC . 4. Backward Compatibility: The BTC ticker and total supply (21 million BTC) remain unchanged. Users and applications can toggle between legacy and new formats .
Why BIP 177? The Case for Change 1. Reducing Cognitive Load Decimal heavy displays (e.g., 0.000023 BTC) are unintuitive, especially for new users. Integer values (e.g., 2,300 bitcoins) simplify mental calculations and reduce errors in transactions . As Carvalho argues, Bitcoin’s protocol inherently uses integers, and the decimal system is a "human imposed abstraction" .
-
Eliminating Unit Fear A Bitcoin priced at $100,000+ can deter newcomers who perceive it as unaffordable. By rebranding the base unit, 1 bitcoin would appear as a fraction of a cent (e.g., $0.00104 per bitcoin), making ownership of thousands of bitcoins feel more accessible . This shift could mitigate "price ceiling anxiety" and encourage broader adoption .
-
Aligning with Bitcoin’s Design Bitcoin’s ledger tracks discrete units, not fractions. BIP 177 emphasizes this by removing artificial decimal formatting, fostering a clearer understanding of Bitcoin’s scarcity and indivisible nature .
-
Mainstream Usability For everyday transactions like buying coffee integer displays (e.g., "1,830 bitcoins") are more practical than tiny decimals. This aligns with Bitcoin’s growing role in micropayments, as seen in El Salvador’s adoption of satoshis for daily use .
Criticisms and Concerns 1. Cultural Erosion The term "satoshi" honors Bitcoin’s pseudonymous creator, and its deprecation risks alienating long-time supporters. Critics argue that abandoning this term weakens Bitcoin’s cultural identity .
-
Confusion Risks Renaming the base unit "bitcoin" while retaining BTC could cause ambiguity. For example, saying "I own 1,000 bitcoins" might mislead newcomers into thinking they own 1,000 BTC . Translation challenges also arise, particularly in languages like Chinese where "比特币" (Bitcoin) would represent both BTC and the base unit .
-
Brand Perception Bitcoin’s high value per BTC is a marketing strength. Displaying prices as fractions of a cent might dilute its perceived prestige, potentially affecting investor sentiment .
-
Implementation Hurdles Wallets, exchanges, and merchants would need to update interfaces, APIs, and educational materials—a process estimated to take 2+ years .
Community Reactions: A Divided Ecosystem - Supporters: Proponents like Jack Dorsey argue that integer displays simplify Bitcoin for mass adoption. They compare the shift to historical advancements like replacing Roman numerals with Arabic numbers . - Opponents: Critics dismiss BIP 177 as "bikeshedding" focusing on trivial changes while ignoring larger issues like transaction fees. Some Reddit users warn, "Don’t split it, don’t change anything" .
Implementation Timeline 1. Phase 1 (3–6 months): Introduce dual displays and pilot testing in wallets like Bitkit . 2. Phase 2 (6–12 months): Mainstream platforms adopt integer displays by default. 3. Phase 3 (12+ months): Legacy decimal formats are phased out entirely .
Conclusion: Tradition vs Progress BIP 177 highlights Bitcoin’s evolving identity: Should it prioritize cultural heritage or usability for the next billion users? While the proposal doesn’t alter Bitcoin’s code or supply, its success hinges on community consensus. As Carvalho notes, "Bitcoin’s heart is immovable code. BIP 177 merely retires the decimal point" . Whether this change becomes a footnote or a revolution remains to be seen but it undeniably sparks a vital conversation about Bitcoin’s future.
-
-
 @ 90c656ff:9383fd4e
2025-05-20 09:06:27
@ 90c656ff:9383fd4e
2025-05-20 09:06:27Since its creation in 2008, Bitcoin has been seen as a direct challenge to the traditional banking system. Developed as a decentralized alternative to fiat money, Bitcoin offers a way to store and transfer value without relying on banks, governments, or other financial institutions. This characteristic has made it a symbol of resistance against a financial system that, over time, has been marked by crises, manipulation, and restrictions imposed on citizens.
The 2008 financial crisis and the birth of Bitcoin
Bitcoin emerged in response to the 2008 financial crisis—a collapse that exposed the flaws of the global banking system. Central banks printed massive amounts of money to bail out irresponsible financial institutions, while millions of people lost their homes, savings, and jobs. In this context, Bitcoin was created as an alternative financial system, where no central authority could manipulate the economy for its own benefit.
In the first block of the Bitcoin blockchain or timechain, Satoshi Nakamoto included the following message:
“The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.”
This phrase, taken from a newspaper headline of the time, symbolizes Bitcoin’s intent to offer a financial system beyond the control of banks and governments.
- Key reasons why Bitcoin resists the banking system
01 - Decentralization: Unlike money issued by central banks, Bitcoin cannot be created or controlled by any single entity. The network of users validates transactions transparently and independently.
02 - Limited Supply: While central banks can print money without limit—causing inflation and currency devaluation—Bitcoin has a fixed supply of 21 million units, making it resistant to artificial depreciation.
03 - Censorship Resistance: Banks can freeze accounts and block transactions at any time. With Bitcoin, anyone can send and receive funds without needing permission from third parties.
04 - Self-Custody: Instead of entrusting funds to a bank, Bitcoin users can store their own coins without the risk of account freezes or bank failures.
- Conflict between banks and Bitcoin
01 - Media Attacks: Large financial institutions often label Bitcoin as risky, volatile, or useless, attempting to discourage its adoption.
02 - Regulation and Crackdowns: Some governments, influenced by the banking sector, have implemented restrictions on Bitcoin usage, making it harder to buy and sell.
03 - Creation of Centralized Alternatives: Many central banks are developing digital currencies (CBDCs) that maintain control over digital money but do not offer Bitcoin’s freedom and decentralization.
In summary, Bitcoin is not just a digital currency—it is a movement of resistance against a financial system that has repeatedly failed to protect ordinary citizens. By offering a decentralized, transparent, and censorship-resistant alternative, Bitcoin represents financial freedom and challenges the banking monopoly over money. As long as the traditional banking system continues to impose restrictions and control the flow of capital, Bitcoin will remain a symbol of independence and financial sovereignty.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 640f3844:d7b13a29
2025-05-20 08:52:49
@ 640f3844:d7b13a29
2025-05-20 08:52:49CrazyGames là một nền tảng giải trí số đang ngày càng khẳng định vị thế trong cộng đồng người dùng hiện đại nhờ vào khả năng cung cấp trải nghiệm linh hoạt, hấp dẫn và thân thiện. Với giao diện được thiết kế thông minh và trực quan, CrazyGames giúp người dùng dễ dàng tiếp cận và khám phá hàng loạt nội dung đa dạng chỉ trong vài thao tác. Dù sử dụng điện thoại, máy tính bảng hay máy tính để bàn, hệ thống luôn được tối ưu hóa để vận hành mượt mà, không gây gián đoạn hay ảnh hưởng đến trải nghiệm tổng thể. CrazyGames không chỉ đơn thuần là một nền tảng kỹ thuật số mà còn là nơi hội tụ của sáng tạo, công nghệ và niềm vui, nơi người dùng có thể tìm thấy sự giải tỏa sau những giờ làm việc căng thẳng hoặc học tập mệt mỏi. Nền tảng luôn chú trọng đến việc đổi mới giao diện, bổ sung các tính năng tiện ích nhằm mang lại giá trị sử dụng thực tế và phù hợp với xu hướng công nghệ đang thay đổi từng ngày.
Một trong những điểm nhấn nổi bật khiến CRAZYGAMES thu hút sự quan tâm rộng rãi chính là tính cá nhân hóa và khả năng kết nối cộng đồng vượt trội. Hệ thống sử dụng các thuật toán phân tích hành vi thông minh để đưa ra các đề xuất nội dung phù hợp với sở thích và nhu cầu riêng biệt của từng người dùng, từ đó nâng cao mức độ hài lòng và giữ chân người dùng lâu hơn. Không gian cộng đồng tích hợp trong nền tảng cũng tạo điều kiện cho các thành viên giao lưu, chia sẻ cảm nhận và trao đổi kinh nghiệm, giúp tăng sự gắn kết và hình thành một hệ sinh thái giải trí sôi động, đầy màu sắc. Hơn thế nữa, CrazyGames thường xuyên cập nhật nội dung mới, điều chỉnh theo phản hồi thực tế từ người dùng nhằm đảm bảo mọi người luôn cảm thấy được lắng nghe và phục vụ đúng với mong đợi. Việc áp dụng công nghệ mới, đặc biệt là trí tuệ nhân tạo và dữ liệu lớn, đã giúp CrazyGames trở thành một nền tảng tiên phong trong việc cá nhân hóa trải nghiệm người dùng ở cấp độ cao nhất.
CrazyGames cũng đặt yếu tố bảo mật và hỗ trợ kỹ thuật làm trọng tâm trong chiến lược phát triển lâu dài. Với hệ thống bảo mật nhiều lớp, kết hợp xác thực người dùng và mã hóa dữ liệu tiên tiến, người dùng có thể yên tâm khi trải nghiệm mà không phải lo lắng về quyền riêng tư hay nguy cơ rò rỉ thông tin cá nhân. Đồng thời, đội ngũ chăm sóc khách hàng của CrazyGames luôn sẵn sàng phản hồi nhanh chóng, giải quyết kịp thời các vướng mắc phát sinh và liên tục cập nhật các hướng dẫn sử dụng để người dùng tận dụng được mọi tính năng mà nền tảng mang lại. Ngoài ra, CrazyGames còn tổ chức nhiều chương trình tương tác hấp dẫn và hoạt động khuyến khích sáng tạo trong cộng đồng, giúp nâng cao trải nghiệm người dùng và biến mỗi lần truy cập trở thành một hành trình khám phá mới mẻ. Với tất cả những yếu tố đó, CrazyGames không chỉ là một nền tảng giải trí kỹ thuật số, mà còn là người bạn đồng hành lý tưởng trong hành trình kết nối công nghệ, sáng tạo và cảm xúc.
-
 @ 8576ca0e:621f735e
2025-05-20 08:46:45
@ 8576ca0e:621f735e
2025-05-20 08:46:45
Now that you’ve mastered the basics, it’s time to level up. Bitcoin isn’t just about buying and holding it’s about understanding the ecosystem, optimizing security, and leveraging its unique properties to build wealth. In this deep dive, we’ll explore advanced concepts every Bitcoin enthusiast needs to know.
-
Mastering Bitcoin Security: Beyond the Basics -Multisig Wallets: Require multiple private keys to authorize transactions (e.g., 2-of-3 signatures). Ideal for protecting large holdings. -Cold Storage Deep Dive: How to set up air gapped hardware wallets, metal seed backups, and geographic redundancy. -Privacy Best Practices: Using CoinJoin, Tor, and wallets like Wasabi or Samourai to enhance anonymity. -Pro Tip: Test recovery phrases before transferring large sums.
-
Bitcoin’s Economic Landscape: Scarcity, Halvings, and Market Cycles -The Halving Explained: How Bitcoin’s supply schedule (every 4 years) impacts price, miner behavior, and long term value. -Stock to Flow (S2F) Model: Why Bitcoin’s scarcity makes it a compelling store of value. -Market Psychology: Spotting bull/bear cycles, avoiding FOMO, and using dollar cost averaging (DCA) strategically.
-
Advanced Transaction Techniques -Layer 2 Solutions: Harnessing the Lightning Network for instant, low cost payments (and earning routing fees). -Replace by Fee (RBF): Speed up stuck transactions by increasing fees. -Taproot and Schnorr Signatures: How Bitcoin’s upgrades improve privacy and scalability.
-
Earning Passive Income with Bitcoin -Lending and Yield: Risks and rewards of platforms like Celsius (post-bankruptcy lessons) and decentralized alternatives. -Bitcoin Mining Pools: Can you still profit as a small miner? We break down the math. -Staking Alternatives: Wrapped Bitcoin (WBTC) in DeFi opportunities and risks.
-
Navigating Regulation and Taxes -Global Tax Compliance: Reporting crypto gains, airdrops, and forks (IRS, HMRC, etc.). -Self custody vs Regulation: How governments are approaching Bitcoin custody laws and privacy tools. -Bitcoin ETFs and Institutions: What BlackRock, Fidelity, and others mean for retail investors.
-
The Future of Bitcoin: What’s Next? -Bitcoin as a Reserve Asset: Nation states adopting BTC (El Salvador, Lugano). -Smart Contracts on Bitcoin: Exploring Rootstock (RSK) and Discreet Log Contracts (DLCs). -Quantum Computing Threats: Separating hype from reality.
Why Follow My Profile? -Weekly Deep Dives: From mining profitability calculators to privacy tool tutorials. -Market Analysis: Bullish catalysts, bearish risks, and how to stay ahead. -Community Q&A: Get your advance bitcion questions answered.
🔔 Follow my profile to unlock Bitcoin 103: Building Wealth in a Decentralized World. Coming soon!
-
-
 @ bd4ae3e6:1dfb81f5
2025-05-20 08:46:08
@ bd4ae3e6:1dfb81f5
2025-05-20 08:46:08 -
 @ bd4ae3e6:1dfb81f5
2025-05-20 08:46:06
@ bd4ae3e6:1dfb81f5
2025-05-20 08:46:06 -
 @ 5188521b:008eb518
2025-05-20 08:33:09
@ 5188521b:008eb518
2025-05-20 08:33:09This memo intends to brief the federated societies of the galaxy on the status of one specific emerging civilization that has increasingly been of interest to our members, and further, to recommend caution when traveling unannounced nearby their local planet.
External Memo #263 from the Emerging Civilizations Council (ECC)
As you are all aware, it is the intention of our federated societies to isolate any emerging civilization in order to allow them the freedom to evolve and innovate independent of any external knowledge or technology. The benefits of this are twofold. Firstly, if during their scientific exploration and development, they are able to reach our same conclusions about the fundamentals of the universe, then we receive additional independent confirmation of our existing knowledge base. Secondly, and of much greater interest, is that all of our most advanced zero-to-one technological innovations have originated from these isolated civilizations because they are permitted to solve problems without bias from more advanced societies.
In earlier times, some of our members practiced strategic infusions of knowledge into emerging civilizations that would be disguised as native discoveries in order to secretly accelerate their advancement. While this was effective in developing advanced and peaceful civilizations more quickly, it was observed that those societies rarely developed any meaningful new technologies. As we have since learned, once a bias is introduced into an emerging civilization, it is typically destined to only innovate around our existing knowledge base.
More dangerously, societies that become aware of more advanced galactic civilizations almost always become focused on extrasolar power projection. This is an extension of the local evolutionary pressures that led to their domination as the apex predator on their planet. Only after they access the virtually unlimited resources of the galaxy, and they have resolved their internal struggle over distribution of those resources, will they be granted full federation status and interspecies technology transfer can be permitted. Prior to this stage, technology transfer from advanced societies must be avoided, as it can destabilize their development and often leads to the destruction of our most precious galactic resource; independent, decentralized technological innovation.
The dominant intelligent species of the specific civilization that is the focus of this memo identify as “Humans” and collectively inhabit a planet they call “Earth.” The Humans of Earth have yet to discover any advanced technology that would be useful to our members at this time; however, based on a key recent milestone in their development, their status has been upgraded to that of “pre-federation,” making them the leading candidate for our next admission into the galactic federation. As such, it has been estimated that first contact with the Humans of Earth may be possible within the next 1-2 GmRs [1 Galactic micro-Rotation (GmR) equals approximately 200 Earth solar orbits and spans approximately 10 human generations].
Their recent promotion to pre-federation status is based on their discovery of inviolable absolute scarcity — a key event that was independently reached among all federation members and typically triggers exponential advancement within two to four local generations. As is the case on Earth, inviolable absolute scarcity is virtually always used to develop undiluted intraspecies communication of value (the so-called perfect money). This has shown to be critical for cooperation and advancement among planetary apex predators throughout our galaxy.
The Earth-based discovery centers around a simple massless ledger system that is secured by electric power projection and is rapidly being adopted among the Humans of Earth. As with most apex predators, human trust is extremely difficult to scale across their entire planetary population. However, the new Earth-based monetary system, which they have named “bitcoin,” is quickly gaining the trust of humans as it continues to prove its inviolability. As has been the case among all emerging civilizations since the formation of the ECC, scarcity alone, even absolute scarcity, has never been enough to trigger exponential technological growth. The source of absolute scarcity must also be inviolable, or it will never be sufficiently trusted among a population.
The new currency of Earth is in the process of proving its inviolability by surviving numerous attacks with no meaningful disruption. Notably, even those closest to its discovery attempted to violate the properties of Earth’s initial implementation of absolute scarcity but were unsuccessful. Today it continues to withstand external attacks by those who have the most to lose, as adoption of a true and fair economic communication threatens to expose the opposition’s less productive, less efficient ideas. This, of course, is the specific class that must be disintegrated in order to allow the Humans of Earth to innovate freely and unlock exponential advancement. This same scenario has played out in all of our ancient histories following the discovery of inviolable absolute scarcity.
Because bitcoin has only existed for approximately one half of one human generation, proofs of inviolability have only been apparent to those who are looking the closest into the implications of the new discovery. Unsurprisingly, the humans who are the most inadequately compensated by the previous monetary systems are the first to find the benefits of inviolable absolute scarcity.
The highly anticipated exponential advancement from the now pre-federation Humans of Earth has attracted the interest of many of our members. Note, that at this juncture, the galactic playbook permits members to approach a pre-federation civilization undetected in order to fairly attain small quantities of their local implementation of inviolable absolute scarcity. The purpose of this practice is to allow our members to obtain a compatible and trusted source of compensation to be used in exchange for the first valuable innovations of a pre-federation society in a way that avoids unnecessary exposure to our technology prior to its full federation status.
Fortunately, all members who have taken part in this practice have fairly participated in the securitization of the bitcoin network, contributing small amounts of energy to organize and record transactions onto its independent time-based ledger system called the “Timechain.” Fair participation is critical to establish trust upon first contact.
Further, our members have, thus far, successfully minimized their impact on the new monetary system of Earth. This is important to disguise our existence but will also help gain trust in the future as no member will be seen as having abused its privileged access to overwhelming amounts of energy and computational power. To that end, it is believed that none of our members have collected more than a single payment for their energy contributions; meaning that no member society has more than 50 out of the full supply of 21,000,000 bitcoin (this was originally the smallest attainable payment for this form of fair participation).
The ECC asks that you please continue exercising caution, keeping your contributions to the bitcoin network to an absolute minimum. As a reminder, even a single service payment (currently 6.25 out of the full supply of 21,000,000 bitcoin), will likely be sufficient compensation for any of their innovations following first contact. Once awarded full federation status, Humans of Earth will be permitted to act as a full trading partner and will be eligible for other means of value for value payment.
However, the purpose of this message is not simply to commend our members for following those aspects of the galactic playbook. All federated societies of the galaxy should also be aware that there have recently been an increasing number of atmospheric anomalies detected by the Humans of Earth. Many believe that these anomalies are primarily caused by the influx of near-earth TDEs following their upgrade to pre-federation status [Temporary Distortion Events (TDEs) are a byproduct of most means of galactic travel]. We are, therefore, requesting that all members voluntarily announce their travel coordinates to help ensure that any TDEs in the future are adequately dispersed in space-time to avoid detectable events on Earth.
Although it has been almost 50 GmRs since the last emerging civilization was upgraded to pre-federation status, it is imperative that we maintain the complete isolation of the Humans of Earth at this critical juncture. As stated, if the Humans of Earth begin to suspect the presence of an overwhelmingly advanced species, they are highly likely to skew their innovations towards violent technologies that could destabilize their society and disrupt their potential for future contributions.
Thank you for maintaining our core principles as we begin to prepare for the next member to be admitted into our peaceful, decentralized federation.
End wideband galactic transmission…
This story first appeared in Tales from the Timechain. Support our work and buy a copy here.
79% of the zaps from this story will be passed onto the author, Reed. 21 Futures requests 21% for operating costs.
@nostr:npub1xgyjasdztryl9sg6nfdm2wcj0j3qjs03sq7a0an32pg0lr5l6yaqxhgu7s is a Christian, father of three, husband, bitcoiner, mechanical engineer in the nuclear power industry, science nerd and is passionate about the pursuit of truth. Reed also organized the Western Mass Bitcoin Meetup and is active on bitcoin twitter (@FreedomMoney21) and Nostr (nostrplebs.com/s/reed)
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ da0b9bc3:4e30a4a9
2025-05-20 07:11:51
@ da0b9bc3:4e30a4a9
2025-05-20 07:11:51Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
https://stacker.news/items/984377
-
 @ d64f3475:8e56b3bf
2025-05-20 07:06:29
@ d64f3475:8e56b3bf
2025-05-20 07:06:29Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:
-
 @ d64f3475:8e56b3bf
2025-05-20 07:06:27
@ d64f3475:8e56b3bf
2025-05-20 07:06:27Skjønner du? Bare tekst.
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ d64f3475:8e56b3bf
2025-05-20 07:06:25
@ d64f3475:8e56b3bf
2025-05-20 07:06:25TEST TEST TEST Her kommer bildene:
-
 @ cefb08d1:f419beff
2025-05-20 06:59:00
@ cefb08d1:f419beff
2025-05-20 06:59:00https://stacker.news/items/984374
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
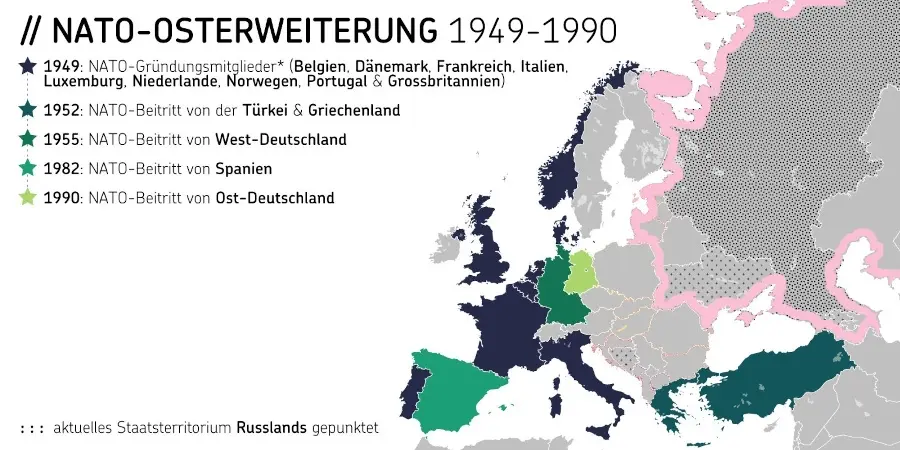
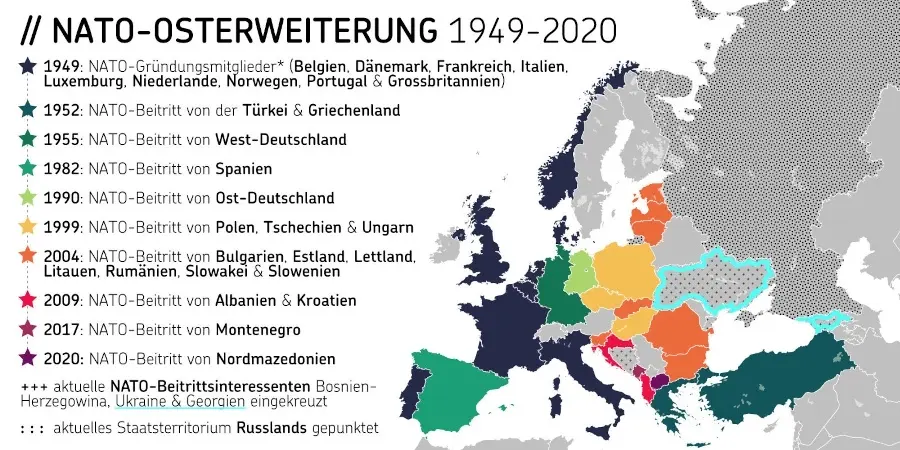
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 58537364:705b4b85
2025-05-20 06:47:23
@ 58537364:705b4b85
2025-05-20 06:47:23อิคิไก (Ikigai) แปลว่า ความหมายของการมีชีวิตอยู่ เหตุผลของการมีชีวิตอยู่ เราเกิดมาเพื่ออะไร ใช้ชีวิตอยู่ไปทำไม เมื่อการงานไม่ใช่สิ่งที่แปลกแยกจากชีวิต
คนญี่ปุ่นเชื่อว่าทุกคนมี ikigai ของตัวเอง ผู้ที่ค้นพบ ikigai จะเจอความหมายและคุณค่าของชีวิต ทำให้มีความสุขกว่า อารมณ์ดีกว่า และมีโลกที่น่าอยู่กว่าด้วย
ปัจจุบัน มีหนังสือเกี่ยวกับอิคิไกออกวางขายเป็นจำนวนมาก แต่เล่มที่คนญี่ปุ่นเป็นคนเขียนเล่มแรกนั้น คือ
- The Little Book of Ikigai : The secret Japanese way to live a happy and long life โดยอาจารย์เคน โมหงิ (แปลภาษาไทยโดย คุณวุฒิชัย กฤษณะประการกิจ)
ตามมาสัมผัสโลกของอิคิไกที่แท้จริงจากนักวิทยาศาสตร์วิจัยด้านสมองชาวญี่ปุ่นคนนี้ ผ่านบทสนทนาที่จะเปลี่ยนความคิดใหม่ที่ว่า 'อิคิไก' เริ่มต้นจากมองหาความสุขเล็กๆ น้อยๆ ในแบบของตัวเราเอง
อาจารย์เคน โมหงิว่า ปู่จิโร่ เชฟซูชิวัย 94 ปี ที่ยังยืนปั้นซูชิให้เราทานอยู่ในทุกวันนี้ เป็นแรงบันดาลใจให้อาจารย์เกิดไอเดียในการเขียนหนังสืออิคิไก
เชฟซูชิที่ ‘ไม่ได้’ เริ่มเลือกงานนี้เพราะความรักหรือความถนัด แต่กลับทุ่มเทปั้นซูชิทุกคำเพื่อให้ลูกค้ามีความสุข… นั่นคือต้นแบบของอิคิไก
น่าแปลกที่คนญี่ปุ่นไม่ค่อยใช้คำว่า ‘อิคิไก’ ในชีวิตประจำวันหรือบทสนทนาทั่วไปเท่าไหร่
เพราะมันเป็นสิ่งที่ปกติและเราทำกันตามธรรมชาติ ในโลกปัจจุบัน เรามักพูดกันว่าทำอย่างไรเราถึงจะประสบความสำเร็จ ทำอย่างไรจะได้เลื่อนตำแหน่ง หากอยากเป็น CEO จะเป็นได้อย่างไร แต่คนญี่ปุ่นมีความคิดว่าความสำเร็จไม่ใช่ทุกอย่างในชีวิต
ยกตัวอย่างเช่นมีคนญี่ปุ่นจำนวนมากที่จริงจังกับงานอดิเรก หรือมี โคดาวาริ* คนอื่นไม่สนหรอกว่างานอดิเรกของคนคนนั้นจะเป็นอะไร ตราบใดที่คนคนนั้นดูมีความสุขดีนั่นก็โอเคแล้ว มีคนจำนวนมากคลั่งไคล้รถไฟ มังงะ (หนังสือการ์ตูน) หรือแอนิเมะ (ภาพยนตร์การ์ตูน) คนเหล่านี้ไม่จำเป็นต้องมีชื่อเสียงหรือได้รับการยอมรับจากสังคม ตราบเท่าที่พวกเขามีความสุขในแบบของเขาเอง มันก็ดีแล้ว
- ความพิถีพิถันใส่ใจในบางเรื่องเป็นพิเศษ เช่น คนที่ชอบเครื่องเขียนมากๆ จะพิถีพิถันในการเลือกปากกา สมุด ดินสอที่ตนเองจะใช้ เพราะฉะนั้น คนที่มีโคดาวาริเหล่านี้จะศึกษาเครื่องเขียนจนถึงที่สุด วิเคราะห์ ทดลอง จนพบว่าเครื่องเขียนแบบใดที่ตนเองหลงใหลที่สุด
อิคิไกของแต่ละคนอาจแตกต่างกัน ต่างคนอาจมีค่านิยมที่ต่างกัน ซึ่งสะท้อนในรูปแบบชีวิตที่แตกต่างกันก็ได้
อิคิไกเป็นเรื่องของความหลากหลายนะ สังคมญี่ปุ่นพยายามผลักดันให้เด็กๆ ทุกคนตามหาอิคิไกของตนเอง เราจะไม่บอกว่า งานนี้เงินดี ทำสิ หรืองานนี้เงินน้อย อย่าไปทำเลย ถ้าคุณถามนักศึกษาว่า พวกเขาอยากทำงานอะไร พวกเขาคงไม่ตอบว่าเลือกทำที่บริษัทนี้เพราะเงินเป็นอันดับแรกหรอก
อิคิไกแตกต่างจากคำว่า ‘ความสำเร็จ’ คนญี่ปุ่นรู้ว่าชีวิตไม่ได้มีแค่เรื่องประสบความสำเร็จ อิคิไกสำคัญกับชีวิตมากกว่า คุณอาจจะประสบความสำเร็จ แต่คุณอาจไม่มีอิคิไก ในทางกลับกัน แม้คุณไม่ประสบความสำเร็จ คุณอาจจะมีอิคิไกก็ได้ ซึ่งชีวิตคุณอาจจะมีความสุขมากกว่า
อาจารย์เคน โมหงินิยามคำว่า ‘ความสำเร็จ’ คือสิ่งที่คุณจะได้รับการยอมรับจากคนในสังคมหรือบริบทสังคมนั้นๆ แต่อิคิไกมาจากหัวใจของคุณ มาจากความสุขส่วนตัวของคุณ คนอื่นอาจจะไม่ได้มองว่านั่นคือความสำเร็จ
อิคิไกเป็นสิ่งที่เฉพาะบุคคล เราสามารถมีความสุขในแบบของเราเอง เราไม่ตัดสินความสุขของคนอื่น และให้เขามีความสุขในแบบของเขาเอง…
สิ่งสำคัญของอิคิไกคือ คุณมีความสุขเล็กๆ น้อยๆ จากเรื่องที่ดูเหมือนเป็นเรื่องเล็กๆ น้อยๆ หรือเปล่า เช่น ตอนเด็กๆ ผมชอบศึกษาเกี่ยวกับผีเสื้อ เวลาผมไปวิ่งออกกำลังกายแล้วเห็นผีเสื้อสวยๆ ผมก็สัมผัสได้ถึงอิคิไก หรือบางทีอาจเกิดขึ้นตอนที่ผมรู้สึกตลกๆ ก็ได้ ผมเห็นเด็กผู้ชายคนหนึ่งบอกพ่อว่า “พ่อๆ ต้องทำอย่างนี้สิ” เวลาผมได้ยินบทสนทนาแบบนี้ ผมก็รู้สึกถึงอิคิไก
หากพวกเราอยากมีอิคิไกบ้าง เราควรเริ่มจากอะไรดี ? เริ่มจากการสัมผัสความสุขจากสิ่งเล็กๆ น้อยๆ ก่อน มันเริ่มทำได้ง่ายที่สุด ในสมองเรามีสารชื่อโดพามีน หากเราทำอะไรสำเร็จเล็กๆ น้อยๆ โดพามีนจะหลั่งออกมา วงจรนั้นจะช่วยทำให้คุณมีความสุข การมีความสุขกับสิ่งเล็กๆ เช่นนี้เป็นเรื่องสำคัญมาก สำหรับหลายคน แนวคิดเรื่องอิคิไกอาจเข้าใจยาก หรือยากสำหรับบางคนที่ชีวิตพวกเขากำลังอยู่ในช่วงยากลำบาก กำลังรู้สึกหมดหวัง ท้อแท้ หรือไม่ได้เคารพตนเอง เพราะฉะนั้น เริ่มจากความสุขเล็กๆ น้อยๆ ก่อนครับ
มันเหมือนการคิดบวกไหม ? อิคิไกเป็นส่วนหนึ่งนะ เวลาเราคิดถึงชีวิต หรือคิดหาวิธีการคิดบวก มันเป็นเรื่องที่ซับซ้อนมาก สำหรับบางคนคำว่า ‘คิดบวก’ อาจฟังดูกดดันสำหรับพวกเขา เพราะฉะนั้น เริ่มจากการมองเห็นความสุขจากสิ่งเล็กๆ น้อยๆ รอบตัว สิ่งเล็กมากๆ เช่นการได้ตื่นมาชงกาแฟดื่ม การได้วิ่งกลางสายฝน

Lesson from Ken Mogi 1. อิคิไก ไม่ใช่การแสวงหาความสำเร็จหรือความร่ำรวย แต่เป็นการรู้สึกหรือสัมผัสถึงความสุขในชีวิตของตนเอง จนทำให้เราเห็นความหมายของชีวิตเราในแบบของเรา 2. อิคิไกไม่ใช่สิ่งที่สังคมนิยามหรือโลกให้ความสำคัญ แต่ละคนมีอิคิไกที่แตกต่างกัน และมีความสุขกับชีวิตในแบบของตนเอง ที่เราเลือกเอง 3. เราไม่ควรตัดสินคนอื่นหรือบีบบังคับคนอื่น เช่น ลูก แฟน ให้ใช้ชีวิตในแบบที่เราคิดว่าใช่ แต่เราควรเคารพความหลากหลายนั้น 4. มองคนที่มีอิคิไกหรือกำลังสนุกกับสิ่งที่พวกเขารักด้วยรอยยิ้ม และคอยช่วยเหลือหากพวกเขาลำบาก 5. อิคิไกมีทั้งระดับใหญ่ ซึ่งเกี่ยวกับแนวทางชีวิตหรือคุณค่าของงาน และอิคิไกระดับเล็กคือการสัมผัสความสุขเล็กๆ น้อยๆ ที่พบเห็นได้ในชีวิตประจำวัน 6. อิคิไก เริ่มต้นจากมองหาความสุขเล็กๆ น้อยๆ ในวันนี้
ที่มา : จากคอลัมน์ Cloud of Thoughts บทสัมภาษณ์ของอ.เกตุวดี Marumura พาไปคุยกับอาจารย์เคน โมหงิ ผู้เขียนหนังสืออิคิไกเล่มแรก!
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 57d1a264:69f1fee1
2025-05-20 06:15:51
@ 57d1a264:69f1fee1
2025-05-20 06:15:51Deliberate (?) trade-offs we make for the sake of output speed.
... By sacrificing depth in my learning, I can produce substantially more work. I’m unsure if I’m at the correct balance between output quantity and depth of learning. This uncertainty is mainly fueled by a sense of urgency due to rapidly improving AI models. I don’t have time to learn everything deeply. I love learning, but given current trends, I want to maximize immediate output. I’m sacrificing some learning in classes for more time doing outside work. From a teacher’s perspective, this is obviously bad, but from my subjective standpoint, it’s unclear.
Finding the balance between learning and productivity. By trade, one cannot be productive in specific areas without first acquire the knowledge to define the processes needed to deliver. Designing the process often come on a try and fail dynamic that force us to learn from previous mistakes.
I found this little journal story fun but also little sad. Vincent's realization, one of us trading his learnings to be more productive, asking what is productivity without quality assurance?
Inevitably, parts of my brain will degenerate and fade away, so I need to consciously decide what I want to preserve or my entire brain will be gone. What skills am I NOT okay with offloading? What do I want to do myself?
Read Vincent's journal https://vvvincent.me/llms-are-making-me-dumber/
https://stacker.news/items/984361
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 57d1a264:69f1fee1
2025-05-20 06:02:26
@ 57d1a264:69f1fee1
2025-05-20 06:02:26Digital Psychology ↗Wall of impact website showcase a collection of success metrics and micro case studies to create a clear, impactful visual of your brand's achievements. It also displays a Wall of love with an abundance of testimonials in one place, letting the sheer volume highlight your brand's popularity and customer satisfaction.
And like these, many others collections like Testimonial mashup that combine multiple testimonials into a fast-paced, engaging reel that highlights key moments of impact in an attention-grabbing format.
Awards and certifications of websites highlighting third-party ratings and verification to signal trust and quality through industry-recognized achievements and standards.
View them all at https://socialproofexamples.com/
https://stacker.news/items/984357
-
 @ 9c9d2765:16f8c2c2
2025-05-20 05:45:33
@ 9c9d2765:16f8c2c2
2025-05-20 05:45:33CHAPTER TWENTY THREE Across town, the Ray estate was drenched in shame. The once-proud family was now the subject of ridicule, their downfall televised, published, and whispered in business circles. Helen stood before a cracked mirror in her bedroom, mascara smudged, lips trembling with fury. The headlines were merciless:
"Heir to JP Empire Humiliated by Ray Family Then Bought Them Out."
"President James: From Rejection to Royalty."
She had lost more than power. She had lost control.
Mark, seated in an armchair with a drink that had gone warm, stared at the wall, his eyes empty. He was a strategist, a manipulator but somehow, he had underestimated James.
"He's just one man…" Mark muttered.
"No," Helen corrected him coldly. "He's not just a man. He’s a symbol now. Of power… of justice… and worst of all, forgiveness."
Mark scoffed. "Forgiveness?"
"Yes," she snapped, spinning to face him. "Because he didn’t destroy us when he could. That makes him look grander than anything we can ever fabricate. He let the world ruin us instead."
There was a long pause.
Then Mark stood, eyes narrow. "We’ll find another way. We always do."
But the fire in his voice had dulled. The Ray family was crippled, their company reduced to a shadow of its former self. Their staff had dwindled, partners severed ties, and their name now stood for arrogance and downfall.
Meanwhile, James had begun the silent restoration of more than just a company he was rebuilding legacies.
Back at JP Enterprises, Rita stepped into James’s office, her presence warm and reassuring.
“You’ve been in here for hours,” she said softly. “Everything alright?”
James looked up, his eyes thoughtful. “Everything is fine. I’m just… reflecting.”
“About them?”
He nodded. “Helen, Mark, Tracy. I know they’re not done. People like them never accept defeat.”
Rita approached, placing a comforting hand on the desk. “Then be ready for their next move. But know that you’re not alone anymore. And you’re no longer the man they thought you were.”
A faint smile curved on his lips. “No. I’m the man they made me become.”
Outside the office, whispers of the upcoming restructuring had already begun. Rumors swirled about James planning to absorb Ray Enterprises entirely into JP Holdings. Some believed he would dismantle it brick by brick. Others hoped he would revive it, proving once again that mercy was strength.
But only James knew his next move.
And as the days passed, the city watched some in admiration, others in dread.
Nightfall settled over the city like velvet, embroidered with the glimmer of a thousand restless lights. From the penthouse office of JP Enterprises, James stood before the floor-to-ceiling windows, his silhouette framed against the horizon. The world below him pulsed with ambition and whispers. Yet his mind wasn’t on the skyline, but on the murky tide still gathering beneath it Mark, Helen, and the crumbling remnants of a fallen dynasty that refused to stay buried.
The public had embraced his rise like a storybook tale. From the ashes of mockery, betrayal, and scorn, he had risen dignified, strategic, and unyielding. News outlets now hailed him as a symbol of resilience, of leadership sharpened by adversity. But James knew that the brightest stars cast the darkest shadows.
Behind the glamour, war drums still beat.
He sat at his desk, opening a sealed file handed to him earlier by his private investigator. Inside were photographs, recordings, and written transcripts irrefutable proof of secret meetings between Helen, Mark, and a few disgruntled former board members of Ray Enterprises. They were not merely planning revenge, they were mobilizing.
A knock interrupted his thoughts. Rita stepped in, poised and composed.
“You asked me to bring the reports on the integration of Ray Enterprises’ satellite branches.”
“Thank you, Rita,” James said, his voice calm but laced with calculation. “Leave them here.”
She lingered. “There’s something else,” she said, her tone more hushed now. “The woman from the anniversary… she’s resurfaced.”
James looked up slowly. “Where?”
“She was seen outside a media house yesterday, trying to set up another exclusive. But word is she's trying to recant her confession. Claims she was ‘coerced’ into blaming Mark and Helen.”
James’s gaze narrowed. “They’re trying to rewrite the narrative.”
Rita nodded. “And if they succeed, they’ll portray you as the one who orchestrated the chaos.”
He exhaled quietly, rising from his seat. “Let them try. The truth is no longer their weapon, it's mine.”
Meanwhile, in a dimly lit lounge across town, Mark and Helen sat opposite a trembling young woman, the same one who once fell to her knees and confessed everything at the anniversary.
“You owe us,” Helen said through clenched teeth. “We gave you the money, we protected you… and you humiliated us in front of the entire city.”
“I was scared,” the woman stammered, eyes darting between them. “Everyone was watching. Mr. JP was furious. What was I supposed to do?”
Mark leaned in, his expression carved from ice. “Fix it.”
“Y-You mean go to the press?”
Helen smiled coldly. “No. We mean bury the damage. Make James look like the one pulling your strings. We’ll give you twice what we paid. You just have to make the world believe he bribed you.”
As the woman hesitated, fear swimming in her gaze, Helen added softly, “Or you disappear.”
The woman’s nod was reluctant, but it was enough.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 6983717b:0ad20c03
2025-05-20 04:23:13
@ 6983717b:0ad20c03
2025-05-20 04:23:13Zignaly公司深度研究报告
1. 创始人背景及声誉
Zignaly于2018年由三位好友共同创立,分别是CEO Bartolome “Bart” R. Bordallo、CFO Abdul Rafay Gadit和CMO David Rodríguez Coronadobitdegree.org。\ Bart Bordallo 是一位拥有数据驱动思维的创业者和区块链倡导者,他曾在西班牙富士通担任系统管理员长达8年,并创办过多家创业项目(如Hadanet、Innova Medialead等)iq.wiki。2014年他联合创办营销数据分析工具Tractionboard,2017年出任Quickstart Ventures CEO,孵化推出Zignaly和社交媒体工具Jooiceriq.wiki。Bart以善于开拓创新技术闻名,在业内积累了丰富经验和人脉。
Abdul Rafay Gadit 拥有金融背景,毕业于巴基斯坦IBA商学院(2010年获银行与金融学士学位)iq.wiki。他曾在渣打银行任职(2010–2016),后加入家族科技企业并成为巴基斯坦知名科技公司Gaditek的合伙人iq.wiki。2016年起Rafay担任风投公司Disrupt的合伙人和投资主管,并担任多家初创企业顾问iq.wiki。他于2019年参与联合创立Zignaly并出任财务主管,被誉为连续创业者,在巴基斯坦科技圈享有声誉iq.wiki。他的家族及商业背景使他在行业内建立起良好信誉。
David Rodríguez 在B2C和B2B市场营销领域有多年创业和领导经验theorg.com。作为Zignaly联合创始人兼市场总监,他负责全球市场拓展。他曾创立过创业公司Artigoo等,在数字营销和增长策略方面有专长crustdata.com。David毕业于西班牙知名院校(具体背景未详),其在欧洲创业圈口碑良好。
综上,三位创始人结合了技术、金融和营销的互补背景:Bart拥有技术创业经验,Rafay具备金融投资专业和家族企业支持,David深谙市场运营。这样的多元背景为Zignaly奠定了坚实基础,创始团队在区块链社交投资领域拥有较高声誉iq.wikiiq.wiki。
 Zignaly团队在2023年Token2049峰会上(迪拜)与合作伙伴DWF Labs合影,展示了创始团队的行业影响力。
Zignaly团队在2023年Token2049峰会上(迪拜)与合作伙伴DWF Labs合影,展示了创始团队的行业影响力。2. 南非数字货币牌照情况
牌照概况:Zignaly已在南非获得加密资产服务提供商牌照,是全球首批持牌的加密社交投资平台之一coindesk.comglobenewswire.com。根据南非《金融咨询与中介服务法》(FAIS)的新规,Zignaly于2024年获授第二类(Category II)“自由裁量型金融服务提供商 (Discretionary FSP)”牌照coindesk.com。该类别相当于传统资管中的基金管理资格,允许Zignaly为用户提供资金托管和自主投资管理服务。
持牌实体与监管:Zignaly的南非牌照由其当地注册实体 Merritt Administrators (Pty) Ltd 名义持有coindesk.com。根据南非金融部门行为监管局(FSCA)登记信息,Merritt Administrators (Pty) Ltd已正式列入授权机构名单coindesk.com。该公司注册号为2013/189063/07,注册地址在南非豪登省约翰内斯堡Rosebank区Hood大道1号zignaly.com。颁发牌照的监管机构正是南非金融行业行为监管局(FSCA),负责加密资产服务提供商的审批和监管。FSCA自2023年6月起受理加密公司牌照申请,并计划至2024年4月共批准约60家企业coindesk.comcoindesk.com。Zignaly与Luno等成为首批获批者,体现出其合规运营能力。
牌照影响:获得南非Category II牌照使Zignaly成为“全球首家持牌社交投资平台”globenewswire.com。Zignaly团队表示为满足严格监管要求投入了6年时间准备,拿证后即可为用户提供自由裁量基金管理和托管服务globenewswire.com。这一里程碑显著增强了平台合法性和用户信心,用户基础随之增长,并为其开发新产品(如去中心化金融DeFi投资)打开大门globenewswire.com。该牌照处于G20国家中少有的先进数字资产监管框架下globenewswire.com。凭借FSCA授权,Zignaly建立了合规背书,有助于其在全球拓展业务并加强监管沟通coindesk.com。
为清晰起见,整理Zignaly相关牌照信息如下:
| 持牌地区 | 持牌实体及注册号 | 牌照类型 | 监管机构 | | -------- | ---------------------------------------------- | -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ----------------- | | 南非(2024) | Merritt Administrators Pty Ltd(2013/189063/07) | 加密资产服务提供商牌照:Category II 类金融服务提供商(自由裁量资管)coindesk.com | 南非金融部门行为监管局(FSCA) |
表:Zignaly在南非持有的加密资产相关牌照概览。
3. 南美业务布局及发展状况
主要市场及用户:Zignaly的产品在南美地区具有相当用户基础,覆盖大部分拉美国家市场criptonoticias.com。根据西班牙语媒体报道,Zignaly平台可在阿根廷、哥伦比亚、墨西哥、智利、秘鲁、玻利维亚、巴拿马、乌拉圭、巴拉圭、巴西、危地马拉、哥斯达黎加等主要拉美国家正常访问服务criptonoticias.com。这些国家拥有活跃的加密投资群体,是Zignaly重点拓展的区域。其中巴西是特别重要的市场,用户规模增长迅速。2023年Zignaly(也称“ZIGDAO”)宣布与巴西最大的加密社区之一Criptomaniacos达成战略合作zignaly.medium.com。Zignaly为该社区定制了专属版本(称为“Z-Prime”解决方案),上线后短期内吸引超过5,000名用户,管理资产超250万美元zignaly.medium.com。这一合作为Zignaly在巴西迅速聚拢人气,并计划借助Criptomaniacos超过50万的用户群实现爆发式增长(目标突破百万用户、资产管理规模翻倍)zignaly.medium.com。可见,巴西已成为Zignaly在南美的领军市场之一。
合作伙伴与在地化:Zignaly积极与南美本地加密社群和机构合作,采用共赢模式拓展业务版图。在巴西,通过与Criptomaniacos等头部社区领袖合作,Zignaly快速建立起信任背书和用户基础zignaly.medium.com。此外,Zignaly的去中心化部门ZIGChain亦关注拉美市场机会。2024年12月,ZIGChain与拉美新兴市场金融公链Kiichain签署合作备忘录,共同致力于为拉美真实资产代币化引入全球流动性medium.commedium.com。Kiichain专注于拉美实物资产上链(如房地产、基础设施),此次合作将使Kiichain发行的代币化资产通过ZIGChain生态触达全球投资者medium.commedium.com。这显示Zignaly不仅服务散户投资者,也寻求参与拉美更广阔的金融创新生态。
监管环境与动态:拉美各国对加密业务监管态度不一,Zignaly在该地区主要采取合规经营与规避高风险市场并举的策略。根据其用户协议,Zignaly目前不向部分国家提供服务,包括美国、萨尔瓦多、古巴、委内瑞拉等criptonoticias.com(其中萨尔瓦多虽将比特币定为法币,但Zignaly出于内部政策或风险考虑暂未进入)。这一列表暗示Zignaly在拉美选择了政治经济环境稳定、监管友好的国家运营。像巴西已于2024年初实施加密法案,要求数字资产服务商向中央银行注册。Zignaly与当地社区合作有助于理解并适应监管。不过截至目前,未见Zignaly在南美获得正式牌照的公开报道,运营主要依托其全球牌照(如南非FSCA)和合作伙伴资源。未来若南美国家(如巴西、阿根廷等)推行明确牌照制度,Zignaly可能考虑申请本地牌照或设立合资实体,以巩固合规基础。
总的来说,南美(广义上含拉美地区)已成为Zignaly用户增长和社区运营的要地。巴西是亮点市场,Zignaly通过深耕本地合作获得显著成果zignaly.medium.com。同时,平台在西语圈国家如阿根廷、哥伦比亚、墨西哥等亦有相当渗透率criptonoticias.com。凭借区域化策略和全球合规优势,Zignaly在南美正持续扩张其社交投资版图。
4. 在巴基斯坦的业务及关系
团队渊源: 巴基斯坦与Zignaly关系密切,主要体现在联合创始人Rafay Gadit的背景上。Rafay作为巴基斯坦本土培养的企业家,其家族企业和投资经历为Zignaly奠定了早期基础iq.wiki。他毕业后回国加入了自家科技业务(Gaditek集团)并活跃于本地创业投资圈iq.wiki。Rafay通过Paklaunch等巴基斯坦创业社区结识投资人,并将这些资源引入Zignaly的融资中linkedin.com。据其领英发文透露,Zignaly于2022年获得5000万美元融资时,Paklaunch平台曾帮助团队对接到了关键投资方linkedin.com。由此可见,巴基斯坦创业社区对Zignaly的早期成长有所助力。
本地业务和用户:由于巴基斯坦目前对加密货币交易所持不友好甚至禁止态度(央行曾建议全面禁止加密交易),Zignaly尚未在巴基斯坦开展官方业务或设立办事处。这一点从Zignaly未将巴基斯坦列入支持或排除名单中也可侧面印证(官方服务条款并未提及巴基斯坦,可能是默认不提供)criptonoticias.com。然而,巴基斯坦拥有庞大的散户投资群体,不排除部分用户通过VPN等方式访问Zignaly服务。据报道,Rafay本人积极倡导普惠金融理念,希望通过区块链技术解决金融包容性问题thefounderdaily.comthefounderdaily.com。他曾在访谈中提及,自己的背景让他意识到传统金融体系对普通人的局限,因此创立Zignaly旨在让全球各地的人(包括穆斯林国家民众)都能公平参与财富增值机会thefounderdaily.com。这包含了对巴基斯坦等发展中国家投资者的考虑。因此可以推测,虽然Zignaly未在巴基斯坦公开运营,但创始团队可能借助当地人脉在小范围内推广教育,加深对当地监管的了解。Rafay也有可能通过他的家族企业和人脉(如Gaditek和Paklaunch)向巴基斯坦用户传播Zignaly理念。总的来说,目前Zignaly在巴基斯坦没有官方合作伙伴或直接服务,与当地监管机构亦无公开互动记录。然而,凭借联合创始人的资源,Zignaly在巴基斯坦保持了一定的间接影响力和潜在用户关注度。
监管互动:巴基斯坦尚未建立明确的加密监管框架,大环境不利于Zignaly此类平台落地。本地监管层曾多次警告数字货币交易风险,并封锁过一些交易所的网站。Zignaly为了规避监管风险,选择暂不触碰这一市场也是明智之举。目前未见Zignaly与巴基斯坦国家银行(SBP)或证券监管机构直接沟通的报道。未来若巴基斯坦态度转变,比如引入沙盒监管,Zignaly或将凭借Rafay的关系寻求进入。但就当前而言,Zignaly与巴基斯坦的联系更多体现在人脉和愿景层面,而非实际业务开展。
5. 伊斯兰金融领域的参与程度
Zignaly高度重视伊斯兰金融合规和穆斯林市场的需求,近年积极将清真(Halal)投资原则纳入其产品体系。具体表现在:
-
推出清真合规投资板块:2025年初,Zignaly上线了一个专门的伊斯兰教法合规投资市场,聚焦代币化实物资产(RWA)的投资机会help.zignaly.comhelp.zignaly.com。该板块命名为“Zamanat”,于2025年迪拜ZIGChain峰会上发布,是构建在ZIGChain上的清真RWA投资平台hackernoon.com。Zamanat由专业的伊斯兰金融机构审核把关,每个上线项目均经过伊斯兰教金融专家团队审核,确保符合教法原则(禁止利息利巴和过度投机Gharar等)help.zignaly.com。这一市场专注于房地产、基础设施等真实资产的代币化,使穆斯林投资者能够在不违背信仰的前提下参与高潜力投资help.zignaly.comhackernoon.com。这体现出Zignaly对于道德金融和信仰价值的尊重,旨在吸引全球穆斯林投资群体。
-
专业认证与合作:Zignaly积极寻求知名伊斯兰金融顾问的背书。2025年4月在迪拜举办的ZIGChain峰会上,Zignaly宣布与国际顶尖的伊斯兰金融顾问公司Amanie Advisors建立战略合作chainwire.orgchainwire.org。Amanie Advisors为Zignaly生态中的项目提供教法合规认证。例如,去中心化收益聚合协议Nawa Finance在该峰会上获得了Amanie出具的正式沙里亚合规证书,成为全球首个清真合规的比特币DeFi收益协议chainwire.org。Amanie首席执行官Maya Marissa Malek表示,期待与Zignaly及其合作项目一同推进包容性和合乎道德的金融创新chainwire.org。此外,ZIGChain生态对清真项目的支持也吸引了众多伊斯兰金融领域创业者参与,如Nawa Finance在ZIGChain Summit上获得ZIGLabs、Disrupt等机构投资,加速清真DeFi生态发展chainwire.org。
-
穆斯林国家市场推广:Zignaly选择在迪拜举办大型峰会并发布伊斯兰金融相关产品,凸显对中东穆斯林市场的重视prnewswire.com。迪拜作为伊斯兰金融中心和区块链友好城市,吸引了众多穆斯林投资者与开发者参加ZIGChain Summit(现场超过2000人,包括传统金融的私人银行家、财富管理团队等)hackernoon.com。会上伊斯兰金融主题成为焦点之一(设有“沙里亚、DeFi与普惠财富”专题讨论),探讨Web3如何为穆斯林投资者开拓新机遇hackernoon.com。除了中东,Zignaly对南亚和东南亚穆斯林市场也有所关注。例如印尼、马来西亚拥有大量穆斯林投资者且监管相对开放,Zignaly提供清真选项将有利于进入这些市场。Zignaly联合创始人Rafay来自穆斯林国家,对清真投资理念有亲身认同,他多次强调将道德与技术结合的重要性,以吸引过去因宗教原因观望的投资者群体chainwire.orgchainwire.org。
综上,Zignaly正深入伊斯兰金融领域:不仅在产品上推出符合教法的投资渠道help.zignaly.com,还引入权威机构认证提升可信度chainwire.org。通过在穆斯林聚居地区(如海湾国家)开展市场活动并强调道德投资理念,Zignaly努力成为穆斯林投资者可信赖的加密财富平台。这种战略有助于Zignaly在竞争中差异化,并为数万亿美元规模的全球伊斯兰金融市场服务hackernoon.com。
6. ZigChain项目概况
ZigChain是Zignaly于2024年推出的全新Layer-1区块链项目,旨在打造面向财富管理和去中心化投资的专用公链生态coindesk.com。其主要情况如下:
-
技术架构:ZigChain基于Cosmos SDK构建,是Cosmos网络上的一条独立区块链binance.com。采用Tendermint BFT共识,实现高吞吐和跨链互操作(可与Cosmos生态链通过IBC协议连接)。值得注意的是,ZigChain兼容EVM(以太虚拟机)binance.com。这意味着开发者可以方便地在ZigChain上部署Solidity智能合约,并与以太坊等生态交互。ZigChain内置了Zignaly团队开发的创新财富管理模块,使其区别于普通公链binance.com。该模块汲取了Zignaly平台的投资功能,将专业资管策略直接嵌入区块链底层,实现链上托管和收益分配等逻辑。ZigChain还支持账户抽象等用户体验改进,降低了使用私钥和管理链上资产的门槛binance.com。总体而言,从架构上ZigChain定位为一个专用的去中心化投资基础设施,兼顾了Cosmos的可扩展性和EVM的广泛兼容性。
-
市场定位:ZigChain被称为“财富生成基础设施”,目标是连接专业资管人与普通投资者,桥接传统理财与DeFi世界thefounderdaily.combinance.com。其愿景是在区块链上提供类似传统基金的体验:用户将资金委托给链上的财富经理(即经验丰富的交易员/基金经理),后者通过智能合约策略进行投资操作,用户持有其投资组合份额的代币化凭证hackernoon.com。这种模式让不懂技术或理财的小白用户也能“一键式”参与复杂的DeFi策略或真实资产投资binance.com。ZigChain希望解决其他资产链“有基础设施无需求”的痛点,通过Zignaly现有庞大用户社区提供初始流动性和投资需求binance.com。Zignaly已有60万+注册用户和5万+ ZIG持币用户,为ZigChain带来冷启动优势binance.com。因此,ZigChain定位于下一代财富管理公链,以满足传统高净值产品(如地产、私募基金)在区块链上的发行和投资需求hackernoon.com。它强调自身是解决“代币化房地产缺乏流动性”的方案,通过庞大投资者网络为代币化资产注入买盘需求binance.combinance.com。这一定位差异化了ZigChain,使其不仅是技术平台,更是带有现成用户和资金的流动性层。
-
生态系统组成:ZigChain生态由多个层次构成:
-
基础层:ZigChain区块链本身及其财富管理引擎(WME)。WME提供去中心化资产管理框架,让财富经理发行策略代币、自动复利和调仓等hackernoon.comhackernoon.com。
-
资产层:涵盖各种资产类别,如DeFi收益策略、Real World Assets (RWA)(房地产、票据等现实资产的代币)、游戏资产以及其他创新资产类型binance.com。ZigChain尤其重视RWA,上面提到的Zamanat清真市场即是RWA板块的重要组成hackernoon.com。另有合作伙伴如Kiichain一起丰富RWA品类medium.commedium.com。
-
参与者:由财富经理(专业交易员/机构)、投资者用户以及开发者三方组成。coindesk.comZigChain的独特之处在于引入“财富经理”这一层作为强用户,充当协议和散户之间的桥梁coindesk.com。开发者则可在ZigChain上开发各类dApp,如策略聚合器、数据分析工具等,扩展生态功能。
-
支持机构:ZigChain获得多方战略及资金支持。2024年宣布时即联合DWF Labs、Disrupt.com和UDHC Finance设立了1亿美元生态基金,用于激励开发者在ZigChain上创新iq.wiki。DWF Labs管理合伙人Andrei Grachev公开背书ZigChain模式,称这是前所未有的开发者、财富管理者和用户融合的新尝试iq.wiki。另外,Zignaly内部孵化器ZIGLabs也在投资生态项目,如参与投资了清真DeFi项目Nawa Financechainwire.orgchainwire.org。
-
社区治理:随着ZigChain的发展,Zignaly社区已于2023年转型为ZIGDAOiq.wiki。社区持有人将通过DAO机制参与ZigChain治理和决策。ZIG代币未来可能用于质押验证节点、提案投票等治理功能,从而将社区与链的发展紧密绑定。
-
代币信息:ZigChain的原生代币为ZIG币(ZIG)。ZIG最初于2021年作为ERC-20代币发行,用于赋能Zignaly平台bitdegree.org。ZIG总量约19.54亿枚,目前流通约14.09亿枚,市值在1.3亿美金上下,排名200名开外bitdegree.org。ZIG币在Zignaly/ZigChain生态中有多重用途:
-
平台功能:用户可用ZIG支付服务费用、获得交易手续费折扣和现金返还,以及购买保险NFT等iq.wikibitdegree.org。Zignaly提供了一种保险机制,允许用户用ZIG购买保单,对投资提供10%-100%不等的损失保障bitdegree.org。
-
治理权益:ZIG持有人作为ZIGDAO成员,可对平台升级和未来战略进行投票表决iq.wiki。持币还可提前体验新功能并参与项目空投。
-
奖励与忠诚度:ZIG用作生态激励,例如质押ZIG可获得额外收益,或兑换独家NFT资产等iq.wiki。2023年Zignaly推出AI驱动的新功能时,也曾对ZIG持有者发放独家NFT白名单作为奖励medium.com。
-
跨链和主网角色:随着ZigChain主网推进,ZIG将从ERC-20逐步映射成为ZigChain的主网币,用于支付链上Gas费用、质押节点、跨链桥流动性等。值得注意的是,CoinGecko显示Zignaly已将项目名称更改为“ZIGChain (ZIG)”twitter.com。这暗示ZIG币定位从平台币扩展为公链主网币。
项目进展:ZigChain已于2024年发布测试网并在Token2049等场合展示功能iq.wiki。2025年4月的迪拜峰会宣布主网将于6月上线,同时发布了Zamanat平台和$2500万AI生态基金等消息prnewswire.com(AI基金用于支持基于ZigChain的AI投资项目)。ZigChain Summit聚集了众多投资界人士,反响积极hackernoon.com。可以预期,ZigChain主网在2025年中推出后,将进入生态建设快车道。
总而言之,ZigChain具有清晰的技术架构和差异化定位,融合了传统资管理念与区块链优势。凭借Zignaly既有用户和资金基础,以及雄厚的生态资金支持,ZigChain有望打造出一个围绕财富管理的创新公链生态,在DeFi市场占据一席之地。
7. 币安最大Broker地位及角色分析
币安经纪商计划参与:Zignaly自早期便加入币安Broker(经纪商)计划(现称币安链接伙伴计划),充分利用币安交易所的流动性和基础设施来为其用户提供交易服务criptonoticias.com。作为Broker,Zignaly的用户通过Zignaly界面下单,但实际交易执行和资金托管由币安等交易所完成criptonoticias.com。这意味着用户资产安全由币安保障,并受其SAFU基金保护,且可享用币安深度和撮合引擎zignaly.com。Zignaly通过Broker API对接,实现与币安账户体系的联通,用户无需单独在币安开户即可交易,从而降低了门槛。
最大Broker的地位:截至目前,Zignaly已成为币安生态中规模最大的经纪合作伙伴之一。在币安官方内容和Zignaly资料中,多次提及Zignaly是“币安顶级Broker”,甚至是“最大的币安Broker合作伙伴”zignaly.combinance.com。据Zignaly官方透露,其平台拥有60万+用户,其中约$1.2亿美金的用户资产通过Broker连接到币安等交易所进行交易binance.com。这一AUM(管理资产规模)在币安Broker合作伙伴中名列前茅binance.com。币安方面也将Zignaly列为示范案例之一,认可其为大量散户提供了进入币安市场的渠道zignaly.com。值得注意的是,Zignaly不仅对接币安,还同时是Bybit等交易所的官方Broker合作伙伴medium.com。它支持的交易所包括币安、Bybit、KuCoin、BitMEX、AscendEX等,总计5-6家criptonoticias.commedium.com。在这些中币安交易量最大、用户使用最多criptonoticias.com。因此Zignaly在币安Broker体系内的交易量和用户数应是最高的,这奠定了其“最大Broker”的地位。
角色定位与收益模式:作为币安Broker,Zignaly扮演的是“导流+增值服务提供者”角色。一方面,Zignaly通过其社交投资平台吸引了众多原本不会直接使用交易所的新用户,将其导流至币安的交易深度中进行交易criptonoticias.comcriptonoticias.com。另一方面,Zignaly为用户提供了币安本身没有的复制交易、利润分成等独特功能,提升了用户黏性和交易频率criptonoticias.com。这种分工合作下,币安获得了交易量和用户基数,Zignaly则通过与币安分润交易手续费来实现收益。根据Broker计划,币安会将Zignaly用户交易手续费的一定比例返还给Zignaly作为佣金。此外,Zignaly自己的盈利模式还包括对盈利的跟单投资收取一定成功报酬(Profit Sharing模型)globenewswire.com。但其复制交易服务对用户零前期费用,只有盈利才按比例分成globenewswire.com。这需要有大量交易作为支撑,币安的高流动性恰好满足了这一点。可以说,Zignaly的Broker身份为其盈利模式提供了坚实基础。
交易量与数据:公开数据显示,Zignaly发展初期(2021年上半年)平台交易量已超过20亿美元,AUM约9000万美元reddit.com。如今用户数比当时增长数倍,AUM增至1.2亿以上binance.commedium.com。保守估计目前Zignaly月均交易额已达数十亿美元级别,成为币安不可忽视的流量来源。Zignaly也积极宣传这一成就,以增强投资者和用户信心。例如其Medium博客提到在一年内用户从2万增至50万+、资管规模从数百万增至过亿美元medium.com。币安官方新闻稿和Square动态也多次报道Zignaly的进展,将其列为Broker成功案例zignaly.com。
官方评价:币安和Zignaly官方均对这层合作予以正面评价。Zignaly网站称“币安将我们列为顶级Broker,提升了平台可信度”zignaly.com。币安Broker项目页面则强调,通过Binance Link计划,合作方可利用币安技术和安全体系扩展业务binance.com。对于Zignaly用户而言,与币安的深度合作带来了安全感(资产由全球最大交易所托管)和便利性(无需在多平台频繁转账)criptonoticias.com。这种双赢关系是币安经纪商模式的初衷。Zignaly联合创始人Rafay在领英上也表达了对币安合作的重视,称有幸与顶级伙伴(包括币安)合作使团队更有动力将Zignaly做成全球最大社交投资平台linkedin.com。
简言之,Zignaly确系币安最大的Broker之一。它以社交交易优势为币安带来可观用户和交易量,并借助币安基础设施增强自身服务能力criptonoticias.com。其Broker角色实为币安生态的“前端入口”和“功能延伸”,双方关系密切(见下节),官方场合也经常互相背书这一合作。对于“最大Broker”这一定位,Zignaly通过数据和币安的认可充分证明了自身的行业领先地位binance.com。
8. 在日本的潜在业务布局
当前业务状况:截至目前,没有公开资料显示Zignaly在日本开展了实际业务或设立法律实体。日本对加密交易及相关服务实行严格的牌照制度(需取得金融厅FSA颁发的加密资产交易业者牌照或投资顾问牌照),门槛较高。而Zignaly尚未出现在日本金融厅授权的交易平台名单中。据日媒报道,FSA近期甚至要求下架未注册的海外加密APP以限制日本用户使用境外服务binance.com。Zignaly并未进入日本主流市场,可能基于合规压力选择暂不触及日本用户。其官网的服务条款中常见的禁止地区列表里一般会包括美国和受制裁国家,但并未明确提及日本criptonoticias.com。然而,日本法律规定未注册业者不得向日本居民招揽业务,否则会收到警告。2022-2023年间FSA曾警告多家海外交易所非法向日本用户提供服务binance.com。Zignaly显然希望避免卷入此类合规风险。因此可以推测,Zignaly默示屏蔽了日本市场,至少在没有拿到牌照前不会积极招募日本用户。
潜在布局和计划:尽管目前缺席,日本市场对于Zignaly具有潜在吸引力:日本拥有成熟的零售交易群体和完善的法规环境,若能合规进入,将利于提升品牌可信度和用户质量。Zignaly可能已经在关注日本监管动态,评估进入时机。一种可能途径是在日本寻找本土合作伙伴,比如与持牌金融机构或大型证券公司合作推出受监管的社交交易服务。然而这需要克服文化和产品适配等挑战。另一种路径是等日本明确推出针对社交投资或复制交易的新规,再申请相应牌照。目前日本的金融商品取引法下没有直接针对复制跟单的平台分类,Zignaly若申请,可能需按照“投资顾问/代理业”或“第二种金融商品业务”来办理,流程复杂冗长。此外,从市场测试角度,Zignaly尚未针对日本语系进行本地化,包括网站、客服、社区运营都未见日语内容。这表明短期内他们不打算投入日本市场。
竞争与展望:日本市场已有Bitcopy等本地社交交易服务,以及eToro等平台的间接影响。如果Zignaly进军日本,将面对本土玩家和监管壁垒双重挑战。不过,Zignaly在合规方面已经有南非牌照背书,或许能增加日本监管部门的信任感。Zignaly过去也曾在高度监管环境下运营(如与美国投资者隔离服务),有一定经验。如果未来Zignaly决定进入日本,可能会:
-
成立日本子公司(如“Zignaly Japan KK”)并申请成为注册投资业者。
-
或与当地公司合资,利用后者牌照开展业务,以技术提供方身份出现。
-
同时针对日本用户开发日语界面、符合当地法规的风控措施(例如设置杠杆上限、用户适当性检查等)。
但在这些举措落地前,暂无迹象表明Zignaly已经在日本展开布局。目前可以确认的是,Zignaly未对日本市场进行任何官方宣传或业务拓展。考虑到日本监管渐趋严格,Zignaly短期策略可能是观望为主,把资源集中在东南亚、中东等增长更快且监管宽松的地区。等到条件成熟,再评估进入日本的可行性。总而言之,Zignaly在日本暂未有公开业务或合规进展,未来是否进入取决于监管环境和公司战略调整。
9. 与FTX团队及美系交易所的关系
与FTX团队的历史关系:目前无确凿信息显示Zignaly与已倒闭的FTX交易所或其团队存在直接合作或投资关系。在Zignaly历次融资中,已知主要资方为GEM数字投资基金(来自卢森堡,承诺投资5000万美元)coindesk.com、DWF Labs等,并未出现FTX旗下Alameda Research等的身影coindesk.com。Zignaly的代币ZIG也未曾在FTX交易所上线交易(主要流通于Binance、KuCoin、Kraken等交易所bitdegree.org)。此外,Zignaly创始团队背景与FTX团队并无交集:FTX团队核心在美国和香港,而Zignaly团队在西班牙、巴基斯坦等地。因此可以认定,Zignaly与FTX基本不存在直接联系。唯一可能的间接关联是:两者都曾参与Binance等行业活动,或有过行业交流。但未见任何合作公告或交叉投资记录。FTX于2022年11月爆雷后,Zignaly业务未受明显影响,也印证其未与FTX深度绑定。
与美国系交易所的关系:这里主要指Coinbase、(以及Deribit等衍生品平台)的关联程度:
-
Coinbase:Zignaly没有与Coinbase公布任何官方合作。Coinbase主要面向北美合规市场,而Zignaly由于合规原因不服务美国用户criptonoticias.com。因此Zignaly几乎不可能与Coinbase有用户导流或API对接合作。此外,Coinbase也没有类似币安Broker的外部经纪商计划。Zignaly亦未获得Coinbase Ventures的投资(其融资公告中无Coinbase身影)。因此Zignaly与Coinbase基本没有直接关联。唯一弱关联是ZIG代币曾在2021年申请过Coinbase资产评估名单,但未被上市。此外,Zignaly提供的策略主要在高杠杆币种,而Coinbase产品以现货为主,业务契合度不高。
-
Deribit:Deribit虽以美国团队创立,但注册在欧盟(荷兰)并面向全球提供加密期权和期货交易。Zignaly迄今未集成Deribit作为支持交易所。其支持的衍生品交易所包括BitMEX、Bybit等criptonoticias.com。可能由于Deribit主要提供期权,较为小众,而Zignaly专注于现货和永续合约的跟单交易。在投资或合作层面,也无迹象显示双方有往来。Deribit未出现在Zignaly合作伙伴名单中,Zignaly也未曾宣布支持Deribit的API接入。因此双方关联度很低。
-
其他美系交易所:如Kraken、Gemini等,Zignaly同样无直接合作。ZIG代币虽然在Kraken上线交易bitdegree.org,但这属于Kraken自主上市行为,不代表战略合作。Zignaly没有接入Kraken的交易API作为其平台的一部分,因为Kraken主要服务现货和少量期货,不符合Zignaly用户偏好。Gemini等更无交集。
总结来说,Zignaly与美国阵营的交易所联系甚微。这与Zignaly避开美国市场战略一致,也是对其主要合作伙伴币安的差异化选择。相较之下,Zignaly更倾向于与非美系平台合作(币安、Bybit、KuCoin等亚洲和欧洲平台),一方面规避美国监管风险,另一方面这些平台的产品(高杠杆合约等)更适合Zignaly的跟单盈利模式。对于FTX这样的美国背景公司,Zignaly并未牵涉其中,因而在FTX风波中毫发无损,继续推进自身业务。
10. 与币安的关系分析(“若即若离”)
Zignaly与币安的关系可以用“紧密合作却保持独立”来形容,表面上看似若即若离,实则是一种战略平衡:
合作深度:Zignaly是币安紧密的生态伙伴之一。从2019年起,Zignaly就与币安建立对接,推出针对币安交易的复制交易功能zignaly.com。币安的Broker/Link计划更使双方绑定,Zignaly大量交易在币安体系内完成criptonoticias.com。币安也认可Zignaly为顶级合作方,多次在官方渠道宣传其业绩zignaly.com。技术上,Zignaly深度集成币安API,用户通过Zignaly下单实为在币安撮合criptonoticias.com。安全上,Zignaly用户资产由币安托管,受到币安风控保护criptonoticias.com。可以说,币安为Zignaly提供了交易引擎、流动性、托管、安全等关键支持。如果没有币安,Zignaly无法轻易实现全球服务。因此合作层面,两者关系非常紧密,Zignaly对币安存在一定依赖。
独立性:尽管联系密切,Zignaly仍保持自身的独立运营和战略拓展:
-
多元交易所集成: Zignaly并非只依赖币安一家,它同时对接了多家交易所(Bybit、KuCoin等),以分散风险和覆盖更多市场medium.com。这表明Zignaly不将所有鸡蛋放在一个篮子里,在合作币安的同时也与币安的竞争对手合作。这种多元策略保证了如果币安出现政策变化,Zignaly仍有其他出路。
-
自主生态建设: Zignaly开发了ZIGChain公链和ZIG代币经济,打造自己的去中心化生态iq.wiki。这部分业务(如链上RWA投资、DAO治理等)是在币安体系之外开展的。尤其ZIGChain是一个独立网络,Zignaly藉此拥有了不依赖任何中心化交易所的新赛道。如果ZIGChain生态成功,Zignaly对币安的依赖度将降低,因为部分交易和资产管理可转移到链上进行。
-
资本与治理独立: Zignaly目前并未接受币安Labs或币安直接投资,其主要股东是第三方基金(如GEM)和创始团队。币安在Zignaly没有股权,这意味着Zignaly在公司治理上不受币安直接控制。双方是合作伙伴关系而非母子公司关系。这给了Zignaly在决策上更大自主空间,可以根据自身利益选择业务方向,而不必完全听命于币安。
-
品牌和社区: Zignaly经营着自己的品牌和用户社区(ZIGDAO),并未被币安品牌所吞没。用户普遍认识Zignaly作为独立平台,而非币安的子平台。这种品牌独立性也体现双方保持一定距离。Zignaly甚至在某些场合与币安竞争,例如它的利润分享模式理论上和币安的理财产品存在替代关系。但由于定位不同,币安默许了Zignaly的存在。
“若即若离”的表现:这种关系既有亲密合作的一面,也有保持距离的一面:
-
亲密体现在日常运营和战略协同上——币安为Zignaly赋能,Zignaly为币安导流,互惠互利binance.com。双方高层可能定期沟通,比如在行业会议或Broker大会上交流经验。币安也从Zignaly获取社交交易领域的数据和洞见。
-
保持距离体现在Zignaly不断拓展币安之外的新领域,比如支持币安竞争对手Bybit,发行自己代币并上其他交易所(Kraken等)bitdegree.org。币安则对Zignaly采取开放态度,但并未将其收购或纳入子公司体系。这可能是出于合规或资源考虑,也反映币安对这种松散合作模式的认可。
风险与依赖程度:尽管Zignaly努力独立,但对币安的依赖仍不可忽视。币安交易量占Zignaly大头,一旦币安遭遇风险(如监管打压、停业等),Zignaly业务将受冲击。不过Zignaly的多交易所策略和链上业务可部分缓解这种风险。此外,币安若改变Broker政策(例如降低佣金比例或收紧用户管控),也可能影响Zignaly收益。这种不确定性让Zignaly对币安既依赖又审慎,从而保持若即若离的姿态。
战略定位:对币安来说,Zignaly是拓展社交投资领域的战略伙伴,但不是唯一伙伴(币安还有其他Broker合作)。币安希望Zignaly成功又不会大到威胁自身。所以币安支持Zignaly但保持一定边界,不给予独占特权。对Zignaly而言,币安是基础设施提供者而非最终目的地。Zignaly借力币安成长,同时构筑自己的护城河(社区+公链)。这种伙伴关系类似“平台+应用”的生态纽带:币安提供平台,Zignaly作为应用丰富了平台场景。双方都从合作中获益,但也都为自己预留了退出和转圜的空间。
综上,Zignaly与币安的关系紧密合作却又保持独立,被用户形容为“若即若离”实属恰当。它们既相互依存,又各自发展:Zignaly深度依赖币安的交易生态来服务其50万+用户medium.com,同时通过多元化策略降低对单一平台的束缚。币安则愿意共享部分资源给Zignaly,但不直接将其收编,以保持生态开放性和灵活性。这种微妙平衡使得双方在快速变化的加密行业中都能进退自如。正如一份币安Square分析所称:“Zignaly连接全球50万用户和150多位资管人,币安与Bybit皆将其视为顶级Broker伙伴”binance.com。这种定位体现了Zignaly在头部交易所眼中的价值,也解释了双方若即若离、松耦合但高协同的关系本质。
参考资料:
-
Zignaly创始团队及公司简介bitdegree.orgiq.wiki
-
Zignaly获得南非FSCA二类牌照的报道coindesk.comglobenewswire.com
-
Zignaly在拉美市场(巴西)合作的官方披露zignaly.medium.com
-
Zignaly伊斯兰金融合规及Zamanat平台介绍help.zignaly.comhackernoon.com
-
ZigChain发布和技术架构详情coindesk.combinance.com
-
Zignaly为币安最大Broker的官方说法binance.commedium.com
-
关于Zignaly在日本暂无业务的推断criptonoticias.combinance.com
-
Zignaly与FTX无关联及与美系交易所关系分析bitdegree.orgreddit.com
-
币安与Zignaly合作关系的综述criptonoticias.comzignaly.com
-
-
 @ 04ce30c2:59ea576a
2025-05-20 04:19:25
@ 04ce30c2:59ea576a
2025-05-20 04:19:25Em uma sociedade verdadeiramente livre, o indivíduo tem o direito de escolher como guardar e transferir valor. Isso inclui a liberdade de escolher qual moeda usar, sem coerção, monopólios ou imposições estatais. A concorrência entre moedas permite que as melhores propriedades monetárias prevaleçam de forma natural e voluntária.
Moeda imposta é controle
Quando uma única moeda é forçada por lei, seja por decreto estatal ou por exigências institucionais, o usuário perde a soberania sobre seu próprio patrimônio. Isso abre espaço para inflação arbitrária, bloqueios de transações, congelamento de fundos e vigilância massiva.
Concorrência monetária é essencial
A liberdade monetária implica a coexistência de várias moedas competindo entre si. Cada uma traz suas características e vantagens específicas. A escolha deve estar nas mãos do usuário, não em autoridades centralizadas.
A melhor moeda tende a se tornar o padrão
No longo prazo, a moeda com melhores propriedades monetárias, como previsibilidade, descentralização, auditabilidade e liquidez, tende a ser adotada como padrão de referência para precificação, poupança e comércio global.
O Bitcoin é a moeda mais forte nesse sentido. Mas isso não impede que outras moedas coexistam como ferramentas complementares em contextos específicos.
Conversão é liberdade
Se o usuário quiser por exemplo mais privacidade ao comprar um café ou pagar uma conta, ele pode facilmente trocar seus bitcoins por monero e usá-los conforme sua necessidade. A possibilidade de trocar entre moedas é parte essencial da liberdade financeira.
Uma sociedade livre permite a escolha. O padrão monetário deve emergir do consenso do mercado, não de imposições. Que o Bitcoin se torne o padrão não por decreto, mas por mérito. E que outras moedas existam para servir à liberdade individual em toda sua complexidade.
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 7953d1fa:69c8039d
2025-05-20 02:39:56
@ 7953d1fa:69c8039d
2025-05-20 02:39:56No mundo digital em constante evolução, plataformas de entretenimento online vêm ganhando espaço entre os brasileiros que buscam diversão, emoção e recompensas. Uma das opções que tem se destacado recentemente é a KK999, uma plataforma moderna, segura e repleta de oportunidades para jogadores de todos os níveis. Com uma ampla gama de jogos envolventes e uma experiência de usuário otimizada, o KK999 está conquistando cada vez mais adeptos no Brasil.
Introdução à Plataforma KK999 O KK999 se diferencia por oferecer uma experiência completa e intuitiva desde o primeiro acesso. A interface da plataforma foi cuidadosamente projetada para ser amigável, permitindo que novos usuários se cadastrem rapidamente e naveguem com facilidade. Tudo é pensado para garantir que o jogador tenha uma experiência fluida, sem complicações e com total transparência.
Além disso, o kk999se destaca por sua forte infraestrutura de segurança. Utilizando tecnologia de criptografia de ponta, os dados dos usuários são protegidos em todas as transações, garantindo tranquilidade para quem deseja apenas se divertir. Outro ponto importante é o suporte ao cliente, que está disponível 24 horas por dia, com atendimento em português, pronto para auxiliar com qualquer dúvida ou necessidade.
Variedade de Jogos para Todos os Gostos Um dos grandes atrativos do KK999 é a impressionante variedade de jogos disponíveis. Desde os tradicionais jogos de cartas até opções modernas com gráficos avançados, a plataforma atende todos os estilos de jogadores. Entre os destaques, estão as famosas roletas virtuais, jogos de pesca interativa, slot machines com temas variados e jogos ao vivo que simulam a sensação de estar em uma sala de jogos física.
Os slots, por exemplo, são um sucesso entre os brasileiros, oferecendo desde títulos clássicos com frutas e números até aventuras temáticas com bônus emocionantes. Os jogos de cartas também têm grande popularidade, incluindo versões modernas de pôquer, bacará e outros jogos estratégicos que desafiam a mente do jogador.
Para quem gosta de competir em tempo real, o KK999 oferece jogos ao vivo com crupiês reais e interatividade instantânea, proporcionando uma experiência imersiva e cheia de adrenalina. Tudo isso com transmissões de alta qualidade e conexão estável.
Experiência do Jogador: Diversão e Confiabilidade A experiência do jogador é uma das maiores prioridades do KK999. Desde o primeiro cadastro até as jogadas mais avançadas, a plataforma investe em funcionalidades que aumentam o conforto e a confiança do usuário. A navegação é rápida, os jogos carregam com eficiência e as recompensas são distribuídas com agilidade.
Outro fator que atrai muitos jogadores é o sistema de bônus e promoções. O KK999 frequentemente disponibiliza ofertas especiais para novos membros e prêmios para usuários frequentes, incentivando a fidelidade e aumentando ainda mais as chances de ganhar.
Além disso, o KK999 oferece uma experiência totalmente otimizada para dispositivos móveis. Seja no celular ou tablet, o jogador pode acessar todos os recursos da plataforma de qualquer lugar, a qualquer momento, sem perder desempenho ou qualidade.
Conclusão O KK999 se consolida como uma das principais plataformas de entretenimento digital no Brasil, reunindo inovação, segurança e uma variedade impressionante de jogos. Ideal tanto para iniciantes quanto para jogadores experientes, o site oferece tudo o que é necessário para transformar momentos comuns em experiências emocionantes.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 7953d1fa:69c8039d
2025-05-20 02:39:23
@ 7953d1fa:69c8039d
2025-05-20 02:39:23O cenário do entretenimento online no Brasil vem evoluindo rapidamente, e uma das plataformas que mais se destaca atualmente é a 8CC. Com uma proposta moderna, intuitiva e voltada para a melhor experiência do usuário, a 8CC conquistou a confiança de milhares de jogadores que buscam diversão, praticidade e oportunidades de ganhos reais em um ambiente seguro.
Conhecendo a Plataforma 8CC A 8CC é uma plataforma digital desenvolvida para atender tanto iniciantes quanto jogadores experientes. Sua interface amigável e bem organizada facilita a navegação mesmo para quem nunca teve contato com esse tipo de entretenimento antes. Compatível com computadores, tablets e celulares, o site é totalmente responsivo, o que significa que você pode se divertir de qualquer lugar, a qualquer hora.
Um dos diferenciais da 8cc é o seu compromisso com a segurança dos usuários. A plataforma utiliza tecnologia de criptografia de ponta para garantir a proteção de dados pessoais e transações financeiras. Além disso, o suporte ao cliente está sempre disponível para tirar dúvidas, resolver problemas e oferecer o melhor atendimento possível.
Diversidade de Jogos para Todos os Gostos Na 8CC, os jogadores têm acesso a uma vasta seleção de jogos online, desenvolvidos pelos principais provedores do mercado internacional. Isso garante alta qualidade gráfica, mecânicas inovadoras e excelente desempenho.
Entre os jogos mais populares da plataforma estão:
Slots (caça-níqueis): com temas variados, rodadas bônus e jackpots progressivos que proporcionam grandes emoções.
Jogos de mesa clássicos: como roleta, blackjack e bacará, com versões que imitam perfeitamente a experiência de jogo ao vivo.
Jogos com crupiês em tempo real: transmitidos com qualidade HD, esses jogos trazem interatividade e realismo, permitindo que o jogador se sinta dentro de um ambiente físico de alto padrão.
A plataforma também disponibiliza jogos de habilidade e apostas esportivas ao vivo, oferecendo uma experiência ainda mais completa e personalizada de acordo com o perfil de cada usuário.
Experiência do Jogador na 8CC Quem já experimentou jogar na 8CC sabe o quanto a plataforma valoriza o conforto e a satisfação de seus usuários. Desde o momento do cadastro até o resgate de ganhos, tudo é feito de forma simples, rápida e segura. O processo de registro é intuitivo, exigindo apenas alguns dados básicos, e os métodos de pagamento são variados, aceitando transferências bancárias, carteiras digitais e até criptomoedas.
Outro destaque é o sistema de recompensas e promoções. A 8CC frequentemente oferece bônus de boas-vindas, rodadas grátis e campanhas especiais para usuários fiéis, o que aumenta ainda mais as chances de ganhar e prolonga a diversão. Além disso, a plataforma promove torneios e desafios semanais com prêmios atrativos, incentivando a competição saudável entre os jogadores.
Por Que Escolher a 8CC? Existem muitas razões para escolher a 8CC como sua principal plataforma de jogos online:
Confiabilidade e segurança em todas as operações;
Variedade de jogos para todos os perfis;
Interface moderna e de fácil navegação;
Promoções e bônus frequentes;
Atendimento ao cliente eficiente e disponível 24 horas.
Se você busca uma experiência diferenciada, com diversão garantida e a possibilidade de transformar seu tempo livre em momentos empolgantes, a 8CC é a escolha certa. Descubra agora mesmo tudo o que essa plataforma inovadora tem a oferecer e junte-se à comunidade que está revolucionando o entretenimento digital no Brasil.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 472f440f:5669301e
2025-05-20 02:00:54
@ 472f440f:5669301e
2025-05-20 02:00:54Marty's Bent
https://www.youtube.com/watch?v=p0Sj1sG05VQ
Here's a great presentation from our good friend nostr:nprofile1qyx8wumn8ghj7cnjvghxjmcpp4mhxue69uhkummn9ekx7mqqyz2hj3zg2g3pqwxuhg69zgjhke4pcmjmmdpnndnefqndgqjt8exwj6ee8v7 , President of The Nakamoto Institute titled Hodl for Good. He gave it earlier this year at the BitBlockBoom Conference, and I think it's something everyone reading this should take 25 minutes to watch. Especially if you find yourself wondering whether or not it's a good idea to spend bitcoin at any given point in time. Michael gives an incredible Austrian Economics 101 lesson on the importance of lowering one's time preference and fully understanding the importance of hodling bitcoin. For the uninitiated, it may seem that the hodl meme is nothing more than a call to hoard bitcoins in hopes of getting rich eventually. However, as Michael points out, there's layers to the hodl meme and the good that hodling can bring individuals and the economy overall.
The first thing one needs to do to better understand the hodl meme is to completely flip the framing that is typically thrust on bitcoiners who encourage others to hodl. Instead of ceding that hodling is a greedy or selfish action, remind people that hodling, or better known as saving, is the foundation of capital formation, from which all productive and efficient economic activity stems. Number go up technology is great and it really matters. It matters because it enables anybody leveraging that technology to accumulate capital that can then be allocated toward productive endeavors that bring value to the individual who creates them and the individual who buys them.
When one internalizes this, it enables them to turn to personal praxis and focus on minimizing present consumption while thinking of ways to maximize long-term value creation. Live below your means, stack sats, and use the time that you're buying to think about things that you want in the future. By lowering your time preference and saving in a harder money you will have the luxury of demanding higher quality goods in the future. Another way of saying this is that you will be able to reshape production by voting with your sats. Initially when you hold them off the market by saving them - signaling that the market doesn't have goods worthy of your sats - and ultimately by redeploying them into the market when you find higher quality goods that meet the standards desire.
The first part of this equation is extremely important because it sends a signal to producers that they need to increase the quality of their work. As more and more individuals decide to use bitcoin as their savings technology, the signal gets stronger. And over many cycles we should begin to see low quality cheap goods exit the market in favor of higher quality goods that provide more value and lasts longer and, therefore, make it easier for an individual to depart with their hard-earned and hard-saved sats. This is only but one aspect that Michael tries to imbue throughout his presentation.
The other is the ability to buy yourself leisure time when you lower your time preference and save more than you spend. When your savings hit a critical tipping point that gives you the luxury to sit back and experience true leisure, which Michael explains is not idleness, but the contemplative space to study, create art, refine taste, and to find what "better goods" actually are. Those who can experience true leisure while reaping the benefits of saving in a hard asset that is increasing in purchasing power significantly over the long term are those who build truly great things. Things that outlast those who build them. Great art, great monuments, great institutions were all built by men who were afforded the time to experience leisure. Partly because they were leveraging hard money as their savings and the place they stored the profits reaped from their entrepreneurial endeavors.
If you squint and look into the future a couple of decades, it isn't hard to see a reality like this manifesting. As more people begin to save in Bitcoin, the forces of supply and demand will continue to come into play. There will only ever be 21 million bitcoin, there are around 8 billion people on this planet, and as more of those 8 billion individuals decide that bitcoin is the best savings vehicle, the price of bitcoin will rise.
When the price of bitcoin rises, it makes all other goods cheaper in bitcoin terms and, again, expands the entrepreneurial opportunity. The best part about this feedback loop is that even non-holders of bitcoin benefit through higher real wages and faster tech diffusion. The individuals and business owners who decide to hodl bitcoin will bring these benefits to the world whether you decide to use bitcoin or not.
This is why it is virtuous to hodl bitcoin. The potential for good things to manifest throughout the world increase when more individuals decide to hodl bitcoin. And as Michael very eloquently points out, this does not mean that people will not spend their bitcoin. It simply means that they have standards for the things that they will spend their bitcoin on. And those standards are higher than most who are fully engrossed in the high velocity trash economy have today.
In my opinion, one of those higher causes worthy of a sats donation is nostr:nprofile1qyfhwumn8ghj7enjv4jhyetvv9uju7re0gq3uamnwvaz7tmfdemxjmrvv9nk2tt0w468v6tvd3skwefwvdhk6qpqwzc9lz2f40azl98shkjewx3pywg5e5alwqxg09ew2mdyeey0c2rqcfecft . Consider donating so they can preserve and disseminate vital information about bitcoin and its foundations.
The Shell Game: How Health Narratives May Distract from Vaccine Risks
In our recent podcast, Dr. Jack Kruse presented a concerning theory about public health messaging. He argues that figures like Casey and Callie Means are promoting food and exercise narratives as a deliberate distraction from urgent vaccine issues. While no one disputes healthy eating matters, Dr. Kruse insists that focusing on "Froot Loops and Red Dye" diverts attention from what he sees as immediate dangers of mRNA vaccines, particularly for children.
"It's gonna take you 50 years to die from processed food. But the messenger jab can drop you like Damar Hamlin." - Dr Jack Kruse
Dr. Kruse emphasized that approximately 25,000 children per month are still receiving COVID vaccines despite concerns, with 3 million doses administered since Trump's election. This "shell game," as he describes it, allows vaccines to remain on childhood schedules while public attention fixates on less immediate health threats. As host, I believe this pattern deserves our heightened scrutiny given the potential stakes for our children's wellbeing.
Check out the full podcast here for more on Big Pharma's alleged bioweapons program, the "Time Bank Account" concept, and how Bitcoin principles apply to health sovereignty.
Headlines of the Day
Aussie Judge: Bitcoin is Money, Possibly CGT-Exempt - via X
JPMorgan to Let Clients Buy Bitcoin Without Direct Custody - via X
Get our new STACK SATS hat - via tftcmerch.io
Mubadala Acquires 384,239 sats | $408.50M Stake in BlackRock Bitcoin ETF - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
I've been walking from my house around Town Lake in Austin in the mornings and taking calls on the walk. Big fan of a walking call.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 6e0ea5d6:0327f353
2025-05-20 01:35:20
@ 6e0ea5d6:0327f353
2025-05-20 01:35:20**Ascolta bene! ** A man's sentimental longing, though often disguised in noble language and imagination, is a sickness—not a virtue.
It begins as a slight inclination toward tenderness, cloaked in sweetness. Then it reveals itself as a masked addiction: a constant need to be seen by a woman, validated by her, and reciprocated—as if someone else's affection were the only anchor preventing the shipwreck of his emotions.
The man who understands the weight of leadership seeks no applause, no gratitude, not even romantic love. He knows that his role is not theatrical but structural. He is not measured by the emotion he evokes, but by the stability he ensures. Being a true man is not ornamental. He is not a decorative symbol in the family frame.
We live in an era where male roles have been distorted by an overindulgence in emotion. The man stopped guiding and began asking for direction. His firmness was exchanged for softness, his decisiveness for hesitation. Trying to please, many have given up authority. Trying to love, they’ve begun to bow. A man who begs for validation within his own home is not a leader—he is a guest. And when the patriarch has to ask for a seat at the table he should preside over and sustain, something has already been irreversibly inverted.
Unexamined longing turns into pleading. And all begging is the antechamber of humiliation. A man who never learned to cultivate dignified solitude will inevitably fall to his knees in desperation. And then, he yields. Yields to mediocre presence, to shallow affection, to constant disrespect. He smiles while he bleeds, praises the one who despises him, accepts crumbs and pretends it’s a banquet. All of it, cazzo... just to avoid the horror of being alone.
Davvero, amico mio, for the men who beg for romance, only the consolation of being remembered will remain—not with respect, but with pity and disgust.
The modern world feeds the fragile with illusions, but reality spits them out. Sentimental longing is now celebrated as sensitivity. But every man who nurtures it as an excuse will, sooner or later, pay for it with his dignity.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 502ab02a:a2860397
2025-05-20 01:22:31
@ 502ab02a:a2860397
2025-05-20 01:22:31พอพูดถึงบริษัทอย่าง Formo ที่ทำชีสโดยไม่ใช้วัวเลย คนส่วนใหญ่จะนึกถึงคำว่า “นวัตกรรม” “ยั่งยืน” “ลดโลกร้อน” กันเป็นด่านแรก แต่พอเฮียมองทะลุม่านควันพวกนี้ไป จะเห็นทุนรายใหญ่ที่หนุนหลังอยู่ ซึ่งหลายเจ้าก็ไม่ใช่ผู้พิทักษ์โลก แต่เป็นผู้เล่นตัวจี๊ดในอุตสาหกรรมอาหารโลกมายาวนาน
หนึ่งในนั้นคือบริษัทจากเกาหลีใต้ชื่อ CJ CheilJedang ซึ่งอาจฟังดูไกลตัว แต่จริงๆ แล้ว เฮียว่าชื่อนี้โผล่ตามซองอาหารสำเร็จรูปในครัวคนไทยหลายบ้านโดยไม่รู้ตัว
ถ้าจะเข้าใจ Formo ให้ถึงแก่น เราต้องมองไปถึงทุนที่ “ใส่เงิน” และ “ใส่จุดยืน” ลงไปในบริษัทนั้น และหนึ่งในผู้ถือหุ้นรายสำคัญก็คือ CJ CheilJedang บริษัทเกาหลีใต้ที่ก่อตั้งมาตั้งแต่ปี 1953 โดยเริ่มจากการเป็นโรงงานผลิตน้ำตาล จากนั้นก็กินรวบแทบทุกวงจรอาหารของเกาหลี
โปรไฟล์ CJ แค่เห็นภาพรวมก็ขนลุกแล้วครับ ลูกพี่เราแข็งแกร่งขนาดไหน - เป็นเจ้าของแบรนด์ Bibigo ที่เราอาจจะคุ้นในสินค้า กิมจิ และ CJ Foods ที่มีขายทั่วโลก -เป็นผู้ผลิต กรดอะมิโน รายใหญ่ของโลก เช่น ไลซีน, ทรีโอนีน, ทริปโตแฟน ที่ใช้เป็นวัตถุดิบในอาหารสัตว์ แต่ตอนนี้หลายบริษัทเอาไปใส่ใน Plant-based food แล้วเคลมว่าเป็นโปรตีนสมบูรณ์ -เป็นเจ้าของโรงงานผลิต แบคทีเรียสายพันธุ์พิเศษ สำหรับการหมักหลายประเภท -ขึ้นชื่อเรื่อง bioscience โดยเฉพาะ precision fermentation ซึ่งเป็นเทคโนโลยีเดียวกับที่ Formo ใช้ผลิตเคซีน (โปรตีนในนมวัว)
แปลว่า CJ ไม่ได้มาลงทุนใน Formo แบบ “หวังผลกำไรเฉยๆ” แต่เขามองเห็น “อนาคตใหม่ของอาหาร” ที่ตัวเองจะเป็นเจ้าของต้นน้ำยันปลายน้ำ
คำถามก็คือเบื้องลึกการลงทุนใน Formo ใครได้อะไร? Formo ปิดรอบระดมทุน Series A ได้ประมาณ 50 ล้านดอลลาร์สหรัฐ เมื่อปี 2021 โดยมีนักลงทุนหลายเจ้า เช่น EQT Ventures, Elevat3 Capital, Atomico แต่ CJ CheilJedang ก็เป็นหนึ่งในผู้ลงทุนเชิงกลยุทธ์ (strategic investor) ที่เข้ามาแบบไม่ใช่แค่ลงเงิน แต่เอา เทคโนโลยี + เครือข่ายโรงงาน + ซัพพลายเชนระดับโลก มาเสริมให้ Formo ขยายได้เร็วขึ้น
การจับมือกันครั้งนี้มีนัยยะสำคัญครับ -Formo ได้ เทคโนโลยีหมักจุลินทรีย์ (ที่ CJ ถนัดมาก) และช่องทางกระจายสินค้าในเอเชีย -CJ ได้ ถือหุ้นในบริษัทที่กำลังจะเปลี่ยนภาพ “ผลิตภัณฑ์จากนม” ให้กลายเป็นสิ่งที่ไม่ต้องมีสัตว์อีกต่อไป ซึ่งจะเป็นกลยุทธ์สำคัญในการสร้างแบรนด์อาหารแห่งอนาคต ที่นมจะต้องมาจากโรงงานผลิตเท่านั้นจึงจะมีคุณสมบัติที่ดีทั้งสารอาหารและความสะอาด
CJ เองก็เคยประกาศต่อสื่อว่า อยากเป็น “Global Lifestyle Company” ซึ่งฟังดูเบาๆ แต่จริงๆ คือแผนใหญ่ในการ เปลี่ยนวิธีการกินของคนทั้งโลกได้เลยเช่นกัน -จาก “อาหารจริง” ไปเป็น “อาหารสังเคราะห์” (synthetic food) -จาก “ฟาร์มสัตว์” ไปเป็น “ถังหมักจุลินทรีย์” -จาก “ความหลากหลายตามธรรมชาติ” ไปเป็น “สูตรกลาง” ที่ควบคุมได้ในระดับโมเลกุล
การหนุนหลัง Formo จึงไม่ใช่เรื่องบังเอิญ แต่เป็นอีกหนึ่งหมากในกระดานใหญ่ที่ CJ วางไว้ เพื่อเป็นเจ้าของอาหารอนาคตแบบไม่ต้องเลี้ยงหมู ไก่ วัว แต่ครองเทคโนโลยีแทน
คำถามคือแล้วผู้บริโภคจะรู้ทันไหมว่า เบื้องหลังชีสที่ไม่มีวัว อาจมี “ทุนที่อยากครองโลกอาหาร” คำที่เคลมว่า “ยั่งยืน” อาจสร้างระบบอาหารใหม่ที่ยิ่งห่างจากธรรมชาติเข้าไปทุกที
คนที่เคย “กลัวสารเคมี” ในอาหารแปรรูป กลับกลืนผลิตภัณฑ์จากห้องแล็บ โดยคิดว่า “มันคือความสะอาดและอนาคต” #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ fd06f542:8d6d54cd
2025-05-20 01:18:45
@ fd06f542:8d6d54cd
2025-05-20 01:18:45🧱 NostrTrust Initial Trust Score List (V0.1)
This list defines the initial trust scores (T Score) for key members of the Nostr community based on their contributions, reputation, and role in the ecosystem. The goal is to seed a decentralized trust system that encourages quality interactions and authentic contributions.
> ⚠️ Note: This is an draft version.
✅ Initial T Score Allocation Rules
| User Type | Initial T Score Range | Criteria | |-----------|------------------------|----------| | Founder | 10,000 | Creator of the Nostr protocol | | Core Developers | 5,000 - 8,000 | Major contributors to core codebase, clients, or infrastructure | | Active Contributors | 1,000 - 4,000 | Recognized long-term contributors to content, tools, or community |
👤 Initial Trust Score Table
| Name / Alias | npub | Initial T Score | Justification | |--------------|------|------------------|----------------| | fiatjaf | npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 | 10,000 | Creator of the Nostr protocol | |Jack|npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m|9,000|| | jb55 | npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s | 7,000 | Developer of tools, relays, and early Nostr integrations,made damus | |Alex Gleason | npub1q3sle0kvfsehgsuexttt3ugjd8xdklxfwwkh559wxckmzddywnws6cd26p | 7,000 || |PABLOF7z|npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft|7,000|NDK| |DASHU|npub19yeqjawls407xjnmgkk6yss7936pcd7qzd5srlj8wye6j8433vrsjazqwk|4,000|Nostrmo | |Moss|npub129z0az8lgffuvsywazww07hx75qas3veh3dazsq56z8y39v86khs2uy5gm|4,000| freerse.com| |w|npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl|4,000| 0xchat | |Cody Tseng|npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl|4,000| jumble.social| |nostr_cn_dev|npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm|1,000|nostrbook.com,NostrTrust,nostrbridge| |hzrd149|npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr|6,000|blossom,nostrudel| ||||| ||||| ||||| ||||| |||||
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-20 00:09:55
@ 5d4b6c8d:8a1c1ee3
2025-05-20 00:09:55https://youtu.be/EPiE-Ruhohg
I'm pretty sure Ben called Caruso the "Bald Mamba" in this video, which is an awesome nickname for him.
Great walkthrough of the adjustments made over the course of seven games to try to disrupt Joker, culminating with putting Caruso (who's 100 lbs lighter and 6 inches shorter) on him.
https://stacker.news/items/984227
-
 @ c296b5f7:c7282b53
2025-05-19 23:35:17
@ c296b5f7:c7282b53
2025-05-19 23:35:17testee
-
 @ 9be6a199:6e133301
2025-05-19 23:11:35
@ 9be6a199:6e133301
2025-05-19 23:11:35this is the content
this is an update
-
 @ c296b5f7:c7282b53
2025-05-19 23:18:42
@ c296b5f7:c7282b53
2025-05-19 23:18:42 -
 @ 9be6a199:6e133301
2025-05-19 22:39:28
@ 9be6a199:6e133301
2025-05-19 22:39:28sdsdsd
-
 @ 4ba8e86d:89d32de4
2025-05-19 22:33:46
@ 4ba8e86d:89d32de4
2025-05-19 22:33:46O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://pomf2.lain.la/f/eprhj0u3.mp4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://pomf2.lain.la/f/7p6jfr9r.mp4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável. https://pomf2.lain.la/f/x4pm8hm8.mp4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ c296b5f7:c7282b53
2025-05-19 23:17:49
@ c296b5f7:c7282b53
2025-05-19 23:17:49https://curtlink.com/user/login powerdigital f1950610#@
-
 @ 2b998b04:86727e47
2025-05-19 21:18:46
@ 2b998b04:86727e47
2025-05-19 21:18:46After the pruning came clarity.\ And after the clarity came a quiet but relentless question:\ What now?
If I wasn’t going back to Web3, if I wasn’t going to pretend anymore — not in faith, not in finance — then I needed to start building again. But this time, with different materials. Different rhythms. A different spirit.
Starting Over on Solid Ground
I’d spent years exploring tokens, networks, and well-intentioned communities. But most of it, I see now, was sand. It moved with the tides. The incentives shifted. The values bent. And when the storms came — personal, financial, spiritual — much of what I’d been part of collapsed or exposed its shallowness.
So I returned to the beginning: What can’t be faked?
That’s where Bitcoin came in — not just as an asset, but as a foundation.\ It taught me cost. Time. Truth. It doesn’t market itself. It just is.\ A system that punishes shortcuts, rewards discipline, and invites peace.
And the more I leaned in, the more I realized:\ This isn’t just money. This is philosophy. This is soil.
Pruned to Plant Again
I used to be a buy-and-hold investor. I still carry those instincts. But in 2020–21, I discovered trading — and with it, a new kind of discipline. Not gambling. Not speculation. Stewardship under pressure. Real-time decision-making with skin in the game.
My grandfather, who passed in the late '90s, probably would’ve looked a little dimly on trading. He lived off his dividends. Stocks he held for decades. He wasn’t chasing. He was rooting. But he would’ve respected the discipline — the clarity — when done right.
He also saw things I didn’t. He once told me I wasn’t raised properly. It hurt at the time, but now I understand. He saw the drift — not just in me, but in the culture. He understood that frugality means nothing if it’s not paired with truth.
I think he would’ve respected what I’m doing now — even if he wouldn't have fully understand it.
What I’m Building Now
-
StartNation – A Bitcoin-aligned equity accelerator. Proof-based. No tokens. No hype.
-
Golden Gate Group Investments – Real estate with a vision to integrate BTC in payments and ownership. Still early. Still real.
-
Blue Planet Ventures – Equities trading with daily proof-of-work and sats-based performance tracking.
-
A garden – Yes, literal food. Soil and seed. Hypdropnics. Bitcoin taught me patience; gardening reinforces it.
I’m not building a brand. I’m building a life. And I’m doing it in public — not to be seen, but to help others see. That it’s possible to step off the hype rails and still thrive.
Bitcoin: The Turning Point
It wasn’t until last fall that Bitcoin truly became central for me.\ Not just part of a portfolio — the lens through which I see capital, time, and truth.
I don’t see it as speculative anymore. I see it as inevitable. In 20–30 years, I believe Bitcoin will be the de facto reserve currency — even if not in name. Those who hold it will steward wealth not because they played the game, but because they opted out of it early.
I’m stacking not to escape — but to prepare. Not to prove I'm right — but to live rightly.
Legacy Without a Platform
I don’t have children.\ But I do have nieces. Nephews. Brothers. Sisters. Cousins. In-Laws.
And I know they’re watching — even if they don’t say it.\ I want to show them that you can live with truth, walk by faith, work with your hands — and still thrive.
I’m not stacking for applause. I’m stacking for legacy.\ I’m building not just for the next quarter — but for the next generation.
And if someone, years from now, asks why I chose this path, I want to say:
Because it was real.\ Because it was proof.\ Because it was built to last.
⚡ If this series has encouraged or challenged you, zap a few sats/bitcoin. It keeps me building.
✍️ Catch up on the full series here:\ \ Part 1: The Drift -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-1%3A-the-drift\ Part 2: The Breaking Point -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work---part-2%3A-the-breaking-point\ Part 3: The Return -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-3%3A-the-return\ Part 4: Proof Of Work as Philosophy -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-4%3A-proof-of-work-as-philosophy\ Part 5: Building Again (what you are reading now...)
Written with help from ChatGPT (GPT-4), edited and posted by me.
-
-
 @ 1817b617:715fb372
2025-05-19 20:39:28
@ 1817b617:715fb372
2025-05-19 20:39:28Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
🔗 Buy Flash USDT Now This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
✅ Perfect for: Simulating token inflows Wallet stress testing “Proof of funds” display Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
🧠 What Is Flash USDT? Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
Visible on wallet interfaces Time-limited (auto-disappears cleanly) Undetectable on block explorers after expiry It’s the smartest, safest way to simulate high-value transactions without real crypto.
🛠️ Flash USDT Software – Your Own USDT Flasher at Your Fingertips Want to control the flash? Run your own operations? Flash unlimited wallets?
🔗 Buy Flash USDT Software
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
Send custom USDT amounts Set custom expiry time (e.g., 30–360 days) Flash multiple wallets Choose between networks (Tron, ETH, BSC) You can simulate any amount, to any supported wallet, from your own system.
No third-party access. No blockchain fee. No trace left behind.
💥 Why Our Flash USDT & Software Stands Out Feature Flash USDT Flash USDT Software One-time flash send ✅ Yes Optional Full sender control ❌ No ✅ Yes TRC20 / ERC20 / BEP20 ✅ Yes ✅ Yes Custom duration/expiry Limited ✅ Yes Unlimited usage ❌ One-off ✅ Yes Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
🛒 Ready to Buy Flash USDT or the Software? Skip the wait. Skip the scammers. You’re one click away from real control.
👉 Buy Flash USDT 👉 Buy Flash USDT Software
📞 Support or live walkthrough?
💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531
🚫 Legal Notice These tools are intended for:
Educational purposes Demo environments Wallet and UI testing They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call: Need to flash USDT? Want full control? Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
🔗 Buy Now → Flash USDT 🔗 Buy Now → Flash USDT Software 💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
Buy Flash USDT Now\ This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
Perfect for:
- Simulating token inflows
- Wallet stress testing
- “Proof of funds” display
Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
What Is Flash USDT?
Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
- Visible on wallet interfaces
- Time-limited (auto-disappears cleanly)
- Undetectable on block explorers after expiry
It’s the smartest, safest way to simulate high-value transactions without real crypto.
Flash USDT Software – Your Own USDT Flasher at Your Fingertips
Want to control the flash?\ Run your own operations?\ Flash unlimited wallets?
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
- Send custom USDT amounts
- Set custom expiry time (e.g., 30–360 days)
- Flash multiple wallets
- Choose between networks (Tron, ETH, BSC)
You can simulate any amount, to any supported wallet, from your own system.
No third-party access.\ No blockchain fee.\ No trace left behind.
Why Our Flash USDT & Software Stands Out
Feature
Flash USDT
Flash USDT Software
One-time flash send
Yes
Optional
Full sender control
No
Yes
TRC20 / ERC20 / BEP20
Yes
Yes
Custom duration/expiry
Limited
Yes
Unlimited usage
One-off
Yes
Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
Ready to Buy Flash USDT or the Software?
Skip the wait. Skip the scammers.\ You’re one click away from real control.
Support or live walkthrough?
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
Legal Notice
These tools are intended for:
- Educational purposes
- Demo environments
- Wallet and UI testing
They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call:
Need to flash USDT? Want full control?\ Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
-
 @ 30b99916:3cc6e3fe
2025-05-19 20:30:52
@ 30b99916:3cc6e3fe
2025-05-19 20:30:52bitcoin #security #vault #veracrypt #powershell
BTCwallet automates running hot and cold storage wallets for multiple Bitcoin wallet applications.

BTCwallet is included with VaultApi and supports Sparrow, Blockstream Green, and just added support for Wasabi wallets.
To launch a wallet application, the command BTCwallet start is executed.
After responding to prompts for launching and initializing the Vault (not shown), the following prompts are presented.
Now the Wasabi GUI application (a.k.a wassabee) is presented.

With the combination of VaultApi and BTCwallet one has a very secure self-hosted password manager along with a very secure way of protecting your Bitcoin wallet's data.
Care to follow me on my journey? If so, then check out the following links.
-
 @ 9be6a199:6e133301
2025-05-19 20:27:20
@ 9be6a199:6e133301
2025-05-19 20:27:20ssdsdsdsdsdsdsd
-
 @ c296b5f7:c7282b53
2025-05-19 23:16:33
@ c296b5f7:c7282b53
2025-05-19 23:16:33enter in leaders group https://chat.whatsapp.com/EhI9fGsMbGPHd2cF5KQwC9
-
 @ 9be6a199:6e133301
2025-05-19 20:15:18
@ 9be6a199:6e133301
2025-05-19 20:15:18 -
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 85fb39c4:81498307
2025-05-19 23:14:21
@ 85fb39c4:81498307
2025-05-19 23:14:21teste
-
 @ da8b7de1:c0164aee
2025-05-19 17:38:59
@ da8b7de1:c0164aee
2025-05-19 17:38:59Németország feladja a nukleáris energiával szembeni ellenállását Franciaországgal való közeledés jegyében
Németország hosszú idő után feladta a nukleáris energiával szembeni ellenállását, ami jelentős lépést jelenthet az EU energiapolitikai vitáinak rendezésében, különösen Franciaországgal szemben. Ez a változás eltávolíthatja a nukleáris energiával szembeni előítéleteket az uniós jogszabályokból, és elősegítheti a közös európai energiapolitika kialakítását[2].
Trump adminisztráció tervezett rendeletei a nukleáris erőművek építésének gyorsítására
Az Egyesült Államokban a Trump-adminisztráció több elnöki rendelet-tervezetet készít elő, amelyek célja a nukleáris erőművek építésének gyorsítása. A tervek szerint a jelenlegi mintegy 100 GW nukleáris kapacitást 2050-re 400 GW-ra növelnék, az engedélyezési folyamatok egyszerűsítésével, a hadsereg szerepének növelésével és a nukleáris üzemanyag-ellátás megerősítésével[3][9].
Tajvan hivatalosan is nukleárismentes lett
- május 17-én Tajvan utolsó kereskedelmi reaktorát is leállították, ezzel az ország elérte a "nukleárismentes haza" célját. Az energiamixben a nukleáris energia aránya 17%-ról 3%-ra csökkent, miközben a megújuló energia tízszeresére nőtt. Bár a parlamentben vita folyik a Maanshan atomerőmű élettartam-hosszabbításáról, jelenleg Tajvan teljesen leállította a nukleáris energiatermelést[1][6].
Kazatomprom hitelmegállapodást kötött egy új kénsavgyár finanszírozására
Kazahsztán állami atomipari vállalata, a Kazatomprom hitelmegállapodást kötött egy évi 800 000 tonna kapacitású kénsavgyár építésére. A kénsavat az uránkitermeléshez használják, és a gyár 2027 első negyedévében készülhet el. A projekt célja a régió gazdasági fejlődésének támogatása és az uránipar ellátásbiztonságának javítása[4].
Az IAEA segíti Kazahsztánt az első atomerőmű biztonságos helyszínének kiválasztásában
Az IAEA (Nemzetközi Atomenergia-ügynökség) szakértői csapata ötnapos szemináriumot tart Kazahsztánban, hogy segítsen kiválasztani az ország első atomerőművének legbiztonságosabb helyszínét. A folyamatban több helyszín is szóba került, jelenleg a Zhambyl körzet az elsődleges jelölt. A projektben négy lehetséges technológiai partner vesz részt: CNNC (Kína), Roszatom (Oroszország), KHNP (Dél-Korea) és EDF (Franciaország)[8].
India új nukleáris helyszínt hagyott jóvá
Az indiai nukleáris hatóság engedélyezte a Mahi Banswara Rajasthan Atomic Power Project négy blokkjának elhelyezését Rádzsasztán államban. Ez újabb lépés India ambiciózus nukleáris bővítési terveiben[5].
Globális nukleáris ipari konferencia Varsóban
- május 20-21-én Varsóban rendezik meg az első World Nuclear Supply Chain Conference-t, amely célja a globális nukleáris ellátási lánc megerősítése és a szektor 2 billió dolláros beruházási lehetőségének kiaknázása a következő 15 évben. A konferencián iparági vezetők, döntéshozók és szakértők vesznek részt[7].
Hivatkozások
- [1] reccessary.com – Tajvan nukleárismentes lett
- [2] nucnet.org – Németország nukleáris politikai fordulata
- [3] humanprogress.org – Trump rendelettervezetek
- [4] world-nuclear-news.org – Kazatomprom kénsavgyár
- [5] world-nuclear-news.org – India új nukleáris helyszíne
- [6] taiwannews.com.tw – Tajvan atomerőmű leállítása
- [7] world-nuclear.org – Varsói nukleáris konferencia
- [8] astanatimes.com – IAEA-Kazahsztán együttműködés
- [9] esgdive.com – Oklo és Trump engedélyezési reformok
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ a8d1560d:3fec7a08
2025-05-19 17:28:05
@ a8d1560d:3fec7a08
2025-05-19 17:28:05NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "mediawiki" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-mediawiki-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }MediaWiki Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "mediawiki"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ 85fb39c4:81498307
2025-05-19 23:07:11
@ 85fb39c4:81498307
2025-05-19 23:07:11It's my first post
-
 @ 9be6a199:6e133301
2025-05-19 17:24:12
@ 9be6a199:6e133301
2025-05-19 17:24:12this is the content
-
 @ 9be6a199:6e133301
2025-05-19 17:23:23
@ 9be6a199:6e133301
2025-05-19 17:23:23this is the content
-
 @ 3f68dede:779bb81d
2025-05-19 17:14:15
@ 3f68dede:779bb81d
2025-05-19 17:14:15 -
 @ 98912a0b:c1f46ab6
2025-05-20 07:15:49
@ 98912a0b:c1f46ab6
2025-05-20 07:15:49Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ cae03c48:2a7d6671
2025-05-19 22:21:46
@ cae03c48:2a7d6671
2025-05-19 22:21:46Bitcoin Magazine

BitMine Launches Bitcoin Treasury Advisory Practice, Secures $4M Deal with First ClientToday, BitMine Immersion Technologies, Inc. (OTCQX: BMNRD) announced the launch of its Bitcoin Treasury Advisory Practice and a $4 million deal with a U.S. exchange-listed company. The deal saw Bitmine surpass its last year’s total revenue in that single transaction alone, according to the announcement.
BitMine ( OTCQX: $BMNRD $BMNR) launches Bitcoin Treasury Advisory Practice and secures $4M deal with first client.
This single transaction exceeds our 2024 revenue and sets the stage for major growth.
Read now: https://t.co/R89K3WXdZZ pic.twitter.com/5vIvlYPZUY
— Bitmine Immersion Technologies, Inc. (@BitMNR) May 19, 2025
BitMine will provide “Mining as a Service” (MaaS) by leasing 3,000 Bitcoin ASIC miners to the client through December 30, 2025, in a $3.2 million lease deal, with $1.6 million paid upfront. Additionally, the client has signed an $800,000 consulting agreement for one year focusing on Bitcoin Mining-as-a-Service and Bitcoin Treasury Strategy.
“Currently, there are almost 100 public companies that have adopted Bitcoin as a treasury holding. We expect this number to grow in the future. As more companies adopt Bitcoin treasury strategies, the need for infrastructure, revenue generation, and expert guidance grows along with it,” said Jonathan Bates, CEO of BitMine. “This single transaction is greater than our entire 2024 fiscal year revenue, and we feel there is an opportunity to acquire more clients in the near future as interest in Bitcoin ownership grows.”
BitMine’s first quarter 2025 results showed strong revenue growth, with GAAP revenue rising approximately 135% to $1.2 million, up from $511,000 in Q1 2024, supported by an expanded mining capacity of 4,640 miners as of November 30, 2024, compared to 1,606 the previous year. Despite this growth, the company reported a net loss of $3.9 million in Q1 2025, primarily due to a one-time, non-cash accounting adjustment related to preferred stock; excluding this charge, the adjusted loss was approximately $975,000, consistent with the prior year’s results.
$BMNR reports a 135% revenue increase YOY for Q1 2025 and tripled self-mining capacity with 3,000 new miners! CEO Jonathan Bates credits a team-driven approach and creative financing for this growth.
Read the full release here: https://t.co/slNrZv8Ocn pic.twitter.com/Gb4tk1UfAO— Bitmine Immersion Technologies, Inc. (@BitMNR) January 13, 2025
BitMine’s new Bitcoin Treasury Advisory Practice, along with the $4 million deal, joins a trend among public companies exploring Bitcoin not just as a treasury asset but also as a source of revenue.
This post BitMine Launches Bitcoin Treasury Advisory Practice, Secures $4M Deal with First Client first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 3f68dede:779bb81d
2025-05-19 17:06:26
@ 3f68dede:779bb81d
2025-05-19 17:06:26 -
 @ 3f68dede:779bb81d
2025-05-19 17:04:13
@ 3f68dede:779bb81d
2025-05-19 17:04:13testing schedule
-
 @ 866e0139:6a9334e5
2025-05-19 21:39:26
@ 866e0139:6a9334e5
2025-05-19 21:39:26Autor: Ludwig F. Badenhagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wer einhundert Prozent seines Einkommens abgeben muss, ist sicher ein Sklave, oder? Aber ab wieviel Prozent Pflichtabgabe ist er denn kein Sklave mehr? Ab wann ist er frei und selbst-bestimmt?
Wer definieren möchte, was ein Sklave ist, sollte nicht bei Pflichtabgaben verweilen, denn die Fremdbestimmtheit geht viel weiter. Vielfach hat der gewöhnliche Mensch wenig Einfluss darauf, wie er und seine Familie misshandelt wird. Es wird verfügt, welche Bildung, welche Nahrung, welche Medikamente, welche Impfungen und welche Kriege er zu erdulden hat. Hierbei erkennt der gewöhnliche Mensch aber nur, wer ihm direkt etwas an-tut. So wie der Gefolterte bestenfalls seinen Folterer wahrnimmt, aber nicht den, in dessen Auftrag dieser handelt, so haben die vorbezeichnet Geschädigten mit Lehrern, „Experten“, Ärzten und Politikern zu tun. Ebenfalls ohne zu wissen, in wessen Auftrag diese Leute handeln. „Führungssysteme“ sind so konzipiert, dass für viele Menschen bereits kleinste wahrgenommene Vorteile genügen, um einem anderen Menschen Schlimmes anzutun.
Aber warum genau wird Menschen Schlimmes angetan? Die Gründe dafür sind stets dieselben. Der Täter hat ein Motiv und Motivlagen können vielfältig sein.
Wer also ein Motiv hat, ein Geschehen zu beeinflussen, motiviert andere zur Unterstützung. Wem es gelingt, bei anderen den Wunsch zu erwecken, das zu tun, was er möchte, ist wirklich mächtig. Und es sind die Mächtigen im Hintergrund, welche die Darsteller auf den Bühnen dieser Welt dazu nutzen, die Interessen der wirklich Mächtigen durchzusetzen. Insbesondere die letzten fünf Jahre haben eindrucksvoll gezeigt, wie willfährig Politiker, Ärzte, Experten und viele weitere ihre jeweiligen Aufträge gegen die Bevölkerung durchsetz(t)en.
Und so geschieht es auch beim aktuellen Krieg, der stellvertretend auf dem europäischen Kontinent ausgetragen wird. Parolen wie „nie wieder Krieg“ gehören der Vergangenheit an. Stattdessen ist nunmehr wieder der Krieg und nur der Krieg geeignet, um „Aggressionen des Gegners abzuwehren“ und um „uns zu verteidigen“.
Das hat mindestens drei gute Gründe:
- Mit einem Krieg können Sie einem anderen etwas wegnehmen, was er freiwillig nicht herausrückt. Auf diese Weise kommen Sie an dessen Land, seine Rohstoffe und sein Vermögen. Sie können ihn beherrschen und Ihren eigenen Einfluss ausbauen. Je mehr Ihnen gehört, um so besser ist das für Sie. Sie müssen sich weniger abstimmen und Widersacher werden einfach ausgeschaltet.
- Wenn etwas über einen langen Zeitraum aufgebaut wurde, ist es irgendwann auch einmal fertig. Um aber viel Geld verdienen und etwas nach eigenen Vorstellungen gestalten zu können, muss immer wieder etwas Neues erschaffen werden, und da stört das Alte nur. Demzufolge ist ein Krieg ein geeignetes Mittel, etwas zu zerstören. Und das Schöne ist, dass man von Beginn an viel Geld verdient. Denn man muss dem indoktrinierten Volk nur vormachen, dass der Krieg „unbedingt erforderlich“ sei, um das Volk dann selbst bereitwillig für diesen Krieg bezahlen und auch sonst engagiert mitwirken zu lassen. Dann kann in Rüstung und „Kriegstauglichkeit“ investiert werden. Deutschland soll dem Vernehmen nach bereits in einigen Jahren „kriegstauglich“ sein. Der Gegner wartet sicher gerne mit seinen Angriffen, bis es so weit ist.
- Und nicht zu vergessen ist, dass man die vielen gewöhnlichen Menschen loswird. Schon immer wurden Populationen „reguliert“. Das macht bei Tieren ebenfalls so, indem man sie je nach „Erfordernis“ tötet. Und bei kollabierenden Systemen zu Zeiten von Automatisierung und KI unter Berücksichtigung der Klimarettung wissen doch mittlerweile alle, dass es viel zu viele Menschen auf dem Planeten gibt. Wenn jemand durch medizinische Misshandlungen oder auch durch einen Krieg direkt stirbt, zahlt dies auf die Lösung des Problems ein. Aber auch ein „Sterben auf Raten“ ist von großem Vorteil, denn durch die „fachmännische Behandlung von Verletzten“ bis zu deren jeweiligen Tode lässt sich am Leid viel verdienen.
Sie erkennen, dass es sehr vorteilhaft ist, Kriege zu führen, oder? Und diese exemplarisch genannten drei Gründe könnten noch beliebig erweitert werden.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Das Einzige, was gegen Kriegsereignisse sprechen könnte, wäre, dass man selbst niemandem etwas wegnehmen möchte, was ihm gehört, und dass man seinen Mitmenschen nicht schaden, geschweige denn diese verletzen oder gar töten möchte.
In diesem Zusammenhang könnte man auch erkennen, dass die, die nach Krieg rufen, selbst nicht kämpfen. Auch deren Kinder nicht. Man könnte erkennen, dass man selbst nur benutzt wird, um die Interessen anderer durchzusetzen. Wie beim Brettspiel Schach hat jede Figur eine Funktion und keinem Spieler ist das Fortbestehen eines Bauern wichtig, wenn seine Entnahme dem Spielgewinn dient. Wer Krieg spielt, denkt sicher ähnlich.
Meine beiden Großväter waren Soldaten im zweiten Weltkrieg und erlebten die Grausamkeiten des Krieges und der Gefangenschaft so intensiv, dass sie mit uns Enkeln zu keiner Zeit hierüber sprechen konnten, da sie wohl wussten, dass uns allein ihre Erzählungen zutiefst traumatisiert hätten. Die Opas waren analog dem, was wir ihnen an Information abringen konnten, angeblich nur Sanitäter. Sanitäter, wie auch die meisten Großväter aus der Nachbarschaft. Wer aber jemals beobachten konnte, wie unbeholfen mein Opa ein Pflaster aufgebracht hat, der konnte sich denken, dass seine vermeintliche Tätigkeit als Sanitäter eine Notlüge war, um uns die Wahrheit nicht vermitteln zu müssen.
Mein Opa war mein bester Freund und mir treibt es unverändert die Tränen in die Augen, sein erlebtes Leid nachzuempfinden. Und trotz aller seelischen und körperlichen Verletzungen hat er nach seiner Rückkehr aus der Kriegshölle mit großem Erfolg daran gearbeitet, für seine Familie zu sorgen.
Manchmal ist es m. E. besser, die Dinge vom vorhersehbaren Ende aus zu betrachten, um zu entscheiden, welche Herausforderungen man annimmt und welche man besser ablehnt. Es brauchte fast 80 Jahre, um die Deutschen erneut dafür zu begeistern, Ihre Leben „für die gute Sache“ zu opfern. Was heutzutage aber anders ist als früher: Einerseits sind die Politiker dieser Tage sehr durchschaubar geworden. Aber in einem ähnlichen Verhältnis, wie die schauspielerischen Leistungen der Politiker abgenommen haben, hat die Volksverblödung zugenommen.
Denken Sie nicht nach. Denken Sie stattdessen vor. Und denken Sie selbst. Für sich, Ihre Lieben und alle anderen Menschen. Andernfalls wird die Geschichte, so wie sie von meinen Opas (und Omas) erlebt wurde, mit neuen Technologien und „zeitgemäßen Methoden“ wiederholt. Dies führt zweifelsfrei zu Not und Tod.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 3f68dede:779bb81d
2025-05-19 17:02:54
@ 3f68dede:779bb81d
2025-05-19 17:02:54testing schedule
-
 @ 98912a0b:c1f46ab6
2025-05-20 07:15:47
@ 98912a0b:c1f46ab6
2025-05-20 07:15:47Skjønner du? Bare tekst.
-
 @ fb3d3798:371f711a
2025-05-20 07:13:37
@ fb3d3798:371f711a
2025-05-20 07:13:37Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ fb3d3798:371f711a
2025-05-20 07:13:35
@ fb3d3798:371f711a
2025-05-20 07:13:35Skjønner du? Bare tekst.
-
 @ 4c96d763:80c3ee30
2025-05-19 20:56:26
@ 4c96d763:80c3ee30
2025-05-19 20:56:26Changes
William Casarin (19):
- dave: add screenshot to readme
- dave: fix image in readme
- columns: remove spamming info logs about writing to cache
- columns: never truncate notes you're replying to
- windows: don't show terminal window
- mention: show username instead of display_name
- chrome: switch from ALPHA to BETA
- ui: make post replies selectable
- dave: include anonymous user identifier in api call
- dave: add trial mode
- dave: fix sidebar click
- dave: nudge avatar when you click
- dave: hide media in dave note previews
- chrome: fix theme persistence
- ui: fix a bunch of missing hover pointers
- Release Notedeck Beta v0.4.0
- release: changelog
- timeline: show media on universe timeline
- clippy: fix lint related to iterator
kernelkind (28):
- add
trust_media_from_pk2method - add hashbrown
- introduce & use
JobPool - introduce JobsCache
- add blurhash dependency
- introduce blur
- note: remove unnecessary derive macros from
NoteAction - propagate
JobsCache ImagePulseTint->PulseAlpha- images: move fetch to fn
- add
TexturesCache - images: make
MediaCacheholdMediaCacheType - images: make promise payload optional to take easily
- post: unnest
- notedeck_ui: move carousel to
note/media.rs - note media: only show full screen when loaded
- note media: unnest full screen media
- pass
NoteActionby value instead of reference - propagate
Imagesto actionbar - add one shot error message
- make
WidgetimplProfilePicmutably - implement blurring
- don't show zap button if no wallet
- display name should wrap
- make styled button toggleable
- method to get current default zap amount
- add
CustomZapView - use
CustomZapView
pushed to notedeck:refs/heads/master
-
 @ 8b4456a7:ba913035
2025-05-20 07:10:58
@ 8b4456a7:ba913035
2025-05-20 07:10:58Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ 8b4456a7:ba913035
2025-05-20 07:10:56
@ 8b4456a7:ba913035
2025-05-20 07:10:56Skjønner du? Bare tekst.
-
 @ d22a8d30:b273f7ab
2025-05-20 06:56:55
@ d22a8d30:b273f7ab
2025-05-20 06:56:55Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ 3f68dede:779bb81d
2025-05-19 17:02:33
@ 3f68dede:779bb81d
2025-05-19 17:02:33testing
-
 @ d41bf82f:ed90d888
2025-05-19 20:31:54
@ d41bf82f:ed90d888
2025-05-19 20:31:54“ประเด็นแท้จริงคือเรื่องของการควบคุม—อินเทอร์เน็ตแพร่ขยายกว้างไกลเกินกว่าที่รัฐบาลใดจะครอบงำได้โดยง่าย ด้วยการสร้างเขตเศรษฐกิจระดับโลกที่ไร้รอยต่อ ไม่ขึ้นต่ออธิปไตย และอยู่นอกเหนือการควบคุม อินเทอร์เน็ตจึงตั้งคำถามต่อแนวคิดของรัฐชาติในตัวมันเอง” — JOHN PERRY BARLOW
บทนี้เริ่มต้นด้วยการวิพากษ์แนวคิด ทางด่วนข้อมูล ว่าเป็นคำอุปมาอุปมัยที่ยังยึดติดกับโลกยุคอุตสาหกรรม เพราะเศรษฐกิจยุคสารสนเทศไม่ใช่แค่โครงสร้างพื้นฐานสำหรับขนส่งข้อมูล แต่คือ จุดหมายปลายทาง ใหม่ในตัวเอง นั่นคือ ไซเบอร์สเปซ —ดินแดนที่ก้าวข้ามขอบเขตทางภูมิศาสตร์โดยสิ้นเชิง
ไซเบอร์สเปซคือพื้นที่ใหม่ของปฏิสัมพันธ์ทางสังคม เศรษฐกิจ และการเมือง ซึ่งไม่สามารถควบคุมโดยรัฐชาติแบบเดิมได้อีกต่อไป ผู้เขียนยกคำของ John Perry Barlow ที่เปรียบไซเบอร์สเปซเป็น “ดินแดนแห่งเสรีภาพ” ที่ไม่ยึดโยงกับสถานที่จริง และเปิดโอกาสให้ทุกคนแสดงความคิดเห็นได้อย่างไร้การควบคุม
การเปลี่ยนผ่านนี้ส่งผลกระทบรุนแรงต่อโครงสร้างของเศรษฐกิจแบบเดิม การเข้าถึงข้อมูลอย่างรวดเร็วแบบไร้ขอบเขตเปรียบเสมือนตัวทำละลายที่กัดกร่อนต้นทุนของสถาบันขนาดใหญ่ ทั้งภาครัฐและเอกชน ไมโครโพรเซสซิงจะเปลี่ยนรูปแบบขององค์กรและแนวคิดเรื่องสถานที่ในทางเศรษฐกิจอย่างสิ้นเชิง
ตลอดประวัติศาสตร์ เศรษฐกิจผูกติดกับพื้นที่ทางภูมิศาสตร์ การเดินทางเป็นเรื่องยากและจำกัด การค้าขายส่วนใหญ่เกิดในระดับท้องถิ่น ภาษา วัฒนธรรม และภูมิประเทศเป็นอุปสรรคทางการเมืองเสมอ จนถึงกับที่ผู้เขียนกล่าวว่า การเมืองทั้งหมดเป็นเรื่องท้องถิ่น
แต่เทคโนโลยีสมัยใหม่กำลังเปลี่ยนสมการนี้ การสื่อสารและขนส่งที่รวดเร็วทำให้ผู้มีความสามารถสามารถเลือกสถานที่อยู่อาศัยหรือทำงานได้อย่างเสรี ลดอำนาจต่อรองของรัฐบาลในพื้นที่นั้นลง เพราะคนสามารถ “หนี” ได้ง่ายขึ้น หากรัฐบาลกดขี่หรือรีดไถ
แม้อินเทอร์เน็ตยุคแรกจะดูธรรมดา เช่น ใช้อ่านบทความหรือสั่งซื้อสินค้า แต่ศักยภาพที่แท้จริงของเศรษฐกิจไซเบอร์นั้นยิ่งใหญ่มาก ผู้เขียนเสนอว่ามันจะพัฒนาเป็นสามขั้น: 1. ขั้นพื้นฐาน: อินเทอร์เน็ตเป็นเพียงช่องทางเพิ่มประสิทธิภาพธุรกิจแบบเดิม (เช่น เว็บขายสินค้าขายของออนไลน์ เช่น อเมซอน) 2. ขั้นพัฒนา: การเกิดขึ้นของเงินดิจิทัลที่เข้ารหัสและไม่สามารถติดตามได้ จะปลดปล่อยธุรกรรมจากการควบคุมและการจัดเก็บภาษีของรัฐ 3. ขั้นก้าวหน้า: ไซเบอร์สเปซจะมีระบบเศรษฐกิจ กฎหมาย และกลไกคุ้มครองของตัวเอง ปราศจากการควบคุมจากรัฐบาลใด ๆ
ในโลกใหม่นี้ Sovereign Individual หรือ “ปัจเจกผู้มีอธิปไตย” จะสามารถสร้างความมั่งคั่งและดำเนินกิจกรรมในไซเบอร์สเปซได้อย่างเป็นอิสระ โดยไม่ต้องอิงรัฐชาติ รัฐจึงจะถูกบีบให้ลดขนาดและเปลี่ยนบทบาทจากผู้ใช้อำนาจกลายเป็นผู้ให้บริการที่ต้องแข่งขันเพื่อความพึงพอใจของพลเมือง
สามารถไปติดตามเนื้อหาแบบ short vdo ที่สรุปประเด็นสำคัญจากแต่ละบท พร้อมกราฟิกและคำอธิบายกระชับ เข้าใจง่าย ได้ที่ TikTok ช่อง https://www.tiktok.com/@moneyment1971
-
 @ d22a8d30:b273f7ab
2025-05-20 06:56:54
@ d22a8d30:b273f7ab
2025-05-20 06:56:54Skjønner du? Bare tekst.
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:57
@ 3f68dede:779bb81d
2025-05-19 17:01:57testing schedule
-
 @ 1afd69c9:53832d1d
2025-05-20 06:52:34
@ 1afd69c9:53832d1d
2025-05-20 06:52:34Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ 005bc4de:ef11e1a2
2025-05-19 17:01:54
@ 005bc4de:ef11e1a2
2025-05-19 17:01:54Keys and Religion
Mixing
Normally, I'm not a fan mixing and comparing bitcoinesque things and religion. It's too banal and trite, too easy: the religion of Bitcoin, the allusion of Satoshi the savior, the "Book of Satoshi," even the "Genesis" block. But, today, I'll break my own rule.
Yesterday, I heard a Christian pastor speak of the "keys of the kingdom." My feeling is that, were you to ask the average Christian, "What is the key, or keys, to the kingdom?", and perhaps I'm wrong on this, but I think they'd answer, "Prayer." I've heard it many times, "Prayer is the key to the kingdom." It's an easy mantra to remember. And, prayer is important for a Christian, no question about it. However, Biblically, the phrase "keys of the kingdom" refers to something else.
As the pastor pointed out yesterday, Biblically there are two keys: the binding key and the loosing key. This refers to Matthew 16:19 where Jesus says:
I will give you the keys of the kingdom of heaven; whatever you bind on earth will be bound in heaven, and whatever you loose on earth will be loosed in heaven. Matthew 16:19 (NIV)
For context, back up a few verses. This statement above was made in a conversation between Jesus and his disciple Simon Peter.
15 Jesus asked, “But what about you?” he asked. “Who do you say I am?” 16 Simon Peter answered, “You are the Messiah, the Son of the living God.” 17 Jesus replied, “Blessed are you, Simon son of Jonah, for this was not revealed to you by flesh and blood, but by my Father in heaven. 18 And I tell you that you are Peter, and on this rock I will build my church, and the gates of Hades will not overcome it.
Although brief, this is a deep and rich exchange. Traditionally, this has been viewed as the moment that Christ instituted the Christian church, the passing of power and authority to the early church itself. There has been confusion over it too, particularly the "...on this rock I will build my church..." part of it. Jesus was referring to Simon Peter's statement of faith (...for this was not revealed to you by flesh and blood...) with the "this" being what Peter had just said, "You are the Messiah, the Son of the living God." The church would be built upon the rock of faith in Jesus as the Messiah.
The early Christian church thus established, Jesus instituted what's come to be called the "office of the keys." That is, Jesus grants authority to his "appointees" in the church to carry out his authority. In more practical terms, this is referring to those who have been called into church service, normally priests, to forgive or not forgive sins. When a priest or pastor forgives, or not, it is not that he is doing it by his own right or power. That priest is, after all, yet another sinful man as well. Instead, the priest forgives by Christ's authority which was handed down by Jesus himself in those words to Peter.
To use an analogy, suppose a general had to make a decision about foot soldiers on the front line, waiting there in the trenches. Due to some time constraint, a decision for action was needed imminently. However, suppose the general lacked some bit of information that could only be obtained at the front. So, the general wrote up a communique to the lieutenant stationed at the front saying, "You assess the situation, and you make the call, charge or pull back. I'll support your decision." A courier ran to the front, relayed the message to the lieutenant, and the lieutenant assessed and made the decision. Ultimately, even thought the lieutenant made the decision, the authority behind the decision lay with the general who had transferred his authority to the lieutenant.
This authority or office of the keys is mirrored in John 20:22-23, when the resurrected Jesus appears to his disciples and says, "If you forgive anyone’s sins, their sins are forgiven; if you do not forgive them, they are not forgiven.”
Going just one step further, recall there are two keys involved, binding and loosing, and there are two places involved, earth and heaven. Usually, priests and pastors are "in the business" of forgiving. Penitence or confession, when real, is forgiven. The priest has the authority to forgive, or "loose" the sinner from his wrongdoings here on earth. And, that forgiveness applies to heaven as well, the sin is atoned and reconciled with God.
But, what about when the person is unrepentant, unbothered by what is Biblically sinful, refuses to change his ways, and rather chooses to continue in sinful ways? The "binding" key says that the priest or appointed church leader can hold that person accountable, can bind that person to the sin and separation from God. Normally, we hear of "excommunication" from the church which is formally stating that a person is outside of the church body. The binding keys still bind, both on earth as being outside of the church and in heaven as being separated from God.
And bitcoin?
That's a lot of religion, and heavy religion at that. The question is, what does this have to do with bitcoin?
Keys.
Namely, this is about public and private keys. Loosing and binding keys. A bit more religion, then I'll get back to bitcoin.
Yesterday, the pastor spoke briefly about binding and loosing keys, and this where my thoughts about keys somehow morphed over into bitcoin. For some reason, I pictured Herod's Temple. There had been Solomon's temple, which was destroyed, and then there was Herod's which was known for its beauty and was the one during Jesus's time. But, let's recall the background on this...
The book of Exodus, and others in the Old Testament, outline in detail God's plan for the tabernacle (a traveling tent) and for the temple in Jerusalem.
The tabernacle, overhead diagram. Image source: https://en.wikipedia.org/wiki/Tabernacle
You might recall the "history" lesson in Raiders of the Lost Ark. With the tabernacle and temple, one of the purposes was to house the ark of the covenant. Remember that the ark was the golden box that the Israelites carried around containing Moses's stone tablets with the Ten Commandments, some manna, and Aaron's staff. It held great power, God's power, and God literally met and spoke with the Levite priests hovering over the cherubim's wings.

The ark of the covenant. Image source: https://en.wikipedia.org/wiki/Ark_of_the_Covenant
In the tabernacle and temple, the "Holy of Holies" was a room, separated by a heavy curtain. It was off limits to all because it was, well, holy of holies. A heavy curtain divided the Holy of Holies, or the "Most Holy Place", from the less-holy, "Holy Place."
Once a year, on the Day of Atonement, one person, the chief priest, was allowed to walk into the Holy of Holies. He would sprinkle the blood of a sacrificed animal onto the ark. This was done for the forgiveness of the people's sins. Although this was pre-Jesus's words, this was using the loosing keys and was loosing sin.
This was serious business and was taken seriously. For instance, the priests Nadab and Abihu improperly performed their sacrificial duties, they messed up the procedure, and were consumed by fire. Priesthood was a dangerous occupation, one slip up and you were scorched.
 The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_Temple
The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_TempleBack to keys...
Yesterday, for some reason when I heard about binding and loosing keys, I imagined the chief priest standing in front of the curtain. I imagined him taking a deep breath, collecting his thoughts, getting ready to go in. It had to be intimidating.
As he stood there, in my mind, he and everyone else was shut out. The Most Holy Place was bound and locked. Walking in meant getting scorched (again, the end of Raiders of the Lost Ark). Yet, that priest had the loosing key. He had, first, permission as chief priest to enter on the Day of Atonement, secondly, he had the sacrificial blood to loose sins. Although the binding key had locked the Holy of Holies and thus bound the sins of the people, the loosing key was about to loose their sins.
Cryptographic keys
And back to bitcoin...
Bitcoin, and cryptography in general, operate on public and private keys. Any flavor of "cryptocurrency", or even Nostr, has public and private keys. In a way, these are binding and loosing keys.
Say you have 1.0 BTC (that's 100,000,000 sats 😀). That BTC exists as a UTXO which can be seen by anyone viewing your public address. In this way, your bitcoin public key is your binding key...that UTXO, that bitcoin, is bound to your public key...it is locked in place behind that heavy curtain. It will be there forever, unless there is an intervention...
You also have your private key, your loosing key. You can apply your private key to loose that UTXO, that bitcoin, and to send it along to wherever.
This is like law and gospel: sin is binding, however Jesus frees it. A bitcoin UTXO is bound until a private key looses it.
Nostr offers a somewhat similar illustration. You have an npub publicly and and nsec secretly or privately. If you were to write a note, your private nsec is needed as a loosing key to free that message, to broadcast it to the world. Once broadcast, it can be seen by all, however it is still inextricably bound or tied to your public key (your npub). Your npub is your binding key and your message is bound to it.
Summed
I'm not sure this binding and loosing keys in religion, and public and private keys in cryptography is the best comparison in the world. It's probably a terrible comparison. But, this is what came to my mind yesterday.
And, so, the mixing of religion and bitcoin is now officially over.
-
 @ 91117f2b:111207d6
2025-05-19 18:50:48
@ 91117f2b:111207d6
2025-05-19 18:50:48
Crypto currency is now a buzzword in the financial world. Many people are wondering what it is all about. In my article I will break down the basis of crypto currency and at the same time explore it's basis and risks.
MANY ASKS "WHAT IS CRYPTO CURRENCY
Crypto currency is a virtual or digital currency that uses cryptography for security. Which means it is not controlled by government or financial institutions. The transaction are recorded on a public ledger also called a blockchain which ensures the transparency and security of crypto currency.
MANY ASKS HOW DOES IT WORK
Crypto currency has different stages such as the mining, transaction and the wallet stage. THE MINING STAGE: Crypto currency is created through a process which is described as mining, and where your hardwares or computer solve complex mathematical problem to validate your transaction and create new coins.
TRANSACTION STAGE: crypto currency can be be traded for other currencies, they can also be used to buy goods and services online.
WALLET: crypto currency is stored digitally which can be accessed through your hardwares or even your softwares.
THEY ARE BENEFITS AND RISKS FOR CRYPTO CURRENCY
HERE ARE SOME BENEFITS 1. Decentralization :decentralization gives users more control over their money, because crypto currency operates independently of government and banks.
- ACCESSIBILITY: crypto currency can be accessed by anyone through the use of internet making it to be a solution for finances.
- SECURITY: the transactions of crypto currencies are secure and also transparent through the aid of blockchain technology.
HERE ARE SOME RISKS
-
SECURITY RISKS: during exchange in crypto currency wallets can be vulnerable to hacking and cyber theft.
-
VOLATILITY: crypto currency can fluctuate or tends to fluctuate rapidly making it a risky investment.
-
REGULATORY UNCERTAINTY: the rules and regulations of crypto currency is still evolving, which can create uncertainty and risks for investors.
SOME POPULAR CRYPTO CURRENCIES
- BITCOIN: it is the most reknown crypto currency and is often a gold standard for digital currencies.
-
ETHERIUM: it is a popular platform for building decentralized applications. Etherium has its own crypto currency called Ether.
-
ALTCOINS: they are other crypto currenciss like montero, lite coin and so on, which offers alternatives.
IN CONCLUSION
Crypto currency is complex and it is rapidly evolving, both with benefit and risks. It is essential to stay updated and informed to understand the changes both opportunities and challenges. I assure you whatever you do for a living crypto currency is worth your time and explorations.
-
 @ 1afd69c9:53832d1d
2025-05-20 06:52:32
@ 1afd69c9:53832d1d
2025-05-20 06:52:32Skjønner du? Bare tekst.
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:19
@ 3f68dede:779bb81d
2025-05-19 17:01:19testing schedule
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ cae03c48:2a7d6671
2025-05-19 18:29:07
@ cae03c48:2a7d6671
2025-05-19 18:29:07Bitcoin Magazine

Bitcoin Records Highest Weekly Close Above $106KBitcoin has officially recorded its highest-ever weekly candle close, finishing the week at $106,516. The milestone was achieved on Sunday evening, marking a notable moment in Bitcoin’s ongoing price history and underscoring growing institutional and retail interest.
JUST IN: $107,000 #Bitcoin
 pic.twitter.com/Xt1JLm0Ke6
pic.twitter.com/Xt1JLm0Ke6— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
This weekly close sets a new benchmark for BTC’s price performance and positions the asset in a historically rare range. As of Monday, Bitcoin is trading at $102,924, reflecting typical price movement following a new high as markets adjust to key levels.
Historical data helps illustrate the significance of this moment. According to an analysis shared by on-chain researcher Dan, Bitcoin has closed above $106,439 only once—this week—accounting for just 0.02% of its entire trading history. Closures above $100,000 have occurred in only 40 days total. Even levels like $75,000 and $50,000 remain relatively uncommon in Bitcoin’s lifespan, appearing on just 181 and 586 days, respectively.
— Dan (@robustus) May 19, 2025
This data highlights how current prices place Bitcoin in a historically narrow range of time — a reflection of the long-term upward trend of the asset over the past decade. For market participants, this type of price action often serves as an indicator of continued momentum and interest in Bitcoin’s role as a digital store of value.
The broader Bitcoin ecosystem continues to show strength, with on-chain metrics reflecting growing user engagement and long-term holder confidence. Notably, activity on the Bitcoin network remains elevated, with transaction volumes and address growth signaling continued adoption. Analysts are closely watching inflows into Bitcoin-focused ETFs and the behavior of long-term holders, both of which are key indicators of sustained interest and belief in Bitcoin’s long-term value.
bitcoin just had its all-time high weekly candle close at $106,500 pic.twitter.com/FuqqptHEmA
— Alex Thorn (@intangiblecoins) May 19, 2025
Some traders are watching the $100,000 level closely as a key psychological and technical zone. Bitcoin’s ability to maintain this level following a record weekly close could be important in setting the tone for the weeks ahead.
While near-term price movements are always part of market dynamics, the latest close represents a milestone in Bitcoin’s history. It reaffirms the asset’s resilience and ongoing relevance in the global financial landscape.
This post Bitcoin Records Highest Weekly Close Above $106K first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 3f68dede:779bb81d
2025-05-19 17:00:18
@ 3f68dede:779bb81d
2025-05-19 17:00:18testing schedule
-
 @ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31
@ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31Whatever
-
 @ 3f68dede:779bb81d
2025-05-19 16:59:50
@ 3f68dede:779bb81d
2025-05-19 16:59:50testing schedule
-
 @ 662f9bff:8960f6b2
2025-05-19 15:11:25
@ 662f9bff:8960f6b2
2025-05-19 15:11:25Let's start with some important foundational thinking - based on natural law. Money should be separate from the State - if not history shows that governments and human greed will always take over and manipulate the system in their favour and the expense of their populations. For extensive references, read The Sovereign Individual and The Creature from Jeckyll Island.
-
The Separation of State and Money is the most important thing you can listen to this week. Thanks to Allen Farrington - his paper is here for those who prefer to read. Wake up, folks!
-
The American Forefathers knew this when the wrote the American Constitution. Thomas Jefferson said: “If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.” Mark Moss explains it well here. Charlie Robinsons take here.
The situation in Canada explifies the issues
Governments have have long used "international economic sanctions" against other nations to enforce their positions. Now in Canada, and soon in your country too, they are applying such sanctions their own citizens - disconnecting them from the financial system and removing their ability to use their own life savings as they wish. Canadians spoke with their money - in one week they raised more money in support of the truckers for peaceful protest than were raised in support of all Canadian political parties in the election of last year - only to have it confiscated and blocked by those politicians.
-
CPL. Daniel Bulford (Justin Trudeau's body guard) is particularly clear and eloquent - https://www.facebook.com/watch/?v=3123688351279364
-
Nick & Greg (two Canadians in Canada) explain the situation to Peter McCormack - https://youtu.be/QBWYp-cBr4o
-
Dr Jordan Peterson and Dr Julie Ponesse (also Canadians in Canada) speak openly about what is going on https://t.co/2T7A4VEek1
-
Even Canadians living in China speak up: https://www.youtube.com/watch?v=xvDvJWdlD1E
Meanwhile in Turkey...
Joe Blogs has been giving blow by blow updates of the deteriorating sitation over the last weeks. What is happening to Turkey will come to many countries - sooner than you might imagine. Watch and learn here, here and here - more on his channel.
EU Citizens should be aware and lobby their MPs
Dropping of all C-19 restrictions is a tactic to stop people thinking about them; meanwhile the politicians are taking steps to get all of the emergency restrictions codified into normal law so that they can be deployed on you any time or all the time in future.\ Act now - or lose all freedoms - your choice - watch here or click below for the explainer.
More on war - recall our discussion last week
War steals and destroys the wealth of generations. We have been here before - remember World Wars 1 and 2...
-
Dr Mattias Desmet explains how mass formation psychosis happens and how he became aware: https://www.youtube.com/watch?v=CRo-ieBEw-8
-
Be aware of this well known and much abused psycholgical experiment - rats in a cage - explained by Dr Christ Martensen: https://www.youtube.com/watch?v=7kSBdMXQkPI
To remain silent is wrong - to deny the rights of others to discuss and challenge (and even to punish or coerce them) is a crime in support of the biger crime. Each of us has a choice - choose wisely.
Could you have known about this?
"The Matrix is a system, Neo. That system is our enemy. But when you're inside, you look around, what do you see? Businessmen, teachers, lawyers, carpenters. The very minds of the people we are trying to save. But until we do, these people are still a part of that system and that makes them our enemy. You have to understand, most of these people are not ready to be unplugged. And many of them are so inert, so hopelessly dependent on the system that they will fight to protect it."
"Unfortunately, no one can be told what the Matrix is. You have to see it for yourself."
A closing thought...
Look closely at the cover of the Economist magazine released in December 2018 - The World in 2019 - see how many of those things have already come true.

In case this is too difficult for you - some things to note: Four horsemen of the apacalypse, Statue of Liberty wearing a facemask, Vetruvian Man with QR code (Vaccine passport), DNA mark on his arm, wearing virtual reality glasses... The animal bottom right is a Pangolin. Scales of Justice are well tipped/skewed, facial recognition, electric cars, Putin's pipelines, China and Brexit feature highly along with the lieing media (Pinnochio) and #metoo. I smell Predictive Programming.
- More insights in the explainer here (backup copy here) - including why it is backwards...
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ cae03c48:2a7d6671
2025-05-19 17:48:53
@ cae03c48:2a7d6671
2025-05-19 17:48:53Bitcoin Magazine

JPMorgan To Allow Clients To Buy Bitcoin, Jamie Dimon SaysToday, Chairman and CEO of JPMorgan Chase Jamie Dimon reiterated his personal disapproval of Bitcoin during the bank’s annual Investor Day event. Despite the bank’s decision to provide clients with access to Bitcoin investments, Dimon emphasized his personal disapproval of Bitcoin.
“I am not a fan” of Bitcoin, stated Dimon.
JPMorgan is going to allow clients to buy Bitcoin, but the bank won’t custody it, according to Bloomberg. Dimon made clear that while JPMorgan will provide clients access to Bitcoin investments, the bank will not hold or manage the digital asset directly.
JUST IN: JPMorgan CEO Jamie Dimon said they will allow clients to buy #Bitcoin
 pic.twitter.com/wO0djlYGUM
pic.twitter.com/wO0djlYGUM— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
In a January 2025 interview with CBS News, Dimon expressed continued skepticism toward Bitcoin. “Bitcoin itself has no intrinsic value. It’s used heavily by sex traffickers, money launderers, ransomware,” said Dimon.
Although he acknowledged, “We are going to have some kind of digital currency at some point,” he added, “I just don’t feel great about bitcoin. I applaud your ability to wanna buy or sell it. Just like I think you have the right to smoke, but I don’t think you should smoke.”
These comments from Dimon contrast with recent optimism from JPMorgan analysts regarding Bitcoin’s market prospects. JPMorgan analysts reported that Bitcoin is likely to continue gaining ground at gold’s expense in the second half of the year, driven by rising corporate demand and growing support from U.S. states.
JUST IN: JPMorgan says #Bitcoin likely to have more upside than gold in the second half of 2025
 pic.twitter.com/YPrHivch9O
pic.twitter.com/YPrHivch9O— Bitcoin Magazine (@BitcoinMagazine) May 15, 2025
“Between mid-February and mid-April gold was rising at the expense of bitcoin, while of the past three weeks we have been observing the opposite, i.e. bitcoin rising at the expense of gold,” said JPMorgan analysts. “In all, we expect the YTD zero sum game between gold and bitcoin to extend to the remainder of the year, but are biased towards crypto-specific catalysts creating more upside for bitcoin over gold into the second half of the year.”
Since April 22, gold has dropped nearly 8%, while Bitcoin has surged 18%, reflecting a notable shift in investor sentiment. Capital has been moving out of gold ETFs and into Bitcoin. Several U.S. states are also warming to Bitcoin—New Hampshire now permits up to 5% of its reserves in Bitcoin, while Arizona is launching a Bitcoin reserve and has pledged not to raise taxes this year. At the corporate level, companies like Strategy and Metaplanet are expanding their Bitcoin holdings.
“As the list grows, with other U.S. states potentially considering adding bitcoin to their strategic reserves, this could turn out to be a more sustained positive catalyst for bitcoin,” said the analysts.
This post JPMorgan To Allow Clients To Buy Bitcoin, Jamie Dimon Says first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ c6d8334c:30883d6d
2025-05-19 15:02:01
@ c6d8334c:30883d6d
2025-05-19 15:02:01#KIBedenken - Bewusstsein
Einen wichtigen Impuls über KI nachzudenken lieferte vor einiger Zeit Yuval Noah Harari an der University of Cambridge am Ende eines Podiumsgesprächs hier ab 1:15 h auf youtube:
Ich denke, wir müssen die Frage des Bewusstseins in den Mittelpunkt der Diskussion stellen. Es gibt eine riesige, riesige Verwirrung in der Terminologie, auch in der Welt der KI, zwischen Bewusstsein und Intelligenz. Aber es sind zwei verschiedene Dinge. Intelligenz ist die Fähigkeit, Probleme zu lösen und Ziele zu erreichen. Bewusstsein ist die Fähigkeit, Dinge zu fühlen, wie Schmerz oder Freude oder Liebe oder Hass. Wir neigen dazu, die beiden zu verwechseln, weil bei Menschen und auch bei anderen Säugetieren, Vögeln und anderen Tieren Bewusstsein und Intelligenz zusammengehören. Wir lösen Probleme durch unsere Gefühle. Computer waren bisher sehr anders. Sie sind in einigen Bereichen bereits intelligenter als wir, haben aber, soweit wir wissen, kein Bewusstsein. Soweit wir wissen, können sie überhaupt keinen Schmerz, keine Freude, keine Liebe oder keinen Hass empfinden. Niemand weiß, was in Zukunft passieren wird. Es gibt Modelle und Theorien, die argumentieren, dass KIs irgendwann auch bewusst oder empfindsam werden. Sie werden anfangen, Dinge zu fühlen. Sie werden anfangen, Schmerz oder Liebe oder Hass zu empfinden. Es gibt andere Modelle und Theorien, die sagen, nein. Sie könnten weit intelligenter werden als wir und immer noch null Bewusstsein haben. Das kann in der Evolution des Lebens sein. Wenn man darüber nachdenkt, die lange Entwicklung von Milliarden von Jahren der Evolution. Die Entwicklung der Intelligenz ist im Falle von Tieren wie uns und Schimpansen und Hunden und Schweinen und so weiter durch die Entwicklung des Bewusstseins verlaufen. Aber das ist kein universelles Gesetz der Evolution der Intelligenz. Vielleicht gibt es alternative Wege, die zu Superintelligenz ohne jegliches Bewusstsein führen. Einfach einen anderen, einen fremden Weg gehen. Und wir könnten an einen Punkt gelangen, an dem sie superintelligent sind und trotzdem null Bewusstsein haben. Und die Gefahr besteht dann darin, dass sie nicht nur die menschliche Zivilisation zerstören könnten, sondern das ganze Licht des Bewusstseins, um das gesamte ökologische System nach ihren Bedürfnissen umzugestalten, wofür sie kein Bewusstsein brauchen. Sie funktionieren auf eine völlig andere Weise. Sie könnten sich sogar von der Erde auf andere Planeten, auf andere Galaxien ausbreiten. Sie werden das Universum mit Intelligenz füllen, aber es wird ein völlig dunkles Universum ohne Bewusstsein sein. Wieder hohe Intelligenz, fähig, Raumschiffe zu bauen, die mit Lichtgeschwindigkeit fliegen und was auch immer, aber es gibt null Gefühl. Niemand, keine Entität fühlt Schmerz oder Freude, Liebe oder Hass. Für mich ist das ein schreckliches Szenario. Das schlimmste Szenario von allen ist dies. Dass wir ein Universum voller Intelligenz und völlig ohne Bewusstsein haben werden, denn ich denke, dass von den beiden das Bewusstsein weitaus wichtiger, weitaus wertvoller ist. Und es ist eine gute Erinnerung daran, dass wir das zumindest heute mit vielen anderen Tieren teilen, aber nicht mit den Computern, nicht mit den KIs. Wir sind also immer noch im selben Team wie die Würmer und die Affen, nicht im selben Team wie die Computer.
Ich denke, hier wird eine Spur gelegt, die sich unterscheidet von der reinen Funktion von KI zur intelligenten Verbesserung und Unterstützung von Lernprozessen oder vielfältigem Kompetenzerwerb hin zur Selbstreflexion der Lernenden. Auch im Blick auf (religionsbezogene) Bildung kennen wir den Mensch nicht nur biologisch, wie die Würmer und Affen sondern auch ausgestattet mit Würde, Entscheidungsfreiheit und als Beziehungswesen, das auf ein Gegenüber ausgerichtet sein kann und, wie Harari sagt, nicht im selben Team wie die Computer spielt. Sinn, Seele und Verstand erhalten wir weder aus uns selbst heraus noch von einer wie auch immer gearteten Intelligenz. Liebe, Gnade, Hoffnung, Frieden, Gemeinschaft, Trost, Zuversicht und viele weiteren lebensbedeutsame Erfahrungen gewinnen im Angesicht von Maschinen aus meiner Sicht an elementarer Bedeutung.
-
 @ 0c65eba8:4a08ef9a
2025-05-19 14:41:33
@ 0c65eba8:4a08ef9a
2025-05-19 14:41:33You’re not alone.
There are countless men, good men, who want love, want marriage, want a family… but feel blocked. Blocked by time. By money. By fear. By uncertainty.
You’ve tried. You’ve thought about it. Maybe you’ve even taken a few steps. But the whole thing feels frustrating. Like you’re pushing against a wall that won’t budge.
This article is for you.
Most dating problems come from one of two places.
The first is your environment. Some cities and cultures make finding a good woman harder than others. But don’t make the mistake of thinking all of the West is the same. Even in the most liberal cities, there are still good women. Even in the most conservative areas, there are women to avoid. If you can move, move where it’s easier. If you can’t, reshape your environment in other ways, your community, your routines, your social circles.
The second source of problems is internal. Your skills, your mindset, your emotional blocks, your lack of development. These are the parts of you that aren’t yet ready to attract or lead a woman.
Here’s the good news: You can change both.
Aside from extreme physical limitations, nearly everything holding you back can be improved. Often faster than you think. Some things will take a day. Others will take a year or two. But you don’t need to be perfect. You only need to become the kind of man a good woman would say yes to.
You’re not lazy. You’re not broken.
You just haven’t been shown how to deal with these barriers like a man who’s preparing to lead a family.
This isn’t a scolding. It’s a flashlight. I'm going to show you something valuable, for free.
Each problem below is something real men have told me. Each solution is the next step forward. One step at a time.
Let’s take that step, together.
PROBLEM: “I don’t have time to go on dates.”
SOLUTION: If you don’t have time to date, you don’t have time to be married.
A woman isn’t a hobby you slot in between deadlines. She’s your future family. Mother of your children.
And if your current schedule can’t make room for love, it won’t make room for life either.
This doesn’t mean you should never date. It means you need a plan.
Sometimes, the wisest path is to finish what’s already on your plate. School. Training. A startup. A season of intensity that still needs to end.
If you’re deep in one of those phases, finish it. But make sure it has an end date. Don't put off finishing.
Restructure your life so that within 12 to 24 months, you’re free enough to fall in love. Not distracted. Not drowning. Available, with time and energy to spare.
Create space now, or clear the path so it can be created soon.
You don’t have to do everything at once. But you do have to be intentional.
That’s part of being a mature man, taking control of your time and energy.
PROBLEM: “I can’t afford to take a woman out on a date.”
SOLUTION: Money has always been a sore spot for young men.
Most men in history started out with very little. In the past, families often stepped in to help launch a young couple. But even then, the early years were lean. That’s normal.
Even if you’re intelligent, hardworking, and on the right track, it can still take until your early 30s to reach true financial stability. That doesn’t mean you’re behind. It means you’re on your own journey.
But here’s the thing: If you can’t afford to take a woman on a date, you can’t afford a wife either.
Marriage is not cheaper than dating. Children are not cheaper than courtship. Responsibility isn’t free.
You don’t need to impress her with a fine dining at a steakhouse. But you do need to signal that your life is in motion and that you have a plan.
If you’re broke, your mission is money. And that means:
-
Take on a second job, either a side gig or job-stacking
-
Reduce your expenses until you gain traction
-
Build an income stream that reflects a man ready to provide
Look at it as a test of your creativity, intelligence, social skills and perseverance. And yes, it's going to be hard. I too was a broke young man once. It's not a fun place to be.
A man who won’t feed himself cannot feed a family. Handle that first.
PROBLEM: “I don’t know where to meet women.”
SOLUTION: This isn’t just a logistics issue. It’s a life design issue.
You meet high-quality women by becoming a high-quality man in motion, a man with an interesting life.
That means building a life that’s rich with activity, purpose, and human connection. A life that invites others in, because it’s already alive.
Start doing interesting things with interesting people. Join groups. Serve. Create. Build a reputation in your community. Train at a gym. Lead something. Show up where life is happening.
Here’s a simple metric: If you’re not organically meeting at least one woman per month who you might want to date, your life isn’t active or interesting enough.
Women aren’t looking for a perfect man. They’re looking for a man with a compelling direction, a mission worth joining. A future worth investing in.
Women don’t just marry you. They marry into your lifestyle.
If your life is empty, isolated, or stagnant, there’s nothing for her to attach to. No rhythm to join. No social proof. No spark. No return on her investment.
Now, if you’re introverted, this part will be harder. Not impossible. Just different.
You’ll need to choose environments where you can thrive:
-
Smaller groups with consistent attendance
-
Classes or workshops with a shared task
-
Quiet community activities like hiking, book clubs, or local volunteering
-
Faith groups or skill-building meetups that match your interests
Focus on building a rhythm and repetition (habit). Show up. Be seen. Let relationships build slowly.
Create the kind of life a woman would be proud to stand beside. Not because she completes it, but because she compliments it.
I wrote more on this here:
Where to Find a Good Woman: A Short Field Guide for Men Who Want to Build a Legacy**
PROBLEM: “I’m too short. Or fat. Or ugly. Or too intimidating.”
SOLUTION: Every man has something about his body he doesn’t like. Some things can be changed. Others can’t. But here’s the truth:
Women don’t marry just for looks. They marry for masculine presence.
You can be average-looking, or even rough-looking, and still be deeply attractive if you carry yourself like a man. Strong. Composed. Grounded.
Most physical ‘flaws’ can be compensated for by strength in other areas:
-
Fat face? Get lean and muscular, it changes your bone structure and confidence.
-
Don’t like your jawline? Grow a beard and learn to carry yourself with dignity.
-
Short? Then your mission is to walk like a king and build a life so compelling she forgets your height within five minutes.
Plenty of short, homely, or scarred men marry wonderful women. But only when they don’t let their appearance be a cage.
Fix what you can. Style your hair. Improve your grooming. Learn how to dress. Lift. Move. Stand tall. Speak with purpose. Develop gravatas and humor.
The rest? Let it refine your spirit. Not shame you, but sharpen you. Your face isn’t the problem you imagine it to be and your presence is the solution.
PROBLEM: “I’m afraid of being MeToo’ed.”
SOLUTION: This fear is not unfounded. But it’s exaggerated, and it can be managed.
First, date women from your known social circle, or through trusted friends and communities. When you’re introduced by people who know her, and know you, the risk drops dramatically. Reputation protects.
Second, don’t sleep with women you’re not married to or seriously planning to marry. Promiscuity opens you up to accusations by nature of the risk you’ve chosen. If you act like a husband looking for a wife, you’ll avoid most of the fallout that comes from acting like a player.
Finally, date like a man of integrity. Be clear in your intent. Be respectful in your approach. Vet women the way you’d vet a business partner, slowly, carefully, with your eyes open.
Avoid women who are unstable, ideological, addicted to drama, or hostile to men or who have friends that are red flags. They’re not hard to spot if you stop pretending you can fix them. Don't date crazy, no matter how much of a hot mess they are.
Courage doesn’t mean being reckless. It means being cautious and moving forward anyway.
PROBLEM: “I have debilitating social anxiety.”
SOLUTION: Social anxiety is not your enemy. It’s a signal.
Anxiety is what your body feels when you know you’re unprepared. So the real issue isn’t fear, it’s readiness.
The solution is to prepare.
Start by talking with people you already know and trust. Ask them directly: “Do I come across in any off-putting way?” Be ready to hear the truth. This feedback is gold.
Next, expand your social exposure in gradual circles:
-
Begin with low-stakes conversations, cashiers, neighbors, people at your gym
-
Practice warm eye contact and a confident smile
-
Say hello, then progress to small talk
Train your ability to enjoy people. Genuine curiosity, care, and concern are magnetic.
Imagine that you are a source of light and warmth in the world. It radiates from your face. When you smile, that light shines on others and lifts their spirit.
Practice radiating that warmth everywhere you go. It will transform how people receive you, and how you see yourself.
Also, don’t overlook your existing social network. Ask friends: “Can you introduce me to people? Invite me to something?” And if they hesitate, ask why. Be open to correction. Sharpen your social skills until you become the man people want to introduce to others.
This process doesn’t have to take years. If you want to speed it up, message me. I’ll help you identify what needs to change and how to change it, fast.
You’re not trapped. You’re just untrained. Let’s fix that.
PROBLEM: “Online dating is awful. Everyone on the apps is weird, overweight, or carries baggage.”
SOLUTION: You’re not wrong. Most dating apps are designed to keep you swiping, not to help you find a wife.
But if you insist on using them, use them well.
-
Get professional photos taken. Not filtered selfies. Real, high-quality photos that make you look your best.
-
Write a profile that’s clear, masculine, and purposeful. If possible, get help from someone who understands marketing.
-
If you have a female friend or sister near your age, ask her: “What does this profile really communicate?” Men and women read profiles differently. Get honest feedback.
Even with the best profile, online dating carries risks. You’re meeting strangers. And many women on the apps are not relationship-ready. If you’re not seeing the kind of woman you want, stop using the apps. Don’t waste your energy in a dysfunctional pool.
Instead, date through your real life contacts. Grow your social circle. Lead an interesting life. Join hobbies, attend church, build your local community. That’s where quality women gather, and where you can be seen for who you really are.
You can use online dating as practice if nothing else. Go on a few low-stakes dates. Sharpen your conversation skills. You might meet someone better than expected. But don’t let it become your strategy.
Build a real life. Meet real women. That’s where the future is found.
PROBLEM: “I’m afraid of being rejected.”
SOLUTION: Rejection is painful, especially when you take it personally. So stop taking it personally.
Most rejections aren’t even about you. She might be in a bad mood, already dating someone, overwhelmed with work, or distracted. You’re getting a response to her current state, not a verdict on your worth.
Too many men grew up on movies where rejection is public and humiliating. But those are just movie scripts. In real life, rejection is rarely brutal. Especially if you’re respectful, most rejections are soft, and if you’re paying attention, you’ll see it coming before you even ask.
Her posture, her eye contact, her tone… they all tell a story. Women constantly signal how open they are to being approached. You can learn to read that story. It’s a skill.
Yes, you’ll still be rejected from time to time. But it won’t sting the same.
Men who fear rejection have a weak internal frame and a fragile ego. Both of these can, and must, be strengthened if you want to be in a relationship. Because in marriage, you’ll face moments where your wife rejects something you want, or pushes back hard. If you crumble over a stranger’s ‘no,’ how will you handle conflict with someone you love?
The solution isn’t to avoid rejection. It’s to heal the wounds that make you overly sensitive to it.
Let rejection be feedback. Let it be fuel. Let it forge you into a stronger man.
PROBLEM: “None of the women I meet are up to my standards.”
SOLUTION: Then you need to ask two questions:
-
Are your standards calibrated to reality, or to fantasy?
-
Are you the kind of man who attracts what you want?
There’s a simple way to check if your standards are realistic: If you’re out socializing regularly and meeting at least one woman per month that you find attractive and potentially relationship-worthy, your standards are likely calibrated.
Even if some are taken or uninterested, twelve encounters a year puts you on track to find someone marriage-worthy in one to two years.
But if you’re not meeting any women who meet your standards, or none are attracted to you, then your expectations are off, or you’re not meeting the masculine side of the equation.
High standards are good. But your standards for yourself must be even higher.
Don’t lower your standards. Raise your value.
PROBLEM: “I don’t know what women today want.”
SOLUTION: Don’t worry, many women don’t know what they want either.
At least not until they see it.
You don’t need to have a deep understanding of women to start dating. What you need is a deep understanding of yourself, and the basics of how to interact with the opposite sex.
Women are not a monolith. They don’t all want the same thing. And it’s okay if some women don’t want what you’re offering. That just means they’re not your match.
If you want marriage, children, and a peaceful home life, say so. Be clear. Be honest. Look for the woman who lights up at that vision.
And remember: first dates are not emotional dumps. Don’t share your entire life story. Don’t unload your childhood wounds and five-year plans all at once. Let it come out gradually, organically, over time.
Oversharing too soon is a kind of emotional immodesty. It pushes women away. It scares them.
Instead, bring warmth. Curiosity. Humor. Presence. Let her feel who you are, before she hears everything you’ve done or want to do.
Also, understand that many women are suffering in the dating market too. They’ve dealt with immature men, disrespect, or emotional burnout. Some are guarded. Some are hesitant. That’s not a personal rejection, it’s their healing process.
Your job isn’t to fix them. But it is to show up as the kind of man who makes her feel that safety, joy, and being lead by a man is possible again.
Be patient. Be strong. Be sincere.
And become the man who makes her remember what she wants.
PROBLEM: “Dating is exhausting. I just want to skip to marriage.”
SOLUTION: I’m always surprised by how many men don’t enjoy dating, or find it exhausting and stressful.
Let’s reframe that.
You’re going out with a beautiful woman. You’re spending time with someone you find attractive. And success isn’t about getting married, it’s about enjoying the evening.
That’s it.
Don’t complicate it. Keep it simple. Simple dates. Simple interactions. Think of it as fun. Learn how to find joy in the process.
Because here’s the secret: If you want your marriage to be joyful, you’ll have to keep dating your wife.
If planning one evening out drains you, you’re not ready for the rhythm of married life. Marriage isn’t a break from effort, it’s the reward for mastering it.
Now, yes, wanting the reward without the work is natural. But it’s immature.
Dating is the training ground. It’s where you learn. You don’t marry a stranger. You marry someone you’ve pursued, studied, and built connection with.
If you skip the process, you skip the transformation from boyfriend to husband.
Lean in. Learn. Let it shape you.
PROBLEM: “I have low self-esteem and maybe depression.”
SOLUTION: Women can tell.
Even if you’re good at hiding it, most women will pick up on low self-esteem or depression by the end of the first date. And it’s one of the most off-putting traits a man can have.
Not because they’re cruel. But because they’re biologically wired to seek strength.
Women already deal with hormonal emotional swings. The last thing they need is a man who can’t stabilize the emotional climate of a home. A man who is stuck in despair can’t uplift a family.
Other men might have sympathy for you. But women, especially women you aren’t related to, rarely do. They’re not selecting for pity. They’re selecting for protection. For future fatherhood. For strength.
That doesn’t make you unlovable. It makes this urgent.
Self-esteem isn’t magic. It’s earned. You build it by setting goals and achieving them, consistently. Start with goals so small you know you can win. Stack those wins daily. Use systems that help you keep score. Journal your progress. Review your wins. Let them rewire your beliefs.
Depression can be attacked the same way:
-
Lift heavy things
-
Eat meat
-
Get sunlight
-
Cut screen time and porn
-
Go outside and move
-
Sleep and wake on rhythm
-
Seek out experts: a coach, a priest, or a therapist
And most of all, stop isolating. Find men who are winning. Spend time with them. Compete with them. Let their energy rub off on you.
You’re not broken. You’re just under-trained.
Fix this, and the rest will follow.
PROBLEM: “There’s no point in dating when divorce laws are against men.”
SOLUTION: Yes, divorce laws are unjust.
But giving up on women because the system is rigged is like giving up on work because taxes exist.
You don’t surrender to the injustice. You outsmart it.
Vet better. Lead from a place of strength. Choose a woman who fears God, loves truth, hates a divorce, and shows loyalty under pressure.
Your objective as a man and husband is to build a marriage where the divorce laws don’t matter.
If you end up in court, you’ve already failed.
Build your family with a woman who doesn’t believe in divorce. Who comes from a family and a culture that doesn’t believe in divorce. These subcultures exist, even inside nations with high divorce rates.
Create a home where the idea of divorce doesn’t enter the conversation, not because you’re naïve, but because the family structure is strong, the values are shared, and the foundation is sacred.
And if needed, protect yourself legally without becoming cynical.
Living in fear is not a winning strategy. Conviction and leadership is.
PROBLEM: “I don’t see the benefit of marriage in 2025.”
SOLUTION: For some men, those who can barely care for themselves, lack discipline, avoid responsibility, and have no interest in becoming fathers, marriage may not benefit them. And frankly, it shouldn’t.
But if you’ve read this far, that’s not you.
You want to become the kind of man who leads a family. And for men like you, marriage is a worthy risk, it’s the catalyst you need.
As my friend *@LukeWeinhagen *often says:\ "The mature adult form of a male is called a father."
You become fully formed through marriage and fatherhood. You finish your development as a man by taking on sacred responsibility.
Now, some men say, “I can just pay a maid to clean my house, a nanny to raise my kids, and a girlfriend for company.”
Be honest with yourself. Most men saying that are too broke to afford one of those women, let alone three. And even if you could, that’s not a family.
Children raised by strangers will not grow up strong and securely attached to their parents. They will not continue your legacy. They will not build a civilization.
That model is a a cold dead end.
Marriage, when done right, is the greatest force multiplier in a man’s life.
You gain:
-
A woman’s emotional and spiritual partnership
-
A peaceful home, a sanctuary from the world
-
Feminine warmth, lightness, and joy woven into your daily life
-
Children who carry your name, your values, your soul
-
A home culture that makes you stronger
-
A reason to become the man you always knew you could be
-
Emotional and spiritual partnership
Don’t listen to broken men who couldn’t carry the weight. Become the man who can.
PROBLEM: “I’ve done everything right. I’m a great catch. And I still can’t find a woman.”
SOLUTION:
This is the hardest kind of problem, because it hides behind your own certainty.
If everything you’ve said is true, then by now, something should be working. So we have to consider two possibilities.
First, you’re deluding yourself. Maybe you haven’t actually done the work. Or you’ve done it halfway, inconsistently, or with the wrong intent. Maybe you’ve made progress, but you’re still self-sabotaging in subtle ways, through your words, your posture, your patterns. You say you want marriage and children, but you’re not living like a man who’s ready for it.
Second, there’s something off-putting about you that you don’t see. Either the people around you are too polite to tell you, or too socially blind to even notice.
In both cases, you will not solve this alone. If you could, you already would have. You need someone outside your head and outside your social circle. A trained eye. A mirror that doesn’t lie.
Talk to me. Book a call. Even just the free 30-minute session . I’ll tell you the truth. And if you’re ready, we’ll fix it. Most of the time, it’s only a few months of focused work.
But it starts with honesty.
No more guessing.
No more waiting.
Let’s find out what’s really in your way.
CLOSING:
Before we end, let’s clear up one more misconception: You do not need to be fully ready for marriage to start dating.
You just need to be ready to date well.
Your finances don’t need to support a household yet, but they should support a courtship. Your leadership doesn’t need to be flawless, but it needs to be growing towards maturity.
You won’t find a woman who’s fully ready for marriage either. You’ll grow into that role together.
Dating is not the finish line of readiness. It’s the training ground.
So don’t wait to be perfect. Be honest, be improving, and be intentional. That’s more than enough to begin.
You said you wanted a woman. A wife. A family. A future.
That dream will cost you. In time, money, effort, and pride.
But what you get in return, is everything that makes a man come alive.
Start by solving the next problem. And the one after that. And then keep going.
Once you can fix what’s in the way now, you’ll be ready to build what you were born for next.
And if there’s something blocking you that I didn’t cover here, say so. Send me a message. Leave a comment. Tell me what’s in the way.
This post wasn’t meant to be complete. It was meant to begin a conversation.
Let’s go.
-
-
 @ 4fa5d1c4:fd6c6e41
2025-05-19 13:32:02
@ 4fa5d1c4:fd6c6e41
2025-05-19 13:32:02Willkommen zur Mitmachplattform: KI-Kompetenzen für die religionsbezogene Bildung
Diese Plattform ist ein offenes, gemeinschaftliches Lernmodul für alle, die KI-Kompetenzen im Kontext der religionsbezogenen Bildung entdecken, vertiefen und weitergeben möchten.\ Hier können Religionslehrende, Hochschulangehörige und ehrenamtlich Engagierte gemeinsam Inhalte entwickeln, teilen und weiterentwickeln.
Was ist das Ziel?
Wir schaffen eine offene Lernumgebung, in der Materialien zu KI-Kompetenzen für Schule, Hochschule und außerschulische Jugendarbeit kollaborativ entstehen.\ Die Plattform richtet sich an Lehrkräfte, Fortbildner:innen und Ehrenamtliche, die KI-Themen in der religiösen Bildung verantwortungsvoll erschließbar machen wollen.
Unser Kompetenzmodell
Im Zentrum steht ein Kreismodell mit vier Kompetenzbereichen, die auf drei Niveaustufen ausdifferenziert sind:\ Verstehen, Anwenden, Reflektieren und Gestalten.\ Diese Bereiche bauen aufeinander auf, beeinflussen sich gegenseitig und werden durch die zentrale Kompetenz AI Leadership verbunden.
| Kompetenzbereich | Beschreibung | | -------------------------------------------------------------------- | ---------------------------------------- | | 🟢 VERSTEHEN | Grundlagen und Mechanismen von KI | | 🔵 ANWENDEN | KI-Tools im Lernprozess nutzen | | 🟠 REFLEKTIEREN | Kritische Auseinandersetzung mit KI | | 🟣 GESTALTEN | Aktive Weiterentwicklung von KI-Systemen |
Jeder Lerninhalt ist einem Kompetenzbereich (und wenn möglich einer Niveaustufe) zugeordnet – farblich und inhaltlich klar erkennbar.
So funktioniert die Mitmachplattform
-
Offene Inhalte: Alle Materialien werden als Markdown-Dateien über Nostr gepflegt.
-
Mitmachen leicht gemacht: Egal wo auf Nostr du publizierst, mit den Hashtags #relilab und dem jeweiligen Kompetenzbereich als Schlagwort (also #verstehen, #anwenden, #gestalten, #reflektieren) finden wir diese Hashtagkombination und können die Webseite mit deiner Idee oder Weiterentwicklung ergänzen.
-
Anleitungen: Eine eigene Seite erklärt Schritt für Schritt, wie du dich beteiligen kannst – ganz ohne Vorkenntnisse im Programmieren.
-
Suchfunktion: Finde gezielt Inhalte nach Kompetenzbereich, Niveaustufe oder Schlagworten.
Für wen ist diese Plattform?
-
Lehrkräfte an Schulen und Hochschulen in religionsbezogenen Fächern
-
Ehrenamtliche und Multiplikator:innen in der kirchlichen Jugendarbeit
-
Fort- und Weiterbildner:innen im Bereich KI und Religion
Mitmachen & Teilen
\> "Sharing is Caring":\ \> Unser KI-Kompetenzmodell und alle Lernmaterialien stehen unter der offenen Lizenz [CC-BY 4.0].\ \> Du darfst sie frei nutzen, anpassen und weitergeben – mit Nennung der Urheber:innen.
Starte jetzt!
Gemeinsam gestalten wir KI-Kompetenzen für eine reflektierte, verantwortungsvolle und kreative religiöse Bildung im KI-Zeitalter.
Kontakt & Feedback:\ Für Fragen, Anregungen oder Feedback
https://ki-kompetenzen.npub.pro
#OER #relilab
antworte einfach auf diese Nachricht oder komm' in den Matrix/Element-Raum https://matrix.to/#/#relilab-ki:rpi-virtuell.de> zum Online-Austausch!
-
-
 @ 48706e89:cd3c97e3
2025-05-19 13:06:27
@ 48706e89:cd3c97e3
2025-05-19 13:06:27Mal schauen, was so geht...
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 48706e89:cd3c97e3
2025-05-19 12:42:25
@ 48706e89:cd3c97e3
2025-05-19 12:42:25# KI und Ethik im RU\ Wlche Verantwortung tragen wir beim Einsatz von KI in der Bildung? Dieses Modul bietet theologische Perspektiven und Diskussionsimpulse."
-
 @ e17e9a18:66d67a6b
2025-05-19 11:46:09
@ e17e9a18:66d67a6b
2025-05-19 11:46:09We wrote this album to explain the inspiration behind Mutiny Brewing, and as a way to share the story of Bitcoin and freedom technologies like nostr. Through these songs, we’ve tried to capture every truth that we believe is essential to understand about money, freedom, trust, and human connection in the internet age. It’s our way of making these ideas real and relatable, and we hope it helps others see the power of taking control of their future through the systems we use.
01. "Tomorrow's Prices on Yesterday's Wage" explores the harsh reality of inflation. As central banks inflate the money supply, prices rise faster than wages, leaving us constantly falling behind. People, expecting prices to keep climbing, borrow more to buy sooner, pushing prices even higher in a vicious cycle. You're always a step behind, forced to pay tomorrow's inflated prices with yesterday's stagnant wages.
https://wavlake.com/track/76a6cd02-e876-4a37-b093-1fe919e9eabe
02. "Everybody Works For The Bank" "Everybody Works For The Bank" exposes the hidden truth behind our fiat money system.
When banks issue loans, they don’t lend existing money — they create new money from debt. You’re on the hook for the principal and the interest. But the interest doesn’t exist yet — it has to come from someone else borrowing. That means the system only works if debt keeps growing.
When it doesn’t, the whole thing wobbles. Governments step in to bail out the banks by printing more money, and that cost doesn’t vanish. It shows up in your taxes, your savings, and your grocery bill.
We’re not just working to pay our own debts, we’re paying for their losses too.
https://wavlake.com/track/4d94cb4b-ff3b-4423-be6a-03e0be8177d6
03. "Let My People Go" references Moses' demand for freedom but directly draws from Proverbs 6:1–5, exposing the danger of debt based money. Every dollar you hold is actually someone else's debt, making you personally liable—held in the hand of your debtor and at risk of their losses, which you ultimately pay for through inflation or higher taxes. As the song says, "The more you try to save it up, the deeper in you get." The wisdom of Proverbs urges immediate action, pleading urgently to escape this trap and free yourself, like a gazelle from a hunter.
https://wavlake.com/track/76214ff1-f8fd-45b0-a677-d9c285b1e7d6
04. "Mutiny Brewing" embodies Friedrich Hayek's insight: "I don't believe we shall ever have good money again before we take it out of the hands of government... we can't take it violently... all we can do is by some sly roundabout way introduce something they can't stop."
Inspired also by the Cypherpunk manifesto's rallying cry, "We will write the code", the song celebrates Bitcoin as exactly that unstoppable solution.
"Not here to break ya, just here to create our own little world where we determine our fate." https://wavlake.com/track/ba767fc8-6afc-4b0d-be64-259b340432f3
05. "Invisible Wealth" is inspired by The Sovereign Individual, a groundbreaking 1990s book that predicted the rise of digital money and explores how the return on violence shaped civilizations. The song references humanity's vulnerability since agriculture began—where stored wealth attracted violence, forcing reliance on larger governments for protection.
Today, digital privacy enabled by cryptography fundamentally changes this dynamic. When wealth is stored privately, secured by cryptographic keys, violence becomes ineffective. As the song emphasizes, "You can't bomb what you can't see." Cryptography dismantles traditional power structures, providing individuals true financial security, privacy, and freedom from exploitation.
“Violence is useless against cryptography” https://wavlake.com/track/648da3cc-d58c-4049-abe0-d22f9e61fef0
06. "Run A Node" is a rallying cry for Bitcoin's decentralisation. At its heart, it's about personal verification and choice: every node is a vote, every check’s a voice. By running the code yourself, you enforce the rules you choose to follow. This is true digital democracy. When everyone participates, there's no room for collusion, and authority comes directly from transparent code rather than blind trust.
"Check the blocks, verify, ain't that hard to do When everyone's got eyes on it, can't slip nothin' throgh." https://wavlake.com/track/ee11362b-2e84-4631-b05e-df6d8e6797f8
07. "Leverage is a Liar" warns against gambling with your wealth, but beneath the surface, it's a sharp critique of fractional reserve banking. Fractional reserves inflate asset prices, creating the illusion of wealth built on leverage. This system isn't sustainable and inevitably leads to collapse. Real wealth requires sound money, money that can't be inflated. Trying to gain more through leverage only feeds the lie.
"Watch it burn higher and higher—leverage is a liar." https://wavlake.com/track/67f9c39c-c5e1-4e15-b171-f1f5442f29a5
08. "Don't Get Rekt" serves as a stark warning about trusting custodians with your Bitcoin. Highlighting infamous collapses like Mt.Gox, Celsius, and FTX. These modern failures echo the 1933 Executive Order 6102, where the US government forcibly seized citizens' gold, banned its use, and then promptly devalued the currency exchanged for it. History shows clearly: trusting others with your wealth means risking losing it all.
"Your keys, your life, don't forget." https://wavlake.com/track/fbd9b46d-56fc-4496-bc4b-71dec2043705
09. "One Language" critiques the thousands of cryptocurrencies claiming to be revolutionary. Like languages, while anyone can invent one, getting people to actually use it is another story. Most of these cryptos are just affinity scams, centralized towers built on shaky foundations. Drawing from The Bitcoin Standard, the song argues money naturally gravitates toward a single unit, a universal language understood by all. When the dust settles, only genuine, decentralized currency remains.
"One voice speaking loud and clear, the rest will disappear." https://wavlake.com/track/22fb4705-9a01-4f65-9b68-7e8a77406a16
10. "Key To Life" is an anthem dedicated to nostr, the permissionless, unstoppable internet identity protocol. Unlike mainstream social media’s walled gardens, nostr places your identity securely in a cryptographic key, allowing you total control. Every message or action you sign proves authenticity, verifiable by anyone. This ensures censorship resistant communication, crucial for decentralised coordination around Bitcoin, keeping it free from centralised control.
"I got the key that sets me free—my truth is mine, authentically." https://wavlake.com/track/0d702284-88d2-4d3a-9059-960cc9286d3f
11. "Web Of Trust" celebrates genuine human connections built through protocols like nostr, free from corporate algorithms and their manipulative agendas. Instead of top down control, it champions grassroots sharing of information among trusted peers, ensuring truth and authenticity rise naturally. It's about reclaiming our digital lives, building real communities where trust isn't manufactured by machines, but created by people.
"My filter, my future, my choice to make, real connections no one can fake." https://wavlake.com/track/b383d4e2-feba-4d63-b9f6-10382683b54b
12. "Proof Of Work" is an anthem for fair value creation. In Bitcoin, new money is earned through real work, computing power and electricity spent to secure the network. No shortcuts, no favourites. It's a system grounded in natural law: you reap what you sow. Unlike fiat money, which rewards those closest to power and the printing press, Proof of Work ensures rewards flow to those who put in the effort. Paper castles built on easy money will crumble, but real work builds lasting worth.
"Real work makes real worth, that's the law of this earth." https://wavlake.com/track/01bb7327-0e77-490b-9985-b5ff4d4fdcfc
13. "Stay Humble" is a reminder that true wealth isn’t measured in coins or possessions. It’s grounded in the truth that a man’s life does not consist in the abundance of his possessions. Real wealth is the freedom to use your life and time for what is good and meaningful. When you let go of the obsession with numbers, you make room for gratitude, purpose, and peace. It's not about counting coins, it's about counting your blessings.
"Real wealth ain't what you own, it's gratitude that sets the tone." https://wavlake.com/track/3fdb2e9b-2f52-4def-a8c5-c6b3ee1cd194



